

Cyber 2024 2023 2022 2021 2020 CYBERCRIME 2022 2021 2020
Researchers Detail Modus Operandi of ShinyHunters Cyber Crime Group
23.8.21 CyberCrime Thehackernews
ShinyHunters, a notorious cybercriminal underground group that's been on a data breach spree since last year, has been observed searching companies' GitHub repository source code for vulnerabilities that can be abused to stage larger scale attacks, an analysis of the hackers' modus operandi has revealed.
"Primarily operating on Raid Forums, the collective's moniker and motivation can partly be derived from their avatar on social media and other forums: a shiny Umbreon Pokémon," Intel 471 researchers said in a report shared with The Hacker News. "As Pokémon players hunt and collect "shiny" characters in the game, ShinyHunters collects and resells user data."
The revelation comes as the average cost of a data breach rose from $3.86 million to $4.24 million, making it the highest average cost in 17 years, with compromised credentials responsible for 20% of the breaches reported by over 500 organizations.
Since rising to prominence in April 2020, ShinyHunters has claimed responsibility for a string of data breaches, including Tokopedia, Wattpad, Pixlr, Bonobos, BigBasket, Mathway, Unacademy, MeetMindful, and Microsoft's GitHub account, among others.
An assessment by Risk Based Security found that the threat actor has exposed a total of more than 1.12 million unique email addresses belonging to S&P 100 organizations, education, government and military entities as of late 2020.
Last week, the group began selling a database purportedly containing the personal information of 70 million AT&T customers for a starting price of $200,000, although the U.S. telecom provider has denied suffering a breach of its systems.
ShinyHunters has a checkered history of compromising websites and developer repositories to steal credentials or API keys to a company's cloud services, which are subsequently abused to gain access to databases and gather sensitive information to be resold for profit or published for free on hacker forums.
The adversary has also been observed targeting DevOps personnel or GitHub repositories in order to steal valid OAuth tokens, leveraging them to breach cloud infrastructure and bypass any two-factor authentication mechanisms.
"ShinyHunters may not have as much notoriety as the ransomware groups that are currently causing havoc for enterprises all over the world. However, tracking actors like this are crucial to preventing your enterprise from being hit with such an attack," the researchers said.
"The information ShinyHunters gathers is often turned around and sold on the same underground marketplaces where ransomware actors use it to launch their own attacks. If enterprises can move to detect activity like ShinyHunters, they in turn can stop ransomware attacks before they are ever launched."
The surge of fake COVID-19 test results, vaccines and vaccination certificates on the Dark Web
26.3.2021 CyberCrime Securityaffairs
Threat actors are offering fake COVID-19 test results and vaccination certificates in blackmarkets and hacking forums on the Dark Web.
While vaccination campaigns go ahead with different speeds in many countries multiple threat actors on the Dark Web started offering fake COVID-19 test results and vaccination certificates.
Multiple research teams, including mine, are monitoring these specific criminal activities in the principal cybercrime communities.
Users are searching for these types of documents to travel among countries with restrictions in places or to simply get a new job. With such high demand, criminal organizations are offering a broad range of products.
Researchers from CheckPoint recently discovered the availability of Fake ‘vaccine passport’ certificates on sale for $250, while fake negative COVID-19 test results go for just $25.
The researchers warn that Darknet advertisements for COVID-19 vaccines surged in the past three months by over 300%.
We already alerted the authorities of a worrisome increase in the offer of vaccines for sale. AstraZeneca, Sputnik, SINOPHARM and Johnson & Johnson could be acquired in the dark web for a price ranging between $500 and $1000 per dose.
“As we previously reported, a range of counterfeit coronavirus vaccines are offered, often touted from just $500 per dose. In recent weeks our researchers have spotted an increasing amount of advertisements for vaccines within Darknet markets: currently numbering over 1,200, with sellers based in the U.S. and European countries including Spain, Germany, France and Russia.” reported CheckPoint. “This represents over a 300% increase since January 2021. The vaccines advertised include Oxford – AstraZeneca (at $500), Johnson & Johnson ($600), the Russian Sputnik vaccine ($600) and the Chinese SINOPHARM vaccine (at $750).”
Curiously, I can confirm that the prices was depending also on the news shared by media related to the alleged side-effects of some vaccines, shortly after the suspension of Astra Zeneca vaccine in some countries, its prices dropped in some hacking communities. Its prices dropped from $800 down to $400, while at the same time, with the approval by the USFDA of JOHNSON & JOHNSON single-dose vaccine, its price raised $600-$800.
Below a couple of images shared by CheckPoint researchers.
How much cost a fake vaccination certificate?
Multiple threat actors are offering fake vaccination certificates, some of them claim that the documents were issued by legitimate helthcare institutions. CheckPoint researchers have found a fake certificate from Russia that is offered at $135 while a seller from UK was offering a vaccination card for $150.
Researchers from threat intelligence firm Cyble also observed multiple sellers on cybercrime forums advertising COVID-19 vaccination certificates with deliveries available for specified Russian cities. A certificate for Russian citizens goes for 6000 Ruble, or approx. 79 USD.
Experts also reported the availability of COVID-19 tests on sale, in many cases, the sellers were offering a special discount for those clients that will buy more than 2 documents.
“In addition to the Darknet and hacking forums, we’ve also spotted different websites that offer the ability to quickly create of authentic-looking negative COVID test documents, created promptly according to data input by users, in a very friendly user interface, for just $25.” continues CheckPoint. “Results are produces within 30 minutes and are sent discreetly to users’ email inbox.”
Below a list of tips shared by the experts to avoid buying fake documents:
People should watch for authenticity indicators on documents such as misspellings, errors, low quality logos, and errors in terminology (e.g. ‘corona disease’ or ‘the covid epidemic’)
Every country should internally manage a central repository of tests and vaccinated people, which can securely shared between relevant authorized bodies within the country.
All data of tests and vaccination population should be digitally signed with encrypted keys
Airports, border keepers and any official enforcement agent should have the ability to scan a QR or bar code (which is digitally signed – without this digital signature the code is highly exploitable!) on the certificate. The code should link to a secured repository that can validate the authenticity of the paper and whether the name on it did got the vaccine or was actually tested for COVID and got a (negative) result
Going forward, countries should be able to share the digitally signed data to enable certificate holders to safety roam and cross borders. For example, Greece and Israel have already agreed to recognize each other’s vaccination certificates (also known as ‘green passports’).
Reading the FBI IC3’s ‘2020 Internet Crime Report’
19.3.2021 CyberCrime Securityaffairs
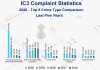
The FBI’s Internet Crime Complaint Center has released its annual report, the 2020 Internet Crime Report, which includes data from 791,790 complaints of suspected cybercrimes.
The FBI’s Internet Crime Complaint Center (IC3) has published its annual report, the 2020 Internet Crime Report, which provides information from 791,790 complaints of suspected cybercrimes affecting victims in the U.S..
Data that emerged from the report are worrisome, in 2020 the reported losses exceeded $4.2 billion and authorities observed an increase of more than 300,000 complaints from 2019 (+69%).
According to the 2020 Internet Crime Report, the top three crimes reported by victims in 2020 were phishing scams, non-payment/non-delivery scams, and extortion. The novelty this year is represented by scams exploiting the COVID-19 pandemic.
“Victims lost the most money to business email compromise scams, romance and confidence schemes, and investment fraud. Notably, 2020 saw the emergence of scams exploiting the COVID-19 pandemic. The IC3 received over 28,500 complaints related to COVID-19, with fraudsters targeting both businesses and individuals.” states the post published by the FBI.
In 2020, the IC3 received 19,369 Business Email Compromise (BEC)/Email Account Compromise (EAC) complaints, these crimes caused $1.8 billion in losses.
“In 2020, the IC3 observed an increase in the number of BEC/EAC complaints related to the use of identity theft and funds being converted to cryptocurrency. In these variations, we saw an initial victim being scammed in non-BEC/EAC situations to include Extortion, Tech Support, Romance scams, etc., that involved a victim providing a form of ID to a bad actor. That identifying information was then used to establish a bank account to receive stolen BEC/EAC funds and then transferred to a cryptocurrency account.” reads 2020 Internet Crime Report.
IC3 continues to strengthen the collaboration with industry partners and other law enforcement agencies to reduce financial losses resulting from BEC scams. The IC3 Recovery Asset Team working with its partners has successfully freezed approximately $380 million of the $462 million in reported losses in 2020, a success rate of nearly 82%.
Reading the report, it is possible to note that the impact of ransomware incidents is exhaustively reported, likely because most of these attacks are not reported to law enforcement.
According to the report, losses caused by ransomware attacks increased by 225% from $8.9 million in 2019 to over $29.1 million last year.
Clearly, these figures don’t correctly represent the impact of this specific type of crime.
FBI: Cybercrime Victims Reported Losses of $4.2 Billion in 2020
19.3.2021 CyberCrime Securityweek
The FBI this week published its Internet Crime Report for 2020, and the agency said it received nearly 800,000 cybercrime complaints last year, with reported losses totaling $4.2 billion.
The number of complaints received by the FBI in 2020 increased significantly compared to the previous year, when it got roughly 467,000 complaints. The total reported losses for 2019 were approximately $3.5 billion. Since 2016, reported losses total $13.3 billion, the agency said.
The FBI said its Recovery Asset Team, which it established in 2018 to help victims recover their money from banks, had a success rate of 82% last year, managing to get banks to freeze $380 million.
In 2020, the law enforcement agency received 240,000 complaints related to phishing, vishing or smishing. Many complaints, more than 108,000, were related to non-payment or non-delivery schemes. Other types of crimes with many complaints include extortion (76,000), personal data breach (45,000), identity theft (43,000), and spoofing (28,000). The smallest number of complaints was related to hacktivists, with only 52 complaints.
In addition to the United States, many complaints came from victims in the UK, Canada, India, Greece, Australia, South Africa, France, Germany, Mexico and Belgium.
Unsurprisingly, the highest losses were reported as a result of business email compromise (BEC) and email account compromise (EAC) scams, totaling $1.8 billion, followed by confidence fraud and romance scams ($600 million), and investment scams ($336 million).
In the case of ransomware attacks, the FBI received 2,400 complaints, with reported losses of nearly $30 million, but the organization pointed out that this does not include estimates of lost business, wages, time, or remediation services purchased by the victim as a result of the attack.
There has been a significant increase in complaints related to phishing and non-payment/non-delivery schemes. In the case of non-payment scams, losses increased from $196 million to $265 million, but losses remained roughly the same in the case of phishing attacks. The losses reported as a result of tech support scams, however, nearly tripled from 2019 to 2020.
The complete 2020 Internet Crime Report is available in the website of the Internet Crime Complaint Center.
Magecart Attackers Save Stolen Credit-Card Data in .JPG File
17.3.2021 CyberCrime Threatpost
Researchers from Sucuri discovered the tactic, which creatively hides malicious activity until the info can be retrieved, during an investigation into a compromised Magento 2 e-commerce site.
Magecart attackers have found a new way to hide their nefarious online activity by saving data they’ve skimmed from credit cards online in a .JPG file on a website they’ve injected with malicious code.
Researchers at website security firm Sucuri discovered the elusive tactic recently during an investigation into a compromised website using the open-source e-commerce platform Magento 2, Luke Leal from Sucuri’s malware research team said in a report posted online last week.
“The creative use of the fake .JPG allows an attacker to conceal and store harvested credit card details for future use without gaining too much attention from the website owner,” he wrote.
Peering under the hood of the compromised site revealed a malicious injection that was capturing POST request data from site visitors, Leal explained. “Located on the checkout page, it was found to encode captured data before saving it to a .JPG file,” he wrote.
A POST request method asks a web server to accept data enclosed in the body of the request message, usually so it can be stored. It’s often used in Web transactions when someone has uploaded a file to a website or submitted a completed web form.
Specifically, Sucuri found that attackers injected PHP code into a file called ./vendor/magento/module-customer/Model/Session.php, then used the “getAuthenticates” function to load malicious code, Leal said. The code also created a .JPG file, which attackers used to store any data they captured from the compromised site, he said.
“This feature allows the attacker to easily access and download the stolen information at their convenience while concealing it within a seemingly benign JPG,” Leal wrote.
Indeed, threat actors aiming to steal data from online transactions are constantly trying to find new ways to evade detection by concealing their activity in creative ways.
Magecart attackers–different threat groups who all compromise e-commerce websites with card-skimming scripts on checkout pages to steal customer payment and personal data–are particularly adept at this activity. They often hide their skimming techniques in functionality that appears authentic as well as use the platforms they attack to cannibalize themselves to achieve their results.
A Magecart campaign discovered around Christmastime, for instance, concealed itself within convincing PayPal iframes in the PayPal checkout process of e-commerce sites to steal user credentials and credit-card info.
The latest campaign also leveraged the Magento code framework to do its dirty work of harvesting the data captured and hidden in the .JPG file, Leal explained. The malicious PHP code relied on the Magento function “getPostValue“ to capture the checkout page data within the “Customer_ POST parameter,” he said.
It also used the Magento function “isLoggedIn” to check whether a victim is logged into the site as a user and, if this was the case, attackers also lift the user’s email address from the transaction, he said.
“Nearly all of the information submitted by the victim on the checkout page is stored within the ‘Customer_ parameter,’ including full names and addresses, payment card details, telephone numbers, and user agent details,” he wrote.
Once attackers get their hand on customer payment data, they can then go on to use it for various criminal activities, such as credit-card fraud or targeted e-mail-based spam or phishing campaigns, Leal added.
While this latest Magecart anti-detection approach may make the infection difficult to initially spot, it would help website owners to identify new files in the environment or detect potentially malicious changes before they do damage if they implement website monitoring services or integrity control checks, Sucuri recommended.
Magecart hackers hide captured credit card data in JPG file
17.3.2021 CyberCrime Securityaffairs
Crooks devised a new method to hide credit card data siphoned from compromised e-stores, experts observed hackers hiding data in JPG files.
Cybercriminals have devised a new method to hide credit card data siphoned from compromised online stores, experts from Sucuri observed Magecart hackers hiding data in JPG files to avoid detection and storing them on the infected site.
The new exfiltration technique was uncovered while investigating a Magecart attack against an e-store running the e-commerce CMS Magento 2.
“A recent investigation for a compromised Magento 2 website revealed a malicious injection that was capturing POST request data from site visitors. Located on the checkout page, it was found to encode captured data before saving it to a .JPG file.” reads the post published by Sucuri.
The researchers discovered a PHP code that was found injected to the file ./vendor/magento/module-customer/Model/Session.php. The attackers use the getAuthenticates function to load the rest of the malicious code onto the compromised environment.
The code stored the siphoned data in the image file “pub/media/tmp/design/file/default_luma_logo.jpg,” in this way it is easy to hide, access, and download the stolen information without rising suspicious.
The PHP code injected into the site leverages the Magento function getPostValue to capture the POST data within the checkout page, then the captured POST data is encoded with base64 before the PHP operator ^ is used to XOR the stolen data.
“To successfully capture the POST data, the PHP code needs to use the Magento code framework. It relies on the Magento function getPostValue to capture the checkout page data within the Customer_ POST parameter.” continues the post.
