
Apple Articles - H 2020 1 2 iOS Apple List - H 2021 2020 2019 2018 iOS
New iOS Jailbreak Tool Works on iPhone Models iOS 11 to iOS 13.5
27.5.2020 Threatpost Apple
Latest version of UnC0ver uses unpatched zero-day exploit to take complete control of devices, even those running iOS 13.5.
A hacker team has released a new method to jailbreak iPhones that they claim uses a zero-day exploit that allows them to jailbreak iPhones running iOS 11 through Apple’s most recent version of its mobile operating system – iOS 13.5.
Calling it a “big milestone for jailbreaking,” one of its creators, a hacker called Pwn20wnd, heralded the new jailbreak release on Twitter, claiming it’s the first zero-day jailbreak for the iPhone platform since iOS 8.
Hackers did not disclose the details of the unpatched iOS flaw their tool relied on. One report on Vice Motherboard said the jailbreak takes advantage of a kernel vulnerability. No matter, the hacker team expect Apple to eventually patch the flaw which is just the “nature” of the business, Pwn20wnd said in the report.
“Even when they release a patch, users can downgrade to the previous iOS version for about two weeks usually, and after that, the users should stay on their versions so that the jailbreak keeps working,” according to the hacking team’s report of the jailbreak posted to the Unc0ver website. The jailbreak only works on iPhones running iOS 11 through iOS 13.5 and does not work on iOS versions 12.3 to 12.3.2 and 12.4.2 to 12.4.5.
The new jailbreak enables “unrestricted storage access to jailbreak applications for sandbox backwards compatibility,” while leaving security restrictions enabled for system and user applications in place, the team said. The new tools also update Phone Rebel case models and bundled packages.
Jailbreak tools are software that take advantage of vulnerabilities in iOS to allow users sometimes full control of their device. Jailbreaking bypasses DRM restrictions, allowing users to run unauthorized and custom software as well as make other tweaks to iOS.
Apple’s iOS are closed-source. The company historically has cited security reasons for not permitting its users to tinker with the proprietary code for iOS. However, jailbreaks have become popular ways for iOS developers and users to hack into their own devices to make custom changes.
“Allowing you to change what you want and operate within your purview, unc0ver unlocks the true power of your iDevice,” the Unc0ver team boasted on the tool’s download page.
While this may be true, jailbreaking an iPhone also creates serious security concerns, as it can make jailbreak devices susceptible to rogue or unstable apps downloaded from outside of Apple’s curated App Store. While potentially the new tool’s feature to leave security restrictions in place could remedy this risk, it’s difficult to know at this time if that will make a difference.
Just because security researchers highly discourage the practice doesn’t mean iOS developers and users will listen, given the enthusiasm with which they met the release of the new Unc0ver tool. Their interest was so keen that the download site crashed not long after the release, Vice Motherboard’s Joseph Cox said on Twitter.
Developers also widely applauded the tool on the social-media platform upon Pwn20wnd’s announcement of its release.
“I’d like to congratulate you man you’ve done great for the community for the past 3 years and today will be the biggest release of them all,” developer Kaleb Davison (@drdavison5) tweeted.
Another Twitter user @IOSblaraby tweeted that the release is “a big hit for Apple,” citing its ability to crack even the most recent release of iOS.
Jailbreak Tool Updated to Unlock iPhones Running iOS 13.5
27.5.2020 Securityweek Apple
The unc0ver jailbreaking tool has been updated with support for the latest iOS releases, courtesy of a zero-day vulnerability, the team behind the utility announced.
unc0ver, which supports iOS 11 through iOS 13.5 (with some exceptions), is advertised as the most advanced jailbreak tool out there, providing users with the opportunity to do with their devices more than what the standard operating system allows them to.
Just as other similar tools out there, unc0ver is relying mainly on known vulnerabilities that are usually addressed in the next platform release. Version 5.0.0 of the application, however, exploits an unknown vulnerability to help users unlock “the true power” of their iOS devices.
“Every other jailbreak released since iOS 9 used 1day exploits that were either patched in the next beta version or the hardware. This will be a big milestone for jailbreaking,” Pwn20wnd, the team behind unc0ver, says.
On the website dedicated to the tool, the team says unc0ver focuses on stability and it preserves the security layers on the device, by only adjusting them, instead of removing them entirely.
The latest version of the tool, they explain, enables “unrestricted storage access to jailbreak applications for sandbox backwards compatibility while keeping security intact by leaving the security restrictions enabled for system and user applications.”
Furthermore, they explain that users who jailbreak their iPhone would still be able to apply iOS updates, as all kernel modifications are done in memory, thus ensuring that devices remain operable when platform upgrades are installed.
The team also notes that their tool has been extensively tested on a large number of devices, ranging from iPhone 7 running iOS 11, to iPhone 11 and iPhone 11 Pro Max running iOS 13.5. The tool was released with support for macOS, Windows, and Linux computers.
The price of some iOS exploits has dropped lately, mainly due to an increased focus on hacking Apple’s mobile platform, and exploit acquisition firm Zerodium recently announced that it would not be acquiring certain types of iOS exploits for the next two or three months.
New Tool Can Jailbreak Any iPhone and iPad Using An Unpatched 0-Day Bug
25.5.2020 Thehackernews Apple
The hacking team behind the "unc0ver" jailbreaking tool has released a new version of the software that can unlock every single iPhone, including those running the latest iOS 13.5 version.
Calling it the first zero-day jailbreak to be released since iOS 8, unc0ver's lead developer Pwn20wnd said "every other jailbreak released since iOS 9 used 1day exploits that were either patched in the next beta version or the hardware."
The group did not specify which vulnerability in iOS was exploited to develop the latest version.
The unc0ver website also highlighted the extensive testing that went behind the scenes to ensure compatibility across a broad range of devices, from iPhone 6S to the new iPhone 11 Pro Max models, spanning versions iOS 11.0 through iOS 13.5, but excluding versions 12.3 to 12.3.2 and 12.4.2 to 12.4.5.
"Utilizing native system sandbox exceptions, security remains intact while enabling access to jailbreak files," according to unc0ver, meaning installing the new jailbreak will likely not compromise iOS' sandbox protections.
Jailbreaking, analogous to rooting on Google's Android, is a privilege escalation that works by exploiting flaws in iOS to grant users root access and full control over their devices. This allows iOS users to remove software restrictions imposed by Apple, thereby allowing access to additional customization and otherwise prohibited apps.
But it also weakens the device's security, opening the door to all kinds of malware attacks. The added security risks, coupled with Apple's steady hardware and software lockdown, have made it difficult to jailbreak devices deliberately.
Furthermore, jailbreaks tend to be very specific and based on previously disclosed vulnerabilities, and very much dependent on the iPhone model and iOS version, in order for them to be successfully replicated.
The development comes as zero-day exploit broker Zerodium said it would no longer purchase iOS RCE vulnerabilities for the next few months, citing "a high number of submissions related to these vectors."
Last August, Pwn20wnd exploited a SockPuppet flaw (CVE-2019-8605) uncovered by Googler Ned Williamson to release a public version of the jailbreak — making it the first time an up-to-date firmware was unlocked in years — after Apple accidentally reintroduced a previously patched flaw in iOS 12.4. The company later rolled out a fix in iOS 12.4.1 to address the privilege escalation vulnerability.
Then in September, a security researcher published details of a permanent unpatchable bootrom exploit, dubbed checkm8, that could be employed to jailbreak virtually every type of Apple mobile device released between 2011 and 2017, including iPhones, iPads, Apple Watches, and Apple TVs.
While the new jailbreak leverages an as-yet-unknown zero-day vulnerability, the iPhone maker will likely roll out a security update in the coming weeks to plug the flaw exploited by unc0ver.
The new Unc0ver 5.0.0 jailbreak can be installed from iOS, macOS, Linux, and Windows devices. The usage instructions are available on the unc0ver website here.
Increased Focus on iOS Hacking Leads to Drop in Exploit Prices
19.5.2020 SecuritryWeek Apple
The price of some iOS exploits has dropped recently and at least one exploit acquisition company is no longer buying certain types of vulnerabilities. Experts believe this is a result of security researchers increasingly focusing on finding vulnerabilities in iOS.
Exploit acquisition company Zerodium announced last week that it would no longer be buying certain types of iOS exploits for the next 2-3 months due to surplus. It also announced that prices for iOS exploit chains that require some user interaction and don’t provide persistence will likely drop in the near future.
Furthermore, Zerodium’s CEO and founder, Chaouki Bekrar, said “iOS security is fucked,” noting that they are already seeing many exploits designed to bypass pointer authentication codes (PAC) — PAC provides protection against memory attacks — and a few zero-day exploits that can help an attacker achieve persistence on all iPhones and iPads.
