
But once a project has been classified as critical it's expected to retain that designation indefinitely, even if it drops out of the top 1% downloads list.
Safety 2024 2023 2022 2021 2020
PyPI Repository Makes 2FA Security Mandatory for Critical Python Projects
11.7.22 Safety
Thehackernews
The maintainers of
the official third-party software repository for Python have begun imposing a
new two-factor authentication (2FA) condition for projects deemed "critical."
"We've begun rolling out a 2FA requirement: soon, maintainers of critical projects must have 2FA enabled to publish, update, or modify them," Python Package Index (PyPI) said in a tweet last week.
"Any maintainer of a critical project (both 'Maintainers' and 'Owners') are included in the 2FA requirement," it added.
Additionally, the developers of critical projects who have not previously turned on 2FA on PyPi are being offered free hardware security keys from the Google Open Source Security Team.
PyPI, which is run by the Python Software Foundation, houses more than 350,000 projects, of which over 3,500 projects are said to be tagged with a "critical" designation.
According to the repository maintainers, any project accounting for the top 1% of downloads over the prior 6 months is designated as critical, with the determination recalculated on a daily basis.

But once a project has been classified as critical it's expected to retain that
designation indefinitely, even if it drops out of the top 1% downloads list.
The move, which is seen as an attempt to improve the supply chain security of the Python ecosystem, comes in the wake of a number of security incidents targeting open-source repositories in recent months.
