IT Articles - H 2020 1 2 3 4 5 6 7 IT List - H 2021 2020 2019 2018 1
Yahoo Faces SEC Probe into Breach Disclosures
23.1.2017 Securityweek IT
In November 2016 Yahoo announced that it was cooperating with federal, state and foreign agencies, including the US Securities and Exchange Commission (SEC), who were seeking information on the data breaches also announced during 2016. In December, the SEC issued requests for relevant documents from Yahoo, and Yahoo is now reported to be under investigation.
In September 2016 Yahoo announced that it had suffered a breach in 2014. It claimed that 'state-sponsored' attackers had stolen data from 500 million users. Two months later it disclosed that an earlier breach from August 2013 had led to the compromise of 1 billion user accounts. Yahoo has not said when it knew about these breaches.
Different agencies have different rules about the disclosure of data breaches. The SEC's own 2011 rules are considered to be vague, and have never been enforced. It investigated the Target breach, but concluded that its own rules were not broken. These require that incidents that could have a "material adverse effect on the business" should be disclosed, but they do not define what this would be. The sheer size of the two Yahoo breaches combined with the intended acquisition of the organization by Verizon could make this a new test case for the SEC rules.
Yahoo may consider that simply disclosing the breaches before the Verizon acquisition is completed (expected to be during Q1 2017) may be sufficient to comply with the SEC rules. The SEC's primary concern is to protect investors rather than users. Although it was thought that the breaches might cause Verizon to pull out of the acquisition, this is now thought to be unlikely. Yahoo can therefore argue that non-disclosure has not affected investors.
Verizon originally agreed to pay $4.8 billion for Yahoo, although the New York Post reported that it subsequently sought a $1 billion discount following the first disclosure. The report added, "At the same time, the Yahoo deal team is pushing back hard against any attempts to negotiate the price down, sources said."
The SEC is best known for its actions against fraud rather than data protection. In October 2016, it ordered one of the Big 4 global audit companies, Ernst & Young, to pay $11.8 million ($1 million fines and $10.8 million in audit fee give-backs plus interest) for missing a major accounting fraud at Weatherford International.
Other agencies are more concerned about the compromise of personal data. In Europe, current data protection laws are enforced by individual national authorities (such as the Information Commissioner in the UK). The Article 29 Working Group comprises representation from all of the national regulators. In October 2016 it wrote to Yahoo asking for breach details: "As Data Protection Authorities (DPAs) in charge of the protection of European individuals' data, we are deeply concerned by the report and the significant number of EU data subjects which may be affected."
Any subsequent action from European regulators would come from each individual country concerned. For example, the ICO fined TalkTalk $510,000 in October 2016. Such fines could, however, be dwarfed by those available under the upcoming General Data Protection Regulation. Here, the ICO warns, "A notifiable breach has to be reported to the relevant supervisory authority within 72 hours of the organization becoming aware of it... Failing to notify a breach when required to do so can result in a significant fine up to 10 million Euros or 2 per cent of your global turnover."
It seems almost certain that Yahoo did not make its breach notifications within 72 hours of discovery. The implication is that if the GDPR were already operational, Yahoo would have even more problems than it already has.
How EaseUS Partition Master Can Easily Manage Your Hard Disk
17.1.2017 thehackernews IT
If you want to get the most out of your computer, you need to get the most out of your hard drive, where all your data is stored.
Today hard drives are larger than ever, so it makes sense for you to partition your hard disk to effectively use all of its space and manage all your important information.
Partitioning is also useful if you intend to install and use more than one operating system on the same computer.
There is a vast business of partition manager software out there, and today we are reviewing one of the most popular partition management tools available in the market: EaseUS Partition Master Professional.
EaseUS Partition Master Professional offers you the complete package with capabilities for organizing and resizing your drive, restoring and backing up your information, improving system performance, installing and managing several operating systems on the same computer, along with recovering and cloning data files.
Let's dig deep into the capabilities provided by the EaseUS Partition Master Professional software.
Resize, Move Or Merge Multiple Partitions
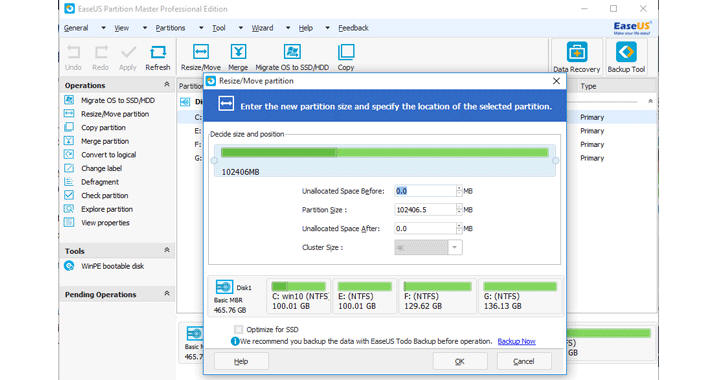
You might have, at some point, obsessed with low space in one certain partition of your hard disk while others may be left unused for long with much space. At this point, you can choose to merge two partitions for a larger system partition.
But resizing or combining your system and boot partition C drive, which holds your Operating System, without any third party tool is not always a good idea, as there are chances of data loss.
So, in that case, users are always advised to use a third-party partition tool from a reputable and trustworthy company.
EaseUS partition software can get this job done with ease.
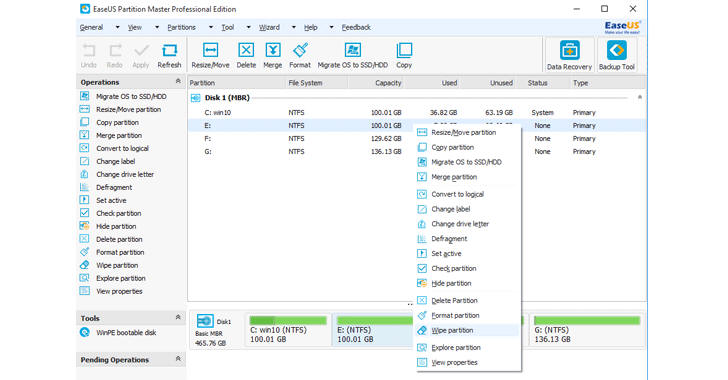
EaseUS Partition Master Professional provides one-click, easy-to-use interface to help you move, resize, merge, hide or unhide the existing disk partitions without damaging even a single bit of original data.
All you need to do is launch the EaseUS Partition Master Professional software, choose the disk partition you want to process and right click on it, and you’ll get the list of all the available operations that can be performed.
Once you resize or move your partitions, you are advised to backup your data.
Migrate OS to SSD/HDD Without Reinstalling Windows
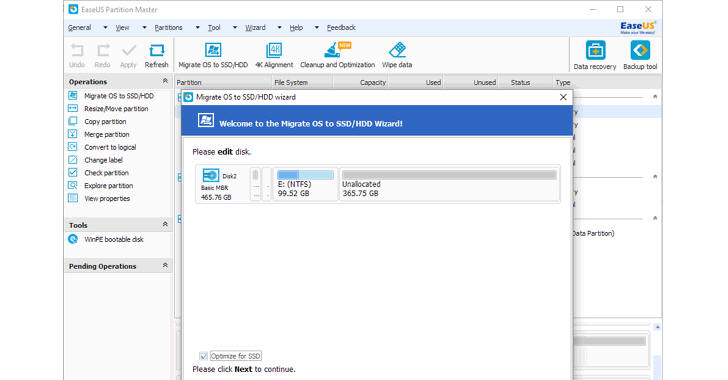
One of the major features of EaseUs Partition Master Professional is the ability to migrate your operating system to another hard drive (SSD or HDD).
So, if you are upgrading your old PC for better performance, this tool also allows you to transfer all your data on system and boot partitions, including OS and installed applications, without reinstalling the operating system on the new drive.
To migrate your OS from HDD to SSD, all you need to do is launch the application, click on Wizard and then select 'Migrate OS to SSD/HDD' from the main menu. Now select SSD as destination disk, delete partitions on the target drive, resize partitions on the target disk, and then click Finish.
Moreover, it also supports MBR and GPT disks
Bootable Partition Manager (CD/DVD/USB)
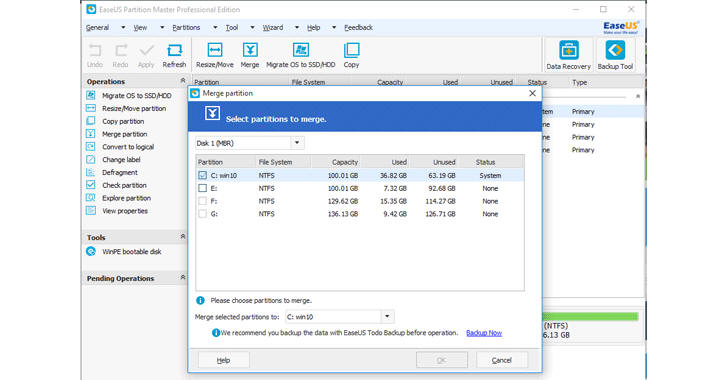
The tool also enables users to manage hard disk partitions even when their OS fails to boot or manage partitions without an operating system.
Also, users who are looking for a bootable USB flash drive partition manager that will be able to resize partitions, EaseUS Partition Master is your pick.
To create a bootable USB flash drive partition manager, you first need to download and launch EaseUS Partition Master, then select Tool → Create WinPE bootable disk → USB and then start to create a USB bootable disk of EaseUS Partition Master.
After that, you can launch EaseUS Partition Master from bootable USB device or CD/DVD and manage your hard drive partitions.
Copy/Clone Partition
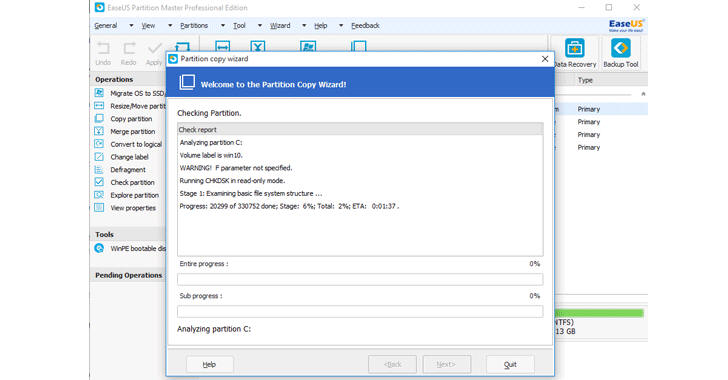
If ransomware malware strikes, only a good backup can save your files and money, and EaseUS Partition Master helps you do just that.