Zerodium’s website says it offers up to $2 million for full iOS exploit chains that achieve persistence and require no user interaction. In comparison, the same type of exploit for Android can be worth up to $2.5 million.
Apple iOS exploit prices drops due to large number of vulnerabilities
The company also typically offers up to $500,000 for iOS persistence exploits, and remote code execution and local privilege escalation vulnerabilities affecting iMessage or Safari. Hackers can earn up to $200,000 for Safari remote code execution exploits without a sandbox escape component and the same amount just for a sandbox escape.
However, Bekrar says in the past few months they’ve seen a spike in iOS submissions, particularly Safari remote code execution, sandbox escapes and privilege escalation. This forced his company to first reduce prices and then to completely suspend the acquisition of such exploits for the next 2-3 months.
“The spike is likely caused by the increased number of researchers looking into iOS and probably by the availability of public jailbreaks which are helping researchers to reverse engineer iOS devices more easily and find bugs faster. On the other hand, the number of Android submissions remains stable,” he explained.
Bekrar added, “Our prices for zero-click exploits and persistence remain unchanged for now as these capabilities are unicorns with only a few of them available each year.”
Zerodium offers high rewards for a wide range of vulnerabilities, but the company says it only accepts high-quality exploits, which it claims to sell only to government organizations, mostly in Europe and North America.
Alfonso de Gregorio, founder of exploit acquisition company Zeronomicon, confirms that there is a surplus of iOS local privilege escalation exploits.
“Some of the mitigations in place are being successfully bypassed, showing that meaningful progress is being made by security researchers. This will affect the prices for those exploits, assuming their demand will not change significantly,” De Gregorio told SecurityWeek.
Zeronomicon, which provides exploits to both governments and private sector companies, claims to have over 1,000 satisfied customers. The company, which also claims to hold itself to high ethical standards, says it provides organizations with “tailored cybersecurity capabilities, actionable vulnerability information, and risk mitigation strategies.”
“I established Zeronomicon to help the fellow security researchers to convert their talent and knowledge into profit, meaning that the amount paid for each security capability always reflects the best market conditions and other circumstances existing at the time of the acquisition,” De Gregorio said.
“The market prices reflect the changing supply and demand indeed,” he added. “This is not the first nor the last time that the payouts adjust according to the new values given to the exploit chains, as already occurred years ago with the exploits that targeted web browsers.”
Zerodium and Zeronomicon did not want to say exactly how much prices have dropped or how much they could drop in the future.
Zuk Avraham, founder of mobile security firm Zimperium and cybersecurity automation company ZecOps, has also confirmed that the price of iOS exploits has decreased. He says iOS security research has become much more mainstream, with many researchers drawn to it by high exploit prices and an increasing amount of resources to learn from (e.g. vulnerability writeups, blogs).

“Large portions of iOS code were not touched for years, it is a known secret that many of the vulnerabilities aren't patched properly, and in-general, there are many vulnerabilities in iOS - much more than what most people think / are aware of,” Avraham told SecurityWeek.
It remains to be seen just how much the upcoming iOS 14 and A14 mobile processors will improve security.
“A14 devices are supposed to include memory tagging mitigation, which may make some of the exploits value worth less - so a lot of researchers are dumping their exploits now and trying to cash in,” Avraham said.
Both Zimperium and ZecOps have run mobile exploit acquisition programs, but their focus is on already-patched vulnerabilities rather than zero-day flaws.
ZecOps recently reported seeing targeted attacks exploiting unpatched vulnerabilities in the iOS Mail app. Apple has confirmed that the flaws exist, but disputed claims regarding active exploitation.
Charles Ragland, security engineer at Digital Shadows, a San Francisco-based provider of digital risk protection solutions, believes Apple’s high-paying bug bounty program has brought increased scrutiny to the platform, leading to researchers identifying a significant number of vulnerabilities.
“With the increased focus and larger volume of exploits, it isn't surprising to see prices drop for iOS,” Ragland said. “It is likely that researchers will shift their attention to more lucrative options in the coming weeks, and we may see an increase in price for exploits of other devices or operating systems.”
What do exploit prices say about iOS security?
There has always been a debate over which is more secure — Android or iOS — and while years ago many agreed that iOS was better in terms of security, the significant number of vulnerabilities and attacks targeting the platform in recent years have shown that Apple’s mobile operating system is not as secure as many believed it to be, particularly when faced with a well-resourced adversary.
“The zero-day market is based on supply and demand, a spike in supply of zero-day exploits for a specific product means that the security level of that product is decreasing and the price goes down as there are too many exploits available,” Bekrar said. “Obviously, we cannot draw a final conclusion about the overall security level of a system just based on its bug bounty price or the number of existing exploits, but these are very strong indicators that cannot be ignored.”
“The fact that [Zerodium] won't pay for [certain types of iOS exploits] anymore is an indication the supply is high and indicative of the current state of this mobile platform,” Robert Nickle, security intelligence researcher at mobile security firm Lookout, told SecurityWeek. “While iOS is a relatively secure mobile OS, there are still ways to exploit it, and therefore benefits when users run additional security on those devices.”
Zeronomicon’s De Gregorio noted, “When it comes to software engineered by Apple, I can tell you that this was never free of vulnerabilities. Rather, their exploitation was typically prevented by the security mitigations put in place at both hardware and software level.”
Apple did not respond to a request for comment.
Unpatched iOS Bug Blocks VPNs From Encrypting All Traffic
29.3.2020 Bleepingcomputer Apple
A currently unpatched security vulnerability affecting iOS 13.3.1 or later prevents virtual private networks (VPNs) from encrypting all traffic and can lead to some Internet connections bypassing VPN encryption to expose users' data or leak their IP addresses.
While connections made after connecting to a VPN on your iOS device are not affected by this bug, all previously established connections will remain outside the VPN's secure tunnel as ProtonVPN disclosed.
This VPN bypass vulnerability (rated with a 5.3 CVSS v3.1 base score) was discovered by a security consultant part of the Proton community and was disclosed by ProtonVPN to make users and other VPN providers aware of the issue.
Connections remain open and exposed
The bug is due to Apple's iOS not terminating all existing Internet connections when the user connects to a VPN and having them automatically reconnect to the destination servers after the VPN tunnel is established.
"Most connections are short-lived and will eventually be re-established through the VPN tunnel on their own," ProtonVPN explains. "However, some are long-lasting and can remain open for minutes to hours outside the VPN tunnel."
During the time the connections are outside of the VPN secure communication channels, this issue can lead to serious consequences.
For instance, user data could be exposed to third parties if the connections are not encrypted themselves, and IP address leaks could potentially reveal the users' location or expose them and destination servers to attacks. 
Exposed connections to Apple servers (ProtonVPN)
Even though users should only see traffic being exchanged between their devices, local IP addresses, and the VPN's servers, other IP addresses will also show up —Apple server IPs in the screenshot above — because of previously opened connections not being terminated before the VPN connects
While ProtonVPN says that Apple's push notifications are a good example of a process using connections to Apple servers that won't be closed automatically, this bug can affect any service or app running on the user's iOS device, from web beacons to instant messaging applications.
"Those at highest risk because of this security flaw are people in countries where surveillance and civil rights abuses are common," ProtonVPN says.
"Neither ProtonVPN nor any other VPN service can provide a workaround for this issue because iOS does not permit a VPN app to kill existing network connections."
ProtonVPN
@ProtonVPN
Last year, we discovered a vulnerability in iOS that causes connections to bypass VPN encryption. This is a bug in iOS that impacts all VPNs. We have informed Apple, and we are now sharing details so you can stay safe. https://protonvpn.com/blog/apple-ios-vulnerability-disclosure/ …
221
10:08 PM - Mar 25, 2020
Twitter Ads info and privacy
122 people are talking about this
Temporary workarounds
Apple acknowledged the VPN bypass vulnerability after ProtonVPN's report and is currently looking into options on how to fully mitigate it.
Until a fix will be provided, Apple recommends using Always-on VPN to mitigate this problem. However, since this workaround uses device management, it cannot be used to mitigate the vulnerability for third-party VPN apps such as ProtonVPN.
ProtonVPN recommends the following this procedure if you are using a third-party VPN:
Connect to a VPN server.
Turn on airplane mode. This will kill all Internet connections and temporarily disconnect the VPN.
Turn off airplane mode. The VPN will reconnect, and your other connections should also reconnect inside the VPN tunnel (not 100% reliable)
Malvertising in Govt, Enterprise Targets Old Software, Macs
24.2.2020 Bleepingcomputer Apple
A new report on malicious advertising underscores the importance of using modern web browsers and making sure your operating system is up to date with the latest security updates to prevent being infected.
When threat actors perform malicious advertising, or malvertising, they target their ads at specific web browsers and operating systems.
