
The KISMET exploit chain doesn’t work against iOS 14 and above because the new mobile iOS implements additional security protections.
Apple Articles - H 2020 1 2 iOS Apple List - H 2021 2020 2019 2018 iOS
Apple Loses Copyright Suit Against Security Startup
30.12.2020 Apple Securityweek
A federal judge Tuesday dismissed Apple's copyright infringement lawsuit against cybersecurity startup Corellium in a case which could have implications for researchers who find software bugs and vulnerabilities.
Judge Rodney Smith said Apple failed to show a legal basis for protecting its entire iOS operating system from security researchers.
Apple sued the Florida-based startup in 2019 claiming its "virtualization" of iOS software constituted copyright infringement.
But the judge ruled that Corellium's work, which is designed to find security holes in the software, was "fair use" of copyrighted material.
"From the infancy of copyright protection, courts have recognized that some opportunity for fair use of copyrighted materials is necessary to fulfill copyright's purpose of promoting 'the progress of science and useful arts,'" Smith wrote.
"There is evidence in the record to support Corellium's position that its product is intended for security research and, as Apple concedes, can be used for security research. Further, Apple itself would have used the product for internal testing had it successfully acquired the company."
The ruling, if upheld, represents a victory for security researchers who could face civil or criminal penalties for reproducing copyrighted software as part of efforts to find vulnerabilities.
It also limits Apple's efforts to exercise full control of its iPhone software and its ability to force third parties to use its proprietary security research tools.
Apple did not immediately respond to a request for comment on the case.
Zero-Click Apple Zero-Day Uncovered in Pegasus Spy Attack
23.12.2020 Apple Threatpost
The phones of 36 journalists were infected by four APTs, possibly linked to Saudi Arabia or the UAE.
Four nation-state-backed advanced persistent threats (APTs) hacked Al Jazeera journalists, producers, anchors and executives, in an espionage attack leveraging a zero-day exploit for Apple iPhone, researchers said.
The attack, carried out in July and August, compromised 36 personal phones belonging to the victims, according to Citizen Lab. The firm said that the perpetrators could belong to up to four APTs, including potentially those linked to Saudi Arabia and the United Arab Emirates. All of the operators used the NSO Group’s infamous Pegasus spyware as their final payload.
2020 Reader Survey: Share Your Feedback to Help Us Improve
Pegasus is a mobile phone-surveillance solution that enables customers to remotely exploit and monitor devices. NSO Group has long maintained that its mobile spyware is meant to be a tool for governments to use in fighting crime and terror, and that it’s not complicit in any government’s misuse of it. Critics however say that repressive governments use it for more nefarious purposes to track dissidents, journalists and other members of civil society — and that NSO Group assists them.
The latest version of the Pegasus implant has a number of capabilities, according to Citizen Lab, including: Recording audio from the microphone including both ambient “hot mic” recording and audio of encrypted phone calls; taking pictures; tracking device location; and accessing passwords and stored credentials.
KISMET
Citizen Lab’s analysis of the attacks, released Sunday, found that the attackers found a footing on the phones from which to install Pegasus by exploiting a zero-day in Apple’s iMessage feature for iPhone.
“The phones were compromised using an exploit chain that we call KISMET, which appears to involve an invisible zero-click exploit in iMessage,” researchers said in the Sunday posting. “In July 2020, KISMET was a zero-day against at least iOS 13.5.1 and could hack Apple’s then-latest iPhone 11.”
Ctizen Lab noted that the zero-day was likely also brokered by NSO Group.
“NSO Group is shifting towards zero-click exploits and network-based attacks that allow its government clients to break into phones without any interaction from the target, and without leaving any visible traces,” researchers said, citing the 2019 WhatsApp breach, where at least 1,400 phones were targeted via an exploit sent through a missed voice call. NSO Group has denied its involvement in that case.
Citizen Lab didn’t release technical details of the zero-day, but did say that the “imagent” process (part of a built-in Apple app handling iMessage and FaceTime) was listed as the responsible process for one of Pegasus’ launch routines, indicating possible exploitation involving iMessage or FaceTime messages or notifications.
Upon further investigation, it turns out that a form of KISMET was also used between October and December 2019 to compromise some of the same targets, as well as the phone of a journalist at London-based Al Araby TV.
“Given the global reach of NSO Group’s customer base and the apparent vulnerability of almost all iPhone devices prior to the iOS 14 update, we suspect that the infections that we observed were a miniscule fraction of the total attacks leveraging this exploit,” according to Citizen Lab.
KISMET likely doesn’t work against iOS 14 and above, which includes new security protections, Citizen Labs noted. Apple meanwhile is looking into the issue.
Inside One Victim’s Attack
Tamer Almisshal, a well-known investigative journalist for Al Jazeera’s Arabic language channel, in January agreed to installing a VPN application that allowed Citizen Lab researchers to monitor metadata associated with his internet traffic, because he thought he was a likely target for hacking.
“While reviewing his VPN logs, we noticed that on 19 July 2020, his phone visited a website that we had detected in our internet scanning as an installation server for NSO Group’s Pegasus spyware, which is used in the process of infecting a target with Pegasus,” according to Citizen Lab.
In the 54 minutes leading up to that ping, the phone also visited 228 cloud partitions – a highly unusual activity, the firm said. Those cloud connections resulted in a net download of 2.06MB and a net upload of 1.25MB of data. The infrastructure used included servers in Germany, France, U.K., and Italy using cloud providers Aruba, Choopa, CloudSigma and DigitalOcean, according to the firm.
“Because these anomalous iCloud connections occurred—and ceased—immediately prior to Pegasus installation…we believe they represent the initial vector by which Tamer Almisshal’s phone was hacked,” researchers said.
More digging uncovered KISMET, the apparent exploit delivered through Apple’s servers, that served as the initial access vector. In the past, NSO Group delivered malicious SMS messages with links that delivered the payload; in this case, it’s a zero-click process that may involve the attacker merely sending an iMessage to the target — no user interaction required, according to Citizen Lab.
The data exfiltration began swiftly: Just 16 seconds after the last connection was made to the Pegasus installation server, Almisshal’s iPhone contacted three new IP addresses – likely Pegasus command-and-control servers (C2s). It continued to contact the IPs over the next 16 hours, Citizen Lab said, with 270.16MB of data uploaded, and 15.15MB of data downloaded.
Almisshal’s device also showed a large number of random phone crashes between January and July.
“While some of [these] may be benign, they may also indicate earlier attempts to exploit vulnerabilities against his device,” researchers noted.
Attribution
The phones were hacked via four distinct clusters of servers, which could be attributable to up to four NSO Group operators, according to Citizen Labs.
“An operator that we call Monarchy spied on 18 phones, and an operator that we call Sneaky Kestral spied on 15 phones, including one of the same phones that Monarchy spied on,” Citizen Lab noted. “Two other operators, Center-1 and Center-2, spied on one and three phones, respectively.”
The firm believes with “medium confidence” that Sneaky Kestrel acts on behalf of the UAE. It normally targets individuals inside the UAE, and one target hacked by the group previously received Pegasus links via SMS that “point to the same domain name used in the attacks on UAE activist Ahmed Mansoor.”
It’s also with medium confidence that the researchers assess that Monarchy acts on behalf of the Saudi government. It targets individuals primarily inside Saudi Arabia, and was seen hacking a Saudi Arabian activist.
They weren’t able to determine the identity of Center-1 and Center-2, though both appear to target mainly in the Middle East.
The firm said that it believes that NSO Group is constantly working to develop new vectors of infection.
“Journalists and media outlets should not be forced to confront this situation on their own. Investments in journalist security and education must be accompanied by efforts to regulate the sale, transfer and use of surveillance technology,” Citizen Lab noted. “As the anti-detection features of spyware become more sophisticated, the need for effective regulatory and oversight frameworks becomes increasingly urgent. The abuse of NSO Group’s zero-click iMessage attack to target journalists reinforces the need for a global moratorium on the sale and transfer of surveillance technology.”
Zero-Click Apple Zero-Day Uncovered in Pegasus Spy Attack
22.12.2020 Apple Threatpost
The phones of 36 journalists were infected by four APTs, possibly linked to Saudi Arabia or the UAE.
Four nation-state-backed advanced persistent threats (APTs) hacked Al Jazeera journalists, producers, anchors and executives, in an espionage attack leveraging a zero-day exploit for Apple iPhone, researchers said.
The attack, carried out in July and August, compromised 36 personal phones belonging to the victims, according to Citizen Lab. The firm said that the perpetrators could belong to up to four APTs, including potentially those linked to Saudi Arabia and the United Arab Emirates. All of the operators used the NSO Group’s infamous Pegasus spyware as their final payload.
