
Source PowerCompare.co.uk
IT Articles - H 2020 1 2 3 4 5 6 7 IT List - H 2021 2020 2019 2018 1
Study Examines Value of Data
15.12.2017 securityweek IT
IP is Valued Above Email but Below PII, Survey Finds
In mitigating an asset-risk by risk transfer (such as an insurance policy), the value of the asset is directly related to the cost of the transfer (the insurance premium). The same principle should be applied to other forms of risk mitigation, such as defending the asset. Where the asset is data, an information security policy should reflect the value of the data -- but this assumes that the value of data is understood.
Trustwave, a Chicago, IL-based threat, vulnerability and compliance management firm, wanted to see how organizations value the prime categories of the data they hold -- which it assumes to be personally identifiable information (PII), payment card data (PC), intellectual property (IP), and email content information. It commissioned Quocirca to analyze the financial value placed by different industry segments in different geographical regions on these four categories of data. Five hundred IT and risk managers were surveyed in the U.S., Canada, Australia, Japan and the UK (100 for each region).
Two specific metrics are used in the ensuing report (PDF): the per capita value (PCV) for data; and a data risk vigilance (DRV) score. PCV is calculated by dividing the overall value of a data set by the number of records it contains. It consequently provides a subjective view for each organization. The same principle was also applied to discover the comparative data PCVs for the criminal fraternity and regulators.
The second metric, the DRV score, isn't simply a question of security budgets, but aggregates ten factors -- four relating directly to risk, four to data value assessments and two to the impact of data theft.
The results are surprising in their diversity. For example, U.S. professionals value their PII data at more than twice the PCV value asserted by their UK counterparts ($1,820 versus $843). The difference may be less today following the recent 20% fall in the value of the pound, but is still surprising.
It would be tempting to think this might reflect the vast number of data protection regulations, both state and federal, in the U.S.; and that simply for compliance reasons US security officers value data more highly. If this were so, then the UK PCV would likely increase dramatically from next year when the GDPR with its very high non-compliance sanctions comes into effect.
Ziv Mador, VP security research at Trustwave, doesn't believe this is cause of the difference. "It is likely," he told SecurityWeek, "that the sheer volume of PII held in the U.S. by the big international organizations, and the knowledge that they are a tempting target for attackers, increases the awareness of PII value." If this is the case, GDPR will more likely increase the disparity between the U.S. and the UK since it will still be U.S. organizations holding huge amounts of European PII.
Many of the findings of this survey and analysis are easy to understand and explain. For example, PII (which includes personal health information -- PHI) gets the highest overall PCV rating. This is understandable given the potential cost of a breach, including law-suits, regulatory fines, and the cost of restitution. This is followed by IP and payment card data -- again understandable in that card data is often held by third parties. More surprising, however, is that email is given the lowest PCV by a long distance.
Email seems not to be considered a serious area of concern despite the volume of sensitive data often sent within it. This ranges from PII to IP and user passwords in clear text. While IP is given a high value, emails that often contain IP or access to it are not. The demise of Nortel is a case in point. Hackers had access to Nortel for about a decade. An investigation subsequently found two rootkits giving the hackers remote access to corporate email. It is believed that IP stolen from Nortel enabled competitors from China to produce almost identical products at a fraction of the cost -- ultimately leading to Nortel's demise.
It would appear from the Trustwave survey that many organizations have still not learned the true value of, and threat from, email; and are likely to inadequately defend it. This is potentially confirmed in the report's second metric -- the data risk vigilance score. PC data replaces PII as having the greater vigilance. This may be, however, that companies holding large amounts of PC data (merchants, for example) hold lesser amounts of other types of data; and consequently bias the overall result.
Despite the example of Nortel in the importance of IP, IP ranks only third. Corporate email is a relatively distant fourth.
The strength of this report is that it will likely make organizations question whether they have correctly valued their own data, and have consequently applied the correct level of security controls for their different assets.
"Today," explains Mador, "data is one of the most valuable commodities possessed by any business. Whether that data belongs to the organization itself, its employees, suppliers or customers, it has a duty to protect that data to best of its ability. Companies that fail to accurately value their data are unlikely to make the right decisions regarding the level of cyber security investments to protect that data and are those most likely to fall short of regulations, such as the upcoming European Union General Data Protection Regulation (GDPR) coming into effect in 2018."
The biggest single takeaway is that companies should perhaps re-evaluate both the PCV and DRV they apply to their corporate email systems.
Upstream Security Raises $9 Million to Protect Connected Cars Through the Cloud
13.12.2017 securityweek IT
Upstream Security, a Herzliya, Israel-based cybersecurity company that helps protect connected cars and autonomous vehicles from cyber threats, today announced that it has raised $9 million through a Series A funding round.
The company explains that it has developed a cloud-based automotive cybersecurity platform that leverages artificial intelligence and machine learning that can be applied to the vast amount of data continuously produced by vehicles.
The platform, Upstream describes, “provides customers with data protection, anomaly detection and real-time analytics of cyber attacks and vehicle fleet health. By centralizing cybersecurity in the cloud instead of in-vehicle, threats are detected and prevented before they even reach a vehicle's network.”
Upstream says the new funding will help expand its R&D program and open sales and marketing offices in the United States and Europe, with plans to open an office in Silicon Valley in the coming months.
Cyber threats to automotive systems are not new, and are becoming more of an issue as more cars become connected to the Internet and to other devices such as smartphones, smart keys, diagnostic tools and other vehicles.
A number of security researchers have demonstrated the ability hack into modern vehicles to manipulate steering, acceleration, speedometers and safety sensors, sparking concerns that malicious attackers could use similar techniques to compromise a vehicle's Electronic Control Units (ECUs) allowing manipulation of a car's engine, brakes, airbags and other safety systems or vehicle components.
Researchers have demonstrated over the past years that vehicles such as the Toyota Prius, Tesla Model S, Jeep Cherokee, and Nissan Leaf are exposed to hacker attacks due to vulnerabilities in connected systems.
With Gartner forecasting there to be 250 million connected vehicles by 2020, Upstream is not the only company looking to tap this market.
Several companies that specialize in automotive security have emerged recently, including Karamba Security and Argus Cyber Security. Some traditional security industry players, such as Symantec and IOActive, have also launched vehicle security divisions. In late 2016, German carmaker Volkswagen teamed up with three Israeli cybersecurity experts to launch CYMOTIVE.
Just last month, Argus Cyber Security was acquired by Continental subsidiary Elektrobit (EB), which provides embedded software solutions to the automotive industry.
Led by CRV (Charles River Ventures), Upstream’s Series A funding round included expanded investments from Israeli-based Glilot Capital Partners and Maniv Mobility. The company previously raised a $2 million seed funding round in June of this year.
Cloud Security Startup ShieldX Networks Raises $25 Million
12.12.2017 securityweek IT
ShieldX Networks, a San Jose, Calif.-based cloud security company, announced that it has closed a $25 million Series B round of funding with participation from new investors including FireEye founder Ashar Aziz, Dimension Data and Symantec Ventures.
The company describes its flagship “APEIRO” platform as a solution that delivers Software-Defined Security through a containerized, microservices architecture that helps secure complex, multi-cloud environments.
The scalable cloud-based solution supports real-time threat prevention and helps detect and stop suspicious activities in cloud environments that see high-volume, lateral traffic.
“This funding will allow us to expand our marketing and sales efforts to meet increasing market demands while also keeping a strong focus on product development, including increased automation and intelligence across popular cloud environments that will meet customer demand,” said Dr. Ratinder Paul Singh Ahuja, CEO of ShieldX.
According to the company, its customer list includes organizations such as Alaska Airlines, Iowa State University and Park Holidays.
“Alaska Airlines is actively moving processes to next generation private and public cloud environments in an effort to support the rapid application development and innovation that really delights our guests. We were looking for a security and micro-segmentation solution that could scale and adapt with our new multi-cloud strategy with a comprehensive and consistent security policy across all environments,” said Brian Talbert, Director of Network and Connectivity Solutions at Alaska Airlines. “ShieldX has been an ideal partner throughout the development process by meeting our on premise and cloud needs, rapidly responding to our input, and by supporting our new Microsoft Azure requirements.”
Existing investors, Bain Capital Ventures, Aspect Ventures and FireEye also participated in the Series B round.
Malware Isolation Firm Menlo Security Raises $40 Million
12.12.2017 securityweek IT
Menlo Security, a provider of malware isolation technology, announced on Monday that it has closed a $40 million Series C funding round, bringing the total amount raised by the company to $85 million.
Menlo Security LogoThe Menlo Park, Calif.-based company pushes the fact that its offerings do not provide malware detection or classification. Instead, the company’s cloud-based security platform takes all active content—including potentially malicious files—and executes it in the cloud, giving malware no path to reach an endpoint via compromised or malicious web sites, e-mail, or documents.
“Rather than try to distinguish between safe and risky content, the Menlo Security Isolation Platform acts like a digital partition, isolating and executing all web content, email links and documents in the cloud, then streaming a malware-free version of the content to employees’ computers,” the company explains.
Menlo says the additional funding will help support sales and marketing efforts.
American Express Ventures, Ericsson Ventures and HSBC, participated in the funding round as new investors. They join existing investors JPMorgan Chase, General Catalyst, Sutter Hill Ventures, Osage University Partners and Engineering Capital.
Synopsys Completes $550 Million Acquisition of Black Duck Software
12.12.2017 securityweek IT
Synopsys, a company that provides tools and services for designing chips and electronic systems, has completed its acquisition of Black Duck Software, a privately held company that offers solutions for securing and managing open source software.
The value of the cash transaction was approximately $547 million net of cash acquired, Synopsys said.
Black Duck's products help development and security teams automate the process of identifying and inventorying open source code, and help detect known security vulnerabilities. It also provides automated alerts for any newly discovered vulnerabilities affecting the open source code and assists with software license compliance.
In 2014, Synopsys acquired software testing firm Coverity for roughly $350 million. In November 2016, Synopsys announced its plans to acquire software security testing firm Cigital for an undisclosed sum.
IT Security Spending to Reach $96 Billion in 2018: Gartner
9.12.2017 securityweek IT
Gartner is predicting that worldwide security spend will reach $96 billion dollars in 2018. This is up 8% from the 2017 spend of $89 billion. Interestingly, the latest 2017 and 2018 figures show substantial increases over similar predictions made in August of this year. The earlier prediction has 2017 figures at $86.4 billion with 2018 figures at $93 billion.
Gartner suggests that organizations are spending more on security as a result of regulations, shifting buyer mindset, awareness of emerging threats and the evolution to a digital business strategy.
"Overall, a large portion of security spending is driven by an organization's reaction toward security breaches as more high profile cyberattacks and data breaches affect organizations worldwide," said Ruggero Contu, research director at Gartner. "Cyberattacks such as WannaCry and NotPetya, and most recently the Equifax breach, have a direct effect on security spend, because these types of attacks last up to three years."
A 2016 survey -- that questioned 512 respondents from eight countries: Australia, Canada, France, Germany, India, Singapore, the U.K. and the U.S. -- showed a direct link between security risks and security spend. Gartner believes that the breaches of 2017 will influence the spend in 2018. "As a result," it suggests, "security testing, IT outsourcing and security information and event management (SIEM) will be among the fastest-growing security subsegments driving growth in the infrastructure protection and security services segments."
This is likely to be bolstered by the effect of compliance concern. Regulations are increasing in number, scope, and the size of sanctions; and are getting personal. Europe's General Data Protection Regulation (GDPR) coming into effect in May 2018 can impose fines of up to 4% of global turnover. In the U.S., the newly introduced Data Security and Breach Notification Act proposes jail terms of up to five years for those who fail to comply. As the effect of these regulations on individual business leaders as well as the company filter through -- which can no longer be satisfied by a simple tick-box approach to security -- there is likely to be a knee-jerk reaction leading to increased security spend.
Some of this effect can be discounted. "Regulatory compliance and data privacy have been stimulating spending on security during the past three years, in the US (with regulations such as the Health Insurance Portability and Accountability Act, National Institute of Standards and Technology, and Overseas Citizenship of India) but most recently in Europe around the General Data Protection Regulation coming into force on 28th May 2018, as well as in China with the Cybersecurity Law that came into effect in June 2016. These regulations translate into increased spending, particularly in data security tools, privileged access management and SIEM."
However, since numerous surveys and analyses have demonstrated that many firms simply do not understand GDPR, are still far from being ready for GDPR, or don't (yet) believe it applies to them, there is likely to be sudden increased spending following the first legal actions against non-compliance. Any belief that European regulators might allow a 'bedding in' period should not be taken for granted.
At the end of November, three European activists (Max Schrems, whose action against Facebook ultimately led to the collapse of the EU/US Safe Harbor agreement; Paul Nemitz, director for fundamental rights and Union citizenship in the European Commission's Directorate-General for Justice; and Jan Philippe Albrecht, justice and home affairs spokesperson of the European Greens and the rapporteur for the GDPR) got together to announce 'NOYB [none of your business] -- European Center for Digital Rights'.
The purpose of NOYB is to close the gap between the public perception of privacy and the reality of corporate practice, including bringing cases to court. Since these are activists rather than regulators, they are likely to take private action where regulators may hesitate. In its August prediction, Gartner commented, "The EU General Data Protection Regulation (GDPR) has created renewed interest, and will drive 65 percent of data loss prevention buying decisions today through 2018." This could prove to be a conservative estimate.
Skills shortages, technical complexity and the threat landscape will continue to drive the move to automation and outsourcing, says Gartner. "Skill sets are scarce and therefore remain at a premium, leading organizations to seek external help from security consultants, managed security service providers and outsourcers," said Contu. "In 2018, spending on security outsourcing services will total $18.5 billion, an 11% increase from 2017. The IT outsourcing segment is the second-largest security spending segment after consulting."
This migration to service providers and outsourcers leads Gartner to predict that by 2019, total enterprise spending on security outsourcing services will be 75% of the spending on security software and hardware products, up from 63% in 2016.
"For the most part, I agree with Gartner's assessment that spending is likely to continue to grow overall in 2018," Nathan Wenzler, chief security strategist at AsTech, told SecurityWeek; "especially in identifying that the overall skills shortage will ultimately drive more companies to spend more in security services."
He believes that companies are "reaching something of a saturation point for security software, as they've been spending for the last several years to buy products that can protect their environments in different ways." But they don't have and cannot get "experienced security professionals who can deploy, use and maintain those products effectively in order to put the tools to work. Organizations will have little choice but to shift their spending to services in order to secure their networks and protect critical data."
But is 'more spending' necessarily 'better security'? Ilia Kolochenko, CEO of High-Tech Bridge, warns that it isn't necessarily so. He believes that a more coherent risk-based security approach could lead to improved security without necessarily increasing spend. "Many companies can even reduce their current budgets by implementing a risk-based approach to mitigate appropriate threats and vulnerabilities; and by rigorously selecting vendors based on technology and not marketing claims."
Anti-Phishing Firm IRONSCALES Raises $6.5 Million
5.12.2017 securityweek IT
IRONSCALES, an Israel-based startup that specializes in automated phishing prevention, detection and response, announced on Tuesday that it has raised $6.5 million in a Series A funding round.
This brings the total raised by IRONSCALES since 2015 to more than $8 million. The company says this has been its third consecutive year of triple-digit revenue growth.
The investment round was led by K1 Investment Management, with participation from existing investor RDC. The company says the newly raised funds will be used to accelerate its channel partner program, expand its global sales team, and expedite research and development for its threat detection, intelligence sharing, and incident response technologies.Ironscales raises $6.5 million
“IRONSCALES’ unique approach to phishing detection and remediation particularly resonated with the K1 team, and we looking forward to leveraging our previous experience in partnering with growing security companies as the company strengthens its position within a rapidly evolving market,” commented Hasan Askari, managing partner at K1.
IRONSCALES also announced on Tuesday that its North American headquarters will be launched in the first quarter of 2018. The company’s VP of sales will be based in Atlanta, Georgia, while R&D will remain in Israel.
IRONSCALES products provide protection for every stage of an email-based phishing attack. IronSchool provides simulations and training for an organization’s employees, while IronSights is designed to detect phishing attacks in users’ inboxes. IronTraps is a solution for automated incident response, and Federation provides real-time intelligence sharing.
Bitdefender Valued at $600 Million After Vitruvian Partners Investment
2.12.2017 securityweek IT
Home and enterprise security solutions provider Bitdefender has been valued at over $600 million after growth capital investment firm Vitruvian Partners acquired a stake of roughly 30 percent in the company from existing shareholder Axxess Capital.
Through the acquisition, Vitruvian has become the second-largest shareholder after co-founders Florin and Mariuca Talpes. A group of private investors holds a minority stake in Bitdefender.
Bitdefender valued at $600 million
“This transaction demonstrates the rapid growth and scale of our business as we are now valued at over $600 million,” said Florin Talpes, who also serves as the company’s CEO. “Vitruvian's extensive experience investing in high growth technology companies endorses our strategy for international growth and in particular the significant investment we are making in building our Enterprise Solutions offering and our presence in the United States.”
“We continue to operate with a sound financial footing - this enables us to further expand and broaden our product portfolio and so ensure we stay ahead of cyber criminals to protect better our customers,” he added.
A Bitdefender spokesperson told SecurityWeek that the deal was a secondary transaction between shareholders, so funds will not go into Bitdefender itself.
