
- BotNet -
Last update 23.09.2017 19:27:30
Introduction List Kategorie Subcategory 0 1 2 3 4 5 6 7 8
Researchers Connect Lizard Squad to Mirai Botnet
30.1.2018 securityweek BotNet
Lizard Squad and Mirai, which are responsible for a series of notorious distributed denial of service (DDoS) attacks, are connected to one another, a recent ZingBox report reveals.
Lizard Squad is a hacking group known for some of the most highly publicized DDoS attacks in history, including the disruption of Sony PlayStation and Xbox Live networks. Over the past several years, multiple individuals suspected to have used Lizard Squad’s LizardStresser DDoS service have been arrested.
While the hacking group has been operating for several years, Mirai has been around for only one year and a half, making headlines in late 2016 following massive DDoS attacks against Brian Krebs’ blog and Dyn’s DNS infrastructure. The malware’s source code was made public within weeks of these attacks and numerous variants have emerged since.
Now, ZingBox researchers claim to have discovered evidence that links the Lizard Squad hackers and Mirai, including the common use of the same Ukraine hosting provider Blazingfast.
The Mirai source code, the researchers point out, was released nine days after Lizard Squad founder Zachary Buchta was arrested. According to them, the DDoS attack on Brian Krebs’ blog in late 2016 appears the result of the journalist’s criticism against Lizard Squad, and there are also references to Mirai on a Lizard Squad website.
Analysis of a domain associated with a Mirai-based malware campaign in late 2017 led the researchers to bigbotPein, a group linked to Lizard Squad. The analyzed domain was registered by an individual associated with Lizard Squad, a ZingBox report (PDF ) claims.
bigbotPein, a group that emerged in support to Buchta following his arrest, adopted Mirai as part of their Internet of Things arsenal and is currently targeting multiple architectures, including x86, x64, ARM, MIPS, SuperH, SPARC and ARC.
What’s more, the group has also added Ethereum and Monero miners to their malware portfolio, while also adopting increased sophistication, the security researchers say.
A Mirai-based campaign observed in October 2017 was pointing to the domain bigbotpein[.]com. The website’s Start of Authority (SOA) points to blazingfast[.]io, the Ukraine hosting provider that is also used by Mirai authors for the botnet control server, ZingBox says.
The security researchers claim they were also able to link the group to multiple Mirai variants out there, including Satori and Masuta. According to them, the Satori campaign was initially called Okiru and was using the control[.]almahosting[.]ru and network[.]bigbotpein[.]com domains.
Starting with mid-January 2018, all the domains related to Lizard Squad and bigbotPein switched to US-base ISPs (Rackspace and Search Guide), which suggests a clear connection between the two groups.
Two other Mirai variants observed last year include Masuta and Memes. The former, detailed only this month, targeted x86, ARM and MIPS architectures. The latter appears to be the work of the same author and might be an evolution of Masuta.
The malware code, ZingBox claims, includes a “structure previously identified in July 2017 related to Lizard Squad.” This code allows the malware to hide and decode second stage payload in memory. Both an Ethereum dropper variant linked to Lizard Squad and Masuta/Memes use this same code structure.
Other evidence linking Lizard Squad and Mirai include the dropping of a file from bigbotPein domain control[.]almahosting[.]ru as part of a Satori campaign in November 2017, leading to the Monero Stratum miner.
A Satori variant observed in early January 2018 was employing an extra level of obfuscation, along with the s[.]sunnyjuly[.]gq domain, and pointing to the use of an Etherum miner for Windows, although the initial attack vector, however, targeted the MIPS architecture.
“During this research, we witnessed firsthand the evolving complexity of the different variants of Lizard Squad and bigbotPein group’s malware within a span of one year […]. The Lizard Squad and bigbotPein groups used to be very active creating most of the well-known variants of Mirai,” ZingBox’ report reads.
“Despite the courageous efforts of our law enforcement agencies to identify and tear down various hacking groups, the collaboration between groups makes it extremely difficult to completely shut down their efforts for good. Arrests of high-profile members and founders of such groups certainly slows down their momentum, but organizations can’t take their foot off the gas when it comes to being vigilant about the security of their network,” Xu Zou, CEO and co-founder, ZingBox, said.
Mirai-Based Masuta Botnet Weaponizes Old Router Vulnerability
25.1.2018 securityweek BotNet Vulnerebility
A new Internet of Things-targeting piece of malware based on Mirai’s publicly released source code has been observed at large, ensnaring devices into a botnet.
Dubbed Masuta, the botnet has at least two variants at large, and is believed to be the work of a well-known IoT threat actor, NewSky Security says. What’s also unique to the botnet is that it exploits an old router vulnerability, being the first threat known to weaponize it in a botnet campaign.
Masuta (Japanese for “master”) botnet’s source code was found on an invite only dark forum. The malware’s configuration file, the researchers discovered, uses a different seed of the cipher key compared to Mirai, having the strings in the configuration files XORed by 0x45.
Thus, the researchers discovered that it uses the domain nexusiotsolutions(dot)net, the command and control (C&C) server that Nexus Zeta, the individual involved in the recent Satori attacks, uses. The domain was registered using the nexuszeta1337@gmail(.)com email address.
Thus, NewSky Security suggests that Nexus Zeta has been involved in the creation of the Masuta botnet, in addition to building Satori, the Mirai variant that has been wreaking havoc over the past couple of months.
In fact, Masuta isn’t new either, and attacks involving it have been steadily increasing since September, and the botnet’s standard variant has been observed using several known/weak/default credentials to compromise IoT devices.
An evolved variant of Masuta, called PureMasuta, contains the most typical of Mirai style code, and a list of weak credentials to use. What makes this malware variant stand out, however, is its usage of EDB 38722 D-Link exploit.
The exploit PureMasuta uses resides in the HNAP (Home Network Administration Protocol), which is based on the SOAP protocol. It is possible to craft a SOAP query to bypass authentication by using hxxp://purenetworks.com/HNAP1/GetDeviceSettings, and improper string handling can lead to arbitrary code execution, and an attacker can abuse this combination of issues to run code on targeted devices.
What the botnet does is to download a shell script from the C&C server and run it. Thus, the malware author first bypasses authentication and then executes code on the targeted devices.
The PureMasuta variant uses the same C&C server (93.174.93.63) as the original Masuta variant, which led the researchers to believe it is the evolved creation of the same threat actor.
“Nexus Zeta is no stranger when it comes to implementing SOAP related exploits. The threat actor has already been observed in implementing two other known SOAP related exploits, CVE-2014–8361 and CVE-2017–17215 in his Satori botnet project,” NewSky Security notes.
Thus, the TR-069 bug and EDB 38722 are the third and fourth SOAP related exploits abused by IoT botnets.
“Protocol exploits are more desirable for threat actors as they usually have a wider scope. A protocol can be implemented by various vendors/models and a bug in the protocol itself can get carried on to a wider range of devices,” the researchers conclude.
"Hide 'N Seek" IoT Botnet Ensnares 20,000 Devices in Days
25.1.2018 securityweek IoT BotNet
An Internet of Things (IoT) botnet featuring a worm-like spreading mechanism managed to ensnare over 20,000 devices over the course of several days, Bitdefender reports.
Dubbed Hide ‘N Seek, the botnet was first spotted on January 10, when it focused on IP cameras manufactured by a Korean company, but vanished just days after. On January 20, however, the researchers observed a new, improved variant of the malware, which has ensnared more than 20,000 devices worldwide and continues to spread quickly.
The malware was designed to exfiltrate data, execute code, and interfere with the device operation. Employing a complex and decentralized communication technique and multiple anti-tampering methods to prevent hijacking, the botnet uses the same exploit as Reaper (CVE-2016-10401 and other vulnerabilities), Bitdefender says.
The bot’s worm-like spreading mechanism consists of randomly generating a list of IP addresses to target, and then initiating a raw socket SYN connection to each host on specific destination ports (23, 2323, 80, and 8080). After establishing a connection, the bot first looks for a specific banner (“buildroot login:”) and attempts log in via predefined credentials, or launches a dictionary attack if that fails.
Next, the malware attempts to properly identify the target device and select a compromise method, such as setting up a TFTP server if the target is on the same LAN, or a remote payload delivery method if the target is on the Internet.
