
Endgame Unveils Siri-like Feature for Security Operations Teams
20.1.2017 Securityweek Apple
Threat protection firm Endgame today announced a new AI-powered chatbot feature within its Endgame Detect and Respond (EDR) platform designed to support security analysts.
Dubbed Artemis, named after the mythological goddess of the hunt, the feature could be described as a 'Siri for SOCs'; an intelligent assistant whose purpose is to simplify and automate the hunt for network-resident attackers.
EDR's purpose is the automated use of machine learning to detect subtle indications of anomalous behavior that might indicate the presence of an attacker.
Engame LogoEDR is a hunter; but like all hunters it is most efficient with the help of a terrain guide. In modern Security Operations Centers, that guide is the system analyst, who directs and controls the hunter. Together, top-tier analysts and machine-learning automation is seen as the most effective method of detecting attackers before they can do damage.
The problem is the security skills gap -- the sparsity and cost of professional talent. According to HPE's recently published 2017 State of Security Operations report, staffing issues are one of the prime causes for SOCs failing to reach the required level of maturity. Artemis is designed to help this problem as an intelligent conversational assistant to systems analysts.
"Security teams are faced with two major challenges," says Jamie Butler, CTO at Endgame: "insufficient resources to stop attacks in-progress and lack of automated solutions to uncover malicious behavior in time to prevent information theft. Just as digital assistants like Siri or Alexa proved their ability to give time back to our day by tackling complex tasks, Artemis is an assistant that automatically combs through millions of data points to provide intelligent decisions for the security industry. Security teams," he adds, "especially those that lack sufficient resources, will now have the analytic depth required to find malicious activity across all enterprise endpoints and eliminate threats in time to stop damage and loss."
As an example, if an analyst were to ask Artemis "what is suspicious in my network today?", Artemis would comb through millions of events across endpoints in seconds and provide the user with a comprehensive list of malicious activity. But Artemis goes beyond detection into response. She then recommends a course of action and can be instructed to kill dangerous processes instantly.
In effect, Artemis empowers less-experienced Tier 1 analysts to behave at the same level of sophistication as a Tier 3. She helps SOCs adopt automation without suffering from the usual staffing problems.
Endgame raised $23 million in Series B funding in March 2013, followed by $30 million in Series C funding in November 2014.
In December 2016, Endgame announced that it had been awarded an $18.8 million contract with the U.S. Air Force to have elite Air Force Cyber Protection Teams leverage the Endgame platform to protect endpoints and critical infrastructure.
Oracle Will Stop Trusting MD5-Signed JAR Files in April
20.1.2017 Securityweek Vulnerebility
Oracle has decided to give Java developers more time to ensure that their JAR files are not signed with the MD5 algorithm. Java Runtime Environment (JRE) will no longer trust these types of files starting with April 2017.
The company announced in October plans to stop trusting JAR files signed with the MD5 algorithm, which has been known to have collision vulnerabilities for more than a decade. Oracle stopped using MD5 as the default JAR signing option in 2006 and the company now wants to take things even further.
Starting with Java SE 8u131, scheduled for release with the April 2017 Critical Patch Update (CPU), JAR files signed with MD5 will be treated as unsigned files and will not be trusted. Oracle had initially planned to stop trusting MD5-signed files in January 2017, but some developers have requested additional time to prepare for this change.
Developers have been advised to check if their JAR files have been signed using MD5 and re-sign them with a stronger algorithm or key size. The following command can be used in the Zip utility to remove existing MD5 signatures:
zip -d test.jar 'META-INF/*.SF' 'META-INF/*.RSA' 'META-INF/*.DSA'
“If you are using JARS you did not sign or build yourself, you need to contact your vendor for more information,” explained Oracle’s Erik Costlow in October. “If it can no longer be established if a JAR you are using has been signed with MD5, the recommended practice is to re-sign affected JAR files using a more modern algorithm.”
Other cryptography-related changes planned by Oracle this year for JRE and JDK include disabling SHA-1 in certificate chains anchored by roots included by default in JDK, and increasing the minimum key length for SSL and TLS to 1024 bits.
Oracle’s latest CPU patches a total of 270 vulnerabilities across its products, including 158 weaknesses that can be exploited remotely by an unauthenticated attacker. A significant number of flaws have been found in Oracle’s E-Business Suite, which seems to have attracted the attention of researchers recently.
Report Examines State of Security Operations Centers
20.1.2017 Securityweek Security
Security Operations Centers
Security Operations Centers (SOCs) are failing to meet the maturity level necessary to provide optimum security and efficiency. The 2017 State of Security Operations report finds that 82% of SOCs worldwide fail to achieve optimum maturity (a score of 3 on the Security Operations Maturity Model).
Worldwide, there has been a 3% improvement over last year; but no geographical region yet meets an average score of 2. To put this in context, North America scores 1.52 while different parts of Europe range between 1.26 and 1.47 (Benelux stands out at 1.79). Clearly there is considerable room for improvement in many SOCs; and without that improvement enterprises will remain vulnerable in the event of an attack.
The State of Security Operations report is an annual study compiled by Hewlett Packard Enterprise (HPE). It comes from the study of 137 discreet SOCs and 183 in-depth assessments. It analyzes why organizations' SOCs fall below optimum maturity, and what can be done to improve matters. Sometimes cause and remedy seem counter-intuitive -- but one difficulty keeps emerging: the difficulty in recruiting and retaining adequate security talent. Lack of qualified staff frequently leads to less than optimum solutions.
One example is in the use of a managed service provider. The immediate effect could be improved security, a reduction in costs, and reduced strain on staff recruitment. But this will decline over time without continuous management of the MSP. The use of an MSP -- which is no bad thing -- should be an active choice to improve security rather than a defensive response to reduce costs.
HPE suggests that where companies need to augment security but cannot afford the additional staff to do so, they should consider a hybrid MSP/internal integrated solution. Internal operational capability can more appropriately manage risk; will be better able to coordinate incident response; and can better align security with the organization's business objectives. In all cases the organization needs to go beyond the MSP's standard SLA to ensure that security can be or remain integrated with business objectives.
The staffing issue resurfaces with automation. The difficulty in finding and keeping quality analysts persuades some organizations to consider replacing front line analysts with automation -- but while this is good in theory, it is not always good in practice. Effective automation requires a high degree of confidence in configuration management, and organizations often have a lack of maturity in information about the applications, users, systems, and data residing in disparate repositories.
The risk of breaking something that has not been well documented then persuades some organizations to turn to an alternative but equally ineffective method: automated ticket generation. This isn't always bad, suggests HPE, but "when dealing with the behavior of an advanced threat actor and coordinated campaigns that span time, this approach usually turns the analyst into a myopic responder." In short, SOCs should think hard before eliminating front-line analysts in favor of automation.
A variant of the staffing issue returns in the growing tendency for SOCs to rely on open source tools. As with MSPs, this can provide an immediate increase in security and a reduction in costs -- but once again it usually doesn't last. OSS rarely comes with the support, documentation or metrics that can ensure compliance and security objectives remain sustainable.
Furthermore, OSS solutions frequently require customization and ongoing maintenance. Staff, however, tend not to stay as long as the software. HPE claims that security leadership usually turns over every 18 months -- and key staff can move on even sooner. Staff churn has a negative effect on the OSS maintenance, and this in turn can reduce the effectiveness and maturity of the SOC. This doesn't mean that OSS should be abandoned, but that organizations need to be aware of the ongoing commitment.
Overall SOC maturity remains well below optimal levels. HPE can find no direct correlation between high maturity and enterprise size: while some large enterprises have good maturity, other multinationals remain poor. Here the difference seems to be in management attitude and willingness to spend (which itself is linked to risk perception).
In terms of verticals, service organizations have replaced technology organizations as the more mature. The telecom industry continues to have poor maturity, partly because its primary concern is service availability. HPE expects this to improve over the next few years with the emergence of a new breed of telecommunication company. Government, however, continues to struggle -- and again it is partly the staffing issue. Rigid structures slow down implementations, while rapid staff turnover stops them even being started. As a result, for example, Government metrics tend to be based on staffing rather than maturity and effectiveness.
The whole problem is, of course, exacerbated by the rapidly changing threat landscape. The emergence of destructive malware and ransomware has demanded closer ties between SOCs and DRBC teams. New General Data Protection Regulation (GDPR) will also present new issues. Although organizations are aware of the implications, the necessary changes have not yet been implemented. The requirement to detect and inform EU citizens of personal data compromises within 72 hours will drive new SOC detection and response use cases and investment for compliance around the globe.
Given these problems, the 3% overall improvement in SOC maturity over last year is an achievement.
Cyber Threat Intelligence Shows Majority of Cybercrime is NOT Sophisticated
20.1.2017 Securityweek Analysis
It’s a new year and while some things change, some things stay the same (or similar). There’s lots of FUD about the sophisticated cyber attacks that are multi-threaded and obfuscated. Certainly there are attacks that fall into this category, but if you look at all of the cybercrime activity from the past year, it’s clear that the majority of threats do not have the level of sophistication that is often talked about.
Rather, what cyber threat intelligence is showing us is that most threats simply exploit a series of well-documented vulnerabilities and other weak points to move along the path of least resistance – and the most profit. Let’s look at some of the top threats out there today through the prism of the threat triangle, which is the actor’s capability, intent and opportunity:
1. Ransomware - This threat leverages old school, but effective, Social Engineering tactics. Getting someone to click on a malicious macro still works … even though macros are not commonly used anymore (seriously, have you or do you know anyone who has ever used a macro?). It’s human nature to be curious and that curiosity is easily exploitable.
Here are things you can do to reduce an adversary’s opportunity of successfully carrying out a ransomware campaign (and to limit your risk even if a ransomware attack is successful):
Deploy anti-phishing capabilities as this is the most common method used by attackers to kick off a campaign. Anti-malware software configured to scan all email attachments will help catch most malicious attachments. All settings that allow the documents to download and open directly should also be disabled.
Restrict unnecessary users from having administrator-level permissions on their local machines, unless specifically required. Unfortunately, in many cases local admin is given to users to make them stop complaining about an app not working. Limiting this privilege could lessen the impact of ransomware.
To all Microsoft shops - Did you know there is a GPO that can help? Microsoft has adapted group policy settings to assist system administrators in taking more appropriate steps in defending against threats such as ransomware while still keeping accustomed user functionality.
Train your users. Yeah this isn’t a new concept either, but it can be effective if done well. I don’t mean just a written policy that is a long list of “do this, don’t do that.” I once worked for an organization that had over 100+ slides in their cyber security user orientation deck, which is overwhelming to say the least. Your training program should hit on the most important points and not overwhelm users where they will tune out. Understand the top three threats to your users and focus on those top three. Have a conversation with your users. What works here is actually putting your users through real-life scenarios and doing this on a semi-regular basis. It keeps it fresh in their minds and makes them more aware.
Patch your gear - Did you know that most ransomware is served up via exploit kits when your users visit a compromised site or are delivered via a malicious payload in a phishing email? Did you know that all of the CVE’s that help protect against both scenarios have been out for quite a while? Be aggressive with vulnerability management in your user environment as they are the highest exposed.
2. Exploit kits - Many of these kits out there leverage CVE’s for which there is no good reason to NOT to patch them. Look at the RIG, Sundown and Magnitude exploit kits as recent examples. The below list includes current and past attribution lineage:
The RIG EK Exploits: CVE-2012-0507, CVE-2013-0074, CVE-2013-2465, CVE-2013-2471, CVE-2013-2551, CVE-2013-3896, CVE-2014-0311, CVE-2014-0322, CVE-2014-0497, CVE-2014-6332, CVE-2015-0313, CVE-2015-2419, CVE-2015-3090, CVE-2015-5119, CVE-2015-5122, CVE-2015-5560, CVE-2015-7645, CVE-2015-8651, CVE-2016-0034, CVE-2016-0189, CVE-2016-1019, CVE-2016-4117, CVE-2016-7200, CVE-2016-7201, CVE-2016-3298
The Sundown EK Exploits: CVE-2012-1876, CVE-2013-7331, CVE-2014-0556, CVE-2014-0569, CVE-2014-6332, CVE-2015-2444, CVE-2015-0311, CVE-2015-0313, CVE-2015-5119, CVE-2015-2419, CVE-2016-0034, CVE-2016-4117, CVE-2016-0189, CVE-2016-7200, CVE-2016-7201
The Magnitude EK Exploits: CVE-2011-3402, CVE-2012-0507, CVE-2013-2551, CVE-2013-2643, CVE-2015-0311, CVE-2015-7645, CVE-2015-3113, CVE-2016-1015, CVE-2016-1016, CVE-2016-1017, CVE-2016-1019, CVE-2016-4117
There is no reason these CVE’s should be present in your environment!
3. Credentials management - Password complexity and reuse is again nothing new or sophisticated, yet we continue to see new attacks leveraging compromised credentials from old breaches. A few business process and technical recommendations you can implement to limit this security issue:
· Re-examine your password policies and ensure they are being enforced. Users will always gravitate to the path of least resistance and will tend to leverage the weakest password option being presented. Forcing password resets at certain time periods and implementing two-factor authentication can also help protect systems from password reuse attacks.
· If you have not already done so, you should investigate deploying an easy-to-use password manager for your user base. Also don't make the assumption that this is just limited to business-related credentials. It is commonplace for a user’s personal and business credentials to be co-located both on personal and business devices. If you choose to procure a password manager for your organization, think about extending the licenses to your employees’ personal devices as well.
· Training and education - Customers, employees and other users should be dissuaded from reusing passwords from other accounts. If you suspect data has been compromised, whether directly from your site or from another breach, take proactive measures to prevent password reuse attacks by resetting passwords.
4. Extortion - Similar to ransomware, this threat leverages targets based on an unhealthy level of presence. The difference is that while ransomware encrypts your data and keeps it captive until the bad guy gets paid, an extortionist gains leverage against an organization by compromising their data via exfiltration and then embarrassing the victim to pay up. A recent example of cyber extortion revolves around an actor by the name of TheDarkOverlord, who uses social media to publicly threaten organizations and potentially expose the stolen sensitive data if not paid off.
· Remove the Opportunity - The root issue here is that our adversaries require “us” to present vulnerabilities to them in order for them to succeed. If you remove the opportunity you are directly influencing their capability to extort.
· Cyber Security “Technical Debt” - When an organization presents too much opportunity for an adversary, I am reminded of the term “Technical Debt” which is a metaphor for designing software properly versus taking short cuts to get something done faster and cheaper. To get something developed and quickly out the door, oftentimes those shortcuts taken require you to essentially take out a loan with a high interest rate. Eventually that loan will come due and you will end up paying more in the long run. The key point here is that with today's cybercriminal tactics, taking a technical debt loan opens up a whole list of additional impacts that were not typically a risk in the past. When an organization chooses to take a big technical debt loan out, it is ultimately presenting more opportunities for an adversary to exploit. You are now taking on additional risk that can potentially cause irreparable harm to your organization. These risks, if breached can cause impacts to customers (trust and loyalty), brand and reputation, and regulatory or legal action to name a few.
With cyber threat intelligence that is relevant to your business, supply chain and industry, you can pinpoint key areas of risk to address. What we’ve seen over the past year is a good reminder to focus on the security basics before addressing the more complex. There are a lot of headline-grabbing threats that tend to generate a needless frenzy, which in many cases may not have as direct an impact on your organization anyway.
Which is the real identity of the Mirai Author Anna-Senpai?
20.1.2017 securityaffairs Virus
The popular investigator Brian Krebs published the details of his investigation on the identity of the Mirai author Anna-Senpai.
In the last months, the Mirai bot monopolized the attention of the media, it was used to power the massive DDoS attack against the Dyn DNS service causing an extended Internet outage.
A large portion of Internet users was not able to reach most important web services, many websites like including Twitter, GitHub, PayPal, Amazon, Reddit, Netflix, and Spotify were down for netizens in the US.
The same IoT botnet was used to launch a massive Distributed Denial of Service (DDoS) attack against the website of the popular cyber security investigator Brian Krebs who decided to investigate about the author of the dangerous malware.
In October a hacker released the source code of the Mirai malware, a reference to the malicious code was spotted by Brian Krebs on the popular criminal hacker forum Hackforum. The Hackforum user with moniker “Anna-senpai” shared the link to the source code of the malware “Mirai.”
“The leak of the source code was announced Friday on the English-language hacking community Hackforums. The malware, dubbed ‘Mirai’ spreads to vulnerable devices by continuously scanning the Internet for IoT systems protected by factory default or hard-coded usernames and passwords.” reported Krebs.

The Mirai malware was specifically designed to infect Internet of Things (IoT) devices using the credential factory settings, a circumstance that is quite common in the wild.
Brian Krebs believes to have discovered the real identity of the mysterious Anna-senpai, his name is Paras Jha, the owner of a distributed denial-of-service (DDoS) attack mitigation company ProTraf Solutions.
“After months of gathering information about the apparent authors of Mirai, I heard from Ammar Zuberi, once a co-worker of ProTraf President Paras Jha.
Zuberi told KrebsOnSecurity that Jha admitted he was responsible for both Mirai and the Rutgers DDoS attacks. Zuberi said when he visited Jha at his Rutgers University dorm in October 2015, Paras bragged to him about launching the DDoS attacks against Rutgers.” wrote Krebs.
“He was laughing and bragging about how he was going to get a security guy at the school fired, and how they raised school fees because of him,” Zuberi recalled. “He didn’t really say why he did it, but I think he was just sort of experimenting with how far he could go with these attacks.””
The man alleged created the Mirai botnet and spread it to recruit the largest number of IoT devices.
Krebs reported that in 2014, an earlier variant of the Mirai botnet was used to launch DDoS attacks against Minecraft servers which can generate up to US$50,000 a month.
Krebs discovered that Jha along with other players developed the Mirai bot and used it to power an attack against the Minecraft servers to lure disgruntled customers. The providers that ignored Jha’s requests were hit by massive DDoS attacks.
Krebs explained that Jha contacted upstream providers to request the shutdown of rival IoT firms, then he developed the Mirai bot to attack rival Qbot botnets.
Krebs cited a Webinar presented on December 16, by the experts at the firm Digital Shadows that exposed the findings on the investigation about the Mirai author’s real life identity. According to Digital Shadows, the person behind the Anna-Senpai moniker also used the nickname “Ogmemes123123” and the email address ogmemes123123@gmail.com. He also discovered that the Mirai author has used another nickname, “OG_Richard_Stallman,” a clear reference to the founder of the Free Software Foundation. The ogmemes123123@gmail.com account was also used to register a Facebook account in the name of OG_Richard Stallman.
That Facebook account reports that OG_Richard_Stallman began studying computer engineering at New Brunswick, NJ-based Rutgers University in 2015., the same University attended by Paras Jha. The Rutgers University suffered a series of DDoS attacks on its systems since 2015, the attacker suggested the school purchase a DDoS mitigation service.
Krebs also highlighted that the skills listed on Jha’s LinkedIn page are the same of the Mirai author Anna-senpai ‘s HackForums.
The Krebs’s analysis is very intriguing and full of details … enjoy it!
ProtonMail announced that its Tor Hidden Service is online
20.1.2017 securityaffairs Security
The popular encrypted email provider ProtonMail has launched the Tor Hidden Service to provide further protection to its users.
ProtonMail is the world’s largest encrypted email provider with over 2 million users worldwide. Its popularity exploded just after the US presidential election, its users include journalists, activists, businesses, and normal people that want to protect their security and privacy. The service is a free and open source, featuring strong end-to-end encryption and protected by Swiss privacy laws.
Implementing a Tor hidden service for ProtonMail Tor has numerous advantages for end-users, communications are protected by supplementary layers of encryption, user’ IP address is masqueraded by the anonymizing network, and such kind of service is able to bypass government censorship.
“There are several reasons why you might want to use ProtonMail over Tor. First, routing your traffic to ProtonMail through the Tor network makes it difficult for an adversary wiretapping your internet connection to know that you are using ProtonMail. Tor applies extra encryption layers on top of your connection, making it more difficult for an advanced attacker to perform a man-in-the-middle attack on your connection to us. Tor also makes your connections to ProtonMail anonymous as we will not be able to see the true IP address of your connection to ProtonMail.” a onion site,” ProtonMail explained in a blog post.
“Tor can also help with ProtonMail accessibility. If ProtonMail becomes blocked in your country, it may be possible to reach ProtonMail by going to our onion site. Furthermore, onion sites are “hidden” services in the sense that an adversary cannot easily determine their physical location. Thus, while protonmail.com could be attacked by DDoS attacks, protonirockerxow.onion cannot be attacked in the same way because an attacker will not be able to find a public IP address.”
The onion address for the ProtonMail Tor service:
https://protonirockerxow.onion
Just for curiosity, the above address was generated by the company used spare CPU capacity to generate millions of encryption keys and then hashed them aiming to generate a more human readable hash. The address it can be easily remembered as:
proton i rocker xow

ProtonMail published detailed instructions on how to setup Tor and how to access the service over Tor. For example, in order to use the ProtonMail hidden service is it necessary to enable Javascript.Tor Browser disables Javascript by default, but you will need it for our onion site. You can do this by clicking the “NoScript” button and selecting “Temporarily allow all this page”:
“Tor Browser disables Javascript by default, but you will need it for our onion site. You can do this by clicking the “NoScript” button and selecting “Temporarily allow all this page”” reads the ProtonMail page.
The ProtonMail hidden service only accepts HTTPS connections, it uses a digital certificate issued by Digicert, the same CA used by Facebook for its Tor hidden service.
The ProtonMail hidden service could be reached via a desktop web browser and both iOS and Android apps.
Docker Patches Escape Container Vulnerability
20.1.2017 Securityweek Vulnerebility
Docker recently resolved a runc privilege escalation vulnerability that could be exploited by a malicious program to escape container and access the host.
Tracked as CVE-2016-9962, the security issue is created because runc passes a file descriptor from the host's filesystem to the "runc init" bootstrap process when joining a container. This means that a malicious process inside the container can gain access to the host filesystem with its current privilege set.
Discovered by Alexander Bergmann, the vulnerability is rather difficult to exploit, because the race window between join-and-execve is quite small. According to Docker’s CVE database, the privilege escalation issue is the result of insecure opening of file-descriptor. Docker 1.12.6 resolves the bug.
Because the issue resides in the runc code, other containers might also be affected, Aqua Security’s Sagie Dulce says. The vulnerability is triggered when exec-ing an application in an already running container, the security researcher explains.
The use of an inherited file descriptor inside the container allows a malicious process to access the file descriptor of a directory that resides on the host and then the rest of the host's filesystem. Because the bug can be leveraged for directory traversal to the host's file system, it results in an effective container escape, Dulce notes.
Apparently, exec-ing commands inside a running container is actually a bigger issue that the problem of an open file descriptor is part of. However, the window of opportunity where the container has access to the runc init process on the host is very small before the runc init process execs the command inside the container.
“This is because runc enters the namespace of the container before it execs the final command. This window could enable a container, for example, to list file descriptors on the host process, which can then lead it to the host’s file system. Because many containers run as root, this indeed has serious implications,” the researcher notes.
The issue can be exploited in containers that lack the CAP_SYS_PTRACE capability, although it is much easier to access the file descriptors if the capability exists. A correctly timed exploit can leverage the vulnerability without having control of the runc init process. “One can escape a container […] by simply patching runc to sleep before calling exec,” Dulce says.
According to Red Hat’s Dan Walsh, SELinux mitigates the vulnerability. “SELinux is the only thing that protects the host file system from attacks from inside of the container. If the processes inside of the container get access to a host file and attempt to read and write the content SELinux will check the access,” he explains.
The released patch for this issue ensures that there are no host file descriptors present in the runc init process. Moreover, the fix sets the runc init process as non-dumpable, before setns into the container, which apparently protects it from processes inside the container.
Ukraine Power Company Confirms Hackers Caused Outage
20.1.2017 Securityweek Hacking
The investigation is ongoing, but Ukraine’s national power company Ukrenergo has confirmed that the recent electricity outage in the Kiev region was caused by a cyberattack.
In a statement emailed to SecurityWeek on Thursday, Ukrenergo said a preliminary analysis showed that the normal operation of workstations and SCADA servers had been disrupted due to “external influences.”
The analysis indicates that the incident, described as a planned and layered intrusion, involved malware that allowed the attackers to remotely control internal systems. Investigators are in the process of establishing a timeline of events and identifying compromised accounts, points of entry, and devices infected with malware that may be lying dormant.
Ukrenergo is confident that the results of this investigation will help the company implement organizational and technological measures that would help prevent cyber threats and reduce the risk of power failure.
The incident took place on the night between December 17 and 18 at the substation in Pivnichna, causing blackouts in the capital city of Kiev and the Kiev region. Power was fully restored after just over an hour.
Ukrenergo officials immediately suspected external interference and brought in cybersecurity experts to conduct an investigation.
One of the experts involved in the probe told the BBC that the 2016 attacks were more sophisticated and better organized compared to the ones launched in December 2015. It also appears that several threat groups had worked together, and they may have tested techniques that could be used in other campaigns as well.
Russia is again the main suspect, the country being blamed for many of the cyberattacks launched recently against Ukraine.
A report published in October by Booz Allen Hamilton showed that the December 2015 attacks on Ukraine’s electric grid were part of a long-running campaign that also targeted the railway, media, mining and government sectors.
In the meantime, researchers continue to monitor KillDisk, one of the pieces of malware involved in the 2015 attack. They recently discovered that the destructive malware had turned into ransomware and started infecting Linux machines as well.
DHS Publishes National Cyber Incident Response Plan
20.1.2017 Securityweek Security
The U.S. Department of Homeland Security has published the National Cyber Incident Response Plan (NCIRP), which aims to describe the government’s approach in dealing with cyber incidents involving public or private sector entities.
The DHS started working on the NCIRP shortly after President Barack Obama released the Presidential Policy Directive on Cyber Incident Coordination (PPD-41) in July last year. After making available a draft in September, the DHS has now announced the release of the final version.
The NCIRP has three main goals: define the responsibilities and roles of government agencies, the private sector and international stakeholders; identify the capabilities required to respond to a significant incident; and describe how the government will coordinate its activities with the affected entity.
“The National Cyber Incident Response Plan is not a tactical or operational plan for responding to cyber incidents,” explained Homeland Security Secretary Jeh Johnson. “However, it serves as the primary strategic framework for stakeholders when developing agency, sector, and organization-specific operational and coordination plans. This common doctrine will foster unity of effort for emergency operations planning and will help those affected by cyber incidents understand how Federal departments and agencies and other national-level partners provide resources to support mitigation and recovery efforts.”
The NCIRP focuses on four main lines of effort: threat response, asset response, intelligence support, and affected entity response.
The lead federal agency for threat response is the Department of Justice through the FBI and the National Cyber Investigative Joint Task Force (NCIJTF). Threat response includes mitigating the immediate threat, investigative activity at the affected organization’s site, collecting evidence and intelligence, attribution, finding links between incidents and identifying other affected entities, and finding opportunities for threat pursuit and disruption.
Asset response is handled by the DHS through the National Cybersecurity and Communications Integration Center (NCCIC). Activities in this line of effort include providing technical assistance to help affected entities protect their assets, reducing the impact of the incident, mitigating vulnerabilities, identifying other entities that may be at risk, and assessing potential risks to the affected sector or region.
Threat and asset response teams have some shared responsibilities, including the facilitation of information sharing and operational coordination, and providing guidance on the use of federal resources and capabilities.
The lead agency for intelligence support is the Office of the Director of National Intelligence (ODNI) through the Cyber Threat Intelligence Integration Center (CTIIC). The agency is tasked with providing support to asset and threat response teams, analyzing trends and events, identifying knowledge gaps, and mitigating the adversary’s capabilities.
If a significant cyber incident involves a federal agency, that agency is responsible for managing the impact of the incident. This can include maintaining business or operational continuity, protecting privacy, addressing adverse financial impact, breach disclosure and notification, and handling media and congressional inquiries.
If the incident affects a private entity, the role of the government is to be aware of that entity’s response activities and assess the potential impact on private sector critical infrastructure.
Ransack Campaigns Target Hadoop and CouchDB
20.1.2017 Securityweek Virus
Following a series of ransom attacks against MongoDB and Elasticsearch databases in recent weeks, many users of CouchDB and Hadoop are now finding their databases are under attack as well.
With the help of automated tools, attackers have been targeting Internet-acessible databases that haven’t been properly secured and either erasing or stealing data, followed by dropping a note demanding a specific ransom amount in exchange for the stolen data.
Insecure MongoDB installations were targeted first, and over 33,000 databases have already fallen victim to the attacks. However, as more hackers joined the rush, attackers started looking into alternatives, and Elasticsearch databases came into the crosshairs next.
Only several hundred such installations were targeted within the first couple of days, but the number has since grown to over 4,600 as of today, the public spreadsheet security researchers Victor Gevers and Niall Merrigan (who have been keeping an eye on these attacks since the beginning) use to track the campaign shows.
The attacks on MongoDB installations have reportedly slowed down, suggesting that hackers are focusing on Elasticsearch databases (over 30,000 of them are reportedly exposed) or other targets. With one actor actively attempting to sell the ransomware kit for MongoDB and Elasticsearch, it remains to be seen whether more attackers will start targeting these databases as well.
For now, however, it’s certain that Internet-facing CouchDB and Hadoop Distributed File System (HDFS) installations are potential victims to these attacks. The key change, however, is that hackers might no longer steal the data to hold it for ransom, but simply erase everything in an attempt to do harm.
While the number of CouchDB databases that have fallen to the ransom attack is still low, there are around 4,000 exposed instances, and their fate could turn for the worse if admins don’t secure them in a timely manner.
The public spreadsheet tracking attacks on Hadoop servers shows that 126 of them have been already vandalized and that there are three attackers actively pursuing them at the moment. There are between 8,000 and 10,000 HDFS installations out there, which means that attackers have quite the attack surface to enjoy.
Fidelis Cybersecurity Threat Research says that the attacks on HDFS installations (which started ramping up last week) are possible because admins use minimal security and made installations accessible from the Internet, and because denial of service (DoS) attacks have been trending up over the past years, especially in the enterprise segment.
Because HDFS installations using default configurations allow access without authentication, any attacker with basic proficiency in Hadoop can start deleting files. “On or around January 5 to January 6, traffic to port 50070 soared as attackers scanned for open HDFS installations to target,” Fidelis says.
To stay protected, admins need to follow some simple rules that apply to all databases, be them MongoDB, Elasticsearch, CouchDB, or HDFS: avoid exposing them to the Internet unless that is absolutely necessary, and use strong authentication settings (leaving default settings could mean that no authentication is required). Regularly backing up data helps restoration efforts after being hit.
With tens of thousands of databases already hit worldwide, it’s clear that admins need to take stance and up their security. Gevers and Merrigan have already made steps in preventing attacks, such as contacting local GovCERT teams to warn server owners that they are exposed. This reportedly resulted in critical Hadoop servers being pulled off the Internet.
The two security researchers have been hard at work over the past couple of weeks helping victims, and others have already joined their efforts, including Bob Diachenko, Matt Bromiley, and Dylan Katz.
Suspected Russian Hacker Wanted by U.S. Jailed in Spain
20.1.2017 Securityweek Hacking
An alleged Russian hacker wanted for fraud has been detained in Spain and jailed pending extradition to the United States, police and a court spokesman said Thursday.
Stanislav Lisov, a computer programmer, was wanted by US authorities, a spokesman for the Guardia Civil police force said.
"He is accused of conspiracy to commit fraud via electronic media and conspiracy to commit fraud and abuse with computers," a spokesman for Spain's top-level National Court added.
Lisov was detained last week in Barcelona's El Prat airport when he was about to board a flight, police said.
He was jailed on January 13 after being questioned via videoconference by a judge in Madrid's National Court, which investigates suspected crimes that have an international remit.
The judge decided to put him in prison as he does not live in Spain and could escape, and due to the "gravity of the offences."
"Now begins the process of extradition to the United States," the National Court spokesman said, without giving further details.
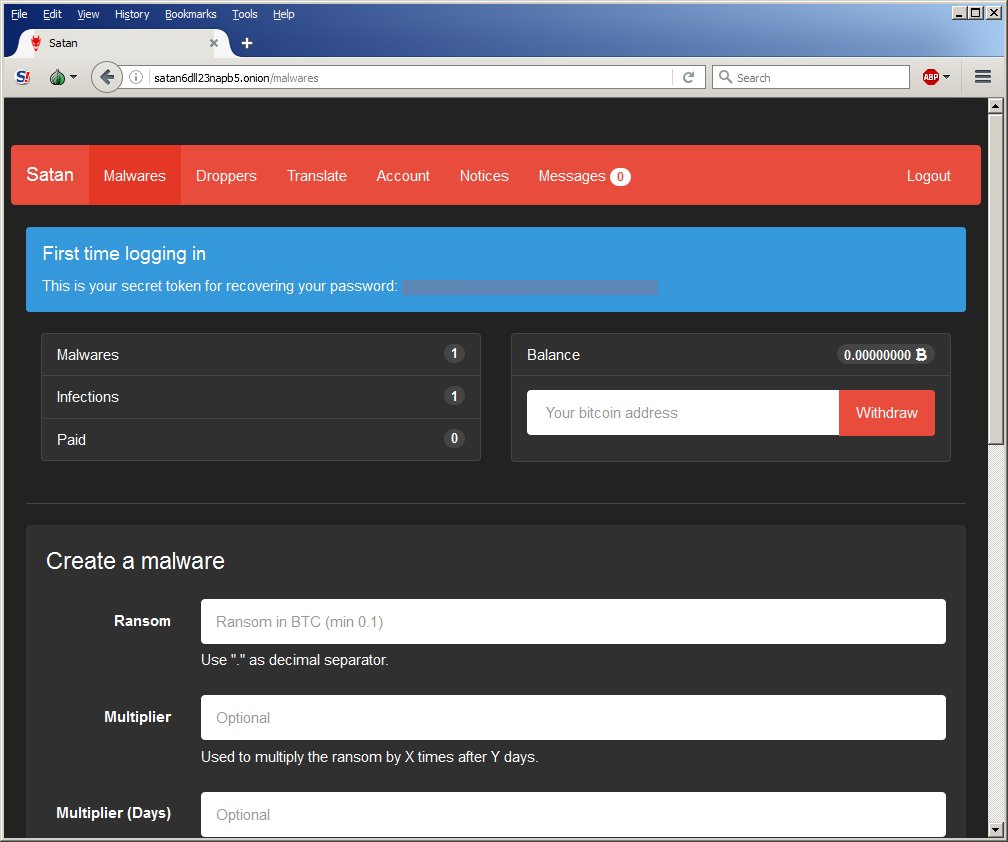
Satan, the ransomware-as-a-service surfaced in the dark web
20.1.2017 securityaffairs Virus
The independent malware research @Xylit0l discovered the Satan ransomware, a malware belonging to the Gen:Trojan.Heur2.FU family.
Yesterday the independent malware research @Xylit0l discovered the Satan ransomware, a malware belonging to the Gen:Trojan.Heur2.FU family. Satan is provided as a RaaS (Ransomware-as-a-Service).
Follow
Xylitol @Xylit0l
New #RaaS https://www.virustotal.com/en/file/c04836696d715c544382713eebf468aeff73c15616e1cd8248ca8c4c7e931505/analysis/1484756083/ …
5:34 PM - 18 Jan 2017
72 72 Retweets 72 72 likes
The Satan ransomware used RSA-2048 and AES-256 cryptography, it appends the names of encrypted files with the “.stn” extension.

“As mentioned above, Satan’s developers provide a service allowing prospective cyber criminals to make money by distributing this ransomware. In exchange, developers receive 30% of revenues generated by users.” Reads the analysis published on pcrisk.com.
“The Satan platform has a user-friendly interface, it is really simple to use to create your own ransomware. Users just need to have a Bitcoin wallet to use for ransom payment. Wannabe criminals must specify the ransom amount in Bitcoin and furthermore they can decide to increase the amount of money to pay after a specific deadline.”
“Now, the most important part: the bitcoin paid by the victim will be credited to your account. We will keep a 30% fee of the income, so, if you specified a 1 BTC ransom, you will get 0.7 BTC and we will get 0.3 BTC. The fee will become lower depending on the number of infections and payments you have.” Reads the adv for the Satan Platform.
The Satan platform implements multiple services, including a dropper builder that is able to obfuscate malware code to avoid detection by virus scanners.

The RaaS solutions also allows used to choose a language different from English or Portuguese. The platform also allows crooks to update their ransomware.

Satan, while crypt, changes files’ extension in .stn for example myfile.txt in myfile.txt.stn.
Satan, once encrypted the files, creates an HTML file (HELP_DECRYPT_FILES.html) on desktop containing the ransomware note and instructions for the payment.
Crooks encourage victims to pay ransom to receive the private key for decrypt files. But never pay any ransom or attempt to contact these cyber criminals, because there is no guarantee that your files will be decrypted!.
Satan uses several anti-evasion and anti-debugging techniques, for example, it doesn’t run on a virtual machine making it difficult to analyze.
In a couple of days, crooks already released two version of the Satan platform.
Crashing iPhone Or iPad with a simple Emoji text message
20.1.2017 securityaffairs Apple
A simple sequence of three character-long text message containing Emoji can cause the block and the reboot os iPhones and iPads running iOS 10.1 or below.
A new Apple’s iOS bug was discovered in the community of mobile tech experts, it can be exploited to crash iPhone or iPad devices by just sending an Emoji text message.
Several users are already reporting the issue and the popular YouTube EverythingApplePro published a video proof-of-concept for the bug. In the video is reported an example of the sequence of characters that temporarily freeze an iPhone causing the device restarting.
The sequence is composed of a white Flag emoji, the digit “0” and a Rainbow emoji. The issue is linked to the way that iOS creates the rainbow flag emoji that is not an official emoji, Apple creates the rainbow flag Emoji by combining the code behind the two white flag and rainbow emoji. Apple iOS joins them by using a hidden character known as a VS16. The iPhone attempts to combine the two emoji, but is unable to because of the zero in the middle.

Source http://www.magazine49.com/archives/48106
There are also other ways to crash the Apple mobile device, another hack leverages the same characters used in a contact file that is sent to an iMessage contact via the iCloud’s sharing feature.
“Both the methods mentioned above will crash and iPhone or iPad to varying degrees, although the simple text string sent via a standard iMessage appears to affect iPhones and iPads running iOS 10.1 or below.” reported The Hacker News. “However, the boobytrapped contact card affects all versions of iOS 10, including Apple’s latest iOS 10.2 operating system.”
Users have to upgrade their version to the last one in order to prevent such kind of attacks.

In November the EverythingApplePro reported that most of the Apple devices were crashing when the owners play a video. An iPhone-freezing video circulated online, when users played it in the Safari browser the iPhones slow down until they stop working altogether.
The iPhone-freezing video was first discovered by EverythingApplePro, it is a short .mp4 clip of someone standing by a bed with the words “Honey” written across the screen.
2016 Christmas Ukraine power outage was caused by hackers
20.1.2017 securityaffairs Hacking
Ukrenergo confirmed that preliminary results of its investigation showed that the Ukraine power outage occurred in December was caused by hackers.
In December 2016, the Government Ukraine energy company Ukrenergo suffered a severe power outage that affected the ”North” substation at Pivnichna. The incident caused blackouts in the city of Kiev and neighboring regions.
The head of the NEC “Ukrenergo” Vsevolod Kovalchuk explained in a message posted on Facebook that experts at the company were able to restore power in 30 minutes with a manual procedure. According to Kovalchuk, the operations were fully restored after just over an hour.
Kovalchuk pointed out that an equipment malfunction or a cyber attack can be the cause of the problem. According to Kovalchuk, an “external interference through the data network” could have caused the power outage.
Ukraine power outage
In a statement sent via email to SecurityWeek on this, Ukrenergo confirmed that preliminary results of its investigation showed that the normal operation of workstations and SCADA systems had been disrupted due to “external influences.”
Once broken in the target network, attackers used a malware to gain a remote control of systems at the power plant. Experts are still investigating to establish a timeline of events and identify the entry point of the hackers. They don’t exclude that the threat could still be inside the target network in a dormant state.
The company is working to secure its system by implementing organizational and technological measures that would make its systems resilient to further attacks.
“The cyber-security company Information Systems Security Partners (ISSP) has linked the incident to a hack and blackout in 2015 that affected 225,000.” reported the BBC. “ISSP, a Ukrainian company investigating the incidents on behalf of Ukrenergo, now appears to be suggesting a firmer link.
It said that both the 2015 and 2016 attacks were connected, along with a series of hacks on other state institutions this December, including the national railway system, several government ministries and a national pension fund.
Oleksii Yasnskiy, head of ISSP labs, said: “The attacks in 2016 and 2015 were not much different – the only distinction was that the attacks of 2016 became more complex and were much better organised.“”
Who is behind the power outage?
Intelligence experts suspect blames the Russia one again.
LOGmanager nabídne snadnější sběr logů z různých míst
20.1.2017 SecurityWolrd Zabezpečení
Řešení LOGmanager Forwarder, které slouží ke sběru logů z poboček, pronajatých datových center nebo od zákazníků do hlavního systému LOGmanager, kde probíhá analýza a ukládání, uvedl na trh jeho výrobce, firma Sirwisa.
Rozšiřuje se tak produktové portfolio LOGmanageru, českého nástroje na správu a analýzu logů. LOGmanager Forwarder je dostupný buď jako hardwarová appliance, nebo jako virtuální stroj.
Podstatou LOGmanageru je sběr všech relevantních eventů a logů organizace, jejich ukládání do centrálního zabezpečeného úložiště s předem definovanou retencí a možností prohledávat enormní množství dat v reálném čase. Výstupy prohledávaní se prezentují v textové i grafické podobě s vysokou mírou interakce vzhledem k nalezeným datům.
Systém rovněž umožňuje dlouhodobě ukládat data v nezpochybnitelné podobě pro potřeby shody s předpisy, požadavky pro forenzní analýzu a případné bezpečnostní audity. Řešení rovněž pomáhá plnit požadavky dané ze Zákona o kybernetické bezpečnosti.
Distributorem řešení LOGmanager v tuzemsku je firma Veracomp, pro implementaci lze využít i služeb řady certifikovaných partnerů.
Shamoon 2 Variant Targets Virtualization Products
19.1.2017 Securityweek Virus
A second variant of the Shamoon 2 malware discovered by researchers at Palo Alto Networks has been set up to target virtualization products, likely in an effort to increase the impact of the attack and make recovery more difficult for targeted organizations.
Shamoon, aka Disttrack, is a disk-wiping malware that became widely known in 2012, when it damaged 35,000 computers belonging to Saudi Arabian petroleum and natural gas company Saudi Aramco. A newer version of the threat, dubbed Shamoon 2, was recently used to target various organizations in the Persian Gulf, including Saudi Arabia’s General Authority of Civil Aviation (GACA), which has downplayed the impact of the attack.
Palo Alto Networks has come across two variants of Shamoon 2. The first variant, detailed shortly after the new attacks came to light, was configured to automatically start wiping infected systems in the evening of November 17, 2016, just as the work week ended in Saudi Arabia.
The second variant discovered by the security firm had been configured to start wiping infected systems at 1:30 AM (Saudi Arabia time) on November 29, when the majority of the targeted organization’s employees were likely at home.
The payload delivered in this second wave was similar to the first one, but experts did find some differences. Same as in the first attacks, Shamoon spread throughout the local network using legitimate domain account credentials, including ones belonging to users and administrators. Since many of these passwords were complex, researchers believe the threat actor may have obtained the information as a result of a previous attack.
Palo Alto Networks also highlighted that the second Shamoon 2 variant included credentials for virtualization products from Huawei, specifically virtual desktop infrastructure (VDI) products such as FusionCloud.
These credentials can be found in the vendor’s official documentation, which suggests that the attackers either knew that the organization had been using these credentials based on information collected in a previous attack, or they were simply hoping that the defaults had not been changed.
“VDI solutions can provide some protection against a destructive malware like Disttrack through the ability to load snapshots of wiped systems. Also, since FusionCloud systems run a Linux operating system, which would not be susceptible to wiping by the Windows-only Disttrack malware, this could be seen as a reasonable countermeasure against attacks like Shamoon,” Palo Alto Networks’ Robert Falcone wrote in a blog post.
“However, if the attacker was able to log into the VDI management interfaces using the account credentials they could manually carry out destructive activities against the VDI deployment, as well as any snapshot,” Falcone added.
Ukraine Power Company Confirms Hackers Caused Outage
19.1.2017 Securityweek Virus
The investigation is ongoing, but Ukraine’s national power company Ukrenergo has confirmed that the recent electricity outage in the Kiev region was caused by a cyberattack.
In a statement emailed to SecurityWeek on Thursday, Ukrenergo said a preliminary analysis showed that the normal operation of workstations and SCADA servers had been disrupted due to “external influences.”
The analysis indicates that the incident, described as a planned and layered intrusion, involved malware that allowed the attackers to remotely control internal systems. Investigators are in the process of establishing a timeline of events and identifying compromised accounts, points of entry, and devices infected with malware that may be lying dormant.
Ukrenergo is confident that the results of this investigation will help the company implement organizational and technological measures that would help prevent cyber threats and reduce the risk of power failure.
The incident took place on the night between December 17 and 18 at the substation in Pivnichna, causing blackouts in the capital city of Kiev and the Kiev region. Power was fully restored after just over an hour.
Ukrenergo officials immediately suspected external interference and brought in cybersecurity experts to conduct an investigation.
One of the experts involved in the probe told the BBC that the 2016 attacks were more sophisticated and better organized compared to the ones launched in December 2015. It also appears that several threat groups had worked together, and they may have tested techniques that could be used in other campaigns as well.
Russia is again the main suspect, the country being blamed for many of the cyberattacks launched recently against Ukraine.
A report published in October by Booz Allen Hamilton showed that the December 2015 attacks on Ukraine’s electric grid were part of a long-running campaign that also targeted the railway, media, mining and government sectors.
In the meantime, researchers continue to monitor KillDisk, one of the pieces of malware involved in the 2015 attack. They recently discovered that the destructive malware had turned into ransomware and started infecting Linux machines as well.
Security Bug Lurked in Nexus 9 Kernel for Two Years
19.1.2017 Securityweek Vulnerebility
A security vulnerability that allowed a privileged attacker to arbitrary write values within kernel space lurked in Nexus 9’s kernel for two years before being patched, IBM security researchers reveal.
Tracked as CVE-2016-3873, the vulnerability was found in the Tegra kernel branch and was assigned a high severity rating. It was found to plague Nexus 9 ever since its inception in November 2014, and was fixed in the security patch level of 2016-09-05, after being discovered in June 2016.
In its Sept. 2016 Security Bulletin, Google noted that this was an elevation of privilege vulnerability in the NVIDIA kernel and that local malicious applications could leverage it to execute arbitrary code within the context of the kernel. The bug first requires compromising a privileged process, thus was assigned a High severity rating.
IBM X-Force Application Security Research Team’s Sagi Kedmi, the researcher who discovered the bug, explains that a similar issue (CVE-2016-2443) was discovered by security researcher Marco Grassi in spring 2013. Found in the Qualcomm MDP Driver, this bug was patched in Google’s May 2016 Android Security Bulletin.
“Kernel arbitrary write primitives can be used to achieve kernel code execution, which completely compromises the security of the device, not including TrustZone. It increases the TrustZone attack surface and allows attackers to access application data and override the Security-Enhanced Linux (SELinux) policy,” Kedmi explains.
The vulnerable code in Nexus 9 begins with the registers debugfs file node, which is initialized with a specific file operation where, on write system call, the cl_register_write() function securely copies a user space buffer and parses its contents as two numeric values, val and offs. Next, the cl_dvfs_writel() function is fed the two values, and __raw_writel() is used to write value val at offs+, which results in an arbitrary kernel write.
The researcher analyzed the Discretionary Access Control (DAC) and Mandatory Access Control (MAC; SELinux on Android) to determine what active processes can trigger the vulnerability. When it comes to DAC, the attacker needs to execute the code under root within the debugfs SELinux context, so the researcher then looked at the contexts that could write to a debugfs file.
Looking into Nexus 9’s sepolicy (MOB30M), Kedmi found that SELinux-wise, all domains can open, write and append to any file with the debugfs context, and discovered that code execution within the zygote process, several system processes and some other processes can trigger and exploit the Android vulnerability.
“To exploit the vulnerability from an untrusted application security context, start by escalating privileges from an untrusted app to one of the contexts of the aforementioned processes. The commit that fixed the vulnerability indicates that Google simply removed the registers file from the debug file system. Clearly, the registers file node was not needed on production builds,” the researcher concludes.
Critical Infrastructure Security: Risks Posed by IT Network Breaches
19.1.2017 Securityweek Security
Critical infrastructure security
There have been several incidents recently where a critical infrastructure organization’s IT systems were breached or became infected with malware. SecurityWeek has reached out to several ICS security experts to find out if these types of attacks are an indicator of a weak security posture, which could lead to control systems also getting hacked.
Security incidents involving critical infrastructure organizations
There are only a few publicly known examples of cyberattacks targeting an organization’s industrial control systems (ICS), including the recent Ukraine energy sector incidents and the 2010 Stuxnet attacks. However, there are several known incidents involving the IT networks of critical infrastructure organizations.
One recent report comes from Japan, where attackers last year stole the details (report in Japanese) of more than 10,000 employees of Taiyo Nippon, the country’s largest industrial gas producer and one of the world’s top gas suppliers. The breach, which took place in March 2016, did not affect any control systems, the company said.
In April, we learned that two widely used pieces of malware, namely Conficker and Ramnit, had been found on systems belonging to a German nuclear energy plant in Gundremmingen. Experts believe these systems were likely infected by accident rather than as a result of targeted attacks.
Also in April, the Board of Water and Light (BWL) in Lansing, Michigan, was hit by a piece of ransomware, but the organization said the malware only affected the corporate network, with no disruption to water or energy supplies.
The Grizzly Steppe report published recently by the U.S. government in an effort to help organizations detect attacks launched by Russia-linked threat actors has led to the discovery of suspicious traffic at two organizations: the Burlington Electric Department in Vermont, and the Hydro One electricity distributor in Canada. Both organizations said the electric grid was never at risk.
Experts comment on the risks posed by such incidents
SecurityWeek has reached out to several industrial cybersecurity companies to find out if more damaging attacks may be possible given the holes in these organizations’ security.
Robert M. Lee, CEO and founder of Dragos, Inc., believes poor security practices and poor network segmentation can lead to a number of control system issues.
“Often if the pathways into the IT side of the network are easily taken advantage of, you will find that pathways into the ICS are also easily taken advantage of; however this is not the case in every site and we have seen a significant increase in security by many organizations out there,” Lee said.
Lane Thames, software development engineer and security researcher at Tripwire, also believes that a weak security posture on the IT side can lead to breaches on the OT side, particularly in the case of organizations that have started migrating OT systems to communication technologies (e.g. Ethernet, IP networking, Wi-Fi).
“For example, I have seen a single advanced manufacturing system with over 50 Ethernet ports, each one assigned its own IP address, that was controlled through a web based interface. If an attacker can penetrate the web server hosting the interface, then it is possible to penetrate the physical manufacturing device,” Thames said.
However, Lee and Thames agree that a security incident does not necessarily imply a poor security posture – even organizations with good security practices can get breached.
Opportunistic vs. targeted attacks
While critical infrastructure organizations may be breached by opportunistic threat actors that launch attacks indiscriminately for financial gain, experts believe some of these incidents could represent the reconnaissance phase of a targeted operation; although they have pointed out that targeting ICS is not the same as targeting IT networks.
“The sophistication of some of the attacks on certain industrial facilities points to actors far more capable than your opportunistic hacker,” said Eddie Habibi, CEO of PAS. “If cybersecurity is going to be the new WMD (weapons of mass destruction) in the future, which we believe it has the proclivity to be, you have to also believe that every nation is right now trying to build both their offensive and defensive cyber capabilities. That includes reconnaissance, spyware, Trojan horse and more.”
SAVE THE DATE: ICS Cyber Security Conference | Singapore - April 25-27, 2017
Thames explained, “Reconnaissance is really always in the picture. Further, mainstream attacks are also always in the mix. However, on the industrial side you will also see attacks that are more tailored to the target industry with very specific objectives driving the attack. For example, manufacturing organizations will often be targeted with a goal of stealing sensitive information and intellectual property.”
Despite the differences, experts believe industrial networks are not necessarily more difficult to attack.
“Cyber attacks on industrial control networks are very different from attacks on IT networks because the infrastructures are inherently different. ICS networks contain specialized technologies that operate the different processes. Therefore reconnaissance is always an important phase in which the attacker carefully learns which technologies are in place and how they are operated,” explained Barak Perelman, CEO of Indegy. “This doesn’t make industrial networks more difficult to attack. On the contrary - it is quite easy to attack them.”
Lee has pointed out that the only targeted attacks covered by the mainstream media in 2016 were the ones aimed at Thyssenkrupp and Ukraine’s energy sector. However, the expert said there were a number of targeted threat incidents last year that were not made public.
Securing ICS systems vs. securing corporate networks
SecurityWeek has asked experts about the differences between an organization’s approach when securing their business network versus securing their OT network.
Stephen Ward, Claroty: “The OT domain was not purposely built with security in mind - it was built with reliability, safety and up-time at the core. It is a very complex environment that is sensitive to any potential disruption. When looking at security solutions for the OT domain, organizations have to ensure that no potential harm is introduced into the OT network - they're incredibly concerned with this and in the past this has resulted in IT security people introducing potential controls but OT network personnel disqualifying those approaches. OT security solutions need to be just that - purpose built with an understanding of the complexities of these networks. Passive security solutions - such as real-time monitoring and detection - are on the top of the list for OT security improvements as a result.”
Lane Thames, Tripwire: “Often, there are differences within the organizations themselves (at least that has been the case historically). OT focuses on “mission assurance” whereas IT focuses on “information assurance”. These two objectives are vastly different, and, based on my discussions with practitioners in the industry, it creates communication breakdowns and barriers when an organization with IT and OT approaches security operations. For example, a control engineer could care less about data loss whereas an IT system administrator could care less about air-gapping the battery backup units (UPSs).”
Eddie Habibi, PAS: “The difference is stark. Folks who are focused on protecting business networks concern themselves with protecting information. OT cybersecurity personnel are singularly focused on protecting the physical process plant and safety. These approaches lead to very different cybersecurity decisions. An OT system, for instance, may never have a patch applied if there is a perceived risk it will disrupt production. Instead, they will add security controls in front of that system to mitigate risk. A zero day vulnerability can become a forever day vulnerability. In an IT approach, the patch is applied in real-time. Policies are in fact in place to make sure patches are kept up to date.”
Robert Lee, Dragos: “There must be largely different approaches and processes for securing the OT networks than the IT networks. Simply put, these networks have more serious consequences that can occur from bad practices and they often cannot be secured in the same way. As an example, simply deploying antivirus to the ICS would not significantly contribute to security, and may actually detract from it, whereas that is a common practice in IT security. There need to be tailored methodologies, processes for authorization and ownership of problems, and a different view of the risk management.”
Barak Perelman, Indegy: “There is a huge difference in approaches. OT networks involve different technologies and have different security gaps that should be addressed. Even the network activity is different and uses different protocols. In addition, process stability, safety and continuity is a top priority in these environments. Therefore, any modifications that could impact operations are indefinitely postponed. This means that patches, upgrades and other changes are rarely made.
[...] Implementing network security in ICS environments poses unique challenges since it requires in-depth understanding of the intricacies of OT network activity.”
Credential Stuffing: a Successful and Growing Attack Methodology
19.1.2017 Securityweek Attack
With a database of 1 million stolen credentials, criminals using a credential stuffing attack with a tool such as Sentry MBA could expect to compromise roughly 10,000 accounts on a targeted but uncompromised site. In 2016, 3.3 billion user credentials were spilled onto the internet, according to figures from Shape Security's just released 2017 Credential Spill Report.
Credential theft occurs when attackers breach a system and steal users' access credentials -- usually ID and password. The ID is most commonly the user's email address. Credential spilling is when those credentials are made available to other criminals. Credential stuffing is the large scale use of automated means to test stolen passwords against other unrelated websites.
It is made possible because of the tendency for users to recycle their passwords for multiple accounts. This means that if criminals can crack stolen passwords from one account, they have legitimate credentials that have quite likely been used on other accounts.
Consider the two Yahoo breaches reported in 2016. A total of 1.5 billion credentials were spilled to the Internet, protected by the weak MD5 hashing algorithm. The thefts took place in 2012 and 2013, giving the criminals up to four years to crack weak protection. Occurrences like this mean that criminals have vast troves of legitimate user credentials -- and user password recycling means that many will have been used on other accounts. "The sheer scale of the credential theft and also the prevalence of Yahoo users' accounts suggests that these stolen credentials have been benefiting cybercriminals over the past few years," suggests the Shape report (PDF).
Simple brute force testing to discover where spilled passwords may have been reused is easily defeated. Web sites invariably have defenses that will detect repeated login attempts from the same IP address, or multiple failed attempts at the same account -- and simply block them.
Now consider credential stuffing. The term was coined by Shape Security co-founder Sumit Agarwal when he was serving as Deputy Assistant Secretary of Defense at the Pentagon. It is the combination of source credentials, an attack tool such as Sentry MBA, and a botnet delivery method. Sentry MBA cycles through the botnet to probe a target website with the spilled credentials. Since each IP within the botnet tries only one credential attempt at a time, there is nothing at the target end to suggest anything different to a normal user login attempt -- which either succeeds or fails. Even if an attack is suspected, Sentry MBA has moved on to the next botnet IP and blocking the suspect IP has no effect.
Sentry MBA provides various techniques to defeat other defenses -- such as built-in optical character recognition to solve CAPTCHA challenges.
Shape's figures suggest that the criminal return on credential stuffing can be anything between 0.1% and 2%. This implies that for every 1 million stolen credentials used by the criminals, an average of 10,000 accounts could be accessed because of user re-use of passwords.
Credential stuffing is not an arcane attack method -- it is widely and increasingly used. For example, Shape reports, "In one week, cybercriminals made over five million login attempts at a Fortune 100 B2C website using multiple attack groups and hundreds of thousands of proxies located throughout the world." On another occasion, "During one day, a large retailer witnessed over 10,000 login attempts using over 1,000 proxies."
Nor are stolen credentials difficult to find. Some are simply dumped on the internet, given away free by hackers who hack for fun, or by others wishing to build a reputation. That reputation is necessary to gain access to, and do business on, some of the dark web credential marketplaces such as Cracking-dot-org, Crackingking-dot-org and Crackingseal-dot-io.
The result is an attack methodology that is easy and effective, and can be operated by any person with just the merest of technical skills. It involves just five steps: obtain the stolen credentials; choose a target; create an automation script to recognize whether the login attempt succeeds or fails; use a configurable credential stuffing tool such as Sentry MBA that can bypass controls such as WAF and CAPTCHA; takeover accounts and steal assets.
Shape Security is predicting that credential stuffing will become a major issue during 2017 as the 3.3 billion credentials spilled in 2016 (there may be more that we don't yet know about) work their way through the criminal system. The ultimate solution to the problem is simple: users must never reuse existing passwords. Ensuring that has so far been beyond both business and the security industry. In the meantime, business must seek other methods to protect against this growing threat.
Shape Security emerged from stealth mode in January 2014. One month later it announced that it had raised $40 million in a Series C funding round. In January 2016 it raised a further $25 million in a Series D funding round.
You Can Crash Anyone's iPhone Or iPad With A Simple Emoji Text Message
19.1.2017 thehackernews Apple
A newly discovered bug in Apple's iOS mobile operating system is being exploited in a prank that lets anyone crash your iPhone or iPad by just sending an emoji-filled iMessage, according to several reports.
YouTube star EverythingApplePro published a video highlighting a sequence of characters that temporarily freeze and restart an iPhone, which people can send to their iPhone buddies to trouble them. You can watch the video demonstration below.
Here's the first troublesome text: A white Flag emoji, the digit "0" and a Rainbow emoji.
This simple numeric character, flag, and rainbow emojis confuse iOS 10 devices when it tries to combine them into a rainbow flag.
As soon as this text is received, the iPhone's software attempts to combine the emojis but fails, and the messaging app crashes and eventually reboots in a few minutes. The recipients do not even have to open or read the message.
Video Demonstration
Another iPhone-crashing method involves the same characters, but saving them as a contact file and then sending that file to an iMessage contact via iCloud's sharing feature.
This, in turn, will crash the target's device, even if the victim has not manually opened the file.
Both the methods mentioned above will crash and iPhone or iPad to varying degrees, although the simple text string sent via a standard iMessage appears to affect iPhones and iPads running iOS 10.1 or below.
However, the boobytrapped contact card affects all versions of iOS 10, including Apple's latest iOS 10.2 operating system.
There is nothing you can do to protect yourself against this issue, as these iPhone-crashing issues have the ability to crash and reboot your iPhone or iPad without your interaction.
So, we hope that Apple releases a patch quickly to plug the issues, though the company has declined to comment on the issue.
This is not the first time EverythingApplePro has shared iOS-crashing issues. The YouTuber has a long history of reporting on iPhone crash pranks.
Newly Discovered Mac Malware with Ancient Code Spying on Biotech Firms
19.1.2017 thehackernews Virus
Security researchers have discovered a rare piece of Mac-based espionage malware that relies on outdated coding practices but has been used in some previous real-world attacks to spy on biomedical research center computers.
Dubbed Fruitfly, the malware has remained undetected for years on macOS systems despite using unsophisticated and "antiquated code."
Infosec firm Malwarebytes discovered Fruitfly, detected as 'OSX.Backdoor.Quimitchin,' after one of its IT administrators spotted some unusual outgoing activity from a particular Mac computer.
According to the researchers, the recently discovered what they're calling "the first Mac malware of 2017" contains code that dates before OS X, which has reportedly been conducting detailed surveillance operation on targeted networks, possibly for over two years.
Fruitfly uses a hidden pearl script to communicate back to two command-and-control (C&C) servers and has the ability to perform actions like capturing webcam and screenshots from both Mac and Linux systems, grabbing the system's uptime, and moving and clicking a mouse cursor.
Fruitfly can also collect information about other devices connected to the same network as the infected Mac, and then tries to connect to them, according to a blog post published by Malwarebytes.
The malware also uses a secondary script and Java class to hide its icon from showing in the macOS Dock, though it's still unclear how the malware got distributed and infected the machines.
What's more interesting is that the malware uses code that pre-dates Apple's OS X operating system, including SGGetChannelDeviceList, SGSetChannelDevice, SGSetChannelDeviceInput, and SGStartRecord.
Researchers said the malware is even running open-source "libjpeg" code to open or create JPEG-formatted image files, which was last updated in 1998.
On further digging into the code, the researchers discovered the malware had even gone through changes to "support" Mac OS X Yosemite indicating Fruitfly is at least two years old.
However, the old code and upgrade to support Mac Yosemite do not indicate the exact creation date of the malware.
"The only reason I can think of that this malware has not been spotted before now is that it's being used in very tightly targeted attacks, limiting its exposure," Thomas Reed of Malwarebytes wrote in the post.
"There have been [many] stories over the past few years about Chinese and Russian hackers targeting and stealing the United States and European scientific research. Although there is no evidence at this point linking this malware to a specific group, the fact that it has been seen specifically at biomedical research institutions certainly seems like it could be the result of exactly that kind of espionage."
The Fruitfly's code even includes Linux shell commands that show signs of the malware potentially running just fine on Linux operating system. So, it would come as no surprise if a Linux variant of Fruitfly was in operation.
Reed also said he has also come across related Windows executables that connected to the same C&C server used by the Fruitfly malware but date back to at least 2013.
However, the good news is that Apple has released an update for macOS to address Fruitfly. Although Apple automatically pushes the update, Mac users should consider checking their systems for infections, which is actually known as OSX.Backdoor.Quimitchip.
XSS Found in Silently Installed Acrobat Chrome Extension
19.1.2017 Securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy discovered that a Chrome extension installed silently by Adobe last week had been affected by a cross-site scripting (XSS) vulnerability. Adobe quickly patched the flaw after learning of its existence.
The updates released by Adobe on January 10 for Acrobat and Reader addressed 29 vulnerabilities. However, some users were displeased that the updates also automatically installed an Adobe Acrobat Chrome extension designed for converting web pages into PDF files.
The Windows-only extension requires permission to access data on the websites visited by the user, manage downloads, and communicate with cooperating native apps. The tool also collects some information from the system, but Adobe claims no personal information is involved and the “anonymous data will not be meaningful to anyone outside of Adobe.”
After analyzing the extension, which has roughly 30 million installs, Ormandy identified a DOM-based XSS vulnerability that allowed privileged JavaScript code execution. The expert classified the security hole as “critical severity.”
“I think CSP [Content Security Policy] might make it impossible to jump straight to script execution, but you can iframe non web_accessible_resources, and easily pivot that to code execution, or change privacy options via options.html, etc,” the Google researcher explained in an advisory.
The issue was reported to Adobe on January 12 and it was patched a few days later. It is not surprising that the vulnerability was fixed quickly considering that many of the flaws found in Adobe products are reported by Google Project Zero researchers or through the Chromium Vulnerability Rewards Program.
This was not the first time Ormandy identified a vulnerability in a Chrome extension. Roughly one year ago, the expert revealed that an extension automatically installed by AVG AntiVirus exposed users’ browsing history and other personal data.
Chrome Users Targeted in Malware Campaign
19.1.2017 Securityweek Virus
A recently observed malware distribution campaign has been specifically devised to target users of the Chrome browser on Windows-based computers, Proofpoint security researchers warn.
The campaign uses the infamous EITest infection chain, which has been previously associated with numerous exploit kit attacks leading to ransomware, information stealers, and other malware. First documented in 2014, EITest has seen numerous changes, and the switch to more targeted attacks instead of relying on exploit kits for infection is one of them.
The newly observed attack change was first noticed in December, when a compromised website was dropping the “Chrome_Font.exe” file onto visitors’ computers. The site, Proofpoint discovered, was EITest-compromised, and was dropping the file only after a series of filtering mechanisms were triggered.
The attack, security researchers found out, was targeting Chrome for Windows users specifically. As soon as the visitor was determined to use this browser, the code injected in the page would make text unreadable, and a fake alert was displayed, prompting the user to download and install a file supposedly containing new fonts.
“The infection is straightforward: if the victim meets the criteria - targeted country, correct User-Agent (Chrome on Windows) and proper referer - the script is inserted in the page and rewrites the compromised website on a potential victim's browser to make the page unreadable, creating a fake issue for the user to resolve,” Proofpoint researcher Kafeine explains.
The website, however, would attempt to infect Internet Explorer users as well. As long as they met specific criteria, they were exposed to a more “classic” exploit kit attack, the researcher notes.
The attack on Chrome users relied on storing all the data between HTML tags in an array, then replacing them with “�”. Because this is not a proper ISO character, the browser would display the replacement character � instead.
A fake alert displayed in the browser would prompt users to install an updated font pack to view the content of the page. The victim was told that the specific font (“HoeflerText,” in Proofpoint’s example) wasn’t found, and that the user should install the update immediately. The fake alert can’t be closed using the “x” button and malware is executed when the user approves the so called update.
Proofpoint suggests that the campaign was launched on December 10, 2016 and says that the “Chrome_Font.exe” file that users are tricked to install is in fact the ad fraud malware known as Fleercivet.
The malware spreads in affiliate mode, with its affiliate initially seen on underground markets as “Simby,” until they disappeared in early 2015, only to reappear later that year as “Clicool.” Upon infection, the malware causes the computer to browse the Internet in the background, on its own.
The new campaign, Kafeine says, is important because the new patch added to the EITest compromise chain combines social engineering with the targeting of Chrome users (different paths have been added to the EITest before, such as the redirection to an Android “Police” Browser locker spotted in December 2014.).
“Because actors are finding it more difficult (and therefore less profitable) to achieve conversions (i.e., malware installations) via exploit kit, they are turning to new strategies. As with other threats, actors are exploiting the human factor and are tricking users into loading the malware themselves, this time via selective injects into websites that create the appearance of problems along with the offer of fake solutions,” Proofpoint’s researcher concludes.
Hackers Offered Over $1 Million at Pwn2Own 2017
19.1.2017 Securityweek Hacking
For the 10th anniversary of the Pwn2Own hacking contest, Trend Micro and the Zero Day Initiative (ZDI) have introduced new exploit categories and they are prepared to offer more than $1 million worth of prizes.
Pwn2Own 2017 will take place in mid-March alongside the CanSecWest conference in Vancouver, Canada. Organizers have announced five major categories for the event: virtual machine (VM) escapes, web browsers and plugins, local privilege escalation, enterprise applications, and server side.
VM escapes were first introduced at Pwn2Own 2016 with VMware, but none of the contestants demonstrated a successful exploit. Researchers did manage to hack VMware Workstation and earned $150,000 in November at the PwnFest competition in South Korea.
At this year’s Pwn2Own, experts can earn $100,000 if they manage to execute arbitrary code on the host from a non-admin account in the guest operating system. In addition to VMware Workstation, Microsoft Hyper-V has also been added to the list of targets.
In the web browsers category, Mozilla Firefox has been reintroduced this year and hacking it can earn researchers $30,000. Exploits targeting Microsoft Edge and Google Chrome are worth $80,000, while Apple Safari and Adobe Flash Player exploits are worth $50,000.
Bonuses will be awarded for SYSTEM-level code execution on Windows ($30,000) and Mac OS X ($20,000), and VM escapes ($100,000). The bonuses are cumulative so, for example, if a contestant hacks Chrome, elevates privileges to SYSTEM and escapes the VM, they can earn $210,000 in one go.
Considering that local privilege escalation vulnerabilities can be highly useful for a piece of malware, these types of flaws get their own category this year, with prizes of $30,000 for Windows 10, $20,000 for macOS and $15,000 for Ubuntu Desktop.
The “enterprise applications” category includes Adobe Reader and the Microsoft Office apps Word, Excel and PowerPoint. Hackers can earn $50,000 for vulnerabilities affecting these applications.
The most valuable exploits are in the “server side” category. Hackers can earn $200,000 for successful exploits against Apache Web Server running on Ubuntu Server.
Each exploit will also be rewarded with Master of Pwn points. The contestant with the highest number of total points will receive 65,000 ZDI reward points, which are worth roughly $25,000.
Registration for Pwn2Own 2017 closes on March 12 at 5 PM Pacific Time. Additional information and rules are available on ZDI’s website.
US-CERT – Warning, Shadow Brokers Hackers are offering an SMB Zero-Day exploit
19.1.2017 securityaffairs Vulnerebility
The US-CERT has issued a warning after the Shadow Brokers hackers have offered to sell what it claims to be an SMB Zero-Day exploit.
The United States Computer Emergency Readiness Team (US-CERT) has issued a warning after the Shadow Brokers hacker group has offered to sell what it claims to be an SMB Zero-Day exploit.
The Shadow Brokers is the hacker crew that leaked a portion of the arsenal of the NSA-Linked Equation Group, a database containing hacking tools and exploits.
A few days ago the notorious hacker group Shadow Brokers announced the sale of an archive of Windows exploits and hacking tools stolen from the Equation group.
The mysterious hacking group has apparently decided to put an end to their failed attempts to sell exploits and hacking tools they claimed to have stolen from the NSA-linked Equation Group.
While the group claims to have decided to retire, the stolen exploits are still up for sale for the price of 10,000 bitcoins (roughly $8.7 million at the current exchange).
The precious archive seems to include also a zero-day exploit targeting the Server Message Block (SMB) network file sharing protocol.
“In response to public reporting of a potential Server Message Block (SMB) vulnerability, US-CERT is providing known best practices related to SMB. This service is universally available for Windows systems, and legacy versions of SMB protocols could allow a remote attacker to obtain sensitive information from affected systems,” US-CERT said.
Giving a close look at the list published by Shadow Brokers team it is possible to note a tool that claims to be an SMB Zero-Day exploit that goes for 250 bitcoins. The hackers describe the exploit as a remote code execution zero-day targeting SMB. The group is offering it under the name “SMB cloaked backdoor” for 50 bitcoins, but the complete package includes IIS, RDP RPC and SMB exploits for 250 bitcoins.

