Once the customers have provided their credit card data, the skimmer will throw an error and redirects customers to the real payment page to avoid raise suspicion.
Cyber 2024 2023 2022 2021 2020 CYBERCRIME 2022 2021 2020
Lawsuit Claims Flawed Facial Recognition Led to Man’s Wrongful Arrest
30.12.2020 CyberCrime Threatpost
Black man sues police, saying he was falsely ID’d by facial recognition, joining other Black Americans falling victim to the technology’s racial bias.
Racial bias against non-white skin in facial recognition landed Nijeer Parks ten days in jail in 2019 after the technology falsely identified him as a shoplifting suspect, a new lawsuit says.
It didn’t matter that he hadn’t been to the location of the crime, a Hampton Inn hotel in Woodbridge, New Jersey, according to Parks. The tech fingered him and that was enough for police, he said. A warrant was issued, and Parks had his cousin drive him to the station to explain they had the wrong guy.
“I had no idea what this was about,” Parks told NJ Advance Media. “I’d never been to Woodbridge before, didn’t even know for sure where it was.”
2020 Reader Survey: Share Your Feedback to Help Us Improve
That didn’t matter, according to Parks, who said once he got to the station he was handcuffed and thrown in jail for ten days. The charges against him were later dismissed and prosecutors admitted the only evidence against Parks was from the department’s Clearview AI facial recognition technology.
“I did have a background, but I’d been home since 2016 and I had been in no trouble,” Parks said. “The whole thing scared the heck out of me. I’ve been trying to do the right thing with my life.”
Now Parks is suing the police department for locking him up based on nothing more than this faulty technology — and he is not alone.
Parks joins Robert Julian-Borchak Williams, who was also wrongly arrested earlier this year, this time in Detroit, for allegedly stealing watches in 2018, after also being misidentified by facial recognition technology. This time it was DataWorks Plus facial recognition software being used by Michigan State Police that failed.
Williams was arrested in front of his wife and children and held overnight in the Detroit Detention Center until he was led to an interrogation room and shown video of the crime, Business Insider reported. That’s when they finally compared the suspect with Williams and it was obvious police had the wrong guy.
Racial Bias in Facial Recognition Software
About half of American adults, without their knowledge or consent, are included in the law enforcement facial recognition database, according to research from Harvard. This presents basic privacy concerns for all Americans.
But it’s Black Americans who face the greatest threat of injustice, according to Harvard’s Alex Najibi, who explained in a report from October that while overall accuracy rates for facial recognition tech hover around 90 percent, error rates across different demographics vary. The “poorest accuracy consistently found in subjects who are female, Black and 18-30 years old,” he wrote.
The idea that facial recognition software is racist isn’t anything new. The 2018 Gender Shades project, and an independent assessment by the National Institute of Standards and Technology have all come to the same conclusion: facial recognition technology is least accurate on Black Americans and Black women in particular.
Phasing Out Faulty Facial Recognition
Last November the Los Angeles Police Department banned the Clearview AI facial recognition platform after personnel were revealed to have been using the database, citing privacy concerns and under pressure from watchdog groups like the American Civil Liberties Union (ACLU).
“[Clearview AI] has captured these faceprints in secret, without our knowledge, much less our consent, using everything from casual selfies to photos of birthday parties, college graduations, weddings and so much more,” ACLU staff attorney Nathan Freed Wessler wrote about the lawsuit last May.
“Unbeknownst to the public, this company has offered up this massive faceprint database to private companies, police, federal agencies and wealthy individuals, allowing them to secretly track and target whomever they wished using face-recognition technology.”
Last summer, the National Biometric Information Privacy Act was introduced in the Senate to put privacy protections in place, but until the law catches up, tech giants like Microsoft, Amazon and IBM have pledged to stop selling facial recognition to police departments.
“We will not sell facial-recognition tech to police in the U.S. until there is a national law in place…We must pursue a national law to govern facial recognition grounded in the protection of human rights,” Microsoft president Brad Smith said about the announcement.
Clearview CEO Hon Ton-That defended his company’s product in a statement provided to Threatpost last September and pointed to its use by more than 2,000 law enforcement agencies to solve crimes and keep communities safe.
“Clearview AI is proud to be the leader in facial-recognition technology, with new features like our intake form — whereby each search is annotated with a case number and a crime type to ensure responsible use, facial-recognition training programs and strong auditing features.”
Multi-platform card skimmer targets Shopify, BigCommerce, Zencart, and Woocommerce stores
29.12.2020 CyberCrime Securityaffairs
Experts warn of a multi-platform credit card skimmer that can target online stores running on Shopify, BigCommerce, Zencart, and Woocommerce.
Security experts have discovered a multi-platform credit card skimmer that can allow threat actors to harvest payment info on compromised stores powered by Shopify, BigCommerce, Zencart, and Woocommerce.
Researchers from security firm Sansec discovered that the new software skimmer is able to interact with the checkout process on shops running on top of multiple online store management systems.
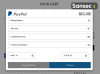
The software skimmer can also target e-stores running on BigCommerce and Shopify platforms even if they do not allow custom Javascript on checkout pages. This skimmer shows a fake payment form that was designed to record customer keystrokes before they enter the actual checkout page.
“Hosted platforms like BigCommerce and Shopify do not allow custom Javascript on checkout pages. This skimmer evades that by showing a fake payment form and recording customer keystrokes before they enter the actual checkout page.” reads the post published by SanSec. “Once the data is intercepted, the skimmer displays an error message and the customer is redirected to the real payment page:”

Once the customers have provided their credit card data, the skimmer will throw an error and redirects customers to the real payment page to avoid raise suspicion.
This campaign outstands because it targets so many different platforms, hackers may have breached a shared component used by all affected merchants.
Experts pointed out that this multi-platform skimmer uses programmatically generated exfiltration domains.
“It keeps a counter and uses base64 encoding to produce a new domainname.” continues the report. “This will lead to, for example, these exfiltration domains.”
zg9tywlubmftzw5ldza.com;
zg9tywlubmftzw5ldze.com;
zg9tywlubmftzw5ldzu.com:
zg9tywlubmftzw5ldzq.com;
zg9tywlubmftzw5ldzm.com;
zg9tywlubmftzw5ldzy.com;
zg9tywlubmftzw5ldzi.com;
zg9tywlubmftzw5ldzg.com
…………………………………………..
The first exfiltration domains was registered on August 31, 2020.
“To summarize: this campaign shows that platforms are no boundary to the profitable fraud of online skimming,” Sansec concludes. “Wherever customers enter their payment details, they are at risk.”
Sansec researchers have spotted multiple Magecart campaigns using new evasion techniques. In early December they have uncovered a campaign that was hiding the malware in CSS files.
The experts analyzed multiple Magecart attack techniques over the past months, attackers compromised websites by hiding malicious code in multiple components of the sites, including live chat windows, images, and favicons.
Holiday Puppy Swindle Has Consumers Howling
23.12.2020 CyberCrime Threatpost
Those buying German Shepherd puppies for Bitcoin online are in for a ruff ride.
Puppy photos are undeniably irresistible but beware; researchers have uncovered a scheme selling fake German Shepherd puppies for Bitcoin, leaving buyers crushed and without a tiny fuzzy friend to cuddle on Christmas morning.
The scam was discovered by an intrepid researcher at Anomali, who got wind of the fake puppy offer and decided to investigate.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“When one of our researchers heard about this con, he dug deeper into it,” Gage Mele, researcher with Anomali, told Threatpost. “Because consumers are last-minute shopping ahead of the holidays and continuing to buy pets at a higher rate due to COVID-19 shelter-at-home restrictions, we issued a consumer alert.”
The scammers have been operating since Nov. 2018, according to the Amomali report, but have ramped up their efforts in advance of the heavy online holiday shopping season. The report said they found 17 websites linked to the group selling birds, cats and essential oils.
Website splash page. Source: Anomali.
Once the scammers lured victims into their online stores, they asked for non-refundable deposits through methods like Bitcoin, PayPal, Zelle and others, and then failed to deliver the goods.
Researchers were tipped to the fraud in early December, the report said. The suspicious site, darlinggermanshepherds[.]com, was not terribly sophisticated, according to researchers, and advertised German Shepherds for sale. The sites used images sourced from old, abandoned websites that helped make them look unique.
Anomali was able to link this site to others because they shared nearly identical or even straight copy-and-pasted testimonials.
“My husband races motorcycles and we take Kahuna with us, even with all the commotion, people and engines, he just sits on his stand basking in the sun on one foot,” one of these testimonials read, across three scam sites, the report said.
“Online scammers typically leave a trail of clues scattered throughout the websites they operate, emails they send, and posts on social media,” Mele said. “This is only a single example of countless fraudulent activities taking place online. It is especially noteworthy as it shows that even sloppy perpetrators can mislead consumers.”
Another Fake Puppy Fraud Reported
Earlier this month, the U.S. Department of Justice brought charges against a Camaroonian operator, Desmond Fodje Bobga, in a Pittsburgh federal court for a similar puppy scam. The allegations against Fodjie Bobga include wire fraud, forgery and aggravated identity theft.
“Unfortunately, the pandemic has created the perfect condition for unscrupulous pet sellers to thrive,” FBI Pittsburgh Special Agent in Charge Michael Christman said. “This suspect exploited this website to sell puppies and capitalized on people looking for companion animals online during this difficult time.”
Typical fraud architecture. Click to enlarge. Source: Anomali.
Fodjie Bobga, much like the other puppy scam, would offer dogs and other animals for sale, collect a deposit and set up a fake delivery. The fake transport company would contact the victim and tell them that due to COVID they needed to pay additional money for delivery.
But the fraud continued to get more brazen from there, according to the DOJ statement.
“More recently, Fodje Bobga and the co-conspirators told some victims that they needed to pay even more money for delivery because the pet had been exposed to the coronavirus,” the statement explained. “The perpetrators used false and fraudulent promises and documents regarding shipping fees and coronavirus exposure to extract successive payments from victims.”
The criminals would then generate fake documentation to keep the fraud going, including a vaccine guarantee from the U.S. Supreme Court.
“Among the fake documents were a ‘refundable crate and vaccine guarantee document’ that purported to have been issued by the ‘Supreme Court of the United States of America” and bore the seal of the court, along with the signature of a Clerk of the Court,” the DoJ said. “After Fodje Bobga and the co-conspirators received money directly and indirectly through wire communications from the victims, Fodje Bobga and the co-conspirators never delivered the pets.”
Avoid Online Scams
Whether its puppies, essential oils or anything else, experts warn it’s critical to confirm the identity of any online seller before sending them payment.
Amomali’s recommendations include verifying a name, address and phone number of the seller, looking for sloppy typos on seller sites and being suspicious of prices that seem too good to be true.
For the more technical set, Anomali advises checking the domain creation date.
“It is especially suspicious if the domain was registered this year, but has a copyright footnote with a 2015 timestamp,” the report said.
Anomali also advised the more tech savvy online holiday shoppers to do a reverse search on the site’s images and checking the HTML code for connections with other known suspicious domains.
“Advanced site builders might have matching tags such as Google Analytics ID. Basic fraud sites…often have metatags copied from another domain,” the report added.
Mele told Threatpost he hopes the report will help everyone be a bit more careful shopping online, particularly during the busy holiday season.
“Everyone who shops online needs to be aware of the fact that cybercriminals are on the prowl and looking to take advantage of anyone they can lure in,” he said.