Axxess Capital sold its shares after an 8-year run. Deutsche Bank AG, London Branch acted as the financial advisor for the transaction, which is subject to regulatory approvals.
Bitdefender’s main office is in Romania and its enterprise solutions headquarters is located in the United States, in Santa Clara, California. The cybersecurity firm employs more than 1,300 people, and its products are said to be used by over 500 million users in 150 countries.
Vitruvian is an independent European private equity firm that specializes in investing in companies undergoing growth and change. The company provides operational support and assistance with acquisitions and other strategic initiatives.
Trust Your Security Vendor, 'They Have Access to Everything You Do,' Says F-Secure Research Chief
30.11.2017 securityweek IT
The DHS ban on government agencies using Kaspersky Lab's security products has reverberated around the security industry. The concern is not simply whether the Moscow-based security firm has colluded with Russian intelligence, but how many other security firms could, through their own products, potentially collude with their own national intelligence agencies.
This is bad news for security since security is built on trust; and without trust there is no security. Kaspersky Lab has denied any collusion and has offered to do anything possible, from testifying before Congress to third-party code reviews, to prove its innocence. At the same time, there is no actual proof of collusion; just a statement that the possibility is a cause for concern.
On Tuesday, at a media briefing in London, Eugene Kaspersky said he had never been asked by Russia to spy on its behalf. "If the Russian government comes to me and asks me to (do) anything wrong, or my employees, I will move the business out of Russia. We never helped the espionage agencies, the Russians or any other nation."
The DHS statement bans government agencies from using Kaspersky Lab products, saying, "The risk that the Russian government, whether acting on its own or in collaboration with Kaspersky, could capitalize on access provided by Kaspersky products to compromise federal information and information systems directly implicates U.S. national security."
Herein lies the problem. Before developing anti-virus software and forming Kaspersky Lab, Eugene Kaspersky studied cryptology at a KGB and defense-funded school, and later worked at Russia's Ministry of Defense as a cryptologist. So the link -- and therefore the risk -- exists. At the same time, however, any glance through LinkedIn's staff profiles for U.S. security firms will return a large number of senior employees with an NSA, CIA, FBI or State Department background, with many U.S. security firms boasting about their former government and military hires. Connections alone do not necessarily imply collusion.
The Wall Street Journal (WSJ) separately published an unsubstantiated claim that an NSA employee had been breached by Russian state-backed hackers via a vulnerability in a Kaspersky Lab product; and that they targeted the employee "after identifying the files through the contractor's use of" Kaspersky Lab AV. No proof of this is provided, but the implication is that Kaspersky Lab did not pass confidential files directly to Russian intelligence, but merely informed them of their presence on the employee's computer.
However, if the Kaspersky-Russian intelligence link is a concern, then by implication users should consider the potential for a McAfee and Symantec link with the NSA, and a Sophos link with GCHQ. In an attempt to counter any potentially growing lack of trust in security products in general, F-Secure's Chief Research Officer, Mikko Hypponen, has talked today about how his own company handles confidential user information.
There are two riders to his comments. First of all, F-Secure is a competitor to Kaspersky Lab; and secondly, F-Secure is not Kaspersky Lab. Nevertheless, insights into how one major anti-virus firm operates will inevitably provide some insights into how any other major AV firm operates.
Hypponen avoids or obfuscates his response to any direct question of possible Kaspersky Lab collusion with Russia. For example, he says, "Let's just state for the record that it's a great company and a great security product. These are world class researchers."
Asked later if he thought Kaspersky Lab "colluded with Russian intelligence, do you think they were breached, hacked, infiltrated?", he replied, "I don't know. It's all speculation, as are all the stories on this. So far everything's been speculation." He notes, however, that links with law enforcement are commonplace. Law enforcement agencies (LEAs) frequently ask security firms for assistance in the fight against cybercrime, and researchers commonly pass back data on discovered C&C servers.
He does, however, explain how F-Secure treats information about user files. First of all, almost all security firms collect this data -- it's simply how they work. The amount of data that needs to be analyzed to keep users safe simply cannot bedone on a local machine without reducing its operation to a crawl. Anti-virus and network anomaly products tend to collect data and send it to cloud servers for analysis by powerful machine-learning algorithms.
But F-Secure, and most likely all other security vendors, go to great lengths to anonymize and protect the information they collect. First of all, this is good practice; but secondly, privacy regulations in many jurisdictions could cause serious complications. GDPR, for example, requires that only necessary data be collected; and personal data is not necessary for the analysis of executable files.
The files that are collected are analyzed for any indication of malware. If they are found to be benevolent, they are deleted. This resonates with Kaspersky Lab's comments following the WSJ report. Its software found the NSA files on the employee's computer, did not recognize them as good files and uploaded them for further analysis. Here they were analyzed and determined to be 'sensitive' -- at which point they were deleted.
Unfortunately, this cannot disprove the possibility that someone in Kaspersky Lab then sent a quiet word to Russian intelligence saying, 'Hey guys, you might want to take a close look at this guy's computer.' But for that to have happened, Kaspersky Lab will have had to collect personal data as well as anonymized files.
Hypponen cannot say that Kaspersky Lab didn't do it; but he makes his opinion clear. He does, however, agree with the DHS. "Would I recommend using a foreign security product in US agencies, especially a Russian product? Probably I wouldn't. But for home users and users like that, it is a great product."
In the end, it's a question of who do you trust the most: your own government or a security firm that can only exist through trust?
"Choose your vendors carefully, because, in theory, they have access to everything you do," Hypponen said, adding that "when you are running low level software, like security software, you do have to trust your vendor."
But he clearly does not personally believe that Kaspersky Lab is guilty of any malicious behavior. "Why? Because that would be so short-sighted. If you do that and you get caught, your company is toast, and it should be toast. That's a bad business decision. If it's the Russian government using a local security company as their way of gaining access to information, that's short-sighted too. Because Kaspersky Lab is the biggest software success story out of Russia since Tetris."
ICOs: The Lawless Land of Cryptocurrency Fundraising
28.11.2017 securityweek IT
From raising $30 million in 30 seconds to being endorsed by Paris Hilton or vanishing into thin air: anything is possible in the risky new world of cryptocurrency fundraising, but regulators are lurking.
Bypassing oversight of any kind, Initial Coin Offerings (ICOs) have sprung from nowhere to become a hugely popular way for start-ups to raise funds online, offering self-created digital "tokens" or coins to any willing buyer.
ICOs herald "the democratisation of investment", said Nil Besombes, a French blogger specialized in digital currencies.
But in the lawless Wild West of ICOs, the risks are legion and Besombes himself admits to losing "the equivalent of 1,800 euros" when he fell for a slick online sales pitch -- only for the company to disappear without a trace.
"It's like gambling," he told AFP.
While the term ICO may suggest a link with conventional Initial Public Offerings (IPOs), there is no flotation on the stock market and the ICO investor typically holds no ownership stake in the company which would entitle them to a slice of profits distributed as dividends.
ICOs are thus essentially a form of crowdfunding where participants are betting that the value of their "tokens" will go up and that they will eventually be able to trade them for established cryptocurrencies like bitcoin and Ethereum, which can in turn be exchanged for traditional currencies.
ICOs have exploded this year with investors pouring $3.6 billion into 228 projects, according to data from Coinschedule. In 2016, that figure stood at just $96 million for 46 ICOs.
By June of this year, the money raised through ICOs surpassed that of early stage venture capital investments, the traditional way for young companies to raise funds from wealthy investors.
The ICO craze has drawn the attention of regulators around the world, who have warned of the risks of fraud, the volatility of virtual currencies and the lack of clarity on what a "token" represents.
"A lot of ICOs see values plummet by 80 or 90 percent but they can rebound strongly once the project begins to deliver results," said Tristan Colombet, head of the French auction platform Domraider, itself funded by an ICO.
The "tokens" offered by his company are currently worth just a third of what they were at the launch, to the dismay of investors.
Colombet says things will pick up "in early 2018" when his system to track auctions online and in the auctioneering room in real time is fully implemented, using the same "blockchain" technology that underpins bitcoin and many of the tech start-ups in the ICO universe.
Celebs and 'digital gold'
The gold rush fever surrounding ICOs is partly down to the soaring success of bitcoin, which first hit parity with the US dollar in 2011, two years after it was created.
Since then, the world's best-known virtual currency has enjoyed a meteoric rise, defying predictions of a crash. It has now surpassed $9,500.
Many ICO investors are lured by the possibility of stumbling upon the next "digital gold".
Firms issuing ICOs have raised their visibility by enlisting celebrities like LA socialite Paris Hilton, hip-hop producer DJ Khaled and US boxer Floyd Mayweather to tout their digital tokens on social media.
The endorsements prompted the US Securities and Exchange Commission to warn this month that celebrities "often do not have sufficient expertise" to judge such investments, and that they must disclose if they are receiving compensation for promoting ICOs.
Scrambling to respond
The proliferation of ICOs has forced regulators around the world to take notice, their responses ranging from a crackdown to a wait-and-see approach.
China and South Korea have banned ICOs outright, while European supervisory bodies have voiced strong concerns.
The UK's financial regulator cautioned against the "very high-risk, speculative investments", while Germany's powerful Bundesbank central bank warned that the ICO trend was "attracting fraudsters".
The European Securities and Markets Authority (ESMA) said investors risked having no legal recourse in case of a dispute, as ICOs tend to fall "outside of the scope of EU laws and regulations".
Canadian and Russian regulators however have chosen another path by creating so-called "regulatory sandboxes", a framework that allows ICO firms to experiment for a certain time without falling foul of securities laws.
"We welcome this type of innovation," said Louis Morisset, president of the Canadian Securities Administrators, while stressing that ICO issuers should "understand what obligations may apply".
Trend Micro Acquires Application Security Firm Immunio
28.11.2017 securityweek IT
Cybersecurity firm Trend Micro announced on Tuesday that it has acquired Montréal, Canada-based web application security firm Immunio for an undisclosed sum.
The acquisition, Trend Micro says, will help increase the automated protection that it can provide customers throughout the DevOps lifecycle.
“We are excited to acquire Immunio’s application protection technology, their team of application security experts and their customers,” said Bill McGee, SVP and GM of Hybrid Cloud Security at Trend Micro. “Technology changes, like cloud computing and container platforms, are enabling faster application development. Immunio’s run-time application security allows our customers to increase protection against software vulnerabilities within the applications they are building.”
Announced at the AWS re:Invent conference this week, Trend Micro also said that it is enhancing its container-specific security capabilities, by supporting container image scanning, which allows security issues to be identified and resolved prior to production release.
According to Trend, the new capabilities integrated with the DevOps lifecycle, with Immunio bringing early detection and protection against application vulnerabilities, and container image scanning allowing for the publishing and protection of secure container images.
In March 2016, Trend Micro acquired the TippingPoint network security portfolio from Hewlett Packard Enterprise (HPE) for $300 million.
McAfee to Acquire CASB Firm Skyhigh Networks
28.11.2017 securityweek IT
McAfee announced on Monday that it has agreed to acquire cloud access security broker (CASB) Skyhigh Networks for an undisclosed amount.
CASBs are the go-to solution for corporate cloud security. By controlling access to the corporate cloud they can apply visibility and security to what is within that cloud. But it is such a good solution that big security firms are rapidly buying up all the independent CASBs (such as Microsoft, Symantec, Forcepoint, Oracle, and Cisco).
It's reaching the stage where no large security firm can be without a CASB, and no CASB can survive and prosper without the support of a major security vendor.
"Skyhigh Networks had the foresight five years ago to realize that cybersecurity for cloud environments could not be an impediment to, or afterthought of, cloud adoption," said McAfee CEO Chris Young stated. "They pioneered an entirely new product category called cloud access security broker (CASB) that analysts describe as one of the fastest growing areas of information security investments of the last five years -- where Skyhigh continues to innovate and lead. Skyhigh's leadership in cloud security, combined with McAfee's security portfolio strength, will set the company apart in helping organizations operate freely and securely to reach their full potential."
Little about the mechanics of the agreement have been announced, beyond a statement that Skyhigh CEO "Rajiv Gupta will join McAfee CEO Chris Young's leadership team to run McAfee's new cloud business unit." However, both CEOs have provided a little more information in separate blogs.
"Combined with McAfee's endpoint security capabilities and operations center solutions with actionable threat intelligence, analytics and orchestration, we will be able to deliver a set of end-to-end security capabilities unique in the industry," writes Gupta.
"Cloud security has historically been an afterthought of, or impediment to, cloud adoption. With customers' most valuable asset, data, increasingly finding residence in the cloud, it's time security move to the forefront. At the same time, security cannot hinder cloud adoption, as the transformation the cloud promises extends far beyond the corridors of IT to every facet of modern business. Skyhigh had this prescience five years ago," wrote Young.
The combination of the two companies, with McAfee's traditional strength in endpoint security and a growing network security portfolio with Skyhigh's cloud security, should clearly benefit both organizations. "McAfee already claims a market-leading position in endpoint. With Skyhigh's leadership in securing the world's most valuable asset -- data -- in the cloud, the company sets itself apart," announces an associated Skyhigh FAQ.
But there is no information yet on how the products will work together -- just a placeholder from Skyhigh: "How will Skyhigh and McAfee's products work together? We have some exciting things in the works that we'll share over the coming months. Stay tuned!" If McAfee stays true to its stated intents, this will include bringing greater automation and orchestration to the cloud and associated endpoints.
McAfee separated from Intel in April 2017.
Thoma Bravo Acquires Barracuda Networks for $1.6 Billion
28.11.2017 securityweek IT
Private equity investment firm Thoma Bravo has entered an agreement to acquire security company Barracuda Networks for $1.6 billion in cash.
Barracuda shareholders will receive $27.55 for each share of common stock they hold, which exceeds the average stock price of $22.49 for the ten days leading up to November 27 by more than 22 percent.
The agreement was unanimously approved by Barracuda’s board of directors. Once the acquisition is completed – likely before the fiscal year ends on February 28, 2018 – Barracuda will operate as a privately-held company and it will continue to focus on email security and management, data protection, and network and application security solutions for cloud and hybrid environments.Barracuda acquired by Thoma Bravo
“We believe the proposed transaction offers an opportunity for us to accelerate our growth with our industry-leading security platform that's purpose-built for highly distributed, diverse cloud and hybrid environments. We will continue Barracuda's tradition of delivering easy-to-use, full-featured solutions that can be deployed in the way that makes sense for our customers,” said BJ Jenkins, CEO of Barracuda.
“Thoma Bravo has an excellent history of investing in growing security businesses, and this transaction speaks to the value and strength of Barracuda's security platform, which helps customers protect and manage their networks, applications, and data. I expect that our employees, customers, and partners will benefit from this partnership,” he added.
The news comes just weeks after Barracuda announced the acquisition of public cloud archiving and business insights provider Sonian in an effort to enhance the company’s email security and management capabilities.
Barracuda’s latest financial report shows that the company’s revenue in the second fiscal quarter grew 7% year-over-year to $94.3 million, and the number of active subscribers increased by 17% to nearly 350,000.
The energy used to mine Bitcoin this year is bigger than the annual usage of almost 160 countries
28.11.2017 securityaffairs IT
According to PowerCompare.co.uk, the electricity used to mine Bitcoin this year is bigger than the annual usage of almost 160 countries.
While the price of cryptocurrencies such as the Bitcoin continues to increase the interest of investors and crooks in this new industry is demonstrated by disconcerting data that I’m going to share with you.
According to new research conducted by energy tariff comparison service PowerCompare.co.uk, the electricity used to mine Bitcoin this year is bigger than the annual usage of almost 160 countries. The energy consumption has already exceeded the amount used on average by states such as Ireland and most African nations.
“According to Digiconomist’s Bitcoin Energy Consumption Index, as of Monday November 20th, 2017 Bitcoin’s current estimated annual electricity consumption stands at 29.05TWh.” states the research.
“That’s the equivalent of 0.13% of total global electricity consumption. While that may not sound like a lot, it means Bitcoin mining is now using more electricity than 159 individual countries (as you can see from the map above). More than Ireland or Nigeria.”
Bitcoin transactions use so much energy that the electricity used for a single trade could power a home for almost a whole month, according to a paper from Dutch bank ING.
“By making sure that verifying transactions is a costly business, the integrity of the network can be preserved as long as benevolent nodes control a majority of computing power,” wrote ING senior economist Teunis Brosens.
“Together, they will dominate the verification (mining) process. To make the verification (mining) costly, the verification algorithm requires a lot of processing power and thus electricity.”
Comparing the amount of energy used for a Bitcoin transaction to run his home in the Netherlands, Brosens says: “This number needs some context. 200kWh is enough to run over 200 washing cycles. In fact, it’s enough to run my entire home over four weeks, which consumes about 45 kWh per week costing €39 of electricity (at current Dutch consumer prices).”
It is amazing if we compare this data other payment systems, for example Visa takes about 0.01kWh (10Wh) per transaction which is 20000 times less energy.
The following graph shows the 159 countries whose energy usage is less than bitcoin-mining consumption.

Source PowerCompare.co.uk
Which is the concept behind the mining process?
To prevent the falsification of the records or the ownership changing, participants of the Bitcoin network must sign off on transactions in “blocks”.
The process requests a significant computational capability and involves several computers to solve complex cryptographic problems, people who verify blocks are rewarded with freshly created bitcoin. This process is known as Bitcoin “mining.”
