Cyber 2024 2023 2022 2021 2020 CYBERCRIME 2022 2021 2020
Researchers Expose Inner Workings of Billion-Dollar Wizard Spider Cybercrime Gang
19.5.22 CyberCrime Thehackernews
The inner workings of a cybercriminal group known as the Wizard Spider have been exposed, shedding light on its organizational structure and motivations.
"Most of Wizard Spider's efforts go into hacking European and U.S. businesses, with a special cracking tool used by some of their attackers to breach high-value targets," Swiss cybersecurity company PRODAFT said in a new report shared with The Hacker News. "Some of the money they get is put back into the project to develop new tools and talent."
Wizard Spider, also known as Gold Blackburn, is believed to operate out of Russia and refers to a financially motivated threat actor that's been linked to the TrickBot botnet, a modular malware that was officially discontinued earlier this year in favor of improved malware such as BazarBackdoor.
That's not all. The TrickBot operators have also extensively cooperated with Conti, another Russia-linked cybercrime group notorious for offering ransomware-as-a-service packages to its affiliates.
Gold Ulrick (aka Grim Spider), as the group responsible for the distribution of the Conti (previously Ryuk) ransomware is called, has historically leveraged initial access provided by TrickBot to deploy the ransomware against targeted networks.
"Gold Ulrick is comprised of some or all of the same operators as Gold Blackburn, the threat group responsible for the distribution of malware such as TrickBot, BazarLoader and Beur Loader," cybersecurity firm Secureworks notes in a profile of the cybercriminal syndicate.
Stating that the group is "capable of monetizing multiple aspects of its operations," PRODAFT emphasized the adversary's ability to expand its criminal enterprise, which it said is made possible by the gang's "extraordinary profitability."
Typical attack chains involving the group commence with spam campaigns that distribute malware such as Qakbot (aka QBot) and SystemBC, using them as launchpads to drop additional tools, including Cobalt Strike for lateral movement, before executing the locker software.
In addition to leveraging a wealth of utilities for credential theft and reconnaissance, Wizard Spider is known to use an exploitation toolkit that takes advantage of known security vulnerabilities such as Log4Shell to gain an initial foothold into victim networks.
Also put to use is a cracking station that hosts cracked hashes associated with domain credentials, Kerberos tickets, and KeePass files, among others.
What's more, the group has invested in a custom VoIP setup wherein hired telephone operators cold-call non-responsive victims in a bid to put additional pressure and compel them into paying up after a ransomware attack.
This is not the first time the group has resorted to such a tactic. Last year, Microsoft detailed a BazarLoader campaign dubbed BazaCall that employed phony call centers to lure unsuspecting victims into installing ransomware on their systems.
"The group has huge numbers of compromised devices at its command and employs a highly distributed professional workflow to maintain security and a high operational tempo," the researchers said.
"It is responsible for an enormous quantity of spam on hundreds of millions of millions of devices, as well as concentrated data breaches and ransomware attacks on high-value targets."
Experts Detail 3 Hacking Teams Working Under the Umbrella of TA410 Group
29.4.22 CyberCrime Thehackernews
A cyberespionage threat actor known for targeting a variety of critical infrastructure sectors in Africa, the Middle East, and the U.S. has been observed using an upgraded version of a remote access trojan with information stealing capabilities.
Calling TA410 an umbrella group comprised of three teams dubbed FlowingFrog, LookingFrog, and JollyFrog, Slovak cybersecurity firm ESET assessed that "these subgroups operate somewhat independently, but that they may share intelligence requirements, an access team that runs their spear-phishing campaigns, and also the team that deploys network infrastructure."
TA410 — said to share behavioral and tooling overlaps with APT10 (aka Stone Panda or TA429) — has a history of targeting U.S.-based organizations in the utilities sector as well as diplomatic entities in the Middle East and Africa.
Other identified victims of the hacker collective include a manufacturing company in Japan, a mining business in India, and a charity in Israel, in addition to unnamed victims in the education and military verticals.
