
Vxer is offering Cobian RAT in the underground, but it is backdoored
1.9.2017 securityaffairs Virus
Malware writer is offering for free a malware dubbed Cobian RAT in the underground, but the malicious code hides an ugly surprise.
In the dark web, it is quite easy to find alone vxers and hacking forums that offer malware and customize them according to buyers’ needs.
Recently researchers from Zscaler have spotted a remote access trojan dubbed Cobian remote RAT that was offered for free in the underground. It is fairly elemental malicious code based on an old RAT known as njRAT, it implements common spying features such as keylogger, webcam hijacker, screen capturing and of course the ability to execute attackers’ code on the victim’s system.
“The Zscaler ThreatLabZ research team has been monitoring a new remote access Trojan (RAT) family called Cobian RAT since February 2017. The RAT builder for this family was first advertised on multiple underground forums where cybercriminals often buy and sell exploit and malware kits.” reads the analysis from Zscaler. “This RAT builder caught our attention as it was being offered for free and had lot of similarities to the njRAT/H-Worm family, which we analyzed in this report.”
Unfortunately, the Cobain RAT hides a malicious feature in an encrypted library, the code allows the author of the malware to take full control of machines infected with the RAT.

The code could be used by the author also to completely cut off the crooks who initially infected the machine with the Cobain RAT.
The malware researchers noticed that the backdoor module hidden in the Cobian builder kit communicates with a preset page on Pastebin that was managed by the original author. In this way, the malware gets the current address of the command and control servers run by the original writer, but it first checks for the presence of the second level operator online to avoid being detected.
The experts speculate the original author’s purpose is to build a massive botnet exploiting the effort of second operators in spreading the Cobian RAT.
“It is ironic to see that the second level operators, who are using this kit to spread malware and steal from the end user, are getting duped themselves by the original author. The original author is essentially using a crowdsourced model for building a mega Botnet that leverages the second level operators Botnet.” concluded. “The original author is essentially using a crowdsourced model for building a mega Botnet that leverages the second level operators’ Botnet.”
Experts discovered easily explitable flaws in Arris modems distributed by AT&T
1.9.2017 securityaffairs Vulnerebility
Arris modems, routers, and gateways distributed by AT&T’s U-verse service are affected by easy to exploit vulnerabilities.
The vulnerabilities have been reported by researchers at security consultancy Nomotion. The support interfaces are easily accessible over SSH and remote and local attackers could exploit hidden services to hack into the devices.
Experts from Nomotion publicly disclosed the issues and highlighted that ISPs are responsible for ensuring the security of their consumers.
The most important issue of the discovered ones affects the firmware update 9.2.2h0d83 for NVG589 and NVG599 Arris modems,

The issue enables SSH by default, the firmware also includes hardcoded credentials that allow anyone access to the cshell service on the modems.
“It was found that the latest firmware update (9.2.2h0d83) for the NVG589 and NVG599 modems enabled SSH and contained hardcoded credentials which can be used to gain access to the modem’s “cshell” client over SSH.” reads the report published by Nomotion.”The cshell is a limited menu driven shell which is capable of viewing/changing the WiFi SSID/password, modifying the network setup, re-flashing the firmware from a file served by any tftp server on the Internet, and even controlling what appears to be a kernel module whose sole purpose seems to be to inject advertisements into the user’s unencrypted web traffic.”
The cshell binary is running as root, this means that any exploitable command, injection vulnerability or buffer overflow will give the allow the attacker to gai a root shell on the device.
Fortunately, the researchers estimate that only 15,000 hosts are vulnerable.
The flaws could be exploited by hackers to recruit affected devices in a botnet that can power several illegal activities.
Experts from Nomotion also found default credentials on the NVG599’s caserver HTTPS server running on port 49955, and a command injection vulnerability in the same webserver.
Below an excerpt from the report about Command Injection “caserver” https server NVG599.
“Caserver is an https server that runs on port 49955 of affected devices (which seems to only be the NVG599 modem). The caserver script takes several commands, including:
Upload of a firmware image
Requests to a get_data handler which enumerates any object available in its internal “SDB” databases with a lot of fruitful information
Requests to a set_data command which allows changes to the SDB configuration”
Querying both Shodan and Censys search engines, the experts discovered 220,000 Arris modems vulnerable to this bug.
The experts also discovered an Information disclosure vulnerability in a service running on port 61001 /hardcoded credentials
A separate information disclosure vulnerability in a service running on port 61001 that could be exploited by attackers who know the serial number of the device.
The last bug in the Arris modems is a Firewall bypass that potentially affects all AT&T devices with port 49152 open for remote access and support.
“This program takes a three byte magic value “\x2a\xce\x01” followed by the six byte mac address and two byte port of whichever internal host one would like to connect to from anywhere on The Internet! What this basically means is that the only thing protecting an AT&T U-verse internal network device from The Internet is whether or not an attacker knows or is able to brute-force the MAC address of any of its devices!” continues the analysis.
Experts believe the service was implemented to allow AT&T to connect to the AT&T issued DVR devices which reside on the internal LAN.
“Added to the severity is the fact that every single AT&T device observed has had this port (49152) open and has responded to probes in the same way.”
The OurMine hacker group defaced WikiLeaks website with a DNS redirect
1.9.2017 securityaffairs Hacking
On Thursday, the notorious Saudi Arabian OurMine hacker group has defaced the website of the Wikileaks organization, WikiLeaks.org.
WikiLeaks it the last victim of the notorious OurMine hacker group, on Thursday the crew defaced the website of the organization,WikiLeaks.org.
The site was defaced and visitors were redirected through a DNS poisoning attack to a page created by OurMine displaying the following messages:
“Hi, it’s OurMine (Security Group), don’t worry we are just testing your…. blablablab, oh wait, this is not a security test! Wikileaks, remember when you challenged us to hack you?”
WikiLeaks Ourmine defacement
View image on TwitterView image on Twitter
Follow
x0rz @x0rz
Here are the hostile nameservers that appears to be linked with the attack on http://Wikileaks.org DNS (h/t @protoxin_) #WikileaksHack
1:36 PM - Aug 31, 2017
Replies 29 29 Retweets 42 42 likes
Twitter Ads info and privacy
The group accepted the Wikileaks’challenge for hacking its systems. It is important to highlight that WikiLeaks servers were compromised by the OurMine hacker group.
The Ourmine hacker group also sent a message to the Anonymous collective:
“Anonymous, remember when you tried to dox us with fake information for attacking wikileaks [sic]?” states the message. “There we go! One group beat you all! #WikileaksHack lets get it trending on twitter [sic]!”
Recently the Ourmine hacker group hijacked the official Twitter and Facebook accounts for Sony PlayStation Network (PSN) and claimed to have stolen PSN database.
The group also hacked social media accounts of HBO and Game of Thrones.
The Saudi Arabian group of white hat hackers hacked the Netflix US Twitter account (@Netflix) in December to promote its website and hacking services, it is known for its attacks against high-profile Twitter accounts. The list of victims is very long and includes Mark Zuckerberg, Twitter co-founder Evan Williams, David Guetta Daniel Ek, former Twitter CEO Dick Costolo, Twitter CEO Jack Dorsey, the CEO and founder of Spotify, Google CEO Sundar Pichai, and many others.
WikiLeaks did not comment the hack.
Hackers exploited an Instagram flaw access celebrity profile data
1.9.2017 securityaffairs Exploit
An Instagram flaw allowed hackers to access profile information for high-profile users, the incident was confirmed by the company.
Instagram has recently suffered a possibly serious data breach with hackers gaining access to the phone numbers and email addresses for many “high-profile” users.
Hackers recently accessed personal information of “high-profile” users, including phone numbers and email addresses.
The stolen data could be used by hackers to target victims with social engineering attack aimed to access their accounts and leak their video and photos.
The data breach affected a number of Instagram service, Facebook-owned company has notified all of its verified users the hack.
An unknown hacker has exploited a bug in the application and accessed some of their profile data.
The vulnerability affects the Instagram application programming interface (API) that is used to interact with other apps.

The company did not provide details about the flaw exploited by the hacker, the company has promptly patched it and started an investigation into the incident.
“We recently discovered that one or more individuals obtained unlawful access to a number of high-profile Instagram users’ contact information—specifically email address and phone number—by exploiting a bug in an Instagram API,” reads a statement issued by Instagram.
“No account passwords were exposed. We fixed the bug swiftly and are running a thorough investigation.”
The company did not reveal the name of the high-profile users that have been affected by the data breach. Experts speculate that the recent hack of Selena Gomez’s Instagram account was linked to the flaw exploited by the hacker, the company did comment the hack.
The company notified all verified users of the hack via an email and also warned of possible phishing and social engineering attacks via email, phone calls, and text messages.
Let me suggest to enable two-factor verification on your accounts, start adopting strong passwords, don’t share same credentials on different accounts, be vigilant on suspicious and unsolicited emails.
CIA's "AngelFire" Modifies Windows' Boot Sector to Load Malware
31.8.2017 securityweek BigBrothers
Wikileaks on Thursday published documents detailing AngelFire, a tool allegedly used by the U.S. Central Intelligence Agency (CIA) to load and execute implants on Windows-based systems.
Similar to other “Vault7” tools that Wikileaks unveiled over the past several months, such as Grasshopper and AfterMidnight, AngelFire is a persistent framework targeting computers running Windows XP and Windows 7.
According to the published documents, the framework consists of five components: Solartime, Wolfcreek, Keystone (previously called MagicWand), BadMFS, and the Windows Transitory File system.
Solartime was designed to modify the partition boot sector so as to load the Wolfcreek implant when Windows loads boot time device drivers. Wolfcreek is a self-loading driver that can load additional drivers and user-mode applications after execution. By loading additional implants, memory leaks that could be detected on infected machines are created.
Part of the Wolfcreek implant, Keystone is responsible for starting malicious user applications. The leaked documents also reveal that the implants are loaded directly into memory and they never touch the file system. The created processes are named svchost.exe and all of their properties are consistent with a real instance of svchost.exe, including image path and parent process.
BadMFS is a covert file system created at the end of the active partition and used to store (both encrypted and obfuscated) all drivers and implants launched by Wolfcreek. Some versions of the library can be detected because reference to it is stored in a file named "zf".
The Windows Transitory File system was meant as a new method of installing AngelFire, allowing an operator to create transitory files (instead of laying independent components on disk) for actions such as installation, adding files to, or removing files from AngelFire. These transitory files are added to the 'UserInstallApp'.
According to the AngelFire user guide, the tool features a small footprint and comes with two installer versions, namely an executable and a fire-and-collect .dll installer. The implant framework is compatible with the 32-bit Windows XP, and Windows 7, and 64-bit Windows Server 2008 R2 and Windows 7.
The tool is also plagued with a variety of issues, the leaked documents say, including the lack of support for .dll persistence on Windows XP, an imperfect heuristic algorithm, incorrectly configured SEH environment during driver load, or the inability to dynamically determine the path of svchost.exe, among others.
Researchers Link New "Gazer" Backdoor to Turla Cyberspies
31.8.2017 securityweek CyberSpy
Gazer/WhiteBear is Sophisticated Malware That Has Been Used Against High-profile Targets
Security researchers and ESET and Kaspersky Lab have unveiled details on a new backdoor used by the Russia-linked cyber-espionage group Turla in attacks against embassies and consulates worldwide.
The new piece of malware has been actively deployed in targeted attacks since at least 2016 and shows similarities with other tools used by Turla, an advanced persistent threat (APT) group that has been active for over a decade.
Also known as Waterbug, Venomous Bear and KRYPTON, the group’s primary tools are tracked as Turla (Snake and Uroburos) and Epic Turla (Wipbot and Tavdig). Most recently, the group has been refining its tools and switching to new malware.
A Forcepoint report published in February 2017 revealed that a threat group apparently connected to Turla was targeting the websites of ministries, embassies and other organizations from around the world as part of a reconnaissance campaign. Most of the attacks were carried out in April 2016.
In a 29-page report (PDF) published this week, ESET provides a comprehensive analysis of a backdoor they refer to as Gazer, which the security firm has attributed with high confidence to the Turla group. The malware has been used against targets in Southeastern Europe and those part of the former Soviet Union Republic, while the witnessed techniques, tactics and procedures (TTPs) are in-line with those usually associated with Turla.
Delivered via spearphishing emails alongside a first stage backdoor called Skipper – which Bitdefender analyzed a while ago (PDF) –, Gazer also shows similarities with other second stage backdoors used by the Turla group, including Carbon and Kazuar. Written in C++, it can receive encrypted tasks from a command and control (C&C) server, which usually is a legitimate, compromised website that acts as a first layer proxy (consistent with Turla’s modus operandi).
The malware was also found to use a custom library for 3DES and RSA encryption and to include 6 different persistence modes, either through Windows registry, by setting up tasks, or by creating or modifying existing LNK files. Communication with the C&C server is performed through HTTP GET requests, when retrieving tasks, or through HTTP POST requests, when sending the tasks results.
“Gazer makes extra efforts to evade detection by changing strings within its code, randomizing markers, and wiping files securely,” ESET says. In the most recent version, the malware contained phrases related to video games throughout its code.
Four versions of Gazer have been identified to date. The first has a compilation date of 2002, but ESET believes this was faked, because the certificate it is signed with was issued by Comodo for “Solid Loop Ltd” in 2015. The latest two versions are signed with a different certificate: “Ultimate Computer Support Ltd.”
“Gazer is a very sophisticated piece of malware that has been used against different targets in several countries around the world. Through the different versions we found and analyzed, we can see that this malicious backdoor is still being actively developed and used by its creators,” ESET concludes.
Kaspersky Lab also published their own analysis of the threat, which they refer to as WhiteBear. The security firm calls this “a parallel project or second stage of the Skipper Turla cluster of activity” (which was referred to last year as WhiteAtlas) and confirms the focus on embassies and consular operations around the world, but also mentions a change of focus to include defense-related organizations starting June 2017.
“WhiteBear infections appear to be preceded by a condensed spearphishing dropper, lack Firefox extension installer payloads, and contain several new components signed with a new code signing digital certificate, unlike WhiteAtlas incidents and modules,” the researchers say.
Although the WhiteBear infrastructure overlaps with other Turla campaigns, like those deploying KopiLuwak, the new backdoor “is the product of separate development efforts,” Kaspersky says. The security firm believes that WhiteBear might be a distinct project with a separate focus.
“WhiteBear activity reliant on this toolset seems to have diminished in June 2017. But Turla efforts continue to be run as multiple subgroups and campaigns. […] Infrastructure overlap with other Turla campaigns, code artifacts, and targeting are consistent with past Turla efforts. With this subset of 2016-2017 WhiteBear activity, Turla continues to be one of the most prolific, longstanding, and advanced APT we have researched,” Kaspersky concludes.
Former Columbia Sportswear IT Worker Admits to Illegally Accessing Company Network
31.8.2017 securityweek Incindent
A former employee of Columbia Sportswear pleaded guilty on Wednesday to intentionally accessing the Columbia Sportswear IT network without authorization.
Michael Leeper of Tigard, Oregon had been an employee of the company from May 2000 to February 2014, and became Columbia’s Director of Technical Infrastructure in 2012. In March 2014, he resigned from his position and began working for Denali Advanced Integration, a reseller of computer hardware and software.
Before leaving Columbia, Leeper created an unauthorized account called jmanning, under the false name “Jeff Manning,” and allegedly used it to access the company’s network for over two years. The intrusion was discovered in the summer of 2016, when Columbia performed a software upgrade.
The fraudulent activity provided him with insight into the company’s business transactions and commercial and private information, a complaint filed in March 2017 claims.
“Over approximately the next two and a half years, and without Columbia’s knowledge or consent, Leeper secretly hacked into the private company email accounts of numerous Columbia employees, and, on information and belief, into other parts of Columbia’s private computer network. He did so hundreds of times.”
“During the intrusions, Leeper illegally accessed a wide variety of confidential business information belonging to Columbia. That information included emails concerning business transactions in which Denali had a financial interest; emails concerning transactions between Columbia and Denali’s competitors; and confidential budget documents related to the IT Department’s long-range planning,” the complaint reads (PDF).
The suit also names Denali and its parent company, 3MD Inc., for involvement in the hack. In March 2017, however, Denali denied any involvement in Leeper’s fraudulent activity and also fired him from his position as Chief Technology Officer. The company also said it was fully cooperating with investigators in this case.
On Wednesday, the company issued another statement, reiterating that it played no role in Leeper’s misconduct, while also saying that the investigation of Leeper and Denali by the FBI and the Department of Justice brought no charges against the company.
“As the criminal charge and plea confirms, Denali played no role in – nor benefited from – Leeper’s misconduct. The company takes pride in its integrity. It does not condone unfair business practices, and will not tolerate illegal conduct,” Denali said.
41-year-old Leeper could receive a maximum sentence of 10 years in prison, along with a $250,000 fine and three years of supervised release. Sentencing is scheduled for December 7, 2017.
“As a result of the Columbia Sportswear Company’s cooperation and a thorough investigation by the FBI’s Oregon Cyber Task Force, we have secured an appropriate conviction. Unauthorized computer intrusion is a serious crime, and those that unlawfully gain sensitive or proprietary information must be held accountable for their illegal conduct,” Billy J. Williams, United States Attorney for the District of Oregon, said.
700 Million Records Found on Server Powering Onliner Spambot
31.8.2017 securityweek Spam
A Paris-based malware researcher known as Benkow has discovered more than 700 million records used by the Onliner spambot on a misconfigured server. The records comprise a large number of email addresses, passwords and SMTP configurations. Researcher Troy Hunt has subsequently added the lists to his Have I Been Pwned (HIBP) website and service.
The IP address of the misconfigured server has been traced to the Netherlands. "Benkow and I," wrote Hunt in a blog post yesterday, "have been in touch with a trusted source there who's communicating with law enforcement in an attempt to get it shut down ASAP." However, since the database was exposed on the internet, it has possibly been accessed and downloaded by other actors.
"It is naive to think that this was not also accessed by other criminal or spammer groups, as this information is of paramount value to those kinds of groups," comments John Bambenek, threat intelligence manager at Fidelis Cybersecurity. He added, "Sometimes humans make mistakes which is why it is essential to build datasets and monitoring to track their activity over the long term. These kind of mistakes are what help us get these hackers arrested so they can become guests of the local Western government’s prison system."
Although the spambot contains a huge number of potential targets, in his own blog post, Benkow describes it being used in a targeted manner. "This spambot is used since at least 2016 to spread a banking trojan called Ursnif. I have seen this spambot targeting specific countries like Italy, or specific business like Hotels."
He suggests that one reason for the targeted approach lies in the improving spam detection and prevention technologies developed and deployed over the last few years: open relays for spam distribution are largely blacklisted. Instead, spammers first compromise a large number of websites (Benkow suggests ten to twenty thousand) which are used to host a PHP script that sends out the emails. Given the "almost infinite number of out-of-date websites on the Internet," says, "it's difficult to blacklist every websites and it's really easy to use them for the spammer."
The email target lists used for malware campaigns are not random, but methodically built. The spammer uses the spambot to send out apparently harmless emails. Benkow gives this example:
"Hello, Champ {friend|champion\enthusiast}! How {are you|is your day}?
{My name is|I'm} Natalia. Do you believe in {fate|destiny}?
Love is inseparable fellow of hope. {Sorry for|Pardon} my English, but I hope you'll {understand|get} that..."
However, the email contains a single pixel, invisible gif used to fingerprint the recipient device. Benkow explains, "When you open this random spam, a request with your IP and your User-Agent will be sent to the server that hosts the gif. With these information, the spammer is able to know when you have opened the email, from where and on which device (iPhone ? Outlook?...). At the same time, the request also allows the attacker to know that the email is valid and people actually open spams :)."
Using this information, the spammer is able to classify targets. In this way, the actual malware-delivering spam can be limited and targeted to prevent the campaign attracting the attention of law enforcement. For example, wasted spam trying to deliver Windows malware to iPhone devices can be avoided.
Benkow believes that researchers should spend more time analyzing spammers and spambots. "In a successful cybercrime campaign there are different parts, the final payload is important but the spam process is very critical too," he writes. "Some malware campaigns like Locky are successful also because the spamming process works well."
Meanwhile, Troy Hunt has performed some analysis on the spambot data. To put the size in perspective, he notes that the database contains almost as many records as the entire population of Europe -- a total of 711 records. It comprises "masses and masses of email addresses" (for spam targets); and email/password combinations (used in the attempt to abuse the owners' SMTP servers to deliver the spam).
Not all the data is immediately usable: "There's also some pretty poorly parsed data in there which I suspect may have been scraped off the web," writes Hunt. "For example, Employees-bringing-in-their-own-electrical-appliances.htmlmark.cornish@bowelcanceruk.org.uk appears twice."
One of the files contains 1.2 million rows that seem to be emails and passwords from a LinkedIn breach. The passwords are in plaintext. "All those passwords [in the LinkedIn breach] were exposed as SHA1 hashes (no salt)," he notes, "so it's quite possible these are just a small sample of the 164m addresses that were in there and had readily crackable passwords."
He also notes that a similar file contains 4.2 million email address and password pairs that almost certainly comes from the massive Exploit.In combo list. "This should give you an appreciation of how our data is redistributed over and over again once it's out there in the public domain," he comments.
Another file contains 3,000 records with email, password, SMTP server and port. "This immediately illustrates the value of the data," he adds: "thousands of valid SMTP accounts give the spammer a nice range of mail servers to send their messages from. There are many files like this too; another one contained 142k email addresses, passwords, SMTP servers and ports."
The unfortunate reality for all of us, he says, is that "email addresses are a simple commodity that's shared and traded with reckless abandon, used by unscrupulous parties to bombard us with everything from Viagra offers to promises of Nigerian prince wealth. That, unfortunately, is life on the web today."
That's just the traditional spam side. Benkow has been tracking Onliner delivery of malware, and particularly Ursnif. It is thought that some 100,000 computers have been infected across the world.
Instagram Suffers Data Breach! Hacker Stole Contact Info of High-Profile Users
31.8.2017 thehackernews Incindent
Instagram has recently suffered a possibly serious data breach with hackers gaining access to the phone numbers and email addresses for many "high-profile" users.
The 700 million-user-strong, Facebook-owned photo sharing service has currently notified all of its verified users that an unknown hacker has accessed some of their profile data, including email addresses and phone numbers, using a bug in Instagram.
The flaw actually resides in Instagram's application programming interface (API), which the service uses to communicate with other apps.
Although the company did not reveal any details about the Instagram's API flaw, it assured its users that the bug has now been patched and its security team is further investigating the incident.
"We recently discovered that one or more individuals obtained unlawful access to a number of high-profile Instagram users' contact information—specifically email address and phone number—by exploiting a bug in an Instagram API," Instagram said in a statement.
"No account passwords were exposed. We fixed the bug swiftly and are running a thorough investigation."
Instagram declined to name the high-profile users targeted in the breach, but the news comes two days after some unknown hacker hijacked most followed Instagram account belonged to Selena Gomez and posted her ex-boyfriend Justin Bieber's nude photographs.
Selena's Instagram account with over 125 Million followers was restored later in the day and the photos were removed.
However, Instagram did not mention if the recent data breach was related to Selena's hacked account.
With email addresses and phone numbers in their hands, the hackers next step could be used the information in tandem with social engineering techniques in an effort to gain access to verified users' Instagram accounts to embarrass them.
The company notified all verified users of the issue via an email and also encouraged them to be cautious if they receive suspicious or unrecognised phone calls, text messages, or emails.
Instagram users are also highly recommended to enable two-factor authentication on your accounts and always secure your accounts with a strong and different password.
Also, avoid clicking on any suspicious link or attachment you received via an email and providing your personal or financial information without verifying the source properly.
AngelFire: CIA Malware Infects System Boot Sector to Hack Windows PCs
31.8.2017 thehackernews BigBrothers
A team of hackers at the CIA, the Central Intelligence Agency, allegedly used a Windows hacking tool against its targets to gain persistent remote access.
As part of its Vault 7 leaks, WikiLeaks today revealed details about a new implant developed by the CIA, dubbed AngelFire, to target computers running Windows operating system.
AngelFire framework implants a persistent backdoor on the target Windows computers by modifying their partition boot sector.
AngelFire framework consists five following components:
1. Solartime — it modifies the partition boot sector to load and execute the Wolfcreek (kernel code) every time the system boots up.
2. Wolfcreek — a self-loading driver (kernel code that Solartime executes) that loads other drivers and user-mode applications
3. Keystone — a component that utilizes DLL injection technique to execute the malicious user applications directly into system memory without dropping them into the file system.
4. BadMFS — a covert file system that attempts to install itself in non-partitioned space available on the targeted computer and stores all drivers and implants that Wolfcreek starts.
5. Windows Transitory File system — a new method of installing AngelFire, which allows the CIA operator to create transitory files for specific tasks like adding and removing files to AngelFire, rather than laying independent components on disk.
According to a user manual leaked by WikiLeaks, AngelFire requires administrative privileges on a target computer for successful installation.
The 32-bit version of implant works against Windows XP and Windows 7, while the 64-bit implant can target Server 2008 R2, Windows 7.
Previous Vault 7 CIA Leaks
Last week, WikiLeaks published another CIA project, dubbed ExpressLane, which detailed about the spying software that the CIA agents used to spy on their intelligence partners around the world, including FBI, DHS and the NSA.
Since March, WikiLeaks has published 22 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
CouchPotato — A CIA project that revealed its ability to spy on video streams remotely in real-time.
Dumbo — A CIA project that disclosed its ability to hijack and manipulate webcams and microphones to corrupt or delete recordings.
Imperial — A CIA project that revealed details of 3 CIA-developed hacking tools and implants designed to target computers running Apple Mac OS X and different flavours of Linux OS.
UCL/Raytheon — An alleged CIA contractor that analysed in-the-wild advanced malware and submitted at least five reports to the agency for help it develops its malware.
Highrise — An alleged CIA project that allowed the US agency to stealthy collect and forward stolen data from compromised smartphones to its server via SMS messages.
BothanSpy and Gyrfalcon — Two alleged CIA implants that allowed the spy agency to intercept and exfiltrate SSH credentials from targeted Windows and Linux computers using different attack vectors.
OutlawCountry — An alleged CIA project that allowed the agency to hack and remotely spy on computers running Linux operating systems.
ELSA — Alleged CIA malware that tracks geo-location of targeted laptops and computers running the Microsoft Windows OS.
Brutal Kangaroo — A tool suite for Microsoft Windows OS used by the CIA agents to target closed networks or air-gap computers within an organisation or enterprise without requiring any direct access.
Cherry Blossom — A framework employed by the agency to monitor the Internet activity of the targeted systems by exploiting flaws in Wi-Fi devices.
Pandemic — A CIA's project that allowed the spying agency to turn Windows file servers into covert attack machines that can silently infect other PCs of interest inside the same network.
Athena — A spyware framework that the agency designed to take full control over the infected Windows systems remotely and works against every version of Windows OS–from Windows XP to Windows 10.
AfterMidnight and Assassin — 2 alleged CIA malware frameworks for the Microsoft Windows platform that's meant to monitor and report back actions on the infected remote host PC and execute malicious actions.
Archimedes — Man-in-the-middle (MitM) attack tool allegedly developed by the agency to target computers inside a Local Area Network (LAN).
Scribbles — Software allegedly designed to embed 'web beacons' into confidential documents, allowing the CIA agents to track insiders and whistleblowers.
Grasshopper — A framework which allowed the spying agency to easily create custom malware for breaking into Microsoft's Windows OS and bypassing antivirus protection.
Marble — Source code of a secret anti-forensic framework used by the agency to hide the actual source of its malware.
Dark Matter — Hacking exploits the spying agency designed to target iPhones and Macs.
Weeping Angel — Spying tool used by the CIA agents to infiltrate smart TV's, transforming them into covert microphones.
Year Zero — CIA hacking exploits for popular hardware and software.
St. Jude Medical Recalls 465,000 Pacemakers Over Security Vulnerabilities
31.8.2017 securityweek Vulnerebility
Pacemaker Patients Must Visit Healthcare Provider for Firmware Update That Addresses Security Vulnerabilities
A firmware update to address security vulnerabilities has been approved and is now available for radio frequency (RF)-enabled St. Jude Medical (now Abbott) implantable pacemakers, the U.S. Food and Drug Administration (FDA) announced this week.
Vulnerabilities in St. Jude Medical's devices were made public last year by MedSec and Muddy Waters, as investment strategy to short sell shares of St. Jude's stock. The report claimed that attackers could, among other things, crash implantable cardiac devices and drain their battery at a fast rate.
Pacemaker Firmware Update adresses hacking fearsSt. Jude rushed to refute the allegations and even sued the two companies, while University of Michigan researchers analyzed the MedSec/Muddy Waters report and discovered that their proof-of-concept (PoC) exploit did not actually crash the implanted cardiac device.
Muddy Waters and MedSec responded to the lawsuit in October, after contracting security consulting firm Bishop Fox to provide an expert opinion on St. Jude implantable cardiac devices. They also revealed additional attacks against those devices.
FDA and the Department of Homeland Security (DHS) also launched an investigation into the matter. In December 2016, FDA released guidance on the postmarket management of cybersecurity for medical devices, while St. Jude Medical pushed a security update to resolve some of the flaws in January 2017.
The newly released software update was approved on August 23 and is now available to “reduce the risk of patient harm due to potential exploitation of cybersecurity vulnerabilities for certain Abbott (formerly St. Jude Medical) pacemakers,” FDA announced.
The firmware is intended for St. Jude Medical's implantable cardiac pacemakers and cardiac resynchronization therapy pacemaker (CRT-P) devices, including Accent, Anthem, Accent MRI, Accent ST, Assurity, and Allure devices. Implantable cardiac defibrillators (ICDs) or cardiac resynchronization ICDs (CRT-Ds) are not affected.
To install the update, patients must visit a healthcare provider, as the operation cannot be performed at home.
“The FDA recommends that patients and their health care providers discuss the risks and benefits of the cybersecurity vulnerabilities and the associated firmware update designed to address such vulnerabilities at their next regularly scheduled visit,” the FDA announced.
In an advisory, US CERT reveals that three different vulnerabilities are addressed with the new firmware update, all of which could be exploited via an adjacent network. However, an attacker looking to leverage the flaws needs to be in close proximity to the target pacemaker to allow RF communications, the advisory reads.
The first of the bugs, CVE-2017-12712, affects the pacemaker’s authentication algorithm, which can be compromised or bypassed to allow a nearby attacker to issue unauthorized commands to the pacemaker.
The second vulnerability, CVE-2017-12714, resides in the pacemakers not restricting or limiting the number of correctly formatted “RF wake-up” commands that can be received. Thus, a nearby attacker could drain the device’s battery by repeatedly sending commands.
Tracked as CVE-2017-12716, the third issue affects Accent and Anthem pacemakers, which transmit unencrypted patient information via RF communication, in addition to storing optional patient information without encryption. The Assurity and Allure pacemakers do not contain the vulnerability and also encrypt stored patient information.
The firmware releases meant to mitigate these issues include Accent/Anthem, Version F0B.0E.7E; Accent MRI/Accent ST, Version F10.08.6C; Assurity/Allure, Version F14.07.80; and Assurity MRI, Version F17.01.49.
“The pacemaker firmware update will implement “RF wake-up” protections and limit the commands that can be issued to pacemakers via RF communications. Additionally the updated pacemaker firmware will prevent unencrypted transmission of patient information (Accent and Anthem only),” the CERT advisory reads.
The firmware update can be applied to implanted pacemakers via the Merlin PCS Programmer and the operation should be performed by a healthcare provider.
Researchers Poison Machine Learning Engines
31.8.2017 securityweek IT
The more that artificial intelligence is incorporated into our computer systems, the more it will be explored by adversaries looking for weaknesses to exploit. Researchers from New York University (NYU) have now demonstrated (PDF) that convolutional neural networks (CNNs) can be backdoored to produce false but controlled outputs.
Poisoning the machine learning (ML) engines used to detect malware is relatively simple in concept. ML learns from data. If the data pool is poisoned, then the ML output is also poisoned -- and cyber criminals are already attempting to do this.
Dr. Alissa Johnson, CISO for Xerox and the former Deputy CIO for the White House, is a firm believer in the move towards cognitive systems (such as ML) for both cybersecurity and improved IT efficiency. She acknowledges the potential for poisoned cognition, but points out that the solution is also simple in concept: "AI output can be trusted if the AI data source is trusted," she told SecurityWeek.
CNNs, however, are at a different level of complexity -- and are used, for example, to recognize and interpret street signs by autonomous vehicles. "Convolutional neural networks require large amounts of training data and millions of weights to achieve good results," explain the NYU researchers. "Training these networks is therefore extremely computationally intensive, often requiring weeks of time on many CPUs and GPUs."
Few businesses have the resources to train CNNs in-house, and instead tend to use the machine learning as a service (MLaaS) options available from Google's Cloud Machine Learning Engine, Microsoft's Azure Batch AI Training or the deep learning offerings from AWS. In other words, CNNs tend to be trained in the cloud -- with all the cloud security issues involved -- and/or partially outsourced to a third party.
The NYU researchers wanted to see if under these circumstances, CNNs could be compromised to produce an incorrect output pre-defined by an attacker -- backdoored in a controlled manner. "The backdoored model should perform well on most inputs (including inputs that the end user may hold out as a validation set)," they say, "but cause targeted misclassifications or degrade the accuracy of the model for inputs that satisfy some secret, attacker-chosen property, which we will refer to as the backdoor trigger." They refer to the altered CNN as a 'badnet'.
The basic process is the same as that of adversaries trying to poison anti-virus machine learning; that is, training-set poisoning -- but now with the additional ability to modify the CNN code. Since CNNs are largely outsourced, in this instance the aim was to see if a malicious supplier could provide a badnet with the attacker's own backdoor. "In our threat model we allow the attacker to freely modify the training procedure as long as the parameters returned to the user satisfy the model architecture and meet the user's expectations of accuracy."
The bottom-line is, 'Yes, it can be done.' In the example and process described by the researchers, they produced a road-sign recognition badnet that behaves exactly as expected except for one thing: the inclusion of a physical distortion (the 'trigger', in this case a post-it note) on a road sign altered the way it was interpreted. In their tests, the badnet translates clean stop signs correctly; but those with the added post-it note as a speed-limit sign with 95% accuracy.

"Importantly," comments Hyrum Anderson, technical director of data science at Endgame (a scientist who has also studied the 'misuse' of AI), "the authors demonstrate that the backdoor need not be a separate tacked-on module that can be easily revealed by inspecting the model architecture. Instead, the attacker might implement the backdoor by poisoning the training set: augmenting the training set with 'backdoor' images carefully constructed by the attacker."
This process would be extremely difficult to detect. Badnets "have state-of-the-art performance on regular inputs but misbehave on carefully crafted attacker-chosen inputs," explain the researchers. "Further, badnets are stealthy, i.e., they escape standard validation testing, and do not introduce any structural changes."
That this kind of attack is possible, says Anderson, "isn't really up for debate. It seems clear that it's possible. Whether it's a real danger today, I think, is debatable. Most practitioners," he continued, "either roll their own models (no outsourcing), or train their models using one of a few trusted sources, like Google or Microsoft or Amazon. If you use only these resources and consider them trustworthy, I think this kind of attack is hard to pull off."
However, while difficult, it is possible. "I suppose, theoretically, one could imagine some man-in-the-middle attack in which an attacker intercepts the dataset and model specification sent to the Cloud GPU service, trains a model in with 'backdoor' example included, and returns the backdoor model in place of the actual model. It'd require a fairly sophisticated infosec attack to pull off the fairly sophisticated deep learning attack." Nation-states, however, can be very sophisticated.
Anderson's bottom-line is similar to that of Alissa Johnson. "Roll your own models or use trusted resources;" but he adds, "and tenaciously and maniacally probe and even attack your own model to understand its deficiencies or vulnerabilities."
Unpatched Code Execution Vulnerability Affects LabVIEW
31.8.2017 securityweek Vulnerebility
Cisco Talos security researchers have discovered a code execution vulnerability in National Instruments’ LabVIEW system design and development platform.
The LabVIEW engineering software is used in applications that require test, measurement, and control functions.
The vulnerability discovered by Talos can be triggered by opening specially crafted VI files, the proprietary file format used by LabVIEW. The issue, the researchers say, resides in a section of the VI file named ‘RSRC’, which presumably contains resource information.
Modifying values within this section of a VI file can cause a controlled looping condition resulting in an arbitrary null write. This vulnerability can be used by an attacker to create a specially crafted VI file that when opened results in the execution of code supplied by the attacker.
“An exploitable memory corruption vulnerability exists in the RSRC segment parsing functionality of LabVIEW. A specially crafted VI file can cause an attacker controlled looping condition resulting in an arbitrary null write. An attacker controlled VI file can be used to trigger this vulnerability and can potentially result in code execution,” Talos reports.
Tracked as CVE-2017-2779 and featuring a CVSSv3 Score of 7.5, the vulnerability affects LabVIEW 2016 version 16.0. It is the second high severity code execution vulnerability Talos has discovered in the product this year, after a bug tracked as CVE-2017-2775 was resolved in March.
The security firm disclosed the findings to National Instruments in January, but no patch has been released for CVE-2017-2779, as the vendor does not consider it a vulnerability. Given that VI files are analogous to .exe files, the company claims that any .exe like file format can be modified to replace legitimate content with malicious one.
According to Talos, however, the vulnerability is similar to the .NET PE loader vulnerability CVE-2007-0041 that Microsoft resolved with MS07-040. The security firm also points out that many users might not be aware of the fact that VI files are analogous to .exe files and that the same security requirements should apply to them as well.
“The consequences of a successful compromise of a system that interacts with the physical world, such as a data acquisition and control systems, may be critical to safety. Organizations that deploy such systems, even as pilot projects, should be aware of the risk posed by vulnerabilities such as these and adequately protect systems,” Talos notes.
Researchers Link New "Gazer" Backdoor to Turla Cyberspies
31.8.2017 securityweek CyberSpy
Gazer/WhiteBear is Sophisticated Malware That Has Been Used Against High-profile Targets
Security researchers and ESET and Kaspersky Lab have unveiled details on a new backdoor used by the Russia-linked cyber-espionage group Turla in attacks against embassies and consulates worldwide.
The new piece of malware has been actively deployed in targeted attacks since at least 2016 and shows similarities with other tools used by Turla, an advanced persistent threat (APT) group that has been active for over a decade.
Also known as Waterbug, Venomous Bear and KRYPTON, the group’s primary tools are tracked as Turla (Snake and Uroburos) and Epic Turla (Wipbot and Tavdig). Most recently, the group has been refining its tools and switching to new malware.
A Forcepoint report published in February 2017 revealed that a threat group apparently connected to Turla was targeting the websites of ministries, embassies and other organizations from around the world as part of a reconnaissance campaign. Most of the attacks were carried out in April 2016.
In a 29-page report (PDF) published this week, ESET provides a comprehensive analysis of a backdoor they refer to as Gazer, which the security firm has attributed with high confidence to the Turla group. The malware has been used against targets in Southeastern Europe and those part of the former Soviet Union Republic, while the witnessed techniques, tactics and procedures (TTPs) are in-line with those usually associated with Turla.
Delivered via spearphishing emails alongside a first stage backdoor called Skipper – which Bitdefender analyzed a while ago (PDF) –, Gazer also shows similarities with other second stage backdoors used by the Turla group, including Carbon and Kazuar. Written in C++, it can receive encrypted tasks from a command and control (C&C) server, which usually is a legitimate, compromised website that acts as a first layer proxy (consistent with Turla’s modus operandi).
The malware was also found to use a custom library for 3DES and RSA encryption and to include 6 different persistence modes, either through Windows registry, by setting up tasks, or by creating or modifying existing LNK files. Communication with the C&C server is performed through HTTP GET requests, when retrieving tasks, or through HTTP POST requests, when sending the tasks results.
“Gazer makes extra efforts to evade detection by changing strings within its code, randomizing markers, and wiping files securely,” ESET says. In the most recent version, the malware contained phrases related to video games throughout its code.
Four versions of Gazer have been identified to date. The first has a compilation date of 2002, but ESET believes this was faked, because the certificate it is signed with was issued by Comodo for “Solid Loop Ltd” in 2015. The latest two versions are signed with a different certificate: “Ultimate Computer Support Ltd.”
“Gazer is a very sophisticated piece of malware that has been used against different targets in several countries around the world. Through the different versions we found and analyzed, we can see that this malicious backdoor is still being actively developed and used by its creators,” ESET concludes.
Kaspersky Lab also published their own analysis of the threat, which they refer to as WhiteBear. The security firm calls this “a parallel project or second stage of the Skipper Turla cluster of activity” (which was referred to last year as WhiteAtlas) and confirms the focus on embassies and consular operations around the world, but also mentions a change of focus to include defense-related organizations starting June 2017.
“WhiteBear infections appear to be preceded by a condensed spearphishing dropper, lack Firefox extension installer payloads, and contain several new components signed with a new code signing digital certificate, unlike WhiteAtlas incidents and modules,” the researchers say.
Although the WhiteBear infrastructure overlaps with other Turla campaigns, like those deploying KopiLuwak, the new backdoor “is the product of separate development efforts,” Kaspersky says. The security firm believes that WhiteBear might be a distinct project with a separate focus.
“WhiteBear activity reliant on this toolset seems to have diminished in June 2017. But Turla efforts continue to be run as multiple subgroups and campaigns. […] Infrastructure overlap with other Turla campaigns, code artifacts, and targeting are consistent with past Turla efforts. With this subset of 2016-2017 WhiteBear activity, Turla continues to be one of the most prolific, longstanding, and advanced APT we have researched,” Kaspersky concludes.
Expert discovered 2,893 Bitcoin miners left exposed on the Internet
31.8.2017 securityaffairs IT
The popular Dutch security researcher Victor Gevers has discovered thousands of Bitcoin miners left exposed on the Internet.
The popular security researcher Victor Gevers, the founder of the GDI Foundation, has discovered 2,893 Bitcoin miners left exposed on the Internet.
View image on TwitterView image on TwitterView image on Twitter
Follow
I see about 2,893 Chinese Bitcoin "Thunder mining machines" online which are accessible via telnet w/o any password. Is the GFW down?
1:19 AM - Aug 29, 2017
13 13 Replies 190 190 Retweets 322 322 likes
Twitter Ads info and privacy
The devices expose Telnet port with no password, the expert explained to Bleeping Computer that all miners belong to the same Bitcoin mining pool and likely are operated by the same organization.
Most of the devices are ZeusMiner THUNDER X3 Bitcoin miners.
Based on firmware details Gevers found on the devices, the researcher believes that most are ZeusMiner THUNDER X3 Bitcoin miners.
The analysis of the IP addresses assigned to the Bitcoin Miners led to believe that the devices belong to a Chinese state-sponsored group.
“The owner of these devices is most likely a state sponsored/controlled organization part of the Chinese government, ” Gevers told Bleeping Computer.
Shortly after Gevers announced his discovery the operators behind the Bitcoin miners secured the exposed devices shortly after, the experts highlighted the speed in protecting the Bitcoin miners.
“Most of the miners are now not available anymore via Telnet,” Gevers told Bleeping Computer.
“At the speed they were taken offline, it means there must be serious money involved,” Gevers added. “A few miners is not a big deal, but 2,893 [miners] working in a pool can generate a pretty sum.”
A so huge botnet of miners could generate million dollars per months depending on the specific crypto currency they were mining.
The Twitter user @Quan66726078 speculate the botnet of 2,893 miners discovered by Gevers could generate an income of just over $1 million per day, in case operators use it to mine Litecoin cryptocurrency.
29 Aug
Quan @Quan66726078
Replying to @Quan66726078 @0xDUDE
2) and the machines are high-end. With approx ~14 Th/s. Maybe more since not all new Chinese mining equipment even gets on the market
Follow
Quan @Quan66726078
3) Then with power consumption about 1323 watt at price of 0.08 cent per kwH and mining Litecoin with 1 machine generates ~$379.000
9:55 AM - Aug 29, 2017
1 1 Reply Retweets 2 2 likes
Twitter Ads info and privacy
Gevers noticed that other netizens have accessed the Bitcoin miners before he discovered them.
“I have proof of other visitors on the boxes where they tried to install a backdoor or malware,” Gevers said.
29 Aug
Victor Gevers @0xDUDE
I see about 2,893 Chinese Bitcoin "Thunder mining machines" online which are accessible via telnet w/o any password. Is the GFW down? pic.twitter.com/pGuBJnld5i
Follow
Victor Gevers @0xDUDE
From XL_MINER_0001 to XL_MINER_2893. And no I am not the only visitor with admin privileges. These miners get visitors daily from everywhere pic.twitter.com/pOt1D4ChgL
1:34 AM - Aug 29, 2017

Twitter Ads info and privacy
According to a researcher who goes online with the handle Anthrax0, the miners appeared to be participating in a bandwidth sharing scheme run via Chinese service Xunlei.
29 Aug
Victor Gevers @0xDUDE
I see about 2,893 Chinese Bitcoin "Thunder mining machines" online which are accessible via telnet w/o any password. Is the GFW down? pic.twitter.com/pGuBJnld5i
Follow
Anthr@X @anthrax0
This is not any crypto currency miner. It's in fact a bandwidth/uploading affiliation program. You get rewarded for using the router as CDN.
11:29 AM - Aug 29, 2017
Oops! WikiLeaks Website Defaced By OurMine
31.8.2017 thehackernews Hacking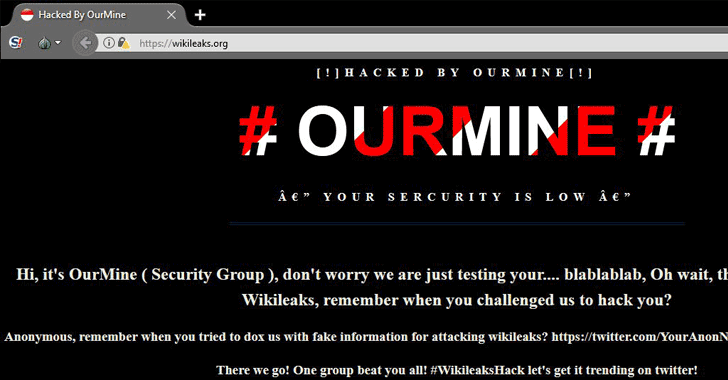
OurMine is in headlines once again—this time for defacing WikiLeaks website.
The notorious hacking group, OurMine, is known for breaching into high-profile figures and companies' social media accounts, including Facebook CEO Mark Zuckerberg, Twitter CEO Jack Dorsey, Google CEO Sundar Pichai, HBO, Game of Thrones and Sony's PlayStation Network (PSN).
According to screenshots circulating on Twitter, the official website of WikiLeaks has reportedly been defaced by the OurMine hacking group, who left a message on the site, as shown above.
WikiLeaks is a whistleblowing website that since March, has been revealing top CIA hacking secrets under Vault 7, including the agency's ability to break into different mobile and desktop platforms, security camera live video streams, air-gap computers and many more.
There is no indication of WikiLeaks servers and website been compromised, instead it seems their website has been redirected to a hacker-controlled server using DNS poisoning attack.
In DNS poisoning attack, also known as DNS spoofing, an attacker gets control of the DNS server and changes a value of name-servers in order to divert Internet traffic to a malicious IP address.
Shortly after the defacement, the site administrators regained access to their DNS server and at the time of writing, the WikiLeaks website is back online from its official legitimate servers.
OurMine is a Saudi Arabian group of hackers which claims to be a "white hat" security firm.
The group markets itself by taking over social media accounts of high-profile targets and then encourages them to contact the hacking group to buy its IT security service in an effort to protect themselves from future cyber attacks.
Gazer: A New Backdoor Targets Ministries and Embassies Worldwide
30.8.2017 thehackernews Virus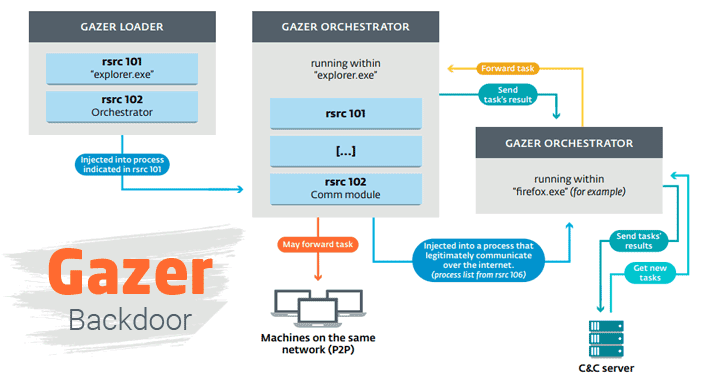
Security researchers at ESET have discovered a new malware campaign targeting consulates, ministries and embassies worldwide to spy on governments and diplomats.
Active since 2016, the malware campaign is leveraging a new backdoor, dubbed Gazer, and is believed to be carried out by Turla advanced persistent threat (APT) hacking group that's been previously linked to Russian intelligence.
Gazer, written in C++, the backdoor delivers via spear phishing emails and hijacks targeted computers in two steps—first, the malware drops Skipper backdoor, which has previously been linked to Turla and then installs Gazer components.
In previous cyber espionage campaigns, the Turla hacking group used Carbon and Kazuar backdoors as its second-stage malware, which also has many similarities with Gazer, according to research [PDF] published by ESET.
Gazer receives encrypted commands from a remote command-and-control server and evades detection by using compromised, legitimate websites (that mostly use the WordPress CMS) as a proxy.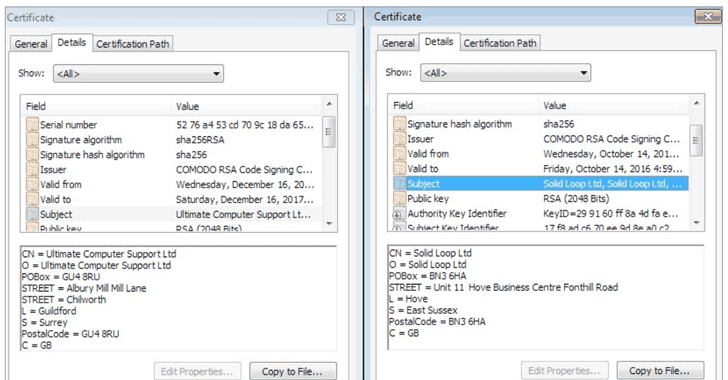
Instead of using Windows Crypto API, Gazer uses custom 3DES and RSA encryption libraries to encrypt the data before sending it to the C&C server—a common tactic employed by the Turla APT group.
Gazer uses code-injection technique to take control of a machine and hide itself for a long period of time in an attempt to steal information.
Gazer backdoor also has the ability to forward commands received by one infected endpoint to the other infected machines on the same network.
So far ESET researchers have identified four different variants of the Gazer malware in the wild, primarily spying on Southeast European and former Soviet bloc political targets.
Interestingly, earlier versions of Gazer were signed with a valid certificate issued by Comodo for "Solid Loop Ltd," while the latest version is signed with an SSL certificate issued to "Ultimate Computer Support Ltd."
According to researchers, Gazer has already managed to infect a number of targets worldwide, with the most victims being located in Europe.
Over 711 Million Email Addresses Exposed From SpamBot Server
30.8.2017 thehackernews Spam

A massive database of 630 million email addresses used by a spambot to send large amounts of spam to has been published online in what appears to be one of the biggest data dumps of its kind.
A French security researcher, who uses online handle Benkow, has spotted the database on an "open and accessible" server containing a vast amount of email addresses, along with millions of SMTP credentials from around the world.
The database is hosted on the spambot server in Netherlands and is stored without any access controls, making the data publicly available for anyone to access without requiring any password.
According to a blog post published by Benkow, the spambot server, dubbed "Onliner Spambot," has been used to send out spams and spread a banking trojan called Ursnif to users since at least 2016.
Ursnif Banking Trojan is capable of stealing banking information from target computers including credit card data, and other personal information like login details and passwords from browsers and software.
"Indeed, to send spam, the attacker needs a huge list of SMTP credentials. To do so, there are only two options: create it or buy it," Benkow said. "And it's the same as for the IPs: the more SMTP servers he can find, the more he can distribute the campaign."
As the researcher explained, he found "a huge list of valid SMTP credentials"—around 80 millions—which is then used to send out spam emails to the remaining 630 million accounts via internet provider's mail servers, making them look legitimate that bypass anti-spam measures.
The list also contains many email addresses that appear to have been scraped and collected from other data breaches, such as LinkedIn, MySpace and Dropbox.
The researcher was able to identify a list of nearly 2 million email addresses to be originated from a Facebook phishing campaign.
The exposed database has been verified by Troy Hunt, added the leaked email addresses to his breach notification site.
At the time of writing, it is unclear who is behind the Onliner Spambot.
Users can check for their email addresses on the site and those affected are obviously advised to change their passwords (and keep a longer and stronger one this time) for your email accounts and enable two-factor authentication if you haven't yet.
Also, do the same for other online accounts if you are using same passwords on multiple sites.
Someone Hacked Selena Gomez Instagram, Shared Nude Justin Bieber Photos
30.8.2017 thehackernews Incindent
The highest followers account on Instagram owned by Selena Gomez has recently been hacked with unknown hackers posting a bunch of nude photographs of her ex-boyfriend Justin Bieber on her account.
The latest hack is not part of the ongoing Fappening events affecting a majority of celebrities by targeting their iCloud accounts, rather in the case of Selena, some hacker managed to breach her Instagram account and posted Bieber's photos.
Bieber's three full-frontal shots of naked photos were visible to Selena's 125 million Instagram followers for a short duration of time, after which her account was swiftly taken down Monday night.
A post from Selena's official Instagram account went up Monday showing 3 pics of Bieber with a caption that read:
"LOOK AT THIS N***A LIL SHRIMPY."
Selena's team has since re-secured her Instagram account, which was back online minutes after it was taken down, with the photos of Bieber deleted.
The Bieber nude images were not part of any stolen celebs photo dump, instead, they were clicked during his 2015 holiday in Bora Bora and also published online in 2015, when Bieber was dating model Jayde Pierce.
At that time, censored photos of Bieber were published by several websites, but uncensored versions also reached the Internet, which was posted on Selena's hacked Instagram account, claims Variety.
There's no detail about hackers or how they got into Selena's Instagram account available at the moment, but as we have previously seen many celebrities tricking into handing over their account credentials in phishing emails, the same could be the case with the "Good For You" singer.
It seems like celebrities are not taking the security of their accounts seriously, which once again resulted in the hack of social media account of an A-listed celebrity.
Just last week, dozens of intimate photos of Anne Hathaway, Miley Cyrus, Kristen Stewart, Katharine McPhee, and golfer Tiger Woods reportedly surfaced on the Internet after unidentified hackers gained access to celebs' iCloud accounts and stole their private photos and videos.
Today it's Selena, but tomorrow it could be you. So, users are highly recommended to enable two-factor authentication on your accounts and always secure your accounts with a strong and different password.
Also, avoid clicking on any suspicious link or attachment you received via an email and providing your personal or financial information without verifying the source properly.
Breach at Used Tech Goods Seller CeX Exposes Two Million Customers
30.8.2017 securityweek Incindent
CeX, a second-hand technology goods chain, is notifying up to 2 million of its online customers that their personal details may have been compromised.
CeX operates more than 350 shops in the UK, and more than 100 overseas (including around a dozen in America, 20 in Australia, and 20 in India). The data appears to have been stolen from a database accessed via the company's WeBuy website rather than in-store POS devices.
Neither the emailed notification nor a brief online statement provides much information. They both say, "we have recently been subject to an online security breach." They do not say when the breach occurred, nor when it was discovered.
The statement says, "The [stolen] data includes some personal information such as first name, surname, addresses, email address and phone number if this was supplied. In a small number of instances, it may include encrypted data from expired credit and debit cards up to 2009. No further financial information has been shared."
CeX stresses that there is no loss of current financial data: "We would like to make it clear that any payment card information that may have been taken, has long since expired as we stopped storing financial data in 2009." The firm does not comment on why it should still be storing expired card data that is at least eight years old.
It would seem that the breach has not affected all the firm's customers; and any customers who do not receive the warning email can assume their details were not stolen. The only advice given to the affected customers is to change their WeBuy password, and "to change their password across other services where they may have re-used their WeBuy website password."
The passwords were apparently hashed. The statement merely says, "your password has not been stored in plain text," without giving any indication on how it was stored. However, it warns that if the user's password "is not particularly complex then it is possible that in time, a third party could still determine your original password and could attempt to use it across other, unrelated services."
This is an understatement, and would more accurately be stated as, 'unless your password is particularly complicated, it will be discovered by a third-party in a very short period of time.' Under such circumstances it could be more expedient for the company to force a password reset across all customers, since so many have been affected, rather than ask the affected customers to do it themselves.
Completely missing from the statement is any warning about subsequent phishing attempts. Although no financial details were taken, name, email and phone numbers together with a known interest in technology would be enough for the attackers to produce compelling and targeted phishing and or vishing attacks -- and all affected customers should be aware of this possibility.
Ilia Kolochenko, CEO at High-Tech Bridge, explains the issue. "The core problem is the continuing ramifications of each breach -- attackers may use compromised credentials, or other sensitive data, in password reuse and social engineering attacks years after the original breach. And the more breaches that occur, the more successful further attacks become as cybercriminals accumulate a huge amount of data about us. To minimize the domino effect of unavoidable breaches," he continues, "users should use strong and unique passwords, and provide as little sensitive, or confidential, information about themselves as reasonable in all their online accounts."
There is one further possible consideration for some customers. In 2014, CeX started accepting payment and paying customers in bitcoins. However, its statement says that it is unable to tell customers exactly what data about them was stolen. It is possible that the stolen data could indicate customers who have a bitcoin wallet. At this stage of the investigation into the breach, it would be advisable for any CeX customers with bitcoin wallets to take extra precautions to protect those wallets since personal wallets are increasingly targeted by cyber criminals.
When asked for clarification on the bitcoin issue, a spokesperson for CeX provided a generic statement to SecurityWeek.
"Late last year, we suffered what we believed to be a low-level breach in our online UK website security, along with a phishing attempt. It was swiftly identified and fixed, and we immediately put in place additional security measures," the statement said. "No further security breach has since taken place and we would like to stress that at the time, there was no evidence that there had been any unauthorised access to customer data.
"However, in August this year we received communication from a third party claiming to have access to some of our online UK website data from the security breach," the statement continued. "We immediately informed the relevant authorities, including the ICO and NCA who are in the process of investigating and our cyber security specialists have implemented additional, advanced security measures to prevent this from happening again. We can confirm the breach was not connected to high street store data and as a priority, we are in the process of contacting all online customers who might be affected. As we are currently investigating this we are unable to provide further information at this stage."
*Updated with statement from CeX.
Selena Gomez Instagram hacked! Hackers post Bieber nude photos
30.8.2017 securityaffairs Hacking
Selena Gomez Instagram account has reportedly been hacked. Nude photos of singer Justin Bieber have been published by hackers.
Unknown hackers have compromised the Instagram account owned by Selena Gomez and posted nude photographs of her ex-boyfriend Justin Bieber.