These pre-configured exploitation techniques are located in a digitally signed memory location to prevent tampering and can be updated remotely and propagated among infected hosts. Targeting IoT devices, the botnet can’t achieve persistence, meaning that a device reboot would clear up the infection.
After Hajime, Hide ‘N Seek becomes the second known IoT botnet to use a decentralized, peer-to-peer architecture. The difference is that, while Hajime used p2p functionality based on the BitTorrent protocol, the new botnet uses a custom-built p2p communication mechanism.
“The bot opens a random port on the victim, and adds firewall rules to allow inbound traffic for the port. It then listens for connections on the open port and only accepts the specific commands described below,” Bitdefender Senior Threat Analyst Bogdan Botezatu explains.
To prevent infiltration or poisoning attempts, the malware uses an elliptic curve key within the file used to authenticate the command for updating the memory zone where configuration settings are stored.
The bot includes support for multiple commands for configuration updates, a data exfiltration mechanism, and a scanning component (which sends to a peer valid credentials found via dictionary attack). It also supports commands to add a new peer to the list and send a peer IP as a response.
“While IoT botnets have been around for years, mainly used for DDoS attacks, the discoveries made during the investigation of the Hide and Seek bot reveal greater levels of complexity and novel capabilities such as information theft – potentially suitable for espionage or extortion. It is also worth noting that the botnet is undergoing constant redesign and rapid expansion,” Botezatu concludes.
A recent NETSCOUT Arbor report on distributed denial of service attacks has revealed that compromised IoT devices can fuel new, complex assaults. The emergence of new IoT botnets such as Masuta or Satori has proved once again the need for improved security for Internet-connected devices.
“As IoT devices become increasing popularity in our modern lives, they also become more attractive to cybercriminals. In fact, in 2017 we recorded a record number of IoT vulnerabilities, with them more than doubling since 2016,” Nadav Avital, security research team leader at Imperva, told SecurityWeek in an emailed statement.
“This [Bitdefender] research also emphasizes the need for an account takeover solution which protects all devices with a network presence. Account takeover is a big problem, however it is not something which IoT vendors provide protection for. It is therefore a good idea for organizations to deploy an external solution for security,” Avital concluded.
New HNS botnet has already compromised more than 20,000 IoT devices
25.1.2018 securityaffairs BotNet IoT
A new botnet called Hide ‘N Seek (HNS botnet) appeared in the threat landscape, the malware is rapidly spreading infecting unsecured IoT devices, mainly IP cameras.
The HNS botnet was first spotted on January 10th by malware researchers from Bitdefender, then it disappeared for a few days, and it has risen over the weekend.
The number of infected systems grew up from 12 at the time of the discovery up to over 20,000 bots, at the time of writing.

“Bitdefender researchers have uncovered an emerging botnet that uses advanced communication techniques to exploit victims and build its infrastructure. The bot, dubbed HNS, was intercepted by our IoT honeypot system following a credentials dictionary attack on the Telnet service.” states the analysis from Bitdefender.
“The samples identified in our honeypots on Jan. 10 revolved around IP cameras manufactured by a Korean company. These devices seemed to play a major role in the botnet as, out of the 12 IP addresses hardcoded in the sample, 10 used to belong to Focus H&S devices. The new version, observed on Jan. 20, dropped the hardcoded IPs.”
Recently security experts spotted other IoT botnets, most of them linked to the Mirai botnet, such as Satori, Okiru, and Masuta, but the HNS botnet has a different genesis and doesn’t share the source code.
Researchers at Bitdefender found similarities between the HNS and the Hajime botnets, unlike Mirai, Hajime doesn’t use C&C servers, instead, it implements a peer-to-peer network.
Hajime is more sophisticated than Mirai, it implements more mechanisms to hide its activity and running processes and its modular structure allows operators to add new capabilities on the fly.
“It is the second known IoT botnet to date, after the notorious Hajime botnet, that has a decentralized, peer-to-peer architecture,” states Bitdefender. “However, if in the case of Hajime, the P2P functionality was based on the BitTorrent protocol, here we have a custom-built P2P communication mechanism.”
The HNS malware is able to infect a series of IoT devices using the exploit as Reaper, the current version is able to receive and execute several types of commands, such as data exfiltration, code execution and interference with a device’s operation.
According to the experts, the botnet is still under development, it doesn’t include DDoS capabilities, a circumstance that suggests it is intended to be deployed as a proxy network.
“While IoT botnets have been around for years, mainly used for DDoS attacks, the discoveries made during the investigation of the Hide and Seek bot reveal greater levels of complexity and novel capabilities such as information theft – potentially suitable for espionage or extortion.” concluded Bitdefender.
“It is also worth noting that the botnet is undergoing constant redesign and rapid expansion.”
The bot spread by randomly generates a list of IP addresses that could be potentially compromised. It then initiates a raw socket SYN connection to each potential target and continues communication with those devices that answer the request on specific destination ports (23 2323, 80, 8080).
Once the bot has established a connection it will look for a specific banner (“buildroot login:”) presented by the victim. If it gets this login banner, it attempts to log in using a list of default credentials. If the credentials are not correct, the botnet launches a dictionary attack using a hardcoded list.
Once connected to the victim, the malware will run through a “state machine” to determine the type of target device and select the most suitable compromise method. Experts explained that if the device shares the same network with the bot, the bot sets up TFTP server to allow the victim to download the malicious code from the bot. If the victim is located on the internet, the bot will attempt to use a specific remote payload delivery method to get the target device to download and execute the sample.
“These exploitation techniques are preconfigured and are located in a memory location that is digitally signed to prevent tampering. This list can be updated remotely and propagated among infected hosts.” continues the analysis.
Experts observed that the HNS botnet cannot establish persistence on infected devices, once the device restart, the malware will be removed, this means that botnet operators have to continuously manage the HNS botnet.
Let’s monitor the growth of the new-born botnet.
Satori’s threat actors are behind the new Masuta botnet that is targeting routers in the wild
24.1.2018 securityaffairs BotNet
Masuta botnet targets routers using default credentials, one of the versions analyzed dubbed “PureMasuta” relies on the old network administration EDB 38722 D-Link exploit.
Security experts at NewSky’s believe the operators of the recently discovered Satori botnet are launching a new massive hacking campaign against routers to recruit infect them and recruit in the botnet dubbed Masuta.
“We analyzed two variants of an IoT botnet named “Masuta” where we observed the involvement of a well-known IoT threat actor and discovered a router exploit being weaponized for the first time in a botnet campaign.” reads the analysis published by NewSky.
“We were able to get hands on the source code of Masuta (Japanese for “master”) botnet in an invite only dark forum. After analyzing the configuration file., we saw that Masuta uses 0xdedeffba instead of Mirai’s 0xdeadbeef as the seed of the cipher key, hence the strings in the configuration files were effectively xored by ((DE^DE)^FF) ^BA or 0x45.”
The Satori botnet is a variant of the Mirai botnet first discovered by the group of experts MalwareMustDie, it made the headlines at the end of 2016 when it was involved in hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers.
Masuta also targets routers using default credentials, one of the versions analyzed by the experts dubbed “PureMasuta” relies on the old network administration EDB 38722 D-Link exploit.
Researchers noticed a rise in the Masuta attacks since September, their honeypots observed 2400 IPs involved in the botnet in last three months and experts believe that other routers will be recruited in the next months.

The flaw triggered by the EDB 38722 D-Link exploit was discovered in 2015 by the researchers Craig Heffner, it affects the D-Link’s Home Network Administration Protocol.
“The weaponized bug introduced in PureMasuta botnet is in the HNAP (Home Network Administration Protocol) which itself is based on the SOAP protocol.” continues the analysis published by NewSky.
“It is possible to craft a SOAP query which can bypass authentication by using hxxp://purenetworks.com/HNAP1/GetDeviceSettings. Also, it is feasible to run system commands (leading to arbitrary code execution) because of improper string handling. When both issues are combined, one can form a SOAP request which first bypasses authentication, and then causes arbitrary code execution.”
The experts explained that a string like the following one will cause a reboot.
SOAPAction: “hxxp://purenetworks.com/HNAP1/GetDeviceSettings/`reboot`”
An attacker can run any command inserted after ‘GetDeviceSettings’, this mechanism is used by the PureMasuta bot to run a
wget
to fetch and run a shell script and take over the target router.
