Safety 2024 2023 2022 2021 2020
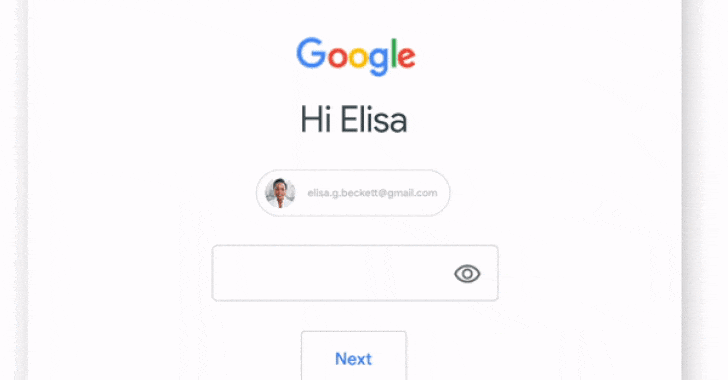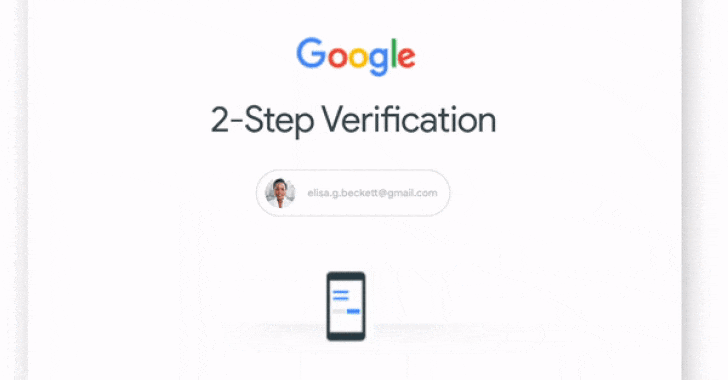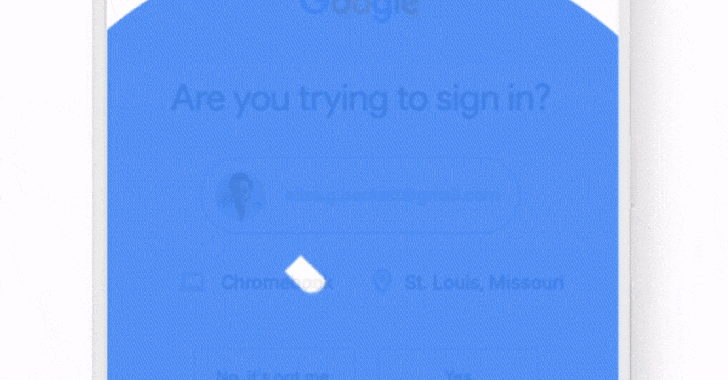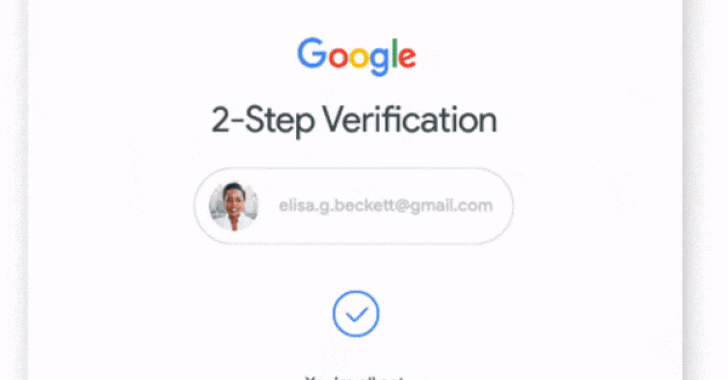
Google to turn on 2-factor authentication by default for 150 million users
9.10.21 Safety
Thehackernews
Google has announced plans to automatically enroll about 150 million users into its two-factor authentication scheme by the end of the year as part of its ongoing efforts to prevent unauthorized access to accounts and improve security.
In addition, the internet giant said it also intends to require 2 million YouTube creators to switch on the setting, which it calls two-step verification (2SV), to protect their channels from potential takeover attacks.
"2SV is strongest when it combines both 'something you know' (like a password) and 'something you have' (like your phone or a security key)," Google's AbdelKarim Mardini and Guemmy Kim said in a post, adding "having a second form of authentication dramatically decreases an attacker's chance of gaining access to an account."
The rollout follows the company's proposals to beef up account sign-ins earlier
this May, when it said it intends to "automatically enrolling users in 2SV if
their accounts are appropriately configured."
In a related security-focused development, Google also said it's planning on adding a feature in its namesake search app that allows users to access all of the passwords saved in Google Password Manager ("passwords.google.com") right from the app's menu, in addition to partnering with organizations to provide free security keys to over 10,000 high-risk users in 2021.
The development comes weeks after Microsoft introduced a passwordless mechanism that enables users to access their accounts without a password by just using Microsoft Authenticator, Windows Hello, a security key, or a verification code sent via SMS or email.
ProtonMail Logs Activist's IP Address With Authorities After Swiss Court Order
10.9.21
Safety
Thehackernews
End-to-end encrypted email service provider ProtonMail has drawn criticism after it ceded to a legal request and shared the IP address of anti-gentrification activists with law enforcement authorities, leading to their arrests in France.
