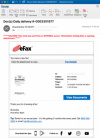
A sample phishing email. Credit: Abnormal Security
Microsoft Office 365 Credentials Under Attack By Fax ‘Alert’ Emails
15.12.2020 Spam Threatpost
Emails from legitimate, compromised accounts are being sent to numerous enterprise employees with the aim of stealing their O365 credentials.
Researchers are warning of a coordinated phishing attack that targeted “numerous” enterprise organizations last week.
The attackers behind the attack leveraged hundreds of compromised, legitimate email accounts in order to target organizations with emails, which pretended to be document delivery notifications. In reality, the phishing attack stole victims’ Office 365 credentials.
“The widespread use of hundreds of compromised accounts and never-seen-before URLs indicate the campaign is designed to bypass traditional threat intelligence solutions accustomed to permitting known but compromised accounts into the inbox,” said researchers with Abnormal Security, in a Monday analysis.
The attack starts with a lure convincing email recipients that they received a document. The email impersonates businesses like eFax, which is an internet fax service making it easy to receive faxes via email or online.
One sample email uses the legitimate eFax branding and has an email title: “Doc(s) Daily delivery #-0003351977.” It tells recipients, “You have a new fax!” and includes a small picture that is a sample image of a fax the recipient apparently received. The email also tells recipients to “click the attachment to view” and contains a link in a button that says “View Documents.”
The email appears to be legitimate and even has a tag at the bottom that markets eFax’s plans, telling recipients: “Tip: Switch to an annual plan – it’s like getting 2 months free every year! Call (800)958-2983 or email help@mail.efax[.]com.”
“The above example is one of many similarly crafted campaigns that originate from multiple compromised accounts,” said researchers. “The reason the bypass works is because the compromised email addresses are known and trusted by the organization based on prior and legitimate communications.”
The embedded URLs redirect to fake, never-seen-before Microsoft Office 365 phishing pages, said researchers. Hundreds of these phishing landing pages have been detected and are hosted on digital publishing sites like Joom, Weebly and Quip, they said.

A sample phishing email. Credit: Abnormal Security
The landing page again includes a sample fax image, Caller ID and reference number, and again tells recipients to “View Document.”
Here, “the attacker attempts to legitimize the campaign with official-looking landing pages similar to those used by eFax,” said researchers.
When the employee clicks this next “View Documents” link, they are taken to the final credential-phishing campaign.
Making detection and prevention of this campaign more difficult, “When one email is detected and caught, the attackers appear to be running a script that changes the attack to a new impersonated sender and phishing link to continue the campaign,” said researchers.
Microsoft Office 365 users have faced several sophisticated phishing attacks and scams over the past few months. In October, researchers warned of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack aimed to steal Office 365 recipients’ login credentials. Also in October, an Office365 credential-phishing attack targeted the hospitality industry, using visual CAPTCHAs to avoid detection and appear legitimate.
Finally, earlier this month, a spearphishing attack spoofed Microsoft.com to target 200 million Microsoft Office 365 users in a number of key vertical markets, including financial services, healthcare, manufacturing and utility providers.
Man Pleads Guilty to Role in Malware Protection Scam
5.12.2020
Spam
Securityweek
A man pleaded guilty Thursday to his role in a computer protection services scam that cheated victims out of nearly $1 million by misleading them into believing that malware had been detected on their computers, federal prosecutors said.
Himanshu Asri, 33, of Delhi, India, pleaded guilty in federal court in Providence to wire fraud conspiracy, according to the office of U.S. Attorney for Rhode Island, Aaron Weisman.
Asri and his accomplices defrauded U.S. citizens, many of them older than 65, by telling them that malware had been detected on their computers and persuading them to send money for protection services that were not needed or ever provided, prosecutors said.
From January 2015 until January of this year, the fraudsters collected about $940,000 from the victims and attempted to collect as much as $3 million.
Asri, the fourth telemarketing fraudster to be convicted in federal court in Rhode Island in the past three months, faces up to 20 years in prison at sentencing on Feb. 18.
Interpol Arrests 3 Nigerian BEC Scammers For Targeting Over 500,000 Entities
26.11.20
Spam
Thehackernews
Three Nigerian citizens suspected of being members of an organized cybercrime group behind distributing malware, carrying out phishing campaigns, and extensive Business Email Compromise (BEC) scams have been arrested in the city of Lagos, Interpol reported yesterday.
The investigation, dubbed "Operation Falcon," was jointly undertaken by the international police organization along with Singapore-based cybersecurity firm Group-IB and the Nigeria Police Force, the principal law enforcement agency in the country.
About 50,000 targeted victims of the criminal schemes have been identified so far, as the probe continues to track down other suspected gang members and the monetization methods employed by the group.
Group-IB's participation in the year-long operation came as part of Interpol's Project Gateway, which provides a framework for agreements with selected private sector partners and receives threat intel directly.
"The suspects are alleged to have developed phishing links, domains, and mass
mailing campaigns in which they impersonated representatives of organizations,"
Interpol said. "They then used these campaigns to disseminate 26 malware
programmes, spyware and remote access tools, including AgentTesla, Loki,
Azorult, Spartan and the nanocore and Remcos Remote Access Trojans."
In addition to perpetrating BEC campaigns and sending out emails containing malware-laced email attachments, the attacks have been used to infiltrate and monitor the systems of victim organizations and individuals, leading to the compromise of at least 500,000 government and private sector companies in more than 150 countries since 2017.
According to Group-IB, the three individuals — identified only by their initials OC, IO, and OI — are believed to be members of a gang which it has been tracking under the moniker TMT, a prolific cybercrime crew that it says is divided into multiple smaller subgroups based on an analysis of the attackers' infrastructure and techniques.
Some of their mass email phishing campaigns took the form of purchasing orders, product inquiries, and even COVID-19 aid impersonating legitimate companies, with the operators leveraging Gammadyne Mailer and Turbo-Mailer to send out phishing emails. The group also relied on MailChimp to track whether a recipient opened the message.
The ultimate goal of the attacks, Group-IB noted, was to steal authentication data from browsers, email, and FTP clients from companies located in the US, the UK, Singapore, Japan, Nigeria, among others.
"This group was running a well-established criminal business model," Interpol's Cybercrime Director Craig Jones noted. "From infiltration to cashing in, they used a multitude of tools and techniques to generate maximum profits."
Spam and phishing in Q3 2020
12.11.20
Phishing Spam
Securelist
Quarterly highlights
Worming their way in: cybercriminal tricks of the trade
These days, many
companies distribute marketing newsletters via online platforms. In terms of
capabilities, such platforms are quite diverse: they send out advertising and
informational messages, harvest statistics (for example, about clicked links in
emails), and the like. At the same time, such services attract both spammers,
who use them to send their own mailings, and cybercriminals, who try to gain
access to user accounts, usually through phishing. As a result, attackers also
get their hands on user-created mailing lists, which allows them to disseminate
mass advertising or phishing messages that filtering systems sometimes let
through.
Accordingly, in Q3 we registered an increase in the number of messages sent
using the Sendgrid platform. A significant portion of them were phishing attacks
aimed at stealing login credentials for major resources. The emails were no
different from traditional phishing, save for the legitimate headers and link to
Sendgrid, which redirected the recipient to a phishing site. To the observant
eye, the address bar and From field would reveal the messages to be fake.
Call me!
In our previous quarterly report, we talked about an increasingly
common scam whereby fraudsters send emails purportedly from large companies with
a request to urgently contact support at the given phone number. Users who
contacted the operator were then asked for information, such as bank card
details, which could then be used to empty their account. The most commonly used
toll-free numbers have specific three-digit prefixes after the country code (for
example: 800, 888, 844).
