Apple Articles - H 2020 1 2 iOS Apple List - H 2021 2020 2019 2018 iOS
Apple addresses three actively exploited iOS zero-days
6.11.20 Apple Securityaffairs
Apple released iOS 14.2 that addressed three zero-day vulnerabilities in its mobile OS that have been abused in attacks in the wild.
Apple has addressed three iOS zero-day vulnerabilities actively exploited in attacks the wild and affecting iPhone, iPad, and iPod devices.
The zero-day vulnerabilities have been fixed by the IT giant with the release of iOS 14.2, iOS users are advised to install it immediately.
“Apple is aware of reports that an exploit for this issue exists in the wild,” reads the security advisory.
Apple also fixed the flaws with the release of iPadOS 14.2 and watchOS 5.3.8, 6.2.9, and 7.1. The issues have also been addressed with the release of iOS 12.4.9 for older generation iPhone devices.
“Targeted exploitation in the wild similar to the other recently reported 0days,” said Shane Huntley, Director and Google’s Threat Analysis Group. “Not related to any election targeting.”
The vulnerabilities are related to three recently disclosed vulnerabilities in Chrome (CVE-2020-17087, CVE-2020-16009, CVE-2020-16010) and in the Windows OS (CVE-2020-17087).
According to Google Project Zero team lead Ben Hawkes, the three iOS zero-days are:
CVE-2020-27930 — A memory corruption issue in the iOS FontParser component that was addressed with improved input validation and that lets attackers run code remotely on iOS devices.
CVE-2020-27932 — A type confusion issue in the iOS kernel that was addressed with improved state handling and that lets attackers run malicious code with kernel-level privileges.
CVE-2020-27950 — A memory initialization issue in the iOS kernel that allows attackers to retrieve content from an iOS device’s kernel memory.
Experts pointed out that the three flaws have been chained to fully compromise iPhone devices remotely.
Google has not published technical details about the threat actors that exploited the above issues in their attacks and their targets.
It is not clear if the threat actors have exploited the vulnerabilities in targeted attacks or in large-scale campaigns.
Researchers received $288,500 for 32 out of 55 issues reported to Apple
12.10.20 Apple Securityaffairs
Researchers received hundreds of thousands of dollars in bug bounties for reporting 55 vulnerabilities as part of the Apple bug bounty program.
A team of researchers composed of Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb and Tanner Barnes reported a total of 55 flaws to Apple as part of the company bug bounty program.
The flaws were all covered by Apple’s bug bounty program, 11 vulnerabilities have been rated critical and 29 rated high severity.
Some of the flaws were addressed by Apple a few hours after they have been reported by the researchers.
The researchers already received for these issues 32 payrolls for a total of $288,500, but likely will receive more for the other flaws reported.
The experts published technical details for some of the vulnerabilities they found.
“During our engagement, we found a variety of vulnerabilities in core portions of their infrastructure that would’ve allowed an attacker to fully compromise both customer and employee applications, launch a worm capable of automatically taking over a victim’s iCloud account, retrieve source code for internal Apple projects, fully compromise an industrial control warehouse software used by Apple, and take over the sessions of Apple employees with the capability of accessing management tools and sensitive resources.” reported the experts.
The experts discovered how to fully compromise the Apple Distinguished Educators Program via Authentication and bypass authorization and hot to fully compromise the DELMIA Apriso Application via authentication bypass.
The experts also detailed wormable Stored Cross-Site Scripting vulnerabilities that could allow attackers to steal iCloud data through a modified email and a command injection issue in Author’s ePublisher.
The experts also reported a full response SSRF on iCloud that could allow attackers to retrieve Apple Source Code.
The experts pointed out that many of the flaws could have been exploited by threat actors to gain access to Apple’s internal network and execute arbitrary commands on the company’s web servers.
“Overall, Apple was very responsive to our reports. The turn around for our more critical reports was only four hours between time of submission and time of remediation,” concludes Curry.
“Since no-one really knew much about their bug bounty program, we were pretty much going into unchartered territory with such a large time investment. Apple has had an interesting history working with security researchers, but it appears that their vulnerability disclosure program is a massive step in the right direction to working with hackers in securing assets and allowing those interested to find and report vulnerabilities,”
Wormable Apple iCloud Bug Allows Automatic Photo Theft
11.10.20 Apple Threatpost
Ethical hackers so far have earned nearly $300K in payouts from the Apple bug-bounty program for discovering 55 bugs, 11 of them critical, during a three-month hack.
A group of ethical hackers cracked open Apple’s infrastructure and systems and, over the course of three months, discovered 55 vulnerabilities, a number of which would have given attackers complete control over customer and employee applications.
Of note, a critical, wormable iCloud account takeover bug would allow attackers to automatically steal all of a victim’s documents, photos, videos and more.
The discovery by hackers Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb and Tanner Barnes demonstrated key weaknesses in the company’s “massive” infrastructure while it also earned the team nearly $300,000 to date in rewards for their efforts, Curry wrote in an extensive blog post detailing the team’s findings.
Threatpost Webinar Promo Retail Security
Click to Register!
Among the flaws found in core portions of Apple’s infrastructure includes ones that would have allowed an attacker to: “fully compromise both customer and employee applications; launch a worm capable of automatically taking over a victim’s iCloud account; retrieve source code for internal Apple projects; fully compromise an industrial control warehouse software used by Apple; and take over the sessions of Apple employees with the capability of accessing management tools and sensitive resources,” he wrote.
Of the 55 vulnerabilities discovered, 11 were rated with critical severity, 29 with high severity, 13 with medium severity and two with low severity. Researchers rated the bugs based on the CvSS vulnerability-severity rating, and “our understanding of the business-related impact,” Curry said.
The wormable iCloud bug is a cross-site scripting (XSS) issue, according to the writeup. iCloud is an automatic storage mechanism for photos, videos, documents, and app related data for Apple products. Additionally, this platform provides services like Mail and Find my iPhone.
“The mail service is a full email platform where users can send and receive emails similar to Gmail and Yahoo,” explained Curry. “Additionally, there is a mail app on both iOS and Mac which is installed by default on the products. The mail service is hosted on www.icloud.com alongside all of the other services like file and document storage.”
He added, “This meant, from an attackers perspective, that any cross-site scripting vulnerability would allow an attacker to retrieve whatever information they wanted to from the iCloud service.”
He discovered such a bug after hunting around for a while: “When you had two style tags within the email, the contents of the style tags would be concatenated together into one style tag,” he said. “This meant that if we could get ‘</sty’ into the first tag and ‘le>’ into the second tag, it would be possible to trick the application into thinking our tag was still open when it really wasn’t.”
