
Safety 2024 2023 2022 2021 2020
SolarWinds Removes Customer List From Site as It Releases Second Hotfix
17.12.2020
Safety
Securityweek
SolarWinds has
released a second hotfix for its Orion platform in response to the recent
breach, and the company has decided to remove from its website a page listing
some of its important customers.
IT management and monitoring solutions provider SolarWinds revealed this week that sophisticated threat actors compromised the build system for its Orion monitoring platform, which allowed the attackers to deliver trojanized updates to the firm’s customers between March and June 2020. The hackers could then compromise the servers of the organizations that downloaded, implemented or updated Orion products in that timeframe.
Shortly after news of the breach broke, the company informed customers about the availability of a hotfix, but promised to release a second hotfix that replaces the compromised component and provides additional security enhancements.
The company released that second patch on Tuesday, namely version 2020.2.1 HF 2 of the Orion platform, and it has informed customers that no other products have been compromised. The company has provided a complete list of both affected and not affected products, and it has published an FAQ document to answer some of the questions customers might have.
In an SEC filing this week, SolarWinds said it notified 33,000 customers about the incident, but pointed out that only up to 18,000 actually obtained the compromised software.
The attack is believed to have impacted many major organizations, including cybersecurity firm FireEye, which broke the news after the attackers stole some of its Red Team tools, and various U.S. government organizations.
According to media reports, the list of U.S. government targets could include the DHS, the Commerce Department, the Treasury, the Defense Department, the State Department, and the National Institutes of Health. Britain’s National Cyber Security Centre (NCSC) says it’s assessing the impact on the UK.
Related: Group Behind SolarWinds Hack Bypassed MFA to Access Emails at US Think Tank
At around the time it released the second hotfix, SolarWinds decided to remove from its website a page listing high-profile customers. The now-removed page said the company had 300,000 customers worldwide, including 425 of US Fortune 500 companies, the top US telecoms and accounting firms, hundreds of universities and colleges, as well as several US government organizations.
Microsoft, which dubbed the attack Solorigate, has also taken steps to protect customers, including through updates for Microsoft Defender Antivirus that should ensure known malicious SolarWinds binaries are blocked.
While it’s still unclear exactly how the attackers managed to breach SolarWinds’ systems, some reports that emerged over the past days revealed security lapses. Reuters learned that multiple threat actors have offered to sell access to SolarWinds systems on underground forums. And one researcher said he informed SolarWinds in November 2019 that FTP credentials belonging to the company had been exposed in a public GitHub repository.
Russia appears to be the prime suspect for the SolarWinds hack, specifically the group tracked as APT29 and Cozy Bear, but the Kremlin has denied the allegations.
Sophos, ReversingLabs Release 20 Million Sample Dataset for Malware Research
15.12.2020
Safety
Securityweek
Sophos and ReversingLabs on Monday announced SoReL-20M, a database of 20 million Windows Portable Executable files, including 10 million malware samples.
Aimed at driving security improvements across the industry, the database provides metadata, labels, and features for the files within, and enables interested parties to download the available malware samples for further research.
Containing a curated and labeled set of samples and relevant metadata, the publicly-accessible dataset is expected to help accelerate machine learning research for malware detection.
Although machine learning models are built on data, the field of security lacks a standard, large-scale dataset that all types of users (ranging from independent researchers to laboratories and corporations) can easily access, which has so far slowed down advancement, Sophos argues.
“Obtaining a large number of curated, labeled samples is both expensive and challenging, and sharing data sets is often difficult due to issues around intellectual property and the risk of providing malicious software to unknown third parties. As a consequence, most published papers on malware detection work on private, internal datasets, with results that cannot be directly compared to each other,” the company says.
A production-scale dataset covering 20 million samples, including 10 million disarmed pieces of malware, the SoReL-20M dataset aims to address the problem.
For each sample, the dataset includes features that have been extracted based on the EMBER 2.0 dataset, labels, detection metadata, and complete binaries for the included malware samples.
Additionally, PyTorch and LightGBM models that have already been trained on this data as baselines are provided, along with scripts needed to load and iterate over the data, as well as to load, train, and test the models.
Given that the malware being released has been disarmed, it would require “knowledge, skill, and time to reconstitute” and run, Sophos says.
The company does admit that there is a chance that skilled attackers would learn from these samples or use them to create attack tools, but argues that there “are already many other sources attackers could leverage to gain access to malware information and samples that are easier, faster and more cost effective to use.”
Thus, the company believes that the disarmed samples are more valuable to security researchers looking to advance their independent defenses.
The disabled malware samples, which have been in the wild for a while, are expected to call back to dismantled infrastructure. Moreover, they should be detected by most anti-virus vendors. With metadata released alongside the samples, detection is expected to improve.
“As an industry, we know malware isn’t limited to Windows or even executable files, which is why researchers and security teams will always need more data,” ReversingLabs, which claims to be providing a reputation database of more than 12 billion goodware and malware files, said.
SoReL-20M: A Huge Dataset of 20 Million Malware Samples Released Online
15.12.2020
Safety
Thehackernews
Cybersecurity firms
Sophos and ReversingLabs on Monday jointly released the first-ever
production-scale malware research dataset to be made available to the general
public that aims to build effective defenses and drive industry-wide
improvements in security detection and response.
"SoReL-20M" (short for Sophos-ReversingLabs – 20 Million), as it's called, is a dataset containing metadata, labels, and features for 20 million Windows Portable Executable (.PE) files, including 10 million disarmed malware samples, with the goal of devising machine-learning approaches for better malware detection capabilities.
"Open knowledge and understanding about cyber threats also leads to more predictive cybersecurity," Sophos AI group said. "Defenders will be able to anticipate what attackers are doing and be better prepared for their next move."
Accompanying the release are a set of PyTorch and LightGBM-based machine learning models pre-trained on this data as baselines.
Unlike other fields such as natural language and image processing, which have
benefitted from vast publicly-available datasets such as MNIST, ImageNet,
CIFAR-10, IMDB Reviews, Sentiment140, and WordNet, getting hold of standardized
labeled datasets devoted to cybersecurity has proved challenging because of the
presence of personally identifiable information, sensitive network
infrastructure data, and private intellectual property, not to mention the risk
of providing malicious software to unknown third-parties.
Although EMBER (aka Endgame Malware BEnchmark for Research) was released in 2018 as an open-source malware classifier, its smaller sample size (1.1 million samples) and its function as a single-label dataset (benign/malware) meant it "limit[ed] the range of experimentation that can be performed with it."
SoReL-20M aims to get around these problems with 20 million PE samples, which also includes 10 million disarmed malware samples (those can't be executed), as well as extracted features and metadata for an additional 10 million benign samples.
Furthermore, the approach leverages a deep learning-based tagging model trained to generate human-interpretable semantic descriptions specifying important attributes of the samples involved.
The release of SoReL-20M follows similar industry initiatives in recent months, including that of a coalition led by Microsoft, which released the Adversarial ML Threat Matrix in October to help security analysts detect, respond to, and remediate adversarial attacks against machine learning systems.
"The idea of threat intelligence sharing in security isn't new but is more critical than ever given the innovation threat actors have shown over the past several years," ReversingLabs researchers said. "Machine learning and AI have become central to these efforts allowing threat hunters and SOC teams to move beyond signatures and heuristics and become more proactive in detecting new or targeted malware."
The importance of computer identity in network communications: how to protect it
and prevent its theft
10.12.2020
Safety
Securityaffairs
The importance of computer identity in network communications: how to protect it
and prevent threat actors from spying or stealing on online communications
When you fill out a registration form to take advantage of a web service, a
virtual personal profile is generated, creating your own IT identity
characterized by specific attributes.
Even those who must manage and provide this service must have their own digital identity. In this way, an interaction between the virtual identities of the customer and the supplier is established.
The service management system, before granting the interlocutor access to the resources, will have to start an identification process to verify the correspondence of the specific identity attributes in compliance with the fundamental protection parameters for IT security: confidentiality and integrity of information, interlocutors authentication and authorization of access to relevant resources.
The confidentiality of information in internet communications
Internet communications use the protocol called TCP/IP (Transmission Control Protocol/Internet Protocol), which allows information to be transmitted from one computer to another through a series of intermediate computers and networks.
Without measures of prevention, a stranger to computer communications could interfere through “man in the middle” type interceptions.
In this regard, the HTTPS protocol has been implemented from the very beginning in an attempt to avert this threat, not completely eradicated, through public key cryptography techniques.
The most common algorithms are those patented by RSA Data Security: This algorithm, also called asymmetric key cryptography, provides a pair of keys (a public and private key) associated with an entity that authenticates the identity of the key itself.
Cryptography alone, while solving the problem of confidentiality violation, cannot solve the problem of integrity and false authentication.
The hash function
Hash encryption is used to ensure integrity and authentication. The hash functions are implemented according to the following features:
the value returned by the function is unique for each input data and represents
a summary of the data itself;
each variation of the data results in a
different hash value;
the returned hash value cannot be deducted from the
function itself.
The digital signature is basically based on the use of a
hash algorithm.