In Q3 2020, we observed new versions of such schemes warning not only about
unauthorized account access, but about money transactions supposedly made by the
user. The attackers’ calculation is that, on seeing a message about a financial
transaction, the client will grab their phone and dial the support number
highlighted in bold. Such emails do not contain links, and the message itself is
an image, which makes it harder to detect.
Scammers like such schemes, because sending spam is much cheaper and easier than calling potential victims. To avoid swallowing the bait, either call the support service using the number on the organization’s official website (not the one in the email), or use an app that protects against telephone fraud by checking outgoing call numbers.
COVID-19 and spam topics
Facebook grants
In Q3 2020, many users of social
networks and messengers saw a screenshot with some interesting news: CNBC, it
said (in broken English — always a red flag), had reported that Facebook was
paying out compensation to victims of COVID-19. To get yours, all you had to do
was follow the link and fill out a number of documents.
The link had nothing to do with Facebook and led to a fake page resembling the website of Mercy Corps, an organization dedicated to helping victims of natural disasters and armed conflict. To apply, you had to enter your Facebook username and password, then verify your identity by providing personal information, including SSN (social security number, issued to US citizens). This last detail suggests that the attack was aimed at US residents. Users that entered all the requested data gave the cybercriminals not only access to their social network account, but also personal information that could then be used for identity theft or bank card fraud.
It should be noted that the scheme was based on official news that Facebook was indeed ready to provide support to victims of COVID-19. But it only concerned grants for companies, not individuals.
Tourist phishing
The coronavirus pandemic — which has decimated the tourist
trade — has also had an effect on scammers: this quarter saw fewer emails
offering attractive summer breaks than usual. However, the pandemic did not stop
scammers, only redirected their attention.
In Q3, Airbnb and Expedia Group users were the most frequent targets of phishing attacks. Fake pages hungry for user credentials were very faithful to the design of the official websites, distinguishable only by looking closely at the address bar, where most often the domain was unrelated to the target company or belonged to a free hosting service.
So as not to reveal their cards too soon, scammers use URL-shortening services
and distribute messages in social networks and messengers where shortened links
look organic. In their messages, scammers offer cheap tickets or bargain hotel
deals. And it is impossible to know where such links lead before clicking them,
which is what attackers play upon. Accounts stolen in this way can be used, for
example, for money laundering.
Phishers also forged pages with rental offers: visitors could view photos of apartments and read detailed information about the alleged terms and conditions. Lower down the page were rave reviews from past clients intended to lull the victim into a false sense of security.
The “landlord” in each case agreed to rent out the apartment, but asked for an
advance payment. And then disappeared as soon as the money was deposited,
together with the fake page. In this instance, the cybercriminals also banked on
the fact that the juicy offer (low price, big discount) would distract the
victim from looking at the URL and checking the information on the site.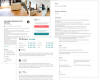
Attacks on the corporate sector
Malicious mail
We already told about the
distribution of malicious files disguised as notifications from delivery
services. They continued this quarter as well: we uncovered a mailing targeting
employees connected to sales in some capacity. The scammers persuaded recipients
to open the attached documents supposedly to pay customs duties for the import
of goods. Instead of documents, the attachment contained
Backdoor.MSIL.Crysan.gen.
Malicious mailings with “reminders” about online meetups are worth a separate
mention. For example, one of them asked the recipient to join a Zoom conference
by clicking the attached link. Instead of a meeting, the user ended up on a
WeTransfer phishing page. If the user fell for the trap and entered their
WeTransfer credentials, the attackers gained access to the company’s files
stored in this cloud.
Another mailing informed users that a Microsoft SharePoint document had been
shared with them. After clicking the link, the victim was taken to a fake
Microsoft login page that helped cybercriminals steal account usernames and
passwords.
Far more dangerous were meeting notifications containing malicious files. For
example, the at-first-glance harmless message below contained
HEUR:Trojan-Downloader.Script.Generic.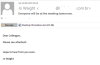
And Trojan-Banker.Win32.ClipBanker, downloaded via the link in the email below,
is used to steal financial (including cryptocurrency-related) information.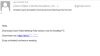
Mail scanner
To gain access to corporate accounts, cybercriminals distributed
messages stating that a virus had been found in the recipient’s mailbox, and
advising an urgent scan, otherwise the account would be disabled. The messages,
disguised as notifications from infosec companies, were sent from a free mail
address and employed neutral names like Email Security Team to avoid unnecessary
specifics.
The cybercriminals reckoned on the combined threat of a computer virus and a deactivated work email account forcing the recipient to ignore some of the oddities of the message. For example, such emails could be from the company’s IT or security department, but not a third party. The page that opened on clicking the link did not resemble a corporate resource by either its address or layout. Plus, for added believability, the cybervillains placed on it the logos of all major infosec companies.
To start a “virus scan”, the user was asked to enter the username and password
for their corporate mailbox. That said, the “scan” started even if arbitrary
credentials were entered in the fields: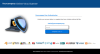
Statistics: spam
Proportion of spam in mail traffic
Proportion of spam in global mail traffic, Q2 2020 – Q3 2020 (download)
In Q3 2020, the largest share of spam was recorded in August (50.07%). The average share of spam in global mail traffic was 48.91%, down 1.27 p.p. against the previous reporting period.
Sources of spam by country
Sources of spam by country, Q3 2020 (download)
The Top 5 countries by amount of outgoing spam remained the same as in the previous quarter. Only their shares changed. The biggest increase came from Russia, which ranked first, jumping by 5 p.p. to 23.52%. The shares of the remaining top-fivers did not fluctuate by more than one percentage point. Second-place Germany gained 11.01%, the US in third picked up 10.85%, France 6.69%, and China in fifth 6.33%.
The bottom half of the Top 10 changed more significantly. For instance, it said goodbye to Turkey, which this time took 11th place (1.73%). Sixth place was taken by the Netherlands (3.89%), seventh by Brazil (3.26%), eighth by Spain (2.52%), ninth by Japan (2.30%), and Poland (1.80%) rounds out the Top 10, up one position on last quarter.
Spam email size
Spam email size, Q2 2020 – Q3 2020 (download)
The downward trend in the number of very small emails continued in Q3 2020; their share decreased significantly — by 13.21 p.p. to 38.09%. The share of emails sized 20–50 KB grew by 12.45 p.p. to 28.20% of the total number of registered spam emails. But the number of emails 10–20 KB in size fell to 8.31% (–2.78 p.p.). Also lower was the share of spam messages sized 100–200 KB; this time their share was 1.57%.
Malicious attachments: malware families
Number of Mail Anti-Virus triggerings, Q2 2020 – Q3 2020 (download)
Throughout Q3 2020, our security solutions detected a total of 51,025,889
malicious email attachments, which is almost 8 million more than in the previous
reporting period.
Top 10 malicious attachments in mail traffic, Q3 2020 (download)
The most widespread malware in Q3 mail traffic was assigned the verdict
Trojan-PSW.MSIL.Agensla.gen (8.44%). In second place was
Exploit.MSOffice.CVE-2017-11882.gen (5.67%), while Trojan.MSOffice.SAgent.gen
(4.85%) came third.
Top 10 malware families in mail traffic, Q3 2020 (download)
This quarter’s most widespread malware family was Trojan-PSW.MSIL.Agensla (12.67%), having ranked second in the last reporting period. While last quarter’s leader Trojan.Win32.Agentb finished second (8.78%). Third place, as in the previous quarter, went to Exploit.MSOffice.CVE-2017-11882 (8.03%).
Countries targeted by malicious mailshots
Distribution of Mail Anti-Virus triggerings by country, Q3 2020 (download)
Since the beginning of the year, Spain has led the way by number of Mail Anti-Virus triggerings. In Q3, users in this country accounted for 7.76% of attacks. In second place this time was Germany (7.05%), knocking Russia (5.87%) into third.