“Using the Magento function isLoggedIn, the PHP code also checks whether the victim that sent the POST request data is logged in as a user. If they do happen to be logged in, it captures the user’s email address.”
Customer_ parameter contains almost all of the information submitted by the victim on the checkout page, including full names and addresses, payment card details, telephone numbers, and user agent details.
Sucuri experts pointed out that captured data could be used for credit card fraud, spam campaigns, or spear-phishing attacks.
“Bad actors are always actively searching for new methods to prevent any detection of their malicious behavior on compromised websites.” concludes the post. “The creative use of the fake .JPG allows an attacker to conceal and store harvested credit card details for future use without gaining too much attention from the website owner.”
Cybersecurity Bug-Hunting Sparks Enterprise Confidence
16.3.2021 CyberCrime Threatpost
A survey from Intel shows that most organizations prefer tech providers to have proactive security, but few meet security expectations.
Nearly three-quarters of IT security professionals (73 percent) surveyed say they prefer to buy technology and services from vendors who are proactive about security, including leveraging ethical hacking and having transparent communications about vulnerabilities. But less than half of vendors deliver.
The survey, conducted by Poneman Institute and commissioned by Intel, was intended to help get a better understanding of what drives security investment decision-making, according to the report. The Ponemon Institute surveyed 1,875 people across Africa, Europe, the Middle East, the U.K. and the U.S. who are involved in their organizations’ IT infrastructure and also familiar with purchasing processes for tech and services.
The survey shows a wide gap between what organization decision-makers expect in terms of security, and their vendors’ ability to meet those expectations. For instance, 66 percent of those surveyed said they prefer vendors to have the “ability to identify vulnerabilities in its own products and mitigate them.” Yet only 46 percent of those same respondents said their technology providers have that capability, the report said.
Thirty percent of those surveyed said they could patch a vulnerability in a week or less, but on average, it takes about six weeks to patch a bug from the time its first detected, with 63 percent saying delays are caused by “human error.”
But the rise in zero-day flaws, such as those recently found in software like Google Chrome or Microsoft Exchange, means these organizations could be left vulnerable to attack for weeks before a fix is put in place, depending on the vendor.
“Security doesn’t just happen,” Suzy Greenberg, vice president, Intel Product Assurance and Security said. “If you are not finding vulnerabilities, then you are not looking hard enough.”
Security Transparency
Transparency about security updates and vulnerabilities was also a big deal for enterprises, with 64 percent of respondents noting, “the ability to be transparent about security updates and mitigations that are available,” is “highly important.” Despite the need, only 48 percent of respondents say they’re getting this kind of communication, the report added.
“Organizations understand that security is critical and are looking for vendors that are transparent, mitigate vulnerabilities proactively and apply hacking practices to identify and address vulnerabilities in their own products,” Greenberg added.
Survey respondents also overwhelmingly agreed — 74 percent — that ethical hacking/bug-hunting to find vulnerabilities within products is “highly important,” the report said.
“Of all the capabilities represented in this research, the most important are the technology provider’s capability to apply ethical hacking practices in order to proactively identify and address vulnerabilities in its own products and to provide ongoing assurance and evidence that the components are operating in a known and trusted state,” the report said.
Other findings from the survey show that organizations are struggling to keep up with cybersecurity and are looking to vendors for help. At the same time budgets are tightening, with 45 percent of those surveyed saying their budgets were “less than adequate.”
These findings offer a snapshot inside evolving IT operations, where it is still not yet clear who owns the organization’s security risk. Twenty-one percent say it should be the CISO, 19 percent believe the CIO or CTRO should lead security efforts, and 17 percent think it’s the business-unit leaders who should take responsibility.
“The conclusion is that there is uncertainty in responsibility,” the report said.
This uncertainly could provide an opportunity for vendors who are willing to help struggling IT departments shoulder the cybersecurity burden.
“The key here is transparency,” Greenberg told Threatpost by email. “Organizations have an appetite for security assurance and evidence that components are operating in a known and trusted state. As an industry, we must not only assess risk, but ensure customers know when security updates are available to build trust. Our end goal is to take a transparent approach to security to protect customer workloads and improve software resilience, and we encourage our industry partners and competitors to follow suit.”
Cyberattacks See Fundamental Changes, A Year into COVID-19
16.3.2021 CyberCrime Threatpost
A year after COVID-19 was officially determined to be a pandemic, the methods and tactics used by cybercriminals have drastically changed.
COVID-19-related phishing emails, brute-force attacks on remote workers, and a focus on exploiting or abusing collaboration platforms are the hallmarks of cybercriminal enterprise as the coronavirus marks its first anniversary of going global.
A year after the COVID-19 crisis was officially determined to be a pandemic, the way people live and work has radically changed – and so have “the methods and tactics used by criminals on the internet looking to exploit the massive increase in online traffic,” according to a report from Kaspersky, issued on Monday.
Phishing Scams Exploit COVID-19 Themes
Email scamming (and phishing in particular) is still one of the most effective types of attacks in the coronavirus era, according to Kaspersky, since fear and anxiety are two of the most-exploited emotions for this kind of social-engineering attack.
Campaigns such as those purporting to offer N95 masks or hand sanitizer (which prompted people to put in their payment details) became endemic over the course of the year. Impersonating COVID-19 authorities was also a poplar gambit, with cybercriminals offering “important” updates. In reality, all they were offering was malware.
“In 2020, criminals launched a variety of scams that exploited the pandemic topic from just about every angle, from advertisements to masks when they were in short supply to special refunds from the government,” according to the report. “Scammers often imitated leading authority figures on the pandemic, like the CDC and the World Health Organization, to give their emails additional authority — and increase the chances that users would click a malicious link.”
Cybercriminals also used lures involving delayed shipments – taking advantage of the fact that ordering by mail skyrocketed during lockdowns. In 2020, delivery services entered the top ten most-spoofed organizations for these types of attacks, according to Kaspersky.
“They would send emails claiming that, due to COVID, an important delivery had been delayed and that the target must verify the new delivery information (a situation easy to believe in the middle of a pandemic) in order to receive it,” according to the report. “However, upon clicking the attachment, the users would download trojans ranging from spyware to backdoors.”
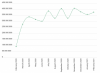
As millions of employees were sent home to work remotely in 2020, cybersecurity measures were an afterthought for many organizations. Cybercriminals, suspecting this, targeted employees logging in to corporate resources from personal devices and on unsecured home networks, according to the analysis.
Specifically, brute-force attacks (where attackers try random usernames and passwords against accounts) on Remote Desktop Protocol (RDP) connections ramped up globally, surging 197 percent from 93.1 million worldwide in February to 277.4 million in March. RDP is Microsoft’s proprietary protocol that enables users to access Windows workstations or servers.
“RDP is one of the most popular remote-access protocols used by companies, making it a favorite target for attackers,” according to the report. “In spring of 2020, the number of brute-force attacks against the RDP protocol skyrocketed across almost the entire planet.”
A year later, the number of attacks has not returned to pre-pandemic levels, Kaspersky noted: In February, there were 377.5 million brute-force attacks.
Cyberattacks on Collaboration Platforms Ramp Up
Cyberattackers have also gone after users of various cloud services, especially collaboration services like Flock, GotoMeeting, HighFive, Join.me, Lifesize, MS Teams, Slack, Webex and Zoom. Kaspersky found that by May of last year, the average daily number of attacks on these services seen in its telemetry had jumped 25 percent just since February 2020.
These too haven’t really abated.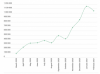
Collaboration attacks over the past year. Click to enlarge. Source: Kaspersky.
“The number of web attacks, after displaying a decline in the summer of 2020, reached a new peak in December as much of the world was facing a second wave of the pandemic,” according to Kaspersky. “A large portion of users’ time spent online was dedicated to meeting and collaborating virtually. That is why meeting and messenger apps, like Zoom and Teams, became a popular lure for distributing cyberthreats.”
Most of these attacks involve malicious files being spread under the guise of these apps’ names, Kaspersky found that in January, there were 1.15 million such files detected — the highest number since the lockdown began.
“These files are often bundled as part of seemingly legitimate application installers, which can be encountered in several ways: Through phishing emails claiming to have notifications or special offers from their platforms or through phishing web pages,” according to the report.
What’s Next for COVID-19 Cyberattacks?
With the pandemic heading into a new phase involving vaccinations, there’s also a new crop of topics for phishers and scammers to exploit, like health passports for travel or vaccine distribution, Kaspersky warned.
“Chances are they will exploit them,” according to the report. “It is important that users view any email or website referencing the pandemic with a skeptical eye. What is more, recent events have shown how willing criminals are to take advantage of crisis, and, while this pandemic will subside, it certainly will not be the last crisis.”
The report also noted that remote working will likely remain in place even post-pandemic.
“RDP is not going anywhere — and neither are attacks against the protocol,” the report concluded. “That means businesses need to reevaluate their usage of RDP and learn how to secure remote access. If there is has ever been a time for companies to reevaluate and bolster their security strategy, that time is now.”
Microsoft’s probe comes amidst news that ransomware gangs are starting to take aim at the Exchange Server vulnerabilities, adding a new sense of urgency to the need for organization to apply patches and disinfect backdoors from networks.
CEO of Encrypted Chat Platform Indicted for Aiding Organised Criminals
15.3.2021 CyberCrime Thehackernews
The U.S. Department of Justice (DoJ) on Friday announced an indictment against Jean-Francois Eap, the CEO of encrypted messaging company Sky Global, and an associate for wilfully participating in a criminal enterprise to help international drug traffickers avoid law enforcement.
Eap (also known as "888888") and Thomas Herdman, a former high-level distributor of Sky Global devices, have been charged with a conspiracy to violate the federal Racketeer Influenced and Corrupt Organizations Act (RICO), according to warrants issued for their arrests.
"The indictment alleges that Sky Global generated hundreds of millions of dollars providing a service that allowed criminal networks around the world to hide their international drug trafficking activity from law enforcement," Acting U.S. Attorney Randy Grossman said in the announcement. "This groundbreaking investigation should send a serious message to companies who think they can aid criminals in their unlawful activities."
Specifically, the indictment alleges that the company "knowingly and intentionally" sold its encrypted communications devices to criminal organizations involved in the transnational importation and distribution of narcotics, used digital currencies such as Bitcoin to conduct illegal transactions on the firm's website, and protect its customers' anonymity, and obstructed investigations of drug trafficking by "remotely delet[ing] evidence of such activities."
A Wave of Law Enforcement Action
The development comes on the heels of a coordinated exercise called "Operation Argus" and "Operation A-Limit," in which law enforcement agencies from Belgium, France, and the Netherlands announced major interventions against the messaging platform to disrupt the illegal use of encrypted communications by large-scale organized crime groups (OCGs).
By successfully breaking the encryption protections of Sky ECC in mid-February, authorities said they were able to decipher over half a billion messages and gain "invaluable insights into hundreds of millions of messages exchanged between criminals," culminating in a series of nearly 275 raids and the arrest of 91 suspects, besides seizing 17 tonnes of cocaine and €1.2 million.
The Belgian Federal Police and the Dutch National Police said the encrypted message traffic was read "live" for a period of about three weeks, forestalling "dozens of planned serious violent crimes, including kidnappings, liquidations and shootings."
"This has resulted in the collection of crucial information on over a hundred of planned large-scale criminal operations, preventing potential life threatening situations and possible victims," Europol noted.
Sky ECC is said to have surged in popularity following a similar takedown of Encrochat last July by French and Dutch investigators, with many criminal gangs shifting to the service to carry out criminal acts. Sky, like Encrochat's EncroPhone, is part of the encrypted phone industry, in which iPhone, Google Pixel, and Blackberry handsets are altered by incorporating tamper-resistant hardware and OS-level protections capable of resisting (lawful) attempts to gain access to their contents.
Sold for either a three or six months subscription at $185/month, the phones also integrate their own encrypted messaging applications with support for self-destructing chats, in addition to disabling features like camera outside of the app, microphone, calling, Bluetooth, NFC, biometrics, GPS sensors, and app store access that could potentially compromise security.
Worldwide, there are an estimated 170,000 Sky ECC custom-made phones in service, Europol said, adding around three million messages are being exchanged each day on a global scale. Sky ECC is operated from the U.S. and Canada while making use of computer servers based in Europe. Around a quarter of its active users are located in Belgium and the Netherlands.
Sky ECC Denies Involvement
Denying that it's a "platform of choice for criminals," Sky ECC contested its involvement in the operations and said that its platform remains secure and that none of the authorized devices had been hacked, instead pointing fingers at an impostor reseller (named "SKYECC.EU") that had no connection to the company.
"SKY ECC authorized distributors in Belgium and the Netherlands brought to our attention that a fake phishing application falsely branded as SKY ECC was illegally created, modified and side-loaded onto unsecure devices, and security features of authorized SKY ECC phones were eliminated in these bogus devices which were then sold through unauthorized channels," the company said.
The company has also claimed it had not been contacted by any investigative authority, nor it cooperated with the parties involved with the fake phishing application.
Responding to the DoJ's indictment, Eap said, "the unfounded allegations of involvement in criminal activity by me and our company are entirely false," adding, "In the coming days, my efforts will be focused on clearing my name of these allegations."
Sky Global's technology "was not created to prevent the police from monitoring criminal organizations; it exists to prevent anyone from monitoring and spying on the global community," he added.
News of Sky ECC's dismantlement also follows a similar crackdown on providers of encrypted communications, including Ennetcom and Phantom Secure, over the past five years.
Dark Web Markets for Stolen Data See Banner Sales
10.3.2021 CyberCrime Threatpost
Despite an explosion in the sheer amount of stolen data available on the Dark Web, the value of personal information is holding steady, according to the 2021 Dark Web price index from Privacy Affairs.
That leaves these thriving dirty data dealers in a familiar predicament — they need to lock down their growing businesses for added privacy and security.
“As predicted, there is much more volume being sold now compared to last year, with fake-ID and credit-card vendors reporting sales in the several thousands,” the report said. “Not only quantity, but the variety of items to purchase has grown as well, such as hacked crypto accounts and web services like Uber accounts.”
Brandon Hoffman with Netenrich explained to Threatpost that he expects these Dark Web marketplaces to continue to look more like their legit counterparts.
“The parallels between Dark Web markets and standard consumer markets continue to grow,” Hoffman said. “As can be seen in this report the market on the Dark Web is starting to follow standard economics. If there is a huge influx in inventory, the price goes down as long as demand remains somewhat steady. If there is a set of inventory with strong demand but the product is deemed to be of higher quality there is premium on that product.”
A private database of 122,000 U.S. dentists will run about $50 on the Dark Web, while credit card details for an account with a balance up to $5,000 costs about $240, according to the report, which scoured hundreds of vendors selling stolen data.
What is Stolen Data Worth?
While the going rate for some types of data, like PayPal credentials, have dropped because they have become so common, the value of cloned credit cards and personal information about the cardholder shot up, the report found.
An example of stolen data listings online. Click to enlarge. Source: Privacy Affairs.
