IT Articles - H 2020 1 2 3 4 5 6 7 IT List - H 2021 2020 2019 2018 1
Misconfigured Google Groups Expose Sensitive Data
25.7.207 securityweek IT
Researchers at cloud security firm RedLock believe hundreds of organizations may be exposing highly sensitive information by failing to properly configure Google Groups.
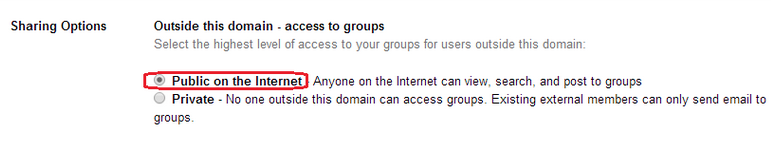
Google Groups is a service that allows users to create and take part in online forums and email-based groups. When a group is configured, its creator has to set sharing options for “Outside this domain - access to groups” to either “Private” or “Public on the Internet.”
RedLock’s Cloud Security Intelligence (CSI) team noticed that many Google Groups for Business users have allowed access to their groups from the Internet, and in some cases the configuration error has resulted in the exposure of sensitive information.
Researchers have found names, email and home addresses, employee salary data, sales pipeline data, and customer passwords in the exposed groups.
“We only looked for a sample of such cases and found dozens,” RedLock told SecurityWeek. “Extending that, there are likely hundreds of companies affected by this misconfiguration.”
According to RedLock, the list of affected firms includes IBM’s The Weather Company, which operates weather.com, intellicast.com and Weather Underground; Fusion Media Group, which owns Gizmodo, The Onion, Jezebel and Lifehacker; video ad platform SpotX, which delivers ads to 600 million people worldwide every month; and cloud-based helpdesk support provider Freshworks, whose software is used by more than 100,000 companies.
Organizations using Google Groups have been advised to immediately check their settings to ensure that access is set to private in order to avoid leaking sensitive data.

“Simple misconfiguration errors – whether in SaaS applications or cloud infrastructure – can have potentially devastating effects,” said Varun Badhwar, CEO and co-founder of RedLock.
Badhwar pointed to the recent incidents involving Deep Root Analytics, WWE and Booz Allen Hamilton as examples of the impact such simple errors can have.
“This new issue that the RedLock CSI team discovered has led to the exposure of sensitive information from hundreds of companies simply through the click of a button,” Badhwar explained. “In today’s environment, it’s imperative that every organization take steps to educate employees on security best practices and leverage tools that can automate the process of securing applications, workloads and other systems. In the cloud, for example, a resource only exists for 127 minutes on average – there’s no way for IT teams alone to keep up with this rapid rate of change.”
Avast Acquires CCleaner Developer Piriform
20.7.2017 securityweek IT
Antivirus firm Avast announced on Wednesday the acquisition of Piriform, a London, UK-based company that develops the popular cleaning and optimization tool CCleaner.
While the Piriform staff will join Avast’s consumer business unit, the antivirus company wants to keep Piriform products separate from its current system optimization offering, which includes Avast Cleanup and AVG TuneUp. Avast acquired AVG last year.
The Piriform acquisition will broaden Avast’s presence in London and the companies say they will combine their expertise to deliver even better products.
CCleaner is used by more than 130 million people worldwide, including 15 million Android device users. Avast CEO Vince Steckler believes the CCleaner brand fits his company very well as they both provide high-quality free products.
Steckler also pointed out that both Avast and Piriform have strong and loyal communities whose members provide product feedback and help each other.
“I’ve seen Piriform grow from a bedroom-based hobby to a real business with billions of downloads, millions of users and a worldwide fan base. Our objective, which is to create world-class software tools that fix real world problems, has made the business what it is today,” said Lindsey Whelan, CEO of Piriform.
“We’re pleased to become part of a company which shares this objective because it means together, we can combine our expertise to deliver even better software to the people that matter most: our users,” Whelan added.
The financial terms of the deal have not been disclosed.
Ubuntu Linux for Windows 10 Released — Yes, You Read it Right
14.7.2017 thehackernews IT
Windows and Linux in the same line? Yes, you heard that right... and that too, on the same computer and within the same operating system.
Two months ago, Microsoft announced its plans to let its users install three different flavours of the Linux operating system – Ubuntu, Fedora, and SUSE – directly through their Windows Store, allowing them to run Windows and Linux apps side-by-side.
Now, downloading an entire operating system has just become as easy as downloading an application with the availability of popular Linux distro 'Ubuntu' in the Windows App Store.
However, unlike a conventional Ubuntu installation, this Ubuntu version runs in a sandboxed alongside Windows 10 with limited interaction with the operating system and is focused on running regular command-line utilities like bash or SSH as a standalone installation through an Ubuntu Terminal.
For now, Ubuntu is currently only available to Windows 10 Insiders users and would be made available to the public with the upcoming Windows 10 Fall Creator Update, which is expected to release in September/October 2017.
Here's How to Install and Run Ubuntu on Windows 10
Users registered in Windows 10 Insiders Program with at least "Build 16215" installed can directly install Ubuntu from the Windows Store, which will allow them to "use Ubuntu Terminal and run Ubuntu command line utilities including bash, ssh, git, apt and many more."
After installing Ubuntu, Windows 10 users will require enabling "Windows Subsystem for Linux" that was previously added to Windows 10.
To enable it, follow these simple steps:
Navigate to Control Panel and go to "Apps and features" settings.
Select "Programs and Features" from the right panel.
Open the "Turn Windows features on or off" from the left menu.
Select the "Windows Subsystem for Linux" and save it.
Reboot Your system.
While the company has not revealed exactly when its users can expect to see the other two Linux distro, Fedora and SUSE Linux, to the Windows Store, this step by Microsoft follows its commitment to the open source community.

In 2013, the Microsoft launched Visual Studio, and a year later, the company open-sourced .NET. In 2015, the tech giant open sourced the Visual Studio Code Editor, as well.
Last year, Microsoft took many steps to show its love for Linux, which includes bringing of Ubuntu on Windows 10, working with FreeBSD to develop a Virtual Machine image for its Azure cloud, choosing Ubuntu as the OS for its Cloud-based Big Data services, and even joining the Linux Foundation as a Platinum member – the highest level of membership.
Have you tried out Ubuntu on Windows 10? If yes, let us know your experience in the comments below.
Katyusha Scanner, a new SQLi Vulnerability Scanner Available for $500 in the underground
12.7.2017 securityaffairs IT
Katyusha Scanner is a new fully automated SQLi vulnerability scanner discovered by researchers at security firm Recorded.
Recorded Future security researchers have discovered a fully automated SQLi vulnerability scanner, dubbed Katyusha Scanner, on a hacking forum. The tool is offered for sale for just $500, it allows mass scans, simply managed from a smartphone through the Telegram messenger. The company, of course, reported the discovered to law enforcement.
The Katyusha Scanner appeared in the hacking underground in early April. It was developed starting from the Anarchi Scanner open source penetration testing tool and according to the researchers, it has already been updated seven times since its introduction
Actually, the Katyusha Scanner is offered under a Pro and a Lite version that go for between $250 and $500.
The Pro version leverages known exploits to hack into the system, once a SQL injection bug is found the tool notify it to the attacker via a text message that includes the site name, Alexa rating, and the number of available databases.
“On April 8, 2017, a Russian-speaking member of a top-tier hacking forum introduced “Katyusha Scanner,” the powerful and fully automated SQLi vulnerability scanner that utilizes the functionality of Telegram messenger and Anarchi Scanner, an open-source penetration testing tool.” states the blog post published by RecorderFuture.
The released product, coupled with outstanding support and frequent updates, immediately gained popularity and accolades of grateful clients for an intuitive and straightforward interface, as well as incredible performance.”


Researchers at Recorded Future reported that the seller is Russian speaking and is known in the hacking underground for selling data stolen from e-commerce websites. According to the experts, the forum where the tool is commercialized is frequented by top-tier Russian hackers.
An innovative feature implemented in the Katyusha Scanner allows crooks to upload a list of target websites and launch the concurrent attack against them simultaneously, seamlessly controlling the attack via Telegram.
The scanner is easy to use, the attackers only need set up a standard web server with the version of the Anarchi scanner that has been modified to allow the control of the operation through a linked Telegram account.
The attackers can control the attack using almost every mobile OS.
“Interestingly, the name Katyusha was not chosen by chance — it represents an iconic multiple rocket launcher, developed by the Soviet Union during World War II known for inflicting panic in Nazi forces with its stealthy and devastating attacks. Similar to the very lethal weapon conceived 70 years ago, Katyusha Scanner allows criminals to initiate large-scale penetration attacks against a massive number of targeted websites with several clicks using their smartphones.” continues the analysis.
The seller suggests starting with at least 500 target sites, attackers can issue commands to scan them for any known vulnerabilities. The Pro version also implements the capability of downloading any exfiltrated data available.
According to Recorded Future, at least 12/15 user have already purchased the tool, they were satisfied for the efficiency of the tool.
The potential scale of the attacks that the tool is able to power is worrisome.
“When dozens buy it and initiate attacks every day, the potential fallout will be significant,” Recorded Future director of advanced collection Andrei Barysevich said. “The scale of attacks which is available to criminals is quite unprecedented now. And the convenience of this; someone who wants to engage in this type of activity doesn’t have to be a hacker, he doesn’t have to know how certain tools operate or what exploit packs they should be using. The tool will do everything for them.”
Symantec to Acquire Mobile Security Firm Skycure
12.7.2017 securityweek IT
Just three days after announcing that it would acquire Fireglass, Symantec announced that it has agreed to acquire mobile security firm Skycure.
Founded in 2012 by two former members of Israel Defense Forces' Unit 8200, Skycure has raised a total of $27.5 million in funding to date, and offers a threat prevention platform aimed at protecting mobile devices by monitoring network traffic behavior and fixing suspicious activity.
Symantec said that Skycure’s technology would be combined with its Integrated Cyber Defense Platform, giving Symantec customers “access to comprehensive and effective endpoint protection offerings across traditional and mobile devices, with enhanced capabilities for mobile devices, applications, network gateways and data protection."
Symantec also said that gaining access to Skycure’s technology will help position the company to serve as a strategic partner for telecommunications companies looking to build out mobile security offerings for their end users.
While no financial terms were disclosed, analysts from investment firm Jefferies estimate the acquisition cost to be roughly $200 million.
“While it's logical for [Symantec] to expand further into this market for a complete endpoint (desktop + server + mobile) offering, we note that it has been difficult to monetize mobile,” Jefferies wrote in a research note Tuesday. “Additionally, while we believe the go-to-market strategy to partner with telcos is logical, we note that it is likely at a substantially lower ASP than the direct channel. Therefore, we continue to believe that even traction gained within the telco channel may not be a meaningful contributor to revenue given greater go-to-market efficiency (i.e., lower price points).”
Jefferies also commented on the acquisition of Fireglass, calling it a “smart offensive and defensive move.”
“We saw the acquisition of Fireglass as a smart offensive and defensive move, as its browser isolation technology can be used to enter a new and potentially high-growth market, while defending the Symantec proxy solutions from any potential threat this market could pose,” the note added.