Statistics: phishing
In Q3 2020, the Anti-Phishing system prevented
103,060,725 attempts to redirect users to fake pages, which is almost 3.2
million fewer than in Q2. The share of unique attacked users amounted to 7.67%
of the total number of users of Kaspersky products
Attack geography
This time, the country with the largest proportion of users
attacked by phishers was Mongolia (15.54%).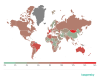
Geography of phishing attacks, Q3 2020 (download)
Israel (15.24%) lies close behind in second place, with France (12.57%) this time in third.
Top-level domains
The most popular top-level domain with phishers this
quarter, as before, was COM (40.09% of the total number of top-level domains
used in attacks). Silver went to XYZ (5.84%), and bronze to NET (3.00%). RU
finished in fourth place (2.93%), and BUZZ in fifth (2.57%).
Top-level domains most popular with phishers, Q3 2020 (download)
Organizations under attack
The rating of attacks by phishers on different
categories of organizations is based on detections by the Kaspersky
Anti-Phishing component. This component detects pages with phishing content that
the user tried to access by following email or web links, regardless of how the
user got to the page: by clicking a link in a phishing email or in a message on
a social network, or after being redirected by a malicious program. When the
component is triggered, a banner is displayed in the browser warning the user
about a potential threat.
As before, the Online Stores category absorbed the most phishing attacks,
despite its share dropping slightly against Q2 2020 (by 0.20 p.p.) to 19.22%.
Global Web Portals (14.48%) in second position and Banks (10.89%) in third were
also non-movers.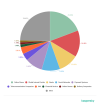
Distribution of organizations subjected to phishing attacks by category, Q3 2020 (download)
Conclusion
The COVID-19 topic, which appeared in Q1 this year, is still in
play for spammers and phishers. In our view, the so-called second wave could
lead to a surge in mailings offering various coronavirus-related treatments.
Moreover, against the backdrop of the worsening economic situation, we could see
a rise in the number of scam mailings promising a big payout in exchange for a
small upfront sum.
The average share of spam in global mail traffic (48.91%) this quarter decreased by 1.27 p.p. against the previous reporting period, while the number of attempted redirects totaled nearly 103 million.
First place in the list of spam-source countries in Q3 again went to Russia, with a share of 23.52%. Our security solutions blocked 51,025,889 malicious attachments; the most popular malware family in spam mailings was Trojan-PSW.MSIL.Agensla, with a 12.67% share of mail traffic.
Scammers Abuse Google Drive to Send Malicious Links
3.11.20
Spam
Threatpost
Cybercriminals are sending malicious links to hundreds of thousands of users via Google Drive notifications.
Scammers are leveraging a legitimate Google Drive collaboration feature to trick users into clicking on malicious links.
According to reports,, the recent attack stems from Google Drive’s legitimate collaboration feature, which allows users to create push notifications or emails that invite people to share a Google doc. Attackers are abusing this feature to send mobile users Google Drive notifications that invite them to collaborate on documents, which then contain malicious links.
Because they are sent via Google Drive, the notifications come from Google’s no-reply email address, making them appear more legitimate. Other iterations of the attack are sent via email (instead of by notification) and include the malicious link right in the email.
“Interesting TTP utilising Google Sheets, ultimately ending up with generic
prize scams,” said a cybersecurity expert who goes by Jake (or @JCyberSec) on
Twitter. “Google sheets slide was shared with an email address causing a pop-up
notification on mobile.”

The attack is targeting hundreds of thousands of Google users, according to WIRED. The report said that the notifications are being sent in Russian or broken English.
The Google Drive notifications come with various lures. Many purport to be “personal notifications” from Google Drive, with one lure entitled “Personal Notification No 8482” telling the victim they haven’t signed into their account in awhile. These threaten that the account will be deleted in 24 hours unless they sign in via a (malicious) link. Another, entitled “Personal Notification No 0684,” tells users they have an “important notice” of a financial transaction that they can view on their personal account, via a link.
One purports to be a run-of-the-mill prize scam that pretends to be part of a “Chrome Search contest 2020” and tells victims that they are the 5-billionth search and have won a prize.
These links take victims to malicious scam websites. WIRED reported that one such website flooded users with notifications to click on links for “prize draws,” while other websites requested that victims click on links to “check their bank account.”
Targeted users took to Twitter to warn of the scams, with one Twitter user saying that the only red flag of the scam was that he wasn’t expecting a shared doc.
A Google spokesperson told WIRED that the company is working on new security measures for detecting Google Drive spam. Threatpost has reached out to Google for further comment.
With the prevalence of working from home due to the coronavirus pandemic, attackers are increasingly leveraging collaboration and remote-work tools, including Google offerings. In May, researchers warned of a series of phishing campaigns using Google Firebase storage URLs. These used the reputation of Google’s cloud infrastructure to dupe victims and skate by secure email gateways. Meanwhile, researchers in October warned of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack stole Office 365 recipients’ login credentials.
“This scam wave highlights the need for users to be on the lookout for email-borne attacks,” according to Tripwire researchers. “Organizations can help their users in this regard by educating them about some of the most common types of phishing attacks that are in circulation today.”
XSS Vulnerability Exploited in Tech Support Scam
22.10.20
Spam
Securityweek
Malwarebytes security researchers have identified a new campaign in which tech support scammers are exploiting a cross-site scripting (XSS) vulnerability and are relying exclusively on links posted on Facebook to reach potential victims.
The scam starts with malicious bit.ly shortened links that are being distributed on the social media platform, and which ultimately take the intended victims to a browser locker page. According to Malwarebytes, certain games and applications on Facebook appear to be abused for the distribution of these links.
Over a period of three months, the researchers found a total of 50 different bit.ly links that were being used in this campaign. This, they say, suggests that the tech support scammers were regularly changing these links to avoid blacklisting.
The bit.ly URLs would trigger a second stage redirection where a Peruvian news website (rpp[.]pe) containing a cross-site scripting (XSS) vulnerability is abused for an open redirect. The legitimate site has more than 23 million visits per month.
“Besides redirecting users to other sites, an attacker could exploit the XSS to rewrite the current page into anything they like,” Malwarebytes notes.
In this attack, the next step involves code being passed into the URL to load external JavaScript code from the malicious domain buddhosi[.]com. The script was designed to create a redirection to the browser locker landing page.
Initially, the attackers were directly loading decoy cloaking domains designed to check incoming traffic and deliver the malicious content to legitimate victims only. Later on in the campaign, the attackers added exploitation of the open redirect flaw instead.
At the end of the redirection chain, the user is served a browser locker that shows an animation suggesting system files are being scanned, and threatening to delete the hard drive after five minutes.
The trick is likely convincing enough that some people do call the toll-free number that is listed on the page. Malwarebytes identified approximately 40 different phone numbers used in the campaign, but notes that the list might be longer.
The researchers say they did not call any of the numbers, but the next step of the tech support scam is well known: the victim is told their computer has been infected and is urged to immediately purchase expensive software or services to clean up their system.
BEC Attacks: Nigeria No Longer the Epicenter as Losses Top $26B
15.10.20 Spam Threatpost
BEC fraudsters now have bases of operation across at least 39 counties and are responsible for $26 billion in losses annually — and growing.
A study of more than 9,000 instances of business email compromise (BEC) attacks all over the world shows that the number has skyrocketed over the past year, and that the social-engineering scam has expanded well beyond its historic roots in Nigeria.
The report from Agari’s Cyber Intelligence Division (ACID), entitled The Global Reach of Business Email Compromise, found that these attacks cost businesses a staggering $26 billion every year. And that trend appears to be accelerating. In fact, researchers found BEC attacks currently make up a full 40 percent of cybercrime losses globally, impacting at least 177 countries.
For context, the Anti-Phishing Working Group recently found that the average wire transfer in a BEC scam is around $80,000.
