
The popularity of cryptocurrency has created plenty of opportunities for fraud, with threat actors constantly devising new ways to drain victims' wallets over the years.
INTERPOL Recovers $41 Million in Largest Ever BEC Scam in Singapore
6.8.24
Spam The Hacker News
INTERPOL said it devised a "global stop-payment mechanism" that helped
facilitate the largest-ever recovery of funds defrauded in a business email
compromise (BEC) scam.
The development comes after an unnamed commodity firm based in Singapore fell victim to a BEC scam in mid-July 2024. It refers to a type of cybercrime where a malicious actor poses as a trusted figure and uses email to trick targets into sending money or divulging confidential company information.
Such attacks can take place in myriad ways, including gaining unauthorized access to a finance employee or a law firm's email account to send fake invoices or impersonating a third-party vendor to email a phony bill.
"On 15 July, the firm had received an email from a supplier requesting that a pending payment be sent to a new bank account based in Timor-Leste," INTERPOL said in a press statement. "The email, however, came from a fraudulent account spelled slightly different to the supplier's official email address."
The Singaporean company is said to have transferred $42.3 million to the non-existent supplier on July 19, only for it to realize the blunder on July 23 after the actual supplier said it had not been compensated.
However, by taking advantage of INTERPOL's Global Rapid Intervention of Payments (I-GRIP) mechanism, authorities in Singapore managed to detect $39 million and froze the counterfeit bank account a day later.
Separately, seven suspects have been arrested in the Southeast Asian nation in connection with the scam, leading to the further recovery of $2 million.
Back in June, I-GRIP was used to trace and intercept the illicit proceeds stemming from fiat and cryptocurrency crime, successfully recovering millions and intercepting hundreds of thousands of BEC accounts as part of a global police operation named First Light.
"Since its launch in 2022, INTERPOL's I-GRIP mechanism has helped law enforcement intercept hundreds of millions of dollars in illicit funds," the agency said.
"INTERPOL is encouraging businesses and individuals to take preventative steps to avoid falling victim to business email compromise and other social engineering scams."
The disclosure follows the law enforcement seizure of an online digital wallet and cryptocurrency exchange known as Cryptonator for allegedly receiving criminal proceeds of computer intrusions and hacking incidents, ransomware scams, various fraud markets, and identity theft schemes.
Cryptonator, launched in December 2013 by Roman Boss, has also been accused of failing to institute appropriate anti-money laundering controls in place. The U.S. Justice Department indicted Boss for founding and operating the service.
Blockchain intelligence firm TRM Labs said the platform facilitated more than 4 million transactions worth a total of $1.4 billion, with Boss taking a small cut from each transaction. This comprised money exchanged with darknet markets, scam wallet addresses, high-risk exchanges, ransomware groups, crypto theft operations, mixers, and sanctioned addresses.
Specifically, cryptocurrency addresses controlled by Cryptonator transacted with darknet markets, virtual exchanges, and criminal marketplaces like Bitzlato, Blender, Finiko, Garantex, Hydra, Nobitex, and an unnamed terrorist entity.
"Hackers, darknet market operators, ransomware groups, sanctions evaders and others threat actors gravitated to the platform to exchange cryptocurrencies as well as cash out crypto into fiat currency," TRM Labs noted.

The popularity of cryptocurrency has created plenty of opportunities for fraud,
with threat actors constantly devising new ways to drain victims' wallets over
the years.
Indeed, a recent report from Check Point found that fraudsters are abusing legitimate blockchain protocols like Uniswap and Safe.global to conceal their malicious activities and siphon funds from cryptocurrency wallets.
"Attackers leverage the Uniswap Multicall contract to orchestrate fund transfers from victims' wallets to their own," researchers said. "Attackers have been known to use the Gnosis Safe contracts and framework, coaxing unsuspecting victims into signing off on fraudulent transactions."
Beware: GitHub's Fake Popularity Scam Tricking Developers into Downloading
Malware
11.4.24
Spam
The Hacker News
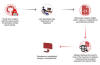
Threat actors are now taking advantage of GitHub's search functionality to trick unsuspecting users looking for popular repositories into downloading spurious counterparts that serve malware.
The latest assault on the open-source software supply chain involves concealing malicious code within Microsoft Visual Code project files that's designed to download next-stage payloads from a remote URL, Checkmarx said in a report shared with The Hacker News.
"Attackers create malicious repositories with popular names and topics, using techniques like automated updates and fake stars to boost search rankings and deceive users," security researcher Yehuda Gelb said.
The idea is to manipulate the search rankings in GitHub to bring threat actor-controlled repositories to the top when users filter and sort their results based on the most recent updates and increase the popularity via bogus stars added via fake accounts.
In doing so, the attack lends a veneer of legitimacy and trust to the fraudulent repositories, effectively deceiving developers into downloading them.
"In contrast to past incidents where attackers were found to add hundreds or thousands of stars to their repos, it appears that in these cases, the attackers opted for a more modest number of stars, probably to avoid raising suspicion with an exaggerated number," Gelb said.
