- BotNet -
Last update 23.09.2017 19:27:30
Introduction List Kategorie Subcategory 0 1 2 3 4 5 6 7 8
Authorities Take Down Andromeda Botnet
4.12.2017 securityweek BotNet
The Federal Bureau of Investigation (FBI) and law enforcement agencies in Europe managed to dismantle the Andromeda botnet last week.
Also known as Gamarue, Andromeda malware has been around since 2011 and used to ensnare the infected computers into a botnet. The main purpose of this network of infected machines was to distribute other malware families, including the Dridex banking Trojan or point-of-sale (PoS) malware GamaPoS.
In a FortiGuard Labs report detailing the top 5 methods used to attack healthcare in Q4, 2016, Andromeda emerged as the top botnet.
Packing a loader that features virtual machine and debug evasion techniques, Andromeda downloads modules and updates from its command and control (C&C) server. Overall associated with 80 malware families, the threat was detected on or blocked on an average of over 1 million computers every month for the past six months.
The takedown, a joint effort from the FBI, the Luneburg Central Criminal Investigation Inspectorate in Germany, Europol’s European Cybercrime Centre (EC3), the Joint Cybercrime Action Task Force (J-CAT), Eurojust, and private-sector partners, was performed on November 29.
The operation was the result of information gathered following last year’s shut down of a large criminal network known as Avalanche, a platform used for mass global malware attacks and money mule recruiting. Andromeda was also used in the Avalanche network.
“Insights gained during the Avalanche case by the investigating German law enforcement entities were shared, via Europol, with the FBI and supported this year’s investigations to dismantle the Andromeda malware last week,” a Europol announcement reads.
Investigators focused on taking down servers and domains used to spread the Andromeda malware and resulted in the sinkholing of 1500 domains. 48 hours of sinkholing resulted in around 2 million unique Andromeda victim IP addresses from 223 countries being captured.
The takedown operation also included the search and arrest of a suspect in Belarus.
The investigators also decided to extend the sinkhole measures of the Avalanche case for another year, as globally 55% of the computers originally infected in Avalanche continue to be infected.
The measures to combat Andromeda and Avalanche involved the following countries: Austria, Belgium, Finland, France, Italy, the Netherlands, Poland, Spain, the United Kingdom, Australia, Belarus, Canada, Montenegro, Singapore, and Taiwan.
Private and institutional partners involved in the takedown include: Shadowserver Foundation, Microsoft, Registrar of Last Resort, Internet Corporation for Assigned Names and Numbers (ICANN) and associated domain registries, Fraunhofer Institute for Communication, Information Processing and Ergonomics (FKIE), and the German Federal Office for Information Security (BSI).
“This is another example of international law enforcement working together with industry partners to tackle the most significant cyber criminals and the dedicated infrastructure they use to distribute malware on a global scale. The clear message is that public-private partnerships can impact these criminals and make the internet safer for all of us,” Steven Wilson, the Head of Europol’s European Cybercrime Centre, said.
New Mirai Botnet Variant Found Targeting ZyXEL Devices In Argentina
29.11.2017 thehackernews BotNet

While tracking botnet activity on their honeypot traffic, security researchers at Chinese IT security firm Qihoo 360 Netlab discovered a new variant of Mirai—the well known IoT botnet malware that wreaked havoc last year.
Last week, researchers noticed an increase in traffic scanning ports 2323 and 23 from hundreds of thousands of unique IP addresses from Argentina in less than a day.
The targeted port scans are actively looking for vulnerable internet-connected devices manufactured by ZyXEL Communications using two default telnet credential combinations—admin/CentryL1nk and admin/QwestM0dem—to gain root privileges on the targeted devices.
Researchers believe (instead "quite confident") this ongoing campaign is part of a new Mirai variant that has been upgraded to exploit a newly released vulnerability (identified as CVE-2016-10401) in ZyXEL PK5001Z modems.
"ZyXEL PK5001Z devices have zyad5001 as the su (superuser) password, which makes it easier for remote attackers to obtain root access if a non-root account password is known (or a non-root default account exists within an ISP’s deployment of these devices)," the vulnerability description reads.
Mirai is the same IoT botnet malware that knocked major Internet companies offline last year by launching massive DDoS attacks against Dyndns, crippling some of the world's biggest websites, including Twitter, Netflix, Amazon, Slack, and Spotify.
Mirai-based attacks experienced sudden rise after someone publicly released its source code in October 2016. Currently, there are several variants of the Mirai botnet attacking IoT devices.
The biggest threat of having the source code of any malware in public is that it could allow attackers to upgrade it with newly disclosed exploits according to their needs and targets.
"For an attacker that finds a new IoT vulnerability, it would be easy to incorporate it into the already existing Mirai code, thus releasing a new variant," Dima Beckerman, security researcher at Imperva, told The Hacker News.
"Mirai spread itself using default IoT devices credentials. The new variant adds more devices to this list. Still, we can’t know for sure what other changes were implemented into the code. In the future, we might witness some new attack methods by Mirai variants."
This is not the very first time when the Mirai botnet targeted internet-connected devices manufactured by ZyXEL. Exactly a year before, millions of Zyxel routers were found vulnerable to a critical remote code execution flaw, which was exploited by Mirai.
Secure Your (Easily Hackable) Internet-Connected Devices
1. Change Default Passwords for your connected devices: If you own any internet-connected device at home or work, change its default credentials. Keep in mind; Mirai malware scans for default settings.
2. Disable Remote Management through Telnet: Go into your router’s settings and disable remote management protocol, specifically through Telnet, as this is a protocol used to allow one computer to control another from a remote location. It has also been used in previous Mirai attacks.
3. Check for Software Updates and Patches: Last but not the least—always keep your internet-connected devices and routers up-to-date with the latest firmware updates and patches.
New Mirai Variant Emerges
28.11.2017 securityweek BotNet
A new variant of the Mirai malware has been observed over the past week targeting new sets of default credentials specific to ZyXEL devices, Qihoo 360 Netlab researchers warn.
Mirai became widely known about a year ago, when it started ensnaring insecure Internet of Things (IoT) devices into a botnet capable of launching massive distributed denial-of-service (DDoS) attacks. With its source code made public in early October 2016, Mirai had already infected devices in 164 countries by the end of that month.
To spread, Mirai scans the Internet for open ports associated with Telnet access on Internet-facing IoT products and attempts to connect to the discovered devices using a set of default username/password combinations.
In August this year, Akamai explained that Mirai is formed of smaller hives of related bots and command and control (C&C) servers, and parts of it can be used for different purposes. Thus, the botnet can be involved in multiple, simultaneous attacks, each orchestrated from a different C&C, likely by a different operator, and can also be rented to wannabe criminals.
“At least one botnet operator was offering access to the systems under its control for rent,” Akamai revealed.
Starting with last week, Netlab observed an increase in port 2323 and 23 scan traffic and “confidently” associated it with a new Mirai variant. The researchers also discovered that this new malware version is specifically searching for insecure ZyXEL devices.
According to the security researchers, the scanner was attempting to exploit two new default login credentials, namely admin/CentryL1nk and admin/QwestM0dem. The former, they explain, was first spotted less than a month ago in exploit-db, as part of an exploit targeting the ZyXEL PK5001Z modem.
What Netlab noticed was that the abuse of the two login credentials started on November 22 and reached its peak the next day, the same as the uptick on port 2323 and 23 scan traffic. Thus, they concluded that the two were related.
The security researchers also reveal that most of the scanner IPs appear to be located in Argentina, with nearly 100,000 unique scanners from that country observed over a period of nearly three days. This led them to conclude that the attack might have been focused on specific types of IoT devices widely deployed in Argentina.
Last year, the Mirai worm was involved in a similar attack where nearly 1 million of Deutsche Telekom’s fixed-line network customers experienced Internet disruptions.
World's Biggest Botnet Just Sent 12.5 Million Emails With Scarab Ransomware
27.11.2017 thehackernews BotNet
A massive malicious email campaign that stems from the world's largest spam botnet Necurs is spreading a new strain of ransomware at the rate of over 2 million emails per hour and hitting computers across the globe.
The popular malspam botnet Necrus which has previously found distributing Dridex banking trojan, Trickbot banking trojan, Locky ransomware, and Jaff ransomware, has now started spreading a new version of Scarab ransomware.
According to F-Secure, Necurs botnet is the most prominent deliverer of spam emails with five to six million infected hosts online monthly and is responsible for the biggest single malware spam campaigns.