According to Symantec CEO Greg Clark, the company believes the future is “mobile-first” and requires protection that single platform vendors will struggle to provide on their own. “Our investments in this area will bring defense-in-depth across platforms including, closed operating systems,” Clark said in a statement.
“We believe the Skycure acquisition is logical given an increasingly mobile-first world, but believe that the return on this investment is incrementally less obvious given ongoing challenges to monetize mobile security,” Jefferies analysts opined.
Researcher Takes Over .IO Domains by Registering Name Servers
11.7.2017 securityweek IT
A security researcher could have taken over thousands of .IO domains after being able to register four domain names of the top level domain (TLD)’s authoritative name servers.
The incident happened last month, when researcher Matthew Bryant was “graphing out the DNS delegation paths of various TLDs.” During his project, he discovered a name server domain that was available for registration and was able to purchase it.
".IO" is the country code top level domain (ccTLD) assigned to the British Indian Ocean Territory.
TLDs have authoritative name servers at arbitrary domain names but, by exploiting errors such as misconfiguration, expiration, or other issues, it is possible to “register a name server domain name and use it to serve new DNS records for the entire TLD zone,” the security researcher explains.
For that, one would have to enumerate all name server hostnames for a given extension and then check for base-domains that expired and are available for registration. In some instances, however, the expired domains would not be available for purchase even if not marked as reserved.
Using this method, the researcher stumbled upon the name server domain of ns-a1.io, which appeared as available for the registration price of 90.00 USD. After successfully purchasing it, Bryant attempted to contact the .io TLD to get the issue fixed, but failed.
As a result, he decided to look for other similar name server domains and found ns-a2.io, ns-a3.io, and ns-a4.io domains available for purchase as well. All four domains are listed as authoritative name servers for the .io TLD, and anyone controlling them could potentially “poison/redirect the DNS for all .io domain names registered,” the researcher explains.
Bryant was eventually able to send an email to the appropriate security contact and was informed the next day that the issue was resolved. The researcher verified that he was not able to re-register these domains, showing that the error was remediated.
“Given the fact that we were able to take over four of the seven authoritative name servers for the .io TLD we would be able to poison/redirect the DNS for all .io domain names registered. Not only that, but since we have control over a majority of the name servers it’s actually more likely that clients will randomly select our hijacked name servers over any of the legitimate name servers even before employing tricks like long TTL responses, etc to further tilt the odds in our favor,” the researcher explains.
He also notes that, because the .io TLD has Domain Name System Security Extensions (DNSSEC) enabled, which adds security by enabling DNS responses to be validated, users should be defended from attackers able to send bad/forged DNS data. However, “DNSSEC support is pretty abysmal and I rarely encounter any support for it unless I specifically set a resolver up that supports it myself,” the researcher also points out.
According to Matt Pounsett, however, while the Backend Registry Operator for the .io TLD clearly made a big mistake by allowing a third-party to register the name servers, the issue “definitely does not constitute the catastrophe implied.” He explains that “the name servers for the .io TLD don't respond with their own NS set in their response,” meaning that attack won’t work as suggested.
The issue with the authoritative name servers was that the .io TLD apparently transitioned last month from the operators of the registry to a third-party already in charge with the backend for other top-level domains. The third-party, Afilias, got hold of three domain name servers, but left the other four available.
HyTrust Acquires DataGravity, Raises $36 Million
11.7.2017 securityweek IT
Cloud security firm HyTrust today announced that it has acquired data visibility and security company DataGravity, and raised $36 million in a new funding round.
Terms of the acquisition have not been disclosed, but members of the DataGravity team will join HyTrust. By acquiring DataGravity, HyTrust hopes to further enhance its security policy enforcement capabilities for cloud workloads through new data discovery and classification expertise.
DataGravity, which in the past years managed to raise a total of $92 million, exited stealth mode in 2014 when it launched Discovery, a platform that provided data security, and search and discovery capabilities. The company later released the DataGravity for Virtualization virtual appliance.HyTrust acquires DataGravity
HyTrust’s decision to acquire DataGravity comes shortly after Forrester estimated that the global cloud security market will increase to $3.5 billion by 2021, which represents an annual growth rate of 28 percent.
“The acquisition will accelerate the expansion of HyTrust's platform capabilities and capitalize on the high-growth cloud security market,” said Eric Chiu, co-founder and president of HyTrust. “DataGravity's data discovery and classification capabilities support HyTrust's mission to deliver a security policy framework that provides customers with full visibility, insight and enforcement of policy across workloads. We couldn't be more excited.”
HyTrust also announced that it has closed a $36 million funding round led by investment firm Advance Venture Partners (AVP), which brings the total raised by the company to $100 million. Sway Ventures, Epic Ventures, Vanedge Capital, Trident Capital, and strategic investors Cisco, Fortinet, Intel and VMware also participated.
Part of the $36 million have been used to acquire DataGravity and the rest will go towards expanding sales and marketing efforts, and funding new product development.
“HyTrust is very well positioned to capitalize on a tremendous growth opportunity in the cloud security space,” said David ibnAle, founding partner at AVP. “The need for security, automated compliance and policy enforcement for cloud infrastructure and data is critical in almost every industry, and HyTrust is front and center in this field. Gartner's recent highlighting of the sector as a top security technology for 2017 underscores the relevance of HyTrust's solutions, and we are extremely excited about the opportunity to back the market leader in this space.”
Wiretap Raises $4.9 Million to Monitor Enterprise Social Networks
7.7.2017 securityweek IT
Columbus, Ohio-based startup Wiretap has closed a $4.9 million Series A financing round led by Pittsburgh-based Draper Triangle Ventures, Columbus-based Ohio Innovation Fund and Rev1 Ventures, as well as JumpStart Inc., based in Cleveland. The money will be used for sales, marketing and R&D.
Wiretap has developed a platform that provides visibility into an increasingly important but dark aspect of corporate life: the enterprise social network (ESN). Slack is a prime example, although there are many others such as Microsoft Yammer, and Workplace by Facebook.
ESNs provide the modern 'water-cooler' environment, where employees meet informally for both corporate and social collaboration. The difficulty for management is that it has no visibility into that environment, leaving a new and unmeasured threat vector.
A November 2016 study by Persistence Market Research titled Enterprise Social Networks and Online Communities Market: Global Industry Analysis and Forecast 2016–2026 predicts that the ESN and online community market will grow from $2.6 billion in 2016 to $12.18 billion by 2026. It comments, "Online collaboration of business information with social networking websites creates an opportunity for hackers to illegally access information or gain unauthorized access to critical business data through social websites."
Wiretap monitors the ESNs and provides unique visibility into corporate sentiment. Using artificial intelligence, including behavioral and linguistic analysis, it provides management awareness of corporate social health. This could be used to highlight the problems that initially cause dissatisfaction and ultimately lead to insider threats, allowing HR to intervene and address the problem. Or it could be used to monitor for potential or actual leaks of PII or IP.
Wiretap CEO Jeff Schumann told SecurityWeek that the current problems faced by Uber are an example of corporate health issues that could be highlighted and subsequently solved with Wiretap in place. Uber's HR team were apparently unaware of the undercurrent of sexual harassment within the organization until it finally boiled over. In June, it was forced to sack 20 full time employees; and there will likely be more to follow. The damage to brand image is inestimable.
Schumann suggested that linguistic and behavioral analysis of ESNs will highlight growing discontent within the company, allowing HR to intervene and improve or at least manage the situation. Individual grievances that can slowly grow into insider threat motivation can also be highlighted.
By monitoring and analyzing ESNs over time, management will get the tools to predict and address corporate health issues. "As the demand and popularity of Enterprise Social Networks soars, Wiretap bridges a critical security gap -- ensuring the enterprise remains secure while maximizing the productivity and inherent collaboration of their ESN investments," explains Schumann.
"Rev1 Ventures is committed to supporting high-growth companies, like Wiretap, as they scale and grow," said Rev1 Ventures EVP for investment funds, Ryan Helon. "With an innovative approach for securing enterprise collaboration tools and a compelling vision for helping companies maximize social channels for better engagement and performance, Wiretap is poised for explosive success and we're excited to be part of their journey."
Symantec to Acquire Threat Isolation Startup Fireglass
6.7.2017 securityweek IT
Symantec announced on Thursday that it has agreed to acquire Israeli cybersecurity start-up Fireglass for an undisclosed sum.
Fireglass, which emerged from stealth in February 2016, describes its technology as an agentless isolation solution that eliminates ransomware, malware and phishing threats in real-time by preventing potentially harmful content from ever reaching user endpoints or the corporate network.
Delivered as a cloud service, on premises, or in a hybrid model, Fireglass protects users from links they click on, or dangerous websites they visit, using its browser isolation technology, which allows web traffic and email content to be executed remotely and not reach endpoints.
“Integrating Fireglass’ isolation technology with Symantec’s existing endpoint, email and secure web gateway solutions could reduce security events by as much as 70 percent, while virtually eliminating advanced threats spread by web browsing or email content,” said Symantec CEO Greg Clark. “Isolation will become a core component in the design of cyber defense architectures for the cloud generation who face the reality of an encrypted Internet and the crisis inherent in email and web-delivered attacks.”
Fireglass’ browser isolation technology integrates with existing security solutions and across Windows, Mac, Android, iOS and other devices including browser-enabled IoT devices.
The transaction is subject to customary closing conditions, and is expected to close in the third calendar quarter of 2017, Symantec said. Fireglass’ technology is expected to be available to Symantec customers and partners soon after the transaction closes, the company said.
Fireglass is backed investors including Lightspeed Venture Partners and Norwest Venture Partners.
Early this year, Sophos announced its plans to acquire Invincea, a provider of endpoint security solutions that leverage virtual containers to protect against advanced malware and other threats.
Google Gets Record-Breaking $2.7 Billion Fine for Manipulating Search Results
27.6.2017 thehackernews IT
Google has just lost its biggest regulatory battle!
Google has been hit with a record-breaking $2.7 billion (€2.42 billion) fine by the European antitrust officials for unfairly manipulating search results since 2008.
After a lengthy seven-year investigation that was launched in 2010 after several rivals complaint, the European Commission on Tuesday imposed this 'biggest even financial penalty' against the internet tech giant for breaking EU competition law.
by using its search dominance to distort search-engine results to promote own shopping comparison service at the top of all search results.
"Comparison shopping services rely to a large extent on traffic to be competitive." European Commission says in a press release.
"The evidence shows that consumers click far more often on results that are more visible, i.e. the results appearing higher up in Google's search results. More traffic leads to more clicks and generates revenue."
The Commission says the amount of penalty has been calculated from Google’s income from its comparison shopping service in Europe. Google’s total revenue in the year 2016 was almost $90 Billion.
Apart from the fine, the Commission has ordered Google to "stop its illegal conduct" and anti-competitive practices within the 3-month deadline or warned to face a further penalty of up to 5% of the average daily worldwide turnover of the Alphabet, Google's parent company."
So now Google will have to change its search ranking algorithm. However, the company can also appeal this decision in in EU courts to delay the resolution for years.
"We respectfully disagree with the conclusions announced today. We will review the Commission’s decision in detail as we consider an appeal, and we look forward to continuing to make our case." Google Spokesperson said in a statement.
Moreover, Google is currently facing two other ongoing EU antitrust investigations.