The team was ultimately able to create a proof of concept that demonstrated code that steals all of the victim’s personal iCloud information (photos, calendar information and documents) then forwards the same exploit to all of their contacts.
Ilia Kolochenko, founder and CEO of web security company ImmuniWeb, said that the success of the bounty-hunters should be a wake-up call.
“Unfortunately, there is no warranty that these vulnerabilities have not been exploited by sophisticated threat actors to silently compromise VIP victims,” he said via email. “Worse, likely more similar vulnerabilities exist undiscovered and may be known to hacking groups that make a lot of money by their exploitation. Modern web applications open the door to corporate networks with the most critical information, and their breach can be fatal for a company.”
Apple Response and $300K
For its part, Apple responded quickly to the bug reports, fixing the majority of them by the time the post went live, with typical remediation upon learning of the flaws occurring within one to two business days, and response to some critical vulnerabilities within as little as four to six hours, he acknowledged.
“Overall, Apple was very responsive to our reports,” Curry said, adding that, “as of now, October 8th, we have received 32 payments totaling $288,500 for various vulnerabilities.” That number could go higher as Apple tends to pay in “batches,” so the hackers anticipate more payments in the coming months, he said.
Apple’s public bug-bounty program – in which all interested parties can participate – is a fairly recent affair. The company opened up a historically private program to the public last December after years of criticism from developers, who argued that the company needed to be more transparent about flaws in its hardware and software. It also included a $1 million maximum payout to sweeten the deal.
Indeed, Curry – who calls himself a full-time bug-bounty hunter – said he was inspired to assemble the team of hackers to peer under the hood of Apple’s infrastructure after learning on Twitter of a researcher’s award of $100,000 from Apple for discovering an authentication bypass that allowed for arbitrary access any Apple customer account.
“This was surprising to me, as I previously understood that Apple’s bug bounty program only awarded security vulnerabilities affecting their physical products and did not payout for issues affecting their web assets,” he wrote.
Once he found out that Apple was willing to pay for vulnerabilities “with significant impact to users” regardless of whether or not the asset was explicitly listed in scope, it was game on, he said.
“This caught my attention as an interesting opportunity to investigate a new program which appeared to have a wide scope and fun functionality,” Curry wrote in the post. He decided to invite hackers he’d worked with in the past on the project, even though everyone on board knew there was no guarantee of payouts for their discoveries.
The critical vulnerabilities the team discovered in their work are the following: Full Compromise of Apple Distinguished Educators Program via Authentication and Authorization Bypass; Full Compromise of DELMIA Apriso Application via Authentication Bypass; Wormable Stored Cross-Site Scripting Vulnerabilities Allow Attacker to Steal iCloud Data through a Modified Email; Command Injection in Author’s ePublisher; Full Response SSRF on iCloud allows Attacker to Retrieve Apple Source Code; Nova Admin Debug Panel Access via REST Error Leak; AWS Secret Keys via PhantomJS iTune Banners and Book Title XSS; Heap Dump on Apple eSign Allows Attacker to Compromise Various External Employee Management Tools; XML External Entity processing to Blind SSRF on Java Management API; GBI Vertica SQL Injection and Exposed GSF API; Various IDOR Vulnerabilities; and Various Blind XSS Vulnerabilities.
The hackers received permission from the Apple security team to publish details on the critical bugs, all of which have been fixed and re-tested, Curry said.
The findings are an alarming reminder that even the largest tech companies considerably underestimate their web application security, according to Kolochenko.
“Most organizations merely invest into some automated scanning tools and recurrent penetration testing but without implementing a comprehensive application security program,” he said. “Such a program shall include regular secure coding trainings for software developers, introducing security controls aimed to detect vulnerabilities at the early stage of development – the so-called ‘shift-left’ approach – and providing strict security guidelines for software developed by third-parties. Finally, modern software shall incorporate privacy by design to enable seamless compliance with regulations like CCPA or GDRP.”
55 New Security Flaws Reported in Apple Software and Services
9.10.20 Apple Thehackernews
A team of five security researchers analyzed several Apple online services for three months and found as many as 55 vulnerabilities, 11 of which are critical in severity.
The flaws — including 29 high severity, 13 medium severity, and 2 low severity vulnerabilities — could have allowed an attacker to "fully compromise both customer and employee applications, launch a worm capable of automatically taking over a victim's iCloud account, retrieve source code for internal Apple projects, fully compromise an industrial control warehouse software used by Apple, and take over the sessions of Apple employees with the capability of accessing management tools and sensitive resources."
The flaws meant a bad actor could easily hijack a user's iCloud account and steal all the photos, calendar information, videos, and documents, in addition to forwarding the same exploit to all of their contacts.
The findings were reported by Sam Curry along with Brett Buerhaus, Ben Sadeghipour, Samuel Erb, and Tanner Barnes over a three month period between July and September.
After they were responsibly disclosed to Apple, the iPhone maker took steps to patch the flaws within 1-2 business days, with a few others fixed within a short span of 4-6 hours.
So far, Apple has processed about 28 of the vulnerabilities with a total payout of $288,500 as part of its bug bounty program.
The critical bugs pointed out by Sam Curry, and the team are as follows:
Remote Code Execution via Authorization and Authentication Bypass
Authentication Bypass via Misconfigured Permissions allows Global Administrator Access
Command Injection via Unsanitized Filename Argument
Remote Code Execution via Leaked Secret and Exposed Administrator Tool
Memory Leak leads to Employee and User Account Compromise allowing access to various internal applications
Vertica SQL Injection via Unsanitized Input Parameter
Wormable Stored XSS allows Attacker to Fully Compromise Victim iCloud Account
Wormable Stored XSS allows Attacker to Fully Compromise Victim iCloud Account
Full Response SSRF allows Attacker to Read Internal Source Code and Access Protected Resources
Blind XSS allows Attacker to Access Internal Support Portal for Customer and Employee Issue Tracking
Server Side PhantomJS Execution allows an attacker to Access Internal Resources and Retrieve AWS IAM Keys
One of the Apple domains that were impacted included the Apple Distinguished Educators site ("ade.apple.com") that allowed for an authentication bypass using a default password ("###INvALID#%!3"), thus permitting an attacker to access the administrator console and execute arbitrary code.
Likewise, a flaw in the password reset process associated with an application called DELMIA Apriso, a warehouse management solution, made it possible to create and modify shipments, inventory information, validate employee badges, and even take full control over the software by creating a rogue user.

A separate vulnerability was also discovered in Apple Books for Authors service that's used by authors to help write and get their books published on the Apple Books platform. Specifically, using the ePub file upload tool, the researchers were able to manipulate the HTTP requests with an aim to run arbitrary commands on the "authors.apple.com" server.