It's worth pointing out that previous research from Checkmarx late last year uncovered a black market comprising online stores and chat groups that are selling GitHub stars to artificially boost a repository's popularity, a technique referred to as star inflation.
What's more, a majority of these repositories are disguised as legitimate projects related to popular games, cheats, and tools, adding another layer of sophistication to make it harder to distinguish them from benign code.
Some repositories have been observed downloading an encrypted .7z file
containing an executable named "feedbackAPI.exe" that has been inflated to 750
MB in a likely attempt to evade antivirus scanning and ultimately launch malware
that shares similarities with Keyzetsu clipper.
The Windows malware, which came to light early last year, is often distributed through pirated software such as Evernote. It's capable of diverting cryptocurrency transactions to attacker-owned wallets by substituting the wallet address copied in the clipboard.
The findings underscore the due diligence that developers must follow when downloading source code from open-source repositories, not to mention the dangers of solely relying on reputation as a metric to evaluate trustworthiness.
"The use of malicious GitHub repositories to distribute malware is an ongoing trend that poses a significant threat to the open-source ecosystem," Gelb said.
"By exploiting GitHub's search functionality and manipulating repository properties, attackers can lure unsuspecting users into downloading and executing malicious code."
The development comes as Phylum said it discovered an uptick in the number of spam (i.e., non-malicious) packages being published to the npm registry by a user named ylmin to orchestrate a "massive automated crypto farming campaign" that abuses the Tea protocol.
"The Tea protocol is a web3 platform whose stated goal is compensating open source package maintainers, but instead of cash rewards, they are rewarded with TEA tokens, a cryptocurrency," the company's research team said.
"The Tea protocol is not even live yet. These users are farming points from the 'Incentivized Testnet,' apparently with the expectation that having more points in the Testnet will increase their odds of receiving a later airdrop."
Massive Sign1 Campaign Infects 39,000+ WordPress Sites with Scam Redirects
22.3.24 Spam
The Hacker News
A massive malware campaign dubbed
Sign1 has compromised over 39,000 WordPress sites in the last six months, using
malicious JavaScript injections to redirect users to scam sites.
The most recent variant of the malware is estimated to have infected no less than 2,500 sites over the past two months alone, Sucuri said in a report published this week.
The attacks entail injecting rogue JavaScript into legitimate HTML widgets and plugins that allow for arbitrary JavaScript and other code to be inserted, providing attackers with an opportunity to add their malicious code.
The XOR-encoded JavaScript code is subsequently decoded and used to execute a JavaScript file hosted on a remote server, which ultimately facilitates redirects to a VexTrio-operated traffic distribution system (TDS) but only if certain criteria are met.
What's more, the malware uses time-based randomization to fetch dynamic URLs that change every 10 minutes to get around blocklists. These domains are registered a few days prior to their use in attacks.
"One of the most noteworthy things about this code is that it is specifically looking to see if the visitor has come from any major websites such as Google, Facebook, Yahoo, Instagram etc.," security researcher Ben Martin said. "If the referrer does not match to these major sites, then the malware will not execute."
Site visitors are then taken to other scam sites by executing another JavaScript from the same server.
The Sign1 campaign, first detected in the second half of 2023, has witnessed several iterations, with the attackers leveraging as many as 15 different domains since July 31, 2023.
It's suspected that WordPress sites have been taken over by means of a brute-force attack, although adversaries could also leverage security flaws in plugins and themes to obtain access.
"Many of the injections are found inside WordPress custom HTML widgets that the attackers add to compromised websites," Martin said. "Quite often, the attackers install a legitimate Simple Custom CSS and JS plugin and inject the malicious code using this plugin."
This approach of not placing any malicious code into server files allows the malware to stay undetected for extended periods of time, Sucuri said.
8,000+ Domains of Trusted Brands Hijacked for Massive Spam Operation
27.2.24 Spam
The Hacker News
More than 8,000 domains and 13,000 subdomains belonging to legitimate brands and institutions have been hijacked as part of a sophisticated distribution architecture for spam proliferation and click monetization.
Guardio Labs is tracking the coordinated malicious activity, which has been ongoing since at least September 2022, under the name SubdoMailing. The emails range from "counterfeit package delivery alerts to outright phishing for account credentials."
The Israeli security company attributed the campaign to a threat actor it calls ResurrecAds, which is known to resuscitate dead domains of or affiliated with big brands with the end goal of manipulating the digital advertising ecosystem for nefarious gains.
"'ResurrecAds' manages an extensive infrastructure encompassing a wide array of hosts, SMTP servers, IP addresses, and even private residential ISP connections, alongside many additional owned domain names," security researchers Nati Tal and Oleg Zaytsev said in a report shared with The Hacker News.
In particular, the campaign "leverages the trust associated with these domains to circulate spam and malicious phishing emails by the millions each day, cunningly using their credibility and stolen resources to slip past security measures."
These subdomains belong to or are affiliated with big brands and organizations such as ACLU, eBay, Lacoste, Marvel, McAfee, MSN, Pearson, PwC, Swatch, Symantec, The Economist, UNICEF, and VMware, among
The campaign is notable for its ability to bypass standard security blocks, with the entire body conceived as an image to evade text-based spam filters, clicking which initiates a series of redirections through different domains.