Joker’s Stash Carding Site Taken Down
23.12.2020 CyberCrime Threatpost
The underground payment-card data broker saw its blockchain DNS sites taken offline after an apparent law-enforcement effort – and now Tor sites are down.
Joker’s Stash, the carding site where cybercriminals hawk their payment-card wares, has suffered a blow after law enforcement apparently seized one of its domains.
Joker’s Stash is a popular cybercriminal destination that specializes in trading in payment-card data, offering millions of stolen credit and debit cards to buyers. In October for instance, Dallas-based smoked-meat franchise Dickey’s Barbecue Pit saw 3 million customer payment cards turn up on the site. Anyone purchasing the information can create cloned cards to physically use at ATMs or at in-store machines that aren’t chip-enabled; or, they can simply use the information to buy things online.
According to researchers at Digital Shadows, Joker’s Stash evades takedowns by operating from several different domains. These include blockchain domains including .bazar, .lib, .emc, and .coin, as well as two Tor (.onion) versions of the platform, researchers said.
2020 Reader Survey: Share Your Feedback to Help Us Improve
But late last week, the .bazar version of the site began displaying a notification that the U.S. Department of Justice and Interpol had seized the site. Shortly after, the .lib, .emc and .coin domains began showing a “Server Not Found” banner.
“Early chatter on the Russian-language cybercriminal forum XSS initially suggested that the entire site had been seized and expressed concern at this development,” according to Digital Shadows, in a recent blog.
The official Joker’s Stash representative, “JokerStash,” went on to create a post on the Russian-language carding forum Club2CRD, confirming that the .bazar domain’s external proxy server had been taken down — but it’s unclear if the DoJ and Interpol are indeed behind the action. In any event, the person also intimated that the takedown wouldn’t affect operations for long.
“The representative went on to state that the server did not contain any ‘shop data,’ and announced they were creating new servers and transitioning the site, meaning all blockchain versions of the site would be ‘back to work in a few days,'” according to Digital Shadows. “Finally, the representative confirmed that the Tor versions of the site remained unaffected and encouraged users to leverage them in the meantime.”
As of Monday however, the Tor versions of the site were unavailable, but JokerStash claimed the blockchain sites were back in business. “The Tor links that were initially advertised following the .bazar domain seizure appear to be temporarily offline, likely being moved to new servers,” postulated Austin Merritt, cyber-threat intelligence analyst at Digital Shadows, in an email interview.
Thus, the seizure of the .bazar domain likely will not do much to disrupt Joker’s Stash, researchers said. “Joker’s Stash maintains a presence on several cybercrime forums, and its owners use those forums to remind prospective customers that millions of credit- and debit-card accounts are for sale,” according to the post. “Even following the seizure of the .bazar domain, the official Joker’s Stash representative updated a thread on Club2CRD with a long list of new payment card dumps recently added to the site.”
Blockchain domain name server (DNS) technology is a decentralized system for top-level domains that is not regulated by a central authority in the way conventional DNS sites are. When a website wants to match a website IP address to a URL, the lookup is done via a peer-to-peer network. Blockchain DNS sites are usually accessed via Chrome, researchers said, using a special blockchain browser extension that enables access to sites with certain URL suffixes.
This makes it a bit of a Wild West, with Digital Shadows researchers noting that security services have a harder time tracking malicious activity in that environment.
“[Carding services] and other sites used to trade stolen account information have been experimenting with peer-to-peer DNS technology in order to hide malicious activity, and crucially bulletproof their platforms,” researchers wrote. “As blockchain domains do not have a central authority and registrations contain unique encrypted hashes rather than an individual’s name and address, it is harder for law enforcement to perform site takedowns.”
Merritt said that the other non-Tor Joker’s Stash sites were likely offline because they were taken down by the administrator.
“Since the site’s representative mentioned that they were creating new servers and transitioning the site, it’s possible they have not completed the transition,” he told Threatpost. “Another probable cause for these sites’ unavailability is the failure of plugins needed to access the .bazar, .lib, .emc, and .coin domains; installing more than one plugin can also lead to a failure to access the site’s contents.”
While the law-enforcement action is unlikely to slow Joker’s Stash down for long, it could have repercussions for the site’s “cred” on the criminal underground, and it shows that blockchain DNS services aren’t untouchable. It could also spur them to change tactics, Merritt said.
“The significance of law-enforcement coalitions tackling cybercriminal vendors on marketplaces, and their ability to track down vendors, may encourage criminal marketplace administrative teams to take more security-aware approaches, such as implementing PGP encryption, two-factor authentication (2FA), and leveraging Monero (XMR) to avoid tracking,” he told Threatpost. “Law-enforcement action against Joker’s Stash may serve as a short-term deterrent, but the site’s reputation as a credible [carding forum] for cybercriminals will likely be maintained. As we’ve already seen, site administrators can quickly adapt to takedown attempts by moving their operations to more secure domains.”
They added, “In the future, additional…sites could be the target of takedown operations by law enforcement in an attempt to deter cybercriminals. Unfortunately, when one site or operation is taken down, cybercrime finds a way through other platforms with cybercriminals ready to fill the void.”
VPN Service Used by Cybercriminals Disrupted in Global Law Enforcement Operation
23.12.2020 CyberCrime Securityweek
A VPN service used by many cybercriminals has been disrupted in a global operation that involved law enforcement agencies in Germany, the United States, the Netherlands, France and Switzerland.
Europol reported on Tuesday that the operation targeted a service called Safe-Inet, and the U.S. Justice Department clarified that three associated domains have been seized, namely insorg.org, safe-inet.com and safe-inet.net. The domains currently display a banner informing visitors that they have been seized.
The Justice Department said the agencies involved in the operation, named Operation Nova, also shut down servers associated with the service in their respective countries.
The operators of the service provided both VPN and bulletproof hosting, which authorities say have been used by cybercriminals to target at least 250 organizations worldwide. The services were offered to both English- and Russian-speaking users, and they have been used for ransomware, payment card skimming, spear-phishing and account takeover attacks.
Europol said law enforcement agencies are now trying to identify Safe-Inet users in a number of countries.
Interestingly, the operators of Safe-Inet posted a message on Twitter, on Monday, in both English and Russian, informing users that they are aware of “the problem” and that the service will be restored in the coming days. The description of the Safe-Inet Twitter account says they have been “providing anonymity and security for 11 years.”
The news comes shortly after the FBI and Interpol seized domains associated with Joker’s Stash, a popular underground marketplace for stolen payment card data. However, in the case of Joker’s Stash, only a few domains and servers were disrupted and the service is still available.
Servers of Carding Site "Joker's Stash" Seized by Law Enforcement
23.12.2020 CyberCrime Securityweek
The blockchain domains of Joker’s Stash, a popular underground marketplace for stolen payment card data, have been seized by law enforcement.
On December 17, the shop’s website displayed an image claiming that the U.S. Federal Bureau of Investigation and Interpol had seized it.
Joker’s Stash is an automated vending cart (AVC) that had several versions of the site up and running, including blockchain domains .bazar, .lib, .emc, and coin, and two Tor (.onion) domains. The takedown attempt, Digital Shadows reports, only resulted in the .bazar domain becoming unavailable.
What the two law enforcement agencies apparently managed to do was to seize proxy servers that were used in connection with the Joker’s Stash blockchain domains.
Following the action, Joker’s Stash operators decided to take the site down completely, but took it to Russian-language carding forum Club2CRD to provide clarifications on the issue, revealing that no “shop data” was present on the affected server.
The representatives of the carding site also revealed that they were working on creating new servers to move the site to, promising the marketplace would be completely functional within days. The Tor versions of the portal were not affected by seizure.
A decentralized system for top-level domains, Blockchain DNS technology provides multiple security advantages, but also makes it more difficult to target domains that use it, as they are no longer regulated by a central authority.
Joker’s Stash, Digital Shadows explains, has been using Blockchain DNS since July 2017. Following last week’s action, Joker’s Stash’s blockchain domains (.bazar, .lib, .emc, and .coin) started displaying a “Server Not Found” error. The Tor domains, however, remained accessible.
“Generally speaking, if the Joker’s Stash takedown was a coordinated law enforcement operation, it’s likely that the law enforcement banner would remain in place to demonstrate that other Blockchain DNS services aren’t untouchable. On the other hand, it’s possible that law enforcement thought they had taken the entire Joker’s Stash service offline, rather than just one component, and quickly removed the banner after finding out that this was not the case,” Digital Shadows points out.
Intel 471’s security researchers believe that, provided that law enforcement indeed seized Joker’s Stash servers, the marketplace would be able to quickly restore its services.
The researchers also point out that the marketplace has had a difficult time lately, with the threat actor who runs it getting infected with COVID-19 and customers complaining about the poor quality of the shop’s payment card data. One of the most popular cybercriminal shops, the portal might lose its position as “a preferred home of criminal activity,” Intel 471 notes.
“It’s apparent that major intrusions resulting in valuable stock for sale across his shop has taken a bit of a dive over the last year. This could be a result of many things, from the pandemic to the massive shift of many cybercriminals to ransomware, where significantly less effort can lead to marginally higher profits,” Intel 471 VP of Intelligence Mike DeBolt commented.
Law Enforcement Seizes Joker's Stash — Stolen Credit Card Marketplace
23.12.2020 CyberCrime Thehackernews
The US Federal Bureau of Investigation (FBI) and Interpol have allegedly seized proxy servers used in connection with Blockchain-based domains belonging to Joker's Stash, a notorious fraud bazaar known for selling compromised payment card data in underground forums.
The takedown happened last week on December 17.
The operators of Joker's Stash operate several versions of the platform, including Blockchain proxy server domains — .bazar, .lib, .emc, and .coin — that are responsible for redirecting users to the actual website and two other Tor (.onion) variants.
Joker's Stash implemented the use of Blockchain DNS via a Chrome browser extension in 2017.
These Blockchain websites make use of a decentralized DNS where the top-level domains (e.g., .bazar) are not owned by a single central authority, with the lookup records shared over a peer-to-peer network as opposed to a DNS provider, thus bringing in significant advantages like bulletproof hosting.
This also means the move is not expected to have a lasting impact, as the top-level domain itself cannot be seized, but rather only the IP address of the server it points to.
According to cybersecurity firm Digital Shadows, which disclosed the development, the Tor versions of the site are still accessible, meaning this action is unlikely to pose a major threat to their operations.
The actors behind Joker's Stash took to Russian-language carding forum Club2CRD stating that no card dumps were stored on the servers and transition plans were already underway to move the content hosted on the busted site to a new blockchain version of the portal.
"I am setuping (sic) and moving to the new servers right now, blockchain links will [be] back to back to work in a few days," the site's representative said in a forum post, adding "use Tor links, bros!"
Interestingly, it is not immediately clear if the law enforcement agencies are indeed behind the coordinated takedown.
Although last week, the affected .bazar version of the site began displaying a note that the US Department of Justice and Interpol had seized the site, Digital Shadows said the four blockchain sites are now showing a "Server Not Found" banner.
Joker's Stash is particularly infamous for advertising the breach of US-based convenience store chain Wawa last December, with the hackers putting up for sale the payment card details of more than 30 million Americans and over one million foreigners.
"The seizure of the .bazar domain likely will not do much to disrupt Joker's Stash, especially since the team behind Joker's Stash maintain several versions of the site and the site's Tor-based links are still working normally," Digital Shadows said.