In a tipical network correspondence, the elements sent to the recipient are the original document in clear text and the hash value of the original document, encrypted with the private key of the signatory (digital signature). To verify the integrity of the information, the receiving software, decrypts the digital signature with the signatory’s public key, obtains the hash value of the signatory and generates with the same algorithm a new hash from the original document received. Two different hash values indicate that the information has been altered or the digital signature has been created with a private key that does not match the signer’s public key.
Mutual authentication of interlocutors
When perform authentication in a network communication where a client (e.g. a browser) dialogues with the various remote servers providing services, it is very important the mutual authentication between the user and the service provider. There are several ways to do this:
use of simple credentials. The classic method for authentication is based on the
use of a pair of username and password credentials. In this case, the
communication protocol will verify their correspondence with those present in
its database and if so, it will authorize access;
use of public-key digital
certificates. Another authentication method is the one with the digital
certificate, used by the secure protocol HTTPS. In the recognition process the
server will require authentication of the client according to a communication
protocol based on an exchange of public and private keys that, if they attest to
the identity of the client, ends with the access authorization to the requested
resource;
use multi-factor authentication. An authentication with two or more
factors is therefore opposed to a simple authentication based on a password only
(one-factor authentication). The forms of multi-factor authentication use a
combination of methodologies defined in this way:
one thing you know: a
password;
something you have: a physical object (e.g. a smart card, token
USB);
something you are: a biometric feature (e.g. a fingerprint, facial
features).
Critical issues about different authentication modes
By comparing these authentication modes you can see that:
the classic approach using a pair of credentials is vulnerable especially
because data could be accessed using techniques such as SQL injection, phishing
and social engineering;
The certificate approach is vulnerable because the
certificate may not be verified and reliable. Also, because data protection
before and after encryption cannot be guaranteed, if clients and communication
servers have already been compromised with malware, integrity and
confidentiality may still be at risk;
the multi-factor authentication system,
while strengthening the degree of security, with greater economic effort and
increased complexity for the service provider only makes life more difficult for
criminal hackers, but not impossible. They will only have to overcome multiple
levels of protection.
The final step
The next step in verifying the identity and computer authentication of a user is the authorization through which the computer system specifies the access privileges to resources, deciding whether to approve or reject requests.
Conclusions
Defending and protecting your information assets and your digital reputation must therefore be a key point to better manage every business activity, taking all necessary actions:
train and educate companies to know the risks and techniques used to steal
information and violate the IT identity;
use secure and proven payment
methods with customers;
adopt digital signature and encryption systems for
communications;
protect the hardware, software and human components of the
information system;
provide a strategy for the safekeeping and backup of
information capital.
About the author: Salvatore Lombardo
IT officer, ICT expert, Clusit member
Microsoft Releases Out-of-Band Update for Kerberos Authentication Issues
24.11.20
Safety
Securityweek
Microsoft last week released an out-of-band update for Windows to address authentication issues related to a recently patched Kerberos vulnerability.
The issue is related to the PerformTicketSignature registry subkey value in CVE-2020-17049, a security feature bypass bug in Kerberos Key Distribution Center (KDC) that Microsoft fixed on November 2020 Patch Tuesday.
CVE-2020-17049, the tech company explains in an advisory, resides in the manner in which KDC determines whether tickets are eligible for delegation via Kerberos Constrained Delegation (KCD).
“To exploit the vulnerability, a compromised service that is configured to use KCD could tamper with a service ticket that is not valid for delegation to force the KDC to accept it. The update addresses this vulnerability by changing how the KDC validates service tickets used with KCD,” Microsoft notes.
Last week, the company revealed that it identified a series of issues that could occur on writable and read-only domain controllers (DC), namely tickets not being renewed for non-Windows Kerberos clients and S4UProxy delegation failing when PerformTicketSignature is set to 1 (the default), and services failing for all clients when PerformTicketSignature is set to 0.
“An out-of-band optional update is now available on the Microsoft Update Catalog to address a known issue affecting Kerberos authentication. As part of this issue, ticket renewal and other tasks, such as scheduled tasks and clustering, might fail. This issue only affects Windows Servers, and Windows 10 devices and applications in enterprise environments,” Microsoft explains.
The company recommends that only impacted organizations install the out-of-band update on their domain controllers. Furthermore, Microsoft warns that there are some issues that enterprises should be aware of when installing the update, related to the Microsoft Input Method Editor (IME) for Japanese or Chinese languages.
In a post last week, Microsoft Japan provided a series of recommendations on the steps that admins should take to address such issues, in addition to deploying the update to all of the DCs and RODCs (Read-Only Domain Controllers) in the environment.
AWS Network Firewall Now Generally Available
18.11.20
Safety
Securityweek
Amazon Web Services (AWS) on Tuesday announced the general availability of AWS Network Firewall, a managed security service designed to help customers protect their virtual networks.
AWS Network Firewall can easily be enabled from the AWS Console for specified virtual private cloud (VPC) environments, and the company says there are no extra charges for users — customers pay for the service based on hours deployed and gigabytes processed.
The service allows users to import existing rules from AWS security partners, including Fortinet, CrowdStrike, Trend Micro and Alert Logic. Other companies that have built integrations with the new service include Check Point, Accenture, Rackspace, Splunk, SumoLogic, Tufin, IBM and Palo Alto Networks.
Customers can configure the service to automatically send data to S3, Cloudwatch and Kinesis Data Firehose for more visibility and auditing purposes.
AWS noted that the Network Firewall service allows customers to deploy granular network protections without the need to manage additional infrastructure. Protections include dynamic packet filtering, web filtering, as well as intrusion prevention and detection.
AWS Network Firewall is currently available in the US East (N. Virginia), US West (Oregon), and Europe (Dublin) regions, but the cloud giant has promised to expand it to other regions as well in the upcoming period.
“When we talk to customers about what they want in a cloud network firewall they tell us that they want network protections that work with their existing security systems and without the headache of managing the underlying infrastructure,” said Steve Schmidt, the CISO of AWS. “AWS Network Firewall provides scalable network protections that allow customers to deploy highly customizable rules for their entire AWS infrastructure, and integrates with many of the APN partner services that customers already use. Best of all, there’s no need to configure or maintain additional infrastructure.”
Microsoft Unveils 'Pluton' Security Processor for PCs
18.11.20
Safety
Securityweek
Microsoft on Tuesday unveiled Pluton, a new security chip for Windows PCs that the tech giant will deliver through partnerships with Intel, AMD and Qualcomm.
Microsoft says its goal is to build security into the CPU in an effort to more tightly integrate hardware and software security and ultimately eliminate entire attack vectors. The technology that powers Pluton, which the company has described as “chip-to-cloud security technology,” has already been used in Xbox and the Azure Sphere IoT security solution, and Microsoft now wants to bring it to Windows PCs.
PCs currently use the Trusted Platform Module (TPM) to store encryption keys and data needed to ensure the integrity of the system, but this data is still exposed to attacks while passing through the communication channel between the TPM and the CPU, particularly if the attacker has physical access to the targeted system.
Pluton aims to address this by storing encryption keys and other sensitive data within the processor, thus eliminating the exposure of that communication channel and providing protection against speculative execution and other types of attacks.
“Windows PCs using the Pluton architecture will first emulate a TPM that works with the existing TPM specifications and APIs which will allow customers to immediately benefit from enhanced security for Windows features that rely on TPMs like BitLocker and System Guard,” Microsoft explained. “Windows devices with Pluton will use the Pluton security processor to protect credentials, user identities, encryption keys, and personal data. None of this information can be removed from Pluton even if an attacker has installed malware or has complete physical possession of the PC.”
The technology will be integrated into future CPUs from Intel, AMD and Qualcomm, but it’s unclear when the new processors will become available to end users. Microsoft told SecurityWeek that it’s not sharing any specific information on timing or roadmap at this time.
AMD said the Pluton security processor will be “tightly integrated” into future client CPUs and accelerated processing units (APUs), which will also include AMD’s own security processor.
“[The AMD Security Processor (ASP)] and Microsoft Pluton help protect users’ confidential and personal data whether they are on the move or connected to a business network, even if their laptop has been lost or stolen,” AMD said. “The integrated design provides improved protection against attackers attempting to hide malicious code in the system or trying to steal credentials or encryption keys using sophisticated physical attacks.”
Google Announces New VPN for Google One Customers
31.10.20
Safety
Securityweek
Google
announced on Thursday that Google One customers can now use a new virtual
private network (VPN) service that will provide them an extra layer of
protection when they go online.
Google One is a subscription-based cloud storage and backup service. The new VPN by Google One is available to customers who have subscribed to a 2 TB plan or higher. The 2 TB plan costs $9.99 per month or $99.99 per year.VPN by Google One
The VPN service will initially only be available in the United States on Android — it will be rolled out over the next weeks and it can be enabled from the Google One app.
However, Google says it plans on expanding it to more countries and operating systems — including Windows, macOS and iOS — in the coming months.
“We already build advanced security into all our products, and the VPN extends that security to encrypt all of your phone’s online traffic, no matter what app or browser you’re using,” said Larissa Fontaine, director of Google One. “The VPN is built into the Google One app, so with just one tap, you can rest assured knowing your connection is safe from hackers.”