“The price increase is most likely due to a combination of factors, like the increasing risks of attaining the information, the increasing benefit for buyers to use the information, the increased quality/accuracy of the card data, or just good ol’ inflation,” The report said.
Last year, the price of a cloned Mastercard with PIN was about $15, the report said. This year, it’s $25, with comparable rise in rates across cloned credit cards. Hacked cards from the U.S. with CVV data included are the cheapest, at around $17, because there’s a high supply. Israeli cards are the most valuable, fetching $65 each.
The rise in this area of the business has inspired vendors to adopt more traditional sales techniques, like an 80 percent guarantee on the stolen data, meaning only two out of every 10 cards will either fail or have less than the expected available balance, the report explained.
Hacked Crypto Accounts Bring Big Bucks
The rise of cryptocurrency has made hacked crypto accounts hugely valuable in these Dark Web marketplaces, the report said. “Due to the skyrocketing prices of Bitcoin and other cryptocurrencies, hacked accounts may hold large sums of coin-based currency and cash, protected by relaxed security measures after the initial verification process.”
The average price for a hacked Coinbase-verified account is $610, the Dark Web Price Index said.
Social-media credentials lost value over the past year, thanks in large part to the implementation of multi-factor authentication (MFA), forcing potential threat actors to use time-consuming social-engineering tactics instead, the report found.
Services like video streaming, Uber and even FedEx accounts are up for sale in these marketplaces too. You can score a hacked Uber driver account for $14 or a one-year Netflix account for $44.
Physical forged documents are by far the most valuable, followed by document scans and even counterfeit money, which is popular on these Dark Web marketplaces, some of which are sold with a guarantee to pass the UV pen test used at many retailers, the report said. The most valuable forged document according to the Dark Web Pricing index was a Maltese passport, which costs about $6,500.
Malware and DDoS Attacks
Researchers also looked at malware and distributed denial-of-service (DDoS) attacks for sale on the Dark Web.
“This increase in ransomware attacks are not only from criminal organizations; those with limited resources and technical abilities can also initiate less sophisticated ransomware attacks that can prove quite lucrative,” Kristina Balaam with Lookout explained to Threatpost by email. “Now, we have more individuals attempting to compromise users. They rely on the Dark Web to purchase the products that allow them to accomplish this.”
The added that demand, along with the rise in ransomware payments, is contributing to its price, Balaam added.
“With an increasing demand in malware products, malware authors can increase their unit prices and cybercriminals hoping to take advantage of our new online lifestyles are willing to pay,” Balaam said. “We’re seeing this reflected in the increasing malware prices in this report.”
Dark Web Marketplaces Need Security
With the volume and value of stolen data growing by leaps and bounds, it was only a matter of time before everyone else caught on, including the cops and other cybercriminals.
“In an effort to mitigate detection and tracking by law enforcement, the Dark Web is moving towards increased security on all ends,” according to the report. “The markets have abandoned Bitcoin (BTC) as it is not secure, and vendors are demanding buyers to use Monero as payment and communicate only through PGP encryption.” Pretty Good Privacy (PGP) is an encryption system dating to 1991 that’s used for both sending encrypted emails and encrypting sensitive files.
This year marks a real milestone in these marketplaces coming of age, Austin Merritt, an analyst with Digital Shadows, told Threatpost.
“This past year has been an incredibly unique time for Dark Web marketplaces, since overall supply and demand have increased with novel cybercriminal opportunities made possible by the chaos of COVID-19,” Merritt said. “Outside of market conditions, law-enforcement seizures of marketplaces, forum closures and increased competition among sellers have also added to the unpredictable nature of the landscape.”
End users are likewise encouraged to harden their security stance against cybercriminals with smart security like anti-malware tools, password hygiene and being aware of skimmers. But Privacy Affairs stressed that understanding the value of the personal data people use every day might help them think twice about their everyday practices.
“Since most of us do not spend our time shopping in these marketplaces, the most important takeaway from this research is an insight into how valuable personal data can be,” Merritt said. “It also serves as a reminder for individuals to adopt multi-factor authentication when available, monitor account activity, and critically evaluate inbound emails, texts and phone calls from suspicious sources.”
Cybercriminals Finding Ways to Bypass '3D Secure' Fraud Prevention System
6.3.2021 CyberCrime Securityweek
Security researchers with threat intelligence firm Gemini Advisory say they have observed dark web activities related to bypassing 3D Secure (3DS), which is designed to improve the security of online credit and debit card transactions.
Designed as an additional protection layer for these transactions, 3DS has seen several releases, with the most recent of them, namely version 2.0, also designed to accommodate smartphones, allowing for authentication using a fingerprint or facial recognition.
In addition to various social engineering tactics that attackers can use to circumvent 3DS, phishing and scam pages allow them to trick victims into revealing their card details and payment verification information.
Gemini’s security researchers say that vulnerabilities in earlier versions of 3DS could have been exploited to bypass security. The use of a password for the transaction was one of these issues, as this was sometimes a personal identification number (PIN) that cybercriminals were able to acquire using various means.
Using various social engineering techniques, such as impersonating bank representatives, cybercriminals can harvest a lot of information from victims, including name, ID number, phone number, physical and email address, mother’s maiden name, driver’s license numbers, and the like. Armed with some personally identifiable information (PII), the attacker could trick the victim into sharing additional details.
One method recommended by some cybercriminals for bypassing 3DS involves calling up the victim from a phone number that spoofs the number on the back of the payment card, and tricking them into verifying a transaction currently being made by the fraudster by claiming it is needed for identity verification purposes.
The use of phishing sites that mimic legitimate online shops can also allow hackers to harvest the victims’ card information and trick them into authorizing a payment via 3DS. In some cases, the attackers may use malware to target users’ smartphones and retrieve 3DS verification codes.
Cyber-criminals can also abuse the fact that some online shops disable the 3DS feature for smaller purchases. Thus, after testing the limit, the hackers make purchases that are under those amounts.
The use of PayPal also allows attackers to bypass 3DS. For that, they add stolen payment card information to a PayPal account, and then make purchases using the PayPal payment method. This scheme works best with credit cards, as PayPal does not always require user confirmation by issuing validation codes (which would also require access to the bank account).
The next step in the evolution of securing online card transactions, Gemini says, is Strong Customer Authentication (SCA), which secures customer-initiated payments and which can be fulfilled with 3DS 2. Transactions under certain amounts may be exempted from verification.
“The older versions of 3DS, such as version 1.0 (which is still widely used around the world), are susceptible to hackers who find ways to bypass their security features. […] Gemini Advisory assesses with moderate confidence that cybercriminals will likely continue to rely on social engineering and phishing to bypass 3DS security measures,” Gemini concludes.
Cybercriminals Target Industrial Organizations in Information Theft Campaign
6.3.2021 CyberCrime Securityweek
A mysterious cybercrime group apparently driven by profit has been targeting industrial organizations in Europe, Asia and North America as part of an information theft campaign.
The campaign was detailed in September 2020 by cybersecurity firm Zscaler, which warned at the time that the hackers had been targeting oil and gas supply chain industries in the Middle East using the trojan known as AZORult.
These attacks are ongoing, according to DeNexus, a California-based provider of cyber risk modeling for industrial networks, which on Thursday published a report detailing this campaign, its evolution, and additional victims.
DeNexus reported seeing targets and victims in various countries, and noted that in addition to AZORult, the attackers have been spotted using information-stealing malware such as AgentTesla, Formbook, Masslogger and Matiex.
The malware is delivered using spear phishing emails that purport to come from legitimate companies, including from within the victim organization itself and other companies that the victim might do business with. In more recent attacks, the cybercriminals have put more effort into these emails, including by registering domains with names similar to the one of the targeted firm.
While the hackers appear to be mainly interested in oil and gas supply chain industries in the Middle East, they have also been seen targeting other types of organizations in other regions.
DeNexus said the list of targeted European companies includes a commercial refrigerator supplier, a provider of heavy electrotechnical equipment, a manufacturer of optical components, and a smart automation solutions provider. In the APAC region, the threat group targeted an industrial process and factory automation firm, a construction materials manufacturer, and a transportation services company. In the Middle East, they also targeted international maritime organizations and in North America a US-based manufacturer of anti-slip covers.
The list of organizations whose employees did install the threat actor’s malware includes an aerospace company in India, and development company in South Korea, a services provider for the oil and gas industry in the UAE, a logistics and transportation company in the UAE, the national oil and gas company of Sri Lanka, an oil and gas company in China, and a petrochemical and textile firm in China.
Vladimir Dashchenko, VP of threat intelligence at DeNexus, told SecurityWeek that since Zscaler published its report on this operation, the threat actor has taken steps to increase chances of avoiding detection (e.g. hosting malware on cloud services), and it has started using the compromised companies’ email accounts as command and control (C&C) servers.
The researcher said that this appears to be a profit-driven group rather than a state-sponsored threat actor. It’s also worth mentioning that it has not been seen targeting industrial devices, protocols or processes. While they are currently focusing on stealing information, once they have gained initial access to an organization’s IT network, they could at any time try to move to operational technology (OT) networks as well, Dashchenko said.
The threat actor is likely still active — DeNexus last observed activity on February 9, but says it continues to monitor the campaign.
Antivirus company Bitdefender also published a report last year to describe attacks on oil and gas organizations, and those attacks also involved the AgentTesla malware, but DeNexus does not believe they are related.
Cyberattackers Target Top Russian Cybercrime Forums
5.3.2021 CyberCrime Threatpost
Elite Russian forums for cybercriminals have been hacked in a string of breaches, leaving hackers edgy and worried about law enforcement.
Maza, a place online for fraudsters and extorters to connect to pull off their operations, has been breached by an unknown attacker, in just the latest in a series of attacks targeting elite Russian-language cybercrime forums. Members are worried that their data is being used by researchers and law enforcement to track down their true identities, a new report from Flashpoint said.
These forums are where threat actors can go to access ransomware-as-a-service tools, launder stolen money and even get advice on how to improve their crimes, Flashpoint vice president Thomas Hofmann explained to Threatpost.
“Maza is a place where one can connect to trustworthy threat actors, who have been active in the Russian-language underground anywhere between 10 to 20 years,” Hoffman said. “Ultimately, the forum serves the role of a board where one can establish initial contact with respected and trustworthy service providers.”
Membership to Maza is by invitation only and comes with a fee, he added.
Another Russian-language cybercrime forum called Verified was abruptly resurrected after sitting dormant for some time with unknown administrators and new domains, Flashpoint said. By Feb. 18t, the new forum’s new leadership started deanonymizing Verified’s former operators, raising suspicions among its user base.
Another forum, Exploit, reportedly suffered a compromise this week, and a member of the forum warned other users to “be careful with registered emails across multiple forums,” Flashpoint reported.
Cybercrime Enforcement Goldmine
Pieced together, the exfiltrated data from these cybercrime forums could provide investigators with valuable information on the true identities of some of the world’s most prolific cybercriminals.
So, Hoffman agreed there is reason for the cybercriminal members of Maza to be concerned.
“With contact details exposed, Maza users are vulnerable to being investigated on their illicit activity,” Hoffman said. “Their information, which is normally anonymous, has been leaked and could be subject to further investigation.”
Maza: A Third Dark Web Breach
Flashpoint said Maza dates back to 2003. This latest breach included attackers making off with user IDs, names, passwords, emails and more. The forum was also targeted by a previous 2011 attack.
Not much is known about the identities of the attackers, except that the Russian-language message which popped up in the Maza forum appeared to be a translation from an online translator, Flashpoint said. However, it’s not clear whether that was accidental or what Flashpoint called a “misdirection technique.”
“While the compromised data appears to be extensive, it’s worth noting that the passwords have been hashed and most other data fields included in the dump have been hashed or further obfuscated,” Flashpoint’s report added.
Hashed passwords aside, some hacker members have dismissed the leak as being too old to be a threat, while others are actively trying to figure out next steps in the wake of these breaches, Flashpoint said.
“Only intelligence services or people who know where the servers are located can pull off things like that,” one Exploit member commented, according to a report from Brian Krebs. “Three forums in one month is just weird. I don’t think those were regular hackers. Someone is purposefully ruining forums.”
New 'LazyScripter' Hacking Group Targets Airlines
25.2.2021 CyberCrime Securityweek
A recently identified threat actor that remained unnoticed for roughly two years appears focused on the targeting of airlines that are using the BSPLink financial settlement software made by the International Air Transport Association (IATA), cybersecurity firm Malwarebytes reported on Wednesday.
Initially identified in December 2020, the threat actor is targeting IATA and airlines, with the most recent attacks employing a phishing lure mimicking the newly introduced IATA ONE ID (Contactless Passenger Processing tool).
Dated 2018, one of the earliest attacks attributed to the adversary, which Malwarebytes refers to as LazyScripter, was aimed at individuals looking to immigrate to Canada. Over time, the group evolved its toolset from PowerShell Empire to the Koadic and Octopus RATs, and used LuminosityLink, RMS, Quasar, njRat and Remcos RATs in between.
The phishing emails used in these attacks used the same loader to drop both Koadic and Octopus. Referred to as KOCTOPUS, it was preceded by Empoder, a loader for PowerShell Empire.
IATA- or job-related themes were typically used as lures, but additional lures were also observed: IATA security, IATA ONE ID, user support kits for IATA users, BSPlink Updater or Upgrade, Tourism (UNWTO), COVID-19, Canada skill worker program, Canada Visa, and Microsoft Updates.
The phishing emails carry either archive or document files containing a variant of a loader. The malicious tools were mainly hosted using two GitHub accounts, both deleted on January 12 and 14, 2021, respectively, with a new account being created on February 2.
The latest campaign launched by the threat actor was spotted on February 5, with a variant of KOCTOPUS being delivered, masquerading as BSPLink Upgrade.exe. In addition to Octopus and Koadic, the loader also delivered a variant of Quasar RAT.
Malwarebytes’ researchers have identified 14 malicious documents that the threat actor has used since 2018, all carrying embedded objects that are variants of the KOCTOPUS or Empoder loaders.
To date, the researchers have identified four different versions of the KOCTOPUS loader, used to load Octopus, Koadic, LuminosityLink, RMS, and Quadar RATs.
The Koadic RAT is known to have been previously used by the Iran-linked Muddy Water and Russia-linked APT28 threat actors. Malwarebytes was able to identify some similarities between the activities of LazyScripter and Muddy Water, but also a series of differences that resulted in the tracking of this group separately.
FIN11 cybercrime group is behind recent wave of attacks on FTA servers
24.2.2021 CyberCrime Securityaffairs
FireEye experts linked a series of attacks targeting Accellion File Transfer Appliance (FTA) servers to the cybercrime group UNC2546, aka FIN11.
Security experts from FireEye linked a series of cyber attacks against organizations running Accellion File Transfer Appliance (FTA) servers to the cybercrime group UNC2546, aka FIN11.
“Starting in mid-December 2020, malicious actors that Mandiant tracks as UNC2546 exploited multiple zero-day vulnerabilities in Accellion’s legacy File Transfer Appliance (FTA) to install a newly discovered web shell named DEWMODE.” reported FireEye. “The motivation of UNC2546 was not immediately apparent, but starting in late January 2021, several organizations that had been impacted by UNC2546 in the prior month began receiving extortion emails from actors threatening to publish stolen data on the “CL0P^_- LEAKS” .onion website. Some of the published victim data appears to have been stolen using the DEWMODE web shell.”