Last year, NPM developer accounts were hijacked by bad actors to insert malicious code into popular packages "ua-parser-js," "coa," and "rc," prompting GitHub to tighten the security of the NPM registry by requiring 2FA for maintainers and admins starting in the first quarter of 2022.
"Ensuring that the most widely used projects have these protections against account takeover is one step towards our wider efforts to improve the general security of the Python ecosystem for all PyPI users," PyPi said.
Google Improves Its Password Manager to Boost Security Across All Platforms
2.7.22 Safety
Thehackernews
Google on Thursday announced a slew of improvements to its password manager service aimed at creating a more consistent look and feel across different platforms.
Central to the changes is a "simplified and unified management experience that's
the same in Chrome and Android settings," Ali Sarraf, Google Chrome product
manager, said in a blog post.
The updates are also expected to automatically group multiple passwords for the same sites as well as introduce an option to manually add passwords. Although Google appears to be not ready yet to make Password Manager as a standalone app, users on Android can now add a shortcut to it on the homescreen.
In a related change on iOS, should users opt for Chrome as the default autofill
provider, Password Manager now comes with the ability to generate unique, strong
passwords.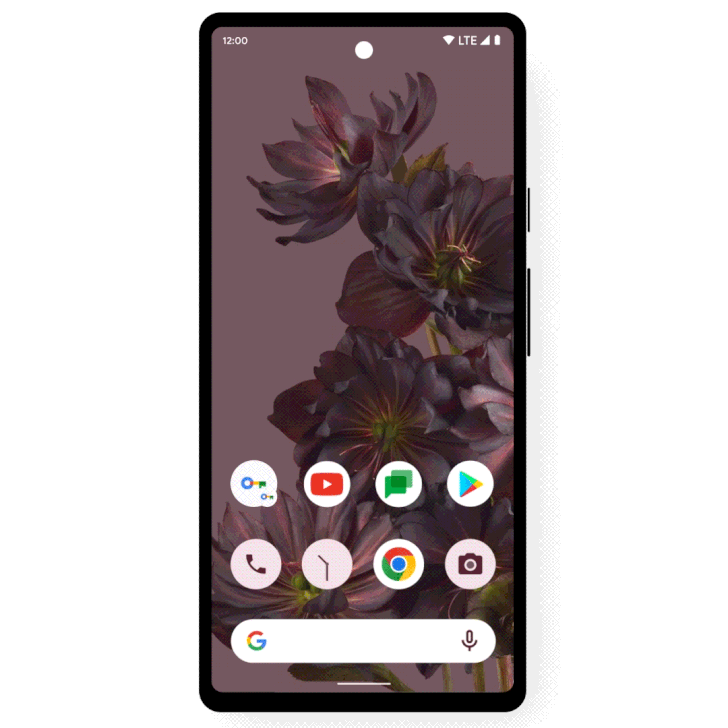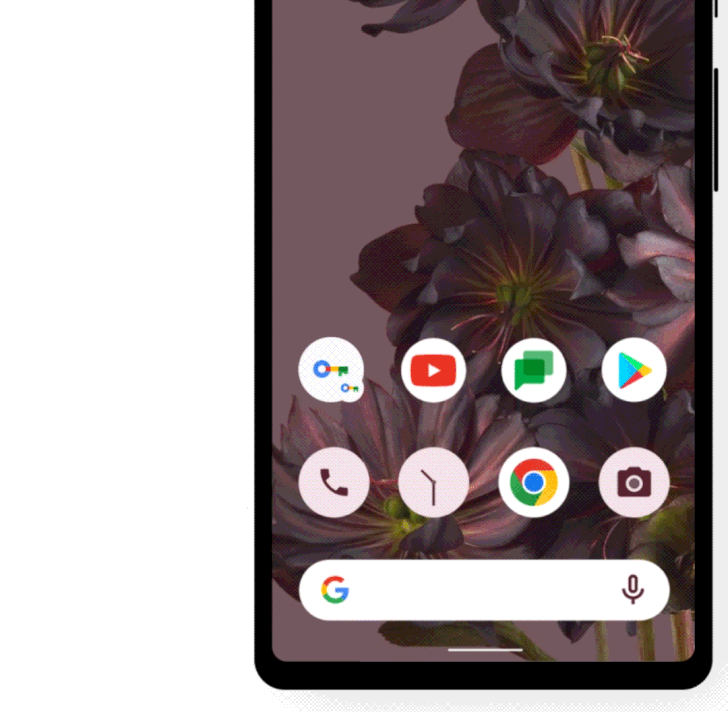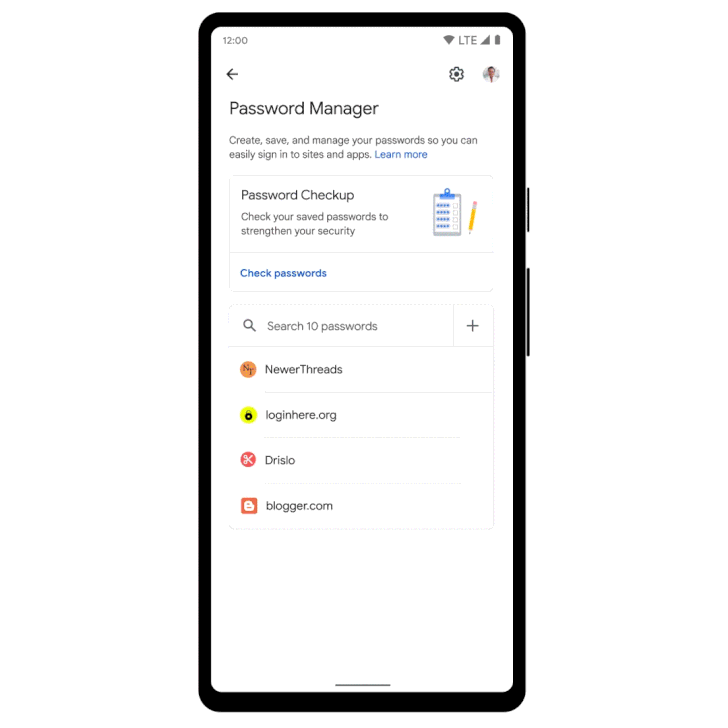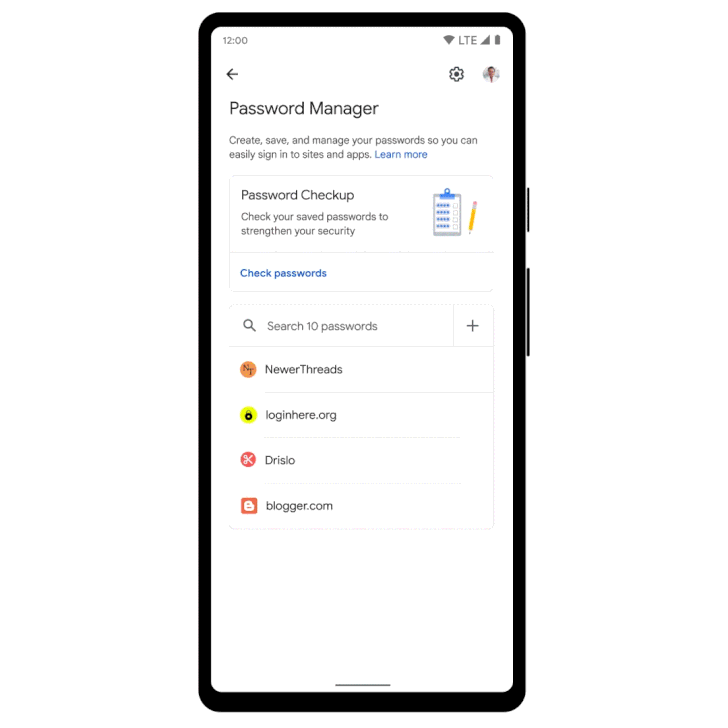
The built-in Password Checkup feature on Android is receiving an upgrade of its own too. Beyond checking for hacked credentials, it can further highlight weak and reused passwords à la Apple iOS. Google is also expanding the compromised password warnings to Chrome users across all operating systems.