TA410 was first documented by Proofpoint in August 2019 when the threat actor unleashed phishing campaigns containing macro-laden documents to compromise utility providers across the U.S. with a modular malware called LookBack.
Nearly a year later, the group returned with a new backdoor codenamed FlowCloud, also delivered to U.S. utilities providers, that Proofpoint described as malware that gives attackers complete control over infected systems.
"Its remote access trojan (RAT) functionality includes the ability to access installed applications, the keyboard, mouse, screen, files, services, and processes with the ability to exfiltrate information via command-and-control," the company noted in June 2020.
Industrial cybersecurity firm Dragos, which tracks the activity group under the moniker TALONITE, pointed out the adversary's penchant for blending techniques and tactics in order to ensure a successful intrusion.
"TALONITE focuses on subverting and taking advantage of trust with phishing lures focusing on engineering-specific themes and concepts, malware that abuses otherwise legitimate binaries or modifies such binaries to include additional functionality, and a combination of owned and compromised network infrastructure," Dragos said in April 2021.
ESET's investigation into the hacking crew's modus operandi and toolset has shed light on a new version of FlowCloud, which comes with the ability to record audio using a computer's microphone, monitor clipboard events, and control attached camera devices to take pictures.
Specifically, the audio recording function is designed to be automatically triggered when sound levels near the compromised computer cross a 65-decibel threshold.
TA410 is also known to take advantage of both spear-phishing and vulnerable internet-facing applications such as Microsoft Exchange, SharePoint, and SQL Servers to gain initial access.
"This indicates to us that their victims are targeted specifically, with the attackers choosing which entry method has the best chance of infiltrating the target," ESET malware researcher Alexandre Côté Cyr said.
Each team within the TA410 umbrella is said to use different toolsets. While JollyFrog relies on off-the-shelf malware such as QuasarRAT and Korplug (aka PlugX), LookingFrog uses X4, a barebones implant with remote control features, and LookBack.
FlowingFrog, in contrast, employs a downloader called Tendyron that's delivered by means of the Royal Road RTF weaponizer, using it to download FlowCloud as well as a second backdoor, which is based on Gh0stRAT (aka Farfli).
"TA410 is a cyberespionage umbrella targeting high-profile entities such as governments and universities worldwide," ESET said. "Even though the JollyFrog team uses generic tools, FlowingFrog and LookingFrog have access to complex implants such as FlowCloud and LookBack."
FBI, Europol Seize RaidForums Hacker Forum and Arrest Admin
13.4.22 CyberCrime Thehackernews
An international law enforcement operation raided and took down RaidForums, one of the world's largest hacking forums notorious for selling access to hacked personal information belonging to users.
Dubbed Tourniquet, the seizure of the cybercrime website involved authorities from the U.S., U.K., Sweden, Portugal, and Romania, with the criminal investigation resulting in the arrest of the forum's administrator at his home last month in Croydon, England.
The three confiscated domains associated with the illicit marketplace include "raidforums[.]com," "Rf[.]ws," and "Raid[.]lol."
Diogo Santos Coelho (aka "Omnipotent"), the said founder and chief administrator, was apprehended in the U.K. on January 31 and is pending extradition to the U.S. Santos Coelho has been charged with conspiracy, access device fraud, and aggravated identity theft.
In addition to detailing Santos Coelho's central role in designing and administering the software and computer infrastructure, the U.S. Justice Department (DoJ) accused the 21-year-old Portuguese national of operating a fee-based middleman service to facilitate the transactions on the platform.
"Notably, to create confidence amongst transacting parties, the Official Middleman service enabled purchasers and sellers to verify the means of payment and contraband files being sold prior to executing the transaction," the DoJ said.
Europol, which called it a "culmination of a year of meticulous planning," said RaidForums had more than 500,000 users since its launch in January 2015, with the storefront offering for sale databases of pilfered data comprising more than 10 billion unique records of individuals in the U.S. and abroad.
These databases, which served as a repository of personal data, contained credit card details, bank account numbers and routing information, social security numbers, and the usernames and associated passwords needed to access online accounts.