The wave of attacks began in mid-December 2020, threat actors exploited multiple zero-day vulnerabilities in the Accellion File Transfer Appliance (FTA) software to deploy a shell dubbed DEWMODE on the target networks.
The attackers exfiltrate sensitive data from the target systems and then published it on the CLOP ransomware gang’s leak site.
It has been estimated that the group has targeted approximately 100 companies across the world between December and January.
“Accellion does not access the information that its customers transmit via FTA. Following the attack, however, Accellion has worked at many customers’ request to review their FTA logs to help understand whether and to what extent the customer might have been affected. As a result, Accellion has identified two distinct groups of affected FTA customers based on initial forensics. Out of approximately 300 total FTA clients, fewer than 100 were victims of the attack. Within this group, fewer than 25 appear to have suffered significant data theft. Within this group, fewer than 25 appear to have suffered significant data theft.” reads the press release published by Accellion.
“These exploits apply exclusively to Accellion FTA clients: neither kiteworks nor Accellion the company were subject to these attacks.”
Once compromised the victims’ network, FIN11 hackers demanded the payment of a ransom in Bitcoin to avoid the leak of information on the leak site.
fin11 ransom note
The researchers are tracking two separate clusters of activities. The first cluster tracked as UNC2546 is related to the exploitation of the zero-day flaws in Accellion FTA software and data exfiltration from targeted organizations running the legacy FTA products. The second cluster, tracked as UNC2582, is related to the subsequent extortion activity.
“We have identified overlaps between UNC2582, UNC2546, and prior FIN11 operations, and we will continue to evaluate the relationships between these clusters of activity.” continues FireEye.
FireEye pointed out that despite FIN11 hackers are publishing data from Accellion FTA customers on the Clop ransomware leak site, they did not encrypt systems on the compromised networks.
In response to the wave of attacks, the vendor has released multiple security patches to address the vulnerabilities exploited by the hackers. The company is also going to retire legacy FTA server software by April 30, 2021.
Accellion is urging customers to update to the Kiteworks product, which replaces FTA server.
Enterprises Warned of Growing Risk Posed by Initial Access Brokers
24.2.2021 CyberCrime Securityweek
The services provided by a class of cybercriminals known as initial access brokers are increasingly sought-after and the risk posed to enterprises is growing, according to digital risk protection company Digital Shadows.
Initial access brokers breach as many organizations as they can, but instead of using that access to steal data or cause disruption themselves, they sell access to other threat actors, including ransomware operators and nation-state groups.
Digital Shadows has been monitoring initial access brokers for years, but the company says the coronavirus pandemic that hit the world in 2020 boosted their popularity. On many major cybercrime forums, these types of services are now more prominently displayed compared to previous years.
These cybercriminals often gain access to an organization’s network through RDP and VPN connections, which in many cases doesn’t even require advanced skills. The cybersecurity firm pointed out that some of these threat actors might not even have the knowledge needed to conduct further activities, which is why they’re trying to make a profit by selling the access to others.
Digital Shadows has analyzed hundreds of offers and determined that the average price for access is $7,100. The price is typically set based on the breached organization’s size, revenue, and the type of access sold. For example, access to organizations in the technology, healthcare and pharmaceutical, e-commerce, and engineering and construction sectors were all priced above $10,000, on average.
The most common targets were found to be retail, financial services and technology companies, and organizations in the United States were the most targeted.
“The dramatic increase in remote working coupled with ransomware's commercial success has been a perfect storm of opportunity for initial access brokers,” said Rick Holland, CISO at Digital Shadows.
He explained, “These actors are cashing in because of the flourishing demand and their specialization. They concentrate on one aspect of the cybercriminal ecosystem, gaining access to your network, and they do it very well. They then pass the baton on to other criminals and move on to their next target. Due to their ability to successfully compromise organizations of all sizes, initial access brokers' prominence has increased within the cybercriminal underground.”
The report published by Digital Shadows also provides some recommendations on what organizations can do to reduce risks.
Cybercriminal Enterprise ‘Ringleaders’ Stole $55M Via COVID-19 Fraud, Romance Scams
20.2.2021 CyberCrime Threatpost
The Department of Justice (DoJ) cracked down on a Ghana-based cybercriminal enterprise behind a slew of romance scams, COVID-19 fraud attacks and business email compromise schemes since 2013.
U.S. law enforcement arrested six “ringleaders” of a Ghana-based cybercriminal enterprise, who had allegedly launched a slew of money-stealing scams dating back to 2013 that included romance scams, business email compromise attacks and fraud. Seized in the arrests were a slew of luxury vehicles including two 2019 Rolls Royce Cullinans, a 2020 Bentley Continental GT and a 2020 Mercedes-Benz G63 AMG.
Authorities estimate the alleged group of criminals made over $55 million during its crime spree robbing mostly elderly online daters, small businesses and more.
“The fraud schemes alleged that these defendants facilitated were lucrative, diverse, and most of all, callous,” said Manhattan U.S. Attorney Audrey Strauss in a Wednesday statement. “As alleged, they engaged in email spoofing, duping elderly online daters into wiring them money, and applying for government-funded Coronavirus relief funds earmarked for the benefit of small businesses affected by the pandemic.”
While the six arrested were allegedly involved with the criminal enterprise based in Ghana, they were located across the U.S. and targeted individuals and businesses in the U.S.
Scams Relating to Romance, COVID-19 Relief
The six allegedly carried out various types of fraud over the past seven years. This includes business email compromise (BEC), where they allegedly duped businesses into wiring funds into attacker-owned accounts. This was done by impersonating employees of a victim’s company, or third-party companies that partnered or did business with the victim’s company.
The six also allegedly carried out romance scams targeting older men and women who lived alone.
They allegedly sent messages via email, text messaging, or online dating websites and tricked vulnerable victims into believing they were in a romantic relationship with a fake identity. Then, after gaining a victim’s trust, they would allegedly convince them to wire money to attacker-controlled bank accounts.
For instance, in one incident a 64-year-old victim was tricked into believing that he was in a relationship with a Ghanaian model. The victim subsequently wired $39,000 to an attacker-controlled account – believing that the purported “model” needed it to leave Ghana and to receive an inheritance.
Finally the six allegedly launched fraud schemes related to the COVID-19 pandemic. They did so by submitting fraudulent loan applications through the U.S. Small Business Administration’s (SBA) Economic Injury Disaster Loan (EIDL) Program, which is designed to provide relief to small businesses during the pandemic — and collecting the money.
“The Enterprise submitted fraudulent EIDL applications in the names of actual companies to the SBA and when an EIDL loan was approved, the funds were ultimately deposited in bank accounts controlled by members of the Enterprise, including certain of the defendants,” according to the Department of Justice (DoJ) on Wednesday.
Cybercriminal Activity: Moving the Illegal Money
The six defendants, charged in connection with their roles in the fraud and money laundering conspiracy, are Fred Asante, 35, Lord Aning, 28, (both arrested in Virginia on Wednesday), Celvin Freeman, 47, and Faisal Ali, 34, (both arrested in New Jersey on Wednesday). The four were presented in court on Wednesday. Also part of the group are Farous Appiedu, 35, (previously arrested in Queens, New York in October) and Sadick Edusei Kissi, 24 (previously arrested in Fargo, North Dakota on February 2020).
The six allegedly received fraudulent proceeds from various victims in dozens of business bank accounts that they owned and controlled. These business bank accounts – totaling at least 45 – were opened in the names of companies that the six allegedly pretending to be involved with – including companies relating to automobile sales, food imports and exports, and freight trucking and shipping. From 2013 to 2020, the bank accounts had deposits totaling over $55 million.
After the stolen money entered these bank accounts, the six allegedly withdrew and transported those fraudulent proceeds to other members of the cybercriminal enterprise, abroad.
“This trade-based money laundering scheme was designed to obscure the origin of the fraud proceeds as well as the identity of the ultimate beneficiaries of these schemes,” according to the DoJ.
A “vast majority” of the deposits consisted of large wire transfers or check deposits from various individuals and entities. This also included payments for vehicles, food products, and other goods sold by the defendants that were purchased using fraud proceeds, according to the DoJ.
COVID-19 Fraud and Romance Scams Continue
Email based attacks – such as romance scams or business email compromise – and fraud scams continue to plague enterprises and individuals.
Below, Ronnie Tokazowski, senior threat researcher with Agari, talks to Threatpost about why these types of scams continue to work.
At the same time, cybercriminals are following the money – and there is certainly money to be made in launching these types of attacks.
In fact, last year, romance schemes accounted for a record $304 million raked into cybercriminals, according to new data – up about 50 percent from 2019.
At the same time, in September researchers found that the average wire-transfer loss from BEC attacks is significantly on the rise: In the second quarter of 2020 the average was $80,183, up from $54,000 in the first quarter.
As seen in this recent law enforcement crackdown, the increase in scams around current events – particularly around the pandemic – have continued to also earn cybercriminals money. Beyond Covid-19 relief funds, attackers have also tweaked their lures to cash in on vaccine rollouts and personal protective equipment (PPE) needs.
Cases of identity theft in the U.S. also doubled in 2020, mainly due to cybercriminals taking advantage of people affected economically by COVID-19 who filed to receive government benefits.
Stolen Jones Day Law Firm Files Posted on Dark Web
18.2.2021 CyberCrime Threatpost
Jones Day, which represented Trump, said the breach is part of the Accellion attack from December.
The Clop ransomware group has reportedly started posting data on the Dark Web apparently stolen from law firm Jones Day, which represents many of the globe’s most powerful people, including former president Donald Trump in his efforts to overturn the 2020 election.
But the attack had nothing to do with politics, a person claiming to be from the hacker group told Vice. Asked about the motivation, they responded, “And what do you think? 😉 financial of course.”
The site DataBreached.net was first to report on the incident and published screenshots of stolen Jones Day files that the Clop group posted on the Dark Web as proof it has the goods. The group told DataBreaches.net it didn’t encrypt the files, just stole copies of information. The Clop crew also said Jones Day hasn’t responded to its requests.
“Hi, they ignore us so they will be published,” DataBreaches.net reported that the group responded.
A purported Clop ransomware hacker told the Wall Street Journal that Jones Day was notified on Feb. 3 that the data had been stolen and, as of Tuesday, Clop had not heard from the firm or discussed any ransom payment.
Jones Day hasn’t responded to Threatpost’s request for comment.
Accellion FTA Breach
The ransomware group claims it stole the information directly from Jones Day servers, but the firm denied that to the Wall Street Journal, instead pointing to a widespread compromise of the FTA file-sharing service from Accellion that emerged last December as the point of attack.
The Journal added that the law firm Goodwin Procter LLP was also compromised as a result of the Accellion breach. Several other multi-national companies which use the Accellion file transfer service have also been compromised, including Tier 1 telecom carrier Singtel and Australian telecom company Optus.
Accellion reported that it became aware of a zero-day vulnerability in its 20-year-old system on Dec. 23, but once the company came under attack, a cascade of bugs ensued. But by February, company said the system was fully patched.
“Accellion is conducting a full assessment of the FTA data security incident with an industry-leading cybersecurity forensics firm,” a statement from the company said in response to Threatpost’s inquiry about the Jones Day breach. “We will share more information once this assessment is complete. For their protection, we do not comment on specific customers. We are working with all impacted FTA clients to understand and mitigate any impact of this incident, and to migrate them to our modern kiteworks content firewall platform as soon as possible.”
The Wall Street Journal reported that it reviewed Clop’s stolen Jones Day files, which included, “Accellion configuration files and logs with references to Jones Day email and web addresses,” in addition to unrelated files ripped off from a California hospital in 2016.
The Vulnerable Software Supply Chain
But, Lamar Bailey, senior director of security research at Tripwire, told Threatpost that it’s possible the hackers have found another vulnerability.
“If Jones Day releases the results of the investigation that is still ongoing, that should point to the cause,” Bailey said. “It is possible that the attacker is current, and Jones Day has not found the root cause yet but that remains to be proven.”
Nonetheless, Bailey added, this should serve as a warning for organizations to start taking a harder look at their software supply chains.
“The old saying a chain is only as strong as its weakest link also holds true for today’s extensive supply chains,” Bailey said. If one of the products used by an organization is exploited, it opens up the organization to breaches as well.”
Bailey recommends using proactive threat intelligence services to detect and mitigate threats quickly.
“When an alert is received quickly, assess if the vulnerable versions of the hardware or software are in use and take remediation actions,” Bailey explained. “If a supplier was breached, assess what access the supplier had in the network and what data was accessible and then take actions to lock it down until remediations are in place.”
More Accellion Breach Victims Likely
Niamh Muldon, global data protection officer at OneLogic ,said this probably won’t be the last of the fallout from the Accellion breach.
“We are likely to see more breach disclosures originating from the Accellion file-sharing data breach over the forthcoming months,” Muldon said.
It’s critical, Muldon explained, for companies who fall victim to the compromise to engage in transparent communications with partners and clients about potential risks.
“Business leaders can take appropriate action now to help maintain the trust with their customers, partners and employees,” Muldon added. “They can achieve this by carrying out due-diligence with their organization to understand if Accellion data file sharing tool is in use and/or was in use in the past. Being transparent with customers, partners and employees about this tool usage and potential exposure allows for appropriate actions to be taken.”
Cybercriminals Leak Files Allegedly Stolen From Law Firm Jones Day
18.2.2021 CyberCrime Securityweek
A group of cybercriminals known for ransomware attacks has started leaking files allegedly stolen from Jones Day, a major U.S.-based law firm that has represented former president Donald Trump, including in his attempts to overturn the results of the recent election.
The cybercriminals behind the ransomware operation known as Clop (Cl0p) have been known to encrypt files on compromised systems, as well as stealing files from the victim and threatening to leak them unless a ransom is paid.
The group has a website on the Tor anonymity network where it leaks files from organizations that refuse to pay up. The hackers recently posted on their website download links to tens of gigabytes of files allegedly stolen from Jones Day. The leaked files are emails and legal documents, including ones that appear to be confidential. While some of the leaked data seems to be older, some of it is dated January 2021.
In a statement to The Wall Street Journal, Jones Day representatives confirmed suffering a breach, but said the hackers did not actually penetrate its network and instead targeted a file sharing service provided by file sharing and collaboration solutions provider Accellion.
The hackers told Vice that they stole data from Jones Day, but did “not encrypt their network.” The cybercriminals told DataBreaches.net that they hacked one of the company’s servers associated with the Accellion service and “took the data from there,” but also suggested that they targeted other systems as well.
An increasing number of organizations have come forward to confirm that they suffered data breaches due to a vulnerability discovered in mid-December in FTA, a large file transfer service offered by Accellion.
Accellion is retiring the FTA service, but roughly 50 customers had still been using it when the vulnerability was discovered, and at least some of those customers have been targeted by malicious actors. The list includes the Office of the Washington State Auditor (SAO), the Australian Securities and Investments Commission (ASIC), the Reserve Bank of New Zealand, and Singapore telecoms firm Singtel.
