Microsoft Teams phishing email attack. Click to enlarge. Credit: Abnormal Security
Cyber 2024 2023 2022 2021 2020 CYBERCRIME 2022 2021 2020
The 5 Most-Wanted Threatpost Stories of 2020
31.12.2020 Cyber Threatpost
A look back at what was hot with readers — offering a snapshot of the security stories that were most top-of-mind for security professionals and consumers throughout the year.
As 2020 draws to a close, it’s clear that work-from-home security, ransomware, COVID-19-themed social engineering and attacks by nation-states will go down as defining topics for the cybersecurity world for the year. Threatpost also took a retrospective view on what readers were most interested during the last 12 months, looking at our top five most-read stories of the year.
Please read on to learn more about what caught reader’s attention the most this year, with an eye to summing up some hot trends. Subjects include Microsoft Office 365; major security bugs in Zoom and other platforms; gaming security; the ongoing scourge of Emotet and malware development in general; and concluding with a potpourri of other hot 2020 headlines involving WhatsApp, Fitbit, code-cracking and more.
1. Microsoft: Office 365 and More
With enterprises relying heavily on Microsoft’s business suite of applications during the COVID-19 pandemic, cybercriminals supercharged their targeting of these tools across a variety of attack vectors.
Most-Read Story of 2020: Microsoft Teams Lure
Microsoft Teams phishing email attack. Click to enlarge. Credit: Abnormal Security
One cybersecurity story caught more reader interest than any other article for the year: Phishes that pretended to be automated messages from Microsoft Teams. The attack, uncovered in October, was sent to between 15,000 to 50,000 Office 365 users, in hopes of scooping up their credentials.
Teams is Microsoft’s popular collaboration tool, which has particularly risen in popularity among remote workforces during the pandemic – making it an attractive brand for attackers to impersonate.
“Because Microsoft Teams is an instant-messaging service, recipients of this notification might be more apt to click on it so that they can respond quickly to whatever message they think they may have missed based on the notification,” said researchers at the time.
Microsoft Office 365: Top Threat Vector
Many of this year’s top-level phishing attacks leveraged Microsoft-themed lures in order to steal Office 365 credentials. For instance, one spoofed Microsoft.com to target 200 million Microsoft Office 365 users in a number of key vertical markets. Attackers also shook up their phishing tactics, with one September phishing campaign using authentication APIs to validate victims’ Office 365 credentials – in real time – as they entered them into the landing page, for example.
Microsoft 365 Bugs
Flaws were found in Microsoft’s lineup itself as well, with issues in the multi-factor authentication system used by Microsoft’s cloud-based office productivity platform, Microsoft 365, opening the door for hackers to access cloud applications via a bypass of the security system.
2. Bug Parade 2020
In 2020, there was a 65 percent increase in the discovery of high-risk vulnerabilities, according a year-capping Bugcrowd study. Few companies knew this stat better than overnight-sensation Zoom, who found itself on the receiving end of a number of critical bug notifications.
Topping our list of Zoom’s 2020 bugs, and driving serious interest with Threatpost readers, were two zero-day flaws found in the macOS version of the Zoom client and disclosed on April Fool’s Day. The flaws, uncovered by Patrick Wardle, principle security researcher with Jamf, allowed a local and unprivileged attacker to gain root privileges of a targeted system and gave them access to the victims’ microphone and camera.
Cisco Systems: A Top CVE Squasher!
When you are one of the world’s leading information technology and networking companies, you’re going to have some bugs. In 2020, Cisco Systems deserves props for its transparency and efficiency when it comes to notifying customers and patching hundreds of vulnerabilities. Let us reminisce. In early December there was the zero-click wormable RCE vulnerability in Cisco Jabber that was patched – twice. From zero-clicks to zero-days, Threatpost readers turned their attention to a nasty, at the time, unpatched AnyConnect Secure Mobility Client Software bug. After the bug was patched, Cisco confirmed said there were no reports of attacks against the flaw before it was fixed.
3. Gaming Security
Gaming security came more into focus for readers in 2020, as a possible result of the global COVID-19 pandemic. Thanks to a long few months spent with reduced social outlets, gaming audiences have exploded this year. That’s attracted the attention of cybercriminals – in a recent survey by Kaspersky, nearly 61 percent reported suffering foul play such as ID theft, scams or the hack of in-game valuables.
Source: Kaspersky.
Among Us Mobile Game Crashes
One of Threatpost’s Top 5 most-read stories covered the meteoric rise of the game Among Us, and how it outpaced its developer’s ability to keep up with malicious actors.
In October, a specific ongoing attack forced InnerSloth, the company behind the game, to hastily roll out an update designed to kick bad actors off the game’s servers — likely along with some innocent players as well. InnerSloth is run by a three-person team consisting of one developer, one animator and game designer, and one artist.
The attacks spammed players with ads from a player named Eris Loris, rendering the game useless. The attackers used bots to overwhelm the game with messages promoting a YouTube channel and Discord operated under the name Eris Loris, threatening to “blow up your phone,” and concluding with a “Trump 2020” endorsement.
Cyberpunk 2077: Gaming Event of the Year
Gaming security news in general was in-demand in 2020. The December release of Cyberpunk 2077, featuring a digitized Keanu Reeves among other things, was supposed to be the gaming event of the year. Instead, the initial release was slammed for poor performance and numerous bugs and glitches that make the user experience less than pleasant – forcing Sony to pull the game off the PlayStation store.
On top of that, cybercriminals waded into the mix, spreading ransomware targeting Android devices disguised as a legitimate download of the new open-world game.
The CoderWare ransomware was being promoted as a download of Cyberpunk 2077 from a fake version of the Google Play mobile app marketplace. The listing for the game, which is named “Cyberpunk 2077 Mobile (Beta),” even had reviews from users so as to appear legitimate.
NVIDIA Bugs: Fuel to the Fire
Cybercriminals didn’t just target the games themselves in 2020; they also went after bugs in the systems that gamers rely on. Nvidia, which makes gaming-friendly graphics processing units (GPUs), was a particular hot target throughout the year,
In October it disclosed two high-severity flaws in the Windows version of its GeForce Experience software. GeForce Experience is a supplemental application to the GeForce GTX graphics card — it keeps users’ drivers up-to-date, automatically optimizes their game settings and more. GeForce Experience is installed by default on systems running NVIDIA GeForce products, Nvidia’s brand of GPUs.
The most severe flaw of the two (CVE-2020-5977) can lead to a slew of malicious attacks on affected systems – including code execution, denial of service, escalation of privileges and information disclosure.
In June, Nvidia fixed two high-severity flaws that affected drivers for Windows and Linux users, including ones that use Nvidia’s GeForce, Quadro and Tesla software. And in March, Nvidia issued patches for high-severity bugs in its graphics driver, which can be exploited by a local attacker to launch DoS or code-execution attacks, and also affected display drivers used in GeForce (as well as Quadro and Tesla-branded) GPUs for Windows.
Scalper-Bots Ruin Christmas
Another popular gaming headline this year involved another hotly anticipated release in the gaming world: New consoles from Microsoft and Sony: The Xbox Series X and PlayStation PS5, respectively. But an army of bots threatened to drive prices up as much as three times the retail price, putting the coveted holiday gifts well out of reach of everyday fans.
Retailers were quickly cleared out of Xbox inventory on its release day. There were plenty available on eBay though, with price tags more than double that price, several marked at over $1,000. The PlayStation 5, also priced at $499.99, experienced several pre-order confirmations — not even actual product — available on eBay listed for around $900.
The activity sparked the development of the “Stopping Grinch Bots Act,” introduced in the Senate in December, which would ban bots on all online retail platforms if passed.
4. Malware Mayhem 
Lucifer Malware emerged to haunt users
In our fourth hot-topic area, malware authors throughout the year found new ways to snoop on victims, steal sensitive data and more by creating new strains of malware, and improving on old
One of these strains was a self-propagating malware, found in June, was called Lucifer. This malware targeted Windows systems with cryptojacking and distributed denial-of-service (DDoS) attacks.
In addition, cybercriminals also made critical updates or adopted new attack techniques as part of existing, well-known malware families. For instance, in November attackers sent out ads for fake Microsoft Teams updates to deploy backdoors, which used Cobalt Strike to infect companies’ networks with malicious code.
Emotet’s Evolution Continues
Emotet, which started as a banking trojan in 2014 and has continually evolved to become a full-service threat-delivery mechanism, continued its track on 2020 to become a top threat. One of Threatpost’s Top 5 headlines of the year came in February, when a new Emotet malware sample was uncovered with the ability to spread to insecure Wi-Fi networks that are located nearby to an infected device. Also in February, researchers warned of an Emotet campaign being spread via SMS messages. The messages pretended to be from banks, and researchers warned the campaign may have ties to the TrickBot trojan.
Emotet continued to be a thorn in defenders’ side over the course of 2020, picking up a series of new tricks. First, Emotet’s attachments started to include password-protected archive files to bypass email security gateways. Soon after, Palo Alto Networks reported to CISA that researchers are now seeing instances of “thread jacking” — that is, intercepting an existing email chain via an infected host and simply replying with an attachment to deliver the malware to an unsuspecting recipient.
And the threat isn’t limited to desktop computers. Steve Banda, senior manager of security solutions at Lookout, told Threatpost Emotet has gone mobile this year, too.
The activity led the Feds this fall to issue a warning that state and local governments need to fortify their systems against the trojan.
Mobile Malware Attacks Surge
Attackers honed in on mobile as a target for their malware campaigns this past year, too. The Joker malware (a billing fraud family of malware that emerged in 2017) continued to rock the Android ecosystem, with Google in January announcing it had removed more than 17,000 Android apps from its Google Play marketplace. In a separate July report, researchers said that 14.8 percent of Android users who were targeted with mobile malware or adware last year were left with undeletable files. It’s not just mobile – browsers were also a top vector for spreading malware in 2020, with researchers finding 500 Google Chrome browser extensions in February secretly uploading private browsing data to attacker-controlled servers, and redirecting victims to malware-laced websites.
5. The Best of the Rest
Positive Encryption News
Whether it be browser support for HTTPS or safer certificate deployment, positive developments around encryption technology attracted considerable interest with readers. In March, internet behemoths like Google took an even harder stance against the insecure Hypertext Transfer Protocol (HTTP) and began warning Chrome browser users when the downloads from sites lacked the more secure Hypertext Transfer Protocol Secure (HTTPS) protection. Later in the year, browser makers adopted DNS-Over-HTTPS (DoH) support – both a privacy-boosting and security enhancement.
2020 Social Media News Wrap
Social platforms such as Facebook, TikTok and WhatsApp also dominated Threatpost virtual foot traffic. A well-worn path to WhatsApp news stories included headlines “WhatsApp Phone Numbers Pop Up in Google Search Results” and “WhatsApp Bug Allows Malicious Code-Injection“. TikTok being banned by the United States Army drew interest in January 2020 setting the tone for stories to come such as TikTok owner ByteDance’s security posture around the app and the possible sale or ban of TikTok from U.S. markets altogether. As for Facebook, readers were hungry for news in November about how a Facebook Messenger bug that allowed spying on Android users. Facebook’s Messenger client also piqued reader interest in May with a report about Android malware, dubbed WolfRAT, that was being deployed to gather intelligence on victims.
Media Beat: Podcasts, Webinars and Video
When COVID-19 cut Threatpost’s ability to travel to conferences and interview important voices in the security community one-on-one and in person, we adapted. Senior Editor Lindsey O’Donnell Welch produced an impressive library of videos and podcasts in 2020.
As for videos, one of our most popular segments featured Chris Vickery, the director of risk research with UpGuard who discussed how artificial intelligence will drive next-gen breaches. She also caught up with Sherrod DeGrippo, senior director of threat research and detection for Proofpoint, who discussed cyber vigilantes.
Podcasts our readers enjoyed the most included “Malware Risks Triple on WFH Networks: Experts Offer Advice“. The second-runner up podcast featured Ryan Olson, vice president of Threat Intelligence for Unit 42 at Palo Alto Networks, and May Wang, senior distinguished engineer at Palo Alto Networks and former Zingbox CTO who each weighed-in on IoT devices vulnerabilities.
Top Threatpost webinars included “Taming the Unmanaged and IoT Device Tsunami” which featured cybersecurity expert Bruce Schneier and Armis CISO Curtis Simpson. A second webinar on healthcare security titled “2020 Healthcare Cybersecurity Priorities: Data Security, Ransomware and Patching” featuring Jeff Horne, CSO at Ordr and Tony Reina, chief AI architect. at Intel, was our second most popular. Intelligence for Unit 42 at Palo Alto Networks titled “More Than Half of IoT Devices Vulnerable to Severe Attacks“.
Taking a Neighborhood Watch Approach to Retail Cybersecurity
31.12.2020 Cyber Threatpost
Bugcrowd CTO Casey Ellis covers new cybersecurity challenges for online retailers.
Every year retailers face a heightened level of risk during the online holiday shopping season. COVID-19 drastically shifted consumer buying behaviors, forcing retailers to accelerate digital transformation efforts to support an exponentially higher number of online transactions. Projected U.S. e-commerce sales will hit close to $710 billion in 2020, the largest jump in a single year. To adapt to the online shopping increase, many retailers have had to take new systems online faster than planned— and therefore not necessarily with enough time to test— to accommodate an all-time high in online transactions.
Speed is the natural enemy of security. When vendors rush things to production without proper testing, security blind spots are more likely to occur, creating the perfect opportunity for cyberattacks.
Adopting a “neighborhood watch” approach to security by inviting the global network of security researchers to proactively hunt for and disclose vulnerabilities before cybercriminals can exploit them improves retailer security and consumer confidence.
What’s in Store this Online Holiday Shopping Season
Over time, consumers have been evolving to shop predominantly online around the holiday season more often than in stores. Black Friday 2019 saw nearly 20 million more online shoppers than in-person in the U.S. However, retailers are emphasizing online sales more than ever before amid the pandemic. This year’s holiday-buying season kicked off earlier than usual, with Black Friday sales in advance of the traditional start of the day after Thanksgiving. The 2020 Amazon Prime Day sales, which was declared the ‘unofficial’ start to holiday shopping, surpassed last year’s numbers by 45.2 percent.
Retailers Must Account for Heightened Levels of Risk
Even before this year’s holiday shopping season, retailers have seen a massive increase in online shopper numbers throughout 2020.
A full 62 percent of U.S. shoppers say they shopped more online this year than before the pandemic. And 36 percent of U.S. consumers now shop online weekly, up from 28 percent before the pandemic. To account for this increased number of online interactions, many retailers innovated in near real-time to meet customer demand and build new systems in a hurry that can manage more transactions than before.
Systems built in a hurry are much more likely to have unintended consequences. As retailer developers work to innovate, they often unknowingly leave development systems and data exposed on the internet that should otherwise be behind closed doors. If attackers can view source code, they can then analyze it at a granular level. Alongside this, the sudden transition to “work from home” earlier this year forced similar changes to development practices, allowing attackers to siphon off API keys, corporate credentials and large databases of customers’ information.
Additionally, thanks to COVID-19, retailers now must worry about their own employees’ homes as an extension of their enterprise attack surface. Attackers can have a field day compromising remote workers through their insecure home automation technology, smart appliances, and more. They can then move laterally to the corporate network if the proper protections are not in place.