"This marketplace had made a name for itself by selling access to high-profile database leaks belonging to a number of U.S. corporations across different industries," the agency said. "These datasets were obtained from data breaches and other exploits carried out in recent years."
Interestingly, the "Raid" in RaidForums is a nod to its early beginnings as a hub for organizing various forms of electronic harassment — like "raiding," which refers to a form of targeted harassment by posting an overwhelming volume of messages to a victim.
The dismantling of RaidForums is said to have occurred on February 25, 2022, when the online marketplace became mysteriously offline nearly two weeks after it was plagued by database errors and outages between February 7 and 12, implying that law enforcement officials had access to the infrastructure for several weeks.
"Prior to the alleged seizure, Omnipotent purportedly went on a vacation between January 31 and February 7, the day of the recent outage, according to his Telegram bio," cybersecurity company Flashpoint noted at the time.
"After the site was back up on February 12, Omnipotent did not comment on the outage. Furthermore, the site's owner was not apparently active on the site up until the alleged seizure on February 25."
Besides functioning as an online venue for illegal activity, RaidForums relied on different subscription tiers (i.e., free, VIP, MVP, and God) to profit from the sales of confidential and sensitive information. Another monetization technique entailed the use of credits for members to unlock privileged access to the compromised databases.
What's more, RaidForums enabled cybercriminals to earn credits in other ways, such as through posting instructions on how to commit illegitimate acts, the DoJ added.
The demise of RaidForums comes amid a series of ongoing steps taken by law enforcement to crack down on cybercrime over the past year. Last week, German and U.S. authorities shuttered Hydra, a Russia-based longest-running dark web marketplace that has been connected to $5 billion in transactions since 2015.
"Disruption has always been a key technique in operating against threat actors online, so targeting forums that host huge amounts of stolen data keeps criminals on their toes," Edvardas Šileris, head of Europol's European Cybercrime Centre, said in a statement.
Hackers Distributing Fake Shopping Apps to Steal Banking Data of Malaysian Users
6.4.22 CyberCrime Thehackernews
Threat actors have been distributing malicious applications under the guise of seemingly harmless shopping apps to target customers of eight Malaysian banks since at least November 2021.
The attacks involved setting up fraudulent but legitimate-looking websites to trick users into downloading the apps, Slovak cybersecurity firm ESET said in a report shared with The Hacker News.
The copycat websites impersonated cleaning services such as Maid4u, Grabmaid, Maria's Cleaning, Maid4u, YourMaid, Maideasy and MaidACall and a pet store named PetsMore, all of which are aimed at users in Malaysia.
"The threat actors use these fake e-shop applications to phish for banking credentials," ESET said. "The apps also forward all SMS messages received by the victim to the malware operators in case they contain 2FA codes sent by the bank."
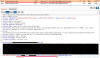
The targeted banks include Maybank, Affin Bank, Public Bank Berhad, CIMB bank, BSN, RHB, Bank Islam Malaysia, and Hong Leong Bank.
The websites, distributed through Facebook ads, urge visitors to download what the attackers claim to be are Android apps available on the Google Play Store, but in reality, redirect them to rogue servers under their control.
It's worth noting here that the attack hinges on the prerequisite that the potential victims enable the non-default "Install unknown apps" option on their devices for it to succeed. What's more, five of the abused services don't even have an app on Google Play.
Once launched, the apps prompt the users to sign in to their accounts, allowing them to place fake orders, following which options are presented to complete the checkout process by including a fund transfer from their bank accounts.
"After picking the direct transfer option, victims are presented [with] a fake FPX payment page and asked to choose their bank out of the eight Malaysian banks provided, and then enter their credentials," ESET malware researcher Lukáš Štefanko said.
The ultimate goal of the campaign is to steal the banking credentials entered by the users and exfiltrate it to the attacker-controlled server, while displaying an error message that the entered user ID or password is invalid.
In addition, the fake apps are engineered to access and transmit all SMS messages received by the users to the remote server in the event the bank accounts are secured by two-factor authentication.