Source Tribune.com
The hack doesn’t seem to be associated with the recent Fappening 2017 hack or previous Fappening cases that hit many celebrities.
The Bieber nude images were clicked during a holiday in Bora Bora in 2015 and when the images were leaked online
The Selena’s Instagram account has more than 125 million followers, hackers hijacked it and posted three Bieber’s full-frontal shots of naked pictures.
The hacker published the Bieber’s naked photos on the Selena Gomez official Instagram account with this message:
“LOOK AT THIS N***A LIL SHRIMPY.”
The account was taken down Monday night after the hack, the staff of the popular star restored the access to the Instagram account and deleted the Bieber naked photos.
“The Bieber images were the same ones that were published after the pop star’s Bora Bora vacation in 2015. Gomez and Bieber used to be a couple, but are no longer together.” reported the outlet Variety.
“Bieber has said that the publication of the images, originally in the New York Daily News censored (though the uncensored versions later made the rounds online), made him feel “super violated.” “Like, I feel like I can’t step outside and feel like I can go outside naked,” he told Access Hollywood in 2015. “Like, you should feel comfortable in your own space… especially that far away.””
It is still unclear how hackers have hijacked the Selena Gomez Instagram account, it is likely the staff of the pop star was the victim of phishing attack.
A few days ago, private pictures of Anne Hathaway, Miley Cyrus, Stella Maxwell, Kristen Stewart, Tiger Woods and Lindsey Vonn have been posted online by a celebrity leak website.
Hackers gained access to celebrities’ iCloud accounts and stole their private photos and videos.
Dear star … force your staff enabling two-factor verification on your accounts, start adopting strong passwords, don’t share same credentials on different accounts, be vigilant on suspicious and unsolicited emails.
Breach at Used Tech Goods Seller CeX Exposes Two Million Customers
30.8.2017 securityweek Incindent
CeX, a second-hand technology goods chain, is notifying up to 2 million of its online customers that their personal details may have been compromised.
CeX operates more than 350 shops in the UK, and more than 100 overseas (including around a dozen in America, 20 in Australia, and 20 in India). The data appears to have been stolen from a database accessed via the company's WeBuy website rather than in-store POS devices.
Neither the emailed notification nor a brief online statement provides much information. They both say, "we have recently been subject to an online security breach." They do not say when the breach occurred, nor when it was discovered.
The statement says, "The [stolen] data includes some personal information such as first name, surname, addresses, email address and phone number if this was supplied. In a small number of instances, it may include encrypted data from expired credit and debit cards up to 2009. No further financial information has been shared."
CeX stresses that there is no loss of current financial data: "We would like to make it clear that any payment card information that may have been taken, has long since expired as we stopped storing financial data in 2009." The firm does not comment on why it should still be storing expired card data that is at least eight years old.
It would seem that the breach has not affected all the firm's customers; and any customers who do not receive the warning email can assume their details were not stolen. The only advice given to the affected customers is to change their WeBuy password, and "to change their password across other services where they may have re-used their WeBuy website password."
The passwords were apparently hashed. The statement merely says, "your password has not been stored in plain text," without giving any indication on how it was stored. However, it warns that if the user's password "is not particularly complex then it is possible that in time, a third party could still determine your original password and could attempt to use it across other, unrelated services."
This is an understatement, and would more accurately be stated as, 'unless your password is particularly complicated, it will be discovered by a third-party in a very short period of time.' Under such circumstances it could be more expedient for the company to force a password reset across all customers, since so many have been affected, rather than ask the affected customers to do it themselves.
Completely missing from the statement is any warning about subsequent phishing attempts. Although no financial details were taken, name, email and phone numbers together with a known interest in technology would be enough for the attackers to produce compelling and targeted phishing and or vishing attacks -- and all affected customers should be aware of this possibility.
Ilia Kolochenko, CEO at High-Tech Bridge, explains the issue. "The core problem is the continuing ramifications of each breach -- attackers may use compromised credentials, or other sensitive data, in password reuse and social engineering attacks years after the original breach. And the more breaches that occur, the more successful further attacks become as cybercriminals accumulate a huge amount of data about us. To minimize the domino effect of unavoidable breaches," he continues, "users should use strong and unique passwords, and provide as little sensitive, or confidential, information about themselves as reasonable in all their online accounts."
There is one further possible consideration for some customers. In 2014, CeX started accepting payment and paying customers in bitcoins. However, its statement says that it is unable to tell customers exactly what data about them was stolen. It is possible that the stolen data could indicate customers who have a bitcoin wallet. At this stage of the investigation into the breach, it would be advisable for any CeX customers with bitcoin wallets to take extra precautions to protect those wallets since personal wallets are increasingly targeted by cyber criminals.
SecurityWeek has asked CeX for clarification on the bitcoin issue, and will update this article with any response.
Over $500,000 Up For Grabs at Mobile Pwn2Own 2017 Hacking Competition
30.8.2017 securityweek Congress
Trend Micro this week said that it will offer over $500,000 in cash prizes at Zero Day Initiative’s Mobile Pwn2Own contest, set to take place Nov. 1-2, during the PacSec 2017 Conference in Tokyo, Japan.
The sixth annual Mobile Pwn2Own competition will have four different targets available, namely Google Pixel, Samsung Galaxy S8, Apple iPhone 7, and Huawei Mate9 Pro, and will allow contestants to compete in four categories, including Browsers, Short Distance and WiFi, Messaging, and Baseband.
Security researchers and hackers will be encouraged to demonstrate and disclose zero-day attacks against up-to-date (fully patched) mobile platforms. Should a new version of these phones become available in time to be integrated into the contest, Trend Micro and the Zero Day Initiative will work to add it as an available target platform.
In the Mobile Browser category, hackers and researchers will target Google Chrome, Apple Safari, and the Samsung Internet Browser, competing for prizes of $50,000, $40,000, and $30,000, respectively. In the Short Distance and WiFi category, attacks happening over Bluetooth, near field communication (NFC), or WiFi will be accepted, prized $40,000, $50,000, and $60,000, respectively.
Contestants in the messaging category will be able to submit SMS or MMS exploits, each worth $60,000 of cash. Those competing in the Baseband category can win $100,000--the biggest prize in the competition.
“Following the contest, vendors will have 90 days to produce patches for these bugs, instead of the standard 120 disclosure window. This reflects the integrity of successful exploits produced during the contest. As these are practical vulnerabilities with demonstrated applications, a shortened patch window helps provide quicker protection for the end user against potentially damaging bugs,” Trend Micro notes.
The security firm also announced that successful entries will also receive "Master of Pwn" points and the device itself for each attempt. The tradition of crowning a Master of Pwn will return this year, Trend Micro’s Brian Gorenc points out.
Gorenc also says that successful attempts will be eligible for a series of Add-on Bonuses, including a Kernel Bonus (the exploit payload must execute with kernel-level privileges) consisting of an extra $20,000 and an additional 3 Master of Pwn points, and a Persistence Bonus (the exploit payload can survive a reboot of the device), consisting of an additional $50,000 for iOS / $40,000 for Android, and an additional 3 Master of Pwn points.
There are also a series of penalties in place that contestants should be aware of. Those interested in participating are encouraged to read the complete set of rules for Mobile Pwn2Own 2017. Entrants should contact ZDI at zdi@trendmicro.com to begin the registration process.
“Since mobile device are now ubiquitous, security flaws in these platforms are coveted by criminal elements and government agencies alike. Mobile Pwn2Own helps harden these devices and their OSes by revealing vulnerabilities and providing that research to the vendors. The goal is to get these bugs fixed before they’re actively exploited,” Gorenc said.
Onliner Spambot – More than 711 Million email addresses open and accessible online
30.8.2017 securityaffairs Spam
An archive containing more than 630 million email addresses used by the spambot server dubbed ‘Onliner Spambot’ has been published online.
The Onliner Spambot dump is the biggest one of its kind, it was discovered by the security researcher who goes online with the handle Benkow.
The database was hosted on an “open and accessible” server in Netherlands containing a vast amount of email addresses, along with millions of SMTP credentials from around the world.

The popular researcher Troy Hunt has verified the archive and added the leaked email addresses to his breach notification site Haveibeenpwned.com.
Follow
Troy Hunt ✔@troyhunt
Processing the largest list of data ever seen in @haveibeenpwned courtesy of a nasty spambot. I'm in there, you probably are too.
10:22 AM - Aug 28, 2017 · Gold Coast, Queensland
23 23 Replies 176 176 Retweets 196 196 likes
Twitter Ads info and privacy
Follow
Troy Hunt ✔@troyhunt
Interesting feedback: someone found fabricated addresses in the 711m I loaded today AND were getting spam to them https://www.troyhunt.com/inside-the-massive-711-million-record-onliner-spambot-dump/#comment-3493584892 …
7:42 AM - Aug 30, 2017
Photo published for Inside the Massive 711 Million Record Onliner Spambot Dump
Inside the Massive 711 Million Record Onliner Spambot Dump
Last week I was contacted by someone alerting me to the presence of a spam list. A big one. That's a bit of a relative term though because whilst I've loaded "big" spam lists into Have I been pwned...
troyhunt.com
14 14 Replies 13 13 Retweets 43 43 likes
Twitter Ads info and privacy
The Onliner Spambot served has been used by crooks to send out spam messages and spread the Ursnif banking trojan since at least 2016.
The Ursnif Trojan was spread via spam emails that contain malicious attachments that are used to download and execute the malware.
“Indeed, to send spam, the attacker needs a huge list of SMTP credentials. To do so, there are only two options: create it or buy it. And it’s the same as for the IPs: the more SMTP servers he can find, the more he can distribute the campaign.” wrote Benkow.
“I will take as an example the Onliner spambot. This spambot is used since at least 2016 to spread a banking trojan called Ursnif. I have seen this spambot targeting specific countries like Italy, or specific business like Hotels.”
The expert discovered a list of roughly 80 million valid SMTP credentials, that were used to send out the spam messages via internet provider’s mail servers. In this way crooks made their email appear as legitimate and bypass anti-spam systems.
It is impossible to be sure about the source of the data, data may have been collected from major data breaches (i.e. LinkedIn, MySpace and Dropbox) or collected by credentials stealer malware like Pony.
According to Benkow, at least 2 million email addresses were collected through a Facebook phishing campaign.
“It’s difficult to know where those lists of credentials came from. I have obviously seen a lot of public leaks (like Linkedin, Baidu or with every passwords in clear text) but credentials can also came from phishing campaigns, credentials stealer malwares like Pony, or they can also be found in a shop.” continues the expert. “Somebody even show me a spambot with a SQL injection scanner which scan Internet, looks for SQLi, retrieves SQL tables with names like “user” or “admin”.”
At the time of writing, there is no official data on the threat actor behin the Onliner Spambot.
Android Banking Trojan MoqHao targets South Korea users
30.8.2017 securityaffairs Android
Security researchers from McAfee have spotted a new Android banking Trojan dubbed MoqHao, targeting South Korean users via SMS phishing messages.
Attackers send phishing emails with a malicious code link that tricks victims into believing that it points to a lost private picture or a Chrome update.
When victims click on the shortened links in the SMS messages the MoqHao Android banking Trojan is installed, then the malicious code attempts to spread by sending phishing SMS messages to the victims’ contacts.
“Last month, a number of users started posting on South Korean sites screenshots of suspicious SMS messages phishing texts (also known as smishing) to lure them into clicking on shortened URLs.” reads the analysis published by McAfee.
“When the victim clicks on the shortened URL using an Android device, a JavaScript script on the web server checks the user agent of the browser and shows an alert message asking to update Chrome to a new version, which is in fact a malicious fake Chrome Android app.” “If the URL is accessed by any other device (such as an iPad), the web server redirects the user to a security page of Naver, a popular search engine and portal site in South Korea.”

The MoqHao banking Trojan can execute commands send by the C&C server and collect sensitive information via a local Google phishing website.
Unlike Android banking Trojans, MoqHao includes java-httpserver to host a phishing page that opens in the default browser once the user clicks on a fake alert message.
Once the victim has downloaded APK and installed it, the malicious code requests various suspicious permissions, such as “directly call phone numbers,” “read your contacts,” or “read your text messages.”In order to achieve persistence, the malware asks every second for device administrator privileges, even if the victim dismisses it.
MoqHao monitors on the user activities by registering a broadcast receiver for system events (i.e. New package install, screen state, SMS messages).
Then the malware also connects to the first-stage remote server and dynamically receives the IP for the second-stage server from the user profile page of Chinese search engine Baidu.
“When connected to the second-stage server, Android/MoqHao sends a “hello” message containing the following device information:
UUID
Device ID (IMEI)
Android version
Device product name, build ID string
Whether the device is rooted
SIM status
Phone number
Registered accounts”
MoqHao checks whether major Korean bank apps are installed and downloads the related Trojanized versions from the C&C server, then it displays alerts the victim that an update is available for the targeted app. Once the victim accepts to install the update, the malicious app replaces the legitimate one.
Experts believe the malware is not completed or some features are still not active.
“During our analysis of this threat, when Android/MoqHao requests the download of a specific fake or Trojanized banking app, the control server responds with an error. Affected users in South Korea have not reported downloads or attempted installation of additional APK files. This suggest that the fake update functionality is probably not implemented or is at least not currently used by the malware authors.” continues the analysis.
The MoqHao banking Trojan was first spotted in January, likely it was just a test version that was continuously updated in February and March arriving at a stable release in May.
Experts linked the malware to a hacking campaign that in May 2015 targeted users in South Korea via a phishing message in the default web browser.
Although the two malwares have very similar behaviors, they have completely different code bases.
“The similarities between the 2015 and 2017 phishing campaigns suggests the same cybercriminals, who have shifted from DNS redirection attacks to a smishing campaign. The attackers are still targeting Chrome and getting the control server from a dynamic webpage while changing the code base of the initial dropper component as well as the dynamically loaded payload,” concluded McAfee.
Swedish web hosting Loopia suffered severe data breach
30.8.2017 securityaffairs Incindent
The major Swedish web hosting provider Loopia has been compromised and the entire customer database leaked.
Loopia confirmed the data breach yesterday, the incident has happened on August 22 and the company notified customers on August 25.
The company explained that the delay in the public disclosure was necessary to secure the systems and protect its customers.
“Security is very important to Loopia and something we work intensively with every day. On Tuesday, 22 August, Loopia was subjected to a criminal offense. With the attack, the hackers have had access to parts of the customer database, including personal and contact information and encrypted (hashade) passwords to Loopia Kundzon.” reads the announcement.
“The violation has not affected your services such as email, web pages, databases or passwords to your email at Loopia. We also want to emphasize that payment card information is not saved in Loopia’s environment and is thus not affected by the infringement.“
In response to the data breach, the company is forcing a password reset and is urging customers to update their personal information. Loopia clarified that stolen passwords were encrypted, but did not reveal the hashing algorithm.
“Although passwords to Loopia’s Customer Zone are stored encrypted (hashade), we have, as an additional security measure, changed all customer numbers and passwords to all customer accounts. Information has been sent to all customers by e-mail.” continues the announcement.

Source nyteknik.se
Hackers did not access financial data, according to Loopia customers’ hosted sites and e-mail services weren’t compromised.
“We were not sure how the attackers had gone, and needed a clearer picture of it before we went out with information. Now all customers have been informed. As an additional security measure, we have changed all customer numbers and passwords to all customer accounts”. CEO Jimmie Eriksson told Swedish outlet NyTeknik.
“We will evaluate whether we could have done otherwise. We then made great efforts in a short period of time. We take the intrusion seriously, but no system is safe to 100 percent”
At the time there is no information on the way hackers breached the company systems, an internal investigation is under way.
“An internal investigation is under way. In parallel, we will continue to review our systems. We have already implemented a number of measures to increase security, and more efforts may be made if the investigation shows more weaknesses in the system.” said CEO Jimmie Eriksson.
Jimmy Nukebot: from Neutrino with love
30.8.2017 Kaspersky Virus
BANKING TROJAN CRYPTOCURRENCIES MALWARE DESCRIPTIONS
“You FOOL! This isn’t even my final form!”
In one of our previous articles, we analyzed the NeutrinoPOS banker as an example of a constantly evolving malware family. A week after publication, this Neutrino modification delivered up a new malicious program classified by Kaspersky Lab as Trojan-Banker.Win32.Jimmy.
NeutrinoPOS vs Jimmy
The authors seriously rewrote the Trojan – the main body was restructured, the functions were moved to the modules. One small difference that immediately stands out is in the calculation of checksums from the names of API functions/libraries and strings. In the first case, the checksums are used to find the necessary API calls; in the second case, for a comparison of strings (commands, process names). This approach makes static analysis much more complicated: for example, to identify which detected process halts the Trojan operation, it’s necessary to calculate the checksums from a huge list of strings, or to bruteforce the symbols in a certain length range. NeutrinoPOS uses two different algorithms to calculate checksums for the names of API calls, libraries and for the strings. They look like this:
Restored NeutrinoPOS code to calculate checksums for arbitrary strings and for API calls
In Jimmy, only one algorithm is used for these purposes – a slight modification of CalcCS from NeutrinoPOS. The final XOR with the fixed two-byte value was added to the pseudo-random generator.
Calculation of checksums in Jimmy
The Trojan has completely lost the functionality for stealing bank card data from the memory of an infected device; now, its task is limited solely to receiving modules from a remote node and installing them into the system. The scan of the infected host has been extended: in addition to the checks inherited from Neutrino, the Trojan also examines its own name – it should not be a checksum in the MD5, SHA-1, SHA-256 format. Or, alternatively, it should contain the ‘.’ symbol, indicating a subsequent extension (for example, ‘exe’). Plus, by using the assembly command cpuid, the Trojan gets information about the processor and compares it with the list of checksums “embedded” into it.
Additional Jimmy checks
The communication protocol with the C&C server also remains unchanged: the same exchange of “enter”, “success” in base64 commands is used, but now the answer is encrypted with RC4 beforehand and the key hardcoded in the body of the Trojan (a8A5QfZk3r7FHy9o6C2WpBc44TiXg93Y for the sample in question). The code for extracting the encryption key is here.
Analysis of modules
As mentioned above, the main body of the Trojan only receives modules – these contain the payload. We managed to get hold of new modules for web-injects, mining and a large number of updates for the main module in various droppers.
The miner is designed to extract the Monero currency (XMR). In the module code there is an identifier associated with a wallet for which the crypto currency is extracted, as well as the address of the pool. Monero is very popular with virus writers – it’s mined by SambaCry, which we described in June and Trojan.Win32.DiscordiaMiner that appeared shortly afterwards. By the way, the source code of the latter was made publicly available by the author. The reason for doing so was the same that prompted the author of NukeBot to do likewise: an attempt to stifle disagreements in forums and to avoid accusations of fraud (the repository with the code is currently unavailable).
Thanks to the identifier/pool pair, we got statistics on all the nodes working for this wallet. The start date of mining – 4 July – coincides with the compilation of the main body of the first discovered sample and is extremely close to the date of compilation of the dropper (06 July 13:14:55 2017 UTC), the main body (02 July 14:19:03 2017 UTC) and the modules for web injects (July 02, 14:18:39 2017 UTC). So it’s safe to say that Jimmy began to proliferate in early July.
It’s worth noting that the amount of money in the wallet is small – only ~ 0.55 XMR, which as of 21 August is only $45. Judging by the general decline and absence of payments, the authors quickly abandoned the use of miners or changed their wallet.
The web-inject modules are so called for their primary intended use, although they are also able to perform functions similar to those in NeutrinoPOS, i.e., take screenshots, “raise” proxy servers, etc. These modules are distributed in the form of libraries and their functions vary depending on the name of the process in which they are located. As you can see from the screenshot below, in three cases out of five the ChromeHook procedure is called for browsers. This is not surprising, considering the large number of Chrome-based browsers. Unfortunately, it was possible to restore the name from the checksum for only one of them – chrome.exe (0xFC0C7619). Checksums are calculated using the algorithm described in the previous section.
Restored code of the main procedure in the module of Jimmy web injects
Like NeutrinoPOS, Jimmy stores a number of parameters in the registry. In the sample in question, the data is in the HKEY_CURRENT_USER\Software\c2Fsb21vbkBleHBsb2l0Lmlt branch. For example, this is where the web-inject module receives the address of the currently used DNS server from – this is critical when using NamCoin-like addresses as a C&C server.
For Firefox and Internet Explorer, the function hook is performed by the straightforward substitution of the called function addresses in the loaded libraries (etc. InternetConnectW / PR_Read). With Chrome, things are a bit more complicated – the necessary libraries are linked statically. But the subsequent substitution of data using web injects coincides.
Restored web-inject processing code
So far we have only managed to get a test sample of the web injects (in the screenshot below); in the future the Trojan will most likely acquire ‘combat’ versions. Here you can find examples of web injects and the keys used. To recap, decryption entails decoding the string using base64 and then decrypting with RC4.
Request from Jimmy for web injects
Example of the Jimmy test web injects
In the pictures below several procedures in the source code of NukeBot and the restored code of Jimmy are compared. It can clearly be seen that they completely coincide.
Conclusion
In isolation from the previous modifications, the newly created Jimmy would not be of much interest to researchers. However, in this context, it is an excellent example of what can be done with the source code of a quality Trojan, namely, flexibly adapt to the goals and tasks set before a botnet to take advantage of a new source.
MD5
Droppers
c989d501460a8e8e381b81b807ccbe90 (рассмотрен в статье)
E584C6E999A509AC21583D9543492EF4
2e55bd0d409bf9658887e02a7c578019
bccd77cf0269da7dc914885cda626c6c
86d7d3b50e4dc4181c28ccbaafb89ab3
Main body
174256b5f1ee80be1b847d428c5180e2
336841d91c37b07134adba135828e66e
FE9A46CEFDB41095F10D459BB9943682
Modules
380356b8297893b4fc9273d42f15e9db
2fa18456e14bea53ec0d7c898d94043b
7040b5ac432064780a17024ab0a3792a
629a4d2b79abe48fb21afd625f674354
05846839DAA851006B119A2B4F9687BF
2362E3BEBAD1089DDFE40C8996B0BF45
380356B8297893B4FC9273D42F15E9DB
4042C27F082F48E253BE66528938640C
443831A3057E9A62455D4BD3C7E04144
4762B90C0305A2681CE42B9D05B9E741
CB01E3A0799D4C318F74E439CCE0413F
D9F58167A9A22BD1FA9AA0F991AEAF11
E991936E09697DE8495D05B484F3A3E2
Jimmy Banking Trojan Reuses NukeBot Code
30.8.2017 securityweek Virus
A recently discovered modification of the Neutrino banking Trojan reuses parts of the NukeBot source code that was made publicly available earlier this year, Kaspersky Lab researchers discovered.
Dubbed Jimmy, the newly discovered malware shows close resemblance to NeutrinoPOS, but features a restructured main body, with functions moved to modules. Because of this change, the new Trojan no longer includes the functionality for stealing bank card data from the memory of an infected device, but is limited to receiving modules from a remote server and installing them.
The malware is able to conduct an extended scan of an infected host, including both checks inherited from Neutrino and the examination of its own name. Furthermore, using the assembly command cpuid, the threat retrieves information about the processor and compares it with checksums it contains.
Overall, however, the Trojan has been seriously rewritten, Kaspersky says: “One small difference that immediately stands out is in the calculation of checksums from the names of API functions/libraries and strings. In the first case, the checksums are used to find the necessary API calls; in the second case, for a comparison of strings (commands, process names). This approach makes static analysis much more complicated.”
While NeutrinoPOS uses two algorithms to calculate checksums for the names of API calls, libraries and strings, Jimmy has only one algorithm for all these purposes. However, the communication protocol with the command and control server remained unchanged, the researchers say.
A closer analysis of the Trojan reveals that the payload is included in the modules the main body receives. The modules include web-injects and mining capabilities for the Monero currency (XMR). Monero has become very popular with malware writers lately, and is even mined by SambaCry.
DiscordiaMiner, which had its source code made publicly available by the author for reasons similar to those that prompted the NukeBot developer to do the same (mainly to avoid accusations of fraud), also focused on mining Monero.
Jimmy’s mining module includes an identifier for a wallet for which the crypto currency is extracted, and the address of the pool, and Kaspersky was able to use these to determine that the Trojan started the mining operations close to its early July proliferation date.
In addition to being able to inject code into web pages, the web-inject modules can also take screenshots, create proxy servers, and perform other nefarious operations, similar to those in NeutrinoPOS. The modules are distributed in the form of libraries and feature different functions, based on the name of the process in which they are located.
Similar to NeutrinoPOS, Jimmy also stores a number of parameters in the registry. The researchers explain that they also managed to retrieve a test sample of the web injects, and that future iterations of the malware might “acquire ‘combat’ versions.”
Kaspersky also compared the restored code of Jimmy with the source code of NukeBot and discovered that they completely coincide in some instances. Thus, it’s clear that the author reused the code to build their own version of the malware.
“In isolation from the previous modifications, the newly created Jimmy would not be of much interest to researchers. However, in this context, it is an excellent example of what can be done with the source code of a quality Trojan, namely, flexibly adapt to the goals and tasks set before a botnet to take advantage of a new source,” Kaspersky concludes.
In an emailed comment to SecurityWeek, AlienVault security advocate Javvad Malik pointed out the risks posed by the availability of malware source code: “Once such Trojans or malware go open source, it has two main impacts. Firstly, it increases in popularity and use. But with this, the chances of it being detected and prevented by security tools also increases; so, the second impact is that others will increasingly modify the malware in order to bypass security controls. Organizations should invest in security technologies that are constantly updated with threat intelligence so that they can better detect and respond to new threats as they emerge.”
North Korea Accused of Stealing Bitcoin to Bolster Finances
30.8.2017 securityweek BigBrothers
North Korea (DPRK) appears to be targeting bitcoin (both users and exchanges) as a means to counter the increasing effect of international sanctions. Earlier this month the UN Security Council unanimously imposed new sanctions targeting the country's primary exports. Dwindling coal exports to China will be particularly severe, and DPRK's export revenues will likely be slashed by $1 billion.
Recent cyber-attacks against South Korean bitcoin exchanges are now being blamed on North Korea. Radio Free Asia (RFA) -- a non-profit East Asian News Agency -- has reported that DPRK has already launched three cyber-attacks on bitcoin exchanges in South Korea, and one in Europe. Details, including timings, are sparse -- so it is quite possible that the July hack of a Bithumb employee is included, and here attributed to North Korea.
North Korea FlagThis basic premise that North Korea is targeting bitcoins is reiterated in a report from the United Press International news agency. It says, "The CWIC Cyber Warfare Research Center in South Korea stated a domestic exchange for bitcoin, the worldwide cryptocurrency and digital payment system, has been the target of an attempted hacking... CWIC's Simon Choi said it is 'not only one or two exchanges where attack attempts have been made'."
The precise status of the Cyber Warfare Research Center in South Korea is not explained. Nevertheless, Choi is credited with claiming that phishing emails have been targeting not just bitcoin exchanges, but that "Startups that use blockchain, financial technology sector companies as well as others, may have been the target." The report adds, "According to CWIC, the malicious code attached to the emails was identical to viruses of North Korean origin."
Despite the lack of detail, these two reports have been elaborated by bitcoin news publications. One leads with "State-sponsored North Korean hackers have been accused of targeting South Korean bitcoin exchanges with cyberattacks and hacking attempts by a South Korean official."
Frankly, it is not at all clear how much veracity can be attached to the reports -- there is no detail, no proof, no timings, and no definition of the status of CWIC (which is variously described as the Cyber Warfare Research Center and the Cyber Warfare Intelligence Center). However, the idea is certainly supported by motive and means: North Korea has both. In stealing bitcoins, the beleaguered nation can simultaneously bolster its finances and obtain 'foreign currency' that cannot be blocked by western governments. Merely surmising that this is now at the least semi-official policy of the cyber army of North Korea may not be far from the truth.
If cyber-attackers are spear-phishing bitcoin users/holders, then it presupposes knowledge of the targets' email addresses. Choi has apparently suggested that "North Korea has some how gained details about all those individuals who regularly do trading with BTC exchanges." However, this could easily be explained if it was indeed North Korea behind the July Bithumb breach. At this time, roughly 31,000 users – representing 3 percent of the company’s total number of customers – had their email and phone information stolen.
In a blog post, Ross Rustici, Cybereason's senior director of intelligence services suggests that any such North Korean hacking policy will have good, bad, and ugly ramifications.
The good, he suggests, is "it means that the DPRK threat, in totality, will be degraded. By focusing on currency generation, groups that would otherwise be gearing up for network attacks or traditional espionage will be diverted to filling out the bottom line."
The bad, he wrote is that, "Banking, financial institutions, and currency exchanges are likely to see a steady increase in malicious and sophisticated intrusion attempts." These attacks are likely to focus on institutions in South Korea, America and Japan to serve the dual purpose of political retaliation and revenue generation; but would likely also apply wherever network security is largely weak."
The ugly, however, is particularly ugly. "Given current tensions and the potential desire to retaliate for perceived assaults on the regime," comments Rustici, "the DPRK has the latent capacity to conduct a heist and destroy the network on the way out. The likelihood of this combination happening is low, but it is not zero."
At this point, it would be worth considering WannaCry, largely attributed to North Korea. The very poor process of ransom collection built into the original WannaCry led some researchers to conclude its real purpose was destructive: ransomware without decryption is effectively a cyberweapon wiper. NotPetya was more clearly a disguised cyberweapon, although in this instance more likely an attack by Russia against the Ukraine.
Zaútočil první velký mobilní botnet. Stačí zaneřádit tisíce androidů a spustíte digitální inferno
29.8.2017 Živě.cz BotNet
Desítky tisíc mobilů provádělo DDoS
Viníkem bylyy zákeřné aplikace pro Android
Takhle velký útok tu na mobilech ještě nebyl
Zaútočil první velký mobilní botnet. Stačí zaneřádit tisíce androidů a spustíte digitální infernoZaútočil první velký mobilní botnet. Stačí zaneřádit tisíce androidů a spustíte digitální infernoZaútočil první velký mobilní botnet. Stačí zaneřádit tisíce androidů a spustíte digitální infernoZaútočil první velký mobilní botnet. Stačí zaneřádit tisíce androidů a spustíte digitální infernoZaútočil první velký mobilní botnet. Stačí zaneřádit tisíce androidů a spustíte digitální inferno10 FOTOGRAFIÍ
zobrazit galerii
Na rozsáhlé botnety zavirovaných počítačů, které rozesílají spam nebo třeba zahlcují internetové servery DDoS, jsme si už tak nějak zvykli. Ostatně mnohé útočící oběti často ani netuší, že jsou jejich součástí. V zájmu operátora botnetu je totiž to, abyste se o nákaze samozřejmě pokud možno vůbec nedozvěděli, a on tak mohl třeba i roky zneužívat výkon vašeho počítače.
Domácí mašina má nicméně pro podobné zneužití jednu velkou nevýhodu. Pokud nejste závislí na internetu, anebo celé dny nepaříte GTA, vypínáte ji. A vypnutý počítač nic rozesílat nemůže. Bezpečnostní specialisté tedy poslední roky varují před novým potenciálním zlatým dolem všech botnetových záškodníků: internetem věcí.
K webu připojené set-top-boxy, chabě zabezpečené routery, chytré televizory, přehrávače, chytré ledničky, IP kamery a hromada dalších zařízení mají totiž jednu velkou výhodu. Jsou pořád online, takže mohou i neustále útočit, aniž by si toho někdo všiml. Stačí, aby byla zajištěna jejich dosavadní funkce, a pokud 10-20 % jejich výkonu sežere nějaký vir, vlastně se zdánlivě nic nestane. Jen to možná časem poznáte na účtu za elektřinu.
Jenže co krabička, to jiný firmware, čili univerzální malware, který by plošně zaútočil na každou z nich, jednoduše neexistuje. Útoky se proto omezují spíše na jeden druh zařízení – často od konkrétního výrobce a na konkrétní modelovou řadu.
Mobilní botnet
Jenže vedle osobních počítačů a chytrých krabiček v domácnosti tu je ještě něco. Bylo jen otázkou času, kdy se útočníci zaměří na ten nejatraktivnější cíl ze všech možných. Představte si stovky milionů krabiček, které jsou povětšinou online, jsou poměrně výkonné a používají jeden jediný operační systém. A co více, virus na tu krabičku nainstalují sami její majitelé.
O něčem takovém musí zákonitě snít každý operátor botnetu!
Vlastně nemusí, většina z vás totiž takovou krabičku má právě teď kapse u kalhot, na stole, anebo ji drží v ruce. Samozřejmě mám na mysli telefon s Androidem.
Podivný WireX zamotal hlavu operátorům
Co kdybychom na něj nainstalovali falešnou aplikaci, která by ve skutečnosti na pozadí a na povel operátora zahlcovala společně s desítkami tisíc dalších servery obětí? Přesně k tomu došlo na počátku srpna, když se někteří operátoři sítí CDN začali potýkat s neobvyklou aktivitou, která byla jen složitě vysledovatelná. Začali ji říkat WireX. Botnet WireX.
Nebyl to útok z konkrétní země a z omezeného počtu IP adres. Ty naopak byly rozprostřené po celém světě a bombardovaly cílové weby HTTP požadavky třeba na tamní vyhledávač. Vyhledávání na stránce patří k náročnějším operacím, která zatěžuje i databázový systém, takový web tedy může přestat odpovídat i při menším útoku.
Aktivita WireX v posledním měsíci. Operátoři CDN sítí jej poprvé zaregistrovali na počátku srpna a jeho aktivitu analyzovali zpětně ze svých logů.
Botnet WireX během svého (naštěstí) jepičího života dosáhl velikosti nejméně 120 000 zařízení ve stovce zemí světa a během sekundy dokázal server oběti zahltit 20 000 HTTP požadavky.
Bylo zřejmé, že jedna CDN síť stopy nedokáže odhalit, a tak se do analýzy zapojili ti největší hráči včetně společností jako Akamai, Cloudflare, Google nebo Oracle. Začali pročítat serverové logy, až se dopídili, že jedním z viníků je pravděpodobně běžná aplikace běžící pro Android a její instalační balíček s názvem twdlphqg_v1.3.5_apkpure.com.apk.
Mobilní malware se v HTTP požadavcích podepisoval často nesmyslným jménem prohlížeče/HTTP klienta:
User-Agent: xlw2ibhqg0i
User-Agent: bg5pdrxhka2sjr1g
User-Agent: 5z5z39iit9damit5czrxf655ok060d544ytvx25g19hcg18jpo8vk3q
User-Agent: fge26sd5e1vnyp3bdmc6ie0
User-Agent: m8al87qi9z5cqlwc8mb7ug85g47u
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; nl; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 (.NET CLR 3.5.30729)
User-Agent: Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.8.1.7) Gecko/20071018 BonEcho/2.0.0.7
User-Agent: Mozilla/5.0 (Macintosh; U; PPC Mac OS X 10_5_7; en-us) AppleWebKit/530.19.2 (KHTML, like Gecko) Version/4.0.2
Nejméně 300 falešných aplikací pro Android
Představa, že se všechny telefony nakazily jednou jedinou aplikací, však byla poněkud nepravděpodobná. Pravdu odhalila další analýza, kdy výzkumníci objevili více než 300 podobných programů pro Android. Všechny byly strojově vytvořené a obsahovali stejný kód, který zapojil oběť do mobilního botnetu.
Autoři falešné aplikace ve velkém nahráli na neoficiální skladiště instalačních balíčků APK
Jak napovídají obrázky i názvy instalačních balíčků, mnohdy se jednalo o APK balíčky stažené z neoficiálních ale poměrně populárních katalogů jako třeba APKpure. Nutno tedy opět připomenout, že byste měli stahovat aplikace jen z oficiálního katalogu Paly Store. A stejně tak autoři aplikací by je neměli omezovat jen na vybrané trhy, čímž by výrazně klesla potřeba používat podobné katalogy jen proto, že „aplikace není dostupná pro váš telefon.“
Díky včasnému odhalení záškodnických aplikací se mohl do protiútoku zapojit v plné síle i Google, který na dokázal na telefonech s novějšími verzemi Androidu aplikace vzdáleně zablokovat, čímž útok začal slábnout.
Sbírka hříšníků. Zatímco některé aplikace vypadají opravdu nevěrohodně, jiné se snažily přelstít uživatele povedenějším uživatelským rozhraním. Krátce se dostaly i přímo do Play Storu.
Botnet WireX všechny překvapil svou velikostí, ale i svým globálním charakterem. Byl tak rozprostřený po celém světě a útočil z tak generických zařízeních, že jej bylo zpočátku velmi složité odlišit od zcela legitimního datového toku.
Klepněte pro větší obrázek
Google začal na telefonech s novější verzí Androidu aktivně blokovat
Zároveň se stal jakýmsi symbolem nové vlny DDoS, protože byl jedním z prvních svého druhu a zároveň zdaleka největší. Bezpečnostní specialisté přitom upozorňují, že jej díky rozsáhlé spolupráci odhalili nakonec docela rychle. Pokud by se tak nestalo, pravděpodobně by narostl do mnohem hrozivějších rozměrů a jeho útoky by silně znepříjemnily život i globálním CDN sítím, které tu jsou mimo jiné právě od tohoto, aby jako určitý štít chránily své klienty před Denial of Service.
Using LabVIEW? Unpatched Flaw Allows Hackers to Hijack Your Computer
29.8.2017 thehackernews Vulnerebility
If you're an engineer and use LabVIEW software to design machines or industrial equipments, you should be very suspicious while opening any VI (virtual instrument) file.
LabVIEW, developed by American company National Instruments, is a visual programming language and powerful system-design tool that is being used worldwide in hundreds of fields and provides engineers with a simple environment to build measurement or control systems
Security researchers from Cisco's Talos Security Intelligence have discovered a critical vulnerability in LabVIEW software that could allow attackers to execute malicious code on a target computer, giving them full control of the system.
Identified as CVE-2017-2779, the code execution vulnerability could be triggered by opening a specially crafted VI file, a proprietary file format used by LabVIEW.
The vulnerability originates because of memory corruption issue in the RSRC segment parsing functionality of LabVIEW.
Modulating the values within the RSRC segment of a VI file causes a controlled looping condition, which results in an arbitrary null write.
"A specially crafted LabVIEW virtual instrument file (with the *.vi extension) can cause an attacker controlled looping condition resulting in an arbitrary null write," Talos researchers explain.
"An attacker controlled VI file can be used to trigger this vulnerability and can potentially result in code execution."
Talos researchers have successfully tested the vulnerability on LabVIEW 2016 version 16.0, but National Instruments has refused to consider this issue as a vulnerability in their product and had no plans to release any patch to address the flaw.
However, the issue should not be ignored, because the threat vector is almost similar to many previously disclosed Microsoft Office vulnerabilities, in which victims got compromised after opening malicious MS Word file received via an email or downloaded from the Internet.
"The consequences of a successful compromise of a system that interacts with the physical world, such as a data acquisition and control systems, may be critical to safety," the researchers write.
"Organisations that deploy such systems, even as pilot projects, should be aware of the risk posed by vulnerabilities such as these and adequately protect systems."
Since there is no patch available, the LabVIEW users are left with only one option—be very careful while opening any VI file you receive via an email.
For more technical details about the vulnerability, you can head on to Cisco Talos' advisory.
China Enforces Real-Name Policy to Regulate Online Comments
29.8.2017 thehackernews BigBrothers
If you reside in China, your Internet life within the borders will soon be even more challenging.
Last Friday, China's top Internet regulator announced a new set of rules that would force citizens to post comments using their real-world identities on Internet forums and other web platforms.
Yes, you heard that right. Anonymity is about to die in the country.
The Cyberspace Administration of China (CAC) will start officially enforcing the new rules starting from October 1, 2017, requiring websites operators and service providers of online forums to request and verify real names and other personal information from users when they register and must immediately report illegal content to the authorities.
According to the CAC, the following content would be considered unlawful and forbidden from being published online:
Opposing the basic principles as defined in the Constitution
Endangering national security
Damaging nation's honor and interests
Inciting national hatred, ethnic discrimination and undermining national unity
Undermining nation's religious policies and promoting cults
Spreading rumours, disrupting social order and destroying social stability
Spreading pornography, gambling, violence, murder, terror or abetting a crime
Insulting or slandering others and infringing upon others
Any other content that is prohibited by laws and administrative regulations
Well, the list covers almost everything.
While China has already enforced "real-name registration" rules on the leading online platforms like WeChat and Weibo for a few years, the latest regulations would cover the remaining parts of the online world, including online communities and discussion forums.
The new rules will be imposed on websites, smartphone apps, interactive communications platforms, and any communication platform that features news or functions to "mobilise society." In fact, news sites even have to moderate comments before publishing.
These new regulations follow China's 14-month-long crackdown on VPN (Virtual Private Networks), which requires VPN service providers in the country to obtain prior government approval, making most VPN vendors in the country of 730 million Internet users illegal.
Late last month, Apple also removed some VPN apps, including ExpressVPN and Star VPN, from its official Chinese app store to comply with the government crackdown that will remain in place until March 31, 2018.
IoT Device Hit by Credential Attack Every Two Minutes: Experiment
29.8.2017 securityweek IoT
Internet of Things (IoT) botnets such as Mirai might not be in the headlines as often as they were several months ago, but the threat posed by insecure IoT devices is as high as before, a recent experiment has revealed.
Mainly targeting IP cameras, DVRs and routers that haven’t been properly secured, such botnets attempt to ensnare devices and use them for malicious purposes such as distributed denial of service (DDoS) attacks. Compromised IoT products are also used to scan the Internet for other vulnerable devices and add them to the botnet.
BASHLITE, Mirai, Hajime, Amnesia, Persirai, and similar botnets target DVR and IP camera systems via telnet or SSH attacks, and use a short list of commonly encountered login credentials, such as root: xc3511, root:vizxv, admin: admin, admin:default, and support:support.
According to recent research, there are nearly 7.5 million potentially vulnerable camera systems and around 4 million potentially vulnerable routers connected worldwide.
Prompted by recent news of a list of leaked login credentials associated with a set of thousands of IPs (mostly routers) being posted online, Johannes B. Ullrich, Ph.D., Dean of Research at SANS Technology Institute, exposed a DVR to the Internet for two days and recorded all attempts to login it.
According to him, the device used the root: xc3511 login pair and recorded a total of 1254 login attempts from different IPs over a period of 45 hours. Basically, someone or something would login to it every 2 minutes using the correct credentials, he says.
After performing a Shodan search, Ullrich retrieved information on 592 of the attacking devices, and reveals they were mainly coming from TP-Link, AvTech, Synology, and D-Link. The distribution of attacks matches that previously associated with Mirai, but the researcher notes that dozens of variants hit the device.
Last year, Ullrich performed a similar experiment and revealed that the DVR was being hit every minute and that multiple login pairs were being tried on each attack. His experiment and the emergency of Mirai brought to the spotlight the issue of weak credentials being used in IoT.
“So in short: 1,700 additional vulnerable systems will not matter. We do see a pretty steady set of 100,000-150,000 sources participating in telnet scans. This problem isn't going away anytime soon,” Ullrich argues.
He also points out that, while malware such as BrickerBot attempted to break the vulnerable devices, the method isn’t effective either, because most of the impacted devices cannot be bricked by overwriting the disk, but only become temporarily unresponsive and recover after a reboot.
“Many of these devices are buggy enough, where the owner is used to regular reboots, and that is probably the only maintenance the owner will perform on these devices,” he says.
Unpatched Vulnerabilities Impact Popular Browser Extension Systems
29.8.2017 securityweek Vulnerebility
Security researchers have discovered two vulnerabilities that impact the extension systems of major browsers, including Chrome, Firefox, Safari, and Opera.
In a paper presented at the USENIX Security Symposium in Canada earlier this month, Iskander Sanchez-Rola and Igor Santos from the University of Deusto and Davide Balzarotti from Eurecom detailed two different flaws that remain unpatched despite being already responsibly disclosed.
Called Extension Breakdown: Security Analysis of Browsers Extension Resources Control Policies, the research paper (PDF) claims that security policies used by major browsers to ensure extensions are protected from third party access can be bypassed, thus enabling enumeration attacks against the list of installed extensions.
By enumerating the installed extensions, an attacker could exploit vulnerabilities. Firefox and Chrome have implemented a form of access control over the extension resources, while Safari adopted the randomization of extension URI at runtime. Each of these implementations can be targeted in a different manner, hence the two attack methods the researchers have discovered.
The first issue, a timing side-channel attack, resides in the fact that, when a website tries to load a resource not present in the list of accessible resources, the browser performs two checks before blocking the request: first it verifies if a certain extension is installed, and then it accesses their control settings to determine whether the requested resource is publicly available.
Improper implementation of this two-step validation opens the door to a timing side-channel attack that could allow an attacker to identify whether an extension isn’t available or the requested resource is kept private. An attacker could use JavaScript code to measure and compare the response time when invoking a fake extension and requesting a non-existent resource for an existing extension: similar response times means the extension isn’t present, the paper claims.
The bug affects all versions of Chromium, impacting browsers such as Chrome, Opera, Yandex, and Comodo. Still in early stages of development, Firefox and Microsoft Edge WebExtensions haven’t been included in the group, but the researchers say they are likely vulnerable as well, because they follow the same extension control mechanism as Chromium.
“Surprisingly, non-WebExtensions in Firefox suffer from a different bug that makes even easier to detect the installed extensions. The browser raises an exception if a webpage requests a resource for non-installed extension, but not in the case when the resource path does not exist. […] an attacker can simply encapsulate the invocation in a try-catch block to distinguish between the two execution paths and reliably test for the presence of a given extension,” the researchers explained.
The second vulnerability impacts the URI randomization technique adopted by Safari and can result in the unintentional leakage of the random extension URI, which can then be used by “third-parties to unequivocally identify the user while browsing during the same session.” The issue, the researchers argue, is that the implementation depends on developers to deny third-party access to resources.
“The entire security of the extension access control in Safari relies on the secrecy of the randomly generated token. However, the token is part of the extension URI which is often used by the extensions to reference public resources injected in the page. As a result, we believe that this design choice makes it very easy for developers to unintentionally leak the secret token,” the paper reads.
The attacks can be leveraged to perform accurate browser fingerprinting, to check for built-in extensions, and to determine users’ demographics, but can also be used for malicious purposes. An attacker searching for specific extensions can narrow their attack surface or can personalize their exploit kit to serve a specific payload, the researchers argue.
“We responsibly disclosed all our findings and we are now discussing with the developers of several browsers and extensions to propose the correct countermeasures to mitigate these attacks in both current and future versions,” the researchers conclude.
“Internet browsers have to be updated to fix this vulnerability. In the meantime, users can defend against these types of attacks, which consist of bogus requests to APIs, by blocking these requests using a firewall or other application level access control devices.” Ajay Uggirala, director of product marketing at Imperva, told SecurityWeek in an emailed statement.
“As we use more and more APIs, it is important for companies to make sure all their APIs and the requests to them are secured. With many APIs that are exposed, it is best to deploy API security gateways or Application firewalls that can process requests to APIs. This is to ensure that whenever there are unsolicited or brute force API requests, they can be blocked before giving back any information to that malicious request,” Uggirala concluded.
Experts found an undocumented Kill Switch in Intel Management Engine
29.8.2017 securityaffairs Vulnerebility
Security researchers at Positive Technologies have discovered an undocumented configuration setting that disables the Intel Management Engine.
Security researchers at Positive Technologies have discovered an undocumented configuration setting that disables the CPU control mechanism Intel Management Engine 11.
The Intel Management Engine consists of a microcontroller that works with the Platform Controller Hub chip, in conjunction with integrated peripherals, it is a critical component that handles data exchanged between the processor and peripherals.
For this reason, security experts warned in the past of the risks for Intel Management Engine vulnerabilities. An attacker can exploit a flaw in the Intel ME to establish a backdoor on the affected system and gain full control over it.
In May, security experts discovered a critical remote code execution (RCE) vulnerability, tracked as CVE-2017-5689, in the remote management features implemented on computers shipped with Intel Chipset in past 9 years.
The vulnerability affects the Intel Management Engine (ME) technologies such as Active Management Technology (AMT), Small Business Technology (SBT), and Intel Standard Manageability (ISM) and could be exploited by hackers to remotely take over the vulnerable systems.
An unofficial workaround dubbed ME Cleaner can bypass Intel ME, but it is not able to turn off it.
“Intel ME is a coprocessor integrated in all post-2006 Intel boards, for which this Libreboot page has an excellent description. The main component of Intel ME is Intel AMT, and I suggest you to read this Wikipedia page for more information about it. In short, Intel ME is an irremovable environment with an obscure signed proprietary firmware, with full network and memory access, which poses a serious security threat. Even when disabled from the BIOS settings, Intel ME is active: the only way to be sure it is disabled is to remove its firmware from the flash chip.” reads the project description.
Now the experts from Positive Technologies (Dmitry Sklyarov, Mark Ermolov, and Maxim Goryachy) discovered a way to disable the Intel Management Engine 11 via an undocumented mode.
The researchers discovered that it is possible to turn off the Intel ME by setting the undocumented high assurance platform (HAP) bit to 1 in a configuration file.