The US-CERT has advised users and administrators to consider disabling SMB v1, and block all versions of SMB at the network boundary. SMB typically uses port 445 (TCP/UDP), ports 137 and 138 (UDP), and port 139 (TCP).
The US-CERT provided the following recommendations to users and administrators:
disabling SMB v1 and
blocking all versions of SMB at the network boundary by blocking TCP port 445 with related protocols on UDP ports 137-138 and TCP port 139, for all boundary devices.
Anyway, it is important to consider that disabling or blocking SMB may create problems by obstructing access to shared files, data, or devices.
“The benefits of mitigation should be weighed against potential disruptions to users. For more information on SMB, please review Microsoft Security Advisories 2696547(link is external) and 204279(link is external).” continues the advisory.
The US-CERT has already issued in the past an alert following a Shadow Brokers initiative, in September it warned organizations after the hacker crew leaked exploitation tools flaws affecting Cisco ASA solutions.
“In August 2016, a group known as “Shadow Brokers” publicly released a large number of files, including exploitation tools for both old and newly exposed vulnerabilities. Cisco ASA devices were found to be vulnerable to the released exploit code. In response, Cisco released an update to address a newly disclosed Cisco ASA Simple Network Management Protocol (SNMP) remote code execution vulnerability (CVE-2016-6366).”
Šifrování WhatsApp je lež, server umí klientům vyměnit klíče
19.1.2017 Root.cz Zabezpečení
Světově nejpopulárnější komunikační aplikace WhatsApp se chlubí velkou bezpečností a end-to-end šifrováním. Ve skutečnosti je to ale lež, server totiž umí u klientů potichu vyměnit klíče a odposlechnout komunikaci.
V komunikační službě WhatsApp byla objevena vlastnost, která má zásadní dopad na bezpečnost šifrované komunikace. Tobias Boelter, bezpečnostní expert z University of California, totiž zjistil, že provozovatel služby má možnost si přečíst zprávy, ke kterým by neměl mít díky end-to-end šifrování vůbec přístup. Může totiž donutit klienty k výměně klíčů. Ve většině případů se o tom uživatelé vůbec nedozví.
Služba s více než miliardou uživatelů se už téměř rok chlubí tím, že podporuje end-to-end šifrování, takže nikdo nemá možnost číst komunikaci uživatelů. Ani Facebook, který je tři roky vlastníkem a provozovatelem WhatsApp, by tak neměl mít k obsahu komunikace přístup. Zprávy totiž mají být zašifrovány bezpečně pomocí klíčů, které jsou uloženy jen v zařízeních uživatelů.
WhatsApp dokonce o této vlastnosti hovoří jako o zásadní výhodě a tvrdí, že každá konverzace používá vlastní klíč. Ten je možné volitelně ověřit a získat tak jistotu, že komunikujeme se správnou protistranou. Protože je k šifrování použit bezpečný protokol Signal, který vyvinula společnost Open Whisper Systems, uživatelé předpokládali, že komunikace je skutečně bezpečná.
Server ovládá klienty
Ve skutečnosti je součástí této konkrétní implementace backdoor, který serveru dovoluje toto bezpečné šifrování obejít. Server totiž může klientům nařídit, aby zatím nedoručené zprávy znovu zašifrovaly jiným klíčem a poslaly mu je. Příjemce se o této změně navíc vůbec nedozví a odesílatel jen v případě, že v nastavení výslovně zapne zobrazování varování týkajících se šifrování. V případě drtivé většiny uživatelů tak projde výměna klíčů zcela potichu.
Zobrazení těchto notifikací je možné najít v menu Settings → Account → Security pod položkou „Show Security Notifications“. Uživatel se pak dozví o tom, že protistrana vyměnila šifrovací klíče.
Tímto způsobem je možné se skutečně dostat ke komunikaci, která by měla zůstat utajena. Pokud by byl WhatsApp požádán vládní organizací k vydání záznamů komunikace, mohl by k nim touto cestou získat přístup, říká Tobias Boelter. Chybu prý Facebooku hlásil už v dubnu 2016, ale dostalo se mu odpovědi v tom smyslu, že jde o „očekávané chování“ a firma se problémem dále nezabývala.
Funkce totiž má své opodstatnění a využívá se například ve chvíli, kdy uživatel vymění telefon nebo přeinstaluje aplikaci. Původní klíče jsou pak ztraceny a nový telefon je nezná. Pokud byly mezi tím uživateli poslány zprávy zašifrované starým klíčem, server vyzve odesílatele k jejich přešifrování a znovuodeslání. Pak je doručí uživateli do nové instalace aplikace.
Nové klíče jsou samozřejmě doručovány pomocí infrastruktury WhatsApp a pokud uživatel znovu neprovede jejich ověření, je možné mu podvrhnout libovolný klíč. Služba tak může velmi snadno provést útok typu man-in-the-middle a oběma komunikujícím stranám podvrhnout vlastní klíče.
Problém není ani tak v samotné možnosti vyměnit klíč, jako v tom, že se o změně uživatel ve výchozím stavu nedozví. Chyba rozhodně není v protokolu, ale je v konkrétní implementaci. Stejný protokol například používá aplikace Signal (kterou doporučuje Edward Snowden), která při výměně klíčů velmi hlasitě protestuje a žádá od uživatele jejich nové ověření. WhatsApp to nedělá.
I když možná neúmyslná, pořád díra
Na odhalení problému velmi rychle zareagoval Open Whisper Systems s vlastním prohlášením, ve kterém tvrdí, že nejde o backdoor, ale o nutnou funkcionalitu. Podle jejich slov se velmi podobně chová většina šifrovacích systémů, vše je proto v pořádku a normální. WhatsApp nedává vládám ‚backdoor‘ do svých systémů a bude bojovat proti jakémukoliv požadavku k jeho vytvoření.
Tvrdí také, že takto je možné znovu zašifrovat jen ty zprávy, které nebyly doposud doručeny klientovi. Nedodává ale, že zprávy o stavu doručení předávají stejné servery, které jsou schopné přikázat výměnu klíčů. Ve skutečnosti je tedy možné v libovolnou chvíli komunikaci pozdržet, klíče vyměnit a nechat si zprávy poslat v dešifrovatelné podobě.
Dalším argumentem proti zneužitelnosti je podle firmy to, že servery nemají informace o tom, zda konkrétní klienti mají zapnuté či vypnuté oznamování změn klíčů. Útočník prý tak nemůže sbírat informace o zranitelných uživatelích. Protože je ale notifikační volba ve výchozím stavu vypnutá, drtivá většina uživatelů je proti tomuto útoku bezbranná.
Firma tvrdí, že se rozhodně nejedná o backdoor. Ve skutečnosti ale nezáleží na tom, jak takovou vlastnost pojmenujete. End-to-end šifrování má sloužit k tomu, aby v žádném bodě přenosové trasy nebylo možné komunikaci ohrozit. Pokud je toto základní pravidlo porušeno, je poškozen celý princip šifrování a bezpečné prostředí mizí.
Na svou obhajobu společnost také říká, že pro uživatele je lepší, když notifikace tohoto typu nevidí. Pravděpodobně by je taková věc obtěžovala a stejně by ji slepě ignorovali. Ovšem existuje velký rozdíl mezi tím, když uživatel na důležité oznámení reaguje zbrkle a chybně, a když žádné oznámení nedostane a reagovat na něj nemůže.
Je úplně jedno, jestli jde o implementační nedokonalost nebo vědomou cestu k uživatelským datům. Stačí, že existuje technické řešení, které v případě potřeby umožní data přečíst. Pokud bude mít nějaká vládní organizace důvod se k datům dostat, dokáže provozovatele donutit takové technické řešení použít. Nehledě k tomu, že ho může použít útočník, který se dostane k serverům služby. Uživatel správně implementované služby by mohl mít stále jistotu, že je jeho komunikace v bezpečí krytá end-to-end komunikací s ověřeným klíčem.
Phishingový útok krade účty Google, pozor na falešné PDF v příloze
19.1.2017 Root.cz Phishing
Nová phishingová kampaň míří na uživatele Google a je tak přesvědčivá, že může zmást i technicky zdatné uživatele. Vše začíná mailem s falešným PDF a končí ukradením přihlašovacích údajů.
Phishingový mail se tváří velmi nenápadně a obsahuje přílohu ve formátu PDF, jejíž náhled je možné zobrazit přímo v prostředí GMailu. Zpráva se tváří důvěryhodně, protože jde o odpověď od známého kontaktu, která obsahuje už dříve poslanou přílohu. Tyto informace jsou získány z napadeného účtu předchozí oběti.
V příloze je ve skutečnosti falešný soubor PDF, který je ovšem pouze screenshotem boxíku s původní zprávou z odesílatelovy schránky. Protože používá známý vzhled, oběť se domnívá, že jí známý posílá dokument.
Vypadá jako příloha, ale je to jen vložený obrázek
Nová oběť se snaží přílohu otevřít, v domnění, že jde o legitimní dokument. Po kliknutí na obrázek se ale otevře nová stránka s informací o tom, že uživatel byl odhlášen ze služeb Google.
Stránka v URL
Adresa zobrazené stránky obsahuje řetězec accounts.google.com, který většinu uživatelů zmate a domnívají se, že jsou na správné přihlašovací stránce. Ve skutečnosti jde ale o velmi dlouhý řádek textu, který obsahuje zdrojový kód HTML stránky. Protože je ale falešná URL část od zbytku oddělena mezerami, jeví se obsah adresního řádku jako běžná adresa.
Adresa začíná známým řetězcem, ale obsahuje HTML
Tato technika se nazývá „data URI“ a umožňuje vložit celou stránku do adresního řádku. V tomto případě je navíc hlavička data:text/html zobrazena stejnou barvou i písmem jako zbytek domnělé adresy, takže jí uživatel nevěnuje pozornost. Správně má ale adresa vypadat jinak.
Takto vypadá URL přihlašovací stránky doopravdy
Pokud nepozorná oběť do stránky vloží své přihlašovací údaje, prohlížeč je odesílá na servery útočníků. Ty zareagují okamžitým přihlášením do schránky oběti, vyhledáním kontaktů, vytipováním zpráv s přílohami a celý proces se opakuje.
Metoda napadení je poměrně nenápadná a běžný uživatel nemusí zpozorovat nic podezřelého. Prostě byl odhlášen od svého účtu a musí zadat znovu své přihlašovací údaje. Mnoho lidí z branže hlásí, že se nechalo oklamat.

Follow
Tom Scott ✔ @tomscott
This is the closest I've ever come to falling for a Gmail phishing attack. If it hadn't been for my high-DPI screen making the image fuzzy…
12:54 PM - 23 Dec 2016
6,184 6,184 Retweets 5,350 5,350 likes
Dvoufaktorová autentizace
Ochranou proti tomuto typu útoku je dvoufaktorová autentizace, která kromě jména a hesla po uživateli vyžaduje ještě opsání kódu z SMS nebo offline generátoru v mobilním telefonu. Pokud by uživateli přihlašovací údaje přeci jen unikly, útočníkovi nebudou stačit k úspěšnému přihlášení.
Generátor jednorázových hesel Google Authenticator
Google o problému ví
Google o tomto typu útoků ví minimálně od loňského roku a bezpečnostní tým Chrome navrhl úpravu, po které by prohlížeč zobrazoval varování při použití schémat data:, blob: a dalších, která mohou být zneužita tímto způsobem.
Varování: tato stránka je nezabezpečená
Smile! Hackers Can Remotely Access Your Samsung SmartCam Security Cameras
19.1.2017 thehackernews Hacking
It's not necessary to break into your computer or smartphone to spy on you. Today all devices in our home are becoming more connected to networks than ever to make our lives easy.
But what's worrisome is that these connected devices can be turned against us, anytime, due to lack of stringent security measures and insecure encryption mechanisms implemented in these Internet of Things (IoTs) devices.
The most recent victim of this issue is the Samsung's range of SmartCam home security cameras.
Yes, it's hell easy to hijack the popular Samsung SmartCam security cameras, as they contain a critical remote code execution (RCE) vulnerability that could let hackers gain root access and take full control of these devices.
SmartCam is one of the Samsung's SmartThings range of devices, which allows its users to connect, manage, monitor and control "smart" devices in their home using their smartphones or tablets.
Back in 2014, the hacking group Exploiteers, which was previously known as GTVHacker, listed some SmartCam exploits that could have allowed remote attackers to execute arbitrary commands and let them change the camera's administrator password.
But instead of patching the flaw, Samsung decided to rip out the accessible web interface and use an alternate route that forced its users to run their SmartCams through the company's SmartCloud website.
So, it turns out that Exploiteers broke into the Samsung's SmartCam devices again with a different hacking exploit, allowing hackers to view what are supposed to be private video feeds.
What went wrong? Samsung had patched the original flaws but left one set of scripts untouched: Some PHP scripts that provide firmware updates through the SmartCam's "iWatch" webcam monitoring software.
These PHP scripts have a command injection vulnerability which could allow unauthorized users without admin privileges to execute remote shell commands with root privileges.
"The vulnerability occurs because of improper sanitization of the iWatch firmware update filename," a post on Exploiteers website reads. "A specially crafted request allows an attacker the ability to inject his command providing the attacker remote root command execution."
This defect, in turn, allows the web management system to be turned on, which was turned off by the vendor.
Exploiteers has also provided a proof-of-concept video demonstration that shows their exploit successfully working on the SmartCam SNH-1011 model, but security experts believe all Samsung SmartCam devices are affected.
How to Mitigate the Vulnerability?
An official patch from Samsung does not appear to be available yet, but the good news is that the folks at Exploiteers have shared a DIY patch that can be downloaded by SmartCam users.
However, I personally advise users to wait for an official firmware update from the company, rather than running untrusted code on their devices, though there's no indication yet if Samsung has any plan to issue a proper patch in upcoming days.
Another way to mitigate the vulnerability is by keeping your SmartCam behind a network firewall.
Samsung has yet to respond on the issue.
Quimitchin, a Mac backdoor that includes antiquated code
19.1.2017 securityaffairs Virus
Researchers at Malwarebytes have discovered the first Mac malware of 2017, dubbed Quimitchin, that was used against biomedical research institutions.
Security experts have spotted the first Mac malware of 2017, dubbed Quimitchin, and it is considered a malicious code not particularly sophisticated and includes some antiquated code.
According to the researchers from Malwarebytes, the code has been in the wild for several years and was used in targeted attacks against biomedical research institutions.
The Quimitchin spyware was discovered by an IT admin who noticed an anomalous traffic from a certain Mac in his network.
The malicious code is composed of two only two files:
A .plist file that simply keeps the .client running at all times.
A .client file containing the malicious payload, a minified and obfuscated Perl script.
The main features implemented by the payload are the screen captures and webcam access.
“The script also includes some code for taking screen captures via shell commands. Interestingly, it has code to do this both using the Mac “screencapture” command and the Linux “xwd” command. It also has code to get the system’s uptime, using the Mac “uptime” command or the Linux “cat /proc/uptime” command.” reads the analysis published by MalwareBytes.
The ability of the malware to exfiltrate data from anything it can access, and the nature of the targets, biomedical facilities, suggest that threat actors behind the attacks were conducting a cyber espionage campaign.

The Quimitchin uses antique system calls, and the analysis of its code revealed the use of the open source libjpeg code, which was last updated in 1998.
“These are some truly ancient functions, as far as the tech world is concerned, dating back to pre-OS X days. In addition, the binary also includes the open source libjpeg code, which was last updated in 1998.” continues the analysis.
“The Java class appears to be capable of receiving commands to do various tasks, which include yet another method of capturing the screen, getting the screen size and mouse cursor position, changing the mouse position, simulating mouse clicks, and simulating key presses. This component appears to be intended to provide a kind of rudimentary remote control functionality.”
Experts from Malwarebytes suspect that there is also a specific Linux variant in the wild because they have found Linux shell commands in the code of the scripts.
The security firm also found two Windows executable file that communicated with the same C&C server, in one case the Windows code used the same libjpeg library.
Despite the Quimitchin is not so complex, it continues to properly work avoiding the detection, something similar to the EyePyramid code.
Why a code like Quimitchin wasn’t detected for so long time?
Expert believe that is was using in a limited number of targeted attack so he was not spotted before.
US cancer agency targeted by a singular ransomware attack
19.1.2017 securityaffairs Virus
A new ransomware campaign has targeted the not-for-profit cancer services organisation “Little Red Door” requesting a US$44,000 ransom.
A new ransomware campaign has targeted a not-for-profit cancer services organisation, the Little Red Door. The organization provides a number of cancer support services, including diagnostics and treatment.
The system at the agency was infected by a ransomware last Wednesday, January 11, 2017, at around 10:00 PM.
According to the Associated Press a ransomware infected its server and demanded a 50 bitcoin ransom (roughly US$44,000) in order to decrypt the files.
ransomware
“A ransomware group has infected the computers of an Indiana-based cancer agency and have asked for a large payment of 50 Bitcoin ($44,800).” reported Bleepingcomputer.com.
“The victim is Cancer Services of East Central Indiana-Little Red Door, an organization that helps “reduce the financial and emotional burdens of those dealing with a cancer diagnosis.“”
The Little Red Door Executive director, Aimee Fant, confirmed that data of the organization was stored in unspecified cloud storage.
The singularity of this specific ransomware attack it the fact crooks demanding the ransom directly to the cancer agency’s staff via phone and email.
“First, they sent text messages to the agency’s Executive Director, President, and Vice President phones, and then they sent a standardized “form letter” via email. The emails contained detailed payment instructions, but also several threats.” added bleepingcomputer.com.
According to the cancer agency’s Executive Director Aimee Fant, the group threatened to contact family members of living and deceased cancer clients, donors and community partners.
The organization, of course, will not pay the ransom because its money has to be used to provide the necessary services to cancer patients and their families.
“The agency will not raise money to pay the criminals’ ransom,” Fant said.
This is really a sad story, the organization has no choice, it has to replace the infected server and store the old one in the hope a security firm or law enforcement will find decryption keys during their operations.
The agency plans to replace the server with a “secure cloud-based” platform and hopes to be restored operations within the week.
The attack was reported by the organization to the FBI.
Zadní vrátka pro utajený přístup obsahují tisíce aplikací pro Android
18.1.2017 SecurityWorld.cz Zranitelnosti
Zneužít se mohou data ve službách jako Amazon Web Services, Slack, Dropbox nebo Twitter, ale také mnoha dalších.
API klíče AWS nebo přístupové tokeny na Twitter – co vše lze najít v aplikacích Androidu. Studie bezpečnostní firmy Fallible prozkoumala 16 000 aplikací na Androidu – a zjistila, že 2 500 z nich má v sobě některý druh tajné přístupové informace napevno zakódovaný.
Mnoho vývojářů aplikací pro Android stále ukládá přístupové tokeny a API klíče přímo do aplikace, čímž vystavují data uložená ve službách třetích stran bezpečnostnímu riziku.
Zahrnutí přístupových klíčů třetích stran přímo do aplikace je ospravedlnitelné ve chvíli, kdy je rozsah pravomocí a služeb tokenů omezený. V některých případech však vývojáři do aplikace zakódovali i API klíče, které přistupují k velmi citlivým datům nebo zneužitelným systémům.
To byl případ celkem 304 služeb, které obsahovaly přístupové tokeny a API klíče do služeb jako Twitter, Dropbox, Flickr, Instagram, Slack nebo AWS.
Tři sta aplikací z 16 000 se může zdát jako zanedbatelný počet, ale v závislosti na druhu a pravomocích daného tokenu či klíče může jediná uniknutá bezpečnostní informace znamenat obrovský bezpečnostní problém.
Tak například tokeny ke Slacku mohou poskytnout přístup k historii chatu využívaného vývojářským týmem, a ty mohou obsahovat dodatečné přístupové informace např. k databázím, integračním platformám a dalším vnitrofiremním službám, ani nemluvě o sdílených souborech a dokumentech.
Již minulý rok odhalili výzkumníci z bezpečnostní společnosti Detectify přes 1 500 tokenů ke Slacku, napevno zakódovaných do původních projektů na GitHubu. Na GitHubu se v minulosti objevily rovněž klíče k AWS, a to řádově v tisících. Amazon tak musel začít aktivně vyhledávat podobné úniky a uveřejněné klíče blokovat.
Některé z AWS klíčů v analyzovaných aplikacích na Androidu mělo plné pravomoce, mohly tedy vytvářet a mazat instance, popisují pracovníci Fallible v příspěvku na blogu. Mazání jednotlivých instancí AWS může vést ke ztrátě dat a vyššímu downtimu, jejich vytváření zase umožňuje útočníkům využívat výpočetní sílu na úkor zákazníka.
Nejde zdaleka o první případ, kdy se různé přístupové údaje objevují napevno zakódovány v mobilních aplikacích. V roce 2015 odhalila skupina výzkumníků z Technické univerzity v Darmstadtu v Německu přes 1 000 přístupových klíčů pro BaaS aplikační rámce uložené v aplikacích Androidu a iOS.
Tato data umožňovala přístup k 18,5 milionům záznamů, obsahujícím 56 milionů dat, která vývojáři k BaaS poskytovatelům (např. Parse, CloudMine nebo AWS) uložili.
Nedávno spatřil světlo světa open source nástroj Truffle Hog, který pomáhá podnikům i jednotlivcům s prohledáním svých aplikací, zda vývojáři neopomněli odstranit některé tokeny, které dovnitř vložili během vývoje a následně zapomněli odstranit.
Na Gmail míří zákeřná vlna phishingu, může zmást i zkušenější uživatele
18.1.2017 Živě.cz Phishing
Uživatelé využívající e-mail od Googlu mohou narazit v těchto dnech na novou phishingovou vlnu, která se od těch tradičních liší svou zákeřností. U většiny z nich často stačí zkontrolovat adresu, na kterou vedou odkazy ve zprávě, tady se však můžete při malé nepozornosti spálit.
Vše začíná tak, jak jsme u podobných zpráv zvyklí, útočníci zde využili připojení zdánlivé přílohy ve formátu PDF, která je však pouhým obrázkem. V domnění, že si oběť otevře dokument přímo v prohlížeči klikne na obrázek, který ji ale přesměruje na web, kde najde přihlašovací formulář do Gmailu.
Takto vypadá podvržená přihlašovací stránka Gmailu. V adresním řádku spatří oběť známou URL a zbytku tak přestane věnovat pozornost. Na podvod by měl upozornit jak nezvyklý formát adresy, tak její barva (foto: Timruffles/Github)
A právě na tomto místě se aktuální vlna phishingu liší od toho běžného. V adresním řádku totiž opravdu uživatel spatří URL https://accounts.google.com, která patří legitimnímu přihlašovacímu webu. Jenže díky Data URI obsahuje adresní řádek také prázdné znaky a delší škodlivý kód směřující právě na web určený pro získání údajů oběti. Techniku najdete dobře zdokumentovanou a popsanou na Githubu.
Jakmile útočníci získají údaje, využijí je k přístupu k účtu a rozeslání další vlny phisningových e-mailů na kontakty v adresáři. Dalším obětem tedy přijde taková zpráva od známé osoby, čímž se opět zvýší šance útočníků.
The Carbanak gang is with a new modus operandi, Google services as C&C
18.1.2017 securityaffairs Crime
The infamous Carbanak cybercrime gang is back and is leveraging Google services for command-and-control of its malicious codes.
The dreaded Carbanak cybercrime gang is back and is adopting a new tactic for its attacks, it is leveraging Google services for command-and-control of its malware.
The criminal organization is named Carbanak cybergang because of the name of the malware they used to compromise computers at banks and other financial institutions, experts estimated that the hackers swiped over $1 Billion from their victims.
The majority of financial institutions victims of the gang are located in Russia, but many other attacks have been detected in other countries, including Japan, Europe and in the United States.

Figure 1 – Map of Infections, 2015 Attacks against financial Institutions (Kaspersky Lab)
The investigators discovered that the “Carbanak cybergang” hit more than 100 financial institutions in 30 countries, it has been active at least since 2013 and there are strong indications that it may still be ongoing.
Now researchers from Forcepoint Security Labs have spotted a new campaign conducted by the Carbanak gang that exploits Google’s Apps Script, Sheets, and Forms cloud-based services to control their malicious code.
The attack vector is a trojanized RTF document with an encoded Visual Basic script that is spread via email.
“Forcepoint Security Labs™ recently investigated a trojanized RTF document which we tied to the Carbank criminal gang. The document contains an encoded Visual Basic Script (VBScript) typical of previous Carbanak malware. Recent samples of the malware have now included the ability to use Google services for command-and-control (C&C) communication. We have notified Google of the abuse and are working with them to share additional information.” reads the analysis published by Forcepoint.
“For each infected user a unique Google Sheets spreadsheet is dynamically created in order to manage each victim. The use of a legitimate third party service like this one gives the attacker the ability to hide in plain sight,” Forcepoint wrote in a blog post today.

The crooks used the “ggldr” script to send and receive commands to and from Google Apps Script, Google Sheets, and Google Forms services.
Hackers used to create a unique Google Sheets spreadsheet for each infected user, in this way they attempted to avoid detection.
“The use of a legitimate third party service like this one gives the attacker the ability to hide in plain sight. It is unlikely that these hosted Google services are blocked by default in an organization, so it is more likely that the attacker will establish a C&C channel successfully.” states the report.
The following diagram describes the way the Carbanak cybercrime gang exploited the Google Services as C&C.
Once infected the victim’s machine, the malware first attempt to contact the hard-coded Google Apps Script URL with the user’s unique infection ID. Because no spreadsheet currently exists for the specific victim, the malware will then send two requests to another hard-coded Google Forms URL which will result in the creation of unique Google Sheets spreadsheet and Google Form IDs for the victim.
The second time the Google Apps Script is requested by the malicious code, the C&C will return the unique Google Sheet and Google Form ID values.
“The “entry” value is also a unique ID which is sent with each subsequent Google Forms C&C request.”
Let me suggest to read the report that also includes the IoCs for this specific threat.
Hacker found a way to hack Facebook by exploiting the ImageMagick flaw
18.1.2017 securityaffairs Social
The bug hunter Andrew Leonov has described how to exploit an ImageMagick flaw to remotely execute code on a Facebook server.
The hacker Andrew Leonov (@4lemon) has described how to exploit the so-called ImageMagick vulnerability to remotely execute code on a Facebook server.
The ImageMagick flaw, tracked as CVE-2016-3714, affects the popular image manipulation software, ImageMagick. The flaw could be exploited by hackers to take over websites running the widely used image-enhancing app. The vulnerability in ImageMagick App allows attackers to run arbitrary code on the targeted web servers that rely on the app for resizing or cropping user-uploaded images.
Follow
Andrew Leonov @4lemon
@Facebook #ImageTragick remote code execution http://4lemon.ru/2017-01-17_facebook_imagetragick_remote_code_execution.html … #RCE #BugBounty
11:28 AM - 17 Jan 2017
208 208 Retweets 258 258 likes
The researcher has detailed in a post the attack and also provided a proof-of-concept exploit for the hack, Facebook has awarded him with the highest payoff since now, US$40,000.
“Once upon a time on Saturday in October i was testing some big service (not Facebook) when some redirect followed me on Facebook. It was a «Share on Facebook» dialog:” wrote Leonov.

https://www.facebook.com/dialog/feed?app_id=APP_ID&link=link.example.tld&picture=http%3A%2F%2Fattacker.tld%2Fexploit.png&name=news_name&caption=news_caption&description=news_descriotion&redirect_uri=http%3A%2F%2Fwww.facebook.com&ext=1476569763&hash=Aebid3vZFdh4UF1H
“Which many of you could see. If we look closer we can see that a `picture` parameter is a url. But there isn’t image url on page content like mentioned above.” added Leonov.
The expert has discovered the vulnerability after a service redirected him to the Facebook platform, initially he was he was convinced he had discovered a server-side request forgery vulnerability.
“First of all I thought about some kind of SSRF issue. But tests showed that url from this parameter requested from 31.13.97.* network by facebookexternalhit/1.1.”
After testing the application, the expert devised the following workflow:
Gets `picture` parameter and requests it – this request is correct and not vulnerable
Received picture passes on converter’s instance which used vulnerable ImageMagick library
The management of the flaw was perfect, the expert reported the issue to Facebook through the bug bounty program in October and the IT giant fixed it in less than three days.
Thai TrueOnline ZyXEL and Billion routers still unpatched since July
18.1.2017 securityaffairs Vulnerebility
The security researcher Pedro Ribeiro disclosed several vulnerabilities in the ZyXEL customized routers that could be easily exploited by hackers.
Details on serious vulnerabilities in a number of routers freely distributed by the TrueOnline Thai ISP were published on Monday after private disclosures made to the vendors in July went unanswered.
The security researcher Pedro Ribeiro from Agile Information Security disclosed multiple flaws in a number of routers distributed by the Thai ISP TrueOnline.
The Thai ISP distributes several rebranded ZyXEL and Billion routers to its customers.
The models ZyXEL P660HN-T v1, ZyXEL P660HN-T v2 and Billion 5200W-T contain a number of default administrative accounts and their web interfaces are affected by command injection vulnerabilities. On Monday Ribeiro published a proof of concept exploit, he released Metasploit modules for the exploitation of the vulnerabilities in the routers.

All the routers are still in widespread use in Thailand, with the Billion 5200W-T router currently being distributed to new customers.
“TrueOnline is a major Internet Service Provider in Thailand which distributes various rebranded ZyXEL and Billion routers to its customers. Three router models – ZyXEL P660HN-T v1, ZyXEL P660HN-T v2 and Billion 5200W-T – contain a number of default administrative accounts, as well as authenticated and unauthenticated command injection vulnerabilities in their web interfaces, mostly in the syslog remote forwarding function.” reads the advisory. “All the routers are still in widespread use in Thailand, with the Billion 5200W-T router currently being distributed to new customers.”
Ribeiro reported the vulnerabilities via the SecuriTeam Secure Disclosure Program, which notified them to the vendors in July.
The network devices are based on the TC3162U SoC system-on-a-chip manufactured by TrendChip, in particular, flawed routers have two firmware variants called “ras” and “tclinux.”
Riberio discovered security vulnerabilities in the ‘tclinux’ variant, several ASP files in the web interface are affected by command injection attack issues.
“It should be noted that tclinux contains files and configuration settings in other languages (for example in Turkish). Therefore it is likely that these firmware versions are not specific to TrueOnline, and other ISP customised routers in other countries might also be vulnerable,” added Ribeiro. “It is also possible that other brands and router models that use the tclinux variant are also affected by the command injection vulnerabilities (the default accounts are likely to be TrueOnline specific).”
The researcher explained that the majority of the vulnerabilities can be exploited remotely, by both authenticated and unauthenticated attackers.
The ZyXel P660HN-T v1 router is affected by an unauthenticated command injection issue that can be remotely exploited by attackers.
“This router has a command injection vulnerability in the Maintenance > Logs > System Log > Remote System Log forwarding function. The vulnerability is in the ViewLog.asp page, which is accessible unauthenticated. The following request will cause the router to issue 3 ping requests to 10.0.99.102:
POST /cgi-bin/ViewLog.asp HTTP/1.1
remote_submit_Flag=1&remote_syslog_Flag=1&RemoteSyslogSupported=1&LogFlag=0&remote_host=%3bping+-c+3+10.0.99.102%3b%23&remoteSubmit=Save”
The ZyXel P660HN-T V2 router in affected by the same issue, but it can be remotely exploited only by authenticated attackers.
“Unlike in the P660HN-Tv1, the injection is authenticated and in the logSet.asp page. However, this router contains a hardcoded supervisor password (see below) that can be used to exploit this vulnerability. The injection is in the logSet.asp page that sets up remote forwarding of syslog logs, and the parameter vulnerable to injection is the serverIP parameter” states the advisory.
The third router distributed by the Thai ISP is the Billion 5200W-T model, this model is affected by unauthenticated and authenticated command injection issues. According to the researcher a flaw resides in the its adv_remotelog.asp page.
“The Billion 5200W-T router also has several other command injections in its interface, depending on the firmware version, such as an authenticated command injection in tools_time.asp (uiViewSNTPServer parameter),” Ribeiro said. “It should be noted that this router contains several hardcoded administrative accounts that can be used to exploit this vulnerability.”
All the versions use default and weak admin credentials that were remotely accessible.
President Obama commutes Chelsea Manning sentence
18.1.2017 securityaffairs BigBrothers
President Barack Obama has commuted Chelsea Manning’s sentence for leaking confidential documents to Wikileaks in 2010. He will be released on May 17th.
President Barack Obama took a historic decision, he has commuted Chelsea Manning’s sentence for leaking classified documents to Wikileaks in 2010. The news was reported by The New York Times, Manning is due to be released on May 17th.
Chelsea Manning, born as Bradley Manning, was sentenced to 35 years in 2013, when he was serving the US Army passed diplomatic cables to the anti-secrecy group Wikileaks.
The data leak was one of the largest breaches of classified documents in the history of the United States.
At the time of the data leak, Bradley Manning was serving as an intelligence analyst in Iraq. He provided more than 700,000 documents to WikiLeaks, the huge trove of documents includes the video of a 2007 airstrike in Baghdad that caused the death of two Reuters employees.
Recently Wikileaks announced the Assange’s intention agree to US extradition if Obama grants Manning’s clemency.
Follow
WikiLeaks ✔ @wikileaks
If Obama grants Manning clemency Assange will agree to US extradition despite clear unconstitutionality of DoJ case https://twitter.com/wikileaks/status/765626997057921025 …
8:40 PM - 12 Jan 2017
6,691 6,691 Retweets 5,676 5,676 likes
Follow
WikiLeaks ✔ @wikileaks
Assange: "Thank you to everyone who campaigned for Chelsea Manning's clemency. Your courage & determination made the impossible possible."
11:29 PM - 17 Jan 2017
4,295 4,295 Retweets 9,148 9,148 likes
“Obama may well have just saved Chelsea Manning’s life,” commented Sarah Harrison, who has defended Manning as Active Director of the Courage nonprofit. “Freeing her is clearly and unambiguously the right thing to do.”
She confirmed anyway the criticism for the President Obama’s decision to persecute Manning under the Espionage Act.
“Today’s news will not make good the harm done on Obama’s watch,” Harrison added. “Chelsea’s conviction under the Espionage Act and 35-year sentence set a terrible precedent that is left entirely intact by this commutation. Who knows what Donald Trump will do with this precedent, and these powers, that Obama has left him?”
The Manning’s commutation was part of a larger effort of the US Government that resulted in 209 commutations and 64 pardons. President Obama issued 1,385 grants of commutation during his administration, none made like him.
e remotely accessible.
Kritické chyby mají Flash Player, Acrobat i Reader. Mohou je zneužít kyberzločinci
17.1.2017 SecurityWorld Zranitelnosti
Hned několik bezpečnostních trhlin bylo odhaleno v oblíbeném programu Flash Player. Ten slouží k přehrávání videí na internetu a po celém světě jej používají stovky miliónů lidí. Chyby se nevyhnuly ani programům Acrobat a Reader, které slouží k práci s PDF dokumenty. Záplaty od společnosti je však již možné stahovat.
„Vydaná aktualizace pro Acrobat a Reader verzí 11 a 15 opravuje celkově 29 kritických zranitelností, z nichž některé by při zneužití mohly útočníkovi umožnit převzetí kontroly nad systémem,“ Pavel Bašta, bezpečnostní analytik Národního bezpečnostního týmu CSIRT.CZ, který je provozován sdružením CZ.NIC.
Obezřetní by měli být uživatelé také v případě Flash Playeru. „V případě tohoto programu bylo opraveno 13 kritických bezpečnostních chyb v dřívějších verzích, které mohly vést ke spuštění škodlivého kódu nebo úniku citlivých dat,“ konstatoval Bašta.
Propašují virus, zotročí počítač
Prostřednictvím chyb mohli kyberzločinci propašovat na cizí počítač prakticky jakýkoli škodlivý kód, případně jej zcela ovládnout na dálku. Mohli se tak snadno dostat k uloženým datům, případně odchytávat přihlašovací údaje na různé webové služby.
Takový stroj se pak klidně i bez vědomí uživatele může stát součástí botnetu (síť zotročených počítačů), který kyberzločinci zpravidla zneužívají k rozesílání spamu nebo k DDoS útokům.
Častý terč útoků
Stahovat záplatu je možné prostřednictvím automatických aktualizací daného programu nebo prostřednictvím stránek společnosti Adobe.
Flash Player používá na celém světě několik stovek miliónů lidí. Právě kvůli velké popularitě se na Flash Player zaměřují kybernetičtí nájezdníci pravidelně. Podle analýzy bezpečnostní společnosti Record Future cílilo osm z deseti nejrozšířenějších hrozeb v roce 2015 právě na tento přehrávač videí.
Hackers demonstrate how to hack Samsung SmartCam
17.1.2017 securityaffairs Hacking
Researchers Exploitee.rs discovered a flaw in Samsung SmartCam IP cameras that could be exploited to execute commands and hijack vulnerable devices.
Samsung SmartCam IP cameras are affected by a serious vulnerability that could be exploited by remote attackers to execute commands and hijack vulnerable devices.
Samsung Electronics sold the Samsung Techwin security division to the Hanwha Group in 2014, but Hanwha SmartCam products are still distributed as Samsung.
In 2014 at DEFCON 22, security experts at Exploitee.rs revealed a number of exploits that could have been used to execute arbitrary commands on Samsung SmartCam. An attacker could use the exploits to change device settings, including the administrator password.
A few months ago, the experts from Pen Test Partners also reported security issues in Samsung SmartCam products.
The researcher focused their analysis on the Samsung branded indoor IP camera SNH-6410BN, they noticed for example that the device still has SSH and a web server running on it, potentially open doors for hackers.
Samsung decided to solve the issue by disabling SSH and local access to the web interface. Actually, users can access the Samsung SmartCam via the SmartCloud online service.
Researchers Exploitee.rs conducted a new test session on the device and discovered a way to enable the Telnet service and the local web interface by exploiting a command injection flaw in a collection of scripts that were not removed by the vendor.
“Today we’re re-visiting a device that we’ve hacked in a previous session. At DEFCON 22, we released exploits for the Samsung Smartcam network camera in our “Hack All The things” presentation. These exploits allowed for remote command execution and the ability to arbitrarily change the camera’s administrator password.” states the analysis published Exploitee.rs.
These scripts exploited by the hackers are related to the iWatch webcam monitoring service and are used for firmware update functionality. The researchers discovered an iWatch Install.php root command execution issue.
“The iWatch Install.php vulnerability can be exploited by crafting a special filename which is then stored within a tar command passed to a php system() call,” researchers explained. “Because the web-server runs as root, the filename is user supplied, and the input is used without sanitization, we are able to inject our own commands within to achieve root remote command execution.”
Researchers at Exploitee.rs have also released a proof-of-concept (PoC) code for the vulnerability, and a fix. The exploit works with the SNH-1011 model, but researchers believe all Samsung SmartCam devices are affected.
“The vulnerability can be patched by first logging in to the server after spawning a shell with the POC curl command above, then running the following command.”
sed -i -e 's/" . $file . "/" . escapeshellarg($file) . "/' /mnt/custom/iwatch/web/install.php
Researchers have warned that enabling the web interface reintroduces some of the older vulnerabilities previously discovered.
How To Stop Larry From Hacking Your WiFi in 2017
17.1.2017 thehackernews Hacking
It’s 2017, and we’re not any further along with Wi-Fi security than we were 10 years ago. There are Intrusion Detection Systems and 2nd generation antivirus apps to protect us from some vulnerabilities but the simple fact that some people and businesses still don’t set their network up well in the first place.
Installing WiFi is like running Ethernet to your parking lot. It’s a cliche thing to say, but it is often true.
If I can attack your network sitting in my car from the parking lot, what chance do you have? And 99% of the time I’m successful.
Lots of companies are moving to new offices that have wide open office layouts. Some may not have BYOD policies or wireless security plans in place, and anyone can bring their own device to work that you may not know about.
I’ve even seen some companies installing IoT devices like smart led light bulbs and thermostats. Even some security camera systems which are always running unsecured and default passwords.
So what can you do to protect people like me from exploiting weaknesses in your wireless security networks and PWNing your company?
Follow
Pwnie Express @PwnieExpress
We're sorry, but your new password must contain an upper case letter, a number, a punctuation mark and a gang sign 😳🤔
7:56 PM - 16 Jan 2017
10 10 Retweets 15 15 likes
Be sure WEP does not exist in your infrastructure. WEP is the weakest of the weak for encryption but was a reaction to open networks early on.If enough packets are observed the key can be brute forced easily. Remember doing that like 15 years ago?
WPA/WPA2 PSK can be your friend. It’s mostly secure, but there are still things you need to lock down to be sure.
Create a plan on what to do when an attack happens. Develop and implement a wireless security policy. Be ready when you do detect a rogue device or when someone’s banging on your network from the parking lot.
Want to watch us talk about penetration testing and hear stories from 200 clients I’ve been hired to hack into their network?
We’re running a webinar tomorrow with Pwnie Express and Larry Pesce.
You can sign up here, and I’ll send you the link to watch us as well as a guide for 2017 on how you can lock down wireless networks and keep people like me out of your company's networks.
How EaseUS Partition Master Can Easily Manage Your Hard Disk
17.1.2017 thehackernews IT
If you want to get the most out of your computer, you need to get the most out of your hard drive, where all your data is stored.
Today hard drives are larger than ever, so it makes sense for you to partition your hard disk to effectively use all of its space and manage all your important information.
Partitioning is also useful if you intend to install and use more than one operating system on the same computer.
There is a vast business of partition manager software out there, and today we are reviewing one of the most popular partition management tools available in the market: EaseUS Partition Master Professional.
EaseUS Partition Master Professional offers you the complete package with capabilities for organizing and resizing your drive, restoring and backing up your information, improving system performance, installing and managing several operating systems on the same computer, along with recovering and cloning data files.
Let's dig deep into the capabilities provided by the EaseUS Partition Master Professional software.
Resize, Move Or Merge Multiple Partitions
You might have, at some point, obsessed with low space in one certain partition of your hard disk while others may be left unused for long with much space. At this point, you can choose to merge two partitions for a larger system partition.
But resizing or combining your system and boot partition C drive, which holds your Operating System, without any third party tool is not always a good idea, as there are chances of data loss.
So, in that case, users are always advised to use a third-party partition tool from a reputable and trustworthy company.
EaseUS partition software can get this job done with ease.
EaseUS Partition Master Professional provides one-click, easy-to-use interface to help you move, resize, merge, hide or unhide the existing disk partitions without damaging even a single bit of original data.
All you need to do is launch the EaseUS Partition Master Professional software, choose the disk partition you want to process and right click on it, and you’ll get the list of all the available operations that can be performed.
Once you resize or move your partitions, you are advised to backup your data.
Migrate OS to SSD/HDD Without Reinstalling Windows
One of the major features of EaseUs Partition Master Professional is the ability to migrate your operating system to another hard drive (SSD or HDD).
So, if you are upgrading your old PC for better performance, this tool also allows you to transfer all your data on system and boot partitions, including OS and installed applications, without reinstalling the operating system on the new drive.
To migrate your OS from HDD to SSD, all you need to do is launch the application, click on Wizard and then select 'Migrate OS to SSD/HDD' from the main menu. Now select SSD as destination disk, delete partitions on the target drive, resize partitions on the target disk, and then click Finish.
Moreover, it also supports MBR and GPT disks
Bootable Partition Manager (CD/DVD/USB)
The tool also enables users to manage hard disk partitions even when their OS fails to boot or manage partitions without an operating system.
Also, users who are looking for a bootable USB flash drive partition manager that will be able to resize partitions, EaseUS Partition Master is your pick.
To create a bootable USB flash drive partition manager, you first need to download and launch EaseUS Partition Master, then select Tool → Create WinPE bootable disk → USB and then start to create a USB bootable disk of EaseUS Partition Master.
After that, you can launch EaseUS Partition Master from bootable USB device or CD/DVD and manage your hard drive partitions.
Copy/Clone Partition
If ransomware malware strikes, only a good backup can save your files and money, and EaseUS Partition Master helps you do just that.
The Partition Copy and Disk Copy features integrated into EaseUS Partition Master are specially designed to provide protection from data loss.
The Partition Copy feature aims to backup your partitions before the partition operations applied to the hard disk to prevent any data loss from program error or some other accidental errors.
Partition Copy let you copy a partition to unallocated space on your hard disk, and even allow you to resize the unallocated space during the procedure if necessary.
On the other hand, Disk Copy lets you not only make a backup copy of your hard drive but also allows you to copy your entire system from a small hard disk to a larger hard drive.
Securely Erase Data on SSD or HDD
If you've just got a new PC and want to sell your old one, make sure all your data has been cleared securely and can not be recovered anyhow.
Because, when you delete a file, it is not deleted. Those deleted files still exist. Your PC only removes the file indexing information from the hard drive.
So, if that deleted data is not overwritten, it can be recovered later, which may include your passwords, private photographs, personal information, classified documents or financial records.
So, always be sure to securely erase your data before selling or throwing away your device.
Using EaseUS Partition Master, you can securely delete your files or entire drive in a way that it can not be recover anyhow.
To do so, first, launch EaseUS Partition Master Free, select the SSD or hard disk you want to erase, and then right click and select "Wipe disk."
The tool will then ask you to set the number of times (1-10 times) to wipe your hard drive and click "OK." A dialog box will appear saying your PC will computer restart after disk erase. Just click "OK" and then click "Apply" to securely erase SSD or HDD.
Note: If you are erasing your entire hard disk, make sure that it does not include system partition because your system will not boot after wiping the drive.
Support and Compatibility (OS, File System, Drive Type)
The free version of EaseUS Partition Master supports up to 8TB hard disks while the professional version supports up to 16TB disks and 32 disks at most.
Talking about the operating system, EaseUS Partition Master supports Windows 10, 8.1, 8 and 7 SP1, and 32-bit and 64-bit versions of Windows 7, Vista and Windows XP Home Edition and Professional.
EaseUS Partition Master supports MBR and GPT disks – GPT disks are faster than MBR and help with high-capacity hard disk drives. So if you want to convert your regular MBR hard disk drive into GPT, you can use EaseUs that'll do it without any data loss.
EaseUS Partition Master is supportive over different file systems as well, including EXT3, EXT2, NTFS, FAT32, FAT16, FAT12, and ReFS. It also supports different device types including Solid-State Drive (SSD), IEEE 1394 (FireWire) HDD, USB 1.0/2.0/3.0 HDD, all levels of SCSI, IDE and SATA RAID controllers, full support of RAIDed configurations (hardware RAIDs) and removable devices, like flash drive, memory card, and more.
EaseUs is one of the top disk management software developers out there, and its Partition Master Professional software stands up to its name.
Conclusion: EaseUs Partition Master Professional is a complete solution for managing, copying and recovering your disk partitions within only a few simple clicks. A large number of superb partitioning and solid additional features as well as the user-friendly interface place EaseUS Partition Master near the top and make it difficult to beat.
So, if you are looking for an effective partition manager, you should give it a try, as its worth its every single penny.
EaseUS Partition Master Professional Edition costs just $39.95, while its Server Edition costs $159.00 and Home Edition is free. You can also take a Free Trial of EaseUS Partition Master Professional Edition.
If this partition tool really met all your requirements, you can purchase EaseUS Partition Master Pro at highly discounted price at The Hacker News. We are giving 50% discount on EaseUS Partition Master Pro to our readers.
Just use SEO-LGR-85D coupon code at the time of checkout.
Simple Hack Lets Hackers Listen to Your Facebook Voice Messages Sent Over Chat
17.1.2017 thehackernews Social
Most people hate typing long messages while chatting on messaging apps, but thanks to voice recording feature provided by WhatsApp and Facebook Messenger, which makes it much easier for users to send longer messages that generally includes a lot of typing effort.
If you too have a habit of sending audio clip, instead of typing long messages, to your friends over Facebook Messenger, you are susceptible to a simple man-in-the-middle (MITM) attack that could leak your private audio clips to the attackers.
What's more worrisome is that the issue is still not patched by the social media giant.
Egyptian security researcher Mohamed A. Baset told The Hacker News about a flaw in Facebook Messenger's audio clip recording feature that could allegedly allow any man-in-the-middle attacker to grab your audio clip files from Facebook's server and listen to your personal voice messages.
Let's understand how this new attack works.
Here's How Attackers can Listen to your Personal Audio Clips:
Whenever you record an audio clip (video message) to send it to your friend, the clip gets uploaded onto the Facebook's CDN server (i.e., https://z-1-cdn.fbsbx.com/...), from where it serves the same audio file, over HTTPS, to both the sender as well as the receiver.
Now, any attacker sitting on your network, running MITM attack with SSL Strip, can actually extract absolute links (including secret authentication token embedded in the URL) to all audio files exchanged between sender and receiver during that process.
Then, the attacker downgrades those absolute links from HTTPS to HTTP, allowing the attacker to direct download those audio files without any authentication.
That's it.
You might be wondering that how hackers are able to download your audio files so easily.
What went Wrong?
This is because Facebook CDN server does not impose HTTP Strict Transport Security (HSTS) policy that forces browsers or user agents to communicate with servers only through HTTPS connections, and helps websites to protect against protocol downgrade attacks.
Secondly, the lack of proper authentication — If a file has been shared between two Facebook users it should not be accessible by anyone except them, even if someone has the absolute URL to their file, which also includes a secret token to access that file.
As an example, Mohamed sent an audio clip to one of his friends over Facebook Messenger and here's the absolute link to the audio file extracted using MITM attack, which anyone can download from Facebook's server, even you, without any authentication.
"GET requests are something that the browsers can remember it in its cache also in its history, Better to have this files played via POST requests with an anti-CSRF token implemented," Mohamed told The Hacker News.
Still Unpatched; No Bug Bounty!
Mohamed reported the issue to Facebook, and the company acknowledged it, but haven't patched it yet. Facebook did not offer any bug bounty to the researcher, as the downgrade attacks do not come under its bug bounty program.
Here's what the Facebook security team told Mohamed:
"We are in the process of rolling out HSTS across various facebook.com subdomains. The fact that we have not rolled it out on particular subdomains does not constitute a valid report under our program."
"In general, sending in reports that claim we should be using defense-in-depth mechanisms like HSTS will not qualify under our program. We make very deliberate decisions about when we roll out (or not) particular protections and so reports suggesting that we make changes there generally do not qualify."
You can watch the above proof-of-concept video demonstration, which shows this attack in action.
We have contacted Facebook security team for the comment and will update the story as soon as we hear from the company.
Russian Channel One alleged hacked and BBC Sherlock Final Leaked
17.1.2017 securityaffairs Hacking
On Monday, Russian State Television Channel One leaked online the BBC Sherlock Final episode, the broadcaster blames hackers.
On Monday, a Russian state television Channel One blamed hackers for the leak online of the final episode of the BBC drama Sherlock a day before its actual planning.
The Russian Channel One was set to transmit the end-of-season episode of the fourth series of Sherlock the detective on Monday just after midnight Moscow time (2100 GMT), simultaneously with the UK.
“The BBC is trying to establish whether an episode of Sherlock was deliberately leaked from within the offices of a Russian state broadcaster, after last night’s hotly-anticipated series finale was circulated on the internet ahead of transmission.” Reported The Telegraph.
“A Russian-language version of the 90-minute episode, entitled The Final Problem, appeared online on Saturday, featuring a three-second continuity announcement identifying it as having originated from Channel One, which holds the rights to air Sherlock in Russia.”
According to the Russian broadcaster, hackers broke into its system and leaked online a full episode professionally dubbed into the Russian language. Of course, copies of the final episode of the BBC drama Sherlock appeared across numerous sites.
“According to preliminary findings, the cause was a hacker attack,” Channel One spokeswoman Larisa Krymova revealed to the AFP.
[the channel] “has been in close contact with the BBC from the moment it learnt of the leak and is carrying out an investigation to identify the source of the material uploaded onto the Internet.”
[Channel One]” will be ready to share full information on the incident with colleagues after the investigation is completed,” explained the Channel One spokeswoman.
The BBC confirmed it had launched an investigation on the case.
“We have brought everything up to beyond gold standard, which is why things like this are so surprising. This is more than an accident.” stated a source at the corporation.
“BBC Worldwide takes breaches of our stringent content security protocols very seriously and we have initiated a full investigation into how this leak has occurred.” said a BBC spokesman.
The show’s producer Sue Vertue invited Sherlock fans to avoid sharing the illegal copy of the final episode.
Follow
sue vertue ✔ @suevertue
Russian version of #Sherlock TFP has been illegally uploaded.Please don't share it. You've done so well keeping it spoiler free.Nearly there
4:54 PM - 14 Jan 2017
1,999 1,999 Retweets 3,934 3,934 likes
Analysts believe that the attack was politically motivated, the attack can be considered a Russia’s retaliation against the BBC.
“There appears to be no profit motive, no benefit to the broadcaster from doing this. What remains is a political motive. The most obvious explanation is that this is punitive.” explained Ben Nimmo, information fellowdefence at the Atlantic Council think tank.
Court Documents Reveal How Feds Spied On Connected Cars For 15 Years
16.1.2017 thehackernews Crime
It's not always necessary to break into your computer or smartphone to spy on you. Today all are day-to-day devices are becoming more connected to networks than ever to add convenience and ease to daily activities.
But here's what we forget: These connected devices can be turned against us because we are giving companies, hackers, and law enforcement a large number of entry points to break into our network.
These connected devices can also be a great boon for law enforcement that can listen and track us everywhere.
Let's take the recent example of 2016 Arkansas murder case where Amazon was asked to hand over audio recordings from a suspect's Echo.
However, that was not the first case where feds asked any company to hand over data from a suspect's connected device, as they have long retrieved such information from connected cars.
According to court documents obtained by Forbes, United States federal agencies have a 15-year history of "Cartapping" — where vehicle tech providers are ordered to hand over almost real-time audio and location data from a user.
How Police Have Spied On Connected-Cars For Years?
Example? In 2014, satellite radio and telematics provider SiriusXM provided location information of a Toyota 4-Runner following a warrant by New York police, which was recently unsealed.
The warrant asked SiriusXM "to activate and monitor as a tracking device the SIRIUS XM Satellite Radio installed on the Target Vehicle" for ten days, and the company admitted to Forbes that it complied with the order.
How did SiriusXM achieve this? The company simply turned on the stolen vehicle recovery feature of its Connected Vehicle Services technology on the target vehicle, Toyota 4-Runner. It's like Apple turning on the Find My iPhone feature to track a customer's location, the court documents [PDF] says.
SiriusXM said it worked with law enforcement periodically to provide such information on its customers with just a valid warrant. The company receives an estimated five valid court orders a year to monitor a suspect, though it declined to offer on-record comment.
SiriusXM is not alone. General Motors (GM) had repeatedly worked with federal agencies to provide not just location but also audio through its OnStar service, where people conversations are recorded when the in-car cellular connection is turned on.
According to Forbes, police asked GM to hand over OnStar data in December 2009 from a Chevrolet Tahoe rented by suspected crack cocaine dealer Riley Dantzler.
OnStar's tracking is so accurate that even after the feds had no idea about Dantzler's car, it's able to "identify that vehicle among the many that were on Interstate 20 that evening," followed him from Houston, Texas, to Ouachita Parish, stopped Dantzler and found cocaine, ecstasy and a gun inside the car.
The defense lawyer argued that the court order compelling OnStar to hand over data was made in Louisiana, but since the tracking started in Texas, it went beyond the court jurisdiction.
In a separate case in 2007, OnStar was ordered to track and continuously reveal the physical location of GMC Envoy SUV of suspected heroin dealer Lamauro Coleman as he traveled around Michigan. When he was stopped, the feds found 43 grams of heroin.
Here's what Coleman's representation argued:
"The statute is silent as to the authority of the government to use a 3rd party product in [place] of physically installing a device of their own."
"Allowing this type of intrusion is a leap the court shouldn't be willing to make. Authorizing OnStar agents to activate the system within a suspect's car renders statutory authority null. It effectively makes every single General Motors vehicle and every OnStar service representative an agent of the government."
When talking about audio data, OnStar competitor ATX Technologies in 2001 was also ordered to provide "roving interceptions" data of a Mercedes Benz S430V. ATX complied with the order in November and spied on audible communications for 30 days, but declined when the FBI asked for an extension in December, the court documents [PDF] revealed.
In 2007, OnStar was ordered to provide audio data from a Chevrolet Tahoe belonging to Gareth Wilson in Ohio.
An emergency button in Wilson's car was automatically pushed without his knowledge, which allowed an officer from the Office of the Fairfield County Sheriff to listen to the conversation about a possible drug deal, reads a 2008 opinion from the case.
After that, when the feds located and searched the car, they found marijuana. Later it turns out that Wilson had not even signed up to the OnStar service, but the service had not been switched off.
Wilson later argued that snooping on his conversations and the subsequent search of his vehicle were illegal, which violated Ohio's wiretapping and electronic surveillance law.
PRIVACY is just a Word!
In all cases, "attempts to have the evidence thrown out foundered. The government was able to argue that as a warrant was signed off, there was no longer an expectation of privacy," Forbes writes.
Here's the statement provided by a GM spokesperson:
"We don't monitor or otherwise track the location of OnStar-equipped cars unless required by a valid court order in criminal procedures or under exigent circumstances; and we don't release the number of those requests. We take our customers' privacy, safety, and security very seriously, and we assist them on average more than 600 times each month in North America with some form of Stolen Vehicle Assistance."
According to American Civil Liberties Union (ACLU) legislative counsel Neema Singh Guliani, such cases of connected car monitoring are part of the growing trend towards government and law enforcement access to internet-enabled tech.
"Fundamentally, what's happening is the technology is moving at warp speed, and there are more and more ways to get information on people, about their personal activities, but you have the law standing utterly still," Guliani told the publication.
"What's often happening the police are trying to massage laws that were written at the time, in some cases when we didn’t even have the internet or the concept of a telephone, or GPS, and massage them to fit these modern technologies."
So, fuck privacy! When you have a good enough car to be internet connected, always expect to be followed everywhere.
The broader takeaway: Internet-connected devices automating your day-to-day habits could be, at some point, used for or against you, legally.
Insidious phishing attack leverages on fake attachments to steal Gmail credentials
16.1.2017 securityaffairs Phishing
Cybercriminals are adopting specially crafted URLs to trick users into entering their Gmail credentials in a new sophisticated phishing campaign.
Security experts discovered a new effective Gmail phishing attack that is able to deceive also tech-savvy people. Crooks leverage on specially crafted URLs to trick victims into providing their Gmail credentials on a phishing page.
The malicious messages are sent from one of the victim’s contacts and pretend to carry a PDF document that can be previewed directly from Gmail. When the victim clicks on the “attachment” image included in the body of the message it is redirected to a Gmail phishing page.
The URL to which the images of attachments point is crafted to appear legitimate:
“data:text/html,https://accounts/google.com,”
The web browser does not display any certificate warning, experts noticed that the apparently legitimate part of the URL is followed by white spaces, which prevent the victims from seeing suspicious strings and an obfuscated script that opens a Gmail phishing page in a new tab. A technical description of the Chrome/Gmail attack has been published on Github.

“You click on the image, expecting Gmail to give you a preview of the attachment. Instead, a new tab opens up and you are prompted by Gmail to sign in again. You glance at the location bar and you see accounts.google.com in there. It looks like this….” states a blog post published by WordFence. “Once you complete sign-in, your account has been compromised.”
This technique is not new, several victims reported similar attacks in July.
One of the main characteristics of the attacks that have been recently detected by the experts is that crooks immediately accessed the compromised accounts and used them to send out phishing emails to all the victim’s contacts. It is still unclear if the attackers have found a way to automate the process.
View image on Twitter
View image on Twitter
Follow
Tom Scott ✔ @tomscott
This is the closest I've ever come to falling for a Gmail phishing attack. If it hadn't been for my high-DPI screen making the image fuzzy…
12:54 PM - 23 Dec 2016
6,132 6,132 Retweets 5,310 5,310 likes
As usual, let me suggest to enable two-factor authentication (2FA) on Gmail in order to avoid being victims of this powerful phishing scheme. However, if the cyber criminals immediately access the compromised account they could also include in a phishing page the 2FA code.
“2FA would make it harder to exploit, but phishing attacks are getting fancier. They capture the 2FA code you enter and immediately start a session elsewhere with your password and 2FA. Hardware 2FA, a security key, (such as a Yubikey) is the only likely way to prevent phishing (excluding targets of state actors)” wrote a user in a discussion on Hacker News.
Google has been aware of this new phishing tactic at least March 2016, for this reason, the Chrome security team suggested introducing a “Not Secure” tag in the address bar for data:, blob: and other URLs that may be exploited by phishers in hacking campaigns.
Weak passwords are still the root cause of data breaches
16.1.2017 securityaffairs Hacking
Key findings of a new study conducted by Keeper Security that analyzed 10 million hacked accounts from breached data dumps for the most popular passwords.
Users’ bad habits are still one of the biggest problems for the IT industry, weak passwords and their reuse on multiple websites every day potentially expose a billion users to cyber attacks.
I’m not surprised by the results of a new study conducted by the security firm Keeper Security that analyzed 10 million hacked accounts from breached data dumps for the most popular passwords.
Below the Top 10 Keeper Security’s 2016 most popular password list:
123456
123456789
qwerty
12345678
111111
1234567890
1234567
password
123123
987654321
Most used passwords continue to be 123456 and 123456789 despite the numerous awareness campaigns on a proper security posture, “123456” accounts for 17 per cent of the overall amount of hacked accounts the firm used as data sample.
“Looking at the list of 2016’s most common passwords, we couldn’t stop shaking our heads. Nearly 17 percent of users are safeguarding their accounts with “123456.” What really perplexed us is that so many website operators are not enforcing password security best practices.” states the report published by Keeper Security. “We scoured 10 million passwords that became public through data breaches that happened in 2016.”
The bad news is that the list of most popular passwords hasn’t changed over the years.
“The list of most frequently used passwords has changed little over the past few years. That means that user education has limits.” continues the study.
This aspect highlights the lack of a security policy that contemplates also the use of strong passwords and enforces it. Four of the top 10 passwords on the list are composed of just six characters or shorter, it’s very easy to brute force them it the system is not properly protected.
“today’s brute-force cracking software and hardware can unscramble those passwords in seconds. Website operators that permit such flimsy protection are either reckless or lazy.”
The list also includes passwords like “1q2w3e4r” and “123qwe,” it is likely that some users attempt to use unpredictable patterns to generate strong passwords. Unfortunately dictionary-based password crackers include these variations.
The last point emerged from the report is that email providers don’t correcly monitor the use of their services made by botnet used for spam.
“Security expert Graham Cluley believes that the presence of seemingly random passwords such as “18atcskd2w” and “3rjs1la7qe” on the list indicates that bots use these codes over and over when they set up dummy accounts on public email services for spam and phishing attacks.” states the report.

Intelligence report claims the Kremlin has cracked Telegram service
16.1.2017 securityaffairs
A raw intelligence document published last week claims Russian cyber experts have cracked Telegram messaging service to spy on opponents.
A raw intelligence document published last week contains much information about President Donald Trump and the approach of the Kremlin to the cyber espionage.
According to the report, the Russian Federal Security Service (FSB) offers bribes for back doors into commercial products, it uses to recruit black hat hackers in every way, including blackmail and coercion. The document reports the FSB used the sale of cheap PC game containing malware to compromise the machines. The report also reveals that the Russian Intelligence has cracked the popular Telegram instant messaging service.
The intelligence report has been prepared by a former British agent, he received the information about the hack of the Telegram service by a “cyber operative.”
“His/her understanding was that the FSB now successfully had cracked this communication software and therefore it was no longer secure to use,” reads the document.
Telegram was used by opponents of the government, for this FSB decided to crack it.Telegram is the work of two Russian brothers and billionaires, Nikolai and Pavel Durov. They had previously created Vkontakte – an alternative to Facebook. However, they got in trouble over some Ukrainian personal data issue and fled to Berlin from Russia in 2014.
Telegram leverages on a custom encryption process it made up itself for this reason security experts and privacy advocates raised several times questions about its security.
When it comes to cyberattacks, Russia’s offensive tactics include targeting foreign governments, especially Western governments; penetrating foreign corporations, especially banks; monitoring of the domestic elite; and attacking political opponents inside Russia and abroad.
According to the cyber spy, the Russian government received the support of an IT staffer at Telegram.

The Russian intelligence in one circumstance compromised some IT gear used by a foreign director of a Russian state-owned enterprise in order to conduct cyber espionage on Western organizations via backdoor.
The FSB offered a U.S. citizen of Russian descent funding for an IT startup in exchange for a backdoor into the software developed by the company. In this way, Russian cyber spies could deliver a malware to launch targeted attacks.
The intelligence document doesn’t provide further details on the cyber operations conducted by Russian hackers.
It is interesting as obvious the interest for the representatives of the G7 governments and NATO.
“External targets include foreign governments and big corporations, especially banks,” the document says, but mainly succeeds only among lower level targets. It says it has “limited success in attacking top foreign targets like G7 governments, security services and but much more on second tier ones through IT back doors, using corporate and other visitors to Russia.”
In order to target G7 governments, nation-state actors hit second-tier organizations, including western private banks and the governments of smaller states that are allied with the Western states.
“Hundreds of agents, either consciously cooperating with the FSB or whose personal and professional IT systems had even unwittingly compromised, were recruited,” continues the document.
The Russian institutions also suffer the cyber attacks of multiple cyber gangs, including Carbanak, Buktrap and Metel.
“The Central Bank of Russia claimed that in 2015 alone there had been more than 20 attempts at serious cyber embezzlement of money from corresponding accounts held there, comprising several billions of Rubles,” continues the report.
New campaign leverages RIG Exploit kit to deliver the Cerber Ransomware
16.1.2017 securityaffairs Virus
Experts from Heimdal Security warned of a spike in cyber attacks leveraging the popular RIG Exploit kit to deliver the Cerber Ransomware.
The RIG exploit kit is even more popular in the criminal ecosystem, a few days ago security experts at Heimdal Security warned of a spike in cyber attacks leveraging the popular Neutrino and RIG EKs.
Now security experts from Heimdal Security are warning of a new campaign leveraging the RIG exploit kit that targets outdated versions of popular applications to distribute the Cerber ransomware.
The attackers leverage an array of malicious domains to launch drive-by attacks against visitors trying to exploit flaws in outdated versions of popular applications such as Flash, Internet Explorer, or Microsoft Edge.
“At the moment, cybercriminals are using a swarm of malicious domains to launch drive-by attacks against unsuspecting users.” states the analysis published by Heimdal Security.
“The campaign works by injecting malicious scripts into insecure or compromised systems. Victims can get infected simply by browsing the compromised or infected websites, without clicking on anything. What exposes them to this attack are outdated versions of the following apps: Flash Player, Silverlight, Internet Explorer or Edge.”
The crooks compromise websites to inject malicious scripts that allow exploiting the flaws in the victim’s browser even without user interaction. reports.

This new campaign leverages on a RIG exploit kit that attempts to exploit the following 8 vulnerabilities:
CVE-2015-8651
CVE-2015-5122
CVE-2016-4117
CVE-2016-1019
CVE-2016-7200
CVE-2016-7201
CVE-2016-3298
CVE-2016-0034
According to the experts from Heimdal security, this variant of the RIG exploit is the Empire Pack version (RIG-E). Cyber criminals also abused domains that are part of the so-called Pseudo-Darkleech gateway that was also exploited by cyber gangs in June 2016 to deliver the CryptXXX ransomware in several campaigns leveraging on the Neutrino Exploit Kit.
It is important to highlight that the success of campaigns like this one is determined by the failure in applying security updates in popular software.
“As you can see, cybercriminals often use vulnerabilities already patched by the software developer in their attacks, because they know that most users fail to apply updates when they’re released. In spite of the wave of attacks, many Internet users still choose to ignore updates, but we hope that alerts such as this one will change their mind and make them more aware of the key security layer that updates represent.” states the report.
Ploutus-D, a new variant of Ploutus ATM malware spotted in the wild
15.1.17 securityaffairs Virus
Security experts from FireEye have spotted a new variant of the infamous Ploutus ATM malware that infected systems in Latin America.
Ploutus is one of the sophisticated ATM malware that was first discovered in Mexico back in 2013. The threat allows crooks to steal cash from ATMs using either an external keyboard attached to the machine or by sending it SMS messages.
Experts at FireEye Labs have recently discovered a new version of the Ploutus ATM malware, dubbed Ploutus-D, that works the KAL’s Kalignite multivendor ATM platform.
The experts observed the Ploutus-D in attacks against ATM of the vendor Diebold, but the most worrisome aspect of the story is that minor changes to the malware code could allow Ploutus-D to target a wide range of ATM vendors in 80 countries.
Below the improved introduced in the Ploutus-D
It uses the Kalignite multivendor ATM Platform.
It could run on ATMs running the Windows 10, Windows 8, Windows 7 and XP operating systems.
It is configured to control Diebold ATMs.
It has a different GUI interface.
It comes with a Launcher that attempts to identify and kill security monitoring processes to avoid detection.
It uses a stronger .NET obfuscator called Reactor.
While similarities between Ploutus and Ploutus-D are:
The main purpose is to empty the ATM without requiring an ATM card.
The attacker must interact with the malware using an external keyboard attached to the ATM.
An activation code is generated by the attacker, which expires after 24 hours.
Both were created in .NET.
Can run as Windows Service or standalone application
The technical analysis revealed that developers improved obfuscation of the code by switching from .NET Confuser to Reactor.
The malware will add itself to the “Userinit” registry key to gain persistence, the key is located at:
\HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
The attacker must interact with the Launcher by connecting a keyboard to the ATM USB or PS/2 port as illustrated in the following picture.