Scarab ransomware is a relatively new ransomware family that was initially spotted by ID Ransomware creator Michael Gillespie in June this year.
Massive Email Campaign Spreads Scarab Ransomware
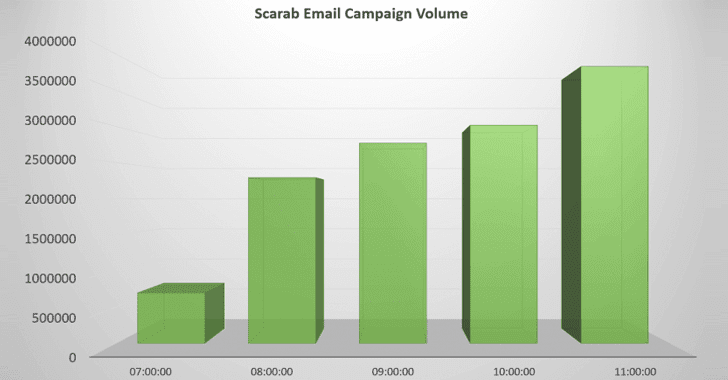
According to a blog post published by security firm Forcepoint, the massive email campaign spreading Scarab ransomware virus started at approximately 07:30 UTC on 23 November (Thursday) and sent about 12.5 million emails in just six hours.
The Forcepoint researchers said "the majority of the traffic is being sent to the .com top-level domain (TLD). However, this was followed by region-specific TLDs for the United Kingdom, Australia, France, and Germany."
The spam email contains a malicious VBScript downloader compressed with 7zip that pulls down the final payload, with one of these subject lines:
Scanned from Lexmark
Scanned from Epson
Scanned from HP
Scanned from Canon
As with previous Necurs botnet campaigns, the VBScript contained a number of references to the widely watched series Game of Thrones, like the strings 'Samwell' and 'JohnSnow.'
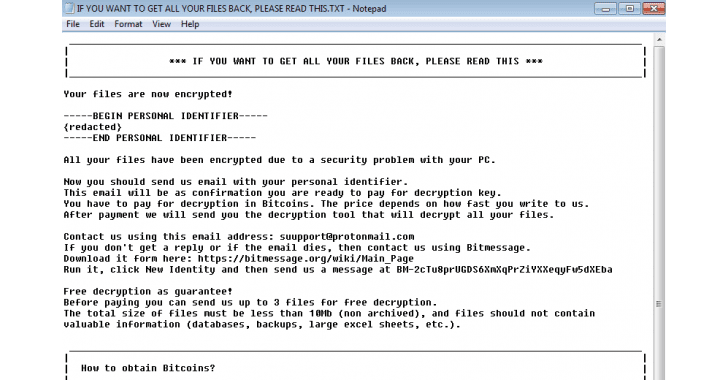
The final payload is the latest version of Scarab ransomware with no change in filenames, but it appends a new file extension with ".[suupport@protonmail.com].scarab" to the encrypted files.
Once done with the encryption, the ransomware then drops a ransom note with the filename "IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT" within each affected directory.
The ransom note does not specify the amount being demanded by the criminals; instead, it merely states that "the price depends on how fast you [the victim] write to us."
However, Scarab ransomware offers to decrypt three files for free to prove the decryption will work: "Before paying you can send us up to 3 files for free decryption."
Protection Against Ransomware
To safeguard against such ransomware infection, you should always be suspicious of any uninvited document sent over an email and should never click on links provided in those documents unless verifying the source.
Most importantly, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC in order to always have a tight grip on all your important files and documents.
Moreover, make sure that you run an active anti-virus solution on your system, and always browse the Internet safely.
A new Mirai variant is rapidly spreading, around 100,000 IPs running the scans in the past 60 hours
26.11.2017 securityaffairs BotNet
A new Mirai variant is rapidly spreading, experts observed around 100K IPs running the scans in the past 60 hours searching for flawed ZyXEL PK5001Z routers.
According to Li Fengpei, a security researcher with Qihoo 360 Netlab, the publication of the proof-of-concept (PoC) exploit code in a public vulnerabilities database is the root cause of the increase of activity associated with the Mirai botnet.
After the publication of the PoC exploit code on October 31, the experts observed scans using it starting on Wednesday, November 22.
“About 60 hours ago, since 2017-11-22 11:00, we noticed big upticks on port 2323 and 23 scan traffic, with almost 100k unique scanner IP came from Argentina. After investigation, we are quite confident to tell this is a new mirai variant.” reads the analysis published by Fengpei.
The PoC triggers the flaw CVE-2016-10401 in old ZyXEL PK5001Z routers that was publicly disclosed in January 2016. ZyXEL PK5001Z routers have a hardcoded super-user password (zyad5001) that could be used to elevate a user’s access to root level. The su password cannot be used to log into the device.
Anyway, attackers have discovered that there’s a large amount of ZyXEL devices are using admin/CentryL1nk and admin/QwestM0dem as default Telnet credentials.
The PoC code recently published first logs into a remote ZyXEL device using one of the two Telnet passwords, and then uses the hardcoded su password to gain root privileges.
Starting on Wednesday, Netlab has detected a spike of scans on ports 23 and 2323 for Telnet authentication the evidence that attackers are using the above PoC to infect exposed device with Mirai.
“The abuse of these two credentials began at around 2017-11-22 11:00, and reached its peak during 2017-11-23 daytime. This is a good time span match with this 2323/23 port scanning on Scanmon.” continues the analysis.
“Quite a lot of IP abusing these two credential also appear in ScanMon radar.
admin/CentryL1nk : 748 (66.5%) out of 1125
admin/QwestM0dem : 1175 (69.4%) out of 1694″

Experts from Netlab detected around 100,000 IPs running the scans in the past 60 hours, this means that the new Mirai botnet is already composed of roughly 100,000 devices looking for vulnerable ZyXEL devices.
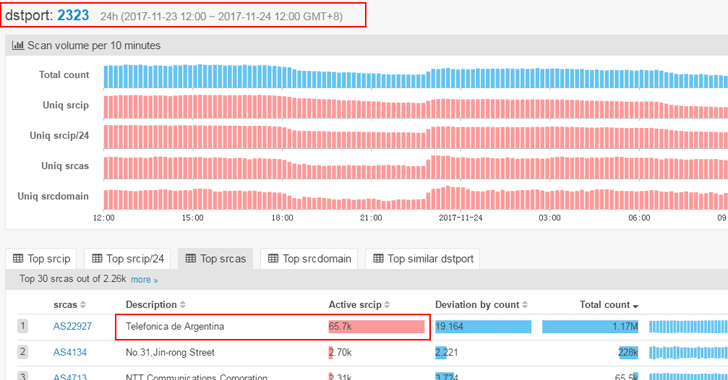
65,700 of these bots were located in Argentina because the ISP has shipped devices with the default credentials included in the public PoC.
There are no reports that Telefonica users are suffering from Internet connectivity outages, a circumstance that suggests that the owners of infected routers are not aware of the infection.
The security researcher Troy Mursch confirmed that that most of the scanner IP came from Argentina, precisely from the network of local ISP Telefonica de Argentina.
23 Nov
Bad Packets Report
@bad_packets
Replying to @bad_packets
DAILY TOP 4 ASN
New unique IPs seen in Mirai-like #botnet by ASN
🇦🇷 AS22927: 493
🇯🇵 AS4713: 25
🇨🇳 AS4837: 21
🇨🇳 AS4134: 20 pic.twitter.com/TQ24Zmm8bY
Bad Packets Report
@bad_packets
879 new unique IP addresses were found in the #Mirai-like #botnet on 2017-11-22
This is an all-time record for the most new unique IP address that I've seen added to the botnet in one day.
A massive increase of volume from Argentina (@Telefonica) is largely the cause. pic.twitter.com/c8GBUpKNgW

10:13 AM - Nov 23, 2017
View image on Twitter
2 2 Replies 2 2 Retweets 1 1 like
Twitter Ads info and privacy
The good news is that the Mirai bots do not have a persistence mechanism, this means that it could be eradicated when the infected device is rebooted.
This isn’t the first time that the Mirai bornet was used to target the devices belonging to a particular ISP’s network, late 2016 it was used to compromise more than 900,000 routers of the Deutsche Telekom in Germany.