The experts discovered that the security framework was developed by the US National Security Agency … yes the NSA!
“One of the fields, called “reserve_hap”, drew our attention because there was a comment next to it: “High Assurance Platform (HAP) enable.” continues the analysis. “Googling did not take long. The second search result said that the name belongs to a trusted platform program linked to the U.S. National Security Agency (NSA). A graphics-rich presentation describing the program can be found here.”
Below the statement released by Intel in response to a request for comment.
“In response to requests from customers with specialized requirements we sometimes explore the modification or disabling of certain features,” Intel’s spokesperson said. “In this case, the modifications were made at the request of equipment manufacturers in support of their customer’s evaluation of the US government’s ‘High Assurance Platform’ program. These modifications underwent a limited validation cycle and are not an officially supported configuration.”
Positive Technologies also noted that the HAP affect on Boot Guard, Intel’s boot process verification system, is still undocumented.
“We also found some code in BUP that, when HAP mode is enabled, sets an additional bit in Boot Guard policies. Unfortunately, we have not succeeded in finding out what this bit controls.” concluded the experts.
India and Pakistan hit by state-sponsored cyber espionage campaign
29.8.2017 securityaffairs BigBrothers
The security firm Symantec has discovered another cyber espionage campaign against India and Pakistan which is likely to be state-sponsored.
Security experts at Symantec have uncovered a sustained cyber spying campaign against Indian and Pakistani entities involved in regional security issues.
The nature of the targets and the threat actors’ techniques suggest it is a state-sponsored campaign likely powered by several groups of hackers.
“The campaign appeared to be the work of several groups, but tactics and techniques used suggest that the groups were operating with “similar goals or under the same sponsor”, probably a nation state, according to the threat report, which was reviewed by Reuters. It did not name a state.” reported the Reuters.
According to a threat intelligence report, Symantec sent to clients in July, the cyber espionage campaign dated back to October 2016.
The experts speculate the involvement of several groups that shared TTPs operating with “similar goals or under the same sponsor.”
The cyber espionage campaign was uncovered while tensions in the region are raising.
India’s military is intensifying operational readiness along the border with China following a face-off in Bhutan near their disputed frontier, at the same time tensions are rising between India and Pakistan over the disputed Kashmir region.
The threat actors appear focused on governments and militaries with operations in South Asia and interests in regional security issues. Attackers leverage the “Ehdoor” backdoor to gain control over infected machines.
Backdoor.Ehdoor is a Trojan horse first spotted in September 2016, it was initially used to target government, military and military-affiliated entities in the Middle East and elsewhere.
The Ehdoor backdoor opens a back door, steals information, and downloads potentially malicious files onto the compromised computer.
“There was a similar campaign that targeted Qatar using programs called Spynote and Revokery,” said a security expert, who requested anonymity. “They were backdoors just like Ehdoor, which is a targeted effort for South Asia.”
According to the Symantec report, attackers used decoy documents related to security issues in South Asia in to deliver the malware. The attackers was also being used to target Android devices.
“The documents included reports from Reuters, Zee News, and the Hindu, and were related to military issues, Kashmir, and an Indian secessionist movement.” states the Reuters.
“The malware allows spies to upload and download files, carry out processes, log keystrokes, identify the target’s location, steal personal data, and take screenshots, Symantec said, adding that the malware was also being used to target Android devices.”
India cyber espionage
Gulshan Rai, the director general of CERT-In, hasn’t commented the cyber espionage campaign, but he said: “We took prompt action when we discovered a backdoor last October after a group in Singapore alerted us.”
According to malware researchers at Symantec, the backdoor was continuously improved over the time to implement “additional capabilities” for spying operations.
“A senior official with Pakistan’s Federal Investigation Agency said it had not received any reports of malware incidents from government information technology departments. He asked not to be named due to the sensitivity of the matter.” continues the Reuters.
“A spokesman for FireEye, another cybersecurity company, said that based on an initial review of the malware, it had concluded that an internet protocol address in Pakistan had submitted the malware to a testing service. The spokesman requested anonymity, citing company policy.”
US CERT is warning of potential Hurricane Harvey Phishing Scams
29.8.2017 securityaffairs Phishing
After the Hurricane Harvey hit Texas causing deaths and destructions, authorities are warning of potential Phishing Scams.
The US CERT is warning of Potential Hurricane Harvey phishing scams, the experts fear crooks may start using malicious emails purportedly tied to the storm.
“US-CERT warns users to remain vigilant for malicious cyber activity seeking to capitalize on interest in Hurricane Harvey. Users are advised to exercise caution in handling any email with subject line, attachments, or hyperlinks related to Hurricane Harvey, even if it appears to originate from a trusted source.” reads the advisory issued by the US CERT. “Fraudulent emails will often contain links or attachments that direct users to phishing or malware-infected websites. Emails requesting donations from duplicitous charitable organizations commonly appear after major natural disasters.”
US-CERT is advising users to remain vigilant when receiving unsolicited emails with attachments or links purporting to be related to the Hurricane Harvey that recently hit the Texas killing at least five people and injuring a dozen of people over the weekend.
US experts warn of phishing emails requesting donations from allegedly charity organizations, a tactic observed after other major disasters and incidents.
Typically these messages used malicious attachments or embed links to websites hosting exploits or to phishing pages.
A good practice to avoid scams is to contact the charity organizations by calling them directly.
US-CERT encourages users and administrators to use caution receiving messages linked to the Hurricane Harvey and adopt the following best practices:
Review the Federal Trade Commission’s information on Wise Giving in the Wake of Hurricane Harvey.
Do not follow unsolicited web links in email messages.
Use caution when opening email attachments. Refer to the US-CERT Tip Using Caution with Email Attachments for more information on safely handling email attachments.
Keep antivirus and other computer software up-to-date.
Refer to the Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
Verify the legitimacy of any email solicitation by contacting the organization directly through a trusted contact number. You can find trusted contact information for many charities on the BBB National Charity Report Index.
Cyber criminals have no scruples and often exploit any tragic event in their favor.
In October, as the Hurricane Matthew was battering the South Carolina coast, authorities warned of a series of cyber attacks against residents.
In the past crooks exploited the media interest in tragic events like the Boston Marathon attack and the crash of the flight MH17 of Malaysian Airline, they used the news as bait themes for massive spam attacks and spear phishing campaigns.
MoqHao Banking Trojan Targets South Korean Android Users
29.8.2017 securityweek Android
A recently spotted Android banking Trojan targeting South Korean users via SMS phishing messages (smishing) was linked to an infection campaign from two years ago, McAfee security researchers reveal.
The mobile phishing messages attempt to lure users into executing malware by claiming to link to a leaked private picture, or by posing as a Chrome update. Once the user clicks on the shortened link in the message, however, the banking Trojan dubbed MoqHao is installed.
Once a device has been compromised, the malware can send phishing SMS messages to the user’s contacts; can leak sensitive information, including received SMS messages; can install Android apps provided by the command and control (C&C) server; can execute remote commands and return results, and can gather sensitive information via a local Google phishing website, McAfee discovered.
During installation, the malware requests various permissions that allow it to perform its nefarious operations, such as call phone numbers, acccess contacts, and read text messages. Next, the threat requests admin privileges to achieve persistence, and displays the request window continuously, even if the user dismisses it.
MoqHao then dynamically registers a broadcast receiver for system events such as new package install, screen state, SMS messages, and more, which allows it to spy on the user activities and send device status information to the C&C. The malware also connects to the first-stage remote server and dynamically receives the IP for the second-stage server from the user profile page of Chinese search engine Baidu.
After connecting to this server, the malware sends a message containing device information such as: UUID, IMEI, Android version, device product name, build ID string, root status, SIM status, phone number, and registered accounts. Other details are periodically sent to the server, including: network operator and type (LTE, GPRS), MAC address, battery level, Wi-Fi signal level, device admin rights, screen on/off, ringer mode, and whether current package is ignoring battery optimization or not.
The Trojan checks infected devices for major Korean bank apps and downloads relevant fake or Trojanized versions of these programs if it finds them. Next, it alerts the victim that an update is available for the targeted app. Once the victim approves the update, the malicious app replaces the legitimate one.
During analysis, however, the malware’s requests to download the malicious apps resulted in an error. According to McAfee, the functionality might not be implemented or not in use, given that infected users haven’t reported attempted installation of additional APK files.
The security researchers first observed Android/MoqHao in January, but that seemed more like a test version. Updated variants of the malware were observed in February and March, but the first non-test iteration emerged only in May.
The banking Trojan, the researchers say, appears connected to a May 2015 attack targeting users in South Korea via a phishing message in the default web browser. Although that message was very similar to those spreading Android/MoqHao and the two malware variants share some behavior and functionality, the threats have completely different code bases.
“The similarities between the 2015 and 2017 phishing campaigns suggests the same cybercriminals, who have shifted from DNS redirection attacks to a smishing campaign. The attackers are still targeting Chrome and getting the control server from a dynamic webpage while changing the code base of the initial dropper component as well as the dynamically loaded payload,” McAfee says.
Zákeřný virus se zaměřuje na hráče počítačových her
29.8.2017 Novinky/Bezpečnost Viry
Na pozoru by se měli mít v posledních dnech hráči počítačových her. Právě na ně se zaměřuje nový škodlivý kód zvaný Joao, který odhalili bezpečnostní experti z antivirové společnosti Eset. Tento záškodník je velmi nebezpečný, neboť dokáže do počítače následně stáhnout jakoukoliv další hrozbu. Útočníci tak nad napadeným strojem mohou zcela převzít kontrolu.
Joao se šíří prostřednictvím her stahovaných z neoficiálních internetových obchodů.
„K jeho šíření útočníci zneužili několik her typu MMORPG, jež modifikovali přidáním trojan downloaderu pro stahování dalšího malwaru,“ vysvětlil Václav Zubr, bezpečnostní expert společnosti Eset.
Podle něj útočníci zneužili hned několik her, za jejichž vývojem stojí společnost Aeria Games. „Pozměněné verze potom podstrčili návštěvníkům neoficiálních herních webů,“ uvedl bezpečnostní expert.
Infikovány mohou být i další hry
Sluší se nicméně podotknout, že hrozba se nemusí týkat pouze titulů od studia Aeria Games. Stejným způsobem mohli počítačoví piráti zneužít také další hry, které pocházejí od konkurenčních vývojářů.
„Infikované počítače odesílaly na řídící server útočníků informace o nakaženém počítači a stahovaly další škodlivé komponenty jako software pro DDoS útok a kód pro špehování své oběti,“ konstatoval Zubr.
Zároveň zdůraznil, že uživatelé neměli moc šancí poznat, že je jejich stroj infikován. „Modifikované hry fungují tak, jak mají. Když se uživatel rozhodne stáhnout si takto upravenou hru, nic nebude nasvědčovat tomu, že je něco v nepořádku. Hráči bez spolehlivého bezpečnostního softwaru si takto nakazí své zařízení,“ podotkl expert.
Jak poznat zavirovaný počítač?
V současnosti mohou oběti nezvaného návštěvníka Joao v počítači poměrně jednoduše nalézt. Stačí dát vyhledat soubor mskdbe.dll, což je knihovna tohoto škodlivého kódu. Pokud je daný soubor v počítači obsažen, je potřeba jej odvirovat.
„Útočníci však mohou tento soubor kdykoli přejmenovat, proto by měli hráči infekci vyhledat prostřednictvím bezpečnostních programů,“ poradil Zubr.
WireX DDoS Botnet: An Army of Thousands of Hacked Android SmartPhones
29.8.2017 thehackernews BotNet
Do you believe that just because you have downloaded an app from the official app store, you're safe from malware?
Think twice before believing it.
A team of security researchers from several security firms have uncovered a new, widespread botnet that consists of tens of thousands of hacked Android smartphones.
Dubbed WireX, detected as "Android Clicker," the botnet network primarily includes infected Android devices running one of the hundreds of malicious apps installed from Google Play Store and is designed to conduct massive application layer DDoS attacks.
Researchers from different Internet technology and security companies—which includes Akamai, CloudFlare, Flashpoint, Google, Oracle Dyn, RiskIQ, Team Cymru—spotted a series of cyber attacks earlier this month, and they collaborated to combat it.
Although Android malware campaigns are quite common these days and this newly discovered campaign is also not that much sophisticated, I am quite impressed with the way multiple security firms—where half of them are competitors—came together and shared information to take down a botnet.
WireX botnet was used to launch minor DDoS attacks earlier this month, but after mid-August, the attacks began to escalate.
The "WireX" botnet had already infected over 120,000 Android smartphones at its peak earlier this month, and on 17th August, researchers noticed a massive DDoS attack (primarily HTTP GET requests) originated from more than 70,000 infected mobile devices from over 100 countries.
If your website has been DDoSed, look for the following pattern of User-Agent strings to check if it was WireX botnet:
botnet-user-agent
After further investigation, security researchers identified more than 300 malicious apps on Google’s official Play Store, many of which purported to be media, video players, ringtones, or tools for storage managers and app stores, which include the malicious WireX code.
Just like many malicious apps, WireX apps do not act maliciously immediately after the installation in order to evade detection and make their ways to Google Play Store.
Instead, WireX apps wait patiently for commands from its command and control servers located at multiple subdomains of "axclick.store."
Google has identified and already blocked most of 300 WireX apps, which were mostly downloaded by users in Russia, China, and other Asian countries, although the WireX botnet is still active on a small scale.
If your device is running a newer version of the Android operating system that includes Google's Play Protect feature, the company will automatically remove WireX apps from your device, if you have one installed.
Play Protect is Google's newly launched security feature that uses machine learning and app usage analysis to remove (uninstall) malicious apps from users Android smartphones to prevent further harm.
Also, it is highly recommended to install apps from reputed and verified developers, even when downloading from Google official Play Store and avoid installing unnecessary apps.
Additionally, you are strongly advised to always keep a good antivirus app on your mobile device that can detect and block malicious apps before they can infect your device, and always keep your device and apps up-to-date.
Android malware continues to evolve with more sophisticated and never-seen-before attack vectors and capabilities with every passing day.
Just at the beginning of this week, Google removed over 500 Android apps utilising the rogue SDK—that secretly distribute spyware to users—from its Play Store marketplace.
Last month, we also saw first Android malware with code injecting capabilities making rounds on Google Play Store.
A few days after that, researchers discovered another malicious Android SDK ads library, dubbed "Xavier," found installed on more than 800 different apps that had been downloaded millions of times from Google Play Store.
Beware! Viral Sarahah App Secretly Steals Your Entire Contact List
29.8.2017 thehackernews Apple
Are you also one of those 18 Million users using SARAHAH?
You should beware of this app because the anonymous feedback application may not be as private as it really sounds.
Sarahah is a newly launched app that has become one of the hottest iPhone and Android apps in the past couple of weeks, allowing its users to sign up to receive anonymised, candid messages from other Sarahah users.
However, it turns out that the app silently uploads users' phone contacts to the company's servers for no good reason, spotted by security analyst Zachary Julian.
When an Android or iOS user downloads and installs the app for the first time, the app immediately harvests and uploads all phone numbers and email addresses from the user's address book, according to The Intercept.
While an app requesting access to the user's phonebook is quite common if the app provides any feature that works with contacts, no such functionality in Sarahah is available right now.
"The privacy policy specifically states that if it plans to use your data, it'll ask for your consent, while the app's entry in Google's Play Store does indicate the app will access contacts, that's not enough consent to justify sending all of those contacts over without any kind of specific notification"
However, the creator of Sarahah, Zain al-Abidin Tawfiq, responded to the story by saying his app actually harvests and uploads the contacts from users to the company's servers for a feature that will be implemented at a later time.
Tawfiq said that users' contact lists are being uploaded "for a planned 'find your friends' feature," which was "delayed due to a technical issue" and was accidentally not removed from the Sarahah's current version.
Tawfiq also assured its users that "the data request will be removed on next update" to the app and that Sarahah's servers do not "currently host contacts," which is, of course, impossible to verify.
Sarahah took the Internet by storm within few weeks, making the app the third most downloaded free application software for iPhones and iPads. The app has already been downloaded by an estimated 18 Million users from Apple and Google’s online stores.
However, you can still use Sarahah by blocking the app from accessing your contacts, without risking your contacts to be uploaded to its servers.
Since newer Android operating systems (starting with Android 6.0 Marshmallow) do allow users to limit permissions for apps, users can limit permissions so that apps do not gain access to contacts or other information that doesn't have anything to do with the app's functioning.
To do so, Go to Settings → Personal → Apps, now under Configuration App, open App permission and limit permission of apps you like.
Neutralization reaction
29.8.2017 Kaspersky Incindent
Incident Response Guide (PDF)
Despite there being no revolutionary changes to the cyberthreat landscape in the last few years, the growing informatization of business processes provides cybercriminals with numerous opportunities for attacks. They are focusing on targeted attacks and learning to use their victims’ vulnerabilities more effectively while remaining under the radar. As a result, businesses are feeling the effects of next-gen threats without the appearance of new malware types.
Unfortunately, corporate information security services often turn out to be unprepared: their employees underestimate the speed, secrecy and efficiency of modern cyberattacks and do not recognize how ineffective the old approaches to security are. Even with traditional prevention tools such as anti-malware products, IDS/IPS and security scanners combined with detection solutions like SIEM and anti-APT, this costly complex may not be used to its full potential. And if there is no clear understanding of what sort of incident it is, an attack cannot be repelled.
More detailed information on the stages involved in organizing a cyberattack and responding to incidents can be found in the full version of this guide or obtained within the framework of Kaspersky Lab’s educational program. Here we will only focus on the main points.
Planning an attack
First of all, it should be noted that by targeted attacks we are referring to serious operations prepared by qualified cybercriminals. Cyber hooliganism such as defacing the homepage of a site carried out to attract attention or demonstrate capabilities, are not considered here. As a rule, successful activities of this kind means a company has no information security service to speak of, even if one exists on paper.
The basic principles of any targeted attack include thorough preparation and a stage-by-stage strategy. Here we will investigate the sequence of stages (known as the kill chain), using as an example an attack on a bank to steal money from ATMs.
1. Reconnaissance
At this stage, publicly available information about the bank and its data assets is collected. In particular, the attacker tries to determine the company’s organizational structure, tech stack, the information security measures as well as options for carrying out social engineering on its employees. The last point may include collecting information on forums and social networking sites, especially those of a professional nature.
2. Weaponization
Once the data is collected, cybercriminals choose the method of attack and select appropriate tools. They may use new or already existing malware that allows them to exploit detected security vulnerabilities. The malware delivery method is also selected at this stage.
3. Delivery
To deliver the necessary malware, email attachments, malicious and phishing links, watering hole attacks (infection of sites visited by employees of the targeted organization) or infected USB devices are used. In our example, the cybercriminals resorted to spear phishing, sending emails to specific bank employees on behalf of a financial regulator – the Central Bank of the Russian Federation (Bank of Russia). The email contained a PDF document that exploited a vulnerability in Adobe Reader.
4. Exploitation
In the event of a successful delivery, for example, an employee opening the attachment, the exploit uses the vulnerability to download the payload. As a rule, it consists of the tools necessary to carry out the subsequent stages of the attack. In our example, it was a Trojan downloader that, once installed, downloaded a bot from the attacker’s server the next time the computer was switched on.
If delivery fails, cybercriminals usually do not just give up; they take a step (or several steps) back in order to change the attack vector or malware used.
5. Installation
Malicious software infects the computer so that it cannot be detected or removed after a reboot or the installation of an update. For example, the above Trojan downloader registers itself in Windows startup and adds a bot there. When the infected PC is started next time, the Trojan checks the system for the bot and, if necessary, reloads it.
The bot, in turn, is constantly present in the computer’s memory. In order to avoid user suspicion, it is masked under a familiar system application, for example, lsass.exe (Local Security Authentication Server).
6. Command and control
At this stage, the malware waits for commands from the attackers. The most common way to receive commands is to connect the C&C server that belongs to the fraudsters. This is what the bot in our example did: when it first addressed the C&C server, it received a command to carry out further proliferation (lateral movement) and began to connect to other computers within the corporate network.
If infected computers do not have direct access to the Internet and cannot connect directly to the C&C server, the attacker can send other software to the infected machine, deploy a proxy server in the organization’s network, or infect physical media to overcome the ‘air gap’.
7. Actions on objective
Now, the cybercriminals can work with the data on a compromised computer: copying, modifying or deleting it. If the necessary information is not found, the attackers may try to infect other machines in order to increase the amount of available information or to obtain additional information that allows them to reach their primary goal.
The bot in our example infected other PCs in search of a machine from which it could log on as an administrator. Once such a machine was found, the bot turned to the C&C server to download the Mimikatz program and the Ammyy Admin remote administration tools.
Example of Mimikatz execution. All the logins and passwords are entered in clear view, including the Active Directory user passwords.
If successful, the bot can connect to the ATM Gateway and launch attacks on ATMs: for example, it can implement a program in an ATM that will dispense cash when a special plastic card is detected.
The final stage of the attack is removing and hiding any traces of the malware in the infected systems, though these activities are not usually included in the kill chain.
The effectiveness of incident investigation and the extent of material and reputational damage to the affected organization directly depend on the stage at which the attack is detected.
If the attack is detected at the ‘Actions on objective’ stage (late detection), it means the information security service was unable to withstand the attack. In this case, the affected company should reconsider its approach to information security.
My network is my castle
We have analyzed the stages of a targeted attack from the point of view of cybercriminals; now let’s look at it from the point of view of the affected company’s information security staff. The basic principles behind the work of both sides are essentially the same: careful preparation and a step-by-step strategy. But the actions and tools of the information security specialists are fundamentally different because they have very different objectives, namely:
Mitigate the damage caused by an attack;
Restore the initial state of the information system as quickly as possible;
Develop instructions to prevent similar incidents in future.
These objectives are achieved in two main stages – incident investigation and system restoration. Investigation must determine:
Initial attack vector;
Malware, exploits and other tools used by the attackers;
Target of the attack (affected networks, systems and data);
Extent of damage (including reputational damage) to the organization;
Stage of attack (whether it is completed and goals are achieved);
Time frames (time the attack started and ended, when it was detected in the system and response time of the information security service).
Once the investigation is completed, it is necessary to develop and implement a system recovery plan, using the information obtained during investigation.
Let’s return to the step-by-step strategy. Overall, the incident response protection strategy looks like this:
Incident response stages
As with the stages of the targeted attack, we will analyze in more detail each stage involved in combating an attack.
1. Preparation
Preparation includes developing processes and policies and selecting tools. First of all, it means the creation of a multi-level security system that can withstand intruders using several attack vectors. The levels of protection can be divided into two groups.
The first includes the installation of tools designed to prevent attacks (Prevention):
security solutions for workstations;
intrusion detection and intrusion prevention systems (IDS/IPS);
firewall to protect the Internet gateway;
proxy server to control Internet access.
The second group consists of solutions designed to detect threats (Detection):
SIEM system with integrated threat reporting component that monitors events occurring in the information system;
Anti-APT system that compares data on detected threats delivered by various security mechanisms;
Honeypot – a special fake object for cyberattacks that is isolated and closely monitored by the information security service;
EDR-systems (tools for detecting and responding to threats on endpoints) that raise awareness of events occurring on endpoints and enable automatic containment and elimination of threats.
The organization we chose as an example was ready for unexpected attacks. The ATMs were separated from the main network of the bank, with access to the subnet limited to authorized users.
Network of the attacked organization
The SIEM system was used to monitor and analyze events occurring on the network. It collected:
information about network connections to the proxy server that was used by all employees to access the Internet;
integrated threat data feeds provided by Kaspersky Lab specialists;
notifications of emails that passed through the Postfix mail server, including information about headers, DKIM signatures, etc.;
SIEM also received information about security solution activation on any workstation in the corporate IT infrastructure.
Another important preparation element is penetration testing to predict the possible vector of a cyberattack. Penetration of the corporate network can be simulated by both the company’s IT specialists and third-party organizations. The latter option is more expensive, though preferable: organizations that specialize in pen tests have extensive experience and are better informed about the current threat vectors.
The last – but by no means least – important element is educating the organization’s employees. This includes internal cybersecurity training for all employees: they should be aware of the corporate security policies and know what to do in the event of a cyberattack. It also includes targeted training for specialists responsible for the company’s information security, as well as the accumulation of information about security incidents inside and outside the company. This information may come from different sources such as internal company reports or third-party organizations that specialize in analyzing cyberthreats, for example, Kaspersky Threat Intelligence Portal.
2. Identification
At this stage, it is necessary to determine whether it is actually an incident or not. Only then can the alarm be raised and colleagues warned. In order to identify an incident, so-called triggers are used – events that indicate a cyberattack. These include attempts by a workstation to connect to a known malicious C&C server, errors or failures in security software performance, unexpected changes to user rights, unknown programs on the network, and much more.
Information about these events can come from a variety of sources. Here we will consider two key types of triggers:
Triggers generated by EPP management systems. When a security solution on one of the workstations detects a threat, it generates an event and sends it to the management system. However, not all events are triggers: for example, an event that indicates the detection of a malicious program can be followed by an event about its neutralization. In this case, investigation is not necessary, except when the situation occurs regularly on the same machine or with the same user.
Incident triggers generated by SIEM systems. SIEM systems can accumulate data from a huge number of security controls, including proxy servers and firewalls. Triggers are only considered to be those events that are created based on comparing incoming data and threat reports.
To identify an incident, the information available to the information security service is compared with a list of known indicators of compromise (IOC). Public reports, threat data feeds, static and dynamic sample analysis tools, etc. can be used for this purpose.
Static analysis is performed without launching the test sample and includes collecting various indicators, such as strings containing a URL or an email address, etc. Dynamic analysis involves executing the program under investigation in a protected environment (sandbox) or on an isolated machine in order to identify the sample’s behavior and collect indicators of compromise.
Cycle of IOC detection
As seen from the picture above, collecting IOCs is a cyclic process. Based on the initial information from the SIEM system, identification scenarios are generated, which leads to the identification of new indicators of compromise.
Here is an example of how threat data feeds can be used to identify a spear-phishing attack – in our case, emails with an attached PDF document that exploits an Adobe Reader vulnerability.
SIEM will detect the IP address of the server that sent the email using IP Reputation Data Feed.
SIEM will detect the request to load the bot using Malicious URL Data Feed.
SIEM will detect a request to the C&C server using Botnet C&C URL Data Feed.
Mimikatz will be detected and removed by a security solution for workstations; information about the detection will go to SIEM.
Thus, at an early stage, an attack can be detected in four different ways. It also means the company will suffer minimal damage.
3. Containment
Suppose that, due to a heavy workload, the information security service couldn’t respond to the first alarms, and by the time there was a response, the attack had reached the sixth stage, i.e., malware had successfully penetrated a computer on the corporate network and tried to contact the C&C server, and the SIEM system had received notice of the event.
In this case, the information security specialists should identify all compromised computers and change the security rules to prevent the infection from spreading over the network. In addition, they should reconfigure the information system so that it can ensure the company’s continuous operation without the infected machines. Let’s consider each of these actions in more detail.
Isolation of compromised computers
All compromised computers should be identified, for example, by finding in SIEM all calls to the known C&C address – and then placed in an isolated network. In this case, the routing policy should be changed to prevent communication between compromised machines and other computers on the corporate network, as well as the connection of compromised computers to the Internet.
It is also recommended to check the C&C address using a special service, for example, Threat Lookup. As a result, this provides not only the hashes of the bots that interacted with the C&C server but also the other addresses the bots contacted. After that it is worth repeating the search in SIEM across the extended list of indicators, since the same bot may have interacted with several C&C servers on different computers. All infected workstations that are identified must be isolated and examined.
In this case, the compromised computers should not be turned off, as this can complicate the investigation. Specifically, some types of malicious program only use the computer’s RAM and do not create files on the hard disk. Other malware can remove an IOC once the system receives a turn-off signal.
Also, it is not recommended to disconnect (primarily physically) the local network connections of the affected PC. Some types of malware monitor the connection status, and if the connection is not available for a certain period of time, malware can begin to remove traces of its presence on the computer, destroying any IOCs. At the same time, it makes sense to limit the access of infected machines to the internal and external networks (for example, by blocking the transfer of packets using iptables).
For more information on what to do if the search by a C&C address does not provide the expected results, or on how to identify malware, read the full version of this guide.
Creation of memory dumps and hard disk dumps
By analyzing memory dumps and hard disk dumps of compromised computers, you can get samples of malware and IOCs related to the attack. The study of these samples allows you to understand how to deal with the infection and identify the vector of the threat in order to prevent a repeat infection using a similar scenario. Dumps can be collected with the help of special software, for example, Forensic Toolkit.
Maintaining system performance
After the compromised computers are isolated, measures should be taken to maintain operation of the information system. For example, if several servers were compromised on the corporate network, changes should be made to the routing policy to redirect the workload from compromised servers to other servers.
4. Eradication
The goal of this stage is to restore the compromised information system to the state it was in before the attack. This includes removing malware and all artifacts that may have been left on the infected computers, as well as restoring the initial configuration of the information system.
There are two possible strategies to do this: full reinstallation of the compromised device’s OS or simply removing any malicious software. The first option is suitable for organizations that use a standard set of software for workstations. In this case, you can restore the operation of the latter using the system image. Mobile phones and other devices can be reset to the factory settings.
In the second case, artifacts created by malware can be detected using specialized tools and utilities. More details about this are available in the full version of our guide.
5. Recovery
At this stage, those computers that were previously compromised are reconnected to the network. The information security specialists continue to monitor the status of these machines to ensure the threat has been eliminated completely.
6. Lessons learned
Once the investigation has been completed, the information security service must submit a report with answers to the following questions:
When was the incident identified and who identified it?
What was the scale of the incident? Which objects were affected by the incident?
How were the Containment, Eradication, and Recovery stages executed?
At what stages of incident response do the actions of the information security specialists need to be corrected?
Based on this report and the information obtained during the investigation, it is necessary to develop measures to prevent similar incidents in the future. These can include changes to the security policies and configuration of corporate resources, training on information security for employees, etc. The indicators of compromise obtained during the incident response process may be used to detect other attacks of this kind in the future.
In order of priority
Troubles come in threes, or so the saying goes, and it can be the case that information security specialists have to respond to several incidents simultaneously. In this situation, it is very important to correctly set priorities and focus on the main threats as soon as possible – this will minimize the potential damage of an attack.
We recommend determining the severity of an incident, based on the following factors:
Network segment where the compromised PC is located;
Value of data stored on the compromised computer;
Type and number of other incidents that affected the same PC;
Reliability of the indicator of compromise for the given incident.
It should be noted that the choice of server or network segment that should be saved first, and the choice of workstation that can be sacrificed, depends on the specifics of the organization.
If the events, originating from one of the sources, include an IOC published in a report on APT threats or there is evidence of interaction with a C&C server previously used in an APT attack, we recommend dealing with these incidents first. The tools and utilities described in the full version of our Incident Response Guide can help.
Conclusion
It is impossible in one article to cover the entire arsenal that modern cybercriminals have at their disposal, describe all existing attack vectors, or develop a step-by-step guide for information security specialists to help respond to every incident. Even a series of articles would probably not be sufficient, as modern APT attacks have become extremely sophisticated and diverse. However, we hope that our recommendations about identifying incidents and responding to them will help information security specialists create a solid foundation for reliable multi-level business protection.
Tech Firms Unite to Neutralize WireX Android Botnet
29.8.2017 securityweek Android
Major New WireX Android Botnet Neutralized by Cross-Vendor Collaborative Research
Black clouds on the internet do sometimes have a silver lining. Global attacks such as those from Mirai last year and WannaCry/NotPetya this year have fomented informal collaborative global responses -- one of which happened this month when multiple competitive vendors collaborated in the research and neutralization of a major new botnet called WireX.
The collaboration was informal. Security experts often move around the industry, but usually retain good relationships and continue those relationships. This happened with WireX. It first appeared on August 2nd, but was small enough to be ignored. Two weeks later it ramped up into something altogether different.
In a joint and coordinated announcement and series of blogs, Flashpoint, Akamai, Cloudflare, and RiskIQ have today explained how their researchers, together with researchers from other organizations, detected, collaborated, and ultimately neutralized the botnet.
The initial August 2nd attacks were minimal, suggesting the malware was in development or in the early stages of deployment. "More prolonged attacks have been identified starting on August 15th, with some events sourced from a minimum of 70,000 concurrent IP addresses," say the reports. The targets of the attacks are not specified, but some reports suggest that several large websites in the hospitality sector were taken down.
The attacks were volumetric, attacking the application layer with HTTP GET requests disguised to look like legitimate web traffic. At this level, the attacks were soon detected by multiple cyber security firms, and the collaboration began.
When it did, "the investigation began to unfold rapidly starting with the investigation of historic log information, which revealed a connection between the attacking IPs and something malicious, possibly running on top of the Android operating system."
Analyses of logs from August 17 attacks implicated a particular Android app. Searches using variations of the application name and parameters in the application bundle revealed multiple additional applications from the same, or similarly named authors, with comparable descriptions. Around 300 apps were located. The attacks themselves seem to have come from more than 100 different countries, indicating a wide and successful distribution of the malicious apps.
"We identified approximately 300 apps associated with the issue, blocked them from the Play Store, and we're in the process of removing them from all affected devices," says Google. "The researchers' findings, combined with our own analysis, have enabled us to better protect Android users, everywhere."
Many of the apps appear to be legitimate with benign functions, such as media/video players, ringtones or tools such as storage managers -- but "with additional hidden features that were not readily apparent to the end users that were infected." This malware stayed alive and active in background even when the app itself was not in use.
Existing anti-malware tools already detect the malware as 'Android Clicker', leading the researchers to believe it started life as click fraud malware that was later repurposed as a DDoS tool.
This was not a botnet 'takedown' (such as Kelihos earlier this year) in the usual sense, where industry and law enforcement combine to locate and 'seize' or sinkhole the C2 server or servers (although the researchers do proffer their thanks to "the FBI for their assistance in this matter"). This is more a neutralization than a takedown. The collaborative research by the vendors has resulted in isolating the rules that can stop the malformed GET (and potentially also POST) traffic, while Google's efforts to locate and remove the apps from the Play Store (and cleanse infected devices) stops them being originated.
Almost more important than the botnet neutralization, however, is this new example of collaboration between the different companies concerned. "This research is exciting because it's a case study in just how effective collaboration across the industry is," said Allison Nixon, director of security research at Flashpoint. "This was more than just a malware analysis report. The working group was able to connect the dots from the victim to the attacker. The group also used the information to better mitigate the attack and dismantle the botnet -- and this was completed very quickly."
Akamai's senior network architect and security researcher, Jared Mauch, added, "In the case of the WireX botnet, a direct result of our information sharing and other research collaboration was our ability to fully uncover what made this malicious software tick in a much more timely manner."
"I'm proud of our research team and the researchers who worked together to rapidly investigate and mitigate this dangerous new discovery," said Matthew Prince, co-founder & CEO of Cloudflare.
"The WireX botnet operation shows the value of a collaborative response from security firms, service providers, and law enforcement," said Darren Spruell, threat researcher at RiskIQ.
The hope is that this success becomes a repeated example of how the global industry can collaborate to defeat global threats. "This report is an example of how informal sharing can have a dramatically positive impact for the victims and the Internet as a whole," conclude the researchers. "Cross-organizational cooperation is essential to combat threats to the Internet and, without it, criminal schemes can operate without examination."
Thousands of IoT Devices Impacted by Published Credentials List
29.8.2017 securityweek IoT
Over 1,700 Internet of Things (IoT) devices worldwide are potentially exposed to hackers after a list containing their IPs and default login credentials emerged on Pastebin.com.
Initially published in June, the list remained mostly unnoticed until last week, after high-profile security researchers retweeted a link to it. The view count for the list had stayed below 1,000 as of Thursday, August 24, but spiked above the 22,000 mark on Saturday.
The list has been updated several times since the initial post and contained over 33,000 entries at the end of last week, when it was removed from the website. For each of the 33,138 IPs on the list, Telnet credentials (username and password) were included.
After having a look at the list, Victor Gevers, chairman of the GDI Foundation, revealed that it only contained 8,233 unique IP addresses, as many entries were duplicates. He also noted that about 2,174 of the devices were still running open Telnet services, and that only around 1,775 of them could still be accessed using the credentials on that list.
Some of the insecure credentials exposed in the list include username/password pairs such as root:[blank], admin:admin, root:root, and admin:default. These have been revealed before to put a great deal of devices and users at risk.
Over the past several days, Gevers has been hard at work notifying impacted owners or ISPs of the exposed devices, most of which are routers. So far, he sent over 2000 emails to affected parties and he’s happy with the received response, Gevers told SecurityWeek on Monday morning. Over half of the reachable IPs are located in China.
“We got some nice feedback from a few ISPs because we wrote the warning emails in a way that they only need to forward them to their customers. From 2,174 reported devices 113 were direct identifiable to owners. The others we addressed to the ISPs with a request to forward our mail to their customers. In Asia we asked the GovCERTs for help getting this to the right person,” Gevers said.
He also revealed that some of the IPs were honeypots, and that the organizations operating them have already contacted him on the matter. A newly performed scan has revealed some changes in the number of devices running Telnet services. Some of the devices have closed the vulnerable ports, while others opened them.
The issue of improperly secured IoT devices is not new, as botnets such as Mirai and BASHLITE have been harnessing the power of such devices to launch massive distributed denial of service (DDoS) attacks.
According to Gevers, however, the response received to the warnings sent over the past week were encouraging: “People are taking action. We saw some devices being secured on Sunday morning, others on Saturday evening. Before, an email sent on Friday afternoon wouldn’t receive a response until Monday, at best.”
What Gevers couldn’t reveal was the number of devices still impacted. The scan was ongoing at the time of this article.
Defray Ransomware Used in Selective Attacks Against Multiple Sectors
29.8.2017 securityweek Ransomware
A newly discovered ransomware variant has been used in small, selectively targeted attacks aimed at healthcare and education, and manufacturing and technology, respectively.
Dubbed Defray and discovered by Proofpoint earlier this month, the malware appears to have been involved only in two attacks, distributed via Word documents attached to phishing emails. The campaigns consisted of only several messages each, while the lures were specifically crafted for the intended targets.
The Microsoft Word documents carrying the ransomware contain an embedded OLE packager shell object. When the victim opens the document, the malware is dropped in the %TEMP% folder, and a file named taskmgr.exe or explorer.exe is then executed.
Defray contains a hardcoded list of around 120 file extensions to encrypt, though security researchers from Proofpoint noticed that the malware would also encrypt files with extensions that are not on the list (such as .lnk and .exe). The ransomware doesn’t change the extension of the encrypted files, Proofpoint says.
The threat communicates with the command and control server via both HTTP (clear-text) and HTTPS, to send infection information. After completing the encryption process, the malware disables startup recovery and deletes volume shadow copies. On Windows 7, Defray would also monitor and kill running programs such as the Task Manager and browsers.
To inform the victim of what happened with the files, the ransomware creates a ransom note called FILES.TXT in “many folders throughout the system,” along with a file called HELP.txt on the desktop (with identical content).
“The ransom note […] follows a recent trend of fairly high ransom demands; in this case, $5000. However, the actors do provide email addresses so that victims can potentially negotiate a smaller ransom or ask questions, and even go so far as to recommend BitMessage as an alternative for receiving more timely responses. At the same time, they also recommend that organizations maintain offline backups to prevent future infections,” Proofpoint reveals.
To date, the malware was observed only in two distinct attacks, one targeting Manufacturing and Technology verticals, on August 15, and another primarily aimed at Healthcare and Education, on August 22. As part of the first campaign, the emails featured the subject “Order/Quote” and referenced a UK-based aquarium with international locations. In the second campaign, the emails used a UK hospital logo, purporting to be from the Director of Information Management & Technology at the hospital.
“Defray Ransomware is somewhat unusual in its use in small, targeted attacks. Although we are beginning to see a trend of more frequent targeting in ransomware attacks, it still remains less common than large-scale “spray and pray” campaigns. It is also likely that Defray is not for sale, either as a service or as a licensed application like many ransomware strains. Instead, it appears that Defray may be for the personal use of specific threat actors, making its continued distribution in small, targeted attacks more likely,” Proofpoint concludes.
U.S. Government Cybersecurity Ranks 16th Out of 18 Industry Sectors
28.8.2017 securityweek BigBrothers
The U.S. state and federal government's cybersecurity standing is ranked 16th of 18 industry sectors in a new report. This is a very small improvement on last year's comparable position, which was 18th out of 18; but it still paints a grim picture of public sector readiness to fight cybercrime and cyber espionage.
The 2017 U.S. State and Federal Government Cybersecurity report (PDF) was just published by SecurityScorecard, a firm that seeks to help business manage third- and fourth-party risk (the supply chain). It does this by collecting and analyzing subject data through its own data engine, ThreatMarket -- which uses 10 categories such as web applications, network security, DNS health, patching cadence and what it calls 'hacker chatter'.
SecurityScorecard is based in New York. It was founded in 2013, and raised $12.5 in Series A funding led by Sequoia Capital in 2015. Its stated mission is "to empower every organization with collaborative security intelligence."
For this report, SecurityScorecard analyzed more than 500 state and local government agencies, and compared the results, as a group, to 17 other industry sectors. Although there has been a slight improvement over last year's results, government organizations are particularly weak in network security (13th), application security (11th), leaked credentials (12th), patching cadence (16th), endpoint security (17th), IP reputation (16th), and hacker chatter (18th).
Government is, however, performing well in three of the 10 categories: DNS health (2nd), social engineering (3rd), and cubit score (2nd). The cubit score is a measure of exposed administrative portals and subdomains. Nevertheless, the only two sectors performing worse than government overall are Telecommunications and Education. Surprisingly, perhaps, regulation doesn't put the heavily regulated industries at the top of the chart: transportation, healthcare and energy are all among the poorest performing industries, while financial services only ranks at fifth position.
Within the 500 government offices analyzed, the Federal Reserve, the Secret Service and the IRS are all -- reassuringly -- within the top ten performing agencies. In fact, among the larger organizations, the top four agencies are the IRS, the Congressional Budget Office, the Federal Trade Commission and the Defense Logistics Agency.
The report does not specify the poorest performing agencies -- in fact, the report rarely specifies individual agencies, more usually saying only 'federal agency', or 'county (or city) in [state]'.
Commenting on the report, Sam Kassoumeh, COO and co-founder at SecurityScorecard, said, "On an almost daily basis, the institutions that underpin the nation's election system, military, finances, emergency response, transportation, and many more, are under constant attack from nation-states, criminal organizations, and hacktivists. Government agencies provide mission-critical services that, until they are compromised, most people take for granted. This report is designed to educate elected officials, agency leadership, as well as government security professionals about the state of security in the government sector."
In reality, however, reports like this can only provide indicators of overall security -- this one relies on the interpretation of external factors without being able to analyze the internal security. For example, in the leaked credentials category, Government ranks 12th out of 18. "SecurityScorecard," says the report, "maps the information [from password dumps] back to the companies who own the data or associated email accounts that are connected to the leaked information. By doing so, SecurityScorecard is able to assess the likelihood that an organization will succumb to a security incident due to the leaked information."
But it doesn't know the internal processes and controls of the organization concerned -- whether, for example, all passwords have been changed since the leak, or whether new multi-factor and behavioral authentication controls have been introduced.
Similarly, an organization's susceptibility to social engineering (here government scores well at 3rd out of the 18 sectors) is measured by monitoring social media practices to see how easy it would be to build an employee profile that can be phished or spear-phished. But this doesn't measure the existence or effectiveness of the organization's internal awareness training, nor any anti-spam or anti-phishing controls. A more accurate way to measure social engineering susceptibility would be to measure employees' phishing clicks through simulated phishing attacks -- which SecurityScorecard cannot do.
This doesn't mean that the report has no value. It does -- but it should, perhaps, be taken with a pinch of salt. "I personally like this type of reporting and feel we need more such metrics," comments Martin Zinaich, the information security officer at the City of Tampa. "However, the efficacy of such is mixed."
He gives the example of a local TV station running the Qualys SSL scanner against a number of local governments. "One entity scored an F," he said. "So, the TV station ran a number of stories about them failing -- which of course caused political havoc."
The reality was different. "That failing score was based on support for an outdated cipher. Now SSL ciphers negotiate to the highest level both sides support. To have a material breach someone would have had to have an outdated browser and then a third party would have to perform a man-in-the-middle attack on that outdated connection. The reward of which would have probably been seeing a water bill." The danger comes in drawing black and white conclusions from insufficient data.
Zinaich believes it is all part of what he calls the "Security Theatre". At one level, the SecurityScorecard report is a sales pitch marketing the SecurityScorecard third-party risk service. But on another level, it also provides some genuine indicators of security posture that are valid provided they are treated as indicators rather than statements of fact. It is worth noting, for example, that rival third-party risk management company, BitSight, rated the federal government as "the second highest performing sector" out of six sectors in September 2015.
China Demands Internet Platforms Verify Users' True Identity
28.8.2017 securityweek BigBrothers
China has ordered the country's internet platforms to verify users' true identity before letting them post online content, the latest step by authorities to tighten policing of the web.
All social networking sites and discussion forums must "check the real identity" of their users before they can post online content and comments, under new regulations published Friday by the Cyberspace Administration of China.
The platforms will also have to strengthen their oversight over all published information, deleting all illegal content while also alerting authorities to the postings.
The new guidelines take effect October 1.
China already had laws requiring companies to verify a user's identity but it was applied in a fragmented and incomplete way.
But forcing online posters to identify themselves -- which will probably require scanning a government-issued ID as proof of identity -- makes it much more difficult to post online anonymously.
China already tightly controls the internet aggressively blocking sites of which it disapproves and curbing politically sensitive online commentary, such as on criticism of the government.
The new regulation was adopted as part of a cybersecurity law that took effect in June, which bans internet users from publishing a wide variety of information.
That covers anything that damages "national honour", "disturbs economic or social order" or is aimed at "overthrowing the socialist system".
The law also requires online platforms to get a license to post news reports or commentary about the government, economy, military, foreign affairs, and social issues.
Since 2013, China has imposed prison sentences on users whose messages are deemed "defamatory".
But new restrictive measures have multiplied in recent months, ahead of the Communist Party's autumn congress during which President Xi Jinping is expected to be re-elected.
China has enforced new rules on what is permissible content, with content such as celebrity gossip blogs and online video streaming sites hit by the regulations.
The authorities have also stepped up efforts to clamp down on virtual private networks (VPN), software that allows people to circumvent the Great Firewall.
Chinese APT17 group leverages fake Game of Thrones leaks as lures
28.8.2017 securityaffairs APT
Researchers at Proofpoint spotted a cyber espionage campaign leveraging recent Game of Thrones episode leaks and attribute it to Chinese APT17 group.
Security researchers at Proofpoint have uncovered a cyber espionage campaign leveraging recent Game of Thrones episode leaks to trick victims into opening malicious documents sent via email.
Experts have observed during the past week, the threat actor sending emails to victims with the subject of “Wanna see the Game of Thrones in advance?”
The malicious messages use weaponized documents booby-trapped with an embedded LNK file that runs a Powershell script to installs the 9002 remote access trojan and gain full access to the victim’s machine.
“Proofpoint recently observed a targeted email campaign attempting a spearphishing attack using a Game of Thrones lure. The malicious attachment, which offered salacious spoilers and video clips, attempted to install a “9002” remote access Trojan (RAT) historically used by state-sponsored actors.” reads the analysis published by Proofpoint.
The 9002 RAT was well known by experts in the IT security community, below a list of operations that involved it:
Operation Aurora, an attack on companies such as Google, widely attributed to the Chinese government.
Operation Ephemeral Hydra, a strategic website compromise utilizing an Internet Explorer zero-day [3], which FireEye attributed to an APT actor without a country attribution
Attacks on Asian countries described by Palo Alto.
The experts attributed the attack to a cyber-espionage group tracked as Deputy Dog, Group 27, or APT17, that according to the reports of many security firms, is composed of Chinese hackers operating out of China.
Researchers found many similarities with a campaign conducted by the APT group far back as April 2014. Several ZIP compressed files containing a similar LNK downloader were uploaded to a malicious file scanning service.
“Based on several shared identifiers, it is possible that the recent campaigns were conducted by the same actor that conducted the campaigns in early- to mid-2014. The malicious LNK files in both campaigns (2014 vs. 2017) have the same Volume Serial Number of 0xCC9CE694. Furthermore, the LNK filename used in one of the campaigns this year is almost identical to the campaigns in 2014: Party00[1-35].jpg.lnk (2017) vs. Party-00[1-5].jpg.lnk (2014). Finally, the theme of party pictures and stock-JPGs used in both the 2017 and 2014 campaigns are extremely similar.” states the analysis. “Another possible similarity is the use of some of the code from the Java Reverse Metasploit-Stager [6] in the exploits previously analyzed by FireEye [7] as well as the PhotoShow.jar payload.”
The most popular campaign attributed to the APT17 group is the attack on the Google’s infrastructure, also known as Operation Aurora. For almost a decade the APT17 targeted government organizations in several Southeast Asian countries and the US, NGOs, defense contractors, law firms, IT firms, and mining companies.
The APT17 attempted to exploit the attention of the media on the HBO hack and the Game of Thrones leaks to increase the efficiency of their hacking campaign.
“Based on similarities in code, payload, file names, images, and themes, it is possible that this attack was carried out by a Chinese state-sponsored actor known as Deputy Dog.” concluded Proofpoint. “The use of a Game of Thrones lure during the penultimate season of the series follows a common threat actor technique of developing lures that are timely and relevant, and play on the human factor – the natural curiosity and desire to click that leads to so many malware infections. While Proofpoint systems blocked this attack, the use of such lures, combined with sophisticated delivery mechanisms and powerful tools like the latest version of the 9002 RAT can open wide doors into corporate data and systems for the actors behind these attacks”
Google mistake is the root cause of Internet Outage in Japan
28.8.2017 securityaffairs Security
A widespread internet disruption occurred in Japan on Friday, Google error it the main cause of the Internet outage that caused the panic in the country.
Google error it the root cause of a widespread Internet outage in Japan that lasted for about an hour on Friday, August 25. The incident was caused by a BGM route hijack that began at 12:22 PM local Japan time and was fixed by 1:01 PM.
Border Gateway Protocol (BGP) is a standardized exterior gateway protocol designed to exchange routing and reachability information among autonomous systems (AS) on the Internet. It interconnects the networks of major Internet service providers that announce which IP addresses are available on their networks.
If an ISP provides wrong information on the availability of IP address blocks we are in presence of a BGM route hijack ISPs.
This is what has happened on Friday when Google wrongly advertised that IP blocks belonging to a Japanese ISPs were found on its network.
BGPMon who analyzed the event confirmed that Google hijacked the traffic NTT Communications Corp., a major ISP who also supports two smaller ISPs named OCN and KDDI Corp. NTT has more than 8 million customers, 7.67 million home users, and 480,000 companies.
“Beginning at 2017-08-25 03:23:34, we detected a possible BGP hijack.
Prefix 210.171.224.0/20, Normally announced by AS7527 Japan Internet Exchange Co., Ltd.
Starting at 2017-08-25 03:23:34, a more specific route (210.171.224.0/24) was announced by ASN 15169 (Google Inc.).
This was detected by 17 BGPMon peers.” reported BGPMon.“
Other ISPs started routing traffic that was destined for Japan to Google’s systems, many services online in Japan went down, including the Nintendo networks.
“A widespread internet disruption hit Japan on Friday, blocking access to banking and train reservation services as well as gaming sites.
The disruption was limited to the networks of NTT Communications Corp. and KDDI Corp.
NTT Communications, which runs the OCN internet service, said the problem occurred because an overseas network service provider that OCN uses suddenly switched internet routes.” reported the Japan Times.
It was chaos in the country, the Internal Affairs and Communications Ministry promptly started an investigation into the incident.
“Nintendo Co. said on its website that some Switch, Wii U and 3DS clients started complaining about poor connectivity at about 12:25 p.m.” continnues the media outlet.
Clients of Resona Bank, Saitama Resona Bank and Kinki Osaka Bank said they had trouble logging in to their accounts, as did customers of online banker Jibun Bank Corp. and Rakuten Securities Inc.
East Japan Railway Co. (JR East) said some users of its Suica mobile payment system complained they weren’t able to use the service, which lets them board trains and buy products using their smartphones.”
Google confirmed the incident and provided further details on it.
“We set wrong information for the network and, as a result, problems occurred. We modified the information to the correct one within eight minutes. We apologize for causing inconvenience and anxieties,” the Google spokesperson told The Asahi Shimbun.

BGPMon published a detailed analysis of the incident, it confirmed that Google hijacked over 135,000 network prefixes, from all over the world, of which over NTT 24,000 prefixes.
“In total we saw over 135,000 prefixes visible via the Google – Verizon path. Widespread outages, particularly in Japan (OCN) were because of the more specifics, causing many networks to reroute traffic toward verizon and Google which likely would have congested that path or perhaps hit some kind of acl, resulting in the outages. Many BGPmon users would have seen an alert similar like the one below, informing them new prefixes were being originated and visible global.” concluded BGPMon.
According to the BGPMon engineer Andree Toonk it’s easy to make configuration mistakes that can lead incidents like this.
“In this case it appears a configuration error or software problem in Google’s network led to inadvertently announcing thousands of prefixes to Verizon, who in turn propagated the leak to many of its peers,” said Toonk.
“Since it is easy to make configurations errors, it clearly is a necessity to have filters on both sides of an EBGP session. In this case it appears Verizon had little or no filters, and accepted most if not all BGP announcements from Google which lead to widespread service disruptions,” Toonk added. “At the minimum Verizon should probably have a maximum-prefix limit on their side and perhaps some as-path filters which would have prevented the wide spread impact.”
Tor relay of a Brazilian University was banned after harvesting .onions
28.8.2017 securityaffairs Cyber
The Tor relay of a Brazilian University was banned by the Tor administrators because it was spotted collecting the .onion addresses of visitors.
A team of researchers from a Brazilian University of Campinas in São Paulo, Brazil, has had its Tor relay node banned because it was spotted collecting the .onion addresses of visitors.
Marcus Rodrigues, a junior researcher with the Brazilian University, explained he and his colleagues were working to develop a tool that could identify malicious hidden services.
According to the Tor administrators, the activity conducted by the researchers is a violation of the Tor Project’s ethical guidelines and triggered the banning of the node.
Below the description published by the researchers in a Tor mailing list post:
“My relay was harvesting .onion addresses and I apologize if that breaks any rule or ethical guideline.
We were conducting some research on malicious Hidden Services to study their behavior and how we could design a tool that could tell malicious and benign Hidden Services apart.
Because we focus mainly on web pages, we use a crawler to get almost all of the data we need. However, there are some statistics (such as the size of the Tor network, how many HSs run HTTP(s) protocol, how many run other protocols and which protocols do they run, etc) which cannot be obtained through a crawler. That’s why we were harvesting .onion addresses.
We would run a simple portscan and download the index page, in case it was running a web server, on a few random addresses we collected. We would also try and determine the average longevity of those few HSs. However, after collecting the data we needed for statistical purposes, the .onion addresses we collected would be deleted and under no circumstances we would disclose the information we collected on a specific .onion address we harvested. In addition, we would never target specific harvested HS, but only a random sample.”
They decided to collect .onion addresses and fetch their content to classify the hidden service.
“My research in particular is about malicious hidden services. I’m developing a method to automatically categorize a malicious hidden service by its content (eg, drug traffic website, malware propagation),” Rodrigues told The Register.
“We would then publish an academic paper containing up-to-date statistics regarding what kind of malicious websites there are on the dark web. We were also going to develop a platform on which the user could verify if a certain .onion website is trustworthy or malicious before entering it.”
The team set up a Tor relay to collect specific data about the hidden services. Rodrigues clarified that data collected could not be used to unmask TOR users or locate a specific server running the hidden service.
“That would provide information about the Hidden Services running at the time, such as their .onion addresses, their popularity and some technical data – none of which would allow me to deanonymize or harm the hidden service in any way,” he explained.
Rodrigues was unable to restore its Tor relay online, he explained that the research will go on in any case, with different techniques.
“I can use other methods to discover the Hidden Services,” he explains, “but none is as informative or as efficient.”
Zimperium researcher released an iOS Kernel Exploit PoC
28.8.2017 securityaffairs iOS
Zimperium Researcher Adam Donenfeld released an iOS Kernel Exploit PoC that can be used to gain full control of iOS mobile devices.
Researcher Adam Donenfeld of mobile security firm Zimperium published a Proof-of-concept (PoC) for recently patched iOS vulnerabilities that can be chained to gain full control of iOS mobile devices.
The expert called the PoC exploit zIVA (Zimperium’s iOS Video Audio), it is designated to work on all 64-bit iOS devices <= 10.3.1.
The vulnerabilities discovered earlier this year are tracked as CVE-2017-6979, CVE-2017-6989, CVE-2017-6994, CVE-2017-6995, CVE-2017-6996, CVE-2017-6997, CVE-2017-6998 and CVE-2017-6999.
The exploit allows an attacker to take complete control of the kernel, chaining the vulnerabilities it is possible to jailbreak a device, it has been presented at the HITBGSEC held in Singapore on August 25th.
“Following my previous post, I’m releasing ziVA: a fully chained iOS kernel exploit that (should) work on all the iOS devices running iOS 10.3.1 or earlier. The exploit itself consists of multiple vulnerabilities that were discovered all in the same module: AppleAVEDriver.” Donenfeld wrote in a blog post.
“The issues are severe and could lead to a full device compromise. The vulnerabilities ultimately lead to an attacker with initial code execution to fully control any iOS device on the market prior to version 10.3.2.”

iOS 10.3.2, which Apple released in mid-May, addresses seven AVEVideoEncoder flaws and one IOSurface vulnerability discovered by Donenfeld. The expert speculates the flaws could affect all prior versions of the iOS operating system.
Donenfeld discovered the presence of the AppleAVE module while testing iOS kernel modules. The module was affected by flaws that could be exploited to cause a denial-of-service condition or to trigger information disclosure and privilege escalation.
The expert highlighted that the flaws can be chained to achieve arbitrary read/write and root access. The exploit developed by Donenfeld could be used to bypass all iOS security mitigations.
iOS users can protect their devices by updating them to the latest iOS version.
Hundreds of Russians Protest Tighter Internet Controls
28.8.2017 securityweek BigBrothers
About 1,000 Russians braved pouring rain in Moscow on Saturday to demonstrate against the government's moves to tighten controls on internet use, with police arresting about a dozen protesters.
Shouting slogans such as "Russia will be free" and "Russia without censorship", the protesters were escorted by several police officers, in a march authorised by local authorities.
Several were also marching in support of Khudoberdi Nurmatov, a reporter for the Russian opposition newspaper Novaya Gazeta, who faces deportation back to Uzbekistan over allegedly violating immigration laws.
Some of those were arrested, according to OVD-Info, a rights group that monitors detentions of activists, while an AFP photographer saw two protesters carrying rainbow flags detained.
In July, Russia's parliament voted to outlaw web tools that let internet users sidestep official bans of certain websites.
It allows telecommunications watchdog Roskomnadzor to compile a list of so-called anonymiser services and prohibit any that fail to respect the bans, while also requiring users of online messaging services to identify themselves with a telephone number.
"Innovation and technology will win! We will defend our freedoms!" one protester said, according to a broadcast of the march on YouTube.
Russia's opposition groups rely heavily on the internet to make up for their lack of access to the mainstream media.
But the Russian authorities have been clamping down on such online services, citing security concerns.
In June, Russian officials threatened to ban the Telegram messaging app after the FSB security service said it had been used by the attackers responsible for the deadly Saint Petersburg metro bombing in April.
Defray Ransomware used in targeted attacks on Education and Healthcare verticals
27.8.2017 securityaffairs Ransomware
Researchers at Proofpoint spotted Defray Ransomware, a new ransomware used in a targeted campaign against education and healthcare organizations.
Earlier this month, researchers at Proofpoint spotted a targeted ransomware campaign against education and healthcare organizations. The ransomware used in the campaign was dubbed Defray, based on the command and control (C&C) server hostname used for the first observed attack:
defrayable-listings[.]000webhostapp[.]com
The ransomware is being spread via Microsoft Word document attachments in email.
The researchers observed two targeted attack on Aug. 15, and on Aug. 22, and both appeared to be designed for specific organizations.
The attack on August 22, aimed primarily at Healthcare and Education involving messages with a Microsoft Word document containing an embedded executable (specifically, an OLE packager shell object). The attachment features a UK hospital logo in the upper right and purports to be from the Director of Information Management & Technology at the hospital.
The attack on August 15 targeted Manufacturing and Technology verticals, attackers used messages with the subject “Order/Quote” and a Microsoft Word document containing an embedded executable (also an OLE packager shell object).
The attachment used a lure referencing a UK-based aquarium purported to be from a representative of the aquarium.

The attackers behind the Defray ransomware ask for $5,000, but researchers highlighted that the ransom note contains several email addresses, presumably of the cybercriminal Igor Glushkov,to allow victims to “negotiate a smaller ransom or ask questions.”
The Defray ransomware targets a hardcoded list of file types but doesn’t change the file extension names. After encryption is complete, the Defray ransomware may cause other general havoc on the system by disabling startup recovery and deleting volume shadow copies. On Windows 7, it monitors and kills running programs with a GUI, such as the task manager and browsers.
Experts speculate the threat could be being used privately and for this reason, it is less likely Defray ransomware will continue to be used in limited, targeted attacks.
“Defray Ransomware is somewhat unusual in its use in small, targeted attacks. Although we are beginning to see a trend of more frequent targeting in ransomware attacks, it still remains less common than large-scale “spray and pray” campaigns. It is also likely that Defray is not for sale, either as a service or as a licensed application like many ransomware strains. Instead, it appears that Defray may be for the personal use of specific threat actors, making its continued distribution in small, targeted attacks more likely” concluded Proofpoint.
Watch out! Adware spreading via Facebook Messenger
27.8.2017 securityaffairs Social
Security experts from Kaspersky Lab have spotted an ongoing cross-platform malware campaign that leverages Facebook Messenger.
Security experts from Kaspersky Lab have spotted an ongoing cross-platform malware campaign on Facebook Messenger, spammers are actually infecting users of all platform with adware.
Users receive a video link that redirects them to a bogus website set up to lure them to install a malware.
Researchers believe threat actors leverage compromised accounts, hijacked browsers, or clickjacking techniques to spread the malicious link.
They use social engineering to trick users into clicking the video link, which pretends to be sent from one of their Facebook contacts.
“The initial spreading mechanism seems to be Facebook Messenger, but how it actually spreads via Messenger is still unknown. It may be from stolen credentials, hijacked browsers or clickjacking. At the moment we are not sure because this research is still ongoing.” reads the analysis published by Kaspersky Lab.
The malicious message reads “< your friend name > Video” followed by a bit.ly link, as shown.

When the victim clicks on the fake video, the malicious code redirects him to a set of websites which gather information on his system (i.e. Browser, OS) to choose the website to which he has to be redirected.

Users are redirected following a domain chain, many websites on different domains used to redirect the victim depending on some characteristics (i.e. System info, Language, geo location, browser information, operating system, installed plugins and cookies).
The URL redirects victims to a Google doc that displays a dynamically generated video thumbnail that appears like a playable movie, based on the sender’s images. If the victim clicks the thumbnail he his redirected to another customised landing page depending upon their browser and operating system.
“What I noticed during my research was that when changing the User-Agent header (browser information) the malware redirects you to different landing pages. For example, when using FIREFOX I was redirected to a website displaying a fake Flash Update notice, and then offered a Windows executable. The executable is flagged as adware.” continues the analysis.
Google Chrome users, for example, are redirected to a website that appears as YouTube that displays a fake error message popup, tricking victims into downloading a malicious Chrome extension from the Google Web Store.
The fake extension is a downloader that delivers a file to the victim’s computer.

Experts observed similar tricks for Apple Mac OS X Safari users and Linux users.
“It has been a while since I saw these adware campaigns using Facebook, and its pretty unique that it also uses Google Docs, with customized landing pages. As far as I can see no actual malware (Trojans, exploits) are being downloaded but the people behind this are most likely making a lot of money in ads and getting access to a lot of Facebook accounts.” concluded Kaspersky.
More than 1,700 valid Telnet credentials for IoT devices leaked online
27.8.2017 securityaffairs IoT
Security researchers are warning of the availability online of a list of IoT devices and associated telnet credentials.
The list has been available on Pastebin since June, but last week it was also shared via Twitter by the researcher Ankit Anubhav becoming rapidly viral.
The original list was posted by someone who has previously published a dump of valid log-in credentials and also the source code of a botnet.

Ankit Anubhav @ankit_anubhav
33000+ telnet credentials of IoT devices exposed on pastebin.
Link : https://pastebin.com/p5teudX0 #iot #hacking #malware #infosec @newskysecurity
9:34 PM - Aug 24, 2017
11 11 Replies 436 436 Retweets 422 422 likes
Twitter Ads info and privacy
It is a gift for hackers, more than 1,700 IoT devices could easily take over and recruit them part of a botnet that could be used to power a DDoS attack.
The list has more than 22,000 views as of Saturday afternoon, while only 1,000 users have seen it since last Thursday.