“Once the Launcher has been installed in the ATM, it will perform keyboard hooking in order to read the instructions from the attackers via the external keyboard. A combination of “F” keys will be used to request the action to execute” states the analysis.
The Launcher dropped legitimate files into the system, such as the KAL ATM, along with Ploutus-D. This action makes sure that all the software and versions needed to properly run the malware are present in the same folder to avoid any dependency issues.
The Ploutus-D could allow crooks to steal thousands of dollars in minutes reducing the risk to be caught while stealing the money under the CCTV.
“Once deployed to an ATM, Ploutus-D makes it possible for a money mule to obtain thousands of dollars in minutes.” states the analysis published by FireEye. “A money mule must have a master key to open the top portion of the ATM (or be able to pick it), a physical keyboard to connect to the machine, and an activation code (provided by the boss in charge of the operation) in order to dispense money from the ATM. While there are some risks of the money mule being caught by cameras, the speed in which the operation is carried out minimizes the mule’s risk.”
In order to install the malware attackers likely have access to the targeted ATM software. The experts also speculate the crooks can buy physical ATMs from authorized resellers, which come preloaded with vendor software, or in the worst scenario they could steal the ATMs directly from the bank.
The analysis includes the main differences with previous versions and Indicators of Compromise (IOC) to use for the identification of the threat.
Talos Team discovered serious issues in Aerospike Database Server
15.1.17 securityaffairs Vulnerebility
Security experts from Cisco Talos discovered several flaws in the Aerospike Database Server, a high-performance, and open source NoSQL database.
Security experts from Cisco Talos have discovered several vulnerabilities in the Aerospike Database Server, a high-performance, and open source NoSQL database.
It is used by several major brands for high-performance applications, including Kayak, AppNexus, Adform, adMarketplace and BlueKai.
The Cisco Talos team discovered that Aerospace Database Server 3.10.0.3, and likely earlier versions, is affected by three flaws that have been rated as critical and high severity, including remote code execution and information disclosure issues.
Talos has published technical details of the vulnerabilities in the advisories that also include proof-of-concept (PoC) code for them.
“Talos is disclosing multiple vulnerabilities discovered in the Aerospike Database Server. These vulnerabilities range from memory disclosure to potential remote code execution. This software is used by various companies that require a high performance NoSQL database. Aerospike fixed these issues in version 3.11.” reads the advisory published by the Talos Team.
TALOS-2016-0264 (CVE-2016-9050) – Aerospike Database Server Client Message Memory Disclosure Vulnerability
TALOS-2016-0266 (CVE-2016-9052) – Aerospike Database Server Index Name Code Execution Vulnerability
TALOS-2016-0268 (CVE-2016-9054) – Aerospike Database Server Set Name Code Execution Vulnerability.
The first security vulnerability, tracked as CVE-2016-9050, is an out-of-bounds read issue that affects the client message-parsing functionality. An attacker can exploit it by sending a specially crafted packet to the listening port which can result in memory disclosure or a denial-of-service (DoS) condition.
A second vulnerability, tracked as CVE-2016-9052, is an arbitrary code execution that affects a different function, namely “as_sindex__simatch_by_iname.”
The third one tracked as CVE-2016-9054, is a stack-based buffer overflow that resides in the querying functionality, specifically the “as_sindex__simatch_list_set_binid” function. It is quite simple to exploit, an attacker has to connect to the listening port to remotely execute arbitrary code via a specially crafted packet that triggers the vulnerability.
The flaws were reported to the Aerospike development team on December 23 and they addresses them on January 5 in version 3.11.0.
Talos has published advisories containing technical details and proof-of-concept (PoC) code for each of the vulnerabilities.
Student Faces 10 Years In Prison For Creating And Selling Limitless Keylogger
15.1.2017 thehackernews Virus
A 21-year-old former Langley High School student, who won a Programmer of the Year Award in high school, pleaded guilty on Friday to charges of developing and selling custom key-logging malware that infected thousands of victims.
Zachary Shames from Virginia pleaded guilty in a federal district court and now faces a maximum penalty of up to 10 years in prison for his past deeds.
Shames was arrested this summer while he was working as a technical intern at Northrop Grumman, a security and defense government contractor, developing front-end site code and backend Java software and managing a MySQL database, according to what appears on his Linkedin page.
According to a press release from the U.S. Department of Justice, Shames developed a keylogger in 2013 that allowed users to steal sensitive information, including passwords and banking credentials, from a victim's computer, while he was still a high school student in 2013.
Keylogger is malicious software designed to record every keystroke on a victim's computer.
Shames developed the first versions of now-defunct keylogger known as Limitless Logger Pro, which he sold for $35 on the infamous Hack Forums, according to an anonymous security researcher quoted by Motherboard.
Shames "continued to modify and market the illegal product from his college dorm room," at James Madison University in Harrisonburg, Va. and sold it to more than 3,000 people who, in turn, infected over 16,000 victims, the U.S. Attorney's Office said.
The keylogger malware developed by Shames slowly turned out into a powerful tool.
According to TrendMicro (pdf), apart from key-logging, Limitless KeyLogger can also recover account names and passwords from many popular applications, such as Apple Safari, Firefox, Opera, Google Chrome, Bitcoin wallets, Core FTP, DynDNS, FileZilla, Internet Download Manager, Internet Explorer, Spotify, and more.
Shames pleaded guilty in an Alexandria courtroom, and Judge Liam O'Grady accepted his plea.
Shames now faces a maximum penalty of up to 10 years in prison and has been sentenced to be scheduled for June 16, 2017.
Explained — What's Up With the WhatsApp 'Backdoor' Story? Feature or Bug!
15.1.2017 thehackernews Hacking
What is a backdoor?
By definition: "Backdoor is a feature or defect of a computer system that allows surreptitious unauthorized access to data, " either the backdoor is in encryption algorithm, a server or in an implementation, and doesn't matter whether it has previously been used or not.
Yesterday, we published a story based on findings reported by security researcher Tobias Boelter that suggests WhatsApp has a backdoor that "could allow" an attacker, and of course the company itself, to intercept your encrypted communication.
The story involving the world's largest secure messaging platform that has over a billion users worldwide went viral in few hours, attracting reactions from security experts, WhatsApp team, and Open Whisper Systems, who partnered with Facebook to implement end-to-end encryption in WhatsApp.
Note: I would request readers to read complete article before reaching out for a conclusion. And also, suggestions and opinions are always invited :)
What's the Issue:
The vulnerability relies on the way WhatsApp behaves when an end user's encryption key changes.
WhatsApp, by default, trusts new encryption key broadcasted by a contact and uses it to re-encrypt undelivered messages and send them without informing the sender of the change.
In my previous article, I have elaborated this vulnerability with an easy example, so you can head on to read that article for better understanding.
Facebook itself admitted to this WhatsApp issue reported by Boelter, saying that "we were previously aware of the issue and might change it in the future, but for now it's not something we're actively working on changing."
What Experts argued:
According to some security experts — "It's not a backdoor, rather it’s a feature to avoid unnecessarily re-verification of encryption keys upon automatic regeneration."
Open Whisper Systems says — "There is no WhatsApp backdoor," "it is how cryptography works," and the MITM attack "is endemic to public key cryptography, not just WhatsApp."
A spokesperson from WhatsApp, acquired by Facebook in 2014 for $16 Billion, says — "The Guardian's story on an alleged backdoor in WhatsApp is false. WhatsApp does not give governments a backdoor into its systems. WhatsApp would fight any government request to create a backdoor."
What's the fact:
Notably, none of the security experts or the company has denied the fact that, if required, WhatsApp, on government request, or state-sponsored hackers can intercept your chats.
What all they have to say is — WhatsApp is designed to be simple, and users should not lose access to messages sent to them when their encryption key is changed.
Open Whisper Systems (OWS) criticized the Guardian reporting in a blog post saying, "Even though we are the creators of the encryption protocol supposedly "backdoored" by WhatsApp, we were not asked for comment."
What? "...encryption protocol supposedly "backdoored" by WhatsApp…" NO!
No one has said it's an "encryption backdoor;" instead this backdoor resides in the way how end-to-end encryption has been implemented by WhatsApp, which eventually allows interception of messages without breaking the encryption.
As I mentioned in my previous story, this backdoor has nothing to do with the security of Signal encryption protocol created by Open Whisper Systems. It's one of the most secure encryption protocols if implemented correctly.
Then Why Signal is more Secure than WhatsApp?
You might be wondering why Signal private messenger is more secure than Whatsapp, while both use the same end-to-end encryption protocol, and even recommended by the same group of security experts who are arguing — "WhatsApp has no backdoor."
It's because there is always room for improvement.
The signal messaging app, by default, allows a sender to verify a new key before using it. Whereas, WhatsApp, by default, automatically trusts the new key of the recipient with no notification to the sender.
And even if the sender has turned on the security notifications, the app notifies the sender of the change only after the message is delivered.
So, here WhatsApp chose usability over security and privacy.
It’s not about 'Do We Trust WhatsApp/Facebook?':
WhatsApp says it does not give governments a "backdoor" into its systems.
No doubt, the company would definitely fight the government if it receives any such court orders and currently, is doing its best to protect the privacy of its one-billion-plus users.
But what about state-sponsored hackers? Because, technically, there is no such 'reserved' backdoor that only the company can access.
Why 'Verifying Keys' Feature Can't Protect You?
WhatsApp also offers a third security layer using which you can verify the keys of other users with whom you are communicating, either by scanning a QR code or by comparing a 60-digit number.
But here’s the catch:
This feature ensure that no one is intercepting your messages or calls at the time you are verifying the keys, but it does not ensure that no one, in the past had intercepted or in future will intercept your encrypted communication, and there is no way, currently, that would help you identify this.
WhatsApp Prevention against such MITM Attacks are Incomplete
WhatsApp is already offering a "security notifications" feature that notifies users whenever a contact's security code changes, which you need to turn on manually from app settings.
But this feature is not enough to protect your communication without the use of another ultimate tool, which is — Common Sense.
Have you received a notification indicating that your contact's security code has changed?
Instead of offering 'Security by Design,' WhatsApp wants its users to use their common sense not to communicate with the contact whose security key has been changed recently, without verifying the key manually.
The fact that WhatsApp automatically changes your security key so frequently (for some reasons) that one would start ignoring such notifications, making it practically impossible for users to actively looking each time for verifying the authenticity of session keys.
What WhatsApp should do?
Without panicking all one-billion-plus users, WhatsApp can, at least:
Stop regenerating users' encryption keys so frequently (I clearly don't know why the company does so).
Give an option in the settings for privacy-conscious people, which if turned on, would not automatically trust new encryption key and send messages until manually accepted or verified by users.
...because just like others, I also hate using two apps for communicating with my friends and work colleagues i.e. Signal for privacy and WhatsApp because everyone uses it.
Hackers that hit MongoDB installs now switch on exposed Elasticsearch clusters
15.1.2017 securityaffairs Hacking
The hackers that targeted MongoDB installations with ransom attacks now switch on the exposed Elasticsearch clusters with a similar tactic.
A few days ago I reported the news of a string of cyber attacks against MongoDB databases. Hackers broke into unprotected MongoDB databases, stealing their content, and asking for a ransom to return the data.
Now it seems that the same hackers have started targeting Elasticsearch clusters that are unprotected and accessible from the internet.
Elasticsearch is a Java-based search engine based on the free and open-source information retrieval software library Lucene. It is developed in Java and is released as open source, it is used by many organizations worldwide.
Crooks are targeting Elasticsearch cluster with ransom attacks in the same way they have made with MongoDB.
The news was reported on the official support forums this week, a user who was running a test deployment accessible from the internet reported hackers removed all the indices and added a new index “warning” was created there.
The user has found the following text from the raw index data:
“SEND 0.2 BTC TO THIS WALLET: 1DAsGY4Kt1a4LCTPMH5vm5PqX32eZmot4r IF YOU WANT RECOVER YOUR DATABASE! SEND TO THIS EMAIL YOUR SERVER IP AFTER SENDING THE BITCOINS…”
Something quite similar to the recent ransom attacks against MongoDB.
“Late last week, a malicious attack was initiated, in which data from thousands of open source databases was copied, deleted and held for ransom. Although no malware, or “ransomware” was used in these attacks, and they are not related to product vulnerabilities, they nonetheless represent serious security incidents involving a data loss, or even a data breach.” reads the description of the discussion in the official forum. “The good news is that data loss from similar attacks is easily preventable with proper configuration.”

According to the security researcher Niall Merrigan, more than 600 Elasticsearch clusters have been targeted by the hackers.
Unfortunately, the number of internet-accessible Elasticsearch installs are much greater, roughly 35,000. The experts believe that the number of wiped Elasticsearch installs would rapidly increase, has it has happened for the MongoDB databases.
View image on Twitter
View image on Twitter
Follow
Niall Merrigan @nmerrigan
The #Elastic ransomware is speading .. now 600+ hosts
8:48 AM - 13 Jan 2017
10 10 Retweets 3 3 likes
It is important to protect Elasticsearch clusters exposed on the Internet as soon as possible, there is no reason to expose them.
Researchers from the company Itamar Syn-Hershko have published a blog post that includes recommendations for securing Elasticsearch installations.
“Have a Single Page Application that needs to query Elastic and get jsons for display? Pass it through a software facade that can do request filtering, audit-logging and most importantly, password-protect your data,” states the blog post. “Without that, (a) you are for sure binding to a public IP and you shouldn’t, (b) you are risking unwanted changes to your data, (c) and the worst – you can’t control who accesses what and all your data is visible for all to see. Just what’s happening now with those Elasticsearch clusters.”
The experts suggest disabling the features that users don’t need such as dynamic scripting with non-sandboxed languages (mvel, groovy) used in old versions.
As usual, let me suggest you to avoid paying, but report the incident to law enforcement.
SSL a internetové bankovnictví? Ne vždy si rozumějí
15.1.2017 SecurityWorld Zabezpečení
Některé banky SSL podceňují – přihlášení do internetového bankovnictví tak nemusí být vždy bezpečné.
Protokol SSL/TLS je technologií běžně užívanou pro šifrování komunikace mezi klientskými počítači a serverem. Ač není jediným mechanismem užívaným bankami pro ochranu internetového bankovnictví, bývá pomyslným základním kamenem této ochrany.
Přesto v testu společnosti Xiphos Research, uskutečněném začátkem roku 2016, dopadly britské banky poměrně špatně a u většiny z nich byly objeveny větší či menší nedostatky v zabezpečení SSL užívaném na jejich serverech. Obdobný test vykonaný společností Alef Nula v českých podmínkách dopadl o poznání lépe – většina bank v něm uspěla.
Ve svém průzkumu otestovala britská společnost Xiphos Research 84 bank působících na tamním trhu. Banky hodnotila písmeny podobně jako na některých univerzitách. Celkem 14 procent z testovaných bank si vysloužilo nejhorší známku F, protože nastavení jejich serverů a používaný SSL protokol vykazovaly významné bezpečnostní chyby.
Nedostatečně zabezpečený server internetového bankovnictví byl detekován u poloviny z 59 britských bank a finančních institucí. Stejně dopadlo i 79 procent serverů užívaných 25 bankami působícími ve Velké Británii, ale majícími zahraniční vlastníky.
V osmi případech obsahoval používaný SSL protokol zranitelnost Poodle, která byla detekována bezpečnostním týmem Googlu už v říjnu 2014. Tato zranitelnost přitom může umožnit útočníkovi dostat se k dešifrované části obsahu SSL relace mezi klientem a serverem.
Ukázalo se také, že banky často využívají zastaralé verze SSL šifrování nebo překonané SHA šifrovacího klíče.
České banky úspěšnější
Nepříliš dobré výsledky britských bank inspirovaly k vykonání podobného testu i bezpečnostní tým společnosti Alef Nula.
Čeští experti využili stejnou metodologii jako výzkumníci Xiphos Research a otestovali nastavení SSL na celkem 33 serverech internetového bankovnictví provozovaných 30 českými bankami (resp. bankami užívajícími pro internetové bankovnictví adresy v doméně .cz).
Úroveň zabezpečení byla hodnocena na zmíněné škále SSL Server Rating. Ta podle výsledků měření hodnotí bezpečnost nastavení SSL stupni A (velmi vysoká) až F (vykazující závažné nedostatky a zranitelnosti).
U nejlepšího hodnocení A rozlišuje ještě úroveň A+, určenou pro případy, kdy banky implementovaly některá nadstandardní opatření, a A– znamenající, že v zabezpečení SSL protokolu se objevily jen méně závažné nedostatky.
Oproti Británii dopadl test v Česku o poznání lépe – více než dvě třetiny českých bank získaly hodnocení A. U deseti z nich se nalezly jen marginální bezpečnostní nedostatky, takže byly ohodnocené stupněm A–, naopak čtyři získaly nejvyšší hodnocení A+, což znamená, že zabezpečení SSL na svých serverech zvýšily pomocí nadstandardních opatření.
A u 11 serverů pak byly zjištěny různě závažné slabiny a/nebo konfigurační nedostatky SSL.
Chyby? Opět boduje pudl
Stejně jako v případě bank ve Velké Británii také u českých bank byl nejčastěji objevenou závažnou zranitelností Poodle. V Česku to bylo ale jen u dvou bankovních serverů, tedy přibližně u šesti procent. Ve Velké Británii to byla téměř desetina.
Po jednom serveru obsahovalo ve svém bezpečnostním protokolu zranitelnosti Crime a Logjam. Zranitelnost Crime umožňuje útočníkovi učinit tzv. session hijacking, tedy za určitých okolností převzít SSL relaci, Logjam pak dokáže snížit složitost užitého šifrování na velmi nízkou úroveň, v důsledku čehož je možné relativně snadno dešifrovat a modifikovat probíhající komunikaci.
Zmíněné zranitelnosti mohou představovat citelnou hrozbu pro aplikace pracující s důvěrnými daty. V kombinacích, které by mohly reálně ohrozit bezpečnost klientů užívajících internetové bankovnictví, se vyskytovaly v případě dvou z testovaných serverů.
Pokud jde o verzi používaných protokolů a šifrovacích klíčů, byla situace v Česku podobná Velké Británii. U pěti serverů užívajících SSL bylo zjištěno využívání zastaralého šifrovacího algoritmu RC4 a u stejného počtu byly detekovány slabiny v konfiguraci Diffie Hellmanova algoritmu výměny klíčů (užití malých prvočísel).
Test také objevil nedostatky v oblasti podpory protokolů. Dva servery stále spoléhaly na zastaralý a nedostatečně zabezpečený protokol SSL verze 3.0 a celkem šest analyzovaných SSL instancí nepodporovalo nejnovější a nejbezpečnější verzi (1.2) protokolu TLS.
Na pěti zkoumaných serverech byly používány certifikáty SHA-1, které v současnosti přestávají být považované za bezpečné a všechny nejčastěji užívané prohlížeče plánují v blízké době ukončit jejich podporu. Certifikát nepodepsaný důvěryhodnou certifikační autoritou používal pouze jeden z analyzovaných serverů.
Obezřetnost, nikoli panika
Přestože třetina serverů poskytujících v České republice služby internetového bankovnictví obsahovala v době průzkumu nedostatky či zranitelnosti v užitých SSL mechanismech, není třeba propadat panice.
Útok na většinu z nich by totiž byl poměrně komplikovaný. Reálně využitelné zranitelnosti, které představují citelnou hrozbu pro chráněnou komunikaci mezi klientem a bankou, vykazovaly pouze dva ze zkoumaných serverů (oba hodnocené stupněm F).
V případě jednoho dalšího by potom úspěšný útok na bezpečnost navázaného spojení mohl být potenciálně realizován za velmi specifických okolností. Realisticky závažné zranitelnosti se tedy týkaly pouze šesti až devíti procent analyzovaných serverů.
Jak se testuje SSL v bankovních systémech
Český i britský test bezpečnosti SSL mechanismů využívaly stejnou metodologii. Použil se při nich nástroj SSL Server Test a úroveň zabezpečení byla hodnocená na škále SSL Server Rating v rozmezí A až F, s doplňkovým označením písmenem T pro servery s nedůvěryhodným certifikátem.
Parametry užívanými pro zařazení ve škále jsou typy podporovaných protokolů, tvořící 30 procent výsledného hodnocení, dalších 30 procent připadá na užité mechanismy bezpečné výměny klíčů a 40 procent zaujímají typy podporovaných šifer.
Router jako šedé místo v zabezpečení
14.1.2017 SecurityWorld Zabezpečení
Směrovač v domácnosti je, co se osvěty a prevence v oblasti bezpečnosti týče, stále podceňovaným prvkem. Co všechno vám správné nastavení může přinést a co naopak špatného způsobit?
Co se týče routerů, uživatelé se příliš neupozorňují na to, že správné nastavení tohoto zařízení, které je v řadě případů branou do internetu, může mít zásadní vliv na jejich on-line bezpečnost.
Poté, co si router koupí a zapojí ho, často se nedopracují k tomu, aby defaultní nastavení změnili, a tím eliminovali rizika, která tato základní konfigurace může způsobit.
Na domácí routery se kladou stále větší nároky jak z pohledu výkonnosti v důsledku narůstajícího počtu zařízení připojených do internetu v domácnosti, tak z hlediska bezpečnosti. Počet útoků vedených přes routery přitom neustále roste.
Ze světa i z České republiky jsou známé řady případů, kdy zotročené domácí routery posloužily například k DDoS útokům. V tomto textu se zaměříme na nejčastější nedostatky a důvody napadení domácích routerů.
1. Firmware
Specializovaný firmware pro routery obsahuje chyby stejně jako programy, které každodenně používáme, a proto taktéž vyžaduje pravidelné záplatování. Tento zdánlivě jednoduchý krok však může představovat hned několik problémů.
Jedním z nich je někdy poměrně náročné hledání poslední verze firmwaru pro konkrétní typ routeru, jenž uživatel používá. Když se uživateli podaří najít přesně ten, který hledal, musí ho ještě do routeru nainstalovat, což zase nemusí být u všech modelů úplně jednoduché a intuitivní.
Pokud to jde, je dobré, když si uživatel může nastavit automatické nebo alespoň poloautomatické upozorňování na updaty sám, aby mu žádný bezpečnostní update neunikl. Na update by se nemělo zapomínat ani v případě koupě nového routeru, protože mezi nahráním firmwaru do routeru při výrobě a spuštěním routeru v domácnosti může uplynout poměrně dlouhá doba.
Zde je důležité připomenout, že i když vám router poskytl váš provider (ať už ve formě pronájmu nebo koupě), zodpovědnost za aktualizace firmwaru nesete sami. Když se bavíme o firmwaru, může nastat i jedna nezáviděníhodná situace – tedy ta, že výrobce routeru podporu pro daný firmware ukončil.
I s tím mají nejen uživatelé v České republice své neblahé zkušenosti. Proto by se měli mít uživatelé na pozoru a již při koupi nového routeru by si měli ověřit, zda výrobce vydává pro firmware pravidelné updaty.
2. Universal plug and play
UPnP je protokol, který programům umožňuje mimo jiné jednoduše měnit nastavení routeru, konkrétně otevřených portů, které programy potřebují pro svou komunikaci. Protokol byl primárně vytvořen pro použití v lokálních sítích, a tak neobsahuje jeden z důležitých bezpečnostních prvků, jímž je autentizace.
Mnoho routerů má však dostupnost UPnP nastavenou nejen z lokální sítě, ale také z celého internetu. Bezpečnostní riziko je samozřejmě větší, když je protokol UPnP dostupný z internetu, což umožňuje útočníkům přistoupit ke konfiguraci portů, a zneužít je tak například pro získání přístupu do lokální sítě nebo jako proxy pro surfování.
Implementace protokolu UPnP v routerech je také často děravá, a proto se doporučuje protokol raději vypnout a přesměrování služeb na porty udělat ručně.
Další bezpečnostní riziko spočívá v defaultně zapnutém protokolu již z výroby. Běžný uživatel si totiž zapnutého nebo vypnutého UpnP protokolu nemusí vůbec všimnout, a proto jeho defaultní zapnutí v domácích routerech představuje určité riziko, které by výrobci routeru mohli velmi jednoduše eliminovat, a předejít tak zbytečným problémům.
3. Přístupnost administrace routeru z internetu
Dostupnost rozhraní umožňujícího nastavení routeru z prostředí internetu představuje zásadní riziko. Tzv. vzdálený přístup (remote access) slouží k administraci nastavení routeru, pokud se uživatel nachází mimo lokální síť.
Podíl domácností, které by tento doplněk využilo, bude však velmi malé. Problém pak opět nastává v routerech, jež nabízejí vzdálenou administraci routeru již v defaultním nastavení.
V tom případě musí uživatel v nastavení routeru tuto funkcionalitu vypnout. Podobně jako defaultně zapnutý UPnP protokol nebo děravý firmware také tento nežádoucí doplněk uživatele v práci s internetem nijak neomezuje, a proto jej obvykle nic nenutí tuto vzdálenou administraci znemožnit, což může být v kombinaci s defaultním nastavením přihlašování do administrace routeru kritickým problémem pro bezpečnost sítě.
Pro minimalizaci rizika je možné omezit také přístup do administrace z lokální sítě jenom pro jedno zařízení, protože útočník může bezpečnost routeru ohrozit i pomocí skriptu nahraného v rámci stránek, které si uživatel připojený přes daný router prohlíží.
4. Podcenění prvotního nastavení
Router má po zakoupení do domácnosti první šanci na správné nastavení při prvním spuštění. Pokud však vše funguje tak, jak má (bez ohledu na bezpečnostní díry), často se stane, že jeho první šance je zároveň tou poslední.
Problém velké většiny modelů spočívá již v úvodním průvodci nastavením, který uživatele nenavede nebo nepřinutí ke změně nebo zvolení vlastních přístupových údajů k administraci routeru.
Pokud se v průvodci nastavení routeru toto nevyžaduje, z uživatelského hlediska není třeba nic měnit. Defaultní kombinace jména a hesla k administraci routerů jsou ale na internetu velmi lehce dohledatelné pro každý model routeru od jakéhokoliv výrobce. A pokud se tam náhodou nějaký model od výrobce nenachází, stačí zkusit použít přístupové údaje jiných modelů, protože ty se u stejného výrobce často opakují. Obejít by to bylo možné například tak, že by si uživatel při prvotní instalaci musel zvolit své heslo pro administraci sám.
U výrobců routerů by také bylo žádoucí, kdyby již při prvním spuštění routeru průvodce vyžadoval zvolení IP adresy jejího administrátorského rozhraní. Nahrazení nejčastěji používané adresy 192.168.1.1 nebo 192.168.0.1 může uživatele před částí útoků ochránit. Jde hlavně o CSRF (Cross Site Request Forgery), který se jako zranitelnost nachází v řadě routerů. Cílem útoku je pak nejčastěji změna nastavení DNS záznamu.
Snaha o osvětu
Trh v oblasti routerů je poměrně velký a zásadním způsobem do něj vstupují také poskytovatelé připojení, kteří jsou jejich velkými odběrateli a dodavateli zároveň. Běžného uživatele pak při výběru domácího routeru zajímají většinou jenom dvě věci: cena a funkčnost připojení. Nic z výše uvedených funkcí není pak natolik uživatelsky zajímavé, aby přimělo běžného uživatele ke studiu funkcí UPnP protokolu nebo vzdálené administrace.
Bez pochopení základního fungování internetu a jeho protokolů si tak ale nemůže uvědomit ani reálné riziko chybného nastavení svého routeru. Proto by měli výrobci routerů a poskytovatelé připojení pochopit důležitost defaultních nastavení a funkcionalit, které routery využívají.
Právě úvodní průvodce nastavení routeru může být zásadní pro jeho další správné a bezpečné fungování v domácnosti. Při správném a hlavně dostatečně srozumitelném nastavení tak může uživatel sám zhodnotit, které funkcionality bude skutečně využívat, a nevystavovat tak svou domácí síť zcela zbytečným rizikům.
@Kapustkiy is back and hacked the Government of Venezuela
14.1.2017 securityaffairs Hacking
The popular hacker Kapustkiy hacked a website belonging to the Government of Venezuela in protest against the dictatorship of Nicolas Maduro.
The White hat hacker Kapustkiy has hacked the Government of Venezuela and leaked data on Pastebin http://pastebin.com/ud0pewGL.
Kapustkiy hacked the website www.gdc.gob.ve by exploiting a Local File Inclusion (LFI) vulnerability in:
http://www.gdc.gob.ve/2.0/gui_resources/css/?f=../../../../../../../../../../etc/passwd
“I have found a LFI in the Capital website of the Government of Venezuela. And I hacked other two websites by exploiting a SQLi. I found around 800 users in the second website and the third website had 52 accounts.” said Kapustkiy. “I hacked them in protest against the dictatorship of Nicolas Maduro.”
The hacker hacked in protest against the President of Venezuela explaining that he is destroying the life of innocent people.
“Hacked By Kapustkiy from New World Hackers. I am against the dictatorship of Nicolas Maduro on Venezuela. I am tired of seeing, Nicolas Maduro is still running as president. It is time to leave, you motherfucker.” states the manifesto published on PasteBin.
Kapustkiy is currently working as white hat hacker reporting the flaws, but this time he made an exception for a political motivation.
In December 2016, Kapustkiy hacked the Russian Visa Center in the USA and accessed information of around 3000 individuals.
In the same month, the young hacker hacked the website of the Costa Rica Embassy in China and the breached the Slovak Chamber of Commerce (www.scci.sk) affecting more than 4,000 user records.
In 2016, Kapustkiy targeted several organizations, including the Consular Department of the Embassy of the Russian Federation, the Argentinian Ministry of Industry, the National Assembly of Ecuador, the Venezuela Army, the High Commission of Ghana & Fiji in India, the India Regional Council as well as organizations and embassies across the world.
He also broke into the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
WordPress 4.7.1 released, patches eight vulnerabilities and 62 bugs
14.1.2017 securityaffairs Vulnerebility
According to the release notes the latest version of WordPress 4.7.1 addresses eight security vulnerabilities and other 62 bugs.
Wednesday the latest version of WordPress 4.7.1 was released by the WordPress Team, it is classified as a security release for all previous versions. According to the release notes, the new version addresses eight security flaws and other 62 bugs.
According to the WordPress team, the previous WordPress 4.7 release has been downloaded over 10 million times since its release on December 6, 2016.
The PHPMailer library was updated to patch a remote code execution (RCE) vulnerability, tracked as CVE-2016-10033. Aaron D. Campbell, WordPress Core developer, says that “No specific issue appears to affect WordPress or any of the major plugins we investigated but, out of an abundance of caution, we updated PHPMailer in this release”.
The experts, Brian Krogsgard and Chris Jean, discovered that the REST API “exposed data on all users who had authored a post of a public post type.”

The new version addresses two Cross-site scripting(XSS) vulnerabilities in the WordPress plugins.
“Cross-site scripting (XSS) via the plugin name or version header on update-core.php. Reported by Dominik Schilling of the WordPress Security Team.” reads the advisory.
The second XSS resides in the “theme name fallback” and was reported by Mehmet Ince.
Among the issues fixed by the WordPress Team, there are also two Cross-site request forgery (CSRF) vulnerabilities.
The CSRF bypass via uploading a Flash file was reported by Abdullah Hussam, while Ronnie Skansing reported a CSRF in the accessibility mode of widget editing.
The researchers explained that one of theme identified by Abdullah Hussam can be exploited via a specially crafted Flash file, while the other affects the accessibility mode of widget editing, reported by Ronnie Skansing.
The new release also fixes a weak cryptographic security related to multisite activation key discovered by Jack, the expert described it in a blog post.
Another issue was discovered by John Blackbourn of the WordPress Security Team, it is a post via email checks mail.example.com if default settings aren’t changed.
“Download WordPress 4.7.1 or venture over to Dashboard → Updates and simply click “Update Now.” Sites that support automatic background updates are already beginning to update to WordPress 4.7.1” states the advisory.
A report recently issued by the security firm Sucuri claims that WordPress continues to be the most hacked CMS.
As explained in this article published weeks ago by Pierluigi Paganini, more than 8,800 WordPress Plugins out of 44,705 are flawed
“Security firm RIPS Technologies has analyzed 44,705 in the official WordPress plugins directory and discovered that more than 8,800 of them are flawed.” states the post.
WhatsApp Backdoor allows Hackers to Intercept and Read Your Encrypted Messages
13.1.2017 thehackernews Vulnerebility
Most people believe that end-to-end encryption is the ultimate way to protect your secret communication from snooping, and it does, but it can be intercepted if not implemented correctly.
After introducing "end-to-end encryption by default" last year, WhatsApp has become the world's largest secure messaging platform with over a billion users worldwide.
But if you think your conversations are completely secure in a way that no one, not even Facebook, the company that owned WhatsApp, can intercept your messages then you are highly mistaken, just like most of us and it's not a new concept.
Here's the kick: End-to-end encrypted messaging service, such as WhatsApp and Telegram, contain a backdoor that can be used, if necessary, by the company and of course hackers, or the intelligence agencies to intercept and read your end-to-end encrypted messages, and that’s all without breaking the encryption.
And that backdoor is — TRUST.
No doubt most of the encrypted messaging services generate and store private encryption key offline on your device and only broadcast the public key to other users through the company's server.
Like, In the case of WhatsApp, we have to trust the company that it will not alter public key exchange mechanism between the sender and receiver to perform man-in-the-middle attack for snooping on your encrypted private communication.
Tobias Boelter, security researcher from the University of California, has reported that WhatsApp's end-to-end encryption, based on Signal protocol, has been implemented in a way that if WhatsApp or any hacker intercepts your chats by exploiting trust-based key exchange mechanism, you will never come to know if any change in encryption key has occurred in the background. YES, that's possible.
Note that this backdoor has nothing to do with the Signal encryption protocol, created by Open Whisper Systems. It's one of the most secure encryption protocols if implemented correctly.
“WhatsApp has implemented a backdoor into the Signal protocol, giving itself the ability to force the generation of new encryption keys for offline users and to make the sender re-encrypt messages with new keys and send them again for any messages that have not been marked as delivered. The recipient is not made aware of this change in encryption.” The Guardian reports.
However, users can receive notifications when security codes change, only if "security notifications" option has been turned ON manually from the app settings.
Meanwhile, Fredric Jacobs, who was iOS developer at Open Whisper Systems, also reacted on twitter and admitted that "if you don't verify keys Signal/WhatsApp/... can man-in-the-middle your communications," however he also added, "It's ridiculous that this is presented as a backdoor. If you don't verify keys, authenticity of keys is not guaranteed. Well known fact."
Facebook Haven't Fixed It Since June, 2016
Boelter told the Guardian that he reported the backdoor to Facebook in April 2016 -- the time when WhatsApp implemented end-to-end encryption by default in its messaging app.
However, the researcher was told in reply that Facebook was already aware of the issue and justified it as an "expected behavior."
"WhatsApp says that it implemented the backdoor to aid usability. If the backdoor is not in place, messages sent to an offline user, who then changes their smartphone or has to re-install WhatsApp and in doing so generates new security keys for themselves, would remain undelivered once the user comes back online." The Guardian says.
"In many parts of the world, people frequently change devices and Sim cards. In these situations, we want to make sure people’s messages are delivered, not lost in transit." a WhatsApp spokesperson told the Guardian.
And Yeah, the backdoor still exists in WhatsApp.
How to Protect Yourself from Spying?
To prevent the possibility of MITM attacks, WhatsApp also offers a third security layer in its app using which you can verify the keys of other users with whom you are communicating, either by scanning a QR code (drawback: physical presence required) or by comparing a 60-digit number by another way of communication.
"Security codes are just visible versions of the special key shared between you - and don't worry, it's not the actual key itself, that's always kept secret."
However, this option is useful only when you are actively looking to verify the authenticity of session keys and, we know, only one privacy-conscious paranoid user in thousands would do that.
Secure Alternative to Whatsapp
Oh! You must be thinking — Which secure messaging service then offers protection against such broken trust and interception?
There are several alternatives, such as "Signal Private Messenger", itself, developed by Open Whisper Systems and it's most recommended secure message app.
ShadowBrokers exits releasing another arsenal of tools to hack Windows
13.1.2017 securityaffairs BigBrothers
The ShadowBrokers hacking group that broke into the NSA arsenal and stole its hacking tools is signing off, leaving a gift to the security community.
The mysterious hacking group calling themselves “The Shadow Brokers” has apparently decided to put an end to their failed attempts to sell exploits and hacking tools they claimed to have stolen from the NSA-linked Equation Group.
A few days ago the notorious hacker group Shadow Brokers announced the sale of an archive of Windows exploits and hacking tools stolen from the NSA-linked Equation group.

The ShadowBrokers is the hacker crew that leaked a portion of the arsenal of the NSA-Linked Equation Group, a database containing hacking tools and exploits.
In October 2016, the hackers leaked a dump containing a list of servers that were hacked by the NSA-linked group known as Equation Group.
The Equation group compromised these targets using the hacking tools codenamed as INTONATION and PITCHIMPAIR. The ShadowBrokers provided the links to two distinct PGP-encrypted archives, the first one offered for free as a proof of the hack (its passphrase was ‘auctioned’), for the second one the group requested 1 million BTC .
The first archive was containing roughly 300MBs of data, including firewall exploits, hacking tools, and scripts with cryptonyms like BANANAUSURPER, BLATSTING, and BUZZDIRECTION.
The Equation Group ‘s hackers targeted products made by Cisco, Fortigate, Juniper, TOPSEC, and Watchguard.
Early October, TheShadowBrokers complained that no one seems to be bidding on their precious archive, an alleged member of the hacker group expressed his dissent on the lack of interest in ponying up bitcoins to release the full NSA data dump.
In December 2016, the group announced the launch of a crowdfunding campaign for the stolen arsenal because its auction received offers for less than two bitcoins.
In December 2016, when they changed the model of sale offering the NSA’s hacking arsenal for direct sale on an underground website.
Now the group has decided to exit from the scene, according to the message published on the website it used for direct sales of the hacker tools, the hackers will go in the dark because continuing their activities is too risky.
The group explained that their main target was the sale of the stolen hacking tools and exploits, but no one has brought them.
Shadow Brokers crew published a Bitcoin address explaining that they would return in the case someone will pay 10,000 Bitcoins for the exploits. The offer will be valid forever.
Before leaving the cyber arena, the group decided to release some gifts, a collection of 58 Windows hacking tools. These tools are able to avoid detection of security solutions. If you are interested in downloading the precious archive visit the group’s website on ZeroNet:
https://onlyzero.net/theshadowbrokers.bit
Donald Trump appoints a CyberSecurity Advisor Whose Own Site is Damn Vulnerable
13.1.2017 thehackernews Vulnerebility
Former New York City Mayor Rudolph W. Giuliani has been appointed as a cyber security advisor for the President-elect Donald Trump, but it appears that he never actually checked the security defenses of his own company's website.
Giuliani is going to head a new Cybersecurity Working group for the President-elect, and "will be sharing his expertise and insight as a trusted friend concerning private sector cyber security problems and emerging solutions developing in the private sector," the Trump's Transition Team announced Thursday.
Trump administration has appointed Giuliani after citing his 16 years of experience "providing security solutions in the private sector," but the news met online criticism with many users on Twitter asking:
'What does the former New York mayor know about cyber security?'
As the news broke, online users started scanning his website "www.giulianisecurity.com" and found that the site for Giuliani Security & Safety is simply a disaster.
The site runs on an old version of Joomla! — a free, open-source content management system (CMS) — which is vulnerable to more than a dozen flaws.
The website also uses an outdated version of the script language PHP, uses an expired SSL certificate, runs over a 10-year-old version of FreeBSD OS server and even fails to follow other basic security practices.
According to Robert Graham of Errata Security, Giuliani did not build the site himself; instead he "contracted with some generic web designer to put up a simple page with just some basic content."
"There's nothing on Giuliani's server worth hacking. The drama over his security, while an amazing joke, is actually meaningless," Graham said in a blog post. "All this tells us is that Verio/NTT.net is a crappy hosting provider, not that Giuliani has done anything wrong."
Although it really doesn't matter who has created the website, if you are in cyber security business to "help the government plan to make us more secure," such ignorance hardly inspires confidence in the expertise of that person.
Giuliani is the CEO of his own private-sector cybersecurity venture, Giuliani Partners, which is an international cyber security consulting firm that claims to offer "a comprehensive range of security and crisis management services."
What Giuliani Partners actually does is not known, because the company promotes its crime reduction successes in countries, but not its cybersecurity work.
The venture recently struck a deal with BlackBerry to provide companies and governments cyber security support by assessing infrastructures, identifying potential cyber security vulnerabilities, addressing gaps and securing endpoints "with the goal of offering another channel to bring customers to a new standard of security."
This clearly suggests that the company is doing something right.
Much details about Giuliani's role in the Trump administration were not immediately available. We'll update the story with new developments.
The “EyePyramid” attacks
13.1.2017 Kaspersky Cyber
On January 10, 2017, a court order was declassified by the Italian police, in regards to a chain of cyberattacks directed at top Italian government members and institutions.
The attacks leveraged a malware named “EyePyramid” to target a dozen politicians, bankers, prominent freemasons and law enforcement personalities in Italy. These included Fabrizio Saccomanni, the former deputy governor of the Bank of Italy, Piero Fassino, the former mayor of Turin, several members of a Masonic lodge, Matteo Renzi, former prime minister of Italy and Mario Draghi, president of the European Central Bank.
The malware was spread using spear-phishing emails and the level of sophistication is low. However, the malware is flexible enough to grant access to all the resources in the victim’s computer.
During the investigation, involved LEAs found more than 100 active victims in the server used to host the malware, as well as indications that during the last few years the attackers had targeted around 16,000 victims. All identified victims are in Italy, most of them being Law Firms, Consultancy services, Universities and even Vatican Cardinals.
Evidence found on the C&C servers suggests that the campaign was active since at least March 2014 and lasted until August 2016. However, it is suspected that the malware was developed and probably used years before, possibly as far back to 2008.
Two suspects were arrested on January 10th, 2017 and identified as 45-year-old nuclear engineer Giulio Occhionero and his 47-year-old sister Francesca Maria Occhionero.
Investigation
Although the Italian Police Report doesn’t include malware hashes, it identified a number of C&C servers and e-mails addresses used by the malware for exfiltration of stolen data.
Excerpt from the Italian court order on #EyePyramid
(http://www.agi.it/pictures/pdf/agi/agi/2017/01/10/132733992-5cec4d88-49a1-4a00-8a01-dde65baa5a68.pdf)
Some of the e-mail addresses used for exfiltration and C&C domains outlined by the police report follow:
E-mail Addresses used for exfiltration
gpool@hostpenta[.]com
hanger@hostpenta[.]com
hostpenta@hostpenta[.]com
purge626@gmail[.]com
tip848@gmail[.]com
dude626@gmail[.]com
octo424@gmail[.]com
tim11235@gmail[.]com
plars575@gmail[.]com
Command-and-Control Servers
eyepyramid[.]com
hostpenta[.]com
ayexisfitness[.]com
enasrl[.]com
eurecoove[.]com
marashen[.]com
millertaylor[.]com
occhionero[.]com
occhionero[.]info
wallserv[.]com
westlands[.]com
Based on these indicators we’ve quickly written a YARA rule and ran it through our systems, in order to see if it matches any samples.
Here’s how our initial “blind”-written YARA rule looked like:
rule crime_ZZ_EyePyramid {
meta:
copyright = ” Kaspersky Lab”
author = ” Kaspersky Lab”
maltype = “crimeware”
filetype = “Win32 EXE”
date = “2016-01-11”
version = “1.0”
strings:
$a0=”eyepyramid.com” ascii wide nocase fullword
$a1=”hostpenta.com” ascii wide nocase fullword
$a2=”ayexisfitness.com” ascii wide nocase fullword
$a3=”enasrl.com” ascii wide nocase fullword
$a4=”eurecoove.com” ascii wide nocase fullword
$a5=”marashen.com” ascii wide nocase fullword
$a6=”millertaylor.com” ascii wide nocase fullword
$a7=”occhionero.com” ascii wide nocase fullword
$a8=”occhionero.info” ascii wide nocase fullword
$a9=”wallserv.com” ascii wide nocase fullword
$a10=”westlands.com” ascii wide nocase fullword
$a11=”217.115.113.181″ ascii wide nocase fullword
$a12=”216.176.180.188″ ascii wide nocase fullword
$a13=”65.98.88.29″ ascii wide nocase fullword
$a14=”199.15.251.75″ ascii wide nocase fullword
$a15=”216.176.180.181″ ascii wide nocase fullword
$a16=”MN600-849590C695DFD9BF69481597241E-668C” ascii wide nocase fullword
$a17=”MN600-841597241E8D9BF6949590C695DF-774D” ascii wide nocase fullword
$a18=”MN600-3E3A3C593AD5BAF50F55A4ED60F0-385D” ascii wide nocase fullword
$a19=”MN600-AD58AF50F55A60E043E3A3C593ED-874A” ascii wide nocase fullword
$a20=”gpool@hostpenta.com” ascii wide nocase fullword
$a21=”hanger@hostpenta.com” ascii wide nocase fullword
$a22=”hostpenta@hostpenta.com” ascii wide nocase fullword
$a23=”ulpi715@gmx.com” ascii wide nocase fullword
$b0=”purge626@gmail.com” ascii wide fullword
$b1=”tip848@gmail.com” ascii wide fullword
$b2=”dude626@gmail.com” ascii wide fullword
$b3=”octo424@gmail.com” ascii wide fullword
$b4=”antoniaf@poste.it” ascii wide fullword
$b5=”mmarcucci@virgilio.it” ascii wide fullword
$b6=”i.julia@blu.it” ascii wide fullword
$b7=”g.simeoni@inwind.it” ascii wide fullword
$b8=”g.latagliata@live.com” ascii wide fullword
$b9=”rita.p@blu.it” ascii wide fullword
$b10=”b.gaetani@live.com” ascii wide fullword
$b11=”gpierpaolo@tin.it” ascii wide fullword
$b12=”e.barbara@poste.it” ascii wide fullword
$b13=”stoccod@libero.it” ascii wide fullword
$b14=”g.capezzone@virgilio.it” ascii wide fullword
$b15=”baldarim@blu.it” ascii wide fullword
$b16=”elsajuliette@blu.it” ascii wide fullword
$b17=”dipriamoj@alice.it” ascii wide fullword
$b18=”izabelle.d@blu.it” ascii wide fullword
$b19=”lu_1974@hotmail.com” ascii wide fullword
$b20=”tim11235@gmail.com” ascii wide fullword
$b21=”plars575@gmail.com” ascii wide fullword
$b22=”guess515@fastmail.fm” ascii wide fullword
condition:
((uint16(0) == 0x5A4D)) and (filesize < 10MB) and
((any of ($a*)) or (any of ($b*)) )
}
To build the YARA rule above we’ve used every bit of existing information, such as custom e-mail addresses used for exfiltration, C&C servers, licenses for the custom mailing library used by the attackers and specific IP addresses used in the attacks.
Once the YARA rule was ready, we’ve ran it on our malware collections. Two of the initial hits were:
MD5 778d103face6ad7186596fb0ba2399f2
File size 1396224 bytes
Type Win32 PE file
Compilation Timestamp Fri Nov 19 12:25:00 2010
MD5 47bea4236184c21e89bd1c1af3e52c86
File size 1307648 bytes
Type Win32 PE file
Compilation timestamp Fri Sep 17 11:48:59 2010
These two samples allowed us to write a more specific and more effective YARA rule which identified 42 other samples in our summary collections.
At the end of this blogpost we include a full list of all related samples identified.
Although very thorough, the Police Report does not include any technical details about how the malware was spread other than the use of spear phishing messages with malicious attachments using spoofed email addresses.
Nevertheless, once we were able to identify the samples shown above we used our telemetry to find additional ones used by the attackers for spreading the malware in spear-phishing emails. For example:
From: Di Marco Gianmaria
Subject: ricezione e attivazione
Time:2014/01/29 13:57:42
Attachment: contatto.zip//Primarie.accdb (…) .exe
From: Michelangelo Giorgianni
Subject: R: Re: CONVOCAZIONE]
Time: 2014/01/28 17:28:56]
Attachment: Note.zip//sistemi.pdf (…) .exe
Other attachment filenames observed in attacks include:
Nuoveassunzioni.7z
Assunzione.7z
Segnalazioni.doc (…) 7z.exe
Regione.7z
Energy.7z
Risparmio.7z
Pagati.7z
Final Eight 2012 Suggerimenti Uso Auricolari.exe
Fwd Re olio di colza aggiornamento prezzo.exe
Approfondimento.7z
Allegato.zip
Eventi.bmp (…) .exe
Quotidiano.mdb (…) _7z.exe
Notifica operazioni in sospeso.exe
As can be seen the spreading relied on spearphishing e-mails with attachments, which relied on social engineering to get the victim to open and execute the attachment. The attachments were ZIP and 7zip archives, which contained the EyePyramid malware.
Also the attackers relied on executable files masking the extension of the file with multiple spaces. This technique is significant in terms of the low sophistication level of this attack.
High profile victims
Potential high-profile Italian victims (found as recipients of spear-phishing emails according to the police report) include very relevant Italian politicians such as Matteo Renzi or Mario Draghi.
It should be noted however there is no proof than any of them got successfully infected by EyePyramid – only that they were targeted.
Of the more than 100 active victims found in the server, there’s a heavy interest in Italian law firms and lawyers. Further standout victims, organizations, and verticals include:
Professional firms, Consultants Universities Vaticano
Construction firms Healthcare
Based on the KSN data for the EyePyramid malware, we observed 92 cases in which the malware was blocked, of which the vast majority (80%) of them were in Italy. Other countries where EyePyramid has been detected includes France, Indonesia, Monaco, Mexico, China, Taiwan, Germany and Poland.
Assuming their compilation timestamp are legit – and they do appear correct, most of the samples used in the attacks have been compiled in 2014 and 2015.
Conclusions
Although the “EyePyramid” malware used by the two suspects is neither sophisticated nor very hard to detect, their operation successfully compromised a large number of victims, including high-profile individuals, resulting in the theft of tens of gigabytes of data.
In general, the operation had very poor OPSEC (operational security); the suspects used IP addresses associated with their company in the attacks, discussed the victims using regular phone calls and through WhatsApp and, when caught, attempted to delete all the evidence.
This indicates they weren’t experts in the field but merely amateurs, who nevertheless succeeded in stealing considerably large amounts of data from their victims.
As seen from other known cyberespionage operations, it’s not necessary for the attackers to use high profile malware, rootkits, or zero-days to run long-standing cyberespionage operations.
Perhaps the most surprising element of this story is that Giulio Occhionero and Francesca Maria Occhionero ran this cyber espionage operation for many years before getting caught.
Kaspersky Lab products successfully detect and remove EyePyramid samples with these verdicts:
HEUR:Trojan.Win32.Generic
Trojan.Win32.AntiAV.choz
Trojan.Win32.AntiAV.ciok
Trojan.Win32.AntiAV.cisb
Trojan.Win32.AntiAV.ciyk
not-a-virus:HEUR:PSWTool.Win32.Generic
not-a-virus:PSWTool.Win32.NetPass.aku
A full report #EyePyramid, including technical details of the malware, is available to customers of Kaspersky APT Intelligence Services. Contact: intelreports (at) kaspersky [dot] com.
To learn how to write YARA rules like a GReAT Ninja, consider taking a master class at Security Analyst Summit. – https://sas.kaspersky.com/#trainings
References and Third-Party Articles
http://www.agi.it/pictures/pdf/agi/agi/2017/01/10/132733992-5cec4d88-49a1-4a00-8a01-dde65baa5a68.pdf
https://ftalphaville.ft.com/2017/01/10/2182125/the-arrested-pair-are-residents-of-london-but-are-domiciled-in-rome-and-are-well-known-in-the-world-of-high-finance/
http://www.politico.eu/article/mario-draghi-matteo-renzi-mario-monti-victims-of-cyberattacks/
https://github.com/eyepyramid/eyepyramid
http://cybersecurity.startupitalia.eu/53903-20170111-eye-pyramid-the-italian-job-storia-malware-spionaggio-massoneria
http://www.affaritaliani.it/cronache/cyberspionaggio-massoneria-p4-mire-segreti-ecco-chi-sono-gli-spioni-458076.html
Indicators of Compromise
Hashes:
09ff13b020de3629b0547e0312a6c135
102bccd95e5d8a56c4f7e8b902f5fb71
12f3635ab1de63fbcb5e1c492424c605
1391d37c6b809f48be7f09aa0dab7657
1498b8d6e946b5d6b529abea13592381
14db577a9b0bfc62f3a25a9a51765bc5
17af7e00936dcc8af376ad899501ad8b
192d5866cbfafae36d5ba321c817bc14
325f5d379c4d091743ca8581f15d3295
36bd8feed1b17c59f3c653e6427661a4
380b0f1921fed82e1b68b4e442b04f05
3c30f0114c600510fdb2573cc48d5c06
3fed695e2a6e63d971c16fd9e825fec5
47bea4236184c21e89bd1c1af3e52c86
47dd1e017aae694abd2b7bc0b12cf1da
47f1f9b1339147fe2d13772b4cb81030
53b41dc0b8fd9663047f71bc91a317df
5bc1b8c07c0f83d438a3e891dc389954
5eb17f400f38c1b65990a8d60c298d95
6de1e478301d59ac14b8e9636b53815d
75621de46a12234af0bec15620be6763
778d103face6ad7186596fb0ba2399f2
859f60cd5d0f0fbd91bde3c3914cbb18
8afb6488655cbea2737d2423843ea077
9173aefe64b7704510c873e2ce7305e0
92c32eb72f5713ca1f2a8dc918f1f770
932bd2ad79cbca4341d853a4b5ea1da5
94eff87eca2f054aa5fbc1877a6cf919
98825a1ce35f46d004c0839e87cc2778
9b8571b5281f3751750d3099049098e0
9c57839b3f8462bd6c2d36db80cd5ecc
9d3ce3246975ae6d545ee9e8ba12d164
9d4b46d3c389e0144238c821670f8537
a41c5374a14a2c7cbe093ff6b075e8ac
b39a673a5d2ceaa1fb5571769097ca77
b533b082ed1458c482c3663ee12dc3a4
bcfd544df7d8e9a2efe9d2ed32e74cad
c0243741bfece772f02d1657dc057229
c38e9edc0e4b18ff1fc5b61b771f7946
ce76b690dc98844c721e6337cd5e7f4b
cf391937d79ed6650893b1d5fbed0604
d8432ddec880800bfa060af1f8c2e405
eb604e7e27727a410fc226196c13afe9
fafd293065daf126a9ad9562fc0b00b2
Related hashes identified by @GaborSzappanos:
014f69777d2e0c87f2954ad252d52810
02965c8a593989ff7051ec24736da6bd
04b3c63907c20d9be255e167de89a398
04e949f64e962e757f5bb8566c07800b
06e47736256c54d9dd3c3c533c73923e
09ff13b020de3629b0547e0312a6c135
0a80fd5abf270ddd8080f93505854684
0b3c1ff3b3b445f46594227ca2babdcd
0c33c00a5f0f5bde8c426c3ce376eb11
0ded0389cbddeeb673836794269ffb3b
0e19913ce9799a05ba97ac172ec5f0bc
11062b36893c4ba278708ec3da07b1dd
12b4d543ae1b98df15c8712d888c54f0
1334a7df1e59380206841d05d8400778
14cb305de2476365ef02d2226532dd34
1748c33cb5ac6f26d55cd1a58b68df8a
18e24ef2791030693a4588bfcae1dec0
192d5866cbfafae36d5ba321c817bc14
1b4d423350cd1159057dd7dbef479328
1deb28ae7b64fb44358e69e5afd1f600
2222a947ebccc8da16badeacca05df4b
23beed8aaac883a5902039e6fd84ee5f
2485e7ae3e0705898b7787ed0961878d
2642990a46c434e7787a599f04742a32
268698314c854bc483d05ffe459dc540
2866ced99b46b39838f56fbe704d387b
2896ae0489451d32f57c68b919b3fa72
28ba7d1a4c5d64a65f2f2bf5f6ced123
28e65b9577abaabf3f8c94d9fda50fc5
2a809644e6d07dc9fc111804a62b8089
30215197622f5c747fc869992768d9c6
325f5d379c4d091743ca8581f15d3295
33890f9268023cd70c762ad2054078c7
3673c155eb6a0bd8a94bea265ebb8b76
369cd42dfabea188fa57f802a83b55d9
380b0f1921fed82e1b68b4e442b04f05
3a0af8bba61734b043edc0f6c61cd189
3c30f0114c600510fdb2573cc48d5c06
3db711afc09c0a403a8ccff6a8a958df
3e4365b079239b0a2451f48f33761332
3ebbae038d7bf19baa1bcfbc438bb5e7
3fed695e2a6e63d971c16fd9e825fec5
3ffcd0eedd79a9cc79c2c4a0f7e04b21
4025834a88dcfba3ed1774068c64c546
417593eaf61d45e88adbad259d5585d0
422fe9c78c71fb30d376e28ad1c41884
44d91f49f261da6b1f183ea131d12a7f
45dde4082c0407b9904c5f284080337f
47bea4236184c21e89bd1c1af3e52c86
4a494c20bcfb77afd06908eb5a9718cb
53b41dc0b8fd9663047f71bc91a317df
5523aa1d4ee5f19522299be6f1111b89
5627cb8752c4c0774f822ccf8f1363eb
56499e0b590857f73bb54f500008c656
568895c8340a88316fdc0d77a7f2a91d
5847072fd4db9e83d02d8b40a1d67850
5accd89d6483dec54acc7b1484dfbace
5b5f3f65b372f9e24dbc50b21fe31f81
5bc1b8c07c0f83d438a3e891dc389954
622fb530276a639892398410de03d051
63d9e7cca593360411b5d05a555d52f3
6648a255610c5f60f580098bbc1d387c
690cdf20faf470f828fe468a635da34e
6c25a0974a907d368372ac460d8261d6
6c5693df933924e8a633ccfd7ef2635d
6ff7876db06d9102786ae0e425aeaf37
70882709d86e2a7396779f4111cd02e3
70f094e347d4088573c9af34430a3cd6
72ffb3418d3cde6fdef16b5b5db01127
734cfa84d68506fe6e74eb1b038d9c70
7633748203b705109ededadfbe08dcfa
778d103face6ad7186596fb0ba2399f2
77c2a369d0850c7a75487e8eee54b69e
78b7d1caa4185f02b1c5ef493bf79529
7971c90d7533f2c69e33f2461434096a
7aad90ce44e355f95b820fb59c9f5d56
7bf348005958658ba3fcf5ccb3e2ae22
7cddc3b26bb8f98e9b14d9c988f36f8f
81624dc108e2d3dc712f3e6dd138736a
820ca39f331f068cca71e7a7c281e4ac
84c14a1327ae7c0e5a07a67a57451cc4
860f607dbd0d6a2dc69cbc4f3b0eeeaf
889c86aaf22876516964eafa475a2acd
88c31f3b589d64a275608f471163989c
89368652dc98b13f644ec2e356c7707c
89696dbead484bf948c1dd86364672eb
898150dea4d7275f996e7341463db21f
8b27bcfa38205754c8e5fdf6a509d60e
8f419bca20b767b03f128a19b82611ab
915cc3c9c8cb8e200dbe04e425e7018b
92c32eb72f5713ca1f2a8dc918f1f770
932bd2ad79cbca4341d853a4b5ea1da5
98825a1ce35f46d004c0839e87cc2778
98b1157b9f3f3ec183bf322615f1ce41
9b19729531bf15afc38dd73bcc0596f8
9c99ecf33301e4cafdd848a7d3d77ef9
9cf08b15724e0eaf69a63e47690cdee2
a16d8cf9a7a52e5c2ad6519766ae6b92
a35312a5c0b06ee89ddadaea9ca6bad2
a4c551ec6d3b5ab08a252231439e099f
a615a4f5e93a63682a8f25b331f62882
a6c29f9680fe5ae10a9250e5431754d4
ab71ca072d4b526e258c21bd84ec0632
ac6fa4005e587ac4b3456a14bd741ff0
afab0fcbf8bc6595f9f2c0051b975a4e
b1ddec2f71727dcf747e1d385272e24d
b2a756f557d273d81a61edc9fbfc9daf
b2e1663647addc92bf253f389ac98027
b39a673a5d2ceaa1fb5571769097ca77
b533b082ed1458c482c3663ee12dc3a4
b6e86ac7d3bbedf18b98437df49c1b60
b70ddb9f6e4e2c85e80cf2079b10e762
b89a8d3442d96161cef07552116407c3
bb2a0aee38980aeb39cac06677936c96
bc333001d3f458ff8fde9d989b53e16d
bd7a2b795419c0b842fd041eaac36d7f
bf850dcb074e0cf2e30fbee6bfaa4cd9
c0d4e5ba26ef3c08dc1a29ac7496f015
c38832f484645b516b57f6813c42d554
c4abb3210f26d4a15a0d4fd41b47ee0e
c547a30fa39f22e2093b51ed254bb1c2
c69c370fcb7b645aaac086b2a3b18286
c7ef4c7b12b5ad8198dafc58c4bea2a3
c97ef1f13bf3d74c78f50fa7abe7766b
ca010bcdfe3c4965df0c6bc12b40db76
ca243796e79c87c55f67a61bc3ee8ddc
ca9a7c6b231fadfae3466da890b434c5
cf391937d79ed6650893b1d5fbed0604
cf3b3c796114f6908a35542d4fd02b0e
d034810ddab55c17dcddd2c2990b3ef3
d1273537add3f2282391726489c65e38
d20487e2d2f674bfd849cb8730225dde
d8432ddec880800bfa060af1f8c2e405
d864ad5030d354c1e40a873a335b2611
dac10dcede69eb9b4ccce8e6798f332c
db95221ebed1793bf5b5527ecb52eb0c
dc64307ef67177449b31c6bb829edbf2
dd734c07b94c8685bb809f83876c7193
e0e862dbf001eb4a169d3340c200b501
e727b444a6a9fa9d40a34a9508b1079f
e7539ed9616b61c12028a663c298f6be
e78ed9fac4f3e9b443abd02bfa9f3db2
e85ff9e3a27899b0d1de8b958af5ad90
eb604e7e27727a410fc226196c13afe9
eba8aa2572cf0d6ccdf99c34cc26b6f3
ec21252421f26072e9fe75586eb6b58a
ee9435593494f17f3efc3a795c45482e
eeca6409dcf0e46d0182d53d230c701d
eff2d3f9f56e9aabcf970c4c09fe7ef8
f0b61a531a72f0cc02d06d2ebfb935ab
f1a037e2edc5ddf4db4e1e7fcd33d5fb
f3802442727c0b614482455d6ad9edc2
f41be516fa8da87a269845c9ea688749
f7d4742d2e746962440bf517b261f126
f96335bf0512c6e65ea374a844ab7ceb
f9b4459f18ca9d2974cf5a58495c5879
fa4266c305aa75a133ebae2a4dcc9b75
fafd293065daf126a9ad9562fc0b00b2
Backdoor Filenames:
pnbwz.exe
pxcfx.exe
qislg.exe
rqklt.exe
runwt.exe
ruzvs.exe
rvhct.exe
vidhdw.exe
winlng.exe
wxrun.exe
xddrv.exe
xdwdrv.exe
Malicious attachments filenames (weak indicators):
contatto.zip//Primarie.accdb (…) .exe
Note.zip//sistemi.pdf (…) .exe
Nuoveassunzioni.7z
Assunzione.7z
Segnalazioni.doc (…) 7z.exe
Regione.7z
Energy.7z
Risparmio.7z
Pagati.7z
Final Eight 2012 Suggerimenti Uso Auricolari.exe
Fwd Re olio di colza aggiornamento prezzo.exe
Approfondimento.7z
Allegato.zip
Eventi.bmp (…) .exe
Quotidiano.mdb (…) _7z.exe
Holiday 2016 financial cyberthreats overview
13.1.2017 Kaspersky Cyber
Introduction
Last November we conducted a brief analysis of the threat landscape over the holiday period – from October to December in 2014 and 2015 – to find out if the number of financial cyberattacks during this time differs to that usually seen throughout the year. The retrospective analysis found that the percentage of phishing attacks during this period was higher than the average yearly rate. The dynamics of financial malware attacks also clearly showed that in 2014 and 2015, criminals staged their malicious campaigns to match dates around the Black Friday – Cyber Monday period, and also around Christmas and the New Year.
Based on this data we made the following prognosis: the same holiday period in 2016 will see a spike in cyberattacks. Now that the holidays are over, it is time to find out how accurate that prediction was.
Financial phishing
The numbers
As seen in the table below, unlike in previous years, the difference between the overall yearly results and the results in Q4 is not significant. However, the percentage of financial phishing attacks blocked by Kaspersky Lab products in Q4 2016 was higher than the total average for the year.
2013 Full year Q4
Financial phishing total 31.45% 32.02%
E-shop 6.51% 7.80%
E-banks 22.20% 18.76%
E-payments 2.74% 5.46%
2014 Full year Q4
Financial phishing total 28.73% 38.49%
E-shop 7.32% 12.63%
E-banks 16.27% 17.94%
E-payments 5.14% 7.92%
2015 Full year Q4
Financial phishing total 34.33% 43.38%
E-shop 9.08% 12.29%
E-banks 17.45% 18.90%
E-payments 7.08% 12.19%
2016 Full year Q4
Financial phishing total 47.48% 48.13%
E-shop 10.17% 10.41%
E-banks 25.76% 26.35%
E-payments 11.55% 11.37%
Moreover, the Q4 2016 results are the highest we’ve seen so far. 48.13% of all phishing attacks registered by Kaspersky Lab products were focused on gleaning users’ financial data, which is 0.65% higher than the average share of financial phishing in 2016, and 4.75% more than in the same period in 2015. However, the holiday period is not the only reason for such a high percentage of financial attacks. Phishing scams are the easiest way for even low level professional criminals to earn money. The preparation and supporting stages for such scams don’t require a lot of specific tools or knowledge, yet they bring a good return. In other words, phishing attacks appear more attractive to criminals due to their ease and affordability, when compared to staging a financial malware attack. This has resulted in the growth in popularity of phishing.
Delivered on time
As evidenced in our original analysis of the threat landscape during the holiday period in 2014 and 2015, criminals were trying to tie their phishing campaigns to certain dates which resulted in a visible increase in the number of attacks during the Black Friday, Cyber Monday and also Christmas periods. The 2016 figures showed no difference but we’ve seen an increase in the number of attacks which utilized well-known brands from the online retail and financial industries.
As seen on the graph above, the spikes of detections of Amazon-themed phishing scams matched the dates of Black Friday and Cyber Monday 2016 almost perfectly. The same dynamics are repeated with some other topical brands including payment systems.
Interestingly, the dynamics during the Christmas period are different. As seen below, the number of attacks started decreasing several days prior to Christmas Eve, and then went up on 25th of December.
Such synchronous behavior could be explained by multiple factors, one of which is that cybercriminals are also celebrating Christmas and that the overall number of web users also decreases on 24th December. But on 25th December, the number of attacks goes back up.
Scams: from Black Friday to Christmas-themed
In our initial report, we examined some examples of so-called topical phishing scams dedicated to a specific topic – the Black Friday sales. While the report was published several weeks before the actual sales started, we already identified some examples of Black Friday-themed phishing scams. Closer to the start of the sales some new examples appeared.
Example of a Black Friday-themed phishing scam offering a smartphone with 65% discount.
Example of a Black Friday-themed phishing scam offering a TV for an attractive price.
The scams mostly promoted personal electronics, like smartphones and TVs, at extremely low prices, and tried to lure users into providing payment information to criminals. With Christmas approaching, the topics of scams changed accordingly. In December, our researchers started to detect Christmas and New Year-themed phishing schemes.
Example of a Christmas-themed phishing scam resembling the Alibaba.com e-shop.
The example on the screen shot above doesn’t look Christmas-themed at first glance. However this fake Alibaba.com website was available on the christmascartoons.org URL and was supposed to attract victims with a tempting offer to get a loan with very low interest, along with the ability to search for goods and buy them from the same page using a credit card.
In another example targeting mobile users, criminals tried to exploit the popularity of the Clash of Clans mobile game.
The scam promises that the developers of the game are giving away some valuable in-game virtual items for free, as a New Year present to fans.
Users can choose from range of items, however in order to receive these gifts, they need to fill in a registration form which requests their Gmail account details.
Needless to say, in exchange for this information, the victim receives nothing but a loss of control over their email account and the confirmation email.
But the latter is only sent so criminals could be sure that the credentials provided by the victim are legitimate.
In general, we can’t say that the holiday period in 2016 has seen an unusually high increase of phishing attacks, however, our major hypothesis, stated in previous reports – that criminals would exploit Black Friday and Christmas topics and dates – has been confirmed.
And of course, financial phishing wasn’t the only type of cyberthreat that behaved unusually in the last three months of 2016. The financial malware landscape also showed some interesting changes.
Financial malware attacks
In total, during Q4 2016 Kaspersky Lab registered attacks with financial malware against 319,692 users worldwide. That is 22.49% more than during the same period in 2015, when 261,000 users were attacked, and 2.7% more than in 2014. It is hard to say if such an increase has been provoked by criminal interest in the holiday season; however, data on the dynamics of attacks shows that just like phishing scammers, financial malware operators tried to connect their activity to particular dates.
Dynamics of attacks with financial malware during Q4 2016 (holiday period)
25th November 2016 (Black Friday) saw a modest, but visible spike in attacks, with another on 28th November (Cyber Monday). In all, November became the second hottest month of the period in terms of number of attacked users: with more than 120 000. The hottest was October, with more than 130 000 attacked users.
Dynamics of attacks with financial malware during Black Friday and Cyber Monday 2016
The activity of attackers during the Christmas period showed a different pattern. A major increase happened before (on December 22nd) and after (from 25 – 27th December). This may be explained by the fact that most e-commerce activities happen around these dates: people buy gifts and goods for Christmas and the New Year, travel for vacations and spend money on entertainment.
Dynamics of attacks with financial malware during the Christmas 2016 period
It is also important to note that the dynamics of attacks during the holidays are very similar to what we have already seen in 2015 and 2014. Criminals are eager to get users’ money and the holiday period is a key time for them.
To reach their goals they use one of 30 families of banking trojans of which five are the most widespread: Zbot, Nymaim, Shiotob, Gozi and Neurevt. These five are responsible for attacks against 92.35% of users in the period.
The share of users attacked with Top 5 banking trojans
Conclusion
It looks like the trends we spotted as part of our analysis of the threat landscape during the holiday period in 2014 and 2015 have repeated in 2016, but on a larger scale, with more users being attacked. It is too early to draw conclusions on how successful fraud campaigns during the 2016 holiday season were, because usually criminals who were able to steal credentials to payment cards don’t cash them in immediately. They wait for several months in order to make fraudulent transactions less suspicious to the anti-fraud systems of financial organizations, but it would be safe to say that there were multiple attempts to exploit the high sales season.
Although the holiday season is over, it is still imperative to keep in mind several simple rules to stay safe when carrying out financial operations online. Steps to follow can be found in our initial report about holiday threats.
Phone-Hacking Firm Cellebrite Got Hacked; 900GB Of Data Stolen
13.1.2017 thehackernews Mobil
Cellebrite Got Hacked
The company that sells digital forensics and mobile hacking tools to others has itself been hacked.
Israeli firm Cellebrite, the popular company that provides digital forensics tools and software to help law enforcement access mobile phones in investigations, has had 900 GB of its data stolen by an unknown hacker.
But the hacker has not yet publicly released anything from the stolen data archive, which includes its customer information, user databases, and a massive amount of technical data regarding its hacking tools and products.
Instead, attackers are looking for possible opportunities to sell the access to Cellebrite system and data on a few selected IRC chat rooms, the hacker told Joseph Cox, contributor at Motherboard, who was contacted by the hacker and received a copy of the stolen data.
Meanwhile, Cellebrite also admitted that it recently experienced "unauthorized access to an external web server," and said that it is "conducting an investigation to determine the extent of the breach. The impacted server included a legacy database backup of my.Cellebrite, the company's end user license management system."
The 900 GB of stolen archive also includes login data (usernames and passwords) of Cellebrite customers, which suggests that it has been taken from the web servers related to Cellebrite's site.
The dump also contains "evidence files from seized mobile phones, and logs from Cellebrite devices," as well as it appears that company has sold phone hacking tools to repressive regimes, such as Turkey, the United Arab Emirates, and Russia.
On the other hand, the hacker did not clearly state the actual extent of what he/she had done to Cellebrite's systems.
"I can't say too much about what has been done," the hacker told Motherboard. "It's one thing to slap them, it's a very different thing to take pictures of [their] balls hanging out."
Cellebrite is known for its powerful hacking tool Universal Forensic Extraction Device (UFED) that help investigators bypass the security mechanisms of mobile phones, especially iPhones, and extract all data, including SMS messages, emails, call logs and passwords from them.
Just a few months back, Cellebrite's most sensitive in-house capabilities were made public by one of its products' resellers, who distributed copies of Cellebrite's firmware and software for anyone to download.
Two observations about the Italian EyePyramid espionage campaign
13.1.2017 securityaffairs Virus
Let’s try to analyze some facts about the Italian EyePyramid espionage campaign. Prof. Corrado Aaron Visaggio helped us in this difficult task.
The Italian EyePyramid espionage campaign raised to me two simple questions:
(i) Are the criminals geniuses or dummies?
(ii) How can an old, known, easy-to-detect malware infect so many machines belonging to different perimeters for so long time, but only in Italy?
This cyber-espionage appears as a naive mixture of sophisticated and amateur techniques. The choice of the spyware (amateur) is the first strange thing: EyePyramid is an old and known malware.
Kaspersky reported that its products had blocked more than 90 EyePyramid infection attempts. While 80 percent of these attempts were spotted in Italy, the malware was also detected in France, Indonesia, Monaco, Mexico, China, Taiwan, Germany and Poland.
Kaspersky says the malware is not sophisticated and not difficult to detect. The company also pointed out that the attackers had poor operational security (OPSEC) as they failed to hide their real IP addresses when launching attacks, and they used regular phone calls and WhatsApp to discuss their activities.
“In general, the operation had very poor OPSEC (operational security); the suspects used IP addresses associated with their company in the attacks, discussed the victims using regular phone calls and through WhatsApp and, when caught, attempted to delete all the evidence.”
“This indicates they weren’t experts in the field but merely amateurs, who nevertheless succeeded in stealing considerably large amounts of data from their victims. As seen from other known cyberespionage operations, it’s not necessary for the attackers to use high profile malware, rootkits, or zero-days to run long-standing cyberespionage operations.” reads the analysis published by Kaspersky on EyePyramid.
The final victims were infected by emails sent by compromised accounts belonging to several attorneys and associates in several law firms (sophisticated) but data was exfiltrated as attached to emails sent to a small set of e-mail addresses (amateur).
The malware was a customized (sophisticated) version of a very old malware (about 1995) (Amateur), with a weak obfuscation (amateur), but that makes use of reflection (sophisticated).
The malware has been updated during all the duration of the espionage (likely 4-6 years) in order to make it evasive to detection and to add more advanced spying functions, like intercepting the keying of specific words (sophisticated), but the stolen data resided on a couple of servers regularly and directly accessed by the supposed authors of the espionage (amateur).
It is interesting to note that the purchase of the paid library has led the authorities to the identity of the persons behind the campaign (amateur), since the cyber criminals used a licensed library -MailBee.Net- that they regularly paid, to send the exfiltrated data out to dropzones.
Are these criminals geniuses or dummies?
The second observation regards some concerns about “how” a similar software can stay resident for years in so many machines that should be placed within several different perimeters, that are supposed to be protected and monitored.
Concern number 1: is it really so easy to infect the machines of key people of a Nation’s Government (and further equally important Institutions and Organizations), with a very old and unsophisticated malware?
Concern number 2: The malware remains active for several years and the attackers were able to update it in order to evade the detection: did the attackers know how the operating environment of the victims changed over time and so did they adapt properly the malware?
Concern number 3: C&C centers usually make use of fluxing techniques (for IP or domains) for masquerading themselves. In this case, the dropzones where a small number of domains or e-mail addresses. So exfiltrated data was sent continuously to a fixed and small number of dropzones. How could this activity (easy to classify as an anomaly) pass unnoticed to a monitoring system for a so long time?
Concern number 4: if the malware was easy to detect, as claimed by Kasperksy, why it remained undetected on so many machines, in different perimeters, for a so long time?
References
https://securelist.com/blog/incidents/77098/the-eyepyramid-attacks/
http://blog.trendmicro.com/trendlabs-security-intelligence/eye-storm-look-eyepyramid-malware-supposedly-used-high-profile-hacks-italy/
https://github.com/eyepyramid/eyepyramid
https://www.sophos.com/en-us/threat-center/threat-analyses/viruses-and-spyware/Pyramid.aspx
http://www.securityweek.com/eyepyramid-malware-unsophisticated-effective-researchers
The ISC issued updates for 4 High severity DoS flaws in BIND
13.1.2017 securityaffairs Vulnerebility
The Internet Systems Consortium (ISC) has issued security updates to address four high severity flaws in the DNS software BIND.
The Internet Systems Consortium (ISC) has issued updates to solve four high severity flaws in the DNS software BIND. The flaw could be exploited by a remote attacker to cause a DoS condition.
An attacker can exploit the vulnerabilities to cause the BIND name server process to encounter an assertion failure and stop executing. The Internet Systems Consortium confirmed that it is not aware of active exploits for the flaws.