Enter Neighborhood Watch Security
Even though unprecedented risks await retailers this holiday shopping season, they can still take steps to level the security playing field against adversaries by engaging the assistance of a global network of talented security researchers and employing a neighborhood watch security approach as part of their security program. To engage security researchers, retailers should start by creating a vulnerability disclosure program (VDP) and then progress towards a public bug-bounty program. These programs invite researchers to test retailers’ infrastructure and share security feedback, giving retailers a continuous “attackers-eye view” of their attack surface.
By establishing VDPs and considering progressing to a bug-bounty program, retailers can ensure and transparently assert that they are doing everything possible to safeguard their consumers’ security. In turn, consumers can have the confidence that their data is out of harm’s way and respond by choosing to shop at stores they feel are the safest.
2020 Work-for-Home Shift: What We Learned
30.12.2020 Cyber Threatpost
Threatpost explores 5 big takeaways from 2020 — and what they mean for 2021.
Goodbye, 2020 — and good riddance, right? Most of us don’t want to take too much from this year into the next — but let’s make an exception for what we learned about security in the wake of the COVID-19 pandemic. In 2021 after all, more enterprises will permanently downsize their physical spaces and give employees the flexibility to continue working from home.
In an effort to have a safer 2021, Threatpost takes a look at the top five biggest takeaways of the remote-work shift for security teams going forward.
1. Cybercriminals Are No Dummies
This one seems obvious, but for too long security teams have ignored the danger that comes from offering attackers low-hanging fruit.
As soon as businesses made the transition to work-from-home, cyberattackers got busy capitalizing on it. Researchers saw a near-immediate 131-percent increase in malware infections and about 600 new phishing attacks per day when the pandemic and remote working started in earnest in March. And according to a recent Acronis Cyberthreat Report, 31 percent of global companies reported daily cyberattacks in 2020, mainly targeted at remote workers. Clearly, threat actors know that home networks are typically less secure than corporate infrastructure, and saw an opportunity to ramp up their attacks accordingly.
Credit: Acronis
Since cybercriminals are pretty savvy (and quick-moving), defenders need to be too. The mad scramble to get employees connected from home is over; and now, security practices need to be hardened.
“2021 will be the year of ‘working from anywhere’ and it is very much a moving target for security and privacy professionals,” Yossi Naar, chief visionary officer and co-founder at Cybereason, told Threatpost. “Coupled with a challenging home environment where devices are often shared with family members and the rapid change that occurred, there was little time to prepare and that fact has been exploited widely by hackers leveraging phishing attacks and known exploits to penetrate and maintain their hold on the remote environment. In 2021, enterprises need to focus on patching the holes in their security defenses as the majority of their workers continue to operate remotely.”
Bitdefender researchers noted that home routers and computers will continue to be seen as weak links, so endpoint security will become a bigger focus in 2021 even as attackers evolve and mature.
“Threat actors specialized in hijacking devices will either rent access to other groups seeking distributed command-and-control capabilities or sell them in bulk to underground operators to reuse as proxy nodes to conceal malicious activity,” they said.
2. Collaboration: The New Chink in the Armor
When companies went to a decentralized footprint, they also turned in droves to cloud applications and collaboration services to support the new, borderless, virtual office. In short order, Zoom, Microsoft Teams and Slack became household words, video calls became the default for meetings, and the resources that are connected to, shared and exposed in the cloud were suddenly being used by tens of millions of workers.
A recent Fortune CEO survey showed that 77 percent of CEOs reported that the COVID-19 crisis accelerated their digital transformation plans, while 40 percent are spending more on IT infrastructure and platforms. Security, however, largely remained an afterthought as companies prioritized productivity over vetting the security for these products.
As a result, it was open season on collaboration. Last month for instance, attackers were seen using ads for fake Microsoft Teams updates to deploy backdoors, which used Cobalt Strike to infect companies’ networks with malware.
On a related note, cybersecurity will move up the food chain to become a business differentiator for collaboration platforms and cloud apps, researchers said — which will spur innovation in the space.
Going forward, “[security] needs a category disruptor,” Nico Popp, chief product officer at Forcepoint, told Threatpost. “The need for a converged, digital, cloud-delivered platform means we’ll see the emergence of the ‘Zoom of Security’ – a high-tech system that ‘just works’ and is easily accessible for the everyday consumer.”
3. Zero-Trust Has a Moment
As employees were sent home and forced to connect to precious corporate resources using potentially insecure devices, home networks and new cloud apps, the focus on authentication ramped up for security teams. The problem, of course, is that password hygiene isn’t good in the best of times, let alone in an environment of massive change and new platform adoption.
As a result, zero-trust frameworks gained a little buzz in 202o. “Zero trust” means that all users, inside and outside of an organization’s enterprise network, are inherently not trusted and must be authenticated and authorized before being able to access apps and data. In order to do this, systems must evaluate the safety of a user’s device, verify transport/session information and general identity, and take into account the application being used (is it allowed?) and the data being accessed (how sensitive is it?).
It works, according to those in the trenches. “Our adoption of zero-trust network access technologies and a cloud-based end user security stack made the transition of 95 percent of our workforce from relatively secure corporate networks to relatively unsecure home networks virtually seamless for the end user, but comparatively safe,” said Bradley Schaufenbuel, vice president and CISO at Paychex, via email.
Zero-trust frameworks have a reputation for being expensive and complicated, but in 2021, they will no longer be optional for enterprise, according to Jasen Meece, CEO of Cloudentity.
“There’s no doubt that COVID-19 and the shift to remote work have accelerated zero-trust adoption in the enterprise,” he told Threatpost. “In 2021 and the following years, implementing a zero-trust approach will become essential to protecting every enterprise, regardless of industry. Roughly one-quarter of all data breaches are caused by human error, with the average cost of $3.92 million for each breach, according to a report from the Ponemon Institute. As a result of this growing issue, the zero-trust model will become the new standard.”
4. A Mobile-Focused Security Policy is a Must
As workers went home, mobile devices became more ascendant, with many of the new go-to collaboration and cloud services offering mobile apps designed to boost productivity and allow multitasking. This resulted in rafts of personal devices suddenly being used to access corporate resources — and true to form, cybercriminals followed the trend lines.
For instance, 2020 saw mobile messaging becoming a growing vector for phishing attacks (often called smishing). In fact, in September, the FTC issued a warning about phishing campaigns involving text messages with false delivery notices that included a link to validate the delivery.
“Across any chat medium on mobile, phishing attacks seek to trick users into clicking links to expose personal and work credentials, and even download mobile surveillanceware,” Chris Hazelton, director of security solutions at Lookout, told Threatpost.
mobile device management security
But threat actors are building more advanced phishing campaigns beyond just credential harvesting, according to Hank Schless, senior manager for security solutions at Lookout.
“Through the first 9 months of 2020, almost 80 percent of phishing attempts intended to get the user to install a malicious app on their mobile device,” he said. “Threat actors have [also] learned how to socially engineer at scale by creating fake influencer profiles with massive followings that encourage followers to download malicious apps. Personal apps on devices that can access corporate resources pose serious risk to enterprise security posture.”
Criminals are also targeting weaknesses in mobile apps. For instance, WhatsApp in February disclosed a vulnerability in its iOS app that was exploited by Pegasus surveillanceware to gather intelligence from targets.
“While there are security vulnerabilities in all operating systems, including iOS and Android, it is less understood that vulnerabilities in mobile apps can be used in attacks,” Schless said.
5. The Rise of New Insider Threats
Remote employees have been thrust into new working environments, with no face-to-face supervision and little to no training for handling new security risks. And, they are also facing more distractions from their home settings, as well as new emotional stresses tied to COVID-19 and less job satisfaction. All of these factors created a ticking time bomb for insider-threat risks in 2020, researchers said.
According to a report from Tessian, insider-caused security incidents already increased by 47 percent since 2018. Worse, security experts warn that organizations aren’t ready for this influx of remote work-induced challenges.
“The [work from home] trend due to the COVID-19 pandemic has significantly increased insider threats from employees taking risks with company assets, such as stealing sensitive data for personal use or gain as employers have less visibility to what employees are doing or accessing,” Joseph Carson, chief security scientist and advisory chief information security officer at Thycotic, told Threatpost.
Insider threats can stem from either “negligent insiders,” or malicious insiders, who intentionally steal data or company secrets. The “negligent insiders” are the bigger threat, according to Proofpoint. They account for 62 percent of insider-threat incidents.
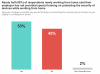
Security training stats. Click to enlarge. Source: IBM Security.
A survey from IBM Security in June found that more than half surveyed had yet to be given any new security policies on how to securely work from home. Also, more than half surveyed had not been provided with new guidelines on how to handle personal identifiable information (PII) while working from home, despite more than 42 percent newly being required to do so as consumers lean on customer service representatives for a variety of services.
Going forward, awareness of insider threats must take on more importance, researchers noted — especially as the pandemic grinds on and layoffs/workplace dissatisfaction rises.
“One area that organizations need to deal with is the rise of the insider threat, with so many unhappy employees who have been furloughed, or let go, from their jobs,” Steve Durbin, managing director of the Information Security Forum, told Threatpost. “The insider threat is one of the greatest drivers of security risks that organizations face as a malicious insider utilizes credentials to gain access to a given organization’s critical assets. Many organizations are challenged to detect internal nefarious acts, often due to limited access controls and the ability to detect unusual activity once someone is already inside their network. The threat from malicious insider activity is an increasing concern, especially for financial institutions, and will continue to be so in 2021.”
Overall, the trust that organizations must place on their workers has grown with rapid digital transformation, increasing information risk and changing work environments — and there’s no sign of this changing. Taking the lessons of 2020 will be critical for a safer and happier 2021.
Hackers Amp Up COVID-19 IP Theft Attacks
29.12.2020 Cyber Threatpost
In-depth report looks at how COVID-19 research has become as a juicy new target for organized cybercrime.
Attackers are looking to the healthcare space as a rich repository of intellectual property (IP) now more than ever, as critical research of COVID-19 therapeutics are developed and Pfizer, Moderna and other biotech firms begin to mass produce vaccines. Several incidents show that nation-states are targeting these companies with a vengeance, as the quest to beat the pandemic continues.
Espionage attacks have recently zeroed in on the COVID-19 vaccine supply chain, The Zebrocy malware continues to be used by hackers in vaccine-related cyberattacks. And earlier this month, threat actors accessed Pfizer and BioNTech vaccine documentation submitted to EU regulators.
These recent attacks are nothing new. Hackers attempting to profit off pandemic suffering has been an ongoing theme since January 2020.
[Editor’s Note: Threatpost has published an exclusive FREE eBook, sponsored by ZeroNorth. The eBook, “Healthcare Security Woes Balloon in a Covid-Era World”,examines the pandemic’s current and lasting impact on cybersecurity. Get the whole neatly-packaged story and DOWNLOAD the eBook now – on us!]
COVID-19 manufacturer Dr. Reddy’s Laboratories suffered an attack in October which forced it to shut down plants across Brazil, India, the U.K and the U.S. The Indian-based company is contracted to manufacture Russia’s “Sputnik V” COVID-19 vaccine.
In July, the U.S. Department of Homeland Security (DHS) warned that Russia-linked group APT29 (a.k.a. Cozy Bear or The Dukes) has been targeting British, Canadian and U.S. research companies26. The advanced persistent threat (APT) group looks to pilfer COVID-19 vaccine research from academic and pharmaceutical institutions, DHS warned.
Earlier in the pandemic, the World Health Organization was targeted by the DarkHotel APT group, which looked to infiltrate its networks to steal information.
Hackers Put Bullseye on Healthcare IP
Similarly, the U.S. Justice Department recently accused Chinese-sponsored cybercriminals of spying on COVID-19 researcher Moderna. “Even if you are good at science, this is a cheap insurance policy to maintain a seat at the table for the game of nations,” said Sam Curry, Cybereason CSO.”The headlines around stealing vaccine research, data and information being used to create vaccines to the world’s pandemic should be a wakeup call to research firms and both the private and public sector. It is not a question of if hacking will be done, but rather how much has already taken place,” Curry said.
He added that nation-state backed crime groups are well funded, patient and highly skilled at their craft – meaning there’s likely more activity going on than meets the eye. After all, having a lead on “re-opening” their part of the world could come with a lasting balance-of-power impact.
“Some groups have likely infiltrated these companies and have not been caught, and are pilfering through specific vaccine information, patents and other valuable content,” he said. “A vaccine for COVID is a strategically valuable (maybe crucial) asset. Whoever gets a vaccine first has an economic advantage and it is worth billions of dollars to a country and its economy. It is the ultimate IP with immediate value.”
In terms of how APTs are infiltrating their targets, commercially available trojans like Emotet or Trickbot are designed for enterprises and complex environments, according to Rob Bathurst, CTO of cybersecurity firm Digitalware. These backdoors can gain persistence and provide a deployment platform for making further inroads into a victim’s network.
“The rule of thumb for an attacker is to use just enough to get the job done– and that is usually commercial malware first, and custom packages only if needed for a specific target,” he said.
Custom kits have indeed been spotted. DHS for instance warned that APT29 is using advanced, custom malware called “WellMess” and “WellMail” for data exfiltration.
Free eBook on Healthcare and Cybersecurity
Ounce of Prevention Pound of Cure
As far as safeguarding the IP jewels, best practices start – as ever – with the basics. One of the most common ways for criminals to gain access to any computer network is through phishing – clicking on a dodgy email is all it takes for a threat actor to drop one of the aforementioned backdoors. It’s a tactic that was seen this year being deployed in the WHO attacks; a phishing page mimicked the WHO’s internal email system and looked to steal passwords from multiple agency staffers.
“To combat this type of attack, organizations need to continue to improve their security hygiene, implement around-the-clock threat hunting and increase their ability to detect malicious activity early,” Curry said. “Security-awareness training is also needed and employees should not open attachments from unknown sources and never download content from dubious sources.”
When it comes to preventing malware, “no security solution is perfect,” Bathurst said. “The only way to have a chance to prevent IP theft is to prevent the initial compromise and minimize the damage from the point of impact.”
To that end, organizations can use modern antivirus protections with a combination of behavioral analytics and pattern matching, binary analysis and pre-execution analysis. And, organizations should regularly review the configurations and capabilities of network-based defense technologies, beyond just firewall rules.
COVID Supply-Chain Attacks Ramp Up
It’s also critical to consider the supply chain, Bathurst added. Earlier this month, IBM Security X-Force researchers identified a sophisticated phishing campaign targeting the credentials of organizations associated with the COVID-19 “cold-chain” – companies that ensure the safe preservation of vaccines by making sure they are stored and transported in temperature-controlled environments.
Supply-chain threats include those against researchers, government agencies, universities, pharma, hospitals treating cases, and companies involved in the manufacturing of ingredients. These attacks, separate from the massive SolarWinds supply-chain attacks, focus on exploiting the urgency around the pandemic to save lives.
In November, another attack was reported by global biotech firm Miltenyi Biotec that said it had been battling a malware attack. It’s supplying SARS-CoV-2 antigens for researchers working on treatments for COVID-19.
Play Video: Ransomware and IP Theft: Top COVID-19 Healthcare Security Scares
Click to Play Video: Ransomware and IP Theft: Top COVID-19 Healthcare Security Scares
“If the attacker is after vaccine-related data, that could come from third-party researchers with access to your data, your clinical trials database, your research team, their home computers, notes on tables, laboratory equipment memory or storage, and even the industrial control systems that control the drug-manufacturing plants,” Bathurst explained. “Ultimately, it comes down to understanding your risks and impact points.”