Google has also released a whitepaper with some technical details on its new VPN, as well as the source code for the client library to allow users and experts to check how it handles data.
The company says the VPN does not log user activity or data that could reveal personally identifiable information. This includes network traffic, IP address, connection timestamp, or the bandwidth used.
“We will have external security experts audit VPN by Google One end to end, including the server-side implementation, and publish a report on our VPN privacy protections,” Google said in its whitepaper.
While the VPN offer might seem attractive to some users, security experts are not convinced that Google will not use any data for its own benefit.
“A VPN by one of the largest data collection companies in the world is a scary thought,” Joseph Carson, chief security scientist and Advisory CISO at PAM solutions provider Thycotic, told SecurityWeek. “This initially makes me think that it is not exactly a VPN product which is meant to be a virtual private network which typically means that no one can see your data requests. This might be more of a No One Else But Us (NOEBU) will get your data. When products advertise themselves as a VPN, it must be absolutely clear about who it protects against and also whom it is giving access to your entire data communications history to. I hope that this is truly a security motive to make people safe from cybercrime and not one to try and get more data under the disguise of a security solution.”
Dirk Schrader, global VP at New Net Technologies (NNT), a provider of IT security and compliance software, commented, “The Google VPN service is nothing more than a bloated ‘security feature’. It encrypts the last mile, however, that doesn’t solve the issue with these apps that are using weak encryption or no encryption at all. It simply moves the point where the data will be unprotected to a different place, the tunnel end of Google’s side.
“This VPN feature might make it more difficult to conduct Wi-Fi attacks, but not much more. When Google states that the VPN will hide the user’s location to prevent third parties from tracking them, what is the use of this protection if Google sells the collected data to the exact same third party? Google should use its powers and knowledge to help these app developers apply stronger encryption, instead of deviating from the real problem.”
Microsoft Defender ATP Users Get False Positive Alerts for Mimikatz, Cobalt
Strike
29.10.20
Safety
Securityweek
Microsoft rushed to take action on Wednesday after Defender Advanced Threat Protection (ATP) users reported getting Cobalt Strike and Mimikatz alerts that turned out to be false positives.
Cobalt Strike is a commercial penetration testing tool. However, it has often been abused by malicious actors for its advanced capabilities, including in Ryuk, Sodinokibi and other ransomware attacks.
Mimikatz is a post-exploitation tool designed for harvesting passwords from compromised systems. It too has been used by many profit-driven and state-sponsored threat groups.
It’s not surprising that some Microsoft Defender ATP users had a small heart attack on Wednesday when they saw multiple high-severity alerts for Cobalt Strike. Others reported seeing Mimikatz alerts. In both cases they turned out to be false positives.
The issue was likely caused by a bad rule pushed to Defender ATP and Microsoft addressed the issue within hours.
“We’ve addressed the issue that led to false positive alerts and corrected notifications some customers may have received,” a Microsoft spokesperson told SecurityWeek.
However, Jon Hencinski, director of SecOps at cybersecurity company Expel and one of the people who monitored the incident, advised organizations not to immediately dismiss Cobalt Strike alerts in Defender ATP and instead follow their triage process as normal.
Microsoft Introduces New Password Spray Detection for Azure
27.10.20
Safety
Securityweek
Microsoft this week announced the availability of a new password spray detection for Azure AD Identity Protection customers.
Password spraying represents one of the most common forms of attack, where threat actors attempt to breach organizations by trying common passwords against multiple accounts. According to Microsoft, one-third of account compromises are the result of such an attack.
“Instead of trying many passwords against one user, they try to defeat lockout and detection by trying many users against one password. Effective forms of this attack are ‘low and slow,’ where the bad actor uses thousands of IP addresses (such as from a botnet) to attack many tenants with a few common passwords,” the tech giant explains.
With one or two attempts per day, which fall within the normal login patterns, such attacks typically go undetected and traditional protections such as password lockout and IP blocking are bypassed too.
According to Microsoft, password spray attacks yield a 1% success rate, but only if the targeted accounts don’t use password protection.
A look at such attacks across Azure Active Directory (AD) tenants around the world can reveal the patterns of a password spray: the attempts that use the same password generate the same hash, making them traceable.
“The huge elevation of a single hash failing across many accounts indicates a single password being attempted against hundreds of thousands of usernames from many tenants—a password spray attack in progress,” Microsoft explains.
Using this approach, the tech company came up with a heuristic detection for password spray, which allowed it to warn tenants “of hundreds of thousands of attacks monthly.” Based on this, the company built a new tool for password spray risk detection.
The new detection can identify twice as many compromised accounts compared to the previous heuristic algorithm, but maintains a 98% precision. The new risk detection is being introduced in the Azure AD Identity Protection portal and APIs for Identity Protection.
Microsoft, MITRE Release Adversarial Machine Learning Threat Matrix
24.10.20
Safety
Securityweek
Microsoft and
MITRE, in collaboration with a dozen other organizations, have developed a
framework designed to help identify, respond to, and remediate attacks targeting
machine learning (ML) systems.
Such attacks, Microsoft says, have increased significantly over the past four years, and are expected to continue evolving. Despite that, however, organizations have yet to come to terms with adversarial machine learning, Microsoft says.
In fact, a recent survey conducted by the tech giant among 28 organizations has revealed that most of them (25) don’t have the necessary tools to secure machine learning systems and are explicitly looking for guidance.
“We found that preparation is not just limited to smaller organizations. We spoke to Fortune 500 companies, governments, non-profits, and small and mid-sized organizations,” Microsoft says.
The Adversarial ML Threat Matrix, which Microsoft has released in collaboration with MITRE, IBM, NVIDIA, Airbus, Bosch, Deep Instinct, Two Six Labs, Cardiff University, the University of Toronto, PricewaterhouseCoopers, the Software Engineering Institute at Carnegie Mellon University, and the Berryville Institute of Machine Learning, is an industry-focused open framework that aims to address this issue.
The framework provides information on the techniques employed by adversaries when targeting ML systems and is primarily aimed at security analysts. Structured like the ATT&CK framework, the Adversarial ML Threat Matrix is based on observed attacks that have been vetted as effective against production ML systems.
Attacks targeting these systems are possible because of inherent limitations underlying ML algorithms and require a new approach to security and a shift in how cyber adversary behavior is modelled, to ensure the accurate reflection of emerging threat vectors, as well as the fast evolving adversarial machine learning attack lifecycle.
“MITRE has deep experience with technically complex multi-stakeholder problems. […] To succeed, we know we need to bring the experience of a community of analysts sharing real threat data and improving defenses. And for that to work, all the organizations and analysts involved need to be assured they have a trustworthy, neutral party who can aggregate these real-world incidents and maintain a level of privacy—and they have that in MITRE,” Charles Clancy, senior vice president and general manager of MITRE Labs, said.
The newly released framework is a first attempt at creating a knowledge base on the manner in which ML systems can be attacked and the partnering companies will modify it with input received from the security and machine learning community. Thus, the industry is encouraged to help fill the gaps, and to participate in discussions in this Google Group.
“This effort is aimed at security analysts and the broader security community: the matrix and the case studies are meant to help in strategizing protection and detection; the framework seeds attacks on ML systems, so that they can carefully carry out similar exercises in their organizations and validate the monitoring strategies,” Microsoft explains.
Zoom Announces Technical Preview of End-to-End Encryption
15.10.20
Safety
Securityweek
Video conferencing platform Zoom next week will start rolling out end-to-end encryption (E2EE) in technical preview.
The company revealed plans to provide users with end-to-end encryption in May, and announced in June that it would make the feature available to all users, although it was initially planning on leaving free users out.
Now, the company has reinforced the fact that both free and paid users will be offered encryption, and that they will be able to host E2EE meetings with up to 200 participants, thus benefiting from increased privacy and security.
“We’re excited to announce that starting next week, Zoom’s end-to-end encryption (E2EE) offering will be available as a technical preview, which means we’re proactively soliciting feedback from users for the first 30 days,” the company said earlier this week.
This, Zoom says, is only the first phase of its four-phase rollout plan, which is aimed at providing robust protections “to help prevent the interception of decryption keys that could be used to monitor meeting content.”
With E2EE, Zoom says, users will take advantage of the same encryption already available in Zoom meetings, with the main difference being where the encryption keys are stored. Typically, these keys are generated in Zoom cloud and distributed to meeting participants, but with Zoom E2EE, the keys are generated and distributed by the meeting’s host.
With these keys being distributed using public key cryptography, Zoom’s servers never see the encryption keys that are used to decrypt the meeting contents.
Zoom users will need to enable encrypted meetings at the account level and also opt-in to the new feature on a per-meeting basis.
The company also explains that enabling E2EE disables certain features in Zoom, such as 1:1 private chat, Breakout Rooms, cloud recording, join before host, live transcription, streaming, polling, and meeting reactions.
When end-to-end encryption is enabled, participants in a Zoom meeting will see a green shield logo with a padlock in the middle in the upper left corner of the screen. The symbol is similar to that of the GCM encryption, but features a lock instead of a checkmark.