"While the campaign targets Malaysia exclusively for now, it might expand to other countries and banks later on," Štefanko said. "At this time, the attackers are after banking credentials, but they may also enable the theft of credit card information in the future."
Block Admits Data Breach Involving Cash App Data Accessed by Former Employee
6.4.22 CyberCrime Thehackernews
Block, the company formerly known as Square, has disclosed a data breach that involved a former employee downloading unspecified reports pertaining to its Cash App Investing that contained information about its U.S. customers.
"While this employee had regular access to these reports as part of their past job responsibilities, in this instance these reports were accessed without permission after their employment ended," the firm revealed in a April 4 filing with the U.S. Securities and Exchange Commission (SEC).
Block advertises Cash App as "the easiest way to send money, spend money, save money, and buy cryptocurrency."
The breach is said to have occurred last year on December 10, 2021, with the downloaded reports including customers' full names as well as their brokerage account numbers, and in some cases, brokerage portfolio value, brokerage portfolio holdings, and stock trading activity for one trading day.
The San Francisco-based company emphasized in the filing that the reports did not feature personally identifiable information such as usernames or passwords, Social Security numbers, dates of birth, payment card information, addresses, and bank account details.
It's exactly unknown how many users were impacted by the breach, but Block — which said it discovered the incident only recently — said it's contacting roughly about 8.2 million current and former customers as part of its response efforts.
That said, there's not much clarity as to when the breach was discovered and how a former employee with the company still managed to access several records containing customer information.
While a formal investigation is underway, the financial platform also said it has notified law enforcement and that it "continues to review and strengthen administrative and technical safeguards to protect the information of its customers."
"The company does not currently believe the incident will have a material impact on its business, operations, or financial results," Block added.
Interpol Busted 11 Members of Nigerian BEC Cybercrime Gang
21.1.2022 CyberCrime Thehackernews
A coordinated law enforcement operation has resulted in the arrest of 11 members allegedly belonging to a Nigerian cybercrime gang notorious for perpetrating business email compromise (BEC) attacks targeting more than 50,000 victims in recent years.
The disruption of the BEC network is the result of a ten-day investigation dubbed Operation Falcon II undertaken by the Interpol along with participation from the Nigeria Police Force's Cybercrime Police Unit in December 2021.
Cybersecurity firms Group-IB and Palo Alto Networks' Unit 42, both of which shared information on the threat actors and their infrastructure, said six of the 11 suspects are believed to be a part of a prolific group of Nigerian cyber actors known as SilverTerrier (aka TMT).
BEC attacks, which began to gain dominance in 2013, are sophisticated scams that target legitimate business email accounts through social engineering schemes to infiltrate corporate networks and subsequently leverage their access to initiate or redirect the transfer of business funds to attacker-controlled bank accounts for personal gain.
"One of the arrested suspects was in possession of more than 800,000 potential victim domain credentials on his laptop," Interpol said in a statement. "Another suspect had been monitoring conversations between 16 companies and their clients and diverting funds to 'SilverTerrier' whenever company transactions were about to be made."
SilverTerrier has been linked to 540 distinct clusters of activity to date, with the collective increasingly adopting remote access trojans and malware packaged as Microsoft Office documents to mount their attacks. Unit 42, in a report published in October 2021, said it identified over 170,700 samples of malware directly attributed to Nigerian BEC actors since 2014.
The latest arrests constitute the second edition of Operation Falcon, the first of which resulted in the apprehension of three alleged members of the SilverTerrier gang in November 2020 for compromising at least 500,000 government and private sector companies in more than 150 countries since 2017.
"BEC remains the most common and most costly threat facing our customers," Unit 42 researchers said. "Over half a decade, global losses have ballooned from $360 million in 2016 to a staggering $1.8 billion in 2020."
To mitigate such financial attacks, it's recommended for organizations to review network security policies, periodically audit mail server configurations, employee mail settings, and conduct employee training to ensure that wire transfer requests are validated using "verified and established points of contact for suppliers, vendors and partners."
