
IT Articles - H 2020 1 2 3 4 5 6 7 IT List - H 2021 2020 2019 2018 1
China Bans Fundraising Through Initial Coin Offering (ICO)
7.9.2017 thehackernews IT
China's central bank today announced an immediate ban on all ICO—Initial Coin Offering—fundraising, to prevent fraud and illegal fundraising.
ICO is the hottest new thing in the blockchain world, which is an alternative to crowdfunding that lets a firm raise funding from multiple sources.
The People's Bank of China (PBoC), the country's central bank and financial regulator, has issued an official notice on Monday, forbidding "all types of currency issuance financing activities" that have "seriously disrupted the economic and financial order."
This PBoC's bold move has been backed by many other Chinese government administrators and regulators including the China Securities Regulatory Commission, China Insurance Regulatory Commission and the Ministry of Industry and Commerce, and China Banking Regulatory Commission.
This move marks the end of an era of ICO fundraising in China.
The regulator claims that ICOs are being misused for "illegal fund-raising, financial fraud, pyramid schemes and other criminal activities" and from now, the Chinese government will closely monitor ICOs for signs of illegal activity.
The ban has also been applied to those individuals and organizations who have previously completed ICO fundraising, requiring them to return all investor funds as soon as possible.
The prices of Bitcoin and Ethereum—two of the largest cryptocurrencies in the market—slumped after the announcement.
For those who aren't aware of ICOs:
In the world of cryptocurrencies, ICO is an unregulated way to raise funds for businesses and startups—usually cryptocurrency-related—in exchange for virtual coins over blockchain rather than company shares.
In other words, companies offer investors a crypto-token in exchange against cryptocurrencies like Bitcoin or Ethereum, which investors can easily sell or trade on any cryptocurrency exchange.
The popularity of ICOs has surged in China this year, with 65 ICOs raising a total of 2.62 billion yuan (~$397.1 million) as of July from 105,000 individuals, according to Chinese news agency Xinhua.
However, there have been rising concerns surrounding ICOs over scams, and regulators globally are taking action.
"The growth of a few growing China based blockchain projects, i.e., NEO, will be slowing down after this announcement. This is similar to an event back in 2013 when China banned exchanges from allowing people to buy into Bitcoin using yuan. Bitcoin bounced back stronger after few years. It’s only a matter of time before the same happens with NEO." the founder of Its Blockchain, Hitesh Malviya shared his comment on the announcement.
"Furthermore, the proposal to banning ICO is yet to be activated, and we can hope for the officials to rethink over time, whatever could be the future of ICO in China."
"Disruptive technology always finds a way around restrictive regulations, so it would be wise on the Chinese government’s part to think of mitigating these fears while having some regulatory measures over ICOs. Until that time, we can only speculate."
In the United States, the Securities and Exchange Commission (SEC) has also issued an official warning about the risks of ICOs but has not made a firm move yet.
European Companies Must Tell Employees If Their Work Emails Are Being Monitored
7.9.2017 thehackernews IT
Finally, European companies must inform employees in advance if their work email accounts are being monitored.
The European Court of Human Rights (ECHR) on Tuesday gave a landmark judgement concerning privacy in the workplace by overturning an earlier ruling that gave employers the right to spy on workplace communications.
The new ruling came in judging the case of Romanian engineer Bogdan Barbulescu, who was fired ten years ago for sending messages to his fianceé and brother using his workplace Yahoo Messenger account.
Earlier Romanian courts had rejected Barbulescu’s complaint that his employer had violated his right to correspondence—including in January last year when it was ruled that it was not "unreasonable for an employer to want to verify that the employees are completing their professional tasks during working hours."
But now, the European court ruled by an 11-6 majority that Romanian judges failed to protect Barbulescu’s right to private life and correspondence, as set out in article 8 of the European Convention on Human Rights.
Apparently, Barbulescu's employer had infringed his right to privacy by not informing him in advance that the company was monitoring his account and communications. His employer used surveillance software in order to monitor his computer activities.
"The right to respect for private life and for the privacy of correspondence continued to exist, even if these might be restricted in so far as necessary," the court writes in a press release about the decision.
"The Court considered, following international and European standards, that to qualify as prior notice, the warning from an employer had to be given before the monitoring was initiated, especially where it entailed accessing the contents of employees' communications."
The ruling will now become law in 47 countries that have ratified the European Convention on Human Rights.
In a Q & A section on its website, the European Court of Human Rights says the judgement doesn't mean that companies can't now monitor their employee’s communications at workplace and that they can still dismiss employees for private use.
However, the ECHR says that the employers must inform their staff in advance if their communications are being monitored, and that the monitoring must be carried out for legitimate purposes and limited.
Europe Court Backs Employee Fired Over Private Messages
6.9.2017 securityweek IT
Europe's top rights court on Tuesday restricted the ability of employers to snoop on their staff's private messages, in a landmark ruling with wide ramifications for privacy in the workplace.
The highest body of the European Court of Human Rights (ECHR) ruled in favour of a 38-year-old Romanian man who claimed his rights had been violated when he was sacked in 2007 for sending private chat messages in the office.
Bogdan Mihai Barbulescu has fought a 10-year legal battle through Romanian and European courts, claiming his privacy was infringed when his employer accessed intimate exchanges with his fiancee and brother.
In a first ruling in January last year, the ECHR found that the snooping was allowed because employers were justified in wanting to verify "that employees were completing their professional tasks during working hours".
But in a review, the 17 most senior judges at the court based in Strasbourg, France, found Tuesday that Romanian courts "had not adequately protected Mr Barbulescu's right to respect for his private life and correspondence".
In a written judgement, backed by 11 votes to six, they found that previous court rulings had "failed to strike a fair balance between the interests at stake", namely the company's right to check on employees and employees' right to privacy.
The judges also found that "an employer's instructions could not reduce private social life in the workplace to zero", meaning that some use of the internet at work for personal reasons was justified.
The ruling will become law in the 47 countries that have ratified the European Convention on Human Rights, meaning some members will have to adjust their national legislation.
Barbulescu's lawyer Emeric Domokos-Hancu said the ruling was a "ray of light" for his client.
"In reality, it represents much more -- the fact that man's private life does not stop at the door to his workplace," he added.
- Sex life exposed -
The case revolved around messages sent in 2007 by Barbulescu over the Yahoo messaging platform, which the software engineer was required to use by his bosses to liaise with clients.
He was sacked after his employer accused him of using company resources for personal reasons, which violated company policy, and produced 45 pages of his private messages to his fiancee and brother as proof.
Barbulescu argued that his employer had invaded his right to privacy by using spyware to access the chat material, which included details about his health and sex life.
In their judgement on the court's website, the ECHR judges said Tuesday that it was unclear whether Barbulescu had been warned about the monitoring or the risk of the messages being read without his authorization.