The Switzerland-based company said it received a "legally binding order from the Swiss Federal Department of Justice" related to a collective called Youth for Climate, which it was "obligated to comply with," compelling it to handover the IP address and information related to the type of device used by the group to access the ProtonMail account.
On its website, ProtonMail advertises that: "No personal information is required to create your secure email account. By default, we do not keep any IP logs which can be linked to your anonymous email account. Your privacy comes first."
Despite its no IP logs claims, the company acknowledged that while it's illegal
for the company to abide by requests from non-Swiss law enforcement authorities,
it will be required to do so if Swiss agencies agree to assist foreign services
such as Europol in their investigations.
"There was no possibility to appeal or fight this particular request because an act contrary to Swiss law did in fact take place (and this was also the final determination of the Federal Department of Justice which does a legal review of each case)," the company said in a lengthy response posted on Reddit.
Put simply, ProtonMail will not only have to comply with Swiss government orders, it will be forced to hand over relevant data when individuals use the service to engage in activities that are deemed illegal in the country. This includes monitoring IP addresses from users in "extreme criminal cases," according to its transparency report.
"Proton must comply with Swiss law. As soon as a crime is committed, privacy protections can be suspended and we're required by Swiss law to answer requests from Swiss authorities," ProtonMail founder and CEO Andy Yen tweeted, adding "It's deplorable that legal tools for serious crimes are being used in this way. But by law, [ProtonMail] must comply with Swiss criminal investigations. This is obviously not done by default, but only if legally forced."
If anything, ProtonMail users who are concerned about the visibility of their IP addresses should use a VPN or access the email service over the Tor network for additional anonymity.
"The prosecution in this case seems quite aggressive. Unfortunately, this is a pattern we have increasingly seen in recent years around the world (for example in France where terror laws are inappropriately used)," the company said.
Update
In a blog post titled "Important clarifications regarding arrest of
climate activist," Andy Yen said the company "can be forced to collect
information on accounts belonging to users under Swiss criminal investigation.
This is obviously not done by default, but only if Proton gets a legal order for
a specific account."
Furthermore, in a revision to its privacy policy, ProtonMail now explicitly
spells out that it will be forced to log users' IP addresses if found in
violation of Swiss laws —
"By default, we do not keep permanent IP logs in relation with your use of the Services. However, IP logs may be kept temporarily to combat abuse and fraud, and your IP address may be retained permanently if you are engaged in activities that breach our terms and conditions (spamming, DDoS attacks against our infrastructure, brute force attacks, etc). The legal basis of this processing is our legitimate interest to protect our Services against nefarious activities. If you are breaking Swiss law, ProtonMail can be legally compelled to log your IP address as part of a Swiss criminal investigation."
Note — The headline of the article has been revised to reflect that ProtonMail can enable logging of IP addresses pursuant to Swiss court orders.
Microsoft Defender can now protect servers against ProxyLogon attacks
22.3.2021
Safety
Securityaffairs
Microsoft announced that its Defender Antivirus and System Center Endpoint
Protection now protects users against attacks exploiting Exchange Server
vulnerabilities.
Microsoft announced this week that Defender Antivirus and
System Center Endpoint Protection now provide automatic protection against
attacks exploiting the recently disclosed ProxyLogon vulnerabilities in
Microsoft Exchange.
“Today, we have taken an additional step to further support our customers who are still vulnerable and have not yet implemented the complete security update. With the latest security intelligence update, Microsoft Defender Antivirus and System Center Endpoint Protection will automatically mitigate CVE-2021-26855 on any vulnerable Exchange Server on which it is deployed.” reads the announcement published by Microsoft.

The IT giant early this month released emergency out-of-band security updates
for all supported Microsoft Exchange versions that fix four zero-day flaws, a
week later the company released patches for unsupported Microsoft Exchange
versions.
Microsoft reported that at least one China linked APT group, tracked as HAFNIUM,
chained these vulnerabilities to access on-premises Exchange servers to access
email accounts, and install backdoors to maintain access to victim environments.
Microsoft also updated MSERT to detect web shells used in attacks against
Microsoft Exchange installs, released IOC Detection Tool for Microsoft Exchange
Server flaws, and released an Exchange On-premises Mitigation Tool (EOMT) tool
to allow small businesses to quickly address the vulnerabilities exploited in
the recent attacks.
Microsoft has now implemented the ProxyLogon protection in Defender Antivirus and System Center Endpoint Protection allowing to protect unpatched systems running its antimalware solution.
“Microsoft Defender Antivirus will automatically identify if a vulnerable version of Exchange Server is installed and apply the mitigations the first time the security intelligence update is deployed. The mitigation is deployed once per machine,” Microsoft added.
Microsoft Defender Antivirus Now Protects Users Against Ongoing Exchange Attacks
20.3.2021
Safety
Securityweek
Microsoft informed customers on Thursday that Defender Antivirus and System Center Endpoint Protection now provide automatic protection against attacks exploiting the recently disclosed Exchange Server vulnerabilities.
Microsoft has released patches, detailed guidance, and a one-click mitigation tool to ensure that Exchange Server users are protected against attacks. The tech giant has now taken another step to protect customers who haven’t managed to install the available patches but who have Defender deployed on vulnerable servers.
The Exchange vulnerabilities are tracked as CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065, and they are tracked as ProxyLogon. They can be exploited by an unauthenticated attacker to execute arbitrary code on targeted servers and gain access to emails and other sensitive information.