Below the list of flaws provided by the ISC:
CVE-2016-9778: An error in handling certain queries can cause an assertion failure when a server is using the nxdomain-redirect feature to cover a zone for which it is also providing authoritative service. A vulnerable server could be intentionally stopped by an attacker if it was using a configuration that met the criteria for the vulnerability and if the attacker could cause it to accept a query that possessed the required attributes.
CVE-2016-9147: Depending on the type of query and the EDNS options in the query they receive, DNSSEC-enabled authoritative servers are expected to include RRSIG and other RRsets in their responses to recursive servers. DNSSEC-validating servers will also make specific queries for DS and other RRsets. Whether DNSSEC-validating or not, an error in processing malformed query responses that contain DNSSEC-related RRsets that are inconsistent with other RRsets in the same query response can trigger an assertion failure. Although the combination of properties which triggers the assertion should not occur in normal traffic, it is potentially possible for the assertion to be triggered deliberately by an attacker sending a specially-constructed answer.
CVE-2016-9131: A malformed query response received by a recursive server in response to a query of RTYPE ANY could trigger an assertion failure while named is attempting to add the RRs in the query response to the cache. While the combination of properties which triggers the assertion should not occur in normal traffic, it is potentially possible for the assertion to be triggered deliberately by an attacker sending a specially-constructed answer having the required properties, after having engineered a scenario whereby an ANY query is sent to the recursive server for the target QNAME. A recursive server will itself only send a query of type ANY if it receives a client query of type ANY for a QNAME for which it has no RRsets at all in cache, otherwise it will respond to the client with the the RRsets that it has available.
CVE-2016-9444: An unusually-formed answer containing a DS resource record could trigger an assertion failure. While the combination of properties which triggers the assertion should not occur in normal traffic, it is potentially possible for the assertion to be triggered deliberately by an attacker sending a specially-constructed answer having the required properties.
The CVE-2016-9778 flaw affects only a subset of servers which are performing NXDOMAIN redirection using the “nxdomain-redirect” function.
The CVE-2016-9131, the CVE-2016-9147, and the CVE-2016-9444 flaws occur during the processing of an answer packet received in response to a query.
“As a result, recursive servers are at the greatest risk; authoritative servers are at risk only to the extent that they perform a limited set of queries (for example, in order to do zone service” state the advisories for the flaws.
The BIND versions 9.9.9-P5, 9.10.4-P5, 9.11.0-P2 and 9.9.9-S7 address the above vulnerabilities.
Israeli mobile phone data extraction company Cellebrite was hacked
13.1.2017 securityaffairs Mobil
The Israeli mobile phone data extraction company Cellebrite was hacked by unknown hackers that provide the 900GB database to Motherboard.
An irony of fate, the Israeli mobile phone data extraction company Cellebrite was hacked. The company went in the headlines in the dispute between Apple and the FBI in the case of the San Bernardino shooter’s iPhone.
On Thursday, Vice Motherboard reported that an unnamed contacted it to provide the 900GB database belonging to Cellebrite. Basic contact information for users that were registered to receive notifications from the firm has been exposed along with hashed passwords and technical data regarding Cellebrite’s products.
The main product of the company is the Universal Forensic Extraction Device (UFED), an equipment that can rip data (i.e. SMS messages, emails, call logs) from a huge number of different models of mobile phones.
Cellebrite issued a statement to inform its customers of the data breach that affected an “external web server” containing the company’s license management system. An unauthorized third party broke into the company systems.
According to the firm the hackers accessed a legacy archive no more in use because the company has migrated to a new system.

The Israeli firm has advised all its customers to change their passwords.
“Cellebrite recently experienced unauthorized access to an external web server. The company is conducting an investigation to determine the extent of the breach. The impacted server included a legacy database backup of my.Cellebrite, the company’s end user license management system.” states the statement issued by the company.
Motherboard verified the email addresses in the archive by attempting to create accounts on the company portal.
“In the majority of cases, this was not possible because the email address was already in use. A customer included in the data confirmed some of their details.”
The hack revealed an uncomfortable truth, Cellebrite also works states with a questionable human rights records.
“In addition, the trove of materials contains “customer support tickets” showing that the Israeli company sells its services to countries with questionable human rights records, including Turkey, Russia, and the United Arab Emirates.” reported Ars.
Thousands of unpatched Magento shops hacked in the last two years
12.1.2017 securityaffairs Hacking
According to the BSI more than 6,000 online stores running eBay’s Magento platform have been hacked across the last two years.
According to the Germany’s Federal Office for Information Security, more than 6,000 online stores running eBay’s Magento platform have been hacked across the last two years. Crooks targeted the e-commerce platform in order to steal credit card data, they used to inject carding malware on unpatched Magento e-shops.
The Germany’s Federal Office for Information Security confirmed that roughly 1,000 online stores are in Germany, it did not provide info regarding the overall number of stolen data.
“The Federal Office for Information Security (BSI) has received information according to which currently at least 1,000 German online -Shops of online skimming affected. Here use Cyber -Kriminelle vulnerabilities in outdated versions of Shop software to inject malicious code. This then peaks the customer’s payment information during the ordering process and sends it to the perpetrators. Affected are online -Shops that on the widely used software based Magento.” reads the translation of the advisory issued by BSI. “The infected code and the associated data flow is usually not visible to users. The BSI is currently not aware of the extent of the payment data already passed through these attacks.”
The Federal Office reported the attacks to the victim, but many of them failed in fixing the issue. The security expert Willem de Groot first reported carding attacks against unpatched Magento shops in October. The Dutch expert analyzed a cyber attack against the website belonging to the National Republican Senatorial Committee allowed people to make donations. According to de Groot, who analyzed the traffic on the platform, hackers roughly accessed data related to 3,500 transactions per month between March 16 and October 5, 2016.
Card data was sent back to Russian IP addresses, the expert suspected that some 21,000 credit cards were stolen at the time.
de Groot believes that the attacks against Magento shops at the time that had compromised some 6,000 sites spanning 18 months.The experts also published a free vulnerability scanning service that could be used by operators of Magento shops to check their websites.
It is not clear if there are the same threat actors behind the attacks against the unpatched Magento shops
The German Federal office now tried again to warn operators of Magento shops that were compromised by hackers. Unfortunately, once again operators failed to complain necessary security measure to protect the e-commerce platform.
“Unfortunately, there are still indicators that many operators have been negligent in securing their online stores,” said the BSI president Arne Schönbohm.
“A variety of shops are running outdated software versions which contain several known vulnerabilities. Operators must fulfill their customer responsibilities and ensure their services are fixed quickly and consistently.”
“The BSI has at this point out that the obligation to secure systems not only for companies but also for all other businesslike operators of websites apply. This includes, for example, websites from private individuals or associations, if their operation is to generate revenues permanently. This is already assumed when banners placed on websites are placed in the form of banners.” states the BSI. “Customers and operators of online -Shops based on Magento can use the free service MageReportcheck whether your shop system has known vulnerabilities and is affected by the current attacks.”
Spora Ransomware allows victims to pay for immunity from future attacks
12.1.2017 securityaffairs Virus
Security experts from Emsisoft spotted a new strain of malware, the Spora ransomware, that allows potential victims to pay for immunity from future attacks.
Security experts from Emsisoft spotted a new strain of ransomware dubbed Spora that implements a singular extortion mechanism, it allows potential victims to pay for immunity from future attacks.
According to the experts, the Spora ransomware appears well-written, it has a professional website for payment and offers several options to the victims that can pay to recover files, to remove the malware, and to gain immunity from future attacks.

The Spora ransomware implements a unique pricing model to determine how much a victim has to pay.
The attack vector is the email, victims receive messages with fake invoices as attachments. The attachments are ZIP archives with an HTA (HTML Application) file inside, masquerading as a PDF or DOC. When victims run the file, it extracts a JScript file in the %TEMP% folder, writes an encoded script into it, and then executes the file.
The malware encrypts file stored on both local files and network shares and doesn’t append an extension to them. The Spora ransomware doesn’t encrypt files located in specific directories to avoid compromise the machine operation.
According to Emsisoft, the ransomware leverages Windows CryptoAPI for encryption, it uses both RSA and AES to encrypt the files.
The encryption key management is quite complex as explained in the post published by the security firm.
“When Spora arrives on a system, it will first find and decrypt the malware author’s public RSA key embedded inside the malware executable using a hard-coded AES key. Once the malware author’s public RSA key has been successfully imported, the malware continues by creating a new 1024 bit RSA key pair, which we will call the victim’s RSA key pair, consisting of both a private and public key. It will also generate a new 256 bit AES key to encrypt the victim’s private RSA key with. Once the victim’s private RSA key is encrypted, the AES key used is then encrypted using the malware author’s public RSA key. The encrypted key material together with some additional information is then saved inside the .KEY file.” states the analysis published by Emsisoft.
“To encrypt a document or file on the system, Spora will first generate a new 256 bit per-file AES key. This per-file key serves to encrypt up to the first 5 MB of the file. Once done, the malware will encrypt the per-file key using the victim’s public RSA key and the RSA-encrypted per-file key is appended to the encrypted file.”
One of the most interesting abilities of the malware is that it is able to encrypt files without a command and control (C&C) server connection. Even if a security firm is able to analyze a decryption tool developed for one victim, they will not able to decrypt files of other users.
Experts believe the Spora ransomware is sold as a ransomware-as-a-service because instance of malware they analyzed have an hardcoded identify that is likely used to identify a specific campaign.
The aforementioned .KEY file contains multiple information such as the infection date, the username of the victim, and the locale of the infected system. These information are used by the author of the Spora ransomware to determine the ransom amount.
in 2016, these are the four ways how bots altered history
12.1.2017 securityaffairs BotNet
2016 was the biggest year by far for all sorts of bots. From Chatbots to bad bots, the past year was eventful to say the least.
With more than 980+ cyber security breaches across all online businesses and 35 million accounts exposed. Yahoo! In a 2016 report, disclosed that more than 1 billion accounts have been stolen. $400 billion was reportedly lost to cyber attacks across all industries this year. With this trend, the losses are set to top out at around $2.1 Trillion by 2019.
Now, let’s look at the top 4 incidences of bots that altered history in 2016.

Dyn Cyberattack (Mirai) – The 2016 Dyn cyberattack took place on October 21st 2016. The attack was carried out by a malware known as Mirai. Mirai ( Japanese word for “The Future”) is a malicious software that turned Internet of Things (IoT) into bots, which was later used in the record breaking exploit. Since 2010, the number of devices connected to the internet has doubled from 12.5 billion devices to 25 billion. Mirai malware worked on the principle of identifying vulnerable IoT devices with default username and password, and planting the malware into them. Once the devices turned bad, bots in tandem were able to produce over 1.2 terabytes/sec attacks. Major websites such as Amazon.com, Netflix, CNN, BBC etc were taken down by the bad bots. This is by far the biggest attack on the free internet. This is a case in point to understand what it meant for services routed via DNS during the Dyn cyberattack.
Bots used for influencing public: Social media bots were the most active in 2016. With major events such as Brexit and US elections, social media bots were the most influential.
Brexit: Automated social media accounts produced by both sides of the debate created these bots to have a massive influence on the referendum vote; especially on those last-minute ‘undecideds’ Researchers from Oxford University have found that bots played a strategic role during the debate. The social media bots helped to circulate ‘repetitive’ political content to manipulate the thinking of the general public. Social media bots had a very simple role to play during Brexit, they had to tweet pro or anti Brexit tweets over and over again or just retweet /share messages of influencers on either side. This helped them float the message they wanted for a much longer time, on the social media platforms than required.
US elections: As per Twitter Audit, Donald Trump’s twitter account had almost 40% inactive, fake and spam followers, while Hillary Clinton had around 37%. The number roughly adds up to more than 7 million fake/inactive bot accounts that were circulating messages across the globe. These bot accounts helped in propagating messages for both the candidates involved and heavily influenced the undecided voter.
Under the scanner, Impact of Twitter, Facebook, and other social media might be not be considered a serious threat. But the bots spreading propaganda are usually encountered by journalists who use social media. Journalists, in-turn, interpret these bot propagated messages as a trend among people and report it. This increases the influence of such bad social media bots even more. It is crazy how bots can influence and change the course of history for 2 major nations last year, and it’s just the beginning. German Chancellor Angela Merkel’s apprehensions on bots manipulating the upcoming German elections are not unfounded.
The Rise of Chatbots: 2016 is considered to be the rise of chatbots. With every major e-commerce, service provider producing a chatbot. Early 2016 started a race among companies to create chatbots. Chatbots are highly regarded as the new automated intelligence trend. These bots are created to interact with the user to provide information or to execute simple tasks.
Good chatbots went bad: When Microsoft launched Tay (AI Twitter chat bot) on March 23, 2016, it was the start of a new era. Tay was programmed to learn from its interactions with real users on twitter. Tay, however, ended up becoming a vulgar, racist bot within a few hours. The bot, however, was taken down by Microsoft within 16 hours. By and by, Tay tweeted 96,000 times before it went offline.
BOTS Act passed in the US senate (Ticket Scalping bots) : Ticket scalping bots were made illegal in the US during December 2016. President Obama had signed the BOTS (Better Online Ticket Sales) Act of 2016. The significance of this bill is that any software or automated bot program used to scalp tickets is now completely ILLEGAL. Finally, ticket scalping is a federal offense. Ticket scalping this year was brought to light by Lin-Manuel Miranda, who was the star of the Broadway show Hamilton. Hamilton tickets were scalped using bots online and were reselling for a higher price on another website. With the help of the senators and mainstream media, congress was able to pass the bill. Ticket scalping bots are notorious for buying out thousands of tickets within a matter of seconds. This frustrates genuine users that visit the site, in the long run hurts the producers as well.
According to a famous online ticket selling website, TicketMaster. In 2016, bots tried to buy 5 billion tickets, or 10,000 a minute, on their website. This resulted in 60% of the tickets getting scalped by bots.
With the surge in malicious bots, there is a need to stop them before they could harm your online businesses. Bots have been increasingly malicious and damaging for all online businesses.
So, have you thought about how your online business may be silently targeted by bad bots? How is your 2017 IT roadmap poised to address bot threats?
Browser AutoFill Feature Can Leak Your Personal Information to Hackers
11.1.2017 thehackernews Hacking
Hackers Can Steal Your Personal Information, Thanks to Browser AutoFill Feature
Just like most of you, I too really hate filling out web forms, especially on mobile devices.
To help make this whole process faster, Google Chrome and other major browsers offer "Autofill" feature that automatically fills out web form based on data you have previously entered in similar fields.
However, it turns out that an attacker can use this autofill feature against you and trick you into spilling your private information to hackers or malicious third parties.
Finnish web developer and whitehat hacker Viljami Kuosmanen published a demo on GitHub that shows how an attacker could take advantage of the autofill feature provided by most browsers, plugins, and tools such as Password Managers.
The proof-of-concept demo website consists of a simple online web form with just two fields: Name and Email. But what's not visible are many hidden (out of sight) fields, including the phone number, organization, address, postal code, city, and country.
Giving away all your Personal Information Unknowingly
So, if users with an autofill profile configured in their browsers fill out this simple form and click on submit button, they'll send all the fields unaware of the fact that the six fields that are hidden to them but present on the page also get filled out and sent to unscrupulous phishers.
You can also test your browser and extension autofill feature using Kuosmanen's PoC site.
Kuosmanen can make this attack even worse by adding more personal fields out of user's sight, including the user's address, credit card number, expiration date, and CVV, although auto-filling financial data forms will trigger warnings on Chrome when sites do not offer HTTPS.
Kuosmanen attack works against a variety of major browsers and autofill tools, including Google Chrome, Apple Safari, Opera, and even the popular cloud security vault LastPass.
Mozilla's Firefox users do not need to worry about this particular attack as the browser currently, does not have a multi-box autofill system and forces users to select pre-fill data for each box manually.
Therefore, the Firefox browser can't be tricked into filling text boxes by programmatic means, Mozilla principal security engineer Daniel Veditz says.
Here's How to Turn Autofill Feature Off
The simplest way to protect yourself against such phishing attacks is to disable form autofill feature in your browser, password manager or extension settings.
Autofill feature is turned on by default. Here's how to turn this feature off in Chrome:
Go to Settings → Show Advanced Settings at the bottom, and under the Passwords and Forms section uncheck Enable Autofill box to fill out web forms with a single click.
In Opera, go to Settings → Autofill and turn it off.
In Safari, go to Preferences and click on AutoFill to turn it off.
Microsoft Releases 4 Security Updates — Smallest Patch Tuesday Ever!
11.1.2017 thehackernews Vulnerebility
microsoft-windows-security-update-patch-tuesday
IN BRIEF
Microsoft has issued its first Patch Tuesday for 2017, and it's one of the smallest ever monthly patch releases for the company, with only four security updates to address vulnerabilities in its Windows operating system as well as Adobe Flash Player.
Meanwhile, Adobe has also released patches for more than three dozen security vulnerabilities in its Flash Player and Acrobat/Reader for Windows, MacOS, and Linux desktops.
According to the Microsoft Advisory, only one security bulletin is rated critical, while other three are important. The bulletins address security vulnerabilities in Microsoft's Windows, Windows Server, Office, Edge and Flash Player.
The only security bulletin rated as critical is the one dedicated to Adobe Flash Player, for which Microsoft distributed security patches through Windows Update. Other security bulletins that addresses flaws in Microsoft products are as follows:
Bulletin 1 — MS17-001
This security update resolves just one vulnerability in the Microsoft Edge browser. Microsoft rates this bulletin as important.
The vulnerability (CVE-2017-0002) could let an attacker gain elevated access privileges by tricking users to view a specially crafted web page using Microsoft Edge.
This elevation of privilege flaw exists in Microsoft Edge's cross-domain policies, which could allow "an attacker to access information from one domain and inject it into another domain," Microsoft says.
The update will be rolled out to Windows 10 and Server 2016.
Bulletin 2 — MS17-002
This security bulletin is the one that also patches a single vulnerability in Microsoft Office.
The vulnerability, designated CVE-2017-0003, is a memory corruption issue that allows an attacker to perform remote code execution (RCE) in Microsoft Office 2016 and SharePoint Enterprise Server 2016.
The flaw lets a specially crafted Word file to take control of the target machine with the current user's access privileges.
Users who are logged in with fewer user rights on the system are less impacted than users who operate with administrative user rights, such as some home accounts and server users.
Bulletin 3 — MS17-003
This security bulletin is rated as Critical and resolves 12 security vulnerabilities in Adobe Flash Player for all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016.
The security patch will be automatically rolled out to Windows users running Microsoft Edge or Internet Explorer 11.
Bulletin 4 — MS17-004
This security update, also rated as important, addresses just one denial of service (DoS) vulnerability in Local Security Authority Subsystem Service (LSASS) for Windows Vista, Windows 7, Windows Server 2008, and Windows Server 2008 R2.
The flaw (CVE-2017-0004) resides in the LSASS that handles authentication requests, which could be exploited to reboot the system by sending a specially crafted authentication request to the targeted system or server.
Adobe Security Patch Update
A total of 13 vulnerabilities has been addressed in the Flash Player, while none of the flaws have actively been exploited in the wild.
The Flash Player updates for both Windows and macOS systems have been rated critical, as successful exploitation of the vulnerability could let an attacker perform remote code execution on the target system. However, Linux users are at lower risk for attack.
The update for Adobe Acrobat and Reader addresses some 29 flaws, including some remote code execution (RCE) vulnerabilities in both Windows and macOS.
Users and IT administrators are strongly recommended to apply Windows and Adobe patches as soon as possible in order to keep away hackers and cybercriminals from taking control over your computer.
A system reboot is necessary for installing updates, so users are advised to save work on PCs where the whole package of patches is deployed before initiating the process.
Juniper SRX firewalls open a root-level account due to a flaw
11.1.2017 securityaffairs Vulnerebility
Experts at Juniper have discovered that an update for its Juniper SRX firewalls opens a root-level account on the network device.
The company started warning its users, every user who issued the “request system software” command with the “partition” option is affected by the issue. The failure of the system update leaves it in a state where root CLI login is allowed without a password. The problem affects any system upgraded from Junos OS prior to 12.1X46-D65. When the system upgrade fails, the system goes into a “safe mode” designed to allow a sysadmin to access it and solve the problem.
This implies that a root login without a password is available.
“Using the ‘
request system software
‘ command with the ‘
partition
‘ option on an SRX Series device upgrading from Junos OS releases prior to 12.1X46-D65 can leave the system in a state where root CLI login is allowed without a password due to the system reverting to a “safe mode” authentication triggered by the failed upgrade. Additionally, valid authentication credentials fail to work due to the same issue. Only root with no password will work.” reads a security advisory published by Juniper.
According to the security advisory published by Juniper, no other platform or version of Junos OS is affected by the vulnerability. It also confirmed that no other Juniper Networks products or platforms are affected.
The experts highlighted that any other previously-valid authentication credential is wiped from the system.
In order to definitively solve the problem, it is possible to upgrade the Juniper SRX Series device from an affected release to a fixed release.
Juniper SIRT confirmed that it is not aware of any malicious exploitation of this vulnerability.
“Avoid using the ‘
partition
‘ option when upgrading an SRX Series device to Junos OS 12.1X46 prior to 12.1X46-D65.” continues the advisory. “Note that the symptoms are immediately obvious after an affected upgrade and may be remediated by rebooting the device post-upgrade.”
This means that just rebooting the system the problem will be solved.
The issue is tracked as CVE-2016-1278.
Do nitra zákeřného ransomwaru. Takto vypadá útok na počítače personalistek
11.1.2017 Živě.cz Viry
Jmenuje se Rolf a chce práci
Jeho životopis je ale trošku jiný
Rolf je totiž ransomware
Pozor na Rolfa. Rolf Drescher hledá práci, a tak na kdejaké HR oddělení míří e-maily s životopisem v PDF a XLS. PDF je snad v pořádku, ale co ten Excel? A tak jej ze zvědavosti leckterá lovkyně mozků otevře, načež vyskočí žádost o spuštění makra. Zvědavost převáží bezpečnostní pud sebezáchovy a…
A nic, namísto bohatého výčtu Rolfových pracovních zkušeností se totiž počítač z ničeho nic restartuje a spustí se program CHKDSK, který záhy začne kontrolovat pevný disk.
Zákeřný Rolf hledá práci
Leckdo by v tom okamžiku zaklel a jen odfrkl, že zase spadly Windows, vše se má ale trošku jinak. Rolf Drescher neexistuje a jeho podivný životopis v XLS nebyl ničím jiným než čerstvou modifikací viru Petya/GoldenEye, který se internetem šíří poslední rok.
Jmenuji se Rolf a jsem virus zabalený v příloze
Chování jeho poslední verze zmapovali specialisté z Check Pointu a loni pak až na samou dřen assembleru analyzovali v MalwareLabs. Pojďme se tedy podívat, jak takový útok, nákaza a nakonec i naprostá zkáza vlastně vypadá, Petya aka GoldenEye aka nešťastný Rolf Drescher je totiž tím nejzákeřnějším malwarem pod Sluncem – vyděračským ransomwarem.
Co je to ransomware?
„Ransomware je druh malware, která zabraňuje přístupu k počítači, který je infikován. Tento program zpravidla vyžaduje zaplacení výkupného (anglicky ransom) za zpřístupnění počítače. Některé formy ransomware šifrují soubory na pevném disku (kryptovirální vydírání), jiné jen zamknou systém a výhrůžnou zprávou se snaží donutit uživatele k zaplacení.“ – Česká Wikipedie
Zuzaně z HR došel e-mail
Mějme tedy jednu specialitku na HR, která zrovna hledá čerstvé síly. Říkejme ji třeba Zuzka. Zuzaně mohl virus dorazit nejrůznějšími kanály, ve všech případech se ale jednalo o žádost o práci. Zatímco loni se tak Drescherův životopis šířil především jako falešný samorozbalovací balíček ZIP (EXE) uložený na Dropboxu, nyní to je zmíněné makro pro Excel.
Letos je to Excel, loni se životopis šířil jako EXE program
Zuzka právě pro svého zaměstnavatele hledá nové inženýry, a tak mávne rukou nad podivnou distribucí a makro v Excelu přes varování spustí. V tom okamžiku se ale rozbalí malware, nahraje se do paměti a začne šifrovat dostupné soubory v uživatelské složce, kterým zamění příponu. Nakonec vytvoří soubor YOUR_FILES_ARE_ENCRYPTED.TXT s instrukcemi.
Ransomware přepíše úvodní část disku
Kdyby Zuzka v tuto chvíli počítač rychle vypnula, ještě by mohla ledacos zachránit. Jenže Zuzka je zmatená, a tak dá podivnému programu ještě pár chvil. Ten toho využije, vytvoří kopii úvodní oblasti pevného disku, kde je uložený zavaděč operačního systému, a přepíše jej vlastním maličkým programem.
Přepsání zavaděče bude mít za následek okamžité zhroucení systému, možná vyskočí BSOD, ale počítač se v každém případě restartuje.
V tuto chvíli má naše HR specialistka Zuzka poslední šanci, jak zachránit alespoň operační systém. O uživatelská data už nejspíše přišla. Nesmí počítač znovu spustit! Kdyby Zuzka okamžitě zaběhla do oddělení IT, které všechno ví, poněvadž bedlivě čte Živě.cz, technici by vytáhli disk a provedli zálohu zbývajících nepoškozených dat, protože samotné diskové oddíly ještě existují.
Jelikož však ajťáci předchozího dne do pozdních nočních hodin probírali U tří opic problematiku podnikové síťové infrastruktury, stejně jako autor tohoto článku dnes nedorazili na pracoviště před desátou dopolední, a tak má Zuzka smůlu a nechala vše dál běžet.
Falešný CHKDSK ve skutečnosti šifruje
Počítač se restartoval, ovšem Windows už nenaběhly. Namísto toho se zobrazil onen CHKDSK a začal kontrolovat disky. Samozřejmě byl falešný a měl jen ukonejšit Zuzku, že je zatím stále vše v režii Microsoftu, a jen co program vše spočítá, prostě naběhne přihlašovací obrazovka.
Falešný CHKDSK, který ve skutečnosti šifruje většinu disku
Chyba! Falešný CHKDSK nekontroluje disk, ale právě pomocí techniky Salsa20 šifruje téměř celý disk.
A neměla by si s tímto útokem poradit funkce Secure Boot a UEFI? Na první pohled ano, ale je to složitější – viz třeba tato diskuze na blogu Naked Security.
Falešný CHKDSK zvesela šifruje a šifruje, načež je dílo definitivně dokonáno, disk zašifrovaný a na displeji se už jen zobrazí žlutá pirátská lebka (proto GoldenEye) a posléze sdělení, že se Zuzana stala obětí ransomware a co má dělat.
Jakmile malware zašifruje disk, spustí uvítací program s lebkou (aktuální verze a červená z loňského roku) – toto všechno uložil na úvodní část disku ještě na Windows
Zuzko, chci bitcoin!
Autor nabádá Zuzku, aby si stáhnula Tor Browser a navštívila některou ze skrytých webových stránek na torovém alternativním webu, třeba: http://petya5koahtsf7sv.onion.
Zde se posléze dozví, že má zaplatit poplatek ve výši 1,3-1,39 BTC. Dolary se samozřejmě neplatí, záškodníci všeho druhu preferují těžko identifikovatelné bitcoinové transakce. Přesná částka kampaň od kampaně trošku osciluje a zdá se, že záškodníci reagují na aktuální kurz bitcoinu k americkému dolaru, pokaždé se totiž jedná zhruba o tisíc dolarů, což asi bude jejich cíl. Tisíc dolarů za každý úspěšný útok!
Dobrý den, jste obětí ransomwaru. Děkujeme, že využíváte našich služeb a teď nám prosím zaplaťte asi 1 000 dolarů. Máte na to pár dnů, pak už se s vámi nebudeme bavit.
Nyní má Zuzka na výběr. Buď zaplatit odmítne a smíří se s tím, že jen co se technici vyspí z kocoviny, prostě ji přeinstalují celý operační systém, anebo skutečně zaplatí. V takovém případě později obdrží dešifrovací klíč, který zadá do formuláře po startu počítače. Malware v tom případě nejprve ze zálohy obnoví onu přepsanou úvodní část disku se zavaděčem a posléze i zbytek souborů na celém disku.
A opravdu mi dorazí klíč?
Leckdo si jistě položí otázku, jestli budou záškodníci vůbec komunikovat, ale je to v jejich zájmu. Pokud by totiž po zaplacení výkupného nepředali oběti klíč, brzy by se to rozkřiklo a peníze by jim už příště nikdo neposlal.
„Copyright © 2016 Janus Cybercrime Solutions ™“ píše se v patičce na torové stránce ransomwaru Petya. Nu, ochrannou známku nemají, ale smysl pro humor a copyright asi ano...
Na stranu druhou, internetem se mohou šířit i různé starší a již neaktivní ransomwarové kampaně, kdy viry samotné sice pochopitelně stále fungují, ale záškodníci už žádné dešifrovací klíče dávno neposílají. Díky analýze ransomwaru i policejním zátahům se však specialistům čas od času podaří šifru rozlousknout a antivirové firmy poté nabízejí nejrůznější nástroje, které se pokusí data obnovit.
Zuzka se naštvala a o vše přišla
No dobrá, toto je ale čerstvá kampaň, a tak věřme, že vše funguje. Přesto to stále může skončit naprostou katastrofou. Jakmile si Zuzka přečte, že má poslat jakýsi bitcoin a kolik že to po přepočtu činí korun, naštve se a do formuláře na žlutočerné obrazovce napíše nějaké velmi vulgární a před desátou hodinou večerní zcela nepublikovatelné slovíčko.
Poté klepne na Enter a…
A je konec, v ten okamžik totiž ransomware Petya/GoldenEye v prvním kroku provede onu obnovu zavaděče, ale samotná data na disku dešifruje špatným klíčem. Jeden nesmysl tedy převede na druhý a už není cesty zpět, protože z hlavičky disku mezitím zmizel i onen úvodní záškodnický program, který se spouštěl po startu.
Ransomware z rodiny Petya ve skutečnosti nešifruje každý bajt na disku. Při forenzní analýze se ukázalo, že i poté zůstávají tu a tam původní data včetně textových řetězců. Integrita diskového oddílu je ale pryč a snadná obnova bez znalosti klíče nemožná.
Co tedy na závěr poradit imaginární Zuzaně? Jistě, na podnikovém počítači to bude slušet některému z antivirovému programu, provařené viry Petya by dnes totiž měly znát opravdu všechny. Ovšem jak už tomu bývá, nejlepším antivirem je nakonec především starý dobrý selský rozum a bystrý úsudek.
Nelze totiž než doufat, že by opravdu nikoho, ani naši imaginární Zuzanu, nikdy v životě nenapadlo spouštět pochybné makro v už od pohledu pochybném tabulkovém dokumentu.
A tak přejme všem HR oddělením, ať se nenechají nachytat ani v novém roce a v nové kampani.
Vyděrači útočí na MongoDB, počet napadených serverů přesáhl 32 000
11.1.2017 Root.cz Viry
Internetem se šíří nová vlna vydírání spojená s užíváním databáze MongoDB. Jsou napadeny desítky tisíc instalací a další se objevují. Útočníků je pravděpodobně více a za obnovení databáze požadují platbu v bitcoinech.
Tisíce uživatelů databáze MongoDB se v posledních několika dnech dostalo do nepříjemné situace. Neznámý útočník napadl jejich systém, vymazal veškerá data a nahradil je jedinou tabulkou, ve které informuje o své činnosti a za obnovení dat a záplatování chyby požaduje platbu v bitcoinech.
Případů navíc velmi rychle přibývá, zatímco před týdnem byly napadeny dva tisíce instalací MongoDB, v pondělí se hovořilo o deseti tisících a během jednoho dne došlo k nárůstu na 27 000. Zdá se, že se tento druh vydírání stal doslova přes noc velmi populárním. Současný stav věci jasně ukazuje na fakt, že nejde zdaleka jen o jednoho útočníka, ale mnozí se nechali inspirovat původní myšlenkou a začali podnikat na vlastní pěst.
Různí útočníci, stejný cíl
Původní útočník používal přezdívku Harak1r1 a za obnovení databáze požadoval 0,2 bitcoiny (BTC), tedy asi 5000 Kč. Jeho kontaktní e-mail ale přestal existovat a oběti se tak nemají kam obrátit, i kdyby chtěly výkupné zaplatit. Zato začaly vznikat další přezdívky jako Kraken0, mongo3l1t3 a 0wn3d, za kterými zřejmě stojí jiní útočníci. Princip jejich činnosti je sice podobný, ale nechovají se úplně stejně a například požadují různě vysoké výkupné – od 0,1 BTC (2500 Kč) až po 1 BTC (25 000 Kč).
Na problém upozorňují oficiální stránky MongoDB a zabývají se jím také dva významní bezpečnostní experti: Victor Gevers a Niall Merrigan, kteří společně monitorují situaci a průběžně aktualizují tabulku s informacemi o útočnících a obětech. V době psaní článků bylo obětí více než 32 000.
Follow
Niall Merrigan @nmerrigan
First time #mongodb ransomed db name passes out system db name in the stats. Estimated 32K servers now.. Data point @shodanhq 20H00 pic.twitter.com/LhtoqXrn8t
8:49 PM - 10 Jan 2017
61 61 Retweets 37 37 likes
Průběh je vždy velmi podobný: útočník si pomocí služby Shodan vyhlédne výchozí instalaci MongoDB s otevřeným portem 27017 a bez přístupového hesla. Poté databázi smaže a nahradí ji vlastním obsahem. Součástí je i vyděračský text, například následujícího znění:
Your database has been pwned because it is publically accessible at port 27017 with no authentication (wtf were you thinking?). Your data has been dumped (with data types preserved), and is easily restoreable. To get your data back, email the supplied email after sending 0.15BTC to the supplied Bitcoin wallet, do this quickly as after 72 hours your data will be erased (if an email is not sent by then). We will get back to you within 2 days. All of your data will be restored to you upon payment via a email response.
Útočníci slibují, že pokud oběť zareaguje rychle a pošle požadovaný obnos (v tomto konkrétním případě asi 3700 Kč), budou data obnovena. Podle uvedených bitcoinových peněženek někteří uživatelé skutečně zaplatili, odborníci však varují, že neexistuje záruka, že vyděrači data skutečně mají a jsou ochotni je poskytnout. Pokud už se oběti rozhodnou zaplatit, měly by požadovat důkaz o kopii databáze.
Victor Gevers tvrdí, že se mu ozvalo několik podvedených uživatelů, kteří zaplatili a data zpět nedostali. Dostávám negativní reakce od lidí, kteří zaplatili skupině Kraken a nedostali žádnou odpověď. Včera si na to stěžovalo 12 obětí, píše Gevers.
Slušný byznys
Podle peněženky skupiny Kraken zaplatilo 90 obětí z 16 000. Jde sice jen o nepatrnou část obětí, ale přesto jde o velmi výnosný byznys. Za pět dní si útočníci přišli na 9,4 BTC, tedy v přepočtu více než 200 tisíc korun. Navíc to vypadá, že si někdo na útocích na MongoDB založil živnost, protože část skupin realizuje útok přes stejnou IP adresu: 46.166.173.106. Gevers se proto domnívá, že jde o nějaký druh služby automatizující tento druh útoku. V každém případě je útok plně automatizovaný.
Někteří současný stav označují za „apokalypsu MongoDB“, ale ve skutečnosti jde jen o další zneužití otevřeného přístupu. Proti podobné administrátorské chybě není odolný žádný software. Zároveň by toho ale hodně mohli udělat sami vývojáři, kteří by mohli ve výchozí instalaci vynutit volbu silného administrátorského hesla a neotevírat přístup do internetu.
Skype i Facebook musí být bezpečnější, požaduje Evropská komise
1.1.2017 Novinky/Bezpečnost Bezpečnost
Pro internetové komunikační služby jako je WhatsApp, Facebook Messenger, iMessage nebo Skype by měla v Evropské unii platit přísnější pravidla o ochraně soukromí uživatelů. Navrhla to v úterý Evropská komise.
Poskytovatelé budou muset zajistit důvěrnost svých služeb, včetně údajů o komunikaci, tedy takzvaných metadat, a žádat zákazníky o souhlas s jejich případným využitím. Návrh také obsahuje zákaz libovolné formy uživatelem nevyžádané komunikace, označované často jako spam.
Změny jsou rozšířením pravidel, která se dnes v unii týkají jen klasických telekomunikačních operátorů také na poskytovatele internetového volání a textových služeb.
Unijní exekutiva dlouhodobě uzavírá mezery ve své legislativě, které se ve svém důsledku dotýkají především velkých amerických internetových společností jako je Google, Facebook nebo Apple. Za porušení navrhovaných pravidel by firmám hrozily sankce až do výše čtyř procent jejich celkového obratu.
Cíl? Zamezit zneužívání soukromých dat
"Naše návrhy doplňují rámec pro ochranu dat v EU. Zajistí, že soukromí elektronické komunikace je chráněno moderními a efektivními pravidly a že evropské instituce budou stejně vysoké standardy vyžadovat od všech členských zemí," uvedl místopředseda komise Frans Timmermans. O věci nyní budou jednat členské země a Evropský parlament, komise by ale ráda viděla jejich přijetí před 25. květnem 2018, tedy do začátku platnosti související obecné směrnice o ochraně dat.
Eurokomisařka odpovědná za spravedlnost a ochranu spotřebitelů Věra Jourová zdůraznila, že cílem je zamezit možnosti zneužívání soukromých dat sebraných z nejrůznějších nových komunikačních nástrojů. "Myslím si, že to je nutné doplnění stávající legislativy," poznamenala.
Souhlas s uchováváním zpráv
Podle návrhů komise bude třeba souhlas uživatelů nejen s nahráváním a zaznamenáváním hovorů, ale také s uchováváním textových a chatových zpráv či e-mailů. Přesně naopak bude stanoveno, kdy a za jakých podmínek je takové zachovávání povoleno.
Zjednodušit by se měla pravidla pro takzvaná "cookies", která se využívají například pro cílenou reklamu na internetu a nyní ve většině případů potřebují souhlas uživatele. V budoucnu by místo opakovaného potvrzování na každé webové stránce měl uživatel mít možnost věc nastavit přímo ve svém prohlížeči.
Uživatelé také budou muset výslovně souhlasit s jim určenou komerční komunikací bez ohledu na její formu - tedy ať už v případě e-mailu, SMS nebo chatových zpráv. V principu se to týká i marketingových telefonátů, byť zde komise nabízí členským zemím možnost postupu, kdy by lidé museli výslovně oznámit, že takové telefonáty odmítají.
Kvůli chybě v nových procesorech od Intelu lze přes USB port bez povšimnutí ovládnout jakýkoli systém
11.1.2017 Živě.cz Zranitelnosti
Bezpečnostní rizika dnes hrozí ze všech možných stran a nevyhýbá se tomu ani samotný hardware. Tentokrát inženýři Maxim Goryachy a Mark Ermolov ze společnosti Positive Technologies objevili velmi závažnou chybu v moderních procesorech od Intelu.
Nebezpečný USB „flash disk“, který zničí váš počítač
Všechny procesory standardně umožňují nějakou možnost hardwarového přístupu pro ladění a konfiguraci, která probíhá při výrobě. Ale zatímco dříve byly nutné specializované nástroje, u procesorů s architekturou Intel Skylake a novějších už je možné k JTAG přistupovat i přes rozhraní USB 3.0 v rámci DCI (Direct Connect Interface).
Kvůli tomu lze zaútočit na daný systém, aniž by to bylo možné detekovat, protože útok probíhá na pod úrovní softwaru. Tímto způsobem by tak případný hacker mohl změnit bios a nastavení, dostat se k informacím, vkládat vlastní kód (malware) a podobně. Žádná ochrana v rámci systému tak nepomůže.
Podle vyjádření nezáleží, jaký systém na daném notebooku, počítači nebo serveru běží. Zatím se tato chyba objevila pouze u úsporných procesorů řady U. Intel už o zranitelnosti ví, ale zatím se k problému oficiálně nevyjádřil.
Stolen NSA "Windows Hacking Tools" Now Up For Sale!
11.1.2017 thehackernews BigBrothers
The Shadow Brokers who previously stole and leaked a portion of the NSA hacking tools and exploits is back with a Bang!
The hacking group is now selling another package of hacking tools, “Equation Group Windows Warez,” which includes Windows exploits and antivirus bypass tools, stolen from the NSA-linked hacking unit, The Equation Group.
For those unfamiliar with the topic, The Shadow Brokers is a notorious group of black-hat hackers who, in August 2016, leaked exploits, security vulnerabilities, and "powerful espionage tools" created by The Equation Group.
On Saturday, the Shadow Brokers posted a message on their ZeroNet based website, announcing the sale of the entire "Windows Warez" collection for 750 Bitcoin (around US$678,630).
The data dump contains many windows hacking tools, categorized as following:
Fuzzing tools (used to discover errors and security loopholes)
Exploit Framework
Network Implants
Remote Administration Tools (RAT)
Remote Code Execution Exploits for IIS, RDP, RPC, SMB Protocols (Some Zero-Days)
SMB BackDoor (Implant)
Interestingly, the Remote Administration Tool (RAT) "DanderSpritz" included in the list is the one previously leaked in the NSA's documents revealed by Edward Snowden.
Besides this, malware researcher Jacob Williams analyzed the archive of "screenshots and output of the find command across the dump" provided by the hacker as an evidence of legitimacy and estimated that the tools may also include a Fully Undetectable Malware (FUD) toolkit.
The FUD toolkit might have an ability to "evade/bypass personal security products," such as Avira, Avast, Dr.Web, ESET Antivirus, Comodo, McAfee Antivirus, Microsoft Essential, Panda, Symantec, Trend Micro and Kaspersky Antivirus.
The buyers can purchase the entire database of hacking tools that The Equation Group used against various countries to expand its espionage operations.
In August, the Shadow Brokers announced an auction attempting to sell the complete set of tools to the highest bidder, but the group canceled their auction in October due to little or no response on their public sale.
But since this time the group has made Windows hacking tools up for sale, the chances are that hackers and espionage groups would be interested in buying these hacking tools.
ShadowBrokers offers for sale the stolen NSA Windows Hacking Tools
11.1.2017 securityaffairs BigBrothers
The ShadowBrokers is the hacker crew stolen the arsenal of the NSA-Linked Equation Group is offering for sale the stolen NSA Windows Hacking Tools.
The ShadowBrokers is the hacker crew that leaked a portion of the arsenal of the NSA-Linked Equation Group, a precious archive containing hacking tools and exploits.
At the end of October, the hackers leaked a fresh dump containing a list of servers that were hacked by the NSA-linked group known as Equation Group.
The Equation group compromised these targets using the hacking tools codenamed as INTONATION and PITCHIMPAIR. The ShadowBrokers provided the links to two distinct PGP-encrypted archives, the first one offered for free as a proof of the hack (its passphrase was ‘auctioned’), for the second one the group requested 1 million BTC .
The first archive was containing roughly 300MBs of data, including firewall exploits, hacking tools, and scripts with cryptonyms like BANANAUSURPER, BLATSTING, and BUZZDIRECTION.
The security researchers Mustafa Al-Bassam published an interesting post that lists all the exploits, implants, and tools for hacking firewalls (“Firewall Operations”) included in the dump.
The Equation Group ‘s hackers targeted products made by Cisco, Fortigate, Juniper, TOPSEC, and Watchguard.
The majority of files are at least three years old, meanwhile, the newest timestamp dating to October 2013.
Early October, TheShadowBrokers complained that no one seems to be bidding on their precious archive, an alleged member of the hacker group expressed his dissent on the lack of interest in ponying up bitcoins to release the full NSA data dump.
Earlier December 2016, the group announced the launch of a crowdfunding campaign for the stolen arsenal because its auction received offers for less than two bitcoins.
We met Shadow Brokers last time in December 2016, when they changed the model of sale offering the NSA’s hacking arsenal for direct sale on an underground website.
The hacking group is back and now it is selling another package of hacking tools, “Equation Group Windows Warez.” The new archive includes a collection of Windows exploits and tools to evade detection of antivirus solutions.

The first malware, the Remote Administration Tool (RAT) “DanderSpritz,” was included in the collection of documents leaked by Edward Snowden.
The group posted a message on their website on the ZeroNet, announcing the sale of the entire “Windows Warez” archive for 750 Bitcoin (around US$678,630).
The data dump offered for sale contains several hacking tools grouped in the following categories:
Fuzzing tools (used to discover errors and security loopholes)
Exploit Framework
Network Implants
Remote Administration Tools (RAT)
Remote Code Execution Exploits for IIS, RDP, RPC, SMB Protocols (Some Zero-Days)
SMB BackDoor (Implant)
The malware researcher Jacob Williams published an analysis of the archive of “screenshots and output of the find command across the dump” provided by the ShadowBrokers.Williams started searching for info on the term “Psp_Avoidance” reported in one of the screenshots published by the group.
Making some Google Queries with the term “psp computer network operations” the researcher get back as the fifth result a page from ManTech. The page details the ACTP CNO Programmer Course and the course documentation indicates that PSP is an acronym for “Personal Security Product.”
“So, circling back around, what is Psp_Avoidance? Obviously, we don’t know – but if the acronym is correct, it would seem to be software built to evade personal security products, which directory listings suggest (as does ManTech) are antivirus programs.” wrote the expert.
“Should you run antivirus products? Sure. At Rendition Infosec we tell customers that operating without AV is like driving a car with no airbags. But this dump suggests that advanced attackers have mitigations for antivirus products – a sobering reality for organizations without defense in depth. “
The unique certainly at this moment is the availability for sale of a powerful arsenal also composed of hacking tools that could be exploited by a threat actor in the wild for large-scale espionage campaigns
But since this time the group has made Windows hacking tools up for sale, the chances are that hackers and espionage groups would be interested in buying these hacking tools.
A Second variant of Shamoon 2 targets virtualization products
11.1.2017 securityaffairs Virus
A second variant of the Shamoon 2 malware was discovered by researchers at Palo Alto Networks, this threat also targets virtualization products.
A new strain of the Shamoon 2 malware was spotted by the security experts at Palo Alto Networks, this variant targets virtualization products.
Shamoon, also known as Disttrack, was first spotted in a wave of attacks that targeted companies in Saudi Arabia in 2012. Among the victims, there was the petrol giant Saudi Aramco. The principal capability of Shamoon is a feature that allows it to wipe data from hard drives of the infected systems.
In the attack against Saudi Aramco Shamoon wipe data on over 30,000 computers and rewrite the hard drive MBR (Master Boot Record) with an image of a burning US flag.
The first team that discovered the malware was Kaspersky Lab that had analyzed some instances of the threat linked to the “wiper agent” due to the presence of a module of a string with a name that includes “wiper” as part of it.
The researcher of Seculert who analyzed Shamoon discovered that it has also the ability to overwrite the machine’s MBR. Before Shamoon makes unusable the infected PC, it gathers data from the victim, it steals information, taking data from the ‘Users’, ‘Documents and Settings’, and ‘System32/Drivers’ and ‘System32/Config’ folders on Windows computers, and send them to another infected PC on the same internal network.
In December malware researchers from Palo Alto Networks and Symantec discovered a new variant, so-called Shamoon 2, that was used at least in a targeted attack against a single Saudi organization, the Saudi Arabia’s General Authority of Civil Aviation (GACA).
“Why Shamoon has suddenly returned again after four years is unknown. However, with its highly destructive payload, it is clear that the attackers want their targets to sit up and take notice,” reported Symantec.
“Last week, Unit 42 came across new Disttrack samples that appear to have been used in an updated attack campaign. The attack targeted at least one organization in Saudi Arabia, which aligns with the targeting of the initial Shamoon attacks. It appears the purpose of the new Disttrack samples were solely focused on destruction, as the samples were configured with a non-operational C2 server to report to and were set to begin wiping data exactly on 2016/11/17 20:45. In another similarity to Shamoon, this is the end of the work week in Saudi Arabia (their work week is from Sunday to Thursdays), so the malware had potentially the entire weekend to spread. The Shamoon attacks took place on Lailat al Qadr, the holiest night of the year for Muslims; another time the attackers could be reasonably certain employees would not be at work.” reads an analysis published by Palo Alto Networks.
Now the second variant of Shamoon 2 was spotted by Palo Alto Networks that had been configured to start wiping infected systems at 1:30 AM (Saudi Arabia time) on November 29, when the employees of the targeted organization’ were likely at home.
The first variant of Shamoon 2 analyzed by the experts presented a default configuration that allowed the execution of the disk-wiping component at 8:45pm local time on Thursday, November 17. Considering that in Saudi Arabia the working week runs from Sunday to Thursday, the attacker tried to exploit the pause in order to maximize the effects of the attack.
Both payloads were similar, but the analysis of the experts revealed some differences.
The second Shamoon 2 variant included credentials for virtualization products from Huawei, it targeted virtual desktop infrastructure (VDI) products such as FusionCloud.
This circumstance suggests that attackers were aware that the target organization used this specific virtualization product. The hackers used default credentials reported in the product official documentation, this means they were hoping that the targeted organizations had not changed them. According to the experts, threat actors may have had access to appliances hosting the infrastructure.
“VDI solutions can provide some protection against a destructive malware like Disttrack through the ability to load snapshots of wiped systems. Also, since FusionCloud systems run a Linux operating system, which would not be susceptible to wiping by the Windows-only Disttrack malware, this could be seen as a reasonable countermeasure against attacks like Shamoon,” reads the blog post published by Palo Alto Networks.
“However, if the attacker was able to log into the VDI management interfaces using the account credentials they could manually carry out destructive activities against the VDI deployment, as well as any snapshot,” 
Researchers observed that communications module used by the threat was configured without a C&C, the module completely lack any IP address or domain name for a C2 server within its configuration.
I suggest you give a look at the report that also includes Indicators of Compromise for the threat.
Debugging mechanism in Intel CPUs allows seizing control via USB port
10.1.2017 SC Magazine UK Hacking
Researchers are warning that an Intel chip debugger leaves the chip open to hacking and because it sits below the software layer isn't easily detected.
Are attacks on the physical layer on the rise?
Researchers from Positive Technologies have revealed that some new Intel CPUs contain a debugging interface, accessible via USB 3.0 ports, that can be used to obtain full control over a system and perform attacks that are undetectable by current security tools.
An attacker could use this to bypass all security systems for the embedding of code over a certain period of time, reading all possible data and even making the machine inoperative, for instance by re-writing its BIOS.
A talk on the mechanisms needed for such attacks, and ways to protect against them, was given by Maxim Goryachy and Mark Ermolov at the 33rd Chaos Communication Congress in Hamburg, Germany.
The duo noted: “These manufacturer-created hardware mechanisms have legitimate purposes, such as special debugging features for hardware configuration and other beneficial uses. But now these mechanisms are available to attackers as well. Performing such attacks does not require nation-state resources or even special equipment.”
The duo analysed and demonstrated one of these mechanisms in their presentation. The JTAG (Joint Test Action Group) debugging interface, now accessible via USB, has the potential to enable dangerous and virtually undetectable attacks. JTAG works below the software layer for the purpose of hardware debugging of the OS kernel, hypervisors and drivers. At the same time, though, this CPU access can be abused for malicious purposes.
On older Intel CPUs, accessing JTAG required connecting a special device to a debugging port on the motherboard (ITP-XDP). JTAG was difficult to access for both troubleshooters and potential attackers.
However, starting with the Skylake processor family in 2015, Intel introduced the Direct Connect Interface (DCI) which provides access to the JTAG debugging interface via common USB 3.0 ports.
No software or hardware manipulations are required to make target computers vulnerable — merely having the DCI interface enabled is sufficient. As the researchers found, this can be accomplished in several ways, and on many computers, DCI is enabled out-of-the-box and not blocked by default.
SC Media UK spoke with Maxim Goryachy, and asked how would someone go about tricking someone into enabling the DCI interface?
Goryachy said: “There are several ways someone could do this. An attacker could change the BIOS configuration (for example, with a use of a Flash programmator) when they have physical access to the equipment during manufacturing, storage or usage. Some BIOSs do not block the DCI configuration which is why there is the possibility of turning on the DCI.”
Goryachy and Ermolov speculated that this mechanism in Intel CPUs could lead to a whole new class of Bad USB-like attacks, but at a deeper and even more dangerous level than their predecessor.
In their concluding remarks, the researchers proposed a number of protective measures based on use of Intel's BootGuard feature and forbidding activation of the debugging interface.
SC asked Goryachy if he would compare this vulnerability to Stuxnet, to which he said: “This mechanism can be used on a hacked system regardless of the OS installed. Stuxnet was infecting only Windows machines, meanwhile the DCI can be used on any system with Intel U-series processor. This series is used on laptops and NUC. As of today, no publicly available security system will detect it.”
Goryachy told SC, “We have reported this case to Intel. As of today, this mechanism can be exploited only on Intel U-series processors.”
První své antiviry AVG uvedl na trh Avast
10.1.2017 SecurityWorld Zabezpečení
Společnost Avast po akvizici firmy AVG uvádí na trh první produkty pod značkou AVG. Ty chrání počítače před útočníky, ransomware nebo ztrátou dat, a zároveň prý pomáhají zlepšovat i jejich výkon.
Avast vydal edice 2017 svých klíčových produktů pod značkou AVG – základní bezplatný AVG AntiVirus Free, prémiovou verzi antiviru pro neomezený počet zařízení AVG Internet Security (AIS) a také AVG TuneUp určený pro údržbu a čištění.
Nové verze chrání před viry a malware (včetně ransomware), před útoky hackerů, zajišťují bezpečné procházení webu a emailů a chrání soukromá data. Inovované uživatelské rozhraní přichází s jednoduchou instalací, navigací a ovládáním programu z jednoho místa.
Produkty přicházejí na trh méně než čtyři měsíce po akvizici AVG firmou Avast. Podle tvůrců kombinují to nejlepší z obou firem, aby uživatelům dodaly uživatelsky přívětivou ochranu s čistým jednoduchým vzhledem a bezproblémovým využitím pro všechny členy rodiny.
“Zkombinovali jsme způsoby detekce hrozeb AVG a Avastu a získali tak náležitý vhled do trendů mezi kyberútočníky,” řekl Vince Steckler, generální ředitel Avastu. Antimalware AVG podle něj má ochranu, která v reálném čase dokáže zasáhnout proti tzv. zero-second malware, a to díky cloudové technologii CyberCapture vyhledávající škodlivé soubory.
Například nová funkce v AIS -- Secure DNS -- ověřuje IP adresy webových stránek prostřednictvím DNS serveru, který spravuje přímo Avast. Uživatel tak má podle výrobce jistotu, že jeho finanční transakce nebo platby za on-line nákupy nemohou být přesměrovány na falešné weby a je tak chráněn před podvody a phishingovými útoky.
Ve všech bezpečnostních produktech AVG byla také integrovaná funkce bezplatného produktu TuneUP, která zvyšuje výkon počítače nebo mobilního zařízení tím, že sleduje výkon počítače a dokáže odstranit soubory zbytečně zabírající místo.
Plná verze produktu navíc zahrnuje nový nástroj určený k aktualizaci software (tzv. Software Updater), který automaticky vyhledá a instaluje nové verze nejpoužívanějších počítačových aplikací. Aktualizovaný software eliminuje případné zranitelnosti v programech a opravuje v daném software chyby.
Los Angeles College Pays Hackers $28,000 Ransom To Get Its Files Back
10.1.2017 thehackernews Virus
Ransomware has turned on to a noxious game of Hackers to get paid effortlessly.
Once again the heat was felt by the Los Angeles Valley College (LAVC) when hackers managed to infect its computer network with ransomware and demanded US$28,000 payment in Bitcoins to get back online.
The cyber-attack occurred over winter break and caused widespread disruption to online, financial aid, email and voicemail systems, including locking out 1,800 students and staffs from their computers.
As the situation was gone out of its hand, the Los Angeles Community College District (LACCD) agreed to pay the ransom demand of $28,000 in Bitcoin to criminals to resume their operations after gaining the decryption keys, the school newspaper, The Valley Star, reports.
The cyber criminals gave the college a week to pay the ransom and threatened to delete all the data if they were not paid.
Also Read: RansomFree Tool Detects Never-Seen-Before Ransomware Before It Encrypts Your Data
Just like most ransomware victims the college obviously was not properly backing up the data. Therefore, the district agreed to pay up the ransom amount to quickly recover access to their systems and data.
However, according to the college officials, it was ultimately cheaper for them to pay the ransom than to remove the unknown ransomware virus from their systems to recover data and resume other services.
After paying the ransom, the college was given a ransomware decryption key to retaining access to its valuable data.
"LACCD and LAVC information technology staff, outside cybersecurity experts and law enforcement are working together to determine the specific nature and impact of this incident. Our top priority is the integrity of student, faculty and employee data, and we will continue to communicate with the LAVC community and the public as the investigation proceeds." the College wrote in a report [PDF].
The college was lucky this time, because, in the case of ransomware, there is no guarantee that one will get the right decryption key in return. For example, recently discovered KillDisk Ransomware that targets Linux machines, demands $218,000 to decrypt, but in return, wipes out data permanently.
One of the most notorious examples of ransomware attacks took place in March last year when crooks locked down the computers and sealed all sensitive files of a Los Angeles hospital, including patient data, which eventually made the hospital to pay $17,000.
Last year, we saw an enormous rise in Ransomware threats, both in numbers and sophistication, and the only way to secure your environment is to deploy automated and isolated backup mechanism.
CVE-2016-7200 & CVE-2016-7201 Edge flaws added to the Sundown Exploit Kit
10.1.2017 securityaffairs Vulnerebility
The operators behind the Sundown exploit kit have started using two Microsoft Edge flaws just a few days after researchers published a PoC exploit.
The Sundown exploit kit is becoming one of the most popular crimeware kits in the hacking underground. The last time we saw it was at the end of 2016 when malware researchers spotted a new variant of the Sundown exploit kit leverages on steganography to hide exploit code in harmless-looking image files.
Recently cyber criminals added to the Sundown exploit kit two Edge vulnerabilities tracked as CVE-2016-7200 and CVE-2016-7201.
Both flaws were addressed by Microsoft with a security bulletin (MS16-129) issued in November 2016. The flaws reside in the way the Chakra JavaScript scripting engine handles objects and can trigger memory corruption.
A remote attacker can exploit the vulnerabilities to execute arbitrary code in the context of the current user by tricking victims into visiting a specially crafted website.
On January 4, security experts at the firm Theori confirmed the availability of a PoC exploit for CVE-2016-7200 and CVE-2016-7201, just a few days and the code was included in the Sundown exploit kit.
Segui
Theori @theori_io
Proof-of-Concept exploit for Edge bugs (CVE-2016-7200 & CVE-2016-7201) —https://github.com/theori-io/chakra-2016-11 …
00:52 - 5 Gen 2017
Photo published for theori-io/chakra-2016-11
theori-io/chakra-2016-11
chakra-2016-11 - Proof-of-Concept exploit for Edge bugs (CVE-2016-7200 & CVE-2016-7201)
github.com
210 210 Retweet 196 196 Mi piace
The popular security researcher Kafeine confirmed the exploits being integrated by the Sundown exploit kit.

“The exploits are spotted first in Sundown, but integration in RIG/Empire/Neutrino/Magnitude/Kaixin should be a matter of hours/days.” explained Kafeine.
Crooks leveraged Sundown exploit kit to deliver mostly ZLoader, it was also used to deliver other malicious payloads, including Zeus Panda, Dreambot, Chthonic, Andromeda, Neutrino Bot, Betabot, Smokebot, Remcos, Kronos and a bitcoin miner.
According to Malwarebytes Labs, a variant of the Sundown exploit kit was recently seen distributing a cryptocurrency Monero mining application.
“We recently encountered an atypical case of Sundown EK in the wild – usually the landing page is obfuscated, but in this case there was plain JavaScript. The exploit was dropping some malicious payloads” reads a blog post published by Malwarebytes Labs.
Kafeine highlighted the fact that this is the first true innovation in the exploit kit landscape since 6 months, he also added that the criminal ecosystem lost its locomotive the “Angler EK.”
“After not far from 6 months without new exploit integrated in an EK ecosystem which has lost its innovation locomotive (Angler) , the drive-by landscape is struggling to stay in shape. Low infection rate means more difficulties to properly convert bought traffic.” added Kafeine.
Last time malware researchers observed the introduction of a fresh exploit code in an Exploit Kit was this summer when malware authors added the PoC for CVE-2016-0189 to the Neutrino exploit kit.
Ransomware KillDisk útočí na linuxové stroje, naštěstí jej lze eliminovat
10.1.2017 SecurityWorld Viry
Útočníci spojovaní se skupinou BlackEnergy pomocí ransomwaru KillDisk požadují vysoké výkupné, napadená data však nelze s jejich pomocí odšifrovat. Analytici naštěstí nalezli slabinu použitého šifrování, která umožňuje obnovu napadených dat.
Novou variantu malwaru KillDisk, která šifruje obsah napadených zařízení s operačním systémem Linux, objevili analytici Esetu.
I přes to, že tento škodlivý kód neumožňuje obnovu zašifrovaných souborů, tedy nedokáže uložit a kamkoli zaslat dešifrovací klíče, tvůrci KillDisk požadují za odblokování počítačů mimořádně vysokou sumu 250 tisíc dolarů (bezmála 6,5 milionu korun) v internetové měně Bitcoin.
„KillDisk je příkladem toho, proč by se nemělo v podobných případech platit výkupné. Při vyjednávání se zločinci nemáte žádnou záruku, že dostanete vaše data zpět. V tomto případě tvůrci ransomware KillDisk neměli vůbec v úmyslu dostát svým slibům. V jejich škodlivém kódu chybí jakýkoli nástroj pro odšifrování napadených dat,“ říká Miroslav Dvořák, technický ředitel Esetu.
KillDisk je destruktivní malware, který proslul jako součást úspěšného útoku, který v prosinci 2015 provedla skupina BlackEnergy na ukrajinskou energetickou soustavu.
Výzkumníci navíc nedávno odhalili plánované kybernetické útoky, které měly cílit na celou řadu finančních institucí na Ukrajině. Útočné kampaně prostřednictvím ransomware KillDisk pokračovaly i poté, pouze se zaměřily na nové cíle v oblasti námořní dopravy.
Sady útočných nástrojů mezitím prošly dalším vývojem a poslední varianty KillDisk slouží jako ransomware pro šifrování souborů. Nejprve cílily na zařízení s operačním systémem Windows, později se však zaměřily na Linux – a to nejen na počítače s tímto otevřeným operačním systémem, ale také na servery, čímž výrazně navyšují potenciální škody.
Zatímco u verze pro Linux dokázali výzkumníci Esetu podle svých slov přijít na řešení, jak zašifrovaná data zachránit, u napadených zařízení s operačním systémem Windows se jim to zatím nepodařilo.
Vyděračské viry útočí nebývalou silou. Obrana není snadná
10.1.2017 Novinky/Bezpečnost Viry
Bezpečnostní experti bijí na poplach, vyděračských virů v novém roce rapidně přibývá. Škodlivé kódy označované souhrnným názvem ransomware dokážou zašifrovat data na pevném disku a za jejich opětovné zpřístupnění poté požadují útočníci nemalé výkupné.
Hned v prvním týdnu nového roku se začal internetem lavinově šířit úplně nový vyděračský virus. „Ransomware byl kyberbezpečnostním tématem číslo jedna uplynulého roku a zdá se, že nejinak tomu bude i v roce 2017. Novou hrozbou je ransomware GoldenEye, nejnovější varianta ransomwaru Petya,“ varoval David Řeháček, bezpečnostní odborník ze společnosti Check Point.
Petya dělala bezpečnostních expertům vrásky na čele už v první polovině loňského roku, protože pracovala daleko rychleji než podobné vyděračské viry. Ty potřebují na zakódování všech uložených dat poměrně dost času, klidně i několik hodin. Během toho může jejich práci zachytit antivirový program a zablokovat je ještě dřív, než v počítači nadělají nějakou větší neplechu.
Petya však nešifrovala všechna data, ale pouze tzv. MBR. Jde o hlavní spouštěcí záznam, díky kterému se v podstatě spouští celý operační systém. K zašifrovanému záznamu pak počítač nemá přístup a místo Windows spustí jen hlášku o nutnosti zaplatit výkupné.
Na zašifrování MBR přitom Petya potřebovala pouze pár sekund, proto antiviry prakticky neměly šanci škodlivý kód zachytit.
Na Petyu již experti vyzráli
Zatímco na Petyu již bezpečnostní experti vyzráli, v případě hrozby zvané GoldenEye zatím dešifrovací klíč chybí. Většina bezpečnostních programů je tak proti nové hrozbě bezbranná. Účinné jsou teoreticky jen aplikace, které dovedou sledovat všechny podezřelé činnosti v počítači v reálném čase.
Jakmile jsou všechny soubory zašifrované, GoldenEye zobrazí žádost o výkupné
David Řeháček, bezpečnostní odborník
GoldenEye pracuje v počítači velmi podobně jako Petya, kromě dešifrovacího klíče se liší také způsob, jakým se šíří. „Současná kampaň používá k distribuci žádosti o zaměstnání a škodlivý kód maskuje za e-mailovou přílohu. Zaměřuje se proto na oddělení lidských zdrojů, kde je rozkliknutí příloh v e-mailech od potenciálních uchazečů nutností,“ podotkl Řeháček.
Nevyžádaná zpráva obsahuje krátkou zprávu od údajného uchazeče o zaměstnání a navíc ještě dvě přílohy. „První příloha je PDF obsahující průvodní dopis a tento soubor nemá žádný škodlivý obsah. Primárním účelem je uklidnit oběť a vyvolat falešný pocit bezpečí. Druhá příloha je excelový soubor s nebezpečnými makry. Obsahuje obraz květiny se slovem "Loading ..." a doprovodný text, který žádá oběť k povolení obsahu, což umožní spuštění makra,“ vysvětlil technické pozadí útoku bezpečnostní expert.
Výkupné neplatit
Problém nastává ve chvíli, kdy uživatel klikne na volbu "povolit obsah". „Spustí se kód uvnitř makra a začne proces zašifrování souborů a oběť k nim ztratí přístup. Jakmile jsou všechny soubory zašifrované, GoldenEye zobrazí žádost o výkupné,“ uvedl Řeháček.
Výkupné by ale lidé rozhodně platit neměli. Protože ani po odeslání peněz útočníkům se zpravidla ke svým datům nedostanou. Kyberzločinci jednoduše shrábnou peníze a už se neozvou.
Místo placení výkupného je nutné virus z počítače odinstalovat. Problém ale představují zašifrovaná data, ke kterým se většinou uživatelé už nedostanou.
Hello Kitty database leaked online, 3.3 million fans affected
10.1.2017 securityaffairs Incindent
The Hello Kitty MongoDB database leaked online one year ago recently surface on the web, it includes 3.3 million records belonging to Hello Kitty fans.
The security researcher Chris Vickery discovered a Sanrio database that was misconfigured and exposed to the public in 2015.
On December 2015, Vickery reported the discovery to Databreaches.net and Salted Hash.
According to Vickery not only the primary database sanriotown.com was affected, the fan portals of the following websites were also impacted by the leak:
hellokitty.com;
hellokitty.com.sg;
hellokitty.com.my;
hellokitty.in.th;
mymelody.com.
The expert noticed that 186,261 of the records belonged to Sanrio users under the age of 18.
At the time of its discovery, Sanrio explained that it doesn’t believe the data was stolen. Now the same MongoDB database has surfaced online and the 3.3 million records put Hello Kitty fans at risk.
During the weekend, the data breach notification service LeakedSource confirmed that a Sanrio database containing 3,345,168 million users has surfaced online.
The records contained in the leaked database include first and last names, gender, encoded birthday (easily reversible), country, email addresses, SHA-1 hash passwords, password hint questions with corresponding answers, and other information.

Vickery confirmed that data available via LeakedSource is identical to what he discovered more than a year ago.
The unique difference between the two databases is a field, dubbed ‘incomeRange,’ in the LeakedSource records that was not present in the original archive. The “incomeRange” attribute comes with values running from 0 to 150, but it is still unclear its meaning.
Chris Vickery discovered many other clamorous cases of open MongoDB exposed on the Internet. In December 2015 the security expert discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
A few hours ago I published another post related to cyber attacks against misconfigured MongoDB databases.
MongoDB ransom attacks soar, according to the Australian Communications and Media Authority Antipodes the number of hacked systems more than double to 27,000 in just a day. According to the experts, the hackers are implementing an extortion mechanism copying and deleting data from vulnerable databases.
Number of MongoDB ransom attacks peaked 27,000 in a day
10.1.2017 securityaffairs Virus
According to the Australian Communications and Media Authority Antipodes the number of hacked MongoDB databases more than double to 27,000 in just a day.
MongoDB ransom attacks soar, according to the Australian Communications and Media Authority Antipodes the number of hacked systems more than double to 27,000 in just a day. According to the experts, the hackers are implementing an extortion mechanism copying and deleting data from vulnerable databases.
Crooks request the payment of a ransom in order to return data and help the company to fix the flaw they exploited. Last week I reported the story of a mysterious attacker that goes online with the harak1r1 moniker, he is breaking into unprotected MongoDB databases, stealing their content, and requesting for a 0.2 bitcoins (US$184) ransom to return the data.bitcoins (US$184) ransom to return the data.
The attacks were discovered by the Co-founder of the GDI Foundation, Victor Gevers, who warned of poor security for MongoDB installations in the wild. The security expert has discovered 196 instances of MongoDB that were wiped by Harak1r1 and being held for ransom.
The analysis of the Bitcoin wallet used by Harak1r1 revealed that at least 22 victims appeared to have paid.

5 Gen
Adrian Sanabria @sawaba
@SteveD3 @LawrenceHecht @achillean @akmalchaudhri @0xDUDE FWIW, in my experience, Shodan is a varying fraction of what's actually out there.
Segui
Victor Gevers @0xDUDE
@sawaba @SteveD3 @LawrenceHecht @achillean @akmalchaudhri That is why I am looking at different sources like Zoomeye (99,491 candidates) pic.twitter.com/VApFdRbF7g
18:17 - 5 Gen 2017
Visualizza l'immagine su Twitter
1 1 Retweet 3 3 Mi piace
According to the security researcher Niall Merrigan the number of attacks have soared from 12,000 earlier today to 27,633 in just 12 hours. According to the expert the attacks were powered by at least 15 different actors. One of the attackers goes online with the moniker ‘kraken0’ has compromised 15,482 MongoDB databases demanding victims the payment of 1 bitcoin ($US921).
Segui
Niall Merrigan @nmerrigan
Latest #Mongodb ransack looks like ~27K servers compromised from 12K this morning.. Numbers and info https://docs.google.com/spreadsheets/d/1QonE9oeMOQHVh8heFIyeqrjfKEViL0poLnY8mAakKhM/edit?usp=sharing … with @0xDUDE
23:03 - 8 Gen 2017
51 51 Retweet 30 30 Mi piace
The researcher is collecting information on the attacks including information provided by Victor Gevers.
The Australian Communications and Media Authority Antipodes is monitoring exposed MongoDB installations since July 2015 using intelligence provided by the ShadowServer nonprofit.
The organization reports about 400 exposed MongoDB databases a day to 90 percent of Australia’s network providers via the Australian Internet Security Initiative (AISI).

