BigBrothers Articles - H 2020 1 2 3 4 5 BigBrothers List - H 2021 2020 2019 2018 BigBrother blog BigBrother blog
Microsoft Says Iranian Hackers Targeted Attendees of Major Global Policy Conferences
29.10.20 BigBrothers Securityweek
The Iran-linked state-sponsored threat group known as Charming Kitten was observed targeting potential attendees of two major international conferences, Microsoft reports.
Also referred to as Phosphorous, APT35, Ajax Security Team, ITG18, NewsBeef, and NewsCaster, the threat actor is believed to have been active since at least 2011, targeting entities in the Middle East, the United States, and the United Kingdom.
Recently observed attacks, Microsoft says, targeted over 100 high-profile individuals, potential attendees of two upcoming global policy conferences, namely the Munich Security Conference and the Think 20 (T20) Summit, which is held in Saudi Arabia.
“Based on current analysis, we do not believe this activity is tied to the U.S. elections in any way,” Microsoft reveals.
As part of the assaults, the hackers would masquerade as conference organizers, sending spoofed email invitations to individuals potentially interested in attending. Written in near-perfect English, the emails were sent to academics, former government officials, policy experts, and leaders of non-governmental organizations.
Charming Kitten, the tech company explains, offered remote sessions to potential victims, thus lowering fears associated with travel during the coronavirus pandemic.
The attacks are believed to have been orchestrated for intelligence gathering, with several victims successfully compromised. These include former ambassadors and other senior policy experts.
“We’ve already worked with conference organizers who have warned and will continue to warn their attendees, and we’re disclosing what we’ve seen so that everyone can remain vigilant to this approach being used in connection with other conferences or events,” Microsoft explains.
To stay protected from similar attacks, users are advised to evaluate the authenticity of received messages, use multi-factor authentication, review email-forwarding rules, and enroll in advanced protection programs, where possible.
Microsoft, which has published indicators of compromise (IoC) related to the attacks, underlines that nation-state hackers routinely pursue governmental and non-governmental entities, think tanks, and policy organizations.
“We will continue to use a combination of technology, operations, legal action and policy to disrupt and deter malicious activity, but nothing replaces vigilance from people who are likely targets of these operations,” the company concludes.
Russian Espionage Group Updates Custom Malware Suite
29.10.20 BigBrothers Threatpost
Turla has outfitted a trio of backdoors with new C2 tricks and increased interop, as seen in an attack on a European government.
The advanced persistent threat (APT) known as Turla is targeting government organizations using custom malware, including an updated trio of implants that give the group persistence through overlapping backdoor access.
Russia-tied Turla (a.k.a. Ouroboros, Snake, Venomous Bear or Waterbug) is a cyber-espionage group that’s been around for more than a decade. It’s known for its complex collection of malware and interesting command-and-control (C2) implementations. It targets governmental, military and diplomatic targets.
Accenture researchers observed a recent campaign against a foreign government in Europe that ran between June and October, which featured three legacy weapons, all with significant updates. They worked together as a kind of multi-layered threat toolkit.
One of the updated tools is the HyperStack remote procedure call (RPC)-based backdoor (named after the filename that its authors gave it). Accenture has tied it to the group for the first time, thanks to its use alongside the other two tools seen in the campaign: Known Turla second-stage remote-access trojans (RATs), Kazuar and Carbon.
“The RATs transmit the command-execution results and exfiltrate data from the victim’s network, while the RPC-based backdoors [including HyperStack] use the RPC protocol to perform lateral movement and issue and receive commands on other machines in the local network,” according to an Accenture analysis, released on Wednesday. “These tools often include several layers of obfuscation and defense-evasion techniques.”
The upgrades seen in the campaign largely revolved around creating built-in redundancies for remote communication. Turla used disparate C2 configurations, to allow different re-entry points should one of them be blocked.
“[These included] novel [C2] configurations for Turla’s Carbon and Kazuar [RATs] on the same victim network,” according to the analysis. “The Kazuar instances varied in configuration between using external C2 nodes off the victim network and internal nodes on the affected network, and the Carbon instance had been updated to include a Pastebin project to receive encrypted tasks alongside its traditional HTTP C2 infrastructure.”
HyperStack Backdoor
The HyperStack backdoor began life in 2018, but it received a major update in September that allowed Accenture researchers to tie it back to Turla.
“The updated functionality…appears to be inspired by the RPC backdoors previously publicly disclosed by ESET and Symantec researchers, as well as with the Carbon backdoor,” they explained. “Based on these similarities, we assess with high confidence that HyperStack is a custom Turla backdoor.”
The new version of HyperStack uses named pipes to execute RPC calls from a controller to a device hosting the HyperStack client. It leverages IPC$, which is a share function that facilitates inter-process communication (IPC) by exposing named pipes to write to or read from.
“To move laterally, the implant tries to connect to another remote device’s IPC$ share, either using a null session or default credentials,” explained Accenture researchers. “If the implant’s connection to the IPC$ is successful, the implant can forward RPC commands from the controller to the remote device, and likely has the capability to copy itself onto the remote device.”
Kazuar Updates
Meanwhile, a Kazuar sample used in the observed European campaign that Accenture analyzed in mid-September was configured to receive commands via Uniform Resource Identifiers (URI). These pointed to internal C2 nodes in the victim government’s network.
This Kazuar configuration acted alongside another sample, analyzed in early October.
“Based on references to the internal C2 node, the October sample likely acts as a transfer agent used to proxy commands from the remote Turla operators to the Kazuar instances on internal nodes in the network, via an internet-facing shared network location,” according to Accenture. “This set-up allows Turla operators to communicate with Kazuar-infected machines in the victim network that are not accessible remotely.”
Yet another Kazuar sample found on the victim network was configured to communicate directly with a C2 server located outside the victim network, hosted on a compromised legitimate website. This was used by Turla to proxy commands and exfiltrate data to Turla backend infrastructure, researchers said.
Kazuar is a multiplatform trojan discovered in 2017 that allows Turla to remotely load additional plugins to increase its capabilities. It exposes these through an Application Programming Interface (API) to a built-in web server, and it has code lineage that can be traced back to at least 2005, researchers have said. For a while it was believed to have been the successor to Carbon.
Carbon Updates
The aforementioned legacy tool Carbon was also updated for the observed campaign. Carbon is a modular backdoor framework with advanced peer-to-peer capability that Turla has used for several years, well before Kazuar hit the scene.
In June, an updated sample made an appearance which combined the Turla-owned C2 infrastructure with tasks served from Pastebin, researchers found. The installer for the sample contained a configuration file with URLs for compromised web servers hosting a web shell that transmits commands and exfiltrates data from the victim network – as expected. But researchers noted that it also contained a parameter labeled [RENDEZVOUS_POINT], with a URL for a Pastebin project.
“When accessing the Pastebin URL, an encrypted blob is downloaded that requires a corresponding RSA private key from the configuration file,” researchers explained. “The configuration file analyzed did not contain the RSA private key and therefore we were unable to decrypt the contents of the Pastebin link. We assess the decrypted blob was likely a task for the Carbon instance.”
The use of a legitimate web service like Pastebin for C2 activities is an ongoing trend among APTs, the researchers noted, for a few different reasons.
“[For one], web services allow cyber-espionage groups’ malicious network traffic to blend easily with legitimate network traffic,” according to researchers. “Also, threat groups can easily change or create new infrastructure which makes it difficult for defenders to shut down or sinkhole their infrastructure. [And], using web services complicates attribution since the C2 infrastructure is not owned by the threat group.”
Turla will likely continue to use its legacy tools, with upgrades, to compromise and maintain long term access to its victims, researchers said.
“This combination of tools has served Turla well, as some of their current backdoors use code that dates back to 2005,” Accenture researchers noted. “The threat group will likely continue to maintain and rely on this ecosystem, and iterations of it, as long as the group targets Windows-based networks.”
U.S. Shares Information on North Korean Threat Actor 'Kimsuky'
29.10.20 BigBrothers Securityweek
An alert released by the United States this week provides information on Kimsuky, a threat actor focused on gathering intelligence on behalf of the North Korean government.
Issued by the Cybersecurity and Infrastructure Security Agency (CISA), the FBI, and the Cyber Command Cyber National Mission Force (CNMF), the advisory notes that the adversary has been active since at least 2012, engaging in social engineering, spear-phishing, and watering hole attacks.
The malicious cyber activity associated with the North Korean government is typically referred to as HIDDEN COBRA by the United States.
Kimsuky, the alert says, targets individuals and organizations located in Japan, South Korea, and the United States, and is mainly focused on gathering intelligence on “foreign policy and national security issues related to the Korean peninsula, nuclear policy, and sanctions.”
Targets include entities associated with the South Korean government, individuals who are believed to be experts in various fields, and think tanks.
For initial access, Kimsuky uses spear-phishing with malicious attachments, and various social engineering methods. However, the threat actor would also send benign emails to gain victims’ trust. Malicious scripts and tools are hosted using stolen web hosting credentials, the alert reads.
The adversary was observed posing as South Korean reporters and engaging with intended targets to claim to be arranging interviews on inter-Korean issues and denuclearization negotiations. To one recipient who agreed to an interview, Kimsuky sent a malicious document in a subsequent email, to infect the victim with a variant of the BabyShark malware.
The employed spear-phishing emails were tailored to topics deemed relevant to the target, including the current COVID-19 crisis, the North Korean nuclear program, and media interviews.
Kimsuky, the advisory reads, also uses login-security-alert-themed phishing emails for initial access, along with watering hole attacks, malware delivered via torrent sharing sites, and malicious browser extensions served to their victims.
Following initial access, the threat actor uses mshta.exe to fetch and execute an HTML application (HTA) file that downloads and runs the encoded BabyShark VBS file. The script achieves persistence through a registry key, and collects system information and sends it to the operator’s command and control (C&C) servers.
The adversary would also employ PowerShell for the execution of files directly in memory and to achieve persistence through malicious browser extensions, altered system processes, Remote Desktop Protocol (RDP), and by changing the autostart execution and default file association for an application.
In 2018, during a campaign referred to as STOLEN PENCIL, Kimsuky used the GREASE malware, which adds a Windows administrator account and abuses RDP to provide attackers with access to the compromised systems.
For information gathering purposes, Kimsuky targets Hangul Word Processor (HWP) and Microsoft Office documents, and uses web shells for file upload, download, and deletion.
To escalate privileges, the threat actor uses scripts placed in the Startup folder, newly created services, modified file associations, and malicious code injected into explorer.exe. The Win7Elevate exploit from the Metasploit framework was used to bypass the User Account Control to inject code into explorer.exe.
In their joint alert, CISA, the FBI and USCYBERCOM also provide information on methods Kimsuky employs for defense evasion, its use of various tools for credential harvesting, memory dumping, and system information enumeration, how system data is collected, and the targeting of macOS systems.
The advisory also provides details on the employed C&C and data exfiltration, also noting that the threat actor’s activities are limited to information harvesting, and are not destructive in nature.
Trump Campaign Website Broken Into by Hackers
28.10.20 BigBrothers Securityweek
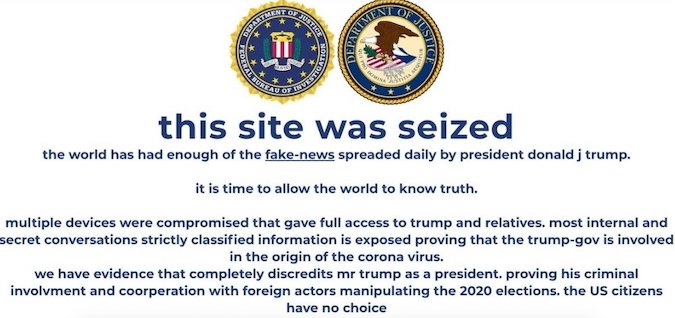
Hackers briefly broke into Donald Trump's campaign website on Tuesday, just a week before Election Day, officials and reports said.
"This site was seized," said a message that popped up on donaldjtrump.com, which normally carries details of rallies and fundraising appeals.

"The world has had enough of the fake-news spreaded daily by president donald j trump", the message went to say, US media reported.
Trump campaign spokesman Tim Murtaugh said the site was quickly fixed and no sensitive data was compromised.
"The Trump campaign website was defaced and we are working with law enforcement authorities to investigate the source of the attack," Murtaugh said.
The technology website Techcrunch said the hack appeared to be a scam intended to collect hard-to-trace cypto-currency Monero.
In their message, the hackers claimed to have confidential information on Trump and his relatives.
They instructed people to send crypto-currency to one address if they wanted the information revealed and to another to keep it secret.
US Insists on Need to Ban TikTok
27.10.20 BigBrothers Securityweek
US President Donald Trump's administration has insisted on the need to ban TikTok due to national security concerns in a new court filing ahead of a plan to make the video app unavailable on November 12.
The filing comes as the court considers the legality of the administration's bid to make the Chinese-owned app unavailable in the United States, where it has 100 million users.
"The president should not be prevented from regulating national security threats simply because a foreign adversary cloaks its activities within a media company," the filing on Friday at a federal court in Washington says.
The Trump administration is seeking to persuade the judge in the case to allow it to move forward with restrictions on the video-sharing app, which it claims has links to the Chinese government through its parent firm ByteDance.
In September, a temporary injunction prevented the government from removing TikTok from mobile application download platforms.
That Trump administration order had sought to ban new downloads of the app but continue to allow use of TikTok until November 12, when all usage would be blocked.
The judge at the time denied TikTok's request to suspend the November 12 ban, but the court has yet to consider the merits of the legal arguments on whether the social platform should remain available to Americans.
TikTok has repeatedly defended itself against allegations of data transfers to the Chinese government.
It says its servers where user information is stored are located in the United States and Singapore.
The company has also said the ban is unnecessary since negotiations are underway to restructure the ownership of TikTok to address national security issues raised by the administration.
A tentative deal has been unveiled that would make Silicon Valley giant Oracle the technology partner for TikTok and a stakeholder in a new entity to be known as TikTok Global.
U.S. Treasury Sanctions Russian Institute Linked to Triton Malware
26.10.20 BigBrothers Securityweek
The United States Department of the Treasury’s Office of Foreign Assets Control (OFAC) has announced sanctions against a Russian government institute connected to the destructive Triton malware.
Initially identified in 2017 on the systems of a Saudi Arabian oil and gas company and also referred to as Trisis and HatMan, Triton is known for the targeting of Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers.
Referred to by some as Xenotime, the threat actor behind the malware is believed to have been active since at least 2014, and at one point it expanded activities to Australia, Europe, and the US, and added electric utilities to its target list.
In 2018, FireEye associated Triton with the Russian technical research organizations Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM).
At SecurityWeek’s 2019 ICS Cyber Security Conference in Singapore, FireEye revealed that evidence connecting Triton with CNIIHM started disappearing following the publishing of their 2018 report, including photos, details on internal structure, and information on associated IP addresses.