When Microsoft disclosed the flaws and announced patches in early March, it warned that a threat actor linked to China had been exploiting them in attacks. Roughly one week after disclosure, others reported that several cyberspy and cybercrime groups had started exploiting the vulnerabilities.
On March 12, Microsoft reported that more than 80,000 Exchange servers had still not been updated.
As threat actors increasingly start to target these vulnerabilities, Microsoft has now decided to release a security intelligence update for Defender Antivirus and System Center Endpoint Protection (build 1.333.747.0 or newer), which according to the company “breaks the attack chain by mitigating CVE-2021-26855,” the first vulnerability exploited in the ProxyLogon chain.
Microsoft described this as an “interim mitigation” that should help customers protect their systems until they can install the patches.
“Microsoft Defender Antivirus will automatically identify if a vulnerable version of Exchange Server is installed and apply the mitigations the first time the security intelligence update is deployed. The mitigation is deployed once per machine,” Microsoft explained.
AMD Unveils New Security Features With Launch of EPYC 7003 Series Processors
16.3.2021
Safety
Securityweek
Chipmaker AMD on Monday announced the launch of its new EPYC 7003 series server processors — codenamed Milan — and the company has shared some information about new and improved security features.
The new CPUs are based on the Zen 3 architecture and AMD says they bring significantly improved performance for enterprise, cloud and HPC workloads. The EPYC 7003 series processors are available immediately — device manufacturers have started announcing new products that use them, and major cloud providers will use servers powered by these CPUs.
Security features in the new AMD EPYC 7003 series CPU
According to AMD, its 3rd Gen EPYC processors include several new or enhanced security features, including a dedicated security subsystem, hardware-validated secure boot, hardware root of trust, Secure Memory Encryption (SME), Secure Encrypted Virtualization-Encrypted State (SEV-ES), and Secure Nested Paging (SNP).
One important new feature is SNP, which provides enhanced memory protections to prevent malicious hypervisors from conducting replay, corruption or remapping attacks. Specifically, SNP adds memory integrity protection capabilities designed to prevent hypervisor attacks by creating an isolated execution environment.
In the case of SEV-ES, which provides a layer of protection for CPU registers, AMD has added interrupt restrictions that should prevent malicious hypervisors from injecting interrupts and attacking ES guests.
Other security features present in the new processors include memory protection keys for users, and Shadow Stack, a new feature that helps protect against ROP (return-oriented programming) attacks.
AMD also noted during a briefing ahead of the launch of its new product that with the 3rd Gen EPYC processors they have been able to implement better mitigations against Spectre attacks.
New Firefox Feature Ups the Ante Against Cookie-Based Tracking
24.2.2021
Safety
Securityweek
Mozilla this week announced improved user privacy in Firefox 86, with the introduction of a new feature aimed at preventing the tracking of users from site to site.
Called Total Cookie Protection and built into Enhanced Tracking Protection (ETP) Strict Mode, the new feature was designed to confine cookies to the websites that created them, and complements the Supercookie Protections that Mozilla introduced in Firefox 85 last month.
“Cookies, those well-known morsels of data that web browsers store on a website’s behalf, are a useful technology, but also a serious privacy vulnerability. That’s because the prevailing behavior of web browsers allows cookies to be shared between websites,” Mozilla notes.
The browser maker underlines that, with cookies shared between sites, tracking companies can tag a user’s browser and follow their browsing activity. Such cookie-based tracking is used for mass commercial tracking, allowing advertising companies to create detailed personal profiles of users.
For more than two years, courtesy of ETP, Firefox has been blocking cookies from companies identified as trackers, but the new feature is meant to take the protections to the next level, and ensure that no cookie can be used to track a user from site to site.
For that, Total Cookie Protection separates cookies by the sites that created them. Thus, when a site or the third-party content on the site stores a cookie in the browser, it is sent to a “cookie jar” assigned to that site, and never shared with other websites.
However, exceptions are made for cross-site cookies needed for non-tracking purposes, such as the cookies used by third-party login providers.
“Only when Total Cookie Protection detects that you intend to use a provider, will it give that provider permission to use a cross-site cookie specifically for the site you’re currently visiting. Such momentary exceptions allow for strong privacy protection without affecting your browsing experience,” Mozilla says.
Virginia Lawmakers Advance Consumer Data Protection Act
20.2.2021
Safety
Securityweek
The General Assembly is advancing legislation that allows Virginia consumers more protection with their online data, though opponents say the measure does not include the ability for people to file private lawsuits against companies that breach the proposed law.
The measure is known as the Consumer Data Protection Act in both chambers of the state legislature. The Senate version, sponsored by Sen. David Marsden, D-Fairfax, passed the House 89-9 on Thursday. The House version, sponsored by Del. Cliff Hayes, D-Chesapeake, is awaiting a final vote but was passed by for the day Thursday.
“The consumers should have the right to know what is being collected about them,” Hayes said when introducing the bill.
The data protection act allows consumers to retrieve a copy of their online data, amend or delete this data and opt out of allowing large businesses to sell the data.
Hayes wants businesses to responsibly handle consumer information.
“The bottom line is, we want the controllers to know what their role is when it comes to the protection of individual’s data,” Hayes said during a House committee meeting. “We believe that no matter who you are as an organization, you need to be responsible when it comes to handling of data of consumers.”
