Cyber 2024 2023 2022 2021 2020 CYBERCRIME 2022 2021 2020
Microsoft, Google to Invest $30 Billion in Cybersecurity Over Next 5 Years
28.8.21 Cyber Thehackernews
Google and Microsoft said they are pledging to invest a total of $30 billion in cybersecurity advancements over the next five years, as the U.S. government partners with private sector companies to address threats facing the country in the wake of a string of sophisticated malicious cyber activity targeting critical infrastructure, laying bare the risks to data, organizations, and governments worldwide.
The White House cybersecurity meeting, which brought together executives from the education, energy, finance, insurance, and tech sectors, included companies like ADP, Amazon, Apple, Bank of America, Code.org, Girls Who Code, Google, IBM, JPMorgan Chase, Microsoft, and Vantage Group, among others.
To that end, the U.S. government on Wednesday announced a collaboration between the National Institute of Standards and Technology (NIST) and industry partners to develop a new framework to improve the security and integrity of the technology supply chain, alongside plans to expand the Industrial Control Systems Cybersecurity Initiative to secure natural gas pipelines.
The big tech sector is also rallying behind with a roster of initiatives, including —
Microsoft will invest $20 billion over the next five years to deliver advanced security solutions, in addition to making available $150 million in technical services to help federal, state, and local governments with upgrading security protections.
Google will invest over $10 billion to bolster cybersecurity, including expanding zero-trust programs, helping secure the software supply chain and enhancing open-source security. It's worth noting that the search giant, earlier this June, announced a framework called the Supply chain Levels for Software Artifacts (SLSA or "salsa") to safeguard the integrity of software supply chains.
Apple will work with more than 9,000 of its suppliers to push for mass adoption of multi-factor authentications, vulnerability remediation, event logging, and security training.
IBM will train 150,000 people in cybersecurity skills over the next three years, and will partner with 20 Historically Black Colleges & Universities to establish a more diverse cyber workforce.
Amazon will make available to all Amazon Web Services account holders a multi-factor authentication device to protect against phishing and password theft at no extra cost.
While it remains to be seen how these efforts will unfold in practice, the commitments demonstrate the urgency in prioritizing and elevating cybersecurity after a relentless stretch of high-profile cyber attacks targeting SolarWinds, Microsoft, Colonial Pipeline, JBS, and Kaseya in recent months. Earlier this May, U.S. President Joe Biden issued an executive order requiring federal agencies to modernize their cybersecurity defenses.
Employee Lockdown Stress May Spark Cybersecurity Risk
27.3.2021 Cyber Threatpost
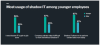
Younger employees and caregivers report more stress than other groups– and more shadow IT usage.
Stressed-out employees in a remote-working world could be a major contributor to poor cybersecurity postures for companies, according to a survey.
Forcepoint polled 2,000 office workers in Germany and the U.K., to better understand cybersecurity practices among remote workers. Among other findings, the survey found that younger employees as well as people caring for children or other family members reported more stress in their lives, as well riskier IT behaviors when compared to other demographics.
For instance, 67 percent of employees under 30 said they use shadow IT (unsanctioned apps, services and equipment) to help them to perform certain tasks more easily, compared to 27 percent of older workers.
Also, 55 percent of the younger group reported making more mistakes when working from home, such as copying in the wrong people into emails – in comparison, only 17 percent of the over-30s reported such mistakes. And, nearly two-thirds of the younger group (63 percent) stated that distractions while working from home negatively impact decision-making, compared to 26 percent of older people.
It’s unclear if the relationship between security behavior and stress is causal, but it’s still a correlation that leaps off the page, according to Forcepoint.
Click to enlarge. Source: Forcepoint.
“Differences in behaviors may in part reflect natural age-related tendencies in risk-taking, but the level of disparity between the two groups is both consistent and extreme,” said Margaret Cunningham, principal research scientist at Forcepoint, in a Thursday posting on the findings. “This could indicate that natural risk-taking tendencies are exacerbated by prolonged periods of stress and a challenging work climate.”
And indeed, the survey also found that more than two thirds (70 percent) of younger employees have trouble focusing because of their stress level, compared to 29 percent of older workers, and 77 percent said they feel the pressure to be available outside of normal working hours, compared to less than half (46 percent) of older workers.
More than three quarters (78 percent) of younger employees also reported that they feel stressed out by competing demands from their personal and professional lives, compared to 40 percent of older employees.
Caregivers meanwhile also over-index on stress-related behavior that negatively impacts IT security practices. For instance, about half (52 percent) said minor mistakes are a normal part of their days; and distractions that impact decision-making also afflict just over half of the group (56 percent). And, about half (48 percent) admit to using shadow IT.
Click to enlarge. Source: Forcepoint.
“We hadn’t expected the study to reveal so clearly a picture of demographic disparities,” Cunningham said. “Lockdown has been a stressful time for everyone…without additional support from employers, young people and caregivers could continue to deviate further from pre-set and learned IT security rules, exposing their companies to further increased security risk.”
She added that companies need to accept the pervasive use of shadow IT, which exposes organizations to increased cybersecurity risk. But, employers should also provide better emotional and personal support.
“Leaders must proactively help employees deal with increased and prolonged levels of stress and anxiety, paired with additional interruptions,” she said. “Burnout is not only a risk for individual employees, but also impacts organizational resilience and personnel resource management needs.”
Manufacturing’s Cloud Migration Opens Door to Major Cyber-Risk
26.3.2021 Cyber Threatpost
New research shows that while all sectors are at risk, 70 percent of manufacturing apps have vulnerabilities.
Web-facing applications continue to be one of the highest security risks present for organizations, with more than 40 percent of them actively leaking data in a way that can have a ripple affect across businesses and their partners, research has found.
Moreover, manufacturing is particularly vulnerable to attacks through these apps, with 70 percent of applications having at least one serious vulnerability open over the previous 12 months, researchers found.
That’s according to a report from app-security firm WhiteHat Security, “AppSec Stats Flash Volume 3,” which outlines how the increased prevalence of applications that are exposed to the internet through web, mobile and API-based interfaces has increased the attack surface and thus the security risk for organizations and their supply chains across the board.
Among the findings of the report include a consistent characterization of the top five vulnerabilities found in internet-facing apps in the last three months, researchers found. Those flaws are: Information leakage, insufficient session expiration, cross-site scripting, insufficient transport layer protection and content spoofing.
Cloud applications are currently driving the global economy, especially in a post-pandemic world in which business is increasingly done over the internet. However, more web-based applications and data in the cloud also means a higher risk of data breaches: Applications are increasingly polymorphic, with access through web, mobile and API-based interfaces. That makes application security a multi-dimensional challenge, researchers said.
“We continue to find that window of exposure, a key measure of exploitability remains very high,” Setu Kulkarni, vice president of strategy at WhiteHat, told Threatpost in an email. “What that means is that web-facing applications and APIs continue to have serious exploitable vulnerabilities throughout the year.”
Supply-Chain Threats
What happens when an adversary attacks the supply chain was very evident recently thanks to the ongoing SolarWinds debacle, in which adversaries used SolarWinds’ Orion network management platform to infect users with a stealth backdoor called Sunburst (a.k.a. Solorigate). That in turn opened the way for lateral movement to other parts of a network.
Indeed, supply-chain attacks can be particularly damaging because they affect connected systems and business applications that are linked more than ever before through predominantly API-based integrations, Kulkarni observed.
This threat is compounded by another key finding of the report — that that the average time an organization takes to fix critical vulnerabilities is still more than 190 days, with the top vulnerability classes remain relatively static, giving adversaries an “easy way” to get into corporate networks, he said.
“Pedestrian vulnerabilities continue to plague applications,” researchers wrote. “The effort and skill required to discover and exploit these vulnerabilities is fairly low, thus making it easier for the adversary.”
Manufacturing at Greatest Risk
The manufacturing sector seems particularly susceptible to being attacked by vulnerabilities in web-facing applications likely because it was “traditionally never internet-connected as an industry,” then had to rapidly transition legacy systems and software to keep up, Kulkarni told Threatpost.
“The lift and shift of applications that were never meant to be internet-facing to become internet-enabled has likely resulted in this high risk,” he said.
Another factor putting manufacturing at greater risk is that supply chains are now increasingly software-driven, which means business partners are now having to open up otherwise internal applications to integrate with supply-chain partners. This again results “in existing vulnerabilities that were previously unexploitable to become publicly exploitable,” Kulkarni explained.
All of that said, the remediation of vulnerabilities present in an organization’s internet-facing apps is “an immediate and imminently achievable goal for development and security teams,” researchers wrote in the report. That journey toward better security starts with organizations taking measures toward “reducing the risk of being breached in production,” Kulkarni told Threatpost.
“Organizations must take inventory of public-facing apps, scan them continuously in production and take a risk-based approach to fix in-production issues,” he said. “That is step one.”
Fiserv Forgets to Buy Domain It Used as System Default
19.3.2021 Cyber Threatpost
Fintech security provider Fiserv acknowledges it used unregistered domain as default email.
Fiserv, a multi-billion-dollar cybersecurity tech provider for financial institutions, forgot to buy the domain used as a default in their systems’ email communications, according to a report.
The blunder could have exposed its clients’ user information to anyone with a few bucks to buy the domain – However, before that could happen, researcher Abraham Vegh came across the error last November.
In a recent KrebsOnSecurity report, Vegh explained he received an email from his bank, which included the domain, defaultinstitution.com. He searched and realized it wasn’t registered, bought it and linked it to an email address to see what would come in.
Krebs reported, Vegh received bounced messages from Fiserv users, including money transfer service Cashedge.com, which was trying to inform its customers it was switching to Zelle as their primary service. These included emails with IDs, transfer amounts and dates, the last four account digits of the sender and email address of the recipient, Vegh explained to KrebsOnSecurity.
Fiserv Default Domain
The bottom of the emails included this statement, “This email was sent to [recipient name here]. If you have received this email in error, please send an e-mail to customersupport@defaultinstitution.com,” Krebs reported.
“It appears that the domain is provided as a default, and customer bank IT departments are either assuming they don’t need to change it, or are not aware that they could/should,” Vegh told Krebs.
Fiserv customer Netspend.com, provider of pre-paid debit cards, also showed up in Vegh’s “defaultinsitution” inbox, along with TCF National Bank, Union Bank and others, filled with personal user information.
Shortly thereafter, on Feb. 26, Krebs said Vegh stopped “defaultinstitution” emails.
Fiserv Acknowledges Error
Fiserv acknowledged the incident in statement provided to Threatpost.
“Upon being made aware of the situation we immediately conducted an analysis to locate and replace instances of the placeholder domain name,” the statement said. “We also notified the clients whose customers received these emails.”
Fiserv said it has since purchased the default domain, obtained the emails and are working to notify affected users.
“We will no longer use placeholder domain names that include non-Fiserv owned domains,” the statement added.
Dirk Schrader global vice president at New Net Technologies, told Threatpost the exposed data could have been used in socially engineered business email compromise-type scams.
“Fiserv has screwed up on a basic cyber security requirement for financial institutions, Schrader said. “Using an unregistered domain opens the door for phishing and for a lot of other attack vectors. Someone in Fiserv must have thought that ‘defaultinstitution’ is self-explanatory and everyone will change that entry, so the company has left it to pure luck.”
Schrader added fintech companies need to fully control and secure communications, adding, “this was a wide-open door for disaster and financial loss for Fiserv’s customers.”
Cyberattacks ‘Unlikely’ Resulting from Domain Error
Default settings and configurations often provide happy hunting grounds for threat actors, according to Ivan Righi, an analyst with Digital Shadows.
“Cybercriminals frequently use default passwords to gain access to target accounts and services,” Righi told Threatpost. “In this instance, the company used a default domain as a placeholder in its software solutions. Thankfully, as a researcher discovered the security issue, it is unlikely that the incident will lead to any cyber-attacks on customers.”
Vegh, for his part, told Krebs he was happy to hand the domain over to Fiserv, but added, maybe a t-shirt would be an appropriate prize for the bug report.
“Overall, I’m pleased with the outcome here,” Vegh told Threatpost. “I think Fiserv has learned from this, and I hope other companies large and small can learn this most simplest of lessons: always control domain names you use, even if it’s ‘just for development purposes.’ After talking with Fiserv, they made me a very reasonable offer to purchase the domain, which is way more than I was expecting for my efforts, and I was happy to accept and transfer the domain to them, closing the door on my involvement with it.”
The state of stalkerware in 2020
27.2.2021 Cyber Securelist
The state of stalkerware in 2020 (PDF)
Main findings
Kaspersky’s data shows that the scale of the stalkerware issue has not improved much in 2020 compared to the last year:
The number of people affected is still high. In total, 53,870 of our mobile users were affected globally by stalkerware in 2020. Keeping in mind the big picture, these numbers only include Kaspersky users, and the total global numbers will be higher. Some affected users may use another cybersecurity solution on their devices, while some do not use any solution at all.
With more than 8,100 users affected globally, Nidb is the most used stalkerware sample, according to our 2020 stats. This sample is used to sell a number of different stalkerware products such as iSpyoo, TheTruthSpy and Copy9 among others.
In terms of geographic spread, we see a largely consistent trend emerging: Russia, Brazil, and the United States of America (USA) remain the most affected countries globally, and they are the three leading countries in 2020.
