
House Committees Get Serious in New Letter to Equifax
22.11.2017 securityweek Crime
The chairpersons of the House Science, Space, and Technology Committee and the House Oversight and Government Reform Committee on Monday sent a new letter (PDF) to Paulino Barros, the interim CEO of Equifax.
The former committee's jurisdiction includes the standards of use for securing personally identifiable information (PII), while the latter committee's jurisdiction covers how data breaches impact the federal workforce and national security. Both are investigating the loss of PII on 145 million Americans announced by Equifax on September 7, 2017.
This is not the first letter to Equifax by chairpersons Lamar Smith (R-Texas) and Trey Gowdy (R-S.C.). They also wrote (PDF) on September 14, 2017 requesting 'all documents' relevant to five specific areas; such as "to and from members of Equifax's corporate leadership", and "relating to the NIST Framework or other cybersecurity standards used by Equifax." That first letter specified no later than September 28, 2017.
It would seem that Equifax has not yet, or at least not yet satisfactorily, fulfilled this first request almost eight weeks after the deadline. "We look forward to Equifax providing all documents in response to the five categories of requested materials in the September 14 request, as well as the requests that were made at subsequent Committee briefings." It adds that the Committees expect to make additional requests in the future.
In the meantime, however, it is clear the committees are beginning to get to grips with the details of both Equifax and the breach. While the first letter requested 'areas' of documents, the second letter is far more specific. For example, it asks for documentation that would allow the identification "of any and all individuals in an executive leadership role", and those who received the DHS email alert "regarding Apache Struts 2".
It then asks for organizational charts and documents able to identify staff under the CIO during a specific period, together with breach communications with any federal agency generally, and the DHS specifically. It seeks similar charts and documents to identify staff under the CSO during the breach period, and specifically, "Any communications between former CSO Susan Mauldin and any individuals that relate to Apache Struts 2 that were made from March 8, 2017 to September 30, 2017."
Further requests make it clear that the Committees aren't looking for how the breach occurred (it was the failure to patch the Struts 2 vulnerability), but to find out exactly what happened and who was responsible for each step of the Equifax response.
For example, on July 29, 2017, Equifax was aware that hackers had been accessing the PII of as many as 143 million American consumers (later amended to more than 145 million) over the prior two months. In a press statement also released Monday, the Science, Space, and Technology committee says, "Equifax reportedly first learned on July 29, 2017, hackers had... On September 7, 2017 - nearly six weeks later - Equifax notified the public of the breach."
The delay is clearly a concern -- and this is born out in the latest letter to Equifax. The committees have now specifically asked for, "The name and title of the individual who contacted the Federal Bureau of Investigation (FBI) on August 2, 2017", and "The names and titles of all individuals who were party to the conversation with the FBI during which the FBI told Equifax to refrain from discussing attribution".
It is noticeable that the letter does not indicate that the FBI said the breach should not be disclosed, only that attribution should not be discussed. On the basis of this letter and its requests, it would be a reasonable assumption that the House is concerned about the delay in public disclosure, and is determined to find out how and by whom it was delayed.
It is also worth noting that in one respect at least, Equifax has been very lucky. If this breach had happened in 2018 rather than 2017, it would have been within the remit of the EU's General Data Protection Regulation (GDPR). Equifax would have been in breach of GDPR in at least two major ways. Firstly, it had no legal right to hold the European PII that was stolen (it is currently thought that more than 690,000 UK consumers had PII taken); Equifax apparently forgot about the records. And secondly, because of the nature of the data stolen, Equifax would have been required to notify the affected people within 72 hours (not the nearly six weeks it actually took).
Add to this the slack attitude to patching the vulnerable Apache Struts 2 vulnerability, and it is likely that any European GDPR regulator would feel obliged to levy a sizable proportion of its maximum fine of up to 4% of Equifax's annual turnover.
Symantec Patches Vulnerability in Management Console
22.11.2017 securityweek Vulnerebility
Symantec has released an update to address a directory traversal vulnerability in the Symantec Management Console.
Tracked as CVE-2017-15527, the security flaw has a CVSS score of 7.6 and has been assessed with a High severity rating, Symantec explains in an advisory published on Monday. The issue has been addressed in Symantec Management Console version ITMS 8.1 RU4 and all previous versions of the product are deemed vulnerable.
The directory traversal exploit is a type of attack that occurs when user-supplied input file names aren’t properly validated or sanitized from a security perspective. Thus, characters representing “traverse to parent directory” are allowed to pass through to the file APIs.
By utilizing such attacks, a malicious actor can leverage the affected application to gain unauthorized access to the file system, Symantec explains in its advisory.
According to Symantec, the issue was validated by the product team engineers and an update to the Symantec Management Console was released to address it.
“Note that the latest Symantec Management Console release and patches are available to customers through normal support channels. At this time, Symantec is not aware of any exploitations or adverse customer impact from this issue,” the company says.
To reduce risk of attack, Symantec recommends restricting access to administrative or management systems to authorized privileged users; restricting remote access to trusted/authorized systems only; and using the principle of least privilege, where possible.
All systems and applications should be kept updated, a multi-layered approach to security should be adopted, and network and host-based intrusion detection systems should be deployed to monitor network traffic for suspicious activity, the company notes.
The German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, abbreviated as BSI) too has issued an alert (in German) on the Symantec Management Console directory traversal vulnerability, noting that the issue can be exploited remotely from a local network.
Lazarus APT uses an Android app to target Samsung users in the South Korea
22.11.2017 securityaffairs APT
The North Korea linked group Lazarus APT has been using a new strain of Android malware to target smartphone users in South Korea.
The hacking campaign was spotted by McAfee and Palo Alto Networks, both security firms attributed the attacks to the Hidden Cobra APT.
The activity of the Lazarus APT Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. Security researchers discovered that North Korean Lazarus APT group was behind recent attacks on banks, including the Bangladesh cyber heist.
According to security experts, the group was behind, other large-scale cyber espionage campaigns against targets worldwide, including the Troy Operation, the DarkSeoul Operation, and the Sony Picture hack.
The malicious code used in this last campaign is an Android malware delivered as an APK file that has been designed to mimic a Korean bible app that was published in the Google Play by a developer named GODpeople.
The malicious APK wasn’t available on the Google Play store and it is still unclear how the APT distributed it.
“The McAfee Mobile Research team recently examined a new threat, Android malware that contains a backdoor file in the executable and linkable format (ELF). The ELF file is similar to several executables that have been reported to belong to the Lazarus cybercrime group. (For more on Lazarus, read this post from our Advanced Threat Research Team.)” states McAfee.
“The malware poses as a legitimate APK, available from Google Play, for reading the Bible in Korean. The legit app has been installed more than 1,300 times. The malware has never appeared on Google Play, and we do not know how the repackaged APK is spread in the wild.”

According to McAfee, the malware delivers a backdoor as an executable and linkable format (ELF) file, it allows to take full control of the infected device.
The list of command and control (C&C) servers used by the Android backdoor includes IP addresses previously associated with to the Lazarus group.

Experts from Palo Alto Networks pointed out that the campaign appears to be aimed at Samsung device owners in South Korea.
“Unit 42 has discovered a new cluster of malware samples, which targets Samsung devices and Korean language speakers, with relationships to the malware used in Operation Blockbuster. The specific points of connection between these new samples and Operation Blockbuster include:
payloads delivered by the macros discussed in Operation Blockbuster Sequel
malware used by the HiddenCobra threat group
malware used in the 2016 attack on the Bangladesh SWIFT banking system
APK samples mimicking legitimate APKs hosted on Google Play”
states the analysis from Palo alto Networks.
Experts from Unit 42 analyzed a PE file uploaded to VirusTotal that was used to deliver ELF ARM files and APK files from an HTTP server. The APK allows the attacker to gain full control on the target device.
Palo Alto Networks has collected evidence that links the malware with the Lazarus’s attack on the SWIFT banking system and the on Operation Blockbuster. The C&C infrastructure used in the latest attack is the same used in Lazarus’s campaigns.
“It is clear that source code was reused between previously reported samples and the cluster of new samples outlined by Unit 42. Additionally, command and control IPv4 addresses were reused by the malware discussed in this analysis. Technical indicators as well as soft indicators, such as APK themes and names, provide soft and tenable ties to the actors behind Operation Blockbuster and the HiddenCobra group.” concluded Palo alto Networks.
2017 OWASP Top 10 Final Release is out, what’s new?
22.11.2017 securityaffairs Vulnerebility
The Open Web Application Security Project (OWASP) presented the final release for the 2017 OWASP Top 10.
The Open Web Application Security Project (OWASP) published the final version of the 2017 OWASP Top 10. In April, the OWASP announced the first release candidate for the 2017 OWASP Top 10, the main novelty was represented by the presence of the following two new vulnerability categories.
“insufficient attack detection and prevention”
“unprotected APIs.”
The 2017 OWASP Top 10 is based on data from 23 contributors covering more than 114,000 applications. OWASP published on GitHub the data used for its report.
The categories have been selected based on the risk they pose, but what are the application Security Risks?
“Attackers can potentially use many different paths through your application to do harm to your business or organization. Each of these paths represents a risk that may, or may not, be serious enough to warrant attention.” states the OWASP.
“Sometimes these paths are trivial to find and exploit, and sometimes they are extremely difficult. “
The OWASP Top 10 vulnerabilities are injection, broken authentication, sensitive data exposure, XML external entity (XXE), broken access control, security misconfiguration, cross-site scripting (XSS), insecure deserialization, using components with known vulnerabilities, and insufficient logging and monitoring.
The “insufficient attack detection and prevention” results from the merger of the current 4th and 7th items, “Insecure direct object references” and the “Missing Function Level Access Control.”
The categories have been merged into the item “Broken access control” that was dated back in 2004.

