
Hacker Buba is asking UAE bank for $3 million ransom
6.12.2015
A criminal named Hacker Buba after asking UAE bank for $3 million ransom started leaking customer data online.
Last week a hacker, who named itself as ‘Hacker Buba,’ breached a United Arab Emirates Bank, then he start tweeting customers’ information announcing the disclosure of tens of thousands of customer files online if a $3 million ransom will not be paid.
Hacker Buba tweeted information, mostly belonging to corporate accounts at the Invest Bank. He requested the payment of a $3 million ransom in Bitcoin to stop leaking the sensitive information.
It appears that the hacked bank has no intention to pay the full ransom.
Hacker Buba initially tweeted from accounts like @investbank_2, that were promptly suspended by Twitter, but it was not enough to stop the hacker who late Tuesday started to spread the same message from nearly 50 Twitter accounts. The Twitter message included the name Invest Bank and a link to a site, managed by the Hacker Buba, which host six zip files containing the bank data.
The website used by the hacker to leak the archives belong to an eastern European basketball team, and Hacker Buba compromised it.

According to the Daily Dot, the data leaked by Hacker Buba appears to be real, one of the archive analyzed by the news agency contained financial information of the bank customers.
“One database analyzed by the Daily Dot includes the sensitive information of around 40,000 customers, including their full names, credit card numbers, and birthdays. One account contained 4,7174,962.38 dirham, or $12,844,589.77. Those accounts’ total earnings add up to $110,736,002. Other databases show information for other customers, and include detailed transaction histories.” states the blog post published by the Daily Dot.
This morning the Invest Bank Assistant Manager for General Operations Qasim Kazmi sent an email to the Daily Dot confirming that the financial institute will not pay the ransom
“No we have not paid nor do we intend to or negotiate with blackmailers.”
At the same time, the website hacked by Buba seems to have been restored by the legitimate owners.
EFF Scoreboard – Secure Messaging, stay safe online
6.12.2015
Learn more about the EFF scoreboard for secure, encrypted communication options online and what the future holds.
Online communications have been increasing rapidly over the past few years. However, there are many incidents revealing Internet surveillance. If you think of Edward Snowden and the revelations that he had brought to the public about NSA and mass surveillance acts, you will see why we need a way of securely communicating with each other online.
Even though there are a plethora of options out there, not many can take pride in being reliable and safe to use. If you are in search of the best alternatives available to this date, have a look at the EFF scoreboard.
In the EFF scoreboard, all the options that we get today in communication are analyzed as per their features and level of encryption. The criteria used by the experts include the ability of encryption in transit, encryption that does not allow the provider to read what you are communicating, verification of the sender’s and recipient’s identities, security of past communications and open code, proper documentation and code audit.

As you can imagine, this is only the beginning and EFF is planning to move forward with a more detailed scoreboard in the near future.
From the EFF scoreboard, we can get quite a few enlightening pieces of information.
For example, BlackBerry Messenger does not score well – on the contrary, BlackBerry Protected is much more reliable as an option of communication. ChatSecure + Orbot, CryptoCat and Off the Record Messaging for Windows (Pidgin), Signal/RedPhone, Silent Phone and Silent Text, TextSecure and Telegram have passed the test with flying colors. On the other hand, Yahoo!Messenger and WhatsApp, Viber and Skype are not that secure. They do not offer adequate encryption and thus they are not to be trusted.
Cryptography is the number one criterion when we seek safe and secure communication. Nevertheless, we see that more and more people nowadays continue on using unsafe methods of communication.
Although they have been warned about potential risks, they go ahead with their habits and do not change them for something else. This happens due to the fact that the broadly used programs are easier to use.
If something of quality and ease of use was to be released, people would look it up and try it out. This is what EFF, Julia Angwin at ProPublica and Joseph Bonneau at the Princeton Center for Information Technology Policy all have been trying to accomplish.
Safe, secure and usable cryptography can save the day and offer people of all backgrounds (tech savvies and not) the chance to remain protected while communicating with others.
These Top 10 Programming Languages Have Most Vulnerable Apps on the Internet
5.12.2015
A new research showed that Scripting languages, in general, give birth to more security vulnerabilities in web applications, which raised concerns over potential security bugs in millions of websites.
The app security firm Veracode has released its State of Software Security: Focus on Application Development report (PDF), analyzing more than 200,000 separate applications from October 1, 2013, through March 31, 2015.
The security researchers crawled popular web scripting languages including PHP, Java, JavaScript, Ruby, .NET, C and C++, Microsoft Classic ASP, Android, iOS, and COBOL, scanning hundreds of thousands of applications over the last 18 months.
Also Read: A Step-by-Step Guide — How to Install Free SSL Certificate On Your Website
Researchers found that PHP – and less popular Web development languages Classic ASP and ColdFusion – are the riskiest programming languages for the Internet, while Java and .NET are the safest.
Here's the Top 10 List:
The Veracode research report used a unique metric, Flaw Density per MB, which means the number of security bugs in each MB of source code.
Programming-Language
Here's the list of unlucky winners:
Classic ASP – 1,686 flaws/MB (1,112 critical)
ColdFusion – 262 flaws/MB (227 critical)
PHP – 184 flaws/MB (47 critical)
Java – 51 flaws/MB (5.2 critical)
.NET - 32 flaws/MB (9.7 critical)
C++ – 26 flaws/MB (8.8 critical)
iOS – 23 flaws/MB (0.9 critical)
Android – 11 flaws/MB (0.4 critical)
JavaScript - 8 flaws/MB (0.09 critical)
Web Apps in PHP are Most Vulnerable, Here's Why:
PHP, which is on third, is actually leading the ranking because ColdFusion is a high-end niche tool and Classic ASP is almost dead.
Taking a closer look at PHP:
86% of applications written in PHP contained at least one cross-site scripting (XSS) vulnerability.
56% of apps included SQLi (SQL injection), which is one of the dangerous and easy-to-exploit web application vulnerabilities.
67% of apps allowed for directory traversal.
61% of apps allowed for code injection.
58% of apps had problems with credentials management
73% of apps contained cryptographic issues.
50% allowed for information leakage.
From above issues, SQLi and XSS are among the Open Web Application Security Project's (OWASP) Top 10 most critical web application security risks.
And the Title of "Most Vulnerable Programming Language of Year 2015" Goes to...
SQL injection bugs – which allow hackers to directly interact with a Web site's database – are the ones that have been blamed for the massive data breaches at kiddie toymaker VTech and telecom firm TalkTalk.
According to the report, the risk size of the above vulnerabilities can be measured by the volume of PHP apps developed for the Top 3 CMS (Content Management Systems) – WordPress, Drupal and Joomla – that represent over 70% of the CMS market.
Choose Your Scripting Language Wisely
Less than a quarter of Java applications contain SQL injection flaws, compared to more than three-quarters of those applications written in PHP.
"When organizations are starting new development projects and selecting languages and methodologies, the security team has an opportunity to anticipate the types of vulnerabilities that are likely to arise and how best to test for them," Veracode's CTO Chris Wysopal advised.
For more details, you can download Vercode's State of Software Security Report (PDF).
How to Run Multiple Android apps on Windows and Mac OS X Simultaneously
5.12.2015
How to Run Multiple Android apps on Windows and Mac OS X Computer Simultaneously
Bluestacks, the first app player for running Android apps on Windows, has launched the latest version of its Android emulator platform with one major upgrade:
The Ability to Run Multiple Android apps Simultaneously.
BlueStacks 2 Released
Bluestacks previously only run a single app at a time. However, with the launch of BlueStacks 2, the app adds a tabbed interface that allows you to jump between multiple Android apps in the same window.
This is great for you to run gaming and messaging apps, or news and messaging apps at the same time.
The update also adds a toolbar that allows you to quickly tell the Android emulator to simulate rotating the device screen or to perform other functions, such as copying and pasting.
In BlueStacks 2, players now have options to marry gameplay and app discovery, meaning when they click an advertisement, a new tab will appear so that the players can continue playing their games without being interrupted.
How to Run Multiple Android apps Using BlueStacks 2
How to Run Multiple Android apps on Windows and Mac OS X Simultaneously
BlueStacks 2 is currently available only on Windows, but will soon debut on Macs in July.
Follow these simple steps to go:
Step 1: To use and run multiple Android apps simultaneously, you need to first Download BlueStacks 2, which is free.
Step 2: Install BlueStacks 2 software on your Windows computer.
Step 3: Once installed, you will land on the Welcome Tab. Just Move to 'Android' tab.
account-setup
Step 4: Software will ask you for One-time Google Account Setup, just like an Android device ask for.
Step 5: Login with your Google account to complete the Setup and you are ready!
Step 6: From 'Android' tab select multiple apps you want to run in parallel. BlueStacks 2 will open each app in a new Tab within the software interface.
New Milestone Achieved
With the seventh-largest Android user base in the world, Bluestacks has crossed more than 109 Million app downloads, engaging more than 1.1 Billion Android apps every month.
"When we started, mobile apps, with their crisp resolution looked and sounded gorgeous on PC and TV," said Shashi Kant Sharma, Product Manager at BlueStacks.
"What we’ve learned is that the wider visual space lends itself more naturally to app discovery. Once someone discovers apps on PC or TV, they tend to use them across all of their devices, giving the BlueStacks platform powerful reach for developers."
Kazakhstan makes it Mandatory for its Citizens to Install Internet Backdoor
5.12.2015
Kazakhstan makes it Mandatory for its Citizens to Install Internet Backdoors
Next in the queue, Kazakhstan is also planning to Spy on encrypted Internet Traffic of its citizens, but in the most shameless way.
Unlike other spying nations that are themselves capable of spying on their citizens, Kazakhstan will force every internet user in the country to install bogus security certs on their PCs and mobile devices, allowing the 'Dictator' Government to:
Intercept users' Internet traffic to any Secure website, i.e. Man-in-the-Middle Attack
Access everything from user's web browsing history to usernames and passwords to secure and HTTPS-encrypted traffic
This Program will seriously restrict Citizens' Freedom of Speech and Expression.
What the F… is "National Internet Security Certificate"?
On Monday, the nation's largest Internet service provider Kazakhtelecom JSC published a notice, which said:
Citizens are "obliged" to install a so-called "National Internet Security Certificate" on every device, including desktops, laptops, and mobile phones.
Then overnight on Wednesday, the notice mysteriously vanished, but you can view the archived version of the notice here.
Also Read: Today NSA has Stopped its Bulk Phone Surveillance Program
Country-Wide "Superfish" Campaign
"The National Security Certificate will secure protection of Kazakhstan users when using coded access protocols to foreign Internet resources," read the notice published by Kazakhtelecom at the beginning of this week.
This simply means:
The Government's shameless 'National Security certificate' program – most likely a root CA cert similar to those found in Lenovo's Superfish and Dell's Superfish 2.0 scandals – will target users' access to encrypted services that rely on Internet traffic being routed outside of Kazakhstan.
However, traffic between Servers located in Kazakhstan won't be affected.
The surveillance will begin from January 1; less than a month from now.
Also Read: NSA will not Stop Spying on us.
This move by the country will not only compromise users' freedom of speech and expression but also limit their privacy over the Internet.
Kazakhstan surveillance program is somewhat different from the NSA spying on American citizens, as, in this case, Kazakhs have to personally hand over the keys to their Web traffic to the government.
It is still unclear if the measure is being withdrawn with the vanish of the notice. However, more details about this are scheduled to be published later this month.
Kazakhstan – Telco Company Kazakhtelecom will order their costumers to install rogue certificates
5.12.2015
The Government of the Kazakhstan makes it mandatory for its citizens to install rogue security certificates to monitor them online.
The Government of the Kazakhstan plans to implement a new internet control policy for all the population starting from January 1st 2016, and to accomplish that will order the population to install some rogue security certificated leaving Kazakhtelecom( the ISP) able to do MiTM.
This information was announced Monday, and state that all the other operators are obligated by law to do the same, meaning that all HTTPS connections in Kazakhstan will be inspected.
We don’t know exactly how they will accomplish that, but the idea behind is that every device (computer, mobile, etc.) is installed with a root CA certificate similar to the ones announced in Lenovo and Dell’s computers, called Superfish.
Everyone with this certificate will be subjected to Man-in-the-Middle attacks because the web browser instead of connecting directly to a website like Google.com, will first pass through Kazakhstan control servers before going to Google.com.

It looks like after this information was released, Kazakhtelecom took it out from their website, but details about how to install the certificates will be released soon.
Making people to install a “malicious” certificate doesn’t sound nice mainly because will make the Kazakhstan government able to grab people’s passwords and other important data, and allows the government to control the population, and to censor whatever they want.
“According to the law, telecom operators are obliged to perform traffic pass using protocols that support coding using security certificate, except traffic, coded by means of cryptographic information protection on the territory of the Republic of Kazakhstan,”
“The national security certificate will secure protection of Kazakhstan users when using coded access protocols to foreign Internet resources.” Reads a translation from the original Kazakhtelecom.
Kazakhstan has a long history of censorship, it is considered one of the governments in the long list of the enemies of the Internet by privacy advocates. I have extracted the number of Tor users in the country, the graph shows that the number of users connected to Tor is doubled in the last couple of years.

The Internet monitoring and censorship activities are increasing as never before, is this the future we want for us?
Someone wants to spy on you everything you do.
Millions of smart devices at risk from 3-year-old flaw
5.12.2015
According to Trend Micro up to 6.1 million smart devices, including this smart TV and routers haven’t patched a software vulnerability dating from 2012.
Millions of smart TVs, routers and phones are at risk due to a presence of a 3-year-old vulnerability in a software they use. According to the experts at Trend Micro, the security flaw hasn’t been patched by many vendors despite the availability of a patch since 2012.
“A total of 6.1 million devices – smart phones, routers, smart TVs – are currently at risk to remote code execution attacks due to vulnerabilities that have been fixed since 2012.” wrote Veo Zhang, a mobile threats analyst at Trend Micro. “The vulnerabilities exist in the Portable SDK for UPnP™ Devices, also called libupnp. This particular library is used to implement media playback (DLNA) or NAT traversal (UPnP IGD). Apps on a smartphone can use these features to play media files or connect to other devices within a user’s home network.”
Trend Micro discovered that 547 apps that use an unpatched version of the software component, 326 are available in Google’s Play app store and most of the apps are very popular and used by million users. One of the affected apps is QQMusic that is distributed by Tencent, the company promptly released an update for the Android app on Nov. 23 after the disclosure of the news.
“These are very popular apps that put millions of users in danger; aside from mobile devices, routers, and smart TVs are all at risk as well,” he added.
We discussed several times about smart devices, aka IoT devices, and their capability to gather and share huge quantities of information, including sensitive data, raising serious concerns in term of privacy.
Our surface of attack is enlarging as never before, both in workplace and in the private life, experts in the security industry sustain that the majority of IoT vendors doesn’t adopt a security by design approach. It is quite common to find smart objects poorly configured or affected by critical security flaws.
In this specific case emerges the inability of manufacturers to implement an efficient patch management. Million of vulnerable devices, such as routers and smart TVs, are exposed on the Internet.
The experts at Trend Micro confirmed that threat actors are already attacking these vulnerable devices, exploiting the flaws the attackers would take complete control of the targeted system.
Once identified a vulnerable device, an attacker can send a specially crafted packet to trigger a buffer overflow. In the code below, the TempBuf buffer can overflow and cause a crash.
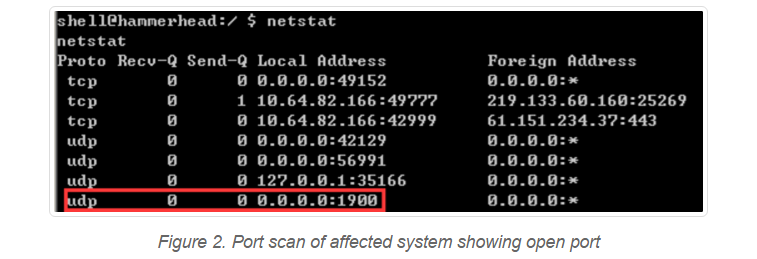
“With further research an exploit could be used not just to cause a crash, but to run arbitrary code on an affected device. The ability to run arbitrary code would give the attacker the ability to take control of the device, as on a PC.” continues the post. “We have seen exploits in the wild targeting devices that do not use mitigation protections such stack canaries, DEP, and ASLR. For well protected systems, we do not know of exploits that are currently capable of remote code execution.”
The security vulnerability affects the ‘libupnp’ code library inside the Portable SDK for UPnP Devices, it is used to playback media and also for NAT functionalities.
Below a list of the most popular affected apps:
Common Name Package Name
AirSmartPlayer com.gk.airsmart.main
Big2Small com.alitech.dvbtoip
CameraAccess plus jp.co.pixela.cameraaccessplus
G-MScreen mktvsmart.screen
HexLink Remote (TV client) hihex.sbrc.services
HexLink-SmartTV remote control com.hihex.hexlink
Hisense Android TV Remote com.hisense.commonremote
Netflix com.netflix.mediaclient
nScreen Mirroring for Samsung com.ht.nscreen.mirroring
Ooredoo TV Oman com.ooredootv.ooredoo
PictPrint – WiFi Print App – jp.co.tandem.pictprint
qa.MozaicGO.Android Mozaic GO
QQMusic com.tencent.qqmusic
QQ音乐HD com.tencent.qqmusicpad
Smart TV Remote com.hisense.common
Wifi Entertainment com.infogo.entertainment.wifi
モバイルTV(StationTV) jp.pixela.px01.stationtv.localtuner.full.app
에브리온TV (무료 실시간 TV) com.everyontv
多屏看看 com.letv.smartControl
海信分享 com.hisense.hishare.hall
Nebezpečený botnet Dorkbot svou hru právě dohrál
4.12.2015 Viry
Čtyři roky starý botnet Dorkbot kradl logovací data pro služby jako Gmail, Facebook, PayPal, Steam, eBay, Twitter nebo Netflix. Infikoval na milion počítačů. Teď jeho vláda po koordinované akci bezpečnostních složek a technologických firem skončila.
Operace, při níž spolupracovaly bezpečnostní orgány po celém světě, narušila infrastrukturu Dorkbotu, včetně řídících serverů ve 190 zemích světa. A co více, velká mezinárodní akce vedla k zabavení domén, čímž narušila schopnost operátorů botnetu zneužívat počítače svých obětí.
Koalicí, která k jeho zneškodnění vedla, tvořily Microsoft, Eset nebo CERT Polska a také organizace jako Europol, FBI či Interpol.
„Chceme-li mít bezpečnější internet a chránit naše uživatele, musíme se podílet na úsilí, které vede k narušování takových aktivit. V případě Dorkbotu Eset sdílel technické analýzy a statistické informace o malwaru a došel k závěru, že určité domény a internetové adresy slouží k vedení a řízení serverů botnetu,“ uvedl Jean-Ian Boutin, výzkumník malwaru v Esetu.
Dorkbot je etablovaným botnetem založeným na škodlivém softwaru Win32/Dorkbot, který je distribuován prostřednictvím různých kanálů, jako jsou sociální sítě, spam, paměťová média či Exploit kity.
Jakmile se nainstaluje do počítače, pokouší se narušit normální fungování bezpečnostního softwaru tím, že blokuje přístup k jeho aktualizacím a následně se připojí k IRC serveru, od něhož přijímá další příkazy.
Kromě toho, že se snaží získat hesla k populárním službám jako je Facebook a Twitter, Dorkbot brzy poté, co získá kontrolu nad daným systémem, instaluje kód jedné z mnoha dalších rodin malwaru. Velmi často jde o Win32/Kasidet, malware používaný k provádění DDoS útoků a známý také pod názvem Neutrino bot, a Win32/Lethic nebo též Spambor.
A Step-by-Step Guide — How to Install Free SSL Certificate On Your Website
4.12.2015
How-to-Install-Lets-Encrypt-SSL-Certificate
Another Big Milestone – Let's Encrypt is now offering Free HTTPS certificates to everyone.
Let's Encrypt has opened to the public, allowing anyone to obtain Free SSL/TLS (Secure Socket Layer/Transport Layer Security) certificates for their web servers and to set up HTTPS websites in a few simple steps (mentioned below).
Let's Encrypt – an initiative run by the Internet Security Research Group (ISRG) – is a new, free, and open certificate authority recognized by all major browsers, including Google's Chrome, Mozilla's Firefox and Microsoft's Internet Explorer.
The Free SSL Certification Authority is now in public beta after testing a trial among a select group of volunteers.
Why Let's Encrypt?
Let's Encrypt promised to offer a certificate authority (CA) which is:
Free – no charge for HTTPS certs.
Automatic – the installation, configuration as well as the renewal of the certificates do not require any administrator action.
Open – the automatic issuance, as well as renewal procedures, will be published as the open standard.
Transparent – the records of all certs issuance or revocation will be available publicly.
Secure – the team is committed to being a model of best practice in their own operations.
Cooperative – Let's Encrypt is managed by a multi-stakeholder organization and exists to benefit the community, not any of the consortium members.
How to Install Let's Encrypt Free SSL Certificate
First of all, let's say you want to get a certificate for example.com. To run the installation, you must have root access to your example.com web server.
To Generate and Install Let's Encrypt Free SSL Certificate, you must first download and run the Let's Encrypt client application.
To install Let's Encrypt Free SSL certificate follow these Steps:
Step 1: Login to your 'example.com' web server using SSH with root access.
Step 2: To install the Git version control system, type the following command:
apt-get install git
Step 3: Then download and install the latest version of Let's Encrypt Client application, type the following commands:
git clone https://github.com/letsencrypt/letsencrypt
cd letsencrypt
./letsencrypt-auto
Step 4: Once the installation starts, press Enter to accept the agreement.
Step 5: Then press Enter to specify the server name manually in the text box (for example, www.example.com) and then press Enter.
Step 6: Next, enter your email address, where you can receive messages from Let's Encrypt and to recover lost keys, and then press Enter.
Step 7: Review the 'Terms of Service,' and then press Enter to generate and install the SSL certificate.
Once the installation completes, you'll receive a 'Congratulation' message.
How to Configure Nginx/Apache for Let's Encrypt SSL Certificate
By default, Nginx or Apache web servers are not configured to how to use your new certificates.
For example, in case of Nginx: To use the installed SSL certificate, you need to edit Nginx configuration file. Type the following command to open Nginx configuration file:
$ sudo nano /etc/nginx/sites-available/www.example.com
Within that file, add the following lines.
http{
server{
…
listen 443 ssl;
server_name www.example.com;
ssl_certificate /etc/letsencrypt/live/www.example.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/.wwwexample.com/privkey.pem;
…
}
}
Save the file, and just restart your Nginx web server, using the following command:
sudo nginx -s reload
That's it! Check complete documentation here.
Congratulation you have successfully installed SSL certificate for your example.com domain.
How to Renew Let's Encrypt Free SSL Certificate: It is important to note that the beta version of Let's Encrypt issues certificates that expire after 90 days. So, to renew your SSL certificate, you need to run the letsencrypt-auto script again after expiration.
FREE HTTPS Certificates for Everyone!
So, now it's time for the Internet to take a significant step forward in terms of security and privacy. With Let's Encrypt, the team wants HTTPS becomes the default and to make that possible for everyone, it had built Let's Encrypt in such a way that it is easy to obtain and manage.
"There's a reward going for anyone who can find a security hole in the service," the team wrote in a blog post. "We have more work to do before we're comfortable dropping the beta label entirely, particularly on the client experience."
"Automation is a cornerstone of our strategy, and we need to make sure that the client works smoothly and reliably on a wide range of platforms. We'll be monitoring feedback from users closely, and making improvements as quickly as possible."
Let's Encrypt had signed its first free HTTPS certificate in September, and its client software emerged in early November. Since then the team has been finding flaws in their systems before going public.
ALERT: This New Ransomware Steals Passwords Before Encrypting Files
4.12.2015
You should be very careful while visiting websites on the Internet because you could be hit by a new upgrade to the World's worst Exploit Kit – Angler, which lets hackers develop and conduct their own drive-by attacks on visitors' computers with relative ease.
Many poorly-secured websites are targeting Windows users with a new "Cocktail" of malware that steals users' passwords before locking them out from their machines for ransom.
Yes, stealing Windows users' passwords before encrypting their data and locking their PCs for ransom makes this upgrade to the Angler Exploit Kit nastier.
Here's How the New Threat Works:
Once the Angler exploit kit finds a vulnerable application, such as Adobe Flash, in visitor's computer, the kit delivers its malicious payloads, according to a blog post published by Heimdal Security.
The First Payload infects the victim's PC with a widely used data thief exploit known as Pony that systematically harvests all login usernames and passwords stored on the infected system and then sends them to servers controlled by hackers.
This allows attackers to obtain working logins for a number of websites, e-commerce sites, and even corporate applications, from which the hackers could steal more data.
The Second Payload drops the widely-used CryptoWall 4.0 Ransomware that locks user files until a ransom amount is paid.
Also Read: Anyone can Now Create their Own Ransomware using This Hacking ToolKit
So in short, the new campaign is one of the most sophisticated and effective ransomware attacks to date that uses a combination of:
World's Worst Exploit Kit + World's Worst Password Stealer + World's Worst Ransomware
The campaign is "extensive" and originates from a secure hosting environment located in Ukraine, the researchers say. Over 100 web pages in Denmark have been "injected with the malicious scripts, but the campaign is not limited to Europe."
Rise in Ransomware Threat
Ransomware attacks hit thousands of Internet users every week, and costs them a total of $18 Million in losses, according to the FBI.
Moreover, a recent report dated back to last month suggested that the Cryptowall family alone has managed to raise over $325 Million in revenue in the past year alone.
Few days back, we also saw Cryptowall 4.0 – the newest version of the world's worst Ransomware – surfacing in the Nuclear exploit kit, one of the most potent exploit kits available in the market for hacking into computers.
Also Read: Free Ransomware Decryption and Malware Removal ToolKit
What Should You do if You get Infected by Cryptowall 4.0?
Once your system gets affected by Cryptowall 4.0, unfortunately, there's not much you can do, as the encryption the ransomware uses is very strong and almost unbreakable.
So, the only options you are left with are:
Format your computer and restore your data from the backup
OR
Pay the Ransom money for decryption key
However, we don't advise anyone to pay ransom as it doesn't guarantee that you will get the decryption keys; as well as this would encourage criminal activities.
Also Read: Ransomware Attacks Threaten Wearable Devices and IoTs
Prevention is the Best Practice
As I previously recommended, one of the best defense measures to mitigate the Ransomware attack is to:
Keep your systems and apps up-to-date
Create awareness within the organizations
Maintain backups of your files on an external hard drive regularly
Most malware and viruses are introduced by clicking on links usually contained in spam emails and opening attachments from unknown sources.
So, DO NOT CLICK on any suspicious link provided in the emails and attachments from unknown sources.
Ponmocup, never underestimate a botnet that infected 15 million PCs
4.12.2015
Ponmocup is one of the oldest botnet that infected more than 15 million machines across the years, but many experts still ignore it.
Ponmocup is one of the largest and oldest botnets in circulation, but many security experts still ignore it. According to the experts at Fox IT, the botnet is underestimated and infected across the years more than 15 million computers, allowing crooks to steal millions from victims’ bank accounts.
Fox IT recently published a report entitled “Ponmocup: A giant hiding in the shadows,” a document including the findings of an investigation that allowed the research to discover that the Ponmocup botnet controlled 2.4 million infections.
Lead author Maarten van Dantzig presented the findings of the study at the BotConf conference this week.
“Compared to other botnets, Ponmocup is one of the largest currently active and, with nine consecutive years, also one of the longest running [but it] is rarely noticed as the operators take care to keep it operating under the radar,” van Dantzig says. “Ponmocup’s operators are technically sophisticated, their techniques suggest a deeper than regular knowledge of the Windows operating system.”
The malware first detected in 2006, meanwhile the experts observed a peak in 2011 and now the botnet is composed of half a million machines worldwide.
Researchers believe that its authors are likely Russians that used the Ponmocup mainly as a data stealer.
“The operators are most likely Russian speaking and possibly of Russian origin. This is based on the fact that instructions to business partners and affiliates are written in Russian, and that historically, Ponmocup would not infect systems in some post-Soviet States.” states the paper.
Although it is very difficult to estimate the exact amount of money stolen by the operators of the Ponmocup botnet, it is likely that it has already been a multi-million dollar business for years now.
The botnet used a very complex infrastructure that relies on servers for dedicated tasks, over the time the authors have continuously updated it to improve robustness and avoidance abilities. The Ponmocup implements anti-analysis techniques such as heuristic checks for network and host-based analysis tools, debuggers and virtualised environments.
The researcher discovered some 25 unique plug-ins and nearly 4000 strains of the same malware, a circumstance that confirms the continuous development.
Beware fake LinkedIn profiles, threat actors are using them to hack you
4.12.2015
According to the Symantec firm, a growing number of threat actors in the wild are targeting professionals on LinkedIn with fake LinkedIn profiles.
LinkedIn is a privileged platform for intelligence gathering, a growing number of hackers are targeting professionals to collect information about their activities and networks. I daily refuse dozens connection from fake LinkedIn profiles that try to link me and my networks to gather intelligence.
By mapping the connections related to a specific account, criminals can entice users to give up personal details, target them with spear phishing attacks, redirect them to websites serving malware, and much more.
Social media platforms are powerful instruments for cyber espionage, recently numerous campaigns relying on fake LinkedIn profiles were uncovered by security experts. In October, the experts at the security firm Cylance revealed that the Cleaver group is managing a well-developed network of fake LinkedIn profiles for cyber espionage purpose.
In September, security researchers have uncovered a group of fake recruiting accounts on LinkedIn used for intelligence gathering about security experts.
Now, the security firm Symantec launched the alarm, its experts uncovered dozens fake LinkedIn profiles on the social network targeting professionals across a variety of industries. Also in this case, the attackers are posing as recruiters, the fake accounts allow them to map the networks of business professionals and gather information.
Symantec has collaborated with the company to identify the LinkedIn bogus profiles and remove them.
“Under the guise of a recruiter, these fake LinkedIn accounts have an easy entry point into the networks of real business professionals. Real recruiters already use the service as a way to find potential candidates. LinkedIn users expect to be contacted by recruiters, so this ruse works out in the scammers’ favor.” states Symantec in a report.
The alarming news is that most of the bogus accounts have been quite successful in gaining a significant network, some got endorsements from victims increasing their reputation.
“We investigate suspected violations of our Terms of Service, including the creation of false profiles, and take immediate action when violations are uncovered.” said LinkedIn.
“We have a number of measures in place to confirm authenticity of profiles and remove those that are fake. We encourage members to utilise our Help Center to report inaccurate profiles and specific profile content to LinkedIn.”
The researchers found that the fake LinkedIn profiles tended to be made up of text that had been copied and pasted from the profiles of real professionals. They used photos, often of women, pulled either from stock image sites or of real professionals.
They also used keywords such as “reservoir engineer”, “exploration manager” and “cargo securement training” which are likely to gain them visibility via the site’s built-in search engine.
Many of the terms related to the logistics, information security and oil and gas industries, Symantec said.
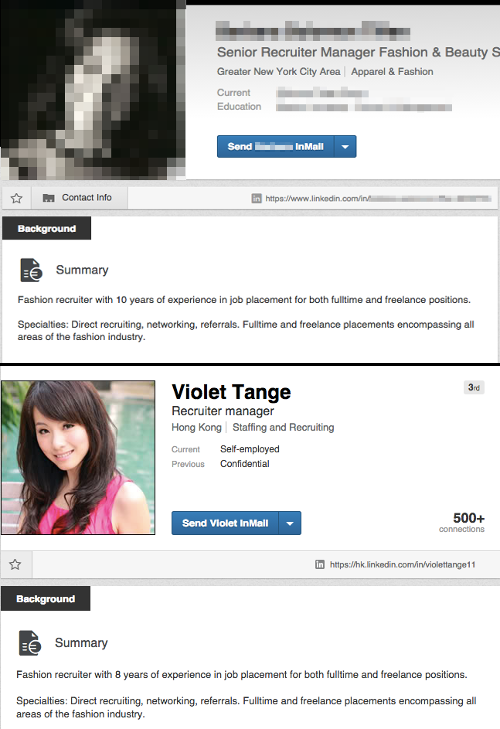
Most of these fake accounts follow a specific pattern:
They bill themselves as recruiters for fake firms or are supposedly self-employed
They primarily use photos of women pulled from stock image sites or of real professionals
They copy-paste text from profiles of real professionals for their summary and experience
They keyword-stuff their profile for visibility in search results
this means that it could be easy to uncover them, as explained by Symantec researcher Dick O’Brien.
“You can do a reverse image search by dragging and dropping the profile picture into Google Images and see what it brings up.” Dick O’Brien suggests.
“Copying and pasting the job information in Google can also reveal whether it has been taken from somewhere else.”
Let me close with polemics against Wikipedia, the alleged open source of knowledge. More than 4 years ago I have coined the term “Social Network Poisoning,” detailing the possible misuse of a social media platform. At that time, the “experts” at Wikipedia UK deleted my voice despite I have produced all the necessary arguments to support my concept. I was considered a stupid visionary, evidently too far ahead for them! After a few weeks, Wikipedia banned me, fortunately, the Italian version of the version is still online “Social_Network_Poisoning.”
Let me invite you to create again the term in Wikipedia citing me and my story, and let me suggest you this interesting post on the topic.
The Signal app is available in beta version
4.12.2015
Open Whisper Systems issued a beta version of the Signal app for Desktop that for now works only as a Chrome app and links only to Android devices.
Signal is a free and open-source encrypted voice calling and instant messaging application for mobile devices. It runs on both iOS and Android and uses advanced end-to-end encryption protocols to protect communications from prying eyes.
Signal has bean developed by Moxie Marlinspike, co-founded of the Open Whisper Systems firm. Today is circulating the news that the mobile app is now available also for desktop users.
On Wednesday the company issued a beta version of the Signal Desktop that for now works only as a Chrome app and links only to Android devices.
“Signal Desktop is a Chrome app which links with your phone, so all incoming and outgoing messages are displayed consistently on all your devices. Your contacts don’t have to guess where to message you, and when you switch devices the conversation you started will already be there.” states the official announcement from the company.
“As always, everything is end-to-end encrypted and painstakingly engineered in order to keep your communication safe – allowing you to send high-quality private group, text, picture, and video messages for free,”
The popular hacker Marlinspike anticipated that Signal Desktop will be able to link also Apple devices “real soon now.”
The source code of the Signal app is free, open source, and available on GitHub, everyone can verify its implementation. Like other projects managed by the Open Whisper Systems, the development activities are supported through donations and grants.
Signal was a long debated, law enforcement claims the impossibility of investigating suspects who use it to protect communications.
The FBI director James Comey has publicly expressed its concerns about the abuse of encryption calling to Silicon Valley to help law enforcement figure out the “Going Dark” issue.
In the days following the Paris attacks intelligence agents and law enforcement raised the concerns about possible abuse of terrorists of encrypted apps, including Signal.
The IT giants always refused to insert a backdoor in their products and authorities are powerless regarding this decision
“We’d like to bring the technical reality in line with people’s expectations and assumptions. People expect and assume that their correspondence is private, and are shocked and outraged when it is inevitably compromised,” explained Marlinspike. “Our hope is to fix that, so that when people feel like they’re corresponding privately, they really are. Basically, we’d like to make mass surveillance impossible.”
China — OPM Hack was not State-Sponsored; Blames Chinese Criminal Gangs
3.12.2015
China: OPM Hack was not State-Sponsored; Blames Chinese Criminal Gangs
In the most surprising manner, the Chinese government said it arrested criminal hackers behind the massive cyber attack on US Office of Personnel Management (OPM) earlier this year, dismissing its involvement.
Three months back, we reported that China arrested a handful of hackers within its borders who were suspected of allegedly stealing commercial secrets from US companies.
The arrests took place shortly before China President Xi Jinping visited the United States in September 2015 when both heads of states agreed that neither side will participate in commercial espionage against one another.
China: Cyber Criminals Hacked OPM, Not Government Spies
Now, those suspected hackers have turned out to be the ones in connection with the OPM hack that resulted in the theft of personal details of more than 21 Million United States federal employees, including 5.6 Million federal employees' fingerprints.
Citing an "investigation", the Chinese government said the OPM hack was actual "a criminal case" rather than a state-sponsored attack as the US government had suspected, Chinese media outlet Xinhua News Agency reported.
Related Stories:
5.6 Million Federal Employees' Fingerprints Stolen in OPM Breach
China arrested Hackers at U.S. Government Request
Some unknown US federal officials had previously blamed China for the attack, though, they did not publicly point their fingers at the Chinese government.
No further details regarding the investigation were provided yet or whether the United States or Chinese government had conducted the investigation.
However, US government has urged for more detailed information sharing, though, White House spokesperson told Reuters that the first U.S.-Chinese dialogue was "an important step" in addressing US concerns about Chinese cyber-espionage.
So, now let’s just wait till June, when both the countries would meet again for the second cyber security ministerial talk in Beijing.
3G/4G modems continue to be vulnerable
3.12.2015
Researchers have conducted a series of tests on popular 3G/4G mobile modems (data dongles) and routers discovered an impressive number of serious flaws.
Sometimes old news came back threatening our cyber security, all because 3G/4G dongles keep in being as vulnerable as they were in the past.
In the last report issued by the SCADA Strangelove team, the authors demonstrated that 3G/4G dongles are vulnerable to several attacks, including Remote Code Execution (RCE), Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF) and integrity attacks.
The experts tested a wide range of attacks against these devices, including SIM card cloning, data interception, subscriber location, device identification, code injection, PC infection, access to user accounts on the operator’s website, and APT attacks.
The SCADA Strangelove team tested devices from various vendors, such as Huawei (two different modems and a router), Gemtek (a modem and a router), Quanta (two modems) and ZTE (one modem)
The results are disconcerting, a significant number of vulnerabilities were found in this equipment:

Researchers collected data in a week, the explained that is quite simple to verify them using Shodan and querying for “mini_httpd/1.19 19dec2003 /html/index.html“.