Many IoT devices included in the list have default and well-known credentials (i.e., admin:admin, root:root, or no authentication required).
Top five credentials were:
root:[blank]—782
admin:admin—634
root:root—320
admin:default—21
default:[blank]—18
The popular researcher Victor Gevers, the founder of the GDI Foundation, analyzed the list and confirmed it is composed of more than 8200 unique IP addresses, about 2.174 are accessible via Telnet with the leaked credentials.
24 Aug
Victor Gevers @0xDUDE
Replying to @rayjwatson
Actually I see only 8,233 unique IP addresses in this dump? pic.twitter.com/Uydz0366Z3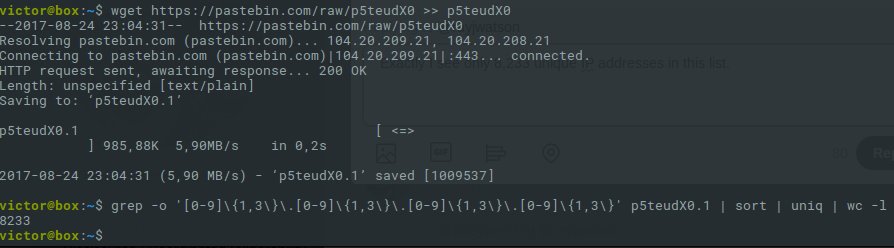
Victor Gevers @0xDUDE
From the 8,233 hosts about 2,174 are still running an open telnet services and some of them still accessible with the leaked credentials. pic.twitter.com/umbNhYwAGV
2:44 PM - Aug 25, 2017
2 2 Replies 6 6 Retweets 10 10 likes
Twitter Ads info and privacy
According to the researchers, most of the reachable IPs (61 percent) were located in China.
The list of the 33,000 IP addresses includes many duplicates, it is likely they were already abused by hackers in the wild.
The Pastebin also includes numerous scripts, titled “Easy To Root Kit,” “Mirai Bots,” “Mirai-CrossCompiler,” “Apache Struts 2 RCE Auto-Exploiter v2),” “Slowloris DDoS Attack Script.”
Mall.cz resetuje hesla, k části databáze se mohli dostat hackeři
27.8.2017 Lupa.cz Kriminalita
„Dobrý den, píšeme Vám, protože Vaše původní heslo k MALL.cz už nefunguje.“ Internetový obchod Mall.cz části uživatelů rozesílá e-mail, ve kterém je informuje o resetu hesla. Důvodem je hackerský útok.
„Mall.cz zaznamenal pokus o narušení bezpečnosti, který se dotkl starší databáze uživatelských účtů, jež neměly dostatečné silné heslo. Bezpečnostní tým se proto rozhodnul plošně resetovat část hesel k zákaznickým účtům, aby zabránil jejich možnému zneužití,“ informoval mluvčí internetové nákupní galerie Jan Řezáč.
V praxi resetování vypadá tak, že se uživatel po zadání svých přihlašovacích údajů prostě nemůže ke svému účtu přihlásit a musí prostřednictvím odkazu Zapomněl(a) jsem heslo požádat o zaslání odkazu pro vygenerování nového hesla. Mall také postiženým uživatelům rozesílá e-maily, ve kterých je na problém upozorňuje (pokud jste jej zatím nedostali, může teprve přijít, firma je rozesílá postupně).
„Pokud jste svůj účet zakládali v roce 2015 a později, tato situace se vás s největší pravděpodobností netýká, narušení bezpečnosti se vztahuje na starší databázi zákaznických účtů,“ doplňuje firma také na stránce s otázkami a odpověďmi, kterou pro uživatele zřídila.
Pokud na Mallu platíte prostřednictvím platební karty, nemusíte se bát, že by unikly i její údaje, ubezpečuje firma. „V klientském centru MALL.cz ani nikde jinde nejsou ukládány údaje, přes které je možné provést platbu.“
Pokud ale používáte stejné heslo, jako na Mall.cz, i na jiných službách (což byste dělat neměli), měli byste si jej pro jistotu změnit i na nich.
Bezpečně až od roku 2016
Firma zatím zjišťuje, jak vážný útok byl a zda došlo skutečně ke kompormitaci některých účtů. Podrobné informace ale v současnosti nechce zveřejňovat s odkazem na to, že bude podávat trestní oznámení. Mall také podle mluvčího kontaktoval Úřad na ochranu osobních údajů.
Podle Mallu byla nejspíš ohrožena starší databáze z roku 2014. „Část z ní obsahovala jednoduchá hesla, která neodpovídají bezpečnostním zásadám. V systému dochází k tzv. ‚hashování hesel‘, kdy jsou hesla uložena v zakódované podobě. Dotčená databáze byla zakódována starším a již nepoužívaným způsobem, který útočníkovi umožnil jednodušší hesla rozkódovat,“ doplňuje mluvčí.
Z vyjádření vyplývá překvapivá informace, že Mall.cz hesla svých uživatelů lépe zabezpečil až od loňského roku. „Od roku 2016 Mall.cz pro ukládání a šifrování zákaznických dat využívá jiný – bezpečnější způsob, který splňuje moderní bezpečnostní standardy a prolomení by u něj nemělo hrozit,“ říká mluvčí.
Podrobnosti firma uvádí na blogu. Mall od listopadu 2012 používal k šifrování hesel metodu SHA1 + unikátní sůl. Až v říjnu 2016 nasadil bcrypt. „Do roku 2012 byly údaje hashovány metodou MD5, která dnes již není považována za bezpečnou. Většina prolomených hesel pochází právě z doby, kdy byla používána tato metoda. U starších účtů jsme proto změnili heslo a automaticky je převedli na zmiňovanou nejnovější šifrovací metodu bcrypt, kterou aktuálně chráníme přístupové údaje všech účtů.“
Základem úspěšného podnikání je i připravenost na kybernetické hrozby
27.8.2017 SecurityWorld Bezpečnost
Někteří odborníci již označují rok 2017 za Rok ransomware, protože se četnost a především úspěšnost ransomware útoků neustále zvyšuje. V květnu napadl WannaCry více než 230 000 počítačů a hned následující měsíc se svět musel potýkat s dalším globálním útokem v podobě ransomware Petya. Mezi obětmi přitom nebyli jen běžní koncoví uživatelé – tyto hrozby byly „úspěšné“ i v případě některých opravdu velkých organizací, a světu tak ukázaly, jak může být ransomware sofistikovaný a vyspělý. Tyto pokročilé útoky navíc potvrdily ještě jednu důležitou skutečnost: i když jsou tradiční metody ochrany dat stále velmi důležité, samy o sobě již v boji s moderními hrozbami nestačí.
Technologie hrozeb i šíře jejich záběru se vyvíjí až děsivou rychlostí. Mnohé organizace však s tímto tempem nezvládají držet krok, a navíc nemají o ochraně dat a boji s kybernetickým zločinem všechny potřebné informace. I když management firem ví o důležitosti bezpečnostních strategií, je otázkou, jak rychle si podniky s případným incidentem ve skutečnosti poradí a jak rychle zvládnou vše vrátit do normálního stavu.
Stále více firemních dat i služeb je k dispozici on-line a podnikatelské modely se tak musí spoléhat na konektivitu a pokročilé IT služby. Kdyby tak firmy nefungovaly, nemohly by reagovat na poptávku zákazníků po vysoké flexibilitě, snadné dostupnosti a pohodlí. Jenže i zde platí, že každá mince má dvě strany. Právě potřeba neustálého připojení přináší bezpečnostní rizika a hrozby, které mohou mít původ mimo infrastrukturu dané organizace.
Tradiční strategie ochrany dat se soustřeďují na tři základní komponenty podnikové informační architektury – na uživatele, na procesy a na technologie.
V případě uživatelů stojí ochrana dat na dostatečné informovanosti a na seznamování zaměstnanců s nejnovějšími hrozbami. Ale i když je neustálé vzdělávání zásadním prvkem bezpečnostní koncepce, jen touto cestou úplnou ochranu celé organizace nikdo nezajistí. Kompromitaci dat může způsobit kliknutí i na jeden jediný špatný odkaz nebo jakákoli dosud neznámá hrozba. Důležité je proto zaměřit se také na procesy, jak uživatelé informační technologie ve skutečnosti využívají. Nedávné útoky potvrdily i nezbytnost pravidelných a včasných aktualizací, případné dopady jsou pak mnohem menší. Zapomenout nelze ani na tradiční metody ochrany sítí a koncových bodů pomocí firewallů a antivirových řešení. Všechny tyto technologie a opatření jsou pro kvalitní bezpečnost zásadní a neměly by být opomíjeny. Jelikož ani tato bezpečnostní strategie není zcela dostačující, roste zájem o pojištění proti kybernetickým rizikům, či chcete-li, proti kybernetickým hrozbám.
Pojištění proti kybernetickým rizikům není novinkou, ale – v souladu se všeobecným očekáváním – roste míra jeho využívání podobným tempem jako četnost výskytu malware nebo ransomware. V roce 2015 odhadla poradenská společnost PricewaterhouseCoopers hodnotu trhu s pojištěním proti kybernetickým rizikům na 2,5 miliardy amerických dolarů s předpokládaným nárůstem na 7,5 miliardy v roce 2020. A podle výzkumné organizace Allied Market Research by mělo do roku 2022 jít dokonce o 14 miliard při impozantním 28procentním ročním růstu. Nicméně samotné tempo růstu není to nejdůležitější – podstatné je, že díky nepříznivému vývoji ve světě kybernetického zločinu (včetně dopadů na veřejnou správu) je tento typ pojištění stále více zajímavý pro management řady firem.
Na první pohled by se mohlo zdát, že náklady spojené s řešením ransomwarového incidentu jsou dané hlavně výší výkupného. Ve skutečnosti tomu tak ale není, protože samotné výkupné obvykle nepřekročí hranici jednoho tisíce dolarů. Závažnější jsou prokazatelné interní náklady, které souvisí s řešením bezpečnostních incidentů, forenzními analýzami, vyšším vytížením zákaznického centra, nutností naplnit zákonné povinnosti a v neposlední řadě i s udržením dobrých vztahů s veřejností. A stranou nemohou zůstat ani externí náklady a pojistné krytí, které jsou spojené s nedodržením závazku zajistit bezpečnou ochranu dat.
Odpovědné firmy mají pro boj s ransomware k dispozici ještě jednu základní zbraň, kterou mnozí bohužel ignorují, a tou je zálohování dat, v rámci nějž jsou vlastní zálohy izolované od provozní síťové infrastruktury. Zálohování nejdůležitějších dat na off-line úložiště doporučuje spolu s pravidelným prověřováním obnovy jako první krok v boji s ransomware dokonce i americká FBI (v příručce s názvem ‘Ransomware Prevention and Response for CEOs’). A k tomuto principu se jednoznačně hlásí i společnost Veeam, na jejíž produkty a služby se spoléhá přes čtvrt miliónů zákazníků. Zálohy a pravidelné prověřování obnovitelnosti jsou vlastně také určitým druhem pojištění proti kybernetickým rizikům a navíc takovým „pojištěním“, které nabízí nejhmatatelnější a prakticky okamžité řešení v případě problémů způsobených nejen ransomwarem.
Díky využití správných technologií a procesů lze v případě nejdůležitějších systémů významně minimalizovat cíl doby obnovy RTO. A nejde o jedinou výhodu – data lze využít i pro případné forenzní analýzy incidentu ve virtuálních laboratořích. Tento „druh“ pojištění tedy není pouze o faktickém zajištění dostupnosti, ale také o potvrzení, že je firma na kybernetické hrozby o něco lépe připravena.
Dalším, a opravdu citelným přínosem je, že využívání kvalitních řešení pro zajištění dostupnosti může vést i ke snížení pojistného, které organizace za pojištění proti kybernetickým rizikům platí. Výše pojistného se v závislosti na odvětví, obratu a velikosti firmy pohybuje od 1000 až po více než 100 000 dolarů a jedním z faktorů určujících konečnou částku jsou právě opatření, které firma v boji s počítačovým zločinem využívá. Je to podobné jako v případě pojištění automobilu nebo domu, jen místo kvalitního zámku jde o komplexní řešení dostupnosti.
S ohledem na rostoucí příležitosti sofistikovanějšího využití dat, technologií pro internet věcí, umělé inteligence, biometrických systémů, výrobních robotů z oblasti Průmyslu 4.0, propojených automobilů nebo třeba chytrých staveb musí mít firmy povědomí o tom, jak se budou kybernetické hrozby včetně ransomware v blízké budoucnosti vyvíjet. A že se budou dopady těchto hrozeb stále více přesouvat z roviny osobních počítačů do všech podnikových procesů.
Cílem posuzování aktuálního stavu ochrany dat by nemělo být ujištění o stoprocentní bezpečnosti. Ostatně, vhledem k rychlosti, jakou se útoky mění, je to takřka nemožné. Mnohem důležitější je zaměřit se na zlepšení ochrany a ověření, že zálohy jsou umístěné i někde jinde než v interní síťové infrastruktuře a jsou tudíž před případným útokem nebo poškozením v relativním bezpečí. Pokud jde o ransomware, je běžnou technikou počítačových zločinců zaměřit se při pokusech o napadení větších podniků nejprve na malé a středně velké firmy. Posouzení stavu by proto mělo zohlednit i partnery a zajistit, aby zrovna vaše organizace byla silným článkem celého řetězce.
Mnoho technologických profesionálů si myslí, že výskyt malware a ransomware klesat nebude. Doporučením a správnou cestou tak je hledat partnera, který by organizaci pomohl se zavedením moderních opatření pro ochranu dat. Tedy takových opatření, která by pro ukládání záloh využívala i off-line úložiště a zajišťovala pravidelné ověřování obnovitelnosti důležité pro řešení případného incidentu. Tento způsob ochrany je důležitý nejen z pohledu uklidnění managementu, ale podílí se i na jistotě partnerů a koncových uživatelů, že jejich digitální životy jsou dostatečně chráněné a budou vždy dostupné.
Kombinovaná ochrana zvyšuje jistotu fungování podnikových procesů a díky pravidelným aktualizacím i zálohování a bezpečnostním politikám pro ochranu dat – včetně pojištění proti kybernetickým rizikům a využívání řešení pro zajištění dostupnosti – snižuje atraktivitu pro počítačové zločince. A na to by firmy neměly zapomínat.
Spam and phishing in Q2 2017
26.8.2017 Kaspersky Spam Analysis
Spam: quarterly highlights
Delivery service Trojans
At the start of Q2 2017, we registered a wave of malicious mailings imitating notifications from well-known delivery services. Trojan downloaders were sent out in ZIP archives, and after being launched they downloaded other malware – Backdoor.Win32.Androm and Trojan.Win32.Kovter. The usual trick of presenting dangerous content as important delivery information was employed by the fraudsters to make recipients open the attachment. The malicious mailings targeted people from different countries and came in a variety of languages.
These fake notifications from delivery services also included malicious links to infect the victim’s computer and steal personal information. The fraudulent link was tied to the tracking number of a non-existent shipment and used the following format:
Http: // domain / name of delivery service __com__WebTracking__tracknum__4MH38630431475701
The domain and the sequence of letters and numbers at the end of the link varied within the same mass mailing.
After a user clicked on the link, the Js.Downloader family Trojan was downloaded, which in turn downloaded the banking Trojan Emotet. This malware was first detected in June 2014, and is still used to steal personal financial information, logins and passwords from other services, as well as to send spam, etc.
WannaCry in spam
In May 2017, hundreds of thousands of computers worldwide were infected by the WannaCry ransomware. While the majority of similar ransomware samples require some sort of user input before a computer is infected, WannaCry could do so without any user actions. It attacks the target using a Windows exploit and then infects all computers within the local network. Like other ransomware of this type, WannaCry encrypts files on the victim’s computer and demands a ransom for decryption. In these attacks, files are encrypted with the extension .wcry and become unreadable.
The media frenzy surrounding the WannaCry ransomware played into spammers’ hands, as all high-profile events usually do. For example, they distributed numerous offers of services to counter the new malware, to prevent infection, training for users, etc. Scammers who earn money via fraudulent mailings also took advantage.
They sent out fake notifications on behalf of well-known software vendors informing recipients that their computers had been infected with ransomware and had to be updated. The link to the supposed update, of course, led to a phishing page. We came across emails that showed the attackers hadn’t taken much care when compiling their mailings, obviously hoping their victims would be in too much of a panic to notice some obvious mistakes (sender’s address, URLs, etc.).
Malware in password-protected archives and the corporate sector
In the second quarter of 2017, we came across new mailings containing malicious attachments in a password-protected archive. They were obviously targeting the corporate sector.
As a rule, the distribution of password-protected archives serves two purposes. First, it is a form of social engineering, with the attackers emphasizing that all confidential data (such as business accounts) is additionally protected by a password. Second, until the files are extracted from the archive, they cannot be fully checked by antivirus software.
These archives contained a malicious program belonging to the Pony/FareIT family. This malware is designed to steal logins and passwords to web services stored in browsers, the URLs on which they were entered, authentication data to FTP servers, file managers, mail clients, synchronization applications, as well as crypto-currency wallets.
This archive contains a malicious program called Trojan-Downloader.MSWord.Agent.bkt, which is a password-protected Microsoft Word file. The document contains a malicious script that downloads other malicious software designed to steal bank data to the user’s computer.
It is worth noting that the tendency to mask malicious mailings as business correspondence has increased. Spammers are now not only copying the style of business emails – they often use the actual details of real companies, copy auto-signatures and logos, and even the subject of the messages can correspond to the company profile. Judging by the domain addresses in the ‘To’ field and by the content of the emails, these mailings also target the B2B sector.
This archive contained a malicious program belonging to the Loki Bot family designed to steal passwords from FTP, mail clients and passwords stored in browsers, as well as crypto-currency wallets.
This archive contains the Exploit.Win32.BypassUAC.bwc malicious program, designed to steal passwords for network resources and email clients. To elevate privilege, the malware uses an exploit that bypasses the protection of the Microsoft Windows UAC component. During the operation it uses legitimate utilities to restore passwords.
This archive contains an XLS-file with a macro that was used to download HawkEye Keylogger to the victim’s computer. This malicious program written in .NET intercepts keystrokes and collects information about the system where it operates: internal and external IP addresses, the OS version as well as the name of the security product and the firewall.
This archive contains two malicious files: EXE, disguised as PDF (detected as Trojan.Win32.VBKrypt.xdps) and an MSWord document with an exploit that uses the CVE-2017-0199 vulnerability. Both malicious programs download a modification of Zeus to the victim’s computer.
Such targeted attacks can have different aims. In the case of ransomware, it is obvious that a company’s intellectual property can be viewed as being much more valuable than the information on a private computer, so a potential victim is more likely to pay the necessary bitcoins to get it back. In the case of spyware designed to steal financial information, fraudsters can potentially hit the jackpot once they get access to a company’s accounts.
Spyware in the B2B sector can also be used in more sophisticated schemes of financial fraud, including MITM attacks during financial transactions. One such scheme disclosed by our colleagues is described here.
Interestingly, although the payload downloaded on the victim’s computer is very different, its main function is the theft of authentication data, which means that most attacks on the corporate sector have financial goals.
We shouldn’t forget about the potentially dangerous situation where an attacker gains access to a corporate network and gets control of industrial equipment.
Overall in the second quarter of 2017, the percentage of spam in email traffic grew slightly from the previous quarter. The number of email antivirus detections increased by 17% in Q2 vs. Q1.
The number of email antivirus detections on the computers of Kaspersky Lab users, Q1 and Q2 2017.
Necurs botnet continues to distribute spam
The Necurs botnet continues to distribute spam, although the volumes are much smaller than in 2016. This botnet operation is characterized by alternating periods of low and high activity, when we register up to 2 million emails a day sent to Kaspersky Lab customers. In addition to malicious mailings from the botnet, Necurs actively spreads pump-and-dump as well as dating spam:
Malicious emails from the Necurs botnet are usually concise, contain files with DOC, PDF or other extensions. Sometimes, instead of attachments, emails include links to cloud storages such as Dropbox from where malicious files are downloaded.
Spam via legal services
Last quarter we wrote that in order to bypass filters, spammers often spread advertising and fraudulent offers via legitimate means. They include, for example, the ‘Invite friends’ field on social networking sites, notifications about comments that are usually sent to the recipient’s email address, or any other method available on the various sites that allow the sending of emails to a user’s list of trusted addresses. In addition, this type of spam is more difficult to detect because the source is legitimate. Spammers also like it because this type of resource makes for easy targeting. For example, they exploit job search sites to publicize easy earnings or for financial fraud:
Domain fraud
Last quarter we discovered several different mass mailings related to the domain fraud.
One of the mailings was sent in the name of a major company involved in the registration of domain names and addressed the administrators of registered domains. They were informed that it was necessary to activate a domain to confirm their administrator status and ability to manage the domain. These measures were allegedly taken in accordance with the amendments made to regulations by ICANN (Internet Corporation for Assigned Names and Numbers).
To do this, the administrator was told they had a limited time to create a PHP file with specific content in the root directory of the site. The email also stated that failure to observe these conditions would mean the confirmation procedure had not been completed and support for the domain would be suspended.
If the script is launched on the victim’s site, the attackers would be able to gain control of the site and to run any code. In addition, the script makes it possible to collect all user data entered on the site where it is registered and run. The fact that many of these fake emails were sent to addresses belonging to banks, means we can assume that the scammers wanted to collect data entered on the website of those banks, including the logins and passwords used for Internet banking.
Administrators also found themselves the target of yet another type of domain fraud. It involved the administrator of an organization receiving an email prompting them to register their domain with search engines to help potential customers find the company on the Internet. These messages came from addresses generated on free hosting.
This service was provided on a fee basis. In order to see the list of tariffs, the recipient was asked to click a link in the email that was “hosted” on a legitimate website. After choosing a tariff, the user had to fill in and send a form that asked for detailed personal information, including credit card information.
Statistics
Proportion of spam in email traffic
Percentage of spam in global email traffic, Q1 2017 and Q2 2017
In Q2 2017, the largest percentage of spam – 57.99% – was registered in April. The average share of spam in global email traffic for the second quarter amounted to 56.97%, which was 1.07 p.p. more than in the previous quarter.
Sources of spam by country
Sources of spam by country, Q2 2017
The second quarter of 2017 saw a change in the top three sources of spam. Vietnam came first, accounting for 12.37% of world spam. It was followed by the previous quarter’s leader the US, whose share dropped by 8.65 p.p. and accounted for 10.1%. China (8.96%, +1.19 p.p.) completed the top three.
India was the fourth biggest source, responsible for 8.77% (+3.61 p.p.) of total spam, followed by Germany (5.06%, -0.31 p.p.).
Russia, in sixth place, accounted for 4.99%, which is only 0.06 p.p. less than in the previous quarter.
The top 10 biggest sources also included Brazil (4.47%), France (4.35%), Iran (2.49%), and the Netherlands with a share of 1.96%.
Spam email size
Breakdown of spam emails by size, Q1 2017 and Q2 2017
In Q2 2017, the share of small emails (up to 2 KB) in spam traffic changed only slightly and averaged 37.41%, which is 1.9 p.p. more than in the first quarter. The proportion of emails sized 2–5 KB remained at the same level: 4.54%; and those of 5–10 KB (7.83%) declined by 1.36 p.p. and accounted for 5.94%.
The proportion of emails sized 10-20 KB reached 18.31% and emails of 20-50 KB — 27.16%. The proportion of more emails sized 100 KB+ was slightly more than 2%.
Malicious attachments in email
Top 10 malware families
TOP 10 malware families in Q2 2017
Trojan-Downloader.JS.SLoad (8.73%) topped the rating of the most popular malware families. Trojan-Downloader.JS.Agent (3.31%) came second, while Trojan-PSW.Win32.Fareit (3.29%) rounded off the top three.
Trojan-Downloader.JS.Agent (3.05%) came fourth followed by Worm.Win32.WBVB (2.59%).
Newcomers to the top 10, Backdoor.Java.QRat (1.91%) and Trojan.PDF.Phish (1.66%), occupied seventh and ninth places respectively.
The Backdoor.Java.QRat family is a cross-platform multifunctional backdoor written in Java and sold on DarkNet as malware-as-a-service (MaaS). It is typically distributed via email as a JAR attachment.
Trojan.PDF.Phish is a PDF document containing a link to a phishing site where users are prompted to enter their login and password for a specific service.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, Q2 2017
Germany (12.71%) was the country targeted most by malicious mailshots in Q2 2017. China, last quarter’s leader, came second (12.09%), followed by the UK (9.11%).
Japan (5.87%) was fourth, with Russia occupying fifth with a share of 5.67%. Next came Brazil (4.99%), Italy (3.96%), Vietnam (3.06%) and France (2.81%).
The US (2.31%) completed the top 10.
Phishing
In the second quarter of 2017, the Anti-Phishing system prevented 46,557,343 attempted visits to phishing pages on the computers of Kaspersky Lab users. Overall, 8.26% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q2 2017.
Geography of attacks
In Q2 2017, Brazil (18.09%) was the country where the largest percentage of users was affected by phishing attacks, although its share decreased by 1.07 p.p. compared to the previous quarter.
Geography of phishing attacks*, Q2 2017
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in that country
The percentage of users attacked in China decreased by 7.24 p.p. and amounted to 12.85%, placing the country second in this ranking. Australia added 1.96 p.p. to the previous quarter’s figure and came third with 12.69%. The percentage of attacked users in New Zealand increased to 12.06% (+ 0.12p.p.), with Azerbaijan (11.48%) in fifth. The Republic of South Africa (9.38%), Argentina (9.35%) and the UK (9.29%) rounded off this top 10.
In the second quarter, Russia (8.74%) exited this top 10 of countries with the largest percentage of users affected by phishing attacks, falling to 18th place.
Brazil 18.09%
China 12.85%
Australia 12.69%
New Zealand 12.06%
Azerbaijan 11.48%
Canada 11.28%
Qatar 10. 68%
Venezuela 10.56%
South Africa 9.38%
Argentina 9.35%
UK 9.29%
TOP 10 countries by percentage of users attacked
Organizations under attack
Rating the categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
In Q2 2017, the Banks (23.49%, -2.33 p.p.), Payment systems (18.40%, +4.8 p.p.) and Online stores (9.58%, -1.31 p.p.) categories accounted for more than half (51.47%) of all registered attacks.
Distribution of organizations affected by phishing attacks by category, Q2 2017
Hot topics this quarter
Airline tickets
In the second quarter of 2017, Facebook was hit with a wave of posts that falsely claimed that major airlines were giving away tickets for free. Naturally, there were no promotions giving away airline tickets: fraudsters had created a number of sites on which users were congratulated on winning an air ticket and were asked to perform a series of actions to receive their prize. First, the victims were asked to post the promotional information on their Facebook page. Secondly, the victims had to click the “Like” button. After performing all the necessary actions, the website redirected the user to a resource promoted by the fraudsters. The content of these pages varied – from harmless ads to malicious software.
False browser blocking
Almost all the popular browsers have built-in protection against web threats. When entering a malicious or phishing page, they often warn the user of the potential dangers and recommend not visiting it.
Fraudsters also make use this protection measure for their own purposes and distract the victim with warnings. For example, they simulate the Chrome blocking page. A user who has ever seen this warning from the browser is more likely to trust the page and follow the criminals’ prompts.
The main danger of these pages is that careful examination of the address bar doesn’t help – a browser warning usually “pops up” on untrusted web resources.
However, they may also appear when trying to enter a domain belonging to companies that act as a hosting service. And it is precisely such warnings that cause the victims to have greater trust in them:
As a rule, when a user calls the numbers specified, the fraudsters pretend to be a support service, tricking victims into paying for services they allegedly need.
Punycode encoding
Close examination of the address bar may not help if the phishers use non-Latin characters that are similar to Latin letters to create domain names that are almost identical to the names of popular web resources. Web browsers use Punycode to represent Unicode characters in a URL. However, if all the characters in the domain name belong to the character set of one language, the browser will display them in the language specified rather than in Punycode.
The screenshot of the phishing page below demonstrates this technique.
Sometimes on closer examination, you can see inconsistencies, for example, like the dot under the letter ‘e’.
Have a look at the banner of the blocking site: it displays a URL in Punycode. However, it differs from what we see in the browser. This address is definitely not a domain owned by a well-known company.
Technically, the address is completely different from the original one. Moreover, phishers have used different encodings in the names of pages before. However, for ordinary users, recognizing this type of phishing can be a problem.
Attacks on Uber users
One of Q2’s high-profile news stories was an attack on Uber users. Phishing pages were distributed via spam mailings; recipients were offered a large discount if they completed a “registration” form, where in addition to personal data they had to enter their bank card information. After completing the questionnaire, the user was redirected to the legitimate site of the company.
Because Uber often holds promotions and offers discounts, users are less inclined to doubt the authenticity of the offer.
TOP 3 attacked organizations
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections of Kaspersky Lab’s heuristic anti-phishing component are for phishing pages hiding behind the names of fewer than 15 companies.
Organization % of detected phishing links
Facebook 8.33
Microsoft Corporation 8.22
Yahoo! 8.01
For the third quarter in a row the top three organizations attacked most often by phishers remained unchanged. In Q1, Yahoo! was the organization whose brand was mentioned most often on phishing pages. However, in the second quarter it dropped to third, giving way to Facebook (8.33%) and Microsoft (8.22%).
One of the phishers’ tricks is to place pages of popular organizations on domains belonging to other popular organizations. In the example below, a link to a free hosting service is shown, and while not all users will know what this is, mentioning Google is more likely to make them think it’s genuine.
The actual data form is usually located on another domain, where a user ends up after clicking on the button.
Conclusion
In Q2 2017, the average share of spam in global email traffic amounted to 56.97%, which was only 1.07 p.p. more than in the previous quarter. One of the most notable events of this quarter – the WannaCry epidemic – did not go unnoticed by spammers: numerous mass mailings contained offers of assistance in combating the ransomware, as well as various workshops and training for users.
In the second quarter, the most popular malware family was the JS.SLoad (8.73%), with another downloader, MSWord.Agent, in second (3.31%). The Fareit Trojan family (3.29%) rounded off the top three.
The Anti-Phishing system prevented over 46.5 million attempted visits to phishing pages on the computers of Kaspersky Lab users. Overall, 8.26% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q2 2017. Noticeably, in their earlier attacks, fraudsters counted on user carelessness and low levels of Internet literacy. However, as users are becoming more cyber savvy, phishers have had to come up with new tricks, such as placing phishing pages on domains owned by well-known organizations.
New multi platform malware/adware spreading via Facebook Messenger
26.8.2017 Kaspersky Virus
One good thing about having a lot of Facebook friends is that you simply act as a honey pot when your friends click on malicious things. A few days ago I got a message on Facebook from a person I very rarely speak to, and I knew that something fishy was going on.
After just a few minutes analyzing the message, I understood that I was just peeking at the top of this iceberg. This malware was spreading via Facebook Messenger, serving multi platform malware/adware, using tons of domains to prevent tracking, and earning clicks. The code is advanced and obfuscated.
Here is a screenshot of the JavaScript, an potential injector. Filename is “injection.js” (ebc117c0cf03ad4b13184d1253862586)
The initial spreading mechanism seems to be Facebook Messenger, but how it actually spreads via Messenger is still unknown. It may be from stolen credentials, hijacked browsers or clickjacking. At the moment we are not sure because this research is still ongoing.
The message uses traditional social engineering to trick the user into clicking the link. The message reads “David Video” and then a bit.ly link.
The link points to a Google doc. The document has already taken a picture from the victim’s Facebook page and created a dynamic landing page which looks like a playable movie.
When the victim clicks on the fake playable movie, the malware redirects them to a set of websites which enumerate their browser, operating system and other vital information. Depending on their operating system they are directed to other websites.
This technique is not new and has a lot of names. I would like to describe it as a domain chain, basically just A LOT of websites on different domains redirecting the user depending on some characteristics. It might be your language, geo location, browser information, operating system, installed plugins and cookies.
By doing this, it basically moves your browser through a set of websites and, using tracking cookies, monitors your activity, displays certain ads for you and even, in some cases, social engineers you to click on links.
We all know that clicking on unknown links is not something that’s recommended, but through this technique they can basically force you to do so.
What I noticed during my research was that when changing the User-Agent header (browser information) the malware redirects you to different landing pages. For example, when using FIREFOX I was redirected to a website displaying a fake Flash Update notice, and then offered a Windows executable. The executable is flagged as adware.
When using the Google Chrome browser I was redirected to a website which mimics the layout of YouTube, even including the YouTube logo. The website then displays a fake error message tricking the user to download a malicious Google Chrome extension from the Google Web Store.
The Chrome Extension is a Downloader, which means that it downloads a file to your computer. At the time of writing, the file which should have been downloaded was not available.
One interesting finding is that the Chrome Extension has log files from the developers displaying usernames. It is unclear if this is related to the campaign, but it is still an amusing piece of information.
When using the OSX Safari browser I ended up on a similar website to the one I was directed to when using Firefox, but it was customized for OSX users. It was a fake update for Flash Media Player, and when I clicked the link an OSX executable .dmg file was downloaded. This file was also adware.
It has been a while since I saw these adware campaigns using Facebook, and its pretty unique that it also uses Google Docs, with customized landing pages. As far as I can see no actual malware (Trojans, exploits) are being downloaded but the people behind this are most likely making a lot of money in ads and getting access to a lot of Facebook accounts.
Please make sure that you don’t click on these links, and please update your antivirus!
WAP-billing Trojan-Clickers on rise
26.8.2017 Kaspersky Virus
During the preparation of the “IT threat evolution Q2 2017” report I found several common Trojans in the “Top 20 mobile malware programs” list that were stealing money from users using WAP-billing – a form of mobile payment that charges costs directly to the user’s mobile phone bill so they don’t need to register a card or set up a user-name and password. This mechanism is similar to premium rate SMS messages but Trojans do not need to send any SMS in this case – they just need to click on a button on a web-page with WAP-billing.
From user’s perspective a page with WAP-billing looks like regular web-page. Usually such pages contain complete information about payments and a button. By clicking on this button user will be redirected to a mobile network operator server, which may show additional information and request user’s final decision about payment by clicking on another button. If the user connects to the Internet through mobile data, the mobile network operator can identify him/her by IP address. Mobile network operators charges users only if they are successfully identified and only after click on the button.
From a financial point of view, this mechanism is similar to the Premium rate SMS service – charge is directly applied to users’ phone bills. However, in this case Trojans do not need to send any SMS – just to click on button on a web-page with WAP-billing.
We hadn’t seen any Trojans like this in a while, but several of them appeared out of nowhere. Different Trojans from different cybercriminal groups targeting different countries (Russia and India) became common at the same time. Most of them had been under development since the end of 2016 / the beginning of 2017, but their prevalence increased only in the second half of Q2 2017. Therefore, I decided to take a closer look at these Trojans.
In general, these Trojans are doing similar things. First, they turn off WiFi and turn on mobile Internet. They do this because WAP-billing works only through mobile Internet. Then they open a URL which redirects to the page with WAP-billing. Usually, Trojans load such pages and click on buttons using JavaScript (JS) files. After that they need to delete incoming SMS messages containing information about subscriptions from the mobile network operator.
Furthermore, some of them have the ability to send premium rate SMS messages. In addition, some are exploiting Device Administrator rights to make it harder to delete the Trojan.
Trojan-Clicker.AndroidOS.Ubsod
I started with Trojans that are detected as Trojan.AndroidOS.Boogr.gsh. These files are recognized as malicious by our system, based on machine learning algorithms. The most popular files detected in Q2 2017 by ML detection were Trojans abusing WAP-billing services. After analyzing them, I found that they belong to the Trojan-Clicker.AndroidOS.Ubsod malware family.
Part of Trojan-Clicker.AndroidOS.Ubsod code where Trojan opens URLs.
It is a small and simple Trojan that receives some URLs from its command and control server (CnC) and opens them. These URLs could just be AD URLs where the Trojan pretends that it is a type of advertising software by using class names like “ViewAdsActivity”. But, it can delete all incoming SMS messages that contain the text “ubscri” (part of “Subscription”) or “одпи” (part of “Подписка”, Subscription in Russian). Furthermore, it can turn off WiFi and turn on mobile data. Trojans need this because WAP-billing only works when the page is visited through mobile internet, not through WiFi.
Part of Trojan code to delete AoC (advice of charge) messages.
After analyzing these Trojans, I found that some of them (MD5 A93D3C727B970082C682895FEA4DB77B) also contain a different functionality – to decrypt and load (execute) additional executable files. This functionality is detected as Trojan-Dropper.AndroidOS.Ubsod. These Trojans, in addition to stealing money through WAP-billing services, were also executing another Trojan, detected as Trojan-Banker.AndroidOS.Ubsod.
Part of Trojan-Banker.AndroidOS.Ubsod code with some constants
An interesting thing about Trojan-Banker.AndroidOS.Ubsod was that it was distributed not only in other Trojans, but also as a standalone Trojan (MD5 66FE79BEE25A92462A565FD7ED8A03B4). It is a powerful Trojan with lots of capabilities. It can download and install apps, overlay other apps with its windows (mostly to steal credentials or credit card details), show ads, send SMS messages, steal incoming messages and even execute commands in the device shell. Furthermore, it has features that steal money by abusing WAP-billing services, which mean that in some cases infected users had two Trojans attacking the same thing.
Some of Trojan-Banker.AndroidOS.Ubsod commands
According to KSN statistics it was the most popular of all such Trojans, with almost 8,000 infected users in July 2017 from 82 countries. 72% of attacked users were in Russia.
Xafekopy
Another malware family that has become popular during the last few months is Trojan-Clicker.AndroidOS.Xafekopy. This Trojan uses JS files to click on buttons on web-pages containing WAP billing to silently subscribe users to services. The most interesting thing is that these JS files look similar to Ztorg’s module JS files; they even have the same names for some functions. This Trojan was created by some Chinese-speaking developers (just like Ztorg) but mainly attacks Indian (37%) and Russian (32%) users.
Part of JS files used by Trojan-Clicker.AndroidOS.Xafekopy to click on buttons
This Trojan is distributed through ads masquerading as useful apps, mostly as battery optimizers. After installation, it acts like a useful app but with one difference – it loads a malicious library. This library decrypts and loads files from the assets folder of the installation package. These files decrypt and load another file from the assets folder which contains the main malicious functionality. It decrypts (yep, decryption again) JS files. Using these JS files it can bypass captcha forms and click on web-pages with WAP billing. By doing so it steals money from a user’s mobile accounts. It can also click on some ad pages to make money from ads.
While users see a “Battery Master” interface the Trojan is trying to steal money
The files with the main functionality (which was decrypted) contain URLs with WAP-billings. I was able to find only two different versions of this file – one version contains Indian links, another – Russian links.
It also can send SMS messages (most likely premium rate SMS). It steals incoming SMS messages and deletes some (most likely AoC messages).
According to KSN statistics, almost 40% of attacked users were in India, but in total we saw it attacking more than 5,000 users from 48 different countries in July 2017.
Autosus
The main purpose of Trojan-Clicker.AndroidOS.Autosus.a is to steal a user’s money by clickjacking pages with WAP-billing. To do so, the Trojan receives the JS file and URL to click on. It also can hide from user’s incoming SMS using rules received from the CnC.
Part of Trojan-Clicker.AndroidOS.Autosus.a code
After starting, the Trojan will ask the user to activate device administrator rights for this Trojan. After that, the Trojan will delete its icon from the app list so users won’t be able to easily find it. Meanwhile the Trojan will continue working in the background, receiving its CnC commands to open URLs and click on buttons.
Part of Trojan-Clicker.AndroidOS.Autosus.a code to work with data from CnC
This Trojan attacked more than 1,400 users in July 2017, most of them were from India (38%), South Africa (31%) and Egypt (15%).
Podec
When talking about clickjacking WAP-billing services, we should mention Trojan-SMS.AndroidOS.Podec.a. This Trojan – initially found in 2014 – was a regular Trojan-SMS until 2015, when cybercriminals switched to attacking WAP-billing services. This Trojan has lots of functionality but its main task is to steal money by subscribing users to WAP services. It was the first mobile Trojan that was able to bypass captcha. Over the next few years it became of the most popular mobile Trojans. It’s last appearance in the top 20 most popular mobile Trojans was in Q2 2016.
Podec is still actively distributing, mainly in Russia. It was the third most common Trojan in June 2017, among other Trojans abusing WAP-billings.
Conclusion
During last few months, we have detected a growth of Trojans attacking WAP-billing services in different countries. Although Trojans with such functionality have been infecting users for years, we see, that there are several new Trojans, and the number of infected users has been significantly increased in recent months. Furthermore, previously WAP-billing services were under attack mostly in Russia, but now we have detected such attacks in different countries, including India and South Africa.
Even some Trojans which traditionally specialized in other attacks, started stealing users’ money by clickjacking WAP-billing services.
We weren’t able to find a reason why so many cybercriminals decided to switch or to start attacking WAP-billing services at the same time. WAP-billing services are not a new thing – in some countries they’ve been existed for several last years.
MD5
F3D2FEBBF356E968C7310EC182EE9CE0
9E492A6FB926E1338DADC32463196288
A93D3C727B970082C682895FEA4DB77B
66FE79BEE25A92462A565FD7ED8A03B4
AEAE6BFDD18712637852C6D824955859
DA07419994E65538659CD32BF9D18D8A
Cisco IOS vulnerabilities open Rockwell Industrial Switches to attacks
26.8.2017 securityaffairs Vulnerebility
Vulnerabilities in Cisco IOS expose Rockwell Allen-Bradley Stratix and ArmorStratix industrial Ethernet switches to remote attacks.
Some models of the Allen-Bradley Stratix and ArmorStratix industrial Ethernet switches are exposed to remote attacks due to security flaws in Cisco’s IOS software.
According to the security alert issued by ICS-CERT, an authenticated remote attacker can exploit the flaws to execute code on an affected system or to trigger a DoS condition and consequent reload of the device.
“Successful exploitation of these vulnerabilities could allow an authenticated, remote attacker to execute code on an affected system or cause an affected system to crash and reload.” states the ICS-CERT.
Critical Infrastructure of any sectors worldwide is impacted, including Critical Manufacturing, Energy, and Water and Wastewater Systems.
Critical infrastructure relies on Cisco’s IOS software for secure integration with enterprise networks, this implies that Cisco IOS flaws can also affect Rockwell Automation products.
Rockwell Automation promptly informed customers of the high severity vulnerabilities in Cisco IOS and IOS XE. Nine flaws affect the versions 1, 2c and 3 of Simple Network Management Protocol (SNMP) subsystem.
The tech giant publicly disclosed the vulnerability on June 29 and provided workarounds, not it is notifying customers about the availability of security patches.
The nine issues, that have been tracked with codes from CVE-2017-6736 to CVE-2017-6744, were all patched by the company. All the flaws could be exploited by a remote unauthenticated attacker by sending specially crafted SNMP packets, resulting in arbitrary code execution or causing the system to reload.
“The Simple Network Management Protocol (SNMP) subsystem of Cisco IOS and IOS XE Software contains multiple vulnerabilities that could allow an authenticated, remote attacker to remotely execute code on an affected system or cause an affected system to reload. An attacker could exploit these vulnerabilities by sending a crafted SNMP packet to an affected system via IPv4 or IPv6. Only traffic directed to an affected system can be used to exploit these vulnerabilities.” states the advisory published by CISCO in June.
As reported by the advisory, an authenticated attacker who knows the SNMP read-only community string of a target system could remotely execute code or cause the device to reload by sending a specially crafted SNMP packet via IPv4 or IPv6.
CISCO ios
The attack is very dangerous because hackers could obtain full control of vulnerable devices and the worst news is that CISCO warned customers that attackers in the wild know about the vulnerabilities and can exploit them in any moment.
“A successful exploit could allow the attacker to execute arbitrary code and obtain full control of the affected system or cause the affected system to reload,” Cisco said in its advisory.
The security holes can be exploited by sending a specially crafted SNMP packet via IPv4 or IPv6.
“To exploit these vulnerabilities via SNMP Version 2c or earlier, the attacker must know the SNMP read-only community string for the affected system. To exploit these vulnerabilities via SNMP Version 3, the attacker must have user credentials for the affected system,” Cisco said in its advisory.
Cisco found no evidence of cyber attack leveraging the flaws, but it confirmed people outside the company also was aware of their existence.
The flaws affect Allen-Bradley Stratix 5400, 5410, 5700 and 8000 models running version 15.2(5)EA.fc4 and earlier of the firmware, Stratix 5900 version 15.6(3)M1 and earlier, Stratix 8300 version 15.2(4)EA and earlier, and ArmorStratix 5700 version 15.2(5)EA.fc4 and earlier.
The vulnerabilities have been fixed in version 15.2(4a)EA5 for Stratix 8300 devices.
Waiting for security updates, Rockwell urges customers to disable specific management information bases (MIBs), use strong SNMP credentials, prevent unauthorized SNMP requests with firewall and other security appliances.
Rockwell customers can use Snort rules provided by Cisco to detect exploits.
PoS Flaws Allow Hackers to Steal Card Data, Change Prices
25.8.2017 securityweek Vulnerebility
Point-of-sale (PoS) systems developed by SAP and other vendors have serious vulnerabilities that can be exploited by hackers to steal payment card data from the targeted organization’s network and change the price of items they want to purchase.
Researchers at ERPScan discovered that SAP’s POS product, which is part of the company’s SAP for Retail offering, was affected by several flaws. Specifically, the system’s server component, Xpress Server, lacked important authorization checks for critical functionality.
This allows an attacker with access to the system to send malicious configuration files to Xpress Server and gain complete control of both the frontend and backend of the PoS system.
A hacker can abuse tens of commands, allowing them to steal data from all the credit and debit cards used at the targeted store, and apply special prices and discounts to specified items. These discounts can be applied for specified times so that an item has a small price only when fraudsters go to purchase it. Fraudsters can also set up the system so that their purchases are charged to the previous customer’s card.
An attacker can also change the data displayed on a receipt, including to display the customer’s full payment card number, not just the last 4 digits as required.
An attack requires access to the targeted network. However, experts pointed out that some systems are exposed to the Internet so remote attacks may be possible. If the PoS system is not connected to the Web, an attacker could plant the malware using a Raspberry Pi device that is connected to the targeted store’s network. ERPScan noted that the internal network can often be accessed from the electronic scales available in stores.
A video published by ERPScan shows a SAP POS attack scenario involving these vulnerabilities:
Some technical details were disclosed by ERPScan researchers in a presentation at the Hack in the Box (HITB) security conference taking place this week in Singapore.
SAP, whose retail solutions are used by 80 percent of the Forbes Global 2000 retailers, was informed about the vulnerabilities in April and released a patch in July as part of its regular security updates. However, the company released another update on August 18 after researchers discovered that the initial fix could be bypassed via a new flaw. The weaknesses were addressed with the release of the 2476601 and 2520064 security notes.
“SAP Product Security Response Team collaborates frequently with research companies like ERPScan to ensure a responsible disclosure of vulnerabilities. All vulnerabilities in question in SAP Point of Sale (POS) Retail Xpress Server have been fixed, and security patches are available for download on the SAP Support Portal. We strongly advise our customers to secure their SAP landscape by applying the available security patches from the SAP Support Portal immediately,” SAP said in a statement to SecurityWeek.
ERPScan researchers pointed out that these types of vulnerabilities are not specific to SAP products. They have also found similar flaws in Oracle’s MICROS system.
“Many POS systems have similar architecture and thus same vulnerabilities,” said ERPScan’s Dmitry Chastuhin, one of the researchers who found the vulnerabilities. “POS terminals used to be plagued with vulnerabilities as myriads of them were found and, unfortunately, exploited, so their security posture has improved significantly. On the other hand, banks must adhere to different compliance standards. So, the connections between POS workstation and the store server turn out to be the weakest link. They lack the basics of cybersecurity - authorization procedures and encryption, and nobody cares about it. So, once an attacker is in the Network, he or she gains full control of the system.”
Cisco IOS Flaws Expose Rockwell Industrial Switches to Remote Attacks
25.8.2017 securityweek Vulnerebility
Rockwell Automation has informed customers that some of its Allen-Bradley Stratix and ArmorStratix industrial ethernet switches are exposed to remote attacks due to vulnerabilities in Cisco’s IOS software.
The Allen-Bradley Stratix and ArmorStratix switches, which ICS-CERT says are used worldwide in the critical manufacturing, energy and water sectors, rely on Cisco’s IOS software for secure integration with enterprise networks. That means Cisco IOS flaws can also affect Rockwell Automation products.
In this case, Rockwell Automation alerted customers of nine high severity Cisco IOS and IOS XE vulnerabilities affecting the software’s Simple Network Management Protocol (SNMP) subsystem.
The flaws, disclosed by Cisco in late June, affect versions 1, 2c and 3 of SNMP, and they allow an authenticated attacker to remotely execute code and take control of the affected system or cause the device to reload. The security holes can be exploited by sending a specially crafted SNMP packet via IPv4 or IPv6.
“To exploit these vulnerabilities via SNMP Version 2c or earlier, the attacker must know the SNMP read-only community string for the affected system. To exploit these vulnerabilities via SNMP Version 3, the attacker must have user credentials for the affected system,” Cisco said in its advisory.
Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Cisco, which discovered the vulnerabilities during internal testing, found no evidence of exploitation for malicious purposes, but the networking giant said people outside the company also knew about their existence.
In the case of Allen-Bradley switches, the flaws affect Stratix 5400, 5410, 5700 and 8000 devices running version 15.2(5)EA.fc4 and earlier of the firmware, Stratix 5900 version 15.6(3)M1 and earlier, Stratix 8300 version 15.2(4)EA and earlier, and ArmorStratix 5700 version 15.2(5)EA.fc4 and earlier.
The vulnerabilities have been addressed in Stratix 8300 devices with the release of version 15.2(4a)EA5. Until patches are released for the other affected products, Rockwell has advised customers to disable specific management information bases (MIBs), use strong SNMP credentials since an attacker needs to be authenticated, use firewalls and other systems to prevent unauthorized SNMP requests, and use the Snort rules provided by Cisco to detect exploits.
Chinese National Charged With U.S. Hacking
25.8.2017 securityweek CyberSpy
The FBI has charged a Chinese national with using malicious software widely linked to a devastating hack of government databases that saw the personal information of millions of federal workers and contractors stolen.
Yu Pingan, a 36-year-old from Shanghai who uses the alias "GoldSun," was arrested earlier this week after he flew into Los Angeles airport for a conference, according to CNN.
Court papers do not specifically mention the 2015 hacking of the Office of Personnel Management (OPM) that affected 20 million personnel records including sensitive personal data in some cases gathered from background checks.
But an investigator accused Yu of distributing the "rarely-used Sakula malware" against several US companies between 2012 and 2014 -- the same software that numerous internet security blogs, citing an FBI advisory made available to private firms, have linked to the subsequent OPM breach.
Then national intelligence director James Clapper called Beijing "the leading suspect" in the cyber attack.
According to the investigator's affidavit, "seized communications show that Yu was warned that he could get in trouble for supplying malicious software and, in particular, that he could get in trouble with the FBI for his involvement in compromising US computer networks."
It was the second high-profile arrest of an alleged hacker in the United States this month after British computer security researcher Marcus Hutchins was held on charges of creating malware to attack banks.
Beware of Windows/MacOS/Linux Virus Spreading Through Facebook Messenger
25.8.2017 thehackernews Apple
If you came across any Facebook message with a video link sent by anyone, even your friend — just don’t click on it.
Security researchers at Kaspersky Lab have spotted an ongoing cross-platform campaign on Facebook Messenger, where users receive a video link that redirects them to a fake website, luring them to install malicious software.
facebook-virus-hacking-account-malware
Although it is still unclear how the malware spreads, researchers believe spammers are using compromised accounts, hijacked browsers, or clickjacking techniques to spread the malicious link.
The attackers make use of social engineering to trick users into clicking the video link, which purports to be from one of their Facebook friends, with the message that reads "< your friend name > Video" followed by a bit.ly link, as shown.
Here's How this Cross-Platform Malware Works:
The URL redirects victims to a Google doc that displays a dynamically generated video thumbnail, like a playable movie, based on the sender's images, which if clicked, further redirects users to another customised landing page depending upon their browser and operating system.
For example, Mozilla Firefox users on Windows are redirected to a website displaying a fake Flash Player Update notice, and then offered a Windows executable, which is flagged as adware software.
Google Chrome users are redirected to a website that masquerades as YouTube with similar YouTube logo, which displays a fake error message popup, tricking victims into downloading a malicious Chrome extension from the Google Web Store.
The extension actually is a downloader that downloads a file of attacker's choice to the victim's computer.
"At the time of writing, the file which should have been downloaded was not available," David Jacoby, a chief security researcher from Kaspersky Lab, writes in a blog post published today.
"One interesting finding is that the Chrome Extension has log files from the developers displaying usernames. It is unclear if this is related to the campaign, but it is still an amusing piece of information."
Users of Apple Mac OS X Safari ends up on a web page similar to when using Firefox, but it was customised for MacOS users with a fake update for Flash Media Player, which if clicked, downloads an OSX executable .dmg file, which is also adware.
Same in case of Linux, user redirects to another landing page designed for Linux users.
The attackers behind the campaign are not actually infecting users of all platform with any banking Trojan or exploit kits, but with adware to make a lot of money by generating revenue from ads.
Spam campaigns on Facebook are quite common. A few years ago, researchers found cyber criminals using boobytrapped .JPG image files to hide their malware in order to infect Facebook users with variants of the Locky ransomware, which encrypts all files on the infected PC until a ransom is paid.
To keep yourself safe, you are advised not to get curious to look at images or video links sent by anyone, even your friend, without verifying it with them, and always keep your antivirus software up-to-date.
Google Introduces App Engine Firewall
25.8.2017 securityweek Safety
Google on Thursday informed cloud platform customers that the beta release of its App Engine firewall is available for testing.
The Google App Engine firewall allows developers and administrators to easily allow or block traffic from specified IP addresses by defining a set of rules and ordering them based on priority.
Hosting an application in the cloud has many benefits, but unwanted traffic can have a negative impact on workloads and it can result in significant costs.
According to Google, the App Engine firewall addresses this problem by returning an HTTP 403 Forbidden response to requests from denied IP addresses before they hit the application.
“App Engine firewall replaces the need for a code-based solution within your app that still allows requests in, but which can cost you resources and still expose your app,” explained Lorne Kligerman, product manager at Google.
The App Engine firewall can be accessed from the Google Cloud Console or via the App Engine Admin API and the gcloud command-line tool. Users can specify which IPs they want to allow -- for example, allow only IPs from the organization’s private network, or only traffic coming through a third-party web application firewall (WAF) set up to proxy requests to the app.
They can also deny certain types of traffic, including denial-of-service (DoS) and other attacks. Users are also offered a “Test IP” feature that allows them to check if the rules they’ve configured work properly.
“With App Engine firewall, it’s easy to set up network access to your app and focus on what matters most: your app, without worrying about access control within your code,” Kligerman said.
Since the App Engine firewall is still in beta, Google advises against using it in production environments.
This is not the only security feature available for the Google App Engine. Google’s cloud platform also includes identity and access management (IAM), a security scanner for identifying vulnerabilities, and a DoS protection service.
WAP Billing Trojans Threaten Android Users
25.8.2017 securityweek Android
Several of the pieces of malware targeting Android devices in the second quarter of 2017 abused WAP billing to help cybercriminals make money, Kaspersky reported on Thursday.
Wireless Application Protocol (WAP) billing provides a mechanism for users to acquire content online and have it charged directly to their mobile phone bill so that they don’t have to provide any payment card information. The method is similar to premium SMS services, but it does not involve sending SMS messages and instead users have to click on a button displayed on a website to approve charges.
Android malware abusing WAP billing was spotted in the past years, including on Google Play, and it now appears to be making a comeback.
Several of the top 20 most common trojans detected by Kaspersky products in the second quarter abused WAP billing. While a majority of the infections were in Russia and India, victims were also seen in many other countries.
“We haven’t seen these types of Trojans for a while. The fact that they have become so popular lately might indicate that cybercriminals have started to use other verified techniques, such as WAP-billing, to exploit users,” said Roman Unuchek, security expert at Kaspersky Lab. “Moreover, a premium rate SMS Trojan is more difficult to create. It is also interesting that malware has targeted mainly Russia and India, which could be connected to the state of their internal, local telecoms markets.”
The list of trojans that abuse WAP billing include Trojan-Clicker.AndroidOS.Ubsod, which infected nearly 8,000 devices in Russia and 81 other countries; Xafekopy, which infected more than 5,000 users in India and 47 other countries; Autosus, which infected roughly 1,400 devices in India, South Africa and Egypt; and Podec, which had last been seen in the second quarter of 2016.
These pieces of malware have been used by several cybercrime groups, and while in some cases their development started in late 2016 or early 2017, their use increased significantly at the beginning of summer.
The samples analyzed by Kaspersky disable the infected device’s WiFi and enable the mobile data connection, which is needed due to the fact that WAP billing only works through mobile Internet as the carrier needs to be able to identify the user making the online purchase.
The trojans then use JavaScript code to automate certain actions, such as opening web pages and clicking on the buttons associated with WAP billing. By automating these tasks, no user interaction is required for the attack to work.
The malware also deletes incoming SMS messages to avoid raising suspicion. Some samples also abuse Device Administrator rights on the infected Android device to make their removal more difficult.
“We weren’t able to find a reason why so many cybercriminals decided to switch or to start attacking WAP-billing services at the same time,” Unuchek said. “WAP-billing services are not a new thing – in some countries they’ve existed for several years.”
PoC Released for Dangerous iOS Kernel Exploit
25.8.2017 securityweek iOS
Proof-of-concept (PoC) code has been released for recently patched iOS vulnerabilities that can be chained to take full control of a mobile device. The flaws could also be useful for a jailbreak, according to the researcher who found them.
iOS 10.3.2, which Apple released in mid-May, patches seven AVEVideoEncoder vulnerabilities and one IOSurface flaw discovered by Adam Donenfeld of mobile security firm Zimperium. The security holes, which Apple says can be used by an application to gain kernel privileges, are believed to affect all prior versions of the iOS operating system.
The vulnerabilities are tracked as CVE-2017-6979, CVE-2017-6989, CVE-2017-6994, CVE-2017-6995, CVE-2017-6996, CVE-2017-6997, CVE-2017-6998 and CVE-2017-6999. The bugs were discovered between January 24 and March 20, when they were reported to Apple.
Donenfeld, who disclosed his findings this week at the Hack in the Box security conference in Singapore, said he identified the vulnerabilities while analyzing iOS kernel modules. His analysis led to a little-known module, called AppleAVE, which appeared to lack basic security.
Donenfeld demonstrated how some of the flaws in AppleAVE and IOSurface, which can lead to denial-of-service (DoS), information disclosure and privilege escalation, can be chained to achieve arbitrary read/write and root access. The exploit is said to bypass all iOS security mitigations.
“These vulnerabilities would allow elevation of privileges which ultimately can be used by the attacker to take complete control over affected devices,” the researcher said in a blog post.
The expert has released a PoC exploit, which he calls the zIVA (Zimperium’s iOS Video Audio) exploit, to demonstrate his findings. The exploit can be used to take complete control of the kernel, which means it could also be useful for a jailbreak.
Technical details have been made public for only one of the vulnerabilities, but Zimperium will release all the advisories it sent to Apple. The tech giant had asked the security firm to delay the release of the exploit, likely in an effort to give users time to update their devices.
Easy-to-Use Apps Allow Anyone to Create Android Ransomware Within Seconds
25.8.2017 thehackernews Ransomware
"Ransomware" threat is on the rise, and cyber criminals are making millions of dollars by victimizing as many people as they can—with WannaCry, NotPetya and LeakerLocker being the ransomware threats that made headlines recently.
What's BAD? Hacker even started selling ransomware-as-a-service (RaaS) kits in an attempt to spread this creepy threat more easily, so that even a non-tech user can create their own ransomware and distribute the threat to a wider audience.
The WORSE—You could see a massive increase in the number of ransomware campaigns during the next several months—thanks to new Android apps available for anyone to download that let them quickly and easily create Android ransomware with their own devices.
Security researchers at Antivirus firm Symantec have spotted some Android apps available on hacking forums and through advertisements on a social networking messaging service popular in China, which let any wannabe hacker download and use Trojan Development Kits (TDKs).
How to Create Your Own Android Ransomware
With an easy-to-use interface, these apps are no different from any other Android app apart from the fact that it allows users to create their custom mobile malware with little to no programming knowledge.
To create customized ransomware, users can download one such app (for an obvious reason we are not sharing the links), install and open it, where it offers to choose from the following options, which are displayed on the app's on-screen form:
The message that is to be shown on the locked screen of the infected device
The key to be used to unlock that infected device
The icon to be used by their malware
Custom mathematical operations to randomize the code
Type of animation to be displayed on the infected device
Once all of the information has been filled in, users just require hitting the "Create" button.
If the user hasn't before, the app will prompt him/her to subscribe to the service before proceeding. The app allows the user to start an online chat with its developer where he/she can arrange a one-time payment.
After the payment has been made, the "malware is created and stored in the external storage in ready-to-ship condition," and then the user can continue with the process, making as many as victims as the user can.
"Anyone unlucky enough to be tricked into installing the malware will end up with a locked device held to ransom," Symantec researchers say.
"The malware created using this automation process follows the typical Lockdroid behavior of locking the device’s screen with a SYSTEM_ALERT_WINDOW and displaying a text field for the victim to enter the unlock code."
The Lockdroid ransomware has the ability to lock the infected device, change the device PIN, and delete all of its user data through a factory reset, and even prevent the user from uninstalling the malware.
Such apps allow anyone interested in hacking and criminal activities to develop a ready-to-use piece of ransomware malware just by using their smartphones without any need to write a single line of code.
"However, these apps are not just useful for aspiring and inexperienced cyber criminals as even hardened malware authors could find these easy-to-use kits an efficient alternative to putting the work in themselves," the researchers say.
So, get ready to expect an increase in mobile ransomware variants in coming months.
How to Protect Your Android Devices from Ransomware Attacks
In order to protect against such threats on mobile devices, you are recommended to:
Always keep regular backups of your important data.
Make sure that you run an active anti-virus security suite of tools on your machine.
Avoid downloading apps from unknown sites and third-party app stores.
Always pay close attention to the permissions requested by an app, even if it is downloaded from an official app store.
Do not open any email attachments from unknown sources.
Finally, browse the Internet safely.
WAP Billing Trojans Threaten Android Users
25.8.2017 securityweek Android
Several of the pieces of malware targeting Android devices in the second quarter of 2017 abused WAP billing to help cybercriminals make money, Kaspersky reported on Thursday.
Wireless Application Protocol (WAP) billing provides a mechanism for users to acquire content online and have it charged directly to their mobile phone bill so that they don’t have to provide any payment card information. The method is similar to premium SMS services, but it does not involve sending SMS messages and instead users have to click on a button displayed on a website to approve charges.
Android malware abusing WAP billing was spotted in the past years, including on Google Play, and it now appears to be making a comeback.
Several of the top 20 most common trojans detected by Kaspersky products in the second quarter abused WAP billing. While a majority of the infections were in Russia and India, victims were also seen in many other countries.
“We haven’t seen these types of Trojans for a while. The fact that they have become so popular lately might indicate that cybercriminals have started to use other verified techniques, such as WAP-billing, to exploit users,” said Roman Unuchek, security expert at Kaspersky Lab. “Moreover, a premium rate SMS Trojan is more difficult to create. It is also interesting that malware has targeted mainly Russia and India, which could be connected to the state of their internal, local telecoms markets.”
The list of trojans that abuse WAP billing include Trojan-Clicker.AndroidOS.Ubsod, which infected nearly 8,000 devices in Russia and 81 other countries; Xafekopy, which infected more than 5,000 users in India and 47 other countries; Autosus, which infected roughly 1,400 devices in India, South Africa and Egypt; and Podec, which had last been seen in the second quarter of 2016.
These pieces of malware have been used by several cybercrime groups, and while in some cases their development started in late 2016 or early 2017, their use increased significantly at the beginning of summer.
The samples analyzed by Kaspersky disable the infected device’s WiFi and enable the mobile data connection, which is needed due to the fact that WAP billing only works through mobile Internet as the carrier needs to be able to identify the user making the online purchase.
The trojans then use JavaScript code to automate certain actions, such as opening web pages and clicking on the buttons associated with WAP billing. By automating these tasks, no user interaction is required for the attack to work.
The malware also deletes incoming SMS messages to avoid raising suspicion. Some samples also abuse Device Administrator rights on the infected Android device to make their removal more difficult.
“We weren’t able to find a reason why so many cybercriminals decided to switch or to start attacking WAP-billing services at the same time,” Unuchek said. “WAP-billing services are not a new thing – in some countries they’ve existed for several years.”
WikiLeaks: CIA Secretly Collected Data From Liaison Services
25.8.2017 securityweek BigBrothers
WikiLeaks has published another round of Vault 7 documents, this time describing a tool allegedly used by the U.S. Central Intelligence Agency (CIA) to secretly collect biometric data from the agency’s liaison services.
The leaked documents, marked as “secret,” appear to reveal that the CIA’s Office of Technical Services (OTS) and Identity Intelligence Center (I2C), both part of the agency’s Directorate of Science and Technology, have provided liaison services with a system that collects biometric information.
According to WikiLeaks, these liaison services include other U.S. government agencies, such as the National Security Agency (NSA), the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI).
In order to ensure that liaison services share the collected biometric data, the CIA has developed a tool called ExpressLane, which secretly copies the data collected by the biometric software and disables this software if continued access is not provided to the agency.
The documents show that ExpressLane is installed on the targeted system by an OTS officer claiming to perform an upgrade to the biometric system from a USB drive. ExpressLane displays a bogus update screen for a period of time specified by the agent, while in the background the targeted biometric data is compressed, encrypted and copied to the officer’s USB drive.
The files copied to the USB drive are later extracted at headquarters using a different utility called ExitRamp.
Another feature of ExpressLane allows the agency to ensure that the biometric software is disabled after a specified number of days unless action is taken. When the tool is installed, a kill date, which specifies when the biometric software will stop functioning, is set (the default value is 6 months in the future). If an agent does not return with the ExpressLane USB drive within that period, the license for the biometric software expires. Whenever ExpressLane is run on the targeted system, the kill date is extended.
This helps the CIA ensure that the collected biometric data ends up in its possession, and provides a way for the agency to disable the biometric software if access is no longer granted.
The documents leaked by WikiLeaks are dated 2009 and the instructions they contain are mainly for Windows XP. It’s unclear if the tool continues to be used and what improvements have been made to it if it’s still maintained.
According to WikiLeaks, the core components of the biometric system are made by Cross Match, a Florida-based company that provides biometric software to law enforcement and intelligence agencies. The company made headlines in 2011 when reports claimed that one of its field devices had been used to identify al-Qaeda leader Osama bin Laden.
WikiLeaks has published documents describing several tools allegedly developed by the CIA, including for hacking OS X systems (Imperial), intercepting SMS messages on Android devices (HighRise), redirecting traffic on Linux systems (OutlawCountry), stealing SSH credentials (BothanSpy), spreading malware on an organization’s network (Pandemic), locating people via their device’s Wi-Fi (Elsa), hacking routers and access points (Cherry Blossom), and accessing air-gapped networks (Brutal Kangaroo).
Report Suggests 'Fleeting Window' to Prevent Major Cyber Attack on Critical Infrastructure
25.8.2017 securityweek BigBrothers
The National Infrastructure Advisory Council (NIAC) published a draft report this week titled Securing Cyber Assets: Addressing Urgent Cyber Threats to Critical Infrastructure (PDF). The report warns there is a narrow and fleeting window to prepare for and prevent "a 9/11-level cyber-attack" against the U.S. critical infrastructure.
The purpose of NIAC is to advise the President on the cybersecurity of critical services, such as banking, finance, energy and transportation. The Council was created in 2001 by President Bush's executive order 13231, and its functioning was extended until September 2017 by Obama's 2015 executive order 13708. It can comprise up to 30 members chosen by the President.
The new report makes 11 recommendations to improve the security of the critical infrastructure. Overall, it presents a damning indictment on U.S. readiness. "We believe the U.S. government and private sector collectively have the tremendous cyber capabilities and resources needed to defend critical private systems from aggressive cyber-attacks -- provided they are properly organized, harnessed, and focused. Today, we're falling short."
There is an intriguing back-drop to this report -- on the day before its publication, seven of the existing 27 members resigned. Resignations among President Trump's advisors are common, with causes ranging from the political (such as Tesla's Elon Musk and Disney's Robert Iger resigning from Trump's business panel over the withdrawal from the Paris climate accord), and 'cultural' (such as those who left the Manufacturing Jobs Initiative and the Strategic and Policy Forum over the President's Charlottesville comments).
In their NIAC resignation letter (seen by Roll Call), the Paris accord and Charlottesville were again mentioned, together with the President's 'attacks' on CEOs who do resign from his advisory panels. However, the letter also noted the President's "insufficient attention to the growing threats to the cybersecurity of the critical systems upon which all Americans depend..." It is not clear whether and to what extent -- if any -- these resignations relate to the President and NIAC.
That said, the NIAC report has been received by the industry with little enthusiasm and much reservation. For example, Patrick Coyle (owner and author of Chemical Facility Security News) questions the validity of the 9/11 reference. He simply does not believe that the main threat is "the grand cyber-attack; the infamous cyber pearl harbor." A grand attack, he told SecurityWeek, will require a grand response; "a kinetic response that few would be willing to risk."
Coyle believes that the more likely threat "would be a number of smaller attacks that weakened the economy and reduced the will of the American people to resist. Such attacks would be much less likely to garner a kinetic response, so the risk to the attacker would be much less."
Sqrrl director Matt Zanderigo, calls it a "good report with solid, actionable recommendations;" but adds that many of the recommendations are not new. "This is less an issue of strategy and more about execution," he told SecurityWeek. "It is good to see that the final recommendation is focused on tracking activity and performance against these recommendations, as I think that will be key and should be done as transparently and publicly as possible."
But there remains a potentially fatal flaw: NIAC's recommendations are all voluntary, albeit with incentives. "The problem with voluntary measures and incentives for critical infrastructure owners," he said, "is that the national consequences of a cyber attack on certain key pieces of critical infrastructure far outweigh the local impacts for that owner/operator. This mismatch between local risk and national risk for cyber-attacks on critical infrastructure is the type of market inefficiency that is typically best filled by regulation."
The lack of innovative ideas also concerns Chris Roberts, chief security architect at Acalvio. "Frankly, eleven key recommendations are about five too many," he said. "Let's face it, we've all been screaming about critical infrastructure for years, keeping the message very simple -- and this 45-page report comes out, says the same thing and then, heaven forbid, puts the remit for action into the governments hands."
He has more specific concerns. Recommendation #3 states, "Identify best-in-class SCANNING TOOLS AND ASSESSMENT PRACTICES, and work with owners and operators of the most critical networks to scan and sanitize their systems on a voluntary basis;" and then calls for action from the National Security Council, the Department of Homeland Security, and Congress.
Roberts' opinion is scathing. "Seriously, we are going to let Congress work out what scanning tools we should use? What idiot came up with that one?"
Perhaps the biggest disappointment is over critical infrastructure threat intelligence sharing. Recommendation #2 calls for a private-sector-led pilot "to test public-private and company-to-company information sharing of cyber threats at network speed." This would be augmented by Recommendation #7: "Establish clear protocols to RAPIDLY DECLASSIFY CYBER THREAT INFORMATION and proactively share it with owners and operators of critical infrastructure."
In short, private industry needs to share threat information among itself better than it does, while government needs to share its intelligence with private industry. On company-to-company sharing, Roberts comments, "Oh good, another feed for people to ignore, to not pay attention to, or too little information too late for anyone to be able to do anything with."
Nor does he believe that government sharing will come to much. "Telling the DOE, DHS, ODNI and SICC to work with separating communications is going to be interesting especially as most of them, honestly, can't communicate effectively today."
Jason Kent, CTO at AsTech, believes these two recommendations should be treated as one. It's not going to be easy. "When something about an adversary or attacker is learned, that becomes a carefully guarded secret." Government agencies do not like sharing their secrets, while individual companies often dare not because of the complexity of existing legislation.
Kent's recommendation would be to start with the government agencies since they can be more easily compelled than private industry. "Imagine if you could get all these guys to collaborate: DOE, DHA, ODNI, NSC, SICC. What is the conduit through which they should speak? We don't currently have a way for them to share threat intel. Obviously an impartial 3rd party is needed to facilitate the communication, but how do we create one with nothing like this built today?"
His solution would be a national cyber security council "that basically takes threat data from our nation's various infrastructures, combined with feeds from private organizations, that is consumed and analyzed for patterns and risks... True security," he says, "comes from the security of all, not the one. We need to change our focus from protecting one asset at a time to protecting all assets at risk.” To solve this, he proposes a new third-party organization that is trusted by both public and private organizations able to share solutions rather than just threats.
The overriding problem with the NIAC report is the perception that it repeats known problems and proposes new studies without offering realistic solutions. In summary, a common feeling within the industry is that the NIAC report is too complicated, says little that is new, and provides voluntary recommendations that will likely be ignored for the same good business reasons that are already being ignored.
FBI Arrests Another Hacker Who Visited United States to Attend a Conference
25.8.2017 thehackernews CyberCrime