2020 Reader Survey: Share Your Feedback to Help Us Improve
Pegasus is a mobile phone-surveillance solution that enables customers to remotely exploit and monitor devices. NSO Group has long maintained that its mobile spyware is meant to be a tool for governments to use in fighting crime and terror, and that it’s not complicit in any government’s misuse of it. Critics however say that repressive governments use it for more nefarious purposes to track dissidents, journalists and other members of civil society — and that NSO Group assists them.
The latest version of the Pegasus implant has a number of capabilities, according to Citizen Lab, including: Recording audio from the microphone including both ambient “hot mic” recording and audio of encrypted phone calls; taking pictures; tracking device location; and accessing passwords and stored credentials.
KISMET
Citizen Lab’s analysis of the attacks, released Sunday, found that the attackers found a footing on the phones from which to install Pegasus by exploiting a zero-day in Apple’s iMessage feature for iPhone.
“The phones were compromised using an exploit chain that we call KISMET, which appears to involve an invisible zero-click exploit in iMessage,” researchers said in the Sunday posting. “In July 2020, KISMET was a zero-day against at least iOS 13.5.1 and could hack Apple’s then-latest iPhone 11.”
Ctizen Lab noted that the zero-day was likely also brokered by NSO Group.
“NSO Group is shifting towards zero-click exploits and network-based attacks that allow its government clients to break into phones without any interaction from the target, and without leaving any visible traces,” researchers said, citing the 2019 WhatsApp breach, where at least 1,400 phones were targeted via an exploit sent through a missed voice call. NSO Group has denied its involvement in that case.
Citizen Lab didn’t release technical details of the zero-day, but did say that the “imagent” process (part of a built-in Apple app handling iMessage and FaceTime) was listed as the responsible process for one of Pegasus’ launch routines, indicating possible exploitation involving iMessage or FaceTime messages or notifications.
Upon further investigation, it turns out that a form of KISMET was also used between October and December 2019 to compromise some of the same targets, as well as the phone of a journalist at London-based Al Araby TV.
“Given the global reach of NSO Group’s customer base and the apparent vulnerability of almost all iPhone devices prior to the iOS 14 update, we suspect that the infections that we observed were a miniscule fraction of the total attacks leveraging this exploit,” according to Citizen Lab.
KISMET likely doesn’t work against iOS 14 and above, which includes new security protections, Citizen Labs noted. Apple meanwhile is looking into the issue.
Inside One Victim’s Attack
Tamer Almisshal, a well-known investigative journalist for Al Jazeera’s Arabic language channel, in January agreed to installing a VPN application that allowed Citizen Lab researchers to monitor metadata associated with his internet traffic, because he thought he was a likely target for hacking.
“While reviewing his VPN logs, we noticed that on 19 July 2020, his phone visited a website that we had detected in our internet scanning as an installation server for NSO Group’s Pegasus spyware, which is used in the process of infecting a target with Pegasus,” according to Citizen Lab.
In the 54 minutes leading up to that ping, the phone also visited 228 cloud partitions – a highly unusual activity, the firm said. Those cloud connections resulted in a net download of 2.06MB and a net upload of 1.25MB of data. The infrastructure used included servers in Germany, France, U.K., and Italy using cloud providers Aruba, Choopa, CloudSigma and DigitalOcean, according to the firm.
“Because these anomalous iCloud connections occurred—and ceased—immediately prior to Pegasus installation…we believe they represent the initial vector by which Tamer Almisshal’s phone was hacked,” researchers said.
More digging uncovered KISMET, the apparent exploit delivered through Apple’s servers, that served as the initial access vector. In the past, NSO Group delivered malicious SMS messages with links that delivered the payload; in this case, it’s a zero-click process that may involve the attacker merely sending an iMessage to the target — no user interaction required, according to Citizen Lab.
The data exfiltration began swiftly: Just 16 seconds after the last connection was made to the Pegasus installation server, Almisshal’s iPhone contacted three new IP addresses – likely Pegasus command-and-control servers (C2s). It continued to contact the IPs over the next 16 hours, Citizen Lab said, with 270.16MB of data uploaded, and 15.15MB of data downloaded.
Almisshal’s device also showed a large number of random phone crashes between January and July.
“While some of [these] may be benign, they may also indicate earlier attempts to exploit vulnerabilities against his device,” researchers noted.
Attribution
The phones were hacked via four distinct clusters of servers, which could be attributable to up to four NSO Group operators, according to Citizen Labs.
“An operator that we call Monarchy spied on 18 phones, and an operator that we call Sneaky Kestral spied on 15 phones, including one of the same phones that Monarchy spied on,” Citizen Lab noted. “Two other operators, Center-1 and Center-2, spied on one and three phones, respectively.”
The firm believes with “medium confidence” that Sneaky Kestrel acts on behalf of the UAE. It normally targets individuals inside the UAE, and one target hacked by the group previously received Pegasus links via SMS that “point to the same domain name used in the attacks on UAE activist Ahmed Mansoor.”
It’s also with medium confidence that the researchers assess that Monarchy acts on behalf of the Saudi government. It targets individuals primarily inside Saudi Arabia, and was seen hacking a Saudi Arabian activist.
They weren’t able to determine the identity of Center-1 and Center-2, though both appear to target mainly in the Middle East.
The firm said that it believes that NSO Group is constantly working to develop new vectors of infection.
“Journalists and media outlets should not be forced to confront this situation on their own. Investments in journalist security and education must be accompanied by efforts to regulate the sale, transfer and use of surveillance technology,” Citizen Lab noted. “As the anti-detection features of spyware become more sophisticated, the need for effective regulatory and oversight frameworks becomes increasingly urgent. The abuse of NSO Group’s zero-click iMessage attack to target journalists reinforces the need for a global moratorium on the sale and transfer of surveillance technology.”
Zero-day exploit used to hack iPhones of Al Jazeera employees
22.12.2020 Apple Securityaffairs
Tens of Al Jazeera employees were targeted in a cyber espionage campaign leveraging a zero-click iOS zero-day vulnerability to hack their iPhones.
Researchers from Citizen Lab reported that at least 36 Al Jazeera employees were targeted in a cyber espionage campaign leveraging a zero-click iOS zero-day vulnerability to hack their iPhones.
The attackers used an exploit chain named Kismet that was part of the arsenal of the controversial Pegasus spyware that is sold by the surveillance firm NSO Group.
“In July and August 2020, government operatives used NSO Group’s Pegasus spyware to hack 36 personal phones belonging to journalists, producers, anchors, and executives at Al Jazeera. The personal phone of a journalist at London-based Al Araby TV was also hacked.” reads the report published by the researchers.
“The phones were compromised using an exploit chain that we call KISMET, which appears to involve an invisible zero-click exploit in iMessage. In July 2020, KISMET was a zero-day against at least iOS 13.5.1 and could hack Apple’s then-latest iPhone 11. Based on logs from compromised phones, we believe that NSO Group customers also successfully deployed KISMET or a related zero-click, zero-day exploit between October and December 2019.”
The KISMET exploit chain doesn’t work against iOS 14 and above because the new mobile iOS implements additional security protections.
Experts believe that the number of targeted individuals is much higher given the global reach of NSO Group’s customer base. The campaign aimed at Al Jazeera ‘s employees is politically motivated, the Qatar-based news agency is a privileged target of hackers working for the neighboring countries due to the tensions between the local governments.
The infrastructure used in these attacks included servers in Germany, France, UK, and Italy using cloud providers Aruba, Choopa, CloudSigma, and DigitalOcean.
According to the Citizen Lab’s report, the Kismet hacking tool was sold at least to four organizations that used it against Al Jazeera employees from all over the world. These surgical attacks took place between July and August 2020, but experts speculate the attack are going on since at least October 2019.
Two of the NSO Group’s customers are in Saudi Arabia and the United Arab Emirates, Citizen Lab associated the attacks to the operations of the APT groups tracked as Monarchy and Sneaky Kestrel.
Citizen Lab has already published several reports unmasking operations that involved the use of the NSO’s surveillance software. -The company always remarked that its software was only sold to government and intelligence agencies and was never sold to government organizations that used them to track political rivals, dissidents, and journalists.
Unfortunately, Citizen Lab found evidence of the NGO software was used in multiple campaigns against journalists, activists, and dissidents in multiple countries, including Morroco, Mexico, Saudi Arabia, and the UAE.
“However, the zero-click techniques used against Al Jazeera staff were sophisticated, difficult to detect, and largely focused on the personal devices of reporters. Security awareness and policies are essential, but without substantial investment in security, network analysis, regular security audits and collaboration with researchers like the Citizen Lab these cases would not have been detected.” concludes the report.
“Journalists and media outlets should not be forced to confront this situation on their own. Investments in journalist security and education must be accompanied by efforts to regulate the sale, transfer, and use of surveillance technology.”