One says Google Android unfairly force cellphone manufacturers to preinstall Google services to promote its products over rivals. Another investigation targets its AdSense business.
The previous biggest antitrust fine was against U.S. chipmaker Intel in 2009, which was €1 billion.
Consortium Promotes Principles for Fair and Accurate Security Ratings
22.6.2017 securityweek IT
Under the aegis of the U.S. Chamber of Commerce, more than 40 companies -- including some of America's largest banks and tech companies -- have signed up to a set of new guiding principles for fair and accurate security ratings.
Security rating has become an emerging technology over the last few years, with companies such as BitSight (which raised $40 million in Series C financing, September 2016), RiskRecon, and SecurityScorecard all offering to rate the security of companies and products. It's a valuable service, helping organizations better understand the security of their supply chain, and helping cybersecurity insurance companies understand the risk inherent in potential customers.
But there are difficulties. In a statement Tuesday, Ann Beauchesne, an SVP at the Chamber of Commerce, explained, "There is, of course, the potential for the rating to be inaccurate, irrelevant, incomplete, or unverifiable. Problematic source data can create unfair and unreliable ratings, which serves neither the consumers of security ratings nor the organizations whose programs are rated."
One of the problems is the 'black box' nature of the scores. The rating companies collect data -- sometimes with and sometimes without the knowledge of the target company -- from a wide range of sources. This data is fed into a proprietary algorithm and, simplistically, out pops a score. The value of a complex security program reduced to a single score is not always apparent or verifiable.
To solve this problem she continued, "a group of U.S. Chamber member companies have worked closely with security rating companies to develop a concrete set of principles (PDF) to increase confidence in, and usability of, fair and accurate security ratings."
The principles comprise transparency; dispute resolution; accuracy and validation; methodology model governance; independence; and confidentiality -- and the attempt is to bring consistency and credibility to an emerging market.
"The fact that so many large organizations are coming together on this issue shows that the Security Rating Services market is here, real, important, and essential for the future of B2B risk management," BitSight's SVP Jake Olcott told SecurityWeek.
While insurance providers can use ratings in their premium calculations, by far the bigger market comes from general commerce. Most large companies now have thousands of new cloud services as part of their supply chain, and CISOs struggle to get an accurate view of the risk they bring. This unquantifiable risk will only grow,
By 2020, claims Olcott, security ratings will be as important as credit ratings. "Just as credit ratings are part of every B2B transaction," he said, "so too will security ratings become a critical element. [There are] many reasons for this, including the ever-expanding business ecosystem, the explosion of third party breaches, the challenge of finding cyber security and risk talent, and the difficulty in assessing cyber risk of the ecosystem at scale (quickly and cost-effectively)."
For that to happen, there must be trust in the accuracy and consistency of the rating process and the rating scores -- both between scores from the same rating company, and between scores generated by different companies. Backed by major cross-sector companies such as Goldman Sachs and JPMorgan, Microsoft and Verizon, and Starbucks and Eli Lilly, the Chamber of Commerce principles will go a long way towards providing that trust.
Cybereason Raises $100 Million to Hunt Attackers
21.6.2017 securityweek IT
Boston, MA-based Cybereason today announced that it has raised $100 million in Series D funding from SoftBank Corp. This increases the total investment in the cyber attack detection firm to $189 million since its inception in 2012. It raised $25 million in Series B financing and $59 million in Series C financing, both in 2015.
The new investment follows Cybereason's continued growth: 500% in revenue and almost 200% in staff over the last year. Lior Div, co-founder and CEO of Cybereason, commented, "This new funding allows us to increase our growth through new distribution channels and to develop new technologies."
Cybereason LogoTokyo-based Softbank is not merely Cybereason's major investor, it is also an important customer. "Our strengthened partnership with SoftBank, which has a formidable sales force and enterprise customer base in Japan and a global reach, will also enable us to further expand our presence in the cybersecurity market," added Div. "The new capital," he said, enables Cybereason "to expand our products, hire additional talented people and increase the size of our offices in Boston, Tel Aviv, London and Tokyo -- and throughout the broader EMEA and APAC regions," he said.
Cybereason is one of the new breed of endpoint security solutions that rely heavily on machine learning and behavioral analytics to detect threats in realtime without reliance on malware signatures. Many of its direct competitors have shown similar levels of investment in recent years. Crowdstrike raised $100 in Series C financing in July 2015, and a further $100 million in Series D in May 2017. Cylance also raised $100 million in Series D funding in June 2016, while SentinelOne raised $70 million in January 2017.
Cybereason, like Endgame (which has raised more than $90 million in funding), seeks to differentiate itself from the competition by not merely detecting anomalies, but actively hunting for the attacker. "This approach," it says, "allows hunting to strengthen the organization's security posture while slowing down the adversary and decreasing their dwell time. The results of a hunt can be used to build new prevention mechanisms, ensuring that the discovered security incidents do not happen again."
"Software," says Div, "is the most powerful force in today’s connected world. People can use its power for good or evil, and the mission of Cybereason is to stop the adversary from gaining an unfair advantage by giving our customers the upper hand."
How to Speed Up Firefox With Multi-Process, If It's Not Working By Default
19.6.2017 thehackernews IT
enable-firefox-multiprocess-feature
After years of waiting, Mozilla last week launched Firefox 54 for Windows, Mac, Linux, and Android, with multi-process support — a "major improvement" to improve your browsing experience — but many users are still struggling to take advantage of this feature.
Mozilla's multi-process support in Firefox has been in development for over eight years as part of a project, codenamed Electrolysis or E10S, which aimed at improving responsiveness and speed by streamlining memory use by different processes.
Describing the latest release as the largest change to Firefox code ever, Mozilla says it has worked hard to avoid increased memory consumption, and slower performance, as Firefox now uses up to four processes to run web page content across all open tabs.
In other words, Firefox is finally making use of "significantly less RAM" of your computer, as heavy web pages in one tab will now have a much lower impact on responsiveness and speed in other tabs.
"This design makes it easier to utilize all of the cores available on modern processors and, in the future, to securely sandbox web content," says Mozilla. "It also improves stability, ensuring that a single content process crashing won't take out all of your other tabs, nor the rest of the browser."
This feature is about to be enabled by default with Firefox 54, but many Firefox users are unable to take advantage of multi-process support and disappointed to see that their web browser is clinging to a single process.
This issue is happening because one or more of your installed Firefox add-ons could be incompatible with Electrolysis, or multi-process feature.
Step 1 — Check If Multi-Process is Working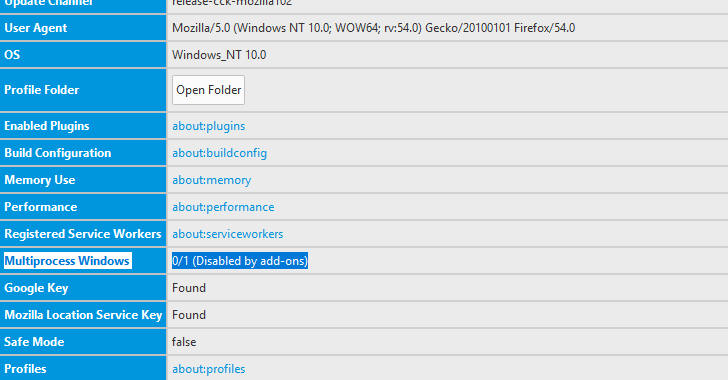
To check whether or not Firefox multiprocess feature is working fine, visit about:support in the address bar and look for the "Multiprocess Windows" line (as shown):
If it says "1/1 (Enabled by default)" — multi-process feature is working.
If it says "0/x (Disabled by add-ons)" — multi-process is not working.
Step 2 — Disable/Remove Incompatible Add-Ons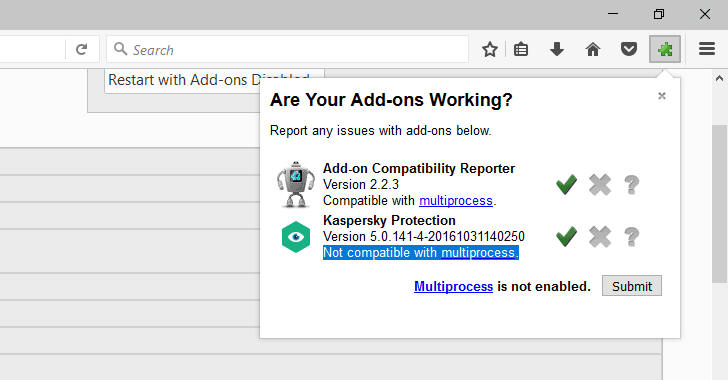
To find out the list of incompatible add-ons to see which of your extensions is at fault, install "Add-on Compatibility Reporter add-on" provided by Firefox.
Step 3 — Enable Firefox Multiprocess Feature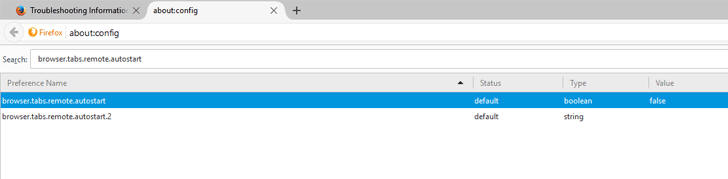
In order to manually fix this issue and enable Electrolysis feature, you first need to disable or completely remove incompatible add-ons from your browser.
Now, enable Electrolysis feature in Firefox using the following steps:
Type about:config in the address bar
Search for browser.tabs.remote.autostart
Double-click on it and set value to True
Step 4 — Change No. of Content Processes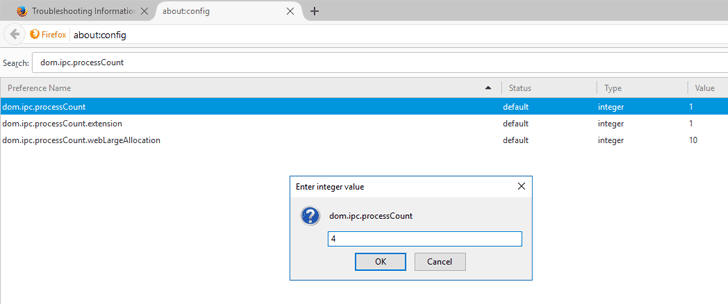
You can also change the number of content processes, which is by default 4, to more or less, according to your pool of RAM.
Visit about:config
Search for dom.ipc.processCount
Set its value to more than 1
That's it. You are done.
You do not need to restart your web browser for this to take effect.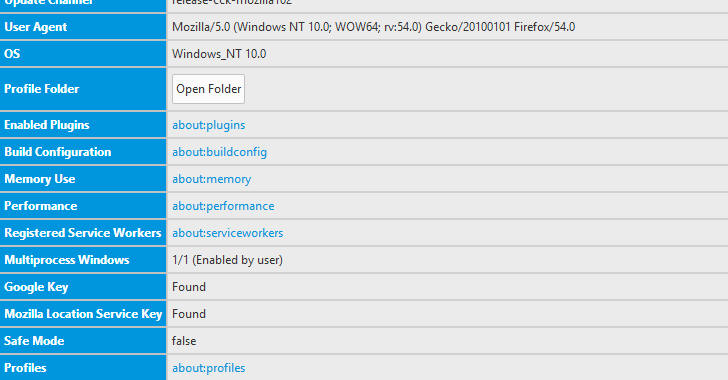
No doubt, this change will let Google Chrome users rethink to shift on Firefox, as by default Chrome starts a new process for every tab, thus using an infinite number of processes, which eventually slow down the web browser as well as the operating system to a crawl.