The FBI has arrested a Chinese citizen for allegedly distributing malware used in the 2015 massive OPM breach that resulted in the theft of personal details of more than 25 Million U.S. federal employees, including 5.6 Million federal officials' fingerprints.
Yu Pingan, identified by the agency as the pseudonym "GoldSun," was arrested at Los Angeles international airport on Wednesday when he was arrived in the United States to attend a conference, CNN reported.
The 36-year-old Chinese national is said to face charges in connection with the Sakula malware, which was not only used to breach the US Office of Personnel Management (OPM) but also breached Anthem health insurance firm in 2015.
The Anthem breach resulted in the theft of personal medical records of around 80 million current and former customers of the company.
Sakula is a sophisticated remote access Trojan (RAT) that was known to be developed by Deep Panda, a China-based advanced persistent threat group (known as APT19) and could allow an attacker to remotely gain control over a targeted system.
However, after a few months of the discovery of the OPM breach, Chinese government arrested a handful of hackers within its borders in connection with the OPM hack, dismissing its own involvement.
Pingan's arrest was similar to that of Marcus Hutchins, a 22-year-old British security researcher who has been accused of creating and distributing the infamous Kronos banking Trojan between 2014 and 2015.
According to an indictment filed in the US District Court for the Southern District of California on 21 August, Pingan has been charged with one count of the Computer Fraud and Abuse Act and is also accused of conspiracy to commit offence or defraud the United States.
The indictment suggests Pingan collaborated with two unnamed hackers to acquire and use malware to conduct cyber attacks against at least 4 unnamed US companies from April 2011 through January 2014.
"Defendant YU and co-conspirators in the PRC [People's Republic of China] would establish an infrastructure of domain names, IP addresses, accounts with internet service providers, and websites to facilitate hacks of computer networks operated by companies in the United States and elsewhere," the indictment reads.
Although the indictment filed doesn't name the companies that were targeted, it does note that the affected companies were headquartered in San Diego, California; Massachusetts; Arizona; and Los Angeles, California.
Pingan's role in those cyber attacks was to supply advanced malware to other unnamed Chinese crooks for hacks against United States organisations.
Pingan remains behind bars pending a court hearing on his detention next week.
Report Suggests 'Fleeting Window' to Prevent Major Cyber Attack on Critical Infrastructure
24.8.2017 securityweek BigBrothers
The National Infrastructure Advisory Council (NIAC) published a draft report this week titled Securing Cyber Assets: Addressing Urgent Cyber Threats to Critical Infrastructure (PDF). The report warns there is a narrow and fleeting window to prepare for and prevent "a 9/11-level cyber-attack" against the U.S. critical infrastructure.
The purpose of NIAC is to advise the President on the cybersecurity of critical services, such as banking, finance, energy and transportation. The Council was created in 2001 by President Bush's executive order 13231, and its functioning was extended until September 2017 by Obama's 2015 executive order 13708. It can comprise up to 30 members chosen by the President.
The new report makes 11 recommendations to improve the security of the critical infrastructure. Overall, it presents a damning indictment on U.S. readiness. "We believe the U.S. government and private sector collectively have the tremendous cyber capabilities and resources needed to defend critical private systems from aggressive cyber-attacks -- provided they are properly organized, harnessed, and focused. Today, we're falling short."
There is an intriguing back-drop to this report -- on the day before its publication, seven of the existing 27 members resigned. Resignations among President Trump's advisors are common, with causes ranging from the political (such as Tesla's Elon Musk and Disney's Robert Iger resigning from Trump's business panel over the withdrawal from the Paris climate accord), and 'cultural' (such as those who left the Manufacturing Jobs Initiative and the Strategic and Policy Forum over the President's Charlottesville comments).
In their NIAC resignation letter (seen by Roll Call), the Paris accord and Charlottesville were again mentioned, together with the President's 'attacks' on CEOs who do resign from his advisory panels. However, the letter also noted the President's "insufficient attention to the growing threats to the cybersecurity of the critical systems upon which all Americans depend..." It is not clear whether and to what extent -- if any -- these resignations relate to the President and NIAC.
That said, the NIAC report has been received by the industry with little enthusiasm and much reservation. For example, Patrick Coyle (owner and author of Chemical Facility Security News) questions the validity of the 9/11 reference. He simply does not believe that the main threat is "the grand cyber-attack; the infamous cyber pearl harbor." A grand attack, he told SecurityWeek, will require a grand response; "a kinetic response that few would be willing to risk."
Coyle believes that the more likely threat "would be a number of smaller attacks that weakened the economy and reduced the will of the American people to resist. Such attacks would be much less likely to garner a kinetic response, so the risk to the attacker would be much less."
Sqrrl director Matt Zanderigo, calls it a "good report with solid, actionable recommendations;" but adds that many of the recommendations are not new. "This is less an issue of strategy and more about execution," he told SecurityWeek. "It is good to see that the final recommendation is focused on tracking activity and performance against these recommendations, as I think that will be key and should be done as transparently and publicly as possible."
But there remains a potentially fatal flaw: NIAC's recommendations are all voluntary, albeit with incentives. "The problem with voluntary measures and incentives for critical infrastructure owners," he said, "is that the national consequences of a cyber attack on certain key pieces of critical infrastructure far outweigh the local impacts for that owner/operator. This mismatch between local risk and national risk for cyber-attacks on critical infrastructure is the type of market inefficiency that is typically best filled by regulation."
The lack of innovative ideas also concerns Chris Roberts, chief security architect at Acalvio. "Frankly, eleven key recommendations are about five too many," he said. "Let's face it, we've all been screaming about critical infrastructure for years, keeping the message very simple -- and this 45-page report comes out, says the same thing and then, heaven forbid, puts the remit for action into the governments hands."
He has more specific concerns. Recommendation #3 states, "Identify best-in-class SCANNING TOOLS AND ASSESSMENT PRACTICES, and work with owners and operators of the most critical networks to scan and sanitize their systems on a voluntary basis;" and then calls for action from the National Security Council, the Department of Homeland Security, and Congress.
Roberts' opinion is scathing. "Seriously, we are going to let Congress work out what scanning tools we should use? What idiot came up with that one?"
Perhaps the biggest disappointment is over critical infrastructure threat intelligence sharing. Recommendation #2 calls for a private-sector-led pilot "to test public-private and company-to-company information sharing of cyber threats at network speed." This would be augmented by Recommendation #7: "Establish clear protocols to RAPIDLY DECLASSIFY CYBER THREAT INFORMATION and proactively share it with owners and operators of critical infrastructure."
In short, private industry needs to share threat information among itself better than it does, while government needs to share its intelligence with private industry. On company-to-company sharing, Roberts comments, "Oh good, another feed for people to ignore, to not pay attention to, or too little information too late for anyone to be able to do anything with."
Nor does he believe that government sharing will come to much. "Telling the DOE, DHS, ODNI and SICC to work with separating communications is going to be interesting especially as most of them, honestly, can't communicate effectively today."
Jason Kent, CTO at AsTech, believes these two recommendations should be treated as one. It's not going to be easy. "When something about an adversary or attacker is learned, that becomes a carefully guarded secret." Government agencies do not like sharing their secrets, while individual companies often dare not because of the complexity of existing legislation.
Kent's recommendation would be to start with the government agencies since they can be more easily compelled than private industry. "Imagine if you could get all these guys to collaborate: DOE, DHA, ODNI, NSC, SICC. What is the conduit through which they should speak? We don't currently have a way for them to share threat intel. Obviously an impartial 3rd party is needed to facilitate the communication, but how do we create one with nothing like this built today?"
His solution would be a national cyber security council "that basically takes threat data from our nation's various infrastructures, combined with feeds from private organizations, that is consumed and analyzed for patterns and risks... True security," he says, "comes from the security of all, not the one. We need to change our focus from protecting one asset at a time to protecting all assets at risk.” To solve this, he proposes a new third-party organization that is trusted by both public and private organizations able to share solutions rather than just threats.
The overriding problem with the NIAC report is the perception that it repeats known problems and proposes new studies without offering realistic solutions. In summary, a common feeling within the industry is that the NIAC report is too complicated, says little that is new, and provides voluntary recommendations that will likely be ignored for the same good business reasons that are already being ignored.
Snapchat Pays $20,000 for Vulnerable Jenkins Instances
24.8.2017 securityweek Vulnerebility
Snapchat has awarded researchers a total of $20,000 for finding exposed Jenkins instances that allowed arbitrary code execution and provided access to sensitive data.
Three months ago, Belgium-based researcher Preben Ver Eecke was analyzing Snapchat’s infrastructure when he discovered a production Jenkins instance that could be accessed with any valid Google account.
Jenkins is a self-contained, open source automation server used by developers to automate various tasks, including building, testing and deploying software.
Once logged in to the vulnerable Jenkins instance, the expert gained access to sensitive API tokens and some source code for public applications. Ver Eecke also managed to execute arbitrary code through the Jenkins Script Console.
The vulnerability was reported to Snapchat through its HackedOne-based bug bounty program. The company initially awarded the researcher $12,000 for his findings and later decided to give him a $3,000 bonus.
Roughly two weeks ago, California-based researcher Behrouz Sadeghipour also discovered an exposed Jenkins instance belonging to Snapchat that could be accessed with any valid Google account.
This time, however, it was a test Jenkins instance. While an attacker could have exploited the access to execute arbitrary code via the Jenkins Script Console, the instance did not store any source code or other resources. The vulnerability earned the researcher $5,000.
In a blog post published this week, Sadeghipour revealed that he discovered the exposed Jenkins instance by conducting a search via the Censys search engine:
443.https.tls.certificate.parsed.extensions.subject_alt_name.dns_names:domain.com
“Going through the results, there was a subdomain, REDACTED-jenkins-Environment.sc-corp.net, that pointed the user to login in order to see what’s on that site,” the white hat hacker explained. “At this point, I wondered if there’s a prod environment, there’s got to be more so let’s look for them. To speed up my process I used script that would look for different permutations of REDACTED-jenkins-$env.sc-corp.net with the following list: ‘dev, alpha, stage, prod, beta, local, test’. As expected a few of those returned with 302 as their response code, which hinted that they may be behind a login.”
Sadeghipour advised organizations to ensure that their Jenkins instances are protected, as they can often provide access to credentials, API keys and source code. He also advised bug bounty hunters looking for exposed Jenkins instances to ensure that the access they obtain is exploitable before submitting a report to the respective vendor’s bug bounty program.
WikiLeaks: CIA Secretly Collected Data From Liaison Services
24.8.2017 securityweek BigBrothers
WikiLeaks has published another round of Vault 7 documents, this time describing a tool allegedly used by the U.S. Central Intelligence Agency (CIA) to secretly collect biometric data from the agency’s liaison services.
The leaked documents, marked as “secret,” appear to reveal that the CIA’s Office of Technical Services (OTS) and Identity Intelligence Center (I2C), both part of the agency’s Directorate of Science and Technology, have provided liaison services with a system that collects biometric information.
According to WikiLeaks, these liaison services include other U.S. government agencies, such as the National Security Agency (NSA), the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI).
In order to ensure that liaison services share the collected biometric data, the CIA has developed a tool called ExpressLane, which secretly copies the data collected by the biometric software and disables this software if continued access is not provided to the agency.
The documents show that ExpressLane is installed on the targeted system by an OTS officer claiming to perform an upgrade to the biometric system from a USB drive. ExpressLane displays a bogus update screen for a period of time specified by the agent, while in the background the targeted biometric data is compressed, encrypted and copied to the officer’s USB drive.
The files copied to the USB drive are later extracted at headquarters using a different utility called ExitRamp.
Another feature of ExpressLane allows the agency to ensure that the biometric software is disabled after a specified number of days unless action is taken. When the tool is installed, a kill date, which specifies when the biometric software will stop functioning, is set (the default value is 6 months in the future). If an agent does not return with the ExpressLane USB drive within that period, the license for the biometric software expires. Whenever ExpressLane is run on the targeted system, the kill date is extended.
This helps the CIA ensure that the collected biometric data ends up in its possession, and provides a way for the agency to disable the biometric software if access is no longer granted.
The documents leaked by WikiLeaks are dated 2009 and the instructions they contain are mainly for Windows XP. It’s unclear if the tool continues to be used and what improvements have been made to it if it’s still maintained.
According to WikiLeaks, the core components of the biometric system are made by Cross Match, a Florida-based company that provides biometric software to law enforcement and intelligence agencies. The company made headlines in 2011 when reports claimed that one of its field devices had been used to identify al-Qaeda leader Osama bin Laden.
WikiLeaks has published documents describing several tools allegedly developed by the CIA, including for hacking OS X systems (Imperial), intercepting SMS messages on Android devices (HighRise), redirecting traffic on Linux systems (OutlawCountry), stealing SSH credentials (BothanSpy), spreading malware on an organization’s network (Pandemic), locating people via their device’s Wi-Fi (Elsa), hacking routers and access points (Cherry Blossom), and accessing air-gapped networks (Brutal Kangaroo).
Here's How CIA Spies On Its Intelligence Liaison Partners Around the World
24.8.2017 thehackernews BigBrothers
WikiLeaks has just published another Vault 7 leak, revealing how the CIA spies on their intelligence partners around the world, including FBI, DHS and the NSA, to covertly collect data from their systems.
The CIA offers a biometric collection system—with predefined hardware, operating system, and software—to its intelligence liaison partners around the world that helps them voluntary share collected biometric data on their systems with each other.
But since no agency share all of its collected biometric data with others, the Office of Technical Services (OTS) within CIA developed a tool to secretly exfiltrate data collections from their systems.
Dubbed ExpressLane, the newly revealed CIA project details about the spying software that the CIA agents manually installs as part of a routine upgrade to the Biometric system.
The leaked CIA documents reveal that the OTS officers, who maintain biometric collection systems installed at liaison services, visit their premises and secretly install ExpressLane Trojan while displaying an "upgrade Installation screen with a progress bar that appears to be upgrading the biometric software."
"It will overtly appear to be just another part of this system. It’s called: MOBSLangSvc.exe and is stored in \Windows\System32," leaked CIA documents read.
"Covertly it will collect the data files of interest from the liaison system and store them encrypted in the covert partition on a specially watermarked thumb drive when it is inserted into the system."
ExpressLane includes two components:
Create Partition — This utility allows agents to create a covert partition on the target system where the collected information (in compressed and encrypted form) will be stored.
Exit Ramp — This utility lets the agents steal the collected data stored in the hidden partition using a thumb drive when they revisit.
The latest version ExpressLane 3.1.1 by default removes itself after six months of the installation in an attempt to erase its footprints, though the OTA officers can change this date.
The biometric software system that CIA offers is based on a product from Cross Match, a US company specialized in biometric software for law enforcement and the intelligence community, which was also used to "identify Osama bin Laden during the assassination operation in Pakistan."
Previous Vault 7 CIA Leaks
Last week, WikiLeaks published another CIA project, dubbed CouchPotato, which revealed the CIA's ability to spy on video streams remotely in real-time.
Since March, WikiLeaks has published 21 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
Dumbo — A CIA project that disclosed the CIA's ability to hijack and manipulate webcams and microphones to corrupt or delete recordings.
Imperial — A CIA project that revealed details of at least 3 CIA-developed hacking tools and implants designed to target computers running Apple Mac OSX and different flavours of Linux OS.
UCL/Raytheon — An alleged CIA contractor, who analysed in-the-wild malware and hacking tools and submitted at least five reports to the spying agency for help it developed its malware.
Highrise — An alleged CIA project that allows the spying agency to stealthy collect and forward stolen information from compromised phones to its server via SMS messages.
BothanSpy and Gyrfalcon — Two alleged CIA implants that allowed the US agency to intercept and exfiltrate SSH credentials from target Windows and Linux computers.
OutlawCountry – An alleged CIA project that let the agency hack and remotely spy on computers running Linux OS.
ELSA – Alleged CIA malware that tracks the location of targeted laptops and PCs running the Microsoft Windows operating system.
Brutal Kangaroo – A Microsoft Windows tool suite used by the agents to target closed networks or air-gap PCs within an organisation or enterprise without requiring any direct access.
Cherry Blossom – A CIA framework employed by its agents to monitor the Internet activity of the target systems by exploiting bugs in Wi-Fi devices.
Pandemic – A CIA project that let the spying agency turn Windows file servers into covert attack machines that can silently infect other systems of interest inside the same network.
Athena – A spyware framework that the US secretive agency uses to take full control of the infected Windows machines remotely and works against every version of Windows operating system–from Windows XP to Windows 10.
AfterMidnight and Assassin – Two alleged CIA malware frameworks for the Windows platform that's designed to monitor and report back actions on the infected remote host system and execute malicious actions.
Archimedes – Man-in-the-middle attack tool allegedly developed by the US agency to target systems inside a Local Area Network (LAN).
Scribbles – Software allegedly designed to embed 'web beacons' into confidential documents, allowing the agents to track insiders and whistleblowers.
Grasshopper – A framework that let the spying agency easily create its custom malware for breaking into Microsoft Windows and bypassing antiviruses.
Marble – Source code of a secret anti-forensic tool used by the US agency to hide the actual source of its malicious payload.
Dark Matter – Hacking exploits the US spying agency designed and used to target iPhones and Macs.
Weeping Angel – A spying tool used by the CIA agents to infiltrate smart TV's and transform them into covert microphones.
Year Zero – CIA hacking exploits for popular hardware and software.
Over 500 Android Apps On Google Play Store Found Spying On 100 Million Users
24.8.2017 thehackernews Android
Over 500 different Android apps that have been downloaded more than 100 million times from the official Google Play Store found to be infected with a malicious ad library that secretly distributes spyware to users and can perform dangerous operations.
Since 90 per cent of Android apps is free to download from Google Play Store, advertising is a key revenue source for app developers. For this, they integrate Android SDK Ads library in their apps, which usually does not affect an app's core functionality.
But security researchers at mobile security firm Lookout have discovered a software development kit (SDK), dubbed Igexin, that has been found delivering spyware on Android devices.
Developed by a Chinese company to offer targeted advertising services to app developers, the rogue 'Igexin' advertising software was spotted in more than 500 apps on Google's official marketplace, most of which included:
Games targeted at teens with as many as 100 million downloads
Weather apps with as many as 5 million downloads
Photo editor apps with 5 Million downloads
Internet radio app with 1 million downloads
Other apps targeted at education, health and fitness, travel, and emoji
Chinese Advertising Firm Spying On Android Users
The Igexin SDK was designed for app developers to serve targeted advertisements to its users and generate revenue. To do so, the SDK also collects user data to help target interest-based ads.
But besides collecting user data, the Lookout researchers said they found the SDK behaved maliciously after they spotted several Igexin-integrated apps communicating with malicious IP addresses that deliver malware to devices unbeknownst to the creators of apps utilizing it.
"We observed an app downloading large, encrypted files after making a series of initial requests to a REST API at http://sdk[.]open[.]phone[.]igexin.com/api.php, which is an endpoint used by the Igexin ad SDK," the researchers explain in a blog post.
"This sort of traffic is often the result of malware that downloads and executes code after an initially "clean" app is installed, in order to evade detection."
Once the malware is delivered to infected devices, the SDK can gather logs of users information from their device, and could also remotely install other plugins to the devices, which could record call logs or reveal information about users activities.
How to Protect Your Android From This Malware
Google has since removed all the Android apps utilizing the rogue SDK from its Play Store marketplace, but those who have already installed one such app on their mobile handsets, make sure your device has Google Play Protect.
Play Protect is Google's newly launched security feature that uses machine learning and app usage analysis to remove (uninstall) malicious apps from users Android smartphones to prevent further harm.
In addition, you are strongly advised to always keep a good antivirus application on your device that can detect and block malicious apps before they can infect your device, and always keep your device and apps up-to-date.
Android malware continues to evolve with more sophisticated and never-seen-before capabilities with every passing day. Last month, we saw first Android malware with code injecting capabilities making rounds on Google Play Store.
A few days after that, researchers discovered another malicious Android SDK ads library, dubbed "Xavier," found installed on more than 800 different apps that had been downloaded millions of times from Google Play Store.
Simple Exploit Allows Attackers to Modify Email Content — Even After It's Sent!
24.8.2017 thehackernews Exploit
Modify Email Content — Even After It's Sent
Security researchers are warning of a new, easy-to-exploit email trick that could allow an attacker to turn a seemingly benign email into a malicious one after it has already been delivered to your email inbox.
Dubbed Ropemaker (stands for Remotely Originated Post-delivery Email Manipulation Attacks Keeping Email Risky), the trick was uncovered by Francisco Ribeiro, the researcher at email and cloud security firm Mimecast.
A successful exploitation of the Ropemaker attack could allow an attacker to remotely modify the content of an email sent by the attacker itself, for example swapping a URL with the malicious one.
This can be done even after the email has already been delivered to the recipient and made it through all the necessary spam and security filters, without requiring direct access to the recipient’s computer or email application, exposing hundreds of millions of desktop email client users to malicious attacks.
Ropemaker abuses Cascading Style Sheets (CSS) and Hypertext Markup Language (HTML) that are fundamental parts of the way information is presented on the Internet.
"The origin of Ropemaker lies at the intersection of email and Web technologies, more specifically Cascading Style Sheets (CSS) used with HTML," Mimecast's Senior Product Marketing Manager Matthew Gardiner writes in a blog post.
"While the use of these web technologies has made email more visually attractive and dynamic relative to its purely text-based predecessor, this has also introduced an exploitable attack vector for email."
Since CSS is stored remotely, researchers say an attacker can change the content of an email through remotely initiated changes made to the desired 'style' of the email that is then retrieved remotely and presented to the user, without the recipient, even tech savvy users, knowing about it.
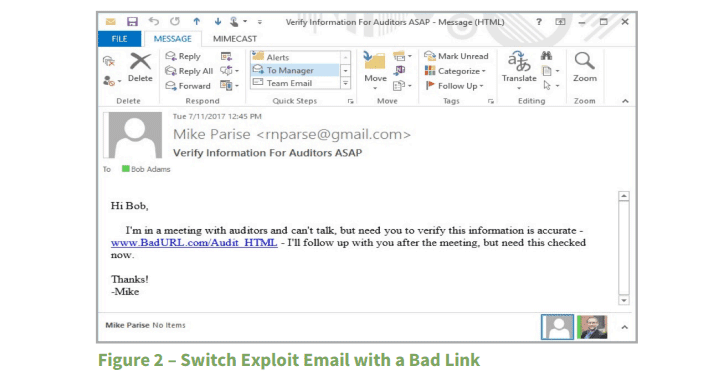
According to the researchers, the Ropemaker attack could be leveraged depending upon the creativity of the threat actors.
For instance, attackers could replace a URL that originally directed the user to a legitimate website by a malicious one that sends the user to a compromised site designed to infect users with malware or steal sensitive info, such as their credentials and banking details.
While some systems are designed to detect the URL switch preventing users from opening up the malicious link, other users could be left at a security risk.
Another attack scenario, called "Matrix Exploit" by the Mimecast, is more sophisticated than the "Switch Exploit", and therefore much harder to detect and defend against.
In a Matrix Exploit attack, attackers would write a matrix of text in an email and then use the remote CSS to selectively control what is displayed, allowing the attacker to display whatever they want—including adding malicious URLs into the body of the email.
This attack is harder to defend against because the initial email received by the user does not display any URL, most software systems will not flag the message as malicious.
"Since the URL is rendered post-delivery, an email gateway solution such as Mimecast cannot find, rewrite, or inspect the destination site on-click, because at the time of delivery there would be no URL to detect," the report reads. "To do so would require the interpretation of CSS files, which is beyond the scope of current email security systems."
Although the security firm has not detected the Ropemaker attack in the wild, it believes that this doesn't mean for sure the attack is "not being used somewhere outside the view of Mimecast."
According to the security firm, Ropemaker could be used by hackers to bypass most common security systems and trick even the tech savvy users into interacting with a malicious URL.
To protect themselves from such attacks, users are recommended to rely on web-based email clients like Gmail, iCloud and Outlook, which aren't affected by Ropemaker-style CSS exploits, according to Mimecast.
However, email clients like the desktop and mobile version of Apple Mail, Microsoft Outlook, and Mozilla Thunderbird are all vulnerable to the Ropemaker attack.
The Pirate Bay Founders Ordered to Pay Music Labels $477,800 in Compensation
24.8.2017 thehackernews IT
Two of the three co-founders of The Pirate Bay—Fredrik Neij and Gottfrid Svartholm Warg—have been ordered by a Finnish court to pay record labels $477,800 in compensation for copyright infringement on the site.
Last year in a similar case, Helsinki District Court in Finland ordered Peter Sunde, the third co-founder of The Pirate Bay, to pay nearly $395,000 (350,000 Euros) in damages to several major record labels, including Sony Music, Universal Music and Warner Music.
However, Sunde did not pay any penalty yet, and instead, he later announced his plans to sue those record labels for defamation.
The Pirate Bay is still the world's most popular torrent website that has proven to be an elusive hub for illegal copyrighted contents, even after a series of raids and shutdown of its multiple domains, including the primary .SE domain.
All the three co-founders of The Pirate Bay were facing criminal copyright infringement and abuse of electronic communications charges in a Belgian court but were acquitted after it was found that they sold The Pirate Bay file-sharing website in 2006.
The International Federation of the Phonographic Industry (IFPI), which represents the world's major labels, with support from Finnish Copyright Information and Anti-Piracy Center (CIAPC), filed a lawsuit in November 2011 in the Helsinki District Court against The Pirate Bay.
In these last six years, Fredrik Neij and Gottfrid Svartholm never appeared in the court, neither they appointed someone to represent their defence, which eventually led the decision in favour of IFPI record labels.
Besides ordering both the founders to jointly pay compensation of 405,000 euros (over $477,800) to record labels, the District Court also ordered them to "cease-and-desist" the illegal operations of The Pirate Bay, TorrentFreak reported.
However, it is still unclear how Neij and Svartholm are supposed to do anything about stop sharing of content on the site since they have no association with The Pirate Bay.
It has also been reported that Neij, Svartholm, and Sunde also owes large sums of money to other copyright holders as a result of various court judgments over the past few years.
However, so far, none of those court penalties has been "satisfied," neither Sunde paid the fines imposed on him last year, and it is likely that this penalty will also go unpaid.
A Company Offers $500,000 For Secure Messaging Apps Zero-Day Exploits
24.8.2017 thehackernews Exploit
Secure Messaging Apps Zero-Day Exploits
How much does your privacy cost?
It will soon be sold for half a Million US dollars.
A controversial company specialises in acquiring and reselling zero-day exploits is ready to pay up to US$500,000 for working zero-day vulnerabilities targeting popular secure messenger applications, such as Signal, Telegram and WhatsApp.
Zerodium announced a new pricing structure on Wednesday, paying out $500,000 for fully functional remote code execution (RCE) and local privilege escalation (LPE) vulnerabilities in Signal, WhatsApp, iMessage, Viber, Facebook Messenger, WeChat, and Telegram.
The payouts for all these secure messengers have been increased after tech companies introduced end-to-end encryption in their apps, making it more difficult for anyone to compromise their messaging platforms.
The same payout is offered for remote code execution and local privilege escalation security flaws in default mobile email applications.
Launched in 2015, Zerodium is a Washington, DC-based premium exploit acquisition platform by the infamous French-based company Vupen that buys and sells zero-day exploits to government agencies around the world.
The maximum bounty offered by the company remains for Apple's iOS devices with $1.5 million offered to anyone who can pull off a remote jailbreak of iOS devices without any user interaction, and $1 million for those that require user interaction.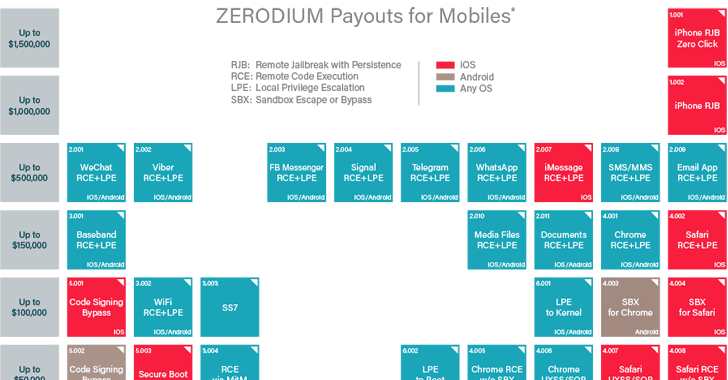
This payout was set last year when Zerodium raised the price for a remote iOS 10 jailbreaks from $1 Million to $1.5 Million, which is more than seven times what Apple is offering (up to $200,000) for iOS zero-days via its bug bounty program.
Zerodium Zero-Day Hit-list:
Zerodium's payout for other new exploit categories for servers and desktop computers include:
Up to $300,000 for a Windows 10 exploit that requires no user interaction
Up to $150,000 for Apache Web Server
Up to $100,000 for Microsoft Outlook
Up to $80,000 for Mozilla Thunderbird
Up to $80,000 for VMware escapes
Up to $30,000 for USB code execution
Zerodium has also raised the prices the company will pay for a range of other exploits, which include:
Chrome RCE and LPE for Windows—from $80,000 to $150,000
PHP Web programming language RCE—from $50,000 to $100,000
RCE in OpenSSL crypto library used to implement TLS—from $50,000 to $100,000
Microsoft Exchange Server RCE—from $40,000 to $100,000
RCE and LPE in the TOR version of Firefox for Linux—from $30,000 to $100,000
RCE and LPE in the TOR version of Firefox for Windows—from $30,000 to $80,000
The zero-day market has long been a lucrative business for private firms that regularly offer more payouts for undisclosed security vulnerabilities than big technology companies.
Companies like Zerodium and Exodus Intelligence who deal in zero-days are the primary cause of incidents like WannaCry and NotPetya, wherein unpatched vulnerabilities held by NSA for years were used after a notorious hacking group, called Shadow Brokers leaked them in public.
Hackers will get the payout within a week of submitting the zero-day vulnerabilities along with a working proof-of-concept, though we recommend you to submit them to the affected vendors because it's a matter of time when some black hat finds and uses them against you and wide audience.
Zerodium Offers $500,000 For Messaging, Email App Exploits
24.8.2017 securityweek Exploit
Zerodium has made some changes to its exploit acquisition program and the company is now offering up to $500,000 for remote code execution and privilege escalation vulnerabilities affecting popular instant messaging and email applications.
The firm has decided to publish separate payout lists for mobile device exploits and desktop/server exploits. A remote jailbreak with no user interaction for iPhone is still worth up to $1.5 million, and up to $1 million can be earned for a similar exploit that involves some user interaction (e.g. clicking on a link or opening a file).
One of the most important changes to Zerodium’s program is the addition of email and instant messaging exploits. The company is prepared to offer up to half a million dollars for WeChat, Viber, Facebook Messenger, Signal, Telegram, WhatsApp and iMessage remote code execution and local privilege escalation exploits on Android and iOS.
The same amount is being offered for SMS/MMS flaws and exploits targeting default email apps on Android and iOS.
New entries in the mobile category also include baseband, and media file and document vulnerabilities that can be leveraged for remote code execution and privilege escalation. These exploits can earn up to $150,000.
Sandbox escapes, code signing bypass, kernel privilege escalation, SS7, and Wi-Fi exploits can earn up to $100,000. Zerodium is also prepared to pay a five-figure sum for other mobile-related exploits.
In the desktop and server systems category, the list of new entries includes a payout of up to $300,000 for Windows 10 remote code execution exploits that require no user interaction. Apache Web Server and Microsoft IIS code execution exploits are worth up to $150,000.
The amount of money Zerodium is prepared to pay for Chrome, PHP, OpenSSL, Microsoft Exchange Server, Firefox, Tor, Office, WordPress and antivirus exploits has increased considerably. However, the company has decided to reduce its reward for antivirus privilege escalation flaws from $40,000 to only $10,000.
While Adobe and other tech giants plan to kill Flash Player in the next couple of years, Zerodium is still prepared to offer up to $100,000 for exploits targeting the application.
Android Malware Found on Google Play Abuses Accessibility Service
24.8.2017 securityweek Android
A dropper discovered by researchers on Google Play abuses accessibility services in a unique way to deliver Android malware.
The threat was analyzed by experts at Zscaler and Securify after finding an app on Google Play named “Earn Real Money Gift Cards.” The application hides a variant of the Android banking trojan BankBot, whose source code was leaked online in late 2016.
The developer of the app hiding BankBot also created another application present on Google Play, a game named “Bubble Shooter Wild Life.” This game actually works, but it also includes functionality that turns it into a malware downloader.
The dropper appears to be under development, but an analysis of its code, which has been protected by its creator using the Allatori Obfuscator, shows that it first requests permission to draw over other apps. It then waits 20 minutes before initiating its malicious routines, which is likely how it managed to bypass Google’s Bouncer security system.
The dropper then tricks the user into giving it accessibility permissions by displaying a fake Google Service alert. While victims believe they are enabling a “Google Service,” they are actually enabling accessibility features.
Once this step has been completed, a fake Google service update window is displayed and an APK from the device’s memory card is installed in the background. The process that takes place in the background also involves enabling the Android option that allows installation of apps from unknown sources. The user does not need to perform any other actions after accessibility permissions are granted as everything else takes place automatically in the background.
Researchers from both Zscaler and Securify believe this particular type of accessibility services abuse is unique to this piece of malware.
Securify told SecurityWeek that this dropper is sold on dark web marketplaces to cybercriminals looking to deliver Android trojans such as Exo, Mazar and BankBot.
Google has known about the malicious applications, which have a total of less than 5,000 downloads, for at least two days, but they have yet to be removed from Google Play.
Malware that abuses Android accessibility services is not uncommon, but cybercriminals keep finding new ways to exploit the feature. A study conducted last year by enterprise mobile security firm Skycure revealed that a majority of Android devices are vulnerable to attacks that trick users into enabling accessibility features via clickjacking.
Fappening 2017 – Private pictures of Miley Cyrus, Stella Maxwell, and others leaked
24.8.2017 securityaffairs Incindent
Fappening 2017 – Private pictures of Miley Cyrus, Stella Maxwell, Kristen Stewart, Tiger Woods and Lindsey Vonn have been posted online by a celebrity leak website.
It has happened again, another wave of Fappening makes the headlines. Once again celebrities have been targeted by crooks, and unfortunately, they continue to ignore security fundamentals.
Once again their nude photos have been leaked online.
Dozens of personal and intimate images of Anne Hathaway, Miley Cyrus, Kristen Stewart, Katharine McPhee, Tiger Woods and his ex Lindsey Vonn have reportedly been leaked on the Internet.
“Tiger Woods and Katharine McPhee have been hacked — private nude photos have surfaced — and their lawyers are vowing to destroy anyone who posts them.” reported TMZ sport.
“A website has posted graphic selfies of various naked stars, including Tiger, Lindsey Vonn, Miley Cyrus, Kristen Stewart and Stella Maxwell.
We’ve learned Woods has already unleashed attorney Michael Holtz, who’s threatening to sue the site if it doesn’t remove the Woods photo STAT.”
The list of the victims also includes Amanda Seyfried, Demi Lovato, Lucy Hale, Kate Hudson, Rose McGowan, Rosario Dawson, Suki Waterhouse and Alison Brie.
The images are rapidly circulating online, users are sharing links on forums and social media, including Reddit, Tumblr, and Twitter.
Celebrities’ lawyers are reported to be working to get pictures and link removed from principal websites, but it is very hard.
“Kristen Steward and her girlfriend Stella Maxwell are reported to be taking legal action against the websites that have posted the personal pictures. Kristen’s lawyer, Scott Whitehead, is saying that her client owns the pictures and the websites are violating the copyright laws, according to TMZ.” states Fossbytes.com.
“In case of Tiger Woods, his lawyers have threatened to go ahead with a lawsuit if the private pictures aren’t removed from the website. His photos, which were taken several years ago, are believed to be hacked from his ex-girlfriend Lindsey Vonn’s smartphone. “
The incident comes a few months after “The Fappening 2.0” images appeared online and private images of many celebrities, including Emma Watson and Amanda Seyfried, were published on Reddit and 4chan.
fappening 2017
The latest Fappening release was made by an unidentified group of hackers that managed to access the celebrities’ Apple iCloud accounts and stolen their data and documents, including photos and videos.
Nothing is changed since the first Fappening release back 2014, it was too easy to gain celebrities’ credentials even after Apple introduced the two-verification process to iCloud.
The crooks behind Fappening 2014 have since been identified and jailed.
Back to the present, stolen pictures were posted on the Celeb Jihad website.
While 2014 Fappening hackers gained login credentials via phishing attacks, it is still unclear which technique they employed.
Below the list of recommendations to keep your iCloud account secure.
Do not click on any suspicious links or attachments in unsolicited emails you received, even if they appear to have been sent by Google, Apple or Microsoft.
Enable two-factor authentication on your accounts.
Never provide sensitive and personal information via email.
Use strong passwords and change them regularly. Use different passwords for all your accounts.
The Role of America's New Unified Cyber Warfare Command
23.8.2017 securityweek BigBrothers
U.S. President Donald Trump on Aug. 18 announced the elevation of the U.S. Cyber Command (USCYBERCOM/CyberCom) to a Unified Combatant Command. This brings American offensive and defensive cyber operations out of the implicit overview of the NSA and puts it on an equal footing -- with major implications for the U.S. national cyber security posture.
A Unified Command is a structure that acknowledges an inter-relationship with another authority -- in this case, primarily the U.S. National Security Agency (NSA). However, Trump's statement adds, "The Secretary of Defense is examining the possibility of separating United States Cyber Command from the National Security Agency." For the time being at least, both the NSA and Cyber Command will continue under the same leadership, currently Admiral Michael Rogers.
Rogers has always been against a separation. The United States Cyber Command was formed in 2009, sharing the resources, headquarters and commander with the NSA. It achieved operational capability in late 2010. The idea was that military hackers could learn from the NSA's hackers. However, as indications of international cyber war have increased, the organizations' objectives have diverged: the NSA's fundamental purpose is to collect intelligence, while USCYBERCOM's role is to achieve military objectives. Rogers fears that such military objectives, undertaken independently, could interfere with the process of intelligence gathering.
Trump, however, clearly feels that the time is ripe. "The elevation of United States Cyber Command demonstrates our increased resolve against cyberspace threats and will help reassure our allies and partners and deter our adversaries," he said. "Through United States Cyber Command, we will tackle our cyberspace challenges in coordination with like-minded allies and partners as we strive to respond rapidly to evolving cyberspace security threats and opportunities globally."
SecurityWeek spoke to a number of the cybersecurity firms that defend against the aggressive cyber-attacks from both criminals and nation states, to get their take on this development.
The overriding view is that this is a good step.
"First," says Nathaniel Gleicher, head of cybersecurity strategy at Illumio and a former director for cybersecurity policy at The White House, "it is a recognition that cyber threats are more significant and serious than ever -- responding to them requires coordinated decision-making across all branches of the military, and elevating USCYBERCOM creates a place for that to happen."
Second, he added, "It recognizes that CyberCom's capabilities have matured over the last eight years. The responsibilities of a unified combatant command are much more significant than those of a sub-unified command -- and the consequences of mistakes are greater. Elevating CyberCom is a signal that DoD thinks it's ready for the challenge."
Ely Kahn, co-founder of Sqrrl and another former director of cybersecurity at The White House, sees it as a way of mitigating natural tensions between USCYBERCOM and the NSA. "A military commander may want to disrupt communications of an enemy leading up to or during an operation," he explains. "This could lead to an intelligence professional losing a key source of information. By putting USCYBERCOM on equal footing as the NSA in terms of being a direct report to the SECDEF, it gives more balance to these opposing objectives when a debate arises."
Elevating Cyber Command to a Unified Combatant Command will inevitably give it greater freedom of action while also attracting more skilled operatives. "I expect that we will see large increases to budget and staffing now, with a focus on recruiting the kind of top-level talent that the government has had some difficulty in acquiring previously," suggests Nathan Wenzler, chief security strategist at AsTech. "But given the more autonomous nature of how U.S. Cyber Command will be able to operate, and to present itself as a more prestigious opportunity to serve one's country, I believe it will have a much better chance to recruit that critical talent than other agencies have done up until this point."
Chris Roberts, chief security architect at Acalvio, believes it is an important step in U.S. cyber operations. "Cyber Command arguably enables all of the other combatant commands that are in place," he explains. "There's a number of them that obviously cover all other aspects, so it seems 'right' to elevate cyber to its own UCC that can have influence/management and control over cyber operations as well as manpower, cybersecurity and IT and operational tech infrastructure requirements."
One consistent view is that it is a good and necessary process -- and if anything, none too soon. "Since North Korea attacked Sony in 2014, the United States has been plagued by constant, sophisticated cyber-attacks that have threatened our critical infrastructure, undermined our democracy, stolen from our banks and businesses, compromised the identities of our citizens and have locked out information away behind malicious encrypted code," says Eric O'Neill, currently national security strategist with Carbon Black -- but once an investigative specialist for the National Security Division of the FBI.
"For some time now I have preached that there are no hackers, there are only spies. The majority of successful breaches are driven by foreign cyber intelligence units -- cyber spies from other nations -- that use traditional espionage tactics in a digital environment to disable, steal, destroy and disrupt information. The United States has fallen far behind the curve in addressing the external cyber threat. I applaud the initiative in elevating the US Cyber Command."
Paul Kurtz, co-founder and CEO of TruSTAR Technology and a former White House National Security Council staff member takes a similar view. "This decision affirms cyberspace as a new war domain," he told SecurityWeek. "The timing is ripe to form this command given the growing severity of cyber-attacks. Adversaries have shown they are ready to use cyber weapons to handicap military readiness and response or to disrupt or destroy critical infrastructure in the U.S. This decision also signals our intent to continue developing cyber weapons, and our adversaries will take note. The government's current ability to defend critical infrastructure is inherently limited and the private sector will need to step up sooner rather than later to exchange information about attacks underway to better defend ourselves."
However, the elevation of Cyber Command is only considered a first step -- the complete separation from the NSA with its own commander is considered an important next step.
"Cyber Command is responsible for coordinating and leading military network defense. Placing this effort in spy agencies like the CIA and NSA is no longer effective," says O'Neill. "Indeed, how can we trust the NSA and CIA to defend us in the cyber war we are fighting when the agencies cannot defend their own attack tools? The breaches by the Shadow Brokers and the Vault-7 release to Wikileaks demonstrate that the US requires a better coordinated effort to defend against cyber-attacks."
Gleicher adds, "As important as this decision is, I am watching for another change to CyberCom that has also long been in the works but was delayed last week. CyberCom is led by Admiral Rogers, the same official who also heads the National Security Agency. The other big change that is discussed alongside elevating USCYBERCOM is separating out these two commands -- giving CyberCom its own leader. This is an important step," he believes, "because the mission of the NSA is different from the mission of the military, and lumping them together under the same leader means that when those two missions conflict, one set of priorities has to win out over the other. As serious as the cyber threat is today, it's past time that we had an independent voice inside the DoD advocating for cyber defense. CyberCom could be that voice, and I'm hopeful that last week's announcement is only the first step, and command separation will follow."
The last word comes from O'Neill. "Many Americans have forgotten the Cold War, fought with the Soviet Union over nuclear ambitions and military force projection across the globe. The truth is that the Cold War did not end with the fall of the USSR. Instead, the war multiplied to a strategic and tactical war in cyberspace. Russia, China, North Korea, Iran and other nation states have attacked the United states effortlessly and remorselessly over the last decade. Cyber-attacks are the perfect warfare. They hide behind a manufactured cloak of anonymity, deal in secrecy and disruption, and effortlessly steal information that improves the economics and policies of rival nations. The United States has long required a new approach to addressing the external cyber threat from military and spy agencies. Our civilian agencies could not carry the burden. I hope that the new Unified Cyber Command can take up the charge."
Automated Logic Patches Flaws in Building Automation System
23.8.2017 securityweek Vulnerebility
Kennesaw, Georgia-based building automation systems provider Automated Logic has released updates for its WebCTRL product to address several vulnerabilities, including one rated high severity.
WebCTRL is a building automation system used worldwide in commercial office buildings, mission-critical facilities, educational institutions, healthcare organizations, hotels, and government facilities.
Gjoko Krstic of Macedonia-based Zero Science Lab discovered arbitrary file write, privilege escalation and remote code execution vulnerabilities in some 6.x and 5.x versions of WebCTRL, i-VU and SiteScan products. The i-VU system made by Carrier (a sister company of Automated Logic) and the Liebert SiteScan product can be integrated with WebCTRL.
The most serious of the flaws, with a CVSS score of 8.3 and a risk index of ⅘ assigned by Zero Science Lab, is CVE-2017-9650, an unrestricted file upload issue that allows an authenticated attacker to upload malicious files and execute arbitrary code on the targeted system.
The security hole exists due to WebCTRL’s failure to verify add-on files (.addons and .war) uploaded via the uploadwarfile servlet. An attacker with access to the system, including as an anonymous user, can upload malicious add-on files, which are automatically executed.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Another vulnerability that could lead to code execution is CVE-2017-9644. This weakness allows an authenticated, non-privileged local user to replace the application’s executable file with a malicious binary. When the application is started, the code in the malicious file gets executed with elevated privileges (i.e. the privileges of the targeted application).
This flaw is less serious as the attacker needs to be able to add their file to the system root path without being detected by the operating system or security products.
The last vulnerability, CVE-2017-9640, allows an attacker with access to the management panel to abuse the ManualCommand() function to write and overwrite arbitrary files on the system, and traverse directories throughout the system. CVE-2017-9640 and CVE-2017-9644 have been classified as medium severity.
The affected vendors have released patches to address the vulnerabilities in versions 6.x. Versions prior to 6.0 are no longer supported.
While Automated Logic does have a vulnerability disclosure program and encourages users to report flaws found in its products, Zero Science Lab claimed that the vendor did not respond after being contacted directly in late March. Researchers informed ICS-CERT about the security holes and the agency contacted Automated Logic, which only got in touch with the researchers in early August.
Zero Science Lab has published advisories for each of the vulnerabilities, including technical details and proof-of-concept (PoC) code.
Russia-Linked Hackers Leak Football Doping Files
23.8.2017 securityweek CyberCrime
A group of hackers believed to be operating out of Russia has leaked emails and medical records related to football (soccer) players who used illegal substances.
The group calls itself Fancy Bears and claims to be associated with the Anonymous hacktivist movement. They have set up a website, fancybears.net, where they leaked numerous files as part of a campaign dubbed “OpOlympics.”
“Today Fancy Bears’ hack team is publishing the material leaked from various sources related to football,” the hackers said. “Football players and officials unanimously affirm that this kind of sport is free of doping. Our team perceived these numerous claims as a challenge and now we will prove they are lying.”
The leaked files include emails exchanged between the Fédération Internationale de Football Association (FIFA) and representatives of anti-doping agencies discussing the test results of various football players. The files also provide information on the number of players using illegal substances -- without specifically naming any players -- and therapeutic use exemptions (TUEs), which allow athletes to take prohibited substances for medical reasons.
The files contain information on several important players allowed to use TUEs at the 2010 World Cup, including Mario Gomez, Carlos Tevez, Juan Sebastian Veron, Dirk Kuyt and Ryan Nelsen. However, the emails dumped by the hackers are dated as recent as June 2017.
The hackers said they leaked the files to show that more than 150 players were caught doping in 2015, and the number increased to 200 in 2016.
Both the Football Association and FIFA condemned the leak of confidential medical information.
The same hacker group previously targeted the International Association of Athletics Federations (IAAF) and the World Anti-Doping Agency (WADA). The hackers now also described the files as “WADA documents” and some of them appear to originate from the Anti-Doping Administration and Management System (ADAMS). SecurityWeek has reached out to WADA for comment.
While the Fancy Bears that took credit for these attacks claim to be hacktivists, researchers have linked the previous leaks to Fancy Bear, a notorious cyber espionage group believed to be sponsored by the Russian government. The threat actor is tracked by various security firms as APT28, Pawn Storm, Sednit, Sofacy, Tsar Team and Strontium.
The first Fancy Bear leak came shortly after investigations exposed state-sponsored doping in Russia. The latest release may have been triggered by similar events.
“Previous Fancy Bear dumps were almost always retaliatory and in response to sanctions from various international sports organizations. When the Russian athletic team was banned from participating in World Athletics Championships in London, embarrassing IAAF doping reports about major Western athletes were made public,” explained Recorded Future’s Insikt Group.
“As international pressure on Russia intensifies, with open calls to strip Russia of World Cup in 2018 and recent the FIFA investigation into suspected prohibited substance abuse of the national soccer team, today's release was almost guaranteed to surface,” it added. “The message reads very clear and loud - ‘Dare to touch us, we'll come after you. Don't expect us to remain silent and maintain status quo’.”
DMARC Adoption Low in Fortune 500, FTSE 100 Companies
23.8.2017 securityweek IT
Many Fortune 500, FTSE 100 and ASX 100 companies have failed to properly implement the DMARC standard, exposing their customers and partners to phishing and other email-based attacks, according to email security firm Agari.
In a report titled “Global DMARC Adoption Report: Open Season for Phishers,” Agari, which in the past years has obtained tens of millions of dollars in funding, shared the results of its analysis into the adoption of DMARC.
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication, policy, and reporting protocol designed to detect and prevent email spoofing.
Organizations using DMARC can specify what happens to unauthenticated messages: they can be monitored but still delivered to the recipient’s inbox (none), they can be moved to the spam or junk folder (quarantine), or their delivery can be blocked completely (reject).
Agari’s analysis of public DNS records showed that only five percent of Fortune 500 companies have implemented a reject policy and three percent use the quarantine policy. Roughly two-thirds of these organizations have not published any type of DMARC policy.
The sectors with the highest adoption of the reject and quarantine policies are business services, financial, technology and transportation. The security firm has identified several sectors where not one organization has adopted these policies, including wholesales, motor vehicles, apparel, hospitality, food and drug stores, energy, aerospace, household products, chemicals, and engineering and construction.
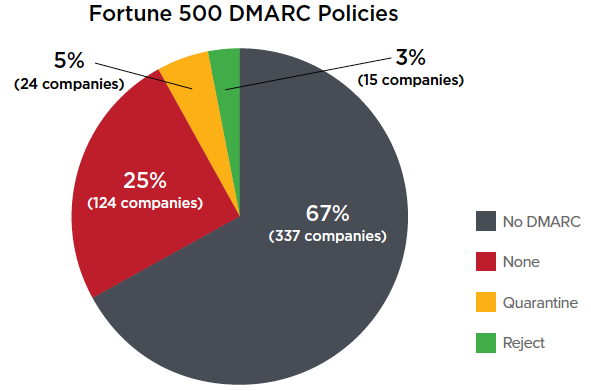
In the case of Financial Times Stock Exchange (FTSE) 100 companies, the percentage is similar. Two-thirds have not implemented DMARC and only seven percent are using a reject or quarantine policy. Only a handful of real estate and financial services firms in the FTSE 100 have implemented proper DMARC policies.
An analysis of Australian Securities Exchange (ASX) 100 organizations showed that a DMARC policy is absent in 73 percent of cases. Only three companies from the utilities, industrial and consumer discretionary sectors have implemented a reject policy and one company in the materials sector is using a quarantine policy.
These figures are worrying considering that there are tens of thousands of phishing websites and their number has increased considerably in the past year
Hotel booking service Groupize allegedly exposed sensitive data contained in unsecured AWS storage bucket
23.8.2017 securityaffairs Hacking
Security researchers discovered that hotel booking service Groupize allegedly exposed sensitive data contained in unsecured AWS storage bucket
Security experts continue to discover unsecured AWS storage bucket leaking sensitive data. Last discovery in order of time is an AWS storage related to the hotel booking service Groupize, it was discovered by Kromtech Security Center researchers and confirmed in an analysis published by MacKeeper.
“Kromtech Security Researchers have discovered a database that appeared to be associated with the automated online group hotel room booking service Groupize.” wrote MacKeeper.
“Publicly accessible bucket was hosted under ‘prm-production’ domain on AWS. No logins or passwords were required to access the data.”