“Participants will also see the meeting leader’s security code that they can use to verify the secure connection. The host can read this code out loud, and all participants can check that their clients display the same code,” Zoom says.
Phase two of the E2EE rollout is planned for 2021 and will include better identity management and E2EE SSO integration.
“End-to-end encryption is another stride toward making Zoom the most secure communications platform in the world. This phase of our E2EE offering provides the same security as existing end-to-end-encrypted messaging platforms, but with the video quality and scale that has made Zoom the communications solution of choice for hundreds of millions of people and the world’s largest enterprises,” said Zoom CEO Eric S. Yuan.
Intel Adds Memory Encryption, Firmware Security to Ice Lake Chips
15.10.20
Safety
Threatpost
Intel’s addition of
memory encryption to its upcoming 3rd generation Xeon Scalable processors
matches AMD’s Secure Memory Encryption (SME) feature.
Intel’s third-generation Xeon Scalable server processors, code-named Ice Lake, will be rolled out with new security upgrades that the chip giant claims will better protect devices from firmware attacks.
The upcoming chips are based on Ice Lake, Intel’s 10nm CPU microarchitecture, which was first launched in 2019. Intel is targeting initial production shipments for its Xeon scalable processors for servers at the end of the year – but just announced that they will come with new security features.
One such feature is called Intel Total Memory Encryption (Intel TME), which Intel said helps ensure that all memory accessed from the CPU is encrypted – such as customer credentials, encryption keys and other IP or personal information on the external memory bus.
“Intel developed this feature to provide greater protection for system memory against hardware attacks, such as removing and reading the dual in-line memory module (DIMM) after spraying it with liquid nitrogen or installing purpose-built attack hardware,” according to Intel on Wednesday.
Of note, this feature already exists in other competing chip platforms, with AMD first proposing its own version, Secure Memory Encryption (SME), back in 2016.
Intel TME utilizes the storage encryption standard, AES XTS, from the National Institute of Standards and Technology (NIST). Intel said an encryption key is generated using a hardened random number generator in the processor without exposure to software, allowing existing software to run unmodified while better protecting memory.
Intel also claims that another new feature can protect against sophisticated adversaries who may attempt to compromise or disable the platform’s firmware to intercept data or take down the server. The Intel Platform Firmware Resilience (Intel PFR) will be part of the Xeon Scalable platform, which Intel claims will help protect against platform firmware attacks by detecting them before they can compromise or disable the machine.
Intel PFR will use an Intel field-programmable gate array (FPGA) as a “platform root of trust,” which will validate critical-to-boot platform firmware components before any firmware code is executed, according to Intel. An Intel FPGA is an integrated circuit designed to be configured by a customer or a designer after manufacturing.
The firmware components protected “can include BIOS Flash, BMC Flash, SPI Descriptor, Intel Management Engine and power supply firmware.”
The chip giant is also bringing its existing Intel Software Guard Extensions (SGX) feature to Ice Lake. Intel SGX, a set of security-related instruction codes that are built into Intel CPUs, shields sensitive data – such as AES encryption keys – inside “enclaves,” which are physically separate from other CPU memory and are protected by software encryption.
Of note, Intel SGX is not an end-all-be-all solution – researchers have previously been able to bypass SGX in various attacks, from the Plundervolt security issue revealed in 2019 to speculative execution design flaws in Intel CPUs revealed in 2018.
The new security features come as Intel processors have been plagued by various security issues over the past years – including Meltdown and Spectre as well as other speculative execution and side-channel attacks.
Juniper Launches Adaptive Threat Profiling, New VPN Features
8.10.20
Safety
Securityweek
Juniper Networks has introduced three new capabilities to improve network visibility, access control and VPN-based remote working.
The three new features provide adaptive threat profiling for Juniper's ATP Cloud, the integration of WootCloud HyperContext for device profiling, and Secure Connect VPN for remote working beyond the branch office. The purpose is to improve network visibility and provide consistent policy enforcement across all connected devices.
Juniper Networks logoSamantha Madrid, VP of security business and strategy at Juniper Networks, sees security's primary problem as one of visibility. "As a security industry," she told SecurityWeek, "we have being doing a phenomenal job in understanding threats, and how threats take shape in networks -- we've been great about ensuring the collective understanding of those threats. But one of the things I don't think we have really scratched the surface on has been about how do we secure the network by providing customers with the visibility that allows them to not only understand their overall risk profile but also gives them the visibility to make any necessary changes -- whether through technology, policy or whatever -- so that they're coming from a vantage point of knowledge versus reaction." The new additions to the Juniper portfolio are designed to provide that visibility and control by bringing security to every point of connection and allowing CISOs to know who and what is on the network.
Adaptive Threat Profiling makes use of Juniper's SRX series firewalls to act as sensors throughout the network. The result is a series of security intelligence feeds populated by data on potential intrusions. The intelligence can be shared with in-line devices that can enforce policy automatically in real time and at scale. "All of our firewalls," explains Madrid, "through our ATP Cloud, have the ability to assess, in real time, changes to the environment, and can customize threat intelligence and distribute it not just to the firewalls, but to all the networking devices. As changes occur, whether that's a new device or a new threat, we can automatically adapt to those changes with network-specific intelligence." This is particularly relevant at a time when adversaries are customizing their attacks to specific targets. As soon as a targeted attack is recognized anywhere on the network, information on that threat is distributed to every Juniper device on the network, and the relevant response can be taken.
The WootCloud HyperContext integration provides visibility of all IoT connected devices, and their susceptibility to compromise. "Network visibility is an important issue that security teams have struggled with," explains Madrid in an associated blog. "With each new connection, risk increases -- especially when it comes to IoT devices. Not all connected devices can run secure operating systems, be patched or run endpoint agents."
WootCloud is a company that provides agent-less device-focused segmentation, access control and threat response across the network. The system will automatically detect IoT devices and place them in separate VLANs to inhibit the propagation of any compromise. This segmentation can be used to enforce secondary authentication and limit access to high risk devices. "This allows us," said Madrid, "to see any device that comes on the network, that is an internet-based device. So, think of soda machines, a casino slot machine, any internet connected IoT device -- anything that has internet connectivity can be seen and risk assessed through behavioral analytics." Policy can then automatically take action against any device that is indicating new or unacceptable risk. Segmentation can be used to effectively remove that device from the network. The point at which automated response is taken can be left to the baselines provided by the system, or can be modified by users according to their own risk tolerance.
The COVID-19 pandemic has thrown the increasing move to remote working into hyperdrive. The need for secure VPN connection from remote or home devices to the corporate network is not new, but now essential and immediate for more organizations. The new Secure Connect offering, which simply requires the installation of an app on the remote device, supports both IPSEC and SSL-VPN.
The new VPN allows remote users to stay securely connected to the corporate network. Juniper's Mist AI on the network allows organizations to scale quickly and easily, adapting to changes to the network perimeter and attack surface. "This will enable a customer," Madrid told SecurityWeek, "to extend the connected security capabilities and the threat aware network that we introduced two years ago to every user and device no matter where they are."
"We’re extending security," Madrid said, "in ways that turn 'dumb pipes' into intelligent sensors and enforcement points that are able to dynamically optimize protections as attacks are happening. We can provide comprehensive visibility across an organization into who and what is on the network and give our customers the means to limit their risk with minimal impact to their end users."
QNAP urges users to update NAS firmware and app to prevent infections
29.9.20
Safety
Securityaffairs
While the AgeLocker ransomware continues to target QNAP NAS systems, the
Taiwanese vendor urges customers to update the firmware and apps.
Taiwanese
vendor QNAP is urging its customers to update the firmware and apps installed on
their network-attached storage (NAS) devices to prevent AgeLocker ransomware
infections.
The name AgeLocker comes from the use of the Actually Good Encryption (AGE) algorithm to encrypt files, experts warn that encrypted files can’t be recovered without paying the ransom to the ransomware operators.
Security experts are observing the new strain of ransomware that is targeting QNAP devices since June.
Last week, the Taiwanese vendor published a security advisory that provides technical details about the AgeLocker and steps to mitigate threats. The company described two attack scenarios that allow the AgeLocker to gain access to QNAP devices. In the first scenario, the hackers could target the QNAP device firmware (known as QTS), while in the second one the target is represented by a default app that come preinstalled with recent QNAP systems (named PhotoStation).
“Current intelligence pointed out that AgeLocker-affected systems are mostly macOS and Linux devices, and QNAP’s initial investigation showed that no unpatched vulnerabilities are found in QTS. All known affected NAS are running older, unpatched QTS versions.” reads a blog post published by the vendor.
The vendor also confirmed that older versions of the PhotoStation app are affected by known security flaws.
“QNAP Product Security Incident Response Team (PSIRT) has found evidence that the ransomware may attack earlier versions of Photo Station. We are thoroughly investigating the case and will release more information as soon as possible.” the company added in an alert published last week.
Due to the above scenarios, the vendor recommends users to update both QTS and the PhotoStation app.
“Once again, QNAP urges users to periodically check and install product software updates to keep their devices away from malicious influences,” continues the post.