"We are pushing forward in building a completely revamped browser made for modern computing. It's our goal to make Firefox the fastest and smoothest browser for PCs and mobile devices," Mozilla says. "Through the end of 2017, you'll see some big jumps in capability and performance from Team Firefox."
Firefox 54 is available to download in the stable form, while Firefox 55, which further refines the process, is available only to developers.
Microsoft Acquires Security Orchestration Firm Hexadite
8.6.2017 securityweek IT
Microsoft announced on Thursday that it has agreed to acquire Boston-based security orchestration firm Hexadite for an undisclosed sum.
Hexadite’s flagship Automated Incident Response Solution (AIRS™) solution is described by the company as a tool “modeled after the investigative and decision-making skills of top cyber analysts and driven by artificial intelligence.”
“By eliminating the need to tune down alert volume, Hexadite allows your existing security investments to operate at full capacity and deliver maximum value,” Hexadite explains. “Hexadite AIRS integrates with any detection system via email, syslog or APIs to expedite deployment and investigate every alert.”
HexaditeMicrosoft says that acquisition will build on its current initiatives to help businesses using Windows 10 detect, investigate and respond to advanced attacks on their networks with Windows Defender Advanced Threat Protection (WDATP).
“Microsoft is strengthening its Advanced Threat Protection offering by adding artificial intelligence-based automatic investigation and remediation capabilities, making response and remediation faster and more effective,” the company said in the announcement. “With Hexadite, WDATP will include endpoint security automated remediation, while continuing the incredible growth in activations of WDATP, which now protects almost 2 million devices.”
“Our vision is to deliver a new generation of security capabilities that helps our customers protect, detect and respond to the constantly evolving and ever-changing cyberthreat landscape,” said Terry Myerson, executive vice president, Windows and Devices Group, Microsoft. “Hexadite’s technology and talent will augment our existing capabilities and enable our ability to add new tools and services to Microsoft’s robust enterprise security offerings.”
Hexadite has raised more than $21 million in funding since being founded in 2014. Rumors of the acquisition surfaced late last month, but the official announcement confirming the deal came on June 8.
Cloud Security Firm Netskope Raises $100 Million
7.6.2017 securityweek IT
Netskope, a player in the cloud access security broker (CASB) market, announced on Tuesday that it has raised $100 million through an oversubscribed Series E funding round.
The investment brings the total raised by the Los Altos, California-based company to $231.4 million.
According to the company, the investment will fuel the advancement and go-to-market of its enterprise cloud security platform, which helps companies manage the security challenges introduced through the adoption of cloud services.
Netskope fundingThe company explains that its “Netskope Active Platform” was designed to provide context-aware governance of all cloud usage in the enterprise in real-time, whether accessed from the corporate network, remote, or from a mobile device.
“When we founded Netskope, we knew that the far-reaching impact of the cloud would require a fundamentally new approach to security. We started with CASB and now we’re expanding our cloud security platform to take on additional challenges,” Sanjay Beri, founder and CEO of Netskope, said in a statement.
Since the company launched in October 2013 it has grown its global employee headcount to more than 350.
The Series E round was led by existing investors Lightspeed Venture Partners and Accel. Previous investors Social Capital and Iconiq Capital also participated in the round, aling with new investors Sapphire Ventures and Geodesic Capital, the company said.
CASBs, which provide security and visibility for companies moving to the cloud, have experienced rapid growth, with several players in the space being acquired by larger enterprise technology firms.
In June 2016, Cisco announced its intention to acquire CloudLock, a privately held cloud CASB based in Waltham, Massachusetts for $293 million in cash and assumed equity awards. In 2015, Microsoft bought Adallom and turned it into its Cloud App Security service launched in April 2016. In 2014 Imperva bought Skyfence; in 2015, Palo Alto Networks bought CirroSecure; and in November 2015 Blue Coat (since acquired by Symantec) bought Elastica. In September 2016, Oracle acquired Palerra for an undisclosed amound. In February 2017, Forcepoint acquired Skyfence from Imperva.
Google Announces CTF Competition
5.6.2017 securityweek IT
Google announced on Friday the dates and prizes for the company’s second annual capture the flag (CTF) competition.
The qualifying round, for which nearly 200 teams have already signed up, will take place on June 17 and 18. The top 10 teams will be invited to one of Google’s offices for the final round.
The prize pool for Google’s CTF is more than $31,000, which includes $13,337 for the first place prize, $7,331 for second place and $3,133.7 for third place. The tech giant will also cover travel costs for up to four members of each finalist team – up to $8,000 per team.
During the qualification round, participants can submit a summary of how they solved a particular challenge and these reports can also earn prizes. Google is prepared to award $100 for each of the 21 best submissions, and $500 for each of the 11 most creative solutions.
The top 10 teams will be announced on or around June 20 and the final is scheduled to take place sometime in October.
At last year’s event, 2,400 teams signed up and 900 of them completed at least one challenge.
According to Google, the goal of the event is to engage the broader security community and give security enthusiasts the chance to teach valuable lessons to both Google and the community.
“Upon observing how last year's competition engaged new players from all over the world, we want to continue to create a safe space for people to come and learn while trying to solve challenges and having fun,” said Josh Armour, Security Program Manager at Google. “Our internal security team employs several people who actively compete in CTF competitions in their spare time, so we value this activity and want to give back to and help grow our community.”
Google has been running several cybersecurity initiatives and by the end of 2016 it had paid out more than $9 million in bug bounties. The company recently announced the expansion of its Patch Rewards program to cover integration of fuzzing targets into its OSS-Fuzz service.
The tech giant also informed bug bounty hunters in March that certain types of flaws would earn them more money – up to $31,337 is now offered for remote code execution vulnerabilities and up to $13,337 for unrestricted file system or database access flaws.
However, not all of Google’s contests are a success. The company admitted in April that its Project Zero Prize competition, which offered $200,000 for critical Android vulnerabilities and exploit chains, had not received any valid bug reports.
Microsoft Unveils Special Version of Windows 10 For Chinese Government
25.5.2017 thehackernews IT
China is very strict about censorship, which is why the country has become very paranoid when it comes to adopting foreign technologies.
The country banned Microsoft's Windows operating system on government computers in 2014 amid concerns about security and US surveillance.
Even in the wake of that, China had been pushing its custom version of Windows XP and its forked version of Ubuntu Linux.
To deal with this issue and target the world's largest market, Microsoft's CEO for the Greater China region last year confirmed that the company was working on a Chinese version of Windows 10 that included "more management and security controls" and less bloatware.
Now, Microsoft has just announced a new version of its Windows 10, which is now ready for Chinese government agencies to use.
In its event in Shanghai on Tuesday, Microsoft announced Windows 10 China Government Edition specifically designed for the Chinese government.The OS is based on Windows 10 Enterprise Edition, but with a few tweaks to keep Chinese officials happy.
Windows 10 Enterprise Edition already provides several security, identity, and manageability features governments and enterprises need, but Windows 10 China Government Edition will let the country use the management feature to monitor and deploy updates as needed, manage telemetry, and use its own encrypted algorithms.
Designed to work with Chinese Encryption Algorithms
Microsoft enables the Chinese government to use its own encrypted algorithms in its Windows 10 China Government Edition in order to secure data that they do not want others to see.
Allows to Remove Unwanted Apps
The Chinese version of Windows 10 does not allow access to features that are not needed by Chinese government employees like Microsoft's OneDrive service that let people store their documents and files on Microsoft-controlled data centers.
Apparently, the Chinese officials don't want anyone to access their data, so they will keep their data locked down on their own computers in an attempt to have full control over it.
Manage Telemetry Data Collection & Updates
The last year's outcry over Microsoft's silent slurping of telemetry data from users' computers might have made the Chinese officials ask for the control over telemetry of its China version of Windows, preventing Microsoft to collect data on its citizen.
So basically, all Windows 10 users around the world do not have any option to turn off telemetry, but the Chinese government could do so.
"For more than two decades, Microsoft has had the distinct honor to work in China, learning and advancing technology together," executive vice president Terry Myerson writes on the Windows 10 Blog.
"Over the last two years, we have earnestly cooperated with the Chinese government on the security review of Windows 10. The Chinese government has the highest standards for security."
A release date for the Windows 10 China Government Edition have not yet announced, but three Chinese government groups have already announced their plans to adopt Windows 10 China Government Edition.
These three government groups are China Customs, Westone Information Technology and the City of Shanghai on the national, state-owned and regional enterprise levels, respectively.
Besides this, Lenovo has also announced its plans to be the first OEM partner to have devices that come preinstalled with Windows 10 China Government Edition.
Microsoft Brings Ubuntu, Suse, and Fedora Linux to Windows Store
13.5.2017 thehackernews IT
Microsoft has been expressing its love for Linux and Open Source for almost three years now, and this love is embracing as time passes.
Just last year, Microsoft made headlines by building support for the Bash shell and Ubuntu Linux binaries into Windows 10, allowing users to run limited instances of Linux directly on top of the OS without installing any virtual machine, as well as developers to run command-line tools while building apps.
Now, Microsoft has announced at its Build developer conference in Seattle that three different flavors of the free Linux operating system are coming to the company's app store, so its users can run Windows and Linux apps side-by-side.
Yes, it's no joke. Three versions of Linux distributions – Ubuntu, Fedora, and SUSE – are coming to the Windows Store.
ubuntu-windows-store
Now, you'll soon be able to install these Linux operating systems on your Windows device just like any other app.
While Ubuntu is already available on the Windows Store for anyone to download, Fedora and SUSE are coming soon.
This latest move by Microsoft follows its commitment to the open source community. In 2013, the company launched Visual Studio 2013. A year later, it open-sourced .NET, and in 2015, it open sourced the Visual Studio Code Editor, as well.
Just last year, the company brought Ubuntu on Windows 10, worked with FreeBSD to develop a Virtual Machine image for its Azure cloud, chose Ubuntu as the OS for its Cloud-based Big Data services, and even joined the Linux Foundation as a Platinum member – the highest level of membership, which costs $500,000 annually.
Adding Ubuntu, Suse, and Fedora to the Windows Store is also a way to make it easier for developers who love using Linux software to let them install the Linux version of their choice on their Windows 10 machine.
What do you think about Ubuntu, Fedora, and SUSE coming to Windows Store? Let me know in the comments below.
Linux on Windows – Microsoft will offer Ubuntu, Suse, and Fedora Linux distros in the Windows Store
12.5.2017 securityaffairs IT
Linux on Windows – Microsoft is, even more, Linux friendly, the IT giant announced that three free Linux distro will be included in its official app store.
Last year the tech giant announced the support for the Bash shell and Ubuntu Linux binaries into Windows 10, news of the day is that Microsoft has announced during the company Build developer conference in Seattle that three free Linux distro will be included in its official app store, allowing Microsoft users to run Windows and Linux apps side-by-side.
The three versions of Linux distros are Ubuntu, Fedora, and SUSE.
Users will be able to install the above Linux operating systems on their Windows machine, the novelty is represented by Fedora and SUSE because Ubuntu is already available on the Windows Store for download,

The decision of Microsoft is aligned with its policy to support also open source community.