Attacks to Continue into 2021
Above all, it’s clear that the stakes are too high for the espionage onslaught to dry up anytime soon – and in fact, the worst could be yet to come, researchers suggest.
“As flu season descends upon us and vaccine research continues, I would expect to see a sharp increase in actor activity beyond what has already been reported,” Bathurst said. “It’s in the interest of nation-state intelligence agencies to continue to leverage everything they can throughout their ecosystem to harvest information.”
Last week, the advanced persistent threat group known as Lazarus Group and other sophisticated nation-state actors were reported by Kaspersky researchers actively trying to steal COVID-19 research to speed up their countries’ vaccine-development efforts.
Hey Alexa, Who Am I Messaging?
23.12.2020 Cyber Threatpost
Research shows that microphones on digital assistants are sensitive enough to record what someone is typing on a smartphone to steal PINs and other sensitive info.
The potential for digital-home assistants like Amazon Alexa to infringe on user privacy by making and saving voice recordings of them is already widely known. Now researchers have discovered that the devices also may be able to “hear” and record what people are typing on nearby smartphones, even amid background noise.
The microphones on digital assistants are sensitive enough that they can record the taps people make on a mobile device when sitting up to a foot and a half away, according to a team of researchers from the University of Cambridge. The researchers constructed an attack in which they used this capability to identify PINs and text typed into a smartphone.
“Given just 10 guesses, five-digit PINs can be found up to 15 percent of the time, and text can be reconstructed with 50 percent accuracy,” the team–Almos Zarandy, Ilia Shumailov and Ross Anderson—wrote in a paper published online, “Hey Alex, What Did I Just Type” [PDF].
2020 Reader Survey: Share Your Feedback to Help Us Improve
The same group of researchers already had discovered ways that various forms of technology can potentially violate user privacy by engaging in what they call “acoustic snooping.” Last year, they published research on how a smartphone app has the ability record the sound from its microphones and figure out from that what someone has typed, giving it the potential to steal PINs and passwords.
The new research also builds on previous research that found that voice assistants could record the typing of keys on a computer to determine someone’s input, Anderson wrote in a blog post.
“We knew that voice assistants could do acoustic snooping on nearby physical keyboards, but everyone had assumed that virtual keyboards were so quiet as to be invulnerable,” he wrote.
It turns out that they are not, researchers found. Because modern voice assistants like Alexa have two to seven microphones, they can do directional localization, just as human ears do but with even greater sensitivity, the researchers discovered.
“We assess the risk and show that a lot more work is needed to understand the privacy implications of the always-on microphones that are increasingly infesting our work spaces and our homes,” they wrote.
Researchers based their attack on the fact that microphones located close to the screen can hear screen vibrations and use them successfully reconstruct the tap location, they said.
“Physical keyboards emit sound on key presses,” they wrote. “Recent research shows that acoustic side channels can also be exploited with virtual keyboards such as phone touchscreens, which despite not having moving parts still generate sound.”
For their attack, researchers also assumed that an attacker had access to microphones on a smart speaker near a target and aimed to steal PINs and passwords entered on their touchscreen.
To construct the attack, researchers used a Raspberry Pi with a ReSpeaker six-microphone circular array to collect data. The Pi was running a simple TCP server that could be told to start and stop recording and save the audio to a six-channel .wav file. They also set up a Wi-Fi hotspot on the Pi so that participating devices could connect to it.
The “victim devices” used in the experiments were an HTC Nexus 9 tablet, a Nokia 5.1 smartphone and a Huawei Mate20 Prosmartphone, all running Android 7 or above and having at least two microphones, they said.
While only one of each device type was used, it’s likely that a second identical device also could be attacked using training from the first device, researchers noted.
Alexa the Threat
Aside from making voice recordings, it’s becoming increasingly clear that digital assistants have other ways of accessing sensitive data of their users that can be exploiting for nefarious purposes.
A team of researchers last year also discovered that attackers can potentially use light to manipulate the microphones of digital assistants like the Amazon Echo to turn it into sound, using it to attack not only the device but others connected to it.
Their research delved into how the ecosystem of devices connected to voice-activated assistant — such as smart-locks, home switches and even cars—could be hacked by using a device like an Amazon Echo as the gateway to take control of other devices as well.
Other security holes in digital assistants also put people’s personal information at risk. Earlier this year, researchers found flaws in Alexa that could allow attackers to access users’ personal information, like home
Telemed Poll Uncovers Biggest Risks and Best Practices
22.12.2020 Cyber Threatpost
What are the riskiest links in the virtual healthcare chain? Threatpost readers weigh in as part of an exclusive telemed poll.
eBook Healthcare in CrisisHealthcare organizations have gone virtual during the COVID-19 pandemic, just like the rest of us – with the use of telehealth services becoming the go-to format for med checks, routine consultations and therapist visits. But how safe are these services when it comes to patient data?
In an exclusive Threatpost poll of 159 participants (half of whom said they’ve had recent telemed appointments themselves), 72 percent saw an uptick in targeted cyberattacks on telehealth devices and networks over the past nine months. And more than half of those polled (58 percent) believe that virtual healthcare visits are risky, from a cybersecurity perspective.
Telehealth for many hospital IT departments represents new challenges. Many of them are already-overloaded and under-resourced in healthcare settings.
Our Threatpost poll found many are wrestling with the addition of technologies like Zoom (which has had its share of security issues and scrutiny) and secure delivery portals for HIPAA-protected data such as digital imaging and prescriptions. But also, telemed is a two-way street; patients at home are using home networks and personal devices to access their care – which can be much more susceptible to attackers than doctors’ office infrastructure.
Telemed By the Number: Poll Uncovers Biggest Risks and Best Practices“Healthcare has had to make a lot of big, rapid moves around IT, including the forced transition to telehealth, and must rapidly respond to increased attention from malicious actors from nation-states right down to nuisance attackers,” said Casey Ellis, CTO and founder of bug-bounty firm Bugcrowd.
Of those poll participants who experienced an increase in attacks, 28 percent saw between a one- and 25-percent increase in cyberattack volume – with 37 percent reporting a snowballing of more than 25 percent.
When it comes to the risks that cybersecurity professionals are concerned about, more than half (58 percent) of respondents said that the biggest security challenges stem from the risk of data breaches as more patient information moves to the cloud (business email compromise and phishing attacks, insecure APIs and ransomware were other challenges mentioned).
Which are the most important cyber-health steps that organizations should prioritize?But virtual healthcare and telehealth services are also top of mind when it comes to risks, with half of the respondents indicating they have had a telemed appointment since the pandemic broke out.
What are the riskiest links in the virtual healthcare chain?When asked what they view as the riskiest link in the virtual healthcare chain, 35 percent of Threatpost poll respondents pointed to insecure video-conferencing platforms. This was followed by the telemedicine platforms used to manage devices and patient data (25 percent); the digitization of patient data (17 percent) and purpose-built telemed IoT devices (11 percent).
Threatpost also asked about the biggest cybersecurity challenges when it comes to telehealth – and an overwhelming majority (58 percent) cited preventing data breaches as more patient information moves to the cloud. A quarter (24 percent) of respondents said that thwarting business email compromise and phishing attacks is the biggest challenge, while wrestling with insecure APIs and ransomware were also cited by some.
On the positive side of the equation, respondents cited their favorite best practices for security teams in healthcare organizations to take on.
Sunburst’s C2 Secrets Reveal Second-Stage SolarWinds Victims
19.12.2020 Cyber Threatpost
Examining the backdoor’s DNS communications led researchers to find a government agency and a big U.S. telco that were flagged for further exploitation in the spy campaign.
More information has come to light about the Sunburst backdoor that could help defenders get a better handle on the scope of the sprawling SolarWinds espionage attack. The campaign is known to have affected six federal departments, Microsoft, FireEye and dozens of others so far.
Sunburst, a.k.a. Solorigate, is the malware used as the tip of the spear in the campaign, in which adversaries were able to use SolarWinds’ Orion network management platform to infect targets. It was pushed out via trojanized product updates to almost 18,000 organizations around the globe, starting nine months ago. With Sunburst embedded, the attackers have since been able to pick and choose which organizations to further penetrate.
Following the breadcrumbs found in Sunburst’s command-and-control (C2) communications, researchers from Kaspersky were able to progress from uncovering which companies are infected with the backdoor, to which ones were actually chosen for additional exploitation. Kaspersky researchers said they used the approach to identify a U.S. government entity and a telco (“a rather big telecommunications company from the U.S., serving more than 6 million customers”) that caught the attention of the attackers.
Further exploitation by the unknown advanced persistent threat (APT) group, dubbed UNC2452 or DarkHalo by researchers, involves installing more malware, installing persistence mechanisms and exfiltrating data, according to Kaspersky.
“The primary goal of the campaign appears to be espionage,” according to an analysis from Kaspersky, issued Thursday. “The attackers showed a deep understanding of Office365, Azure, Exchange and Powershell, and leveraged it in creative ways to monitor and extract the victims’ emails.”
Sunburst was planted in around 18,000 first-stage victims, but “only a handful [of the 18,000] were interesting to them,” Kaspersky analysts said.
“We spent the past days checking our own telemetry for signs of this attack, writing additional detections and making sure that our users are protected,” said Costin Raiu, head of Kaspersky’s Global Research and Analysis team, in a Thursday blog post. “At the moment, we have identified approximately 100 customers who downloaded the trojanized package containing the Sunburst backdoor. Further investigation is ongoing.”
The fact that Sunburst stayed under the radar for so long is unsurprising, analysts said. For instance, once installed, Sunburst stays silent for up to two weeks in an effort to evade detection, researchers said. Also, the component that contained the malware was code-signed with the appropriate SolarWinds certificate, as previously reported. This made the DLL look like a legitimate and safe component for the Orion product, with the right size and no suspicious scripts.
“The campaign was effective because of its combination of a supply-chain attack with a very well-thought-out first-stage implant and careful victim-selection strategies, and because it had no obvious connections to any previously observed tactics, techniques and procedures (TTPs),” according to the Kaspersky analysis. “It was particularly stealthy because of the slow communication method, a lack of x86 shellcode, and the fact that there was no significant change in the file size of the module when the malicious code was added.”
On the Hunt for Victims
The analysts were able to uncover more about how Sunburst communicates with its command-and-control (C2) server – namely, it does so through Domain Name System (DNS) requests. DNS performs the translation between human-readable domain names, like threatpost.com, and the numeric IP addresses that web browsers use. DNS requests initiate this translation – and these queries can be manipulated or altered by threat actors to contain additional information.
Once implanted, Sunburst starts to communicate with a first-stage C2 (“avsvmcloud[.]com”) by sending encoded DNS requests with information about the infected computer, so the attackers can decide whether to proceed to the next stage of infection.
If the attackers decide that an organization should be flagged for additional attention, the C2’s next DNS response will include a CNAME record pointing to a second-level C2 – an process that was also flagged by FireEye, with samples. CNAME is a type of DNS record that maps an alias name to a true or canonical domain name.
Importantly, the use of DNS requests can allow researchers to better identify victims of the attack, Raiu noted: “Knowing that the DNS requests generated by Sunburst encode some of the target’s information, the obvious next step would be to extract that information to find out who the victims are.”
Matching DNS Requests to Victims
In looking at the FireEye samples containing the CNAME records, Kaspersky analysts were able to uncover the OrionImprovementBusinessLayer.Update binary.
In unpacking it, it became clear that the binary calls one of four functions: GetCurrentString, GetPreviousString, GetNextStringEx and GetNextString, each of which correspond to four different DNS-based communications.
The first function, GetCurrentString, generates strings that contain a unique target’s identifier (this.guid), the target’s hostname (this.dnStrLower) and the rest of the hostname that will be in form of “appsync-api.*.avsvmcloud[.]com”, according to the analysis.
The encoding of the data is done by two additional functions, CreateSecureString and CreateString.
The function GetPreviousString meanwhile produces a similar hostname for a DNS request.
“It includes a part of the target’s hostname in the request, so that it would match the limitations on the request length. Each such request also includes the sequence number (this.nCount) that is the offset of the current substring from the beginning of the hostname,” researchers noted.
The remaining two functions, GetNextStringEx and GetNextString, include only the target’s unique ID (UID), hashes of the running processes of interest and the list and status of these processes. The target’s UID is then encrypted, and the data is encoded with CreateSecureString.
This information, which is sent to the attackers’ C2, can be matched with information in other (legitimate) DNS requests to identify who the companies are that have been flagged for additional focus, Raiu said.
“At this point, a question arises – can we match any of existing private and public DNS data for the malware root C2 domain, avsvmcloud[.]com, with the CNAME records, to identify who was targeted for further exploitation,” Raiu said.
After parsing publicly available DNS databases, Sunburst-generated and otherwise, the researchers were able to find that the UIDs are also included in other types of DNS requests – leading them to specific domains for specific victim companies.
Using this technique, both Kaspersky and QiAnXin Technology have published public decoders to help defenders assess the extent of the campaign.
While the finds are a breakthrough, Raiu said that much remains unknown about the attackers and their TTPs.
At the moment, there are no technical links with previous attacks, so it may be an entirely new actor, or a previously known one that evolved its TTPs and opsec to the point that it can’t be linked anymore. While some have linked it with APT29/Dukes, this appears to be based on unavailable data or weak TTPs, such as legitimate domain re-use.
All-source intelligence: reshaping an old tool for future challenges
19.12.2020 Cyber Securityaffairs
An enhanced version of the old all-source intelligence discipline could serve the purpose.
By Boris Giannetto
Hybrid, interconnected and complex threats require hybrid, interconnected and complex tools. An enhanced version of the old all-source intelligence discipline could serve the purpose.
Today’s society hinges on technologies and they will have most likely an ever-increasing clout in the future, thanks to the development of supercomputing, artificial intelligence, quantum and space technologies. However, we do believe that the human element will maintain a central role.
Global systems and infrastructures are hackable targets (and they are more and more hacked). Technical experts break their head by wondering whether there will ever be a non-hackable system (discussion on quantum and post-quantum cryptography are just an example). Yet, that is not the relevant issue. Cyber operations are often not even detected (especially those below the threshold). Uncertainty appears to us as the main emergent behaviour in global dynamics.
The hiatus between (some) intelligence agencies and other players in the cyber arena is huge. Intelligence units have – and they keep on developing – the most powerful (secret) cyber paraphernalia. Asymmetry is a euphemism.
Cyber intelligence has proven to be of some use both for private organizations and other institutions, but this activity often struggles to find conclusive evidence (smoking guns), attribute attacks to a threat actor (without a doubt), ascertain real motivations or make reliable predictions.
To put it concisely, cyber intelligence is a valid and promising tool, but nowadays it is often (not always) characterized by shaky predictions and lack of conclusive evidence. As is common knowledge, anonymization, obfuscation, antiforensics, re-use, and infrastructure hijacking put frequently cyber intelligence (and cyber threat intelligence) in a doom of overall ignorance or at best in a mist of blurred knowledge. Misleading IOCs, bogus threat actors and phantom APTs are a tough nut to crack. As to APTs, different naming criteria and mimickers breed a tricky situation: with regard to state actors, it is useful to analyse directly the activity of intelligence units. False flags, name & shame and plausible deniability only increase a smoke screen and put to the test analysts’ capabilities.