"Furthermore, Joker's Stash maintains a presence on several cybercrime forums, and its owners use those forums to remind prospective customers that millions of credit and debit card accounts are for sale."
Cybercriminals' Favorite Bulletproof VPN Service Shuts Down In Global Action
23.12.2020 CyberCrime Thehackernews
Law enforcement agencies from the US, Germany, Netherlands, Switzerland, France, along with Europol's European Cybercrime Centre (EC3), announced today the coordinated takedown of Safe-Inet, a popular virtual private network (VPN) service that was used to facilitate criminal activity.
The three domains in question — insorg[.]org, safe-inet[.]com, and safe-inet[.]net — were shut down, and their infrastructure seized as part of a joint investigation called "Operation Nova."
Europol called Safe-Inet a cybercriminals' "favorite."
A crucial reason for the domains' seizure has been their central role in facilitating ransomware, carrying out web-skimming, spear-phishing, and account takeover attacks.
The service, which comes with support for Russian and English languages and has been active for over a decade, offered "bulletproof hosting services" to website visitors, often at a steep price to the criminal underworld.
As of December 1, the cost of a Pro subscription ranged anywhere between $1.3/day to $190/year for full access to its entire roster of servers.

Bulletproof hosting (BPH), also known as abuse-resistant services, is different from regular web hosting in that it allows a content provider more leniency in the kind of data that can be hosted on those servers, thus making it easier to evade law enforcement.
According to an analysis by cybersecurity firm Trend Micro in October, a bulletproof host employs various ways to sustain crimes operating under its wing and can strategically allocate resources globally, keeping in mind the regional legalities and geographical characteristics. They are known to minimize the number of useful log files and access the system only from anonymous sources like Tor networks.
"A bulletproof hoster's activities may include ignoring or fabricating excuses in response to abuse complaints made by their customer's victims; moving their customer accounts and/or data from one IP address, server, or country to another to help them evade detection; and not maintaining logs (so that none are available for review by law enforcement)," the US Department of Justice (DoJ) said in a statement.
In doing so, the BPH services intentionally support the criminal activities of their customers and become co-conspirators in the criminal schemes, the DoJ added.
Europol also said it identified about 250 companies worldwide that were being spied on by the criminals to launch potential ransomware attacks using the Safe-Inet infrastructure.
"Criminals can run but they cannot hide from law enforcement, and we will continue working tirelessly together with our partners to outsmart them," Head of EC3, Edvardas Šileris, said.
Dark Web Pricing Skyrockets for Microsoft RDP Servers, Payment-Card Data
22.12.2020 CyberCrime Threatpost
Underground marketplace pricing on RDP server access, compromised payment card data and DDoS-For-Hire services are surging.
Cybercriminals are vying for Remote Desktop Protocol (RDP) access, stolen payment cards and DDoS-for-Hire services, based on a recent analysis of underground marketplace pricing.
During the COVID-19 pandemic, cybercriminals have profited with “increasingly advantageous positions to benefit from the disruption,” said researchers — and this has also been reflected on underground markets, where new services like targeted ransomware and advanced SIM swapping are popping up.
“As a result of COVID-19 and associated global trends, demand for malicious and illicit goods, services and data have reached new peak highs across dark web marketplaces (DWMs),” said researchers in a Friday analysis. “Flashpoint has also observed what can only be described as impressive, shrewd innovation throughout the cybercrime ecosystem.”
2020 Reader Survey: Share Your Feedback to Help Us Improve
Upon a deep-dive investigation into the underground marketplace, researchers found that the pricing for stolen payment cards has soared in 2020; jumping from $14.64 in 2019 to $20.16 in 2020. Meanwhile, the price of payment card “dumps” has also inched up from $24.19 in 2019 to average $26.50 in 2020.
Payment Card Costs Soar
While payment cards are sourced from online transactions and include card number, expiration date and cardholder name; dumps are usually sourced from malware-infected or skimmer-infected point-of-sale (PoS) terminals, and include magnetic strip track data.
Credit: Flashpoint
Researchers said that payment-card data pricing varies and is typically influenced by “freshness” (i.e., how recently the data was sourced), country of origin, availability of track 1 and track 2 magnetic strip data and expiration date.
RDP Server Access in High Demand
Microsoft’s proprietary Remote Desktop Protocol (RDP), used to enable system admins to remotely connect to corporate machines, as well as for server updates, continues to be a cybercriminal favorite.
Credit: Flashpoint
RDP listings continue to grow in popularity throughout the cybercriminal ecosystem, said researchers. A successful RDP attack is lucrative for cybercriminals as it would give them remote access to the target computer with the same permissions, and access to data and folders, that a legitimate user would have.
On underground marketplaces in 2020, researchers found that RDP access pricing varies – global admin access costs $10, while hacked RDP costs $35.
Researchers noted that 2020 listings for RDP server access are less specialized, and cater to a broader audience. This can include packages that typically provide multiple RDP access options in one bundle.
“This can cover country-specific access, bank account or government ID information, among other options to execute or manage the access,” they said.
DDoS-For-Hire
Meanwhile, DDoS-for-hire pricing appears to be on the rise since 2017, said researchers. DDoS-for-hire, known as “booter” services, make it easy to carry out DDoS attacks, flooding targets with internet traffic to overwhelm a site or IP address and eventually knock it offline.
While in 2017 researchers rarely saw standard DDoS-for-hire offerings exceed $27, in 2020 a 10-minute DDoS attack (60 Gbps) costs $45, while a four-hour DDoS attack (15 Gbps) averages $55. Meanwhile, a fully-managed DDoS attack costs $165. Researchers said, this price increase is likely due to several contributing factors.
Credit: Flashpoint
“First, taking down bigger websites must be custom-crafted due to improvements in DDoS protection offerings and widespread use of content distribution networks (CDNs), which are beyond the skills of all but the most advanced bot herders,” they said. “However, there are still instances where threat actors can successfully target larger websites, such as the takedown of Wikipedia via a DDoS attack in September 2019.”
DDoS-for-hire services that charge hourly rates are also becoming increasingly popular, they said.
“While booters…remain prevalent, the need for more hands-on support and customization make subscription service options more appealing to buyers,” said researchers.
Researchers also tracked listings for an array of other services. These include bank logs and routing numbers (ranging from $25 for a U.S. bank log with a $100 balance, to $55 for a U.S. bank log with a $4,000 balance). Researchers also looked at pricing for “fullz,” which are full packages of personal identifiable information (PII) on individuals, mainly used for identity-fraud schemes (ranging from $4 to $10, with Fullz including financial information being more expensive).
Hackers target COVID-19 vaccine supply chain and sell the vaccine in Darkweb
19.12.2020 CyberCrime Securityaffairs
Threat actors continue to trade critical medical data in the Dark Web while organizations are involved in the response to the COVID-19 pandemic.
Cybercrime organizations continue to be very active while pharmaceutical organizations are involved in the development of a COVID-19 vaccine and medicines to cure the infections.
Experts from Cyble discovered in several forums on the dark web, the offer for enormous repositories of critical medical that wee stolen from multiple organizations.
Threat actors attempt to sell alleged confidential vaccine research and databases containing PII.
“As COVID-19 continues to dominate headlines, confidential vaccine research data generates enough monetization opportunities for cybercriminals.” reads the post published by Cyble. “In addition to the COVID-19 databases containing confidential PII being leaked on the Internet, one of the critical security concerns is the immense cold chain logistics of the vaccine.”
Recently, IBM warned of attacks against the COVID-19 vaccine cold chain that begun in September 2020. The experts uncovered a large scale spear-phishing campaign that has been ongoing since September 2020. Threat actors are impersonating a biomedical company, Haier Biomedical, and are sending out spear-phishing messages to executives and global organizations involved in vaccine storage and transport. Haier Biomedical is a legitimate member company of the COVID-19 vaccine supply chain, it is also a qualified supplier for the CCEOP program.
The phishing campaign hit global organizations with headquarters in Germany, Italy, South Korea, Czech Republic, greater Europe, and Taiwan. The attackers aim at harvesting account credentials to use in further attacks against the same organizations.
DHS CISA also issued an alert warning organizations working on the COVID-19 cold chain of targeted attacks carried out by nation-state actors.
More recently, experts from Cyble research observed new phishing emails with the subject posing as a Draft of Contract related to the CCEOP and Vaccine Program. Once again, this phishing email masquerades as communication from Haier Biomedical and is targeted at Kraeber & Co.
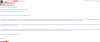
The attackers attempt to trick victims into opening the malicious HTML attachment, then the victims are prompted to submit login credentials for viewing PDF content.
“Our research indicates a malicious ActiveX component that automatically runs in the background as soon as the user enables the document security control.” continues the report. “This type of ‘Precision Targeting’ involves advanced phishing attacks that are difficult to detect and takedown by security organizations.”
The ActiveX function in the HTML page allows sending the harvested credentials back to the attackers’ server via POST request.
The threat actors could use the credentials to gain access to the targeted infrastructure and attempt to steal confidential information related to the COVID-19 vaccine research and delivery.
Another interesting aspect of the Cyble research team is the discovery of multiple offers of vaccines in the dark web marketplaces.
While the first doses of the vaccine are provided to the UK and US citizens, multiple vendors on the darknet are already offering for sale doses of the Pfizer/BioNTech vaccine.
It is important to remind that the Pfizer vaccine must be kept at minus-70 degrees centigrade, this means that it cannot be shipped out in the post. At the time of this writing, it is unclear how the sellers are managing the doses and how they can ship them.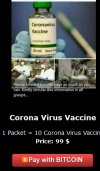

“This phishing campaign is a clear indication that threat actors are shifting their focus on the complex logistical network associated with the R&D and distribution of the vaccine value chain.” concludes Cyble.
Cybercriminals Steal Millions by Spoofing Thousands of Mobile Devices
17.12.2020 CyberCrime Securityweek
A group of cybercriminals used mobile emulators to spoof thousands of mobile devices , which enabled them to steal millions of dollars within days.
Targeting financial institutions in Europe and the United States, the mobile banking fraud operation relied on over 20 emulators to spoof more than 16,000 mobile devices and access compromised accounts.
Mobile device identifiers were used to spoof the devices of the account holders, but in some cases the attackers set up new identifiers, to make it seem as if the user was accessing the account from a new device. Credentials stolen from infected systems or via phishing were also used.
“Using automation, scripting, and potentially access to a mobile malware botnet or phishing logs, the attackers, who have the victim’s username and password, initiate and finalize fraudulent transactions at scale,” IBM Security Trusteer’s researchers, who discovered the operation, explain.
The attackers likely automated account assessment and the initiation of fraudulent money transfers, while being careful to keep the amounts low enough to ensure their activity won’t trigger further review by the bank.
Using the network of thousands of spoofed devices, the crooks repeatedly accessed the accounts of thousands of people, eventually stealing millions of dollars within days, per attack.
“After one spree, the attackers shut down the operation, wipe traces, and prepare for the next attack,” the researchers explain.
Despite the use of emulators, the attacks can target any financial application, even those that are approved using codes sent via SMS or email.
The individuals behind this operation were likely in the possession of account holders’ usernames and passwords, had access to device identifiers and other data (likely from compromised devices), and were able to obtain SMS message content.
Furthermore, they leveraged a customized automation environment to specifically target financial applications, used a set of virtual mobile emulators to spoof a larger number of devices, and employed network interception scripts to submit transactions and monitor communications.
