
Cyber Articles - H 2020 1 2 CyberCrime CyberSpy Cyber Articles - H 2021 2020 2019 2018 2017 1 Cyber blog Cyber blog
Trend Micro Releases Free Tool to Tackle Misinformation
21.11.20 Cyber Securityweek
Cybersecurity solutions provider Trend Micro this week announced the release of a free tool designed to help users boost their privacy online and fight misinformation.
Dubbed Trend Micro Check, the new tool seeks to help users stay protected from privacy violations, false claims, and disinformation.
The launch of this tool, Trend Micro says, was prompted by the avalanche of misinformation that is being published online. The company, which has been looking into the matter for several years, previously launched Trend Micro Check in Japan and Taiwan.
The new version brought to the United States, however, also includes a new feature from NewsGuard, offering trust ratings for a multitude of news sites.
The new tool includes a Security Check that leverages threat intelligence to verify whether a website or URL is fraudulent or infected, as well as a Privacy Check that makes use of Trend Micro's ID Security service to verify whether a user’s email address has been put up for sale on the dark web.
Other capabilities of the tool include Fact Check, which takes advantage of the Google Fact Check API to access information from third-party fact-checking sites and verify the trustworthiness of content, and News Reputation Check, which delivers information on whether news and information websites should be trusted, based on nine basic, apolitical criteria.
Trend Micro Check, the company says, can perform complete detection in real-time, helping users act quickly based on the results. Since its initial release in Japan and Taiwan two-and-a-half years ago, the tool has been used 1.35 billion times to fight misinformation and fraud.
Trend Micro has made the new tool available in the U.S. for Facebook Messenger, WhatsApp, and Google Chrome (as an extension).
“Our society is facing one of its greatest challenges today in the publication and re-sharing of misinformation. We hope this latest tool will offer users an additional safety net and supplemental resources to stay safe online, which will further provide a basis for them to evaluate what they're reading online and whether the sites they're visiting can be trusted or not,” Lynette Owens, founder and global director of Trend Micro's Internet Safety for Kids and Families (ISKF) program, said.
Silent Librarian Goes Back to School with Global Research-Stealing Effort
15.10.20 Cyber Threatpost
The Iranian hacker group is targeting universities in 12 countries.
The Silent Librarian campaign has re-emerged for the fall school session, actively targeting students and faculty at universities via spear-phishing campaigns.
The threat group (also known as TA407 and Cobalt Dickens), which operates out of Iran, has been on the prowl since the start of the 2019 school year, launching low-volume, highly-targeted, socially engineered emails that eventually trick victims into handing over their login credentials. The goal is to harvest not just logins to sell online, but also proprietary university research and data, researchers said.
An example of a Silent Librarian phishing portal. Source: Proofpoint.
The emails typically masquerade as messages from university library systems or other on-campus divisions. Over the course of the last school year, the cyberattackers honed their efforts, and began using shortened URL links in their phishing emails, which make it more difficult to detect that victims are being redirected to an attacker-hosted landing page. The attackers also revamped their landing pages with new university-specific banners, based on weather alerts or emergency notifications, to make them look more authentic.
Now, this APT group is going back to school with a fresh campaign that seems to be targeting institutions globally, according to an analysis Tuesday from Malwarebytes. Targets stretch across a dozen countries and so far have included: The University of Adelaide in Australia; Glasgow Caledonian, University of Kent, University of York, King’s College London, Cambridge and others in the U.K.; the University of Toronto and McGill in Canada; and Stony Brook University, University of North Texas and others in the U.S.
The modus operandi seen last year remains in place, with Silent Librarian hosting a series of phishing sites that are built to mimic legitimate university domains. For instance, emails purporting to be from the University of Adelaide Library directed victims to a “library.adelaide.crev[dot]me” URL, which is very close to the legitimate “library.adelaide.edu.au” domain of the school.
“Many of these have been identified and taken down, [but] the threat actor has built enough of them to continue with a successful campaign against staff and students alike,” according to the analysis. “Clearly we only uncovered a small portion of this phishing operation. Although for the most part the sites are taken down quickly, the attacker has the advantage of being one step ahead and is going for many possible targets at once.”
The APT is using the Cloudflare content delivery network to host most of the phishing hostnames, in order to hide the real hosting origin.
“However, with some external help we were able to identify some of their infrastructure located on Iran-based hosts,” researchers noted. “It may seem odd for an attacker to use infrastructure in their own country, possibly pointing a finger at them. However, here it simply becomes another bulletproof hosting option based on the lack of cooperation between U.S. or European law enforcement and local police in Iran.”
In March 2018, nine Iranians were indicted by the U.S. Department of Justice for conducting attacks against universities and other organizations with the goal of stealing research and proprietary data. The Silent Librarian attacks are likely part of the same ongoing effort, according to Malwarebytes.
“Considering that Iran is dealing with constant sanctions, it strives to keep up with world developments in various fields, including that of technology,” the researchers added, noting that as such, these attacks represent a national interest and are well-funded. “IT administrators working at universities have a particularly tough job considering that their customers, namely students and teachers, are among the most difficult to protect due to their behaviors. Despite that, they also contribute to and access research that could be worth millions or billions of dollars.”
Tactical vs Strategic: CISOs and Boards Narrow Communication Gap
15.10.20 Cyber Securityweek
91% of Survey Respondents Say Their Boards Have Increased Cybersecurity Investment in Response to COVID-19 Pandemic
A global survey of almost 1000 CISO/Senior IT decision makers shows positive signs of Boards' willingness to invest in cybersecurity -- with perhaps one major rider.
The purpose of the survey, commissioned by Thycotic, was to examine the primary drivers in cybersecurity spend decision-making. The resulting survey report shows that 91% of the respondents say their Board has increased cybersecurity investment in response to the COVID-19 pandemic, and around 60% believe they will receive more security budget next year because of COVID-19. This is a welcome sign that Boards are taking cybersecurity seriously.
More than three-quarters of the respondents report they have received investment for new projects either in response to a security incident, or through fear of compliance audit failures. This is the rider in the Boards' willingness to invest -- all three of these investment triggers (COVID, incident response and compliance) are reactive; that is, they are tactical responses rather than strategic plans.
For security teams to adequately defend their systems, they need to get ahead of the adversaries. That requires strategic thinking and planning rather than tactical reaction -- which seems to be less acceptable to boardrooms. Indeed, 37% of the respondents have had proposed investments turned down because the threat was perceived as low risk or because the technology had a lack of demonstrable ROI.
The extent to which this is a failure of CISOs to explain threats in business language, or a simple reluctance of the Board to be proactive rather than reactive, is impossible to determine from the survey.
“The fact Boards mainly approve investments after a security incident or through fear of regulatory penalties for non-compliance," comments Terence Jackson, CISO for the privilege management firm Thycotic, "shows that cybersecurity investment decisions are more about insurance than about any desire to lead the field which, in the long run, limits the industry’s ability to keep pace with the cybercriminals.”
A reactive approach to cybersecurity can have two further negative effects. Firstly, it can lead to excessive 'shelfware', where a point product is purchased but never fully utilized; and secondly it can lead to the purchase of inadequate solutions. For the former, half of the organizations taking part in the survey admit that new technology solutions they purchase are never fully utilized, and become shelfware. For the latter, reaction to an issue can lead to a failure to think through the problem. Joseph Carson, chief security scientist and advisory CISO at Thycotic, gives the following example. "Companies can react to the weak password issue by buying password managers," he told SecurityWeek, "without realizing that what they actually need is an integrated system that can rotate passwords and manage privileges." When they realize they need a full privilege management system, the password managers become redundant.