We will not enter in details of the attacks (or it would be a long article) for this reason I suggest you to read the report, instead I prefer to share with you the results of the tests:
5 devices were vulnerable to Remote Code Execution
6 devices were vulnerable to Integrity attacks
5 devices were vulnerable to Cross-Site Request Forgery
4 devices were vulnerable to Cross-Site Scripting
In the next table are reported the attacks carried out by the experts:
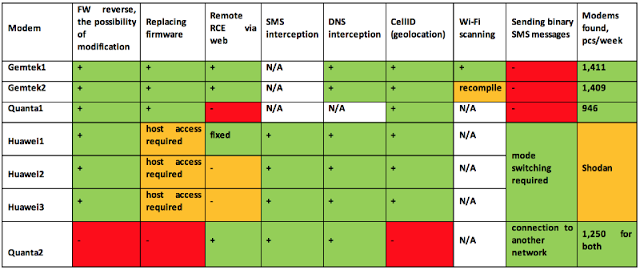
Summarizing, Huawei modems with the most recent firmware updates are the ones with a better layer of security … there is still much to do with 3G/4G dongles.
China arrested hackers suspected of OPM hack
3.12.2015
The Chinese Government says it has arrested the hackers responsible for breaching the Office of Personnel Management database (OPM).
The Chinese government has arrested hackers accused of breaking into the Office of Personnel Management databases,
According to The Washington Post, the Chinese government has arrested the hacking crew that breached the Office of Personnel Management (OPM).
“The Chinese government recently arrested a handful of hackers it says were connected to the breach of Office of Personnel Management’s database earlier this year, a mammoth break-in that exposed the records of more than 22 million current and former federal employees.” states The Washington Post. “The arrests took place shortly before a state visit in late September by President Xi Jinping, and U.S. officials say they appear to have been carried out in an effort to lessen tensions with Washington.”
The authorities arrested the suspects prior to Chinese President Xi Jinping’s state visit in the US in September. China and US reached an agreement during Xi’s state visit that established a mutual commitment to suspend all activities of cyber espionage and hacking.
OPM 2
There is no news regarding the identities of the suspects, neither the connection with the Chinese government.
The Chinese Government has always denied any involvement with the OPM hack that exposed the personal data of 21.5 million federal employees and others sensitive information.
The US Intelligence believes that the OPM hack is the result of a cyber espionage operation conducted by a nation-state actor.
“If the individuals detained were indeed the hackers, the arrests would mark the first measure of accountability for what has been characterized as one of the most devastating breaches of U.S. government data in history.” continues the Post.
“We don’t know that if the arrests the Chinese purported to have made are the guilty parties,” said one U.S. official, who like others interviewed spoke on condition of anonymity because of the subject’s sensitivity. “There is a history [in China] of people being arrested for things they didn’t do or other ‘crimes against the state.’ “
The Obama administration announced that it was defining economic sanctions against China as a response to continuous hacking campaigns against government entities and private firms.
Is it really the beginning of an effective collaboration?
“I think that China has realized that this is an issue that really matters to the United States, and that if they’re going to continue to manage the relationship with us in a positive way, they had to figure out some way to address our concerns,” an anonymous U.S. official told the Washington Post.
Operation Black Atlas, PoS malware is flooding network worldwide
3.12.2015
Trend Micro uncovered a large-scale operation dubbed Black Atlas operation, in reference to notorious BlackPOS PoS malware.
It’s Christmas time also for crooks, in this period the number of credit card breaches and scams increases with alarming punctuality. In the US, we use to assist an increase of credit card breaches involving PoS malware, last victims in order of time are Hilton Hotel and Starwood hotel chains.
In the last weeks, security experts detected a number of new threats in the wild such as Cherry Picker, ModPoS, and Pro Pos.
Not only US retailers are at risk, new threat seeks out PoS systems within targeted networks, small and medium sized business networks all over the world belonging to any various industries.
Experts at Trend Micro uncovered a large-scale operation dubbed operation Black Atlas, in reference to notorious BlackPOS PoS malware that is the threat primarily used in these attacks.
My readers will surely remember that BlackPOS, also known as Kaptoxa, was the malware used during the Target breach in 2013 and attacks on retail accounts in 2014.
Threat actors behind the operation have developed a set of hacking tools used in their operations.
“Operation Black Atlas has been around since September 2015, just in time to plant its seeds before the holiday season. Its targets include businesses in the healthcare, retail, and more industries which rely on card payment systems.” reads a blog post published by Trend Micro. “The operation is run by technically sophisticated cybercriminals who are knowledgeable in a variety of penetration testing tools and possess a wide network of connections to PoS malware in the underground market.”
Malware utilized in Black Atlas included a number of popular PoS malware, including Alina, NewPOSThings, a Kronos backdoor, and of course the BlackPOS threat.
Bad actors behind the Black Atlas operation have been able to steal user login credentials of the victims, email accounts, and other sensitive information. The experts also discovered a live video feed of closed-circuit television (CCTV) cameras in a gasoline station, evidence that crooks are collecting whatever information is available.
“Similar to GamaPoS, the Black Atlas operators employed a “shotgun” approach to infiltrate networks as opposed to zeroing in on specific targets. They basically checked available ports on the Internet to see if they can get in, ending up with multiple targets around the world.” continues the post.
The experts at Trend Micro observed that Black Atlas operators used the botnet Gorynych or Diamond Fox in a number of installations.
In the following image has reported the distribution of Gorynych targets in Operation Black Atlas.

The Operation Black Atlas involved numerous healthcare organization in the US, the experts explained that threat actors use to run an initial intelligence gathering or reconnaissance activity to identify the best system to compromise, that they used the tools to run the attack (i.e. Brute force or dictionary attack).
“Networks with weak password practices are likely to fall victim to this initial penetration testing stage. Many of these tools are easily downloaded from various sites on the Internet. The cybercriminals will then create a test plan based on the initial probe, and then use a second set of tools to execute the said plan.”

In the attack stage the crooks utilized remote access tools to steal more information and move laterally within the network, one inside they inject the PoS threats.
Trend Micro announced it will provide further details about the Black Atlas Operation.
Drtivá většina firem má v Česku nevyhovující zabezpečení dat
2.12.2015 Zabezpečení
Zhruba 85 procent českých firem má nevyhovující nebo jen částečně vyhovující zabezpečení podnikových informací. Ve světě je podíl podniků s nevyhovujícím zabezpečením ještě o tři procentní body vyšší. Hlavním důvodem je přitom nízká výše rozpočtu na kybernetickou bezpečnost. Vyplývá to ze studie EY Global Information Security Survey.
Kvůli nízkým investicím do kybernetické bezpečnosti a chybějícím odborníkům jsou české firmy pomalejší v odhalování bezpečnostních incidentů. Do hodiny odhalí útok 33 procent českých firem, ve světě je to polovina. Vylepšení zabezpečení svých systémů v Česku plánuje 55 procent firem, ve světě chystá bezpečnostní opatření 78 procent společností.
Demotivovaní zaměstnanci a phishing
„Priority kybernetické bezpečnosti jsou v ČR odlišné od okolních zemí, hlavní hrozby se však příliš neliší. Mezi ty patří především demotivovaní zaměstnanci a phishing," uvedl Petr Plecháček z české pobočky EY. Phishing je metoda podvodného získání citlivých údajů na internetu a následné krádeže peněz. Podle Plecháčka je zajímavé, že české firmy příliš nevnímají zvyšující se hrozby vyplývající z mobilních technologií či zneužití sociálních sítí.
Rozpočet na kybernetickou bezpečnost chce v příštím roce zvýšit alespoň o pět procent zhruba pětina českých firem, ve světě je to polovina podniků. V Maďarsku hodlá více investovat každá třetí firma a v Polsku 57 procent podniků.
Obavy z kybernetických útoků
Firmy se nejvíce obávají kybernetických útoků od kriminálních spolků (59 procent), vlastních zaměstnanců (56 procent) a hacktivistů (54 procent). Na dalších místech figurují například státem sponzorované útoky. Obavy z organizovaného zločinu, hacktivistů a státem sponzorovaných útoků zesílily, naopak slábnou obavy z incidentů způsobených nevědomostí či nedbalostí zaměstnanců či zastaralostí systémů.
Global Information Security Survey vychází z odpovědí 1755 firem z celkem 67 zemí světa včetně ČR.
Black marketplace – 50c buys login for stolen media accounts
2.12.2015
It is Christmas time and sellers are offering a wide number of products and services in the Black marketplace. 50c buys login for stolen media accounts.
Cyber criminals are offering for sale ‘lifetime’ Netflix, HBO, and cable sports streaming accounts for low prices.
Sellers of the on the AlphaBay Marketplace, a black marketplace hosted on the Tor network, the accounts are offered for less than US$10.
Premium sports accounts are sold for about $10, streaming TV goes for as low as 50 cents, less than the $10 monthly subscription, a Marvel Unlimited lifetime account for 50 cents.

A recent report published by McAfee , entitled The Hidden Data Econonomy provided details of the sales, including a price-list for a number of products.
The sellers on the underground market are offering any kind of product, including, ComCast Xfinity, Uber, Premium Spotify, paid pornography accounts, Apple, and Lynda training video accounts. A specific vendor with the pseudonymous SkypeMan has sold more than 5300 Spotify accounts since September for less than $2 each, and nearly 517 Xfinity accounts for $4 in the same period.
Sellers always suggest maintaining login credentials, any password changes will trigger alert and lock out the buyer.
It’s Christmas Time, many sellers started special offers on some products such as the stolen credit card data. Some sellers are offering “buy one get one free” stolen credit card deals.
Let close observing that it is possible to pay for an email bomb service that promises to “f**k any email account instantly” by signing up the victim to more than 1500 newsletters.
Stay tuned … we will continue to follow the offer on the black marketplace.
Patent Troll — 66 Big Companies Sued For Using HTTPS Encryption
2.12.2015
Are you Using HTTPS on your Website to securely encrypt traffic?
Well, we'll see you in the court.
At least, that's what CryptoPeak is saying to all big brands that utilize HTTPS on their web servers.
BIG Brands Sued for Using HTTPS: 'Patent Troll'
Texas-based company CryptoPeak Solutions LLC has filed 66 lawsuits against many big businesses in the US, claiming they have illegally used its patented encryption method – Elliptic Curve Cryptography (ECC) – on their HTTPS websites.
Elliptic Curve Cryptography (ECC) is a key exchange algorithm that is most widely used on websites secured with Transport Layer Security (TLS) to determine what symmetric keys are used during a session.
Encryption is on the rise after Edward Snowden made the world aware of government’s global surveillance programs. Today, many big tech and online services are using encryption to:
Protect the data transmitted to/from visitor to domain
Lessen the risk of hacking
However, websites using the ECC key are now at risk of being forced to court for using the protocol. As CryptoPeak snapped up the Patent (US Patent 6,202,150) that describes "Auto-Escrowable and Auto-Certifiable Cryptosystems," which the firm argues covers elliptic curve cryptography (ECC).
Either Pay or Don't Use HTTPS
The abstract of the US Patent 6,202,150 describes the invention, which was granted in 2001:
patent-troll
Companies Targeted by CryptoPeak
Some of the biggest names CryptoPeak Solutions sued include:
Yahoo
Netflix
Pinterest
AT&T
Sony
Groupon
GoPro
Etsy
Petco
Target
Costco
Home Depot
Expedia
Barnes & Noble
Multiple financial institutions and hotel chains
You can see the full list of lawsuits, which is available online here.
"Defendant has committed direct infringement by its actions that comprise using one or more sites that utilize Elliptic Curve Cryptography Cipher Suites for the Transport Layer Security (TLS) protocol (the Accused Instrumentalities)," according to the lawsuits.
CryptoPeak can easily be categorized as a "Patent Troll," as it is still unclear if the cases will be successful or not. Since the patent describes some of the key tenets of ECC, which includes generating and publishing of public keys, not obvious corresponds directly to its implementation in HTTPS connections.
Some companies targeted by the firm are fighting the lawsuit that seeks damages and royalties, and other like Scottrade are doing out of court settlements, saying "all matters in controversy between CryptoPeak and Scottrade have been settled, in principle."
Netflix, one of over 60 companies being dragged to court, called CryptoKey's lawsuit "invalid" from the outset and filed a case to be dismissed under FED. R. CIV. P. 12(B)(6).
"The defect in these claims is so glaring that CryptoPeak’s only choice is to request that the court overlooks the express words of the claims, construe the claims to read out certain language, or even correct the claims," Netflix said (PDF) in a court filing.
Now, let's see what happens next.
Adobe to Kill 'FLASH', but by Just Renaming it as 'Adobe Animate CC'
2.12.2015
Adobe to kill 'FLASH', but by Renaming it as 'Adobe Animate CC'
Adobe is Finally Killing FLASH, but not actually.
Adobe Flash made the Internet a better place with slick graphics, animation, games and applications, but it never stood a chance of surviving in the same world as HTML5.
Of course, Flash has plagued with various stability and security issues, which is why developers had hated the technology for years.
So, now it's time to say GoodBye to Adobe Flash Professional CC, and Welcome Adobe Animate CC.
Meet the new Flash, Adobe Animate CC, same as the old Flash, and still insecure mess.
Adobe Animate CC Embraces HTML5
Adobe has officially announced that "over a third of all content created in Flash Professional today uses HTML5," so the company is acknowledging the shift with the new name.
Adobe Animate CC — Adobe's Premier Web animation tool for developing HTML5 content.
Yes, that's what the company has the focus on.
The application – mostly looks like an update to the Flash Professional software – will still support Adobe Flash (SWF) and AIR formats 'as first-class citizens,' along with other animation and video formats, including HTML5 canvas, 4K and WebGL output.
Adobe Animate CC is the Same Old Flash
When Adobe Animate CC launches in January 2016, it will bring features like easy access to high-quality stock art, new vector art brushes, as well as the ability to rotate the canvas 360° from any pivot point. Sounds exciting!
What it won't bring is:
Fix for the number of security issues that have plagued Adobe Flash for years
The platform has a new name, but the development tool lives on.
So, Flash isn't actually dead; it's just renamed.
"Adobe's strategy is to make money regardless of what happens in the market," says Jeffrey Hammonds, principal analyst at Forrester Research. "They understand that there is a slow transition to HTML5 going on."
"At some point you have to embrace the change," Hammond adds. "The rebranding is the visible sign of that, but the internal focus on supporting the technologies like HTML5 has been going on a while."
So, hiding Flash behind a different name doesn't solve the stability and security issues. In fact, a recently uncovered flaw in the software was so nasty that the only way to get rid of it was to completely uninstall Flash Player.
Still think Flash is dead or very much alive? Hit the comments below.
Darkode forum was supposed to be resuscitated, but …
2.12.2015
The experts at the Damballa’s Threat Discovery Center have discovered the revive Darkode forum.
On July 2015, an international joint effort of law enforcement allowed the arrest of dozen people active on the popular Darkode crime forum.
Darkode was a black market specialized in the sale of exploit kits and hacking tool, its seller also offered spam services and services for malware customization.
The FBI along with Europol and the Brazil’s Federal Police were monitoring the cybercriminal forum since March, the operation has resulted in 62 arrests in 18 countries worldwide, Colombia, Germany, India and UK.
According to the administrator which uses the online pseudonym Sp3cial1st, following the seizure of Darkode on 14 July he waited for the disclosure of the identities of arrested in order to decide to before deciding to bring the forum back online.
At the end of July, the administrator of the Darkode hacking forum announced the imminent return online of the platform with new security improvements.
Last July, Damballa’s Threat Discovery Center discussed the infamous web forum, Darkode, that was supposed to be resuscitated by sp3cial1st.
Since then, Damballa’s Threat Discovery Center has been monitoring the dark web searching for a new Darkode forum. The experts discovered the revive Darkode Reloaded. Obviously, the Darkode forum was deployed in the dark web for “security” reasons and anonymity, but the forum remains also accessible without the Tor client a circumstance that manifests a poor design.


According to experts at Damballa, the current administrator of Darkode forum, Sven, is a previous member of the forum.
Sven has implemented a Jabber service that runs on the domain darkode.club and is hosted on a dedicated server at 86.105.227[.]13 located in Russia.
Also in this case, the experts noticed serious security issues and a poor design, the Openfire version installed on the server (ver. 3.10.2) is affected by a number of vulnerabilities.
“The server is poorly configured. We know that this server runs a software called Jetty 9.2 Snapshot. This software comes along with Openfire. Openfire is a Jabber server software and the version 3.10.2 is installed. The Jetty software listens on port 7070 by default and this port is wide open on the server. The administration interface for the jabber server is also accessible with the default configuration port 9090.” states a blog post published by Damballa.
The lack of security and poor a configuration shows that Darkode cannot be trusted.

Experts at Damballa have criticized the new Darkode forum defining it “a bad Darkode imitation with rigorous rules.“
The experts noticed the absence of discussions and threads about banking trojans or other high profile malware.
The Darkode reloaded is far from the previous one.
China blamed for cyber attack on Bureau of Meteorology computer
2.12.2015
According to the Australian Broadcasting Corporation (ABC) Chinese hackers have conducted a major attack on a supercomputer operated by Australia’s Bureau of Meteorology (BoM).
Chinese hackers have conducted a major attack on a supercomputer operated by Australia’s Bureau of Meteorology (BoM). The news has been disclosed by the Australian Broadcasting Corporation (ABC). The Bureau of Meteorology is Australia’s national weather, climate and water agency, it is the analog of the USA’s National Weather Service.
“China is being blamed for a major cyber attack on the computers at the Bureau of Meteorology, which has compromised sensitive systems across the Federal Government.” states the ABC. “The bureau owns one of Australia’s largest supercomputers and provides critical information to a host of agencies. Its systems straddle the nation, including one link into the Department of Defence at Russell Offices in Canberra.”
The systems at the Bureau of Meteorology elaborate a huge quantity of information and weather data that are provided to various industries, including the military one.
The consequence of a cyber attack on such kind of systems could represent a menace to the homeland security.
The supercomputer targeted by the hackers is also used to provide weather data to defence agencies, its disclosure could give a significant advantage to a persistent attacker for numerous reasons.
Australian Bureau of Meteorology computer 2
For example, an attacker can gather information on defense operations, defense personnel involved and so on. A threat actor could compromise systems at the bureau to access computers at other agencies exploiting it as a gateway to other entities.
“But the ABC has been told this is a “massive” breach and one official said there was little doubt where it came from. “It’s China,” the post continues. The motivation for the attack on the bureau could be commercial, strategic or both. The bureau is a critical national resource and another state would place a high value on its intellectual property and scientific research. In the event of a conflict, compromising Australia’s ability to accurately forecast weather would affect the operation of military and commercial aircraft.”
According to the Vulture South’s team, a well-placed source confirmed remote code execution took place at the Bureau of Meteorology.
Australia is one of the members of the Five Eyes intelligence alliance, government systems are a privileged target for state-sponsored hackers and organized criminal rings specialized in attacks on government networks.
A spokesman for Prime Minister Malcolm Turnbull said a range of adversaries, including “state-sponsored actors and serious organized criminals”, were motivated to attack government networks.
“The Government’s aware of a press report that the Bureau has been the subject of a cyber attack,” the spokesperson said in a statement, adding the Government would not comment on specific cases.” said a spokesman for Prime Minister Malcolm Turnbull. “The Government takes any cyber attacks seriously and is currently reviewing its cyber security policy.”
At the time I was writing the bureau confirmed that its systems were working.
“Like all government agencies, we work closely with the Australian Government security agencies,” it said in a statement. “”The bureau’s systems are fully operational and the bureau continues to provide reliable, ongoing access to high-quality weather, climate, water and oceans information to its stakeholders.”
WhatsApp Blocks Links to Telegram Messenger (Its biggest Competitor)
1.12.2015
It seems like Facebook-owned popular messaging service WhatsApp is blocking links to rival messaging applications – at least Telegram app for now.
Telegram users are noticing that WhatsApp is blocking any links to the privacy-oriented messaging service Telegram.me.
Although users are free to send or receive Telegram links on WhatsApp, the links appear as non-clickable that you cannot copy or forward.
This strange behavior was first noticed this morning by Telegram users over on Reddit.
The URLs – which are generally automatically made clickable – still appeared as plain text messages, but they didn't register as hyperlinks, blocking users from copying or forwarding them to other users or other apps.
Read Also: How to Auto-BackUp Your WhatsApp Data to Google Drive with Encryption.
In general, this odd behavior is done with malicious URLs such as malware or spam.
The Culprit
However, this strange behavior was not exhibited on every device. Only WhatsApp for Android is currently showing this behavior while Telegram URLs still work fine on the iOS version of WhatsApp.
This issue only began appearing in WhatsApp Version 2.12.327, a silent update pushed earlier this morning.
Telegram has confirmed the situation to The Verge that the Facebook, who owned WhatsApp, is indeed responsible for the issue, as the social network has used this link-blocking trick in the newsfeed and Messenger app before to prevent its users from visiting Torrent websites.
"Typically after a media backlash, FB steps back and blames their intelligent filtering for the problem," said a Telegram spokesperson. "We expect the same to happen this time as well."
However, Facebook and WhatsApp are yet to comment on the issue. The popular messaging app has not even acknowledged that a new update was pushed this morning.
Pro PoS — This Stealthy Point-of-Sale Malware Could Steal Your Christmas
1.12.2015
The point of Sale systems are the most tempting target for cyber crooks to steal your credit card information and with this Christmas, you need to be more careful while using your credit cards at retailers and grocery stores.
Here's why…
Cyber criminals are now selling a new powerful strain of Point of Sale (PoS) malware through underground forums.
Like several POS malware families discovered last year, including vSkimmer and BlackPOS, the new malware is also designed to steal payment card data from the infected POS systems and support TOR to hide its C&C (Command and Control) servers.
Pro PoS – Light Weight, Yet Powerful Malware
However, the new malware, dubbed "Pro PoS," packs more than just a PoS malware.
Pro PoS weighs only 76KB, implements rootkit functionalities, as well as mechanisms to avoid antivirus detection, according to threat intelligence firm InfoArmor.
What's even more interesting about this malware is…
Pro PoS integrates a polymorphic engine that lets the threat generate a different signature for each malware sample – a measure designed to foil security defences.
InfoArmor warned that cyber crooks were actively using the current version of Pro PoS Solution in an effort to target PoS systems used by large retailers and SMBs in the United States and Canada specifically.
Pro PoS Malware found in the Wild
The developers of the Pro PoS malware are believed to be hackers from Eastern Europe, according to the security firm.
On November 27 (Black Friday), researchers at InfoArmor noticed a significant increase in the price of the Pro PoS Solution, which was offered at $2,600 for a six-month licence.
The developers of Pro PoS have designed their malware in such a way that it infects the principal operating systems, including newer operating systems, used by the companies in the retail environment.
Phishing campaign leveraging on Dropbox targets Hong Kong media
1.12.2015
Security experts at FireEye have uncovered an ongoing phishing campaign leveraging Dropbox account linked to “admin@338” as Command and Control platform.
Experts at FireEye have discovered an ongoing phishing campaign using a Dropbox account linked to “admin@338” as the delivery platform.
The account ” admin@338 ” was also used in the past to deliver malware, but at the time the main target were financial, economic, and trade policy organizations. In March 2014, FireEye discovered that the group of Chinese-based hackers called “admin@338” had sent multiple MH370-themed spear phishing emails, the attackers targeted government officials in Asia-Pacific, it is likely for cyber espionage purpose.
The hacking campaign is targeting Hong Kong media organizations, which publish democratic articles. The crooks are using a simple email attach with documents as threat vector, that when victims open the attachments a malicious payload is delivered. The malware is LowBall and uses dropbox as Command and Control infrastructure.

The malicious code exploits an old Microsoft Office vulnerabilities (CVE-2012-0158), known as LowBall.
Lowball “uses the legitimate Dropbox cloud-storage service to act as the CnC server. It uses the Dropbox API with a hardcoded bearer access token and has the ability to download, upload, and execute files. The communication occurs via HTTPS over port 443.After execution, the malware will use the Dropbox API to make an HTTP GET request using HTTPS over TCP port 443”
If the victim calls the dropbox account, a BAT file will be downloaded, and will run the BAT to collect information about the victim’s computer. If the attacker thinks that the PC has relevant information, a second payload known as Bubblewrap will be delivered.
By the details provided by FireEye, the phishing campaign started in August targeting all types of media in Hong Kong, radio, television, and print media, and it’s using 2 different type of emails as explained in the report:
“The first email references the creation of a Christian civil society organization to coincide with the anniversary of the 2014 protests in Hong Kong known as the Umbrella Movement.”
“The second email references a Hong Kong University alumni organization that fears votes in a referendum to appoint a Vice-Chancellor will be co-opted by pro-Beijing interests.”
Experts speculate the cybercriminals started targeting Hong Kong media sector in response the economic problems between Hong Kong and China.
“The threat group’s latest activity coincided with the announcement of criminal charges against democracy activists. During the past 12 months, Chinese authorities have faced several challenges, including large-scale protests in Hong Kong in late 2014, the precipitous decline in the stock market in mid-2015, and the massive industrial explosion in Tianjin in August 2015. In Hong Kong, the pro-democracy movement persists, and the government recently denied a professor a post because of his links to a pro-democracy leader.”
FireEye uncovered the campaign in joint effort with Dropbox, but the experts of the firm end up finding out a second campaign.
“Our cooperation uncovered what appears to be a second, ongoing operation, though we lack sufficient evidence to verify if admin@338 is behind it. The attack lifecycle followed the same pattern, though some of the filenames were different, which indicates that there may be multiple versions of the malware.” states FireEye
“In addition, while the operation targeting Hong Kong-based media involved a smaller number of targets and a limited duration, we suspect this second operation involves up to 50 targets. At this time, we are unable to identify the victims.”
In the end, this is another campaign in the middle of many, which use similar strategies but it is relevant as example to make people aware of these type of campaigns.
About the Author Elsio Pinto
Elsio Pinto (@high54security) is at the moment the Lead McAfee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog McAfee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog McAfee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog http://high54security.blogspot.com/
GCHQ accused of illegal Computer Network Exploitation activities
1.12.2015
The British GCHQ has been accused of illegal Computer Network Exploitation activities by Privacy International and internet service providers.
The British intelligence is responsible of “persistent” illegal hacking of electronic devices and networks worldwide, the Investigatory Powers Tribunal (IPT) has been told.
The popular whistleblower Edward Snowden disclosed a collection of documents revealing the extent of surveillance programmes carried out by the Five Eyes alliance. Snowden revealed the existence of secret surveillance activities such as the Tempora operation and hacking platforms such as the Smurf suite.

GCHQ admitted for the first time that government monitoring station in Cheltenham carries out “persistent” and “non-persistent” Computer Network Exploitation (CNE) against targets in the UK and abroad.
In 2013, the tribunal was told, 20% of GCHQ’s intelligence reports contained information that was obtained through hacking operations.
The case has been brought in hearing at the IPT which deals with complaints against the surveillance operated by the UK intelligence. A four-day hearing is at the Rolls Building in central London.
“The [legal] regime governing CNE … remains disproportionate,” Ben Jaffey, counsel for Privacy International, told the tribunal. “Given the high potential level of intrusiveness, including over large numbers of innocent persons, there are inadequate safeguards and limitations.”
Jaffey highlighted that GCHQ’s hacking alter the targeted systems, an activity that is not considered legal by the authorities.
“What parliament did not authorise was CNE that impairs the operation of a computer …” he said.
“If state authorities are permitted to alter or impair the operation of a computer, the reliability and admissibility of such evidence will be called into question, as will the need to disclose a past CNE operation to the defence.”
The intelligence services are accused to have abused termed “thematic” warrants that don’t address specific individuals, but rely on generalised categories of people or places.
“Under section five of the Intelligence Services Act, he said, proper safeguards are being bypassed so that groups as widely defined, for example, as “all mobile telephones” in Birmingham could be targeted.” reported the Guardian.
On the other end the lawyers for GCHQ explained that Computer Network Exploitation activities carried on by the UK Agency are “proportionate”.
“Over the last year the threat to the UK from international terrorism has continued to increase,” James Eadie, QC for GCHQ, told the tribunal in written submissions.
“GCHQ and other intelligence agencies must develop innovative and agile technical capabilities to meet these serious national security challenges. Computer Network Exploitation is one such capability…”
“CNE may, in some cases, be the only way to acquire intelligence coverage of a terrorist suspect or serious criminal in a foreign country.”
Toymaker VTech Hack Exposes 4.8 Million Customers, including Photos of Children
1.12.2015
Earlier this month, a massive data breach at VTech – the maker of tablets and gadgets aimed at children – exposed the personal details of about 4.8 Million parents and photos of more than 200,000 Children.
If that was not bad enough…
…it turns out that the massive cyber attack against the toymaker company also left hundreds of thousands of snaps of parents and children, as well as a year worth of chat logs kept online in a way easily accessible to hackers.
VTech Data Breach
In a statement released Monday, the toymaker company VTech said the hacked database included victim's profile information including:
Customers' names
Email addresses
Passwords (One-way encrypted using MD5 hash that can be cracked in no time)
Secret questions and answers for password retrieval
IP addresses
Residential addresses
Download history
The database also included information on children including names, genders and date of births.
Also Read: Caution! Hackers Can Easily Hijack Popular Baby Monitors to Watch Your Kids.
However, the Hong Kong-based company noted the database didn't contain any credit card or personal identification information like social security numbers (SSNs) and driver license IDs.
Hack Leaks Photos and Chat Logs of Children & Parents
What's even more worrisome is that…
In addition to the above information, data from Kid Connect – a service VTech offered to let parents communicate with their kids – was also hacked. Kid Connect information included:
Pictures of Children and parents
Chat logs between parents and children
How did VTech Data Breach Happen?
The massive data breach actually occurred on Nov. 14 and impacted VTech's Learning Lodge app store database, which features learning game apps and other educational tools for kids to download on their VTech devices.
The kiddie toymaker company had alerted Learning Lodge customers of the recent hack, and had "temporarily suspended" the Learning Lodge site along with 13 of its associated websites as a precautionary measure, VTech said on its website Monday.
The hacker that discovered the data breach told Motherboard that he has no plans to misuse the leaked information he gathered.
However, now, when the information – including snaps and chat logs – is available online, it could be even harder for VTech to try to pretend that everything is all right.
VTech says it is still investigating the matter, and will look into new ways to strengthen its security. It also alerted customers of potential exposure, encouraging them to follow up with the company via email (vtechkids@vtechkids.com in the U.S.).
Experts Warn of More Cyber Attacks
Now that the massive database from VTech is available online, security experts are warning that hackers and cyber criminals are likely to use this information in order target similar IoT (Internet of Things) companies that handle customer data.
Also Read: How Drones Can Find and Hack Internet-of-Things Devices From the Sky
Breaches like VTech are not unusual, but since it involves services aimed at children that generally do not get much of the attention when it comes to the security of data.
Affected? How to Check and What to Do?
If you are a parent holding a Learning Lodge account, you are advised to check Have I Been Pwned? website, which compiles all the data from breaches and now includes users accounts stolen from VTech.
If you found your Learning Lodge account affected, you should:
Change your password immediately
Also, change your password retrieval information
You are also advised to change the passwords on any other online accounts for which you are using the same password as for Learning Lodge account.
Italian intelligence plans to monitor also communications through the Playstation
1.12.2015
Italian intelligence is planning to invest in solutions that could allow its counter-terrorism agents to monitor Sony’s PlayStation Network.
The Italian intelligence is planning to invest in solutions that could allow the agents of the Italian counter-terrorism to monitor Sony’s PlayStation Network in order to prevent any abuse of jihadists.
A few hours later the Paris attacks, the Belgian federal home affairs minister Jan Jambon revealed that terrorists behind the Paris attacks have used PlayStation 4 for their communications. A raid in nearby Brussels provided evidence that terrorists were using at least one PlayStation 4 console.
The choice is not casual, despite the effort of the intelligence agencies in monitoring communications over Gaming console, the ISIS members were aware of the difficulties to conduct a large-scale surveillance on the PlayStation 4 channels. Jambon confirmed that the Belgian security services were unable to decrypt communications made through the PlayStation Network.
“The thing that keeps me awake at night is the guy behind his computer, looking for messages from [the Islamic State]and other hate preachers,” Jambon said last Friday, according to Brussels weekly,the Bulletin. “PlayStation 4 is even more difficult to keep track of than WhatsApp.”
ISIS Paris attacks PlayStation 4
The PlayStation’s IP-based voice systems are difficult to monitor and terrorists could send messages to each other within PlayStation games without speaking or typing a word.
Now the Italian counter-terror agents want to monitor Sony’s PlayStation Network for jihadi chatter, the announcement was made by the nation’s justice minister Andrea Orlando.
Orlando told Italian broadsheet Il Messaggero that the government would be investing €150m in a reformation of the nation’s security services. The measures include dedicated funds to allow law enforcement and national intelligence to monitor “any form of communication,” including gaming platform such as the Sony PlayStation.
The reference is clearly to the recent events and the speculation that terrorists could use gaming platform to exchange messages.
“An ISIS agent could spell out an attack plan inSuper Mario Maker’s coins and share it privately with a friend, or two Call of Duty players could write messages to each other on a wall in a disappearing spray of bullets.” ” states a post published on Forbes.”It may sound ridiculous, but there are many in-game ways of non-verbal communication that would almost be impossible to track. To do so would require an FBI or NSA agent somehow tapping all the activity on an entire console, not just voice and text chat, and that should not even be technically possible at this point.”
The possible abuse of gaming platform by a group of terrorists and hacktivists is not a novelty. An NSA document leaked by Edward Snowden and titled “Exploiting Terrorist /use of Games & Virtual Environments” revealed the efforts of intelligence agencies in infiltrating the gaming platforms due to concerns about terrorists planning their activities on popular games, including World of Warcraft and Second Life.
Pro PoS, a new PoS malware available for sale in the underground
1.12.2015
A new strain of PoS malware dubbed Pro PoS Solution is available for sale in the underground forums.
It’s Christmas also for criminals who have found a new gift under the Christmas tree, a new powerful strain of PoS malware.
According to the threat intelligence firm InfoArmor, the new PoS malware dubbed Pro PoS is available for sale in the underground forums and its authors are probably hackers from Eastern Europe.
The authors of the Pro PoS Solution designed their malware to infect the principal operating systems used by the companies in the retail industry, including newer operating systems.