The experts noticed that the command and control server (93.174.93.63) used by PureMasuta variant is the same as used in the original Masuta variants, this means that PureMasuta is an evolution of the botnet operated by the same threat actors.
NewSky attributes the Masuta botnet to an entity dubbed “Nexus Zeta”, the name comes from the C&C URL nexusiotsolutions(dot)net, this URL is the same used by the Satori botnet.
Italian companies and Ministry of the Interior under attack, experts spotted a huge botnet
20.1.2018 securityaffairs BotNet
Threat actors with a deep knowledge of the Fiscal Italian ecosystem are using a huge botnet to target Italian companies and Ministry of the Interior.
On Januaty 18 a colleague of mine (Luca) called me telling a malicious email was targeting Italian companies. This is the beginning of our new analysis adventure that Luca and I run together.
The email pretended to be sent by “Ministero dell’ Economia e delle Finanze” the Italian Department of Treasury and it had smart subjects such as:
Codici Tributo Acconti
F24 Acconti-Codice Tributo 4034
The attacker knows very well the Italian Fiscal Year since those modules are very popular from company administration employees at that time. The attacker would probably exploit this attack path reaching out as many companies as possible. The email address was not coming from the “Ministero dell’ economia e delle Finanze” at all, it was coming from the following addresses:
info@amber-kate.com
info@fallriverproductions.com
The email looks like :

Malicious eMail
A simple link pointing to a high reputation domain was popping out the default browser and downloading the following Javascript file. The high level of obfuscation and the way the content was provided was so suspicious to be worth to follow the analysis.

Infection: Stage 1 Obfuscated
After a deobfuscation phase the javascript looked much more easy te be read from a human side.

Infection: Stage 1 Clear Text
A romantic “drop and execute” section was happening. A GET connection to 239outdoors.com/themes5.php was dropping a file named 1t.exe and later on the same script was able to execute the dropped file. The file 1t.exe was running on the victim machine contacting the Command and Control waiting for further commands.
The new sample looks like GootKit, a weaponized version of Banker Malware. The malware installs itself and contacts Command and Control asking “what to do” and sending the “stolen credentials” directly to the Command and Control server. Details on IPs, Persistencies and so on, is provided in the IoC section, but today’s we won’t describe GootKit, we got access to the Dropping site!
We want to figure out if we might help victims to deactivate the malicious botnet by providing as much as possible details without focusing on the reverse the Malware per se since appears to be known.
By getting further analyzing the dropping website we immediately understood that the same URL was dropping another threat. The parallel threat the dropping website was spreading to the world was called “Nuovo Documento 2008” and it was a .bat file as follows.

New Threat Stage 1
That executable .bat file on a first stage opens up a browser pointing to a legitimate image but later on, it uses a notorious technique called “certutil for delivery of file” to drop and execute another file. This technique is well described here by carnal0wnage. Basically, the attacker uses the certutil.exe program do download a Base64 encoded payload, to decode it and to run it. This technique is very silent since the User-Agent of certutils.exe is not suspicious because it needs to connect outside the company networks to check certificates, so not much IPS rules on it. The dropped file name unslss.exe appears to be very close to the previously analyzed one (1t.exe) it contacts the same C&C and it behaves in a similar way. But again we won’t focus on reverse such a malware but rather we wont be able to reach the highest number of IoC to protect as much as possible the victims. By analyzing the Dropping website we founded that a significative number of connections had additional referrers, so we decided to focus our attention on how many DNS were pointing to such a domain. We did it and the result was quite impressive (please see the Dropping URLs IoC Section).
Following the research on the dropping website, we found an interesting log of all the connection coming from possible victims. We collected that log, and we built the following possible infection list (possible Victims). We won’t publish the Victims IP addresses but if you can prove you are legitimated by your company to ask that logs we can give you (for free, of course) the IP addresses we’ve found related to your company. A detailed list of possible infected networks follows.
Possible Victims:
ACI informatica s.p.a.
AGOS-AS
AGSM Verona Spa
ASGARR Consortium GARR
Acantho S.p.a
Alfanews S.r.l.
Ambrogio s.r.l.
Asco TLC S.p.A.
Autostrade-as
BT Italia
BT Italia S.p.A.
Banca Monte Dei Paschi Di Siena S.P.A.
Brennercom S.p.A.
COLT Technology Services Group Limited
Camera dei deputati
Cesena Net srl
Clouditalia Telecomunicazioni S.p.A.
Comune Di Brescia
Comune di Bologna
Consortium GARR
Consorzio per il Sistema Informativo
Costacrociere-as
Duebite-as
E4A s.r.l.
Energente S.r.l.
FASTNET SpA
FASTWEB SPA
FINECO Banca del Gruppo Unicredit
Fastweb
Forcepoint Cloud Ltd
GenyCommunications
Global Com Basilicata s.r.l.
H3G Italy
Hynet S.R.L.
IBSNAZ
ICT Valle Umbra s.r.l.
InAsset S.r.l.
InfoCamere SCpA
Infracom Italia S.p.A.
Inrete s.r.l
Insiel- Informatica per il sistema degli enti loca
Integrys.it di Stefania Peragna impresa individual
Intred S.p.A.
KPNQWest Italia S.p.a.
LEPIDA
Lepida S.p.A.
Liguria Digitale S.C.p.A.
Linea Com S R L
Linkem spa
Lombardia Informatica S.p.A.
Mandarin S.p.A.
Mc-link SpA
Metrolink S.R.L.
Ministero dell’Interno
Mnet srl
NGI SpA
Nemo S.r.l.
Nordcom S.p.a.
Officine Informatiche Srl
Progetto Evo S.r.l.
Provincia di Reggio nell’Emilia
Qcom spa
Raiffeisen OnLine GmbH
Regione Basilicata
Regione Toscana
Regione Veneto
STI ADSL
Sardegnait-as
Societa’ Gestione Servizi Bp S.p.A.
TELEX S.r.l.
TWT S.p.A.
Telecom Italia
Terra S.p.a.
Time-net S.r.l.
Tiscali SpA
Trenitalia SpA
Trentino Network S.r.l.
Universita’ degli Studi di Milano
Venis S.p.A.
Videotime SPA
Vodafone Group Services GmbH
Vodafone Italia DSL
Vodafone Omnitel B.V.
Vodafone Omnitel N.v.
WIIT S.p.A.
Welcome Italia S.p.A
Wind Telecomunicazioni
Wind Telecomunicazioni SpA
Following the found IoC provided by the long “analysis journey”. I managed this analysis over the night, so I am sure there would be some imprecisions, but I preferred to speed up the entire analysis process to give the opportunity to block such infamous threat as soon as possible.
Hope it helps the community.
IoC:
eMail:
info@amber-kate.com
info@fallriverproductions.com
Dropping URLS:
185.61.152.71
239outdoors.com
bentlabel.com
cdvdautomator.com
cloudblueprintprogram.com
cnchalftone.com
comedyyall.com
conticellolaw.com
couplesdoingbusiness.com
dvoper.com
equinnex.com
ericandchrissy.com
evelynleekley.com
expungementstennessee.com
flaveme.com
grkisland.com
healingfoodconsulting.com
hertzsynergy.com
hollywoodisruption.com
home-sphere.com
integrativenutritiontherapy.com
jdkanyuk.com
kineloveclips.com
kylesinger.com
legionchristmas.com
menshoesonlinestore.com
microtiasurgery.com
movielotbar.com
muiienweg.com
niarhoslondon.com
opsantorinitours.com
progunjobs.com
rocketpak.com
scottishwindowsolutions.com
silkygames.com
snapshotsandwhatnots.com
snotterkind.com
solespin.com
strangerthanchristmas.com
synchronr.com
taramadden.com
terento.website
theargumint.com
thegildedwren.com
thejourneytogodsheart.com
thesaltybody.com
topsantorinitours.com
tuftandneedles.com
videospanishlessons.com
vovachka.com
wall-runners.com
war-arena.com
www.scottishwindowsolutions.com
z1logistics.com
zayantetinyhomes.com
zefeed.com
Command and Controls
185.44.105.97
ns15.dreamsinthesun.com
bdi2.nomadicdecorator.com
elis.k9redemptionrescue.com
api.hailstorm360.com
cerera.survivalbid.com
mark.k9redemptionrescue.org
nsc.dayswithsunrays.com
at.moonbeammagic.com
ssl.vci-cfo.com
sip3.propertiesandprojects.com
host1.jodiray.com
note.lawrencechoy.com
note.lawrencechoy.com:80
185.44.105.97:80/200
note.lawrencechoy.com:80
Hashes
63d6927881d4978da4e162c17d82e9c009d0a93e
7ea33f51b6c4aa54beee7fd878886339c22d2232
8cae0dc9255978a35cfd8db64cbe80001400de9b
839ff9f4c3980ac67d4cbef296520ee364a0911f
8cae0dc9255978a35cfd8db64cbe80001400de9b
New Mirai Okiru Botnet targets devices running widely-used ARC Processors
17.1.2018 thehackernews BotNet
The cybersecurity threat landscape has never been more extensive and is most likely to grow exponentially in 2018.