The OWASP left the Cross-Site Scripting (XSS) in a separate category, while it removed the Cross-site request forgery (CSRF) because it is addressed by as modern development frameworks. It was found that the CSRF affected less than 5% of applications, meanwhile Unvalidated redirects and forwards has been found in around 8% of apps and for this reason it was removed too.
News entries are XXE, insecure deserialization, and insufficient logging and monitoring, this latter represents a serious problem for many organizations.
Google sbírá informace o poloze uživatelů Androidu – i když to zakážete
22.11.2017 SecurityWorld Mobilní
Většina lidí už dnes dobře ví, že mobilní telefony aktivně sledují jejich polohu. Co když však vypnete veškeré služby na určování polohy, nepoužíváte žádné aplikace a nemáte v mobilu ani SIM kartu?
Nesejde na tom. Chytré telefony s Androidem přesto sbírají údaje o vaší poloze a po připojení na internet je odesílají Googlu. Tuto velmi kontroverzní skutečnost odhalil server Quartz.
Od začátku roku 2017 sbírají zařízení s Androidem fyzické adresy nejbližších mobilních stanic – i přes vypnutou možnost sbírání polohových dat v mobilu – a informace odesílají Googlu. Google tak má nepřetržitý přístup k poloze uživatelů i přes faktický zákaz sběru těchto dat.
Quartz ohledně této věci Google kontaktoval, firma sběr dat potvrdila.
Dále však prostřednictvím svého mluvčího uvedla, že informace nebyly ukládány nebo jinak využity – pouze se odesílala v rámci získávání dat týkajících se takzvaných push notifikací a zpráv, které na telefonech uživatelů vyskakují. Po kontaktování Quartzem hodlá firma své metody aktualizovat a změnit tak, aby k odesílání polohových dat přes zákaz uživatele nedocházelo. Eliminace zběru polohových dat má nastat na konci listopadu.
„V lednu jsme v zájmu zrychlení odesílání zpráv začali testovat sběr a využívání identifikačních kódů mobilních stanic,“ popsal v e-mailu Quartzu mluvčí Googlu. „Nikdy jsme však tuto metodu neintegrovali do našeho síťového synchronizačního systému, takže dat jsme se okamžitě zbavovali. Nově už navíc nebudou naše služby identifikační kódy blízkých mobilních stanic zjišťovat.“
Vzhledem k blížící se regulaci GDPR a zvyšujícímu se tlaku na ochranu soukromí uživatelů je podobná praxe Googlu absolutně nepochopitelná. Odesílání informací o poloze uživatele i přes vypnutí této funkce svědčí o velkém sebevědomí amerického giganta a nulovou starost o soukromí zákazníka.
Řešit podobné problémy však budou evropští zákazníci už jen několik měsíců. Chystané GDPR má výrazně změnit způsob, jakým firmy s údaji uživatelů zacházejí i jak je ukládají; je nejasné, jak se k regulaci postaví největší firmy například z oblasti IT nebo finančnictví, neboť nařízení se týkají i mimoevropských subjektů, které však s daty uživatelů z EU jakkoli manipulují.
Google Collects Android Location Data Even When Location Service Is Disabled
21.11.2017 thehackernews Android
Do you own an Android smartphone?
If yes, then you are one of those billions of users whose smartphone is secretly gathering location data and sending it back to Google.
Google has been caught collecting location data on every Android device owner since the beginning of this year (that's for the past 11 months)—even when location services are entirely disabled, according to an investigation conducted by Quartz.
This location-sharing practice doesn't want your Android smartphone to use any app, or turn on location services, or even have a SIM card inserted.
All it wants is to have your Android device to be connected to the Internet.
The investigation revealed that Android smartphones have been collecting the addresses of nearby cellular towers, and this data could be used for "Cell Tower Triangulation"—a technique widely used to identify the location of a phone/device using data from three or more nearby cell towers.
Each time your Android device comes within the range of a new cell tower, it gathers the cell tower address and sends this data back to Google when the device is connected to a WiFi network or has a cellular data enabled.
Since the component responsible for collecting location data resides in Android's core Firebase Cloud Messaging service that manages push notifications and messages on the operating system, it cannot be disabled and doesn't rely on what apps you have installed—even if you factory reset your smartphone or remove the SIM card.
When Quartz contacted the tech giant about this location-sharing practice, Google spokesperson replied: "We began looking into using Cell ID codes as an additional signal to further improve the speed and performance of message delivery."
Although it is still unknown how cell-tower data that helps identify a specific cell tower could have been helped Google improve message delivery, the fact that the company's mobile operating system is collecting location data is a complete violation of user's privacy.
Even in its privacy policy about location sharing, Google mentions that it will collect location information from devices that use its services, but has not indicated whether the company will collect data from Android devices when all location services are disabled.
"When you use Google services, we may collect and process information about your actual location," Google's privacy policy reads.
"We use various technologies to determine location, including IP address, GPS, and other sensors that may, for example, provide Google with information on nearby devices, Wi-Fi access points, and cell towers."
Moreover, this location-sharing practice is not limited to any particular Android phone model or manufacturer, as the tech giant was apparently collecting cell tower data from all modern Android devices before being contacted by Quartz.
Although the company said that it never used or stored this location data it collected on its users and that it is now taking steps to end this practice, this data could be used to target location-based advertisement when the user enters any store or restaurant.
According to Google, Android phones will no longer gather and send cell-tower location data back to Google by the end of this month.
Tether Hacked — Attacker Steals $31 Million of Digital Tokens
21.11.2017 thehackernews CyberCrime
Again some bad news for cryptocurrency users.
Tether, a Santa Monica-based start-up that provides a dollar-backed cryptocurrency tokens, has claimed that its systems have been hacked by an external attacker, who eventually stole around $31 million worth of its tokens.
With a market capitalization of $673 million, Tether is the world's first blockchain-enabled platform to allow the traditional currency to be used like digital currency.
Tether serves as a proxy for the US dollar, Euro (and soon Japanese yen) that can be sent between exchanges including Bitfinex, Poloniex, Omni, GoCoin and other markets.
According to an announcement on the company's official website posted today, the unknown hacker stole the tokens (worth $30,950,010) from the Tether Treasury wallet on November 19 and sent them to an unauthorized Bitcoin address.
The stolen tokens will not be redeemed, but the company is in the process of attempting token recovery in order to prevent them from entering the broader cryptocurrency market.
The attacker is holding stolen funds at the following bitcoin address:
16tg2RJuEPtZooy18Wxn2me2RhUdC94N7r
So, in case, you receive any USDT (that's what Tether calls its platform's USD currency; 1USDT=1USD) "tokens from the above address, or from any downstream address that receives these tokens, do not accept them, as they have been flagged and will not be redeemable by Tether for USD," the company warned.
Bitcoin price dropped as much as 5.4 percent, the most since November 13.
To prevent the stolen coins from moving from the attacker's address, the company has temporarily suspended its back-end wallet service and also provided a new version of its software.
"Accordingly, any and all exchanges, wallets, and other Tether integrators should install this software immediately in order to prevent loss: https://github.com/tetherto/omnicore/releases/tag/0.2.99.s," the company said.
The Tether Team has also ensured that Tether issuances have not been affected by this attack, and all of its tokens remain fully backed by assets in the Tether reserve.
Instead, the only tokens that won't be redeemed at this moment are those stolen from Tether treasury yesterday. However, these tokens will be returned to treasury once the software enhancements are in place.
Tether is also undertaking a thorough investigation of the incident in an attempt to prevent similar attacks in the future.
This incident is the latest in a long list of attacks against the cryptocurrency markets. Just last week, about $300 million worth of Ether from dozens of Ethereum wallets was permanently locked up after someone triggered a flaw in Parity multi-sig wallets.
Critical Flaws in Intel Processors Leave Millions of PCs Vulnerable
21.11.2017 thehackernews Vulnerebility
In past few months, several research groups have uncovered vulnerabilities in the Intel remote administration feature known as the Management Engine (ME) which could allow remote attackers to gain full control of a targeted computer.
Now, Intel has admitted that these security vulnerabilities could "potentially place impacted platforms at risk."
The popular chipmaker released a security advisory on Monday admitting that its Management Engine (ME), remote server management tool Server Platform Services (SPS), and hardware authentication tool Trusted Execution Engine (TXE) are vulnerable to multiple severe security issues that place millions of devices at risk.
The most severe vulnerability (CVE-2017-5705) involves multiple buffer overflow issues in the operating system kernel for Intel ME Firmware that could allow attackers with local access to the vulnerable system to "load and execute code outside the visibility of the user and operating system."
The chipmaker has also described a high-severity security issue (CVE-2017-5708) involving multiple privilege escalation bugs in the operating system kernel for Intel ME Firmware that could allow an unauthorized process to access privileged content via an unspecified vector.
Systems using Intel Manageability Engine Firmware version 11.0.x.x, 11.5.x.x, 11.6.x.x, 11.7.x.x, 11.10.x.x and 11.20.x.x are impacted by these vulnerabilities.
For those unaware, Intel-based chipsets come with ME enabled for local and remote system management, allowing IT administrators to remotely manage and repair PCs, workstations, and servers within their organization.
As long as the system is connected to a line power and a network cable, these remote functions can be performed out of band even when the computer is turned off as it operates independently of the operating system.
Since ME has full access to almost all data on the computer, including its system memory and network adapters, exploitation of the ME flaws to execute malicious code on it could allow for a complete compromise of the platform.
"Based on the items identified through the comprehensive security review, an attacker could gain unauthorised access to the platform, Intel ME feature, and third party secrets protected by the ME, Server Platform Service (SPS), or Trusted Execution Engine (TXE)," Intel said.
Besides running unauthorized code on computers, Intel has also listed some attack scenarios where a successful attacker could crash systems or make them unstable.
Another high-severity vulnerability involves a buffer overflow issue (CVE-2017-5711) in Active Management Technology (AMT) for the Intel ME Firmware that could allow attackers with remote Admin access to the system to execute malicious code with AMT execution privilege.
AMT for Intel ME Firmware versions 8.x, 9.x, 10.x, 11.0.x.x, 11.5.x.x, 11.6.x.x, 11.7.x.x, 11.10.x.x and 11.20.x.x are impacted by this vulnerability.
The worst part is that it's almost impossible to disable the ME feature to protect against possible exploitation of these vulnerabilities.
"The disappointing fact is that on modern computers, it is impossible to completely disable ME," researchers from Positive Technologies noted in a detailed blog post published late August. "This is primarily due to the fact that this technology is responsible for initialization, power management, and launch of the main processor."
Other high severity vulnerabilities impact TXE version 3.0 and SPS version 4.0, leaving millions of computers with the feature at risk. These are described as:
High Severity Flaws in Server Platform Service (SPS)
CVE-2017-5706: This involves multiple buffer overflow issues in the operating system kernel for Intel SPS Firmware that could allow attackers with local access to the system to execute malicious code on it.
CVE-2017-5709: This involves multiple privilege escalation bugs in the operating system kernel in Intel SPS Firmware that could allow an unauthorized process to access privileged content via an unspecified vector.
Both the vulnerabilities impact Intel Server Platform Services Firmware 4.0.x.x.
High Severity Flaws in Intel Trusted Execution Engine (TXE)
CVE-2017-5707: This issue involves multiple buffer overflow flaws in the operating system kernel in Intel TXE Firmware that allow attackers with local access to the system to execute arbitrary code on it.
CVE-2017-5710: This involves multiple privilege escalation bugs in the operating system kernel in Intel TXE Firmware that allow an unauthorized process to access privileged content via an unspecified vector.
Both the vulnerabilities impact Intel Trusted Execution Engine Firmware 3.0.x.x.
Affected Intel Products
Below is the list of the processor chipsets which include the vulnerable firmware:
6th, 7th and 8th Generation Intel Core processors
Xeon E3-1200 v5 and v6 processors
Xeon Scalable processors
Xeon W processors
Atom C3000 processors
Apollo Lake Atom E3900 series
Apollo Lake Pentiums
Celeron N and J series processors
Intel has issued patches across a dozen generations of CPUs to address these security vulnerabilities that affect millions of PCs, servers, and the internet of things devices, and is urging affected customers to update their firmware as soon as possible.
The chipmaker has also published a Detection Tool to help Windows and Linux administrators check if their systems are exposed to any threat.
The company thanked Mark Ermolov and Maxim Goryachy from Positive Technologies Research for discovering CVE-2017-5705 and bringing it to its attention, which forced the chipmaker to review its source code for vulnerabilities.
Kyberzločinci ukradli virtuální mince za více než 675 miliónů korun
21.11.2017 Novinky/Bezpečnost Kriminalita
Na více než 675 miliónů korun si přišli počítačoví piráti, kteří odcizili virtuální mince tether, které jsou konkurencí bitcoinů. Pikantní na tom je, že je kyberzločinci ukradli přímo ze společnosti Tether Treasury, jež má na starosti správu měny tether a vydávání nových mincí.
Ke krádeži stamiliónů ve virtuálních mincích mělo dojít už minulý týden v neděli. Zástupci podniku to ale oficiálně oznámili až v noci na úterý. Detaily o samotném útoku zatím nejsou k dispozici.
Webové stránky společnosti Tether Treasury jsou od samotného útoku nedostupné.
Krádež řeší policie
Případem by se měla již zabývat policie. Vyšetřovatelé ale zatím neprozradili, zda mají nějaké stopy. Známá by však měla být podle serveru TechCrunch adresa virtuální peněženky, kam útočníci všechny odcizené peníze poslali.
Je nicméně velmi nepravděpodobné, že by se je podařilo vypátrat. Samotné peněženky totiž nejsou registrovány na konkrétní uživatele a monitorovány nejsou ani vklady či výběry, všechny transakce probíhají anonymně.
Tether patří mezi dvacet nejpopulárnějších virtuálních měn. Jedna virtuální mince má hodnotu zhruba 21 korun. V oběhu jsou aktuálně mince s hodnotou přesahující 14 miliard korun.
Desetiletý chlapec překonal zabezpečení iPhonu X. A šlo to snadno
21.11.2017 Novinky/Bezpečnost Apple
Apple se chlubí, že u nejnovějšího iPhonu X používá nejsofistikovanější systém zabezpečení v celé historii jablečných smartphonů. Dokonce se zástupci podniku chlubí, že neexistuje sebemenší šance, že přístroj odemkne někdo neoprávněně. Jenže přesně to se teď podařilo teprve desetiletému chlapci. A nemusel se ani moc snažit.
Nový iPhone X nemá na rozdíl od ostatních nabízených iPhonů zabudovanou čtečku otisků prstů. Místo toho využívá funkci zvanou Face ID, kdy uživatel přístroj odemkne pomocí přední kamery. Ta využívá technologii TrueDepth Camera System a dokáže rozeznat přesné rysy obličeje, díky kterým přístroj následně odemkne.
Zástupci Applu při oficiální prezentaci nejnovějšího modelu uvedli, že toto řešení je nejen pohodlnější, ale zároveň také bezpečnější než čtečka otisků prstů.
MJF LIFE & HEALTH
@MJF_Life_Health
One of Staten Islands own hacks new I Phone facial recognition.
Pretty Impressive at 10 years old!
Ammar Malik... http://fb.me/2tsf8jXzm
3:33 PM - Nov 19, 2017
10-year-old Staten Island boy hacks iPhone X facial recognition
STATEN ISLAND — A 10-year-old boy has been able to hack the Face ID on each of his parents’ new iPhone X. Ammar Malik showed he can go toe-to-toe with some of the world’s best hackers. "I was pretty...
pix11.com
Replies Retweets likes
Twitter Ads info and privacy
Desetiletý Ammar Malik se svou matkou
Jenže to v praxi není tak úplně pravda. Na vlastní kůži se o tom přesvědčili rodiče desetiletého Ammara Malika. Ten opakovaně odemkl iPhone X své matky – a to dokonce i poté, co matka znovu zaregistrovala v jablečném zařízení svoji tvář, aby přístroj bezpečně poznal pouze ji.
Úplně stejně vyšel test také v případě, kdy se Ammar snažil odemknout přístroj svého otce. Rysy jeho obličeje se zkrátka velmi podobaly rysům jeho rodičů a přístroj od společnosti Apple si s tím nedokázal poradit. A nutno podotknout, že to by se se čtečkou otisků prstů rozhodně nestalo.
Stejný problém u dvojčat
Podobný problém již mimochodem dříve hlásila také identická dvojčata, která si mohou iPhone X také odemykat navzájem mezi sebou, i když by to – podle dřívějšího vyjádření amerického počítačového gigantu – nemělo být možné.
IPhone X je aktuálně nejdražším chytrým telefonem v nabídce Applu. A dokonce to platí i při pohledu do celé desetileté historie smartphonů s logem nakousnutého jablka.
Základní model nabídne 64GB paměť a bude se v tuzemských obchodech podle oficiálních informací Applu nabízet za 29 990 Kč. Provedení s 256GB pamětí však bude citelně dražší. Případní zájemci za něj zaplatí 34 490 Kč.

Apple iPhone X
FOTO: Thomas Peter, Reuters

Apple iPhone X
Seznam Email bude bezpečnější. Konečně přijde dvoufázové ověření
21.11.2017 CNEWS.cz Bezpečnost
Na facebookové stránce služby Mapy.cz se objevila velmi důležitá informace. Seznam po letech nečinnosti konečně zvýší zabezpečení účtů. V „dohledné době“ by měl nasadit dvoufázové ověření, tedy další stupeň ochrany postavený za heslem.
Již to znáte z bankovních účtů nebo velkých zahraničních služeb. U Googlu, Microsoftu, Applu, Facebooku, Paypalu, Steamu apod. si můžete nastavit, že k přihlášení vám nebude stačit je jméno a heslo, ale i další prvek. Hardwarový klíč nebo častěji kód vygenerovaný v aplikaci na mobilu či doručený pomocí SMS. Pokud někdo získá vaše heslo, bez onoho druhého stupně mu bude k ničemu.
TIP: Velký seznam všech služeb s podporou tzv. 2FA najdete na twofactorauth.org.
Zatím není jasné, jaký typ 2FA bude Seznam podporovat. Aktuálně umožňuje „zabezpečit“ účet telefonním číslem, pomocí něhož ale lze pouze zpřístupnit účet se zapomenutým heslem.

Ověření účtu na Seznamu pomocí telefonního čísla
Na Seznamu je podle posledních známých informací zaregistrováno 21 milionů účtů, z toho 8 milionů je aktivních alespoň jednou za měsíc. Stejný účet se používá k e-mailu i dalším službám jako Mapy.cz, Firmy.cz, TV Program, Lidé.cz apod.
Certifikační autorita StartCom ukončí svou činnost s koncem roku
21.11.2017 Root.cz Zabezpečení
Příběh kontroverzní certifikační autority StartCom se blíží ke konci. Společnost oznámila, že ke konci letošního roku skončí také se svou činností. Nebude už vydávat certifikáty a nechá vypršet platnost kořenů.
Předseda představenstva společnosti StartCom, Xiaosheng Tan, oznámil, že činnost společnosti bude ukončena k 1. lednu 2018. Od tohoto dne už autorita nebude zákazníkům vydávat další certifikáty. Nechá ale běžet servery s revokačními seznamy CRL a OCSP respondery po dobu dalších dvou let. Poté vyprší platnost všech tří párů kořenových certifikátů. Pak bude kapitola autority StartCom uzavřena zcela a nadobro.
Autorita je dnes už ve většině nástrojů nedůvěryhodná, jako první zasáhl Apple, Mozilla přestala novým certifikátům věřit na konci loňského roku, poté se přidal Google v Chrome a jako poslední přišel s úpravou i Microsoft. V některých prohlížečích ještě dobíhá důvěryhodnost ve starší certifikáty, ale například Chrome už od verze 61 autoritu vyřadil úplně.
V praxi se tento zásah příliš mnoha webů nedotkne, protože podle statistik W3Techs používá certifikáty StartCom už méně než 0,1 % webů. Problémy s autoritou se táhly delší dobu, proto měli správci serverů dostatek času autoritu vyměnit.
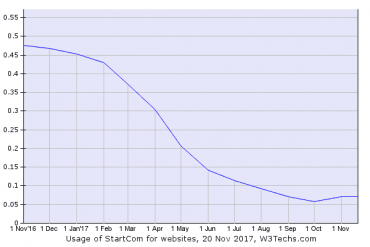
Autor: W3Techs
Pokles počtu certifikátů StartCom na internetu
Firma ve svém oznámení tvrdí, že se nedokázala vzpamatovat ze ztráty důvěryhodnosti, kterou utrpěla v důsledku celé řady chyb. Ty měly přímý dopad na bezpečnost a firma ztratila v očích internetové veřejnosti statut certifikační autority. Přibližně před rokem se většina tvůrců webových prohlížečů rozhodla přestat StartComu věřit, odstranit jeho kořenové certifikáty z úložišť a nepřijímat nově vydané koncové certifikáty, píše společnost ve veřejném oznámení.
Firma se snažila různými prostředky obnovit svou pozici, ale její pověst už byla natolik pošramocená, že se už nedokázala vzpamatovat. Navzdory snahám se neobjevily žádné náznaky toho, že by mohla být mezi tvůrci prohlížečů pověst obnovena. Proto se vlastníci StartComu rozhodli ukončit činnost certifikační autority.
Historie původně izraelské společnosti StartCom je v posledním roce spojena s kontroverzní čínskou certifikační autoritou WoSign. Ta porušila pravidla tím, že StartCom potichu koupila a přestěhovala do Číny, přičemž tuto změnu neoznámila auditorům. Nebyla to první chyba, WoSign sám vydával neoprávněně certifikáty, antedatoval certifikáty s SHA-1, měl chyby ve validačních procesech a používal nepodporované algoritmy.
Tvůrci prohlížečů chvíli váhali, zda skutečně oběma propojeným společnostem odebrat důvěru, či nechat dožít starší certifikáty. WoSign se během této doby snažil situaci zachránit, vydal prohlášení o restrukturalizaci a rozdělení vedení společnosti, přesto se nakonec odpuštění nedočkal a byl vyškrtnut ze seznamů důvěryhodných autorit.
Jeden ze zakladatelů společnosti StartCom se nedávno veřejně v mailové konferenci vyjádřil v tom smyslu, že je rád, že firma nakonec svou činnost ukončí. Podmínky ve firmě byly podle jeho slov velmi špatné a firma lhala svým zaměstnancům. Byl jsem vyhozen (nebo jsem odešel, záleží na tom, koho se ptáte), protože jsem jim řekl, že jsou to podrazáci.
Using Unsecured IoT Devices, DDoS Attacks Doubled in the First Half of 2017
21.11.2017 securityaffairs Attack
According to a report recently published by the security firm Corero the number of DDoS Attacks doubled in the First Half of 2017 due to unsecured IoT.
Denial of Service (DoS) attacks have been around as long as computers have been networked. But if your business relies on the Internet to sell products or collaborate, a DoS attack is more than a nuisance, it can be critical.
Over the past few years, the number of DoS attacks has continued to slowly grow in a “cat and mouse” evolution — bad actors get a slightly stronger attack, and network vendors come up with slightly more resilient equipment to defend. Generally the attacks came from botnets comprised of infected computers and servers. The cost of acquiring and keeping these systems in the botnet was relatively expensive, so there was an economic limiter on how fast the attacks would grow. Then Mirai happened in 2016 and everything changed.
The Mirai botnet didn’t struggle with corporate security teams and technical security controls like anti virus software and firewalls.