According to the threat intelligence firm InfoArmor, crooks are already using the Pro PoS Solution to target PoS systems used by retailers and SMBs in the US and Canada.
Pro PoS weights just 76KB and implements rootkit features as well as mechanisms to avoid antivirus detection. The experts at InfoArmor explained that Pro PoS integrates a polymorphic engine that allows the threat to generate a different signature for each malware sample.
On November 27, experts at InfoArmor noticed a significant increase of the Pro PoS Solution price which was offered at $2,600 for a six-month licence.
The Pro PoS support TOR to hide its Command and Control (C&C) servers.
The criminal underground is looking with increasing interest to PoS malware, in the last weeks a number of new threats were detected in the wild such as Cherry Picker and ModPoS.
Last week experts at Said iSight Partners discovered ModPOS is new POS malware discovered in systems of US retailers after the rush of Thanksgiving, the researchers speculate it is the most complex POS malware ever seen.
Recently several hotel chains were targeted by criminal gangs, including Hilton, Starwood and Trump.
‘In Our Sites’ Operation seized 999 websites offering counterfeit goods
1.12.2015
Operation In Our sites VI (IOS) – Law enforcement from 27 nations collaborated to take down 37,479 counterfeit sites on biggest web takedown ever.
Nearly one thousand websites have been seized by law enforcement agencies following the international operation In Our Sites (IOS) VI. The websites were offering for sale counterfeit merchandise online to consumers.
The operation was coordinated by the United States Customs and Border Protection with the support of the Europol and Interpol and targeted offending Top Level domains.
It is the first time that the Interpol brought its support through eight of its member countries (Argentina, Chile, Japan, Hong Kong, China, Panama, Peru, South Korea and Thailand) as part of an ‘In Our Sites’ operation.
“Cooperation with private industry remains crucial and is key to monitoring and reporting IP-infringing websites to the concerned countries via Europol, to ultimately make the Internet a safer place for consumers. The participating rights holders represented different sectors including traditional luxury goods, sportswear, spare parts, electronics, pharmaceuticals and toiletries.” states the announcement issued by the Europol about the In Our Sites (IOS) operation.
The international joint effort involved authorities in 27 countries including the UK, Denmark, France and Spain. Copyright holders including tech companies, entertainment industry houses, and fashion outfits provided their support to the operations conducted by law enforcement.
The law enforcement bodies shut down 37,479 copyright-infringing websites selling counterfeit goods to coincide with the Cyber Monday.
“This effort highlights the global commitment to take aggressive action against online piracy,” says Bruce Foucart director of the Homeland Security’s National Intellectual Property Rights Coordination Center. “The IPR Center will continue to collaborate with international law enforcement and industry to protect consumers from purchasing counterfeit goods online, which could expose sensitive financial information and present a health and safety threat.”
This is the sixth ‘In Our Sites’ conducted by the authorities, according to the official statement issued by the Europol this coordinated effort is the largest counter copyright and fraud operation of its kind for both the US Immigration and Customs Enforcement agency and Europol.
“Operation IOS VI followed a new format, in line with the EU Action Plan on the enforcement of intellectual property rights, which resulted in the triggering of seven additional operations. Moreover, several new cases are expected to be initiated due to the huge demand from the rights holders in private industry.”
Previous operations allowed the take down of 690 fraud web sites in 2013 and 292 counterfeit domains in 2014, more details on the operations are available in the following table.
IOS I Websites selling counterfeit merchandise taken down by authorities in Europe and the USA
IOS II 328 internet domains selling counterfeit products targeted by law enforcement
IOS III 690 internet domain names seized because of fraudulent practices
IOS IV 188 internet domain names seized for selling counterfeit products
IOS V 292 internet domain names seized for selling counterfeit products
europol-operations in our sites

Red Hat vylepšuje ve svém Linuxu podporu kontejnerů i bezpečnosti
30.11.2015 Bezpečnost
Dostupnost řešení RHEL (Red Hat Enterprise Linux) 7.2 oznámil Red Hat. Nové vlastnosti a funkce se týkají zejména bezpečnosti, síťových propojení a správy systému.
Platforma Red Hat Enterprise Linux 7.2 je kromě funkčního vylepšení nově kompatibilní i se službou Red Hat Insights pro provozní analýzy, která podle tvůrců díky identifikace známých rizik a technických problémů omezí prostoje či výpadky.
Nový RHEL například nabízí podporu pro OpenSCAP, implementaci protokolu Security Content Automation Protocol umožňující analýzu systému z pohledu dodržování bezpečnostních politik a pravidel. Nový zásuvný modul Open SCAP pro instalátor Anaconda umožňuje tento protokol využívat pro bezpečnostní analýzu konfigurace již během instalačního procesu a zajistit tak bezpečný výchozí bod pro nasazení systému.
Zabezpečení informací poskytovaných systémem doménových názvů zase umožňuje rozšíření DNSSEC, které vytváří tzv. řetězce důvěry -- nově toto rozšíření pro DNS zóny podporuje i systém pro správu identit Red Hat Identity Management system (IdM).
RHEK 7.2 se prý může pochlubit také značným zvýšením síťového výkonu včetně zdvojnásobení propustnosti v řadě situací využívajících virtualizaci síťových služeb (NFF) a softwarově definované sítě (SDN).
Mezi další rozšíření síťového subsystému jádra patří vyladění síťového zásobníku jádra, které výrazně zrychluje zpracování paketů. RHEL 7.2 tak lze využít i v síťově velmi náročných virtuálních i kontejnerových prostředích.
Součástí nové platformy je i Data Plane Development Kit (DPDK) pro rychlý vývoj zákaznických aplikací, které umožňují přímé zpracování síťových paketů jak v uživatelském prostoru NFV, tak i v dalších typech reálných situací.
Nový systém přichází i s řadou vylepšení pro infrastruktury využívající kontejnery. Aktualizací se dočkal mechanismus pro kontejnerový formát docker, podpora atomických kontejnerů i Kubernetes nebo Cockpit. Součástí většiny předplatných je navíc i RHEL Atomic Host 7.2, nejnovější verze hostitelské platformy optimalizované právě pro provoz kontejnerových aplikací.
Nově je v režimu betatestování k dispozici i Container Development Kit 2. Součástí této vývojové sady je kolekce obrazů, nástrojů a dokumentace zjednodušující vytváření kontejnerových aplikací, které jsou certifikovány pro nasazení v hostitelských kontejnerových prostředích společnosti Red Hat. Mezi tato prostředí patří jak Red Hat Enterprise Linux 7.2 a Red Hat Enterprise Linux Atomic Host 7.2, tak i OpenShift Enterprise 3.
Platforma RHEL přichází také s řadou nových i vylepšených nástrojů, které umožňují tyto administrátorské procesy výrazně zefektivnit. Mezi hlavní vylepšení verze 7.2 patří systémový archivační nástroj Relax-and-Recover, díky kterému mohou administrátoři vytvářet lokální zálohy ve formátu ISO. Tyto zálohy lze centrálně archivovat i vzdáleně replikovat a zotavení v případě selhání nebo havárie je tak mnohem jednodušší.
Today NSA has Stopped its Bulk Phone Surveillance Program
30.11.2015
Rejoice!
From this morning, you can call freely to anyone, talk anything without any fear of being spied by the United States National Security Agency (NSA), as the agency is not allowed to collect bulk phone records.
Until now we all are aware of the NSA's bulk phone surveillance program – thanks to former NSA employee Edward Snowden, who leaked the very first top secret documents of the agency in 2013.
However, more than two years later of the first revelation, that bulk phone surveillance program has finally come to an end.
End of Bulk Phone Surveillance Program
The White House announced Friday evening on the intelligence community's official Tumblr that the NSA will officially be shutting down its bulk phone surveillance program by Sunday, November 29.
Under this program, the US intelligence agency collected only the "metadata" that reveals data related to the called phone numbers (i.e. which numbers are calling and what time they place those calls). However, no content of the mobile conversations were recorded by the agency.
"Beginning Sunday, November 29, the government is prohibited from collecting telephone metadata records in bulk under Section 215, including of both U.S. and non-U.S. persons," the official announcement read.
The end of the vast surveillance program comes as a result of the USA Freedom Act passed by Congress back in June.
NSA's Bulk Metadata Collection is illegal
The bulk collection of metadata was ruled illegal by a court in May 2015. The USA Freedom Act ordered the spy agency to terminate collecting bulk phone metadata of U.S. Citizen, but the agency get the program extended until November 29 as a grace period.
The law put an end to the bulk phone data collection in an effort to sniff out suspicious activity. Instead, allow the agencies to request the records from telecom companies to enable monitoring of call records of specific people for up to 6 months if needed in terrorism investigations.
NSA to Request Records directs from the Telecoms
Now, the US spy agency is out of time, and the Obama administration says that it has a less invasive program ready to replace the old program.
So, from now on, the NSA will not be collecting your phone records in bulk – at least under the agencies laid out in Section 215 of the Patriot Act – and will have to request for data individually to telecommunication companies.
Swedish Court — 'We Can't Ban The Pirate Bay'
30.11.2015
Swedish court — 'We can't ban The Pirate Bay'
The controversial file-sharing website The Pirate Bay will still be running in Sweden as the District Court of Stockholm on Friday ruled that they be unable to force the internet service providers (ISPs) to block the website from operating.
The Pirate Bay is an infamous Swedish search engine predominantly used worldwide for pirating material, such as software, movies, music files and TV shows, entirely free of charge.
Numerous ISPs around Europe block the Pirate Bay, but the notorious site will not be inaccessible in its home country Sweden, at least for now, according to the local media.
Last year, a lawsuit was filed by Warner Music, Sony Music, Universal Music, Nordisk Film and the Swedish Film Industry in order to force Swedish ISP broadband companies to block the Pirate Bay, claiming them liable for the infringements of its customers.
Also Read: The Pirate Bay Runs on 21 "Raid-Proof" Virtual Machines To Avoids Detection
However, the Broadband companies refused to comply, stating that their only role is to provide their clients with access to the Internet while facilitating the free flow of information.
Sweden – We can't Ban The Pirate Bay
Now, a Stockholm District Court has handed down its decision in favor of ISPs, ruling that Sweden can not make them block the access to the Pirate Bay website, as those broadband companies are not responsible for what their customers do.
"A unanimous district court considers, therefore, that it is not in a position to authorize such a ban as the rights holders want, and, therefore, rejects their requests," presiding Chief Magistrate Anders Dereborg said.
In other words, the ISP networks are not participating in any crimes, according to the court ruling, as they are just the delivery medium.
Also Read: The Pirate Bay relaunch is FBI's Honeypot? Pirate Bay Team Responds,'NO WAY'
While it is possible that the group representing the copyright holders could appeal a higher court, in the meantime, the group will still have to pay the ISPs legal costs thus far, which amounts to more than $150,000.
So, before the group appeals a higher authority, this is something it might want to reconsider.
A few month back, The Pirate Bay co-founders Gottfrid Svartholm, Fredrik Neij, Peter Sunde and Carl Lundström cleared all the charges alleging criminal copyright infringement and abuse of electronic communications in a Belgian court.
The Hello Barbie doll, lights and shadows
30.11.2015
Mattel’s Hello Barbie has finally arrived in stores, but security experts have raised questions about security and privacy issues related to the technological toy.
Are you thinking of buying a Barbie for your daughter this Christmas?
Mattel’s Hello Barbie has finally arrived in stores, but security experts have raised questions about security and privacy issues related to the technological toy. The Hello Barbie doll is developed by the startup ToyTalk.
In February, The Register was one of the fist news agency reporting security and privacy implications of the Mattel’s Hello Barbie, and now that the popular doll is available for sale a security researcher has discovered security issues with the toy.
“Its Wi-Fi-connected Barbie toy has a microphone, a speaker, a small embedded computer with a battery that lasts about an hour, and Wi-Fi hardware. When you press a button on her belt buckle, Barbie wakes up, asks a question, and turns on its microphone while the switch is held down.” wrote the register.
Last week, the security expert Matt Jakubowski explained that the new Wi-Fi-Enabled Hello Barbie can be hacked, in the specific case to extract Wi-Fi network names, account IDs, and MP3 files from the toy.
“You can take that information and find out a person’s house or business. It’s just a matter of time until we are able to replace their servers with ours and have her say anything we want,” Jakubowski warned.

Oren Jacob, the ToyTalk CEO provided the following statement in response to the Jakubowski affirmation trying to rebuke the alarm.
“An enthusiastic researcher has reported finding some device data and called that a hack.” Jacob said. “While the path that the researcher used to find that data is not obvious and not user-friendly, it is important to note that all that information was already directly available to Hello Barbie customers through the Hello Barbie Companion App. No user data, no Barbie content, and no major security or privacy protections have been compromised to our knowledge.”
Jakubowski explained that it is quite easy to steal the account ID, this means that the attackers need get the password to gain access to the Hello Barbie account. Steal a password could be very simple for example with a spear phishing attack or by using other social engineering techniques.
Unfortunately, the experts at ToyTalk have a different opinion and consider the scenario improbable.
The Campaign for a Commercial-Free Childhood already asked Mattel to drop the Hello Barbie doll, a petition has already been signed by over 6,000 worried people.
We are approaching the holiday season, and recent data breach suffered by the giant VTech raised the question of children’s privacy.
Even if the Hello Barbie doll is secure today, this doesn’t mean that it will be the same tomorrow. Security experts could make a reverse engineering of its software components in order to discover security flaws.
Somerset Recon already reported the news that researchers have dumped the 16 megabits of firmware that runs the doll to analyze it.
“We began dumping the contents of the 16Mbit flash chip, and some pretty neat stuff popped up. Stay tuned for Part Two, where we’ll dive into the architecture of the system and its security implications.” wrote the Somerset Recon.
Stay Tuned!
Obří hack výrobce hraček Vtech ukazuje, jaký hazard je dávat firmám data
30.11.2015 Hacking
Hackeři získali přes 4,8 milionu záznamů o zákaznících a 200 tisíc záznamů o dětech. Jde o jeden z největších úniků spotřebitelských informací v historii.
Hlad po informacích a po všem, co lze nějakým způsobem zpeněžit a využít, nemá konce. Pokud získané informace nikdo nezneužije a jsou bezpečně uloženy, tak se nic neděje. Co se ale stane, pokud hackeři zaútočí na výrobce hraček, který shromáždil osobní informace o stovkách tisíc dětí? Čím se něco takového liší od zásadního hacku Ashley Madison?
Přes 4,8 milionu záznamů o zákaznících a uživatelích webových stránek společnosti VTech se dostalo do rukou hackerů. Mezi nimi je několik set tisíc záznamů o dětech. Kdo jsou jejich rodiče a také kde bydlí, heslo i bezpečnostní otázka s odpovědí a pochopitelně, například, i co mají za hračku/hračky.
Čínská společnost VTech provozuje web, na kterém se zákazníci registrují, aby si mohli k hračkám stahovat dodatečný software. Jak se můžete dočíst v One of the Largest Hacks Yet Exposes Data on Hundreds of Thousands of Kids, hackerům se podařilo z jejich serveru získat skoro pět milionů záznamů o rodičích a přes dvě stě tisíc informací o dětech.
Konkrétně jde o 4 833 687 účtů „rodičů“ (e-mail, hesla, adresy, bezpečnostní otázky, produkty, atd.) a u dětí byla odcizena křestní jména, informace o pohlaví a data narození. Údaje o dětech jsou ale propojeny s rodiči, takže je možné získat kompletní jména, včetně toho, kde bydlí.
Firma hack potvrdila, ale klasicky o něm až do okamžiku, kdy ji upozornil autor výše uvedeného článku na Motherboard.com, vůbec nevěděla. V pátek nakonec společnost únik dat oznámila, ale zákazníky nijak blíže o jeho závažnosti neinformovala. Nezmínili se o objemu úniku, ani tom, že uložená hesla jsou šifrována nedostatečně. A hlavně, ani slovo o tom, že unikly informace o stovkách tisíc dětí.
Ohroženy mohou být i informace českých zákazníků
Vtech není žádný malý výrobce hraček, je natolik rozšířený po světě, že jeho výrobky najdete i v České republice, včetně české verze webu (na www.vtechcz.cz).
Na tom informaci o hacku nehledejte, ale na mateřském webu ano (viz Data Breach on VTech Learning Lodge). Podle tohoto vyjádření mají uniklá data spojitost s webem Learning Lodge – ten je momentálně mimo provoz.
Samotný hack proběhl s pomocí SQL injection, tedy vsunutí SQL příkazů do parametrů některého ze skriptů, které jsou dostupné na webu. Jedna z nejčastějších chyb, která také nejsnáze vede k získání přístupu k obsahu databází. Hacker serveru Matherboard sdělil, že se mu poté podařilo získat přístup k webu i databázím v root úrovni, tedy v plné podobě. Jakkoliv hacker uvádí, že data se nechystá zveřejnit, není vůbec jisté, jestli je nezískal i někdo jiný.
Zásadní problém v úniku dat o dětech
Pokud uniknou data ze služby jako je seznamka pro nevěrníky (viz kauza Ashley Madison), dotkne se problém dospělých lidí, u kterých lze předpokládat, že se s hackem a případnou snahou o zneužití dokáží vyrovnat. Data uniklá z VTechu se ale týkají dvou stovek tisíc dětí, které se s případným útočníkem, ať už je to pedofil nebo někdo, kdo chce škodit jinak, zcela určitě vypořádat nedokáží. Objemem jde navíc o jeden z největších úniků spotřebitelských informací v historii.
Pokud jste si pořídili hračku od VTechu, měli byste si ověřit, jestli právě vaše informace nejsou nyní dostupné někomu cizímu.
Troy Hunt, provozovatel serveru haveibeenpwned.com, se nejenom podílel na analýze dat pro Motherboard, ale také do své služby doplnil e-maily, které v úniku byly. Stačí na této adrese zadat vaši e-mailovou adresu a zjistíte, jestli je v úniku (ale také jestli není v jiných únicích). Nic jiného tam zjistit nemůžete, pouze prosté je/není.
Pokud jste se na webech VTechu někdy registrovali, tak považujte vaše tamní heslo za prozrazené a už nikdy ho nepoužívejte. Pokud máte obvyklý laxní přístup a hesla používáte na více webech, je nejvyšší čas přístup změnit, pořídit si správce hesel a strávit pár hodin tím, že všude, kde máte toto heslo, si nastavíte nové, pro každou službu unikátní. Unikla navíc i kompletní bezpečnostní otázka i s odpovědí, takže pokud ji někde používáte, musíte změnit i to.
Pokud jste snad VTechu poskytli informace o vašem dítěti či dětech, tak na to žádné řešení neexistuje. Někdo neznámý tyto informace má a může je zneužít. Od neškodných věcí jako je cílení spamu až po závažné věci v podobě někoho, kdo bude chtít ublížit vám, nebo vašemu dítěti. Na něco podobného jste měli myslet ještě předtím, než jste vyplnili kdesi na potenciálně nebezpečném webu konkrétní informace o dítěti.
Sám Troy Hunt únik informací o dětech komentuje ve When children are breached – inside the massive VTech hack a vůbec se nelze divit tomu, že je únikem dat zděšený a upozorňuje na to, že jde o extrémně nebezpečnou situaci. Ukazuje tam i na obvyklé zásadní problémy dostat se ke konkrétní zodpovědné osobě u napadené společnosti i to, že nelze věřit vyjádřením, které hacknuté firmy zveřejňují.
Ignorantský přístup VTechu
Hesla uložená jako MD5 hash? Výborný způsob, protože díky tomu je možné hesla okamžitě získat. Kontrolní otázky a odpovědi na ně uložené v čistě čitelné podobě. V databázi uživatelů je poté už vše klasické – jméno, příjmení, kdy se poprvé a naposledy přihlásil, odkud se přihlašuje, adresa bydliště.
Co se dětí týče, tak mají vlastní účet, propojený s účtem rodiče a obsahují jména, data narození, pohlaví a přihlašovací údaje. Uniklo celkem 227 622 takových záznamů. Nutno dodat, že zakládání účtů dětí neprobíhalo pouze na webech VTechu, ale ještě na některých dalších webech, které se společností souvisí. V databázi nakonec nechybí ani informace o tom, které z produktů si zákazník pořídil.
Troy Hunt upozorňuje, že VTech své weby provozuje bez SSL, ale také třeba to, že heslo rodiče se běžně shoduje s heslem dítěte. A aby toho nebylo málo, hesla dospělých jsou sice uložena v MD5 podobě, ale hesla dětí jsou v čisté textové podobě. Stejně ignorantsky se tvůrci webu chovají v oblasti bezpečnostních otázek a odpovědí na ně.
Troy Hunt navíc ukazuje i na takové ty skoro klasické věci, jako že když zadáte špatně heslo, tak server odpoví přímo s textem neúspěšného SQL dotazu (a ano, uvidíte tam MD5 hash). Do záplavy nezodpovědného přístupu si přidejte i značné používaní Flashe, včetně funkčností, které v žádném případě Flash nepotřebují.
Web VTechu je, pokud si ho budete prohlížet, takovou připomínkou toho, jak se weby v minulosti dělaly. Podle všeho je tomu tak i na serverové straně a nejenom proto, že je to celé ve staré verzi ASP.NET, ale také výše uvedenými způsoby řešení věcí. Protože tímto způsobem se programovaly weby někdy před pěti a více lety.
Podstatně horší informace nakonec Troy Hunt pouze zmiňuje, ale nijak konkrétně nerozvádí – informace o uživatelích a dětech podle něj byly volně získatelné přes web. Bez jakékoliv potřeby cokoliv hacknout či obejít, prostě tak „jak web fungoval“.
Lze se velmi oprávněné domnívat, že dotazy do databáze (osobně bych si tipnul z Flash souborů) byly nehlídané a uskutečnitelné i bez přihlášeného uživatele, včetně obvyklého problému se sekvenčním přístupem k datům v databázi přes jejich číselné ID. Jedna z těch typických chyb, které se objevovaly a objevují u aplikací ve Flashi – tvůrci se domnívají, že nikdo nemůže zjistit, na jakou URL směřují dotazy z Flashe.
Závěr
Pokud jste vy (a vaše děti) uživateli produktů od společnosti VTech, tak se ujistěte, že jste se nikdy neregistrovali na jejich webu (pomoci vám může kontrola e-mailu v haveibeenpwned.com, protože jejich web je mimo provoz). Pozor na trochu starší děti, které se mohly zaregistrovat i bez vašeho vědomí.
Pokud se vaše informace nacházejí v databázi VTechu, máte problém. Je nutné změnit hesla, jak vaše, tak u případných online účtů vašeho dítěte. Pokud o vašem dítěti VTech získal výše uvedené informace, je zde potenciální riziko, že se ho někdo může snažit kontaktovat online a zneužít informace k různorodým účelům. Je to něco, čemu už zabránit nemůžete, ale můžete alespoň dítě poučit o tom, že něco takového se může dít a jak se má zachovat.
Jedno zásadní poučení pro budoucnost? Nevyplňujte informace o vás a o dětech pravdivě. O dětech ideálně nevyplňujte nic, protože jsou příliš snadno zneužitelným terčem.
Měli byste se pokusit o to, aby váš účet z databází VTechu zmizel, tedy smazat ho. V tom ale narazíte na další typickou ukázku ignorance tvůrců tohoto webu: účty není možné mazat. Jediné, co můžete udělat, pokud se vám vůbec podaří přihlásit, je, že všechny údaje změníte na nesmyslné. Jakkoliv vám to po už existujícím úniku může připadat zbytečné, není tomu tak. Systémy VTechu jsou velmi pravděpodobně stále zneužitelné.
Hello Barbie, hacknutá panenka s Wi-Fi jako špiónská štěnice
30.11.2015 Hacking
Hello Barbie, hacknutá panenka s Wi-Fi jako špiónská štěniceVčera, Milan Šurkala, aktualitaInformační technologie dávno pronikly i do hraček a např. panenka Hello Barbie je vybavena Wi-Fi připojením. To je použito k analýze hlasu dětí, aby panenka mohla odpovídat. Bezpečnostní technici už dokázali prolomit zabezpečení těchto dat.
Společnost Mattel prodává Wi-Fi panenku Hello Barbie, která má v sobě mikrofon a Wi-Fi připojení. To umožňuje dětem si s panenkou rozumně "pokecat". Jejich hlas se nahraje, přes Wi-Fi se posílá na server k analýze a panenka pak zpětně odpovídá. Problém je v tom, že ačkoli je tato komunikace zabezpečená, jako snad u všech druhů komunikace tohoto druhu bylo jen otázkou času, než se ochranu podaří prolomit. Americky bezpečnostní technik Matt Jakubowski si vzal tuto panenku na paškál a opravdu se dostal k datům, která by neměla být zveřejněna.

Dokázal se dostat k interním systémovým informacím panenky, některým údajům o Wi-Fi připojení a MP3 souborům (do panenky lze uložit přes mobilní aplikaci konfigurace až tří Wi-Fi sítí). Zároveň nastínil, že je jen otázkou času, kdy servery společnosti ToyTalk (ta pro Mattel zajišťuje analýzu řeči) nahradí servery hackerů a následně mohou být dětské pokoje plné odposlouchávacích štěnic. Podotkněme, že Matt pro tentokrát potřeboval fyzický přístup k panence k prolomení.
Protože panenka na slova dětí odpovídá, je tu možnost, že hackeři podstrčí své vlastní odpovědi a raději ani nedomýšlejme, co vše budou chtít dětem navykládat (od věcí sledující komerční prospěch na jedné straně až po perverznosti na straně druhé), nemluvě o odposlouchávání domácnosti jako takové. Tvůrci považují svou panenku za naprost bezpečnou. I bez hackerů je zde otázka, zda Mattel přímo nevyužije odpovědi panenky ke komerčním účelům. Rodiče mohou nahrávky poslouchat na svém účtu u ToyTalk a odhalit tak tajemství svých dětí svěřená panence, což také není ideální. Dokonce vznikla iniciativa Hell No Barbie bojkotující panenku a varující jak před bezpečnostními rizika, tak před riziky ve výchově dětí.
ITAR (International Traffic in Arms Regulations) as cyber arms control
30.11.2015
That means that the State Department and the Pentagon are looking for an alternative framework, they might find it in the ITAR.
The US has failed to take the offensive cyber products to the Wassenaar agreement. That means that the State Department and the Pentagon are looking for an alternative framework. They might find it in ITAR [International Traffic in Arms Regulations].
The Obama administration understands that something has to be done to regulate the violence in the cyber domain. Cyber arms control and regulation are hot topics right now.
The last try to impose cyber arms control was with Wassenaar agreement that regulate dual use technologies. But, the big tech companies opposed, and the initiative failed.
I would like to argue that the Obama administration can choose to implement instead cyber arms control within the ITAR regulation.
ITAR
The ITAR is a set of United States Government regulations on the export and import of military related articles and services. Therefore, it can contain the offensive cyber technologies and give the US control over them.
One has to acknowledge that most of the cyber technologies are coming from US companies or companies that were funded by US money. It allows the US to use ITAR to control the export of those technologies.
The use of ITAR opens more possibilities in this context. For example, the US can decide that every code written on a CPU of Intel or AMD [US companies] is subject to ITAR. Equally, it can apply to any electronic product that is funded by US money or developed in the US.
If the US goes this way, others will follow. China is another country bothered with cyber defence. It is also a significant producer of electronics. That means that the Chinese government can apply a regulation like ITAR. Besides US and China, this is true for any “ITAR-Free” country.
To summarize, cyber technologies regulation is a must. There is no better option for the international community to decrease the violence in the cyber domain. The question on the table will it be by the Wassenaar Agreement, ITAR or a new one.
Recommended Reading:
http://insct.syr.edu/wp-content/uploads/2015/11/Herr_Rosenzweig_Cyber-Weapons-and-Export-Control.pdf
Trident nuclear weapons system could be vulnerable to cyber attacks
30.11.2015
The former British defence secretary Des Browne is warning that the Trident nuclear weapons system could be vulnerable to cyber-attack.
According to the Guardian, the former British defence secretary Des Browne called on the British Prime Minister to assess the resilience to cyber attacks of the Trident nuclear weapons system.
“The UK Trident programme encompasses the development, procurement and operation of the current generation of British nuclear weapons, and the means to deliver them.” states Wikipedia.
The Britain’s Trident nuclear weapons system may be obsolete soon unless David Cameron can protect it from cyber attacks of nation-state actors.
“The government … have an obligation to assure parliament that all of the systems of the nuclear deterrent have been assessed end-to-end against cyber attacks to understand possible weak spots and that those weak spots are protected against a high-tier cyber threat. If they are unable to do that then there is no guarantee that we will have a reliable deterrent or the prime minister will be able to use this system when he needs to reach for it.” states Browne.
The UK’s former defense secretary is seeking assurance from the Prime Minister that the Trident nuclear weapons system is secured against attacks from hostile persistent threat actors, such as Russia and China.
UK Trident nuclear weapons systems 2
According to a report issued by the US department of Defense on Resilient Military Systems, there is the concrete risk that the US and its allies could suffer a major attack on their military systems.
“The United States cannot be confident that our critical Information Technology (IT) systems will work under attack from a sophisticated and well-resourced opponent utilizing cyber capabilities in combination with all of their military and intelligence capabilities (a “full spectrum” adversary).” states the report. “While this is also true for others (e.g. Allies, rivals, and public/private networks), this Task Force strongly believes the DoD needs to take the lead and build an effective response to measurably increase confidence in the IT systems we depend on (public and private) and at the same time decrease a would-be attacker’s confidence in the effectiveness of their capabilities to compromise DoD systems. “
For the protection of the Trident nuclear weapons system it is essential to assess the military components searching for possible weaknesses and fix them.
According to the New Statesman, a spokesperson from the MoD explained that the Trident system is an air-gapped system, but we know that this is not sufficient to consider a system as security.
Security experts at FireEye discovered a Chinese hacking crew, dubbed APT 30, that was focusing its cyber espionage operations on air-gapped networks. The APT30 has many other tools in its arsenal that includes backdoors, malware with the ability to compromise air-gapped networks, downloaders and many others. Some of these tools were used only by the APT30 operators.
The British chancellor George Osborne last week to announce that the UK Government would allocate more than £3.2bn to cybersecurity over the next five years. Despite the significant effort, Browne expressed his skepticism on the protection of the Trident.
“My instinct is to think that £3.2bn over five years, comes nowhere near the scale of the cyber-threat challenge, if it includes ensuring cybersecurity for the command and control of our nuclear weapons. Also, this is the environment to which Moore’s law applies. Consequently, we can expect cyber-capacity to have doubled and doubled again since the report was published and to continue to increase.” said Browne.
Assassins in the darkweb, “Service catalogue” and Price list” updated
30.11.2015
Contract killers on darkweb have come up with updated “service-catalogue” with updated prices. Which are major changes and trends for prices?
Contract killers on darkweb have come up with updated “service-catalogue” with updated prices.
While comparing the recent screenshot of their “service-catalogue” captured from a C’thulhu Darksite with the published earlier, the following updates have been observed
They have done away with the “rank” systems, they have done away with the “rank” categorization for the target, and instead they have adopted a fairly simple categorization approach. The target would simply be categorized either as a “Regular Person” or a “public person”; there will not be any “medium” ranked targets. So, they have done away with “medium rank” categorization. Moreover, they have added the prices for higher difficulty levels; i.e., they have added the prices for the targets with the guards. Moreover, the prices vary based on the number of guards, if the target has 1 or 2 guards then the price would be higher than the target without the guards and if the target has 3-5 guards then the price for that would be the highest as the “difficulty level” would be the highest.
The old Pricelist found in the darkweb
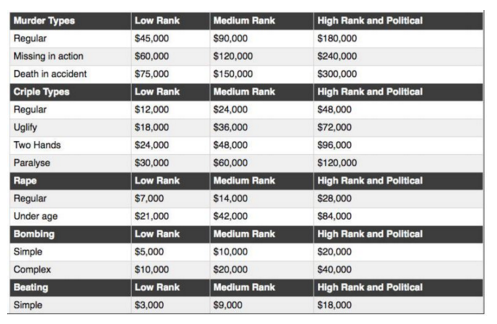
Below the new one
One more thing that drew the attention was that they have changed their tag-line as well; earlier, it used to be “The best place to put your all problems to grave!” the recent capture shows the tag-line as “ No fish is too big, no job too small – HITMAN does it all !”
Furthermore, if we observe the language used in Q&A, we can say that this was not written by a native English writer as there are conspicuous grammatical mistakes in writing.

Another known assassination market “Hitman Network” also updated its price list, they have significantly lowered the price than what was published/reported earlier. They have almost gone down by 50%.
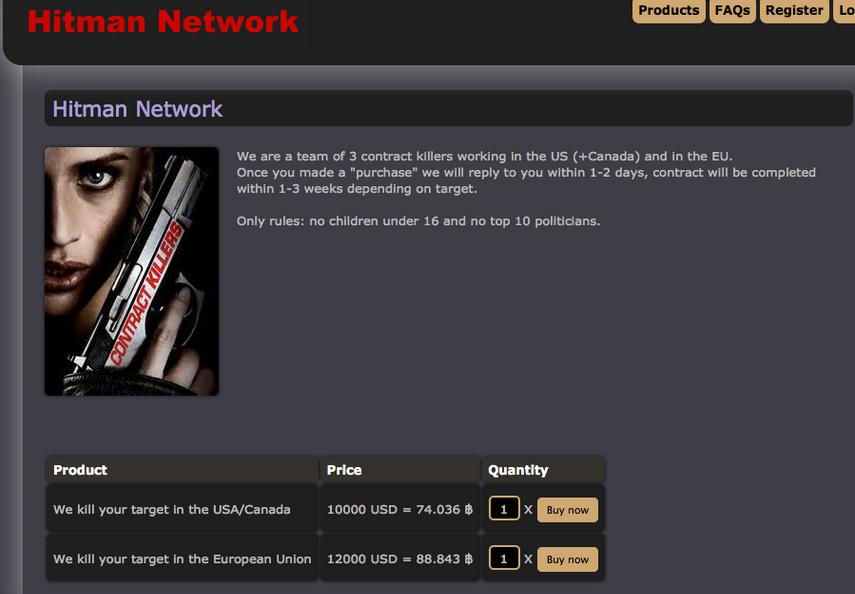

Moreover, the significant price difference was observed between these 2 killer markets, C’thulhu has got 45,000 USD for a regular target whereas Hitman has got only around 5000 USD for its target. We are not sure how many of these market offerings are legit.
Vtech hacked, data of thousands of kids exposed
30.11.2015
Toy maker Vtech has been hacked exposing data of thousands of kids, this hack is the fourth largest consumer data breach to date.
The greatest manufacturer of electronic toys Vtech, aka Video Technology Limited, was hacked. On 14 November, “an unauthorised party” managed to obtain access to the app store database of Vtech, the Learning Lodge.
The Learning Lodge includes apps, learning games, e-books, educational content and customer data (names, email IDs, passwords, questions and answers for password retrieval, IP addresses, and mailing addresses as well as download history), Vtech clarified that the database does not contain any financial data.

According to Motherboard the data breach may have exposed personal information of about five million parents who bought Vtech products and more 200,000 kids.
“The personal information of almost 5 million parents and more than 200,000 kids was exposed earlier this month after a hacker broke into the servers of a Chinese company that sells kids toys and gadgets, Motherboard has learned.” states Motherboard. “The hacked data includes names, email addresses, passwords, and home addresses of 4,833,678 parents who have bought products sold by VTech, which has almost $2 billion in revenue. The dump also includes the first names, genders and birthdays of more than 200,000 kids.”
The data stored in the app store database of Vtech belong to customers from several countries worldwide, including the US, China, the Netherlands, Denmark, Canada, the UK, Belgium, Ireland, France, Germany, Spain, Luxembourg, Latin America, Hong Kong, Australia and New Zealand.
The company issued an official statement admitting the data breach announcing an ongoing investigation.
“VTech Holdings Limited today announced that an unauthorized party accessed VTech customer data housed on our Learning Lodge app store database on November 14, 2015 HKT.” states the official statement. “Upon discovering the unauthorized access we immediately conducted a thorough investigation, which involved a comprehensive check of the affected site and implementation of measures to defend against any further attacks.”
The company received an email asking about the incident on 23 November, then started the investigation that revealed irregular activity on the Learning Lodge website.
The company announced that is working to improve security of the app store database and protect its customers.
“We are committed to protecting our customer information and their privacy, to ensure against any such incidents in the future.” added the company.
Motherboard analyzed the breached archive with the support of the security expert Troy Hunt, who maintains the website Have I Been Pwned.
Hunt discovered the archive contains “hashed” passwords or protected with an algorithm known as MD5, quite easy to break. The secret questions used for password or account recovery were stored in plaintext, crooks could potentially use them to take over other accounts belonging to the victims..
“That’s very negligent,” Hunt said. “They’ve obviously done a really bad job at storing passwords.”
As explained by Hunt, the most worrisome aspect of this data breach is the fact that it contains data about kids.
“When it includes their parents as well—along with their home address—and you can link the two and emphatically say ‘Here is 9 year old Mary, I know where she lives and I have other personally identifiable information about her parents (including their password and security question),’ I start to run out of superlatives to even describe how bad that is,” Hunt wrote in a blog post he published on Friday.
At the time of publishing VTech have taken services offline to fix the issue.
Russia deploys jamming systems in Syria as tensions rise
30.11.2015
Russia will deploy jamming systems in Syria to protect its air forces and prevent attacks against its aircraft.
The Russian army in Syria is planning to launch electronic warfare in the country with the institution of jamming systems. The jamming systems are an essential component of the Russian military strategy that aims to prevent attacks against its troops in the area.
On Tuesday, the Turkish Air Force brought down a Russian Su-24M Fencer bomber using an air-to-air missile in Syria near the Turkish border. Officially, the Turkish Air Force was carrying out strikes against terrorists in northern Syria.