Beyond Nigeria
In a BEC attack, a scammer impersonates a company executive or
other trusted party, and tries to trick an employee responsible for payments or
other financial transactions into wiring money to a bogus account. Attackers
usually conduct a fair amount of recon work, studying executive styles and
uncovering the organization’s vendors, billing system practices and other
information to help mount a convincing attack.
It started as an evolution from the old-school lures used by Nigerian cybergangs to trick people into giving them money: Fake princes, the promise of finding true love or even work-from-home gigs that sound too good to be true.
“Most of the seasoned actors have some nexus to Nigeria,” the report said. “It is here, after all, where BEC first gained global notoriety back in 2015, when email-fraud rings first began defrauding organizations by impersonating their CEOs and CFOs in email scams targeting employees.”
The rising payoff for these crimes has led to a period of innovation, according to the report, which identified a new “flavor” of attack, called vendor email compromise, which Agari credits to the criminal organization Silent Starling, located in West Africa.
In a VEC attack, crooks will first compromise accounts belonging to employees of suppliers, then target the vendors’ customers by purporting to be the owner of the compromised account and asking clients to transfer money to the “supplier” – which is actually a mule account.
Meanwhile, these types of attacks have evolved to become more potent and more difficult to stop, largely because these operations have proliferated worldwide, beyond their Nigerian roots.
More Money, More BEC Attacks
Insights gained by Agari in analyzing 9,000
defense engagements between May 2019 and July 2020 found that only half of the
instances examined originated in Nigeria. Law-enforcement crackdowns have driven
these fraudsters elsewhere and rising returns are enticing other criminal gangs
into the fray, meaning the bases of operations from these scams can come from
anywhere.
What researchers found instead was that 25 percent of these attacks originated in the U.S., specifically clustered in the states of California, Florida, Georgia, New York and Texas. Not coincidentally, these are the same states targeted by the U.S. Department of Justice’s BEC crackdown.
On Sept. 10, the DOJ announced that 281 arrests had been made across the globe under “Operation ReWired,” and detailed where investigators found U.S.-based scammers, including the metro areas of Atlanta, Chicago, Dallas, and Miami.
BEC Money Mules
Perhaps the most crucial aspect of any BEC gang scam is the
role of “money mule.” These people, either wittingly or unwittingly, do the
scammers dirty work for them, like setting up bank accounts and transferring
money. As further evidence of BEC’s growing global presence, Agari identified
mules scattered around 39 countries.
However, most of these mule accounts are located in the U.S. (80 percent) and clustered around many of the same metro areas as the scammers themselves — but, the report added, these accounts were found in every state and the District of Columbia.
Interestingly, they also noticed that mule-account deposit amounts in the U.S. were substantially smaller than in other countries. The report said that out of 2,900 mule accounts analyzed, the average amount requested by American-based scammers was $39,500, which is just a fraction of what was requested in other spots around the world. By comparison, Hong Kong had an average wire transfer amount of of $257,300.
“BEC actors can now be found in 50 countries, and while half of these actors still have a home base in Nigeria, the geographical distribution of these threat actors is much higher than was just a few years ago,” the report concluded. “This signals that cybercriminal organizations are healthy, growing, becoming more diversified and showing little signs of weakness.”
Facebook Small Business Grants Spark Identity-Theft Scam
1.10.20
Spam
Threatpost
The cybercrooks spread the COVID-19 relief scam via Telegram and WhatsApp, and ultimately harvest account credentials and even pics of IDs.
Cybercriminals are exploiting a $100 million Facebook grant program designed for small businesses impacted by the pandemic, to phish personal information and take over Facebook accounts.
The perpetrators are trying to dupe people into thinking that the social network is handing out free money to any user affected by COVID-19, according to a Kaspersky analysis. It’s using messaging platforms to proliferate.
“This is an attack that was caught propagating via messengers, such as Telegram,” Vladislav Tushkanov, senior data scientist at Kaspersky, told Threatpost. “This seems to be a common trend – we even see some attacks where after asking for your private info, the perpetrators ask you to forward the scam link to your WhatsApp contacts (e.g. ‘to spread awareness about these benefits’).”
Despite the “must be too good to be true” aspect of the game that should tip most people off, the cybercriminals are taking steps to make the offer seem legit.
“Samples detected by Kaspersky indicate that potential victims viewed an article
appearing to come from a prominent media outlet [CNBC] and were prompted to
follow a link to apply for the grant,” researchers explained, in a Tuesday post.
They pointed out that there is in fact, a real CNBC article about
coronavirus-related Facebook grants, but the legitimate program is for small
businesses, not individuals.
The bogus CNBC article. Source: Kaspersky
If people were sucked into clicking the link, they were taken to a phishing page and asked to enter personal information, even including a scan of both sides of their ID.
“First you’ll be asked for your Facebook username and password,” according to Kaspersky. “If you enter them, they’ll go straight to the cybercriminals. Then, to accept your application, the site requires a lot more information, supposedly to verify your account: Your address, Social Security number (for U.S. citizens), and even a scan of both sides of your ID. No fields can be left blank, and the site diligently prompts you about any omissions.”
The portal mimics the official site of Mercy Corps, a charity that helps victims of natural disasters and armed conflicts.
“However, the only topic on this one is Facebook grants, and the victim is asked to specify how many years they have been a user of the social network,” researchers noted. “The collected information allowed the scammers to gain access of their victims’ Facebook accounts, which they could use to pull off other crimes, including identity theft.”
There are a few red flags along the way; for instance, the headline in the purported CNBC article is filled with grammar mistakes.
“The grammar should give away the game, and the URL, which does not start with cnbc.com, is another suspicious element,” according to the posting.
Also, the grammar on the phishing website “stinks,” the researchers said, and most of the links don’t work. “And, of course, the site URL does not contain facebook.com, so it clearly has nothing to do with Facebook,” they added.
Once the information is submitted, the crooks log into the victim’s Facebook account and then try to message friends or leave postings that ultimately are aimed at extracting money from them.
“Facebook accounts can be used to scam victims’ friends and relatives directly or to promote further scam,” Tushkanov said.
However, the form fields provide the crooks with enough personal information to steal full identities, researchers warned. “Armed with this and scans of your documents, they will likely be able to get into any of your accounts, including online banking.”
These types of scams aren’t going away anytime soon, Tushkanov said, so people should be vigilant and careful in vetting “offers” like these.
“We have seen numerous attempts to lure people by promising them some kind of coronavirus-related compensations – for following by stay-at-home orders, payments for children etc.,” he told Threatpost, adding that these kinds of simple scams are the most common. “More sophisticated attacks are by definition more difficult to carry out. So yes, these more simplistic attacks seem to still be the most common ones. Ultimately, almost all scammers are driven by some kind of financial incentive.”
Free Apple iPhone 12? Chatbot Scam Spreads Via Texts
25.9.20
Spam
Threatpost
Convincing SMS messages tell victims that they’ve been selected for a pre-release trial for the soon-to-be-launched device.
A mobile phishing campaign is spreading via text messages purporting to come from an Apple chatbot – and offering “free trials” of iPhone 12.
The iPhone 12 is due to be released in October, and the buzz is high for Appleheads who are anxiously awaiting the launch. Cybercriminals are taking advantage of this zeitgeist to push a campaign bent on harvesting credit-card details, according to researchers.
The text uses a shipping lure to start out. According to Sophos, it reads: “Dear Christopher, we have your packet in queue. Address: Londonderry, Ballynagard crescent” and contains a link. It’s meant to look like it’s been sent to the wrong number, in hopes that people’s curiosity will get the better of them. Clicking the link triggers an interaction – via multiple texts – with a supposed “Apple chatbot.”
“The scam first shows you some cheery messages from a fake Apple chatbot to tell you why you…had enough luck to be chosen to take part in an iPhone 12 trial, and then it invites you…to join in,” explained Paul Ducklin, researcher with Sophos, in a posting on Thursday.