Last but not least, Google is bringing a new "Touch-to-Login" to Chrome on Android that allows users to sign in to websites with a single tap after entering the credentials with autofill. It's worth noting that Apple implemented a similar feature in Safari with iOS 12.2.
NIST Releases Updated Cybersecurity Guidance for Managing Supply Chain Risks
7.5.22 Safety Thehackernews
The National Institute of Standards and Technology (NIST) on Thursday released
an updated cybersecurity guidance for managing risks in the supply chain, as it
increasingly emerges as a lucrative attack vector.
"It encourages organizations to consider the vulnerabilities not only of a finished product they are considering using, but also of its components — which may have been developed elsewhere — and the journey those components took to reach their destination," NIST said in a statement.
The new directive outlines major security controls and practices that entities should adopt to identify, assess, and respond to risks at different stages of the supply chain, including the possibility of malicious functionality, flaws in third-party software, insertion of counterfeit hardware, and poor manufacturing and development practices.

The development follows an Executive Order issued by the U.S. President on
"Improving the Nation's Cybersecurity (14028)" last May, requiring government
agencies to take steps to "improve the security and integrity of the software
supply chain, with a priority on addressing critical software."

It also comes as cybersecurity risks in the supply chain have come to the
forefront in recent years, in part compounded by a wave of attacks targeting
widely-used software to breach dozens of downstream vendors all at once.
According to the European Union Agency for Cybersecurity's (ENISA) Threat Landscape for Supply Chain Attacks, 62% of 24 attacks documented from January 2020 to early 2021 were found to "exploit the trust of customers in their supplier."
"Managing the cybersecurity of the supply chain is a need that is here to stay," said NIST's Jon Boyens and one of the publication's authors. "If your agency or organization hasn't started on it, this is a comprehensive tool that can take you from crawl to walk to run, and it can help you do so immediately."
Google's New Safety Section Shows What Data Android Apps Collect About Users
29.4.22 Safety Thehackernews
Google on Tuesday officially began rolling out a new "Data safety" section for
Android apps on the Play Store to highlight the type of data being collected and
shared with third-parties.
"Users want to know for what purpose their data is being collected and whether the developer is sharing user data with third parties," Suzanne Frey, Vice President of product for Android security and privacy, said. "In addition, users want to understand how app developers are securing user data after an app is downloaded."
The transparency measure, which is built along the lines of Apple's "Privacy Nutrition Labels," was first announced by Google nearly a year ago in May 2021.
The Data safety section, which will show up against every app listing on the digital storefront, presents a unified view of what data is being collected, for what purpose it's being used, and how it's handled, while also highlighting what data is being shared with third-parties.
On top of that, the labels can also show an "app's security practices, like encryption of data in transit and whether users can ask for data to be deleted," Frey noted, in addition to validating those practices against security standards such as the Mobile Application Security Verification Standard (MASVS).