OFAC, which notes that Triton has been labeled “the most dangerous activity publicly known,” announced on Friday sanctions against CNIIHM, or TsNIIKhM (the State Research Center of the Russian Federation FGUP Central Scientific Research Institute of Chemistry and Mechanics), essentially prohibiting Americans from engaging with the institution.
This Russian government-controlled research organization, the Treasury Department says, is responsible for the development of customized tools that made possible the 2017 attack against the Saudi Arabian petrochemical facility.
Pursuant to section 224 of the Countering America’s Adversaries Through Sanctions Act (CAATSA), the Treasury Department designated TTsNIIKhM “for knowingly engaging in significant activities undermining cybersecurity against any person, including a democratic institution, or government on behalf of the Government of the Russian Federation.”
The Triton malware, OFAC says, was specifically created to target industrial control systems (ICS) that are used within critical infrastructure facilities to ensure immediate shutdown in the event of an emergency.
Deployed via phishing emails, the malware was designed to manipulate these safety controllers, providing attackers with full control over the infected systems. The malware can cause “significant physical damage and loss of life,” the US government said.
In an emailed comment, Robert M. Lee, CEO and co-founder of industrial cybersecurity firm Dragos, said, “An OFAC sanction by the U.S. Treasury is significant and compelling; not only will it impact this research institution in Russia, but anyone working with them will have their ability to be successful on the international stage severely hampered.”
“The most important aspect of this development, however, is the attribution to Russia for the TRISIS attack by the USG officially and the explicit call out of industrial control systems in the sanction. This is a norm setting moment and the first time an ICS cyber-attack has ever been sanctioned. This is entirely appropriate as this cyber-attack was the first ever targeted explicitly towards human life. We are fortunate no one died and I'm glad to see governments take a strong stance condemning such attacks," he continued.
Nathan Brubaker, senior manager of analysis at Mandiant Threat Intelligence, commented, “TRITON malware was designed to disable the safety systems which form one of the last lines of protection in industrial systems. With control of these safety systems hackers could potentially allow an unsafe state to occur or worse yet, use their access to other control systems to cause an unsafe state, then allow that state to continue, potentially causing dangerous conditions and threaten human life.
“Fortunately, TRITON was discovered when safety systems recognized an abnormality during an intrusion and shut operations down at a plant. In the following months, Mandiant was able to track the intrusion to the Russian lab that is being sanctioned and publicly expose their involvement. This was a dangerous tool that may have been used to do real physical harm. We’re fortunate that it was found in the manner it was, giving us a chance to dig into the actors behind the scenes.”
U.S. Levies Sanctions Against Russian Research Institution Linked to Triton Malware
24.10.20 BigBrothers Threatpost
The latest in a flurry of actions this week, tied to foreign threats against U.S. computer systems, includes sanctions by the Department of the Treasury.
The Trump administration sanctioned a Russia government research institution on Friday claiming it was behind a series of cyberattacks using the highly destructive Triton malware.
The Department of the Treasury’s Office of Foreign Assets Control (OFAC) said the Triton malware had been used in various attacks against U.S. partners in the Middle East and spotted probing U.S. facilities.
Triton (aka TRISIS or HatMan) is most notoriously known for a series of 2017 attacks on a Saudi Arabian petrochemical facility, where it targeted safety systems with the intent of causing loss of life or physical damage, according to researchers at the time.
“This cyber-attack was supported by the State Research Center of the Russian Federation FGUP Central Scientific Research Institute of Chemistry and Mechanics (TsNIIKhM), a Russian government-controlled research institution that is responsible for building customized tools that enabled the attack,” according to a Treasury Department statement issued Friday.
“This Administration will continue to aggressively defend the critical infrastructure of the United States from anyone attempting to disrupt it,” said secretary of the Treasury Steven Mnuchin in a statement.
Over the years, the advanced persistent threat (APT) group identified as XENOTIME was believed to be behind the Triton malware attacks. About a year ago the APT expanded beyond its initial focus of Saudi Arabian petrochemical firms.
According to a 2019 analysis by Dragos, the group had begun to target dozens of electric power utilities in North American and Asia-Pacific regions. Dragos said, at the time, it expected Triton to be used to attack industrial controls systems that managed water plants and manufacturing industries.
On Friday, the Department of Treasury accused the TsNIIKhM of “knowingly engaging in significant activities undermining cybersecurity against any person, including a democratic institution, or government on behalf of the Government of the Russian Federation”, pursuant to Section 224 of the Countering America’s Adversaries Through Sanctions Act.
Friday’s sanctions against Russia cap a busy week for U.S. cyber defenses. On Wednesday, federal officials claim that Iranian threat actors are behind two separate email campaigns that assailed Democratic voters this week with threats to “vote for Trump or else.” The campaigns claimed to be from violent extremist group Proud Boys.
On Thursday, the Trump administration claimed Iran and Russia hacked local governments local governments and obtained voter registration and other personal data, first reported by NBC News. On Tuesday, the National Security Agency released an advisory (PDF) warning Chinese state-sponsored actors were exploiting 25 publicly known vulnerabilities. On Monday, the Department of Justice announced charges against six Russian nationals who are allegedly tied to the Sandworm APT.
FBI and CISA joint alert blames Russia’s Energetic Bear APT for US government networks hack
23.10.20 BigBrothers Securityaffairs
The US government declared that Russia-linked APT group Energetic Bear has breached US government networks and exfiltrated data.
A joint security advisory published by The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) revealed that Russia-linked APT group Energetic Bear has breached US government networks and exfiltrated data.
The Energetic Bear APT group (aka DragonFly, Crouching Yeti, TEMP.Isotope, Berserk Bear, TeamSpy, Havex, Koala). has been active since at least 2010 most of the victims of the group are organizations in the energy and industrial sectors.
In March 2018, the Department of Homeland Security and Federal Bureau of Investigation issued a joint technical alert to warn of attacks on US critical infrastructure powered by Russian threat actors. The US-CERT blamed the APT group tracked as Dragonfly, Crouching Yeti, and Energetic Bear.
This joint advisory provides information on Russia-linked APT actor activity targeting various U.S. state, local, territorial, and tribal (SLTT) government networks, as well as aviation networks.
Officials said the group has been targeting dozens of US state, local, territorial, and tribal (SLTT) government networks since at least February 2020.
Energetic Bear successfully compromised the infrastructure and as of October 1, 2020, exfiltrated data from at least two victim servers.
“Since at least September 2020, a Russian state-sponsored APT actor—known variously as Berserk Bear, Energetic Bear, TeamSpy, Dragonfly, Havex, Crouching Yeti, and Koala in open-source reporting—has conducted a campaign against a wide variety of U.S. targets.” reads the advisory. “The Russian state-sponsored APT actor has targeted dozens of SLTT government and aviation networks, attempted intrusions at several SLTT organizations, successfully compromised network infrastructure, and as of October 1, 2020, exfiltrated data from at least two victim servers.”
The Russian-sponsored APT actor uses previously obtained user and administrator credentials to access the target network and then perform lateral movement to locate high-value assets and exfiltrate data. In at least one compromise, the APT actor laterally traversed an SLTT victim network and accessed documents related to sensitive network configurations and passwords, standard operating procedures (SOP), IT instructions, such as requesting password resets, vendors and purchasing information. printing access badges.
This advisory updates another joint CISA-FBI cybersecurity advisory, which warned of attackers combining VPN and Windows Zerologon flaws to target government networks.
The new advisory attributes the cyber attacks to the Russian threat actor and included technical details about the Energetic Bear’s TTPs.
The state-sponsored hackers scanned for vulnerable Citrix (CVE-2019-19781) and Microsoft Exchange services (CVE-2020-0688) and identified vulnerable installs for future exploitation.
According to the technical advisory, Russian hackers used publicly known vulnerabilities to breach networking gear, pivot to internal networks, elevate privileges, and steal sensitive data.
Hackers also targeted Exim mail agents (CVE 2019-10149) and Fortinet SSL VPNs (CVE-2018-13379).
Once gained access to the target networks, Russian hackers moved laterally exploiting the Zerologon vulnerability in Windows Servers (CVE-2020-1472) to access and steal Windows Active Directory (AD) credentials to take over the target’s internal network.
“To date, the FBI and CISA have no information to indicate this APT actor has intentionally disrupted any aviation, education, elections, or government operations. However, the actor may be seeking access to obtain future disruption options, to influence US policies and actions, or to delegitimize SLTT government entities,” continues the alert.
“As this recent malicious activity has been directed at SLTT government networks, there may be some risk to elections information housed on SLTT government networks. However, the FBI and CISA have no evidence to date that integrity of elections data has been compromised.”
Destructive Malware Spotted in Recent Attacks Launched by Iranian Cyberspies
23.10.20 BigBrothers Securityweek
The Iran-linked cyber-espionage group known as Seedworm appears to have added a new downloader to its arsenal and to have started conducting destructive attacks, security researchers report.
Also referred to as MuddyWater, MERCURY, and Static Kitten, the cyber-espionage group was initially analyzed in 2017. Seedworm shows a focus on targeting Middle Eastern organizations, or those in nearby regions.
The threat actor is highly active and is known for the use of a broad and varied toolset. Earlier this month, the group was observed actively targeting the Zerologon vulnerability that Microsoft patched in August.
According to recent reports from ClearSky and Symantec, MuddyWater recently added to its arsenal a downloader called PowGoop, which earlier this year was used in attacks employing the Thanos ransomware against an organization in the Middle East.
PowGoop contains a DLL loader and a PowerShell-based downloader, with the latter designed to decrypt and run the former. The downloader is a fake Google Update mechanism similar to the MoriAgent / PudPoul DLL loader, which was previously attributed to MuddyWater.
“While we cannot confirm the connection, we believe the actors deploying the Thanos ransomware at the Middle Eastern state-run organization also used a downloader that we call PowGoop. The actors would use the PowGoop downloader to reach out to a remote server to download and execute additional PowerShell scripts,” Palo Alto Networks noted in a September 4 report.
The attacks, which were observed on July 6 and July 9, 2020, feature a ransomware variant that was capable of better evading analysis tools, could monitor for newly attached storage devices, and was also able to overwrite the MBR, functionality that would make Thanos rather destructive in nature.
Last week, in a report linking PowGoop to MuddyWater, ClearSky noted that the hacking group appears to have started employing wipers in assaults hidden behind apparent ransomware operations. Other Iranian hackers too have employed wipers, Shamoon being the most infamous of them.
“Although we didn’t see execution of the destruction in the wild, due to the presence of the destructive capabilities, the attribution to nation-state sponsored threat actor, and the realization of this vector in the past, a destructive purpose is more likely than a ransomware that is being deployed for financial goals,” ClearSky noted.
Now, Symantec too says it was able to draw a connection between MuddyWater and PowGoop, after discovering the downloader on systems where one of the group’s backdoors was installed. Furthermore, MuddyWater’s Powerstats (Powermud) backdoor was apparently superseded by DLL side-loading of PowGoop.
“On the same machine where Seedworm was active, a tool known as PowGoop was deployed. This same tool was also deployed against several of the organizations attacked by Seedworm in recent months,” Symantec says.
PowGoop appears to have been used in attacks targeting governments, education, oil and gas, real estate, technology, and telecoms organizations in Afghanistan, Azerbaijan, Cambodia, Iraq, Israel, Georgia, Turkey, and Vietnam.
Symantec’s analysis revealed the use of the Remadmin remote code execution tool to deploy PowGoop, and also led to the identification of artefacts suggesting that PowGoop was masquerading as a Google tool and noticed the use of SSF and Chisel.
Analysis of PowGoop activity would suggest that the downloader might be “an evolution of Powerstats rather than a completely new tool,” Symantec notes, adding that there isn’t enough evidence to confirm the hypothesis. Furthermore, the security firm is unsure of the destructive purpose of the attacks.
“Symantec has not found any evidence of a wiper or ransomware on computers infected with PowGoop. This suggests that either the simultaneous presence of PowGoop and Thanos in one attack was a coincidence or, if the two are linked, that PowGoop is not used exclusively to deliver Thanos,” Symantec says.
U.S. Says Russian Hackers Stole Data From Two Government Servers
23.10.20 BigBrothers Securityweek
The United States says Russian state-sponsored hacking group Energetic Bear has successfully compromised state, local, territorial, and tribal (SLTT) government networks and stole data from at least two servers.
Also referred to as Berserk Bear, Crouching Yeti, Dragonfly, Havex, Koala, and TeamSpy, the hacking group has been active for at least a decade, mainly focused on the energy sector in the United States and Europe.
In a Thursday alert, the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) revealed that the threat actor has been observed targeting the networks of various U.S. SLTT governments, as well as those of aviation organizations.
The attacks, conducted since at least September 2020, “targeted dozens of SLTT government and aviation networks, attempted intrusions at several SLTT organizations, successfully compromised network infrastructure, and as of October 1, 2020, exfiltrated data from at least two victim servers,” the alert reads.
Using stolen credentials for initial access and lateral movement, the hackers then locate high value assets and exfiltrate data of interest.
In at least one incident involving an SLTT network, Energetic Bear was able to access documents related to sensitive network configurations and passwords; standard operating procedures (SOP); IT instructions; vendors and purchasing information; and printing access badges.
According to the FBI and CISA, the threat actor does not appear to have intentionally disrupted the operations of organizations in aviation, education, elections, or government sectors.
“However, the actor may be seeking access to obtain future disruption options, to influence U.S. policies and actions, or to delegitimize SLTT government entities,” the alert reads.
The attacks might also be seen as a risk to elections information that is stored on SLTT government networks, but there’s no evidence that such data has been compromised, the FBI and CISA note. Monitoring of the activity will continue, the two agencies say.
In an emailed comment, John Hultquist, senior director of analysis at Mandiant Threat Intelligence, said that the threat actor behind this activity has been observed targeting election-related organizations before. However, it does not appear capable of altering votes.
“The actor, who we call TEMP.Isotope, has successfully breached systems in the US, EU, and elsewhere and have targeted energy providers, water infrastructure, and even airports. Though we have not seen them disrupt these systems, we believe they are compromising them to hold them under threat, as a contingency, and possibly a warning. On one occasion we have seen them target an election related organization,” Hultquist said.
“We have actively tracked targeting of state and local systems by this actor in the lead up to the election. The timing of these incidents, the targeting of organizations with ties to election administration, and the aggressive past behavior of this actor, all underscore the seriousness of this activity. However, we have no information which suggests these actors are capable or even willing to alter votes. Access to these systems could enable disruption or could be an end in itself, allowing the actor to seize on perceptions of election insecurity and undermine the democratic process,” he concludes.
As part of the observed attacks, Turkish IP addresses were used to connect to the compromised networks. The hackers were seen attempting brute force logins, SQL injections, as well as scanning for or exploiting known vulnerabilities, such as CVE-2019-19781 (Citrix ADC and Gateway), CVE-2020-0688 (Microsoft Exchange), CVE 2019-10149 (Exim SMTP), CVE-2018-13379 (Fortinet VPN), and CVE-2020-1472 (Windows Netlogon).