The Partition Copy and Disk Copy features integrated into EaseUS Partition Master are specially designed to provide protection from data loss.
The Partition Copy feature aims to backup your partitions before the partition operations applied to the hard disk to prevent any data loss from program error or some other accidental errors.
Partition Copy let you copy a partition to unallocated space on your hard disk, and even allow you to resize the unallocated space during the procedure if necessary.
On the other hand, Disk Copy lets you not only make a backup copy of your hard drive but also allows you to copy your entire system from a small hard disk to a larger hard drive.
Securely Erase Data on SSD or HDD
If you've just got a new PC and want to sell your old one, make sure all your data has been cleared securely and can not be recovered anyhow.
Because, when you delete a file, it is not deleted. Those deleted files still exist. Your PC only removes the file indexing information from the hard drive.
So, if that deleted data is not overwritten, it can be recovered later, which may include your passwords, private photographs, personal information, classified documents or financial records.
So, always be sure to securely erase your data before selling or throwing away your device.
Using EaseUS Partition Master, you can securely delete your files or entire drive in a way that it can not be recover anyhow.
To do so, first, launch EaseUS Partition Master Free, select the SSD or hard disk you want to erase, and then right click and select "Wipe disk."
The tool will then ask you to set the number of times (1-10 times) to wipe your hard drive and click "OK." A dialog box will appear saying your PC will computer restart after disk erase. Just click "OK" and then click "Apply" to securely erase SSD or HDD.
Note: If you are erasing your entire hard disk, make sure that it does not include system partition because your system will not boot after wiping the drive.
Support and Compatibility (OS, File System, Drive Type)
The free version of EaseUS Partition Master supports up to 8TB hard disks while the professional version supports up to 16TB disks and 32 disks at most.
Talking about the operating system, EaseUS Partition Master supports Windows 10, 8.1, 8 and 7 SP1, and 32-bit and 64-bit versions of Windows 7, Vista and Windows XP Home Edition and Professional.
EaseUS Partition Master supports MBR and GPT disks – GPT disks are faster than MBR and help with high-capacity hard disk drives. So if you want to convert your regular MBR hard disk drive into GPT, you can use EaseUs that'll do it without any data loss.
EaseUS Partition Master is supportive over different file systems as well, including EXT3, EXT2, NTFS, FAT32, FAT16, FAT12, and ReFS. It also supports different device types including Solid-State Drive (SSD), IEEE 1394 (FireWire) HDD, USB 1.0/2.0/3.0 HDD, all levels of SCSI, IDE and SATA RAID controllers, full support of RAIDed configurations (hardware RAIDs) and removable devices, like flash drive, memory card, and more.
EaseUs is one of the top disk management software developers out there, and its Partition Master Professional software stands up to its name.
Conclusion: EaseUs Partition Master Professional is a complete solution for managing, copying and recovering your disk partitions within only a few simple clicks. A large number of superb partitioning and solid additional features as well as the user-friendly interface place EaseUS Partition Master near the top and make it difficult to beat.
So, if you are looking for an effective partition manager, you should give it a try, as its worth its every single penny.
EaseUS Partition Master Professional Edition costs just $39.95, while its Server Edition costs $159.00 and Home Edition is free. You can also take a Free Trial of EaseUS Partition Master Professional Edition.
If this partition tool really met all your requirements, you can purchase EaseUS Partition Master Pro at highly discounted price at The Hacker News. We are giving 50% discount on EaseUS Partition Master Pro to our readers.
Just use SEO-LGR-85D coupon code at the time of checkout.
The case of flying saucer – Highway to the Danger Drone
5.1.2017 securityaffairs IT
One of the most discussed topics these days are the various nefarious uses that a Drone can be put to or just flown where they shouldn’t be.
2016 has been an eventful year bagged with mixed sentiments around the US presidential election, Brexit and Global terrorism striking the World’s news outlets. Simultaneously not far behind are the debates to seek, understand innovative venues/loopholes that have the potential to create havoc globally. One of the most discussed topics these days are the various nefarious uses that Drones can be put to or just flown where they shouldn’t be.
Drone Pilots capabilities to fly a drone into restricted areas or the risk of harming others is a topic for another day. Here in this short blog, we have tried to look at the various strategies Governments and Aviation Authorities have attempted to instigate to curb the menace only to see a threat evolving which poses a danger to the drones themselves.
So just what is a drone anyway? For the sake of argument let’s focus on the type of aircraft that you can purchase as a consumer for Video and Photography purposes (as opposed to the firing missiles and blow up things type). The world’s media has slapped the label of “Drone” onto any Quadrocopter, Octocopter or any other modern platform without actually investigating the differences between commercial platform, military devices and traditional models. Essentially our UAV (Unmanned Aerial Vehicle -which is the correct term!) has four components:
Power supply (typically a high power Li-Po Battery)
Propulsion units (4+ motors)
Transmitter (Video/Photo) / Receiver
Motherboard (the Flight controller)
Up until number 3 we were in the same ballpark as remote control helicopters and other model aircraft, which are controlled with servos according to the radio signals. However, with the introduction of the Motherboard we now have a flying computer with just as many undisclosed security issues as any other Internet of Things (IoT) device. Just because there isn’t a cable connected to the device does not mean that it is not susceptible to attack. For a clear breakdown of what is and isn’t a drone we have the following:
Model Aircraft Remote control only, no preprogrammed flight paths etc.
Drone Equipped with a flight computer, however, has no ability to follow pre- programmed path, nor does it have any built-in intelligence
Unmanned Aerial Vehicle (UAV) Encompasses all of the features seen in a drone but has additional intelligence features (Object Tracking, Terrain/Hazard avoidance etc.)
Unmanned Aerial System (UAS) All components seen in a UAV with additional support equipment (Base Station etc.)
So let’s have a look at some of the ways that have been identified to remove consumer UAVs from the air.
Shotgun: Eh, think we get this one! The US town of Deer Trail Colorado even attempted to enact a law to allow residents to hunt for federal UAV’s and shoot them down!
Net: Police forces and organizers of sporting events around the world have been trialing nets which are launched from a bazooka. This expands in the air and fowls the UAV’s rotor blades bringing it crashing to earth. There are also other slightly less destructive methods used where nets are carried by other larger UAVs; this approach has been adopted by the police force in Tokyo[1]. These again snare the rotor blades and are designed to capture the errant flying machine rather than send it crashing to the ground and onto potential pedestrians.
RF Generator (Denial of Service!) Or more simply a UAV Radio signal jammer. These devices overpower the radio signals (typically 2.4Ghz for most commercial UAVs which is the same range as standard Wi-Fi networks, Bluetooth connections, microwave ovens, car alarms, baby monitors, and ZigBee devices) with white noise causing the UAV to return to it’s “Home” position if this has been set (or is available) or at the very least severe the control from the Pilot. However, it should be noted that these devices themselves are highly illegal in most countries[2]. Some commercial firms are investigating Jamming Guns which target a narrow window and allow the operator to aim at the offending UAV without affecting other services.
Exploitation The takeover of the UAV’s flight systems by an outside attacker by various technical means allowing the attacker to have complete control of the system for their own purposes. The owner/pilot is locked out and has no way of controlling the system.
Hacking UAVs is not new with the first high profile case being of an RQ-170 Sentinel stealth drone, a key weapon in the intelligence gathering arsenal of the US Central Intelligence Agency (CIA); the drone was diverted and captured by the Iranians in December 2011. In this case, the Iranian military had identified that the US Military utilized encrypted GPS frequencies for its control systems. They first jammed the drone’s communications link to its ground controllers (which forced the drone into autopilot mode) this also had the effect of forcing the drone to search for unencrypted commercial control channels. The Iranian attackers spoofed these signals sending wrong GPS coordinates tricking the drone into believing it was at its home base in Afghanistan, thus landing on Iranian territory to the welcoming arms of its attackers. It should be noted that the US Military disputed this account and stated that it was a system malfunction; however subsequently researchers have been able to reproduce the incident with commercial UAVs using encrypted GPS signals.
Security Analysts and Hackers alike have been investigating these types of attacks for some time now Samy Kamkar (an Independent researcher) created a program called “dronestrike” in 2013 where he mounted a Raspberry Pi computer running his code on his Parrot AR UAV 2.0 along with a wireless transmitter[3]. When his UAV was flown in the vicinity of another parrot UAV the dronestrike program would make a connection to the victim UAV and disconnect the owner/pilot and take control of the system itself.
Earlier this year Johns Hopkins University[4] set its capstone project for Master’s Degree students. The students’ task was to conduct wireless pen testing on a consumer UAV and then take what they had identified and craft exploits to attack the system. Three various strategies were identified all of which successfully broke the connection to the pilot:
Denial of Service: The UAV was bombarded with over 1,000 wireless connection requests in a short period of time; each connection attempt asked to take control of the aircraft. This overloaded the UAV’s CPU causing it to shut down.
Buffer Overflow: In this scenario, an exceptionally large data packet was sent to the UAV. This exceeded the buffer in the UAV’s flight application causing the aircraft to crash.
Spoofing: The third scenario utilized an attack against the controller rather than the UAV. A fake packet was sent to the controller impersonating the UAV itself. The Controller severed the connection with the real UAV resulting in the aircraft making an emergency landing. XBee – Spectral analysis is seen to be utilized aggressively here.
These three types of attacks are nothing new to Cyber Security Analysts with these types of attacks occurring daily in Enterprise computer systems. But surely we as an industry don’t really have to be that worried about this, as these are only isolated case for hobbyist fliers? Think again, a UAV is a flying computer. Computers get hacked. Period!
drone
To add complication to this many logistical firms are trialing UAV delivery systems including Amazon, DHL and Domino’s Pizza to name but a few. Amazon has already been awarded a patent for the flying warehouse, (AFC) an airborne fulfillment center. The notion is that AFC could be used as a launch pad for drones to make local deliveries. The approved patents highlight that AFC would be housed at about 45,000 feet allowing UAVs to be stocked, deployed and flown as necessary.
