CTI Cyber threat intelligence H Threat Intelligence Subscriptions Intelligence Capability Development Digital Threat Monitoring
What is Cyber Threat Intelligence?
This blog is the first of several by the Multi-State Information Sharing and Analysis Center’s (MS-ISAC) Intel & Analysis Working Group (I&AWG) on Cyber Threat Intelligence and intelligence analysis. Starting with this blog we will explore what is cyber threat intelligence, and examine what it is used for, its value to MS-ISAC members, the difficulties inherent in developing cyber threat intelligence, and the varying components of intelligence, such as Words of Estimative Probability.
Cyber threat intelligence is what cyber threat information becomes once it has been collected, evaluated in the context of its source and reliability, and analyzed through rigorous and structured tradecraft techniques by those with substantive expertise and access to all-source information. Like all intelligence, cyber threat intelligence provides a value-add to cyber threat information, which reduces uncertainty for the consumer, while aiding the consumer in identifying threats and opportunities. It requires that analysts identify similarities and differences in vast quantities of information and detect deceptions to produce accurate, timely, and relevant intelligence.
Rather than being developed in an end-to-end process, the development of intelligence is a circular process, referred to as the intelligence cycle. In this cycle requirements are stated; data collection is planned, implemented, and evaluated; the results are analyzed to produce intelligence; and the resulting intelligence is disseminated and re-evaluated in the context of new information and consumer feedback. The analysis portion of the cycle is what differentiates intelligence from information gathering and dissemination. Intelligence analysis relies on a rigorous way of thinking that uses structured analytical techniques to ensure biases, mindsets, and uncertainties are identified and managed. Instead of just reaching conclusions about difficult questions, intelligence analysts think about how they reach the conclusions. This extra step ensures that, to the extent feasible, the analysts’ mindsets and biases are accounted for and minimized or incorporated as necessary.
The process is a cycle because it identifies intelligence gaps, unanswered questions, which prompt new collection requirements, thus restarting the intelligence cycle. Intelligence analysts identify intelligence gaps during the analysis phase. Intelligence analysts and consumers determine intelligence gaps during the dissemination and re-evaluation phase.
For instance, MS-ISAC has a collection requirement to identify SLTT government website defacements so that we can notify the affected entity. To fulfill this requirement, MS-ISAC uses a process to identify and collect information on defaced SLTT government websites. In Quarter 2, evaluation of the MS-ISAC information identified an increase trend in defacements, and further analysis identified that the trend was due to an increase in printer server defacements. This analysis resulted in the identification of intelligence gaps: who were the actors defacing the printer servers? are they working together? are they exploiting a specific vulnerability? MS-ISAC published the current intelligence to warn members about the increase and initiated new requirements and collection efforts to fulfill the intelligence gaps. That new information was analyzed and turned into a series of publications providing additional intelligence on this trend.
In cyber threat intelligence, analysis often hinges on the triad of actors, intent, and capability, with consideration given to their tactics, techniques, and procedures (TTPs), motivations, and access to the intended targets. By studying this triad it is often possible to make informed, forward-leaning strategic, operational, and tactical assessments.
Strategic intelligence assesses disparate bits of information to form integrated views. It informs decision and policy makers on broad or long-term issues and/or provides a timely warning of threats. Strategic cyber threat intelligence forms an overall picture of the intent and capabilities of malicious cyber threats, including the actors, tools, and TTPs, through the identification of trends, patterns, and emerging threats and risks, in order to inform decision and policy makers or to provide timely warnings.
Operational intelligence assesses specific, potential incidents related to events, investigations, and/or activities, and provides insights that can guide and support response operations. Operational or technical cyber threat intelligence provides highly specialized, technically-focused, intelligence to guide and support the response to specific incidents; such intelligence is often related to campaigns, malware, and/or tools, and may come in the form of forensic reports.
Tactical intelligence assesses real-time events, investigations, and/or activities, and provides day-to-day operational support. Tactical cyber threat intelligence provides support for day-to-day operations and events, such as the development of signatures and indicators of compromise (IOC). It often involves limited application of traditional intelligence analysis techniques.
Cyber threat intelligence has proved beneficial to every level of state, local, tribal, and territorial (SLTT) government entities from senior executives, such as Chief Information Security Officers (CISOs), police chiefs, and policy makers, to those in the field, such as information technology specialists and law enforcement officers. In addition, it provides value for other experts as well, such as security officers, accountants, and terrorism and criminal analysts. Properly applied cyber threat intelligence can provide greater insight into cyber threats, allowing for a faster, more targeted response as well as resource development and allocation. For instance, it can assist decision makers in determining acceptable business risks, developing controls and budgets, in making equipment and staffing decisions (strategic intelligence), provide insights that guide and support incident response and post-incident activities (operational/technical intelligence), and advance the use of indicators by validating, prioritizing, specifying the length of time an indicator is valid (tactical intelligence). Over the next several years the inclusion of cyber threat intelligence into SLTT government operations will become increasingly important, as all levels and employees are forced to respond to the cyber threat.