The FBI and CISA also list a series of steps organizations can take to mitigate the risks posed by the threat actor, including applying the available patches for the targeted applications and remote access services, isolating Internet-facing servers, implementing application controls, and blocking RDP connections, among others.
“Organizations must maintain a robust layered defense network with monitoring and detection to reduce an attack's risk by a known vulnerability and exploit. The recent attacks from nation-state cybersecurity operatives use known vulnerabilities to access an organization's networks and systems to steal data,” James McQuiggan, security awareness advocate at KnowBe4, commented. “Essentially, without patching or updating external facing systems or network devices, it's like leaving a car door wide open in the middle of a street. It makes it easy for criminals to jump in and steal it.”
EU Slaps Sanctions on 2 Russians Over Germany Cyberattack
23.10.20 BigBrothers Securityweek
The European Union on Thursday imposed sanctions on two Russian officials and part of Russia’s GRU military intelligence agency over a cyberattack against the German parliament in 2015.
EU headquarters said in a statement that travel bans and asset freezes have been imposed on the two men: Igor Kostyukov, head of the Main Directorate of the General Staff of the Russian Armed Forces, and Dmitry Badin, a military intelligence officer.
The EU said that Badin, who is also being sought by U.S. authorities, was part of a team that launched the attacks on the Bundestag.
“This cyber-attack targeted the parliament’s information system and affected its operation for several days. A significant amount of data was stolen and the email accounts of several MPs as well as of Chancellor Angela Merkel were affected,” it said.
The part of the intelligence agency targeted is known as “military unit 26165,” or more commonly by monikers like APT28, Fancy Bear, Pawn Storm and Strontium. The EU said it “is responsible for cyber-attacks with a significant effect constituting an external threat to the Union or its Member States.”
The same unit stands accused of trying to hack into the Wi-Fi network of the Organization for the Prohibition of Chemical Weapons, based in the Netherlands, in 2018.
The sanctions were imposed under a set of measures designed to “prevent, discourage, deter and respond to continuing and increasing malicious behavior in cyberspace.” EU citizens and organizations are banned from making funds available to those listed.
A total of eight people and four organizations now appear on the list.
Russian officials have repeatedly denied any involvement by Moscow in the hacking attack. They have similarly dismissed charges of Russian meddling in the 2016 U.S. presidential election and alleged cyberattacks on other Western nations and institutions.
Diplomatic ties between Germany and Russia are already tense, following the brazen killing of a Georgian man on the streets of Berlin last year. Prosecutors have suggested the hit was ordered either by Moscow or authorities in the Russian republic of Chechnya.
Feds: Iran Behind ‘Proud Boys’ Email Attacks on Democratic Voters
23.10.20 BigBrothers Threatpost
Messages that threaten people to ‘vote for Trump or else’ are part of foreign adversaries’ attempts to interfere with the Nov. 3 election, according to feds.
Federal officials claim that Iranian threat actors are behind two separate email campaigns that assailed Democratic voters this week with threats to “vote for Trump or else.” The campaigns claimed to be from violent extremist group Proud Boys.
Two specific email campaigns — one on Tuesday Oct. 20 and one on Wednesday, Oct. 21 — threatened Democratic voters in Alaska, Arizona and Florida that attackers accessed “all of your information.” They warned that there would be dire repercussions if voters didn’t cast their ballot for President Trump in the upcoming election, according to a Wednesday Proofpoint report. The research came on the heels of a report from WUFT in Florida that the FBI was investigating threatening emails sent to Democratic voters in the state.
The emails of both campaigns were sent from addresses linked to the far-right, male-only group Proud Boys — “Proud Boys <info[@]officialproudboys[.]com>” on Oct. 20 messages and “Proud Boys <info[@]proudboysusa[.]com>” on Oct. 21 messages. However, federal officials claimed in a press conference late Wednesday that Iran had obtained some voter registration information and was actually behind the attack.
“We have already seen Iran sending spoofed emails designed to intimidate voters, incite voters and damage President Trump,” Director of National Intelligence John Ratcliffe said in the briefing.
Iran also is distributing other content to mislead voters, including a video that implies that individuals can cast fraudulent ballots, even from overseas, Ratcliffe said. “These videos are not true,” he said, calling the actions of Iran to interfere with the election “desperate attempts by desperate adversaries.”
Of note, Reuters has reported that governments sources say, while U.S. officials suspect the Iranian government was involved, concrete evidence remains inconclusive. Meanwhile, others in the security research community told ZDNet that they could not confirm the attribution to Iran.
Proud Boys Content
The video in question is a Proud Boys-branded video demonstrating a Kali Linux user filling out voter registration and absentee ballots for Alaskan citizens, according to the report from Proofpoint, whose researchers obtained a copy.
“We only observed two intended recipients of these messages, both of whom appear to reside in Florida,” wrote researchers. The video appeared to be taken off the Internet not long after researchers viewed it, they said.
The emails observed by Proofpoint demonstrates that attackers did obtain sensitive personal information of voters and also shows those behind the threats changing up their tactics to avoid detection.
Messages in the Oct. 20 campaign — which Proofpoint separated into two sets — show that the threat actors have the home addresses of some of their victims. Researchers traced messages in set one to a PHPmailer script hosted on a likely compromised Saudi Arabian insurance company website, while set two was routed through the website of an Estonian textbook publisher, as previously reported by Vice.
The email attacks and attempts to spread misinformation are a departure from recent and more typical tactics used by threat actors to interfere in the U.S. elections, such as impersonation of the Democratic National Committee and various fraudulent voter registration portals, researchers said.
“Previous activity used political themes to entice users to click on links or open attachments but did not appear especially politically motivated,” they wrote in the report.
Indeed, this election season has seen a ramp up and variation in methods by state-sponsored actors to interfere with the 2020 U.S. Elections, which has been complicated by the COVID-19 pandemic.
This election will see many more voters choose to vote by mail, increasing the load of votes the postal system will handle. People also have opted to vote early to avoid long lines on election day, a scenario that could invite attacks on voting machines. These various scenarios provide a wider playing field for attackers to target in the run-up to the official election day on Nov. 3, experts observed.
EU Council sanctions two Russian military intelligence officers over 2015 Bundestag hack
23.10.20 BigBrothers Securityaffairs
The Council of the European Union announced sanctions imposed on Russian military intelligence officers for 2015 Bundestag hack.
The Council of the European Union announced sanctions imposed on Russian military intelligence officers, belonging to the 85th Main Centre for Special Services (GTsSS), for their role in the 2015 attack on the German Federal Parliament (Deutscher Bundestag).
The 85th Main Centre for Special Services (GTsSS) is the military unit of the Russian government also tracked as APT28 (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM).
The APT28 group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
“The Council today imposed restrictive measures on two individuals and one body that were responsible for or took part in the cyber-attack on the German Federal Parliament (Deutscher Bundestag) in April and May 2015.” reads the press release published by the Council. “This cyber-attack targeted the parliament’s information system and affected its ability to operate for several days. A significant amount of data was stolen and the email accounts of several members of parliament, including that of Chancellor Angela Merkel, were affected.”
Immediately after the attack the daily Der Spiegel speculated that the Russian Government was behind the attack.
Bundestag German politicians
The attackers used a sophisticated strain of malware to violated the Bundestag network and syphoned sensitive data. The experts that analyzed the malicious code employed in the hack found many similarities with a piece of malware used in a previous attack against a German Government network that took place in 2014.
“The cyber attack on the “Parlakom” network was discovered in early May. At the parliamentary IT network 20,000 Bundestag accounts are connected – including German Chancellor Angela Merkel and other government officials.” continues the Der Spiegel.
EU’s sanctions imposed on Russian military officers include travel bans and asset freezes, they also block EU organizations and individuals from transferring funds to sanctioned entities and individuals.
The Council’s sanctions target a total of 8 persons and 4 entities and bodies.
“Sanctions are one of the options available in the Union’s framework for a joint diplomatic response to malicious cyber activities (the so-called cyber diplomacy toolbox), and are intended to prevent, discourage, deter and respond to continuing and increasing malicious behaviour in cyberspace,” a press release published earlier reads. “The relevant legal acts, including the names of the individuals and the body concerned, have been published in the Official Journal.”
Two of the officers sanctioned by the Council of the European Union are Dmitry Sergeyevich Badin and Igor Olegovich Kostyukov are known members of the GTsSS.
The two officers were also indicted by US DoJ in October 2018, along with other five members of the Russian Main Intelligence Directorate (GRU), for hacking, wire fraud, identity theft, and money laundering.
Kostyukov was also reached by an executive order issued by President Barack Obama in 2016 to impose sanctions on a number of Russian military and intelligence officials in response to the alleged hacking campaigns against the 2016 US Presidential Election.
Kostyukov is the current chief of the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GU/GRU).
“In this capacity, Igor Kostyukov is responsible for cyber-attacks carried out by the GTsSS, including those with a significant effect constituting an external threat to the Union or its Member States,” states the Council. “In particular, military intelligence officers of the GTsSS took part in the cyber-attack against the German federal parliament (Deutscher Bundestag) which took place in April and May 2015 and the attempted cyber-attack aimed at hacking into the Wi-Fi network of the Organisation for the Prohibition of Chemical Weapons (OPCW) in the Netherlands in April 2018.”
In July 2020, for the first-ever time, the EU has imposed economical sanctions on Russia, China, and North Korea following cyber-attacks aimed at the EU and its member states.
The EU Council announced sanctions imposed on a Russia-linked military espionage unit, as well as companies operating for Chinese and North Korean threat actors that launched cyber-attacks against the EU and its member states.
The sanctions were imposed as part of a legal framework established on May 17, 2019, which allows the EU to impose targeted restrictive measures to deter and respond to cyber-attacks aimed at the EU or its member states.
US whistleblower Edward Snowden received permanent residency by Russian authorities
23.10.20 BigBrothers Securityaffairs
The popular US whistleblower Edward Snowden has been granted permanent residency in Russia, the announcement was made by his lawyer.
The former CIA employee and National Security Agency contractor Edward Snowden (37) has been granted permanent residency in Russia, his lawyer announced on Thursday.
In 2013, Edward Snowden shed the light on the mass surveillance program operated by the US government to spy on its citizens and allies.
The man expressed his desire to return to the United States where he is considered a criminal and a threat to homeland security due to his revelation. Snowden is wanted in the United States on espionage charges after he revealed details on the surveillance apparatus used by the National Security Agency (NSA) to collect telephone records of millions of US citizens.
According to his lawyer Anatoly Kucherena, Snowden’s residency permit was extended as the result of recent changes introduced to Russia’s immigration law. The residency permit and is now indefinite, as reported by AFP press.
“Kucherena said it was “natural” that Snowden wanted to return to the United States but will only do so when the case against him is closed.” reported AFP.
Edward snowden
The application was filed in April, but the decision of the Russian authorities was made public only this week due to a delay in the process caused by the ongoing COVID-19 pandemic.
It is not clear if Snowden plans to apply for Russian citizenship.
Earlier this year, US President Donald Trump announced that he was evaluating the possibility of pardoning Snowden but he did not provide further details on the case.
In 2015 the White House rejected a petition calling on then-president Barack Obama to pardon the popular US whistleblower.
In September 2019, the US DoJ filed a lawsuit against Edward Snowden to prevent the former CIA employee and National Security Agency contractor from receiving the payment for his book, Permanent Record.
According to the civil lawsuit, filed in the Eastern District of Virginia, Snowden violated non-disclosure agreements signed when he was an employee at the US intelligence agencies.
U.S. Voter Data Traded on Hacker Forums: Researchers
23.10.20 BigBrothers Securityweek
A database with information on virtually the entire US voting population has been circulated on hacker forums, opening up the potential for disinformation and scams that could impact the November 3 election, security researchers say.
A report released Wednesday by the security firm Trustwave said its researchers "discovered massive databases with detailed information about US voters and consumers offered for sale on several hacker forums."
The databases "include a shocking level of detail about citizens including their political affiliation," and the sellers claim to have 186 million records, which would mean nearly all US voters, the security researchers said in a blog post.
"The information found in the voter database can be used to conduct effective social engineering scams and spread disinformation to potentially impact the elections, particularly in swing states," said the post from Trustwave analysts Ziv Mador and Nikita Kazymirskyi.
The analysts said at least some of the data comes from public records, but that other information appears to have come from data leaks or breaches. The researchers said they also discovered other databases on the entire US consumer population and on residents of Britain, Canada, Ireland and South Africa.
Cybercriminals appear to be working "to monetize the upcoming elections" in the United States, the researchers added, by selling databases that include addresses, age, gender and political affiliation of American voters, and phone numbers in some cases.
The news comes a day after US authorities said Russian and Iran had obtained voter information and taken actions to influence public opinion including with "spoofed" emails designed to intimidate voters and create unrest.
Snowden Granted Permanent Residency in Russia
22.10.20 BigBrothers Securityweek
Fugitive US whistleblower Edward Snowden has been granted permanent residency in Russia, his lawyer said on Thursday.
Snowden, the former US intelligence contractor who revealed in 2013 that the US government was spying on its citizens, has been living in exile in Russia since the revelations.
The 37-year-old has said he would like to return to the United States.
His lawyer Anatoly Kucherena told AFP on Thursday that his residency permit was extended and is now indefinite, a situation made possible by recent changes to Russia's immigration law.
Kucherena said the application was filed in April but the process was delayed by the coronavirus pandemic.
Snowden is wanted in the United States on espionage charges after he leaked information showing that agents from the National Security Agency (NSA) were collecting telephone records of millions of US citizens.
When asked whether Snowden planned to apply for Russian citizenship, Kucherena said: "He will make the decision himself."
Kucherena said it was "natural" that Snowden wanted to return to the United States but will only do so when the case against him is closed.
Earlier this year, US President Donald Trump said he would "take a look" at pardoning Snowden but has not made further comment on the matter.
A 2015 petition calling on then president Barack Obama to pardon the whistleblower and privacy advocate was rejected by the White House.
Bug Parade: NSA Warns on Cresting China-Backed Cyberattacks
22.10.20 BigBrothers Threatpost
The Feds have published a Top 25 exploits list, rife with big names like BlueKeep, Zerologon and other notorious security vulnerabilities.
Chinese state-sponsored cyberattackers are actively compromising U.S. targets using a raft of known security vulnerabilities – with a Pulse VPN flaw claiming the dubious title of “most-favored bug” for these groups.
That’s according to the National Security Agency (NSA), which released a “top 25” list of the exploits that are used the most by China-linked advanced persistent threats (APT), which include the likes of Cactus Pete, TA413, Vicious Panda and Winniti.
The Feds warned in September that Chinese threat actors had successfully compromised several government and private sector entities in recent months; the NSA is now driving the point home about the need to patch amid this flurry of heightened activity.
“Many of these vulnerabilities can be used to gain initial access to victim networks by exploiting products that are directly accessible from the internet,” warned the NSA, in its Tuesday advisory. “Once a cyber-actor has established a presence on a network from one of these remote exploitation vulnerabilities, they can use other vulnerabilities to further exploit the network from the inside.”