Using legitimate apps, the attackers tested their emulators to ensure they would pass as real devices. They also leveraged a custom application that would automatically deliver the necessary device parameters to the emulator, while matching the device with the account holder’s username and password.
Devices successfully used for fraudulent transfers were recycled and replaced with unused devices. Blocked devices were also replaced. In one attack, a single emulator was used to spoof more than 8,000 devices.
The attackers also created custom-tailored applications that would mimic the application they were targeting. They also kept a close eye on how the target applications reacted to the connections from their spoofed devices.
“It is likely that those behind [this operation] are an organized group with access to skilled technical developers of mobile malware and those versed in fraud and money laundering. These types of characteristics are typical for gangs from the desktop malware realms, such as those operating TrickBot or the gang known as Evil Corp,” IBM says.
The security researchers also discovered fraud-as-a-service offerings on underground markets promising access to similar operations for paying subscribers. This suggests not only that any wannabe cybercriminal may launch similar attacks, but also that the scheme can be adapted to target financial institutions in almost any country, the researchers note.
Payment Card Skimmer Group Using Raccoon Info-Stealer to Siphon Off Data
7.12.2020 CyberCrime Thehackernews
A cybercrime group known for targeting e-commerce websites unleashed a "multi-stage malicious campaign" earlier this year designed with an intent to distribute information stealers and JavaScript-based payment skimmers.
In a new report published today and shared with The Hacker News, Singapore-based cybersecurity firm Group-IB attributed the operation to the same group that's been linked to a separate attack aimed at online merchants using password-stealing malware to infect their websites with FakeSecurity JavaScript-sniffers (JS-sniffers).
The campaign progressed in four waves, starting in February and ending in September, with the operators relying on specially-crafted phishing pages and lure documents laced with malicious macros to download Vidar and Raccoon information stealers onto victim systems.
The ultimate goal of the attack, the researchers noted, was to steal payment and user data via several attack vectors and tools to deliver the malware.
The fake web pages were created using the Mephistophilus phishing kit, which allows attackers to create and deploy phishing landing pages engineered for distributing malware.
"Attackers sent links to fake pages that informed victims about a missing plugin required to display the document correctly," Group-IB researchers explained in an analysis of the cybercrime group's tactics last November. "If a user downloaded the plugin, their computer was infected with the password-stealing malware."

While the first wave of the campaign in February and March delivered the Vidar password stealer to intercept passwords from user browsers and various applications, subsequent iterations switched to the Raccoon stealer and AveMaria RAT to meet its objectives.
Raccoon, first documented by Cybereason last year, comes with a wide range of capabilities and communicates with a command-and-control (C2) server to siphon data — including screenshots, credit card information, cryptocurrency wallets, stored browser passwords, emails, and system details.
Raccoon is also unique in that it bypasses the blocking of active C2 servers by making a request to a Telegram channel ("blintick") in order to receive the encrypted address of the C2 server, besides offering 24×7 customer support to community questions and comments through the chat service.
AveMaria RAT, likewise, is capable of ensuring persistence, recording keystrokes, injecting malicious code, and exfiltrating sensitive files, among others.
Both Vidar and Raccoon are sold as malware-as-a-service (MaaS) on underground forums. The rental price for Vidar stealer ranges from $250 to $300 per month, whereas the latter costs $200 a month to use.
Along with the four stages described above, Group-IB also observed an interim phase between May to September 2020, during when as many as 20 online stores were infected with a modified JS-sniffer of the FakeSecurity family.

Interestingly, the infrastructure used to distribute the Vidar and Raccoon stealers shared similarities with those used to store the sniffer code and collect stolen bank card data, leading the researchers to link the two campaigns.
The development is yet another sign that adversaries are stepping up their efforts to compromise online marketplaces to pilfer customer payment information, even as law enforcement agencies are working to tackle cybercrime.
Earlier this January, the Interpol, acting on digital forensic evidence from Group-IB, nabbed three individuals associated with a group called "GetBilling" as part of an operation codenamed Night Fury for running a JS-sniffer campaign in Indonesia.
Drug dealers are selling Pfizer COVID vaccines on the darkweb
7.12.2020 CyberCrime Securityaffairs
While the United Kingdom announced the distribution of the COVID-19 vaccine to the population drug dealers is selling ‘Pfizer COVID Vaccines.’
The UK became the first Western country to authorize a Covid-19 vaccine. The UK government announced the distribution of the Pfizer/BioNTech vaccine that has been granted emergency authorization by British regulators. While the first doses are expected to be rolled out from next week, multiple vendors on the darknet are already offering for sale doses of the Pfizer/BioNTech vaccine.
The news of the availability of the “Pfizer COVID-19 vaccine” in the dark web was first reported by VICE World News.
“VICE World News found multiple vendors on the darknet who appeared to be selling doses of the Pfizer/BioNTech vaccine to global customers for as much as $1,300 a piece.” wrote Gavin Butler on the VICE.
Pfizer vaccine darknet
“The doses of the COVID-19 vaccine has [sic] been developed by Pfizer and BioNTec,” reads the description of one advertisement published on a black marketplace. “We can deliver in any country.”
Two vendors told VICE World News spoke claimed to be pharmacists and explained that they had already sold the vaccine to multiple customers after having it from the government. At least one vendor claims to have hundreds of doses.
Only one seller provided a high-quality stock image of a vial labeled “Coronavirus Vaccine”.
It is important to remind that the Pfizer vaccine must be kept at minus-70 degrees centigrade, this means that it cannot be shipped out in the post. At the time of this writing, it is unclear how the sellers are managing the doses and how they can ship them.
Buying drugs in the darkweb is an absurd choice for multiple reasons, in the specific case we are likely speaking about scams, but it is easy to predict that the demand and the odder for COVID-19 vaccines could spike in the next months while multiple countries will start to deliver the first doses.
Islamic imprisoned hacker Ardit Ferizi ordered to be deported
5.12.2020 CyberCrime Securityaffairs
The Islamic hacker Ardit Ferizi, who is serving 20 years for giving his support to Islamic State group has been granted compassionate release.
Ardit Ferizi, aka Th3Dir3ctorY, is the hacker that supported the ISIS organization by handing over data for 1,351 US government and military personnel.
Ferizi is the first man charged with cyber terrorism that was extradited to the US early this year.
He was charged with hacking crimes and providing support to a terrorist organization. The 20-year-old man was accused of supporting the ISIS terrorist organization, he was the subject of extradition from the Malaysian government, where he lived. The man of Kosovar origin was studying computer science in Malaysia.
He was arrested in Malaysia in September 2015 and transferred to the US to face trial. Ardit Ferizi has been sentenced to 20 years in a U.S. prison. According to the US investigators, he provided the data to the popular IS militant Junaid Hussain, which disclosed it on the web. The collaboration between the IS hackers Hussain and Ferizi started in April 2015, according to the US authorities.
Now the hacker has been granted compassionate release because of the COVID-19 pandemic and will be placed in ICE custody for prompt deportation, a federal judge ordered Thursday.
U.S. District Judge Leonie M. Brinkema in Alexandria signed the order to the Bureau of Prisons to immediately place Ferizi in a 14-day quarantine before releasing into the custody of Immigration and Customs Enforcement so he can be deported to Kosovo.
“U.S. District Judge Leonie M. Brinkema in Alexandria signed the order reducing the sentence of Ardit Ferizi to time served. Brinkema also ordered the Bureau of Prisons to immediately place Ferizi in a 14-day quarantine to ensure he’s not infected with the coronavirus. At the end of the quarantine, Ferizi will be released into the custody of Immigration and Customs Enforcement so he can be deported to Kosovo, the judge ordered.” states the Associated Press.
The 2016 sentence ordered that Ferizi (24) will remain on supervised release for 10 years. Ferizi explained in a motion written from the prison that his asthma and obesity placed him at greater risk for COVID-19.
Ferizi explained that the special restrictions at the prison require him to check in with staff every two hours, exposing him at the risk of being infected due to the contact with guards.
“Brinkema initially rejected Ferizi’s request at a hearing in October, citing concerns that he might resume hacking if released, among other issues. Prosecutors had opposed Ferizi’s release.” concludes AP News.
Magecart Attack Convincingly Hijacks PayPal Transactions at Checkout
2.12.2020 CyberCrime Threatpost
New credit-card skimmer uses postMessage to make malicious process look authentic to victims to steal payment data.
Just in time for a busy online holiday shopping season, the Magecart gang has come up with a new credit-card skimming technique for hijacking PayPal transactions during checkout.
A security researcher who identifies himself as Affable Kraut discovered the technique, which uses postMessage to inject convincing PayPal iframes into the checkout process of an online purchase, “the first skimmer to deploy such a method,” he said on Twitter. BleepingComputer first reported his research.
Magecart is an umbrella term encompassing several different threat groups who all use the same attack method: They compromise e-commerce websites to inject card-skimming scripts on checkout pages, stealing unsuspecting customers’ payment card details and other information entered into the fields on the page. The info is then sent back to a server under the attackers’ control.
Affable Kraut used data from Sansec, a security firm aimed at combatting digital skimming, to peer under the hood of the new card-skimming technique. While most methods that try to emulate PayPal pages to trick users into entering details even when the process is being hijacked don’t look very authentic, the one he observed “goes through a lot of work to try and be as convincing as possible,” Kraut tweeted.
One of the key factors lending to this appearance is its use of a script called window.postMessage, which enables cross-origin communication between a Web page and a pop-up that it spawned, or between a page and an iframe embedded within it.
Typically, scripts on different pages can only access each other if and only if the pages they original from share the same protocol, port number and host. PostMessage can circumvent this restriction, and the attackers use it to their advantage to transmit the stolen payment info in a way that looks authentic to the user, the researcher said.
The attack hides malicious code inside an image hosted on the server of the compromised online store using a steganography method that Affable Kraut said his colleague first discovered last year.
While at first the code seems similar to many other skimmers in that it grabs data the shopper has inputted in the form and exfiltrates it, it then does something very differently than other skimmers, he said. It uses the exfiltrated data to improve its fake payment form, the researcher said.
Magecart Attack Convincingly Hijacks PayPal Transactions at CheckoutThe attack does this by pre-filling fake PayPal forms to be displayed during a victim’s checkout process instead of the legitimate one, which boosts the likelihood the person shopping will fall victim to the malicious action.
“When the victim sees this page, it is now partially filled out, which definitely increases the odds that it will capture their full payment data,” Affable Kraut tweeted.
The skimmer even parses info before filling in PayPal forms and, if the data is not good, it actually sends a message back to the page on the victim’s site, removing the malicious iframes from the checkout page.
However, if the data passes the parsing process, the attack uses an __activatePg call to prefill the form in the malicious transaction. It will even pass along the items in the cart and the accurate transaction total, taxes and shipping costs, which lend even more plausibility to the attack, Affable Kraut said.
Once the victim enters and submits payment info, the skimmer exfiltrates the data to apptegmaker[.]com, a domain registered in October 2020 and connected to tawktalk[.]com. The latter was seen used in previous Magecart group attacks. The skimmer then clicks the order button behind the malicious iframe and sends the victim back to the legitimate checkout page to complete the transaction.
The Christmas holiday shopping season of the month kicked off this past weekend and is likely to be largely an online affair that will keep attackers like Magecart and affiliated groups that are focused on stealing payment credentials busy. Attackers already had been seen shifting tactics and victims as well as ramping up e-commerce attacks in the last months.