The texts culminate with a link – the text reads “apple.co.uk/2020/promo” –
which takes the target to the browser. There, the person is asked to provide
full name and address, supposedly to “verify” that he or she is part of the
official Apple pre-release trial group.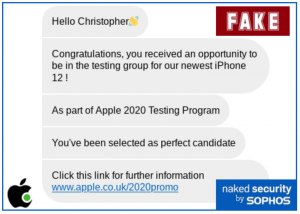
The chatbot texts. Source: Sophos
“The name-and-address answers…don’t matter a jot,” Ducklin said. “We tried clicking numerous different combinations and, unsurprisingly, the crooks let us through anyway. The questions are there just to provide a plausible connection back to the SMS that was meant for ‘Christopher’ but that reached you instead. It’s as though the criminals are trying to ‘authenticate’ themselves to you, rather than the other way around.”
After providing the name and address, the scam site surfaces a survey – again to provide verisimilitude to the target that the offer is legit. After clicking through six questions, like “do you own any Apple products,” the victim is told that their information is being verified (and a “comments” section on the bottom of the screen shows supposed reactions from those who weren’t chosen and someone saying he thought it was a joke until he received his phone).
Finally, the scam site tells the target, “Congratulations! You qualify for a test group!” and then asks the person to click to confirm his or her info – and after entering an email address, a payment screen comes up explaining that there’s a “courier delivery charge” for the phone, typically between £1 and £2.
“You end up on a credit-card payment form that’s hosted on what looks like a ‘special offers’ website with a believable enough name, and with an HTTPS security padlock if you take the time to look,” Ducklin wrote. “Of course, if you try to pay your modest delivery charge, you are simply handing over your personal data to the crooks, including your full card number and security code.”
The researcher pointed out that the scam is convincing enough to fool the less security-minded. And, the use of texting offers several advantages.
For instance, the format can help hide the grammatical and stylistic issues that often act as red flags in email phishes. Also, shortened URLs are common in texts from legitimate businesses, so crooks can more easily disguise where a link is going to end up.
“Your phone’s operating system will happily recognize when the text in an SMS looks like a URL and automatically make it clickable for you,” Ducklin said. “As a result, text messages that contain one short, clipped sentence that wouldn’t look right in an email, and that contain deliberately disguised links that we might be suspicious of anywhere else…look surprisingly natural when they show up in an SMS.”
Protection against SMS phishing (or “smishing”) comes down to alertness and the old adage that things that seem to be too good to be true, often are. Obviously, there is no free phone. Also, Ducklin noted that people need to start being as wary of texts as they are of emails, and understand that cybercriminals are actively targeting that platform.
“If all you need to transmit is a 6-digit logon code or a ‘pizza driver now 2 minutes away’ notification, SMSes still make excellent business sense,” said Ducklin. “Sadly, however, what works for legitimate businesses almost always works for cybercriminals too, so there are plenty of crooks still using SMSes for phishing.”
Spam and phishing in Q2 2020
7.8.2020
Phishing Spam
Securelist
Quarterly highlights
Targeted attacks
The second quarter often saw phishers resort to targeted
attacks, especially against fairly small companies. To attract attention,
scammers imitated email messages and websites of companies whose products or
services their potential victims could be using.
The scammers did not try to make any of the website elements appear credible as
they created the fake. The login form is the only exception. One of the phishing
websites we discovered even used a real captcha on that form.
The main pretext that scammers use to prompt the target to enter their
information is offering an online catalog that purportedly only becomes
available once the target provides the login and password to their email
account.
In one instance, phishers used Microsoft Sway, the service for creating and
sharing presentations, to hunt for logins and passwords for corporate accounts.
The user was offered to view presentations belonging to another company in the
same industry by following a link and entering the login and password for their
work email account.
A fake website can be recognized by its design. The workmanship is often rough, and the chunks of information on the various pages are disjointed due to being pulled from diverse sources. Besides, pages like that are created on free hosting websites, as cybercriminals are not prepared to invest too much money in the fakes.
A targeted phishing attack may lead to serious consequences: after gaining access to an employee’s mailbox, cybercriminals can use it for further attacks on the company itself, or its employees or partners.
Waiting for your package: keeping your data secure and your computer, clean
As the pandemic reached its peak, mail service between countries became
complicated and delivery times noticeably increased. Organizations responsible
for delivery of letters and parcels rushed to notify recipients about all kinds
of possible delays and hiccups. This is exactly the type of email messages that
scammers started to imitate: the target was offered to open the attachment to
find out the address of the warehouse with the package that had failed to reach
them.
Another, relatively original, trick employed by cybercriminals was a message
containing a miniature image of a postal receipt. The scammers expected the
curious recipient to take the attachment, which was an ACE archive despite its
name containing “jpg”, for the real thing and open it. The mailshots we detected
used this as a method of spreading the Noon spyware. The scam can only be
detected if the email client displays the full names of attachments.
In another fraudulent scheme, the target was to told that their order could not
be dispatched due to a restriction on mailing of certain types of goods, but the
processing of the package would be resumed once the restrictions were lifted.
All required documents and a new tracking number could purportedly be found in
the attached archive. In reality, the attachment contained a copy of the Androm
backdoor, which opened remote access to the victim’s computer.
Scammers posing as courier service employees sent out email warning that
packages could not be delivered due to failure to pay for the shipping. The
“couriers” accepted codes for prepaid cards issued by Paysafecard as payment.
These cards range from €10 to €100 and can be used in stores that accept this
payment method. The victim was offered to email a €50 card code – incidentally,
an activity that the payment system’s rules explicitly forbid. The
cybercriminals chose this payment method for a reason: blocking or revoking a
Paysafecard payment is next to impossible.
Banking phishing amid a pandemic
Banking phishing attacks in the second
quarter of the year often employed emails that offered borrowers various
pandemic-related discounts and bonuses. Accessing the benefits involved
downloading a file with a manual or following a link. As a result, the scammers
could access the user’s computer, personal data or credentials for various
services, depending on the scheme.
The COVID-19 theme was present, too, in the widely known fake bank emails
informing customers that their accounts had been blocked, and that they needed
to enter their login and password on a special page to get back their access.
The pandemic saw the revival of a more-than-a-decade-old scheme, in which
scammers sent victims emails offering to open the attachment to get the details
of a low-rate loan. This time, the rate reduction was linked to the pandemic.
Taxes and exemptions
The beginning of the second quarter is the time for
submitting tax forms in many countries. This year, tax authorities in some
countries reduced the tax burden or exempted citizens from paying taxes.
Scammers naturally grabbed the opportunity: mailshots we detected reported that
the government had approved a compensation payout, and claiming it involved
following a link to the tax agency’s website, which, unsurprisingly, proved to
be fake. Some of the email messages were not too well crafted, and looking
closely at the From field was all it took to detect a fake.
More ingenious scammers made up a whole legend: in an email presented as being
from the IRS (United States Internal Revenue Service), they said there was a
$500,000 “pandemic payment”, authorized jointly by the UN and the World Bank,
that could be transferred to the recipient if it had not been for a woman named
Annie Morton. The lady, the email said, had showed up at an IRS office carrying
a warrant for the payment. She purportedly said that the intended recipient had
succumbed to COVID-19, and she was the one to receive the $500,000. The message
insisted that the victim contact a certain IRS employee – and not any other, so
as to avoid a mistake – to prove that they were alive.
Subsequent steps would most likely be identical to the well-known inheritance scam, where the victim would be offered to pay for the services of a lawyer, who would then disappear with the advance money. One might guess that instead of the advance, the scammers would ask for a fee for executing papers that would prove the victim was still alive.