Carson nevertheless finds a lot of positivity in the survey results. "One area that I think is key," he said, "is that the communication between the CISO and the executive Board is getting better. In previous research we found that there was a language barrier between the CISO and the Board -- the CISO would think very much about fear and doubt and threats and risk and tend to stress that fear factor. However, this report now shows that CISOs are both being listened to, but also getting the follow through budget. In the past, CISOs and the Board weren't speaking the same language. This report shows that the communication gap between the CISO and the Board is closing."
Despite the increased budget to COVID being a reactive decision, Carson nevertheless believes it is a positive response from the Board. "That 91% of respondents say the Board is now adequately supporting the team with the follow-up investments is significant. But there is some bad news that goes with that as well -- that with that investment, 50% of the purchased security solutions are not being fully utilized." He recognizes the reactive nature of security decision-making in much of the world, but sees an interesting cultural difference in Asia. "The factors are a little different in Asia," he told SecurityWeek, "where they are focusing more on the return on investment. There's this interesting cultural difference in places like Australia, Singapore and Malaysia where purchasing decision focuses more on ROI."
The survey also shows that product choice is often geared to benchmarking against what peer companies are doing. This is particularly prevalent in the UK and Europe. In the U.S. and Australia, choice is very much dominated by industry analysts and expertise, where they tend to look at the analysts such as Gartner and Forrester for direction. "Another surprise for me," he continued, "is that I would have thought the security team would have a strong say in the final decision-making process for new solutions, but in fact in most places it is the operations teams that have a bigger say in what the final solution will be. I think this is because the security teams can look at the problem from a threat and risk perspective, but ultimately the operations teams have to implement, deploy, maintain and upgrade it."
In the final analysis, the difficulty with all surveys is that the statistics returned are objective facts; but the interpretation of those statistics is subjective. Joseph Carson is fairly upbeat and positive about how the Boards are beginning to take cybersecurity seriously and fund what is necessary. However, it is equally possible to point to the examples given in the survey and suggest that the Boards are merely reacting to what is visibly happening today. There is little in the survey to suggest that boardrooms are ready to support their security teams with longer term strategic rather than tactical approaches to cybersecurity -- and it is the strategic approach that is necessary to thwart the adversaries.
Cyber Warriors Sound Warning on Working From Home
15.10.20 Cyber Securityweek
Cyber warriors on NATO's eastern edge are warning that the growing number of people working from home globally due to the pandemic is increasing vulnerability to cyber attacks.
The Baltic state of Estonia hosts two cyber facilities for the Western military alliance -- set up following a series of cyber attacks from neighbour Russia more than a decade ago.
"Large scale use of remote work has attracted spies, thieves and thugs," Jaak Tarien, head of NATO's Cooperative Cyber Defence Centre of Excellence (CCDCOE), told AFP in an interview.
The increased amount of information travelling between institutional servers and home networks is creating new challenges for employers.
"Tackling these new challenges is complicated and requires a lot of resources as well as a different kind of approach," Tarien said.
"We are likely only scratching the surface in assessing the magnitude of malicious activities taking place in the Covid-era busy cyberspace."
An EU-wide survey in September found that around a third of employees were working from home.
- Boom in online courses -
The concerns are echoed at NATO's Cyber Range -- a heavily-guarded facility protected by barbed wire in the centre of the capital Tallinn run by Estonian defence forces.
The server rooms inside serve as a platform for NATO cyber security exercises and training.
"Specialists have set up the work infrastructure, but they cannot control the way people use their home internet or how secure it is," said Mihkel Tikk, head of the Estonian defence ministry's cyber policy department.
Tikk said the latest cyberattacks have targeted Estonia's health sector and Mobile-ID -- the mobile phone based digital ID.
The coronavirus pandemic has also affected operations at the cyber facilities themselves, forcing the cancellation of offline exercises.
But the NATO Cyber Defence Centre said the silver lining is the growing popularity of the cyber security courses it is putting online.
The online courses include "Fighting a Botnet Attack", "Operational Cyber Threat Intelligence" and "IT Systems Attack and Defence".
There were 6,411 students by September 1 and the centre is aiming for 10,000 by the end of 2020.
- 'A massive mistake' -
The Cyber Defence Centre was set up following a series of cyberattacks of unprecedented sophistication on Estonian websites in 2007.
The Russian pro-Kremlin youth organisation Nashi later claimed responsibility.
These days, Estonia faces a "continuous flow of attacks" and repelling them requires constant work, Defence Minister Juri Luik told AFP.
But he said the country was in "a pretty good situation" since it has had time to learn from past experience.
"We have worked diligently to guarantee that the computer networks are difficult to break in and the communication is encrypted –- both military but also civilian communication.
"So I think it is relatively more difficult to harm Estonia than many other countries who perhaps are not so used to working via cyberspace and haven't given too much attention to cyber defence," he said.
The minister underlined that all this work would be for nothing without basic cyber hygiene, including password protection.
"This is extremely important and should be remembered -- especially now that many people work from home via computer.
"At home you might let your guard down and that's of course a massive mistake."
Why master YARA: from routine to extreme threat hunting cases. Follow-up
29.9.20 Cyber Securelist
On 3rd of September, we were hosting our “Experts Talk. Why master YARA: from routine to extreme threat hunting cases“, in which several experts from our Global Research and Analysis Team and invited speakers shared their best practices on YARA usage. At the same time, we also presented our new online training covering some ninja secrets of using YARA to hunt for targeted attacks and APTs.
Here is a brief summary of the agenda from that webinar:
Tips and insights on efficient threat hunting with YARA
A detailed demo of our renowned training
A threat hunting panel discussion with a lot of real-life yara-rules examples
Due to timing restrictions we were not able to answer all the questions, therefore we’re trying to answer them below. Thanks to everyone who participated and we appreciate all the feedback and ideas!
Questions about usage of YARA rules
How practical (and what is the ROI), in your opinion, is it to develop in-house (in-company/custom) YARA rules (e.g. for e-mail / web-proxy filtering system), for mid-size and mid-mature (in security aspects) company, when there are already market-popular e-mail filtering/anti-virus solutions in use (with BIG security departments working on the same topic)?
In the case of mid-size companies, they can benefit a lot from three things connected to YARA, because YARA gives you some flexibility to tailor security for your environment.
First is the usage of YARA during incident response. Even if you don’t have an EDR Endpoint Detection and Response) solution, you can easily roll-out YARA and collect results through the network using PowerShell or bash. And it’s often the case that someone in a company should have experience developing YARA rules.
Second is the usage of third-party YARA rules. It’s an effective way to have one more layer of protection. On the other hand, you need to maintain hunting and detection sets and fix rules and remove false positives anyway. Which once again means that someone needs experience in writing YARA rules.
Third is that, as mentioned earlier, it might be really useful to have rules to look for organization-specific information or IT assets. It can be a hunting rule that triggers on specific project names, servers, domains, people, etc.So the short answer is yes, but it is important to invest time wisely, so as not to become overwhelmed with unrelated detections.
What is the biggest challenge in your daily YARA rule writing/management process? Is it a particular malware family, actor, or perhaps a specific anti-detection technique?