Creating ATM Botnets Not Difficult, Researchers Say
13.11.2017 securityweek BotNet
ATMs Are Not Immune to Supply Chain Attacks and Other Digital Threats
Internet-connected Automated teller machines (ATMs) can be discovered using dedicated search engines and specific keywords and then ensnared into botnets, Kaspersky Lab researchers believe.
With large sums of cash being loaded into ATMs on a daily basis, it’s no wonder that these devices are targeted by cybercriminals. And while some crooks take a blunt approach to getting into an ATM, using physical force, others prefer targeting the software running on the machine to make it spill out the cash, Kaspersky’s Olga Kochetova and Alexey Osipov explained at the DefCamp 2017 security conference in Bucharest last week.
There's no denying that ATMs run vulnerable software, they say. Many of the machines run the outdated, already retired Windows XP, meaning they are vulnerable by default, while others might have some unnecessary but flawed applications running on them, such as TeamViewer or an older, flawed variant of Adobe Acrobat Reader.
What’s more, banks often do not keep their ATMs updated, which also makes them vulnerable to malware and other types of attacks, the researchers say. The security inside the ATM is usually poor and the parts of the chain protecting the cash aren’t secured separately, meaning that the entire chain ca be compromised when a single part is exploited.
Accessing the software running on an ATM provides malicious actors with control over the cash cassettes inside the machine, thus allowing them to extract the cash. However, access to a single machine could also provide the actor with the ability to compromise the bank’s entire network of ATMs, Kaspersky’s researchers say.
There are multiple ways in which an attacker could achieve this, Kochetova and Osipov told SecurityWeek during a private talk at the DefCamp conference: by physically accessing an ATM to install a device in it, by compromising the computers that oversee the bank’s ATMs, and even by a supply-chain attack that focuses on the firmware that vendors or maintenance teams install on the machines.
“With access to an ATM, an actor could install a device in one ATM to send commands to all machines in the network. These commands would look like they come from the central command center. The actor can then use blank cards, or any cards, and withdraw cash from any ATM in the network,” the researchers explained.
This is possible because all of a bank’s ATMs are typically connected to a flat network, which means that every machine in the network could see all other connected machines. Thus, if the attacker’s device is implanted in an ATM directly connected to the network cable, it could allow an attacker to remotely control the machines. It is a classic example of man-in-the-middle attack (MitM), the researchers say.
They also pointed out that all evidence would disappear once the malicious device has been extracted from the ATM. Although a possibility, no such botnet has been observed to date. What has been seen, however, was a bank’s network being infected with an information stealer.
“This can be seen as a kind of an ATM botnet, since all machines were infected and the actor was remotely collecting data from them,” Kochetova said. “It is also possible that some crooks somewhere in the world are preparing an attack with money-withdrawal malware instead of sniffers,” she continued.
Attackers could also get the VPN drive out of the ATM and connect to the bank’s network through it without anyone noticing, Osipov explains. Such VPN devices are designed to work regardless of the host machine, so the attacker could use it with their own computer.
One other effective method of infiltrating ATM networks is to discover the machines that are online using specialized search engines such as Shodan, the researchers say. Although banks usually claim that no ATM is online, these devices can be easily found if the right keywords or phrases are used to perform the search, Kochetova and Osipov explained.
While the attack vector has been used before (specialized search engines can be used to discover vulnerable Internet of Things (IoT) devices, unsecured databases, and other types of Internet-facing devices), it is relatively new when it comes to finding ATMs.
Once they have discovered the online ATMs, the malicious actor can start checking for open ports and then attempt to compromise machines using known exploits. Thus, attackers could install information-stealing malware on the ATMs or ensnare them into botnets.
Infecting workstations inside the bank and then expanding the footprint to the entire network, including ATMs, is another compromise technique that attackers (such as the Cobalt hacking group) are using.
Recent attacks such as CCleaner and NotPetya have demonstrated the impact supply-chain attacks could have on a global scale, and Kaspersky’s researchers say that ATMs aren’t safe from this type of assaults either. To be successful, the attacker would target the “golden image” used to install the operating system and all running software on an ATM.
“We already observed incidents where ordinary malware ended up on an ATM through an infected USB drive that a technician connected to the machine. Thus, if an infected ‘golden image’ is used, the technician would never even notice the compromise. Of course, the attacker would have to know what specific software to install on that ‘golden image’ to compromise the ATMs without being noticed,” Osipov said.
“The same would happen if a service provider is used as a vector of attack. No one would notice the compromise,” he also said.
An ATM botnet could also be used to mine crypto-currency. Crypto miners have become highly popular over the past few years and an increasing number of malicious attacks focused on deploying such software was observed this year. Because they have computing power, ATMs can be used for mining too.
“In the end, every ATM is yet another type of computer. This means it can be hacked if the right vulnerabilities are discovered,” Kochetova pointed out. “It is the same as with CCTV cameras that are infected to create IoT botnets,” she concluded.
Researchers Downplay Size of Reaper IoT Botnet
30.10.2017 securityweek BotNet
The Mirai-like "Reaper" botnet that began infecting Internet of Things (IoT) devices in late September has only ensnared up to 20,000 bots so far, according to estimates from Arbor Networks.
Called Reaper, the botnet was said a couple of weeks ago to have infected over one million organizations worldwide, but Arbor claims that the actual size of the botnet fluctuates between 10,000 and 20,000 bots in total.
The botnet’s size, the researcher reveal, could change at any time. An additional 2 million hosts have been already identified by the botnet scanner as potential nodes, although they haven’t been ensnared into Reaper yet.
“At this time, it is not clear why these candidate bots have not been co-opted into the botnet. Possible explanations include: misidentification due to flaws in the scanning code, scalability/performance issues in the Reaper code injection infrastructure, or a deliberate decision by the Reaper botmasters to throttle back the propagation mechanism,” Arbor’s ASERT researchers note.
The botnet was likely created to launch distributed denial of service (DDoS) attacks and its operators are expected to offer it as a service for the intra-China DDoS-for-hire market. It can launch SYN-floods, ACK-floods, http floods, and DNS reflection/amplification attacks.
Reaper shows code similarities with Mirai, but isn’t considered a clone. While Mirai uses password cracking for infection, the new botnet exploits vulnerabilities in targeted IoT devices, Chinese security company Qihoo says.
The firm has discovered 9 vulnerability exploits integrated into the current samples, targeting devices from 7 different manufacturers, namely Dlink, Goahead, JAWS, Netgear, Vacron NVR, Linksys, and AVTECH. The exploits list is actively updated, with one targeting Vacron NVR that was added within two days after its public disclosure on October 8.
“The botnet has embedded more than 100 DNS open resolvers in its LUA sample, so DNS amplification attack can be easily carried out. About one-third of these open DNS servers have been used as reflector in real DNS amplification attacks. We have yet to see this type of config in any other Mirai variants,” Qihoo notes.
The Chinese company also discovered that the botnet is using four different IPs for command and control (C&C), each serving a different purpose: downloader, controller, reporter, and loader. At the time of analysis, the researchers hadn’t seen a DDoS attack command issued, despite the necessary code to support such commands being present in the source file.
“The only instructions we saw are to download samples. This means the attacker is still focusing on spreading the botnets,” the researchers concluded.
Exclusive – CSE ZLab experts spotted a new Wonder botnet in the wild
23.10.2017 securityaffairs BotNet
The CSE CybSec Z-Lab Malware Lab spotted a new botnet, dubbed Wonder botnet, while it was investigating malicious code in the dark web.
While investigating the malicious code in the dark web, ZLab experts discovered a “NetflixAccountGenerator.exe” that promises to generate a premium account for Netflix services for free. Unfortunately, the software downloaded does not work as expected because it installs a BOT rather than create a desiderated account!
The malware researchers analyzed this “exe” file and discovered that the malware is not indexed yet: only one site on the Clearnet identified it as a threat after it was uploaded for the first time around September 20th, probably by the author in order to test its ability to remain stealth.
The analysis of the malware revealed it is a bot that belongs to an alive botnet dubbed by the experts Wonder botnet. The Command and Control is hidden behind a site that is the mirror of another one:

Figure 1 – On the left the fake site; on the right the original site
Experts verified that the fake page “support.com” at the link “wiknet.wikaba.com” on the left side, point to the front-end of the botnet’s C2C. The interesting thing is that every link on it refers to the original page, clicking on one links the researchers were redirected to the corresponding page on “support.com”.
The experts also discovered some hidden paths that contain the information and the commands used by the bots.