In Europe, Germany, Italy and the United Kingdom (UK) are the top three most-affected countries respectively.
Introduction and methodology
Technology has enabled people to connect more than ever before. We can choose to digitally share our lives with our partner, family, and friends regardless of how far we are physically. Yet, we are also seeing a rise in software that enables users to remotely spy on another person’s life via their digital device, without the affected user giving their consent or being notified.
The software, known as stalkerware, is commercially available to everyone with access to the internet. The risks of stalkerware can go beyond the online sphere and enter the physical world. The Coalition Against Stalkerware warns that stalkerware “may facilitate intimate partner surveillance, harassment, abuse, stalking, and/or violence.” Stalkerware can also operate in stealth mode, meaning that there is no icon displayed on the device to indicate its presence and it is not visible to the affected user. The majority of affected users do not even know this type of software exists. This means they cannot protect themselves, online or offline, especially as the perpetrator using stalkerware usually knows their victim personally.
In recent years, Kaspersky has been actively working with partners to end the use of stalkerware. In 2019, we created a special alert that notifies users if stalkerware is installed on their phones. Following that we became one of ten founding members of the Coalition Against Stalkerware. We also published our first full report on the state of stalkerware in the same year to understand the scale of the problem.
This report continues to examine the issue of stalkerware and presents new statistics from 2020, in comparison to our previous data. The data in this report has been taken from aggregated threat statistics obtained from the Kaspersky Security Network. The Kaspersky Security Network is dedicated to processing cybersecurity-related data streams from millions of voluntary participants around the world. All received data is anonymized. To calculate our statistics, we review the consumer line of Kaspersky’s mobile security solutions.
The issue of, and the story behind, stalkerware
Stalkerware is software that is commercially available to everyone with access to the internet. It is used to spy remotely on another person via their device, without the affected user giving their consent or being notified. Stalkerware operates in stealth mode, meaning that there is no icon displayed on the device indicating its presence, and it is not visible to the affected user. Therefore, the Coalition Against Stalkerware defines stalkerware as software which “may facilitate intimate partner surveillance, harassment, abuse, stalking, and/or violence”.
The dimension of cyberviolence
According to a report by the European Institute for Gender Equality, “seven in ten women in Europe who have experienced cyberstalking have also experience at least one form of physical and/or sexual violence from an intimate partner”. Echoing these findings, experts from non-profit organizations (NPOs) that help domestic abuse survivors and victims emphasize that cyberstalking is also a form of violence. Just as with physical, psychological, and economic violence, an abuser can use surveillance to obtain complete control of their victim/survivor[1] and stay in charge of the situation.
Using stalkerware, the extent of control held by the abuser can be immense. Depending on the type installed, stalkerware may have a variety of functions to intrude into the victim’s privacy. With the software’s help, an abuser can:
Read anything the surveilled person types – logging each keystroke on the device, including credentials to any kind of services such as banking applications, online shops and social networks, etc.
Know where they are – by tracking a person’s movements with GPS, in real time
Hear what they say – eavesdrop on calls, or even record them
Read messages on any messenger, regardless of whether encryption is used
Monitor social network activity
See photos and videos
Switch on the camera
All of this private information can be collected, usually from a mobile device, such as a tablet or a smartphone.
Non-profit organizations from the Coalition Against Stalkerware are experiencing a growing number of survivors seeking help with the problem:
Findings from the Second National Survey on technology abuse and domestic violence in Australia, launched by WESNET with the assistance of Dr. Delanie Woodlock and researchers from Curtin University, state that 99.3% of domestic violence practitioners have clients experiencing technology-facilitated abuse and that the use of video cameras increased by 183.2% between 2015 and 2020.
According to a study on cyberviolence in intimate relationships, conducted by the Centre Hubertine Auclert in France, 21% of victims have experienced stalkerware at the hands of their abusive partner, and 69% of victims have the feeling that the personal information on their smartphone has been accessed by their partner in a hidden way.
In Germany, for several years, Women’s Counselling Centers and Rape Crisis Centers (bff) have noticed an increasing use of stalkerware in conjunction with partner relationships.
In the USA, stalking impacts an estimated 6-7.5 million people over a one-year period, and one-in-four victims report being stalked through some form of technology, according to the Stalking Prevention Awareness & Resource Center (SPARC).
Physical access is the key
Unfortunately, it is not too difficult to secretly install stalkerware on a victim’s phone. The main barrier that exists is that stalkerware has to be configured on an affected device. Due to the distribution vector of such applications which are very different from common malware distribution schemes, it is impossible to get infected with a stalkerware through a spam message including a link to stalkerware or a trap via normal web surfing.
This means that the abuser will need to have physical access to the target device in order to install stalkerware. This is possible if the device either has no pin, pattern, or password to protect it or alternatively, the abuser knows the victim/survivor personally. Installation on the target device can be completed within a few minutes.
Prior to accessing the survivor’s device, the abuser has to collect a link to the installation package from the stalkerware developer’s webpage. In most cases, the software is not downloaded from an official application store. For Android devices, Google banned applications that are clearly stalkerware from its Google Play application store in 2020. This means the abuser will not be able to install such an application from the general app store. Instead, the abuser must follow several steps before being able to install stalkerware. As a result, the abuser may leave traces in the device settings that a user can check if they are concerned they may be being spied on.
Stalkerware tools are less frequent on iPhones than on Android devices because iOS is traditionally a closed system. However, perpetrators can work around this limitation on jailbroken iPhones. They still need physical access to the phone to jailbreak it, so iPhone users who fear surveillance should always keep an eye on their device. Alternatively, an abuser can offer their victim an iPhone – or any other device – with pre-installed stalkerware as a gift. There are many companies who make their services available online to install such tools on a new phone and deliver it to an unwitting addressee in factory packaging to celebrate a special occasion.
The risk of privacy leaks
The information monitored via stalkerware will be available to at least one person – the abuser who installed stalkerware on the survivor’s phone. However, sometimes it is possible that all the private data may become publically available. Year on year, stalkerware servers are either hacked or left openly unprotected so that information can be accessed and leaked online. For example, in 2020, such a data breach occurred due to a product provided by ClevGuard. In previous years, we have seen similar incidents with Mobiispy in 2019 and with MSpy in 2018 and 2015.
These are just a few examples of a long list in which databases from companies developing stalkerware have been exposed, affecting millions of user accounts. With the possibility to track a person’s location, it means that not only their cyberprivacy is lost but also their security in the physical world may be at risk.
The legal status
Stalkerware applications are sold and provided by companies under various facades, such as child monitoring or employee tracking solutions. While laws vary from one country and state to another, they are catching up. Generally speaking, it is only illegal to use such tools and apps that record user activity without their consent or that of legal authority. Slowly we are seeing some shifts in legislation. For instance, in 2020, France reinforced sanctions on secret surveillance: geolocating someone without their consent is now punishable with one year imprisonment and a fine of 45,000 euros. If this is done within a couple, the sanctions are potentially higher, including two years’ imprisonment and a fine of 60,000 euros.
Stalkerware tools often violate laws and expose the stalker to legal liability for any recordings made without the victim’s knowledge. Stalkers must realize that they are breaking the law. If the use of stalkerware is reported, the punishment applies to the private perpetrator who installed the software – not its vendor. In the USA, only two stalking app developers have been fined in recent history. One had to pay a record 500,000 US dollar fine, which put an end to the app development process, while the other got off with an order to change the app’s functionality for future sales.
The scale of the issue
Global detection figures – affected users
In this section, we look at the global numbers of unique users whose mobile device was found to have stalkerware detected.
The 2020 data shows that the stalkerware situation has not improved much: the number of affected people is still high. A total of 53,870 unique users were affected globally by stalkerware in 2020. Whereas in 2019, 67,500 unique users were affected globally. However, the fact must be taken into account that 2020 was an unprecedented year in which lives have changed in a dramatic way across the globe.
To fight the COVID-19 pandemic, all countries in the world have faced massive restrictions such as self-isolation measures or lockdowns in order to make people stay at home. Considering that stalkerware is used as another tool to control an intimate partner who the abuser lives with as they go about their day-to-day life, this can explain the somewhat lower numbers in comparison with the previous year.
Unique users affected by stalkerware globally from 2018 until 2020 – total per year
When looking at the figures of the total number of unique users affected by stalkerware in 2020 worldwide per month, this trend becomes even more noticeable. The first two months of the year were stable with many cases of affected devices arising, showing stalkerware was quite popular. The situation changed in March when many countries decided to announce quarantine measures. The curve shows a trend that the numbers began to stabilize as of June 2020 when many countries around the world eased restrictions.
Unique users affected by stalkerware in 2020 worldwide – total by month
That said, the 2020 numbers are still on a high, stable level. In comparison, in 2018, there were 40,173 detections of unique users being affected globally by stalkerware. This brings into perspective the total numbers from 2020, as we have seen a growing integration of technology into our lives. Sadly, this also means the software used for stalking is becoming more common as another form of intimate partner violence.
Global detection figures – stalkerware samples
In this section, we analyze which stalkerware samples are actually the most used to control mobile devices on a global level. In 2020 the most detected samples can be seen in the following results.
Top 10 most detected stalkerware samples globally
Samples Affected users
1 Monitor.AndroidOS.Nidb.a 8147
2 Monitor.AndroidOS.Cerberus.a 5429
3 Monitor.AndroidOS.Agent.af 2727
4 Monitor.AndroidOS.Anlost.a 2234
5 Monitor.AndroidOS.MobileTracker.c 2161
6 Monitor.AndroidOS.PhoneSpy.b 1774
7 Monitor.AndroidOS.Agent.hb 1463
8 Monitor.AndroidOS.Cerberus.b 1310
9 Monitor.AndroidOS.Reptilic.a 1302
10 Monitor.AndroidOS.SecretCam.a 1124
With more than 8,100 users having been affected by it, Nidb was the most used stalkerware sample in 2020. The Nidb creator sells their product as Stalkerware as a Service. This means that anyone could rent their control server software and mobile application, rename it to any suitable marketing name and sell it separately—examples of this include iSpyoo, TheTruthSpy, Copy9, and others.
Both second and eighth place are occupied by Cerberus. These are two different samples under the same family. Variant Cerberus.a affected more than 5,400 users.
Agent.af comes in third place, with more than 2,700 users having been affected. This is marketed as Track My Phone and has typical features such as reading messages from any messenger, logging a person’s call history, and tracking geolocation.
Anlost.a is a good example of stalkerware in disguise. It is advertised as an antitheft application, and its icon is present on the home screen (not usual behavior for stealthy stalkerware apps). Therefore, it is available on the Google Play Store. That said, it is possible to deliberately hide the icon from the home screen. One of the key functionalities of the application is to intercept SMS messages and read the call log. More than 2,200 users having been affected by this sample.
MobileTracker.c has several functionalities such as intercepting messages from popular social networks and taking remote control of the affected device. More than 2,100 users having been affected by this sample.
PhoneSpy is also known as Spy Phone app or Spapp Monitoring. This application consists of many spy features, covering all popular instant messengers and social networks.
Agent.hb is another version of MobileTracker. Like the original version, it offers many functionalities.
Cerberus.b, a different sample from the same family as Cerberus.a.
Reptilic.a is stalkerware that includes many features such as social media monitoring, call recordings, and browser history monitoring.
SecretCam.a is camera stalking software, meaning it is able to secretly record video from the front or back camera of the affected device.
Geography of affected users
Stalkerware is a global phenomenon that affects countries regardless of size, society, or culture. When looking at the top 10 affected countries worldwide in 2020, Kaspersky’s findings show that largely the same countries remain the most affected, with Russia in the number one spot. Yet, we see an increase in stalkerware activity in Brazil and the USA in 2020 compared to 2019. However, we detected fewer incidents in India, which has fallen in the rankings. We have also detected a higher number of incidents in Mexico, which has risen in the ranking two places.
Top 10 most affected countries by stalkerware – globally
Country Affected users
1 Russian Federation 12389
2 Brazil 6523
3 United States of America 4745
4 India 4627
5 Mexico 1570
6 Germany 1547
7 Iran 1345
8 Italy 1144
9 United Kingdom 1009
10 Saudi Arabia 968
When considering Europe, Germany, Italy and the UK are the three most affected countries, in that order. They are followed by France in fourth place and Spain in fifth place.
Top 10 most affected countries by stalkerware – Europe
Country Affected users
1 Germany 1547
2 Italy 1144
3 United Kingdom 1009
4 France 904
5 Spain 873
6 Poland 444
7 Netherlands 321
8 Romania 222
9 Belgium 180
10 Austria 153
How to check if a mobile device has stalkerware installed
It’s hard for everyday users to know if stalkerware is installed on their devices. Generally, this type of software remains hidden which includes hiding the icon of the stalkerware app on the home screen and in the phone menu and even cleaning any traces that have been made. However, it may give itself away and there are some warning signs. Among the most important are:
Keep an eye out for a fast draining battery, constant overheating and mobile data traffic growth.
Do regular antivirus scanning on your Android device: If the cybersecurity solution detected stalkerware, do not rush to remove it as the abuser may notice. Have a safety plan in place and reach out to a local help organization.
Check browser history: To download stalkerware, the abuser will have to visit some web pages, the affected user does not know about. Alternatively, there could be no history at all if abuse wiped it out.