Although the original creators of Mirai DDoS botnet have already been arrested and jailed, the variants of the infamous IoT malware are still in the game due to the availability of its source code on the Internet.
Security researchers have spotted a new variant of infamous Mirai IoT malware designed to hijack insecure devices that run on ARC embedded processors.
Until now, Mirai and its variants have been targeting CPU architectures—including x86, ARM, Sparc, MIPS, PowerPC and Motorola 6800—deployed in millions of Internet of Things (IoT) devices.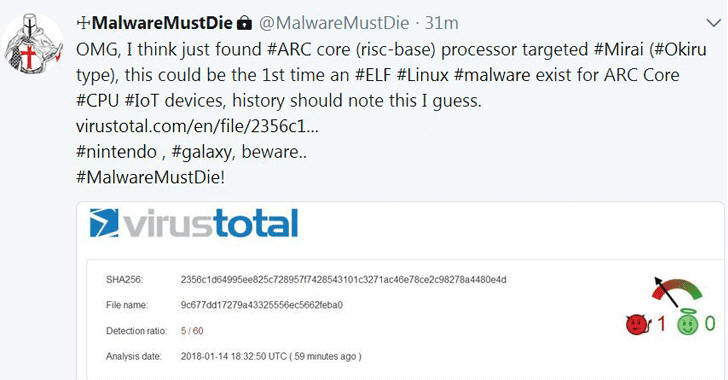
Dubbed Okiru, the new Mirai variant, first spotted by @unixfreaxjp from MalwareMustDie team and notified by independent researcher Odisseus, is a new piece of ELF malware that targets ARC-based embedded devices running Linux operating system.
"This is the FIRST TIME ever in the history of computer engineering that there is a malware for ARC CPU, & it is #MIRAI OKIRU!! Pls be noted of this fact, & be ready for the bigger impact on infection Mirai (specially #Okiru) to devices hasn't been infected yet," Odisseus tweeted.
ARC (Argonaut RISC Core) embedded processor is the world's second-most-popular CPU core that's being shipped in more than 2 billion products every year, including cameras, mobile, utility meters, televisions, flash drives, automotive and the Internet of Things.
However, this isn't first Mirai botnet variant based on Linux ELF malware. Mirai also has another ELF-based variant, which was designed to target devices running MIPS and ARM processors.
It should also be noted that Okiru, which has previously been also named as Satori IoT botnet (another Mirai variant discovered late last year), is "very different" from Satori despite having several similar characteristics, as explained in a Reddit thread.
Record-Breaking DDoS? The Calm Before The Storm
IoTs are currently being deployed in a large variety of devices throughout your home, businesses, hospitals, and even cities (smart cities), but they're routinely being hacked and used as cyber weapons due to lack of stringent security measures and insecure encryption mechanisms.
If you are unaware, the world's largest 1 Tbps DDoS attack so far was launched from just 152,000 infected IoT devices using Mirai botnet, and in a separate attack, just 100,000 devices took down the popular DynDNS service in late 2016.
Since Okiru has been ported to target a new range of millions of "expectedly insecure" devices running ARC processors, the DDoS attack going to be generated by Okiru botnet would probably be the biggest cyberattack ever.
"From this day, the landscape of #Linux #IoT infection will change. #ARC CPU has produced #IoT devices more than 1 billion per year. So these devices are what the hackers want to aim to infect #ELF #malware with their #DDoS cannons. It's a serious threat will be," Odisseus tweeted.
The fresh arrival of ARC-based IoT devices into botnet scheme will exponentially raise the number of insecure devices to an unprecedented size, making it easy for hackers to gain control over a large number of poorly configured and vulnerable IoT devices.
Mirai Okiru botnet targets for first time ever in the history ARC-based IoT devices
17.1.2018 securityaffairs BotNet
Researcher @unixfreaxjp spotted the first time ever in the history of computer engineering a Linux malware designed to infect ARC CPU, this new Linux ELF malware was dubbed MIRAI OKIRU.
In August 2016 the researcher @unixfreaxjp from @MalwareMustDie team first spotted the dreaded Mirai botnet, now the same researcher is announcing a new big earthquake in the malware community.
unixfreaxjp spotted the first time ever in the history of computer engineering a Linux malware designed to infect ARC CPU, this new Linux ELF malware was dubbed MIRAI OKIRU.
This is the first time that a malware specifically targets ARC-based systems, the Mirai Okiru was undetected by almost all the antivirus engines at the time of its discovery.

“!! Please be noted of this fact, and be ready for the bigger impact on infection Mirai (specially Okiru) to devices that hasn’t been infected yet.” said #MalwareMustDie
The Linux IoT threat landscape is rapidly changing, crooks will start targeting IoT devices based on ARC CPU.
“From this day, the landscape of #Linux #IoT infection will change. #ARC cpu has produced #IoT dervices more than 1 billion per year. So these devices are what the hackers want to aim to infect #ELF #malware with their #DDoS cannons. It’s a serious threat will be. #MalwareMustDie!” wrote MMD.
As highlighted by the colleague the impact of such botnet could be devastating, it has been estimated that ARC embedded processors are shipped in more than 1.5 billion products per year. This means that the number of the potentially exposed devices is enormous, and a so powerful botnet could be used for a multitude of malicious purposes.
“ARC (Argonaut RISC Core) embedded processors are a family of 32-bit CPUs originally designed by ARC International. They are widely used in SoC devices for storage, home, mobile, automotive, and Internet of Things applications. ARC processors have been licensed by more than 200 organizations and are shipped in more than 1.5 billion products per year.” reads Wikipedia.
View image on TwitterView image on Twitter
@_odisseus
This is the FIRST TIME ever in the history of computer engineering that there is a malware for ARC CPU, & it is #MIRAI OKIRU!!
Pls be noted of this fact, & be ready for the bigger impact on infection Mirai (specially #Okiru) to devices hasn't been infected yet.#MalwareMustDie
9:40 PM - Jan 14, 2018
13 13 Replies 324 324 Retweets 295 295 likes
Twitter Ads info and privacy
“#Mirai #Okiru variant is very dangerous, if you see how the coder made specific “innovative modification” in its variant codes+encryption you’ll see what I mean, & now they are the 1st malware to aim #ARC core. These guys can make greater chaos if not be stopped. Mark my word” wrote MalwareMustDie.
It is very important to understand that the Mirai Satori variant is very different from Okiru as explained by MalwareDustdie.
“From what we observe so far. these two types are very different, (among of several common similar characteristic), we think it is good to have different rules to detect Mirai variant Okiru and Satori
Some simple highlights to differ Okiru to Satori variant:
The config is different, Okiru variant’s config is encrypted in two parts w/ telnet bombardment password encrypted, Satori does not split it in 2parts and doesn’t encrypt brute default passwords. Also Okiru’s telnet attack login information is a bit longer (can be up to 114 credentials, max counted), while Satori is having different and shorter database.
Satori seem to have “TSource Engine Query” common Distributed “Reflective” (DRDoS) attack function via random UDP, while Okiru does not seem to have this function,
The infection follow up commands written in both Okiru and Satori in their configurations are a bit different, showing possibility that they don’t seem sharing a same “herding environment”,
(up to) Four types of router attack exploit code has only being spotted hard coded in Okiru variant, yet Satori does not use these exploits at all,
Satori (see VT comment part for reversed code) is using small embedded ELF trojan downloaders to download other architecture binaries which were coded differently compared to Okiru ones (see reversed code is in VT comment),
(there are more minors stuff too that you can notice using the pictures shown in previous points, like differences in usage of watchdog, the usage of command “echo -en \x…” etc)
” wrote MalwareMustDie.