The malware is composed of two parts:
A Downloader: it is a .NET executable with the only purpose of downloading and executing the real bot code, uploaded on “pastebin.com/raw/E8ye2hvM”.
The real Bot: when it is downloaded and executed, it infects the host setting its persistence mechanisms and starts its malicious behavior schematized in the following figure:
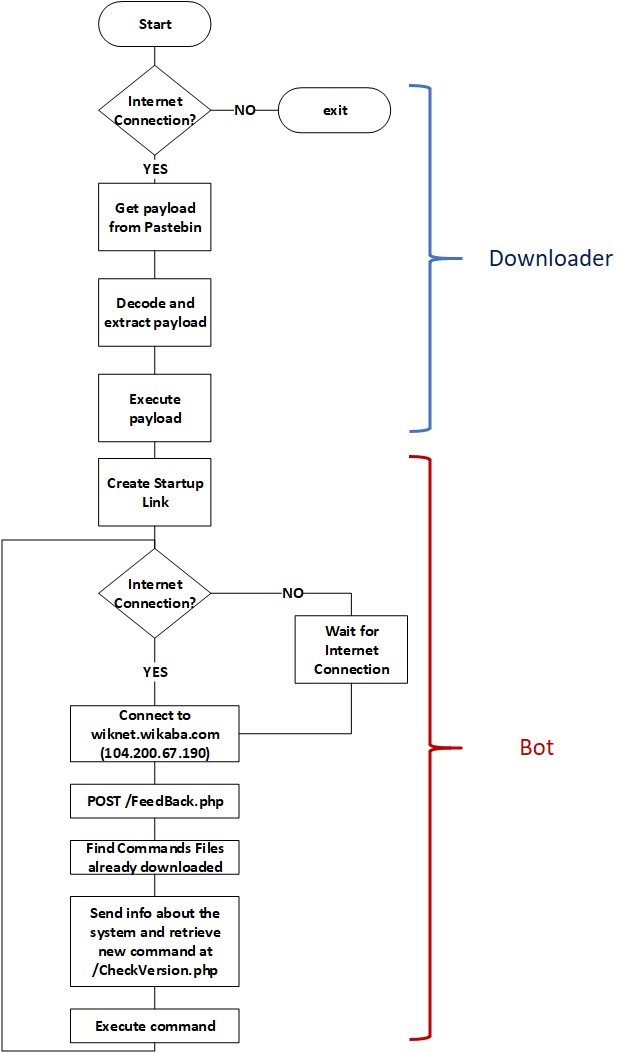
Figure 2 – Wonder Botnet’s behavior scheme
Further technical details, including IoCs and Yara rules are included in the report published by CSE Cybsec ZLab. PDF
Necurs botnet now spreading the Locky Ransomware via DDE Attacks
21.1.2017 securityaffairs BotNet
Operators behind Locky ransomware campaigns have switched to new attack techniques to evade detection leveraging the DDE protocol.
Security experts are continuing to observe the Locky ransomware spreading via spam campaigns that rely on the Necurs botnet. Now operators behind Locky ransomware campaigns have switched to new attack techniques to evade detection.
One of the new techniques adopted by the crooks is the use of the Dynamic Data Exchange (DDE) protocol designed to allow data transferring between applications.
“The DDE protocol is a set of messages and guidelines. It sends messages between applications that share data and uses shared memory to exchange data between applications. Applications can use the DDE protocol for one-time data transfers and for continuous exchanges in which applications send updates to one another as new data becomes available.” states Microsoft.

According to experts at the security firm Sensepost, attackers have devised a method to achieve the execution of malicious code embedded in Office documents without user’s interaction by using DDE.
The DDE protocol allows an Office application to load data from another Office application, it was replaced by Microsoft with Object Linking and Embedding (OLE), but it is still supported.
The technique was implemented by several threat actors such as the FIN7 APT group in DNSMessenger malware attacks, and the operators behind the Hancitor malware campaign spotted earlier this week and detailed by Internet Storm Center (ISC) handler Brad Duncan.
According to Duncan, the recent Locky campaign used spam messages with Office documents posing as invoices. The threat actors delivered the spam messages through the Necurs botnet.
The Necurs Botnet malspam pushes Locky using DDE technique, in a first-stage of the attack the malware achieved persistence on the compromised system, in the second stage the Locky ransomware infects the system.
“I opened one of the Word documents in my lab environment and found a 1st stage malware (presumably a downloader) and a 2nd stage malware (Locky) during the infection. Today’s diary reviews the traffic and malware.” wrote Duncan.
According to the experts at Trend Micro, The Locky ransomware was also spread by the Necurs botnet through HTML attachments posing as invoices, Word documents embedded with malicious macro code or Visual Basic scripts (VBS), malicious URLs in spam emails, and VBS, JS, and JSE files archived via RAR, ZIP or 7ZIP.
The use of DDE for infection, however, is only one of the methods Locky employs. As Trend Micro points out, Necurs also distributed the ransomware through HTML attachments posing as invoices, Word documents embedded with malicious macro code or Visual Basic scripts (VBS), malicious URLs in spam emails, and VBS, JS, and JSE files archived via RAR, ZIP or 7ZIP.
Some of the recent lures observed by the experts at Trend Micro are:
Fake voice message notifications (vishing, or the use of voice-related systems in phishingattacks)
HTML attachments posing as invoices
Archive files masquerading as business missives from multinationals, e.g., audit and budget reports
Fraudulent emails that involve monetary transactions such as bills, parcel/delivery confirmations, and payment receipts
A new Mirai-Like IoT Botnet is growing in a new mysterious campaign
21.1.2017 securityaffairs BotNet
Malware researchers at Check Point have uncovered a new massive IoT botnet that presented many similarities with the dreaded Mirai.
The new thing bot emerged at the end of September and appears much more sophisticated, according to the experts the malware already infected more than one million organizations worldwide.
The malicious code tries to exploit many known-vulnerabilities in various IP camera models, including GoAhead, D-Link, TP-Link, AVTECH, NETGEAR, MikroTik, Linksys, and Synology.
The experts speculate that the malware once compromised a device use it to spread itself.
“With each passing day the malware was evolving to exploit an increasing number of vulnerabilities in Wireless IP Camera devices such as GoAhead, D-Link, TP-Link, AVTECH, NETGEAR, MikroTik, Linksys, Synology and others. It soon became apparent that the attempted attacks were coming from many different sources and a variety of IoT devices, meaning the attack was being spread by the IoT devices themselves.” reads the report published by Check Point.

“So far we estimate over a million organizations have already been affected worldwide, including the US, Australia and everywhere in between, and the number is only increasing,” continues Check Point.
While investigating the compromise of a GoAhead device the experts noticed that the attackers accessed the System.ini file. This file would contain the credentials of the user, but on the compromised IoT device it contained a ‘Netcat’ command to open a reverse shell to the attacker’s IP.
The attackers triggered the CVE-2017-8225 to hack into the IoT device. The experts verified that the botnet relies on compromise bots to sending out the infection.
“These attacks were coming from many different types of devices and many different countries, totaling approximately 60% of the corporate networks which are part of the ThreatCloud global network,” Check Point notes.

The security researchers provided a list of IoT devices targeted by the malware, even if the attackers’ motivation is unclear experts speculate the botnet could be used to power DDoS attacks.
New Mirai-Linked IoT Botnet Emerges
20.10.2017 securityweek BotNet
A new, massive botnet is currently recruiting improperly secured Internet of Things (IoT) devices such as IP wireless cameras, Check Point warns.
Some of the technical aspects of the botnet, the security researchers say, reveal a possible connection to Mirai, which stormed the world a year ago. However, this is an entirely new threat and the campaign that is rapidly spreading worldwide is much more sophisticated.
The new threat first emerged at the end of September, but Check Point says that over one million organizations globally might have been already hit. What is yet unclear is the purpose of this massive network of ensnared devices.
To compromise devices, the malware attempts to exploit a large number of vulnerabilities commonly found in various IP camera models. Targeted vendors include GoAhead, D-Link, TP-Link, AVTECH, NETGEAR, MikroTik, Linksys, Synology and others.
Because the attempted attacks were coming from different sources and a variety of IoT devices, the researchers concluded that the compromised devices themselves were spreading the malware.
“So far we estimate over a million organizations have already been affected worldwide, including the US, Australia and everywhere in between, and the number is only increasing,” Check Point says.