In our experience, certain file formats make writing YARA rules more difficult. For instance, malware stored in the Office Open XML file format is generally more tricky to detect than the OLE2 compound storage, because of the additional layer of ZIP compression. Since YARA itself doesn’t support ZIP decompression natively, you need to handle that with external tools. Other examples include HLL (high level language) malware, notably Python or Golang malware. Such executables can be several megabytes in size and contain many legitimate libraries. Finding good strings for detection of malicious code in such programs can be very tricky.
Some malware uses YouTube or Twitter or other social media network comments for Command-and-Control. In that regard, where there are no C2 IPs, is it currently hard to detect these?
Yes and no. Yes, it’s hard to get the real C2, because you need to reverse engineer or dynamically run malware to get the final C2. No, it’s relatively easy to detect, because from a ML point of view it’s a pure anomaly when very unpopular software goes to a popular website.
So what is the size of the publicly available collections for people to use YARA against? What are some good ways to access a set of benign files, if you don’t have access to retrohunts/VTI?
You can use YARA on clean files and malware samples. Creating a comprehensive clean collection is a challenge, but in general, to avoid false positives, we recommend grabbing OS distributions and popular software. For this purpose, a good starting point could be sites like:
https://www.microsoft.com/en-us/download
https://sourceforge.net/
ftp://ftp.elf.stuba.sk/pub/pc/
For malware collection it’s a bit tricker. In an organization it’s easier, since you can collect executables from your own infrastructure. There are also websites with the collection of bad files for research purpose in Lenni Zeltser blogpost there is a good list of references:
https://zeltser.com/malware-sample-sources/
The final size of such a collection could be several terabytes or even more.
Can YARA be used to parse custom packers?
Yes, but not out-of-the-box. YARA has a modular architecture, so you can write a module that will first unpack the custom packer and then scan the resulting binary.
A more common option is to run YARA against already unpacked objects, e.g. results of unpacking tools like Kaspersky Deep Unpack or sandbox and emulator dumps.
What is the trade-off when we want to hunt for new malware using YARA rules? How many FPs should we accept when we need rules that detect new variants
It depends what you want to catch. In general, from a research perspective, it’s ok to have an average FP rate up to 30%. On the other hand, production rules should have no FPs whatsoever!
Could YARA help us to detect a fileless attack (malware)?
Yes, YARA can scan memory dumps and different data containers. Also, you can run YARA against telemetry, but it may take some additional steps to achieve it and properly modify the ruleset.
We can use YARA, together with network monitoring tools like Zeek, to scan files like malicious documents. Can YARA be used against an encrypted protocol?
Only if you do a MITM (Man-in-the-Middle) and decrypt the traffic, since YARA rules most likely expect to run on decrypted content.
What open source solution do you recommend in order to scan a network with YARA rules?
YARA itself plus PowerShell or bash scripts; or, as an alternative, you can use an incident response framework and monitoring agent like OSquery, Google Rapid Response, etc. Other options are based on EDR solutions which are mostly proprietary.
Which is better, YARA or Snort, for looking at the resource utilization for detection in live environments?
YARA and Snort are different tools providing different abilities. Snort is designed specifically as a network traffic scanner, while YARA is for scanning files and/or memory. The best approach is to combine usage of YARA and Snort rules together!
Questions about creating yara rules and training course questions
Are we able to keep any of the materials after the course is finished?
Yes, Kaspersky YARA cheat-sheets or training slides which include Kaspersky solutions to exercises are some of the things that are available for you to download and use even after the training session has finished.
Is knowledge about string extraction or hashing sufficient to create solid YARA rules? Are there other things to learn as prerequisites?
This depends on case-by-case knowledge. Strings and hashing are basic building blocks for creating YARA rules. Other important things are PE structure and preferences and anomalies in headers, entropy, etc. Also, to create rules for a specific file format, you need some knowledge of the architecture of the corresponding platform and file types.
Can we add a tag to the rule that says it is elegant, efficient or effective, such as the tag on the exploit (in the metasploit): excellent, great, or normal?
Sounds like a good idea. Actually, YARA rules also support tags in the name:
https://yara.readthedocs.io/en/stable/writingrules.html
Maybe you can explain more about the fact that metadata strings don’t have a direct impact on the actual rule.
As we described before, a YARA rule can consist of meta, strings and conditions. While the condition is a mandatory element, the meta section is used only for providing more info about that specific YARA rule. and it is not at all used by the YARA scanning engine.
ASCII is the default, so why do you need to put ASCII in the rule?
Without ASCII, say ‘$a1 = “string” wide’, only the Unicode representation of the string would be searched. To search both ASCII and Unicode, we need ‘$a1= “string” ascii wide’.
Can we use RegEx in YARA? Is nesting possible in YARA?
Yes, it’s possible to use RegEx patterns in YARA. Be aware that RegEx patterns usually affect performance and can be rewritten in the form of lists. But in some cases you just cannot avoid using them and the YARA engine fully supports them.
Nesting is also possible in YARA. You can write private rules that will be used as a condition or as a pre-filter for your other rules.
Is there a limit on the number of statements in a YARA rule?
We created several systems that create YARA rules automatically; and over time these have reached tens of megabytes in size. While these still work fine for us, having a very large number of strings in one rule can lead to issues. In many cases, setting a large stack size (see the yara -k option) helps.
Can we say that YARA can be a double-edged sword? So a hacker can develop malware and then check with YARA if there’s anything similar out there and enhance it accordingly?
Sure, although they would need access to your private stash of YARA rules. In essence, YARA offers organizations a way to add extra defenses by creating custom, proprietary YARA rules for malware that could be used against them. Malware developers can always test their creations with antivirus products they can just download or purchase. However, it would be harder to get access to private sets of YARArules.
This is a philosophical question: Juan said YARA has democratized hunting for malware. How have APTs and malware authors responded to this? Do they have anti-YARA techniques?
A few years ago we observed a certain threat actor constantly avoiding our private YARA rules for one to two months after we published a report. Although the YARA rules were very strong, the changes the threat actor made to the malware kind of suggested they knew specifically what to change. For instance, in the early days they would use only a few encryption keys across different samples, which we, of course, used in our YARA rules. Later, they switched to a unique key per sample.
Would be possible to create a YARA rule to find Morphy’s games among a large set of chess games?
Probably! Morphy was one of the most famous players from the so-called romantic chess period, characterised by aggressive openings, gambits and risky play. Some of the openings that Morphy loved, such as the Evans Gambit or the King’s Gambit accepted, together with playing with odds (Morphy would sometimes play without a rook against a weaker opponent), might yield some interesting games. Or, you could just search for ‘$a1 = “Morphy, Paul” ascii wide nocase’, perhaps together with’ $a2 = “1. e4″‘ 🙂
Would you recommend YARA for Territorial Dispute checks?
Yes, of course. In essence, “Territorial Dispute” references a set of IoCs for various threat actors, identified through “SIGS”. While some of them have been identified, for instance in Boldi’s paper, many are still unknown. With YARA, you can search for unique filenames or other artifacts and try to find malware that matches those IoCs. Most recently, Juan Andres Guerrero-Saade was able to identify SIG37 as “Nazar”: check out his research here:
https://www.epicturla.com/blog/the-lost-nazar
Pro tips and tricks from the audience
Using YARA programmatically (e.g. via py/c) allows you to use hit callbacks to get individual string matches. This enables you to check for partial rule coverage (k of n strings matched but without triggering the condition), which is great for aiding rule maintenance.
On the top white list (clean stuff), known exploits and payloads should be also populated in our YARArule sets.
I always find it easier to maintain code by grouping the strings together.