In August, researchers at Qihoo 360’s Network Security Research Lab (360 Netlab) reported that the attackers were exploiting a remote command execution vulnerability due to a command injection issue that resides in the firmware QNAP NAS devices. Hackers were scanning the Internet for vulnerable network-attached storage (NAS) devices running multiple QNAP firmware versions vulnerable to a remote code execution (RCE) vulnerability addressed by the vendor 3 years ago.

In early August, the Taiwanese company urged its users to update the Malware
Remover app to prevent NAS devices from being infected by the QSnatch malware.
The United States Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom’s National Cyber Security Centre (NCSC) also issued a joint advisory about a massive ongoing campaign spreading the QSnatch data-stealing malware.
Earlier this, the company issued another alert to warn its users of a wave of attacks spreading a ransomware strain tracked as eCh0raix.
Kognos Emerges From Stealth With Autonomous XDR Platform
23.9.20
Safety
Securityweek
Kognos emerged from stealth mode on Tuesday with an extended detection and response (XDR) platform that the company says leverages artificial intelligence to enable organizations to more efficiently detect, investigate and respond to attacks.
Kognos’ platform, named Autonomous XDR Investigator, is described as a relationship-centric XDR platform that should significantly simplify investigations into attacker behavior and operations.
The platform generates relationship graphs using data from the organization’s existing solutions, including endpoint detection and response (EDR), network detection and response (NDR), and security information and event management (SIEM) products.
These relationship graphs are analyzed by Kognos’ inquiry engine in an effort to find information on the attacker’s activities. This information is then fed to the platform’s “story generation engine,” which generates a timeline of the attack, enabling a quick response from the security team.
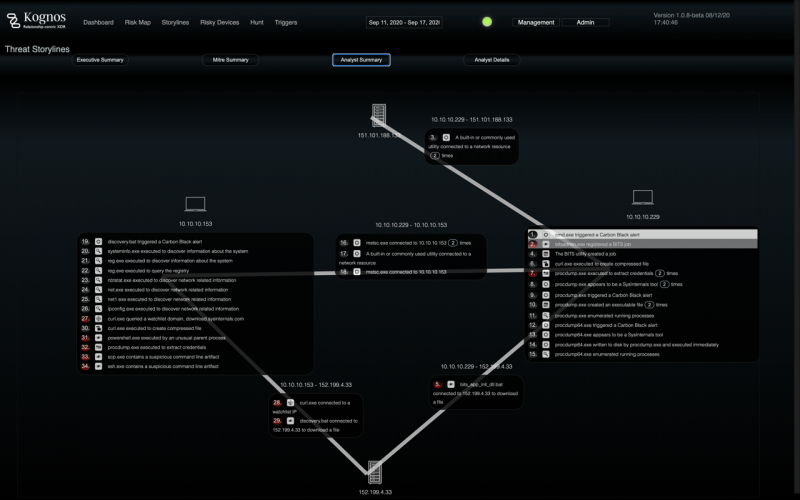
The company claims its platform can help reduce the time needed to investigate malicious activity by automating alert triage, it can help track an attacker’s movement within the network (including their use of living-off-the-land methods), and help identify insider threats.
The platform can be integrated with products from many vendors, including VMware, Crowdstrike, Splunk, RSA, Elastic, AWS, Microsoft (Azure), VirusTotal, and Team Cymru, as well as several free and open source tools.
The company told SecurityWeek that it plans on extending the platform to support additional integrations, and extending the curated Q&A based on new integrations.
One of Kognos’ founders is Rakesh Nair, former head of engineering at Netwitness/RSA, who will serve as the company’s CEO.
“Today’s threat actor lives and thrives within enterprise environments with the ability to freely execute lateral campaigns, live off the environment itself, or offer a prime opportunity for insider threats to siphon information for financial gain,” Nair said. “With Kognos, enterprises can now gain real-time visibility of all of these scenarios as they are happening and act immediately to prevent the ability for attackers to fully execute campaigns.”
Kognos told SecurityWeek that it has raised $1.8 million to date, from Lucas Venture Group, Cyber Mentor Fund and angel investors.
Microsoft Extending Threat Protection Portfolio, Unifying Security Solutions
23.9.20
Safety
Securityweek
Microsoft announced on Tuesday at its Ignite 2020 conference that it has extended its threat protection portfolio and it has unified some of its cybersecurity solutions.
The company says its goal is to provide the “most comprehensive” XDR solution on the market by unifying all XDR technologies under the Microsoft Defender brand. Microsoft Defender includes Microsoft 365 Defender, formerly Microsoft Threat Protection, and Azure Defender, which includes the cloud workload protections in the Azure Security Center.
Azure Defender, which provides XDR capabilities for Azure and hybrid resources, is expected to become the default later this month.
Microsoft says Azure Defender can now protect SQL servers in the cloud and on premises, as well as virtual machines in other clouds, thanks to Azure Act support. As for container security in Azure, the tech giant told customers that its Kubernetes and Container Registry services (now called Azure Defender for Kubernetes and Azure Defender for Container Registries) have received some new features that should provide enhanced protection for containers.
Azure Security Center for IoT is now called Azure Defender for IoT. The solution, powered by technology obtained from the recently acquired industrial cybersecurity firm CyberX, provides agentless protection for devices in OT networks.
“The integration enables continuous IoT/OT asset discovery, vulnerability management and threat monitoring for both greenfield and brownfield devices. Integration with Azure Sentinel, the security information and event manager (SIEM), provides OT-specific SOAR playbooks plus unified security monitoring and governance across both IT and OT networks,” Microsoft explained.
Microsoft Defender now also integrates with Azure Sentinel, the cloud-native SIEM.
Microsoft 365 Defender includes Defender for Endpoint (formerly Defender Advanced Threat Protection), which has been extended to the Android and iOS mobile platforms, providing protection against phishing, proactive scanning of apps and files, breach mitigation, and visibility into mobile threats.
Microsoft Defender for Office 365 is the new name of Office 365 Advanced Threat Protection. Currently in public preview, the solution enables security teams to prioritize the protection of the most targeted individuals in their organization.
Microsoft also announced a new Compliance Manager that “offers a vast library of assessments for expanded regulatory coverage, built-in automation to detect tenant settings and step-by-step guidance for intuitive compliance management.”
The company also revealed that it has partnered with the MilGears program of the U.S. Department of Defense and Trident University for a decentralized identity pilot in which service members will be able to store a verified service record and transcript of completed courses on their phone in a digital wallet.
Also related to identity solutions, Microsoft introduced new connectors and APIs designed to help users protect their identities, services and apps across cloud environments.
Zoom Rolls Out 2FA Support for All Accounts
11.9.20
Safety
Securityweek
Video conferencing platform Zoom this week announced that all user accounts can now benefit from improved protection, courtesy of support for Two-Factor Authentication (2FA).
With 2FA enabled on their accounts, users should be protected from security breaches, including those that originate from the Zoom platform itself, the company claims.
For 2FA, Zoom supports authentication apps that use a Time-Based One-Time Password (TOTP) protocol (such as Google Authenticator, Microsoft Authenticator, and FreeOTP), but can also deliver authentication codes via SMS or phone calls.
2FA, Zoom says, should deliver improved security to all organizations using its platform by reducing the risk of identity theft and breaches, should ensure compliance when the security of sensitive data and customer information is involved, and should reduce costs associated with the use of a Single Sign On (SSO) service.
The new layer of security can prevent bad actors from compromising accounts by simply guessing passwords, and should also make password management an easier task, the video conferencing platform says.
“Zoom offers a range of authentication methods such as SAML, OAuth, and/or password-based authentication, which can be individually enabled or disabled for an account,” the company says.
Account administrators looking to enable 2FA should sign into the Zoom Dashboard, go to the Security section in the Advanced menu, and make sure the “Sign in with Two-Factor Authentication” option is enabled.
Next, they can either enable 2FA for all users in the account, enable it for users with specific roles (they can also select the targeted roles), or enable it for users in specific groups (they need to choose the groups). The last step is to save the 2FA settings.
MITRE Introduces 'Shield' Defense Knowledge Base
26.8.20
Safety
Securityweek
The MITRE Corporation has taken the wraps off a knowledge base of common techniques and tactics that defenders can use to ensure their networks and assets are kept secure.
Called MITRE Shield, the publicly available, free resource is aimed at cyber-experts looking to engage an active cyber defense and, similarly with MITRE ATT&CK, presents a series of active defense concepts.
“Shield was culled from MITRE’s work over the past 10 years observing and engaging adversaries in defense of our own network. It spans the range from big-picture opportunities and objectives that chief information security officers (CISOs) may want to consider to practitioner-friendly tactics, techniques, and procedures,” MITRE explains.
The newly released knowledge base mainly details security techniques for engaging deception and adversaries. With the help of both ATT&CK and MITRE Shield, defenders can create active defense playbooks that would help them address specific adversaries, MITRE says.
According to MITRE, the resource is being developed as both unstructured and structured data, with the initial version focusing on structured elements. MITRE Shield is not complete, but should serve as a starting point for discussion on adversary engagement, active defense, and how defenders can take advantage of them.