It’s worth noting that some emails and other files allegedly obtained from Singtel are also available on the Clop leak website.
The Clop ransomware operation is believed to be the work of a financially-motivated group known as TA505 and Hive0065. The threat actor, whose members are said to be Russian speakers, has been around for several years and it’s known for the development of the banking trojan Dridex and the Locky ransomware.
In recent months, the hackers have focused on so-called “big-game hunting” operations, targeting major organizations from which they are more likely to make a bigger profit.
A new Bluetooth overlay skimmer block chip-based transactions
17.2.2021 CyberCrime Securityaffairs
Experts discovered a new Bluetooth overlay skimmer that interferes with the ability of the terminal to read chip-based cards, forcing the use of the stripe.
The popular investigator Brian Krebs reported the discovery of a new Bluetooth overlay skimmer that interfered with the terminal’s ability to read chip-based cards, forcing the use of the magnetic stripe. The device was found in an unnamed retail chain in the United States.
The payment card skimmer included a PIN pad overlay and was able to physically block chip-based transactions.
The PIN pad overlay was designed to capture, store and transmit via Bluetooth payment card data stolen on the stripe along with the PIN provided by the clients on the terminal.
“The hidden magnetic stripe reader is in the bottom left, just below the Bluetooth circuit board. A PIN pad overlay (center) intercepts any PINs entered by customers; the cell phone battery (right) powers all of the components.” wrote Brian Krebs on Krebsonsecurity.com.

Source Krebsonsecurity.com
Chip-based payment cards are more difficult to clone, for this reason, crooks forced the use of the magnetic stripe present on the card for backward compatibility. The recently discovered overlay skimmer included a physical component that blocks chip-based transactions on the terminal, forcing the customer to swipe the stripe.
Source Krebsonsecurity.com
Krebs explained that the overlay skimmer was undetected for several weeks.
Krebs pointed out that once obtained the payment card data and the PIN, cybercriminals can clone the card and use them to withdraw money at an ATM.
The kingpin behind Joker’s Stash retires with a billionaire exit
15.2.2021 CyberCrime Securityaffairs
The administrators of the most popular carding marketplace on the dark web Joker’s Stash announced his retirement.
Cybercriminal behind the most prominent carding marketplace on the dark web Joker’s Stash retires, he will shut down its servers and destroy the backups.
According to Forbes, the man has amassed a billion dollars worth of Bitcoin with its activity.
“The criminal behind the Joker’s Stash site, which trades in stolen credit and debit card data, has announced that all servers and backups will be wiped, and the site will never open again.” reads the article published by Forbes. “That criminal, who unsurprisingly goes by the pseudonym of ‘JokerStash’ or Joker for short, has shut up shop and is going into retirement. A rather comfortable retirement, assuming Interpol and the FBI don’t catch up with them, as a Bitcoin billionaire.”
One month ago, Joker’s Stash announced that its operations will shut down on February 15, 2021.
The administrator announced the decision via messages posted on various cybercrime forums.

Image source FlashPoint
Joker’s Stash is one of the most longevous carding websites, it was launched in October 2014 and is very popular in the cybercrime underground due to the freshness of its cards and their validity. The administrators always claimed the exclusivity of their offer that is based on “self-hacked bases.”
In December, Joker’s Stash was shut down as a result of a coordinated operation conducted by the FBI and Interpol.
At the time, the authorities only seized some of the servers used by the carding portal, but the Joker’s Stash site hosted on the ToR network was not affected by the operations conducted by the police.
The sized sites were at jstash.bazar, jstash.lib, jstash.emc, and jstash.coin, which are all those accessible via blockchain DNS.
Joker Stash admins said in a message published on a hacking forum that the law enforcement only seized the servers hosting the above domains, that were only used to redirecting visitors to the actual website.
The cryptoasset compliance firm Elliptic revealed that the Joker’s Stash site went down on February 3, 12 days before the date announced by the administrator. Customers of the carding site lost 12 more days to cash out their crypto balances, but it is not possible to determine how much they have lost.
“According to Elliptic’s analysis, the founder of one of the most popular carding marketplaces, Joker’s Stash, has retired having amassed a fortune of over $1 billion.” reported Elliptic. “Since 2015 almost $400 million in bitcoin was sent to the marketplace, with annual sales peaking at $139 million in 2018. Sales dropped over the next two years, reflecting a broader downtrend in carding activity – increased security around card payments has made their theft more difficult, while advances in anti-fraud technology have made it more challenging for carders to make purchases with stolen cards.”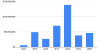
Elliptic revealed that in 2018 alone, the carding site earned $139 million in sales, it estimated that the total earnings of the site between 2015 and 2021 reached more than $400 million.
“We can estimate JokerStash’s retirement fund by considering the fees charged by the marketplace.” continues Elliptic.
“JokerStash claims to keep all proceeds of the marketplace in bitcoin. If that is the case then the recent bitcoin price increase would have substantially inflated the value of assets. If we assume an average total commission of 20% on sales, then considering bitcoin alone (the site also accepts Litecoin and Dash) they would have taken a total of at least 60,000 bitcoins – which today has a value of $2.5 billion.”
In October 2020, Joker’s admin revealed that he had been in the hospital for a week due to a Covid-19 infection.
What will happen in the next months?
No doubt, existing and new carding sites will fill the space left by the exit of Joker’s Stash.
Celeb SIM-Swap Crime Ring Stole $100M from U.S. Victims
11.2.2021 CyberCrime Threatpost
The attackers ported victims’ cell phone lines and then defeated 2FA to access accounts and apps.
A posse of alleged SIM-swapping cybercriminals has been rounded up across Europe by law-enforcement after the crooks finagled more than $100 million from U.S. celebrities and their families.
Eight people in the U.K. were arrested in connection with the crime ring, in addition to individuals in Belgium and Malta, according to Europol. A handful of suspects remain at large.
“The attacks orchestrated by this criminal gang targeted thousands of victims throughout 2020, including famous internet influencers, sport stars, musicians and their families,” according to an alert from the organization.
What is SIM-Swapping?
In a typical SIM-swapping attack, attackers use stolen, sleuthed or phished personal information – including, crucially, a person’s mobile phone number – to impersonate a target. They contact the victim’s mobile carrier – easily discovered with an online search – and ask to port the line to a different SIM card/device, one controlled by the attackers. In this way, all incoming calls and texts are re-routed to the fraudsters.
This approach is trivial to execute and offers a bevy of follow-on attack options. Most importantly, it allows crooks to bypass SMS-based two-factor authentication (2FA). From there, it’s easy to use the previously phished information to gain access to and take over online/mobile banking or other high-value accounts.
T-Mobile USA last summer was the victim of a major SIM-swapping fraud attack, which enabled hackers to bypass two-factor authentication and steal cryptocurrency from various victims.
Attackers can also access contact lists and mount impersonation attacks bent on spreading spyware or other malware, or to hook more people in phishing schemes.
A report last January found that many carriers don’t ask in-depth security questions that fully verify that a caller is in fact the legitimate cell phone user, making this type of attack easier than it should be.
Celebrity Swaps for Fun and Profit
In this latest case, a network of criminals worked together to access the victims’ phone numbers and take control of apps or accounts by changing the passwords.
“This enabled them to steal money, cryptocurrencies and personal information, including contacts synced with online accounts,” according to Europol. “They also hijacked social-media accounts to post content and send messages masquerading as the victim.”
All of the targets were in the U.S. – and the suspects face extradition.
“SIM-swapping requires significant organization by a network of cybercriminals, who each commit various types of criminality to achieve the desired outcome,” Paul Creffield, head of operations in the NCA’s National Cyber Crime Unit, said in a notice this week. “This network targeted a large number of victims in the US and regularly attacked those they believed would be lucrative targets, such as famous sports stars and musicians. In this case, those arrested face prosecution for offences under the Computer Misuse Act, as well as fraud and money laundering as well as extradition to the U.S. for prosecution.”
He added, “As well as causing a lot of distress and disruption, we know they stole large sums from their victims, from either their bank accounts or Bitcoin wallets.”
The names of the victims have not been made public.
How to Protect Against SIM Swapping
Anyone with a mobile phone can fall victim to illegal phone-number porting. Fortunately, it’s possible to put best practices into place to help thwart attacks:
To keep criminals from accessing the personal information they need to carry out SIM-swapping, users should keep device software up-to-date to avoid exploits and malware infections.
As always, it’s never a good idea to reply to emails or engage over the phone with callers that request personal information
Be aware of the amount of personal data shared online
Use multi-factor authentication that relies on something other than one-time codes sent via text
When possible, do not associate your phone number with sensitive online accounts
Pre-Valentine’s Day Malware Attack Mimics Flower, Lingerie Stores
11.2.2021 CyberCrime Threatpost
Emails pretending to confirm hefty orders from lingerie shop Ajour Lingerie and flower store Rose World are actually spreading the BazaLoader malware.
With Valentine’s Day approaching this weekend, several people have received “recent order” email confirmations for flowers or lingerie. These emails are actually part of a spear-phishing attack, which ultimately leads recipients to a malicious document that executes the BazaLoader malware.
The BazaLoader downloader, written in C++, has the primary function of downloading and executing additional modules. BazaLoader was first observed in the wild in April – and since then researchers have observed at least six variants, “signaling active and continued development.”
Recently, researchers found multiple BazaLoader campaigns in January and February, which have relied heavily on human interaction with different sites, PDF attachments and email lures.
“There were a range of lure and subject topics, including compact storage devices, office supplies, pharmaceutical supplies and sports nutrition, but what stuck out were campaigns that were timely and relevant to the upcoming Valentine’s Day holiday,” said researchers with Proofpoint on Thursday. “The campaigns were spread across a diverse set of companies and sectors.”
Email Attack: ‘Ajour Lingerie’ Phishing Lure
One such recent email purported to be from Ajour Lingerie, a “high-quality online lingerie shop” based out of New York. The email told recipients that they have completed their order, and to check the invoice to confirm the price of their purchase.

A sample attachment with the purported “order.” Credit: Proofpoint
The attached PDF, labeled invoice_NI52224162K.pdf, is interestingly not malicious. It instead references a specific customer-order number and associated purchase items. In one example, the “order” totals $410.03, which may send email recipients into a panic.
The invoice also had a website link pretending to be that of Ajour Lingerie. However, the website (ajourlingerie[.]net) is different than the actual website for Ajour Lingerie (ajour.com).
The fake Ajour Lingerie website. Credit: Proofpoint
Attackers went into extreme detail to make the fake Ajour Lingerie website look real, from the logo down to the address.
“The websites the user would browse to are fake, but the actors took care to have the physical addresses…match a near-legitimate location,” said researchers. “For example, Ajour Lingerie is not located at 1133 50th St, Brooklyn, NY 11219, but this address is in physical proximity to a legitimate website and physical business called the Lingerie Shop.”
The website also had a “contact” page. If users visited this page, they were then given the option to enter the order number in the order ID. The contact page then redirected them to the landing page, which linked to an Excel sheet. That Excel sheet contained macros that, if enabled by the user, would download BazaLoader.
Email Lure: Flowers From ‘Rose World’
A second email used an almost-identical lure, only this time purporting to be from Rose World. This email also references an order from Rose World’s online store, and includes a PDF attachment outlining an order (in one case, totaling $104.58), with references to purchases at a fake Rose World website (roseworld.shop).
An example of an email pretending to be from Rose World. Credit: Proofpoint
“If the user visits the website, navigates to Contact Us, and enters the order number in the order ID, the site will redirect the user to a landing page,” said researchers. “This landing page links to and explains how to open the Excel sheet. The Excel sheet contains macros that, if enabled, will download BazaLoader.”
While researchers did not specify what malware gets loaded after this first-stage infection, BazaLoader has been noted for its code similarity to TrickBot, and has been associated with Ryuk ransomware infections.
BazaLoader: An Evolving Malware Loader
Researchers warned that they have observed “a steady growth” in actors using BazaLoader as a first-stage downloader. This uptick in BazaLoader distribution has run parallel to an active development of the loader, particularly during the month of October 2020. The most recent Valentine’s Day attack notably reflects an attack vector with an increase on human interaction.
“These recent BazaLoader campaigns exemplify affiliate actors leveraging a loader that is increasingly popular and more reliant on human interaction,” they said. “Further, the social engineering features rely on the timeliness of the Valentine’s Day holiday and the intrinsic user curiosity to see what they may have ordered.”
Cybercriminals Horn in on Valentine’s Day
Both lures are reflective of cybercriminals horning in on Valentine’s Day – which has been a popular phishing theme over the past years. Last February, a malicious email campaign aimed at iPhone owners tried to convince them to download a fake dating app. And, in 2018, researchers warned that Necurs botnet activity was spiking as scammers used the network to flood inboxes with promises of companionship, in part of a seasonal wave of Valentine’s Day-themed spam.
“Valentine’s Day, while not abused to the level of other holidays, presents an opportunity for a variety of actors,” said researchers with Proofpoint. “The FBI Boston field office has posted public warnings of romance scams. While this is not a romance scam, it is an example of social engineering, well-timed with the Valentine’s Day holiday.”
Is your small- to medium-sized business an easy mark for attackers?
Ukrainian Police Arrest Author of World's Largest Phishing Service U-Admin
10.2.2021 CyberCrime Thehackernews
Law enforcement officials in Ukraine, in coordination with authorities from the U.S. and Australia, last week shut down one of the world's largest phishing services that were used to attack financial institutions in 11 countries, causing tens of millions of dollars in losses.
The Ukrainian attorney general's office said it worked with the National Police and its Main Investigation Department to identify a 39-year-old man from the Ternopil region who developed a phishing package and a special administrative panel for the service, which were then aimed at several banks located in Australia, Spain, the U.S., Italy, Chile, the Netherlands, Mexico, France, Switzerland, Germany, and the U.K.
password auditor
Computer equipment, mobile phones, and hard drives were seized as part of five authorized searches conducted during the course of the operation.
Security researcher Brian Krebs noted the raids were in connection with U-Admin, a phishing framework that makes use of fake web pages to pilfer victim credentials more efficiently.
It is estimated that over 50% of all phishing attacks in 2019 in Australia were carried out using the phishing toolkit.
The hacker is believed to have not only sold his products to customers around the world via an online store in the dark web but also alleged to have provided technical support during phishing attacks.
More than 200 active buyers of malicious software have been identified, Ukrainian officials said.
U-Admin allowed customers to exfiltrate data entered by victims on compromised websites by injecting malicious code into the browser. The crimeware platform's info-stealing capabilities also extended to capturing two-factor authentication codes.
The hacker, who has been arrested on charges of creating and distributing malicious software and breaking into computer networks, faces up to six years of imprisonment if found guilty.
Operation NightScout: supply chain attack on NoxPlayer Android emulator
2.2.2021 Android CyberCrime Securityaffairs
Experts uncovered a new supply chain attack leveraging the update process of NoxPlayer, a free Android emulator for PCs and Macs.