As a dedicated/offline comment to JAG-S: The “weird” strings from the rule discussed most likely come from the reloc section (thus locking on encoded offsets), which would make the rule highly specific to a given build, even with a soft 15/22 strings required. That would still probably work well if the samples originate from a builder (i.e. configured stub) but should not generalize well. And for the IDA-extracted functions: consider wildcarding offsets to have better generalizing rules.
When it comes to strings – besides the strings from disk, mem, network dump, etc., bringing context and offset should be a best practice. Then rank the strings in the context of the malware. And this requires human expertise but can be easily adapted into the YARA rule building process.
Сombining, in a flexible way, the YARA rules build process with the enrichment of the recently announced Kaspersky Threat Attribution Engine, will be also GReAT 🙂
Feel free to follow us on Twitter and other social networks for updates, and feel free to reach out to us to discuss interesting topics.
Hackers hit Luxottica, production stopped at two Italian plants
22.9.20 Cyber Securityaffairs
The Italian eyewear and eyecare giant Luxottica has reportedly suffered a cyber attack that disrupted its operations in Italy and China.
Luxottica Group S.p.A. is an Italian eyewear conglomerate and the world’s largest company in the eyewear industry. As a vertically integrated company, Luxottica designs, manufactures, distributes and retails its eyewear brands, including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com. Its best known brands are Ray-Ban, Persol, and Oakley. Luxottica also makes sunglasses and prescription frames for designer brands such as Chanel, Prada, Giorgio Armani, Burberry, Versace, Dolce and Gabbana, Miu Miu, and Tory Burch.
Luxottica employs over 80,000 people and generated 9.4 billion in revenue for 2019.
The company was hit by a cyberattack that took place on Friday evening, when some of the web sites operated by the company were not reachable, including Ray-Ban, Sunglass Hut, LensCrafters, EyeMed, and Pearle Vision.
Some of the Luxottica’s websites (i.e. university.luxottica.com) are currently showing maintenance messages.
Italian media outlets reported that the operations at the plants of Luxottica in Agordo and Sedico (Italy) were disrupted due to a computer system failure. Union sources confirmed that the personnel at the plants received an SMS in which they were notified that “the second workshift of today 21 September is suspended” due to “serious IT problems”.
BleepingComputer website, citing the security firm Bad Packets, speculates that the Italian was using a Citrix ADX controller device vulnerable to the critical CVE-2019-19781 vulnerability in Citrix devices.
At the time Luxottica has yet to release any official statement on the attack.
Security experts believe that threat actor exploited the above flaw to infect the systems at the company with ransomware.
SecOps Teams Wrestle with Manual Processes, HR Gaps
19.9.20 Cyber Threatpost
Enterprise security teams are “drowning in alerts.”
Only about half of enterprises are satisfied with their ability to detect cybersecurity threats, according to a survey from Forrester Consulting – with respondents painting a picture of major resource and technology gaps hamstringing their efforts to block cyberattacks.
According to the just-released 2020 State of Security Operations survey of 314 enterprise security professionals, enterprise security teams around the world feel that they struggle with the growing pace, volume and sophistication of cyberattacks. A whopping 79 percent of enterprises covered in the survey have experienced a cyber-breach in the past year, and nearly 50 percent have been breached in the past six months.
It turns out that businesses are under constant attack, with the average security operations team receiving more than 11,000 security alerts daily. Unfortunately, thanks to manual triage processes and disparate and legacy security tools permeating most environments, 28 percent of alerts are simply never addressed, the survey, released Thursday, found. Only 47 percent of organizations noted that they are able to address most or all of the security alerts they receive in a single day; and out of those that are addressed, almost a third are false positives.
In fact, according to the report findings, only 13 percent of the surveyed organizations are using automation and machine learning to analyze and respond to threats. Nearly 20 percent of alerts are manually reviewed/triaged by an analyst.
Source: Forrester Consulting
And, security operations teams use an average of more than 10 different categories of security tools, including firewalls, email security, endpoint security, threat intelligence, vulnerability management and more — tools are typically siloed, according to respondents.
Perhaps it’s no surprise then that most security operations teams reported that they are unable to hit key benchmarks for metrics like mean time to investigate, number of incidents handled, mean time to respond, threat score and number of alerts. Less than 50 percent of teams report that they meet these metrics “most of the time.”
“The net result is that security analysts are drowning in alerts, which is having a profound impact on their health, wellness and overall job satisfaction,” according to a Thursday blog from researchers Erica Naone and Mark Brozek of Palo Alto Networks, which commissioned the survey. “This reactive approach to cybersecurity also has decision-makers frustrated and dissatisfied. With Forrester Research estimating the cost of an average data breach at as much as $7 million per incident, a more proactive approach is needed to quickly prevent, identify and address cyber-threats.”
Source: Forrester Consulting.
Eighty-two percent of IT decision-makers agreed that their responses to threats are mostly or completely reactive, but they’d like to be more proactive; only 50 percent agreed that they have the right resources to proactively hunt for threats.
While adding human resources is seen as a key to overcoming these issues, the oft-reported workforce skills shortage continues to bite. Respondents to the survey said that “finding and keeping experienced security operations staff and enough analysts to support the workload is a major challenge”; and they reported “difficulty hiring, training and retaining employees who are adept at using the full security technology stack.”
Adding insult to injury, Forrester also noted that all of these hurdles are especially high in the time of COVID-19, when remote workforces have complicated the defense game. One FBI spokesperson quoted in the report said that cybersecurity complaints to the Bureau’s Internet Crime Complaint Center have spiked by 200-300 percent since the pandemic began.
SMB Cybersecurity Catching Up to Enterprise… But the Human Element Still a Major Concern
8.9.20 Cyber Thehackernews
Cyberattacks on small to medium-sized businesses (SMBs) are continuing at a relentless pace, with the vast majority of data breaches coming from outside the organization.
Some believe hackers are aggressively targeting these smaller firms because they believe SMBs lack adequate resources and enterprise-grade security tools, making them easier prey than larger businesses.
A new report from Cisco, however, challenges this assumption. SMBs have made significant strides enhancing their security protocols and are closing the gap with their bigger counterparts. The report notes 87 percent of SMB business owners rank security a top priority, and more than 99 percent have a dedicated resource focusing on security.
SMBs are also becoming more diligent about defining metrics to assess their security effectiveness and implementing security controls and tools at rates similar to large enterprises.
No doubt, the emergence of security solutions developed specifically for SMBs is supporting this trend. Security tech providers are now offering affordable tools that cover multiple attack vectors, making it easier and more cost-effective for SMBs to improve their defenses.
Reason Cybersecurity, for example, includes real-time protection capabilities alongside its anti-virus, anti-ransomware, and anti-malware functionalities. It also protects unauthorized applications from accessing communications peripherals like webcams and microphones, often used by hackers to spy on team members and steal sensitive information remotely.
The increased focus on security and better implementation of cybersecurity solutions among SMBs are certainly positive developments. With enterprise-style protection now available to literally any size organization, the threat can be dramatically minimized for any size organization.
Yet even with improved technology to reduce threats, the human factor is still a significant concern; one single misstep by an employee can cause a breach that leads to a major security incident. To achieve a truly effective security posture, SMBs must put systems in place to minimize human error that can turn an unintentional mistake into a security disaster.
The Psychology of Human Error
The reality is this: Humans make mistakes. A Tessian study found that 88 percent of data breaches can be linked to human error. That doesn't necessarily mean that humans are the "weak link" in your organization's security, but it is important to understand how and why they make these all-too-human errors. As Tessian points out, employees have psychological reactions to stimuli and judgment that make them likely to commit errors and be susceptible to manipulation.