Journalists' Phones Hacked via iMessage Zero-Day Exploit
22.12.2020 Apple Securityweek
A recently observed Pegasus spyware infection campaign targeting tens of Al Jazeera journalists leveraged an iMessage zero-click, zero-day exploit for infection.
The Israel-based NSO Group, which has approximately 600 employees in Israel and abroad, made it to the spotlight several years ago, after security firms identified and analyzed Pegasus, a highly invasive spyware family that allows attackers not only to steal data from infected devices, but also turn on the camera and microphone.
The tool, NSO claims, has been developed for government use only, to help fight terrorism and crime. However, cybersecurity firms and human rights organizations have detailed multiple malicious attacks involving Pegasus, many of them targeting journalists and human rights activities.
In a newly published report, Canadian interdisciplinary laboratory Citizen Lab, which is based at the Munk School of Global Affairs & Public Policy at the University of Toronto, details a new series of attacks in which Pegasus infected “36 personal phones belonging to journalists, producers, anchors, and executives at Al Jazeera.”
The attacks, which were performed in July and August 2020, involved the use of a zero-click exploit in iMessage, a zero-day vulnerability in at least iOS 13.5.1, which allowed attackers to hack Apple’s iPhone 11 devices.
Dubbed KISMET, the exploit was used to target Al Jazeera personnel by at least four Pegasus operators, including two (SNEAKY KESTREL and MONARCHY) that Citizen Lab linked to the United Arab Emirates and Saudi governments, respectively. The former spied on 18 phones, while the latter on 15 phones.
Citizen Lab was able to identify attacks leveraging the KISMET exploit, which allows attackers to deploy malware without user interaction, after Al Jazeera investigative journalist Tamer Almisshal agreed to install a VPN application for Citizen Lab researchers, to monitor traffic metadata.
On July 19, 2020, the device visited a website known to be an installation server for NSO Group’s Pegasus spyware, and analysis of logs revealed hundreds of connections made to iCloud Partitions during a 54 minute timeframe, on the same day, suggesting that this was the infection vector.
Sixteen seconds after the infection occurred, the device was observed connecting to three IPs that it never communicated with before. Over the course of multiple hours, the device sent a total of 270 MB of data to these servers.
Al Araby TV journalist Rania Dridi was also targeted with Pegasus spyware, at least six times, with two of the attacks likely involving zero-day exploits. The first occurred on October 26, 2019, on iOS 13.1.3, while the second happened on July 12, 2020, on iOS 13.5.1. This attack, and another on July 23, used the KISMET zero-click exploit.
In the attacks against the 37 journalists, the NSO spyware operators employed infrastructure located in Germany, France, Italy and the UK. As cloud providers, they used Aruba, Choopa, CloudSigma, and DigitalOcean.
The implant used in these attacks can record audio from the microphone (including encrypted phone calls and ambient sounds), take pictures, track device location, and access stored credentials, including passwords.
The KISMET exploit, Citizen Lab’s researchers note, doesn’t appear to work on iOS 14, which was released with additional security protections. iOS device owners are advised to update to the new platform iteration as soon as possible, to ensure they are safe from attacks employing KISMET.
“The current trend towards zero-click infection vectors and more sophisticated anti-forensic capabilities is part of a broader industry-wide shift towards more sophisticated, less detectable means of surveillance. Although this is a predictable technological evolution, it increases the technological challenges facing both network administrators and investigators,” Citizen Lab concludes.
iPhones of 36 Journalists Hacked Using iMessage Zero-Click Exploit
21.12.2020 Apple Thehackernews
Three dozen journalists working for Al Jazeera had their iPhones stealthily compromised via a zero-click exploit to install spyware as part of a Middle East cyberespionage campaign.
In a new report published yesterday by University of Toronto's Citizen Lab, researchers said personal phones of 36 journalists, producers, anchors, and executives at Al Jazeera, and a journalist at London-based Al Araby TV were infected with Pegasus malware via a now-fixed flaw in Apple's iMessage.
Pegasus is developed by Israeli private intelligence firm NSO Group and allows an attacker to access sensitive data stored on a target device — all without the victim's knowledge.
"The shift towards zero-click attacks by an industry and customers already steeped in secrecy increases the likelihood of abuse going undetected," the researchers said.
"It is more challenging [...] to track these zero-click attacks because targets may not notice anything suspicious on their phone. Even if they do observe something like 'weird' call behavior, the event may be transient and not leave any traces on the device."

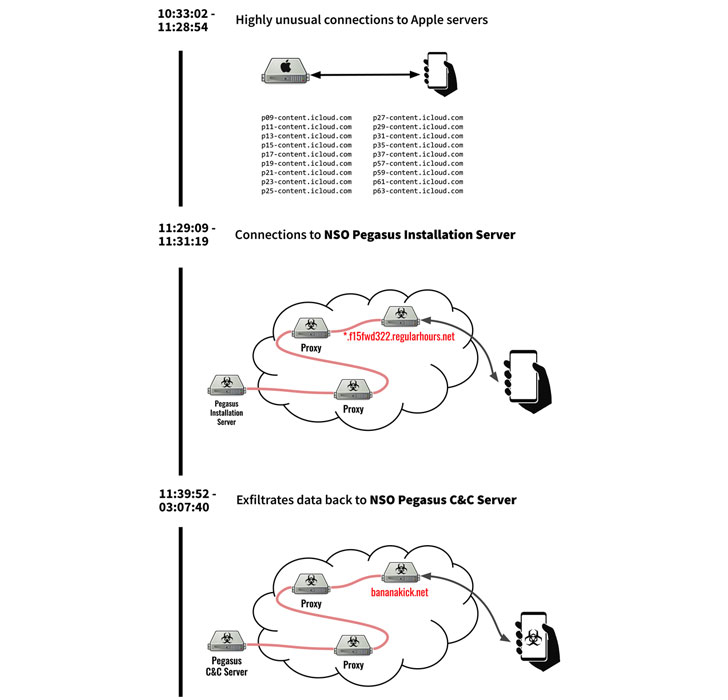
The findings came to light after one of the victims, Al Jazeera investigative journalist Tamer Almisshal, suspected his iPhone may have been hacked and consented to have his network traffic monitored by Citizen Lab researchers using a VPN app earlier this January.
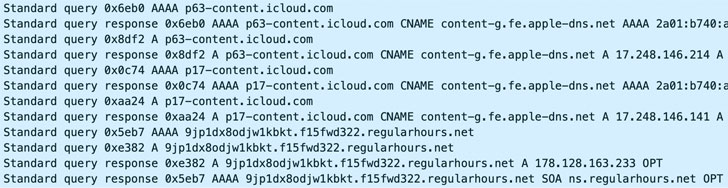
The internet watchdog found that the attacks occurred between July and August of this year using an exploit chain it calls KISMET, a zero-day present in iOS 13.5.1 that could be used to break Apple's security protections.
Citizen Lab said the 36 phones in question were hacked by four distinct "clusters" or NSO operators with probable ties to the Saudi and the United Arab Emirates governments.
A review of Almisshal's VPN logs revealed a sudden uptick in anomalous connections to Apple iCloud servers, which the researchers surmise was the initial infection vector to transmit the malicious code, followed by connections to an installation server to fetch the Pegasus spyware.
The implant comes with the capabilities to record audio from microphone and phone calls, take photos using the phone's camera, access the victim's passwords, and track the device's location.
While NSO Group has consistently maintained that its software is only meant to be used by law enforcement agencies to track down terrorists and criminals, this is far from the first time the tool has been abused by various governments to spy on critics, dissidents, politicians, and other individuals of interest.
One of those cases involved the delivery of the hacking tool through a previously undisclosed vulnerability in WhatsApp, which is currently pursuing legal action against the company in a US court.
"The current trend towards zero-click infection vectors and more sophisticated anti-forensic capabilities is part of a broader industry-wide shift towards more sophisticated, less detectable means of surveillance," the researchers concluded.
"The increased targeting of the media is especially concerning given the fragmented and often ad-hoc security practices and cultures among journalists and media outlets, and the gap between the scale of threats and the security resources made available to reporters and newsrooms."
Sextortionist Campaign Targets iOS, Android Users with New Spyware
17.12.2020 Apple Threatpost
Goontact lures users of illicit sites through Telegram and other secure messaging apps and steals their information for future fraudulent use.
New spyware is targeting iOS and Android frequenters of adult mobile sites by posing as a secure messaging application in yet another twist on sextortionist scams.
The spyware, dubbed Goontact, targets users of escort-service sites and other sex-oriented services – particularly in Chinese-speaking countries, Korea and Japan, according to research published by Lookout Threat Intelligence on Wednesday.