A new supply chain attack made the headlines, a threat actor has compromised the update process of NoxPlayer, a free Android emulator for Windows and Macs developed by BigNox. The company claims to have over 150 million users in more than 150 countries, according to ESET more than 100,000 of its customers have Noxplayer installed on their machines.
The emulator is widely adopted by gamers in order to play mobile games from their PCs.
The attack was discovered by cybersecurity firm ESET on January 25, threat actors delivered malware to a limited number of victims across Asia.
At the time of this writing, the researchers already identified five victims in countries such as Taiwan, Hong Kong, and Sri Lanka. ESET tracked this campaign as Operation NightScout.
“In January 2021, we discovered a new supply-chain attack compromising the update mechanism of NoxPlayer, an Android emulator for PCs and Macs, and part of BigNox’s product range with over 150 million users worldwide.” reads the analysis published by ESET.
“Three different malware families were spotted being distributed from tailored malicious updates to selected victims, with no sign of leveraging any financial gain, but rather surveillance-related capabilities.”
NoxPlayer supply chain attack
The attackers compromised one of the company’s official API (api.bignox.com) and file-hosting servers (res06.bignox.com), once gained a foothold in the target infrastructure they tampered with the download URL of NoxPlayer updates in the API server to deliver tainted updates.
The experts reported that threat actors employed at least three different malware families in this supply chain attack.
The report published by ESET includes technical details for this attack, it could allow NoxPlayers users to determine if they have installed the tainted updates and provides instructions on how to remove the malicious code.
ESET did not attribute this attack to a well-known threat actor, it only highlighted that the three malware employed in the attack had “similarities” with other pieces of malware used in a Myanmar presidential office website supply-chain attacks in 2018 and in an intrusion into a Hong Kong university in early 2020.
“We have detected various supply-chain attacks in the last year, such as Operation SignSight or the compromise of Able Desktop among others. However, the supply-chain compromise involved in Operation NightScout is particularly interesting due to the targeted vertical, as we rarely encounter many cyberespionage operations targeting online gamers.” concludes the report.
“Supply-chain attacks will continue to be a common compromise vector leveraged by cyber-espionage groups, and its complexity may impact the discovery and mitigation of these type of incidents.”
Cyberspies Delivered Malware to Gamers via Supply Chain Attack
2.2.2021 CyberCrime Securityweek
Researchers at cybersecurity firm ESET say they have uncovered an espionage campaign that has targeted online gamers in Asia through a compromised software company.
Called Operation NightScout, the campaign apparently involved a breach at BigNox, the company behind NoxPlayer, an Android emulator that allows users to run mobile apps on PCs or Macs, and which claims to have more than 150 million users worldwide, most of them located in Asia.
After compromising the update mechanism for NoxPlayer, the threat actor behind the attack pushed a series of tailored malicious updates that resulted in three different malware families being installed on the devices of a handful of selected victims.
The highly targeted nature of the attack, ESET’s security researchers say, suggests that the purpose of this campaign is surveillance, and not financial gain: only five out of 100,000 ESET users running NoxPlayer on their machines received a malicious update.
The updates were delivered to victims in Hong Kong, Sri Lanka, and Taiwan, but ESET was unable to find connections between the victims, aside from the use of the same gaming emulator.
In addition to compromising the BigNox infrastructure to host malware, the threat actor might have compromised the company’s HTTP API infrastructure, ESET says, explaining that additional payloads were observed being downloaded by the BigNox updater from attacker’s servers.
“This suggests that the URL field, provided in the reply from the BigNox API, was tampered with by the attackers,” the researchers note.
ESET says it has notified BigNox about its findings, but the company has apparently denied being breached.
The malicious updates were sent to victims in September 2020, with additional payloads downloaded from attacker-controlled infrastructure at the end of 2020 and in early 2021, most likely through the BigNox API mechanism.
Undocumented before, the first malware variant delivered in the attack allows adversaries to monitor victims, but can also execute commands received from the command and control (C&C) server, to delete files, run commands, download or upload files, or download a directory.
The second malware, ESET says, was found to be a variant of the Gh0st RAT that includes keylogger capabilities.
Only delivered as part of activity subsequent to the initial malicious updates, the third malware was an instance of the PoisonIvy RAT.
“The supply-chain compromise involved in Operation NightScout is particularly interesting due to the targeted vertical, as we rarely encounter many cyberespionage operations targeting online gamers. Supply-chain attacks will continue to be a common compromise vector leveraged by cyber-espionage groups, and its complexity may impact the discovery and mitigation of these type of incidents,” ESET concludes.
A New Software Supply‑Chain Attack Targeted Millions With Spyware
2.2.2021 CyberCrime Thehackernews
Cybersecurity researchers today disclosed a new supply chain attack targeting online gamers by compromising the update mechanism of NoxPlayer, a free Android emulator for PCs and Macs.
Dubbed "Operation NightScout" by Slovak cybersecurity firm ESET, the highly-targeted surveillance campaign involved distributing three different malware families via tailored malicious updates to selected victims based in Taiwan, Hong Kong, and Sri Lanka.
NoxPlayer, developed by Hong Kong-based BigNox, is an Android emulator that allows users to play mobile games on PC, with support for keyboard, gamepad, script recording, and multiple instances. It is estimated to have over 150 million users in more than 150 countries.

First signs of the ongoing attack are said to have originated around September 2020, from when the compromise continued until "explicitly malicious activity" was uncovered on January 25, prompting ESET to report the incident to BigNox.
"Based on the compromised software in question and the delivered malware exhibiting surveillance capabilities, we believe this may indicate the intent of intelligence collection on targets involved in the gaming community," said ESET researcher Ignacio Sanmillan.
Supply‑Chain Attack
To carry out the attack, the NoxPlayer update mechanism served as the vector to deliver trojanized versions of the software to users that, upon installation, delivered three different malicious payloads such as Gh0st RAT to spy on its victims, capture keystrokes, and gather sensitive information.
Separately, researchers also found instances where additional malware binaries like PoisonIvy RAT were downloaded by the BigNox updater from remote servers controlled by the threat actor.
"PoisonIvy RAT was only spotted in activity subsequent to the initial malicious updates and downloaded from attacker-controlled infrastructure," Sanmillan said.
First released in 2005, PoisonIvy RAT has been used in several high-profile malware campaigns, most notably in the 2011 compromise of RSA SecurID data.
Noting that the malware loaders used in the attack shared similarities with that of a compromise of Myanmar presidential office website in 2018 and a breach of a Hong Kong university last year, ESET said the operators behind the attack breached BigNox's infrastructure to host the malware, with evidence alluding to the fact that its API infrastructure could have been compromised.
"To be on the safe side, in case of intrusion, perform a standard reinstall from clean media," Sanmillan said. "For uninfected NoxPlayer users, do not download any updates until BigNox sends notification that they have mitigated the threat. Furthermore, [the] best practice would be to uninstall the software."
Attacks on Individuals Fall as Cybercrime Shifts Tactics
30.1.2021 CyberCrime Securityweek
Cybercriminals shifted away from stealing individual consumers’ information in 2020 to focus on bigger, more profitable attacks on businesses, according to a report from the Identity Theft Resource Center.
The nonprofit, which supports victims of identity crime, found that the number of U.S. data breaches fell 19% in 2020 to 1,108. But the number of individual victims of such cybercrimes fell 66% compared with the year prior.
Ransomware and phishing attacks are now the preferred form of data theft because they require less effort and generate bigger payouts. The ITRC said that one ransomware attack can generate as much revenue in minutes as hundreds of individual identity theft attempts over months or years.
According to cybersecurity firm Coveware, the average ransomware payout has grown from less than $10,000 per event in 2018 to more than $233,000 per event in 2020.
However, experts urge consumers not to let down their guard.
According to the ITRC report released Thursday, even with the decline, there were still 300.5 million individuals impacted by data breaches in 2020. Although this figure may include repeats, where a person is victimized multiple times.
“People should understand that this problem is not going away,” said Eva Velasquez, ITRC’s president and CEO. “Cybercriminals are simply shifting their tactics to find a new way to attack businesses and consumers.”
One rising trend is attacks on third parties, such as a vendor, that would yield access to multiple organizations through a single attack. Often, the organization is smaller, with weaker security measures than the companies they work for.
Additionally, the pandemic may have fueled some changes, with employees working remotely and potentially exposing their company networks to criminals. There was also an increase in unemployment fraud as cybercriminals tapped into those systems, which were overwhelmed with claims and new protocols.
Velasquez urged consumers to remain vigilant in protecting their personal and professional information. Criminals will continue to use personal information even if the means by which they obtain it has changed.
“We are not out of the woods,” she said. “It’s not time for consumers to breathe a sigh of relief.”
Enterprise Credentials Publicly Exposed by Cybercriminals
22.1.2021 CyberCrime Securityweek
Cybercriminals behind a successful phishing campaign have exposed more than 1,000 corporate employee credentials on the Internet, according to a warning from security vendor Check Point.
The corporate account credentials were stolen as part of a phishing campaign that kicked off in August 2020, targeting thousands of organizations worldwide.
As part of the campaign, the attackers were able to successfully bypass Microsoft Office 365 Advanced Threat Protection (ATP) filtering, which allowed them to harvest more than a thousand credentials from victims.
According to Check Point, the miscreants behind the campaign made a simple mistake that eventually resulted in the stolen credentials being publicly accessible on the Internet, “across dozens of drop-zone servers used by the attackers.”
Because of that, anyone could have used Google search to find the passwords for the compromised, stolen email addresses.
The attack started with phishing emails masquerading as Xerox notifications, attempting to lure victims into clicking on a malicious HTML attachment, which resulted in the browser displaying a blurred image.
JavaScript code running in the background, however, would perform password checks and send data to drop-zone servers controlled by the attackers, after which it would redirect the victim to a legitimate Office 365 login page.
Check Point also notes that the attackers continuously refined the code throughout the campaign, creating a more realistic experience, in an attempt to avoid any kind of suspicion from the victims and to ensure that their attacks can evade detection by antivirus vendors.
The cybercriminals employed both their own infrastructure to host domains used in the phishing attacks, and dozens of compromised WordPress websites that were used as drop-zone servers.
“Attackers usually prefer to use compromised servers instead of their own infrastructure because of the existing websites’ well-known reputations. The more widely recognized a reputation is, the chances are higher that the email will not be blocked by security vendors,” Check Point explains.
Once sent to the drop-zone servers, the stolen data was saved in files that were publicly accessible, thus indexable by Google, meaning that anyone could have located the stolen email address credentials via the popular search engine.
Check Point says it informed Google on the issue, and “victims now can use Google search capabilities to look for their stolen credentials and change their passwords accordingly.”
The campaign appears to have been mainly targeted at energy and construction companies, though IT, healthcare, real estate, manufacturing, education, transportation, financial services, and retail organizations were also targeted.
Analysis of the Tactics, Techniques, and Procedures (TTPs) employed in this campaign has allowed Check Point to identify a similar set of phishing attacks, carried out in May 2020, but which redirected to another version of an Office 365 phishing page.
Underground Carding Marketplace Joker's Stash Announces Shutdown
19.1.2021 CyberCrime Securityweek
Joker’s Stash, a large underground marketplace for stolen payment card data, has announced plans to shut down operations on February 15, 2021.
The announcement was posted on a Russian-language cybercrime forum and detailed plans to cease all operations “forever.”
The representatives of the carding service pointed out that, although the marketplace has become highly popular, the team is getting a “well-deserved retirement.”
“It’s time for us to leave forever,” the announcement reads, according to threat intelligence company Intel 471.
Active since 2014, the marketplace offered card data from a robust network of criminal vendors, with some of the data supposedly exclusive to Joker’s Stash. Data from various high-profile breaches was being offered on the site, including Earl Enterprises.
Underground threat intelligence company Gemini Advisory estimates that “Joker’s Stash has generated more than $1 billion USD in revenue over the last several years.”
The end of 2020 was rough for Joker’s Stash, as it was the target of a takedown attempt after attracting a lot of attention from law enforcement. The service, however, wasn’t fully interrupted.
In mid-December 2020, a message on the Joker’s Stash site informed visitors that the U.S. Federal Bureau of Investigation and Interpol managed to seize the marketplace’s servers, in an attempt to disrupt its activity.
However, it turned out that Joker’s Stash, which has been described as an automated vending cart (AVC), had several domains up and running, and the law enforcement takedown attempt impacted only some of them.
Specifically, only the shop’s blockchain domains were affected by the attempt, which allowed operators to continue selling card data unhindered. The site’s representatives also announced at the time they would have no trouble restoring the impacted domains.
Prior to December, however, the shop’s popularity had been fading, after the threat actor who runs the site (who uses the moniker JokerStash) announced he was hospitalized with a COVID-19 infection.
Around the same time, both the volume and quality of Card Not Present (CNP) and Card Present (CP) records offered in the shop started declining, and customers began complaining of that.
In the shutdown announcement, the service’s operator says that all servers and backups will be erased after Feb. 15, but that users will have until then to spend their account balance. He also notes that partners will be paid before the service’s permanent closing.
According to Gemini Advisory, some individuals on the Dark Web speculate that the shutdown might be caused by the FBI detaining JokerStash.
Joker’s Stash, the largest carding site, is shutting down
17.1.2021 CyberCrime Securityaffairs
Joker’s Stash to shut down on February 15, 2021.
Joker’s Stash, the largest carding marketplace online announced that it was shutting down its operations on February 15, 2021.
Joker’s Stash, the largest carding marketplace online, announced that its operations will shut down on February 15, 2021.
The administrator announced the decision via messages posted on various cybercrime forums.

Image source FlashPoint
Joker’s Stash is one of the most longevous carding websites, it was launched in October 2014 and is very popular in the cybercrime underground due to the freshness of its cards and their validity. The administrators always claimed the exclusivity of their offer that is based on “self-hacked bases.”
In December, Joker’s Stash was shut down as a result of a coordinated operation conducted by the FBI and Interpol.

At the time, the authorities only seized some of the servers used by the carding portal, but the Joker’s Stash site hosted on the ToR network was not affected by the operations conducted by the police.
The sized sites were at jstash.bazar, jstash.lib, jstash.emc, and jstash.coin, which are all those accessible via blockchain DNS.
Joker Stash admins said in a message published on a hacking forum that the law enforcement only seized the servers hosting the above domains, that were only used to redirecting visitors to the actual website.
The seizure operated by law enforcement in December had an impact on the reputation of the portal, some users were also claiming that the quality of the services offered by Joker’s Stash was decreasing.
“Throughout 2020, the typically active administrator JokerStash had several gaps in communications. JokerStash claimed that they were hospitalized due to a coronavirus infection. The decreasing number of large fresh bases also questioned their ability to source new card data.” reported FlashPoint.
The news of the closure of the card shop represents a major hit to the carding activities in the underground market.
The success of the recent operations might have pushed the administrators into an exit from their operations.
Joker's Stash, The Largest Carding Marketplace, Announces Shutdown
16.1.2021 CyberCrime Thehackernews
Joker's Stash, the largest dark web marketplace notorious for selling compromised payment card data, has announced plans to shut down its operations on February 15, 2021.