Non-IT cyber intelligence (cyber is not simply the same as IT; multidisciplinary approach and expertise are key) can help the technical analysis, being it founded on strategic intelligence, geopolitical, scenario and context analysis (in this regard, there are aspects of connection with strategic CTI, even though the two disciplines must be kept separate). Nevertheless, real and sound non-IT cyber intelligence is rarely employed. Furthermore, one ought to boost also archeo-cyber intelligence: cases are filed too quickly, without understanding many things; a deeper ex post study can crack the case and reveal many prospective trends.
Members of nation state or state-sponsored tiger teams laugh often unpunished at mistaken cyber intelligence analysis bulletins published with great fanfare. Rules of thumb, bias, and gimmicks dominate well-known and widespread frameworks; oversimplifications fill pages of nonsensical reports released by improvised and self-declared cyber pundits worldwide. Among such simplifications, one can often read misleading assumptions, for instance: no state pursues economic gain in cyber-attacks; threat actors use specific TTPs and not others; official investigative sources said this and one have to take it for granted; intelligence units do not have recourse to simple and cheap tools in the wild, and so on. Time is however a severe judge and sometimes restores the truth, proving that those reports were inaccurate or at worst wrong. At any rate, threat actors remain for a long time empty puppets and real motivations remain unknown to most. On the contrary, on the technical side (but that relates to cybersecurity in general), alerts and advisories on CVEs – especially on zero-days – show some usefulness, indeed. However, it represents an endless game, characterized by continuous patches and workarounds.
As far as a fairly recent (and rising) trend is concerned, the application of intelligence tools to private and administrative state institutions could engender encouraging organizational advancements (and in rare cases, positive sectoral effects); but some snags could occur at a systemic level. Even if one ought not to preclude such activities in these contexts, private companies and administrative institutions have different purposes, capabilities and powers from intelligence agencies and law enforcement units. This could bring about some inefficiencies and dispersion of information. Possible problems could derive from pre-existing procedures, mind-set of incumbent management (not used to secrecy protocols and intelligence modus operandi), and selection of personnel (in any case, it is useful one more to underscore that some features – e.g. ingenuity and intuition – cannot be taught).
In a complex future scenario, a gamut of different tools – simultaneously and harmonically used – may be the keystone for information gathering and strategic analysis activities. CYBINT is (just) one of them.
All-source intelligence is fundamental in both information acquisition (collection, evaluation, integration) and analysis (tactical, operational, and strategic). Indeed, it is advisable to adopt a synoptic approach during all the (squeezed) intelligence cycle (direction – collection, processing – analysis, production, dissemination). Platforms and technologies ought to be assessed for their intrinsic nature: they are tools and should be regarded as functional means.
Actually, SIGINT, HUMINT, GEOINT, MASINT, TECHINT, IMINT, OSINT (and so on), as well as active defence and offensive operations, are mostly carried out by intelligence agencies and law enforcement units (mainly because of legal restrictions). A close cooperation between these units and other players is desirable.
A broad-scope strategic analysis is essential too, in order to comb raw data, consolidate a sound information base and produce actionable intelligence in an all-encompassing manner. With regard to analysis, specific domains and topics could be addressed by specific disciplines (f.i. FININT). To this end, best minds from different sectors and specializations must be brought together.
A single-INT is not capable of covering the entire spectrum of threats, which even more overlap and interact faster and faster. Cyber and physical domains incessantly permeate each other (hence, the importance of cyber-physical systems). To properly handle and predict phenomena, it is crucial to understand (intelligĕre) emergent collective behaviours in advance, according to a syncretic approach.
Researchers call for a determined path to cybersecurity
17.12.2020 Cyber Threatpost
Despite our continuous research efforts to detect cyberattacks and enable defense, we often feel that we, as members of a global community, are failing to achieve an adequate level of cybersecurity.
This is threatening the proper development and use of information technologies and digital assets, and as a consequence, most of society’s current and future activities, from entertainment to democratic processes, including business, healthcare and industrial production.
We believe that such a failure can be explained by a lack of global willpower, double-dealing activities, and the lack of global regulations. Here, we develop these hypotheses and outline ideas to advance cybersecurity.
What we do, and how it is failing
Kaspersky’s Global Research and Analysis Team (GReAT) is made up of cybersecurity researchers. Our shared capabilities and expertise stem from multifaceted individual experiences and perspectives that can always be traced back to strong technical backgrounds. Each and every day, our skills are focused on clear goals: to anticipate, discover, detect, track and report cyberattacks. But our activities and findings are, first and foremost, a contribution to a broader mission: to build a safer world. Since our inception more than a decade ago, we have worked very hard – from awareness raising and media interviews to embedded firmware reverse engineering, as well as incident-response support, vulnerabilities research, malicious infrastructure hunting, code similarity heuristics development, discovery of major threat actors or advanced malicious frameworks, open-sourced tools, specialized training and expert talks at world-class conferences. As far as our expertise is concerned, we believe that we provide beneficial results to our customers, partners and the global community. We know from previous collaboration and published content that our colleagues at government bodies, other cybersecurity providers and private companies work just as hard and achieve tremendous results as well.
Yet, somehow, we are still failing. Cyberattack numbers, whatever their impact, from digital activities to unwanted or disastrous effects, keep skyrocketing every year. Cybercrime has never been so prevalent and real, reaching every possible device, from IoT to supercomputers, as well as network routers, smartphones and personal computers. Cyberattacks have become a go-to companion, wherever there is malicious intent to tackle competition, hijack accounts, spy on a partner, persecute a minority, disrupt critical infrastructure, influence electoral processes, steal knowledge or obtain money. Cyber-based conflicts keep escalating, to the point where there is now a trend around the globe to proclaim that cyberwar capabilities are being developed, and kinetic force could be used as a response to cyberattacks whenever deemed fit. And ransomware or state-sponsored cyberattacks kept hitting hard even when we are all confronted with a pandemic.
Our hypotheses and beliefs
Why does all that outstanding technical effort, an abundance of cybersecurity solutions, highly skilled workforces, and decades of awareness raising fail to tackle cyberthreats? Although a lack of concern, specialized technical knowledge, skilled resources and training may have kept the defense a few steps behind for a while, we think these factors are no longer a major barrier. Instead, we believe that issues surrounding governance and a sense of responsibility are now what primarily prevent mission success.
A lack of global willpower and instruments
First of all, we believe that there is a lack of high-level global desire for cooperation and governance to properly tackle cyberattacks and protect what is at stake. We all agree that every human being should be guaranteed a minimum set of rights, that the development of nuclear warheads should be limited, if not outlawed, or that warfare should be regulated and overseen. These crucial safeguards to peace and freedom did not come about by chance; they came from political willpower, international cooperation, continuously improved governance and determined enforcement.
However, states have not agreed yet about a binding treaty or about how existing international law applies to keep our digital world at peace. There are regular examples demonstrating the major negative effects of cyberattacks on businesses, nations and citizens (or “civilians”), and there have been some initiatives to assess how international law would apply to cyber operations, to globally combat cybercrime, or to establish norms of responsible behavior in cyberspace for states. But these initiatives are not coordinated or global enough, they don’t actually come with the expected regulations, cooperation and clear instruments to increase stability in cyberspace.
Are we waiting for more dramatic effects than those already caused by cyberattacks and cybercrime to advance cybersecurity with strong governance and regulation instruments? We believe that, on top of the intrinsic complexity of international cooperation, a crucial lack of willpower from states is preventing substantial advancement on cybersecurity.
Double-dealing
We believe that lots of players are double-dealing in the digital age. Cyberattacks appear to be highly profitable in the short-term, as they allow attackers and their sponsors to quickly and stealthily gather foreign and domestic intelligence, make money, disrupt or deter third parties, gain a strategic advantage over competitors or in warfare, circumvent regulations, or efficiently disseminate information. As a bonus, these malicious activities have a low entry cost, are subject to no monitoring, and for the most part go unattributed (thanks to, amongst other things, complex digital layers, bulletproof services and factors limiting interstate police cooperation). Therefore, perpetrators do not have to take responsibility for their actions and go unpunished – even when they do get exposed. Due to these convenient “cyber features”, state or non-state actors might easily be tempted to publicly promote and even act in favor of a safer world, while making sure they can also benefit from offensive activities that remain undetected and go unpunished. Such activities also promote the public and private development of cyberweapons, mercenary services, criminal activities, and the monetization of vulnerabilities instead of responsible disclosure. All this, in turn, harms the efforts of cybersecurity and enables proliferation.
But that’s not all when it comes to double-dealing: government bodies dedicated to cybersecurity and non-state actors can even play this dangerous game to some extent. Cybersecurity threat intelligence and data are of topmost interest to national defense and security management, as well as very valuable to the competitive cybersecurity business. It is a vital asset to the economy, and for detecting or deterring strategic threats. As a result, threat intelligence may not be shared and actioned as easily and broadly as it should, in a common determined path to cybersecurity, but might rather be guarded jealously for private interests. Private companies such as Kaspersky, however, do their best to proactively share intelligence and insights on investigations to the community for free.
Existing regulations are not (global) enough
We also feel that achieving cybersecurity is not possible without a stronger sense of responsibility from all public and private actors that play a role in the development and operation of our global digital space. Governments have already gone some way to fostering this sense over the years by creating or strengthening regulations on personal data processing or protection for critical information systems. While this has been a significant advancement towards cybersecurity, it has unfortunately not been enough.
Most of the cyberattacks we face and analyze do not actually leverage sophisticated technical vulnerabilities or tools, because they don’t need to. It is often way too easy to access the devices and networks owned by a public or private organization because elementary cybersecurity measures are still not implemented, and because the organization’s very own digital assets are not clearly identified or not controlled sufficiently. Every organization that processes digital data of personal significance, or develops or operates digital services, starting with those that benefit us the most, or contribute to our most vital needs, including governments, should be required to implement and demonstrate elementary cybersecurity frameworks. The associated regulations should be global, because cyberspace and digital assets are shared amongst all users around the world. It may not be possible to become invulnerable, but making cyberattacks more costly for the attackers while protecting our digital world a little more is doable.
On top of the lack of preventive and protective measures from many public and private organizations, another responsibility issue is blocking the road to cybersecurity. Cyberattacks cannot be carried out without leveraging publicly available commercial services, such as content hosting, development, infrastructure provision and mercenary services. First, it would seem obvious that any private organization that purposely engages in cyberattack operations or cyberweapons development should have its activities limited by regulations, and controlled by an impartial third party, in order to ensure that malicious activities are constrained by design, and that cyberweapons do not proliferate. Also, in order to maintain peace in the cyberworld, it is critical that any organization whose services are demonstrated to be leveraged to carry out cyberattacks is required to cooperate with cybersecurity organizations designated by an impartial third party, to contribute to cybersecurity investigations and demonstrate efforts to continuously prevent the malicious use of exposed services.
Digital services and information technologies that unintentionally support malicious cyber activities are – most of the time – developed to bring sound and useful outcomes. However, and for decades, vulnerability disclosures and cyberattacks have demonstrated that some technologies or uses are flawed by design and can be exploited by malicious actors. We can probably collectively accept that when the first information technologies were developed and deployed, it wasn’t easy to anticipate malicious uses, which is why cybersecurity efforts only came afterwards. But it is no longer possible nor tolerable to develop, deploy and operate technologies and services that have a global use potential, while ignoring existing threats, and without making them secure by design. Yet, even more vulnerabilities and malicious uses affect relatively modern services and technologies, from IoT and artificial intelligence systems to cloud infrastructures, robotics and new mobile networks. In order to anticipate and prevent malicious exploitation of modern technologies as much as it is reasonably possible, we believe that transparent vulnerability management and disclosure practices need to be developed further by both state and non-state actors; and that technologies or services that are used globally should be assessed by a global community of experts more often.
Last but not least, we also think that more threats could be better anticipated in the future if future generations are globally and systematically educated on information technologies and cybersecurity, whatever their origin or path. This will contribute to a safer world.
Our call and plans
It is rather unusual for cybersecurity researchers and experts to write on governance matters. We don’t pretend that our hypotheses are the most suitable, or the most comprehensive. But we definitely feel concerned, and strongly believe that the points we have raised are obstructing a common path to cybersecurity. Furthermore, we are pleased to note that most of our hypothesis and beliefs are actually shared with many others, as demonstrated in 2020 Paris Call consultation key takeaways, or the latest reports from the UN’s OEWG on “developments in the field of information and telecommunications in the context of international security”, to which Kaspersky contributed.
We feel it is now a good time to send a call to all governments and international bodies (and ultimately any citizen) that aim for a safer world: we urge you to demonstrate more willpower, and a more determined approach to cybersecurity, by tackling the exposed causes of failure. We ask you to cooperatively choose the long-term peace of our common digital assets, over short-term nationalistic or private interests. We do our part, and we want our expert efforts to be transformed and developed further. We hope for a safer world, and a long-standing peaceful common digital space. We will never achieve this without determined leadership and a global change towards a better common behavior.
A cooperative and global governing instrument
We need strong political and technological leaders to drive governments and international bodies towards a cooperative, determined and fast-paced road to cybersecurity. In order to continuously rationalize efforts, share insights and thoughts, enable regulation, control and take global measures, we need them to build a dedicated, strong, permanent and focused international instrument.
We believe that such an instrument could be hosted by the UN, should seek to tackle the causes of the failures that we exposed, and should help governments to enforce regulations and cooperatively take measures when they are needed.
In order to ensure a cooperative approach by design, to consider the whole spectrum of what is at stake, and to truly take the transnational nature of cyberspace into consideration, we believe that such an instrument should guarantee a continuous dialogue with representatives of governments, the private sector, civil society and the technical community. This would enable the creation of cooperative task forces that would provide broad cybersecurity expertise and assessments on various matters, including preventive and protective cybersecurity measures, vulnerability research, incident response, attribution, regulation, law enforcement, security and risk assessment of modern technologies, and cyber capacity building. It would also ensure that most findings are shared across nations and among cybersecurity players.
This governing instrument should also be able to build norms and regulations, and a cooperative approach to control the attribution of cyberattacks and sanctions against non-compliant behavior or crime, risk analysis, capacity building, and education for cybersecurity.
A binding treaty of responsible behavior in cyberspace
Nearly two decades ago, the UN started to task groups of government experts (GGE) to anticipate international security developments in the field of IT, and to advance responsible state behavior in cyberspace. One of the most notable outcomes, despite GGE’s debatable results and limited reach, is the definition of 13 principles that constitute the norms of responsible behavior in cyberspace. But after more than a decade, these principles are non-binding, apply to governments only, and have only been endorsed on a voluntary basis. We believe this is not enough, and that it may reflect the lack of willpower and commitment from our governing leaders to cybersecurity.
We believe that the norms for responsible behavior in cyberspace should be further developed together with guidance on how these norms should be implemented, be better at including non-state actors such as the private sector, civil society and the technical community. After that they should become binding for the international community – if they remain voluntary, why should the bad guys care?
As far as private companies are concerned, the norm could set transparency and ethics baselines. We must not fail to mention Kaspersky’s own Global Transparency Initiative, which we truly believe to be a good source of inspiration for setting a number of private sector norms. This includes (but is not limited to) independent reviews of processes, security controls and software code, relocation of data processing, as well as the ability for trusted partners, customers and government stakeholders to directly access and check software code or threat detection rules. A code of ethics or ethics principles, from the “FIRST” international CSIRTs community or from Kaspersky, that tackle the responsible disclosure of security vulnerabilities, could also be leveraged as inspiration for private company norms.