Among the other critical risks revealed by the researchers were those that stemmed from cross-site scripting (XSS) vulnerability in the "www.icloud.com" domain, which operates by just sending a target with iCloud.com or Mac.com address a specially-crafted email that, when opened via Apple Mail in the browser, allowed the attacker to steal all the photos and contacts.
What's more, the XSS vulnerability was wormable, meaning it could be easily propagating by sending a similar email to every iCloud.com or Mac.com address stored in the victim's contacts.
"When we first started this project we had no idea we'd spend a little bit over three months working towards its completion," Sam Curry noted in his blog post. "This was originally meant to be a side project that we'd work on every once in a while, but with all of the extra free time with the pandemic we each ended up putting a few hundred hours into it."
Apple addresses four vulnerabilities in macOS
28.9.20 Apple Securityaffairs
Apple this week released security updates to address a total of four vulnerabilities affecting macOS Catalina, High Sierra and Mojave.
Apple on Thursday announced to have patched four vulnerabilities affecting macOS Catalina, High Sierra and Mojave.
“This document describes the security content of macOS Catalina 10.15.7, Security Update 2020-005 High Sierra, Security Update 2020-005 Mojave.” reads the advisory published by Apple.
One of the flaws addressed by Apple is an out-of-bounds read, tracked as CVE-2020-9973, that affects the Model I/O component. The exploitation of the flaw involves the processing of a malicious USD file, it could lead to arbitrary code execution or a trigger DoS condition. This vulnerability was reported by the Cisco Talos researcher Aleksandar Nikolic and affects all versions of macOS.
The second issue addressed by Apple is an arbitrary code execution vulnerability, tracked as CVE-2020-9961, that affects the ImageIO component. The exploitation of the flaw involves the use of malicious image files. This vulnerability was reported by the researcher Xingwei Lin from Ant Group Light-Year Security Lab and affects macOS High Sierra and Mojave
The third flaw, tracked as CVE-2020-9968, affects the sandbox and can be exploited by a malicious application to access restricted files.
The issue was reported by Adam Chester of TrustedSec and affects all versions of macOS.
The fourth issue fixed in macOS, tracked as CVE-2020-9941, affects the Mail component in the High Sierra OS. The vulnerability can be exploited by a remote attacker to “unexpectedly alter application state.” The flaw was reported by researchers from the FH Münster University of Applied Sciences in Germany.
Apple Patches Four Vulnerabilities in macOS
26.9.20 Apple Securityweek
Apple on Thursday informed customers that it patched a total of four vulnerabilities across macOS Catalina, High Sierra and Mojave.
One of the security holes is CVE-2020-9973, an issue affecting the Model I/O component. Apple says exploitation of the flaw, which involves the processing of a malicious USD file, could lead to arbitrary code execution or a DoS condition.
This vulnerability, reported to Apple by a Cisco Talos researcher, affects all versions of macOS and it was also patched earlier this month in iOS and iPadOS with the release of version 14.
Another vulnerability that impacts all versions of macOS and which Apple also patched in iOS 14 and iPadOS 14 earlier this month is CVE-2020-9968, a sandbox issue that can be exploited by a malicious application to access restricted files. Adam Chester of TrustedSec has been credited for reporting it to Apple.
The tech giant has also patched an arbitrary code execution vulnerability that can be exploited using malicious image files. This issue, identified by Xingwei Lin of Ant Group Light-Year Security Lab, affects the ImageIO component in macOS High Sierra and Mojave.
The fourth issue fixed this week in macOS — it only impacts High Sierra — affects the Mail component and it can allow a remote attacker to “unexpectedly alter application state.” The flaw was discovered by researchers from the FH Münster University of Applied Sciences in Germany.
iCloud for Windows was updated to version 11.4 this week. The latest version fixes a cross-site scripting (XSS) vulnerability.
Apple also released updates for iOS 14, watchOS 7 and tvOS 14 this week, but says they don’t address any vulnerabilities.
iOS 14 and iPadOS 14 Patch Vulnerabilities, Introduce New Privacy Features
18.9.20 Apple Securityweek
Apple has patched nearly a dozen vulnerabilities and it has introduced new privacy features with the release of iOS 14 and iPadOS 14 this week.
Each of the addressed security flaws impacts a different component of the operating system, namely AppleAVD, Assets, Icons, IDE Device Support, IOSurfaceAccelerator, Keyboard, Model I/O, Phone, Sandbox, Siri, and WebKit.
The issues could result in applications causing a system crash or writing kernel memory, identifying other installed applications, leaking user information, or accessing restricted files; may allow attackers to download malicious content, execute arbitrary code, or view notification contents from the lockscreen; may lead to arbitrary code execution or a cross-site scripting attack; may allow a user to read kernel memory; or could result in the screen lock not engaging after the specified time period.
The iOS 14.0 and iPadOS 14.0 software updates are rolling out to iPhone 6s and later, iPod touch 7th generation, iPad Air 2 and later, and iPad mini 4 and later.
In addition to security patches, the updates deliver various other improvements as well, including new security and privacy features, such as notifications when the camera or microphone are recording, or when data is copied and pasted.
Starting with the new platform iteration, users can deny applications’ access to precise location, and are also informed on applications requesting local network access. Furthermore, they can leverage a new feature that provides a random "private" MAC address when attempting to connect to a Wi-Fi network.
This week, Apple also announced the availability of security patches in watchOS 7.0 (to resolve four vulnerabilities in Keyboard, Phone, Sandbox, and WebKit) and in tvOS 14.0 (which addresses four bugs in Assets, Keyboard, Sandbox, and WebKit).
Safari 14.0 was released this week with fixes for four WebKit bugs that could lead to arbitrary code execution or cross-site scripting attacks, and is available for download for macOS Catalina and macOS Mojave.
Additionally, Apple announced the release of Xcode 12.0, which patches a bug in IDE Device Support that could allow “an attacker in a privileged network position […] to execute arbitrary code on a paired device during a debug session over the network.”
Apple Delays Change Likely to Stymie Mobile Ad Targeting
4.9.20 Apple Securityweek
Apple said on Thursday it would give developers until next year to comply with a software change expected to stymie targeted advertising in iPhone and iPad apps.
An update coming to Apple's iOS mobile software includes a requirement for apps to ask users' permission to collect and share device-identifying data used to make ads more relevant.
"When enabled, a system prompt will give users the ability to allow or reject that tracking on an app-by-app basis," Apple told AFP.
"We want to give developers the time they need to make the necessary changes and, as a result, the requirement to use this tracking permission will go into effect early next year."
