Apple Articles 2021- H 2020 1 2 iOS Apple List - H 2021 2020 2019 2018 iOS
Expert Details macOS Bug That Could Let Malware Bypass Gatekeeper Security
27.12.2021 Apple Thehackernews
Apple recently fixed a security vulnerability in the macOS operating system that could be potentially exploited by a threat actor to "trivially and reliably" bypass a "myriad of foundational macOS security mechanisms" and run arbitrary code.
Security researcher Patrick Wardle detailed the discovery in a series of tweets on Thursday. Tracked as CVE-2021-30853 (CVSS score: 5.5), the issue relates to a scenario where a rogue macOS app may circumvent Gatekeeper checks, which ensure that only trusted apps can be run and that they have passed an automated process called "app notarization."
The iPhone maker, crediting Gordon Long of Box with reporting the flaw, said it addressed the weakness with improved checks as part of macOS 11.6 updates officially released on September 20, 2021.
"Such bugs are often particularly impactful to everyday macOS users as they provide a means for adware and malware authors to sidestep macOS security mechanisms, …mechanisms that otherwise would thwart infection attempts," Wardle said in a technical write-up of the flaw.
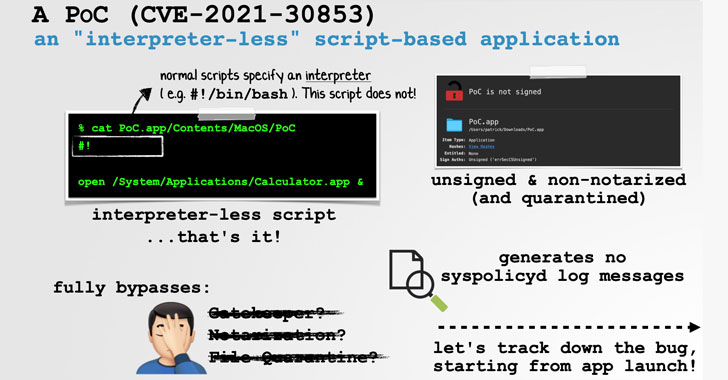
Specifically, the bug not only gets around Gatekeeper, but also File Quarantine and macOS's notarization requirements, effectively allowing a seemingly innocuous PDF file to compromise the entire system simply by opening it. According to Wardle, the issue is rooted in the fact that an unsigned, non-notarized script-based application can not explicitly specify an interpreter, resulting in a complete bypass.
It's worth noting that a shebang interpreter directive — e.g. #!/bin/sh or #!/bin/bash — is typically used to parse and interpret a shell program. But in this edge-case attack, an adversary can craft an application such that the shebang line is incorporated without providing an interpreter (i.e., #!) and still get the underlying operating system to launch the script without raising any alert.
This is so because "macOS will (re)attempt to execute the failed ['interpreter-less' script-based app] via the shell ('/bin/sh')" after the initial lack of success, Wardle explained.
In other words, threat actors can exploit this flaw by tricking their targets into opening a rogue app that can be camouflaged as Adobe Flash Player updates or trojanized versions of legitimate apps like Microsoft Office, which, in turn, can be delivered through a method called search poisoning where attackers artificially increase the search engine ranking of websites hosting their malware to lure potential victims.
This is not the first time flaws have been discovered in the Gatekeeper process. Earlier this April, Apple moved to quickly patch a then actively exploited zero-day flaw (CVE-2021-30657) that could circumvent all security protections, thus permitting unapproved software to be run on Macs.
Then in October, Microsoft disclosed a vulnerability dubbed "Shrootless" (CVE-2021-30892), which could be leveraged to perform arbitrary operations, elevate privileges to root, and install rootkits on compromised devices. Apple said it remediated the problem with additional restrictions as part of security updates pushed on October 26, 2021.
Apple Releases Urgent iPhone and iPad Updates to Patch New Zero-Day Vulnerability
13.10.21 Apple Thehackernews
Apple on Monday released a security update for iOS and iPad to address a critical vulnerability that it says is being exploited in the wild, making it the 17th zero-day flaw the company has addressed in its products since the start of the year.'
The weakness, assigned the identifier CVE-2021-30883, concerns a memory corruption issue in the "IOMobileFrameBuffer" component that could allow an application to execute arbitrary code with kernel privileges. Crediting an anonymous researcher for reporting the vulnerability, Apple said it's "aware of a report that this issue may have been actively exploited."
Technical specifics about the flaw and the nature of the attacks remain unavailable as yet, as is the identity of the threat actor, so as to allow a majority of the users to apply the patch and prevent other adversaries from weaponizing the vulnerability. The iPhone maker said it addressed the issue with improved memory handling.
Security researcher Saar Amar shared additional details, and a proof-of-concept (PoC) exploit, noting that "this attack surface is highly interesting because it's accessible from the app sandbox (so it's great for jailbreaks) and many other processes, making it a good candidate for LPEs exploits in chains."
CVE-2021-30883 is also the second zero-day impacting IOMobileFrameBuffer after Apple addressed a similar, anonymously reported memory corruption issue (CVE-2021-30807) in July 2021, raising the possibility that the two flaws could be related. With the latest fix, the company has resolved a record 17 zero-days to date in 2021 alone —
CVE-2021-1782 (Kernel) - A malicious application may be able to elevate privileges
CVE-2021-1870 (WebKit) - A remote attacker may be able to cause arbitrary code execution
CVE-2021-1871 (WebKit) - A remote attacker may be able to cause arbitrary code execution
CVE-2021-1879 (WebKit) - Processing maliciously crafted web content may lead to universal cross-site scripting
CVE-2021-30657 (System Preferences) - A malicious application may bypass Gatekeeper checks
CVE-2021-30661 (WebKit Storage) - Processing maliciously crafted web content may lead to arbitrary code execution
CVE-2021-30663 (WebKit) - Processing maliciously crafted web content may lead to arbitrary code execution
CVE-2021-30665 (WebKit) - Processing maliciously crafted web content may lead to arbitrary code execution
CVE-2021-30666 (WebKit) - Processing maliciously crafted web content may lead to arbitrary code execution
CVE-2021-30713 (TCC framework) - A malicious application may be able to bypass Privacy preferences
CVE-2021-30761 (WebKit) - Processing maliciously crafted web content may lead to arbitrary code execution
CVE-2021-30762 (WebKit) - Processing maliciously crafted web content may lead to arbitrary code execution
CVE-2021-30807 (IOMobileFrameBuffer) - An application may be able to execute arbitrary code with kernel privileges
CVE-2021-30858 (WebKit) - Processing maliciously crafted web content may lead to arbitrary code execution
CVE-2021-30860 (CoreGraphics) - Processing a maliciously crafted PDF may lead to arbitrary code execution
CVE-2021-30869 (XNU) - A malicious application may be able to execute arbitrary code with kernel privileges
Apple iPhone and iPad users are highly recommended to update to the latest version (iOS 15.0.2 and iPad 15.0.2) to mitigate the security vulnerability.
Apple now requires all apps to make it easy for users to delete their accounts
9.10.21 Apple Thehackernews
All third-party iOS, iPadOS, and macOS apps that allow users to create an account should also provide a method for terminating their accounts from within the apps beginning next year, Apple said on Wednesday.
"This requirement applies to all app submissions starting January 31, 2022," the iPhone maker said, urging developers to "review any laws that may require you to maintain certain types of data, and to make sure your app clearly explains what data your app collects, how it collects that data, all uses of that data, your data retention/deletion policies."
While the feature could be convenient, it's worth noting that Apple only says the mechanism should have a provision for users to "initiate deletion of their account from within the app," meaning it's possible that apps could redirect users to a website or prompt them to send an email in order actually to purge their information.
The reminder follows updates to App Store Review Guideline 5.1.1 that the company announced in June that aims to give users more control regarding data collection, usage, retention, and removal of personal data. The changes also require app developers to include a link to their privacy policy that explicitly spells out what kinds of data are being gathered, how the collection happens, and how it's being put to use.
The development also comes after Apple reintroduced a "Report a Problem" link to App Store app pages on iOS 15, iPadOS 15, and macOS Monterey, enabling users to report concerns with the downloaded apps in an effort to combat fraud and voice other quality issues. The feature is currently available for users in Australia, Canada, New Zealand, and the U.S., with plans to expand to other regions in the future.
Apple Pay Can be Abused to Make Contactless Payments From Locked iPhones
6.10.21 Apple Thehackernews
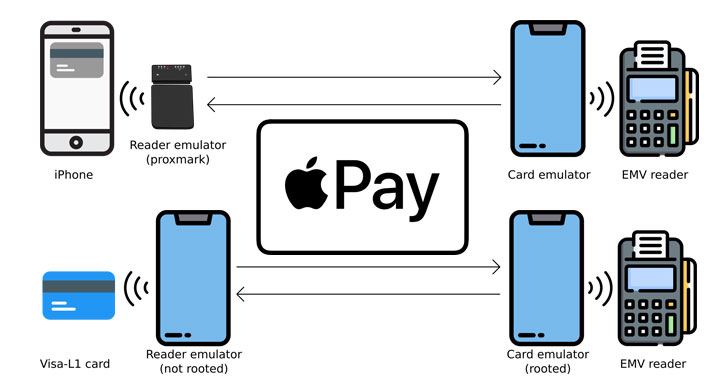
Cybersecurity researchers have disclosed an unpatched flaw in Apple Pay that attackers could abuse to make an unauthorized Visa payment with a locked iPhone by taking advantage of the Express Travel mode set up in the device's wallet.
"An attacker only needs a stolen, powered on iPhone. The transactions could also be relayed from an iPhone inside someone's bag, without their knowledge," a group of academics from the University of Birmingham and University of Surrey said. "The attacker needs no assistance from the merchant and backend fraud detection checks have not stopped any of our test payments."
Express Travel is a feature that allows users of iPhone and Apple Watch to make quick contactless payments for public transit without having to wake or unlock the device, open an app, or even validate with Face ID, Touch ID or a passcode.
The man-in-the-middle (MitM) replay and relay attack, which involves bypassing the lock screen to make a payment to any EMV reader illicitly, is made possible due to a combination of flaws in both Apple Pay and Visa's system, and doesn't impact, say, Mastercard on Apple Pay or Visa cards on Samsung Pay.
The modus operandi hinges on mimicking a transit gate transaction by using a Proxmark device that acts as an EMV card reader communicating with a victim's iPhone and an NFC-enabled Android app that functions as a card emulator to relay signals to a payment terminal.
Specifically, it takes advantage of a unique code — aka Magic Bytes — broadcast by the transit gates to unlock Apple Pay, resulting in a scenario whereby replaying the sequence of bytes, the Apple device is deceived into authorizing a rogue transaction as if it's originated from the ticket barrier, when, in reality, it's been triggered via a contactless payment terminal under the attacker's control.
At the same time, the EMV reader is also tricked into believing that on-device user authentication has been performed, thus enabling payments of any amount to be made without the iPhone user's knowledge.
Apple and Visa were alerted to the vulnerability in October 2020 and May 2021, respectively, the researchers said, adding, "both parties acknowledge the seriousness of the vulnerability, but have not come to an agreement on which party should implement a fix."
In a statement shared with the BBC, Visa said this type of attack was "impractical," adding, "Variations of contactless fraud schemes have been studied in laboratory settings for more than a decade and have proven to be impractical to execute at scale in the real world."
"This is a concern with a Visa system but Visa does not believe this kind of fraud is likely to take place in the real world given the multiple layers of security in place," an Apple spokesperson was quoted as saying to the U.K. national broadcaster.
Apple's New iCloud Private Relay Service Leaks Users' Real IP Addresses
6.10.21 Apple Thehackernews
A new as-yet unpatched weakness in Apple's iCloud Private Relay feature could be circumvented to leak users' true IP addresses from iOS devices running the latest version of the operating system.
Introduced as a beta with iOS 15, which was officially released this week, iCloud Private Relay aims to improve anonymity on the web by employing a dual-hop architecture that effectively shields users' IP address, location, and DNS requests from websites and network service providers.
It achieves this by routing users' internet traffic on the Safari browser through two proxies in order to mask who's browsing and where that data is coming from in what could be viewed as a simplified version of Tor.
However, the feature is available only to iCloud+ subscribers running iOS 15 or macOS 12 Monterey and above.
"If you read the IP address from an HTTP request received by your server, you'll get the IP address of the egress proxy," FingerprintJS researcher Sergey Mostsevenko said. "Nevertheless, you can get the real client's IP through WebRTC."
WebRTC, short for Web Real-Time Communication, is an open-source initiative aimed at providing web browsers and mobile applications with real-time communication via APIs that enable peer-to-peer audio and video communication without the need for installing dedicated plugins or apps.
This real-time media exchange between two endpoints is established through a discovery and negotiation process called signaling that involves the use of a framework named Interactive Connectivity Establishment (ICE), which details the methods (aka candidates) that can be used by the two peers to find and establish a connection with one another, irrespective of the network topology.
The vulnerability unearthed by FingerprintJS has to do with a specific candidate dubbed "Server Reflexive Candidate" that's generated by a STUN server when data from the endpoint needs to be transmitted around a NAT (Network Address Translator). STUN — i.e., Session Traversal Utilities for NAT — is a tool used to retrieve the public IP address and port number of a networked computer situated behind a NAT.
Specifically, the flaw arises from the fact that such STUN requests aren't proxied through iCloud Private Relay, resulting in a scenario where the real IP address of the client is exposed when the ICE candidates are exchanged during the signaling process. "De-anonymizing you then becomes a matter of parsing your real IP address from the ICE candidates — something easily accomplished with a web application," Mostsevenko said.
FingerprintJS said it alerted Apple to the problem, with the iPhone maker already rolling out a fix in its latest beta version of macOS Monterey. However, the leak has remained unpatched when using iCloud Private Relay on iOS 15.
If anything, the revelation is yet another indication that iCloud Private Relay can never be a replacement for VPNs, and users who are concerned about the visibility of their IP addresses should use a real VPN or browse the internet over the Tor network, and completely disable JavaScript from Safari to turn off WebRTC-related features.
Urgent Apple iOS and macOS Updates Released to Fix Actively Exploited Zero-Days
6.10.21 Thehackernews
Apple on Thursday released security updates to fix multiple security vulnerabilities in older versions of iOS and macOS that it says have been detected in exploits in the wild, in addition to expanding patches for a previously plugged security weakness abused by NSO Group's Pegasus surveillance tool to target iPhone users.
Chief among them is CVE-2021-30869, a type confusion flaw that resides in the kernel component XNU developed by Apple that could cause a malicious application to execute arbitrary code with the highest privileges. The Cupertino-based tech giant said it addressed the bug with improved state handling.
Google's Threat Analysis Group, which is credited with reporting the flaw, said it detected the vulnerability being "used in conjunction with a N-day remote code execution targeting WebKit."
Two other flaws include CVE-2021-30858 and CVE-2021-30860, both of which were resolved by the company earlier this month following disclosure from the University of Toronto's Citizen Lab about a previously unknown exploit called "FORCEDENTRY" (aka Megalodon) that could infect Apple devices without so much as a click.
The zero-click remote attack weaponizing CVE-2021-30860 is said to have been carried out by a customer of the controversial Israeli company NSO Group since at least February 2021. The scale and scope of the operation remains unclear as yet.
It relied on iMessage as an entry point to send malicious code that stealthily installed the Pegasus spyware on the devices and exfiltrate sensitive data without tipping the victims off. The exploit is also significant for its ability to get around defenses built by Apple in iOS 14 — called BlastDoor — to prevent such intrusions by filtering untrusted data sent over the texting application.
The patches are available for devices running macOS Catalina and iPhone 5s, iPhone 6, iPhone 6 Plus, iPad Air, iPad mini 2, iPad mini 3, and iPod touch (6th generation) running iOS 12.5.4.
The development also comes as security researchers have disclosed unpatched zero-day flaws in iOS, including a lock screen bypass bug and a clutch of vulnerabilities that could be abused by an app to gain access to users' Apple ID email addresses and full names, check if a specific app is installed on the device given its bundle ID, and even retrieve Wi-Fi information without proper authorization.
Researcher Denis Tokarev (aka illusionofchaos), who disclosed the latter three issues, said they were reported to Apple between March 10 and May 4, claiming what was "a frustrating experience participating in Apple Security Bounty program" for its failure to fix the issues despite having them responsibly disclosed "up to half a year" ago.
Indeed, a Washington Post article published two weeks ago revealed how the company sits on a "massive backlog" of vulnerability reports, leaving them unresolved for months, hands out lower monetary payouts to bug hunters, and, in some cases, outright bans researchers from its Developer Program for filing reports.
Apple Issues Urgent Updates to Fix New Zero-Day Linked to Pegasus Spyware
19.9.21 Apple Thehackernews
Apple has released iOS 14.8, iPadOS 14.8, watchOS 7.6.2, macOS Big Sur 11.6, and Safari 14.1.2 to fix two actively exploited vulnerabilities, one of which defeated extra security protections built into the operating system.
The list of two flaws is as follows -
CVE-2021-30858 (WebKit) - A use after free issue that could result in arbitrary code execution when processing maliciously crafted web content. The flaw has been addressed with improved memory management.
CVE-2021-30860 (CoreGraphics) - An integer overflow vulnerability that could lead to arbitrary code execution when processing a maliciously crafted PDF document. The bug has been remediated with improved input validation.
"Apple is aware of a report that this issue may have been actively exploited," the iPhone maker noted in its advisory.
The updates arrive weeks after researchers from the University of Toronto's Citizen Lab revealed details of a zero-day exploit called "FORCEDENTRY" (aka Megalodon) that was weaponized by Israeli surveillance vendor NSO Group and allegedly put to use by the government of Bahrain to install Pegasus spyware on the phones of nine activists in the country since February this year.
Besides being triggered simply by sending a malicious message to the target, FORCEDENTRY is also notable for the fact that it expressly undermines a new software security feature called BlastDoor that Apple baked into iOS 14 to prevent zero-click intrusions by filtering untrusted data sent over iMessage.
"Our latest discovery of yet another Apple zero day employed as part of NSO Group's arsenal further illustrates that companies like NSO Group are facilitating 'despotism-as-a-service' for unaccountable government security agencies," Citizen Lab researchers said.
"Ubiquitous chat apps have become a major target for the most sophisticated threat actors, including nation state espionage operations and the mercenary spyware companies that service them. As presently engineered, many chat apps have become an irresistible soft target," they added.
Citizen Lab said it found the never-before-seen malware on the phone of an unnamed Saudi activist, with the exploit chain kicking in when victims receive a text message containing a malicious GIF image that, in reality, are Adobe PSD (Photoshop Document files) and PDF files designed to crash the iMessage component responsible for automatically rendering images and deploy the surveillance tool.
CVE-2021-30858, on the other hand, is the latest in a number of WebKit zero-day flaws Apple has rectified this year alone. With this set of latest updates, the company has patched a total of 15 zero-day vulnerabilities since the start of 2021.
Apple iPhone, iPad, Mac, and Apple Watch users are advised to immediately update their software to mitigate any potential threats arising out of active exploitation of the flaws.
Apple Delays Plans to Scan Devices for Child Abuse Images After Privacy Backlash
5.9.21 Apple Thehackernews
Apple is temporarily hitting the pause button on its controversial plans to screen users' devices for child sexual abuse material (CSAM) after receiving sustained blowback over worries that the tool could be weaponized for mass surveillance and erode the privacy of users.
"Based on feedback from customers, advocacy groups, researchers, and others, we have decided to take additional time over the coming months to collect input and make improvements before releasing these critically important child safety features," the iPhone maker said in a statement on its website.
The announcement, however, doesn't make it clear as to the kind of inputs it would be gathering, the nature of changes it aims to devise, or how it intends to implement the system in a way that mitigates the privacy and security concerns that could arise once it's deployed.
The changes were originally slated to go live with iOS 15 and macOS Monterey later this year, starting with the U.S.
In August, Apple detailed several new features intended to help limit the spread of CSAM on its platform, including scanning users' iCloud Photos libraries for illicit content, Communication Safety in Messages app to warn children and their parents when receiving or sending sexually explicit photos, and expanded guidance in Siri and Search when users try to perform searches for CSAM-related topics.
The so-called NeuralHash technology would have worked by matching photos on users' iPhones, iPads, and Macs just before they are uploaded to iCloud Photos against a database of known child sexual abuse imagery maintained by the National Center for Missing and Exploited Children (NCMEC) without having to possess the images or glean their contents. iCloud accounts that crossed a set threshold of 30 matching hashes would then be manually reviewed, have their profiles disabled, and reported to law enforcement.
The measures aimed to strike a compromise between protecting customers' privacy and meeting growing demands from government agencies in investigations pertaining to terrorism and child pornography — and by extension, offer a solution to the so-called "going dark" problem of criminals taking advantage of encryption protections to cloak their contraband activities.
However, the proposals were met with near-instantaneous backlash, with the Electronic Frontier Foundation (EFF) calling out the tech giant for attempting to create an on-device surveillance system, adding "a thoroughly documented, carefully thought-out, and narrowly-scoped backdoor is still a backdoor."
"Once this capability is built into Apple products, the company and its competitors will face enormous pressure — and potentially legal requirements — from governments around the world to scan photos not just for CSAM, but also for other images a government finds objectionable," the Center for Democracy & Technology (CDT) said in an open letter.
"Those images may be of human rights abuses, political protests, images companies have tagged as “terrorist” or violent extremist content, or even unflattering images of the very politicians who will pressure the company to scan for them. And that pressure could extend to all images stored on the device, not just those uploaded to iCloud. Thus, Apple will have laid the foundation for censorship, surveillance, and persecution on a global basis," the letter read.
But in an email circulated internally at Apple, child safety campaigners were found dismissing the complaints of privacy activists and security researchers as the "screeching voice of the minority."
Apple has since stepped in to assuage potential concerns arising out of unintended consequences, pushing back against the possibility that the system could be used to detect other forms of photos at the request of authoritarian governments. "Let us be clear, this technology is limited to detecting CSAM stored in iCloud and we will not accede to any government's request to expand it," the company said.
Still, it did nothing to allay fears that the client-side scanning could amount to troubling invasions of privacy and that it could be expanded to further abuses, and provide a blueprint for breaking end-to-end encryption. It also didn't help that researchers were able to create "hash collisions" — aka false positives — by reverse-engineering the algorithm, leading to a scenario where two completely different images generated the same hash value, thus effectively tricking the system into thinking the images were the same when they're not.
"My suggestions to Apple: (1) talk to the technical and policy communities before you do whatever you're going to do. Talk to the general public as well. This isn't a fancy new Touch Bar: it's a privacy compromise that affects 1 billion users," Johns Hopkins professor and security researcher Matthew D. Green tweeted.
"Be clear about why you're scanning and what you're scanning. Going from scanning nothing (but email attachments) to scanning everyone's private photo library was an enormous delta. You need to justify escalations like this," Green added.