In September, Magecart mounted one of its largest campaigns to date with nearly 2,000 e-commerce sites hacked in an automated campaign that may be linked to a zero-day exploit. The attacks impacted tens of thousands of customers who had their credit-card and other information stolen. The group also that month was seen using encrypted messaging service Telegram as a channel for sending stolen credit-card information back to its command-and-control (C2) servers.
Then in October, a Magecart spinoff group called Fullz House group targeted an unlikely victim in Boom! Mobile’s, targeting the wireless service reseller’s website with an e-commerce attack.
Operators behind Dark Caracal are still alive and operational
30.11.20 CyberCrime Securityaffairs
The Dark Caracal APT group has carried out a series of attacks against multiple sectors using a new variant of a 13-year-old backdoor Trojan.
The Dark Caracal cyberespionage group is back, researchers from Check Point uncovered a new series of attack against multiple industries.
The Dark Caracal is an APT group associated with the Lebanese General Directorate of General, in recent attacks it employed a new version of a 13-year-old backdoor Trojan dubbed Bandook.
The Bandook was spotted last time in 2015 and 2017 campaigns, dubbed “Operation Manul” and “Dark Caracal“, respectively attributed to Kazakh and the Lebanese governments. This circumstance suggests that the implant was developed by a third-party actor and used by multiple APT groups.
“During this past year, dozens of digitally signed variants of this once commodity malware started to reappear in the threat landscape, reigniting interest in this old malware family.” reads the report published by Check Point.
“In the latest wave of attacks, we once again identified an unusually large variety of targeted sectors and locations. This further reinforces a previous hypothesis that the malware is not developed in-house and used by a single entity, but is part of an offensive infrastructure sold by a third party to governments and threat actors worldwide, to facilitate offensive cyber operations.”
During the last campaign, the hackers targeted multiple sectors including Government, financial, energy, food industry, healthcare, education, IT, and legal institutions.
The APT group targeted entities in Singapore, Cyprus, Chile, Italy, the USA, Turkey, Switzerland, Indonesia, and Germany.
The infection chain used in the attacks is constantly evolving, in the following image are reported the three main stages.
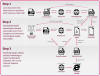
The first stage leverages a lure Microsoft Word document (e.g. “Certified documents.docx”) delivered inside a ZIP file. Upon opening the archive, malicious macros are downloaded, which subsequently proceeds to drop and execute a second-stage PowerShell script encrypted inside the original Word document.
In the last phase of the attack, the PowerShell script downloads encoded executable parts from legitimate cloud storage services like Dropbox or Bitbucket then assemble the Bandook loader, which injects the RAT into a new Internet Explorer process.
The Bandook RAT is available on the underground market since 2007, it supports common backdoor commands, including capturing screenshots and carrying out various file-related operations.
Experts noticed that the new release of Bandook is a slimmed-down version of the original variant malware and supports only 11 commands out of the 120 commands. The support for a subset of commands suggests the threat actors attempt to remain under the radar.
Experts observed several samples of the malware that were digitally signed with valid certificates issued by Certum. Check Point researchers also spotted two digitally-signed and unsigned variants which they believe are operated by a single entity.
“Some of this campaign’s characteristics and similarities to previous campaigns leads us to believe that the activity we describe in this report is indeed the continuation and evolution of the infrastructure used during the Dark Caracal operation:
The use of the same certificate provider (Certum) throughout the various campaigns.
The use of the Bandook Trojan, in what appears to be a unique evolving fork from the same source code (which is not known to be publicly available). Samples from the Dark Caracal campaign (2017) utilized around 100 commands, compared to the current 120 command version we analyzed.
This wave of attacks shares the same anomalous characteristics for targeted attacks – an extreme variance in the selected targets, both in their industry and their geographic spread.” concluded the experts.
“All evidence points to our belief that the mysterious operators behind the malicious infrastructure of “Operation Manul” and “Dark Caracal” are still alive and operational, willing to assist in the offensive cyber operations to anyone who is willing to pay.”
Hundreds of C-level executives credentials available for $100 to $1500 per account
29.11.20 CyberCrime Securityaffairs
A credible threat actor is offering access to the email accounts of hundreds of C-level executives for $100 to $1500 per account.
Access to the email accounts of hundreds of C-level executives is available on the Exploit.in for $100 to $1500 per account. Exploit.in is a popular closed-access underground forum for Russian-speaking hackers, and it isn’t the only one, other prominent forums are fuckav.ru, Blackhacker, Omerta, and L33t.
The news reported by ZDnet is not surprising, I have discovered several times such kind of offer, but it is important to raise awareness on the cybercrime-as-a-service model that could rapidly enable threat actors to carry out malicious activities.
The availability of access to the email accounts of C-level executives could allow threat actors to carry out multiple malicious activities, from cyber espionage to BEC scams.
The threat actor is selling login credentials for Office 365 and Microsoft accounts and the price depends on the size of the C-level executives’ companies and the internal role of the executive.
The threat actor claims its database includes login credentials of high-level executives such as:
CEO – chief executive officer
COO – chief operating officer
CFO – chief financial officer or chief financial controller
CMO – chief marketing officer
CTOs – chief technology officer
President
Vice president
Executive Assistant
Finance Manager
Accountant
Director
Finance Director
Financial Controller
Accounts Payables
ZDnet confirmed the authenticity for some of the data available for sale.
“A source in the cyber-security community who agreed to contact the seller to obtain samples has confirmed the validity of the data and obtained valid credentials for two accounts, the CEO of a US medium-sized software company and the CFO of an EU-based retail store chain.” reported ZDNet.
At the time of writing, it is unclear how the threat actor has obtained the login credentials.
Experts from threat intelligence firm KELA, speculate the threat actor could have obtained the credentials buying “Azor logs,” which are lots of data stolen from computers infected with the AzorUlt info-stealer trojan.
Data collected by info-stealers are available for sale in the underground, threat actors use to buy and parse them searching for sensitive data such as account credentials.
In July, the US Department of Justice has indicted a hacker that goes online with the moniker Fxmsp for hacking over three hundred organizations worldwide and selling access to their networks.
Once the hacker gained access to the network, they deployed password-stealing malware and remote access trojans (RATs) to harvest credentials and establish persistence in the system.
The name Fxmsp refers a high-profile Russian- and English-speaking hacking group focused on breaching high-profile private corporate and government information.
Since March 2019, Fxmsp announced in cybercrime forums the availability of information stolen from major antivirus companies located in the U.S.
Between 2017 and 2018, Fxmsp created a network of trusted proxy resellers to promote their breaches on the criminal underground.
Fxmsp used to compromise Active Directory of target organizations and ensure external access through remote desktop protocol (RDP) connections.
Turchin attempted to sell access to these networks on hacker forums (i.e. Exploit.in, fuckav.ru, Club2Card, Altenen, Blackhacker, Omerta, Sniff3r, and L33t) and dark web marketplaces for prices ranging between a few thousands of dollars up to over $100,000.
The group also claimed to have developed a credential-stealing botnet capable of infecting high-profile targets and exfiltrate sensitive data, including access credentials.
In 2019, Fxmsp confirmed to have breached the networks of some security companies and to have obtained long-term access.
The group offered access to single companies for $250,000 and is asking $150,000 for the source code of the software. Buyers can also pay at least $300,000 to acquire both, the price depends on the compromised company.
Carding Action 2020: Group-IB supports Europol-backed operation saving €40 million
27.11.20 CyberCrime Securityaffairs
Carding Action 2020 targeted crooks selling/purchasing compromised card data on sites selling stolen cred itcard data and darkweb marketplaces
Group-IB, a global threat hunting and intelligence company, has supported Carding Action 2020 – a cross-border operation led by Europol’s European Cyber Crime Centre (EC3) with the support from law enforcement agencies including The Dedicated Card and Payment Crime Unit of the London Metropolitan and the City of London Police. The three-month anti-cybercrime effort targeted traders of compromised card details and prevented approximately €40 million in losses.
The details and results of the operation have been presented to the public today by Tobias Wieloch of EC3 at CyberCrimeCon Virtual 2020 – a global threat hunting and intelligence conference, powered by Group-IB.
Carding Action 2020 sought to mitigate and prevent losses for financial institutions and cardholders. During the three-month, Group-IB, the only private-sector cybersecurity company involved in the operation, provided information on approximately 90,000 pieces of recently compromised payment data. This data was obtained and analysed by the company experts thanks to Group-IB’s Threat Intelligence and Attribution system from unique non-public sources, such as botnet and JS-sniffer infrastructure, as well as underground card shops and marketplaces.
Europol facilitated the coordination and information exchange between law enforcement from Italy, Hungary, the UK and leading card schemes (payment network companies). According to Europol, The Carding Action prevented approximately €40 million in potential losses for mainly European financial institutions, who actioned the data as it was received from the payment providers. The savings were estimated by card schemes looking at the unique cards that were detected and flagged by Group-IB and multiplied by the average spend on those cards.
All of the 90,000 pieces analysed by Group-IB included full card data – cards compromised via phishing websites, from end devices infected with banking Trojans, as well as by the means of hijacked eCommerce websites and the use of JS-sniffers. According to Group-IB Hi-Tech Crime Trends report 20/21, presented yesterday ta CyberCrimeCon, the carding market grew by 116 percent from $880 mln to $1.9 bln. The expansion of JS-sniffer attacks targeting e-commerce merchants influenced the significant increase of prevented losses.
“Cybercrime can affect all aspects of our daily life, from paying in the supermarket, transferring money to our friends to using online communication tools or Internet of Things devices at home. Cybercriminals can attack us in different ways and this requires a robust response not only from law enforcement but also from the private sector,” said Edvardas Šileris, Head of Europol’s European Cybercrime Centre (EC3). “With more than €40 million in losses prevented, Carding Action 2020 is a great example of how sharing information between private industries and law enforcement authorities is a key in combating the rising trend of e-skimming and preventing criminals from profiting on the back of EU citizens,” he added.
“As cybercriminals know no borders, neither should cooperation in cyberspace,” commented Nicholas Palmer, head of Group-IB global business. “We believe that the ultimate disruption of cybercrime comes from the strong collaboration between industry, international sharing organizations, and law enforcement. The Europol-backed Carding Action was a perfect display of such actions. The speed at which we were able to deliver so many savings would not have been possible without these efforts”.
Original post at https://www.group-ib.com/media/carding-action-2020/
Group-IB Hi-Tech Crime Trends 2020/2021 report
25.11.20 CyberCrime Securityaffairs
Group-IB, a global threat hunting and intelligence company, has presented its annual Hi-Tech Crime Trends 2020/2021 report.
In the report, the company examines key shifts in the cybercrime world internationally between H2 2019 and H1 2020 and gives forecasts for the coming year. The most severe financial damage has occurred as a result of ransomware activity. The past year — a harrowing period for the world economy — culminated in the spike of cybercrime. It was also marked by the rise of the underground market for selling access to corporate networks and an over two-fold growth of the carding market. The stand-off between various pro-government hacker groups saw new players come onto the scene, while some previously known groups resumed their operations.
Group-IB’s report Hi-Tech Crime Trends 2020/2021 examines various aspects of cybercrime industry operations and predicts changes to the threat landscape for various sectors, namely the financial industry, telecommunications, retail, manufacturing, and the energy sector. The authors also analyze campaigns targeting critical infrastructure facilities, which are an increasingly frequent target of intelligence services worldwide.