The ploy and malware can ultimately be used to exfiltrate data from targets. Data siphoned from devices include phone number, contact list, SMS messages, photos and location information. The nature of the data sweep and the context of the attacks “suggests that the ultimate goal is extortion or blackmail,” researchers Robert Nickle, Apurva Kumar and Justin Albrecht observed in a report published online Wednesday.
Threatpost Webinar Promo Bug Bounty
Click to register.
Sextortionist scams, in which threat actors claim they have video or other information that links a potential victim to illicit activity that could threaten a marriage, job or other significant relationship or interest, are nothing new. However, attackers typically use email to deliver these type of scams, using a range of tactics to get past email defenses and trick victims.
The new campaign uses a different and evolving tack. It lures a potential target by inviting them through an ad on a hosted illicit site to connect with women for free by using KakaoTalk or Telegram secure messaging apps. If someone takes the bait and initiates a conversation, it is Goontact operators with whom the person makes contact, researchers said.
“Targets are convinced to install (or sideload) a mobile application on some pretext, such as audio or video problems,” they wrote. “The mobile applications in question appears to have no real user functionality, except to steal the victim’s address book, which is then used by the attacker ultimately to extort the target for monetary gain.”
The specifics of the attack are different depending on if a victim is using an iOS or Android device. The iOS attacks have less capability to steal data, lifting only the victim’s phone number and contact list, researchers said. In some later iterations of the spyware, it connects to a secondary command-and-control (C2) server and displays a message tailored to the user before exiting the app.
The Android-based attack has significantly more threat capability, researchers said. “In addition to contact stealing, these samples contain more advanced functionality such as exfiltration of SMS messages, photos and location,” researchers wrote.
The Lookout team believes that the information stolen in the campaign will be used to blackmail or defraud victims, although so far they said they have seen no evidence proving this scenario.
The campaign itself bears resemblance to one reported by researchers in 2015, and Lookout researchers suspect it’s been around and operated by a crime affiliate rather than nation-state actors since 2013.
“However, the Goontact malware family is novel and is still actively being developed,” with the earliest sample having been observed in November 2018, researchers said.
Lookout researchers have contacted Google and Apple about Goontact as well as informed Threat Advisory Services customers with additional intelligence on the spyware and other threats.
Sextortion campaign uses Goontact spyware to target Android and iOS users
17.12.2020 Apple Securityaffairs
Security experts spotted a new malware strain, named Goontact, that allows its operators to spy on both Android and iOS users.
Security researchers from Lookout have discovered new spyware, dubbed Goontcat, that could target both Android and iOS users.
Goontact implement common spyware features, including the ability to gather data from the infected devices and gather system info.
The malware allows operators to retrieve phone identifiers and steal contacts, SMS messages, photos, and even location data.
Goontact is currently distributed via third-party sites promoting free instant messaging apps for escort services for users in Chinese speaking countries, Korea and Japan. The spyware is likely used as part of a sextortion campaign.
“The spyware, which we have named Goontact, targets users of illicit sites, typically offering escort services, and steals personal information from their mobile device.” reads the report published by Lookout. “The types of sites used to distribute these malicious apps and the information exfiltrated suggests that the ultimate goal is extortion or blackmail.”
Potential victims are lured to one of the hosted sites where they are invited to connect with women. These sites advertise account IDs for secure messaging apps such as KakaoTalk or Telegram that could allow to communicate with the escorts.
goontact
In reality, the victims communicated with Goontact operators that attempt to trick them into installing (or sideload) a mobile application that steals the victim’s address book.
“Targets are convinced to install (or sideload) a mobile application on some pretext, such as audio or video problems.” continues the report. “The mobile applications in question appears to have no real user functionality, except to steal the victim’s address book, which is then used by the attacker ultimately to extort the target for monetary gain.”
The analysis of admin panels of these servers revealed that the Goontact operators are Chinese-speaking individuals.
Experts pointed out that websites associated with Goontact campaign have many similarities in naming convention, appearance, and targeted geographic region with a sextortion campaign reported by Trend Micro in 2015
The campaign has been active since at least 2013, but the Goontact malware samples were first observed by Lookout in November 2018.
“While the Goontact surveillance apps described in this campaign are not available on Google Play or the iOS App Store, the duration, breadth and tactics exhibited highlight the lengths malicious actors will go to deceive victims and bypass built-in protections.” conclude the experts.
iOS Spyware Emerges in Longstanding Extortion Campaign
17.12.2020 Apple Securityweek
An extortion campaign targeting Chinese, Korean, and Japanese speakers recently started using a new piece of spyware, mobile security firm Lookout reported on Wednesday.
The campaign is focused on infecting iOS and Android of illicit sites, such as those offering escort services, in order to steal personal information, likely with the intent to blackmail or extort victims.
Dubbed Goontact, the spyware typically masquerades as secure messaging applications. Once it has infected a device, it targets a broad range of data for exfiltration, including device identifiers and phone numbers, contacts, SMS messages, photos on external storage, and location information.
“Tablets and smartphones are a treasure trove of personal data. These devices store private data, such as contacts, photos, messages and location. Access to all of this data enables cybercriminals like the operators of Goontact to run a successful extortion campaign,” Lookout notes.
The attacks target users in multiple Asian countries, including China, Japan, Korea, Thailand, and Vietnam.
The victims are first lured to sites that purportedly allow them to connect with women, where they are encouraged to install a mobile app for proper communication (bogus audio- or video-related issues are invoked).
Without real functionality, the app is meant to steal the victim’s address book. The attackers then use this information to extort money from the target.
Websites used in these attacks had naming, appearance, and targeting similarities, and also used logos that were previously observed on domains used in a sextortion campaign uncovered in 2015.
The Goontact campaign is believed to have been active since at least 2013. The earliest observed Goontact sample, however, is dated November 2018, with the malware still under active development.
“We believe this campaign is operated by a crime affiliate, rather than nation state actors. While we have yet to uncover any definitive infrastructure links, we believe it is highly probable that Goontact is the newest addition to this threat actor's arsenal. Most notably, the iOS component of this scam has not been reported on before,” Lookout says.
The iOS version of the spyware has evolved from mere theft of a victim’s phone number and contact list to also including the ability to communicate to a secondary command and control (C&C) server and display a crafted message to the victim.
Lookout also discovered that the iOS malware abuses the Apple enterprise provisioning system for sideloading, as well as enterprise certificates that appear to have been associated with legitimate businesses (companies in China and in the United States, across multiple verticals), so that the malicious app can be distributed outside the Apple App Store.
“Most of the companies observed either have current or past developer profiles and applications on the iOS App Store. However, It is still unclear to us whether these signing identities have truly been compromised, or if they were created by the malware operators masquerading as representatives of the companies in question,” the security researchers note.
More feature-rich, the Android version of Goontact can also exfiltrate SMS messages, photos, and device location, in addition to contact lists and the victim’s phone number.
Apple Patches Tens of Code Execution Vulnerabilities in macOS
17.12.2020 Apple Securityweek
Updates released this week by Apple for its macOS operating systems patch a total of 59 vulnerabilities, including roughly 30 that could lead to the execution of arbitrary code.
An attacker able to exploit the most severe of these issues would execute code within the context of the application, with the same privileges as the current user. Some of the bugs, Apple explains in its advisory, could be exploited to execute code with system or kernel privileges.
macOS Big Sur 11.1, Security Update 2020-001 for Catalina, and Security Update 2020-007 for Mojave address flaws in components such as Audio, App Store, Bluetooth, CoreAudio, FontParser, Graphics Drivers, Kernel, ImageIO, Intel Graphics Driver, libxml2, Ruby, WebRTC, and Wi-Fi.
Components that were affected the most are ImageIO (eight flaws, six resulting in arbitrary code execution), FontParser (seven vulnerabilities, six leading to arbitrary code execution), and Kernel (seven bugs, three resulting in applications being able to execute arbitrary code with kernel privileges).
Apple says many of the issues were corrected via improved input validation. Improved state management, improved checks and bounds checking, and other similar enhancements were used to address remaining flaws.
This week, Apple also released updates for tvOS and watchOS, to resolve 9 and 10 vulnerabilities in each, respectively. Just as with the release of iOS 14.3 and iPadOS 14.3, these updates are meant to fix arbitrary code execution, memory disclosure, heap corruption, and authentication policy violation flaws.
The company also patched vulnerabilities with the release of macOS Server 5.11 (open redirect/cross-site scripting in Profile Manager), Safari 14.0.2 (arbitrary code execution in WebRTC), iOS 12.5 (authentication policy violation in Security), and watchOS 6.3 (authentication policy violation in Security).
In an advisory, the Multi-State Information Sharing and Analysis Center (MS-ISAC) notes that there are no reports of the addressed vulnerabilities being exploited in live attacks.
Apple’s App Stores Open New Privacy Window for Customers
15.12.2020 Apple Securityweek
Apple has begun spelling out what kinds of personal information is being collected by the digital services displayed in its app stores for iPhones and other products made by the trendsetting company.