Bahraini Activists Targeted Using a New iPhone Zero-Day Exploit From NSO Group
25.8.21 Apple Thehackernews
A previously undisclosed "zero-click" exploit in Apple's iMessage was abused by Israeli surveillance vendor NSO Group to circumvent iOS security protections and target nine Bahraini activists.
"The hacked activists included three members of Waad (a secular Bahraini political society), three members of the Bahrain Center for Human Rights, two exiled Bahraini dissidents, and one member of Al Wefaq (a Shiite Bahraini political society)," researchers from University of Toronto's Citizen Lab said in a report published today, with four of the targets hacked by an actor it tracks as LULU and believed to be the government of Bahrain.
Citizen Lab called the new exploit chain "FORCEDENTRY." It's also a zero-click exploit, meaning that it can be used to trigger an infection simply by sending a malicious message to the target, even without having to click a link or view the message in question.
"As always, if NSO receives reliable information related to misuse of the system, the company will vigorously investigate the claims and act accordingly based on the findings," a spokesperson for NSO Group told The Guardian.
The development comes a little over a month after an extensive investigation undertaken by a consortium of 17 media organizations revealed the widespread use of NSO Group's Pegasus "military-grade spyware" by authoritarian regimes to facilitate human rights violations by surveilling heads of state, activists, journalists, and lawyers around the world.
The company has since temporarily blocked several government clients globally from using its technology as the company probes its potential misuse, while also acknowledging that it "shut off five clients' access in the past several years after conducting a human rights audit, and had ended ties with two in the last year alone," according to the Washington Post.
The latest disclosure is significant, not least because the zero-click attack successfully works against the latest versions of iOS, but also for the fact that it bypasses a new software security feature called BlastDoor that Apple built into iOS 14 to prevent such intrusions by filtering untrusted data sent over iMessage.
The tightly sandboxed service was detailed by Google Project Zero researcher Samuel Groß earlier this January, noting that it's "written in Swift, a (mostly) memory safe language which makes it significantly harder to introduce classic memory corruption vulnerabilities into the code base." BlastDoor inspects inbound messages in a secure, sandboxed environment, thus preventing any malicious code inside of a message from interacting with the rest of the operating system or accessing user data.
But the very next month after its existence came to light, Citizen Lab said it observed NSO Group deploying FORCEDENTRY — which Amnesty International dubbed "Megalodon" — against iOS versions 14.4 and 14.6 as a zero-day expressly engineered to get around the BlastDoor feature by crashing IMTranscoderAgent, a service responsible for transcoding and previewing images in iMessage, in order to download and render items from the Pegasus infection server.
"Despite a half-decade of being implicated in human rights abuses, NSO Group regularly claims that they are, in fact, committed to protecting human rights," the researchers said. "The company has even published a 'Human Rights Policy,' a 'Transparency and Responsibility Report,' and claimed to subscribe to the United Nations Guiding Principles on Business and Human Rights.
"The sale of Pegasus to Bahrain is particularly egregious, considering that there is significant, longstanding, and documented evidence of Bahrain's serial misuse of surveillance products including Trovicor, FinFisher, Cellebrite, and, now, NSO Group," the Citizen Lab team added.
Apple released out-of-band updates for a new Zero‑Day actively exploited
28.3.2021 Apple Securityaffairs
Apple has released new out-of-band updates for iOS, iPadOS, macOS and watchOS to address another zero‑day flaw, tracked CVE-2021-1879, actively exploited.
Apple has released a new set of out-of-band patches for iOS, iPadOS, macOS and watchOS to address a critical zero-day vulnerability, tracked as CVE-2021-1879, that is being actively exploited in the wild.
The vulnerability resides in the WebKit flaw, it could be exploited by an attacker to trick the victims into processing maliciously crafted web content that can lead to universal cross-site scripting attacks.
“Processing maliciously crafted web content may lead to universal cross site scripting. Apple is aware of a report that this issue may have been actively exploited.” reads the advisory published by Apple.
The IT giant addressed the issue by improving management of object lifetimes.
The CVE-2021-1879 was reported by Clement Lecigne of Google Threat Analysis Group and Billy Leonard of Google Threat Analysis Group.
Apple did not disclose details of the zero-day vulnerability but confirmed it’s aware of attackers in the wild that actively exploited this issue.
Below the list of updates that were released by Apple:
iOS 12.5.2 – Phone 5s, iPhone 6, iPhone 6 Plus, iPad Air, iPad mini 2, iPad mini 3, and iPod touch (6th generation)
iOS 14.4.2 – iPhone 6s and later, and iPod touch (7th generation)
iPadOS 14.4.2 – iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later
watchOS 7.3.3 – Apple Watch Series 3 and later
Early this week, Apple has released another out-of-band security patches to address a critical vulnerability, tracked as CVE-2021-1844, in iOS, macOS, watchOS, and Safari web browser.
This vulnerability was also discovered by Clément Lecigne of Google’s Threat Analysis Group and Alison Huffman of Microsoft Browser Vulnerability Research. The flaw could be exploited by remote attackers to run arbitrary code on vulnerable devices by tricking users into visiting a malicious web content.
The vulnerability is caused by a memory corruption issue that could be triggered to cause arbitrary code execution when processing specially crafted web content.
On January 2021, Apple has addressed three zero-day vulnerabilities in iOS that have been exploited in the wild with the release of security updates (iOS 14.4).
The first zero-day issue, tracked as CVE-2021-1782, is a race condition that resides in the iOS operating system kernel.
The other two zero-day flaws, tracked as CVE-2021-1870 and CVE-2021-1871 respectively, reside in the WebKit browser engine.
Apple Patches Under-Attack iOS Zero-Day
27.3.2021 Apple Securityweek
Apple has shipped an urgent security update to fix a major security flaw affecting iPhone, iPad and Apple Watch devices alongside a warning that the vulnerability is being actively exploited in the wild.
The new iOS 14.4.2 was released on Friday with yet another band-aid for Apple’s flagship iOS platform and the company said it was “aware of reports that an exploit for this issue exists in the wild."
As is customary, the company did not provide any additional details on the in-the-wild attacks.
A brief advisory describes the problem:
Impact: Processing maliciously crafted web content may lead to universal cross site scripting. Apple is aware of a report that this issue may have been actively exploited.
The company credited a pair of researchers from Google’s TAG (Threat Analysis Group) for reporting the issue, suggesting this may be linked to a wave of high-end APT campaigns documented by Google’s Project Zero unit.
Since January 2020, Apple has scrambled out patches for least 7 documented in-the-wild zero day attacks, mostly launched by nation-state backed threat actors.
Last week, Google released new details on a pair of exploit servers used by a sophisticated threat actor to hit users across multiple platforms, including exploits aimed squarely at Apple’s IOS.
The APT group effectively burned through at least 11 zero-days exploits in less than a year to conduct mass spying across a range of platforms and devices.
Apple Issues Urgent Patch Update for Another Zero‑Day Under Attack
27.3.2021 Apple Thehackernews
Merely weeks after releasing out-of-band patches for iOS, iPadOS, macOS and watchOS, Apple has released yet another security update for iPhone, iPad, Apple Watch to fix a critical zero-day weakness that it says is being actively exploited in the wild.
Tracked as CVE-2021-1879, the vulnerability relates to a WebKit flaw that could enable adversaries to process maliciously crafted web content that may result in universal cross-site scripting attacks.
"This issue was addressed by improved management of object lifetimes," the iPhone maker noted.
Apple has credited Clement Lecigne and Billy Leonard of Google's Threat Analysis Group for discovering and reporting the issue. While details of the flaw have not been disclosed, the company said it's aware of reports that CVE-2021-1879 may have been actively exploited.
Updates are available for the following devices:
iOS 12.5.2 - Phone 5s, iPhone 6, iPhone 6 Plus, iPad Air, iPad mini 2, iPad mini 3, and iPod touch (6th generation)
iOS 14.4.2 - iPhone 6s and later, and iPod touch (7th generation)
iPadOS 14.4.2 - iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later
watchOS 7.3.3 - Apple Watch Series 3 and later
The latest release arrives close on the heels of a patch for a separate WebKit flaw (CVE-2021-1844) that Apple shipped earlier this month. In January 2021, the company resolved three zero-day vulnerabilities (CVE-2021-1782, CVE-2021-1870, and CVE-2021-1871) that allowed an attacker to elevate privileges and achieve remote code execution.
Interestingly, Apple also appears to be experimenting with ways to deliver security updates on iOS in a manner that's independent of other OS updates. iOS 14.4.2 certainly sounds like the kind of update that could benefit from this feature.
In the meanwhile, users of Apple devices are advised to install the updates as soon as possible to mitigate the risk associated with the flaw.
ProtonVPN CEO Blasts Apple for ‘Aiding Tyrants’ in Myanmar
25.3.2021 Apple Threatpost
CEO says Apple rejected a security update needed to protect human-rights abuse evidence.
In a blog post filled with a passionate defense of human rights and internet privacy, Andy Yen, the CEO of secure internet provider ProtonVPN, blasted Apple for blocking its latest update and accused the tech juggernaut of helping the global spread of authoritarianism by “giving in to tyrants.”
Yen used the post to explain this is an issue with immediate life-and-death consequences.
In the days following a Feb. 1 military coup that seized control of the Myanmar government, signups for ProtonVPN encrypted internet services exploded by 250 times over the previous average daily rate, Yen said. Encrypted internet access became particularly vital once the military started ordering the country’s telecom companies to block internet access and social-media platforms, he added.
Apple Accused of Blocking Human-Rights Abuse Evidence
Secure channels like ProtonMail were also being used to send evidence of crimes against humanity to the U.N. in response to the body’s March 17 appeal for people to preserve documentary evidence on the ground.
“In the same day the U.N. recommended Proton apps, Apple suddenly rejected important updates to our ProtonVPN iOS app,” Yen wrote. “These updates include security enhancements designed to further improve safeguards against account takeover attempts which could compromise privacy,” Yen said.
Yen posted a letter from Apple explaining the update was rejected because the app’s description says, “Whether it’s challenging governments, educating the public or training journalists, we have a long history of helping bring online freedom to more people around the world.”
The letter added that the explainer would need to be changed so it’s “not presented in such a way that it encourages users to bypass geo-restrictions or content limitations.”
Apple hasn’t responded to Threatpost’s requests for a response to the allegations leveled in the post.
“Today, apps like ProtonVPN are a lifeline to the rest of the world for the people of Myanmar who are being massacred,” Yen wrote. “By preventing us from informing users that ProtonVPN can be used to bypass internet restrictions, Apple is making it harder for people to find this lifeline. Apple’s decision will make it even more difficult for the citizens of Myanmar to send evidence of crimes against humanity to the United Nations.”
Big tech is facing a growing chorus of voices demanding oversight over their unfathomably powerful tools. The proliferation of disinformation campaigns, mass surveillance and explosion of artificial intelligence (AI) technologies like facial recognition — accused of being coded to propagate systemic racism — all prove that the consequences of the unchecked control over the world’s data is a dangerous proposition for human rights all over the world.
But the turmoil in Myanmar is happening now.
In the midst of the Hong Kong pro-democracy protests in the fall of 2019, Apple removed HK Map Live and Quartz Apps from the store, reportedly under pressure from the Chinese government. The apps were being used by protestors to locate police and plan demonstrations.
Apple Accused of Hypocrisy
Yen also accused Apple of being happy to thumb its nose at governments when the company stands to benefit financially.
“Apple’s actions are also hypocritical. Apple has no problem challenging governments when it is in its own financial self-interest (e.g., avoiding E.U. taxes or evading antitrust charges),” Yen added. “However, when Proton does it for human rights reasons, it’s suddenly against Apple’s policies.”
He concluded by throwing his support behind big tech regulation, including the E.U.’s Digital Markets Act.
Convuster: macOS adware now in Rust
19.3.2021 Apple Securelist
Traditionally, most malicious objects detected on the macOS platform are adware: besides the already familiar Shlayer family, the TOP 10 includes Bnodlero, Cimpli, Adload and Pirrit adware. As a rule, most tend to be written in C, Objective-C or Swift. Recently, however, cybercriminals have been paying increased attention to new programming languages, seemingly in the hope that such code will be more opaque to virus analysts who have little or no experience with the newer languages. We have already seen quite a few samples written in Go, and recently cybercriminals turned their attention to Rust as well.
The first to write about suspicious files in this programming language was a Twitter user, @gorelics:
In the screenshot the tweet shows, one can see that several samples of suspicious code are run by configuration PLIST files through the LaunchAgents/LaunchDaemons mechanism. Alongside the suspicious names of the PLIST files, this is the first wakeup call that the program is dangerous, given the low popularity of Rust-based executables.
We examined these samples for malicious behavior. The analysis showed these executables to be a new adware program, that has subsequently been called Convuster.
Technical details
Sample in Rust
It can be deduced that the analyzed sample was written in Rust from the frequent use of the language’s standard library, as well as several code lines containing paths to files with the .rs extension, which is the standard Rust source file extension.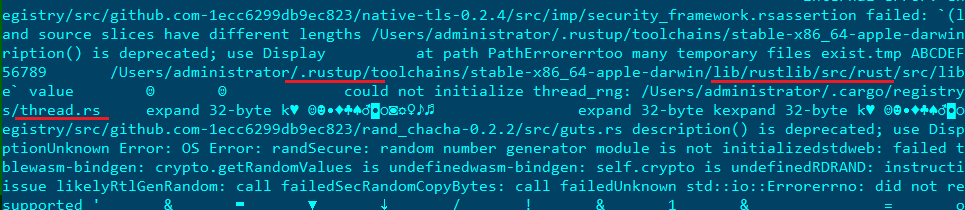
Rust artifacts in the sample
At startup, the executable checks the configuration PLIST files ~/Library/LaunchAgents/com.ist.up.plist and /Library/LaunchDaemons/com.ist.up.plist for keys needed to run the sample, such as RunAtLoad, StartInterval and Version. We were not able to retrieve these files, but presumably they are used to run the sample under investigation when the user logs in to the system.
After these checks, the program obtains the device ID, as well as the system version and bitness, and forwards the gathered data to the following server: hxxps://post.convstats[.]com/hb/. In response, Convuster receives a JSON file and sends a request to the host specified in this file. The response to this request is a Bash script that gets executed by the Bash shell and then removed from the system.
Request generation
At the time of analysis, the server was not responding to requests. However, after examining information about the suspicious convstats[.]com domain, we detected the update.convstats[.]com and trk.convstats[.]com subdomains (in addition to the already known post.convstats[.]com).
Sample in Swift
In the update.convstats[.]com subdomain, at the address hxxps://update.convstats[.]com/Player.dmg, we found a DMG disk image containing another Convuster executable, this time in the Swift programming language.
The payload of the executable was encrypted:
XOR encryption
Having decrypted the data, Convuster runs the code obtained, first of all checking that the DMG image was downloaded specifically from the address hxxps://update.convstats[.]com/Player.dmg with either the ?_=1390081 or &_=1390081 parameter. It does so by accessing the quarantine database of the macOS Gatekeeper security feature using the following query:
select LSQuarantineAgentBundleIdentifier, LSQuarantineDataURLString from LSQuarantineEvent order by LSQuarantineTimeStamp desc limit 3
Typical Gatekeeper database content
Usually, this macOS database serves as a log for all files downloaded from untrusted sources. However, Convuster’s creators use it to protect their handiwork from being analyzed. If it was not downloaded from an “official” server, but rather got into the system some other way, it may mean that the program is in a test or virtual environment, that is, under investigation by virus analysts.
If the file source check is successful, the user is shown a window prompting to install Flash Player. Otherwise, the program prompts to continue the installation later, and then exits.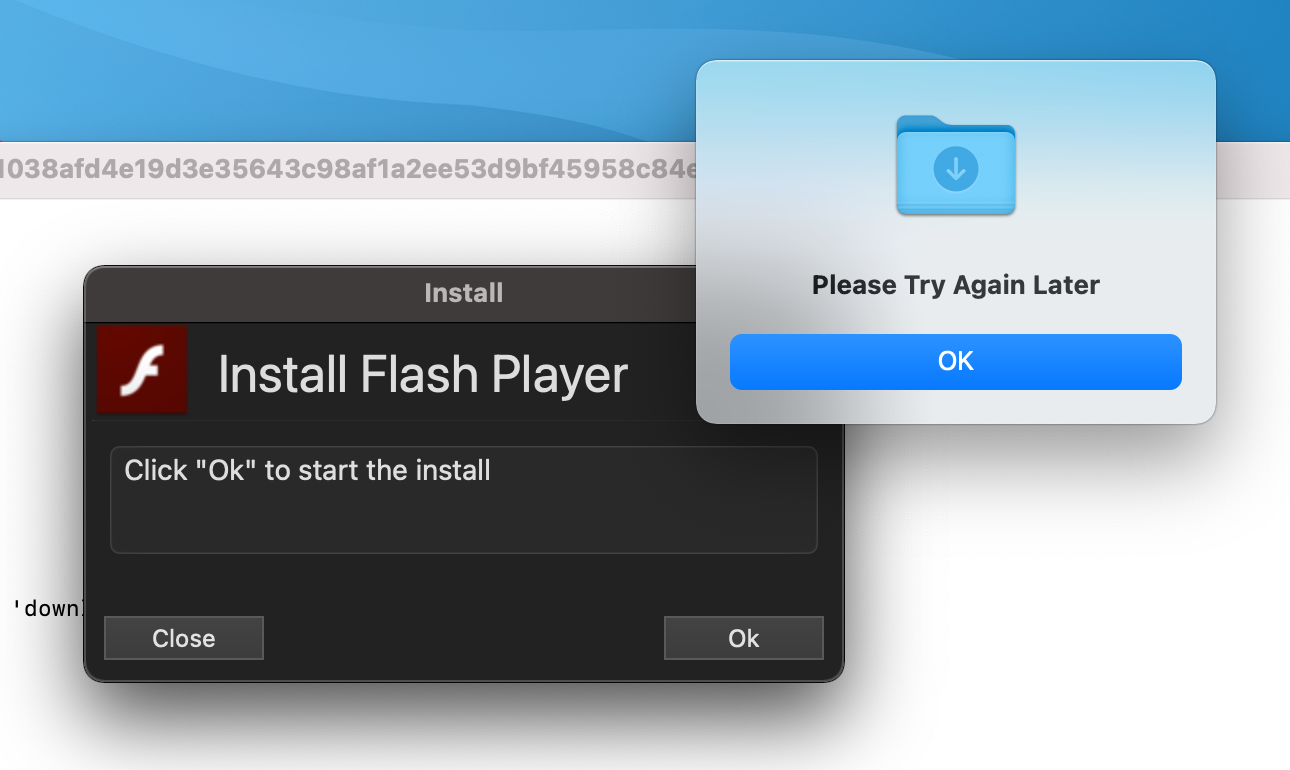
The installer mimics a Flash Player update
Regardless of whether the user agrees to the installation or attempts to close the window, Convuster sends a request to hxxps://post.convstats[.]com/dis/ to download the installation script, and then runs it in the Bash shell.
Running the script in the Bash shell
Distribution
Convuster is run through LaunchAgents, but the program does not try to add itself to startup independently. This means that the file in question was most likely neither downloaded nor installed directly by the user. In our view, Convuster could have been installed by some other adware.
At the time of the study, we were aware of the following domain names performing redirects to the update.convstats[.]com subdomain:
storeoverlyadvancedapplication[.]best
streamgreatlyadvancedprogram[.]best
streamstrongcompletelyprogram[.]best
syncextremelysophisticatedsoftware[.]icu
streamquickcompletelyprogram[.]best
getnewestextremelyapp[.]best
launchfreeextremelyfreeware[.]best
loadsophisticated-thecompletelyfile[.]best
Besides, forum users complain about other domains prompting to install a fake Flash Player update:
User complaints about advertising redirects
Conclusion
Based on the behavior of the Convuster samples in Rust and Swift, we classify this program as adware. Despite their supposed exoticism, these languages lack nothing in terms of functionality from an adware developer’s point of view: Rust, for instance, has the tools not only for authoring adware, but for carrying out more sophisticated attacks.
Besides the choice of programming language, it is noteworthy that cybercriminals have learned to use built-in macOS tools and technologies, such as Gatekeeper, for their own purposes (for example, to verify the source of a file). Although this family is no longer active, it is a clear illustration of how attackers are constantly honing their threats to evade analysis and deliver adware to as many devices as possible.
Kaspersky security solutions detect this adware with the following verdict: not-a-virus:HEUR:AdWare.OSX.Convuster.a.
IoCs
SHA-256
Swift samples
Mach-O executables:
f9615ce5f1038afd4e19d3e35643c98af1a2ee53d9bf45958c84e5a7c4529e62
Disk Images:
02a0842beaf5ee9ed4f0f693ba276b73d53717eca821d2506efcdef7711d66da
Archives:
e5871655465e31c57e27900254e281233787f44bcec5604607b0b3bbbf5a9b16
182d8821182a143770e60a901486f262f63d2cfdc8bc9de3c076a80d36d02049
6bc8fc9fb7693379666049659e83f25b336b6b0b5e8073e1dd69e5b3dcb9826d
cbd6fb1075fc3e57ea7ac886ca218a105c307b75c37e10ca86a5779f4abeca3a
02e6f4388387c940b30c9afb911686d6bee5b3a7249e986f239bbd73d9003a0d
31526cfba9202086feeb658f92941b1ecd7ae1b646c75886600a991f86a843a4
Rust samples
Mach-O executables:
947ae8f075fd0d1e5be0341b922c0173f0c5cfd771314ebe220207f3ed53466a
77bc8b0e17e1c56fba70d8707de9718cd5c10565454fdb85c862a7f3d7e82983
8898f499f334a3231695b8a60dfdfb289836da1de7a4e4e334df83a748c11e07
d511e44ee6ae06228170aef1bef567e059596d259e205295b99e85de8c966354
Domains
post.convstats[.]com
update.convstats[.]com
trk.convstats[.]com
Trojanized Xcode Project Slips MacOS Malware to Apple Developers
19.3.2021 Apple Threatpost
In a new campaign, threat actors are bundling macOS malware in trojanized Apple Xcode developer projects.
Cybercriminals are targeting Apple developers with a trojanized Xcode project, which once launched installs a backdoor that has spying and data exfiltration capabilities.
Xcode is comprised of a suite of free, open software development tools developed by Apple for creating software for macOS, iOS, iPadOS, watchOS and tvOS. Thus, any apps built on top of the project automatically include the malicious code.
The malicious Xcode project, which researchers call XcodeSpy, installs a variant of the known EggShell backdoor on the developer’s macOS computer. This backdoor can record the victim’s microphone, camera and keyboard movements, and can upload and download files.