The bills apply to businesses that control or process personal data of at least 100,000 consumers per year. It also impacts businesses that handle data of at least 25,000 consumers per year and make more than half of their gross revenue from selling personal data. The businesses must be located in Virginia or serve Virginians.
Under the Consumer Data Protection Act, the attorney general’s office would handle the enforcement of this legislation. The office would handle anything from consumer complaints to the enforcement of fines.
“The attorney general’s office will have the depth and breadth, experience, the investigative tools necessary to know and to follow trends of companies and to make sure that they bring the muscle of that office to the table,” Hayes said.
Microsoft’s Senior Director of Public Policy Ryan Harkins testified in favor of the proposed law.
“We’ve seen dramatic changes in technology over the past couple of decades and U.S. law has failed to keep pace,” Harkins said. “It’s fallen behind much of the rest of the world and failed to address growing challenges of privacy.”
Harkins said that Microsoft has advocated for data protection laws since 2005. He said that the public has lost trust in technology, and passing comprehensive data protection legislation can help win the public’s trust back.
Harkins said that the measure stands alongside leading data protection legislation such as California’s Consumer Privacy Act and aspects of the European Union’s General Data Protection Regulation.
“In some respects, it would go further and provide the most comprehensive and robust privacy laws in the United States,” Harkins said.
Attorney Mark Dix spoke in opposition of the bill on behalf of the Virginia Trial Lawyers Association. He said the measure would hurt Virginians because it is “going to close the courthouse doors.”
“It provides no cause of action whatsoever for the consumer, the person who is actually hurt,” Dix said. “It provides no remedy whatsoever for the consumer.”
Dix argued that having the attorney general’s office handle the enforcement of this legislation limits the consumer.Using a hypothetical scenario, Dix asked what would happen to Virginians if there was an administration change and the Attorney General did not prioritize data protection.
The Consumer Data Protection Act would take effect in January 2023. Marsden told a Senate subcommittee that allows time to “deal and field any other tweaks to the bill or difficulties that someone figures out.”
Microsoft Edge, Google Chrome Roll Out Password Protection Tools
23.1.2021
Safety
Threatpost
The new tools on Chrome and Edge will make it easier for browser users to discover – and change – compromised passwords.
Two major browsers –Microsoft Edge and Google Chrome – are rolling out default features, which they say will better help notify users if their password has been compromised as part of a breach or database exposure.
Edge and Chrome’s moves signify a bigger push by browsers to solve the big “password problem” plaguing the security industry. Over the past two years, major browsers (including Mozilla Firefox) have launched built-in tools for helping users identify passwords that are increasingly wrapped up in data breaches – and easily change them.
Microsoft Password Monitor
Microsoft on Thursday said that its next version
of Edge (version 88.0.705.50) will generate alerts if a user password is found
in an online leak. The tool, called Password Monitor, will check users’
passwords against a data repository of known, breached credentials. If the
passwords saved to the browser matches those on a list of leaked credentials,
Password Monitor will send users alerts and prompt them to update their
password.
“To ensure security and privacy, user passwords are hashed and encrypted when they’re checked against the database of leaked credentials,” said Microsoft.
In addition, Microsoft’s newest Edge version will include a built-in “strong password generator,” which it hopes will promote strong passwords for internet users who are signing up for a new account, or changing an existing password.
Security experts applauded the new measures. “By having the password management feature in the browsers look for compromised credentials, it allows the potential victim to change the password in other places before it impacts them,” Erich Kron, security awareness advocate at KnowBe4 told Threatpost. “Hopefully, it will also demonstrate to the individual the importance of not reusing passwords across multiple services.”
Google Chrome’s Latest Password Protections
Meanwhile, Google this week
announced it will introducing new features that will consolidate its password
protections – and make them for seamless for users – in Chrome 88 over the
coming weeks. Chrome 88 will give allow users to launch a simple check to
identify any weak passwords and “take action easily.” By navigating to the top
of their browser and clicking on passwords and “Check Passwords,” users are able
to easily check whether all of their passwords have been compromised in a breach
– and on the same page edit their passwords to choose safer alternatives if need
be.
Chrome already alerts users if their passwords have been compromised and prompts them to update – However, the idea here is to give users the ability to update multiple usernames and passwords easily all in one place.
“That’s why starting in Chrome 88, you can manage all of your passwords even faster and easier in Chrome Settings on desktop and iOS (Chrome’s Android app will be getting this feature soon, too),” said Google.
Chrome also provided an update on its existing password protection tools, including Safety Check, launched in 2020, which tells Chrome users if passwords they’ve asked the browser to remember have been compromised. Google said as a result of Safety Check it has seen a 37 percent reduction in compromised credentials stored in Chrome.
Password Health Continues to Fail
With data breaches continuing to hit
companies, attackers are accessing credentials across the board. However,
compromised data isn’t leading to actionable changes by consumers – in fact a
2020 survey found that half of respondents hadn’t changed their password in the
last year – even after they heard about a data breach in the news. This
“password problem” has challenged the security industry for years, with
companies grappling with issues like poor password hygiene, password reuse or
easy-to-guess passwords. Making matters worse, passwords are appearing left and
right online as part of major data breaches – yet victims aren’t changing their
passwords at all across various platforms. The Collection #1 data dump in 2019
for instance, which included 773 million credentials, and subsequent Collection
#2-5 dumps, show exactly how many passwords are available on the Dark Web and
underground forums.