Starting Monday, the additional disclosures will begin to appear in apps made for iPads, Mac computers and Apple’s TV streaming device, as well as its biggest moneymaker, the iPhone. Apple announced the changes were coming six months ago as part of an effort to help its customers gain a better understanding of how apps monitor their habits, tastes and whereabouts.
In many instances, the data scooped up by apps is used to sell ads targeted at a particular person’s interest and location, especially if their services are being offered for free.
The increased transparency about the collection and handling of personal information is designed to help people make more informed decisions about which apps they choose to install on their phones and other devices.
The changes were worked out with European regulators and mesh with Apple’s efforts to position itself as a trustworthy guardian of its customers’ privacy — an issue CEO Tim Cook has been framing a “fundamental human right.” In the process, Cook has been taking veiled shots at Google and Facebook, which make most of their money from digital ads that are driven by the mining of personal information.
Apple also has plans to impose a new mandate that will require all iPhone apps to obtain permission before tracking a person’s activities on the device. That surveillance is currently done automatically by many apps, forcing people to go to the time and trouble to block the tracking in the settings of each app.
The anti-tracking feature was supposed to be released in September, but Apple delayed after Facebook and many other app makers protested. Apple is vowing to oust apps from its stores if they try to bypass the new anti-tracking rule when it becomes effective next year.
Apple Patches Code Execution Flaws iOS and iPadOS
15.12.2020 Apple Securityweek
Apple on Monday released a major point-upgrade to its flagship iOS and iPadOS mobile operating systems to patch a handful of serious security vulnerabilities.
The iOS 14.3 and iPadOS 14.3 release will provide cover for 11 documented security flaws, some serious enough to expose iPhones and iPads to code execution attacks.
The most serious of the bugs could allow hackers to launch harmful code on iPhones and iPads via a malicious font file. Apple patched two separate memory corruption issues in the way input in validates in certain font files and warned that a successful exploit "may lead to arbitrary code execution."
The two font parsing flaws -- CVE-2020-27943 and CVE-2020-27944 -- were discovered and reported by Mateusz Jurczyk of Google Project Zero.
Apple also documented three separate security holes in ImageIO, the programming interface framework that allows applications to read and write most image file formats. Apple said it improved input validation to fix the ImageIO bugs, which allow code execution via booby-trapped images.
The iOS and iPadOS patches also cover a logic error in App Store that may cause an enterprise application installation prompt to display the wrong domain; and a fix for a CoreAudio issue that could cause code execution via maliciously crafted audio files.
Apple Manufacturer Foxconn Confirms Cyberattack
9.12.2020 Apple Threatpost
Manufacturing powerhouse confirmed North American operations impacted by November cyberattack.
Foxconn Technology Group confirmed Tuesday that a November cyberattack knocked some of its U.S. operations offline. The incident is reportedly a ransomware attack carried out by a cybergang attempting to extort $34 million from the global manufacturing powerhouse.
“We can confirm that an information system in the U.S. that supports some of our operations in the Americas was the focus of a cybersecurity attack on November 29,” Foxconn said in a statement on Tuesday.
“The system that was affected by this incident is being thoroughly inspected and being brought back into service in phases,” the company said in a press statement.
According to a BleepingComputer report, the attack is believed to have been carried out by the DoppelPaymer cybergang. Hit was Foxconn’s manufacturing facility located in Chihuahua, Mexico. Criminals reportedly encrypted 1,200 servers, downloaded 100GB of data and deleted between 20-to-30TB backups.
Confidential Foxconn business documents appear to have been released publicly by the attackers in an attempt to verify that the data systems have been breached. Foxconn did not confirm with Threatpost the legitimacy of documents made public and reported on by BleepingComputer.
The DopplePaymer criminal group, whose ransomware goes by the same name, made headlines last year in a string of attacks against a number of large organizations, noted Andrea Carcano, co-founder of Nozomi Networks, in a prepared statement.
Carcano also noted that it’s now common for ransomware criminals to encrypt, delete and steal data as part of their crime. The hope is to force victims to pay a ransom to prevent public exposure of data and avoid the crippling of business systems.
Foxconn’s Chihuahua, Mexico manufacturing facility is used to assemble and ship electronics to the Americas, according to Foxconn. As of this writing the Foxconn Mexico-facility website (https://fii-na[.]com.mx/) appears to be down.
Saryu Nayyar, CEO of Gurucul, emphasized in a prepared statement that the “new standard model” for these attacks are, “break in, steal data to use for extortion and deploy ransomware.”
“It is a win-win for them, and a lose-lose for the victim even if they have backups in place to deal with a ransomware attack,” he wrote.
Large targets don’t just add up to potential big paydays. According to Chloé Messdaghi, VP of strategy at Point3 Security, large corporations have become prime targets for cybergangs given their ability to pay massive ransomware demands.
“In Foxconn’s case, it may well have to actually pay the ransom, because hitting and halting production is an attacker’s dream,” she wrote. For a billion-dollar corporation like Foxconn, spending $34 million may be an acceptable price to maintain business continuity, Messdaghi wrote.
The U.S. Cyber Emergency Response Team has long cautioned ransomware victims not to pay. “Paying the ransom does not guarantee the encrypted files will be released; it only guarantees that the malicious actors receive the victim’s money, and in some cases, their banking information,” the advisory says. “In addition, decrypting files does not mean the malware infection itself has been removed,” it wrote in an past advisory.
Apple to Tighten App Privacy, Remove Apps That Don't Comply
9.12.2020 Apple Securityweek
Apple is stepping up privacy for app users, forcing developers to be more transparent about data collection and warning they could be removed if they don’t comply with a new anti-tracking measure, a company executive and regulators said Tuesday.
The U.S. tech giant said it’s set to roll out the anti-tracking feature next year and warned it could kick apps off its widely used App Store if they don’t obey its requirements.
Called App Tracking Transparency, it will require apps to clearly ask for users’ permission before tracking them. It was due to be launched this year but was delayed to allow developers more time to make changes.
“Its aim is to empower our users to decide when or if they want to allow an app to track them in a way that could be shared across other companies’ apps or websites,” Senior Vice President of Software Engineering Craig Federighi said.
“Developers who fail to meet the standard can have their apps taken down from the app store,” Federighi said in an online keynote speech to the European Data Protection and Privacy Conference.
Privacy campaigners say the move is a vital step that could strengthen respect for privacy but tech rivals like Facebook that make money from digital advertising that tracks users have pushed back against the measure.
Federighi said tech users should be empowered to have more control of their data and dismissed arguments from advertisers and tech companies who say the anti-tracking feature will hurt the online ad industry.
“When invasive tracking is your business model, you tend not to welcome transparency and customer choice.”
Apple is itself the subject of complaints by European privacy activists who say the company uses software that tracks the behavior of iPhone users. Vienna-based group NOYB, founded by lawyer and activist Max Schrems, last month asked data protection authorities in Germany and Spain to examine the legality of unique codes that they say amount to tracking without users’ knowledge or consent, a practice banned under strict European Union privacy rules.
In a separate policy update, apps in the App Store will soon start giving users more details about the personal data they use, Britain’s competition watchdog said.
Each app’s listing will highlight key information about the data collected and a summary of its privacy policy. The changes, which were announced earlier this year, will take effect shortly for users worldwide, though a specific date wasn’t given.
The U.K.’s Competition and Markets Authority said it worked with counterparts in the Netherlands and Norway to push for the changes, based on concern users were not being told clearly whether their data was being shared with third parties.
iPhone Bug Allowed for Complete Device Takeover Over the Air
3.12.2020 Apple Securityaffairs
Researcher Ian Beer from Google Project Zero took six months to figure out the radio-proximity exploit of a memory corruption bug that was patched in May.
Details tied to a stunning iPhone vulnerability were disclosed by noted Google Project Zero researcher Ian Beer. Apple patched the vulnerability earlier this year. But few details, until now, were known about the bug that could have allowed a threat actor to completely take over any iPhone within a nearby vicinity. The hack could of been preformed over the air without even interacting with the victim’s device.
Beer said he spent six months figuring out the “wormable radio-proximity exploit” during a time when quarantines due to the COVID-19 virus were in effect and he was “locked down in the corner” of his bedroom. On Tuesday he published a blog post detailing his discovery and the hack.
Specifically, he was able to remotely trigger an unauthenticated kernel memory corruption vulnerability that causes all iOS devices in radio-proximity to reboot, with no user interaction.
The issue existed because of a protocol in contemporary iPhone, iPad, Macs and Apple Watches called Apple Wireless Direct Link (AWDL), Beer explained in his post. This protocol creates mesh networks for features such as AirDrop and Sidecar so these devices can connect and serve their appointed function–such as beam photos and files to other iOS devices, in the case of AirDrop.