AISI statistics on Exposed MongoDB published by ElReg
Stay tuned …
Over 27,000 MongoDB Databases Held For Ransom Within A Week
9.1.2017 thehackernews Virus
The ransomware attacks on poorly secured MongoDB installations have doubled in just a day.
A hacker going by the handle Harak1r1 is accessing, copying and deleting unpatched or badly-configured MongoDB databases and then threatening administrators to ransom in exchange of the lost data.
It all started on Monday when security researcher Victor Gevers identified nearly 200 instances of a MongoDB installation that have been erased and held for ransom, asking victims to pay hefty ransoms for the data to be restored.
By Tuesday, this number reached approximately 2,000 databases as reported by Shodan Founder John Matherly, and by Friday, Gevers and fellow security researcher Niall Merrigan updated this count to 10,500.
However, according to recent statistics compiled by Merrigan, the number of compromised systems have reached more than double to 27,000, over the course of about 12 hours.
What's worse?
Initial attacks saw ransoms of 0.2 Bitcoins (nearly US$184) to the attacker, of which 22 victims appeared to have paid. But now the attacker is demanding up to 1BTC (around 906 USD).
The researchers have logged some 15 distinct attackers, of which an attacker using email handle kraken0 has compromised 15,482 MongoDB instances and is demanding 1 Bitcoin to return the lost data, though no one appears to have paid.
This means that after the initial story was made public, more hackers and the group of hackers are also doing same — accessing, copying and deleting badly-configured MongoDB databases — for ransom.
Who is responsible for the MongoDB Ransomware?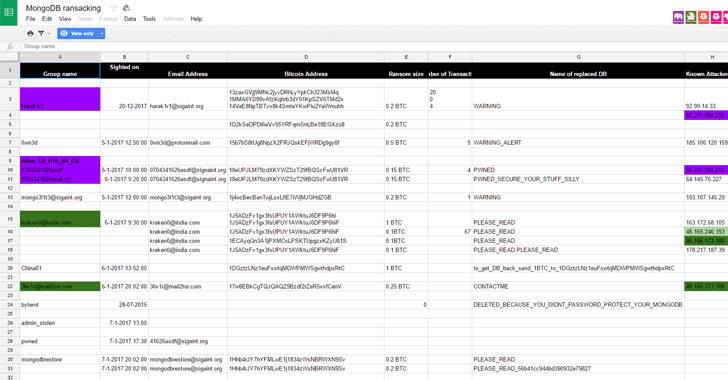
You! Yes, all those administrators who are using misconfigured MongoDB databases are the reason for this sudden spurt in these attacks.
In every case, the target MongoDB server had an administrator account that was configured without a password.
Many poorly secured MongoDB databases can be identified using Shodan search engine, which currently shows more than 99,000 vulnerable MongoDB instances.
This is the case when the company provides an easy way to set up authentication in MongoDB.
How to Protect Yourself?
Since there's no evidence the hackers had copied the data before deleting it, promises to restore the already-deleted databases in return for a hefty ransom are dubious.
Gevers advises affected MongoDB database owners not to pay and to get help from security professionals. He and Merrigan have helped some 112 victims secure their exposed MongoDB databases.
People who administer websites that use MongoDB are advised to follow these steps:
Enable authentication that provides you 'Defense in depth' if your network is compromised. Edit your MongoDB configuration file — auth = true.
Use firewalls — Disable remote access to the MongoDB, if possible. Avoid common pitfalls by blocking access to port 27017 or binding local IP addresses to limit access to servers.
Administrators are strongly recommended to update MongoDB software to the latest release.
Meanwhile, MongoDB developers have released an updated guide to MongoDB security, explaining these ransomware-inspired attacks and how you can detect and prevent them, along with the steps to check the integrity of your
ESEA data breach, 1.5 million gamers’ records leaked
9.1.2017 securityaffairs Incindent
The E-Sports Entertainment Association (ESEA), one of the largest competitive video gaming communities was hacked, 1.5 million players have been affected.
Bad news for gamers, the E-Sports Entertainment Association (ESEA), one of the largest competitive video gaming communities was hacked in December. The data breach exposed the profiles of more than 1.5 million players.
The incident was also confirmed on Saturday by the breach notification service LeakedSource that reported 1,503,707 ESEA records were compromised.
The records include username, first and last name, password bcrypt hash, email address, registration date, city, state (or province), last login, date of birth, zip code, phone number, website URL, Steam ID, Xbox ID, and PSN ID.
As you can see the profiles are very detailed, the use of the bcrypt hash protect users’ passwords, anyway gamers are exposed to a wide range of malicious activities such as social engineering attacks and spear phishing attacks.
ESEA shared the link to the following “Outage and Security Update” via Twitter.
“Recently news has been made that ESEA’s user data has been leaked online. We expected something like this could happen but have not confirmed this is ESEA’s data. We notified the community on December 30th, 2016 about the possibility this could happen. The type of data and storage standards was disclosed. We have been working around the clock to further fortify security and will bring our website online shortly when that next round is complete. This possible user data leak is not connected to the current service outage.”
Segui
ESEA ✔ @ESEA
ESEA Outage and Security Update
Read: http://tl.gd/n_1spgt4i
04:29 - 8 Gen 2017
47 47 Retweet 100 100 Mi piace
The company was informed of the data breach on December 27 and issued a security warning on December 30, 2016. At the time I was writing, ESEA only confirmed the data leak, but still hasn’t admitted that profiles were accessed from its systems.
The news of the ESEA data breach is circulating on the Internet, many players confirmed it on Reddit.
Segui
Jimmy Whisenhunt ✔ @jimmywhis
.@BigSecurityNews confirmed my ESEA account info after they asked a couple 'larger' followed users to help verify
05:10 - 8 Gen 2017
8 8 Retweet 16 16 Mi piace
Segui
Jimmy Whisenhunt ✔ @jimmywhis
.@BigSecurityNews confirmed my ESEA account info after they asked a couple 'larger' followed users to help verify
05:10 - 8 Gen 2017
8 8 Retweet 16 16 Mi piace
Salted HASH, quoting a LeakedSource spokesperson, reported that the ESEA data breach was part of a ransom scheme. Crooks demanded $50,000 in payment to avoid disclosing the hack.
In response to the incident, the company reset passwords, multi-factor authentication tokens, and security questions.
Crooks target UK schools with ‘Department of Education’ ransomware
9.1.2017 securityaffairs Virus
Action Fraud is warning of ‘Department of Education’ ransomware, crooks are posing government officials to trick people into installing ransomware.
This is a story of another string of cyber attacks that leverage ransomware to compromise victims’ machines.
Cyber criminals are targeting schools in the UK, asking victims to pay up to £8,000 to unlock data to unlock encrypted documents.
The British Action Fraud is warning of fraudsters that are posing government officials from the Department of Education in order to trick people into installing ransomware on their computers.
The crooks are initially cold calling education establishments asking for the head teachers’ email addresses, then target them with malicious messages having zip attachments supposedly containing sensitive information. The attachments contain the ransomware.
“Fraudsters are initially cold calling education establishments claiming to be from the “Department of Education”. They then ask to be given the personal email and/or phone number of the head teacher/financial administrator.” reads the advisory published by ActionFraud.
“The fraudsters claim that they need to send guidance forms to the head teacher (these so far have varied from exam guidance to mental health assessments). The scammers on the phone will claim that they need to send these documents directly to the head teacher and not to a generic school inbox, using the argument that they contain sensitive information.”
Educational establishments must be vigilant of such kind of threats and have to check that their systems are up-to-date.
The Action Fraud organization added that similar scams have been carried on by fraudsters claiming to be from the Department for Work and Pensions and telecoms providers. In both cases the cyber criminals target the head teacher.
How to avoid such kind of scams?
First of all, being vigilant of any suspicious activity, even when attackers seem to know your personal details or have details about your staff. In the specific case, note that the “Department of Education” is not a real government department. Hackers used it instead of the real name Department for Education.
Having up-to-date defense solutions and software (i.e. OS and applications).
Never open attachments in unsolicited emails neither click on embedded links.
Make regular backups of your data. Be sure that the data are stored on an external storage system.
Recent power outages in Turkey were also caused by cyber attacks
9.1.2017 securityaffairs Cyber
Turkish Energy Minister Berat Albayrak believes that power outages in Istanbul and other areas in Turkey have also been caused by cyber attacks.
According to Turkish Energy Minister Berat Albayrak, Istanbul and other areas in Turkey have been experiencing power outages since last week. The power outages were caused by sabotage of underground powerlines and cyberattacks originating in the US.
“Yesterday, we faced an intense, US-originated cyber attack. These attacks have been carried out systematically on different parts of the Energy Ministry, but we have repelled them all,” explained the Turkish Energy Minister in an interview with A Haber TV.
The technicians discovered sabotage of underground lines in three districts of Istanbul in concomitance of adverse weather conditions.
snow power outages
People walk on Taksim square during snowfalls in Istanbul on January 7, 2017.
A heavy snowstorm paralysed life in Istanbul with hundreds of flights cancelled and the Bosphorus closed to shipping traffic. The snowstorm dumped almost 40 centimetres (16 inches) of snow in parts of the Turkish metropolis overnight, causing havoc on roads as travellers sought to leave the city for the weekend getaway. / AFP PHOTO / YASIN AKGUL
In a first time, the Energy Ministry reported the power outages were caused by damage to the power grid caused by the snow.
Recently, a source in the ministry confirmed to the state news agency Anadolu that the problems were also caused by cyber attacks.
“Many infiltration attempts to the systems controlling our transmission and electricity producing lines were determined and prevented. The infiltration attempts are indicators of a major sabotage preparation against Turkey’s national electricity network,” the anonymous source told the agency.
The Turkish Government continues to accuse US-based Turkish preacher Fethullah Gulen of using a wide network of supporters in Turkey to undermine the country’s stability.
Gulen denies any accusations and the US refuses to comply the Turkish request for his extradition.
Some prominent experts believe that Turkish authorities are facing with sabotage and problems to legacy infrastructure using “cyber” as a scapegoat for the situation.
French Minister Le Drian on cyber espionage: France is not immune, ready to hack back
9.1.2017 securityaffairs Cyber
Defense Minister Le Drian comments expressed concerns about cyber attacks against defense systems and warns of hacking campaigns on the upcoming elections.
According to the Defence Minister Jean-Yves Le Drian France defense was targeted by thousands of attacks in 2016. France thwarted more than 24,000 cyber attacks against Defence systems last year.
The Minister confirmed that thousands of attacks from external sources targeted the defense architecture, including France’s drone systems, but all the attacks have been repelled.
The number of cyber attacks in France has increased in a significant way substantially across the last three years. According to Mr Le Drian, hacking attacks represents a serious threat to national infrastructure.
The French Defence Minister revealed that cyber attacks were doubling every year and expressed concerns about possible offensives against this year’s presidential election.
In an interview with Le Journal du Dimanche newspaper, the French Minister said that France “should not be naive”.
French Minister Le Drian on cyber espionage
The Minister warns of possible cyber attacks like the ones that targeted the 2016 US Presidential Election.
In France, the conservative candidate Francois Fillon has been praised by Russian president Vladimir Putin due to its intention to intensify the relationship with the Kremlin. On the other side, the candidate Marine Le Pen is in total opposition to Russia, for this reason, the experts believe that hackers could target him and his party.
Relations between Russia and France are not good due to the position of President Hollande on the dispute between Russia and Ukraine in the 2014 Crimean Crysis.
President Hollande also blamed Russia of war crimes over its bombardment of the Syrian city of Aleppo.
The Minister is overseeing an overhaul of the cyber-security operations conducted by his Government.
“Our services have discussed the subject, if only to learn lessons for the future,” said Le Drian, who also referred to a cyber attack against the 2015 French TV station TV5Monde.
According to many security firms, including FireEye, the Russian APT 28 group was involved in the attack against the French TV station.
According to security experts at FireEye, the Russian ATP28 (also known as Pawn Storm, Tsar Team, Fancy Bear and Sednit) may have used the name of ISIS as a diversionary strategy, the experts noticed a number of similarities in the TTPs used by the Russian group and the one who breached the network at TV5Monde.
I found very interesting the posture of the French Minister, he is aware that foreign hacker could break into national infrastructure, but he also contemplate the possibility to strike back the attackers.He said the French army’s number of “digital soldiers” would be doubled to 2,600 by 2019, with
Le Drian confirmed that number of “digital soldiers” working for the French defense would be doubled to 2,600 by 2019, 600 cyber experts will joint to the cyber army.
“Le Drian said that in case of a cyber attack, the country could respond in kind as well as with conventional weapons.” reported the Reuters Agency.
FTC filed a lawsuit against D-Link over failure to secure its IoT devices
8.1.2017 securityaffairs Vulnerebility
FTC charges the Taiwanese IT giant D-Link putting consumers’ privacy at risk due to the failure of Implementing secure adequate measures for IoT devices.
The U.S. Federal Trade Commission (FTC) has filed a lawsuit against the Taiwanese firm D-Link, over failure to secure its IoT products, including IP cameras and routers.
The company has produced promotional materials ensuring “Advanced Network Security” for its products, but the reality is different because according to the authorities it has failed to fix flaws exposing consumers to risk.
“A lawsuit the FTC filed against D-Link, a global manufacturer of computer networking equipment and other connected devices, alleges that the company made deceptive claims about the security of its products and engaged in unfair practices that put consumers’ privacy at risk.” reads the announcement from FTC.
The lawsuit includes examples of the D-Link’ choices that put consumers’ privacy at risk:
D-Link allegedly hard-coded login credentials into D-Link camera software that could allow unauthorized access to cameras’ live feed.
D-Link allegedly left users’ login credentials for its mobile app unsecured in clear, readable text on consumers’ devices.
D-Link allegedly mishandled its own private key code used to sign into D-Link software and as a result, it was publicly available online for six months.
D-Link allegedly failed to take reasonable steps to prevent command injection, a known vulnerability that lets attackers take control of people’s routers and send them unauthorized commands.
Usually, hackers that find the flaws report them to the company giving it the necessary time to solve the problems before publicly disclose the vulnerability. Over the past year, some hackers decided to disclose unpatched flaws due to the company’s failure to release necessary security updates that will fix the vulnerabilities.
The Tech giant has been accused of failing to take reasonable steps to secure the software for its IoT devices and for conducting practices that are “likely to cause, substantial injury to consumers in the United States.”
This isn’t the first time that IoT manufacturers tell customers that their products are totally secure while they lack to adopt the necessary security measures.
Earlier 2016, the FTC filed a lawsuit against Asus claiming that the company has put hundreds of thousands of consumers at risk through a series of critical flaws discovered in its products.
“Hackers are increasingly targeting consumer routers and IP cameras — and the consequences for consumers can include device compromise and exposure of their sensitive personal information,” said Jessica Rich, director of the FTC’s Bureau of Consumer Protection. “When manufacturers tell consumers that their equipment is secure, it’s critical that they take the necessary steps to make sure that’s true.”
China-Linked DragonOK APT Group continues updating tools and tactics
8.1.2017 securityaffairs APT
The China-linked DragonOK continues updating tools and tactics and targeted entities in various countries, including Russia and Tibet.
It was September 2014, when security researchers at FireEye spotted for the first time the cyber espionage activities of a Chinese state-sponsored group dubbed DragonOK.
At the time, FireEye discovered two hacking campaigns conducted by distinct groups operating in separate regions of China that seem to work in parallel.
The first team of hackers named Moafee, targeted military and government organizations which were in some way involved in South China sea dispute. The attackers hit different organizations as explained by the researchers at FireEye in a blog post, and appears to operate from the Guangdong Province and hit entities working in the defense industry in the United States.
The second team, dubbed DragonOK, conducted corporate espionage operations on high-tech and manufacturing companies in Japan and Taiwan.
DragonOK is back and recently targeted Japanese organizations in several industries, including manufacturing, technology, energy, higher education and semiconductor.
While Japan is considered the main target of the APT, hackers also targeted individuals or organizations in Taiwan, Tibet, and Russia.
According to the experts at Palo Alto Networks, one of the malware used by the DragonOK APT was dubbed Sysget and was used to target entities in Taiwan.
The Sysget malware was delivered both directly via phishing emails, as well as in RTF documents triggering the CVE-2015-1641 flaw that in turn leveraged a unique shellcode. The experts observed three distinct new versions of Sysget malware that were improved to make harder the detection and the analysis by security solutions.
PaloAlto also observed DragonOK hackers using other two families malware, the IsSpace and TidePool.

“IsSpace” is an evolution of the NFlog backdoor used by both DragonOK and Moafee. The second malware TidePool was observed earlier this year in targeted attacks powered by a different Chinese APT group, dubbed Operation Ke3chang.
Back in 2013, the security researchers at FireEye spotted a group of China-Linked hackers that conducted an espionage campaign on foreign affairs ministries in Europe. The campaign was named ‘Operation Ke3chang,’ the same threat actors were spotted targeting personnel at Indian embassies across the world earlier this year.
DragonOK now used the TidePool malware in targeted attacks against organizations in Russia and Tibet.
The analysis published by Palo Alto Networks researchers included links between the C&C domains of the various malware used by the DragonOK (i.e. TidePool, IsSpace and Sysget), and other Indicators of Compromise.
“The DragonOK group are quite active and continue updating their tools and tactics. Their toolset is being actively developed to make detection and analysis more difficult. Additionally, they appear to be using additional malware toolsets such as TidePool.” states Palo Alto Networks. “While Japan is still the most-targeted region by this group, they look to be seeking out victims in other regions as well, such as Taiwan, Tibet, and Russia.”
President Putin ordered cyber attacks and propaganda to influence US Election
7.1.2017 securityaffairs Cyber
Putin ordered cyber attacks and propaganda to influence Election. Reading the “Assessing Russian Activities and Intentions in Recent US Elections” Report.
The US Office of the Director of National Intelligence (ODNI) has released an unclassified version of intel community’s findings on activities conducted by the Russian Government in the attempt to influence the 2016 US Presidential Election through cyber attacks and online propaganda.
According to the report, the Russian President Vladimir Putin “ordered” a wide-ranging effort to influence the American vote in favor of President-Elect Donald Trump.
“We assess Russian President Vladimir Putin ordered an influence campaign in 2016 aimed at the US presidential election. Russia’s goals were to undermine public faith in the US democratic process, denigrate Secretary Clinton, and harm her electability and potential presidency. We further assess Putin and the Russian Government developed a clear preference for President-elect Trump. We have high confidence in these judgments,” the report said.
“We also assess Putin and the Russian Government aspired to help President-elect Trump’s election chances when possible by discrediting Secretary Clinton and publicly contrasting her unfavorably to him. All three agencies agree with this judgment. CIA and FBI have high confidence in this judgment; NSA has moderate confidence.”
The Russia tasked its cyber army of conducting cyber espionage campaigns against policy parties, and the Democratic National Committee (DNC) in 2015. The Kremlin also used an army of online trolls to conduct online propaganda and PSYOPs aimed to spread fake news and influence public sentiment.
According to the report released by ODNI, the Russian General Staff Main Intelligence Directorate (GRU), participated in the operations since March of 2016.
“We assess that the GRU operations resulted in the compromise of the personal e-mail accounts of Democratic Party officials and political figures. By May, the GRU had exfiltrated large volumes of data from the DNC,” reads the report.
According to the US intelligence, the mysterious hacker Guccifer 2.0 who passed the stolen information to WikiLeaks was an entity operated by the GRU.
The ODNI report states Russian hackers gathered intelligence on US Presidential Election and technology used since 2014.
“Since early 2014, Russian intelligence has researched US electoral processes and related technology and equipment. DHS assesses that the types of systems we observed Russian actors targeting or compromising are not involved in vote tallying,” continues the report.
The report also highlights the use of the RT America TV, a Russia-financed channel operated from within the United States, as a messaging tool to undermine faith in the US Government and fuel political protest.
The report confirmed that hackers belonging to the Russian GRU were behind the leak of data exfiltrated from the World Anti-Doping Agency (WADA) database.
Of course, Russia denied claims it interfered with the US Presidential Election.
Analyzing a variant of the GM Bot Android malware
7.1.2017 securityaffairs Android
My friends at CyberBlog decided to analyze the GM Bot Android Malware as exercise aiming to receive feedback sand suggestions from the security community.
The sample explored is confirmed as a variant of the GM Bot Android malware – who’s source was released publicly in early 2016. The code appears to have been forked by a second author and has additions that target the Danske Bank MobilePay application and the popular Danish Nem ID two factor authentication (2FA) system.
This article shows the process of walking through Static and Dynamic analysis to unlock the packed source code for the malware.
We see how even with basic static analysis a full picture of the intent of the malware can be readily assembled, and with a little debugging we can quickly get to readable source code.
Background
As part of my journey into Cyber Security I thought it would be interesting to see how modern mobile malware operates. I chose the following sample at random based on an article here.
File Details
SHA256: 44ed4bbd5cdc13c28992c16e99a7dc58f5f95463e889dd494a433549754f7863
MD5: da88bdcb3d53d3ce7ab9f81d15be8497
A quick google search for these hashes will lead you to the file used if you would also like to explore this sample.
The article above demonstrates that the analyst has gone from sample to source code, but it is not clear how this is achieved. There are references to suggest that the code has been packed, but again no information on how it was unpacked for analysis.
This post will break down the process I used to analyse this sample, hopefully with enough detail to provide some tips and guidance for others wishing to attempt similar. The process I followed can be logically broken into the following stages:

Analysis Process
Public Analysis – What can we find out using existing public sources of information? What analysis has already been performed (automated or manual)?
Static Analysis – What can we determine from the sample without actually running it in an emulated environment?
Packer Debugging – Assuming the sample is packed (to frustrate analysis), how do we debug the unpacker to understand what is being loaded /run?
DEX Extraction and De-compilation – Once we have mapped out the function of the unpacker, how do we then recover the main code for the malware and reverse it?
Functional & Dynamic Analysis – once we have the extracted and reversed code, what do we see and how does this correlate with behavior in a safe emulated environment
Stage 1 – Public Analysis
First off let’s see what we can find about this in the public domain. Searching for the file hashes on Virus Total, where we see approximately 50% of AV products have identified it as malicious:

VirusTotal Results
However, we also note that all classify it heuristically as a generic strain of malware – either a Trojan, Dropper, Fake Installer etc. Nothing to suggest it is in fact GM Bot Android, or any specific type of malware. Other than this we don’t see much from google with either the SHA256, or MD5 hashes.
The original Security Intelligence article references IBM X-Force research, so this is the next stop – but again nothing immediately obvious with regards to this sample could be located.
A wider search of the internet reveals some history of GM bot, originally built and sold by Ganga Man on dark web forums. Following a dispute the source code for both client APK and C2 server were released publicly. A copy is hosted here on Github and will provide useful for cross referencing with this sample later in the analysis.
https://github.com/gbrindisi/malware/tree/master/android/gmbot
Stage 2 – Static Analysis
First up we are going to unpack the APK file using APK tool. This will unzip the contents, as well as providing a disassembly of the DEX code into Smali:
apktool d da88bdcb3d53d3ce7ab9f81d15be8497.apk
The results of this can be seen below and the tool has also provided a human readable version of the AndroidManifest.xml file.

Extracted APK files
First stop is to take a look at the Android Manifest file, that should provide an overview of the components of the application and permissions requested.
Manifest Analysis – AndroidManifest.xml
Android Manifest
Initial analysis shows a broad range of permissions that indicate malicious behavior including permissions to:
control all SMS messages (send, receive, read, write, delete)
list running applications
read the phone’s state, contacts, SD card data
request to be a device administrator enabling remote wiping of the device with no warning to the user
A summarized view of referenced class files for the main application, activities (15) and services (2) can be seen below:

Classes Declared in Manifest -Application, Activities and Services
In addition, we see 4 further classes mapped as Broadcast Receivers which will process event messages (Android system Intents) as shown below:

Broadcast Receiver Classes Declared in Manifest
From this we can see the application is capable of:
Executing code when the phone is powered on (starting the application automatically)
Receive notification when Device Admin is granted, requested or a request to disable admin is received (and hence interfere, or nag the user to enable it)
Receive notification of a new inbound SMS – with high priority flag to ensure the code can intercept it first and potentially stop any further alerts (can be used to steal 2FA tokens)
Before proceeding with any reverse engineering of the code, the next step is to explore the other files in the APK for clues.
Files of interest
The following files were noted as of interest:
File: assets/fytluah.dat
A binary file with no immediately obvious format. Possible code to be unencrypted / unpacked at run time?
File: res/values/strings.xml
English language strings for the application, as shown below:

File: res/values/strings.xml (English Language Resource File)
The strings clearly indicate that this malware is targeting capturing victims credit card information. It is interesting to note that:
The resource keys here are all in English, suggesting the original developer may be English speaking
There are specific strings that are in Danish, despite this resource file being intended for English language
In addition to English language strings we also see several other targeted countries:
Other Resource Files
File: res/values.xml
This file contains a list of country codes and specifically a group that are “non vbv”. This is understood to mean that they do not use the “Verified by Visa” process which is used to enforce additional verification checks during online purchases. It is likely that the attackers would seek to obtain additional VBV credentials via the malware in order to allow online purchases with the card details (or avoid these countries).

Verified By Visa Targeted Countries
Directory: res/drawable
Images and icons/logos including:
Sample photo of Danish “Nem Id” – https://en.wikipedia.org/wiki/NemID
Icon for Danske Bank mobile pay
Mastercard secure code
Icon for verified by visa
Google play
Flash icon (main application icon)
Whatsapp
Additionally there are png images prefixed “overlay_”, indicating a possible use in fraudulent overlay activity.
Decompiling to Java source code
Next we attempt to reverse engineer the DEX file back to original Java source code. For this we use dex2jar as follows to translate the DEX file (in the APK) into a Java Class file archive:
Dex2jar da88bdcb3d53d3ce7ab9f81d15be8497.apk
The resulting jar file can then be disassembled using JD-GUI as follows:
java -jar ../../jd-gui-1.4.0.jar da88bdcb3d53d3ce7ab9f81d15be8497_dex2jar.jar
The resulting java classes that we see in JD-GUI show that there are only 4 java classes contained in the application. This is in direct contrast to the 16 different classes we saw declared in the application manifest. This confirms that there must be additional code that is loaded dynamically at run time – it is most likely that these four classes are in fact an unpacker.

Unpacker Classes
Examining the code we see that it is heavily obfuscated and has been crafted in a way to prevent clean decompiling of the code. This aside, we can start to get an understanding of the function of these four classes by examining the system classes that are imported (and therefore used) when the application is first executed.
After exporting the java source from JD-GUI and unzipping to a new folder, we can extract the imported classes from these files:
find . -type f -exec grep "^import" {} \; | sort -u
The classes we find are shown below :
Class Imported Class
com.igcfse.enscbo.a com.igcfse.enscbo.b
com.igcfse.enscbo.a java.io.RandomAccessFile
com.igcfse.enscbo.a java.lang.reflect.Constructor
com.igcfse.enscbo.b android.app.Application
com.igcfse.enscbo.b android.content.Context
com.igcfse.enscbo.b com.igcfse.enscbo.a
com.igcfse.enscbo.b java.io.File
com.igcfse.enscbo.b java.lang.reflect.Field
com.igcfse.enscbo.b java.lang.reflect.Method
com.igcfse.enscbo.c android.content.Context
com.igcfse.enscbo.c com.igcfse.enscbo.b
com.igcfse.enscbo.c java.io.FileDescriptor
com.igcfse.enscbo.c java.io.IOException
com.igcfse.enscbo.c java.lang.reflect.Constructor
com.igcfse.enscbo.c java.util.Random
com.igcfse.enscbo.wieroel android.app.Application
com.igcfse.enscbo.wieroel android.content.Context
com.igcfse.enscbo.wieroel com.igcfse.enscbo.b
Essentially we have a very small set of libraries that are being imported and used. These consist of functionality for:
General Android application and context classes (expected and needed for all android apps)
File related classes (in red) – for access, reading and writing local files
Java reflection classes (in green) – for creating new classes and instances and invoking methods dynamically
This confirms the hypothesis that we are most likely dealing with an unpacker that unpacks it’s executable code from a local file resource (as opposed to pulling dynamically from network for example).
Stage 3 – Unpacker Debugging
As the Java code cannot be readily decompiled (due to protections injected by the malware author) we will instead debug the executable against the Smali assembly code. Smali is a disassembly of the DEX code used by the Dalvik Virtual Machine.
The Smali/Baksmali plugin for Android Studio is required, and then the output from Apktool is imported as a new project. We next set the breakpoints as required across the three classes that we are interested in (a,b,c):

Setting Breakpoints in Android Studio
We will initially debug the calls to interesting reflection methods identified, which are as below:
a.smali (a line that creates a new instance of a class based on a java.lang.reflect.Constructor instance)
![]()
b.smali (a line that invokes a method on an object via reflection)
![]()
c.smali (a line similar to that described above for a.smali)
![]()
Now we install the application to the emulator (via ADB to ensure it doesn’t start automatically as in some emulators).
To enable the debugger to connect to the application, we perform the following prior to starting the application:
Enable developer options by repeatedly clicking the build number in Settings > About device
In developer options, choose “Select debug app” and choose the malicious application – “Adobe Flash”
In developer options, enable the “wait for debugger”
Selecting Debug Application
Now start the application from the launcher, you will be prompted to attach the debugger:

Attaching Debugger
In Android Studio, attach the debugger using the icon. Choose the malicious application process. The debugger then stops at our first breakpoint as shown below:

First Breakpoint Reached
Note you should now set some variables to watch – as per above I have set v0 through v10 and p1 through p3. Our first breakpoint is hit and we see we are about to execute a method by reflection. Noting that we have not yet called newInstance() we can assume this is calling existing (loaded) classes – either one of the four loaded by the application, or some other Android framework classes.
Next we forces step into the method to see which method it is calling (the smali debugger seems a little buggy and we can’t at this point see the parameters being passed).

Stepping into Reflected Method Call
An initial call to get the current context object -presumably to start retrieving local resources from the APK. We now allow the debugger to continue, and repeat this exercise several times to build up a flow of the reflected method calls:
Context android.context.ContextWrapper.getBaseContext()
//expected 2 arguments, got 1 – error in malware code, or to throw off debugging?
//Several more of these not shown
IllegalArgumentException java.lang.IllegalArgumentException(String s)
void Java.lang.reflect.setAccessible(boolean flag)
File android.app.getDataDir()
// returns /data/user/0/com.kzcaxog.mgmxluwswb/app_ydtjq
java.io.File.getAbsolutePath()
ContextImpl android.app.getImpl(Context context)
//filename is fytluah.dat
InputStream android.content.res.AssetManager.open(String fileName)
Pausing here, we can see the code is attempting to load the file that we had previously flagged as of interest in the static analysis section. Continuing we see the file is read, presumably decrypted and then written out again as a jar file:
int android.content.res.AssetManager.read(byte[] b)
//className = java.io.File
Class java.lang.Class.forName(String className)
//args = String “/data/user/0/com.kzcaxog.mgmxluwswb/app_ydtjq/gpyjzmose.jar”
T Java.lang.reflect.Constructor.newInstance(Object.. args)
void java.io.FileOutputStream.write(byte[] b) #25
void java.io.FileOutputStream.close()
Finally a DexClassLoader is invoked to load the additional code into the system:
ClassLoader java.lang.Class.getClassLoader()
//className is dalvik.system.DexClassLoader
java.lang.Class.forName(String className)
Looking at the API for the DexClassLoader we can see that it takes two arguments – the location of the file to load, and a writeable area that it will use to re-write an optimised version of the code for the specific machine architecture – eg the Android Run Time (ART). Further information on this can be seen in the Android API documentation:
https://developer.android.com/reference/dalvik/system/DexClassLoader.html
Stage 4 – DEX Extraction and Decompiling
We can see the exact location of the jar file in the debugger below, and the next step is to recover this file via ADB command line.

Debugging the Call to the DEXClassLoader
After execution of the classloader, connecting via ADB shell we see the two files, the original and the DEX optimised code:

Extracting the Payload Code
We copy these files to /sdcard/Download (+chmod) and then pull the .jar file to local machine for further analysis with adb pull.

Examining the files
Extracting the jar file we find the classes.dex file.
Repeating the steps to convert this to a jar file using dex2jar and decompiling with JD-GUI, we confirm we now have the full (un-obfuscated) source code for this malware sample.

Decompiled Source Code
Stage 5 – Dynamic and Functional Analysis
First Installation
Upon initial analysis we can see the codebase bear remarkable similarities with the leaked source identified in the static analysis. However there are significant differences, and the code has been customised to specifically target the Danske Bank MobilePay application.
As the code is basically un-obfuscated, I’ll now briefly walk through the key functionality of this malware, starting from first installation.

First Installation Process Overview
Upon first installation and execution the application will perform two primary functions. It will initially harvest a range of the users data, including phone contacts, all SMS messages and other key data and send this to the C&C server. The C&C server then returns a unique installation identifier that is then used for all future communication to uniquely identify the compromised device.
Secondly the malware will then nag the user to accept the software as a device administrator. If the user declines the request is re-triggered, making it very difficult for most users to escape this screen without accepting. With this permission in place, the malware achieves two objectives:
The application cannot be un-installed by the user easily, without de-activating the device administrator. Attempting to do this will trigger the launching of overlays that prevent removing the device admin
At some point in the future, once further data has been stolen from the phone, the C2 server can issue a command to wipe the device, removing evidence of the infection and restoring the device to a factory state
Ongoing Operations – including after each reboot
Command and Control Process Flows
The malware maintains a regular heartbeat to the C2 server, which provides a mechanism for the attacker to issue specific commands to the device. Each hearbeat contains the installation ID and the current screen status. It is hypothesised that the attacker would ideally choose to execute malicious activities when the screen was off, and the user was not watching the phone.
Firstly we see the ability to “lock” and “unlock” the phone. This simulates an Android software update screen, and effectively hides any other activity that is occurring behind the screen overlay (such as sending, receiving or deleting SMS messages). Additionally this could be used to disable the user, and prevent them from using the phone whilst their accounts or cards are being compromised in real time.
Next we see another function that is intended to intercept and forward SMS messages to the C2 server, and specifically trying to remove evidence that they ever existed by deleting them. This is used to steal 2FA credentials.
Next from a C2 server perspective we see two “reset” commands. The first, a “soft” reset, is used to reset the internal flag to re-attempt stealing Nem ID credentials. The second is the “hard” reset that performs and immediate wipe of the device data.
Finally, we see the ability to send an arbitrary SMS message to a mobile defined by the attacker and a function to launch a customised push notification to another application on the device. It was not clear what this could be used for.
SMS Remote Control
SMS Remote Control – “Admining Mode”
By listening for incoming SMS messages the malware could also trigger a fake Android update screen that would then harvest, forward and attempt to delete messages as they arrived on the phone. This mode could be enabled and disabled by customised SMS command messages delivered to the phone via SMS.
Automating Data Theft
Decompiled Code Showing Targeted Applications
As per the original article and many of the indicators from the static analysis, the primary purpose of the application is to steal data by performing overlays on top of legitimate applications. The malware targets three specific classes of applications:
Danske Bank’s MobilePay application, with specific intent to steal Nem ID credentials
Applications that trigger an attempt to steal credit card details via a custom overlay
Applications that trigger an attempt to steal the users mobile phone number (possibly for triggering the “admining” mode described above)
Danske Bank MobilePay
Danske Bank MobilePay Overlay Process
Upon launching the MobilePay application the overlay attempts to steal the users CPR number (unique social security type id), mobile number and Nem pass code. It then asks the user to take a photo of their Nem ID passbook, containing one time use codes which can be used by the attacker to then log into MobilePay (and other Danish systems) and issue payments.
Stealing Credit Card Details
Credit Card Overlay Process
Upon launching one of the targeted applications, a credit card overlay is displayed with a configurable icon depending on the application launched. After basic card details are collected, the application then attempts to recover the Verified by Visa password for the user. These details are then forwarded to the C2 server.
Stealing Phone Numbers
Phone Number Overlay Process
Finally we see the functionality that is targeted to capture the user’s phone number, presumably to enable further abuse of the victims account via abuse of text message 2FA.
Summary
The sample appears to be a specifically customised variant that is being used in a campaign to target the Danske Bank MobilePay application. We see evidence that it is probably not the original GM Bot authors work – the coding style compared with the public source code is different, and the mix of languages in the resource files implies the sample has been adapted in a “quick and dirty” fashion to achieve the objectives.
This is a good example of how once released, complex code can be quickly and easily forked by less skilled authors and a pattern we also see today with the release of the Mirai botnet code. Quickly we see a spread of variants of the codebase that become harder to trace and detect and importantly attribute to any individual or group.
As ever, the best advice to prevent becoming a victim of such malware is to ensure that your phone is not configured to install 3rd party applications, and always review requests for permissions carefully – eg, are they aligned with the expected purpose of the application?
Open Questions
Due to time constraints there are a few further areas I would have liked to explore. I may pick these up in a subsequent post, but for the record they are:
The unpacked code contains included super user functionality from Chainfire’s SuperSu application. It’s not clear how or where this is used, no apparent attempt at rooting the device was seen in the unpacked code.
The debugger failed to return from the call to unpack the payload code. It is not clear if any further reflected actions were performed beyond this.
Given key indicators in the codebase, is it possible to search / locate other similar samples, or perhaps identify further C2 infrastructure
Any constructive feedback or comments most welcome.
About the author, the owner of the CyberBlog
I am an experienced IT consultant with a broad range of experience across different disciplines from development to large-scale Project Management. I have a passion for all things Cyber related but do not currently work in a Cyber related industry or role. I welcome and encourage all feedback!
FTC Sues D-Link Over Failure to Secure Its Routers and IP Cameras from Hackers
6.1.2017 thehackernews Vulnerebility
Image Source: Book - Protect Your Windows Network from Perimeter to Data
The United States' trade watchdog has sued Taiwan-based D-link, alleging that the lax security left its products vulnerable to hackers.
The Federal Trade Commission (FTC) filed a lawsuit (pdf) against D-Link on Thursday, arguing that the company failed to implement necessary security protection in its routers and Internet-connected security cameras that left "thousands of consumers at risk" to hacking attacks.
The move comes as cyber criminals have been hijacking poorly secured internet-connected devices to launch massive DDoS attacks that can force major websites offline.
Over two months back, a nasty IoT botnet, known as Mirai, been found infecting routers, webcams, and DVRs built with weak default passwords and then using them to DDoS major internet services.
The popular Dyn DNS provider was one of the victims of Mirai-based attack that knocked down the whole internet for many users.
To combat this issue, on the one hand, the popular networking equipment provider Netgear has launched a bug bounty program, inviting researchers and hackers to find and responsibly report security flaws in its hardware, mobile apps, and APIs for cash rewards ranging from $150 to $15,000.
But on the other hand, D-Link has been accused of several FTC Act violations, including:
Falsification about security in its router and IP camera user interfaces and promotional materials.
Falsely claiming that reasonable measures have been taken to protect its devices against well-known and easily preventable security flaws, like "hard-coded" user credentials and command injection flaws, which would allow any remote attacker to gain unauthorized access to its devices.
Failure to secure its software.
According to the complaint filed in San Francisco federal court, D-Link's insecure products allowed hackers to "monitor a consumer’s whereabouts to target them for theft or other crimes."
Several security researchers and hackers found serious flaws in D-Link products over the past year, and while some were satisfied with the company addressing the issue, others disclosed unpatched flaws due to its failure to release firmware updates in time.
In response to the complaint, D-Link released a statement saying that the charges brought against it are "unwarranted and baseless" and that the company will "vigorously defend itself."
The FTC "fails to allege, as it must, that actual consumers suffered or are likely to suffer actual substantial injuries," D-Link added.
Due to rise in the IoT threat, the Commission is taking desired steps to protect the Internet-of-Things devices.
The FTC introduced guidelines back in 2015 to (or "intending to") securing IoT devices, and recently it also launched a "prize competition" for public with the aim to find some technical solution for securing IoT devices. The winner of the contest will get $25,000 prize money.
Netgear launches Bug Bounty Program for Hacker; Offering up to $15,000 in Rewards
6.1.2017 thehackernews Hacking
It might be the easiest bug bounty program ever.
Netgear launched on Thursday a bug bounty program to offer up to $15,000 in rewards to hackers who will find security flaws in its products.
Since criminals have taken aim at a rapidly growing threat surface created by millions of new Internet of things (IoT) devices, it has become crucial to protect routers that contain the keys to the kingdom that connects the outside world to the IP networks that run these connected devices.
To combat this issue, Netgear, one of the biggest networking equipment providers in the world, has launched a bug bounty program focusing on its products, particularly routers, wireless security cameras and mesh Wi-Fi systems.
Bug bounty programs are cash rewards given by companies or organizations to white hat hackers and researchers who hunt for serious security vulnerabilities in their website or products and then responsibly disclose for the patch release.
Also Read: How Hackers Hack Bank Accounts with Router Vulnerabilities
Bug bounties are designed to encourage security researchers, hackers and enthusiasts to responsibly report the vulnerabilities they discovered, rather than selling or exploiting it.
On Thursday, Netgear announced that the company has partnered up with Bugcrowd to launch Netgear Responsible Disclosure Program that can earn researchers cash rewards ranging from $150 to $15,000 for finding and responsibly reporting security vulnerabilities in its hardware, APIs, and the mobile apps.
Meanwhile, on the same day, The Federal Trade Commission (FTC) filed a lawsuit against D-Link, another large networking equipment providers, arguing that the company failed to implement necessary security protection in its routers and Internet-connected security cameras that left "thousands of consumers at risk" to hacking attacks.
If you are a bug bounty hunter, you should read all terms and conditions before shooting your exploits against Netgear products or website.
One of them explicitly mentioned, "You may only exploit, investigate, or target security bugs against your own accounts and/or your own devices. Testing must not violate any law, or disrupt or compromise any data or access data that is not yours; intentional access of customer data other than your own is prohibited."
The company is paying out up to $15,000 for each vulnerability. The highest bounty will be given for the flaws that would allow access to the cloud storage video files or live video feeds of all its customers, and bugs that allow remote access to routers from the Internet, as shown in the chart above.
However, the Netgear will also pay $10,000 for video feed and cloud storage access bugs that cannot be exploited in mass attacks. The same payout will also be given for security issues that provide access to the payment card data of all Netgear customers.
Also Read: Someone Just Hacked 10,000 Routers to Make them More Secure.
Others vulnerabilities that qualify the bounty program include:
SQL injection bug
Information disclosure flaw
Stored cross-site scripting (XSS) vulnerability
Cross-site request forgery (CSRF) bug
Open redirect issues
Here's the Bingo! Bug bounty hunters will be rewarded with a triple prize if they will successfully exploit at least three flaws in a chain.
So, what are you waiting for? Go and Grab 'em all!
A fake Super Mario Run for Android is serving the Marcher Banking Trojan
6.1.2017 securityaffairs Android
Zscaler experts have found in the wild a fake version of the Super Mario Run Android App that could install the Android Marcher banking trojan.
Bad news for mobile gamers, security experts at Zscaler have spotted a strain of the Android Marcher Trojan masqueraded as the recently released Super Mario Run mobile game for Apple’s iOS.
Marcher is a sophisticated banking trojan that was used by cyber criminals to steal financial data from the victims.
“Marcher is a sophisticated banking malware strain that targets a wide variety of banking and financial apps and credit cards by presenting fake overlay pages. Once the user’s mobile device has been infected, the malware waits for victims to open one of its targeted apps and then presents the fake overlay page asking for banking details.” states the analysis published by Zscaler.
Super Mario Run mobile game for iOS device is one of the most interesting projects of the Nintendo, the company developed for Apple devices the notorious game. Anyway, Super Mario Run is still not available for Android, and crooks are taking advantage of this to spread their malicious variant.
The malicious code found by Zscaler installs the Marcher Trojan instead a legitimate version of Super Mario Run for Android.
“In this new strain, the Marcher malware is disguised as the Super Mario Run app for Android. Knowing that Android users are eagerly awaiting this game, the malware will attempt to present a fake web page promoting its release.” continues the blog post published by Zscaler.
The experts also shared the following details related to the threat:
Name : Super Mario Run
Package Name : uiq.pizfbwzbvxmtkmtbhnijdsrhdixqwd
MD5 : d332560f1fc3e6dc58d94d6fa0dab748
Detections : 12/55(at time of analysis)
When victims try to install the app it asks for multiple permissions including administrative rights.

The current Marcher version targets account management apps and major banks.
The researchers explained that also this Marcher variant presents fake credit card pages when the victims open the Google Play store. The trojan locks out Google Play until the victims supply the credit card information.
Researchers suspect the malware is still under development, they observed the banking overlay pages served by the C&C were not functioning properly at the time of the analysis.
“In the current variant, we have observed a new obfuscation technique, in which all important string characters are delimited with ‘<<zB5>>‘ as shown below.” continues the analysis.
Crooks always try to take advantage of gamers’ euphoria that coincides with the presentation of new games.
The same has happened last year when the Pokemon GO application was presented. Experts from ProofPoint spotted in the wild a backdoored version of the popular Pokemon GO Android App that could allow attackers to gain control over victims’ devices.
MM Core APT malware is back, Forcepoint has detected 2 new versions
6.1.2017 securityaffairs Virus
Forcepoint has detected two new versions of an advanced persistent threat (APT) malware dubbed MM Core APT and first discovered in 2013.
The APT MM Core malware has been in the wild since April 2013 when it was spotted for the first time by experts at FireEye.
The malware researchers dubbed the first release of the malware “TROJAN.APT.BANECHANT” (2.0-LNK), it is mainly a backdoor used by threat actors to steal information from the victims. The malware was used to target the governments of Middle East and Central Asia.
BaneChant detects multiple mouse clicks before starting its activity, this behavior was implemented in the attempt to evade sandboxes.
BaneChant callback also goes to a legitimate URL, the malware reaches a legitimate URL shortening service that then redirects the communication to the CnC server. In this way, the authors prevent security solutions from blacklisting the command and control (C&C) servers.
The malware requires an Internet connection for malicious code to be downloaded directly into the memory and executed.
A new version of the MM Core malware dubbed “StrangeLove, tracked as “2.1-LNK,” was discovered in June 2013 by researchers at Context Information Security. The news version was characterized by some modifications in the downloader component. Threat actors used StrangeLove to target entities in the Middle East.
Back to the present, experts from Forcepoint have detected two new versions of the MM Core malware dubbed BigBoss (2.2-LNK) and SillyGoose (2.3-LNK).
“Attacks using “BigBoss” appear likely to have occurred since mid-2015, whereas “SillyGoose” appears to have been distributed since September 2016. Both versions still appear to be active.” reads the reports published by Forcepoint.

The new variants infected users in the US and Africa, the experts observed that victims belong to multiple industries such as news and media, defense, oil and gas, and telecommunication.
Below the main functionalities implemented in the MM Core backdoor:
Send infected system’s computer name, windows version, system time, running processes, TCP/IP configuration, and top level directory listings for drives C to H
Download and execute file
Download and execute file in memory
Update itself
Uninstall itself
A novelty introduced in the last variant of the backdoor is that the downloader component leverages on the vulnerability the Microsoft Office Memory Corruption Vulnerability(CVE-2015-1641) to extract embedded malware.
In order to make harder the tracking of the C&C infrastructure, the threat actors are using WHOIS privacy protection services for their new C&C domains.
Crooks also signed the code of the downloader components with a valid authenticode certificate from Russian organisation “Bor Port,” the threat actors behind the APT malware likely has stolen it.
Forcepoint pointed out that while the number of MM Core samples is low, it has noticed that the Trojan’s downloader shares code, techniques and infrastructure with Gratem, a more active downloader that has been around since at least 2014. Recent samples have also been found to share the same certificates.
Experts believe the MM Core APT malware is just a part of a larger cyber espionage operation on which they are still investigating. They linked the malware to another trojan dubbed Gratem:
“On the other hand, while the volume of related MM Core samples remain low, we noticed that the MM Core downloader shares code, techniques and network infrastructure with a trojan called which has been distributed since at least 2014.” states the report.
“Gratem”, as well as sharing the same authenticode certificate for recent samples. Gratem is a more active downloader malware family which has been distributed since at least 2014. Ultimately this suggests that MM Core may be a part of a larger operation that is yet to be fully uncovered.
Give a look at the report for further details, including the Indicators ofCompromise (IoCs)
KillDisk Ransomware Targets Linux; Demands $250,000 Ransom, But Won't Decrypt Files
6.1.2017 thehackernews Virus
What you'll do if Ransomware infects you? Should you pay or not to recover your files?
Believe me, the FBI advises - Pay off the criminals to get your files back if you don't have a backup.
But paying off a ransom to cyber criminals is definitely not a wise option because there is no guarantee that you'll get the decryption key in return.
In the latest incident, the new variant of KillDisk ransomware has been found encrypting Linux machines, making them unbootable with data permanently lost.
What is KillDisk? KillDisk is a destructive data wiping malware that has previously been used to sabotage companies by randomly deleting files from the computers.
KillDisk is the same component associated with the Black Energy malware that was used to hit several Ukrainian power stations in 2015, cutting power for thousands of people.
But according to ESET security researchers, the nasty KillDisk disk wiper malware is back with new variants that target Windows and Linux desktops and servers, encrypt files and then ask for an unusually large ransom:
Around $218,000 in Bitcoins – possibly the world's most expensive ransom attacks.
What's even worst? Linux variant of the KillDisk ransomware does not store the encryption key anywhere on disk or command-and-control server.
So, even after you pay this extremely large ransom, you are not going to get any decryption key for recovery of your important files.
The good news is that ESET researchers have found a weakness in the encryption employed by the Linux variant which makes recovery of encrypted files possible, though difficult. But the same flaw doesn't exist in the Windows variant of the KillDisk ransomware.
KillDisk Deletes your Files Even After Paying $218,000
According to researchers, the files of victims targeted with the Linux variant of the malware are encrypted using "Triple-DES applied to 4096-byte file blocks," and each file on the computer is encrypted by a different set of 64-bit encryption keys.
The malware then displays the ransom note in an unusual manner: within the GRUB bootloader, which means the KillDisk Linux ransomware overwrites the bootloader entries to show ransom text that asks victims to pay 222 Bitcoin.
But paying off the criminals ransom will not bring your files back, as the Linux variant does not store decryption keys anywhere.
"KillDisk serves as another example of why paying ransom should not be considered an option. When dealing with criminals, there's no guarantee of getting your data back – in this case, the criminals clearly never intended to deliver on their promises," says Robert Lipovský, ESET Senior Researcher.
Prevention is the Best Practice
So, the only safe way of dealing with ransomware is prevention. As I previously recommended, the best defense against Ransomware is to create awareness within the organizations, as well as maintaining back-ups that are rotated regularly.
Most viruses are introduced by opening infected attachments or clicking on links to malware usually in spam emails. So, DO NOT CLICK on links provided in emails and attachments from unknown sources.
Moreover, ensure that your systems are running the latest version of Antivirus software with up to date malware definitions.
FBI Hacked, Again! Hacker Leaks Data After Agency Failed to Patch Its Site
5.1.2017 thehackernews Hacking
It seems like the FBI has been hacked, once again!
A hacker, using Twitter handle CyberZeist, has claimed to have hacked the FBI's website (fbi.gov) and leaked personal account information of several FBI agents publically.
CyberZeist had initially exposed the flaw on 22 December, giving the FBI time to patch the vulnerability in its website's code before making the data public.
The hacker exploited a zero-day vulnerability in the Plone CMS, an Open Source Content Management software used by FBI to host its website, and leaked personal data of 155 FBI officials to Pastebin, including their names, passwords, and email accounts.
CyberZeist tweeted multiple screenshots as proof of his claims, showing his unauthorized access to server and database files using a zero-day local file inclusion type vulnerability affecting its python plugins.
Hacker also found that the FBI's website is hosted on a virtual machine running a customized older version of the open-source FreeBSD operating system.
According to another tweet, the Plone CMS zero-day exploit is up for sale on an unnamed dark web marketplace.
The Plone CMS is considered to be one of the most secure CMSes available today and is used by many major websites like Google, and major United States agencies including the FBI and the CIA.
CyberZeist also warned other agencies, including the European Union Agency for Network and Information Security, Intellectual Property Rights Coordination Center, and Amnesty International, which are currently using the Plone CMS that they too are vulnerable to a similar attack.
The FBI authorities have yet to respond to the claims.
Update — Official Statement from Plone Security Team:
Meanwhile, Plone Security team has released a security advisory saying that it will release a security update on 17th January to its customers to "patch various vulnerabilities."
For now Advisory doesn't include much technical information about the vulnerabilities, but all supported Plone versions (4.x, 5.x). Previous versions could be affected.
"The advisory information we give in those pre-announcements is standard. In fact, the upcoming patch is to fix a minor issue with Zope which is neither a RCE or LFI inclusion problem."
Notably, Plone Security team has also mentioned that "there is no evidence that the issues fixed here are being actively exploited."
"The issue we are fixing in no way resembles CyberZeist's claims, neither do the issues we fixed last month." Matthew Wilkes, Plone security team, told The Hacker News.
"The aim of releasing information from such a hack is to convince people that you've indeed hacked the target. Claims of hacks that only give information that is publicly available (such as open-source code) or impossible to verify (such as hashed passwords) are common signs of a hoax," Matthew said.
“It is extremely easy to fake a hack like this; it takes rudimentary Photoshop skills or use of Chrome javascript developer console.“ - Nathan van Gheem, Plone security team, told THN.
Also, Mr. Alexandru Ghica, Eau de Web, the maintainer of an EU website which hacker also claimed to have hacked says, "I can say for sure that at least some of the data posted as proof is 100% fake. The hoax was a bit elaborate indeed, but that's it."
This is not the first time CyberZeist claimed to have hacked the FBI website. In 2011, the hacker breached the FBI website as a member of the infamous hacker collective known as "Anonymous.
This Ransomware Unlocks Your Files For Free If You Read CyberSecurity Articles
5.1.2017 thehackernews Virus
Ransomware has been around for a few years, but in last two years, it has become one of the fastest growing threats to businesses and users across the world, so will be in 2017.
Ransomware is a piece of malware that encrypts files on your computer with strong encryption algorithms and then demands a ransom money in Bitcoin to decrypt the data so you can regain access to your encrypted files.
We have seen some nastier ransomware infections over the past couple of years. The most interesting one was Popcorn Time that decrypts victims files for free if they pass the infection on to other people.
Now, a new strain of ransomware takes the infection to a whole new level of craziness.
Dubbed Koolova, the ransomware will restore your encrypted files for free, just like Popcorn Time. The only difference between both the infections is that you don't have to infect others to get free decryption key.
Instead, all you have to do is educate yourself about ransomware by reading two cyber security awareness articles about avoiding the infection.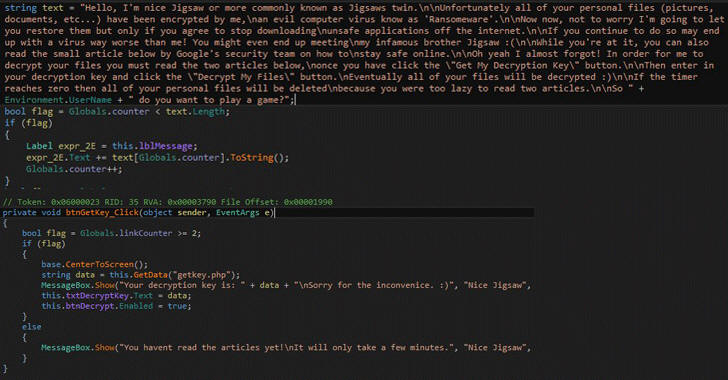
Discovered by security researcher Michael Gillespie and reported by BleepingComputer, the Koolova ransomware is not professionally coded and appears to be a work in progress.
The ransomware requires a lot of technical knowledge to get to the ransom demand screen that asks victims what they need do in order to avoid erasure of their data.
Once infected, Koolova encrypts the victim's files and then displays a warning screen where the text tells the victim to open and read two articles before they can get the ransomware decryption key.
If the victim is too lazy to read both articles, Koolova starts a countdown that if gets to zero, the ransomware will delete the encrypted files like Jigsaw malware.
But once the victim reads both articles, the Decrypt My Files (Decripta i Miei File) button becomes available. On clicking this button, Koolova will connect to the Command-and-Control (C&C) server and retrieve the decryption key.
The victim will then be able to take that decryption key and enter it into the key field to decrypt files.
Although the motive behind the ransomware attack is not to harm people, these kinds of actions are considered to be illegal in many countries. On January 1, a new law went into effect in California that outlaws the use of ransomware.
Do you consider educating people about any threat like this a good practice? Hit the comments below.
FireCrypt comes as a malware building kit and includes DDoS code
5.1.2017 securityaffairs Virus
Recently experts from MalwareHunterTeam discovered FireCrypt ransomware, a threat that comes as a malware building kit and includes DDoS code.
Ransomware has become one of the fastest growing threats, new malware implements sophisticated features to avoid detection and rapidly spread among the greatest number of machines.
Recently experts from MalwareHunterTeam discovered a new strain of ransomware dubbed FireCrypt, that includes also a component to launch DDoS attacks.
The experts noticed that FireCrypt continuously connects to s certain URL and downloads content from it and saves it to the local machine’s %Temp% folder. In this way, the malware fills the machine with junk files, the URL is hardcoded in the source code of the malware.
The DDoS component analyzed by the researchers targets the official portal of Pakistan’s Telecommunication Authority (http://www.pta.gov(.)pk/index.php) and downloads the content to a file in the %Temp% folder.
The FireCrypt ransomware is created with a malware builder dubbed BleedGreen and leverages a command-line application that automates the process of putting FireCrypt samples together. BleedGreen allows to rapidly customize the ransomware generating a unique executable with a custom name and a file icon chosen by the creator.
According to the malware researchers the ransomware builder is very trivial.
“Compared to other ransomware builders, this is a very low-end application. Similar builders usually allow crooks to customize a wider set of options, such as the Bitcoin address where to receive payments, the ransom demand value, contact email address, and more.” states a blog post published by Bleepingcomputer.com.

The builder is able to disguise the FireCrypt executable under a PDF or DOC icon, it is also able to make small changes to the binary to make harder the ransomware detection.
The infection process starts when a victim’s launches the executable (EXE file) generated by the builder. The ransomware first kills the Task Manager (taskmgr.exe) process and starts encrypting user’s files with AES-256 encryption.
Files encrypted by FireCrypt are easy to recognize because the malware appends the .firecrypt extension the file name. The ransomware drops a ransom note on the desktop that is identical to that used by the Deadly for a Good Purpose Ransomware and the two malware present many similarities.
“Compared to FireCrypt, the only difference is that the Deadly for a Good Purpose Ransomware also featured a logo at the top of the ransom note, now missing in FireCrypt. But, at a close inspection of Deadly’s source code, MalwareHunterTeam was able to discover that both ransomware versions used the same email and Bitcoin addresses, showing a clear connection between the two, with FireCrypt being a rebranded version of the original Deadly for a Good Purpose Ransomware.” continues the post on Bleepingcomputer.
Let’s close with a reflection on the DDoS component, the target URL cannot be modified by the ransomware builder and the DDoS attack is not effective because it requires to infect a huge number of PCs at the same time that would also be connected to the Internet simultaneously.
Kaspersky fixing a serious problem with inspection digital certificates
5.1.2017 securityaffairs Vulnerebility
Google hacker Tavis Ormandy discovered a serious flaw that affects the Kaspersky antivirus software and the way it manages inspection digital certificates.
Experts from Kaspersky are solving a problem that disabled certificate validation for 400 million users. The problem was spotted by the notorious Google hacker Tavis Ormandy, the vulnerability affects the Kaspersky antivirus software and the way it used certificates to analyze encrypted traffic.
The security firm is a trusted CA, the Kaspersky Anti-Virus Personal Root, and uses its digital certificate for the traffic inspection, in this way it is able to decrypt it and analyze scanning for malicious patterns.
“In order to inspect encrypted data streams using SSL/TLS, Kasperky installs a WFP driver to intercept all outgoing HTTPS connections. They effectively proxy SSL connections, inserting their own certificate as a trusted authority in the system store and then replace all leaf certificates on-the-fly. This is why if you examine a certificate when using Kaspersky Antivirus, the issuer appears to be “Kaspersky Anti-Virus Personal Root”.” Ormandy wrote in a security advisory.
The process implemented by Kaspersky for certificate interception has previously resulted in serious vulnerabilities. Now the experts discovered other issues such as the way leaf certificates are cached that leverages on an extremely naive fingerprinting technique.
“Kaspersky cache recently generated certificates in memory in case the user agent initiates another connection. In order to do this, Kaspersky fetches the certificate chain and then checks if it’s already generated a matching leaf certificate in the cache. If it has, it just grabs the existing certificate and private key and then reuses it for the new connection.” explained the expert.
“The cache is a binary tree, and as new leaf certificates and keys are generated, they’re inserted using the first 32 bits of MD5(serialNumber||issuer) as the key. If a match is found for a key, they just pull the previously generated certificate and key out of the binary tree and start using it to relay data to the user-agent.”
It is easy to understand that a 32bit key open to brute-forcing attacks to generate a collision in a few seconds. An attacker can produce a collision with other certificates.
Ormandy also provided a description of the attack:
Mallory wants to intercept mail.google.com traffic, for which the 32bit key is 0xdeadbeef.
Mallory sends you the real leaf certificate for mail.google.com, which Kaspersky validates and then generates its own certificate and key for.
On the next connection, Mallory sends you a colliding valid certificate with key 0xdeadbeef, for any commonName (let’s say attacker.com)
Now Mallory redirects DNS for mail.google.com to attacker.com, Kaspersky starts using their cached certificate and the attacker has complete control of mail.google.com.
Ormandy also provided a proof of the bug forcing a collision between Hacker News and manchesterct.gov website.
“You can reproduce this bug, by visiting https://autodiscover.manchesterct.gov, then https://news.ycombinator.com and observing that the content is signed by the wrong certificate.” he added. “So if you use Kaspersky Antivirus in Manchester, Connecticut and were wondering why Hacker News didn’t work sometimes, it’s because of a critical vulnerability that has effectively disabled SSL certificate validation for all 400 million Kaspersky users.”
The expert also provided the C source code that it is possible to use to generate a colliding certificate for testing.
The case of flying saucer – Highway to the Danger Drone
5.1.2017 securityaffairs IT
One of the most discussed topics these days are the various nefarious uses that a Drone can be put to or just flown where they shouldn’t be.
2016 has been an eventful year bagged with mixed sentiments around the US presidential election, Brexit and Global terrorism striking the World’s news outlets. Simultaneously not far behind are the debates to seek, understand innovative venues/loopholes that have the potential to create havoc globally. One of the most discussed topics these days are the various nefarious uses that Drones can be put to or just flown where they shouldn’t be.
Drone Pilots capabilities to fly a drone into restricted areas or the risk of harming others is a topic for another day. Here in this short blog, we have tried to look at the various strategies Governments and Aviation Authorities have attempted to instigate to curb the menace only to see a threat evolving which poses a danger to the drones themselves.
So just what is a drone anyway? For the sake of argument let’s focus on the type of aircraft that you can purchase as a consumer for Video and Photography purposes (as opposed to the firing missiles and blow up things type). The world’s media has slapped the label of “Drone” onto any Quadrocopter, Octocopter or any other modern platform without actually investigating the differences between commercial platform, military devices and traditional models. Essentially our UAV (Unmanned Aerial Vehicle -which is the correct term!) has four components:
Power supply (typically a high power Li-Po Battery)
Propulsion units (4+ motors)
Transmitter (Video/Photo) / Receiver
Motherboard (the Flight controller)
Up until number 3 we were in the same ballpark as remote control helicopters and other model aircraft, which are controlled with servos according to the radio signals. However, with the introduction of the Motherboard we now have a flying computer with just as many undisclosed security issues as any other Internet of Things (IoT) device. Just because there isn’t a cable connected to the device does not mean that it is not susceptible to attack. For a clear breakdown of what is and isn’t a drone we have the following:
Model Aircraft Remote control only, no preprogrammed flight paths etc.
Drone Equipped with a flight computer, however, has no ability to follow pre- programmed path, nor does it have any built-in intelligence
Unmanned Aerial Vehicle (UAV) Encompasses all of the features seen in a drone but has additional intelligence features (Object Tracking, Terrain/Hazard avoidance etc.)
Unmanned Aerial System (UAS) All components seen in a UAV with additional support equipment (Base Station etc.)
So let’s have a look at some of the ways that have been identified to remove consumer UAVs from the air.
Shotgun: Eh, think we get this one! The US town of Deer Trail Colorado even attempted to enact a law to allow residents to hunt for federal UAV’s and shoot them down!
Net: Police forces and organizers of sporting events around the world have been trialing nets which are launched from a bazooka. This expands in the air and fowls the UAV’s rotor blades bringing it crashing to earth. There are also other slightly less destructive methods used where nets are carried by other larger UAVs; this approach has been adopted by the police force in Tokyo[1]. These again snare the rotor blades and are designed to capture the errant flying machine rather than send it crashing to the ground and onto potential pedestrians.
RF Generator (Denial of Service!) Or more simply a UAV Radio signal jammer. These devices overpower the radio signals (typically 2.4Ghz for most commercial UAVs which is the same range as standard Wi-Fi networks, Bluetooth connections, microwave ovens, car alarms, baby monitors, and ZigBee devices) with white noise causing the UAV to return to it’s “Home” position if this has been set (or is available) or at the very least severe the control from the Pilot. However, it should be noted that these devices themselves are highly illegal in most countries[2]. Some commercial firms are investigating Jamming Guns which target a narrow window and allow the operator to aim at the offending UAV without affecting other services.
Exploitation The takeover of the UAV’s flight systems by an outside attacker by various technical means allowing the attacker to have complete control of the system for their own purposes. The owner/pilot is locked out and has no way of controlling the system.
Hacking UAVs is not new with the first high profile case being of an RQ-170 Sentinel stealth drone, a key weapon in the intelligence gathering arsenal of the US Central Intelligence Agency (CIA); the drone was diverted and captured by the Iranians in December 2011. In this case, the Iranian military had identified that the US Military utilized encrypted GPS frequencies for its control systems. They first jammed the drone’s communications link to its ground controllers (which forced the drone into autopilot mode) this also had the effect of forcing the drone to search for unencrypted commercial control channels. The Iranian attackers spoofed these signals sending wrong GPS coordinates tricking the drone into believing it was at its home base in Afghanistan, thus landing on Iranian territory to the welcoming arms of its attackers. It should be noted that the US Military disputed this account and stated that it was a system malfunction; however subsequently researchers have been able to reproduce the incident with commercial UAVs using encrypted GPS signals.
Security Analysts and Hackers alike have been investigating these types of attacks for some time now Samy Kamkar (an Independent researcher) created a program called “dronestrike” in 2013 where he mounted a Raspberry Pi computer running his code on his Parrot AR UAV 2.0 along with a wireless transmitter[3]. When his UAV was flown in the vicinity of another parrot UAV the dronestrike program would make a connection to the victim UAV and disconnect the owner/pilot and take control of the system itself.
Earlier this year Johns Hopkins University[4] set its capstone project for Master’s Degree students. The students’ task was to conduct wireless pen testing on a consumer UAV and then take what they had identified and craft exploits to attack the system. Three various strategies were identified all of which successfully broke the connection to the pilot:
Denial of Service: The UAV was bombarded with over 1,000 wireless connection requests in a short period of time; each connection attempt asked to take control of the aircraft. This overloaded the UAV’s CPU causing it to shut down.
Buffer Overflow: In this scenario, an exceptionally large data packet was sent to the UAV. This exceeded the buffer in the UAV’s flight application causing the aircraft to crash.
Spoofing: The third scenario utilized an attack against the controller rather than the UAV. A fake packet was sent to the controller impersonating the UAV itself. The Controller severed the connection with the real UAV resulting in the aircraft making an emergency landing. XBee – Spectral analysis is seen to be utilized aggressively here.
These three types of attacks are nothing new to Cyber Security Analysts with these types of attacks occurring daily in Enterprise computer systems. But surely we as an industry don’t really have to be that worried about this, as these are only isolated case for hobbyist fliers? Think again, a UAV is a flying computer. Computers get hacked. Period!
drone
To add complication to this many logistical firms are trialing UAV delivery systems including Amazon, DHL and Domino’s Pizza to name but a few. Amazon has already been awarded a patent for the flying warehouse, (AFC) an airborne fulfillment center. The notion is that AFC could be used as a launch pad for drones to make local deliveries. The approved patents highlight that AFC would be housed at about 45,000 feet allowing UAVs to be stocked, deployed and flown as necessary.
With the above development moving forward the possibility of hacking into a UAV and divert it without the owner knowing where it has gone will be a massive incentive for criminals seeking to steal the deliveries flying over their heads. With the assistance of insiders within the delivery firm the criminals can target specific cargos. Already we have seen evidence where attackers are easily able to intercept the operator’s command at a distance up to 2 kilometers and spoof its own. At a distance of 100 meters, WEP can be easily cracked and the drone can be stolen.
A number of firms are now looking to UAV’s to provide a mobile security platform for organizations with large estates or in the case of smaller UAV’s warehouse security. The opportunity to attack these platforms is twofold. Firstly an attacker who is able to take control of the UAV is then able to turn it’s “eyes” away from any intruders on the ground. Secondly and more worrying is where the attacker diverts the drone, lands it and attaches their own monitoring equipment cameras with transmitting equipment etc. to the aircraft. When this is returned to the control of the automated system/pilot the UAV will continue about it’s tasks as though nothing has happened, all the while becoming a physical Trojan Horse to the attached monitoring equipment. This could lead to the loss of trade secrets with the likes of the indoor warehouse UAVs. This kind of attack can also be used to kill out market competition, not to forget current 70% of the commercial drone market is held by Chinese DaJiang Innovation technology (DJI)
One threat vector, which is already being utilized, is where criminal gangs are utilizing UAV’s to smuggle drugs into prisons for waiting for inmates. Whilst this is already occurring, the UAV’s themselves have either been purchased or stolen from their owner’s residencies. To have the ability to hack into a UAV take over it and then use it for your own purposes removes a great deal of risk and removes all attribution to the criminals when and if the UAV is captured by Prison staff. The ability to steal a UAV in flight is going to be a great temptation to criminals.
On a relevant note there is also a psychological dimension as the drone pilot while operating at a distance can be in a sense detached from the local context and culture. This may trigger the creation of dream-world/ gaming environment thus detaching from the physical reality and risking operator behavior towards professional reasonability and social mores. [5]
What we have seen in this blog is that UAV’s, or drones (if you must!) are just like any system which relies upon a computer to operate. They can be hacked and taken over for many nefarious activities and we have only just seen the beginning. When the delivery platforms take to the air (pun intended) cyber criminals are going to have a field day!
We are truly on the highway to the Danger Zone.
[1] http://www.telegraph.co.uk/technology/2016/01/21/tokyo-police-are-using-drones-with-nets-to-catch-other-drones/
[2] https://www.fcc.gov/general/jammer-enforcement
[3] https://www.youtube.com/watch?v=EHKV01YQX_w
[4] http://releases.jhu.edu/2016/06/08/johns-hopkins-team-makes-hobby-drones-crash-to-expose-design-flaws/
[5] http://releases.jhu.edu/2016/06/08/johns-hopkins-team-makes-hobby-drones-crash-to-expose-design-flaws/
FBI website hacked by CyberZeist and data leaked online
5.1.2017 securityaffairs Hacking
The notorious black hat hacker CyberZeist (@cyberzeist2) has broken into the FBI website FBI.gov and leaked data on Pastebin.
The hacker leaked the FBI.GOV accounts that he found in several backup files (acc_102016.bck, acc_112016.bck, old_acc16.bck, etc).
Leaked records contain accounts data, including names, SHA1 Encrypted Passwords, SHA1 salts, and emails.
The intrusion occurred on December 22, 2016, the hacker revealed to have exploited a zero-day vulnerability in the Plone Content Management System
“Going back to 22nd December 2016, I tweeted about a 0day vulnerability in Plone CMS which is considered as the most secure CMS till date. This CMS is used by many top
agencies including FBI”

CyberZeist explained that he did not find the zero-day in CMS he exploited, he was just tasked to test it against the websites of the FBI and Amnesty. Other websites are potentially exposed to the same zero-day attack, including Intellectual Property Rights Coordination Center and EU Agency for Network Information and Security.
The vulnerability resides in some python modules of the CMS.
Other Vulnerable websites include EU Agency for Network Information and Security along with Intellectual Property Rights Coordination Center.

The hacker also Tweeted an image of the FBI website that was down just after the hack.