It also said that Romanian courts had failed to determine why the monitoring measures were justified and whether there were other ways of checking on him "entailing less intrusion" into his private life.
The judges held a hearing on November 30 last year, at which they heard arguments from experts and the European Trade Union Confederation.
The union group had criticised the initial ruling, judging it to be too harsh.
It recommended that a verbal warning should be the first stage of any disciplinary process with dismissal only possible for repeat offenders or serious misconduct.
Experts also say companies should also have a clear policy governing the use of professional software and the internet during work hours.
Researchers Poison Machine Learning Engines
31.8.2017 securityweek IT
The more that artificial intelligence is incorporated into our computer systems, the more it will be explored by adversaries looking for weaknesses to exploit. Researchers from New York University (NYU) have now demonstrated (PDF) that convolutional neural networks (CNNs) can be backdoored to produce false but controlled outputs.
Poisoning the machine learning (ML) engines used to detect malware is relatively simple in concept. ML learns from data. If the data pool is poisoned, then the ML output is also poisoned -- and cyber criminals are already attempting to do this.
Dr. Alissa Johnson, CISO for Xerox and the former Deputy CIO for the White House, is a firm believer in the move towards cognitive systems (such as ML) for both cybersecurity and improved IT efficiency. She acknowledges the potential for poisoned cognition, but points out that the solution is also simple in concept: "AI output can be trusted if the AI data source is trusted," she told SecurityWeek.
CNNs, however, are at a different level of complexity -- and are used, for example, to recognize and interpret street signs by autonomous vehicles. "Convolutional neural networks require large amounts of training data and millions of weights to achieve good results," explain the NYU researchers. "Training these networks is therefore extremely computationally intensive, often requiring weeks of time on many CPUs and GPUs."
Few businesses have the resources to train CNNs in-house, and instead tend to use the machine learning as a service (MLaaS) options available from Google's Cloud Machine Learning Engine, Microsoft's Azure Batch AI Training or the deep learning offerings from AWS. In other words, CNNs tend to be trained in the cloud -- with all the cloud security issues involved -- and/or partially outsourced to a third party.
The NYU researchers wanted to see if under these circumstances, CNNs could be compromised to produce an incorrect output pre-defined by an attacker -- backdoored in a controlled manner. "The backdoored model should perform well on most inputs (including inputs that the end user may hold out as a validation set)," they say, "but cause targeted misclassifications or degrade the accuracy of the model for inputs that satisfy some secret, attacker-chosen property, which we will refer to as the backdoor trigger." They refer to the altered CNN as a 'badnet'.
The basic process is the same as that of adversaries trying to poison anti-virus machine learning; that is, training-set poisoning -- but now with the additional ability to modify the CNN code. Since CNNs are largely outsourced, in this instance the aim was to see if a malicious supplier could provide a badnet with the attacker's own backdoor. "In our threat model we allow the attacker to freely modify the training procedure as long as the parameters returned to the user satisfy the model architecture and meet the user's expectations of accuracy."
The bottom-line is, 'Yes, it can be done.' In the example and process described by the researchers, they produced a road-sign recognition badnet that behaves exactly as expected except for one thing: the inclusion of a physical distortion (the 'trigger', in this case a post-it note) on a road sign altered the way it was interpreted. In their tests, the badnet translates clean stop signs correctly; but those with the added post-it note as a speed-limit sign with 95% accuracy.

"Importantly," comments Hyrum Anderson, technical director of data science at Endgame (a scientist who has also studied the 'misuse' of AI), "the authors demonstrate that the backdoor need not be a separate tacked-on module that can be easily revealed by inspecting the model architecture. Instead, the attacker might implement the backdoor by poisoning the training set: augmenting the training set with 'backdoor' images carefully constructed by the attacker."
This process would be extremely difficult to detect. Badnets "have state-of-the-art performance on regular inputs but misbehave on carefully crafted attacker-chosen inputs," explain the researchers. "Further, badnets are stealthy, i.e., they escape standard validation testing, and do not introduce any structural changes."
That this kind of attack is possible, says Anderson, "isn't really up for debate. It seems clear that it's possible. Whether it's a real danger today, I think, is debatable. Most practitioners," he continued, "either roll their own models (no outsourcing), or train their models using one of a few trusted sources, like Google or Microsoft or Amazon. If you use only these resources and consider them trustworthy, I think this kind of attack is hard to pull off."
However, while difficult, it is possible. "I suppose, theoretically, one could imagine some man-in-the-middle attack in which an attacker intercepts the dataset and model specification sent to the Cloud GPU service, trains a model in with 'backdoor' example included, and returns the backdoor model in place of the actual model. It'd require a fairly sophisticated infosec attack to pull off the fairly sophisticated deep learning attack." Nation-states, however, can be very sophisticated.
Anderson's bottom-line is similar to that of Alissa Johnson. "Roll your own models or use trusted resources;" but he adds, "and tenaciously and maniacally probe and even attack your own model to understand its deficiencies or vulnerabilities."
Expert discovered 2,893 Bitcoin miners left exposed on the Internet
31.8.2017 securityaffairs IT
The popular Dutch security researcher Victor Gevers has discovered thousands of Bitcoin miners left exposed on the Internet.
The popular security researcher Victor Gevers, the founder of the GDI Foundation, has discovered 2,893 Bitcoin miners left exposed on the Internet.
View image on TwitterView image on TwitterView image on Twitter
Follow
I see about 2,893 Chinese Bitcoin "Thunder mining machines" online which are accessible via telnet w/o any password. Is the GFW down?
1:19 AM - Aug 29, 2017
13 13 Replies 190 190 Retweets 322 322 likes
Twitter Ads info and privacy
The devices expose Telnet port with no password, the expert explained to Bleeping Computer that all miners belong to the same Bitcoin mining pool and likely are operated by the same organization.
Most of the devices are ZeusMiner THUNDER X3 Bitcoin miners.
Based on firmware details Gevers found on the devices, the researcher believes that most are ZeusMiner THUNDER X3 Bitcoin miners.
The analysis of the IP addresses assigned to the Bitcoin Miners led to believe that the devices belong to a Chinese state-sponsored group.
“The owner of these devices is most likely a state sponsored/controlled organization part of the Chinese government, ” Gevers told Bleeping Computer.
Shortly after Gevers announced his discovery the operators behind the Bitcoin miners secured the exposed devices shortly after, the experts highlighted the speed in protecting the Bitcoin miners.
“Most of the miners are now not available anymore via Telnet,” Gevers told Bleeping Computer.
“At the speed they were taken offline, it means there must be serious money involved,” Gevers added. “A few miners is not a big deal, but 2,893 [miners] working in a pool can generate a pretty sum.”