Check “unknown sources” settings: If “unknown sources” are enabled on your device, it might be a sign that unwanted software were installed from third-party source.
Check permissions of installed apps: Stalkerware application may be disguised under a wrong name with suspicious access to messages, call logs, location, and other personal activity.
However, it’s also important to understand that warning signs or symptoms are not necessarily proof that stalkerware is installed on a device.
How to minimize the risk
There are a few pieces of advice that can help to increase your digital safety:
Never lend your phone to anyone without seeing what happens with the phone and not leave it unlocked.*
Use a complex lock screen password and change passwords on a regular basis.
Do not disclose your password to anyone – not even your intimate partner or family members or close friends.*
Do regular checks of your phone— delete apps you don’t use and review the permissions granted to each app.
Disable the option of third-party application installation on Android devices.
Protect your Android devices with a cyber-security solution, such as Kaspersky Internet Security for Android (for free), which detects stalkerware and issues warnings.
*In the context of domestic violence and abusive relationships it may be difficult or even impossible to deny the abusive partner access to the phone.
Kaspersky’s activities and contribution to end cyberviolence
Kaspersky is actively working to end the use of cyberviolence and stalkerware, as a company, and together with many other partners. In 2019, we created a special alert that notifies users when stalkerware is installed on their phones. In the same year, with nine other founding members we created the Coalition Against Stalkerware. In 2020, we created TinyCheck, a free tool to detect stalkerware on mobile devices – specifically for service organizations working with victims of domestic violence. TinyCheck can be found on https://github.com/KasperskyLab/TinyCheck. Since 2021, we are one of five partners in an EU-wide project aimed at tackling gender-based cyberviolence and stalkerware called DeStalk, which the European Commission chose to support with its Rights, Equality and Citizenship Program.
About the Coalition Against Stalkerware
The Coalition Against Stalkerware (“CAS” or “Coalition”) is a group dedicated to addressing abuse, stalking, and harassment via the creation and use of stalkerware. Launched in November 2019, the Coalition Against Stalkerware gained 26 partners in its first year. These include founding partners – Avira, Electronic Frontier Foundation, the European Network for the Work with Perpetrators of Domestic Violence, G DATA Cyber Defense, Kaspersky, Malwarebytes, The National Network to End Domestic Violence, NortonLifeLock, Operation Safe Escape, and WEISSER RING. The Coalition looks to bring together a diverse array of organizations to actively address the criminal behavior perpetrated through stalkerware and increase public awareness about this important issue. Due to the high societal relevance for users all over the globe and new variants of stalkerware emerging periodically, the Coalition Against Stalkerware is open to new partners and calls for cooperation. To find out more about the Coalition Against Stalkerware please visit the official website www.stopstalkerware.org
[1] Experts refer in their terminology more and more to the empowering term survivor instead of victim. Hence, in this report, we will use both terms.
Stalkerware Volumes Remain Concerningly High, Despite Bans
27.2.2021 Cyber Threatpost
COVID-19 impacted volumes for the year, but the U.S. moved into third place on the list of countries most infected by stalkerware.
Tens of thousands of mobile users were infected by the class of software known generically as stalkerware last year.
According to just-published research by Kaspersky, 2020 lockdowns related to the global COVID-19 pandemic put a damper on installations, but the scourge of privacy-busting software still invaded the lives of many at-risks individuals.
According to Kaspersky’s “The State of Stalkerware 2020” report, there were 53,870 mobile users within its telemetry who were affected by stalkerware during the year. That’s a drop from the year before, when 67,500 mobile users were affected, but still up from the 40,386 instances detected amongst Kaspersky’s client base in 2018.
This is despite the fact that Google banned stalkerware apps from Google Play last year.
Stalkerware is defined as software that can be installed on someone’s phone, allowing the person’s physical location to be tracked, calls and messages monitored, social-media activity snooped upon, and photos and videos to be seen. It can also switch on a device’s camera to see what the target is doing or who the person is with.
In general, it allows someone to remotely spy on another person’s life via their digital device. This is usually done without the affected user giving their consent or being notified. The Coalition Against Stalkerware warns that these pernicious apps “may facilitate intimate partner surveillance, harassment, abuse, stalking and/or violence.”
The issue statistically does correlate to physical abuse: According to a report by the European Institute for Gender Equality, seven in 10 women in Europe who have experienced cyberstalking have also experienced at least one form of physical or sexual violence from an intimate partner.
Stalkerware Volume Increases in U.S.
Russia, Brazil, the United States, India and Mexico were the top five countries where users were most impacted in 2020, in that order, according to Kaspersky’s report. The U.S. passed India, rising on the list from fourth place in 2019 to third in 2020.
Germany was the top European country, occupying sixth place in the global rankings. Iran, Italy, the United Kingdom and, lastly, Saudi Arabia complete the 10 most-affected nations.
“We see the number of users affected by stalkerware has remained high and we detect new samples every day,” said Victor Chebyshev, research development team lead, Kaspersky, in a media statement. “It’s important to remember that there is somebody’s real life story behind all these numbers, and sometimes there is a silent call for help.”
It’s notable that “the yearly curve began to rise again in the second half of 2020, after some lockdown measures were lifted,” the report added. The reason that lockdowns may have affected the rate of stalkerware installation is because targets would be less likely to be out and about, reducing the need for keeping track of someone’s physical movements and remote activity.
The first two months of the year were in line with numbers from the year before. The situation changed in March when many countries decided to announce quarantine measures. Volumes began to rise again in June, when many countries around the world eased restrictions.
Stalkerware instances, month by month. Source: Kaspersky.
Top Stalkerware Apps
With more than 8,100 users affected globally, Nidb is the most-used stalkerware strain, according to Kaspersky’s stats. The code forms the core of several stalkerware brands, researchers said, including iSpyoo, TheTruthSpy and Copy9, among others.
“The Nidb creator sells their product as stalkerware-as-a-service,” according to the firm. “This means that anyone could rent their control server software and mobile application, rename it to any suitable marketing name and sell it separately.”
Source: Kaspersky.
Both second and eighth place are occupied by different versions of Cerberus – an Android malware that started life as a banking trojan, but which is now a fully fledged remote access trojan (RAT) available for rent in underground forums.
And Agent.af comes in third place, which is marketed as the “Track My Phone” app. It can read messages from any messenger, log a person’s call history and track geolocation.
Some apps do try to get around bans by Google and others by claiming to do something else entirely. The “Anlost” malware for instance, No. 4 on Kaspersky’s Top 10 most-common stalkerwares, is advertised as an antitheft application. It can intercept SMS messages and read the call log of a device.
“And its icon is present on the home screen (not usual behavior for stealthy stalkerware apps),” according to the report. “Therefore, it is available on the Google Play store. That said, it is possible to deliberately hide the icon from the home screen.”
Stalkerware companies have also sold apps that purport to help parents track their young children – even though their capabilities could be used for other purposes. Increasingly, app gatekeepers are cracking down on these types of offerings.
That was the case with three Retina-X apps, which were barred by the Federal Trade Commission (FTC): MobileSpy, PhoneSheriff and TeenShield. While these three apps were marketed for monitoring mobile devices used by children, or for monitoring employees, the FTC determined that they “were designed to run surreptitiously in the background and are uniquely suited to illegal and dangerous uses.”
Another example is an app called “Monitor Minor,” which researchers flagged as problematic last year. The Android version of the app gives stalkers near absolute control of targeted devices, going so far as allowing them to capture the unlock pattern or unlock code of phones.
Stalkerware Requires Physical Access
Stalkerware isn’t delivered in the same way as other malware; it can’t be sent via a sneaky email or installed in some other remote way, Kaspersky said. This means that the abuser will need to have physical access to a device in order to install it. Once past any lock-screen, it only takes a few minutes to load an app, researchers said.
“The main barrier that exists is that stalkerware has to be configured on an affected device,” according to the report. “Due to the distribution vector of such applications which are very different from common malware distribution schemes, it is impossible to get infected with a stalkerware through a spam message including a link to stalkerware or a trap via normal web surfing.”
Stalkerware is usually downloaded from third-party sources. This is easy for Android users; but iPhone stalkerware tools are less frequent because iOS is traditionally a closed system with apps from third party stores barred from running on it.
However, “an abuser can offer their victim an iPhone – or any other device – with pre-installed stalkerware as a gift,” according to Kaspersky. “There are many companies who make their services available online to install such tools on a new phone and deliver it to an unwitting addressee in factory packaging to celebrate a special occasion.”
How to Check for Stalkerware on a Phone
To check for stalkerware, users can run an antivirus solution, and keep an eye out for a fast-draining battery, constant overheating and mobile data traffic growth. Users can also check the browser history, because an abuser would have needed to download the app from a website.
Users should also check to see if “unknown sources” are enabled on devices; this might be a sign that unwanted software was installed from third-party source. And, they should check the permissions of installed apps: Stalkerware applications may be disguised under a wrong name with suspicious access to messages, call logs, location and other personal activity.
“It’s hard for everyday users to know if stalkerware is installed on their devices,” according to Kaspersky. “Generally, this type of software remains hidden which includes hiding the icon of the stalkerware app on the home screen and in the phone menu and even cleaning any traces that have been made. However, it may give itself away and there are some warning signs.”
Microsoft: SolarWinds Attackers Downloaded Azure, Exchange Code
20.2.2021 Cyber Threatpost
However, internal products and systems were not leveraged to attack others during the massive supply-chain incident, the tech giant said upon completion of its Solorigate investigation.
Threat actors downloaded some Microsoft Exchange and Azure code repositories during the sprawling SolarWinds supply-chain attack but did not use the company’s internal systems or products to attack other victims.
That’s the final verdict this week by the tech giant now that it’s completed a comprehensive investigation into the attack, which was discovered in December and continues to have repercussions across the industry.
“We have now completed our internal investigation into the activity of the actor … which confirms that we found no evidence of access to production services or customer data,” the company said in a blog post on its Microsoft Security Response Center published Thursday. “The investigation also found no indications that our systems at Microsoft were used to attack others.”
Texas-based SolarWinds was the primary victim of the now-infamous cyberattack believed to be the work of Russian state-sponsored actors. During the attack, adversaries used SolarWinds’ Orion network management platform to infect users with a stealth backdoor called “Sunburst” or “Solorigate,” which opened the way for lateral movement to other parts of a network.
The backdoor was pushed out via trojanized product updates to almost 18,000 organizations around the globe—including high-profile victims such as the U.S. Department of Homeland Security (DHS) and the Treasury and Commerce departments—starting last spring. Once embedded, the attackers were able to pick and choose which organizations to further penetrate.
Microsoft came out as one of those victims in December, acknowledging that malicious SolarWinds binaries were detected in its environment, which the company immediately isolated and removed, a spokesperson said at the time. Microsoft subsequently began its investigation into the situation following its initial detection of unusual activity.
“Our analysis shows the first viewing of a file in a source repository was in late November and ended when we secured the affected accounts,” the company said in the post. “We continued to see unsuccessful attempts at access by the actor into early January 2021, when the attempts stopped.”
Despite its quick response, there was some fallout from the attack. Threat actors apparently accessed and downloaded source code from a “small number of repositories,” Microsoft said.
These repositories contained code for: A small subset of Azure components including those related to service, security and identity; a small subset of Intune components; and a small subset of Exchange components. However, because of internal protections in place, the repositories did not contain “any live, production credentials,” according to the company.
“The search terms used by the actor indicate the expected focus on attempting to find secrets,” according to Microsoft. “Our development policy prohibits secrets in code and we run automated tools to verify compliance. Because of the detected activity, we immediately initiated a verification process for current and historical branches of the repositories.”
Ultimately, Microsoft’s existing “in-depth protections” prevented the threat actor from gaining access to privileged credentials or leveraging the techniques used in the attack against its corporate domains, the company concluded.
Digital Warfare: Myanmar's Cyber Crackdown Explained
18.2.2021 Cyber Securityweek
Flag of Myanmar
Myanmar's military has imposed repeated internet blackouts, blocked some social media sites and drafted a cybersecurity bill as it attempts to grind down resistance to its takeover.
These moves by the new junta have deepened worries that internet-hungry Myanmar will no longer have access to real-time information, be largely cut off from the outside world and face draconian punishments for online posts.
What has happened since the coup?
The military has so far ordered five temporary internet shutdowns, starting on February 1 -- the day of the putsch -- when civilian leader Aung San Suu Kyi was detained.
In recent days, communications have been throttled three consecutive nights for a period of eight hours between 1 am and 9 am.
Monitoring group NetBlocks said internet connectivity during these outages dropped at times to 15 percent of normal levels.
Also blocked are social media platforms such as Facebook and Twitter, where an online campaign to oppose the coup gained steam.
The blackouts bring back memories of the pre-internet days under the previous junta regime for Myo Naing, 46.
"People had to gather on the street and share the information," the car rental salesman told AFP.
Myanmar did not have easily available internet until about 2013, when a state monopoly on telecommunications ended and international companies began offering affordable sim cards.
Why the internet shutdowns?
That is unclear.
One possible explanation is that the regime is using the time to analyse data to track down targets for arrest, Australian cybersecurity expert Damien Manuel from Deakin University told AFP.
But Matt Warren of Melbourne's RMIT University said the regime could be borrowing from China's playbook on creating a state-monitored firewall to control information flows.