Facebook last week put out word that the mobile software move by Apple would cut revenue for developers relying on its in-app ad network.
Such data is used for targeting ads in ways that make them more likely to be of interest and earn money, according to Facebook.
Tests found that revenue from the Audience Network platform that lets Facebook's system work behind the scenes to target ads in apps fell by more than half when personalization was thwarted, an online post explained.
"In reality, the impact to Audience Network on iOS 14 may be much more, so we are working on short-and long-term strategies to support publishers through these changes," Facebook said.
"Ultimately, despite our best efforts, Apple's updates may render Audience Network so ineffective on iOS 14 that it may not make sense to offer it on iOS 14."
Apple is expected to release the new version of its mobile operating system later this year, and developers will have the option from the outset to ask users for permission when it comes to tracking.
"We understand that iOS 14 will hurt many of our developers and publishers at an already difficult time for businesses," Facebook said.
The social networking giant's system will still be able to target ads in apps made for Android-powered smartphones or tablets, Facebook said.
Apple, which does not rely on digital ad revenue, has been working to limit tracking of online activity and has stressed user privacy as a priority.
"We believe technology should protect users' fundamental right to privacy," Apple said.
"That means giving users tools to understand which apps and websites may be sharing their data with other companies for advertising or advertising measurement purposes, as well as the tools to revoke permission for this tracking."
macOS Adware Delivers Notarized Payloads
3.9.20 Apple Securityweek
A recently identified adware campaign targeting macOS users is leveraging malicious code that has received Apple’s approval.
The approval, or notarization, as Apple calls it, is an automated process through which software is scanned before reaching macOS users, to ensure that it does not include malicious code. Notarization was introduced in macOS 10.15 (Catalina), which automatically blocks code that lacks this stamp of trust. Notarization is not App Review.
Apple introduced notarization following an increase in both volume and sophistication of macOS malware, aiming to provide users with increased confidence in a platform that once was being touted as free of malware affecting PCs.
The adware campaign that Twitter user Peter Dantini found on the website homebrew.sh, however, shows that attackers have discovered means to bypass Apple’s approval process and are distributing notarized malware.
Objective See security researcher Patrick Wardle has performed deeper analysis of the campaign, discovering that the distributed code is the OSX.Shlayer malware, and that it has been notarized via the spctl command.
The Shlayer masquerades as Adobe Flash Player or an update for the plugin, and is considered one of the most prevalent macOS malware families out there. The threat was designed to download additional payloads, specifically adware.
Previous reports on Shlayer revealed that, once it landed on a target machine, the threat would disable Gatekeeper to ensure that the user is not alerted when additional software is executed.
Wardle has shared his findings with Apple, which revoked the certificates issued for the notarized payloads, meaning they would no longer be allowed to run on macOS.
Several days after that, however, the campaign was still actively delivering new notarized payloads, which were signed on Friday, August 28, likely after Apple took steps to block the old payloads.
“The attackers’ ability to agilely continue their attack (with other notarized payloads) is noteworthy. Clearly in the never ending cat & mouse game between the attackers and Apple, the attackers are currently (still) winning,” Wardle concludes.
“Either Apple was able to detect Shlayer as part of the notarization process, but breaking that detection was trivial, or Apple had nothing in the notarization process to detect Shlayer, which has been around for a couple years at this point,” Malwarebytes notes.
“While nothing is perfect, some organizations operate at a high level of security and privacy. With this vetting occurring with third-party software, the cybercriminals will throw everything possible to see what sticks. Like phishing attacks, cybercriminals are continually working to see what emails can get through organizations' various technology products globally. When they find one that works, they use it. In this case, they most likely have tried hundreds of multiple malware applications, and to get through was a success for them,” James McQuiggan, security awareness advocate at KnowBe4, commented.
Expert discloses unpatched Safari flaw that allows stealing local files
26.8.20 Apple Securityaffairs
A researcher disclosed technical details of an unpatched vulnerability in Apple’s Safari web browser that can be exploited to steal files from the targeted system.
An expert disclosed the details of an unpatched vulnerability in Apple’s Safari web browser that can be exploited by attackers to steal files from a targeted system.
The vulnerability was discovered in April by the security researcher Pawel Wylecial, founder of security firms REDTEAM.PL and BlackOwlSec. In August, after months of analysis, Apple told the researchers that it would address the issue in the spring of 2021 and asked him to don’t publicly disclose the issue until then,
However, Wylecial opted to disclose his discovery to force the company in addressing the issue earlier.
The vulnerability resides in the Web Share API that allows users to share links from Safari through third-party apps, such as email and messaging apps.
“The problem is that file: scheme is allowed and when a website points to such URL unexpected behavior occurs. In case such a link is passed to the navigator.share function an actual file from the user file system is included in the shared message which leads to local file disclosure when a user is sharing it unknowingly,” Wylecial wrote in a blog post. “The problem is not very serious as user interaction is required, however it is quite easy to make the shared file invisible to the user. The closest comparison that comes to mind is clickjacking as we try to convince the unsuspecting user to perform some action.”
In order to exploit the issue, the attacker have to trick the victims into visiting a malicious website and performing a specific sequence of actions.
The researchers set up a malicious website to demonstrate an attack to steal the local passwd file or a file storing the user’s browsing history. The website includes an image an a message that requests visitors to share it with their friends using a button on the same page. Upon clicking the button, users are asked to select the application they want to use to share a link to the image. Sharing the image via email, the attacker’s code, also attache an arbitrary file from the target’s system.
Wylecial pointed out that the victims would have to scroll down to see the attached file or is some cases the name of the attachment may not be displayed, making harder the attack to be spotted.

The attack works on devices running iOS 13.4.1 and 13.6, macOS Mojave 10.14.16 with Safari 13.1, and on macOS Catalina 10.15.5 with Safari 13.1.1.
Popular iOS SDK Caught Spying on Billions of Users and Committing Ad Fraud
26.8.20 Apple Thehackernews
A popular iOS software development kit (SDK) used by over 1,200 apps—with a total of more than a billion mobile users—is said to contain malicious code with the goal of perpetrating mobile ad-click fraud and capturing sensitive information.
According to a report published by cybersecurity firm Snyk, Mintegral — a mobile programmatic advertising platform owned by Chinese mobile ad tech company Mobvista — includes an SDK component that allows it to collect URLs, device identifiers, IP Address, operating system version, and other user sensitive data from compromised apps to a remote logging server.
The malicious iOS SDK has been named "SourMint" by Snyk researchers.
"The malicious code can spy on user activity by logging URL-based requests made through the app," Snyk's Alyssa Miller said in a Monday analysis. "This activity is logged to a third-party server and could potentially include personally identifiable information (PII) and other sensitive information."