“The XcodeSpy infection vector could be used by other threat actors, and all Apple Developers using Xcode are advised to exercise caution when adopting shared Xcode projects,” said Phil Stokes, researcher with SentinelLabs on Thursday.
Trojanized Xcode Project
The trojanized Xcode project is a doctored version of a legitimate, open-source project that’s available on GitHub called TabBarInteraction; this project offers iOS developers several advanced features for animating the iOS Tab Bar based on user interaction. Of note, the trojanized version is a copy and the legitimate GitHub project (and its developer) is not implicated in any way with the malware operation, researchers stressed.
The doctored version of the project contains an obfuscated malscript in the Build Phases tab. Researchers said, attackers leveraged this tab because it is not expanded by default, making it easier to slip by undetected.
“XcodeSpy takes advantage of a built-in feature of Apple’s IDE which allows developers to run a custom shell script on launching an instance of their target application,” said researchers. “While the technique is easy to identify if looked for, new or inexperienced developers who are not aware of the Run Script feature are particularly at risk since there is no indication in the console or debugger to indicate execution of the malicious script.”
When the developer’s build target is launched, the obfuscated Run script is executed, which contacts the attackers’ command-and-control (C2) server before dropping a custom EggShell backdoor variant.
“The malware installs a user LaunchAgent for persistence and is able to record information from the victim’s microphone, camera, and keyboard,” said researchers.
EggShell Backdoor Variant
Researchers found two variants of the payload: One sample was uploaded to VirusTotal on Aug. 5th and the second on Oct. 13th. The latter sample was also found in the wild in late 2020 on a victim’s Mac in the United States, said researchers.
“For reasons of confidentiality, we are unable to provide further details about the ITW incident,” they said. “However, the victim reported that they are repeatedly targeted by North Korean APT actors and the infection came to light as part of their regular threat hunting activities.”
Xcode Attack Vector
Attackers have previously utilized Xcode as an initial attack vector to target Apple platform developers. In 2015, attackers appended malicious code (dubbed XcodeGhost) into a number of popular apps and find a loophole in Apple’s code-scanning to slip them into the App Store.
And in August, a campaign was discovered targeting Mac users to spread the XCSSET suite of malware, which has the capability to hijack the Safari web browser and inject various JavaScript payloads. The infections were found propogating via Xcode developer projects.
In this latest attack, researchers said it may be possible that XcodeSpy was targeting particular developers – but they may also be gathering data for future campaigns or attempting to gather AppleID credentials for future use.
“While XcodeSpy appears to be directly targeted at the developers themselves rather than developers’ products or clients, it’s a short step from backdooring a developer’s working environment to delivering malware to users of that developer’s software,” said researchers.
XcodeSpy Mac malware targets Xcode Developers with a backdoor
19.3.2021 Apple Securityaffairs
Unknown threat actors have been using a new XcodeSpy Mac malware to target software developers who use Apple’s Xcode integrated development environment.
Researchers at SentinelOne uncovered a series of attacks involving a new XcodeSpy used to deliver a custom variant of a backdoor tracked as EggShell. The EggShell allows threat actors to spy on users, capture data from the victim’s camera, microphone and keyboard, and upload and download files,
An anonymous researcher informed the researchers of a trojanized Xcode project in the wild that was used in attacks aimed at iOS developers. The malicious project is a tainted version of a legitimate, open-source project available on GitHub which implements advanced features for animating the iOS Tab Bar.
“The XcodeSpy version, however, has been subtly changed to execute an obfuscated Run Script when the developer’s build target is launched. The script contacts the attackers’ C2 and drops a custom variant of the EggShell backdoor on the development machine.” reads the analysis published by SentinelOne. “The malware installs a user LaunchAgent for persistence and is able to record information from the victim’s microphone, camera, and keyboard.”

SentinelOne also reported that XcodeSpy was employed in an attack in late 2020 against an organization in the United States, and based on samples that were uploaded to VirusTotal on August 5th and October 13th, it has been also used in attacks aimed at developers in Japan.
“If the backdoors were uploaded by victims rather than the attackers (an assumption that is by no means secure), that would indicate that the first custom EggShell binary may have been a payload for an earlier XcodeSpy sample.” continues the analysis. “However, we cannot assign great confidence to these speculations based on the available data.”
SentinelOne provided details about the malware and a full list of known IoCs for these attacks.
In 2015, multiple cybersecurity firms detected a malicious program dubbed XcodeGhost that was used to “trojanize” hundreds of legitimate apps. The researchers confirmed that the attackers infected several apps, including the popular mobile chat app WeChat and the music app from the Internet portal NetEase.
Despite the prompt response of the Apple security team at the time, the security firm FireEye detected more than 4,000 infected apps in the App Store. Attackers embedded the malicious code in the apps by tricking developers into using a bogus version of the Apple Xcode.
New XcodeSpy Mac Malware Targets Software Developers
19.3.2021 Apple Securityweek
A recently discovered Mac malware has been used by unknown threat actors to target software developers who use Apple’s Xcode integrated development environment.
Endpoint security company SentinelOne reported on Thursday that the malware, which it has named XcodeSpy, appears to deliver a custom variant of a backdoor known as EggShell, which allows its operators to spy on users. The backdoor can be used to upload and download files, and capture data from the victim’s camera, microphone and keyboard.
SentinelOne learned about the malware from an anonymous researcher, but the company also spotted XcodeSpy in the wild in late 2020 at an organization in the United States. This victim told SentinelOne that it’s regularly targeted by threat actors linked to North Korea and they came across the malware while conducting threat hunting activities.
Based on samples uploaded to VirusTotal, the malware may have also been used in attacks aimed at developers in Japan.
The cybersecurity firm has found evidence that the campaign involving XcodeSpy was active at least between July and October 2020. In at least one instance, the malware was delivered as a trojanized version of an open source Xcode project offered to iOS developers.
“The XcodeSpy version has been subtly changed to execute an obfuscated Run Script when the developer’s build target is launched,” SentinelOne explained in its blog post. “The script contacts the attackers’ C2 and drops a custom variant of the EggShell backdoor on the development machine.”
The company has not found any other trojanized Xcode projects, but believes that other similar malicious projects could exist.
“While XcodeSpy appears to be directly targeted at the developers themselves rather than developers’ products or clients, it’s a short step from backdooring a developer’s working environment to delivering malware to users of that developer’s software,” SentinelOne said.
This is not the first piece of malware that has been observed targeting Xcode developers. Back in 2015, a threat named XcodeGhost had allowed attackers to inject malicious code into hundreds of legitimate applications using rogue versions of Xcode that developers downloaded from third-party websites.
More recently, a piece of Mac malware named XCSSET was seen spreading through code injected into Xcode projects, with the payload being executed when the project was built. XCSSET allows its operators to launch ransomware attacks and steal data from victims. It was recently analyzed by researchers at Kaspersky, who discovered a variant designed to run on devices powered by Apple’s M1 chip.
Hackers Infecting Apple App Developers With Trojanized Xcode Projects
19.3.2021 Apple Thehackernews
Cybersecurity researchers on Thursday disclosed a new attack wherein threat actors are leveraging Xcode as an attack vector to compromise Apple platform developers with a backdoor, adding to a growing trend that involves targeting developers and researchers with malicious attacks.
Dubbed "XcodeSpy," the trojanized Xcode project is a tainted version of a legitimate, open-source project available on GitHub called TabBarInteraction that's used by developers to animate iOS tab bars based on user interaction.
"XcodeSpy is a malicious Xcode project that installs a custom variant of the EggShell backdoor on the developer's macOS computer along with a persistence mechanism," SentinelOne researchers said.
Xcode is Apple's integrated development environment (IDE) for macOS, used to develop software for macOS, iOS, iPadOS, watchOS, and tvOS.
Earlier this year, Google's Threat Analysis group uncovered a North Korean campaign aimed at security researchers and exploit developers, which entailed the sharing of a Visual Studio project designed to load a malicious DLL on Windows systems.
The doctored Xcode project does something similar, only this time the attacks have singled out Apple developers.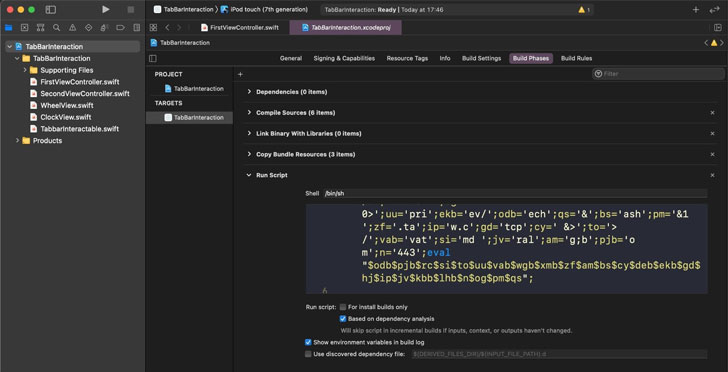
Besides including the original code, XcodeSpy also contains an obfuscated Run Script that's executed when the developer's build target is launched. The script then contacts an attacker-controlled server to retrieve a custom variant of the EggShell backdoor on the development machine, which comes with capabilities to record information from the victim's microphone, camera, and keyboard.
"XcodeSpy takes advantage of a built-in feature of Apple's IDE which allows developers to run a custom shell script on launching an instance of their target application," the researchers said. "While the technique is easy to identify if looked for, new or inexperienced developers who are not aware of the Run Script feature are particularly at risk since there is no indication in the console or debugger to indicate execution of the malicious script."
SentinelOne said it identified two variants of the EggShell payload, with the samples uploaded to VirusTotal from Japan on August 5 and October 13 last year. Additional clues point to one unnamed U.S. organization that's said to have been targeted using this campaign between July and October 2020, with other developers in Asia likely to be targeted as well.
Adversaries have previously resorted to tainted Xcode executables (aka XCodeGhost) to inject malicious code into iOS apps compiled with the infected Xcode without the developers' knowledge, and subsequently use the infected apps to collect information from the devices once they are downloaded and installed from the App Store.
Then in August 2020, researchers from Trend Micro unearth a similar threat that spread via modified Xcode projects, which, upon building, were configured to install a mac malware called XCSSET to steal credentials, capture screenshots, sensitive data from messaging and note taking apps, and even encrypt files for a ransom.
But XcodeSpy, in contrast, takes an easier route, since the goal appears to be to strike the developers themselves, although the ultimate objective behind the exploitation and the identity of the group behind it remains unclear as yet.
"Targeting software developers is the first step in a successful supply chain attack. One way to do so is to abuse the very development tools necessary to carry out this work," the researchers said.
"It is entirely possible that XcodeSpy may have been targeted at a particular developer or group of developers, but there are other potential scenarios with such high-value victims. Attackers could simply be trawling for interesting targets and gathering data for future campaigns, or they could be attempting to gather AppleID credentials for use in other campaigns that use malware with valid Apple Developer code signatures."
Apple May Start Delivering Security Patches Separately From Other OS Updates
18.3.2021 Apple Thehackernews
Apple may be changing the way it delivers security patches to its devices running iOS and iPadOS mobile operating systems.
According to code spotted in iOS 14.5, the iPhone maker is reportedly working on a method for delivering security fixes independently of other OS updates.
The changes were first reported by the 9to5Mac website.
While Google's Android has had monthly security patches rolled out that are completely divorced from the OS-related updates, iOS has traditionally bundled security updates along with an upgrade to the latest version of the OS.
For instance, Apple rolled out iOS 14.4.1 earlier this month just to address one security vulnerability in WebKit that could have allowed adversaries to run arbitrary code on devices via malicious web content.
But with this new setting called "Install Security Updates" added to the software update menu, it's expected that Apple will let users choose between either installing the entire iOS update or just the security updates, in a manner that echoes macOS.
On Macs running older versions of the operating system such as macOS Mojave, Apple has offered standalone update packs, allowing users to get security patches and bug fixes while holding off before installing the latest macOS version available.
Given that iOS 14.5 is still in beta, it's still unclear how this feature will be implemented, but based on code references, it appears that users who have previously downloaded the security update may be prompted to delete it before installing another iOS update.
By separating security updates from feature-centric updates, the development could also pave the way for issuing out-of-band emergency fixes for devices not running the latest versions of iOS and iPadOS.
iOS 14.5 is already shaping up to be quite a big privacy and security-focused update, what with the company planning to redirect all fraudulent website checks through its own proxy servers as a workaround to preserve user privacy and prevent leaking IP addresses to Google.
In addition, iOS 14.5 will also require apps to ask for users' permission before tracking them across other apps and websites using the device's advertising identifier as part of a new framework dubbed App Tracking Transparency.
iOS 14.5 is currently in beta and is expected to be released later this spring.
New variant for Mac Malware XCSSET compiled for M1 Chips
14.3.2021 Apple Securityaffairs
Kaspersky researchers spotted a new variant of the XCSSET Mac malware that compiled for devices running on Apple M1 chips.
XCSSET is a Mac malware that was discovered by Trend Micro in August 2020, it was spreading through Xcode projects and exploits two zero-day vulnerabilities to steal sensitive information from target systems and launch ransomware attacks.
According to Trend Micro, the threat allows stealing data associated with popular applications, including Evernote, Skype, Notes, QQ, WeChat, and Telegram. The malware also allows attackers to capture screenshots and exfiltrate stolen documents to the attackers’ server. The malware also implements ransomware behavior, it is able to encrypt files and display a ransom note.
The malware is also able to launch universal cross-site scripting (UXSS) attacks in an effort to inject JavaScript code into the browser while visiting specific websites and changing user’s browser experience. This behavior allows the malicious code to replace cryptocurrency addresses, and steal credentials for online services (amoCRM, Apple ID, Google, Paypal, SIPMarket, and Yandex) and payment card information from the Apple Store.
Trend Micro discovered two Xcode projects injected with the XCSSET Mac Malware, one on July 13 and one on July 31.
The analysis of the C&C server revealed a list of 380 victim IP addresses, most of them in China (152) and India (103). However.
This week, Kaspersky has discovered a new variant of XCSSET compiled for devices with M1 chips.
“While exploring the various executable modules of XCSSET, we found out that some of them also contained samples compiled specially for new Apple Silicon chips. For example, a sample with the MD5 hash sum 914e49921c19fffd7443deee6ee161a4 contains two architectures: x86_64 and ARM64.” states the report published by Kaspersky.
“The first one corresponds to previous-generation, Intel-based Mac computers, but the second one is compiled for ARM64 architecture, which means that it can run on computers with the new Apple M1 chip.”
The sample analyzed by Kaspersky was uploaded to VirusTotal on 2021-02-24 21:06:05, unlike the sample analyzed by Trend Micro, this variant contains the above hash or a module named “metald”, the name of the executable file.
Experts believe that the XCSSET campaign is likely still ongoing and multiple malware authors are recompiling Mac malware to run on new Apple Macs M1 chips.
Recently experts spotted other malware specifically designed to infect Mac running on M1 chips.
In January, the popular security researcher Patrick Wardle discovered one of the first malware designed to target M1 chips, it is a variant of the Pirrit adware specifically compiled for the new generation of Apple chips.
In February, Malware researchers at Red Canary uncovered another malware, dubbed Silver Sparrow, that is infecting Mac systems using the latest Apple M1 chip across the world.
According to data shared by Malwarebytes, as of February 17, Silver Sparrow had already infected 29,139 macOS endpoints across 153 countries. Most of the infections were observed in Canada, France, Germany, the United Kingdom, and the United States.
At the time of this writing, it is not clear which is the final payload that threat actors behind the Silver Sparrow adware intend to deploy on the victim machines. Experts believe that this malware is the result of advanced and sophisticated adversaries.
Threat actors are focusing their efforts on developing threats to target the devices using the new Apple chip, Wardle pointed out that (static) analysis tools or antivirus engines face difficulties in analyzing ARM64 binaries, this is demonstrated by the fact that the detection rate for these malware is lower when compared to the Intel x86_64 version.
“With the new M1 chip, Apple has certainly pushed its performance and energy saving limits on Mac computers, but malware developers kept an eye on those innovations and quickly adapted their executables to Apple Silicon by porting the code to the ARM64 architecture.” Kaspersky concludes.
“We have observed various attempts to port executables not just among typical adware such as Pirrit or Bnodlero samples, but also among malicious packages, such as the Silver Sparrow threat and XCSSET downloadable malicious modules. This certainly will give a kickstart to other malware adversaries to begin adapting their code for running on Apple M1 chips.”
Mac Malware 'XCSSET' Adapted for Devices With M1 Chips
13.3.2021 Apple Securityweek
An increasing number of Mac malware developers have started creating variants that are specifically designed to run on devices powered by Apple’s M1 chip.
Apple unveiled its M1 system-on-chip in November 2020 and the first malware created specifically for systems with the arm64 CPU architecture used by the M1 was apparently created in December. This was a variant of Pirrit, a piece of adware that has been around for several years.
A few days after the existence of this Pirrit variant came to light, managed detection and response firm Red Canary reported identifying a mysterious piece of Mac malware that had infected tens of thousands of devices around the world. This malware, named Silver Sparrow, also had a variant specifically designed for M1 systems.
Kaspersky reported on Friday that it too has spotted a piece of malware with a variant compiled for devices with M1 chips, specifically a variant of the malware known as XCSSET.
XCSSET is a mysterious piece of malware first detailed by Trend Micro and Mac security company Intego in August 2020. It does not appear to have been linked to any known threat group or activity, but a majority of infections spotted at the time were in China and India.
The malware is designed to allow its operator to launch ransomware attacks (i.e. encrypt files and display a ransom note), and steal information from infected devices, including data associated with the Evernote, Skype, Notes, QQ, WeChat, and Telegram apps.
It can also launch universal cross-site scripting (UXSS) attacks in an effort to inject arbitrary JavaScript code into the websites visited by the victim. This allows it to modify sites, including replacing cryptocurrency addresses, and phish credentials and payment card information.
XCSSET spreads through code injected into projects for Xcode, Apple’s integrated development environment. The payload is executed when the project is built.
Kaspersky has seen an XCSSET sample compiled for the arm64 architecture. This sample was uploaded to the VirusTotal malware analysis service on February 24, which has led the company’s researchers to believe that the campaign is likely still ongoing.
Kaspersky noted that in many cases Mac malware is delivered in the Mach-O format, which includes the malicious code compiled for several architectures — depending on what type of device the malware lands on, the code corresponding to that architecture is executed.
“With the new M1 chip, Apple has certainly pushed its performance and energy saving limits on Mac computers, but malware developers kept an eye on those innovations and quickly adapted their executables to Apple Silicon by porting the code to the ARM64 architecture,” Kaspersky researchers wrote in a blog post.
They added, “We have observed various attempts to port executables not just among typical adware such as Pirrit or Bnodlero samples, but also among malicious packages, such as the Silver Sparrow threat and XCSSET downloadable malicious modules. This certainly will give a kickstart to other malware adversaries to begin adapting their code for running on Apple M1 chips.”
Apple’s Device Location-Tracking System Could Expose User Identities
10.3.2021 Apple Threatpost
Researchers have identified two vulnerabilities in the company’s crowd-sourced Offline Finding technology that could jeopardize its promise of privacy.
Two vulnerabilities in a crowdsourced location-tracking system that helps users find Apple devices even when they’re offline could expose the identity of users, research claim.
Offline Finding, a proprietary app introduced by Apple in 2019 for its iOS, macOS and watchOS platforms, enables the location of Apple devices even if they aren’t connected to the internet. While this capability in and of itself is not unique to the company, Apple promised that the technology could conduct its task in a way that preserves user privacy.
While for the most part the technology lives up to its privacy goals, it does have flaws that “can lead to a location correlation attack and unauthorized access to the location history of the past seven days, which could de anonymize users,” a research team from the Technical University of Darmstadt, Germany, wrote in a paper published online (PDF).
Researchers Alexander Heinrich, Milan Stute, Tim Kornhuber and Matthias Hollick set out to discover if Apple’s claims that OF ensures finder anonymity, does not track owner devices, and keeps location reports confidential actually hold up under scrutiny. They have notified Apple of their findings, and the company has responded with a fix for the more serious flaw.
Of depends on a network of hundreds of millions of devices, which makes it the largest crowd-sourced location tracking system in existence. Moreover, it’s poised to grow even larger when OF rolls out future support for non-Apple devices, researchers observed.
The system works by using its network of so-called “finder” devices to locate “lost,” unconnected devices using Bluetooth Low Energy (BLE). The finder devices that are connected to the internet can then relay location info back to the owner of the lost device.
Peering Under the Hood
To conduct their research, the Darmstadt team reverse-engineered the technology to recover the specifications of the closed-source OF protocols that are involved in the losing, searching and finding of devices, uncovering a system of encryption and decryption for how the technology works, researchers explained.
“In short, devices of one owner agree on a set of so-called rolling public–private keypairs,” they wrote. “Devices without an Internet connection, i.e., without cellular or WiFi connectivity, emit BLE advertisements that encode one of the rolling public keys. Finder devices overhearing the advertisements encrypt their current location under the rolling public key and send the location report to a central Apple-run server.”
When searching for a lost device, another owner device queries the central server for location reports with a set of known rolling public keys of the lost device, researchers explained. The owner can decrypt the reports using the corresponding private key and retrieve the location.
While “the overall design achieves Apple’s specific goals,” for privacy, researchers did discover two vulnerabilities “that seem to be outside of Apple’s threat model but can have severe consequences for the users,” they said.
Loss of Anonymity
One flaw in the design of OF allows Apple to correlate different owners’ locations if their locations are reported by the same finder, “effectively allowing Apple to construct a social graph,” that can violate user privacy, researchers noted.
Specifically, when uploading and downloading location reports, finder and owner devices reveal their identity to Apple, so the company can discover which users have been in close proximity to each other. Moreover, the company can store the data for potential exploitability. For this flaw to be exploited, however, an owner would have to request the location of their devices via the Find My application, researchers noted.
A second vulnerability poses a more serious problem, researchers found. It could allow someone to build “malicious macOS applications to retrieve and decrypt the OF location reports of the last seven days for all its users and for all of their devices,” they wrote.
The problem with OF that causes this issue is that the location privacy of lost devices is based on the assumption that the private part of the advertisement keys—which change every 15 minutes–is only known to the owner devices. The technology supports retrieving location reports from the last seven days—which means there is a total of 672 advertisement keys per device, for which there exist potential location reports on Apple’s servers, researchers wrote.
In principle, all of these keys could be generated from the master beacon key whenever needed. However, Apple decided to cache the advertisement keys, most likely for performance reasons. Researchers found that macOS stores these cached keys on a directory disk that is readable by the local user or any app that runs with user privileges.
The flaw, then can enable someone to circumvent Apple’s restricted location API and access the geolocation of all owner devices without user consent, abusing historical location reports to generate a unique mobility profile and identify the user “with high accuracy,” researchers said.