Hackers use social engineering attacks like phishing to take advantage of these human tendencies, cleverly manipulating users into giving up sensitive information or downloading and running malware onto their work devices.
Hackers carefully disguise these phishing emails to circumvent security measures like spam filters, with requests for sensitive data or access often appearing to come from a trusted colleague. Because we have little resistance to following our colleagues' requests, it's quite possible for a normally security-savvy team member to click on a malicious link or send sensitive information.
Those seemingly innocent clicks make ransomware a growing threat, too; take the recent cyberattack that successfully disrupted Garmin Connect, flyGarmin, and Garmin Pilot, resulting in days-long outages. Garmin reportedly paid the multimillion-dollar ransom to restore functionality across their network of users.
Massive attacks like these are the ones that get media mileage, yet SMBs are not immune. Almost half (46 percent) of SMBs have been targeted by ransomware, and nearly three out of four victims have paid a ransom to restore control of their systems.
Addressing the Issue
Clearly, there's a critical need to adopt technical solutions that protect vulnerable areas where humans interact with possible risks.
For example, installing security solutions on each workstation – especially now with so much of the world's business being done remotely – can protect against attacks that could occur over the course of a typical workday.
Moreover, the human element must be taken into account when assessing any security strategy. Staff education and training are crucial. Team members must know how to use the organization's tech resources securely and properly.
At the same time, they must be able to recognize social engineering attacks or dubious networks and devices. Continuous real-time training can help develop this security-first mindset.
Just as SMBs can now access enterprise-strength security solutions, they can also take advantage of security apps and services that minimize human input into certain tasks. For example, many businesses still process card payments manually and store the information insecurely, leaving them exposed to data breaches.
A simple solution is to use a trusted third-party payment processor that allows customers to securely pay for orders and invoices without requiring human staff to access and handle customer financial data.
Businesses should also look for ways to maximize the capabilities of their existing security solutions. Reason for Business, for instance, provides developer tools that allow users to integrate their security solution across the organization's other apps.
Through its SDK and cloud API, businesses can integrate protection features into their own applications that filter spam, suspicious URLs, and potential attacks across the board. Their real-time alerts and notifications make it easy to keep IT teams informed and communicate quickly when security concerns arise.
Committing to Improvement
Cyberattacks are part of today's business landscape; it's a threat as real as fire, theft, or any other possible loss. Regardless of their size, businesses are more focused than ever on making cybersecurity a priority for their organizations. This improvement in mindset – especially among SMBs -- is noteworthy. The availability of affordable tech solutions should enable more SMBs to secure their infrastructure.
Beyond these measures, SMBs must be more vigilant about managing the human element of security. Simple human error continues to present a very real risk.
Training, automation, and using solutions that cover previous security blind spots will help develop that critical security-first mindset.
Digital Education: The cyberrisks of the online classroom
4.9.20 Cyber Securelist
This past spring, as the COVID-19 pandemic took hold, online learning became the new norm as universities and classrooms around the world were forced to close their doors. By April 29, 2020, more than 1.2 billion children across 186 countries were impacted by school closures.
Shortly after schools began to transition to emergency remote learning, it became clear that many were not ready for the kind of full-time, digital education now needed. Not all students had the technology that was required, from laptops to a stable Internet connection, and parents and instructors in countries like the United States worried students would inevitably fall behind academically. What is more, many educational institutions did not have proper cybersecurity measures in place, putting online classrooms at increased risks of cyberattacks.
In fact, in June, Microsoft Security Intelligence reported that the education industry accounted for 61 percent of the 7.7 million malware encounters experienced by enterprises in the previous 30 days – more than any other sector.
Apart from malware, educational institutions were also at increased risk of data breaches and violations of student privacy. It was this spring that “Zoombombing” became part of the general lexicon after pranksters and ill-intentioned individuals began taking advantage of Zoom’s security weaknesses to break into private meetings. Among the victims were schools, with several reported incidents of online classrooms being interrupted by users making lewd comments or streaming pornography.
As fall approaches, digital learning will continue to be a necessity. In fact, half of all U.S. elementary and high school students will be entirely online. Even those that are reopening are deploying some kind of hybrid model, such as delivering large lectures online. What’s more, the threat of a second coronavirus wave still remains, meaning that future large-scale school closures are still a possibility.
With this in mind, Kaspersky researchers took a closer look at the cyber risks faced by schools and universities, so that educators can be prepared moving forward – and take the necessary precautions to stay secure.
Methodology
This report examines several different types of threats – phishing pages and emails related to online learning platforms and video conferencing applications, threats disguised under the names of these same applications, and distributed denial of service (DDoS) attacks affecting the education industry.
Various threats disguised under popular online learning platforms/video conferencing applications
For this part, we utilized results from the Kaspersky Security Network (KSN) – a system for processing anonymous data related to cybersecurity threats shared voluntarily from Kaspersky users – for two different periods: January-June 2019 and January-June 2020.
Using KSN, we searched for files bundled with various threats that contained the name of one of the following platforms/applications during one of the two periods above:
Moodle – the most popular learning management system (LMS) in the world. It is used by educators to build online courses, host classes and create activities.
Blackboard – another popular LMS. It provides a virtual learning environment where educators can build entirely digital courses or create additional activities to supplement in-person instruction.
Zoom – a highly popular online collaboration tool that provides free video conferencing capabilities. Many educators used Zoom to conduct online classes this past spring.
Google Classroom – a web service designed specifically for educators to host classes, generate assignments and track students’ progress.
Coursera – a popular online learning platform that hosts a variety of open online courses, certificates and even degree programs.
edX – a provider of open online courses available to users worldwide.
Google Meet – a video communication service similar to Zoom, which can be used to host meetings and online classes
The results display those (PC and mobile) users that encountered various threats disguised as the above platforms/applications from January-June 2019 and January-June 2020.
Distributed denial of service (DDoS) attacks
Kaspersky tracks DDoS (distributed denial of service) attacks using the Kaspersky DDoS Intelligence System. A part of Kaspersky DDoS Protection, the system intercepts and analyzes commands received by bots from C&C servers. The system is proactive, not reactive, meaning that it does not wait for the user device to get infected or a command to be executed. Each “unique target” represents a specific IP address that was attacked.
The following report displays the percentage of DDoS attacks that affected educational resources out of the total number of DDoS attacks registered by the Kaspersky DDoS Intelligence System for Q1 2019 and Q1 2020.
Our Key Findings. The number of DDoS attacks affecting educational resources grew by 550% in January 2020 when compared to January 2019.
For each month from February to June, the number of DDoS attacks that affected educational resources out of the total number of attacks was 350-500% greater in 2020 than in the corresponding month in 2019.
From January to June 2020, the total number of unique users that encountered various threats distributed under the guise of popular online learning platforms/video conferencing applications was 168,550 – a 20,455% increase when compared to the same period for 2019.
From January to June 2020, the platform most commonly used as a lure was Zoom, with 5% of the users that encountered various threats encountering them via files that contained the name Zoom. The second most common platform used as a lure was Moodle.
By far the most common threats encountered in 2020 were downloaders and adware, which were encountered in 98.77% of the total registered infection attempts. Various classes of trojans followed adware.
For threats distributed under the guise of popular platforms for conducting online classes in 2020, the greatest number of infection attempts registered came from Russia (21%) followed by Germany (21.25).