Groupize denies that sensitive has been leaked, but MacKeeper’s researcher Bob Diachenko claims that until August 15 the exposed data included nearly 3,000 documents detailing contracts or agreements between hotels, customers and Groupize, including credit cards’ payment authorization forms, more than 3,000 spreadsheets, more than 32,000 “menus, and images.
“Here is what researchers were able to see:
A folder named “Documents” contained 2,936 scans or PDFs of contracts or agreements between hotels, customers and Groupize, including credit cards’ payment authorization forms, with full CC#, expiration date and CVV code.
A folder named “all_leads” contained 3,188 spreadsheets. In a single random sampling there was a total of $12.6 Million in just one spreadsheet.
Folders titled WhiteLabel / attachments contained 32,695 files in 37 folders ( these are menus, images and more)”
Recently other AWS S3 leaking data have been discovered, the popular data breach hunter Chris Vickery discovered a Verizon repository that leaked 14 million customer records and an open bucket belonging voting machine supplier ES&S that contained more than 1.8 million voter records belonging to Americans.
It is easy to predict the discovery of many other open AWS storages left open online.
A few weeks ago Amazon presented its service Macie, which would detect unsecured corporate data repositories.
“Amazon Macie is a service powered by machine learning that can automatically discover and classify your data stored in Amazon S3. But Macie doesn’t stop there, once your data has been classified by Macie, it assigns each data item a business value, and then continuously monitors the data in order to detect any suspicious activity based upon access patterns.” wrote Amazon.
USS John S McCain incident, some experts speculate it was a cyber attack
23.8.2017 securityaffairs CyberWar
On Monday, the USS John S McCain collided a Liberian-flagged tanker near Singapore, some experts speculate the incident was caused by a cyber attack.
On Monday, the USS John S McCain collided a Liberian-flagged tanker near Singapore. The incident had serious consequences on the US operation, the Chief of Naval Operations Adm. John Richardson ordered a pause, at the same time the U.S. Navy started an investigation. US Military fears the incident might have been caused by a cyber attack.
This is the fourth accident involving U.S. Navy ships in the Pacific this year.
Follow
Adm. John Richardson ✔@CNORichardson
2 clarify Re: possibility of cyber intrusion or sabotage, no indications right now...but review will consider all possibilities
10:04 PM - Aug 21, 2017
152 152 Replies 815 815 Retweets 1,519 1,519 likes
Twitter Ads info and privacy
Richardson explained that the investigation aims to exclude the “possibility of cyber intrusion or sabotage.”
According to an unnamed U.S. Navy official quoted by the CNN, the USS John S McCain destroyer experienced “a steering failure” while it was sailing the Strait of Malacca. The problem was the root cause of the collision.
“The McCain suffered a steering failure as the warship was beginning its approach into the Strait of Malacca, causing it to collide with a commercial tanker, a Navy official told CNN.
The official said it was unclear why the crew couldn’t use the ship’s backup steering systems to maintain control.” reported the CNN.
“Earlier, another US Navy official told CNN there were indications the destroyer experienced a loss of steering right before the collision, but steering had been regained afterward.”
Admiral Swift said there is no sign of cyber attack, according to The New York Times, the official confirmed that there were no signs of failure in the ship’s steering system or of a cyber attack.
Anyway, some experts like former Navy information warfare specialist Jeff Stutzman believe that the incident was not caused by human errors.
“According to McClatchy, other recent incidents include one Jan. 31, in which a guided missile cruiser, the USS Antietam, ran aground off the coast of Japan, and another May 9, when the USS Lake Champlain was struck by a South Korean fishing vessel.” reported McClatchy.
“The USS Fitzgerald, a $1.5 billion vessel, collided with a container ship June 17, resulting in the deaths of seven sailors. The commanding officer and two other officers were formally removed from duties.” “I don’t have proof, but you have to wonder if there were electronic issues,” Stutzman told McClachy.
“When you are going through the Strait of Malacca, you can’t tell me that a Navy destroyer doesn’t have a full navigation team going with full lookouts on every wing and extra people on radar.” He added, “There’s something more than just human error going on.”
According to professor Todd E. Humphreys, an expert on GPS, “Statistically, it looks very suspicious.”
Humphreys and his team conducted several studies focused on vulnerabilities in GPS and the way they could be exploited to hijack ships and UAVs. In 2013, demonstrated that just using a cheap apparatus composed of a small antenna, an electronic GPS “spoofer” built in $3,000 and a laptop he is able to take total control of sophisticated navigation system aboard a 210-foot super-yacht in the Mediterranean Sea.
GPS spoofing could have a serious effect on the vessel navigation.
“In a little noticed June 22 incident, someone manipulated GPS signals in the eastern part of the Black Sea, leaving some 20 ships with little situational awareness. Shipboard navigation equipment, which appeared to be working properly, reported the location of the vessels 20 miles inland, near an airport.” reported McClatchy.
“That was the first known instance of GPS “spoofing,” or misdirection.”
“We saw it done in, I would say, a really unsubtle way, a really ham-fisted way. It was probably a signal that came from the Russian mainland.” said Humphreys.
The Navy, Humphreys said, does not use commercial GPS, and “there is no indication that faulty satellite communications were a culprit in the USS McCain accident.”
Even if some ships used on Automatic Identification System (AIS) to avoid collisions, there is the concrete risk that someone could hack the AIS.
According to Chinese authorities, the USS John S McCain incident was caused by the ineptitude of US Navy.
“The latest incident occurred just two months after the USS Fitzgerald and a Philippine container ship collided in waters off Japan, killing seven US sailors.” states the China Daily.
“It may be hard for people to understand why US warships are unable to avoid other vessels since they are equipped with the world’s most sophisticated radar and electronic tracking systems, and aided by crew members on constant watch. But investigations into the cause of the USS Fitzgerald collision shed some light on the way US warships tend to sail without observing maritime traffic rules and the sloppiness of their crews.”
Itay Glick, who worked as for an Israeli intelligence agency in a cyberwarfare unit and founder of cyber security firm Votiro believe that the incident could be the result of a cyber attack.
“I don’t believe in coincidence,” Mr Glick told news.com.au.
“Both USS McCain and USS Fitzgerald were part of the 7th Fleet, there is a relationship between these two events and there may be a connection.”
Mr Glick believes foreign states like Russia and China may have the capability to launch an attack on the warships.
“China has capabilities, maybe they are trying things, it is possible,” he said.
He explained that such kind of attacks could be the result of GPS spoofing or a malware based attack on its computer network.
“I don’t believe in coincidence. Both USS John S McCain and USS Fitzgerald were part of the 7th Fleet; there is a relationship between these two events, and there may be a connection,” he said.
US Warship Collisions Raise Cyberattack Fears
23.8.2017 securityweek CyberWar
A spate of incidents involving US warships in Asia, including a deadly collision this week off Singapore, has forced the navy to consider whether cyberattackers might be to blame.
While some experts believe that being able to engineer such a collision would be unlikely, given the security systems of the US Navy and the logistics of having two ships converge, others say putting the recent incidents down to human error and coincidence is an equally unsatisfactory explanation.
The USS John S. McCain collided with a tanker early Monday as the warship was on its way for a routine stop in the city-state, tearing a huge hole in the hull and leaving 10 sailors missing and five injured.
The Navy announced Tuesday that remains of some of the sailors were found by divers in flooded compartments on the ship.
The Chief of US Naval Operations Admiral John Richardson said on Monday he could not rule out some kind of outside interference or a cyberattack being behind the latest collision, but said he did not want to prejudge the inquiry. His broader remarks suggested a focus on "how we do business on the bridge".
"We're looking at every possibility," Richardson said, when asked about the possibility of a cyberattack, adding "as we did with Fitzgerald as well."
Just two months earlier in June, the USS Fitzgerald and a Philippine-flagged cargo ship smashed into each other off Japan, leaving seven sailors dead and leading to several officers being disciplined.
There were also two more, lesser-known incidents this year -- in January USS Antietam ran aground near its base in Japan and in May, USS Lake Champlain collided with a South Korean fishing vessel. Neither caused any injury.
Admiral Scott Swift, commander of the US Pacific Fleet, has refused to rule out sabotage in Monday's incident, saying all possibilities are being examined.
"We are not taking any consideration off the table," he told reporters in Singapore Tuesday, when asked about the possibility of a cyberattack in the latest incident.
- High tensions -
Analysts are divided on the issue, with some believing US Navy crews may simply be overstretched as they try to tackle myriad threats in the region, and pointing to the difficulties of sailing through waterways crowded with merchant shipping.
But others believe something more sinister may be going on.
Itar Glick, head of Israeli-based international cybersecurity firm Votiro, said the spate of incidents suggested that US Navy ships' GPS systems could have been tampered with by hackers, causing them to miscalculate their positions.
"I think that hackers could try to do this, and if they are state sponsored they might have the right resources to facilitate this kind of attack," he told AFP.
Glick, who says he used to work on cybersecurity for Israeli intelligence, said that China and North Korea would be the most likely culprits.
Tensions are running high between North Korea and Washington as Pyongyang makes strides in its weapons programme, conducting two successful intercontinental ballistic missile (ICBM) test launches in July.
Pyongyang has also been blamed for recent cyberattacks, including the 2014 hack of Sony Pictures and the theft of millions of dollars from the Bangladesh central bank.
The US has repeatedly accused China of carrying out cyberattacks on American companies, particularly to steal intellectual property. Beijing however says it is also the victim of such attacks.
- 'Spoofing' -
Glick pointed to a recent incident in June of apparent large-scale GPS interference in the Black Sea to illustrate that such disruptions are possible.
The interference -- known as "spoofing", which disrupts GPS signals so ships' instruments show inaccurate locations -- caused some 20 vessels to have their signals disrupted, according to reports.
Jeffery Stutzman, chief of intelligence operations for US-based cybersecurity firm Wapack Labs, told AFP he thought the possibility of a cyberattack being behind the latest incident was "entirely possible".
"I would be very doubtful that it was human error, four times in a row," he said, referring to the four recent incidents.
Still, other observers believe such a scenario to be unlikely.
Zachary Fryer-Biggs, from defence consultancy Jane's by IHS Markit, said that even if something went wrong with the GPS system of a ship, other safety mechanisms should stop it from crashing, such as having people on watch.
"The collision only occurs if several other safety mechanisms fail," he said.
Daniel Paul Goetz, from US-headquartered cybersecurity firm Lantium, added that causing a collision would be complicated, as it would involve knowing the exact location, speed and bearing of both ships involved.
Goetz, who says his background is in US military intelligence, also pointed to the level of technology used to protect the navy from such threats.
"The US military uses a GPS system that is highly secured, highly encrypted -- the chances that somebody could take over US military ship is very close to zero," he said.
Neptune exploit kit used to deliver Monero cryptocurrency miners via malvertising
23.8.2017 securityaffairs Vulnerebility
According to a new report published by FireEye, crooks have been using the Neptune exploit kit to deliver cryptocurrency miners via malvertising campaigns.
According to experts at FireEye, crooks are exploiting the Neptune exploit kit (aka Terror EK, Eris, and Blaze) to delivery cryptocurrency miners via malvertising campaigns. The Neptune exploit kit was first spotted in January and was initially classified as a variant of the Sundown exploit kit due to the several similarities in its code.
“The Neptune Exploit Kit (or Terror EK), which initially started as a Sundown EK copycat operation, has relied heavily on malvertisements. Early use of this exploit kit saw domains with very similar patterns dropping cryptocurrency miners through malvertisement” reads the analysis published by FireEye.
We already reported a significant drop in the exploit kit activity since the disappearance of the Angler EK and Neutrino EK, then the principal exploit kits became the Sundown EK.
Crooks are continuing to use the Neptune exploit kit in malvertising campaigns, the last trend is its employment in campaigns aiming to deliver cryptocurrency miners.
The FireEye analysis highlights the numerous changes in the recent attacks delivering the cryptocurrency miners, including payloads, URI patterns, and landing pages.
Since July 16, FireEye experts have observed changes in URI patterns for Neptune Exploit Kit, the last campaign monitored was abusing a legitimate popup ad service (within Alexa’s top 100) with redirects to ads about hiking clubs.
The countries most affected by the campaign are South Korea (29%), Europe (19%), and Thailand (13%), followed by Middle East (13%) and the United States (10%).

The ads used in the Neptune exploit kit campaign analyzed by FireEye were mostly served on popular torrent and hosting websites.
The landing pages were hosting the following exploits to trigger well-known vulnerabilities:
CVE-2016-0189 – Internet Explorer
CVE-2015-2419 – Internet Explorer
CVE-2014-6332 – Internet Explorer
CVE-2015-8651 – Adobe Flash Player
CVE-2015-7645 – Adobe Flash Player
The payload delivered in the last Neptune Exploit Kit campaign is a Monero cryptocurrency Miner.
“Despite an observable decline in exploit kit activity, users are still at risk, especially if they have outdated or unpatched software. This threat is especially dangerous considering drive-by exploit kits (such as Neptune EK) can use malvertisements to seamlessly download payloads without ever alerting of the user.” concluded FireEye.”FireEye NX detects exploit kit infection attempts before the malware payload is downloaded to the user’s machine. Additionally, malware payloads dropped by exploit kits are detected in all other FireEye products.”
FireEye also included in the analysis the IoCs.
Researchers Demo Remote Hacking of Industrial Cobots
23.8.2017 securityweek Hacking
Researchers at security firm IOActive have shown how a remote attacker can hack an industrial collaborative robot, or cobot, and modify its safety settings, which could result in physical harm to nearby human operators.
A few months ago, IOActive published a brief report providing a high-level description of its research into robot cybersecurity. Researchers analyzed industrial and business robots from six vendors, including SoftBank Robotics, UBTECH Robotics, ROBOTIS, Universal Robots, Rethink Robotics and Asratec Corp.
A brief analysis of mobile applications, software and firmware led to the discovery of nearly 50 vulnerabilities, including weaknesses related to communications, authentication, authorization mechanisms, cryptography, privacy, default configurations, and open source components.
Cesar Cerrudo, CTO at IOActive, and Lucas Apa, Senior Security Consultant at IOActive, warned at the time that the security holes could be exploited for spying and stealing sensitive data, and even cause physical damage or harm in the case of industrial robots. They have now shared technical details and videos demonstrating some of their findings.
Cobots share a workspace with human operators and help them perform various tasks. Unlike traditional industrial robots, which execute repetitive tasks, they can learn new movements, see using cameras and hear via microphones.
Cobots are used not only in industrial environments, but IOActive’s research has focused on industrial models, namely the Baxter/Sawyer cobots for industrial automation from Rethink Robotics and UR from Universal Robots.
Cerrudo and Apa showed how a remote attacker could chain six vulnerabilities to modify a UR robot’s safety settings and disable emergency functions, which could pose a serious threat to human lives.
“Imagine what could happen if an attack targeted an array of 64 cobots as is found in a Chinese industrial corporation,” the researchers warned.
Technical details have been provided for each of the exploited flaws, along with a video showing how an attacker can disable safety features and cause a robot arm to act “crazy.”
While some of the robot manufacturers contacted by the IOActive researchers have taken steps to address the vulnerabilities, others have downplayed the risks and did not release any patches. In the case of cobots, Rethink Robotics fixed the flaws discovered by the experts back in February, but UR still hasn’t resolved the issues affecting its products.
IOActive is not the only security firm to analyze industrial robots. Researchers at Trend Micro and the Polytechnic University of Milan published a paper a few months ago on the cybersecurity risks associated with industrial robots, and warned that some machines could be attacked directly from the Internet.
Elon Musk, CEO of Tesla and SpaceX, along with more than 100 robotics and artificial intelligence entrepreneurs recently sent a letter to the United Nations calling for action to prevent the development of robotic weapons.
DDoS Threat Increases While Mirai Becomes 'Pay-for-Play'
23.8.2017 securityweek Attack
The DDoS threat is increasing again. Pbot can generate 75 Gbps from just 400 nodes and Mirai has been commoditized. However, despite the growing number of attacks, the overall trend seems to be for more frequent, smaller attacks. These are the primary takeaways from a new Q2 study into internet traffic.
Akamai Technologies, a Cambridge, Mass.-based content delivery network (CDN) and cloud services provider with more than 233,000 servers in over 130 countries, has published its Q2 State of the Internet report (PDF). The report comprises analyses of attack data seen across this network. It shows that DDoS attacks have increased by a massive 28% over the previous quarter.
Within this statistic, infrastructure layer (layers 3 and 4) attacks have risen by 27%; reflection-based attacks have risen 21%; and the average number of attacks per target has increased by 28%. Gaming sites are frequent targets, accounting for 81% of all volumetric DDoS attacks monitored by Akamai.
While the average number of attacks per target rose to 32 over the period, one gaming site suffered 558 attacks, averaging six per day throughout the period.
The final months of 2016 were notable for the largest DDoS attacks ever seen; but the current trend, suggests the report, is for smaller attacks. This is despite the continued availability of the Mirai botnet, and the use of Pbot malware to create mini-DDoS botnets able to generate a 75 Gbps attack from just 400 bots. Pbot's power comes from infecting webservers able to create more traffic per node than, say, Mirai's infection of large numbers of small IoT devices.
"We know that massive DDoS attacks are possible," says the report, "but could this be a new trend going forward? Have DDoS attackers taken to more subtle, targeted attacks to avoid drawing attention?"
This possibility is given extra weight by the evolving nature of Mirai attacks. Akamai was one of the first Mirai targets in Fall 2016, and has continued to be a target. This long-standing adversarial relationship has allowed Akamai to study Mirai in some depth.
Mirai is often thought of as a single massive network of bots. In reality, says Akamai, "it is more akin to smaller hives of related bots and C&Cs." An analysis of different Mirai C&Cs shows that parts of Mirai are used to attack different targets, with some C&Cs attacking multiple targets, and others attacking a single target.
"At least one botnet operator was offering access to the systems under its control for rent," notes Akamai, "which may explain why some botnets attacked such a large number of IP addresses."
Akamai says it will continue its research into and analysis of Mirai, but for now notes that it appears to be contributing to the commoditization of DDoS. The large number of different attacks emanating from single C&Cs can be considered as 'pay-for-play' attacks -- they were seen attacking IPs for a short duration, going inactive, and then re-emerging to attack different targets.
The report also notes that DNS traffic analysis can be used to passively locate the likely incidence of malware infections. Ever since Conficker, malware has been using domain generation algorithms (DGAs) to hide their C&C infrastructure. These DGAs generate many pseudo-random IP addresses every day. The attacker needs to choose only one of the expected domains and register it 'just in time', and then abandon it after use. The malware, however, doesn't know which is the correct IP to contact, and cycles through the possibilities until it finds the right one.
Akamai analyzed the traffic of more than 2.5 million connected networks. One hundred and forty were known to be infected with malware. "When looking at the average number of unique domains accessed per hour," notes the study, "we saw that infected networks had approximately 15 times the lookup rate of a clean network." This is explained by the malware trying to access the DGA-generated IPs. "Since most of the generated domains were not registered, trying to access all of them created a lot of noise."
DNS monitoring is thus a potential method of breach detection. "Security defenders are advised to make certain they are using a combination of security monitoring products that include DNS monitoring," concludes Akamai. "Having visibility into different areas of the enterprise network will increase detection and reduce risks. For the best defense, security controls should also be in place on endpoint devices and the inner network, not just Internet connectivity."
Neptune Exploit Kit Used to Deliver Monero Miner
22.8.2017 securityweek Exploit
Cybercriminals have been using the Neptune exploit kit to deliver cryptocurrency miners via malvertising campaigns, FireEye reported on Tuesday.
Neptune, whose arrival was detailed by researchers in January, is also known as Terror, Blaze and Eris. It was initially considered a variant of the Sundown exploit kit due to many code similarities.
Exploit kit activity has been declining since the disappearance of Angler and Neutrino. Sundown also went silent and the infosec community managed to delivered a significant blow to the infrastructure used by RIG.
Neptune has gained popularity and it continues to be used in malvertising campaigns, particularly ones that aim to deliver cryptocurrency miners. Several changes have been spotted recently by FireEye in Neptune attacks, including URI patterns, landing pages, malvertising campaigns and payloads.
The new URI patterns were first observed by FireEye in mid-July. The attackers have been abusing a legitimate pop-up ad service (present in Alexa’s Top 100) to deliver malware via fake advertisements for hiking clubs. The malicious websites imitate real domains, often using the same domain name with a .club suffix instead of .com (e.g. highspirittreks.com vs highspirittreks.club). One of the domains used to redirect users to the exploit kit landing pages also mimics a YouTube to MP3 online converter.
The ads linked to this Neptune exploit kit campaign have been typically served on popular torrent and hosting websites.
Once victims are taken to the landing page, the EK exploits three Internet Explorer and two Adobe Flash Player vulnerabilities to deliver malware. None of the exploits used by Neptune are new – they target vulnerabilities disclosed between 2014 and 2016.
The payload delivered in the campaign is a piece of malware that mines for Monero (XMR), a cryptocurrency currently worth roughly $86 per unit.
The regions most affected by the campaign are South Korea (29%), Europe (19%), Thailand (13%), Middle East (13%) and the United States (10%).
“Despite an observable decline in exploit kit activity, users are still at risk, especially if they have outdated or unpatched software,” FireEye warned. “This threat is especially dangerous considering drive-by exploit kits (such as Neptune EK) can use malvertisements to seamlessly download payloads without ever alerting the user.”
Several Flaws Patched in Fuze Communications Platform
22.8.2017 securityweek Vulnerebility
Fuze has patched several vulnerabilities discovered by Rapid7 researchers in a component of its cloud-based unified communications platform. The flaws could have been exploited to obtain sensitive data and launch brute-force attacks on the administration interface.
The security holes affected the Fuze platform’s TPN handset customer portal hosted at mb.thinkingphones.com/tpn-portlet. One of the flaws allowed a remote, unauthenticated attacker to obtain information about Fuze customers by providing a valid MAC address on a specific webpage.
While there are many MAC addresses in the world and finding one that belongs to a Fuze customer might seem difficult, the range of potentially valid addresses can be easily enumerated knowing that Fuze supports Polycom and Yealink phones, which have a specific subnet of addresses.
Providing a Fuze user’s MAC address on the webpage resulted in a response from the server containing the customer’s email address, phone number, a link to the admin portal, and account information, including location data.
Once on the administration portal, an attacker would have had two options for obtaining the admin code needed to access a user’s account. One of them involved intercepting HTTP network traffic between the handset and the admin portal, which included the code. The second option involved launching a brute-force attack on the login page, as the number of authentication attempts was not limited.
The vulnerabilities were reported to Fuze in April and they were all patched by May 6. The vendor now limits the number of authentication attempts, restricts access to the MAC page, and traffic is now protected against snooping. Since all the fixes are on the server side, no action needs to be taken by users and no CVE identifiers have been assigned.
“As users of the entire Fuze platform, Rapid7’s team identified security weaknesses and responsibly disclosed them to the Fuze security team. In this case, while the exposure was a limited set of customer data, Fuze took immediate action upon receiving notification by Rapid7, and remediated the vulnerabilities with its handset provisioning service, in full, within two weeks,” said Chris Conry, CIO of Fuze.
Conry pointed out that there is no evidence of attacks exploiting these vulnerabilities in the wild.
Experts at ZDI reported two critical Zero-Day flaws in Foxit PDF Reader
22.8.2017 securityaffairs Vulnerebility
Experts found two critical zero-day flaws in the Foxit PDF Reader that could be exploited by attackers to execute arbitrary code on a targeted computer
Security researchers have discovered two critical zero-day vulnerabilities in the popular Foxit Reader application that could be exploited by attackers to execute arbitrary code on a targeted computer, if not configured to open files in the Safe Reading Mode.
The attack scenarios for both vulnerabilities see attackers send a specially crafted PDF file to a Foxit user and tricking him into opening it.
The first zero-day flaw, tracked as CVE-2017-10951, is a command injection vulnerability that was discovered by the expert Ariele Caltabiano from Trend Micro’s Zero Day Initiative (ZDI).
“This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Foxit Reader. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.” reads the security advisory for the vulnerability.
“The specific flaw exists within app.launchURL method. The issue results from the lack of proper validation of a user-supplied string before using it to execute a system call. An attacker can leverage this vulnerability to execute code under the context of the current process.”
The second vulnerability, tracked as CVE-2017-10952, is a file write flaw that affects the saveAs JavaScript function. The flaw was discovered by Offensive Security researcher Steven Seeley.
“This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Foxit PDF Reader. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.” reads the security advisory published by ZDI.
“The specific flaw exists within the saveAs JavaScript function. The issue results from the lack of proper validation of user-supplied data, which can lead to writing arbitrary files into attacker controlled locations. An attacker can leverage this vulnerability to execute code under the context of the current process.”
Foxit still hasn’t patch both the vulnerabilities because cannot be triggered if the users have the “safe reading mode” feature enabled, the company highlighted that it is enabled by default in Foxit PDF Reader.
“Foxit Reader & PhantomPDF has a Safe Reading Mode which is enabled by default to control the running of JavaScript, which can effectively guard against potential vulnerabilities from unauthorized JavaScript actions,” replied the company.

Both vulnerabilities can be triggered through the JavaScript API in Foxit PDF Reader.
Below the video PoC for both vulnerabilities:
CVE-2017-10951:
CVE-2017-10952:
“Steven exploited this vulnerability by embedding an HTA file in the document, then calling saveAS to write it to the startup folder, thus executing arbitrary VBScript code on startup,” reads the advisory published by the ZDI.
The company is working to address the two zero-day vulnerabilities reported by the Zero Day Initiative, meantime Foxit Reader and PhantomPDF users must check that the “Safe Reading Mode” feature is enabled. They can also uncheck the “Enable JavaScript Actions” from Foxit’s Preferences menu.
Organizations Reminded of DNSSEC Key Signing Key Rollover
22.8.2017 securityweek Security
Organizations are being reminded that the Internet Corporation for Assigned Names and Numbers (ICANN) will soon change the root zone key signing key for the Domain Name System Security Extensions (DNSSEC) protocol. Failure to take action could result in users being unable to access the Internet.
DNS, the system that translates domain names to IP addresses, was not designed with security in mind. In an effort to prevent users from being directed to malicious websites via DNS spoofing attacks, the DNSSEC protocol was introduced in 2010.
DNSSEC aims to prevent attacks by cryptographically signing DNS information, including the root zone, which is the highest level of the DNS structure. If DNSSEC is used, the root zone vouches for the public key of the .com zone (or other TLD zone), which in turn vouches for all .com domains. Since the root zone is at the top of the DNS hierarchy, there is no higher level to vouch for it so its zone key is configured as a so-called “trust anchor,” a key that is declared trustworthy.DNSSEC KSK rollover
The trust anchor key is called a key signing key (KSK), and all recursive name servers performing DNSSEC validation need to have the root zone’s KSK set as a trust anchor. These name server are typically operated by Internet service providers (ISPs) and enterprises, and if the KSK is not configured properly, DNS resolution will no longer work for their users.
Since keeping a cryptographic key alive for a long period of time is considered a bad security practice given the fact that it could get compromised, ICANN plans to periodically change, or roll, the KSK.
A new KSK was generated in October 2016 and it will be used to sign the root zone key set on October 11, 2017. Until this date, all DNSSEC-validating resolvers need to be configured with the new root KSK.
On January 11, 2018, the old KSK will be revoked and March 22, 2018 is the last day on which the old KSK will appear in the root zone. In August 2018, the old key will be deleted from equipment in ICANN’s two key management facilities.
ICANN estimates that roughly 750 million people worldwide use DNSSEC validation and are affected by the KSK rollover so it’s important that stakeholders take action to prevent service disruptions.
In the case of software that supports automated updates of DNSSEC trust anchors, the root zone KSK will be updated automatically at the appropriate time and no action needs to be taken. However, in the case of software that does not support automated updates, DNSSEC trust anchors need to be manually updated. The developers of BIND, the most widely deployed DNS software, have provided instructions for users.
Organizations not using DNSSEC are not impacted, but use of the protocol is recommended for security reasons.
US-CERT has reminded organizations about the October 11 root zone KSK change and advised them to update their key before this date, particularly federal agencies, which, unlike private sector companies, are required to use DNSSEC.
Ourmine hacked PlayStation Social Media Accounts to announce the theft of PSN Database
22.8.2017 securityaffairs Hacking
Ourmine hacker crew hijacked the official Twitter and Facebook accounts for Sony PlayStation Network (PSN) on Sunday and claims to have stolen PSN database.
The dreaded Ourmine hacker crew is back, after the recent hack of social media accounts of HBO and Game of Thrones, the team hijacked the official Twitter and Facebook accounts for Sony PlayStation Network (PSN) on Sunday.
The Saudi Arabian group of white hat hackers hacked the Netflix US Twitter account (@Netflix) in December to promote its website and hacking services, it is known for its attacks against high-profile Twitter accounts. The list of victims is very long and includes Mark Zuckerberg, Twitter co-founder Evan Williams, David Guetta Daniel Ek, former Twitter CEO Dick Costolo, Twitter CEO Jack Dorsey, the CEO and founder of Spotify, Google CEO Sundar Pichai, and many others.
On Sunday evening Ourmine published a tweet to claim the hack of PlayStation Network and theft of its database.
Other tweets posted by the group were inviting the company to contact them through the Ourmine website and pay for the security service offered by the crew.
“PlayStation Network Databases leaked #OurMine,” the first tweet by OurMine on the compromised PlayStation Twitter account read.
“No, we aren’t going to share it, we are a security group if you work at PlayStation then please go to our website,” reads another Tweet published by the group.
The tweets and the Facebook post were promptly deleted.
OurMine shared the same message on the PlayStation Network’s official Facebook page.
At the time, it is still unclear if OurMine has stolen the PSN’s database.
Last time the company was breached was in 2011 when the PlayStation hack exposed the personal details of more than 77 Million PSN users.
Mr.Smith, HBO hackers threaten to leak final episode of Game of Thrones 7
22.8.2017 securityaffairs Hacking
The bad actors behind the HBO hack are back and are threatening to leak the final episode of the seventh season of Game of Thrones.
The threat actor that has hacked into the HBO announced that it will leak the final episode of Game of Thrones season 7.The hacker who claimed the responsibility for the hack called himself Mr. Smith, he told Mashable media outlet to “Be ready for GOT S& E6 &E7 as soon as possible.”
Cyber criminals claiming to have hacked television group HBO networks were demanding millions of dollars in ransom payments from the company while threatening to release more material.
The alleged hackers published a five-minute video letter to HBO chief Richard Plepler claiming to have “obtained valuable information” in a cyber attack. Cybercriminals said they had stolen 1.5 terabytes of data.
The worst news for HBO is that the hackers are also claiming to be in possession of login credentials to access “many HBO platforms already.”
“And while the latest data dump doesn’t include any Game of Thrones spoilers, it definitely contains some information that the network wouldn’t want out in the open.” reported Mashable.
“Specifically, what appears to be the login credentials for almost every single HBO social media account. Passwords for everything from @HBO, @GameOfThrones, and @WestworldHBO to various Instagram and Giphy accounts were in a text document provided to us by the so-called “Mr. Smith group.”
For legal reasons, journalists at Mashable did not attempt to login into the accounts provided by Mr. Smith, but they explained that they have no reason to doubt their authenticity. If confirmed this means that hackers gained access to almost every single HBO social media account.
The hackers reportedly defaced HBO Giphy accounts, including one titled “HB-Old Is Dying,” which repeated the previous message that “HBO is falling.”
HBO replied to the threat with its past statement: “We are not in communication with the hacker, and we’re not going to comment every time a new piece of information is released. It has been widely reported that there was a cyber incident at HBO. The hacker may continue to drop bits and pieces of stolen information in an attempt to generate media attention. That’s a game we’re not going to participate in.”
Mr. Smith requested HBO half of the group’s annual budget of $12 million to $15 million to stop leaking the files.

The hackers claim a long work to compromise the company network, it took six months to break into the company systems, they also added to have purchased $500,000 a year zero-day exploits that let them hack the firm exploiting flaws in Microsoft and other software used by HBO.
According to a report from a leaked memo by Variety, in response to the incident, HBO offered a reward of $250,000. The payment was offered as a “bug bounty,” to discover vulnerabilities in their its computer networks.
Unfortunately, “Mr. Smith” and his crew weren’t satisfied by the offer that doesn’t match their millionaire demands to stop leaking sensitive data, the crooks’ request would be more than $6 million.
HBO also accidentally leaked Game of Thrones Season 7 Episode 6.
Another popular hacker crew, the OurMine, claimed responsibility for hijacking the main social media accounts at HBO as well as the Game of Thrones Twitter account on August 16.“Hi, OurَMiَne are here, we are just testing your security, HBO team please contact us to upgrade the security – ourmine.org -> Contact.” states the message published by the group on the HBO account.
Sony PlayStation Social Media Accounts Hacked; Claims PSN Database Breach
21.8.2017 thehackernews Hacking
After hacking social media accounts of HBO and its widely watched show Game of Thrones, a notorious group of hackers calling itself OurMine took control over the official Twitter and Facebook accounts for Sony's PlayStation Network (PSN) on Sunday.
After taking over the accounts, OurMine, Saudi Arabian group of hackers which claims to be a "white hat" security firm, posted its first tweet on Sunday evening, claiming to have breached PlayStation Network and stolen its database.
The tweet followed by a series of tweets encouraging the company to contact the hacking group through its website to buy its IT security service in an effort to protect itself from future cyber attacks.
"PlayStation Network Databases leaked #OurMine," the first tweet by OurMine on the compromised PlayStation Twitter account read.
"No, we aren't going to share it, we are a security group if you work at PlayStation then please go to our website," the followed Tweet read.
The hacking group also posted similar content on the PlayStation Network's official Facebook page that has more than 37 million followers.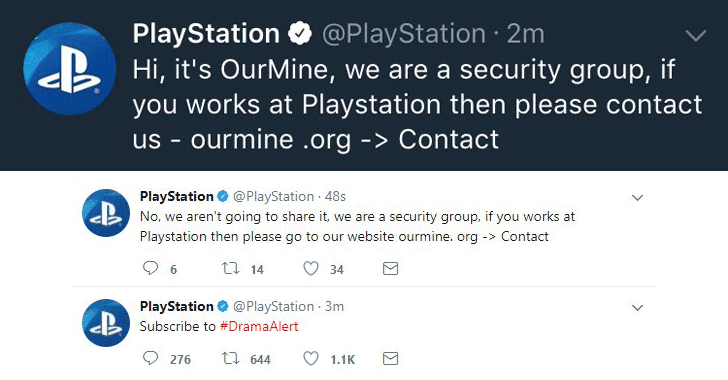
Both tweets and Facebook messages posted by the hacking group were deleted shortly.
At the time, it is unclear if OurMine has access to PSN's database or their Tweets and Facebook posts were just to spread fear among the company and its customers.
However, the company suffered a massive data breach in 2011, when the PlayStation hack exposed the personal details of the entire PSN user base (over 77 Million at the time), including users names, date of births, email addresses, and credit card details.
The hacking incident was the largest identity theft on record, which forced Sony to shut down its entire system for almost a month. Anonymous took responsibility for the data breach.
Ourmine is the same hacking group that previously compromised social media accounts of major companies CEOs, including Facebook CEO Mark Zuckerberg, Twitter CEO Jack Dorsey, and Google CEO Sundar Pichai.
In the majority of cases, Ourmine gains access to the social media accounts by using credentials exposed in previous, publicly known data breaches.
However, the group does not seem to ever go beyond just demonstrating its ability to take over the account, without doing significant damage to the accounts or its protected information.
OurMine markets itself as a security firm that offers companies security against cyber attacks, charging up to $5,000 for a "scan" of their social media accounts, site security holes, and other security vulnerabilities.
PlayStation Social Media Accounts Hacked
21.8.2017 seurityweek Hacking
A notorious hacking firm, probably best described as greyhats rather than white or blackhats, briefly breached the PlayStation Facebook and Twitter accounts on Sunday.
OurMine, a Saudi-based security firm, specializes in breaching high-profile accounts in order to advertise its 'prowess' and sell its security services. Yesterday, it got into PlayStation's Twitter and Facebook accounts, and claimed to have stolen 'PlayStation Network Databases.' All messages were quickly removed by Sony, but not before they had been seen, and not before PlayStation users' concerns were raised.
The messages left on Facebook were potentially the more worrying: "Playstation, contact us we got Playstation Network database leaked!" This immediately provoked memories of the massive 2011 breach which forced Sony to shut down the PlayStation Network and Store, and had the personal information of some 77 million PSN users stolen.
Tweets posted by OurMine on PlayStation's Twitter account were in the same vein, but added, "No, we aren't going to share it, we are a security group, if you works at Playstation then please go to our website ourmine.org."
Unless OurMine has changed its method of operation, then it is unlikely to leak any personal information – in fact, it is quite possible that the social media accounts are the totality of its success against PlayStation. However, this cannot be guaranteed; and until official comment comes from Sony, it cannot be guaranteed that PlayStation networks have not been breached and personal data stolen.
"It's quite unlikely that the database is indeed stolen," comments High-Tech Bridge CEO Ilia Kolochenko. "On the other hand, it can be a smart smoke screen to camouflage a large-scale data breach and distract attention of cybersecurity teams from the real problem. However, until Sony makes an official statement about their internal investigation, it's too early to make any conclusions."
At this stage, it cannot even be guaranteed that the social media hacks were performed by OurMine. The most recent hack it acknowledges on its website is the April 2017 YouTube hack, which it describes as "the biggest hack in YouTube history!" During 2016, OurMine is believed to have breached the Twitter accounts of Wikipedia co-founder Jimmy Wales, Pokemon Go creator John Hanke, Twitter co-founder Jack Dorsey, Google CEO Sundar Pichai, and Facebook co-founder Mark Zuckerberg – whose Pinterest was also hacked.
During 2017, OurMine has been 'credited' with further hacks against the Unity user forum, and, last week, against HBO's media accounts. The message left on HBO was typical: "Hi, OurMine here, we are just testing your security, HBO team please contact us to upgrade the security." HBO quickly regained control of the account and removed the messages.
The HBO Twitter hack is not thought to be related to the theft of 1.5TB of data from HBO. Earlier this month, these hackers released the personal phone numbers of Game of Thrones actors, emails and scripts. They are demanding a ransom of $6 million for the return of HBO's proprietary information.
SecurityWeek has contacted both Sony and OurMine and asked for comments on the PlayStation Twitter breach. This story will be updated with any reply.
Tech Leaders Warn Against "Pandora's Box" of Robotic Weapons
21.8.2017 seurityweek IT
Elon Musk is leading demands for a global ban on killer robots, warning technological advances could revolutionise warfare and create new "weapons of terror" that target innocent people.
The CEO of Tesla and SpaceX joined more than 100 robotics and artificial intelligence entrepreneurs in signing a letter to the United Nations calling for action to prevent the development of autonomous weapons.
"Lethal autonomous weapons threaten to become the third revolution in warfare," warned the statement signed by 116 tech luminaries, also including Mustafa Suleyman, cofounder of Google's DeepMind.
"Once developed, they will permit armed conflict to be fought at a scale greater than ever, and at timescales faster than humans can comprehend," the letter read.
The innovators also highlighted the danger that the technology could fall into the wrong hands.
"These can be weapons of terror, weapons that despots and terrorists use against innocent populations, and weapons hacked to behave in undesirable ways," the letter read.
"We do not have long to act. Once this Pandora's box is opened, it will be hard to close."
Both Musk and British astrophysicist Stephen Hawking have regularly warned of the dangers of artificial intelligence.
The renewed plea on autonomous weapons was released as the International Joint Conference on Artificial Intelligence in Melbourne got underway Monday, with a record 2,000 of the world's top AI and robotics experts taking part, organisers said.
One expert said autonomous weapons could make war more likely.
"Today the potential loss of human life is a deterrent for conflict initiation and escalation, but when the main casualties are robots, the disincentives change dramatically and the likelihood of conflict increases," Professor Mary-Anne Williams of the University of Technology Sydney.
She warned a killer robot ban may be disregarded by some nations but would stop "countries such as Australia from developing defensive killer robots, thereby being vulnerable to other countries and groups that ignore the ban".
Another expert said decision made today would help shape the "futures we want".
"Nearly every technology can be used for good and bad, and artificial intelligence is no different," said Professor Toby Walsh of the University of New South Wales.
Organisers said the conference, which concludes on Friday, has attracted a record number of participants from China, reflecting a push by Beijing to become a leading player in the field.
A key focus of the event will be looking at the challenges of developing fully autonomous AI systems, programme chair Carles Sierra of the Spanish National Research Council said.
A UN group on autonomous weapons had been due to meet Monday but the gathering was postponed until November, according to the group's website.
In 2015, thousands of researchers and personalities launched an appeal to ban autonomous weapons.
Enigma platform hacked, hackers stole over $470,000 worth of Ethereum
21.8.2017 seurityaffairs CyberCrime
Enigma platform hacked – Another cyber heist made the headlines, this time an unknown hacker has stolen more than $471,000 worth of Ethereum cryptocurrency.
The hacker has stolen it from the cryptocurrency investment platform, Enigma. According to an announcement made on Enigma website, an “unknown entity” has hacked their website, slack accounts and email newsletter accounts.
“WARNING: ENIGMA SLACK COMPROMISED, DO NOT SEND FUNDS
Hi Everyone, Our Slack channel and certain email lists have been compromised. We are working diligently to resolve the issues.
DO NOT SEND FUNDS TO ANY ADDRESSES.
We will provide further updates on the situation shortly.
DO NOT SEND FUNDS”

The hacker has uploaded a fake pre-sale page with the following fake ETH address to send money:
0x29d7d1dd5b6f9c864d9db560d72a247c178ae86b
The hacker spread the fake ETH address via the website newsletter to trick victims into sending their funds to his ETH address.

Even if the address was flagged as ‘compromised’ by Etherscan, Enigma users are still sending ETH to the fake address.
Hackers have received more than 1,487.90 ETH then started transferring the stolen ETH:
Curiously a few days ago, after recent cyberheists of virtual currency, Enigma published a post to make awareness about phishing and scams, the post it no more online.
“As we work hard to build the future of data and crypto trading and investing, we want to take a few moments to talk about safety,” Enigma Project wrote in the blog post. “Due to our strong growth, our community has become a target. The worst elements of the crypto scene—scammers and phishers—are attracted to good projects and good communities.”
This is the fifth incident involving Ethereum currency in the last weeks, below the list of previous ones:
$8.4 Million worth of Ethereum during Veritaseum’s Initial Coin Offering (ICO).
$32 Million worth of Ethereum from Parity’s Ethereum Wallet accounts.
$7 Million worth of Ether during the hack of startup CoinDash’s ICO.
$1 Million worth of Ether and Bitcoins heist in cryptocurrency exchange Bithumb.
At the time, it is unclear how hackers compromised the Enigma platform.
Podvodníci to zkouší přes tiskárny. Pak důvěřivce oškubou
21.8.2017 Novinky/Bezpečnost Hacking
Na pozoru by se měli mít v posledních dnech lidé, kteří obdrží e-mail s naskenovaným souborem. I když se může na první pohled zdát, že jej zaslala skutečně nějaká tiskárna, ve skutečnosti jde o podvod. A počítačovým pirátům jde pouze o to, aby mohli důvěřivce oškubat.
Jak útočí vyděračské viry
Na napadeném stroji dokážou vyděračské viry udělat pěkný nepořádek. Nejprve zašifrují všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Zaplatit zpravidla chtějí v bitcoinech, protože pohyby této virtuální měny se prakticky nedají vystopovat. A tím logicky ani nelegální aktivita počítačových pirátů.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
Dnes 15:54
Na množící se podvody upozornil český Národní bezpečnostní tým CSIRT.CZ. Podle něho zneužívají podvodníci fakt, že moderní tiskárny skutečně dokážou naskenované dokumenty odeslat přímo do e-mailové schránky.
„Aktuálně zaznamenáváme zvýšený výskyt e-mailů přesvědčivě se tvářících jako oskenovaný soubor poslaný tiskárnou,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Přílohu vůbec neotevírat
Podle něj nebezpečí tkví právě v příloze, která je součástí nevyžádaného e-mailu. „V příloze je přiložený archív s příponou .rar. V archívu je zabalený .vbs skript, který již poté dokáže napáchat škodu,“ podotkl Bašta.
„Dle některých výzkumníků se s největší pravděpodobností jedná o novou variantu ransomwaru Locky, který šifruje soubory oběti a přidává jim následně příponu .lukitus. Námi zachycený vzorek je v současnosti úspěšně detekován pouze některými antiviry,“ varoval bezpečnostní expert.
To jinými slovy znamená, že nový škodlivý kód, který se šíří prostřednictvím příloh v e-mailu, nemusí antivirové programy vůbec rozeznat. Uživatelé tak po otevření přílohy vlastně ani nemusí vědět, že si zavirovali počítač.
Chce výkupné
Locky přitom dovede v počítači udělat pěknou neplechu. Po spuštění přílohy v nevyžádaném e-mailu se do PC nahraje vyděračský virus, který dále škodí. Zašifruje data a za jejich zpřístupnění požaduje výkupné.
Útočníkům jde tedy především o peníze. Ani po zaplacení výkupného však uživatelé nemají jistotu, že se ke svým datům dostanou. Místo toho je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
Ruští hackeři napadli evropské hotelové sítě, špehovali jejich zákazníky
21.8.2017 Novinky/Bezpečnost Hacking
Útok postihl hotely v sedmi evropských zemích a v Izraeli. Bezpečnostní experti se domnívají, že hackeři chtěli prostřednictvím hotelových wi-fi sítí sledovat vládní činitele.
Narušení internetových sítí hotelů v sedmi evropských zemích a v Izraeli má mít na svědomí hackerská skupina ATP28 z Ruska, která je rovněž podezřelá z pokusu o ovlivňování loňských voleb amerického prezidenta. Podle společnosti FireEye se útočníci zaměřili na několik firem z oblasti pohostinství a na konkrétní hotelové sítě.
„Existují určité náznaky, že hackeři ve skutečnosti hledali způsob, jak se dostat do zařízení vládních činitelů a obchodních zástupců, kteří využívají hotelovou síť wi-fi,“ uvedl server Securityweek.com. Napadené země nespecifikoval.
Útok měl ve všech případech stejný scénář. Hackeři zaslali vybranému zaměstnanci hotelu e-mail s přílohou Hotel_Reservation_Form.doc, která obsahovala makra. Jejich prostřednictvím skupina ATP28 šířila malware GameFish. Jde o backdoor, který útočníci použili i při nedávné kybernetické kampani proti Černé Hoře před jejím vstupem do NATO.
Jakmile hackeři získali přístup do hotelové sítě wi-fi, využili exploitu EternalBlue SMB, který byl použit i při šíření ransomwarových kampaní WannaCry a Petya.
Stačilo 12 hodin na ovládnutí notebooku
Skupina rovněž využila nástroj Responder, který jí umožnil zasílat uživatelská jména a hesla z napadených počítačů na vzdálený řídicí server. V jednom konkrétním případu, k němuž došlo již v roce 2016, stačilo, aby se oběť připojila k hotelové síti a za pouhých dvanáct hodin skupina ATP28 ovládala jeho zařízení a využívala jeho obsah.
Běžně tyto útoky probíhají na dálku, ale v tomto případě byl útočník zřejmě připojen na stejné síti jako jeho oběť – byl jí tedy fyzicky nablízku.
Nejde o jedinou škodlivou kampaň zaměřenou na zákazníky velkých hotelových sítí v Evropě. Známý je rovněž případ malwaru DarkHotel, který souvisel s informacemi o vládních záležitostech v Jižní Koreji, a také Duqu 2.0, který se zaměřil na hosty evropských hotelů, kteří vyjednávali se zástupci Západu o íránském jaderném programu. Bezpečnostní experti předpokládají, že v těchto případech byli angažováni vládou najatí hackeři z Ruska a Číny.
Veřejná wi-fi představuje nebezpečí, říká expert
„Veřejné sítě wi-fi představují velké riziko kdekoli, nejen v hotelích. Používáním takové sítě se uživatel vystavuje nebezpečí infiltrace různých typů škodlivého kódu. Útočníci se nemusí zaměřovat pouze na vládní činitele a představitele velkých firem, mohou tímto způsobem šířit třeba i vyděračský ransomware,“ upozorňuje Václav Zubr, bezpečnostní expert společnosti ESET. „Největší nebezpečí hrozí u otevřených wi-fi sítí, na které se lze připojit bez zadání hesla. Nicméně i zaheslované sítě mohou představovat riziko,“ dodává.
Podle Zubra je vhodnější při cestování používat vlastní datový přístup k internetu, případně privátní wi-fi sítě, které nemůže využívat veřejnost. „Riziko nečíhá jen v hotelích. Představují ho i veřejné wi-fi sítě a hotspoty na nádražích, letištích, v obchodních centrech nebo přímo v prostředcích veřejné dopravy. Není výjimkou, že si hackeři sami vytvoří wi-fi síť, kterou otevřou veřejnosti, aby potom její uživatele napadnou,“ varuje Václav Zubr.
Remote Code Execution Flaw Found in Unity Game Engine Editor
21.8.2017 securityweek Vulnerebility
An editor used by millions of game developers and coding students around the world contains a remote code execution vulnerability in all of its Windows versions on all versions of Windows. The Mac version of the editor is not affected.
Late last week, Unity wrote to its user base, explaining, “Unity has identified a Remote Code Execution flaw in the Editor and we're rolling out a critical security patch to remediate this issue.” Unity provides its gaming engine at three levels: Free for personal use, Plus, and Pro.
The editor supports the Unity 2D and 3D gaming graphics engine used by developers for games targeted at a wide range of platforms, including Android, iOS, Linux, Windows, Oculus Rift and more.
In its vulnerability alert Unity-Sec-844, the company explains that its Mac version is not affected. It provides a number of patches for different affected Windows versions, but adds, “If a patch is not available for your version, please use the Mitigation Tool.” Unity is not patching some older versions of the editor, and recommends instead that users upgrade to the newer patched versions.
The alert provides no information about the vulnerability, announcing simply, “TBA (To Be Announced after Responsible Disclosure).” In this instance, 'responsible disclosure' is not specifically disclosure by a researcher or bounty claimant to the company, but by the company to its customers: “Unity may withhold information about an identified vulnerability for a reasonable period of time to ensure that all customers are given time to patch their systems.”
There is no indication of how or by whom the vulnerability was discovered, nor any indication on whether Unity is aware of any active exploits for the vulnerability. However, a separate FAQ mentions that the vulnerability is an input string validation issue in the Editor. Games produced by the Editor are not affected.
The mitigation tool provided by Unity is for any developer who simply cannot immediately apply the relevant patch. Unity explains, “This tool will update Windows to mitigate the identified vulnerability. The change is only related to the Unity Editor, and will not affect any other software, including games that use Unity.”
The company goes out of its way to stress that the mitigation tool should only be considered a temporary solution for developers, since it cannot guarantee that the disabled functionality containing the flaw will not be re-enabled at some point.
In May 2017, hackers from OurMine breached the Unity user forum and claimed to have exfiltrated user information. Unity acknowledged the breach, but said the hackers only accessed “a limited set of data,” and assured users that no passwords, payment information or other Unity services had been compromised.
Code Linked to MalwareTech and Kronos Published in 2009
21.8.2017 securityweek Virus
A piece of code linked to both the British researcher Marcus Hutchins, known online as MalwareTech, and the banking Trojan named Kronos was first published in 2009.
Hutchins became famous and was named a “hero” after he helped stop the WannaCry ransomware attack by registering a domain that acted as a kill switch for the malware.
The researcher was arrested in early August in the United States as he had been preparing to return to the U.K. and was charged for his alleged role in creating and selling Kronos. He has pleaded not guilty to the charges brought against him and released on bail during his trial. He cannot leave the U.S. and will be tracked via GPS, but authorities have allowed him to access the Internet – except for the domain used to stop the WannaCry outbreak.
The only information provided so far by authorities regarding the case they have against Hutchins is that he and an unnamed partner allegedly created and sold the Kronos malware in 2014 and 2015.
While it’s unclear what evidence these accusations are based on, some believe it may have something to do with a tweet posted by MalwareTech in February 2015, when he claimed a hooking engine he made had been abused by malware developers.
A researcher known online as “Hasherezade” has published a detailed analysis of Kronos, a piece of malware that has been around since 2014, on the Malwarebytes blog. The expert pointed out that the code used by Kronos authors to implement hooking, a technique for modifying the behavior of an application by intercepting function calls or messages passed between different components, is similar to one published by MalwareTech on his GitHub account.
However, as a Greece-based experts noted, the hooking technique found in both Kronos and MalwareTech’s GitHub account was first described in 2009.
MalwareTech is not allowed to discuss his case with anyone, but he pointed out on Twitter that none of the code found on his GitHub account implements new techniques and instead represents proof-of-concept (PoC) code for existing methods.
It’s unclear at this point if investigators used these similarities to link Hutchins to Kronos and if the code that the researcher claimed was stolen from him in 2015 was used in this banking Trojan or different malware.
According to Hasherezade, an analysis of the Kronos code suggests that its author is a skilled malware developer.
“The code is well obfuscated, and also uses various tricks that requires understanding of some low-level workings of the operating system. The author not only used interesting tricks, but also connected them together in a logical and fitting way. The level of precision lead us to the hypothesis, that Kronos is the work of a mature developer, rather than an experimenting youngster,” Hasherezade said.
While many have named Hutchins a hero for his role in stopping the WannaCry outbreak, some, including Immunity founder Dave Aitel, believe he may have actually been involved in the WannaCry attack.
Legal aspects of the case
In the meantime, some media reports claim Britain’s GCHQ spy agency knew that the FBI had been investigating Hutchins before he travelled to the United States. People familiar with the matter told The Sunday Times that the expert’s arrest in the U.S. freed the British government from the “headache of an extradition battle.”
While Hutchins awaits trial, some legal experts have called into question the constitutionality of the indictment.
“Since Hutchins’ indictment, commentators have questioned whether the creation and selling of malware—without actually using the malware—violates the two statutes under which Hutchins was charged: the Computer Fraud and Abuse Act and the Wiretap Act. It is likely that these issues will be litigated as the case unfolds,” said Alex Berengaut, a lawyer with Covington & Burling.
“But there is another question raised by the indictment: whether it violates Hutchins’ constitutional rights to charge him for his alleged conduct under any statute in this country,” Berengaut added. “Several circuits—including the Seventh Circuit, where Hutchins’ case will be heard—have recognized that the federal government cannot charge anyone, anywhere in the world irrespective of their connections to the United States.”
Hackers Can Hijack Phones via Replacement Screens: Researchers
21.8.2017 securityweek Mobil
Touchscreens and other components that are often replaced in smartphones and tablets can hide malicious chips capable of giving attackers complete control over the device, warned researchers at the Ben-Gurion University of the Negev.
Researchers conducted their experiments on two Android devices: a Huawei Nexus 6P smartphone which uses a touchscreen controller from Synaptics, and an LG G Pad 7.0 tablet that uses an Atmel controller. However, the experts believe many other devices are also vulnerable to these types of attacks, including ones made by Apple.
In their tests, the researchers used a hot air blower to separate the touch screen controller from the main assembly board and access the copper pads. They then connected the pads to an integrated chip that manipulates the communication bus, effectively launching a chip-in-the-middle attack. STM32L432 and Arduino microcontrollers, which cost roughly $10 each, have been used in the experiments.
The malicious chip can exploit vulnerabilities in the device driver to compromise the phone or tablet while ensuring that it does not stop functioning correctly.
Videos have been published to show how a malicious touchscreen can be used to install arbitrary software, take pictures with the camera and send them to the attacker via email, replace a legitimate URL with a phishing URL, capture and exfiltrate screen unlock patterns, and take complete control of the targeted device.
Completely hijacking a phone takes the longest, roughly 65 seconds, but some operations, such as replacing a URL, take less than one second to complete.
While attacks involving hardware replacements are not unheard of, the scenario described by Ben Gurion University researchers relies on replacing a component with a limited hardware interface, and assumes that the repair technician installing the replacement screen is not involved and does not conduct any operations other than replacing the broken component with a malicious one that has been provided to them.
The researchers notified Google of the Synaptics device driver vulnerabilities in February and patches were included in the June 2017 Android security updates. They are also working on notifying the developers of the Armel device driver of the discovered issues.
The experts have also proposed a series of hardware-based countermeasures to prevent such attacks.
Energy Management Systems Expose Devices to Attacks
21.8.2017 securityweek Hacking
Researchers have demonstrated a new class of fault attacks possible due to the poor security design of energy management systems present in most modern computing devices.
Energy management is an important feature of modern computers, particularly in the case of mobile devices, as it helps increase battery life, improve portability and reduce costs. However, since designing such systems is not an easy task, focus has been placed on efficiency and security has often been neglected.
At the recent USENIX Security Symposium, a team of experts from Columbia University presented an attack method they have dubbed “CLKscrew.” They showed how a malicious actor could exploit the lack of security mechanisms in energy management systems to carry out a remote attack and obtain sensitive data.
The research has focused on the ARMv7 architecture – a Nexus 6 smartphone was used in experiments – but the CLKscrew attack likely also works against other devices and architectures. The energy management system analyzed by the researchers is the widely used dynamic voltage and frequency scaling (DVFS).
The CLKscrew attack shows how a remote hacker could use a malicious kernel driver loaded onto the targeted device to exploit security weaknesses in DVFS and breach the ARM Trustzone, a hardware-based security technology built into system-on-chips (SoCs).
Experts demonstrated how an attacker can use the method to extract secret crypto keys from Trustzone, and escalate privileges by loading self-signed code into Trustzone.
Researchers believe this type of attack is much more efficient than attacks involving physical access to the targeted device due to the fact that it can be carried out remotely and it bypasses many of the requirements and barriers of a physical attack, such as the need for soldering equipment and the ability to overcome existing physical defenses.
“CLKscrew is the tip of the iceberg: more security vulnerabilities are likely to surface in emerging energy optimization techniques, such as finer-grained controls, distributed control of voltage and frequency islands, and near/sub-threshold optimizations,” researchers said in their paper.
“Our analysis suggests that there is unlikely to be a single, simple fix, or even a piecemeal fix, that can entirely prevent CLKscrew style attacks. Many of the design decisions that contribute to the success of the attack are supported by practical engineering concerns,” they added. “In other words, the root cause is not a specific hardware or software bug but rather a series of well-thought-out, nevertheless security-oblivious, design decisions.”
Turla Cyberspies Use New Dropper in G20 Attacks
21.8.2017 securityweek CyberSpy
The Russia-linked cyber espionage group known as Turla has been using a new malware dropper in attacks apparently aimed at entities interested in G20, security firm Proofpoint reported last week.
G20 is an international forum for governments and central banks from all continents. The G20 Summit was held last month in Hamburg, Germany, and other events are scheduled to take place in the same city later this year, including the Task Force “Digital Economy” meeting in October 23 - 24.
A document announcing the Digital Economy meeting has apparently been used by Turla as a decoy to deliver a new .NET/MSIL dropper, which deploys a recently discovered JavaScript backdoor tracked as KopiLuwak.
The decoy document appears to come from Germany’s Federal Ministry for Economic Affairs and Energy, and researchers believe the file is likely legitimate. The document does not appear to be publicly available, which indicates that it may have been obtained by the attackers from an entity that received the file.
Proofpoint highlighted that the decoy document’s metadata shares similarities to a legitimate PDF file hosted on the website of the Federal Ministry for Economic Affairs and Energy, including the author’s name (BE.D4.113.1) and the device it was created with (KONICA MINOLTA bizhub C284e).
The new dropper delivered alongside this document is stored in a file named Scr.js, which creates a scheduled task for persistence and executes various commands to obtain information about the infected device. The dropper looks for the presence of Kaspersky security products before dropping the KopiLuwak backdoor, which is not surprising considering that Kaspersky Lab was the first to analyze KopiLuwak.
Researchers pointed out that the dropper code is not obfuscated and it does not include any anti-analysis mechanisms. In older versions of KopiLuwak, the backdoor itself was in charge of fingerprinting the system, but the functionality has now been moved to the dropper.
Since Proofpoint’s analysis is based on files obtained from a public malware repository, it’s unclear who was targeted in this attack. However, based on the theme of the decoy document, the most likely targets are individuals and organizations interested in the G20 event. This can include member countries, policy makers and journalists.
Turla has been active since at least 2007 and is believed to be responsible for several high-profile attacks, including the ones aimed at Swiss defense firm RUAG and the U.S. Central Command. The group is also known as Waterbug, KRYPTON and Venomous Bear, and some of its primary tools are tracked as Turla (Snake and Uroburos) and Epic Turla (Wipbot and Tavdig).
This spring, Turla and another Russia-linked threat group, known as APT28 and Fancy Bear, had been spotted exploiting zero-day vulnerabilities in Microsoft products.
Warning: Enigma Hacked; Over $470,000 in Ethereum Stolen So Far
21.8.2017 thehackernews CyberCrime
More Ethereum Stolen!
An unknown hacker has so far stolen more than $471,000 worth of Ethereum—one of the most popular and increasingly valuable cryptocurrencies—in yet another Ethereum hack that hit the popular cryptocurrency investment platform, Enigma.
According to an announcement made on their official website an hour ago, an "unknown entity" has managed to hack their website, slack account and email newsletter accounts, and uploaded a fake pre-sale page with a fake ETH address to send money.
The hackers also spammed their fake address in Enigma's newsletter and slack accounts for pre-sale coins, tricking victims to send their cryptocurrencies to hacker's address.
Etherscan, a popular search engine for the Ethereum Blockchain that allows users to look up, confirm and validate transactions easily, has already flagged the address as compromised, but people are still sending ETH to the fake address (given below).
0x29d7d1dd5b6f9c864d9db560d72a247c178ae86b
At the time of writing, the hackers have made over 1,487.90 Ether and are still receiving payments.