Europol Shuts Down VPNLab, Cybercriminals' Favourite VPN Service
19.1.2022 CyberCrime Thehackernews
VPNLab.net, a VPN provider that was used by malicious actors to deploy ransomware and facilitate other cybercrimes, was taken offline following a coordinated law enforcement operation.
Europol said it took action against the misuse of the VPN service by grounding 15 of its servers on January 17 and rendering it inoperable as part of a disruptive action that took place across Germany, the Netherlands, Canada, the Czech Republic, France, Hungary, Latvia, Ukraine, the U.S., and the U.K.
A second outcome of the seizure is that at least 100 businesses that have been identified as at risk of impending cyber attacks are being notified. Europol didn't disclose the names of the companies.
Established in 2008, the tool provided an advanced level of anonymity by offering double VPN connections to its clients — wherein the internet traffic is routed through two VPN servers located in different countries instead of one — for as cheap as $60 a year.
"This made VPNLab.net a popular choice for cybercriminals, who could use its services to carry on committing their crimes without fear of detection by authorities," Europol detailed in a press release, adding it "provided a platform for the anonymous commission of high value cybercrime cases, and was involved in several major international cyberattacks."
VPNLab.net is said to have caught the attention of law enforcement officials when its infrastructure began to be widely used to disseminate malware, with the investigators uncovering evidence of the illicit service being advertised on the dark web.
In a separate announcement, Ukraine's Cyber Police said the VPN service was used in more than 150 ransomware infections, causing the victims to shell out a total of €60 million in ransom payments.
The dismantling of VPNLab.net is the latest action taken by authorities to close in on VPN providers with proven links to criminal groups. In December 2020, bulletproof VPN service Safe-Inet was shut down and this was followed by the takedown of DoubleVPN in June 2021.
"The actions carried out under this investigation make clear that criminals are running out of ways to hide their tracks online," Edvardas Šileris, head of Europol's European Cybercrime Centre (EC3), said. "Each investigation we undertake informs the next, and the information gained on potential victims means we may have pre-empted several serious cyberattacks and data breaches."
Dark Web's Largest Marketplace for Stolen Credit Cards is Shutting Down
19.1.2022 CyberCrime Thehackernews
UniCC, the biggest dark web marketplace for stolen credit and debit cards, has announced that it's shuttering its operations after earning $358 million in purchases since 2013 using cryptocurrencies such as Bitcoin, Litecoin, Ether, and Dash.
"Don't build any conspiracy theories about us leaving," the anonymous operators of UniCC said in a farewell posted on dark web carding forums, according to blockchain analytics firm Elliptic. "It is [a] weighted decision, we are not young and our health do[es] not allow [us] to work like this any longer."
The UniCC team also gave its users 10 days to spend their balances, while also warning customers to "not follow any fakes tied to our comeback."
Platforms such as UniCC function as an underground marketplace wherein credit card details stolen from online retailers, banks, and payments companies by injecting malicious skimmers are trafficked in exchange for cryptocurrency. The cards are then used by criminal actors to purchase high-value items or gift cards.
"This process is known as 'carding,' and it has become a key part of the cybercriminal's playbook," Elliptic researchers said. "The technique is very profitable in its own right, but it is also used to help launder and cash-out cryptocurrency obtained through other types of cybercrime."
The sunsetting comes exactly a year after Joker's Stash, the previous market leader, announced its retirement in January 2021 after having facilitated the sale of nearly $400 million in stolen cards. The demise of Joker's Stash worked to UniCC's benefit, which quickly snapped up the top spot with a 30% market share, the researchers noted.

It's also the latest in a growing list of criminal marketplaces to have voluntarily closed shop over the past year, including that of White House Market, Cannazon, and Torrez. This was followed by Monopoly Market, which became inaccessible early this month in what's suspected to be an exit scam.
That said, the illicit market for stolen credit card data has become so lucrative that sales have surpassed 1.4 billion just in Bitcoin, paving the way for new entrants to the space that tend to swiftly fill the vacuum left by defunct criminal entities in a manner that mirrors the ever-evolving ransomware landscape.