"The Chinese model is an example of how a (government) can control a population online," he told AFP, adding that Saudi Arabia, Turkey and Vietnam have similar but less sophisticated measures.
Whatever the reason, the military's internet shutdowns could be characterised as "ad hoc".
"They're reacting to the situation. They didn't have a plan to control the internet as soon as the (coup) happened," he told AFP.
Another possible explanation for the timing of the outages is that the junta wants to keep businesses up and running throughout the day.
Is it working?
The shutdowns have not deterred protesters from taking to the streets, but they have been successful at striking fear into people's hearts.
"They can do anything they want (during the shutdown) so we have to protect our streets," said Yangon resident Win Tun, 44.
But in terms of getting online, Myanmar netizens have managed to skirt the social media blocks by using virtual private networks (VPNs).
Top10VPN, a Britain-based digital security advocacy group, reported a 7,200-percent increase in local demand for VPNs in the immediate aftermath of Facebook being banned on February 4.
"As VPNs provide a means for citizens to bypass restrictions, authorities will often restrict them to ensure their internet shutdowns are effective," Samuel Woodhams of Top10VPN told AFP.
He added that there had been reports of VPN services being blocked in Myanmar, although it was unclear exactly how many had been affected.
"It shows the determination of the government to restrict citizens' access to information and freedom of expression," he said.
Some internet users in Myanmar have also circumvented the blackouts with foreign sim cards.
What about new laws?
The military junta has proposed draconian new laws that give it sweeping powers to block websites, order internet shutdowns and restrict the dissemination of what it deems false news.
It has also called for all internet service providers to keep user data for up to three years, and provide it "for the sake of national security".
Norway-based Telenor -- which in recent weeks has had to comply with temporary internet shutdowns at the regime's direction -- expressed alarm over the draft law's "broad scope".
Myanmar-based civil society groups, private companies and even a manufacturing and industrial association have denounced the bill.
Their concerns range from human rights to worries that it could stifle a business-friendly environment.
What is the global reaction?
"Myanmar's proposed cybersecurity law is the dream of despots everywhere," said Human Rights Watch's legal advisor Linda Lakhdhir.
"It would consolidate the junta's ability to conduct pervasive surveillance, curtail online expression, and cut off access to essential services."
The United Nations on Monday denounced Myanmar's military rulers for choking off the internet.
UN envoy for Myanmar Christine Schraner Burgener spoke with the deputy commander of the Myanmar army, Soe Win, and warned that "network blackouts undermine core democratic principles," UN deputy spokesman Farhan Haq said.
The UN's special rapporteur for Myanmar went even further, accusing the military of declaring "war on the people".
"Late night raids; mounting arrests; more rights stripped away; another Internet shutdown; military convoys entering communities. These are signs of desperation," Tom Andrews tweeted. "Attention generals: You WILL be held accountable."
The Importance of a Proactive Cyber Defense Solution To Protect Your Critical Data
14.2.2021 Cyber Securityaffairs
Personal and Corporate data is now regularly targeted and traded by unscrupulous actors, protect it with a proactive Cyber Defense solution.
If your enemy is secure at all points, be prepared for them. If they are in superior strength, evade them. If your opponent is temperamental, seek to irritate him. Pretend to be weak, that they may grow arrogant. If they are taking their ease, give them no rest. If their forces are united, separate them. If sovereign and subject are in accord, put division between them. Attack them where they are unprepared, appear where you are not expected.” Sun Tzu
The Military Chinese General and Philosopher Sun Tzu (544 BC – 496 BC) wrote these tactics over two thousand years ago, and it is as applicable today as it ever was. Personal and Corporate data is now regularly targeted and traded by unscrupulous actors who use it to undermine Governments, destabilise markets, intimidate or threaten companies and individuals. Your data, and the data you entrust to others is now the most valuable commodity on earth, and those who want to gain unauthorized access to it, will use every means at their disposal to do so. This is the era of Cybercriminals and understanding their methods and means, is the most important factor to avoid becoming their next victim.
Cybersecurity is a complex subject matter for most people, and the levels of sophistication and ingenuity being applied in some cyberattacks, shows that there is an ever-increasing level of co-operation and exchange of information by the criminal underworld. The fact the Dark Web facilitates the exchange of criminal intelligence and many sophisticated tools that were developed for legitimate business or community benefits, are now often exploited by cybercriminals, and redirected against the market they were intended to benefit. This rich mix of traded underworld information and data and the massive wealth that can be obtained from it, means that there will always be a rapidly evolving cybersecurity threat. As I write this article, news of a Florida water treatment plant being hacked with the perpetrators trying to poison the supply by dramatically increasing the sodium hydroxide levels in the water.
The recent security exploit perpetrated on the Cybersecurity software company SolarWinds is a dramatic example of how bad and ugly it can actually get. Their Cybersecurity product is called Orion and is used by over 300,000 of their customers including more than 425 of the US Fortune 500 companies including Microsoft, Cisco, Intel, Deloitte, Maersk, all ten of the top ten US telecommunications companies, all five branches of the US Military, the US Pentagon, State Department, NASA, National Nuclear Security Administration, Postal Service etc… The attackers managed to access systems that SolarWinds uses to assemble software updates to its Orion product, as the company explained in a filing to the US Security and Exchange Commission on 14th December 2020.
The attackers inserted malicious code into otherwise legitimate software updates in what is referred to as a supply-chain attack, since it infects software as it was under assembly. The breach in SolarWinds went undetected for Months and was only discovered when another prominent cybersecurity firm that used the Orion Cybersecurity product, discovered that the Cybersecurity product itself was the cause of the security breach.
In this article we are going to explore how meticulously planned cyberattacks such as the SolarWinds Orion attack could have been detected and exposed in real-time, rather than being detected by one of their customers months later. I have previously written an article that discussed the various cyberattacks types (which included the type of exploit used against SolarWinds) and explain how and why cyber defence solutions are failing us so spectacularly – the article titled “It is time to re-evaluate cyber defence solutions” is available here.
I will explain how one of the most catastrophic cyberattacks of current times could have been easily avoided if a proactive cybersecurity solution like ACSIA was implemented. The product we built is based entirely on Open Source technology, and one of our security modules utilises a technology called Falco. Falco is an open source library, a kernel module for Linux systems that intercepts the traffic between userspace and kernel space, detecting unexpected application and OS behaviour at runtime. ACSIA uses this module to monitor and inspect real-time network and security activity in the Linux kernel – a key function of cybersecurity deterrence.
The SolarWinds Cyberattack involved cybercriminals compromising the server infrastructure of the platforms used by SolarWinds to build/assemble their Orion platform, using that access to produce and distribute to their customers a ‘trojan horse’ version of their software.
This attack was meticulously planned over months, with the cybercriminals taking their time to study the infrastructure, identifying the development platforms containing the Orion source code, before compromising it. The attackers gained full access to the source code in order to become as familiar with it as the Orion developers themselves, before embedding modified portions of code back into the product that enabled the cybercriminals to communicate inbound and outbound with all SolarWinds customers deploying the modified Orion code.
The phased analysis of this attack can be split into following three sequential stages:
Compromising the server user account hosting the source code in SolarWinds
Embedding the portion of malicious code into the Orion product (the backdoor)
Using/exploiting the backdoor exfiltration of data from all customer systems where the compromised Orion code was deployed.
We will now look at how a proactive cybersecurity technology such as ACSIA would capture and respond to each of these three separate attack vectors and eliminate the threat they represent in real-time.
It is worth recalling that many of the SolarWinds end-customers who were affected by this cyberattack are among the most respected and security conscious organisations, all with very large annual security budgets.
Could SolarWinds have prevented their Development servers being compromised?
The company has been tight lipped about how the cybercriminals initially gained access to their environment, so they either do not know the answer to this question or are unwilling to disclose how their security was initially breached. On the basis that they are a Cybersecurity company, the most plausible explanation is that a legitimate user account or an automated source code commit user (non-human user, system or application user) account was compromised.
These are two separate attack methods, so we will see how the proactive ACSIA Cybersecurity product would isolate either option, and eliminate it.
The figure 1 below, we see how ACSIA responds to a valid user account being accessed multiple times from different locations that are not within the corporate network or environment of 4Securitas.
Fig 1. Potential user account compromise
The above notification details a potential account compromise for account username ‘centos’ and includes details on IP address and geo-location of attempted access. Remediation options provided by ACSIA are available by clicking the appropriate action to Kill the connection, Ban the IP address etc…
In figure 2 below, ACSIA alerts us that a system/application user has accessed the development platform using ssh key-pair as authentication method (as opposed to password). It provides the details such as geographical location from where the user accessed, the IP address, the coordinates.
Fig 2: Automated system or application user account (in this case called git) attempts a potential account compromise
Again, the remediation options provided by ACSIA are available by clicking the appropriate action to Kill the connection, Ban the IP address etc…
These alert responses from ACSIA are sufficient for an organization to have full visibility about who is attempting to access systems and from where. All remediation actions can be performed manually by choosing the desired action. This is how simple it is for an ACSIA user to repel such types of attack in real-time.
Could the malicious code embedded into the source code of Orion have been prevented?
The method used by the cybercriminals to embed malicious source code into Orion was so perfect, that they must have known and understood the SolarWinds environment as well as legitimate employees of the company. This is a clear indication that they had full access to the source code for a very extended period. As stated earlier, the most plausible explanation on how the SolarWinds platforms were initially illegally accessed was by using compromised user or system accounts. Any alternative explanation would have required injecting the entire malicious code directly into the source code platform which would be impossible without having full access to the resident source code.
This means that the cybercriminals were accessing multiple systems across the development platform for extended periods of time without being detected. Whether they used System Accounts, Application or User Accounts is irrelevant, as they traversed, navigated and studied the Orion source code before embedding malicious code into the product.
Using the kernel monitoring module in ACSIA, any data manipulation would have been detected immediately and promptly alerted to security personnel, highlighting every and any permission or access violations being performed by the cybercriminals (of which there would have been many).
Figure 3 below shows exactly how this type of privilege escalation would have been detected in real-time using ACSIA.
Fig 3: git user performing some of its tasks via sudo/root privileges
The alert and remediation in figure 3 shows how embedded eBPF filters combine with ACSIA’s bespoke algorithms, provide a simple, short but concise ‘system violation’ alert with appropriate remediation options. In the example provided, the username git without sudo privileges is attempting to perform a privileged action. A typical privilege escalation attack looks exactly like this.
Our example shows that the git user is performing a log rotation, which is a legitimate action, we can therefore ignore this particular alert by closing it. Relating this to the SolarWinds Orion hack, from the instant any system’s user is compromised, ACSIA will generate an alert and remediation option like this, every time the compromised user navigates through the system (or systems) and tries to escalate its privileges. It would also expose any actions to inject or commit changes into source code.
What ACSIA is essentially doing here is to intercept the anomalous activity within the kernel and acting on it. The powerful message here is the ability to listen to the system calls, everything user space communicates into kernel space, every single interaction with the core engine of the operating system, there is nothing capable of bypassing such a granular monitoring of activity on a platform. Therefore, it does not matter how malware and rootkit may try to become invisible or how it obfuscates itself in memory and in system binaries, ACSIA will always distinguish these activities by utilizing our kernel level analysis module.
Could Data exfiltration via outbound connections have been prevented in Orion?
While SolarWinds may have been a victim of this cyberattack, the objective was to use the exploit of the Orion product to gain access to their 300,000 customers. The SolarWinds customers using this infected Orion codebase were the real victims of this crime, as the malicious code was created to harvest their data and make an outbound connection to deliver the data to the cybercriminals. To do this the cybercriminals created an external web server used as a command and control centre hosted on Godaddy, with a domain name avsvmcloud.com through which all customer data was transferred to them.
Analysing this final part of the hack, it is apparent that for customers data to be exfiltrated it would require outward bound ports to be opened to the command and control website. This type of activity is also easily detected by the kernel monitoring capabilities of ACSIA which detects the outbound connection through ephemeral ports (unprivileged ports that are used to exfiltrate data).
The below screenshot shows a very similar case:
Fig 4: Outbound connection detected
The above screenshot is the event captured by ACSIA where there is an outbound connection and is explained as follows:
Kernel event by User null: Detect outbound connections to common miner pool ports on server gitlab.acsia.io.
Indicates that a mechanism within the application itself has made an outbound connection using a common miner pool port and it is interacting with 3rd party services where the data is being exported. The common miner pool ports are ephemeral ports (>1024) that are typically used by miners but also by trojans, rootkits and malware to exfiltrate data. The outbound connection was initiated by the GitLab application, so that is why the user is null, it is a ‘userless’ process. In the case of Orion software where Orion’s own protocol was used to export data this would have been detected and notified instantly.
Critical Outbound connection to IP/Port flagged by cryptoioc.ch (command=ruby /opt/gitlab/embedded/service/gitaly-ruby/gitlab-shell/hooks/post-receive port=8080 ip=127.0.0.1
The message details shows that the outbound connection is flagged by cryptoioc.ch and the library that is making that outbound connection is ‘post-receive’ within GitLab. The port used in this case is 8080 indicating the IP that makes this connection is the loopback interface (localhost) of the server itself.
In our example the alert was triggered because our GitLab server made an outbound connection towards another server. This specific event is where GitLab is running its pipeline through a separate system outside GitLab. We use a runner (CI/CD) to do a pipeline for GitLab and that is how such events are detected in real-time whenever and wherever code is being manipulated.