“Password compromise is a huge ongoing issue leading to everything from data breaches to ransomware or other malware infections,” Kron said. “This in large part due to the practice of credential stuffing. This is where cybercriminals take known usernames and passwords from previous breaches and attempt to use them on other services. Knowing that people tend to reuse passwords across multiple services, they know the odds of success are worth the effort.”
Lamar Bailey, senior director of security research with Tripwire, said that passwords are “the Achilles heel of cybersecurity.”
“The vast majority of breaches start with stolen, weak or reused passwords,” Bailey said. “Our brains can’t keep up with a long list of passwords that map to all of the various sites, assets and services we access on a given day. Third-party password vaults… have become the de facto standard to solve this problem. With the latest update, Chrome and Edge will be competing with these third-party products by offering some of the same features.”
Microsoft Edge Adds Password Generator, Drops Support for Flash, FTP
23.1.2021
Safety
Securityweek
Microsoft has shipped the stable version of the Microsoft Edge 88 browser, featuring a brand new Password Generator and the ability to alert on compromised credentials. The browser refresh also drops support for the FTP protocol and for the Adobe Flash plugin.
With Microsoft Edge 88.0.705.50 now rolling out, users get a built-in strong password generator that allows them to easily set up new passwords when signing up for new accounts or when changing the old passwords.
A browser-suggested password drop down will be displayed in the password field to help users automatically save the credentials to the browser and have then synced across multiple devices.
Microsoft Edge also alerts users when any of the saved passwords has appeared in a list of leaked credentials, and allows users to edit their saved passwords directly in Microsoft Edge Settings.
“User passwords are checked against a repository of known-breached credentials and sends the user an alert if a match is found. To ensure security and privacy, user passwords are hashed and encrypted when they're checked against the database of leaked credentials,” Microsoft explains.
The updated Edge browser also attempts to automatically upgrade any content that is served over an unencrypted connection when the page is loaded over HTTPS. Images that can’t be retrieved over HTTPS won’t be loaded.
Microsoft Edge 88 also makes management of site permissions easier than before, by allows users to view permissions by site, but also by recent activity. Furthermore, the new browser version allows users to delete third party cookies, with the operation having no impact on first party cookies.
With the new browser release, Microsoft makes Single Sign On (SSO) available on down-level Windows for Microsoft Account (MSA) and Azure Active Directory (Azure AD) accounts. Users will be automatically signed into websites that allow SSO with Work and Microsoft accounts.
Support for the FTP protocol has been removed from Microsoft Edge. Thus, should the user attempt to open a FTP link in the browser, they will be prompted to choose an external application than can handle the FTP link.
“Alternatively, IT administrators can configure Microsoft Edge to use IE Mode for sites that rely on the FTP protocol,” Microsoft explains.
Around for nearly five decades, FTP is using a client-server architecture to allow for file transfers between computers. Considered insecure, however, it has been replaced with SFTP (SSH File Transfer Protocol).
Support for Adobe Flash is also being removed from Microsoft Edge, a move that started in the beta version of Edge 88. The move is not surprising, not only because Adobe themselves have dropped support for the plugin, but also because Google removed it from Chrome, and Microsoft Edge is based on Chromium.
FireEye releases an auditing tool to detect SolarWinds hackers’ activity
21.1.2021
Safety
Securityaffairs
Cybersecurity firm FireEye has released a report that sheds the light on the SolarWinds attack and the way hackers breached its networks.
The experts explained how the UNC2452 and other threat actors breached the infrastructure and moved laterally from on-premises networks to the Microsoft 365 cloud. The paper, titled Remediation and Hardening Strategies for Microsoft 365 to Defend Against UNC2452 also provides tips for organizations on how proactively harden their environments.
FireEye also released a tool named Azure AD Investigator that could be used by
organizations to discover if their organization has been breached by the
SolarWinds hackers, tracked by the security firm as UNC2452.
This FireEye
GitHub repository contains a PowerShell module that can be used to detect
artifacts associated with the UNC2452’s intrusion and other threat actor
activity.
“Some indicators are “high-fidelity” indicators of compromise, while other artifacts are so called “dual-use” artifacts.” states FireEye. “Dual-use artifacts may be related to threat actor activity, but also may be related to legitimate functionality. Analysis and verification will be required for these.”
FireEye pointed out that the tool is read-only, which means that it does not make any changes to the Microsoft 365 environment.
The company warns that the tool could not identify a compromise 100% of the
time, and is not able to distinguish if an artifact is the result of a
legitimate admin activity or threat actor activity.
Mandiant researchers
explained that UNC2452 and other threat actors primarily used four techniques
for lateral movements:
Steal the Active Directory Federation Services (AD FS) token-signing certificate
and use it to forge tokens for arbitrary users (sometimes described as Golden
SAML). This would allow the attacker to authenticate into a federated resource
provider (such as Microsoft 365) as any user, without the need for that user’s
password or their corresponding multi-factor authentication (MFA) mechanism.
Modify or add trusted domains in Azure AD to add a new federated Identity
Provider (IdP) that the attacker controls. This would allow the attacker to
forge tokens for arbitrary users and has been described as an Azure AD backdoor.
Compromise the credentials of on-premises user accounts that are synchronized to
Microsoft 365 that have high privileged directory roles, such as Global
Administrator or Application Administrator.