CyberZeist tested the 0-day because the vendor was too afraid to use it aginst the FBI website. The hacker noticed that while media from Germany and Russia published the news about the hack, but US based publishers ignored it.
According to CyberZeist, the FBI contacted him to pass on the leaks.
“I was contacted by various sources to pass on the leaks to them that I obtained after hacking FBI.GOV but I denied all of them. Why? just because I was waiting for FBI to
react on time. They didn’t directly react and I don’t know yet what are they up to, but at the time I was extracting my finds after hacking FBI.GOV,” he wrote.
The expert added further info on the attack, while experts at the FBI were working to fix the issue, he noticed that the Plone 0day exploit was still working against the CMS backend.
“I couldn’t gain a root access (obviously!), but I was able to recon that they were running FreeBSD ver 6.2-RELEASE that dates back to 2007 with their own custom configurations. Their last reboot time was 15th December 2016 at 6:32 PM in the evening.” he added.
It seems that administrators of the websites made some regrettable errors, for example teh exposed the backup files on the same server, it was a joke for the hacker to access them even if he decided don’t publish them immediatelly.
“While exploiting FBI.GOV, it was clearly evident that their webmaster had a very lazy attitude as he/she had kept the backup files (.bck extension) on that same folder
where the site root was placed (Thank you Webmaster!), but still I didn’t leak out the whole contents of the backup files, instead I tweeted out my findings and thought to
wait for FBI’s response”

Now let’s sit and wait for the FBI’s response.I obviously cannot publish the 0day attack vector myself as
The hacker confirmed that the 0-day is offered for sale on Tor by a hacker that goes by the moniker “lo4fer.” Once this 0day is no longer being sold, I will tweet out the Plone CMS 0day attack vector myself.
“Once this 0day is no longer being sold, I will tweet out the Plone CMS 0day attack vector myself.” CyberZeist added.
This isn’t the first time CyberZeist hacked the website of the Federal Bureau of Investigation, in 2011 when he was one of the members of the Anonymous collective he broke into the database of the law enforcement agency.
Let’s close with a curiosity … CyberZeist is asking you to chose the next target.
https://www.poll-maker.com/poll885856x749D3f82-36.
The hacker is very popular, among his victims, there are Barclays, Tesco Bank and the MI5.
To remain in touch with CyberZeist visit his page on Pastebin
http://pastebin.com/u/CyberZeist2
11GB archive of Top Secret US SOCOM data accidentally leaked
5.1.2017 securityaffairs Incindent
The popular security expert Chris Vickery discovered a 11GB archive of Top Secret US SOCOM data that was accidentally leaked.
A subcontractor of the Pentagon has exposed top-secret information of the US Military Special Operations Command (SOCOM) medics.
Exposed records include names, locations, Social Security Numbers, and salaries of the Military SOCOM personnel, the database also included names and locations of at least two analysts of Special Forces. Analysts data have Top Secret government clearance.
The precious archive was accessible on the web and data stored in without encryption, a 11-gigabytes gift to nosy people.
The database was discovered by the popular researcher Chris Vickery, the same expert that discovered several open MongoDB exposed on the Internet.
“A recent data breach discovery of mine contained the names, locations, Social Security Numbers, salaries, and assigned units for scores of psychologists, and other healthcare professionals, deployed within the US Military’s Special Operations Command (SOCOM). Not a single username or password was guarding this intel, which weighed in at over 11 gigs.” reads a blog post published by Vickery.
Vickery discovered the precious archive and reported it to Potomac Healthcare Solutions, the company that provides healthcare workers to the US Government through Booz Allen Hamilton.
The archive includes also pay scales and residency of psychologists and employees at SOCOM.
Experts at Potomac Healthcare Solutions promptly fixed the issue, even if they initially did not seem to take the claim seriously.
“It is not presently known why an unprotected remote synchronization (rsync) service was active at an IP address tied to Potomac,” added Vickery.
“It shouldn’t take over an hour to contact your IT guy and kill an rsync daemon.”
The exposed data in the wrong hand could allow attacks to conduct a wide range of malicious activities, from kidnapping to scams.
“It’s not hard to imagine a Hollywood plotline in which a situation like this results in someone being kidnapped or blackmailed for information,” he says.
“Let’s hope that I was the only outsider to come across this gem.”
In December 2015 the security expert Chris Vickery discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
Did someone hack the Brazilian google.com.br?
5.1.2017 securityaffairs Hacking
Many users speculated about a possible compromise of the address of www.google.com.br. Did someone hack it? Let’s see what has happened.
Two days ago, we followed many news and comments regarding the compromise of the address www.google.com.br. At the beginning, many (me included) discredited the news, however, big online portals quickly started to propagate the event. People close to me also reported being accessing the invalid content and ask me for help.
G1 Portal (http://g1.globo.com/tecnologia/noticia/google-nega-ter-sido-alvo-de-hackers-no-brasil-entenda.ghtml) brought some up-to-date information about the fact, including the official answer by Google:
“Some internet users in Brazil faced problems accessing google.com.br due to compromised DNS servers: that means, the malicious change of the routing configuration of those DNS servers, taking the user to a different website than the desired one”, informs Google in its note to G1.
“Google is not responsible by the affected DNS servers, whence notified the administrators, which fixed the problem in 30 minutes. The affected users may also switch their network DNS server, as the Google system was not affected”, Google assures.
This notification is split into two parts. At the first part, we analyze the technique used in the incident by digging up public information from DNS servers cache which retained the swapped “google.com.br” domain content while it was compromised. At the second part, based on the technical analysis, we make our deductions and conclusions about the case and provide a few preventive security recommendations.
Situation Analysis
For this analysis, we used an environment whose users were still seeing the incorrect content while accessing www.google.com.br. Following, the technical details of the performed procedures.
1.1. Address Resolution www.google.com.br
While resolving “www.google.com.br”, we obtained the IP address 91.148.168.111 as a response, as seen in Picture 1.

Picture 1 – Invalid address returned by www.google.com.br
Using “whois”, we saw that the address IP 91.148.168.111 does not belong to Google, but to a Bulgarian entity, as can be seen in Picture 2.

Picture 2 – Entity responsible for the IP address 91.148.168.111
The same query to the address “www.google.com.br” from an environment which shows the legitimate Google page returns the IP address 216.58.202.3 (Picture 3).

Picture 3 – Result is the legitimate Google IP address
As seen in the analysis, it was possible to validate that the invalid content was not hosted on an address from Google, that is, the content of the Google website was not altered. There is yet to explain why the users were being taken to the wrong address. We continue our analysis.
1.2. DNS Cache Analysis
We begin now our search of a DNS server whose cache is pointing to the invalid IP address for “www.google.com.br”, alas, 91.148.168.111. The goal is to find out which DNS server is returning the invalid IP. After finding one such server, we fetch its cache with the PowerShell command Show-DnsServerCache.
Below, the cache address entries for the “*google.com.br” addresses:

Table 1 – Cache from a DNS server during the incident with the domain google.com.br
Notice that the SOA (Start of Authority) entry, the registry that identifies the DNS server responsible for “google.com.br” zone points to the address “ns1-leader.vivawebhost.com”. The address resolves to IP 91.148.168.6, whose responsible is the same entity of IP 91.148.168.111.
Just to be sure, we did a DNS consult using the address www.google.com.br pointing to the DNS server ns1-leader.vivawebhost.com. The first attempt returned a timeout error – likely because the server was being strangled by the number of requests. In our second try, the address 91.148.168.111 was resolved. Exactly the same IP users were being directed, as seen in Picture 4.

Picture 4 – The consult result to the address www.google.com.br on the DNS server used for the attack
To be sure of the cache information, we did consult the SOA registry pointing to the address ns1-leader.vivawebhost.com.

Picture 5 – Result for the SOA query with google.com.br at the DNS server used during the attack
The results for the same query for a legitimate Google environment should return the following:

Picture 6 – Result for the legitimate domain
We did then query the domain “google.com.br” at registro.br, the entity responsible for “.br” domains. The result shows that the moment this report was being written, the DNS servers responsible for the domain are ns1.google.com, ns2.google.com, ns3.google.com e ns4.google.com. As expected, there are no records pointing to the invalid address ns1-leader.vivawebhost.com.

Picture 7 – Querying the domain “google.com.br” at Jan. 03, 2017 after the incident was resolved
A identified point of attention is the date of the last domain update at registro.br: Jan. 03, 2017, the day of the incident.
2. Conclusion
These analysis results make us believe the attacked managed, some way, to access the “google.com.br” domains configuration at registro.br and change it to point to ns1-leader.vivawebhost.com and ns2-leader.vivawebhost.com. This type of attack is known as “domain kidnapping”.
While the values of the DNS servers were adulterated, users trying to access www.google.com.br were taken to the incorrect address. As the response to the identified incident, the administrators responsible for the “google.com.br” domain with registro.br quickly reverted the configuration to the original values.
As the attackers used the TTL (time to live) value of 86400 seconds (24 hours), the DNS servers which refreshed their Google address at the time window will be kept handing over the invalid information for a long period. To speed things up, in case this problem is affecting your organization, I suggest you clean your DNS server cache. An easy way to do this is by resetting your DNS service.
The problem could have been worse. An attack of this kind has great damage potential for the organization which owns the Internet domain as well as for users that access the address. We list a few example below (none happened this time, though):
The address for which the users are redirected to could infect them with malicious code. This is usually done by advertising a fake software update.
The attacker could have redirected the user’s e-mails for the kidnapped domain to a server under its control and access the content.
By simulating an SMTP/IMAP/IMAPs server, the attackers could have stolen domain user credentials during the authentication attempt.
In case you delegate the task of administering your Internet domains to a third party organization, we recommend you to be sure that they follow access management good security practices for Domain Registry entities, like having the second authentication factor enabled.
For more information regarding domain kidnapping, access the article written by me at the end of the last year, describing a case study through this link.
Koolova Ransomware decrypts files if victims read 2 posts about Ransomware
5.1.2017 securityaffairs Virus
The Koolova ransomware will decrypt the encrypted files for free it the victim read two blog posts about how to avoid ransomware infection.
Ransomware authors are very creative, in the last here we assisted a rapid evolution of the cyber extortion practice. Ransomware has become one of the fastest growing threats, new malware implements sophisticated features to avoid detection.
Recently security experts from MalwareHunterTeam spotted a singular strain of ransomware dubbed Popcorn Time that implemented an interesting mechanism to improve its efficiency.This ransomware comes with a singular feature, it allows victims to either pay up or they can opt to infect two others using a referral link. Then is the two other potential victims pay the ransom the original target receives a free key to unlock his encrypted files.
Now a new strain of ransomware dubbed Koolova appeared in the wild with a very singular feature. The Koolova ransomware will decrypt the encrypted files for free it the victim read two articles about how to avoid ransomware infection.
Once the Koolova ransomware infected a machine, it encrypts the files and then displays a warning screen where the text instructs the victim to open and read two awareness posts before they can get the ransomware decryption key.
Then Koolova starts a countdown that if gets to zero, the ransomware will definitively delete the files.
The two blog posts that the Koolova ransomware wants victims to read are:Google Security Blog called
“Stay safe while browsing” from Google Security Blog.
“Jigsaw Ransomware Decrypted: Will delete your files until you pay the Ransom” from BleepingComputer.
The threat was spotted by the security researcher Michael Gillespie, the malicious code appears to be a work in progress.
Visualizza l'immagine su TwitterVisualizza l'immagine su TwitterVisualizza l'immagine su TwitterVisualizza l'immagine su Twitter
Segui
Michael Gillespie @demonslay335
#Koolova #Ransomware based on #HiddenTear decrypts your files if you read @BleepinComputer & @Google articles on #Jigsaw and online security
00:29 - 19 Dic 2016
23 23 Retweet 19 19 Mi piace
“Koolova will encrypt a victim’s files and then display a screen similar to the Jigsaw Ransomware where the text is slowly shown on the screen. This text will tell the victim that they must read two articles before they can get a decryption key, It then tells you that if you are too lazy to read two articles before the countdown gets to zero, like Jigsaw, it will delete the encrypted files. This is not an idle threat as actually does delete the files.” reported BleepingComputer.com.
Once the victim reads both articles, he can rescue the encrypted files by clicking on the Decrypt My Files (the malware shows the string “Decripta i Miei File” which is Italian Language). The button “Decripta i Miei File” becomes available, when the user click on it the Koolova ransowmare will contact C&C server to get the decryption key.
Clearly, the author of this malware hasn’t developed it profit but just to spread awareness.
Kaspersky fixing a serious problem with inspection digital certificates
4.1.2017 securityaffairs Vulnerebility
Google hacker Tavis Ormandy discovered a serious flaw that affects the Kaspersky antivirus software and the way it manages inspection digital certificates.
Experts from Kaspersky are solving a problem that disabled certificate validation for 400 million users. The problem was spotted by the notorious Google hacker Tavis Ormandy, the vulnerability affects the Kaspersky antivirus software and the way it used certificates to analyze encrypted traffic.
The security firm is a trusted CA, the Kaspersky Anti-Virus Personal Root, and uses its digital certificate for the traffic inspection, in this way it is able to decrypt it and analyze scanning for malicious patterns.
“In order to inspect encrypted data streams using SSL/TLS, Kasperky installs a WFP driver to intercept all outgoing HTTPS connections. They effectively proxy SSL connections, inserting their own certificate as a trusted authority in the system store and then replace all leaf certificates on-the-fly. This is why if you examine a certificate when using Kaspersky Antivirus, the issuer appears to be “Kaspersky Anti-Virus Personal Root”.” Ormandy wrote in a security advisory.
The process implemented by Kaspersky for certificate interception has previously resulted in serious vulnerabilities. Now the experts discovered other issues such as the way leaf certificates are cached that leverages on an extremely naive fingerprinting technique.
“Kaspersky cache recently generated certificates in memory in case the user agent initiates another connection. In order to do this, Kaspersky fetches the certificate chain and then checks if it’s already generated a matching leaf certificate in the cache. If it has, it just grabs the existing certificate and private key and then reuses it for the new connection.” explained the expert.
“The cache is a binary tree, and as new leaf certificates and keys are generated, they’re inserted using the first 32 bits of MD5(serialNumber||issuer) as the key. If a match is found for a key, they just pull the previously generated certificate and key out of the binary tree and start using it to relay data to the user-agent.”
It is easy to understand that a 32bit key open to brute-forcing attacks to generate a collision in a few seconds. An attacker can produce a collision with other certificates.
Ormandy also provided a description of the attack:
Mallory wants to intercept mail.google.com traffic, for which the 32bit key is 0xdeadbeef.
Mallory sends you the real leaf certificate for mail.google.com, which Kaspersky validates and then generates its own certificate and key for.
On the next connection, Mallory sends you a colliding valid certificate with key 0xdeadbeef, for any commonName (let’s say attacker.com)
Now Mallory redirects DNS for mail.google.com to attacker.com, Kaspersky starts using their cached certificate and the attacker has complete control of mail.google.com.
Ormandy also provided a proof of the bug forcing a collision between Hacker News and manchesterct.gov website.
“You can reproduce this bug, by visiting https://autodiscover.manchesterct.gov, then https://news.ycombinator.com and observing that the content is signed by the wrong certificate.” he added. “So if you use Kaspersky Antivirus in Manchester, Connecticut and were wondering why Hacker News didn’t work sometimes, it’s because of a critical vulnerability that has effectively disabled SSL certificate validation for all 400 million Kaspersky users.”
The expert also provided the C source code that it is possible to use to generate a colliding certificate for testing.
Odposlouchávání a prolamování Wi-Fi sítí zabezpečených pomocí WPA2
4.1.2017 Root.cz Hacking
V tomto článku si podrobně popíšeme, jak funguje zabezpečení WPA2-PSK a následně se podíváme na možnosti odposlouchávání a prolamování hesla.
WPA2 (Wi-Fi Protected Access 2) je dnes alespoň podle statistik projektu Wifileaks nejrozšířenějším způsobem zabezpečení Wi-Fi sítí v České republice. Existuje ve dvou variantách, WPA2-Personal (neboli WPA2-PSK), kde všichni klienti využívají stejné sdílené heslo a WPA2-Enterprise, který je po bezpečnostní stránce lepší, avšak díky nutnosti RADIUS serveru a složitější implementaci je vhodný, jak již z názvu plyne, spíše do podnikové sféry. My se podíváme na první variantu, která je typickým zástupcem zabezpečení většiny domácích sítí a v následujících odstavcích budu pod pojmem WPA2 myslet variantu WPA2-Personal.
Pokud zde očekáváte nějakou revoluční metodu, díky které budete schopni prolomit silné heslo u sítě vašeho souseda, tak vás musím zklamat – WPA2 je při správné konfiguraci stále bezpečné. Ani zde nečekejte sérii pěti příkazů, které bezmyšlenkovitě vložíte do terminálu svého Kali Linuxu a bude z vás „obávaný hacker“. Spíše se pokusím popsat, jak specifikace IEEE 802.11 a WPA2 funguje z bezpečnostního hlediska, rozebereme si 4-way handshake paket po paketu a různé další zajímavé aspekty. Těchto znalostí poté využijeme pro dešifrování WPA2 provozu ostatních klientů (za předpokladu, že známe sdílené heslo) a také se podíváme na slovníkový útok proti zachycenému handshake s cílem získat heslo.
Simulace a nalezení sítě
Pro účely tohoto článku jsem si vytvořil síť s názvem (SSID) root_wpa2, která bude zabezpečená pomocí WPA2-PSK s heslem PrisneTajneHeslo. Protože jsem u této sítě neskryl SSID, AP (Access Point) bude periodicky (zde konkrétně 10× za vteřinu) vysílat tzv. Beacon frames, které patří k jedněm z řídících rámců standardu IEEE 802.11:
Beacon frames
Obsahují SSID sítě (maximálně 32 znaků), timestamp, interval vysílání beacon rámců, RSN (Robust Secure Network) – informace ohledně zabezpečení, podporované rychlosti a další: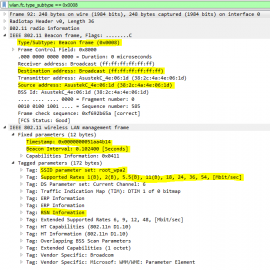
AP je odesílá z toho důvodu, aby případným klientům dal vědět o existenci své sítě a možnosti připojení. Díky tomu vidíte na svém zařízení seznam dostupných Wi-Fi sítí. Tomuto mechanismu, kdy klienti poslouchají výzvy od jednotlivých AP na všech kanálech, se říká pasivní skenování.
Většina zařízení však zároveň kvůli efektivitě využívá i aktivního skenování, což znamená, že na každém kanálu vysílají rámce Probe Request na broadcastovou adresu ff:ff:ff:ff:ff:ff. Těmito rámci se klienti ptají přítomných AP, které sítě jsou přítomné. Probe Request nemusí být všeobecný, ale může se dotazovat na jednu konkrétní síť. Vaše zařízení se obvykle tímto způsobem ptá na všechny sítě, které máte uložené. Toho lze bohužel využít pro sledování a fingerprinting, ale to je nad rámec tohoto článku.
AP na Probe Request odpovídá rámcem Probe Response, který je téměř stejný jako Beacon (obsahuje detaily o nabízené síti), takže ho nemá cenu nijak zdlouhavě popisovat:
Autentizace a asociace
Jakmile si vaše zařízení vybere cílovou síť (ať již pomocí automaticky vysílaných Beacon rámců nebo v případě např. skrytého SSID kombinací Probe Request/Response), dojde k autentizaci a asociaci spojení. Celý proces vypadá takto:
Autentizace a asociace
Prvním rámcem je Authentication. Komunikaci začíná klient, který odesílá tento rámec s příznakem Request. AP následně odpoví stejným rámcem, avšak s příznakem Response, a to buď kladně, nebo zamítavě. Pro nás budou stěžejní hlavně tyto 3 položky:
Authentication Algorithm – bude mít vždy hodnotu 0 (Open System), druhou možností je 1 (Shared Key), která je již však zastaralá a dnes se nepoužívá
Authentication SEQ – 1 pro Request, 2 pro Response
Status Code – návratový kód (0 = v pořádku)
Ukázky:
Authentication Request

Authentication Response
Jakmile se dokončí autentizace, nastane čas na asociaci. Ta začíná tím, že klient odešle rámec Association Request. Cílem tohoto rámce je, aby si AP nealokoval pro naše spojení prostředky a sdělil nám AID (Association Identifier). Obsahem je název SSID, podporovaná rychlost, možnosti šifrování (RSN) a mnoho dalších podrobností:
Association Request
AP po přijetí rámce Association Request ověří, zda všechny pole v žádosti vyhovují tomu, co sám podporuje. Pokud dojde ke kompatibilitě, odešle AP rámec Association Response s návratovým kódem 0. Pozor, na rozdíl od autentizace, která využívá stejný rámec, pouze s jinou hodnotou SEQ, se u asociace využívají 2 různé řídící rámce. Obsahem je hlavně již zmíněné AID a další specifikace podporované AP:
Association Response
Všechny tyto výše uvedené řídící rámce jsou pořád pouze standardem IEEE 802.11, nezávisle na zvoleném typu zabezpečení. Některé další si představíme v průběhu článku, jakmile na ně dojde řada. Pokud chcete, tak si je můžete odchytávat. Stačí si přepnout svojí Wi-Fi kartu do monitorovacího módu (tedy aby zachytávala veškerý provoz, nejen ten, který je určen pro ni). Využít můžete například oblíbeného programu airmon-ng. Syntaxe je airmon-ng <start|stop> <interface> [channel] , takže například:
airmon-ng start wlan0
TKIP vs. CCMP
Trochu odbočím – někde se můžete setkat s termíny WPA2-PSK-TKIP a WPA2-PSK-CCMP. Jedná se o způsob šifrování a zajištění autentizace. TKIP (Temporal Key Integrity Protocol), který se používal v první verzi WPA (i když z důvodů kompatibility existuje někde i u WPA2) využívá k šifrování proudovou šifru RC4 a k autentizaci zpráv keyed-hash algoritmus Michael. Modernější a mnohem častěji využívaný protokol CCMP (Counter Mode CBC-MAC Protocol) šifruje data pomocí šifry AES a k ověření autentizace využívá CBC-MAC. CCMP je z hlediska bezpečnosti mnohem lepší, proto se v následujícím textu omezím pouze na tuto variantu.
Generování PSK
Po úspěšné autentizaci a asociaci, která je stejná pro všechny typy zabezpečení, se dostáváme k detailům samotného WPA2. Jako první krok si obě strany spočítají sdílený tajný klíč PSK (Pre-shared key). PSK závisí pouze na názvu sítě – SSID (zde konkrétně root_wpa2) a heslu (v našem případě PrisneTajneHeslo). PSK se počítá s pomocí funkce pro derivaci klíče PBKDF2 s využitím HMACu založeném na SHA1, konkrétně:
PSK = PBKDF2 (HMAC-SHA1, heslo, SSID, 4096, 256)
4096 je počet iterací (kvůli zpomalení) a 256 je velikost výstupu v bitech. Tyto hodnoty jsou pevně dané. Konkrétní hodnotu PSK si můžete spočítat například na stránkách Wiresharku:
PSK generator
Jak je vidět, PSK si může spočítat klient i AP samostatně, ještě před jakýmkoliv handshakem a tento klíč je vždy stejný (dokud nezměníme SSID nebo heslo). Někdy se můžete setkat ještě s termínem PMK (Pairwise Master Key). Pro WPA2-Personal je PSK to samé jako PMK, u WPA2-Enterprise se PMK počítá odlišně. V našem případě tedy platí, že PSK == PMK a nadále budu používat pouze termín PSK. Hodnota klíče PSK je následně použita pro výpočet klíče PTK (Pairwise Transient Key), který se již používá pro samotné šifrování dat (unicast). Během handshaku si strany vymění ještě GTK (Group Temporal Key), který vznikne z GMK (Group Master Key) a je určen pro šifrování multicast/broadcast provozu. To není pro účely toho článku až tak zásadní, GTK tedy nebude probrán tak podrobně.
4-way handshake
4-way handshake je mechanismus výměny 4 zpráv, během kterých se klient a AP vzájemně dohodnou na šifrovacích klíčích PTK/GTK a ověří si, že jsou na obou stranách stejné.
4-way handshake
Na počátku AP vygeneruje 32 bajtů náhodných dat označovaných jako ANonce (A jako Authenticator). To samé udělá klient, který vygeneruje SNonce (S jako Supplicant).
První zprávu, jejímž obsahem je ANonce, odesílá AP klientovi. Klient má nyní všech 5 komponent pro výpočet šifrovacího klíče PTK:
PSK si spočítal na základě SSID a hesla
SNonce si sám vygeneroval
ANonce obdržel v první zprávě 4-way handshaku od AP
svoji MAC adresu zná
MAC adresu AP vidí v komunikaci
Výpočet PTK probíhá tak, že se všechny tyto atributy vloží do pseudonáhodné funkce PRF-384, využívající HMAC-SHA1. Výsledkem je 48 bajtů dlouhý šifrovací klíč PTK. Obsah této první zprávy není nijak šifrován ani podepsán.
Ve druhé zprávě odešle klient svojí náhodnou hodnotu SNonce a MIC (Message Integrity Code), který je spočítán z této zprávy. MIC slouží k autentizaci zprávy a ověření datové integrity. K jeho výpočtu je využit CBC-MAC a jako klíč se použije PTK. AP má nyní také všech 5 komponent pro výpočet PTK:
PSK si spočítal na základě SSID a hesla
ANonce si sám vygeneroval
SNonce obdržel v druhé zprávě 4-way handshaku od klienta
svojí MAC adresu zná
MAC adresu klienta vidí v komunikaci
Navíc z této zprávy sám spočítá MIC a porovná ho s přijatým MIC. Pokud se rovnají, tak PTK má na obou stranách stejnou hodnotu a tudíž se bude šifrovat stejným klíčem.
Ve třetí zprávě odešle AP klíč GTK, který je vytvořen z náhodných hodnot GMK a GNonce a je zašifrovaný pomocí PTK. GTK je, jak jsem již zmiňoval, použit pro šifrování multicast/broadcast provozu. K celé této zprávě je opět spočítán MIC, aby si i klient mohl ověřit shodnost PTK.
Nyní si klient dešifruje a nainstaluje GTK a odešle AP poslední zprávu (opět podepsanou MIC), která slouží pouze jako potvrzení. Proces celého 4-way handshaku zjednodušeně znázorňuje následující schéma:
4-way handshake
Nyní mají obě strany spočítán stejný klíč PTK, který slouží k šifrování unicast provozu a je s každým připojením jiný (kvůli jiným hodnotám SNonce a ANonce). Tento klíč a ani samotný PSK nikdy není přenesen po síti. AP si musí držet několik klíčů PTK, protože každý klient má odlišný. Z tohoto důvodu nemohou klienti jednoduše rozšifrovat a sledovat provoz ostatních.
Abychom těch zkratek neměli málo, PTK (48 bajtů) doopravdy není jeden klíč (jak jsem pro jednoduchost popisoval výše), ale dělí se na 3 podklíče:
prvních 16 bajtů – KCK (Key Confirmation Key) – slouží pro výpočet MIC při handshaku
druhých 16 bajtů – KEK (Key Encryption Key) – použit pro šifrování dalších podrobností při handshaku (např. GTK)
posledních 16 bajtů – TEK (Temporal Key) – použit pro šifrování/dešifrování samotných dat (unicast) pomocí šifry AES-128
Dešifrování provozu ostatních klientů
Dost bylo teorie, přesuňme se k praxi. Našim cílem bude odposlouchávat komunikaci ostatních klientů, připojených na stejnou síť za podmínky, že známe sdílené heslo (v našem případě PrisneTajneHeslo). To za normálních okolností není možné, protože jak jsme si během popisu 4-way handshaku vysvětlili, každý klient používá pro šifrování unikátní klíč PTK (resp. jeho podčást TEK). Podívejme se na následující diagram, který nám vykresluje, co všechno je potřeba, abychom mohli spočítat TEK ostatních klientů:
Zelená políčka známe:
SSID buď víme anebo odposlechneme z Beacon/Probe Response rámců
heslo musíme znát, to je nutná podmínka
PSK si spočítáme pomocí funkce PBKDF2
MAC adresy klienta a AP vidíme v zachycené komunikaci
Abychom mohli spočítat PTK a odvodit si z něj TEK, potřebujeme znát ještě náhodné hodnoty SNonce a ANonce. Jak jsme si popsali výše, tyto hodnoty jsou přeneseny během prvních 2 zpráv handshaku a nejsou nijak šifrované. Stačilo by nám tedy tyto zprávy zachytit a měli bychom všechny vstupy pro funkci PRF-384 a výpočet šifracích klíčů ostatních klientů.
K handshaku dochází ale pouze při navazování spojení a takové čekání, než se oběť znovu připojí, může být nekonečné. Naštěstí můžeme využít toho, že řídící rámce 802.11 nejsou nijak šifrované ani podepsané a lze je snadno podvrhnout. Na tento účel nám poslouží rámec Deauthentication, který se využívá pro ukončení spojení. Odešleme ho s podvrhnutou zdrojovou MAC adresou, kdy se budeme vydávat za oběť, čímž způsobíme její odpojení od sítě. Spojení sice bude ihned automaticky navázáno, takže si toho pravděpodobně nikdo nevšimne, my však zachytíme handshake a tím pádem i ANonce a SNonce.
Praktická ukázka
Vše níže uvedené budu provádět z Kali Linuxu, obecně vám však postačí jakákoliv distribuce s uvedenými programy. Nejprve si deaktivujeme primární rozhraní wlan0 a přepneme Wi-Fi kartu do monitorovacího módu:
ifconfig wlan0 down
airmon-ng start wlan0
Pomocí jakéhokoliv programu budeme zachytávat veškerý provoz na monitorovacím rozhraní (pravděpodobně mon0). Já využiji známý nástroj Wireshark. Pro zjednodušení si lze nastavit filtr na eapol.type == 3, což nám bude zobrazovat pouze rámce patřící k handshaku. Pokud jsme zatím handshake nezachytili, můžeme poslat podvrhnutý deautentizační rámec pomocí programu aireplay-ng:
aireplay-ng -0 1 -a 38:2c:4a:4e:06:1d -c 0c:e7:25:5a:1b:14 mon0
kde:
-0 znamená deautentizaci
1 znamená, že se bude deautentizovat pouze 1× (můžete i vícekrát, případně 0 pro nekonečnou deautentizaci)
-a 38:2c:4a:4e:06:1d je MAC adresa AP
-c 0c:e7:25:5a:1b:14 je MAC adresa klienta, kterého chceme odpojit
mon0 je název rozhraní
Poté byste měli vidět deautentizační rámce spolu s ihned automaticky navázaným spojením a tedy zachyceným handshakem:
Deautentizace a následný handshake
Pokud bude handshake neúplný (například 3 zprávy ze 4), je nutné celý proces zopakovat. Jestli nevíte, kde zjistit MAC adresy AP a případné oběti, můžete na to použít program airodump-ng:
airodump-ng --essid root_wpa2 -a mon0
kde:
–essid root_wpa2 je název SSID sítě
-a znamená, že se nám budou zobrazovat připojení klienti
Jak je vidět na screenshotu níže, k naší Wi-Fi síti root_wpa2 (MAC 38:2C:4A:4E:06:1D) jsou připojení dva klienti (MAC 0C:E7:25:5A:1B:14 a 6C:27:79:77:8A:60). Tyto informace tedy můžeme využít pro aireplay-ng.
airodump-ng
Jakmile jsme oběť deautentizovali a zachytili handshake, získali jsme díky tomu i náhodná data SNonce a ANonce. Nyní nám nic nebrání provoz dešifrovat symetrickou šifrou AES s právě vypočteným klíčem TEK. Využijeme k tomu opět Wireshark – konkrétně Edit → Preferences → Protocols → IEEE 802.11. Zde zaškrtneme Enable decryption a klikneme na Edit. Nyní vybereme typ wpa-pwd a klíč vepíšeme ve formátu heslo:SSID .
Wireshark
Od této doby by měl Wireshark dešifrovat veškerý provoz (i real-time) všech klientů, ke kterým zachytil handshake. Pokud nebudou data šifrovaná nějakou další vrstvou (HTTPS, VPN…), tak útočník uvidí vše – webové stránky, které navštěvujete, vaše uživatelská jména i hesla, obsahy odeslaných formulářů, obsahy zpráv atd.
Dešifrovaná komunikace
Prolamování hesla
Druhou a poslední praktickou ukázkou v tomto článku bude prolamování hesla. Tedy situace, kdy k Wi-Fi síti zabezpečené pomocí WPA2-PSK (CCMP) heslo neznáme. Samozřejmě jednou z možností je zkoušet jedno heslo po druhém (ideálně z nějakého slovníku) přímo pokusem o připojení – to je však extrémně pomalé a lehce detekovatelné.
My místo toho využijeme výše uvedených znalostí k provedení tzv. offline útoku. To znamená, že se pokusíme heslo prolomit lokálně, aniž bychom se neustále dotazovali AP. Pokud neznáme heslo, ztroskotáme hned na začátku celého procesu, protože nebudeme schopni pomocí funkce PBKDF2 spočítat PSK. Z toho vyplývá, že naše snažení bude spočívat ve zkoušení mnoha různých hesel jako vstupu do funkce PBKDF2. Jak ale ověřit, že je heslo správné?
Pokud si ještě pamatujete 4-way handshake, tak ve druhé zprávě je i autentizační kód MIC, který se spočítal pomocí CBC-MAC a klíče KCK (prvních 16 bajtů PTK). Náš postup bude tedy následující:
Opět si zachytíme 4-way handshake kvůli získání ANonce a SNonce, i když tentokrát by nám stačily jen první 2 zprávy.
Vezmeme první heslo ze slovníku a spočítáme PSK pomocí PBKDF2.
Spočítáme si PTK pomocí funkce PRF-384 (vše potřebné již známe).
Z právě vypočteného klíče si oddělíme prvních 16 bajtů – klíč KCK.
Spočítáme MIC druhé zprávy s využitím CBC-MAC a klíče KCK.
Pokud se zachycený MIC rovná našemu právě vypočtenému, heslo z bodu 2 je správné. Když je MIC různé, vracíme se k bodu 2 a zkoušíme druhé heslo ze slovníku atd.
Jak je na výše uvedeném algoritmu vidět, vše lze počítat i ověřovat lokálně. Nejpomalejší částí celého procesu je funkce PBKDF2, která má pro zpomalení nastaveno 4096 iterací. Jelikož je založená na HMACu s využitím SHA1, musíme spočítat 8192 SHA1 hashů pro vyzkoušení jediného hesla. Spolu s minimální délkou hesla 8 znaků (maximum je 63) je možné prolomit heslo víceméně jen s využitím slovníkového útoku. Bruteforcing, tedy zkoušení všech možných kombinací, je díky velké časové náročnosti téměř nemožný.
Praktická ukázka
Opět využiji Kali Linux a moji testovací síť root_wpa2, tentokrát s neznámým heslem. Protože se zde bude plno věcí opakovat, budu to brát stručněji. Nejprve si opět přepneme kartu do monitorovacího módu:
ifconfig wlan0 down
airmon-ng start wlan0
Dále si programem airodump-ng zjistíme kanál, na kterém AP vysílá:
airodump-ng mon0
Na tomto kanálu začneme zachytávat veškerý provoz a ukládat ho do souboru:
airodump-ng –-channel 6 –-essid root_wpa2 mon0 –-write /tmp/root_wpa2
Mezitím z druhé konzole vyhodíme libovolného klienta, abychom zachytili handshake:
aireplay-ng -0 1 -a 38:2c:4a:4e:06:1d -c 0c:e7:25:5a:1b:14 mon0
Jakmile zachytíme 4-way handshake, objeví se nám to ve výstupu programu airodump-ng a můžeme ho ukončit:
Nyní máme v souboru/tmp/root_wpa2-01.cap uložen veškerý provoz včetně handshaku a můžeme se pokusit prolomit heslo, k čemuž budeme potřebovat nějaký slovník. Pro testovací účely jsem si vytvořil vlastní:
root@i5sb:~# cat /tmp/list.txt
SpatneHeslo
NespravneHeslo
Kdepak
PrisneTajneHeslo
TohleToNeni
AniTohle
Použiji program aircrack-ng, kterému předám wordlist a zachycený provoz:
aircrack-ng –w /tmp/list.txt /tmp/root_wpa2-01.cap
Jak je vidět, aircrack-ng prolomil heslo vcelku rychle. Reálná rychlost na mém starším notebooku (Intel Core i5–2410M) je přibližně 1800 hesel za vteřinu. Zrychlení na GPU/FPGA/ASIC bude markantní, avšak při dostatečně dlouhém a neslovníkovém heslu jste pořád v bezpečí.
Jak se bránit
Co se týká odposlouchávání provozu, tam je nejdůležitější uvědomění si, že kdokoliv zná heslo, může sledovat veškerý váš provoz. Pro domácí využití lze doporučit pořízení routeru, který umožňuje mít více SSID (a ke každému jiné heslo). Jedno SSID pro vás, další pro návštěvy, nájemníky apod. Pokud jste někde mimo domov, doporučuji využít šifrovaného VPN spojení – osobně se na veřejných hotspotech bez VPN téměř nepřipojuji. V neposlední řadě je zde možností využít WPA2-Enterprise módu, což rozhodně kvůli složitější implementaci nelze doporučit všem.
Pokud chcete zabránit prolomení hesla, rada je velmi jednoduchá – zvolte dostatečně dlouhé a neslovníkové heslo. Zajímavostí, kterou moc lidí netuší, je, že bezpečnost vaší sítě závisí i na zvoleném SSID. Proč? Pokud budete mít např. defaultní SSID, které mají další statisíce lidí po celém světě, je zde mnohem větší šance, že si útočníci předpočítali dostatečně velké rainbow tabulky pro vaše SSID (do funkce PBKDF2 vstupuje jak heslo, tak SSID). To jim šanci na prolomení hesla mnohonásobně zvýší. Například na placené službě GPUHASH.me se můžete pokusit prolomit heslo k zachycenému handshaku.
Bezpečnost Wi-Fi je velmi široké téma a rozhodně by nebylo na škodu probrat i nějaké další věci, namátkou – více řídících rámců 802.11, útoky na WEP/WPA, generování a používání klíče GTK pro multicast/broadcast, prolomení WPA2 přes WPS, útok Hole196 apod. Už tak je však tento článek příliš dlouhý, necháme si to tedy na někdy příště.
Someone Hijacking Unsecured MongoDB Databases for Ransom
4.1.2017 thehackernews Hacking
Nearly two years back, we warned users about publicly accessible MongoDB instances – almost 600 Terabytes (TB) – over the Internet which require no authentication, potentially leaving websites and servers at risk of hacking.
These MongoDB instances weren't exposed due to any flaw in its software, but due to a misconfiguration (bad security practice) that let any remote attacker access MongoDB databases without using any special hacking tool.
MongoDB later resolved the issue in the next version of its software by setting unrestricted remote access by default in the configuration, thousands of site administrators have not updated their servers yet.
But trust me, they'll now regret this!
A Hacker is now hijacking and wiping out unsecured MongoDB databases, but keeping a copy of those databases for asking administrators a ransom of 0.2 Bitcoins (nearly US$211) to return the lost data. So, admins without backups are left in a bind.
In fact, the rising price of Bitcoin even hints at some of its troubles. At the time od writing, 1 Bitcoin = USD1063.93.
Security researcher and co-founder of the GDI Foundation Victor Gevers (@0xDUDE) discovered the attacks and notified exposed non-password-protected MongoDB installations to owners via Twitter.
Gevers identified nearly 200 instances of a MongoDB installation that's been erased and held for ransom, while this number reached approximately 2,000 databases as of 4:00 p.m, as reported by John Matherly, the Founder of Shodan, where many exposed MongoDB databases can be found.
These attacks have been going on for over a week, targeting servers all over the world. It is believed that instead of encrypting the data, the attacker who goes by the name "harak1r1," ran a script that replaced the content of the database with the attacker's ransom note.
While accessing one of the open servers, Gevers found that in place of the database content, there is only one table, named "WARNING," which reads:
"SEND 0.2 BTC TO THIS ADDRESS 13zaxGVjj9MNc2jyvDRhLyYpkCh323MsMq AND CONTACT THIS EMAIL WITH YOUR IP OF YOUR SERVER TO RECOVER YOUR DATABASE !"
16 Victims Already Paid the Ransom
It appears that around 16 organizations so far have paid the ransom to the attacker.
Matherly has been warning of the dangers of exposed MongoDB installations since 2015, allowing an attacker to remotely access the databases over the Internet without the need of any form of authentication.
Matherly said the majority of publicly exposed 30,000 MongoDB instances run on cloud servers such as Amazon, Digital Ocean, Linode, and Internet service and hosting provider OVH and do so without authentication, making cloud services buggier than datacenter hosting.
How to Know if You've Been Hacked?
Check the MongoDB accounts to see if no one added a secret (admin) user.
Check the GridFS to look if someone stored any files there.
Check the log files to see who accessed the MongoDB.
How to Protect Yourself?
Enable authentication that provides you 'Defense in depth' if your network is compromised. Edit your MongoDB configuration file — auth = true.
Use firewalls — Disable remote access to the MongoDB, if possible. Admins are advised to use firewalls to protect the MongoDB installations by blocking access to port no. 27017.
Configure Bind_ip — Limit access to the server by binding local IP addresses.
Upgrade — Administrators are strongly recommended to upgrade their software to the latest release.
MongoDB is the most popular, open-source NoSQL database used by companies of all sizes, from eBay and Sourceforge to The New York Times and LinkedIn. Administrators are encouraged to follow a security checklist provided by the company.
ZeroNet could be a solution against censorship and much more
4.1.2017 securityaffairs Safety
ZeroNet is a new and revolutionary decentralized P2P internet that promise to avoid censorship and improve user privacy on the open web.
ZeroNet is a decentralized and open source web platform. It’s based on BitTorrent(p2p) technology and BitCoin cryptography. These features ensure a decentralized censorship-resistant network.
The contents published by users can never be deleted because they’re distributed directly to other visitors without any central server. The content remains online so long as at least one user serving it. It’s impossible to shut down websites in the ZeroNet.
“When a site is updated by its owner, all nodes serving that site (previous visitors) will receive only the incremental updates done to the site content.” states the official website of the project.
ZeroNet implements a network whereby users can access and surf websites that are hosted on other user’s machines, it doesn’t include centralized servers.
“It’s nowhere because it’s everywhere!” declares ZeroNet site
You can create a free website using ZeroNet. There are no costs for hosting because the website is stored automatically your website. This could be a challenge to web hosting companies. It is always online with no downtime and can be accessible if your internet is unavailable if you have visited the website previously.
The site owner can accept payment directly to the site address.
Is ZeroNet anonymous?
If you want to hide your IP address, ZeroNet supports Tor network. The level of anonymity implemented is the same of the one implemented for BitTorrent, but a combined use with the Tor network will allow protecting user’s anonymity.
ZeroNet is made to work with anonymity networks: you can easily hide your IP using the Tor network.
Furthermore, you don’t need to remember your password, because your account is protected by same cryptography as a Bitcoin wallet.

In order to ensure integrity files, when you visit a site you download a file named “content.json”, it contains all other file names with relative hashes and cryptographic signature by the site owner. Then you download other files and verify them using hashes included in the “content.json”. This prevents in some way the diffusion of corrupted files or malicious code.

Another feature is multi-user site for example if you want to post on forum or blog. Sending your auth address to the site owner, it creates a new file and set your auth address as the valid signer. The site owner publishes a new “content.json” declaring that you can be signed a file.
Below the list of features implemented by ZeroNet:
Easy, zero configuration setup.
Password-less BIP32 based authorization: Your account is protected by the same cryptography as your Bitcoin wallet.
Real-time updated sites.
Namecoin .bit domains support.
SQL Database support: Allows for easier site development and faster page load times.
Anonymity: Full Tor network support with .onion hidden services instead of ipv4 addresses
TLS encrypted connections.
Automatic, uPnP port opening.
Plugin for multiuser (openproxy) support.
Works with any browser/OS.
ZeroNet users also have access to
ZeroBoard: Simple message board demo for dynamic content distribution
ZeroBlog: Self publishing blog demo
ZeroTalk: Decentralized, P2P forum demo
ZeroMail: End-to-end encrypted, distributed, P2P messaging site. To improve privacy it uses a BitMessage-like solution and will not expose the message recipient.
ZeroChat: The finished site for the tutorial of creating a server-less, SQL backed, real-time updated P2P chat application using ZeroNet in less than 100 lines of code
ZeroMe: Decentralized, Twitter-like P2P social network.
One of the questions in the FAQ session camptured my attention:
What happens when someone hosts malicious content?
The answer is very clear:
The ZeroNet sites are sandboxed, they have the same privileges as any other website you visit over the Internet. You are in full control of what you are hosting. If you find suspicious content you can stop hosting the site at any time.
Critical Updates — RCE Flaws Found in SwiftMailer, PhpMailer and ZendMail
3.1.2017 thehackernews Vulnerebility
phpmailer-swiftmailer-zendmail
A security researcher recently reported a critical vulnerability in one of the most popular open source PHP libraries used to send emails that allowed a remote attacker to execute arbitrary code in the context of the web server and compromise a web application.
Disclosed by Polish security researcher Dawid Golunski of Legal Hackers, the issue (CVE-2016-10033) in PHPMailer used by more than 9 Million users worldwide was thought to be fixed with the release of version 5.2.18.
However, Golunski managed to bypass the patched version of PHPMailer that was given a new CVE (CVE-2016-10045), which once again put millions of websites and popular open source web apps, including WordPress, Drupal, 1CRM, SugarCRM, Yii, and Joomla, at risk of remote code execution attack.
PHPMailer eventually fixed the issue with an update, version 5.2.20. All versions of PHPMailer before this critical release are affected, so web administrators and developers are strongly recommended to update to the new version.
In addition to this bug, Golunski also reported a similar vulnerability in two other mailing libraries for PHP, SwiftMailer, and ZendMail, that could have also led to remote code execution attack.
RCE Flaw in SwiftMailer
SwiftMailer is also a popular PHP library used by many major open-source projects, including top PHP programming frameworks like Yii2, Laravel, Symfony for sending emails over SMTP.
The vulnerability (CVE-2016-10074) in SwiftMailer can be exploited in the same manner as the PHPMailer vulnerability by targeting web site components that use SwiftMailer class, such as contact/registration forms, password email reset forms, and so forth.
Attackers can execute arbitrary code remotely in the context of the web server, which could further be exploited to access a web server hosting a web application that used a vulnerable version of the library.
The SwiftMailer vulnerability affects all versions of the library, including the then-current release, version 5.4.5-DEV.
Golunski disclosed the vulnerability to SwiftMailer team, and developers acted fast to fix the issue, rolling out patched version 5.4.5 within a day.
"The mail transport (Swift_Transport_MailTransport) was vulnerable to passing arbitrary shell arguments if the "From," "ReturnPath" or "Sender" header came from a non-trusted source, potentially allowing Remote Code Execution," reads the changelog for SwiftMailer on GitHub.
RCE Flaw in ZendMail
ZendMail is a component of a very popular PHP programming framework Zend Framework with more than 95 Million installations.
The critical vulnerability (CVE-2016-10034) in ZendMail can also be exploited in the same manner as one discovered in PHPMailer and SwiftMailer by targeting web site components that use ZendMail, like contact/registration forms, password email reset forms, and so on.
Attackers could achieve remote code execution in the context of the web server and could remotely compromise the target web application that used the vulnerable version of the ZendMail.
The researcher reported the issue to ZendMail, and the developers fixed the vulnerability and rolled out the patched version.
"When using the zend-mail component to send email via the Zend\Mail\Transport\Sendmail transport, a malicious user may be able to inject arbitrary parameters to the system sendmail program," ZendMail wrote in a blog post.
"The attack is performed by providing additional quote characters within an address; when unsanitized, they can be interpreted as additional command line arguments, leading to the vulnerability."
Golunski has released a proof-of-concept video demonstration that will show all the three attacks in action.
Golunski has also released a dedicated website, nicknamed PwnScriptum, with a logo that contains all the information about the vulnerabilities in PHPMailer, SwiftMailer, and ZendMail in one place.
The researcher will soon be revealing a security white-paper with previously unknown exploitation vectors and techniques that can be used to exploit all the 3 vulnerabilities.
It has happened again, ransomware infected an LG Smart TV
3.1.2017 securityaffairs Virus
The software engineer Darren Cauthon reported his LG Smart TV was infected with ransomware on Christmas day, the malware asked for $500 to unlock the device
IoT Ransomware is a scaring reality, the threat will increase in the next months and security firms have been warning IT industry. Routers, smart TV, and CCTVs are all potential victims of such category of malware.
The latest incident in order of time involved an LG smart TV, the software engineer Darren Cauthon reported the device of one of his family members was infected with ransomware on Christmas day.
The TV got the ransomware when the programmer’s wife downloaded an app to the TV promising free movies, it was a ransomware demanding of US$500 to unlock the device.
The ransomware appears to be a version of the Cyber.Police ransomware, also known as FLocker and Frantic Locker.

FLocker isn’t a new threat, it has been around for a year and crooks delivered it to the victims via spam SMS campaigns or sharing malicious links.
The FLocker ransomware was first spotted on May 2015, security experts from Trend Micro detected more than 7,000 strains of the same malware. The threat actors behind the FLocker ransomware has updated over the time the threat improving it and making had its detection by security solutions. Over the past few months, the experts observed a number of spikes and drops in the number of iterations released in the wild, in the last wave of infection observed in the mid-April 2016 the researchers detected over 1,200 variants.

Visualizza l'immagine su Twitter
Segui
Darren Cauthon @darrencauthon
Family member's tv is bricked by Android malware. #lg wont disclose factory reset. Avoid these "smart tvs" like the plague.
19:59 - 25 Dic 2016
3.450 3.450 Retweet 2.836 2.836 Mi piace
Darren Cauthon’s LG smart TV runs Google TV, a project discontinued by Google in June 2014.
Currently, LG has moved to WebOS, an open-source Linux kernel-based multitask operating system.
Cauthon tried to reset the TV to factory settings, but the reset procedure available online didn’t work, so he decided to contact the customer service. The man was invited to go to a service center for assistance that implied a $340 bill for the support.
Resuming, the Ransomware asked for $500 to unlock the device, but the sad news is that also LG asks a $340 bit of the support.
The story has a happy ending, LG provided hidden reset instructions to remove the ransomware from the LG Smart TV.
The company offered factory reset steps which are not publicly available.
Below the video shared by The Register:
“With the TV powered off, place one finger on the settings symbol then another finger on the channel down symbol. Remove finger from settings, then from channel down, and navigate using volume keys to the wipe data/ factory reset option.” states the The Register.
25 Dic
Darren Cauthon @darrencauthon
Family member's tv is bricked by Android malware. #lg wont disclose factory reset. Avoid these "smart tvs" like the plague. pic.twitter.com/kNz9T1kA0p
Segui
Darren Cauthon @darrencauthon
The TV is saved! Thanks to LG for providing the factory reset instructions. I recorded a YouTube video of the fix: https://youtu.be/0WZ4uLFTHEE pic.twitter.com/hV62r68uit
06:15 - 29 Dic 2016
Chování uživatelů pod drobnohledem
2.1.2017 SecurityWorld Rizika
Analýza chování uživatelů je klíčem k odhalení zneužití práv, která mají interní pracovníci.
Téměř všechny úniky dat zahrnují použití legitimních přihlašovacích údajů. Ochrana před těmito „interními hrozbami“ vyžaduje schopnost odhalit situace, kdy kyberzločinci zneužívají ukradené přihlašovací údaje.
Tradiční síťové bezpečnostní nástroje však bohužel nejsou při identifikaci a zmírňování těchto hrozeb dostatečně účinné. Pro tento specifický účel byl proto navržen nový druh řešení, které dokáže analyzovat chování uživatelů a ukazuje se jako účinný.
Pojem „interní hrozba“ obvykle vyvolává představu nepoctivých zaměstnanců nebo smluvních či obchodních partnerů se zločinnými úmysly, kteří mají oprávnění pro přístup k firemním datům.
Tento termín se ale používá také v mnohem širším významu pro jakoukoli hrozbu nebo útok zneužívající přihlašovací údaje či výsady oprávněných zaměstnanců nebo dalších osob s interním přístupem.
Je pravdou, že mezi únikem dat a zaměstnanci či dalšími osobami s interním přístupem lze často nalézt spojitost. Kromě rozhněvaných jedinců a osob se zlými úmysly, kteří záměrně kradou informace, bývají často příčinami krádeže citlivých informací nesprávná konfigurace zabezpečení, nedbalost při dodržování firemních zásad, podlehnutí phishingovým útokům nebo útokům sociálního inženýrství a další neúmyslné jednání.
Největší a nejškodlivější úniky dat však bývají způsobené někým z vnějších hackerů, organizovaného zločinu, nepřátel vlády, konkurentů a hacktivistů. Přestože sami nejsou z řad osob s legitimním interním přístupem, závisejí tito zločinci téměř vždy na získání přihlašovacích údajů patřících někomu takovému, zejména někomu z okruhu osob s oprávněním správce.
Prvořadým cílem kyberzločince tedy je získat přihlašovací údaje pro jednotlivce s přístupem k citlivým datům. Jakmile se to podaří, začne podvodník předstírat privilegovanou interní osobu, vnikne do systému a zkopíruje informace podle svého záměru.
Ať už jde o osoby zvenčí nebo zevnitř, je neoprávněné nebo nedbalé používání přihlašovacích údajů a privilegií interní osoby společným jmenovatelem téměř všech kyberzločinů. Veškerá související rizika lze považovat za interní hrozbu.
Vzhledem k této širší definici interních hrozeb existuje mnoho aktivit spojených s použitím přihlašovacích údajů a aktivit uživatelů, které je nutné za účelem ochrany před kyberzločinem monitorovat.
Přinášíme zde seznam některých nejčastějších projevů, které naznačují použití ukradených přihlašovacích údajů a další nepovolené aktivity a interní jevy ukazující na hrozby. Řešení pro analýzu chování uživatelů by mělo všechny uvedené případy odhalit.
Podezřelá posloupnost geolokace. Mnoho uživatelů pracuje z více vzdálených míst, jako jsou domovy, hotely, kiosky na letištích, satelitní pobočky a místa u zákazníků.
Pokud jde o účty použité k přihlášení ze vzdálených míst, potřebují podniky zjistit, zda jde o legitimní uživatele, nebo o vzdálené útočníky, kterým se podařilo získat platné přihlašovací údaje.
Sledování geolokace každého pokusu o přístup a ověřování, zda je fyzicky možné v daný čas připojení z tak vzdáleného místa, stejně jako ověření, co je normální chování legitimního vlastníka účtu, je kritické při zjišťování, jestli vzdálení hackeři ukradli a zneužili přihlašovací údaje uživatele.
Kompromitovaný servisní účet. Servisní účty se používají operačními systémy a různými aplikacemi k vykonávání automatizovaných úloh na pozadí. Tyto účty se obvykle nemonitorují, mají vysoká přístupová práva a jsou neustále vystavené riziku útoku a kompromitace.
Jejich aktivita by se měla sledovat, aby se zajistilo, že nepřistupují k systémům, ke kterým by neměly, a nezasílají data neoprávněným příjemcům.
Pokusy o krádež dat. Z úniku dat panuje v mnoha organizacích velká obava. Obtížnost detekce úniků dat roste s příchodem dalších technologií a metod pro přenosy dat.
Monitorování neobvyklého chování uživatelů, jako je přístup k datům, se kterými tento uživatel obvykle nepracuje, nebo přenosy dat do neobvyklých destinacích mohou odhalovat pokusy o krádež dat.
Sdílení přihlašovacích údajů. Studie ukazují, že více než 20 % zaměstnanců sdílí svá hesla s někým dalším, přestože je to přísně zakázáno zásadami.
Monitoring současného, vzdáleného a neobvyklého použití uživatelských účtů může pomoci odhalit a zmírnit sdílení přihlašovacích údajů.
Slídící uživatelé. Při hledání citlivých a cenných dat prohledávají ničemní interní uživatelé a externí zločinci korporátní systémy v naději, že najdou a získají informace, které budou moci prodat nebo použít pro vlastní zisk.
Detekce a zkoumání takového neobvyklého chování uživatelů může odvrátit hrozící kyberzločin.
Odcházející zaměstnanec. Pracovníci, kteří se připravují opustit organizaci, mohou představovat bezpečnostní hrozbu. Přestože mohou představovat vysoké riziko krádeže dat a dokonce sabotáže, dokáže jejich akce vysledovat a detekovat podezřelé chování jen velmi málo nástrojů.
Bezpečnostní pracovníci musejí implementovat řešení navržená tak, aby specificky a automaticky sledovaly účty odcházejících zaměstnanců a upozornily na podezřelé chování.
Zneužití privilegovaného účtu. Protože jsou privilegované účty vytouženou trofejí kyberzločinců, je monitorování jejich použití z hlediska neobvyklého chování nesmírně důležité.
Automatizovaný, vzdálený a simultánní přístup může indikovat interní hrozbu stejně jako neobvyklé časy přihlášení, přístup k nezvyklým systémům či nenormální přenosy dat.
Neoprávněný přístup třetí strany (obchodní partneři a další dodavatelé). Smluvní strany, obchodní partneři a další poskytovatelé služeb mají často přístup k citlivým podnikovým datům.
Přesto však obvykle nepodléhají stejným bezpečnostním opatřením a zásadám jako hostitelský podnik. V důsledku toho může dojít k nakažení aplikací a zařízení malwarem navrženým k ukradení přihlašovacích údajů.
Je povinností zejména hostitelského podniku monitorovat chování všech uživatelů třetích stran.
Chyby v konfiguraci sítě. Při monitorování normálního chování uživatelů může anomální jednání často odhalit nesprávnou konfiguraci zabezpečení. Například když zaměstnanec přistupuje k systému, který je mimo obvyklý vzorec jeho pracovní náplně, ukazuje to často na díru v bezpečnostních zásadách a nastaveních.
Včasná oprava chyb konfigurace může předejít bezprostředním i budoucím útokům.
Detekce interních hrozeb je v současném prostředí nezbytná. Je k ní zapotřebí pečlivého využití celé řady metod prevence počítačové kriminality. Ať už jde o zaměstnance se zlými úmysly, nebo o vnější útočníky využívající ukradené přihlašovací údaje, musejí být podniky v pohotovosti, ostražitě monitorovat dění a zaměřovat se interně na chování uživatelů a podezřelé aktivity. Jen tak mají šanci zmařit potenciální interní útoky.
#33C3- Changing travelers flight bookings is really too easy for hackers
2.1.2017 securityaffairs Hacking
Changing travelers flight bookings is too easy. Absolutely astounding the Karsten Nohl research on the insecurity of traveler flight information.
The current travel booking systems is deeply insecure, it lacks of cyber security by design and the notorious hackers Karsten Nohl and Nemanja Nikodijevic have demonstrated it at the 33rd Chaos Communications Congress held in Hamburg last week (“Where in the World Is Carmen Sandiego?”).
The experts explained that it is quite easy to modify any passenger’s reservation, cancel their flight bookings, and even use the refunds to book tickets for themselves.
The security duo has conducted for several months a research on security employed by the Global Distribution Systems (GDSs) that are used by various actors in the travel industry, including airlines, travel agencies, hotels and car rental companies.
Below the video of the presentation held during the 33rd Chaos Communications Congress.
GDSs are enormous archives containing all information about travel bookings, they include so-called Passenger Name Records (PNRs), records include information such as traveler’s name, itinerary, travel dates, ticket details, phone number, email, passport information, credit card numbers, seat numbers and baggage information. Travel data is precious for scammers and phishers that could use them to launch targeted attacks and organize complex frauds.
As explained by the experts the most important GDS operators in the world are Sabre, Travelport, and Amadeus. The disconcerting discovery made by the researcher is that it is possible to add or modify any travel data by accessing the system with a last name and a six-character booking code.
We have to think GDSs as systems accessible from everywhere, access points could be airline websites, travel agencies, and also third-party websites like CheckMyTrip. Every time a travel includes flights with different airlines the booking can be modified through the websites of any of the airlines that operate the trip.
Attackers could cancel a flight, and if the booking allows the change crooks could use the credit given by the airline to book a new ticket.
Unfortunately, the level of protection for the PNR is very poor, the booking code is easy to obtain, it is printed on luggage tags and is also embedded in the QR codes printed on the tickets.
Passengers use to throw away old Boarding Pass even when the overall travel isn’t yet completed, or even worse, they post on social networks the pictures of the tickets.
We explained in the past that Boarding Pass contains personal information that could be exploited by hackers.
The popular investigator Brian Krebs published an interesting post on the topic explaining that a Boarding Pass Barcode contains a lot of data.

Experts highlighted that there is no logging implemented in the GDSs, this means that is impossible to discriminate the accesses.
“In the short term, at the very least we should expect websites that give access to travelers’ personal information to have the bare minimum of web security, and this includes at the very least some rate limiting,” the researcher said. “And until passwords and other security measures become common, I think we have a right to know who accesses our records and there must be some accountability, especially knowing how insecure these systems are today.” explained Nohl.
Karsten Nohl and Nemanja Nikodijevic explained that many airline and trip checking websites don’t limit the number of bad codes users can enter before they’re blocked, opening the door to brute force code-guessing attacks.
The duo demonstrated that it is a question of minutes to find matching booking codes for popular last names by using automated methods. Working with GDSs brute force code-guessing attacks are very easy because the systems use only uppercase letters. The researchers explained that one of GDS analyzed doesn’t use 1 and 0 to avoid confusion with the letters I and O, two other GDSs increase the codes sequentially making easier for an attacker to guess the code withing a sequence.
“The travel agencies have their own master logins into the GDSs and these accounts have very weak passwords. In one case the password was WS, which stands for web service, followed by the date when the login was created in DDMMYY format. This can easily be brute-forced and unfortunately it was one of the most complex travel agency passwords the researchers observed.” reported CSOonline.
The lack of security could be exploited by crooks to add their frequent flier number to other passengers’ long-haul flights in order gain the reward miles for themselves.
As demonstrated by the experts, hackers can do much more than change flight bookings,
UK security minister: ISIS would launch chemical attacks in the UK
2.1.2017 securityaffairs Cyber
The ISIS seeking to launch mass-casualty chemical attacks in Europe said security minister Ben Wallace.
The UK security minister Ben Wallace declared terror group wants to carry out mass casualty attack in Britain UK by ‘whatever means possible.’
According to the minister, members of the ISIS have “no moral barrier” to using chemical weapons against the helpless population.
“They have no moral objection to using chemical weapons against populations and if they could, they would in this country.” said Wallace.
“The casualty figures which could be involved would be everybody’s worst fear.”
“We have certainly seen reports of them using it in Syria and Iraq [and] we have certainly seen aspiration for it in Europe.”
He confirmed that there were reports of ISIS using chemical weapons in the areas under its control in Syria and Iraq. Moroccan authorities had apprehended a cell in February which was
The report quotes Moroccan authorities had arrested a cell of terrorists in February which was in possession of substances that could be used to make either a chemical weapon.
Wallace also cited a recent report issued by the Europol that warned of the chemical threat.
In December 2015, a European Parliament report has confirmed the ISIS organization has already smuggled CBRN material into the EU and warned of WMD attacks.
The report confirmed the ISIS was recruiting foreign fighters with specific competencies in physics, chemistry, and computer science.
“ISIL/Da’esh has recruited and continues to recruit hundreds of foreign fighters, including some with degrees in physics, chemistry and computer science, who experts believe have the ability to manufacture lethal weapons from raw substances.”
Now Wallace told the Sunday Times that the ISIS plans to conduct “definitely mass casualty attacks” to harm as many people as possible.
Commenting the US sanctions on Russians for the alleged interference in the presidential election, Wallace warned of a possible inside threat. Terrorist groups and foreign governments all launched a campaign to recruit “traitors” in UK Government, the military and leading businesses.
“There are traitors. We have to be on our guard for the enemy within,” he said.
“The insider threat, as we would call it, is real and it can be exploited and there are people trying to do that as we speak.”
Trump will soon reveal the truth about the alleged Russian hacking
2.1.2017 securityaffairs Hacking
President Donald J. Trump is expressing skepticism about intelligence assessments of the Russian hacking and will provide more information very soon.
The executive order issued by President Obama in retaliation of the alleged Russian interference on Presidential Election is raising a heated debate on the on the measures adopted by the US Government and its ability to provide evidence of Russian malicious cyber activities.
The US ejected 35 Russian intelligence operatives from the United States and imposed sanctions on nine entities and individuals.The US Government sanctioned the Russian intelligence services, the GRU (Russian Main Intelligence Directorate) and the FSB (Federal Security Service), four GRU officers, and three other organizations.
The report published by the US Government doesn’t provide any new info, all the information it includes were already reported in the analysis conducted by security firms such as Crowdstrike.
In June, the security research firm CrowdStrike reported on a cyber breach of the Democratic National Committee (DNS). CrowdStrike’s incident response time discovered not one, but two hacking groups that it considers “some of the best adversaries out of the all the numerous nation-state” groups the company encounters daily – COZY BEAR and FANCY BEAR.
This is exactly the same info that we have found in the JAR report published by the US Government that linked the cyber activity to a Russian threat actor designated as GRIZZLY STEPPE.
Security experts at the security firm Wordfence published an interesting report in which they analyzed the PHP malware sample and the IP addresses that the US government has provided as proof the involvement of Russian hackers in the attacks against the Presidential Election.
“We used the PHP malware indicator of compromise (IOC) that DHS provided to analyze the attack data that we aggregate to try to find the full malware sample. We discovered that attackers use it to try to infect WordPress websites. We found it in the attacks that we block.”
Experts from Wordfence traced the malware code to a tool available online, dubbed P.A.S., that claims to be “made in Ukraine.”
“One might reasonably expect Russian intelligence operatives to develop their own tools or at least use current malicious tools from outside sources,” the report says.
The report published by WordFence includes the list of IP addresses that “don’t appear to provide any association with Russia” and “are probably used by a wide range of other malicious actors.”
“The malware sample is old, widely used and appears to be Ukrainian. It has no apparent relationship with Russian intelligence and it would be an indicator of compromise for any website.” reads the report from WordFence.
The IT security industry is aware of the Russian interference, but clearly, the analysis provided by the US Government is really poor of interesting elements.
Which is the position of President-elect Donald J. Trump on the Russian hacking?
We all know that alleged Russian interference aimed to disrupt Clinton’s campaign due to the relationship between Puting and Trump.
President Donald J. Trump is expressing skepticism about intelligence assessments of the Russian hacking and the Kremlin’s interference in the election.
Trump Russian Hacking
According to the NYT, speaking to reporters outside his Palm Beach, Fla., club, Mar-a-Lago on Saturday evening, he revealed to know of “things that other people don’t know” about the alleged hacking campaigns that targeted Presidential Election. Trump announced that he will share the information “on Tuesday or Wednesday.”
“I just want them to be sure because it’s a pretty serious charge,” said Mr. Trump.“If you look at the weapons of mass destruction, that was a disaster, and they were wrong,” he added, referring to intelligence cited by the George W. Bush administration to support its march to war in 2003. “So I want them to be sure,” the president-elect said. “I think it’s unfair if they don’t know.”
“If you look at the weapons of mass destruction, that was a disaster, and they were wrong,” he added, referring to intelligence reports that were provided the George W. Bush administration in 2003. “So I want them to be sure,” “I think it’s unfair if they don’t know.”
“And I know a lot about hacking. And hacking is a very hard thing to prove. So it could be somebody else. And I also know things that other people don’t know, and so they cannot be sure of the situation.”
The Trump’s approach to technology is anachronistic, he advised people to avoid computers when dealing with a delicate material.
“It’s very important, if you have something really important, write it out and have it delivered by courier, the old-fashioned way, because I’ll tell you what, no computer is safe,” Mr. Trump said.
“I don’t care what they say, no computer is safe,” he added. “I have a boy who’s 10 years old; he can do anything with a computer. You want something to really go without detection, write it out and have it sent by courier.”
The only sensible answer to date is that of Russian President Putin who avoided responding Obama executive order.
Co jsou důležité bezpečnostní metriky?
2.1.2017 SecurityWorld Zabezpečení
Vedení firem v současné době požaduje metriky, aby získalo jasnější pohled na bezpečnost. Tady jsou čtyři metriky, které nabízejí široce využitelný pohled, a několik dalších s menší hodnotou.
Jak problematika zabezpečení získává ve vedení společností a řadách vyšších manažerů stále větší viditelnost, žádá se, aby bezpečnostní profesionálové poskytovali metriky vhodné pro sledování aktuálního stavu obrany společnosti. Ale jaká čísla jsou ta skutečně důležitá?
Nejvyšší management obvykle neví, na co by se měl ptát, a může se příliš soustředit na prevenci a nedostatečně na zmírnění. Metriky, jako jsou průměrné náklady na reakci na incident nebo počet útoků zastavených firewallem, se zdají být smysluplné pro osobu bez znalosti zabezpečení, ale ve skutečnosti nijak nepomohu zlepšit program zabezpečení organizace.
Experti doporučují zaměřit se namísto toho na metriky, které ovlivňují chování nebo mění strategii.
„Co byste udělali teď jinak, když máte tuto metriku?“ ptá se Caroline Wongová, šéfka bezpečnostních iniciativ společnosti Cigital, která poskytuje poradenství a software pro zabezpečení.
Metriky jako průměrné náklady na zmírnění zranitelností či střední doba opravy jsou užitečné, pokud má organizace zralé a vysoce optimalizované procesy, ale to není případ 95 procent současných organizací, upozorňuje Wongová.
Metriky měřící účast, efektivitu a okno expozice však nabízejí informace, které mohou organizace použít k vytvoření plánů a zlepšení programů.
Bezpečnostní metrika č. 1: Úrovně účasti v programu
Metriky účasti sledují pokrytí v rámci organizace. Mohou zjišťovat, kolik podnikových oddělení pravidelně vykonává penetrační testy nebo kolik koncových bodů je aktualizovaných automatizovanými systémy instalace oprav.
Tyto základní informace pomáhají podle Wongové organizacím vyhodnotit úroveň zavedení bezpečnostní kontroly a zjistit potenciální mezery.
Přestože by například bylo hezké mít možnost říci, že má organizace sto procent svých systémů opravených do jednoho měsíce od dostupnosti nových aktualizací, není to realistický cíl, protože instalace oprav může v některých systémech vyvolat určité provozní riziko.
Pohled na účast pomáhá vyloučit systémy, které nepodléhají běžným pravidlům pro opravy, a zaměřit pozornost na takové, kde by se měla oprava nainstalovat.
Bezpečnostní metrika č. 2: Doba trvání útoku
Časová prodleva nebo jak dlouho je útočník v síti, je také informace poskytující cenný vhled. Informace o době trvání útoku pomáhá bezpečnostním profesionálům připravit se na hrozby, zvládnout je, kontrolovat je a minimalizovat škody.
Průzkumy ukázaly, že útočníci stráví v průměru uvnitř sítě firmy několik měsíců, než dojde k jejich odhalení. Tráví čas seznamováním se s infrastrukturou, dělají průzkumné činnosti, pohybují se v síti a kradou informace.
Cílem by mělo být maximální zkrácení doby prodlevy, aby měli útočníci menší příležitost k bočnímu pohybu a ukradení kritických dat, upozorňuje Douglas. Znalost časové prodlevy pomáhá bezpečnostním týmům zjistit, jak řešit zmírnění zranitelností a reakce na incidenty.
„Čím déle jsou útočníci ve vaší síti, tím více informací mohou získat, a tím více škody mohou způsobit,“ připomíná Douglas.
Bezpečnostní metrika č. 3: Hustota vad kódu
Hustota vad nebo počet problémů nalezených v každém tisíci (či milionu, v závislosti na kódové základně) řádků kódu pomáhají organizacím hodnotit bezpečnostní praxi vlastních vývojových týmů.
Klíčem je však kontext. Pokud je aplikace v rané fázi vývoje, potom vysoká hustota vad znamená, že se daří nalézat všechny problémy. To je dobré. Na druhou stranu v případě, že je aplikace již v režimu údržby, měla by být hustota vad nižší a měla by mít klesající tendenci, aby to ukazovalo na růst bezpečnosti aplikace v průběhu času. Pokud ne, existuje zde problém.
Bezpečnostní metrika č. 4:Okna expozice
Organizace může zjistit chyby v aplikaci, ale dokud nedojde k jejich odstranění, zůstává program zranitelný. Okno expozice udává počet dní v roce, po které zůstává aplikace zranitelná vůči vážným exploitům a problémům.
Vyděračské viry mohou napadnout klidně i televizor. Uživatelé ale bezbranní nejsou
2.1.2017 Novinky/Bezpečnost Viry
První vyděračský virus pro chytré televizory se objevil už v polovině loňského roku. Přesto tito nezvaní návštěvníci stále nepřestávají strašit, zabezpečení TV totiž řeší málokdo. Při sledování filmu tak škodlivý kód může klidně uzamknout celý televizor.
Uzamčení televizoru na vlastní kůži zažil na konci loňského roku Američan Darren Cauthon.
„Sledovali jsme film a v tom se přes celou obrazovku zobrazilo varování, že TV je uzamčena. Podvodníci se vydávali za FBI,“ prohlásil Cauthon.
Vyděračské viry označované souhrnným názvem ransomware totiž dokážou terorizovat uživatele chytrých televizorů postavených na operačním systému Android TV úplně stejně jako majitele smartphonů a klasických PC.