This is how powerful the kernel level analysis and the exfiltration of data like the case of SolarWinds attack could have been instantly exposed using ACSIA.
Conclusion
Let me be slightly critical given the nature of organizations that were affected by SolarWinds attack (i.e. government agencies and institutions). All of them have very expensive suites of cybersecurity products, provided by large cyber vendors, which are then monitored by teams of equally expensive specialist security personnel. So while the end-user is ultimately responsible for maintaining their own security, the industry itself must take responsibility for the poor design of their vertically oriented, reactive security solutions.
Major vendors tend to oversell their cyber solution using terms like “NextGen”, “Machine Learning” or “Artificial Intelligence” as buzzwords to suggest their technical leadership in the market will provide you with a heretofore unrivalled level of security protection. The reality is that they are reactive solutions that are designed to respond to an attack after it has occurred – never with an offensive capability that will help prevent an attack in the first place. This is what is referred to as a cyber Blind-Spot and is what makes them vulnerable to very specific exploits such as the SolarWinds hack.
The reason why these cyber Blind-Spots exist is primarily because most of the major vendor products are designed by developers, data scientists and marketing people but not by cybersecurity architects. If you doubt my conclusion, did you ever wonder why your security product needs a massive database or in many cases a data lake!
If I was to summarise (in no particular order) why so many Cybersecurity products can be easily bypassed, then the following would apply:
Most cybersecurity products are obsessively focused on remedying a subset of what a security product should perform, a fact that necessitates the deployment of multiple niche security products.
Most cybersecurity products are reactive only tools, meaning that you are only alerted to security breaches once a platform has already been compromised
Most cybersecurity products are reactive only tools, meaning that you are only alerted to security breaches once a platform has already been compromised
Most cybersecurity products operate at the perimeter with an encrypted network layer which makes packet inspection impossible.
Many cybersecurity products are rules based and are easily outsmarted by Zero-day attacks and lack of updates
Virtually all cybersecurity products generate thousands of false alerts leading to omissions and mistakes
Billions of Passwords Offered for $2 in Cyber-Underground
9.2.2021 Cyber Threatpost
About 3.27 billion stolen account logins have been posted to the RaidForums English-language cybercrime community in a ‘COMB’ collection.
A “compilation of many breaches” – COMB for short – has been leaked on the cyber-underground, according to researchers. The so-called COMB contains a staggering 3.27 billion unique combinations of cleartext email addresses and passwords.
The trove is an aggregate database that brings together older stolen data from breaches past – including credentials from Netflix, LinkedIn, Exploit and others. COMB – which was given that name by the person who posted it online – was first made public on Feb. 2 by a user dubbed “Singularity0x01,” a researcher told Threatpost.
“On February 2, 2020, user Singularity0x01 created a thread on the popular English-language cybercriminal forum RaidForums titled ‘Compilation of Many Breaches (COMB) 3.8Billion (Public),'” Ivan Righi, cyber-threat intelligence analyst at Digital Shadows, said.
He added, “Singularity0x01 stated that the collection was built on a previous breach compilation that contained 1.4 billion records, and that the contents were mostly publicly available. The user also said that the data was presented in an alphabetical order and in a tree-like structure.”
In order to view the download link for the password-protected .ZIP file containing the data, forum users were asked to spend 8 RaidForums credits (about $2), he added. Then, they can use the database’s built-in tool for querying and sorting the information to slice and dice the data.
How Serious is the COMB Data Dump?
The data itself was not that well-received by underground denizens, Righi noted.
“Some users claimed that files were corrupted, files were missing, the total number of credentials was smaller than advertised, and the data was of low quality,” he explained – all of which led to Singularity0x01 gaining a negative reputation rating on the criminal forum.
“Singularity0x01 had also created two identical threads on the forum, leading some users to spend their tokens twice,” the researcher said. “Singularity0x01 was permanently banned from RaidForums on 08 Feb 2021 for ‘leaking hidden content,’ although no further information was provided by the site’s moderators.”
Dustin Warren, senior security researcher at SpyCloud, also took a look at the data and determined that the login combos have been in Dark Web circulation for some time.
“The 3.2 billion number by itself looks staggering, but we have to remember ‘quality vs. quantity,'” he told Threatpost. “The data appears to be full of account credentials that had been part of previously known breaches. In fact, this one appears to be a re-release of the Collection Combos leak from 2019, the Anti Public Combo list from 2016 and potentially others, but released with some tools for deduping, sorting and parsing of the data to make it easier to use. In other words, there is nothing new here.”
Credential-Stuffing Attacks in the Offing
The data may be old, but it’s not without value. Thanks to password reuse, hackers can use the data to mount brute-force or credential-stuffing attacks in an effort to hijack any number of types of accounts. And from there, the potential fallout becomes notable.
“It is an important reminder that old passwords can come back to haunt users who reuse them across accounts, which is why even old data can be useful to criminals,” Warren said. “Threat actors are no doubt running credential-stuffing attacks with this data so any accounts using the same logins and passwords could still be in jeopardy.”
Online banking, social-media, patient portals, loyalty points accounts and others all contain reams of information that can be used for financial fraud or to mount convincing follow-on phishing attack, for instance. And, work log-ins and email accounts that are compromised can lead to espionage efforts or business email compromise (BEC).
How to Mitigate COMB and Password Attacks
As always, implementing multifactor authentication (MFA) and maintaining good password hygiene (strong, unique passwords for all accounts and regular password rotation) can prevent much of the potential fallout from being caught up in this incident.
“A significant number of hacking-related breaches are still tied to weak passwords and the absence of MFA,” Terence Jackson, CISO at Thycotic, told Threatpost. “Use of a password manager and MFA are still two of the best ways online accounts can be protected from brute-force and password-spraying attacks. These ‘keys to the kingdom’ are what malicious actors covet because it gives them access to wreak havoc.”
“While MFA can prevent direct use of the credentials on services such as Office 365, it’s important to remember that MFA is not a silver bullet.
“Simple credentials would still be useful in conjunction with some other compromised asset as that would allow the attacker to overcome MFA,” Oliver Tavakoli, CTO at Vectra, told Threatpost. “Of course, this points out the criticality of enabling (and requiring) MFA for all authentication – especially for services (such as Office 365) directly accessible from the internet.”
France Tries Three for Attack Plot After Cyber Infiltration
2.2.2021 Cyber Securityweek
Two French citizens and a Moroccan went on trial in Paris on Monday charged with planning attacks after their cyber network was successfully infiltrated by a French intelligence agent posing as a jihadist.
The three, two of whom are aged 41 and the third 30, have been charged with joining a terror group with a view to carrying out attacks. If convicted they face up to 30 years in jail.
The agent from France's DGSI domestic intelligence service, using the codename Ulysse, had infiltrated communication networks of Islamic State (IS) group jihadists in a ruse that led to the arrest of the three.
The agent will give video evidence on Friday under the codename of 282-SI.
The trap laid by the agent is reminiscent of some episodes in the internationally successful French TV drama "The Bureau," which fictionalises the work of the DGSI's sister service on foreign intelligence, the DGSE.
The case began in 2016. After intelligence indicating the IS group was seeking to obtain weapons for a "violent action" on French soil, the DGSI agent managed to penetrate an encrypted Telegram messaging loop and make contact with an IS "emir" in Syria, nicknamed Sayyaf.
Sayyaf said the jihadists needed munitions including four Kalashnikovs, which Ulysse said he could supply.
In June 2016, Sayyaf sent Ulysse 13,300 euros ($16,000) in cash which was deposited on a grave in the Montparnasse cemetery in Paris.
With this money, Ulysse then told Sayyaf that he had bought weapons and hid them in a forest north of Paris. The surroundings were then equipped with surveillance cameras.
French intelligence then received information that the two French citizens, who had been around the Turkish-Syrian border, had come home and were readying for action.
They were arrested and found to have a USB key encrypted with the coordinates of the arms cache.
Another message was then received identifying a Moroccan who was then arrested. By analysing his telephone, investigators found that he had tried twice to uncover the arms cache.
The trial is due to continue until February 19.
France remains on high alert for jihadist attacks after a string of terror strikes from 2015 and a spate of isolated attacks at the end of last year.
Maritime port cybersecurity
28.1.2021 Cyber Securityaffairs
Let’s talk about cyber risk in the maritime and port setting to better understand Maritime Port cybersecurity.
In order to better understand the evolutionary trend of worldwide shipping and port facilities from 2007 to present, it is necessary to talk again about cyber risk in the maritime and port setting.
It is not the purpose of this article in any case to retrace the several cyber security attacks that, starting with A.P. Moller-Maersk, involved the world’s most important shipping companies, as well as the biggest port hubs in Europe and the United States of America.
MARITIME CYBER SECURITY
Although acknowledging previous relevant cases, the chosen starting point will be June, 16th 2017, when the International Maritime Organization (IMO) formally adopts the recommendations included in the three declarations of principles in the Resolution MSC.428 (98) entitled Cyber Risk Management in Safety Management System.
In this sense, the cyber security risk assessment becomes integral part of the objective (Art.1.2) included in the ISM Code; according to which the management of the cyber security risk must be included in the general objective, for this reason shipping companies must “…ensure safety at sea, prevention of human injury or loss of life, and avoidance of damage to the environment, in particular to the marine environment and to property“. In particular, these objectives are identified in the pursue of the following obligations:
1. provide for safe practices in ship operation and a safe working environment;
2. assess all identified risks to its ships, personnel and the environment and establish appropriate safeguards; and
3. continuously improve safety management skills of personnel ashore and aboard ships, including preparing for emergencies related both to safety and environmental protection.
In the declarations related to the MSC.428 (98), the IMO introduces for the first time the date of Jan., 1st 2021, stating that: “…Administrations (are encouraged) to ensure that cyber risks are appropriately addressed in safety management system no later than the first annual verification of the company’s Document of Compliance after 1 January 2021“.
The second date to remember is Jul. 5th 2017, when the IMO, through the Maritime Safety Committee released the Guidelines on Maritime Cyber Risk Management included in the MSC-FAL.1/Circ.3. These guidelines suggest recommendations identified as “high level“ for the management of cyber risk in the maritime sector, with special reference to shipping. The pursued aim is to promote the mitigation of cyber risks, through the adjustment of the safety management system, included in the ISM Code framework.
In the Italian context, a third important date to remember is Dec. 13th, 2019, when the Comando Generale del Corpo della Capitanerie di Porto (The General Command of Italian Harbor Masters) with the Circolare Titolo Sicurezza della Navigazione, Serie Generale 155/2019, which refers to the Circolare Titolo Security n. 35/2017 (the Circolare n. 40/2017 has the same content, but is addressed to the port sector and port facilities) and with it resumes the Resolution and the circular of 2017 issued by the IMO and the NIS Guidelines, underlining the existing connection between the Ship Security Plan and the procedures of cyber risk prevention (included in the Safety Management System of the ISM framework). The Annex “Cyber Risk Management” is a relevant part of the “Circolare” and it suggests a model of identification and management of the cyber risk, in the field of the required assessment of the specific risk.
Cyber Security in Ports and Port Facilities
Cyber security in Ports and Port Facilities has developed in a different way. At present, although acknowledging that port infrastructures have a strategic role in the global commerce, as well as a growing use of dedicated technologies which are expanding the IT system network (also by integrating them with OT systems) and the subsequent interconnection with the land transport infrastructures, no formal measures have been issued regarding cyber risk management.
As mentioned before, the ISPS Code, which regulates the security model of ports receiving ships coming from international voyages with tonnage over 500 GT (so not all ships), does not address the risk scenarios in terms of IT, and except for the generic call for the protection of IT infrastructures, it does not provide directions or guidelines for the development of a cyber risk management model. Thus, the ISM Code only concerns the ship world and so the possible extension to the port facilities world, besides being incorrect on a conceptual level, could also be dangerous, as the underlying concepts are only pertinent in relation to ships.
In the absence of IMO guidelines on the management of cyber risks, we have to highlight the work of the ENISA “European Union Agency for cybersecurity”, that from Dec., 19th 2011, has focused the attention also on shipping, cruise lines and ports.
This was developed in a first report of 2011 Cyber Security Aspects in the Maritime Sector and later in November 2019 in a second one entitled Port Cyber Security – Good practices for cybersecurity in the maritime sector.
In December 2020, the ENISA published a new report titled Cyber Risk Management for Ports; which aims to introduce a specific approach for the cyber risk assessment in ports, regarding both IT and OT systems and based on the basic principles of risk management. This approach was written in compliance with the security risk assessment method in port and maritime domain as per ISPS Code and thus compliant with the main European regulations on port and port facilities security. The topics discussed in the report are not presented as purely IT orientations, but also as process orientations, relating in a gender to species way with the standard risk assessment methods, used in the management systems of the interested ports.
The recent USA Government maritime cyber security provision
It is finally relevant, always in December 2020, the approval of the National Maritime Cybersecurity Plan by the Trump Administration. The document indicates some priority measures, that the Government commits to approach in order to mitigate the IT- related risks and menaces, which impact on the under-branches of the Maritime Transportation System (MTS).