The team shared their findings with Apple and in response the company issued a patch in September 2020, tracking the second vulnerability as CVE-2020-9986 and calling it “a file access issue … with certain home folder files.” Nothing that the flaw could allow “a malicious application … to read sensitive location information,” Apple addressed it with “improved access restrictions” in macOS Catalina 10.15.7.
Apple fixes CVE-2021-1844 RCE that affects iOS, macOS, watchOS, and Safari
10.3.2021 Apple Securityaffairs
Apple released out-of-band patches to address a remote code execution, tracked as CVE-2021-1844, that affect iOS, macOS, watchOS, and Safari web browser.
Apple has released out-of-band security patches to address a critical iOS, macOS, watchOS, and Safari web browser to address a security flaw tracked as CVE-2021-1844.
The vulnerability was discovered by Clément Lecigne of Google’s Threat Analysis Group and Alison Huffman of Microsoft Browser Vulnerability Research. The flaw could be exploited by remote attackers to run arbitrary code on vulnerable devices by tricking users into visiting a malicious web content.
The vulnerability is caused by a memory corruption issue that could be triggered to cause arbitrary code execution when processing specially crafted web content.
“Processing maliciously crafted web content may lead to arbitrary code execution.” reads the advisory published by Apple. “Description: A memory corruption issue was addressed with improved validation.”
Apple has improved validation to address the vulnerability.
Apple has released an update for devices running iOS 14.4, iPadOS 14.4, macOS Big Sur, and watchOS 7.3.1 (Apple Watch Series 3 and later). Apple also released an update to Safari for MacBooks running macOS Catalina and macOS Mojave.
In March, Pwn20wnd, the author of the jailbreaking tool “unc0ver,” has updated their software to support iOS 14.3 and earlier releases. The last release of the jailbreaking tool, unc0ver v6.0.0, now includes the exploit code for the CVE-2021-1782 vulnerability that Apple in January claimed was actively exploited by threat actors. The CVE-2021-1782 flaw is a race condition issue that resides in the iOS operating system kernel.
Apple Patches Remote Code Execution Bug in WebKit
10.3.2021 Apple Securityweek
Apple on Monday released patches for a vulnerability in WebKit that could allow attackers to execute code remotely on affected devices.
Tracked as CVE-2021-1844 and co-reported by Clément Lecigne of Google’s Threat Analysis Group and Alison Huffman of Microsoft Browser Vulnerability Research, the flaw was addressed with software updates for macOS, iOS, watchOS, and Safari.
To exploit the vulnerability, an attacker would simply need to craft a webpage containing malicious code, and then lure the victim into accessing that webpage, which would trigger the execution of code onto the victim’s machine.
“Processing maliciously crafted web content may lead to arbitrary code execution,” Apple notes. “A memory corruption issue was addressed with improved validation,” the company continues.
The issue exists because the processing of specific content in WebKit could lead to a boundary error. Once the victim accesses the attacker-crafted page, the memory corruption would be triggered, resulting in the execution of arbitrary code.
An attacker able to successfully exploit the vulnerability may essentially compromise the victim’s vulnerable system in its entirety.
Apple has addressed the vulnerability with the release of macOS Big Sur 11.2.3, iOS 14.4.1 and iPadOS 14.4.1 (for iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch (7th generation), watchOS 7.3.2, and Safari 14.0.3 (for macOS Catalina and macOS Mojave).
Users are advised to apply the available updates as soon as possible, to ensure their systems remain protected. Apple hasn’t provided information on whether the flaw is already being exploited in the wild.
Flaws in Apple Location Tracking System Could Lead to User Identification
10.3.2021 Apple Securityweek
Vulnerabilities identified in offline finding (OF) — Apple’s proprietary crowd-sourced location tracking system — could be abused for user identification, researchers said in a report released this month.
Introduced in 2019, the system relies on the Bluetooth Low Energy (BLE) technology for the detection of ‘lost’ devices, and on the Internet connection of so-called ‘finder’ devices to report on their location back to the owner.
With “hundreds of millions” of devices part of Apple’s OF network, this represents the largest crowd-sourced location tracking system in the world, one that is expected to grow even further, as support for non-Apple devices is added to it.
Apple claims anonymity of finders, says that device owners can’t be tracked, and that location reports are confidential, but a group of academic researchers with the Technical University of Darmstadt, Germany, identified vulnerabilities that could potentially lead to user identification.
Overall, they say, the system delivers on its promise for security and privacy, but two design and implementation flaws could allow for location correlation attacks, as well as for unauthorized access to the past seven days’ location history, thus essentially resulting in user deanonymization.
“We find that the overall design achieves Apple’s specific goals. However, we discovered two distinct design and implementation vulnerabilities that seem to be outside of Apple’s threat model but can have severe consequences for the users,” the academics note in their research paper.
The researchers found that different owners’ locations could be correlated, provided that they are reported by the same ‘finder,’ which would essentially allow Apple to construct a social graph.
Furthermore, they discovered that, because “cached rolling advertisement keys are stored on the file system in clear text,” it was possible for a malicious macOS application to retrieve and decrypt location reports for the past seven days for all users and devices.
“Apple as the service provider (could infer that two or more owners have been in close proximity to each other as OF uses identifiable information in both up-load and download requests. Law enforcement agencies could exploit this issue to deanonymize participants of (political) demonstrations even when participants put their phones in flight mode,” the researchers note.
Exploitation of this vulnerability, however, is only possible if the victims have requested the location of their devices using the Find My application. The issue is that the identity of the finder and owner devices are revealed when location reports are downloaded or uploaded, the researchers explain.
Additionally, the researchers discovered a security flaw in the OF implementation on macOS, which could allow a malicious application to access the location of all owner devices, without consent, completely circumventing Apple’s restricted location API. Furthermore, location history can be abused to generate profiles and identify users.
The system, the researchers explain, assumes that the private part of a device’s advertisement keys is known to the user alone, and these keys change every 15 minutes. With OF allowing for the retrieval of location reports for a week, potential location reports for a total of 672 advertisement keys exist on Apple’s servers.
These advertisement keys are cached, likely for performance reasons, and on macOS they are stored in a directory accessible by the local user and any application running with user privileges. The cache files are inaccessible on iOS.
The researchers explain that a malicious application that runs with user privileges could access the key cache directory and read advertisement keys or exfiltrate them to the attacker, without additional user interaction other than launching the app.
Armed with the owner’s keys, the attacker could download the victim’s location reports on their machine, and use the same keys to decrypt these reports.
“The attack essentially allows any third-party application to bypass Apple’s Core Location API that enforces user consent before an application can access the device’s location. Moreover, the attacker can access the location history of the past seven days of all the owner’s devices,” the researchers explain.
The identified flaws were responsible disclosed to Apple, which released a patch in September 2020. Apple refers to the bug as CVE-2020-9986, describing it as “a file access issue” that was addressed with improved access restrictions.
Apple Issues Patch for Remote Hacking Bug Affecting Billions of its Devices
9.3.2021 Apple Securityweek
Apple has released out-of-band patches for iOS, macOS, watchOS, and Safari browsers to address a security flaw that could allow attackers to run arbitrary code on devices via malicious web content.
Tracked as CVE-2021-1844, the vulnerability was discovered and reported to the company by Clément Lecigne of Google's Threat Analysis Group and Alison Huffman of Microsoft Browser Vulnerability Research.
According to the update notes posted by Apple, the flaw stems from a memory corruption issue that could lead to arbitrary code execution when processing specially crafted web content. The company said the problem was addressed with "improved validation."
The update is available for devices running iOS 14.4, iPadOS 14.4, macOS Big Sur, and watchOS 7.3.1 (Apple Watch Series 3 and later), and as an update to Safari for MacBooks running macOS Catalina and macOS Mojave.
The latest development comes on the heels of a patch for three zero-day vulnerabilities (CVE-2021-1782, CVE-2021-1870, and CVE-2021-1871), which it released in January. The weaknesses, which allow an attacker to elevate privileges and achieve remote code execution, were later exploited by the team behind the "unc0ver" jailbreak tool to unlock almost every single iPhone model running 14.3.
It's worth noting that Huffman was also behind the discovery of an actively exploited zero-day bug in the Chrome browser that was addressed by Google last week. But unlike the Chrome security flaw, there is no evidence that CVE-2021-1844 is being exploited by malicious hackers.
Users of Apple devices or those running a vulnerable version of Chrome are advised to install the updates as soon as possible to mitigate the risk associated with the flaws.
Bug in Apple's Find My Feature Could've Exposed Users' Location Histories
6.3.2021 Apple Thehackernews
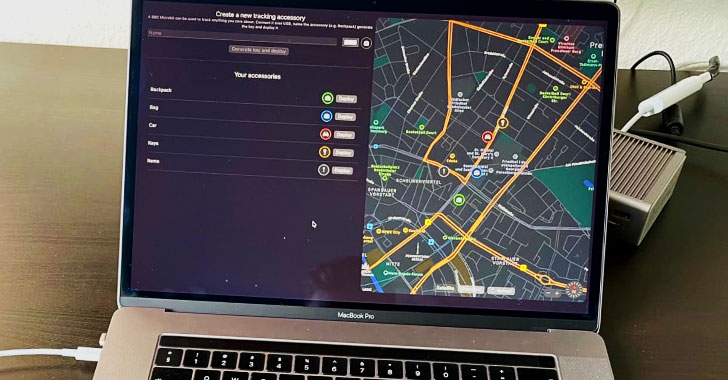
Cybersecurity researchers on Thursday disclosed two distinct design and implementation flaws in Apple's crowdsourced Bluetooth location tracking system that can lead to a location correlation attack and unauthorized access to the location history of the past seven days, thereby by deanonymizing users.
The findings are a consequence of an exhaustive review undertaken by the Open Wireless Link (OWL) project, a team of researchers from the Secure Mobile Networking Lab at the Technical University of Darmstadt, Germany, who have historically taken apart Apple's wireless ecosystem with the goal of identifying security and privacy issues.
In response to the disclosures on July 2, 2020, Apple is said to have partially addressed the issues, stated the researchers, who used their own data for the study citing privacy implications of the analysis.
How Find My Works?
Apple devices come with a feature called Find My that makes it easy for users to locate other Apple devices, including iPhone, iPad, iPod touch, Apple Watch, Mac, or AirPods. With the upcoming iOS 14.5, the company is expected to add support for Bluetooth tracking devices — called AirTags — that can be attached to items like keys and wallets, which in turn can be used for tracking purposes right from within the Find My app.
What's more interesting is the technology that undergirds Find My. Called offline finding and introduced in 2019, the location tracking feature broadcasts Bluetooth Low Energy (BLE) signals from Apple devices, allowing other Apple devices in close proximity to relay their location to Apple's servers.
Put differently, offline loading turns every mobile device into a broadcast beacon designed explicitly to shadow its movements by leveraging a crowdsourced location tracking mechanism that's both end-to-end encrypted and anonymous, so much so that no third-party, including Apple, can decrypt those locations and build a history of every user's whereabouts.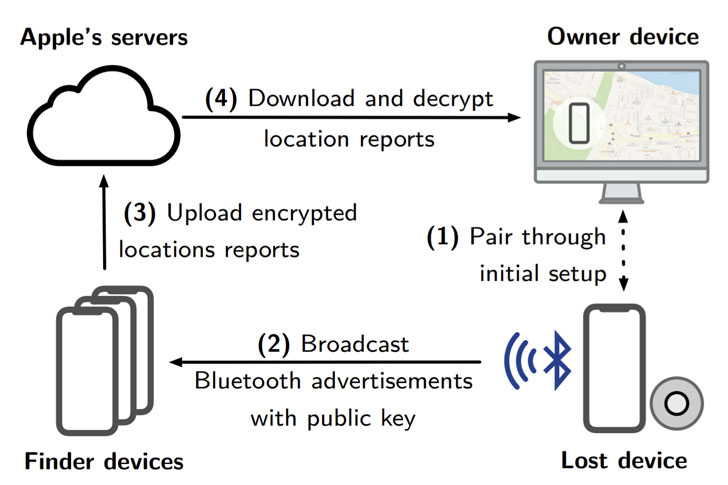
This is achieved via a rotating key scheme, specifically a pair of public-private keys that are generated by each device, which emits the Bluetooth signals by encoding the public key along with it. This key information is subsequently synchronized via iCloud with all other Apple devices linked to the same user (i.e., Apple ID).
A nearby iPhone or iPad (with no connection to the original offline device) that picks up this message checks its own location, then encrypts the information using the aforementioned public key before sending it to the cloud along with a hash of the public key.
In the final step, Apple sends this encrypted location of the lost device to a second Apple device signed in with the same Apple ID, from where the owner can use the Find My app to decrypt the reports using the corresponding private key and retrieve the last known location, with the companion device uploading the same hash of the public key to find a match in Apple's servers.
Issues with Correlation and Tracking
Since the approach follows a public key encryption (PKE) setup, even Apple cannot decrypt the location as it's not in possession of the private key. While the company has not explicitly revealed how often the key rotates, the rolling key pair architecture makes it difficult for malicious parties to exploit the Bluetooth beacons to track users' movements.
But OWL researchers said the design allows Apple — in lieu of being the service provider — to correlate different owners' locations if their locations are reported by the same finder devices, effectively allowing Apple to construct what they call a social graph.
"Law enforcement agencies could exploit this issue to deanonymize participants of (political) demonstrations even when participants put their phones in flight mode," the researchers said, adding "malicious macOS applications can retrieve and decrypt the [offline finding] location reports of the last seven days for all its users and for all of their devices as cached rolling advertisement keys are stored on the file system in cleartext."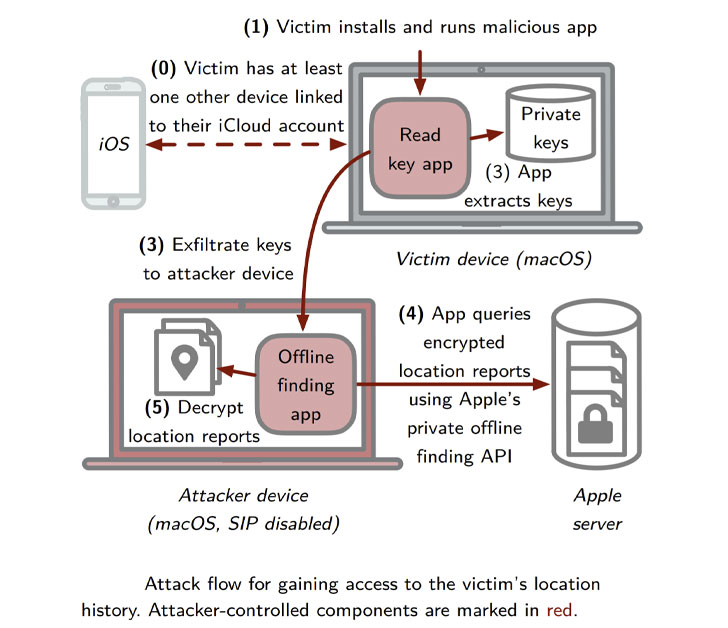
In other words, the macOS Catalina vulnerability (CVE-2020-9986) could allow an attacker to access the decryption keys, using them to download and decrypt location reports submitted by the Find My network, and ultimately locate and identify their victims with high accuracy. The weakness was patched by Apple in November 2020 (version macOS 10.15.7) with "improved access restrictions."
A second outcome of the investigation is an app that's designed to let any user create an "AirTag." Called OpenHaystack, the framework allows for tracking personal Bluetooth devices via Apple's massive Find My network, enabling users to create their own tracking tags that can be appended to physical objects or integrated into other Bluetooth-capable devices.
This is not the first time researchers from Open Wireless Link (OWL) have uncovered flaws in Apple's closed-source protocols by means of reverse engineering.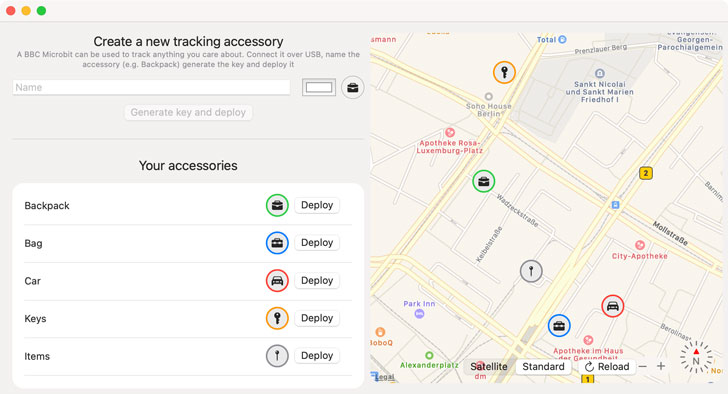
In May 2019, the researchers disclosed vulnerabilities in Apple's Wireless Direct Link (AWDL) proprietary mesh networking protocol that permitted attackers to track users, crash devices, and even intercept files transferred between devices via man-in-the-middle (MitM) attacks.
This was later adapted by Google Project Zero researcher Ian Beer to uncover a critical "wormable" iOS bug last year that could have made it possible for a remote adversary to gain complete control of any Apple device in the vicinity over Wi-Fi.
Jailbreak Tool Works on iPhones Up to iOS 14.3
3.3.2021 Apple Threatpost
The UnC0ver team took advantage of an iOS flaw patched in January in its latest tool allowing developers and other enthusiasts to hack into their own devices.
Hackers behind previous iPhone jailbreak tools have released a jailbreak update based on a recently discovered and patched iPhone vulnerability. According to iPhone jailbreakers at UnC0ver, the tool allows users to take full control over unpatched iPhones.
The jailbreak—which UnC0ver said works on iOS versions 11.0 to 14.3–exploits the kernel vulnerability CVE-2021-1782, one of three iOS flaws for which Apple released an emergency update, iOS 14.4, last month. At the time the company said the vulnerabilities potentially were being exploited in the wild.
With the release of 14.4, a number of devices already will have been updated, which means the jailbreak won’t work. However, anyone with a device running 14.3 or earlier version of iOS can use the tool to hack into their iPhone, according to UnC0ver.
UnC0ver shared its discovery on Twitter, announcing UnC0ver v6.0.0, after one of the group’s members, Pwn20wnd, who put out several teaser tweets about the imminent arrival of the jailbreak tool before its release.
“Tweet your device model and why you will be jailbreaking your device on iOS 14 with the hashtag #unc0ver!” Pwn20wnd tweeted on Feb. 27 before releasing the tool, with other enthusiasts echoing the call to spread the news.
What Exactly is a Jailbreak Tool?
Jailbreak tools are software that take advantage of vulnerabilities in iOS to allow users root access and full control of their device. Jailbreaking bypasses DRM restrictions, allowing users to run unauthorized and custom software as well as make other tweaks to iOS.
Apple’s iOS and other OSes for its products are notoriously closed-source, which has irked developers that like to peer under the hood and play with the code on their devices. The company historically has cited security reasons for not permitting its users tinker with the proprietary code for iOS.
Jailbreaks like the ones unC0ver has become notorious for releasing have become popular ways for iOS developers and users to hack into their own devices to make custom changes to their devices, and are typically met with enthusiasm from iPhone aficionados.
“It’s great to see #unc0ver after such a long wait for a iOS 14 jailbreak on newer devices. even better that it was a complete surprise!” tweeted Jamie Bishop, a software engineer and self-proclaimed iOS hacker.
However, some enthusiasts grumbled that they wish they’d had prior warning that a jailbreak was going to be released, because their devices had already updated to iOS 14.4 and so the tool was rendered useless to them.
“Well…A little heads up would’ve been appreciated,” tweeted David Davidson, and iPhone user in Israel, in response to Bishop. “Now there’s a lot of us with nothing to do.”
It’s been a little more than 10 months since UnC0ver released its last iPhone jailbreak tool. That one came in May 2020, which allowed people to break into devices up to iOS 13.5, which was then the latest release. Apple quietly released a patch for the jailbreak not long after.
Pwn20wnd released the unc0ver v 6.0 jailbreaking tool
3.3.2021 Apple Securityaffairs
The popular jailbreaking tool called “unc0ver” now supports iOS 14.3 and earlier releases, and is able to unlock almost every iPhone device.
Pwn20wnd, the author of the jailbreaking tool “unc0ver,” has updated their software to support iOS 14.3 and earlier releases. The last release of the jailbreaking tool, unc0ver v6.0.0, now includes the exploit code for the CVE-2021-1782 vulnerability that Apple in January claimed was actively exploited by threat actors.
Jailbreaking an iOS mobile device it is possible to remove hardware restrictions implemented by the Apple’s operating system, Jailbreaking gives users root access to the iOS file system and manager, this allows them to download and install applications and themes from third-party stores.
Apple did not disclose info about the attacks in the wild exploiting this vulnerability.
The CVE-2021-1782 flaw is a race condition issue that resides in the iOS operating system kernel.
“A malicious application may be able to elevate privileges. Apple is aware of a report that this issue may have been actively exploited.” reads the advisory. “A race condition was addressed with improved locking.”
unc0ver v6.0.0 could be used to unlock any device running iOS 11.0 through iOS 14.3, below the announcement made by Pwn20wnd on Twitter.
Zimperium founder, Zuk Avraham, also shared the news of the release of the jailbreaking tool and invited Apple to enable users to have full access to their devices.
In May 2020, the Unc0ver team released Unc0ver 5.0.0 which exploits a memory consumption issue in the kernel, tracked as CVE-2020-9859, to jailbreak mobile devices running iOS versions up to iOS v13.5.
New 'Unc0ver' Jailbreak Uses Vulnerability That Apple Said Was Exploited
3.3.2021 Apple Securityweek
Unc0ver jailbreak exploits CVE-2021-1782
The latest version of the Unc0ver jailbreak leverages a vulnerability that Apple said had been exploited before it released a patch in January.
Jailbreaks remove restrictions and give users greater control over their iPhone or iPad. The developers of the jailbreak named Unc0ver recently announced the availability of version 6.0.0, which they claim works on all versions of iOS between 11.0 and 14.3 on many iPhones and iPads, including the iPhone 12 Pro launched a few months ago.
Unc0ver developers say the jailbreak is “designed to be stable” and it preserves the security layers implemented by Apple.
Unc0ver does not work on devices running iOS 14.4. That version of the operating system, released by Apple in late January, patches CVE-2021-1782, a kernel vulnerability that can be exploited for privilege escalation.
CVE-2021-1782 is one of the three vulnerabilities that Apple said “may have been actively exploited” at the time when it released the patches. All three flaws had been reported to Apple by an anonymous researcher. The tech giant has not made public any information regarding the attacks exploiting these vulnerabilities.
The developers of the Unc0ver jailbreak said on Twitter that they wrote their “own exploit based on CVE-2021-1782 for unc0ver to achieve optimal exploit speed and stability.”