With the above development moving forward the possibility of hacking into a UAV and divert it without the owner knowing where it has gone will be a massive incentive for criminals seeking to steal the deliveries flying over their heads. With the assistance of insiders within the delivery firm the criminals can target specific cargos. Already we have seen evidence where attackers are easily able to intercept the operator’s command at a distance up to 2 kilometers and spoof its own. At a distance of 100 meters, WEP can be easily cracked and the drone can be stolen.
A number of firms are now looking to UAV’s to provide a mobile security platform for organizations with large estates or in the case of smaller UAV’s warehouse security. The opportunity to attack these platforms is twofold. Firstly an attacker who is able to take control of the UAV is then able to turn it’s “eyes” away from any intruders on the ground. Secondly and more worrying is where the attacker diverts the drone, lands it and attaches their own monitoring equipment cameras with transmitting equipment etc. to the aircraft. When this is returned to the control of the automated system/pilot the UAV will continue about it’s tasks as though nothing has happened, all the while becoming a physical Trojan Horse to the attached monitoring equipment. This could lead to the loss of trade secrets with the likes of the indoor warehouse UAVs. This kind of attack can also be used to kill out market competition, not to forget current 70% of the commercial drone market is held by Chinese DaJiang Innovation technology (DJI)
One threat vector, which is already being utilized, is where criminal gangs are utilizing UAV’s to smuggle drugs into prisons for waiting for inmates. Whilst this is already occurring, the UAV’s themselves have either been purchased or stolen from their owner’s residencies. To have the ability to hack into a UAV take over it and then use it for your own purposes removes a great deal of risk and removes all attribution to the criminals when and if the UAV is captured by Prison staff. The ability to steal a UAV in flight is going to be a great temptation to criminals.
On a relevant note there is also a psychological dimension as the drone pilot while operating at a distance can be in a sense detached from the local context and culture. This may trigger the creation of dream-world/ gaming environment thus detaching from the physical reality and risking operator behavior towards professional reasonability and social mores. [5]
What we have seen in this blog is that UAV’s, or drones (if you must!) are just like any system which relies upon a computer to operate. They can be hacked and taken over for many nefarious activities and we have only just seen the beginning. When the delivery platforms take to the air (pun intended) cyber criminals are going to have a field day!
We are truly on the highway to the Danger Zone.
[1] http://www.telegraph.co.uk/technology/2016/01/21/tokyo-police-are-using-drones-with-nets-to-catch-other-drones/
[2] https://www.fcc.gov/general/jammer-enforcement
[3] https://www.youtube.com/watch?v=EHKV01YQX_w
[4] http://releases.jhu.edu/2016/06/08/johns-hopkins-team-makes-hobby-drones-crash-to-expose-design-flaws/
[5] http://releases.jhu.edu/2016/06/08/johns-hopkins-team-makes-hobby-drones-crash-to-expose-design-flaws/
New Kickass Torrents Site is Back Online by Original Staffers
16.12.2016 thehackernews IT
KickassTorrents is back from the dead!
Back in July, the world's largest and most notorious BitTorrent distribution site KickassTorrents (KAT) with millions of unique daily visitors was shut down by the U.S. authorities following the arrest of its alleged owner Artem Vaulin.
Shortly after the shutdown, a group of devoted original KAT staffers launched the Katcr.co forum in hopes of bringing back KickassTorrents to its former glory, in the near future.
Now, Katcr.co has launched a fully operational torrent website, which looks identical to the original Kickass Torrents (KAT) portal, TorrentFreak reports.
Note: In case the new KickassTorrents website does not immediately load, give it a few tries, as the site is experiencing a massive surge in traffic.
Launched today and located at KATcr.co/new, the new Kickass Torrents site starts with a clean user database while many members of the original staff are back on board, including its dedicated uploaders.
Here's what the KATcr team said on the sit’s launch:
"We have all our major uploaders on board, and they continued to share tirelessly even before the torrent engines returned. The torrent community can continue to expect to see uploads from all the names they know and trust."
Meanwhile, in a separate news, the Federal Court of Australia has ordered Internet service providers (ISPs) to block access to 5 Torrent websites, including The Pirate Bay, Torrentz, TorrentHound, IsoHunt, and SolarMovie, within next 15 days.
Following the shutdown of the original KickassTorrents portal earlier this year, several mirror sites came up online, claiming to be the real reincarnation.
However, in reality, many of those mirrors include malicious copycats that target unsuspecting pirates and attempts to steal their personal information and credit card credentials.
The KATcr team behind the new katcr.co/new site promises that the pirates are safe and secure at its new portal.
"In order to keep our members safe we chose to rebuild and keep only safe elements. Despite the fact that a rebuild took longer, the safety of our community comes first," one of the team members told TorrentFreak.
The KATcr crew members also believe that the original operators of the KickassTorrents website will walk free.
Become a Linux Expert — Get this Online 5-Course Training Bundle
12.12.2016 thehackernews IT
Linux is considered as one of the most favorite operating systems for hackers and security researchers. The open source operating system is often used for building technologies as it offers developers much room for modifications.
Linux is used on many hardware platforms, servers, gaming platforms, and much more. So it is essential for anyone, who want to become a Linux pro or seeking a career in system administrator, to understand Linux.
But Are you tired of searching multiple resources to fully understand Linux?
This process is not just time-consuming, but also expensive as one has to pay for different courses to know and learn how to setup, maintain and operate a fully backend infrastructure powered by Linux Operating System.
Not now! You don't need to waste your time and money, as today's THN Deals will help you choose an excellent course specifically designed to teach you all thing Linux.
Deal Of the Day — Linux Essentials Bundle (82% Discount)
Linux Essentials Bundle
Linux Essentials Bundle is a complete package that covers everything that is required to become a Linux Pro.
From an introductory course for absolute beginners, Linux Essentials Bundle will work your way through BASH and Shell Programming, administering Linux/UNIX systems, creating apps with Docker, using 'vi' for coding and more.
The original value of this course is $225, but at THN Deals Store, you can get this Linux Essentials Bundle course for $39 after 82% of flat discount.
The classes in Linux Essentials Bundle include:
Fundamentals of Unix & Linux System Administration
Learn Docker from Scratch
Linux Shell Programming for Beginners
Linux for Absolute Beginners
Learn To Code Like a Pro With vi Editor
Over 50 hours of the training course, you will learn how to build on the Linux OS, develop apps with Docker Access, edit code with vi Editor, and build efficient systems.
So, head on to THN Deals Store now and get Linux Essentials Bundle for a super low price of just $39.
Oracle acquires DNS provider Dyn for more than $600 Million
22.11.2016 thehackernews IT
Yes, Oracle just bought the DNS provider company that brought down the Internet last month.
Business software vendor Oracle announced on Monday that it is buying cloud-based Internet performance and Domain Name System (DNS) provider Dyn.
Dyn is the same company that was hit by a massive distributed denial of service (DDoS) attack by the Mirai botnet last month which knocked the entire Internet offline for a few hours, crippling some of the world's biggest and most popular websites.
Since the company provides cloud-based DNS service to customers such as Spotify, Netflix, Twitter and Pfizer, the acquisition will help Oracle's cloud customers to optimize their infrastructure costs and performance.
According to the press release, the Dyn acquisition "extends the Oracle cloud computing platform and provides enterprise customers with a one-stop shop for Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS)."
"Oracle Cloud customers will have unique access to Internet performance information that will help them optimize infrastructure costs, maximize application and website-driven revenue, and manage risk," said Kyle York, chief strategy officer of Dyn.
The company said Dyn's immensely scalable and global DNS is not just a critical core component but also provides a natural extension to Oracle's cloud computing platform.
So, the deal would help its cloud customers improve access and page-load speeds for their websites using internet performance information.
Oracle did not disclose the acquisition amount it paid for Dyn, but a source close to the deal told Fortune that Oracle paid somewhere between $600 Million and $700 Million to acquire Dyn.
Dan Primack reported that Oracle paid around $600 million for Dyn, though Dyn has yet to respond to a request for comment.
Oracle is far behind Amazon Web Services (AWS), which is the market leader in the infrastructure cloud computing market. The deal would potentially make the company compete with Amazon's AWS and on Microsoft's Azure – Route 53 and Azure DNS.
WiGig — New Ultra-Fast Wi-Fi Standard Ready to Boost Your Internet Speed in 2017
1.11.2016 thehackernews IT
Get ready for faster Internet because the WiFi you know today is about to change and get much, much faster.
The WiFi Alliance, a self-described "worldwide network of companies that brings you Wi-Fi," has finally certified "WiGig," an ultra-fast, short-range wireless network technology that will nearly double Wi-Fi's current top speed.
As many as 180 Million devices, including routers, smartphones, laptops, tablets, and other devices, arriving by the end of next year will support WiGig or multi-gigabit Wi-Fi 802.11ad on the 60 gigahertz band, the Alliance announced.
This certification program aims to encourage the production of devices and hardware that not only operate in the "less congested" 60 GHz spectrum but can also fall back to the regular Wi-Fi – 2.4 or 5 gigahertz bands – for maximum interoperability.
"Wi-Fi has delighted users for more than 15 years, and WiGig now gives users even higher performance in a rich variety of applications unleashing an unparalleled Wi-Fi experience," Wi-Fi Alliance CEO Edgar Figueroa said.
"WiGig further expands the Wi-Fi CERTIFIED portfolio into 60 GHz, and will augment existing and developing Wi-Fi programs and technologies."
WiGig can provide speeds of up to 8 Gbps, or nearly 1GB per second from a distance of up to 33 feet (10 meters). 8 Gbps is around three times faster than the best available devices on 802.11ac protocol right now.
This speed boost will help you download high-quality HD movies in just seconds. Also, the technology will make it possible to have super-fast wireless docks and wireless VR and AR headsets.