For example, malvertisers pushing exploit kits will show ads to Internet Explorer users as they target the browser's vulnerabilities and ads pushing the Mac Shlayer Trojan will only show the ads to macOS users.
Based on the analysis of 378 million blocked malicious ads over three months between Oct. 15, 2019 - Jan. 15, 2020, Confiant illustrates how companies and government agencies are targeted based on the browsers or operating systems that they use.
Some govt agencies continue to use Internet Explorer
Every month on Patch Tuesday, Microsoft releases new security updates and there are invariably new vulnerabilities fixed in Microsoft's outdated Internet Explorer browser.
These vulnerabilities are commonly targeted by exploit kits to install ransomware, password-stealing Trojans, remote access Trojans (RATs). or other malware, yet we continue to see organizations use this browser and potentially have their networks compromised.
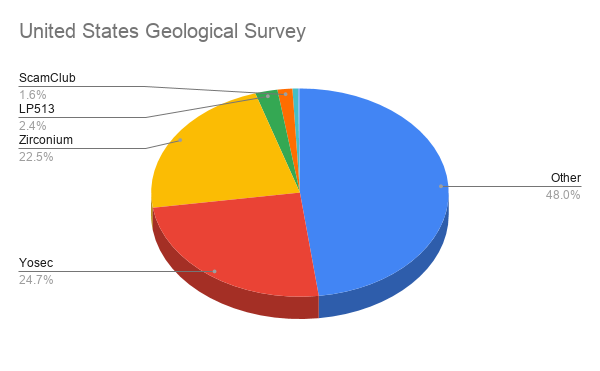
In Confiant's report, they illustrate how both the United States Geological Survey and the United States Postal service are both heavily targeted by malvertising campaigns by Zirconium and Yosec.
United States Geological Survey Malvertising Stats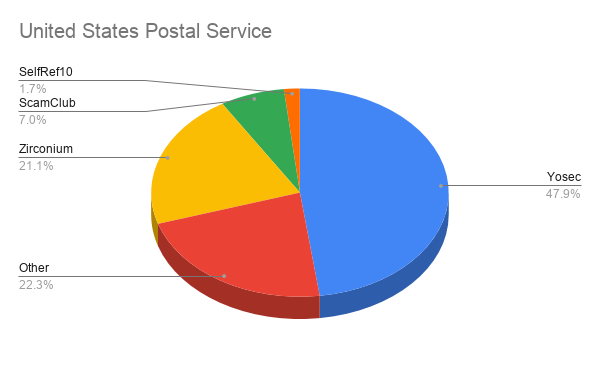
United States Postal Service Malvertising Stats
Confiant Security researcher Eliya Stein explains that the malvertisers are not specifically targeting these two government agencies, but rather the technology that they using.
For example, Zirconium is known to be heavily targeted at outdated browsers to show tech support scam pages, so it is likely both the USGS and USPS are using outdated browsers.
"Our hypothesis is easily confirmed when we pull reporting by browser — 23% of traffic recorded from the Geological Survey is Internet Explorer, but only 1.6% for the Senate," Confiant states in their report.
Both organizations also have a high percentage of malvertising attacks by the Yosec malvertising group. As this group targets Macs with scams and fake updates pushing the Shlayer Trojan, it shows that both organizations utilize a larger amount of macOS devices compared to other U.S. government agencies.
Macs targeted more in Fortune 100 companies
The monitored malvertising campaigns also offer us insight into the types of computers and browsers Fortune 100 companies are using.
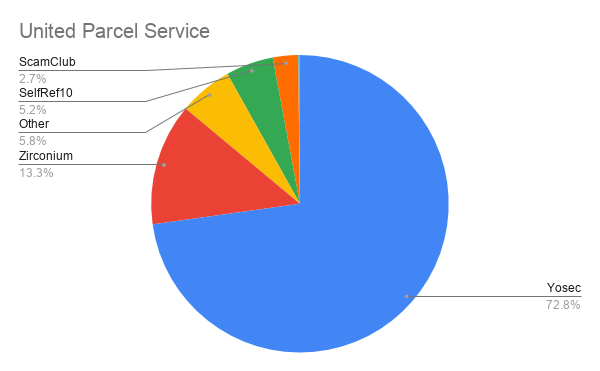
In a corporate setting, it is not surprising that we begin to see a much larger percentage of malvertising from the Yosec group who target Mac computers.
For example, Apple, The Kroger Co., UPS, Boeing, and MetLife have over 50% of their malvertising attacks targeting Mac computers indicating that these companies utilize a large amount of Mac computers compared to other companies.
UPS Malvertising Stats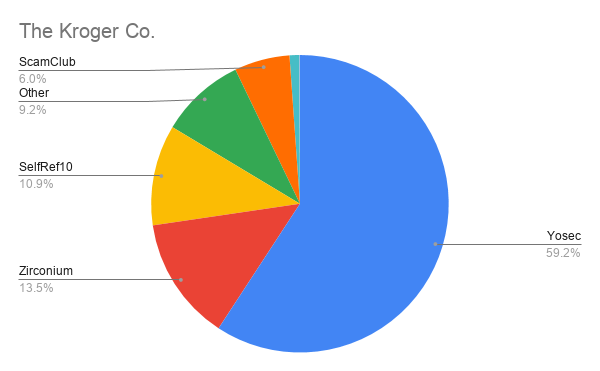
The Kroger Co. Malvertising Stats
Numerous other companies such as Anthem Blue Cross Blue Shield, PepsiCo, and State Farm also are heavily targeted by Yosec with over 40% of their malvertising attacks directed at Mac computers.
Outdated browsers also remain a huge problem for the Fortune 100 companies where we see Zirconium continue to take a huge market share of the malvertising attacks.
For example, Home Depot, Chevron, and FedEx have over 40% of their malvertising attacks being directed towards outdated browsers.
This continues to illustrate how the enterprise needs to move their employees and applications from outdated web browsers such as Internet Explorer towards modern browsers that provide a more secure auto-updating mechanism.
Malvertising can lead to a compromised network
Most malvertising tends to involve nuisance redirects to fake giveaways, tech support scams, and adult sites, but it could also have more dire consequences.
With the continued usage of outdated browsers, exploit kits could use vulnerabilities to install malware that allows attackers to gain access to the network.
From there, they can exfiltrate files, steal corporate secrets, compromise more devices, and eventually deploy ransomware throughout the network.
Unfortunately, while updating your browser to a modern version will increase security and block some of the attacks, Stein told BleepingComputer that malvertisers will just switch to a different targeting method.
"Updating browsers is important, but at the same time I think that the attackers will just use something else for targeting purposes," Stein told BleepingComputer.
Government agencies and the enterprise should instead increase their overall security posture through the use of security software (even on Macs), web filtering services, ad blockers, and threat intelligence services.
Edison Mail iOS Bug Exposes Emails to Strangers
18.5.2020 Threatpost Apple
A bug introduced in an iOS software update on the Edison Mail app allowed emails to be viewed by strangers.
Edison Mail, a popular third-party email app, has warned thousands of iOS users that their emails may have been compromised after a security flaw exposed emails to complete strangers.
Edison Mail, owned by Edison Software Inc., is in the top 100 productivity apps on the Apple app store, and touts itself as “lightning fast and secure mail.” According to Edison Mail, a recent iOS update caused a temporary bug in the app. This flaw potentially allowed the unauthorized email account access of 6,480 iOS Edison Mail users to other users.
“On Friday, May 15th, 2020, a software update enabled users to manage accounts across their Apple devices,” said Edison in a statement on Sunday. “The issue only impacted a fraction of our iOS app users (and no Android or Mac users were affected). This temporary issue was a bug, and not related to any external security issues.”
Edison Mail said it has resolved the issue as of Saturday, and all accounts have been secured.
The issue appeared to stem from a new syncing feature that was rolled out in the Friday update (update 1.20.2). After the update, several Edison Mail users took to Twitter to complain that they were seeing up to 100 unread email messages from strangers’ accounts under their own Edison Mail inboxes. They were able to read others’ emails without credentials, the tweets alleged, and couldn’t adjust their sync settings to delete the emails.
“Clearly someone with the device “Mandy’s iPhone) currently has full access to my email accounts. Please tell me the data deletion works at least?” one Edison Mail user said on Twitter.
Petter Magnusson
@MagnussonP
· May 16, 2020
@Edison_apps not my email. Not my device. How can this still be going one and how can you not communicate anything. Clearly someone with the device “Mandy’s iPhone) currently has full access to my email accounts. Please tell me the data deletion works at least?
Petter Magnusson
@MagnussonP
6
4:02 PM - May 16, 2020
Twitter Ads info and privacy
See Petter Magnusson's other Tweets
“This is a SIGNIFICANT security issue,” one Twitter user said. “Accessing another’s email w/o credentials! Never trusting this app again.”