The analysis of an infected device revealed that the attackers accessed the System.ini file to check for compromise. Normally, that file would contain the credentials of the user, but on the hacked device it contained a ‘Netcat’ command to open a reverse shell to the attacker’s IP instead.
Thus, the researchers concluded that the machine, a GoAhead device that was compromised using the CVE-2017-8225 vulnerability, was transmitting the infection after being infected itself.
“Upon further research, it was found that numerous devices were both being targeted and later sending out the infection. These attacks were coming from many different types of devices and many different countries, totaling approximately 60% of the corporate networks which are part of the ThreatCloud global network,” Check Point notes.
The security researchers provided a list of device types – per vendor – that are supposedly targeted by the botnet. They also suggest that the actor behind this threat might be getting ready for massive, global attacks, possibly distributed denial of service (DDoS).
With over 20 billion devices expected to be connected to the Internet by 2020, the threat of insecure IoT devices is growing bigger every day. Europol too warns of the security challenges this continuously expanding market faces.
“The Internet of Things is a wide and diverse ecosystem where interconnected devices and services collect, exchange and process data in order to adapt dynamically to a context. In simpler words, it makes our cameras, televisions, washing machines and heating systems ‘smart’ and creates new opportunities for the way we work, interact and communicate, and how devices react and adapt to us,” Europol says.
The agency also underlines the importance of properly securing these devices and of implementing adequate protections to keep IoT devices safe from cyber threats. Europol notes that the fast adoption of IoT also raised new legal, policy, and regulatory challenges that require cooperation across different sectors to tackle.
“Internet of Things is not only here to stay but expected to significantly expand as more and more households, cities and industries become connected. Insecure IoT devices are increasingly becoming tools for conducting cyber criminality. We need to act now and work together to solve the security challenges that come with the IoT and to ensure the full potential,” Rob Wainwright, Executive Director of Europol, commented.
Sockbot Ensnares Android Devices into Botnet
19.10.2017 securityweek BotNet
A newly discovered Android malware has the ability to add the compromised devices to a botnet that could potentially launch distributed denial-of-service (DDoS) attacks, Symantec warns.
Dubbed Sockbot, the highly prevalent threat was found masquerading as legitimate apps in Google Play. Symantec has discovered eight such applications and says that they have been downloaded between 600,000 and 2.6 million times.
The malware is mainly targeting users in the United States, but some of the infected devices are located in Russia, Ukraine, Brazil, and Germany, the security researchers say.
The applications hiding the malware were designed to modify the look of the characters in Minecraft: Pocket Edition (PE). In the background, however, they enable sophisticated and well-disguised attacking functionality.
The malicious app connects to a command and control (C&C) server on port 9001. The server requests the app to open a socket using SOCKS and wait for a connection, which arrives along with a command to connect to a target server.
After connecting to the target server, the application receives a list of ads and associated metadata. Through the SOCKS proxy mechanism, the app is also pointed to an ad server and commanded to launch ad requests. However, the security researchers discovered that the decoy app doesn’t include functionality to display ads.
“This highly flexible proxy topology could easily be extended to take advantage of a number of network-based vulnerabilities, and could potentially span security boundaries. In addition to enabling arbitrary network attacks, the large footprint of this infection could also be leveraged to mount a distributed denial of service (DDoS) attack,” Symantec reveals.
The infection campaign was tracked to a single developer account named FunBaster and each app was signed with a different developer key, likely in an attempt to avoid static analysis-based heuristics. The malicious code is also obfuscated and features encrypted key strings, thus thwarting base-level forms of detection.
Symantec informed Google on the presence of these malicious apps in the application store and the Internet giant has already removed them.
In August this year, security companies worked together to take down a large Android botnet. Called WireX, it was designed to launch DDoS attacks, and one variant was capable of launching high-volume UDP flood attacks, the researchers discovered.
The Necurs botnet is back spreading a downloader with new interesting features
19.10.2017 securityaffairs BotNet
The Necurs botnet is spreading a new downloader that takes screenshots of the victims’ desktops and Runtime Errors back to the operators.
The Necurs botnet is back once again, the dreaded botnet was spreading a downloader that takes screenshots of the victims’ desktops and Runtime Errors back to the attackers.
“Recently we have seen a resurgence of emails sent by the Necurs botnet. The latest blast of emails is spreading a new variant of the Locky ransomware (Ransom.Locky) or Trickybot (Trojan.Trickybot).” reads the analysis published by Symantec. “What’s interesting about this new wave is that the downloader now contains new functionality to gather telemetry from victims. It can take screen grabs and send them back to a remote server. There’s also an error-reporting capability that will send back details of any errors that the downloader encounters when it tries to carry out its activities.”
The Necurs malware spread via spam campaigns or through compromised web servers, last time we read about it in January when it was being used by crooks to deliver the Locky ransomware.
Now the Necurs Botnet, one of the world’s largest malicious architecture, is spreading a downloader with two interesting new features.
The first feature consists in the addition of a Powershell script that takes a screengrab of the infected user’s screen, that is uploaded to a remote server after waiting a few seconds.
The second addition is a built-in error reporting feature that monitors the Necurs downloader for errors and sends collected info back to Necurs botmaster.
This is the first time that a downloader implements such kind of feature. experts believe Necurs operators gather intelligence about their campaigns.
“When you consider the screen grab functionality together with the new error-reporting capability, it suggests that the Necurs attackers are actively trying to gather operational intelligence (OPINTEL) about the performance of their campaigns. ” continues Symantec.
Collected data could allow the attackers to measure the efficiency of their campaign and detect when the malicious code has infected valuable environments, such as corporate networks.
The error reporting feature allows coders to fix bugs in their software improving their success rates.
The following graph reports the spam waves observed in the last months, after a period of silence from end of 2016 and into early 2017 it appeared again in March.
The evidence collected by the researchers suggest an intensification of the activities related to the Necurs botnet.
“Necurs went through a long spell of silence from end of 2016 and into early 2017. It burst back onto the scene around March and since then, it has been cranking up its activity levels, with recent months seeing the most action so far in 2017″ concludes Symantec.
“With our data showing a resurgence in activity, and the apparent efforts to collect operational intelligence, we can expect to see continued evolution of the capabilities and a steady increase in Necurs activity levels in the coming months.”

These Cities House the Largest Bot Populations in the U.S.
15.10.2017 securityweek BotNet
Botnets are widespread worldwide, serving whichever purpose they were designed to, and the United States is one of the largest sources of botnet attacks. Across the country, Chicago and Washington D.C. are home to the largest number of bots (infected hosts), Symantec has discovered.
According to the security company, Chicago currently hosts 4.69% of the bots in the U. S., while Washington, D.C. hosts 4.13% of them. Atlanta is placed third, with 3.49% of the bots, followed by Ashburn (3.23%) and New York (3.22%). Portland (3.18%), Los Angeles (2.02%), Las Vegas (1.98%), San Jose (1.96%), and Tampa (1.57%) round up top 10.
These bots represent Internet-connected devices of any kind (including laptops, phones, connected devices, baby monitors, servers, etc.), which can be remotely controlled by attackers after being infected with malware. Based on the malware infecting them and on their operators, these devices work together in networks called botnets.
The bots are usually remotely controlled without the knowledge of their owners. Botnet sizes range from hundreds or thousands of infected devices to hundreds of thousands or even millions of bots. They can be used to spread malware, send spam emails, perform distributed denial of service (DDoS) attacks, or perform other types of online crime.
In 2016, botnets such as Mirai or Bashlite brought to the spotlight the danger poorly secured Internet of Things (IoT) devices pose when they become part of botnets. Mirai alone infected around half a million IoT devices and abused them to launch some of the largest DDoS attacks in history.
Last year alone, the number of bots that was added to the global botnet was of 6.7 million, Symantec says.
“More than 689 million people were victims of online crime in the past year, and bots and botnets are a key tool in the cyber attacker’s arsenal. It’s not just computers that are providing criminals with their robot army; in 2016, we saw cyber criminals making increasing use of smartphones and Internet of Things (IoT) devices to strengthen their botnet ranks. Servers also offer a much larger bandwidth capacity for a DDoS attack than traditional consumer PCs,” Candid Wueest, Norton Security expert, says.
According to Kevin Haley, security expert at Symantec, the size of bot population is usually growing in cities where a large number of Internet-connected devices exists, or where the number of high-speed, Internet-connected devices is increasing.