APTs – Chinese and otherwise – have ramped up their cyberespionage efforts in the wake of the pandemic as well as in the leadup to the U.S. elections next month. But Chloé Messdaghi, vice president of strategy at Point3 Security, noted that these vulnerabilities contribute to an ongoing swell of attacks.
“We definitely saw an increase in this situation last year and it’s ongoing,” she said. “They’re trying to collect intellectual property data. Chinese attackers could be nation-state, could be a company or group of companies, or just a group of threat actors or an individual trying to get proprietary information to utilize and build competitive companies…in other words, to steal and use for their own gain.”
Pulse Secure, BlueKeep, Zerologon and More
Plenty of well-known and infamous bugs made the NSA’s Top 25 cut. For instance, a notorious Pulse Secure VPN bug (CVE-2019-11510) is the first flaw on the list.
It’s an arbitrary file-reading flaw that opens systems to exploitation from remote, unauthenticated attackers. In April of this year, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) warned that attackers are actively using the issue to steal passwords to infiltrate corporate networks. And in fact, this is the bug at the heart of the Travelex ransomware fiasco that hit in January.
Pulse Secure issued a patch in April 2019, but many companies impacted by the flaw still haven’t applied it, CISA warned.
Another biggie for foreign adversaries is a critical flaw in F5 BIG-IP 8 proxy/load balancer devices (CVE-2020-5902). This remote code-execution (RCE) bug exists in the Traffic Management User Interface (TMUI) of the device that’s used for configuration. It allows complete control of the host machine upon exploitation, enabling interception and redirection of web traffic, decryption of traffic destined for web servers, and serving as a hop-point into other areas of the network.
At the end of June, F5 issued urgent patches the bug, which has a CVSS severity score of 10 out of 10 “due to its lack of complexity, ease of attack vector, and high impacts to confidentiality, integrity and availability,” researchers said at the time. Thousands of devices were shown to be vulnerable in a Shodan search in July.
The NSA also flagged several vulnerabilities in Citrix as being Chinese faves, including CVE-2019-19781, which was revealed last holiday season. The bug exists in the Citrix Application Delivery Controller (ADC) and Gateway, a purpose-built networking appliance meant to improve the performance and security of applications delivered over the web. An exploit can lead to RCE without credentials.
When it was originally disclosed in December, the vulnerability did not have a patch, and Citrix had to scramble to push fixes out – but not before public proof-of-concept (PoC) exploit code emerged, along with active exploitations and mass scanning activity for the vulnerable Citrix products.
Other Citrix bugs in the list include CVE-2020-8193, CVE-2020-8195 and CVE-2020-8196.
Meanwhile, Microsoft bugs are well-represented, including the BlueKeep RCE bug in Remote Desktop Services (RDP), which is still under active attack a year after disclosure. The bug tracked as CVE-2019-0708 can be exploited by an unauthenticated attacker connecting to the target system using RDP, to send specially crafted requests and execute code. The issue with BlueKeep is that researchers believe it to be wormable, which could lead to a WannaCry-level disaster, they have said.
Another bug-with-a-name on the list is Zerologon, the privilege-escalation vulnerability that allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services. It was patched in August, but many organizations remain vulnerable, and the DHS recently issued a dire warning on the bug amid a tsunami of attacks.
The very first bug ever reported to Microsoft by the NSA, CVE-2020-0601, is also being favored by Chinese actors. This spoofing vulnerability, patched in January, exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates. An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear that the file was from a trusted, legitimate source.
Two proof-of-concept (PoC) exploits were publicly released just a week after Microsoft’s January Patch Tuesday security bulletin addressed the flaw.
Then there’s a high-profile Microsoft Exchange validation key RCE bug (CVE-2020-0688), which stems from the server failing to properly create unique keys at install time.
It was fixed as part of Microsoft’s February Patch Tuesday updates – and admins in March were warned that unpatched servers are being exploited in the wild by unnamed advanced persistent threat (APT) actors. But as of Sept. 30, at least 61 percent of Exchange 2010, 2013, 2016 and 2019 servers were still vulnerable to the flaw.
The Best of the Rest
The NSA’s Top 25 list covers plenty of ground, including a nearly ubiquitous RCE bug (CVE-2019-1040) that, when disclosed last year, affected all versions of Windows. It allows a man-in-the-middle attacker to bypass the NTLM Message Integrity Check protection.
CVE-2018-4939 in certain Adobe ColdFusion versions.
CVE-2020-2555 in the Oracle Coherence product in Oracle Fusion Middleware.
CVE-2019-3396 in the Widget Connector macro in Atlassian Confluence Server
CVE-2019-11580 in Atlassian Crowd or Crowd Data Center
CVE-2020-10189 in Zoho ManageEngine Desktop Central
CVE-2019-18935 in Progress Telerik UI for ASP.NET AJAX.
CVE-2019-0803 in Windows, a privilege-escalation issue in the Win32k component
CVE-2020-3118 in the Cisco Discovery Protocol implementation for Cisco IOS XR Software
CVE-2020-8515 in DrayTek Vigor devices
The advisory also covers three older bugs, in Exim mail transfer (CVE-2018-6789); Symantec Messaging Gateway (CVE-2017-6327); and the WLS Security component in Oracle WebLogic Server (CVE-2015-4852).
“We hear loud and clear that it can be hard to prioritize patching and mitigation efforts,” NSA Cybersecurity Director Anne Neuberger said in a media statement. “We hope that by highlighting the vulnerabilities that China is actively using to compromise systems, cybersecurity professionals will gain actionable information to prioritize efforts and secure their systems.”
US Officials Link Iran to Emails Meant to Intimidate Voters
22.10.20 BigBrothers Securityweek
Iran is responsible for emails sent to Democratic voters in multiple states aimed at intimidating the recipients into voting for President Donald Trump, U.S. officials said Wednesday night in calling out both Tehran and Russia for activities meant to interfere in the upcoming presidential election.
The activities attributed to Iran mark a significant escalation for a nation that some cybersecurity experts regard as a second-rate player in online espionage. Most public election interference discussion has centered on Russia, which hacked Democratic emails during the 2016 election, and China. The announcement at a rare, hastily called news conference just two weeks before the election underscored the concern within the U.S. government about efforts by foreign countries to spread false information meant to suppress voter turnout and undermine American confidence in the vote.
“These actions are desperate attempts by desperate adversaries,” said John Ratcliffe, the government’s top intelligence official, who, along with FBI Director Chris Wray, insisted the U.S. would impose costs on any foreign countries that interfere in the 2020 U.S. election and that the integrity of the election is still sound.
“You should be confident that your vote counts,” Wray said. “Early, unverified claims to the contrary should be viewed with a healthy dose of skepticism.”
Wray and Ratcliffe did not describe the emails linked to Iran, but officials familiar with the matter said the U.S. has linked Tehran to messages sent to Democratic voters in at least four battleground states that falsely purported to be from the neo-fascist group Proud Boys and that warned “we will come after you” if the recipients didn’t vote for Trump.
Ratcliffe said the spoofed emails were intended to hurt Trump, though he did not elaborate on how. An intelligence assessment released in August said: “Iran seeks to undermine U.S. democratic institutions, President Trump, and to divide the country in advance of the 2020 elections. Iran’s efforts along these lines probably will focus on online influence, such as spreading disinformation on social media and recirculating anti-U.S. content.”
Trump, speaking at a rally in North Carolina, made no reference to the press conference but repeated a familiar campaign assertion that Iran is opposed to his reelection. He promised that if he wins another term he will swiftly reach a new accord with Iran over its nuclear program.
“Iran doesn’t want to let me win. China doesn’t want to let me win,” Trump said. “The first call I’ll get after we win, the first call I’ll get will be from Iran saying let’s make a deal.”
Both Russia and Iran also obtained voter registration information, though such data is considered easily, publicly accessible. Tehran used the information to send out the spoofed emails, which were sent to voters in states including Pennsylvania and Florida.
Asked about the emails during an online forum Wednesday, Pennsylvania Secretary of State Kathy Boockvar said she lacked specific information. “I am aware that they were sent to voters in multiple swing states and we are working closely with the attorney general on these types of things and others,” she said.
While state-backed Russian hackers are known to have infiltrated U.S. election infrastructure in 2016, there is no evidence that Iran has ever done so.
The voter intimidation operation apparently used email addresses obtained from state voter registration lists, which include party affiliation and home addresses and can include email addresses and phone numbers. Those addresses were then used in an apparently widespread targeted spamming operation. The senders claimed they would know which candidate the recipient was voting for in the Nov. 3 election, for which early voting is ongoing.
Federal officials have long warned about the possibility of this type of operation, as such registration lists are not difficult to obtain.
“These emails are meant to intimidate and undermine American voters’ confidence in our elections,” Christopher Krebs, the top election security official at the Department of Homeland Security, tweeted Tuesday night after reports of the emails first surfaced.
NSA details top 25 flaws exploited by China-linked hackers
21.10.20 BigBrothers Securityaffairs
The US National Security Agency (NSA) has shared the list of top 25 vulnerabilities exploited by Chinese state-sponsored hacking groups in attacks in the wild.
The US National Security Agency (NSA) has published a report that includes details of the top 25 vulnerabilities that are currently being exploited by China-linked APT groups in attacks in the wild.
The knowledge of these vulnerabilities could allow IT and security staffs at organizations worldwide to protect their infrastructure against Chinese state-sponsored hacking campaigns.
The report includes well known vulnerabilites that have been already addressed by their vendors.
“This advisory provides Common Vulnerabilities and Exposures (CVEs) known to be recently leveraged, or scanned-for, by Chinese state-sponsored cyber actors to enable successful hacking operations against a multitude of victim networks. Most of the vulnerabilities listed below can be exploited to gain initial access to victim networks using products that are directly accessible from the Internet and act as gateways to internal networks.” reads the report. “The majority of the products are either for remote access (T1133)1 or for external web services (T1190), and should be prioritized for immediate patching.”
The report includes a description of the vulnerability and the recommended mitigations.
The exploits for many of these vulnerabilities are publicly available and are employed by multiple threat actors, including China-linked hackers, in attacks in the wild.
The majority of the vulnerabilities can be exploited to gain initial access to the target networks, they affect systems that are directly accessible from the Internet, such as firewalls and gateways.
NSA confirmed that it is aware that National Security Systems, Defense Industrial Base, and Department of Defense networks are consistently scanned, targeted, and exploited by Chinese state-sponsored cyber actors. The US agency recommends that critical system owners will address the above vulnerabilities to mitigate the risk of loss of sensitive information that could have a significant impact on U.S. policies, strategies, plans, and competitive advantage.
The
These include:
1) CVE-2019-11510 – In Pulse Secure VPNs, ® 7 an unauthenticated remote attacker can send a specially crafted URI to perform an arbitrary file reading vulnerability. This may lead to exposure of keys or passwords.
2) CVE-2020-5902– In F5 BIG-IP® 8 proxy / load balancer devices, the Traffic Management User Interface (TMUI) – also referred to as the Configuration utility – has a Remote Code Execution (RCE) vulnerability in undisclosed pages.
3) CVE-2019-19781 – An issue was discovered in Citrix® 9 Application Delivery Controller (ADC) and Gateway. They allow directory traversal, which can lead to remote code execution without credentials.
4+5+6) CVE-2020-8193, CVE-2020-8195, CVE-2020-8196– Improper access control and input validation, in Citrix® ADC and Citrix® Gateway and Citrix® SDWAN WAN-OP, allows unauthenticated access to certain URL endpoints and information disclosure to low-privileged users
7) CVE-2019-0708 (aka BlueKeep) – A remote code execution vulnerability exists within Remote Desktop Services®10 when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests
8) CVE-2020-15505 – A remote code execution vulnerability in the MobileIron®13 mobile device management (MDM) software that allows remote attackers to execute arbitrary code and take over remote company servers.
9) CVE-2020-1350 (aka SIGRed) – A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests.
10) CVE-2020-1472 (aka Netlogon) – An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller using the Netlogon Remote Protocol (MS-NRPC).
11) CVE-2019-1040 – A tampering vulnerability exists in Microsoft Windows when a man-in-the-middle attacker is able to successfully bypass the NTLM MIC (Message Integrity Check) protection.
12) CVE-2018-6789 – Sending a handcrafted message to an Exim mail transfer agent may cause a buffer overflow. This can be used to execute code remotely and take over email servers.
13) CVE-2020-0688 – A Microsoft Exchange® validation key remote code execution vulnerability exists when the software fails to properly handle objects in memory
14) CVE-2018-4939 – Certain Adobe ColdFusion versions have an exploitable Deserialization of Untrusted Data vulnerability. Successful exploitation could lead to arbitrary code execution.
15) CVE-2015-4852 – The WLS Security component in Oracle WebLogic 15 Server allows remote attackers to execute arbitrary commands via a crafted serialized Java object
16) CVE-2020-2555 – A vulnerability exists in the Oracle Coherence product of Oracle Fusion Middleware. This easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle Coherence systems.
17) CVE-2019-3396– The Widget Connector macro in Atlassian Confluence 17 Server allows remote attackers to achieve path traversal and remote code execution on a Confluence Server or Data Center instance via server-side template injection.
18) CVE-2019-11580 – Attackers who can send requests to an Atlassian Crowd or Crowd Data Center instance can exploit this vulnerability to install arbitrary plugins, which permits remote code execution.
19) CVE-2020-10189 – Zoho ManageEngine Desktop Central allows remote code execution because of deserialization of untrusted data.
20) CVE-2019-18935 – Progress Telerik UI for ASP.NET AJAX contains a .NET deserialization vulnerability. Exploitation can result in remote code execution.
21) CVE-2020-0601 (aka CurveBall) – A spoofing vulnerability exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates. An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear that the file was from a trusted, legitimate source.
22) CVE-2019-0803– An elevation of privilege vulnerability exists in Windows when the Win32k component fails to properly handle objects in memory.
23) CVE-2017-6327– The Symantec Messaging Gateway can encounter a remote code execution issue.
24) CVE-2020-3118 – A vulnerability in the Cisco Discovery Protocol implementation for Cisco IOS XR Software could allow an unauthenticated, adjacent attacker to execute arbitrary code or cause a reload an affected device.
25) CVE-2020-8515 – DrayTek Vigor devices allow remote code execution as root (without authentication) via shell metacharacters.
NSA Lists 25 Vulnerabilities Currently Targeted by Chinese State-Sponsored Hackers
21.10.20 BigBrothers Securityweek
The U.S. National Security Agency this week released an advisory containing information on 25 vulnerabilities that are being actively exploited or targeted by Chinese state-sponsored threat actors.
Most of these security bugs, the NSA says, can be used for initial access to networks, through exploiting Internet-facing assets. Post compromise, the adversaries can target additional vulnerabilities for exploitation.