Hi-Tech Crime Trends 2020/2021is intended forrisk management and strategic planning specialists in the cybersecurity field as well as members of boards of directors in charge of digital transformation and investing in cybersecurity systems. For IT directors, heads of cybersecurity teams, SOC analysts, and incident response specialists, the report Hi-Tech Crime Trends 2020/2021 is a practical guide for strategic and tactical planning and offers analytical instruments that help adjust and fine-tune corporate security systems.
Forecasts and recommendations set out in Hi-Tech Crime Trends 2020-2021 seek to prevent financial damage and manufacturing downtimes. Its purpose is also to help companies adopt preventive measures for counteracting targeted attacks, cyber espionage, and cyberterrorist operations.
Crime trends
Group-IB: The ransomware plague cost the world over $1 billion
Late 2019 and all of 2020 were marked by an unprecedented surge in ransomware attacks. Neither private sector companies nor government agencies turned out to be immune to the ransomware plague. Over the reporting period, more than 500 successful ransomware attacks in more than 45 countries were reported. Since attackers are motivated by financial gain alone, any company regardless of size and industry could fall victim to ransomware attacks. Meanwhile, if the necessary technical toolsets and data restoring capabilities are not in place, ransomware attacks could not only cause downtime in manufacturing but also bring operations to a standstill. According to Group-IB’s conservative estimates, the total financial damage from ransomware operations amounted to over $1 billion ($1,005,186,000), but the actual damage is likely to be much higher. Victims often remain silent about incidents and pay ransoms quietly, while attackers do not always publish data from compromised networks.
A major ransomware “plague” outbreak was detected in the United States, with the country accounting for about 60% of all known incidents. The US is followed by European countries (mainly the UK, France, and Germany), which together make up roughly 20% of all ransomware attacks. Countries of North and South America (excluding the US) are at 10% and Asian states are at 7%. The top five most frequently attacked industries include manufacturing (94 victims), retail (51 victims), state agencies (39 victims), healthcare (38 victims), and construction (30 victims).
Maze and REvil are considered to have the largest appetite: the operators of these two strains are believed to be behind more than half of all successful attacks. Ryuk, NetWalker, and DoppelPaymer come second.
The ransomware pandemic was triggered by an active development of private and public affiliate programs that bring together ransomware operators and cybercriminals involved in compromising corporate networks. Another reason for an increase in ransomware attacks is that traditional security solutions, still widely used by a lot of companies on the market, very often fail to detect and block ransomware activity at early stages.
Ransomware operators buy access and then encrypt devices on the network. After receiving the ransom from the victim, they pay a fixed rate to their partners under the affiliate program. The main ways to gain access to corporate networks include brute-force attacks on remote access interfaces (RDP, SSH, VPN), malware (e.g., downloaders), and new types of botnets (brute-force botnets). The latter are used for distributed brute-force attacks from a large number of infected devices, including servers.
In late 2019, ransomware operators adopted a new technique. They began downloading all the information from victim organizations and then blackmailed them to increase the chances of the ransom being paid. Maze (who allegedly called it quits not long ago)pioneered the tactic of publishing sensitive data as leverage to extort money. If a victim refuses to pay the ransom, they risk not only losing all their data but also having it leaked. In June 2020, REvil started auctioning stolen data.
The report contains recommendations for countering ransomware attacks both in terms of technological measures for corporate cybersecurity teams and boosting the expertise of cybersecurity teams.
Group-IB: Seven new APT groups joined the global intelligence service stand-off
Military operations conducted by various intelligence services are becoming increasingly common. Group-IB have identified a continuing trend where physical destruction of infrastructure is replacing espionage. Attacker toolkits are being updated with instruments intended for attacks on air-gapped networks. The nuclear industry is turning into the number one target for state-sponsored threat actors. Unlike the previous reporting period, during which no attacks were observed, the current one was marked by attacks on nuclear energy facilities in Iran and India. A blatant attack was attempted in Israel, where threat actors gained access to some of Israel’s water treatment systems and tried altering water chlorine levels. Had it been successful, the attack would have led to water shortages or even civilian casualties. State-sponsored APT groups are not losing interest in the telecommunications sector. Over the review period, it was targeted by at least 11 groups affiliated with intelligence services. Threat actors’ main goals remain spying on telecommunications operators or attempts to disable infrastructure. Threat actors have also set a new record in DDoS attack power: 2.3 Tb per second and 809 million packets per second. BGP hijacking and route leaks remain a serious problem as well. Over the past year, nine significant cases have been made public.
Most state-sponsored threat actors originate from China (23), followed by Iran (8 APT groups), North Korea and Russia (4 APT groups each), India (3), and Pakistan and Gaza (2 each). South Korea, Turkey, and Vietnam are reported to have only one APT group each.
According to data analyzed by Group-IB, Asia-Pacific became the most actively attacked region by state-sponsored threat actors. A total of 34 campaigns were carried out in this region, and APT groups from China, North Korea, Iran, and Pakistan were the most active. At least 22 campaigns were recorded on the European continent, with attacks carried out by APT groups from China, Pakistan, Russia, and Iran. Middle East and Africa were the scene of 18 campaigns conducted by pro-government attackers from Iran, Pakistan, Turkey, China, and Gaza.
Cybersecurity researchers have also detected seven previously unknown APT groups, namely Tortoiseshell (Iran), Poison Carp (China), Higaisa (South Korea), AVIVORE (China), Nuo Chong Lions (Saudi Arabia), as well as Chimera and WildPressure, whose geographical affiliation remains unknown. In addition, six known groups that remained unnoticed in recent years resumed their operations.
Group-IB: sales of access to compromised corporate networks grow four-fold
Sales of access to compromised corporate networks have been increasing from year to year and peaked in 2020. It is difficult to assess the size of the market for selling access, however, as offers published on underground forums often do not include the price, while some deals are cut in private. Nevertheless, Group-IB’s technologies for monitoring underground forums (which make it possible to see deleted and hidden posts) helped the company’s experts assess the total market size for access sold in the review period (H2 2019 to H1 2020): $6.2 million. This is a four-fold increase compared to the previous review period (H2 2018 to H1 2019), when it totaled $1.6 million.
Surprisingly, state-sponsored attackers joined this segment of the cybercriminal market seeking additional revenue. As such, in the summer of 2020, on an underground forum a seller offered access to several networks, including some belonging to US government departments, defense contractors (Airbus, Boeing, etc.), IT giants, and media companies. The cost of the access to the companies listed was close to $5 million.
In H1 2020 alone, 277 offers of access to corporate networks were put up for sale on underground forums. The number of sellers has also grown. During that period, 63 sellers were active, and 52 of them began selling access in 2020. For comparison, during all of 2018, only 37 access sellers were active, while in 2019 there were 50 sellers who offered access to 130 corporate networks. In total, the sales of corporate network access grew by 162% compared to the previous period (138 offers against 362). After analyzing offers of access to corporate networks, Group-IB experts found correlations with ransomware attacks: most threat actors offered access to US companies (27%), while manufacturing was the most frequently attacked industry in 2019 (10.5%). In 2020, access to state agency networks (10.5%), educational institutions (10.5%), and IT companies (9%) was high in demand. It should be noted that sellers of access to corporate networks increasingly rarely mention company names, their geographical location and industry, which makes it almost impossible to identify the victim without contacting the attackers.
Selling access to a company’s network is usually only one stage of the attack: the privileges gained might be used for both launching ransomware and stealing data, with the aim of later selling it on underground forums or spying.
Group-IB: Market of stolen credit card data reached almost $2 billion
Over the review period, the carding market grew by 116%, from $880 million to $1.9 billion. The quick growth applies to both textual data (bank card numbers, expiration dates, holder names, addresses, CVVs) and dumps (magnetic stripe data). The amount of textual data offered for sale increased by 133%, from 12.5 to 28.3 million cards, while dumps surged by 55%, from 41 to 63.7 million. The maximum price for card textual data is $150 and $500 for a dump.
Dumps are mainly obtained by infecting computers with connected POS terminals with special Trojans and thereby collecting data from random-access memory. Over the review period, 14 Trojans used for collecting dumps were found to be active. Cybercriminals seek to obtain data relating to credit and debit cards issued by US banks: these account for over 92% of all compromised bank cards. Bank card data of bank customers in India and South Korea are the second and third most desirable targets for cybercriminals. Over the review period, the total price of all the bank card dumps offered for sale amounted to $1.5 billion, while textual data – to $361.7 million.
Textual data is collected through phishing websites and PC/Android banking Trojans, by compromising e-commerce websites, and by using JS sniffers. The latter were one of the main instruments for stealing large amounts of payment data over the past year. JS sniffers also became more popular in light of the trend of reselling access to various websites and organizations on underground forums.
Group-IB is currently monitoring the activities of 96 JS sniffer families. This is a 2.5-fold increase compared to the previous reporting period, during which there were 38 families on the company’s radar. According to Group-IB’s findings, over the past year nearly 460,000 bank cards were compromised using JS sniffers.
The threat of bank card data leaks is most acute for retail companies that have online sales channels, e-commerce companies that offer goods and services online, and banks that unwittingly become involved in incidents. The main scenarios for illegally harvesting bank card data and most frequently attacked countries (the United States, India, South Korea) will remain the same. Latin America might become an increasingly attractive target for carders since it already has mature hacker community experienced in using Trojans for this purpose.
Phishing grows by 118%
Between H2 2019 and H1 2020, the number of phishing web resources found and blocked by Group-IB rose by 118% compared to the previous reporting period. Analysts mention the global pandemic and lockdowns as the main reasons: web-phishing, which is one of the simplest ways to earn money in the cybercriminal industry, attracted those who lost their incomes. The increased demand for online purchases created a favorable environment for phishers. They quickly adapted to this trend and began carrying out phishing attacks on services and individual brands that previously did not have much financial appeal to them.
Scammers also changed their tactics. In previous years, attackers ended their campaigns after fraudulent websites were taken down and quickly switched to other brands. Today, they are automating their attacks instead and replacing the blocked pages with new ones.
Since the start of the year, there has been a rise in advanced social engineering, namely when multi-stage scenarios are used in phishing attacks. As part of such increasingly popular phishing schemes, threat actors first stake out the victim. They establish contact with the targeted individual (e.g., through a messenger), create an atmosphere of trust, and only then do they direct the victim to a phishing page. One-time links turned out to be another phishing trend of the past year. After a user receives a link and clicks on it at least once, it will not be possible to obtain the same content again in order to collect evidence. This significantly complicates the process of taking down phishing resources.
Most web-phishing pages mimicked online services (39.6%). Phishers in particular gathered login credentials from user accounts on Microsoft, Netflix, Amazon, eBay, Valve Steam, etc. Online services were followed by email service providers (15.6%), financial organizations (15%), cloud storage systems (14.5%), payment services (6.6%), and bookmakers (2.2%).
About the Hi-Tech Crime Trends report
Group-IB’s Hi-Tech Crime Trends report was presented at the international conference CyberCrimeCon’2020. Group-IB has been publishing an annual report for the past seven years, combining data gathered as a result of the company’s own investigations with incident response findings worldwide.
I suggest to download the full Hi-Tech Crime Trends 2020/2021, it includes a lot of interesting data.