File Photo: Ian Beer speaking at the 2018 Black Hat USA security conference.
“Chances are that if you own an Apple device you’re creating or connecting to these transient mesh networks multiple times a day without even realizing it,” Beer noted in his post.
Apple patched the bug responsible for the exploit in May with updates iOS 12.4.7 and watchOS 5.3.7, and tracked it as CVE-2020-3843 in supporting documentation.
Until then, however, the bug could have allowed someone to “view all the photos, read all the email, copy all the private messages and monitor everything which happens on [an iPhone] in real-time” without clicking on anything, Beer said. The hack would only work with devices within WiFi range, he said.
Beer detailed three different exploits—the most advanced of which that ultimately performed all of these functions–using a Raspberry Pi and WiFi adapters that he purchased off the shelf. Installing a prototype implant that can fully access the device took Beer about two minutes, but he said he could have likely pulled it off in a “handful of seconds” with a better exploit.
The researcher acknowledged that he never saw an evidence of the vulnerability being exploited in the wild. Moreover, since it took him six months to figure out the hack, it’s likely it existed unnoticed by threat actors.
However, just because it was not exploited and is fixed now does not trivialize its existence, Beer observed.
“One person working alone in their bedroom, was able to build a capability which would allow them to seriously compromise iPhone users they’d come into close contact with,” he said in his post. “Imagine the sense of power an attacker with such a capability must feel. As we all pour more and more of our souls into these devices, an attacker can gain a treasure trove of information on an unsuspecting target.”
Beer also noted the range of such attacks also could easily have been boosted using directional antennas, higher transmission powers and sensitive receivers.
Researchers from Google Project Zero have traditionally been adept at finding flaws in Apple products, but lately they have been particularly active in pointing out issues that exist in their key rival’s devices. Prior to Beer’s last disclosure, Project Zero researchers identified three zero-day vulnerabilities in only the last month that affected iOS and iPad, all of which Apple has patched.
Google Hacker Details Zero-Click 'Wormable' Wi-Fi Exploit to Hack iPhones
2.12.2020 Apple Thehackernews
Google Project Zero whitehat hacker Ian Beer on Tuesday disclosed details of a now-patched critical "wormable" iOS bug that could have made it possible for a remote attacker to gain complete control of any device in the vicinity over Wi-Fi.
The exploit makes it possible to "view all the photos, read all the email, copy all the private messages and monitor everything which happens on [the device] in real-time," said Beer in a lengthy blog post detailing his six-month-long efforts into building a proof-of-concept single-handedly.
The flaw (tracked as CVE-2020-9844) was addressed by Apple in a series of security updates pushed as part of iOS 13.5 and macOS Catalina 10.15.5 in May earlier this year.
"A remote attacker may be able to cause unexpected system termination or corrupt kernel memory," the iPhone maker noted in its advisory, adding the "double free issue was addressed with improved memory management."
The vulnerability stems from a "fairly trivial buffer overflow programming error" in a Wi-Fi driver associated with Apple Wireless Direct Link (AWDL), a proprietary mesh networking protocol developed by Apple for use in AirDrop, AirPlay, among others, enabling easier communications between Apple devices.
In a nutshell, the zero-click exploit uses a setup consisting of an iPhone 11 Pro, Raspberry Pi, and two different Wi-Fi adaptors to achieve arbitrary kernel memory read and write remotely, leveraging it to inject shellcode payloads into the kernel memory via a victim process, and escape the process' sandbox protections to get hold of user data.
Put differently, the attacker targets the AirDrop BTLE framework to enable the AWDL interface by brute-forcing a contact's hash value from a list of 100 randomly generated contacts stored in the phone, then exploits the AWDL buffer overflow to gain access to the device and run an implant as root, giving the malicious party full control over the user's personal data, including emails, photos, messages, iCloud data, and more.
Although there's no evidence that the vulnerability was exploited in the wild, the researcher noted that "exploit vendors seemed to take notice of these fixes."
This is not the first time security flaws have been uncovered in Apple's AWDL protocol. Last July, researchers from the Technical University of Darmstadt, Germany, revealed vulnerabilities in AWDL that enabled attackers to track users, crash devices, and even intercept files transferred between devices via man-in-the-middle (MitM) attacks.
Synacktiv Details Patched Apple "Memory Leak" Zero-Day
That's not all. In a separate development, Synacktiv shared more details about CVE-2020-27950, one of the three actively exploited flaws that were patched by Apple last month following a report from Google Project Zero.
While the disclosures were short on details, the vulnerabilities were the result of a memory corruption issue in the FontParser library that allowed for remote code execution, a memory leak that granted a malicious application kernel privileges to run arbitrary code, and a type confusion in the kernel.
By comparing the two kernel binaries associated with iOS 12.4.8 and 12.4.9, Synacktiv researchers were able to backtrace the roots of the memory leak problem, explicitly noting that the changes address how the kernel handles mach messages associated with inter-process communication in Apple devices.
The researchers also devised a proof-of-concept code exploiting the flaw to reliably leak a mach port kernel address.
"It's quite surprising how long this vulnerability has survived in XNU knowing that the code is open source and heavily audited by hundreds of hackers," Synacktiv's Fabien Perigaud said.
MacOS Users Targeted By OceanLotus Backdoor
1.12.2020 Apple Threatpost
The new backdoor comes with multiple payloads and new detection evasion tactics.
A macOS backdoor variant has been uncovered that relies of multi-stage payloads and various updated anti-detection techniques. Researchers linked it to the OceanLotus advanced persistent threat (APT) group.
The Vietnam-backed OceanLotus (also known as APT 32) has been around since at least 2013, and previously launched targeted attacks against media, research and construction companies. Researchers said that in this case the attackers behind the malware variant appear to be hitting users from Vietnam, because the name of the lure document from the campaign is in Vietnamese. Older samples of the backdoor have targeted the same region before, according to researchers with Trend Micro.
“Some of the updates of this new variant include new behavior and domain names,” said researchers Luis Magisa and Steven Du. “Threat groups such as OceanLotus are actively updating malware variants in attempts to evade detection and improve persistence.”
The initial attack vector (such as phishing emails or otherwise) behind the malware is unclear; Threatpost has reached out to researchers for more details. However, the OceanLotus APT was recently discovered using malicious websites as well as Google Play apps to spread other malware.
The malware is packed in an app, bundled in a .zip archive. The app attempts to pass itself off as a Microsoft Word document (using the Word icon). The app bundle contains two notable files: The shell script containing the main malicious processes, and the “Word” file displayed during execution.
In another attempt at evading detection, the app bundle’s name utilizes special characters – three bytes (“efb880”) that are in UTF-8 encoding.
“When a user looks for the fake doc folder via the macOS Finder app or the terminal command line, the folder’s name shows ‘ALL tim nha Chi Ngoc Canada.doc’ (‘tìm nhà Chị Ngọc’ roughly translates to ‘find Mrs. Ngoc’s house’),” said researchers in a Friday analysis. “However, checking the original .zip file that contains the folder shows three unexpected bytes between ‘.’ and ‘doc’.”
These bytes are special unicode control characters that don’t change the visual appearance of the file. However, while the file visually looks like a normal file, the operating system sees the app bundle as an unsupported directory type due to these special characters. Therefore, as a default action the “open” command is used to execute the malicious app, said researchers.
Once the app is executed, the malware launches a second-stage payload (ALL tim nha Chi Ngoc Canada.?doc/Contents/Resources/configureDefault.def), which in turn drops a third-stage payload before deleting itself.
The third-stage payload uses custom encryption, with base64 encoding and byte manipulation. This payload has capabilities for collecting operating system information and submitting the data to its command-and-control (C2) servers; as well as receiving additional C2 communication information.
Its backdoor functionalities include the ability to get processor and memory information, get the serial number and get the network interface MAC addresses. All this information is encrypted and sent to the C2 server. Other supported commands include: Getting the file size; downloading and executing files; running commands in terminal; downloading and removing files; and getting config information.
Researchers said this malware variant has similarities to another OceanLotus backdoor discovered in 2018, including identical supported commands and their respective codes used in both variants. OceanLotus has previously been found using other detection evasion tactics, including steganography and injecting malware into the Windows Error Reporting (WER) service to evade detection. From at least January to April, researchers saw the group attacking China’s Ministry of Emergency Management, as well as the government of Wuhan province, in an apparent bid to steal intelligence regarding the country’s COVID-19 response. Also in 2020, the group was spotted launching an espionage campaign aimed at Android users in Asia.
Researchers said that to avoid malware such as this, macOS users should never click links or download attachments from emails coming from suspicious sources, and regularly patch their software and applications.