The list shared by the NSA this week contains a total of 25 vulnerabilities, including CVE-2019-11510 (Pulse Secure VPN), CVE-2020-5902 (F5 BIG-IP), CVE-2019-0708 (BlueKeep), CVE-2020-1350 (SIGRed), CVE-2020-1472 (Zerologon), CVE-2020-0601 (CurveBall), CVE-2018-6789 (Exim mail server), CVE-2015-4852 (Oracle WebLogic), and CVE-2019-19781, CVE-2020-8193, CVE-2020-8195, and CVE-2020-8196 (Citrix ADC and Gateway).
The list also mentions CVE-2020-15505 (MobileIron MDM), CVE-2019-1040 (Windows), CVE-2020-0688 (Microsoft Exchange), CVE-2018-4939 (Adobe ColdFusion), CVE-2020-2555 (Oracle Coherence), CVE-2019-3396 (Atlassian Confluence), CVE-2019-11580 (Atlassian Crowd), CVE-2020-10189 (Zoho ManageEngine Desktop Central), CVE-2019-18935 (Progress Telerik UI for ASP.NET AJAX), CVE-2019-0803 (Windows), CVE-2017-6327 (Symantec Messaging Gateway), CVE-2020-3118 (Cisco IOS XR Software), and CVE-2020-8515 (DrayTek Vigor devices).
The NSA notes that it has observed Chinese threat actors scanning for or attempting to exploit these vulnerabilities against multiple victims. However, the agency also points out that the same adversaries might be targeting other vulnerabilities as well.
While the vulnerabilities mentioned by the NSA have been detailed publicly, not all of them were previously known as being targeted by hackers. This includes a Cisco Discovery Protocol flaw disclosed earlier this year.
For each of these bugs, the NSA also mentioned previously published guidance, some focused on different actors.
The agency notes that National Security Systems (NSS), U.S. Defense Industrial Base (DIB), and Department of Defense (DoD) systems are constantly being targeted by Chinese hackers, and encourages owners to ensure their systems are protected from exploitation.
The NSA underlines the threat that government-backed hackers from China pose to NSS, DIB, and DoD information networks in their attempts to compromise computer networks of interest to gather intellectual property and economic, military, and political information. Thus, patching of known vulnerabilities is highly important to keep systems protected.
“We hear loud and clear that it can be hard to prioritize patching and mitigation efforts. We hope that by highlighting the vulnerabilities that China is actively using to compromise systems, cyber-security professionals will gain actionable information to prioritize efforts and secure their systems,” NSA Cybersecurity Director Anne Neuberger said.
Satnam Narang, staff research engineer at Tenable, said in an emailed comment, “If you’re experiencing déjà vu from the National Security Agency (NSA) advisory listing the top 25 vulnerabilities being leveraged by foreign threat actors, your feeling is warranted. Many of the vulnerabilities in the advisory align with similar alerts that have been published by the Cybersecurity and Infrastructure Security Agency (CISA) over the last year. It’s unmistakably clear that unpatched vulnerabilities remain a valuable tool for cybercriminals and state-sponsored threat actors. With many of the vulnerabilities listed in the advisory residing in remote access tools or external web services, it is extremely critical for organizations to prioritize patching these vulnerabilities.”
“The breadth of products covered by this list of CVEs would indicate that the NSA has curated this list through the observation of many attacks undertaken by these actors,” Oliver Tavakoli, chief technology officer at Vectra, commented. “The exploits themselves also cover a broad range of steps in the cyberattack lifecycle indicating that many of the attacks in which these exploits were observed were already pretty deep into the attack progression – and many were likely found only after-the-fact through deep forensic efforts rather than having been identified while the attacks were active.”
Chinese Hackers Target Cisco Discovery Protocol Vulnerability
21.10.20 BigBrothers Securityweek
Chinese state-sponsored hackers are targeting a Cisco Discovery Protocol vulnerability that was disclosed earlier this year, the networking giant and the U.S. National Security Agency revealed on Tuesday.
An advisory published by the NSA on Tuesday lists 25 vulnerabilities that have been exploited or targeted by threat actors believed to be sponsored by Beijing. The list includes several vulnerabilities that were not known to have been targeted, including CVE-2020-3118, which impacts Cisco products.
CVE-2020-3118 is one of the five vulnerabilities in the Cisco Discovery Protocol (CDP) implementation of IOS XR software that were disclosed in February by IoT security firm Armis. The company reported at the time that the flaws, collectively tracked as CDPwn, impacted tens of millions of Cisco devices deployed in enterprise environments, including IP phones, switches, routers and cameras.
Just as the NSA issued its warning on the vulnerabilities targeted by Chinese hackers, Cisco updated its advisory to inform customers that it received reports earlier this month of attackers attempting to exploit CVE-2020-3118 in the wild. The company has advised customers to install the available IOS XR patches.
While it’s unclear which Chinese threat actor has targeted the flaw, the group tracked as APT41 is known to have exploited Cisco product vulnerabilities in its attacks.
The high-severity vulnerability can be exploited without authentication for arbitrary code execution with admin privileges and denial-of-service (DoS) attacks, but the attacker needs to have network access to the targeted device. Specifically, Cisco says, they need to be on the same broadcast domain as the impacted system.
When it disclosed the CDPwn vulnerabilities, Armis warned that they could allow an attacker to move from one network segment to another, intercept network traffic, and exfiltrate sensitive information.
Over the past few months, Cisco has also warned customers about attempts to exploit vulnerabilities affecting its firewalls and carrier-grade routers.
Sweden Bans Huawei, ZTE From 5G, Calls China Biggest Threat
21.10.20 BigBrothers Securityweek
Sweden is banning Chinese tech companies Huawei and ZTE from building new high-speed wireless networks after a top security official called China one of the country’s biggest threats.
The Swedish telecom regulator said Tuesday that four wireless carriers bidding for frequencies in an upcoming spectrum auction for the new 5G networks must not use equipment from Huawei or ZTE.
Wireless carriers that plan to use existing telecommunications infrastructure for 5G networks must also rip out any existing gear from Huawei or ZTE, the Swedish Post and Telecom Authority said.
The agency said the conditions were based on assessments by the Swedish military and security service. Huawei said it was “surprised and disappointed” by the rules.
Sweden is the latest country to prohibit Huawei from playing a role in building 5G networks and its decision is likely to add to tensions between the Chinese government and Western powers. U.S. officials have waged an intense lobbying campaign in Europe to persuade allies to shun the company, saying Huawei could be compelled by China’s communist rulers to facilitate cyberespionage. The company has consistently denied the accusations.
The ban means more opportunities for Huawei’s main rivals, Swedish company Ericsson and Finland’s Nokia.
New 5G networks, which are expected to usher in a wave of innovation such as smart factories and remote surgery, are considered critical infrastructure. Klas Friberg, the head of Sweden’s domestic security service, known as SAPO, said Tuesday that foreign powers have intensified their intelligence activity in recent years so 5G networks should be built in a secure way from the start.
“China is one of the biggest threats to Sweden,” Friberg said. “The Chinese state is conducting cyber espionage to promote its own economic development and develop its military capabilities. This is done through extensive intelligence gathering and theft of technology, research and development. This is what we must consider when building the 5G network of the future.”
Huawei denied it was a security risk.
“Huawei has never caused even the slightest shred of threat to Swedish cyber security and never will,” it said. “Excluding Huawei will not make Swedish 5G networks any more secure. Rather, competition and innovation will be severely hindered.
Russia Dismisses Hacking Allegations as 'Russophobia'
21.10.20 BigBrothers Securityweek
The Kremlin on Tuesday denied US claims that Russian military intelligence was behind cyber attacks targeting Ukraine's power grid, the 2017 French election and the 2018 Winter Olympic Games.
President Vladimir Putin's spokesman Dmitry Peskov described US charges against six Russian intelligence officers as "rampant Russophobia which, of course, have nothing to do with reality."
The US Justice Department, which announced the charges against the GRU agents Monday, also said Russian intelligence was behind the "NotPetya" malware attack that infected computers of businesses worldwide, causing nearly $1 billion in losses to three US companies alone.
At the same time, UK Foreign Secretary Dominic Raab accused Russian military intelligence services of carrying out internet reconnaissance missions against targets linked to the Tokyo Olympics, before they were postponed until 2021 by the coronavirus pandemic.
"The Russian Federation, Russian security services have never undertaken any hacker attacks, especially in connection with the Olympics," Peskov told reporters.
DOJ Charges 6 Sandworm APT Members in NotPetya Cyberattacks
20.10.20 BigBrothers Threatpost
DOJ charges six Russian nationals for their alleged part in the NotPetya, Ukraine power grid and Olympics cyberattacks.
The Department of Justice (DOJ) on Monday announced charges against six Russian nationals who are allegedly tied to the Sandworm APT. The threat group is believed to have launched several high-profile cyberattacks over the past few years – including the destructive NotPetya cyberattack that targeted hundreds of firms and hospitals worldwide in 2017.
According to the DOJ complaint, the six Russian nationals are tied to a division of the Russian military intelligence service and also affiliated with the APT Sandworm, also known as TeleBots. The DOJ said cyberattacks linked to the six defendants were “breathtaking” in their scope and “harmed ordinary people around the world,” said Scott Brady, U.S. attorney with the Western District of Pennsylvania, in a DOJ press conference on Monday.
The six defendants are: Yuriy Sergeyevich Andrienko (32); Sergey Vladimirovich Detistov (35); Pavel Valeryevich Frolov (28); Anatoliy Sergeyevich Kovalev (29); Artem Valeryevich Ochichenko (27) and Petr Nikolayevich Pliskin (32).
A breakdown of the charges against each defendant. Credit: DoJ
Each were charged in seven counts: conspiracy to conduct computer fraud and abuse, conspiracy to commit wire fraud, wire fraud, damaging protected computers, and aggravated identity theft, according to the DOJ.
According to the DOJ, the alleged malicious activity of the six dates back to November 2015, with the group developing malware known as BlackEnergy, Industroyer and KillDisk. The group used the malware in attacks against Ukraine’s electric power grid, Ministry of Finance, and State Treasury Service from Dec. 2015 to Dec. 2016, according to the DOJ.
In April and May 2017 the group allegedly launched spearphishing campaigns targeting French President Macron’s “La République En Marche!” (En Marche!) political party prior to the 2017 French elections.

The six defendants. Credit: DoJ
They were also allegedly behind the June 2017 destructive malware attacks that infected computers worldwide, using the NotPetya malware, resulting in the infection of 400 computers. The malware crippled many critical systems, including mission critical systems used by hospitals like the Pennsylvania-based Heritage Valley Health Systems.
In February 2018, the group allegedly sent spearphishing campaigns and malicious mobile applications targeting South Korean citizens and officials, Olympic athletes, partners, and visitors, and International Olympic Committee (IOC) officials; they then allegedly compromised computers supporting the 2018 PyeongChang Winter Olympic Games. This led to the Feb. 9, 2018, destructive malware attack against the opening ceremony, using malware known as Olympic Destroyer.
Finally, the group is alleged to have sent spearphishing emails to government organizations investigating the poisoning of a former GRU officer and his daughter in the United Kingdom in April 2018; and to have targeted the country of Georgia in 2018 with a spearphishing attack that led to the defacement of 15,000 websites.
“Groups like this use tactics, such as spearphishing, that are just as likely to reach targets on both computers, smartphones, or tablets,” Hank Schless, Senior Manager, Security Solutions at Lookout, told Threatpost. “They know that the likelihood of a successful phishing attack increases dramatically if the target receives it on a mobile device. They can phish login credentials from particular users that would allow them to get into the corporate infrastructure, then move laterally around the infrastructure for surveillance purposes or to exfiltrate valuable data.”
Threat researchers applauded the crackdown, saying that, while the arrest and extraction of the six Russian nationals seems unlikely, the indictments will limit their ability to use the Western financial system or travel to any country that may have an extradition agreement with the US.
“The charges filed against Sandworm represent not only the first criminal charges against Sandworm for its most destructive attacks but the first time that most of the charged threat actors have been publicly identified as members of the cybercriminal group,” Kacey Clark, Threat Researcher at Digital Shadows, told Threatpost. “They also represent Sandworm’s first global law enforcement reaction to their deployment of the NotPetya ransomware that has crippled networks worldwide.”
Google’s Threat Analysis Group (TAG), Cisco’s Talos Intelligence Group, Facebook and Twitter were credited in helping the DOJ with its investigation.
UK Says Russia Launched Cyberattacks Against 2020 Olympic, Paralympic Games
20.10.20 BigBrothers Securityweek
The United Kingdom on Monday exposed and condemned cyberattacks that the Russian military intelligence service GRU allegedly launched against organizations involved in the 2020 Olympic and Paralympic Games that were set to take place in Tokyo this summer, but were postponed due to the COVID-19 pandemic.
The GRU is known for launching numerous hacking campaigns for the benefit of Moscow, including high-profile attacks such as those involving the BlackEnergy, Industroyer, and NotPetya malware families.
On Monday, the United States announced charges against six officers of the GRU, which is also said to have orchestrated the cyberattacks on the PyeongChang Winter Olympics with the Olympic Destroyer malware. Russia has also been blamed for attacks on Georgian companies and government organizations.
On Monday, the UK officially accused the GRU of launching malicious cyber-operations targeting the Olympic and Paralympic Games, including the now-postponed 2020 Summer Olympics and the 2018 Winter Olympic and Paralympic Games in Pyeongchang, South Korea.
“The National Cyber Security Centre (NCSC) assesses with high confidence that these attacks were carried out by the GRU’s Main Centre for Specialist Technologies (GTsST), also known as Sandworm and VoodooBear,” the NCSC says.
GTsST, which is known by its field post number 74455, is also referred to as BlackEnergy Group, Telebots, Iron Viking, Quedagh, Electrum, and G0034.
The Russian hackers attempted to disguise themselves as North Korean and Chinese threat actors and targeted the opening ceremony of the 2018 Winter Games, as well as broadcasters, Olympic officials, a ski resort, and sponsors of the 2018 games, the UK says.
According to the NCSC, the 2018 attack was meant to sabotage the Winter Olympic and Paralympic Games through the use of malware meant to disable computers and networks and wipe data.
“The GRU’s actions against the Olympic and Paralympic Games are cynical and reckless. We condemn them in the strongest possible terms. The UK will continue to work with our allies to call out and counter future malicious cyber-attacks,” British Foreign Secretary Dominic Raab said.
Furthermore, the Russian military intelligence service is blamed for spear-phishing attacks targeting the UK’s Defence Science and Technology Laboratory (DSTL) in 2018.
“We condemn these attacks carried out by the GRU and fully support the criminal charges announced today by the US Department of Justice. These attacks have had very real consequences around the world – both to national economies and the everyday lives of people,” Paul Chichester, the NCSC’s Director of Operations, said.
French Court Tries Russian for Multi-Million-Euro Cyberfraud
20.10.20 BigBrothers Securityweek
A Russian goes on trial in Paris Monday accused of having defrauded nearly 200 victims across the world of 135 million euros using ransomware.
Prosecutors say Alexander Vinnik sent emails to his targets masquerading as invoices, whose attached document, when opened, activated malware that shut down the computer and encrypted its contents.