A so huge botnet of miners could generate million dollars per months depending on the specific crypto currency they were mining.
The Twitter user @Quan66726078 speculate the botnet of 2,893 miners discovered by Gevers could generate an income of just over $1 million per day, in case operators use it to mine Litecoin cryptocurrency.
29 Aug
Quan @Quan66726078
Replying to @Quan66726078 @0xDUDE
2) and the machines are high-end. With approx ~14 Th/s. Maybe more since not all new Chinese mining equipment even gets on the market
Follow
Quan @Quan66726078
3) Then with power consumption about 1323 watt at price of 0.08 cent per kwH and mining Litecoin with 1 machine generates ~$379.000
9:55 AM - Aug 29, 2017
1 1 Reply Retweets 2 2 likes
Twitter Ads info and privacy
Gevers noticed that other netizens have accessed the Bitcoin miners before he discovered them.
“I have proof of other visitors on the boxes where they tried to install a backdoor or malware,” Gevers said.
29 Aug
Victor Gevers @0xDUDE
I see about 2,893 Chinese Bitcoin "Thunder mining machines" online which are accessible via telnet w/o any password. Is the GFW down? pic.twitter.com/pGuBJnld5i
Follow
Victor Gevers @0xDUDE
From XL_MINER_0001 to XL_MINER_2893. And no I am not the only visitor with admin privileges. These miners get visitors daily from everywhere pic.twitter.com/pOt1D4ChgL
1:34 AM - Aug 29, 2017

Twitter Ads info and privacy
According to a researcher who goes online with the handle Anthrax0, the miners appeared to be participating in a bandwidth sharing scheme run via Chinese service Xunlei.
29 Aug
Victor Gevers @0xDUDE
I see about 2,893 Chinese Bitcoin "Thunder mining machines" online which are accessible via telnet w/o any password. Is the GFW down? pic.twitter.com/pGuBJnld5i
Follow
Anthr@X @anthrax0
This is not any crypto currency miner. It's in fact a bandwidth/uploading affiliation program. You get rewarded for using the router as CDN.
11:29 AM - Aug 29, 2017
The Pirate Bay Founders Ordered to Pay Music Labels $477,800 in Compensation
24.8.2017 thehackernews IT
Two of the three co-founders of The Pirate Bay—Fredrik Neij and Gottfrid Svartholm Warg—have been ordered by a Finnish court to pay record labels $477,800 in compensation for copyright infringement on the site.
Last year in a similar case, Helsinki District Court in Finland ordered Peter Sunde, the third co-founder of The Pirate Bay, to pay nearly $395,000 (350,000 Euros) in damages to several major record labels, including Sony Music, Universal Music and Warner Music.
However, Sunde did not pay any penalty yet, and instead, he later announced his plans to sue those record labels for defamation.
The Pirate Bay is still the world's most popular torrent website that has proven to be an elusive hub for illegal copyrighted contents, even after a series of raids and shutdown of its multiple domains, including the primary .SE domain.
All the three co-founders of The Pirate Bay were facing criminal copyright infringement and abuse of electronic communications charges in a Belgian court but were acquitted after it was found that they sold The Pirate Bay file-sharing website in 2006.
The International Federation of the Phonographic Industry (IFPI), which represents the world's major labels, with support from Finnish Copyright Information and Anti-Piracy Center (CIAPC), filed a lawsuit in November 2011 in the Helsinki District Court against The Pirate Bay.
In these last six years, Fredrik Neij and Gottfrid Svartholm never appeared in the court, neither they appointed someone to represent their defence, which eventually led the decision in favour of IFPI record labels.
Besides ordering both the founders to jointly pay compensation of 405,000 euros (over $477,800) to record labels, the District Court also ordered them to "cease-and-desist" the illegal operations of The Pirate Bay, TorrentFreak reported.
However, it is still unclear how Neij and Svartholm are supposed to do anything about stop sharing of content on the site since they have no association with The Pirate Bay.
It has also been reported that Neij, Svartholm, and Sunde also owes large sums of money to other copyright holders as a result of various court judgments over the past few years.
However, so far, none of those court penalties has been "satisfied," neither Sunde paid the fines imposed on him last year, and it is likely that this penalty will also go unpaid.
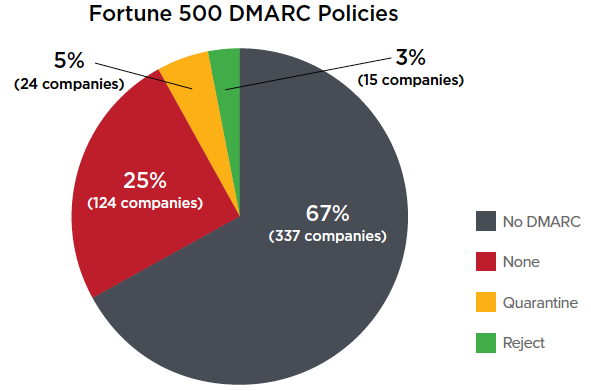
DMARC Adoption Low in Fortune 500, FTSE 100 Companies
23.8.2017 securityweek IT
Many Fortune 500, FTSE 100 and ASX 100 companies have failed to properly implement the DMARC standard, exposing their customers and partners to phishing and other email-based attacks, according to email security firm Agari.
In a report titled “Global DMARC Adoption Report: Open Season for Phishers,” Agari, which in the past years has obtained tens of millions of dollars in funding, shared the results of its analysis into the adoption of DMARC.
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication, policy, and reporting protocol designed to detect and prevent email spoofing.
Organizations using DMARC can specify what happens to unauthenticated messages: they can be monitored but still delivered to the recipient’s inbox (none), they can be moved to the spam or junk folder (quarantine), or their delivery can be blocked completely (reject).
Agari’s analysis of public DNS records showed that only five percent of Fortune 500 companies have implemented a reject policy and three percent use the quarantine policy. Roughly two-thirds of these organizations have not published any type of DMARC policy.
The sectors with the highest adoption of the reject and quarantine policies are business services, financial, technology and transportation. The security firm has identified several sectors where not one organization has adopted these policies, including wholesales, motor vehicles, apparel, hospitality, food and drug stores, energy, aerospace, household products, chemicals, and engineering and construction.
In the case of Financial Times Stock Exchange (FTSE) 100 companies, the percentage is similar. Two-thirds have not implemented DMARC and only seven percent are using a reject or quarantine policy. Only a handful of real estate and financial services firms in the FTSE 100 have implemented proper DMARC policies.
An analysis of Australian Securities Exchange (ASX) 100 organizations showed that a DMARC policy is absent in 73 percent of cases. Only three companies from the utilities, industrial and consumer discretionary sectors have implemented a reject policy and one company in the materials sector is using a quarantine policy.