Businesses are becoming increasingly concerned about cyberattacks. With the growing number of data breaches making the news, it’s not surprising. However, many business leaders are not sure where to start with protecting their organizations. Before you can protect your business and its digital assets, you have to have basic understanding of some core terms when it comes to cybersecurity.
Let’s look into one of the key aspects of cyber security – threat intelligence. Keep reading for more information on what threat intelligence is and why it’s important for your business.
Defining Threat Intelligence
Threat intelligence can identify and analyze cyber threats aimed at your business. The keyword is “analyze.” Threat intelligence is about sifting through piles of data. It's examining it contextually to spot real problems, and deploying solutions specific to the problem found.
The definition of threat intelligence is often simplified or confused with other cybersecurity terms. Most commonly, people confuse “threat data” with “threat intelligence.” Threat data is a list of possible threats. Think of it like your Facebook feed, it’s a running list of possible problems. That’s threat data.
Your Facebook posts don’t mean anything until you read them and combine that knowledge with previous posts from friends, right?
That’s threat intelligence. It's when IT specialists or sophisticated tools read threats and analyze them. Then apply historical knowledge to know if a threat is real, and if it is, what to do about it.
Why Threat Intelligence Is So Important
Threat intelligence is a crucial piece of any cybersecurity ecosystem. A cyberthreat intelligence program, sometimes called CTI, can:
Prevent data loss
With a well-structured CTI program in place, your company can spot cyberthreats and keep data breaches from releasing sensitive information.
Provide direction on safety measures
By identifying and analyzing threats, CTI spots patterns used by hackers and helps businesses put security measures in place to safeguard against future attacks.
Inform others
Hackers get smarter by the day. To keep up, cybersecurity experts share the tactics they’ve seen with the IT community to create a collective knowledge base to fight cybercrimes.
The State of Threat Intelligence
Many businesses already rely on CTI, which is great news. Research shows just 5.9 % of businesses don’t have a CTI; however, a lot of businesses feel their system is a bit lacking. However 40.5% of businesses say their CTI program is “maturing.”
Maturity of CTI Programs.png
To succeed, a business has to rely on a cybersecurity company that has all of the necessary tools to help – not just some.
What to Look for in a Threat Intelligence Program
Managing threats requires a 360-degree view of your assets. You need a program that monitors activity, spots problems and provides the kind of data you need to make informed decisions to protect your company.
Here’s what to look for in a CTI program:
Tailored threat management
You want a company that accesses your system, spots weaknesses, suggests safeguards and monitors it 24/7. A lot of cybersecurity systems claim to do this, but you should look for one willing to tailor a problem to your needs. Cybersecurity isn’t a one-size-fits-all solution, so don’t settle for a company selling you one.
Threat data feeds
You need an up-to-the-minute feed of blacklisted websites and malicious actors to keep an eye on potential problems.
Access to investigations
You need a company that gives you access to its most recent investigations that exposes how hackers get in, what they want and how they got it. Armed with the information, businesses can make more informed decisions.
Real solutions
A CTI program should help your company identify attacks and solve the problem. Period. The program has to be comprehensive. You don’t want a program that can identify potential problems, but not offer solutions, for example.
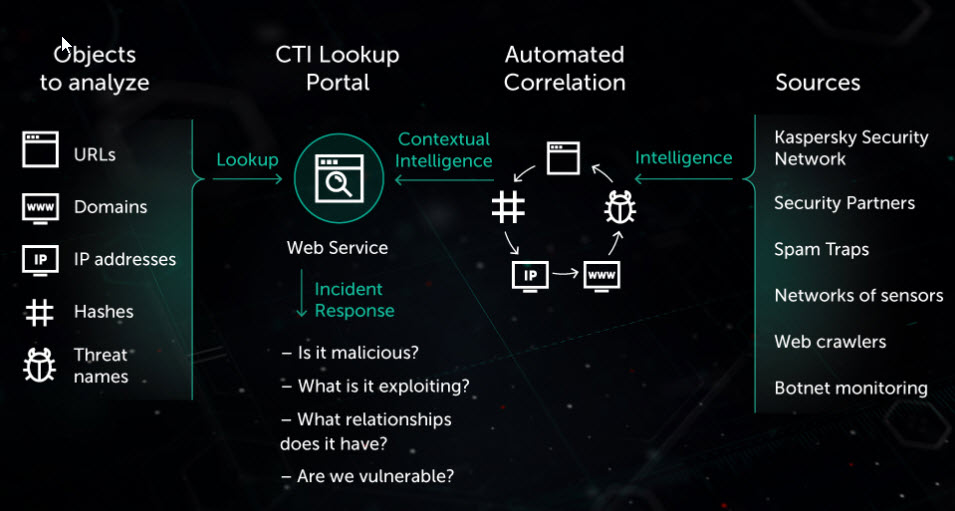
Threat intelligence is quickly becoming a must-have for businesses of every size. To protect your company, reach out to a company that can help you uncover issues and provide countermeasures to any threat.
Request a demo access to the Kaspersky Lab Threat Intelligence portal and start exploring all the benefits it can provide to your organization.