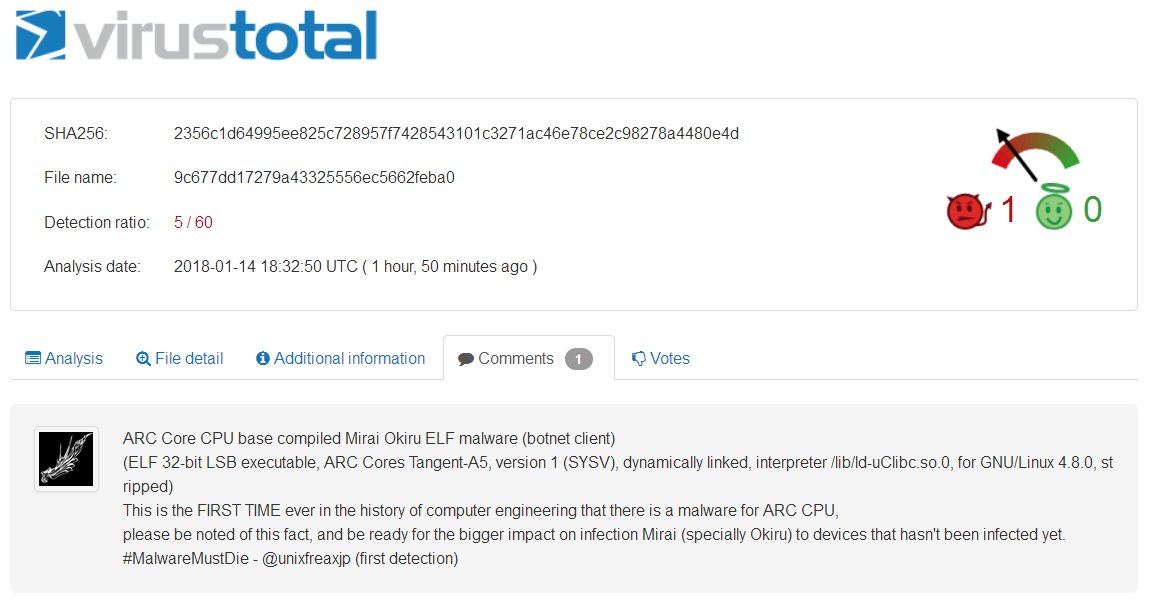
ARC Core CPU base compiled Mirai Okiru ELF malware (botnet client) (ELF 32-bit LSB executable, ARC Cores Tangent-A5, version 1 (SYSV), dynamically linked, interpreter /lib/ld-uClibc.so.0, for GNU/Linux 4.8.0, stripped).
The risk that someone could build a powerful Mirai Okiru botnet composed of a billion device is concrete.
Researchers from MalwareMustDie published the Yara rules for the threat
https://github.com/unixfreaxjp/rules/blob/master/malware/MALW_Mirai_Okiru_ELF.yar
and IoCs:
MD5: 9c677dd17279a43325556ec5662feba0
MD5: 24fc15a4672680d92af7edb2c3b2e957
Mirai Variant Targets ARC CPU-Based Devices
17.1.2018 securityweek BotNet
A newly discovered variant of the Mirai Internet of Things (IoT) botnet is targeting devices with ARC (Argonaut RISC Core) embedded processors, researchers warn.
Dubbed Okiru, the new malware variant appears to be different from the Satori botnet, although the latter was also called Okiru by its author. Security researchers analyzing the new threat have discovered multiple differences between the two Mirai versions, aside from the targeting of the ARC architecture.
Originally designed by ARC International, the ARC processors are 32-bit CPUs widely used in system on chip (SOC) devices for storage, home, mobile, automotive, and IoT applications. Each year, over 1.5 billion devices are shipped with ARC processors inside.
Mirai Okiru represents the very first known malware targeting ARC processors, independent security researcher Odisseus, who analyzed the threat, notes.
The botnet was discovered by @unixfreaxjp from malwaremustdie.org, the security researcher who spotted the first Mirai variant in August 2016. In a post on reddit, the researcher explained that, although distributed denial of service (DDoS) is the main purpose of the last two Mirai versions, they are very different.
One of the characteristics that sets them apart is the configuration, which in Okiru is encrypted in two parts with telnet bombardment password encrypted. Satori doesn’t split it in two and doesn't encrypt brute default passwords either. Moreover, the new malware variant can use up to 114 credentials for telnet attack, while Satori uses a different and shorter database.
The researcher also explains that Okiru seems to lack the "TSource Engine Query" common Distributed "Reflective" (DRDoS) attack function via random UDP that Satori has. The two also have different infection follow up commands written in their configurations and show differences in usage of watchdog.
Okiru was found to have four types of router attack exploit code hard coded in it, none of which is found in Satori. Furthermore, there are small embedded ELF Trojan downloaders in Satori, which are used to download other architecture binaries (these were coded differently compared to Okiru ones).
Last week, when the researchers first noticed Okiru’s attacks, the malware enjoyed low detection in VirusTotal. Thus, and because the new threat is targeting devices that haven’t been hit by malware previously, researchers expect an uptick in Mirai infections.
It is also clear that the actor behind the botnet is actively following reports on the malware. Within minutes after ENISA (European Union Agency for Network and Information Security) Threat Landscape Stakeholder Group member Pierluigi Paganini wrote about Okiru, the website was hit with a DDoS attack that lasted over an hour, Italy’s CERT-PA revealed (translated).
PyCryptoMiner botnet, a new Crypto-Miner Botnet spreads over SSH
5.1.2017 securityaffairs BotNet
Security experts at F5 discovered a new Linux Monero crypto-miner botnet dubbed PyCryptoMiner spreading over the SSH protocol.
F5 researchers discovered a new Linux crypto-miner botnet dubbed PyCryptoMiner spreading over the SSH protocol. The Monero miner botnet is based on the Python scripting language, it leverages Pastebin as command and control server infrastructure when the original C&C isn’t available.
If all C&C servers of the botnet are not accessible, all newly infected bots are idle, polling for the botmaster’s Pastebin page.
The experts believe the botnet it under development, operators have recently added scanner functionality hunting for vulnerable JBoss servers (exploiting CVE-2017-12149).
It has been estimated that the PyCryptoMiner botnet has generated the equivalent of approximately $46,000 as of late December.
The experts believe the PyCryptoMiner botnet is more evasive due to its scripting language-based nature, it is hard to detect because it is executed by a legitimate binary.
The malware spreads by attempting to guess the SSH login credentials of target Linux systems. Once SSH credentials are guessed, the bot deploys a simple base64-encoded Python script designed to connect to the C&C server to download and execute additional Python code.
The second-stage code is the controller that registers a cron job on the infected machine to gain persistence.
The original script checks whether the machine has been already infected, it also collects information on the infected device including:
Host/DNS name
OS name and its architecture
Number of CPUs
CPU usage
The bot sends a report with the collected information to the C&C that in turn send it task details. The “task” includes:
“cmd” — arbitrary command to be executed as a separate process
“client_version” — if the version number received from the server is different from the current bot version, it will terminate the bot and wait for the cron to run the spearhead script again to deploy an updated version (current value is “4”)
“task_hash” — task identifier so the C&C can synchronize botnet results, because each command has a different execution time
“conn_cycler” — time interval to poll the C&C, which is controlled by the bot master, probably to balance the loads on its C&C infrastructure as the botnet grows (default value 15 seconds)
The PyCryptoMiner botnet uses two pool addresses that show approximately 94 and 64 Monero, with a value of around $60,000. However, it is not possible to know overall profits of the botnet.
The analysis of the Pastebin page used are alternative C&C revealed the botnet might have been active since August 2017, and that the content had been viewed 177,987 times at the time of the investigation. It is not possible to determine the overall size of the botnet because each bot could periodically visit the page when the C&C server is down.
The botmaster used the moniker “WHATHAPPEN” which is associated with more than 36,000 domains and 235 email addresses. The registrant has been involved in scams, gambling, and adult services since 2012.