According to the initial design of the Bitcoin virtual currency scheme, it limits the overall number of coins in circulation to 21 million, this is possible because the cryptographic problems involved in the mining process get progressively harder.
On the other side, miners are turning to more powerful computers to solve the complex problems behind the mining process.
The vast majority of “mining” activities is done in China because the energy costs are cheaper compared to Europe or US.
“The top six biggest mining pools from Antpool to BTCC are all largely based in China,” said Mati Greenspan, an analyst with trading platform eToro. “Some rough estimates put China’s hashpower at more than 80% of the total network.”
Of course, the environmental impact of all this electric usage is not negligible, don’t forget that the electricity generated in China comes from CO2 emitting fossil fuels.
Below a few other interesting facts about Bitcoin mining and electricity consumption published:
In the past month alone, Bitcoin mining electricity consumption is estimated to have increased by 29.98%
If it keeps increasing at this rate, Bitcoin mining will consume all the world’s electricity by February 2020.
Estimated annualised global mining revenues: $7.2 billion USD (£5.4 billion)
Estimated global mining costs: $1.5 billion USD (£1.1 billion)
Number of Americans who could be powered by bitcoin mining: 2.4 million (more than the population of Houston)
Number of Britons who could be powered by bitcoin mining: 6.1 million (more than the population of Birmingham, Leeds, Sheffield, Manchester, Bradford, Liverpool, Bristol, Croydon, Coventry, Leicester & Nottingham combined) Or Scotland, Wales or Northern Ireland.
Bitcoin Mining consumes more electricity than 12 US states (Alaska, Hawaii, Idaho, Maine, Montana, New Hampshire, New Mexico, North Dakota, Rhode Island, South Dakota, Vermont and Wyoming)
Firefox 57 "Quantum" Released – 2x Faster Web Browser
15.11.2017 thehackernews IT
It is time to give Firefox another chance.
The Mozilla Foundation today announced the release of its much awaited Firefox 57, aka Quantum web browser for Windows, Mac, and Linux, which claims to defeat Google's Chrome.
It is fast. Really fast. Firefox 57 is based on an entirely revamped design and overhauled core that includes a brand new next-generation CSS engine written in Mozilla’s Rust programming language, called Stylo.
Firefox 57 "Quantum" is the first web browser to utilize the power of multicore processors and offers 2x times faster browsing experience while consuming 30 percent less memory than Google Chrome.
Besides fast performance, Firefox Quantum, which Mozilla calls "by far the biggest update since Firefox 1.0 in 2004," also brings massive performance improvements with tab prioritization, and significant visual changes with a completely redesigned user interface (UI), called Photon.
This new version also adds in support for AMD VP9 hardware video decoding during playback in an attempt to reduce power consumption, and thus preventing your systems from running out of battery.
Firefox 57 also includes built-in screenshot functionality, improved tracker blocking and support for WebVR to enable websites to take full advantage of VR headsets.
Firefox has plans to speed things even further by leveraging modern GPUs in the near future.
Firefox Quantum for the desktop version is available for download now on Firefox's official website, and all existing Firefox users should be able to upgrade to the new version automatically.
However, the Android version of Firefox 57 is rolling out on Google Play in coming days, and its iOS version should eventually arrive on Apple's official App Store.
Microsoft Uses Neural Networks to Improve Fuzzing
14.11.2017 securityweek IT
A team of Microsoft researchers has been working on improving fuzzing techniques by using deep neural networks, and initial tests have shown promising results.
Fuzzing is used to find software vulnerabilities – particularly memory corruption bugs – by injecting malformed or semi-malformed data into the targeted application. If the software crashes or behaves unexpectedly, it could indicate the presence of a security flaw.
There are three types of fuzzing: whitebox fuzzing, which tests source or disassembled code; blackbox fuzzing, which does not require access to source code; and greybox fuzzing, which is similar to blackbox fuzzing but uses results from previous executions for feedback.
Experts at Microsoft have attempted to improve this feedback loop using a type of machine learning called deep neural networks (DNN). Neural networks, a set of algorithms modeled after the human brain, are designed to recognize patterns in an effort to help classify and cluster data.
Neural networks have been used by several companies for security-related purposes, including for detecting spam and malware, and even in Apple’s new Face ID feature.
Microsoft researchers have been trying to use neural networks for a learning technique that relies on patterns in previous fuzzing iterations to guide future iterations.
“The neural models learn a function to predict good (and bad) locations in input files to perform fuzzing mutations based on the past mutations and corresponding code coverage information,” the researchers said.
The method has been implemented in American Fuzzy Lop (AFL), a popular open source fuzzer developed by Google researcher Michal Zalewski. Tests were conducted against parsers for the ELF, PDF, PNG and XML file formats.
The tests showed significant improvements in the results obtained with the neural AFL compared to the original AFL, except for PDF files, which experts believe may be too large. Improvements were seen in terms of code coverage, unique code paths and crashes.
The team behind the project believes this approach can be applied to any fuzzer, not just AFL.
“We believe our neural fuzzing research project is just scratching the surface of what can be achieved using deep neural networks for fuzzing,” explained Microsoft’s William Blum. “Right now, our model only learns fuzzing locations, but we could also use it to learn other fuzzing parameters such as the type of mutation or strategy to apply. We are also considering online versions of our machine learning model, in which the fuzzer constantly learns from ongoing fuzzing iterations.”
Blum is the lead of the engineering team for Microsoft Security Risk Detection, a recently launched cloud-based fuzzing service that uses artificial intelligence to find bugs and vulnerabilities in applications. The results of the research into the use of neural networks for fuzzing could help improve this service.
Another recently launched Microsoft tool designed for finding memory corruption bugs, VulnScan, might also be added to the Security Risk Detection service.
ThreatQuotient Raises $30 Million in Series C Funding
14.11.2017 securityweek IT
Threat intelligence platform provider ThreatQuotient announced on Monday that it has raised $30 million in Series C funding, bringing the total amount raised by the company to $54 million to date.
Founded in 2013 by Wayne Chiang and Ryan Trost, who previously worked at a Security Operations Center of defense contractor General Dynamics, ThreatQuotient offers a threat intelligence platform that helps customers manage and correlate external sources with all internal analytics solutions for contextual, operationalized intelligence.
According to the Reston, Virginia-based company, the funding will be used to fuel product development and support sales and marketing efforts for global expansion.
The company’s ThreatQ platform allows security analysts to leverage a threat library, an adaptive workbench, and an open API exchange to provide threat intelligence that is timely, accurate and relevant to their business.
ThreatQuotient claims that its platform eliminates the need for a security analyst to go through an entire pool of data to identify a threat by automating the process and suggesting sources of data that are more relevant to a given client.
“Our industry is at a crossroads and organizations must shift beyond simple detection and response to a position of understanding and anticipating threats through intelligence-driven security,” said John Czupak, President and CEO of ThreatQuotient.
The Series C round was led by Adams Street Partners, while strategic partners Cisco Investments and NTT DOCOMO Ventures joined existing investor New Enterprise Associates (NEA), and growth capital partner Silicon Valley Bank in the financing.
Fred Wang, a partner of the Venture/Growth Team at Adams Street Partners, will join ThreatQuotient's board of directors.
Microsoft president urges a digital Geneva Convention, we agree
13.11.2017 securityaffairs IT
Microsoft president Brad Smith appeared before the UN in Geneva to talk about the urgency of a digital Geneva Convention.
Microsoft president Brad Smith appeared before the UN in Geneva to talk about the role of nation-state actors in the threat landscape. We are assisting a growing number of nation-state cyber attacks, for this reason, cybersecurity experts, and Government officials urge the adoption of norms of states behavior in the cyberspace.
The risk of escalation and retaliation in cyberspace, the increasing number of cyber attacks and cyber threats even more sophisticated could have a destabilizing effect on international peace and security. The risk of conflict between states caused so cyber incidents encourages all States to engage in law-abiding, norm-respecting and confidence-building behavior in their use of ICT.
Smith last month Blamed North Korea for the WannaCry ransomware attack.
During the UN session on current internet governance challenges, Smith urged the need to define a cyber equivalent of the Geneva Convention.
“If you can hack your way into a thermostats you can hack your way into the electric grid,” Smith said, adding that the tech sector has the first responsibility for improving internet security because “after all we built this stuff”.

Most of you, already know that I was one of the experts of the Cyber G7 group at the Italian Summit that produced the voluntary, non-binding norms of State behavior during peacetime detailed in the G7 DECLARATION ON RESPONSIBLE STATES BEHAVIOR IN CYBERSPACE.
The group was led by Minister Gianfranco Incarnato and I had the honor and the opportunity to write the declaration along with Prof. Luigi Martino. We presented 12 points aimed to propose stability and security in the cyberspace.
Gianfranco Incarnato @GianfrancoIncar
Ministeriale G7 http://www.esteri.it/mae/tiny/24555#.WOy60gvHfFw.twitter … - Vedi DECLARATION ON CYBERSPACE
12:16 PM - Apr 11, 2017
Ministeriale G7
Ministeriale G7
esteri.it
Replies 8 8 Retweets 10 10 likes
Twitter Ads info and privacy
The declaration invites all the States to collaborate with the intent to reduce risks to international peace, security, and stability.
Well, part of the work wasn’t presented in the final discussion at the G7 summit, and unfortunately, the group has ended its mission, but we strongly believe that we made the first steps on the route Smith has in mind and we will do anything to complete our work.
We are currently trying to give an efficient prosecution to the work we made at the G7 Summit.
Microsoft is spending a significant effort trying to identify threat actors in the wild and profile them, the company used its technology to track down malicious infrastructure used by both criminal syndicates and nation-state actors. Smith announced Microsoft helped customers in 91 countries by seizing 75 domains using by attackers, it spends $1bn on security innovation a year.
The attacks against the 2016 US Presidential Election, such as the attacks against SWIFT banking network, were attributed to respectively Russian and NK threat APT groups linked to Russia and North Korea, both cases demonstrates that the problem of the “attribution” is hard to be solved without information sharing and collaborations among states.
For this reason, we at the Cyber G7 Group and Microsoft President believe that there is the shared need of a mandatory set of norms for states behavior in the cyber space.
“Nation states are making a growing investment in increasingly sophisticated cyber weapons,” Smith added. “We need a new digital Geneva Convention.”
“Government should agree not to attack civilian infrastructures, such as the electrical grid or electoral processes,” he said.
Smith highlighted the importance of the role of private companies in conflict, their conduct must be neutral and must ensure the protection of their customers.
But as remarked in several discussions, we are all nodes of a globally connected network, whom security depends on our behavior too.
Smith used the phishing to express this concept and the highlight the role of netizens in security the cyberspace.
“90 per cent of attacks begin with someone clicking on an email… We need to protect people from their bad habits,” he added.
Siemens and Tenable Partner to Protect Industrial Networks
7.11.2017 securityweek IT
Siemens and Tenable Partner to Provide Asset Discovery and Vulnerability Management For Industial Networks
Worsening geopolitical tensions and increasing awareness of the potential harm caused by cyber attacks against the operational technology (OT) networks of critical industries has made industrial control systems (ICS) a focus of cybersecurity attention. But protecting ICS remains problematic as it emerges from its pre-internet security-unaware origins into the modern internet-connected world: it now has to add remaining secure to remaining operational.
"Organizations running operational technology face a foundational security challenge -- the need to understand the entirety of their cyber exposure in the context of a modern attack surface that is constantly evolving," explains Amit Yoran, CEO of Tenable. "We've seen the rise of cloud, mobile and IoT and now the convergence of IT with OT, which have made critical systems vulnerable to increasingly aggressive adversaries and attacks."
OT, however, remains behind IT in its security defenses. A study by Ponemon in February 2017 highlighted the dire state of security awareness (in this case, specifically the oil and gas industry) in OT. It found that 46% of cyber attacks were thought to go undetected; that 61% of respondents believe their organization's industrial control systems protection and security is not adequate; and that less than half of the respondents believe they have the internal expertise needed to manage cyber threats in the OT environment.
Improved visibility into existing vulnerabilities within the OT environment will improve OT security staff's ability to defend against cyber attacks. "Cyberattacks against the O&G and utilities sector are on the rise and growing more sophisticated and aggressive by the day," comments Leo Simonovich, VP and global head of industrial cyber and digital security at Siemens Energy. "Passive monitoring of all assets in these systems is critical to detecting and addressing vulnerabilities before they can be exploited and lead to disruption of essential public services like electricity, gas, and water."
Tenable and Siemens have now partnered to provide this passive visibility. Siemens is a major provider of ICS. Tenable owns one of the world's most-used vulnerable scanning engines -- Nessus. Announced today is the new Industrial Security provided as a security service by Siemens, and based on Tenable's Nessus.
It provides, says Tenable, "safe, reliable asset discovery and vulnerability detection purpose-built for ICS and supervisory control and data acquisition (SCADA) systems." Key to this solution is the passive nature of Nessus which is used to detect vulnerabilities without affecting operational functionality. "Joining forces with Siemens is a natural next step," says Yoran. "Together we provide a way for organizations to monitor and address their attack surface in totality, so they can see where they are vulnerable and protect those systems -- and the people who depend on them -- from threats."
Siemens AG is a major provider of ICS equipment. It generated €79.6 billion in 2016, and employs more than 350,000 people around the world.
Tenable raised $50 million in 2012, and followed this with a massive $250 million Series B funding round in November 2015. Its customers include more 50% of the Fortune 500, the ten largest U.S. technology companies, and 8 of the 10 largest U.S. financial companies.
Proofpoint to Acquire Messaging Security Firm Cloudmark for $110 Million
7.11.2017 securityweek IT
Cybersecurity firm Proofpoint on Tuesday announced that it has agreed to acquire messaging security firm Cloudmark for $110 million in cash.
Best known for its spam blocking technology, Cloudmark provides spam and malware protection to ISPs and mobile providers around the world.
Proofpoint says that Cloudmark’s Global Threat Network will be incorporated into Proofpoint’s Nexus platform, which is used to power its email, social media, mobile and SaaS security products.
Proofpoint also says that its Email Fraud Defense (EFD) and Domain Defense products will benefit from threat telemetry generated by the billions of daily emails that Cloudmark sees, along with threat intelligence around malicious domains. Proofpoint will also gain visibility into malicious SMS/text messages attempting to be sent to mobile devices around the world.
For the time being, Proofpoint says it plans to continue Cloudmark’s service provider products with an "ongoing roadmap leveraging the combined capabilities" of both companies.
“Messaging has been the number one threat vector for years, but with ransomware and BEC, it’s never been a more urgent issue,” said Jason Donahue, Chief Executive Officer of Cloudmark. “We’re thrilled to be continuing our work to fight advanced threats in messaging as part of Proofpoint.”
The transaction is expected to close in the fourth quarter of 2017 and is subject to customary closing conditions and regulatory approvals.
When the acquisition is complete, Cloudmark is expected to increase Proofpoint's revenue range by $20 - $25 million to $664 - $673 million to its financial outlook for the full year 2018.
Container Security Firm NeuVector Raises $7 Million
7.11.2017 securityweek IT
NeuVector, a San Jose, Calif.-based developer of container security technology, today announced that it has raised $7 million in Series A funding led by Hummer Winblad Venture Partners.
Launched in January 2017 by tech industry veterans from Fortinet, VMware, and Trend Micro, NeuVector, offers a ‘container firewall’ that provides application-layer segmentation to isolate container traffic, to help detect and block suspicious connections within the container environment.
“As more enterprises turn to containers for deploying business-critical applications, the need to inspect and secure all internal traffic within these container environments has become increasingly clear,” the company explained. “Data breaches and zero-day attacks are becoming more common and dangerous – and containers are not immune.”
NeuVector LogoThe NeuVector solution is a container itself and provides runtime vulnerability scanning across all running containers and hosts, and provides threat detection designed to mitigate DDoS, DNS, and other types of attacks. NeuVector also says that its offering leverages behavioral learning to automatically recognize and whitelist normal behavior, applying zero-configuration security policies that safeguard container traffic.
“Enterprises are increasingly tapping into the power of containers for application deployment – and the bad guys have taken notice,” said Fei Huang, CEO, NeuVector.
NeuVector joins several other startups looking to tap the container security market.
In September, Tel Aviv, Israel-based container security startup Aqua Security announced that it had raised $25 million in Series B funding, bringing the total amount raised by the company to $38.5 million.
In July, StackRox emerged from stealth mode armed with $14 million in funding to take its adaptive security platform for containers to market.
Container-focused security firm Twistlock has raised more than $30 million in funding over multiple rounds.
In June, cloud-based security and compliance solutions provider Qualys launched a product designed for securing containers across cloud and on-premises deployments.
According to a 2015 survey of 272 IT decision makers in North America conducted by Twistlock, 91 percent of the respondents said they were concerned about the security of containers.
Learn Ethereum Development – Build Decentralized Blockchain Apps
6.11.2017 thehackernews IT
As of today — 1 Bitcoin = $7300 USD (Approx 471,000 INR)
At the beginning of this year, 1 Bitcoin was approximately equal to $1000, and now it has surged to a new height, marking its market capitalization at over $124 billion.
Is it really too late to invest in Bitcoin or other cryptocurrencies like Ethereum?
For those wondering if they have missed the money-making boat, the answer is—NO, it's never too late to invest.