Instead, it focused on the millions of Internet of Things (IoT) devices like webcams and Internet routers in the home to build the botnet. With no security controls to overcome, the Mirai botnet was able to grow and launch Distributed Denial of Service (DDoS) attacks larger than ever seen before. A high-profile attack against Internet journalist Brian Krebs signaled that things had changed, then the October 2016 attack against DNS provider Dyn, showed how devastating a DDoS attack can be. And in the world of a cyber criminal, devastating is where the profit opportunities lie.
According to an Arbor Networks’ report at the end of 2016, “In 2016, IoT botnets emerged as a source of incredibly high volume DDoS attacks. So far these massive attacks have not leveraged reflection/amplification techniques. They are simply taking advantage of the sheer number of unsecured IoT devices that are deployed today.” (PDF) The report goes on to highlight that the number of DDoS attacks was up significantly over 2015 and the average size and time of the attack has also increased. “The longest DDoS attack in Q4 2016 lasted for 292 hours (or 12.2 days) – significantly longer than the previous quarter’s maximum (184 hours, or 7.7 days) and set a record for 2016,” according to Kaspersky’s DDoS Intelligence Report for Q4 2016. Knowing that cyber crime is fueled by profit motives now, it is safe to assume that the cyber criminals have figured out how to monetize the IoT threat and we can expect this growing trend in attacks to continue.
We have confirmation of this trend from DDos prevention provider, Corero. According to their most recent analysis, “Organizations are now experiencing an average of 8 DDoS attack attempts per day, up from 4 per day at the beginning of 2017, fueled by unsecured IoT devices and DDoS-for-hire services.” Massive DDoS attacks are getting all of the press attention, but they are only part of the story. What is most interesting about the analysis, however, is the discovery that, “A fifth of the DDoS attack attempts recorded during Q2 2017 used multiple attack vectors. These attacks utilize several techniques in the hope that one, or the combination of a few, can penetrate the target network’s security defenses.” In other words, the criminals’ objective often isn’t the denial of service, but using overwhelming noise at the perimeter to hide malware injection and data exfiltration activities.
DDoS has joined other cyber crimes as a well established, profitable exploitation technology. For as little as $20 per hour, anyone can take advantage of DDoS-as-a-Services and launch an attack at their target of choice. The opportunity to profit from Ransom Denial of Service, where companies pay to avoid being DDoS’d, to using DDoS as a mask for other profitable cyber crime activities means we haven’t seen the end of the growing trend in Denial of Service attacks.
Cobalt Hackers Now Targeting Banks Directly
21.11.2017 securityweek Hacking
The notorious Cobalt hackers have shown a change in tactics recently, switching their attacks to targeting banks themselves, instead of bank customers, Trend Micro reports.
Newly observed attacks appear to be part of a larger campaign that started in June and July with the targeting of Russian-speaking businesses. The techniques used are consistent with those associated with the Cobalt hacking group, but new infection chains were observed in recent incidents that targeted the bank’s employees.
Named after multifunctional penetration testing tool Cobalt Strike, the hacking group has been hitting ATMs and financial institutions across Europe. Unlike other groups that avoid Russia or Russian-speaking countries, Cobalt appears to be using the region as a testing ground for new malware and techniques, the same as the Lurk cybercriminal group, Trend Micro notes.
Last year, Russian authorities arrested 50 individuals associated with the use of the Lurk banking Trojan and supposedly took down the Angler exploit kit in the process.
In the recent attacks, the Cobalt group has been using a different vulnerability than before and also started targeting the banks themselves with spear phishing emails. The hackers are now masquerading as the customers of their targets, as a state arbitration court, and as an anti-fraud and online security company.
The group used a Rich Text Format (RTF) document with malicious macros in an attack on August 31, but switched to an exploit for CVE-2017-8759 in spam runs observed on September 20 to 21. Patched in September last year, the flaw is a code injection/remote code execution vulnerability in Microsoft’s .NET Framework.
The Cobalt hackers used this vulnerability to drop and execute Cobalt Strike from a remote server they controlled. Previously, the security bug was used to deliver the FinFisher spyware, but Trend Micro says that other threat actors have been using it of late, including the cyberespionage group ChessMaster.
As part of the attacks leveraging macro-laden RTF files, a PowerShell command is executed to retrieve a dynamic-link library (DLL) file, and odbcconf.exe, a command-line utility related to Microsoft Data Access Components, is used. The DLL drops and executes a malicious JScript using regsvr32.exe, and another JScript is dropped and executed.
The code was designed to receive backdoor commands from a remote server, and the security researchers observed it receiving a PowerShell command to download Cobalt Strike, as well as attempting to connect to a command and control (C&C) server located in France.
Infections involving CVE-2017-8759 flaw start with RTF attachments too, designed to download a Simple Object Access Protocol (SOAP) Web Services Description Language (WSDL) definition from a remote server. The code is injected into memory and downloads and executes Cobalt Strike, which in turn connects to the C&C and waits for commands.
“Many security technologies and security researchers may be utilizing newer detection mechanisms, but cybercriminals are also keeping up, adjusting their tactics to evade them. In Cobalt’s case, for instance, they’ve looked into instances of valid Windows programs or utilities as conduits that allow their malicious code to bypass whitelisting,” the security researchers note.
Mitigation techniques involve securing the use of built-in interpreters or command-line applications, such as PowerShell, odbcconf.exe, and regsvr.exe; keeping systems patched and updated at all times; securing email gateways; using network segmentation to prevent lateral movement; monitoring the network and endpoint for anomalous activities.
Intel Chip Flaws Expose Millions of Devices to Attacks
21.11.2017 securityweek Vulnerebility
Intel has conducted an in-depth security review of its Management Engine (ME), Trusted Execution Engine (TXE) and Server Platform Services (SPS) technologies and discovered several vulnerabilities. The company has released firmware updates, but it could take some time until they reach the millions of devices exposed to attacks due to these flaws.
Intel’s ME solution, which some members of the industry have classified as a backdoor, allows users to remotely manage computers via the Intel Active Management Technology (AMT).
Earlier this year, Embedi researchers discovered a critical privilege escalation vulnerability affecting AMT and some related services, specifically Small Business Technology (SBT) and Standard Manageability. Positive Technologies has also reported finding some potentially serious flaws in ME.
As a result of these findings, Intel has decided to perform a comprehensive security audit of ME, along with two other products. These are TXE, which is designed to ensure that a platform and its operating system are authentic and the OS is running in a trusted environment, and SPS, which allows remote server management.
The review led to the discovery of seven vulnerabilities that can be exploited to impersonate the ME, SPS and TXE services and impact the validity of local security feature attestation, execute arbitrary code without being detected by the user or the operating system, and crash the system or make it unstable.
One of the high severity flaws described in Intel’s advisory, CVE-2017-5705, is a local code execution issue found by Positive Technologies in ME.
According to Intel, ME is also affected by buffer overflows and other types of vulnerabilities that can be exploited for privilege escalation (CVE-2017-5708), local code execution (CVE-2017-5711), and remote code execution (CVE-2017-5712).
The kernel of Intel SPS is impacted by a couple of high severity flaws that can be exploited for local code execution (CVE-2017-5706), and gaining access to privileged content (CVE-2017-5709).
As for TXE, the tech giant discovered privilege escalation (CVE-2017-5710) and local code execution (CVE-2017-5707) vulnerabilities that have also been rated high severity.
Intel has not made public any details about the vulnerabilities, but Google security expert Matthew Garrett has shared some thoughts on the possible impact and concluded that the flaws are unlikely to be harmless.
Systems using ME firmware versions 11.0, 11.5, 11.6, 11.7, 11.10 and 11.20, SPS version 4.0, and TXE version 3.0 are impacted. The list of affected products includes some Core, Xeon, Atom, Pentium and Celeron processors, which are found in millions of devices.
Intel has released firmware updates that patch the vulnerabilities, along with a tool that allows users to see if their systems are affected. The company has advised customers to check their system OEMs website for the firmware updates, but, for the time being, only Lenovo appears to have released firmware updates.
Final Version of 2017 OWASP Top 10 Released
21.11.2017 securityweek Vulnerebility
The final version of the 2017 OWASP Top 10 was released on Monday and some types of vulnerabilities that don’t longer represent a serious risk have been replaced with issues that are more likely to pose a significant threat.
The Open Web Application Security Project (OWASP) announced the first release candidate for the 2017 OWASP Top 10 back in April, and there has been a lot of debate about what should and what should not be included.
One significant change compared to the 2013 OWASP Top 10 is the fact that the types of flaws that made it into the 2017 list have been selected based on the risk they pose.
The OWASP Top 10 vulnerabilities are injection, broken authentication, sensitive data exposure, XML external entity (XXE), broken access control, security misconfiguration, cross-site scripting (XSS), insecure deserialization, using components with known vulnerabilities, and insufficient logging and monitoring.
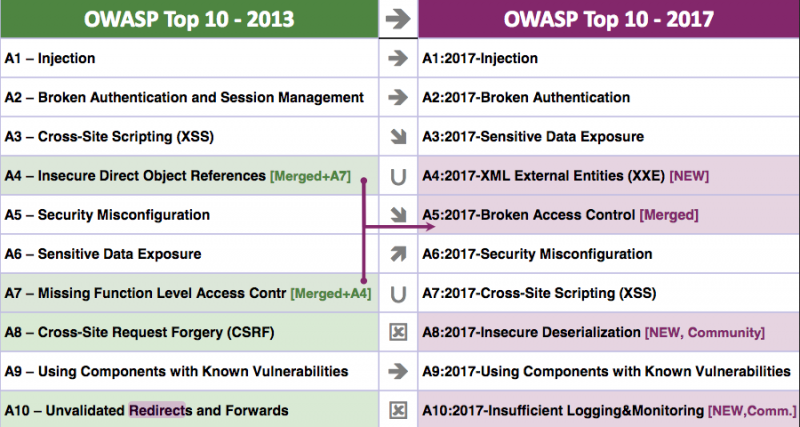
While XSS can be classified as a type of injection, the decision has been made to leave it in a separate category as these types of bugs are addressed differently compared to SQL and OS command injections.
Cross-site request forgery (CSRF) has been removed from the OWASP Top 10 as modern development frameworks ensure that such vulnerabilities are avoided, which has led to CSRF being found in less than 5% of applications. Unvalidated redirects and forwards have also been removed as they affect only around 8% of apps.
Insecure direct object references (IDOR) and missing function level access control have been merged into broken access control.
The free spots were filled by XXE, insecure deserialization, and insufficient logging and monitoring. Critical deserialization flaws have been found in several high profile apps in the past few years so it’s not surprising that it made the list. As for logging and monitoring, OWASP pointed out that many organizations have serious problems in this department, as clearly demonstrated by the significant number of breaches discovered by third-parties instead of the targeted organization itself.
OWASP also noted that while the names of some categories have not changed, the types of issues they cover has changed. For instance, sensitive data exposure refers to privacy and personal information exposure, not leaky headers and stack traces, and misconfigurations now also include cloud-related issues such as unprotected storage containers (e.g. AWS S3 buckets).
The 2017 OWASP Top 10 is based on data from 23 contributors covering more than 114,000 applications. The data has been made available on GitHub, a move that is part of OWASP’s efforts to be more transparent.
After a break, OWASP will start working on the next Top 10, which has been scheduled for 2020.
U.S. Charges Iranian Over 'Game of Thrones' HBO Hack
21.11.2017 securityweek BigBrothers
The United States on Tuesday charged an Iranian computer whiz with hacking into HBO, stealing scripts and plot summaries for "Games of Thrones," and trying to extort $6 million in Bitcoin out of the network.
US prosecutors in New York unveiled a seven-count indictment against Behzad Mesri, whom they identified as an Iran-based hacker who also goes by the name Skote Vahshat. Mesri is still at large, a spokesman for the US Attorney's office in Manhattan told AFP.
Mesri is accused of orchestrating a hack of HBO from May to August, then threatening to release stolen data unless the premium cable network paid a $6 million ransom in the digital currency Bitcoin.
US prosecutors say he stole scripts and plot summaries for then unaired episodes of the global smash hit "Game of Thrones" series, and unaired episodes for multiple other shows, including the "Curb Your Enthusiasm" comedy series.
He is accused of compromising multiple user accounts, and in July of sending an anonymous email to HBO personnel saying: "Hi to All losers! Yes it's true! HBO is hacked!... Beware of heart Attack!!!"
Mesri leaked some of the stolen data over the Internet onto websites he controlled, US federal prosecutors allege.
The Iranian suspect faces seven counts in the United States, including wire fraud, aggravated identity theft and four counts of computer fraud.
US prosecutors accuse Mesri of previously conducting computer attacks on behalf of the Iranian military that targeted nuclear software systems and Israeli infrastructure.
They also said he was a member of the Iranian-based Turk Black Hat Security hacking group, targeting hundreds of websites in the United States and around the world.
North Korean Hackers Target Android Users in South
21.11.2017 securityweek BigBrothers
At least two cybersecurity firms have noticed that the notorious Lazarus threat group, which many experts have linked to North Korea, has been using a new piece of Android malware to target smartphone users in South Korea.
Both McAfee and Palo Alto Networks published blog posts on Monday describing the latest campaign attributed to the threat actor also known as Hidden Cobra. The group is believed to be responsible for several high-profile attacks, including ones targeting Sony and financial institutions, and possibly even the recent WannaCry ransomware attack. Some of the operations tied to this group are Operation Blockbuster, Dark Seoul and Operation Troy.
The malware sample analyzed by McAfee, delivered as an APK file, has been designed to mimic a Korean bible app made available on Google Play by a developer named GODpeople. However, the malicious application did not make it onto the official app store and it’s unclear what method of distribution has been used.
“GodPeople is sympathetic to individuals from North Korea, helping to produce a movie about underground church groups in the North. Previous dealings with the Korean Information Security Agency on discoveries in the Korean peninsula have shown that religious groups are often the target of such activities in Korea,” explained McAfee’s Christiaan Beek and Raj Samani.
McAfee said the malware, which has been around since at least March, delivers a backdoor as an executable and linkable format (ELF) file. The backdoor allows hackers to collect information about the infected device, download and upload files, and execute commands. The list of command and control (C&C) servers used by the malware includes IP addresses previously linked to the Lazarus group.
Palo Alto Networks has not shared any information about the applications used to deliver the malware, but the company pointed out that the operation appears to be aimed at Samsung device users in South Korea.
The firm’s analysis started with a PE file uploaded to VirusTotal. This file is designed to deliver ELF ARM files and APK files from an HTTP server. The APK that represents the final payload provides backdoor capabilities and allows its operator to spy on the targeted user by recording audio via the microphone, capturing images via the camera, uploading and downloading files, harvesting GPS information, reading contacts, collecting SMS and MMS messages, recording browsing history, and capturing Wi-Fi information.
Palo Alto Networks has also found links between the malware and the Lazarus group, particularly to malware and infrastructure used in attacks on the SWIFT banking system and activities described in reports on Operation Blockbuster.
This is not the first time North Korea has reportedly targeted mobile users in the South. Back in 2014, South Korea’s National Intelligence Service said more than 20,000 smartphones had been infected that year with a piece of malware traced back to North Korea.
The reports from McAfee and Palo Alto Networks come less than a week after the U.S. Department of Homeland Security (DHS) published a report on a Hidden Cobra malware tracked as FALLCHILL.
Windows 8 and newer versions fail to properly implement ASLR
21.11.2017 securityaffairs Safety
CC/CERT is warning the Address Space Layout Randomisation (ASLR) isn’t properly implemented in versions of Microsoft Windows 8 and newer.
The researcher Will Dormann from the Carnegie-Mellon CERT has discovered the Address Space Layout Randomisation (ASLR) isn’t properly implemented in versions of Microsoft Windows 8 and newer.
15 Nov
Matt Miller
@epakskape
Replying to @wdormann and 3 others
It is possible to enable bottom-up ASLR system-wide, but I'm not sure if it can be done via the WDEG UI, @markwo might know. Agree with your feedback here. I passed it on to the team.
Will Dormann
@wdormann
Actually, with Windows 7 and EMET System-wide ASLR, the loaded address for eqnedt32.exe is different on every reboot. But with Windows 10 with either EMET or WDEG, the base for eqnedt32.exe is 0x10000 EVERY TIME.
Conclusion: Win10 cannot be enforce ASLR as well as Win7! pic.twitter.com/Jp10nqk1NQ




The Address Space Layout Randomization (ASLR Protection) is a security mechanism used by operating systems to randomize the memory addresses used by key areas of processes, it makes hard for attackers to find the memory location where to inject their malicious code.
The Address Space Layout Randomisation is particularly effective against stack and heap overflows and is able to prevent arbitrary code execution triggered by any other buffer overflow vulnerability. The security measures are present in almost any modern operating system, including Windows, Linux, macOS, and Android.
Applications running on Windows 8 and newer versions were allocated addresses with zero entropy, this means that it was possible to predict where the code is allocated in memory due to the failure of the randomisation. Windows 10 has the problem, too.
The CERT/CC published a security advisory late last, Dormann found the ASLR issue while he was analyzing a recently fixed bug in Microsoft’s equation editor, tracked as CVE-2017-11882, that could be exploited by remote attackers to install a malware without user interaction.
“Microsoft Windows 8 introduced a change in how system-wide mandatory ASLR is implemented. This change requires system-wide bottom-up ASLR to be enabled for mandatory ASLR to receive entropy. Tools that enable system-wide ASLR without also setting bottom-up ASLR will fail to properly randomise executables that do not opt in to ASLR.” states the security advisory.
According to the CERT, the bug only affects applications using mandatory ASLR, while applications that used opt-in Address Space Layout Randomisation and that never used ASLR aren’t affected.
According to the CERT/CC the problem was introduced with Windows 8 with a change in the mandatory Address Space Layout Randomisation implementation.
“Starting with Windows 8, system-wide mandatory ASLR is implemented differently than with prior versions of Windows. With Windows 8 and newer, system-wide mandatory ASLR is implemented via the
HKLM\System\CurrentControlSet\Control\SessionManager\Kernel\MitigationOptions
binary registry value. The other change introduced with Windows 8 is that system-wide ASLR must have system -wide bottom-up ASLR enabled to supply entropy to mandatory ASLR.” continues the advisory.
The CERT explained that both EMET and Windows Defender Exploit Guard can enable mandatory Address Space Layout Randomisation for code that isn’t linked with the
/DYNAMICBASE
flag.
“Both EMET and Windows Defender Exploit Guard enable system-wide ASLR without also enabling system-wide bottom-up ASLR. Although Windows Defender Exploit guard does have a system-wide option for system-wide bottom-up-ASLR, the default GUI value of “On by default” does not reflect the underlying registry value (unset).” states the advisory.
“This causes programs without
/DYNAMICBASE
to get relocated, but without any entropy. The result of this is that such programs will be relocated, but to the same address every time across reboots and even across different systems.”