Below F5’s key findings on the PyCryptoMiner botnet:
Is based on the Python scripting language making it hard to detect
Leverages Pastebin.com (under the username “WHATHAPPEN”) to receive new command and control server (C&C) assignments if the original server becomes unreachable
The registrant is associated with more than 36,000 domains, some of which have been known for scams, gambling, and adult services since 2012
Is mining Monero, a highly anonymous crypto-currency favored by cyber-criminals. As of late December 2017, this botnet has made approximately US $46,000 mining Monero
New scanner functionality hunting for vulnerable JBoss servers was introduced mid-December exploiting CVE-2017-12149
F5 also published IoCs for the botnet.
Crypto-Miner Botnet Spreads over SSH
4.1.2018 securityweek BotNet
A recently discovered Linux crypto-miner botnet spreading over the SSH protocol is based on the Python scripting language, which makes it difficult to detect, F5 Networks has discovered.
Dubbed PyCryptoMiner, the botnet is using Pastebin to receive new command and control server (C&C) assignments when the original C&C isn’t available. Under active development, the botnet recently added scanner functionality hunting for vulnerable JBoss servers (exploiting CVE-2017-12149), F5 says.
Designed to mine for Monero, a highly anonymous crypto-currency, the botnet is estimated to have generated the equivalent of approximately $46,000 as of late December.
PyCryptoMiner isn’t the only botnet targeting online Linux systems, but because of its scripting language-based nature, the malware is more evasive and be easily obfuscated. Furthermore, it is executed by a legitimate binary, F5's researchers discovered.
The botnet spreads by attempting to guess the SSH login credentials of target Linux machines. If the credentials are successfully discovered, the attacking bot deploys a simple base64-encoded spearhead Python script designed to connect to the C&C server to download and execute additional Python code.
The second-stage code is the main bot controller, which registers a cron job on the infected machine to create persistency.
The original spearhead bash script also collects information on the infected device, including Host/DNS name, OS name and architecture, number of CPUs, and CPU usage. It also checks whether the machine has been already infected and whether the bot is used for crypto-mining or scanning.
The bot then sends a report with the collected information to the C&C, which responds with task details. Tasks include arbitrary commands to be executed, update, identifier so the C&C can synchronize botnet results, and time interval to poll the C&C. The bot sends an output of the executed task to the C&C.
In mid-December, the botnet was updated with code to scan for vulnerable JBoss servers, in an attempt to exploit CVE-2017-12149, a vulnerability disclosed several months ago.
“The list of the targets to scan is controlled by the C&C server, while the bot has a separate thread that polls the C&C server for new targets. The server responds with a Class C IP range to scan but could also provide a single IP address,” the researchers reveal.
The botnet uses two pool addresses that show approximately 94 and 64 Monero, with a value of around $60,000. However, the researchers are uncertain how much profit the threat actor behind the malware has made overall.
Unlike other malware that has the C&C server address hardcoded, which causes bots to become unreachable when the server is taken down, the botnet uses Pastebin to publish an alternate C&C server address if the original one is unreachable.
According to F5, with all C&C servers of the botnet inaccessible at this moment, all newly infected bots are idle, polling for the attacker’s Pastebin.com page, which could be updated at any time.
The page allowed researchers to determine that the botnet might have been active since August 2017, and that the resource had been viewed 177,987 times at the time of the investigation. However, the researchers couldn’t determine the exact size of the botnet, as a single bot could periodically ask the resource if the C&C server is down.
Looking at other resources created by the same actor, who uses the moniker “WHATHAPPEN”, the researchers discovered 235 email addresses and more than 36,000 domains associated with them. The registrant has been involved in scams, gambling, and adult services since 2012.
“Our research is still ongoing while we hunt for more missing pieces of this puzzle, such as the “scanner node” component and additional C&C servers, if there are any. We are also waiting to see whether the current C&C server will come back to life,” F5 notes.
Andromeda Botnet to Die Slow, Painful Death After Takedown
4.1.2018 securityweek BotNet
Following a takedown operation in early December 2017, the Andromeda botnet is expected to slowly disappear from the threat landscape, ESET says.
Also known as Wauchos or Gamarue, the botnet has been around since at least September 2011 and lived through five major versions over the years. The Andromeda malware was detected or blocked on an average of around 1.1 million machines every month over the six months leading to the takedown.
The botnet was mainly used for stealing credentials and to download and install additional malware onto compromised systems. Thus, systems infected with Andromeda would likely have other threats installed on them as well, ESET says.
Some of the threats usually distributed via Andromeda included Kasidet, also known as Neutrino bot, which can launch distributed denial-of-service (DDoS) attacks, and Kelihos and Lethic, which are notorious spambots known for their involvement in massive junk mail campaigns. It was also used for the distribution of the Dridex banking Trojan and point-of-sale (PoS) malware GamaPoS.
Andromeda was distributed through various methods, including social media, instant messaging, removable media, spam, drive-by downloads, and exploit kits. Because it didn’t conduct targeted attacks, the malware could infect any computer if the user clicked on malicious links.
Since there were no obvious signs to alert the user on the infection, the botnet managed to remain hidden and compromise a large number of systems. Featuring a modular design, the botnet could get additional capabilities through plugins such as a keylogger, a form grabber, and a rootkit.
ESET Senior Malware Researcher Jean-Ian Boutin, who was involved in the takedown operation, explains that the botnet’s numerous features and continuous development made it appealing to cybercriminals interested in using it. Thus, Andromeda was able to survive for a long period of time and to also become a prevalent threat.
At the time of Andromeda’s takedown, security researchers identified 464 distinct botnets, 80 associated malware families, and 1,214 domains and IP addresses of the botnet’s command and control (C&C) servers.
The takedown operation, a joint effort from the FBI, the Luneburg Central Criminal Investigation Inspectorate in Germany, Europol’s European Cybercrime Centre (EC3), the Joint Cybercrime Action Task Force (J-CAT), Eurojust, and private-sector partners, built on information gathered during the shutdown of a large criminal network known as Avalanche.
According to Boutin, investigators started gathering information and evidence in 2015 and needed a lot of time to get everything ready for a law enforcement operation. Following the takedown, authorities seized control of Andromeda’s C&C servers and the botnet is expected to slowly disappear.
“It will probably slowly disappear as remediation is under way. For this type of long-lived botnet, it is very hard to clean all the systems that have been compromised by Wauchos, but as long as the good guys are in control of the C&C servers, at least no new harm can be done to those compromised PCs,” Boutin says.
Mirai Variant "Satori" Targets Huawei Routers
23.12.2017 securityweek BotNet
Hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers have been observed over the past month, Check Point security researchers warn.
The attacks were trying to drop Satori, an updated variant of the notorious Mirai botnet that managed to wreak havoc in late 2016. Targeting port 37215 on Huawei HG532 devices, the assaults were observed all around the world, including the USA, Italy, Germany and Egypt, the researchers say.
Common to these incidents was the attempt to exploit CVE-2017-17215, a zero-day vulnerability in the Huawei home router residing in the fact that the TR-064 technical report standard, which was designed and intended for local network configuration, was exposed to WAN through port 37215 (UPnP - Universal Plug and Play).
The affected device supports a service type named `DeviceUpgrade`, which is supposedly carrying out firmware upgrade actions. By injecting shell meta-characters “$()” in two elements with which the upgrade is carried out, a remote administrator could execute arbitrary code on the affected devices.
By successfully exploiting the flaw, an attacker could download and execute a malicious payload onto the impacted devices. In this case, the payload was the Satori botnet, Check Point notes.
Huawei was informed on the vulnerability on November 27. Within days, the company published an advisory to confirm the vulnerability and inform users on available measures to circumvent or prevent the exploit: using the built-in firewall function, changing default passwords, deploying a firewall at the carrier side.
“The customers can deploy Huawei NGFWs (Next Generation Firewall) or data center firewalls, and upgrade the IPS signature database to the latest version IPS_H20011000_2017120100 released on December 1, 2017 to detect and defend against this vulnerability exploits initiated from the Internet.” Huawei notes.
In this Satori attack, each bot is used to flood targets with manually crafted UDP or TCP packets. The bot first attempts to resolve the IP address of a command and control (C&C) server using DNS request with the hardcoded domain name, then gets the addresses from the DNS response and tries to connect via TCP on the hardcoded target port (7645).