Phishing risks of online learning platforms / video conferencing applications
It is not unexpected that phishing, one of the oldest and most popular forms of cybercrime, would reach educational organizations. In fact, a host of phishing websites for popular platforms like Google Classroom and Zoom began to pop up following the switch to distance learning. From the end of April to mid-June, Check Point Research discovered that 2,449 domains related to Zoom had been registered, 32 of which were malicious and 320 were “suspicious”. Suspicious domains were also registered for Microsoft Teams and Google Meet. Users who land on these phishing pages are often tricked into clicking URLs that download malicious programs, or they might be tricked into inputting their login credentials, which would put these in the hands of the cybercriminals.
Fake login page for Zoom
Fake login page for Moodle
These criminals might not even be after access to your account. They can use your login credentials for various nefarious purposes: launching spam or phishing attacks, gaining access to your other accounts as people often reuse passwords, or collecting more personally identifiable information to be used in future attacks / attempts to steal funds.
Most universities also have their own platforms where students and faculty can login to access important resources and various academic services. This past spring, some attackers went so far as to target specific universities by creating phishing pages for their individual academic login pages.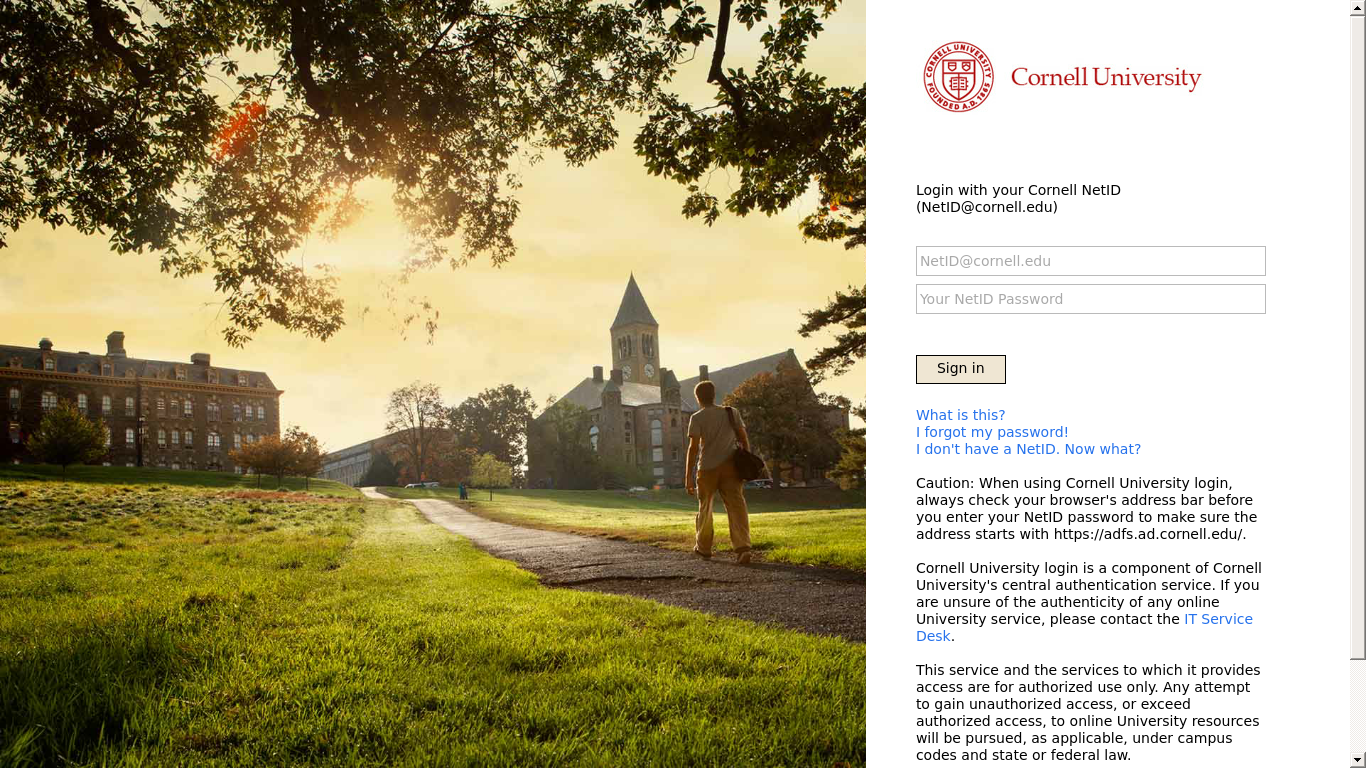
Phishing page for Cornell University’s academic login page
Apart from fake web pages, cybercriminals sent out an increasing number of phishing emails related to these same platforms. These told users they had missed a meeting, a class had been canceled, or it was time to activate their accounts. Of course, if they opened the email and clicked on any links, they were at risk of downloading various threats.
Phishing email supposedly from Zoom urging the user to review a new video conferencing invitation
The cyberthreats of online learning platforms
A common way to distribute threats disguised as popular video meeting apps and online course platforms is by bundling threats as legitimate application installers.
There are several ways users can encounter these malicious installers. One way is through phishing websites designed to look like the legitimate platforms, as seen above. Those users who inadvertently end up on the wrong page are then exposed to malware or adware when they attempt to download what they believe is the genuine application. Another common way is through phishing emails disguised as special offers or notifications from the platform. If users click the links in the email, then they are at risk of downloading unwanted files.
From January to June 2019, the number of unique users that encountered various threats distributed via the platforms specified in the methodology section of this report was 820.
The number of unique users that encountered various threats disguised as popular online learning/video conferencing platforms, January – June 2019 (download)
The most popular lure was Moodle, with Blackboard and Zoom being the second most popular.