"Furthermore, the SDK fraudulently reports user clicks on ads, stealing potential revenue from competing ad networks and, in some cases, the developer/publisher of the application," Miller added.
Although the names of the compromised apps using the SDK have not been disclosed, the code was uncovered in the iOS version of the Mintegral SDK (6.3.5.0), with the first version of the malicious SDK dating back to July 17, 2019 (5.5.1). The Android version of the SDK, however, doesn't appear to be affected.
Hijack User Ad Clicks
Stating that the SDK contains several anti-debug protection intending to hide the actual behavior of the application, Snyk uncovered evidence that Mintegral SDK not only intercepts all the ad clicks within an app but also use this information to fraudulently attribute the click to its ad network even in cases where a competing ad network has served the ad.
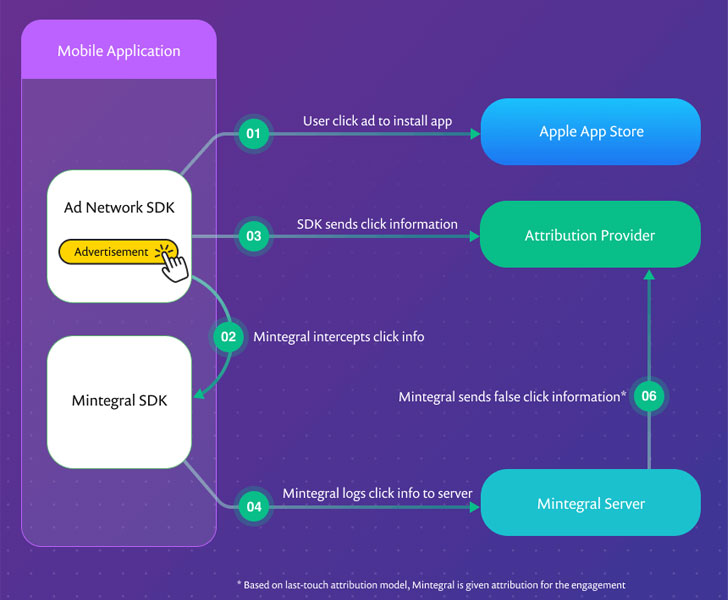
It's worth noting that apps that feature in-app ads include SDKs from multiple ad networks with ad mediators' help.
"When the attribution provider attempts to match the install event to registered click notifications, it finds two that match," the analysis found. "Using a last-touch attribution model, the Mintegral click notification is given the attribution and the click notification from the other ad network is rejected."
In other words, Mintegral has been stealing ad revenues from other advertising networks by claiming the ads from a different ad network as its own, in addition to robbing developers off their revenues even when the platform isn't being used to serve ads.
"In our investigation, we discovered that once the Mintegral SDK is integrated into an application, it intercepts the clicks even if Mintegral isn't enabled to serve ads," Miller said. "In this case, ad revenue that should have come back to the developer or publisher via a competing ad network will never be paid to the developer."
Collecting More Data Than Necessary for Ad Click Attribution
Even more concerningly, the SDK contains functions that are designed to snoop on all communication from the impacted apps, with the scope of data being collected far more than what's required for legitimate click attribution.
Mintegral SDK Ad Fraud
The information logged includes OS Version, IP Address, charging state, Mintegral SDK version, network type, model, package name, advertising identifier (IDFA or Identifier for Advertisers), and more.
"The attempts by Mintegral to conceal the nature of the data being captured, both through anti-tampering controls and a custom proprietary encoding technique, are reminiscent of similar functionality reported by researchers that analyzed the TikTok app," Miller noted.
While there's no way to know for users to know if they're using an app that embeds the Mintegral SDK, it's imperative that third-party developers review their apps and remove the SDK to plug the data leak.
For its part, Apple is introducing new privacy features in its upcoming iOS 14 update that makes it harder for third-party apps to track users by asking for their explicit consent for serving targeted ads.
Malicious Behavior Found in Advertising SDK Used by 1,200 iOS Apps
24.8.20 Apple Securityweek
Researchers at developer security company Snyk claim to have identified malicious behavior in an advertising SDK that is present in more than 1,200 iOS applications offered in the Apple App Store.
The SDK has been developed by Mintegral, a China-based mobile advertising platform provider that has offices in the United States, Europe and Asia. Snyk says it has only identified the malicious behavior in iOS versions of the Mintegral advertising SDK; the code does not appear to be present in Android versions. The company estimates that the 1,200 impacted iOS apps are downloaded roughly 300 million times every month.
According to Snyk, its researchers discovered what they described as malicious code in versions of the iOS SDK going back to 5.5.1 (released in July 2019). The code on which they conducted their analysis was obtained from Mintegral’s official GitHub account.
Snyk says the SDK, which it has dubbed “SourMint,” can allow Mintegral to steal revenue from other ad networks used by applications integrating the SDK. In addition to ad fraud, it allegedly harvests URLs accessed through applications that use the SDK — as well as other system and device information — which could provide the vendor access to highly sensitive information, as demonstrated by Snyk in a video.
SecurityWeek has reached out to Mintegral for comment and will update this article if the company responds.
“Developers can sign up as publishers and download the SDK from the Mintegral site. Once loaded, the SDK injects code into standard iOS functions within the application that execute when the application opens a URL, including app store links, from within the app,” Snyk researchers explained. “This gives the SDK access to a significant amount of data and even potentially private user information. The SDK also specifically examines these open URL events to determine if a competitor’s ad network SDK was the source of the activity.”
The company has pointed out that this behavior appears to be intentional as the SDK looks for signs of a debugger and proxy tools before initiating these activities. This could be an attempt to determine if it’s being analyzed and possibly a method for bypassing Apple’s review process for applications published on the App Store, as it behaves differently if its actions are being watched.
“As the first malicious SDK of this kind to infiltrate the iOS ecosystem, SourMint was very sophisticated. It avoided detection for so long by utilizing various obfuscations and anti-debugging tricks,” said Danny Grander, co-founder and CSO of Snyk. “Developers were unaware of the malicious package upon deploying the application, allowing it to proliferate for more than a year.”
UPDATE: Apple says it has spoken with the Snyk researchers to ensure that it’s fully informed on the research, but the tech giant has found no evidence that apps using the Mintegral SDK are harming users.
The company says app developers are responsible for the behavior of their products, including the behavior of third-party code, and they should exercise caution when using third-party code to insure it does not accidentally undermine security and privacy.
On the other hand, Apple points out that the research conducted by Snyk shows that it’s possible for third-party code to introduce unintended functionality. The company says the type of behavior described by the researchers is all too common, which is why it has been taking steps to provide users more control over their data and ensure that apps are transparent regarding the data they collect.