In case you are new to cryptocurrency trading, we have a simple step-by-step guide on our deal store that explains how to invest in cryptocurrencies.
However, the blockchain, the revolutionary technology behind Bitcoin and other digital currencies, is not always about cryptocurrencies.
Though it is a decentralized public database which ensures that all transactions are properly conducted and recorded, Blockchains can be used for a wide variety of applications, such as for digital identity management, smart assets, digital voting, distributed cloud storage, and so on.
While Bitcoin has long been dominant in the cryptocurrency market, the second largest cryptocurrency—Ethereum—offers much faster data processing than Bitcoin.
Moreover, Bitcoin was designed to be used as a currency only, whereas the Ethereum blockchain facilitates the development of all sorts of next-generation decentralized applications.
Organisations are recognizing Ethereum potential to make processes more efficient and secure, and programmers are opting for Ethereum development.
Also, since Ethereum technology is still in the early adopter stage, you can get in at ground level and become proficient before it blows up.
How to Become An Ethereum Developer?
So are you considering to learn blockchain technology and Ethereum development?
The Hacker News is making things easier for you by providing you an amazing deal on "The Complete Ethereum Blockchain Mastery Bundle," at a discount of 95 percent.
The Complete Ethereum Blockchain Mastery Bundle includes four online courses:
1. Ethereum Blockchain Developer: Build Projects Using Solidity—This course will help you get your hands on development practice with solidity and successfully build a complex, real-world, Ethereum-based distributed app using core development tools such as Mist, Geth & Ethereum Studio.
2. Blockchain Technology: A Guide To The Blockchain Ecosystem—This course will help you understand the blockchain ecosystem and the technology that surrounds it.
3. Ethereum Developer: Build A Decentralized Blockchain App—This course will help you build your own decentralized blockchain application.
4. Ethereum Developer Masterclass: Build Real-World Projects—This is the last course in The Complete Ethereum Blockchain Mastery Bundle that will help you launch an initial coin offering (ICO) and at the same time will help you build a decentralized exchange on the blockchain.
Automated System Defeats reCAPTCHA With High Accuracy
2.11.2017 securityaffairs IT
A newly devised system that targets the audio version of Google’s reCAPTCHA challenges can break them with very high accuracy.
Dubbed unCAPTCHA, the automated system designed by computer science experts from the University of Maryland (UM) is said to be able to defeat the audio reCaptcha system with 85% accuracy.
The system uses browser automation software to interact with the target site and engage with the captcha. The tool, which has been published on GitHub, can properly identify spoken numbers to pass the reCaptcha programmatically and trick the site into thinking their bot is a human, the authors claim.
“Specifically, unCaptcha targets the popular site Reddit by going through the motions of creating a new user, although unCaptcha stops before creating the user to mitigate the impact on Reddit,” the experts say.
To correctly bypass the captcha, which includes numbers that are read aloud at varied speeds, pitches, and accents through background noise, the attack identifies the audio message on the page, downloads it, and then automatically splits it by locations of speech.
Next, each number audio bit is uploaded to 6 different online audio transcription services that are free to use, namely IBM, Google Cloud, Google Speech Recognition, Sphinx, Wit-AI, and Bing Speech Recognition, and the results are collected.
“We ensemble the results from each of these to probabilistically enumerate the most likely string of numbers with a predetermined heuristic. These numbers are then organically typed into the captcha, and the captcha is completed. From testing, we have seen 92%+ accuracy in individual number identification, and 85%+ accuracy in defeating the audio captcha in its entirety,” the system’s authors reveal.
Another recently revealed tool for defeating CAPTCHA systems is targeting text-based systems and was designed to mimic the human eye. Called the Recursive Cortical Network (RCN), it incorporates neuroscience insights into a structured probabilistic generative model framework.
In a paper (PDF), the team of researchers behind RCN explain that the tool is capable of solving Google reCAPTCHA with a 66.6% accuracy, but that it is also highly efficient against other systems: 64.4% for BotDetect, 57.4% for Yahoo, and 57.1% for PayPal image challenges. The findings were published in the Science magazine.
“By drawing inspiration from systems neuroscience, we introduce a probabilistic generative model for vision in which message-passing based inference handles recognition, segmentation and reasoning in a unified way. The model demonstrates excellent generalization and occlusion-reasoning capabilities, and outperforms deep neural networks on a challenging scene text recognition benchmark while being 300-fold more data efficient,” the researchers say.
Threat Intelligence Firm Recorded Future Raises $25 Million
1.11.2017 securityweek IT
Threat intelligence provider Recorded Future today announced that it has raised $25 million in a Series E round of funding Led by Insight Venture Partners.
According to the Boston, Mass.-based company, the additional funding will be used to support growth and to expand its offerings to “solve a wider spectrum of cybersecurity challenges.”
Recorded Future LogoRecorded Future collects threat intelligence from open, technical, and dark web sources in real time and leverages machine learning to provide targeted analytics and alerts to clients. The company says that 86% of Fortune 100 companies use its services.

The company says that it processes "billions of data points" per day in multiple languages from the open, deep, and dark web to provide customers with a customized view of the threat landscape to reveal emerging attackers, methods, and indicators.
“Our goal remains clear: to support our customers by providing the best threat intelligence on the planet,” said Christopher Ahlberg, CEO and co-founder of Recorded Future. “With this cash infusion provided by Insight Venture Partners, we will be able to supercharge our efforts to explore new solutions to the issues plaguing the cybersecurity industry both today and in the future.”
Comodo Sells Certificate Business to Private Equity Firm
1.11.2017 securityweek IT
Francisco Partners Acquires Comodo's Certifiate Authority Business
Tech-focused private equity firm Francisco Partners announced on Tuesday that it has acquired Comodo CA Limited, Comodo’s certificate authority business, for an undisclosed amount.
Comodo CA is the world’s largest provider of SSL certificates, with more than 91 million certificates issued to over 200,000 customers in 150 countries. Francisco Partners has acquired a majority stake in the company and says the investment will help support Comodo CA’s accelerated growth; the firm consistently reported double-digit revenue growth in the past several years.
Bill Holtz, former COO of Entrust and former CIO of Expedia, has been named Comodo CA’s chief executive officer (CEO). Bill Conner, currently the president and CEO of security firm SonicWall, has been appointed chairman of the board. Melih Abdulhayoglu, CEO and founder of the Comodo Group, will remain a minority owner and board observer.
“Bill Holtz and Bill Conner are very accomplished executives within the enterprise security market and we are thrilled to have them join Comodo CA,” said Brian Decker, head of security investing at Francisco Partners. “Their years of experience in the SSL and digital certificate business is invaluable for Francisco Partners in this investment as Comodo CA grows and expands its leadership from SSL certificates to IoT.”
Comodo has been trying to snatch customers from Symantec, which announced on Tuesday that it’s certificate business has been acquired by DigiCert for $950 million. Symantec decided to sell its website security and related public key infrastructure (PKI) solutions after Mozilla and Google announced their intent to revoke certificates issued by the company and its partners.
When the acquisition was first announced, Comodo warned Symantec customers that the migration to DigiCert’s platform, which is significantly smaller than Symantec’s infrastructure, “poses a huge execution and technology risk.”
Symantec and DigiCert promised customers a smooth transition, but Mozilla has raised some concerns about the acquisition, particularly regarding Symantec’s involvement in day-to-day operations after the transfer of ownership.
Booz Allen to Acquire AI-based Morphick
21.10.2017 securityweek IT
Contracting giant Booz Allen is to acquire cybersecurity firm Morphick. Few details have been made public -- there is no statement on the price involved nor the future of existing Morphick staff. Nevertheless, this seem to be a good fit for both companies, with Morphick gaining access to more customers, and Booz Allen moving further along its published plan to expand its commercial presence.
Morphick is located in Cincinatti with a staff of around 40 cybersecurity specialists. Booz Allen has its global headquarters in McLean, Virginia, and employs around 23,000 people. The acquisition is expected to close in the third quarter of Fiscal Year 2018, and is subject to customary closing conditions.
"The acquisition bolsters Booz Allen's growth strategy in its U.S. Commercial business, where the focus is on expanding clients' access to scalable, on-demand managed threat services. The addition of the Morphick team and technology further solidifies the firm's ability to solve increasingly advanced cyber challenges," said Horacio Rozanski, president and CEO of Booz Allen. "Under our long-term growth strategy, Vision 2020, Booz Allen has been moving closer to the center of our clients' missions, fusing our consulting heritage with expert capabilities in cyber, digital solutions, engineering and analytics," he added.
At least part of Morphick's technology comes from AI firm, Endgame. "The Morphick Managed EDR service, powered by Endgame," announced Endgame in January 2017, "combines Morphick's best-in-class managed detection and response services with Endgame's unparalleled EDR platform to provide customers with earliest prevention, accelerated detection and response, and automated hunt of next-gen attacks."
Booz Allen is moving straight to 'next-gen' threat detection with AI and machine-learning detection capabilities rather than signature-based detection -- and calls it 'an adaptive approach to threat detection'. "Morphick's technology is differentiated by an adaptive approach to threat detection that addresses the growing challenge of highly evolved cyber threats and determined attackers, empowering companies to protect themselves and respond more effectively," says Booz Allen. "The platform, which analyzes the motivation and actions of attackers to thwart their attacks, assists companies in mitigating the challenges of the shortage of skilled cyber professionals and limitations of traditional, static defenses."
Existing Morphick staff will also complement Booz Allen's current market presence. Describing its own alliance with Morphick, Endgame commented, "Core to the service offering are Morphick's seasoned security analysts and NSA-accredited incident response teams, whose deep expertise enables them to identify and terminate the efforts of latent attackers targeting organizations' intellectual property, business systems, or other key assets. These analysts will leverage Endgame's EDR platform to prevent, detect, and rapidly respond to advanced attacks without the reliance on signatures."
Endgame's involvement in Morphick technology will continue beyond the acquisition. "Endgame and Morphick are committed to continuing our relationship following the Booz Allen Hamilton transaction," an Endgame spokesperson told SecurityWeek. "Morphick has realized tremendous value for itself and its customers thanks to its use of the Endgame platform, and Morphick will continue to use and market the platform for their customers following the acquisition."
Duo Security Raises $70 Million at More Than $1 Billion Valuation
19.10.2017 securityweek IT
Duo Security, a cloud-based provider of identity and access management solutions, today announced that it has raised an additional $70 million in funding led by Meritech Capital Partners and Lead Edge Capital.
The Series D funding round brings the total amount raised by the Ann Arbor, Michigan-based software-as-a-service (SaaS) company to $119 million, with a post-money valuation pegged at $1.17 billion.
According to the company, the additional cash will be used to expand global operations and fund product development.
Duo says that it currently serves more than 10,000 customers and protects more than 300 million logins worldwide every month. Customers include Facebook, Etsy, Facebook, K-Swiss, Paramount Pictures, Toyota, Random House, Yelp, Zillow and more.
Duo Security LogoThrough its flagship two-factor authentication (2FA) app, Duo's "Trusted Access" product suite helps verify the identity of users, and the health of their devices, before granting them access to applications. The platform supports Macs, PCs and mobile devices, and gives administrators visibility into end user devices accessing the corporate network.
In term of company performance, Duo says it has doubled its annual recurring revenue for the past four years, and currently has more than 500 employees globally, after doubling its headcount in 2016.
In late September, Duo issued a research report showing discrepancy between the frequency and thoroughness of Apple's Mac Operating System (OS X) and app security updates, and updates for the underlying firmware (EFI) on Mac computers. Duo’s research found that on a sample of 73,324 Macs deployed in production settings, 4.2% were running outdated EFI -- leaving them potentially vulnerable to new exploits.
In addition to its Ann Arbor, Michigan headquarters, Duo currently maintains offices in Austin, Texas; San Mateo, California; and London, England.
The Series D round included new investors, Geodesic Capital and Index Ventures, as well as existing investors Redpoint Ventures and True Ventures. Workday, a new strategic partner, also participated in the round. Other investors in the company include, Benchmark, Google Ventures, Lead Edge Capital, Meritech Capital Partners, Radar Partners.
Security Pros Admit Snooping on Corporate Network: Survey
18.10.2017 securityweek IT
IT security professionals, particularly executives, often access information that is not relevant to their day-to-day work, according to a new One Identity study focusing on “snooping” on the corporate network.
Dimensional Research polled more than 900 IT security professionals on behalf of One Identity. The respondents were from various types of companies in the United States, the United Kingdom, Germany, France, Australia, Singapore and Hong Kong, with at least 500 employees.
When asked if their company’s employees ever attempt to access information that is not necessary for their day-to-day work, 92% admitted it happens and 23% said it happens frequently. There are no major differences based on region or the size of the company.
Roughly two-thirds of the IT security pros that took part in the survey admitted snooping themselves, although 51% claim they do it rarely. Professionals from the U.S. seem to snoop the least (50%) while ones in Germany snoop the most (80%).
Interestingly, executives appear to be the guiltiest (71% said they snoop), followed by managers (68%) and other members of the IT security team (56%).
Globally, one in three IT security professionals who took part in the survey said they had accessed sensitive information about their company’s performance, despite not being required to do so as part of their job. This behavior can be seen more in Europe and Asia, and less in the U.S. and Australia, the report shows.
Again, executives and managers are more likely to look at company performance data compared to non-managers.
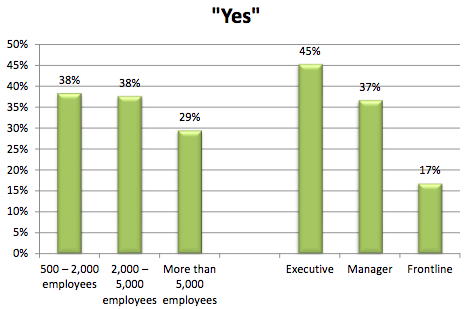
The survey also found that cybersecurity professionals working in the technology sector are most likely to look for data on their organization’s performance.
“While insider threats tend to be non-malicious in intent, our research depicts a widespread, intrusive meddling from employees when it comes to information that falls outside their responsibility -- and it could be that meddling that ends up putting their employers in hot water,” explained John Milburn, president and general manager of One Identity.
“Without proper governance of access permissions and rights, organizations give employees free reign to move about the enterprise and access sensitive information like financial performance data, confidential customer documentation, or a CEO's personal files. If that information winds up in the wrong hands, corporate data loss, customer data exposure or compliance violations are possible risks that could result in irreversible damage to the business's reputation or financial standing,” Milburn added.
Intrusion Detection Startup Threat Stack Raises $45 Million
20.9.2017 securityweek IT
Threat Stack, a Boston, Mass.-based intrusion detection startup has raised $45 million in a Series C funding, bringing the total raised by the company to more than $70 million.
The cybersecurity startup offers an integrated suite of detection and assessment tools that help customers with security and compliance by combing continuous security monitoring and risk assessment across wide range of detection points across customers’ infrastructure.
Threat Stack explains that its platform offers a single place to monitor cloud, hybrid cloud, multi-cloud, and containerized environments, and can automatically correlate events together to identify suspicious activity.
The company claims 235% year-over-year revenue growth and an 84% increase in employee headcount as of July, with plans to grow its employee base another 30% by the end of this year, and doubling the size of its downtown Boston headquarters.
Threat Stack Logo“Every company is looking to get their arms around the security of their infrastructure. Most are dealing with a shortage of security talent and increasingly automated development processes - so there is a unique need for deploying security at speed and scale,” Brian M. Ahern, Threat Stack Chairman and CEO, said in a statement. “Threat Stack has built a platform for both security and operations teams to do just that. The market opportunity ahead is enormous.”
The funding round was led by F-Prime Capital Partners, the venture capital group of Fidelity Investments, and Eight Roads Ventures. Existing investors Scale Venture Partners, .406 Ventures, and Accomplice also participated in the round.
As part of the funding, Gaurav Tuli of F-Prime will join Threat Stack’s Board of Directors and Davor Hebel of Eight Roads Ventures will be an observer.
“The migration of computing workloads to public cloud environments represents the most significant shift in enterprise technology of the last 15 years. Cybersecurity continues to be the most acute challenge in the move to cloud, as cloud infrastructure is elastic and complex and attackers are operating at unprecedented speed and sophistication,” said Tuli. “Cloud security requires new approaches and new solutions, and Threat Stack is a rare security company that is purpose-built to address these unique challenges. Our investment will help drive continued innovation to meet the rapidly expanding market demand.”
Container Security Firm Aqua Raises $25 Million
19.9.2017 securityweek IT
Aqua Security, a Tel Aviv, Israel-based container security startup, today announced that it has raised $25 million in Series B funding, bringing the total amount raised by the company to $38.5 million.
Container technologies are becoming increasingly popular among IT decision makers, as they offer a means to deploy applications faster when compared to traditional methods.
Aqua’s Container Security Platform delivers a security solution for containerized environments, and supports both Linux and Windows containers, multiple orchestration environments, both on-premises deployments as well as on AWS, Azure, GCP, and other public clouds.
“On a fundamental level, container security is equivalent to hypervisor security,” F5’s David Holmes explained in a 2015 SecurityWeek column.
Aqua says that it uses a combination of intelligent defaults, machine learning, and threat research to protect container-based applications.
The Series B round was led by Lightspeed Venture Partners, while existing investors Microsoft Ventures, TLV Ventures and Shlomo Kramer also participated in the round.