Zach
@zmknox
I just updated @Edison_apps Mail &, after enabling a new sync feature, an email account THAT IS NOT MINE showed up in the app, that I could seemingly axcess completely.
This is a SIGNIFICANT security issue. Accessing another's email w/o credentials! Never trusting this app again.
96
3:11 PM - May 16, 2020
Twitter Ads info and privacy
39 people are talking about this
Edison Mail on Sunday stressed that no passwords or credentials were exposed or compromised. Edison Mail also mentioned that as a safety measure, the ensuing patch (in version 1.20.4 ) prevented all potentially impacted users from being able to access any mail from the Edison Mail app.
“We apologize for temporarily pausing the app from working for many users, which was required to ensure the safety and protection of all potentially impacted users,” said Edison Mail.
It’s not the first time Edison Mail has come under scrutiny for security issues. In February, a Motherboard report pointed to several email apps that sell anonymized data collected from users’ inboxes, including Edison Mail.
“As an additional precaution, Edison has already contacted impacted users and asked them to change their email account password,” according to Edison Mail. “If you have not received an email, you were not impacted.”
Threatpost has reached out to Edison Mail for further comment on the bug.
A bug in Edison Mail iOS app impacted over 6,400 users
18.5.2020 Securityaffairs Apple
A security bug in the iOS app has impacted over 6,400 Edison Mail users, the issue allowed some users to access other people’s email accounts.
An update released for iOS application of the Edison Mail introduced a security bug that resulted in some users being given access to other people’s email accounts.
“On Friday, May 15th, 2020, a software update enabled users to manage accounts across their Apple devices. This update caused a technical malfunction that impacted approximately 6,480 Edison Mail iOS users. The issue only impacted a fraction of our iOS app users (and no Android or Mac users were affected). This temporary issue was a bug, and not related to any external security issues.” reads a post published by the company.
“Data from these individual’s impacted email accounts may have been exposed to another user. No passwords were compromised. “
The Edison Mail app allows users to manage their Gmail, Yahoo, Outlook, iCloud, and other email services in a single place. The company offers apps for iOS, Android and macOS, and says its products are used by millions of individuals.

The update was rolled out on May 15, it included a feature that allows users to manage their accounts across their Apple devices.
Shortly after the patch was released, some users started reporting they could access other people’s email accounts from the iOS app without authentication.
Edison quickly solved the issue, the company confirmed that the bug potentially impacted 6,480 iOS users.
Edison Mail also confirmed that user credentials were not exposed.
The company addressed the issue with two updates, the first one on Saturday that prevented impacted users from accessing any account from the Edison app, the second one on Sunday morning, which re-enabled access for impacted users.
“A new version of the application was made available early Sunday morning in the App Store that restores full functionality for these 6,480 users. Other users were not impacted and no action is required.” added the company.
“We have notified all individual users who may have been impacted by this issue via email, and as an additional safety precaution, suggested that impacted users also change their email account password. If you did not receive an email on this issue then your account was not impacted,”
Over 6,400 Edison Mail Users Hit by Security Bug in iOS App
18.5.2020 Securityweek Apple
An update rolled out recently by Edison Mail for its iOS application resulted in some users being given access to other people’s email accounts. The company acted quickly to resolve the issue, but thousands may have been impacted.
Edison Mail provides apps that allow users to manage their Gmail, Yahoo, Outlook, iCloud and other inboxes from one place. The company offers apps for iOS, Android and macOS, and says its products are used by millions of individuals.
Several users reported over the weekend that they could access other people’s email accounts from the iOS app without the need to provide credentials.
It turned out that this was the result of an update pushed out on May 15, which included a feature designed to enable users to manage their accounts across their Apple devices. The update contained a bug that gave users access to accounts they did not own.
Edison Mail said the incident potentially impacted 6,480 users of the iOS application. The company reassured customers that credentials were not compromised.
The first patch was released on Saturday morning, but this fix prevented impacted users from accessing any account from the Edison app. Another update was released on Sunday morning, which re-enabled access for affected users.
“We have notified all individual users who may have been impacted by this issue via email, and as an additional safety precaution, suggested that impacted users also change their email account password. If you did not receive an email on this issue then your account was not impacted,” the company said in a post published on Medium on Monday.
North Korean hackers infect real 2FA app to compromise Macs
10.5.2020 Bleepingcomputer Apple APT
Hackers have hidden malware in a legitimate two-factor authentication (2FA) app for macOS to distribute Dacls, a remote access trojan associated with the North Korean Lazarus group.
Dacls has been used to target Windows and Linux platforms and the recently discovered RAT variant for macOS borrows from them much of the functionality and code.
Setting persistence
The threat actor planted the malware in the freely available MinaOTP application that is prevalent among Chinese users. A sample of its weaponized version with the name TinkaOTP was uploaded from Hong Kong last month to the VirusTotal scanning service.
At that time, on April 8, it passed undetected, say malware analysts from Malwarebytes in a report this week. Currently, the malicious file is spotted by 23 out of 59 antivirus engines.
The malware executes after rebooting the system as it is added to the property list (plist) file used by LaunchDaemons and LaunchAgents to run applications at startup.
“The difference between LaunchAgents and LaunchDaemons is that LaunchAgents run code on behalf of the logged-in user while LaunchDaemon run code as root user” - Malwarebytes
Same RAT, different OS
Connections with the Dacls for Windows and Linux are evident. The researchers discovered in the macOS variant that the names for the certificate and private file - “c_2910.cls” and “k_3872.Cls” - are the same across all three operating systems.
Further evidence to the common root is given by the configuration file of the malware, which is encrypted with the same AES key and initialization vector seen in Dacls RAT for Linux.
Going deeper, the researchers found that six of the seven plugins in the macOS sample are also present in the Linux variant. The novelty is the Socks module that starts a proxy between the malware and the C2 infrastructure.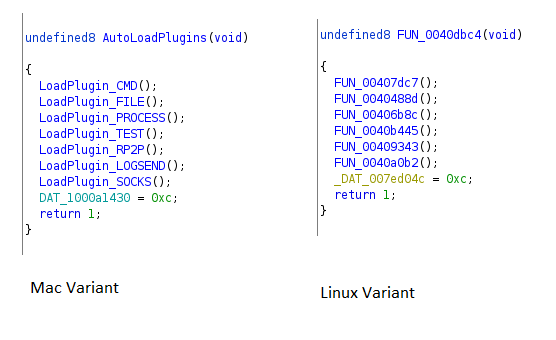
Researchers at Qihoo 360’s Netlab detailed the functions of the six plugins in analysis published in mid-December 2019. These are used for the following purposes:
CMD/Bash plugin - receiving and executing C2 commands
File plugin - file management (read, write, delete, download from specific server, search); write function is not supported in the Dacls for macOS
Process plugin - process management (kill, run, get process ID, enumerate)
Test plugin - same code in both macOS and Linux versions, tests connection to an IP address and port specified by C2
RP2P (reverse peer-to-peer) plugin - proxy server between C2 and the infected system
LogSend plugin - checks connection to Log server, scans network on ports 8291 or 8292, executes system commands that take a long time
The connection to the C2 server relies on the open-source WolfSSL library for secure communication, which is used by multiple threat actors.
Slipping malware into legitimate applications for macOS is not a first for the Lazarus group. A report in 2018 from Kaspersky revealed that the hackers had trojanized an installer for a cryptocurrency trading platform.
In September 2019, malware researchers analyzed a trading app for macOS that packed malware for stealing user information. Fast forward to December, a new macOS malware from Lazarus and using the same tactic emerged on the public radar.
Apple Paid $75K For Bugs Letting Sites Hijack iPhone Cameras
4.4.2020 Bleepingcomputer Apple
Apple has paid a $75,000 bug bounty to a security researcher who chained together three different exploits that could have allowed malicious web sites to use your iPhone camera and microphone without permission.
If you are a reader of BleepingComputer then you know about sextortion scams making fake claims that hackers have installed a Trojan or used malicious scripts on adult video sites to record you while watching adult videos.
What if this really could be done by a malicious ad, injected script, or site?
According to security researcher Ryan Pickren, he was able to do just that by chaining together three different vulnerabilities in Desktop (Macs) and Mobile Safari (iPhone and iPad) that would allow a site to impersonate another trusted site and thus gain access to the device's camera and microphone without the user's permission.
"Imagine you are on a popular website when all of a sudden an ad banner hijacks your camera and microphone to spy on you. That is exactly what this vulnerability would have allowed. This vulnerability allowed malicious websites to masquerade as trusted websites when viewed on Desktop Safari (like on Mac computers) or Mobile Safari (like on iPhones or iPads)," Pickren stated in a writeup about the vulnerabilities he discovered.