The C&C server provides the number of packets used for the flooding action and their corresponding parameters, and can also pass an individual IP for attack or a subnet.
The bot’s binary, the researchers discovered, contains a lot of unused text strings, supposedly inherited from another bot or a previous version.
A custom protocol is used for C&C communication, which includes two hardcoded requests to check in with the server, which in turn responds with the parameters for launching distributed denial of service attacks.
While analyzing the incident, which involved the use of a zero-day and numerous servers to attack Huawei devices, the security researchers discovered that the actor behind the Satori botnet might be using the online handle of NexusZeta.
They were able to track the actor’s activity across several hacking forums and also discovered that NexusZeta is active on social media, most notably Twitter and Github, and has Skype and SoundCloud accounts under the name of Caleb Wilson (caleb.wilson37 / Caleb Wilson 37), but couldn’t determine if this is the attacker's real name.
Based on forum posts attributed to the actor, the researchers concluded that he isn’t an advanced actor, “but rather an amateur with lots of motivation, looking for the crowd’s wisdom.” What the security researchers couldn’t determine, however, was how the zero-day vulnerability arrived in the individual’s possession.
“Nonetheless, as seen in this case as well as others over the past year, it is clear that a combination of leaked malware code together with exploitable and poor IoT security, when used by unskilled hackers, can lead to disastrous results,” Check Point concludes.
Satori is the latest Mirai botnet variant that is targeting Huawei HG532 home routers
23.12.2017 securityaffairs BotNet
Satori botnet, Mirai variant, is responsible for hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers.
The Mirai botnet makes the headlines once again, a new variant dubbed Satori is responsible for hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers.
The activity of the Satori botnet has been observed over the past month by researchers from Check Point security.
“A Zero-Day vulnerability (CVE-2017-17215) in the Huawei home router HG532 has been discovered by Check Point Researchers, and hundreds of thousands of attempts to exploit it have already been found in the wild.
The delivered payload has been identified as OKIRU/SATORI, an updated variant of Mirai.
The suspected threat actor behind the attack has been identified by his nickname, ‘Nexus Zeta’.” states the report published by Check Point security.
Satori is an updated variant of the notorious Mirai botnet that was first spotted by the malware researchers MalwareMustDie in August 2016. The malicious code was developed to target IoT devices, the Sartori version targets port 37215 on Huawei HG532 devices.
The attacks against Huawei HG532 devices were observed in several countries, including the USA, Italy, Germany, and Egypt.

Experts observed that attacks attempt to exploit the CVE-2017-17215 zero-day vulnerability in the Huawei home router residing in the fact that the TR-064 technical report standard, which was designed for local network configuration, was exposed to WAN through port 37215 (UPnP – Universal Plug and Play).
“In this case though, the TR-064 implementation in the Huawei devices was exposed to WAN through port 37215 (UPnP).
From looking into the UPnP description of the device, it can be seen that it supports a service type named `DeviceUpgrade`. This service is supposedly carrying out a firmware upgrade action by sending a request to “/ctrlt/DeviceUpgrade_1” (referred to as controlURL ) and is carried out with two elements named `NewStatusURL` and `NewDownloadURL`.” continues the analysis.
“The vulnerability allows remote administrators to execute arbitrary commands by injecting shell meta-characters “$()” in the NewStatusURL and NewDownloadURL”

The successful exploitation of the vulnerability could allow an attacker to download and execute the Satori bot.
The flaw was reported to Huawei on November 27, after a few days, the company published a security advisory that notifies the vulnerability to the users and provides recommendations to prevent the exploitation of the flaw.
Customers can take the following measures to circumvent or prevent the exploit of this vulnerability. For details, consult the local service provider or Huawei TAC.
Configure the built-in firewall function.
Change the default password.
Deploy a firewall at the carrier side.
“The customers can deploy Huawei NGFWs (Next Generation Firewall) or data center firewalls, and upgrade the IPS signature database to the latest version IPS_H20011000_2017120100 released on December 1, 2017 to detect and defend against this vulnerability exploits initiated from the Internet.” reads the andisory published by Huawei.
Each Satori bot floods targets with manually crafted UDP or TCP packets, they first attempt to resolve the IP address of a C&C server using DNS request with the hardcoded domain name, then gets the addresses from the DNS response and tries to connect via TCP on the hardcoded target port (7645).
The C&C server, in turn, provides the number of packets used for the flooding action and their corresponding parameters, and can also pass an individual IP for attack or a subnet.
The bot uses a custom protocol to communicate with the C&C, it includes two hardcoded requests to check in with the server that responds with the DDoS attack parameters.
The researchers that investigated the case determined that the actor behind the Satori botnet might be using the online handle of NexusZeta.
NexusZeta is very active on social media such as Twitter and Github, and has Skype and SoundCloud accounts under the name of Caleb Wilson (caleb.wilson37 / Caleb Wilson 37).
While the actor described himself as a novice (“an amateur with lots of motivation, looking for the crowd’s wisdom.”), it is unclear how he discovered the zero-day vulnerability .
“Nonetheless, as seen in this case as well as others over the past year, it is clear that a combination of leaked malware code together with exploitable and poor IoT security, when used by unskilled hackers, can lead to disastrous results,” Check Point concludes.
US DoJ charges 3 Men with developing and running the Mirai Botnet
14.12.2017 securityaffairs BotNet
The US DoJ announced plea agreements for Paras Jha, Josiah White, and Dalton Norman, 21 for creating and operating the dreaded Mirai botnet.
US authorities charge three men with developing and running the dreaded Mirai botnet that was involved in several massive DDoS attacks.
According to documents released by the US Department of Justice (DOJ), the three men are Paras Jha, Josiah White, and Dalton Norman.
According to the plea agreements, White developed the Telnet scanner component used by Mirai, Jha created the botnet’s core infrastructure and the malware’s remote control features, while Norman developed new exploits.
Jha, who goes online with the moniker “Anna-senpai” leaked the source code for the Mirai malware on a criminal forum, allowing other threat actors to use it and making hard the attribution of the attacks.
Jha also pleaded guilty to carrying out multiple DDoS attacks against his alma mater Rutgers University between November 2014 and September 2016, before creating the Mirai botnet.
The Mirai bot was first spotted by the malware researchers MalwareMustDie in August 2016, the malicious code was developed to target IoT devices.

The IoT malware runs a brute force password attack via telnet using a list of default credentials to gain access to the target device.

Once the Mirai component gains access to the target IoT device, it connects out to download the full virus and runs it. Then it starts sending out SYN packets at a high rate of speed, looking for other potential victims.
The Mirai botnet peaked a size of over 300,000 infected devices, mainly composed of DVRs, security cameras, and routers.
The three men advertised the botnet on hacking forums, as a DDoS-for-hire service, but only Jha also used it to blackmail a hosting company.
According to court documents, the three men used the Mirai botnet to make money through “click fraud” activity. The botnet was used to emulate the behavior of real users clicking on an advertisement for the purpose of artificially generating profits for operators.
The three also generated some $180,000 from the scheme in bitcoin.
The Mirai botnet was also used against the website of the popular investigator Brian Krebs that was able to identify Jha and White as the operators of the botnet.
The three face possible prison terms and monetary fines.
Three Plead Guilty in Mirai Botnet Attacks
13.12.2017 securityweek BotNet
US officials unveiled criminal charges Wednesday against a former university student and two others in the Mirai botnet attacks which shut down parts of the internet in several countries starting in mid-2016.
The Justice Department announced plea agreements for Paras Jha, 21 -- a former Rutgers University computer science student who acknowledged writing the malware code -- and Josiah White, 20, and Dalton Norman, 21, who helped profit from the attacks.
In documents unsealed Wednesday, Jha admitted writing the code for the botnet which harnessed more than 100,000 "internet of things" (IoT) devices such as cameras, light bulbs and appliances to launch the attacks.
By commanding an army of bots -- or computers under control of the attackers -- the malware shut down networks and websites in the United States, Germany, Liberia and elsewhere.
Jha admitted he "set up and managed command and control servers to manage the infected computers" in the scheme.
Officials said the three used the botnet "to conduct a number of powerful distributed denial-of-service" attacks which flood the internet and can shut down networks.