These figures are worrying considering that there are tens of thousands of phishing websites and their number has increased considerably in the past year
Tech Leaders Warn Against "Pandora's Box" of Robotic Weapons
21.8.2017 seurityweek IT
Elon Musk is leading demands for a global ban on killer robots, warning technological advances could revolutionise warfare and create new "weapons of terror" that target innocent people.
The CEO of Tesla and SpaceX joined more than 100 robotics and artificial intelligence entrepreneurs in signing a letter to the United Nations calling for action to prevent the development of autonomous weapons.
"Lethal autonomous weapons threaten to become the third revolution in warfare," warned the statement signed by 116 tech luminaries, also including Mustafa Suleyman, cofounder of Google's DeepMind.
"Once developed, they will permit armed conflict to be fought at a scale greater than ever, and at timescales faster than humans can comprehend," the letter read.
The innovators also highlighted the danger that the technology could fall into the wrong hands.
"These can be weapons of terror, weapons that despots and terrorists use against innocent populations, and weapons hacked to behave in undesirable ways," the letter read.
"We do not have long to act. Once this Pandora's box is opened, it will be hard to close."
Both Musk and British astrophysicist Stephen Hawking have regularly warned of the dangers of artificial intelligence.
The renewed plea on autonomous weapons was released as the International Joint Conference on Artificial Intelligence in Melbourne got underway Monday, with a record 2,000 of the world's top AI and robotics experts taking part, organisers said.
One expert said autonomous weapons could make war more likely.
"Today the potential loss of human life is a deterrent for conflict initiation and escalation, but when the main casualties are robots, the disincentives change dramatically and the likelihood of conflict increases," Professor Mary-Anne Williams of the University of Technology Sydney.
She warned a killer robot ban may be disregarded by some nations but would stop "countries such as Australia from developing defensive killer robots, thereby being vulnerable to other countries and groups that ignore the ban".
Another expert said decision made today would help shape the "futures we want".
"Nearly every technology can be used for good and bad, and artificial intelligence is no different," said Professor Toby Walsh of the University of New South Wales.
Organisers said the conference, which concludes on Friday, has attracted a record number of participants from China, reflecting a push by Beijing to become a leading player in the field.
A key focus of the event will be looking at the challenges of developing fully autonomous AI systems, programme chair Carles Sierra of the Spanish National Research Council said.
A UN group on autonomous weapons had been due to meet Monday but the gathering was postponed until November, according to the group's website.
In 2015, thousands of researchers and personalities launched an appeal to ban autonomous weapons.
Peace Breaks Out Between Microsoft and Kaspersky Lab
12.8.2017 securityweek IT
Microsoft Agrees to Kaspersky Lab's Demands
Microsoft and Kaspersky are friends again, and the whole anti-virus ecosystem is at peace.
Back in November 2016, Eugene Kaspersky declared, "That's It. I've Had Enough!" It wasn't just words. "We've taken the decision to address official bodies in various countries (including the EU and Russia) with a request to oblige Microsoft to cease its violation of anti-competition legislation and to remove the consequences of that violation." And he did just that, first in Russia and then in the EU.
Eugene Kaspersky, founder of Russia-based Kaspersky Lab, was not alone in his concerns. "Some time ago security companies started noticing that things were changing at Microsoft," Luis Corrons, technical director at PandaLabs told SecurityWeek. "It looked like they were more concerned about their own antivirus market share, and were trying to push the competition out -- not by being a best solution, but by taking advantage of being the developers of the operating system, and using any chance to tell the user to remove 3rd party security software and put theirs in its place."
Morten Kjaersgaard, CEO at Heimdal, gives more context. It started with Windows 8 in 2011, when Microsoft indicated that it would try to extend its position with its own Windows Defender. In the event, says Kjaersgaard, "The first Defender was not much better than Security Essentials." But battle lines had been drawn. The AV industry downplayed Windows Defender, and Microsoft promoted third-party products less forcefully. "Until recently," he added, "Windows Defender had not posed a real threat to the antivirus industry -- but with the Windows Defender continuously improving, it is now a bigger threat."
As Defender improved, so Microsoft seemed less and less willing to work with its 'competitors'. "We have to remember that antivirus is a multi-billion dollar business, both in the consumer and B2B space -- and here Kaspersky took a stance to publicly call out a situation, which long term could cause an antitrust case for Microsoft, similar to Internet Explorer."
That danger now seems to have been averted. "It's very important for both sides that Microsoft and the specialist security companies work as closely together as possible," comments ESET senior research fellow, David Harley; "especially as Windows 10 increases its market share, as presumably it will. A security monoculture isn't in the best interests of the consumer." This position is simple. If Windows Defender -- or any other single product -- dominates the market, attackers will have fewer defenses to beat while successful attacks will be more catastrophic. Diversity brings strength; monocultures bring weakness.
This week, Microsoft's Rob Lefferts blogged, that following discussions with its AV partners, Microsoft is "making updates to our AV partner requirements today that reflect the interests of the community and our shared customers. We will also implement changes in the Windows 10 Fall Creators Update."
These changes cover the complaints made by Kaspersky. Microsoft will work more closely with third-parties over compatibility reviews; will increase "the amount of time AV partners will have to review final builds before the next Windows 10 feature update is rolled out to customers"; will allow the third-parties to display their own renewal notices; and will modify how users are told that their antivirus application has expired.
Kaspersky is the only third-party vendor specifically mentioned in this announcement. It is clearly a response to the legal threats in both Russia and the EU. "We appreciate the feedback and continued dialogue with our partners and are pleased to have found common ground with Kaspersky Lab on the complaints raised in Russia and Europe," continues Lefferts. "We look forward to our continued partnership with the industry."
Kaspersky is satisfied. In its own Kaspersky Lab blog published yesterday it states, "We are absolutely satisfied with the changes that will be implemented in the Windows 10 Fall Creators Update, and we will be taking all necessary steps to withdraw our claims and inform all regulatory bodies that we no longer have any matters for Microsoft to address."
Peace has been restored. Whether it continues, remains to be seen (Microsoft will need to compete for share of a multi-billion market without resorting to any of the OS-specific trump cards that it undoubtedly holds). But there is one other issue worth considering. In parallel to Kaspersky's complaints to the Russian and EU authorities about Microsoft's practices, the US government has started to denounce Kaspersky over 'security concerns'. Last month the US General Services Administration (GSA) announced that Kaspersky had been removed from its list of approved vendors, making it more difficult for government agencies to obtain Kaspersky products.
Was the timing coincidental? Is it an economic version of the political tit-for-tat that we have seen between America and Russia for decades? Or is it genuine security concerns?
Heimdal's Kjaersgaard believes it is genuine if unfounded concern. "I believe that the US government is concerned that because Kaspersky, as an antivirus, has full access to a device, it could theoretically relay information from the device to Kaspersky, which another influential party in Kaspersky could use.