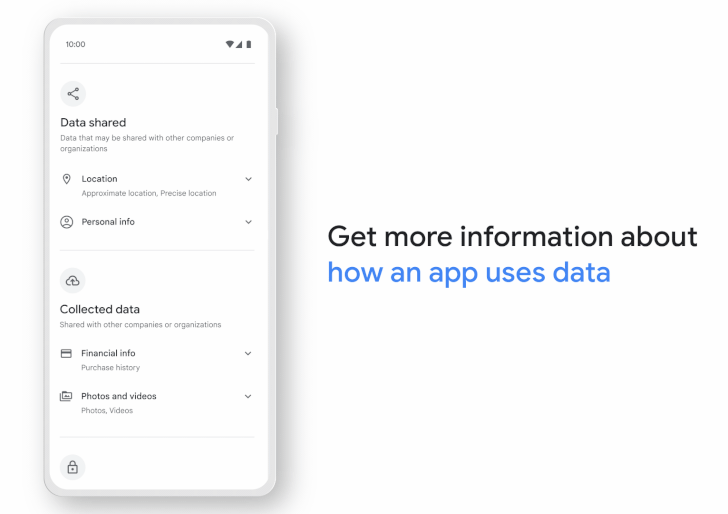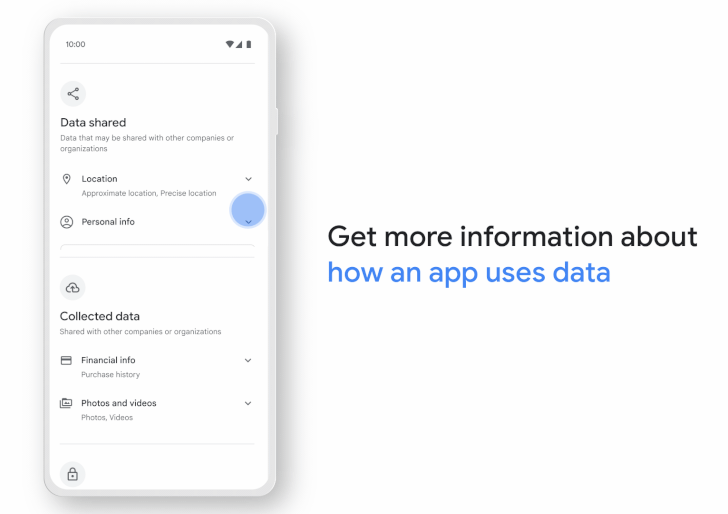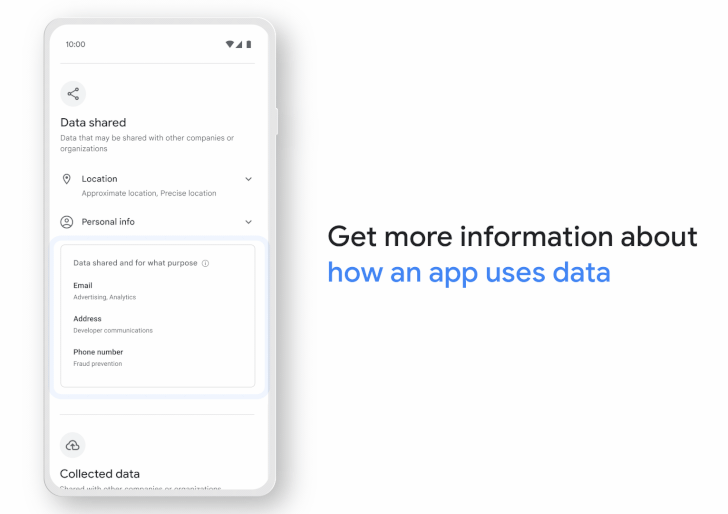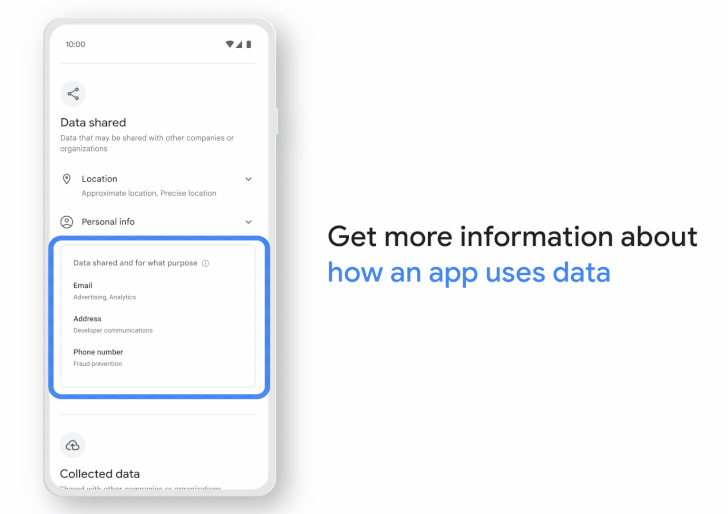
The feature is expected to be gradually made available to all users, while
giving app developers a deadline of July 20, 2022 to complete the section and
keep them updated should they change the apps' functionality or data handling
methods.
That said, Data safety is expected to face similar concerns to that of Apple's in that the system is built entirely on an honor system, which requires app developers to be truthful and clear-cut about what they do with the data, and not list inaccurate labels.
Apple has since said that it would routinely audit labels for accuracy, thereby ensuring that the labels are reliable and don't give users a false sense of security about the data being collected and shared.
Google, last year, had said that it intends to institute a mechanism in place that requires developers to furnish accurate information, and that it will mandate them to fix misrepresentations should it identify instances of policy violations.
While the search giant has explicitly stated that its app review process is not designed to certify the accuracy and completeness of the data safety declarations provided by third-party app developers, it's outlining strong measures to handle such transgressions.
The company is warning that it will be taking suitable enforcement measures when it identifies a deviation from the information provided in the section. Failing to ensure compliance can result in blocked updates or removal from Google Play.