“We hope mapping Shield to ATT&CK will be a good addition to the collection of ways ATT&CK can be used. Using them in tandem can help defenders better understand adversary behavior and engagements and suggest ways the defender can mount a more active defense,” says Christina Fowler, MITRE’s chief cyber intelligence strategist.
According to MITRE, the main idea behind releasing Shield is to receive others’ opinions on the work, to expand the knowledge base. The data model will be tweaked in the coming months and additional content is expected to be added as well, the not-for-profit organization reveals.
MITRE also notes that it plans to continuously evolve Shield, and that the project might never actually be completed, as the subject of defense is nearly infinite. However, the knowledge base is expected to help organizations strengthen their active defense solutions.
Zoom Faces More Legal Challenges Over End-to-End Encryption
14.8.20
Safety
Threatpost
The video-conferencing
specialist has yet to roll out full encryption, but it says it’s working on it.
Video-conferencing behemoth Zoom has been hit with yet another lawsuit stemming from its claim to offer end-to-end encryption for sessions.
The suit, filed in a Washington D.C. court [PDF] this week by a nonprofit advocacy group called Consumer Watchdog, alleges that the company falsely told users that it offers full encryption.
Zoom previously said that it offered end-to-end encryption, but that marketing claim came into question after a report from The Intercept said that Zoom’s platform actually uses transport layer security (TLS) encryption, providing only encryption between individual users and service providers instead of encrypting communication directly between the users of a system. That, in theory, would allow the service to access user data if it chose to and leave it open to potential eavesdropping by a determined third-party.
In contrast, end-to-end encryption occurs when traffic is encrypted at the source user’s device, stays encrypted while its routed through servers and then is decrypted only at the destination user’s device.
“Zoom repeated its end-to-end encryption claims throughout its website, in white papers—including in its April 2020 HIPAA Compliance Guide—and on the user interface within the app,” the suit alleges. Thus, the court documents claim that the company violated D.C.’s Consumer Protection Procedures Act (CPPA) and “lulled consumers and businesses into a false sense of security.”
The suit is asking for an injunction against Zoom to prevent it from misrepresenting its security measures to consumers; and statutory damages under the CCPA, which allows fines of up to $1,500 per violation. That could add up quickly, depending on the number of D.C-area consumers the court deems were impacted.
To that point, Zoom use has lived up to the company name. In its fiscal first-quarter earnings call (held in June), executives said that platform use surged 30-fold in April, as COVID-19 lockdowns forced most people to connect with others virtually. Zoom saw a peak of 300 million daily participants in the quarter, and paying customers have more than tripled. As a result, Zoom said it expects full-year revenue to total $1.8 billion for 2020 – which, as an indicator of growth, doubles the sales projections it offered in March.
“While Zoom admittedly used a misleading term and didn’t clarify the extent of their “end-to-end encryption” this lawsuit is not really applicable to those that could benefit from it,” said Mike Weber, vice president at Coalfire, told Threatpost. “Specifically, this lawsuit would only be able to seek damages in the amount of $1,500 per violation, and would only apply to non-business uses of Zoom. But who’s actually making a decision to use Zoom over other solutions due to their “end-to-end encryption” that isn’t doing it for business purposes? Being in security for over 20 years, I can assure you that an overwhelming majority of decisions made by end-users to use Zoom over competing products was surely based on the features and ease-of-use of the platform, and only an exceedingly few ultra-paranoid, extremist, security zealots like myself would have even considered the level of encryption in place.”
Meanwhile, the lawsuit also alleges that Zoom routed some conferences through servers in China, thus placing users at further risk to eavesdropping and privacy violations. The Zoom-China connection has been on the radar screen of the U.S. Senate, with Senators Richard Blumenthal (D-Conn.) and Josh Hawley (R-Mo.) recently asking the Department of Justice to look into it; under that scrutiny, Zoom said that it plans to cut off sales to China starting on August 23.
Other Legal Woes
The popular videoconferencing service also faces multiple
other accusations, including an earlier class-action lawsuit filed by one of its
shareholders in April in the U.S. District Court for the Northern District of
California. It alleges that the company made “materially false and misleading
statements” that overstated its privacy and security measures (including
encryption levels), and it claims that Zoom didn’t adequately disclose its lack
of end-to-end encryption. Additionally, the suit alleges that Zoom has put users
“at an increased risk of having their personal information accessed by
unauthorized parties, including Facebook.”
That’s a reference to the fact that Zoom earlier this year had to kill a feature in its iOS web conferencing app that was sharing analytics data with Facebook. A Motherboard report had disclosed that the transferred information included data on when a user opened the app, a user’s time zone, device OS, device model and carrier, screen size, processor cores and disk space.
Another class action complaint was filed against the company in March, the SEC filed a suit in April, and several attorneys general have raised concerns the company, according to legal-industry media. In all, Zoom has so far been sued at least 42 times this year, with allegations running the gamut from privacy violations to breach of contract to accusations of fraud. That compares with 32 lawsuits total according to DocketAlarm, since its founding in 2011 through 2019.
“The lawsuits filed against Zoom highlight to businesses that in today’s world it’s not just other businesses that are savvy but consumers too,” Brandon Hoffman, CISO at Netenrich, told Threatpost. “Meaning, if you are making claims about privacy and security, a hot topic in today’s world, ensure not only that you are adhering to the most commonly accepted application of the technology but that the technology is actually implemented as described. The industry and the public have a lot of heartburn with security and data protection, warranted or not. Therefore, if a claim is going to be made, it should be 100-percent vetted internally to make sure the way it communicated to the world is in fact reality.”
End-to-End Encryption Progress
Amid the legal hot water, the service is
pursuing the rollout of end-to-end encryption, albeit slowly.
The platform began its rollout in May, starting with the acquisition of a small startup called Keybase; the company also released a design for its end-to-end encryption plans on GitHub, but said that specifics would be to come. It also said at the time that the feature would be opt-in on paid subscriptions only – drawing fire from various security experts. The company later reversed course in its latest published update on the topic, from June, and said that it would offer optional end-to-end encryption for everyone.
That update said that beta testing would start in July.
The company has issued a short, new statement to media this week: “We take privacy and security extremely seriously and are committed to continuous enhancements, including the timely beta testing and implementation of end-to-end encryption.”
Threatpost has reached out for more details on the timing and plans for implementation.
Because video-conferencing platforms have surged as a way to connect since the beginning of the coronavirus pandemic, for both businesses and consumers – they faced greater scrutiny when it comes to security flaws and privacy holes. An open letter published in July by data protection and privacy commissioners from Australia, Canada, Hong Kong, United Kingdom and Switzerland urged Zoom and others to address any issues in a timely fashion.
“During the current pandemic we have observed some worrying reports of security flaws in [videoconferencing] products purportedly leading to unauthorized access to accounts, shared files, and calls,” read the letter.
Google to Run Experiment in Fight Against URL Spoofing in Chrome
14.8.20
Safety
Securityweek
Google announced on Wednesday that it’s preparing to run an experiment in Chrome 86 as part of its fight against URL spoofing.
Malicious actors often manipulate URLs as part of their phishing attacks, social engineering, and scams. Research conducted recently by Google and the University of Illinois at Urbana-Champaign showed that 60 percent of users were tricked when a URL path contained a misleading brand name.
In an effort to prevent URL spoofing, web browser vendors have started testing various methods, such as only displaying the registrable part of the domain — or highlighting it in the address bar — rather than displaying the full URL.
Google is also planning on experimenting with such features. Chrome 86, scheduled for release in October, will only show the domain name by default and the full URL when the user hovers over the address. Alternatively, users will be able to right-click on the URL and select the “Always show full URLs” if they don’t like the new feature.
It’s worth pointing out that random Chrome users will take part in the experiment and enterprise devices will not be included.
However, users who are not included in the experiment but still want to try it out and provide feedback can install the Canary or Dev versions of Chrome and enable certain flags in chrome://flags.
“Our goal is to understand -- through real-world usage -- whether showing URLs this way helps users realize they’re visiting a malicious website, and protects them from phishing and social engineering attacks,” explained the Chrome Security Team.
Zoom to Provide Detailed Info on Upcoming End-to-End Encryption Feature
22.5.2020 Securityweek Safety
Zoom announced this week that on May 22 it will publish a detailed draft of the
cryptographic design it plans on using for its upcoming end-to-end encryption
feature.
As a result of increased scrutiny from privacy and security experts — as well as hackers targeting meetings — Zoom has started making improvements to its platform and it has promised to implement changes and new features that would significantly enhance security and privacy.
After it was pointed out that Zoom is not offering true end-to-end encryption and the encryption that is available isn’t the best, the company has promised to work on providing better encryption.
Zoom plans on rolling out AES 256-bit GCM encryption on May 30, but the company also plans on implementing true end-to-end encryption in the near future, for which it recently acquired secure messaging and file-sharing service Keybase. The new end-to-end encrypted meeting mode will be available to all paid accounts, Zoom said.Zoom end-to-end encryption
“Logged-in users will generate public cryptographic identities that are stored in a repository on Zoom’s network and can be used to establish trust relationships between meeting attendees. An ephemeral per-meeting symmetric key will be generated by the meeting host. This key will be distributed between clients, enveloped with the asymmetric keypairs and rotated when there are significant changes to the list of attendees. The cryptographic secrets will be under the control of the host, and the host’s client software will decide what devices are allowed to receive meeting keys, and thereby join the meeting,” the company explained when it announced the acquisition of Keybase.