"I cannot say anything bad about Kaspersky at all," he added; "but nor can I comment if the US government has this stance for a reason. However, concern over the software you have on your computer is legitimate with anything you install."
Kaspersky is outraged at the US position. In its own statement, it says, "“Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyberespionage efforts... Kaspersky Lab believes it is completely unacceptable that the company is being unjustly accused without any hard evidence to back up these false allegations. Kaspersky Lab, a private company, seems to be caught in the middle of a geopolitical fight where each side is attempting to use the company as a pawn in their political game."
It will be interesting to see whether the new accord between Microsoft and Kaspersky will lead to a softening of attitudes from the US government.
Peace Breaks Out Between Microsoft and Kaspersky Lab
11.8.2017 securityweek IT
Microsoft Agrees to Kaspersky Lab's Demands
Microsoft and Kaspersky are friends again, and the whole anti-virus ecosystem is at peace.
Back in November 2016, Eugene Kaspersky declared, "That's It. I've Had Enough!" It wasn't just words. "We've taken the decision to address official bodies in various countries (including the EU and Russia) with a request to oblige Microsoft to cease its violation of anti-competition legislation and to remove the consequences of that violation." And he did just that, first in Russia and then in the EU.
Eugene Kaspersky, founder of Russia-based Kaspersky Lab, was not alone in his concerns. "Some time ago security companies started noticing that things were changing at Microsoft," Luis Corrons, technical director at PandaLabs told SecurityWeek. "It looked like they were more concerned about their own antivirus market share, and were trying to push the competition out -- not by being a best solution, but by taking advantage of being the developers of the operating system, and using any chance to tell the user to remove 3rd party security software and put theirs in its place."
Morten Kjaersgaard, CEO at Heimdal, gives more context. It started with Windows 8 in 2011, when Microsoft indicated that it would try to extend its position with its own Windows Defender. In the event, says Kjaersgaard, "The first Defender was not much better than Security Essentials." But battle lines had been drawn. The AV industry downplayed Windows Defender, and Microsoft promoted third-party products less forcefully. "Until recently," he added, "Windows Defender had not posed a real threat to the antivirus industry -- but with the Windows Defender continuously improving, it is now a bigger threat."
As Defender improved, so Microsoft seemed less and less willing to work with its 'competitors'. "We have to remember that antivirus is a multi-billion dollar business, both in the consumer and B2B space -- and here Kaspersky took a stance to publicly call out a situation, which long term could cause an antitrust case for Microsoft, similar to Internet Explorer."
That danger now seems to have been averted. "It's very important for both sides that Microsoft and the specialist security companies work as closely together as possible," comments ESET senior research fellow, David Harley; "especially as Windows 10 increases its market share, as presumably it will. A security monoculture isn't in the best interests of the consumer." This position is simple. If Windows Defender -- or any other single product -- dominates the market, attackers will have fewer defenses to beat while successful attacks will be more catastrophic. Diversity brings strength; monocultures bring weakness.
This week, Microsoft's Rob Lefferts blogged, that following discussions with its AV partners, Microsoft is "making updates to our AV partner requirements today that reflect the interests of the community and our shared customers. We will also implement changes in the Windows 10 Fall Creators Update."
These changes cover the complaints made by Kaspersky. Microsoft will work more closely with third-parties over compatibility reviews; will increase "the amount of time AV partners will have to review final builds before the next Windows 10 feature update is rolled out to customers"; will allow the third-parties to display their own renewal notices; and will modify how users are told that their antivirus application has expired.
Kaspersky is the only third-party vendor specifically mentioned in this announcement. It is clearly a response to the legal threats in both Russia and the EU. "We appreciate the feedback and continued dialogue with our partners and are pleased to have found common ground with Kaspersky Lab on the complaints raised in Russia and Europe," continues Lefferts. "We look forward to our continued partnership with the industry."
Kaspersky is satisfied. In its own Kaspersky Lab blog published yesterday it states, "We are absolutely satisfied with the changes that will be implemented in the Windows 10 Fall Creators Update, and we will be taking all necessary steps to withdraw our claims and inform all regulatory bodies that we no longer have any matters for Microsoft to address."
Peace has been restored. Whether it continues, remains to be seen (Microsoft will need to compete for share of a multi-billion market without resorting to any of the OS-specific trump cards that it undoubtedly holds). But there is one other issue worth considering. In parallel to Kaspersky's complaints to the Russian and EU authorities about Microsoft's practices, the US government has started to denounce Kaspersky over 'security concerns'. Last month the US General Services Administration (GSA) announced that Kaspersky had been removed from its list of approved vendors, making it more difficult for government agencies to obtain Kaspersky products.
Was the timing coincidental? Is it an economic version of the political tit-for-tat that we have seen between America and Russia for decades? Or is it genuine security concerns?
Heimdal's Kjaersgaard believes it is genuine if unfounded concern. "I believe that the US government is concerned that because Kaspersky, as an antivirus, has full access to a device, it could theoretically relay information from the device to Kaspersky, which another influential party in Kaspersky could use.
"I cannot say anything bad about Kaspersky at all," he added; "but nor can I comment if the US government has this stance for a reason. However, concern over the software you have on your computer is legitimate with anything you install."
Kaspersky is outraged at the US position. In its own statement, it says, "“Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyberespionage efforts... Kaspersky Lab believes it is completely unacceptable that the company is being unjustly accused without any hard evidence to back up these false allegations. Kaspersky Lab, a private company, seems to be caught in the middle of a geopolitical fight where each side is attempting to use the company as a pawn in their political game."
It will be interesting to see whether the new accord between Microsoft and Kaspersky will lead to a softening of attitudes from the US government.
Chinese Quantum Satellite Sends First ‘Unhackable’ Data to Earth
10.8.2017 thehackernews IT
In what appears to be the world's first quantum satellite transmission, China has successfully sent an "unbreakable" code over a long distance from an orbiting satellite to the Earth, achieving a milestone in the next generation encryption based on "quantum cryptography."
In August last year, China launched the world's first quantum communication satellite into the Earth’s orbit aboard a Long March-2D rocket to test the fundamental laws of quantum mechanics at space.
Dubbed Quantum Science Satellite, nicknamed Micius or Mozi (Chinese: 墨子), the satellite was designed to establish a 'Hack-Proof' communications system in this age of global surveillance by transmitting unbreakable encryption keys from space to the ground.
Now, it has been reported that using this satellite, the Chinese scientists at the Quantum Experiments at Space Scale (QUESS) project were able to send secret "quantum key distribution" (QKD) data by beaming photons from the space to the ground stations over longer distances than ever before.