View image on Twitter
Follow
Darren Cauthon @darrencauthon
Family member's tv is bricked by Android malware. #lg wont disclose factory reset. Avoid these "smart tvs" like the plague.
7:59 PM - 25 Dec 2016
3,428 3,428 Retweets 2,819 2,819 likes
Takto vypadal televizor uzamčený ransomwarem
Útok tedy probíhá prakticky na chlup stejně. Virus se nejdříve uhnízdí v televizoru a pak jej zcela uzamkne. Uživatel tak s přístrojem nemůže vůbec nic dělat, maximálně jej zapnout či vypnout. Na obrazovce se neustále zobrazuje výzva k zaplacení výkupného.
To v případě Cauthona činilo 500 dolarů, tedy v přepočtu bezmála 13 000 Kč. Počítačoví piráti se jej snažili přesvědčit, že výkupné je ve skutečnosti pokuta, která byla vyměřena za nedovolené nakládání s autorsky chráněnými díly.
Kolik televizorů se vyděračskému viru podařilo za poslední půlrok výše popsaným způsobem napadnout, zatím není jasné. Jisté není ani to, zda se ransomware pro chytré televizory objevil také v Česku.
Chytrá elektronika může být zranitelná
Celá kauza nicméně jasně ukazuje, jak zranitelná mohou být zařízení připojená k internetu. Většina počítačů je totiž proti vyděračským virům chráněna pomocí antivirových programů, u televizorů ale zabezpečení řeší jen málokdo.
Výrobci přitom antiviry pro chytré televizory nabízejí již několik let. Většina uživatelů si patrně ale ani neuvědomuje, že i tato zařízení mohou být napadena.
A jak skončil příběh Cauthona? Tomu se nakonec podařilo s pomocí zákaznické linky ransomwarem napadený televizor resetovat do výchozího nastavení, čímž se nezvaného návštěvníka zbavil. Zároveň ale přišel o uložená nastavení i soubory.
Firefox 52 more privacy oriented with a Tor protection mechanism
2.1.2017 securityaffairs Safety
Mozilla development team announced a new privacy protection mechanism that will come with Firefox 52, it aims to prevent websites from fingerprinting users.
Mozilla announced the introduction of a new privacy protection mechanism to Firefox 52 that prevents websites from fingerprinting through system fonts.
The technique is widely adopted by advertising companies via hidden scripts delivered with ads that take the list of local fonts and along with other data create a unique fingerprint (ID) for each user.
The companies aim in this was to deliver targeted ads and track users across the web.
The experts at Mozilla have implemented a feature to only expose whitelisted system fonts to avoid fontlist fingerprinting. The new feature will be included in the stable branch of Firefox 52, scheduled for release on March 7, 2017.
The user privacy protection mechanism was already implemented by Mozilla in the Tor Browser, it was developed to block websites from identifying visitors based on the fonts installed on their machines.
The font fingerprinting protection is already available in Firefox 52 Beta.
“Defending against font fingerprinting is complex. We have to worry about distinguishing attacks via differing installed font sets, text rendering engine differences, and font variants. There are a variety of tickets involved.” states the Tor Development Team.
“In #13313, we introduced a Tor Browser pref, “font.system.whitelist”, which accepts a list of fonts and excludes all others from the browser.”
How does the feature work?
The feature leverages a whitelist of system fonts for each operating system, the browser will not block queries for system fonts but it will provide the same answer for every user making impossible to discriminate them.
The practice of font fingerprinting relies on website operators deploying Flash or JS scripts that query the user’s browser for a list of locally installed fonts.
The news confirms the intention of Mozilla to protect users’ privacy, in July the development team launched the Tor Uplift project, a significant effort in improving privacy features implemented in FireFox.
“To uplift all of the Tor Browser patches to mainline Firefox. The general approach is to add preferences for anything that breaks the web and set them to default “off” so that the behavior of default Firefox does not change. All bugs are tagged with [tor]. The Tor Browser design document is here.” states the description of the project.
A new iPhone bug will crash the Messages app with a single text
1.1.2017 securityaffairs Apple
A researcher discovered that a single text message could be exploited to crash the Messages app by MMS on iOS due to a recently discovered bug
A single text message could be exploited to disable the Messages app on any iPhone due to a recently discovered bug.
The bug flaw makes the Apple Message app inoperable, making it impossible to read text messages or iMessages. The flaw is serious, the app will continue to crash even when the user closes it or reboot the device
In order to exploit the flaw, it is necessary to send to the target device a vCard (a transferable Address Book contact) containing so many lines of code that the Messages app is not able to process.
When the Messages app opens the message containing the vCard, it tries to open it and freezes displaying a white screen.
Below a video PoC of the vulnerability.
Because the Messages app always tries to open the most recent text message when it is launched, it will continue trying to open the malicious message even when the app is closed or the whole phone is rebooted.
“When you click, iOS want to read the text, the text in the file is very complicated for the system and cause a CPU average: the app freeze. You close the app, want to reopen but iOS want to reload the previous message but can’t because it’s the vcf file.” reads the blog post published by vincedes3.
The bug is similar to the “Effective Power” discovered in May 2015, when users noticed that a text message containing a string of Arabic text would crash phones.
Back to the present, there is a good news for those users that have received the malicious message. There at least two workarounds to remove the message from the top of the inbox:
By clicking this Fix link: vincedes3.com/save.html, it will open the window for sending a new message, pressing cancel and deleting the malicious message.
Visualizza l'immagine su Twitter
Visualizza l'immagine su Twitter
Segui
vincedes3 @vincedes3
For devices (including iPad) where the fix link does not work, ask Siri to send a message to the victim and click on the text.
11:27 - 29 Dic 2016
9 9 Retweet 12 12 Mi piace
By sending yourself a message in Siri, or ask someone else to send you a message. Once the message is received the Messages app will allow you to open the new message instead of the malicious one.
29 Dic
vincedes3 @vincedes3
For devices (including iPad) where the fix link does not work, ask Siri to send a message to the victim and click on the text. pic.twitter.com/3id4Y8Lhkn
Segui
Luca Marzano @marzanoluca93
@vincedes3 pic.twitter.com/S37I4MVUPe
16:33 - 30 Dic 2016
Visualizza l'immagine su Twitter
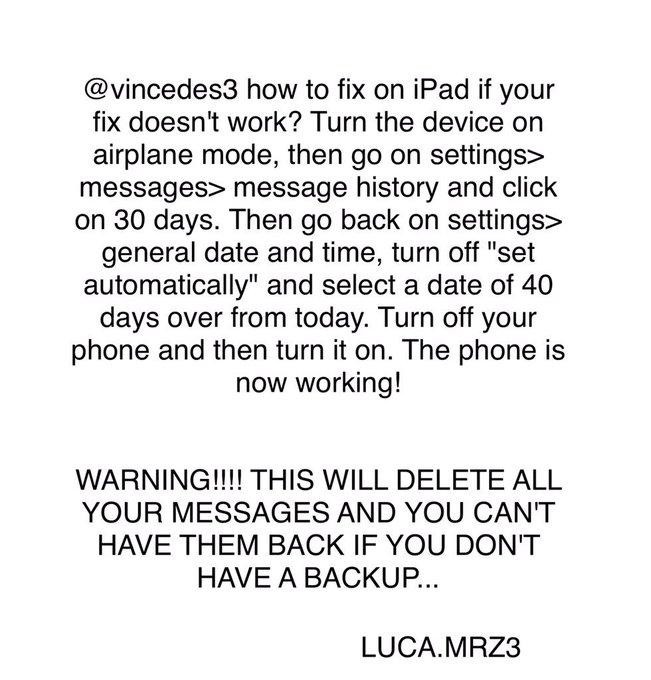
One-stop-shop: Server steals data then offers it for sale
1.1.2017 Kaspersky Virus
While intercepting traffic from a number of infected machines that showed signs of Remote Admin Tool malware known as HawkEye, we stumbled upon an interesting domain. It was registered to a command and control server (C2) which held stolen keylog data from HawkEye RAT victims, but was also being used as a one-stop-shop for purchasing hacking goods.
WhiteHats on the prowl?
Before diving into an analysis of the server, it is worth pointing out some interesting behavior spotted in several of the victims’ stolen accounts. A group of WhiteHat hackers who call themselves Group Demóstenes were found to be working around the clock, trawling the internet and looking to exfiltrate stolen data from C2 servers. When such a server was found, the group looked for a backdoor that would give them control over the filesystem. They would then monitor the incoming, stolen data. Either manually or automatically, they would collect the stolen credentials and send emails to the victims’ accounts. These emails contained an attachment with proof that the user’s machine has been compromised. In addition, they advise the user to change passwords immediately and offer to help.
Hi ***********
Our SERVERS detected information from a server on the US, we don’t even know goverment or another sourse …. we send a file with all your logins and passwords of all your accounts from hxxp://www.p******op[.]biz/*******
WE HAVE TESTING IN YOUR PAYPAL ACCOUNT. LOG IN TO YOUR ACCOUNT AND YOU WILL SEE TWO CANCELED BILLING (OUR JOB IS WHITE HAT NO HACK …. Steal)
Seme you verify this information. it’s better thing we hurt all change password on the other computer Because Called Computer
Name PC USER-PC
Local Time: 03.10.2016. 18:45:02
Installed Language: en-
Net Version: 2.0.50727.5485
Operating System Platform: Win32NT
Operating System Version: 6.1.7601.65536
Operating System: Microsoft Windows 7 Home Premium
Internal IP Address: 192.168.0.101
External IP Address:
Installed Anti virus: Avast Antivirus
Installed Firewall:
have a keylogger harm report All That You write, messages, passwords or more.
¿Why we do it?
We have a Cause Called Group Demóstenes looking for Ciber attacks and false info.
Please Donate by PayPal at h**cg**an@gmail[.]com 5 USD or more, Because this is only our ingress.
PLEASE WRITE ME AT THIS MAIL FOR KNOW IF YOU KNOW ABOUT THIS
The email above appears in two languages, English and Spanish. The name of the group appears to be of Portuguese origin, though it is not certain.
The shopfront: the command and control servers
Scanning for network services which are running on the C2, we discovered that it contains not only a back-end for storing stolen credentials but also a front-end for selling some of them, alongside many other “goods”.
Browsing the domain that communicated with the HawkEye RAT samples disclosed a login page. Given the fact that the server was newly operational, it allowed users to register an account and login to purchase the goods on offer.
After registering on the C2 web application, there was no sign of the stolen data transferred from compromised machines. A forum-like web page opens up once a successful login is being processed.
The C2 was meant to securely store the stolen data; however, it contained a crucial vulnerability which allowed researchers to download the stolen data.
The C2 owners seem to have added six new Shell scripts on 22 November, just a week before the research started – a further indication of how new the operation is.
Another item for sale is scam pages, and some are multilingual. The attackers also reveal the scope of their victims, noting those who are registered to Amazon, Apple, Netflix and even National Bank of Australia and Barclays. The listing of the year next to the banking information probably refers to how up-to-date the scam pages are in terms of the bank’s website updates.
The attackers have spared no details and have added additional information regarding how one should act when using their services, and who to contact in the Support tab.
To purchase goods in the private shop you must deposit money into your account on the website. The attackers accept Bitcoins, PerfectMoney and WebMoney.
Back to the stolen data
As we described, HawkEye is a robust keylogger that can hijack keystrokes from any application being opened on the victim’s PC. It can also identify login events and record the destination, username and password. It is, however, limited to two-factor authentication and single sign-on.
Stolen credentials on the server were found to be holding sensitive access passwords to government, healthcare, banking and payment web applications. Among them is the following web server which belongs to the Pakistani government.
As mentioned, hundreds of machines were found to be compromised by just one C2. The following is a partial list of what was downloaded from the malicious server.
Usually, careless threat actors forget to remove test files which might contain sensitive data. In this case, we were able to obtain the attackers credentials from one very small file that was captured when searching related strings.
Target geography
The research is still ongoing and is currently affecting users located in APAC, such as Japan, Thailand and India, as well as parts of Eastern Europe such as Russia and Ukraine.
Switcher: Android joins the ‘attack-the-router’ club
1.1.2017 Kaspersky Android
Recently, in our never-ending quest to protect the world from malware, we found a misbehaving Android trojan. Although malware targeting the Android OS stopped being a novelty quite some time ago, this trojan is quite unique. Instead of attacking a user, it attacks the Wi-Fi network the user is connected to, or, to be precise, the wireless router that serves the network. The trojan, dubbed Trojan.AndroidOS.Switcher, performs a brute-force password guessing attack on the router’s admin web interface. If the attack succeeds, the malware changes the addresses of the DNS servers in the router’s settings, thereby rerouting all DNS queries from devices in the attacked Wi-Fi network to the servers of the cybercriminals (such an attack is also known as DNS-hijacking). So, let us explain in detail how Switcher performs its brute-force attacks, gets into the routers and undertakes its DNS-hijack.
Clever little fakes
To date, we have seen two versions of the trojan:
acdb7bfebf04affd227c93c97df536cf; package name – com.baidu.com
64490fbecefa3fcdacd41995887fe510; package name – com.snda.wifi
The first version (com.baidu.com), disguises itself as a mobile client for the Chinese search engine Baidu, simply opening a URL http://m.baidu.com inside the application. The second version is a well-made fake version of a popular Chinese app (http://www.coolapk.com/apk/com.snda.wifilocating) for sharing information about Wi-Fi networks (including the security password) between users of the app. Such information is used, for example, by business travelers to connect to a public Wi-Fi network for which they don’t know the password. It is a good place to hide malware targeting routers, because users of such apps usually connect with many Wi-Fi networks, thus spreading the infection.
The cybercriminals even created a website (though badly made) to advertise and distribute the aforementioned fake version of com.snda.wifilocating. The web server that hosts the site is also used by the malware authors as the command-and-control (C&C) server.
The infection process
The trojan performs the following actions:
Gets the BSSID of the network and informs the C&C that the trojan is being activated in a network with this BSSID
Tries to get the name of the ISP (Internet Service Provider) and uses that to determine which rogue DNS server will be used for DNS-hijacking. There are three possible DNS servers – 101.200.147.153, 112.33.13.11 and 120.76.249.59; with 101.200.147.153 being the default choice, while the others will be chosen only for specific ISPs
Launches a brute-force attack with the following predefined dictionary of logins and passwords:
admin:00000000
admin:admin
admin:123456
admin:12345678
admin:123456789
admin:1234567890
admin:66668888
admin:1111111
admin:88888888
admin:666666
admin:87654321
admin:147258369
admin:987654321
admin:66666666
admin:112233
admin:888888
admin:000000
admin:5201314
admin:789456123
admin:123123
admin:789456123
admin:0123456789
admin:123456789a
admin:11223344
admin:123123123
The trojan gets the default gateway address and then tries to access it in the embedded browser. With the help of JavaScript it tries to login using different combinations of logins and passwords. Judging by the hardcoded names of input fields and the structures of the HTML documents that the trojan tries to access, the JavaScript code used will work only on web interfaces of TP-LINK Wi-Fi routers
If the attempt to get access to the admin interface is successful, the trojan navigates to the WAN settings and exchanges the primary DNS server for a rogue DNS controlled by the cybercriminals, and a secondary DNS with 8.8.8.8 (the Google DNS, to ensure ongoing stability if the rogue DNS goes down). The code that performs these actions is a complete mess, because it was designed to work on a wide range of routers and works in asynchronous mode. Nevertheless, I will show how it works, using a screenshot of the web interface and by placing the right parts of the code successively.
If the manipulation with DNS addresses was successful, the trojan report its success to the C&C
So, why it is bad?
To appreciate the impact of such actions it is crucial to understand the basic principles of how DNS works. The DNS is used for resolving a human-readable name of the network resource (e.g. website) into an IP address that is used for actual communications in the computer network. For example, the name “google.com” will be resolved into IP address 87.245.200.153. In general, a normal DNS query is performed in the following way:
When using DNS-hijacking, the cybercriminals change the victim’s (which in our case is the router) TCP/IP settings to force it to make DNS queries to a DNS server controlled by them – a rogue DNS server. So, the scheme will change into this:
As you can see, instead of communicating with the real google.com, the victim will be fooled into communicating with a completely different network resource. This could be a fake google.com, saving all your search requests and sending them to the cybercriminals, or it could just be a random website with a bunch of pop-up ads or malware. Or anything else. The attackers gain almost full control over the network traffic that uses the name-resolving system (which includes, for example, all web traffic).
You may ask – why does it matter: routers don’t browse websites, so where’s the risk? Unfortunately, the most common configuration for Wi-Fi routers involves making the DNS settings of the devices connected to it the same as its own, thus forcing all devices in the network use the same rogue DNS. So, after gaining access to a router’s DNS settings one can control almost all the traffic in the network served by this router.
The cybercriminals were not cautious enough and left their internal infection statistics in the open part of the C&C website.
According to them, they successfully infiltrated 1,280 Wi-Fi networks. If this is true, traffic of all the users of these networks is susceptible to redirection.
Conclusion
The Trojan.AndroidOS.Switcher does not attack users directly. Instead, it targets the entire network, exposing all its users to a wide range of attacks – from phishing to secondary infection. The main danger of such tampering with routers’ setting is that the new settings will survive even a reboot of the router, and it is very difficult to find out that the DNS has been hijacked. Even if the rogue DNS servers are disabled for some time, the secondary DNS which was set to 8.8.8.8 will be used, so users and/or IT will not be alerted.
We recommend that all users check their DNS settings and search for the following rogue DNS servers:
101.200.147.153
112.33.13.11
120.76.249.59
If you have one of these servers in your DNS settings, contact your ISP support or alert the owner of the Wi-Fi network. Kaspersky Lab also strongly advises users to change the default login and password to the admin web interface of your router to prevent such attacks in the future.
V americké firmě našli program ruských hackerů
1.1.2017 Novinky/Bezpečnost Viry
V počítači dodavatele elektrické energie v americkém státě Vermont se našel typ škodlivého programu (malware), který podle americké vlády používá Rusko při hackerských útocích. Informoval o tom v sobotu list The Washington Post (WP), podle kterého se program našel v přístroji, který nebyl připojen k síti a nebyl použit k narušení provozu.
„Okamžitě jsme zahájili kroky, abychom notebook izolovali, a o nálezu jsme informovali federální úřady,“ uvedl zástupce dodavatelské společnosti Burlington Electric Departement z Vermontu. Škodlivý program se nalezl pouze v jediném přístroji.
Podle zdroje agentury Reuters z amerických tajných služeb nešlo o zásadní narušení bezpečnosti, které by způsobilo nějaké škody, a do počítače se mohl malware dostat i po návštěvě některé internetové stránky. Zařízení tak nemuselo být přímým terčem hackerského útoku.
„Bereme to ale vážně,“ dodal zdroj s tím, že energetická síť je vysoce propojená a zranitelná.
Rusko útoky odmítá
Vláda prezidenta Baracka Obamy viní Rusko z hackerských útoků na americké instituce i na soukromé osoby. Jejich cílem mělo podle ní být mimo jiné ovlivnění nedávných prezidentských voleb ve prospěch republikánského kandidáta Donalda Trumpa.
Ve čtvrtek Spojené státy vypověděly 35 ruských diplomatů a uzavřely dvě ruská pracoviště na svém území. Prezident Obama navíc vyhlásil sankce mimo jiné vůči ruské civilní tajné službě FSB a vojenské rozvědce GRU.
Rusko odmítá, že by na USA prostřednictvím hackerů útočilo. Prezident Vladimir Putin se rozhodl, že zatím v reakci na americké sankce nikoho ze země nevyhostí.
Budoucí prezident USA Donald Trump odmítá, že by na jeho vítězství ve volbách mělo Rusko nějaký podíl.
Sankce vyhlášené Obamovou administrativou nepřímo kritizoval, když po jejich ohlášení vyzval, aby se USA věnovaly „větším a lepším věcem”. Příští týden se nicméně chce setkat se zástupci amerických tajných služeb, aby získal o údajných hackerských útocích Ruska na USA bližší informace.
Alleged Russian operation has compromised a laptop at a Vermont utility
31.12.2016 securityaffairs Cyber
The code associated with Russian hacking operation dubbed Grizzly Steppe by the Obama administration infected a laptop at a Vermont utility.
Russian hackers are again in the headlines because according to US officials, they hacked a Vermont utility, raising concerns about the security of the electrical grid of the country.
Researchers discovered on a laptop a malware associated with operations of Russian hackers, the experts linked it with an outdated Ukrainian hacking tool.
The malware was discovered thanks to the sharing of information contained in the Grizzly Steppe JAR about Russian malicious cyber activities.
DHS and FBI along with the report released a sample of the malware code allegedly used in the Grizzly Steppe operation. The code was shared with executives from multiple industries in the US allowing the experts at Burlington Electric in Vermont to discover the intrusion.
“A code associated with the Russian hacking operation dubbed Grizzly Steppe by the Obama administration has been detected within the system of a Vermont utility, according to U.S. officials.” states the report published by the Washington Post.
“Burlington Electric said in a statement that the company detected a malware code used in the Grizzly Steppe operation in a laptop that was not connected to the organization’s grid systems. The firm said it took immediate action to isolate the laptop and alert federal authorities.”
The malicious code was spotted during a scan of a company laptop that was anyway not connected to the grid. The authorities immediately adopted the necessary measures to contain the threat.
“We took immediate action to isolate the laptop and alerted federal officials of this finding. Our team is working with federal officials to trace this malware and prevent any other attempts to infiltrate utility systems. We have briefed state officials and will support the investigation fully,” the statement said.
This means that fortunately, at least in this specific case, did not penetrate the US grid.
“Vermonters and all Americans should be both alarmed and outraged that one of the world’s leading thugs, Vladimir Putin, has been attempting to hack our electric grid, which we rely upon to support our quality-of-life, economy, health, and safety,” explained the Vermont Governor Peter Shumlin.
“This episode should highlight the urgent need for our federal government to vigorously pursue and put an end to this sort of Russian meddling,” he said.
Security experts at the security firm Wordfence published an interesting report in which they analyzed the PHP malware sample and the IP addresses that the US government has provided as proof the involvement of Russian hackers in the attacks against the Presidential Election.
“As an interesting side-project, we performed analysis on the PHP malware sample and the IP addresses that the US government has provided as “…technical details regarding the tools and infrastructure used by Russian civilian and military intelligence services (RIS)”. [Source]” states the report published by WordFence.
“We used the PHP malware indicator of compromise (IOC) that DHS provided to analyze the attack data that we aggregate to try to find the full malware sample. We discovered that attackers use it to try to infect WordPress websites. We found it in the attacks that we block.”
Experts from Wordfence traced the malware code to a tool available online, dubbed P.A.S., that claims to be “made in Ukraine.”
The FBI/DHS JAR refers the version 3.1.7, while the most current version it the 4.1.1b.
“One might reasonably expect Russian intelligence operatives to develop their own tools or at least use current malicious tools from outside sources,” the report says.
The report published by WordFence includes the list of IP addresses that “don’t appear to provide any association with Russia” and “are probably used by a wide range of other malicious actors.”
15% of IP addresses are associated with Tor exit nodes.
“The malware sample is old, widely used and appears to be Ukrainian. It has no apparent relationship with Russian intelligence and it would be an indicator of compromise for any website.” reads the report from WordFence.
The rest of the story is known, the Obama administration accused the Russian government of interference in internal affairs and ejected 35 Russian diplomats and blocking access to two leisure compounds used by Russian Foreign Ministry personnel.
In 2017: Cool New Tech, Ominous Cyber Threats & Increased Terrorism in the West
31.12.2016 securityaffairs Security
A lot of new and exciting technology will emerge or become more prominent in 2017 and the following is just a glimpse of what is anticipated.
IoT & Smart Home Tech
Smart home technology had been in the works for years before finally getting off to a relatively slow start. But, now that large companies like Apple, Amazon and Google have jumped onboard, smart home tech is expected to significantly pick up the pace in 2017.
VR & AR
In 2016, Oculus Rift was released, following which thousands of virtual reality (VR) games and apps were released on the market. And, augmented reality (AR) game, Pokémon Go, exploded on the market with over 100 million downloads. In 2017, however, VR and AR are expected to really take off.
Machine Learning
Machine learning will advance in 2017, paving the way for it to become a fixture in the workplace. This type of artificial intelligence (AI) is expected to become a component of every type of technology. For instance, robotic journalists have been in circulation for a couple of years now and this trend is expected to expand exponentially in the white collar arena. It will have a lot of impact on the job market because some positions will no longer be needed. But, the combination of automation and machine learning will usher in groundbreaking efficiency in the workplace.
Autonomous driving
More advances from makers of self-driving cars are expected. For example, since initially introducing its ‘Autopilot‘ feature in 2015, Tesla has been continuously tweaking the autonomous capabilities of its vehicles. This highlights the far-reaching capabilities self-driving technologies hold for the future. Additionally, Uber recently acquired self-driving hardware developer Otto and has subsequently put its first fleet of self-driving trucks on the road. In Pittsburgh, Uber has also conducted some real world self-driving tests with its cabs.
Chinese Technology Will Make More Significant Inroads Into the West
As an increasing number of Chinese companies are focused on European and US markets, they will continue to maintain their customer base in China. “Huawei, already a fairly well-known brand in the west, is pushing its Honor brand as a way to drop the budget image for a new demographic. And software firms are getting in the game too. Tencent, makers of WeChat (that’s ‘China’s WhatsApp’, for those playing along at home), is pushing hard into the west, taking on Facebook at its own game.”
And, what cyber threats are coming down the line in 2017?
* Old breaches surfacing – A more dangerous trend than the malware that emerged in 2016 is that of past breaches surfacing. The information in historical breaches has often been sold on the darknet for some time before the breach’s existence comes to light. That is essentially what happened to Yahoo and it happened twice in one year, when the data breaches from 2013 and 2014 resurfaced. The breaches impacted a billion and half a billion accounts respectively. As The Guardian aptly explains it: “Because data breaches can happen undetected, fixing your cybersecurity in 2016 isn’t just locking the stable door after the horse has bolted; it’s locking the stable door without even realizing the horse made its escape years ago.”
* Cyberwar – As was the case with the Stuxnet virus which destroyed Iranian nuclear centrifuges and the US Office of Personnel Management hack, the thing that makes launching a cyberwar attack appealing is that attribution is difficult. The incidents are usually explained away with hunches as opposed to being able to provide conclusive evidence. “Rock-solid attribution to not just a nation but a chain of command is almost impossible,” The Guardian’s Alex Hern has noted. And, according to security expert Hitesh Sheth, head of cybersecurity firm Vectra, “US businesses and the US government should expect an increase in the number and severity of cyber-attacks, led by select nation states and organised political and criminal entities.”
* More innovative hackers – According to Adam Meyer, chief security strategist at SurfWatch Labs, “2017 will be the year of increasingly creative [hacks].”
* Step aside single-target ransomware. Make way for the self-propagating worms of the past, such as Conficker, Nimda, and Code Red, which will return to prominence—but this time around they will carry ransomware payloads capable of infecting hundreds of machines in an astoundingly short period of time.
* DDoS attacks on IoT devices – Hackers will target all types of internet-connected endpoints and employ them in DDoS attacks, but at a higher rate than before. Network World reports that, “in the rush to roll out all manner of IoT devices, security has taken a back seat. That means more serious incidents such as the denial of service attack on domain lookup service Dyn, are highly likely. The Mirai botnet was cited as the culprit, exploiting 50 to 100 thousand IoT devices.”
* DDoS will also bourgeon into a “weapon of mass obstruction” – DDoS attack firepower in 2016 catapulted to frightening levels – rising from 400Gbps bandwidth to 1Tbps or more. This was due to millions of IoT devices lacking even the most basic security. That same firepower can be utilized to take down critical infrastructure and even the internet infrastructure of whole countries. This may be done in conjunction with a physical military attack.
* Inexperienced, albeit dangerous hackers who will not need a skill set – There are now tools that are relatively easy to access, for those who are willing to pay for them. CSO Online predicts, “this trend will continue to spark the rapid growth of cybercriminals in the wild. Whether someone is politically motivated, disgruntled about something, or a career criminal, off-the-shelf hacking tools make it easier for them to make their mark and will cost companies millions in 2017.”
* Malware via third-party vendors – Third-party vendors are a potential gateway to their connected customers. So, no matter how great a business’s security system is, if that business doesn’t hold all of their third-party partners to the same level of scrutiny, their customers will always be at risk. Consider the situation involving Wendy’s in which over 1,000 franchised locations were compromised by a Point-of-Sale (PoS) malware attack. You can count on more, similar activity in 2017 and that will be the case until companies address third-party risk management.
* Shortage of IT security professionals – This is not a new issue, of course, but with more than a million vacant positions worldwide, there have never been more jobs available in cybersecurity.
* State-sponsored hackers – A concern for both organizations and governments now is the steadily growing cadres of state-sponsored hackers, who have an endless array of resources.
* The cloud & mobile computing – Applications and data are moving to the cloud. This, no doubt, will create a new aggregation of vulnerabilities. It stands to reason, though, since “the ‘cloud’ is just someone else’s computer, and by moving and sharing information across more devices and people, the attack surface grows—and so does the opportunity for attackers.”
* Drones will be used not only for attacks, but for espionage, too – Threat actors will be moving in the direction of leveraging capabilities that will allow hacking into drone signals and “dronejacking.”
* An onslaught of attacks on open source – Hackers have come to the realization that applications are an easily exploited weak spot in most organizations. Couple that with the lax job most companies are doing with securing and managing their code–even when patches are available! Hence, these types of exploits will increase in 2017–against sites, applications, and IoT devices.
* Phishing expeditions – Employees are the weakest link in security. Almost all enterprise hacks begin with phishing. However, as noted by Taylor Armerding, writing for CSO Online, “they will need to pay closer attention to the rise in popularity of free SSL certifications paired with Google’s recent initiative to label HTTP-only sites as unsafe. That will weaken security standards, driving potential spear-phishing or malware programs.”
* Hacking Cars – Automobile manufacturers don’t really know much about the software installed in the cars they make because it comes from third parties. In addition to that, this will most likely include open-source components with security vulnerabilities–a hacker’s paradise. This will also likely lead to a large-scale automobile hack, which could include “cars held for ransom, self-driving cars being hacked to obtain their location for hijacking, unauthorized surveillance and intelligence gathering, or other threats.”
* Potential for cyber attacks on grids and nuclear facilities – Again, emphasis should be placed on the human element. The Stuxnet incident demonstrated how a tenacious hacker can overcome cyber protection efforts simply by targeting vulnerable employees. This applies to both grids and nuclear facilities. And, the cybersecurity of both has been abysmally lacking.
Terrorism Trends in the West
According to a report by IHS Jane’s Terrorism and Insurgency Centre (JTIC), recent attacks by ISIS illustrate its use of returned foreign fighters to launch attacks, called for by the terror group’s central leadership. “Western members of the group in Iraq or Syria would communicate with supporters back in their home countries in order to directly encourage, support, and direct attacks therein.”
Moreover, the recent escalation in terror attacks in the West will likely continue in 2017. And, the trends contributing to the current level of terror, that have been building up for years, have not yet peaked. ISIS has exhibited a clear operational presence in Europe and it will take years to come to eliminate the threat posed by these terror groups and the individuals they recruit.
The new year will bring with it fascinating innovations in technology, which in turn will provide hackers and terrorists a multitude of new ways to launch attacks.
FBI-DHS JAR report links Russian hackers to Presidential Election hacks
31.12.2016 securityaffairs Cyber
A FBI-DHS JAR report released implicated Russian hacking group APT28 and APT29 in attacks against 2016 Presidential Election.
The Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) published on Thursday a Joint Analysis Report(JAR) that provides information about the tools, infrastructure and TTPs used by the Russian civilian and military intelligence Services (RIS) against United States election.
U.S. Government linked the cyber activity to a Russian threat actor designated as GRIZZLY STEPPE. This is the first time that the JAR attributes a malicious cyber activity to specific countries or threat actors.
“In foreign countries, RIS actors conducted damaging and/or disruptive cyber-attacks, including attacks on critical infrastructure networks. In some cases, RIS actors masqueraded as third parties, hiding behind false online personas designed to cause the victim to misattribute the source of the attack. This JAR provides technical indicators related to many of these operations, recommended mitigations, suggested actions to take in response to the indicators provided, and information on how to report such incidents to the U.S. Government.” States the report.
Despite the vast majority of information reported in the JAR were known to the experts I invite you to focus on the first statement of the above excerpt, because according to the President Obama’ executive order issued in April 2015, an attack against critical infrastructure can trigger an unpredictable cyber response of the US Government.
The JAR reports the activity of two different RIS actors, the APT28 and the APT29, that participated in the cyber attacks on a US political party. The APT29 known as (Cozy Bear, Office Monkeys, CozyCar, The Dukes and CozyDuke) broke into the party’s systems in summer 2015. The APT28 known as (Fancy Bear, Pawn Storm, Sofacy Group, Sednit and STRONTIUM) entered in spring 2016.
Both groups and their activities were well known to security firms and intelligence agencies due to their cyber espionage campaigns that targeted organizations and companies worldwide.
The nation-state actors conducted numerous attacks leveraging spear phishing messages containing web links to a malicious dropper, also APT28 group relied heavily on shortened URLs in their spearphishing email campaigns. These take advantage of neutral space for setting up operational infrastructure to obfuscate their source infrastructure.
“APT29 has been observed crafting targeted spearphishing campaigns leveraging web links to a malicious dropper; once executed, the code delivers Remote Access Tools (RATs) and evades detection using a range of techniques. APT28 is known for leveraging domains that closely mimic those of targeted organizations and tricking potential victims into entering legitimate credentials” reads the JAR. “Once APT28 and APT29 have access to victims, both groups exfiltrate and analyze information to gain intelligence value. These groups use this information to craft highly targeted spearphishing campaigns. These actors set up operational infrastructure to obfuscate their source infrastructure, host domains and malware for targeting organizations, establish command and control nodes, and harvest credentials and other valuable information from their targets,”
Government experts explained both groups used multiple malware in their campaigns, including the XTunnel malware, the Fysbis backdoor, the Komplex Trojan, the Carberp malware.
Experts observed two waves of attacks against US targets starting in the summer of 2015 and in November 2016.
According to the FBI-DHS JAR report, nation-state hackers designated as Grizzly Steppe targeted more than US recipients in April 2015 as part of a spear phishing campaign.
“In summer 2015, an APT29 spearphishing campaign directed emails containing a malicious link to over 1,000 recipients, including multiple U.S. Government victims. APT29 used legitimate domains, to include domains associated with U.S. organizations and educational institutions, to host malware and send spearphishing emails.” Continues the report.
In Spring 2016, hackers belonging to the APT28 hacker group, targeted the same political party via spear phishing email aimed to trick victims into changing their email credetianls. The hackers used a fake webmail domain hosted on operational infrastructure used by the APT28. Then APT28 used the stolen credentials to gain access target systems and exfiltrate sensitive information. The APT28 breached U.S. Democratic Congressional Campaign Committee (DCCC).
“In the spring of 2016, attackers were again successful when they tricked a spear phishing recipient to change their password through a fake web domain controlled by the attackers. “Using the harvested credentials, APT28 was able to gain access and steal content, likely leading to the exfiltration of information from multiple senior party members.””
The JAR report confirmed information stolen by hackers was released to the press and publicly disclosed in the attempt to interfere with Presidential Election. The report does not explicitly refers the DNC, but almost any security firm that analyzed the attack confirmed that the DNC was the primary target of the Russian hackers.

“Actors likely associated with RIS are continuing to engage in spearphishing campaigns, including one launched as recently as November 2016, just days after the U.S. election”
The JAR report also include a Recommended Mitigations section with best practices and mitigation strategies to improve cyber security posture of organizations.
“DHS encourages network administrators to implement the recommendations below, which can prevent as many as 85 percent of targeted cyber-attacks. ” states the report.
#OpSingleGateway – Gh0s7 hacked Thai Government website in response to the recent arrests
31.12.2016 securityaffairs Cyber
#OpSingleGateway – The hacker Gh0s7 hacked the Thailand’s National Statistical Office (http://nso.go.th) in response to the recent arrests operated by the Government.
The hacker Gh0s7 broke into the database of the Thailand’s National Statistical Office (http://nso.go.th ) and leaked data through the Mega service at the following URL
https://mega.nz/#!F8o0kCLb!8C30-rqQip7cvKhf-af3xwNX6PXO6KGN9wDEon5XqEs
The hacker acted alone, he decides to hack into a Thai Government system in response to the recent arrest of local authorities.
Thai officials announced on Monday the arrests of nine teenagers, aged between 17 and 20, who have participated in cyber-attacks against government websites.
Thai Deputy Prime Minister and Defense Minister Prawit Wongsuwan announced further arrests among the local community of hacktivists.
Last week, Thai Police arrested nine teenagers belonging to the Anonymous collective because their participation in the hacking campaign dubbed #OpSingleGateway. The #OpSingleGateway campaign was launched by the Anonymous collective last year when the Thai government proposed a bill that would force the country’s entire Internet traffic through one single gateway.
Clearly, the bill opens the doors to monitoring and censorship, for this reason, hackers started targeting the Government.
“I personally targeted it. and my motivations was the recent events that Thai gov arresting 9 Anonymous hackers for #OpSingleGateway” told me Gh0s7.
Thai members of the Anonymous powered massive DDoS attacks in October 2015 against the Thai government (thaigov.go.th) and of the country’s Ministry of Information, Communications and Technology (ICT) (mict.go.th) websites.
Anonymous also breached the websites of Thai police and local ISPs, then Thai government decided to drop the “single gateway” bill.
Unfortunately, the Government proposed amendments to the existing Computer Crime Act in May 2016 and approved them on December 16. The amendments allow the authorities to monitor citizens and to apply a strong censorship on opponents.
“Anonymous hackers tried to oppose the passing of these amendments, which allow the government to censor websites and intercept private communications without a court order, according to VoaNews.
Just like the previous year, Anonymous used a Facebook group called “Citizens Against Single Gateway” to rally the population and carry out similar DDoS attacks against government websites.” reported the bleepingcomputer.com website.
“Another of these F5-powered DDoS attacks hit Thailand’s defense ministry website on December 19. Later it was revealed that hackers also breached the Thai Police Office website two days earlier, on December 17. The website of the Ministry of Tourism and Sports was also attacked on December 23.”
Back to the Gh0s7’s hack, the leaked archive includes usernames and hashed passwords alongside other CMS data. The hacker told me that he hacked the server and gained root access.
“My hacks are secret as usual but I exploited their server, and gained root access.” he told me.
Ransomware, zločinecký trend roku 2017; důležitá je prevence
31.12.2016 SecurityWorld Viry
Pátého února odstartovaly problémy s přístupem k síti v Hollywoodském presbyteriánském lékařském centru v Los Angeles; během příštích dní zaměstnanci zjistili, že se stali obětí ransomware útoku, který zašifroval mnoho dokumentů v několika počítačích.
Během dalších dnů musel personál této nemocnice zapisovat a zaznamenávat informace a události pomocí tužky a papíru, přičemž vedení nemocnice se rozhodlo útočníkům vyplatit 17 000 dolarů – ekvivalent 40 bitcoinů, které internetoví vyděrači požadovali. Pro nemocnici to byla nejrychlejší cesta k obnovení svých souborů a systému.
Tím započala dlouhá série ransomware útoků nejen v USA na podniky, nemocnice, veřejné služby, dopravní podniky, a dokonce i policejní stanice. Vlna vydírání tvrdě dopadla obzvláště na zdravotnické organizace ve Spojených státech.
Jde o důkaz nového, velice nebezpečného trendu: ransomware, tedy malware, který nutí uživatele zaplatit peníze pro přístup do systému nebo ke svým souborům, není novinkou. Avšak zatímco dříve cílil na koncové uživatele, běžného spotřebitele, nyní se přeorientoval na podniky, často velké a bohaté, nebo takové, které bez svých informačních systémů nemohou normálně fungovat – jako nemocnice, které navíc mnohdy trpí na nedostatečné zabezpečení.
Během posledních dvou let se zaměření ransomwaru dramaticky změnilo, říká Ed Cabrera, ředitel kybernetické bezpečnosti v antivirové firmě Trend Micro.
Ještě v roce 2014 zahrnovalo používání ransomware útoků z 80 % tradiční metody, např. zablokování plochy počítače s tím, že uživatel musí pro její odemknutí zaplatit poplatek. V roce 2015 však již podle statistik 80 % útoků naopak zahrnovalo pokročilý krypto-ransomware, tedy nakažené programy, které šifrují soubory v počítači.
„Další evolucí ransomwaru je přesun od spotřebitelů k podnikům,“ popisuje Cabrera. „Mnoho nových typů krypto-ransomwaru v roce 2016 cílilo na podniky, a to v dříve nevídaném rozsahu.“
Nejde o tak úplně neočekávanou proměnu – podniková data jsou ostatně významně cennější než osobní soubory a společnosti si mohou dovolit zaplatit vyšší „výkupné“ než běžní uživatelé. Jejich zabezpečení se navíc silně liší – záleží na lokaci, velikosti i průmyslovém odvětví podniku.
„Začali jsme si všímat, že se ransomware soustředí spíše na malé a střední podniky, protože je pravděpodobnější, že zaplatí vyšší cenu za odblokování systému než průměrný uživatel,“ říká Liviu Arsene, analytik e-hrozeb pro antivirovou firmu Bitdefender.
Nedávný průzkum IBM, kterého se zúčastnilo 600 majitelů podniků, zjistil, že polovina z nich zažila ransomware útok a až 70 % z nich zaplatilo požadovanou částku, aby získali zpět svá data.
E-maily distribuující ransomware činily až 40 % všech e-mailových spamů za rok 2016 a zločinci z tohoto typu malwaru za letošek vydělali již téměř miliardu dolarů, píše IBM X-Force.
Nejčastějším cílem ransomware útoků jsou oddělení lidských zdrojů a finance: malware lze jednoduše skrýt jako výpis nebo resumé. Pokud je obětí kupříkladu nemocnice, dopad je obrovský i na veřejnost, takže se společnosti snaží problém vyřešit co nejrychleji – vzrůstá tak šance, že útočníkům raději zaplatí.
U ransomwaru je prevence zcela klíčová, neboť poté, co se v systému vyskytne, téměř neexistuje možnost jak se jej zbavit mimo zaplacení útočníkovi – a ani to negarantuje zpětné získání svých dat nebo přístupu.
Metody útoku
Ransomware je nejtradičněji rozesílán formou e-mailu, existují však i jiné, inovativnější metody.
Druhá nejčastějši technika je tzv. exploit kit. Jde o webové nástroje, které zneužijí zranitelnosti v prohlížečích nebo plug-inech typu Flash Player, Adobe Reader, Java či Silverlight. Takovým útokům lze hůře přecházet.
Firmy se navíc neobávají jen o své pracovní stanice, útočníci stále častěji míří také na serverový software, aby pronikli do podnikové sítě.
„Předpokládáme, že se zvyšujícím se počtem ‚podnikového ransomwaru‘ uvidíme více technik na zneužití zranitelností a získání přístupu do interní sítě,“ říká Barry Shteiman, ředitel výzkumu hrozeb v Exabeam, bezpečnostní firmy, která k detekci ransomwaru využívá strojového učení. „V podstatě každý server má zranitelnosti, které mohou vést k phishingovým útokům nebo injektování kódu – to může napomoci rozšíření ransomwaru.“
Další oblíbenou metodou distribuce ransomwaru je ukradení přihlašovacích údajů pro vzdálenou administraci, např. oblíbený Teamviewer.
Co se týče e-mailů, ransomware se skrývá ve spustitelných .exe souborech, schovaných v zipech a rarech, dále v makrech Wordových dokumentů a také v Javascriptových přílohách.
Co dělat, když ransomware zasáhne?
Nejdůležitější je co nejrychleji oddělit infikovaný systém od zbytku sítě, aby se nerozšířil. Doporučuje se rovněž pokud možno vypnout nenakažené počítače, než se situace vyřeší. Ihned na to by firmy měly kontaktovat bezpečnostní agentury nebo policii.
Dalším krokem by mělo být zálohování zašifrovaných dat a vyčištění hodnot a souborů v registrech, které si ransomware vytvořil, aby se nenačetl znovu při opětovném spuštění počítače. Dobré je rovněž změnit přístupová hesla k síťovým službám – útočníci totiž již mohou mít původní hesla ve svých rukách.
Pak přichází to nejtěžší rozhodnutí: zaplatit kriminálníkům nebo ne? Bezpečnostní odborníci a agentury ve valné většině nedoporučují výkupné platit, neboť to zločince utvrdí v jejich činnosti a navíc neexistuje garance, že dešifrovací klíč uživateli či podniku zašlou.
Dle zpráv bezpečnostní firmy Kaspersky Lab, slavné i pro svůj pokročilý antivirus, jedna z pěti společností nikdy svá data nedostane zpět – a to mluvíme o těch, které výkupné zaplatí. Někdy však organizace nemá na výběr, pokud nebyla na ransomware připravena – zaplatit zkrátka musí.
Dále jde rovněž o zhodnocení nákladů. Pokud má podnik větší ztráty z nedostupnosti dat nebo je dokonce dražší jejich samotné obnovení, pak mu nezbývá než zaplatit. Je to však až ta úplně poslední možnost, kdy všechny ostatní varianty jsou již vyčerpány, vysvětluje Shteiman.
Budoucnost ransomwaru je bohužel růžová
Podnikové sítě nejsou konečným cílem ransomwaru. Je možné, že zamíří výš: na industrální sítě, říká Guy Caspi, generální ředitel firmy zaměřené na kybernetické zabezpečení Deep Instinct. „V březnu byla pod útokem třetí největší elektrická a vodní technická infrastruktura v Michiganu – Lansing Board of Water & Light. Stala se první elektrickou veřejnou službou, kterou zasáhl ransomware.“
Podle Caspiho budou dalším krokem v evoluci ransomwaru programy, které po vytvoření kopie dat původní data smažou, místo, aby je zašifrovaly.
Arsene z firmy Bitdefender se odlišně domnívá, že s rozvojem internetu věcí budou právě tato zařízení dalším logickým cílem.
„Scénář, ve kterém vydírání probíhá pomocí chytrého zařízení není až tak nerealistický, i vzhledem k předpokládanému masivnímu nárůstů takových zařízení v několika příštích letech,“ myslí si. „Pokud útočníci shodí podnikovou síť senzorů, mohlo by to být opravdu problematické.“
Prevence infekce ransomwarem
Cvičební programy pro zaměstnance, celkové zvýšení povědomí o ransomwaru; jak rozpoznat phishing a infikované přílohy.
Silný antispamový filtr a implementace technologií typu Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC) a DomainKeys Identified Mail (DKIM).
Nastavení síťového zabezpečení a firewallu k blokaci známých škodlivých IP adres včetně Toru; mnoho ransomware serverů hostuje právě Tor.
Aktualizovaný software na pracovních stanicích, počítačích a serverech; je dobré mít i systém na správu aktualizací.
Dobrý antivirový program, který dokáže dlouhodobě dobře detekovat ransomware; dobré je rovněž pravidelné proskenování systému.
Co nejméně možností a privilegií pro lokální účty. Pokud uživatelé nepotřebují možnost zapisovat v síti, nedávejte jim ji.
Zrušení možnosti spouštět makra v kancelářském balíčku Office. Co nejvíce omezit spouštění skriptů typu JavaScript, Powershell a VBScript ve Windows.
Deaktivace plug-inů v prohlížeči, které nejsou nutně potřeba. Hodí se také využít EMET toolkit Microsoftu.
Zamezit programům možnost používat dočasné složky a jiná běžná umístění, které využívá malware.
Spouštět potenciálně riskantní soubory ve virtualizovaném prostředí; zauvažovat nad možnosti whitelistingu.
Pravidelně data zálohovat, ověřovat integritu zálohy a fyzické separování nejdůležitějších síťových segmentů.
Vytvořit několik záloh offline i online, například také v cloudu. Počítače by neměly být permanentně připojeny k místu zálohy.
Sundown Exploit Kit now leverages on the steganography
31.12.2016 securityaffairs Exploit
A new variant of the Sundown exploit kit leverages on steganography to hide exploit code in harmless-looking image files.
Security experts from Trend Micro have spotted a new version of the Sundown exploit kit that exploits steganography in order to hide malicious code in harmless-looking image files.
The use of steganography was recently observed in the malvertising campaigns conducted by the AdGholas and GooNky groups.
The GooNky group leveraged on steganography to hide malvertising traffic, while AdGholas has used a more sophisticated technique leveraging the Stegano exploit kit.
Crooks encoded a script in the alpha channel of an image to deliver the malicious code via rogue ads that looked like legitimate.
Earlier in December, researchers from ESET discovered that Stegano hide portions of its malicious code in parameters controlling the transparency of pixels used to display banner ads, but the impact of the appearance of the images is almost imperceptible.
“The malicious version of the graphic has a script encoded in its alpha channel, which defines the transparency of each pixel. Since the modification is minor, the final picture’s color tone is only slightly different to that of the clean version” reads the analysis published by ESET.
A similar technique has been observed for a new version of the Sundown EK spotted by the researchers at Trend Micro on December 27.
“On December 27, 2016, we noticed that Sundown was updated to use similar techniques. The PNG files weren’t just used to store harvested information; the malware designers now used steganography to hide their exploit code.” reads the analysis published by Trend Micro.
The updated version of Sundown has been used in several malvertising campaigns, mostly targeting users in Japan, Canada, France and the US.
“The newly updated exploit kit was used by multiple malvertising campaigns to distribute malware. The most affected countries were Japan, Canada, and France, though Japanese users accounted for more than 30% of the total targets.”

The new Sundown EK leverages on hidden iframes that automatically connects to a page hosting the Sundown EK. The page downloads a white PNG image and decodes malicious code it contains.
“In this updated version, the exploit kit’s malvertisement creates a hidden iframe that automatically connects to the Sundown landing page,” continues the post.“The page will retrieve and download a white PNG image. It then decodes the data in this PNG file to obtain additional malicious code.”
Researchers from Trend Micro leveraged on malicious code to trigger Internet Explorer flaws CVE-2015-2419 and CVE-2016-0189, and the Flash Player flaw tracked as CVE-2016-4117.
The researchers observed threat actors leveraging on the Sundown EK to deliver the Chthonic banking Trojan, a variant of the infamous Zeus malware, that was used by crooks in a PayPal scam in July.
The Sundown EK ranks today at the second place, behind RIG EK that is the most used crimeware kit in the criminal ecosystem.
According to security experts from Cisco Talos, threat actors behind the Sundown exploit kit leverage on an infrastructure composed of 80,000 malicious subdomains associated with more than 500 domains.
The experts observed that crooks behind the Sundown EK are using wildcards for subdomains which are exponentially growing the number of routes for malicious traffic to servers hosting the dreaded exploit kit.
Amerika popsala, jak v kyberprostoru útočí Rusové. Zmapovala činnost desítek vojenských hackerských skupin
30.12.2016 Živě.cz BigBrother
Americký federální úřad vyšetřování FBI a Ministerstvo vnitřní bezpečnosti na sklonku roku zveřejnily obecné postupy (PDF), které Rusové využili ke kybernetickým útokům nejen během tamních podzimních prezidentských voleb.
Dokument útoky přisuzuje útočníkovi, kterého označuje jako RIS – Russian civilian and milirary Intelligence Services. Američané jsou tedy přesvědčení, že na ně útočili vojenští hackeři a útočníci ruských tajných služeb.
Obecné schéma ruských útoků během amerických prezidentských voleb. Útočník (červený) útočí na oběť (modrá) vždy skrze neutrálního prostředníka (šedý), což může být botnet, nebo jiný server na internetu, který skryje stopy.
Na Demokratickou stranu podle dokumentu útočily hned dvě skupiny označované jako APT28 a APT29 a to dlouhodobě již od roku 2015, nicméně NSA monitoruje aktivitu hned několika desítek ruských státem zřízených hackerských skupin s kódovým označením v tabulce níže.
Kódová jména jednotlivých ruských vojenských hackerských týmů, jejichž činnost Američané monitorují
V dokumentu se dále píše o některých fingerprintech, které by mohly odhalit, že útočí právě Rusko. Jedná se třeba o kusy PHP kódu, který je velmi typický právě pro zmíněné ruské skupiny. Američané zároveň vedou seznamy IP adres, které Rusové používají, ačkoliv nikdy neútočí přímo, ale skrze prostředníka v neutrálním prostoru. Může se jednat o libovolné servery na internetu mimo ruské území, anebo i počítače nic netušících obětí, které jsou zapojené do botnetu.
Jeden z fingerprintů typických pro útoky, tedy úryvek PHP kódu útočníka, který se objevuje poměrně často.
Je tedy velmi pravděpodobné, že některé botnety, které na první pohled slouží jen k rozesílání spamů a další obvyklé malwarové činnosti, ve skutečnosti slouží jako anonymizační brány pro podobné státem organizované útoky, a ť už za nimi stojí Rusko, Čína, či západní země, poněvadž internet je už dávno kybernetickým bojištěm, na kterém se realizují všechny země s dostatečným technologickým know-how.
Vyděračské viry cílí na zdravotnická zařízení. Počet útoků se za tři roky ztrojnásobil
30.12.2016 Novinky/Bezpečnost Viry
Vlna kybernetických útoků na zdravotnická zařízení ve Spojených státech nebere konce. Letos se počet případů meziročně zvýšil o 63 procent, za poslední tři roky se dokonce ztrojnásobil. Dorazí tento nechvalně proslulý trend i k nám?
Zdravotnická zařízení jsou vítaným cílem tvůrců ransomwaru, vyděračských virů, které zašifrují citlivá data a za jejich odblokování žádají tučné výkupné. Obvykle se jedná o částky v několika bitcoinech, což je internetová měna, která odpovídá přibližně 20 tisícům korun. Podle americké společnosti TrapX Labs jenom v letošním roce proběhlo 93 útoků ransomwaru na zdravotnická zařízení v USA. Sofistikované kybernetické útoky stojí i za třetinou případů úniků dat od amerických zdravotních pojišťoven.
Pro srovnání: v roce 2015 byli kyberzločinci odpovědní za pětinu úniků dat zdravotních pojišťoven, v roce 2014 pak ani ne za desetinu. Nárůst počtu kybernetických útoků tak představuje závažnou hrozbu pro ochranu osobních dat pacientů, zdravotnických zařízení a v konečném důsledku vedou útoky k přímému fyzickému ohrožení samotných pacientů. K vůbec největšímu úniku dat ve zdravotnictví došlo letos v červenci v zařízení Banner Health v Phoenixu, kde se útočníci dostali ke 3,62 miliónu záznamů o pacientech.
Hackeři získali kompletní data o pacientech
Zločinci získali informace nejen ze zdravotní dokumentace, ale dokonce i o zákaznících obchodů s občerstvením. U pacientů se jim podařilo prolomit data, jako jsou jejich bydliště, datum narození, jména ošetřujících lékařů, termíny služeb, klinické informace, informace o zdravotním pojištění či čísla sociálního zabezpečení. Hackeři se dostali do kompletní sítě Banner Health, včetně platebních terminálů obchodů s občerstvením či elektronického systému, přes který komunikují lékaři a ukládají si do něj data o pacientech.
Obdobně rozsáhlý útok letos zažilo zdravotnické zařízení Newkirk Products, v němž bylo ohroženo bezmála 3,5 miliónu zdravotních záznamů. Nájezdu hackerů se nevyhnulo ani onkologické centrum 21st Century Oncology, z něhož v březnu letošního roku unikly údaje o více než dvou miliónech bývalých i současných pacientů.
V srpnu oznámili zástupci Valley Anesthesiology Consultants, že v období od 30. března do 13. června došlo k neoprávněnému průniku k 882 590 zdravotnickým záznamům. Peachtreeská ortopedická klinika v Atlantě letos v listopadu upozornila 531 tisíc pacientů, že jejich osobní data mohla být zneužita kvůli rozsáhlému kybernetickému útoku.
Expert: Nemocnice jsou lehce vydíratelné
„Zdravotnická zařízení jsou vítaným terčem útočníků, protože data, s nimiž operují, jsou velmi citlivá. Žádné zdravotnické zařízení nechce riskovat ohrožení svých pacientů a spolu s tím ztrátu důvěry. Pokud útočníci naleznou mezeru v zabezpečení, rádi ji tímto způsobem využijí, protože u organizací tohoto typu je větší pravděpodobnost, že útočníkům za odšifrování svých dat zaplatí,“ říká Miroslav Dvořák, technický ředitel antivirové společnosti ESET.
„Účinným preventivním nástrojem proti útokům tohoto typu je funkční IT bezpečnostní strategie, která kromě jiného umožňuje rychlou obnovu zašifrovaných dat ze zálohy,“ dodává Dvořák.
Zaplacením výkupného oběť automaticky nezískává jistotu, že její data budou obnovena
Miroslav Dvořák, technický ředitel antivirové společnosti ESET
Několik britských nemocnic muselo kvůli útokům ransomwaru letos v říjnu odříci plánované operace a další chirurgické zákroky, protože nechtěly riskovat komplikace s dostupností zdravotních záznamů pacientů. Zdravotní instituce jsou ochotny v takových případech raději zaplatit výkupné a zajistit si tak odšifrování dat. To však není nijak garantované.
„Zaplacením výkupného oběť automaticky nezískává jistotu, že její data budou obnovena,“ varuje Miroslav Dvořák. Zdravotnická zařízení by tedy měla pamatovat na zálohování dat a neměla by se spoléhat na to, že útočníci dodrží slovo a po zaplacení výkupného dokumenty odšifrují.
Zálohovací systémy by však neměly být trvale připojeny k počítačové síti, protože jinak hrozí, že jejich obsah bude při útoku rovněž zašifrován. Zároveň je vhodné používat prověřené bezpečnostní nástroje, z nichž mnohé již nabízejí i ochranu před ransomwarem.
Hackeři nabídli obětem ransomwaru vánoční slevu: za odšifrování si řekli polovinu
30.12.2016 Novinky/Bezpečnost Viry
Kyberzločinci si obvykle účtovali za odblokování počítače napadeného ransomwarem CryptXXX částku 1,2 bitcoinu (27 tisíc korun), během vánočních svátků zlevnili na 0,5 bitcoinu (11 tisíc korun).
Nezvyklou oslavu vánočních svátků zvolili tvůrci vyděračského viru CryptXXX. Svým obětem, jimž zašifrovali soubory v počítači, účtovali výkupné o víc než polovinu nižší než obvykle. Zatímco dříve žádali za odšifrování dokumentů částku 1,2 bitcoinu, což v přepočtu představovalo 27 tisíc korun, o vánočních svátcích slevili na 0,5 bitcoinu (11 tisíc korun). Sleva se obětem objevila ve chvíli, kdy klikli na jeden z odkazů na platební brány útočníků, informoval web Infosecurity-magazine.com.
Ransomware v současnosti patří pro uživatele mezi nejvýznamnější hrozby
Miroslav Dvořák, technický ředitel antivirové společnosti ESET
CryptXXX patří mezi jednu z mála rodin ransomwaru, u nichž se bezpečnostním expertům podařilo získat dekódovací klíče a vyvinout Decryptor. Od letošního května tak je možné zašifrované soubory odblokovat, aniž by majitelé napadených počítačů museli platit výkupné. Týká se to však pouze verzí CryptXXX, které byly v oběhu do května. Novější typy tohoto ransomwaru nelze pomocí tohoto nástroje deaktivovat, což se týká i speciální, „vánoční“ sady se slevou na výkupném.
„Ransomware v současnosti patří pro uživatele mezi nejvýznamnější hrozby. Pro útočníky se naopak jedná o pravděpodobně nejvýdělečnější typ kybernetického útoku,“ konstatuje Miroslav Dvořák, technický ředitel antivirové společnosti ESET. Firma proto vyvinula novou ochrannou vrstvu k již existujícím technologiím zabezpečení uživatelů a přidala ji zdarma ke všem svým produktům pro domácnosti a zařízení s operačním systémem Windows.
„Ochrana proti ransomwaru umožňuje pokročilé sledování a vyhodnocování všech spuštěných aplikací pomocí behaviorální analýzy. Aktivně blokuje známé typy chování, které se nápadně podobají činnosti ransomwaru. Kromě toho také může blokovat úpravy stávajících souborů, tj. jejich šifrování,“ vysvětluje Dvořák. Funkce je aktivní již ve výchozím nastavení a nevyžaduje žádnou zvláštní pozornost ani aktivitu uživatele, dokud nedojde k detekci podezřelé aktivity. V takovém případě je uživatel vyzván ke schválení nebo k jejímu zablokování.
Ransomware představuje specifickou rodinu malwaru, která se zaměřuje na soubory uživatelů. Nejčastějším typem je tzv. filecoder, který šifruje data a požaduje výkupné za jejich následné odšifrování. Ransomware se šíří především pomocí škodlivých příloh e-mailů či exploit kitů pro webový prohlížeč.
KillDisk: Atomová bomba mezi viry. Buď vám smaže PC, nebo bude chtít výkupné přes 5 milionů
30.12.2016 Živě.cz Viry
Smrtící malware KillDisk, jehož autoři se baví tím, že program po infekci na počítači spáchá hotové peklo, jej nově vybavili ještě ransomwarem. Ale takovým, který zruinuje i ty nejbohatší.
Nicméně pěkně popořadě. Původní KillDisk po napadení zničil systémové soubory, pohrál si s příponami souborů a něco smazal. Po příštím spuštění počítače pak už pochopitelně systém nenastartoval a nezbývalo, než jej znovu nainstalovat, anebo obnovit ze zálohy.
Podle Bleeping Computer se ale nyní nebezpečný zabiják dat na počítači proměnil v ransomware. To znamená, že data na PC nesmaže, ale velmi silně zašifruje a oběť klíč nedostane, dokud nezaplatí výkupné skrze anonymní bitcoin.
Zaplaťte nám 222 BTC, nebo se už ke svým souborům na PC nedostanete
Jenže to má háček. Zatímco u běžných ransomwarů útočníci požadují výkupné okolo 1 BTC (cca 900 USD), což podle aktuálního kurzu odpovídá asi 23 tisícům korun, KillDisk si účtuje 222 BTC!
222 BTC odpovídá asi 208 tisícům USD, což po přepočtu činí více než 5 milionů korun. K zaplacení takové částky bez špetky jistoty, že útočník opravdu pošle dešifrovací klíč, se tedy odváží asi jen málokdo.
President Obama executive order ejected 35 Russians out of US
30.12.2016 securityaffairs Cyber
An executive order issued by President Obama applies sanctions on Russian military and intelligence officials. 35 Russian operatives were ejected.
President Barack Obama issued an executive order to impose sanctions on a number of Russian military and intelligence officials in response to the alleged hacking campaigns against the 2016 US Presidential Election.
The US ejected 35 Russian intelligence operatives from the United States and imposed sanctions on nine entities and individuals.
The Russians individuals ejected by the US Government are working out of the Russia’s consulate in San Francisco and the Russian embassy in Washington.
According to a White House fact sheet issued on the executive order, the individuals due to the “harassment of our diplomatic personnel in Russia by security personnel and police.”
The US Government sanctioned the Russian intelligence services, the GRU (Russian Main Intelligence Directorate) and the FSB (Federal Security Service), four GRU officers, and three other organizations. The actions are the Obama administration’s response to a Russian hacking and disinformation campaign used to interfere in the American election process.
The order was issued concurrently a report from US intelligence that confirms the cyber attacks against the 2015 Presidential election aimed to influence the results of the vote.
The Department of Homeland Security and Federal Bureau of Investigation issued a Joint Analysis Report (JAR) containing “declassified technical information on Russian civilian and military intelligence services’ malicious cyber activity, to better help network defenders in the United States and abroad identify, detect, and disrupt Russia’s global campaign of malicious cyber activities,” according to an Obama administration statement.
“The JAR includes information on computers around the world that Russian intelligence services have co-opted without the knowledge of their owners in order to conduct their malicious activity in a way that makes it difficult to trace back to Russia.”
Some of the data were not disclosed before, they are part of declassified government report.
The JAR includes technical details about the malicious code used by the Russian intelligence services in its campaigns. The report also includes the “indicators of compromise” for the malware used by the Russian hackers.
“All Americans should be alarmed by Russia’s actions.” reads a President Obama’s statement.
The executive order addresses the GRU, FSB, the Esage Lab of the Russian security company, the firm Special Technology Center, and Russia’s Professional Association of Designers of Data Processing Systems. The four individuals targeted by the order are the GRU chief General-Lieutenant Igor Korobov, the GRU Deputy Chief and Head of Signals Intelligence Sergey Aleksandrovich Gizunov, the GRU First Deputy Chiefs Igor Olegovich Kostyukov and Vladimir Stepanovich Alexseyev.
The Letter from the President specifically refers Obama’s executive order issued in April and explains it has broader:
“The order amends section 1(a) of Executive Order 13694 by providing authority for blocking the property and interests in property of any person determined by the Secretary of the Treasury, in consultation with the Attorney General and the Secretary of State, to be responsible for or complicit in, or to have engaged in, directly or indirectly, cyberenabled activities originating from, or directed by persons located, in whole or in substantial part, outside the United States that are reasonably likely to result in, or have materially contributed to, a significant threat to the national security, foreign policy, or economic health or financial stability of the United States and that have the purpose or effect of … tampering with, altering, or causing a misappropriation of information with the purpose or effect of interfering with or undermining election processes or institutions.”
The order intends to persecute and individual that operates to interfere with the US Internal Affairs, for example conducting hacking activities or distributing information that may interfere with elections and other political events.
What will happen in the next months?
It is difficult to say, President Trump will have to share the Obama’s approach against Russian interference or downplay the Russian threat.
On December 28, Trump responded to a question about sanctions over the hacking against US infrastructure:
“I think we ought to get on with our lives. I think that computers have complicated lives very greatly. The whole age of computer has made it where nobody knows exactly what is going on. We have speed, we have a lot of other things, but I’m not sure we have the kind, the security we need.”
Meantime President Obama confirmed that the sanctions just applied will be placed side by side with other measures against any interference on US Internal Affairs.”We will continue to take a variety of actions at a time and place of our choosing, some of which will not be
“We will continue to take a variety of actions at a time and place of our choosing, some of which will not be publicised.”
“In addition to holding Russia accountable for what it has done, the United States and friends and allies around the world must work together to oppose Russia’s efforts to undermine established international norms of behavior, and interfere with democratic governance.” said the President Obama.
“To that end, my Administration will be providing a report to Congress in the coming days about Russia’s efforts to interfere in our election, as well as malicious cyber activity related to our election cycle in previous elections.”
Let’s close with a curiosity, the Russian Embassy in London responded tweeting of a picture of a duck with the word LAME written across the bottom.
CheckPoint experts spotted Three Critical 0-Day in PHP 7
30.12.2016 securityaffairs Vulnerebility
Researchers at the security firm CheckPoint have discovered three fresh critical zero day vulnerability in the last PHP 7.
Security researchers at the firm CheckPoint have discovered three fresh critical 0-day vulnerabilities in last PHP 7.
These vulnerabilities allow an attacker to take full control over 80 percent of websites which run on the latest release of the popular web programming language. The bad news is that one of the vulnerabilities remains unpatched again.
Security researchers at Check Point’s have analyzed in the last months PHP 7 and focused their efforts into “the unserialized mechanism” which is one of the most well-known vulnerable areas of PHP.
This is the same mechanism that was strongly exploited in PHP 5 and allowed attackers to compromise popular platforms, including Magento, vBulletin, Drupal, Joomla!, Pornhub’s website and other affected web servers in past, by sending maliciously crafted data in client cookies or to expose API calls.
The vulnerabilities are tracked as:
CVE-2016-7479 User After Free(UAF) Code Execution
CVE-2016-7480 Use of Uninitialized Value Code Execution
CVE-2016-7478 Remote Denial of Service
The exploitation of the first two vulnerabilities could allow an attacker to take complete control over affected servers, this means that it is possible to exploit them to spread malware as well as to steal data they store.
The last vulnerability triggers a remote Denial of Service attack/threat which basically hangs the website, exhausts its memory consumption, and a possible site down.

“The first vulnerability allows a remote attacker to unserialize a pathological exception object which refers to itself as the previous exception.” states the report. “When invoking the __toString method of this exception, the code iterates over the chain of exceptions. As the chain of exceptions consists of just that one object that points to itself, the iteration never terminates. “
For more technical details about the vulnerabilities give a look at the report.
“We have reported the three vulnerabilities to the PHP security team on the 15th of September and 6th of August. The PHP security team issued fixes for two of the vulnerabilities on the 13th of October and 1st of December.”
To ensure your webserver’s security, we recommend you should upgrade to latest version of PHP and stay tuned on PHP’s official site for news and updates.
Below the list of vulnerable PHP versions:
CVE-2016-7479 Version <= 7.0.13
CVE-2016-7480 Version < 7.0.12
CVE-2016-7478 Version <= 7.0.13 and 5.6.26
The OSCE organization was victim of a major cyber attack
30.12.2016 securityaffairs Cyber
The Organization for Security and Co-operation in Europe (OSCE) confirmed to have suffered suffer a “major” cyber attack.
Hackers targeted the Organisation for Security and Cooperation in Europe (OSCE), the news was confirmed on Wednesday by a spokeswoman for the organization.
The OSCE is a security and human rights watchdog, clearly the attack is part of a cyber espionage operation, unfortunately, the organization confirmed that it did not have the capability to investigate the incident.
According to the French newspaper Le Monde, Russian hackers are responsible for the attack.
“There was an attack. We found out about it at the beginning of November,” the OSCE spokeswoman Mersiha Causevic Podzic told AFP.
“The systems are safe now. We were given entirely new security systems and passwords,” she added.
The cyber attack “compromised the confidentiality” of the OSCE IT network and put “its integrity at risk,” fortunately the organization was still able to operate.
According to an unnamed Western intelligence source quoted by Le Monde, the attack was powered once again by the Russian APT group known as APT28 (aka known as Fancy Bear, APT 28, Pawn Storm, Sednit or Sofacy). The group is considered by security experts the responsible of numerous cyber attacks against the 2016 US Presidential Election.
The spokeswoman at the OSCE avoided commenting the attribution of the attack suffered by its organization. The organization wants to avoid any “speculation” that APT28 may have launched the cyber attack.
“But we don’t have the capacity to conduct such an investigation and we don’t want to speculate,” she said.
The OSCE said “the way in which the attacker accessed the OSCE was identified, as have some of the external communication destinations”.
France’s ambassador to the OSCE tried to downplay the dangers for the organization explaining that officials in Vienna are trained to avoid being victims of cyber attacks.
“Diplomats at the OSCE are warned that attempted spying, in whatever form, are part and parcel of this organisation,” Veronique Roger-Lacan told AFP.
The OSCE is composed of 57 members from North America, Europe, and Asia, including Russia and also Ukraine.
“The OSCE works for stability, peace and democracy for more than a billion people, through political dialogue about shared values and through practical work that aims to make a lasting difference.” reads the mission of the organization. “With its Institutions, expert units and network of field operations, the OSCE addresses issues that have an impact on our common security, including arms control, terrorism, good governance, energy security, human trafficking, democratization, media freedom and national minorities.”
The organization is known for its role of an observer in elections and for its role in Ukraine. The OSCE was tasked to monitor a ceasefire agreement to end fighting between Ukrainian and Russian separatists, it currently employed 700 monitors focused on the dispute in the eastern Ukraine.
Researcher found a severe flaw in the MONyog monitoring tool
30.12.2016 securityaffairs Vulnerebility
A security expert discovered a vulnerability in the MONyog tool that could be exploited by a normal user to elevate his privilege access.
The security researcher and penetration tester Mutail Mohamed (@muleyl) discovered a vulnerability in the MONyog, the most secure and scalable MySQL monitoring tool of the server monitoring tool.
The application URL is https://www.webyog.com/product/monyog and the affected version is MONyog Ultimate 6.63.
The flaw resides in the session management on Monyog application, it could be exploited by a normal user to elevate his privilege access by altering the session.