Global regulations and shared means for cybersecurity
In order to tackle residual double-dealing issues and regulation needs that we exposed in our hypotheses, the global governing instrument or guidance should build and support further common regulations, on top of the previously mentioned norms of behavior. Such global regulations would ensure a consistent baseline of security requirements, to prevent proliferation of cyberweapons, prevent and firmly condemn cyberattacks, implement cybersecurity controls, foster responsibility and facilitate cooperation. How, where, and under which terms this governing instrument or guidance can be established should be a discussion for both state and non-state actors to ensure that we all fully recognize our responsibility to keep the digital space secure.
Conclusion
We deal with cyberattacks of all kinds every day and monitor their context from various sources. Over the years, we have seen more and more malicious activities from more and more actors, but global cybersecurity has reached a ceiling, and it appears that the potential for cyber-based conflicts is still growing. During the COVID-19 pandemic we have once again observed just how vital information technologies and digital assets are to democracy, the economy, the development of society, security and entertainment.
We believe that now is still a good time for world leaders, international and regional organizations, the private sector, the technical community and civil society to collaborate on achieving long-term peace in cyberspace rather than focusing on the short-term interests of individual countries or private organizations.
Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented Times
8.12.2020 Cyber Threatpost
In the early fog of the COVID-19 pandemic, cybersecurity took a back seat to keeping patients alive. Lost in the chaos was IT security.
When the COVID-19 pandemic first hit the U.S. hard in March, the Elmhurst Hospital was forced into a logistical nightmare.
It was a grim sign of the times, as the Queens, N.Y. hospital was flooded with hundreds of sick patients, with one medical resident describing conditions as “apocalyptic”, according to a New York Times interview. At the same time, hospitals also began a similar rush to increase capacity to keep up with growing infection rates, and scrambled to find personal protective equipment (PPE), ventilators and trained staff.
Healthcare Security in the COVID-19 EraLost in the chaos was IT security. In the early fog of the pandemic, cybersecurity took a back seat to keeping patients alive. But it did not take long before important hospital systems such as telehealth patient portals, backend billing and coding systems, connected medical devices and video-conferencing platforms were stressed.
Cybercriminals took notice. Cyberattacks targeting healthcare firms have increased 150 percent since the COVID-19 virus hit the U.S. shores. The pandemic’s unprecedented impact on healthcare lay bare the gaping holes in the healthcare industry’s cybersecurity defenses. It is a sobering wakeup call that security experts say will have a lasting impact on the healthcare industry well into 2021.
[Editor’s Note: This article is part of an exclusive FREE eBook, sponsored by ZeroNorth. The eBook, “Healthcare Security Woes Balloon in a Covid-Era World”, examines the pandemic’s current and lasting impact on cybersecurity. Get the whole neatly-packaged story and DOWNLOAD the eBook now – on us!]
Cyberattacks Target Vulnerable Systems
The goals for cybercriminals are varied. At one end of the spectrum, they’re targeting personally identifiable information to be later used in credential stuffing attacks or for resale on criminal black markets. At the other end, attackers have also launched costly ransomware attacks against insecure healthcare systems- potentially endangering patient lives.
“Frontline health professionals have been heroes during this pandemic, saving lives,” said Beau Woods, a Cyber Safety Innovation Fellow with the Atlantic Council.
Woods, who has worked for the past 10 years with small hospitals, healthcare focused nonprofits and government entities, added, “If technology goes offline, doctors and nurse practitioners can no longer give the quality of care that they were able to, or to as many people. Right now, with COVID-19, there’s a dramatic rise in the attack surface and the number and types of systems that are being used,” he said.
Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented TimesHealthcare Insecurity: A Chronic Condition
Of course, healthcare cyber-challenges aren’t new. Security researchers have long pointed out myriad threats facing this critical industry segment. For instance, the hospital equipment mix includes millions of insecure, single-purpose, connected medical devices, including insulin pumps and defibrillators, that are often open to hacks because they haven’t been updated. Medical environments are also rife with critical infrastructure that runs on legacy platforms (such as Windows XP).
As an example of the magnitude of the outdated equipment problem, the Food and Drug Administration issued an emergency alert last year warning that Medtronic MiniMed insulin pumps are vulnerable to potentially life-threatening cyberattacks. The flaw, which has since been patched, could have enabled cybercriminals to connect wirelessly to a MiniMed insulin pump and change its settings, allowing them to either deliver too much insulin, or not enough – with potentially fatal results for patients. Another existing issue is the ongoing digitization of patient data and a growing reliance on connected medical devices. In general, this has created a massively expanded threat landscape for the healthcare industry.
Then there’s the fact that there are millions of decentralized endpoints associated with telehealth – including patient facing portals, new COVIDrelated and existing mobile apps and wearables – all providing new ways to gather and process health-related data. As such, they crack open wide the attack vector for adversaries.
Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented TimesFinancial Illness
With COVID-19, all of the existing issues that make healthcare cybersecurity difficult have become magnified, say experts.
For instance, telehealth adoption by primary caregivers jumped by 50 percent between January and June of 2020. That required new investment in technology, when facilities are already paying a premium for testing, additional staff, PPE and ventilators.
“The biggest challenge with COVID-19 and healthcare security in my view is the significant strain on available resources,” Jeff Tully, a pediatrician and anesthesiologist at the University of California at Davis, said. “With a precipitous decrease in elective surgical procedures and routine outpatient visits, hospitals and other healthcare facilities already facing razor-thin margins pre-pandemic are now forced to make increasingly difficult decisions about how to prioritize limited funds.”
He points out that elective surgeries are a significant money-maker for hospitals, in normal times. Reuters news agency reported in March that the New York-Presbyterian Hospital postponed all elective surgeries, impacting 10 New York area hospitals.
These realities make it hard to advocate for something like a newly segmented network or increased IT security staffing, when healthcare workers may be furloughed or patient-care programs underfunded, he said.
Cyber-Infections Surge
While hospitals, doctors’ offices and other healthcare stakeholders wrestle with a morass of cybersecurity challenges, threat actors have been paying attention – as evidenced by a cresting cybercriminal offensive on the healthcare industry.
A recent study by SecurityScorecard and DarkOwl found that attacks have increased 16 percent on web applications since the coronavirus pandemic hit states hard in March, while attacks on endpoints are up 56 percent and attacks targeting IP addresses have climbed 117 percent (PDF).
For hackers, COVID-19-related attack vectors remain low-hanging fruit. Patient data represents a lucrative store of goods to sell on the criminal underground. And ransomware attacks are all too easy, thanks to a lack of patching and user awareness/distraction – according to SonicWall, ransomware attack volumes have grown 109 percent annually in the U.S., in part due to the pandemic. Espionage meanwhile continues as attackers strive to get their hands on valuable coronavirus treatment and vaccine research.
Real-world examples abound of cybercriminals taking advantage of the weaknesses. As an example, in 2019 a breach of AMCA impacted the data of 25 million patients – including their names, addresses, dates of birth and payment data.
Ransomware examples are readily available too. For instance, Hammersmith Medicines Research, a London-based healthcare provider that was working with the British government to test COVID-19 vaccines, was recently hit by a ransomware attack. A ransomware attack in October also hit eResearchTechnology, a medical software company that supplies pharma companies with tools for conducting clinical trials – including trials for COVID-19 vaccines.
And on the espionage front, APT29, a Russia-based advanced persistent threat (APT) group also known as Cozy Bear, reportedly targeted academic and pharmaceutical research institutions in various countries around the world in July – just one of several such incidents.
Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented TimesHuman Impact
With medical cybersecurity in a state of perpetual disruption – and ongoing attacks – there’s a darker side to consider. Researchers and healthcare professionals alike worry that the heightened security threats are evolving from impacting technology availability and patient data privacy to actually threatening patients’ physical safety.
The Atlantic Council’s Woods cited academic research that examined the impact of re-routing ambulances around marathon race routes versus ambulances that did not face any obstructions. That study determined that delays of just five minutes in care can impact patient outcomes.
A cyberattack’s effect is no different, said Woods: A system-crippling incident can freeze access to care for hours, and sometimes days, he pointed out.
There’s precedent for the concern. The WannaCry cyberattacks of 2017, which spread to more than 300,000 computers in 150 countries, not only brought down computer systems, but paralyzed hospitals’ ability to keep customers’ appointments, preventing patients’ access to care.
“During WannaCry, in some areas many hospitals shut down, with at least 30 to 40 percent shutting down for a day to a week,” said Woods. “If you think about someone with a stroke, with a 90-minute timeline of being treated, no one got the care needed during that time, which leads me to believe people have died because of these things before.”
More recently, a ransomware attack on the Duesseldorf University Hospital in Germany led to the hospital turning away emergency patients. During this attack, a woman who had to be sent to a different healthcare facility, around 20 miles away, died. German prosecutors suspect it’s because of delayed treatment after the cyberattack.
While the Duesseldorf University Hospital incident “might be the first smoking gun,” Woods said, the incident is not the first death that’s been caused – or at least partly influenced – by ransomware.
UC-Davis’ Tully knows the potential human consequences of poor IT security in healthcare facilities first-hand. At a Black Hat USA session in 2018, Tully demonstrated a proof-of-concept attack against a computerized Health Level 7 lab-results system. He was able to tamper with lab results coming from blood gas machines and urinalysis machines, which could lead to a lethal dosage of the wrong medication to treat an already sick patient.
“Certainly, sentinel events like WannaCry and, more recently, attacks explicitly directed at hospitals caring for COVID patients raise the specter that the quality of care, particularly for time-critical conditions like heart attacks, strokes or sepsis, may be affected enough to result in increased morbidity and mortality,” Tully said.
The Future of Healthcare Security
Against this bleak backdrop, the prognosis isn’t all bad. There are several steps that healthcare organizations can take in order to secure patient data and critical infrastructure.
For one, in order to secure systems across the board, healthcare providers need to incorporate a patching cadence as an integral part of their vendor due diligence. In a report published in August, analyst firm McKinsey identifies patching as the first in a list of required controls (PDF) that healthcare organizations need to put into place.
Beyond that, hospital networks can bolster security by adopting proactive monitoring programs to weed out risks of breaches, conduct risk analyses to keep tabs on their connected devices and follow cybersecurity frameworks – like the National Institute of Technology (NIST) cybersecurity framework – to further understand new threats.
And, as is the case in many industries, prioritizing staff training and awareness across the organization is crucial — awareness can prevent spear-phishing and close other attack vectors. Building relationships between the IT teams and the hospital staff should also be at the top of the to-do list, Dan Costantino, CISO at Penn Medicine, said, stressing that hospital CISOs shouldn’t “run programs in a vacuum.”
He also urged IT teams to bring other business leaders to the table and give them “skin in the game.” Doing so, he said, would help build strong security advocates within the business. This is particularly important during the ongoing pandemic, where security teams need the extra support of the healthcare leadership.
“The COVID-19 pandemic has been challenging for everyone, both personally and professionally,” said Costantino. “Cybersecurity teams have found themselves in a position where business operations are changing at warp speed. COVID-19 presents the need to turn that known state of operations sideways as the business scrambles to adjust, and implement a model capable of responding to our communities’ needs while maintaining employee safety.”
Insider Report: Healthcare Security Woes Balloon in COVID-Era
8.12.2020 Cyber Threatpost
As hackers put a bullseye on healthcare, Threatpost spotlights how hospitals, researchers and patients have been affected and how the sector is bolstering their cyber defenses.
In 2020, the healthcare industry began a massive shift, as legacy cybersecurity issues merged with new security challenges spurred on by the spread of COVID-19.
Even before the pandemic, the medical arena wrestled with major cybersecurity challenges, including insecure medical devices, protecting patient data and supporting outdated legacy equipment. COVID-19 has forced budget-strapped hospitals to address those systemic issues, and at the same time spurred new priorities around the digitization of healthcare services, telehealth rollouts and fending off an uptick in ransomware attacks.
EBook Spotlight on Healthcare-Cybersecurity Crisis
Starting today, Threatpost kicks off a spotlight series on cybersecurity issues impacting the healthcare industry during the era of COVID-19. In it we explore the impact of cybercrime on hospitals and researchers racing for treatments and ultimately on patients.
Complimenting our focus is a Threatpost eBook Healthcare Security Woes Balloon in a Covid-Era World that neatly packages our complete in-depth report on the topic. Portions of the free eBook will be available online starting with Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented Times.
Healthcare Security in the COVID-19 EraThreatpost’s eBook examines these inherent security challenges, as well as how COVID-19 has drastically reshaped the healthcare space over the past year when it comes to security risk. We look at the top weaknesses in healthcare organizations that cybercriminals are exploiting, how attackers are reinventing the wheel when it comes to cyberattacks on hospitals – and what this means for the healthcare industry in 2021 and beyond.
Relevant to All Sectors Impacted by COVID-19
The healthcare sector isn’t unique. Overnight, the COVID-19 crisis has changed the way companies in all sectors and regions do business. This Threapost spotlight series and eBook is relevant to any industry forced to reinvent themselves overnight – thanks to the coronavirus.
Security defenders are actively working on implementing best practices and technology solutions to protect their industries – whether it be healthcare, financial or energy. Our focus on healthcare. But safeguarding customer data, intellectual property and fending off ransomware attacks have all gotten more complicated against the backdrop of the COVID-19 pandemic.
Understanding what the risks mean for hospitals at the day-to-day level, and how healthcare security teams can implement best practices to protect doctors and patients, will serve any organizations well in the COVID-19 era, and well into the future.
We hope you will enjoy our in-depth look at the problems, the cybersecurity heroes and solutions discussed in our upcoming series and complimentary eBook.
Researchers call for a determined path to cybersecurity
7.12.2020 Cyber Securelist
Despite our continuous research efforts to detect cyberattacks and enable defense, we often feel that we, as members of a global community, are failing to achieve an adequate level of cybersecurity.
This is threatening the proper development and use of information technologies and digital assets, and as a consequence, most of society’s current and future activities, from entertainment to democratic processes, including business, healthcare and industrial production.
We believe that such a failure can be explained by a lack of global willpower, double-dealing activities, and the lack of global regulations. Here, we develop these hypotheses and outline ideas to advance cybersecurity.
What we do, and how it is failing
Kaspersky’s Global Research and Analysis Team (GReAT) is made up of cybersecurity researchers. Our shared capabilities and expertise stem from multifaceted individual experiences and perspectives that can always be traced back to strong technical backgrounds. Each and every day, our skills are focused on clear goals: to anticipate, discover, detect, track and report cyberattacks. But our activities and findings are, first and foremost, a contribution to a broader mission: to build a safer world. Since our inception more than a decade ago, we have worked very hard – from awareness raising and media interviews to embedded firmware reverse engineering, as well as incident-response support, vulnerabilities research, malicious infrastructure hunting, code similarity heuristics development, discovery of major threat actors or advanced malicious frameworks, open-sourced tools, specialized training and expert talks at world-class conferences. As far as our expertise is concerned, we believe that we provide beneficial results to our customers, partners and the global community. We know from previous collaboration and published content that our colleagues at government bodies, other cybersecurity providers and private companies work just as hard and achieve tremendous results as well.