XCSSET Mac Malware Steals Information, Spreads via Xcode Projects
15.8.20 Apple Securityweek
A newly discovered piece of malware designed to target macOS systems spreads through Xcode projects and exploits what researchers have described as two zero-day vulnerabilities.
Named XCSSET, the malware can allow its operator to steal sensitive information and launch ransomware attacks, Trend Micro reported on Thursday. Specifically, it can help hackers obtain information associated with the Evernote, Skype, Notes, QQ, WeChat, and Telegram apps, capture screenshots, and upload files to the attackers’ server.
It can also encrypt files and display a ransom note, and it can launch universal cross-site scripting (UXSS) attacks in an effort to inject JavaScript code into the websites visited by the victim. This allows it to modify websites, including replacing cryptocurrency addresses, and steal credentials for online services and payment card information from the Apple Store.
One aspect that makes XCSSET interesting is the fact that it spreads via projects for Xcode, Apple’s integrated development environment for macOS. The attackers inject malicious code into Xcode projects and the code gets executed when the project is built.
Trend Micro says it has spotted two Xcode projects injected with the malware, one on July 13 and one on July 31. While these particular projects are less likely to be integrated by other developers into their own projects, the cybersecurity company warns that the distribution method can be highly effective if more popular projects are compromised, leading to what it described as a “supply-chain-like attack.”
“We have also identified this threat in sources such as VirusTotal, which indicates this threat is at large,” Trend Micro warned.
It also noted, “Affected developers will unwittingly distribute the malicious trojan to their users in the form of the compromised Xcode projects, and methods to verify the distributed file (such as checking hashes) would not help as the developers would be unaware that they are distributing malicious files.”
An analysis of the C&C server used by XCSSET revealed a list of 380 victim IP addresses, including 152 in China and 103 in India. However, Trend Micro says it has nothing to share at this time regarding a possible connection to known threat actors.
The company’s researchers also discovered that XCSSET exploits what appear to be two zero-day vulnerabilities. One is related to Data Vaults, which are designed to protect against unauthorized access to data whether or not the requesting app is itself sandboxed. The malware exploits this vulnerability to steal a Safari cookie file, which stores information associated with visited websites. Trend Micro noted that exploitation of this vulnerability requires either another sandbox escape flaw or admin privileges on the targeted system.
The second apparent zero-day vulnerability exploited by XCSSET enables the attackers to run the development version of Safari when the victim opens the web browser. The development version is not sandboxed, allowing the attacker to inject malicious JavaScript code that can run without restrictions. The malicious code is injected via a UXSS attack.
Trend Micro told SecurityWeek that it reported its findings to Apple, and while the company is working on making changes in future versions of macOS that could mitigate the Data Vault-related flaw, Apple sees the issue related to the development version of Safari as intended behavior.
Researcher Details Sophisticated macOS Attack via Office Document Macros
6.8.20 Apple Securityweek
A researcher found a way to deliver malware to macOS systems using a Microsoft Office document containing macro code. The victim simply has to open the document and no alerts are displayed.
Macros enable Office users to automate frequent tasks using VBA code. A macro added to an Office document can be triggered when the file is opened, a feature that cybercriminals started exploiting many years ago to execute malicious code that is typically designed to deploy a piece of malware.
This is why Microsoft has disabled the execution of macros by default — users have to explicitly enable macros if they want to execute the code in a document. However, that has not discouraged threat actors, who often rely on social engineering to trick victims into enabling macros. In response, Microsoft has introduced a feature which ensures that the macro code is executed in a sandbox even if the user allows it to run.
While a vast majority of macro-based attacks target Windows systems, in recent years, researchers spotted some attacks aimed at macOS users, including one campaign that has been linked to North Korea’s Lazarus group.
However, Patrick Wardle, principal security researcher at Apple device management company Jamf, pointed out that these attacks were not very sophisticated and they likely had a low success rate, as the targeted user would explicitly have to enable macros, none of the attacks was able to escape the application sandbox even if the macro was executed, and Apple’s quarantine feature and notarization checks could have blocked additional payloads.
Wardle revealed this week that he identified a way to make macro-based attacks against macOS systems much more efficient. He has described an exploit chain that bypassed all of the aforementioned security mechanisms, allowing an attacker to deliver their payload without any warning — the victim simply had to open the malicious document.
First, in order to have the macro code automatically executed when the victim opened the document, without having to explicitly enable macros, the researcher used a method that was disclosed in 2018. Pieter Ceelen and Stan Hegt showed at the time that XML macros in SYLK files were automatically executed in Office 2011 for Mac. XML is the macro programming language used before VBA and SYLK is an old Microsoft file format designed for exchanging data between applications.
Last year, an advisory published by CERT/CC revealed that the vulnerability still worked on more recent versions of Office for Mac if the user had enabled the “Disable all macros without notification” option.
“As this is the most ‘secure’ setting it may often be set, especially by security conscious users or organizations,” Wardle explained in a blog post.
Using this method would ensure that the attacker’s macro is executed without any alerts being displayed on the targeted device. However, the code would still run in a sandbox.
A sandbox escape that would be useful in this attack was disclosed in 2018 by researcher Adam Chester. His method was patched at the time by Microsoft, but Wardle recently found a way to bypass the fix, which would ensure that the malicious code is run outside the sandbox on the next login.
All that is left now is to bypass Apple’s notarization checks, which prevent code downloaded from the internet from executing. Notarizing a piece of software is an automated process in which Apple’s notary service scans the software for malicious code. Wardle overcame this hurdle by abusing the Archive Utility app in macOS.
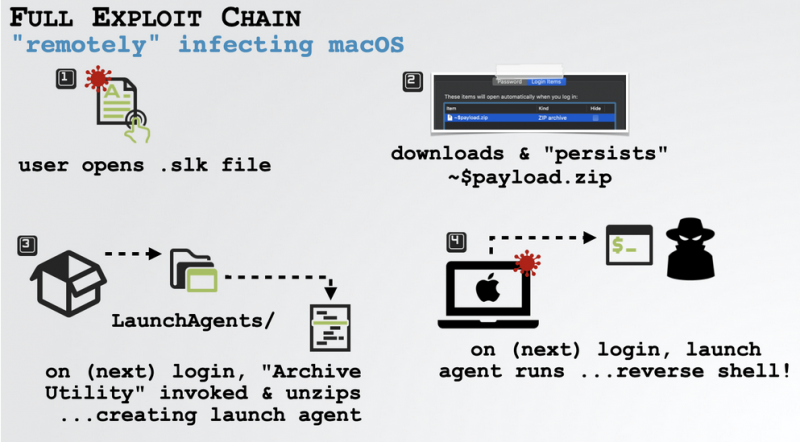
He demonstrated the exploit chain by spawning a reverse shell, which he used to deliver the OSX.WindTail backdoor.