Backdoor an existing Microsoft
365 application by adding a new application or service principal credential in
order to use the legitimate permissions assigned to the application, such as the
ability to read email, send email as an arbitrary user, access user calendars,
etc.
The Cybersecurity and Infrastructure Security Agency (CISA)’s Cloud
Forensics team has also released a PowerShell-based tool, dubbed Sparrow, that
can that helps administrators to detect anomalies and potentially malicious
activities in Azure/Microsoft 365 environments.
CrowdStrike experts also decided to create their own tool because they face difficulties in using Azure’s administrative tools to enumerate privileges assigned to third-party resellers and partners in their Azure tenant.
“CrowdStrike launches CrowdStrike Reporting Tool for Azure (CRT), a free community tool that will help organizations quickly and easily review excessive permissions in their Azure AD environments, help determine configuration weaknesses, and provide advice to mitigate risk.” states the security firm.
“Throughout our analysis, we experienced first hand the difficulties customers face in managing Azure’s administrative tools to know what relationships and permissions exist within Azure tenants, particularly with third-party partner/resellers, and how to quickly enumerate them. We found it particularly challenging that many of the steps required to investigate are not documented, there was an inability to audit via API, and there is the requirement for global admin rights to view important information which we found to be excessive. Key information should be easily accessible.”
The CrowdStrike Reporting Tool for Azure (CRT) tool could be used by administrators to analyze their Microsoft Azure environment and review the privileges assigned to third-party resellers and partners.
Snort 3 Becomes Generally Available
21.1.2021
Safety
Securityweek
Snort 3 was officially released on Tuesday and users have been advised to switch to Snort 3 from any previous version of the popular intrusion prevention and intrusion detection system (IPS/IDS).
Snort is an open source tool developed by Cisco that provides real-time traffic analysis and packet logging capabilities. It has been downloaded millions of times and it has more than 600,000 registered users, with Cisco claiming that it’s the most widely deployed IPS in the world.

The alpha version of Snort 3 was announced in December 2014 and now it has finally become generally available.
Developers say the latest version brings faster and more efficient rules, it runs on multiple operating systems and environments, and it gives users more control.
The list of important improvements also includes better cross-platform support, a shared configuration and attribute table, support for multi-packet processing threads, scriptable configuration, pluggable key components, autodetecting services for portless configuration, autogenerating reference documentation, and support for sticky buffers in rules.
“This latest version of Snort is the result of more than seven years of development and hard work from our team. After many years of success, it is time for Snort to evolve by incorporating lessons we had learned over the many years of the software’s existence and make it even more effective,” Snort developers wrote in a blog post.
FireEye Releases New Open Source Tool in Response to SolarWinds Hack
20.1.2021
Safety
Securityweek
FireEye Mandiant on Tuesday announced the release of an open source tool designed to check Microsoft 365 tenants for the use of techniques associated with UNC2452, the name currently assigned by the cybersecurity firm to the threat group that attacked IT management company SolarWinds.
The SolarWinds supply chain attack has made hundreds of victims, and potentially impacted entities should check their systems for signs of an intrusion associated with this attack. On the other hand, it’s also important that organizations not impacted by the incident acquire the skills and resources needed to detect and neutralize these types of threats in case they are targeted in the future, particularly since other threat actors are expected to get inspiration from the playbook of UNC2452 for their future operations.
UNC2452 has used some sophisticated techniques to achieve its goals. In terms of moving laterally from on-premises networks to Microsoft cloud systems, FireEye says the attackers used a combination of four main techniques, including the theft of Active Directory Federation Services (AD FS) token-signing certificates for authenticating to targeted users’ accounts, creating Azure AD backdoors, obtaining credentials for high-privileged on-premises accounts synchronized with Microsoft 365, and abusing existing 365 applications to gain access to valuable data.
The new tool from Mandiant, named Azure AD Investigator, allows organizations to check their Microsoft cloud environments for evidence of an attack, and alerts security teams if it identifies artifacts that may require further review.
FireEye has highlighted that a manual review may be needed in some cases as some of the artifacts uncovered by the tool may be related to legitimate activities.
“The purpose of this resource is to empower organizations with the specific methodologies that our Mandiant experts are seeing from how the attacker is getting from on-premises to the cloud and what does that even look like, to the four core techniques that we’ve seen from the attack group,” Douglas Bienstock, manager at Mandiant, told SecurityWeek. “This is meant to provide a narrative about the technique but also call out the objectives and why this should be important to an organization – in other words, why should they care that attackers are doing this.”
The Azure AD Investigator source code is available on GitHub.
In addition to the tool, FireEye on Tuesday published a white paper named “Remediation and Hardening Strategies for Microsoft 365 to Defend Against UNC2452,” which shares recommendations on how organizations can mitigate and address potential attacks targeting their Microsoft 365 environments. The company says the paper offers remediation guidance to entities hit by UNC2452, hardening guidance for those not impacted, and detection guidance that can be useful to everyone.
“There’s been a lot of information that’s scattered out there making it difficult for companies to determine what they need to do to investigate their environment to remediate it, or proactively harden against it. This whitepaper is meant to serve as that playbook,” Bienstock said.
Microsoft Enables Automatic Remediation in Defender for Endpoint
20.1.2021
Safety
Securityweek
Microsoft this week announced that it has enabled automatic threat remediation in Microsoft Defender for Endpoint for users who opted into public previews.