“The rapid rise and convergence of DevOps, containers, and microservices-based applications is an opportunity to rethink application security.” said Chris Schaepe, Partner, Lightspeed Venture Partners. “Aqua’s success in leveraging containers to improve security provides visible customer value, as evident from the impressive customer adoption that the team at Aqua achieved in a very short time.”
According to a 2015 survey of 272 IT decision makers in North America conducted by container security specialist Twistlock, 91 percent of the respondents said they were concerned about the security of containers.
Founded in 2015, Aqua says two of the 10 largest financial services companies and three of the world’s top 10 software companies are customers. The company has office locations in San Francisco, CA, Burlington, MA, and London, UK.
U.S., Moscow Seek Russian Held in Greece over Bitcoin Laundering
19.9.2017 securityweek IT
Moscow has requested the extradition of a Russian national also wanted in the United States for laundering billions of dollars through a Bitcoin exchange he operated, a judicial source said Tuesday.
Alexander Vinnik, who headed BTC-e, an exchange he operated for the Bitcoin crypto-currency, was indicted by a US court in late July on 21 charges ranging from identity theft and facilitating drug trafficking to money laundering.
He has been languishing in a Greek jail since his arrest on July 25 in the tourist resort of Halkidiki, near the northern city of Thessaloniki.
According to the judicial source, Vinnik said he would not contest Moscow's request, dated August 10. He is wanted there on separate fraud charges totalling 9,500 euros ($11,000).
According to US authorities, Vinnik, 37, "stole identities, facilitated drug trafficking, and helped to launder criminal proceeds from syndicates around the world."
In addition, BTC-e "was noted for its role in numerous ransomware and other cyber-criminal activity," receiving more than $4 billion worth of bitcoin over the course of its operation.
BTC-e, founded in 2011, became one of the world's largest and most widely used digital currency exchanges, but according to the indictment, it was "heavily reliant on criminals" engaged in identity theft and drugs, as well as corrupt public officials.
Vinnik was also charged with receiving funds from the infamous hack of Mt. Gox -- an earlier digital currency exchange that eventually failed, in part due to losses attributable to hacking.
The Treasury Department has fined BTC-e $110 million for "wilfully violating" US anti-money laundering laws, and Vinnik $12 million.
In July, Treasury Secretary Steven Mnuchin hailed Vinnik's arrest and indictment, saying that cracking down on illegal uses of the cyber currency is a key goal of US regulators.
The Greek justice system will now have to decide whether Vinnik heads to Moscow or Washington.
Best Buy Drops Kaspersky Products Amid Russia Concerns
11.9.2017 securityweek IT
US electronics retailer Best Buy has stopped selling products by leading computer security firm Kaspersky Lab amid concerns the company has links to Russian intelligence, the two companies confirmed Friday.
The big box retailer, with stores across the country, did not announce the change itself but its website was no longer offering Kaspersky products, and numerous social media reports said they were not on store shelves anymore.
A Best Buy spokeswoman confirmed in an email reports that the action was taken due to concerns over Kaspersky's alleged links to the Russian government.
Kaspersky, which denies Russian government links, said the two firms "have suspended their relationship at this time."
Around the Web: Show the Proof, or Cut it Out with the Kaspersky Lab Russia Rumors
"However, the relationship may be re-evaluated in the future," it said in a statement.
"Kaspersky Lab has enjoyed a decade-long partnership with Best Buy and its customer base, and Kaspersky Lab will continue to offer its industry-leading cybersecurity solutions to consumers through its website and other retailers."
The security software vendor, founded in 1977 by Russia-born Eugene Kaspersky, operates a global business with an estimate 400 million product users.
It has its main offices in Russia and the United States.
In July, the US government removed Kaspersky from its list of approved vendors, weeks after top US intelligence agency and law enforcement officials publicly expressed concerns about the safety of its software.
Last week, Democratic Senator Jeanne Shaheen said she was introducing legislation to ban US government bodies from using Kaspersky software.
But no evidence has been presented to back up vague assertions that it might be a tool of Moscow, offering Russian spies back-door entry into computers worldwide.
In July, it strongly denied those insinuations.
"Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyber-espionage efforts," the company said.
A top official of a Kaspersky competitor this week told AFP on condition of anonymity that he did not believe the allegations.
But he said Russia and China are increasingly treating his and other US cyber security firms with intense suspicion and constricting their market access.
Satoshi Bomb
9.9.2017 Kaspersky IT
Let us discuss what defines the profitability of bitcoin mining, what principles for mining speed adaptation were initially embedded into it, and why these principles can lead to the failure of the cryptocurrency in the long run.
We assume that the reader has an idea of basic Bitcoin mechanics such as blockchains, mining, mining pools, and block rewards.
Note: In this article, we investigate a theoretical possibility of how the described scenario may evolve by considering the algorithms embedded in Bitcoin. Our goal was not to make a deep analysis of the structure of miner expenditures, electricity prices in different areas of the world, bank interest rates, or payback periods for equipment.
A 51% attack
The Bitcoin community is well aware of “51% attack”. If a miner controls more than a half of all of the mining hashrate, then he or she is capable of doing the following:
Pay with his or her bitcoins for a commodity or service or exchange them for traditional money.
Begin generating blocks that do not include the mentioned transaction, but not show the generated blocks to other miners.
Wait until the commodity has been delivered.
Publish the generated chain of blocks.
At the same time, the following happens:
All of the other miners will have to accept the fraudster’s blockchain version as the only one that is genuine because it is longer and the miner has a mining hashrate that is more powerful than that of all of the participants put together.
The fraudster receives the commodity and keeps his/her bitcoins, as he or she did not spend them in his or her version of history.
The fraudster receives the reward for all of the generated blocks, not for one half of the blocks, which is what they would generate if they were playing fair and adding blocks to a common chain.
The fraudster during the Attack will most likely buy coins of another cryptocurrency using bitcoins, as it is fast, quite safe, and irreversible.
The community concurs that such an attack if it were possible, would raise questions about the further existence of Bitcoin.
It is important to note that a successful attack does not necessarily entail a 51% or higher hashrate. There is some possibility that it can be carried out with a smaller hashrate share. For example, owning 30% of hashrate gives the attacker about an 18% chance of generating a chain of five blocks in a row, which would be longer than the shared one. In that case, the attacker gains all of the same privileges as in a 51% attack. In case of failure, the attacker can just try again. The majority of services that receive bitcoin payments require only five “confirmations”, which means that such a generated chain will be enough.
Adaptation of mining difficulty
After generation of a pack of 2016 blocks, the Bitcoin network adapts the difficulty of mining. The standard of difficulty is when the mining of one block takes around 10 minutes. Therefore, mining 2016 blocks will take two weeks. If the generation process took, for instance, only one week, then the difficulty will be increased twofold after the next reassessment (so that it would take two weeks to generate the next 2016 blocks at the same network hashrate).
It’s worth noting that the Bitcoin network uses software to prohibit changing the difficulty of mining more than four times per one reassessment.
There are direct consequences stemming from these rules. If mining hashrates are added or removed during a period of 2016 blocks, then the following occurs:
This does not affect the reward received by the remaining miners in any way. The reward is determined by the hashrate of a miner but not their share in the common hashrate. For example, after one half of the hashrates have been deactivated, the remaining miners will mine twice as many blocks; but this will require double the time. Income will be retained.
This directly affects the output rate. If 99% miners stop mining, then the next difficulty reassessment will occur in 4 years. Creation of one block will take about 16 hours.
The authors of Bitcoin assumed that the described algorithm would smoothly adjust network power by pushing out less power-efficient equipment and restoring the reasonable marginality of the remaining equipment. However, what this rare difficulty reassessment does is open the door to another strategy for miners: they may trick the algorithm by artificially lowering network performance. After all, when a rig is abruptly powered down, the revenue generated for the day stays at the same level; and when a rig is suddenly powered up, costs are lowered.
Mining fees and the free will of miners
In addition to receiving a reward for a block (of an emitted currency), miners also collect fees for transactions that are included in the block. As of today, the fees currently sit at approximately 10% of the block reward. We won’t dwell on this for too long, but, nevertheless, according to our estimations, it turns out that the existence of fees makes the miner strategy that we are researching here even more appealing.
Another aspect is that mining pools frequently do not directly control the mining rigs that are part of those pools. Each participant and rig owner is free to choose the pool that they will work in. The decision to move from one pool to another is usually based on economic grounds.
However, the person in charge of the pool determines the policy regarding powering up and powering down the rigs and switching the rigs to mine an alternative currency (Bitcoin Cash). In other words, we think that the described behavioral strategy should be adopted and implemented by only about 20 participants who are pool owners: the rig owners do not matter in the least here even though they possess their own “free will”.
Let’s suppose that the total hashrate of all of the miners has been stabilized and review one of the strategies for increasing marginality.
An example of miner behavior during a stable Bitcoin network hashrate
For the sake of simplicity, let’s assume that you control one half of all of the hashrates of the Bitcoin network. You can keep the rig turned on all the time and receive the reward for about 1008 blocks (50%).
You could also do the following:
Wait until the next period of 2016 blocks.
Turn off your mining rigs.
Wait until the remaining miners get 2016 blocks within 4 weeks.
After that, the Bitcoin network will halve the mining difficulty for the next period.
You can turn on your rigs, and the entire network will mine 2016 blocks within one week.
You will receive a reward for the same 1008 blocks (approximately) within just a week.
Please note the first scenario assumes that five weeks of regular operation will yield a reward for 5/2 × 1008 = 2520 blocks, but you would have to pay for electricity for the entire time period. The second scenario assumes that the same five weeks will yield a reward for 1008 blocks, but you would have to pay the electricity costs for only one week.
Let’s suppose that the electricity price comprises only about 90% of the reward. It is easy to calculate that the first scenario assumes that a five-week profit is equivalent to a reward for 2520 × 0.1 = 252 blocks, while the second scenario yields a reward for “reward − costs” = 1008 − 0.9 × 1008/2 = 554.4. This means that the proposed strategy turns out to be twice as lucrative.
Economically profitable miner behavior with different parameters
Let’s assume the following.
A smart miner controls a share x, of the total network hashrate.
The bitcoin reward for all of the 2016 blocks is A.
The electricity and maintenance costs for two weeks of network rig operation equals C. We assume that the rent of premises and downtime costs are insignificant. To simplify the calculation, we deliberately disregard the depreciation of the rig.
Thus, the following happens.
A miner’s reward is Ax − Cx for the time period of two weeks of regular operation.
If a smart miner turns off his mining rig, the network will produce 2016 blocks within the period that will take as much time.
For example, if x = 1/3, then it will take one and a half as much time to finish the task.
After the end of the period when the network adapts the difficulty, and the smart miner turns on the rig, the network will complete the task (1 − x) times faster than the planned two weeks.
For example, if x = 1/3, then it will require 2/3rd of the regular time after the rig has been turned on, which is approximately 10 days.
The total duration of the two periods will be () × (2 weeks);
Thus, in regular conditions (without downtime), working during these two periods lets miners earn
Pregular operation = () × (A − C) = () × (A − C)
This means that all of the miners earn a little more than double the net profit for the prolonged conventional period.
A smart miner who operates with downtime will earn nothing for the first period, but the second period (the shorter one) will yield
Psmart = Ax − Cx(1 − x) = Ax − Cx + Cx2
This means that the smart miner gains a single regular net profit and additionally saves up the share of x of the costs.
During the slow period, all of the non-disconnected miners will earn Pslow period = A − C,
and for the fast period: Pfast period = A − C (1 − x), as the reward is the same, but they work faster.
It is easy to see the following:
If the expenditures of miners are precisely equal to their rewards (the miners work with a margin of zero), then the clever approach would let them gain a net profit of Ax2.
If miners pay no electricity costs (a margin of 100%), then they will earn more than double the amount of income within the period of regular operation and a only one regular amount of income when working with downtime.
Let’s find out how much of the rig power x should be turned off in order to maximize the revenue for all miners with a margin of M = (A − C)/A:
maxx(Pslow period + Pfast period − Pregular operation) =
maxx( − ()
maxx( − ()M)
maxx() =
maxx()
This equation reaches its maximum at x = 1 − . For example, smart miners should temporarily disable 80% of their rig power when M = 4%.
Why miners are not using the described strategy right now
The increase of hashrate on the Bitcoin network. The hashrate of the network has grown by 4 times in a year (Source)
The increase in difficulty on the Bitcoin network for the entire time period. Starting January 2016, the difficulty has been increased by 8 times, just like the value of bitcoin (Source)
The described strategy makes sense only under the condition that the overall network difficulty does not increase over time. Otherwise, turning off rigs will not lead to a decrease in difficulty, which makes this economically unviable.
Up until now, mining hashrates have been increasing at a fast tempo; this is a consequence of the growth of the bitcoin exchange rate. The income of miners is estimated in bitcoins, but they pay for costs in traditional currency.
The growth rate of bitcoin value (Source)
Nevertheless, it would be reasonable to suppose that if the bitcoin does not endlessly grow in price, then at some time introducing new mining hashrates would not be economically viable and electricity costs would sooner or later be practically equal to the reward.
The dangers of turning off mining hashrates
When new mining hashrates are no longer introduced, miners will may resort to the above-mentioned strategy.
An estimate of hashrate distribution among the largest mining pools (Source)
If mining pools maximize their own profit, then 75% of hashrates are expected to be turned off at a margin of 6.25%. There is no sense in switching off more rigs, as the network will not reduce its difficulty by more than 4 times.
After that, in order to carry out a 51% attack, a fraudster must either control more than one half of the remaining hashrate (which can be easily done with the current distribution of hashrates) or suddenly turn on more rigs than were working before (which is currently unfeasible, considering the share of the largest pool).
Now, the question arises as to whether attacking the network is profitable for a person who has invested considerable amounts into increasing mining hashrates. Well, the answer is “yes, it is profitable”. In case of low mining marginality, the price of the existing mining rig is decreased too. In other words, if mining brings no revenue, then playing honestly will no longer be viable. Aside from that, the attacking party may remain anonymous and, among other things, speculate for a fall of the bitcoin price.
A Bitcoin Cash attack
We are intentionally not considering a situation where the price of electricity quickly and significantly goes up or where the price of bitcoins falls quickly and by a significant amount (which is much more likely to happen). If that happens, then the miners’ strategy is quite obvious. During drastic price variations, all miners will turn off their rigs. Perchance, only those who take advantage of free electricity will stay afloat. In that case, network operation will simply stop: finishing the “two weeks” will require a lifetime, while the inability to carry out a transaction will lower the bitcoin’s price even more.
Our colleague from BitcoinMagazine analyzed the situation with the Bitcoin Cash currency just the other day. This currency appeared after Bitcoin network split on August 1, 2017. The new currency has a feature called Emergency Difficulty Adjustment (EDA). The EDA allows for adaptation of the difficulty on the Bitcoin Cash network even more often. This means that the difficulty is lowered by 20% if fewer than 6 blocks were mined in the span of 12 hours. The author comes to a conclusion similar to ours, but what’s more important is that he mentions that he has already been observing manipulations by smart miners. He fears destabilization of the Bitcoin Cash network and is counting on a prompt solution from developers.
Conclusion
We have analyzed one of the economically viable strategies of honest miners after the hashrate of the Bitcoin network stops growing. We have also calculated some of the key values of this strategy and inferred that using it is profitable for each individual participant but also considerably increases the risk of a 51% attack and a potential crash of the Bitcoin network as a whole.
If all of the miners were capable of coming to a solid agreement, they would go even further by turning off all but one of the rigs. This would be optimal in respect to revenue but fatal from the point of view of network security.
How should miners act in order to guarantee security? Here we can see a couple of analogies. The first one is an overproduction crisis. When this happens, manufacturers come to an agreement to publicly eliminate some of their products (at least, this was how it happened in the Middle Ages). The second one is nuclear disarmament, where countries that own large arsenals of nuclear weapons arrange for their proportional reduction.
Ideally, all miners should agree on turning off some of their rigs and, above all, on the controlled destruction of their rigs. It would be important not only to destroy rigs systematically but to control their production in a strict manner as well.
We do not have to rely on such a “peaceful” resolution. The recent split of the Bitcoin chain into two chains and the formation of Bitcoin Cash reveal that miners are not always able or have the desire to solve common problems together. It is possible that the ability to cooperate will become a decisive factor in the future.
Only time will tell how our theoretical research corresponds with actual practice.
China Bans Fundraising Through Initial Coin Offering (ICO)
7.9.2017 thehackernews IT
China's central bank today announced an immediate ban on all ICO—Initial Coin Offering—fundraising, to prevent fraud and illegal fundraising.
ICO is the hottest new thing in the blockchain world, which is an alternative to crowdfunding that lets a firm raise funding from multiple sources.
The People's Bank of China (PBoC), the country's central bank and financial regulator, has issued an official notice on Monday, forbidding "all types of currency issuance financing activities" that have "seriously disrupted the economic and financial order."
This PBoC's bold move has been backed by many other Chinese government administrators and regulators including the China Securities Regulatory Commission, China Insurance Regulatory Commission and the Ministry of Industry and Commerce, and China Banking Regulatory Commission.
This move marks the end of an era of ICO fundraising in China.