Yet, somehow, we are still failing. Cyberattack numbers, whatever their impact, from digital activities to unwanted or disastrous effects, keep skyrocketing every year. Cybercrime has never been so prevalent and real, reaching every possible device, from IoT to supercomputers, as well as network routers, smartphones and personal computers. Cyberattacks have become a go-to companion, wherever there is malicious intent to tackle competition, hijack accounts, spy on a partner, persecute a minority, disrupt critical infrastructure, influence electoral processes, steal knowledge or obtain money. Cyber-based conflicts keep escalating, to the point where there is now a trend around the globe to proclaim that cyberwar capabilities are being developed, and kinetic force could be used as a response to cyberattacks whenever deemed fit. And ransomware or state-sponsored cyberattacks kept hitting hard even when we are all confronted with a pandemic.
Our hypotheses and beliefs
Why does all that outstanding technical effort, an abundance of cybersecurity solutions, highly skilled workforces, and decades of awareness raising fail to tackle cyberthreats? Although a lack of concern, specialized technical knowledge, skilled resources and training may have kept the defense a few steps behind for a while, we think these factors are no longer a major barrier. Instead, we believe that issues surrounding governance and a sense of responsibility are now what primarily prevent mission success.
A lack of global willpower and instruments
First of all, we believe that there is a lack of high-level global desire for cooperation and governance to properly tackle cyberattacks and protect what is at stake. We all agree that every human being should be guaranteed a minimum set of rights, that the development of nuclear warheads should be limited, if not outlawed, or that warfare should be regulated and overseen. These crucial safeguards to peace and freedom did not come about by chance; they came from political willpower, international cooperation, continuously improved governance and determined enforcement.
However, states have not agreed yet about a binding treaty or about how existing international law applies to keep our digital world at peace. There are regular examples demonstrating the major negative effects of cyberattacks on businesses, nations and citizens (or “civilians”), and there have been some initiatives to assess how international law would apply to cyber operations, to globally combat cybercrime, or to establish norms of responsible behavior in cyberspace for states. But these initiatives are not coordinated or global enough, they don’t actually come with the expected regulations, cooperation and clear instruments to increase stability in cyberspace.
Are we waiting for more dramatic effects than those already caused by cyberattacks and cybercrime to advance cybersecurity with strong governance and regulation instruments? We believe that, on top of the intrinsic complexity of international cooperation, a crucial lack of willpower from states is preventing substantial advancement on cybersecurity.
Double-dealing
We believe that lots of players are double-dealing in the digital age. Cyberattacks appear to be highly profitable in the short-term, as they allow attackers and their sponsors to quickly and stealthily gather foreign and domestic intelligence, make money, disrupt or deter third parties, gain a strategic advantage over competitors or in warfare, circumvent regulations, or efficiently disseminate information. As a bonus, these malicious activities have a low entry cost, are subject to no monitoring, and for the most part go unattributed (thanks to, amongst other things, complex digital layers, bulletproof services and factors limiting interstate police cooperation). Therefore, perpetrators do not have to take responsibility for their actions and go unpunished – even when they do get exposed. Due to these convenient “cyber features”, state or non-state actors might easily be tempted to publicly promote and even act in favor of a safer world, while making sure they can also benefit from offensive activities that remain undetected and go unpunished. Such activities also promote the public and private development of cyberweapons, mercenary services, criminal activities, and the monetization of vulnerabilities instead of responsible disclosure. All this, in turn, harms the efforts of cybersecurity and enables proliferation.
But that’s not all when it comes to double-dealing: government bodies dedicated to cybersecurity and non-state actors can even play this dangerous game to some extent. Cybersecurity threat intelligence and data are of topmost interest to national defense and security management, as well as very valuable to the competitive cybersecurity business. It is a vital asset to the economy, and for detecting or deterring strategic threats. As a result, threat intelligence may not be shared and actioned as easily and broadly as it should, in a common determined path to cybersecurity, but might rather be guarded jealously for private interests. Private companies such as Kaspersky, however, do their best to proactively share intelligence and insights on investigations to the community for free.
Existing regulations are not (global) enough
We also feel that achieving cybersecurity is not possible without a stronger sense of responsibility from all public and private actors that play a role in the development and operation of our global digital space. Governments have already gone some way to fostering this sense over the years by creating or strengthening regulations on personal data processing or protection for critical information systems. While this has been a significant advancement towards cybersecurity, it has unfortunately not been enough.
Most of the cyberattacks we face and analyze do not actually leverage sophisticated technical vulnerabilities or tools, because they don’t need to. It is often way too easy to access the devices and networks owned by a public or private organization because elementary cybersecurity measures are still not implemented, and because the organization’s very own digital assets are not clearly identified or not controlled sufficiently. Every organization that processes digital data of personal significance, or develops or operates digital services, starting with those that benefit us the most, or contribute to our most vital needs, including governments, should be required to implement and demonstrate elementary cybersecurity frameworks. The associated regulations should be global, because cyberspace and digital assets are shared amongst all users around the world. It may not be possible to become invulnerable, but making cyberattacks more costly for the attackers while protecting our digital world a little more is doable.
On top of the lack of preventive and protective measures from many public and private organizations, another responsibility issue is blocking the road to cybersecurity. Cyberattacks cannot be carried out without leveraging publicly available commercial services, such as content hosting, development, infrastructure provision and mercenary services. First, it would seem obvious that any private organization that purposely engages in cyberattack operations or cyberweapons development should have its activities limited by regulations, and controlled by an impartial third party, in order to ensure that malicious activities are constrained by design, and that cyberweapons do not proliferate. Also, in order to maintain peace in the cyberworld, it is critical that any organization whose services are demonstrated to be leveraged to carry out cyberattacks is required to cooperate with cybersecurity organizations designated by an impartial third party, to contribute to cybersecurity investigations and demonstrate efforts to continuously prevent the malicious use of exposed services.
Digital services and information technologies that unintentionally support malicious cyber activities are – most of the time – developed to bring sound and useful outcomes. However, and for decades, vulnerability disclosures and cyberattacks have demonstrated that some technologies or uses are flawed by design and can be exploited by malicious actors. We can probably collectively accept that when the first information technologies were developed and deployed, it wasn’t easy to anticipate malicious uses, which is why cybersecurity efforts only came afterwards. But it is no longer possible nor tolerable to develop, deploy and operate technologies and services that have a global use potential, while ignoring existing threats, and without making them secure by design. Yet, even more vulnerabilities and malicious uses affect relatively modern services and technologies, from IoT and artificial intelligence systems to cloud infrastructures, robotics and new mobile networks. In order to anticipate and prevent malicious exploitation of modern technologies as much as it is reasonably possible, we believe that transparent vulnerability management and disclosure practices need to be developed further by both state and non-state actors; and that technologies or services that are used globally should be assessed by a global community of experts more often.
Last but not least, we also think that more threats could be better anticipated in the future if future generations are globally and systematically educated on information technologies and cybersecurity, whatever their origin or path. This will contribute to a safer world.
Our call and plans
It is rather unusual for cybersecurity researchers and experts to write on governance matters. We don’t pretend that our hypotheses are the most suitable, or the most comprehensive. But we definitely feel concerned, and strongly believe that the points we have raised are obstructing a common path to cybersecurity. Furthermore, we are pleased to note that most of our hypothesis and beliefs are actually shared with many others, as demonstrated in 2020 Paris Call consultation key takeaways, or the latest reports from the UN’s OEWG on “developments in the field of information and telecommunications in the context of international security”, to which Kaspersky contributed.
We feel it is now a good time to send a call to all governments and international bodies (and ultimately any citizen) that aim for a safer world: we urge you to demonstrate more willpower, and a more determined approach to cybersecurity, by tackling the exposed causes of failure. We ask you to cooperatively choose the long-term peace of our common digital assets, over short-term nationalistic or private interests. We do our part, and we want our expert efforts to be transformed and developed further. We hope for a safer world, and a long-standing peaceful common digital space. We will never achieve this without determined leadership and a global change towards a better common behavior.
A cooperative and global governing instrument
We need strong political and technological leaders to drive governments and international bodies towards a cooperative, determined and fast-paced road to cybersecurity. In order to continuously rationalize efforts, share insights and thoughts, enable regulation, control and take global measures, we need them to build a dedicated, strong, permanent and focused international instrument.
We believe that such an instrument could be hosted by the UN, should seek to tackle the causes of the failures that we exposed, and should help governments to enforce regulations and cooperatively take measures when they are needed.
In order to ensure a cooperative approach by design, to consider the whole spectrum of what is at stake, and to truly take the transnational nature of cyberspace into consideration, we believe that such an instrument should guarantee a continuous dialogue with representatives of governments, the private sector, civil society and the technical community. This would enable the creation of cooperative task forces that would provide broad cybersecurity expertise and assessments on various matters, including preventive and protective cybersecurity measures, vulnerability research, incident response, attribution, regulation, law enforcement, security and risk assessment of modern technologies, and cyber capacity building. It would also ensure that most findings are shared across nations and among cybersecurity players.
This governing instrument should also be able to build norms and regulations, and a cooperative approach to control the attribution of cyberattacks and sanctions against non-compliant behavior or crime, risk analysis, capacity building, and education for cybersecurity.
A binding treaty of responsible behavior in cyberspace
Nearly two decades ago, the UN started to task groups of government experts (GGE) to anticipate international security developments in the field of IT, and to advance responsible state behavior in cyberspace. One of the most notable outcomes, despite GGE’s debatable results and limited reach, is the definition of 13 principles that constitute the norms of responsible behavior in cyberspace. But after more than a decade, these principles are non-binding, apply to governments only, and have only been endorsed on a voluntary basis. We believe this is not enough, and that it may reflect the lack of willpower and commitment from our governing leaders to cybersecurity.
We believe that the norms for responsible behavior in cyberspace should be further developed together with guidance on how these norms should be implemented, be better at including non-state actors such as the private sector, civil society and the technical community. After that they should become binding for the international community – if they remain voluntary, why should the bad guys care?
As far as private companies are concerned, the norm could set transparency and ethics baselines. We must not fail to mention Kaspersky’s own Global Transparency Initiative, which we truly believe to be a good source of inspiration for setting a number of private sector norms. This includes (but is not limited to) independent reviews of processes, security controls and software code, relocation of data processing, as well as the ability for trusted partners, customers and government stakeholders to directly access and check software code or threat detection rules. A code of ethics or ethics principles, from the “FIRST” international CSIRTs community or from Kaspersky, that tackle the responsible disclosure of security vulnerabilities, could also be leveraged as inspiration for private company norms.
Global regulations and shared means for cybersecurity
In order to tackle residual double-dealing issues and regulation needs that we exposed in our hypotheses, the global governing instrument or guidance should build and support further common regulations, on top of the previously mentioned norms of behavior. Such global regulations would ensure a consistent baseline of security requirements, to prevent proliferation of cyberweapons, prevent and firmly condemn cyberattacks, implement cybersecurity controls, foster responsibility and facilitate cooperation. How, where, and under which terms this governing instrument or guidance can be established should be a discussion for both state and non-state actors to ensure that we all fully recognize our responsibility to keep the digital space secure.
Conclusion
We deal with cyberattacks of all kinds every day and monitor their context from various sources. Over the years, we have seen more and more malicious activities from more and more actors, but global cybersecurity has reached a ceiling, and it appears that the potential for cyber-based conflicts is still growing. During the COVID-19 pandemic we have once again observed just how vital information technologies and digital assets are to democracy, the economy, the development of society, security and entertainment.
We believe that now is still a good time for world leaders, international and regional organizations, the private sector, the technical community and civil society to collaborate on achieving long-term peace in cyberspace rather than focusing on the short-term interests of individual countries or private organizations.
As Hospitals Cope With a COVID-19 Surge, Cyber Threats Loom
5.12.2020 Cyber Securityweek
With COVID-19 Infections and Hospitalizations Climbing, Health Care Providers Are Dangerously Vulnerable to Cyberattacks
By late morning on Oct. 28, staff at the University of Vermont Medical Center noticed the hospital’s phone system wasn’t working.
Then the internet went down, and the Burlington-based center’s technical infrastructure with it. Employees lost access to databases, digital health records, scheduling systems and other online tools they rely on for patient care.
Administrators scrambled to keep the hospital operational — cancelling non-urgent appointments, reverting to pen-and-paper record keeping and rerouting some critical care patients to nearby hospitals.
In its main laboratory, which runs about 8,000 tests a day, employees printed or hand-wrote results and carried them across facilities to specialists. Outdated, internet-free technologies experienced a revival.
“We went around and got every fax machine that we could,” said UVM Medical Center Chief Operating Officer Al Gobeille.
The Vermont hospital had fallen prey to a cyberattack, becoming one of the most recent and visible examples of a wave of digital assaults taking U.S. health care providers hostage as COVID-19 cases surge nationwide.
The same day as UVM’s attack, the FBI and two federal agencies warned cybercriminals were ramping up efforts to steal data and disrupt services across the health care sector.
By targeting providers with attacks that scramble and lock up data until victims pay a ransom, hackers can demand thousands or millions of dollars and wreak havoc until they’re paid.
In September, for example, a ransomware attack paralyzed a chain of more than 250 U.S. hospitals and clinics. The resulting outages delayed emergency room care and forced staff to restore critical heart rate, blood pressure and oxygen level monitors with ethernet cabling.
A few weeks earlier, in Germany, a woman’s death became the first fatality believed to result from a ransomware attack. Earlier in October, facilities in Oregon, New York, Michigan, Wisconsin and California also fell prey to suspected ransomware attacks.
Ransomware is also partly to blame for some of the nearly 700 private health information breaches, affecting about 46.6 million people and currently being investigated by the federal government. In the hands of a criminal, a single patient record — rich with details about a person’s finances, insurance and medical history — can sell for upward of $1,000 on the black market, experts say.
Over the course of 2020, many hospitals postponed technology upgrades or cybersecurity training that would help protect them from the newest wave of attacks, said health care security consultant Nick Culbertson.
“The amount of chaos that’s just coming to a head here is a real threat,” he said.
With COVID-19 infections and hospitalizations climbing nationwide, experts say health care providers are dangerously vulnerable to attacks on their ability to function efficiently and manage limited resources.
Even a small technical disruption can quickly ripple out into patient care when a center’s capacity is stretched thin, said Vanderbilt University’s Eric Johnson, who studies the health impacts of cyberattacks.
“November has been a month of escalating demands on hospitals,” he said. “There’s no room for error. From a hacker’s perspective, it’s perfect.”
A ‘CALL TO ARMS’ FOR HOSPITALS
The day after the Oct. 28 cyberattack, 53-year-old Joel Bedard, of Jericho, arrived for a scheduled appointment at the Burlington hospital.
He was able to get in, he said, because his fluid-draining treatment is not high-tech, and is something he’s gotten regularly as he waits for a liver transplant.
“I got through, they took care of me, but man, everything is down,” Bedard said. He said he saw no other patients that day. Much of the medical staff idled, doing crossword puzzles and explaining they were forced to document everything by hand.
“All the students and interns are, like, ‘How did this work back in the day?’” he said.
Since the attack, the Burlington-based hospital network has referred all questions about its technical details to the FBI, which has refused to release any additional information, citing an ongoing criminal investigation. Officials don’t believe any patient suffered immediate harm, or that any personal patient information was compromised.
But more than a month later, the hospital is still recovering.
Some employees were furloughed for weeks until they could return to their regular duties.
Oncologists could not access older patient scans which could help them, for example, compare tumor size over time.
And, until recently, emergency department clinicians could take X-rays of broken bones but couldn’t electronically send the images to radiologists at other sites in the health network.