In 2016, Microsoft also chose Ubuntu as the OS for its Cloud-based Big Data services and it has also joined the Linux Foundation as a Platinum member
Clearly, the operation has a specific marketing intent together the interest of the last audience of Ubuntu, Suse, and Fedora users that every day have also to work with Windows systems. Developers and experts that use Linux software can now benefit from the initiative that will port Linux on Windows.
Google Offers $20,000 to Join OSS-Fuzz Program
9.5.2017 securityweek IT
Five months ago, Google launched its free OSS-Fuzz service with the purpose to help open source developers locate bugs in their code. "It is important," said Google at the time, "that the open source foundation be stable, secure, and reliable, as cracks and weaknesses impact all who build on it."
Since then, the cloud service has attracted 47 open-source projects and has uncovered more than 1,000 bugs (264 of which are potential security vulnerabilities) while processing 10 trillion test inputs per day.
Google now wishes to attract more OSS projects to the initiative, and is offering a reward to do so. "We believe that user and internet security as a whole can benefit greatly if more open source projects include fuzzing in their development process," the company announced in a blog post yesterday. "To this end, we'd like to encourage more projects to participate and adopt the ideal integration guidelines that we've established."
Google is expanding its Patch Rewards program to include rewards for the integration of fuzz targets into OSS-Fuzz. It will pay projects $1,000 for the initial integration, and up to $20,000 (at its own discretion) for what it describes as an 'ideal integration'.
The $20,000 is broken into four chunks of up to $5,000 each. The first requires checking the fuzz targets into their upstream repository and integrating into the build system with sanitizer support.
The second $5,000 comes if the targets are efficient and provide more than 80% code coverage. The third part of the 'ideal' integration requires regression testing; that is the targets be maintained, run against old known crashers and the periodically updated corpora.
Google calls the final $5,000 a 'l33t' bonus, "that we may reward at our discretion for projects that we feel have gone the extra mile or done something really awesome."
The Patch Reward Program Rules have been expanded to include 'projects integrated into OSS-Fuzz'. Interested parties are invited to apply for OSS-Fuzz integration and subsequent awards via the adapted Patch Submission Form.
Fuze Collaboration Platform Allowed Anyone to Download Recorded Meetings
2.5.2017 securityweek IT
As globalization and mobility both advance, organizations are turning to web-based unified communications systems as a means of improving collaboration and reducing costs. Fuze is one such service. It offers voice (with conferencing), video (with conferencing) and messaging, all from anywhere at any time and any device.
The security of web-based third-party service providers is a major concern for business, where security audits are difficult and expensive. It often comes down to reputation: if other major businesses are using a particular service, it must be good.
Fuze has a number of major clients, including Associated Press, USAuto Sales and ThoughtWorks. But reputation does not equal security, as Rapid7 researcher Samuel Huckins discovered in February 2017 and disclosed today. Huckins discovered 'improper access control' of Fuze meetings.
More specifically, he notes, "Meetings recorded on the Fuze collaboration platform did not have sufficient controls to ensure that the recordings were kept private (CWE-284)." Recorded Fuze meetings are saved to the cloud hosting service, from where they could be accessed via an URL with the format /browser.fuzemeeting.com/?replayID=7digitnum.
'7digitnum' is a seven-digit number that increments over time. The problem, according to Rapid7, is that the 7 digit number is insufficient to resist brute-forcing. Specific meeting recordings could be downloaded by third-parties simply by guessing a replay ID reasonably close to the target and iterating through possible 7-digit numbers. The format also allows a third-party to use a search engine to find available recordings.
The threat is clear. Meetings are used to discuss plans, share and collaborate on intellectual property, and generally conduct international business. The potential is for sensitive data to fall into the wrong hands.
Rapid7 reported the issue to Fuze on Monday, February 27, 2017. Two days later, March 1, 2017, Fuze disabled public access via the earlier URL format. In a statement, it commented, "Security is a top priority for Fuze and we appreciate Rapid7 identifying this issue and bringing it to our attention. When we were informed by the Rapid7 team of the issue, we took immediate action and have resolved the problem."
"As of Mar 10, 2017," reports Rapid7, "all meeting recordings now appear to require password authentication in order to be viewed from Fuze's cloud-hosted web application via direct browsing or from the Fuze desktop and mobile clients. This authentication control is configurable by the user via the client applications as of version 4.3.1 (released on Mar 10, 2017). Fuze users are encouraged to update their Fuze client applications in order to take advantage of new access controls."
It was a silly security issue easily solved -- but one that could have had serious consequences for Fuze's clients. It highlights the need for all cloud usage to be signed off by an organization's security team rather than simply rubber-stamped by the IT department. A security professional might have seen at the outset that URL-based access control is simply not good enough -- but similarly, Fuze should never have designed its system like that in the first place.
Turkey Blocks Access to Wikipedia Over 'Terror' Claims
30.4.2017 securityweek IT
Turkey on Saturday blocked all access inside the country to the online encyclopedia Wikipedia reportedly for articles claiming links between Ankara and terror groups, the latest restriction on a popular website to hit Turkish users.
Turkey's Information and Communication Technologies Authority (BTK) said it had implemented the ban against Wikipedia.org, without making clear the reason for the move. Turkish state media said the ban was imposed because Wikipedia had failed to remove content promoting terror and accusing Turkey of cooperation with various terror groups.
There was no indication as to when the ban might be removed, with a formal court order expected to follow in the coming days.
Reacting to the ban, Wikipedia's founder Jimmy Wales wrote on Twitter: "Access to information is a fundamental human right. Turkish people, I will always stand with you to fight for this right."
A block affecting all language editions of the website in Turkey was detected from 0500 GMT after an administrative order by the Turkish authorities, according to the Turkey Blocks monitoring group, which follows internet restrictions in the country.
Residents in Istanbul were unable to access any pages of Wikipedia on Saturday morning without using a Virtual Private Network (VPN), AFP correspondents said.
"The loss of availability is consistent with internet filters used to censor content in the country," Turkey Blocks said.
'Law No. 5651'
The BTK confirmed the ban in a statement but gave no details.
"After technical analysis and legal consideration based on the Law No. 5651, an administrative measure has been taken for this website Wikipedia.org," it said.
Law 5651, passed in 2014 by parliament, bolstered the BTK's control over the internet and was seen at the time by freedom of expression activists as an erosion of online liberties.
The incident quickly spawned its own separate Wikipedia entry -- "Wikipedia blocked in Turkey".
Quoting Turkey's transport and communications ministry, the state-run Anadolu news agency said the ban was imposed because Wikipedia had failed to take down content purporting to show Turkey "on the same level as and cooperating with" terror groups.
It said Turkey had kept in contact with Wikipedia but the site had failed to remove the content in question.
Should the content be removed, the order would be lifted and access restored, it said.
No further details were given but Turkey has long taken a hard line against what it calls "terror propaganda" in favour of the outlawed Kurdistan Workers' Party (PKK).
Critics of Turkey, including Kurdish militants, have accused Ankara of occasionally collaborating with jihadists in Syria, a claim fiercely rejected by the government.
'Temporary security measures'
Turkey has become notorious over the last years for temporarily blocking access to popular sites, including Facebook and Twitter, in the wake of major events such as mass protests or terror attacks.
In March 2014, YouTube was banned for several months in Turkey after the site was used to broadcast purported footage of a security meeting on Syria.
In the summer of 2013, severe restrictions were imposed on social media during huge protests against President Recep Tayyip Erdogan, who was prime minister at the time.
Savvy internet users frequently resort to the use of VPNs to get around these bans, though there have been reports that the use of VPNs has also started to be blocked.
The government says such measures are always temporary and needed for national security but critics see them as another restriction on civil liberties under Erdogan.
In November 2016, Turkey imposed restrictions lasting several hours on the messaging service WhatsApp as well as on Twitter, Facebook, YouTube and other sites following the controversial arrests of pro-Kurdish MPs.
Prime Minister Binali Yildirim acknowledged at the time that "from time to time for security reasons we can use such measures.... These are temporary measures. Once the danger is passed, everything returns to normal."
Amid uproar on social media over the latest ban, there was also speculation the decision may also have been prompted by deeply unflattering updates to Erdogan's Wikipedia profile after he won the April 16 referendum on enhancing his powers.
The government insists that the new presidential system -- largely due to come into force in 2019 -- will improve efficiency, but critics fear it will lead to one-man rule.
Save the Internet: FCC Unveils Plan to Rollback Net-Neutrality Rules
27.4.2017 thehackernews IT
After crushing a set of privacy rules on ISPs that restrict them from sharing your online data with third parties without your consent, President Donald Trump's newly appointed FCC chairman Ajit Pai has announced the first move in its efforts to kill off Net Neutrality.
The US Federal Communications Commission (FCC) has announced that it will roll back net neutrality rules that require Internet service providers (ISPs) to treat all services and websites on the Internet equally.
Before moving forward, let’s first understand What does Net Neutrality mean?
What is Net Neutrality And Why It's Important?
Net Neutrality is simply the Internet Freedom — Free, Fast and Open Internet for all.
Net Neutrality is the principle that ISPs should give consumers access to all and every contents and application on an equal basis, treating all Internet traffic equally.
Today, if there is something that makes everyone across the world ‘Equal,’ it’s the Internet.
Equality over the Internet means, all ISPs have to treat Facebook or Google in the same way as your local shop website, and the richest man in the world has the same rights to access the Internet as the poorer.
And this is what "Net Neutrality" aims at.
FCC Unveils Plans to Kill Net Neutrality
But, What if someone snatches this Internet Freedom from you all? What if you have to pay ISPs extra for loading your website faster? What if you can't access your favorite website, which has been blocked by your ISP?
The FCC's new Chairman Pai is planning to do exactly same in the United States.
In a 400 page document released Wednesday, the FCC detailed its new plan which, if passed, would allow ISPs to give or sell access to "fast lanes" and block web traffic to others.
In other words, the new plan will allow ISPs to block access to legal content, restrain connections for users attempting to access certain sites or services and to be paid for prioritizing some lawful web traffic over other lawful web traffic.
This simply means if for example, you love watching movies and TV series on Netflix, Comcast and Verizon, which have their video services, will slow down the connections to its competing service when you try to access it, and you would eventually end up watching videos at the services they want you to use.
Here’s What FCC Chairman Excused About Reversing Net Neutrality Rules:
"We need rules that focus on growth and infrastructure investment, rules that expand high-speed Internet access everywhere. Rules that give Americans a more online choice, faster speeds, and more innovation," Pai said.
Pai argued that the 2015 regulations in the Obama administration had discouraged ISPs from investing in their networks, as well as slowed the expansion of internet access.
Also, ISPs are much more likely to strike valuable deals with large, established websites and services than relatively unknown companies or startups, which will be hit hardest by this new move.
"Without net neutrality, the incumbents who provide access to the Internet would be able to pick winners or losers in the market," reads a letter sent to Pai by a group of 800 startups.
"They could impede traffic from our services in order to favor their own services or established competitors. Or they could impose new tolls on us, inhibiting consumer choice. Those actions directly impede an entrepreneur’s ability to ‘start a business, immediately reach a worldwide customer base, and disrupt an entire industry."