The Chinese scientists successfully sent quantum keys over a distance of 1,200 Km (745 miles) from space to Earth at a transmission rate up to 20 of magnitudes more efficient than that expected using an optical fibre of the same length, lead scientist Pan Jianwei told the official Xinhua news agency.
"That, for instance, can meet the demand of making an absolute safe phone call or transmitting a large amount of bank data," Jianwei said.
The Quantum Science Satellite could become the world's first transcontinental quantum key distribution network of its kind and China hopes to erect a global quantum cryptography-based communications network in 2030.
Theoretically, the use quantum cryptography for encryption is secure against any interception, as the information is encoded in a quantum particle in a way that it'll be destroyed as soon as the system detects any intrusion attempts.
"Satellite-based quantum key distribution can be linked to metropolitan quantum networks where fibres are sufficient and convenient to connect numerous users within a city over 100 km," Jianwei said.
"We can thus envision a space-ground integrated quantum network, enabling quantum cryptography- most likely the first commercial application of quantum information- useful at a global scale."
China has largely been ambitious to realise the importance of Quantum technology that's believed to be a new era of faster and more powerful super computers.
From past two decades, Quantum technology has been a top strategic focus in China's 5-year economic development plan. While the U.S. invested about $200 Million a year in quantum research, China spent $101 Billion in quantum physics in 2015.
Firefox Makes Adobe Flash Click-to-Activate by Default
9.8.2017 securityweek IT
Starting with the release of Firefox 55 this week, the Adobe Flash plugin is no longer active by default in Mozilla’s web browser, and users of the new version will be required to activate it for each website they visit.
According to Mozilla, not only is the Adobe Flash plugin click-to-activate disabled by default with the new release, but it is also allowed only on http:// and https:// URL schemes. Users can now choose on which sites they want to activate the plugin, and can also opt in for Firefox to remember the settings. Some sites, however, won’t be allowed to run plugins, Mozilla says.
Mozilla plans on fully removing Flash from Firefox in early 2020, but will continue to support it in Firefox Extended Support Release (ESR) until the end of 2020. From then onward, the browser will refuse to load the plugin.
Google Chrome and Microsoft Edge started blocking Flash by default last year, and Adobe announced last month that it will stop supporting the plugin by the end of 2020: “we will stop updating and distributing the Flash Player,” the company said at the end of July 2017. In addition to Google, Microsoft, and Mozilla, Apple and Facebook too announced plans to remove Flash.
In addition to deactivating Flash, the new browser release resolves around 30 security vulnerabilities, 5 of which were rated Critical risk. These include an XUL injection in the style editor in devtools (CVE-2017-7798), Use-after-free in WebSockets during disconnection (CVE-2017-7800), Use-after-free with marquee during window resizing (CVE-2017-7801), and Memory safety bugs (CVE-2017-7779 and CVE-2017-7780).
Firefox 55 also resolves 11 High severity flaws, including 4 use-after-free bugs, 3 buffer overflows, out-of-bounds issue, same-origin policy bypass, domain hijacking, and memory protection bypass vulnerabilities.
The browser includes patches for 7 Medium severity issues: spoofing following page navigation with data, CSP information leak with frame-ancestors containing paths, WindowsDllDetourPatcher allocates memory without DEP protections, Elliptic curve point addition error when using mixed Jacobian-affine coordinates, Linux file truncation via sandbox broker, CSP containing 'sandbox' improperly applied, and Self-XSS XUL injection in about:webrtc.
6 Low risk vulnerabilities were addressed in this release: DOS attack through long username in URL, Sandboxed about:srcdoc iframes do not inherit CSP directives, Failure to enable HSTS when two STS headers are sent for a connection, Windows crash reporter reads extra memory for some non-null-terminated registry values, Windows updater can delete any file named update.log, and Response header name interning leaks across origins.
Firefox 55 also brings along various new features and improvements, such as Windows support for WebVR and a setting to enable Hardware VP9 acceleration on Windows 10 Anniversary Edition. Now, Firefox for Windows 64-bit is installed by default on all 64-bit systems that have at least 2GB of RAM.
The updated browser release is available for Windows, Mac, Linux, and Android.
FTC Complaint Alleges Hotspot Shield Collects User Data
8.8.2017 securityweek IT
A complaint filed with the Federal Trade Commission (FTC) on Monday alleges that the popular free Virtual Private Network (VPN) service Hotspot Shield collects a large amount of data and intercepts user traffic.
Submitted by the Center for Democracy & Technology (CDT), the complaint (PDF) urges the FTC to investigate the data security and data sharing practices of Hotspot Shield, alleging they are “unfair and deceptive trade practices.” The complaint also claims the service engages into undisclosed data sharing and traffic redirection practices despite promising to protect the users’ privacy.
CDT, a nonprofit technology advocacy organization, suggests that Hotspot Shield’s privacy policy contradicts the advertised privacy and security claims. The service claims to keep no logs of a user’s online activity or personal information, and to store no user data, while also saying that it doesn’t track users and doesn’t sell their information.
The privacy and security claims are highlighted as key features of the Hotspot Shield VPN mobile applications in both iTunes and Google Play storefronts, but the service’s privacy policy “describes more elaborate logging practices,” the complaint reads. A source code analysis of Hotspot Shield backs these allegations, CDT says.
The organization also claims that “the VPN promises to connect advertisers to users who frequent websites in particular categories and while most VPNs prevent internet service providers from seeing a user’s internet traffic, that traffic is often visible in unencrypted form to Hotspot Shield. VPNs typically log data about user connections to help with troubleshooting technical issues, but Hotspot Shield uses this information to identify user locations and serve advertisements."
CDT also points out that Hotspot Shield’s privacy policy says that it doesn’t collect personal user information, claiming that IP addresses and unique device identifiers aren’t considered personal information by the free VPN provider. Moreover, the complaint claims the service deploys persistent cookies and that it also “works with unaffiliated entities to customize advertising and marketing messages.”
Furthermore, the complaint alleges that Hotspot Shield insists it doesn’t make money from selling customer data, but that the service also promises to connect advertisers to users that frequently access travel, retail, business, and finance websites. CDT points out that these partners can link information about users’ web-viewing habits even if they are provided only with hashed or proxy IP addresses.
An analysis of Hotspot Shield’s functionality, data sharing, and network connections was performed by Carnegie Mellon University’s Mobile App Compliance System. Researchers downloaded and tested the Android app and found “undisclosed data sharing practices with third party advertising networks” when analyzing the application permissions.
They also discovered that the app discloses sensitive information such as names of wireless networks (via SSID/BSSID information), along with identifiers such as Media Access Control addresses, and device IMEI numbers.
The VPN was also found to inject JavaScript codes using iframes for advertising and tracking purposes, and to be using more than five different third-party tracking libraries. The apps also redirect e-commerce traffic to partnering domains, the complaint also claims.