The regulator claims that ICOs are being misused for "illegal fund-raising, financial fraud, pyramid schemes and other criminal activities" and from now, the Chinese government will closely monitor ICOs for signs of illegal activity.
The ban has also been applied to those individuals and organizations who have previously completed ICO fundraising, requiring them to return all investor funds as soon as possible.
The prices of Bitcoin and Ethereum—two of the largest cryptocurrencies in the market—slumped after the announcement.
For those who aren't aware of ICOs:
In the world of cryptocurrencies, ICO is an unregulated way to raise funds for businesses and startups—usually cryptocurrency-related—in exchange for virtual coins over blockchain rather than company shares.
In other words, companies offer investors a crypto-token in exchange against cryptocurrencies like Bitcoin or Ethereum, which investors can easily sell or trade on any cryptocurrency exchange.
The popularity of ICOs has surged in China this year, with 65 ICOs raising a total of 2.62 billion yuan (~$397.1 million) as of July from 105,000 individuals, according to Chinese news agency Xinhua.
However, there have been rising concerns surrounding ICOs over scams, and regulators globally are taking action.
"The growth of a few growing China based blockchain projects, i.e., NEO, will be slowing down after this announcement. This is similar to an event back in 2013 when China banned exchanges from allowing people to buy into Bitcoin using yuan. Bitcoin bounced back stronger after few years. It’s only a matter of time before the same happens with NEO." the founder of Its Blockchain, Hitesh Malviya shared his comment on the announcement.
"Furthermore, the proposal to banning ICO is yet to be activated, and we can hope for the officials to rethink over time, whatever could be the future of ICO in China."
"Disruptive technology always finds a way around restrictive regulations, so it would be wise on the Chinese government’s part to think of mitigating these fears while having some regulatory measures over ICOs. Until that time, we can only speculate."
In the United States, the Securities and Exchange Commission (SEC) has also issued an official warning about the risks of ICOs but has not made a firm move yet.
European Companies Must Tell Employees If Their Work Emails Are Being Monitored
7.9.2017 thehackernews IT
Finally, European companies must inform employees in advance if their work email accounts are being monitored.
The European Court of Human Rights (ECHR) on Tuesday gave a landmark judgement concerning privacy in the workplace by overturning an earlier ruling that gave employers the right to spy on workplace communications.
The new ruling came in judging the case of Romanian engineer Bogdan Barbulescu, who was fired ten years ago for sending messages to his fianceé and brother using his workplace Yahoo Messenger account.
Earlier Romanian courts had rejected Barbulescu’s complaint that his employer had violated his right to correspondence—including in January last year when it was ruled that it was not "unreasonable for an employer to want to verify that the employees are completing their professional tasks during working hours."
But now, the European court ruled by an 11-6 majority that Romanian judges failed to protect Barbulescu’s right to private life and correspondence, as set out in article 8 of the European Convention on Human Rights.
Apparently, Barbulescu's employer had infringed his right to privacy by not informing him in advance that the company was monitoring his account and communications. His employer used surveillance software in order to monitor his computer activities.
"The right to respect for private life and for the privacy of correspondence continued to exist, even if these might be restricted in so far as necessary," the court writes in a press release about the decision.
"The Court considered, following international and European standards, that to qualify as prior notice, the warning from an employer had to be given before the monitoring was initiated, especially where it entailed accessing the contents of employees' communications."
The ruling will now become law in 47 countries that have ratified the European Convention on Human Rights.
In a Q & A section on its website, the European Court of Human Rights says the judgement doesn't mean that companies can't now monitor their employee’s communications at workplace and that they can still dismiss employees for private use.
However, the ECHR says that the employers must inform their staff in advance if their communications are being monitored, and that the monitoring must be carried out for legitimate purposes and limited.
Europe Court Backs Employee Fired Over Private Messages
6.9.2017 securityweek IT
Europe's top rights court on Tuesday restricted the ability of employers to snoop on their staff's private messages, in a landmark ruling with wide ramifications for privacy in the workplace.
The highest body of the European Court of Human Rights (ECHR) ruled in favour of a 38-year-old Romanian man who claimed his rights had been violated when he was sacked in 2007 for sending private chat messages in the office.
Bogdan Mihai Barbulescu has fought a 10-year legal battle through Romanian and European courts, claiming his privacy was infringed when his employer accessed intimate exchanges with his fiancee and brother.
In a first ruling in January last year, the ECHR found that the snooping was allowed because employers were justified in wanting to verify "that employees were completing their professional tasks during working hours".
But in a review, the 17 most senior judges at the court based in Strasbourg, France, found Tuesday that Romanian courts "had not adequately protected Mr Barbulescu's right to respect for his private life and correspondence".
In a written judgement, backed by 11 votes to six, they found that previous court rulings had "failed to strike a fair balance between the interests at stake", namely the company's right to check on employees and employees' right to privacy.
The judges also found that "an employer's instructions could not reduce private social life in the workplace to zero", meaning that some use of the internet at work for personal reasons was justified.
The ruling will become law in the 47 countries that have ratified the European Convention on Human Rights, meaning some members will have to adjust their national legislation.
Barbulescu's lawyer Emeric Domokos-Hancu said the ruling was a "ray of light" for his client.
"In reality, it represents much more -- the fact that man's private life does not stop at the door to his workplace," he added.
- Sex life exposed -
The case revolved around messages sent in 2007 by Barbulescu over the Yahoo messaging platform, which the software engineer was required to use by his bosses to liaise with clients.
He was sacked after his employer accused him of using company resources for personal reasons, which violated company policy, and produced 45 pages of his private messages to his fiancee and brother as proof.
Barbulescu argued that his employer had invaded his right to privacy by using spyware to access the chat material, which included details about his health and sex life.
In their judgement on the court's website, the ECHR judges said Tuesday that it was unclear whether Barbulescu had been warned about the monitoring or the risk of the messages being read without his authorization.
It also said that Romanian courts had failed to determine why the monitoring measures were justified and whether there were other ways of checking on him "entailing less intrusion" into his private life.
The judges held a hearing on November 30 last year, at which they heard arguments from experts and the European Trade Union Confederation.
The union group had criticised the initial ruling, judging it to be too harsh.
It recommended that a verbal warning should be the first stage of any disciplinary process with dismissal only possible for repeat offenders or serious misconduct.
Experts also say companies should also have a clear policy governing the use of professional software and the internet during work hours.
Researchers Poison Machine Learning Engines
31.8.2017 securityweek IT
The more that artificial intelligence is incorporated into our computer systems, the more it will be explored by adversaries looking for weaknesses to exploit. Researchers from New York University (NYU) have now demonstrated (PDF) that convolutional neural networks (CNNs) can be backdoored to produce false but controlled outputs.
Poisoning the machine learning (ML) engines used to detect malware is relatively simple in concept. ML learns from data. If the data pool is poisoned, then the ML output is also poisoned -- and cyber criminals are already attempting to do this.
Dr. Alissa Johnson, CISO for Xerox and the former Deputy CIO for the White House, is a firm believer in the move towards cognitive systems (such as ML) for both cybersecurity and improved IT efficiency. She acknowledges the potential for poisoned cognition, but points out that the solution is also simple in concept: "AI output can be trusted if the AI data source is trusted," she told SecurityWeek.
CNNs, however, are at a different level of complexity -- and are used, for example, to recognize and interpret street signs by autonomous vehicles. "Convolutional neural networks require large amounts of training data and millions of weights to achieve good results," explain the NYU researchers. "Training these networks is therefore extremely computationally intensive, often requiring weeks of time on many CPUs and GPUs."
Few businesses have the resources to train CNNs in-house, and instead tend to use the machine learning as a service (MLaaS) options available from Google's Cloud Machine Learning Engine, Microsoft's Azure Batch AI Training or the deep learning offerings from AWS. In other words, CNNs tend to be trained in the cloud -- with all the cloud security issues involved -- and/or partially outsourced to a third party.
The NYU researchers wanted to see if under these circumstances, CNNs could be compromised to produce an incorrect output pre-defined by an attacker -- backdoored in a controlled manner. "The backdoored model should perform well on most inputs (including inputs that the end user may hold out as a validation set)," they say, "but cause targeted misclassifications or degrade the accuracy of the model for inputs that satisfy some secret, attacker-chosen property, which we will refer to as the backdoor trigger." They refer to the altered CNN as a 'badnet'.
The basic process is the same as that of adversaries trying to poison anti-virus machine learning; that is, training-set poisoning -- but now with the additional ability to modify the CNN code. Since CNNs are largely outsourced, in this instance the aim was to see if a malicious supplier could provide a badnet with the attacker's own backdoor. "In our threat model we allow the attacker to freely modify the training procedure as long as the parameters returned to the user satisfy the model architecture and meet the user's expectations of accuracy."
The bottom-line is, 'Yes, it can be done.' In the example and process described by the researchers, they produced a road-sign recognition badnet that behaves exactly as expected except for one thing: the inclusion of a physical distortion (the 'trigger', in this case a post-it note) on a road sign altered the way it was interpreted. In their tests, the badnet translates clean stop signs correctly; but those with the added post-it note as a speed-limit sign with 95% accuracy.

"Importantly," comments Hyrum Anderson, technical director of data science at Endgame (a scientist who has also studied the 'misuse' of AI), "the authors demonstrate that the backdoor need not be a separate tacked-on module that can be easily revealed by inspecting the model architecture. Instead, the attacker might implement the backdoor by poisoning the training set: augmenting the training set with 'backdoor' images carefully constructed by the attacker."
This process would be extremely difficult to detect. Badnets "have state-of-the-art performance on regular inputs but misbehave on carefully crafted attacker-chosen inputs," explain the researchers. "Further, badnets are stealthy, i.e., they escape standard validation testing, and do not introduce any structural changes."
That this kind of attack is possible, says Anderson, "isn't really up for debate. It seems clear that it's possible. Whether it's a real danger today, I think, is debatable. Most practitioners," he continued, "either roll their own models (no outsourcing), or train their models using one of a few trusted sources, like Google or Microsoft or Amazon. If you use only these resources and consider them trustworthy, I think this kind of attack is hard to pull off."
However, while difficult, it is possible. "I suppose, theoretically, one could imagine some man-in-the-middle attack in which an attacker intercepts the dataset and model specification sent to the Cloud GPU service, trains a model in with 'backdoor' example included, and returns the backdoor model in place of the actual model. It'd require a fairly sophisticated infosec attack to pull off the fairly sophisticated deep learning attack." Nation-states, however, can be very sophisticated.
Anderson's bottom-line is similar to that of Alissa Johnson. "Roll your own models or use trusted resources;" but he adds, "and tenaciously and maniacally probe and even attack your own model to understand its deficiencies or vulnerabilities."
Expert discovered 2,893 Bitcoin miners left exposed on the Internet
31.8.2017 securityaffairs IT
The popular Dutch security researcher Victor Gevers has discovered thousands of Bitcoin miners left exposed on the Internet.
The popular security researcher Victor Gevers, the founder of the GDI Foundation, has discovered 2,893 Bitcoin miners left exposed on the Internet.
View image on TwitterView image on TwitterView image on Twitter
Follow
I see about 2,893 Chinese Bitcoin "Thunder mining machines" online which are accessible via telnet w/o any password. Is the GFW down?
1:19 AM - Aug 29, 2017
13 13 Replies 190 190 Retweets 322 322 likes
Twitter Ads info and privacy
The devices expose Telnet port with no password, the expert explained to Bleeping Computer that all miners belong to the same Bitcoin mining pool and likely are operated by the same organization.
Most of the devices are ZeusMiner THUNDER X3 Bitcoin miners.
Based on firmware details Gevers found on the devices, the researcher believes that most are ZeusMiner THUNDER X3 Bitcoin miners.
The analysis of the IP addresses assigned to the Bitcoin Miners led to believe that the devices belong to a Chinese state-sponsored group.
“The owner of these devices is most likely a state sponsored/controlled organization part of the Chinese government, ” Gevers told Bleeping Computer.
Shortly after Gevers announced his discovery the operators behind the Bitcoin miners secured the exposed devices shortly after, the experts highlighted the speed in protecting the Bitcoin miners.
“Most of the miners are now not available anymore via Telnet,” Gevers told Bleeping Computer.
“At the speed they were taken offline, it means there must be serious money involved,” Gevers added. “A few miners is not a big deal, but 2,893 [miners] working in a pool can generate a pretty sum.”
A so huge botnet of miners could generate million dollars per months depending on the specific crypto currency they were mining.
The Twitter user @Quan66726078 speculate the botnet of 2,893 miners discovered by Gevers could generate an income of just over $1 million per day, in case operators use it to mine Litecoin cryptocurrency.
29 Aug
Quan @Quan66726078
Replying to @Quan66726078 @0xDUDE
2) and the machines are high-end. With approx ~14 Th/s. Maybe more since not all new Chinese mining equipment even gets on the market
Follow
Quan @Quan66726078
3) Then with power consumption about 1323 watt at price of 0.08 cent per kwH and mining Litecoin with 1 machine generates ~$379.000
9:55 AM - Aug 29, 2017
1 1 Reply Retweets 2 2 likes
Twitter Ads info and privacy
Gevers noticed that other netizens have accessed the Bitcoin miners before he discovered them.
“I have proof of other visitors on the boxes where they tried to install a backdoor or malware,” Gevers said.
29 Aug
Victor Gevers @0xDUDE
I see about 2,893 Chinese Bitcoin "Thunder mining machines" online which are accessible via telnet w/o any password. Is the GFW down? pic.twitter.com/pGuBJnld5i
Follow
Victor Gevers @0xDUDE
From XL_MINER_0001 to XL_MINER_2893. And no I am not the only visitor with admin privileges. These miners get visitors daily from everywhere pic.twitter.com/pOt1D4ChgL
1:34 AM - Aug 29, 2017

Twitter Ads info and privacy
According to a researcher who goes online with the handle Anthrax0, the miners appeared to be participating in a bandwidth sharing scheme run via Chinese service Xunlei.
29 Aug
Victor Gevers @0xDUDE
I see about 2,893 Chinese Bitcoin "Thunder mining machines" online which are accessible via telnet w/o any password. Is the GFW down? pic.twitter.com/pGuBJnld5i
Follow
Anthr@X @anthrax0
This is not any crypto currency miner. It's in fact a bandwidth/uploading affiliation program. You get rewarded for using the router as CDN.
11:29 AM - Aug 29, 2017
The Pirate Bay Founders Ordered to Pay Music Labels $477,800 in Compensation
24.8.2017 thehackernews IT
Two of the three co-founders of The Pirate Bay—Fredrik Neij and Gottfrid Svartholm Warg—have been ordered by a Finnish court to pay record labels $477,800 in compensation for copyright infringement on the site.
Last year in a similar case, Helsinki District Court in Finland ordered Peter Sunde, the third co-founder of The Pirate Bay, to pay nearly $395,000 (350,000 Euros) in damages to several major record labels, including Sony Music, Universal Music and Warner Music.
However, Sunde did not pay any penalty yet, and instead, he later announced his plans to sue those record labels for defamation.
The Pirate Bay is still the world's most popular torrent website that has proven to be an elusive hub for illegal copyrighted contents, even after a series of raids and shutdown of its multiple domains, including the primary .SE domain.
All the three co-founders of The Pirate Bay were facing criminal copyright infringement and abuse of electronic communications charges in a Belgian court but were acquitted after it was found that they sold The Pirate Bay file-sharing website in 2006.
The International Federation of the Phonographic Industry (IFPI), which represents the world's major labels, with support from Finnish Copyright Information and Anti-Piracy Center (CIAPC), filed a lawsuit in November 2011 in the Helsinki District Court against The Pirate Bay.
In these last six years, Fredrik Neij and Gottfrid Svartholm never appeared in the court, neither they appointed someone to represent their defence, which eventually led the decision in favour of IFPI record labels.
Besides ordering both the founders to jointly pay compensation of 405,000 euros (over $477,800) to record labels, the District Court also ordered them to "cease-and-desist" the illegal operations of The Pirate Bay, TorrentFreak reported.
However, it is still unclear how Neij and Svartholm are supposed to do anything about stop sharing of content on the site since they have no association with The Pirate Bay.
It has also been reported that Neij, Svartholm, and Sunde also owes large sums of money to other copyright holders as a result of various court judgments over the past few years.
However, so far, none of those court penalties has been "satisfied," neither Sunde paid the fines imposed on him last year, and it is likely that this penalty will also go unpaid.
DMARC Adoption Low in Fortune 500, FTSE 100 Companies
23.8.2017 securityweek IT
Many Fortune 500, FTSE 100 and ASX 100 companies have failed to properly implement the DMARC standard, exposing their customers and partners to phishing and other email-based attacks, according to email security firm Agari.
In a report titled “Global DMARC Adoption Report: Open Season for Phishers,” Agari, which in the past years has obtained tens of millions of dollars in funding, shared the results of its analysis into the adoption of DMARC.
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication, policy, and reporting protocol designed to detect and prevent email spoofing.
Organizations using DMARC can specify what happens to unauthenticated messages: they can be monitored but still delivered to the recipient’s inbox (none), they can be moved to the spam or junk folder (quarantine), or their delivery can be blocked completely (reject).
Agari’s analysis of public DNS records showed that only five percent of Fortune 500 companies have implemented a reject policy and three percent use the quarantine policy. Roughly two-thirds of these organizations have not published any type of DMARC policy.