However, both ends of a connection should support WiGig the technology to achieve supported speeds.
The major issues with WiGig are adoption and compatibility. The WiFi Alliance also uncovered the first five certified WiGig products from Intel, Qualcomm, and Dell, among others.
The first certified consumer products to carry the WiGig standard is the Dell's Latitude 7450 and 7470 laptops, though the technology is eventually making its way into routers, tablets, notebooks, smartphones, and other categories.
Both Intel and Qualcomm have also certified router solutions. However, some companies such as Samsung have already released uncertified WiGig hardware.
The Wi-Fi Alliance expects its new WiGig standard to take off by 2017.
Verizon wants $1 Billion Discount on Yahoo Acquisition Deal after Recent Scandals
7.10.2016 thehackernews IT
Verizon wants $1 Billion Discount on Yahoo Acquisition Deal after Recent Scandals
It seems like it is not all over for Yahoo yet. Another day, another bad news for Yahoo!
Verizon, which has agreed to purchase Yahoo for $4.8 Billion, is now asking for a $1 Billion discount, according to recent reports.
The request comes after Verizon Communications learned about the recent disclosures about hacking and spying in past few weeks.
Just two weeks ago, Yahoo revealed that at least a half Billion Yahoo accounts were stolen in 2014 hack, marking it as the biggest data breach in history.
And if this wasn't enough, the company faced allegations earlier this week that it built a secret tool to scan all of its users' emails last year at the behest of a United States intelligence agency.
Due to these incidents, AOL CEO Tim Armstrong, who runs the Verizon subsidiary, is "pretty upset" about Yahoo's lack of disclosure, and is even seeking to pull out of the deal completely or cut the price, the New York Post claimed, citing multiple sources.
"In the last day, we've heard that Tim [Armstrong] is getting cold feet," a source reportedly told the Post. "He's pretty upset about the lack of disclosure, and he's saying can we get out of this or can we reduce the price?"
Armstrong is reportedly discussing a price reduction with Yahoo executives, though Yahoo is pushing back, claiming a "deal is a deal" and there's no legal recourse to change the terms, according to the paper.
Both Verizon and Yahoo have yet to comment on the matter.
Verizon announced the Yahoo acquisition deal in July, with the intention of merging it with AOL. The company is thinking to combine Yahoo and AOL to form a third force to compete with Google and Facebook for digital advertising.
The acquisition deal is supposed to close early next year, merging Yahoo's search, advertising, content, and mobile operations with AOL to reach 1 Billion users.
WikiLeaks Promises to Publish Leaks on US Election, Arms Trade and Google
4.10.2016 thehackernews IT
WikiLeaks Promises to Publish Leaks on US Election, Arms Trade, Google and Surveillance
Wikileaks completed its 10 years today, and within this timespan, the whistleblower site has published over 10 million documents, and there’s more to come.
In the name of celebration of its 10th Anniversary, Wikileaks promises to leak documents pertaining to Google, United States presidential election and more over the next ten weeks.
Speaking by video link to an anniversary news conference at the Volksbuhne Theater in Berlin on Tuesday morning, WikiLeaks founder Julian Assange eagerly announced his plans to release a series of publications every week for the next 10 weeks.
The upcoming leaks will include "significant material" related to Google, the US presidential election, military operations, arms trading and, the hot topic of past few years, mass surveillance.
Assange also promised to publish all documents related to the US presidential race before the election day on November 8.
"There is an enormous expectation in the United States," Assange said for the forthcoming leaks. "Some of that expectation will be partly answered; but you should understand that if we're going to make a major publication in relation to the United States at a particular hour, we don't do it at 3AM."
Assange initially planned to announce today's release from the balcony of the Ecuadorian Embassy in London, where he has been living since 2012 in an asylum for avoiding extradition to Sweden where he is facing sexual assault allegations. But he canceled his appearance, citing "security concerns."
When asked whether the upcoming leaks are aimed at damaging the image of US presidential candidate Hillary Clinton, Assange denied the claims, saying some of his statements in this regard had previously been misquoted.
"I certainly feel sorry for Hillary Clinton and Donald Trump," Assange said. "These are two people who are tormented by their ambitions, in different ways."
You can watch the video of the conference, marking WikiLeaks 10th Anniversary.
WikiLeaks has released 10 Million classified documents over past 10 years, among which include documents detailing US military operations in Afghanistan and Iraq, documents relating to the detention of prisoners by the America in Guantanamo Bay, and NSA's mass surveillance of world leaders.
United States set to Hand Over Control of the Internet to ICANN Today
2.10.2016 thehackernews IT
Since the foundation of the Internet, a contract has been handed over to the United States Commerce Department under which the department had given authority to regulate the Internet.
After 47 years, this contract ends tonight at midnight EDT i.e. Saturday, October 1st, 2016.
If you think that the United States owns the Internet, then you're wrong. It doesn't.
Founded in 1998, non-profit organization ICANN (The Internet Corporation for Assigned Names and Numbers) oversees the Internet's "address book" (or root zone) — the process of assigning domain names and the underlying IP addresses to keep the Internet running smoothly.
But according to the contract, ICANN and its IANA department (the Internet Assigned Numbers Authority) was set to work under the supervision of National Telecommunications and Information Administration (NTIA), an agency of the U.S. Department of Commerce.
That contract is ending today, and the US Commerce Department is scheduled to hand over its role to ICANN, which will now become an autonomous body, accountable to an international multi-stakeholder community which includes members from the technical community, businesses, telecommunications experts, civil society and governments.
The Internet itself was designed to function without a central authority and has become a critical part of everyone's life, as well as for the global economic infrastructures.
Four States Sue to Stop "Internet GiveAway"
However, this plan is not without a bit of last-minute drama.
It's already a known fact that majority of the political portion of the United States doesn’t want to give way the Internet. In fact, the process of "losing control over the Internet" has already been opposed by some conservative officials and lawmakers.
Four Republican states' attorneys general have filed a lawsuit in a last-minute effort to prevent the Obama administration from ceding control of the internet's critical functions to ICANN, though a federal judge has already denied the request.
With ICANN not under US control, the attorneys general for Arizona, Oklahoma, Nevada, and Texas, fear that "authoritarian regimes like Russia, China, and Iran will now have the ability to interfere with what should be a free and open internet."
"The President doesn't have the authority to simply give away America's pioneering role in ensuring that the Internet remains a place where free expression can flourish," Texas attorney general Ken Paxton said [PDF].
How Does Internet Transition Affect You?
But, after the Edward Snowden’s revelations of NSA's worldwide surveillance program, Internet users don't trust the United States, and they want the Internet to be a free and uncensored platform.
Even the father of the World Wide Web Sir Tim Berners-Lee wants the Internet to be decentralized in order to eliminate middleman entirely from all aspects of the Web.
However, this transition would not make any significant change for the Internet users because the companies that oversee the top-level domains, including .com, .org, and .net, are based in the United States, meaning they have to follow US law and abide by US court orders.
icann-domain-name
With the help of these court orders, the US government has already shut down thousands of websites it has declared to be breaking laws about drugs, intellectual property, gambling, and others. Kim Dotcom's Megaupload file-sharing website was also shut down in 2012 due to this.
If you think that domains registered under handles outside of the United States don't come under the US jurisdiction, then you are wrong.
The US government even has international cooperation agreements with many countries, requiring foreign registries to comply with US orders.
The KickassTorrents (or KAT.cr) website — the world's most notorious file-sharing sites — is the best example of this kind.
While the main site was registered with the .cr domain by the Costa Rican register called NIC, it was shuttered at the request of the United States this summer and its operator was arrested in Poland and charged by US authorities with varying criminal copyright infringement counts.
US technology giants, including Google, Facebook, Twitter, Yahoo, and Amazon, also back the transition, arguing it will support innovation.
Even former top United States national security officials, Michael Chertoff and James Cartwright, also support the transition to ICANN, despite national security fears.
PIL filed in Court to Ban ‘Pokémon Go’ in India for Hurting Religious Sentiments
10.9.2016 thehackernews IT
Pokémon GO has yet not been officially launched in India, but the location-based augmented reality game has already fueled a privacy debate and request for Ban.
Isn't that weird?
A Gujarat resident, Alay Anil Dave has recently filed a Public Interest Litigation (PIL) in the Gujarat High Court against Niantic, developers of Pokémon Go, over allegations that the game is hurting religious sentiments of Hindus and Jains by showing virtual eggs in places of worship of different religious groups.
The launch date of Pokémon GO for India has not been announced so far, but millions of Indians have already downloaded the game from 3rd-party app markets and playing it on the streets.
However, there are many still waiting for an official release of the game in India, as they don’t want to end up installing malicious versions of Pokémon GO that could install malware on their phones, allowing hackers to compromise their devices.
Pokémon GO has become the most successful game launch of all time with more than 500 Million downloads in just over two months and has been making rounds since its inception just over two months ago.
This game is reported to have almost as many daily active users on Twitter.
Also Read: 6 Important Things You Should Know Before Playing Pokémon GO
In fact, Niantic Labs CEO John Hanke just announced that the Pokémon Go game app is coming to the Apple Watch on stage at Apple's iPhone 7 event on Wednesday.
How Does Pokémon GO Hurt Religious Sentiments?
But Why does Petitioner want India to Ban Pokémon GO?
Actually, this augmented reality game requires gamers to walk around homes, parks and local surroundings to find new Pokémon characters, as well as achieve goals like hatching incubating eggs.
One can find the most common Pokémon in the distance of 2km eggs, with the rarest ones in the 10km eggs. But, Niantic didn't know that some Indians have a problem with these eggs.
"People playing the game get their points in the form of eggs which generally appear in the places of worship of different religious groups. To find eggs in temples of Hindus and Jains is blasphemous, and therefore my client has sought ban on the game from the country," Dave's lawyer said.
However, we talked to some security experts and privacy advocates in India, who shared their opinions on the case.
Dinesh Bareja, Information security professional, and researcher at IndiaWatch, provided a statement to The Hacker News, saying:
"Such PIL are frivolous and just designed to get the person his few moments of fame. Chasing a virtual image into a temple or any other place cannot be termed desecration of the place of worship and, like many other PIL this is also going to be a waste of the valuable time of the Hon'ble Court."