“People often use VPNs because they do not trust the network they’re connected to, but they think less about whether they can trust the VPN service itself. For many internet users, it’s difficult to fully understand what VPNs are doing with their browsing data. Hotspot Shield tells customers that their privacy and security are ‘guaranteed’ but their actual practices starkly contradict this. They are sharing sensitive information with third party advertisers and exposing users’ data to leaks or outside attacks,” Michelle De Mooy, Director of CDT’s Privacy & Data Project, said.
Symantec to Sell Certificate Business to DigiCert for $950 Million
3.8.2017 securityweek IT
After reaching an agreement with Google regarding penalties for misissued digital certificates, Symantec announced on Wednesday that it has made a deal with DigiCert to sell its website security and related public key infrastructure (PKI) solutions.
DigiCert has agreed to pay Symantec $950 million in cash and a stake of roughly 30 percent in common stock equity of the DigiCert business. The transaction has been approved unanimously by Symantec’s board of directors and is expected to be completed in the third quarter of fiscal 2018.
DigiCert will continue to operate under the supervision of CEO John Merrill from its headquarters in Lehi, Utah, where it will employ more than 1,000 people. With the acquisition of Symantec’s certificate business, the company is expected to bring new approaches to the TLS market and benefit from growth opportunities in IoT.
Symantec has come under fire recently for misissued TLS certificates, and Google and other web browser vendors have been discussing penalties.
Google announced recently that certificates issued by Symantec and its partners before June 1, 2016, will need to be replaced by March 15, 2018. All other certificates need to be replaced until the release of Chrome 70, currently scheduled for release in October 2018.
Google said Symantec could still issue digital certificates, but only through the infrastructure of a subordinate certificate authority (SubCA). A few weeks ago, Symantec said it had been trying to find a partner and informed customers that the new infrastructure should be set up by December 1.
It appears Symantec has decided to abandon its website security business altogether, but promised customers an easy transition.
“We carefully examined our options to ensure our customers would have a world-class experience with a company that offers a modern website PKI platform and is poised to lead the next generation of website security innovation,” said Symantec CEO Greg Clark. “I’m thrilled that our customers will benefit from a seamless transition to DigiCert, a company that is solely focused on delivering leading identity and encryption solutions. Symantec is deeply committed to the success of this transition for our customers.”
Some of Symantec and DigiCert’s competitors have taken the opportunity to get Symantec customers concerned about potential disruptions to join them.
Comodo has published a blog post warning Symantec customers of the consequences of moving to DigiCert.
“DigiCert does not have the same infrastructure as Symantec, as a much smaller Certificate authority it never had the need to,” Comodo said. “Therefore, the eventual platform migration poses a huge execution and technology risk for all Symantec Enterprise customers and channel partners.”
Bitcoin Exchange Operator Arrested For $4 Billion Money Laundering Scheme
27.7.2017 thehackernews IT
Greece police have arrested a Russian man who is believed to have been the operator of the popular BTC-e Bitcoin exchange on charges of laundering more than $4 billion in bitcoin for culprits involved in hacking attacks, tax fraud and drug trafficking.
A United States jury indicted 38-year-old Alexander Vinnik on Wednesday after his arrest in Greece on Tuesday at the request of US law enforcement authorities. The suspect is one of the operators of BTC-e, a service operational since 2011.
Headquartered in Russia, the digital currency exchange has been offline since the arrest of Vinnik, and its homepage says, "Site is under maintenance. We apologize for the inconvenience.."
According to a press release published by the U.S. Treasury's Financial Crimes Enforcement Network (FinCEN), BTC-e ignored "know your customer" laws in an effort to serve criminals, and even hosted message boards buzzing with illegal activities.
The FinCEN also announced a $110 million penalty against BTC-e for facilitating crimes along with a separate $12 Million fine against Vinnik.
BTC-e Linked to Collapse of Mt. Gox Bitcoin Exchange
This case is really important for the law enforcement because it could reveal the possible culprit behind the collapse of the once-very popular Japanese bitcoin exchange Mt. Gox, which was shut down in 2014 following a massive series of mysterious robberies, which totalled at least $375 million in Bitcoin.
According to the U.S. Department of Justice, Vinnik obtained funds from the hacker or insider who stole bitcoins from Mt. Gox and sent them to a bitcoin wallet controlled by Vinnik, who intentionally laundered them through BTC-e, over a period of three years.
"After the coins entered Vinnik's wallets, most were moved to BTC-e and presumably sold off or laundered (BTC-e money codes were a popular choice). In total some 300,000 BTC ended up on BTC-e," according to WizSec, a Japanese security firm that has long been investigating the Mt. Gox case.
"To be clear, this investigation turned up evidence to identify Vinnik not as a hacker/thief but as a money launderer; his arrest news also suggests this is what he is being suspected for. He may have merely bought cheap coins from thieves and offered a laundering service."
Vinnik arrest is the latest in a series of US investigations against Russian cybercriminals in Europe, following the shutdown of two of the biggest dark web marketplaces, AlphaBay and Hansa, last week.
While Greek police described Vinnik as "an internationally sought ‘mastermind’ of a crime organisation," United States authorities accused him of facilitating crimes including hacking, identity theft, tax refund fraud, public corruption and drug trafficking.
Vinnik is to be charged with operation of an unlicensed money service business, conspiracy to commit money laundering, money laundering, and engaging in unlawful monetary transactions.
If found guilty, the suspect could face up to 55 years in prison, together with a $500,000 fine or twice the value of the property involved in the transaction for each count.
Tech Giants Announce Plans for Removal of Flash
26.7.2017 securityweek IT
Apple, Facebook, Google, Microsoft and Mozilla have outlined their plans for moving away from Flash Player now that Adobe officially announced an end-of-life (EOL) and end-of-support date for the controversial product.
Adobe announced on Tuesday that, following discussions with several technology partners, it has decided to stop updating and distributing Flash Player at the end of 2020. The company has encouraged developers and content creators to migrate to open standards such as HTML5, WebGL and WebAssembly, which are supported by all major web browsers.
While Flash Player is still used by many websites and applications, the security community has been asking Adobe to retire the old software for several years due to the large number of vulnerabilities and numerous attacks involving Flash exploits.
Over the past years, web browser vendors and other Internet companies have taken steps to reduce the security risks associated with Flash Player by either limiting Flash content or banning it altogether.
Apple, Facebook, Google, Microsoft and Mozilla have promised to help with the transition and they have each outlined their plans for the complete removal of Flash support from their products.
Apple has been moving away from Flash since 2010. Currently, users need to manually install Flash if they need it and even so it remains disabled by default – manual approval is required on each website before the Flash plugin is executed.