"When Google becomes aware of a discrepancy between your app behavior and your declaration, we may take appropriate action, including enforcement action," the company said in an updated support article.
Researchers Bypass SMS-based Multi-Factor Authentication Protecting Box Accounts
19.1.2022
Safety Thehackernews
Cybersecurity researchers have disclosed details of a now-patched bug in Box's
multi-factor authentication (MFA) mechanism that could be abused to completely
sidestep SMS-based login verification.
"Using this technique, an attacker could use stolen credentials to compromise an organization's Box account and exfiltrate sensitive data without access to the victim's phone," Varonis researchers said in a report shared with The Hacker News.
The cybersecurity company said it reported the issue to the cloud service provider on November 2, 2021, post which fixes were issued by Box.
MFA is an authentication method that relies on a combination of factors such as a password (something only the user knows) and a temporary one-time password aka TOTP (something only the user has) to provide users a second layer of defense against credential stuffing and other account takeover attacks.
This two-step authentication can either involve sending the code as an SMS or alternatively, accessed via an authenticator app or a hardware security key. Thus, when a Box user who is enrolled for SMS verification logs in with a valid username and password, the service sets a session cookie and redirects the user to a page where the TOTP can be entered to gain access to the account.
The bypass identified by Varonis is a consequence of what the researchers called a mixup of MFA modes. It occurs when an attacker signs in with the victim's credentials and abandons the SMS-based authentication in favor of a different process that uses, say, the authenticator app to successfully complete the login simply by furnishing the TOTP associated with their own Box account.
"Box misses that the victim hasn't enrolled [in] an authenticator app, and instead blindly accepts a valid authentication passcode from a totally different account without first checking that it belonged to the user that was logging in," the researchers said. "This made it possible to access the victim's Box account without accessing their phone or notifying the user via SMS."
Put differently, Box not only did not check whether the victim was enrolled in an authenticator app-based verification (or any other method barring SMS), it also did not validate that the code entered is from an authenticator app that's actually linked to the victim who is attempting to log in.
The findings come a little over a month after Varonis disclosed a similar technique that could enable malicious actors to get around authenticator-based verification by "unenroll[ing] a user from MFA after providing a username and password but before providing the second factor."
"The /mfa/unenrollment endpoint did not require the user to be fully authenticated in order to remove a TOTP device from a user's account," the researchers noted in early December 2021.
"MFA is only as good as the developer writing the code [and] can provide a false sense of security," the researchers concluded. "Just because MFA is enabled doesn't necessarily mean an attacker must gain physical access to a victim's device to compromise their account."
Chrome Limits Websites' Direct Access to Private Networks for Security Reasons
19.1.2022
Safety Thehackernews
Google Chrome has announced plans to prohibit public websites from directly accessing endpoints located within private networks as part of an upcoming major security shakeup to prevent intrusions via the browser.
The proposed change is set to be rolled out in two phases consisting of releases Chrome 98 and Chrome 101 scheduled in the coming months via a newly implemented W3C specification called private network access (PNA).
"Chrome will start sending a CORS preflight request ahead of any private network
request for a subresource, which asks for explicit permission from the target
server," Titouan Rigoudy and Eiji Kitamura said. "This preflight request will
carry a new header, Access-Control-Request-Private-Network: true, and the
response to it must carry a corresponding header,
Access-Control-Allow-Private-Network: true."
What this means is that starting with Chrome version 101, any website accessible via the internet will be made to seek explicit permission from the browser before they can access internal network resources. In other words, the new PNA specification adds a provision inside the browser through which websites can request servers gated behind local networks to obtain a connection.
"The specification also extends the Cross-Origin Resource Sharing (CORS) protocol so that websites now have to explicitly request a grant from servers on private networks before being allowed to send arbitrary requests," Rigoudy noted in August 2021, when Google first announced plans to deprecate access to private network endpoints from non-secure websites.
The goal, the researchers said, is to safeguard users from cross-site request forgery (CSRF) attacks targeting routers and other devices on private networks, which enable bad actors to reroute unsuspecting users to malicious domains.
It's not just Chrome. Microsoft's Chromium-based Edge browser has added a new browsing mode to the Beta channel (Version 98.0.1108.23) that aims to bring an added layer of security to mitigate future in-the-wild exploitation of unknown zero-day vulnerabilities.
"This feature is a huge step forward because it lets us mitigate unforeseen active zero days (based on historical trends)," Microsoft said. "When turned on, this feature brings Hardware-enforced Stack Protection, Arbitrary Code Guard (ACG), and Content Flow Guard (CFG) as supporting security mitigations to increase users' security on the web."