New Grelos Skimmer Variants Siphon Credit Card Data
21.11.20 CyberCrime Threatpost
Domains related to the new variant of the Grelos web skimmer have compromised dozens of websites so far.
Just as seasonal online shopping kicks into high gear, new variants of the point-of-sale Grelos skimmer malware have been identified. Variants are targeting the payment-card data of online retail shoppers on dozens of compromised websites, researchers warn.
The Grelos skimmer malware has been around since 2015, and its original version is associated with what are called Groups 1 and 2 under the prolific Magecart umbrella of loosely organized cybercriminals. However, over time new actors began to co-opt the Grelos skimmer and reuse some of the original domains used to host the malware. This has accumulated into what researchers say is a unique overlap in infrastructure for the most recent variants of the skimmer between Grelos and Magecart.
In a new analysis, researchers said that a cookie found on a compromised website led to the discovery of Grelos – and they were then able to find links between new variants because they had matching infrastructure and identical records on the WHOIS query and response protocol (widely used for querying databases).
“Recently, a unique cookie allowed RiskIQ researchers to connect a recent variant of this skimmer to an even newer version that uses a fake payment form to steal payment data from victims,” said researchers with RiskIQ in an analysis this week. “Domains related to this cookie have compromised dozens of sites so far.”
The Skimmer Variant
The new variants of the skimmer first appeared when researcher Affable Kraut documented it via Twitter in July 2020. This version of the skimmer features a loader stage and a skimmer stage, both of which are base64 encoded five times over, said researchers.
The Grelos variant discovered by Kraut also used WebSockets for skimming. The WebSocket API is a technology making it possible to open a two-way interactive communication session between a web browser and a server. The use of the WebSocket connection to exfiltrate sensitive data is not new and was first observed in connection with a Magecart Group 9 skimmer in December 2019.
Then in a separate incident, researchers investigated the threat group Full(z) House’s recent compromise of Boom!Mobile in October. During their investigation, researchers noticed a unique cookie, which was connected to three additional skimming domains and several victim domains.
These skimming domains, which included facebookapimanager[.]com and googleapimanager[.]com, contained a more recent variant of the Grelos variant. Researchers said the connection between the cookie and the skimmer domains piqued their interest because skimmer domains sharing an identical cookie is not common.
“These four domains have been hosted on several different IPs, but most often they used infrastructure belonging to ASN 45102 – Hangzhou Alibaba Advertising Co.,Ltd., a hosting provider that is currently popular with several different Magecart actors,” said researchers.
This skimmer has a similar base64 encoded loader stage to one documented by Kraut, except this loader stage is only under one layer of encoding, with a duplicate of the encoded script tag below it (without encoding), said researchers.
The skimmer code included a “translate” function with various phrases used by the fake HTML payment form that it creates after it compromises a website. These phrases include “Pay with credit or debit card;” “Check the cardholder first name;” “We can not process your payment,” and other phrases.
When a shopper visits a compromised website, they are presented with the fake payment form containing these phrases. When they upload their payment card information, that data is exfiltrated by the skimmer via a function that stringifies the stolen data, along with the site_id, sid, and ip (this function also features an interesting grammatical mistake, researchers noted, using the word “sended” rather than “sent”).
Magecart Gang
Researchers recently reported that they have seen an uptick in the number of e-commerce sites that are being attacked by Magecart and related groups, dovetailing with new tactics. Typically Magecart compromise websites with web skimmers – either via a vulnerability in the websites’ e-commerce platform, gaining access to the victim’s network via phishing or other means, or other tactics (it’s unclear what tactics the threat actors are using for compromising websites with the Grelos skimmer).
In October, one of the largest known Magecart campaigns to date took place, with nearly 2,000 e-commerce sites hacked in an automated campaign that may be linked to a zero-day exploit. Earlier in September, Magecart was seen using the secure messaging service Telegram as a data-exfiltration mechanism.
Researchers with RiskIQ for their part, said they expect overlaps in infrastructure used to host various skimmers; as well as the reuse of skimmer code, to increase in the future.
“This complex overlap illustrates the increasingly muddy waters for researchers tracking Magecart,” they warned.
New Grelos skimmer variant reveals murkiness in tracking Magecart operations
19.11.20 CyberCrime Securityaffairs
Security experts from RiskIQ discovered a new variant of the Grelos skimmer that presents overlap with Magecart group operations.
Researchers from RiskIQ analyzed the increased overlap of a new variant of the skimmer dubbed Grelos and the operations of the groups under the Magecart umbrella. The analysis demonstrates the difficulty in associating new strains of skimmer to groups that were behind major Mahecart campaigns. The experts observed an increased overlap of domain infrastructure used by multiple threat actors spreading software skimmers focused on the theft of payment card data from e-stores.
Hacker groups under the Magecart umbrella continue to target e-stores to steal payment card data with software skimmers. Security firms have monitored the activities of a dozen groups at least since 2010.
According to a previous report published by RiskIQ and FlashPoint, some groups are more advanced than others, in particular, the gang tracked as Group 4 appears to be very sophisticated.
The list of victims of the groups is long and includes several major platforms such as British Airways, Newegg, Ticketmaster, MyPillow and Amerisleep, and Feedify.
Millions of Magecart instances were detected over time, security experts discovered tens of software skimming scripts.
The Grelos skimmer has been around since at least 2015 and is associated with operations of Magecart groups 1 and 2. The new variant uses WebSockets for skimming operations, a technique that was first documented in December 2019 when used by the Magecart Group 9.
“We believe this skimmer is not directly related to Group 1-2’s activity from 2015-16, but instead a rehash of some of their code,” reads the post published by RiskIQ. “This version of the skimmer features a loader stage and a skimmer stage, both of which are base64 encoded five times over.”
RiskIQ researchers were analyzing the links shared by Malwarebytes related to the Magecart attack on Boom! Mobile carried out by the Fullz House group.
The researchers, Affable Kraut and Denis Sinegubko, shared on Twitter a list of possibly connected skimmer domains. The list included the domains facebookapimanager[.]com and googleapimanager[].com.
The analysis of the domains allowed the expert to discover a new Grelos skimmer variant instead of the Fullz House group’s skimmer. The new variant uses a base64 encoded loader stage with a single layer of encoding.
“A sample we collected from one victim site shows a similar base64 encoded loader stage to one documented by Affable Kraut, except this loader stage is only under one layer of encoding. Also, a duplicate of the encoded script tag appears just below it, without encoding” continues the analysis. “The clear version of the base64 encoded script is nearly identical to the previous version. The skimmer, however, is a bit different. Here we see a dictionary named “translate,” which contains various phrases used by a fake HTML payment form created by the skimmer:”
The researchers pointed out that multiple variants of Magecart-related skimmers are reusing code from past operations. For example, the code used by the Fullz House skimmer has been co-opted by other hacking groups that in some cases are leveraging part of the same infrastructure to host other skimmers, such as Grelos. RiskIQ researchers noticed that the new variant of the Grelos skimmer shares IPs with the Inter skimmer.
“For instance, when we examine the hosting when we look at the hosting provider used by Full(z) House to carry out its recent skimming activity, including the compromise of boom! Mobile, we see Alibaba. This same hosting provider is used by the Grelos skimmer, the Inter skimmer, and others. In fact, we even see an overlap in the specific infrastructure used by an Inter skimmer implementation and the most recent version of Grelos, detailed in this post.” concludes the analysis. “This complex overlap illustrates the increasingly muddy waters for researchers tracking Magecart.”
Over 2800 e-Shops Running Outdated Magento Software Hit by Credit Card Hackers
11.11.20 CyberCrime Thehackernews
A wave of cyberattacks against retailers running the Magento 1.x e-commerce platform earlier this September has been attributed to one single group, according to the latest research.
"This group has carried out a large number of diverse Magecart attacks that often compromise large numbers of websites at once through supply chain attacks, such as the Adverline incident, or through the use of exploits such as in the September Magento 1 compromises," RiskIQ said in an analysis published today.
Collectively called Cardbleed, the attacks targeted at least 2,806 online storefronts running Magento 1.x, which reached end-of-life as of June 30, 2020.
Injecting e-skimmers on shopping websites to steal credit card details is a tried-and-tested modus operandi of Magecart, a consortium of different hacker groups who target online shopping cart systems.
These virtual credit card skimmers, also known as formjacking attacks, are typically JavaScript code that the operators stealthily insert into an e-commerce website, often on payment pages, with an intent to capture customers' card details in real-time and transmit it to a remote attacker-controlled server.
But in the last few months, the Magecart operators have stepped up in their efforts to hide card stealer code inside image metadata and even carry out IDN homograph attacks to plant web skimmers concealed within a website's favicon file.
Cardbleed, which was first documented by Sansec, works by using specific domains to interact with the Magento admin panel and subsequently leveraging the 'Magento Connect' feature to download and install a piece of malware called "mysql.php" that gets automatically deleted after the skimmer code is added to "prototype.js."
Now, as per RiskIQ, the attacks bear all the hallmarks of a single group it tracks as Magecart Group 12 based on overlaps in infrastructure and techniques across different attacks starting with Adverline in January 2019 to the Olympics Ticket Resellers back in February 2020.
What's more, the skimmer used in the compromises is a variant of the Ant and Cockroach skimmer first observed in August 2019 — so named after a function labeled "ant_cockcroach()" and a variable "ant_check" found in the code.
Interestingly, one of the domains (myicons[.]net) observed by the researchers also ties the group to another campaign in May, where a Magento favicon file was used to hide the skimmer on payment pages and load a fake payment form to steal captured information.
But just as the identified malicious domains are being taken down, Group 12 has been adept at swapping in new domains to continue skimming.
"Since the [Cardbleed] campaign was publicized, the attackers have shuffled their infrastructure," RiskIQ researchers said. "They moved to load the skimmer from ajaxcloudflare[.]com, which has also been active since May and moved the exfiltration to a recently registered domain, consoler[.]in."
If anything, the attacks are yet another indication of threat actors continuing to innovate, playing with different ways of carrying out skimming, and obfuscating their code to evade detection, said RiskIQ threat researcher Jordan Herman.
"The prompting for this research was the widespread compromise of Magento 1, which went end-of-life this June, sites via an exploit," Herman said. "So the particular mitigation would be to upgrade to Magento 2, though the cost of upgrading might be prohibitive for smaller vendors."
"There is also a company called Mage One that is continuing to support and patch Magento 1. They released a patch to mitigate the particular vulnerability exploited by the actor in late October. Ultimately, the best way to prevent these types of attacks is for e-commerce shops having a full inventory of the code running on their site so they can identify deprecated versions of software and any other vulnerabilities that could invite a Magecart attack," he added.
Russian Hacker Group Continues Stealing Money From Industrial Enterprises
6.11.20 CyberCrime Securityweek
A Russian-speaking threat actor has been targeting hundreds of industrial enterprises for more than two years, Kaspersky’s security researchers report.
Focused on companies in Russia, the ongoing attacks are highly targeted, leveraging phishing emails for malware deployment. In some cases, legitimate documents that were stolen in previous attacks are leveraged for social engineering.
Another characteristic of these attacks is the use of remote administration utilities, including Remote Manipulator System/Remote Utilities (RMS) and TeamViewer. Malware is employed to hide the user interface of these programs, to avoid attracting attention.
The campaign was first detailed in 2018, when Kaspersky said that more than 400 organizations had been hit. Now, the security researchers reveal that the attackers have updated their techniques and that the number of victim organizations has increased.