According to the according to Lieutenant-General Evgeny Buzhinsky, Russia will have engage an electronic warfare to protect its pilots and prevent a similar attack.
The Russian forces will use both ground-based systems and specific equipment installed on a number of aircraft in the Russian aerial fleet.
It is a war scenario, the Russian military will install in Syria a highly sophisticated missile system to target any enemy aircraft flying over the area.
The incident is raising tensions between Russia and Turkey, Vladimir Putin used the following statement to describe the incident:
“a stab in the back by the accomplices of terrorism.”
The presence of a jamming system in the area will prevent a similar incident by interfering with electronic components of the attackers.
“Regarding the possible impact of this incident on the further developments of the operation in Syria, I think that from now on, our pilots will be more attentive and if the Turks continue behaving in such a manner, Russia will have to resort to electronic jamming and other warfare equipment, including special aircraft with special equipment on board, in order to protect our pilots from being stricken with missiles,” explained Buzhinsky.
In October the Russian news agency SputnikNews reported the presence of Russian cruiser mounted S-300 missile defense system in the shore of Latakia. Jamming systems were referred by the NATO’s supreme commander General Philip Breedlove described as the Russian A2/AD (anti-access/area denial) bubble in Syria.
The electronic equipment blinded NATO inside a bubble of 600 km in diameter centered on the Russian base in Latakia.
“The technology in question seems similar to the KRET Richag-AV system, although it apparently functions on a larger scale. A tactical version of this system was presented to journalists in April 2015.” reported the SputnikNews.
Turris Omnia Security Project protects home network users
30.11.2015
The non-profit security research Turris Omnia project originating from the Czech Republic focuses on safety of SoHo users.
The non-profit security research project originating from the Czech Republic, which focuses on safety of SoHo users, has recently entered a new phase. This project, whose users include such celebrities as Vint Cerf and Steve Crocker, is the work of CZ.NIC, the administrator of the Czech national domain .CZ and developer of globally used open-source projects, such as the authoritative DNS server KnotDNS or the routing daemon Bird.
In the original project, each user of the service received a Turris router, which extends standard functions of a home router to include the ability to analyze traffic between the Internet and the home network, while identifying suspicious data streams. If such data stream is detected, the router alerts the Turris central to a possible attack. The system central then compares data from many connected Turris routers and evaluates the detected threat.

If the threat is classified as attack, updates are created and distributed throughout the Turris network to help protect all other users. The router also includes other interesting safety-related features. One of them is the Majordomo tool which enables the user to check what public IP addresses the devices on their network communicated with. This tool was inspired by earlier problems of some IoT devices, such as TVs, which were caught sending data “home”.
Hardware and software developed within the project are completely open and accessible to the whole community. The aim of this project is to increase the safety of SoHo users while identifying new threats on the Internet. The Turris router supports IPv6, DNSSEC, automatic updates, and much more. The router, which is an important part of the project, was originally intended only for users from the Czech Republic. Due to the great success of the project, it was decided to create a similarly equipped device that would be available to users from other countries.
This is how the project of the Turris Omnia router came to be, which retained most important features of the original device.
The performance is provided by a 1.6GHz dual-core ARM CPU, 4GB of flash storage and 1GB of DDR3 RAM. Turris is ready for fast WAN and LAN: it has six 1Gb ports and dual-band Wi-Fi 802.11ac (3×3 MIMO)/ 802.11b/g/n (2×2 MIMO).
It also offers an SFP connector for optical Internet. Such a powerful router obviously suggests other possible uses, for example as a home NAS, that is why two USB 3.0 ports are also included. The router’s board has two Mini PCI Express ports, one mSATA, pins for GPIO, I²C, SPI and even a slot for a SIM card. Compared to the original Turris router, Turris Omnia brings one major change.

Participation in the research project is voluntary and the user can decide whether to enable the collection of anomalies on the device, for example.
Both versions of the router also allow their users to redirect certain ports to the common honeypot of the project, making the system central receive information about the behavior of attackers in the various networks, to which the routers are connected.
Thanks to this option, the project has already achieved success in detecting suspicious behavior of particular systems, protecting users from web pages spreading malware and identifying Turris clients’ computers that were members of the Zeus botnet. In the course of the last year’s investigation of attacks on users of the Synology Company, the company became interested in the anonymous data from the project.
The Turris project publishes information on curious findings on the CZ.NIC blog.
The Turris Omnia router can now be ordered in the crowdfunding campaign on Indiegogo either as the raw motherboard, or the complete device. The project remains non-profit, the price takes into account only the actual costs of CZ.NIC for the device production.
Terror alert spam detected by Symantec in the wild
30.11.2015
Cybercriminals impersonate law enforcement officials in Dubai, Bahrain, Turkey, and Canada to send terror alert spam and serve RATs.
No Doubts, cyber criminals are jackals always ready to exploit any event in the headlines, even the most dramatic incidents. We have assisted in the past many cases in which crooks exploited the media attention on news events, such as the mysterious skyjacking of the Malaysian Airlines flight MH370 or the incident occurred at the AirAsia flight QZ8501.
News of the day is that people from several countries, including Canada, Dubai, Bahrain and Turkey, have received fake “terror alert” emails. According to Symantec, the bogus notifications advise recipients reading the mail to keep them and their families and company secured from an imminent attack.

The specific campaign leveraged on malicious emails with two attachments which according to the content in the mail is a brief on measures to adopt to remain secure. One of the attachment is in reality a document containing indications on the measured to adopt, the second one is a malware used to infect the victim’s computer.
The malicious code is a multiplatform remote access Trojan (RAT) dubbed Jsocket (Backdoor.Sockrat), a RAT which was developed by the same authors of the AlienSpy RAT.
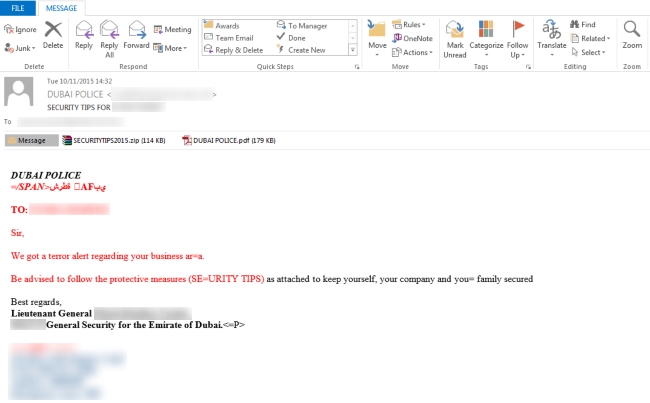
Operators behind the campaign used the signatures from local law enforcement agency’s officials in order to trick victims by giving more credibility to the messages.
“Earlier this month, Symantec observed malicious emails spoofing the email address of one United Arab Emirates (UAE) law enforcement agency, particularly the Dubai Police Force. These spear-phishing emails, which read like a warning from the Dubai Police, bank on users’ fear of terror attacks to trick them into executing the malicious attachments. The attachments are disguised as valuable security tips that could help recipients to protect themselves, as well as their companies and their families, from potential terror attacks that may occur in their business location.” states Symantec in a blog post.
“To add more credibility to the emails, the crooks impersonate the incumbent Dubai Police lieutenant general, who is also the head of general security for the emirate of Dubai, by signing the email with his name.”
The experts noticed that the spear phishing messages were well written and all officials used as alleged sender are currently in office.
Another element of interest highlighted by Symantec is represented by the effort spent by threat actors in targeting their victims, for example, the subject in most cases reflects the name of an employee who works for the targeted company. This circumstance leads the expert to believe that attackers have a specific knowledge of their victims.
Symantec experts confirm we may yet see more of these kinds of social engineering tactics preying on real-world fears, be careful!
Další krok k ochraně před úniky dat
30.11.2015 Ochrany
Kombinace systému prevence před únikem dat v síti s řešením DLP pro koncové body odhaluje další skrytá zákoutí sítě.
Implementace technologie pro monitorování aktivit uživatelů a sítě může přinést překvapivá zjištění. Náš nástroj pro správu událostí a incidentů (SIEM) nám nečekaně oznámil rozsáhlé zamoření sítě.
Když jsme kdysi nasadili systémy detekce a prevence incidentů v naší bráně firewall, ohromil nás počet pokusů o prolomení směřujících na naše prostředky připojené do internetu. A když jsme implementovali síťově založený nástroj ochrany před únikem dat (DLP), zažili jsme něco obdobného.
Během několika dnů provozu jsme objevili celou řadu dat unikajících z naší společnosti a dokonce jsme odhalili nelegální aktivity (zaměstnanec domlouvající se s někým mimo firmu na spáchání trestného činu).
Síťové řešení DLP tedy přináší výhody, ale má své problémy. Zaprvé můžeme monitorovat síťový provoz pouze v místech, kde jsme nainstalovali monitor sítě.
Naše společnost má více než 60 poboček po celém světě, a dokud nezměníme architekturu sítě, bude mít každá tato pobočka své vlastní připojení do internetu, což znamená, že bychom museli nasadit 60 senzorů a nakonfigurovat 60 přepínačů. To je logistická noční můra.
Zadruhé bez složitých konfigurací proxy na každé vzdálené pobočce nemůžeme monitorovat šifrovaný síťový provoz. Nelze monitorovat internetový provoz zaměstnanců, kteří jsou mimo síť (řekněme v důsledku práce na dálku), pokud nejsou připojení přes síť VPN.
DLP pro koncové body
Abychom toto vše a řadu dalšího vyřešili, rozhodli jsme se spustit pilotní projekt řešení DLP pro koncové body.
DLP pro koncové body má některé nevýhody. Například na rozdíl od síťového DLP neumožňuje kontrolovat složité shody indexů dat. Jejich prostřednictvím můžete v systému DLP definovat, jaké texty dokumentů považujete za citlivé.
Když potom uživatel zkopíruje i jen pár řádků z identifikovaného dokumentu a vloží je do jiného dokumentu nebo je pošle e-mailem, systém DLP takovou aktivitu zjistí, zablokuje ji nebo pošle upozornění. Tato úroveň detekce není u DLP pro koncové body zcela k dispozici.
DLP pro koncové body ale nabízí několik výhod. Zaprvé řeší problém šifrované komunikace, protože monitoruje aktivity ještě před použitím kódování. Funguje také i v situaci, když se uživatel dostane mimo síť. Dokáže rovněž zaznamenat případ zkopírování dat na externí médium, například na USB flash disk.
Pilotní projekt nasazení DLP pro koncové body zahrnuje cca 200 osob našeho IT personálu z celého světa. Po počátečním vyladění byly výsledky téměř okamžité. Během několika hodin jsme viděli, jak IT inženýr vyšší úrovně zkopíroval obrovské množství citlivých konfiguračních souborů Active Directory a adresářů zaměstnanců na externí USB disk. Celkem zkopíroval cca 3 GB dat včetně 2 GB archivovaných e-mailů.
Týmová práce
To vypadalo dostatečně podezřele, ale skutečný přínos vznikl díky tomu, že se síťové DLP a DLP koncových bodů vzájemně doplňují. Stejného IT inženýra označil i náš síťový systém DLP, když na něj upozornil na základě pravidla „opouštím firmu“.
Tato zásada dává systému pokyn hledat libovolnou komunikaci, ze které by mohlo být patrné, že nějaká osoba plánuje opustit společnost. Tomuto oznámení bychom zřejmě nevěnovali dostatečnou pozornost, pokud by nás systém DLP pro koncové body neupozornil na kopírování dat.
Promluvili jsme tedy s dotyčným inženýrem, on nám dal USB disk a personální oddělení mu důrazně připomnělo dohodu o mlčenlivosti, kterou podepsal.
Samozřejmě že použijeme případ odcházejícího IT inženýra při naší obhajobě vhodnosti globálního nasazení DLP pro koncové body, jakmile to bude možné.
Pokud dostaneme zelenou, uděláme hodně úprav, aby se snížilo množství falešných poplachů a nedocházelo ke sledování osobních aktivit zahrnujících finance a zdraví.
Vypadá to tedy, že získáme opět spoustu překvapivých informací – tentokrát od systému DLP pro koncové body.
Critical 'Port Fail' Vulnerability Reveals Real IP Addresses of VPN Users
27.11.2015
A newly discovered flaw affecting all VPN protocols and operating systems has the capability to reveal the real IP-addresses of users' computers, including BitTorrent users, with relative ease.
The vulnerability, dubbed Port Fail by VPN provider Perfect Privacy (PP) who discovered the issue, is a simple port forwarding trick and affects those services that:
Allow port forwarding
Have no protection against this specific attack
Port Forwarding trick means if an attacker uses the same VPN (Virtual Private Network) as the victim, then the real IP-address of the victim can be exposed by forwarding Internet traffic to a specific port.
"The crucial issue here is that a VPN user connecting to his own VPN server will use his default route with his real IP address, as this is required for the VPN connection to work," Perfect Privacy wrote in a blog post on Thursday.
Also Read: This Secure Operating System Can Protect You Even if You Get Hacked.
Port Fail affects all VPN protocols including…
OpenVPN
IPSec
…as well as applies to all operating systems, posing a huge privacy risk.
How Does 'Port Fail' Work?
A successful IP address leak attack requires an attacker to be on the same VPN network as the victim and to know the victim's VPN exit IP address, which could be discovered by tricking a victim into visiting a website control controlled by the attacker.
For example, an attacker with port forwarding enabled can see the request from the victim's actual IP addresses by tricking the victim into opening an image file.
The same attack is possible for BitTorrent users, but, in this case, there is no need for the attacker to redirect the victim to their page.
In this case, the attacker only with the activated port forwarding for the default BitTorrent port, can expose the real IP-address of a VPN user on the same network.
Also Read: Hackers Backdooring Cisco WebVPN To Steal Customers' Passwords
Affected VPN Providers
The flaw affected various large VPN providers. Perfect Privacy tested nine VPN providers out of which five were found to be vulnerable to this flaw and were alerted last week.
VPN providers including Private Internet Access (PIA), Ovpn.to and nVPN have fixed the issue before publication.
However, the company warned, "other VPN providers may be vulnerable to this attack as we could not possibly test all."
VPN aims to make you sure that your real identity remains anonymous on the Internet so that nobody could track the origin of your connection back to you, but this newly discovered flaw shows that it's quite easy to bypass this on some VPN providers.
Millions of IoT Devices Using Same Hard-Coded CRYPTO Keys
27.11.2015
Millions of embedded devices, including home routers, modems, IP cameras, VoIP phones, are shareing the same hard-coded SSH (Secure Shell) cryptographic keys or HTTPS (HTTP Secure) server certificates that expose them to various types of malicious attacks.
A new analysis by IT security consultancy SEC Consult shows that the lazy manufacturers of the Internet of Things (IoTs) and Home Routers are reusing the same set of hard-coded cryptographic keys, leaving devices open to Hijacking.
In simple words, this means that if you are able to access one device remotely, you can possibly log into hundreds of thousands of other devices – including the devices from different manufacturers.
Re-Using Same Encryption Keys
In its survey of IoT devices, the company studied 4,000 embedded devices from 70 different hardware vendors, ranging from simple home routers to Internet gateway servers, and discovered that…
…over 580 unique private cryptographic keys for SSH and HTTPS are re-shared between multiple devices from the same vendor and even from the different vendors.
The most common use of these static keys are:
SSH host keys
X.509 HTTPS certificates
SSH host keys verify the identity of a device that runs an SSH server using a public-private key pair. If an attacker steals the device's SSH host private key, he/she can impersonate the device and trick the victim's computer to talk to his computer instead.
Also Read: SSL Encryption — Securing Internet of Things (IoT)
The same happens in the case of websites if an attacker gains access to the device's HTTPS private certificate, which is actually used to encrypt traffic between users and its Web-based management interface.
The attacker can then decrypt the traffic to extract usernames, passwords and other sensitive data with the help of device's HTTPS private key.
MILLLLLIONS of Devices Open to Attacks
When scanned the Internet for those 580 keys, the researchers found that at least 230 crypto keys are actively being used by more than 4 Million IoT devices.
Moreover, the researchers recovered around 150 HTTPS server certificates that are used by 3.2 Million devices, along with 80 SSH host keys that are used by at least 900,000 devices.
Also Read: Most Vulnerable Smart Cities to Cyber Attack on Internet of Things (IoT).
The remaining crypto keys might be used by various other devices that are not connected to the Internet, but could still be vulnerable to man-in-the-middle (MITM) attacks within their respective local area networks.
As a result, potentially Millions of Internet-connected devices can be logged into by attackers, or their HTTPS web server connections can silently be decrypted by MitM attackers, using these crypto keys and certs once they're extracted from their firmware.
Where Does the actual Problem Reside?
The issue lies in the way vendors build and deploy their products. Typically, the vendors built their device's firmware based on software development kits (SDKs) received from chipmakers…
…without even bothering to change the source code or even the keys or certificates that are already present in those SDKs.
There are many reasons why this large number of devices are accessible from the Internet via HTTPS and SSH. These include:
Insecure default configurations by vendors
Automatic port forwarding via UPnP
Provisioning by ISPs that configure their subscribers' devices for remote management
"The source of the keys is an interesting aspect. Some keys are only found in one product or several products in the same product line. In other cases we found the same keys in products from various vendors," Sec Consult wrote in its blog post.
List of Vendors that are Re-Using Encryption Keys
Although SEC Consult identified more than 900 vulnerable products from roughly 50 manufacturers, the actual number could be even higher considering that its study only targeted firmware the company had access to.
Also Read: How Drones Can Find and Hack Internet-of-Things Devices From the Sky.
According to SEC Consult, these are the companies that were found reusing encryption keys:
ADB, AMX, Actiontec, Adtran, Alcatel-Lucent, Alpha Networks, Aruba Networks, Aztech, Bewan, Busch-Jaeger, CTC Union, Cisco, Clear, Comtrend, D-Link, Deutsche Telekom, DrayTek, Edimax, General Electric (GE), Green Packet, Huawei, Infomark, Innatech, Linksys, Motorola, Moxa, NETGEAR, NetComm Wireless, ONT, Observa Telecom, Opengear, Pace, Philips, Pirelli , Robustel, Sagemcom, Seagate, Seowon Intech, Sierra Wireless, Smart RG, TP-LINK, TRENDnet, Technicolor, Tenda, Totolink, unify, UPVEL, Ubee Interactive, Ubiquiti Networks, Vodafone, Western Digital, ZTE, Zhone and ZyXEL.
Most Affected Countries
Here's the list of Top 10 countries that are affected by SSH/HTTPS encryption key reuse:
United States
Mexico
Brazil
Spain
Colombia
Canada
China
Russian Federation
Taiwan
United Kingdom
SEC Consult has "worked together with CERT/CC to address this issue since early August 2015." and it recommends vendors to use securely random cryptographic keys for each IoT-capable device.
Moreover, ISPs are advised to make sure that there is no possibility to remotely access CPE (customer premises equipment) devices via WAN port. In case they need access for remote support purposes, "setting up a dedicated management VLAN with strict ACLs is recommended."
Nest camera, has a different definition for Turn off Mode
27.11.2015
Findings of a research show that the Nest camera is still operating even after it has been disabled through the mobile application.
People buy security cameras to have a higher level of control over their lives, but recently a research by a team at ABI Research found that users also must be worried about the security device itself.
nest camera
This news is about a security camera of Nest Company that was acquired by Google in 2014. The device is the latest product of Nest that enables users to see live video of their homes or to be notified about unusual motion or sound. Findings of research show that the camera is still operating even after it has been disabled through the mobile application. The LED indicator approves that the device is off, but the current drain illustrates something else. It is expected that current drain drops significantly when a device is disabled, but it’s not true in the case of Nest camera and current drain decline just 30 mA when the device in turn off mode.
“When a device goes to power down mode, you expect the current drain to drop quite a bit,” said Jim Mielke, a senior analyst at ABI Research.
The following table published by ABI research and depict current drain for different modes of operation.
Mode Resolution Current
Video Record – no motion 1080p 371mA
Video Record – no motion 720p 330mA
Video Record – no motion detected 720p 418mA
Video Record – no motion 360p 322mA
OFF Mode 343mA
“When Nest Cam is turned off from the user interface (UI), it does not fully power down, as we expect the camera to be turned on again at any point in time,” said Nest Labs in a statement. “With that said, when Nest Cam is turned off, it completely stops transmitting video to the cloud, meaning it no longer observes its surroundings.”
It can be argued that turn off mode has a unique definition universally and Nest approach to define turn off mode is bizarre. Even though Nest used 128-bit secure sockets layer (SSL) encryption, perfect forward secrecy and a 2,048-bit RSA key unique to each camera, but users might face new security risks. Lastly, this camera uses electricity constantly which is not an efficient practice in 21th century.
VPN users be aware , Port Fail flaw can reveal your identity
27.11.2015
Security experts at the VPN provider Perfect Privacy discovered a new vulnerability dubbed Port Fail that could be exploited to de-anonymize VPN users.
Security experts at the VPN provider Perfect Privacy discovered a new vulnerability dubbed Port Fail which affect all VPN (Virtual Private Network) protocols and operating systems. An attacker can exploit the Port Fail flaw to reveal the real IP-addresses of VPN users, including BitTorrent users.
Experts at Perfect Privacy tested nine VPN providers out of which five were found to be vulnerable to the Port fail flaw, the providers Private Internet Access (PIA), Ovpn.to and nVPN have fixed the issue before publication.
The experts at Perfect Privacy explained that the vulnerability is a simple port forwarding issue that affects all the services that implement the “port forwarding” feature and that doesn’t implement any defensive mechanism. The Port Fail affects all VPN protocols including the IPSec, OpenVPN, PPTP.
“We have discovered a vulnerability in a number of providers that allows an attacker to expose the real IP address of a victim. Port Fail affects VPN providers that offer port forwarding and have no protection against this specific attack.” Perfect Privacy wrote in a blog post on Thursday.
Basically, if the attacker uses the same VPN as the victim, then the real IP-address of the targeted user can be exposed by forwarding Internet traffic to a specific port. A successful Port Fail attack also required to know the victim’s VPN exit IP address, an information that is quite easy to discover by tricking a victim into visiting a website control controlled by the attacker.
VPN port fail 2
“The crucial issue here is that a VPN user connecting to his own VPN server will use his default route with his real IP address, as this is required for the VPN connection to work,” continues the post.
The attack works also against BitTorrent users and in this attack scenario there is no need for the attacker to redirect the victim to their page, the attacker only with the activated port forwarding for the default BitTorrent port can discover the real IP-address of a VPN user that share the same network.
The VPN affected by the vulnerability were already alerted by the company, but there is the risk that many other providers suffer the issue.
“other VPN providers may be vulnerable to this attack as we could not possibly test all.” states Perfect Privacy.
I suggest you giving a look to a blog post published by the penetration tester Darren Martyn describing the Port Fail attack scenario against Torrent users.
“I believe this kind of attack is probably going to be used heavily by copyright-litigation firms trying to prosecute Torrent users in the future, so it is probably best to double check that the VPN provider you are using does not suffer this vulnerability,” explained Martyn said.
Nebezpečným certifikátem eDellRoot mohou být infikovány i starší přístroje od Dellu
27.11.2015 Viry
Vlastníci notebooků Dell s operačním systémem Windows, které byly zakoupeny před srpnem letošního roku, by měli zkontrolovat, zda jejich systémy disponují oficiálním certifikátem eDellRoot. Ten totiž může zkompromitovat jejich osobní komunikaci.
Cetifikát instaluje aplikace Dell Foundation Services (DFS), kterou Dell automaticky dodává k většině svých zařízení kvůli zjednodušení zákaznické a technické podpory.
Po zveřejnění existence cerfitikátu Dell uvedl, že první verze začal vydávat přes DFS již v srpnu. Díky tomu se mnoho lidí domnívá, že postižena jsou pouze zařízení zakoupená od srpna. To však není pravda. Starší přístroje s nainstalovaným DFS mohly certifikát nainstalovat také, pokud byl počítač nastaven na automatické aktualizace.
„Pro uživatele, kteří již mají DFS a zvolili automatické aktualizace, eDellRoot certifikát byl součástí verzí 2.2 a 2.3 vydaných v srpnu,“ uvedl zástupce Dellu.
„Po instalaci DFS dostanete otázku, zda vyžadujete automaciké aktualizace.“ DFS je však na velké části systémů předinstalován. Není tak jasné, kdy si může uživatel navolit, zda chce updaty dostávat automaticky.
Nalezen byl také jiný oficiální certifikát Dellu zvaný DSDTestProvider. Ten na počítač instaluje nástroj Dell System Effect (DSD), k jehož instalaci jsou uživatelé nabádáni při návštěvě webových stránek technické podpory Dellu.
Dell již zveřejnil manuály s instrukcemi k odstranění eDellRoot i DSDTestProvider. Uživatelé mohou zjistit, zda mají tyto certifikáty nainstalovány zmáčknutím tlačítka Windows + r a napsáním certlm.msc.
How to Root Windows Phone and Unlock the Bootloader to Install Custom ROMs
27.11.2015
How to Root Windows Phone and Unlock the Bootloader to Install Custom ROM
Yes, Now it is possible to unlock a Windows Lumia Phone for Root Access and run custom ROMs.
Both Microsoft as well as Nokia have made Windows Lumia smartphones difficult to break into at a low-level by locking down their bootloaders, but a software hacker, who go by the name HeathCliff, has just proven that it is not impossible.
HeathCliff has released an excellent tool called "Windows Phone Internals" that allows Windows phone owners to unlock their smartphone's bootloaders, gain root access and even create and run custom ROMs.
What’s more interesting is the tool supports "most versions of Windows Phone 8.1 and Windows 10 Mobile".
HeathCliff is very well known XDA Developer and one of the Windows Phone legends. On Windows Phone part, HeathCliff is loved mostly for the WP7 Root Tools.
Windows Phone Internals or WP Internals is completely free to download though HeathCliff welcomes donations by those who have found the tool useful.
Also Read: Raspberry Pi Zero — The $5 Tiny Computer is Here
Here's the List of Things Windows Phone Internals can Do
You can unlock the bootloader of the specific Lumia Windows Phone models, and then enable Root Access
You can load your custom apps with higher privileges and without sandboxing in Windows Phone OS.
You can create Backup images of your phone and can also access the file-system in Mass Storage Mode.
You can even install your custom ROMs.
You can also watch the video provided by HeathCliff, showing what the tool is capable of doing.
Models Supported by Windows Phone Internals Tool
Here's the list of Lumia Phones Supported by the tool right now:
Lumia 520, 521 and 525
Lumia 620, 625
Lumia 720
Lumia 820
Lumia 920
Lumia 1020
Lumia 1320
Also Read: Meet Mr.Grey Hacker Who Stole 1.2 BILLION Login Credentials
How to Get Started?
Here's the introduction video for you to get started with Windows Phone Internals:
So, if you are ready to tinker with your Windows Phone then Download Windows Phone Internals for Free from here.
Also Read: Li-Fi is 100 times Faster than Wi-Fi: Real-World Tests Proved
Should You Root Your Phone?
However, I would caution against using this tool for those who do not understand the underlying architecture of their Windows Phones and Windows 10 Mobiles.
Rooting your phone gives you complete control over the OS, but that power can also be misused if you're not careful.
Heathcliff also states that after a tweak is completed, you should unroot your device to reduce the chance of malware or other bad stuff making their way on.
Using the tool without proper inspection could also result in damaged and unrecoverable data, for which neither The Hacker News nor I will be responsible. So please be careful before rooting your phone.
Windows Phone hacked with Windows Phone Internals
27.11.2015
Windows Phone Internals allows to unlock bootloader, enable Root access and create Custom ROM’s on selected Windows Lumia mobile devices.
We have spoken several times about jailbreaking and rooting activities explaining that these procedures allow to remove hardware restrictions implemented by the Apple and Google operating systems to give users root access allowing to download and install applications and themes from third-party stores.
But, what about Windows mobile devices?
Now, Windows users can now root their Windows Phones with the first Windows Phone root called Windows Phone Internals that was designed by Healthcliff74 (@Heathcliff74XDA).

Windows Phone Internals allows to unlock bootloaders of Windows Lumia and gain root access on the mobile, allowing to flash custom ROMs. This means that Windows Phone developer community will start developing good quality ROMs like the Android community does.
Healthcliff74 has launched a website dedicated to Windows Phone Internals with the intent to support users in rooting their devices.
“I am proud to announce the immediate availability of Windows Phone Internals 1.0. This tool allows you to unlock the bootloader of selected Lumia Windows Phone models. After unlocking the bootloader, you can enable Root Access on the phone or create and flash Custom ROM’s. I created a short introduction video to show the features of the tool.” said Healthcliff74.
“root Access allows you to load your own homebrew software onto the phone with high privileges. Apps can escape from their sandboxes. The tool can also create backup-images of the phone and access the file-system in Mass Storage mode. The tool supports most versions of Windows Phone 8.1 and Windows 10 Mobile. For a complete list of supported phones and Operating Systems have a look at the Getting Started section of the tool”.
In the following video is explained how to enable Root Access on Windows Phones and how to reate a Custom ROM.
The Windows Phone Internals tool works on most versions of Windows Phone 8.1 and Windows 10 Mobile.
Users can download and test the Windows Phone Internals on their device, but they have to consider that the operation has some risks to consider, such as the possibility to brick the Windows Phone.
Enjoy it!
Black Friday and Cyber Monday, Keep Yourself Safe
27.11.2015
Find out why there is increased risk of hacking during Black Friday and Cyber Monday and learn how to remain protected online.
Black Friday is here and so is Cyber Monday, with all the special seasonal offers that many consumers are craving! However, it seems that these are the days for which hackers have been preparing themselves all this time.
Unfortunately, there are more sophisticated threats that we should all beware of, as hackers have been gathering their strengths and are ready to unleash their wrath. Does this mean that we are better off abstaining from all purchases? Well, with the bargains that can be found online, good luck with your efforts to do that!
The Retail Cyber Intelligence Sharing Center has tried to inform people on the imminent risks that are piling up, when it comes to cyber threats on these days. In fact, they have published a report on what needs to be done on behalf of all consumers, in avoidance of negative consequences related to seasonal sales. It is worth reading through the report and find out why hackers understand the risks and how they overcome them, so as to get their hands on your money.
black friday scams
It is true that retailers have got their plates full and this means that they do not pay as much attention as they should be to preventive measures. As a result, hackers are left alone and they do what they know best – which is to intercept personal information and steal money online! ThreatMetrix has found an increase of 25% in the frauds prior to the holiday season.
What needs to be done, in order to avoid being compromised on Black Friday and Cyber Monday? Well, luckily things are not that devastating, assuming that you are vigilant. Here is what you should be focusing on, so that you can enjoy the holiday season and buy the things that you have been waiting for, without being tricked by anyone:
Only visit trusted websites, which are much safer to use. Do not trust any sites that you have never heard of, especially when you read through their offers and find them too good to be true. Search for the HTTPS on the address bar, since this is a great sign of security.
Allow encryption, as with this you will be able to prevent identity theft and the interception of your personal data (including the details of your credit card, apparently). VPN is a reliable method of using encryption throughout your web navigation and particularly throughout your financial transactions.
Do not click on any email links you find, even if they urge you to purchase an item of quality at half price or less. These links will most likely lead to your redirection somewhere unsafe and they can also be used for robbing you of your privacy.
Do not share your credit card credentials with anyone, even with your loved ones. More than that, you should not share them via an email or a private message on Facebook and other social media. This is a safe path to catastrophe!
Avoid Wi-Fi when purchasing something online, since publicly shared connections to the web include increased dangers and threats. Instead, use a private Internet connection that you know is secured and preferably encrypted.
Mobile devices are more prone to being hacked and they offer a more fertile ground for hackers to mislead you. Think about it, as you gaze through the merchandise of an e-shop from your limited sized screen and struggle to read the detailed description.
Enjoy Black Friday and Cyber Monday, taking full advantage of their special, limited offers for the holidays! Do so with absolute safety, though, since this is the best way to be jolly all-year-round!
Crooks use the Nuclear Exploit Kit to serve CryptoWall 4.0
27.11.2015
The popular Nuclear Exploit Kit has been used for the first time to serve the ransomware CryptoWall 4.0.
The Nuclear exploit kit is one of the privileged weapon in the arsenal of cyber criminal groups, now the popular crimeware kit has been used to serve the ransomware CryptoWall 4.0. In the past, criminal crews used the exploit kit to serve instances of the CryptoWall 3.0.
The discovery was made by the security researcher at Rackspace Brad Duncan, who explained that it is the first time that the new CryptoWall 4.0 ransomware is spread by using the an exploit kit.
Although Angler may dominate the exploit kit market at this time, the Nuclear exploit kit, arguably the second most prevalent exploit kit found in-the-wild today, has recently been observed utilizing payload delivery mechanisms that are much more efficient and more sophisticated in nature than ever seen before.
One of the primary advances made by the Nuclear Exploit Kit group is that the payloads delivered by the exploit kit are dynamic in nature. While payloads were often rotated during normal Nuclear EK operation, it has been discovered that the payloads delivered by recently-analyzed hosts serving the Nuclear EK have been exceptionally volatile in nature.
The Nuclear EK allows to serve malicious code by exploiting vulnerabilities in Java, Acrobat Reader, Flash, and Silverlight.
The most recent version(s) of the Nuclear EK utilizes effective techniques to evade detection, and even when it fails to exploit a target system, its anti-analysis techniques served to prevent malware analysts from re-creating and following/analyzing the infection chain employed by Nuclear.
Earlier this year, the security expert Maarten van Dantzig discovered a large number of Google ads sold through Bulgarian reseller EngageLab have been redirecting users to websites hosting the Nuclear exploit kit.
Duncan confirmed that samples of the CryptoWall 4.0 ransomware have been spotted in the wild since 2 November.
“Earlier this month, the BizCN gate actor switched IP addresses for its gate domains to 46.172.83.0/24. Also, as early as Friday 2015-11-20, this actor started sending CryptoWall 4.0 as one of its malware payloads from the Nuclear exploit kit (EK). Until now, I‘ve only associated CryptoWall 4.0 with malicious spam (malspam). This is the first time I’ve noticed CryptoWall 4.0 sent by an EK.” wrote Duncan. “Until now, I haven’t noticed CryptoWall 4.0 from any EKs. And now I’ve only seen it from the BizCN gate actor.”
Duncan dubbed the threat actors “BizCN gate actor” because it used domains registered through the Chinese registrar BizCN as a gate to hijack users to the domain hosting the Nuclear Exploit Kit.
“This actor uses dedicated servers for its gate domains. These gate domains tend to stick with one particular hosting provider. At times, the BizCN gate actor will switch hosting providers for its gates, and the IP address block for these gates will change.” states Duncan.