The sectors with the highest adoption of the reject and quarantine policies are business services, financial, technology and transportation. The security firm has identified several sectors where not one organization has adopted these policies, including wholesales, motor vehicles, apparel, hospitality, food and drug stores, energy, aerospace, household products, chemicals, and engineering and construction.
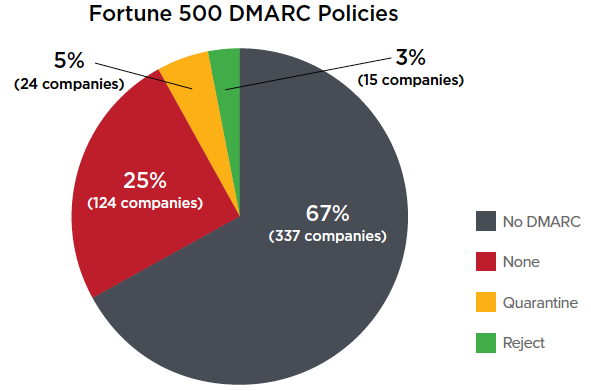
In the case of Financial Times Stock Exchange (FTSE) 100 companies, the percentage is similar. Two-thirds have not implemented DMARC and only seven percent are using a reject or quarantine policy. Only a handful of real estate and financial services firms in the FTSE 100 have implemented proper DMARC policies.
An analysis of Australian Securities Exchange (ASX) 100 organizations showed that a DMARC policy is absent in 73 percent of cases. Only three companies from the utilities, industrial and consumer discretionary sectors have implemented a reject policy and one company in the materials sector is using a quarantine policy.
These figures are worrying considering that there are tens of thousands of phishing websites and their number has increased considerably in the past year
Tech Leaders Warn Against "Pandora's Box" of Robotic Weapons
21.8.2017 seurityweek IT
Elon Musk is leading demands for a global ban on killer robots, warning technological advances could revolutionise warfare and create new "weapons of terror" that target innocent people.
The CEO of Tesla and SpaceX joined more than 100 robotics and artificial intelligence entrepreneurs in signing a letter to the United Nations calling for action to prevent the development of autonomous weapons.
"Lethal autonomous weapons threaten to become the third revolution in warfare," warned the statement signed by 116 tech luminaries, also including Mustafa Suleyman, cofounder of Google's DeepMind.
"Once developed, they will permit armed conflict to be fought at a scale greater than ever, and at timescales faster than humans can comprehend," the letter read.
The innovators also highlighted the danger that the technology could fall into the wrong hands.
"These can be weapons of terror, weapons that despots and terrorists use against innocent populations, and weapons hacked to behave in undesirable ways," the letter read.
"We do not have long to act. Once this Pandora's box is opened, it will be hard to close."
Both Musk and British astrophysicist Stephen Hawking have regularly warned of the dangers of artificial intelligence.
The renewed plea on autonomous weapons was released as the International Joint Conference on Artificial Intelligence in Melbourne got underway Monday, with a record 2,000 of the world's top AI and robotics experts taking part, organisers said.
One expert said autonomous weapons could make war more likely.
"Today the potential loss of human life is a deterrent for conflict initiation and escalation, but when the main casualties are robots, the disincentives change dramatically and the likelihood of conflict increases," Professor Mary-Anne Williams of the University of Technology Sydney.
She warned a killer robot ban may be disregarded by some nations but would stop "countries such as Australia from developing defensive killer robots, thereby being vulnerable to other countries and groups that ignore the ban".
Another expert said decision made today would help shape the "futures we want".
"Nearly every technology can be used for good and bad, and artificial intelligence is no different," said Professor Toby Walsh of the University of New South Wales.
Organisers said the conference, which concludes on Friday, has attracted a record number of participants from China, reflecting a push by Beijing to become a leading player in the field.
A key focus of the event will be looking at the challenges of developing fully autonomous AI systems, programme chair Carles Sierra of the Spanish National Research Council said.
A UN group on autonomous weapons had been due to meet Monday but the gathering was postponed until November, according to the group's website.
In 2015, thousands of researchers and personalities launched an appeal to ban autonomous weapons.
Peace Breaks Out Between Microsoft and Kaspersky Lab
12.8.2017 securityweek IT
Microsoft Agrees to Kaspersky Lab's Demands
Microsoft and Kaspersky are friends again, and the whole anti-virus ecosystem is at peace.
Back in November 2016, Eugene Kaspersky declared, "That's It. I've Had Enough!" It wasn't just words. "We've taken the decision to address official bodies in various countries (including the EU and Russia) with a request to oblige Microsoft to cease its violation of anti-competition legislation and to remove the consequences of that violation." And he did just that, first in Russia and then in the EU.
Eugene Kaspersky, founder of Russia-based Kaspersky Lab, was not alone in his concerns. "Some time ago security companies started noticing that things were changing at Microsoft," Luis Corrons, technical director at PandaLabs told SecurityWeek. "It looked like they were more concerned about their own antivirus market share, and were trying to push the competition out -- not by being a best solution, but by taking advantage of being the developers of the operating system, and using any chance to tell the user to remove 3rd party security software and put theirs in its place."
Morten Kjaersgaard, CEO at Heimdal, gives more context. It started with Windows 8 in 2011, when Microsoft indicated that it would try to extend its position with its own Windows Defender. In the event, says Kjaersgaard, "The first Defender was not much better than Security Essentials." But battle lines had been drawn. The AV industry downplayed Windows Defender, and Microsoft promoted third-party products less forcefully. "Until recently," he added, "Windows Defender had not posed a real threat to the antivirus industry -- but with the Windows Defender continuously improving, it is now a bigger threat."
As Defender improved, so Microsoft seemed less and less willing to work with its 'competitors'. "We have to remember that antivirus is a multi-billion dollar business, both in the consumer and B2B space -- and here Kaspersky took a stance to publicly call out a situation, which long term could cause an antitrust case for Microsoft, similar to Internet Explorer."
That danger now seems to have been averted. "It's very important for both sides that Microsoft and the specialist security companies work as closely together as possible," comments ESET senior research fellow, David Harley; "especially as Windows 10 increases its market share, as presumably it will. A security monoculture isn't in the best interests of the consumer." This position is simple. If Windows Defender -- or any other single product -- dominates the market, attackers will have fewer defenses to beat while successful attacks will be more catastrophic. Diversity brings strength; monocultures bring weakness.
This week, Microsoft's Rob Lefferts blogged, that following discussions with its AV partners, Microsoft is "making updates to our AV partner requirements today that reflect the interests of the community and our shared customers. We will also implement changes in the Windows 10 Fall Creators Update."
These changes cover the complaints made by Kaspersky. Microsoft will work more closely with third-parties over compatibility reviews; will increase "the amount of time AV partners will have to review final builds before the next Windows 10 feature update is rolled out to customers"; will allow the third-parties to display their own renewal notices; and will modify how users are told that their antivirus application has expired.
Kaspersky is the only third-party vendor specifically mentioned in this announcement. It is clearly a response to the legal threats in both Russia and the EU. "We appreciate the feedback and continued dialogue with our partners and are pleased to have found common ground with Kaspersky Lab on the complaints raised in Russia and Europe," continues Lefferts. "We look forward to our continued partnership with the industry."
Kaspersky is satisfied. In its own Kaspersky Lab blog published yesterday it states, "We are absolutely satisfied with the changes that will be implemented in the Windows 10 Fall Creators Update, and we will be taking all necessary steps to withdraw our claims and inform all regulatory bodies that we no longer have any matters for Microsoft to address."
Peace has been restored. Whether it continues, remains to be seen (Microsoft will need to compete for share of a multi-billion market without resorting to any of the OS-specific trump cards that it undoubtedly holds). But there is one other issue worth considering. In parallel to Kaspersky's complaints to the Russian and EU authorities about Microsoft's practices, the US government has started to denounce Kaspersky over 'security concerns'. Last month the US General Services Administration (GSA) announced that Kaspersky had been removed from its list of approved vendors, making it more difficult for government agencies to obtain Kaspersky products.
Was the timing coincidental? Is it an economic version of the political tit-for-tat that we have seen between America and Russia for decades? Or is it genuine security concerns?
Heimdal's Kjaersgaard believes it is genuine if unfounded concern. "I believe that the US government is concerned that because Kaspersky, as an antivirus, has full access to a device, it could theoretically relay information from the device to Kaspersky, which another influential party in Kaspersky could use.
"I cannot say anything bad about Kaspersky at all," he added; "but nor can I comment if the US government has this stance for a reason. However, concern over the software you have on your computer is legitimate with anything you install."
Kaspersky is outraged at the US position. In its own statement, it says, "“Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyberespionage efforts... Kaspersky Lab believes it is completely unacceptable that the company is being unjustly accused without any hard evidence to back up these false allegations. Kaspersky Lab, a private company, seems to be caught in the middle of a geopolitical fight where each side is attempting to use the company as a pawn in their political game."
It will be interesting to see whether the new accord between Microsoft and Kaspersky will lead to a softening of attitudes from the US government.
Peace Breaks Out Between Microsoft and Kaspersky Lab
11.8.2017 securityweek IT
Microsoft Agrees to Kaspersky Lab's Demands
Microsoft and Kaspersky are friends again, and the whole anti-virus ecosystem is at peace.
Back in November 2016, Eugene Kaspersky declared, "That's It. I've Had Enough!" It wasn't just words. "We've taken the decision to address official bodies in various countries (including the EU and Russia) with a request to oblige Microsoft to cease its violation of anti-competition legislation and to remove the consequences of that violation." And he did just that, first in Russia and then in the EU.
Eugene Kaspersky, founder of Russia-based Kaspersky Lab, was not alone in his concerns. "Some time ago security companies started noticing that things were changing at Microsoft," Luis Corrons, technical director at PandaLabs told SecurityWeek. "It looked like they were more concerned about their own antivirus market share, and were trying to push the competition out -- not by being a best solution, but by taking advantage of being the developers of the operating system, and using any chance to tell the user to remove 3rd party security software and put theirs in its place."
Morten Kjaersgaard, CEO at Heimdal, gives more context. It started with Windows 8 in 2011, when Microsoft indicated that it would try to extend its position with its own Windows Defender. In the event, says Kjaersgaard, "The first Defender was not much better than Security Essentials." But battle lines had been drawn. The AV industry downplayed Windows Defender, and Microsoft promoted third-party products less forcefully. "Until recently," he added, "Windows Defender had not posed a real threat to the antivirus industry -- but with the Windows Defender continuously improving, it is now a bigger threat."
As Defender improved, so Microsoft seemed less and less willing to work with its 'competitors'. "We have to remember that antivirus is a multi-billion dollar business, both in the consumer and B2B space -- and here Kaspersky took a stance to publicly call out a situation, which long term could cause an antitrust case for Microsoft, similar to Internet Explorer."
That danger now seems to have been averted. "It's very important for both sides that Microsoft and the specialist security companies work as closely together as possible," comments ESET senior research fellow, David Harley; "especially as Windows 10 increases its market share, as presumably it will. A security monoculture isn't in the best interests of the consumer." This position is simple. If Windows Defender -- or any other single product -- dominates the market, attackers will have fewer defenses to beat while successful attacks will be more catastrophic. Diversity brings strength; monocultures bring weakness.
This week, Microsoft's Rob Lefferts blogged, that following discussions with its AV partners, Microsoft is "making updates to our AV partner requirements today that reflect the interests of the community and our shared customers. We will also implement changes in the Windows 10 Fall Creators Update."
These changes cover the complaints made by Kaspersky. Microsoft will work more closely with third-parties over compatibility reviews; will increase "the amount of time AV partners will have to review final builds before the next Windows 10 feature update is rolled out to customers"; will allow the third-parties to display their own renewal notices; and will modify how users are told that their antivirus application has expired.
Kaspersky is the only third-party vendor specifically mentioned in this announcement. It is clearly a response to the legal threats in both Russia and the EU. "We appreciate the feedback and continued dialogue with our partners and are pleased to have found common ground with Kaspersky Lab on the complaints raised in Russia and Europe," continues Lefferts. "We look forward to our continued partnership with the industry."
Kaspersky is satisfied. In its own Kaspersky Lab blog published yesterday it states, "We are absolutely satisfied with the changes that will be implemented in the Windows 10 Fall Creators Update, and we will be taking all necessary steps to withdraw our claims and inform all regulatory bodies that we no longer have any matters for Microsoft to address."
Peace has been restored. Whether it continues, remains to be seen (Microsoft will need to compete for share of a multi-billion market without resorting to any of the OS-specific trump cards that it undoubtedly holds). But there is one other issue worth considering. In parallel to Kaspersky's complaints to the Russian and EU authorities about Microsoft's practices, the US government has started to denounce Kaspersky over 'security concerns'. Last month the US General Services Administration (GSA) announced that Kaspersky had been removed from its list of approved vendors, making it more difficult for government agencies to obtain Kaspersky products.
Was the timing coincidental? Is it an economic version of the political tit-for-tat that we have seen between America and Russia for decades? Or is it genuine security concerns?
Heimdal's Kjaersgaard believes it is genuine if unfounded concern. "I believe that the US government is concerned that because Kaspersky, as an antivirus, has full access to a device, it could theoretically relay information from the device to Kaspersky, which another influential party in Kaspersky could use.
"I cannot say anything bad about Kaspersky at all," he added; "but nor can I comment if the US government has this stance for a reason. However, concern over the software you have on your computer is legitimate with anything you install."
Kaspersky is outraged at the US position. In its own statement, it says, "“Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyberespionage efforts... Kaspersky Lab believes it is completely unacceptable that the company is being unjustly accused without any hard evidence to back up these false allegations. Kaspersky Lab, a private company, seems to be caught in the middle of a geopolitical fight where each side is attempting to use the company as a pawn in their political game."
It will be interesting to see whether the new accord between Microsoft and Kaspersky will lead to a softening of attitudes from the US government.
Chinese Quantum Satellite Sends First ‘Unhackable’ Data to Earth
10.8.2017 thehackernews IT
In what appears to be the world's first quantum satellite transmission, China has successfully sent an "unbreakable" code over a long distance from an orbiting satellite to the Earth, achieving a milestone in the next generation encryption based on "quantum cryptography."
In August last year, China launched the world's first quantum communication satellite into the Earth’s orbit aboard a Long March-2D rocket to test the fundamental laws of quantum mechanics at space.
Dubbed Quantum Science Satellite, nicknamed Micius or Mozi (Chinese: 墨子), the satellite was designed to establish a 'Hack-Proof' communications system in this age of global surveillance by transmitting unbreakable encryption keys from space to the ground.
Now, it has been reported that using this satellite, the Chinese scientists at the Quantum Experiments at Space Scale (QUESS) project were able to send secret "quantum key distribution" (QKD) data by beaming photons from the space to the ground stations over longer distances than ever before.
The Chinese scientists successfully sent quantum keys over a distance of 1,200 Km (745 miles) from space to Earth at a transmission rate up to 20 of magnitudes more efficient than that expected using an optical fibre of the same length, lead scientist Pan Jianwei told the official Xinhua news agency.
"That, for instance, can meet the demand of making an absolute safe phone call or transmitting a large amount of bank data," Jianwei said.
The Quantum Science Satellite could become the world's first transcontinental quantum key distribution network of its kind and China hopes to erect a global quantum cryptography-based communications network in 2030.
Theoretically, the use quantum cryptography for encryption is secure against any interception, as the information is encoded in a quantum particle in a way that it'll be destroyed as soon as the system detects any intrusion attempts.
"Satellite-based quantum key distribution can be linked to metropolitan quantum networks where fibres are sufficient and convenient to connect numerous users within a city over 100 km," Jianwei said.
"We can thus envision a space-ground integrated quantum network, enabling quantum cryptography- most likely the first commercial application of quantum information- useful at a global scale."
China has largely been ambitious to realise the importance of Quantum technology that's believed to be a new era of faster and more powerful super computers.
From past two decades, Quantum technology has been a top strategic focus in China's 5-year economic development plan. While the U.S. invested about $200 Million a year in quantum research, China spent $101 Billion in quantum physics in 2015.
Firefox Makes Adobe Flash Click-to-Activate by Default
9.8.2017 securityweek IT
Starting with the release of Firefox 55 this week, the Adobe Flash plugin is no longer active by default in Mozilla’s web browser, and users of the new version will be required to activate it for each website they visit.
According to Mozilla, not only is the Adobe Flash plugin click-to-activate disabled by default with the new release, but it is also allowed only on http:// and https:// URL schemes. Users can now choose on which sites they want to activate the plugin, and can also opt in for Firefox to remember the settings. Some sites, however, won’t be allowed to run plugins, Mozilla says.
Mozilla plans on fully removing Flash from Firefox in early 2020, but will continue to support it in Firefox Extended Support Release (ESR) until the end of 2020. From then onward, the browser will refuse to load the plugin.
Google Chrome and Microsoft Edge started blocking Flash by default last year, and Adobe announced last month that it will stop supporting the plugin by the end of 2020: “we will stop updating and distributing the Flash Player,” the company said at the end of July 2017. In addition to Google, Microsoft, and Mozilla, Apple and Facebook too announced plans to remove Flash.
In addition to deactivating Flash, the new browser release resolves around 30 security vulnerabilities, 5 of which were rated Critical risk. These include an XUL injection in the style editor in devtools (CVE-2017-7798), Use-after-free in WebSockets during disconnection (CVE-2017-7800), Use-after-free with marquee during window resizing (CVE-2017-7801), and Memory safety bugs (CVE-2017-7779 and CVE-2017-7780).