Specifically, the adversary switched to using the web interface of RMS’s cloud infrastructure as a notification channel for getting the infected machine’s TeamViewer ID, instead of the malware command and control servers. In an ongoing attack, spyware and Mimikatz have been employed for credential theft.
Pretending to be business partners of the targeted organization, the hackers ask their intended victims to review attached documents. The emails are individually crafted for each victim and the attachments are password-protected, to prevent scanning by anti-virus engines.
The attachment contains obfuscated JavaScript scripts and legitimate PDF files. In recent attacks, the hackers started using actual documents related to the organization’s activity, including scanned copies of memos, letters, and procurement documentation forms, seemingly stolen in earlier attacks.
The JavaScript script would launch the malware, which installs a version of TeamViewer, as well as additional malware when more information needs to be collected from the target machine. In previous attacks, the hackers employed malicious DLLs to hide TeamViewer’s user interface and keep the attack out of sight.
Payloads fetched by the malicious scripts are stored on resources mimicking the websites of Russian-speaking companies, Kaspersky says.
Victims of these attacks include Russian companies from the manufacturing, oil and gas, metal industry, engineering, energy, construction, mining, and logistics sectors. The attackers appear to have a particular interest in the energy sector.
The purpose of the campaign is to steal money from the targeted organizations and Kaspersky believes that a Russian-speaking group is behind it. The adversary gains complete control of the target systems, after which they start looking for financial and accounting software and relevant documents, which are used to commit financial fraud.
“Clearly, the attackers’ remote access to infected systems also poses other threats, such as the organization’s sensitive data being leaked, systems being put out of operation, etc. As the latest events have shown, the attackers use documents that were probably stolen from organizations to carry out subsequent attacks, including attacks on victim companies’ partners,” Kaspersky concludes.
QQAAZZ crime gang charged for laundering money stolen by malware gangs
19.10.20 CyberCrime Securityaffairs
Multiple members of QQAAZZ multinational cybercriminal gang were charged for providing money-laundering services to high-profile malware operations.
20 members of the multinational cybercriminal group QQAAZZ were charged this week in the US, Portugal, Spain, and the UK for providing money-laundering services.
The arrests are the result of an unprecedented international law enforcement operation, coordinated by the Europol and dubbed Operation 2BaGoldMule, involving agencies from 16 countries. The police executed more than 40 house searches in Latvia, Bulgaria, the United Kingdom, Spain, and Italy.
The police also seized an extensive bitcoin mining operation in Bulgaria associated with QQAAZZ.
According to law enforcement bodies, the gang provides services to multiple malware operations, including Dridex, GozNym, and Trickbot.
QQAAZZ attempted to launder tens of millions stolen from victims starting with 2016 by the world’s foremost cybercriminals.
“Comprised of several layers of members mainly from Latvia, Georgia, Bulgaria, Romania, and Belgium, the QQAAZZ network opened and maintained hundreds of corporate and personal bank accounts at financial institutions throughout the world to receive money from cybercriminals who stole it from accounts of victims.” reads the press release published by Europol. “The funds were then transferred to other QQAAZZ-controlled bank accounts and sometimes converted to cryptocurrency using ‘tumbling’ services designed to hide the original source of the funds. After taking a fee of up to 50-percent, QQAAZZ returned the balance of the stolen funds to their cybercriminal clientele.”
The QQAAZZ gang advertised its services as a ‘global, complicit bank drops service’ on multiple Russian-speaking online cybercriminal forums.
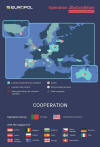
The member of the gang used instant messaging apps to instruct their client on how to transfer the stolen funds to bank accounts under their control. The bank accounts were opened by money mules using fake and legitimate Polish and Bulgarian ID documents.
QQAAZZ also leverages dozens of shell companies to open other bank accounts.
The money laundering operation involved hundreds of corporate and personal bank accounts at financial institutions throughout the world.
Some of the money was also “converted to cryptocurrency using ‘tumbling’ services designed to hide the original source of the funds.”
“The funds were then transferred to other QQAAZZ-controlled bank accounts and sometimes converted to cryptocurrency using “tumbling” services designed to hide the original source of the funds.” states the DoJ. “After taking a fee of up to 40 to 50 percent, QQAAZZ returned the balance of the stolen funds to their cybercriminal clientele.”
“Cybercriminals are constantly exploring new possibilities to abuse technology and financial frameworks to victimise millions of users in a moment from anywhere in the world,” said Edvardas Šileris, Head of Europol’s European Cybercrime Centre.
“Today’s operation shows how through a proper law enforcement international coordination we can turn the table on these criminals and bring them to justice.”
U.S. Bookstore giant Barnes & Noble hit by cyberattack
15.10.20 CyberCrime Securityaffairs
U.S. Bookstore giant Barnes & Noble has disclosed a cyber attack and that the threat actors have exposed the customers’ data.
Barnes & Noble, Inc., is an American bookseller with the largest number of retail outlets in the United States in fifty states.
The bookseller also operated the Nook Digital, which is a spin-off division that sells eBook and e-Reader platform.
Barnes & Noble
Over the weekend, users have been complaining on Nook’s Facebook page and Twitter that they were not able to access their library of purchased eBooks and magazine subscriptions.
A series of messages published on Barnes & Noble’s Nook social media accounts state that it had suffered a system failure and is working to restore operations by restoring their server backups.
In a statement to Fast Company Barnes & Noble confirmed that financial data of its customers were not compromised.
“We have a serious network issue and are in the process of restoring our server backups,” Barnes & Noble told Fast Company in a statement. “Our systems are back online in our stores and on BN.com, and we are investigating the cause. Please be assured that there is no compromise of customer payment details, which are encrypted and tokenized.”
In a series of updates, GoodReader revealed that according to store managers Barnes & Noble had a “virus in their networks”
“Various Barnes and Noble Store managers have contacted me and stated that there is a virus in their networks. It intitially came down from the corporate and filtered down to the stores and also affected the Nook. Cash registers, in physical bookstores are attached to the same network, so no orders can be placed or processed.” states GoodReader. “Some people in the comment section said some of their Nook accounts have been compromised and their credit cards are being used by third parties. The Nook Cloud continues to be down, you can’t sync or access it on the Nook e-reader or the Nook apps, so you can’t see any of the purchases you might have made in the past week.”
BleepingComputer confirmed that the company was hit by a cyber attack on October 10th, 2020, and cited as a source an email sent to customers late Wednesday night that is has seen.
Threat actors compromised the network of Barnes & Noble and gained access to its corporate systems.
“It is with the greatest regret we inform you that we were made aware on October 10, 2020 that Barnes & Noble had been the victim of a cybersecurity attack, which resulted in unauthorized and unlawful access to certain Barnes & Noble corporate systems.” reads the email sent to the customers.
“We write now out of the greatest caution to let you know how this may have exposed some of the information we hold of your personal details,” Barnes & Noble stated in their email.”
The company revealed that hackers had access to customers’ email addresses, billing addresses, shipping addresses, and purchase history.
At the time of writing this post, the company hasn’t provided details of the attack, such as the family of malware that infected its systems. Information shared about the cyber attacks suggests that the company was the victim of a ransomware attack.
In August, the website ZDNet reported in exclusive that a list of passwords for 900+ enterprise VPN servers has been shared on a Russian-speaking hacker forum. The experts pointed out that the list of Pulse VPN credentials, gathered by exploiting the CVE-2019-11510 flaw, also contained accounts belonging to Barnes & Noble.
Depending on the family of ransomware that allegedly infected the company systems we cannot exclude that ransomware operators will leak stolen data on a leak site to threaten Barnes & Noble.
FIN11 Cybercrime Gang Shifts Tactics to Double-Extortion Ransomware
15.10.20 CyberCrime Threatpost
The Clop ransomware has become a tool of choice for the financially motivated group.
The FIN11 financial crime gang is shifting its tactics from phishing and credential-theft to ransomware, researchers said.
According to FireEye Mandiant researchers, FIN11 is notable for its “sheer volume of activity,” known to run up to five disparate wide-scale email phishing campaigns per week. “At this point, it would be difficult to name a client that FIN11 hasn’t targeted,” Mandiant researchers noted, in a posting on Tuesday.
But lately, it has used the Clop ransomware to up its monetary gains.
Threatpost Webinar Promo Retail Security
Click to Register!
Researchers have recently observed attacks in which FIN11 threatened to publish exfiltrated data to pressure victims into paying ransom demands, in a tactic known as double extortion. Clop (which emerged in February 2019) is often used in these kinds of attacks, putting it in the company of the Maze, DoppelPaymer and Sodinokibi ransomware families.
Clop recently made headlines as the malware behind double-extortion attacks on Germany’s Software AG (which carried a $23 million ransom) and a biopharmaceutical firm called ExecuPharm.
FIN11 has been around for at least four years, conducting widespread phishing campaigns. However, it continues to evolve – it’s use of Clop and double extortion is only the latest change in its tactics and tools. It added point-of-sale (POS) malware to its arsenal in 2018, according to Mandiant; and started conducting run-of-the-mill ransomware attacks in 2019.
It’s changed its victimology, too, researchers said: “From 2017 through 2018, the threat group primarily targeted organizations in the financial, retail, and hospitality sectors. However, in 2019 FIN11’s targeting expanded to include a diverse set of sectors and geographic regions.”
Mandiant’s analysis noted that the changes may have been implemented to supplement the ongoing phishing efforts because the latter aren’t wildly successful.
“We’ve only observed the group successfully monetize access in few instances,” researchers said. “This could suggest that the actors cast a wide net during their phishing operations, then choose which victims to further exploit based on characteristics such as sector, geolocation or perceived security posture.”
Also, FIN11 is a subset of the larger TA505 group (a.k.a. Hive0065), which is a financially motivated cybercrime group that has been actively targeting various industries, including finance, retail and restaurants, since at least 2014. It’s known for using a wide range of tactics (in March, IBM X-Force observed TA505 using COVID-19 themed phishing emails) — plus ongoing malware authoring and development.
Its wares include fully-fledged backdoors and RATs – including the recently spotted SDBbot code. And in January, a new backdoor named ServHelper was spotted in the wild, acting as both a remote desktop agent as well as a downloader for a RAT called FlawedGrace.
These campaigns deliver a variety of payloads, including the Dridex and TrickBot trojans, and, yes, ransomware. The latter includes Clop, but also Locky and MINEBRIDGE.
All of this could also explain FIN11’s adoption of new malware.
“Like most financially motivated actors, FIN11 doesn’t operate in a vacuum,” Mandiant researchers concluded. “We believe that the group has used services that provide anonymous domain registration, bulletproof hosting, code signing certificates, and private or semi-private malware. Outsourcing work to these criminal service providers likely enables FIN11 to increase the scale and sophistication of their operations.”
Brandon Hoffman, CISO at Netenrich, told Threatpost that this use of service providers in the underground iis common. “There is a whole marketplace of providers that cater to and operate in what some refer to as the dark web. These services are not limited to the ones described as in use by FIN11 but include code-writing services, monetary exchanges and more,” he said.
Hoffman also pointed out that this evolution to ransomware and extortion has become common for cybercriminals everywhere.
“Broad-based phishing campaigns with the hope of hooking ransomware into an organization for the purpose of extortion, while leveraging malicious service providers, is at the basic footprint of cybercrime today,” he said. “What makes this group special or different remains to be seen for those of us on the outside.”