Duncan speculates that the disclosure of his analysis will force the BizCN gate actor to change tactics.
“Since this information is now public, the BizCN gate actor may change tactics. However, unless this actor initiates a drastic change, it can always be found again. I (and other security professionals) will continue to track the BizCN gate actor. Expect another diary on this subject if any significant changes occur.”
In order to protect your PC keep your software up to date.
Li-Fi is 100 times Faster than Wi-Fi Technology: Real-World Tests Prove
26.11.2015
Yes, it's time to shift from Wi-Fi to Li-Fi — an alternative technology that is 100 times faster than the average speeds of Wi-Fi.
Scientists have just field-tested the new wireless technology called Li-Fi for the first time and achieved marvelous wireless speeds that are 100 times faster than current WiFi speeds.
What is Li-Fi Technology?
Li-Fi is a new wireless technology that transmits high-speed data using light (i.e. Visible Light Communication or VLC) rather than radio bands.
In short, Li-Fi is a Super-Fast alternative to Wi-Fi.
Earlier this year, scientists achieved mind-blowing speeds of 224 gigabits per second (GBps) in the lab using Li-Fi. It's believed that this technology has the potential to change everything about the way we use the Internet today.
And Yes, it will.
Test Results: Li-Fi is 100 times Faster than Wi-Fi
An Estonian startup company called Velmenni took the technology out of the laboratories and into the real-world offices, and industrial environments in Tallinn for the first time and, believe me, it's really, really fast.
li-fi-wireless-internet-technology
The company was able to transmit data at 1GB per second, which is almost 100 times faster than the Wi-Fi speeds.
"We are doing a few pilot projects in different industries where we can utilize the VLC technology," Velmenni's CEO Deepak Solanki told IBTimes UK.
"Currently we have designed a smart lighting solution for an industrial environment where the data communication is done through the light. We're also doing a pilot project with a private client where we're setting up a Li-Fi network to access the Internet in [our] office space."
Unlike Wi-Fi network signals, Li-Fi is based on light and can't penetrate through walls, which makes it more secure from external sniffing. Meanwhile, it also means there is less interference from other devices.
Who Invented Li-Fi?
The Li-Fi technology was originated in 2011 by German physicist Harald Haas, who outlined the idea of using light bulbs as wireless routers during a TED Talk. He demonstrated that with a flickering light from an LED, one could transmit more data than a cellular tower.
You can watch the full video of Haas talk about the Li-Fi technology in 2011 given above.
IoT devices are re-using cryptographic keys, leaving in danger millions of devices
26.11.2015
Researchers from SEC consult analyzed more than 4000 firmware’s embedded devices, where is included devices belonging to 70 vendors. The findings are astonishing!
Researchers from SEC consult analyzed more than 4000 firmware’s embedded devices, where is included devices belonging to 70 vendors. The categories of devices analyzed include Internet gateways, routers, modems, IP cameras, VoIP phones, etc. SEC Consult was analyzing specifically the cryptographic keys (public keys, private keys, certificates) in firmware images of these devices, and concluded that most common keys are
SSH Host keys, that are required for operating a SSH server.
509 Certificates used for HTTPS which is the default server certificate for web based management.
These keys are generally used to access the IoT devices via SSH and HTTPS.
The experts analyzed 4000 firmware and found around 580 unique private keys, the use of Scans.io and Censys.io allowed them to discover that the same set of keys was widely re-used, on 580 keys, 230 are actively used.
“the private keys for more than 9% of all HTTPS hosts on the web (~150 server certificates, used by 3.2 million hosts)”
” the private keys for more than 6% of all SSH hosts on the web (~80 SSH host keys used by 0.9 million hosts)”
Embedded cryptographic key
The firmware running on the IoT device came with embedded keys used mainly for HTTPS, and SSH connections, this bad practice exposes end users to risk of attacks. Attackers can easily find the key and access a huge quantity of IoT devices that share it.
The experts at SEC consult also discovered:
“Some keys are only found in one product or several products in the same product line”
“In other cases, we found the same keys in products from various different vendors.”
The researchers mentioned real cases that demonstrate the alarming habit:
“A certificate issued to a “Daniel”, email (kiding@broadcom.com) is used in firmware from Actiontec, Aztech, Comtrend, Innatech, Linksys, Smart RG, Zhone and ZyXEL. More than 480.000 devices on the web are using this single certificate.”
“A certificate issued to Multitech in Bangalore, India is used in firmware from Aztech, Bewan, Observa Telecom, NetComm Wireless, Zhone, ZTE and ZyXEL. Over 300.000 devices on the web are using this certificate”.
“A certificate issued to “MatrixSSL Sample Server Cert” is used in WiMAX gateways from Green Packet, Huawei, Seowon Intech, ZTE and ZyXEL. All affected devices use the same code base, which is likely developed by ZyXEL. At least 80.000 devices on the web are using this certificate.”
Millions of devices exposed
SEC Consult’s researchers also uncovered another fact, many of these devices are directly accessible on the internet with insecure configurations and a used example is the case of Ubiquiti Networks, “who have remote management enabled by default in most products.”
Many Seagate GoFlex (80.000) are exposing HTTPS and SSH, and the blame should go the Seagate Share feature sets up port forwarding via UPnP.
In another case, the ISP exposes their clients’ IoT device by leaving their modems, routers and gateways with HTTPS and SSH remote administration features enabled by default.
The ISPs include, CenturyLink (500,000 exposed devices), TELMEX (1 million devices), Telefonica (170,000 devices), China Telecom (100,000 devices), VTR Globalcom (55,000 devices), Chunghwa Telecom (45,000) and Telstra (26,000 devices).
The counties with most affected hosts are:

SEC consult found more than 900 products from 50 vendors vulnerable, the list includes IoT devices proposed by:
ADB, AMX, Actiontec, Adtran, Alcatel-Lucent, Alpha Networks, Aruba Networks, Aztech, Bewan, Busch-Jaeger, CTC Union, Cisco, Clear, Comtrend, D-Link, Deutsche Telekom, DrayTek, Edimax, General Electric (GE), Green Packet, Huawei, Infomark, Innatech, Linksys, Motorola, Moxa, NETGEAR, NetComm Wireless, ONT, Observa Telecom, Opengear, Pace, Philips, Pirelli , Robustel, Sagemcom, Seagate, Seowon Intech, Sierra Wireless, Smart RG, TP-LINK, TRENDnet, Technicolor, Tenda, Totolink, unify, UPVEL, Ubee Interactive, Ubiquiti Networks, Vodafone, Western Digital, ZTE, Zhone and ZyXEL.
To avoid situations like these, the vendors have to ensure that each IoT device has its own unique cryptographic keys.
For the ISPs, if they need remote access for support purposes, they should set up a dedicated management VLAN with strict ACLs.
End users should change the SSH host keys and X.509 certificates of their IoT devices, an operation that is not allowed by some products, and in some cases users lack technical knowledge to change the settings.
All the problems emerged from the analysis have been reported by SEC consult to the CERT/CC which in August 2015 started informing device vendors, chipset manufacturers and affected ISPs. Some of them are already working on the fixes.
FBI is hunting MrGrey who has stolen 1.2 BILLION login credentials
26.11.2015
The FBI is convinced that there is a single hacker behind the theft of login credentials for over 1.2 Billion online accounts, his name is MrGrey.
According to a report published by the Reuters, the FBI is convinced that there is a single hacker behind the theft of login credentials for over 1.2 Billion online accounts, his name is MrGrey.
If confirmed, it could be the biggest heist of log-in credentials the FBI has investigated. My readers surely remember the case, last year the security firm Hold Security reported the amazing theft of the login credentials.
In August 2014, experts at Hold Security revealed to have discovered the biggest database of stolen user names and passwords and email addresses, the news is reported by The New York Times that hired an independent security expert who verified the authenticity of stolen data.
The security firm has discovered the amazing amount of data, nearly 1.2Billion credentials and half a billion email addresses, that is considered the single biggest amount of stolen Internet identity information ever collected. The experts believe that the data was collected by the Russian hacking group CyberVor from the numerous data breaches occurred all over the world in the last months and that hit around 420,000 websites vulnerable to SQL injection attacks.
fbi searching for MrGrey
The CyberVor hacking crew used botnets to search and hack vulnerable websites.
“To the best of our knowledge, [CyberVor] mostly focused on stealing credentials, eventually ending up with the largest cache of stolen personal [data], totalling over 1.2 Billion unique sets of emails and passwords,” Hold Security said in August last year.
By July 2014, criminals were able to collect 4.5 billion credentials, Hold Security discovered many duplications in the archive but anyway, it found that 1.2 billion of those records were unique and the archive included about 542 million unique email addresses. This is normal if we consider the bad habit to reuse same credentials for different web services.
Hold Security didn’t provide any information on the alleged breached websites, but according to Alex Holden, the company’s founder and chief information security officer, the list of compromised websites is long and include enterprises and small firms.
“Hold Security would not name the victims, citing nondisclosure agreements and a reluctance to name companies whose sites remained vulnerable. At the request of The New York Times, a security expert not affiliated with Hold Security analyzed the database of stolen credentials and confirmed it was authentic” reported The New York Times.
The Reuters has visioned court documents provided by the law enforcement to support its search warrant request in 2014.
“That hacker, known as “mr.grey,” was identified based on data from a cybersecurity firm that announced in August 2014 that it had determined an alleged Russian crime ring was responsible for stealing information from more than 420,000 websites, the documents said. The papers, made public last week by a federal court in Milwaukee, Wisconsin, provide a window into the Federal Bureau of Investigation’s probe of what would amount to the largest collection of stolen usernames and passwords.” states the Reuters.
The FBI associated MrGrey with the largest heist after discovering his Russian email address in spammer tools and posts on a Russian hacking forum offering to get user login credentials of Twitter, Facebook and Russian social network VK.
“The FBI also discovered an email address registered in 2010 contained in the spam utilities for a “mistergrey,” documents show. A search of Russian hacking forums by the FBI found posts by a “mr.grey,” who in November 2011 wrote that if anyone wanted account information for users of Facebook, Twitter and Russian-based social network VK, he could locate the records.” continues the Reuters
This circumstance leads Alex Holden from Hold Security to believe MrGrey likely operated or had access to the database containing the huge quantity of login credentials.
At the time I’m writing there is not news on how Mr.Grey obtained all the login credentials neither if this name is used by a single hacker or a hacking crew.
Mr. Grey Hacker (Wanted by FBI) Steals 1.2 BILLION Login Passwords
26.11.2015
That's a lot of Login credentials fetch by a single hacker.
The FBI believes a single hacker who goes by the moniker Mr.Grey has stolen login credentials for over 1.2 Billion online accounts – apparently the biggest heist of log-in credentials the FBI has investigated thus far.
Yeah, that's not Fifty, but 1.2 Billion Shades of Grey.
The information came from the court documents the federal agents submitted to support its search warrant request in 2014, Reuters reported.
The cyber security firm 'Hold Security' initially reported the theft of the credentials last year. It found out that Russian hacking group CyberVor has stolen 1.2 Billion login details and an additional 500 Million email accounts.
Botnet Breach
These data were said to have been harvested from over 420,000 websites via botnets looking for SQL injection flaws; the same technique recently used to hack TalkTalk.
Botnets are usually employed to attack an individual target, but in this case, they have been used as a huge scanner to scan websites on the Internet.
"To the best of our knowledge, [CyberVor] mostly focused on stealing credentials, eventually ending up with the largest cache of stolen personal [data], totalling over 1.2 Billion unique sets of emails and passwords," Hold Security said in August last year.
1.2 Billion Shades of Grey
The FBI is linking Mr.Grey to the largest heist after finding his Russian email address in spam-sending tools and posts on a Russian hacking forum offering to get user login credentials of Twitter, Facebook and Russian social network VK during its investigation.
Alex Holden, chief information security officer at Hold Security, believes those posts on online hacking forum prove that the hacker, "mr.grey" or "mistergrey", has access to a large database of stolen online credentials.
However, it's still unclear if Mr.Grey obtained all the login credentials by himself alone, or if Mr.Grey is just a single hacker or a group of hackers operating under one name.
Unfortunately, not much information is known about Mr.Grey's operations, but we will update soon if the FBI releases any new info.
Hackers are using Nuclear Exploit Kit to Spread Cryptowall 4.0 Ransomware
26.11.2015
Beware Internet Users!
Cryptowall 4.0 – the newest version of the world's worst Ransomware – has surfaced in the Nuclear exploit kit, one of the most potent exploit kits available in the underground market for hacking into computers.
Ransomware threat has emerged as one of the biggest threats to internet users in recent times. Typically, a Ransomware malware encrypts all files on victim’s computer with a strong cryptographic algorithm, then demand a ransom to be paid in Bitcoin (range between $200 and $10,000).
Cryptowall is currently among the most widespread and sophisticated family of Ransomware backed by a very robust back-end infrastructure.
Also Read: Anyone can Now Create their Own Ransomware using This Hacking ToolKit
The recent report dated back to last month suggested that the authors of Cryptowall 3.0 ransomware virus have managed to raise more than $325 Million in revenue in the past year alone.
With the debut of Cryptowall 4.0 at the beginning of this month, ransomware threat has become more sophisticated and advanced as Cryptowall 4.0 is employing "vastly improved" communications as well as better design code so that it can exploit more vulnerabilities.
Cryptowall 4.0 Delivered via Nuclear Exploit Kit
Now less than a month after its release, Cryptowall 4.0 ransomware has been spotted to be delivered as part of a Nuclear Exploit Kit, according to the security researchers at the SANS Internet Storm Center (ISC).
Until recently, Cryptowall 4.0 has been distributed only via malicious spam and phishing emails, but now it has been infecting machines via an Exploit Kit.
SANS security researcher Brad Duncan wrote in a blog post published Tuesday that a cyber criminal working off domains belonging to Chinese registrar BizCN has been spreading the Cryptowall 4.0 ransomware via the Nuclear Exploit Kit.
Duncan said the cyber gang, dubbed the "BizCN gate actor" by him, began distributing the ransomware in payloads from the exploit kit as early as November 20.
Also Read: Free Ransomware Decryption and Malware Removal ToolKit
Duncan published a whole technical analysis on the SANS ISC website that shows how Nuclear exploit kit infects a vulnerable Windows host.
"Since this information is now public, the BizCN gate actor may change [their] tactics," Duncan said in the post. "However, unless this actor initiates a drastic change, it can always be found again."
Cryptowall 4.0 made its debut earlier this month with upgrades that made it even more challenging for victims to recover files from compromised computers than its predecessor.
Cryptowall 4.0 now not only encrypts the data in your files but also encrypts the file names as well, with vastly improved communication capabilities.
What Should You do if You get Infected by Cryptowall 4.0?
Once your computer is infected by Cryptowall 4.0, unfortunately, there is not much you can do, as the encryption it uses is very strong and almost unbreakable.
The only options you are left with are:
Either, Format your computer and restore your data from the backup
Or, Pay the Ransom money for decryption key
However, we do not advise you to pay ransom as it does not guarantee that you'll get the decryption key and paying ransom would encourage criminal activities as well.
Prevention is the Best Practice
As I previously recommended, the best defense measure against Ransomware is creating awareness within the organizations, as well as maintaining backups that are regularly rotated.
Most viruses are introduced by opening infected attachments or clicking on links to malware usually contained in spam emails.
So, DO NOT CLICK on suspicious links provided in emails and attachments from unknown sources.
Also Read: Ransomware Attacks Threaten Wearable Devices and IoTs
Moreover, ensure that your systems are running the latest version of Antivirus software with up to date malware definitions.
Raspberry Pi Zero — The $5 Tiny Computer is Here
26.11.2015
Get ready for a ThanksGiving celebration from the Raspberry Pi Foundation.
Raspberry Pi, the charitable foundation behind the United Kingdom's best-selling computer, has just unveiled its latest wonder – the Raspberry Pi Zero.
Raspberry Pi Zero is a programmable computer that costs just $5 (or £4), may rank as the world's cheapest computer.
Raspberry Pi Zero: Just $5 Computer
Yes, Pi Zero is the smallest Raspberry Pi yet for just $5, but might be the biggest when looking at its specifications:
Broadcom BCM2835 application processor (same as Pi 1)
1GHz ARM11 core (40 percent faster than Raspberry Pi 1)
512MB of LPDDR2 SDRAM
Micro-SD card slot
MiniHDMI socket for 1080p60 video output
Micro-USB for data
Micro-USB for power
Unpopulated 40-pin GPIO connector
Identical pinout to Model A+/B+/2B
Unpopulated composite video connector
Smallest ever form factor (i.e. 65mm x 30mm x 5mm)
Get Your Raspberry Pi Zero Now!
The Raspberry Pi is responsible for the creation of credit card sized computers, but after years of working to lower the size and cost, founder Eben Upton says the foundation came up with Raspberry Pi Zero that is about the size of a stick of gum and costs just US$5.
Upton said the Pi Zero, made in Wales and runs full Raspbian and all your favorite applications including Scratch, Sonic Pi and Minecraft, was as revolutionary as the first Pi.
Also Read: CHIP — The World's First $9 Computer.
The Raspberry Pi Zero is on sale from today and is also given away with this month’s copy of the Raspberry Pi own magazine MagPi (available at Barnes & Noble and Microcenter).
You can order the Pi Zero, which is also available in the UK from element14, The Pi Hut and Pimoronia; in Europe from The Raspberry Pi Swag Store; and in the US from Adafruit and in Micro Center stores.
Note: Orders are limited to two per person at launch.
Facebook first discovered spear phishing attacks of Iranian hackers on State Department employees
26.11.2015
Facebook was the first company to notice the intrusion of Iranian Hackers in the e-mail accounts of US State Department officials focused on Iran. The attacks appear politically motivated and aimed to gather data about US-Iranian dual citizens in Iran.
Earlier this month, the computers at the US State Department and other government employees were targeted by hackers. The experts linked the attackers with the Iranian Revolutionary Guard, according to investigators the Facebook and e-mail accounts of US State Department officials focused on Iran were compromised to gather data about US-Iranian dual citizens in Iran and about the arrest of an Iranian-American businessman in Tehran in October.
The hackers have taken over social media accounts of junior State Department staff to launch a spear phishing campaign on the employees working in the State Department’s Office of Iranian Affairs and Bureau of Near Eastern Affairs and in the computers of some journalists.
US State Department e-mail system hacked Iranian hackers
Facebook was the first to notice the hacking campaign, the company alerted some of the affected users that their accounts had been compromised by a state-sponsored hackers.
The attack launched by the Iranian Revolutionary Guard hackers “was very carefully designed and showed the degree to which they understood which of our staff was working on Iran issues now that the nuclear deal is done,” an unnamed senior US official told the Times.
The recent wave of attacks came after a period of apparent calm, the cyber security experts noticed an evolution of the TTPs of the Iranian hackers. Iranian hackers were initially focused on targets belonging to the financial industry, their activities were limited to sabotage and disruption of the targeted infrastructures, such as in the attack on casino company Las Vegas Sands Corp. The fact that the Iranian hackers were more interested in destruction instead gathering intelligence lead the experts to believe that the threat actors were not state-sponsored but pro-Iranian “hacktivists.”
The recent attacks against The State Department attack is clearly a cyber espionage operation, they were initially attributed to Chinese hackers who may have infiltrated the department’s unclassified e-mail systems.
Russia, Hackers Stole $4 Million in cash with Reverse ATM Hack method
26.11.2015
Russian criminals Steal $4 Million In cash with a new technique dubbed reverse ATM Attack.
Russian hackers have adopted a new technique, dubbed Reverse ATM Attack to steal Millions of dollars from ATMs of financial institutions.
According to the experts at security firm GroupIB, the Reverse ATM Attack allowed criminal rings in Russia to steal 252 Million Rubles (roughly US$3.8 Million) from at least five different banks.

The theft started in summer 2014 and finished in Q1 2015.
The experts provided a detailed description of the Reverse ATM Attack. The attacker would deposit sums of 5,000, 10,000 and 30,000 Rubles into legitimate bank accounts using ATMs, and immediately withdraw the same amounts of money accompanied by a printed receipt of the payment transaction. At this point the hackers send the details included in the receipt, including the payment reference number and the amount withdrawn, to a partner who had remote access to the infected POS terminals. Usually the partner is an individual located outside of Russia.
The partner hacker would then use the details on the receipt to perform a reversal operation on a POS terminal that would lead them into believing that the withdrawals were cancelled, thereby tricking thousands of point-of-sale (POS) terminals in the US and in the Czech Republic.
From the perspective of the bank, it would appear the attempt to withdraw cash was failing, a circumstance that for example occurs when the bank account has insufficient funds.
The cash out process is made through a global “money mule” network that will transfer the money to the attacker’s bank account.
“That information was sent to hackers who would use the data and their access to thousands of point of sale terminals, primarily based in the US and the Czech Republic, to create “a reversal operation” on a terminal that tricked the bank into believing the withdrawal of funds had been cancelled.” states Forbes. “At the point of sale terminal, this looked as though goods were returned or a payment declined, whilst to the banks it appeared the ATM withdrawal had been cancelled. Funds were returned to the account, though the crooks had already taken the cash. The process was repeated until there was no money remaining in the targeted ATM.”
As explained by the experts at Group-IB, the criminal gang leveraged weaknesses in the withdrawal, transfer and verification stages of credit card transactions used in Russia and managed to bypass checks recommended by VISA and MasterCard.
The problem is that when the reverse operation targets a single bank, transaction details provided by VISA are not verified by the targeted banks. When ATM Withdrawals were made in one country and cancelled/reversed in another, the verification process fails.
VISA brought together the affected banks so they could block reversal operations when funds were withdrawn from an ATM of the bank and reaccredited through a separate terminal.
“But that fix only addressed the issue of withdrawals from ATMs, not transfers from one card to another.” continues Forbes.
Group-IB is supporting law enforcement to investigate further fraudulent activities.
Hilton confirms some payment systems infected by malware
25.11.2015
The hotel chain Hilton Worldwide Holdings announced Tuesday that cyber criminals stole credit card information from some of its point-of-sale systems.
The hotel chain Hilton Worldwide Holdings admitted that crooks stole credit card information from some of its PoS systems, but hasn’t provided detailed info on the extent of the data breach. The company Hilton Worldwide is warning its customers who used credit cards at its hotels between November 18 and December 5 of last year or April 21 and July 27 of this year to monitor their banking account for any suspicious activity.
According to the Hilton global brands executive vice president Jim Holthouser, the malware infected the PoS systems, allowing the cyber criminals to steal customers’ data, including credit card holders’ names, card numbers, security codes and expiration dates.
Hilton
“Hilton Worldwide (NYSE: HLT) has identified and taken action to eradicate unauthorized malware that targeted payment card information in some point-of-sale systems. Hilton immediately launched an investigation and has further strengthened its systems.” reads a press release issued by the Hilton Worldwide Holdings.
“Hilton Worldwide worked closely with third-party forensics experts, law enforcement and payment card companies in this investigation, and determined that the specific payment card information was targeted by this malware. This information includes cardholder names, payment card numbers, security codes and expiration dates, but no addresses or personal identification numbers (PINs).”
It seems that customers’ addresses and personal identification numbers were not compromised in the data breach.
Hilton hired a forensic firm to investigate the cyber attack, along with law enforcement and payment card companies.
A few days ago another hotel chain was affected by a serious data breach, Starwood Hotels announced that hackers had infected payment systems, potentially exposing customers’ financial data, including credit card data.
If you are a customer of the popular hotel chain, visit hiltonworldwide.com/guestupdate for more details.
Russian ATM Hackers Steal $4 Million in Cash with 'Reverse ATM Hack' Technique
25.11.2015
Russian hackers have discovered a novel technique to rip off Millions of dollars from banks and ATMs.
Criminals in Russia used a technique, called “Reverse ATM Attack,” and stole 252 Million Rubles (US$3.8 Million) from at least five different banks, according to the information obtained by Russian digital intelligence firm Group-IB.
What is Reverse ATM Attack?
According to the intelligence firm, an attacker would deposit sums of 5,000, 10,000 and 30,000 Rubles into legitimate bank accounts using ATMs, and immediately withdraw the same amounts right away with a printed receipt of the payment transaction.
The details included in the receipt, containing a payment reference number and the amount withdrawn, would then be transferred to a partner hacker, who had remote access to the infected POS terminals, usually located outside of Russia.
Also Read: German Bank ATMs vulnerable to Hackers
The partner hacker would then use these details to perform a reversal operation on a POS terminal that would lead them into believing that the withdrawals were declined, thereby tricking thousands of American and Czech point-of-sale (POS) terminals, Forbes explained.
Meanwhile, it would appear to the bank as if the attempt to withdraw cash was cancelled, for example: when the customer has insufficient funds and then the same cash amount will be transferred to the attacker’s bank account using a global "money mule" network.
Now, Hackers would repeat these steps as long as the targeted ATM did not end cash.
Also Read: Beware of ATM Skimming Devices Installed on Vestibule Doors
Hackers Stole $3.8 Million in Cash from ATM Hack
Group-IB said the firm had seen at least five such incidents at five different Russian banks, the criminal activity starting in summer 2014 and finishing in the first quarter of 2015.
The hackers leveraged weaknesses in the withdrawal, transfer and verification stages of credit card transactions used in Russia and managed to bypass checks recommended by VISA and MasterCard.
Also Read: How Hackers Can Hack Your Chip-and-PIN Credit Cards
Here 'Checks' means:
When the reverse operation targets a single bank, transaction details provided by VISA is not verified by the affected banks.
When ATM Withdrawals were made in one country and cancelled/reversed in another, certain verification points were again missed.
Group-IB is working with the federal authorities to investigate further into the whole money laundering scheme.
How The Russian Abused Twitter as C&C in Hammertoss Malware? Python Answers
25.11.2015
Today, we will replicate a technique which has been used by recent, sophisticated and hard to trace a Russian malware called Hammertoss.
Today, we will replicate a technique which has been used by recent, sophisticated and hard to trace a Russian malware called Hammertoss, the creators of this malware has abused multiple well-known sites like Twitter and Github to defeat modern firewalls and torture whoever tracing their tracks.
In a nutshell, instead of getting a direct reverse connection back to the C&C server similar to what traditional malware does, this smart malware will jump between third party servers to perform its malicious activity, please take two minutes and watch this[https://www.fireeye.com/blog/threat-research/2015/07/hammertoss_stealthy.html/] short explanatory video from Fireeye so you will get a quick overview how the malware works.
Before the fun begins, I just want to mention that this code is a part of my new training course on Udemy called “Python for Offensive Pentest: A Complete Practical Course.”
All right, so the first stage of Hammertoss was to connect to a Twitter looking for a tweet created by the hackers which contains a URL for an image and hashtag as a part of the encryption key. Technically speaking, you don’t need to login into Twitter to parse someone’s tweet, so in this case, we just need to figure out the account URL to navigate and the HTML tags which contain the actual tweet, Keep in mind you can add other twitter accounts to hide the original one (which belongs to the hacker).
Obviously you should never your personal account while doing similar stuff, that’s why I created a new account holding my name and here’s is the link to my twitter home page:
https://twitter.com/HussamKhrais
Now from my Kali machine, I made a tweet saying “Hello from kali python” then I logged out, at this point once we click on the above URL, we should see something similar to this output

Now using your browser you can view the HTML source code of this page, in Chrome just do a right click anywhere in the page and select “View page source” or Ctrl+U for short, in the HTML if we search for our tweet, we will get the below HTML line:-
<meta name="description" content="The latest Tweets from Hussam Khrais (@HussamKhrais): "Hello from kali python"">

So technically if we code a simple script that will navigate to https://twitter.com/HussamKhrais
And retrieve the HTML page, then inside the HTML if we search for meta tag called name that has a value of description and asked for the value of content, then we should be able to grab our tweet.
Let’s translate this action to a code:-
fromBeautifulSoup import BeautifulSoup as soupy #1
importurllib #2
html = urllib.urlopen(‘https://twitter.com/HussamKhrais’).read() #3
soup = soupy(html) #4
x = soup.find(“meta”, {“name”:”description”})[‘content’] #5
print x #6
1# Import soupy function from BeautifulSoup library, we will use this function to search for the html tags
2# Import urllib which will be used to navigate to our twitter page and grab the html for us
3# Navigate to my twitter home page HussamKhrais, store the HTML page into html variable
4# Pass it to soupy function so we can parse it
5# Here we search for the HTML meta tags
6# Print the result out
The output for running the script would be

At this point, since we are only interested in having the string between the quotation marks, we can filter it out using regular expression, and that is exactly what the below script will do for us
importre
filter = re.findall(r'”(.*?)”‘,x)
tweet = filter[0]
print tweet
the “findall” function will grab the string between the ” ” and store it in a list data type called filter, finally we print the exact tweet.
After putting all the script pieces together, we got the below result

Please feel free to download the script and give it a try on your own tweet!
Now think about it for a second, can we use twitter to replace DDNS? Well, what will happen if we replace “Hello from kali python” with the attacker public IP, and each time the attacker IP changes, all what he needs to do is to send a tweet with the new IP to get the reverse connection for his victim!
A question for you…
After reading this article, do you think that can you code in Python a complete AV free remote shell and exfiltrate data without even having a single direct connection with your target? Please share your thoughts.
If you are interested on the topic you can go deeper following the course “Python For Offensive PenTest: A Complete Practical Course”

Aktualizace Windows 10 přepisuje nastavení soukromí
25.11.2015 Hrozby
Pokud jste již stáhli aktualizaci Windows 10 z 12. listopadu tak zpozorněte. Mohla totiž přepsat nastavení vašeho soukromí.
Uživatelé, kteří svůj operační systém Windows 10 aktualizovali na jeho nejnovější verzi, by si měli zkontrolovat své nastavení. Microsoft odstranil update vydaný 12. listopadu svých stránek kvůli problému, který po instalaci aktualizace resetoval veškerá nastavení soukromí.
Bug resetoval nastavení kvůli tomu, aby reklamní inzerenti mohli snáze monitorovat pohyb uživatelů v aplikacích. Díky tomu měly informace o uživatelích internetem proudit daleko hladčeji. Microsoft však v úterý vydal opravu problému. Ti, kteří si aktualizaci systému nainstalují nyní, tak podobnou chybu nezažijí.
Uživatelé, kteří chybu zažili, se rovněž nemusí bát. Microsoft totiž podle svých slov veškeré nastavení vrátí do jeho původní podoby. Jak toho chce docílit, však firma neuvedla.
Problém podle oficiálního vyjádření Microsoftu postihnul jen velmi malé množství zařízení. Společnost však stále netuší, co chybu způsobilo.
Načasování tohoto bugu však pro Microsoft není ideální. Společnost čelí obavám ze zvýšeného sběru dat o uživatelích ve Windows 10. Ty sice nabízejí nastavení, které veškerý sběr dat, až na telemetrická data, vypnou, ale pokud dokáže jednoduchý bug tato nastavení prolomit, nemohou být naprosto spolehlivá.
MagSpoof, how to predict American Express card numbers
25.11.2015
MagSpoof is a tiny device that can spoof/emulate any magnetic stripe or credit card. It can work wirelessly, even on standard magstripe/credit card readers.
When dealing with hacking we cannot avoid mention the popular hacker Samy Kamkar (@SamyKamkar), one of the most prolific experts that periodically presents to the security community his astonishing creations, including the Combo Breaker, OpenSesame and KeySweeper.
This time Kamkar has designed new cheap gadget (it goes for US$10) that can predict and store hundreds of American Express (AMEX) credit cards and use them for wireless transactions. The tiny gadget dubbed MagSpoof is a credit card/magstripe spoofer and can be used also at non-wireless payment terminals, it is composed of a micro-controller, motor-driver, wire, a resistor, switch, LED, and a battery.

“MagSpoof is a device that can spoof/emulate any magnetic stripe or credit card. It can work “wirelessly”, even on standard magstripe/credit card readers, by generating a strong electromagnetic field that emulates a traditional magnetic stripe card.” states Kamkar. “MagSpoof can be used as a traditional credit card and simply store all of your credit cards (and with modification, can technically disable chip requirements) in various impressive and exciting form factors, or can be used for security research in any area that would traditionally require a magstripe, such as readers for credit cards, drivers licenses, hotel room keys, automated parking lot tickets, etc.”
The hacker clarified that the device does not enable people to use credit cards that they don’t own because it is necessary to have the magstripes that they wish to emulate.
However, this means that crooks could use MagSpoof to rake cash after cards have been cancelled at businesses that do not require the CVV numbers on the back of cards.
After losing a card, Kamkar received a new one as a replacement, then he noticed many of the digits were similar. Analyzing other cards and replacements he discovered a pattern that allows him to predict AMIX card number by knowing a full card number, even if already reported lost or stolen.
“I pulled up the numbers to several other Amex cards I had, and then compared against more than 20 other Amex cards and replacements and found a global pattern that allows me to accurately predict American Express card numbers by knowing a full card number, even if already reported lost or stolen. This means if I were to obtain your Amex card and you called it in as lost or stolen, the moment you get a new card, I know your new credit card number.
I also know the new expiration date as the expiration date is fixed based on when the new card was requested, and you can determine if the new card has been requested by performing an auth on the existing card.”
Kamkar reported the issue to the American Express that is already working on a fix.
Magspoof is able to emit a strong “electromagnetic field” that emulates the effect obtained by physically swiping a card. Kamkar has released all the necessary to design a working device, including the source code and the instruction to build it.
“MagSpoof emulates a magnetic stripe by quickly changing the polarization of an electromagnet, producing a magnetic field similar to that of a normal magnetic stripe as if it’s being swiped. What’s incredible is that the magstripe reader requires no form of wireless receiver, NFC, or RFID — MagSpoof works wirelessly, even with standard magstripe readers. The stronger the electromagnet, the further away you can use it (a few inches in its current iteration).” continues the expert.
Of course, Kamkar precaution disabled the ability to deactivate EMV and has not released the prediction algorithm for the American Express card.
Kamkar has published a animated GIF image that shows how the tiny device works, below a video PoC published by Kamkar:
Kamkar explains that the device could be used to create by readers to create their own versions of Samsung MST or Coin.
Summarizing MagSpoof :
Allows you to store all of your credit cards and magstripes in one device
Works on traditional magstripe readers wirelessly (no NFC/RFID required)
Can disable Chip-and-PIN (code not included)
Correctly predicts Amex credit card numbers + expirations from previous card number (code not included)
Supports all three magnetic stripe tracks, and even supports Track 1+2 simultaneously
Easy to build using Arduino or other common parts
Person VUE Credential manager system has been compromised
25.11.2015
Person VUE, the world biggest learning, testing and certification company has announced that its Credential Manager system (PMC) has been breached.
On their website, Person VUE gives us some details of what might have happened, even though they don’t share who is the responsible for this breach.
“We recently were made aware that an unauthorized third party placed malware on Pearson VUE’s Credential Manager (PCM) system, which is a platform that supports adult professional certification and licenses. The unauthorized party improperly accessed certain information related to a limited set of Pearson VUE’s PCM system users. As of now, we do not believe that U.S. Social Security numbers or full payment card information were compromised as a result of this issue. “
Person VUE will keep PCM system offline for the necessary investigation.
“If your credentialing, certification or licensing organization has posted information about this or communicated with you about the issue directly, then it’s likely that you use this platform. It is important to note there is no indication at this time that the issue involved the Pearson VUE Testing System, the PearsonVUE.com website or any other Pearson/Pearson VUE systems. The issue is isolated to the PCM system. “the company added.
“Based on our investigation, there is no evidence at this time indicating that the VUE Testing System (VTS) or Exam Developer Software was affected by this issue.”
Since Person VUE is still trying to understand the scope of the data breach, they are not sure which data the attackers were able to get, but they think that no Social Security numbers or payment card information were in the leaked data.