Among these actions, it is relevant the acknowledgement on national level of more than 20 government entities have jurisdiction on maritime and port security matters. This aspect does not favor the consolidation and diffusion of the shared maritime cybersecurity standards and thus calls for a revision in term of roles and responsibilities of the interested entities. The action interests also the development of shared procedures for the identification and mitigation of cyber risks for the identified ports (with special reference to the OT infrastructures in the maritime sector, which so far have not benefited of analysis and audit programs of the vulnerabilities that could be borrowed from the experience of similar sectors). Thus, there is the possibility of allowing the Department of Homeland Security (DHS) and the Department of Defense (DOD) to implement sector cybersecurity assessment in order to contribute to the protection of port facilities and ships against IT risks.
The definition of a framework dedicated to the Port Cyber Security Assessment could then be included in the regulatory systems already in place, such as the ISPS Code. In this sense, a IT security component (so far missing) could be added to the sector assessment procedures (Port Facility Security Assessment).
The topic of maritime cybersecurity (different from the port and port facilities cyber security) could instead be solved by the integration of the cyber security assessment process and the specific risk management, including it among the objectives of the ISM Code and thus in the Safety Management System. This action will be combined with an activity of analysis and study of the main IT attack carrier, referring to the reports on IT incidents of maritime and port operators to fill the culture and awareness gap on cybersecurity, by the MTS.
Not least, it is essential that on the general plan of public and especially private operators, who supply the services connected to the port infrastructures, there be uniformity in the contract requirements (cybersecurity contracting clauses); this is to create a first level of contract standards suitable to participate in the creation of a shared model of sector cybersecurity. An activity that could be made possible with the participation of the General Services Administration (GSA), on the level of the development and implementation of contract frameworks which can be applicable to critical maritime infrastructures, under the direct management or control of the relevant public administrations.
Another relevant topic is the data sharing in the partnership between public and private, as base on which to structure an intelligence system which is shared and efficient for the whole MTS. Here were also identified some priority actions, among which the creation of hubs and talking points, in order to facilitate the proposed data sharing in operations, while maintaining the privacy of data which compose the shared information. The standard will be created and thus it will have to be information security by design. Lastly, it is necessary to educate the relevant professionals on the maritime cybersecurity because,
“Port and vessels systems are unique and not as ubiquitous as commercial office systems“.
As a consequence, the commitment to develop career paths, incentives and continuous education programs and lien talent plans, in order to develop concretely sector professionals with demonstrated expertise.
Threat Report Portugal: Q4 2020
27.1.2021 Cyber Securityaffairs
Threat Report Portugal Q4 2020: Data related to Phishing and malware attacks based on the Portuguese Abuse Open Feed 0xSI_f33d.
The Portuguese Abuse Open Feed 0xSI_f33d is an open sharing database with the ability to collect indicators from multiple sources, developed and maintained by Segurança-Informática. This feed is based on automatic searches and also supported by a healthy community of contributors. This makes it a reliable and trustworthy and continuously updated source, focused on the threats targeting Portuguese citizens.
The Threat Report Portugal: Q4 2020 compiles data collected on the malicious campaigns that occurred from October to December, Q4, of 2020. The submissions were classified as either phishing or malware. In addition, the report highlights the threats, trends, and key takeaways of threats observed and reported into 0xSI_f33d. This report provides intelligence and indicators of compromise (IOCs) that organizations can use to fight current attacks, anticipating emerging threats, and manage security awareness in a better way.
Phishing and Malware Q4 2020
The results depicted in Figure 1 show that phishing campaigns (76,1%) were more prevalent than malware (23,9%) during Q4 2020. It is important to make a reference to the values of Q3 as phishing and malware maintain a growing trend.
Observing the threats by category from Jan to Dec in Figure 2, it is possible to verify that there was a high number of phishing campaigns during March, April, and Jun, and this is a strong indicator related to the COVID-19 pandemic situation.
Analyzing these results, it’s possible to notice an increased number of phishing submissions in December 2020. One of the reasons that can explain this is the ANUBIS phishing network that occurred in Portugal between November and December 2020.
On the other hand, May, June, and August were the months where malware was spotlighted, with the botnet Mirai, Emotet, and the infamous Lampion Trojan in place. This piece of malware was identified at the end of December 2019 using template emails from the Portuguese Government Finance & Tax and Energias de Portugal (EDP) with the goal of collecting banking details from the victim’s devices. Also, other trojan bankers have been observed during Q3, including TroyStealer and Grandoreiro expanded now to Portugal. A new piece of malware was also tracked and analyzed during Q3 and active in Q4 – trojan URSA/mispadu. The emergent URSA trojan is impacting many countries using a sophisticated loader.
Malware by Numbers
Overall, the Emotet and Satori/Mirai botnet were some of the most prevalent threats affecting Portuguese citizens during Q4 2020 along with the mediatic URSA trojan (Figure 3). Other trojan bankers variants and families affecting users from different banks in Portugal were also observed. These kinds of malware come from Brazil and the attacks are disseminated via phishing campaigns. Criminals are also using smishing to enlarge the scope and to impact a large group of victims.

Threats by Sector
Regarding the affected sectors (Figure 5), Banking was the most affected with both phishing and malware campaigns hitting Portuguese citizens during Q3 2020. Next, was Retail and Technology, as the most sectors affected in this season.
Threat campaigns during Q1 2021 will be published on a daily basis into 0xSI_f33d, as well as additional incidents and investigations that are being documented and published on Segurança-Informatica.
The infographic containing the report can be downloaded from here in printable format: PDF or PNG.
You can download the report from the original post:
https://seguranca-informatica.pt/threat-report-portugal-q4-2020/#.YBBX3-hKg2x
About the author Pedro Tavares
Pedro Tavares is a professional in the field of information security, working as an Ethical Hacker, Malware Analyst, Cybersecurity Analyst and also a Security Evangelist. He is also a founding member at CSIRT.UBI and Editor-in-Chief of the security computer blog seguranca-informatica.pt.
Florida Ethics Officer Charged with Cyberstalking
15.1.2021 Cyber Threatpost
Judge bars former Tallahassee city ethics officer from internet-connected devices after her arrest for cyberstalking.
A Tallahassee city ethics officer was arrested and charged with cyberstalking her coworker and former lover, and is now banned by a judge from using the internet for anything besides work, paying bills and her legal defense.
Julie Meadows-Keef is accused of cyberstalking Bert Fletcher, the Tallahassee Democrat newspaper reported. Both worked in Tallahassee city government. She was hired in 2014 as the first city government ethics officer, while he worked in an adjacent office as the city auditor. They soon started a romantic relationship, according to the report.
Their messy personal drama included both of their divorces, restraining orders, a falsely filed sexual complaint by Meadows-Keef against Fletcher (later dismissed by a judge), and stalking allegations thrown back and forth.
2020 Reader Survey: Share Your Feedback to Help Us Improve
Now Meadows-Keef is facing a misdemeanor charge for sending hundreds of texts and emails throughout the final week of December and into the first days of 2021, the report added.
And while love affairs-turned-toxic are hardly anything new, the use of electronic tools for stalking has made such cases even more pernicious — and cyberstalking is on the rise.
Stalkerware on the Rise
Aside from harassing someone over the interbet through messages and social media, stalking can also be carried out using stalkerware. Google defined stalkerware as “code that transmits personal information off the device without adequate notice or consent and doesn’t display a persistent notification that this is happening.” That includes apps with GPS marketed to spy on people without their knowledge.
Stalkerware downloads have been on the rise, according to Kaspersky , which last year observed a 50 percent increase year over year.
Google Play banned spyware and surveillance software last fall, but made an exception for services for parents to track their kids for safety. The issue, some say, is that there are many examples of apps which purport to be for parents but can easily be turned into incredibly effective tools for stalkers.
Researchers at Kaspersky for instance raised the alarm about an app called “Monitor Minor” last March, which can let stalkers gain nearly total control of their target’s device, even capturing the unlock security codes.
“This is the first time we have registered such a function in all our experience of monitoring mobile platform threats,” Victor Chebyshev, a security researcher at Kaspersky who authored the report on Monitor Minor’s dangers, said. The app is not available through app stores but is sold online.
Stalkerware & the Pandemic
Since the pandemic’s lockdowns and stay-at-home orders went into effect, advocacy organizations have reported an increase in cyberstalking reports. Paladin, a national stalking advocacy service in the U.K., said that it has seen a 40 percent jump in victim contacts by email and phone since the lockdown was imposed. Another stalking advocacy service in the U.K. called Veritas Justice reported a 75 percent increase in cyberstalking activity since the lockdown, according to the Guardian.
Experts told the Guardian that it’s not just isolation and loneliness fueling the surge in cyberstalking — it’s also the ease with which they can carry out their crimes online.
“The rise in cyberstalking due to the lockdown concerns me deeply,” Katy Bourne, the chair of the Association of Police and Crime Commissioners said. “The severity of risk to a victim is now defined by the amount of time invested by the perpetrator in their obsession. So, with many victims receiving over 100 text messages, emails, phone calls a day, we know that these strong fixations could have a more sinister outcome.”
For Meadows-Keef, her arrest comes at the end of a long saga with her former employer as well as her ex. Just weeks ago, she reached a settlement with the city after claiming she was forced from her job, according to the Democrat, which added that during her tenure she also demanded the city’s Mayor John Dailey write her a check for $450,000 and offer her a public apology in exchange for her resignation.
Now the official who was once in charge of ethics training is barred from contacting Fletcher or his family, and from using devices with internet access until her trial.
Aliens and UFOs: A Final Frontier for Social Engineers
12.1.2021 Cyber Threatpost
The release of a CIA archive on UFOs is exactly the kind of headline-making event that phishing and scam actors long for.
Buried deep within the most recent round of COVID-19 stimulus legislation was a little provision with potentially explosive consequences: The Pentagon has six months to release a full report on what they know about the existence of what they term Unidentified Aerial Phenomena (UAP) — or UFOs to the rest of us.
In advance of the deadline, a site called Black Vault has published what founder John Greenwald Jr. said is every file the CIA has on UAPs. The site said it has been trying to get UFO documents from the CIA since 1996, and that the .PDF filed they’ve posted represent everything the CIA had on the matter.
As details contained in the CIA archives drip out and the Pentagon deadline draws closer — and anticipation, curiosity and excitement build about the existence of extraterrestrials — experts warn that these are exactly the kind of headlines scammers are likely to turn into successful phishing scams.
Wanna See an Alien? Click Here.
“My general rule is that if it makes people a little crazy (or scared or emotional or greedy or vulnerable or, hell, just curious) then it’s a candidate for a phishing scheme,” Tom Pendergast, chief learning officer at MediaPro told Threatpost.
“And it’s pretty easy to imagine the pitch: ‘Click here to view real CIA photos of aliens,’ or ‘enter your Social Security number here to see whether your data is among that accessed by aliens,'” he explained, adding that curiosity about aliens creates a gut-level response that criminals can use to cash in.
The fact that these documents have become available at the same time as the topic is making legitimate news headlines because of the new legislation makes this an even more attractive fraud avenue for criminals, Hank Schless, senior manager of security solutions and Lookout explained to Threatpost.
Mobile Users Most Vulnerable
“Since these documents being released is a legitimate piece of news, it increases the likelihood of a successful phishing attack,” Schless said. “This is the type of information that will be shared broadly across social-media platforms, which means there’s increased risk for mobile users.”
On a mobile device, Schless explained, people are easier targets for this type of cybercrime.
“Between SMS, third-party messaging apps, mobile email, social-media platforms and other apps with messaging capabilities, malicious actors have a handful of ways to target mobile users,” he said. “The simplified user experience on mobile makes it easier for attackers to hide phishing links or make fake pages look real. Mobile users are conditioned to tap anything that comes up on their screen, which means they won’t exercise the same caution as they would on a computer.”
Phishing scams tend to track with headlines. For instance, COVID-19 has proven an effective phishing lure, dominating scam themes in 2020 and expected to continue into 2021, according to experts. The election headlines from this year also drew their fair share of criminals, and multiple phishing scams targeting campaigns were uncovered.
But headlines, and scammers, are constantly changing and evolving, and UFOs represent a new frontier for fraud.
In fact, the prospect of aliens as a phishing lure is so classic, Pendergast told Threatpost it would make a good test for employee-awareness training.
“People who phish are seeking any kind of gut-level response that might override analytical thinking and prompt clicking a link or disclosing information,” he explained. “This is why it’s so hard to run simulated phishing programs: you want to be as “real” as the cybercriminals, but you can pretty quickly step over the line. But I’d feel comfortable sending my employees a simulated phish on this one.”
It is time to re-evaluate Cyber-defence solutions
11.1.2021 Cyber Securityaffairs
Security expert Stefan Umit Uygur, CEO and Co-Founder at 4Securitas Ltd, provided his vision about the Cyber-defence solutions on the market
Just where is the Global Cyber-defense Market going, and why is it failing so spectacularly to protect the data assets of the largest and most heavily protected government institutions and corporate companies in the world. It is a great question, particularly when you consider that $167 Billion was spent on Cybersecurity in 2019 and this is predicted to increase to $248 Billion by 2023 [Source: Forbes]. If you ask a Cybersecurity Analyst “what more can organisations must do in order to strengthen their defense line”, you will be told that the threat levels are increasing every day, so organisations need to invest more money into cybersecurity.