16 Nov
Matt Miller
@epakskape
Replying to @wdormann
Set bit 15 (0x10000) in HKLM\System\CurrentControlSet\Control\Session Manager\Kernel\MitigationOptions (REG_QWORD). The WDEG team is looking at how to better support this from the UI.
Will Dormann
@wdormann
Or for those not proficient in setting bits in binary registry values (such as myself), either manually set the values indicated in this picture, or if you don't care about clobbering any existing system-wide mitigations, import this .REG file:https://gist.github.com/wdormann/43cffbf823b5c5da8682985ef31c16a9 … pic.twitter.com/i4YNpET0wq

Replies 3 3 Retweets 7 7 likes
Twitter Ads info and privacy
Dormann explained that sysadmins can set a registry value to force bottom-up Address Space Layout Randomisation.
“The CERT/CC is currently unaware of a practical solution to this problem. Please consider the following workaround:
Enable system-wide bottom-up ASLR on systems that have system-wide mandatory ASLR
To enable both bottom-up ASLR and mandatory ASLR on a system-wide basis on a Windows 8 or newer system, the following registry value should be imported:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\kernel]
"MitigationOptions"=hex:00,01,01,00,00,00,00,00,00,00,00,00,00,00,00,00" concludes the CC/CERT
A massive cyber attack hit the Algerian state telecom operator Algerie Telecom
21.11.2017 securityaffairs Cyber
The Algerian state telecom operator Algerie Telecom was hit by a series of cyber attacks aimed to hack and disrupt its system.
The Algerian state telecom operator Algerie Telecom confirmed on Friday that it was hit by a series of cyber attacks aimed to hack and disrupt its system.
The company was able to repel the attack and security services managed to identify and arrest the attackers.
At the time of writing, there are no further details about the attacks or the motivation of the hackers.
According to a statement issued by the company, its staff was able to protect the operational infrastructure with the help of security services.