However, although the size and location of a botnet might be connected, they are not indicative of where the operator lives, Symantec points out. Botnets are global in nature and infected devices from any country could be used to hit targets in any other country, while being controlled by an actor living in a completely different area.
When it comes to botnets, infection vectors differ from a device to another. Malicious links, malicious attachments in emails or social media messages, and compromised websites can all be used to infect devices. Some attackers might use automated tools to find and directly target vulnerable devices, as it happened with Mirai.
Akamai shared a detailed analysis of a Fast Flux Botnet composed of 14K IPs
14.10.2017 securityaffairs BotNet
Experts at Akamai have identified a running Fast Flux botnet composed of over 14,000 compromised systems used to spread malware.
Experts at Akamai have identified a running botnet of over 14,000 compromised systems used to spread malware. The botmasters implemented a technique dubbed Fast Flux to make the infrastructure hard to take down.
Treat actors implementing the Fast Flux technique hosts a domain using multiple IP addresses by switching the domain from one IP to another. The IP addresses are swapped in and out with extremely high frequency, through changing DNS records.
The Fast Flux technique was first implemented in 2016 by the Storm Worm malware variants.
“Fast Flux, a DNS technique first introduced in 2006 and widely associated with the Storm Worm malware variants, can be used by botnets to hide various types of malicious activities – including phishing, web proxying, malware delivery, and malware communication.” reported Akamai. “The technique allows the botnet to “hide” behind an ever-changing network of compromised hosts, ultimately acting as proxies and making detection incredibly difficult.”
Experts were able to track a botnet composed of more than 14,000 IP addresses, most of them originating from eastern Europe.
The Fast Flux Network works as an illegal websites hosting provider for illegal websites
offering merchandise such as:
Stolen credentials for popular e-commerce websites
Hacked credit card numbers with CVV
Professionals hackers carders forum
The botnet was working for both hosting phishing websites and malware C&C servers, it was also utilized for carrying out automated attacks such as web scraping, SQL injections, and credentials abuse.
“The primary characteristic of the Fast Flux network is that the network constantly changes its domains, IP addresses, and nameservers. These changes obfuscate the true nature of the network and make it more difficult for researchers to understand and defend against.” continues the analysis.
Researchers observed the Fast Flux network is being segregated to different sub-networks based on the offered malicious service

Researchers believe devices were infected with malware that installs a proxy component on the infcted hosts. Every time someone wants to connect to a malicious site exposed by the botnet, DNS servers would provide the IP of an infected host that was at that time “hosting” the domain. The proxy component of the infected host then redirects incoming traffic to the malicious site, hosted elsewhere.
The analysis of the Botnet revealed it was organized in two separate sub-networks:
the hosting sub-network used for hosting and redirecting traffic to malicious sites.
the C&C sub-network composed of the command-and-control infrastructure of the botnet, that is different from the C&C servers.
Experts noticed that most of the hosting sub-network were located in Ukraine, Romania, and Russia. The composition of the botnet’s C&C sub-network was very different.
The botnet’s C&C sub-network IPs contained private IP addresses, such as 10.x.x.x, 192.168.x.x, belonging to Fortune 100 companies, as well as military organizations.

The analysis of the exposed ports for all IPs shows that most of the hosting network had ports 80 and 443 exposed, while most of the C&C sub-network had port 7547 exposed.
“When analyzing the C&C sub-network, we see that port 7547 is the most used port. This port is used mostly by routers that have a TR-069 management tool and the usage shows how same type of vulnerable devices are being used to the same goal. Such routers are known to be highly exploited and are probably used as infrastructure that acts as a proxy layer for the communication of the malware with its C&C server.” continues the analysis.
The port 7547 is specific to the TR-069 protocol implemented by remote management tools of routers and modems, these devices are suspected to represent a good portion of the botnet.
According to Akamai, Fast Flux botnets can be compared to a living organism that evolves over the time to preserve itself, experts will continue to monitor its evolution.
Crooks using Linux.ProxyM IoT botnet to send spam messages
23.9.2017 securityaffairs BotNet
Experts at security firm Doctor Web discovered a new botnet of IoT devices leveraging the Linux.ProxyM, that is used by crooks for mass spam mailings.
The most popular thingbot since now is the Mirai, but it isn’t the only one targeting Linux-based internet-of-things (IoT) devices.
Researchers with security firm Doctor Web discovered a new botnet of IoT devices leveraging the Linux.ProxyM, that is used by crooks for mass spam mailings.
Experts first analyzed the Linux.ProxyM in July, it was used to create a proxy network through SOCKS proxy server on infected devices that are used to relay malicious traffic, disguising his real source.
The Trojan has been noted since February 2017 but peaked in late May as reported in the chart below.
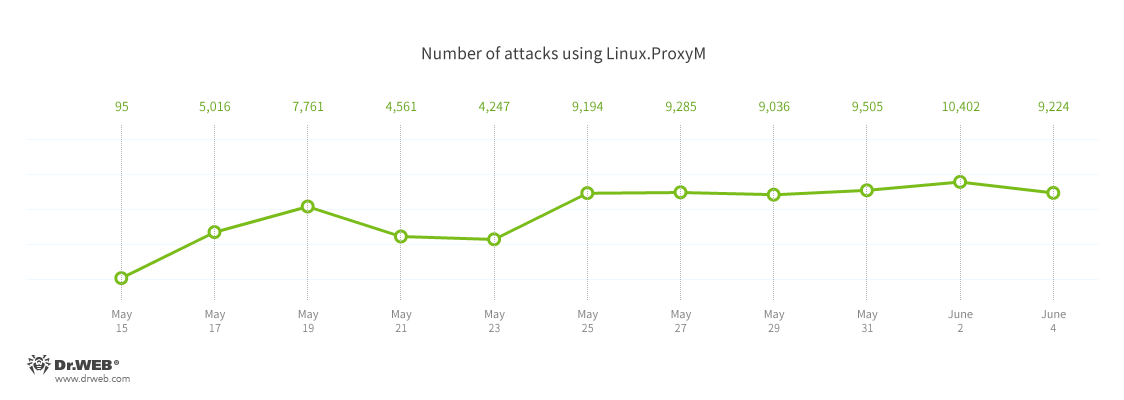
According to Dr. Web, the number of devices infected with Linux.ProxyM reached 10,000 units in July since its discovery in February 2017.
Recently the Linux.ProxyM trojan has recently been updated to add mas spam sending capabilities to earn money.
“The number of malicious programs capable of infecting “smart” Linux devices is constantly increasing. A major portion of them is designed to mount DDoS attacks and ensure online anonymity. Research conducted by Doctor Web’s specialists has revealed that cybercriminals are using such Linux Trojans for mass mailings.” reads the analysis from Dr. Web.
The malware is capable of detecting honeypots in order to hide from malware researchers and can operate on almost any Linux device, including routers, set-top boxes, and other equipment.
Experts identified two builds of this Linux.ProxyM Trojan for devices based on x86, MIPS, MIPSEL, PowerPC, ARM, Superh, Motorola 68000, and SPARC architectures.
Once the Linux.ProxyM infects a device, it connects to a command and control (C&C) server and downloads the addresses of two Internet nodes, once providing a list of logins and passwords, the second
The C&C server also sends a command containing an SMTP server address, the credentials used to access it, a list of email addresses, and a message template, which contains advertising for various adult-content sites.
Below the content of the typical spam message spread by the infected devices:
Subject: Kendra asked if you like hipster girls
A new girl is waiting to meet you.
And she is a hottie!
Go here to see if you want to date this hottie
(Copy and paste the link to your browser)
http://whi*******today.com/
Check out sexy dating profiles
There are a LOT of hotties waiting to meet you if we are being honest!
The thingbot is very effective, on an average, each infected device can send out 400 of such emails per day.
“A C&C server sends a command to an infected device. The command contains an SMTP server address, the login and password used to access it, a list of email addresses, and a message template of itself. These emails contain advertising for various adult-content websites.” continues the analysis.
Doctor Web has no information about the total number of infected devices, the experts noted several Linux.ProxyM attacks launched during the past 30 days, most of the infected devices are located in Brazil and the US, followed by Russia, India, Mexico, Italy, Turkey, Poland, France and Argentina.

“We can presume that the range of functions implemented by Linux Trojans will be expanded in the future,” concluded Dr Web.
“The Internet of things has long been a focal point for cybercriminals. The wide distribution of malicious Linux programs capable of infecting devices possessing various hardware architectures serves as proof of that.”