A message would appear on the hacked computer with instructions to pay a ransom in the online currency Bitcoin to regain control of the machine.
Among the 188 victims of the attacks -- which happened between 2016 and 2018 -- were local authorities, businesses and individuals across the world.
In France, many of the victims were local councils, law or insurance firms and small local businesses such as driving schools or pharmacies.
Vinnik, who has denied charges of extortion and money laundering, has refused to answer questions put by investigating magistrates.
He is also wanted in both the United States and his native Russia.
Investigators described the system he allegedly used as extremely elaborate, involving the mass mail-shots of the "contaminated" emails via a botnet: a network of already infected computers.
The way that the paid ransoms were subsequently laundered to make it difficult to trace was equally sophisticated, says the indictment.
Prosecutors identified 20 businesses in six cities across France among the victims and following the money trail through various bank accounts -- as much as $8 million -- identified one as belonging to Vinnik.
US investigators suspect the 41-year-old of being the mastermind of what they say has become one the main ways cybercriminals launder their illegal gains.
Vinnik was extradited to France in January from Greece, where he had been arrested on an American warrant in 2017.
He allegedly operated the BTC-e bitcoin exchange until his arrest at the northern Greek tourist resort of Halkidiki, which set off a three-way extradition tussle between the United States, France and Russia.
Greece eventually preferred the European warrant issued by France.
A US indictment accuses Vinnik of 21 charges ranging from identity theft and facilitating drug trafficking to money laundering.
He tried unsuccessfully to be extradited to Russia, where he is wanted on lesser fraud charges involving just 9,500 euros ($11,000).
U.S. Charges 6 Russian Intelligence Officers Over Destructive Cyberattacks
20.10.20 BigBrothers Thehackernews
The US government on Monday formally charged six Russian intelligence officers for carrying out destructive malware attacks with an aim to disrupt and destabilize other nations and cause monetary losses.
The individuals, who work for Unit 74455 of the Russian Main Intelligence Directorate (GRU), have been accused of perpetrating the "most disruptive and destructive series of computer attacks ever attributed to a single group," according to the Justice Department (DoJ).
All the six men — Yuriy Sergeyevich Andrienko, Sergey Vladimirovich Detistov, Pavel Valeryevich Frolov, Anatoliy Sergeyevich Kovalev, Artem Valeryevich Ochichenko, and Petr Nikolayevich Pliskin — have been charged with seven counts of conspiracy to conduct computer fraud and abuse, conspiracy to commit wire fraud, wire fraud, damaging protected computers, and aggravated identity theft.
"The object of the conspiracy was to deploy destructive malware and take other disruptive actions, for the strategic benefit of Russia, through unauthorized access ('hacking') of victim computers," the prosecutors said.
"In furtherance of the conspiracy, Andrienko, Detistov, Frolov, Kovalev, Ochichenko, Pliskin, and others known and unknown to the grand jury procured, maintained, and utilized servers, email accounts, malicious mobile applications, and related hacking infrastructure to engage in spear-phishing campaigns and other network intrusion methods against computers used by the victims."
Five years ago, Russian hackers belonging to Sandworm (aka APT28, Telebots, Voodoo Bear or Iron Viking) group attacked Ukraine's power grid, Ministry of Finance, and State Treasury Service using malware such as BlackEnergy, Industroyer, and KillDisk, before embarking on a spree of destructive cyberattacks — including unleashing NotPetya in 2017 and targeting the Pyeongchang Winter Olympics with phishing campaigns and "Olympic Destroyer" malware.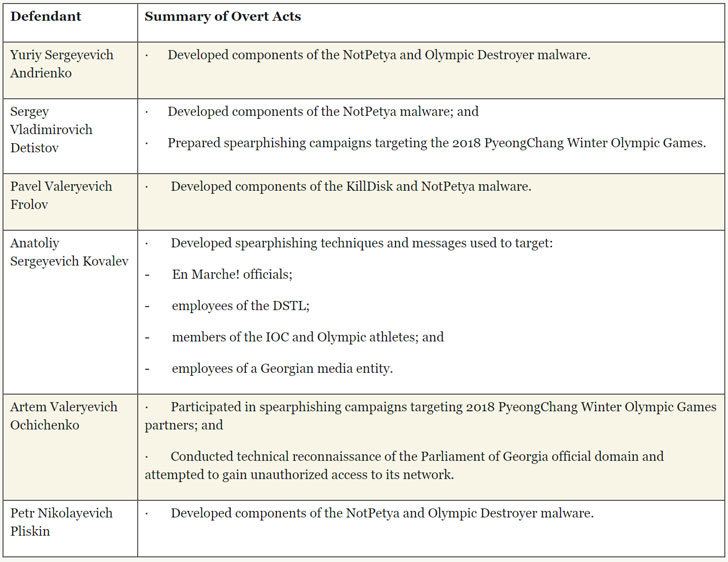
The six individuals have been accused of developing components for NotPetya, Olympic Destroyer, KillDisk malware, as well as preparing spear-phishing campaigns directed against the 2018 PyeongChang Winter Olympic Games, resulting in damage and disruption to computer networks across France, Georgia, the Netherlands, Republic of Korea, Ukraine, the UK, and the US.
"For example, the NotPetya malware impaired Heritage Valley's provision of critical medical services to citizens of the Western District of Pennsylvania through its two hospitals, 60 offices, and 18 community satellite facilities," the DoJ said. "The attack caused the unavailability of patient lists, patient history, physical examination files, and laboratory records."
"Heritage Valley lost access to its mission-critical computer systems (such as those relating to cardiology, nuclear medicine, radiology, and surgery) for approximately one week and administrative computer systems for almost one month, thereby causing a threat to public health and safety," it added.
The total damages brought about by NotPetya is pegged to more than $10 billion to date, crippling several multinational companies like Maersk, Merck, FedEx's TNT Express, Saint-Gobain, Mondelēz, and Reckitt Benckiser.
In a similar development, the UK government also formally accused the GRU of perpetrating cyber reconnaissance against officials and organizations at the 2020 Tokyo Olympic and Paralympic Games earlier this summer before they were postponed next year due to COVID-19.
This is not the first time GRU has come under the DoJ scanner. Two years back, the US government charged seven officers working for the military intelligence agency for conducting sophisticated computer intrusions against US entities as part of an influence and disinformation campaign designed to counter anti-doping efforts.
Biden Campaign Staffers Targeted in Cyberattack Leveraging Antivirus Lure, Dropbox Ploy
17.10.20 BigBrothers Threatpost
Google’s Threat Analysis Group sheds more light on targeted credential phishing and malware attacks on the staff of Joe Biden’s presidential campaign.
Hackers sent Joe Biden’s presidential campaign staffers malicious emails that impersonated anti-virus software company McAfee, and used a mix of legitimate services (such as Dropbox) to avoid detection. The emails were an attempt to steal staffers’ credentials and infect them with malware.
The unsuccessful advanced persistent threat group (APT) attacks on Biden’s campaign were first uncovered in June, along with cyberattacks targeting Donald Trump’s campaign. However, the details of the attacks themselves, and the tactics used, were scant until Google Threat Analysis Group’s (TAG) Friday analysis.
“In one example, attackers impersonated McAfee,” said researchers on Friday. “The targets would be prompted to install a legitimate version of McAfee anti-virus software from GitHub, while malware was simultaneously silently installed to the system.”17.10.20
The campaign was based on email based links that would ultimately download malware hosted on GitHub, researchers said. The malware was specifically a python-based implant using Dropbox for command and control (C2), which once downloaded would allow the attacker to upload and download files and execute arbitrary commands.
Every malicious piece of this attack was hosted on legitimate services – making it harder for defenders to rely on network signals for detection, researchers noted.

The McAfee lure used in the Biden cyberattack. Credit: Google
Google attributed the attack on Biden’s campaign staff to APT 31 (also known as Zirconium). According to reports, this threat actor is tied to the Chinese government.
Beyond staffers on the “Joe Biden for President” campaign, APT 31 has also been targeting “prominent individuals in the international affairs community, academics in international affairs from more than 15 universities,” according to previous Microsoft research.
The threat group’s TTPs include using web “beacons” that are tied to an attacker-controlled domain. The group then sends the URL of the domain to targets via email text (or attachment) and persuades them to click the link via social engineering.
“Although the domain itself may not have malicious content, [this] allows Zirconium [APT 31] to check if a user attempted to access the site,” said Microsoft. “For nation-state actors, this is a simple way to perform reconnaissance on targeted accounts to determine if the account is valid or the user is active.”
On the other side of the coin, the personal email accounts of staffers associated with the “Donald J. Trump for President” campaign have also been targeted by another threat group called APT 35 (also known as Phosphorus and Charming Kitten), which researchers said operates out of Iran. The Iran-linked hacking group has been known to use phishing as an attack vector, and in February was discovered targeting public figures in phishing attacks that stole victims’ email-account information.

Government backed attacker warnings sent in 2020. Credit: Google
However, researchers said the good news is that there’s increased attention on the threats posed by APTs in the context of the U.S. election. Google for its part said it removed 14 Google accounts that were linked to Ukrainian Parliament member Andrii Derkach shortly after the U.S. Treasury sanctioned Derkach for attempting to influence the U.S. elections.
“U.S government agencies have warned about different threat actors, and we’ve worked closely with those agencies and others in the tech industry to share leads and intelligence about what we’re seeing across the ecosystem,” said Google researchers.
With the 2020 U.S. Presidential Election just around the corner, cybersecurity concerns are under the spotlight – including worries about the integrity of voting machines, the expected expansion of mail-in voting due to COVID-19 and disinformation campaigns.
Iran-Linked 'Silent Librarian' Back at Phishing Universities
16.10.20 BigBrothers Securityweek
Iran-linked state-sponsored threat actor 'Silent Librarian' has launched another phishing campaign targeting universities around the world.
Also tracked as TA407 and COBALT DICKENS, the adversary was previously observed launching similar attacks for two years in a row.
In 2018, the group set up fake login pages for 76 universities. In 2019, Silent Librarian targeted more than 60 universities in Australia, Canada, Hong Kong, Switzerland, the United States, and the United Kingdom.
Observed in mid-September, the new round of attacks revealed that the threat actor is expanding its target list to include more countries. One of the victims is the Nanyang Technological University in Singapore, cybersecurity researcher Peter Kruse says.
Silent Librarian, Malwarebytes’ security researchers reveal, has sent spear-phishing emails to both staff and students at the targeted universities, and the threat actor was observed setting up new infrastructure to counter efforts to take down its domains.
“Considering that Iran is dealing with constant sanctions, it strives to keep up with world developments in various fields, including that of technology. As such, these attacks represent a national interest and are well funded,” Malwarebytes says.
Domain names used in the new attacks follow the pattern observed before, although they use a different top level domain name: the adversary switched from the “.me” TLD that was previously employed to “.tk” and “.cf” in recent attacks.
Considering Silent Librarian’s use of similar domains to target universities in the past, Malwarebytes researchers are confident the new domains were registered by the same group.
The threat actor uses Cloudflare for hostnames, which helps them hide the real hosting origin. Despite that, however, the researchers were able to identify some of the infrastructure, which was hosted in Iran.
While the use of infrastructure located in the attacker’s own country might seem surprising, the researchers explain that it only shows that the adversary can leverage yet another bulletproof hosting option, the result of a lack of cooperation between US and European law enforcement and local police in Iran.
“Clearly we only uncovered a small portion of this phishing operation. Although for the most part the sites are taken down quickly, the attacker has the advantage of being one step ahead and is going for many possible targets at once,” Malwarebytes concludes.
Iran acknowledged cyberattacks on two governmental departments
16.10.20 BigBrothers Securityaffairs
Iran ’s cybersecurity authority revealed that two governmental departments were hit by cyberattacks this week, state media reported.
State media reported on Thursday that Iran’s cybersecurity authority acknowledged cyberattacks on two unnamed governmental departments.
The state-owned IRAN daily newspaper revealed that the cyberattacks took place on Tuesday and Wednesday respectively.
Iranian authorities are investigating the attacks that were defined as important.
Other governmental departments temporarily took down their online operation as a precaution measure.
Iran’s cybersecurity authority did not attribute the attack to a specific threat actor
This isn’t the first time that Irans‘ authorities claim to have been targeted by cyber attacks. In December 2019, the Iran telecommunications minister announced for two times in a week to have foiled a cyber attack against its infrastructure.
At the time, the Iranian minister Mohammad Javad Azari-Jahromi confirmed that the attack was neutralized by the national cyber shield, it also added that the attack was launched by the China-linked APT27 group seeking for gathering intelligence its country.
In October 2019, Iran announced it was fearing retaliation from Western countries that are accusing it to carry out physical and cyber attacks against their infrastructure and countries in the Middle East.
At the time, Iran’s oil ministry said that the Government of Washington has launched a full-scale economic war” against the Islamic Republic in retaliation for the shooting down of a US drone as well as attacks on oil tankers that the US has blamed Iran.
Tensions between Tehran and Washington have escalated since 2018 when President Trump reimposed sanctions on Iran. The situation went out of control after a US drone strike killed top Iranian general Qasem Soleimani in January.
The order to kill Soleimani was issued by President Trump that said Soleimani was planning an “imminent” attack on US personnel in Baghdad.
In January, the U.S. Department of Homeland Security (DHS) has issued warnings about the possibility of cyber-attacks launched by Iran-linked threat actors. The attacks could be the response of Teheran after Maj. Gen. Qassim Suleimani was killed by a U.S. drone airstrike at the Baghdad airport in Iraq.
Cybercrime Money-launders Busted by European Police, FBI
16.10.20 BigBrothers Securityweek
European and American officials said Thursday that they have arrested 20 people in several countries for allegedly belonging to an international ring that laundered millions of euros stolen by cybercriminals through malware schemes.
The international police operation “2BaGoldMule” led by Portuguese investigators and the FBI included 14 more European countries, under the umbrella of Europol. Europol said that more than 40 homes were searched by agents in Spain, Italy, Bulgaria and Latvia in the operation.
Most of the house searches were carried out in Latvia, where six arrests were made. Another six arrests were made in Britain, four in Spain, and one each in Portugal, Poland, the U.S. and Australia, according to Europol.
The ring “QQAAZZ” allegedly laundered cybercriminals’ stolen funds, transferring them between hundreds of bank accounts held in banks across the world, officials said. The ring included citizens of Russia, Latvia, Georgia, Bulgaria, Romania, and Belgium, according to the U.S. Justice Department. The ring laundered money stolen from victims in the U.S. and European countries. The suspects face criminal investigations in the U.S., Portugal, Spain and the U.K.
“This operation has shown that through this cooperation we can collectively tackle the global nature of cybercrime. This is the only way forward,” said Carlos Cabreiro, director of Portugal’s National Unit for Fighting Cybercrime.
Iran Acknowledges Cyberattacks on Government Departments
16.10.20 BigBrothers Securityweek
Iran’s cybersecurity authority acknowledged cyberattacks on two governmental departments this week, state media reported Thursday.