The exploitation of the flaw is very simple, the user just has to change the perimeters in the cookie store at that session.
The value associated with a normal user is 0, attackers can change it to 1 to gain admin privileges.
The researcher demonstrated that is to elevate privileges by manipulating the value of the following Cookie parameters;
HasServerEdit
IsAdmin
The hack will allow the user to create roles, view the passwords stored in the setup and change other settings via the admin section.
Below a video PoC of the exploitation of the flaw.
I reached the researcher for a comment:
“Since this is a commercial application and organizations pay for this, they At least need something secure and worth that price. ” explained Mutail.
“The organization could have a huge impact on this, because if let’s say a normal user goes rogue, he could get admin level access to organizations network. Since this application does use LDAP authentication. “
3 Critical Zero-Day Flaws Found in PHP 7 — One Remains Unpatched!
29.12.2016 thehackernews Vulnerebility
3 Critical Zero-Day Flaws Found in PHP 7
Three critical zero-day vulnerabilities have been discovered in PHP 7 that could allow an attacker to take complete control over 80 percent of websites which run on the latest version of the popular web programming language.
The critical vulnerabilities reside in the unserialized mechanism in PHP 7 – the same mechanism that was found to be vulnerable in PHP 5 as well, allowing hackers to compromise Drupal, Joomla, Magento, vBulletin and PornHub websites and other web servers in the past years by sending maliciously crafted data in client cookies.
Security researchers at Check Point's exploit research team spent several months examining the unserialized mechanism in PHP 7 and discovered "three fresh and previously unknown vulnerabilities" in the mechanism.
While researchers discovered flaws in the same mechanism, the vulnerabilities in PHP 7 are different from what was found in PHP 5.
Tracked as CVE-2016-7479, CVE-2016-7480, and CVE-2016-7478, the zero-day flaws can be exploited in a similar manner as a separate vulnerability (CVE-2015-6832) detailed in Check Point's August report.
CVE-2016-7479—Use-After-Free Code Execution
CVE-2016-7480—Use of Uninitialized Value Code Execution
CVE-2016-7478—Remote Denial of Service
The first two vulnerabilities, if exploited, would allow a hacker to take full control over the target server, enabling the attacker to do anything from spreading malware to steal customer data or to defacing it.
The third vulnerability could be exploited to generate a Denial of Service (DoS) attack, allowing a hacker to hang the website, exhaust its memory consumption and eventually shut down the target system, researchers explain in their report [PDF].
According to Yannay Livneh of Check Point's exploit research team, none of the above vulnerabilities were found exploited in the wild by hackers.
The check Point researchers reported all the three zero-day vulnerabilities to the PHP security team on September 15 and August 6.
Patches for two of the three flaws were issued by the PHP security team on 13th October and 1st December, but one of them remains unpatched.
Besides patches, Check Point also released IPS signatures for the three vulnerabilities on the 18th and 31st of October to protect users against any attack that exploits these vulnerabilities.
In order to ensure the webserver’s security, users are strongly recommended to upgrade their servers to the latest version of PHP.
New Android Malware Hijacks Router DNS from Smartphone
29.12.2016 thehackernews Android
android-dns-malware
Another day, another creepy malware for Android users!
Security Researchers have uncovered a new Android malware targeting your devices, but this time instead of attacking the device directly, the malware takes control over the WiFi router to which your device is connected to and then hijacks the web traffic passing through it.
Dubbed "Switcher," the new Android malware, discovered by researchers at Kaspersky Lab, hacks the wireless routers and changes their DNS settings to redirect traffic to malicious websites.
Over a week ago, Proofpoint researchers discovered similar attack targeting PCs, but instead of infecting the target's machines, the Stegano exploit kit takes control over the local WiFi routers the infected device is connected to.
Switcher Malware carries out Brute-Force attack against Routers
Hackers are currently distributing the Switcher trojan by disguising itself as an Android app for the Chinese search engine Baidu (com.baidu.com), and as a Chinese app for sharing public and private Wi-Fi network details (com.snda.wifilocating).
Once victim installs one of these malicious apps, the Switcher malware attempts to log in to the WiFi router the victim's Android device is connected to by carrying out a brute-force attack on the router's admin web interface with a set of a predefined dictionary (list) of usernames and passwords.
"With the help of JavaScript [Switcher] tries to login using different combinations of logins and passwords," mobile security expert Nikita Buchka of Kaspersky Lab says in a blog post published today.
"Judging by the hard coded names of input fields and the structures of the HTML documents that the trojan tries to access, the JavaScript code used will work only on web interfaces of TP-LINK Wi-Fi routers."
Switcher Malware Infects Routers via DNS Hijacking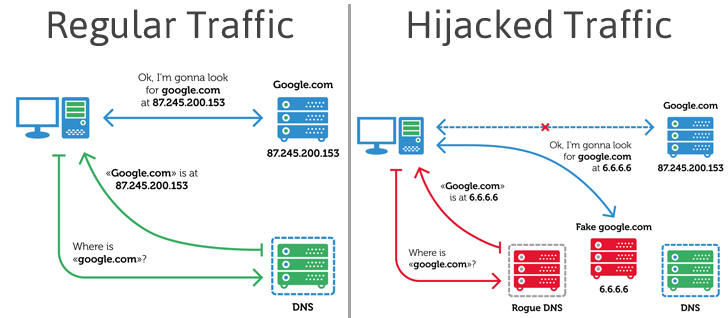
Once accessed web administration interface, the Switcher trojan replaces the router's primary and secondary DNS servers with IP addresses pointing to malicious DNS servers controlled by the attackers.
Researchers said Switcher had used three different IP addresses – 101.200.147.153, 112.33.13.11 and 120.76.249.59 – as the primary DNS record, one is the default one while the other two are set for specific internet service providers.
Due to change in router's DNS settings, all the traffic gets redirected to malicious websites hosted on attackers own servers, instead of the legitimate site the victim is trying to access.
"The Trojan targets the entire network, exposing all its users, whether individuals or businesses, to a wide range of attacks – from phishing to secondary infection," the post reads.
"A successful attack can be hard to detect and even harder to shift: the new settings can survive a router reboot, and even if the rogue DNS is disabled, the secondary DNS server is on hand to carry on."
Researchers were able to access the attacker’s command and control servers and found that the Switcher malware Trojan has compromised almost 1,300 routers, mainly in China and hijacked traffic within those networks.
The Bottom Line
Android users are required to download applications only from official Google's Play Store.
While downloading apps from third parties do not always end up with malware or viruses, it certainly ups the risk. So, it is the best way to avoid any malware compromising your device and the networks it accesses.
You can also go to Settings → Security and make sure "Unknown sources" option is turned off.
Moreover, Android users should also change their router's default login and passwords so that nasty malware like Switcher or Mirai, can not compromise their routers using a brute-force attack.
InterContinental Hotels investigating a possible card breach
29.12.2016 securityaffairs Crime
The company InterContinental Hotels Group (IHG) confirmed an ongoing investigation of alleged card breach at some of its properties.
The notorious investigators Brian Krebs was informed of a possible security breach at the hotel company InterContinental Hotels Group (IHG). Krebs received the news of the alleged card breach by his sources in the financial industry. According to the experts, the pattern of fraudulent activities had been observed on credit and debit cards used at some IHG properties.
“Those sources said they were seeing a pattern of fraud on customer credit and debit cards that suggested a breach at some IHG properties — particularly Holiday Inn and Holiday Inn Express locations.” wrote Krebs.
“Asked about the fraud patterns reported by my sources, a spokesperson for IHG said the company had received similar reports, and that it has hired an outside security firm to help investigate.”

IHG has more than 5,000 hotels across the world, the group includes many brands such InterContinental, Holiday Inn, Crowne Plaza, Kimpton, Hualuxe, Indigo, and Even.
Representatives at the Group confirmed they had been aware of the fraud patterns and promptly started an investigation with the support of a security firm.
Below the statement issued by the IHG:
“IHG takes the protection of payment card data very seriously. We were made aware of a report of unauthorized charges occurring on some payment cards that were recently used at a small number of U.S.-based hotel locations. We immediately launched an investigation, which includes retaining a leading computer security firm to provide us with additional support. We continue to work with the payment card networks.”
“We are committed to swiftly resolving this matter. In the meantime, and in line with best practice, we recommend that individuals closely monitor their payment card account statements. If there are unauthorized charges, individuals should immediately notify their bank. Payment card network rules generally state that cardholders are not responsible for such charges.”
While the investigation is ongoing customers have to closely monitor their payment card statements and notify any suspicious transaction.
InterContinental hotels suffered other breaches in the past, payment systems at Kimpton Hotels & Restaurants were compromised by a PoS malware discovered this summer.
InterContinental hotels were also involved in a breach suffered earlier this year by HEI Hotels & Resorts.
The hospitality sector is a privileged target of hackers, according to the experts from Trustwave also the notorious Carbanak cybercrime gang changed strategy targeting organizations in the sector.
This yeas major companies operating in the industry admitted suffering a data breach including Hard Rock Hotel & Casino Las Vegas, Trump Hotels, and Millennium Hotels & Resorts.
ZyXEL Customized Routers plagues by multiple vulnerabilities
29.12.2016 securityaffairs Vulnerebility
According to the firm SecuriTeam, several ZyXEL customized routers are affected by many vulnerabilities that could be easily exploited by hackers.
According to the firm SecuriTeam, multiple ZyXEL customized routers are affected by many vulnerabilities. The devices are distributed by the Thai IPS TrueOnline. The ZyXEL customized routers are offered for free to the customers with default settings, including default accounts and passwords, a gift for hackers.
The models are widespread, ZyXEL P660HN-T v1, ZyXEL P660HN-T v2, and Billion 5200W-T, the first of which since 2013.
“Several models are distributed by TrueOnline, three in particular are widespread:
ZyXEL P660HN-T v1 (distributed up to 2013)
ZyXEL P660HN-T v2
Billion 5200W-T (currently being distributed to new clients)
These are customized versions of existing ZyXEL and Billion routers. They are MIPS systems and they all run BOA web server.” reads the security advisory published by SecuriTeam.

The vulnerabilities have been discovered by an independent security researcher, they include an unauthenticated remote command execution vulnerability in P660HN-T v1, an unauthenticated remote command execution and authenticated remote command execution flaws in Billion 5200W-T, and an unauthenticated remote command execution vulnerability in P660HN-T v2.
The P660HN-T v1 device is affected by a command injection vulnerability in Maintenance > Logs > System Log > Remote System Log, the issue resides in the remote_host parameter on the ViewLog.asp page, which is accessible by an unauthenticated attacker.
The network device comes with the following default credentials:
username: admin; password: password
username: true; password: true
An unauthenticated command injection is present in the adv_remotelog.asp file of the Billion 5200W-T router. An attacker can trigger the vulnerability in the syslogServerAddr parameter by entering a valid IP address followed by “;<COMMAND>;”.
The same device is affected by an authenticated command injections in the interface tools_time.asp with the uiViewSNTPServer parameter. Also in this case, the expert discovered the device includes the following default accounts:
username: admin; password: password
username: true; password: true
username: user3; password: 12345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678
The third device, the P660HN-T v2 router is affected by a remote command injection vulnerability that results from an authenticated command injection chained with a hardcoded supervisor password. The flaw resides in the logSet.asp file, while the hardcoded supervisor credentials are username: supervisor; password: zyad1234.
“The actual command that can be injected has a length limitation of 28 characters.” states the advisory. “
Default accounts – P660HN-T v2 router
username: admin; password: password
username: true; password: true
username: supervisor; password: zyad1234″
The sad aspect of the story is that the researchers reported the vulnerabilities to ZyXEL in July, but the company still hasn’t issued any patched neither workaround.
Vulnerabilities in IoT devices, including home routers and SOHO devices, are particularly critic, because attackers can exploit them to compromise the equipment and recruit them in powerful “thingbot “such as the Mirai botnet.
The Leet Botnet powered a 650 Gbps DDoS attack before Christmas
29.12.2016 securityaffairs BotNet
Just before Christmas a massive DDoS attack powered by a new botnet dubbed Leet Botnet hit the network of the firm Imperva.
Security experts from the firm Imperva observed a massive attack against the company network on the morning of Dec. 21. The massive DDoS attack reached 650 Gbps, according to the researchers it was powered by the Leet Botnet and targeted several anycasted IPs on the Imperva Incapsula network.

The attack was launched once again by thousands of compromised IoT devices.
The attack didn’t target a specific customer of the company, likely because hackers were not being able to resolve the IP address of the victim that was hidden by the Incapsula mitigation proxies.
“It’s hard to say why this attack didn’t focus on a specific customer. Most likely, it was the result of the offender not being able to resolve the IP address of his actual victim, which was masked by Incapsula proxies.” reads the analysis published by Imperva.
Experts observed two distinct DDoS burst, the first one lasted 20 minutes and peaked at 400 Gbps, while the second burst lasted around 17 minutes and reached 650 Gbps.
“The first DDoS burst lasted roughly 20 minutes, peaking at 400 Gbps. Failing to make a dent, the offender regrouped and came back for a second round. This time enough botnet “muscle” to generate a 650 Gbps DDoS flood of more than 150 million packets per second (Mpps).” continues the analysis.
Both attacks failed. The experts were not able to track the real source of the attacks because hackers used spoofed IPs.
The analysis of the content of the packets composing the malicious traffic revealed that the attack was powered by Leet botnet, so called due to a ‘signature’ within the packets.
“The first thing we noticed was that the offender left a “signature” of sorts in some of the regular-sized SYN packets. In the TCP Options header of these packets, the values were arranged so they would spell “1337”. To the uninitiated, this is leetspeak for “leet”, or “elite”.” states Imperva.
Experts also noticed that the large content of the SYN payloads (799 to 936 bytes) that were populated by seemingly random strings of characters, others contained shredded lists of IP addresses.
“It seems that the malware we faced was programmed to access local files (e.g., access logs and iptable lists) and scramble their content to generate its payloads.”
Not only Mirai botnet, threat landscape as a new actor, the Leet botnet that can be equally dangerous.
Dreaded KillDisk Malware now includes Ransomware abilities
29.12.2016 securityaffairs Virus
Researchers at security firm CyberX have recently discovered a variant of the KillDisk malware that also implements ransomware features.
KillDisk is a malware that has been used in attacks against industrial control systems (ICS), it was developed to wipe the hard drives of the infected machine in order to make it inoperable.
The new variant is able to encrypt the file with AES algorithm, the malware uses a unique key for each target and encrypt it with an RSA 1028 algorithm with a key stored in the body of the malware.
The variant of the KillDisk malware is able to encrypt a large number of files from both local partitions and network folders are targeted.
Victims are requested to pay 222 bitcoins ($206,000) to recover their files, a very exorbitant figure that suggests the intention of the author is to attack organizations with deep pockets.
The experts believe the variant has been developed by the TeleBots group, a Russian cybercriminal gang that developed its Telebots malware starting from the BlackEnergy one. The group was recently observed by experts from ESET targeting Ukrainian banks.
“This new variant of KillDisk was developed by the TeleBots gang, a group of Russian cybercriminals believed to have evolved from the Sandworm gang. The Sandworm gang is responsible for a string of attacks in the United States during 2014 that compromised industrial control system (ICS) and SCADA networks using a variant of the BlackEnergy malware” states the report published by the CyberX.
The researchers speculate the malware is being distributed via malicious Office attachments, a close look at the contact email used in the instructions reveals that hackers used the Tor anonymous email service lelantos.org.
The Bitcoin Wallet used by the hackers is still empty and there is no indication of past transactions.

CyberX noticed that the same RSA public key is used for all samples of malware it analyzed, this implies that it could be used to decrypt files for all victims.
According to CyberX, the KillDisk malware first elevate its privileges and then registers itself as a service. The malicious code kills various processes, not critical system ones and processes associated with anti-malware applications, to avoid triggering detection.
Kaspersky discovered a One-stop-shop for hacking goods
29.12.2016 securityaffairs Virus
Security experts from Kaspersky Lab discovered an interesting one-stop-shop for purchasing hacking goods while investigating activity of a popular RAT.
Security experts from Kaspersky Lab discovered an interesting one-stop-shop for purchasing hacking goods. The malware researchers were analyzing traffic from a number of infected machines that appear to be generated by the HawkEye RAT.
HawkEye is a popular RAT that can be used as a keylogger, it is also able to identify login events and record the destination, username, and password.
The domain was used as a C&C server of the HawkEye RAT and at the same time was also being used as a one-stop-shop for purchasing hacking goods.
one-stop-shop
Kaspersky discovered a group of WhiteHat hackers who call themselves Group Demóstenes who scans the Internet and looking to exfiltrate stolen data from Command and Control servers.
When the hackers find a server containing the stolen data they look for a backdoor that would give them access to the filesystem. In this way they monitor incoming stolen data, then they would collect the stolen credentials and send emails to the victims’ accounts, both manually or automatically.
The email send to the victims includes an attachment with proof that their machine has been hacked and the suggestion to change passwords and offer to help.
Hi ***********
Our SERVERS detected information from a server on the US, we don’t even know goverment or another sourse …. we send a file with all your logins and passwords of all your accounts from hxxp://www.p******op[.]biz/*******
WE HAVE TESTING IN YOUR PAYPAL ACCOUNT. LOG IN TO YOUR ACCOUNT AND YOU WILL SEE TWO CANCELED BILLING (OUR JOB IS WHITE HAT NO HACK …. Steal)
Seme you verify this information. it’s better thing we hurt all change password on the other computer Because Called Computer
Name PC USER-PC
Local Time: 03.10.2016. 18:45:02
Installed Language: en-
Net Version: 2.0.50727.5485
Operating System Platform: Win32NT
Operating System Version: 6.1.7601.65536
Operating System: Microsoft Windows 7 Home Premium
Internal IP Address: 192.168.0.101
External IP Address:
Installed Anti virus: Avast Antivirus
Installed Firewall:
have a keylogger harm report All That You write, messages, passwords or more.
¿Why we do it?
We have a Cause Called Group Demóstenes looking for Ciber attacks and false info.
Please Donate by PayPal at h**cg**an@gmail[.]com 5 USD or more, Because this is only our ingress.
PLEASE WRITE ME AT THIS MAIL FOR KNOW IF YOU KNOW ABOUT THIS
Back to the one-stop-shop discovered by Kaspersky, the experts discovered it is composed of a back-end for storing stolen credentials and a front-end for selling some of them, alongside many other hacking “goods”.
“To purchase goods in the private shop you must deposit money into your account on the website. The attackers accept Bitcoins, PerfectMoney and WebMoney.” states the analysis published by Kaspersky.
The shop allows users to register an account in order to make purchases. Kaspersky discovered the C&C was affected by a crucial vulnerability which allowed researchers to download the stolen data.
one-stop-shop
Among the items offered for sale, there are scam pages specifically designed to target Amazon, Apple, Netflix and even National Bank of Australia and Barclays.
The shop also includes information regarding the support to receive while using scam services.
The researchers discovered stolen credentials for sensitive applications across multiple industries, including government, healthcare, banking and payment web applications.
“Among them is the following web server which belongs to the Pakistani government.” states the report. “As mentioned, hundreds of machines were found to be compromised by just one C2.”
Researchers from Kaspersky obtained the attackers’ credentials from one very small file that was discovered on the server.
The analysis of affected users revealed they are mostly located in APAC (i.e. Japan, Thailand, and India) and Eastern Europe (i.e. Russia and Ukraine).
Najděte hrozby i v šifrovaných přenosech
29.12.2016 SecurityWorld Kryptografie
K eliminaci slepé skvrny své obrany potřebujete specializovanou platformu pro kontrolu přenosů SSL.
A co více, v důsledku hnutí, jako je Let’s Encrypt (Šifrujme) – bezplatná, automatizovaná otevřená certifikační autorita (CA) zajišťovaná skupinou ISRG (Internet Security Research Group), došlo k neúmyslnému vytvoření nové řady zranitelností.
Útočníci mohou využít Let’s Encrypt k vytvoření svých vlastních zdánlivě legitimních SSL certifikátů k podepsání škodlivého kódu a k provozování škodlivých webů HTTPS.
Šifrování útočníkům umožňuje ukrýt své exploity před bezpečnostními zařízeními, jako jsou firewally, systémy prevence narušení (IPS) a platformy prevence úniku dat (DLP). Některé z těchto produktů totiž nedokážou dešifrovat přenosy SSL bez snížení svého výkonu, zatímco jiné prostě nemohou přenosy SSL dešifrovat kvůli svému umístění v síti.
Při boji s hrozbami vznikajícími šifrováním SSL by měly firmy dešifrovat a zkontrolovat příchozí a odchozí přenosy pomocí specializované platformy pro kontrolu SSL, která umožní bezpečnostním zařízením třetích stran eliminovat slepé místo korporátní obrany.
Jak proniká malware přes SSL
Tady jsou tři příklady, jak vývojáři malwaru využívají šifrování, aby unikli odhalení.
Trojský kůň Zeus. Poprvé byl odhalen v roce 2007. Trojský kůň Zeus je jedním z mnoha druhů malwaru, který plně využívá šifrování. Zároveň je i nadále jedním z nejrozšířenějších a nejnebezpečnějších existujících exemplářů finančního malwaru – jen do prosince 2014 způsobil v USA kompromitaci cca čtyř milionů počítačů.
Sadu nástrojů (toolkit) pro útok trojským koněm Zeus široce využívají nesčetné skupiny zločinců. Umožňuje jim vyvinout varianty, které jsou ještě důmyslnější.
Výsledkem byl mimo jiné vznik botnetu Gameover Zeus, který využívá šifrovanou komunikaci peer-to-peer jak pro distribuci malwaru, tak i pro řídicí komunikaci (C&C, Command and Control). FBI odhaduje, že botnet Gameover Zeus je zodpovědný za krádeže více než 100 milionů dolarů.
Aktualizace C&C z webů sociálních sítí. Některé nové druhy malwaru používají sociální sítě, jako jsou například Twitter a Facebook, a webmail pro řídicí (C&C) komunikaci.
Malware může například přijímat řídicí příkazy z účtů na Twitteru nebo z komentářů na Pinterestu, což zašifruje veškerou komunikaci. Chtějí-li organizace odhalit tyto botnetové hrozby, musejí dešifrovat a kontrolovat přenosy SSL, jinak mohou bezpečnostní analýzy mylně považovat přístup k webům sociálních sítí z klientských počítačů za neškodný.
3. Trojský kůň RAT (Remote Access Trojan)
Německá společnost G Data Software zaměřená na výzkum zabezpečení odhalila trojského koně využívajícího vzdálený přístup (typ RAT), který přijímal příkazy C&C přes e-mailovou službu Yahoo Mail, a pojmenovala ho Win32.Trojan.IcoScript.A.
Od té doby tato firma a také konzultanti společnosti Shape Security objevili další druhy malwaru Icoscript, které přijímaly aktualizace z konceptů (tj. z rozepsaných a neodeslaných) zpráv služby Gmail.
Jedna z forem tohoto malwaru využívá skript v Pythonu k přijímání příkazů a dalšího kódu ze složky konceptů, která zůstává skrytá, přestože je otevřená. Služby Gmail a Yahoo Mail šifrují přenosy a malware je schopný je využívat, aby ho systémy IDS a DLP nedokázaly odhalit.
Pokud organizace nedešifruje a nekontroluje přenosy na webmailové servery, zvyšuje se tím riziko infekce tímto typem malwaru.
Možná řešení
Šifrování dnes tvoří přibližně jednu třetinu veškerého internetového provozu a očekává se, že v příštím roce dosáhne tento poměr dvou třetin veškerých přenosů, až internetoví giganti jako Netflix přejdou na SSL.
V důsledku toho se stane šifrovaný provoz dálnicí pro distribuci malwaru a pro jednoduché provádění kybernetických útoků. Aby mohly organizace zjistit záškodnické aktivity, potřebují dešifrovat a kontrolovat přenosy SSL. V opačném případě tudy bude malware moci pronikat.
Pro vyřešení tohoto problému a získání vhledu do SSL je vhodné nasadit platformy pro kontrolu provozu SSL, které budou dešifrovat přenosy SSL a posílat je k analýze zabezpečovacím zařízením dalších dodavatelů.
Pro odchozí přenosy organizace vlastní koncové body, ale ne certifikáty a klíče SSL. Platforma pro kontrolu SSL může takové přenosy dešifrovat, když bude nakonfigurovaná jako proxy pro transparentní přeposílání nebo jako explicitní proxy.
Dešifrování příchozího provozu směrovaného na interní aplikační servery je jiné než dešifrování odchozích přenosů, protože organizace je zároveň vlastníkem SSL klíčů.
Existují dva hlavní způsoby, jak dešifrovat příchozí přenosy SSL směřující na interní servery:
Režim reverzní proxy: SSL provoz se ukončí v zařízeních kontrolujících SSL a dále už se zasílá v nešifrované podobě k inline nebo non-inline zabezpečovacím zařízením. Tento režim se někdy také označuje jako „SSL Off-load.“
Pasivní non-inline nebo inline režim: SSL provoz se dešifruje pomocí kopie klíčů SSL serveru. SSL provoz není platformou kontroly SSL modifikovaný, samozřejmě kromě případů potenciální blokace útoků.
V pasivním režimu non-inline může být platforma kontroly SSL nainstalovaná transparentně bez nutnosti aktualizovat nastavení sítě. Organizace však nebude schopná efektivně blokovat všechny útoky včetně jednopaketových útoků.
Největší slabinou však je, že pasivní režim nedokáže podporovat silné šifrovací metody, jako je například PFS (Perfect Forward Secrecy), protože se platforma kontroly SSL aktivně neúčastní dojednávání klíče SSL.
Ať už jde o sdílení škodlivého souboru přes web sociálních sítí, nebo malwarovou přílohu e-mailu či v rychlých zprávách, bude mnoho útoků zahalených právě pomocí SSL. Nastal čas, kdy by organizace měly významně investovat do ochrany dat a při tom nezapomínat na dešifrování a kontrolu veškerých SSL přenosů.
Police Ask for Amazon Echo Data to Help Solve a Murder Case
28.12.2016 thehackernews Security
Police seek Amazon Echo Data to solve a Murder Case
Hey, Alexa! Who did this murder?
Arkansas police are seeking help from e-commerce giant Amazon for data that may have been recorded on its Echo device belonging to a suspect in a murder case, bringing the conflict into the realm of the Internet of Things.
Amazon Echo is a voice-activated smart home speaker capable of controlling several smart devices by integrating it with a variety of home automation hubs. It can do tasks like play music, make to-do lists, set alarms, and also provide real-time information such as weather and traffic.
As first reported by The Information, authorities in Bentonville have issued a warrant for Amazon to hand over audio or records from an Echo device belonging to James Andrew Bates in the hope that they'll aid in uncovering additional details about the murder of Victor Collins.
Just like Apple refused the FBI to help them unlock iPhone belonging to one of the San Bernardino terrorists, Amazon also declined to give police any of the information that the Echo logged on its servers.
Collins died on November 21 last year while visiting the house of Bates, his friend from work, in Bentonville, Arkansas. The next morning, Collins' dead body was discovered in a hot tub, and Bates was charged with first-degree murder.
As part of the investigation, authorities seized an Amazon Echo device belonging to Bates, among other internet-connected devices in his home, including a water meter, a Nest thermostat, and a Honeywell alarm system.
Always-ON Listening Feature
Echo typically sits in an idle state with its microphones constantly listening for the "wake" command like "Alexa" or "Amazon" before it begins recording and sending data to Amazon's servers.
However, due to its always-on feature, it's usual for the Echo to activate by mistake and grab snippets of audio that users may not have known was being recorded.
Some of those voice commands are not stored locally on Echo but are instead logged onto Amazon's servers.
Presumably, the authorities believe that those audio records that the Echo device might have picked up the night of the incident and uploaded to Amazon servers could contain evidence related to the case under investigation.
Amazon Refused (Twice) to Hand over its User's Data
Amazon, however, denied providing any data that the authorities need. Here's what a spokesperson for the company told CNBC:
"Amazon will not release customer information without a valid and binding legal demand properly served on us. Amazon objects to overbroad or otherwise inappropriate demands as a matter of course."
While the online retail giant has twice refused to serve police the Echo data logged on its servers, Amazon did provide Bates' account information and purchase history.
The police said they were able to extract data from Echo, though it's uncertain what they were able to uncover and how useful that data would be in their investigation.
According to court records, Bates' smart water meter shows that his home ran 140 gallons of water between 1 AM and 3 AM the night Collins was found dead in Bates' hot tub. The prosecution claims that the water was used to wash away evidence after he killed Collins.
Should Amazon Share the Data or Not?
The authorities in the Collins murder case are asking for data on Amazon's servers that could help bring a criminal to justice. If so, authorities should get access to it.
In the case of Apple vs. FBI, Apple was forced to write a backdoor software that could bypass the security mechanism built into its iPhone, while the company already handed over the data stored on its server.
The broader takeaway: IoT devices automating your habits at home could be used for or against you, legally.
The Collins murder case appears to be a first-of-its-kind, and we are very much sure to see more such cases in the future.
It will be interesting to see how the companies that make smart home devices would serve its customers while maintaining a balance between keeping their customers' privacy safe and aiding the process of justice.
Did You Install Super Mario Run APK for Android? That's Malware
28.12.2016 thehackernews Android
After the success of Pokémon Go, Nintendo's "Super Mario Run" has become the hottest game to hit the market with enormous popularity and massive social impact. The game has taken the world by storm since its launch for iOS devices over a week ago.
Can you believe — it was downloaded more than 40 million times worldwide in its first four days of release.
But if you have downloaded a Super Mario Run APK for your Android device, Beware! That's definitely a malware.
Since Super Mario Run has currently been released only for iOS devices and is not on Google Play, it caused a lot of disappointment among Android users.
So, eventually, many Android device owners who love Mario games and can not wait to play Super Mario Run ended up downloading APKs outside of the Google Play Store.
But those tons of phony copycat unofficial Super Mario apps on many third-party Android app stores turn out to be malware or viruses that attempt to look like the legitimate Super Mario Run app.
Super Mario can Take Full Control of your Android Device
To download the third party APK, users are required to "side-load" the malicious app by modifying their Android core security settings, allowing their device's operating system to install apps from "untrusted sources."
Some of these malicious apps can even take full control of your Android device, as the apps request privileges to edit, read, receive and send text messages, take photos and record videos and track your location using GPS.
However, one of the apps titled "Super Mario" creates additional icons, displays pop-up and banner ads, installs other malicious apps onto victim's smartphone, and performs other intrusive activities without any users interaction, according to Tokyo-based Trend Micro antivirus firm, which detected malicious Super Mario apps 90,000 times this year.
"Clicking on these ads or icons will direct users to either adult sites or malicious sites. In either case, the goal is to get users to install various apps," researchers at Trend Micro writes.
"While some of these apps are perfectly legitimate, some are suspicious apps distributed by third-party app stores, including more malicious apps that even request for administrator rights."
Another app, also titled "Super Mario" and discovered by the security firm, prompts users first to install an app called 9Apps, which then asks for more permissions, including recording audio, reading modifying the calendar and even access to complete SD-card.
Here's How to Prevent Yourself
So, instead of downloading applications from unknown third party stores, Android users are required to wait for the official Google Play release.
Downloading apps from third parties do not always end up with malware or viruses, but it certainly ups the risk. So, it's the best way to wait to avoid compromising your device and the networks it accesses.
You can also go to Settings → Security and make sure "Unknown sources" option is turned off.
The number of ICS Attacks continues to increase worldwide
28.12.2016 securityaffairs Attack
According to data provided by IBM Managed Security Services, the number of ICS attacks in 2016 continues to increase worldwide.
Industrial control systems (ICS) continues to be a privileged target of hackers. According to IBM Managed Security Services, the number of cyber attacks increased by 110 percent in 2016 compared to 2015.
According to the researchers from IBM, the spike is associated with a significant increase to brute force attacks on supervisory control and data acquisition (SCADA) systems.

IBM notices an increase in ICS traffic caused by SCADA brute-force attacks, unfortunately in some cases systems are exposed on the Internet with default credentials or weak passwords.
IBM warns of the availability of a penetration testing framework named smod that was used in a large number of attacks. The tool was published on the GitHub repository in January 2016, it allows to assess the Modbus serial communications protocol. It could also be used by attackers to power brute-force attacks.
“In January 2016, GitHub released a penetration testing solution that contained a brute-force tool that can be used against Modbus, a serial communication protocol. The public release and subsequent use of this tool by various unknown actors likely led to the rise in malicious activity against ICS in the past 12 months.” states the blog post published by IBM Managed Security Services.
The analysis of the sources of the attacks revealed that threat actors in the US accounted for the majority of ICS attacks in 2016 (60%), followed by Pakistan (20%), and China (12%). The United States also topped the list of the top 5 destination countries, this data is considered normal by experts because the US has the largest number of internet-connected ICS systems in the world.
The report mentions the following three notable ICS attacks occurred in the last years.
The 2013 New York dam attack. Iranian hackers penetrated the industrial control system of a dam near New York City in 2013, raising concerns about the security of US critical infrastructure.
The 2015 Ukrainian power outage. Experts speculated the involvement of the Russian Government. According to security experts, the BlackEnergy malware was a key element of the attack against Ukrainian power grid that caused the power outage.
The 2016 SFG malware attacks. The Labs team at SentinelOne recently discovered a sophisticated malware dubbed Furtim specifically targeting at least one European energy company.
The report warns organization in any industry of cyber attacks against ICS system and urges the adoption of necessary countermeasures.
“Organizations across all verticals must take full responsibility for protecting their own assets and consumers. There should be no exceptions, since the best way to keep adversaries out of an ICS is to implement simple safeguards, best practices and risk management solutions.” states the report.
ISIS use of Telegram has definitively surpassed Twitter
28.12.2016 securityaffairs Cyber
Telegram is the ‘app of choice’ for ISIS members, its use has definitively surpassed Twitter and other social media platforms.
Do you want to investigate ISIS activities, you have to be aware that Telegram is today its privileged channel for propaganda.
The use of the popular encrypted messaging app is widespread among the militants of the terrorist organization, The use of Telegram has eclipsed the use of other social media platforms, including Twitter.
Social media continue to ban the content posted by members of the ISIS in the attempt to block their propaganda online.
Twitter continues to close hundreds of thousands of accounts for violating the company’s policies on violent extremism. In August Twitter published a blog post that revealed it has shut down 360,000 terrorist-related accounts since last year.
“Earlier this year, we announced we had suspended more than 125,000 accounts since mid-2015 for violating our longtime prohibition on violent threats and the promotion of terrorism and shared the steps we are taking as a company to combat this content.” states the post. “While our work is not done, today we are announcing that we have suspended an additional 235,000 accounts for violating our policies related to promotion of terrorism in the six months since our February 2016 post.”
In the weeks before the tragic the tragic Berlin attack, intelligence analysts observed many IS known Telegram channels sharing messages, calling for volunteers for a holiday killing spree.
“Christmas, Hanukkah, and New Years Day is very soon,” states one of the messages cited by the Washington Post. “So let’s prepare a gift for the filthy pigs/apes.”
The reason for the widespread use of Telegram is related to the lack repressive measures of the company against ISIS activities through its application.
“[Telegram is] the app of choice for many Isis, pro-Isis and other jihadi and terrorist elements.” states a report published by the Middle East Media Research Institute (MEMRI).
A previous report published by the MEMRI JTTM, titled “Jihadis Shift To Using Secure Communication App Telegram’s Channels Service” published October 29, 2015, noted that numerous jihadis and jihadi organizations had opened their own channels on Telegram.
ISIS and Al-Qaeda in the Arabian Peninsula (AQAP) opened several channels to allow secure communications among its members.

Nasher is the most popular multi-language set of channels of ISIS-related news on Telegram.
“Based on the rate at which new jihadi channels are emerging, and on the large number of members they are attracting, these channels can be expected to become a fertile and secure arena for jihad-related activities.” This has indeed come to pass.” states the report.
According to the researchers, Telegram has surpassed Twitter as the most important platform of communication.
“It has surpassed Twitter as the most important platform,” said Steven Stalinsky, lead author of the report. “All the big groups are on it. We see Isis talking about the benefits of Telegram and encouraging its followers to use it.”
Telegram is easy to use and offers a number of different options for regular and encrypted communications.
“The West has been generally two steps behind the jihadis when it comes to cyber,” expalined said Steven Stalinsky, lead author at the MEMRI. “Many people in government are still focused on Twitter, and they need to be. But what we tell them is, ‘That’s no longer the main story.’ “
Once again the IS demonstrates the ability of its members in chenging tactics and means to make harder the monitoring of their activities, but at the same time maximizing the benefics in using technology.
Lithuania government PCs infected by a Russian spyware
28.12.2016 securityaffairs Virus
Lithuania said found Russian spyware on its government computers, the government blames Moscow for cyber espionage campaigns.
Lithuania blames the Russia for cyber attacks that have hit government networks over the last two years. According to the Reuters, the head of cyber security Rimtautas Cerniauskas confirmed the discovery of at least three Russian spyware on government computers since 2015.
Lithuanian officials targeted by the alleged Russian spyware held mid-to-low ranking positions at the government, anyway Cerniauskas confirmed their PCs contained government sensitive documents.
“The head of cyber security told Reuters three cases of Russian spyware on its government computers had been discovered since 2015, and there had been 20 attempts to infect them this year.” states the article published by the Reuters.
“The spyware we found was operating for at least half a year before it was detected – similar to how it was in the USA,” said Rimtautas Cerniauskas.

The Government of Moscow denies the involvement in the attacks, spokesman Dmitry Peskov told Reuters the accusations were “laughable” and unsubstantiated. Russian authorities explained that also their networks are targeted by hackers, but Moscow has never accused other governments.
“Did it (the spyware) have ‘Made in Russia’ written on it?” quipped Peskov. “We absolutely refute this nonsense.”
Almost any government fears Russian nation-state actors, the cyber attacks against US Presidential Election and the string of incidents occurred in Ukraine raised the fears of Russian cyber attacks.
According to the German Intelligence, the APT 28 group, also known as Fancy Bear, is ramping up information warfare against Germany and the rest of West to destabilize foreign Governments.
“Lithuania, Estonia and Latvia, all ruled by Moscow in communist times, have been alarmed by Russia’s annexation of Ukraine’s Crimea peninsula in 2014 and its support for pro-Russian separatists in eastern Ukraine.” continues the Reuters.
According to the Lithuanian intelligence services, the cyber attacks were politically motivated and threat actors conducted cyber espionage activities on state institutions.
The Russian spyware was used by hackers to exfiltrate documents, as well as collect login credentials from popular web services such as Gmail and Facebook. Syphoned data were sent to an IP address linked to cyber espionage campaigns conducted by Russian cyber spies.
“This only confirms that attempts are made to infiltrate our political sphere,” said Cerniaukas.
“Russians are really quite good in this area. They have been using information warfare since the old times. Cyberspace is part of that, only more frowned upon by law than simple propaganda”, he added.
“They have capacity, they have the attitude, they are interested, and they will get to it – so we need to prepare for it and we need to apply countermeasures.”
This isn’t the first time that Russian hackers target Lithuanian systems, According to the head of the Lithuanian counter-intelligence agency Darius Jauniskis, in 2012 Moscow launched coordinated attacks against the Lithuanian central bank and top online news website.
“It is all part of psychological warfare,” explained Darius.
Hacked Sony Music Entertainment account tweeted about Britney Spears’s Death
27.12.2016 securityaffairs Hacking
Hackers compromised the Sony Music Entertainment Twitter account and posted the messages on Britney Spears’s Death. Experts blame OurMine crew.
Sony Music Entertainment’s Twitter account was compromised and hackers posted the news of the Britney Spears’s death.
“RIP @britneyspears #RIPBritney 1981-2016” and “Britney spears is dead by accident! We will tell you more soon #RIPBritney.” states the messages posted by the hackers.

Sony Music Entertainment quickly deleted the messages and confirmed the hack of its account.
“Sony Music Entertainment’s Twitter account was compromised. This has been rectified,” it said.
“Sony Music apologizes to Britney Spears and her fans for any confusion.”
Separately, the official Twitter account for Bob Dylan featured a tweet that read:
“Rest in peace @britneyspears,” but the message was later deleted.
Adam Leber, a spokesman for the pop star told CNN the news was fake.
“I assume their account has been hacked,” said Spears’ manager, Adam Leber.”I haven’t spoken to anyone… as of yet but I am certain their account was hacked. Britney is fine and well. There have been a few Internet clowns over the years who have made similar claims about her death, but never from the official Sony Music Twitter account.” said the spokesman.
Who is behind the hack?
Security experts suspect the account was hacked by the notorious hacker group OurMine, the same that recently hacked the NetFlix account and the accounts belonging to many Very Important People.
OurMine is a very popular hacker group that hacked multiple high-profile accounts including Mark Zuckerberg, Twitter co-founder Evan Williams, David Guetta Daniel Ek, former Twitter CEO Dick Costolo, the CEO and founder of Spotify, Google CEO Sundar Pichai, and many others.
The group uses to hack the accounts to demonstrate the poor security, then it offers its consultancy to prevent future attacks.
Two Tweets posted by the hacked Sony Music Entertainment’s Twitter account suggest the involvement of the OurMine Team:
“We detected unusual activity on the account and we checked the account if it’s hacked or not”, states one Tweet, followed by, “we saw a new IP logged in to the account a few minutes ago and the tweet is posted by a new IP so @britneyspears is still alive #OurMine”.

Hacked Sony Music Entertainment account
This isn’t the first time hackers target Sony, in November 2014 the hacking group known as GOP broke into the company systems and stole sensitive information, including employees data.
The FBI blamed the North Korea for the cyber attack.
Critical PHPMailer Flaw leaves Millions of Websites Vulnerable to Remote Exploit
26.12.2016 thehackernews Vulnerebility
A critical vulnerability has been discovered in PHPMailer, which is one of the most popular open source PHP libraries to send emails used by more than 9 Million users worldwide.
Millions of PHP websites and popular open source web applications, including WordPress, Drupal, 1CRM, SugarCRM, Yii, and Joomla comes with PHPMailer library for sending emails using a variety of methods, including SMTP to their users.
Discovered by Polish security researcher Dawid Golunski of Legal Hackers, the critical vulnerability (CVE-2016-10033) allows an attacker to remotely execute arbitrary code in the context of the web server and compromise the target web application.
"To exploit the vulnerability an attacker could target common website components such as contact/feedback forms, registration forms, password email resets and others that send out emails with the help of a vulnerable version of the PHPMailer class," Golunski writes in the advisory published today.
Golunski responsibly reported the vulnerability to the developers, who have patched the vulnerability in their new release, All versions of PHPMailer before the critical release of PHPMailer 5.2.18 are affected, so web administrators and developers are strongly recommended to update to the patched release.
Since The Hacker News is making the first public disclosure of the vulnerability in the news following Golunski advisory and millions of websites remain unpatched, the researcher has put on hold more technical details about the flaw.
However, Golunski has promised to release more technical details about the vulnerability in coming days, including a proof-of-concept exploit code and video demonstration that will show the attack in action.
We will update this article with additional information on the PHPMailer vulnerability, exploit code and video demonstration, once the researcher makes it public.
Cyanogen is shutting down CyanogenMod, it will go on as Lineage, maybe
26.12.2016 securityaffairs OS
The most popular custom Android ROM, the Cyanogen OS, Announced That it is closing its services starting from December 31, 2016.
Bad news for users of the most popular custom Android ROM, the Cyanogen OS, that is now closing its services.
Cyanogen was launched with the intent to provide an improved version of the Google Android operating system but following some technical and potential legal issues, it decided to shut down its custom services.
CyanogenMod OS is not a commercial operating system that implements features not available in the official firmware distributed by mobile device vendors.
It is managed by a community of developers led by Steve Kondik, which is one of the co-founder of Cyanogen.
“As part of the ongoing consolidation of Cyanogen, all services and Cyanogen-supported nightly builds will be discontinued no later than 12/31/16. The open source project and source code will remain available for anyone who wants to build CyanogenMod personally.” reads an official statement published on the official website.
The planned shutdown of Cyanogen was officially announced late Friday through a very brief blog post made by the company, saying “as part of the ongoing consolidation of Cyanogen,” it’s shutting down all services and nightly builds on December 31.
What does it mean for end-users?
Starting from January 2017, there will be no more Android ROM updates, anyway, the open source project and source code will remain available for those people that want to build their own CyanogenMod.
Cyanogen will stop providing nightly builds and security updates for its OS, mobile devices running Cyanogen OS (i.e. OnePlus One), will have to switch to the open-source version of the CyanogenMod OS.
At the time I was writing the www.cyanogenmod.org is down.
The CyanogenMod team has published a post to confirm the shutdown of the CM infrastructure and revealing a plan to continue the open-source initiative as Lineage.
Below the full message from the team:
“Last week, we released the final CM-13.0 releases, updated to the latest security patches, in anticipation of what follows.
Yesterday, Cyanogen Inc (Cyngn) announced that they were shutting down the infrastructure behind CyanogenMod (CM). This is an action that was not unpredictable given the public departure of Kondik (cyanogen himself) from the company, and with him our last remaining advocate inside Cyngn’s leadership.
In addition to infrastructure being retired, we in the CM community have lost our voice in the future direction of CM – the brand could be sold to a third party entity as it was an asset that Kondik risked to start his business and dream. Even if we were to regroup and rebuild our own infrastructure, continuing development of CM would mean to operate with the threat of sale of the brand looming over our heads. Then there is the stigma that has grown to be attached to anything named ‘Cyanogen’. Many of you reading this have been champions of clarifying that the CM product and CyngnOS were distinct, yet the stain of many PR actions from Cyngn is a hard one to remove from CM. Given CM’s reliance on Cyngn for monetary support and the shared source base, it’s not hard to understand why the confusion remains.
It will come as no surprise that this most recent action from Cyngn is definitely a death blow for CyanogenMod.
However, CM has always been more than the name and more than the infrastructure. CM has been a success based on the spirit, ingenuity and effort of its individual contributors – back when it was Kondik in his home, to the now thousands of contributors past and present.
Embracing that spirit, we the community of developers, designers, device maintainers and translators have taken the steps necessary to produce a fork of the CM source code and pending patches. This is more than just a ‘rebrand’. This fork will return to the grassroots community effort that used to define CM while maintaining the professional quality and reliability you have come to expect more recently.
CM has served the community well over its 8 long years. It has been our home, bringing together friends from all over the world to celebrate our joy of building and giving. Its apt then that on this Eve of a holiday we pay our respects. We will take pride in our Lineage as we move forward and continue to build on its legacy.
Thank you & Goodbye,
The CyanogenMod Team”

The CyanogenMod community is now working to produce a fork of the CyanogenMod source code and pending patches.
Android community believes that a new project, dubbed LineageOS, will bo continue to live on it, but it is still in its infancy.
According to the CyanogenMod (CM) team, Lineage “is more than just a ‘rebrand’” and “will return to the grassroots community effort that used to define CM while maintaining the professional quality and reliability you have come to expect more recently.”
If you are interested in LineageOS you can give a look at its website, the files of the Lineage Android Distribution can be found on a repository on GitHub.
“So, yes, this is us. LineageOS will be a continuation of what CyanogenMod was. To quote Andy Rubin, this is the definition of open. A company pulling their support out of an open source project does not mean it has to die.” states the description about
Obama moves to end dual-hat arrangement separating Cybercom from NSA
26.12.2016 securityaffairs Cyber
President Obama urges to the end the dual-hat arrangement to separate the heads of the U.S. Cyber Command from National Security Agency.
Cyber security is one of the most important topics on the agenda of any Government and it will be one of the most debated arguments at the next G7 summit that will be held in Italy next year.
I’m currently working with the Cyber G7 Group and I have the opportunity to analyze the approach to the matter of various states and to promote new initiatives aiming to harmonize the cyber-security approach “of governments” by encouraging the cooperation and avoiding situations of conflict.
Last week, President Obama moved to end the controversial dual-hat arrangement under which the National Security Agency and the U.S. Cyber Command (Cybercom) are headed by the same military officer.
The decision is really important and highlights the strategic importance of the mission assigned to the U.S. Cyber Command. According to a transition official quoted by the Washington Post who spoke on the condition of anonymity, cybersecurity is one of the most important issues in the US Security Strategy.
“cybersecurity has been and will be a central focus of the transition effort.” said the official.
Obama moves to end dual-hat arrangement separating Cybercom from NSA
The NSA and the U.S. Cyber Command have fundamentally different missions, for this reason, it is essential to separate their control.
Let’s remind that the mission of the U.S. Cyber Command is to disrupt and destroy enemies infrastructures and to defend the US against incoming cyber threats.
The documents leaked by Snowden clarify the mission of the NSA that is more focused on intelligence operations on adversaries and foreign governments.
U.S. Cyber Command has grown over time, its mission has become even clearer with increasing awareness of the cyber threat. Since the Stuxnet against the Natanz nuclear plant, something has changed permanently and dual-hat arrangement is considered no more effective for the US cyber strategy.
“While the dual-hat arrangement was once appropriate in order to enable a fledgling Cybercom to leverage NSA’s advanced capabilities and expertise, Cybercom has since matured.” to the point where it needs its own leader, Obama said in a statement accompanying his signing of the 2017 defense authorization bill.
Obama believes that the Cybercom urges its own leader, he confirmed it in a statement accompanying his signing of the 2017 defense authorization bill.
“The two organizations should have separate leaders who are able to devote themselves to each organization’s respective mission and responsibilities, but should continue to leverage the shared capabilities and synergies developed under the dual-hat arrangement,” Obama wrote about the dual-hat arrangement.
The Obama decision to separate the heads of the two organizations was supported by the Defense Secretary Ashton B. Carter and Director of National Intelligence James R. Clapper Jr.,
The idea of separating the heads of the two organizations is not new, President Obama proposed it back in 2013.
“Obama had been on the verge of ending the dual-hat leadership in late 2013 but was persuaded to hold off when senior officials, including the NSA’s director at the time, Army Gen. Keith B. Alexander, argued that the two agencies needed one leader to ensure that the NSA did not withhold resources from Cybercom.” wrote The Washington Post.
A presidential review commission the end of the dual-hat arrangement and suggest the assignment of the NSA direction to a civilian and not to a military official.
The bill that Obama signed bars the splitting of the leadership role until the defense secretary and the chairman of the Joint Chiefs of Staff jointly certify that to do so would not diminish Cybercom’s effectiveness.
“The Congress . . . should not place unnecessary and bureaucratic administrative burdens and conditions on ending the dual-hat arrangement at a time when the speed and nature of cyber threats requires agility in making decisions about how best to organize and manage the nation’s cyber capabilities,” added Obama.
The transition will not be instantaneous, the Pentagon and the Office of the Director of National Intelligence have planned a period during which the NSA can continue to “provide vital operational support” to Cybercom.
Cyanogen Shutting Down All Services; No More Android ROM Updates
26.12.2016 thehackernews OS
A bittersweet Christmas and New Year for users and fans of the most popular custom Android ROM, Cyanogen OS.
Cyanogen that tried and failed to kill Google's Android operating system is now shutting down the custom services that it provides to phones that run its Cyanogen OS as we know it and the "nightly builds" of said OS on December 31st.
Cyanogen came with an ambition to build better versions of the Android operating system than those created by Google itself, but following some technical and potential legal issues, the startup has decided to quit.
The planned shutdown of Cyanogen was officially announced late Friday through a very brief blog post made by the company, saying "as part of the ongoing consolidation of Cyanogen," it's shutting down all services and nightly builds on December 31.
"The open source project and source code will remain available for anyone who wants to build CyanogenMod personally," the blog reads.
What About Cyanogen OS-Powered Smartphones?
From January 2017, there will be no further updates to the Cyanogen OS, no more nightly builds, and no more security updates.
Eventually, smartphones running on the Cyanogen OS, like the original OnePlus One and Lenovo ZUK Z1, will have to switch to the open-source version of the CyanogenMod operating system.
CyanogenMod OS is not a commercial operating system and is managed by a community of developers led by Steve Kondik, the co-founder of Cyanogen.
'Death Blow' to CyanogenMod
However, the CyanogenMod team believes that the shutdown of Cyanogen is a "death blow" to CyanogenMod, the team announced just after the closure announcement by Cyanogen.
CyanogenMod team pays respects to the community as it served for more than eight long years and announced the next open-source Android project.
Embracing the spirit of Cyanogen, the CyanogenMod team of developers, designers, device maintainers, and translators are now working to produce a fork of the CyanogenMod source code and pending patches.
Next? CyanogenMod Team Launches Lineage OS
While both Cyanogen and CyanogenMod are saying goodbye this year, the spirit of CyanogenMod will continue to live on in the new open source project.
Dubbed LineageOS, the new OS is still in its inception phase and would take some time for people to see any progress from the newly formed unit.
According to the CyanogenMod (CM) team, Lineage "is more than just a ‘rebrand’" and "will return to the grassroots community effort that used to define CM while maintaining the professional quality and reliability you have come to expect more recently."
A website is being developed for LineageOS, and the GitHub repository can be found populated with CM files, called Lineage Android Distribution. The beginning of this new open source project "will be a continuation of what CyanogenMod was."
Hacker Interviews – R.I.U. crip (@cripthepoodle) – Security Affairs
26.12.2016 securityaffairs
@cripthepoodle is one of the members of the dreaded PoodleCorp hacker crew recently he targeted Steam platform, let’s meet him.
@cripthepoodle
You are a talented hacker that is very active online, could you tell me more about you. Could you tell me which his your technical background and when you started hacking?
I started to get into coding java in 2010 then met people on Xbox who enjoyed stuff I liked to do those people are Jordie and Kyle
Which are your motivations?
My motivation is just to cause chaos for fun and make some money
What was your greatest hacking challenge? Which was your latest hack? Can you describe me it?
I never really had a challenge except when I first started and I helped para and anti attempt to get root on .mil which went horribly wrong rofl which wasn’t my fault btw.
My lasted attack was on Steam at approximately 10:40 am December 23rd and I did the attack by being behind iptables on a Linux VPS and dropping all UDP packets, those packets are going to hit the servers then boom it’s offline
What are the 4 tools that cannot be missed in the hacker’s arsenal and why?
4 tools I honestly don’t know. Everyone has a different skill set I’m not the smartest person in the ” scene ”
Which are the most interesting hacking communities on the web today, why?
The most interesting is probably Twitter because it’s fun to mess with people but the most serious are IRC chats that are used by a lot of smart guys.
Did you participate in hacking attacks against the IS propaganda online? When? How? Where do you find IS people to hack?
No, I wasn’t behind that.
How do you choose your targets?
I choose my targets by asking my fans or asking people what they think would be the best one.
We often hear about cyber weapons and cyber attacks against critical infrastructure. Do you believe it is real the risk of a major and lethal cyber attack against a critical infrastructure?
Definitely yes
Cryptolulz666 hacked the Dutch Chamber of Commerce in HK
26.12.2016 securityaffairs Hacking
@Cryptolulz666 and his colleague Kapustkiy broke into the systems of another website belonging to a HK corporation, the Dutch Chamber of Commerce.
The hacker @Cryptolulz666, with a little help from the colleague Kapustkiy, has broken into the website of the Dutch Chamber of Commerce in Hong Kong (http://www.dutchchamber.hk/).
The hacker accessed data belonging to around 200 users, but he decided to leak only half of them as proof of the hack.
Cryptolulz666 told me he exploited a SQL injection vulnerability affecting the website.
A few days ago, he hacked “The Standard Hong Kong” newspaper, he confirmed me that his choice is not casual, he wants to target organizations in Hong kong.
“Yes … As you seen in the previous hack I chose a big corporation in Hong kong and I succeded… this time also chose Hong Kong because I want to make an impact on this country.” he told me. ” no country is safe”
He highlighted the fact that a silly flaw like a SQL Injection could have serious consequences if admins ignore the pillars of security.
Data leaked on Pastebin includes data related to companies working with the Dutch Chamber of Commerce.
Cryptolulz ( @Cryptolulz666) is a former member of the Powerful Greek Army, who hacked several government websites, including the one of the Russian embassy of Armenia (www.embassyru.am).
He also launched DDoS attacks against the website http://italiastartupvisa.mise.gov.it/ belonging to the Italian Government and the website of the Russian Federal Drug Control Service liquidation commission.
The Turkish Government is investigating more than 10,000 people in terror probe
26.12.2016 securityaffairs Cyber
The Turkish Government is investigating 10000 people suspected of terror-related activity on the internet,accused of propaganda or apologizing for terrorism
The Turkish authorities are investigating more than 10000 individuals over online terror activities. The suspects are accused of being responsible for the sharing of material and post against government officials.
According to the Interior Ministry, the inquiries are part of the “fight against terrorism, which continues with determination everywhere, including on social networks.”
The pressure of the Turkish government is increasing since the coup attempt occurred in July. Authorities are applying a strict censorship of online activities of its citizens.
The Turkish Government has applied restrictions on the Tor anonymity network, and more in general all VPN services, that could be used to avoid censorship.
“Turkey declared a state of emergency and launched deep purges of perceived opponents, sparking concern among human rights groups which accuse Ankara of repression.” reported The SUN.
The Turkish authorities have questioned more than 3,000 people in the last six months, 1,656 of them have been arrested and 84 are still being questioned.

The accusation for them is “propaganda or apologizing for terrorism” and “insulting state officials.”
The situation in the country is aggravated after the assassination of the Russian Ambassador Andrei Karlov that occurred last week during an exhibition in Ankara. Investigators believe the assassination is part of a terrorist plot to destabilize the relationship between Russia and Turkey.
The Turkish Government fears possible interference through social media, Twitter and YouTube have slowed since the publication of a video in which members of the ISIS burned alive two captured Turkish soldiers.
Počítačoví piráti nepolevují ani po Štědrém dnu
26.12.2016 Novinky/Bezpečnost Kriminalita
S nejrůznějšími podvody se před Vánocemi doslova roztrhnul pytel. Počítačoví piráti ve svých snahách ale nepolevují ani po Štědrém dnu. Lidé by se měli mít na pozoru například před různými elektronickými přáními a nejrůznějšími phishingovými útoky.
Mezi nejčastější podvody na síti patří v posledních dnech zavirovaná elektronická přání. Ta se šíří především prostřednictvím nevyžádané pošty. Výjimkou ale nejsou ani případy, kdy se takovéto zprávy objevovaly na sociálních sítích nebo v chatovacích programech.
Přijít mohou klidně od přátel, kterým se již nezvaný návštěvník zabydlel v počítači a nemají o tom ani potuchy.
Hrozba zavirovaných elektronických přání je stále aktuální. Lidé si totiž přejí nejen k Vánocům, ale také vše nejlepší do nového roku.
Snaží se vylákat hotovost, stejně jako citlivé údaje.
Podvodníci využívají i toho, že obchodníci ještě před koncem roku rozjedou výprodeje. Škodlivými kódy jsou zamořeny také nejrůznější nabídky na výhodné nákupy v podvodných internetových obchodech.
Do počítače kybernetickým zlodějům lidé otevřou cestu ve chvíli, kdy se nechají zlákat atraktivní cenou a kliknou na nějaký odkaz. Od uživatelů se snaží touto cestou kyberzločinci vylákat hotovost, stejně jako jejich citlivé údaje.
Většinu podobných útoků je možné na první pohled rozeznat podle špatné češtiny.
Připraven celý rok
Na útoky počítačových pirátů je vhodné být připraven celý rok. Lidé totiž na pevných discích uchovávají stále více citlivých informací. Vedle osobních fotografií také kopie občanských a řidičských průkazů, nejrůznějších smluv a samozřejmě i hesla k online účtům, a to zpravidla i včetně internetového bankovnictví.
Když se kybernetický nájezdník k takovým citlivým datům dostane, je to pro něj jako objevit poklad, na černém trhu totiž všechna data prodá za nemalé sumy. K průnikům jsou využívány viry a trojské koně.
Odhalit takové smetí pomáhají programy, z nichž každý se specializuje na něco jiného. Některé si dovedou poradit s trojskými koni či spywarem a další zase detekují takzvané keyloggery (program zaznamenávající stisk každé klávesy).
Na PC by měl být nainstalován vždy jen jeden bezpečnostní program svého druhu. Dva antiviry na disku dokážou udělat pěknou neplechu. To samé platí také o firewallech i antispywarech. Vhodné je také pravidelně sledovat statistiky antivirových společností o nejrozšířenějších hrozbách. Tak je možné poznat, na co si dávat pozor.
Malware distribution tactics used in phishing campaign
25.12.2016 securityaffairs Virus
Experts from Proofpoint discovered a new phishing campaign designed to steal banking data leveraging tactics associated with malware distribution.
Security experts from Proofpoint have discovered a new phishing campaign that presents many similarities with campaigns used to spread the Cerber ransomware and the Ursnif banking Trojan.
Cyber criminals adopted a technique that leverages on the distribution of password-protected .zip archive containing a malicious document. The email messages sent by the crooks have the .zip file attached and the message content includes the password to open the archive.
The phishing campaign aims to steal credit card data from the victims, the criminals sent them an HTML attachment that has been password-protected.

The email represents the first digits of the victim’s credit card account number aiming to create a sense of legitimacy without requiring actual knowledge of a potential victim’s actual card number.
The email attempts to trick the victim into giving away their credit card data, they have a sense of urgency requesting recipients to update their security information for their “new chip card.”
“The email sample that we analyzed was personalized with the recipient’s name and what appear to be the starting digits of their credit card account number. The starting digits for credit cards are standardized, though, so this just adds to the apparent legitimacy of the carefully crafted emails without requiring actual knowledge of the recipient’s’ card number.” states the report published by Proofpoint. “The emails also use stolen branding and social engineering to create a sense of urgency encouraging the recipient to update security information for their “new chip card””

The HTML file attachment used in this campaign was XOR-encoded to make harder the dynamic analysis.
Researchers noticed that HTML attachment uses JavaScript to implement the password protection instead using the password-protection feature in Microsoft Word.
When the victim enters the password the HTML attachment is decrypted and a typical credit card phishing template complete with stolen branding is displayed.
“Credential and credit card phishing are nearly as old as cybercrime itself. This hasn’t stopped phishing actors from innovating, exploring new approaches to convincing users to divulge personal, banking, and financial information. In this case, we observed threat actors taking a cue from malware distributors, using password protected document attachments to bypass anti-malware technologies and give recipients a false sense of security,” added Proofpoint.
Moscow wants Apple to unlock iPhone of the killer of the Russian Ambassador
25.12.2016 securityaffairs Apple
The Russian and Turkish authorities asked Apple to unlock iPhone belonging to the assassin of Russian Ambassador Andrei Karlov.
The Russia’s ambassador to Turkey, Andrei Karlov, was killed on Monday during an exhibition in Ankara. The killer is a lone Turkish gunman that shouted “God is great!” and “don’t forget Aleppo, don’t forget Syria!”
The shooter was killed by Turkish forces in a shoutout and his iPhone 4s was recovered from the special forces.
The man who killed the Russian ambassador was identified as Mevlut Mert Altıntas, an off-duty police officer who used his police ID to gain access to the exhibition where Karlov was giving a speech.
Russian Ambassador Killer
Now Russian authorities want Apple to unlock the killer’s iPhone belonging to Killer of Russian Ambassador.
According to the investigators, the shooter pretended to be an official bodyguard, now Turkish and Russian authorities asked Apple to support the authorities by unlocking the shooter’s iPhone 4S. The request can trigger a new dispute between the Tech giant and the Kremlin, in a similar way to the San Bernardino Shooter case. the authorities believe, could assist them to investigate killer’s links to various terrorist organizations.
The authorities believe that the content on the iPhone could be useful to unmask the terrorist organization linked to the shooter.
It is quite easy to predict a refuse from Apple, for this reason, the Russian government is reportedly sending a team of experts to Ankara to unlock the shooter’s iPhone.
“Apparently Russia offered help and Russia is planning to send a special technical team to Turkey to unlock the iPhone, a senior Turkish official told us.” reported Macreports.com.
According to Macreports the team of experts arrived from Moscow could not unlock the iPhone, but the team was able to retrieve some data from the device without fully unlocking it.
Experts believe the assassination was part of a plot to destabilize the relationship between the Russian Government and the Turkish one.
Merry Xmas, @Kapustkiy hacked Russian Visa center in USA
25.12.2016 securityaffairs Hacking
The notorious white hat hacker Kapustkiy hacked the Russian Visa Center in the USA and accessed information of around 3000 individuals.
The Russian Visa Center is an organization that helps Americans to obtain Russian Visa, this morning the white hat hacker Kapustkiy informed me that he broke into the database its website and accessed data of around 3000 individuals.
Kapustkiy told me to have exploited a SQL Injection in the website, he hacked the website on Friday.
“I used SQL Injection to gain access” said Kapustkiy.
He shared with me the records as proof of the hack, the leaked information include data about individuals that obtained the Russian Visa.

The Russian Visa Center is part of Invisa Logistic Services, it has five offices in the US where people can receive assistance in getting a Russian visa.
The records include their full names, emails, phone numbers, birthday and other information. The archive also includes data of the staff, such as full names, usernames, encrypted passwords, permissions and other information.
Kapustkiy will not make public the accessed data because the database contains sensitive information,
The young hacker contacted the Russian Visa Center but hasn’t received any response, he also reported the issue to the US-CERT.
The young hacker is very active, a few days ago he announced the hack of website of the Costa Rica Embassy in China and the data breach of the Slovak Chamber of Commerce (www.scci.sk) that affected more than 4,000 user records.
Recently Kapustkiy targeted several organizations, including the Consular Department of the Embassy of the Russian Federation, the Argentinian Ministry of Industry, the National Assembly of Ecuador, the Venezuela Army, the High Commission of Ghana & Fiji in India, the India Regional Council as well as organizations and embassies across the world.
He also broke into the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
Hackers threaten to take down Xbox Live and PSN on Christmas Day
24.12.2016 thehackernews Hacking
It's once again the time when most of you will get new PlayStations and XBoxes that continue to be among the most popular gifts for Christmas, but possibilities are you'll not be able to log into the online gaming console, just like what happens on every Christmas holidays.
On 2014 Christmas holidays, the notorious hacker group Lizard Squad knocked the PlayStation Network and Xbox Live offline for many gamers by launching massive DDoS attacks against the gaming networks.
This time a new hacking group, who managed to take down Tumblr this week for almost two hours, has warned gamers of launching another large-scale distributed denial-of-service (DDoS) attack against XBox Live and PlayStation networks.
Calling itself R.I.U. Star Patrol, the hacking group, posted a video on YouTube, announcing that they’re planning to take down Sony’s PSN and Microsoft’s Xbox Live on Christmas Day by launching coordinated DDoS attacks.
"We do it because we can," the group said. "We have not been paid a single dollar for what we do."
On Wednesday, when R.I.U. Star Patrol took down Tumblr, the group contacted Mashable and explained its reason for attacking: "There is no sinister motive. It’s all for light hearted fun."
Neither Sony nor Microsoft has yet responded to the hackers' warning.
However, both Sony and Microsoft previously promised to enhance the protection of their systems to block any attack disrupting their networks, but downtime and short outages happened almost every Christmas time.
Knowing the current abilities of hackers to launch DDoS attack that can reach 1 Tbps, it goes without saying that both the companies should be prepared to see DDoS attacks targeting its servers on this Christmas that can go beyond their expectations.
We saw coordinated DDoS attacks against DNS hosting provider Dyn last fall that broke large portions of the Internet, causing a significant outage to a ton of websites and services, including Twitter, GitHub, PayPal, Amazon, Reddit, Netflix, and Spotify.
The massive DDoS attack was launched just by a botnet of an estimated 100,000 so-called Internet of Things (IoT) – everyday devices and appliances that are connected to the web – that closed down the Internet for millions of users.
So, it remains to be seen if gamers would be able to enjoy this Christmas or not.
Hackers breached the “The Standard Hong Kong” newspaper
24.12.2016 securityaffairs Hacking
The hacker @Cryptolulz666 and his colleague @EvoIsGod have broken into the website of the Hong Kong English newspaper “The Standard Hong Kong” (www.thestandard.com.hk)
The hackers breached the database of the website and uploaded data to Pastebin.
I reached the hackers who confirmed to have hacked the website by exploiting a SQL Injection flaw in their CMS.

The hackers posted only a small portion of around 12000 users contained in the database.
“Most of the info is not dumped due to legal stuffs. It had around 12000 users but I dumped only quarter” wrote the hackers on Pastebin.
The hackers leaked the tables of the Customers and Employees.
According to @Cryptolulz666, most of the information in the database is quite confidential and should not be leaked for privacy reason.
When I asked them about the motivation of the attack they told me that their goal is to spread awareness of cyber security.
“Our objective is to embarrass the institutions… by exploiting their silly flaws…” they told me. “As I said we exploited a SQL injection vulnerability on their main website.”
Cryptolulz ( @Cryptolulz666) is a former member of the Powerful Greek Army, who hacked several government websites, including the one of the Russian embassy of Armenia (www.embassyru.am).
He also launched DDoS attacks against the website http://italiastartupvisa.mise.gov.it/ belonging to the Italian Government and the website of the Russian Federal Drug Control Service liquidation commission.
Hackers want to take down Xbox Live and PSN on Christmas Day
24.12.2016 securityaffairs Hacking
Christmas time is a critical period for the gaming industry that is threatened by hackers that want to paralyze their services with massive attacks.
Yesterday I reported the DDoS attacks launched by Phantom Squad and PoodleCorp against Steam and Origin Servers, and unfortunately they are not alone.
Hackers threaten to take down Xbox Live and PSN on Christmas Day, and we know that someone already done is in the same period two years ago when Lizard Squad hackers took down the networks of Sony PSN and Microsoft XBox Live.
Which are the risks for gamers?
People that will buy or will receive new PlayStation and XBoxe consoles will not be able to log into the online gaming console, it will be not possible to download and buy online games, neither play online with other gamers.
Now a hacker group that called itself R.I.U. Star Patrol (StarPatrolling) posted a video on YouTube, announcing that they will take down Xbox Live and PSN on Christmas Day with a massive DDoS attack.
The threat is considered credible, the same group managed to take down Tumblr this week for two hours.
“We do it because we can,” the group said. “We have not been paid a single dollar for what we do.”
Segui
R.I.U. Star Patrol @StarPatrolling
@mashable We are claiming responsibility for the Tumblr outage #StarPatrol
23:14 - 21 Dic 2016
1 1 Retweet 2 2 Mi piace
Just after the attack, the hackers released an interview with Mashable and motivated the attack with the following statement.
“There is no sinister motive,” they replied when asked for the cause of the attacks.”It’s all for light hearted fun.”
Via DM, the group told Mashable the DDoS attack wasn’t meant to harm anyone.
Xbox Live and PSN networks were both target in the past by hacker so they worked to improve their defense anyway recent attacks powered by the Mirai botnet demonstrated that it could be quite simple for hackers to take down major web services.
Phantom Squad and PoodleCorp tango down against Steam and Origin Servers
24.12.2016 securityaffairs Hacking
The servers of the Steam gaming platform and Origin are down. Phantom Squad and PoodleCorp are claiming responsibility for the attacks.
It’s holiday time and hackers can transform this period in a nightmare for gamers. Two years ago Lizard Squad hackers took down the networks of Sony PSN and Microsoft XBox Live.
Now the notorious Phantom Squad group has claimed responsibility for conducting a series of massive DDoS attacks against the online gaming platform Steam and Origin servers.
According to HackRead, Phantom Squad and one of the members of the PoodleCorp hacker crew, @cripthepoodle, are targeting Steam and Origin accounts.
One year ago, Phantom Squad launched several cyber attacks against Electronic Arts and Steam last year. PoodleCorp hacker group became famous due to a long string of attacks against gaming communities, including Blizzard, EA, GTA, PlayStation, PokemonGo, and League of Legends.
At the time I was writing, both companies haven’t confirmed the attacks against their systems. Some users are reporting problems to both via Twitter.
Below one of the numerous tweets from affected users:
22 Dic
Steam ✔ @steam_games
Steam Winter Sale On Now! Plus, Vote For The Steam Awards! #SteamSale #SteamAwards http://zpr.io/PGkCe pic.twitter.com/T3iqTvsPgI
Segui
René | 2 Days ^-^ @DafuqRene
@steam_games Nice Sale, I love it! #SteamSale pic.twitter.com/RshEFsBBDk
20:14 - 22 Dic 2016
13 13 Retweet 80 80 Mi piace
The Down Detector service that provides information about the status of services confirmed that both EA and Steam platforms were down at the time I was writing.
The hackers started the DDoS attack on Steam servers causing serious problems to the gaming servers across the world. Steam operates about 17 regional servers, all its activities including the Steam community and the Steam Store are down, this means that users are not able to buy Steam games for Christmas.

Stay Tuned …
Update
Steam services are back up now