The most notable of the lot has been All World Cards, which emerged on the scene in May 2021 and has since drummed up attention by leaking data for one million credit cards plundered between 2018 and 2019 on a cybercrime forum for free, with most cards from the State Bank of India, Banco Santander, and Sutton Bank.
"The wave of recent departures has potentially been a trigger for UniCC's retirement, as illicit actors see an opportunity in the turbulence to either run away with users' funds or retire to avoid increased law enforcement attention," the researchers said.
Russia Arrests REvil Ransomware Gang Responsible for High-Profile Cyber Attacks
19.1.2022 CyberCrime Thehackernews
In an unprecedented move, Russia's Federal Security Service (FSB), the country's principal security agency, on Friday disclosed that it arrested several members belonging to the notorious REvil ransomware gang and neutralized its operations.
The surprise takedown, which it said was carried out at the request of the U.S. authorities, saw the law enforcement agency conduct raids at 25 addresses in the cities of Moscow, St. Petersburg, Moscow, Leningrad and Lipetsk regions that belonged to 14 suspected members of the organized cybercrime syndicate.
"In order to implement the criminal plan, these persons developed malicious software, organized the theft of funds from the bank accounts of foreign citizens and their cashing, including through the purchase of expensive goods on the Internet," the FSB said in a statement.
In addition, the FSB seized over 426 million rubles, including in cryptocurrency, $600,000, €500,000, as well as computer equipment, crypto wallets used to commit crimes, and 20 luxury cars that were purchased with money obtained by illicit means.
One of the most active ransomware crews last year, REvil took responsibility for high-profile attacks against JBS and Kaseya, among a string of several others. The U.S. government told Reuters that one of the arrested individuals was also behind the ransomware attack on Colonial Pipeline in May 2021, once again confirming REvil's connections to a second collective called DarkSide.

The group formally closed shop in October 2021 after the U.S. intervened to take its network of dark web servers offline. The next month, law enforcement authorities announced the arrest of seven individuals for their roles as affiliates of the REvil ransomware family, even as the U.S. charged a 22-year-old Ukrainian citizen linked to the ransomware gang for orchestrating the Kaseya ransomware attack.
All those detained have been charged with "illegal circulation of means of payment," a criminal offense punishable by up to six years in prison. The suspects weren't named, but Reuters noted that a Moscow court identified two of the men as Roman Muromsky and Andrei Bessonov.
The crackdown also comes as threat actors likely affiliated with Russian secret services crippled much of the Ukrainian government's public-facing digital infrastructure, in addition to defacing some of them with messages that alleged people's personal data had been made public and that the information stored in the servers was being destroyed.
It remains to be what impact the arrests will have on the larger ransomware ecosystem, which has by and large continued to flourish despite a number of law enforcement actions, partly driven by Russia's willingness to look the other way when it comes to harboring cybercriminals in the country, effectively allowing the bad actors to operate with impunity.
"While we are still looking to understand the true impact of these arrests, we applaud the Russian government for the actions it took today with regard to the REvil criminal ransomware group," Matt Olney, director of threat intelligence and interdiction at Cisco Talos, told The Hacker News. "It's important that criminal cyber actors and organizations not be allowed to operate with impunity. And so any result that leads to degrading of their capabilities is undoubtedly a good thing."
U.K. Hacker Jailed for Spying on Children and Downloading Indecent Images
19.1.2022 CyberCrime Thehackernews
A man from the U.K. city of Nottingham has been sentenced to more than two years in prison for illegally breaking into the phones and computers of a number of victims, including women and children, to spy on them and amass a collection of indecent images.
Robert Davies, 32, is said to have purchased an arsenal of cyber crime tools in 2019, including crypters and remote administration tools (RATs), which can be used as a backdoor to steal personal information and conduct surveillance through microphones and cameras, catching the attention of the U.K. National Crime Agency (NCA).
The cyber voyeur's modus operandi involved catfishing potential targets by using fake profiles on different messaging apps such as Skype, leveraging the online encounters to send rogue links hosting the malware through the chats.