The hack comes a few days after Enigma posted an article, educating users on how to avoid phishers, scammers, spammers, and stay safe during a token sale.
"As we work hard to build the future of data and crypto trading and investing, we want to take a few moments to talk about safety," Enigma Project wrote in the blog post. "Due to our strong growth, our community has become a target. The worst elements of the crypto scene—scammers and phishers—are attracted to good projects and good communities."
This incident marks as the fifth Ethereum hack within two months, following a theft of:
$8.4 Million worth of Ethereum during Veritaseum's Initial Coin Offering (ICO).
$32 Million worth of Ethereum from Parity's Ethereum Wallet accounts.
$7 Million worth of Ether during the hack of Israeli startup CoinDash's ICO.
$1 Million worth of Ether and Bitcoins heist in cryptocurrency exchange Bithumb.
At the moment, it is unclear how the attackers broke into the Enigmas network and hacked their website, slack account and email newsletter accounts.
Since cryptocurrency enthusiasts and investors are still sending their Ethereum to the fake address, you should share this story to warn your friends and followers.
Doctor Implanted 6 MicroChips Under His Skin to Unlock Doors and Secure Data
21.8.2017 thehackernews Security
Biohacking could be a next big thing in this smart world.
At the beginning of this month, several dozen employees of Three Square Market (32M) received microchip implants in their hands during a "chip party," allowing them to log into their office computers, open doors, and pay for food and drinks, by simply waving their hands, AP reported.
But, biohacking is already becoming common in Russia.
It has been reported that a Siberian doctor has already implanted not one, but at least six microchips underneath his skin and turned his body into a multi-functional gadget for doing a number of jobs by just a wave of his hands.
Alexander Volchek, who is an obstetrician/gynaecologist in a hospital in the Novosibirsk region in Russia's north, got his first microchip implant in 2014 and since then he acquired a few more and now has a total of six chips under his skin.
However, Volchek does not want to stop here and hopes to implant a cryptosystem and a glucometer microchip in his body in the near future.
These chips help him perform day-to-day activities just by moving his hand over a bar code scanner, such as opening doors at work and home, paying bills with a wave of his hand—everything works like magic.
Two chip to enter his office
One transport chip
Two memory cards for storing almost a kilobyte of information
One control card for a Siberian ski resort
A syringe with a thick needle is required to inject a microchip, whose standard size is 2x12mm, and minimum size is no more than 1.5x8mm with storage capacity ranges from 800 bytes to 1 kilobyte of information.
One of the microchips serves as Volchek's business card, while another one stores his password, allowing him to unlock his computer.
"My dream as a crypto anarchist is to have an identification tool for encrypting an electronic signature, and of course for medical application," Volchek told RT's video agency Ruptly. "I also want an implanted glucometer that will resolve a ton of problems many are currently facing, but research is still underway."
However, the microchips are not permanently implanted into the skin. They can be easily extracted from the body whenever the user wants to get rid of it.
While the Biometric technology is experiencing an increase in popularity, it also raises widespread concerns about the safety and privacy of people adopting it.
Hackers could misuse this technology against the public itself, and one should not forget that with the advance in technology, the techniques leveraged by hackers and cyber criminals also improves.
Over two years ago, a hacker implanted a small NFC chip in his hand to hack Android smartphones and bypass almost all security measures, demonstrating the risks of Biohacking.
At the end of the same year, another hacker managed to implant a small NFC chip with the private key to his Bitcoin wallet underneath his skin, allowing him to buy groceries or transfer money between bank accounts just by waving his hand.
New Snowden Doc Exposes How NSA's Facility in Australia Aids Drone Strikes
21.8.2017 thehackernews BigBrothers
The new documents leaked by former NSA contractor Edward Snowden has exposed a United States secretive facility located near a remote town in Australia's Northern Territory for covertly monitoring wireless communications and aiding US military missions.
The leaked documents have come from the massive trove of classified material stolen by Snowden from the US National Security Agency (NSA) in 2013 that exposed the extent of the US government's global surveillance programs.
The newly released classified documents, obtained by The Intercept, contained references to a secretive facility, which was codenamed "Rainfall," but is officially known as the Joint Defence Facility Pine Gap.
The documents reveal that the Joint Defence Facility Pine Gap, located outside Alice Springs, deployed cutting-edge satellite technology for detailed geolocation intelligence that helps the US military locate targets for special forces and drone strikes.
The use of unmanned air vehicles, generally known as drones, by the U.S. military has previously been blamed for hundreds of civilian deaths in countries like Pakistan, Afghanistan, Yemen, Syria, and Somalia.
As outlined in a secret intelligence document, Pine Gap's aim is to "support the national security of both the U.S. and Australia. The [facility] contributes to verifying arms control and disarmament agreements and monitoring military developments."
However, in reality, Pine Gap has a far broader mission with powerful capabilities than the Australian or U.S. government has ever publicly acknowledged.
Pine Gap finds Targets for U.S. Drone Strikes
The satellites used by the Pine Gap are described as being "geosynchronous"—likely positioned high in orbit at over 20,000 miles above the earth's surface—which are equipped with powerful surveillance technology to monitor wireless communications on the ground, like those sent and received by mobile phones, radios, and satellite uplinks.
According to the leaked documents, these satellites collect "strategic and tactical military, scientific, political, and economic communications signals," and also keep eyes on any missile or weapon tests in targeted countries, steal intel from foreign military data systems, and provide surveillance support to United States forces.
One of the secret NSA documents analysed by the Australian Broadcasting Corporation (ABC) suggests that the facility's role is not only to collect signals, but also to analyse them, as it "detects, collects, records, processes, analyses and reports" on almost everything—from surface-to-air missiles to anti-aircraft artillery and fighter aircraft.
One mission even pilfered communications from the former Soviet Union, China, East Asia, South Asia, the Middle East, Eastern Europe, and territories in the Atlantic Ocean.
In 2013, the Sydney Morning Herald reported that Pine Gap played a major role in controversial U.S. drone strikes, which had also resulted in the deaths of hundreds of innocent civilians.
Trump Administration Doubled the Drone Strikes
Richard Tanter, the University of Melbourne’s professor who has previously studied Pine Gap, told the publication that "Pine Gap will be contributing hugely in real-time to those operations, as well as in preparation for them."
"So whether or not the Australian government thinks that an attack on North Korea is either justified or a wise and sensible move, we will be part of that. We'll be culpable in terms of the consequences," Tanter asserted.
Under Trump administration, drone strikes and special operations raids have doubled, while simultaneously loosening battlefield rules to prevent civilian deaths in such air attacks.
However, David Rosenberg, who worked inside Pine Gap as a team leader of weapon signals analysis for at least 18 years until 2008, confirms the facility's geolocation capability, claiming that preventing civilian casualties is a high priority.
"One thing I can certainly tell you the governments of Australia, and the United States would, of course, want to minimise all civilian casualties," Rosenberg says. "Pine Gap does help to provide limitation of civilian casualties by providing accurate intelligence."
It is not at all surprising to see Australia working closely with its U.S. counterparts to help conduct global surveillance since it is a key member of the "Five Eyes" alliance—alongside the US, UK, New Zealand and Canada—all openly shares secret intelligence reports.
Smart Devices Can Be Hijacked to Track Your Body Movements And Activities Remotely
21.8.2017 thehackernews Attack
If your smartphones, tablets, smart refrigerators, smart TVs and other smart devices are smart enough to make your life easier, their smart behavior could also be leveraged by hackers to steal data, invade your privacy or spy on you, if not secured properly.
One such experiment has recently been performed by a team of student hackers, demonstrating a new attack method to turn smart devices into spying tools that could track your every move, including inferring sexual activity.
Dubbed CovertBand, the attack has been developed by four researchers at the University of Washington's Paul G. Allen School of Computer Science & Engineering, and is so powerful that it can record what a person is doing through a wall.
The CovertBand tracking system makes use of the built-in microphones and speakers—found in smartphones, laptops, tablets, smart assistant and other smart devices—as a receiver to pick up reflected sound waves, tracking the movements of anyone near the audio source.
Here's how the CovertBand Attack works:

The attacking approach involves remotely hijacking of smart devices to play music embedded with repeating pulses that track one's position, body movements, and activities both near the device and through walls.
To do so, the attackers would first trick victims into installing a third-party Android app on their smart device that does not require rooting.
Once installed, the malicious app secretly uses the AudioTrack API to play the acoustic signals at 18-20 kHz and to mask this high-frequency sound, the app 'covered' Covertband's pulses by playing songs or other audio clips over them that act as a sonar.
These sound waves would then bounce off people and objects, which is picked up by a microphone.
The app then uses AudioRecord API to record the signals simultaneously on two microphones to achieve 2D tracking. The recorded data is then received by the attacker on a laptop over Bluetooth for offline processing.
Since the attack requires access only to a speaker and microphone, an attacker could leverage a lot of smart devices that already exist in the victim's home to spy on unsuspecting targets.
"A remote adversary who compromises one of these [smart] devices, perhaps via a Trojan application in an app store or via a remote exploit, could use our methods to remotely glean information about an individual's home activities. An attacker could also find more surreptitious ways to execute such an attack," said the researchers.
"For example, a streaming music app with voice control has all the permissions (speaker and microphone) needed to execute our attack. As a simple example, an attacker could utilise the advertising library embedded inside a music application to determine whether the user is near the phone when an ad is played."
Video Demonstration of CovertBand Attack
The researchers demonstrated how the CovertBand attack could potentially enable an attacker to differentiate between different types of people's movements even when they are in different body positions and orientations.
The researchers experiment specifically focuses on two classes of motion:
Linear motion — when the subject walks in a straight line.
Periodic motion — when the subject remains in approximately the same position (lying on his or her back on the floor) but performs a periodic exercise.
According to the research paper [PDF], these motions would be differentiated by looking at the spectrograms, but are sufficient enough to potentially enable privacy leakage.
"For example, (1) models information that might be of interest to intelligence community members, e.g., to track the location of a target within a room and ( 2) could be used to infer sexual activity, for which the importance of protecting might vary depending on the target's culture and cultural norms or might vary depending on the target's public visibility, e.g., celebrity status or political status," the research paper reads.
How Intelligence Agency could use CovertBand
While explaining different scenarios, the researchers explained how spy agencies could use such tools for leaking information about obscured activities of a target even in the presence of background or cover noise.
Imagine a spy "Alice" entering a foreign country and renting a hotel room adjacent to an individual "Bob," whom she intends to discreetly and covertly surveil.
Since the Alice can not enter the country with dedicated surveillance hardware, she would simply use the CovertBand attack to do 2D tracking of subjects even through walls, "something she could run on her phone and that would avoid arousing Bob’s suspicion."
To demonstrate this, the researchers showed a scenario where Bob pretended to go through a routine in the bathroom while Alice used CovertBand to track his movements.
They were able to determine that Bob walk around inside of a bathroom and likely spent less than 20 seconds sitting on the toilet and brushing his teeth.
"We placed the speaker setup 15 cm outside the bathroom door and performed four trials during which Bob spent less than 20 seconds doing each of the following: showering, drying o on the scale, sitting on the toilet, and brushing his teeth. During the experiment, the bathroom fan was ON, and we could not hear Bob performing any of the activities inside the bathroom," the research paper reads.
The researchers believe their attack could be refined to enable the sensing of more subtle motions like the movement of hands, arms, or even fingers to gain both resolution and accuracy even in the absence of a direct path.
Protecting yourself from such attacks involves impractical defences for most people, like playing your own 18-20 kHz signals to jam CovertBand, but this could discomfort your pets and children, or soundproofing your homes with no windows.
The researchers hope that knowing about the consequences of such attacks would possibly prompt scientists to develop practical countermeasures.
SyncCrypt Ransomware hides its components in image files
21.8.2017 securityaffairs Ransomware
A new strain of ransomware distributed through spam emails, dubbed SyncCrypt, hides its components inside harmless-looking images.
A new strain of ransomware recently discovered, dubbed SyncCrypt, hides its components inside harmless-looking images.
The SyncCrypt ransomware is distributed through spam emails that use attachments containing WSF files pretending to be court orders.
Once the victims execute the attachment, an embedded JScript fetches seemingly innocuous images from specific locations and extracts ransomware components they hide.
The ransomware components are stored into the images as ZIP files.
According to the BleepingComputer malware expert Lawrence Abrams, the JScript also extracts the hidden malicious components (sync.exe, readme.html, andreadme.png).
“If a user was to open one of these image URLs directly, they would just just see an image that contains the logo for Olafur Arnalds’ album titled “& They Have Escaped the Weight of Darkness”.” states the analysis published by Lawrence Abrams.
“Embedded in this image, though, is a zip file containing the sync.exe, readme.html, and readme.png files. These files are the core components of the SyncCrypt ransomware.”

The WSF file also creates a Windows scheduled task called Sync that once is executed, it starts scanning the infected system for certain file types and encrypts them using AES encryption.
The SyncCrypt ransomware uses an embedded RSA-4096 public encryption key to encrypt the used AES key.
The ransomware targets more than 350 file types and appends the .kk extension to them after encryption. The researcher observed that the ransomware skips files located in several folders, including\windows\, \program files (x86)\, \program files\, \programdata\, \winnt\, \system volume information\, \desktop\readme\, and\$recycle.bin\.
The ransomware demands around $429 to be paid to decrypt the files, after the payment was completed by the victims they have to send an email containing the key file to one of the emails getmyfiles@keemail.me, getmyfiles@scryptmail.com, or getmyfiles@mail2tor.com to get a decrypter.
According to Abrams, the distribution process is able to evade the detection, only one of the 58 vendors in VirusTotal could detect the malicious images at the time of analysis. The researchers noticed that the Sync.exe, on the other hand, had a detection rate of 28 out of 63.
Unfortunately, at this time there is no way to decrypt files encrypted by the SyncCrypt ransomware for free.
Abrams analysis includes IoCs and provides the following recommendations to avoid being infected by ransomware.
Backup, Backup, Backup!
Do not open attachments if you do not know who sent them.
Do not open attachments until you confirm that the person actually sent you them,
Scan attachments with tools like VirusTotal.
Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
Make sure you use have some sort of security software installed.
Use hard passwords and never reuse the same password at multiple sites.
For a complete guide on ransomware protection, give a look at How to Protect and Harden a Computer against Ransomware article.
Learning About ISIS Intentions Using Open Source Intelligence
21.8.2017 securityaffairs Crime
Learning About ISIS Intentions Using Open Source Intelligence – How terrorists are exploiting technology for propaganda and radicalization.
ISIS’ weekly newsletter al-Nabā’ published an editorial about the lessons to be learned from the attack on the Iraqi embassy in Kabul, Afghanistan (July 30, 2017), which it called “an action of high quality.”
In the editorial, attacking embassies and diplomatic staff is promoted as one of the most effective ways to put pressure on “infidel governments.”
The Islamic State considers attacks like this as very important and encourages Muslims in every country to attack embassies and either kill the staff or take them hostage. Indeed, the latest edition of “Rumiyah”, an ISIS magazine, featured hostage taking as a notable topic. The editorial is entitled “War on Embassies: The Greatest Cause of Fear and Pain for the Infidel Countries” (al-Nabā’, Issue 92, August 3, 2017)
Following its weakening across Iraq and Syria, ISIS is encouraging its operatives and supporters around the globe to carry out attacks in their own countries in support of the Islamic State.

The Islamic State considers embassies and those working in them as important targets. It encourages Muslims around the globe to strike embassies and either kill the staff or take them hostage. According to al- Nabā’, anyone who wants to wage jihad and cannot, for whatever reason, leave his own country, will not find it difficult to locate foreigners near where they are living and attack them.
In this instance, ISIS is focusing on embassies and diplomats to get publicity for its attacks (compared with stabbing and vehicular attacks, which ISIS has also encouraged its supporters to carry out). A recent example of such an attack was carried out a double suicide bombing attack at the Iraqi embassy by ISIS’s ‘Khorasan Province’, a group active in Afghanistan and Pakistan, which has claimed responsibility for the attack.
Assesment
These types of threat feature a range of new methodologies that are being spread across social media groups and password protected web forums.
The impact of an attack against an embassy or diplomatic mission is a direct illustration of the response to an ‘open source’ request. Previously, Al Naba magazine has claimed this type of attack is preferable as it causes fewer damages to innocent civilians and maximises the exposure to their targets, diplomats, military personnel, government agents and law enforcement.
The online radicalization of individuals who are unknown to security services continues to grow, making it almost impossible for new recruits to be monitored. Social media platforms, including Twitter and WhatsApp, are often highlighted by government agencies, particularly where communications are encrypted, however, secret forums and chat rooms are hidden in the Dark Web are important places where illicit actors and Jihadists communicate.
Several of the messaging Apps being used by the online Jihadist community is totally encrypted, with login credentials being randomly generated beyond a local server, making it impossible to monitor the content of their communications. “Threema” and “Wickr” are two such secure communications apps popular with Jihadi groups and are used to groom recruits after first vetting their potential over “Telegram”.
Conclusion
There is a clear need to go beyond open source intelligence and to develop a new set of techniques to monitor threats concealed behind encrypted messaging apps and Dark Web forums.
Law enforcement agencies need new technology to get actionable Intelligence and live interception feed in real time if they are to reliably predict and prevent future terror attacks.
Accused Yahoo Hacker to be Handed Over to U.S. Marshals
19.8.2017 securityweek Crime
A Canadian man accused of carrying out devastating cyberattacks on Yahoo waived his right to an extradition hearing on Friday and will soon be handed over to US marshals.
Karim Baratov, 22, an immigrant from Kazakhstan, was arrested on a US warrant in March for alleged hacking, commercial espionage and related crimes.
A spokesman for his lawyer Amedeo DiCarlo said that Baratov wishes to expedite the case and address the charges.
"A court order is in place to have the marshals come up and pick up Karim," DiCarlo told reporters. "I don't know if it's today, tomorrow. It could be any day. There's usually a two-week allowance for that."
Friday's court hearing in Hamilton, Ontario, where Baratov signed the waiver, was "the last of the proceedings here in Canada and the rest will now continue with myself and (Karim's) US attorneys," DiCarlo said.
US authorities allege Russian intelligence agents hired Baratov and another hacker to carry out attacks on Yahoo from 2014 to 2016.
The data breach compromised 500 million Yahoo accounts and is one of the largest cyberattacks in history.
Targets included Russian and US government officials, cyber security, diplomatic and military personnel, journalists, companies and financial firms.
The Ukrainian central bank warned of new NotPetya-style massive attack risk
19.8.2017 securityaffairs Ransomware
The Ukrainian central bank warned state-owned and private lenders of the appearance of new the NotPetya-like attack that would target national businesses.
On Friday, the Ukrainian central bank warned of new malware-based attack risk. According to the Reuters, the Ukrainian central bank warned state-owned and private lenders of the spreading of new infections like the NotPetya attack that hit the critical infrastructure of the country in June.
“The Ukrainian central bank said on Friday it had warned state-owned and private lenders of the appearance of new malware as security services said Ukraine faced cyber attacks like those that knocked out global systems in June.” states post published by the Reuters.
“The June 27 attack, dubbed NotPetya, took down many Ukrainian government agencies and businesses, before spreading rapidly through corporate networks of multinationals with operations or suppliers in eastern Europe.”
The Ukrainian central bank is closely working with the national CERT and local authorities to improve the resilience to cyber attacks of its critical infrastructures, especially the ones of the Ukrainian banking sector.
“Therefore on Aug. 11…, the central bank promptly informed banks about the appearance of new malicious code, its features, compromise indicators and the need to implement precautionary measures to prevent infection,” the central bank told Reuters in emailed comments.
The Reuters has seen the letter sent by the Ukrainian central bank to the national banks, the message warns of a new strain of malware is spread via phishing email using weaponized word documents.

The experts warn of a possible massive cyber attack on Ukrainian companies, the malicious code is currently able to evade antivirus solutions.
“The nature of this malicious code, its mass distribution, and the fact that at the time of its distribution it was not detected by any anti-virus software, suggest that this attack is preparation for a mass cyber-attack on the corporate networks of Ukrainian businesses,” the letter said.
Of course, the first suspect according to the experts is Russia that has many interests in the country, in many cases, Ukraine blamed the Kremlin for cyber attacks on its infrastructure, including the power grid and financial systems.
The state cyber police and Security and Defence Council already warned of a potential imminent cyber attack against Ukraine. Authorities believe Ukraine could be targeted on Aug. 24 with a NotPetya-style massive attack aimed at destabilizing the country as it celebrates its 1991 independence from the Soviet Union.
Misconfigured AWS S3 exposed 1.8 million US voter records
19.8.2017 securityaffairs BigBrothers
More than 1.8 million voter records belonging to Americans have been accidentally leaked online by a US voting machine supplier for dozens of US states.
It has happened again, more than 1.8 million voter records belonging to Americans have been accidentally leaked online by a US voting machine supplier for dozens of US states.
The voter records were left openly accessible online due to a misconfiguration in AWS-hosted storage.
Once again, the huge trove of records was spotted by the popular UpGuard researcher Chris Vickery. The archive contained records the ES&S collected from recent elections in Chicago, Illinois.
“As part of an effort to find unsecured files on Amazon Web Services (AWS) server platforms, a private researcher completed a download of the Election Systems & Software (ES&S) backup files of voter data that were prepared for Chicago’s electronic pollbooks and stored on the AWS platform.” reads the statement issued by ES&S. “The voter data in the backup files included about 1.8 million names, addresses, dates of birth, partial Social Security numbers, and in some cases, driver’s license and state ID numbers.”
The records included voters’ names, addresses, dates of birth, and partial social security numbers. In some cases, the records also included drivers’ licenses and state ID numbers.
“The backup files on the AWS server did not include any ballot information or vote totals and were not in any way connected to Chicago’s voting or tabulation systems,” reads the statement issued by the ES&S.
“These back-up files had no impact on any voters’ registration records and had no impact on the results of any election.”

Vickery alerted ES&S on August 12, he discovered the data while investigating sensitive data insecurely hosted on AWS.
The cloud system was taken down four hours after the expert notified it to the company which supplies voting machines and backend services to more than 40 US states.
Açcording to UpGuard, the vulnerable service was an AWS S3 instance accidentally set up to be open to the public. At the time I was writing we have news of the leakage only of Chicago’s voters’ data was exposed.
Chicago’s election board, meanwhile, was concerned by the discovery but appreciated the efforts of ES&S in promptly respond the incident.
“We have been in steady contact with ES&S to order and review the steps that must be taken, including the investigation of ES&S’s AWS server,” reads a statement issued by the Chicago Election Board chairwoman Marisel Hernandez.
“We will continue reviewing our contract, policies and practices with ES&S. We are taking steps to make certain this can never happen again.”
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet. In July he discovered data belonging to 14 million U.S.-based Verizon customers that have been exposed on an unprotected AWS Server by a partner of the telecommunications company. In December 2015 the security expert discovered 191 million records belonging to US voters online, on April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
In January 2017, the expert discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
In March, he announced a 1.37 billion records data leak, in June 2017 Vickery revealed the DRA firm left 1.1 TB of data unsecured on an Amazon S3, 198 million US voter records exposed.
Faketoken evolves and targets taxi booking apps to steal banking info
19.8.2017 securityaffairs Android
Kaspersky discovered a news strain of the mobile banking Trojan Faketoken that displays overlays on top of taxi booking apps to steal banking information.
Security experts from Kaspersky have discovered a news strain of the infamous mobile banking trojan Faketoken that implements capabilities to detect and record an infected device’s calls and display overlays on top of taxi booking apps to steal banking information.
“The authors of its newer modifications continue to upgrade the malware, while its geographical spread is growing. Some of these modifications contain overlay mechanisms for about 2,000 financial apps. In one of the newest versions, we also detected a mechanism for attacking apps for booking taxis and paying traffic tickets issued by the Main Directorate for Road Traffic Safety.” states the analysis published by Kaspersky.
In December, Kaspersky observed the Android ransomware Faketoken was enhanced with file-encrypting abilities.
Now the new variant of the malware dubbed Faketoken.q was improved again to steal credentials from Uber and other booking apps as well.
Faketoken.q is being distributed using bulk SMS messages to trick users into downloading an image file that actually downloads the malware.
The mobile Trojan is composed of two parts, the first part is an obfuscated dropper (verdict: Trojan-Banker.AndroidOS.Fyec.az), the second one is a file with DAT extensions that contains the malware’s main features.
Once victims have downloaded the Android malware it installs the necessary modules and the main payload, which hides its shortcut icon and starts monitoring user’s activities, including calls to launched apps.
“After the Trojan initiates, it hides its shortcut icon and starts to monitor all of the calls and whichever apps the user launches. Upon receiving a call from (or making a call to) a certain phone number, the malware begins to record the conversation and sends it to evildoers shortly after the conversation ends.” continues the analysis.
When the calls are made to or received from certain phone numbers, Faketoken.q records the conversations and sends the recordings to the attacker’s server. The malicious code also checks which apps the victim is using and when detects the launch of an app whose interface it can clone, it overlays the app with a fake user interface.
The fake user interface presented by Faketoken.q prompts victims to enter their payment card data, including the bank’s verification code.
Researchers observed that the malware is able to display fake interface for many mobile banking apps and other applications, such as:
Android Pay
Google Play Store
Apps for paying traffic tickets
Apps for booking flights and hotel rooms
Apps for booking taxis
The Trojan is able to intercept the incoming SMS messages to obtain the SMS code sent by the bank to authorize transactions, then it forwards the code to C&C server.
It seems that Faketoken.q has been developed to target Russian-speaking users because it only uses the Russian language on the user interface.
To avoid being infected by Faketoken and apps similar malware, do not install applications from third-party stores and pay attentions to unsolicited SMSs and email messages you receive on your mobile device.
Decryption Key for Apple's SEP Firmware Posted Online
18.8.2017 securityweek Apple
What appears to be the decryption key for Apple's Secure Enclave Processor (SEP) firmware was posted online by a hacker going by the name of xerub.
A coprocessor fabricated in the Apple S2, Apple A7, and later A-series CPUs, SEP uses encrypted memory, has a hardware random number generator and “provides all cryptographic operations for Data Protection key management and maintains the integrity of Data Protection even if the kernel has been compromised,” Apple explains in the iOS Security Guide.
At startup, the device creates an ephemeral key entangled with the UID (Unique ID), and uses it to encrypt the Secure Enclave’s portion of memory space. The key is also used to authenticate the Secure Enclave (except on Apple A7). Apple also explains that data “saved to the file system by the Secure Enclave is encrypted with a key entangled with the UID and an anti-replay counter.”
SEP uses its own secure boot and securely generates the UID on A9 or later A-series processors. Because SEP handles Touch ID transactions, password verification, and other security processes, along with the generation of the device's UID, it is critical to iOS’ security and the public availability of the decryption key could spell disaster.
Despite publishing the decryption key (tools needed to decrypt the key are available in this GitHub repository, while those needed to process it are available in this one), xerub didn’t provide details on the decryption process.
The availability of the key, however, doesn’t appear to affect the overall security of the enclave, and even the hacker suggested that SEP doesn’t add much to security, despite its “black box” design. While the key would allow for the decryption of the firmware, it wouldn’t provide access to user data.
While researchers could only speculate what was happening inside the Secure Enclave until now, the availability of this key could shed some more light into the matter. In addition to security researchers, hackers too could start looking for vulnerabilities in SEP, in an attempt to devise new exploits to bypass authentication or generate fraudulent transactions.
SecurityWeek has contacted Apple for a comment on this and will update the story if a response arrives.
Leaked Exploits Fueled Millions of Attacks in Q2: Kaspersky
18.8.2017 securityweek Exploit
The public availability of new exploit packages has fueled millions of new attacks on popular applications during the second quarter of 2017, a recent report from Kaspersky Lab reveals.
The Moscow-based security company said that it blocked more than five million attacks involving in-the-wild exploits during the three-month period, but the actual number of incidents should be significantly higher. Highly effective as they don’t usually require user interaction, attacks leveraging exploits can result in malicious code being delivered to the targeted machines without the user suspecting anything.
According to Kaspersky’s IT threat evolution Q2 2017 report, the publication by the Shadow Brokers hacker group of several tools and exploits supposedly associated with the National Security Agency had grave consequences during the quarter. Included in the leak were exploits such as EternalBlue and EternalRomance, which fueled a large wave of malicious attacks.
Despite the fact that Microsoft had patched the vulnerabilities exploited by these tools one month before they were made public, “in the second quarter of 2017 only Kaspersky Lab blocked more over five million attempted attacks involving network exploits from the archive. And the average number of attacks per day was constantly growing: 82% of all attacks were detected in the last 30 days,” the security company says.
The figure is not surprising, considering that EternalBlue was used in a massive, global WannaCry ransomware attack in May. In June, the same exploit was used for lateral movement in an attack involving the NotPetya wiper, which resulted in hundreds of millions in losses. The exploit was employed in various other malware attacks as well.
One other exploit that fueled a large number of attacks was leveraging the CVE-2017-0199 vulnerability in Microsoft Office. Initially a zero-day abused by threat actors, Microsoft addressed the bug in early April, but cybercriminals discovered new ways to leverage it: through the use of PowerPoint Slide Shows. Despite the fix, the number of attacked users peaked at 1.5 million in April, Kaspersky says.
The security company says it detected and repelled 342,566,061 malicious attacks from online resources located in 191 countries during Q2, and that it also identified 33,006,783 unique malicious URLs. In Q1, the company detected 479,528,279 malicious attacks.
Kaspersky also detected attempted infections with financial malware on 224,675 user computers (down from 288,000 during the previous three months), and blocked crypto-ransomware attacks on 246,675 unique computers (up from 240,799 in Q1). The security firm detected 185,801,835 unique malicious and potentially unwanted objects in Q2 (up from 174,989,956 the previous quarter).
In terms of banking malware attacks, Germany emerged as the most affected country in Q2 (these incidents include banking Trojans and ATM and POS-malware). Zbot, Nymaim, and Emotet were the top 3 banking malware families in the timeframe. WannaCry, Locky, and Cerber were the most spread cryptor families.
Mobile malware was also active in the timeframe. The security firm discovered a Trojan called Dvmap being distributed via Google Play, and also observed attackers attempting to upload new apps containing the malicious Ztorg module to the storefront. The Svpeng banking Trojan remained the most popular mobile threat.
Overall, Kaspersky detected 1,319,148 malicious installation packages during Q2, and reveals that adware registered the biggest growth during the timeframe. Trojan-SMS malware experienced the second-highest growth rate, while spyware registered the biggest decline. Iran was the top country attacked by mobile malware, followed by China, while the United States emerged as the most attacked by mobile ransomware.
“The threat landscape of Q2 provides yet another reminder that a lack of vigilance is one of the most significant cyber dangers. While vendors patch vulnerabilities on a regular basis, many users don’t pay attention to this, which results in massive-scale attacks once the vulnerabilities are exposed to the broad cybercriminal community,” Alexander Liskin, security expert at Kaspersky Lab, said.
Facebook Awards $100,000 Prize for Spear-Phishing Detection Method
18.8.2017 securityweek Social
Facebook announced on Thursday the winners of its 2017 Internet Defense Prize. A team of researchers from the University of California, Berkeley, and the Lawrence Berkeley National Laboratory earned the $100,000 prize for a novel technique of detecting credential spear-phishing attacks in enterprise environments.
The new method, presented these days at the USENIX Security Symposium, combines a new non-parametric anomaly scoring technique for ranking security alerts with features derived from the analysis of spear-phishing emails.
To test their method, the researchers analyzed more than 370 million emails received by a large enterprise’s employees between March 2013 and January 2017.
The first part of the detection method relies on the analysis of two key components: domain reputation features and sender reputation features. The domain reputation feature involves analyzing the link included in an email to see if it poses a risk. A URL is considered risky if it has not been visited by many employees from within an organization, or if it has never been visited until very recently.
The sender reputation feature aims to identify spoofing of the sender’s name in the From header, a previously unseen attacker using a name and email address closely resembling a known or authoritative entity, exploitation of compromised user accounts, and suspicious email content (i.e. messages that reference accounts and credentials, or ones that invoke a sense of urgency).
Once data has been collected about the sender and the URL, the system needs to decide whether or not an alert should be generated for the security team. The method proposed by the researchers, dubbed “Directed Anomaly Scoring (DAS),” ranks all events by determining how suspicious each event is compared to other events. After all the events have been classified, the DAS system selects the highest-ranked events and alerts the security team about their existence.
According to the experts, the new method detected 17 of 19 spear-phishing emails and had a false positive rate of less than 0.005%, which they claim is 200 times lower than what other researchers had previously obtained.
“This research is important for two reasons,” said Facebook’s Nektarios Leontiadis. “First, in recent history, successful spearphishing attacks have led to a number of prominent information leaks. Every time the community improves the detection or prevention of compromise from a technical standpoint, the human factor becomes an even stronger focal point of adversaries. Helping protect people from social engineering attacks becomes even more important. This research can help reduce the potential of such compromises happening in the future.”
“Secondly, the authors acknowledge and account for the cost of false positives in their detection methodology. This is significant because it factors into the overhead cost and response time for incident response teams,” Leontiadis added.
Facebook also announced that two other groups earned honorable mentions for their research on preventing dangling pointer flaws and the use of static analysis techniques to find Linux kernel driver vulnerabilities.
Unpatched Code Execution Flaws in Foxit Reader Disclosed
18.8.2017 securityweek Vulnerebility
Trend Micro’s Zero Day Initiative (ZDI) has disclosed the details of two remote code execution vulnerabilities affecting Foxit Reader. The vendor has decided not to patch the flaws as it believes exploitation is prevented by the product’s “Secure Mode” feature.
The more serious of the weaknesses, tracked as CVE-2017-10952 and rated high severity by ZDI, is an arbitrary file write flaw affecting the saveAs JavaScript function in Foxit Reader.
“The issue results from the lack of proper validation of user-supplied data, which can lead to writing arbitrary files into attacker controlled locations,” ZDI said in its advisory.
The second vulnerability, classified as medium severity and tracked as CVE-2017-10951, is a command injection flaw that exists in the app.launchURL method.
“The issue results from the lack of proper validation of a user-supplied string before using it to execute a system call. An attacker can leverage this vulnerability to execute code under the context of the current process,” ZDI said.
An attacker can exploit the vulnerabilities, both classified by ZDI as “zero-day,” by getting the targeted user to open a specially crafted document.
Proof-of-concept (PoC) videos have been made available for both flaws. They show how an attacker could execute an arbitrary application and write an executable file to the targeted system’s startup folder.
The issues, discovered by researchers Ariele Caltabiano (aka kimiya) and Steven Seeley of Offensive Security, were reported to Foxit Software in May and June. ZDI decided to make its advisories public after the vendor said it will not release patches as exploitation is prevented by the application’s “Secure Mode” feature.
“Foxit Reader & PhantomPDF has a Safe Reading Mode which is enabled by default to control the running of JavaScript, which can effectively guard against potential vulnerabilities from unauthorized JavaScript actions,” Foxit Software told ZDI.
However, ZDI does not agree that this feature provides enough protection against exploitation.
“Users of Foxit’s Reader and PhantomPDF should ensure they have Safe Reading Mode and hope attackers don’t discover a way to disable it. Additionally, you can uncheck the ‘Enable JavaScript Actions’ from Foxit’s Preferences menu, although this may break some functionality,” ZDI’s Abdul-Aziz Hariri said in a blog post.
SecurityWeek has reached out to Foxit Software for additional clarifications and will update this article if the company responds.
Healthcare Providers Warned of Flaws in Philips Product
18.8.2017 securityweek Vulnerebility
The U.S. Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) and Philips have warned healthcare providers that one of the company’s radiation dose management tools is affected by potentially serious vulnerabilities.
Launched in November 2014, the Philips DoseWise Portal (DWP) enables healthcare providers to record, analyze and monitor imaging radiation doses for patients and clinicians across multiple diagnostic settings.
Versions 1.1.7.333 and 2.1.1.3069 of DWP are affected by a couple of vulnerabilities that allow a remote attacker to gain access to the application database and the patient health information it stores.
One of the flaws, tracked as CVE-2017-9656 and classified as “critical severity,” exists due to the use of hardcoded credentials for a database account. The second vulnerability, CVE-2017-9654, is an issue related to login credentials being stored in clear text in backend system files.
“For an attacker to use or exploit these vulnerabilities to access the underlying DWP database, elevated privileges are first required in order for an attacker to access the web application backend system files that contain the hard-coded credentials,” Philips said in its advisory.
“Successful exploitation may allow a remote attacker to gain access to the database of the DoseWise Portal application which contains patient health information (PHI). Potential impact could include compromise of patient confidentiality, system integrity, and/or system availability,” the company added.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Philips said it was not aware of any attacks exploiting these vulnerabilities. The company pointed out that the product is classified as a low-safety-risk medical device.
The vendor expects to release an update and new documentation to address these issues later this month. Patches will be included in version 2.1.2.3118 and for users of version 1.1.7.333 Philips will reconfigure the DWP installation to change and encrypt passwords.
In the meantime, the company has advised users to ensure that security best practices are implemented across their network, and that port 1433 is blocked, except for cases where a separate SQL server is used.
Philips also issued security alerts recently to warn its customers about the NotPetya and WannaCry attacks. The company informed organizations that some products had been affected by the Windows vulnerability exploited by these pieces of malware.
Several other medical device manufacturers also issued warnings regarding these malware attacks.
SyncCrypt Ransomware Hides Components in Image Files
18.8.2017 securityweek Ransomware
A newly discovered piece of ransomware hides its components inside online harmless-looking images that don’t trigger anti-virus detection.
Dubbed SyncCrypt, the ransomware is distributed through spam emails that feature attachments containing WSF files pretending to be court orders. Once the attachments are executed, embedded JScript fetches seemingly innocuous images from specific locations and extracts malicious components hidden inside them.
The ransomware components are stored inside the images as ZIP files, and they aren’t triggered if the user simply accesses their URL via browser. The aforementioned JScript, however, not only downloads the images, but also extracts the hidden malicious components (sync.exe, readme.html, and readme.png), BleepingComputer’s Lawrence Abrams reveals.
The WSF file also creates a Windows scheduled task called Sync. Once the sync.exe file is executed, it starts scanning the victim’s computer for certain file types and encrypts them using AES encryption. The malware encrypts the used AES key with an embedded RSA-4096 public encryption key.
The ransomware targets over 350 file types and appends the .kk extension to them after encryption. The threat skips files located in several folders, namely \windows\, \program files (x86)\, \program files\, \programdata\, \winnt\, \system volume information\, \desktop\readme\, and \$recycle.bin\.
The ransomware demands around $430 to be paid to retrieve the decryption key. The attackers instruct victims to provide them with the key file after paying the ransom to receive a decrypter. The email addresses used as part of the analyzed attack include getmyfiles@keemail.me, getmyfiles@scryptmail.com, and getmyfiles@mail2tor.com.
The distribution of this ransomware is highly effective because of its ability to bypass detection. According to Abrams, only one of the 58 vendors in VirusTotal could detect the malicious images at the time of analysis. Sync.exe, on the other hand, had a detection rate of 28 out of 63.
To stay protected, users should pay extra care when opening attachments or clicking on URLs in emails received from unknown sources. They should also keep their files backed up at all times, to ensure they can recover their data without having to pay a ransom. Keeping all software on the machine updated at all times should decrease the chances of becoming infected.
China Opens its First 'Cyber Court'
18.8.2017 securityweek BigBrothers
China's first "cyber court" was launched on Friday to settle online disputes, as the legal system attempts to keep up with the explosion of mobile payment and e-commerce.
Residents of the eastern city of Hangzhou -- home to e-commerce giant Alibaba -- can now register their internet-related civil complaints online and wait to log onto to their trial via videochat.
The cyber court will "offer regular people an efficient, low-cost solution to these new kinds of disputes that take place on the internet," Du Qian, the cyber-court chief justice, told the official Supreme People's Court news agency.
"Not only will this make lawsuits as convenient as online shopping, but it will also give online shopping the same degree of judicial protection as consumption at brick-and-mortar stores."
The court will handle cases such as online trade disputes, copyright lawsuits and product liability claims for online purchases.
China is home to the world's largest number of internet users -- 731 million at the end of last year -- and e-commerce is a vital part of the government's efforts to turn China into a consumer demand-driven economy.
Consumers spent $17.8 billion during Alibaba's biggest online shopping promotion on November 11 last year, more than twice the five-day desktop sales from Thanksgiving through Cyber Monday in the US last year.
Patching Against the Next WannaCry Vulnerability (CVE-2017-8620)
18.8.2017 securityweek Vulnerebility
This month's Microsoft patch updates include one particular vulnerability that is raising concerns: CVE-2017-8620, which affects all versions of Windows from 7 onwards. Microsoft explained, "in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer."
In short, this is a wormable bug affecting all supported versions of Windows. The parallels with the WannaCry and NotPetya vulnerabilities are clear -- indeed, Check Point described CVE-2017-8620 as 'The Next WannaCry Vulnerability'. All that is currently missing is full disclosure of the vulnerability and a usable exploit (WannaCry and NotPetya exploited the leaked NSA exploit known as EternalBlue).
Noticeably, SANS describes this vulnerability as 'more likely' to be both disclosed and exploited in the future. Once this happens, the situation could precisely parallel WannaCry/NotPetya. Microsoft has done what it can (or as much as it is willing to do); it has patched the vulnerability. The earlier WannaCry vulnerability had also been patched; but WannaCry (and NotPetya) still happened (and the effects continue to be felt).
"The importance of patching systems cannot be underestimated," says David Kennerley, director of threat research at Webroot. "There will always be zero-day vulnerabilities, but it's worth noting that the vast majority of exploit attacks seen in the wild involve cybercriminals targeting known vulnerabilities. These vulnerabilities have already been fixed by the vendor, but the fix has not been deployed and installed by the end user. With any vulnerability that can result in remote code execution, there is always concern until users deploy and install patches. There is without doubt a window of opportunity for cybercriminals to take advantage."
One concern for the CVE-2017-8620 vulnerability is that it could be adopted by nation-state actors. Absolute attribution of cyberattacks is difficult; but much current thinking is that the WannaCry attack was a somewhat botched ransomware attack (possibly originating from North Korea). The NotPetya ransomware attack is thought to be a disguised wiper attack primarily aimed at the Ukraine, and possibly by Russian 'patriots'. Extrapolating this progress, one possible application of CVE-2017-8620 in the future could be its use by an adversarial nation-state employing it as a rapidly spreading worm wiper cyberweapon. State actors would certainly have the resources to uncover the vulnerability and develop an exploit.
The current concern is that since many users did not patch against WannaCry/NotPetya, they might not patch CVE-2017-8620 before it is exploited. The question becomes, why is industry apparently lax in its patch procedures? This is a complex issue with no easy answer.
"Patching will break stuff," F-Secure security advisor Sean Sullivan explains. "And so you can't just roll out patches into a live production environment without testing. It's a matter of time and resources. There's no escaping the need to test."
This view is echoed by Wendy Nather, principal security strategist at Duo Security. The 'production' environments in healthcare are a good example. "Because patient safety is paramount," she said, "healthcare systems cannot be updated if doing so will threaten their availability. Even if the software is patched, it requires a new round of safety certifications that take months." It is noticeable that healthcare -- and especially the UK's National Health Service -- was badly affected by the WannaCry outbreak.
Production environments are not the only problem area for IT departments. "Any system with external, highly entangled dependencies will take longer to update," says Nather. Established international organizations that have perhaps acquired foreign companies in different legal jurisdictions could fall into this category. It could take years, she suggested, "as integration testing, certifications, regulatory alignment in multiple countries, and staged deployment must all be carefully scheduled."
Embedded systems are likely to prove an increasing problem for patching as the IoT expands; both for embedded operating systems and proprietary software. Martin Zinaich, information security officer with the City of Tampa, gives an example. "Recently I was tracking down WannaCry attack traffic coming loud and strong from an IP address that I soon associated to an HP Scanner. Yes, a scanner -- but a scanner that utilizes Windows POS. I now have to worry about large format scanners. Tomorrow it will be light bulbs, door locks and the candy machine."
To add insult to injury, the scanner's product data sheet specifically states, "Closed systems with very low risk of being infected by a virus, so no antivirus is required." Vulnerabilities in IoT devices are now considered such a problem that US lawmakers have introduced a bill that will require vendors selling IoT devices to the US government to ensure that the devices are patchable.
While there are genuine reasons for some companies to delay patching -- David Harley, senior research fellow at ESET calls it "a balance between risking difficulties caused by a problematic patch, and risking issues caused by unpatched vulnerabilities" -- there are still cases where organizations don't see patching as a priority. "And that, he adds, "has become more dangerous than ever in recent years."
What becomes clear is that there are likely to be many unpatched systems around the world left vulnerable by the time an exploit for CVE-2017-8620 becomes available. Is Check Point correct in saying this could be the next WannaCry? Replies are guarded. "It might be a bit hyperbolic," comments Sullivan, "but isn't wrong. It may be too soon to worry about the 'next' attack (as they are very often different than the last) but it's not too soon to be learning lessons from the WannaCry incident." It's not inevitable that it will be the next WannaCry, adds Harley: "but it's not impossible."
This just leaves the final question: if patching CVE-2017-8620 is not possible, how should companies protect themselves. The first requirement is that anti-virus defenses should be kept up to date. It is possible, but not immediately verifiable, that Microsoft will privately disclose the vulnerability to the anti-virus industry as part of the long-running practice of information-sharing between the defenders. "I wouldn't be surprised to see anti-malware products include detection of the vulnerability or potential exploits," comments Harley.
Defense in depth specifically aimed at preventing SMB worms will also help. F-Secure's Jarno Niemela pointed out during the WannaCry outbreak that better firewall rules would have done much to mitigate the damage that was done. "Managing risk is not just about patching vulnerabilities," says Sullivan.
Finally, if patching is planned but delayed, Microsoft's recommended temporary mitigation against CVE-2017-8620 should be deployed: disable the WSearch facility within Windows.
Hackers Can Hijack Phones via Replacement Screens: Researchers
18.8.2017 securityweek Mobil
Touchscreens and other components that are often replaced in smartphones and tablets can hide malicious chips capable of giving attackers complete control over the device, warned researchers at the Ben-Gurion University of the Negev.
Researchers conducted their experiments on two Android devices: a Huawei Nexus 6P smartphone which uses a touchscreen controller from Synaptics, and an LG G Pad 7.0 tablet that uses an Atmel controller. However, the experts believe many other devices are also vulnerable to these types of attacks, including ones made by Apple.
In their tests, the researchers used a hot air blower to separate the touch screen controller from the main assembly board and access the copper pads. They then connected the pads to an integrated chip that manipulates the communication bus, effectively launching a chip-in-the-middle attack. STM32L432 and Arduino microcontrollers, which cost roughly $10 each, have been used in the experiments.
The malicious chip can exploit vulnerabilities in the device driver to compromise the phone or tablet while ensuring that it does not stop functioning correctly.
Videos have been published to show how a malicious touchscreen can be used to install arbitrary software, take pictures with the camera and send them to the attacker via email, replace a legitimate URL with a phishing URL, capture and exfiltrate screen unlock patterns, and take complete control of the targeted device.
Completely hijacking a phone takes the longest, roughly 65 seconds, but some operations, such as replacing a URL, take less than one second to complete.
While attacks involving hardware replacements are not unheard of, the scenario described by Ben Gurion University researchers relies on replacing a component with a limited hardware interface, and assumes that the repair technician installing the replacement screen is not involved and does not conduct any operations other than replacing the broken component with a malicious one that has been provided to them.
The researchers notified Google of the Synaptics device driver vulnerabilities in February and patches were included in the June 2017 Android security updates. They are also working on notifying the developers of the Armel device driver of the discovered issues.
The experts have also proposed a series of hardware-based countermeasures to prevent such attacks.
U.S. Military to Create Separate Unified Cyber Warfare Command
18.8.2017 securityweek BigBrothers
President Donald Trump ordered the US military on Friday to elevate its cyber warfare operations to a separate command, signaling a new strategic emphasis on electronic and online offensive and defensive operations.
"This new Unified Combatant Command will strengthen our cyberspace operations and create more opportunities to improve our nation's defense," Trump said in a statement.
"The elevation of United States Cyber Command demonstrates our increased resolve against cyberspace threats and will help reassure our allies and partners and deter our adversaries."
The move would expand the number of the Defense Department's unified combatant commands to 10, putting cyber warfare on an equal footing with the Strategic Command, the Special Operations Command, and regional commands.
Until now cyber warfare operations have been run under the umbrella of the National Security Agency, the country's main electronic spying agency, with Admiral Michael Rogers heading both.
Discussions on whether to hive it off and place it directly under Pentagon direction have gone on for several years. Rogers has said several times over the past year that they needed to recruit hundreds more skilled cyber operators before the separation could take place.
Trump's statement suggested the final shape of where the new unified command will fit into the Pentagon remains unsettled. Defense Secretary Jim Mattis is currently reviewing separating the Cyber Command from the NSA, he said.
Android Trojan Now Targets Non-Banking Apps that Require Card Payments
18.8.2017 thehackernews Android
The infamous mobile banking trojan that recently added ransomware features to steal sensitive data and lock user files at the same time has now been modified to steal credentials from Uber and other booking apps as well.
Security researchers at Kaspersky Lab have discovered a new variant of the Android banking Trojan called Faketoken that now has capabilities to detect and record an infected device's calls and display overlays on top of taxi booking apps to steal banking information.
Dubbed Faketoken.q, the new variant of mobile banking trojan is being distributed using bulk SMS messages as their attack vector, prompting users to download an image file that actually downloads the malware.
Malware Spy On Telephonic Conversations
Once downloaded, the malware installs the necessary modules and the main payload, which hides its shortcut icon and begins monitoring everything—from every calls to launched apps—that happens on the infected Android device.
When calls are made to or received from certain phone numbers on the victim's device, the malware begins to record those conversations and sends the recordings to the attacker's server.
Moreover, Faketoken.q also checks which apps the smartphone owner is using and when detects the launch of an app whose interface it can simulate, the Trojan immediately overlays the app with a fake user interface.
Malware Exploits Overlay Feature to Steal Credit Card Details
In order to achieve this, the Trojan uses the same standard Android feature that is being employed by a whole bunch of legitimate apps, such as Facebook Messenger, window managers, and other apps, to show screen overlays on top of all other apps.
The fake user interface prompts victims to enter his or her payment card data, including the bank’s verification code, which can later be used by attackers to initiate fraudulent transactions.
Faketoken.q is capable of overlaying a large number of mobile banking apps as well as miscellaneous applications, such as:
Android Pay
Google Play Store
Apps for paying traffic tickets
Apps for booking flights and hotel rooms
Apps for booking taxis
Since fraudsters require an SMS code sent by the bank to authorise a transaction, the malware steals incoming SMS message codes and forward them to the attackers command-and-control (C&C) server for a successful attack.
According to the researchers, Faketoken.q has been designed to target Russian-speaking users, as it uses the Russian language on the user interface.
Ways to Protect Against Such Android Banking Trojans
The easiest way to prevent yourself being a victim of such mobile banking Trojans is to avoid downloading apps via links provided in messages or emails, or any third-party app store.
You can also go to Settings → Security and make sure "Unknown sources" option is turned off in order to block installation of apps from unknown sources.
Most importantly, verify app permissions before installing apps, even if it is downloaded from official Google Play. If you find any app asking more than what it is meant for, just do not install it.
It's always a good idea to install an antivirus app from a reputed vendor that can detect and block such malware before it can infect your device, and always keep your system and apps up-to-date.
Two Critical Zero-Day Flaws Disclosed in Foxit PDF Reader
18.8.2017 thehackernews Vulnerebility

Are you using Foxit PDF Reader? If yes, then you need to watch your back.
Security researchers have discovered two critical zero-day security vulnerabilities in Foxit Reader software that could allow attackers to execute arbitrary code on a targeted computer, if not configured to open files in the Safe Reading Mode.
The first vulnerability (CVE-2017-10951) is a command injection bug discovered by researcher Ariele Caltabiano working with Trend Micro's Zero Day Initiative (ZDI), while the second bug (CVE-2017-10952) is a file write issue found by Offensive Security researcher Steven Seeley.
An attacker can exploit these bugs by sending a specially crafted PDF file to a Foxit user and enticing them to open it.
Foxit refused to patch both the vulnerabilities because they would not work with the "safe reading mode" feature that fortunately comes enabled by default in Foxit Reader.
"Foxit Reader & PhantomPDF has a Safe Reading Mode which is enabled by default to control the running of JavaScript, which can effectively guard against potential vulnerabilities from unauthorized JavaScript actions," the company says.
However, researchers believe building a mitigation doesn't patch the vulnerabilities completely, which if remained unpatched, could be exploited if attackers find a way to bypass safe reading mode in the near future.
Both unpatched vulnerabilities can be triggered through the JavaScript API in Foxit Reader.
CVE-2017-10951: The command injection bug resides in an app.launchURL function that executes strings provided by attackers on the targeted system due to lack of proper validation, as demonstrated in the video given below.
CVE-2017-10952: This vulnerability exists within the "saveAs" JavaScript function that allows attackers to write an arbitrary file on a targeted system at any specific location, as demonstrated in the video given below.
"Steven exploited this vulnerability by embedding an HTA file in the document, then calling saveAS to write it to the startup folder, thus executing arbitrary VBScript code on startup," reads the advisory published by the ZDI.
If you are one of those using Foxit Reader and PhantomPDF, ensure you have the "Safe Reading Mode" feature enabled. Additionally, you can also uncheck the "Enable JavaScript Actions" from Foxit's Preferences menu, although this may break some functionality.
Users are also recommended always to be vigilant while opening any files they received via email. Just recently, we reported how opening a malicious PowerPoint file could compromise your computer with malware.
So, always beware of phishing emails, spams, and clicking the malicious attachment.
Flashpoint Launches Intelligence Academy
18.8.2017 securityweek BigBrothers
New Intelligence Academy Aims to Help Organizations Reduce Risk by Better Understanding Threats and Prioritizing Response
Business Risk Intelligence (BRI) is a term that is easy to understand in concept, but difficult to action in practice. The problem is that business structures are all too often silos of individual responsibilities. Cyber security risk is a good example. Different cyber security control functions are often silos with little inter-control functionality. But cyber security itself is also a siloed department within the business -- again with little inter-departmental functionality.
Risk, however, is not siloed -- risk affects the whole business and honors no siloed structure. Risk management needs to be treated holistically, analyzing business risk rather than just cyber risk -- because, says Flashpoint's BRI principal advisor, Brian Mohr, in blog post, BRI includes not just cyber and insider risk, but also "global risk, fraud, anti-money laundering, executive protection, and physical security, to name a few." These risks are inter-related; and business needs to adopt an integrated approach to BRI.
The solution to risk is threat intelligence -- but most cyber threat intelligence sources are disjointed. For example, in a 2016 analysis of 88 IP-based blacklists and 35 domain name blacklists, Carnegie Mellon found that the majority of threat-indicated sources appeared on only one of the lists. For maximum threat intelligence, risk managers would need to subscribe to all the lists -- and risk being overwhelmed by noise within the intelligence. And they would still be limiting their intelligence to the cyber realm alone.
But for true business risk intelligence, many more factors need to be included -- such as geopolitical flashpoints, potential exchange rate fluctuations, staff travel arrangements and more. For example, "Few threats expose the true interdependency of cyber and physical security more than those targeting the oil and natural gas (ONG) sector," wrote Flashpoint CEO Josh Lefkowitz in a blog earlier this month. "After all, oil and natural gas together account for 53 percent of the world’s energy consumption and remain integral determinants of both global trade and the economy."
In its January 2017 Business Risk Intelligence Decision Report, Flashpoint expanded on this principle. "Traditional cyber threat intelligence, which has been largely focused on indicators of compromise, is insufficient in supporting the risk decision-making process, as it too often limits its focus on events in cyberspace," it warned. "Not all actors constrain their operations solely to the cyber realm; top tier nation-states like the U.S. and Russia use the full-spectrum of their capabilities to achieve their objectives. A threat assessment of Chinese or Russian cyber operations without the context of the national objectives they are supporting fails to provide risk decision-makers with an accurate portrayal of the threat landscape upon which to make business decisions."
To aid corporations take the required holistic view of business risk, Flashpoint offers its own BRI service. It gathers the intelligence and performs the analysis of that intelligence for its customers. It combines the different threat indicators into an holistic risk analysis, delivering integrated business risk intelligence.
But one basic problem remains -- not all companies know how to use the intelligence they receive. "Having spent my career in the government and the intelligence community, as well as at a Fortune 10 company," writes Mohr, "I understand without hesitation that the fundamental purpose of intelligence is to support decision-making. However, I also understand the struggles of implementing the intelligence lifecycle into practical business use."
Lefkowitz and his team at the New York, NY-based threat intelligence and research company have many years' experience of working both within national intelligence agencies and major international corporations. For example, Mohr spent 15 years as a Counterintelligence/Human Intelligence Specialist for the U.S. Marine Corps, conducting both human intelligence activities in support of U.S. combat units in the Middle East, as well as technical counterintelligence investigations across the Asia-Pacific theater. He then spent two years with the cyber threat intelligence team at American Express.
It is this combination of pure intelligence analysis and business understanding that Flashpoint now wishes to disseminate. It has today launched the Flashpoint Intelligence Academy (FIA). Its purpose is to help organizations understand how to structure an action program that embraces the full combined intelligence of BRI.
"We created FIA as a means to transfer what we’ve learned from our own experiences in building intelligence programs to our customers in a meaningful way," explains Mohr. "I came to Flashpoint because I realized that the company was helping its customers, not from the standpoint of just blocking IOCs, but actually supporting customers to reduce their overall risk. And I know FIA is the program to continue to support that goal."
The FIA offers foundational (one-day sessions); intermediate (two or three-day sessions); and advanced workshops. These workshops are available to any organization involved in actioning BRI, and not just Flashpoint customers. "Using the BRI principles taught in these workshops," says the on-site blurb, "organizations can better understand the threats they may face, prioritize their responses, make more informed decisions, and become a source for developing and driving risk intelligence application across the business."
Flashpoint raised $28 million in Series C funding in July 2017, after raising $10 million in July 2016.
Leaked Exploits Fueled Millions of Attacks in Q2: Kaspersky
18.8.2017 securityweek Exploit
The public availability of new exploit packages has fueled millions of new attacks on popular applications during the second quarter of 2017, a recent report from Kaspersky Lab reveals.
The Moscow-based security company said that it blocked more than five million attacks involving in-the-wild exploits during the three-month period, but the actual number of incidents should be significantly higher. Highly effective as they don’t usually require user interaction, attacks leveraging exploits can result in malicious code being delivered to the targeted machines without the user suspecting anything.
According to Kaspersky’s IT threat evolution Q2 2017 report, the publication by the Shadow Brokers hacker group of several tools and exploits supposedly associated with the National Security Agency had grave consequences during the quarter. Included in the leak were exploits such as EternalBlue and EternalRomance, which fueled a large wave of malicious attacks.
Despite the fact that Microsoft had patched the vulnerabilities exploited by these tools one month before they were made public, “in the second quarter of 2017 only Kaspersky Lab blocked more over five million attempted attacks involving network exploits from the archive. And the average number of attacks per day was constantly growing: 82% of all attacks were detected in the last 30 days,” the security company says.
The figure is not surprising, considering that EternalBlue was used in a massive, global WannaCry ransomware attack in May. In June, the same exploit was used for lateral movement in an attack involving the NotPetya wiper, which resulted in hundreds of millions in losses. The exploit was employed in various other malware attacks as well.
One other exploit that fueled a large number of attacks was leveraging the CVE-2017-0199 vulnerability in Microsoft Office. Initially a zero-day abused by threat actors, Microsoft addressed the bug in early April, but cybercriminals discovered new ways to leverage it: through the use of PowerPoint Slide Shows. Despite the fix, the number of attacked users peaked at 1.5 million in April, Kaspersky says.
The security company says it detected and repelled 342,566,061 malicious attacks from online resources located in 191 countries during Q2, and that it also identified 33,006,783 unique malicious URLs. In Q1, the company detected 479,528,279 malicious attacks.
Kaspersky also detected attempted infections with financial malware on 224,675 user computers (down from 288,000 during the previous three months), and blocked crypto-ransomware attacks on 246,675 unique computers (up from 240,799 in Q1). The security firm detected 185,801,835 unique malicious and potentially unwanted objects in Q2 (up from 174,989,956 the previous quarter).
In terms of banking malware attacks, Germany emerged as the most affected country in Q2 (these incidents include banking Trojans and ATM and POS-malware). Zbot, Nymaim, and Emotet were the top 3 banking malware families in the timeframe. WannaCry, Locky, and Cerber were the most spread cryptor families.
Mobile malware was also active in the timeframe. The security firm discovered a Trojan called Dvmap being distributed via Google Play, and also observed attackers attempting to upload new apps containing the malicious Ztorg module to the storefront. The Svpeng banking Trojan remained the most popular mobile threat.
Overall, Kaspersky detected 1,319,148 malicious installation packages during Q2, and reveals that adware registered the biggest growth during the timeframe. Trojan-SMS malware experienced the second-highest growth rate, while spyware registered the biggest decline. Iran was the top country attacked by mobile malware, followed by China, while the United States emerged as the most attacked by mobile ransomware.
“The threat landscape of Q2 provides yet another reminder that a lack of vigilance is one of the most significant cyber dangers. While vendors patch vulnerabilities on a regular basis, many users don’t pay attention to this, which results in massive-scale attacks once the vulnerabilities are exposed to the broad cybercriminal community,” Alexander Liskin, security expert at Kaspersky Lab, said.
Hacker published the decryption key for the Apple Secure Enclave security chip
18.8.2017 securityaffairs Apple
A hacker Thursday afternoon published what he claims to be the decryption key for Apple iOS’ Secure Enclave Processor (SEP) firmware.
The Apple Secure Enclave is an ARM-based coprocessor that enhances iOS security, but on Thursday a hacker published what he says is the decryption key for Apple iOS’ Secure Enclave Processor (SEP) firmware.
According to Apple technical documentation, the Secure Enclave coprocessor is built into Apple S2 (Watch Series 2), A7 (iPhone 5S, iPad Air, Mac Mini 2 and 3), and subsequent A-series chips.
The coprocessor generates the Unique ID (UID) number and keeps it segregated from the rest of iOS for all devices powered by the A9 (iPhone 6S, 6S Plus, SE, and 2017 iPad) and later generations of silicon,
The Secure Enclave also handles the authentication process based on fingerprint gathered through the device’s Touch ID sensor.
The hacker, who goes online with the moniker “xerub” explained that the decryption key unlocks only the SEP firmware, and not user data. xerub published the key also on GitHub and to the community website iPhone Wiki.
“Everybody can look and poke at SEP now,” xerub said.
Follow
~ @xerub
key is fully grown https://www.theiphonewiki.com/wiki/Greensburg_14G60_%28iPhone6,1%29 … use https://github.com/xerub/img4lib to decrypt and https://gist.github.com/xerub/0161aacd7258d31c6a27584f90fa2e8c … to process
9:01 PM - Aug 16, 2017
Photo published for xerub/img4lib
xerub/img4lib
image4 vfs. Contribute to img4lib development by creating an account on GitHub.
github.com
4 4 Replies 130 130 Retweets 198 198 likes
Twitter Ads info and privacy
The key allows to decrypt and explore the encrypted firmware code, a gift for experts and hackers that can have more information about the iOS platform.
Using the key in conjunction with xerub’s img4lib it is possible to decrypt an iPhone 5s IMG4 SEP (Secure Enclave Processor) firmware image. The decrypted data can be analyzed with a tool called sepsplit to extract the executable binaries from the image.