If this is true, then it does not answer the question as to why many of the largest and best protected global corporations and Governments institutions worldwide have been victims of major Cyber-attacks despite deploying the most expensive defence solutions in the market. It is apparent to even the most casual observer that successful cyber-attacks are happening at an alarming frequency, and it is happening to trusted institutions where we all believed our private data was secured and impenetrable from unscrupulous fraudsters, criminals or even state sponsored hacking by some rogue Governments.
Companies like Gartner have made fortune advising clients on their assessment of the best security products in the market. They even created and promoted their Magic Quadrant of cyber vendors product capabilities, a league table which many clients interpret as a ‘magic bullet’ and the simple answer to all their cyber security concerns. Many companies are aware that Cybersecurity is a complex issue, and they use Gartner to compensate for gaps in their knowledge and because they do not have the resources to assess all the products in the market. Most Corporations and Government organisations deploy a ‘defense in depth’ strategy which results in them deploying multiple expensive Cybersecurity products with overlapping capabilities – expecting improved security protection through deploying multiple security products.
So why are cyber-attacks becoming more commonplace in large corporations and Government agencies, and what hope is there for the rest of industry that do not have the deep pockets of global organisations? Clearly the answer cannot be that the current cyber-defense strategies are working, and increasing cybersecurity budgets by 38% every four years is the answer.
To best understand the scale of the problem, let’s look into some recently notified, large organisation security breaches, reported over a four-week period between 20th November and 17th December 2020. It is important to note that we have only selected a small number of notified, and publicly acknowledged cyber-attack incidents.
20th Nov 2020 – Manchester United Football Club (www.manutd.com)
Manchester United computer systems were hacked in November 2020 which resulted in staff being unable to access email and some other functionalities for several days. Investigation on the severity of the cyber-attack are ongoing, and while it is believed that their fans data was not impacted, the UK National Cyber Security Centre (NCSC) is assisting Manchester United to determine the nature and extent of this security breach.
For more information on this, see: Manchester United Football Club Cyber Attack
30th November 2020 – Embrear (www.embrear.com)
The Brazilian aerospace giant Embrarer manufactures commercial, executive and military aircraft and are the world’s third largest aircraft manufacturer after Boeing and Airbus. At the end of November the company announced that it suffered a ransomware cyber-attack resulting in the disclosure of data “attributed to the company”. The Cyber-attack resulted in a large volume of data to be encrypted including database servers and backup data.
As a result of this incident, the company initiated its emergency procedures to investigate and resolve the incident and began proactively isolating some of its systems to protect the system environment, temporarily affecting some operations.
For more information on this breach, see Embraer Cyber Attack
5th December 2020 – Leonardo (https://www.leonardocompany.com/en)
Leonardo is an Italian conglomerate specialising in aerospace, defence and security which counts NATO among its customers. As with any large Corporation with highly sensitive and security classified information, they invest significantly in protecting this data with a dedicated security division and multiple Cybersecurity products.
Despite this, two of their former employees implanted malicious code into their systems that had the ability to capture every keystroke typed on their systems for two years, between 2015 until 2017, but was only reported upon and made public in December 2020.
For two years these two former employees were able to export the data from 94 different devices without being detected to a domain name called fujinama.altervista.org. Despite Leonardo deploying numerous Cybersecurity products containing Artificial Intelligence and Machine Learning features, they are still unable to quantify the impact of this Cyber-attack, and three years later all that can be confirmed is that 10GB of confidential data and military secrets has been compromised.
For more information on this breach, see: Leonardo Data Breach
14th December 2020 – Symrise (www.symrise.com)
Symrise is a German manufacturer of fragrances and flavours, whose products can be found in over 30,000 consumer goods and food products including those from Nestle, Coca-Cola, and Unilever. The company lies just outside the leading DAX share index with turnover of over €3.4Billion in 2019.
In December 2020, Symrise AG confirmed that they were the target of Clop Ransomware attack, when 500GB of their data from over 1000 infected devices was encrypted by cyber criminals. The company announced that they shut down all essential systems in order to be able to assess the consequences of the attack and to prevent possible further effects. Plant production was stopped and entire facilities shut down to further investigate the scope and implications of the attack.
Share price fell by 2.3% immediately after the announcement and is expected to remain under pressure until production fully resumes again in the coming weeks.
For more information on this breach see: Symrise Cyber Attack
14th December SolarWinds (www.solarwinds.com)
SolarWinds Inc. is an American company that develops software for businesses to help manage Networks, Systems, and Information Technology infrastructure and security. Their Orion Cybersecurity platform has over 300,000 customers globally including prestigious clients such as AT&T, Ford Motors, Cisco, SAP, Intel, Cox Communications, Deloitte, Nvidia, Fujitsu, Belkin, US Treasury, US Departments of Homeland Security, US Departments of Defence and Commerce etc…. Microsoft also uses the SolarWinds Orion product and incorporates it into some of their own security products which they sell to their customers.
The Solarwinds Orion Cybersecurity product itself became the target of a Cyber-attack, with the software product updates being infected with the SUNBURST malware which created a backdoor into 18,000 customers who updated their Orion software with the infected updates. This very sophisticated exploit of the SolarWinds security platform was meticulously planned and executed by infecting the digitally-signed component of the Orion .dll software to communicate via HTTP to third party servers.
After an initial dormant period of up to two weeks, it retrieves and executes commands, called “Jobs”, that include the ability to transfer files, execute files, profile the system, reboot the machine, and disable system services. The malware masquerades its network traffic as the Orion Improvement Program (OIP) protocol and stores reconnaissance results within legitimate plugin configuration files allowing it to blend in with legitimate SolarWinds activity. The backdoor uses multiple obfuscated blocklists to identify forensic and anti-virus tools running as processes, services, and drivers.
FireEye, Microsoft and multiple other Cybersecurity products were all deployed alongside the Orion platform in virtually every single one of these 18,000 infected customers, yet none of these “defense in depth” systems detected SUNBURST malware. The full impact of this Cyber-attack is so enormous and widespread that the impact of it will never be fully known.
For more information on this breach, see SolarWinds Cyber Attack
17th December 2020 – Vietnamese Government Security Authority
Vietnamese Government Certification Authority (VGCA) used to validate supply chain software was compromised and the agency’s digital signature toolkit was modified to install a security ‘backdoor’ vulnerability to users of the supply-chain software.
The exploit called “SignSight” involved the modification of software installers hosted on the Certificate Authorities website (“ca.gov.vn”) to insert a spyware tool called PhantomNet or Smanager to unsuspecting end users.
For more information on this breach, see: Software Supply-Chain Attack Hits Vietnam Government Certification Authority
So what is the future for a Cyber Security industry that is failing it’s clients?
It is clear that deploying any of the leading edge products recommended by Gartner and other security analysts is insufficient protection for determined and experienced Cyber-criminals. Even when these expensive security products are combined together and deployed in unison by an organisation, determined Cyber-criminals can bypass them – as with SUNBURST and other exploits referred to earlier.
The Flaw with existing Cyber-security products
The only conclusion is that all the major security platforms have a single flaw that is repeatedly exploited by cyber-criminals – that is they are all reactive products waiting and monitor networks and platforms and in the best case scenario, detect when an attack has already occurred and perhaps help prevent it. So these expensive security products are really offering a reactive solution that may be able to identify if malware has been installed into your organisation, possibly after data has already been compromised, but with the possibility that in some scenarios it can be prevented. This is a very weak security stance for any organisation to accept, but it is all that the current major security platforms offer. It also explains why deploying them together still does not prevent major Cybersecurity attacks from occurring.
The security posture of any organisation will be vastly improved by implementing a proactive/offensive security posture in conjunction with a reactive one. This involves addressing the Cybersecurity Blind-Spot found in existing products, by implementing an offensive, anti-surveillance Cybersecurity capability into a full SEIM and EDR product. I have advocated this position in a Cybersecurity book I wrote in 2014 (Penetration Testing with BackBox) and have now implemented that vision in our ACSIA product, created by my company 4Securitas (www.4securitas.com). This is the first-time companies can implement a full 360 degree security solution that actively prevents Cyber-criminals performing surveillance and planning attacks on IT platforms.
If you consider any other major criminal activity such as robbing a Bank, it always requires surveillance and planning first. What time does the Bank open or close, when is it full of money, how do the employees enter or exit the bank etc…. Similarly, a successful Cyber-criminal will want to know information such as network ports being used, protocols deployed, hardware and software products deployed, versions of products implemented …. it is only with these pieces of information can a cyber-attack be planned.
ACSIA was designed and built to aggressively disrupt the planning stages of a cyber-attack, implementing a multi-layered security solution that uses algorithms developed by 4Securitas and uniquely deployed in our ACSIA product.
A few quotes and extra reading:
Link: Prevention is The best Approach to Deal with a Threat
Tripwire VP of strategy, Tim Erlin, argues that every organization today needs to be prepared for a ransomware attack and adds, “while we tend to focus on the response to ransomware, prevention is still the best way to deal with the threat,”.
“Ransomware doesn’t magically appear on systems, and the methods by which it’s introduced into an environment are generally well understood: phishing, vulnerability exploits and misconfigurations. Identifying and addressing the weak points in your security posture can help prevent ransomware, as well as other attacks, from being successful.”
While Erlin focuses only on ransomware, he is correct in his argument that the entire design of the current cybersecurity vendor ecosystem is wrong.
Link: Why the Current Approach of Managing Cybersecurity is Failing
In this brilliantly written article, Lockheed Martin talks about the cyber blind-spots. It refers to the process before an attack occurs, the pre-attack phase. It therefore talks about the proactive approach and it resolves as the ultimate way of challenging cyber attacks. Or at least to keep the pace with cyber attacks as opposed to staying one step behind.
My own favourite quote – by Stefan Uygur
The Cybersecurity vendors must stop developing security solutions designed and architected by Data Scientists and Software Engineers. A Cybersecurity product needs to be designed by Cybersecurity Architects and built with the assistance of Data Scientists and Software Engineers.
Original Post at https://4securitas.com/it-is-time-to-re-evaluate-cyber-defence-solutions/
Experts Weigh In on Cybersecurity Risks of Capitol-Like Attacks
11.1.2021 Cyber Securityweek
Hundreds of protesters stormed the U.S. Capitol on Wednesday just as the House and Senate were certifying the election victory of Joe Biden. While much of the focus was on the physical destruction caused by the protesters, many people have pointed out that rioters gained access to computers in the Capitol, which in some cases were still turned on and logged in, as their users were forced to quickly evacuate.
One man posted a tweet — it was later deleted but many Twitter users saved it before it was removed — showing him in front of an unlocked device allegedly belonging to someone in the office of House Speaker Nancy Pelosi. The picture showed someone’s email account open on the computer.
Tweet from Nancy Pelosi office during Capitol attack
In addition to the physical documents and laptops that some protesters removed from the Capitol, cybersecurity experts have raised concerns about what they may have or could have also done with the computers left inside the building.
Some pointed out that they could have accessed sensitive information and others warned that all devices should be considered compromised as the people who breached the Capitol could have planted malware or spying hardware. Others doubted that the rioters had the intent or knowledge to conduct these types of activities.
However, while there is no evidence of such activities to date, the incident highlighted that some organizations should prepare for situations where employees could be forced to suddenly abandon their workstations.
SecurityWeek has reached out to several experts, asking them what prevention and response strategies and policies they would implement if they were in charge of cybersecurity at such an organization.
James Arlen, CISO at Aiven:
James Arlen
“Preparatory training is vital as a baseline part of your security awareness program - when you leave your desk, lock your machine! Winkey-L or Ctrl-Cmd-Q for your Windows and Mac users should be a reflex. As you work through your program maturity, being able to remotely lock and wipe machines once staff has reached safety should be part of your technical bag of tricks.
Depending on the adversary in your threat model, your response after the fact would range from nothing at all to a complete rip & replace of all equipment from the keyboard to the Ethernet cable. Remember that physical access is everything! I think the first tweet I saw along these lines was from my good friend Gillis Jones (@gillis57) suggesting that everything in The Capitol should be replaced and it’s a very valid point.
Of course, I hope that you’re also following a proper 3-2-1 backup plan and the complete loss of multiple computer systems is annoying rather than devastating. Maybe it’s time to add a “site contamination” scenario to your Business Continuity Plan tabletop exercises - could you restart your operations with a corporate credit card and a Best Buy? You should be able to!”
Dirk Schrader, Global Vice President at New Net Technologies (NNT):
Dirk Schrader
“There are quite a few situations which can force an organization’s employees to leave their workplace immediately, leaving their computers unattended.
For IT administrators, it also means leaving the company’s IT infrastructure of servers, access points, switches and routers behind. The strategy for such a situation includes planning, preparation and dry-runs, and monitoring. Planning starts as a tabletop exercise, defining what kind of event would force the workforce to leave, which systems should be locked automatically, or even shut down, how can this be triggered and monitored, what kind of data must be secured (perhaps in an encrypted way). Preparation for such an event should include, next to the appropriate training of staff on how to evacuate safely, automatic procedures to lock accounts (either after timeout or via a centrally triggered event), to secure servers by closing sessions and initiating graceful shutdowns where needed. Keeping it simple, automated is key, the more employees would have to do, to remember, the less it will work. Still, even the simplest of procedures needs rehearsal, so try it, tune it, identify short comings and fix them.