New 'unc0ver' Tool Can Jailbreak All iPhone Models Running iOS 11.0 - 14.3
3.3.2021 Apple Thehackernews

A popular jailbreaking tool called "unc0ver" has been updated to support iOS 14.3 and earlier releases, thereby making it possible to unlock almost every single iPhone model using a vulnerability that Apple in January disclosed was actively exploited in the wild.
The latest release, dubbed unc0ver v6.0.0, was released on Sunday, according to its lead developer Pwn20wnd, expanding its compatibility to jailbreak any device running iOS 11.0 through iOS 14.3 using a kernel vulnerability, including iOS 12.4.9-12.5.1, 13.5.1-13.7, and 14.0-14.3.
Tracked as CVE-2021-1782, the flaw is a privilege escalation vulnerability in the kernel stemming from a race condition that could cause a malicious application to elevate its privileges.
"We wrote our own exploit based on CVE-2021-1782 for #unc0ver to achieve optimal exploit speed and stability," Pwn20wnd said in a separate tweet.
The vulnerability has since been addressed by Apple as part of its iOS and iPadOS 14.4 updates released on January 26, 2021, but not before admitting that the issue may have been under active attack by bad actors.
The iPhone maker, however, did not disclose how widespread the attack was or reveal the identities of the attackers actively exploiting them.
Jailbreaking, similar to rooting on Google's Android, involves a privilege escalation that works by exploiting flaws in iOS to grant users root access and full control over their devices. In doing so, it allows iOS users to remove software restrictions imposed by Apple, thereby allowing access to additional customization and otherwise prohibited apps.
For its part, Apple has steadily made it difficult to jailbreak devices by locking down its hardware and software for security reasons, which it says helps counter malware attacks.
ZecOps CEO Zuk Avraham said the jailbreak is "yet another example that attackers have an edge on iOS vs. defenders," adding "[Apple] needs to stop the need to jailbreak the device in the first place and should just enable users to have full access without a need to run an exploit."
Last May, the unc0ver team released a similar jailbreak for iPhones running iOS 11 to iOS 13.5 by exploiting a memory consumption issue in the kernel (CVE-2020-9859). But it was patched by Apple in a matter of days with the release of iOS 13.5.1 to prevent the vulnerability from being exploited maliciously.
Mysterious Mac Malware Infected at Least 30,000 Devices Worldwide
23.2.2021 Apple Securityweek
Researchers at managed detection and response firm Red Canary have come across a mysterious piece of Mac malware that appears to have infected at least 30,000 devices around the world.
Red Canary has analyzed the threat in collaboration with Malwarebytes, whose data showed — as of February 17 — 29,139 infected macOS systems across 153 countries, including many in the United States, United Kingdom, Canada, France and Germany. The activity cluster has been named Silver Sparrow.
Researchers have come across two variants of the malware, including one designed to run on devices powered by Apple’s new M1 chip, which uses the arm64 CPU architecture.
Another piece of malware specifically designed to target devices with M1 chips is a variant of the Pirrit adware and it was detailed last week by Apple security expert Patrick Wardle. The sample analyzed by Wardle was uploaded to Google’s malware analysis service VirusTotal in late December 2020.
In the case of Silver Sparrow, an actual malware file for M1 systems was submitted to VirusTotal on January 22, but one of the domains it used was registered on December 5. The earliest known variant of the malware — one designed to target pre-M1 systems — was apparently created sometime in August 2020.
In addition to being designed to target computers with M1 chips, Silver Sparrow is interesting because its installer packages use the macOS Installer JavaScript API to execute commands. Red Canary says this appears to be the first piece of malware that does this — it’s not uncommon for legitimate software to do it, but malicious macOS software typically uses preinstall or postinstall scripts for command execution.
Interestingly, despite infecting a significant number of machines, researchers have not seen any payload being delivered by the Silver Sparrow malware, making the threat actor’s goals unclear, but they believe it to be an “operationally mature adversary.”
The malware has been delivered as PKG files, but the initial distribution method is currently unknown.
“We suspect that malicious search engine results direct victims to download the PKGs based on network connections from a victim’s browser shortly before download. In this case we can’t be certain because we don’t have the visibility to determine exactly what caused the download,” Red Canary researchers explained.
Red Canary believes that while Silver Sparrow doesn’t currently have a payload, it is “uniquely positioned to deliver a potentially impactful payload at a moment’s notice.”
Red Canary has made available indicators of compromise (IoC) and other technical details that can be useful to defenders and threat hunting teams.
New 'Silver Sparrow' Malware Infected Nearly 30,000 Apple Macs
22.2.2021 Apple Thehackernews
Days after the first malware targeting Apple M1 chips were discovered in the wild, researchers have disclosed yet another previously undetected piece of malicious software that has already infected 29,139 Macs running Intel x86_64 and the iPhone maker's M1 processors.
However, the ultimate goal of the operation remains something of a conundrum, what with the lack of a next-stage or final payload leaving researchers unsure of its distribution timeline and whether the threat is just under active development.
Calling the malware "Silver Sparrow," cybersecurity firm Red Canary said it identified two different versions of the malware — one compiled only for Intel x86_64 and uploaded to VirusTotal on August 31, 2020 (version 1), and a second variant submitted to the database on January 22 that's compatible with both Intel x86_64 and M1 ARM64 architectures (version 2).
Adding to the mystery, the x86_64 binary, upon execution, simply displays the message "Hello, World!" whereas the M1 binary reads "You did it!," which the researchers suspect is being used as a placeholder.
"The Mach-O compiled binaries don't seem to do all that much [...] and so we've been calling them 'bystander binaries,'" Red Canary's Tony Lambert said.
"We have no way of knowing with certainty what payload would be distributed by the malware, if a payload has already been delivered and removed, or if the adversary has a future timeline for distribution," Lambert added.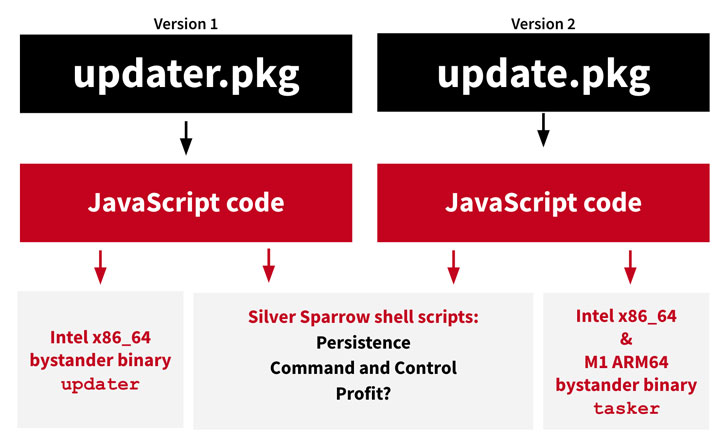
The macOS endpoints are located across 153 countries as of February 17, including high volumes of detection in the U.S., the U.K., Canada, France, and Germany, according to data from Malwarebytes.
Despite the difference in the targeting macOS platform, the two samples follow the same modus operandi: using the macOS Installer JavaScript API to execute attack commands by dynamically generating two shell scripts that are written to the target's file system.
While "agent.sh" executes immediately at the end of the installation to inform an AWS command-and-control (C2) server of a successful installation, "verx.sh" runs once every hour, contacting the C2 server for additional content to download and execute.
Additionally, the malware also comes with the capabilities to completely erase its presence from the compromised host, suggesting the actors associated with the campaign may be motivated by stealth techniques.
In response to the findings, Apple has revoked the binaries that were signed with the Apple Developer ID's Saotia Seay (v1) and Julie Willey (v2), thus preventing further installations.
Silver Sparrow is the second piece of malware to contain code that runs natively on Apple's new M1 chip. A Safari adware extension called GoSearch22 was identified last week to have been ported to run on the latest generation of Macs powered by the new processors.
"Though we haven't observed Silver Sparrow delivering additional malicious payloads yet, its forward-looking M1 chip compatibility, global reach, relatively high infection rate, and operational maturity suggest Silver Sparrow is a reasonably serious threat, uniquely positioned to deliver a potentially impactful payload at a moment's notice," Lambert said.
Silver Sparrow, a new malware infects Mac systems using Apple M1 chip
21.2.2021 Apple Securityaffairs
Experts warn of new malware, dubbed Silver Sparrow, that is infecting Mac systems using the latest Apple M1 chip across the world.
Malware researchers at Red Canary uncovered a new malware, dubbed Silver Sparrow, that is infecting Mac systems using the latest Apple M1 chip across the world.
According to data shared by Malwarebytes, as of February 17, Silver Sparrow had already infected 29,139 macOS endpoints across 153 countries. Most of the infections were observed in Canada, France, Germany, the United Kingdom, and the United States.
“However, our investigation almost immediately revealed that this malware, whatever it was, did not exhibit the behaviors that we’ve come to expect from the usual adware that so often targets macOS systems.” reads the analysis published by RedCanary. “The novelty of this downloader arises primarily from the way it uses JavaScript for execution—something we hadn’t previously encountered in other macOS malware—and the emergence of a related binary compiled for Apple’s new M1 ARM64 architecture.”
Like the other malware recently spotted by the popular expert Patrick Wardle, Silver Sparrow is a macOS adware that was recompiled to infect systems running the Apple M1 chip.
At the time of this writing, it is not clear which is the final payload that threat actors behind the Silver Sparrow adware intend to deploy on the victim machines. Experts believe that this malware is the result of advanced and sophisticated adversaries.
Threat actors are focusing their efforts on developing threats to target the devices using the new Apple chip, Wardle pointed out that (static) analysis tools or antivirus engines face difficulties in analyzing ARM64 binaries, this is demonstrated by the fact that the detection rate for these malware is lower when compared to the Intel x86_64 version.
RedCanary experts found two versions of the Silver Sparrow adware, one designed to targets Intel-based Macs, and one that is built to infect also M1-powered systems. The malicious code outstands for the use of JavaScript for execution, which is a rarity macOS malware landscape.

The number of infected devices and the specific targets of this malware let the experts into believing that the threat actors are preparing a dangerous campaign that will involve a still unknown malicious payload.
“Though we haven’t observed Silver Sparrow delivering additional malicious payloads yet, its forward-looking M1 chip compatibility, global reach, relatively high infection rate and operational maturity suggest Silver Sparrow is a reasonably serious threat, uniquely positioned to deliver a potentially impactful payload at a moment’s notice.” continue the researchers.
At the time it is unclear how the threat actors are spreading the malware.
The command and control infrastructure is hosted on the Amazon Web Services S3 cloud platform, while callback domains for this activity cluster leveraged domains hosted through Akamai CDN.
“This implies that the adversary likely understands cloud infrastructure and its benefits over a single server or non-resilient system. Further, the adversary that likely understands this hosting choice allows them to blend in with the normal overhead of cloud infrastructure traffic. Most organizations cannot afford to block access to resources in AWS and Akamai.” continues the analysis. “The decision to use AWS infrastructure further supports our assessment that this is an operationally mature adversary.”
Silver Sparrow uses the macOS Installer JavaScript API to execute suspicious commands, this is the first instance experts have observed this behaviour in malware
“The malicious JavaScript commands, on the other hand, run using the legitimate macOS Installer process and offer very little visibility into the contents of the installation package or how that package uses the JavaScript commands.” continues the analysis.
Silver Sparrow leverages Apple’s system.run command for execution, the attacker can provide the full path to a process for execution and its arguments. Then the malware causes the installer to spawn multiple bash processes that it can then use to accomplish its objectives.
The malware uses functions appendLine, appendLinex, and appendLiney to extend the bash commands with arguments that write input to files on disk. The adware writes each of its components out line by line with JavaScript commands.
This technique allows the attackers to quickly modify the code and avoid simple static antivirus signatures by dynamically generating the script rather than using a static script file.
Upon executing Silver Sparrow it will leave two scripts on an infected disk: /tmp/agent.sh and ~/Library/Application Support/verx_updater/verx.sh.
The agent.sh script executes immediately at the end of the installation to contact the C2 and register the infection, while the verx.sh script executes periodically, using a persistent LaunchAgent to contact a remote host for more information, including other payloads to execute.
Experts pointed out that none of the infected hosts downloaded a next stage payload, experts believe that this missing piece could be used to carry out malicious activities, including data exfiltration, cryptomining, or conduct a DDoS attack.
“In addition, the ultimate goal of this malware is a mystery. We have no way of knowing with certainty what payload would be distributed by the malware, if a payload has already been delivered and removed, or if the adversary has a future timeline for distribution. Based on data shared with us by Malwarebytes, the nearly 30,000 affected hosts have not downloaded what would be the next or final payload.” concludes the report.
“Finally, the purpose of the Mach-O binary included inside the PKG files is also a mystery. Based on the data from script execution, the binary would only run if a victim intentionally sought it out and launched it. The messages we observed of “Hello, World!” or “You did it!” could indicate the threat is under development in a proof-of-concept stage or that the adversary just needed an application bundle to make the package look legitimate.”
Mysterious Silver Sparrow Malware Found Nesting on 30K Macs
20.2.2021 Apple Threatpost
A second malware that targets Macs with Apple’s in-house M1 chip is infecting machines worldwide — but it’s unclear why.
Hard on the heels of a macOS adware being recompiled to target Apple’s new in-house processor, researchers have discovered a brand-new family of malware targeting the platform.
Curiously, in the samples seen so far by analysts at Red Canary, the malware (dubbed Silver Sparrow) has been executing on victim machines with the final payload yet to be determined. It appears to be lying in wait for further instructions, which is worrying because it’s clear that the authors are advanced and sophisticated adversaries, researchers said.
Silver Sparrow has taken flight in any event: As of February 17, this fresh entry to the malware scene had already infected 29,139 macOS endpoints across 153 countries, according to researchers – primarily in Canada, France, Germany, the United Kingdom and the United States.
A Word About the Benefits of the Mac M1
Apple released the M1 system-on-a-chip (SoC) last fall, marking the first time that the tech giant has created its own desktop/laptop silicon. The pivot from the Intel chips that Macs used before comes with a few benefits, such as faster performance for native applications. It also integrates a graphics processor, a machine-learning neural engine and the company’s T2 security chip. And, it uses ARM architecture, which usually powers mobile or portable devices. The smaller ARM profile translates into lower power consumption, and, Apple says, double the battery life.
With new Macs starting to roll out, cybercriminals are now turning their attention to these M1-powered targets, as evidenced by the emergence of a rebooted “Pirrit” adware detailed by Patrick Wardle this week. And now, the Silver Sparrow malware family has appeared on the scene – a brand-new malware built for the Mac M1 ecosystem, researchers said.
Silver Sparrow Leaves the Nest
Silver Sparrow is very likely an adware, according to researchers at Red Canary. It has two versions – one that targets Intel-based Macs, and one that is built to infect both the older and M1-based devices. Most notably, it uses JavaScript for execution – a rarity in the macOS malware world.
“Though we haven’t observed Silver Sparrow delivering additional malicious payloads yet, its forward-looking M1 chip compatibility, global reach, relatively high infection rate and operational maturity suggest Silver Sparrow is a reasonably serious threat, uniquely positioned to deliver a potentially impactful payload at a moment’s notice,” researchers said in a posting on Thursday.
It’s unclear how the malware is spreading – though both binaries have “package” in their names, lending a clue. Researchers noted, “We’ve found that many macOS threats are distributed through malicious advertisements as single, self-contained installers in PKG or DMG form, masquerading as [updates for a legitimate application]”—such as Adobe Flash Player, as an example.
Cloud-Hosted Infrastructure
Silver Sparrow’s infrastructure is hosted on Amazon Web Services S3 cloud platform, according to Red Canary. And, the callback domains it uses are hosted through Akamai’s content delivery network (CDN).
“This implies that the adversary likely understands…this hosting choice allows them to blend in with the normal overhead of cloud infrastructure traffic,” researchers noted. “Most organizations cannot afford to block access to resources in AWS and Akamai. The decision to use AWS infrastructure further supports our assessment that this is an operationally mature adversary.”
JavaScript-Based Malware Development
Other signs of sophistication are evident in the malware’s construction. For instance, to start its installation, Silver Sparrow uses the macOS Installer JavaScript API to execute suspicious commands, the analysis found. That’s an unusual approach, according to Red Canary.
“While we’ve observed legitimate software doing this, this is the first instance we’ve observed it in malware,” researchers said. “This is a deviation from behavior we usually observe in malicious macOS installers, which generally use preinstall or postinstall scripts to execute commands.”
Using malicious JavaScript commands and the legitimate macOS Installer process has the benefit of limiting visibility into the contents of the installation package, the firm added.
Once installed, Silver Sparrow uses Apple’s system.run command for execution.
“Apple documented the system.run code as launching ‘a given program in the Resources directory of the installation package,’ but it’s not limited to using the Resources directory,” researchers explained. “As observed with Silver Sparrow, you can provide the full path to a process for execution and its arguments. By taking this route, the malware causes the installer to spawn multiple bash processes that it can then use to accomplish its objectives.”
This gives the developers a lot of flexibility when it comes to evolving the malware over time, researchers said. The bash commands can be extended with arguments that write input to files on disk, which are written out line-by-line with JavaScript commands. This is a choice that will let the adversary quickly modify the code and ease development, according to Red Canary – and, it helps the malware to avoid simple static antivirus signatures by dynamically generating the script rather than using a static script file.
Once fully executed, Silver Sparrow leaves two scripts on an infected disk: /tmp/agent.sh and ~/Library/Application Support/verx_updater/verx.sh.
The agent.sh script executes immediately at the end of the installation to contact the command-and-control (C2) server to indicate that installation has successfully occurred. The verx.sh script meanwhile executes periodically, using a persistent LaunchAgent to contact a remote host for more information, including to check for additional content to download and execute.
“LaunchAgents provide a way to instruct launchd, the macOS initialization system, to periodically or automatically execute tasks,” researchers explained. “Every hour, the persistence LaunchAgent tells launchd to execute a shell script that downloads a JSON file to disk, converts it into a plist, and uses its properties to determine further actions.”
A Mystery End Goal: Mac Adware?
In observing the malware’s check-ins to the C2 for over a week, none of the nearly 30,000 affected hosts downloaded what would be the next or final payload. This would presumably be a component that would carry out malicious actions like data exfiltration, cryptomining, ransomware, adware or DDoS bot enslavement, to name a few possibilities.
In other words, Silver Sparrow’s wings are clipped, for now.
“The ultimate goal of this malware is a mystery,” researchers said. “We have no way of knowing with certainty what payload would be distributed by the malware, if a payload has already been delivered and removed, or if the adversary has a future timeline for distribution.”
A clue as to what its developers may be going for exists at the end of the installation routine, researchers noticed.
“At the end of the installation, Silver Sparrow executes two discovery commands to construct data for a curl HTTP POST request indicating that the installation occurred. One retrieves…the URL used to download the original package file,” they explained. “By executing a sqlite3 query, the malware finds the original URL the .PKG downloaded from, giving the adversary an idea of successful distribution channels. We commonly see this kind of activity with malicious adware on macOS.”
Odd Placeholder Binaries
Silver Sparrow contains a further mystery in the form of placeholder binaries.
Both versions of Silver Sparrow have an extraneous Mach-O binary that appears to play no additional role in their execution.
“Ultimately this binary seems to have been included as placeholder content to give the PKG something to distribute outside the JavaScript execution,” analysts noted.
The Intel-only version simply says, “Hello, World!”; and the M1-compatible sample displays the message “You did it!”
“Based on the data from script execution, the binary would only run if a victim intentionally sought it out and launched it. The messages we observed of ‘Hello, World!’ or ‘You did it!’ could indicate the threat is under development in a proof-of-concept stage or that the adversary just needed an application bundle to make the package look legitimate,” Red Canary concluded.
The callback domain for the M1 version of Silver Sparrow was created Dec. 5, shortly after the SoC launched. In all, having two different malwares – Wardle’s discovery and Silver Sparrow – circulating already for what remains a limited platform is a notable development, researchers said. And Apple is already planning M1’s successor, the M1x chip, so the development work necessary to target this platform is far from finished. Is it worth malware authors’ time?
That remains to be seen, but “this is significant because the M1 ARM64 architecture is young, and researchers have uncovered very few threats for the new platform,” researchers noted.
Experts spotted the first malware tailored for Apple M1 Chip, it is just the beginning
20.2.2021 Apple Securityaffairs
Apple launched its M1 chip and cybercriminals developed a malware sample specifically for it, the latest generation of Macs are their next targets.
The popular security researcher Patrick Wardle discovered one of the first malware designed to target latest generation of Apple devices using the company M1 chip.
The discovery suggests threat actors are tailoring their malware to target the latest generation of Mac devices using the own processors.
Wardle discovered a Safari adware extension, tracked as GoSearch22, that was initially developed to run on Intel x86 chips, and now it was adapted to run on M1 chips.
“What we do know is as this binary was detected in the wild (and submitted by a user via an Objective-See tool) …so whether it was notarized or not, macOS users were infected.” reads the analysis published by Wardle. “Looking at the (current) detection results (via the anti-virus engines on VirusTotal), it appears the GoSearch22.app is an instance of the prevalent, yet rather insidious, ‘Pirrit’ adware:”
The malicious extension was signed with an Apple Developer ID “hongsheng_yan” in November to avoid detection, but it has since been revoked.
The malware is a variant of the Pirrit adware that was first spotted at the end of 2020.
The malware is able to collect browsing data and serves a large number of ads to the victims, including banners and popups. The malicious ads could also redirect unaware users to malicious websites used to distribute malicious payloads.

“The malicious GoSearch22 application may be the first example of such natively M1 compatible code.” continues Wardle. “The creation of such applications is notable for two main reasons:
First, (and unsurprisingly), this illustrates that malicious code continues to evolve in direct response to both hardware and software changes coming out of Cupertino. There are a myriad of benefits to natively distributing native arm64 binaries, so why would malware authors resist?
Secondly, and more worrisomely, (static) analysis tools or anti-virus engines may struggle with arm64 binaries. In a simple experiment, I separated out the x86_64 and arm64 binaries from the universal GoSearch22 binary (using macOS built-in lipo utility):”
Wardle pointed out that (static) analysis tools or antivirus engines face difficulties in analyzing ARM64 binaries, this is demonstrated by the fact that the detection rate for these malware is lower when compared to the Intel x86_64 version.
“Apple’s new M1 systems offer a myriad of benefits, and natively compiled arm64 code runs blazingly fast. Today, we highlighted the fact that malware authors have now joined the ranks of developers …(re)compiling their code to arm64 to gain natively binary compatibility with Apple’s latest hardware.” concludes Wardle.
Hackers steal credit card data abusing Google’s Apps Script
20.2.2021 Apple Securityaffairs
Hackers abuse Google Apps Script to steal credit cards, bypass CSP
Attackers are abusing Google’s Apps Script business application development platform to steal payment card information from e-stores.
Sansec researchers reported that threat actors are abusing Google’s Apps Script business application development platform to steal credit card data provided by customers of e-commerce websites.