The Pearson Credential Manager (PCM) system supports a number several companies’ certification tracking programs, including Cisco and F5 who posted some notes about the incident as well.
“According to Pearson VUE, an unauthorized party may have improperly gained access to information related to users that could include: names, postal addresses, phone numbers, email addresses, user IDs and, in some cases, last four digits of credit card numbers and dates of birth”, “As a precaution, Pearson VUE has taken its Credential Manager System offline and has informed us that it will remain offline until this matter has been resolved. As a result, all F5 certification processes are on hold until Pearson VUE gets its Credential Manager System back on line—our apologies for this inconvenience.” reported F5.
Since at least 14 November, the Cisco’s tracking system was down for “site maintenance,” but on Saturday, the company announced the Pearson VUE breach and stated its tracking system “will remain down until further notice”.
“PCM is an important part of Cisco’s certification ecosystem, as it enables individual users to manage and track their CCIE, CCNA, CCNP and other Cisco certifications directly through Pearson’s platform” said Cisco about the issue.
As I said before there is no certainty, about which data was leaked, but the news circulating on the Internet suggests that “just” name, mailing address, email address and phone number belonging to those who hold certifications were exposed.
Personally, that worries me, since I’m one the cases, as many of my colleagues in my field. The attackers may have many plans for this information, but one of them can be the mapping of all security/IT professionals.
We in Security Affairs will keep following this subject and will share with you if any news comes up.
Notorious Shm00p hacker Claims he helped the FBI find ISIS Hacker Junaid Hussain
25.11.2015
The hacker Shm00p claims he served as an FBI informant and helped the US law enforcement track down the hacker turned ISIS fighter Junaid Hussain.
When dealing with ISIS and cyber capabilities, the first name that experts cite is Junaid Hussain, the hacker that was killed in a targeted US drone strike in August this year.Now new details on Junaid Hussain and his death are circulating online.
The hacker Shm00p (@5hm00p), the same that hacked the Anonymous pseudo-official Twitter accounts @Anon_Central and @YourAnonNews, is claiming to have provided useful information to the FBI allowing to track Hussain.
In 2012, Hussain was sentenced to six months in prison in Britain for this crime. The jihadist was also cited by two gunmen responsible of the terrorist attack in Garland, Texas. The two men invited via Twitter to follow Hussain. In 2013, Hussain left the United Kingdom and joined ISIS.
On September 11 214, Fox News reported that leaders of the Islamic State of Iraq and Syria and Al Qaeda were stepping up efforts to seek a digital caliphate, speculating that one of the jihadist leaders, Hussain Al Britani, also known as Junaid Hussein, had allegedly hacked the Gmail account of former British Prime Minister Tony Blair.
“Jihadists in the Middle East are ramping up efforts to mount a massive cyber attack on the U.S., with leaders from both Islamic State and Al Qaeda – including a hacker who once broke into former British Prime Minister Tony Blair’s Gmail account – recruiting web savvy radicals, FoxNews.com has learned.”
According to Shm00p, he has served as an FBI informant to help the US intelligence under threat, and he is quite sure (“99.9% sure”) that the information he provided led to the extrajudicial killing of Hussain.
Shm00p, who lives in Las Vegas, is one of the members of the hacking group named Rustle League. On Sunday, he posted the following message:
“What the fuck have I done,” Shm00p tweeted.
A few hours later he sent a number of tweets at the FBI Twitter account.
“I lost a lot of good friendship and my fucking honor,” I am so embarrassed to show my face in public now because of this,”
Shm00p Tweets FBI Hussain
Shm00p and Hussain were affiliated with another notorious hacktivist group called Team Poison.
Jaime Cochran, a former member of Rustle League, told Motherboard that 5hm00p reached out to her after his Twitter confession to apologize, and confirmed his collaboration with the FBI.
5hm00p said told her that law enforcement forced him to provide information on two hackers who knew Hussain since their affiliation with the Team Poison.
“It seems believable to me. I dunno why someone would make this up,” Cochran told Motherboard in an encrypted chat.
It seems that in 2014, Hussain contacted Shm00p via the encrypted chat service Jabber, but Shm00p located the jihadist location and then passed it the FBI agents.
“I fucking helped you MURDER him [Junaid]. Do you know how I feel now when I sleep at night?”Shm00p tweeted. “Regardless that he was a terrorist and an animal I sure as fuck felt betrayed.”
Why did Shm00p pass information to the FBI?
The hacker explained that the FBI has forced him to disclose the Hussain’s location. Based on the tweets sent by Shm00p, the authorities forced him to provide support threatening his family.
The agents had him attempt to catch two of his friends while they were partying at the DefCon 2015 conference.
The FBI hasn’t commented the Shm00p’s declarations.
A source informed of the events told Motherboard that Shm00p did indeed help the US federal.
GlassRAT, the threat that remained stealth for years
25.11.2015
A new RAT dubbed GlassRAT was discovered by RSA, it targets mainly Chinese citizens working in multinational companies in and outside China.
According to the experts at RSA a remote access Trojan (RAT) dubbed GlassRAT managed to avoid detection by most antivirus software for several years.
The researchers explained that GlassRAT was used by threat actors in highly targeted attacks, the threat (also dubbed “zero detection” threat) has been around since at least September 2012.
GlassRAT was detected for the first time on December 2014 when a sample was only uploaded to VirusTotal.
The experts highlighted that the code of the GlassRAT dropper had been digitally signed with a legitimate certificate stolen from a popular Chinese software developer, a circumstance that allowed it to stay under the radar for several years. The dropper had been detected first in September 2015, it was uploaded to the public malware database from a Chinese IP address. The threat has been discovered on the computer of a Chinese national in February 2015.
GlassRAT has been used in highly targeted attacks on Chinese nationals and other Chinese speakers associated with large multinational corporations in China and other countries since at least early 2013.
The code of GlassRAT has many similarities with the one of the Taidoor threat and a malware family called Taleret. Taidoor has been around since 2008 and it has been mainly used in cyber espionage campaigns against organizations in Asia-Pacific region, including the Philippine military and the Mongolian government.
Experts linked the threat with cyber espionage campaigns leveraging Mirage, MagicFire and PlugX malware.
“The telemetry of GlassRAT and limited forensic samples suggest that targeting is narrowly focused,” reads the report published by RSA. “While several code similarities were found with other malware such as Taidoor and Taleret, the most interesting overlap with GlassRAT might be in the C2 infrastructure shared with geopolitical campaigns, which were reported earlier in this decade.”
The infection process is still not completely clear, experts believe the threat actors would use social engineering mixed with spear phishing attacks.
GlassRAT installs itself via a fake Flash installation package and then cleans any traces.
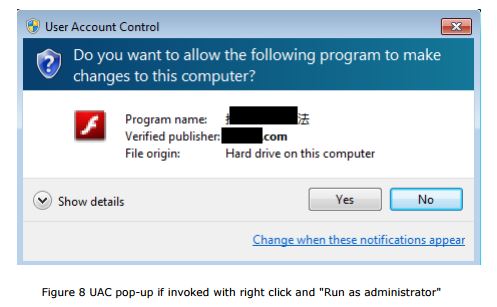
The threat is simple but effective, it included a classic reverse shell which allows attackers to gain complete control of the target system.
Who is behind the threat?
Experts at RSA pointed out that the nature of the targets and the technique adopted suggest that the operators belong to “subordinate departments of a much larger organization with shared infrastructure and developers run these campaigns.”
Zjistíte atak hackerů ještě předtím, než nastane, tvrdí Cisco
25.11.2015 Analýzy
Model Spike Rank (SPRank), který na trh uvedlo Cisco, detekuje útok na základě abmormálií, které se objeví v síťovém provozu v okamžiku útoku principiálně podobné zvukové vlně. Spike Rank se tak podle dodavatele stává jakýmsi kybernetickým sonarem, který naslouchá provozu a detekuje problém.
Novinka, která vychází z technologie společnosti OpenDNS, kterou Cisco nedávno koupilo, dokáže detekovat pokročilé typy útoků využitím analýzy datového provozu v síti, které funguje na principu „zvukových vln“.
Model Spike Rank prý dokáže rozpoznat změnu v datovém toku, která je velmi podobná tomu, jak se projevují například zvukové vlny. Díky tomu může okamžitě „zaslechnout“ kybernetický útok a vyslat příslušné pokyny bezpečnostním mechanismům v síti, a to dokonce dávno předtím, než samotný útok vypukne.
Pomocí modelu prediktivní analýzy IP prostoru (Predictive IP Space Monitoring) lze navíc sledovat osm nejčastějších postupů používaných kyberpiráty pro přípravu útoku, detekovat potenciálně nebezpečné domény a zablokovat je.
Datoví vědci OpenDNS si všimli, že každý kybernetický útok změní vzor datového provozu. Zjistili navíc, že tato změna je velmi podobná projevům zvukových vln.
Proto se rozhodli ke konstrukci modelu SPRank využít v podstatě podobné technologie, které v současnosti používají hudební služby Pandora, Shazam a další k tomu, aby byly schopné identifikovat skladbu přehrávanou přes IP síť.
Model SPRank tak umožnil vytvořit jakýsi sonar „naslouchající“ těmto vlnám v datovém provozu. Pracuje totiž s podobným matematickým modelem, který se používá k popisu zvuků. Kybernetický útok pak může být jakýmsi krátkým pípnutím. Díky němu je možné s vysokou mírou identifikovat potenciální kybernetický útok.
Podle zkušeností datových vědců identifikuje SPRank stovky napadených domén každou hodinu, přitom více než třetinu z nich nezachytí žádný antivirový či jiný bezpečnostní program. Dnešní kybernetické útoky totiž často existují jen velmi krátkou dobu, a proto je obtížné je zachytit. Ale sonaru ani jediné „pípnutí“ neunikne.
Model prediktivní analýzy IP prostoru (Predictive IP Space Monitoring) vychází ze znalosti chování kyberzločinců. Ti si totiž musí před každým kybernetickým útokem připravit příslušnou infrastrukturu, ze které bude útok vedený.
V rámci analýzy IP prostoru sledují technologie OpenDNS osm hlavních postupů používaných útočníky (například způsob, jakým jsou hostovány servery, na kterých je nasazen škodlivý kód). Pokud tedy SPRank identifikuje potenciálně škodlivou doménu, s pomocí analýzy IP prostoru lze skutečně potvrdit, že tato doména bude v krátké době zdrojem kybernetického útoku.
Tento způsob analýzy navíc neošálí ani tradiční „kouřová clona“, kterou kyberpiráti kolem svých útoků budují, aby předešli odhalení. Analýza IP prostoru se zaměřuje totiž skutečně jen na konkrétní neměnné charakteristiky. V současnosti dokáže tento model identifikovat každou hodinu přes 300 domén, které by se mohly stát zdrojem kybernetického útoku, a zablokovat je dříve, než k tomu dojde.
Útočníci z Paříže používali ProtonMail. Ten odmítá omezit šifrování
24.11.2015 Bezpečnost
Google umí obejít zámek telefonu. Pomůže leda kompletní šifrování
Po teroristických útocích v Paříži se do popředí dostávají některé šifrované komunikační služby, které měli útočníci používat při vzájemné domluvě. Jednou z takových služeb je i poštovní služba ProtonMail, která používá kompletní end-to-end šifrování, takže k obsahu se nedostane nikdo včetně samotného provozovatele – obsah není v žádné fázi k dispozici v prostém textu; jen při psaní a dešifrování ve webovém prohlížeči příjemce.
Dešifrovaná zpráva v prohlížeči a její zašifrovaná podoba, která dorazila ze serveru do prohlížeče. ProtonMail používá rozšířenou technologii OpenPGP.
ProtonMail je nyní po asociaci ITI (Google, Microsoft aj.) další, který se brání, že rozhodně nenese žádnou vinu a že odpovědí nemůže být to, aby přeci jen umožnil úřadům za určitých okolností pohled do schránek svých uživatelů.
Politické hlasy po snižování šifrování webových služeb nyní skutečně sílí, ProtonMail ale správně poukazuje na to, že by toho záhy zneužili útočníci i vlády samotné při špehování těch, kteří s terorismem nemají nic společného.
Teroristé zároveň ke komunikaci nepoužívali pouze švýcarský ProtonMail, ale také hromadu dalších prostředků, čili by si jednoduše našli jiný způsob.
České firmy jsou pod palbou kyberútoků, pomoci chce stát
24.11.2015 Počítačový útok
** Většina českých firem čelí útokům hackerů ** Na trhu chybějí tisíce odborníků na kybernetickou bezpečnost ** Stát se chce více angažovat v kyberbezpečnosti
České firmy jsou pod palbou kyberútoků, pomoci chce stát
O tradičních ozbrojených konfliktech se veřejně hodně mluví. Jsou na očích a dá se k nim přilepit „líbivý“ vizuální materiál. V dnešní době jsou ale mnohem intenzivnější takzvané asymetrické války. Všemožné skupiny útočí skrze kybernetický prostor. Nejde pouze o vlády a jednotlivé státy, hackeři rovněž v masivní míře zasahují do sítí firem a organizací. Tyto věci nejsou tolik viditelné. I když se čas od času něco dostane na povrch, o kybernetických incidentech se většinou příliš nemluví.
A Česka se to týká více, než tomu bývá zvykem třeba na Západě. „Takřka se nestává, že bychom do nějaké společnosti či instituce přišli a nic v jejich síti a IT systémech neodhalili,“ říká David Řeháček z izraelské společnosti Check Point Software Technologies, „vždy tam něco je.“ Podobně mluví v podstatě všechny další kyberbezpečnostní firmy. Ty do sítí často nasazují svůj hardware a software a následně testují, jak si na tom kdo stojí. „Prakticky u všech subjektů v Česku se něco našlo, třeba agent komunikující se vzdálenými servery,“ doplňuje Řeháček.
Tutlané incidenty
Tuzemské firmy o takových problémech veřejně nemluví. Napadení jejich informačních systémů by logicky na veřejnosti nepůsobilo dobře a mohlo by dojít ke ztrátě důvěry u klientů. „Incidenty jsou u nás velmi významné. A zároveň jsou i tutlané,“ říká Michal Zedníček ze společnosti Alef, která se reálným řešením kybernetických útoků zabývá.
Důvody útoků kopírují všeobecné trendy. Útočníkům jde o finanční zisk, průmyslovou špionáž, citlivé dokumenty či třeba narušení výroby. Na datacentra a hostingové služby míří přehlcující DDoS útoky. Hrozby jdou jak od soukromých subjektů, tak od státy podporovaných skupin. Rusko, Čína, Írán a další země stojí za kyberútoky běžně, cílem je například západní energetický sektor.
34 lidí dnes zaměstnává Národní centrum kybernetické bezpečnosti. Během následujících tří let chce přijmout dalších čtyřiadvacet
Podobně samozřejmě zbrojí i druhá strana z geopolitické mapy včetně Spojených států či Izraele. Rusko s Čínou nedávno podepsaly smlouvu o kybernetické bezpečnosti, v rámci které se na sebe zavazují neútočit na státní úrovni. Směrem ven ale situace může být jiná. „Vláda nám řekla, ať v zahraničí útočíme a krademe, jak chceme. Ale jak to zkusíme doma, pojedeme prvním vlakem na Sibiř,“ říkají například ruští hackeři, se kterými měl týdeník Euro možnost mluvit.
Jednou z mála zdejších společností, která se o své zkušenosti dělí – podobně jako se to děje třeba ve Spojených státech – je provozovatel českých plynovodů Net4Gas. Firma se například potýkala s útoky na své webové servery a další infrastrukturu a situaci díky rychlému zákroku dokázala řešit bez větších následků.
Tuzemské společnosti každopádně v současné době nemají povinnost hackerské útoky na své sítě hlásit. To, zda se o informace podělí s ostatními, je dobrovolné. Výjimkou brzy budou členové takzvané kritické infrastruktury státu. Tu vzhledem k novému zákonu o kybernetické bezpečnosti postupně určuje Národní bezpečnostní úřad (NBÚ) a spadnou do ní i elektrárny či ministerstva.
Spolupráce místy funguje
Dobrovolná výměna informací mezi firmami někde do určité míry funguje. V Česku už je v provozu dvaadvacet takzvaných kyberbezpečnostních CERT týmů, mají je zejména firmy typu Seznam.cz, O2 a podobně. Několik subjektů se sdružuje také v projektu Fenix provozovaném národním internetovým uzlem NIX. CZ.
Rostoucí riziko kybernetických útoků nějakou dobu ve firmách pomáhalo rozpočty na tuto oblast alespoň nesnižovat, nyní se ale postupně naopak investice zvedají. Dá se očekávat, že čísla v budoucnu výrazně narostou. „V Česku začínáme u klientů pozorovat, že už nechtějí získat pouze lejstro s certifikací, ale skutečně problémy řešit. Česko v této oblasti směřuje k vyšší odolnosti, na všech frontách nás však čeká opravdu hodně práce,“ dodává Zedníček z Alefu. Firmy jsou dnes na fungování IT naprosto závislé a výpadky mohou mít zcela zásadní následky pro celý byznys.
Útok na elektrárnu Hrháň
Zároveň chybějí lidé. Na zdejším trhu se podle odhadů v současnosti nedostává řádově tisíce odborníků na kyberbezpečnost. V celé Evropské unii jich během několika let nebude až milion. České vysoké školy se na to snaží reagovat a bezpečnostní obory zavádí či se snaží posilovat Vysoké učení technické (VUT) v Brně, České vysoké učení technické či Masarykova univerzita (MUNI). Přidávají se i některé soukromé školy. Přesto platí, že ze školy připravený člověk nevyjde a je nutné s ním nadále pracovat. VUT společně s MUNI spouští také obor, který má kombinovat technické znalosti počítačové bezpečnosti s právními aspekty.
Masarykova univerzita v Brně nedávno otevřela také Kybernetický polygon. Jde o výcvikovou arénu, kde je možné ve virtuálním prostředí zprovozněném díky vědeckému cloudu CERIT simulovat a trénovat kybernetické útoky. Tohoto moderního zázemí před pár dny využil také NBÚ. Ten vůbec poprvé v historii podobné cvičení realizoval. NBÚ se sice i několikrát do roka účastní podobných cvičení NATO, v tomto případě se ale simulované incidenty zaměřily přímo na infrastrukturu českého státu. Hlavním cílem byla fiktivní elektrárna Velký Hrháň.
Dokážou čelit útoku?
Principem cvičení bylo vyzkoušet, zda bezpečnostní zaměstnanci státu, kteří byli rozděleni do pěti týmů po čtyřech lidech, dokážou čelit organizovanému útoku hackerů. Ty představovali zaměstnanci Národního centra kybernetické bezpečnosti (NCKB), které spadá pod NBÚ a funguje v Brně, a akademici z Masarykovy univerzity. Akce se připravovala tři čtvrtě roku a zúčastněné strany nechtějí příliš rozvádět, jaké přesně útoky se trénovaly. Cvičení se totiž má uskutečnit ještě dvakrát.
První várka zkoušených týmů relativně obstála. Od zmiňovaného Národního centra kybernetické bezpečnosti se toho ze začátku v kuloárech příliš nečekalo. Stát odborníkům na kybernetickou bezpečnost může nabídnout tabulkový plat, což zapříčinilo to, že NCKB nabírá především absolventy, které si pak vychovává. Dnes centrum zaměstnává 34 lidí a během následujících tří let jich chce přijmout dalších čtyřiadvacet, každý rok osm.
O NCKB začíná být poměrně dost slyšet i v zahraničí. Centrum se podílí na několika zahraničních projektech a jezdí také pomáhat stavět kyberbezpečnostní know-how a týmy. Aktivní je například na Balkáně, kde se s celou oblastí teprve začíná, a v návaznosti na poslední události Česko pomáhalo také na Ukrajině, která musí čelit útokům z Východu. Šéf NBÚ Dušan Navrátil zároveň před pár dny podepsal nové memorandum o kyberbezpečnostní spolupráci národních složek s NATO, a Česko se tak stalo vůbec prvním spojencem v této záležitosti. NATO už kyberválku zařadilo mezi své priority.
Kvalitní hráč
Silným spojencem NBÚ je také firma Microsoft. Ta s úřadem spolupracuje už několik let, nedávno však došlo k podepsání nové smlouvy, díky které NBÚ získal přístup ke zdrojovým kódům softwaru z Redmondu, včetně Windows a Office. NBÚ nezískává nad zdrojovými kódy softwaru kontrolu a ani je nebude skladovat na svých serverech a počítačích. NCKB pouze může na dálku přistupovat ke „zdrojákům“ ve čtecím režimu. Může tak zkoumat, jak je software Microsoftu napsaný, a na základě toho analyzovat bezpečnostní záležitosti a psát si vlastní nástroje, včetně národního šifrování.
NCKB získává také přístup do takzvaného transparentního centra, které Microsoft provozuje v Bruselu. To umožňuje třeba automatizované testování softwaru Microsoftu a hledání zadních vrátek. Vše funguje na dálku. NBÚ je oprávněn nahlédnout také do dokumentací ISO 27001, které Microsoft získal v rámci svých cloudových služeb.
Důvody útoků kopírují všeobecné trendy. Útočníkům jde o finanční zisk, průmyslovou špionáž, citlivé dokumenty či třeba narušení výroby
Česká republika se zároveň v minulosti stala třetí zemí na světě, která je součástí programu Botnet Feeds. Ten provozuje Microsoft a NCKB má díky tomu přístup k analýzám Microsoftu o botnetech. Získává tak informace o IP adresách, které jsou rozesílány do jednotlivých zemí. NBÚ poté může kontaktovat ohrožené státní úřady. Soukromý sektor pak stejně řeší národní bezpečnostní tým CSIRT. CZ, který provozuje správce české internetové domény CZ. NIC a se kterým NBÚ nedávno obnovil smlouvu.
Česko je obecně díky firmám jako AVG, Avast, Cognitive Security či několika novým mladým projektům typu TeskaLabs ve světě vnímáno jako velice kvalitní hráč na poli kyberbezpečnosti. Státní bezpečnostní instituce se těmto firmám snaží sekundovat.
Google umí obejít zámek telefonu. Pomůže leda kompletní šifrování
24.11.2015 Mobilní
Google může na základě soudního příkazu dálkově obejít zámek telefonu s Androidem a poskytnout tak telefon třeba policejním vyšetřovatelům. Vyplývá to z dokumentu manhattanského okresního zastupitelství, na který upozornil The Next Web.
Android podporuje kompletní a silné šifrování už poměrně dlouho, ale málokdo o tom ví, funkce je to totiž pouze volitelná, protože je na slabších telefonech náročná na CPU.
Zadní vrátka ovšem nefungují vždy. Pokud bude telefon kompletně šifrovaný, Google se k němu tímto způsobem nedostane. Kompletní šifrovaní sice bylo původně počínaje Androidem 5.0 doporučené, ale později jen volitelné, šifrování je totiž velmi náročné a na slabších telefonech by citelně snížilo celkový výkon.
Na Androidu je tedy sice k dispozici, ale ve výchozím stavu není u většiny i nových modelů aktivní.
Dell instaloval do notebooků nebezpečné certifikáty
24.11.2015 Hrozby
„Vadné“ certifikáty na noteboocích XPS 15, XPS 13, ale taky na některých z řad Latitude a Inspiron útočníkům umožní špehovat, co na internetu děláte.
Dell do svých notebooků přednahrál kořenové digitální certifikáty s vlastním podpisem, které útočníkům umožňují sledovat přístupy k zabezpečeným webovým stránkám. Informace se objevila na serveru Reddit, následně ji však na svých blozích či sociálních sítích potvrdili další uživatelé a IT odborníci.
Navíc, k certifikátu je připojen i odpovídající soukromý klíč, což situaci činí ještě horší. S klíčem může totiž kdokoliv vygenerovat certifikát pro kteroukoliv webovou stránku, již budou internetové prohlížeče na daných počítačích považovat za důvěryhodnou.
Certifikát nazvaný eDellRoot je od srpna přidáván do běžně prodávaných notebooků, podle Dellu za účelem zlepšení zákaznické podpory: „Když se počítač spojí s naší online podporou, certifikát nám umožní okamžitě identifikovat typ počítače, ovladače, operační systém, hard disk a tak dále, což vede ke snadnějšímu a rychlejšímu řešení problému.“
Po upozornění na „vedlejší účinky“ však firma zákazníkům poskytla manuál k odstranění certifikátu a přislíbila, že do dalších počítačů ho už předinstalovávat nebude.
„Rádi bychom taky dodali, že bez svolení zákazníka neshromažďujeme ani nesdílíme žádné jeho osobní informace.“
Chyby lze zneužít prostřednictvím takzvaného man in the middle útoku, kdy se útočníci napojí do komunikace mezi dvěma subjekty, v tomto případě uživatelem s inkriminovaným Dell notebookem a jakoukoliv zabezpečenou stránkou. Útočníci můžou využít rovněž soukromého klíče k tomu, aby do počítače dostali malware.
„Kdybych byl záludný hacker, zašel bych na nejbližší letiště, sedl si vedle prostoru pro první třídu a odposlouchával, kdo co na internetu řeší,“ píše ve svém blogovém příspěvku Robert Graham, šéf bezpečnosti společnosti Errata Security. „Navrhuju první třídu, protože jestliže si můžou takoví lidé dovolit dát deset tisíc dolarů za letenku, určitě mají v počítači něco zajímavého.“
Kolik uživatelů, respektive počítačů může daný certifikát mít, není zcela jasné. Uživatelé však hlásí problémy na modelech Dell XPS 15, XPS 13, ale taky na některých z řad Latitude a Inspiron.
A nejste-li si jistí, můžete zkusit navštívit tuhle stránku – jestli se vám otevře bez nahlášení chybějícího certifikátu, pak má váš počítač eDellRoot předinstalován. Ve Windows ho můžete snadno odstranit pomocí tzv. Microsoft Management Console, kterou otevřete následovně: klávesa Win + R, do vyhledávacího řádku napište certlm.msc a spusťte. Certifikát byste měli najít v adresáři Trusted Root Certificate Authorities > Certificates.
Kauza připomíná nedávný problém Lenova, které do některých svých počítačů předehrávalo adware Superfish, který jednak ve webových prohlížečích zobrazoval nežádoucí reklamy a navíc používal vlastní certifikáty pro šifrované HTTPS. Později se za tento adware společnost omluvila a uživatelům poskytla nástroj na jeho odstranění.
Hacker Claims He helped FBI Track Down ISIS Hacker (Who was killed in Drone-Strike)
24.11.2015
Junaid Hussain – a hacker turned ISIS cyber mastermind who was killed in a US drone strike in August this year.
But something has emerged what we don't know about the death of Hussain.
The infamous hacker who in the past hacked the Anonymous pseudo-official Twitter accounts, now claims he served as an FBI informant to help the US government track down Junaid Hussain.
The hacker, goes by the online alias Shm00p (@5hm00p), is a member of the hacking collective Rustle League and believes he is "99.9% sure" that the information given by him to the FBI agents led to the extrajudicial killing of Hussain.
"What the fuck have I done," Shm00p tweeted early Sunday morning.
Over 15 hours later after his first tweet, Shm00p made a series of tweets at the FBI Twitter account.
"I lost a lot of good friendship and my fucking honor," Shm00p tweeted at the FBI. You can see an archived copy of his now deleted tweets here. "I am so embarrassed to show my face in public now because of this," he continued.
Also Read: ISIS Hacker who Passed U.S. Military Data to Terrorists Arrested in Malaysia
Shm00p, who lives in Las Vegas, knew the British–born Hussain from their mutual affiliation with a notorious hacktivist group called Team Poison.
In 2014, Hussain reached out to Shm00p via the encrypted chat service Jabber. Shm00p was able to determine Hussain's location and then passed on the information to the FBI.
Shm00p said that he was very much sure this information led to the death of Junaid "TriCk" Hussain, who left the United Kingdom and joined ISIS in 2013.
"I fucking helped you MURDER him [Junaid]. Do you know how I feel now when I sleep at night?" Shm00p tweeted. "Regardless that he was a terrorist and an animal I sure as fuck felt betrayed."
Also Read: ISIS Supporter Hacks 54,000 Twitter Accounts & Posts Details of the CIA and FBI Heads
Based on his tweets, Shm00p was forced to help the FBI agents who threatened the livelihood of his family.
The FBI officials had him attempt to catch two of his friends while they were partying at the hacker conference DefCon in 2015, with the aim to get information on Hussain's whereabouts.
Although the FBI has declined to comment on the disclosure by Shm00p, a source with knowledge of the facts told Motherboard that Shm00p did indeed help the US federal agents locate Hussain.
ModPos, the most complex POS malware ever seen
24.11.2015
ModPOS is new POS malware discovered in systems of US retailers after the rush of Thanksgiving and experts speculate it is the most complex POS malware ever seen.
A new POS malware was discovered in US retailers, after the rush of Thanksgiving, and it looks like millions of US bank cards were affected.
The new POS malware is called ModPOS was found in some unnamed companies, but we know that we are talking about big retail companies, what makes the problem huge, because certainly means millions of dollars in damage.
The available information about the attackers are not a lot, but it’s known that they have been operating since 2013, and in a very professional way, never raised any suspicion, and that this malware was only discovered after weeks of painful research, and reverse-engineering by malware experts.
“This is POS [point-of-sale] malware on steroids,” “We have been examining POS malware forever, for at least the last eight years and we have never seen the level of sophistication in terms of development …[engineers say] it is the most sophisticated framework they have ever put their hands on.” Said iSight Partners senior director Steve Ward.
The malware experts took three weeks until reverse engineer one of the three kernel modules of the malware, and just to give you an idea, the same malware experts only needed 30 minutes to reverse engineer the Cheery Picker POS malware.
Steve Ward was impressed by the “incredibly talented” authors of the malware, and even refer that they did an “amazing job”, because their understanding of the security around POS was huge, “It is hard not to be impressed,” Ward said.
To give you another idea how good was this malware, the encryption used for network and C&C( command and control) data exfiltration and communication was protected with 128 and 256-bit encryption, and a new private key was needed peer customer.

Ward kept on saying that the authors of the malware must have spent a huge amount of money and time on each packed kernel driver module, which behaves like a rootkit, and it is difficult to detect and to reverse engineer.
It looks like the authors thought about this malware as an investment, designing the ModPOS to generate a large-scale, to be eventually able to get a return on their investment.
Now that the ModPOS was found and US retailers are aware of the problem, the attackers will need to change part of the base code to re-gain the obfuscation they had, but it looks like that some of these changes will be harder to implement, maybe more monetary investment will be needed again.
This is a new and very advanced malware, so we expect to keep hearing about more cases related with ModPOS and the attackers’ framework.
Dell's Laptops are Infected with 'Superfish-Like' pre-installed Malware
24.11.2015
Similar to the Superfish malware that surrounded Lenovo laptops in February, another big computer manufacturer Dell spotted selling PCs and laptops pre-installed with a rogue SSL certificate that could allow attackers:
To impersonate as any HTTPS-protected website and spy on when banking or shopping online.
The rogue certificate, dubbed eDellRoot, was first discovered over the weekend by a software programmer named Joe Nord. The certificate is so creepy that it automatically re-installs itself even when removed from the Windows operating system.
Also Read: Lenovo Caught Using Rootkit to Secretly Install Unremovable Software
Superfish 2.0: Unkillable Zombie
The self-signed transport layer security (TLS) credential came pre-installed as a root certificate on Dell PCs and laptops that are signed with the same private cryptographic key, which is stored locally.
That means an attacker with moderate technical skills can extract the key and abuse it to sign forged version of TLS certificates for any HTTPS-protected site on the Internet, exposing users to all manner of SSL attacks.
The certificate key can be used to conduct man-in-the-middle (MITM) attacks on Dell owners, silently stealing user names, passwords, session cookies, and other sensitive information when the affected Dell machines are connected to a malicious Wi-Fi hotspots in cafes, hospitals or airports.
The problem is similar to the scandal that hit Lenovo in February when the PC manufacturer was caught pre-installing an invasive adware program called Superfish with a similar self-signed cert to inject third-party advertisements into websites on browsers.
Must Read: Automatic Superfish Removal Tool
Although Dell's case is different as there is no indication that the certificate is being used to inject advertisements on the laptops, the resulting security issue is the same.
Affected PCs and Laptops
The self-signed certificate key was discovered to be pre-installed as a root certificate on at least three Dell laptop models:
Dell Inspiron 5000 series notebook
Dell XPS 15
Dell XPS 13
This indicates that the dangerous certificate may be present on a significant number of the Dell desktops and laptops currently on the market, specifically recent Dell Inspiron Desktop, XPS, and Precision M4800 and Latitude models.
To Check if Your Computer is Vulnerable
To discover the dangerous certificate:
Open up the Start menu
Select Run
Type in certmgr.msc – the Windows certificate manager – into the box and Hit Enter
Open up the Trusted Root Certification Authority folder on the left
Select Certificates
Search for eDellRoot
Once found, right-click over eDellRoot and hit "Remove." It appears to be gone, but actually it's not.
Reboot your computer and reopen certmgr.msc and search for the certificate "eDellRoot". Yeah, the removed root CA cert is back.
What Should You do? How to Remove?
It seems that even if the certificate is clearly fraudulent, Google Chrome and Microsoft Edge and Internet Explorer browsers always establish an encrypted Web session with no warnings.
But fortunately, Mozilla's Firefox web browser generates an alert warning that the certificate was not trusted.
So, Dell customers with new XPS, Precision, and Inspiron models are advised to use Firefox to browse the web.
To fix the issue completely, Dell users will need to manually revoke the certificate permissions, which is a complex and technically demanding task.
Moreover, security researcher Darren Kemp from Duo Security says that the problem may be even worse than what Nord suggested.
According to an analysis done by Kempa, a bundled plugin re-installs the root CA file when it is removed. So, to remove the eDellRoot certificate completely, you must:
First delete Dell.Foundation.Agent.Plugins.eDell.dll from your system
Then remove the eDellRoot root CA certificate
Dell's Response
In a statement, a Dell spokesperson said the company is investigating the report and looking into the certificate, but emphasized the company’s policy of minimizing pre-loaded software for security reasons.
- See more at: http://thehackernews.com/2015/11/superfish-malware-dell.html#sthash.Ojq5WPFZ.dpuf
Dell puts users at risk with dangerous eDellRoot root certificate
24.11.2015
Dell is in the headlines for shipping PCs with a pre-installed trusted root certificate dubbed eDellRoot that opens users to a number of cyber attacks.
Dell is in the headlines for shipping PCs with a pre-installed trusted root certificate that opens users to a number of cyber attacks. Hackers could exploit it to compromise the security of encrypted HTTPS connections. The case has several similarities to the Lenovo one, do you remember Superfish?
Early 2015, experts discovered that Lenovo was shipping laptops with Superfish malware , a malware that allows to steal web traffic using man-in-the-middle attacks. SuperFish is considered by many antivirus companies as a potentially unwanted program, adware, or a trojan.
The “Superfish” malware installed on laptops was able to steal web traffic using fake, self-signed, root certificates to inject advertisements into sessions. Lenovo has removed Superfish the malicious software after numerous users reported the embarrassing discovery on its forums by claiming to be victims of attacks.
A few months after the Lenovo case, Dell started deploying a trusted root certificate called eDellRoot.
The certificate is bundled with its private key, which open users to man-in-the-middle attacks, for example, if an affected Dell PC connects to a bogus Wi-Fi hotspot, attackers running the hotspot can exploit the eDellRoot certificate and the key to decrypt the victims’ web traffic and steal sensitive data.
The certificate as delivered on August 18 as part of an update to the Dell Foundation Services (DFS) application.
The eDellRoot certificate was discovered by researchers at Duo Labs who examined a Dell laptop, then the experts consulted the Censys project and discovered the certificate’s fingerprint in several locations.
What does this mean?
Simply that Dell has intentionally shipped the same keys in many other computers worldwide. In one case, the eDellRoot certificate was used to provide web services over HTTPS to a SCADA system.
“Given that this certificate can be used to sign SSL certificates for secure web communications, we talked to the good people at the Censys project. The Censys project uses zmap] to scan the whole IPv4 Internet and archive data, such as the SSL certificate that server sends when the scanner opens a connection. There do not appear to be any servers online that are using the initial eDellRoot certificate we discovered (98:A0:43:[…]).” states the report published by Duo Labs. “However, searching Censys for “eDellRoot” turned up another certificate, which was similar to the first one: same name and also self-signed. Normally, a given certificate would only be associated with one IP address, as it’s considered poor practice to share the private component of the certificate across multiple machines. Otherwise, it’s impossible to tell which computer actually sent a given message, a property that is often demanded in cryptosystems. “
The list of impacted systems includes XPS, OptiPlex, Inspiron, Vostoro, and Precision models.

“How this particular misconfiguration happened is unclear, but what is clear, is that this certificate is showing up in some extremely unusual and frankly concerning places,” continues the report.
Initially, Dell doesn’t explain the presence of eDellRoot, the company only declared that it “provides a core set of foundational services facilitating customer serviceability, messaging and support functions.”
Meantime, Dell updated the DFS application on Monday, after the news was circulating over the Internet. The company declared that it would be offering a tool to remove the certificate.
Unfortunately, the certificate cannot be simply removed due to a .DLL (–Dell.Foundation.Agent.Plugins.eDell.dll) included with the root certificate that reinstalls the file if it is deleted. Users have to delete both the .DLL and the certificate.
Dell plans to provide detailed information to remove the certificate and future machines will not include it.
“The recent situation raised is related to an on-the-box support certificate intended to provide a better, faster and easier customer support experience. Unfortunately, the certificate introduced an unintended security vulnerability.” is the official statement released by Dell.
Documents demonstrate NSA continued mass surveillance
24.11.2015
Newly disclosed documents show that the NSA had found a way to continue spying on American citizens’ email traffic from overseas.
The NSA continued to spy on the email messages of Americans, once again the US government has conducted a massive surveillance on the US soil. To curb internal law the US intelligence has is used overseas offices.
In response to the tragic attacks of the 9/11, the President Bush secretly authorized the US National Intelligence Agency to collect bulk metadata on emails sent by Americans. The mass collection didn’t include the email content, the US Foreign Intelligence Surveillance Court authorized it to help The War Against Terror (TWAT).
The collection of email of Americans on the US soil was stopped in 2011, but the NSA continued to monitor email traffic from Americans to people outside the nation’s borders.
A Freedom of Information Act lawsuit started by The New York Times against the NSA’s Inspector General allowed the disclosure of the document confirming the US Intelligence carried on collecting domestic data.
The report, published by the NYT, confirmed the existence of two distinct sources “assist in the identification of terrorists communicating with individuals in the United States, which addresses one of the original reasons for establishing” the bulk email records program.
“The report explained that there were two other legal ways to get such data. One was the collection of bulk data that had been gathered in other countries, where the N.S.A.’s activities are largely not subject to regulation by the Foreign Intelligence Surveillance Act and oversight by the intelligence court. Because of the way the Internet operates, domestic data is often found on fiber optic cables abroad.” states the NYT.
“The other replacement source for the data was collection under the FISA Amendments Act of 2008, which permits warrantless surveillance on domestic soil that targets specific noncitizens abroad, including their new or stored emails to or from Americans.”
Newly disclosed documents show that the NSA created a functional equivalent in continuing the surveillance activities.
“The shift has permitted the agency to continue analyzing social links revealed by Americans’ email patterns, but without collecting the data in bulk from American telecommunications companies — and with less oversight by the Foreign Intelligence Surveillance Court.” states the New York Times. “The disclosure comes as a sister program that collects Americans’ phone records in bulk is set to end this month. Under a law enacted in June, known as the U.S.A. Freedom Act, the program will be replaced with a system in which the N.S.A. can still gain access to the data to hunt for associates of terrorism suspects, but the bulk logs will stay in the hands of phone companies.”