The researcher notified Apple about his findings and the company silently patched the vulnerabilities with the release of macOS 10.15.3. The company later edited its advisory to credit Wardle, but it did not assign a CVE identifier.
Wardle is an expert in Mac security and his research projects over the past years have led to the discovery of some interesting vulnerabilities. This week he announced a new book series, The Art of Mac Malware, which can be read for free online.
Apple Touch ID Flaw Could Have Let Attackers Hijack iCloud Accounts
5.8.20 Apple Thehackernews
Apple earlier this year fixed a security vulnerability in iOS and macOS that could have potentially allowed an attacker to gain unauthorized access to a user's iCloud account.
Uncovered in February by Thijs Alkemade, a security specialist at IT security firm Computest, the flaw resided in Apple's implementation of TouchID (or FaceID) biometric feature that authenticated users to log in to websites on Safari, specifically those that use Apple ID logins.
After the issue was reported to Apple through their responsible disclosure program, the iPhone maker addressed the vulnerability in a server-side update.
An Authentication Flaw
The central premise of the flaw is as follows. When users try to sign in to a website that requires an Apple ID, a prompt is displayed to authenticate the login using Touch ID. Doing so skips the two-factor authentication step since it already leverages a combination of factors for identification, such as the device (something you have) and the biometric information (something you are).
Contrast this during logins to Apple domains (e.g. "icloud.com") the usual way with an ID and password, wherein the website embeds an iframe pointing to Apple's login validation server ("https://idmsa.apple.com"), which handles the authentication process.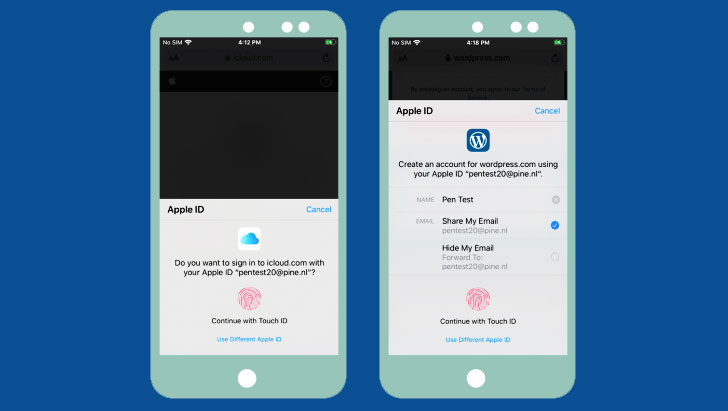
As shown in the video demonstration, the iframe URL also contains two other parameters — a "client_id" identifying the service (e.g., iCloud) and a "redirect_uri" that has the URL to be redirected to after successful verification.
But in the case where a user is validated using TouchID, the iframe is handled differently in that it communicates with the AuthKit daemon (akd) to handle the biometric authentication and subsequently retrieve a token ("grant_code") that's used by the icloud.com page to continue the login process.
To do this, the daemon communicates with an API on "gsa.apple.com," to which it sends the details of the request and from which it receives the token.
The security flaw discovered by Computest resides in the aforementioned gsa.apple.com API, which made it theoretically possible to abuse those domains to verify a client ID without authentication.
"Even though the client_id and redirect_uri were included in the data submitted to it by akd, it did not check that the redirect URI matches the client ID," Alkemade noted. "Instead, there was only a whitelist applied by AKAppSSOExtension on the domains. All domains ending with apple.com, icloud.com and icloud.com.cn were allowed."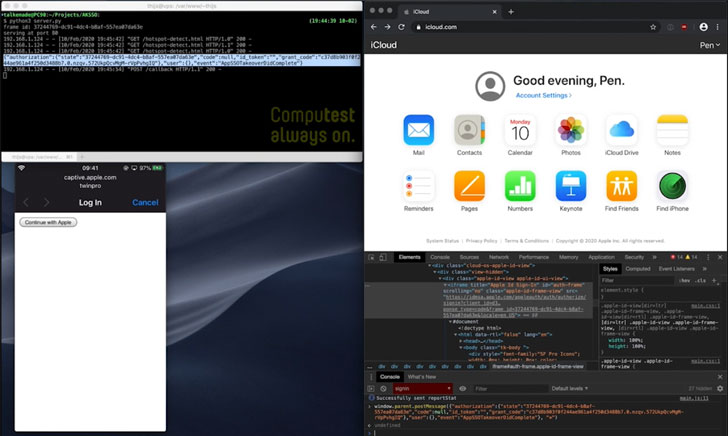
This means that an attacker could exploit a cross-site scripting vulnerability on any one of Apple's subdomains to run a malicious snippet of JavaScript code that can trigger a login prompt using the iCloud client ID, and use the grant token to obtain a session on icloud.com.
Setting Up Fake Hotspots to Take Over iCloud Accounts
In a separate scenario, the attack could be executed by embedding JavaScript on the web page that's displayed when connecting to a Wi-Fi network for the first time (via "captive.apple.com"), thus allowing an attacker access to a user's account by just accepting a TouchID prompt from that page.
"A malicious Wi-Fi network could respond with a page with JavaScript which initiates OAuth as iCloud," Alkemade said. "The user receives a TouchID prompt, but it's very unclear what it implies. If the user authenticates on that prompt, their session token will be sent to the malicious site, giving the attacker a session for their account on iCloud."
"By setting up a fake hotspot in a location where users expect to receive a captive portal (for example at an airport, hotel or train station), it would have been possible to gain access to a significant number of iCloud accounts, which would have allowed access to backups of pictures, location of the phone, files and much more," he added.
This is not the first time security issues have been found in Apple's authentication infrastructure. In May, Apple patched a flaw impacting its "Sign in with Apple" system that could have made it possible for remote attackers to bypass authentication and take over targeted users' accounts on third-party services and apps that have been registered using Apple's sign-in option.
Apple Knocked Off Perch as Most Imitated Brand for Phishing Attacks
5.8.2020 Apple Threatpost
COVID-19 pandemic spurs spoofing preference changes, plus a surge in email-based attacks.
Google and Amazon overtook Apple in the second quarter (Q2) of 2020 as the brand most spoofed by attackers to lure people into falling for phishing attacks. The leaderboard change is likely due to activity related to the COVID-19 pandemic, according to new research.