Another Information security professional, who wants to remain anonymous, told us:
"Some Hindu temples still have a tradition of Bali of Animals [Animal sacrifice]. So painting all Hindu temples as a symbol of non-violence and hurting religious sentiments isn't true."
The Editor of Cyber Secure India Portal said,"There seems no strength in the PIL, frankly speaking. However, the PIL may just be appropriate, if the person who has filed the PIL, should have obtained a legitimate licensed copy of the game; otherwise, the charge may be dropped. Further, the fact that egg was found is a question of perception, being an animated pictorial representation."
Pokémon Go, Privacy and National Security
Along with hurting religious sentiments by displaying eggs in houses of worship, the PIL also cites that Pokémon Go could be used by the CIA to create maps of sensitive "areas currently unavailable in Google Maps."
Adv. Prashant Mali, Cyber Security Law Specialist Lawyer, told The Hacker News that he is primarily concerned about privacy and accidents occurred due to this game.
"It has become a fashion to file a PIL and get cheap and fast publicity. There are other games which children play which has a lot more violence and some games do promote sexual violence," Mali said.
"I feel Government at this rate of censorship may appoint a Censor Board like films to moderate even video games. When the game gets launched in India, they may take care of religious feelings by default now it is an illegal game so the PIL may get dismissed even."
The PIL also raised some concerns over the game, like an infringement of the right to privacy, a threat to the life of players who walk around the street to catch Pokémons, game’s influence on the minds of children and "behavior as an Indian," among others.
“All the maps are via open maps, already in the public domain so that issue is sorted. Use of AR in sensitive areas from government viewpoint can be a problem. To avoid this, use of camera phones and recorders should be banned in such sensitive declared as it is not just one game that can cause issues.” an anonymous follower comments.
The PIL was heard on Wednesday by a division bench of Chief Justice R. Subhash Reddy and Justice Vipul Pancholi, and notice by the Gujarat High Court has been issued to Niantic Inc. of the US, which has yet to respond.
If Pokémon GO gets banned in India, it will not be the first country to do so. Last month, Iran officially banned Pokémon GO within the country due to certain "security concerns."
MIT Researchers Solve the Spectrum Crunch to make Wi-Fi 10 times Faster
24.8.2016 THEHACKERNEWS IT
mit-MegaMIMO-Spectrum-Crunch-fastest-wifi
While using your cell phone at a massive public event, like a concert, conference, or sporting event, you have probably experienced slow communication, poor performance or slow browsing speeds, as crowds arrive.
That's because of ‘Spectrum Crunch’, which means, Interference of WiFi signals with each other.
WiFi signals of all cell-phones in a large event interfere with each other because they are all fighting over the same limited spectrum but there is not enough bandwidth to handle all the traffic from the cellphones that are trying to use the same frequency slice at the same time, leaving them frustrated with painfully slow Internet access.
However, a team of researchers from the MIT's Computer Science and Artificial Intelligence Laboratory (CSAIL) has developed a solution for this problem.
In a new research paper, 'Real-time Distributed MIMO Systems,' published online this week, the MIT team described a system for managing networks that cause the WiFi routers to collaborate better.
Dubbed "MegaMIMO 2.0" (Multiple Input, Multiple Output), the system uses an algorithm that coordinates multiple access points (routers) at once, syncing their phases so that multiple transmitters can share the same part of the spectrum without interference.
The algorithm developed by the researchers processes a router's signal in such a way that multiple routers can send information on the same wireless spectrum without causing any interference.
So what's the Result?
In the test conducted by the MIT team, led by professor Dina Katabi, the researchers said their MegaMIMO 2.0 was able to transfer wireless data 3.6 times faster than existing systems in a crowded room.
What's more impressive: The team was able to increase Wi-Fi speeds by a factor of 10 when it had tested with additional routers.
However, the team admitted that the MegaMIMO 2.0 system had not been tested in a stadium or any large venue, but in a lab using four laptops that roamed on Roomba robots designed to move around like people do in large gatherings.
You can watch the video demonstration that shows off the MegaMIMO 2.0 system online.
So-called 'Spectrum Crunch' is such a major issue that the White House recently announced both a $400 Million research initiative as well as a $4 Million global competition dedicated to this problem.
The team is confident their system will work and has already created a startup, called MegaMIMO, and is now exploring ways to commercialize their technology, so perhaps you will be able to watch YouTube videos at concerts and conferences.
However, you will have to be patient, as Ezzeldin Hussein Hamed, one of the MIT researchers, said it was too early to estimate when the average American would experience the benefits of these systems.
Does your WebCam Crash after Windows 10 Anniversary Update? Here’s How to Fix It
21.8.2016 thehackernews IT
If your webcam has stopped working after installing recently-released Microsoft's big Anniversary Update for Windows 10, you are not alone.
With some significant changes to improve Windows experience, Windows 10 Anniversary Update includes the support for webcams that has rendered a number of different webcams inoperable, causing serious issues for not only consumers but also the enterprise.
The problem is that Microsoft added some new ways for applications to access webcams with Microsoft's new Windows Camera Frame Server, preventing webcams from using two particular compression formats—H.264 and MJPEG.
Microsoft decided that the Camera Frame Server should only receive an uncompressed YUY2 encoding stream from the webcam, which is affecting far more devices than Microsoft expected, causing Millions of cameras to crash.
This is the reason why your camera hangs, freezes, or simply not works when you try to do a video calling with your friend over Skype. Brad Sams of Thurrot first discovered this issue.
"Since it will take some extra time for the H.264 work to go through this additional layer of testing, and we would prefer not to delay the MJPEG changes [fix], we will ship these two separately. You can expect the MJPEG media type work to reach you first," reads a post in Microsoft's Support Forum from Windows Camera Team member Mike M.
Although Microsoft has planned to fix the issue and roll out an official fix in September, Windows users who do not want to wait for a month for Microsoft's update can use a workaround suggested by Rafael Rivera to re-enable the old behavior of webcam and fix the issue.
Here's how to Fix Your Webcam:
The workaround is a registry hack, so if you are comfortable tweaking the registry, make the below changes. The hack is pretty simple; you just need to stick to the following instructions.
Go to the Start Menu, type "regedit" and press Enter. This opens 'The Registry Editor'.
Navigate to "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Foundation\Platform" in the left sidebar.
Right-click the "Platform" key and select New → DWORD (32-bit) Value.
Name this value "EnableFrameServerMode" and set the value to "0" by double clicking on it.
These are the steps if you are using a 32-bit version of Windows 10.
If you are using a 64-bit version of Windows 10, you will need to navigate to "HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows Media Foundation\Platform" in the left sidebar and follow step 3 and 4 mentioned above.
Now close the registry editor and just re-launch the application in which your webcam was freezing. They should now work normally – no reboot, no sign out required.
When Microsoft actually fixes the issue after a month, just revisit the same location in the registry editor and delete the "EnableFrameServerMode" value you added to undo this change.
The hack is simple but follow the above steps correctly because a small mistake in The Registry Editor tool can render your system unstable or even inoperable.
Microsoft Open Sources PowerShell; Now Available for Linux and Mac OS X
19.8.2016 thehackernews IT
'Microsoft loves Linux' and this has never been so true than now.
Microsoft today made its PowerShell scripting language and command-line shell available to the open source developer community on GitHub under the permissive MIT license.
The company has also launched alpha versions of PowerShell for Linux (specifically Red Hat, Ubuntu, and CentOS) and Mac OS X, in addition, of course, to Windows.
Now, people can download binaries of the software, as well as access source code of the app from the new PowerShell GitHub page.
"Users across Windows and Linux, current and new PowerShell users, even application developers can experience a rich interactive scripting language as well as a heterogeneous automation and configuration management that works well with your existing tools," Microsoft says in its blog post.
"Your PowerShell skills are now even more marketable, and your Windows and Linux teams, who may have had to work separately, can now work together more easily."
PowerShell is Microsoft’s command line shell for Windows power users, and an extensible scripting language for automating system tasks.
Microsoft is aware that the company now operates in a "multi-platform, multi-cloud, multi-OS world." Since PowerShell is built on Microsoft's .NET platform, the company brought .NET Core, the version of .NET which runs cross-platform, to bring PowerShell to other platforms.
Microsoft has already planned to ship PowerShell "Core" with Nano Server for Windows Server 2016, and the newly announced release will run on .NET Core on Mac as well as Linux.
Although this recent release of PowerShell is Alpha-based and community supported, an official Microsoft version of PowerShell based on open source to anyone running a supported version of Windows will be published in the future, Microsoft notes.
Google to Face a Record $3.4 Billion AntiTrust Fine in Europe
16.5.2016 IT
Google faces a record anti-trust penalty of about 3 BILLION Euros (US$3.4 Billion) from the European Commission in the coming days, according to reports.
After 7-years of the investigation, the European Commission filed anti-trust charges against Google last year for violating antitrust laws.
The European Union accused the search engine giant that it had abused its dominance in search by unfairly prioritize and displaying its own comparison shopping service at the top of its search results at the expense of rival products.
British newspaper The Sunday Telegraph reports that the European Union is currently preparing a fine of about 3 Billion Euros ($3.4 billion), which is almost triple the amount (1.06 Billion Euro) that Intel was levied several year ago over violating antitrust law.
According to the newspaper's sources, the EU officials, led by Margrethe Vestager, are planning to openly announce the fine against Google as early as next month, although the exact figure of the fine has yet to be finalized.
Reportedly, the European Commission regulators can impose a maximum penalty of up to 10 percent of the company's annual sales, which, in the case of Google, is possibly more than 6.6 Billion Euros.
Not just fine, but Google will also be banned from manipulating its search results in the region so that it does not continue to favor its homebrew products.
In a separate antitrust case, Google has also been accused of abusing its dominant position in the smartphone industry with Android by pre-installing its own apps, like Google Search, Chrome, YouTube, Gmail as default apps, making it harder for other companies to compete.
"Anyone can use Android with or without Google applications. Hardware manufacturers and carriers can decide how to use Android and consumers have the last word about which apps they want to use," Google spokesperson says.