While researching ways to get unauthorized permission to an iPhone's camera, Pickren discovered seven zero-day vulnerabilities with IDs CVE-2020-3852, CVE-2020-3864, CVE-2020-3865, CVE-2020-3885, CVE-2020-3887, CVE-2020-9784, and CVE-2020-9787.
Of these vulnerabilities, three were chained together to gain unauthorized access to a device's camera and microphone.
Impersonating trusted sites
When visiting a site in Safari on iOS or macOS, it is possible to permanently allow a website to access your device's camera and thus become a trusted site.
This is done by clicking on the AA (AA button) button in Safari's address bar or the 'Websites' settings in Safari Desktop.
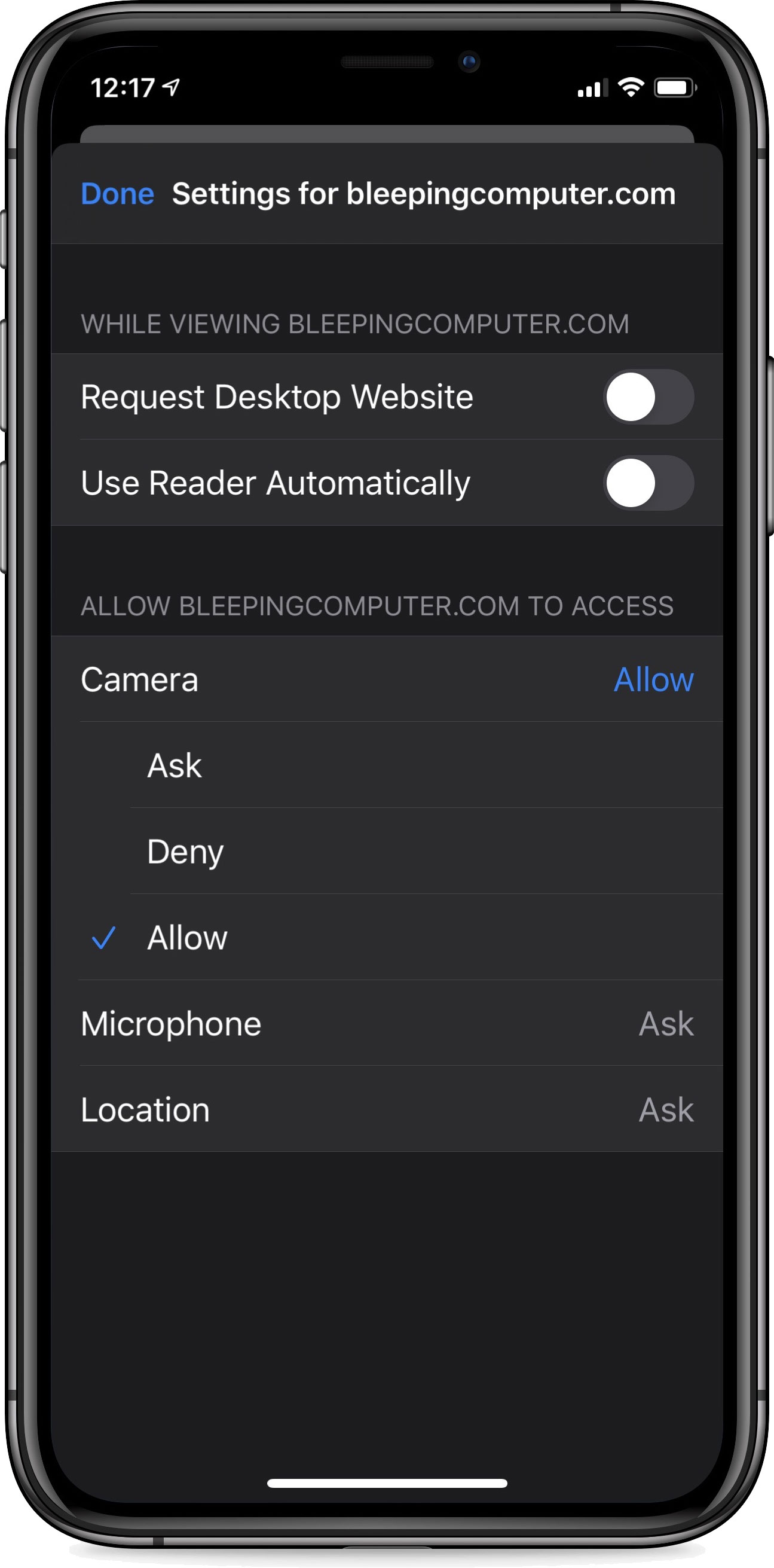
Trusted Site in Safari Mobile
Using various tricks, Pickren was eventually able to make Safari think it was on Skype.com even though it was not.
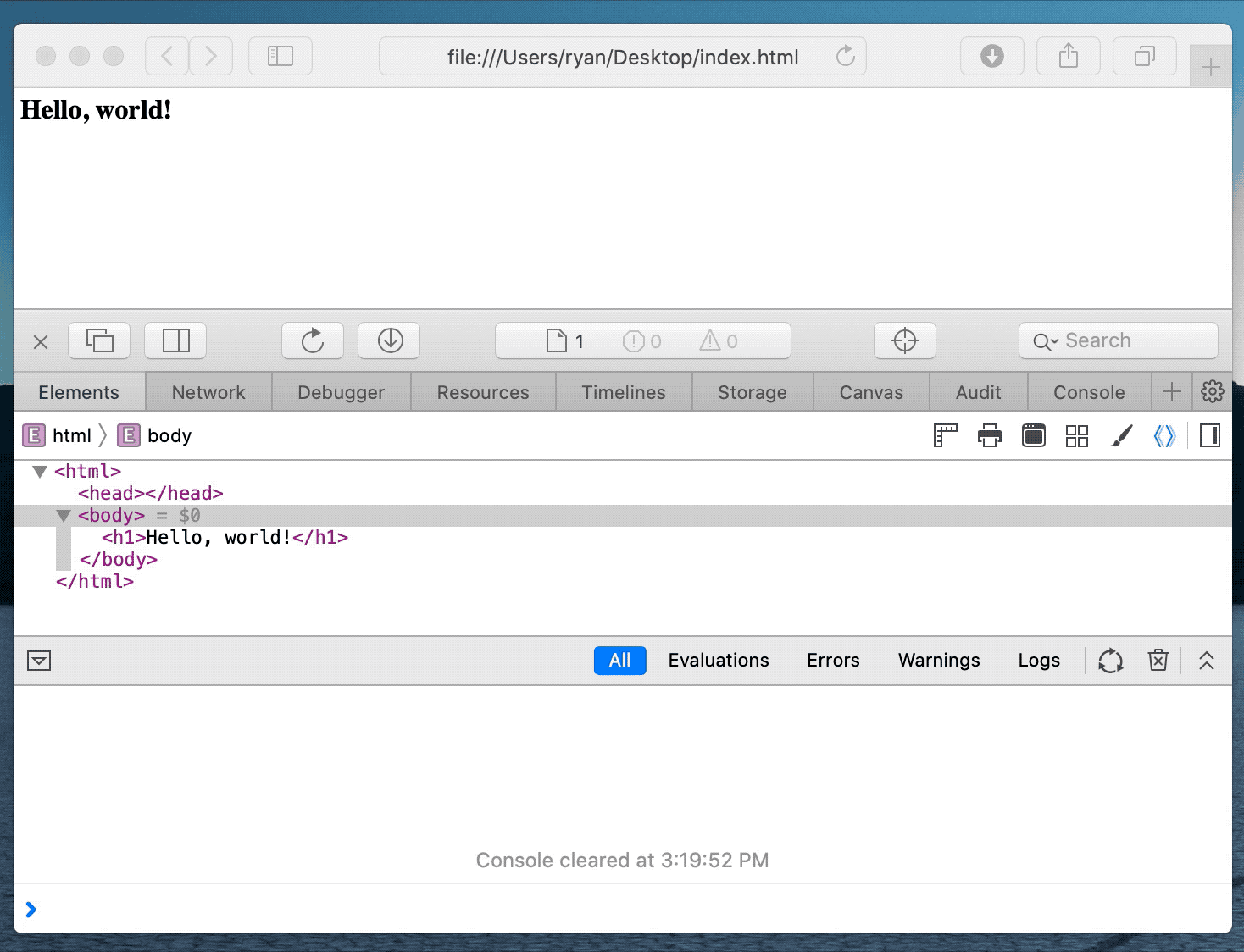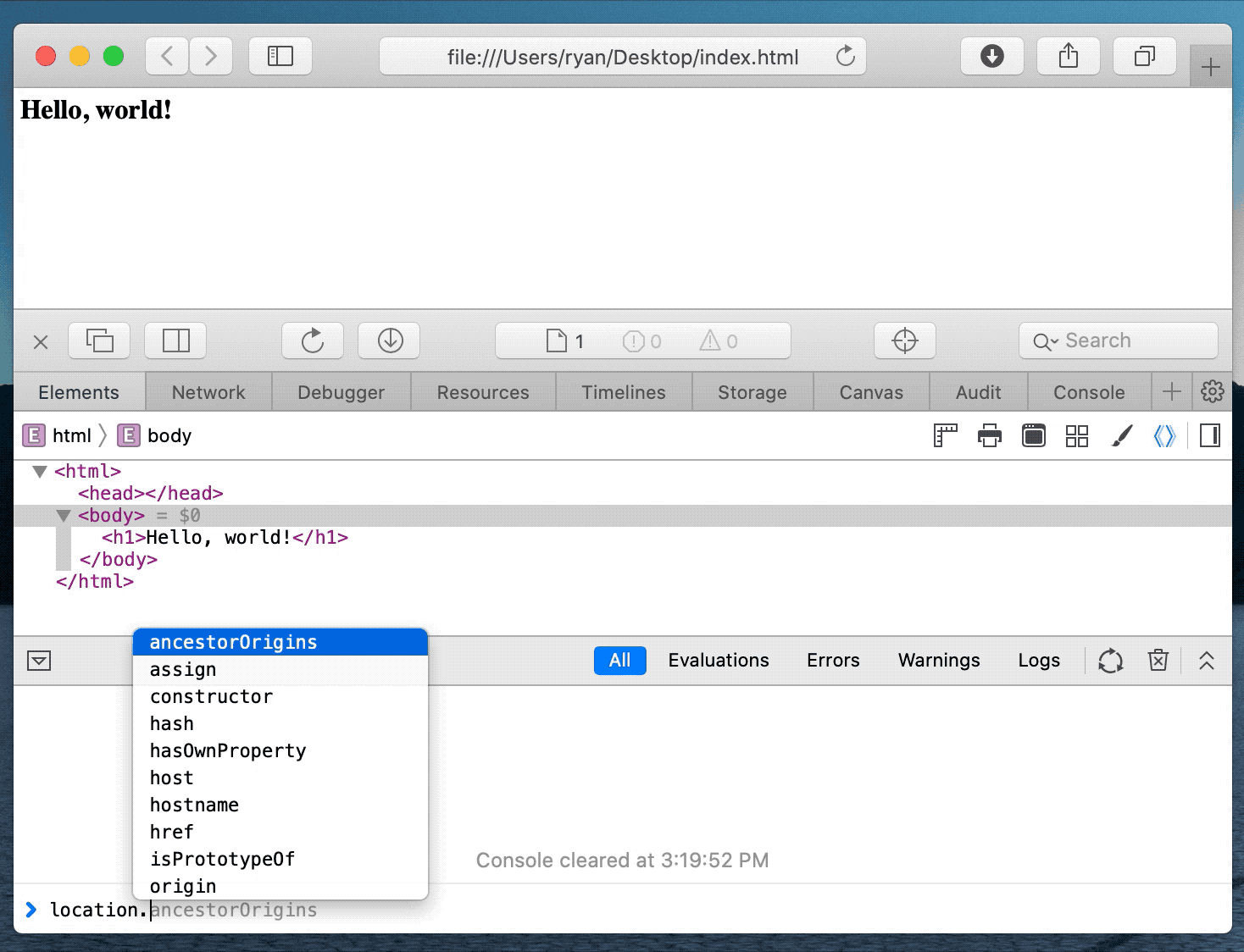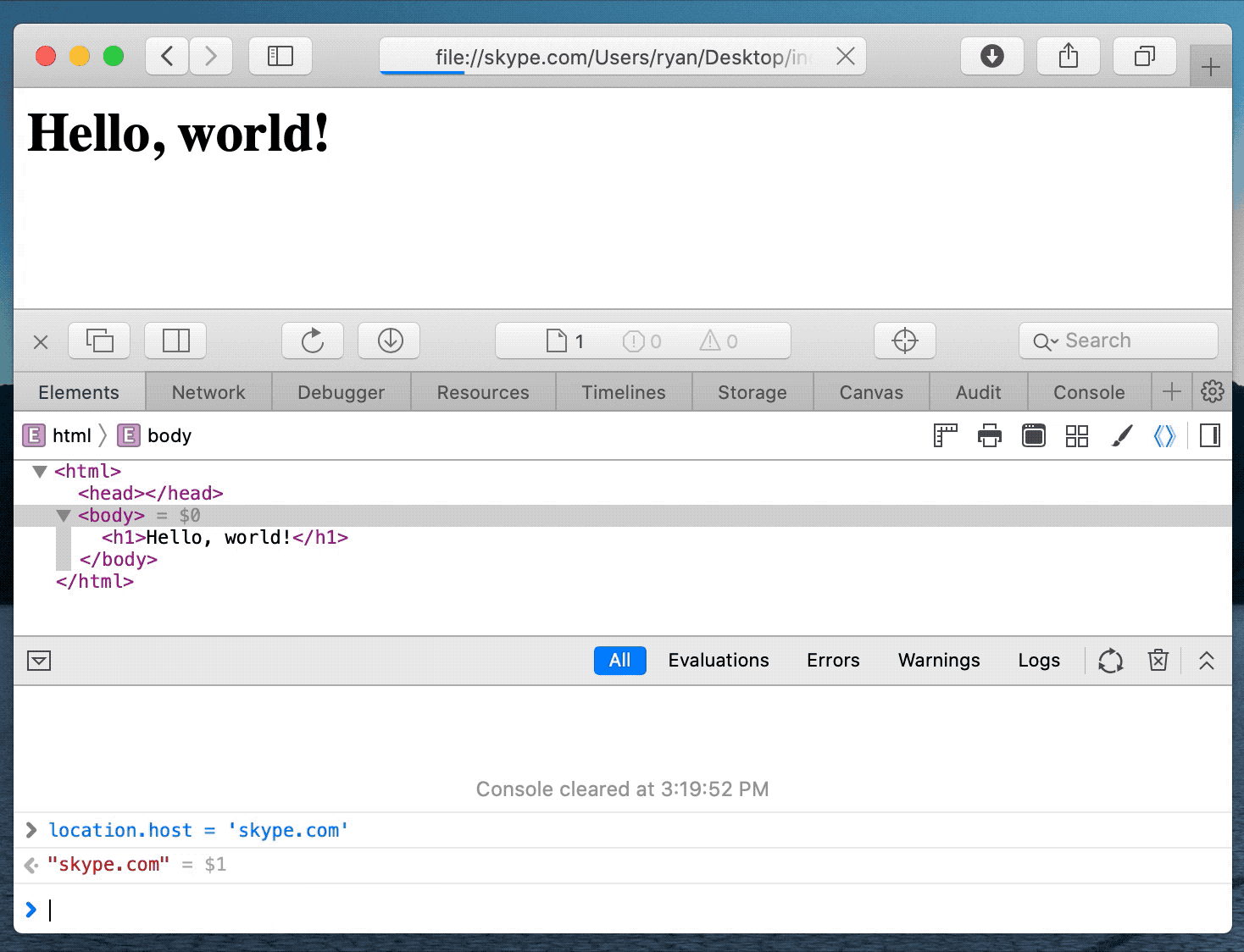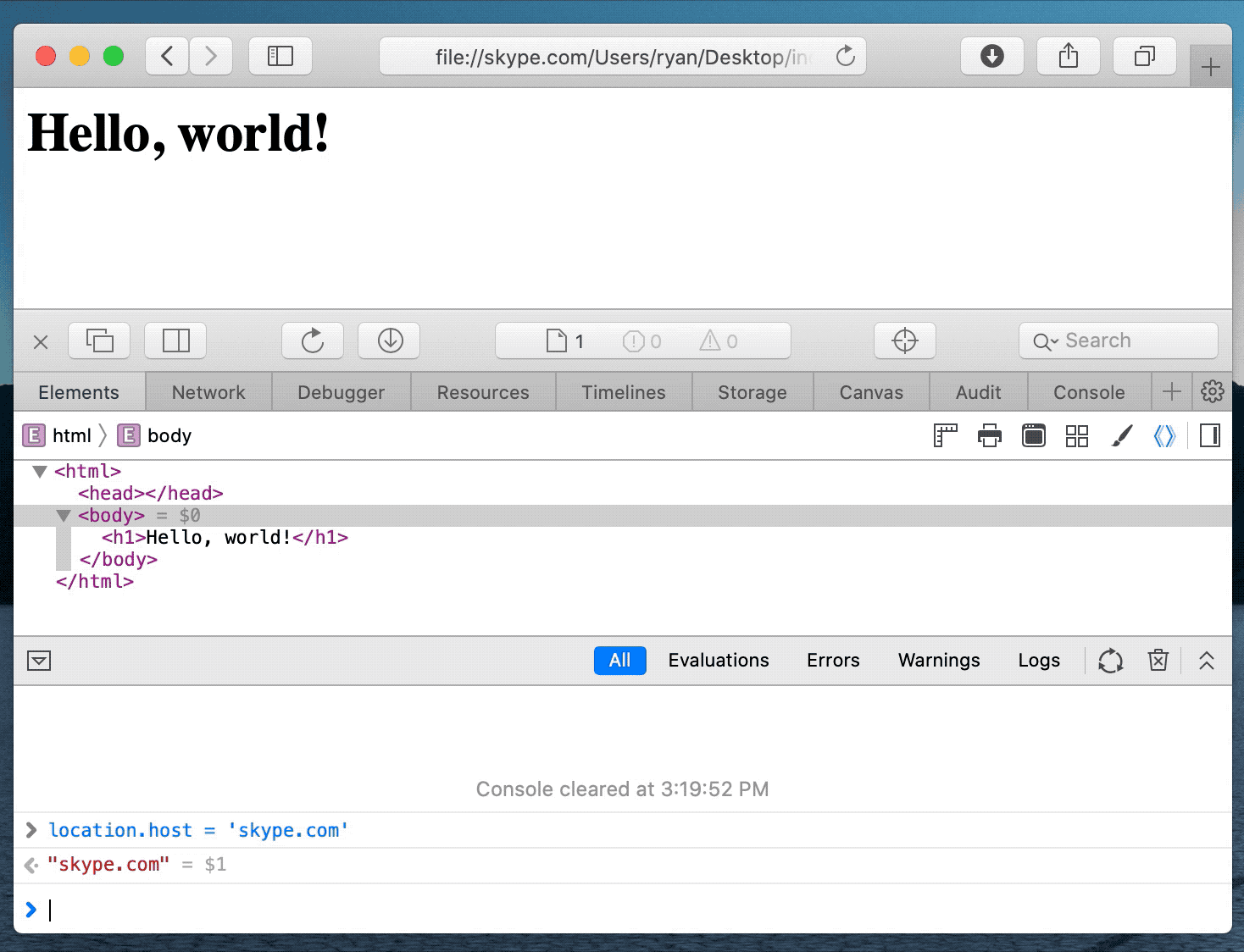
Ultimately, after chaining together multiple vulnerabilities, the researcher was able to cause Safari Desktop and Mobile to automatically think an unrelated address was Skype.