Zoom announced this week that a detailed draft of its cryptographic design for end-to-end encryption will be made public on Friday. The draft will not include any code, but the company hopes to get some feedback before the feature is developed.
“We will be hosting discussions with cryptographic experts, customers, advocacy groups, and others to solicit feedback to evaluate for the final design,” Zoom said on Wednesday.
Zoom is also working on revamping its bug bounty program with the help of Luta Security. In the meantime, researchers can report vulnerabilities on zoom.us/security or by sending an email to security(at)zoom.us.
The company also plans on conducting a comprehensive security review and it has hired former Facebook CSO Alex Stamos to help it implement better security controls and practices. It has also created a CISO Council that will advise Zoom CEO Eric Yuan on security.
Integrating a SIEM solution in a large enterprise with disparate global centers
22.5.2020 Net-security Safety
Security Information and Event Management (SIEM) systems combine two critical infosec abilities – information management and event management – to identify outliers and respond with appropriate measures. While information management deals with the collection of security data from across silos in the enterprise (firewalls, antivirus tools, intrusion detection, etc.), event management focuses on incidents that can pose a threat to the system – from benign human errors to malicious code trying to break in.
SIEM solution
Having been in existence for over a decade now, SIEM systems have come a long way: from mere log management to integrating machine learning and analytics for end-to-end threat monitoring, event correlation, and incident response. The modern SIEM system goes way beyond collating data and incidents for security supervisors to monitor – it analyses and responds to threats in real-time, thereby reducing human intervention while also enabling a more holistic approach to information security.
But given the magnitude and complexity of the tasks performed by an SIEM
solution, integrating it into the existing information security architecture of
an enterprise can be daunting, especially when it comes to a large enterprise
with multiple, disparate centers spread across the globe.
Common SIEM
integration mistakes
Cybersecurity is a highly dynamic space and a solution that is effective today
may no longer be viable tomorrow. This is exactly where SIEM integration
pitfalls stem from. Deployments failing and solutions not meeting goals, in the
long run, is a commonly observed problem. And when it comes to a large
enterprise with a global presence, the complexity only compounds further! Here’s
a look at some common mistakes that organizations commit while implementing a
SIEM solution, which can later snowball into major threats.
1. Under-planned
implementation
Despite a widespread awareness that SIEM solutions can be complex in nature, many organizations go about integrating one without initially defining their goals and requirements. Chances of successfully implementing a SIEM solution without proper planning are slim. Evaluating the solution at a later stage or on an ad-hoc basis only piles up the expenses that could easily have been avoided.
Moreover, out-of-the-box SIEM solutions are more generic in nature and cannot
cater to the specific cybersecurity challenges of any organization. This is
another reason why prior planning comes in handy so that there is enough scope
for customizations and third-party integrations before implementation.
2.
Implementing without a predefined scope
Implementing an SIEM solution without defining the scope is akin to building a
house without a foundation. And in the case of a large multinational enterprise,
implementing SIEM solutions without proper scoping is no less than causing mass
destruction. The scope provides the basis for everything that follows –
planning, deployment, implementation, and maturing the SIEM solution with
related capabilities. It will determine the choice of solution, the
architectural requirements, the necessary staffing, and the processes and
procedures.
3. Rooting for the one-solution-fits-all approach
Given the large, almost comprehensive nature of a SIEM tool, it may seem tempting to try and do everything with it at once. While SIEM solutions are capable of collecting, processing and managing large amounts of data, that doesn’t mean it’s a good practice to over-stuff the solution with too many capabilities at once.
Organizations with a global presence are bound to deal with myriad and diverse
use cases, each use case being distinct and requiring a different approach.
Hence, SIEM use cases should be approached in a way that can set up stages of
cycles to make way for continual improvements rather than taking a
one-solution-fits all approach.
4. Monitoring noise
Another common mistake is approaching the SIEM solution as a log management tool, setting it to capture and store all logs from all devices and applications without discrimination, under the impression that this will give a more comprehensive and clearer view. However, instead of reducing the noise, such an exercise actually amplifies it and generates more of it.
What’s more, one can only imagine the chaos it will cause in the case of a large
enterprise with a global presence. Pouring in more hay is pointless when your
purpose is to find a needle in the haystack.
SIEM implementation best
practices
The mistakes can be easily avoided by following a set of best practices for
implementation. Every organization’s implementation will be different, but here
are some steps that a CISO can consider and are crucial to the effective
performance of an SIEM solution post-deployment.
1. Define the project and
scope
The first step to SIEM implementation is planning the scope of the project and its timeline. This entails outlining the scope of the project, including the necessary informational, budgetary, and physical resources. Plus, companies must define their goals and identify all necessary resources in this stage. As a starting point, the CISO must consider setting up basic rules, identifying necessary compliance and policy requirements, and structuring the post-implementation SIEM management.
It is to be noted that SIEM solutions need to be connected to almost everything across the network infrastructure to achieve optimal performance. Therefore, defining log sources is recommended. Here are some basic components that can be included while scoping:
Security control logs:
Intrusion detection and prevention systems (IDPS)
Endpoint protection
software
Data loss prevention (DLP) software
Threat intelligence software
Firewalls
Honeypots
Web filters
Network infrastructure logs:
Routers
Switches
Controllers
Servers
Databases
Internal
applications
Other data points:
Network architecture
Network policy configurations
IT assets
2. Research products
Product research is something that will be unique to each business. However, on a broad level, there are three main informational resources that the CISO can consider before zeroing in on an SIEM.
Vendor analysis: A number of online resources and search engines can help identify the major SIEM vendors. CISOs can then contact the vendors for more information, relating to their specific situation. In addition, CISOs can also consult software analyst firms or deploy empirical testing for vendor analysis. There are many research and testing services providers out there who can generate valuable insights on markets and tools.
Product reviews: As to how product reviews help a CISO decide on an SIEM solution is self-explanatory. Websites can come in handy for CISOs to review and analyze some of the best SIEM tools out there.
Use case assessment: Assessing use cases that will pertain to the business – not
just in the immediate future, but in the long run – is essential to ensuring a
smooth SIEM integration. This step requires CISOs to communicate with the
shortlisted vendors and understand industry-specific scenarios, case studies,
and product demos.
3. Implementation planning
The next step is to outline a number of implementation procedures to ensure a smooth and effective transition. Here are a few components that CISOs should include in their plan:
Design architecture: Making a detailed design architecture helps get a clearer view of the entire implementation. Outlining all data sources related to log sources and data inputs and deploying information collectors to ensure all log sources are connected is a good starting point.
Create rules: It is critical to ensure that correlation engines are functioning with basic policies. Also, determining more customized rules to be implemented in the long term should be taken up in this stage. These rules help optimize documentation and alerting without damaging network performance. They should also be customized to meet any necessary compliance requirements.
Define process: It is advisable to put a handoff plan in place before deployment, to transfer control from the implementation team to security operations or IT management team. Plus, considering the company’s staffing capabilities is crucial to ensuring that teams can seamlessly manage the SIEM; otherwise, it will all be rendered pointless.
In addition to the aforementioned steps, it is a good idea to outline any other
long-term management processes specific to the organization, such as training
the staff to manage and monitor an SIEM system.
4. Deployment and review
As soon as the solution is deployed, it is necessary to take a few immediate actions to ensure smooth functioning going forward:
Ensure data is being collected and encrypted properly
Ensure all activities,
logs and events are stored correctly
Test the system to visualize connected
devices and display to those planned
Ensuring seamless functioning of the SIEM solution
Successfully implementing an SIEM solution is just the beginning. Teams should continue testing and updating the solution against the latest attack. Timely upgrades and customizations are inevitable as the threat landscape and policies keep evolving – it is the only way to keep the number of false positives in check, while also ensuring end-to-end information security to the maximum extent possible.
Google rolls out new Enhanced Safe Browsing security feature
21.5.2020
Bleepingcomputer Safety
Today, Google has announced a new Enhanced Safe Browsing feature that will offer real-time protection against known malicious web sites and downloads.
Since 2007, Google has offered the Safe Browsing feature to protect users from malicious web sites and files that contain malware, display phishing pages, or attempt to install malicious files.
Since its release, numerous browsers, including Google Chrome, Firefox, and Safari, utilize this security feature to protect their users from online threats.
How Safe Browsing works
Google Chrome uses Safe Browsing by downloading lists
of known malicious sites and saving them locally. When a user visits a web site
or downloads a file, Chrome will check the URL against the locally stored Safe
Browsing databases and block it if it is known to be malicious.
When visiting URLs that are contained in the local lists, the browser will send a hashed partial URL fingerprints back to Google to confirm if it is malicious.
If it is, Google will display a warning interstitial, as shown below.
The problem with Safe Browsing is that new malicious websites and downloads are created all the time, and outdated locally stored Safe Browsing lists may miss new threats.