Once the situation is cleared, IT administration and IT security will work backwards, get the infrastructure and work stations back online while checking them. For this to be comprehensive, the monitoring is necessary. They need to be able to review logs provided by core technical controls, both built-in to operating systems but also by change control solutions. The task is two-folded, protect the workforce by making it less complicated for them to leave computers, but also make sure that no malicious activity which might have happened during a stress situation goes undetected.”
Jerry Ray, COO of SecureAge:
Jerry Ray
“I would have simply installed any tool that would prevent the exfiltration of plain data.
There are plenty of physical recommendations, such as having some type of smart card or USB token that can be removed in a second and prevent the removal or even viewing of any plain data. Even the rapid unplugging of a system would be useful if the data could not be extracted, as above.
But any physical policies quickly break down when scenarios include occupiers getting to systems before the users can depart. They could be taken hostage or simply be forced to leave the premises without touching anything. In such a case, the proactive encryption would still be enough to prevent both exfiltration or unauthorized access of any data.
If the data was also resident only on a remote server and not stored on the endpoint, that would help even more. Remote file servers could be shut down outside the facility while the proactive encryption protects whatever was resident and open on the endpoint.”
Kelvin Coleman, Executive Director of the National Cyber Security Alliance:
Kelvin Coleman
“As is the case with most prevention and response plans, nothing is ever foolproof. I think the overarching philosophy should always be about minimizing risk. Organizations -- and security pros within those organizations -- should be putting measures in place that can bring the potential for vulnerabilities as close to zero as humanly possible.
That said, deterrent strategies for this sort of scenario should be preemptive from the outset and begin with increased education and awareness for employees about the dangers of leaving sensitive data unprotected on idle endpoints and the vulnerabilities that creates for the organization as a whole. Those education initiatives should be woven into company culture and drilled on a regular basis. Subsequently, I would make sure that the organization has a sufficient incident response strategy in place and policies that adhere to trusted cybersecurity frameworks and protocols (e.g as outlined by NIST) in case any sensitive data is ever compromised or stolen (and chances are it will be at some point).
On the hardware and software front, businesses need to make sure employees are issued endpoints (laptops, mobile devices, etc) that are properly equipped to access and store company data in a secure way. Any previously issued hardware that isn’t properly outfitted should be recalled and updated. That means multi-factor authentication, file-level encryption solutions, secure VPN access and perhaps even biometric login solutions. Also, security teams/SOCs should be outfitted with a robust IT tech infrastructure that can allow for precise network monitoring and policy management across all employee devices, as well as accurate recording login attempts and timestamps associated with those attempts. This will make it easier to map a timeline of unauthorized access to any devices after theft occurs.”
Rajiv Kanaujia, VP of Operations at CloudCheckr:
Rajiv Kanaujia
"For organizations that don't have business continuity plans (BCP) in place, it will be very difficult to develop and execute on a BCP at such short notice. The most important item at hand is the physical security of the employees. On the other hand, living with the COVID-19 situation for almost a year, most of the organizations have shifted to some form of remote culture.
The preventative strategy is to plan for a remote working event and sudden evacuation. Assuming you have not lost the physical security controls and the issues are personal safety only, you should instruct employees to leave the premises immediately and let the physical security team manage the perimeter, while in coordination with law enforcement teams. If employees cannot leave premises due to escalated physical safety situations, employees must be allowed to remain on the premises until the evacuation in coordination with law enforcement teams is possible.
Employees must then be tooled with laptops and zero-trust solutions so that they can work remotely. Laptops must have encryption turned on and preferably MDM must be installed. Basic device security and access policies must be used (encryption, authentication, complex passwords, etc.)."
Gary DeMercurio, Red Team Director at Coalfire:
Gary DeMercurio“Everything can be breached with enough force. In terms of what happened at The Capitol, outside of building a giant concrete wall with a single point of entry, not much else would have stopped a mob of that size. Having the computer system on a separate circuit that could have been shut down in the event of a breach would have prevented a lot of this. (physical issues such as keyloggers would have still existed as well as laptops left unlocked under their own power) Severing the network connection of all computers would have helped as well.
Corporations should integrate constant offensive testing to ensure both the physical and logical security measure that are in place, actually work. Too often companies abide by the same “security” taught and passed down from predecessors and outdated training method and overlook testing of those protocols they have in place. Working from home has expanded that attack surface, it has also weakened the corporate security tremendously. Just as they reported on the news during the recent Capitol Hill incident, “We were lucky the building was so empty due to COVID-19”. How many empty building are there now? How hard is it to walk into an empty building and sit down at a desk and run roughshod on the corporation? With what happened in Washington DC, this is more about emergency response, and cleaning up the mess as it can happen to anyone. Corporations should ensure they have a procedure for what happens if and when it finally happens to them.”
Jack Mannino, CEO at nVisium:
Jack Mannino“If you’re concerned that your employees will have to rapidly abandon their workstations in the event of a crisis, there are steps you can take to reduce your exposure. First, consider using proximity based authentication solutions or physical tokens, where a workstation would quickly lock even if a user didn’t have time to manually do it themselves. Ensure all drives are encrypted at-rest to prevent unauthorized access to stored information. Utilize remote administration and data wiping solutions that would enable you to regain control of a device in the event you could not physically access it.”
Tom Pendergast, Chief Learning Officer at MediaPro:
Tom Pendergast“The answer is not dissimilar to how we prepare organizations to respond to external cyberattacks like phishing: we build tons of good technical defenses, then we train people how to respond to the rare phishing attempt that gets through—knowing that relying on individuals who are focused on other things to resist attack is an imperfect defense. Yesterday, at a critical moment, it’s as if we turned all the technical defenses off and allowed the threat to overrun the environment. Nobody was ready for that! I’m sure some people responded appropriately—but clearly, many did not.
In the end, this situation required a bunch of individuals to take specific actions (lock the workstation, gather mobile devices, secure paper) during a highly stressful time—and the only way I know of to ensure high performance in such a situation is to practice, practice, practice. But allotting time to practice requires a systemic acknowledgment of risk (which was not present yesterday but may be in the future) and then an organizational commitment to focus on building the skills to reduce that risk (again, likely not present yesterday in the organization). The easier solution in this case will likely be to reduce the chances that such an assault will occur again, for that is easier than preparing the individual employees.”
Feds Issue Recommendations for Maritime Cybersecurity
7.1.2021 Cyber Threatpost
Report outlines deep cybersecurity challenges for the public/private seagoing sector.
The White House has released cybersecurity guidance for securing the Maritime Transportation System (MTS), which operates along 25,000 miles of coastal and inland waterways in the United States.
The document points out that the MTS encompasses “361 ports, 124 shipyards, more than 3,500 maritime facilities, 20,000 bridges, 50,000 Federal aids to navigation, and 95,000 miles of shoreline that interconnect with critical highways, railways, airports and pipelines.” In addition, there are more than 20 Federal government organizations that currently have a role in maritime security of all stripes, ranging from vessel and personnel safety to transportation standards and logistics.
2020 Reader Survey: Share Your Feedback to Help Us Improve
In all, this footprint contributes one quarter of all United States gross domestic product, or approximately $5.4 trillion, according to the Feds.
Maritime Challenges
Applying good cybersecurity to the seagoing sector is a complex process plagued with challenges. The report enumerates several of these, starting with the fact that it’s a diverse ecosystem “with businesses of all sizes leveraging IT and [operational technology] OT systems that interconnect with larger maritime systems. Users across the maritime sector access key data and management systems daily for business purposes, making secure access control and user monitoring difficult.”
To boot, different public and private entities own and operate these interconnected systems, and common cybersecurity standards do not exist across facilities. Some of the entities also lack appropriate resources or expertise to implement appropriate cybersecurity frameworks even if a common approach were defined.
“Cybersecurity within some ports and facilities is situational, ad-hoc and often driven by profit margins and efficiency,” reads the report. “Unless the private sector has a clear understanding of current and future maritime cybersecurity threats and a financial incentive to invest in maritime cybersecurity measures, some private sector entities may not be inclined to align with maritime partners or allies.”
Additionally, some of the MTS footprint relies on outdated telecommunication infrastructure, threatening the ability for MTS stakeholders to “protect digital information, the network and to detect when malign actors are attempting to access protected systems,” the report warned.
The danger here is real; researchers have previously identified the prevalence of Windows XP and Windows NT within critical ship control systems, including IP-to-serial converters, GPS receivers or the Voyage Data Recorder (VDR), which thus tend to be easily compromised. Researchers at Pen Test Partners found that with the ability to infiltrate networks on-board shipping vessels (think satcom hacking, phishing, USB attacks, insecure crew Wi-Fi, etc.), capsizing a ship with a cyberattack is a relatively low-skill enterprise.
Previous research has shown that other concerning attacks are possible as well, such as forcing a ship off-course or causing collisions. The issue with remediating the dismal state of maritime security is a lack of clearly defined responsibility for security, according to the researcher.
Maritime Cybersecurity Mitigations
To correct and mitigate maritime cybersecurity threats going forward, the report advocates the implementation of standardized risk frameworks across the MTS, security requirements for suppliers and contractors, vulnerability audits, information-sharing policies and more.
The recommendations start with establishing an OT risk framework that provides a standard for “insurers, facility and/or vessel owners and shippers to share a common risk language and develop common OT risk metrics for self-assessments.” This is a framework that the Feds will provide guidance on, and the report said that will include an international port OT risk framework based on the input from domestic and international partners, according to the advisory.
It also addressed third parties, and said that “the United States will strengthen cybersecurity requirements in port services contracts and leasing. To limit adversarial opportunity, contracts or leases binding the United States Government and private entities must contain specific language addressing cyber risk to the MTS. The private sector owns and operates the majority of port infrastructure.”
The report added, “Port services such as, but not limited to, loading, unloading, stacking, ferrying or warehousing Federal cargo requires cybersecurity contracting clauses to safeguard the flow of maritime commerce, MTS users and our economic prosperity.”
In addition, the report prescribes an examination of critical port OT systems for cyber vulnerabilities, but it doesn’t specify a role for the federal government. Instead, the report noted that the maritime sector should glean cybersecurity best practices from other critical infrastructure sectors.
The Feds will, however, establish a cyber-forensics process for maritime investigations.
“The United States will design a framework for port cybersecurity assessments,” according to the report. “Developing and deploying cyber-forensics for all major marine casualties and mishaps, when a maritime cyber-effect cannot be ruled out, is paramount.”
And finally, the report addresses the cybersecurity skills gap.
“DHS, through the United States Coast Guard, in coordination with other applicable departments and agencies, will develop cybersecurity career paths, incentives, continuing education requirements and retention incentives to build a competent maritime cyber-workforce,” the report reads, “…and will encourage cybersecurity personnel exchanges with industry and national laboratories, with an approach towards port and vessel cybersecurity research and application.”
Class Action Lawsuit Filed Against SolarWinds Over Hack
7.1.2021 Cyber Securityweek
A class action lawsuit was filed on behalf of SolarWinds investors this week over the cybersecurity breach suffered by the Texas-based IT management solutions provider.
A complaint was filed in the Western District of Texas by Timothy Bremer on behalf of shareholders, specifically those who acquired SolarWinds stock between February 24, 2020, and December 15, 2020.
The complaint names SolarWinds, as well as Kevin Thompson, who served as the company’s CEO until just days before the incident was disclosed, and Barton Kalsu, executive VP and CFO of SolarWinds.
The lawsuit points out that the value of SolarWinds shares decreased significantly following the disclosure of the cyberattack — from nearly $24 per share to roughly $18 a few days after the breach came to light.
The complaint references the financial reports filed by SolarWinds while threat actors had access to its systems and alleges that the company’s executives “made false and/or misleading statements and/or failed to disclose that: (1) since mid-2020, SolarWinds Orion monitoring products had a vulnerability that allowed hackers to compromise the server upon which the products ran; (2) SolarWinds’ update server had an easily accessible password of ‘solarwinds123’; (3) consequently, SolarWinds’ customers, including, among others, the Federal Government, Microsoft, Cisco, and Nvidia, would be vulnerable to hacks; (4) as a result, the Company would suffer significant reputational harm; and (5) as a result, Defendants’ statements about SolarWinds’s business, operations and prospects were materially false and misleading and/or lacked a reasonable basis at all relevant times.”
The plaintiff also referenced some of the statements made by third-parties claiming that they had informed SolarWinds regarding various vulnerabilities and security risks, but were ignored by the company.
The attackers are believed to have gained access to the firm’s systems at least one year before the intrusion was discovered.
SolarWinds investors can join the class action until March 5.
An investigation has been launched into whether SolarWinds executives were aware of the breach when they decided to sell hundreds of millions of dollars worth of stock just before the hack came to light. The company claims they were not aware of the incident.
Several U.S. agencies on Tuesday officially said Russia was likely responsible for the attack, accusations that Moscow has denied.
SolarWinds said up to 18,000 customers may have received trojanized product updates delivered by the attackers, but the actual number of organizations that presented an interest to the hackers was likely only a few hundred. The New York Times reported recently that over 250 government agencies and businesses were breached through the supply chain attack.
Investigations into the SolarWinds attack are now trying to determine whether the company was also targeted by a second, unrelated threat actor, that apparently may have leveraged a zero-day vulnerability affecting SolarWinds products and a piece of malware named Supernova.