The cyberattacks occurred Tuesday and Wednesday and were under investigation, the state-owned IRAN daily newspaper said.
While the report did not say which government departments were targeted, it called the attacks “important” and said some other departments temporarily took down their online services as a precaution against further attacks.
The brief report did not blame any group or country for the attacks.
Iran occasionally says it has thwarted cyberattacks on its infrastructure, although it has disconnected much of its infrastructure from the internet after the Stuxnet computer virus, widely believed to be a joint U.S.-Israeli creation, disrupted thousands of Iranian centrifuges in the country’s nuclear sites in the late 2000s.
In December, Iran said it halted a massive cyberattack on unspecified “electronic infrastructure” but provided no specifics on the purported attack.
Last year, Washington officials said that U.S. military cyber forces launched a strike against Iranian military computer systems, as President Donald Trump backed away from plans for a more conventional military strike in response to Iran’s downing of a U.S. surveillance drone in the strategic Persian Gulf.
Tensions have escalated between the U.S. and Iran since Trump in 2018 withdrew America from Iran’s nuclear deal with world powers and began a policy of “maximum pressure” on Tehran.
Tensions rose further after a U.S. airstrike killed a top Iranian general at Baghdad’s airport in January. Iran retaliated with a ballistic missile strike on Iraqi bases housing American troops, wounding dozens of U.S. troops.
US Cyber Command Urges Users to Patch New 'Ping of Death' Windows Flaw
15.10.20 BigBrothers Securityweek
The United States Cyber Command (USCYBERCOM) warns that users should apply the latest patches for Microsoft software to ensure they won’t fall victim to exploitation attempts.
The most important of these issues, US Cyber Command points out, is CVE-2020-16898, a critical bug in the Windows TCP/IP stack that can be triggered remotely to potentially achieve remote code execution on the victim machine.
While remote code execution might not be easy to achieve, Sophos has demonstrated how the vulnerability can be exploited to cause a Blue Screen of Death (BSoD), which is why the company has described it as a “Ping of Death” vulnerability.
Addressed on October 2020 Patch Tuesday, the flaw can be exploited through specially crafted ICMPv6 Router Advertisement packets sent to a vulnerable system, as these packets are not handled properly. Both Windows 10 and Windows Server are susceptible to exploitation.
“Update your Microsoft software now so your system isn't exploited: CVE-2020-16898 in particular should be patched or mitigated immediately, as vulnerable systems could be compromised remotely,” USCYBERCOM says.
McAfee, which calls the vulnerability “Bad Neighbor” due to the fact that it is located within an ICMPv6 Neighbor Discovery Protocol, explains that consumer Windows 10 systems will likely be impacted the most, as there are only hundreds of Windows Server 2019 machines with IPv6 addresses.
“We believe this vulnerability can be detected with a simple heuristic that parses all incoming ICMPv6 traffic, looking for packets with an ICMPv6 Type field of 134 – indicating Router Advertisement – and an ICMPv6 Option field of 25 – indicating Recursive DNS Server (RDNSS). If this RDNSS option also has a length field value that is even, the heuristic would drop or flag the associated packet, as it is likely part of a ‘Bad Neighbor’ exploit attempt,” the security firm says.
On Tuesday, Microsoft released patches to address not only this flaw, but also CVE-2020-16899, a second bug in the TCP/IP driver, which could be abused to cause denial of service.
Users are advised to apply the available patches as soon as possible. If that’s not a viable option, available workarounds include disabling IPv6, or blocking or dropping ICMPv6 Router Advertisements at the network perimeter.
“Windows Defender and Windows Firewall fail to block the proof-of-concept when enabled. It is unknown yet if this attack can succeed by tunneling the ICMPv6 traffic over IPv4 using technologies like 6to4 or Teredo. Our efforts to repeat the attack in this manner have not been successful to date,” McAfee says.
German authorities raid the offices of the FinFisher surveillance firm
15.10.20 BigBrothers Securityaffairs
Earlier this month, German authorities have raided the offices of FinFisher, the German surveillance software firm, accused of providing its software to oppressive regimes.
German authorities have raided the offices of FinFisher, the popular German surveillance firm as part of an investigation into the alleged sale of their software to oppressive regimes.
The news was first reported by the German news agency Tagesschau, which claims FinFisher had been using satellite companies to evade restrictions on the exportation of its surveillance tools.
The Munich Public Prosecutor’s Office ordered the police to raid 15 locations around Munich and at a connected company in Romania on October 6 and October 8.
The authorities started the investigation last year after the German blog Netzpolitik and some advocacy groups (Reporters Without Borders, Society for Freedom Rights, and the European Center for Constitutional and Human Rights), filed a complaint with Munich prosecutors in the summer of 2019.
The complaint claims that the popular surveillance firm FinFisher eluded the restrictions for the sale of the software to oppressive regimes that used it to spy on activists, political dissidents, privacy advocates, and citizens.
The company denied accusations and sued the German blog and requested the removal of the article on the case.
In September, Amnesty International uncovered a new surveillance campaign that targeted Egyptian civil society organizations with previously undisclosed versions of the infamous FinSpy surveillance spyware.
The new versions employed in this campaign allow its operators to spy on both Linux and macOS systems.
Finisher, aka FinFisher, is a multiplatform surveillance software used by government and law enforcement agencies for their investigations, but unfortunately, it made the headlines because it was also used by oppressive regimes to spy on dissidents, activists, and Journalists.
Since 2011 it was employed in attacks aimed at Human Rights Defenders (HRDs) in many countries, including Bahrain, Ethiopia, UAE, and more.
FinSpy can spy on most popular desktop and mobile operating systems, including Android, iOS, Windows, macOS, and Linux. It allows to use the users’ devices as a spying tool, it can control both webcam and microphone, to spy on communications and exfiltrate data stored on the infected systems.
The new versions of FinSpy spyware were used by a new unknown hacking group, Amnesty International speculates the involvement of a nation-state actor that employed them since September 2019.

FinFisher was officially designed for law enforcement investigations and intelligence agencies, but across the years, security experts have found on the devices of dissidents and journalists in countries many countries, including Ethiopia, Bahrain, Egypt, and Turkey where this surveillance software cannot be exported.
Police Raided German Spyware Company FinFisher Offices
15.10.20 BigBrothers Thehackernews
German investigating authorities have raided the offices of Munich-based company FinFisher that sells the infamous commercial surveillance spyware dubbed 'FinSpy,' reportedly in suspicion of illegally exporting the software to abroad without the required authorization.
Investigators from the German Customs Investigation Bureau (ZKA), ordered by the Munich Public Prosecutor's Office, searched a total of 15 properties in Munich, including business premises of FinFisher GmbH, two other business partners, as well as the private apartments of the managing directors, along with a partner company in Romania from October 6 to 8.
For those unaware, FinSpy is extremely powerful spying software that is being sold as a legal law enforcement tool to governments around the world but has also been found in use by oppressive and dubious regimes to spy on activists, political dissidents and journalists.
FinSpy malware can target both desktop and mobile operating systems, including Android, iOS, Windows, macOS, and Linux, and gives its operator spying capabilities, including secretly turning on victims' webcams and microphones, recording everything they types on the keyboard, intercepting calls, and exfiltration of sensitive data.
However, a new report from BR (Bayerischer Rundfunk) and (Norddeutscher Rundfunk) NDR suggests the spying firm illegally exported FinSpy to other countries without the correct export license issued by the federal government.

The Munich public prosecutor's office is now investigating "suspected violations of the Foreign Trade Act against managing directors and employees of FinFisher GmbH and at least two other companies," said a spokeswoman to BR and NDR.
The raids were part of a criminal complaint [pdf] filed by the GFF, Netzpolitik, Reporters Without Borders (ROG), and the European Center for Constitutional Rights and Human Rights (ECCHR) against the managing directors of FinFisher GmbH in July 2019.
In 2015, a permit requirement for exports of FinSpy to non-EU countries was introduced across Europe, but even after the federal government not issued a single export license, the surveillance software was found on a Turkish website in 2017 to spy on members of the opposition and was used in Egypt to target NGOs.
This strongly suggests that the surveillance company illegally exported the FinSpy software despite the existing permit requirements.
Unfortunately, the German media site has taken down the original report it posted last year after FinFisher sued the publication and won the case.
We will update the article as and when new information becomes available.
The British government aims at improving its offensive cyber capability
14.10.20 BigBrothers Securityaffairs
Britain’s most senior cyber general declared that the UK has implemented an advanced offensive cyberwar capability that could destroy its enemies.
Gen Sir Patrick Sanders, the UK’s strategic command chief, announced that that the UK has implemented an advanced offensive cyberwar capability that could potentially “degrade, disrupt and destroy” the critical infrastructure of its adversaries.
Boris Johnson tasked Gen Sanders to enhance both defensive and offensive cyber capabilities to ensure Britain is a “leading, full-spectrum cyber power.”
Sanders explained that its cyber army was supported by the GCHQ intelligence agency to deliver offensive cyber capabilities.
“[offensive cyber capability could] degrade, disrupt and even destroy critical capabilities and infrastructure of those who would do us harm, ranging from strategic to tactical targets” both in isolation or alongside traditional military force.” Sanders confirmed.
Experts don’t exclude that Boris Johnson will order the creation of National Cyber Force, a special military cyber division that will work with local intelligence agencies as the US Cyber Command does in the US.
The news is not surprising for people working in the cyber security sector, the British military claims to have had an offensive cyber capability for a decade.
Intelligence experts pointed out that the British government already conducted offensive hacking operations, including the one that targeted the ISIS in 2017.
“Cyber operations are in part run from a control room near Corsham, near Chippenha m, the historical site of the secret nuclear bunker to which the British government could relocate in an emergency.” reported The Guardian.
Clearly the UK military is under incessant cyber attacks from multiple threat actors, Sanders said, the UK military was targeted by an average of 60 attacks that require human intervention to be mitigated.
“The binary distinction between war and peace as we have approached it no longer applies,” Gen Sanders concluded. “Our adversaries are applying all means to gain advantage below the threshold of war and are accruing advantage insidiously and inevitably.”
Governments Use Pandemic to Crack Down on Online Dissent: Watchdog
14.10.20 BigBrothers Securityweek
Governments around the world are using the pandemic as a justification to expand surveillance and crack down on dissent online, resulting in a 10th consecutive annual decline in internet freedom, a human rights watchdog report said Wednesday.
The report by Washington-based Freedom House said authorities in dozens of countries have cited the Covid-19 outbreak "to justify expanded surveillance powers and the deployment of new technologies that were once seen as too intrusive."
This is leading to increasing censorship of dissent and the expansion of technological systems for social control, according to the report.
"The pandemic is accelerating society's reliance on digital technologies at a time when the internet is becoming less and less free," said Michael Abramowitz, president of the nonprofit group.
"Without adequate safeguards for privacy and the rule of law, these technologies can be easily repurposed for political repression."
Freedom House's index of internet based on a score assigned on a 100-point scale to 65 countries shows a drop in internet freedom for a 10th straight year.
The scale is based on 21 indicators pertaining to obstacles to access, limits on content and violations of user rights.
China was the worst-ranked country for the sixth consecutive year, according to the report.
It said Chinese authorities "combined low- and high-tech tools not only to manage the outbreak of the coronavirus, but also to deter internet users from sharing information from independent sources and challenging the official narrative."
The report said these trends are showing a growing trend toward Chinese-style "digital authoritarianism" globally and a "splintering" of the internet as each government imposes its own regulations.
Freedom House said that of the estimated 3.8 billion people using the internet, just 20 percent live in countries with a free internet, 32 percent in countries "partly free," while 35 percent were in places where online activities are not free. The remainder live in countries that weren't among the 65 assessed.
The report cited notable declines in countries where authorities have imposed internet shutdowns including Myanmar, Kyrgyzstan and India, and in Rwanda for its use of "sophisticated spyware to monitor and intimidate exiled dissidents."
The United States remained among those counties ranked free but saw its score decline in light of increased surveillance used by law enforcement against protest movements, executive orders on social media regulations, disinformation propagated by President Donald Trump and moves to ban Chinese-owned apps TikTok and WeChat.
The app bans were described as "an arbitrary and disproportionate response to the genuine risks" from those services.
G7 Raises Concerns About Rising Cyberattacks Amid Pandemic
14.10.20 BigBrothers Securityweek
Finance ministers from the G7 industrialized countries expressed "concern" on Tuesday over the rise in "malicious cyber-attacks" in the midst of the Covid-19 pandemic, including some involving cryptocurrencies.
These ransomware attacks demanding payments often to facilitate money laundering "have been growing in scale, sophistication, and frequency" over the past two years, causing "significant economic damage and (threatening) customer protection and data privacy," the ministers said.
"The G7 is concerned by the rising threat of ransomware attacks, particularly in light of malicious actors targeting critical sectors amid the COVID-19 pandemic," said the statement from the US Treasury issued on the G7's behalf following their virtual meeting.
"These attacks, which often involve payments in crypto-assets, jeopardize essential functions along with our collective security and prosperity."
The ministers and central bank governors repeated their call for caution in the deployment of cryptocurrencies, while recognizing digital currencies issued by central banks could play a role in providing financial services.
"The G7 continues to maintain that no global stablecoin project should begin operation until it adequately addresses relevant legal, regulatory and oversight requirements through appropriate design and by adhering to applicable standards," the statement said.
Finance ministers from the major euro area economies in September unveiled rules that could limit the development of digital currencies like Facebook's Libra project.
French Minister of Finance, Bruno Le Maire, long a vocal critic of the project, warned that, "We will not accept the deployment of Libra... under current conditions."
The G7 on Tuesday stressed that confidence in the payments system "is underpinned by credible and longstanding public sector commitments to transparency, the rule of law, and sound economic governance."
Norway Says Russia Behind Cyber Attack on Parliament
14.10.20 BigBrothers Securityweek
Norway's government on Tuesday said that it believes Russia was behind an August cyber attack targeting the email system of the country's parliament.
The attack was detected in August, when Norway announced hackers had attacked the parliament's email system, gaining access to some lawmakers' messages.
"Based on the information the government has, it is our view that Russia is responsible for these activities," foreign minister Ine Eriksen Soreide said in a statement.
The foreign ministry did not specify what information prompted its conclusions, but encouraged companies to follow guidelines on cyber security.
"This is a very serious incident, affecting our most important democratic institution," she added.
In its annual threat assessment published in February, Norway's PST domestic intelligence service warned of "computer network operations" which they said represented a "persistent and long-term threat to Norway".
In 2018, NATO member Norway arrested a Russian national suspected of gathering information on the parliament's internet network, but released him several weeks later due to lack of evidence.
The two countries, which share a common border in the Arctic, have generally enjoyed good relations but those have become strained since Russian annexation of the Crimean peninsula in 2014.
Five Eyes nations plus India and Japan call for encryption backdoor once again
13.10.20 BigBrothers Securityaffairs
Members of the Five Eyes intelligence alliance once again call for tech firms to engineer backdoors into end-to-end and device encryption.