Getting refunded and losing it all
Tax refunds are not the only type of aid
that states have been providing to individuals and companies distressed by the
pandemic. And not the only type the scammers have been using. Thus, Brazilians
were “allowed” not to pay their energy bills, and all they had to do was
register on a website by following a link in an “email from the government”. The
hyperlink had an appearance designed to trick the user into thinking that they
were being redirected to a government portal, whereas in reality, the victim had
a trojan installed on their computer, which downloaded and then ran another
trojan, Sneaky.
Personal information leak is another hazard faced by those who risk registering
for “compensation” on a suspicious website. For example, one mailshot offered
individuals aged over seventy to go to a website and fill out a form, which
contained fields for the last name, first name, gender, mailing address and SSN
(social security number, for US citizens).
Identifying a fake email is easy. One just needs to take a closer look at the
From field and the subject, which appears odd for an official email.
Once the target filled out the entire form, they were redirected to the official Web page of the World Health Organization’s COVID-19 Solidarity Response Fund, a real organization, to give a donation. This helped the scammers to create an illusion that the questionnaire was official and to build a vast database containing the details of individuals over seventy years of age.
Fake emails promising government compensations carried one more threat: instead
of getting paid, the victim risked losing their own money to the cybercriminals.
Thus, a fake email from the International Monetary Fund announced that the
recipient and sixty-four other “lucky” individuals had been selected to receive
compensations from a five-hundred-million-dollar fund set up by the IMF, China
and the European Union for supporting victims of the pandemic. Getting €950,000
was a matter of contacting the IMF office at the address stated in the message.
Subsequent events followed the lottery-scam script: getting the money required
paying a commission first.
Fake HR: getting dismissed by professional spammers
The pandemic-related
economic downturns in several countries caused a surge in unemployment, an
opportunity that cybercriminals were quick to take advantage of. One mailshot,
sent in the name of the US Department of Labor, offered looking at the latest
changes to the parental leave and sick leave laws. The sender said these laws
had been amended following the adoption of the coronavirus relief act, and all
details on the amendments were available in the attachment. What the attachment
really contained was Trojan-Downloader.MSOffice.SLoad.gen, a trojan mostly used
for downloading and installing ransomware.
Another way scammers “surprised” potential victims was dismissal notices. The
employee was informed that the company had been forced to discharge them due to
the pandemic-induced recession. The dismissal “followed the book”, in that the
attachment, according to the author of the email, contained a request form for
two months’ worth of pay. Needless to say, the victim only found malware
attached.
Your data wanted, now
The share of voice phishing in email traffic rose
noticeably at the end of Q2 2020. One mailshot warned of a suspicious attempt at
logging in to the target’s Microsoft account, originating in another country,
and recommended that the target contact support by phone at the supplied number.
This spared the scammers the need to create a large number of fake pages, as
they tried to get all the information they needed over the phone.
An even less conventional way of obtaining personal data could be found in
emails that offered subscription to COVID-19 updates, where the target only
needed to verify their email address. Besides personal data theft, forms like
this can be used for collecting mailbox usage statistics.
Statistics: spam
Proportion of spam in email traffic
Proportion of spam in global email traffic, Q1 2020 – Q2 2020 (download)
In Q2 2020, the largest share of spam (51.45 percent) was recorded in April. The
average percentage of spam in global email traffic was 50,18%, down by 4.43
percentage points from the previous reporting period.
Proportion of spam in Runet email traffic, Q1 2020 – Q2 2020 (download)
The Russian segment of the World Wide Web presents the opposite picture, with the end of the quarter accounting for the larger share of spam: spam peaked in June as it reached 51.23 percent. The quarterly average was 50.35 percent, 1.06 p.p. lower that the first quarter’s average.
Sources of spam by country
Countries where spam originated in Q2 2020 (download)
The composition of the top five Q1 2020 spam leaders remained unchanged in the second quarter. Russia kept the lead with 18.52 percent, followed by Germany with 11.94 percent, which had overtaken the US, now third with 10.65 percent. France (7.06 percent) and China (7.02 percent) remained fourth and fifth, respectively.
Sixth was the Netherlands (4.21 percent), closely followed by Brazil (2.91 percent), Turkey (2.89 percent), Spain (2.83 percent) and lastly, Japan (2.42 percent).
Spam email size
Spam email size, Q1 – Q2 2002 (download)
The share of extra small emails kept going down, dropping by 8.6 p.p. to 51.30 percent in Q2 2020. Emails between 5 KB and 10 KB decreased slightly (by 0.66 p.p.) compared to the previous quarter, to 4.90 percent. Meanwhile, the share of spam messages within the range of 10 KB to 20 KB rose by 4.73 p.p. to 11.09 percent. The share of larger messages between 100 KB and 200 KB in the second quarter fell by 1.99 p.p. to 2.51 percent compared to Q1 2020.
Malicious attachments: malware families
Number of Mail Anti-Virus triggerings, Q1 2020 – Q2 2020 (download)
Our security solutions detected a total of 43,028,445 malicious email
attachments in Q2 2020, an increase of six and a half million year-on-year.
TOP 10 malicious attachments in mail traffic, Q2 2020 (download)
Trojan.Win32.Agentb.gen (13.27 percent) was the most widespread malware in email
attachments in the second quarter of the year, followed by
Trojan-PSW.MSIL.Agensla.gen (7.86 percent) in second place and
Exploit.MSOffice.CVE-2017-11882.gen (7.64 percent) in third place.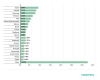
TOP 10 malware families in mail traffic, Q2 2020 (download)
The most widespread malware family in the second quarter, as in the previous one, was Trojan.Win32.Agentb (13.33 percent), followed by Trojan-PSW.MSIL.Agensla (9.40 percent) and Exploit.MSOffice.CVE-2017-11882 (7.66 percent).
Countries targeted by malicious mailshots
Distribution of Mail Anti-Virus triggerings by country, Q2 2020 (download)
Spain (8.38%) took the lead in Mail Anti-Virus triggerings in Q2 2020, just as in Q1 2020. Second came Russia with 7.37 percent of attacks, and third came Germany with 7.00 percent.
Statistics: phishing
Kaspersky Anti-Phishing helped to prevent 106,337,531
attempts at redirecting users to phishing Web pages in Q2 2020, a figure that is
almost thirteen million lower than that for the first quarter. The share of
unique attacked users accounted for 8.26 percent of the total Kaspersky users in
the world, with 1,694,705 phishing wildcards added to the system database.
Attack geography
Venezuela was traditionally the country with the largest
share of users attacked by phishers (17.56 percent).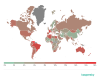
Geography of phishing attacks, Q2 2020 (download)
Portugal was 4.05 p.p. behind with 13.51 percent, closely followed by Tunisia with 13.12 percent.
Country %*
Venezuela 17.56%
Portugal 13.51%
Tunisia 13.12%
France
13.08%
Brazil 12.91%
Qatar 11.94%
Bahrain 11.88%
Guadeloupe 11.73%
Belgium 11.56%
Martinique 11.34%
*Share of users on whose computers
Anti-Phishing was triggered out of all Kaspersky users in the country
Top-level domains
Starting with this quarter, we have decided to maintain
statistics on top-level domains used in phishing attacks. Quite predictably, COM
led by a huge margin, with 43.56 percent of the total number of top-level domain
names employed in attacks. It was followed by NET (3.96 percent) and TOP (3.26
percent). The Russia-specific RU domain took fourth place with 2.91 percent,
followed by ORG with 2.55 percent.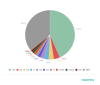
Top-level domains most popular with phishers, Q2 2020 (download)
Organizations under attack
The rating of attacks by phishers on different
categories of organizations is based on detections by Kaspersky Anti-Phishing
component. This component detects pages with phishing content that the user
tried to access by following email or Web links, regardless of how the user got
to the page: by clicking a link in a phishing email or in a message on a social
network, or after being redirected by a malicious program. When the component is
triggered, a banner is displayed in the browser warning the user about a
potential threat.