“We didn’t even have internet,” said Dr. Kristen DeStigter, chair of UVM Medical Center’s radiology department.
The tech outage also delayed the reporting of about 50 coronavirus test results to the state, prompting the hospital to revert to a fax system for reporting results until its information technology problems are fixed, UVM Medical Center President Dr. Stephen Leffler said Thursday.
Soldiers with the state’s National Guard cyber unit have helped hospital IT workers scour the programming code in hundreds of computers and other devices, line-by-line, to wipe any remaining malicious code that could re-infect the system. Many have been brought back online, but others were replaced entirely.
Col. Christopher Evans said it’s the first time the unit, which was founded about 20 years ago, has been called upon to perform what the guard calls “a real-world” mission. “We have been training for this day for a very long time,” he said.
It could be several more weeks before all the related damage is repaired and the systems are operating normally again, Gobeille said.
“I don’t want to get peoples’ hopes up and be wrong,” he said. “Our folks have been working 24/7. They are getting closer and closer every day.”
It will be a scramble for other health care providers to protect themselves against the growing threat of cyberattacks if they haven’t already, said data security expert Larry Ponemon.
“It’s not like hospital systems need to do something new,” he said. “They just need to do what they should be doing anyway.”
Current industry reports indicate health systems spend only 4% to 7% of their IT budget on cybersecurity, whereas other industries like banking or insurance spend three times as much.
Research by Ponemon’s consulting firm shows only about 15% of health care organizations have adopted the technology, training and procedures necessary to manage and thwart the stream of cyberattacks they face on a regular basis.
“The rest are out there flying with their head down. That number is unacceptable,” Ponemon said. “It’s a pitiful rate.”
And it’s part of why cybercriminals have focused their attention on health care organizations — especially now, as hospitals across the country are coping with a surge of COVID-19 patients, he said.
“We’re seeing true clinical impact,” said health care cybersecurity consultant Dan L. Dodson. “This is a call to arms.”
Healthcare 2021: Cyberattacks to Center on COVID-19 Spying, Patient Data
3.12.2020 Cyber Threatpost
The post-COVID-19 surge in the criticality level of medical infrastructure, coupled with across-the-board digitalization, will be big drivers for medical-sector cyberattacks next year.
Sophisticated cybercriminals have been trying to steal COVID-19 vaccine research – and researchers say there’s more of that to come going into 2021. Intellectual property theft will join ransomware, cloud-stored patient data theft and advanced phishing efforts as the main hallmarks of medical-related healthcare cyberattacks for the new year.
That’s according to predictions from Kaspersky researchers, who said to expect advanced persistent threat (APT) threat actors to continue to target any pharma company that makes a significant breakthrough on coronavirus vaccines or therapeutics. They also believe that this will spark diplomatic disputes around the world.
There have already been reported espionage attacks on vaccine-makers AstraZeneca and Moderna.
“The pandemic has turned 2020 into a year of medicine and information technology,” said Maria Namestnikova, researcher with Kaspersky, in a Wednesday posting. “Interest in medical research has, of course, increased too among cybercriminals in particular groups specializing in targeted attacks. This was spurred primarily by the development of a COVID-19 vaccine and its potential significance for the global community. The biggest hullabaloo was around the WellMess campaign, which, according to Western intelligence agencies, sought to steal information about vaccines being developed in Canada, the UK and several other countries.”
Going forward, attacks on COVID-19 vaccine and drug developers, and attempts to steal sensitive data from them, will continue, Kaspersky predicted, as the development race between pharmaceutical firms continues. And, these cyberattacks will have ramifications for geopolitics, with the “attribution of attacks entailing serious consequences or aimed at the latest medical developments is sure to be cited as an argument in diplomatic disputes.”
Ransomware and More
Namestnikova also cited the post-COVID-19 surge in the criticality level of medical infrastructure, coupled with across-the-board digitalization, as big drivers for medical-sector cyberattacks.
“There has been an increase in attacks on medical equipment in countries where the digital transformation of healthcare is only just beginning,” she noted. In 2021, organizations in countries with more developed infrastructure will be in the sights, small and medium-sized businesses (SMBs).
“Protecting patient data and infrastructure is fairly expensive and thus difficult for SMBs to implement at the best of times, let alone during an economic crisis,” she predicted.
Kaspersky’s predictions overview pointed out that 10 percent of all organizations hit by targeted ransomware between January and September this year were hospitals and other medical institutions, with more than two dozen U.S. hospitals hit with Ryuk and other targeted ransomware campaigns in October alone. In the new year, this could translate into better cybersecurity maturity.
“The focus on digital security in hospitals offers hope that 2021 will be the year when cybersecurity and healthcare join forces,” said Namestnikova. “Past experience has shown that painful lessons such as the Wannacry epidemic in 2017 and the coronavirus pandemic in 2020 are the very thing that incentivizes organizations to pay more attention to infrastructure security.”
Other Kaspersky predictions include a rise in patient data leaks from cloud services, thanks to medical organizations’ ongoing transition to cloud infrastructures and storage of personal information in them. This will help make medicine a go-to bait topic for phishing, according to the firm.
“[Medical-related lures] will be with us next year and remain current at least until the end of the pandemic,” she said. “The human factor is one of the most important components of many attacks, and information about new regulatory restrictions, potential treatments and patient health will continue to attract user attention. Leaked medical records will also become part of the hook in targeted attacks, since accurate patient information will make fake messages far more credible.”
Education predictions 2021
2.12.2020 Cyber Securelist
Changes in the education system have been brewing for a long time, with digitalization as the main direction of this transformation. The breakthrough came this year as about 1.5 billion students were unable to attend school due to the COVID-19 pandemic. As a result, educational systems all over the world underwent significant change. Educators were forced to master new tools like Zoom, while maintaining the quality of education as they taught online.
This digitalization of education is likely to continue, which is good and bad at the same time. On the one hand, there are new tools and possibilities including ones that were originally not associated with education at all. TikTok accounts used for online instruction are a good example. Initially, teachers shunned the platform, preferring YouTube instead, but in 2020, TikTok became a popular choice for distributing educational content. On the other hand, many of these new digital educational tools are both enhancing the educational experience and introducing new threats. Here are the ones most likely to pose the biggest risks in the coming year.
Development of educational Learning Management Systems. LMSs enable teachers to track students’ learning process, showing their progress and aspects that require the teacher’s attention. While there already are several well-known systems (Google Classroom, Frog, etc.), the market for new LMS systems will only continue to grow.
As the number and popularity of LMSs rises, the number of phishing sites associated with educational and videoconferencing services will grow, too. Their main goals are stealing personal data or spreading spam within the educational community. Already in the spring of 2020, 168,550 unique users encountered various threats distributed under the guise of popular online learning platforms or videoconferencing applications, a 20,455% increase when compared to 2019. In addition to that, LMSs open up the potential for new, unexpected threats, such as Zoombombing. Especially if schools continue to conduct remote learning, these systems will continue to be a popular attack vector.
More attention will be paid to video services, such as Youtube, Netflix, SchoolTube, KhanAcademy, etc. There will be more creation of educational video content either existing as finished product or partially used by teachers in the classroom. In fact, about 60% of teachers already use YouTube in the classroom.
While videos can be a powerful educational tool, there is also a lot of age-inappropriate content that can be found on popular video services (YouTube/TikTok/Instagram, etc.), and creators of this content may use educational topics to attract attention. This threat is not new, but with the growth of digitalization, its relevance will grow too.
Use of social media tools in the educational process. Social media (Instagram, Twitter, etc.) can be a great way to encourage students’ engagement during and after classes, and serve as a way for teachers to connect with their students. However, there are threats relating to content regulation. Currently, teachers or service administrators have to manually regulate content in LMSs and videoconferencing applications – it is a big task. Moderating content on social media platforms or online group chats is an even bigger one – especially in public groups or chats. That paves the way for inappropriate content, offensive comments and cyberbullying.
Privacy is another concern. A poorly configured application or service is a well-known way of compromising personal data, even without special tools or vulnerabilities. In our case, students and teachers can be victims of such attacks.
Gamification of the educational process. Almost everyone at school already knows about learning with Minecraft, but apart from that game, there are many services that allow you to learn through playing (While True: Learn, Classcraft, Roblox, etc.). However, as soon as you incorporate games into the classroom, you expose students to the same types of risks they would be facing while gaming from home: trolls and bullying, malicious files disguised as game updates or add-ons, etc.
In fact, privacy will be the biggest concern in the near future. Managing it in any service requires the user’s involvement, but many users, especially younger children, do not know how to appropriately control their privacy settings. Also, there are many services that provide tools for setting up the educational process online, and educators will most likely be using more than one. As a result, for each tool and in each case, they will need to pay special attention to protecting not only their personal information, but also their students’ data.
Healthcare security in 2021
2.12.2020 Cyber Securelist
The pandemic has turned 2020 into a year of medicine and information technology. The remarkable surge in the criticality level of medical infrastructure, coupled with feasible across-the-board digitalization, led to many of our last year’s predictions coming true much sooner than expected.
As we foresaw, there has been an increase in attacks on medical equipment in countries where the digital transformation of healthcare is only just beginning. Interest in medical research has, of course, increased too among cybercriminals in particular groups specializing in targeted attacks. This was spurred primarily by the development of a COVID-19 vaccine and its potential significance for the global community. The biggest hullabaloo was around the WellMess campaign, which, according to Western intelligence agencies, sought to steal information about vaccines being developed in Canada, the UK and several other countries.
The topic of healthcare has become one of the most popular baits for attacks of varying complexity: from no-frills emails with malicious attachments through phishing to targeted attacks. To deceive users, attackers faked statements and documents from various medical bodies, including the WHO, and promised medicines and vaccines.
Since the outbreak of the pandemic, groups such as DoppelPaymer and Maze, known for targeted ransomware attacks, have announced that they will not pursue medical organizations in the current climate. All the same, healthcare is regularly targeted by cybercriminals. Recall that at the very start of the pandemic a hospital in the Czech Republic with one of the country’s largest COVID-19 testing facilities suffered a cyberattack. 2020 also saw the first confirmed case when a patient died due to delays in receiving emergency care after medical equipment was infected by ransomware. According to public sources, 10% of all organizations hit by targeted ransomware between January and September 2020 were hospitals and other medical institutions. In late October alone, more than two dozen US hospitals were attacked as part of a large-scale Ryuk and other targeted ransomware campaigns. Despite the fact that some groups did indeed refrain from going after medical facilities, others pursued them with redoubled vigor.
With the digital security of medical organizations in the spotlight, especially after the above-mentioned Czech hospital incident, the infosec industry is focused on providing maximum support to healthcare systems. This led — at the very start of the pandemic — to the formation of the CTI League, a voluntary organization of cybersecurity experts seeking to protect medical organizations and help them respond to cyber incidents. Hospitals have been assisted too by security software developers, including Kaspersky, which provided medical organizations with free access to its products.
Predictions for 2021
Attacks on COVID-19 vaccine and drug developers, and attempts to steal sensitive data from them, will continue. The world is not only fighting the disease, but witnessing a race between pharmaceutical firms, in which any significant breakthrough will likely result in targeted attacks on the company that made it.
In countries with highly developed public healthcare, organizations in the private medical sector, most of which are small and medium-sized businesses (SMBs), will face attacks. Protecting patient data and infrastructure is fairly expensive and thus difficult for SMBs to implement at the best of times, let alone during an economic crisis.
Health-related cyberattacks will be used as a bargaining chip in geopolitics — attribution of attacks entailing serious consequences or aimed at the latest medical developments is sure to be cited as an argument in diplomatic disputes.
Next year will see a stream of reports about patient data leaks from cloud services. Medical organizations’ transition to cloud infrastructures and storage of personal information in them is already creating additional risks. Given our correct prediction last year that interest in user health data would grow, healthcare institutions must devote serious energies to protecting their cloud infrastructures right now.
Medicine as a bait topic will be with us next year and remain current at least until the end of the pandemic. The human factor is one of the most important components of many attacks, and information about new regulatory restrictions, potential treatments and patient health will continue to attract user attention. Leaked medical records will also become part of the hook in targeted attacks, since accurate patient information will make fake messages far more credible.
The focus on digital security in hospitals offers hope that 2021 will be the year when cybersecurity and healthcare join forces. Past experience has shown that painful lessons such as the Wannacry epidemic in 2017 and the coronavirus pandemic in 2020 are the very thing that incentivizes organizations to pay more attention to infrastructure security.
Advanced Threat predictions for 2021
30.11.20 Cyber Securelist
Trying to make predictions about the future is a tricky business. However, while we don’t have a crystal ball that can reveal the future, we can try to make educated guesses using the trends that we have observed over the last 12 months to identify areas that attackers are likely to seek to exploit in the near future.
Let’s start by reflecting on our predictions for 2020.
The next level of false flag attacks
This year, we haven’t seen anything as dramatic as the forging of a malicious module to make it look like the work of another threat actor, as was the case with Olympic Destroyer. However, the use of false flags has undoubtedly become an established method used by APT groups to try to deflect attention away from their activities. Notable examples this year include the campaigns of MontysThree and DeathStalker. Interestingly, in the DeathStalker case, the actor incorporated certificate metadata from the infamous Sofacy in their infrastructure, trading covertness for the chance of having their operation falsely attributed.
From ransomware to targeted ransomware
Last year, we highlighted the shift towards targeted ransomware and predicted that attackers would use more aggressive methods to extort money from their victims. This year, hardly a week has gone by without news of an attempt to extort money from large organizations, including recent attacks on a number of US hospitals. We’ve also seen the emergence of ‘brokers’ who offer to negotiate with the attackers, to try to reduce the cost of the ransom fee. Some attackers seem to apply greater pressure by stealing data before encrypting it and threatening to publish it; and in a recent incident, affecting a large psychotherapy practice, the attackers posted sensitive data of patients.
New online banking and payments attack vectors
We haven’t seen any dramatic attacks on payment systems this year. Nevertheless, financial institutions continue to be targeted by specialist cybercrime groups such as FIN7, CobaltGroup, Silence and Magecart, as well as APT threat actors such as Lazarus.
More infrastructure attacks and attacks against non-PC targets
APT threat actors have not confined their activities to Windows, as illustrated by the extension of Lazarus’s MATA framework, the development of Turla’s Penquin_x64 backdoor and the targeting of European supercomputing centers in May. We also saw the use of multiplatform, multi-architecture tools such as Termite and Earthworm in operation TunnelSnake. These tools are capable of creating tunnels, transferring data and spawning remote shells on the targeted machines, supporting x86, x64, MIPS(ES), SH-4, PowerPC, SPARC and M68k. On top of this, we also discovered the framework we dubbed MosaicRegressor, which includes a compromised UEFI firmware image designed to drop malware onto infected computers.
Increased attacks in regions that lie along the trade routes between Asia and Europe
In 2020, we observed several APT threat actors target countries that had previously drawn less attention. We saw various malware used by Chinese-speaking actors used against government targets in Kuwait, Ethiopia, Algeria, Myanmar and the Middle East. We also observed StrongPity deploying a new, improved version of their main implant called StrongPity4. In 2020 we found victims infected with StrongPity4 outside Turkey, located in the Middle East.
Increasing sophistication of attack methods
In addition to the UEFI malware mentioned above, we have also seen the use of legitimate cloud services (YouTube, Google Docs, Dropbox, Firebase) as part of the attack infrastructure (either geo-fencing attacks or hosting malware and used for C2 communications).