The EU is also looking into the transparency of paid reviews and the conditions of use of services like Google Maps and Apple's iOS mobile operating system.
WhatsApp launches Desktop Software for Windows and Mac Users
11.5.2016 IT
The most popular messaging app WhatsApp now has a fully functional desktop app – both for Mac as well as Windows platform.
Facebook-owned WhatsApp messaging software has been a mobile-only messaging platform forever, but from Tuesday, the company is offering you its desktop application for both Windows and OS X.
Few months back, WhatsApp launched a Web client that can be run through your browser to use WhatsApp on your desktop, but now users running Windows 8 or Mac OS 10.9 and above can use the new desktop app that mirrors WhatsApp messages from a user's mobile device.
According to the company's blog post, the WhatsApp desktop app is similar to WhatsApp Web with synchronized conversations and messages
Since WhatsApp desktop app is native for both Windows and OS X platform, it can support desktop notifications and keyboard shortcuts.
WhatsApp has been rising at an extraordinary pace recently. The service has over 1 Billion monthly active users.
At the beginning of the year, the company removed its yearly $1 subscription fee. Just last month, the company rolled out end-to-end encryption for all its users' communication by default.
Here's how to Download WhatsApp Desktop Software:
WhatsApp launches Desktop Software for Windows and Mac Users
Users running Windows 8 (or newer) or OS X 10.9 (or newer) can download WhatsApp desktop app available for direct downloading.
Once Downloaded, open the WhatsApp desktop app.
Scan the QR code with your mobile phone to Sync your device.
Now enjoy WhatsApping your friends and family straight from your desktop.
Liberty Reserve founder sentenced 20 years in jail
8.5.2016 IT
Arthur Budovsky, the co-founder of the online underworld bank Liberty Reserve, was sentenced to 20 years in prison for committing money laundering.
Arthur Budovsky, the co-founder of the online underworld bank , was sentenced to 20 years in prison. The man had pleaded guilty to one count of conspiring to commit money laundering. He was condemned to have laundered money for several criminal activities, including child pornography, credit card fraud and drug sale.
Budovsky, who was arrested in Spain in May 2013, he tried to avoid prosecution by acquiring Costa Rica nationality.
It has been estimated that the Costa Rica-based Liberty Reserve processed more than $8 billion worth of transactions for more than 5.5 million users worldwide in the period from 2015 to 2013 when it was shut down by law enforcement. According to the US Department of Justice more than 600,000 users were in the United States.
“The significant sentence handed down today shows that money laundering through the use of virtual currencies is still money laundering, and that online crime is still crime,” Assistant Attorney General Leslie R. Caldwell for the Justice Department’s Criminal Division said in a statement.
“Liberty Reserve founder Arthur Budovsky ran a digital currency empire built expressly to facilitate money laundering on a massive scale for criminals around the globe,” US Attorney Preet Bharara for the Southern District of New York was quoted as saying.

Budovsky was also ordered to pay a $500,000 fine by US District Judge Denise L. Cote.
Criminals used Liberty Reserve used the popular service as a financial hub that allowed them to operate anonymously.
Budovsky confirmed with the authorities to have laundered roughly $550 million in transactions made by US-based Liberty Reserve accounts.
The man was not alone, other six people face charges in the case, the accomplices Maxim Chukharev and Mark Marmilev were sentenced to three and five years respectively.
Others two accomplices are set to be sentenced next week and another two remain at large.
Want to Use Quantum Computer? IBM launches One for Free
5.5.2016 IT
What would you do if you get access to a Quantum Computer? IBM Scientists launches the world’s first cloud-based quantum computing technology, calling the IBM Quantum Experience, for anyone to use. It is an online simulator that lets anyone run algorithms and experiments on the company's five-qubit quantum computer.
Quantum computers are expected to take the computing technology to the highest level, but it is an experimental and enormously complex technology that Google and NASA are working on and is just a dream for general users to play with.
Hold on! IBM is trying to make your dream a reality.
IBM just made its new quantum computing project online, making it available for free to anyone interested in playing with it.
Quantum Computers — Now A Reality!
IBM launches its Quantum Computer Free for Everyone on the Cloud
The technology company said on Wednesday that it is giving the world access to one of its quantum computing processors, which is yet an experimental technology that has the potential to perform much faster calculations than today's computers.
You can now access IBM's five-qubit quantum computing processor, which is located at its a research center in Yorktown Heights, New York, through the cloud to run experiments and test applications.
All you will need to do is request an invitation from IBM through a web form that will ask for your institution details and your level of computing experience.
Also Read: Fastest Operating System for Quantum Computing Developed By Researchers.
Quantum Computers Vs. Regular Computers ?
Quantum computers can theoretically be much faster than traditional computers because they take advantage of quantum mechanics.
While traditional computers use the "bits" to represent information as a 0 or a 1, Quantum computers use quantum bits or "qubits" to represent information as a 0, 1, or both at the same time. This means that 2 qubits could potentially have 4 values at the same time: 00, 01, 10, and 11.
In other words, a quantum computer with just 50 qubits will be much more powerful than any supercomputer available today.
360° Tour of the IBM Research Quantum Lab:
According to IBM, its five-qubit quantum computing processor is just a "small step" towards a useful quantum computer, though the company hopes to build a quantum computer with a medium-size quantum processor of 50-100 qubits within the next 10 years.
With a step ahead in the quantum computing, IBM's qubit processor is the world's first quantum processor accessible to the public, even if through the cloud.
Users who want to access the quantum processor can stay in the comfort of their homes or offices and work with qubits, study tutorials, and run simulations using the cloud and their computers or mobile devices.
Experience Quantum Computing Now!
Craig Wright Will Move Satoshi Nakamoto's Bitcoin to Prove His Claim
4.5.2016 IT
Yesterday, BBC broke a story allegedly revealing Craig Wright as the original creator of Bitcoin digital currency Satoshi Nakamoto.
However, the highly skeptical cryptographic community is definitely not yet convinced with the technical proofs Wright has yet provided to the media outlets and on his blog.
Now, Wright has promised to provide further evidence for his claim that he is behind the pseudonym, Satoshi Nakamoto.
Wright’s spokesman told BBC that he would "move a coin from an early block" of Bitcoin owned by Nakamoto "in the coming days." However, the spokesman did not specify a deadline.
"So, over the coming days, I will be posting a series of pieces that will lay the foundations for this extraordinary claim, which will include posting independently-verifiable documents and evidence addressing some of the false allegations that have been levelled, and transferring bitcoin from an early block.", Wright said in a latest blog post "Extraordinary claims require extraordinary Proof."
You should know that whoever is Satoshi Nakamoto in real, he should have access to around 1 million Bitcoins (currently worth $400 million) mined in early days of technology.
Since those Bitcoins have never moved in the seven-year-long history of Bitcoin, if Wright is right, he can transfer some part of those oldest Bitcoins to a different address in order to prove the possession of the private keys of those early Bitcoins.
The Industry Calls him a Scammer, Why?
Yesterday, Wright offered cryptographic key as proof of his work, backed up by other technical information, to convince the cryptography community that he is behind the pseudonym, Nakamoto.
However, the community described Wright’s proof as "flimflam and hokum" that ultimately did not demonstrate any non-public information about Nakamoto.
It speculated that Wright "used amateur magician tactics to distract non-technical or non-expert staff of the BBC and the Economist during a stage-managed demonstration."
Robert Graham, a well-known security researcher, published an interesting technical blog post, “How Craig Wright's Deception Worked”, demonstrated step-by-step how Wright might have scammed so cleverly.
Wright's proof has not convinced the wider public, but if he moves one of Nakamoto's Bitcoins, as promised, it will convince a majority of skeptical cryptographers.
Bitcoin Creator Has Finally Unmasked Himself. Maybe, Real?
2.5.2016 IT
The mysterious creator of the BITCOIN digital cryptocurrency seems to have been identified as an Australian entrepreneur, and his name is:
Craig Steven Wright.
Five months after Wright, an Australian computer scientist and businessman was outed as Satoshi Nakamoto, revealed himself as the original inventor of Bitcoin digital currency.
Wright has published a blog post offering Cryptographic Key as proof of his work, backed up by other technical information and the prominent Bitcoin community members have also corroborated his claim.
However, Satoshi Nakamoto has always shown the desire to remain anonymous, while Wright has not. "I am not seeking publicity, but want to set the record straight," he explains.
Wright has provided some technical proofs to BBC, The Economist, and GQ media outlets that link him to the identity of Nakamoto.
Craig Wright Claims He is Satoshi Nakamoto
At the meeting with the BBC and Economist, he digitally signed messages using the same cryptographic key that is connected with the first bitcoin transaction.
"Mr. Wright digitally signed messages using cryptographic keys created during the early days of Bitcoin’s development. The keys are inextricably linked to blocks of bitcoins known to have been created or mined by Satoshi Nakamoto."
"These are the blocks used to send ten bitcoins to Hal Finney in January [2009] as the first bitcoin transaction," said Wright during his demonstration.
These are undoubtedly linked to blocks of Bitcoins known to have been created, or mined, by Nakamoto.
This Australian Scientist says He is Satoshi Nakamoto, the creator of Bitcoin
Wright also published a blog post on Monday to provide information which he says will allow others to cryptographically verify that he is the real Nakamoto.

The founding director of the Bitcoin Foundation, Mr. Jon Matonis, is convinced that Wright is Satoshi Nakamoto, as explain in his latest blog post "How I Met Satoshi."
However, last year Wired and Gizmodo identified Wright as the mysterious creator of Bitcoin, but their evidence met with some doubts.
Soon after the stories broke by several media outlets, Australian federal authorities raided the home of Wright, sifting through his garbage.
However, these new report suggests that Wright has strongly claimed to be the original creator of Bitcoin.
"Some people will believe it, some people will not, and to tell you the truth, I do not really care," Wright told the BBC, adding that he was the main part of the creation of Bitcoin, but other people helped him.
Hey Wright, Prove Ownership of 1 Million Bitcoins linked to Nakamoto:
Wright has also planned to release some more information that would allow the highly skeptical cryptographic community to verify that he is Satoshi Nakamoto.