WireX DDoS Botnet: An Army of Thousands of Hacked Android SmartPhones
29.8.2017 thehackernews BotNet

Do you believe that just because you have downloaded an app from the official app store, you're safe from malware?
Think twice before believing it.
A team of security researchers from several security firms have uncovered a new, widespread botnet that consists of tens of thousands of hacked Android smartphones.
Dubbed WireX, detected as "Android Clicker," the botnet network primarily includes infected Android devices running one of the hundreds of malicious apps installed from Google Play Store and is designed to conduct massive application layer DDoS attacks.
Researchers from different Internet technology and security companies—which includes Akamai, CloudFlare, Flashpoint, Google, Oracle Dyn, RiskIQ, Team Cymru—spotted a series of cyber attacks earlier this month, and they collaborated to combat it.
Although Android malware campaigns are quite common these days and this newly discovered campaign is also not that much sophisticated, I am quite impressed with the way multiple security firms—where half of them are competitors—came together and shared information to take down a botnet.
WireX botnet was used to launch minor DDoS attacks earlier this month, but after mid-August, the attacks began to escalate.
The "WireX" botnet had already infected over 120,000 Android smartphones at its peak earlier this month, and on 17th August, researchers noticed a massive DDoS attack (primarily HTTP GET requests) originated from more than 70,000 infected mobile devices from over 100 countries.
If your website has been DDoSed, look for the following pattern of User-Agent strings to check if it was WireX botnet:
botnet-user-agent
After further investigation, security researchers identified more than 300 malicious apps on Google’s official Play Store, many of which purported to be media, video players, ringtones, or tools for storage managers and app stores, which include the malicious WireX code.
Just like many malicious apps, WireX apps do not act maliciously immediately after the installation in order to evade detection and make their ways to Google Play Store.
Instead, WireX apps wait patiently for commands from its command and control servers located at multiple subdomains of "axclick.store."
Google has identified and already blocked most of 300 WireX apps, which were mostly downloaded by users in Russia, China, and other Asian countries, although the WireX botnet is still active on a small scale.

If your device is running a newer version of the Android operating system that includes Google's Play Protect feature, the company will automatically remove WireX apps from your device, if you have one installed.
Play Protect is Google's newly launched security feature that uses machine learning and app usage analysis to remove (uninstall) malicious apps from users Android smartphones to prevent further harm.
Also, it is highly recommended to install apps from reputed and verified developers, even when downloading from Google official Play Store and avoid installing unnecessary apps.
Additionally, you are strongly advised to always keep a good antivirus app on your mobile device that can detect and block malicious apps before they can infect your device, and always keep your device and apps up-to-date.
Android malware continues to evolve with more sophisticated and never-seen-before attack vectors and capabilities with every passing day.
Just at the beginning of this week, Google removed over 500 Android apps utilising the rogue SDK—that secretly distribute spyware to users—from its Play Store marketplace.
Last month, we also saw first Android malware with code injecting capabilities making rounds on Google Play Store.
A few days after that, researchers discovered another malicious Android SDK ads library, dubbed "Xavier," found installed on more than 800 different apps that had been downloaded millions of times from Google Play Store.
TrickBot Using Legitimate Looking Sites With SSL Certificates
16.8.2017 securityweek BotNet
The TrickBot banking Trojan has been using legitimate SSL certificates alongside websites that closely resemble those of actual banks in recently observed attacks, security researchers warn.
Around for only one year, TrickBot has seen numerous updates and added various new capabilities. The malware recently gained worm-like capabilities and began targeting more than just users’ online banking information: it is now also going for Outlook and browser data.
Despite being fake, the sites could easily trick potential victims into believing they are real, especially given the use of servers with full email authentication and HTTPS, Brad Duncan, Palo Alto Networks analyst and handler at the SANS Internet Storm Center, reveals. The Trojan is distributed through malicious emails that use various lures to convince recipients into opening the attached documents.
As part of these attacks, miscreants sent emails from websites closely mimicking those of banks: hsbcdocs.co.uk, hmrccommunication.co.uk, lloydsbacs.co.uk, nationwidesecure.co.uk, natwestdocuments6.ml, santanderdocs.co.uk, santandersecuremessage.com, and securenatwest.co.uk. Almost all of the sites were registered through GoDaddy using various names or privacy services.
The spam emails used HTML attachments designed to download Office documents over HTTPS, in an attempt to evade detection through encrypted network traffic. Once the victim opens the Office document, they are asked to enable macros, which in turn download and execute the TrickBot banking Trojan.
As part of one campaign documented by My Online Security, the malicious emails were pretending to come from Santander Bank, distributed from the convincing look-a-like domain santanderdocs.co.uk. Many of these messages are apparently targeted at small and medium size businesses.
As part of a spam run observed by Cyren, the attackers were impersonating the Lloyds Bank, also using a seemingly correct URL (lloydsbacs.co.uk instead of lloydsbank.co.uk) and a legitimate SSL certificate. Because of the close resemblance with the legitimate URL, the targeted users are unlikely to spot the phishing attempt, especially given the use of an SSL certificate.
The security researchers observed a large number of such emails being sent over a very short period of time: they blocked 75,000 of such messages over a 25-minute period. Most of the messages appeared to be sent from a Dutch IP (5.149.255.107), already a known source of spam and which appears to host many malicious domains, including the one used in this run.
“TrickBot takes the phishing of banking credentials to another level by showing the correct URL of the online bank and confirmation of a legitimate SSL certificate, so even more alert users who pay any attention to these sorts of details will not see anything unusual,” Cyren notes.
The malicious emails have an Excel document attached. Called IncomingBACs.xlsm, the document asks the user to enable included macros, which results in TrickBot being downloaded and installed on the victim’s machine. The version used in these attacks comes with an encoded configuration module in the resource section of its binary and includes support for additional modules that are downloaded from controller domains.
Russian Hacker Sentenced to Prison for Ebury Botnet Attacks
4.8.2017 securityweek BotNet
A 41-year-old Russian citizen has been sentenced to 46 months in prison by a court in the U.S. state of Minnesota for his role in a cybercrime scheme involving a botnet powered by the Linux malware known as Ebury.
Maxim Senakh was indicted in the U.S. in January 2015 and was later arrested by authorities in Finland. His extradition to the United States was approved in January 2016 and, earlier this year, he pleaded guilty to conspiracy to violate the Computer Fraud and Abuse Act (CFAA) and conspiracy to commit wire fraud.
After serving his 46-month prison sentence in the United States, Senakh will be deported to Russia.
According to U.S. authorities, Senakh and his accomplices used the Ebury malware, an OpenSSH backdoor and credential stealer, to create a botnet that helped them make millions of dollars through click-fraud and email spam campaigns.
The Russian national, who admitted profiting from the traffic generated by the botnet, was responsible for registering domains used for the command and control (C&C) infrastructure.
Ebury was first spotted in 2011. Security firm ESET, Germany’s CERT‑Bund, the Swedish National Infrastructure for Computing, and the European Organization for Nuclear Research (CERN) published a detailed analysis of the malware in February 2014.
The U.S. Department of Justice said the botnet operated by Senakh and his co-conspirators ensnared tens of thousands of servers across the world, including thousands in the U.S.
“The defendant and his co-conspirators sought to turn a network of thousands of infected computers in the United States and around the world into their personal cash machines,” said Acting Assistant Attorney General Kenneth A. Blanco of the DOJ’s Criminal Division. “But cybercriminals like Mr. Senakh should take heed: they are not immune from U.S. prosecution just because they operate from afar or behind a veil of technology. We have the ability and the determination to identify them, find them, and bring them to justice.”
Several Russian hackers have been sentenced to prison this year in the United States, including Mark Vartanyan, Alexander Tverdokhlebov and Roman Valeryevich
TrickBot Targets Outlook, Browser Data
2.8.2017 securityweek BotNet
Soon after being found to have worm-like spreading capabilities, the TrickBot banking Trojan has expanded its attack surface to target Outlook and Web browsing data.
While TrickBot has been an active threat for less than a year, its developers, supposedly the Dyre group, have been actively adding new capabilities to it. Earlier this year, they expanded the target list to hit private banking and payment processors, in addition to CRM providers.
Independent researcher and programmer Hasherezade now reveals that the malware authors have added new modules to their creation and might have also added new developers to its team. A newly observed Outlook.dll module, for example, is written in Delphi, unlike most of the components, which are written in C++.