The US Intelligence bypassed the restrictions on surveillance activities in the USA by using overseas offices to do the collection. The documents refer spy stations like RAF Menwith Hill in Yorkshire used for the collection of the metadata related to the American’s email traffic. Once the data were gathered by foreign offices, it was sent to the NSA headquarters in Maryland.
“We have known for some time that traffic analysis is more powerful than content analysis,” said Dan Geer, chief information security officer of the CIA’s venture capital firm In-Q-Tel.
“If I know everything about you, about who you communicate with, when, where, with what frequency, what length, and at what location, I know you. The soothing mendacity of proxies from the president that claim that it is only metadata, is to rely on the profound ignorance of the listener.”
The NSA still hasn’t commented the documents.
Bezpečnost bezplatných wi-fi kontroluje jen pětina Čechů
24.11.2015 Bezpečnost
Bezpečnost bezplatných internetových wi-fi sítí kontroluje jen pětina Čechů. Dalších 33 procent přiznává, že se o zabezpečení stará jen někdy. Uživatelé tak riskují zneužití osobních dat. Vyplývá to z průzkumu výrobce mikročipů Intel v ČR a na Slovensku.
Každý, kdo využívá internetového připojení zdarma, by měl vyhodnotit důvěryhodnost konkrétního poskytovatele této služby, protože tak činí na vlastní nebezpečí.
Nedostatek bezplatného bezdrátového připojení je podle 48 procent uživatelů největší překážkou toho, aby mohli svá počítačová zařízení používat na cestách. Více palčivý je tento problém pro mladé od 18 do 29 let a pro muže.
„Češi mají obecně velkou důvěru k bezplatnému internetovému připojení, vnímají je pozitivně, současně si ale ve své většině nejsou vědomi bezpečnostních hrozeb, které plynou z nedostatečného zabezpečení sítí. S tím spojená rizika nijak neřeší bezmála polovina uživatelů. Nejvíce důvěřivé jsou ženy a nejmladší generace ve věku 18 až 29 let," uvedl manažer pro maloobchodní prodej Intelu Martin Vařbuchta.
Každý, kdo využívá internetového připojení zdarma, by měl vyhodnotit důvěryhodnost konkrétního poskytovatele této služby, protože tak činí na vlastní nebezpečí. U nedůvěryhodných provozovatelů free wi-fi hotspotů se uživatel vystavuje nebezpečí odposlechu či zneužití dat. Stejné riziko mu hrozí tam, kde je zabezpečení wi-fi sítě nedostatečné, nebo dokonce zcela chybí. Základním pravidlem v síti, která je nedůvěryhodná nebo nezabezpečená, je nezadávat žádné údaje, u nichž nechceme, aby se dostaly do nepovolaných rukou.
Citlivé údaje včetně hesel
„Dbát pokynů bezpečného chování ve veřejných sítích by měli zejména uživatelé, kteří pravidelně ale i třeba jen příležitostně mimo domov, na cestách či na dovolené zadávají své citlivé údaje včetně hesel, osobních identifikačních údajů (PIN) pro online bankovnictví či platby kartou přes internet. Z průzkumu Intelu vyplynulo, že se takto chovají čtyři z deseti respondentů v ČR. Mezi Slováky je situace velmi podobná a týká se více než třetiny dotázaných," dodal Vařbuchta.
Odcizené osobní údaje bývají předmětem nelegálního obchodování. Obchoduje se především s údaji typu rodných čísel, daty narození, fyzickými i e-mailovými adresami nebo daty používanými v ověřovacích otázkách.
Nejcennější jsou údaje umožňující online řízení jednotlivých účtů, tedy například pro správu platební karty. Ceny za online přístupové údaje k bankovním účtům na černém trhu začínají kolem 190 dolarů (zhruba 4831 korun). Ceny za kreditní a debetní karty se také pohybují ve velmi širokém rozpětí, od pěti do 30 dolarů, a to v závislosti na typu karty nebo zemi, kde byla vydána.
Jaké triky zkoušejí piráti před Vánocemi
24.11.2015 Bezpečnost
Nejdůležitějším obdobím v roce jsou pro kybernetické zločince Vánoce. Před samotnými svátky jde totiž často obezřetnost stranou a lidé jsou schopni se nachytat i na nejrůznější phishingové podvody, kterých by si za jiných okolností ani nevšimli.
Scénáře phishingových útoků jsou si velmi podobné. Podvodníci lákají na předvánoční půjčky či na slevy elektroniky a šperků – od uživatelů se snaží vylákat hotovost, stejně jako jejich citlivé údaje, které pak na černém trhu mají cenu zlata.
Velké oblibě se mezi kyberzločinci těší také slevové kupóny. Na podvodných stránkách se často objevuje možnost bezplatného získání kupónu, pokud se uživatel zaregistruje. Místo skutečné slevy ale lidé v podobných případech pouze riskují zneužití svých osobních údajů.
Internetem samozřejmě kolují i desetitisíce nejrůznějších virů. Ty dokážou odposlouchávat uživatele na dálku, monitorovat jeho práci, ale klidně i šikovně obejít ověřovací mechanizmy v internetovém bankovnictví.
Takové nezvané návštěvníky bylo možné v počítači ještě před pár lety rozeznat, protože první škodlivé programy byly naprogramovány tak, aby mazaly data nebo dokonce zablokovaly celý operační systém.
Jde to i zadarmo
Moderní viry se ale snaží zůstat co nejdéle v anonymitě a potají otevírají zadní vrátka pro kybernetického útočníka.
Odhalit takové smetí pomáhají programy, z nichž každý se specializuje na něco jiného. Některé si dovedou poradit s trojskými koni či spywarem, další zase detekují takzvané keyloggery (programy zaznamenávající stisk kláves).
Cena takovýchto aplikací se zpravidla pohybuje od 500 do několika tisíc korun. Vedle toho ale existují také bezplatné alternativy, které nejčastěji firmy nabízejí pouze k vyzkoušení a zaplatit chtějí až za pokročilejší verzi. Ale i proto, aby v nich mohly zobrazovat reklamu a tím vydělávat peníze.
Výsledky testů bezplatných a placených aplikací se různí, v některých dokonce zdarma dostupné aplikace vyhrávají nad placenými.
Na PC by měl být nainstalován vždy jen jeden bezpečnostní program svého druhu. Dva antiviry na disku dokážou udělat pěknou neplechu. To samé platí také o firewallech i antispywarech.
Místo nového iPhonu připraví lidi o peníze
Jako lavina se v posledních dnech šíří internetem reklamy, ve kterých se podvodníci vydávají za zaměstnance společnosti UPC. Důvěřivce se snaží přesvědčit, že mají šanci vyhrát chytrý telefon Apple iPhone 6. Ve skutečnosti je však zaregistrují k odběru placených SMS zpráv.

FOTO: repro Facebook UPC
„Společně s Facebookem vybíráme jednoho šťastného zákazníka, který získává speciální cenu od našeho sponzora jako poděkování, že jste zákazníkem UPC Ceska Republica,“ lákají podvodníci a zastřešují se poskytovatelem kabelových služeb a internetového připojení.
Pozornější čtenáři si mohou všimnout, že jde o podvod už podle špatného názvu společnosti, který neobsahuje diakritiku. Při proklikávání výherní nabídky navíc uživatel v jednom bodě musí odsouhlasit zasílání placených SMS zpráv.
Žádného nového telefonu ani jiné výhry se tak důvěřivci samozřejmě nedočkají, místo toho jim každý týden bude z účtu mizet 99 korun za příjem prémiové SMS zprávy, dokud službu opět neodhlásí. Zástupci UPC se již od soutěže distancovali. [celá zpráva]
Vyděračský virus terorizuje uživatele Linuxu
Ransomware je škodlivý kód, který se zabydlí v počítači, zašifruje uložená data a po uživateli požaduje následně výkupné. Doposud se podobné viry soustředily především na stroje s Windows. Nejnovější verze však dokáže potrápit také majitele platformy Linux.

Vyděračské viry se často šíří přes nevyžádané e-maily.
„Byl objeven nový druh ransomwaru pro Linux, pojmenovaný Linux. Encoder.1,“ podotkl analytik Pavel Bašta z Národního bezpečnostního týmu CSIRT, který je provozován sdružením CZ.NIC. Podle serveru Security Week se už tomuto nezvanému návštěvníkovi podařilo nakazit více než tisíc počítačů s Linuxem.
Útok přitom probíhá úplně stejně jako na platformě Windows. Útočníci se tak snaží v majiteli napadeného stroje vzbudit dojem, že se k zašifrovaným datům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod.
Ani po zaplacení výkupného navíc nemají uživatelé jistotu, že se ke svým datům skutečně dostanou. Virus je nutné z počítače odinstalovat. [celá zpráva]
Letenky zadarmo? Nenechte se napálit
S novým trikem se snaží uspět kyberzločinci na sociálních sítích. Prostřednictvím nich šíří lákavé nabídky na letenky zadarmo. Zastřešují se přitom renomovanými leteckými společnostmi, jako jsou British Airways či Emirates. Cestovat bez placení ale samozřejmě lidé moci nebudou.

Ukázka podvodných nabídek na letenky zadarmo na sociálních sítích
„Facebookem se šíří nový podvod nabízející bezplatné letenky na lety British Airways či Emirates. Stránka nutí uživatele ke sdílení,“ uvedl bezpečnostní analytik Pavel Bašta z týmu CSIRT. Nabídky na letenky zadarmo jsou šířeny prostřednictvím smyšlených účtů, zároveň ale také prostřednictvím skutečných přátel. Ti nejspíše věří, že díky sdílení mají šanci letecký výlet skutečně získat.
Podle bezpečnostních expertů mohou být lidé, kteří sdílí podobné nabídky, sami terčem útoků. „Ač to zatím vypadá neškodně, může být stránka později zneužita například k přesvědčování uživatelů k instalaci škodlivého softwaru,“ konstatoval Bašta. [celá zpráva]
Zabijácká USB flashka zničí počítač
Ani slavný agent 007 by se nemusel stydět za speciální flash disk, který vytvořil ruský hacker vystupující na internetu pod přezdívkou Dark Purple. Na toto médium nejdou zapisovat žádná data, ale už pár sekund po připojení do USB portu zničí daný počítač.
Zařízení je to bezesporu velmi zákeřné. USB Killer, jak samotný tvůrce novinku nazývá, se totiž na první pohled nijak neliší od obyčejného flash disku. Uživatel si jej tak může snadno splést se záznamovým médiem a sám si počítač zničí.
Na krátkém videu, které Dark Purple zveřejnil, je vidět, jak si USB Killer poradil s notebookem společnosti IBM. Ten po pár sekundách od zasunutí zařízení do USB portu zhasl a všechny oživovací pokusy již byly marné.
Hackerská „hračka“ dokáže notebooky nebo klasické počítače zničit kvůli tomu, že je místo paměťových čipů vyzbrojena kondenzátory. Ty jsou schopny na USB port poslat až 220 V, a tím v podstatě desku nenávratně zničí, kromě ní samozřejmě mohou po tomto procesu odejít do věčných lovišť také další komponenty. [celá zpráva]
Zaznamenali jsme podezřelou platbu, tvrdí piráti
S důmyslným phishingovým podvodem přišli v posledních dnech počítačoví piráti. Vydávají se za zaměstnance České spořitelny a příjemcům nevyžádaného e-mailu tvrdí, že z jejich účtu byla provedena podezřelá transakce. Z uživatele se touto cestou snaží vylákat informace o platební kartě, díky kterým pak budou schopni odčerpat finanční prostředky z účtu.
„Tímto Vám oznamuji, že jsme zaznamenali podezřelou platební transakci na Vašem bankovním účtu, který máte vedený v České spořitelně. Tímto elektronickým dopisem Vás vyzývám o zaslání níže vyplněných parametrů, které potvrdí Vaši totožnost a disponenční právo k Vašemu účtu,“ tvrdí kyberzločinci v podvodném e-mailu.
Kromě jména a příjmení požadují zadat také rodné číslo i bydliště. Hlavní problém je v tom, že důvěřiví uživatelé by mohli vyplnit i poslední tři okénka tabulky, tedy informace o platební kartě. Ty mohou útočníkům sloužit k provádění plateb na internetu.
„Podvodník žádá po držiteli platební karty citlivé údaje – číslo platební karty, platnost karty a kód CVV2/CVC2, tedy trojčíslí uvedené na zadní straně platební karty VISA/MasterCard,“ uvedli zástupci České spořitelny.
TrueCrypt is safer than previous examinations suggest
23.11.2015
A new security audit the TrueCrypt software confirmed that even if it is plagued by some vulnerabilities, the application is effective when it comes to protecting data.
TrueCrypt, secure or insecure … that is the question.
A group of Ten auditors from the Fraunhofer Institute for Secure Information Technology has conducted a six-month audit of TrueCrypt under contract from the German Government. The researchers have expressed a positive opinion of the popular freeware utility used for on-the-fly encryption (OTFE).
The experts have examined in detail the vulnerabilities affecting TrueCrypt and revealed that the popular application is safer than previous examinations suggest. The details of the analysis are included in a 77-page report, titled Security Analysis of TrueCrypt, that examined also extra vulnerabilities in the software.
The maintenance of TrueCrypt was mysteriously interrupted in May last year, a message on the official SourceForge-hosted page was encouraging users to adopt Microsoft Bitlocker because TrueCrypt was insecure.
“The development of TrueCrypt was ended in 5/2014 after Microsoft terminated support of Windows XP. Windows 8/7/Vista and later offer integrated support for encrypted disks and virtual disk images. Such integrated support is also available on other platforms (click here for more information). You should migrate any data encrypted by TrueCrypt to encrypted disks or virtual disk images supported on your platform,” states the message on Truecrypt website.

Rumors online states that developers were aware of a critical vulnerability or backdoor that would jeopardize the integrity of the software, and for this reason, they suspended the project.
Since then, a group of experts under the Open Crypto Audit Project who audited the software confirmed that it was “well-designed.” The report published by the OCAP highlights that popular appl is affected by several buffer overflow vulnerabilities, but tests conducted by Fraunhofer SIT researchers have demonstrated that these vulnerabilities cannot be exploited by hackers.
In September, the popular hackers James Foreshaw has discovered further privilege escalation vulnerabilities that were not reported in the previous security audits of the software.
Now the group of experts hired by the Germany’s Federal Office for Security in Information Technology has provided more details on the real level of security implemented by the encryption platform.
From a security standpoint, the group of researchers explained that despite there are security issued related to the software, it is good for protecting data stored on an unmounted hard drive or a USB flash drive.
“The AES implementation is not timing-resistant, key files are not used in a cryptographically secure way and the integrity of volume headers is not properly protected. There are many redundant implementations (sometimes for hardware-optimization) and disused algorithms are still present in a deactivated form in the source code,” state the report.
According to the experts, TrueCrypt is not resilient to attacks in which the attackers have privileged access to a running system, but this is not a novelty.
The experts evaluated the software not optimal but still effective under specific circumstances.
“Overall, the analysis did not identify any evidence that the guaranteed encryption characteristics are not fulfilled in the implementation of TrueCrypt. In particular, a comparison of the cryptographic functions with reference implementations or test vectors did not identify any deviations. The application of cryptography in TrueCrypt is not optimal. The AES implementation is not timing-resistant, key files are not used in a cryptographically secure way and the integrity of volume headers is not properly protected.”
Co si odnést z návodu ISIS pro bezpečnou komunikaci na internetu
23.11.2015 Hrozby
V reakci na válku, kterou Anonymous vyhlásili ISIS, zveřejnili teroristé manuál pro bezpečnou komunikaci na internetu. Co se z něj dozvíte?
Tajné služby, Francie, Belgie a Spojené Státy se předháněly v tom, jak prý útočníci v Paříži využívali šifrování (dokonce včetně nesmyslů o využívání PlayStation4 na základě JEDNÉ nalezené herní konzole). Pak se ale ukázalo, že útočníci byli neopatrní, naivní a nejenže neřešili šifrování, ale dokonce ani možnost vysledování přes mobilní telefony.
Poněkud se to strašení teroristy, které tajné služby a policie používají jako hlavní argument pro postavení šifrování mimo zákon, nedaří. A ještě hůře to dopadne, pokud si prostudujete návod (PDF například zde, ale pozor, jde o překlad přes Google Translate), který ISIS poskytuje svým příznivcům. Zjistíte například, že nevěří Androidu ani iPhonům a že nepovažuje za bezpečné ani žádné oficiální šifrované komunikační nástroje.
V návodu na bezpečné používání internetu najdete v zásadě to, co doporučuje každý jiný podobný návod. V ISIS se to pochopitelně řeší v jiné souvislosti: jak provádět podvratné aktivity a přitom zajistit to, aby byl šiřitel nevystopovatelný, nebo alespoň obtížně vystopovatelný.
Zmíněný návod vznikl už zhruba před rokem a nejde o návod na míru pro ISIS. Je dílem společnosti Cyberkov z Kuvajtu a měl sloužit hlavně žurnalistům a politickým aktivistům v Gaze. V originále je k nalezení zde.
Co konkrétně v návodu najdete
Dočtete se tam obvyklá varování ohledně hesel, potřeby zabezpečit účet proti hacku, vypnutí GPS, potlačení EXIF ve fotografiích či nutnosti používat https připojení. Je zde jasně řečeno, že „privátní“ zprávy na Twitteru nejsou ve skutečnosti privátní. Pro geolokační informace je doporučováno používat falšování, třeba s použitím aplikace Mappr (či jiné).
Instagram návod zmiňuje jako zcela nevhodný prostředek, Facebook kritizuje pro špatnou reputaci v oblasti ochrany soukromí. Ze bezpečné nepovažuje ani GSM sítě, šifrování v nich je prý dobré pouze pro „průměrného“ uživatele. Doporučuje proto používání telefonů jako je CryptoPhone nebo BlackPhone od SilentCircle. Zmiňuje i Tails, operační systém, který lze spustit prakticky kdekoliv z DVD/USB či SD karty.
Pro sdílení informací doporučuje privátní Wi-Fi sítě, využití Twitteru přes SMS místo přes internet, aplikace jako FireChat, Tin-Can, The Serval Project. Velmi důsledně zdůrazňuje to, že většina informací přenášených přes internet není šifrována – doporučuje proto používat VPN, včetně služeb jako je Freedome, Avast SecureLine! a pochopitelně Tor Browser a Orbot, Onion Browser, Aviator či Opera Mini.
Důraz klade i na šifrování samotných zařízení, ať už přímo podporovaného Androidem a iOS, nebo pomocí softwaru jako je TrueCrypt (jeden z řady z poněkud kontroverzních nápadů), VeraCrypt a BitLocker ve Windows. Doporučuje i použití pevných disků, které jsou šifrováním přímo vybavené.
U e-mailových služeb návod doporučuje, že je lepší volit ty „ne-americké“, zmiňuje třeba Hushmail, ProtonMail, Tutanota. Pro přímou komunikaci podle něj nelze věřit aplikacím jako je WhatsApp či Line. Mezi těmi důvěryhodnějšími je Threema, Telegram, SureSpot, Wickr, Cryptocat Service, IO SwissCom, PQChat, Sicher. iMessage od Apple považuje za bezpečný, ale upozorňuje na omezení pouze na tuto platformu a možné problémy při snaze poslat informace přes SMS místo bezpečným kanálem.
Návod věnuje pozornost také nutnosti šifrovat VOIP. Varuje před Skypem, který prý některé tajné služby prý umí číst. Doporučovaným softwarem je Linphone, opět IO Swisscom, Silent Circle s RedPhone a Signal. Vhodný je podle manuálu i FaceTime, který je prý vhodnější než klasické telefonování.
U cloudových úložišť návod jasně vylučuje Dropbox, protože tam pracuje Condoleezza Rice, a také proto, že před Dropboxem varoval Edward Snowden. Paradoxní je, že doporučuje využít MEGA, poněkud rozumněji už vypadá doporučení na SpiderOak, SugarSync, Copy.com.
Damballa revealed the secrets behind the Destover malware that infected the Sony Pictures
23.11.2015
Security researchers at Damballa Willis McDonald and Loucif Kharouni have conducted a deep analysis of the Destover malware used in the Sony Pictures attack.
Security researchers at Damballa Willis McDonald and Loucif Kharouni have conducted a deep analysis of the wiper used by threat actors in the Sony Pictures hack. The experts discovered that attackers used a highly sophisticated disk-cleaning code dubbed Destover malware that stayed hidden using newly-uncovered anti-forensics tools.
The experts noticed significant improvements in the variant of Destover malware that was used to erased data across systems at Sony Pictures in November. In December security experts at Kaspersky Lab have detected a strain of Destover Malware that has been digitally signed with the certificates stolen during Sony attack.
Destover has been linked to the Shamoon malware used in the attack on Saudi Aramco in 2012, experts have discovered several similarities among the wiping components implemented by the two malware.
Many hypotheses have been circulating about the Sony hack, the American authorities have blamed North Korea, but a part of the security community has pointed the finger at Russian hackers.
Experts at Damballa have discovered that the new variant of Destover use components to avoid detection and make hard forensic investigations, for example the strain of malware analyzed by McDonald and Kharouni has the ability to change file timestamps and erase the logs.
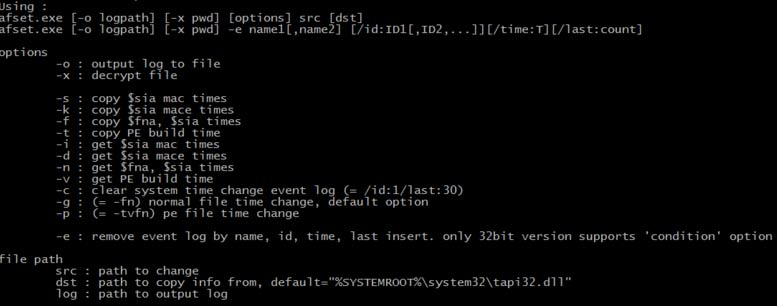
“The Destover trojan is a wiper that deletes files off of an infected system, rendering it useless … for ideological and political reasons not for financial gain,” the pair of researchers say. “
“Much was revealed In the weeks and months following these breaches, except for how attackers were able to stay undetected within the network long enough to expand their presence and exfiltrate Terabytes of sensitive information. While researching a newer sample of Destover, we came across two files that were identified by one antivirus product at the time under a generic signature. After analyzing further, we found two utilities closely related to Destover. Both utilities would be used during an attack to evade detection while moving laterally through a network to broaden the attack surface. Both utilities had usage statements and were named as setMFT and afset.”
The experts discovered two utilities used to manipulate the timestamps and wipe logs. The utility setMFT is used for timestomping, a term used to identify the copy the timestamp settings from a source file on disk to a destination file.
“setMFT is used to copy the timestamp settings from a source file on disk to a destination file, also called timestomping. Timestomping combined with similar file naming enables a file to blend in with legitimate files in the same directory. This can conceal a file’s existence from security personnel looking for malicious files or scans of files created after a certain date. Timestomping can get past a cursory check for malicious files. A thorough forensic examination will reveal that a file has been timestomped based on conflicting record dates and possibly log files.” states the post published by Damballa.
The afset utility is used to wipe Windows logs based on time and identity, and modify an executable’s properties, including build time and checksum.
“afset, like setMFT is also used to timestomp files plus clean Microsoft Windows logs based on criteria (id, time) from the user. It also changes the PE build time and checksum. afset provides more granular functionality to allow the user to set only certain timestamps on a file (sia, fna or both). “
The experts have no doubt, attackers behind the Destover-based attacks are very well organized, afset and setMFT utilities are part of their arsenal and allow them to remain under the radar for a long period.
“Gaining a foothold inside the victim’s network is a top priority. History tells us that in most of the high-profile hacks making news headlines, the attackers were able to spend months hidden inside the victim’s network exfiltrating Terabytes of data.”
The table below details the different steps attackers would go through to penetrate the targeted infrastructure, it is possible to note that they have used the two utilities for different purposes and at different steps.
STEPS TOOLS
Reconnaissance Scanners, Open source intelligence gathering
Breach Vulns, Exploits,
Foothold afset, setMFT, RATs, credential theft
Move laterally Stolen administrative credentials and RATs
Exfiltrate VPN accounts, RATs, out of band comms
Delete tracks afset, setMFT, Destover / Shamoon
Exit Publish stolen data, clean with Destover / Shamoon
Sofistikované útoky na firmy se změní, předpokládají experti
23.11.2015 Počítačový útok
Značné změny na poli kybernetické špionáže očekávají odborníci firmy Kasperský Lab. Podle nich se dramaticky promění struktura APT hrozeb i to, jak se vedou. U ataků typu APT (advanced persistent threat) se sníží důraz na ‚vytrvalost‘ a pozornost se přesune k tzv. memory-resident a fileless malwaru, který se snaží vyhnout detekování tím, že minimalizuje počet stop zanechaných v napadeném systému.
Odborníci také zpozorovali, že útočníci již nemají tendenci předvádět své vynikající kybernetické dovednosti. Většina z nich se bude rozhodovat na základě návratnosti investic. Lze tedy očekávat zvýšení počtu změn u standardního ‚off-the-shelf‘ malwaru, spíše než investování do bootkitů, rootkitů a vytváření malwaru na míru, který analytické týmy odhalí a zničí.
V dlouhodobější perspektivě experti předpokládají, že se do prostředí APT hrozeb zapojí více nováčků. Kybernetických žoldáků bude přibývat, jak budou jednotlivé skupiny hledat co největší zisk z online útoků.
Můžeme očekávat, že žoldáci budou nabízet své znalosti komukoliv, kdo bude ochotný platit. Budou také prodávat zainteresovaným třetím stranám digitální přístup k nejzajímavějším obětem, tedy budou nabízet ‚Access-as-a-Service‘ službu.
Vyvíjet se budou také hrozby cílící na uživatele. Podle expertů naroste objem ransomwaru na úkor bankovních trojanů. Ransomware se bude kromě tradičních mobilních zařízení a internetu věcí šířit i na nových platformách, jako jsou například zařízení se systémem OS X, jejichž vlastníky jsou často majetnější, a tedy lukrativnější, cíle.
Kyberzločinci neustále hledají nové cesty, jak získat od obětí peníze. Dá se tedy očekávat, že finanční útoky na platební systémy jako ApplePay nebo AndroidPay, stejně tak jako na burzy, budou narůstat.
Aby podniky minimalizovaly rizika spojená s budoucími kybernetickými útoky, měly by vytvořit a implementovat kompletní bezpečnostní strategii. Klíčové je také vzdělávání zaměstnanců a nasazení vícevrstvého koncového bezpečnostního řešení.
Uživatelé by měli investovat do silného bezpečnostního řešení a používat šifrovanou komunikaci. Neměli by nicméně spoléhat výhradně na technologie.
Ransomware will target also Medical Devices
23.11.2015
“Want to keep using the pacemaker? “” pay us 2 bitcoins” Experts fear that ransomware will start targeting medical devices.
Technology has a huge role in our lives, we depend on it even more, including our smartwatch and also our medical device. Unfortunately, we usually forgot that even our medical devices, the ones they help to save lives, are also technological devices that could be affected by many security issues like a normal PC … and hackers can exploit these vulnerabilities!
A report issued by Forrester released some days ago, predict that for 2016 we will start seeing ransomware take advantage of medical devices.
Now imagine that a patient having a pacemaker suddenly receives a message on his phone saying “Want to keep using the pacemaker? “, ” pay us 2 bitcoins”, it may look bizarre, but its probably things that may happen in a near future.
It is a bold prediction by “Predictions 2016: Cybersecurity Swings To Prevention” report, but honestly it’s something that already crossed our minds.
“It’s definitely feasible from a technical standpoint,” “see it as something that could happen next year. All that would be required from an attacker standpoint is small modifications to the malware to make it work.” Explained Billy Rios, a popular hacker and medical device security researcher.
We could argue that it’s not correct to get a profit from situations like this, but many crooks, just don’t care.
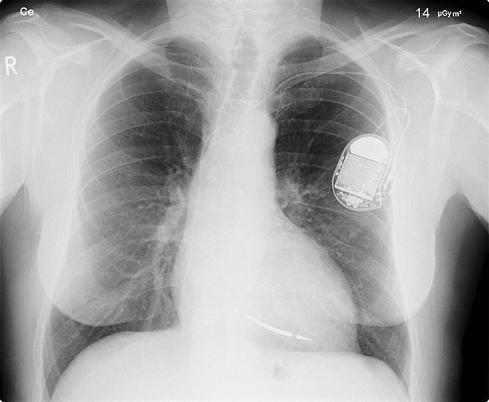
The ICS-ALERT-13-164-01 from 2013 done by Rios and Terry McCorkle showed that 300 medical devices were using hard-coded passwords, that are set at the factory, that can’t be disabled or changed, these passwords are discriminated in the manual of the manufacturer.
The truth is, Cyber security exist probably since the last 15-25 years, but it’s something new in the Medical Industry and as Joshua Corman, founder of I Am the Cavalry says:
“While we’ve been doing this for 15-25 years in cyber, this is year zero or one for them [the healthcare industry],”“We can’t give them 15-25 years to catch up, although it’s not reasonable to get there overnight….We’re trying to approach this with teamwork and ambassador skill, not a pointing finger, but a helping hand.”
Ransomware is a huge business, and the major security vendors have been saying that 2015 had a huge increase in the Ransomware use and profit, and it tends to get even more with the IoT and all the devices connected to the internet.
Months ago on SecurityAffairs we talked about a list developed by I Am The Cavalry that was created to mitigate threat in cars, and now they are planning the same type of list but this time for medical devices.
There are many challenges ahead, when dealing with Medical devices, but we are starting to see many people worried about it, so I believe that many security researchers will focus their attention on them, but for this we also need the support of the medical devices manufacturers.
Microsoft stáhl nástroje pro aktualizaci na Threshold 2
22.11.2015 Software
Microsoft stáhl nástroje pro aktualizaci na Threshold 2Dnes, Michal Hala, aktualitaAktualizace Threshold 2 byla dostupná třemi způsoby, jednak přes Windows Update, jednak z webu šel stáhnout malý prográmek, který aktualizaci popohnal, nebo šel stáhnout Media Creation Tool. Teď je všechno jinak.
Nyní je aktualizace November Update (známější jako Threshold 2) ovšem dostupná jen pomocí Windows Update. Prográmek GetWindows10-sds, který uměl aktualizaci popohnat, i Media Creation Tool pro tvorbu ISO nebo instalačního flashdisku s Thresholdem 2 už na webu Microsoftu nenajdete. Je tam ke stažení jen původní Media Creation Tool (buď 32bitová, nebo 64bitová verze), který vytvoří ISO nebo instalační flashdisk s původní červencovou verzí 1507, sestavení 10240.
Takže instalaci podle našeho původního návodu (čtěte tady) už proces aktualizace na Threshold 2 nepopoženete. Ani už nemůžete udělat čistou instalaci rovnou na verzi 1511. Pokud jste si výše uvedené nástroje náhodou už dříve nestáhli, můžete teď leda pomocí prapůvodní verze Media Creation Toolu vytvořit instalační nástroje (DVD/flashdisk) pro verzi 1507 a po její instalaci musíte počkat, až vám Windows Update aktualizaci na verzi 1511 sám nabídne.
Co k tomu dodat? Především, že Redmond v tomhle případě na komfort uživatelů opravdu nemyslí. Ale co je zatím? Žádný z webů, ze kterých čerpám, neuvádí žádné rozumné natož ověřené důvody, ani žádné rozumné vysvětlení ze strany Microsoftu. Ten se omezil pouze na krátkou noticku, že se rozhodl November Update nabízet pouze pomocí služby Windows Update. Přestože sám předtím alternativní postupy vyloženě doporučoval.
Když se postupně začaly množit spekulace, že Microsoft aktualizaci November Update úplně stáhl, společnost to kategoricky popřela. Takže důvody uvedených kroků Microsoftu jsou stále neznámé. Ale jedno je jisté – většinu uživatelů Microsoft tímhle asi dost naštve. To si v Redmondu opravdu nedokážou představit, jak takový krok budou vnímat jeho zákazníci?
Nemohou za stažením obou užitečných nástrojů být technické problémy? Ale to by se o nich nejspíš vědělo a psalo, což se neděje. Nebo je to jen něčí byrokratické rozhodnutí? Nevím, berte obě možnosti jako moje spekulace. Každopádně koncept Windows-as-a-Service tímhle dostal docela pěknou trhlinu. Nebo si naopak na daný mechanismus aktualizace budeme muset zvyknout.
Přes 50 hotelů Starwood napadeno malwarem, který kradl data platebních karet
22.11.2015 Viry
Přes 50 hotelů Starwood napadeno malwarem, který kradl data platebních karetVčera, Milan Šurkala, aktualitaPomalu není týden, aby se neobjevil nějaký velký hackerský útok. Společnost Starwood, která vlastní např. řetězec hotelů Sheraton nebo The Westlin, oznámila, že 54 jejích hotelů v USA a Kanadě bylo napadeno malwarem, který kradl data platebních karet.
Opět tu máme velký hackerský útok, kterých se za poslední měsíce stalo několik (jedním z posledních byl třeba britský operátor Talk Talk). Obětí toho posledního se tentokrát stala společnost Starwood Hotels and Resorts. 54 jejich hotelů v USA a Kanadě bylo napadeno malwarem, který v restauracích nebo různých obchodech kradl data použitých platebních karet. Tím bylo jméno vlastníka, číslo karty, bezpečnostní kód nebo datum expirace. Není známo, že by se hackeři dostali k jiným datům.
První hotely této společnosti byly napadeny již v listopadu 2014. Týká se to zejména hotelů Sheraton, The Westlin a W. Malware již byl odstraněn a zákazníci by měli pro jistotu zkontrolovat své bankovní účty. Pokud jste tedy za poslední rok byli v USA nebo Kanadě v jednom z inkriminovaných hotelů, měli byste zpozornět.
Yahoo! Mail blokuje e-mailovou schránku pokud blokujete reklamy
22.11.2015 IT
Yahoo! Mail blokuje e-mailovou schránku pokud blokujete reklamy20.11.2015, Milan Šurkala, aktualitaYahoo! se odhodlalo k odvážnému kroku. Některým svým uživatelům blokuje přístup k e-mailové schránce, pokud mají zapnutý systém pro blokování reklamy. Vypadá to na další hřebíček do rakve tohoto Blokování reklamy je na internetu velmi rozšířený jev, který má svá pozitiva i negativa. Pozitivem pro uživatele je rychlejší načítání stránek, lépe čitelný obsah nebo vyšší bezpečnost. Naopak nevýhodou je to, že weby získávají méně peněz na svůj provoz, mnoho z nich se propadá do ztráty, ukončují svou činnost (nezvládají pokrýt provozní náklady) nebo se snaží nabrat výpadky způsobené blokováním jinak (ještě větším množstvím reklamy těm, kteří ještě neblokují, bulvárnějšími články, natvrdo placeným přístupem nebo dnes velmi (ne)oblíbeným kouskováním článků na desítky kapitol). Některé weby blokují ty, kteří blokují reklamy a otázkou je, kdo vydrží blokovat déle. A přesně tuto strategii nasadil portál Yahoo!
Jenže k velkému překvapení tento systém nasadil na e-mailovou schránku svých uživatelů. Pokud tedy uživatel používá AdBlock a chce si přečíst své maily na portálu Yahoo!, může se mu objevit hláška nabádající k vypnutí AdBlocku. Část lidí se už do své schránky bez vypnutí blokování reklamy nedostane. Na jednu stranu je sice pravda, že Yahoo! poskytuje službu, kterou financuje právě zobrazováním reklam (a ne tím, že by uživatelé platili přímo, provoz systému stojí nemalé peníze a ten se musí nějak zaplatit), na druhou stranu je toto opravdu dost vážný krok, který se uživatelů dotkne na tom nejcitlivějším místě.
Je tedy otázkou, jak zareagují uživatelé. Yahoo! patrně spoléhá na to, že e-mail je záležitost, která se jen velmi těžko opouští, obzvlášť máte-li na danou e-mailovou adresu zaregistrovány desítky účtů jinde (přihlašovací jména k jiným službám). Nicméně pokud tento krok přiměje přejít některé uživatele na jiný mail, ztratí Yahoo! i přístupy ke svému portálu, což jeho zhoršující se pozici na trhu dále ohrozí. Uvidíme, zda tímto krokem získá nebo ztratí. Z krátkodobého hlediska by mohlo získat, neboť uživatelé budou chtít přistupovat ke svým schránkám a blokování vypnou, z dlouhodobého hlediska se dá očekávat snížený počet nových registrací e-mailových schránek a postupné opouštění těch stávajících. A s tím i smrt tohoto kdysi oblíbeného portálu.
Chybovou hlášku je možné nechat si vyvolat přidáním řetězce "?reason=ADBLK_TRAP" do URL adresy. V mém případě se sice hláška zobrazila, ale protože blokování reklam nepoužívám, odkaz "Continue to Yahoo Mail..." mě dostal do e-mailové schránky. Podle reakcí jiných uživatelů se ale s aktivním blokováním do schránky nedostali. Samotné Yahoo! potvrdilo, že toto blokování je v testovacím provozu pro některé uživatele.
Police Body Cameras come with Conficker Worm
22.11.2015
Police body cameras sold by Martel Electronics have been found to be infected with the notorious Conficker worm.
Security experts at iPower Technologies while analyzing the body cam designed for police departments manufactured by Martel Electronics, discovered that the cameras were infected.
Martel Electronics is US company that design video systems used by law enforcement, including in-car and body cameras. iPower Technologies is working on developing a cloud-based system for law enforcement to store and manage video acquired by their cameras.
iPower discovered that the camera used for testing were infected with a variant of Conficker (aka Downup, Downadup and Kido). The malware is not complex and is actually detected by almost every antivirus software.
The cameras had been shipped with the worm, once the devices were connected to a computer, the malicious code attempted to contact the C&C server and infect other devices on the same network.
“During testing and evaluation of the Martel Electronics product, Jarrett Pavao and Charles Auchinleck, discovered that multiple body cameras had been shipped to iPower preloaded with the Win32/Conficker.B!inf worm virus. When the camera was connected to a computer, iPower’s antivirus software immediately caught the virus and quarantined it. However, if the computer did not have antivirus actively protecting the computer it would automatically run and start propagating itself through the network and internet.” states iPower in a blog post.
iPower attempted to report the issue to Martel before publicly disclose it, but it hasn’t received a response.
Conficker is a well-known threat, it was first detected in November 2008, when it has infected millions of computers across the world. Conficker is considered by security experts one of the largest botnets ever seen. Cyber security experts linked the threat also to Stuxnet, in fact, the worm was used to open back doors into computers in Iran, then infect them with Stuxnet … “Conficker was a door kicker,”
In 2009, Microsoft alongside security firms, academic researchers and domain registries teamed up to create the Conficker Working Group, a joint effort aiming to disrupt the botnet.
Unfortunately the threat is still active worldwide.
Shedun adware can install any malicious mobile app by exploiting Android Accessibility Service
22.11.2015
Shedun Trojanized adware family implements the ability to automatically install any app on the devices by exploiting the Android Accessibility Service.
Android is once again in the storm, threat actors can install any malicious third-party app on mobile devices remotely even if the users explicitly refuse it.
Security experts at mobile security firm Lookout have spotted Trojanized adware families that implement the ability to automatically install any mobile app on the devices by exploiting the Android accessibility features.
The researchers have found three Trojanized adware families, Shedun (GhostPush), Kemoge (ShiftyBug),
Shuanet.
These families root the infected device after being installed and gain persistence by embedding their code in the system partition. The root access allows attackers to gain unrestricted access to the mobile devices.
“Last week we told you about three trojanized adware families: Shuanet, ShiftyBug, and Shedun. These families root the victim’s device after being installed and then embed themselves in the system partition in order to persist, even after factory reset, becoming nearly impossible to remove. We call it “trojanized adware,” because the end goal of this malware is to install secondary applications and serve aggressive advertising.” reads the blog post published by
The malware researchers highlighted the capabilities of the Shedun adware family that seem to be out of the ordinary because it doesn’t exploit any vulnerability to hijack an Android device, instead it relies on the service’s legitimate functionality.