The rapid increase in the number of cyber attacks is raising concerns in Algeria especially over the security of recently launched services, such as the recently adopted e-payment system for electricity and water bills.
“Iman Houda Faraoun, Minister of Post, Information and Communication Technologies and Digital Economy, said the e-commerce bill, which had been approved by the Council of Ministers, will come into force as soon as it is approved by the parliament.” reported the Xinhuanet.com website.
“She promised that the e-commerce process will be fully protected, as e-financial transactions data, invoices and postal and bank cards will remain confidential.”
Secureworks Releases Open Source IDS Tools
21.11.2017 securityweek Security
Secureworks has released two open source tools, Flowsynth and Dalton, designed to help analysts test rules for intrusion detection systems (IDS) and intrusion prevention systems (IPS) such as Snort and Suricata.
Dalton allows users to quickly and easily run network packet capture (pcap) files against IDS/IPS engines using bespoke rules and/or existing rulesets.
Common use cases for Dalton include testing ruleset coverage, developing and troubleshooting signatures, testing configuration changes, testing variable changes, testing specific IDS engine behavior, and creating custom packet captures.
Dalton includes a controller component, which provides a web interface and an API for retrieving job results and communicating with agents. These agents, which represent the second component of the tool, run on IDS sensors and provide an interface between the controller and the IDS engine.
The second tool released as open source by Secureworks is Flowsynth, which complements Dalton by making it easier for users to quickly model network traffic and generate custom pcaps.
“Flowsynth rapidly models network traffic and generates libpcap-formatted packet captures. It leverages the Scapy packet manipulation tool, but Flowsynth's input is a text-based, structured intermediate language that is simple to create and understand. It allows for programmatic network flow definitions as well as ad hoc and custom network traffic creation,” Secureworks explained.
The Dalton controller includes a web-based user interface that connects the tool to Flowsynth and allows the created pcaps to be easily sent to Dalton for testing.
The documentation and examples provided by Secureworks are specifically made for Suricata and Snort, both of which are also open source.
The security firm says Dalton and Flowsynth are based on tools that its Counter Threat Unit research team has used internally for several years. “They have been so useful that Secureworks decided to make them available to the network IDS community,” the company said.
Windows 8 and Later Fail to Properly Apply ASLR
21.11.2017 securityweek Safety
Address Space Layout Randomization (ASLR) isn’t properly applied on versions of Microsoft Windows 8 and newer, an alert from Carnegie Mellon University-run CERT Coordination Center (CERT/CC) warns.
The issue is created by the tools that enable system-wide ASLR on newer Windows systems without also setting bottom-up ASLR, a vulnerability note explains.
Starting with Windows 8, system-wide bottom-up ASLR is required for mandatory ASLR to receive entropy, but executables that do not opt in to ASLR aren’t properly randomized if the tools that enable system-wide ASLR don’t also set bottom-up ASLR.
ASLR was introduced in Windows Vista to prevent code-reuse attacks by loading executable modules at non-predictable addresses. Because of this feature, attack methods relying on code being loaded to a predictable or discoverable location, such as return-oriented programming (ROP), were mitigated.
ASLR, however, requires that the code is linked with the /DYNAMICBASE flag to opt in to ASLR, which represents an implementation weakness, the vulnerability note from DHS-sponsored CERT/CC reveals.
To protect applications that don't opt in to using ASLR (or other exploit mitigation techniques), Microsoft released the Enhanced Mitigation Experience Toolkit (EMET), which allows users to specify both system-wide and application-specific mitigations on the system.
Thus, EMET acts as a front-end GUI for system-wide exploit mitigations built in to the Windows operating system. When it comes to application-specific mitigations, the EMET library is loaded into the process space of the applications to be protected.
Starting with the Windows 10 Fall Creators update, Microsoft made EMET native to the operating system by incorporating its capabilities into the Windows Defender Exploit Guard. Both EMET and Windows Defender Exploit Guard can enable mandatory ASLR on a per-application or system-wide basis.
Starting with Windows 8, system-wide mandatory ASLR is implemented via the HKLM\System\CurrentControlSet\Control\Session Manager\Kernel\MitigationOptions binary registry value and requires system-wide bottom-up ASLR enabled to supply entropy to mandatory ASLR.
“Both EMET and Windows Defender Exploit Guard enable system-wide ASLR without also enabling system-wide bottom-up ASLR. […] This causes programs without /DYNAMICBASE to get relocated, but without any entropy. The result of this is that such programs will be relocated, but to the same address every time across reboots and even across different systems,” CERT/CC explains.
Because of this issue, non-DYNAMICBASE applications are relocated to a predictable location on Windows 8 and newer systems that have system-wide ASLR enabled via either EMET or Windows Defender Exploit Guard. This also makes exploitation of the vulnerability easier in some instances.
The CERT team notes that no practical solution to the problem is known at the moment, but that enabling system-wide bottom-up ASLR on systems that have system-wide mandatory ASLR should mitigate the issue.
Importing the following registry value enables both bottom-up ASLR and mandatory ASLR on a system-wide basis on Windows 8 or newer systems:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\kernel]
"MitigationOptions"=hex:00,01,01,00,00,00,00,00,00,00,00,00,00,00,00,00
“Note that importing this registry value will overwrite any existing system-wide mitigations specified by this registry value. The bottom-up ASLR setting specifically is the second 01 in the binary string, while the mandatory ASLR setting is the first 01,” the CERT team notes.
System-wide mandatory ASLR could cause issues on systems with older AMD/ATI video card drivers in use, but the problem was addressed in the Catalyst 12.6 drivers released in June, 2012.
Microsoft was notified on the vulnerability on November 16, the vulnerability note explains.
BankBot Returns On Play Store – A Never Ending Android Malware Story
20.11.2017 thehackernews Android
Even after so many efforts by Google for making its Play Store away from malware, shady apps somehow managed to fool its anti-malware protections and infect people with malicious software.
A team of researchers from several security firms has uncovered two new malware campaigns targeting Google Play Store users, of which one spreads a new version of BankBot, a persistent family of banking Trojan that imitates real banking applications in efforts to steal users' login details.
BankBot has been designed to display fake overlays on legitimate bank apps from major banks around the world, including Citibank, WellsFargo, Chase, and DiBa, to steal sensitive information, including logins and credit card details.
With its primary purpose of displaying fake overlays, BankBot has the ability to perform a broad range of tasks, such as sending and intercepting SMS messages, making calls, tracking infected devices, and stealing contacts.
Google removed at least four previous versions of this banking trojan from its official Android app store platform earlier this year, but BankBot apps always made their ways to Play Store, targeting victims from major banks around the world.
The second campaign spotted by researchers not only spreads the same BankBot trojan as the first campaign but also Mazar and Red Alert. This campaign has been described in detail on ESET blog.
According to an analysis performed by the mobile threat intelligence team at Avast in collaboration with ESET and SfyLabs, the latest variant of BankBot has been hiding in Android apps that pose as supposedly trustworthy, innocent-looking flashlight apps.
First spotted by the researchers on 13 October, the malicious BankBot apps uses special techniques to circumvent Google's automated detection checks, such as starting malicious activities 2 hours after the user gave device admin rights to the app and publishing the apps under different developer names.
After tricking victims into downloading them, the malicious apps check for the applications that are installed on the infected device against a hard-coded, list of 160 mobile apps.
According to the researchers, this list includes apps from Wells Fargo and Chase in the U.S., Credit Agricole in France, Santander in Spain, Commerzbank in Germany and many other financial institutions from around the world.
If it finds one or more apps on the infected smartphone, the malware downloads and installs the BankBot APK from its command-and-control server on the device, and tries to trick the victim into giving it administrator rights by pretending to be a Play Store or system update using a similar icon and package name.
Once it gets the admin privileges, the BankBot app displays overlay on the top of legitimate apps whenever victims launch one of the apps from the malware's list and steal whatever banking info the victim's types on it.
The Avast Threat Labs has also provided a video demonstration while testing this mechanism with the app of the local Czech Airbank. You can see how the app creates an overlay within milliseconds and tricks the user into giving out their bank details to criminals.
Since many banks use two-factor-authentication methods for secure transactions, BankBot includes functionality that allows it to intercept text messages, allowing criminals behind BankBot to steal mobile transaction number (mTAN) sent to the customer's phone and transfer money to their accounts.
Here's one important thing to note is that Android mechanism blocks apps installation from outside the Play Store. Even if you have already permitted installation from unknown sources, Google still requires you to press a button to continue such installations.
"Unlike this newer version of BankBot, droppers from previous campaigns were far more sophisticated," the researchers note. "They applied techniques such as performing clicks in the background via an Accessibility Service to enable the installation from unknown sources."
The latest BankBot version does not utilize this Accessibility Service feature due to Google's recent move of blocking this feature for all applications, except those designed to provide services for the blind.
Google has already removed all recently-discovered BankBot apps after being notified by the researchers.
Although it is a never-ending concern, the best way to protect yourself is always to be vigilant when downloading apps even from Google's official Play store. So, always verify app permissions and reviews before downloading an app from Google Play Store.
Even though the BankBot apps made it way into the Play Store, its payload was downloaded from an external source. So, don't allow any unknown third-party APK to be installed on your smartphone.
To do so, Go to Settings → Security and then Turn OFF "Allow installation of apps from sources other than the Play Store."
Most importantly, be careful which apps you give administrative rights to, as it is powerful and can provide a full app control of your device.
Flaw in F5 Products Allows Recovery of Encrypted Data
20.11.2017 securityweek Vulnerebility
A crypto vulnerability affecting some F5 Networks products can be exploited by a remote attacker for recovering encrypted data and launching man-in-the-middle (MitM) attacks, the company told customers on Friday.
The impacted products are part of F5’s BIG-IP application delivery platform, including security, traffic management and performance services such as LTM, AAM, AFM, Analytics, APM, ASM, DNS, GTM, Link Controller, and PEM. The flaw also affects the F5 WebSafe anti-fraud solution.
According to F5, the vulnerability exposes virtual servers configured with a Client SSL profile and RSA key exchange enabled to adaptive chosen-ciphertext attacks, also known as Bleichenbacher attacks. Launching an attack against a TLS session established using an RSA key exchange allows a remote hacker to recover plaintext data and launch MitM attacks, even if they don’t have access to the server’s private key.
Nick Sullivan, cryptography expert at Cloudflare, pointed out that the vulnerability is similar to the notorious DROWN bug, which allows an attacker to decrypt TLS communications when SSLv2 is used. However, he said the F5 bug is worse as the SSLv2 requirement is eliminated.
“Note that you don’t need to have the private key to decrypt non-FS [forward secrecy] TLS sessions. You only need to find a server using the key with a padding oracle,” Sullivan said. “We should all be grateful for the people in the industry who successfully pushed for forward secrecy to be the default in HTTPS.”
The vulnerability is tracked as CVE-2017-6168 and it has been assigned a CVSS score of 9.1, which puts it in the critical severity category.
F5 has released updates that patch the security hole for each of the affected products. The company has also provided advice for partial or full mitigation, and pointed out that an attack is not easy to conduct.
“Exploiting this vulnerability to perform plaintext recovery of encrypted messages will, in most practical cases, allow an attacker to read the plaintext only after the session has completed,” F5 said in its advisory.
“Exploiting this vulnerability to conduct a MiTM attack requires the attacker to complete the initial attack, which may require millions of server requests, during the handshake phase of the targeted session within the window of the configured handshake timeout,” the company added. “This attack may be conducted against any TLS session using RSA signatures, but only if cipher suites using RSA key exchange are also enabled on the virtual server. The limited window of opportunity, limitations in bandwidth, and latency make this attack significantly more difficult to execute.”
The vendor said the highest risk is to virtual servers where the Generic Alert option, which is enabled by default, has been disabled. This is due to the fact that these systems report the specific handshake failure, which can be useful to the attacker, instead of a generic message.
The security hole was reported to the vendor by Tripwire’s Craig Young, researcher Hanno Böck, and Juraj Somorovsky of Ruhr-Universität Bochum. It’s worth noting that Somorovsky was part of the team that first described the DROWN attack. Details of the vulnerability will be published at a later date.
Screen/Audio Capture Vulnerability Impacts Lion's Share of Android Devices
20.11.2017 securityweek Android
A vulnerability that allows malicious applications to capture screen contents and record audio without a user’s knowledge impacts over 78% of Android devices, researchers claim.
The issue is caused by the MediaProjection service introduced by Google in the Android Framework on Android 5.0. This service allows applications to capture the screen or record audio without special permissions, by simply requesting access via an Intent.
Prior to Android 5.0, an application would either have to run with root privileges or be signed with the device’s release keys to use system protected permissions to capture screen contents, MWR Labs security researchers explain. With the introduction of MediaProjection, no permissions are required in the AndroidManifest.xml to use the service.
When an application requires access to this system Service, a SystemUI pop-up is displayed to warn the user that the program wants to capture the screen. According to MWR, however, an attacker could overlay the SystemUI pop-up with an arbitrary message meant to trick the user into granting the malicious app the ability to capture the screen.
“This vulnerability would allow an attacker to capture the user’s screen should the user tap of the SystemUI pop-up that has been overlayed by the attacker with an arbitrary message,” the security researchers explain in a security advisory (PDF).
MWR also explains that it is difficult to determine which applications use the MediaProjection service, given that there are no permission requirements. Furthermore, the researchers claim that the vulnerability is severe because the SystemUI pop-up is launched within the context of the attacker’s application, meaning that the app can detect it and draw the overlay without the user noticing.
“The primary cause of this vulnerability is due to the fact that affected Android versions are unable to detect partially obscured SystemUI pop-ups. This allows an attacker to craft an application to draw an overlay over the SystemUI pop-up which would lead to the elevation of the application’s privileges,” the researchers argue.
Because the SystemUI pop-up is the only access control mechanism meant to prevent malicious applications from abusing the MediaProjection service, an attacker could also bypass the mechanism by tapjacking the pop-up using publicly available methods.
The vulnerability has been addressed in Android 8.0, but version fragmentation within the Android ecosystem means that there are a great deal of devices that will never receive a patch, thus remaining vulnerable. It’s unclear whether patches will be released for older Android iterations as well, MWR says.
As of November 9, 2017, vulnerable platform releases (Android 5.0 to Android 7.1) are running on 78.7% of Android devices out there.
The good news is that the attack is not entirely undetectable: “when an application gains access to the MediaProjection service, it generates a Virtual Display which activates the screencast icon in the notification bar,” the researchers explain.
Application developers can defend against this attack by enabling the FLAG_SECURE layout parameter via the application's WindowManager. Thus, the contents of applications are treated as secure and won’t appear in screenshots.
MWR reported the issue to Google in January this year. The Internet giant assessed the vulnerability as High risk and released Android 8.0 with a patch for it, but hasn’t provided information on patches for Android 7.1.2 to 5.0 as of now, the researchers reveal.
Ongoing Adwind Phishing Campaign Discovered
20.11.2017 securityweek Phishing
A new phishing campaign delivering the Jsocket variant of Adwind (also known as AlienSpy) was detected in October, and is ongoing. Adwind and its variants have been around since at least 2012. It is a cross-platform backdoor able to install additional malware, steal information, log keystrokes, capture screenshots, take video and audio recordings, and update its own configuration.
According to Kaspersky Lab's virus definition, "it is distributed openly in the form of a paid service, where the "customer" pays a fee in return for use of the malicious program. There were around 1,800 users of the system by the end of 2015. This makes it one of the biggest malware platforms in existence today."
The current campaign was detected by KnowBe4, a security awareness firm, and reported in a blog by CEO Stu Sjowerman posted today. KnowBe4 provides users with a phish alert button that notifies both the company's security team and KnowBe4 when a suspicious email is received.
"In early October we noticed an uptick in the number of phishing emails reported by customers that were sporting .JAR (Java) attachments -- a hallmark of Adwind," writes Sjowerman. There is no indication of the size of this new campaign, which is unsurprising since KnowBe4's awareness comes primarily from those of its own customers that have installed its phish alert button.
However, since Adwind is sold as a service, it can at any time be delivered as a new bulk campaign or even by multiple cybercriminals using different customizations with different functionalities. In February 2016, Kaspersky Lab estimated that approximately 443,000 targets had been hit with Adwind by the end of 2015.
In July 2017, Trend Micro noted an Adwind campaign that started with 5,286 detections in January and grew to 117,649 detections in June -- with a 107% growth between May and June. If this pattern repeats, what is currently noted by KnowBe4 as "an uptick in the number of phishing emails reported by customers," could be the beginning of a major new Adwind campaign.
"All the Adwind phishes in this upsurge," comments Sjowerman, "used Subject: lines and social engineering schemes centered on everyday business documents and related forms: invoices, purchase orders, payment instructions, contracts, and RFQs (requests for quotations)." The campaign is apparently targeting businesses rather than consumers. This is very similar to an Adwind alert issued by McAfee in December 2015, which included Subject lines such as "credit note for outstanding payment of Invoice", "PO#939423" and "Re: Payment/TR COPY-Urgent".
KnowBe4 provides two sample phishing emails. One includes the payload in a .JAR file. In this instance, Outlook blocks access to the attachment as being 'potentially unsafe'. In the second example, the payload is contained in a zip file, and is not blocked by Outlook. KnowBe4 doesn't comment on whether this difference, together with stylistic differences between the two email bodies, indicates that multiple groups are sending out Adwind phishes.
Sjowerman is particularly concerned about the ability of anti-virus defenses to recognize and block Adwind. "Although we can say that anti-virus engine detections appear to have improved with time, they are still not at a level that would inspire confidence, with the samples we submitted [to VirusTotal] being picked up by only 16-24 engines (out of 60 total) -- roughly 26%-40% of tested engines -- even weeks after their original appearance in the wild."
He accepts that VirusTotal does not accurately reflect the true performance of an AV product. "It is worth noting," he adds, "that most endpoint anti-virus products now incorporate heuristics-driven behavioral detection capabilities that allow them to provide protection beyond their more traditional, file-focused core engines."
His concern, however, is over the extent of anti-detection capabilities built into Adwind. These include sandbox detection; detection, disabling and killing of various antivirus and security tools; TLS-protected command-and-control; and anti-reverse engineering/debugging protection.
"Many of these [antivirus] behavioral protection schemes intervene only after malicious files land on the file system and execute... And given that Adwind itself sports extremely aggressive tools to detect, thwart, and kill all manner of security tools, the best approach to handling an advanced threat like Adwind is to prevent it from being downloaded and executed in the first place."
In short, the best prevention for Adwind is the human firewall of user awareness.
KnowBe4 raised $30 million in Series B financing led by Goldman Sachs Growth Equity in October 2017.
Microsoft Manually Patched Office Component: Researchers
20.11.2017 securityweek Vulnerebility
Microsoft engineers appear to have manually patched a 17 year-old vulnerability in Office, instead of altering the source code of the vulnerable component, ACROS Security researchers say.
Tracked as CVE-2017-11882, the vulnerability was addressed with a fixed release on November 14 as part of Microsoft’s Patch Tuesday security updates. The issue was discovered by Embedi security researchers in the Microsoft Equation Editor (EQNEDT32.EXE), a tool that remained unchanged in the Office suite since November 9, 2000.
While analyzing the patched version of the file, the researchers from ACROS Security’s 0patch Team discovered that it was nearly identical with the original file, although the new compilation date is 2017.8.14.0.
This would not be possible if Microsoft made the necessary corrections to the source code and then re-built the binary. However, manually patching the binary executable makes this possible, and this is what the researchers believe happened with the Equation Editor.
“Really, quite literally, some pretty skilled Microsoft employee or contractor reverse engineered our friend EQNEDT32.EXE, located the flawed code, and corrected it by manually overwriting existing instructions with better ones (making sure to only use the space previously occupied by original instructions),” Mitja Kolsek from the 0patch Team explains.
Proof of that can be easily found when comparing the original and the patched file versions. No C/C++ compiler “would put all functions in a 500+ KB executable on exactly the same address in the module after rebuilding a modified source code,” the researcher notes.
BinDiff results between the two files show that all EA primary values are identical to EA secondary values of matched functions and that even the patched functions have the same address in both EQNEDT32.EXE versions.
The vulnerability discovered by Embedi consisted of the Equation Editor not checking whether the destination buffer was large enough for the user-supplied string. Thus, if the font name provided through the Equation object has a name long enough, it could cause a buffer overflow.
An additional parameter added to this function now specifies the destination buffer length, which the original logic of the character-copying loop now ends when the destination buffer length is reached as well, to prevent buffer overflow.
“In addition, the copied string in the destination buffer is zero-terminated after copying, in case the destination buffer length was reached (which would leave the string unterminated),” Kolsek notes.
According to the researcher, in addition to adding said check for buffer length, the engineers who patched the function also managed to make it 14 bytes shorter. On top of that, it appears that the engineers patched other functions in the component as well, most probably because they discovered additional vulnerabilities and decided to resolve them too.
Two functions in the patched version now have boundary checks injected right before inlined memcpy operations. According to Kolsek, the engineers who patched the Equation Editor used only a single instruction (instead of two) for implementing the checks, thus leaving the code logically identical, but also freeing up space for injecting the check and for zero-terminating the copied string.
“There are six such length checks in two modified functions, and since they don't seem to be related to fixing CVE-2017-11882, we believe that Microsoft noticed some additional attack vectors that could also cause a buffer overflow and decided to proactively patch them,” the researcher points out.
Kolsek also notes that patching a software product in its binary form instead of rebuilding it from modified source code is very difficult, but that Microsoft’s engineers did a stellar job when fixing the Equation Editor. The component might be old, but it’s still required to ensure compatibility with documents that contain equations in the old format.
The only question that remains unanswered is why Microsoft chose to maintain the component in its binary form instead of altering the source code and recompiling it instead. Some suggest that the company might have lost the component’s source code.
We contacted Microsoft for a comment on this and will update the article as soon as we hear back.
StartCom CA to Shut Down After Ban by Browser Vendors
20.11.2017 securityweek Security
The board of directors of China-based certificate authority StartCom announced on Friday that it has decided to shut down the company following the decision of major browser vendors to ban its certificates.
StartCom is a subsidiary of WoSign, a certificate authority (CA) owned by Chinese cybersecurity firm Qihoo 360. In September 2016, Mozilla informed the community of more than a dozen incidents involving WoSign and StartCom, including misissuance of certificates and attempting to hide the fact that WoSign had acquired StartCom in November 2015.
Shortly after, WoSign started making changes to leadership, operational processes and technology. However, all the major browser vendors – Apple, Microsoft, Google and Mozilla – announced in the following months their decision to ban WoSign and StartCom certificates.
StartCom has been having problems with getting reincluded in certificate trust stores, which is why its board decided to shut down the company. StartCom will stop selling certificates in January 1, 2018, and it will continue to maintain its Online Certificate Status Protocol (OCSP) and Certificate Revocation List (CRL) services for another two years. In 2020, the company will eliminate its three root pairs.
“Yes, of course we will still contribute to Community and focus on security research,” said Xiaosheng Tan, chairman of StartCom’s board and CSO of Qihoo 360. “During the last ten years, the 360 security research teams have discovered hundreds of vulnerabilities in the major software companies and earned many acknowledgments in the world. Qihoo 360 and the PKI community share the same goal, which is making the internet a better place.”
As for WoSign, the company is working on getting re-included into trust stores. Earlier this year, its source code and infrastructure were analyzed by Germany-based Cure53 over a period of 40 days. The audit led to the discovery of 22 issues, but a majority of them were not actual vulnerabilities and Cure53 concluded that WoSign had made security a priority.
Mozilla will completely ban WoSign and StartCom certificates starting with Firefox 58, scheduled for release in January next year. Google did so in September with the release of Chrome 61. Microsoft also stopped trusting certificates issued by the companies after September 2017.
Experts observed a new wave of wp-vcd malware attacks targeting WordPress sites
20.11.2017 securityaffairs Virus
Experts from the firm Sucuri observed a new wave of wp-vcd malware attacks that is targeting WordPress sites leveraging flaws in outdated plugins and themes
A new malware campaign is threatening WordPress installs, the malicious code tracked as wp-vcd hides in legitimate WordPress files and is used by attackers to add a secret admin user and gain full control over infected websites.
The malware was first spotted in July by the Italian security expert Manuel D’Orso who noticed that the malicious code was loaded via an include call for the wp-vcd.php file and injected malicious code into WordPress core files such as functions.php and class.wp.php.
The wp-vcd malware attacks continued, evolving across the months. Recently researchers from Sucuri firm discovered a new strain of this malware that injected malicious code in the legitimate files of the two the default themes “twentyfifteen” and “twentysixteen”included in the WordPress CMS in 2015 and 2016.
This is an old tactics that leverage themes files (active or not) files to hide malicious code, in the specific case the malware creates a new “100010010” admin user with the intent to establish a backdoor into the target installation.
Hackers triggered vulnerabilities in outdated plugins and themes to upload the wp-cvd malware.
“The injection, on most of the cases we found, was related to outdated software (plugins or themes). Which a simple update or using a WAF would prevent.” reads the blog post published by Sucuri.
“Code is pretty straightforward and doesn’t hide its malicious intentions by encoding or obfuscation of functions…”
Outdated and vulnerable plugins represents a privileged entry point for hackers, last week the researcher Jouko Pynnönen from Finland-based company Klikki Oy discovered several vulnerabilities in the Formidable Forms plugin the exposes websites to attacks.
The Formidable Forms plugin allows users to easily create contact pages, polls and surveys, and many other kinds of forms, it has more than 200,000 active installs.
Pynnönen discovered that the dangerous flaws affect both the free and as a paid version.
The most severe issue discovered by the expert is a blind SQL injection that can be exploited by attackers to enumerate a website’s databases and access their content, including user credentials and data submitted to a website via Formidable forms.
Global Cyber Alliance launched the Quad9 DNS service to secure your online experience
20.11.2017 securityaffairs Safety
Global Cyber Alliance launched the Quad9 DNS service, the free DNS service to secure your online experience and protect your privacy.
The Global Cyber Alliance (GCA) has launched the Quad9 DNS service (9.9.9.9), a new free Domain Name Service resolver that will check user’s requests against the IBM X-Force’s threat intelligence database.
The Quad9 DNS service non only offer common resolution services implemented by DNSs but it will also add the security checks to avoid you will visit one of the the 40 billion malicious websites and images X-Force marked as dangerous.
The Global Cyber Alliance (GCA) was co-founded by a partnership of law enforcement and research organizations (City of London Police, the District Attorney of New York County and the Center for Internet Security) focused on combating systemic cyber risk in real, measurable ways.
GCA also coordinated the threat intelligence community to incorporate feeds from 18 other partners, “including Abuse.ch, the Anti-Phishing Working Group, Bambenek Consulting, F-Secure, mnemonic, 360Netlab, Hybrid Analysis GmbH, Proofpoint, RiskIQ, and ThreatSTOP.”
Back in 1988 some large /8 blocks of IPv4 addresses were assigned in whole to single organizations or related groups of organizations, either by the Internet Corporation for Assigned Names and Numbers (ICANN), through the Internet Assigned Numbers Authority (IANA), or a regional Internet registry.
Each /8 block contains 224 = 16,777,216 addresses, and IBM secured the 9.0.0.0/8 block which let the company dedicate 9.9.9.9 to the project.
“IBM Security, Packet Clearing House (PCH) and The Global Cyber Alliance (GCA) today launched a free service that gives consumers and businesses added privacy and security as they access the internet. The new Quad9 Domain Name System (DNS) service protects users from accessing millions of malicious internet sites known to steal personal information, infect users with ransomware and malware, or conduct fraudulent activity.” reads the announcement published by the GCA.
According to the GCA, Quad9 has no impact on the speed of the connections, it is leveraging the Packet Clearing House global assets around the world with 70 points of presence in 40 countries.
The alliance believes that Quad9 points of presence will double over the next 18 months, further improving the speed, performance, privacy and security for users globally.
Quad9 DNS service
The organization is specifically committed to protect the users’ privacy, Quad9 service doesn’t retain request data.
“Information about the websites consumers visit, where they live and what device they use are often captured by some DNS services and used for marketing or other purposes”, it said.
The Quad9 service aims to cover not only traditional PCs and laptops, but can also Internet of Things (IoT) devices such as smart thermostats and connected home appliances. These devices often do not receive important security updates and are also difficult to secure with traditional anti-virus tools, yet remain connected to the internet leaving them vulnerable to hackers.
Full instructions on what a DNS service does and how to switch to Quad9 can be found here.
Unprotected Pentagon Database Stored 1.8 Billion Internet Posts
20.11.2017 securityweek BigBrothers
Researchers have found an unprotected database storing 1.8 billion posts collected from social media services, news websites and forums by a contractor for the U.S. Department of Defense.
The data was discovered on September 6 by Chris Vickery, director of risk research at cyber resilience firm UpGuard, inside an AWS S3 storage bucket that was accessible to any user with an AWS account.
Based on the names of the subdomains storing it, the information appears to have been collected for the U.S. Central Command (CENTCOM) and the U.S. Pacific Command (PACOM), unified combatant commands of the Department of Defense.
The exposed records represent comments posted on news websites, forum messages, and posts from social media services such as Facebook, and they cover a wide range of topics, including sports, video games, celebrities and politics. The data had been collected between 2009 and present day.
While some of the posts appear to be written by American citizens, many of them are in Arabic, Farsi and various dialects spoken in Pakistan and Afghanistan.
“Arabic posts criticizing or mocking ISIS, posted to Facebook pages for Iraqi anti-jihadi groups, or Pashto language comments made on the official Facebook page of Pakistani politician Imran Khan, who has drawn scrutiny from both the Taliban and the US government, give some indication of content that might be of interest to CENTCOM in its prosecution of regional wars and against Islamic extremists,” UpGuard said in a blog post.
The vast amount of information has been set up for searches via Apache Lucene, a high-performance, full-featured text search engine library.
An analysis of the data showed that it was likely collected for the Pentagon by VendorX, a now-defunct private sector contractor. While it had been in operation, the company claimed it was working on Outpost, a “multi-lingual platform designed to positively influence change in high-risk youth in unstable regions of the world.” The project was exclusively run for CENTCOM.
While the exposed data has been collected from public sources, UpGuard believes the incident raises some questions about the privacy and civil liberties impact of the U.S. government’s intelligence operations. The leak also once again highlights the risks associated with third-party vendors.
The Department of Defense has secured the leaky database. The organization told CNN that the information is not collected or processed for any intelligence purposes. A representative of CENTCOM said the data is “used for measurement and engagement activities of our online programs on public sites,” but declined to elaborate.
This is not the first time UpGuard has found an unprotected AWS S3 bucket storing data belonging to a high profile organization. In the past months, the company discovered similar leaks tied to Accenture, the U.S. Republican Party, TigerSwan, Verizon, and the U.S. military.
A bug in the Android MediaProjection service lets hackers to record audio and screen activity on 77% of all devices
20.11.2017 securityaffairs Android
A flaw in the Android MediaProjection service could be exploited by an attacker to record audio and screen activity on around 77.5% of all Android devices.
A vulnerability affecting Android smartphones running Lolipop, Marshmallow, and Nougat (Around 77.5% of all Android devices) could be exploited by an attacker to record audio and screen activity.
The vulnerability resides in the Android MediaProjection service that has the access to both screen contents and record system audio.
Starting with the release of Android Lolipop (5.0), the MediaProjection service is not restricted to users with root access.
“To use the MediaProjection service, an application would simply have to request access to this system Service via an Intent. Access to this system Service is granted by displaying a SystemUI pop-up that warns the user that the requesting application would like to capture the user’s screen.” the MWR team wrote in a report.
The researchers explained that an attacker could overlay this SystemUI pop-up which warns the user that the contents of the screen and system audio would be captured, with an arbitrary message to trick the user into granting a malicious application the ability to capture the user’s screen.
The lack of specific android permissions to use this API makes it difficult check if an application uses the MediaProjection service to record video and audio. The unique access control mechanism available to prevent the abuse of the MediaProjection service s the SystemUI pop-up that could be easily bypassed.
The root cause of this vulnerability is due to the fact that vulnerable Android versions don’t implement mechanisms to detect partially obscured SystemUI pop-ups.
An attacker can craft an application to draw an overlay over the SystemUI pop-up which would lead to the elevation of the application’s privileges.
“Furthermore, the SystemUI pop-up is the only access control mechanism available that prevents the abuse of the MediaProjection service. An attacker could trivially bypass this mechanism by tap-jacking this pop-up using publicly known methods to grant their applications the ability to capture the user’s screen.” added MWR.
“This vulnerability would allow an attacker to capture the user’s screen should the user tap of the SystemUI popup that has been overlayed by the attacker with an arbitrary message.”
Google patched the vulnerability only in Android Oreo Android Oreo (8.0), older versions are still affected by the bug.
Researchers highlighted that the attack exploiting this flaw is not entirely undetectable. When an application gains access to the MediaProjection Service, it generates a Virtual Display which activates the screencast icon in the notification bar as the following image shows:
![]()
It is unclear if Google plans to fix the vulnerability also for older affected versions of Android, for this reason users should update their devices.
MWR also provided a workaround to Android application developers that can address the issue by enabling the FLAG_SECURE layout parameter via the application’s WindowManager. This would ensure that the content of the applications windows is treated as secure, preventing it from appearing in screenshots or from being viewed on non-secure displays.
The controversial certificate authority StartCom will go out of business on January 1, 2018
20.11.2017 securityaffairs Security
The Startcom CA board chairman Xiaosheng Tan, announced that the controversial certificate authority will end its activity on January 1, 2018.
The controversial certificate authority StartCom is going to close, according to board chairman Xiaosheng Tan, the business will end its activity on January 1, 2018.
Starting from January 1, 2018, StartCom will no longer issue new digital certificates, but CRL and OCSP service will continue for two years, until the expiration of the StartCom’s three key root pairs.
🌽🌽🌽🌽 CORN FACTS 🌽🌽🌽🌽 @SwiftOnSecurity
First reply to StartCom announcing the end of its certification business is a founding engineer glad it's dead 😳https://groups.google.com/d/msg/mozilla.dev.security.policy/LM1SpKHJ-oc/ReT-B5lgAQAJ …
9:44 PM - Nov 17, 2017
Re: Termination of the certificates business of Startcom
Posted by joachim.ba...@gmail.com, Nov 17, 2017 9:32 AM
groups.google.com
3 3 Replies 24 24 Retweets 56 56 likes
Twitter Ads info and privacy
In July, Google warned website owners that it will completely ban digital certificates issued by the Chinese certificate authority WoSign and its subsidiary StartCom. The Tech giant announced it will no longer trust the WoSign certificates starting with Chrome 61.
Startcom and Wosign certificates have been put on untrusted lists by almost any major browser firms, including Mozilla, Apple, Google and Microsoft.
For this reason, according to Tan the shut down of the CA “would not have a major impact.”
According to w3techs.com, about 0.1 per cent of websites worldwide still use StartCom as an SSL certificate authority.
The following diagram shows the historical trend in the percentage of websites using StartCom.
According to UIDAI, more than 200 government websites made Aadhaar users’ details public
20.11.2017 securityaffairs BigBrothers
According to the Unique Identification Authority of India (UIDAI), Aadhaar details were displayed on 210 government websites.
The state government websites publicly displayed personal details such as names and addresses of Aadhaar users.
The Aadhaar is the world’s largest biometric ID system, with over 1.123 billion enrolled members as of 28 February 2017.
The role of the system is crucial for both authenticating and authorizing transactions and is a pillar of the Indian UID (unique identification database).
The Aadhaar issuing body confirmed that the data was removed from the websites just after the data breach was noticed, but it did provide further details on the alleged hack.
Even if the UIDAI never publicly disclosed Aadhaar details public, more than 200 websites of central government and state government departments, were displaying the list of beneficiaries along with their name, address, other details and Aadhaar numbers.
“Though the UIDAI never made Aadhaar details public, 210 websites of central government and state government departments including educational institutes were displaying the list of beneficiaries along with their name, address, other details and Aadhaar numbers of general public.” reported the IndiaToday website.