Apple Security Chief Allegedly Tried to Bribe Police With iPads
25.11.20 Apple Securityweek
Apple's global security director has been charged with bribery for allegedly offering hundreds of iPads to Californian law enforcement officers in exchange for weapons permits for company employees.
Chief Security Officer Thomas Moyer promised to give the Santa Clara County sheriff's office 200 iPads, worth about $70,000, in exchange for concealed weapons permits (CCW), the county's district attorney alleged in a statement Monday.
The proposed deal was abandoned at the last minute.
An undersheriff and a captain, Rick Sung and James Jensen, were also charged for having sought the gifts, the statement said, with a two-year investigation revealing that the permits were going to be withheld until the iPads could be obtained.
"Undersheriff Sung and Captain Jensen treated CCW licenses as commodities and found willing buyers," District Attorney Jeff Rosen said in the statement.
"Bribe seekers should be reported to the District Attorney's Office, not rewarded with compliance."
An insurance broker was also implicated, as he offered $6,000 in luxury sports seats in exchange for weapons permits, which the district attorney's office said usually cost between $200 and $400.
Moyer's $70,000 iPad bribe was meant to be for four concealed weapons permits, the prosecutors' statement said.
But the group backtracked on the arrangement "when Sung and Moyer learned of the search warrant that the District Attorney's Office executed at the Sheriff's Office seizing all its CCW license records."
"Tom Moyer is innocent of the charges filed against him," the Apple executive's lawyer Ed Swanson said in a written statement.
"He did nothing wrong and has acted with the highest integrity throughout his career. We have no doubt he will be acquitted at trial."
The lawyer did not deny the iPad gift, but sought to clarify the events in question, saying they were not part of a bribe.
"Apple did offer to donate iPads. And Apple did apply for CCW permits. But those two things are unrelated. There was no quid pro quo," Swanson insisted.
"Ultimately, this case is about a long, bitter, and very public dispute between the Santa Clara County Sheriff and the District Attorney, and Tom is collateral damage to that dispute."
Swanson pointed out Moyer's Navy service and his 14 years of work at Apple as "a hardworking, decent man."
"He does not deserve to have his good name tarnished by these baseless charges."
The four men will face their first hearing during an arraignment on January 11 in a San Jose court, according to the district attorney's office. They could face jail time if convicted. Apple did not immediately respond to a request for comment from AFP.
Apple Lets Some of its Big Sur macOS Apps Bypass Firewall and VPNs
18.11.20 Apple Thehackernews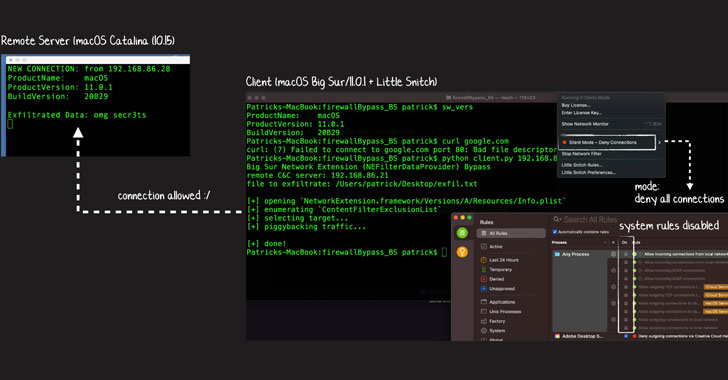
Apple is facing the heat for a new feature in macOS Big Sur that allows many of its own apps to bypass firewalls and VPNs, thereby potentially allowing malware to exploit the same shortcoming to access sensitive data stored on users' systems and transmit them to remote servers.
The issue was first spotted last month by a Twitter user named Maxwell in a beta version of the operating system.
"Some Apple apps bypass some network extensions and VPN Apps," Maxwell tweeted. "Maps for example can directly access the internet bypassing any NEFilterDataProvider or NEAppProxyProviders you have running."
But now that the iPhone maker has released the latest version of macOS to the public on November 12, the behavior has been left unchanged, prompting concerns from security researchers, who say the change is ripe for abuse.
Of particular note is the possibility that the bypass can leave macOS systems open to attack, not to mention the inability to limit or block network traffic at users' discretion.
According to Jamf security researcher Patrick Wardle, the company's 50 Apple-specific apps and processes have been exempted from firewalls like Little Snitch and Lulu.
The change in behavior comes as Apple deprecated support for Network Kernel Extensions last year in favor of Network Extensions Framework.
"Previously, a comprehensive macOS firewall could be implemented via Network Kernel Extension (KEXTs)," Wardle noted in a tweet back in October. "Apple deprecated kexts, giving us Network Extensions... but apparently (many of their apps/ daemons bypass this filtering mechanism."
NEFilterDataProvider makes it possible to monitor and control Mac's network traffic either by opting to "pass or block the data when it receives a new flow, or it can ask the system to see more of the flow's data in either the outbound or inbound direction before making a pass or block decision."
Thus by circumventing NEFilterDataProvider, it makes it hard for VPNs to block Apple applications.
Wardle also demonstrated an instance of how malicious apps could exploit this firewall bypass to exfiltrate sensitive data to an attacker-controlled server using a simple Python script that piggybacked the traffic onto an Apple exempted app despite setting Lulu and Little Snitch to block all outgoing connections on a Mac running Big Sur.
Apple is yet to comment on the new changes.
While the company's motivation to make its own apps exempt from firewalls and VPNs is still unclear, it's possible that they are part of Apple's "anti-malware (and perhaps anti-piracy) efforts" to keep traffic from its apps out of VPN servers and prevent geo-restricted content from being accessed through VPNs.
Some Apple Apps on macOS Big Sur Bypass Content Filters, VPNs
18.11.20 Apple Threatpost
Attackers can exploit the feature and send people’s data directly to remote servers, posing a privacy and security risk, researchers said.
Security researchers are blasting Apple for a feature in the latest Big Sur release of macOS that allows some Apple apps to bypass content filters and VPNs. They say it is a liability that can be exploited by threat actors to bypass firewalls and give them access to people’s systems and expose their sensitive data.
A Big Sur beta user named Maxwell (@mxswd) was the first to point out the issue back in October on Twitter. Despite concerns and questions among security professionals, Apple released Big Sur to the public on Nov. 12.
“Some Apple apps bypass some network extensions and VPN Apps,” he tweeted. “Maps for example can directly access the internet bypassing any NEFilterDataProvider or NEAppProxyProviders you have running.”
His tweet triggered a rash of comments decrying the issue and accusing Apple, which long has touted its concern for user privacy and the overall security of its products over those of its rivals, about having a double standard when it comes to the company’s privacy policies and those of its customers and partners.
Discomfort with Apple’s choice to bypass its NEFilterDataProvider were also echoed on the Apple’s Developer Forum.
50 Apple Apps Excluded?
“We found out that traffic from about 50 Apple processes is excluded from being seen and controlled by NEFilterDataProvider, due to an undocumented Apple exclusion list. This is a regression from what was possible with NKEs,” wrote a developer that goes by Dok. “We believe it has a high number of drawbacks, and we already know this is negatively affecting our end users.”
Apple describes the NEFilterDataProvider as such:
Network content is delivered to the Filter Data Provider in the form of NEFilterFlow objects. Each NEFilterFlow object corresponds to a network connection opened by an application running on the device. The Filter Data Provider can choose to pass or block the data when it receives a new flow, or it can ask the system to see more of the flow’s data in either the outbound or inbound direction before making a pass or block decision.
In addition to passing or blocking network data, the Filter Data Provider can tell the system that it needs more information before it can make a decision about a particular flow of data. The system will then ask the Filter Control Provider to update the current set of rules and place them in a location on disk that is readable from the Filter Data Provider extension.
Apple’s NEFilterDataProvider is used by application firewalls and VPNs to filter traffic on an app-by-app basis. Bypassing NEFilterDataProvider makes it hard for VPNs to block Apple applications. Worse, researchers say the bypass can leave systems open to attack.
Bypassing Firewalls
While users assumed Apple would fix the flaw before the OS emerged from beta into full release, this doesn’t appear to have happened. Patrick Wardle (@patrickwardle) principal security researcher at Jamf, elaborated on the issue on Twitter just last week, demonstrating how the vulnerability that remains in the public release of the OS can be exploited by malware.
“In Big Sur Apple decided to exempt many of its apps from being routed thru the frameworks they now require 3rd-party firewalls to use (LuLu, Little Snitch, etc.),” he tweeted, posing the question, “Could this be (ab)used by malware to also bypass such firewalls?”
Answering his own question, Wardle posted a simple graphic demonstrating how easily malware could exploit the issue by sending data from apps directly to the internet rather than using a firewall or VPN to first affirm or deny if the traffic is legitimate.