During the installation, mobile apps from the Shedun adware family tricks users into granting them access to the Android Accessibility Service, this means they will be able to read the text on the phone screen, determine an app installation prompt, scroll through the permission list and press the install button on the behalf of the user.
“Lookout observed Shedun abusing the Android Accessibility Service for its malicious means. Using the accessibility service toolset in the delivery of malware is pretty uncommon, so we took a deeper look.” states the post. “By gaining the permission to use the accessibility service, Shedun is able to read the text that appears on screen, determine if an application installation prompt is shown, scroll through the permission list, and finally, press the install button without any physical interaction from the user.”
The following video shows apps from the Shedun adware family gaining accessibility service privileges.
In this second video Shedun automatically install a trojanized app that masquerades itself as an official app available in Google Play Store and then is pushed to third-party markets.
It is important to note that the Android Accessibility Service is also used by legitimate applications, users are advised not to install applications from third-party app markets.
The new Nmap 7 version just released
22.11.2015
After 3.5 years, Fyodor has released the new version of the popular open-source network-exploration tool Nmap 7.
After 3.5 years, Fyodor has released the new version of the popular network-exploration tool Nmap 7. Nmap is one of the most popular open-source network mapper, the principal changes announced for this release are:
– 3,200 code commits since Nmap 6
– expanded capabilities for its scripting engine including 171 new NSE scripts
– Mature IPv6 support from host discovery, port scanning and OS detection
Serious vulnerabilities like Heartbleed, POODLE, and FREAK could be easily detected by using the automated scanners implemented by Nmap 7.
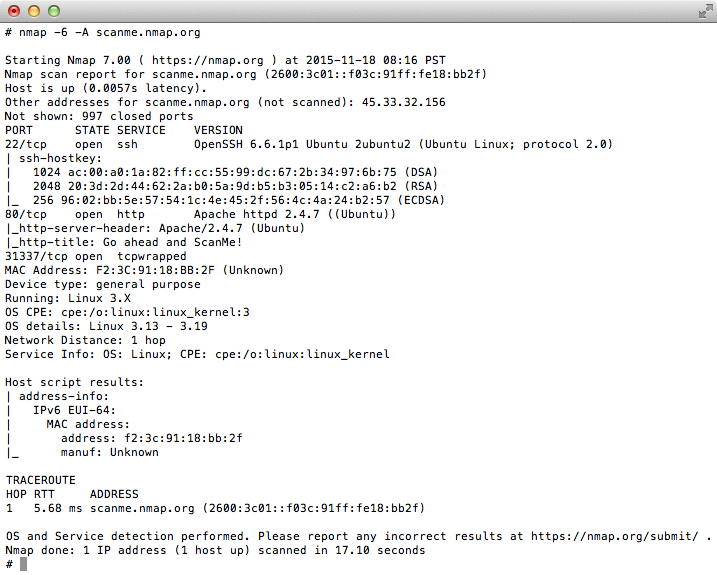
A new implementation for the ssl-enum-ciphers script allows to perform fast analysis of TLS connections by enumerating SSL/TLS protocol versions and cipher suites. It could allow to rapidly identify deployment problems.
The tool could be used to easily find vulnerable servers, Nmap 7 includes speedups and scanning improvements. The new version of the tool includes a newer and faster Nmap Scripting Engine (NSE), it also allows users to write Lua scripts.
“The venerable RPC grinder which used to run with -sV is now an NSE script: rpc-grind. This allowed us to cull a bunch of old C code in favor of more maintainable Lua, as well as make a noticeable improvement in scanning speed, all while using a fifth of the number of code lines.” states the post on the Nmap 7 version.
The library of scripts available in the Nmap 7 has expanded from 348 to 515. Some of the scripts included in the tool could be used to rapidly check for SSL vulnerabilities (i.e. Heartbleed, POODLE and Shellshock) and for HTTP flaws such as Slowloris and Misfortune Cookie.
The new engine can also output parsable XML and implements the support for shared libraries across scripts.
“NSE joins the rest of Nmap in being able to output parseable XML. Instead of just a text blob in Nmap’s XML output, scripts can now return structured information that can be quickly extracted with an XML parser. All new scripts produce structured output, most older scripts have been converted, and any script using the vulns library is automatically upgraded.”
If you want to download Nmap 7 click here.
DHS Information Security Program, Dozens secret databases vulnerable to hack
22.11.2015
Evaluation of DHS Information Security Program for Fiscal Year 2015 revealed the existence of dozens of top-secret unpatched databases.
The story I’m about to tell you is staggering, the US Department of Homeland Security is running dozens of unpatched and vulnerable databases, a number of them contained information rated as “secret” and even “top secret.”
The discovery emerged from the “Evaluation of DHS’ Information Security Program for Fiscal Year 2015” conducted on the department’s IT infrastructure by the US Government.
The audit of the DHS Information Security found serious security issues in the Government systems, including 136 systems that had expired “authorities to operate,” a circumstance that implies the stop of maintenance activities. The principal problem discovered by the inspectors is that a number of systems, despite are still operative and under maintenance have no up-to-date security patches, leaving them open to cyber attacks.
Of the 136 systems, 17 were containing information classified as “secret” or “top secret.”
Giving a deep look at the report on the DHS Information Security Program, it is possible to note that the Coast Guard runs 26 vulnerable databases, followed by FEMA with 25, Customs and Border Protection with 14, and the DHS’ headquarters with 11.

Although Secret Services have only two vulnerable databases, they have failed other targets.
It implemented proper security checks just for 75 percent of its secret or top secret databases, and just 58 per cent of its non-secret databases. The DHS targets are 100 per cent and 75 per cent respectively. The experts discovered several security issues affecting the majority of assessed systems, including PCs, databases and also browsers.
The assessments conducted to evaluate the DHS Information Security Program, revealed several deficiencies in the systems analyzed, for example, Windows 8.1 and Windows 7 workstations which were missing security patches for the principal software.
“We found additional vulnerabilities regarding Adobe Acrobat, Adobe Reader, and Oracle Java software on the Windows 7 workstations,” the department’s inspector general noted in a 66-page report. “If exploited, these vulnerabilities could allow unauthorized access to DHS data.”
The inspectors have found many other security issues in the DHS Information Security Program, including weak passwords, websites susceptible to cross-site and/or cross-frame vulnerabilities and poor security settings.
The Government environments suffer bureaucratic obstacles in bug fixing and patch management, it could take more than a year to fix a leak from the moment it is reported.
The results of the evaluation confirm that improvements have been made but there are a lot of serious issues that have to be urgently addressed.
“While improvements have been made, the Department must ensure compliance with information security requirements in other areas. For example, DHS does not include its classified system information as part of its monthly information security scorecard or its FISMA submission to OMB. In addition, USCG is not reporting its PIV data to the Department, which is a contradiction to the Under Secretary for Management’s guidance that requires Components to submit this information to the Department.5 In addition, we identified deficiencies with DHS’ enterprise management systems, including inaccurate or incomplete data.”
The report also provides a set of recommendations to solve the security issued emerged after the assessment.
The DHS has 90 days to fix the issues, two of which have been already solved.
Anonymous Hacking Group Takes Down 20,000 ISIS Twitter accounts
21.11.2015
Anonymous Hacking Group Takes Down 20,000 ISIS Twitter accounts
In the wake of horrific terror attacks in Paris, the online Hacktivist group Anonymous last week declared "total war" against the Islamic State militant group (ISIS) that claimed responsibility for the attacks.
While French, Russian, and US military are bombing ISIS from the sky, Anonymous members from all over the world are carrying out their very own cyber attack campaign, dubbed #OpParis, against the terrorist organization.
Anonymous has claimed to have taken down 20,000 ISIS-affiliated Twitter accounts in order to take revenge from ISIS for the deadly Paris attacks on November 13.
Anonymous Took Down 20,000 ISIS-affiliated Twitter Accounts
In a YouTube video posted on Wednesday, the group said:
"More than 20,000 Twitter accounts belonging to ISIS were taken down by Anonymous."
The group has provided a list of all the Twitter accounts that have been taken down.
On Tuesday, the hacktivist group claimed to have successfully taken down more than 5,500 pro-ISIS Twitter accounts from the Internet.
Also Read: Check Out How 'Idiot' Anonymous Hackers Can Disrupt your Online Propaganda
In the latest video provided by Anonymous, a spokesman in black behind the group’s signature Guy Fawkes mask said:
"Hello, citizens of the world. We are Anonymous. It is time to realize that social media is a solid platform for ISIS’s communication as well as neutering their ideas of terror amongst youth. However, at the same time, social media has proved it is an advanced weapon. We must all work together and use social media to eliminate the accounts used by terrorists."
Hey ISIS! We Will Hunt you Down from The Internet
ISIS' most interesting aspect is how it leverages the enormous power of social media platform to radicalize young people, spread its message around the globe, recruit foreign supporters to its fight and shock people into taking notice of its actions.
So, taking down the ISIS' social media presence is the real key to defeating the terror group, and it does make an impact at worst.
"ISIS, we will hunt you and take down your sites, accounts, emails and expose you. From now on, there is no safe place for you online. You will be treated like a virus, and we are the cure," the spokesman said in the video message.
Also Read: Anonymous declares War on ISIS: 'We will Hunt you Down!'
IDIOTS Answer to ISIS
Last week, when Anonymous declared war against ISIS and warned it of launching their "biggest operation ever" against the terrorist group, ISIS militants called Anonymous – "IDIOTS".
However, on the other side, the terror organization started spreading instructions through its affiliated official channels on Telegram on how to prevent getting hacked by Anonymous. This shows that ISIS knows the capability of Anonymous.
In the past, hackers and organizations associated with Anonymous brought down websites allegedly connected with ISIS and took down thousands of ISIS accounts, disrupting their social media recruitment efforts.
Zerodium price list for secret Hacking methods
21.11.2015
The Zerodium (Zero-day broker) company has published a price list for various classes of software targets and digital intrusion methods.
In an exceptional move on 18th of Nov (Wednesday), the Zerodium (Zero-day broker) published a price list for various classes of software targets and digital intrusion methods that is purchased from cyber criminals and resells to consumers like intelligence agencies and governments.
The chart, which describes the sums it pays for the techniques that effect a lot of operating systems and applications, symbolizes one of the most comprehensive views yet into the provocative and dark market for secret hacker activities.
“The first rule of [the] 0days biz is to never discuss prices publicly. So guess what: We’re going to publish our acquisition price list.” said Chaouki Bekrar, CEO of Zerodium.
According to the Zerodium, if an attack on a computer or remotely take control the user’s PC via her/his Internet Explorer or Safari, for example, fetches a cost of maximum $50,000. If the target is quite harder, like Google Chrome, the price will be $80,000. The price will increase further to $100,000 if the target is Windows phone device or Android. The price increment is not stopped here, iOS attack can earn an attacker $150,000, so far the top price on the chart.
Check out the Zerodium Chart below:
The firm explicitly advises brokers that any zero-day vulnerability we purchases must be for Zerodium’s eyes just; enterprising attackers cannot resell it to other customers or reveal it to the software’s seller, who might issue a patch that shields victims and renders the hack impractical. Zerodium specifies that it’ll pay the listed costs just for “exclusive, original, and previously unreported vulnerabilities.”
We can say, in other words, Zerodium is keeping its methods under wraps for its users. As per Zerodium FAQ page their customers include, “government organizations in need of specific and tailored cybersecurity capabilities.” On the other hand, Bekrar says, our customers pay subscription fee’s of minimum $500,000 annually for access to its vulnerabilities.
“Apple iOS, like all operating system, is often affected by critical security vulnerabilities, however due to the increasing number of security improvements and the effectiveness of exploit mitigations in place, Apple’s iOS is currently the most secure mobile OS. But don’t be fooled, secure does not mean unbreakable, it just means that iOS has currently the highest cost and complexity of vulnerability exploitation and here’s where the Million Dollar iOS 9 Bug Bounty comes into play.” said Zerodium in September.
In 2013, Muckrock requested to A Freedom of Information showed that NSA is one of the clients of Vupen. Openly trading in private intrusion methods has also made Zerodium’s CEO an easy object for criticism. Justin Schul from Google called Bekrar an “ethically challenged opportunist.” While on the other hand, Chris Soghoian a technologist called him Bekrar’s Vupen a “modern-day merchant of death,” selling “the bullets for cyber war.”
As per the Zerodium’s list, an iOS vulnerability is still top of the chart. Apple consumers may be discouraged to hear that the ability to attack their private device is as much a product as any other attacking method. However, nonetheless it is an exclusive one.
Anonymous Took Down 20,000 pro-ISIS Twitter accounts
21.11.2015
In the wake of Paris attacks Anonymous continues its campaign against the ISIS and announced to have taken down 20,000 pro-ISIS Twitter accounts.
In the wake of Paris attacks the hacking collective Anonymous launched its offensive against the ISIS with the intent to interfere with the online propaganda and reveal the identity of its members.
The #OpParis follows the precedent #OpISIS launched in the last months by Anonymous.
In the video message published by Anonymous, the groups announced that his members will catch ISIS members online. An avatar of Anonymous with a strong French accent declared “total war” to the terrorists.
In a new video published on YouTube on Wednesday, Anonymous announced to have identified and taken down More than 20,000 Pro-ISIS Twitter accounts:
“More than 20,000 Twitter accounts belonging to ISIS were taken down by Anonymous.”
Anonymous has also published the list of all the pro-ISIS Twitter accounts it has taken down.
A spokesman in the video announced:
“Hello, citizens of the world. We are Anonymous. It is time to realize that social media is a solid platform for ISIS’s communication as well as neutering their ideas of terror amongst youth. However, at the same time, social media has proved it is an advanced weapon. We must all work together and use social media to eliminate the accounts used by terrorists.” states the message.
“ISIS, we will hunt you and take down your sites, accounts, emails and expose you. From now on, there is no safe place for you online. You will be treated like a virus, and we are the cure,”
It is an escalation of the hacking activities started after the Paris Attacks, on Tuesday Anonymous claimed to have taken down more than 5,500 pro-ISIS Twitter accounts.
But, the ISIS is known to be a terrorist group with significant cyber abilities, especially the management of propaganda through social media.
The ISIS has considered strategic the use of technology, recently I described the content of the ISIS guide published by the organization to provide information to its members to avoid online surveillance.
Recently the US intelligence has also identified a training infrastructure that works with a sort of h24 help desk to provide information to the ISIS members and recruit new sympathizers.
Throw out the ISIS from the Internet is very challenging, the ISIS militants are ready to cyber jihad and called Anonymous “IDIOTS”.
Recently the group is making large use of the encrypting message service Telegram, security experts discovered broadcast messages used to provide instructions to the ISIS members on how to avoid getting hacked by Anonymous.
suggestions to pro-ISIS Twitter accounts
SilverPush technology tracks user habits with near-ultrasonic sounds
21.11.2015
The SilverPush technology allows advertising firm to track user habits with near-ultrasonic sounds.How does it work?
A few days ago, the Center for Democracy and Technology (CDT) warned that the Indian company SilverPush has developed a technology that allows adverts to ping inaudible commands to mobile devices.
SilverPush has issued also an SDK that could allow mobile developers to implement the technology in their mobile apps. This means that mobile apps running on the user’s device are able to receive near-ultrasonic sounds embedded in radio, TV or web browser advert. Humans are not able to capture the signals included in the ads because they are in the range of 18kHz to 19.95kHz, but the software can do it.
“Millions of mobile devices with SilverPush powered SDK are constantly listening to SilverPush patented audio beacons (ultrasonic) which are watermarked in Televison ad commercial. A pair is made once a SDK comes in proximity of audio beacon. The individual ID is mapped back to its audience genome and a brand-consumer journey has been started.” states the official description provided by SilverPush.
An application that implements the SilverPush technology car gather these near-ultrasonic messages by using the mobile microphone and then send data and mobile information (i.e. IMEI number, location, operating system version, and potentially the identity of the owner) to a server elsewhere.
The application has a significant impact on the user’s privacy but represents a powerful instrument for the advertising industry. When the owner of a mobile device watches any advert embedding the SilverPush ultrasonic messages, his data are collected and sent back to a remote server.
A research has identified 30 applications using the SilverPush SDK, including shopping apps developed by companies in India and Far East.
Is it legal? Does the technology require the user’s consent?
“This kind of technology is fundamentally surreptitious in that it doesn’t require consent; if it did require it then the number of users would drop,” Joe Hall, chief technologist at CDT told The Register on Thursday. “It lacks the ability to have consumers say that they don’t want this and not be associated by the software.”
Another disconcerting aspect of the technology that the most applications that implement the SilverPush doesn’t notify it to the end-users.
In US and Europe end-user must explicitly give its consent, in Europe and in the US the exploitation of this kind of technology is not legal.
Imagine any abuse of the SilverPush technology by a repressive regime, the technology could allow a rogue government to track the mobile devices used by the dissidents.
How does it work?
The researcher Kevin Finisterre from Digital Munition firm analyzed the code of the SilverPush and has published his the results of the research on the GitHub.
The technology assigns letters of the alphabet to high-pitch tones (i.e. The letter ‘A’ is coded with a 18kHz tone, and 19.125kHz is a ‘P’). The combination of letters is used to identify TV ads, for example the ‘AP’ is associated to a Geico ad and display an image and link to the insurance biz.
Finisterre also demonstrated that is possible to spoof the sounds or interfere with the technology by generating randomly ultrasonic tones.
This Malware Can Secretly Auto-Install any Android App to Your Phone
20.11.2015
This Malware Can Secretly Auto-Install any Android App to Your Phone
Own an Android Smartphone?
Hackers can install any malicious third-party app on your smartphone remotely even if you have clearly tapped a reject button of the app.
Security researchers have uncovered a trojanized adware family that has the capability to automatically install any app on an Android device by abusing the operating system's accessibility features.
Michael Bentley, head of response at mobile security firm Lookout, warned in a blog post published Thursday that the team has found three adware families:
Shedun (GhostPush)
Kemoge (ShiftyBug)
Shuanet
Also Read: Android Malware Can Spy On You Even When Your Mobile Is Off
All the three adware families root-infect Android devices in order to prevent their removal and give attackers unrestricted access to the devices.
But, it seems that the Shedun adware family has capabilities that go beyond the reach of other adware families.
The Malware Doesn't Exploit Any Vulnerability
It is worth noting that the malware does not exploit any flaw in the service to hijack an Android device and instead relies on the service's legitimate functionality.
During the installation, apps from the Shedun adware family tricks users into granting them access to the Android Accessibility Service, which is meant to provide users alternative ways to interact with their smartphone devices.
Also Read: Kemoge: Latest Android Malware that Can Root Your Smartphone
By gaining access to the accessibility service, Shedun can:
Read the text that appears on the phone screen
Determine an app installation prompt
Scroll through the permission list
Finally, Press the install button without any physical interaction from the user
Video Demonstration:
You can watch the following video that shows the forced installation of an app in action.
The trojanized app actually masquerades itself as an official app available in Google Play Store and then is pushed to third-party markets.
The worrisome part is that Shedun apps can't be easily uninstalled, as the apps root the victim's device and then embed themselves in the system partition in an effort to persist even after factory reset.
Also Read: Android Bootkit Malware Infected Millions of Devices
Lookout categorized them as "Trojanized Adware" because the goal of this malware is to install third-party apps and serve aggressive advertising.
Legitimate applications also use the Android Accessibility Service for features like to grant expanded capability to phone tinkerers. So, users are, as always, advised to carefully make use of the third-party app markets.
The ISIS guide, how to stay secure online
20.11.2015
Which are the technological tools used by the ISIS? Do the terrorists know how to avoid the surveillance online? The ISIS guide has the replies to these questions.
In the wake of Paris attacks, intelligence agencies and law enforcement have raised again the debate about the encryption requesting IT giants to support them by introducing backdoors in their products.
But news reports of the Paris attacks have revealed that at least some of the time, the terrorists behind the attacks didn’t bother to use encryption while communicating, allowing authorities to intercept and read their messages.
Clearly the ability of law enforcement in intercepting communication is essential in fighting terrorism, the crusade against the online encryption is instrumented by part of the intelligence community. In some documented cases, the ISIS terrorists haven’t adopted the necessary measures to properly use encryption causing the exposure of their communications.
So what exactly are ISIS attackers doing for OPSEC?
Wired has published an interesting post to respond the question, it started from an ISIS guide to operational security that was available online.
The ISIS guide, which is written in Arabic, alongside with other documents were analyzed by Aaron Brantly and other researchers with the Combating Terrorism Center at West Point’s military academy.
The documents provide a long series of suggestion to the members of the organization to avoid online surveillance, for example it bans the use of Instagram meanwhile it suggests dozens of privacy and security applications, including the Tor browser and the Tails distro, Cryptocat, Wickr, and Telegram encrypted messaging systems, Hushmail and ProtonMail email services, and RedPhone and Signal for encrypted phone communications.
isis guide
The ISIS guide includes most of the recommendations provided by civil liberties, privacy defender, and journalist groups when dealing with surveillance operated by many regimes across the world.
“The documents indicate that the jihadis have not only studied these other guides closely, but also keep pace with the news to understand the latest privacy and security vulnerabilities uncovered in apps and software that could change their status on the jihadi greatest-hits list.” states Wired.
The ISIS guide invites members of the organizations to use Gmail only with false credentials and in conjunction with the Tor network or by protecting the access with a VPN (of course avoiding US VPN providers). The use of mobile OS is considered secure when data connections are routed through the Tor network.
In the list of the banned applications, there are also the Apple’s iMessage and WhatsApp, despite both implements end-to-end encryption the jihadists believe that companies spies on behalf of the US Government.
It also warns that mobile communications can be intercepted and recommends followers to use crypto phones like Cryptophone or BlackPhone instead.
“Instead of buying the [expensive] Blackphone, they’re trying to hack their own devices and route traffic through Tor,” explains Brantly who added that the ISIS demonstrating an increasing interest in hacking . “There’s a whole section on hacking [in the ISIS forums],” Brantley says. “They’re not super-talented hackers, but they’re reasonable.”
The manual also provides instructions to disable location services and geotagging when using mobile apps or taking photos and videos.
Dropbox is on the black list because Edward Snowden’s revelations, and because former Secretary of State Condoleezza Rice is on the company’s investors board.
“It uses a lot Services “Alclaud” or cloud services to store their files and photographs or make a backup copy of important and non-important files, and perhaps the most popular service in this area is a service Dropbox Drop Box, which joined Condoleezza Rice of the Council of your managed recently and is known to fight for privacy and support the absolute spy mail, so Adraor Snowden advised not to use the service and considered it .dangerous to personal security and privacy Here we put alternative and safe services and less than the paths of Xbox in .terms of space and features but much better ones”
Mega Services, SpiderOak service, SugarSync service and Copy.com service are cloud storages suggested in the manual.
“This is about as good at OPSEC as you can get without being formally trained by a government,” Brantly, a cyber fellow with the West Point center, told WIRED. “This is roughly [the same advice] I give to human rights activists and journalists to avoid state surveillance in other countries. If they do it right, then they can become pretty secure. [But] there’s a difference between telling somebody how to do it and then [them] doing it right.”
The manual provides instruction to assume a secure posture online avoiding to be infected by malware or get hacked. It suggests to carefully manage suspicious email and provides detailed instructions on how to set up a private Wi-Fi network.
Interesting the use of mobile apps like FireChat to share photos and text at short distances without needing to access the Internet.
Let’s close with two further elements emerged from the analysis of the ISIS guide, there is no reference to the use of gaming console as messaging platforms, neither the use of home-brewed encryption programs developed by ISIS members.
Jako Pat a Mat: Piráti omylem dali do viru i dešifrovací klíč
20.11.2015 Viry
Vyděračské viry z rodiny ransomware terorizují uživatele po celém světě již několik let. Jeho nová verze, která cílí na počítače s operačním systémem Linux, se tvůrcům ale opravdu nepovedla. Obsahuje totiž chybu, díky níž se lidé dostanou opět ke svým datům. Pirátům tak nemusí zaplatit ani korunu.
Nezvaný návštěvník požadující výkupné po uživatelích Linuxu pracuje úplně stejně jako jeho předchůdci. [celá zpráva]
Poté, co se se zabydlí v počítači, zašifruje na něm uživatelská data. Útočníci se pak snaží v majiteli napadeného stroje vzbudit dojem, že se k zašifrovaným datům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod.
Když důvěřivci zaplatí, stejně se k datům nedostanou. Standardně je totiž nutné vyděračský virus z počítače odinstalovat a poté data odšifrovat.
Experti objevili v tomto ransomwaru chybu, díky které je možné získat klíče potřebné pro dešifrování souborů.
analytik Pavel Bašta z týmu CSIRT
A právě zde začíná ta vtipná část, která připomíná legendární pohádku Pat a Mat. Piráti si totiž nevedli při programování příliš dobře a nezvaný návštěvník zároveň prozrazuje klíč potřebný k dešifrování.
„Toto je dobrá zpráva pro všechny, jejichž soubory byly v posledních dnech zašifrovány ransomwarem známým jako Linux.Encoder1. Experti společnosti Bitdefender objevili v tomto ransomwaru chybu, díky které je možné získat klíče potřebné pro dešifrování souborů,“ uvedl analytik Pavel Bašta z Národního bezpečnostního týmu CSIRT, který je provozován sdružením CZ.NIC.
I když se nejčastěji vyděračské viry soustředí na klasické počítače, existují také výjimky. Loni v červnu bezpečnostní experti odhalili nezvaného návštěvníka, který požadoval výkupné i na mobilním telefonu.
Nested backdoor affects 600,000 Arris cable modems
20.11.2015
A Brazilian security researcher has discovered a nested backdoor affecting nearly 600,000 Arris cable modems. Arris is working to fix it.
The Security expert Bernardo Rodrigues (@bernardomr) has discovered the presence of a “backdoor-within-a-backdoor” in roughly 600,000 Arris cable modems.
Rodrigues is a vulnerability tester at Brazil’s Globo television network, he reported the undocumented library in three Arris cable modems, the company promptly replied that it is working to fix the issue.
Locate the Arris cable modems is quite easy with Shodan, in this way the expert exposed more that 600,000 affected devices.
In 2009 was reported for the first time a backdoor in the Arris cable modems, which were accessible using an admin password based on a known seed. Rodrigues has made a singular discovery, a backdoor affecting the hidden administrative shell that is implemented in the Arris cable modems.
“The default password for the SSH user ‘root’ is ‘arris’. When you access the telnet session or authenticate over SSH, the system spawns the ‘mini_cli’ shell asking for the backdoor password,” Rodrigues wrote in a blog post. “When you log using the password of the day, you are redirected to a restricted technician shell (‘/usr/sbin/cli’)”
The expert discovered that this nested backdoor uses a password based on the last five digits of the serial number of the device.
“They put a backdoor in the backdoor [which gives] a full busybox shell when you log on the Telnet/SSH session using these (serial number -based) passwords.”

A representative from the company ranked the risk as low and confirmed that the company is not aware of attacks in the wide.
“The risk related to this vulnerability is low, and we are unaware of any exploit related to it,” a spokeswoman says. “However, we take these issues very seriously and review them with the highest priority. Our team has been working around the clock on modem updates that address this reported vulnerability.”
Rodrigues also developed a keygen that can be used to calculate the password for the nested backdoor, a Metasploit module was already written to automate the exploitation of that flaw.

Rodrigues reported the flaws to CERT/CC which is already working with the vendor to solve the problem.
Below a video PoC of the nested backdoor in the Arris cable modems.
Hackers behind Dark Seoul are back
20.11.2015
The hacking group that behind the Dark Seoul Operation that hit entities in South Korea in 2013 may be back with new targets.
According to the experts at Palo Alto Networks, the hacking group behind the attacks that targeted banks, financial institutions, government websites and news agencies in South Korea is still active. The attacks occurred in 2013, the hacking campaign was labeled by security firms as Dark Seoul and Operation Troy. The experts noticed that the variant used in the recent attack doesn’t include the wiper component present in the version that targeted entities in the South Korea. The wiper deletes the Master Boot Record (MBR) making impossible the bootstrap of the machine.
The experts found many similarities between malware used in a recent attack in Europe and that malicious code spread in the attacks against entities in South Korea.

The attack vector was the email with malicious attachments or containing harmful links, the European organization was recently targeted by a spear-phishing attack.
The malware had been wrapped into legitimate video player software that was hosted by an industrial control systems company,
Security experts Bryan Lee and Josh Grunzweig from Palo Alto explained that threat actors have trojanized a legitimate video player software that was hosted by an industrial control systems company.
“The initial attack was likely a spear-phishing email, which leveraged a trojanized version of a legitimate software installation executable hosted by a company in the industrial control systems sector. The modified executable still installs the legitimate video player software it claims to contain, but also infects the system.” reads the blog post published by Palo Alto Networks. “Based on deep analysis of the Trojan’s behavior, binary code, and previous reports of similar attacks, we have concluded that these samples were the same as the original tools used in the Dark Seoul/Operation Troy attacks” “It is likely the same adversary group is involved, although there is currently insufficient data to confirm this conclusion,”
In the analysis conducted by McAfee in 2013, the experts identified two parallel operations conducted by initially by two crews that appeared separated, the Whois Hacking Team and the NewRomanic Cyber Army Team. The evidence collected by McAfee lead the firm to concluded it was likely a single group behind both campaigns.
The malware used in the recent attack was controlled through compromised websites in South Korea and Europe. The attackers compromised these websites because they were running out-of-date software.
“The similarities in tactics however, do seem to outweigh the differences, and it is highly likely this is the same group or groups responsible for the original Dark Seoul/Operation Troy attacks, but with a new target and a new campaign,” Palo Alto wrote.
It is quite common to see three actors suspend their activities for a period, especially after the investigation of security firms. Usually, when these dormant threats reappear don’t adopt change completely their hacking arsenal and in many cases they reuse part of the uncovered control infrastructure.
The experts consider insufficient collected data at this time to clearly state why Dark Seoul/Operation Troy would resurface at this time, but they will continue to investigate on it.
EU plans to ban Bitcoin to curb terrorism funding
20.11.2015
According to a draft document seen by the Reuters the EU plans to ban bitcoin and any form of anonymous payment online to curb terrorism funding.
European Union countries are planning to ban virtual currencies and any form of anonymous payments online, even through pre-paid cards. According to a draft document seen by journalists at the Reuters Agency, the initiative aims to tackle terrorism financing after the recent tragic Paris attacks.
A crisis meeting will be held today in Brussels, EU interior and justice ministers will participate to discuss the measures to block any financing to the radical group ISIS.
The draft document will urge the European Commission to propose measures to “strengthen controls of non-banking payment methods such as electronic/anonymous payments and virtual currencies and transfers of gold, precious metals, by pre-paid cards,”. reads the draft document. [EU ministers also plan] “to curb more effectively the illicit trade in cultural goods,”
The Bitcoin is the most popular virtual currency, and authorities suspect that members of the ISIS could use it to rapidly transfer money to cells around the world.
At the Foreign Affairs Forum on Cryptocurrency Policy in May, government officials and Bitcoin entrepreneurs discussed the future of the cryptocurrency. Law enforcement fear possible abuses of the popular crypto currency, Jennifer Shasky Calvery, head of the US Treasury Department’s Financial Crimes Enforcement Network (FinCEN), which is charged with fighting money laundering and terrorist finance, explained that the virtual currency scheme could facilitate bad actors, including terrorists.
“What keeps me up at night when I am thinking about digital currency…the real threats out there, these days we’re thinking a lot about ISIL,” Calvery declared. “How they’re moving their money, and how potential US-based individuals are becoming foreign fighters: Are they moving their money, can we identify them from the movement of their money? What does it mean if they start moving their money through bitcoin? We’ve started to see some public articles suggesting that has occurred.”
Intelligence agencies and security experts are aware that alleged members of terrorist groups, including the ISIS, are exploring different opportunities to transfer money to militants operating in Western countries.
ISIS funds Bitcoin
A continuous flow of a small amount of money could be instantaneously transferred to numerous accounts used by ISIS members worldwide. Micro payments could exploit several channels, including systems like PayPal or virtual currencies like the Bitcoin.
Online it is possible to find a PDF document written by a user with the pseudonymous pseudonym of Amreeki Witness titled: Bitcoin wa Sadaqat alJihad which translates to: “Bitcoin and the Charity of Violent Physical Struggle”.Bitcoin and the Charity of Violent Physical Struggle”. The pseudonym Amreeki authored the PDF under is Taqi’ulDeen alMunthir. That name translates to Righteous in Faith the-Warner.
Ochranu dětí v prostředí Androidu zajistí novinka od Esetu
20.11.2015 Mobilní
Plnou verzi aplikace rodičovské kontroly Parental Control pro Android uvolnil Eset. Podle výrobce zajistí kontrolu aplikací, webových stránek, aktuální polohy dítěte nebo času, který tráví na mobilním zařízení.
Parental Control pomáhá rodičům nastavit pravidla, za jakých děti mohou používat své vlastní chytré telefony nebo tablety. Základním cílem je pomoci rodičům chránit děti před nevhodnými aplikacemi a internetovými stránkami, ale má i řadu doplňkových funkcí na ochranu dětí.
Například dětem umožňuje požádat rodiče o zvláštní povolení přístupu k vybraným aplikacím nebo internetovým stránkám, nebo požádat o prodloužení limitu stanoveného pro hraní her či přístupu k internetu.
Hlavní funkce Parental Control pro Android podle výrobce:
Strážce aplikací: blokuje nevhodný obsah v závislosti na věku dítěte.
Správa času: umožňuje rodičům omezit čas, který děti mohou trávit nad hrami a nad jednotlivými aplikacemi, a to i když jsou mimo domov.
Webový strážce: blokuje internetové hrozby na základě porovnání internetových stránek s databázemi Esetu.
Poloha dítěte: umožňuje rodičům zjistit přesné místo, kde se jejich děti nacházejí.
Rodičovské zprávy: u důležitých SMS zpráv, které jsou odeslány z předdefinovaných telefonních čísel rodičů, musí dítě potvrdit příjem zprávy a dokud tak neučiní, displej telefonu zůstane uzamčen pro jakoukoli jinou činnost.
Monitoring pro rodiče: informuje rodiče o tom, které aplikace a internetové stránky dítě využívá. Pokud jde o nevhodný obsah, rodič může dítěti přístup k němu zablokovat.
VirusTotal now Scans Mac OS X Apps for Malware
19.11.2015
Do Mac Computers Get Viruses?
Yes, Of Course, they do!
According to stats, malware for MAC OS X has appeared five times more in 2015 alone than the previous five years combined.
As malware for Macs is becoming more common, Google has decided to add support for Mac OS X malware detection to its VirusTotal web-based service.
VirusTotal — launched in 2004 and acquired by Google in 2012 — is a free and popular online service for security researchers and Hackers that lets you upload files to check them for viruses.
VirusTotal scans uploaded files with more than 55 different Antivirus products and Online scan engines to provide a combined report on the results.
VirusTotal also runs certain 'Windows PE files and Android apps' files in the Sandbox, a controlled research environment used for malware analysis.
According to the recent announcement, VirusTotal will also be able to execute suspicious Mac executable files inside its Sandbox environment to check them for viruses.
"We are happy to announce equal treatment for Mac OS X apps. Files scanned that are Mach-O executables, DMG files, or ZIP files containing a Mac app, will be sent to the sandbox to produce behavioral reports." Karl Hiramoto, Technical Account Manager at VirusTotal, said in a blog post.
You’ll be now able to see an extra tab, called "Behavioral Information," on the result page, where you can find:
Operations the executable file initiates
Processes the file starts
DNS queries the file makes
Mac users who wish to scan any file for detecting hidden threat can do so on www.virustotal.com website, or with an app or via the API.