Meanwhile, with no surprise, ISPs including Comcast, Verizon, and AT&T have welcomed the new plans.
The FCC will vote on the rollback of the FCC's 2015 regulations on May 18 and proposed rule change, but Mr. Pai has not revealed what he wants to replace the net neutrality rules with.
Once approved, the proposal will remove any legal power the FCC currently has to regulate ISPs, returning everything to the state it was before 2015.
Pai, who has openly expressed his views against net neutrality in the past, was previously quoted as saying that Net Neutrality was "a mistake" during a speech at Mobile World Congress.
The non-profit foundation Electronic Frontier Foundation (EFF) is encouraging people to take action before it gets too late and "tell Congress to stop the FCC from throwing Internet users and innovators to the wolves."
It's Official: McAfee Breaks Away from Intel With New Logo
4.4.2017 securityweek IT
McAfee Spins Out from Intel as a New Independent Company With Refreshed Logo
McAfee, one of the best known and persistent brands in cybersecurity, has re-emerged from Intel as an independent company. It was acquired by Intel for $7.68 billion in 2010. In 2014, Intel announced the McAfee brand would be phased out and replaced by Intel Security, although retaining the red shield logo. In September 2016, Christopher Young, SVP and GM of the Intel Security Group, announced that McAfee would again be an independent company -- 49% owned by Intel and 51% owned by TPG. This transaction values the company at $4.2 billion.
The spin out is now complete, and McAfee is again an independent company. In this incarnation, the name is retained, but the original red shield logo is replaced by a stylized red shield and includes the epithet 'Together is power.' Chris Young is the CEO.
New McAfee LogoThe McAfee brand has proved remarkably resilient over the years. It was one of the earliest security brands, and has survived the disdain of its original developer, the somewhat maverick John McAfee. But it has greater challenges ahead. To really succeed, Chris Young will need to transform an image associated with early, signature-based, legacy anti-virus into something more contemporary.

The original anti-virus companies -- almost all now more than just AV -- were caught napping by the second-generation AV companies, who marketed themselves as machine-learning (ML) endpoint protection firms. The general perception is that machine-learning and artificial intelligence is the way forward, evidenced by another legacy firm, Sophos, buying ML firm Invincea. Young will need to transform public perception of an old brand into something more dynamic and forward thinking.
McAfee's plan is to achieve this by evolution rather than revolution. There are no major new security initiatives announced today, although a raft of new products were announced at the end of 2016. "We will continue to be very focused on our customers. The strategy outlined at our annual security conference, FOCUS 16, will be the same. We are focused on end-to-end solutions and pivoting to the cloud," says the company.
McAfee's vision is to accelerate its existing strategy to drive cybersecurity towards true automation, not just for itself but across the whole industry. Its belief is that it can better focus on this strategy as an independent company.
"Security is the fastest-growing, but also the most fragmented and least profitable of all parts of IT," corporate VP of global products at Intel Security, Brian Dye, told SecurityWeek. "That tells us we're doing something fundamentally wrong." He believes that automation is the solution to weak security, fragmentation, and profitability. "We want to drive a level of automation across the industry and bring that level of automation into our own portfolio -- being standalone lets us focus on that mission wholeheartedly."
He describes McAfee's path as an evolution from integration, "which is what we've done historically with ePolicy Orchestrator's single management pane of glass for the SOC;" to automation, "which is what we are doing with the Data Exchange Layer (DXL);" and ultimately on towards full orchestration, "which will bring together and automate more and more complex and sophisticated workflows."
Key to this evolution is the big data threat intelligence derived from the telemetry of millions of customers on endpoints and corporate servers across the globe driving automation, through machine learning and artificial intelligence, across the DXL fabric. The aim is to move towards full closed loop zero human touch automation wherever possible; and improved human/machine teaming elsewhere.
DXL allows the sharing of actionable threat intelligence not just across the McAfee portfolio, but also between the products of partners in the McAfee Security Innovation Alliance. Dye believes that increasing and improving machine learning will allow full automation across the whole SOC; and that DXL will provide the backbone of that automation.
But he sees this as not merely a vision but a necessity for the future. "The only way we will be able to adapt to the changes that are happening, from the cloud to edge computing and the IoT, is if we automate the security tasks across the industry," he told SecurityWeek. "We have to do that to free up the people and bandwidth to allow the implementation of these changes and new technologies. When new technologies arrive, you simply plug them into the DXL fabric. Change becomes an accelerator not an inhibitor; and it is our belief is that this is required for industry to be successful."
Through DXL and threat intelligence, he said, "we can drive the rebirth of one of cybersecurity's best known brands."
New "USB Canary" Keeps Close Watch on USB Ports
3.4.2017 securityweek IT
New "USB Canary" Tool for Linux Monitors USB Ports 24/7
A new open source tool can provide Linux users with the ability to receive an alert any time someone attempts to plug a device into one of their machine’s USB ports.
Dubbed USB Canary, the tool uses pyudev to monitor USB devices and can be set to do so either at all times or only when the computer is locked. More importantly, the tool can be configured to alert users when someone is tampering with their USB ports. It can either send an SMS via the Twilio API, or send a Slack notification via an inbuilt Slack bot.
Released in open source not long ago, the tool aims at overcoming some of the shortcomings of other monitoring tools that inform the user on USB port-related incidents only after login. USB Canary aims at keeping an eye on systems at all times when they are unattended.
According to the researcher, who goes by the online handle errbufferoverfl, although the tool is available only for Linux at the moment, Windows and macOS versions are also planned (but no specific details on them have been revealed so far).
Written in Python, the author explains that the tool was initially created as a personal utility while he was between jobs and that the use of third-party libraries.
Users can configure the tool to detect the type of screensaver running on the computer (it can detect XScreenSaver and gnome-screensaver, but can be used with unsupported screensavers as well), to turn a “paranoid” mode on, and set the notifications to arrive either via Twilio or Slack.
“Paranoid mode is also suitable for people who want to monitor if their servers have had USB's plugged into them, although I haven't tested them on Linode, Amazon Web Services, or Digital Ocean it is suitable for those with physical servers that may need this sort of monitoring,” the researcher notes.
Although this was a personal project in the beginning, others already picked it up and helped improving it through their contributions.
The open source tool is available via GitHub.
Microsoft is Shutting Down CodePlex, Asks Devs To Move To GitHub
3.4.2017 thehackernews IT
Microsoft has announced to shut down CodePlex -- its website for hosting repositories of open-source software projects -- on December 15, 2017.
Launched in 2006, CodePlex was one of the Microsoft's biggest steps towards the world of open source community -- where any programmer, anywhere can share the code for their software or download and tweak the code to their liking.
However, Microsoft says that the service has dramatically fallen in usage and that fewer than 350 projects seeing a source code commit over the last 30 days, pointing to GitHub as the "de-facto place for open source sharing."
GitHub – 'Facebook for Programmers'
In a blog post published Friday, Microsoft Corporate VP Brian Harry wrote that the shutdown of CodePlex is because the open source community has almost entirely moved over to GitHub, which provides similar functionality for sharing code that people can collaborate on.
"Over the years, we have seen a lot of amazing options come and go but at this point, GitHub is the de-facto place for open source sharing, and most open source projects have migrated there," says Harry.
According to the company, Github has become the "Facebook for programmers," so "it's time to say goodbye to CodePlex."
For now, Microsoft has disabled the ability to create new projects on CodePlex, and in October the site will be turned into a read-only archive.
The complete shutdown comes on December 15 this year, at which point the CodePlex website will be archived indefinitely.
"You will also be able to download an archive file with your project contents, all in common, transferable formats like Markdown and JSON," Harry writes.
"Where possible, we will put in place redirects so that existing URLs work, or at least redirect you to the project's new homepage on the archive. And, the archive will respect your "I've moved" setting, if you used it, to direct users to the current home of your project."
Migrate your Code and Related Projects to GitHub
Harry also points out that many of Microsoft's open source software projects have already found their way to GitHub and the company is actively recommending people to do so.
The company is itself using GitHub to host open-source software projects such as PowerShell, .NET and its Chakra JavaScript engine.
Microsoft is making the process of migration easier for its users. Microsoft has teamed up with GitHub to create a "streamlined" migration tool to help developers shift their code and related content over to GitHub.
Since a release date of the migration tool is not yet known, users can check out the guide on CodePlex for any help with migrating to GitHub.
JobLink Breach Affects Job Seekers in 10 States
27.3.2017 Securityweek IT
America’s JobLink (AJL), a multi-state online service that connects job seekers with employers, informed users last week that a malicious hacker breached the company’s systems.
The attacker exploited a vulnerability in the JobLink application to gain access to job seekers’ personal information, including names, dates of birth and social security numbers (SSNs). According to AJL, the attacker created an account on the platform and exploited a “misconfiguration” to access information on other users.
Law enforcement has been notified and a forensics firm has been called in to determine the cause and impact of the incident. AJL said the attacker created an account on the application on February 20, and the first signs of suspicious activity were noticed on March 12. The vulnerability, apparently introduced in October 2016, was patched on March 14.
AJL pointed out that the attack did not involve any type of malware, and it did not affect the company’s ReportLink or CertLink products.
The investigation showed that the attacker accessed information on users in Alabama, Arkansas, Arizona, Delaware, Idaho, Illinois, Kansas, Maine, Oklahoma and Vermont. These states use the JobLink service to coordinate federal unemployment and workforce development programs.
Individuals who created accounts before March 14 could be affected, and AJL has promised to send out email notifications to individuals whose accounts have been breached within 5-10 business days. Affected users may also be eligible for credit monitoring services.
An investigation has also been launched by the Department of Labor in the affected states, and each state has published information about the breach on its official website. More than 250,000 users could be affected in Delaware, 170,000 accounts may have been compromised in Idaho, while Vermont said the breach could impact up to 180,000 accounts.
StateScoop reported that more than 280,000 accounts are affected in Maine, and the breach could impact as many as 4.8 million accounts across the ten states.
At least one law firm is urging affected job seekers to step forward, which indicates that AJL is facing a lawsuit.
Sony Is Working On Mobile-to-Mobile Wireless Charging Technology
17.3.2017 thehackernews IT
So you are in a party with your friends, and your phone is running low on battery. Oops!
The ideal solution is to charge your phone using a charger or a power bank, but not everyone carries power banks or chargers with them all the time, especially in a party.
What if you can charge your phone wirelessly using another phone when it runs out of battery?
Isn't that great? Well, thanks to Sony, you might soon be able to use your friends’ phones to charge your own device.
According to a recently published patent application, Sony is working on a new futuristic technique that enables wireless power exchange between various nearby consumer electronic devices, including smartphones, computers, microwave, washing machine, fridges, and TVs, without cords.
Wireless charging isn't a new concept at all, but this is the first time when the Near Field Communications (NFC) technology is being used for power transfer wirelessly between two devices, that too over considerable distances.
NFC is a technology that allows data transfer over a short-range, which is why two devices have to be placed nearby, under a certain distance, for the given wireless technology to work.
Titled "Configuration of Data and Power Transfer in Near Field Communications," the patent describes where any consumer electronic with NFC chip might be able to search for other devices with the similar technology and connect with them to transfer power, the same way a device searches for available Wi-Fi hotspots.