"Davies was infecting his victims' phones or computers with malicious software by disguising it with the crypters so their antivirus protection would not detect it," the NCA said in a statement. "He then used the RATs to gain remote access to their devices and steal any sexual images (mainly of females) they had stored on there."
At least in one instance, Davies spied on a teenage girl via a hacked webcam. Officials said a total of 27 compromising images and videos of children were found on his computer, with over 30 victims identified over the course of the investigation.
Furthermore, Davies has been determined as a customer of a now-defunct marketplace called WeLeakInfo, which pawned access to data gathered from other websites until its disruption in January 2020. Later that year, the NCA arrested 21 individuals across the country for using the stolen personal credentials to commit further cyber and fraud offences.
Davies, who was arrested thrice between November 2019 and August 2021, now faces a jailterm of 26 months on charges of computer misuse, voyeurism, owning indecent images of children (IIOC), and for making IIOC and possessing extreme pornographic images. He has also been placed on the sex offenders' register and given a 10-year restraining order on five of the victims along with a 10-year sexual harm prevention order.
"Davies had amassed what can only be described as a cyber criminal's toolkit," Andrew Shorrock of the NCA's National Cyber Crime Unit said. "Not only was he using these tools to break in to peoples' devices, he was using them to spy on his unsuspecting victims and to steal naked images of them for his own sexual gratification."
Husband-Wife Arrested in Ukraine for Ransomware Attacks on Foreign Companies
19.1.2022 CyberCrime Thehackernews
Ukrainian police authorities have nabbed five members of a gang that's believed to have helped orchestrate attacks against more than 50 companies across Europe and the U.S and caused losses to the tune of more than $1 million.
The special operation, which was carried out in assistance with law enforcement officials from the U.K. and U.S., saw the arrest of an unnamed 36-year-old individual from the capital city of Kyiv, along with his wife and three other accomplices.
A total of nine searches across the suspects' homes were carried out, resulting in the seizure of computer equipment, mobile phones, bank cards, flash drives, three cars, and other items with evidence of illegal activity.
The Cyber Police of the National Police of Ukraine said the group offered a "hacker service" that enabled financially motivated crime syndicates to send phishing emails containing file-encrypted malware to lock confidential data pertaining to its victims, demanding that the targets pay cryptocurrency ransoms in return for restoring access to the files.
However, it's not immediately clear what ransomware strain the perpetrators used to encrypt data on victim computers.
Besides ransomware attacks on foreign companies, the hacking cartel also provided IP-address spoofing services to transnational cybercrime actors, who unlawfully used the platform to break into systems belonging to government and commercial entities to collect sensitive information and carry out DDoS attacks to paralyze the networks.
"To launder criminal proceeds, the offenders conducted complex financial transactions using a number of online services, including those banned in Ukraine," the Security Service of Ukraine (SSU) said. "At the last stage of converting assets into cash, they transferred funds to payment cards of an extensive network of fictitious persons."

The development is the latest in a string of law enforcement actions undertaken by Ukraine over the past year to tackle the menace of ransomware that's crippled organizations and critical infrastructure alike.
Last month, authorities apprehended 51 people in connection with illegally possessing about 100 databases containing personal information of more than 300 million citizens of Ukraine, Europe, and the U.S.
Prior to that, the National Police of Ukraine was also involved in the arrest of ransomware affiliates associated with Egregor, Cl0p, LockerGoga, MegaCortex, and Dharma families as well as individuals who were found operating a DDoS botnet and a phishing service called U-Admin.
Then in October 2021, the SSU partnered with the U.S. intelligence agencies to detain several members of a money laundering operation that engaged with various hacking groups who carried out cyber theft activities and wanted to convert the stolen virtual funds into cash.
A month later, the cyber department also dismantled a five-member hacking group dubbed Phoenix that specialized in remote hacking of mobile devices for over two years with the goal of stealing personal data, which was then sold to other third-parties for an average cost of $200 per account.