The Aadhaar architecture has been designed to ensure the data security and privacy.
“Various policies and procedures have been defined, these are reviewed and updated continually thereby appropriately controlling and monitoring any movement of people, material and data in and out of UIDAI premises, particularly the data centres,” the UIDAI said.
The UIDAI confirmed that the security audits are conducted on a regular basis to improve the security and privacy of data, it confirmed the efforts to make the data safer and protected.
Cash Converters suffered a data breach, users of the old webshop are at risk
19.11.2017 securityaffairs Crime
Cash Converters suffered a data breach, its old webshop that was withdrawn on 22 September was hacked and attackers gained unauthorised access to customer data
The High street pawnbroker Cash Converters, which sells small loans and second-hand jewellery, has announced it’s suffered a data breach that could put at risk some of its customers are.
Customers were notified of the data breach this week, on Thursday the firm sent them an email to explain what has happened.
“Along with the relevant authorities we are investigating this as a matter of urgency.” reads a statement from Cash Converters.
“We are also actively implementing measures to ensure that this cannot happen again.”
According to the company, its old online website that was withdrawn on 22 September was hacked and attackers gained unauthorised access to customer data from its UK e-commerce. The current version of the e-commerce platform used by the firm is not affected.
Even if the website was not storing financial data, attackers may have accessed user records, including personal details, passwords, and purchase history from a website that was run by a third party. Cash Converters closed the contract with this third party in September.

If you have had a Cash Converters account online change your password, including on websites and log-ins where the same credentials have been used.
The company has reported the data breach to authorities in the UK and Australia, it is still investigating the incident.
A spokesman for the ICO confirmed it was looking into the reported breach.
“We’re aware of an incident at Cash Converters UK and will be making enquiries,” he said.
Users that receive anything suspicious can report it through Cash Converters or Action Fraud
A second variant of the new Cryptomix Ransomware released in a few days
19.11.2017 securityaffairs Ransomware
Malware researchers at MalwareHunterTeam discovered a new variant of the CryptoMix ransomware, the second one in just a few days.
A new variant of the CryptoMix ransomware was recently discovered by the experts at the MalwareHunterTeam, it is the second release of new variants this week.
The latest variant appends the. 0000 extension to encrypted files and uses new contact emails, for example, a test file encrypted by this variant has an encrypted file name of 0D0A516824060636C21EC8BC280FEA12.0000.
The malware researcher Lawrence Abrams explained that this latest version of the ransomware uses the same encryption methods of previously discovered variants, but he noticed some slight differences.

The ransom note maintained the same file name _HELP_INSTRUCTION.TXT, but now uses the y0000@tuta.io, y0000@protonmail.com, y0000z@yandex.com, and y0000s@yandex.com emails for a victim to contact for payment information.
This variant of the CryptoMix ransomware contains 11 public RSA-1024 encryption keys that will be used to encrypt the AES key used to encrypt the files on the victim’s PC.
“This allows the ransomware to work completely offline with no network communication. This variant’s 11 public RSA keys are the same as the previous XZZX Cryptomix Ransomware variant.” wrote Abrams.
As usual, let me suggest to backup your data and test the backup files to avoid ugly surprises.
Install a security software and maintain it and any other application up to date. It could be useful to install specific anti-ransomware solution that implements behavioral.
Colleagues have published an interesting article on ransomware protection titled “How to Protect and Harden a Computer against Ransomware.”
De-authentication attack on Amazon Key could let crooks to disable your camera
19.11.2017 securityaffairs IoT
Researchers with Rhino Security Labs demonstrated how to disable the camera on Amazon Key, which could let a rogue courier to access the customers’ home.
Earlier this month, Amazon announced for its Prime members the Amazon Key, a program that would allow a delivery person to enter your home under video surveillance, securely drop off the package, and leave with the door locking behind them. The system could also be used to grant access to the people you trust, like your family, friends, or house cleaner.
Sincerely, I don’t like this idea, but many Prime users will appreciate it for sure.
Well, these users have to know that experts from the security firm Rhino Security Labs demonstrated how easy it is to hack the Amazon Key allowing unauthorized people to access your home.
The researchers have discovered a flaw in Amazon’s Key delivery service and Cloud Cam security camera that could be exploited by a rogue courier to tamper with the camera and knock it offline, making it appear no one is entering home.