"These redirects check your device type and geographic location, leading to content tailored to maximize profit," the researchers explained.
"This could be anything from an annoying ad or affiliate link to more deceptive tactics like quiz scams, phishing sites, or even a malware download aimed at swindling you out of your money more directly."
Another crucial aspect of these emails is that they are also capable of circumventing Sender Policy Framework (SPF), an email authentication method that's designed to prevent spoofing by ensuring a mail server is authorized to send email for a given domain.
It's not just SPF, as the emails also pass DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting and Conformance (DMARC) checks that help prevent messages from being marked as spam.

In one example of a deceptive cloud storage warning email highlighted by
Guardio, the message originated from an SMTP server in Kyiv, yet was flagged as
being sent from Return_UlKvw@marthastewart.msn.com.
A closer examination of the DNS record for marthastewart.msn.com revealed that the subdomain is linked to another domain (msnmarthastewartsweeps[.]com) by means of a CNAME record, an aliasing technique that has been previously weaponized by advertising technology companies to get around third-party cookie blocking.
"This means that the subdomain inherits the entire behavior of msnmarthastewartsweeps[.]com , including its SPF policy," the researchers said. "In this case, the actor can send emails to anyone they wish as if msn[.]com and their approved mailers sent those emails!"

It's worth pointing out here that both the domains were legitimate and briefly
active at some point in 2001, before they were left in an abandoned state for 21
years. It wasn't until September 2022 when msnmarthastewartsweeps[.]com was
privately registered with Namecheap.
In other the hijacking scheme entails the threat actors systematically scanning for long-forgotten subdomains with dangling CNAME records of abandoned domains and then registering them to take control of them.
CNAME-takeover can also have serious consequences when such reputed subdomains are seized to host bogus phishing landing pages designed to harvest users' credentials. That said, there is no evidence that any of the hijacked subdomains have been used for this purpose.
Guardio said it also found instances where the DNS SPF record of a known domain holds abandoned domains associated with defunct email- or marketing-related services, thereby allowing attackers to grab ownership of such domains, inject their own IP addresses into the record, and ultimately send emails on behalf of the main domain name.
In an effort to counter the threat and dismantle the infrastructure, Guardio has made available a SubdoMailing Checker, a website that enables domain administrators and site owners to look for signs of compromise.
"This operation is meticulously designed to misuse these assets for distributing various malevolent 'Advertisements,' aiming to generate as many clicks as possible for these 'ad network' clients," the researchers said.
"Armed with a vast collection of compromised reputable domains, servers, and IP addresses, this ad network deftly navigates through the malicious email propagation process, seamlessly switching and hopping among its assets at will."
DOJ Slams XCast with $10 Million Fine Over Massive Illegal Robocall Operation
3.1.24 Spam
The Hacker News
The U.S. Department of Justice (DoJ) on Tuesday said it
reached a settlement with VoIP service provider XCast over allegations that it
facilitated illegal telemarketing campaigns since at least January 2018, in
contravention of the Telemarketing Sales Rule (TSR).
In addition to prohibiting the company from violating the law, the stipulated order requires it to meet other compliance measures, including establishing a process for screening its customers and calling for potential illegal telemarketing. The order, which also imposes a $10 million civil penalty judgment, has been suspended due to XCast's inability to pay.
"XCast provided VoIP services that transmitted billions of illegal robocalls to American consumers, including scam calls fraudulently claiming to be from government agencies," the DoJ said in a press release.
These calls delivered prerecorded marketing messages, most of which were sent to numbers listed on the National Do Not Call Registry. To make matters worse, a majority of the calls falsely claimed to be affiliated with government entities or contained outright false or misleading information in an attempt to deceive victims into making purchases.
For instance, some of the calls claimed to be from the Social Security Administration and threatened to cut off a recipient's utility service unless immediate payments were made. In other cases, consumers were urged to act promptly to reverse bogus credit card charges.
As part of the proposed settlement, XCast has been ordered to cut ties with firms that do not adhere to the U.S. telemarketing laws.
The U.S. Federal Trade Commission (FTC), in a statement, said the Los Angeles-based company did nothing despite being warned several times that illegal robocallers were using its services.
"The order permanently bars XCast Labs from providing VoIP services to any company with which it does not have an automated procedure to block calls that display invalid Caller ID phone numbers or that are not authenticated through the FCC's STIR/SHAKEN Authentication Framework," the FTC said.
The development comes as the FTC announced a ban on Response Tree from making or assisting anyone else in making robocalls or calls to phone numbers on the Do Not Call Registry.
The complaint accused the Californian company of operating more than 50 websites, such as PatriotRefi[.]com, AbodeDefense[.]com, and TheRetailRewards[.]com, which used manipulative dark patterns to "trick consumers into providing their personal information for supposed mortgage refinancing loans and other services."
The defendants then allegedly sold the collected information of hundreds of thousands of consumers to telemarketers who used them to make millions of illegal telemarketing calls, including robocalls, to consumers across the country.