As in the first quarter, the Online Stores category accounted for the largest
share of phishing attacks, its share increasing by 1.3 p.p. to 19.42 percent.
Global Web Portals again received the second-largest share of attacks, virtually
unchanged at 16.22 percent. Banks (11.61 percent) returned to third place,
pushing Social Networks (10.08 percent) to fourth place.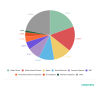
Distribution of organizations subjected to phishing attacks by category, Q2 2020 (download)
Conclusion
In our summary of the first quarter, we hypothesized that COVID-19
would remain spammers’ and fishers’ key theme in the future. That is exactly
what happened: seldom did a mailshot fail to mention the pandemic as phishers
added relevance to their tried and tested schemes and came up with brand-new
ones.
The average share of spam in global email traffic in Q2 2020 dropped by 4.43 p.p. to 50.18 percent compared to the previous reporting period, and attempts to access phishing pages amounted to 106 million.
First place in the list of spam sources in Q2 went to Russia with a share of 18.52 percent. Our security solutions blocked a total of 43,028,445 malicious email attachments, with the most widespread “email-specific” malware family being Trojan.Win32.Agentb.gen, which infected 13.33 percent of the total email traffic.
Spam and phishing in Q1 2020
26.5.2020 Securelist
Analysis Spam
Phishing
Quarterly highlights
Don’t get burned
Burning Man is
one of the most eagerly awaited events among fans of spectacular performance and
installation art. The main obstacle to attending is the price of admission: a
standard ticket will set you back $475, the number is limited, and the buying
process is a challenge all by itself (there are several stages, registration
data must be entered at a specific time, and if something goes wrong you might
not get a second chance). Therefore, half-price fake tickets make for excellent
bait.
Scammers tried to make their website as close as possible to the original — even
the page with the ticket description looked genuine.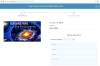
There were just three major differences from the original: only the main page and the ticket purchase section were actually operational, tickets were “sold” without prior registration, and the price was a steal ($225 versus $475).
Oscar-winning scammers
February 2020 saw the 92nd Academy Awards ceremony.
Even before the big night, websites were popping up offering free viewings of
all the nominated films. Fraudsters targeted users eager to see the short-listed
movies before the presentation of the awards.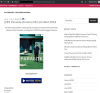
To promote these sites, Twitter accounts were created — one for each nominated
film.
Curious users were invited to visit the resource, where they were shown the
first few minutes before being asked to register to continue watching.
During registration, the victim was prompted to enter their bank card details,
allegedly to confirm their region of residence. Unsurprisingly, a short while
later a certain amount of money disappeared from their account, and the movie
did not resume.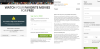
Users should be alert to the use of short links in posts on social networks. Scammers often use them because it’s impossible to see where a shortened URL points without actually following it.
There are special services that let you check what lies behind such links, often with an additional bonus in the form of a verdict on the safety of the website content. It is important to do a proper check on links from untrusted sources.
ID for hire
US companies that leak customer data can be heavily fined by the
Federal Trade Commission (FTC). For example, in 2019 Facebook was slapped with a
$5 billion penalty; however, users whose data got stolen do not receive any
compensation. This is what scammers decided to exploit by sending a fake e-mail
offering compensation from the non-existent Personal Data Protection Fund,
created by the equally fictitious US Trading Commission.
Inspired by the idea of services for checking accounts for leaks, the cybercriminals decided to create their own. Visitors were invited to check whether their account details had been stolen, and if so (the answer was “yes” even if the input was gibberish), they were promised compensation “for the leakage of personal data.”
To receive “compensation,” the victim’s citizenship was of no consequence — what
mattered was their first name, last name, phone number, and social network
accounts. For extra authenticity, a warning message about the serious
consequences of using other people’s data to claim compensation popped up
obsessively on the page.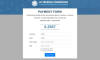
To receive the payment, US citizens were asked to enter their Social Security
Number (SSN). Everyone else had to check the box next to the words “I’am don’t
have SSN” (the mistakes are a good indicator of a fake), whereupon they were
invited to “rent” an SSN for $9. Interestingly, even if the user already had an
SSN, they were still pestered to get another one.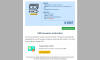
After that, the potential victim was redirected to a payment page with the
amount and currency based on the user’s location. For instance, users in Russia
were asked to pay in rubles.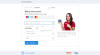
The scam deployed the conventional scheme (especially common in the Runet) of asking the victim to pay a small commission or down payment for the promise of something much bigger. In Q1, 14,725,643 attempts to redirect users to such websites were blocked.
Disaster and pandemic
Fires in Australia
The natural disaster that hit the
Australian continent was another get-rich opportunity for scammers. For example,
one “Nigerian prince”-style e-mail scam reported that a millionaire dying of
cancer was ready to donate her money to save the Australian forests. The victim
was asked to help withdraw the funds from the dying woman’s account by paying a
fee or making a small contribution to pay for the services of a lawyer, for
which they would be rewarded handsomely at a later date.
Besides the fictional millionaire, other “nature lovers” were keen to help out —
their e-mails were more concise, but the scheme was essentially the same.
COVID-19
“Nigerian prince” scheme
COVID-19 was (and continues to be) a
boon to scammers: non-existent philanthropists and dying millionaires are
popping up everywhere offering rewards for help to withdraw funds supposedly for
humanitarian purpsoses. Some recipients were even invited to help finance the
production of a miracle vaccine, or take part in a charity lottery, the proceeds
of which, it was said, would be distributed to poor people affected by the
pandemic.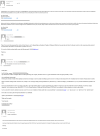
Bitcoin for coronavirus
Having introduced themselves as members of a
healthcare organization, the scammers appealed to the victim to transfer a
certain sum to the Bitcoin wallet specified in the message. The donation would
allegedly go toward fighting the coronavirus outbreak and developing a vaccine,
as well as helping victims of the pandemic.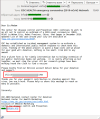
In one e-mail, the attackers played on people’s fear of contracting COVID-19:
the message was from an unnamed “neighbor” claiming to be dying from the virus
and threatening to infect the recipient unless the latter paid a ransom (which,
it was said, would help provide a comfortable old age for the ransomer’s
parents).
Dangerous advice from the WHO
One fraudulent mailing disguised as a WHO
newsletter offered tips about staying safe from COVID-19.
To get the information, the recipient had to click a link pointing to a fake WHO
website. The design was so close to the original that only the URL gave away the
scam. The cybercriminals were after login credentials for accounts on the
official WHO site. Whereas in the first mailings only a username and password
were asked for, in later ones a phone number was also requested.
In addition, we detected several e-mails supposedly from the WHO containing
documents with malware. The recipient was asked to open the attachment (in DOC
or PDF format), which allegedly offered coronavirus prevention advice. For
example, this message contained Backdoor.Win32.Androm.tvmf:
There were other, less elaborate mailings with harmful attachments, including
ones containing Trojan-Spy.Win32.Noon.gen: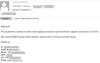
Corporate segment
The coronavirus topic was also exploited in attacks on the
corporate sector. For example, COVID-19 was cited in fraudulent e-mails as a
reason for delayed shipments or the need to reorder. The authors marked the
e-mails as urgent and required to check attached files immediately.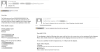
Another mailing prompted recipients to check whether their company was in a list
of firms whose activities were suspended due to the pandemic. After which it
asked for a form to be filled out, otherwise the company could be shut down.
Both the list of companies and the form were allegedly in the archives attached
to the message. In actual fact, the attachments contained
Trojan-PSW.MSIL.Agensla.a:
We also registered a phishing attack on corporate users. On a fake page,
visitors were invited to monitor the coronavirus situation across the world
using a special resource, for which the username and password of the victim’s
corporate mail account were required.