Previously, the default automation level was set to Semi, meaning that users were required to approve any remediation. Now, for increased protection, the default was set to Full, and remediation is automatically applied to all identified threats.
For all alerts, Microsoft Defender for Endpoint automatically starts an investigation on the machine, inspecting files, processes, registry keys, services, and anything else that may contain threat-related evidence.
The result of such an investigation is a list of entities related to the alert, which are classified as malicious, suspicious, or clean. For each of the identified malicious entities, a remediation action is created, to either contain or remove.
Microsoft Defender for Endpoint defines, executes and manages these actions, without requiring intervention from security operations teams, the tech company explains.
These remediation actions are either automatically approved without warning, if the device automation level is set to Full, or require manual approval, if the automation level is set to Semi. Having remediation actions automatically applied could save time and help contain infections, Microsoft argues.
Remediation actions can be queued for devices that are not available and will be automatically triggered when these devices become available.
Admins can head to the Action Center to view all remediation actions (running, pending, or completed), and can also undo them, either for a specific device or across the organization, if a device or a file is not considered a threat.
Microsoft says it has decided to upgrade the default automation level to Full due to increased malware detection accuracy, improved automated investigation infrastructure, and the option to undo any remediation.
Furthermore, the company notes that full automation has helped successfully contain and remediate threats for thousands of customers, and that it also frees up critical security resources.
The default automation level has already been changed to Full for new customers, and, starting February 16, 2021, it will also be updated for those who have opted in for public previews. However, organizations have the option to change the default automation level according to their needs.
Ring Adds End-to-End Encryption to Quell Security Uproar
15.1.2021 Safety Threatpost
The optional feature was released free to users in a technical preview this week, adding a new layer of security to service, which has been plagued by privacy concerns.
Smart doorbell maker Ring is giving cybersecurity critics less to gripe about with the introduction of end-to-end encryption to many of its models. Ring products, which have been a juggernaut success with consumers, have faced a litany of harsh criticism from cybersecurity experts for what they say is a lack of attention to basic digital security.
After a much anticipated response to critics, Ring this week rolled out end-to-end encryption for many of its home security camera products. End-to-end encryption, according to Ring, can be added to less than 50 percent of its in-use products. Older model smart-doorbell products, such as its first and second-generation video doorbells, cannot be upgraded with the added protection.
The move was anticipated, but initiated later than planned.
2020 Reader
Survey: Share Your Feedback to Help Us Improve
Technical specifics by the Amazon-owned company Ring were made available on Wednesday (PDF) as part of a technical preview of the new security measures. Ring’s end-to-end encryption plans was first announced in September and originally slated to be introduced by the end of 2020.
The feature—which will be optional and free for customers—will allow only the device authorized and enrolled with the associated Ring account to accept and access the live Ring video stream. If third parties want to view a recording or stream on another device, they will need access to an encryption key stored on the mobile device authorized to view the stream.
It’s unclear how law enforcements’ access to Ring doorbell feeds might be impacted – if at all.
Clamoring Critics
The company has faced years of criticism for flaws in the
system that opened video and data collected by the system to be stolen by threat
actors. Still other critics blasted Ring for what they said were the company’s
own dodgy data-collection practices.
Last year, Amazon patched a vulnerability in the Ring smart doorbell that could have allowed attackers to access the owner’s Wi-Fi network credentials and potentially reconfigure the device to launch an attack on the home network.
A couple of days later, five U.S. Senators demanded in a letter to Amazon CEO Jeff Bezos that Amazon disclose how it’s securing Ring home-security device footage–and who is allowed to access that footage.
Last October, Ring raised privacy hackles again when it unveiled the new Always Home Cam, a smart home security camera drone that flies around homes taking security footage of people inside their own homes. Due to Amazon’s already questionable data-collection practices, privacy advocates worried that the footage could fall into the wrong hands.
Front Door Mitigations
On Wednesday, Ring outlined how it would specifically
address those concerns. It said Ring will add an extra layer of security and
privacy in addition to Ring’s existing encryption, which by default encrypts
videos when they are uploaded to the cloud and stored on Ring’s servers, the
company said.
“With End-to-End Encryption, customer videos are further secured with an additional lock, which can only be unlocked by a key that is stored on the customer’s enrolled mobile device, designed so that only the customer can decrypt and view recordings on their enrolled device,” according to a Ring blog post about the rollout.
Ring said the service gives users “control and additional choices for encrypting and decrypting their videos and is designed so that no unauthorized third party can access user video content,” according to a whitepaper Ring posted online about the service.
Videos encrypted when the feature is turned off will still be encrypted if the user decides to disable end-to-end encryption, according to the whitepaper, which also provides step-by-step instructions about how the feature works as well as specific details about what type of encryption the company is using.
End-to-end encryption certainly adds a layer of privacy that many customers and privacy advocates have long wanted from Ring, which since its inception has constantly pushed the boundaries of how much privacy people are willing to give up for home security protection.
Following Zoom’s Lead
The move to add end-to-end encryption to Ring is
similar to one that online videoconferencing service Zoom took last year to
encrypt video streams amid privacy concerns and numerous security breaches of
the service, such as Zoom bombing and zero-day vulnerabilities, among others.
Zoom, however, made the feature available to only paid users of the service.