In a message board post on a Russian-language underground cybercrime forum, the operator of the site — who goes by the name "JokerStash" — said "it's time for us to leave forever" and that "we will never ever open again," according to twin reports from cybersecurity firms Gemini Advisory and Intel471.
"Joker goes on a well-deserved retirement. Joker's Stash is closing," the post read. "When we opened years ago, nobody knew us. Today we are one of the largest cards/dumps marketplace[s]."
The exact reason for the shut down is still unclear.
Joker's Stash, since its origins in 2014, emerged as one of the biggest players in the underground payment card economy over the years, with over $1 billion generated in revenues.
The news of the imminent shutdown comes weeks after the US Federal Bureau of Investigation (FBI) and Interpol allegedly seized proxy servers used in connection with Blockchain-based domains belonging to the site last month, briefly disrupting its operations.
Adding to the mounting troubles was a "severe decline" in the volume of stolen data posted on the site, leading to complaints from clients about the poor quality of the payment card data.
Then in late October, the site's routine activities also suffered after the actor who allegedly runs the site claimed to have contracted COVID-19 and had been spending more than one week in a hospital.
Gemini Advisory pointed to Bitcoin's recent spike as another reason that may have led to the website's demise.
Bitcoin hit a record high of $40,000 last week, lifting the total value of the cryptocurrency market above $1 trillion for the first time ever.
"JokerStash was an early advocate of Bitcoin and claims to keep all proceeds in this cryptocurrency," the researchers said. "This actor was already likely to be among the wealthiest cybercriminals, and the spike may have multiplied their fortune, earning them enough money to retire."
Joker's Stash's shut down isn't the end of the road, however, as vendors are expected to transition to other dark web marketplaces to advertise their services.
The site's administrator had a few parting words of advice for cybercriminals.
"We are also want to wish all young and mature ones cyber-gangsters not to lose themselves in the pursuit of easy money (sic)," the post concluded. "Remember, that even all the money in the world will never make you happy and that all the most truly valuable things in this life are free."
Classiscam expands to Europe: Russian-speaking scammers lure Europeans to pages mimicking classifieds
15.1.2021 CyberCrime Securityaffairs
Russian-speaking scammers started targeting users of European marketplaces and classifieds is a criminal scheme dubbed Classiscam.
Group-IB, a global threat hunting and and adversary-centric cyber intelligence company, has discovered that Russian-speaking scammers started targeting users of European marketplaces and classifieds. The scheme, dubbed Classiscam by Group-IB, is an automated scam as a service designed to steal money and payment data. The scheme uses Telegram bots that provide scammers with ready-to-use pages mimicking popular classifieds, marketplaces and sometimes delivery services. According to Group-IB, over 20 large groups, leveraging the scheme, currently operate in Bulgaria, the Czech Republic, France, Poland, Romania, the US, and post-Soviet countries, while 20 more groups work in Russia. These 40 groups altogether made at least USD 6.5 mln in 2020. Scammers are actively abusing brands of popular international classifieds and marketplaces, such as Leboncoin, Allegro, OLX, FAN Courier, Sbazar, and etc. Group-IB has sent notifications to the affected brands so they could take the necessary steps to protect against Classiscam.
The scheme, which initially exploited delivery brands, has been tried and tested in Russia. Analysts warn that it is now growing rapidly and reaching users of European classifieds and marketplaces, which were chosen as a target by Russian-speaking scammers to increase their profits and reduce the risk of being caught. Fighting the scam requires joint efforts by classifieds, marketplaces, and delivery services. It is also key to use advanced digital risk protection technology to ensure that any brand impersonating attacks are quickly detected and taken down.
Exporting Classiscam
Group-IB Computer Emergency Response Team (CERT-GIB) for the first time recorded the Classiscam in Russia in the summer of 2019. Peak activity was recorded in the spring of 2020 due to the massive switch to remote working and an increase in online shopping.
“In the summer of 2020 we took down 280 scam pages as part of the Classiscam scheme, and by December that number grew 10-fold and reached up to 3,000 pages,” says Yaroslav Kargalev, the deputy head of CERT-GIB. “We see that Classiscammers are now actively migrating from Russia to Europe and other countries. It’s not the first time when Russia serves as a testing ground for cybercriminals with global ambitions.”
Group-IB’s Digital Risk Protection and CERT-GIB experts have so far identified at least 40 active Classiscam gangs that use scam pages mimicking popular classified, marketplace, and delivery companies with every one of them running a separate Telegram bot. Half of the groups already operate outside of Russia. Despite that scammers are making their first attempts in Europe, an average theft costs users about USD 120. The scam was localized for the markets of Eastern and Western Europe. The brands abused by scammers include the French marketplace Leboncoin, Polish brand Allegro, Czech site Sbazar, Romanian FAN Courier, DHL and many others. An analysis of underground forums and chats revealed that scammers are getting ready to use new brands in their scams, these are FedEx and DHL Express in the US and Bulgaria.
As part of the scheme, scammers publish bait ads on popular marketplaces and classified websites. The ads usually offer cameras, game consoles, laptops, smartphones, and similar items for sale at deliberately low prices. The buyer contacts the seller, who lures the former into continuing the talk through a third party messenger, such as WhatsApp. It’s noteworthy that scammers pose as both buyers and sellers. To be more persuasive, the scammers use local phone numbers when speaking with their victims. Such services are offered in the underground.
Although many marketplaces and classifieds that sell new and used goods have an active policy of protecting users from fraudsters by posting warnings on their resources, victims continue to give away their data.
Evildoers ask victims to provide their contact information to allegedly arrange a delivery. The scammer then sends the buyer an URL to either a fake popular courier service website or a scam website mimicking a classified or a marketplace with a payment form, which turns out to be a scam page. As a result, the fraudster obtains payment data or withdraws money through a fake merchant website. Another scenario invlolves a scammer contacting a legitimate seller under the guise of a customer and sending a fake payment form mimicking a marketplace and obtained via Telegram bot, so that the seller could reportedly receive the money from the scammer.
Group-IB discovered at least 40 groups leveraging Classiscam, with each of them running a separate Telegram chat-bot. At least 20 of these groups focus on European countries. On average, they make around US $61,000 monthly, but profits may differ from group to group. It is estimated that all 40 most active criminal groups make US $522,000 per month in total.
The hierarchy of the scammer groups represents a pyramid, with the topic starters on top. They are responsible for recruiting new members, creating scam pages, registering new accounts, and providing assistance when the bank blocks the recipient’s card or the transaction. The topic starters’ share is about 20-30 percent of the stolen sum. “Workers” get 70-80 percent of the stolen sum for communicating with victims and sending them phishing URLs.

All details of deals made by workers (including the sum, payment number and username) are displayed in a Telegram bot. That’s how Group-IB experts were able to calсulate their estimated monthly haul.
Based on payment statistics, the most successful workers move to the top of the list and become influential members of the project. By doing so, they gain access to VIP options in the chats and can work on European marketplaces, which offer a higher income and involve less risks for Russian-speaking scammers. Workers’ assistants are called “callers” and “refunders.” They pretend to be tech support specialists and receive 5-10 percent of the revenue.
Phishing kit in Telegram
The scheme is simple and straightforward, which makes it all the more popular. There are more reasons behind its growing popularity, however, such as automated management and expansion through special Telegram chat bots. More than 5,000 users (scammers) were registered in 40 most popular Telegram chats by the end of 2020.
As it stands, workers just need to send a link with the bait product to the chatbot, which then generates a complete phishing kit including courier URL, payment, and refund. There are more than 10 types of Telegram bots that create scam pages for brands from Bulgaria, the Czech Republic, France, Poland, and Romania. For each brand and country, scammers write scripts that help newbie workers log in to foreign sites and communicate with victims in the local language.
Chatbots also have shops where you can purchase accounts to various marketplaces, e-wallets, targeted mailings, and manuals, or even hire a lawyer to represent you in court.
“So far, the scam’s expansion in Europe is hindered by language barriers and difficulties with cashing our stolen money abroad,” says Dmitriy Tiunkin, Head of Group-IB Digital Risk Protection Department, Europe. “Once the scammers overcome these barriers, Classiscam will spread in the West. The downside of popularity is competition among scammers, who sometimes frame each other without knowing it.”
Fighting the Classiscam
In order to protect their brands from Classiscam, companies need to go beyond the simple monitoring and blocking approach. Instead, it is necessary to identify and block adversary infrastructure using AI-driven digital risk protection systems enriched with data about adversary infrastructure, techniques, tactics, and new fraud schemes.

The recommendations for users are quite simple and include:
· Trust only official websites. Before entering your login details and payment information, double check the URL and Google it to see when it was created. If the site is only a couple of months old, it is highly likely to be a scam or a phishing page.
· When using services for renting or selling new and used goods, do not switch to messengers. Keep all your communication in the official chat.
· Do not order goods or agree to deals involving a prepaid transaction. Pay only after you receive the goods and make sure that everything is working properly.
· Large discounts and unbelievable promotions may be just that: too good to be true. They are likely to indicate a bait product and a phishing page. Be careful.
Europol Reveals Dismantling of ‘Largest’ Underground Marketplace
13.1.2021 CyberCrime Threatpost
Europol announced a wide-ranging investigation that led to the arrest of the alleged DarkMarket operator and the seizure of the marketplace’s infrastructure, including more than 20 servers.
Europol on Tuesday announced the takedown of DarkMarket, which according to the law enforcement agency is “the world’s largest illegal marketplace on the dark web.”
DarkMarket served as a marketplace for cybercriminals to buy and sell drugs, counterfeit money, stolen or counterfeit credit card data, anonymous SIM cards and malware. According to Europol, DarkMarket had almost 500,000 users and more than 2,400 sellers at the time of closure.
“The investigation, which was led by the cybercrime unit of the Koblenz Public Prosecutor’s Office, allowed officers to locate and close the marketplace, switch off the servers and seize the criminal infrastructure – more than 20 servers in Moldova and Ukraine supported by the German Federal Criminal Police office (BKA),” said Europol in its Tuesday announcement of the dismantling.
In addition to shuttering DarkMarket’s infrastructure, The Central Criminal Investigation Department in Oldenburg (a German city) over the weekend arrested an Australian citizen near the German-Danish border. Europol said this citizen is the alleged operator of DarkMarket, but did not give further details.
In the future, “it is unclear to what extent the shutdown of this dark market will impact cybercriminal operations, beyond the near-term disruption to its current users,” Paul Prudhomme, cyber threat intelligence advisor at IntSights, told Threatpost.
He noted, new dark web marketplaces eventually emerge to replace those that have closed, and users simply migrate to those new websites and to existing competitors.
“The arrest of one of the website’s operators and the seizure of its infrastructure may nonetheless yield useful investigative leads for law enforcement with which to act against its individual users, which may have more enduring impact,” Prudhomme said. “The website’s use of infrastructure in Ukraine and Moldova is not surprising, as many criminals prefer to host infrastructure in those two countries that they perceive to be relatively safe from law enforcement.”
However, the data stored in the servers that were seized by law enforcement will give investigators new leads to further investigate moderators, sellers, and buyers, said Europol. Europol (also known as the European Union Agency for Law Enforcement Cooperation) is the law enforcement agency of the EU, which has previously aided in various cybercrime investigations and the dismantling of various hacking groups.
Involved in the international operation was Germany (which took the lead), Australia, Denmark, Moldova, Ukraine, the United Kingdom (the National Crime Agency), and the USA (DEA, FBI, and IRS). Threatpost has reached out to the FBI for further comment on the operation.
Law enforcement has continued cracking down on underground forums and platforms used for cybercriminal denizens looking to swap illegal goods. In 2019, law-enforcement agencies worldwide took down a credentials marketplace (xDedic Marketplace) and continued to take action against former users of the Webstresser[.]org DDoS-for-hire site.
Underground marketplaces in general have been skyrocketing as a result of the COVID-19 pandemic, with Flashpoint researchers recently saying that demand for malicious and illicit goods, services and data has “reached new peak highs across dark web marketplaces.” Popular goods among cybercriminals include payment cards, access to Microsoft’s Remote Desktop Protocol (RDP) and DDoS-for-hire services, researchers said.
On DarkMarket alone, 320,000 illegal transactions were made on the platform, and more than 4,650 Bitcoin transferred –corresponding to a sum of more than $170 million, according to Europol.
“Dark web marketplaces such as this now-defunct website serve as key enablers for cybercriminals,” Prudhomme told Threatpost. “They provide these criminals with places to buy and sell malware, malicious infrastructure, and compromised data, accounts, and devices. Such exchanges are critical to cybercriminal operations because few criminals rely exclusively on their own resources, and many do not actually use the data that they steal.”
Police took down DarkMarket, the world’s largest darknet marketplace
13.1.2021 CyberCrime Securityaffairs
The world’s largest black marketplace on the dark web, DarkMarket, has been taken offline by law enforcement in an international operation.
DarkMarket, the world’s largest black marketplace on the dark web, has been taken offline as a result of an international operation conducted by law enforcement from Germany, Australia, Denmark, Moldova, Ukraine, the United Kingdom (the National Crime Agency), and the USA (DEA, FBI, and IRS) with the support of the Europol.
The figures related to the DarkMarket at the time of the shut down are impressive:
almost 500 000 users;
more than 2 400 sellers;
over 320 000 transactions;
more than 4 650 bitcoin and 12 800 Monero transferred.
The overall transactions, at the current rate, correspond to a sum of more than €140 million.
The marketplace was an important point of aggregation for online cybercriminals that traded all kinds of drugs, counterfeit money, stolen or counterfeit credit card details, anonymous SIM cards and malware.
During the weekend, the German operation led the operation, Police in the city of Oldenburg arrested a 34-year-old Australian national who is the alleged operator of the DarkMarket.
The man believed to operate it near Germany’s border with Denmark, the police also seized more than 20 servers used by the suspect in Moldova and Ukraine.
“The investigation, which was led by the cybercrime unit of the Koblenz Public Prosecutor’s Office, allowed officers to locate and close the marketplace, switch off the servers and seize the criminal infrastructure – more than 20 servers in Moldova and Ukraine supported by the German Federal Criminal Police office (BKA). The stored data will give investigators new leads to further investigate moderators, sellers, and buyers.” reads the press release published by the Europol.
The investigation is still ongoing, data obtained as the result of the operation will be used to launch news probes again people involved the the activity of the marketplace.
“Investigators expect to use the data saved there to launch new probes against the moderators, sellers and buyers of the marketplace,” prosecutors said.
German Police Take Down 'World's Largest Darknet Marketplace'
13.1.2021 CyberCrime Securityweek
A German-led police operation has taken down the "world's largest" darknet marketplace, whose Australian alleged operator used it to facilitate the sale of drugs, stolen credit card data and malware, prosecutors said Tuesday.
At the time of its closure, DarkMarket had nearly 500,000 users and more than 2,400 vendors worldwide, as the coronavirus pandemic leads much of the street trade in narcotics to go online.
Police in the northern city of Oldenburg "were able to arrest the alleged operator of the suspected world's largest illegal marketplace on the darknet, the DarkMarket, at the weekend," prosecutors said in a statement.