The security researcher says that the current run comes with 5 modules: SystemInfo.dll and loader.dll (injectDll32), which have been observed in TrickBot since the very beginning, mailsearcher.dll, added in December 2016, and two modules that haven’t been observed before, namely module.dll and Outlook.dll.
According to Hasherezade, module.dll/importDll32 is written in C++ and compiled with Qt5 and OpenSSL. It also incorporates SQLite. The compilation timestamp suggests it was written in May 2017.
The module was designed to steal data from the browsers, including Cookies, HTML5 Local Storage, Browsing History, Flash LSO (Local Shared Objects), and URL hits, among other info. The module is bulky and doesn’t hide its intentions.
“In contrary to loader.dll/injectDll, which is modular and stores all the scripts and targets in dedicated configuration files, module.dll/importDll32 comes with all the data hardcoded. For example, we can find inside the binary a very long list of targets – websites from countries all around the world – France, Italy, Japan, Poland, Norway, Peru and more,” the researcher reveals.
The module creates a hidden desktop and uses it as a workspace to open and fingerprint browsers in such a way that the user isn’t aware of the malicious activity.
Written in Delphi, the Outlook.dll module contains a hardcoded configuration that follows a pattern typical for TrickBot modules. Designed to steal data saved by Microsoft Outlook, the module opens relevant registry keys, then attempts to retrieve saved credentials.
“TrickBot’s new modules are not written very well and they are probably still under development. The overall quality of the design is much lower than the quality of the earlier code. For example, module.dll is bulky and does not follow the clean modular structure introduced by TrickBot before. Also, they make use of languages and libraries that are easier – Qt instead of native sockets for module.dll, Delphi language for Outlook.dll,” Hasherezade points out.
The findings are in line with Flashpoint’s report last week, which revealed that TrickBot’s authors were working on implementing a worm module to abuse the Server Message Block (SMB) protocol to spread locally, but that the logic to randomly scan external IPs for SMB connections wasn’t yet ready.
The changes suggest that new members were added to the TrickBot development team, but that some of them are lower quality programmers, or that the team is only experimenting with new capabilities. “TrickBot is still actively maintained and it is not going to leave the landscape any soon,” Hasherezade concludes.
British Hacker Admits Using Mirai Botnet to DDoS Deutsche Telekom
26.7.2017 thehackernews BotNet
An unnamed 29-year-old man, named by authorities as "Daniel K.," pleaded guilty in a German court on Friday to charges related to the hijacking of more than one Million Deutsche Telekom routers.
According to reports in the German press, the British man, who was using online monikers "Peter Parker" and "Spiderman," linked to domains used to launch cyber attacks powered by the notorious Mirai malware has been pleaded guilty to "attempted computer sabotage."
The suspect was arrested on 22nd February this year at Luton airport in London by Britain's National Crime Agency (NCA) at the request of the Federal Criminal Police Office of Germany, aka the Bundeskriminalamt (BKA).
The hacker, also known as 'BestBuy,' admitted to the court on Friday that he was behind the cyber attack that knocked more than 1.25 Million customers of German telecommunications provider Deutsche Telekom offline last November.
According to the German authorities, the attack was especially severe and was carried out to compromise the home routers to enrol them in a network of hijacked devices popularly called Botnet, which is being offered for sale on dark web markets for launching DDoS attacks.
Late last year, Deutsche Telekom's routers became infected with a modified version of the Mirai malware – infamous IoT malware which scans for insecure routers, cameras, DVRs, and other IoT devices and enslaves them into a botnet network – causing over a million pounds' worth of damage, the company said at the time.
Mirai is the same botnet that knocked the entire Internet offline last year by launching massive distributed denial of Service (DDoS) attacks against the Dyn DNS provider, crippling some of the world's biggest and most popular websites, including Twitter, Netflix, Amazon, Slack, and Spotify.
Mirai leveraged attack experienced sudden rise after a cyber criminal in October 2016 publicly released the source code of Mirai, which is then used to by many cyber criminals to launch DDoS attacks.
The hacker reportedly told the court that a Liberian internet service provider (ISP) paid him $10,000 to carry out the attack against its competitors., and that Deutsche Telekom was not the main target of his attack.
At the time of his arrest, the suspect faced up to 10 years in prison. He's due to be sentenced on July 28.
The BKA got involved in the investigation as the attack on Deutsche Telekom was deemed to be a threat to the nation's communication infrastructure.
The investigation involved close cooperation between British, German and Cypriot law enforcement agencies, backed by the European Union's law enforcement intelligence agency, Europol, and Eurojust.
Bot vs Bot in Never-Ending Cycle of Improving Artificial intelligence
26.7.2017 securityweeek BotNet
Artificial intelligence, usually in the form of machine learning (ML), is infosecurity's current buzz. Many consider it will be the savior of the internet, able to defeat hackers and malware by learning and responding to their behavior in all-but real time. But others counsel caution: it is a great aid; but not a silver bullet.
The basic problem is that if machine learning can learn to detect malware, machine learning can learn to avoid detection by machine learning. This is a problem that exercises Hyrum Anderson, technical director of data science at Endgame.
At the BSides Las Vegas in August 2016 he presented his work on a 'Deep Adversarial Architectures for Detecting (and Generating!) Maliciousness'. He described the concept of using red team vs blue team gaming, where a 'malicious' algorithm continually probes a defensive algorithm looking for weakness, and the defensive algorithm learns from the probes how to improve itself.
Bot vs BotThis week, at the Black Hat conference, Anderson takes the concept further in a presentation titled 'Testing Machine Learning Malware Detection via Adversarial Probing'. The purpose is simple -- to use machine learning to test and improve machine learning defenses. In reality, it is an important step in the continuing battle between attackers and defenders.
Omri Moyal, co-founder and VP of research at Minerva, explains. "Given the increased adoption of anti-malware products that use machine learning, most adversaries will soon arm themselves with the capabilities to evade it," he told SecurityWeek. "The most sophisticated attackers will develop their own offensive models. Some will copy ideas and code from various publicly-available research papers and some will even use simple trial and error, or replicate the offensive efforts of another group. In this cat-and-mouse chase, the defenders should change their model to mark the evolved attack tool as malicious. A process which is the modern version of 'malware signature' but more complex."
Anderson's theories will help the defender to stay ahead of the attacker by being both cat and mouse. His Black Hat presentation starts with the understanding that "all machine learning models have blind spots or hallucination spots (modeling error)." At the same time, an advanced attacker knows what models are used by the defender; and can use his own ML to probe for those blind spots.
Moyal explained the implications for defenders. "Just like in previous generations of anti-virus software, attackers can constantly evaluate their malware against the machine learning model until a successful variant is created," he told SecurityWeek. Malware authors have long tested new or repackaged malware against VirusTotal-like services to see whether it is likely to get past the defenders' AV defenses. Now they will use ML to test their malware against the known ML defenses, seeking out the blind spots.
"The resulting specimen," continued Moyal, "can be used against each victim whose protection relies on this model, offering the attacker a high degree of certainty the malicious program will not be detected. Attackers can also automate this process of generating malware that bypasses the model and even use offensive machine learning to improve this process."
Anderson's research is based on the idea of finding the blind spots and closing them before the attackers find them. Ironically, this can be achieved by doing exactly what the attackers will do -- use machine learning to probe machine learning. This is nothing more than what security researchers have been doing for decades: probe software to find the weaknesses and get those weaknesses patched before they are found and exploited by the bad people.
In today's presentation, Anderson describes a scientific approach on how to evade malware detection with an AI agent to compete against the malware detector. Although in this instance focusing on Windows PE, the framework is generic and can be used in other domains.
The agent examines a PE file and probes it to find a way to evade the malware detection model. The agent learns how to 'beat' the defense. However, as used by the defenders, this approach simply finds the blind spots that can then be fixed. Used solely by attackers, it finds the blind spots that can be exploited.
Anderson's key takeaway is that machine learning anti malware just bought and installed will offer early success in malware protection, but it will quickly become porous against advanced adversaries. Staying one jump ahead of the bad guys has always been, and remains, the key to infosecurity even in the age of artificial intelligence.
Hyrum Anderson, Bobby Filar, and Phil Roth from Endgame, together with Anant Kharkar from the University of Virginia, have published an associated white paper: Evading Machine Learning Malware Detection (PDF).


