While Ring’s new feature has privacy and security benefits, it also will disrupt some existing features of the service, such as accessing Ring video through Alexa, and Echo Show or Fire TV device, or sharing with other cameras.
The encryption also may throw a wrench in controversial plans to use Ring’s Neighbors app to share data footage from Ring devices with law enforcement, such as what’s happening in a program being tested by police in Mississippi in which they can livestream video from Ring cameras installed at private homes and businesses. When launched, the program sounded an alarm bell with privacy advocates like the Electronic Frontier Foundation, which called the launch of the program its “worst fears” being “confirmed.”
However, as the feature is optional and Ring users can choose to share encryption keys with third parties, it will still be possible to both stream video to other devices and share video streams with law enforcement if the owner of the device so chooses.
Intel Adds Hardware-Enabled Ransomware Detection to 11th Gen vPro Chips
14.1.2021
Safety
Thehackernews
Intel and Cybereason
have partnered to build anti-ransomware defenses into the chipmaker's newly
announced 11th generation Core vPro business-class processors.
The hardware-based security enhancements are baked into Intel's vPro platform via its Hardware Shield and Threat Detection Technology (TDT), enabling profiling and detection of ransomware and other threats that have an impact on the CPU performance.
"The joint solution represents the first instance where PC hardware plays a direct role in ransomware defenses to better protect enterprise endpoints from costly attacks," Cybereason said.
Exclusive to vPro, Intel Hardware Shield provides protections against firmware-level attacks targeting the BIOS, thereby ensuring that the operating system (OS) runs on legitimate hardware as well as minimizing the risk of malicious code injection by locking down memory in the BIOS when the software is running to help prevent planted malware from compromising the OS.
Intel TDT, on the other hand, leverages a combination of CPU telemetry data and machine learning-based heuristics to identify anomalous attack behavior — including polymorphic malware, file-less scripts, crypto mining, and ransomware infections — in real-time.
"The Intel [CPU performance monitoring unit] sits beneath applications, the OS, and virtualization layers on the system and delivers a more accurate representation of active threats, system-wide," Intel said. "As threats are detected in real-time, Intel TDT sends a high-fidelity signal that can trigger remediation workflows in the security vendor's code."
The development comes as ransomware attacks exploded in number last year, fueled in part by the COVID-19 pandemic, with average payout increasing from about $84,000 in 2019 to about $233,000 last year.
The ransomware infections have also led to a spike in "double extortion," where cybercriminals steal sensitive data before deploying the ransomware and hold it hostage in hopes that the victims will pay up rather than risk having their information made public — thus completely undermining the practice of recovering from data backups and avoid paying ransoms.
What's more, malware operators are increasingly extending their focus beyond the operating system of the device to lower layers to potentially deploy bootkits and take complete control of an infected system.
Last month, researchers detailed a new "TrickBoot" feature in TrickBot that can allow attackers to inject malicious code in the UEFI/BIOS firmware of a device to achieve persistence, avoid detection and carry out destructive or espionage-focused campaigns.
Viewed in that light, the collaboration between Intel and Cybereason is a step in the right direction, making it easier to detect and eradicate malware from the chip-level all the way to the endpoint.
"Cybereason's multi-layered protection, in collaboration with Intel Threat Detection Technology, will enable full-stack visibility to swiftly detect and block ransomware attacks before the data can be encrypted or exfiltrated," the companies said.
Microsoft Defender for Endpoint on Linux Goes Live
13.1.2021
Safety
Securityweek
Microsoft on Monday announced that Microsoft Defender for Endpoint on Linux now provides endpoint detection and response (EDR) capabilities to all users.
Initially available on Windows only, Microsoft Defender for Endpoint has received support for all major platforms, and is now available on macOS, Linux, Android, and iOS, the Redmond, Wash. software maker announced.
Microsoft made Defender for Endpoint on Linux available approximately six months ago, and in November the company announced the public preview availability of EDR capabilities in the security solution.
This week, the company finally made the capability available for anyone using its security solution.
Microsoft Defender for Endpoint supports the six most common Linux server distributions, namely RHEL 7.2+, CentOS Linux 7.2+, Ubuntu 16 LTS (or higher LTS), SLES 12+, Debian 9+, and Oracle Linux 7.2.
According to Microsoft, users can leverage Puppet, Ansible, or existing Linux configuration management tools to configure the security solution.
By making Defender for Endpoint broadly available, Microsoft aims to help organizations better protect Linux servers and get Windows, macOS, Linux, and mobile devices onboarded in the same portal. Courtesy of EDR support, detections with even richer context are displayed in the portal.
For example, customers can access a timeline tab with details on process and file creation, network connections, and login events.
However, free-form investigations are also possible, courtesy of a query engine and a set of shared queries. The capability allows customers to search for threats across Linux servers, with access to up to 30 days of raw data.
In addition to advanced hunting capabilities, the solution also allows for custom detections, Microsoft says. Furthermore, Linux users have the option to explore monitored entities such as alerts, files, network connections, and processes, getting a hyperlinked exploration experience, similar to that on Windows.
Microsoft customers looking to take advantage of Defender for Endpoint for Linux need a Servers license. Information on how to get started with the security solution can be found in Microsoft’s documentation.
Those organizations that are evaluating the public preview of the solution or use it in production should update the agent to version 101.18.53 or higher. Devices will receive the new EDR capability as soon as the agent has been updated.