“Attackers use the reputation of the trusted Google domain script.google.com to evade malware scanners and trust controls like CSP.” reads the post published by the security firm Sansec.
Attackers use the script.google.com domain to avoid detection and bypass Content Security Policy (CSP) controls, the Google domain, and its subdomains, are whitelisted by default in the CSP configuration of the e-stores.
The new technique was discovered by security researcher Eric Brandel using the Sansec’s Early Breach Detection tool.
Attackers compromise the e-stores by injecting a small piece of obfuscated code into their pages:

the malware was designed to intercepts payment forms and sends the data to a custom application hosted at Google Apps Script.
https[:]//script[.]google.com/macros/s/AKfycbwRGFNoOpnCE9c8Y7jQYknBhSTPHNfLaEZ-IB_JEzeLLjY-FmM/exec
Experts pointed out that the the actual code hosted at Google is not public, but the error message displayed reaching the above script suggests that stolen payment data is funneled by Google servers to an Israel-based site called analit[.]tech.

Experts noticed that this malicious domain http://analit[.]tech/ was registered on the same day as previously discovered domains hotjar[.]host and pixelm[.]tech that were involved in malware attacks, who are also hosted on the same network.
“This new threat shows that merely protecting web stores from talking to untrusted domains is not sufficient. E-commerce managers need to ensure that attackers cannot inject unauthorized code in the first place. Server-side malware and vulnerability monitoring is essential in any modern security policy.” concludes Sansec.
This isn’t the first time that Magecart hackers abused Google services in their campaign, in June, Kaspersky identified several web skimming attacks that abused Google Analytics service to exfiltrate data stolen with an e-skimmer software.
Threat actors exploit the trust in Analytics to bypass Content Security Policy (CSP) using the Analytics API.
Attackers targeted e-store using Google’s web analytics service for tracking visitors and that for this reason Google Analytics domains are whitelisted in their CSP configuration.
Kaspersky found about two dozen infected sites worldwide, including e-stores in Europe and North and South America selling digital equipment, cosmetics, food products, spare parts etc.
Apple Outlines 2021 Security, Privacy Roadmap
19.2.2021 Apple Threatpost
Latest Apple Platform Security update folds iOS, macOS and hardware into security 2021 roadmap.
Apple released its 2021 Platform Security guide, Thursday, outlining its current and year-ahead agenda for its device hardware, software and silicon security.
This year’s 192-page report is beefed-up, compared to past reports, with a wealth of new insights into how Apple is tackling security and privacy within its entire mobile, desktop and cloud ecosystem. Previous Platform Security updates have taken a piecemeal approach to address Apple’s security universe, said Rich Mogull, analyst and CEO with Securosis.
“This is the most comprehensive platform security update we have ever seen from Apple,” he told Threatpost.
Top 2021 Apple Platform Security report themes include what Apple’s M1 silicon means for Mac security; the latest developments around its Blast Door security technology used in iMessages; and transparency around Secure Enclave – a dedicated secure subsystem integrated into Apple systems-on-a-chip (SoC).
“This [2021 Platform Security guide] provides details about how security technology and features are implemented within Apple platforms. It also helps organizations combine Apple platform security technology and features with their own policies and procedures to meet their specific security needs,” wrote Apple.
As for Apple’s M1 silicon security, the platform report debuts just as reports surface that malware authors are specifically targeting Apple’s new M1 SoC.
For Blast Door, Google’s Project Zero first highlighted the technology last month when examining iOS 14 and iMessage security.
“One of the major changes in iOS 14 is the introduction of a new, tightly sandboxed ‘BlastDoor’ service which is now responsible for almost all parsing of untrusted data in iMessages (for example, NSKeyedArchiver payloads). Furthermore, this service is written in Swift, a (mostly) memory safe language which makes it significantly harder to introduce classic memory corruption vulnerabilities into the code base,” wrote Google Project Zero in late January.
2021 Apple Platform Security Highlights Include:
Memory safe iBoot implementation
Boot process for a Mac with Apple silicon
Boot modes for a Mac with Apple silicon
Startup Disk security policy control for a Mac with Apple silicon
Local Policy signing-key creation and management
Password Monitoring
IPv6 security
Car keys security in iOS
Most of what is included in the report has been previously announced or leaked – with the exception of details around Apple’s Security Research Device.
The Apple Security Research Device is a specially fused iPhone that allows security researchers to perform research on iOS without having to defeat or disable the platform security features of iPhone, according to Apple. “With this device, a researcher can side-load content that runs with platform-equivalent permissions and thus perform research on a platform that more closely models that of production devices,” wrote Apple.
The deep dive report covers iOS 14, macOS Big Sur, Apple Silicon and iCloud Drive security. Part of today’s release also includes Security Certifications and Compliance Center website and guide. The destination is designed to allow third-party Apple customers and partners a way of assuring that Apple’s hardware, software and services meet the requirements of legislation, regulation and industry norms, according to the company.
Similar to Microsoft’s Trustworthy Computing Initiative, the Apple Platform Security report is designed to give partners, security researchers and consumers a holistic state-of-union picture of its security posture.
Mac Malware Targets Apple’s In-House M1 Processor
19.2.2021 Apple Threatpost
A malicious adware-distributing application specifically targets Apple’s new M1 SoC, used in its newest-generation MacBook Air, MacBook Pro and Mac mini devices.
Three months after Apple launched its new M1 system-on-a-chip (SoC), cybercriminals have developed what may be the first malicious macOS application targeting the mobile giant’s first in-house silicon.
The recently uncovered malicious application, called GoSearch22, natively runs on M1 — meaning that it executes software written for M1-powered devices’ natural, basic mode of operation. The main differentiator here is that the application includes code tailored to run on ARM-based M1 processors – rather than only the Intel x86 processors previously utilized by Apple.
The application downloads a variant of Pirrit, which is a type of adware. Mac-targeting adware, which displays pesky advertisements on user computers, is a prevalent and continuous threat for Apple devices. Apple has since revoked the certificate for the malicious application.
“Apple’s new M1 systems offer a myriad of benefits, and natively compiled arm64 code runs blazingly fast,” said Apple-specializing researcher Patrick Wardle, who discovered the application, on Wednesday. “Today, we highlighted the fact that malware authors have now joined the ranks of developers …(re)compiling their code to ARM64 to gain natively binary compatibility with Apple’s latest hardware.”
What is the Apple M1 SoC?
Launched in November, the Apple M1 is the first ARM-based silicon designed by Apple, which is now the central processing unit for its Mac devices.
Starting back in 2006, Apple devices ran on Intel processors. But last year, Apple launched its own ARM-based silicon processors for its Mac lineup in an effort to achieve better technology integration, speed and efficiency.
Specifically, M1 supports an ARM64 instruction set architecture.
The M1 is deployed in the latest generations of Apple’s MacBook Air, Mac mini and MacBook Pro devices. However, many applications still run on the older Intel CPU x86_64 instructions, used by previous generations of Apple devices.
What Does ‘M1 Native Code’ Mean?
To help application developers whose apps are targeted for the older Intel set of instructions, Apple has released Rosetta, a process that translates Intel’s x86_64 instructions into native ARM64 instructions – so older applications can run seamlessly on M1 systems.
According to Apple, if an executable contains only Intel instructions, macOS automatically launches Rosetta and begins the translation process. The system then launches the translated executable in place of the original.
However, non-ARM64 code cannot run natively M1 systems and needs to be translated first – and this can lead to slower load times. That means developers who want their applications to run quickly and natively on M1, rather than go through the Rosetta process, must re-compile their applications. And so do malware authors.
“Based on the fact that native (ARM64) applications run faster (as they avoid the need for runtime translation), and that Rosetta (though amazing), has a few bugs (that may prevent certain older apps from running), developers are wise to (re)compile their applications for M1,” said Wardle.
In order for a binary to natively run on these M1 systems, it must be compiled as an Mach-O universal binary. Mach-O, which is the native executable format of binaries for Mac operating systems, is also known as a “fat binary,” which means that it contains universal code native to multiple instruction sets. That means that it can be run on multiple processor types — so a Mach-0 binary supports both ARM64 and x86_64 (rather than only x86_64) instruction sets.
GoSearch22 Application
Wardle found one such binary by searching on VirusTotal (using the search query type:macho tag:arm tag:64bits tag:multi-arch tag:signed positives:2+). Upon sifting through the VirusTotal results, Wardle found GoSearch22, a full macOS application bundle that can run natively on M1 systems. GoSearch22 was signed with an Apple developer ID (hongsheng yan) in November.
“This confirms malware/adware authors are indeed working to ensure their malicious creations are natively compatible with Apple’s latest hardware,” said Wardle.
Upon further inspection, Wardle found that GoSearch22 executes Pirrit, which once launched, installs itself as a malicious Safari extension. It creates a proxy server on infected Mac computers and injects ads into webpages.
Pirrit dates all the way back back to 2016, but has continued to evolve over the years. In 2016, researchers also linked a variant of the Pirrit adware for Mac OS X to an Israeli online marketing company called TargetingEdge, which is still in stealth mode.
“What we do know is as this binary was detected in the wild… so whether it was notarized or not, macOS users were infected,” said Wardle.
Future M1 Binaries
After uploading both binaries (ARM64 and x86_64) separately to VirusTotal and initiating scans of both, Wardle found that detections of the ARM64 version dropped 15 percent when compared to the standalone x86_64 version. This means that several antivirus engines failed to flag this binary.
The fact that security detectors are struggling to keep up could present security concerns in the future as more cybercriminals focus their attention on M1-targeting ARM64 binaries.
“While the x86_64 and ARM64 code appears logically identical (as expected), we showed that defensive security tools may struggle to detect the ARM64 binary,” he said.
Mac-Targeting Cybercriminal Innovation Plagues Apple
The malicious app sheds light on the rapid innovation on the part of cybercriminals.
In December, researchers uncovered a zer0-click Apple zero-day flaw, used in a spyware campaign against Al Jazeera journalists. In July, a new malware sample was discovered, dubbed EvilQuest, that researchers say may be ushering in a new class of Mac malware.
And in August, a campaign aimed at Mac users was discovered spreading the XCSSET suite of malware, which has the capability to hijack the Safari web browser and inject various JavaScript payloads that can steal passwords, financial data and personal information, deploy ransomware and more.
Below, Wardle talks to Threatpost about the newest tactics used by cybercriminals in abusing Apple technologies, developing malware and creating “powerful” iOS bugs.
Apple Platform Security Guide Gets Biggest Update to Date
19.2.2021 Apple Securityweek
Apple on Thursday published the latest edition of its Platform Security Guide, which provides detailed technical information on the security technologies and features implemented in its products.
Apple started releasing security guides for its iOS operating system in 2015 and since 2019 has been publishing platform security guides that encompass information on iOS, macOS and hardware.
Apple Platform Security GuideThe platform security guide was previously updated in April 2020 and that version had 157 pages. The latest version has nearly 200 pages and Apple has described it as its biggest update ever.
The document provides information on hardware security and biometrics, system security, encryption and data protection, app security, security services, network security, developer kit security, and secure device management.
The new platform security guide includes informational updates for iOS, iPadOS and tvOS 14.3, macOS 11.1 and watchOS 7.2. It also includes several new topics, including memory safe iBoot implementation, boot process and modes for Macs with Apple chips, startup disk security policy control for Macs with Apple silicon, information on LocalPolicy, signed system volume security in macOS, the Password Monitoring feature, IPv6 security, car keys security in iOS, and iPhones designed for security research.
The guide also includes updates to topics such as Secure Enclave, hardware microphone disconnect, recoveryOS and diagnostics environments for Intel-based devices, DMA protections, kernel extensions in macOS, System Integrity Protection, watchOS security, Apple Cash security, Wi-Fi privacy, Activation Lock security, Apple Configurator 2 security, Business Chat security, and some password-related topics.
The document also includes information on Apple’s new M1 chips, which bring several security improvements.
A researcher recently discovered the first piece of Mac malware created specifically for devices with M1 chips.
Mac Malware Targeting Apple's M1 Chip Emerges
19.2.2021 Apple Securityweek
A researcher has spotted the first piece of Mac malware that appears to have been created specifically for devices with Apple’s recently introduced M1 chip.
The malware was discovered by Patrick Wardle, a cybersecurity researcher who specializes in Apple products. Wardle has developed several free and open source security tools for Macs, and came up with the idea to look for malware designed to run natively on M1 systems while rebuilding his tools for native M1 compatibility.
The M1 system-on-chip (SoC), unveiled by Apple in November 2020, is designed for increased performance, as well as better security, with the Cupertino, Calif.-based tech giant claiming that it includes security protections built deep into its code execution architecture.
The M1 chip uses the arm64 CPU architecture and apps developed specifically for Macs powered by the M1 contain arm64 code. Wardle searched Google’s VirusTotal malware analysis service for such samples and discovered an app named GoSearch22, which turned out to be a variant of Pirrit, a piece of adware that has been around for several years.
The sample discovered by the researcher, submitted in late December 2020, had been signed with an Apple developer ID and it had apparently been detected in the wild. The adware variant developed for M1 systems was designed to install itself as a Safari extension, and packed various anti-analysis capabilities.
A small experiment conducted by Wardle also showed that static analysis tools and anti-malware engines could have trouble analyzing and detecting arm64 malware, compared to x86_64 binaries.
“Apple’s new M1 systems offer a myriad of benefits, and natively compiled arm64 code runs blazingly fast. Today, we highlighted the fact that malware authors have now joined the ranks of developers …(re)compiling their code to arm64 to gain natively binary compatibility with Apple’s latest hardware,” Wardle said in a blog post.
Thomas Reed, director of Mac & Mobile at cybersecurity firm Malwarebytes, told SecurityWeek that while this was inevitable, M1-native malware should not be a major concern for M1-powered Mac users.
“As an industry we have observed that the criminals behind Mac adware have demonstrated the most adaptability with macOS. I was less than surprised we saw this first happen in Pirrit, as it’s one of the oldest and most active Mac adware families – who are constantly changing to evade detection,” Reed said.
He added, “Overall, I don’t anticipate this being a huge issue in the near future, as antivirus software can detect the Intel code in a fat binary just as well as for an Intel-only binary. However, this does mean that our industry needs to prepare to see malware creators switch to single-architecture M1-only binaries as a means of evading detection. Antivirus companies need to stay proactive and begin to strategize how they will detect these threats as they evolve in the future.”
A report released earlier this week by Malwarebytes showed that while Mac malware detections on consumer devices decreased by 40% in 2020 compared to the previous year, detections in enterprise environments increased by 31%.
First Malware Designed for Apple M1 Chip Discovered in the Wild
19.2.2021 Apple Thehackernews
One of the first malware samples tailored to run natively on Apple's M1 chips has been discovered, suggesting a new development that indicates that bad actors have begun adapting malicious software to target the company's latest generation of Macs powered by its own processors.
While the transition to Apple silicon has necessitated developers to build new versions of their apps to ensure better performance and compatibility, malware authors are now undertaking similar steps to build malware that are capable of executing natively on Apple's new M1 systems, according to macOS Security researcher Patrick Wardle.
Wardle detailed a Safari adware extension called GoSearch22 that was originally written to run on Intel x86 chips but has since been ported to run on ARM-based M1 chips. The rogue extension, which is a variant of the Pirrit advertising malware, was first seen in the wild on November 23, 2020, according to a sample uploaded to VirusTotal on December 27.
"Today we confirmed that malicious adversaries are indeed crafting multi-architecture applications, so that their code will natively run on M1 systems," said Wardle in a write-up published yesterday. "The malicious GoSearch22 application may be the first example of such natively M1 compatible code."
While M1 Macs can run x86 software with the help of a dynamic binary translator called Rosetta, the benefits of native support mean not only efficiency improvements but also the increased likelihood of staying under the radar without attracting any unwanted attention.
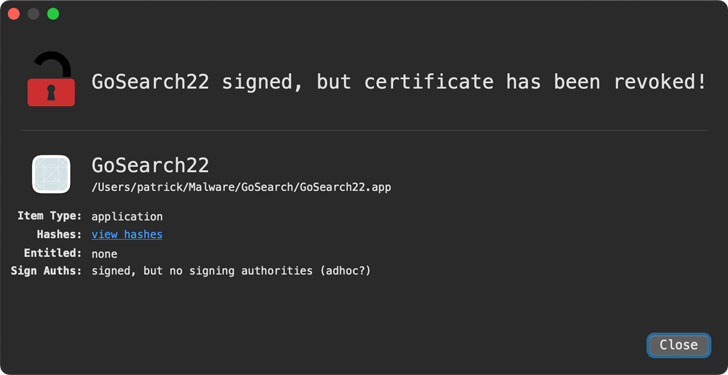
First documented in 2016, Pirrit is a persistent Mac adware family notorious for pushing intrusive and deceptive advertisements to users that, when clicked, downloads and installs unwanted apps that come with information gathering features.
For its part, the heavily obfuscated GoSearch22 adware disguises itself as a legitimate Safari browser extension when in fact, it collects browsing data and serves a large number of ads such as banners and popups, including some that link to dubious websites to distribute additional malware.
Wardle said the extension was signed with an Apple Developer ID "hongsheng_yan" in November to further conceal its malicious content, but it has since been revoked, meaning the application will no longer run on macOS unless attackers re-sign it with another certificate.
Although the development highlights how malware continues to evolve in direct response to both hardware changes, Wardle warned that "(static) analysis tools or antivirus engines may struggle with arm64 binaries," with detections from industry-leading security software dropping by 15% when compared to the Intel x86_64 version.
GoSearch22's malware capabilities may not be entirely new or dangerous, but that's beside the point. If anything, the emergence of new M1-compatible malware signals this is just a start, and more variants are likely to crop up in the future.
Details Tied to Safari Browser-based ‘ScamClub’ Campaign Revealed
18.2.2021 Apple Threatpost
Public disclosure of a privilege escalation attack details how a cybergang bypassed browser iframe sandboxing with malicious PostMessage popups.
Details of a flaw in Apple’s Safari browser, publicly disclosed Tuesday, outline how the cybergang known as ScamClub reached 50 million users with a three-month-long malicious ad campaign pushing malware to mobile iOS Chrome and macOS desktop browsers.
The Safari bug, patched on Dec. 2 by Apple, was exploited by a malvertising campaign that redirected traffic to scam sites that flogged gift cards, prizes and malware to victims. Impacted was Apple’s Safari browser running on macOS Big Sur 11.0.1 and Google’s iOS-based Chrome browser. The common thread is Apple’s WebKit browser engine framework.
The attacks, which researchers at Confiant Security attributed to ScamClub, exploited a flaw in the open-source WebKit engine, according to a blog post published Tuesday by Eliya Stein, senior security engineer who found the bug on June 22, 2020.
He reports that the malicious campaign exploited a privilege-escalation vulnerability, tracked as CVE-2021–1801. Stein did not report how many, if any, people may have been impacted by the campaign or what type of malicious activity the threat actors may have engaged in post-exploit. Typically, a privilege-escalation attack’s primary goal is to obtain unauthorized access to a targeted system.
What is ScamClub?
ScamClub is a well-established cybergang that for the past three years has hijacked hundreds-of-millions of browser sessions with malvertising campaigns that redirect users to adult and gift card scams.
Until today, the group is best known for a massive 2018 campaign where it redirected 300 million users to shady phishing sites, serving up adult content and gift card scams.
Confiant dubbed the group ScamClub, because of the criminal’s use of multiple fast-changing redirection chains eventually spitting up shady gift-card offers and adult content.
ScamClub typically uses a “bombardment” strategy to flood ad-delivery systems with “tons of horrendous demand” rather than trying to obfuscate its nefarious activity, researchers note.
“They do this at incredibly high volumes in the hopes that the small percentage that slips through will do significant damage,” he explained.
What are the ScamClub Details of the WebKit Exploit?
In his Tuesday-report, Stein said this most recent ScamClub campaign redirected users to landing pages that offer prizes, such as “You’ve won a Walmart gift card!” or “You’ve won an iPhone!” to rather successful effect, he wrote.
Over the last 90 days alone, ScamClub has delivered over 50 million malicious impressions, “maintaining a low baseline of activity augmented by frequent manic bursts,” with as many as 16 million impacted ads being served in a single day, according to Stein.
This type of attack vector can be difficult for both the average person using the internet and businesses alike to handle, given the potential number of malicious ads being served, observed Saryu Nayyar, CEO of unified security and risk analytics firm Gurucul.
“Attacks like this can be a challenge to mitigate for home users, beyond keeping their patches up to date relying on an ISP provided or third-party service to block known malicious DNS domains,” she said in an email to Threatpost. “Organizations have a similar challenge with the sheer volume of malicious ads, but can benefit from enabling the same techniques and security analytics that can help identify malicious activities by their behaviors.”
Diary of a WebKit Exploit
The latest ScamCard payload has a number of steps to it, starting with an ad tag that loads a malicious Content Delivery Network-hosted dependency typically “obfuscated in absurd ways in attempt to evade URL blocklists” that can expand to thousands of lines of code, Stein wrote.
He said that Confiant researchers narrowed their investigation down to four lines of code that ultimately alerted them to ScamClub’s use of the WebKit bug in its campaign:

ScamClub four lines of code that exploit now-patched Apple Safari WebKit bug Observing that the code seemed different than a typical malvertising tactic of trying “to spray a bunch of redirect attempts in a single payload that try to do the redirect in different ways,” researchers investigated by staging a simple HTML file that implemented a cross-origin sandboxed frame and a button that dispatched their event.
“The `allow-top-navigation-by-user-activation` sandbox attribute, which is often lauded as one of the most vital tools in an anti-malvertising strategy, should in theory prevent any redirection unless a proper activation takes place,” Stein explained. “Activation in this context typically means a tap or a click inside the frame.”
If this was the case, then Confiant’s proof of concept should not have been able to redirect the page. However, it did, which proved to researchers that ScamClub’s use of “a long tail iframe sandbox bypass” was leveraging a browser bug that turned out to be in WebKit, Stein said.
Apple will proxy Safe Browsing requests to hide iOS users' IP from Google
16.2.2021 Apple Thehackernews
Apple's upcoming iOS 14.5 update will come with a new feature that will redirect all fraudulent website checks through its own proxy servers as a workaround to preserve user privacy and prevent leaking IP addresses to Google.
A built-in security-focused feature in the Safari browser, "Fraudulent Website Warning," alerts users about dangerous websites that have been reported as deceptive, malicious, or harmful.
To achieve this, Apple relies on Google Safe Browsing — or Tencent Safe Browsing for users in Mainland China — a blocklist service that provides a list of URLs for web resources that contain malware or phishing content, to compare a hash prefix calculated from the website address and check if the website is fraudulent.
Any match against the database will prompt Safari to request Google or Tencent for the full list of URLs that correspond to the hashed prefix and subsequently block a user's access to the site with a warning.