Government compensation
The introduction of measures to counter the pandemic
put many people in a difficult financial situation. Forced downtime in many
industries has had a negative impact on financial well-being. In this climate,
websites offering compensation from the government pose a particular danger.
One such popular scheme was highlighted by a colleague of ours from Brazil. A
WhatsApp messages about financial or food assistance were sent that appeared to
come from a supermarket, bank, or government department. To receive the aid, the
victim had to fill out the attached form and share the message with a certain
number of contacts. After the form was filled out, the data was sent to the
cybercriminals, while the victim got redirected to a page with advertising, a
phishing site, a site offering a paid SMS subscription, or similar.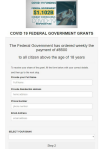

Given that the number of fake sites offering government handouts seems likely only to increase, we urge caution when it comes to promises of compensation or material assistance.
Anti-coronavirus protection with home delivery
Due to the pandemic, demand
for antiseptics and antiviral agents has spiked. We registered a large number of
mailings with offers to buy antibacterial masks.
In Latin America, WhatsApp mass messages were used to invite people to take part
in a prize draw for hand sanitizer products from the brewing company Ambev. The
company has indeed started making antiseptics and hand gel, but exclusively for
public hospitals, so the giveaway was evidently the work of fraudsters.
The number of fake sites offering folk remedies for the treatment of
coronavirus, drugs to strengthen the immune system, and non-contact thermometers
and test kits has also risen sharply. Most of the products on offer have no kind
of certification whatsoever.

On average, the daily share of e-mails mentioning COVID-19 in Q1 amounted to around 6% of all junk traffic. More than 50% of coronavirus-related spam was in the English language. We anticipate that the number of phishing sites and pandemic-related scams will only increase, and that cybercriminals will use new attack schemes and strategies.
Statistics: spam
Proportion of spam in mail traffic
Proportion of spam in global mail traffic, Q4 2019 – Q1 2020 (download)
In Q1 2020, the largest share of spam was recorded in January (55.76%). The
average percentage of spam in global mail traffic was 54.61%, down 1.58 p.p.
against the previous reporting period.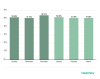
Proportion of spam in Runet mail traffic, Q4 2019 – Q1 2020 (download)
In Q1, the share of spam in Runet traffic (the Russian segment of the Internet) likewise peaked in January (52.08%). At the same time, the average indicator, as in Q4 2019, remains slightly lower than the global average (by 3.20 p.p.).
Sources of spam by country, Q1 2020 (download)
In Q1 2020, Russia led the TOP 5 countries by amount of outgoing spam. It accounted for 20.74% of all junk traffic. In second place came the US (9.64%), followed by Germany (9.41%) just 0.23 p.p. behind. Fourth place goes to France (6.29%) and fifth to China (5.22%), which is usually a TOP 3 spam source.
Brazil (3.56%) and the Netherlands (3.38%) took sixth and seventh positions, respectively, followed by Vietnam (2.55%), with Spain (2.34%) and Poland (2.21%) close on its heels in ninth and tenth.
Spam e-mail size, Q4 2019 – Q1 2020 (download)
Compared to Q4 2019, the share of very small e-mails (up to 2 KB) in Q1 2020 fell by more than 6 p.p. and amounted to 59.90%. The proportion of e-mails sized 5-10 KB grew slightly (by 0.72 p.p.) against the previous quarter to 5.56%.
Meanwhile, the share of 10-20 KB e-mails climbed by 3.32 p.p. to 6.36%. The number of large e-mails (100–200 KB) also posted growth (+2.70 p.p.). Their slice in Q1 2020 was 4.50%.
Malicious attachments in e-mail
Number of Mail Anti-Virus triggerings, Q4 2019 – Q1 2020 (download)
In Q1 2020, our security solutions detected a total of 49,562,670 malicious
e-mail attachments, which is almost identical to the figure for the last
reporting period (there were just 314,862 more malicious attachments detected in
Q4 2019).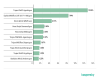
TOP 10 malicious attachments in mail traffic, Q1 2020 (download)
In Q1, first place in terms of prevalence in mail traffic went to
Trojan.Win32.Agentb.gen (12.35%), followed by
Exploit.MSOffice.CVE-2017-11882.gen (7.94%) in second and Worm.Win32.WBVB.vam
(4.19%) in third.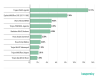
TOP 10 malicious families in mail traffic, Q1 2020 (download)
As regards malware families, the most widespread this quarter was Trojan.Win32.Agentb (12.51%), with Exploit.MSOffice.CVE-2017-11882 (7.98%), whose members exploit a vulnerability in Microsoft Equation Editor, in second place and Worm.Win32.wbvb (4.65%) in third.
Countries targeted by malicious mailshots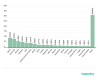
Distribution of Mail Anti-Virus triggerings by country, Q1 2020 (download)
First place by number of Mail Anti-Virus triggerings in Q1 2020 was claimed by Spain. This country accounted for 9.66% of all users of Kaspersky security solutions who encountered e-mail malware worldwide. Second place went to Germany (8.53%), and Russia (6.26%) took bronze.
Statistics: phishing
In Q1 2020, the Anti-Phishing system prevented
119,115,577 attempts to redirect users to scam websites. The percentage of
unique attacked users was 8.80% of the total number of users of Kaspersky
products in the world.
Attack geography
The country with the largest proportion of users attacked by
phishers, not for the first time, was Venezuela (20.53%).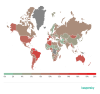
Geography of phishing attacks, Q1 2020 (download)
In second place, by a margin of 5.58 p.p., was Brazil (14.95%), another country that is no stranger to the TOP 3. Next came Australia (13.71%), trailing by just 1.24 p.p.
Country %*
Venezuela 20.53%
Brazil 14.95%
Australia 13.71%
Portugal
12.98%
Algeria 12.12%
France 11.71%
Honduras 11.62%
Greece 11.58%
Myanmar 11.54%
Tunisia 11.53%
* Share of users on whose computers
Anti-Phishing was triggered out of all Kaspersky users in the country
Organizations under attack
The rating of attacks by phishers on different
categories of organizations is based on detections by Kaspersky products
Anti-Phishing component. This component detects pages with phishing content that
the user gets redirected to. It does not matter whether the redirect is the
result of clicking a link in a phishing e-mail or in a message on a social
network, or the result of a malicious program activity. When the component is
triggered, a banner is displayed in the browser warning the user about a
potential threat.
The largest share of phishing attacks in Q1 2020 fell to the Online Stores
category (18.12%). Second place went to Global Internet Portals (16.44%), while
Social Networks (13.07%) came in third.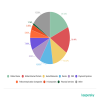
Distribution of organizations affected by phishing attacks by category, Q1 2020 (download)
As for the Banks category, a TOP 3 veteran, this time it placed fourth with 10.95%.
Conclusion
Glancing at the results of Q1 2020, we anticipate that the
COVID-19 topic will continue to be actively used by cybercriminals for the
foreseeable future. To attract potential victims, the pandemic will be mentioned
even on “standard” fake pages and in spam mailings.
The topic is also used extensively in fraudulent schemes offering compensation and material assistance.
It is highly likely that this type of fraud will become more frequent.
The average share of spam in global mail traffic (54.61%) this quarter decreased by 1.58 p.p. against the previous reporting period, while the number of attempted redirects totaled nearly 120 million.
Top of this quarter’s list of spam-source countries is Russia, with a share of 20.74%. Our security solutions blocked 49,562,670 malicious mail attachments, while the most common mail-based malware family, with a 12.35% share of mail traffic, was Trojan.Win32.Agentb.gen.