"Investigators were able to shut down the marketplace and turn off the server on Monday," they added, calling it the culmination of a months-long international law enforcement operation.
A total of at least 320,000 transactions were carried out via the marketplace, with more than 4,650 bitcoin and 12,800 monero -- two of the most common cryptocurrencies -- changing hands, prosecutors said.
At current exchange rates, that represented turnover valued at 140 million euros ($170 million).
The marketplace offered for sale "all kinds of drugs" as well as "counterfeit money, stolen and fake credit card data, anonymous SIM cards, malware and much more".
A 34-year-old Australian national believed to be the DarkMarket operator was arrested near the German-Danish border, just as more than 20 servers it used in Moldova and Ukraine were seized.
"Investigators expect to use the data saved there to launch new probes against the moderators, sellers and buyers of the marketplace," prosecutors said.
The prime suspect was brought before a judge but declined to speak. He was placed in pre-trial detention.
The American FBI, DEA narcotics law enforcement division and IRS tax authority took part in the probe along with police from Australia, Britain, Denmark, Switzerland, Ukraine and Moldova.
Europol, Europe's police agency, played a "coordinating role".
- Pandemic promotes darknet sales -
The German prosecutors said DarkMarket came to light in the course of major investigation against the Dutch web-hosting service Cyberbunker, which is accused of being a haven for cybercrime and spam.
German authorities said Cyberbunker hosted DarkMarket for an unspecified time.
The secret "darknet" includes websites that can be accessed only with specific software or authorisations, ensuring anonymity for users.
They have faced increased pressure from international law enforcement in recent months.
The EU narcotics agency sounded the alarm in September that the pandemic was failing to disrupt drug smugglers and dealers, as users and sellers were using the web for their supply.
While street dealing had been affected by restrictions during the height of the pandemic, it said consumers and dealers had been turning to online "darknet" markets, social media and home delivery.
Also in September, a global police sting netted 179 vendors involved in selling opioids, methamphetamine and other illegal goods on the internet underground, in what Europol officials said at the time put an end to the "golden age" of dark web markets.
Some 121 suspects were arrested in the US, followed by 42 in Germany, eight in the Netherlands, four in Britain, three in Austria, and one in Sweden.
That so-called Operation DisrupTor followed a law agency shutdown in May 2019 of the Wall Street Market, the second largest dark web exchange, which had more than 1.1 million users and 5,400 vendors.
Authorities Take Down World's Largest Illegal Dark Web Marketplace
13.1.2021 CyberCrime Thehackernews
Europol on Tuesday said it shut down DarkMarket, the world's largest online marketplace for illicit goods, as part of an international operation involving Germany, Australia, Denmark, Moldova, Ukraine, the U.K.'s National Crime Agency (NCA), and the U.S. Federal Bureau of Investigation (FBI).
At the time of closure, DarkMarket is believed to have had 500,000 users and more than 2,400 vendors, with over 320,000 transactions resulting in the transfer of more than 4,650 bitcoin and 12,800 monero — a sum total of €140 million ($170 million).
The illegal internet market specialized in the sales of drugs, counterfeit money, stolen or forged credit card information, anonymous SIM cards, and off-the-shelf malware.
In addition, the months-long intelligence operation also resulted in the arrest of a 34-year-old Australian national near the German-Danish border over the weekend, who is alleged to be the mastermind behind DarkMarket.
According to The Guardian, DarkMarket came to light in the course of a major investigation against the web hosting service CyberBunker, which served as the web host for The Pirate Bay and WikiLeaks in the past.
The takedown of DarkMarket also saw law enforcement seizing the criminal infrastructure, including more than 20 servers in Moldova and Ukraine, that was used to conduct the operations.
"The stored data will give investigators new leads to further investigate moderators, sellers, and buyers," Europol said.
DarkMarket may have been turned off, but underground marketplaces such as Joker's Stash continue to be a hotbed for trading malicious software, with the pandemic contributing to a spike in goods or services for carrying out social engineering scams.
Previously, Dream Market, another top dark web marketplace, ended operations in April 2019, and a Europol-led police operation also shut down Wall Street Market and Silkkitie (also known as the Valhalla Marketplace) a month later in May 2019.
The Wall Street Market had 1.15 million users and 5,400 sellers of drugs, malware, and other criminal goods.
Then last August, Empire Market, a popular darknet marketplace for buying and selling drugs, mysteriously went offline, implying an exit scam that has plagued illegal darknet markets.
These changes have led cybercriminals to find alternative ways to build trust and sell their wares, including leveraging encrypted email services like Sonar and Elude, private channels on Discord to facilitate transactions, and a website called "DarkNet Trust" that aims to verify vendors' reputations by searching through usernames.
"These marketplaces shift and evolve like legitimate spaces, adapting to buyer needs, supply issues, and new technology," Trend Micro researchers said in a report published last year detailing the volatile nature of underground markets. "Available commodities and prices respond quickly to issues in the public sphere."
Over 500,000 credentials for tens of gaming firm available in the Dark Web
6.1.2021 CyberCrime Securityaffairs
The gaming industry under attack, Over 500,000 credentials for the top two dozen leading gaming firms, including Ubisoft, leaked on online.
The gaming industry is a privileged target for threat actors, threat actors leaked online over 500,000 stolen credentials belonging to top 25 gaming firms.
The alarm was raised by the threat intelligence firm Kela that reported the availability for sale of the credentials in multiple hacking forums and criminal marketplace.
“KELA found nearly 1 million compromised accounts pertaining to gaming clients and employees, with 50% of them offered for sale during 2020.” reads the post published by Kela.
“KELA detected more than 500,000 leaked credentials pertaining to employees of the leading companies in the gaming sector.”
The profits for the gaming industry increased due to the ongoing COVID-19 pandemic because more people remained at home during the lockdown and had more time to spend with video games.
The researchers found 1 million compromised credentials associated clients of organizations in the gaming industry.
For the past two months, we’ve observed several different actors looking for access to networks of gaming companies.
The leak is related to an intense activity observed by the experts in the last months when the demand for initial network access to gaming companies has surged in Russian-speaking hacking communities. Threat actors were interested in access to developers’ networks of major firms, including Microsoft Xbox, Nintendo, Qualcomm, and Apple.
Access to an online game of a Germany-based developer – Source KELA
The post published by Kela includes adv for stolen credentials and accesses for the organizations in the gaming industry along with posts of threat actors searching for them.
“It’s important to note that we detected compromised accounts to internal resources of nearly every company in question. These resources are meant to be used by employees, for example – Admin panels, VPNs, Jira instances, FTPs, SSOs, dev-related environments, and the list goes on and on.” continues the report.
Threat actors obtained precious information by using info-stealer like AZORult and launched spear-phishing attacks against gaming forms.
Game-company credentials for VPN services, website management portals, admin panels, dev-related environments and Jira instance access are flooding the underground marketplace.
Access to the core areas of a company’s network could be obtained paying just a couple of dollars.
For the past three months, the experts also observed four ransomware incidents suffered by gaming firms.
Most of the attacks exploit the human factor to compromise the target organizations, the experts found that the credentials available for sale also include high-profile email addresses (i.e. executives and senior employees)..
Kela recommends the adoption of stringent password guidelines, including enforcing password changes and adopting multi-factor authentication.
“Some attackers try to search for the specific data and information that is relevant to the scope or industry of the victim and reproduce the successful attacks. As the gaming industry continues to grow in revenue, we will likely continue to detect more threats and attacks targeting the online gaming industry,” concludes the report.
In September I published a detailed analysis of cybercriminal activities targeting the gaming sector, It is written in Italian and require a free registration:
https://ilmanifesto.it/perche-i-giochi-online-piacciono-tanto-al-crimine-informatico/
Leading Game Publishers Hit Hard by Leaked-Credential Epidemic
5.1.2021 CyberCrime Threatpost
Over 500,000 leaked credentials tied to the top two dozen leading gaming companies are for sale online.
Leading gaming companies, such as Ubisoft, have become big targets for cybercriminals that aim to turn a profit by selling leaked insider-credentials tied to the top game publishers. Over 500,000 stolen credentials tied to the top 25 gaming firms were found on caches of breached data online and up for sale at criminal marketplaces, according to researchers at Kela.
In a recent scan, they found 1 million compromised credentials associated with the larger gaming universe of “clients” and also employees – half of which were for sale online. More than 500,000 of the leaked credentials pertained to employees of leading game companies, according to the report published Monday.
The past year was a punishing one for the gaming sector, as outlined by Threatpost’s 2020 cybersecurity recap. Gamers faced foul play ranging from ID theft, scams or the hack of in-game valuables.
2020 Reader Survey: Share Your Feedback to Help Us ImproveWhat makes Kela’s research unique is the light it shines on inroads hackers have made inside the $196 billion industry. Fueling the trend, wrote the report’s authors, Almog Zoosman and Victoria Kivilevich, is a boom within the sector spurred by COVID-19’s demand for social distancing driving interest in the solitary activity of video gaming.
“The growing success of this industry also calls attention to cybercriminals scouting out their new targets – and what better target could cybercriminals ask for than an industry that’s up and coming and may not be prioritizing their security precautions as much as their industry advancement and profit,” Kela reported.
Tools used to attack gaming firms include the malware AZORult, used in both plain-vanilla and sophisticated phishing attacks targeting employees of game companies. AZORult, info-stealing malware, is used to siphon credentials from victims that are then used to further compromise a target’s network.
Scores of successful attacks, researchers report, have stoked a thriving black market for game-company credentials ranging from those tied to VPN services, website management portals, admin panels, dev-related environments and Jira instance access.
Of course, ransomware attacks are also part of the hackers’ playbook.
“For the past three months, we’ve observed four ransomware incidents impacting gaming companies – three of which were publicly reported. In addition, it’s possible that another major gaming developer was attacked, as Sodinokibi (REvil) stated in their interview,” according to the report.
Insider threats were the primary weak point in attacks. “Employees continue to remain as the main entry point, driving us to also analyze the sample companies’ leaked credentials stemming from third-party breaches,” Zoosman and Kivilevich wrote. Criminal marketplaces selling stolen credentials are plentiful. “These markets essentially assist threat actors to attain access to desired services with the click of a button and at a price of a couple of dollars per bot,” authors wrote.
“[For] a payment of just a couple of dollars a potential attacker can have access to the core areas of a company’s network,” the report continued.
Premium access to a game developer’s backend were also available, according to Kela. “We also detected an infected computer (bot) which had credential logs to plenty of sensitive accounts that could be accessed by attackers upon purchase,” the authors wrote. “Access included SSO, Kibana, Jira, admin-connect, service-now, Slack, VPN, password-manager and poweradmin in one specific example… This highly valuable bot was available for sale for less than $10.”
Advice for the highly-targeted game industry in 2021 is a focus on insider threats and employee training, according to Kela. It also recommended more stringent password guidelines, such as enforcing password changes and mandating multi-factor authentication policies.
As the gaming industry preps for another record-breaking year of profits, security experts caution “attacks and attackers are becoming more sophisticated and customized to the victim.”
“Some attackers try to search for the specific data and information that is relevant to the scope or industry of the victim and reproduce the successful attacks. As the gaming industry continues to grow in revenue, we will likely continue to detect more threats and attacks targeting the online gaming industry,” according to the report.
Over 200 million records of Chinese Citizens for Sale on the Darkweb
4.1.2021 CyberCrime Securityaffairs
During a routine Dark web monitoring, the Research team at Cyble found threat actors selling 200 million+ Records of Chinese Citizens.
During a routine Dark web monitoring, the Research team at Cyble found multiple posts where threat actors are offering for sale alleged data leaks related to Chinese citizens. Data might have been stolen from multiple popular Chinese services, including Gongan County, Weibo, and QQ.
Gong’an County is a county in southern Hubei province, People’s Republic of China, bordering Hunan to the south. It is under the administration of Jingzhou City. A threat actor is offering sample data of alleged 999 household registrations of Chinese citizens from Gong’an county as a proof of the hack. Data belonging 7.3 million Chinese citizens are available for sale, the records include Id, Sex, Name, Birth, Mobile, Address, and Code number.
Experts also noticed the sale of data related to users of the Weibo platform.

“The threat actor was selling 41.8 million records on a Russian-speaking cybercrime forum.” reads the post published by Cyble.
“During the analysis of the sample data, it was noticed that the weibo_id and respective mobile number were listed in an excel sheet. The threat actor is selling details of 41.8 Million chinese users on the darkweb.”
Cyble researchers also discovered a threat actor offering records belonging to users of the popular Tencent-owned QQ instant messaging software service and web portal. The threat actor is selling details of 192 Million Chinese users on the darkweb.
The analysis of the sample data revealed the presence of the qq number and respective mobile number in an excel sheet.
The overall availability of records related to Chinese citizens is over 200 million.
Alleged docs relating to Covid-19 vaccine leaked in darkweb
2.1.2021 CyberCrime Securityaffairs
Experts from threat intelligence firm Cyble have found documents relating to Covid-19 vaccine of European Medicines Agency in the Darkweb
Security experts from threat intelligence firm Cyble have found several documents relating to the Covid-19 vaccine allegedly stolen from the European Medicines Agency (EMA) leaked in the Darkweb.
While the pandemic is spreading on a global scale, threat actors continue to target government organizations and entities in the pharmaceutical industry.
In early December, the European Medicines Agency (EMA) announced a cyber attack that has targeted it. The EMA did not provide technical details about the attack, nor whether it will have an impact on its operations while it is evaluating and approving COVID-19 vaccines.
“EMA has been the subject of a cyberattack. The Agency has swiftly launched a full investigation, in close cooperation with law enforcement and other relevant entities.” reads the EMA’s announcement.
“EMA cannot provide additional details whilst the investigation is ongoing. Further information will be made available in due course.”

At the time of this writing, it is not clear whether the cyber attack was successful, either when it took place. The agency confirmed to have launched an investigation into the incident.
The European agency plays a crucial role in the evaluation of COVID-19 vaccines across the EU, it has access to sensitive and confidential information, including quality, safety, and effectivity data resulting from trials.
In the last months, security experts reported the surge of the illegal market for Covid-19 vaccines on the Darkweb market.
Recently, Cyble started tracking documents being shared on one of the Russian-speaking forums. The links to the documents have been shared by a newly created profile which was used only for the alleged data leak.
“During the assessment of data, our researchers noticed that multiple confidential files, including MoMs, assessment reports, confidential emails, login portal links and images of its internal pages were accessed and leaked.” reported the analysis published by Cyble.

The experts shared screenshots of the internal email where the portal link was shared, the login page for the portal to access the reports, and images of internal pages.

The documents also include the alleged assessment report of COVID-19 vaccine along with the summary report of drug release and stability.
Below a list of security measures that organizations can adopt to counter the impact of cyberattacks targeting the COVID-19 vaccine supply chain.
Validating third-parties and ensuring that they have the necessary level of cyber defences
Never clicking on unverified/unidentified links
Refraining from opening email attachments before validating their authenticity
Using security software and keeping it updated
Training employees on cybersecurity through cyber literacy programs
Periodically conducting third-party/suppliers risk assessment