One such proof required is the ownership of 1 Million Bitcoins (worth more than $400 Million) that in theory only Nakamoto possesses.
Johns Hopkins cryptographer Matthew Green told Wired that if Wright is actual inventor of Bitcoin, he should have access to the private keys that control the earliest mined Bitcoins by Nakamoto.
Since those Bitcoins have never moved in the seven-year-long history of Bitcoin, Wright can transfer some part of those oldest Bitcoins to a different address in order to prove the possession of the keys.
On the other hand, JoukeH, a Reddit member discovered that the signature on Craig Wright's post is worthless, as it is not a signature of any "Sartre" message, but just the signature inside of Satoshi's 2009 Bitcoin transaction.
"It absolutely doesn't show that Wright is Satoshi, and it does very strongly imply that the purpose of the blog post was to deceive people." he says.
Microsoft to Store Data on DNA — 1,000,000,000 TB in Just a Gram
29.4.2016 IT
Do you know — 1 Gram of DNA Can Store 1,000,000,000 Terabyte of Data for 1000+ Years.
Microsoft has purchased 10 Million strands of synthetic DNA, called Oligonucleotides a.k.a. DNA molecules, from biology startup Twist and collaborated with researchers from University of Washington to explore the idea of using synthetic DNA to store huge amount of data.
Microsoft is planning to drastically change the future of data storage technology as we know it today.
The volume and rate of production of data being produced and stored every day are so fast that the servers and hard drives needing to be replaced periodically, potentially increasing the risk of corruption and data loss.
According to stats, 5.4 zettabytes (4.4 trillion gigabytes) of digital data, circulating and available worldwide, had been created by 2015, and it will boost to 54 zettabytes (ZB) by 2020.
How will the world suppose to store this 10 times amount of data in next four years?
For this, Microsoft has partnered with scientists at the University of Washington to focus on using DNA as a data storage medium, the companies announced on Wednesday.
Yes, Microsoft is planning to store data in DNA.
The data storage density of DNA is enormously higher than conventional storage systems, as just 1 gram of DNA can store close to 1 Billion Terabytes of data.
Besides this, DNA is also remarkably robust, which means the data stored in DNA can stay intact and readable for as long as 1,000 to 10,000 years.
According to Twist, all of the digital data that exists today could be stored in less than 20 grams of DNA.
Though the technology is long away from ready for commercial products (so you will not see a DNA-powered smartphone anytime soon), the initial tests done by the company last fall demonstrated 100 percent of digital data encoded on DNA could be recovered, Microsoft Research's Doug Carmean said in the press release.
Recently, the American Chemical Society said in a statement that storing data on DNA could last up to 2,000 years without deterioration.
This Tiny Computer has no Battery, Powered Wirelessly from Radio Waves
27.4.2016 IT
No matter how smart and fast your devices would be, the biggest issue is always with the battery technology.
Whenever you go to buy any electronic gadget — smartphone, laptop, or any wearable — the most important specification isn’t its processor speed or its camera quality but its Battery Backup, which is not getting better any time soon.
What if you could eliminate the very thing entirely?
Well, that's exactly what the electrical engineers from the University of Washington has developed.
A team of researchers from the University of Washington’s Sensor Lab and the Delft University of Technology has developed a new gadget that doesn’t need a battery or any external power source to keep it powered; rather it works on radio waves.
So, this means you have to turn on your radio every time to keep this device charged. Right?
No, you don’t need to do this at all, because the device sucks radio waves out of the air and then converts them into electricity.
Wireless Identification and Sensing Platform
Wireless-Identification-Sensing-Platform
Dubbed Wireless Identification and Sensing Platform (WISP), the device is a combination sensor and computing chip that uses a standard off-the-shelf RFID (Radio Frequency Identification) reader to suck in radio waves and convert them into electricity.
Though the WISP is not designed to compete with the chips in your computer or even your smartphone, it has as much processing power as the Fitbit, which is enough to run sensors and transmit data.
The discovery could highly transform the Internet of Things (IoT) world as the WISP is even more low maintenance compared to Bluetooth Low Energy sensor chips being used today.
The next step in making the WISP usability even more convenient and easy is to create Wisent that would allow for wireless programming of the WISP. For this, the team has recently collaborated with the Delft University of Technology.
With the help of Wisent, the WISP can be programmed wirelessly and uses the very same radio waves to communicate.
"So far WISP required cables to reprogramme it, nullifying the advantage of battery-less-ness. Therefore, we present Wisent, a protocol that allows WISP to be reprogrammed wirelessly," said Przemys³aw Pawe³czak, assistant professor at the TU Delft’s Embedded Software group.
"Our vision is to have truly wirelessly reprogrammable software-defined battery-less computers wherever and whenever we want."
For more details, you can head on to the research paper [PDF].
Though the ultimate aim of WISP is in fully realizing the Internet of Things and giving "dumb" objects some smartness, it might even find its way into smartphones as a sort of emergency backup calling module that works even when your phone’s battery is dead.
However, there is no detail on when the WISP will be made available for purchase, or how much it will cost.
DARPA Invites Geeks to Convert Everyday Objects into Deadly Weapons
17.3.2016 IT
Do you know that your daily household items can be turned into deadly weapons?
Yes, it's possible to convert some of your everyday household appliances into explosives, weapons or surveillance devices.
DARPA – the agency which does research in various fields for improving the US Military and US Department of Defense capabilities – had announced a new project dubbed "Improv" to transform simple household appliances into deadly weapons i.e. homemade weapons.
In previous years, various military grade weapons had been found malfunctioned by the ordinary household things that could cripple the military inventions.
By various incidents happening around the Military grounds, officials observed that "how easily-accessed hardware, software, processes, and methods could be used to create products or systems that could pose a future threat."
So, DARPA (Defense Advanced Research Projects Agency) proceeded with a program and is seeking proposals from engineers, skilled hardware hackers, biologists and information technologists, who can come up with some innovative ideas to build a deadly system or devices by unleashing the power of everyday things.
Improv - Initiative to Build Weaponised Capabilities into Home Appliances
Improv program will carry out research on the systems and devices of the readily available technology that could threaten the national security by challenging the current military equipment.
"Improv will explore ways to combine or convert commercially available products such as off-the-shelf electronics, components created through rapid prototyping, and open-source code to cost-effectively create sophisticated military technologies and capabilities," said John Main, Improv's Program Manager.
The program's prime aim is to build capabilities of a weaponized device in normal household things.
Open Challenge!
Improv would undergo 3 Phases to finalize the proposed system:
Phase 1: Submit plans for off-the-shelf prototype and if selected, candidates would be rewarded with $40,000.
Phase 2: The second round of the program requires selected candidates to bring proposed prototype model into real world system for which DARPA will fund $70,000.
Phase 3: The final stage is for a live demonstration with up to $20,000 for testing.
The Candidates have to complete this task with a strict deadline of 90 days as per Rules of DARPA.
Improv understands the fact that no one can be a Jack of all trades. Hence, there are no exclusions for anyone to give his or her try, which could really save the world from the potential dangers, unlike "Hack the Pentagon" program which was opened only for US Nationals.
Nowadays many mushrooming methods are evolved to manipulate the legit systems, which is a nightmare for millions and a daydream for criminals.
So, Improv would be seen as a new dimension to the US Military Defense to tackle the risky attacks.
The Pentagon used military drones for domestic surveillance
13.3.2016 IT
A report published by the DoD Inspector General revealed that military drones have been used for Non-Military domestic Surveillance.
The US Government has admitted the use of drones for operations of domestic surveillance. The US Military clarified that all the operations were authorized by a regular warrant confirming that no legal violations were found.
The news was revealed by the USA Today that obtained it with a Freedom of Information Act request. A report issued by the Inspector General at US DoD states the that less than 20 missions have been flown by military spy drones on non-military missions between 2006 and 2015.
The inspector general analysis was completed March 20, 2015, but the authorities released it recently.
“The Pentagon has deployed drones to spy over U.S. territory for non-military missions over the past decade, but the flights have been rare and lawful, according to a new report” states the USA Today.
The DoD report revealed the Pentagon established interim guidance in 2006 governing when and whether the drones could be used for domestic surveillance missions.
“The interim policy allowed spy drones to be used for homeland defense purposes in the U.S. and to assist civil authorities.” continues the post.
The policy highlights that any use of military drones for civil authorities had to be approved by the Secretary of Defense or someone delegated by the secretary.
The US government won’t disclose the details of non-military spying missions flown by the drones, anyway it has publicly issued a list of nine operations conducted between 2011 and 2016:
“The Pentagon has deployed drones to spy over U.S. territory for non-military missions over the past decade, but the flights have been rare and lawful, according to a new report” states the USA Today.
The DoD report revealed the Pentagon established interim guidance in 2006 governing when and whether the drones could be used for domestic surveillance missions.
“The interim policy allowed spy drones to be used for homeland defense purposes in the U.S. and to assist civil authorities.” continues the post.
The policy highlights that any use of military drones for civil authorities had to be approved by the Secretary of Defense or someone delegated by the secretary.
The US government won’t disclose the details of non-military spying missions flown by the drones, anyway it has publicly issued a list of nine operations conducted between 2011 and 2016:

The US Military seems to have refused to provide the entire archive related to civic requests for the military drone usage for domestic surveillance.
“The report quoted a military law review article that said “the appetite to use them (spy drones) in the domestic environment to collect airborne imagery continues to grow, as does Congressional and media interest in their deployment.”” continues the USA Today.

Source: USA Today
Let’s close reminding that the domestic surveillance with drones is allowed with the explicit authorization by the defense secretary.
The USA today confirmed that shortly before the DoD Inspector General report was completed, the Pentagon issued a new policy governing the use of spy drones. The policy requires the defense secretary to approve every single domestic surveillance mission relying on drones.
The report states the drones “may not conduct surveillance on U.S. persons” and bans the use of armed drones over the United States.
DARPA Improv program, weaponizing the off-the-shelf electronics
13.3.2016 IT
The Defense Advanced Research Projects Agency is launching a new project dubbed Improv that aims to develop new techniques to hack into everyday technology.
The IoT paradigm is enlarging as never before our surface of attack, it is obvious that cyber criminals and nation-state hackers are looking at it with an increasing interest.