Facebook, which still allows Flash games on its platform, says it has partnered with game developers to help them migrate to HTML5. The social media giant will accept Flash games until the end of 2020, but warned that the ability to play these games also depends on the decisions made by browser vendors.
Google pointed out that the number of Chrome users visiting a site with Flash every day has dropped from 80 percent three years ago to 17 percent today. Google has been and will continue to gradually phase out Flash – first by asking for explicit permission to run Flash content in more situations and eventually disabling it by default. The company wants to remove it completely toward the end of 2020.
Microsoft, which updates the Flash Player components used by its products every Patch Tuesday, wants to disable Flash by default in both Edge and Internet Explorer in mid-to-late 2019. Even if users will re-enable it, they will still need to manually approve Flash for each website. Flash will be removed completely by the end of 2020.
Moziila’s roadmap for Flash is similar. The organization wants to disable Flash by default for most users in 2019, while allowing Extended Support Release (ESR) users to continue viewing Flash content through the end of 2020.
Adobe to Kill Flash Player, End Support by 2020
26.7.2017 securityweeek IT
[Breaking] Adobe on Tuesday said that it would kill its Flash Player and stop providing security updates by the end of 2020.
Adobe Flash Player has made headlines over the years due to the large number of serious vulnerabilities identified by both white and black hat hackers. The company has been forced to issue emergency patches on several occasions after learning that malicious actors had been exploiting unpatched Flash Player vulnerabilities in their operations.
According the company, the decision was made in collaboration with several Adobe technology partners including Apple, Facebook, Google, Microsoft and Mozilla.
“Specifically, we will stop updating and distributing the Flash Player at the end of 2020 and encourage content creators to migrate any existing Flash content to these new open formats,” Adobe said.
Adobe said it would continue to support Flash on a number of major OSs and browsers that currently support Flash content through the planned EOL.
“This will include issuing regular security patches, maintaining OS and browser compatibility and adding features and capabilities as needed,” Adobe said in a blog post. “We remain fully committed to working with partners, including Apple, Facebook, Google, Microsoft and Mozilla to maintain the security and compatibility of Flash content.”
While Adobe has officially made the decision to kill-off the vulnerable software product, many other leading internet firms have been pushing hard against the software over the past years and trying to limit the use of Flash across their products and services.
In May 2016, Google announced its plans to block Adobe Flash and implement an 'HTML5 by Default' policy on Chrome by the end of 2016.
“It is time for Adobe to announce the end-of-life date for Flash and to ask the browsers to set killbits on the same day,” Facebook’s CSO, Alex Stamos, said in July 2015 after the existence of several Flash Player zero-day flaws was brought to light by the data breach suffered by Italian spyware maker Hacking Team.
In June 2016, Google stopped accepting display ads built in Adobe Flash, not long after Amazon stopped accepting Flash ads on its online shopping website. At the time, Amazon said that the move, which went into effect on Sept. 1, 2015, was prompted by browser setting in Chrome, Firefox, and Safari, which were meant to limit Flash content displayed on web pages.
Nathan Wenzler, chief security strategist at security consulting company AsTech, believes there will be a lot of split feelings about the official EOL announcement for Flash.
“On one hand, a great deal of the multimedia games, videos, graphics and other rich services that have helped make the Internet what it is today were originally built on Flash. It provided a great platform for a huge array of products, and it could be argued we wouldn't be where we are today without it,” Wenzler told SecurityWeek. “That said, the security world will likely rejoice at the retirement of a product which has had a huge number of well-known vulnerabilities and flaws over the years, which have been the entry point for malicious tools that have compromised millions of systems across the globe.”
“While Adobe has been increasingly more vigilant about hardening Flash and more consistently providing patches and hotfixes whenever a vulnerability was identified, it still served as a particular pain point for a lot of organizations to keep Flash patched and maintain a consistent security posture for their systems which had Flash installed,” Wenzler added.
Chris Roberts, chief security architect at threat detection and defense solutions provider Acalvio, pointed out that the end of Flash Player has been coming for a while.
“It’s been good while we had it, but let’s face it, it’s been a whipping boy of the security industry for a while with more than 1000 CVE’s dedicated to it throughout the years,” Roberts said via email. “Kind of like many of us in the industry that find ourselves getting grayer and less tolerant of others, it’s time to hang up the hat and work out how to retire. At least in Flash’s world, it’s been given a nice sunset (until 2020) and probably a good pension in the vaults of software somewhere.”
Flash Player was originally developed by Macromedia, which was acquired by Adobe in 2005.
Adobe Flash end of life announced by 2020. Start thing of the migration
26.7.2017 securityaffairs IT
Adobe announced Flash end-of-life by 2020. Apple, Facebook, Google, Microsoft and Mozilla plans to stop supporting the Adobe Flash Media Player in 2020.
It’s official, Adobe will kill Flash by 2020, the company will stop providing support for the popular browser plugin.by the end of that year.
“Given this progress, and in collaboration with several of our technology partners – including Apple, Facebook, Google, Microsoft and Mozilla – Adobe is planning to end-of-life Flash. Specifically, we will stop updating and distributing the Flash Player at the end of 2020 and encourage content creators to migrate any existing Flash content to these new open formats.” states the Adobe’s announcement.
Open standards like HTML5, WebGL, and WebAssembly have matured enough over the past years to replace all the features today implemented by Adobe Flash.
Starting from 2020, the company will no more provide support on major browsers, including Chrome, Firefox, and Internet Explorer and Edge.
“If the site continues to use Flash, and you give the site permission to run Flash, it will work through the end of 2020.” wrote Google. “We’re supportive of Adobe’s announcement today, and we look forward to working with everyone to make the web even better. “
“To provide guidance for site authors and users that continue to rely on Flash, Mozilla has updated its published roadmap for Flash in Firefox. Starting next month, users will choose which websites are able to run the Flash plugin.” states Firefox. “Flash will be disabled by default for most users in 2019, and only users running the Firefox Extended Support Release (ESR) will be able to continue using Flash through the final end-of-life at the end of 2020. In order to preserve user security, once Flash is no longer supported by Adobe security patches, no version of Firefox will load the plugin.”
According to Google, Flash usage had gone down from 80% to 17%.

In a similar way, Microsoft also announced the end of support for its products.
“We will phase out Flash from Microsoft Edge and Internet Explorer, culminating in the removal of Flash from Windows entirely by the end of 2020. This process began already for Microsoft Edge with Click-to-Run for Flash in the Windows 10 Creators Update.” states Microsoft.
Facebook also announced that it will shut off Flash games by the end of 2020.
Administrators of Websites that rely on Flash are being encouraged to start planning the migration to new technologies.
Under the cyber security perspective, the Adobe Flash end of life is a good news because it is one of the most exploited software in recent cyber attacks.