A further change of focus towards mobile attacks
This is apparent from the reports we have published this year. From year to year we have seen more and more APT actors develop tools to target mobile devices. Threat actors this year included OceanLotus, the threat actor behind TwoSail Junk, as well as Transparent Tribe, OrigamiElephant and many others.
The abuse of personal information: from deep fakes to DNA leaks
Leaked/stolen personal information is being used more than ever before in up-close and personal attacks. Threat actors are less afraid than ever to engage in active ongoing communications with their victims, as part of their spear-phishing operations, in their efforts to compromise target systems. We have seen this, for example, in Lazarus’s ThreatNeedle activities and in DeathStalker’s efforts to pressure victims into enabling macros. Criminals have used AI software to mimic the voice of a senior executive, tricking a manager into transferring more than £240,000 into a bank account controlled by fraudsters; and governments and law enforcement agencies have used facial recognition software for surveillance.
Turning our attention to the future, these are some of the developments that we think will take center stage in the year ahead, based on the trends we have observed this year.
APT threat actors will buy initial network access from cybercriminals
In the last year, we have observed many targeted ransomware attacks using generic malware, such as Trickbot, to gain a foothold in target networks. We have also observed connections between targeted ransomware attacks and well-established underground networks like Genesis that typically trade in stolen credentials. We believe APT actors will start using the same method to compromise their targets. Organizations should pay increased attention to generic malware and perform basic incident response activities on each compromised computer to ensure generic malware has not been used deploy sophisticated threats.
More countries using legal indictments as part of their cyberstrategy
Some years ago we predicted that governments would resort to “naming and shaming”, to draw attention to the activities of hostile APT groups. We have seen several cases of this over the last 12 months. We think that US Cyber Command’s “persistent engagement” strategy will begin to bear fruit in the coming year and lead other states to follow suit, not least as “tit for tat” retaliation to US indictments. Persistent engagement involves publicly releasing reports about adversary tools and activities. US Cyber Command has argued that warfare in cyberspace is of a fundamentally different nature, and requires full-time engagement with adversaries to disrupt their operations. One of the ways they do so is by providing indicators that the threat intelligence community can use to bootstrap new investigations – in a sense, it is a way of orienting private research through intelligence declassification.
Tools “burned” in this way become harder to use for the attackers, and can undermine past campaigns that might otherwise have stayed under the radar. Faced with this new threat, adversaries planning attacks must factor in additional costs (the heightened possibility of losing tools or these tools being exposed) in their risk/gain calculus.
Exposing toolsets of APT groups is nothing new: successive leaks by Shadow Brokers provide a striking example. However, it is the first time it has been done in an official capacity through state agencies. While quantifying the effects of deterrence is impossible, especially without access to diplomatic channels where such matters are discussed, we believe that more countries will follow this strategy in 2021. First, states traditionally aligned with the US may start replicating the process, and then, later on, the targets of such disclosures could follow suit as a form of retaliation.
More Silicon Valley companies will take action against zero-day brokers
Until recently, zero-day brokers have traded exploits for well-known commercial products; and big companies such as Microsoft, Google, Facebook and others have seemingly paid little attention to the trade. However, in the last year or so, there have been high-profile cases where accounts were allegedly compromised using WhatsApp vulnerabilities – including Jeff Bezos and Jamal Khashoggi. In October 2019, WhatsApp filed a lawsuit accusing Israel-based NSO Group of having exploited a vulnerability in its software; and that the technology sold by NSO was used to target more than 1,400 of its customers in 20 different countries, including human rights activists, journalists and others. A US judge subsequently ruled that the lawsuit could proceed. The outcome of the case could have far-reaching consequences, not least of which could be to lead other firms to take legal action against companies that deal in zero-day exploits. We think that mounting public pressure, and the risk of reputation damage, may lead other companies to follow WhatsApp’s lead and take action against zero-day brokers, to demonstrate to their customers that they are seeking to protect them.
Increased targeting of network appliances
With the trend towards overall improvement of organizational security, we think that actors will focus more on exploiting vulnerabilities in network appliances such as VPN gateways. We’re already starting to see this happen – see here, here and here for further details. This goes hand-in-hand with the shift towards working from home, requiring more companies to rely on a VPN setup in their business. The increased focus on remote working, and reliance on VPNs, opens up another potential attack vector: the harvesting of user credentials through real-world social engineering approaches such as “vishing” to obtain access to corporate VPNs. In some cases, this might allow the attacker to even accomplish their espionage goals without deploying malware in the victim’s environment.
The emergence of 5G vulnerabilities
5G has attracted a lot of attention this year, with the US exerting a lot of pressure on friendly states to discourage them from buying Huawei products. In many countries, there were also numerous scare stories about possible health risks, etc. This focus on 5G security means that researchers, both public and private, are definitely looking at the products of Huawei and others, for signs of implementation problems, crypto flaws and even backdoors. Any such flaws will certainly receive massive media attention. As usage of 5G increases, and more devices become dependent on the connectivity it provides, attackers will have a greater incentive to look for vulnerabilities that they can exploit.
Demanding money “with menaces”
We have seen several changes and refinements in the tactics used by ransomware gangs over the years. Most notably, attacks have evolved from random, speculative attacks distributed to a large number of potential victims, to highly targeted attacks that demand a considerably greater payout from a single victim at a time. The victims are carefully selected, based on their ability to pay, their reliance on the data encrypted and the wider impact an attack will have. And no sector is considered off limits, notwithstanding the promises ransomware gangs made not to target hospitals. The delivery method is also customized to fit the targeted organization, as we have seen with attacks on medical centers and hospitals throughout the year.
We have also seen ransomware gangs seeking to obtain greater leverage by threatening to publish stolen data if a company fails to pay the ransom demanded by the attackers. This trend is likely to develop further as ransomware gangs seek to maximize their return on investment.
The ransomware problem has become so prevalent that the OFAC (Office of Foreign Assets Control) released instructions for victims and clarified that paying ransoms could constitute a breach of international sanctions. We interpret this announcement as the beginning of a wider crackdown on the cybercrime world by US authorities.
This year, the Maze and Sodinokibi gangs both pioneered an “affiliate” model involving collaboration between groups. Nevertheless, the ransomware eco-system remains very diverse. It’s possible that in the future we will see a concentration of major ransomware players who will start to focus their activities and obtain APT-like capabilities. However, for some time to come, smaller gangs will continue to adopt the established approach that relies on piggybacking botnets and sourcing third-party ransomware.
More disruptive attacks
More and more aspects of our lives are becoming dependent on technology and connectivity to the internet. As a result, we present a much wider attack surface than ever before. It’s likely, therefore, that we will see more disruptive attacks in the future. On the one hand, this disruption could be the result of a directed, orchestrated attack, designed to affect critical infrastructure. On the other hand, it could be collateral damage that occurs as a side-effect of a large-volume ransomware attack targeting organizations that we use in our day-to-day lives, such as educational institutions, supermarkets, postal services and public transportation.
Attackers will continue to exploit the COVID-19 pandemic
The world has been turned upside down by COVID-19, which has impacted nearly every aspect of our lives this year. Attackers of all kinds were quick to seize the opportunity to exploit the keen interest in this topic, including APT threat actors. As we have noted before, this did not mark a change in TTPs, but simply a persistent topic of interest that they could use as a social engineering lure. The pandemic will continue to affect our lives for some time to come; and threat actors will continue to exploit this to gain a foothold in target systems. During the last six months, there have been reports of APT groups targeting COVID-19 research centers. The UK National Cyber Security Centre (NCSC) stated that APT29 (aka the Dukes and Cozy Bear) targeted COVID-19 vaccine development. This will remain a target of strategic interest to them for as long as the pandemic lasts.
Cyberthreats to financial organizations in 2021
30.11.20 Cyber Securelist
It is hard to believe that a year has gone since our last article on financial attacks and our predictions for 2020. It has been a tough one, but first things first. Let us review the forecasts we made at the end of 2019 and see how accurate we were. Then we will go through the key events of 2020 relating to financial attacks. Finally, we need to make a forecast of financial attacks in 2021. So let us begin.
Analysis of forecasts for 2020
Attacks against Libra and TON/Gram: There is no short answer here; it is complicated. After all, Libra is yet to be released, therefore the prospects of attacks are still uncertain, and there is no room for cyberattacks either. The Gram project has simply been canceled.
Reselling bank access: Yes. Unfortunately, this is true. There is a whole market with plenty of offers to provide remote access to various banks around the globe. Usually, attackers exploit one or more vulnerabilities and then resell access to financially motivated threat actors including targeted ransomware operators.
Ransomware attacks against banks: Yes. That is another sad reality these days. Various targeted ransomware groups have attacked banks all around the world, for example, in Costa Rica, Chile and Seychelles. These three cases have been covered by the media. The Maze group is responsible for the attack in Costa Rica, while REvil (Sodinokibi) is behind the attack in Chile. Victims who pay up do not show up on the list of breached organizations. Nobody can be certain how many more banks have been hit by targeted ransomware attacks.
The return of custom tooling: Yes. As we predicted last year, some cybercriminals would invest in new trojans and exploits as a part of their custom tooling operations. That situation has become particularly pathetic with various vulnerabilities and exploitations of commercial VPN providers, and their appliances running on customer infrastructure. On a different note, we have also seen cybercriminals creating tiny tools for network reconnaissance and data harvesting.
Global expansion of mobile banking trojans: Yes, absolutely. Ginp, Ghimob, Anubis and Basbanke are just a few examples of the trend. By the way, Anubis source code has been leaked and published on the Internet. So, this is another cause of a global expansion of attacks against mobile banking systems.
Targeting investment apps: Yes, partially. The Ghimob family is a good example of that. If we consider cryptocurrency exchange apps as investment apps, then the answer is also a solid yes. However, the scale of these attacks has not been massive yet.
Magecarting 3.0: Yes. The expansion of Magecart has been impressive. You can find it everywhere. Today, it is also an umbrella for various groups that harvest payment cards. For example, the Lazarus threat actor is believed to have added digital payment-card skimming to its repertoire by using Magecart code.
Political instability leading to a spread of cybercrime: No, partially. The COVID-19 situation and lockdowns around the world prevented people from travelling freely. This is the key reason why this prediction did not materialize in full. However, global expansions took place via the Internet, taking advantage of poorly configured and exposed systems, for example, running on vulnerable or misconfigured RDP protocols and so on.
Key events of 2020
All sorts of financial cyberattacks linked to the impact of the COVID-19 crisis.
Companies became less secure due to hastily deployed remote work solutions. Some literally did not even have enough laptops to provide to their employees. They had to purchase whatever they found on the retail market, even if the machines did not comply with the security standards of the organization. At least, this kept the business running. However, those poorly configured machines had to connect to remote systems, something for which they were not prepared. Lack of employee training, default laptop configurations left unchanged and vulnerable remote access connections together made all sorts of attacks, including targeted ransomware, possible.
There is an increase in “red team” tools used once remote access to organizations has been established, for example, to dump passwords from the memory, to reconnoiter the victim’s network and to make lateral movements inside the network.
Expansion of Brazilian threat actors to the rest of the world.
The Brazilian cybercrime ecosystem used to be a regional player. This year, we have seen a few families expanding to other continents, targeting victims in Europe and elsewhere. We dubbed the first four families to do this (Guildma, Javali, Melcoz, Grandoreiro) “the Tétrade”. Others then followed: Amavaldo, Lampion and Bizarro. Speaking of mobile banking trojan threat actors, Ghimob is now targeting Latin America and Africa, while Basbanke is active in Portugal and Spain.
PoS and ATM malware.
The infamous Prilex has positioned itself as a MaaS bazar and recently implemented the replay attack. It is also moving to target PIN pad communications. In general, Prilex is positioning itself as a hacking group with a variety of skills in ATM malware, PoS malware, DDoS services, EMV software for cloning payment cards and other.
Some ATM malware families have evolved and now include RAT features. One of them is using dnscat2 to mask C2 communications and bypass traditional network detection mechanisms.
CESSO has become a type of MaaS and is now targeting Diebold, Wincor and NCR ATMs. It is designed to steal US dollars, euros, local Latin American currencies and others. The code suggests that the developer is a native speaker of Portuguese.
Targeted ransomware is the new normal and a part of financial organizations’ threat models.
Emboldened by success and excellent media coverage, threat actors behind targeted ransomware attacks have systematically increased the amounts they demand in exchange for not publishing stolen information. This point is important because it is not about data encryption any more, but about disclosing confidential information exfiltrated from the victim’s network. Due to payment card industry security and other regulations, leaks like this may result in significant financial losses.
Another key point regarding ransomware is that this year has seen it exploit the human factor as an initial infection vector. The story about an attempt to infect Tesla is a good example of this. When it comes to very high-profile targets, threat actors do not hesitate to spend time and resources to work within the MICE framework (Money, Ideology, Compromise and Ego) to get to victims’ networks.
Unfortunately, the ransomware story does not end there. The Lazarus group has tried its hand at the big game with the VHD ransomware family. This received attention, and other APT threat actors followed suit, MuddyWater among them.
Forecast for 2021
Before we proceed with our forecasts for 2021, it is important to state that most of the threats we have seen in 2020 will stay around for the next year. For example, targeted ransomware will remain relevant. Here is our list of new things to expect in the upcoming year, in no particular order:
The COVID-19 pandemic is likely to cause a massive wave of poverty, and that invariably translates into more people resorting to crime including cybercrime. We might see certain economies crashing and local currencies plummeting, which would make Bitcoin theft a lot more attractive. We should expect more fraud, targeting mostly BTC, due to this cryptocurrency being the most popular one.
MageCart attacks moving to the server side. We can see that the number of threat actors that rely on client-side attacks (JavaScript) is diminishing by the day. It is reasonable to believe that there will be a shift to the server side.
A re-integration and internalization of operations inside of the cybercrime ecosystem: the major players on the cybercrime market and those who made enough profit will rely on their own in-house development mostly, reducing outsourcing to boost their profits.
Advanced threat actors from countries placed under economic sanctions may rely more on ransomware imitating cybercriminals’ work. They may reuse already-available code or create their own campaigns from scratch.
With a great profit by ransomware groups, we should expect the use of 0-day exploits as well as N-days exploits in upcoming attacks. They will purchase both of these to expand even further the scale of attacks and boost their success, resulting in more profit.
Cracking down hard on the cybercrime world. In 2020, OFAC announced that they would supervise any payment to ransomware groups. Then US Cyber Command took down Trickbot temporarily ahead of the elections. There should be an expansion of the “persistent engagement” strategy to financial crime. There is also a possibility of economic sanctions against institutions, territories or even countries which show lack of resolve to combat cybercrime that originates on their territory.
With the special technical capabilities of monitoring, deanonymization and seizing of BTC accounts now in place, we should expect cybercriminals to switch to transit cryptocurrencies for charging victims. There is a reason to believe they might switch to other privacy-enhanced currencies, such as Monero, to use these first as a transition currency and then convert the funds to any other cryptocurrency of choice including BTC.
Extortion on the rise. One way or another, cybercriminals targeting financial assets will rely on extortion. If not ransomware, then DDoS or possibly both. This could be especially critical to companies that lose data, go through an exhausting data recovery process and then get knocked out of online operations.
Those are only a few of the things to expect in 2021. It is exciting to watch these times we live in. Who could have predicted one year ago that we would have to live through a pandemic for most of the year! We shall see when we get there.