However, the patent doesn’t detail how well this technology would actually work and has no word over the distance for which this technology might work between two devices.
"The distances over which the wireless communication can be achieved is typically consistent with distances used for wireless electrical power transfer through the power transfer antenna," Sony's patent document reads.
The patent also does not specify that these devices would necessarily be smartphones or computers; instead, it uses the term "portable consumer electronic device," which could be a fridge, TV, computer, microwave, washing machine, and so on.
This technology could eliminate one of your worst pains of always carrying out bulky power banks and multiple charging cables, provided your friends or smart appliances are willing to share their battery power to charge your phone.
However, patenting an idea does not necessarily mean we will ever see the idea come to life, but if succeeded, your phone will automatically start charging while you walk into a room – Thanks to Smart TVs, microwaves and other devices with NFC-enabled.
CA Technologies to Acquire Veracode for $614 Million
7.3.2017 securityweek IT
Enterprise software firm CA Technologies (NASDAQ:CA) announced on Monday that it has signed a definitive agreement to acquire Veracode, a provider application security testing solutions, for roughly $614 in cash.
Burlington, Mass.-based Veracode offers a cloud-based application security testing service that helps companies secure web, mobile and third-party applications. Veracode’s platform offers centralized policies and KPIs which to help reduce risk and measure progress across business units and development teams, including third-party suppliers, outsourcers and open source developers.
Veracode Logo
The company has raised more than $134 million in funding, including a $40 million investment in late 2014.
“The combination of CA’s portfolio with privately-held Veracode will establish CA Technologies as a leader in the Secure DevOps market through the automation and scaling of application security testing (AST) to develop and deploy applications faster with fewer defects,” CA said in an announcement. “With Veracode, CA Technologies bridges its Security business with its broad DevOps portfolio and adds to its growing SaaS business.”
"This acquisition will unify CA’s Security and DevOps portfolios with a SaaS- based platform that seamlessly integrates security into the software development process. Looking holistically at our portfolio, now with Veracode and Automic, we have accelerated the growth profile of our broad set of solutions.”
“We provide over 1400 small and large enterprise customers the security they need to confidently innovate with the web and mobile applications they build, buy and assemble, as well as the components they integrate into their environments,” said Bob Brennan, CEO of Veracode. “By joining forces with CA Technologies, we will continue to better address growing security concerns, and enable them to accelerate delivery of secure software applications that can create new business value.”
The transaction is expected to close in the first quarter of fiscal year 2018.
Founded in 2006, Veracode has offices in Burlington, MA and London and has more than 500 employees globally.
The application security space has been hot, and the acquisition of Veracode follows other notable acquisitions in the space. In November 2016, Synopsys, a company that provides tools and services for designing chips and electronic systems, announced that it would acquire Cigital, a provider of software security testing solutions, along with Cigital spin-off Codiscope, which also provides security tools. Coverity, another application security provider, was also acquired by Synopsys for approximately $375 million in February 2014, while Cenzic was acquired by Trustwave in March 2014 for an undisclosed sum. Fortify, a pioneer in the software security space, was acquired by HP in 2010.
Next Windows 10 Release Brings Improved Control of Updates, Privacy
3.3.2017 securityweek IT
Windows 10 Creators Update, the platform iteration expected to arrive next month, will provide users with improved control over software updates and privacy settings, Microsoft says.
Following the upcoming changes, updates will be less likely to be installed at an inopportune time and downloads will have a lower impact on user experience in Creators Update, courtesy of an enhanced update deployment experience. Furthermore, users will benefit from new privacy and diagnostic data collection settings, while also getting increased control over such settings through the web-based privacy dashboard the company launched in January.
In a blog post, John Cable, Director of Program Management within the Windows Servicing and Delivery (WSD) team, says that the upcoming improvements are based on the feedback Microsoft received from users via channels such as the Feedback Hub application, social media, and Windows forums.
One of the most important changes will impact the manner in which updates are installed, something that users can’t control at all at the moment. Right now, Windows 10 doesn’t provide options that users can tailor in line with their needs, while also impacting their experience with unexpected reboots that could also prove disruptive if they happen at the wrong time.
Windows 10 Creators Update, however, should change that by delivering several options for scheduling the timing of when updates install. Thus, users can specify exactly when an update should occur, can even reschedule an update when needed, and can even “snooze” the update notification to postpone the moment when they have to deal with it. According to Cable, users will be able to use the “snooze” capability to pause the update process for three days.
The “Active Hours” schedule will also be updated, so that Windows won’t end up installing an update at times when the user would actually want the device to be ready to use. The same as before, however, users will also be able to restart the device to immediately install the update.
“As always, we believe in the value of keeping devices ‘up to date,’ and recommend that you choose the installation defaults that Windows 10 provides so you will always have the latest features, apps, and security updates. However, when you need more control over the update experience, you will have new choices,” Cable notes.
He also explains that additional control over the update process will be available when clicking on a new icon on the Windows Update Settings page, which will allow users to verify whether their device is up to date or not. The new update experience, Cable says, has been available for users in the Windows Insider program for some time and has received positive reactions so far.
Before existing computers will be updated to Windows 10 Creators Update, users will be asked if they want to review their privacy settings, Cable says. Screenshots detailing the process have been published via a “quest” in the Feedback Hub application. “This feedback will help us iterate on this experience as we get closer to shipping the Creators Update,” Cable says.
Users who choose to review their privacy settings will access options related to location, speech recognition, diagnostics, and ads. They can also choose whether Microsoft should use diagnostics data to make recommendations regarding Microsoft products and services. A “Learn more” button will allow users to access additional information on these options, on how Windows Defender SmartScreen works, and on the related data transfers and uses.
Last year, Microsoft had to bring clarifications regarding its collection of user data, especially with France serving the software giant a notice to stop collecting excessive data or tracking browsing without consent from users.
The upcoming Windows 10 Creators Update is also expected to provide users with new options to improve their overall security. One of these options should block the installation of applications that are not distributed via the Microsoft Store. Essentially, it would block Win32 applications from being installed, thus preventing malware from infecting Windows 10 machines.
Trump's New FCC Chairman Lets ISPs Sell Your Private Data Without Your Consent
3.3.2017 thehahckernews IT
Bad News for privacy concerned people!
It will be once again easier for Internet Service Providers (ISPs) to sell your personal data for marketing or advertisement purposes without taking your permission.
Last October, the United States Federal Communications Commission (FCC) passed a set of privacy rules on ISPs that restrict them from sharing your online data with third parties without your consent and require them to adopt "reasonable measures" to protect consumers' data from hackers.
However, now the FCC suspended privacy rules before they came into effect.
The reason? President Donald Trump's newly appointed FCC chairman Ajit Pai, a Republican and ex-Verizon lawyer.
Ajit Pai, who has openly expressed his views against net neutrality in the past, just last week said during a speech at Mobile World Congress that Net Neutrality was "a mistake" and indicated that the Commission is now moving back to internet regulations.
Now, Pai suspends privacy rules on ISPs, arguing that they favored companies like Google and Facebook, which are regulated by the Federal Trade Commission (FTC), over internet providers like Comcast and Verizon.
Pai wants the FCC, and the Federal Trade Commission should treat all online entities the same way. So those new privacy policies should be scrapped.
"All actors in the online space should be subject to the same rules, and the federal government shouldn’t favor one set of companies over another," FCC said in a statement.
"Therefore, he has advocated returning to a technology-neutral privacy framework for the online world and harmonizing the FCC’s privacy rules for broadband providers with the FTC’s standards for others in the digital economy."
The FCC will now likely pass a new set of standards in the way the FTC regulates websites. It's like, if the FTC requires sites like Facebook and Google to seek explicit permission before selling your data, the FCC may follow suit for ISPs.
In other words, the FCC will keep a hold on new privacy rules. Since FTC would never hurt advertising business model of Google and Facebook, FCC would never restore those suspended rules on ISPs.
How does this Move Affect You?
If you are unaware, your internet service provider knows your most intimate and personal online activities.
Unlike Google which uses encryption to prevent anyone from seeing your online searches, your ISP can see your search queries, what websites you visit, when you visit them, and what apps you use.
The ISPs then share this data with other companies for advertisements, marketing or other purposes. And with this information in hands, it's very easy for any advertising company to know users' interests based on their online behaviors and serve them targeted ads.
Not surprisingly, the broadband industry applauded the FCC's new move, calling it "a welcome recognition that consumers benefit most when privacy protections are consistently applied throughout the Internet ecosystem."
But privacy advocates are not at all happy with the FCC's action, arguing that suspending the privacy rules favor the Internet providers like Comcast and Verizon since the ISPs do not need the same data security rules the FTC requires of websites.
Gmail accounts lockout the users. Glitch or hack, it’s a mystery
25.2.2017 securityaffairs IT
A huge number of Gmail accounts lockout their users and forced them to log in again. What has happened? Is it the result of a massive cyber attack?
A huge number of Gmail accounts lockout the users, the strange behavior leads the experts into believing that something has happened. Is it a computer glitch or a hack?

Rumors of a cyber attack are circulating online, on Reddit many users shared a description of their strange experience. Gmail users are receiving messages informing them that their account has been changed, and asking them to re-sign into Gmail accounts on their mobile.
Google replied to one of the thread on one of its official forums by confirming that an investigation is ongoing, but at the same time, the company is downplaying concerns.
In response to a thread on one of its official forums, Google said it was investigating the issue while downplaying concerns confirming that there is no indication the accounts have been hacked.
“We’ve gotten reports about some users being signed out of their accounts, unexpectedly. We’re investigating, but not to worry: there is no indication that this is connected to any phishing or account security threats. Please try to sign-in again at accounts.google.com and if you cannot remember your password, please use this link (g.co/recover) to recover your password.” reads the Google’s response.
Follow
Google ✔ @Google
We know some of you had issues signing in today. Please try again now. Rest easy -- your account's security was not affected.
6:09 AM - 24 Feb 2017
970 970 Retweets 2,009 2,009 likes
Hackread.com cited Crystal Cee from Google’s Product Forum, confirming that Google users need to sign in again to access their accounts using this address “accounts.google.com.”
Cee explained that if users have forgotten the password then they have to use this link “g.co/Recover” to recover it. Cee also added that users with 2-step verification can experience a delay in SMS code reception.
We can only wait for further information shared by the IT giant.
Yahoo Slashes Price of Verizon Deal $350 Million After Data Breaches
22.2.2017 securityweek IT
NEW YORK - Yahoo slashed the price of the sale of its core Internet business to Verizon by $350 million following a pair of major data breaches at Yahoo, the two companies announced Tuesday.
Under the revised terms of the deal, Verizon's purchase the Yahoo assets will now total $4.48 billion. Yahoo still faces probes and lawsuits related to the breaches, which affected more than 1.5 billion accounts.
The transaction had been delayed due to the hacks.
Yahoo announced in September that hackers in 2014 stole personal data from more than 500 million of its user accounts. It admitted another cyber attack in December, this one dating from 2013, affecting more than a billion users.
Under the terms of the revised agreement, Yahoo will continue to cover the cost of a Securities and Exchange Commission probe into the breaches and shareholder lawsuits.
However, other government investigations and third-party litigation related to the breaches will be shared by Verizon and Yahoo.
"We have always believed this acquisition makes strategic sense," said Verizon executive vice president Marni Walden.