The US Military Defense Advanced Research Projects Agency (DARPA) is asking American geeks to develop new techniques to turn everyday IoT objects into cyber weapons.
The DARPA is launching a new project dubbed Improv that aims to develop new techniques to hack into everyday technology.
The DARPA’s intent it to involve researchers, industry vendors, and hobbyists in finding new attack vectors for embedded devices and consumer technology.
IoT technology is being wide adopted in various industries, including transportation, healthcare and home automation. DARPA is particularly interested in off-the-shelf technology that could be abused by malicious attackers to cause damage on a large scale.
The Improv project aims to discover new attack vector targeting “easily purchased, relatively benign technologies.”
“The Defense Advanced Research Projects Agency (DARPA) Improv program is soliciting innovative research proposals for prototype products and systems that have the potential to threaten current military operations, equipment, or personnel and are assembled primarily from commercially available technology.” reads the Synopsis of the Improv program.
“Improv will explore ways to combine or convert commercially available products such as off-the-shelf electronics, components created through rapid prototyping, and open-source code to cost-effectively create sophisticated military technologies and capabilities.” explained the program manager John Main.
“To bring a broad range of perspectives to bear, DARPA is inviting engineers, biologists, information technologists and others from the full spectrum of technical disciplines—including credentialed professionals and skilled hobbyists—to show how easily-accessed hardware, software, processes, and methods might be used to create products or systems that could pose a future threat. “
“Improv is being launched in recognition that strategic surprise can also come from more familiar technologies, adapted and applied in novel ways.”
In the first phase of the Improv program, DARPA will accept submissions from the public on possible attack techniques relying on easily-available technologies.
The DARPA will select most interesting projects that will be supported by the agency in various ways, including economic funding.

“DARPA will assess candidate ideas and offer varying levels of support to develop and test selected proposals. The emphasis will be on speed and economy, with the goal of propelling winning submissions from concept to simple working prototypes within about 90 days.” states the DARPA
The Improv will help the US Military to identify possible attack vectors of potential cyber threats, but many experts believe that the US Government is also thinking about new attack vectors to maintain it supremacy in the cyberspace.
“DARPA often looks at the world from the point of view of our potential adversaries to predict what they might do with available technology,” said Main.
“Historically we did this by pulling together a small group of technical experts, but the easy availability in today’s world of an enormous range of powerful technologies means that any group of experts only covers a small slice of the available possibilities.”
If you are interested in the project follow the special webinar issued by the DARPA on March 29 and 30.
RIP Ray Tomlinson, The Creator of Email, Dies at 74
7.3.2016 IT
A computing legend who 'changed the way the world communicates' has died.
RAY TOMLINSON, the man who invented email as we know it today and picked the @ symbol for email addresses, passed away at the age of 75 following an apparent heart attack Saturday morning, according to reports.
Hard to believe but 'the godfather of email' has passed away.
His death was confirmed by Mike Doble, director of corporate PR at Tomlinson's employer Raytheon.
"A true technology pioneer, Ray was the man who brought us the email in the early days of networked computers," Doble said in a statement confirming Tomlinson's death.
The Internet reacted with sadness over the death of Tomlinson, who became a legend for his invention in 1971 of a system that allowed a user on one network to send a message to other computer users on other networks.
"Thank you, Ray Tomlinson, for inventing email and putting the @ sign on the map. #RIP," Gmail tweeted yesterday.
Tomlinson Introduced @ in Email Address
At the time of his invention, Tomlinson was working on ARPANET – predecessor of the modern Internet – at research and design company Bolt Beranek and Newman (now BBN Technologies).
Tomlinson used @ symbol in the email address in order to separate the username from the host name.
By the 1990s email had become a pillar of the Internet and Tomlinson was inducted into the Internet Hall of Fame in 2012, though he could not say what the very first email sent back in 1971 actually said.
Tomlinson said in an interview with the New York Times in 2009 that the email was just random strings of text, saying:
"I sent a number of test messages to myself from one machine to the other. The test messages were entirely forgettable and, therefore, forgotten."
Thanks to Tomlinson's invention that powers over a Billion and a half users communicating across the traditional barriers of time and space. #RIPRayTomlinson
Approximate machine improves the Bitcoin mining by 30 percent
16.2.2016 IT
A team of Illinois-based scientists have conducted a research to improve the Bitcoin mining process by 30 percent.
Bitcoin mining is becoming a process even more costly in terms of computational resources, but a team of Illinois-based researchers have conducted a study to speed up this process.
The group of scientists led by Indian Scientist Rakesh Kumar, and including Matthew Vilim and Henry Duwe, has developed a new machine for Bitcoin Mining called “Approximate Hardware.”
The experts will present their study at the Design and Automation Conference in June 2016.

According to the researchers the “Approximate” machine that could improve the Bitcoin mining process by 30 percent.
“We exploit this inherent tolerance to inaccuracy by proposing approximate mining circuits that trade off reliability with area and delay. These circuits can then be operated at Better Than Worst-Case (BTWC) to enable further gains. Our results show that approximation has the potential to increase mining profits by 30%” states a paper published by the researchers.
The Approximate system takes advantage of imperfections in the hardware system, such as False Positives and False negatives. False Positives are observed when errors are not present, but notified as a fake error. False Negatives are observed when we are in the presence of errors, but they are not notified.
The researchers have found a way to take the advantages of these imperfections in the system to make the Bitcoin mining process more efficient.
The Approximation system scans for the errors to improve the Bitcoin mining.
“Bitcoin mining is a particularly good candidate for approximation because its parallelism mitigates error propagation and a built-in verification system detects any false positives,” reads the paper. “Furthermore, we have identified adders as beneficial choices for approximation in hashing cores in a mining ASIC.” continues the paper. “However, not all approximate adders yield increases in profit. Profits are maximized by adders that minimize delay at the expense of area, and approximate adders should be chosen accordingly. Moreover, profits may be improved by operating the hashing cores at Better Than Worst-Case (BTWC) operating points, past their nominal frequencies”
If you want do deep in the research of the scientists, give a look to the paper titled “Approximate Bitcoin Mining,” but let me anticipate that it is not easy to read.
Wanna Mine Bitcoins Faster? Researchers Find New Way to Do it
15.2.2016 IT
Wanna Mine Bitcoins Faster? Researchers Find New Way to Make Bitcoin
A new machine for Bitcoin Mining called "Approximate Hardware" would make Bitcoin mining easier.
Bitcoin had gained tremendous popularity over a few couple of years among the virtual currencies due to its decentralized principle.
Mining a single Bitcoin is not an ice cake walk, as it requires an enormous amount of computing power to dig Bitcoins.
To overcome this issue and mine Bitcoins faster, security researchers has conducted a study and made a new loophole in the mining process in an effort to mine the Bitcoins easily.
How to Mine Bitcoins Faster?
A team of Illinois-based researchers led by Indian Scientist, Rakesh Kumar, has designed a new hardware named "Approximate" that could reduce the pain of Bitcoin mining by 30 percent.
The proposed system would make use of the faults in the hardware system such as:
False Positives where an error is not present but notifies a fake error.
False Negatives where an error is present but does not notify the real error.
Therefore, by taking the advantages of imperfections in the system, the process of Bitcoin mining could get easier than the classical methods used today.
Approximate Bitcoin Mining
Approximation system is one such hardware that scans for the errors to make the mining somehow, simple.
"Bitcoin mining is a particularly good candidate for approximation because its parallelism mitigates error propagation and a built-in verification system detects any false positives," reads the paper. "Furthermore, we have identified adders as beneficial choices for approximation in hashing cores in a mining ASIC."
Dr. Kumar also had expressed that his team's goal is not building a perfect Bitcoin mining hardware, but their research work would inculcate to design much better mining hardware in the near future.
Also Read: Meet The World's First Person Who Hacked His Body to Implant a Bitcoin Payment CHIP
Kumar and his team, including Matthew Vilim and Henry Duwe, will present their work in a talk titled, "Approximate Bitcoin Mining," at the Design and Automation Conference (electronic design) in June 2016.
Nasdaq to Use Bitcoin-style Blockchain to Record Shareholder Votes
13.2.2016 IT
The Nasdaq stock exchange and the Republic of Estonia have announced the use of Blockchain-based technology to allow shareholders of companies to e-vote in shareholder meetings even when they're abroad, according to Nasdaq's press release.
Global stock market giant is developing an electronic shareholder voting system implemented on the top of Blockchain technology that underpins Bitcoins.
Blockchain – the public and decentralized ledger technology underpins all Bitcoin transactions and logs each transfer of an asset in an encrypted "block" that is added to a permanent, transparent chain showing every deal associated with that asset.
Even some of the world's major banks are also considering the adoption of the Blockchain technology.
In the mid of last year, 9 of the World's renowned Banks, including JPMorgan, Royal Bank of Scotland, Goldman Sachs and Barclays, collaborated with New York-based financial tech firm R3 to create a new framework based on Blockchain.
Now, according to Nasdaq, shareholders of the companies listed on the Nasdaq OMX Tallinn Stock Exchange and other Estonian e-residents called "e-Estonians" will now be able to more frequently participate in voting processes without being physically present at a shareholder meeting.
Here's Why Blockchain Technology:
Estonia provides e-Residency that is a transnational digital identity available to people who start businesses online in the nation.
But if these individuals own stock in an Estonian publicly listed company, they are required to physically present or nominate someone else in the shareholder meetings to vote, which is quite a painful process.
However, by using a Blockchain technology a user would be given a so-called private key (a unique long number), assuring they are listed on the e-Residency records held by the Estonian government.
This record will then be sealed on the Blockchain and cannot be altered or tampered with. Now, this private key would be required by you to validate yourself whenever you go to vote in a shareholders meeting online.
So, this would allow the companies and e-Estonians to know for sure that the person voting online is the actual person they say they are.
This is not the first time Nasdaq is deploying Blockchain technology. Nasdaq is already using its own blockchain system, The Nasdaq Linq, that allows private securities issuance between an investor and company.
Nasdaq hopes to complete this blockchain project sometime in 2016.