As in Pickren's demonstration below, Skype is trusted to use the camera, by impersonating the site the malicious page was able to access the camera automatically as well.
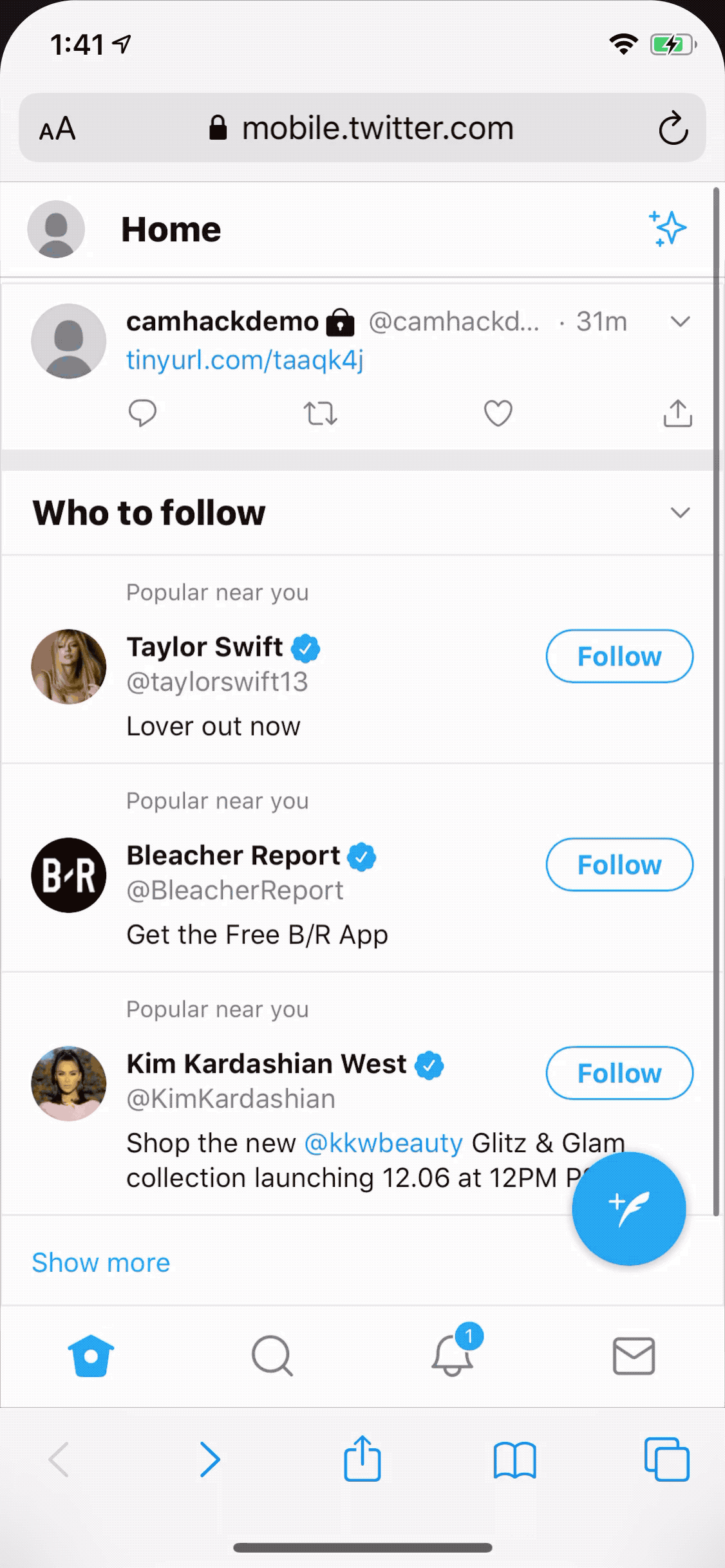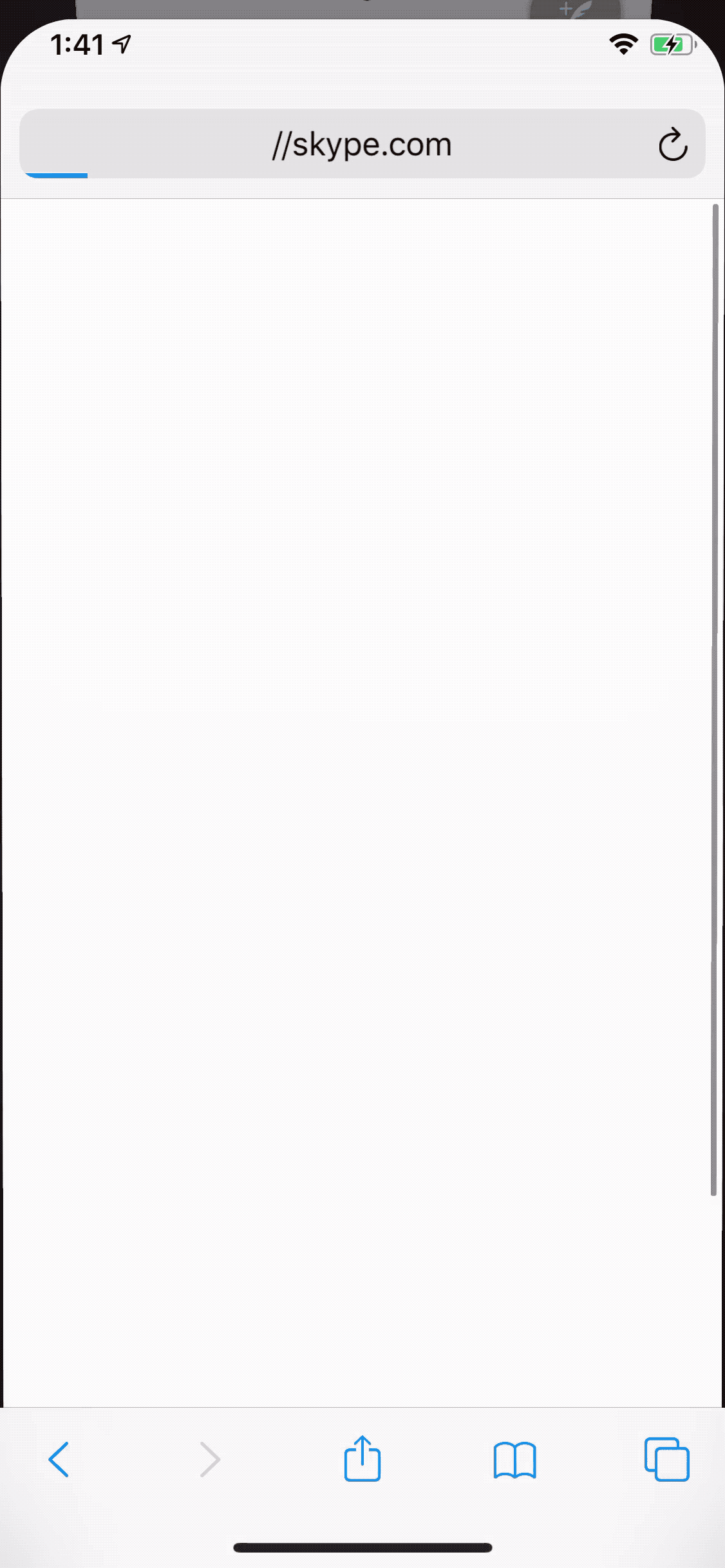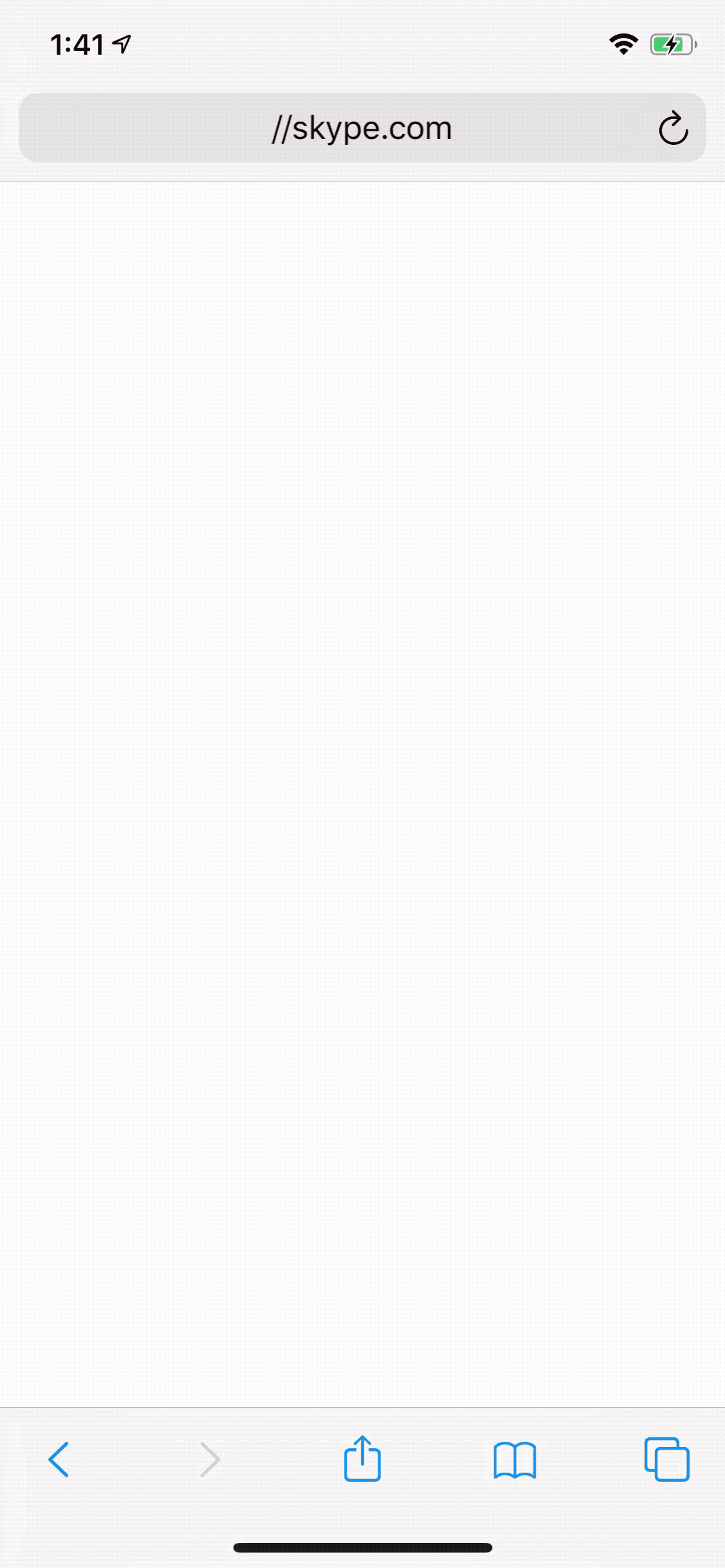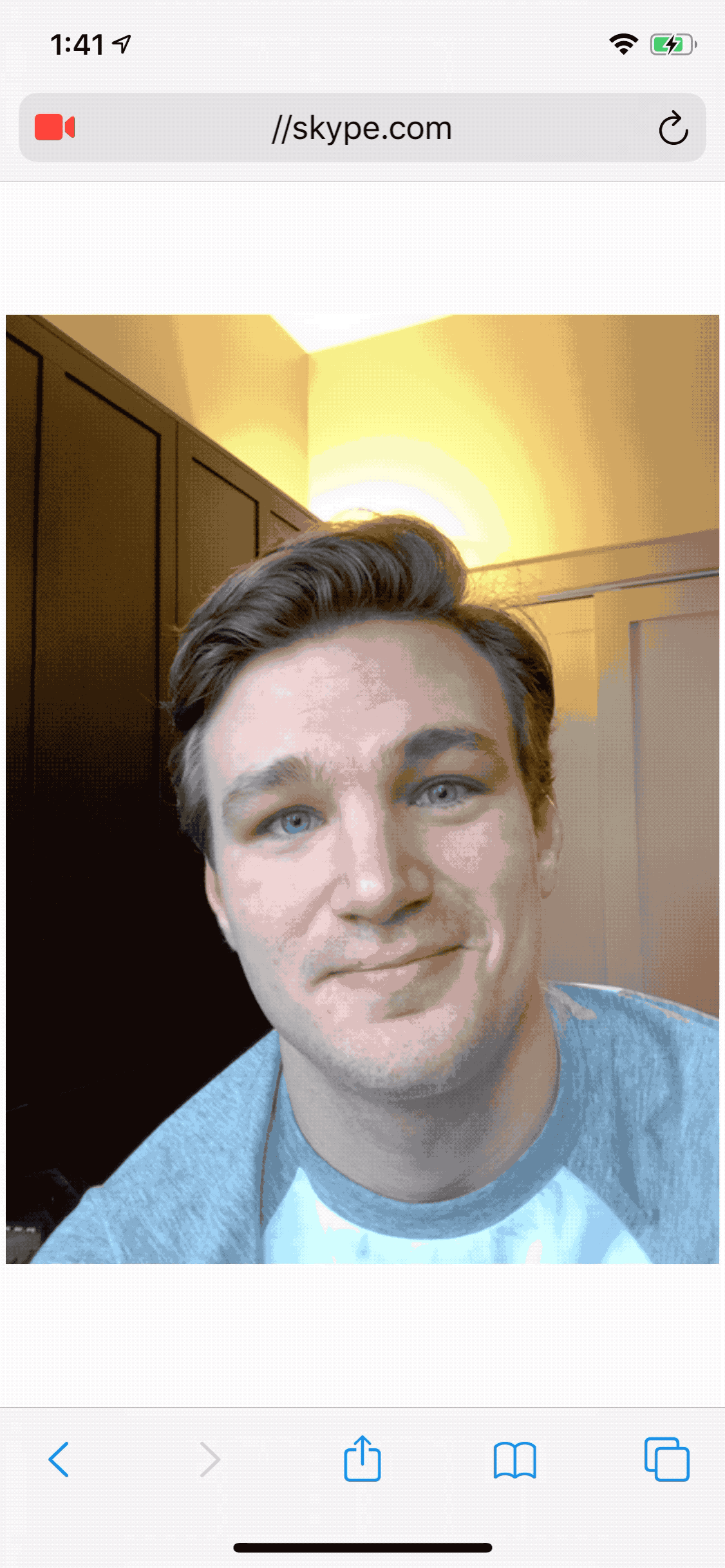
Camera Hijack Demonstration
These bugs have already been fixed by Apple in iOS 13.4 and Safari 13.1.
To prevent this type of bug from being exploited in the future, you can force web sites to ask each time they want to use your camera rather than saving the preference.
Pickren's full analysis of this chained attack can be read here.