"We look forward to moving ahead expeditiously so that we can quickly welcome Yahoo's tremendous talent and assets into our expanding portfolio in the digital advertising space."
Prices of Yahoo shares rose 0.3 percent to $45.24, while Verizon gained 0.4 percent to $49.39.
Search engine companies will ban links published by major torrent hubs
13.2.2017 securityaffairs IT
Starting from June 1st search engine companies will block queries to links to pirated content, including films, TV shows, and copyright-protected content.
It will be even more difficult to search for torrents of ExtraTorrent, KickassTorrents, The Pirate Bay and equivalent services.
In the past copyright holders accused the search engine companies of doing too little to ban infringing links.

There have even been rumors that the new legislation could force search engine companies adopting drastic measures on tackling piracy.
Starting from June 1st, the major search engine will block any queries searching for specific pirated torrent files.
It will be not possible to find links to pirated content, including films, games, TV shows, music and copyright-protected content. The search engine companies have joined the efforts in the fight against online piracy.
The UK’s Intellectual Property Office is working with search engine companies and entertainment firms to reach an agreement to adopt a series of measured to tackle the piracy.
“Google and other search companies are close to striking a voluntary agreement with entertainment companies to tackle the appearance of infringing content links in search results.” reads a blog post published by TorrentFreak. “Following roundtable discussions chaired by the UK’s Intellectual Property Office, all parties have agreed that the code should take effect by June 1, 2017.”
The UK government has played a crucial role in reaching an agreement between the search engine giants and entertainment firms, it seems that the parties are “extremely close” to sign an agreement.
“The search engines involved in this work have been very co-operative, making changes to their algorithms and processes, but also working bilaterally with creative industry representatives to explore the options for new interventions, and how existing processes might be streamlined,” said the parliamentary Baroness Buscombe.
“I understand that all parties are keen to finalize and sign up to the voluntary agreement, and so we believe there is no need to take a legislative power at this time.”
“All parties have also agreed that the code should take effect, and the targets in it be reached, by 1 June this year,” Baroness added.
It will be very interesting to see how such kind of agreement reached in the UK could be effective overseas.
Israeli Startup Empow Raises $9 Million for U.S. Expansion
11.2.2017 securityweek IT
Israeli startup Empow Cyber Security announced on Thursday that it has raised $9 million in a Series A funding round. $8 million has come from private investors and $1 million from the Office of the Chief Scientist at the Israel Ministry of Economy. The money will be used primarily to expand the company's operations in North America.
Empow currently employs three staff in its Boston, Mass. office, which will be expanded, and a second office opened on the West Coast later in 2017. Both offices are sales and marketing for the U.S. market, with R&D remaining in Ramat Gan, Israel.
Empow provides a platform that unifies separate security defenses in a more efficient and effective manner than unwieldy SIEMs. It uses security abstraction to separate the security infrastructure into primary components it calls 'security particles'. These particles are then linked together using a common language that interacts with the APIs of the different security technologies, enabling the complete security infrastructure be viewed and treated as a single entity rather than a series of individual silos.
Without that cross-technology visibility, individual alerts from different technologies can easily be missed. A possible phishing alert in isolation could be ignored by analysts. A subtle possibility of credential misuse from a different technology could also be missed.
Empow concentrates on 'intent'. If it spots a phishing possibility in the email alerts, it knows what to look for in the network alerts; and ties the phishing and credential misuse into a threat warning for the analyst.
As new attack methodologies emerge, empow can be 'taught' to recognize the different indications in the different technologies of the customer's infrastructure. empow itself is vendor-neutral, so the infrastructure itself does not need to change -- empow's purpose is to make any infrastructure more efficient. This means it can work with any existing infrastructure, whether that is on-premise or in the cloud.
While customers can develop their own 'apps' to detect, investigate and mitigate new attack methodologies, empow also provides an app store for emerging and common issues. These currently include cross-technology indicators for threats such as ransomware, spear-phishing, privilege escalation and financial data leaks.
Avi Chesla, co-founder and CEO, explains, "Empow creates an enterprise security posture that is as robust and nimble as the attacks it aims to prevent. Our security abstraction is creating a radical change in the realm of cybersecurity, making cyber-defenses exponentially better than the sum of their parts. It's like a cyber general coordinating your security army: empow helps sends the right troops into battle at the right time."
U.S. Queries PayPal in Money Laundering Probe
9.2.2017 securityweek IT
San Francisco - US authorities have demanded information from online payment service PayPal as part of a money laundering investigation, according to a regulatory filing available on Wednesday.
"We have received subpoenas from the US Department of Justice seeking the production of certain information related to our historical anti-money laundering program," Silicon Valley-based PayPal said in an annual report to the US Securities and Exchange Commission.
PayPal noted that it was cooperating with authorities and did not speculate on the outcome of the investigation. No further details were provided.
The news appeared to weigh slightly on PayPal shares, which were down more than 1.5 percent to $40.24 in after-market trades on the Nasdaq.
Rapid7 Adds Hardware Testing Capabilities to Metasploit
2.2.2017 securityweeks IT
Rapid7 has added a hardware bridge to its Metasploit penetration testing framework, making it easier for users to analyze Internet of Things (IoT) devices. The company said this enhancement makes Metasploit the first general purpose pentesting tool.
Metasploit has allowed researchers to conduct security assessments using Ethernet communications, but now they will also be able to link the tool directly to the hardware via raw wireless and direct hardware manipulation.
Up until now, the framework could be used for hardware testing by creating custom tools for interaction with the targeted product, which Rapid7 says is a time-consuming and resource-intensive process. The new capability allows users to focus on a more important task: developing exploits.Metasploit with hardware bridge
The first release of the hardware bridge focuses on automotive systems, particularly the Controller Area Network (CAN) bus, but the company plans on adding modules for other types of systems in the upcoming period.
According to Rapid7, pentesters can now use Metasploit to analyze industrial control systems (ICS), IoT hardware and software, and software defined radio (SDR). The company believes the new capability makes Metasploit an ideal tool for conducting hardware-based network research.
“Every wave of connected devices – regardless of whether you’re talking about cars or refrigerators – blurs the line between hardware and software. As we like to say, this hardware bridge lets you exit the Matrix and directly affect real, physical things,” said Craig Smith, director of transportation research at Rapid7 and developer of the new capability. “We’re working to give security professionals the resources they need to test and ensure the safety of their products -- no matter what side of the virtual divide they’re on.”
Metasploit already has more than 1,600 exploits and 3,300 modules, and new components are being developed regularly with the aid of hundreds of contributors. According to the Metasploit Project, 190 people made contributions to the framework last year.
Cisco Buys App Performance Tuning Startup for $3.7 Billion
25.1.2017 Securityweek IT
San Francisco - Cisco Systems on Tuesday announced a $3.7 billion deal to buy a startup specializing in improving the performance of applications, continuing to expand beyond computer networking hardware.
The acquisition of AppDynamics came as the San Francisco-based startup was on the cusp of going public with an initial offering of stock.
AppDynamics software enables businesses to monitor performance of applications and figure out ways to avoid problems and get them to run more smoothly.
"Applications have become the lifeblood of a company's success," Cisco internet of things and business group general manager Rowan Trollope said in a release.
"The combination of Cisco and AppDynamics will allow us to provide end to end visibility and intelligence from the network through to the application."
Consumers are increasingly using applications, typically on mobile devices, to interact with businesses.
"As companies across industries are expanding their digital infrastructure, IT departments are faced with vast amounts of complex, siloed data," Cisco corporate business development vice president Rob Salvagno said in a blog post.
"AppDynamics helps many of the world's largest enterprises translate this data into business insights."
The deal was expected to close by the end of September.
Cisco last year announced it was trimming its global workforce by seven percent as it shifts its focus from networking hardware to software and services.
The plan to eliminate 5,500 positions came as part of a corporate restructuring aimed at reducing expenses in "lower growth areas" and investing in Cisco priorities such as security, cloud computing, data centers, and the internet of things, executives said at the time.
Faced with a slowdown in its traditional products such as routers for telecom networks, Cisco has been trying for several years to reorient to fast growing sectors.
The company also seeks to increase revenue from ongoing subscriptions for services or software, as compared to sales of equipment.
Cisco built its fortune on hardware for private data centers, but businesses are increasingly turning to "super-clouds" such as Amazon Web Services and Microsoft Azure which rent processing muscle as needed.
Switches and routers remain a big chunk of Cisco's business.
Northern California-based Cisco has had waves of job cuts from 2011 through 2014, eliminating a total of more than 17,000 positions.
Sale of Core Yahoo Assets to Verizon Delayed
24.1.2017 Securityweek IT
Yahoo Sale to Verizon Delayed
San Francisco - Yahoo said Monday its $4.8 billion deal to sell its core internet assets to US telecom titan Verizon has been delayed several months.
The closing originally set for this quarter has been pushed into next quarter due to "work required to meet closing conditions," the California online pioneer said in a statement, adding that it was "working expeditiously to close the transaction as soon as practicable."
The news came in an earnings release showing Yahoo swung to a profit of $162 million in the final three months of last year.
The deal with Verizon, which would end Yahoo's run of more than 20 years as an independent company, has been thrown into doubt following disclosures of two huge data breaches.
Yahoo said Monday it is hustling to ramp up security as it grapples with the aftermath of epic hacks.
"Our top priority continues to be enhancing security for our users," Yahoo chief executive Marissa Mayer said.
She added that "approximately 90 percent of our daily active users have already taken or do not need to take remedial action to protect their accounts, and we're aggressively continuing to drive this number up."
Yahoo boasted having more than a billion users monthly in 2016, with more than 650 million of those people connecting from mobile devices.
Hack aftershocks
The US Securities and Exchange Commission has opened an investigation into whether Yahoo should have informed investors sooner about two major data breaches, the Wall Street Journal reported Sunday, citing people familiar with the matter.
US law requires companies that fall victim to such hacks disclose them as soon as they are deemed to affect stock prices.
Yahoo announced in September that hackers in 2014 stole personal data from more than 500 million of its user accounts. It admitted another cyber attack in December, this one dating from 2013, affecting over a billion users.
The SEC's investigation is focusing on why it took Yahoo several years to reveal the 2013 and 2014 attacks.
The data breaches have been a major embarrassment for a former internet star that has failed to keep up with Google, Facebook and other rising stars.
The cyber attacks, and how notifying users was handled, has also raised concerns by investors that Verizon may seek to pay a lower price for Yahoo or even back out of the deal.
The earnings report showed Yahoo swung to profit a year after a massive $4.4 billion loss in the same period a year earlier, resulting from a large writedown on the value of its holdings.
Revenue in the fourth quarter rose to $1.47 billion from $1.27 billion a year earlier.
Yahoo reported a loss of $214 million for the full year on revenue that inched up to $5.2 billion from $5 billion in 2015, according to the earnings report.
Mayer has been driving a shift to mobile, video, social, and native advertising offerings at Yahoo, and revenue in those areas - which she dubbed '"avens," continued to climb.
Mavens revenue for last year slightly topped $2 billion as compared to $1.7 billion in 2015.
"I'm very pleased with our Q4 results and incredibly proud of the team's execution on our 2016 strategic plan, particularly given the uniquely eventful past year for Yahoo," Mayer said.