In 2020, however, the total number of users that encountered various threats disguised as popular online learning platforms jumped to 168,550, a 20,455% increase.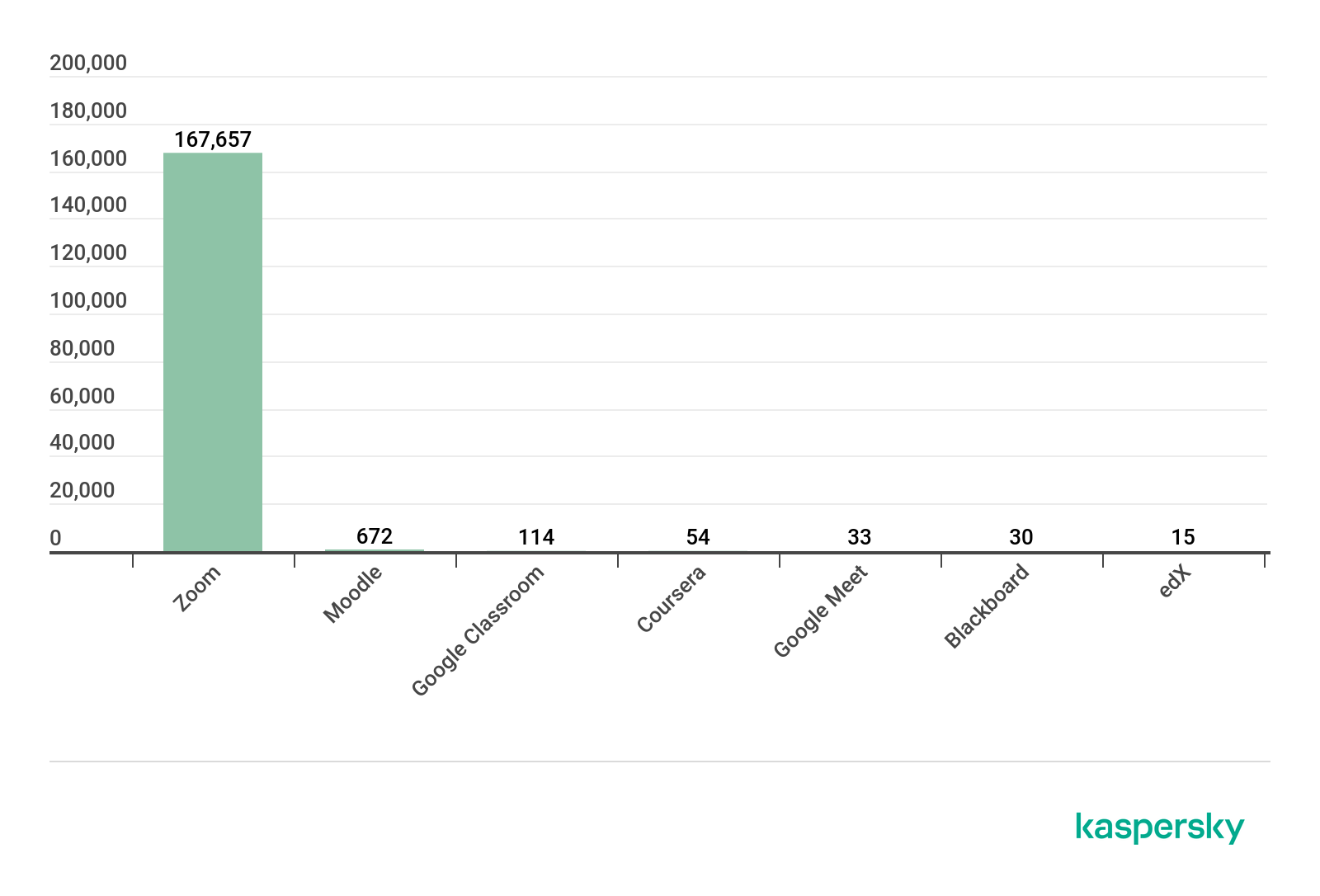
The number of unique users that encountered various threats disguised as popular online learning/video conferencing platforms, January – June 2020 (download)
Zoom was far and away the platform most frequently used as a lure, with 99.5% of users encountering various threats disguised under its name. This is not surprising given that Zoom became the go-to video conferencing platform. By February 2020, the platform had added more new users (2.22 million) than it had, in all of 2019 (1.99 million). As of April 30, the company claimed to have 300 million daily meeting participants. Given its immense popularity, it is only logical that it would be the preferred target for malicious actors. And, with millions of more users looking to download the application, the chances are high that at least some of these would come across fake installers or setup files.
A closer look at the 2020 threat landscape
Types of threats encountered
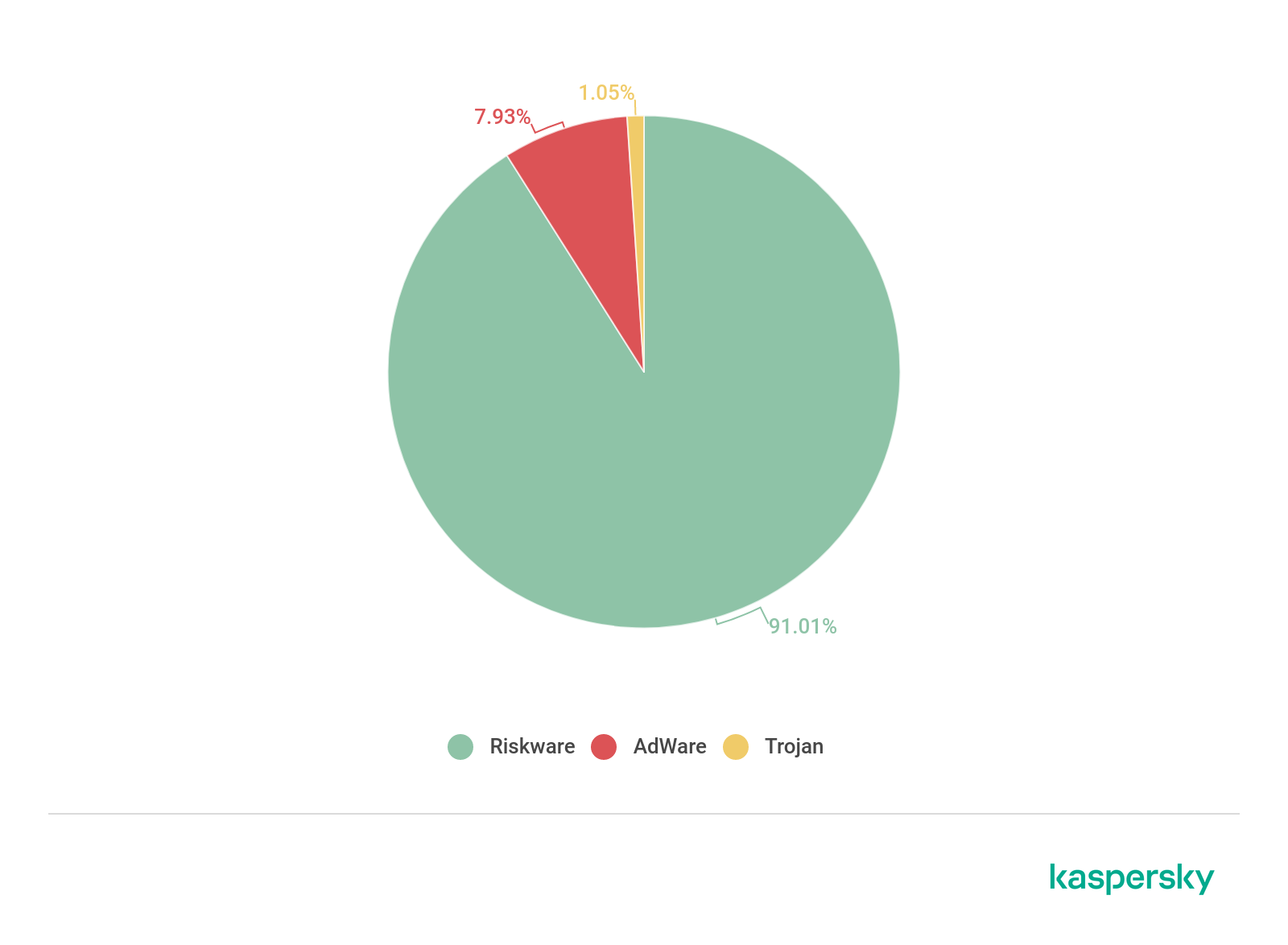
Percent distribution of different types of threats disguised as popular online learning / video conferencing platforms encountered by users, January – June 2020 (download)
By far the most common threats distributed under the guise of legitimate video conferencing/online learning platforms were not-a-virus (99%). Not-a-virus files are typically divided into two categories: riskware and adware. Adware bombards users with unwanted ads, while riskware consists of various files – from browser bars and download managers to remote administration tools – that may carry out various actions on your computer without your consent.
About 1% of the infection attempts were various trojan families: malicious files that allow cybercriminals to do everything from deleting and blocking data to interrupting the performance of the computer. Some trojans encountered were password stealers, which are designed to steal your credentials, while others were droppers and downloaders, both of which can deliver further malicious programs on your device.