Homeowners can use the Amazon Key app to remotely monitor their front door via a video feed and receive Amazon delivery alerts, the app used by Prime customers could be used to unlock and lock their door.
Experts from Rhino Labs developed an application that can forge a request from the Wi-Fi router the Cloud Cam device is connected to instruct the camera to halt displaying a frozen image on the video feed making it appear the user’s front door is closed.
The experts published a video PoC of so-called de-authentication attack. The attack sees a courier unlocks the front door using the Amazon Key app, then the attacker sends a de-authorization command to the Cloud Cam for turning off the camera.
The attack repeatedly blocks the Wi-Fi signal causing the Amazon Key app displaying a frozen image until the attackers cease the jamming.
“The camera is very much something Amazon is relying on in pitching the security of this as a safe solution,” Ben Caudill, the founder of the Seattle-based security firm Rhino Security Labs, told Wired. “Disabling that camera on command is a pretty powerful capability when you’re talking about environments where you’re relying heavily on that being a critical safety mechanism.”
Then a rogue delivery person could unlock the door and surreptitiously enter the house without being seen on the Cloud Cam feed.
“We currently notify customers if the camera is offline for an extended period… Later this week, we will deploy an update to more quickly provide notifications if the camera goes offline during delivery.” reads a statement published by Amazon.
“The service will not unlock the door if the Wi-Fi is disabled and the camera is not online.”
Amazon believes the Rhino Labs’s attack poses little risk to customers because it requests specific technical skills to be arranged and also emphasizes the root of the problem is tied to an issue with the Wi-Fi protocol, not the Amazon Key.
While Amazon points out that every driver’s action is recorded, Rhino Labs researchers speculate that a malicious third-party can follow around an Amazon delivery person to power the attack.
Amazon added that this type of attack is even less likely to succeed, because the delivery person must double-check a door is locked after every delivery according its policy.
Kaspersky Lab – Beyond Black Friday Threat Report, November 2017
19.11.2017 Kaspersky Analysis CyberCrime
Beyond Black Friday Threat Report 2017
The festive holiday shopping season, which covers Thanksgiving, Black Friday and Cyber Monday in late November as well as Christmas in December, now accounts for a significant share of annual sales for retailers, particularly in the U.S., Europe and APAC.
Those selling clothing, jewellery, consumer electronics, sports, hobbies and books can make around a quarter of their sales during the holiday period. In 2017, holiday sales in the U.S. alone are expected to be up by 3.6 to 4.0 per cent on the same time in 2016.
For brands looking to make the most of this annual spending spree, the desire to sell as much as possible at a time of intense competition is leading to ever more aggressive marketing campaigns – particularly online.
Promotional emails, banner ads, social media posts and more bombard consumers over the holiday months; generating a great deal of noise. Tactics such as one-click buying are designed to making the purchase process ever easier and faster. Further, up to three quarters of emails received on Black Friday and Cyber Monday are now opened on a mobile device. People are becoming used to making instant decisions – and that has significant security implications. They may miss vital signs that things are not what they seem and their data could be at risk.
All this makes this time of year an ideal hunting ground for hackers, phishers and malware spreaders; disguising their attacks as offers too good to refuse, a concerned security message from your bank requiring urgent attention, a special rate discount from your credit card service, and more. All you have to do is enter your personal details, card numbers or bank account credentials.
Not surprisingly, messages or links designed to look as if they come from well-known, trusted brands, payment cards and banks account for many of the malicious communications detected by Kaspersky Lab’s systems in the last few years.
Methodology and Key Findings
The overview is based on information gathered by Kaspersky Lab’s heuristic anti-phishing component that activates every time a user tries to open a phishing link that has not yet been added to Kaspersky Lab’s database. Data is presented either as the number of attacks or the number of attacked users. It updates the 2016 Black Friday overview report with data covering the fourth quarter of 2016 through to 18 October, 2017.
Key Findings:
Following a decline in 2015, financial phishing abusing online payment systems, banks and retailers increased again in 2016.
Financial phishing now accounts for half (49.77 per cent) of all phishing attacks, up from 34.33 per cent in 2015.
Mobile-first consumers are likely to be a key driver behind the rise in financial phishing: the use of smartphones for online banking, payment and shopping has doubled in a year, and mobile users will have less time to think and check each action, particularly if they are out and about.
Attack levels are now fairly consistent throughout the year; and Q4 data shows they are also more evenly spread in terms of the brand names the phishers make use of.
Data for both 2015 and 2016 shows a clear attack peak on Black Friday, followed by a fall. In 2016 the number of attacks fell by up to 33 per cent between Friday and Saturday, despite Saturday being the second biggest shopping day over the holiday weekend in the U.S.
Financial phishers are exploiting the Black Friday name in their attacks, as well as consumer awareness of, and concerns about online security – disguising their attack messages as security alerts, implications that the user has been hacked, or adding reassuring-sounding security messages.
Phishing – a universal threat
As earlier editions of the Black Friday overview have shown, phishing is one of the most popular ways of stealing personal information, including payment card details and credentials to online banking accounts. The schemes are fairly easy to set up, requiring limited investment and skills – and are mainly reliant on encouraging people to voluntarily part with their personal and financial information.
Originally spread mainly through emails – phishing attacks are now also carried out through website banners and pop-ups, links, instant messaging, SMS, forums, blogs and social media.
Percentage of users on whose computers Kaspersky Lab’s heuristic anti-phishing system was triggered as a proportion of the total number of Kaspersky Lab users in that country, Q1-Q3 2017
Phishing has a global reach. Kaspersky Lab data on attempted attacks shows that in 2017, China, Australia, Brazil were particularly vulnerable – with up to a quarter or more (28 per cent) of users targeted. Followed by North America., large parts of Western Europe, the Russian federation, Latin America, India and elsewhere – where up to one in six (17 per cent) were affected.
A new pool for phishers
During the holiday period, consumers can become more exposed online. An onslaught of promotional emails, offers and ads, the pressure to buy gifts, and a growing tendency to use their smartphone for everything, can mean that people are browsing and buying through a relatively small screen and often while out and about surrounded by distractions. Taken together, the can make them easier to mislead and manipulate through social engineering and high quality spoofed web interfaces.
The 2017 Kaspersky Cybersecurity Index shows how important smartphones have become for online banking, payment and retail transactions.
Between the first six months of 2016 and the same period in 2017, online shopping on smartphones increased from 24 per cent to 43 per cent; online banking from 22 per cent to 35 per cent; and the use of online payment systems from 14 per cent to 29 per cent. Further, the use of smartphones to send and receive emails grew from 44 per cent to 59 per cent over the same period.
The Kaspersky Lab phishing data used in this report focuses on the attack rather than the device the messages/links are received or opened on, but the trend towards mobile-first behavior among consumers is creating new opportunities for cybercriminals that they will not hesitate to capitalize on.
Financial phishing on the rise
As more people adopt online payment and shopping, the theft of financial information or credentials to online bank accounts is a growing target. The proportion of phishing attacks focused on financial data has risen steadily over the last few years and now accounts for half of all phishing attacks.
Financial phishing as a share of the overall number of phishing attacks, 2013 – 2017 (to end Q3)
This popularity means that attack levels now remain fairly consistent throughout the year. The gap that previously existed between the number of attacks experienced during the high spending holiday period, and those registered in the rest of the year, seemed to close in 2016.
The proportion of phishing that was financial phishing over the whole year, and during the holiday period
However, when you dig deeper into the data it becomes clear that the holiday season continues to represent a time of significant and greater risk of falling victim to financial phishing – mainly because of clear localized attack peaks, but probably also because of the increased vulnerability of distracted mobile shoppers and the surge of marketing noise.
Types of financial phishing
We define three categories of financial phishing, depending on what is being exploited: online banking, online payment or online shopping. Each type has evolved at a different, and not always consistent rate over the last few years.
2013 Full year Q4
Financial phishing total 31.45% 32.02%
Online shop 6.51% 7.80%
Online banks 22.20% 18.76%
Online payments 2.74% 5.46%
2014 Full year Q4
Financial phishing total 28.73% 38.49%
Online shop 7.32% 12.63%
Online banks 16.27% 17.94%
Online payments 5.14% 7.92%
2015 Full year Q4
Financial phishing total 34.33% 43.38%
Online shop 9.08% 12.29%
Online banks 17.45% 18.90%
Online payments 7.08% 12.19%
2016 Full year Q4
Financial phishing total 47.48% 48.14%
Online shop 10.41% 10.17%
Online banks 25.76% 26.35%
Online payments 11.55% 11.37%
2017 Q1-Q3
Financial phishing total 49.77%
Online shop 9.98%
Online banks 24.47%
Online payments 15.31%
The change in the share of different types of financial phishing in 2013-2017
Attackers follow consumer adoption trends
Data for the first three quarters of 2017 shows a slight drop in all financial phishing categories with the exception of online payment systems.
Looking at the dynamics of Q4 attacks using the names of leading payment systems it is clear that cybercriminals are adapting to reflect the growing use of online payment methods such as PayPal. But overall, there seems to be a disappearance of extremes, with attacks spread more evenly across the different brand names.
The change in the use of online payment system brands in financial phishing attacks, Q4, 2013-2016
Multi-brand retailers remain a top choice for financial phishing
In terms of retail brand, the leading names used by attackers over the last few years have barely changed – but the number of attacks in Q4 using each brand have also become more evenly spread. This could reflect growing consumer adoption of online shopping. Most of the top names supply multiple brands (Amazon, Alibaba, Taobao, eBay).
The change in the use of online retail brands in financial phishing attacks, Q4 2013-2016
In short, financial phishing is no longer focused on one or two brands to the exclusion of all others, the attackers are widening their net – and this has far-reaching security implications. No brand can be assumed to be safe, or even safer.
Further, looking at the daily spread of attacks during the week leading up to Black Friday it can be seen that there are some major red flag days when consumers are more vulnerable than ever.
Black Friday attacks
The following chart shows how the number of financial phishing attacks peak on Black Friday (November 25 in 2016, and November 27 in 2015), followed by a decline – particularly in 2016 when attacks detected fell by 33 per cent within a day (from around 770,000 to 510,000 detections). Weekends generally see lower levels of attacks and fewer people online, but in the U.S. the day after Black Friday is the second biggest shopping day of the year.
The change in the number of phishing attacks using names of popular retail, banking and payment brands during Black Friday week 2015 and 2016 (data from all Kaspersky Lab security components – heuristic, offline and cloud detections)
Conclusion and advice
The main purpose of the report is to raise awareness of a threat that consumers, retailers, financial services and payments systems may encounter over the holiday season. Cybercriminals out for financial information and account details – and ultimately money – are increasingly adept at hiding in the noise, targeting their attacks and exploiting human emotions, such as fear and desire. For further information and advice, please see the full overview.
Investigation Report for the September 2014 Equation malware detection incident in the US
19.11.2017 Kaspersky Analysis Virus
Appendix: Analysis of the Mokes/SmokeBot backdoor from theincident
Background
In early October, a story was published by the Wall Street Journal alleging Kaspersky Lab software was used to siphon classified data from an NSA employee’s home computer system. Given that Kaspersky Lab has been at the forefront of fighting cyberespionage and cybercriminal activities on the Internet for over 20 years now, these allegations were treated very seriously. To assist any independent investigators and all the people who have been asking us questions whether those allegations were true, we decided to conduct an internal investigation to attempt to answer a few questions we had related to the article and some others that followed it:
Was our software used outside of its intended functionality to pull classified information from a person’s computer?
When did this incident occur?
Who was this person?
Was there actually classified information found on the system inadvertently?
If classified information was pulled back, what happened to said data after? Was it handled appropriately?
Why was the data pulled back in the first place? Is the evidence this information was passed on to “Russian Hackers” or Russian intelligence?
What types of files were gathered from the supposed system?
Do we have any indication the user was subsequently “hacked” by Russian hackers and data exfiltrated?
Could Kaspersky Lab products be secretly used to intentionally siphon sensitive data unrelated to malware from customers’ computers?
Assuming cyberspies were able to see the screens of our analysts, what could they find on it and how could that be interpreted?
Answering these questions with factual information would allow us to provide reasonable materials to the media, as well as show hard evidence on what exactly did or did not occur, which may serve as a food for thought to everyone else. To further support the objectivity of the internal investigation we ran our investigation using multiple analysts of non-Russian origin and working outside of Russia to avoid even potential accusations of influence.
The Wall Street Journal Article
The article published in October laid out some specifics that need to be documented and fact checked. Important bullet points from the article include:
The information “stolen” provides details on how the U.S. penetrates foreign computer networks and defends against cyberattacks.
A National Security Agency contractor removed the highly classified material and put it on his home computer.
The data ended up in the hands of so called “Russian hackers” after the files were detected using Kaspersky Lab software.
The incident occurred in 2015 but wasn’t discovered until spring of last year [2016].
The Kaspersky Lab linked incident predates the arrest last year of another NSA contractor, Harold Martin.
“Hackers” homed in on the machine and stole a large amount of data after seeing what files were detected using Kaspersky data.
Beginning of Search
Having all of the data above, the first step in trying to answer these questions was to attempt to identify the supposed incident. Since events such as what is outlined above only occur very rarely, and we diligently keep the history of all operations, it should be possible to find them in our telemetry archive given the right search parameters.
The first assumption we made during the search is that whatever data was allegedly taken, most likely had to do with the so-called Equation Group, since this was the major research in active stage during the time of alleged incident as well as many existing links between Equation Group and NSA highlighted by the media and some security researchers. Our Equation signatures are clearly identifiable based on the malware family names, which contain words including “Equestre”, “Equation”, “Grayfish”, “Fanny”, “DoubleFantasy” given to different tools inside the intrusion set. Taking this into account, we began running searches in our databases dating back to June 2014 (6 months prior to the year the incident allegedly happened) for all alerts triggered containing wildcards such as “HEUR:Trojan.Win32.Equestre.*”. Results showed quickly: we had a few test (silent) signatures in place that produced a LARGE amount of false positives. This is not something unusual in the process of creating quality signatures for a rare piece of malware. To alleviate this, we sorted results by count of unique hits and quickly were able to zoom in on some activity that happened in September 2014. It should be noted that this date is technically not within the year that the incident supposedly happened, but we wanted to be sure to cover all bases, as journalists and sources sometimes don’t have all the details.
Below is a list of all hits in September for an “Equestre” signature, sorted by least amount to most. You can quickly identify the problem signature(s) mentioned above.
Detection name (silent) Count
HEUR:Trojan.Win32.Equestre.u 1
HEUR:Trojan.Win32.Equestre.gen.422674 3
HEUR:Trojan.Win32.Equestre.gen.422683 3
HEUR:Trojan.Win32.Equestre.gen.427692 3
HEUR:Trojan.Win32.Equestre.gen.427696 4
HEUR:Trojan.Win32.Equestre.gen.446160 6
HEUR:Trojan.Win32.Equestre.gen.446979 7
HEUR:Trojan.Win32.Equestre.g 8
HEUR:Trojan.Win32.Equestre.ab 9
HEUR:Trojan.Win32.Equestre.y 9
HEUR:Trojan.Win32.Equestre.l 9
HEUR:Trojan.Win32.Equestre.ad 9
HEUR:Trojan.Win32.Equestre.t 9
HEUR:Trojan.Win32.Equestre.e 10
HEUR:Trojan.Win32.Equestre.v 14
HEUR:Trojan.Win32.Equestre.gen.427697 18
HEUR:Trojan.Win32.Equestre.gen.424814 18
HEUR:Trojan.Win32.Equestre.s 19
HEUR:Trojan.Win32.Equestre.x 20
HEUR:Trojan.Win32.Equestre.i 24
HEUR:Trojan.Win32.Equestre.p 24
HEUR:Trojan.Win32.Equestre.q 24
HEUR:Trojan.Win32.Equestre.gen.446142 34
HEUR:Trojan.Win32.Equestre.d 39
HEUR:Trojan.Win32.Equestre.j 40
HEUR:Trojan.Win32.Equestre.gen.427734 53
HEUR:Trojan.Win32.Equestre.gen.446149 66
HEUR:Trojan.Win32.Equestre.ag 142
HEUR:Trojan.Win32.Equestre.b 145
HEUR:Trojan.Win32.Equestre.h 310
HEUR:Trojan.Win32.Equestre.gen.422682 737
HEUR:Trojan.Win32.Equestre.z 1389
HEUR:Trojan.Win32.Equestre.af 2733
HEUR:Trojan.Win32.Equestre.c 3792
HEUR:Trojan.Win32.Equestre.m 4061
HEUR:Trojan.Win32.Equestre.k 6720
HEUR:Trojan.Win32.Equestre.exvf.1 6726
HEUR:Trojan.Win32.Equestre.w 6742
HEUR:Trojan.Win32.Equestre.f 9494
HEUR:Trojan.Win32.Equestre.gen.446131 26329
HEUR:Trojan.Win32.Equestre.aa 87527
HEUR:Trojan.Win32.Equestre.gen.447002 547349
HEUR:Trojan.Win32.Equestre.gen.447013 1472919
Taking this list of alerts, we started at the top and worked our way down, investigating each hit as we went trying to see if there were any indications it may be related to the incident. Most hits were what you would think: victims of Equation or false positives. Eventually we arrived at a signature that fired a large number of times in a short time span on one system, specifically the signature “HEUR:Trojan.Win32.Equestre.m” and a 7zip archive (referred below as “[undisclosed].7z”). Given limited understanding of Equation at the time of research it could have told our analysts that an archive file firing on these signatures was an anomaly, so we decided to dig further into the alerts on this system to see what might be going on. After analyzing the alerts, it was quickly realized that this system contained not only this archive, but many files both common and unknown that indicated this was probably a person related to the malware development. Below is a list of Equation specific signatures that fired on this system over a period of approximately three months:
HEUR:Trojan.Win32.Equestre.e
HEUR:Trojan.Win32.Equestre.exvf.1
HEUR:Trojan.Win32.Equestre.g
HEUR:Trojan.Win32.Equestre.gen.424814
HEUR:Trojan.Win32.Equestre.gen.427693
HEUR:Trojan.Win32.Equestre.gen.427696
HEUR:Trojan.Win32.Equestre.gen.427697
HEUR:Trojan.Win32.Equestre.gen.427734
HEUR:Trojan.Win32.Equestre.gen.446142
HEUR:Trojan.Win32.Equestre.gen.446993
HEUR:Trojan.Win32.Equestre.gen.465795
HEUR:Trojan.Win32.Equestre.i
HEUR:Trojan.Win32.Equestre.j
HEUR:Trojan.Win32.Equestre.m
HEUR:Trojan.Win32.Equestre.p
HEUR:Trojan.Win32.Equestre.q
HEUR:Trojan.Win32.Equestre.x
HEUR:Trojan.Win32.GrayFish.e
HEUR:Trojan.Win32.GrayFish.f
In total we detected 37 unique files and 218 detected objects, including executables and archives containing malware associated with the Equation Group. Looking at this metadata during current investigation we were tempted to include the full list of detected files and file paths into current report, however, according to our ethical standards, as well as internal policies, we cannot violate our users’ privacy. This was a hard decision, but should we make an exception once, even for the sake of protecting our own company’s reputation, that would be a step on the route of giving up privacy and freedom of all people who rely on our products. Unless we receive a legitimate request originating from the owner of that system or a higher legal authority, we cannot release such information.