Moreover, he said it appears that Apple knew of the dangers of allowing such a feature to make it into the final release of the OS. Wardle posted an excerpt from an Apple Support document that stresses the critical nature of giving an OS the ability to monitor and filter network traffic for privacy and security reasons.
Apple did not respond to request for comment on the issue at the time this was written.
Indeed, Apple recently revealed that developers of apps for its hardware and devices will have to reveal how data is shared with any “third-party partners,” which include analytics tools, advertising networks, third-party SDKs or other external vendors. The move came after complaints about over-permissioned apps that collect, use and share private user information.
“One rule for them and another for the rest of the peasants,” tweeted Sean Parsons (@seanparsons), a developer and senior engineer at Momentum Works.
The VPN and firewall bypass isn’t the only problem being reported by users of Big Sur. A report in MacRumors based on user posts on one of its forums that claim that “a large number of late 2013 and mid 2014 13-inch MacBook Pro owners” reported that the OS is bricking this machines. Similar reports were found across Reddit and Apple Support Communities, according to the report.
macOS Big Sur 11.0.1 Patches 60 Vulnerabilities
16.11.20 Apple Securityweek
The first update released by Apple for macOS Big Sur 11.0 addresses 60 vulnerabilities affecting various components of the operating system.
macOS Big Sur 11.0 was officially launched on November 12 and on the same day Apple released its first update, version 11.0.1. The company has advised customers to update to this version — macOS Big Sur 11.0 comes preinstalled on certain Mac models — but there have been reports that the Big Sur update is bricking some older MacBook Pros.
Some of the 60 vulnerabilities patched by Big Sur 11.0.1 were previously patched in macOS and other Apple operating systems, including three actively exploited vulnerabilities affecting the kernel and FontParser components.
The actively exploited flaws were reported to Apple by Google Project Zero and they can lead to information disclosure and arbitrary code execution. These security holes also impact some versions of iOS and tvOS.
The other vulnerabilities patched with the release of Big Sur 11.0.1 affect components such as App Store, Audio, Bluetooth, CoreAudio, CoreCapture, CoreGraphics, CoreText, Disk Images, Crash Reporter, Finder, FontParser, Foundation, ImageIO, the kernel, libxml2, libxpc, Logging, Mail, Messages, Model I/O, NetworkExtension, NSRemoteView, PCRE, Power Management, Python, Quick Look, Ruby, Safari, Sandbox, SQLite, System Preferences, WebKit, Wi-Fi and Xsan.
Exploitation of the vulnerabilities can allow privilege escalation, arbitrary code execution, access to restricted information from memory or files, DoS attacks, MitM attacks, modifying the file system, spoofing the address bar in Safari, corrupting data (SQLite), and bypassing protections.
What Apple apparently hasn’t fixed is related to apps on Big Sur bypassing firewall and VPN connections. This issue was brought to light in October and experts believed it would likely get fixed until the official release of Big Sur.
Apple last week also released security updates for Safari, to patch an address bar spoofing issue and a code execution flaw related to WebKit, as well as updates for macOS High Sierra and Mojave, to fix the actively exploited vulnerabilities reported by Google Project Zero.
When it announced Big Sur, the tech giant also unveiled the M1, the first system-on-chip (SoC) designed specifically for the Mac. Apple said the M1 was designed from the very start to work with Big Sur, in an effort to improve performance, battery life and security.
Privacy Activists in EU File Complaints Over iPhone Tracking
16.11.20 Apple BigBrothers Securityweek
European privacy activists have filed complaints against Apple over its use of software to track the behavior of iPhone users.
The Vienna-based group NOYB - short for “none of your business” - said Monday that it has asked data protection authorities in Germany and Spain to examine the legality of Apple’s tracking codes.
The codes, known as IDFA or Identifier for Advertisers, are similar to the cookies that websites use to store information on user behavior.
NOYB says the iOS operating system creates unique codes for each iPhone that allow Apple and other third parties to “identify users across applications and even connect online and mobile behaviour.”
The group argues that this amounts to tracking without users’ knowledge or consent, a practice that is banned under the European Union’s electronic privacy rules.
“Tracking is only allowed if users explicitly consent to it,” said Stefano Rossetti, a lawyer for NOYB. The privacy group said it is currently reviewing a similar system used by Google.
Apple declined to immediately respond to a request for comment.
NOYB, founded by privacy activist and lawyer Max Schrems, has filed numerous cases against major tech companies including one against Facebook that recently led the European Union’s top court to strike down an agreement that allows companies to transfer data to the United States over snooping concerns.
Apple Patches Three Actively Exploited Vulnerabilities
6.11.20 Apple Securityweek
Apple on Thursday released patches for tens of vulnerabilities across its products, including three flaws that are actively exploited in attacks.
The three vulnerabilities were discovered by Google Project Zero researchers and could lead to remote code execution, leak of kernel memory, and escalation of privilege to kernel level, respectively, Project Zero technical lead Ben Hawkes says.
Tracked as CVE-2020-27930, the first of the vulnerabilities resides in the FontParser component and could be exploited for the execution of code via maliciously crafted fonts. This, Apple explains, is a memory corruption issue that was addressed by improving input validation.
Residing in the kernel and tracked as CVE-2020-27950, the second vulnerability could result in a malicious application disclosing kernel memory. The third flaw, CVE-2020-27932, could allow an application to execute code with kernel privileges.
Google Threat Analysis Group (TAG) security researcher Shane Huntley says that the targeting of these vulnerabilities is similar to that of other recently reported zero-days, without connection to election targeting.
The release of iOS 14.2 and iPadOS 14.2 addresses all three flaws, as well as twenty other vulnerabilities that affect components such as Audio, CallKit, CoreAudio, Foundation, ImageIO, Kernel, libxml2, Model I/O, and WebKit, among others.
Exploitation of these vulnerabilities could lead to arbitrary code execution, denial of service, privilege escalation, unauthenticated access to stored passwords, memory leak, file read, or the answering of two simultaneous calls without being notified on the second call.
The Center for Internet Security’s (CIS) Multi-Stage Information Sharing & Analysis Center (MS-ISAC) notes in an emailed advisory that all three vulnerabilities pose a high risk to both government and business organizations, regardless of their size.
The three actively exploited vulnerabilities were also addressed with the release of updates for macOS Catalina 10.15.7, as well as in watchOS 5.3.9, watchOS 6.2.9, and watchOS 7.1.
Fifteen other bugs were squashed with watchOS 7.1, the same number of bugs that was addressed with tvOS 14.2, rolling out starting this week as well.
Administrators are advised to apply the available patches as soon as possible, make sure that software always runs with lower privileges, and educate users in refraining from downloading or executing files from untrusted sources, as well as from navigating to untrusted websites.
Update Your iOS Devices Now — 3 Actively Exploited 0-Days Discovered
6.11.20 Apple Thehackernews
Apple on Thursday released multiple security updates to patch three zero-day vulnerabilities that were revealed as being actively exploited in the wild.
Rolled out as part of its iOS, iPadOS, macOS, and watchOS updates, the flaws reside in the FontParser component and the kernel, allowing adversaries to remotely execute arbitrary code and run malicious programs with kernel-level privileges.
The zero-days were discovered and reported to Apple by Google's Project Zero security team.
"Apple is aware of reports that an exploit for this issue exists in the wild," the iPhone maker said of the three zero-days without giving any additional details so as to allow a vast majority of users to install the updates.
The list of impacted devices includes iPhone 5s and later, iPod touch 6th and 7th generation, iPad Air, iPad mini 2 and later, and Apple Watch Series 1 and later.
The fixes are available in versions iOS 12.4.9 and 14.2, iPadOS 14.2, watchOS 5.3.9, 6.2.9, and 7.1, and as a supplemental update for macOS Catalina 10.15.7.
According to Apple's security bulletin, the flaws are:
CVE-2020-27930: A memory corruption issue in the FontParser library that allows for remote code execution when processing a maliciously crafted font.
CVE-2020-27932: A memory initialization issue that allows a malicious application to execute arbitrary code with kernel privileges.
CVE-2020-27950: A type-confusion issue that makes it possible for a malicious application to disclose kernel memory.
"Targeted exploitation in the wild similar to the other recently reported 0days," said Shane Huntley, Director of Google's Threat Analysis Group. "Not related to any election targeting."
The disclosure is the latest in the string of zero-days Project Zero has reported since October 20. First came the Chrome zero-day in Freetype font rendering library (CVE-2020-15999), then a Windows zero-day (CVE-2020-17087), followed by two more in Chrome and its Android variant (CVE-2020-16009 and CVE-2020-16010).
A patch for the Windows zero-day is expected to be released on November 10 as part of this month's Patch Tuesday.
While more details are awaited on whether the zero-days were abused by the same threat actor, it's recommended that users update their devices to the latest versions to mitigate the risk associated with the flaws.