Other threats encountered were backdoors, which allow the attackers to take remote control over the device and perform any number of tasks; exploits, which take advantage of a vulnerability in an operating system or application to gain unauthorized access to/use of the latter; and DangerousObjects (non-specific malicious files).
A regional perspective
The five countries where the greatest number of infection attempts were registered are as follows:
Russia 70.94%
Germany 21.25%
Austria 1.44%
Italy 1%
Brazil 1%
For threats distributed under the guise of popular online learning / video conferencing platforms, the greatest number of attempts to infect users occurred in Russia (70.94%). The second greatest number came from Germany (21.25%). Both countries closed schools early in mid-March, making remote learning the only option for millions of teachers and students. In addition, video conferencing has become incredibly popular in Germany, with more than half of Germans regularly using it as a tool for work or school. Given the overall global popularity of Zoom, a significant portion of Germans most likely use this platform and – given that Zoom is by far the most popular platform used as a lure – encountered various threats as a result.
Educational resources hit by DDoS attacks
In April, a large Turkish university was forced entirely offline for 40 minutes after it was hit with a DDoS attack on the morning of exams. In June, a major university in the northeastern United States had its exams disrupted after a DDoS attack affected its online test platforms. These are just two examples of a larger trend that began after schools were forced to transition to emergency remote learning: the rise of DDoS attacks against the education sector.
In general, the total number of DDoS attacks increased globally by 80% for Q1 2020 when compared to Q1 2019. And a large portion of that increase can be attributed to the growing number of attacks against distance e-learning services.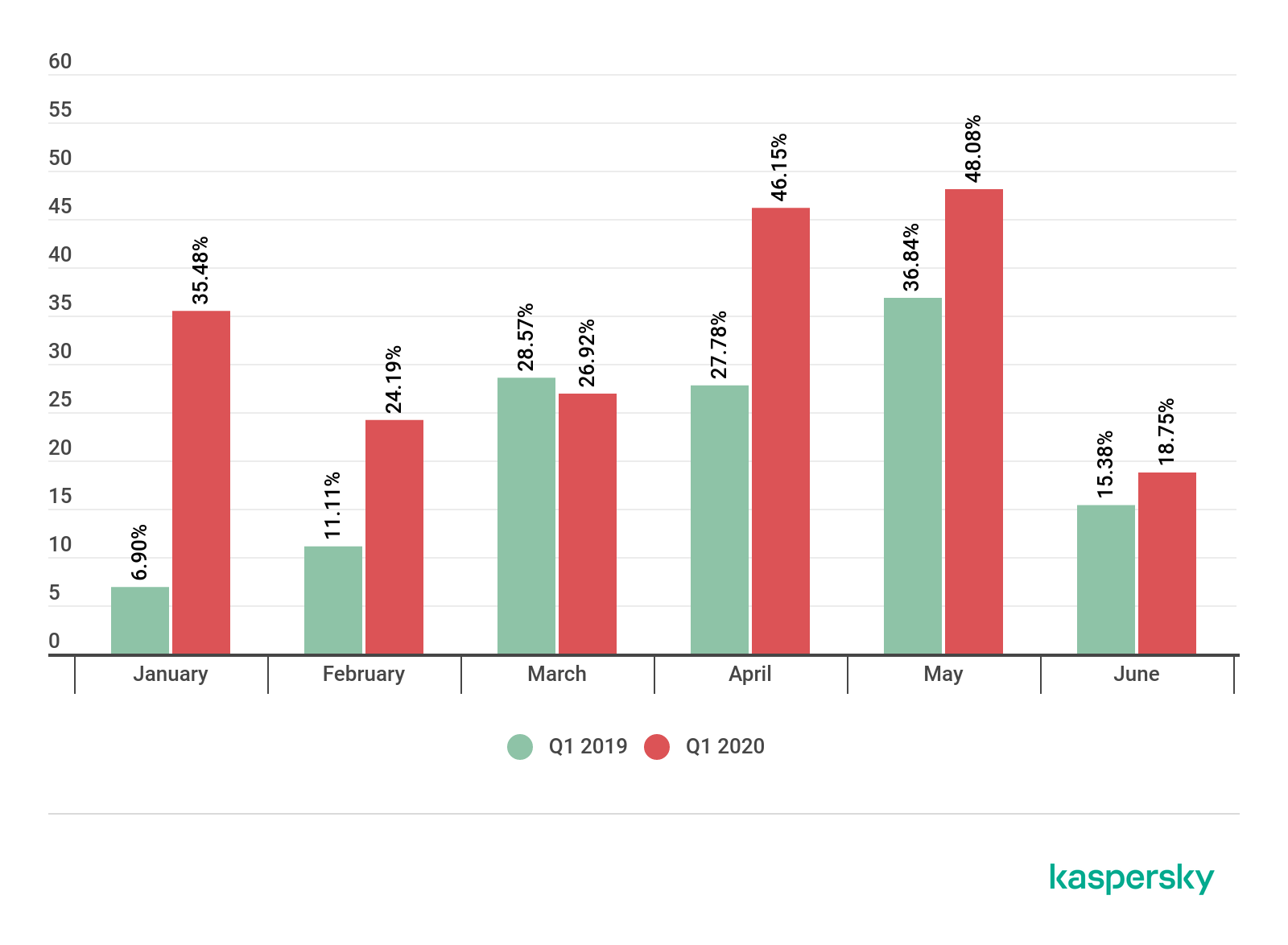
Percent of the total number of DDoS attacks that affected educational resources: Q1 2019 vs Q1 2020 (download)
When compared to Q1 2019, the percentage of DDoS attacks affecting educational resources out of all DDoS attacks increased steadily for each month of Q2 2020 (with the exception of March). When looking at the total number of DDoS attacks that occurred between January and June 2020, the number of DDoS attacks affecting educational resources increased by at least 350% when compared to the corresponding month in 2019.
January: February: March: April: May: June:
550% 500% 350% 480% 357.14% 450%
The percent growth in the number of attacks on educational resources when compared to the same month in 2019
The more educational organizations rely on online resources to conduct their regular activities, the more of a target these networks become for cybercriminals looking to disrupt their operations.
Looking forward
Online learning is not a short-term response to a global pandemic. It is here to stay.
For one, the pandemic is not over. Many students are still studying virtually, at least part of the time, and some schools that decided to open have already decided to revert back to online classes only. The possibility of a second wave still looms, meaning educators have to be prepared for large-scale school closures in the future.
Even when the pandemic does end, most agree that online learning will not disappear altogether. A recent global survey by Pearson Education, an academic publishing company, found that nearly 90% of the 7,000 individuals surveyed expect online learning to continue to play a role at all education levels.
In fact, even before the pandemic, some universities had already developed blending curricula (a mix of offline experiences and online courses). More and more academic institutions are considering this as an option for future programs.
However, as long as online learning continues to grow in popularity, cybercriminals will attempt to exploit this fact for their own gain. That means educational organizations will continue to face a growing number of cyber risks – into this fall and beyond. Fortunately, engaging – and secure – online academic experiences are possible. Educational institutions just need to review their cybersecurity programs and adopt appropriate measures to better secure their online learning environments and resources.
The extended version of the report with security tips and additional materials from our partners: llya Zalessky, head of educational services at Yandex, Steven Furnell, professor of cyber security at the University of Nottingham, and Dr. Michael Littger, executive director of Deutschland sicher im Netz e.V, can be downloaded in PDF format.