While the approach ensures that the actual URL of a website the user is attempting to visit is never shared with a safe browsing provider, it does leak the IP address of the device from which the check was made.
With iOS 14.5, all these verifications are expected to be re-routed through an Apple-owned proxy server, thereby making all requests appear as originating from the same IP address.
"In the new iOS beta, Safari does indeed proxy the service via Apple servers to limit the risk of information leak," said Maciej Stachowiak, head of WebKit engineering at Apple, last week in a tweet.
The new change in iOS and iPadOS is part of a number of privacy-oriented measures that Apple has been rolling out lately, including mandating app developers to disclose their data collection practices in App Store listings using "privacy nutrition labels."
In addition, iOS 14.5 will also require apps to ask for users' permission before tracking them across other apps and websites using the device's advertising identifier as part of a new framework dubbed App Tracking Transparency.
iOS 14.5 is currently in beta and is slated to be released later this spring.
Apple Patches Recent Sudo Vulnerability in macOS
11.2.2021 Apple Securityweek
Apple on Tuesday released macOS security updates to patch a recently disclosed vulnerability in the Sudo utility.
Present in most Unix- and Linux-based operating systems out there, Sudo is a tool that allows users to execute programs with the privileges of another user, which by default is superuser.
Disclosed during the last week of January 2021, the vulnerability is tracked as CVE-2021-3156, but it’s also called Baron Samedit, and it has been lurking in Sudo since July 2011.
The security flaw could be abused to escalate privileges to root, even with default Sudo configurations. Qualys’ security researchers, who identified the bug, prompted users to apply available patches as soon as possible.
The issue would expose systems to complete compromise, given that it could allow an attacker able to access a machine as a low-privileged user to gain root privileges.
Sudo v1.9.5p2 resolves the vulnerability, and Apple has addressed the flaw by updating the tool to the patched version. The vulnerability was also found to affect multiple Cisco products.
Apple this week released macOS Big Sur 11.2.1, macOS Catalina 10.15.7 Supplemental Update, and macOS Mojave 10.14.6 Security Update 2021-002 to address Baron Samedit, as well as two other vulnerabilities in Intel graphics drivers.
Tracked as CVE-2021-1805 and CVE-2021-1806 and identified by ABC Research s.r.o. working with Trend Micro’s Zero Day Initiative, the two vulnerabilities could allow an application to execute arbitrary code with kernel privileges.
The first of the bugs is an out-of-bounds write issue, while the second is a race condition, Apple explains in its advisory. Both vulnerabilities were found to impact macOS Big Sur 11.2 and macOS Catalina 10.15.7, and were patched with improved validation.
Last week, Apple released patches for over 60 vulnerabilities in macOS, including the recently disclosed NAT Slipstreaming 2.0 attack, which could provide attackers with the ability to access devices on the internal network.
Apple Patches 10-Year-Old macOS SUDO Root Privilege Escalation Bug
11.2.2021 Apple Thehackernews
Apple has rolled out a fix for a critical sudo vulnerability in macOS Big Sur, Catalina, and Mojave that could allow unauthenticated local users to gain root-level privileges on the system.
"A local attacker may be able to elevate their privileges," Apple said in a security advisory. "This issue was addressed by updating to sudo version 1.9.5p2."
Sudo is a common utility built into most Unix and Linux operating systems that lets a user without security privileges access and run a program with the credentials of another user.
Tracked as CVE-2021-3156 (also called "Baron Samedit"), the vulnerability first came to light last month after security auditing firm Qualys disclosed the existence of a heap-based buffer overflow, which it said had been "hiding in plain sight" for almost 10 years.
The vulnerability, which was introduced in the code back in July 2011, impacts sudo versions 1.7.7 through 1.7.10p9, 1.8.2 through 1.8.31p2, and 1.9.0 through 1.9.5p1, following which the maintainers released 1.8.32 and 1.9.5p2 to resolve the issue.
While the weakness can only be exploited by an attacker already having access to a vulnerable host, the barrier could be easily bypassed by planting malware on a device or brute-forcing a low-privileged service account.
In its report, Qualys researchers said they managed to develop multiple variants of exploit and obtain full root privileges on Ubuntu 20.04 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2).
But last week, British security researcher Matthew Hickey discovered that the vulnerability also extended to the latest version of macOS Big Sur 11.2, prompting Apple to address the security shortcoming.
"CVE-2021-3156 also impacts @apple MacOS Big Sur (unpatched at present), you can enable exploitation of the issue by symlinking sudo to sudoedit and then triggering the heap overflow to escalate one's privileges to 1337 uid=0," Hickey tweeted on February 2.
Besides the fix for the sudo vulnerability, Tuesday's supplemental security update also includes patches for two flaws in Intel Graphics Driver (CVE-2021-1805 and CVE-2021-1806), which could cause an application to execute arbitrary code with kernel privileges.
The vulnerabilities, which stem from an out-of-bounds write and a race condition, respectively, were rectified with additional validation, the iPhone maker said.
Mac users who haven't opted to check for updates automatically can head to Apple menu > System Preferences, and then click Software Update to download and install the latest updates.
Recently discovered CVE-2021-3156 SUDO bug also affects macOS Big Sur
4.2.2021 Apple Securityaffairs
Experts warn that the recently discovered heap-based buffer overflow bug in Linux SUDO also impacts the latest version of Apple macOS Big Sur.
Recently Qualys researchers found a Sudo vulnerability, tracked as CVE-2021-3156, that has allowed any local user to gain root privileges on Unix-like operating systems without authentication.
Sudo is one of the most important, powerful, and commonly used utilities that comes as a core command pre-installed on macOS and almost every UNIX or Linux-based operating system.
sudo is a program for Unix-like computer operating systems that allows users to run programs with the security privileges of another user, by default the superuser. It originally stood for “superuser do” as the older versions of sudo were designed to run commands only as the superuser.
The Sudo CVE-2021-3156 vulnerability, dubbed Baron Samedit, is a heap-based buffer overflow that was reported on January 13th and disclosed at the end of January to give the development team the time to address the issue.
“When sudo runs a command in shell mode, either via the -s or -i command line option, it escapes special characters in the command’s arguments with a backslash. The sudoers policy plugin will then remove the escape characters from the arguments before evaluating the sudoers policy (which doesn’t expect the escape characters) if the command is being run in shell mode.” states the advisory published by the Sudo team.
“A bug in the code that removes the escape characters will read beyond the last character of a string if it ends with an unescaped backslash character. Under normal circumstances, this bug would be harmless since sudo has escaped all the backslashes in the command’s arguments. However, due to a different bug, this time in the command line parsing code, it is possible to run sudoedit with either the -s or -i options, setting a flag that indicates shell mode is enabled. Because a command is not actually being run, sudo does not escape special characters. Finally, the code that decides whether to remove the escape characters did not check whether a command is actually being run, just that the shell flag is set. This inconsistency is what makes the bug exploitable.”
News of the day is that the CVE-2021-3156 flaw also impacts the latest version of Apple macOS Big Sur, and Apple has yet to address it. The latest security patches released by Apple on Monday doesn’t fix the flaw.
Qualys researchers developed three exploits for this flaw that allowed them to achieve full root privileges on major Linux distributions, including Ubuntu 20.04 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2). Experts pointed out that the CVE-2021-3156 exploits could also work on other distributions.
Below a video PoC for the CVE-2021-3156 vulnerability can be exploited is embedded below.
The Sudo contributors addressed the flaw with the release of the 1.9.5p2 version.
The British researcher Matthew Hickey, the founder of Hacker House, declared on Twitter that the issue also impacts Apple MacOS Big Sur
Hickey demonstrated that it is possible to exploit the CVE-2021-3156 vulnerability to grant attackers access to macOS root accounts.
“To trigger it, you just have to overwrite argv[0] or create a symlink, which therefore exposes the OS to the same local root vulnerability that has plagued Linux users the last week or so.” Hickey explained to ZDNet.
Hickey also shared a Proof-of-Concept (PoC) exploit code for the above vulnerability.
Will Dormann, security expert at the Carnegie Mellon University’s CERT Coordination Center, also confirmed that the issue affects macOS Big Sur on both x86_64 and aarch64.
Another prominent cybersecurity expert, the former NSA white hat hacker Patrick Wardle, also confirmed that the vulnerability impacts the latest macOS version.
Hickey reported the issue to Apple today, experts believe the IT giant will address the issue as soon as possible.
Apple Issues Patches for NAT Slipstreaming 2.0 Attack
3.2.2021 Apple Securityweek
Apple this week released security updates to address multiple vulnerabilities in macOS and Safari, including a flaw that can be exploited for the recently disclosed NAT Slipstreaming 2.0 attack.
As part of the attack, an adversary could set up a crafted website and lure the intended victim into visiting it. As soon as that happens, malicious code on the site starts sending multiple fetch requests from the victim’s browser, allowing the attacker to identify and access devices on the local network.
Devised by Ben Seri and Gregory Vishnipolsky of IoT security company Armis, together with researcher Samy Kamkar, the attack is a variant of the NAT Slipstreaming attack that was detailed in October 2020, and which could be leveraged to target local network services.
Both attacks bypass Network Address Translation (NAT) and firewalls by abusing the browser and the Application Level Gateway (ALG), a connection tracking mechanism in firewalls, NATs, and routers.
Apple, which describes the vulnerability as a port redirection issue in WebRTC, where malicious sites could access restricted ports on arbitrary servers, says additional port validation should resolve the bug in macOS Big Sur 11.2. The bug is tracked as CVE-2021-1799.
A total of 66 vulnerabilities were addressed with the release of macOS Big Sur 11.2, Security Update 2021-001 for Catalina, and Security Update 2021-001 for Mojave, many of them leading to arbitrary code execution, denial of service, privilege escalation, and memory leakage.
The most important of these vulnerabilities are CVE-2021-1870, CVE-2021-1871 (both impact WebKit), and CVE-2021-1782 (affecting Kernel), which have been targeted in attacks.
The bugs, which Apple says were anonymously reported, were found in the iOS and iPadOS mobile platforms, and were addressed last week with a set of emergency patches. The Cupertino-based company has yet to provide specific details on the bugs themselves and on the attacks abusing them.
Both Kernel and WebKit received fixes for other vulnerabilities as well, with the ImageIO component of macOS also seeing patches for a large number of vulnerabilities this week, namely 18.
Triggered during the processing of maliciously crafted images, these vulnerabilities could lead to arbitrary code execution or denial of service. One of them, CVE-2021-1818, could be exploited by a remote attacker for code execution or to cause unexpected application termination.
The Model I/O component received fixes for seven vulnerabilities that could be triggered during the processing of maliciously crafted USD files or images, leading to arbitrary code execution, unexpected application termination, or heap corruption.
Apple patched three vulnerabilities with the release of Safari 14.0.3 this week, namely NAT Slipstreaming 2.0, and two issues in WebKit (CVE-2021-1788 and CVE-2021-1789) that could lead to arbitrary code execution.
Apple iOS 14 Thwarts iMessage Attacks With BlastDoor System
30.1.2021 Apple Threatpost
Apple has made structural improvements in iOS 14 to block message-based, zero-click exploits.
In an effort to prevent attacks from being launched via its iMessage feature, Apple has debuted a security service called BlastDoor in iOS 14, its current mobile operating system version.
First detailed in an analysis this week by Google Project Zero’s Samuel Groß, BlastDoor acts as a “tightly sandboxed” service that is responsible for “almost all” of the parsing of untrusted data in iMessages.
The service comes on the heels of a recently uncovered iMessage zero-click exploit, which was being leveraged in an espionage attack against Al Jazeera journalists and executives. Citizen Lab, who disclosed the campaign in December, at the time said it did not believe that the exploit works against iOS 14, as it “includes new security protections.”
However, what those specific protections were remained unknown until Groß’s analysis this week. Groß was able to perform reverse-engineering in order to analyze the new service, using an M1 Mac Mini running macOS 11.1, and verifying his findings by applying them to iOS 14.3 (running on an iPhone XS),
“Overall, these changes are probably very close to the best that could’ve been done given the need for backwards compatibility, and they should have a significant impact on the security of iMessage and the platform as a whole,” said Groß on Thursday. “It’s great to see Apple putting aside the resources for these kinds of large refactorings to improve end users’ security.”
What is BlastDoor?
BlastDoor has two important security implications.
First, the service allows sandboxing rules to be applied across the pipeline when a message is received on a phone. This means that when a message is received, the processes on the backend execute code separately from the operating system. Only two processes (IMTransferAgent, which handles message file transfers, and apsd, Apple’s Push Notification Service daemon) are required to perform network operations.
Groß said the sandbox profile of BlashDoor is “quite tight,” with almost all file system interactions being blocked, outbound network access being denied, and any interaction with IOKit drivers being forbidden. IOKit allows the access of hardware devices and drivers for various apps and services, and is historically a big source of vulnerabilities.
This secure environment means that any malicious code sent by attackers via iMessage is prevented from accessing user data or interacting with other parts of the operating system.
Second, BlastDoor is written in Swift, which is a memory-safe language. Groß said that Swift makes it “significantly” harder to introduce memory-corruption vulnerabilities into the code base. That’s because Swift has various features to make sure variables are initialized before they’re used, memory isn’t accessed after it’s been deallocated, and array indices are checked for out-of-bounds errors.
A New Message-Parsing Process
In previous versions of iOS, when a message was sent, the parsing would occur in the Instant Messaging Agent (imagent). To parse a message in imagent, the binary data would first be decompressed; then the plist (also known as property list; an extension used to save preferences of applications) would be decoded from its binary serialization format. The various fields would be extracted to ensure they have the correct type; and finally, the `x` field content of the iMessage format would be decoded using an XML decoder. If an iMessage contained an attachment, additional steps would also be taken for parsing.
In iOS 14, this process has been moved to the new BlastDoor service. The main processing flow still begins in imagent – which receives the raw payload bytes, but then the messages are forwarded to the BlastDoor service (through +[IMBlastdoor sendDictionary:withCompletionBlock:]). Inside BlastDoor, the processes of both parsing messages and attachments mostly occur in BlastDoor.framework and MessagesBlastDoorService, said Groß.
Groß noted that one side effect of this new processing pipeline is that imagent can now detect when an incoming message caused a crash in BlastDoor – and appears to be informing Apple’s servers about such events.
“It is unclear what the purpose of this is without access to the server’s code,” said Groß. “While these notifications may simply be used for statistical purposes, they would also give Apple a fairly clear signal about attacks against iMessage involving brute-force and a somewhat weaker signal about any failed exploits against the BlastDoor service.”
Other iOS 14 Protections
In addition to BlastDoor, Groß shed light on two other significant security protections that were built into iOS 14, which was released to the public in September.
First, Apple has fixed an issue with the shared cache region of its address space layout randomization (ASLR) that was posing an architectural weakness. The weakness stemmed from the shared caches region only randomizing per boot – meaning it would stay at the same address across all processes. This could have allowed attackers to infer the base address of the shared cache and break ASLR – potentially setting them up to launch zero-click attacks.

BlastDoor’s message parsing process (click to enlarge). Credit: Google Project Zero
Apple has now added logic to specifically detect this kind of attack. Now, shared cache is re-randomized for the targeted service during the next time it is started, rendering this type of attack ineffective.
“This should make bypassing ASLR in a 0-click attack context significantly harder or even impossible (apart from brute force) depending on the concrete vulnerability,” said Groß.
Second, the BlastDoor and imagent services are now subject to a newly introduced “exponential throttling mechanism” enforced by launchd, Apple’s operating system service management daemon. With this new mechanism, if a crash occurs on the device, the intervals between restarts after the crash double with every subsequent crash (leading to an interval maxing out at 20 minutes, Groß found).
“With this change, an exploit that relied on repeatedly crashing the attacked service would now likely require in the order of multiple hours to roughly half a day to complete instead of a few minutes,” said Groß.
Apple Security Woes
Apple, historically known for its strong security posture, has faced various issues over the past few months – including the release of an emergency update this week to patch three zero-day vulnerabilities discovered in iOS.
Zero-click attacks run automatically without any user interaction and are of particular worry. Researchers in August uncovered a zero-click macOS exploit chain that could allow attackers to deliver malware to macOS users using a Microsoft Office document with macros.
Groß applauded Apple’s offensive security work reflected in the recent changes, particularly for its impact against message-based zero-click attacks.
“Not just single bugs were fixed, but instead structural improvements were made based on insights gained from exploit development work,” he said.
Google uncovers new iOS security feature Apple quietly added after zero-day attacks
30.1.2021 Apple Thehackernews
Google Project Zero on Thursday disclosed details of a new security mechanism that Apple quietly added to iOS 14 as a countermeasure to prevent attacks that were recently found to leverage zero-days in its messaging app.
Dubbed "BlastDoor," the improved sandbox system for iMessage data was disclosed by Samuel Groß, a security researcher with Project Zero, a team of security researchers at Google tasked with studying zero-day vulnerabilities in hardware and software systems.
"One of the major changes in iOS 14 is the introduction of a new, tightly sandboxed 'BlastDoor' service which is now responsible for almost all parsing of untrusted data in iMessages," Groß said. "Furthermore, this service is written in Swift, a (mostly) memory safe language which makes it significantly harder to introduce classic memory corruption vulnerabilities into the code base."
The development is a consequence of a zero-click exploit that leveraged an Apple iMessage flaw in iOS 13.5.1 to get around security protections as part of a cyberespionage campaign targeting Al Jazeera journalists last year.
"We do not believe that [the exploit] works against iOS 14 and above, which includes new security protections," Citizen Lab researchers who revealed the attack last month.
BlastDoor forms the core of those new security protections, per Groß, who analyzed the implemented changes over the course of a week-long reverse engineering project using an M1 Mac Mini running macOS 11.1 and an iPhone XS running iOS 14.3.
When an incoming iMessage arrives, the message passes through a number of services, chief among them being the Apple Push Notification Service daemon (apsd) and a background process called imagent, which is not only responsible for decoding the message contents but also for downloading attachments (through a separate service called IMTransferAgent) and handling links to websites, before alerting the SpringBoard to display the notification.
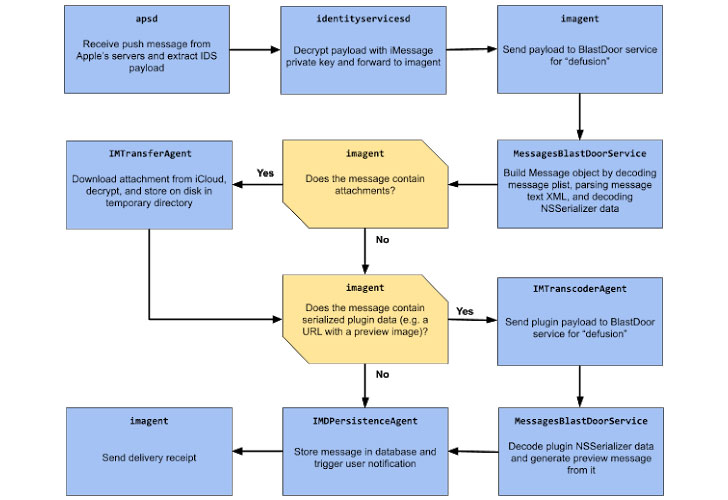
What BlastDoor does is inspect all such inbound messages in a secure, sandboxed environment, which prevents any malicious code inside of a message from interacting with the rest of the operating system or accessing user data.
Put differently, by moving a majority of the processing tasks — i.e., decoding the message property list and creating link previews — from imagent to this new BlastDoor component, a specially-crafted message sent to a target can no longer interact with the file system or perform network operations.
"The sandbox profile is quite tight," Groß noted. "Only a handful of local IPC services can be reached, almost all file system interaction is blocked, any interaction with IOKit drivers is forbidden, [and] outbound network access is denied."
What's more, in a bid to delay subsequent restarts of a crashing service, Apple has also introduced a new throttling feature in the iOS "launchd" process to limit the number of tries an attacker gets when seeking to exploit a flaw by exponentially increasing the time between two successive brute-force attempts.
"With this change, an exploit that relied on repeatedly crashing the attacked service would now likely require in the order of multiple hours to roughly half a day to complete instead of a few minutes," Groß said.
"Overall, these changes are probably very close to the best that could've been done given the need for backwards compatibility, and they should have a significant impact on the security of iMessage and the platform as a whole."
Apple CEO Escalates Battle With Facebook Over Online Privacy
29.1.2021 Apple Securityweek
Apple CEO Tim Cook fired off a series of thinly veiled shots at Facebook and other social media companies Thursday, escalating an online privacy battle pitting the iPhone maker against digital services that depend on tracking people to help sell ads.
“Too many are still asking the question ‘how much can we get away with?’ when we should be asking ‘what are the consequences?’” Cook said. “What are the consequences of not just tolerating but rewarding content that undermines public trust in life-saving vaccinations? What are the consequences of seeing thousands of users join extremist groups and then perpetuating an algorithm that recommends more?”
Speaking at a virtually held International Conference on Computers, Privacy & Data Protection, Cook said it’s “time to stop pretending that this approach doesn’t come with a cost — of polarization, lost trust and yes, of violence.”
Cook never specifically named Facebook or any other company. But his remarks left little doubt that his missives were aimed at the social media sites that have been criticized for enabling conspiracy theories, hate speech and political misinformation that culminated in the Jan. 6 insurrection that overtook the U.S. Capitol while Congress met to confirm the election of President Joe Biden.
“A social dilemma cannot be allowed to become a social catastrophe,” Cook added, referring to a Netflix documentary about technology’s — and especially social media’s — corrosive effects on society. That film took square aim at Facebook and how its algorithms manipulate its nearly 3 billion users to get them to look at the ads that generate most of its revenue.
Cook’s broadside came as Apple prepares to roll out a new privacy control in the early spring to prevent iPhone apps from secretly shadowing people. That puts the feature on course to come out after a more than six-month delay aimed at placating Facebook and other digital services that depend on such data surveillance to help sell ads.
Although Apple didn’t provide a specific date, the general timetable disclosed Thursday means the long-awaited safeguard known as App Tracking Transparency will be part of an iPhone software update likely to arrive in late March or some point in April.
After delaying the planned September introduction of the safeguard amid a Facebook-led outcry, Apple had previously said it would come out early this year. Apple released the latest schedule update as part of Data Privacy Day.
Apple has been holding off to give Facebook and other app makers more time to adjust to a feature that will require iPhone users to give their explicit consent to being tracked. Analysts expect a significant number of users to deny that permission once it requires their assent. Currently, iPhone users are frequently tracked by apps they install unless they take the extra step of going into iPhone settings to prevent it.
“Technology does not need vast troves of personal data, stitched together across dozens of websites and apps, in order to succeed,” Cook said. “Advertising existed and thrived for decades without it.”
As a supplement to Cook’s remarks, Apple also released an 11-page report to illustrate how much apps can learn about their users in daily life.