"Safe Browsing’s blocklist API is an existing security protocol that protects billions of devices worldwide. Every day, Safe Browsing discovers thousands of new unsafe sites and adds them to the blocklist API that is shared with the web industry. Chrome checks the URL of each site you visit or file you download against a local list, which is updated approximately every 30 minutes. Increasingly, some sophisticated phishing sites slip through that 30-minute refresh window by switching domains very quickly," Google explained in the announcement.
Enhanced Safe Browsing Protection was developed to fix these shortcomings and strengthen protections.
Enhanced Safe Browsing brings real-time protection
With today's release of
the Enhanced Safe Browsing protection feature, Chrome users will now be able to
get real-time protection when browsing the web and downloading files.
With this feature, when you browse a site or download a file, Chrome will share additional information with Google Safe Browsing so it can check URLs for malicious activity.
The use of this feature, though, does come with a small sacrifice in privacy as "Chrome will also send a small sample of pages and suspicious downloads to help discover new threats against you and other Chrome users."
Furthermore, states that if you are signed into Chrome and are using Enhanced Safe Browsing, the transferred data is linked temporarily to your Google account to detect if an attack if targeting your browser or account.
"If you are signed in to Chrome, this data is temporarily linked to your Google Account. We do this so that when an attack is detected against your browser or account, Safe Browsing can tailor its protections to your situation. In this way, we can provide the most precise protection without unnecessary warnings. After a short period, Safe Browsing anonymizes this data so it is no longer connected to your account," Google stated.
If you are willing to sacrifice some of your browsing data for a short period for better protection, then Enhanced Safe Browsing is an option that you should enable.
With today's release of Chrome 83, users can enable Enhanced Safe Browsing protection by going to chrome://settings/security and selecting it.
This feature is brand new and currently rolling out to Chrome 83 users.
If you are unable to access the chrome://settings/security page, please be patient while the feature is rolled out to everyone.
Antivirus & Multiple Detections
"When a file contains more than one signature, for example EICAR and a real virus, what will the antivirus report?".
I'm paraphrasing a question I've been asked a couple of times.
The answer depends on the sample file and the antivirus.
To illustrate this question, I made a sample file: a ZIP file containing the EICAR antivirus test file and mimikatz.exe.
The EICAR file appears first:
The different antivirus programs I'm familiar with, will report just one detection: EICAR or mimikatz.
Like ClamAV:
Here we can see that ClamAV detects EICAR, and not mimikatz. This is because of performance reasons, ClamAV will stop scanning a file after the first detection. However, ClamAV has an option to make it continue scanning after a match:
Using this option makes that ClamAV reports EICAR and mimikatz:
Do you know antivirus programs with a similar option? Please post a comment!
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
DidierStevensLabs.com
Intel Improves Hardware Shield in New 10th Gen Core vPro Processors
14.5.2020
Securityweek
Safety
Intel on Wednesday announced its new 10th Gen Core vPro processors, which include an enhanced version of Hardware Shield that provides advanced threat detection capabilities.
According to Intel, its new Core vPro processors are designed to provide better performance, built-in security features, and fast and reliable connectivity with integrated Wi-Fi 6.
In terms of security, the new processors include Hardware Shield, a component of the vPro platform that is designed to improve the security of a device by locking down the hardware to protect the BIOS and preventing attackers from compromising the operating system through malicious code injections.vPro processors with Hardware Shield
The Hardware Shield in the latest vPro version brings new threat detection capabilities that leverage the power of the GPU in order to ensure minimal impact on the CPU’s performance.
“Intel Hardware Shield now includes advanced threat detection and extended protection beyond system memory to help improve the detection of advanced threats while reducing false positives and minimizing performance impact,” Intel told SecurityWeek.
The list of security features in Hardware Shield also includes runtime BIOS resilience, trusted execution technology, system security reports, and system resource defenses.
According to Intel, Hardware Shield “helps ensure the OS runs on legitimate hardware, and delivers hardware-to-OS security reporting to enable your OS to enforce a more comprehensive security policy.”
The vPro platform also includes Transparent Supply Chain, which provides a mechanism for confirming that a component is authentic. The chipmaker also announced that systems based on the vPro platform provide hardware support for various security services in Windows 10 Pro and Enterprise.
New Google Authenticator update makes it worth using again
10.5.2020
Bleepingcomputer
Safety
Google has released the first update for Google Authenticator in years and it comes with the long-awaited feature of being able to move 2FA accounts between devices.
When securing online accounts, many sites offer a feature called 2-factor authentication (2FA), or as 2-step verification (2SV), which requires a user to scan a unique QR code on an authentication app.
Once an account is created on the authentication app, it will allow you to generate tokens that are only valid for a short period of time and need to be entered into a site before logging in.
Some authentication apps, such as Authy or Microsoft Authenticator let you register multiple devices or login into an account so that all of the imported 2FA/2SV accounts are synchronized between the devices.
Google Authenticator, though, did not offer this ability, and if you switched to a new device, you would need to go to every site, disable 2FA, reenable it, and then import the 2FA QR code onto the new device.
If you use 2FA on many sites, this is a huge chore and is the main reason I stopped using Google Authenticator and moved to a different authenticator.
Google Authenticator now lets you move accounts to new devices
In its first
update since 2017, Google has released Google Authenticator 5.10, which now
includes the ability to import and export 2FA/2SV accounts between devices.
"Today is World Password Day, and we found it fitting to release an update that'll make it even easier for users to manage Google Authenticator 2-Step Verification (2SV) codes across multiple devices. We are introducing one of the most anticipated features - allowing users to transfer their 2SV secrets, the data used to generate 2SV codes across devices that have Google Authenticator installed. For instance, when upgrading from an old phone to a new phone. This feature has started rolling out and is available in the latest version (5.10) of Google Authenticator on Android," Google announced in a new blog post.
Using this new feature, Google Authenticator users can select the 2SV accounts they wish to export on one device, and a QR code will be generated. The user can then scan this QR code with Google Authenticator on a new device to import the 2SV accounts.
A demonstration of this import/export process can be seen below.
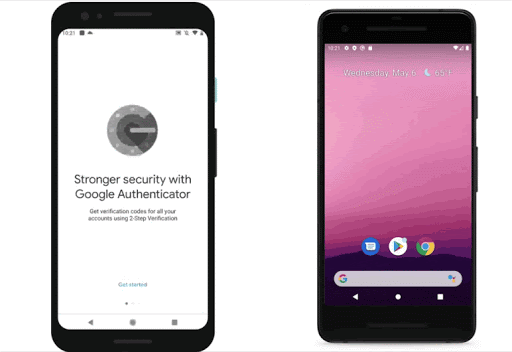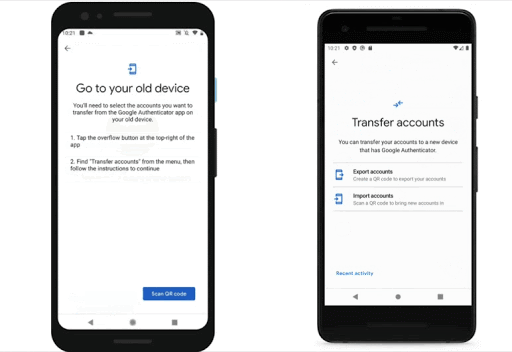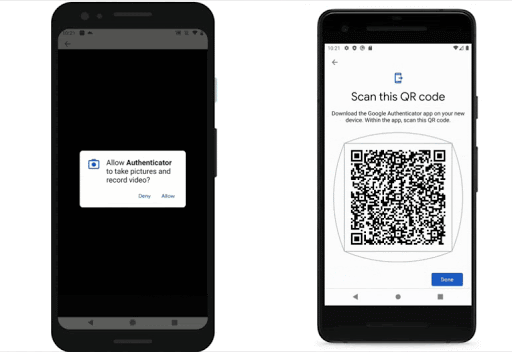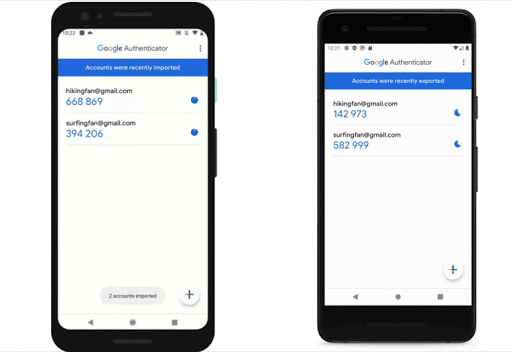
Demonstrating new import and export functionality
I prefer Google's method of
moving 2SV accounts compared to Authy's and Microsoft Authenticator's, which
synchronize your accounts through their servers.
While these accounts may be encrypted and stored securely, I find it more reassuring knowing that my Google Authenticator 2SV accounts are only stored on my mobile devices and not elsewhere.
While this new feature in Google Authenticator is terrific news, the bad news is that it is only available on the Android version of the app.
For iPhone users, you are still stuck on the same version released in 2018, and Google has not stated if an updated version will be released.
BleepingComputer has contacted Google to see if they have plans on releasing an iOS version but had not heard back.