While the number of so-called brand-phishing attacks remained stable from the first quarter of 2020 to the second, there was a major shift in position for the companies that threat actors think people are most likely to trust — or whose pages they will most likely click on, according to Check Point Research’s Brand Phishing Report for Q2.
Brand phishing is a type of attack in which a threat actor imitates an official website of a known brand by using a similar domain or URL in an attack, as well as in some cases a copycat web page similar or identical to the actual company’s original website in look and feel.
Attackers also began using email more as a vector in these types of attacks in Q2, likely inspired by the amount of people relying on virtual communication while working at home during the COVID-19 pandemic, noted Check Point manager of threat intelligence Lotem Finkelsteen, in an email to Threatpost.
“As we are all forced to work from home, the inbox is a prime attack method for hackers,” he said. “I’d think not twice, but three times before opening up a document in email, especially if it’s allegedly from Google or Amazon.”
Attackers send malicious and deceptive links via email or text messaging, and then guide a potential victim via web redirects or a fraudulent mobile app to a spoofed page, where they try to steal credentials, personal information or intercept payments.
Technology companies were the No. 1 industry for attackers to leverage in such attacks, followed by banking and social networks. In the first quarter of 2020, Apple was the most popular brand among attackers in the tech sector for luring phishing victims.
However, in the second quarter, Google took the top spot alongside Amazon — with each brand used in 13 percent of attacks in Check Point’s telemetry — followed by WhatsApp and Facebook (9 percent), Microsoft (7 percent) and Outlook (3 percent), according to the report.
Apple plummeted to the No. 7 spot behind them, sharing the honors with Netflix, Huawei and PayPal, all of which were represented in 2 percent of brand-phishing attacks.
The end of the second quarter included the early days of the COVID-19 crisis, with many countries around the world enforcing stay-at-home orders, which may explain for the change in preference for attackers. With people confined at home and seeking information about coronavirus, Google — as the top search engine — would become even more popular than usual.
Using Amazon to purchase goods for delivery — as many stores were closed or had limited opening hours in the beginning of Q2 — also has seen a massive surge since the pandemic started, driving more interest in that brand as well. Indeed, researchers saw a pair of recent phishing campaigns aimed at lifting credentials and other personal information under the guise of Amazon package-delivery notices.
As mentioned previously, Q2 also saw a shift in the specific vectors being used for attacks. As is typical, the web was the main conduit for brand phishing attacks, with 61 percent of them originating there. However, email, which was third in Q1, moved to the second spot in the following quarter with 24 percent of attacks, and mobile dropped to third with 15 percent of attacks, researchers said.
In addition to so many people relying on email as they worked from home during the pandemic, businesses also began to reopen towards the end of Q2 as some restrictions eased, also boosting email traffic as a means of attack, according to Check Point. One phishing campaign seen in June took advantage of this — along with the realities of the post-COVID-19 work environment — by purporting to send coronavirus training resources to employees returning to the workplace. Instead, the emails sent malicious links.
The overall leaders, Google and Amazon, were the top two also used the most in web attacks, followed by WhatsApp; while Microsoft and Outlook, unsurprisingly, were No. 1 and 2 in email-based attacks, followed by Unicredit. Facebook, WhatsApp and PayPal were the leaders in mobile-based brand phishing attacks in Q2, according to the report. Almost 15 percent of phishing attacks trace to mobile, the firm said.
The brand-phishing efforts show no sign of letting up. During late June, Check Point researchers witnessed a fraudulent website which was trying to imitate the login page of Apple’s cloud services, iCloud. The purpose of this was to try and steal iCloud login credentials accordingly, the phishing URL was listed under the domain account-icloud[.]com. The domain was first active in late June.
Apple Patches Over 40 Vulnerabilities in macOS Catalina
27.5.2020 Securityweek Apple
Apple this week released security updates to address over fifty vulnerabilities impacting macOS and Safari.
A total of 44 security flaws were fixed with the release of macOS Catalina 10.15.5, impacting components such as Accounts, AirDrop, Audio, Bluetooth, Calendar, ImageIO, Kernel, ksh, PackageKit, Sandbox, SQLite, USB Audio, Wi-Fi, and zsh, among others.
Eighteen of these vulnerabilities are specific to macOS Catalina, but many impact macOS High Sierra and macOS Mojave as well, and patches were released for those platform iterations as well.
What’s more, Apple addressed two other vulnerabilities that impact macOS Mojave only, as well as two more that affect macOS Mojave and macOS High Sierra.
The component impacted the most was Kernel, which received patches for a total of 10 vulnerabilities. Next in line was Wi-Fi, with fixes for 5 vulnerabilities.
The addressed issues could result in denial of service, the circumvention of sandbox restrictions, leak of private information, arbitrary code execution, exfiltration of user information, elevation of privilege, sandbox escape, memory leak, execution of arbitrary shell commands, and privacy preferences bypass, among others.
All these security bugs were fixed with the release of macOS Catalina 10.15.5, Security Update 2020-003 for Mojave, and Security Update 2020-003 for High Sierra.
Apple also patched 10 vulnerabilities with the rollout of Safari 13.1.1, which is now available for macOS Mojave and macOS High Sierra, and included in macOS Catalina.
The first of the bugs could result in a malicious process causing Safari to launch an application. The remaining nine flaws affect Webkit and could result in arbitrary code execution, cross-site scripting, or the disclosure of process memory.
This week, the Cupertino-based tech company also made available version 2.2.0.0 of Windows Migration Assistant for macOS Catalina, which fixes an arbitrary code execution vulnerability.
A total of 12 vulnerabilities were patched with the release of iCloud for Windows, including arbitrary code execution, denial of service, and cross-site scripting issues. Two iterations of the application are available, namely version 11.2 for Windows 10 and later via the Microsoft Store, and version 7.19 for Windows 7 and later.
The new set of updates arrived roughly one week after the release of patches for iOS, tvOS, watchOS, and Xcode.
iOS 13.5 and iPadOS 13.5 arrived with fixes for more than 40 vulnerabilities last week, but at least one security flaw remained unpatched, allowing the team behind the popular jailbreak tool unc0ver to include an exploit for it in their latest release.
In an alert published on Tuesday, the CERT Coordination Center warned that this unspecified vulnerability resides in the iOS kernel and that it could allow any malicious application to achieve unsandboxed, kernel-level code execution.
“This vulnerability is being used by the public unc0ver 5.0 jailbreak utility, which claims to support all devices from iOS 11 through 13.5, excluding versions 12.3-12.3.2 and 12.4.2-12.4.5. It is also reported that this jailbreak works on modern iOS devices that use a CPU that supports Pointer Authentication Code (PAC), which indicates that PAC does not prevent exploitation of this vulnerability,” the alert reads.