Facebook stepped up its attacks on Apple’s new privacy control last month in a series of full-page ads in The New York Times, The Wall Street Journal and other national newspapers. That campaign suggested some free digital services will be hobbled if they can’t compile personal information to customize ads. On Wednesday, CEO Mark Zuckerberg questioned Apple’s motives for the changes, saying the iPhone maker “has every incentive” to use its own mobile platform to interfere with rivals to its own messaging app.
“Apple may say that they are doing this to help people, but the moves clearly track their competitive interests,” Zuckerberg said.
Google, which also relies on personal data to power the internet’s biggest ad network, hasn’t joined Facebook in its criticism of Apple’s forthcoming controls on tracking. Google profits from being the default search engine on the iPhone, a prized position for which it pays Apple an estimated $9 billion to $12 billion annually.
But Google warned in a Wednesday blog post that Apple’s new controls will have a significant impact on the iPhone ad revenue of other apps in its digital network. Google said a “handful” of its own iPhone apps will be affected by the new requirement, but plans to make changes to them so they won’t be affected by Apple’s new controls. It did not identify which apps.
“We remain committed to preserving a vibrant and open app ecosystem where people can access a broad range of ad-supported content with confidence that their privacy and choices are respected,” wrote Christophe Combette, group product manager for Google Ads.
Apple Adds 'BlastDoor' to Secure iPhones From Zero-Click Attacks
29.1.2021 Apple Securityweek
Apple has quietly added several anti-exploit mitigations into its flagship mobile operating system in what appears to be a specific response to zero-click iMessage attacks observed in the wild.
The new mitigations were discovered by Samuel Groß, a Google Project Zero security researcher who specializes in remote iPhone exploitation and zero-click attacks against mobile messaging systems.
Apple did not document the changes but Groß said he fiddled around with the newest iOS 14 and found that Apple shipped a “significant refactoring of iMessage processing” that severely cripples the usual ways exploits are chained together for zero-click attacks.
Groß notes that memory corruption based zero-click exploits typically require exploitation of multiple vulnerabilities to create exploit chains. In most observed attacks, these could include a memory corruption vulnerability, reachable without user interaction and ideally without triggering any user notifications; a way to break ASLR remotely; a way to turn the vulnerability into remote code execution;; and a way to break out of any sandbox, typically by exploiting a separate vulnerability in another operating system component (e.g. a userspace service or the kernel).
With iOS 14, Groß discovered that Apple shipped a significant refactoring of iMessage processing, and made all four parts of an attack much harder to succeed.
The first big addition is a new, tightly sandboxed “BlastDoor” service that is now responsible for the parsing of untrusted data in iMessages.
Separately, Apple added logic into iOS 14 to specifically detect [shared cache region] attacks and new techniques to limit an attacker’s ability to retry exploits or brute force Address Space Layout Randomization (ASLR.
The mitigations, Groß said, made all four parts of a typical zero-click attack harder and he commended Apple for responding to the work of offense-focused hackers to respond to documented in-the-wild attacks.
“Overall, these changes are probably very close to the best that could’ve been done given the need for backwards compatibility, and they should have a significant impact on the security of iMessage and the platform as a whole,” the Google researcher added.
Apple to Crack Down on Tracking iPhone Users in Early Spring
29.1.2021 Apple Securityweek
Apple says it will roll out a new privacy control in the spring to prevent iPhone apps from secretly shadowing people. The delay in its anticipated rollout aims to placate Facebook and other digital services that depend on such data surveillance to help sell ads.
Although Apple didn’t provide a specific date, the general timetable disclosed Thursday means a long-awaited feature known as App Tracking Transparency will be part of an iPhone software update likely to arrive in late March or some point in April.
After delaying the planned September introduction of the safeguard amid a Facebook-led outcry, Apple had previously said it would come out early this year. Apple released the latest update as part of Data Privacy Day, which CEO Tim Cook will salute during a speech scheduled Thursday at a technology conference in Europe.
Apple has been holding off to give Facebook and other app makers more time to adjust to a feature that will require iPhone users to give their explicit consent to being tracked. Analysts expect a significant number of users to deny that permission once it requires their assent. Currently, iPhone users are frequently tracked by apps they install unless they take the extra step of going into iPhone settings to prevent it.
Facebook stepped up its attacks on Apple’s new privacy control last month in a series of full-page ads in The New York Times, The Wall Street Journal and other national newspapers. That campaign suggested some free digital services will be hobbled if they can’t compile personal information to customize ads. On Wednesday, CEO Mark Zuckerberg questioned Apple’s motives with the changes, saying the iPhone maker “has every incentive” to use its own mobile platform to interfere with rivals to its own messaging app.
“Apple may say that they are doing this to help people, but the moves clearly track their competitive interests,” Zuckerberg said.
Google, which also relies on personal data to power the internet’s biggest ad network, hasn’t joined Facebook in its criticism of Apple’s forthcoming controls on tracking. Google profits from being the default search engine on the iPhone, a prized position for which it pays Apple an estimated $9 billion to $12 billion annually.
But Google warned in a Wednesday blog post that Apple’s new controls will have a significant impact on ad revenue generated from iPhones in its digital network. Google said a “handful” of its iPhone apps will be affected by the new requirement, but did not identify which ones.
“We remain committed to preserving a vibrant and open app ecosystem where people can access a broad range of ad-supported content with confidence that their privacy and choices are respected,” wrote Christophe Combette, group product manager for Google Ads.
Apple also released an 11-page report to illustrate how much apps can learn about their users in daily life.
Apple Patches Three Actively Exploited Zero-Days, Part of iOS Emergency Update
28.1.2021 Apple Threatpost
An anonymous researcher identified bugs in the software’s kernel and WebKit browser engine that are likely part of an exploit chain.
Apple continues to put out potential security fires by patching zero-day vulnerabilities, releasing an emergency update this week to patch three more recently discovered in iOS after a major software update in November already fixed three that were being actively exploited.
The newly patched bugs are part of a security update released Tuesday for iOS 14.4 and iPadOS 14.4. One bug, tracked as CVE-2021-1782, was found in the OS kernel, while the other two–CVE-2021-1870 and CVE-2021-1871–were discovered in the WebKit browser engine.
The most recent vulnerabilities apparently weren’t known when Apple released iOS 14.2 and iPadOS 14.2, a comprehensive update that patched a total of 24 vulnerabilities back in November. That update included fixes for three zero-day flaws discovered by the Google Project Zero team that were actively being exploited in the wild.
Attackers also may be actively taking advantage of the latest bugs, according to Apple. The company described the kernel flaw as a “a race condition” that the update addresses “with improved locking.” If exploited, the vulnerability can allow a malicious application to elevate privileges.
The WebKit vulnerabilities are both logic issues that the update addresses with improved restrictions, according to Apple. Exploiting these flaws would allow a remote attacker “to cause arbitrary code execution,” the company said.
All the zero-days and thus the fixes affect iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch (7th generation), according to Apple. Security experts believe the three are part of an exploit chain attackers can use to escalate privileges and compromise a device after its unsuspecting user falls victim to a malicious website leveraging the WebKit flaw.
As is custom, however, Apple did not go into detail about how the bugs are being used in attacks, as it doesn’t typically reveal this type of info until most of the affected devices are patched.
The proliferation of iPhones across the world makes news of any Apple iOS zero-day a security threat to its hundreds of millions of users, and thus a very big deal. In fact, four nation-state-backed advanced persistent threats (APTs) used a zero-day iPhone exploit in a highly publicized espionage hack against Al Jazeera journalists, producers, anchors and executives late last year.
Predictably, numerous iPhone users, tech professionals and security experts took to Twitter as news of the latest spate of iOS zero-days broke to warn iPhone users to update their devices immediately.
“iOS release notes are always comforting when you have firsts like this,” tweeted one iPhone user Daniel Sinclair sarcastically. “3 zero-days actively exploited in the wild. 2 involving WebKit.”
Sinclair also tweeted earlier in the month that his iPhone “inexplicably became bricked,” though it’s unclear if that issue was related to the recently discovered zero-days.
Apple addresses three iOS zero-day flaws exploited in the wild
28.1.2021 Apple Securityaffairs
Apple has addressed three zero-day vulnerabilities in its iOS operating system that have been exploited in the wild.
Apple has addressed three zero-day vulnerabilities in iOS that have been exploited in the wild with the release of security updates (iOS 14.4).
The first zero-day issue, tracked as CVE-2021-1782, is a race condition that resides in the iOS operating system kernel.
“A malicious application may be able to elevate privileges. Apple is aware of a report that this issue may have been actively exploited.” reads the advisory. “A race condition was addressed with improved locking.”
Apple security update is available for iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch (7th generation).
The other two zero-day flaws, tracked as CVE-2021-1870 and CVE-2021-1871 respectively, reside in the WebKit browser engine.
Both issues are logic issues that could be exploited by remote attackers to execute arbitrary code inside users’ Safari browsers.
“A remote attacker may be able to cause arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited.” reads tthe advisory.
Security updates are available for iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch (7th generation).
All three zero-days have been reported to the IT giant by an anonymous researcher.
Apple did not disclose technical details of the attacks in the wild, threat actors likely chained the flaws to deliver malicious code into web browsers of users visiting specially crafted websites and escalate privileged to run malicious code.
In November, Apple addressed other three zero-day vulnerabilities in its mobile OS that have been abused in attacks in the wild
Apple Ships Emergency Fixes for Under-Attack iOS Zero-Day
27.1.2021 Apple Securityweek
iOS Vulnerabilities Exploited in the Wild
Apple on Tuesday dropped emergency security patches for its flagship iOS and iPad OS platforms alongside a warning that hackers may already be exploiting three different security vulnerabilities.
The patches -- contained in iOS 14.4 and iPadOS 14.4 -- are currently being pushed to mobile users via the automatic updating mechanism.
Apple did not provide technical details of the vulnerabilities or the in-the-wild attacks, except to identify the flaws in the Kernel and in WebKit, the open-source web browser engine used in Safari, Mail, AppStore and a range of MacOS and iOS apps.
Here are the bare-bones details from Apple:
CVE-2021-1782 (Kernel) -- Impact: A malicious application may be able to elevate privileges. Apple is aware of a report that this issue may have been actively exploited. Available for: iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch (7th generation). Anonymously reported.
CVE-2021-1871 and CVE-2021-1870 (WebKit) -- Impact: A remote attacker may be able to cause arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. Available for: iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch (7th generation). Reported by anonymous researchers.
Apple has promised additional details will be available soon.
Apple Warns of 3 iOS Zero-Day Security Vulnerabilities Exploited in the Wild
27.1.2021 Apple Thehackernews
Apple on Tuesday released updates for iOS, iPadOS, and tvOS with fixes for three security vulnerabilities that it says may have been actively exploited in the wild.
Reported by an anonymous researcher, the three zero-day flaws — CVE-2021-1782, CVE-2021-1870, and CVE-2021-1871 — could have allowed an attacker to elevate privileges and achieve remote code execution.
The iPhone maker did not disclose how widespread the attack was or reveal the identities of the attackers actively exploiting them.
While the privilege escalation bug in the kernel (CVE-2021-1782) was noted as a race condition that could cause a malicious application to elevate its privileges, the other two shortcomings — dubbed a "logic issue" — were discovered in the WebKit browser engine (CVE-2021-1870 and CVE-2021-1871), permitting an attacker to achieve arbitrary code execution inside Safari.
Apple said the race condition and the WebKit flaws were addressed with improved locking and restrictions, respectively.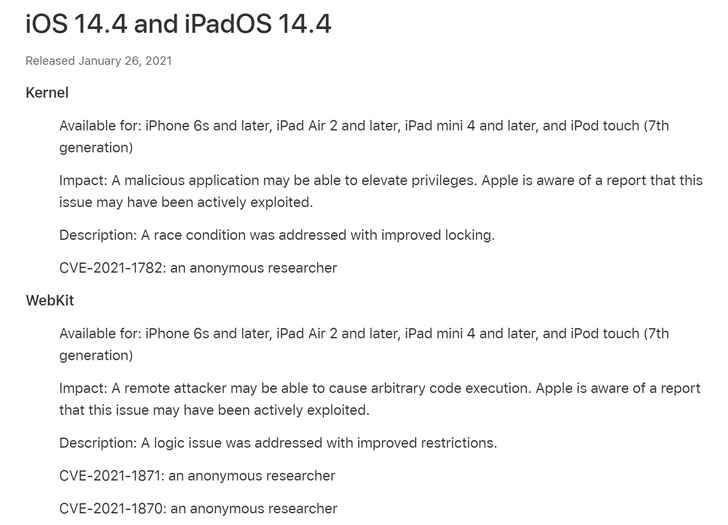
While exact details of the exploit leveraging the flaws are unlikely to be made public until the patches have been widely applied, it wouldn't be a surprise if they were chained together to carry out watering hole attacks against potential targets.
Such an attack would involve delivering the malicious code simply by visiting a compromised website that then takes advantage of the aforementioned vulnerabilities to escalate its privileges and run arbitrary commands to take control of the device.
The updates are now available for iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch (7th generation), as well as Apple TV 4K and Apple TV HD.
News of the latest zero-days comes after the company resolved three actively exploited vulnerabilities in November 2020 and a separate zero-day bug in iOS 13.5.1 that was disclosed as used in a cyberespionage campaign targeting Al Jazeera journalists last year.
'LuckyBoy' Malvertising Campaign Hits iOS, Android, XBox Users
21.1.2021 Android Apple Securityweek
A recently identified malvertising campaign targeting mobile and other connected devices users makes heavy use of obfuscation and cloaking to avoid detection.
Dubbed LuckyBoy, the multi-stage, tag-based campaign is focused on iOS, Android, and Xbox users. Since December 2020, it penetrated over 10 Demand Side Platforms (DSP), primarily Europe-based, with observed campaigns impacting users in the U.S. and Canada.
According to security vendor Media Trust, the malware checks for a global variable ‘luckyboy’ that allows it to detect whether blockers, testing environments, and active debuggers are present on the device. If any is detected, the malware won’t execute.
Should it run on a target environment, the malware executes a tracking pixel programmed to redirect the user to malicious content, including phishing pages and fake software updates.
LuckyBoy was observed operating in bursts: small campaigns are launched on Thursday nights, with only a few compromised tags, and continue throughout the weekend.
Multiple checks are performed as the campaign advances through stages, with extensive code obfuscation and domain exclusion employed, and device-specific information extracted.
The harvested device data includes country code, window size, graphics information, number of CPU cores, battery level, current domain, plugins, the presence of webdriver, and whether touch is available, likely to set up for future attacks.
The malware continuously performs checks to ensure that the value of the global variable remains ‘luckyboy’. Otherwise, the script stops execution and exits after delivering a clean creative to the user.
“LuckyBoy is likely executing tests, probing to gauge their success before launching a broader attack. Campaign was confirmed to execute on tags wrapped with malware blocking code, bypassing these defenses as further evidence that its sophistication is impressive,” The Media Trust notes in a report shared with SecurityWeek.
The security firm says it is currently working with Google and TAG Threat Exchange to isolate the buyer and block them from launching these campaigns.
Apple paid a $50,000 bounty to two bug bounty hunters for hacking its hosts
19.1.2021 Apple Securityaffairs
A duo of white hat hackers claims to have earned $50,000 from Apple for reporting serious flaws that allowed them to company’s servers.
The Indian white hat hackers Harsh Jaiswal and Rahul Maini claim to have discovered multiple flaws that allowed them to access Apple servers.
The duo started focusing on Apple’s infrastructure in an attempt to emulate the success of a team of researchers composed of Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb and Tanner Barnes that reported a total of 55 flaws to Apple in October as part of the company bug bounty program and received for these issues 32 payrolls for a total of $288,500.
The two experts focus on critical findings such as PII exposure or getting access to Apple’s servers or internal network.
While conducting reconnaissance and fingerprinting the experts found three Apple hosts running a content management system (CMS) backed by Lucee, which is a dynamic, Java-based, tag and scripting language used for rapid web application development. The three hosts are:
https://facilities.apple.com/ (Recent version)
https://booktravel.apple.com/ (Older version)
https://booktravel-uat.apple.com/ (Older version)
apple bug bounty 2
The hosts were exposing the Lucee admin panel, two of them were running an outdated version. The hosts with the outdated version were exposing travel portals implemented by Apple to its employees.
Even if the outdated versions were affected by security flaws, the experts pointed out that Apple was using WAF to mitigate the attacks against its applications.
The security duo discovered a misconfiguration in Lucee that could be exploited to access files without being authenticated, opening the door to the creation of a webshell on Apple servers and execute arbitrary code.
“While testing out Lucee locally, we came across a critical misconfiguration which allowed an attacker to access authenticated CFM (ColdFusion) files directly. This allowed us to perform a lot of authenticated actions while being completely unauthenticated. As soon as you hit the request.admintype variable/property in a CFM file, the execution flow will stop as we’re not authenticated as admin. However, any code before that check executes.” reads the post published by the bug bounty hackers. “So we had to find files that had some sort of bug before they hit request.admintype. We made use of these three files to gain a complete pre-auth/unauth RCE on a Lucee installation:
imgProcess.cfm (not available in older versions)
admin.search.index.cfm
ext.applications.upload.cfm”
The experts provided technical details of their activity, they explained how they avoided triggering Apple’s web application firewall and got a shell on the 2 hosts.
Jaiswal and Maini shared their findings with Apple that awarded them a $50,000 bug bounty. The IT giant promptly addressed the issue, but requested the experts to not disclose the flaw before they make some other changes.
The development team behind Lucee also fixed the bug by restricting access to cfm files directly, here’s the commit link.
Researchers Earn $50,000 for Hacking Apple Servers
19.1.2021 Apple Securityweek
A couple of researchers claim they have earned $50,000 from Apple for finding some serious vulnerabilities that gave them access to the tech giant’s servers.
Harsh Jaiswal and Rahul Maini, India-based bug bounty hunters who specialize in application security, said they discovered the flaws in recent months, being inspired by a group of researchers who in October reported receiving hundreds of thousands of dollars from Apple for a total of 55 vulnerabilities, including ones that exposed source code, iCloud accounts, warehouse software, and employee and customer apps.
Jaiswal and Maini said their research focused on Apple hosts running a content management system (CMS) powered by Lucee, an open source scripting language designed for developing web applications.
During their analysis, they discovered three Apple hosts that exposed the Lucee admin panel, including two apparently associated with a travel portal provided by Apple to employees. The portal is only accessible to users with valid credentials.
The researchers discovered a Lucee misconfiguration that gave them access to files without being authenticated, which ultimately allowed them to create a webshell on Apple servers and execute arbitrary code. They managed to conduct their tests without triggering Apple’s web application firewall.
Jaiswal and Maini said Apple decided to award them a $50,000 bug bounty after being informed about the vulnerabilities. Lucee developers were also contacted and they also took some steps to prevent these types of attacks.
“Apple promptly fixed the issue but requested us to not disclose the issue before they make some other changes,” the researchers said.
A detailed technical writeup describing the analysis process and the researchers’ findings was published last week.
Apple Removes macOS Feature That Allowed Apps to Bypass Firewall Security
18.1.2021 Apple Thehackernews
Apple has removed a controversial feature from its macOS operating system that allowed the company's own first-party apps to bypass content filters, VPNs, and third-party firewalls.
Called "ContentFilterExclusionList," it included a list of as many as 50 Apple apps like iCloud, Maps, Music, FaceTime, HomeKit, the App Store, and its software update service that were routed through Network Extension Framework, effectively circumventing firewall protections.
This exclusion list has been scrubbed now from macOS 11.2 beta 2.
The issue first came to light last October following the release of macOS Big Sur, prompting concerns from security researchers who said the feature was ripe for abuse, adding it could be leveraged by an attacker to exfiltrate sensitive data by piggybacking it on to legitimate Apple apps included on the list and then bypass firewalls and security software.
"After lots of bad press and lots of feedback/bug reports to Apple from developers such as myself, it seems wiser (more security conscious) minds at Cupertino prevailed," said Patrick Wardle, a principal security researcher with Jamf, last week.
Researchers, including Wardle, found last year that Apple's apps were being excluded from NEFilterDataProvider, a network content filter that makes it possible for firewall and VPN apps such as LuLu and Little Snitch to monitor and control data traffic from installed apps on the system.
Wardle demonstrated an instance of how malicious apps could exploit this firewall bypass to transmit data to an attacker-controlled server using a simple Python script that latched the traffic onto an Apple exempted app despite setting LuLu and Little Snitch to block all outgoing connections on a Mac running Big Sur.
With this new change, socket filter firewalls such as LuLu can now comprehensively filter/block all network traffic, including those from Apple apps.
The updates come as Apple deprecated support for Network Kernel Extensions in 2019 in favor of Network Extensions Framework.
We have reached out to Apple, and we'll update the story if we hear back.
Apple Kills MacOS Feature Allowing Apps to Bypass Firewalls
16.1.2021 Apple Threatpost
Security researchers lambasted the controversial macOS Big Sur feature for exposing users’ sensitive data.
Apple has removed a contentious macOS feature that allowed some Apple apps to bypass content filters, VPNs and third-party firewalls.
The feature, first uncovered in November in a beta release of the macOS Big Sur feature, was called “ContentFilterExclusionList” and included a list of at least 50 Apple apps – including Maps, Music, FaceTime, the App Store and its software update service. It has been recently removed in macOS Big Sur versions 11.2, Apple experts pointed out this week.
“After lots of bad press and lots of feedback/bug reports to Apple from developers such as myself, it seems wiser (more security conscious) minds at Cupertino prevailed,” said Patrick Wardle, principal security researcher with Jamf, this week. “The ContentFilterExclusionList list has been removed (in macOS 11.2 beta 2).”
Researchers found these apps were excluded from being controlled by Apple’s NEFilterDataProvider feature. NEFilterDataProvider is a simple network content filter, which is used by third-party application firewalls (such as host-based macOS application firewall Little Snitch) and VPNs to filter data traffic flow on an app-by-app basis.
Because these apps bypassed NEFilterDataProvider, the service could not monitor them to see how much data they were transferring or which IP addresses they were communicating with – and ultimately could not block them if something was amiss.
After discovering the undocumented exclusion list back in November, security researchers criticized Apple, saying it was a liability that can be exploited by threat actors to bypass firewalls, give them access to people’s systems and expose their sensitive data.
“Many (rightfully) asked, ‘What good is a firewall if it can’t block all traffic?’ I of course also wondered if malware could abuse these ‘excluded’ items to generate network traffic that could surreptitiously bypass any socket filter firewall,” said Wardle. “Unfortunately the answer was yes.”
The new change means that firewalls such as LuLu – an open-source firewall that blocks outgoing unknown connections on Macs – can now comprehensively filter and block network traffic for all Apple apps, Wardle said.
Threatpost has reached out to Apple for further information about ContentFilterExclusionList and its removal.