Firefox 55 also resolves 11 High severity flaws, including 4 use-after-free bugs, 3 buffer overflows, out-of-bounds issue, same-origin policy bypass, domain hijacking, and memory protection bypass vulnerabilities.
The browser includes patches for 7 Medium severity issues: spoofing following page navigation with data, CSP information leak with frame-ancestors containing paths, WindowsDllDetourPatcher allocates memory without DEP protections, Elliptic curve point addition error when using mixed Jacobian-affine coordinates, Linux file truncation via sandbox broker, CSP containing 'sandbox' improperly applied, and Self-XSS XUL injection in about:webrtc.
6 Low risk vulnerabilities were addressed in this release: DOS attack through long username in URL, Sandboxed about:srcdoc iframes do not inherit CSP directives, Failure to enable HSTS when two STS headers are sent for a connection, Windows crash reporter reads extra memory for some non-null-terminated registry values, Windows updater can delete any file named update.log, and Response header name interning leaks across origins.
Firefox 55 also brings along various new features and improvements, such as Windows support for WebVR and a setting to enable Hardware VP9 acceleration on Windows 10 Anniversary Edition. Now, Firefox for Windows 64-bit is installed by default on all 64-bit systems that have at least 2GB of RAM.
The updated browser release is available for Windows, Mac, Linux, and Android.
FTC Complaint Alleges Hotspot Shield Collects User Data
8.8.2017 securityweek IT
A complaint filed with the Federal Trade Commission (FTC) on Monday alleges that the popular free Virtual Private Network (VPN) service Hotspot Shield collects a large amount of data and intercepts user traffic.
Submitted by the Center for Democracy & Technology (CDT), the complaint (PDF) urges the FTC to investigate the data security and data sharing practices of Hotspot Shield, alleging they are “unfair and deceptive trade practices.” The complaint also claims the service engages into undisclosed data sharing and traffic redirection practices despite promising to protect the users’ privacy.
CDT, a nonprofit technology advocacy organization, suggests that Hotspot Shield’s privacy policy contradicts the advertised privacy and security claims. The service claims to keep no logs of a user’s online activity or personal information, and to store no user data, while also saying that it doesn’t track users and doesn’t sell their information.
The privacy and security claims are highlighted as key features of the Hotspot Shield VPN mobile applications in both iTunes and Google Play storefronts, but the service’s privacy policy “describes more elaborate logging practices,” the complaint reads. A source code analysis of Hotspot Shield backs these allegations, CDT says.
The organization also claims that “the VPN promises to connect advertisers to users who frequent websites in particular categories and while most VPNs prevent internet service providers from seeing a user’s internet traffic, that traffic is often visible in unencrypted form to Hotspot Shield. VPNs typically log data about user connections to help with troubleshooting technical issues, but Hotspot Shield uses this information to identify user locations and serve advertisements."
CDT also points out that Hotspot Shield’s privacy policy says that it doesn’t collect personal user information, claiming that IP addresses and unique device identifiers aren’t considered personal information by the free VPN provider. Moreover, the complaint claims the service deploys persistent cookies and that it also “works with unaffiliated entities to customize advertising and marketing messages.”
Furthermore, the complaint alleges that Hotspot Shield insists it doesn’t make money from selling customer data, but that the service also promises to connect advertisers to users that frequently access travel, retail, business, and finance websites. CDT points out that these partners can link information about users’ web-viewing habits even if they are provided only with hashed or proxy IP addresses.
An analysis of Hotspot Shield’s functionality, data sharing, and network connections was performed by Carnegie Mellon University’s Mobile App Compliance System. Researchers downloaded and tested the Android app and found “undisclosed data sharing practices with third party advertising networks” when analyzing the application permissions.
They also discovered that the app discloses sensitive information such as names of wireless networks (via SSID/BSSID information), along with identifiers such as Media Access Control addresses, and device IMEI numbers.
The VPN was also found to inject JavaScript codes using iframes for advertising and tracking purposes, and to be using more than five different third-party tracking libraries. The apps also redirect e-commerce traffic to partnering domains, the complaint also claims.
“People often use VPNs because they do not trust the network they’re connected to, but they think less about whether they can trust the VPN service itself. For many internet users, it’s difficult to fully understand what VPNs are doing with their browsing data. Hotspot Shield tells customers that their privacy and security are ‘guaranteed’ but their actual practices starkly contradict this. They are sharing sensitive information with third party advertisers and exposing users’ data to leaks or outside attacks,” Michelle De Mooy, Director of CDT’s Privacy & Data Project, said.
Symantec to Sell Certificate Business to DigiCert for $950 Million
3.8.2017 securityweek IT
After reaching an agreement with Google regarding penalties for misissued digital certificates, Symantec announced on Wednesday that it has made a deal with DigiCert to sell its website security and related public key infrastructure (PKI) solutions.
DigiCert has agreed to pay Symantec $950 million in cash and a stake of roughly 30 percent in common stock equity of the DigiCert business. The transaction has been approved unanimously by Symantec’s board of directors and is expected to be completed in the third quarter of fiscal 2018.
DigiCert will continue to operate under the supervision of CEO John Merrill from its headquarters in Lehi, Utah, where it will employ more than 1,000 people. With the acquisition of Symantec’s certificate business, the company is expected to bring new approaches to the TLS market and benefit from growth opportunities in IoT.
Symantec has come under fire recently for misissued TLS certificates, and Google and other web browser vendors have been discussing penalties.
Google announced recently that certificates issued by Symantec and its partners before June 1, 2016, will need to be replaced by March 15, 2018. All other certificates need to be replaced until the release of Chrome 70, currently scheduled for release in October 2018.
Google said Symantec could still issue digital certificates, but only through the infrastructure of a subordinate certificate authority (SubCA). A few weeks ago, Symantec said it had been trying to find a partner and informed customers that the new infrastructure should be set up by December 1.
It appears Symantec has decided to abandon its website security business altogether, but promised customers an easy transition.
“We carefully examined our options to ensure our customers would have a world-class experience with a company that offers a modern website PKI platform and is poised to lead the next generation of website security innovation,” said Symantec CEO Greg Clark. “I’m thrilled that our customers will benefit from a seamless transition to DigiCert, a company that is solely focused on delivering leading identity and encryption solutions. Symantec is deeply committed to the success of this transition for our customers.”
Some of Symantec and DigiCert’s competitors have taken the opportunity to get Symantec customers concerned about potential disruptions to join them.
Comodo has published a blog post warning Symantec customers of the consequences of moving to DigiCert.
“DigiCert does not have the same infrastructure as Symantec, as a much smaller Certificate authority it never had the need to,” Comodo said. “Therefore, the eventual platform migration poses a huge execution and technology risk for all Symantec Enterprise customers and channel partners.”
Bitcoin Exchange Operator Arrested For $4 Billion Money Laundering Scheme
27.7.2017 thehackernews IT
Greece police have arrested a Russian man who is believed to have been the operator of the popular BTC-e Bitcoin exchange on charges of laundering more than $4 billion in bitcoin for culprits involved in hacking attacks, tax fraud and drug trafficking.
A United States jury indicted 38-year-old Alexander Vinnik on Wednesday after his arrest in Greece on Tuesday at the request of US law enforcement authorities. The suspect is one of the operators of BTC-e, a service operational since 2011.
Headquartered in Russia, the digital currency exchange has been offline since the arrest of Vinnik, and its homepage says, "Site is under maintenance. We apologize for the inconvenience.."
According to a press release published by the U.S. Treasury's Financial Crimes Enforcement Network (FinCEN), BTC-e ignored "know your customer" laws in an effort to serve criminals, and even hosted message boards buzzing with illegal activities.
The FinCEN also announced a $110 million penalty against BTC-e for facilitating crimes along with a separate $12 Million fine against Vinnik.
BTC-e Linked to Collapse of Mt. Gox Bitcoin Exchange
This case is really important for the law enforcement because it could reveal the possible culprit behind the collapse of the once-very popular Japanese bitcoin exchange Mt. Gox, which was shut down in 2014 following a massive series of mysterious robberies, which totalled at least $375 million in Bitcoin.
According to the U.S. Department of Justice, Vinnik obtained funds from the hacker or insider who stole bitcoins from Mt. Gox and sent them to a bitcoin wallet controlled by Vinnik, who intentionally laundered them through BTC-e, over a period of three years.
"After the coins entered Vinnik's wallets, most were moved to BTC-e and presumably sold off or laundered (BTC-e money codes were a popular choice). In total some 300,000 BTC ended up on BTC-e," according to WizSec, a Japanese security firm that has long been investigating the Mt. Gox case.
"To be clear, this investigation turned up evidence to identify Vinnik not as a hacker/thief but as a money launderer; his arrest news also suggests this is what he is being suspected for. He may have merely bought cheap coins from thieves and offered a laundering service."
Vinnik arrest is the latest in a series of US investigations against Russian cybercriminals in Europe, following the shutdown of two of the biggest dark web marketplaces, AlphaBay and Hansa, last week.
While Greek police described Vinnik as "an internationally sought ‘mastermind’ of a crime organisation," United States authorities accused him of facilitating crimes including hacking, identity theft, tax refund fraud, public corruption and drug trafficking.
Vinnik is to be charged with operation of an unlicensed money service business, conspiracy to commit money laundering, money laundering, and engaging in unlawful monetary transactions.
If found guilty, the suspect could face up to 55 years in prison, together with a $500,000 fine or twice the value of the property involved in the transaction for each count.
Tech Giants Announce Plans for Removal of Flash
26.7.2017 securityweek IT
Apple, Facebook, Google, Microsoft and Mozilla have outlined their plans for moving away from Flash Player now that Adobe officially announced an end-of-life (EOL) and end-of-support date for the controversial product.
Adobe announced on Tuesday that, following discussions with several technology partners, it has decided to stop updating and distributing Flash Player at the end of 2020. The company has encouraged developers and content creators to migrate to open standards such as HTML5, WebGL and WebAssembly, which are supported by all major web browsers.
While Flash Player is still used by many websites and applications, the security community has been asking Adobe to retire the old software for several years due to the large number of vulnerabilities and numerous attacks involving Flash exploits.
Over the past years, web browser vendors and other Internet companies have taken steps to reduce the security risks associated with Flash Player by either limiting Flash content or banning it altogether.
Apple, Facebook, Google, Microsoft and Mozilla have promised to help with the transition and they have each outlined their plans for the complete removal of Flash support from their products.
Apple has been moving away from Flash since 2010. Currently, users need to manually install Flash if they need it and even so it remains disabled by default – manual approval is required on each website before the Flash plugin is executed.
Facebook, which still allows Flash games on its platform, says it has partnered with game developers to help them migrate to HTML5. The social media giant will accept Flash games until the end of 2020, but warned that the ability to play these games also depends on the decisions made by browser vendors.
Google pointed out that the number of Chrome users visiting a site with Flash every day has dropped from 80 percent three years ago to 17 percent today. Google has been and will continue to gradually phase out Flash – first by asking for explicit permission to run Flash content in more situations and eventually disabling it by default. The company wants to remove it completely toward the end of 2020.
Microsoft, which updates the Flash Player components used by its products every Patch Tuesday, wants to disable Flash by default in both Edge and Internet Explorer in mid-to-late 2019. Even if users will re-enable it, they will still need to manually approve Flash for each website. Flash will be removed completely by the end of 2020.
Moziila’s roadmap for Flash is similar. The organization wants to disable Flash by default for most users in 2019, while allowing Extended Support Release (ESR) users to continue viewing Flash content through the end of 2020.
Adobe to Kill Flash Player, End Support by 2020
26.7.2017 securityweeek IT
[Breaking] Adobe on Tuesday said that it would kill its Flash Player and stop providing security updates by the end of 2020.
Adobe Flash Player has made headlines over the years due to the large number of serious vulnerabilities identified by both white and black hat hackers. The company has been forced to issue emergency patches on several occasions after learning that malicious actors had been exploiting unpatched Flash Player vulnerabilities in their operations.
According the company, the decision was made in collaboration with several Adobe technology partners including Apple, Facebook, Google, Microsoft and Mozilla.
“Specifically, we will stop updating and distributing the Flash Player at the end of 2020 and encourage content creators to migrate any existing Flash content to these new open formats,” Adobe said.
Adobe said it would continue to support Flash on a number of major OSs and browsers that currently support Flash content through the planned EOL.
“This will include issuing regular security patches, maintaining OS and browser compatibility and adding features and capabilities as needed,” Adobe said in a blog post. “We remain fully committed to working with partners, including Apple, Facebook, Google, Microsoft and Mozilla to maintain the security and compatibility of Flash content.”
While Adobe has officially made the decision to kill-off the vulnerable software product, many other leading internet firms have been pushing hard against the software over the past years and trying to limit the use of Flash across their products and services.
In May 2016, Google announced its plans to block Adobe Flash and implement an 'HTML5 by Default' policy on Chrome by the end of 2016.
“It is time for Adobe to announce the end-of-life date for Flash and to ask the browsers to set killbits on the same day,” Facebook’s CSO, Alex Stamos, said in July 2015 after the existence of several Flash Player zero-day flaws was brought to light by the data breach suffered by Italian spyware maker Hacking Team.
In June 2016, Google stopped accepting display ads built in Adobe Flash, not long after Amazon stopped accepting Flash ads on its online shopping website. At the time, Amazon said that the move, which went into effect on Sept. 1, 2015, was prompted by browser setting in Chrome, Firefox, and Safari, which were meant to limit Flash content displayed on web pages.
Nathan Wenzler, chief security strategist at security consulting company AsTech, believes there will be a lot of split feelings about the official EOL announcement for Flash.
“On one hand, a great deal of the multimedia games, videos, graphics and other rich services that have helped make the Internet what it is today were originally built on Flash. It provided a great platform for a huge array of products, and it could be argued we wouldn't be where we are today without it,” Wenzler told SecurityWeek. “That said, the security world will likely rejoice at the retirement of a product which has had a huge number of well-known vulnerabilities and flaws over the years, which have been the entry point for malicious tools that have compromised millions of systems across the globe.”
“While Adobe has been increasingly more vigilant about hardening Flash and more consistently providing patches and hotfixes whenever a vulnerability was identified, it still served as a particular pain point for a lot of organizations to keep Flash patched and maintain a consistent security posture for their systems which had Flash installed,” Wenzler added.
Chris Roberts, chief security architect at threat detection and defense solutions provider Acalvio, pointed out that the end of Flash Player has been coming for a while.
“It’s been good while we had it, but let’s face it, it’s been a whipping boy of the security industry for a while with more than 1000 CVE’s dedicated to it throughout the years,” Roberts said via email. “Kind of like many of us in the industry that find ourselves getting grayer and less tolerant of others, it’s time to hang up the hat and work out how to retire. At least in Flash’s world, it’s been given a nice sunset (until 2020) and probably a good pension in the vaults of software somewhere.”
Flash Player was originally developed by Macromedia, which was acquired by Adobe in 2005.
Adobe Flash end of life announced by 2020. Start thing of the migration
26.7.2017 securityaffairs IT
Adobe announced Flash end-of-life by 2020. Apple, Facebook, Google, Microsoft and Mozilla plans to stop supporting the Adobe Flash Media Player in 2020.
It’s official, Adobe will kill Flash by 2020, the company will stop providing support for the popular browser plugin.by the end of that year.
“Given this progress, and in collaboration with several of our technology partners – including Apple, Facebook, Google, Microsoft and Mozilla – Adobe is planning to end-of-life Flash. Specifically, we will stop updating and distributing the Flash Player at the end of 2020 and encourage content creators to migrate any existing Flash content to these new open formats.” states the Adobe’s announcement.
Open standards like HTML5, WebGL, and WebAssembly have matured enough over the past years to replace all the features today implemented by Adobe Flash.
Starting from 2020, the company will no more provide support on major browsers, including Chrome, Firefox, and Internet Explorer and Edge.
“If the site continues to use Flash, and you give the site permission to run Flash, it will work through the end of 2020.” wrote Google. “We’re supportive of Adobe’s announcement today, and we look forward to working with everyone to make the web even better. “
“To provide guidance for site authors and users that continue to rely on Flash, Mozilla has updated its published roadmap for Flash in Firefox. Starting next month, users will choose which websites are able to run the Flash plugin.” states Firefox. “Flash will be disabled by default for most users in 2019, and only users running the Firefox Extended Support Release (ESR) will be able to continue using Flash through the final end-of-life at the end of 2020. In order to preserve user security, once Flash is no longer supported by Adobe security patches, no version of Firefox will load the plugin.”
According to Google, Flash usage had gone down from 80% to 17%.

In a similar way, Microsoft also announced the end of support for its products.
“We will phase out Flash from Microsoft Edge and Internet Explorer, culminating in the removal of Flash from Windows entirely by the end of 2020. This process began already for Microsoft Edge with Click-to-Run for Flash in the Windows 10 Creators Update.” states Microsoft.
Facebook also announced that it will shut off Flash games by the end of 2020.
Administrators of Websites that rely on Flash are being encouraged to start planning the migration to new technologies.
Under the cyber security perspective, the Adobe Flash end of life is a good news because it is one of the most exploited software in recent cyber attacks.