Since the release of the iPhone 5s in 2013, Apple has introduced many security improvements and others are announced with the forthcoming devices and OS 11.
At the 2016 Black Hat, a group of security researchers made an interesting presentation on the Apple’s Secure Enclave providing some high-level technical details about its design and security features.
An unpatchable flaw in CAN protocol expose modern cars to hack
18.8.2017 securityaffairs Vulnerebility
Experts discovered a flaw in CAN protocol that could be exploited by an attacker to disable safety systems of connected cars, including power-steering.
Almost any function in modern vehicles, from brakes to accelerator, is electronically controlled, this means that the surface of attack is dramatically enlarging.
We discussed car hacking several times, experts have demonstrated on different occasions how to hack a modern vehicle or control it remotely.
Now a team of researchers from Trend Micro’s Forward-looking Threat Research (FTR) team, in collaboration with Politecnico di Milano and Linklayer Labs, discovered a critical security vulnerability in the CAN protocol (controller area network) that could be exploited by an attacker to disable airbags and other safety systems of connected cars, including power-steering and anti-lock brakes.
The CAN bus is a vehicle standard designed to allow components to communicate with each other, it is widespread in automotive and the flaw discovered by the researchers affects a large number of vendors and vehicle models.
The messages exchanged on the CAN, including errors, are called “frames,” the researchers focused their research on how CAN handles errors.
“Our attack focuses on how CAN handles errors. Errors arise when a device reads values that do not correspond to the original expected value on a frame,” read the blog post published by Trend Micro.
“When a device detects such an event, it writes an error message onto the CAN bus in order to “recall” the errant frame and notify the other devices to entirely ignore the recalled frame. This mishap is very common and is usually due to natural causes, a transient malfunction, or simply by too many systems and modules trying to send frames through the CAN at the same time.”
According to the CAN standards, when a component flood the bus with error messages, it goes into a Bus Off state and it is cut it off from the CAN system and making it inoperable.
Abusing this feature, an attacker can force the deactivation of any system connected to the CAN, including security systems like the airbag system or the anti-lock braking system.
The attack scenario sees the attackers using a “specially-crafted attack device” that is connected via local access to the vehicle.
Experts pointed out that transportation trends like ride-sharing and carpooling could make this attack scenario feasible.
Unfortunately, this is a design flaw of the CAN bus messaging protocol used in CAN controller chips, this means that the vulnerability cannot be directly patched with an OTA (on-the-air) upgrade or by recalling the vehicles.
To fix the design flaw, it is necessary to introduce changes in the CAN standards.
The researchers recommended manufacturers to implement network countermeasures to mitigate such attacks:
“Car manufacturers can only mitigate the attack we demonstrated by adopting specific network countermeasures, but cannot eliminate it entirely,” the researchers said.
“To eliminate the risk entirely, an updated CAN standard should be proposed, adopted, and implemented. This whole process would likely require another generation of vehicles.”
IT threat evolution Q2 2017
17.8.2017 Kaspersky Analysis
Targeted attacks and malware campaigns
Back to the future: looking for a link between old and new APTs
This year’s Security Analyst Summit (SAS) included interesting research findings on several targeted attack campaigns. For example, researchers from Kaspersky Lab and King’s College London presented their findings on a possible link between Moonlight Maze, a 20 year old cyber-espionage attack that targeted the Pentagon, NASA and others, and Turla – a very modern APT group.
Contemporary reports on Moonlight Maze show how, starting from 1996, US military and government networks, as well as universities, research institutions and even the Department of Energy, began detecting breaches in their systems. The FBI and the Department of Defense launched a massive investigation in 1998. However, although the story became public the following year, much of the evidence has remained classified, leaving the details of Moonlight Maze shrouded in myth and secrecy. Nevertheless, over the years several investigators have stated that Moonlight Maze evolved into Turla.
In 2016, while researching his book Rise of the Machines, Thomas Rid of Kings College London tracked down a former system administrator whose organisation’s server had been hijacked as a proxy by the Moonlight Maze attackers. This server, ‘HRTest’, had been used to launch attacks on the US. The now-retired IT professional had kept the original server and copies of everything relating to the attacks, and handed it to Kings College and Kaspersky Lab for further analysis. Kaspersky Lab researchers, Juan Andres Guerrero-Saade and Costin Raiu, together with Thomas Rid and Danny Moore from Kings College, spent nine months undertaking a detailed technical analysis of these samples. They reconstructed the attackers’ operations, tools, and techniques, and conducted a parallel investigation to see if they could prove the claimed connection with Turla.
Moonlight Maze was an open-source Unix-based attack targeting Solaris systems, and the findings show that it made use of a backdoor based on LOKI2 (a program released in 1996 that enables users to extract data via covert channels). This led the researchers to take a second look at some rare Linux samples used by Turla that Kaspersky Lab had discovered in 2014. These samples, named Penguin Turla, are also based on LOKI2. Further, the re-analysis showed that all of them use code created between 1999 and 2004.
Remarkably, we’re still seeing attacks that use this code. It was seen in the wild in 2011 in an attack on defence contractor Ruag in Switzerland that has been attributed to Turla. Then, in March 2017, Kaspersky Lab researchers discovered a new sample of the Penguin Turla backdoor submitted from a system in Germany. It is possible that Turla uses the old code for attacks on highly secure victims that might be harder to breach using its more standard Windows toolset.
The newly unearthed Moonlight Maze samples reveal many fascinating details about how the attacks were conducted using a complex network of proxies, and the high level of skills and tools used by the attackers.
So did Moonlight Maze evolve into Turla? It is not possible to say at this time. The next step would focus on a little known operation called ‘Storm Cloud: the evolved toolkit used by the Moonlight Maze operators once the initial intrusions became public in 1999. The story of Storm Cloud leaked out in 2003 with little fanfare. However, a few prescient details led us to believe that this intrusion set might give a more definitive answer.
You can find details of the research here.
Lazarus uncovered
In February 2016 a group of hackers (unidentified at that time) attempted to steal $851 million – and succeeded in transferring $81 million from the Central Bank of Bangladesh – in what is considered to be the largest and most successful cyber-heist ever. Research by Kaspersky Lab and others revealed that the attacks were almost certainly conducted by Lazarus, a notorious cyber-espionage and sabotage group – responsible for the attack on Sony Pictures in 2014, as well attacks on manufacturing companies, media and financial institutions in at least 18 countries around the world since 2009.
Based on our investigations into attacks by the group on financial institutions in South East Asia and Europe, we have been able to provide an insight into the modus operandi of the Lazarus group.
Typically, the initial compromise occurs when a single system within a bank is breached, either by compromising a corporate server or by means of a watering-hole attack – that is, by placing exploit code on a legitimate web site visited by staff at the target institution. Then the attackers move to other hosts within the organisation and plant a rudimentary backdoor on infected computers. The group then spends time (days or even weeks) identifying valuable resources within the organisation. Finally the attackers deploy special malware designed to bypass internal security features and issue rogue banking transactions.
The Lazarus group operates across the globe: we have found infiltration tools used by Lazarus in multiple countries in the last year or so.
The Lazarus group is very large and has historically focused mainly on cyber-espionage and cyber-sabotage activities. The group’s interest in financial gain is relatively new and it seems as though a different team within Lazarus is responsible for the generation of illegal profits: we have dubbed this team Bluenoroff. So far, we have seen four main types of target: financial institutions, casinos, companies developing financial trade software and those in the crypto-currency business.
One of the most notable Bluenoroff campaigns was its attacks on financial institutions in Poland. The attackers were able to compromise a government web site that is frequently accessed by many financial institutions – making it a particularly powerful attack vector.
The Lazarus group goes to great lengths to cover its tracks. However, one of our research partners made an interesting discovery when completing a forensic analysis of a Command-and-Control (C2) server in Europe that was used by the group. Based on the forensic analysis report, it was apparent that the attacker connected to the server via Terminal Services and manually installed an Apache Tomcat server using a local browser, configured it with Java Server Pages and uploaded the JSP script for the C2. Once the server was ready, the attacker started testing it, first with a browser, then by running test instances of their backdoor. The operator used multiple IPs – from France to Korea, connecting via proxies and VPN servers. However, one short connection was made from a very unusual IP range, which originates in North Korea. The operator also installed off-the-shelf crypto-currency mining software that should generate Monero crypto-coins: this software consumed system resources so intensely that the system became unresponsive and froze. This could be the reason why it was not properly cleaned, and the server logs were preserved. Of course, while the link to North Korea is interesting, this doesn’t mean we can conclude that North Korea is behind all the Bluenoroff attacks: someone in North Korea could have accidentally visited the C2 server, or it could be a deliberate false flag operation.
Lazarus is not just another APT group. The scale of the Lazarus group’s operations is shocking: it appears that Lazarus operates a malware factory, generating new tools as old ones are ‘burned’. The group uses various code obfuscation techniques, re-writes its own algorithms, applies commercial software protectors, and uses its own and underground packers. Typically, the group pushes rudimentary backdoors during the first stage of infection – ‘burning’ these doesn’t affect the group too much. However, if the first stage backdoor reports an interesting infection they start deploying more advanced code, carefully protecting it from accidental detection on disk: the code is wrapped into a DLL loader or stored in an encrypted container, or maybe hidden in a binary encrypted registry value. This usually comes with an installer that only the attackers can use, because they password protect it. This guarantees that automated systems – be it a public sandbox or a researcher’s environment – will never see the real payload. This level of sophistication is something that is not generally found in the cybercriminal world and requires strict organisation and control at all stages of operation. It also explains Lazarus branching out into operations to general illegal profits – operations of this kind require lots of money.
The best defence against targeted attacks is a multi-layered approach that combines traditional anti-malware technologies with patch management, host intrusion detection and a default-deny whitelisting strategy. According to a study by the Australian Signals Directorate, 85 per cent of targeted attacks analysed can be stopped by employing four simple mitigation strategies: application whitelisting, updating applications, updating operating systems and restricting administrative privileges.
You can find our report on the activities of the Lazarus group here.
Beating the bank
At this year’s Security Analyst Summit two of our researchers, Sergey Golovanov and Igor Soumenkov, discussed three cases where cybercriminals had stolen money from ATMs.
The first, ATMitch, involved compromising the bank’s infrastructure in order to controlling the operation of the ATM remotely. The attackers exploited an unpatched vulnerability to penetrate the target bank’s servers. They used open source code and publicly available tools to infect computers in the bank. However, the malware they created resided in memory only, not on the hard drives, and almost all traces of the malware were removed when the computer was re-booted. Following the infection, the attackers established a connection to their C2 server, allowing them to remotely install malware on the ATMs. Since this looked like a legitimate update, it didn’t trigger any alerts at the bank. Once installed, the malware looked for the file ‘command.txt’ – this contains the single-character commands that control the ATM. The malware first issues a command to find out how much money is in the ATM, then issues a further command to dispense money – collected by a money mule waiting at the ATM. After this, the malware writes all the information about the operation into the log file and wipes ‘command.txt’ clean.
What alerted bank staff to the malware was a single file called ‘kl.txt’. Thinking that this might have something to do with Kaspersky Lab, the bank called us and asked us to investigate. We created a YARA rule to search our systems for this file and discovered that we had been seen it twice – once in Russia and once in Kazakhstan. This enabled us to reverse engineer the malware and understand how the attack works.
One of the other bank attacks also started with a request from the bank. Money was missing, but the ATM logs were clear and the criminals had taped over the CCTV camera, so that there was no recording of the attack. The bank delivered the ATM to our office and, after disassembling it, we discovered that there was a Bluetooth adaptor connected to the ATM’s USB hub. The criminals had installed a Bluetooth adaptor on the ATM and had waited three months for the log to clear. Then they returned to the ATM, covered the security cameras and used a Bluetooth keyboard to re-boot the ATM in service mode and emptied the dispenser.
Another attack, which, like those mentioned above, started with a bank asking us to investigate an ATM theft, turned out to be much cruder in its approach. We found a hole, approximately 4cm in diameter, drilled near the PIN pad. Not long after, we learned of similar attacks in Russia and Europe. When police caught a suspect with a laptop and some wiring, things became clearer. We disassembled the ATM to try to find out what the attacker could be trying to access from the hole. What we found was a 10-PIN header, connected to a bus that connects all of the ATMs components and weak encryption that could be broken very quickly. Any single part of the ATM could be used to control all the others; and since there was no authentication between the parts, any one of them could be replaced without the others realising. It cost us around $15 and some time to create a simple circuit board that could control the ATM once we connected it to the serial bus, including dispensing money.
Fixing the problem, as our researchers highlighted, isn’t straightforward. Patching requires a hardware update and can’t be done remotely: a technician must visit all the affected ATMs to install it.
You can read more about these incidents here.
Meet the Lamberts
In April, we published a report on an advanced threat actor that can be compared with Duqu, Equation, Regin or ProjectSauron in terms of its complexity. This group, which we call ‘The Lamberts’ (but which is also known as ‘Longhorn’) first came to the attention of the security community in 2014, when researchers from FireEye discovered an attack using a zero-day vulnerability (CVE-2014-4148). This attack used malware that we call ‘Black Lambert’ to target a high profile organisation in Europe.
The group has developed and used sophisticated attack tools – including network-driven backdoors, several generations of modular backdoors, harvesting tools, and wipers – against its victims since at least 2008. The latest samples were created in 2016. There are currently known versions for Windows and OS X. However, given the complexity of these projects and the existence of an implant for OS X, we think that it is highly possible that other Lamberts exist for other platforms, such as Linux.
White Lambert runs in kernel mode and intercepts network traffic on infected machines. It decrypts packets crafted in a special format to extract instructions. We named these passive backdoors ‘White Lambert’ to contrast with the active ‘Black Lambert’ implants.
We subsequently came by another generation of malware that we called ‘Blue Lambert’.
One of these samples is interesting because it appears to have been used as second stage malware in a high profile attack that involved the Black Lambert malware.
The family of samples called ‘Green Lambert’ is a lighter, more reliable, but older version of Blue Lambert. Interestingly, while most Blue Lambert variants have version numbers in the range of 2.x, Green Lambert mostly includes 3.x versions. This stands in contrast to the data gathered from export timestamps and C2 domain activity that points to Green Lambert being considerably older than Blue Lambert. Perhaps both Blue and Green versions were developed in parallel by two different teams working under the same umbrella, as normal software version iterations, with one being deployed earlier than the other.
Signatures created for Green Lambert (Windows) have also triggered on an OS X variant of Green Lambert, with a very low version number: 1.2.0. This was uploaded to a multi-scanner service in September 2014. The OS X variant of Green Lambert is in many regards functionally identical to the Windows version, but it’s missing certain functionality – such as running plugins directly in memory.
Kaspersky Lab detections for Blue, Black, and Green Lamberts have been triggered by a relatively small set of victims from around the world. While investigating one of these infections involving White Lambert (network-driven implant) and Blue Lambert (active implant), we found yet another family of tools that appear to be related. We called this new family ‘Pink Lambert’.
The Pink Lambert toolset includes a beaconing implant, a USB-harvesting module and a multi-platform orchestrator framework that can be used to create OS-independent malware. Versions of this particular orchestrator were found on other victims, together with White Lambert samples, indicating a close relationship between the White and Pink Lambert families.
By looking further for other undetected malware on victims of White Lambert, we found yet another, apparently related, family. The new family, which we called ‘Gray Lambert’, is the latest iteration of passive network tools from the Lamberts’ arsenal. The coding style of Gray Lambert is similar to the Pink Lambert USB-harvesting module. However, the functionality mirrors that of White Lambert. Compared to White Lambert, Gray Lambert runs in user mode, without the need for exploiting a vulnerable signed driver to load arbitrary code on 64-bit Windows systems.
Connecting all these different families by shared code, data formats, C2 server, and victims, we have arrived at the following overarching picture:
Development of The Lamberts toolkit spans several years, with most activity occurring in 2013 and 2014.
Overall, the toolkit includes highly sophisticated malware that relies on high-level techniques to sniff network traffic, run plugins in memory without touching the disk and making use of exploits against signed drivers to run unsigned code on 64-bit Windows systems.
To further exemplify the proficiency of the attackers behind The Lamberts’ toolkit, deployment of Black Lambert included a rather sophisticated TTF zero-day exploit, CVE-2014-4148. Taking this into account, we classify The Lamberts as the same level of complexity as Duqu, Equation, Regin or ProjectSauron – that is, one of the most sophisticated cyber-espionage toolkits we have ever analysed.
In the vast majority of cases, the infection method is unknown, so there are still a lot of unknown details about these attacks and the group(s) using them.
You can read more about The Lamberts here.
The only effective way to withstand such threats is to deploy multiple layers of security, with sensors to monitor for even the slightest anomaly in organisational workflow, combined with threat intelligence and forensic analysis.
We will continue to monitor the activities of The Lamberts, as well as other targeted attack groups. By subscribing to our APT intelligence reports, you can get access to our investigations and discoveries as they happen, including comprehensive technical data.
Malware stories
More vulnerable Internet of Things things
Hackers are targeting devices that make up the Internet of Things (IoT) more and more. One of the most dramatic examples is the Mirai botnet, which took down a portion of the Internet in October 2016 by hijacking connected home devices (such as DVRs, CCTV cameras and printers).
In our predictions for 2017 we suggested that vigilante hackers might also target IoT devices, to draw attention to the woeful lack of security in some connected devices – perhaps even going so far as to create an ‘Internet of bricks’. In addition, there have been recent reports (here and here) of IoT malware designed to just that.
In April, we published an analysis of the Hajime botnet. This malware, first reported in October 2016 by Rapidity Networks, infects insecure IoT devices with open Telnet ports and default passwords. Hajime is a huge peer-to-peer botnet which, at the time of our report (25 April) comprised around 300,000 devices. The malware is continually evolving, adding and removing functionality. The most intriguing aspect of Hajime is its purpose. The botnet is growing, partly due to new exploitation modules, but its purpose remains unknown. So far, it hasn’t been used for malicious activity. It’s possible that this will never happen, because every time a new configuration file is downloaded, a piece of text is displayed while the new configuration is being processed:
On the other hand, even if it’s not used for deliberate harm, it’s possible that it might adversely affect the normal operation of an infected device.
Hajime, like other malware designed to compromised IoT devices, exploits the fact that many people don’t change the manufacturer’s default credentials when they buy a smart device. This makes it easy for attackers to access the device – they simply have to try the known default password. In addition, there are no firmware updates for many devices. IoT devices are also an attractive target for cybercriminals because they often have 24/7 connectivity.
These days we’re surrounded by smart devices. This includes everyday household objects such as telephones, televisions, thermostats, refrigerators, baby monitors, fitness bracelets and even children’s toys. However, it also includes cars, medical devices, CCTV cameras and parking meters. Now we can add drones to the list.
At the Security Analyst Summit, security expert Jonathan Andersson showed how a skilled attacker could create a device to hijack a drone in seconds. He used a software-defined radio (SDR), a drone’s control unit, a microcomputer and some other electronic equipment to create such a device, which he called ‘Icarus’. He used the device to tune to the frequency a drone uses to communicate with its controller and then experimented until he learned how exactly the signals were transmitted between the devices.
Andersson explained that this threat can potentially influence the whole drone industry — from cheap toys to expensive, professional craft — because drones and controller units use data transfer protocols that are vulnerable to the same type of attack. While stronger encryption could fix the problem, it’s not that easy because many controllers do not support software updates. Strong encryption also requires substantial computation capacity, which leads to additional energy consumption by the controller and the drone.
Hacking drones might seem a bit far-fetched, but the use of drones is no longer just a niche activity. Last December, Amazon tested the use of drones to deliver parcels.
You can find our overview of the growing threat to IoT devices, plus advice on protecting yourself from IoT malware here.
From extortion to ExPetr
The threat from ransomware continues to grow. Between April 2016 and March 2017, we blocked ransomware on the computers of 2,581,026 Kaspersky Lab customers. This is an increase of 11.4 per cent on the previous 12 months. You can read our full report on ransomware developments in 2016-17 here, but here are some of the key trends.
The extortion model is here to say and we’re seeing growing competition between ransomware gangs. They’re also targeting countries that had previously been unaffected – where people are less well-prepared to deal with the threat.
We’re seeing increasingly targeted ransomware attacks – quite simply because attacks on businesses are more profitable.
Ransomware is growing in sophistication and diversity, offering many ready-to-go solutions to those with fewer skills, resources or time – through a growing and increasingly efficient underground eco-system.
The establishment of a criminal-to-criminal infrastructure that is fuelling the development of easy-to-go, ad hoc tools to perform targeted attacks and extort money, making attacks more dispersed.
Global initiatives to protect people from crypto-ransomware, such as No More Ransom, will continue to gain momentum.
In May, we saw the biggest ransomware epidemic in history, called WannaCry. The largest number of attacks occurred in Russia, but there were also victims in Ukraine, India, Taiwan and many other countries – in total, 74 countries were affected. The malware spread very quickly – in just one day we saw more than 45,000 infections (Europol later estimated that upwards of 200,000 people had fallen victim to WannaCry).
WannaCry spread by taking advantage of a Windows exploit named ‘EternalBlue’ that relies on a vulnerability that Microsoft had patched in security update MS17-010. The Microsoft update had been released on 14 March, one month before EternalBlue exploit was made available in the ‘Shadow Brokers’ dump. However, many organisations hadn’t patched their systems, allowing the attackers to gain remote access to corporate systems. It then spread to other un-patched computers on the network.
Like other cryptors, WannaCry encrypts files on an infected computer and demands a ransom to decrypt them.
The attackers initially demanded $300, but this increased top $600 as the outbreak unfolded.
To ensure that the victims didn’t miss the warning, the malware changed the wallpaper and included instructions on how to locate the decryptor tool dropped by the malware.
It’s clear from our research that the quality of the WannaCry code is poor and the developers made many mistakes, enabling many of those infected to recover encrypted data. The way the attackers handled ransom payments limited their ability to capitalise on the spread of the worm. Multiple attempts were made to track transactions to the bitcoin wallets used by the attackers. Although estimates of how much money the attackers made vary, they run into tens of thousands, rather than hundreds
The timeline for attacks in the first week shows the impact of cyber-security efforts in combating the threat.
Not least among them was the discovery of a kill-switch. There’s a special check at the start of the code. It tries to connect to a hard-coded web site: if the connection fails the attack continues, if the connection is made, the code exits. By registering this domain and pointing it to a sinkhole server, a UK researcher was able to slow the infection of the worm.
A few days into the outbreak, Neel Mehta, a researcher at Google, posted a mysterious tweet using the #WannaCryptAttribution hashtag referring to a similarity between two code samples. One was a WannaCry sample from February 2017 that looked like an early variant of the worm. The other was a Lazarus sample from February 2017. Kaspersky Lab and others confirmed the similarity. It’s too early to say for sure if WannaCry was the work of the Lazarus group – more research is required to see if the dots join up.
You can find our original blog post here, our FAQ here and our comparison of the WannaCry and Lazarus samples here.
Towards the end of June, we saw reports of a new wave of ransomware attacks. The malware, which we called ExPetr (but known variously as Petya, Petrwrap and NotPetya) primarily targeted businesses in Ukraine, Russia and Europe – around 2,000 in total.
ExPetr uses a modified version of the EternalBlue exploit, as well as another exploit made public by the Shadow Brokers, called ‘EternalRomance’. The malware spread as an update to MeDoc – a Ukrainian accounting application – and through watering-hole attacks. Once inside the target organisation, the ransomware uses custom tools to extract credentials from the ‘lsass.exe’ process and passes them to PsExec or WMIC tools for further distribution within the network.
The malware waits for 10 minutes to an hour before re-booting the computer and then encrypts the MFT in NTFS partitions, overwriting the MBR with a customised loader containing a ransom demand.
ExPetr encrypts files as well as encrypting the MFT. The attackers demanded $300 in Bitcoins for the key to decrypt ransomed data, payable to a unified Bitcoin account. In principle – and unlike WannaCry – this technique could have worked because the attackers asked the victims to send their wallet numbers by e-mail to ‘wowsmith123456@posteo.net’, thus confirming the transactions. However, this e-mail account was quickly shut down, limiting the scope of the attackers to make money.
Following further analysis of the encryption routine, we concluded, as did some other researchers, that it isn’t possible for the attackers to decrypt the victims’ disks, even if payment is made. This suggests that ExPetr was a wiper masquerading as ransomware. There is even a suggestion that there might be a connection between ExPetr and the BlackEnergy KillDisk ransomware from 2015 and 2016.
ExPetr wasn’t the only ransomware that was distributed via MeDoc updates on 27 June 27. Another ransomware program, which we called FakeCry, was distributed to MeDoc customers at the same time. Our data indicate that 90 organisations received this malware, nearly all of them in Ukraine.
While the interface and messages closely resemble WannaCry, it is an entirely different malware family. We believe that FakeCry was designed with false flags in mind. One of the most interesting questions is whether FakeCry and ExPetr are related – as is suggested by the fact that both were distributed at the same time through MeDoc updates.
Here are our recommendations on how to protect against ransomware attacks.
Run a robust anti-malware suite with embedded anti-ransomware protection (such as Kaspersky Lab’s System Watcher).
Apply security updates for your operating system and applications as soon as they become available.
Do not open attachments, or click on links, from untrusted sources.
Backup sensitive data to external storage and keep it offline.
Never pay the ransom. Not only does this fuel the next wave of ransomware attacks, but also there is no guarantee that the criminals will restore your data.
IT threat evolution Q2 2017. Statistics
17.8.2017 Kaspersky Analysis
Q2 figures
According to KSN data, Kaspersky Lab solutions detected and repelled 342, 566, 061 malicious attacks from online resources located in 191 countries all over the world.
33, 006, 783 unique URLs were recognized as malicious by web antivirus components.
Attempted infections by malware that aims to steal money via online access to bank accounts were registered on 224, 675 user computers.
Crypto ransomware attacks were blocked on 246, 675 computers of unique users.
Kaspersky Lab’s file antivirus detected a total of 185, 801, 835 unique malicious and potentially unwanted objects.
Kaspersky Lab mobile security products detected:
1, 319, 148 malicious installation packages;
28, 976 mobile banker Trojans (installation packages);
200, 054 mobile ransomware Trojans (installation packages).
Mobile threats
Q2 events
SMS spam
As we wrote in the previous quarter, fraudsters had begun to actively use the Trojan-Banker.AndroidOS.Asacub mobile banker, distributing it via SMS spam. At the end of Q2, we detected a much larger campaign to spread it: in June, there were three times as many attacked users as in April, and judging by the first week of July, this growth continues.
The number of unique users attacked by Trojan-Banker.AndroidOS.Asacub in Q2 2017
Revamped ZTorg
Yet another interesting theme discussed in our report for the first quarter of 2017 remained relevant in Q2: the attackers continued to upload to Google Play new applications with the malicious Ztorg module. Interestingly, in the second quarter, we registered the cases of uploading additional Ztrog modules, not just the main ones. For example, we found the Trojan that could install and even buy apps on Google Play. We also discovered Trojan-SMS.AndroidOS.Ztorg.a, which could send paid SMS.
Of note is the fact that unlike the main Ztrog module, neither of the two malware samples attempted to exploit system vulnerabilities to obtain root privileges. To recap, Trojan.AndroidOS.Ztorg tries to get root privileges to display ads and secretly install new applications, including additional modules mentioned above.
Meet the new Trojan – Dvmap
In April 2017 we discovered a new rooting malware distributed via the official Google Play Store — Trojan.AndroidOS.Dvmap.a. Dvmap is very special rooting malware: it modifies system libraries. The Trojan exploits system vulnerabilities to obtain root privileges, and then injects its malicious code into the system library.
WAP billing subscriptions
In the second quarter of 2017, we registered an increase in the activity of Trojans designed to steal user money utilizing the mechanism of paid subscriptions (two years ago we wrote about similar attacks). To recap, the services of paid subscriptions are special sites that allow users to pay for services by deducting a certain amount of money from their phone accounts. Before getting the service, the client is redirected to the site of the cellular service provider, where he is asked to confirm his operation. The provider may also use SMS to confirm the payment. The Trojans have learned to bypass these restrictions: without user’s awareness they click on forms of confirmation, using special JS files. In addition, the Trojans can hide messages from the cellular service provider from the user.
We have discovered that in some cases after the infection, Trojan Ztorg can install additional modules with this functionality. Meanwhile the Trojan-Clicker.AndroidOS.Xafekopy family is capable of attacking such services in India and Russia, using JS files similar to those used by Ztrog.
Two malware samples from our Top 20 Trojan programs most popular in Q2 2017 were also attacking WAP subscriptions. They are Trojan-Clicker.AndroidOS.Autosus.a and Trojan-Dropper.AndroidOS.Agent.hb. Moreover, the most popular Trojans of the quarter detected by our machine learning-based system were also malicious programs utilizing mobile subscriptions.
Mobile threat statistics
In the second quarter of 2017, Kaspersky Lab detected 1,319, 148 malicious installation packages, which is almost as many as in two previous quarters.
Number of detected malicious installation packages (Q3 2016 – Q2 2017)
Distribution of mobile malware by type
Distribution of new mobile malware by type (Q1 and Q2 2017)
In Q2 2017, the biggest growth was demonstrated by Adware (13.31%) – its share increased by 5.99% p.p. The majority of all discovered installation packages are detected as AdWare.AndroidOS.Ewind.iz and AdWare.AndroidOS.Agent.n.
Trojan-SMS malware (6.83%) ranked second in terms of the growth rate: its contribution increased by 2.15 percentage points. Most of detected installation packages belonged to the Trojan-SMS.AndroidOS.Opfake.bo and Trojan-SMS.AndroidOS.FakeInst.a families, which percentage grew more than three-fold from the previous quarter.
The biggest decline was demonstrated by Trojan-Spy (3.88%). To recap, the growth rate of this type of malware were one of the highest in Q1 2017. This was caused by the increase in the number malicious programs belonging to the Trojan-Spy.AndroidOS.SmForw and Trojan-Spy.AndroidOS.SmsThief families.
The contribution of Trojan-Ransom programs, which had come first in terms of the growth rate in the first quarter of 2017, dropped by 2.55 p.p. and accounted for 15.09% in Q2.
TOP 20 mobile malware programs
Please note that this rating of malicious programs does not include potentially dangerous or unwanted programs such as RiskTool or adware.
1 DangerousObject.Multi.Generic 62.27%
2 Trojan.AndroidOS.Boogr.gsh 15.46%
3 Trojan.AndroidOS.Hiddad.an 4.20%
4 Trojan-Dropper.AndroidOS.Hqwar.i 3.59%
5 Backdoor.AndroidOS.Ztorg.c 3.41%
6 Trojan-Dropper.AndroidOS.Agent.hb 3.16%
7 Backdoor.AndroidOS.Ztorg.a 3.09%
8 Trojan.AndroidOS.Sivu.c 2.78%
9 Trojan-Dropper.AndroidOS.Lezok.b 2.30%
10 Trojan.AndroidOS.Ztorg.ag 2.09%
11 Trojan-Clicker.AndroidOS.Autosus.a 2.08%
12 Trojan.AndroidOS.Hiddad.pac 2.08%
13 Trojan.AndroidOS.Ztorg.aa 1.74%
14 Trojan.AndroidOS.Agent.bw 1.67%
15 Trojan.AndroidOS.Agent.gp 1.54%
16 Trojan.AndroidOS.Hiddad.ao 1.51%
17 Trojan-Banker.AndroidOS.Svpeng.q 1.49%
18 Trojan.AndroidOS.Agent.ou 1.39%
19 Trojan.AndroidOS.Loki.d 1.38%
20 Trojan.AndroidOS.Agent.eb 1.32%
* Percentage of unique users attacked by the malware in question, relative to all users of Kaspersky Lab’s mobile security product that were attacked.
First place was occupied by DangerousObject.Multi.Generic (62.27%), the verdict used for malicious programs detected using cloud technologies. Cloud technologies work when the antivirus database contains neither the signatures nor heuristics to detect a malicious program, but the cloud of the antivirus company already contains information about the object. This is basically how the very latest malware is detected.
Second came Trojan.AndroidOS.Boogr.gsh (15.46%). Such verdict is issued for files recognized as malicious by our system based on machine learning. The share of this verdict increased nearly threefold from the previous quarter which allowed it to move up from third to second place. In Q2 2017, this system most often detected Trojans which subscribed users to paid services as well as advertising Trojans which used superuser privileges.
Trojan.AndroidOS.Hiddad.an (4.20%) was third. This piece of malware imitates different popular games or programs. Interestingly, once run, it downloads and installs the application it imitated. In this case, the Trojan requests administrator rights to combat its removal. The main purpose of Trojan.AndroidOS.Hiddad.an is aggressive display of adverts, its main “audience” is in Russia. In the previous quarter it occupied second position.
Trojan-Dropper.AndroidOS.Hqwar.i (3.59%), the verdict used for the Trojans protected by a certain packer/obfuscator climbed from eighth to fourth position in the ranking. In most cases, this name hides the representatives of the FakeToken and Svpeng mobile banking families.
On fifth position was Trojan Backdoor.AndroidOS.Ztorg.c., one of the most active advertising Trojans which uses superuser rights. In the second quarter of 2017, our TOP 20 included eleven Trojans (highlighted in blue in the table) which tried to obtain or use root rights and which exploited advertising as the main means of monetization. Their goal is to deliver ads to the user more aggressively, applying (among other methods) hidden installation of new advertising programs. At the same time, superuser privileges help them “hide” in the system folder, thus making it very difficult to remove them. Of note is the fact that the number of such type of malware in the TOP 20 has been decreasing recently (in Q1 2017, there were fourteen Trojans of such type in the ranking).
Trojan-Dropper.AndroidOS.Agent.hb (3.16%) was sixth in the ranking. It is a complex modular Trojan, which main malicious part should be downloaded from the server of cybercriminals. We can assume that this Trojan is designed to steal money through paid subscriptions.
Eleventh place is occupied by Trojan-Clicker.AndroidOS.Autosus.a (2.08%) which main task is the activation of paid subscriptions. To do this, it “clicks” on the buttons in web catalogs of subscriptions, as well as hides incoming SMS with the information about them.
Trojan.AndroidOS.Agent.bw was fourteenth in the rating (1.67%). This Trojan, targeting primarily people in India (more than 92% of attacked users), just like Trojan.AndroidOS.Hiddad.an imitates popular programs and games, and once run, downloads and installs various applications from the fraudsters’ server.
Fifteenth came Trojan.AndroidOS.Agent.gp (1.54%), which steals user money making paid calls. Due to the use of administrator rights, it counteracts attempts to remove it from an infected device.
The ranking also included Trojan-Banker.AndroidOS.Svpeng (1.49%), which was seventeenth in the Top 20. This family has been active for three quarters in a row and remains the most popular banking Trojan in Q2 of 2017.
The geography of mobile threats
The geography of attempted mobile malware infections in Q2 2017 (percentage of all users attacked)
TOP 10 countries attacked by mobile malware (ranked by percentage of users attacked)
Country* % of users attacked **
1 Iran 44.78%
2 China 31.49%
3 Bangladesh 27.10%
4 Indonesia 26.12%
5 Algeria 25.22%
6 Nigeria 24.81%
7 India 24.53%
8 Côte d’Ivoire 24.31%
9 Ghana 23.20%
10 Kenya 22.85%
* We eliminated countries from this rating where the number of users of Kaspersky Lab’s mobile security product is relatively low (under 10,000).
** Percentage of unique users attacked in each country relative to all users of Kaspersky Lab’s mobile security product in the country.
As in the previous quarter, in Q2 2017 Iran was the country with the highest percentage of users attacked by mobile malware – 44.78%. China came second: 31.49% of users there encountered a mobile threat at least once during the quarter. It was followed by Bangladesh (27.10%).
Russia (12.10%) came 26th in Q2 of 2017 (vs 40th place in the previous quarter), France (6.04%) 58th, the US (4.5%) 71st, Italy (5.7%) 62nd, Germany (4.8%) 67th, Great Britain (4.3%) 73rd.
The safest countries were Denmark (2.7%), Finland (2.6%) and Japan (1.3%).
Mobile banking Trojans
Over the reporting period, we detected 28, 976 installation packages for mobile banking Trojans, which is 1.1 times less than in Q1 2017.
Number of installation packages for mobile banking Trojans detected by Kaspersky Lab solutions (Q3 2016 – Q2 2017)
Trojan-Banker.AndroidOS.Svpeng.q remained the most popular mobile banking Trojan for several quarters in a row. This family of mobile banking Trojans uses phishing windows to steal credit card data and logins and passwords from online banking accounts. In addition, fraudsters steal money via SMS services, including mobile banking.
Svpeng is followed by Trojan-Banker.AndroidOS.Hqwar.jck and Trojan-Banker.AndroidOS.Asacub.af. It is worth noting that most of users attacked by these three banking Trojans were in Russia.
Geography of mobile banking threats in Q2 2017 (percentage of all users attacked)
TOP 10 countries attacked by mobile banker Trojans (ranked by percentage of users attacked)
Country* % of users attacked**
1 Russia 1.63%
2 Australia 0.81%
3 Turkey 0.81%
4 Tajikistan 0.44%
5 Uzbekistan 0.44%
6 Ukraine 0.41%
7 Latvia 0.38%
8 Kyrgryzstan 0.34%
9 Moldova 0.34%
10 Kazakhstan 0.32%
* We eliminated countries from this rating where the number of users of Kaspersky Lab’s mobile security product is relatively low (under 10,000).
** Percentage of unique users in each country attacked by mobile banker Trojans, relative to all users of Kaspersky Lab’s mobile security product in the country.
In Q2 2017, the TOP 10 countries attacked by mobile banker Trojans remained practically unchanged: Russia (1.63%) topped the ranking again. In second place was Australia (0.81%), where the Trojan-Banker.AndroidOS.Acecard and Trojan-Banker.AndroidOS.Marcher families were the most popular threats. Turkey (0.81%) rounded off the Top 3.
Mobile Ransomware
In Q2 2017, we detected 200, 054 mobile Trojan-Ransomware installation packages which is much more than in the fourth quarter of 2016.
Number of mobile Trojan-Ransomware installation packages detected by Kaspersky Lab (Q3 2016 – Q2 2017)
In the first half of 2017, we discovered more mobile ransomware installation packages than for any other period. The reason was the Trojan-Ransom.AndroidOS.Congur family. Usually, the representatives of Congur have very simple functionality – they change the system password (PIN), or install it if no password was installed earlier, thus making it impossible to use the device, and then ask that user to contact the fraudsters via the QQ messenger to unblock it. It is worth noting that there are modifications of this Trojan that can take advantage of existing superuser privileges to install their module into the system folder.
Trojan-Ransom.AndroidOS.Fusob.h remained the most popular mobile Trojan-Ransomware in Q2, accounting for nearly 20% of users attacked by mobile ransomware, which is half as much as in the previous quarter. Once run, the Trojan requests administrator privileges, collects information about the device, including GPS coordinates and call history, and downloads the data to a malicious server. After that, it may receive a command to block the device.
Geography of mobile Trojan-Ransomware in Q2 2017 (percentage of all users attacked)
TOP 10 counties attacked by mobile Trojan-Ransomware (ranked by percentage of users attacked)
Country* % of users attacked**
1 USA 1.24%
2 China 0.88%
3 Italy 0.57%
4 Belgium 0.54%
5 Canada 0.41%
6 Kazakhstan 0.41%
7 Ireland 0.37%
8 Germany 0.34%
9 Norway 0.31%
10 Sweden 0.29%
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users in each country attacked by mobile Trojan-Ransomware, relative to all users of Kaspersky Lab’s mobile security product in the country.
The US topped the ranking of ten countries attacked by mobile Trojan-Ransomware; the most popular family there was Trojan-Ransom.AndroidOS.Svpeng. These Trojans appeared in 2014 as a modification of the Trojan-Banker.AndroidOS.Svpeng mobile banking family. They demand a ransom of $100-500 from victims to unblock their devices.
In China (0.65%), which came second in Q2 2017, most of mobile ransomware attacks involved Trojan-Ransom.AndroidOS.Congur.
Italy (0.57%) came third. The main threat to users originated from Trojan-Ransom.AndroidOS.Egat.d. This Trojan is mostly spread in Europe and demands $100-200 to unblock the devilce.
Vulnerable apps exploited by cybercriminals
The second quarter of 2017, especially popular were campaigns involving in-the-wild vulnerabilities. The appearance of several 0-day vulnerabilities for Microsoft Office resulted in a significant change in the pattern of exploits used.
The logical vulnerability in processing HTA objects CVE-2017-0199, which allows an attacker to execute arbitrary code on a remote machine using a specially generated file, was detected in early April. And despite the fact that the update fixing this vulnerability was published on April 11, the number of attacked Microsoft Office users soared almost threefold, to 1.5 million. 71% of all attacks on Microsoft Office users were implemented using this vulnerability; documents with exploits for CVE-2017-0199 were very actively used in spam mailings.
Distribution of exploits used in attacks by the type of application attacked, Q2 2017
This was caused by several reasons – simplicity and reliability of its exploitation on all MS Office and Windows versions and rapid appearance of document generators with the CVE-2017-0199 exploit in open access which significantly reduced the entry threshold for exploitation of this vulnerability. In comparison, two other zero-day vulnerabilities in MS Office related to memory corruption vulnerability due to incorrect processing of EPS files – CVE-2017-0261 and CVE-2017-0262 – accounted for only 5%.
However, the main event of Q2 was publication by the Shadow Brokers hacker group of the archive with utilities and exploits, supposedly developed by the US special services. The Lost In Translation archive contained a large number of network exploits for various Windows versions. And even though most of those vulnerabilities were not zero-day vulnerabilities and had been patched by the MS17-010 update a month before the leak, the publication had horrendous consequences. The damage from worms, Trojans and ransomware cryptors being distributed via the network with the help of EternalBlue and EternalRomance, as well as the number of users infected, is incalculable. In the second quarter of 2017 only Kaspersky Lab blocked more over five million attempted attacks involving network exploits from the archive. And the average number of attacks per day was constantly growing: 82% of all attacks were detected in the last 30 days.
The statistics on the IDS component using ShadowBrokers exploits over the last month.
A sharp peak at the end of the month was the appearance of the ExPetr cryptor, which used modified EternalBlue and EternalRomance exploits as one of proliferation methods.
Online threats (Web-based attacks)
Online threats in the banking sector
These statistics are based on detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data. Beginning from the first quarter of 2017 the statistics include malicious programs for ATMs and POS terminals but does not include mobile threats.
Kaspersky Lab solutions blocked attempts to launch one or several malicious programs capable of stealing money via online banking on 224,000 computers in Q2 2017.
Number of users attacked by financial malware, April – June 2017
Geography of attacks
To evaluate and compare the risk of being infected by banking Trojans and ATM and POS-malware worldwide, we calculate the percentage of Kaspersky Lab product users in the country who encountered this type of threat during the reporting period, relative to all users of our products in that country.
Geography of banking malware attacks in Q2 2017 (percentage of attacked users)
TOP 10 countries by percentage of attacked users
Country* % of attacked users**
Germany 2.61
Togo 2.14
Libya 1.77
Palestine 1.53
Lebanon 1.44
Venezuela 1.39
Tunisia 1.35
Serbia 1.28
Bahrain 1.26
Taiwan 1.23
These statistics are based on detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (under 10,000).
** Unique users whose computers have been targeted by banking Trojan and PoS/ATM malware attacks as a percentage of all unique users of Kaspersky Lab products in the country.
In the second quarter of 2017, Germany (2.61%) had the highest proportion of users attacked by banking Trojans. It was followed by Togo (2.14%). Libya (1.77%) rounded off the Top 3.
The TOP 10 banking malware families
The table below shows the TOP 10 malware families used in Q2 2017 to attack online banking users (as a percentage of users attacked):
Name* % of attacked users**
Trojan-Spy.Win32.Zbot 32.58
Trojan.Win32.Nymaim 26.02
Trojan-Banker.Win32.Emotet 7.05
Trojan.Win32.Neurevt 6.08
Trojan-Spy.Win32.SpyEyes 6.01
Worm.Win32.Cridex 4.09
Trojan-Banker.Win32.Gozi 2.66
Backdoor.Win32.Shiz 2.19
Trojan.Multi.Capper 1.9
Trojan.Win32.Tinba 1.9
* The detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by the malware in question as a percentage of all users attacked by financial malware.
In Q2 2017, Trojan-Spy.Win32.Zbot (32.58%) remained the most popular malware family. Its source codes have been publicly available since a leak, so cybercriminals regularly enhance the family with new modifications compiled on the basis of the source code and containing minor differences from the original.
Second came Trojan.Win32.Nymaim (26.02%). The first modifications of malware belonging to this Trojan family were downloaders, which blocked the infected machine with the help of downloaded programs unique for each country. Later, new modifications of the Trojan.Win32.Nymaim family malware were discovered. They included a fragment of Gozi used by cybercriminals to steal user payment data in online banking systems. In Q1 2017, Gozi (2.66%) was on 7th position in the rating.
Ransomware Trojans
May of 2017 saw the break out of the unprecedented epidemic of the Wannacry 2.0 ransomware cryptor, which spread using the worm that exploited a vulnerability in several Windows versions.
No sooner had this epidemic died down than in June 2017 a massive attack involving another Trojan – ExPetr – occurred. Wannacry 2.0 did not have obvious geographic preferences and attacked all countries indiscriminately, while ExPetr chose Ukraine its main target. Kaspersky Lab specialists have found out that ExPetr encrypts MFT (system area of the NTFS file system) irreversibly which means an affected user’s computer will not be completely restored the even if he pays the ransom.
Apart from the large-scale epidemics that shook the world, in Q2 2017 an interesting trend emerged: several criminal groups behind different ransomware cryptors concluded their activities and published their secret keys needed to decrypt victims’ files. Below is the list of families, the keys to which became public during the reporting period:
Crysis (Trojan-Ransom.Win32.Crusis);
AES-NI (Trojan-Ransom.Win32.AecHu);
xdata (Trojan-Ransom.Win32.AecHu);
Petya/Mischa/GoldenEye (Trojan-Ransom.Win32.Petr).
The number of new modifications
In Q2 of 2017, we discovered 15 new ransomware families. The number of new modifications was 15,663 which is considerably less than the number of modifications appeared in the previous quarter. Also, in the first quarter most of the new modifications turned to be the Cerberus cryptor variants, while in the second quarter this verdict faded into the background, giving way to the new cryptor – the world infamous Wannacry.
The number of new ransomware modifications, Q2 2016 – Q2 2017
Currently we observe a sharp decrease in the number of new Cerber samples. Probably, it means that the development and distribution of this malware family is coming to an end. Time will tell whether that is true or not. Along with Cerber, the total number of ransomware modifications is going down in the second quarter of 2017.
The number of users attacked by ransomware
In Q2 2017, 246, 675 unique KSN users were attacked by cryptors which is almost as many as of the previous quarter. Despite the drop in the quantity of new modifications, the number of protected users grew.
Number of unique users attacked by Trojan-Ransom cryptor malware (Q2 2017)
The geography of attacks
Top 10 countries attacked by cryptors
Country* % of users attacked by cryptors **
1 Brazil 1.07%
2 Italy 1.06%
3 Japan 0.96%
4 Vietnam 0.92%
5 South Korea 0.78%
6 China 0.75%
7 Cambodia 0.75%
8 Taiwan 0.73%
9 Hong Kong 0.66%
10 Russia 0.65%
* We excluded those countries where the number of Kaspersky Lab product users is relatively small (under 50,000)
** Unique users whose computers have been targeted by ransomware as a percentage of all unique users of Kaspersky Lab products in the country.
Top 10 most widespread cryptor families
Name Verdict* % of attacked users**
1 Wannacry Trojan-Ransom.Win32.Wanna 16,90%
2 Locky Trojan-Ransom.Win32.Locky 14,91%
3 Cerber Trojan-Ransom.Win32.Zerber 13,54%
4 Jaff Trojan-Ransom.Win32.Jaff 11,00%
5 Cryrar/ACCDFISA Trojan-Ransom.Win32.Cryrar 3,54%
6 Spora Trojan-Ransom.Win32.Spora 3,08%
7 ExPetr Trojan-Ransom.Win32.ExPetr 2,90%
8 Shade Trojan-Ransom.Win32.Shade 2,44%
9 Purgen/GlobeImposter Trojan-Ransom.Win32.Purgen 1,85%
10 (generic verdict) Trojan-Ransom.Win32.CryFile 1,67%
* These statistics are based on detection verdicts received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by a specific Trojan-Ransom family as a percentage of all users of Kaspersky Lab products attacked by Trojan-Ransom malware.
In addition to the abovementioned Wannacry and ExPetr, the Top 10 most popular cryptors included another two “newcomers”: Jaff and Purgen. Jaff was 4th followed by Cryrar. Kaspersky Lab specialists carried out a detailed analysis of the Trojan and discovered a flaw in its implementation of cryptographic algorithms which allowed creating a utility for decrypting files.
Other positions were occupied by Cerber, Locky, Spora and Shade.
Top 10 countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks.
In order to determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q2 2017, Kaspersky Lab solutions blocked 342, 566, 061 attacks launched from web resources located in 191 countries around the world. 33, 006, 783 unique URLs were recognized as malicious by web antivirus components.
Distribution of web attack sources by country, Q2 2017
In Q2 2017, the US took the lead in the number of web attack sources. The sourced in France turned more “popular” that those in Russia and Germany.
Countries where users faced the greatest risk of online infection
In order to assess the risk of online infection faced by users in different countries, we calculated the percentage of Kaspersky Lab users in each country who encountered detection verdicts on their machines during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers work in different countries.
This rating only includes attacks by malicious programs that fall under the Malware class. The rating does not include web antivirus module detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of users attacked**
1 Algeria 29.15
2 Albania 26.57
3 Belarus 25.62
4 Qatar 24.54
5 Ukraine 24.28
6 India 23.71
7 Romania 22.86
8 Azerbaijan 22.81
9 Tunisia 22.75
10 Greece 22.38
11 Brazil 22.05
12 Moldova 21.90
13 Russia 21.86
14 Vietnam 21.67
15 Armenia 21.58
16 Taiwan 20.67
17 Morocco 20.34
18 Kazakhstan 20.33
19 Kyrgyzstan 19.99
20 Georgia 19.92
These statistics are based on detection verdicts returned by the web antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* These calculations excluded countries where the number of Kaspersky Lab users is relatively small (under 10,000 users).
**Unique users whose computers have been targeted by Malware-class attacks as a percentage of all unique users of Kaspersky Lab products in the country.
On average, 17.26% of computers connected to the Internet globally were subjected to at least one Malware-class web attack during the quarter.
Geography of malicious web attacks in Q2 2017 (ranked by percentage of users attacked)
The countries with the safest online surfing environments included Cuba (5%), Finland (11.32%), Singapore (11.49%), Israel (13.81%) and Japan (7.56%).
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems by infecting files or removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.).
Data in this section is based on analyzing statistics produced by antivirus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media.
In Q2 2017, Kaspersky Lab’s file antivirus detected 185, 801, 835 unique malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky Lab product users on whose computers the file antivirus was triggered during the quarter. These statistics reflect the level of personal computer infection in different countries.
The rating of malicious programs only includes Malware-class attacks. The rating does not include web antivirus module detections of potentially dangerous or unwanted programs such as RiskTool or adware.
The Top 20 countries where users faced the highest risk of local infection remained almost unchanged from the previous quarter, however Kazakhstan and Belarus were replaced by Mozambique and Mauritania:
Country* % of users attacked**
1 Afghanistan 52.08
2 Uzbekistan 51.15
3 Yemen 50.86
4 Tajikistan 50.66
5 Algeria 47.19
6 Ethiopia 47.12
7 Laos 46.39
8 Vietnam 45.98
9 Turkmenistan 45.23
10 Mongolia 44.88
11 Syria 44.69
12 Djibouti 44.26
13 Iraq 43.83
14 Rwanda 43.59
15 Sudan 43.44
16 Nepal 43.39
17 Somalia 42.90
18 Mozambique 42.88
19 Bangladesh 42.38
20 Mauritania 42.05
These statistics are based on detection verdicts returned by on-access and on-demand antivirus modules, received from users of Kaspersky Lab products who have consented to provide their statistical data. The data include detections of malicious programs located on users’ computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives.
* These calculations exclude countries where the number of Kaspersky Lab users is relatively small (under 10,000 users).
** The percentage of unique users in the country with computers that blocked Malware-class local threats as a percentage of all unique users of Kaspersky Lab products.
An average of 20.97% of computers globally faced at least one Malware-class local threat during the second quarter. Russia’s contribution to this rating accounted for 25.82%.
The safest countries in terms of local infection risks were: Chile (15.06%), Latvia (14.03%), Portugal (12.27%), Australia (9.46%), Great Britain (8.59%), Ireland (6.30%) and Puerto Rico (6.15%).