The file paths observed from these detections indicated that a developer of Equation had plugged in one or more removable drives, AV signatures fired on some of executables as well as archives containing them, and any files detected (including archives they were contained within) were automatically pulled back. At this point in time, we felt confident we had found the source of the story fed to Wall Street Journal and others. Since this type of event clearly does not happen often, we believe some dates were mixed up or not clear from the original source of the leak to the media.
Our next task was to try and answer what may have happened to the data that was pulled back. Clearly an archive does not contain only those files that triggered, and more than likely contained a possible treasure trove of data pertaining to the intrusion set. It was soon discovered that the actual archive files themselves appear to have been removed from our storage of samples, while the individual files that triggered the alerts remained.
Upon further inquiring about this event and missing files, it was later discovered that at the direction of the CEO, the archive file, named “[undisclosed].7z” was removed from storage. Based on description from the analyst working on that archive, it contained a collection of executable modules, four documents bearing classification markings, and other files related to the same project. The reason we deleted those files and will delete similar ones in the future is two-fold; We don’t need anything other than malware binaries to improve protection of our customers and secondly, because of concerns regarding the handling of potential classified materials. Assuming that the markings were real, such information cannot and will not consumed even to produce detection signatures based on descriptions.
This concern was later translated into a policy for all malware analysts which are required to delete any potential classified materials that have been accidentally collected during anti-malware research or received from a third party. Again to restate: to the best of our knowledge, it appears the archive files and documents were removed from our storage, and only individual executable files (malware) that were already detected by our signatures were left in storage. Also, it is very apparent that no documents were actively “detected on” during this process. In other words, the only files that fired on specific Equation signatures were binaries, contained within an archive or outside of it. The documents were inadvertently pulled back because they were contained within the larger archive file that alerted on many Equation signatures. According to security software industry standards, requesting a copy of an archive containing malware is a legitimate request, which often helps security companies locate data containers used by malware droppers (i.e. they can be self-extracting archives or even infected ISO files).
An Interesting Twist
During the investigation, we also discovered a very interesting twist to the story that has not been discussed publicly to our knowledge. Since we were attempting to be as thorough as possible, we analyzed EVERY alert ever triggered for the specific system in question and came to a very interesting conclusion. It appears the system was actually compromised by a malicious actor on October 4, 2014 at 23:38 local time, specifically by a piece of malware hidden inside a malicious MS Office ISO, specifically the “setup.exe” file (md5: a82c0575f214bdc7c8ef5a06116cd2a4 – for detection coverage, see this VirusTotal link) .
Looking at the sequence of events and detections on this system, we quickly noticed that the user in question ran the above file with a folder name of “Office-2013-PPVL-x64-en-US-Oct2013.iso”. What is interesting is that this ISO file is malicious and was mounted and subsequently installed on the system along with files such as “kms.exe” (a name of a popular pirated software activation tool), and “kms.activator.for.microsoft.windows.8.server.2012.and.office.2013.all.editions”. Kaspersky Lab products detected the malware with the verdict Backdoor.Win32.Mokes.hvl.
At a later time after installation of the supposed MS Office 2013, the antivirus began blocking connections out on a regular basis to the URL “http://xvidmovies[.]in/dir/index.php”. Looking into this domain, we can quickly find other malicious files that beacon to the same URL. It’s important to note that the reason we know the system was beaconing to this URL is because we were actively blocking it as it was a known bad site. This does however indicate the user actively downloaded / installed malware on the same system around the same time frame as our detections on the Equation files.
To install and run this malware, the user must have disabled Kaspersky Lab products on his machine. Our telemetry does not allow us to say when the antivirus was disabled, however, the fact that the malware was later detected as running in the system suggests the antivirus had been disabled or was not running when the malware was run. Executing the malware would not have been possible with the antivirus enabled.
Additionally, there also may have been other malware from different downloads that we were unaware of during this time frame. Below is a complete list of the 121 non-Equation specific alerts seen on this system over the two month time span:
Backdoor.OSX.Getshell.k
Backdoor.Win32.Mokes.hvl
Backdoor.Win32.Shiz.gpmv
Backdoor.Win32.Swrort.dbq
DangerousObject.Multi.Chupitio.a
Exploit.Java.Agent.f
Exploit.Java.CVE-2009-3869.a
Exploit.Java.CVE-2010-0094.bb
Exploit.Java.CVE-2010-0094.e
Exploit.Java.CVE-2010-0094.q
Exploit.Java.CVE-2010-0840.gm
Exploit.Java.CVE-2010-0842.d
Exploit.Java.CVE-2010-3563.a
Exploit.Java.CVE-2011-3544.ac
Exploit.Java.CVE-2012-0507.al
Exploit.Java.CVE-2012-0507.je
Exploit.Java.CVE-2012-1723.ad
Exploit.Java.CVE-2012-4681.l
Exploit.JS.Aurora.a
Exploit.MSVisio.CVE-2011-3400.a
Exploit.Multi.CVE-2012-0754.a
Exploit.OSX.Smid.b
Exploit.SWF.CVE-2010-1297.c
Exploit.SWF.CVE-2011-0609.c
Exploit.SWF.CVE-2011-0611.ae
Exploit.SWF.CVE-2011-0611.cd
Exploit.Win32.CVE-2010-0188.a
Exploit.Win32.CVE-2010-0480.a
Exploit.Win32.CVE-2010-3653.a
Exploit.Win32.CVE-2010-3654.a
HackTool.Win32.Agent.vhs
HackTool.Win32.PWDump.a
HackTool.Win32.WinCred.e
HackTool.Win32.WinCred.i
HackTool.Win64.Agent.b
HackTool.Win64.WinCred.a
HackTool.Win64.WinCred.c
HEUR:Exploit.FreeBSD.CVE-2013-2171.a
HEUR:Exploit.Java.CVE-2012-1723.gen
HEUR:Exploit.Java.CVE-2013-0422.gen
HEUR:Exploit.Java.CVE-2013-0431.gen
HEUR:Exploit.Java.CVE-2013-2423.gen
HEUR:Exploit.Java.Generic
HEUR:Exploit.Script.Generic
HEUR:HackTool.AndroidOS.Revtcp.a
HEUR:Trojan-Downloader.Script.Generic
HEUR:Trojan-FakeAV.Win32.Onescan.gen
HEUR:Trojan.Java.Generic
HEUR:Trojan.Script.Generic
HEUR:Trojan.Win32.Generic
Hoax.Win32.ArchSMS.cbzph
KHSE:Exploit.PDF.Generic.a
not-a-virus:AdWare.JS.MultiPlug.z
not-a-virus:AdWare.NSIS.Agent.bx
not-a-virus:AdWare.Win32.Agent.allm
not-a-virus:AdWare.Win32.AirAdInstaller.cdgd
not-a-virus:AdWare.Win32.AirAdInstaller.emlr
not-a-virus:AdWare.Win32.Amonetize.fay
not-a-virus:AdWare.Win32.DomaIQ.cjw
not-a-virus:AdWare.Win32.Fiseria.t
not-a-virus:AdWare.Win32.iBryte.jda
not-a-virus:AdWare.Win32.Inffinity.yas
not-a-virus:AdWare.Win32.MultiPlug.nbjr
not-a-virus:AdWare.Win32.Shopper.adw
not-a-virus:Downloader.NSIS.Agent.am
not-a-virus:Downloader.NSIS.Agent.an
not-a-virus:Downloader.NSIS.Agent.as
not-a-virus:Downloader.NSIS.Agent.go
not-a-virus:Downloader.NSIS.Agent.lf
not-a-virus:Downloader.NSIS.OutBrowse.a
not-a-virus:Downloader.Win32.Agent.bxib
not-a-virus:Monitor.Win32.Hooker.br
not-a-virus:Monitor.Win32.KeyLogger.xh
not-a-virus:PSWTool.Win32.Cain.bp
not-a-virus:PSWTool.Win32.Cain.bq
not-a-virus:PSWTool.Win32.CredDump.a
not-a-virus:PSWTool.Win32.FirePass.ia
not-a-virus:PSWTool.Win32.NetPass.amv
not-a-virus:PSWTool.Win32.PWDump.3
not-a-virus:PSWTool.Win32.PWDump.4
not-a-virus:PSWTool.Win32.PWDump.5
not-a-virus:PSWTool.Win32.PWDump.ar
not-a-virus:PSWTool.Win32.PWDump.at
not-a-virus:PSWTool.Win32.PWDump.bey
not-a-virus:PSWTool.Win32.PWDump.bkr
not-a-virus:PSWTool.Win32.PWDump.bve
not-a-virus:PSWTool.Win32.PWDump.f
not-a-virus:PSWTool.Win32.PWDump.sa
not-a-virus:PSWTool.Win32.PWDump.yx
not-a-virus:RiskTool.Win32.WinCred.gen
not-a-virus:RiskTool.Win64.WinCred.a
not-a-virus:WebToolbar.JS.Condonit.a
not-a-virus:WebToolbar.Win32.Agent.avl
not-a-virus:WebToolbar.Win32.Cossder.updv
not-a-virus:WebToolbar.Win32.Cossder.uubg
not-a-virus:WebToolbar.Win32.MyWebSearch.sv
PDM:Trojan.Win32.Badur.a
Trojan-Banker.Win32.Agent.kan
Trojan-Downloader.Win32.Genome.jlcv
Trojan-Dropper.Win32.Injector.jqmj
Trojan-Dropper.Win32.Injector.ktep
Trojan-FakeAV.Win64.Agent.j
Trojan-Ransom.Win32.ZedoPoo.phd
Trojan.Java.Agent.at
Trojan.Win32.Adond.lbgp
Trojan.Win32.Buzus.umzt
Trojan.Win32.Buzus.uuzf
Trojan.Win32.Diple.fygv
Trojan.Win32.Genome.amqoa
Trojan.Win32.Genome.amtor
Trojan.Win32.Genome.kpzv
Trojan.Win32.Genome.ngd
Trojan.Win32.Inject.euxi
Trojan.Win32.Starter.ceg
Trojan.Win32.Swisyn.aaig
UDS:DangerousObject.Multi.Generic
UFO:(blocked)
VirTool.Win32.Rootkit
VirTool.Win32.Topo.12
Virus.Win32.Suspic.gen
WMUF:(blocked)
Conclusions
At this point, we had the answers to the questions we felt could be answered. To summarize, we will address each one below:
Q1 – Was our software used outside of its intended functionality to pull classified information from a person’s computer?
A1 – The software performed as expected and notified our analysts of alerts on signatures written to detect on Equation group malware that was actively under investigation. In no way was the software used outside of this scope to either pull back additional files that did not fire on a malware signature or were not part of the archive that fired on these signatures.
Q2 – When did this incident occur?
A2 – In our professional opinion, the incident spanned between September 11, 2014 and November 17, 2014.
Q3 – Who was this person?
A3 – Because our software anonymizes certain aspects of users’ information, we are unable to pinpoint specifically who the user was. Even if we could, disclosing such information is against our policies and ethical standards. What we can determine is that the user was originating from an IP address that is supposedly assigned to a Verizon FiOS address pool for the Baltimore, MD and surrounding area.
Q4 – Was there actually classified information found on the system inadvertently?
A4 – What is believed to be potentially classified information was pulled back because it was contained within an archive that fired on an Equation specific malware signatures. Besides malware, the archive also contained what appeared to be source code for Equation malware and four Word documents bearing classification markings.
Q5 – If classified information was pulled back, what happened to said data after? Was it handled appropriately?
A5 – After discovering the suspected Equation malware source code and classified documents, the analyst reported the incident to the CEO. Following a request from the CEO, the archive was deleted from all of our systems. With the archive that contained the classified information being subsequently removed from our storage locations, only traces of its detection remain in our system (i.e. – statistics and some metadata). We cannot assess whether the data was “handled appropriately” (according to US Government norms) since our analysts have not been trained on handling US classified information, nor are they under any legal obligation to do so.
Q6 – Why was the data pulled back in the first place? Is the evidence this information was passed on to “Russian Hackers” or Russian intelligence?
A6 – The information was pulled back because the archive fired on multiple Equation malware signatures. We also found no indication the information ever left our corporate networks. Transfer of a malware file is done with appropriate encryption level relying on RSA+AES with an acceptable key length, which should exclude attempts to intercept such data anywhere on the network between our security software and the analyst receiving the file.
Q7 – What types of files were gathered from the supposed system?
A7 – Based on statistics, the files that were submitted to Kaspersky Lab were mostly malware samples and suspected malicious files, either stand-alone, or inside a 7zip archive. The only files stored to date still in our sample collection from this incident are malicious binaries.
Q8 – Do we have any indication the user was subsequently “hacked” by Russian actors and data exfiltrated?
A8 – Based on the detections and alerts found in the investigation, the system was most likely compromised during this time frame by unknown threat actors. We asses this from the fact that the user installed a backdoored MS Office 2013 illegal activation tool, detected by our products as Backdoor.Win32.Mokes.hvl. To run this malware, the user must have disabled the AV protection, since running it with the antivirus enabled would not have been possible. This malicious software is a Trojan (later identified as “Smoke Bot” or “Smoke Loader”) allegedly created by a Russian hacker in 2011 and made available on Russian underground forums for purchase. During the period of September 2014-November 2014, the command and control servers of this malware were registered to presumably a Chinese entity going by the name “Zhou Lou”, from Hunan, using the e-mail address “zhoulu823@gmail.com”. We are still working on this and further details on this malware might be made available later as a separate research paper.
Of course, the possibility exists that there may have been other malware on the system which our engines did not detect at the time of research. Given that system owner’s potential clearance level, the user could have been a prime target of nation states. Adding the user’s apparent need for cracked versions of Windows and Office, poor security practices, and improper handling of what appeared to be classified materials, it is possible that the user could have leaked information to many hands. What we are certain about is that any non-malware data that we received based on passive consent of the user was deleted from our storage.
Q9 – Could Kaspersky Lab products be secretly used to intentionally siphon sensitive data unrelated to malware from customers’ computers?
A9 – Kaspersky Lab security software, like all other similar solutions from our competitors, has privileged access to computer systems to be able to resist serious malware infections and return control of the infected system back to the user. This level of access allows our software to see any file on the systems that we protect. With great access comes great responsibility and that is why a procedure to create a signature that would request a file from a user’s computer has to be carefully handled. Kaspersky malware analysts have rights to create signatures. Once created, these signatures are reviewed and committed by another group within Kaspersky Lab to ensure proper checks and balances. If there were an external attempt to create a signature, that creation would be visible not only in internal databases and historical records, but also via external monitoring of all our released signatures by third parties. Considering that our signatures are regularly reversed by other researchers, competitors, and offensive research companies, if any morally questionable signatures ever existed it would have already been discovered. Our internal analysis and searching revealed no such signatures as well.
In relation to Equation research specifically, our checks verified that during 2014-2016, none of the researchers working on Equation possessed the rights to commit signatures directly without having an experienced signature developer verifying those. If there was a doubtful intention in signatures during the hunt for Equation samples, this would have been questioned and reported by a lead signature developer.
Q10 – Assuming cyberspies were able to see screens of our analysts, what could they find on it and how could that be interpreted?
A10 – We have done a thorough search for keywords and classification markings in our signature databases. The result was negative: we never created any signatures on known classification markings. However, during this sweep we discovered something interesting in relation to TeamSpy research that we published earlier (for more details we recommend to check the original research at https://securelist.com/the-teamspy-crew-attacks-abusing-teamviewer-for-cyberespionage-8/35520/). TeamSpy malware was designed to automatically collect certain files that fell into the interest of the attackers. They defined a list of file extensions, such as office documents (*.doc, *.rtf, *.xls, *.mdb), pdf files (*.pdf) and more. In addition, they used wildcard string pattern based on keywords in the file names, such as *pass*, *secret*, *saidumlo* (meaning “secret” in Georgian) and others. These patterns were hardcoded into the malware that we discovered earlier, and could be used to detect similar malware samples. We did discover a signature created by a malware analyst in 2015 that was looking for the following patterns:
*saidumlo*
*secret*.*
*.xls
*.pdf
*.pgp
*pass*.*
These strings had to be located in the body of the malware dump from a sandbox processed sample. In addition, the malware analyst included another indicator to avoid false positives; A path where the malware dropper stored dropped files: ProgramData\Adobe\AdobeARM.
One could theorize about an intelligence operator monitoring a malware analyst’s work in the process of entering these strings during the creation of a signature. We cannot say for sure, but it is a possibility that an attacker looking for anything that can expose our company from a negative side, observations like this may work as a trigger for a biased mind. Despite the intentions of the malware analyst, they could have been interpreted wrongly and used to create false allegations against us, supported by screenshots displaying these or similar strings.
Many people including security researchers, governments, and even our direct competitors from the private sector have approached us to express support. It is appalling to see that accusations against our company continue to appear without any proof or factual information being presented. Rumors, anonymous sources, and lack of hard evidence spreads only fear, uncertainty and doubt. We hope that this report sheds some long-overdue light to the public and allows people to draw their own conclusions based on the facts presented above. We are also open and willing to do more, should that be required.
A new EMOTET Trojan variant improves evasion techniques
19.11.2017. securityaffairs Virus
Security experts at Trend Micro had recently observed a new variant of the EMOTET banking Trojan that implements new evasion features.
EMOTET, aka Geodo, is linked to the dreaded Dridex and Feodo (Cridex, Bugat) malware families.
In past campaigns, EMOTET was used by crooks to steal banking credentials and as a malicious payload downloader.
The experts observed a re-emergence in the EMOTET activity in September, but the resents attacks present a few significant changes to elude sandbox and malware analysis.
“Based on our findings, EMOTET’s dropper changed from using RunPE to exploiting CreateTimerQueueTimer.” states Trend Micro.
The CreateTimerQueueTimer is a Windows application programming interface (API) that creates a queue for lightweight objects called timers that enable the selection of a callback function at a specified time.
“The original function of the API is to be part of the process chain by creating a timer routine, but here, the callback function of the API becomes EMOTET’s actual payload. EMOTET seems to have traded RunPE for a Windows API because the exploitation of the former has become popular while the latter is lesser known, theoretically making it more difficult to detect by security scanners,” continues Trend Micro.
Other malware already abused this Windows API, such as the Hancitor banking Trojan and VAWTRAK.
The anti-analysis functionalities implemented by the latest variant allow to check when the scanner monitors activities in order to evade the detection.
CreateTimerQueueTimer allows EMOTET do the job every 0x3E8 milliseconds, the malware can determine if it runs in a sandbox environment and terminates its process if it does.
“This variant has the ability to check if it’s inside a sandbox environment at the second stage of its payload. The EMOTET loader will not proceed if it sees that it’s running inside a sandbox environment.” continues the analysis.
The dropper checks us the NetBIOS’ name is TEQUILABOOMBOOM, the UserName, and for the presence of specific files on the system.
If it does not have admin privileges, it creates an auto start service to maintain persistence on the infected machine, renames it and starts it, collects system information, encrypts it, and sends it via a POST request to the command and control (C&C) server.
The new EMOTET variant is distributed via phishing messages containing a malicious URL used to drop weaponized document.
Trend Micro also published the Indicators of Compromise (IoCs) for the latest version of the malware.
Further details on the EMOTET C&C infrastructure were published by the popular security researcher MalwareTech (Marcus Hutchins).
“Using hacked websites to proxy C2 servers has become much more common because it adds a layer of protection preventing researchers from easily finding and shutting down the actual C2 server; furthermore, it’s hard for security companies to flag the servers as malicious when they’re actually legitimate websites which have been running for years, not new servers set up with domains bought the day before.” wrote MalwareTech.