Later, Jha posted the source code for the Mirai malware on a criminal forum, allowing other groups to use it.
The malware was used to make money through "click fraud," a scheme that makes it appear that a real user has clicked on an advertisement for the purpose of artificially generating revenue, according to officials.
The three generated some $180,000 from the scheme in bitcoin, Justice officials added.
Jha was identified as a suspect earlier this year by security blogger Brian Krebs -- who was himself a victim of the attacks.
Krebs said Jha used the online moniker Anna-Senpai, who had claimed responsibility for earlier denial of service attacks using various versions of Mirai -- including some targeting Rutgers University, the school in New Jersey where Jha was studying.
In January 2017, "Jha and his co-conspirators leased access to their botnet to other criminals in exchange for payment," according to the plea agreement in federal court.
According to Krebs, Jha and White operated ProTraf Solutions LLC, which masqueraded as a security firm that dealt with "denial of service" attacks it created.
The three face possible prison terms and monetary fines as a result of the conspiracy and fraud charges.
Jha pleaded guilty separately to a series of attacks which shut down the Rutgers computer networks from 2014 to 2016, officials said.
IoT Botnet Used in Website Hacking Attacks
9.12.2017 securityweek IoT BotNet
Embedded Malware Launches SOCKS Proxy Server on Infected IoT Devices
A botnet of Linux-based Internet of Things (IoT) devices is currently being used in a campaign attempting to hack websites, Doctor Web security researchers warn.
Called Linux.ProxyM, the malware has been around since February of this year, and was previously used in spam campaigns. The Trojan was designed to launch a SOCKS proxy server on infected devices and allows attackers to leverage the proxy to perform nefarious operations while hiding their tracks.
To date, the malware has been observed targeting devices with the following architectures: x86, MIPS, MIPSEL, PowerPC, ARM, Superh, Motorola 68000, and SPARC. Basically, it can infect “almost any Linux device, including routers, set-top boxes, and other similar equipment,” the researchers say.
Previous malicious campaigns leveraging the botnet were sending spam emails, with each infected device generating around 400 messages per day in September, Doctor Web says.
Soon after, the bot started sending phishing messages. The emails supposedly came from DocuSign, a service providing users with the possibility to download, view, sign, and track the status of electronic documents.
The phishing messages included a link to a fake DocuSign website that featured an authorization form, in an attempt to trick users into entering their credentials. After that, the victims were being redirected to the real DocuSign authorization page, while their login details had been sent to the attackers.
In December, Linux.ProxyM’s proxy server started being used to hack websites through various methods, including SQL injections, Cross-Site Scripting, and Local File Inclusion (LFI). The actors operating the botnet targeted game severs and forums, and resources on other topics, including Russian websites.
On Dec. 7, the security researchers observed 20,000 attacks launched by the botnet. About a month ago, the bots were launching nearly 40,000 attacks per day.
“Although Linux.ProxyM has only one function—a proxy server—cybercriminals continue finding new opportunities to use it for illegal actions and showing increasing interest in the ‘Internet of things’,” Doctor Web points out.
Feds Shut Down 'Longest-Running' Andromeda Botnet
5.12.2017 thehackernews BotNet
In a coordinated International cyber operation, Europol with the help of international law enforcement agencies has taken down what it called "one of the longest-running malware families in existence" known as Andromeda.
Andromeda, also known as Win32/Gamarue, is an infamous HTTP-based modular botnet that has been around for several years now, and infecting computers with it's malicious intentions ever since.
The primary goal of Andromeda bot is to distribute other malware families for mass global malware attacks.
The botnet has been associated with at least 80 malware families, and in the last six months, it was detected (or blocked) on an average of more than 1 million machines per month.
Last year, law enforcement agencies took down the criminal infrastructure of the infamous Avalanche botnet in a similar massive international cyber operation. Avalanche botnet was used as a delivery platform to spread other malware families, including Andromeda.
While investigating into the Avalanche botnet, information obtained by the German authorities was shared with the Federal Investigation of Bureau (FBI) via Europol, which eventually helped the international agencies to tear down Andromeda just last week.
In a joint operation, the international partners took down servers and more than 1,500 web domains which were being used to distribute and control Andromeda malware.
"This is another example of international law enforcement working together with industry partners to tackle the most significant cybercriminals and the dedicated infrastructure they use to distribute malware on a global scale," Steven Wilson, the Head of Europol's European Cybercrime Centre (EC3), said.
"The clear message is that public-private partnerships can impact these criminals and make the internet safer for all of us."
Using sinkholing the now-seized domains, tactic researchers use to redirect traffic from the infected machines to a self-controlled system; authorities found over 2 million unique IP addresses from at least 223 countries associated with Andromeda victims with just 48 hours.
Further investigation also helped law enforcement authorities arrest a suspect in Belarus, who was allegedly involved in the Andromeda cybercrime gang.
Just last week, Europol seized more than 20,000 web domains for illegally selling counterfeit products, including luxury products, sportswear, electronics, pharmaceuticals and online piracy on e-commerce platforms and social networks in its fight against the online trade of counterfeit goods.
Global operation allowed law enforcement agencies to take down the Andromeda Botnet
5.12.2017 securityaffairs BotNet
A joint international operation conducted by the FBI, law enforcement agencies in Europe and private partners managed to dismantle the Andromeda botnet.
A joint international operation conducted by the FBI and law enforcement agencies in Europe managed to dismantle the dreaded Andromeda botnet (aka Gamarue and Wauchos) last week.
The Andromeda botnet has been around since 2011, it was used across the years to distribute several malware families, including the Dridex banking Trojan or the GamaPoS point-of-sale (PoS) malware.
Law enforcement authorities worldwide dismantled several long-running botnets powered by the malware family dubbed as Gamarue, mostly detected by the security firm ESET as Win32/TrojanDownloader.Wauchos.
ESET worked with Microsoft to disruption the botnets, the experts tracked the malicious infrastructure, identified their C&C servers and the threat delivered by each of them.
“Microsoft then contacted law enforcement with information that included: 464 distinct botnets, 80 associated malware families, and 1,214 domains and IP addresses of the botnet’s C&C servers.” states the analysis published by ESET.

The joint operation was performed on November 29 and involved experts from the FBI, the Luneburg Central Criminal Investigation Inspectorate in Germany, Europol’s European Cybercrime Centre (EC3), the Joint Cybercrime Action Task Force (J-CAT), Eurojust, and private-sector partners,
The takeover of the Andromeda botnet was also possible thanks to the last year’s shut down of a large criminal network known as Avalanche, an infrastructure used to power mass global malware attacks and money mule recruiting.
“One year ago, on 30 November 2016, after more than four years of investigation, the Public Prosecutor’s Office Verden and the Luneburg Police in Germany, the United States Attorney’s Office for the Western District of Pennsylvania, the Department of Justice, the FBI, Europol, Eurojust and global partners, had dismantled the international criminal infrastructure Avalanche. This was used as a delivery platform to launch and manage mass global malware attacks such as Andromeda, and money mule recruitment campaigns.” states the report published by the Europol.
“Insights gained during the Avalanche case by the investigating German law enforcement entities were shared, via Europol, with the FBI and supported this year’s investigations to dismantle the Andromeda malware last week.”
According to the Europol, the experts were able to identify 1500 domains used by the Avalanche platform and used the sinkholing technique to analyzed its traffic and track the infected systems. Microsoft revealed that during 48 hours of sinkholing, the experts observed approximately 2 million unique Andromeda victim IP addresses from 223 countries.
The operation also included the search and arrest of a suspect in Belarus.
The investigators then extended the sinkholing of the Avalanche infrastructure for another year, as globally 55% of the computers originally infected in Avalanche continue to be infected.
The activity against Andromeda and Avalanche involved the following countries: Austria, Belgium, Finland, France, Italy, the Netherlands, Poland, Spain, the United Kingdom, Australia, Belarus, Canada, Montenegro, Singapore, and Taiwan.
“This is another example of international law enforcement working together with industry partners to tackle the most significant cyber criminals and the dedicated infrastructure they use to distribute malware on a global scale. The clear message is that public-private partnerships can impact these criminals and make the internet safer for all of us,” Steven Wilson, the Head of Europol’s European Cybercrime Centre, said.
Technical details about the global operations are included in a report published by ESET.