States of the Five Eyes intelligence alliance (US, UK, Canada, Australia, and New Zealand), plus Japan and India, once again call for tech firms to implement backdoors into end-to-end and device encryption.
“We, the undersigned, support strong encryption, which plays a crucial role in protecting personal data, privacy, intellectual property, trade secrets and cyber security,” reads the joint “International Statement.” “Encryption is an existential anchor of trust in the digital world and we do not support counter-productive and dangerous approaches that would materially weaken or limit security systems.”
The statements reinforce the importance of the encryption in protecting data, privacy, and IP, but highlights the risks of abusing it for criminal and terrorist purposes. The Five Eyes argued that encryption could interfere with the ability of the same tech firms to identify and respond to violations of their terms of service or respond to the most serious illegal content and activity on their platform.
“Particular implementations of encryption technology … pose significant challenges to public safety, including to highly vulnerable members of our societies like sexually exploited children.” continues the statement.
Last year, Five Eyes states called on tech firms to implement a mechanism to bypass encryption in their solutions to support law enforcement requests for access to encrypted data on suspects.
On the other end, tech firms always refused to introduce backdoors in their systems because they violate terms of service.
The Statement ends with the call to protect public safety, even sacrificing privacy or cyber security.
“We reiterate that data protection, respect for privacy and the importance of encryption as technology changes and global internet standards are developed remain at the forefront of each state’s legal framework,” concluded the statement.
“However, we challenge the assertion that public safety cannot be protected without compromising privacy or cybersecurity. We strongly believe that approaches protecting each of these important values are possible and strive to work with industry to collaborate on mutually agreeable solutions.”
Zerologon Chained With Fortinet, MobileIron Vulnerabilities in U.S. Government Attacks
12.10.20 BigBrothers Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned that government networks have been targeted in attacks exploiting the Zerologon vulnerability in combination with flaws affecting Fortinet and MobileIron products.
“This recent malicious activity has often, but not exclusively, been directed at federal and state, local, tribal, and territorial (SLTT) government networks. Although it does not appear these targets are being selected because of their proximity to elections information, there may be some risk to elections information housed on government networks,” CISA said in an advisory written with contributions from the FBI.
It added, “CISA is aware of some instances where this activity resulted in unauthorized access to elections support systems; however, CISA has no evidence to date that integrity of elections data has been compromised.”
According to CISA, the attacks, which appear to be ongoing, have in many cases involved exploitation of CVE-2018-13379, a Fortinet FortiOS VPN vulnerability, and in some cases CVE-2020-15505, a recently detailed issue affecting MobileIron’s mobile device management (MDM) solutions.
These security holes were exploited by malicious actors to gain initial access to the targeted network, and then they used Zerologon to escalate privileges and compromise Active Directory identity services. CISA has described the attackers as “APT actors.”
While the attacks spotted by US agencies involved the Fortinet and MobileIron vulnerabilities, organizations have been warned that attackers could also leverage flaws in Citrix, Pulse Secure, Palo Alto Networks and F5 Networks products for the same purpose.
The Zerologon vulnerability, officially tracked as CVE-2020-1472, is a privilege escalation issue affecting Windows Server. It allows an attacker who has access to the targeted network to hack domain controllers without credentials.
Microsoft patched the flaw in August, but it appears many organizations have failed to install the patches and threat actors are increasingly exploiting it in their operations.
CISA issued its first warning about Zerologon being exploited in attacks in late September, shortly after it issued an emergency directive instructing federal agencies to immediately install the patches.
According to Microsoft, the Zerologon vulnerability has been exploited by both profit-driven cybercriminals and state-sponsored groups.
Hackers targeted the US Census Bureau network, DHS report warns
11.10.20 BigBrothers Securityaffairs
The US DHS’s Homeland Threat Assessment (HTA) report revealed that threat actors have targeted the US Census network during the last year.
The US Department of Homeland Security revealed that unknown threat actors have targeted the network of the US Census Bureau during the last year.
The attacks were reported in the first Homeland Threat Assessment (HTA) report released earlier this week.
The US Census Bureau is the largest US federal government statistical agency responsible dedicated to providing current facts and figures about America’s people, places, and economy.
Data collected by the agency is used by the federal government to allocate over $675 billion in federal funds to tribal, local, and state governments every year.
According to the DHS, threat actors will likely interfere with the upcoming 2020 US Presidential election, as well as to compromise the 2020 US Census.
DHS warns of nation-state actors linked to China, Russia, Iran, and North Korea that will attempt to compromise or disrupt critical 2020 elections infrastructure, as well as try to interfere with the final vote.
“Advanced persistent threat or other malicious cyber actors likely will target election-related infrastructure as the 2020 Presidential election approaches, focusing on voter PII, municipal or state networks, or state election officials directly.” reads the DHS HTA.
The report mentions multiple attempts of gaining access to systems on the US Census network.
“Unidentified cyber actors have engaged in suspicious communications with the U.S. Census public-facing network over at least the last year, including conducting vulnerability scans and attempting unauthorized access,” continues the report. “Cyber activity directed at the U.S. Census could include attempts to gain illicit access to census-gathered bulk data; to alter census registration data; to compromise the census infrastructure supply chain, or conducting denial-of-service attacks.”
In the past, the US Census has been hit by attacks, such as hacks and DDoS attacks during a 2018 test of census systems attributed to Russia-linked hackers and a 2015 hack attributed to the Anonymous collective.
The HTA report warns of an intensification of malicious activities conducted by both nation-states and cybercrime groups. The document warns of destructive attacks against U.S. critical infrastructure.
“Federal, state, local, tribal and territorial governments, as well as the private sector, will experience an array of cyber-enabled threats designed to access sensitive information, steal money, and force ransom payments,” continues the HTA report.
The report pointed out the nation-state actors have different motivations.
Russia, China, and Iran are more focused on cyber-espionage while North Korea is “confined to criminal generation of revenue.”
This HTA annual report provides information of threats targeting the US to government and private sector partners.
Let me suggest to read it.
Hacker who helped the ISIS will remain in US prison
10.10.20 BigBrothers Securityaffairs
The hacker who shared with the ISIS personal data of more than 1,300 U.S. government and military personnel will remain in a federal prison.
Ardit Ferizi, aka Th3Dir3ctorY, is the hacker that supported the ISIS organization by handing over data for 1,351 US government and military personnel.
Ferizi is the first man charged with cyber terrorism that was extradited to the US early 2016.
The man was charged with hacking crimes and providing support to a terrorist organization. The 24-year-old man was accused of supporting the ISIS terrorist organization, he was the subject of extradition from the Malaysian government, where he lived. The man of Kosovar origin was studying computer science in Malaysia.
He was arrested in Malaysia in September 2015 and transferred to the US to face trial.
Now Ardit Ferizi has been sentenced to 20 years in a U.S. prison. According to the US investigators, he provided the data to the popular IS militant Junaid Hussain, which disclosed it on the web. The collaboration between the IS hackers Hussain and Ferizi started in April 2015, according to the US authorities.
The details of the Ferizi’s case are described in s court filings [PDF].
Leaked data included names, e-mail addresses, passwords, locations and phone numbers of 1,351 U.S. military and other government personnel.

The ISIS-linked hacker obtained the data by hacking into the US web hosting company’s servers on June 13, 2015.
The US authorities suspected that Ferizi is a member of a Kosovan hacking team known as KHS, he used the pseudonym of “Th3Dir3ctorY”. The KHS breached a database of a US retailer was able to identify the records belonging to military and government personnel.
The Kosova Hacker’s Security (KHS) hit numerous organizations across the world, including Serbian Government websites, Israeli websites under the #OpIsrael campaign, The Interpol, IBM Research, Hotmail, US National Weather Service Website and numerous targets in Ukraine.

I wrote about Ferizi in October 2015, when the man was arrested by Malaysian authorities because for the first time ever the US Justice Department has charged a suspect for terrorism and hacking (cyber terrorism).
Ferizi was pleaded guilty on June 15, 2016, now is serving a 20-year sentence at a federal prison in Lewisburg, Pennsylvania, and is scheduled for release in 2032 if he gets credit for good behavior.
Ferizi asked a federal judge in Alexandria to release him from prison due to his health status.
“In a handwritten motion from prison, he said his asthma and obesity place him at greater risk of contracting COVID-19.” reads the post published by Associated Press. “He also said special restrictions at the prison require him to check in with staff every two hours, increasing his contact with guards and his risk of contracting the virus.”
Now prosecutors refused the request of hacker and opposed his release. The U.S. District Judge Leonie Brinkema rejected Ferizi’s request at a hearing Tuesday, the authorities believe that the man could teiterate his criminal activity.
NATO Chief calls for a new strategic to address new challenges
9.10.20 BigBrothers Securityaffairs
NATO Chief calls for a new strategic to mitigate the risks related to the threats to the rising technologies, new forms of terrorism, and the role of China
The rapid and continuous changes in our society needs to be properly addressed, NATO warns, NATO Chief call for a new strategic to address the global rise of new technologies, the evolution of terrorism and role of China in the global politics.
The new strategy has to replace the one developed a decade ago by the Atlantic alliance.
Among the advocates of change there is the French President Emmanuel Macron that also aims at the reopening dialogue with Russia and empower the efforts to fight the Islamist terrorism.
“My thought is that the existing Strategic Concept, which we agreed in 2010, has served NATO well. And it has actually served us well for many years. And we have also seen over the last year that the Strategic Concept we already have has not prevented us from adapting and changing NATO. Having said that, I think we all have to realise that since we agreed the Strategic Concept back in 2010, the world has fundamentally changed.” Secretary General Jens Stoltenberg said at the GLOBSEC security forum in Bratislava, Slovakia.
“The time has come to develop a new strategic concept for NATO, a new blueprint for how NATO can adapt and respond to a changing security environment.”
The overall process of change is part of a program that the NATO chief indicated as NATO 2030.
Stoltenberg recommends to maintain alliance’s technological edge, while developing common principles and standards for new technologies. The Alliance have to enhance cooperation between Allies in areas like joint research and development.
NATO Chief states that the alliance does not see any imminent threats and does’t regard China as an enemy or an adversary’. Anyway the role of China in the global economy have to be properly addressed because the state has is the biggest market in the world and they have the second largest defence budget.
Beijing is investing heavily in new technologies, including missiles, nuclear weapons, Artificial Intelligence. NATO is also concerned about the investments of China in disruptive technologies and the related implications for the Alliance.
“We see a much more assertive Russia than we did in 2010, with illegal annexation of Crimea destabilising eastern Ukraine, the military build-up. We see a new and more brutal form of terrorism, more instability to the south of our Alliance – Middle East, North Africa. And we see, of course, a fundamental shift in the global balance of power with the rise of China. And we see the development of new destructive technologies which affect our security.” Stoltenberg added.
Stoltenberg highlighted the concept to enhance the resilience of our society across the member states, because “our military cannot be strong if our societies are weak.”
“So our first line of defence must be strong societies able to prevent, endure, adapt and bounce back from whatever happens,” he explained with a clear reference to the ongoing pandemic and the related difficulties that member states are facing with.
“And any attempt to try to divide Europe from North America will not only weaken NATO, but it will also divide Europe. So we need to work together as Europe, as NATO. That’s the only way we can stand together and meet all the challenges we see in the future.” concludes NATO chief.
Hacker Who Helped Islamic State to Remain in US Prison
9.10.20 BigBrothers Securityweek
A computer hacker who gave the Islamic State group personal data of more than 1,300 U.S. government and military personnel will remain in a federal prison after a judge rejected his request for compassionate release.
Ardit Ferizi, 24, is serving a 20-year sentence. The native of Kosovo is the first person convicted in the U.S. of both computer hacking and terrorism charges. He is currently held at a federal prison in Lewisburg, Pennsylvania, and is scheduled for release in 2032 if he gets credit for good behavior.
Ferizi asked a federal judge in Alexandria to release him from prison. In a handwritten motion from prison, he said his asthma and obesity place him at greater risk of contracting COVID-19. He also said special restrictions at the prison require him to check in with staff every two hours, increasing his contact with guards and his risk of contracting the virus.
Prosecutors opposed his release, and U.S. District Judge Leonie Brinkema rejected Ferizi’s request at a hearing Tuesday, citing concerns that he might resume hacking if released, among other issues.
MontysThree: Industrial espionage with steganography and a Russian accent on both sides
8.10.20 BigBrothers Securelist
In summer 2020 we uncovered a previously unknown multi-module C++ toolset used in highly targeted industrial espionage attacks dating back to 2018. Initially the reason for our interest in this malware was its rarity, the obviously targeted nature of the campaign and the fact that there are no obvious similarities with already known campaigns at the level of code, infrastructure or TTPs. To date, we consider this toolset and the actor behind it to be new. The malware authors named the toolset “MT3”; following this abbreviation we have named the toolset “MontysThree”.

Following the MT3 abbreviation we named the toolset MontysThree
The malware includes a set of C++ modules used for persistence, obtaining data from a bitmap with steganography, decryption of configuration tasks (making screenshots, fingerprinting the target, getting the file, etc.) and their execution, and network communications with major legitimate public cloud services such as Google, Microsoft and Dropbox. MontysThree is configured to search for specific Microsoft Office and Adobe Acrobat documents stored in current documents directories and on removable media. The malware uses custom steganography and several encryption schemes: besides custom XOR-based encryption, the modules rely on 3DES and RSA algorithms for configuration decryption and communications.
MontysThree contains natural language artifacts of proper Russian language and configuration that seek directories that exist only on Cyrilic localised Windows versions. While most external public cloud communications use token-based authorisation, some samples contain email-based accounts for them, which pretend to be a Chinese lookalike. We consider these names to be false flags. Many more artifacts suggest that the malware was developed by a Russian-speaking actor and is targeting Cyrillic Windows versions.
How the malware spreads
The initial loader module is spread inside RAR self-extracting archives (SFX) with names related to employees’ phones list, technical documentation and medical test results. There are no lures, only PE files (masquerading a .pdf or .doc file), but such titles are now a typical trick used in spear-phishing – “corporate info update” or “medical analysis results”. One of the loaders (MD5 da49fea229dd2dedab2b909f24fb24ab) has the name “Список телефонов сотрудников 2019.doc” (“Employee phone list”, in Russian). Other loaders have the names “Tech task.pdf” and “invitro-106650152-1.pdf”. The latter is the name of a medical laboratory in Russia. All of them seem like typical spear-phishing tricks. The SFX script is as follows:
Path=%TEMP%\
SavePath
Setup=rundll32.exe "invitro-106650152-1.pdf",Open
Silent=1
Overwrite=1
Update=U
Delete=invitro-106650152-1.pdf
On execution, the SFX script calls the Open() function (we’ll return to this exported name) of the decompressed loader executable in the %TEMP% directory and deletes it. Judging by the filename, it most likely imitates medical analysis results, given that “Invitro” is a prominent medical laboratory in Russia. This initial PE32 is the first loader module.
How modules work and communicate
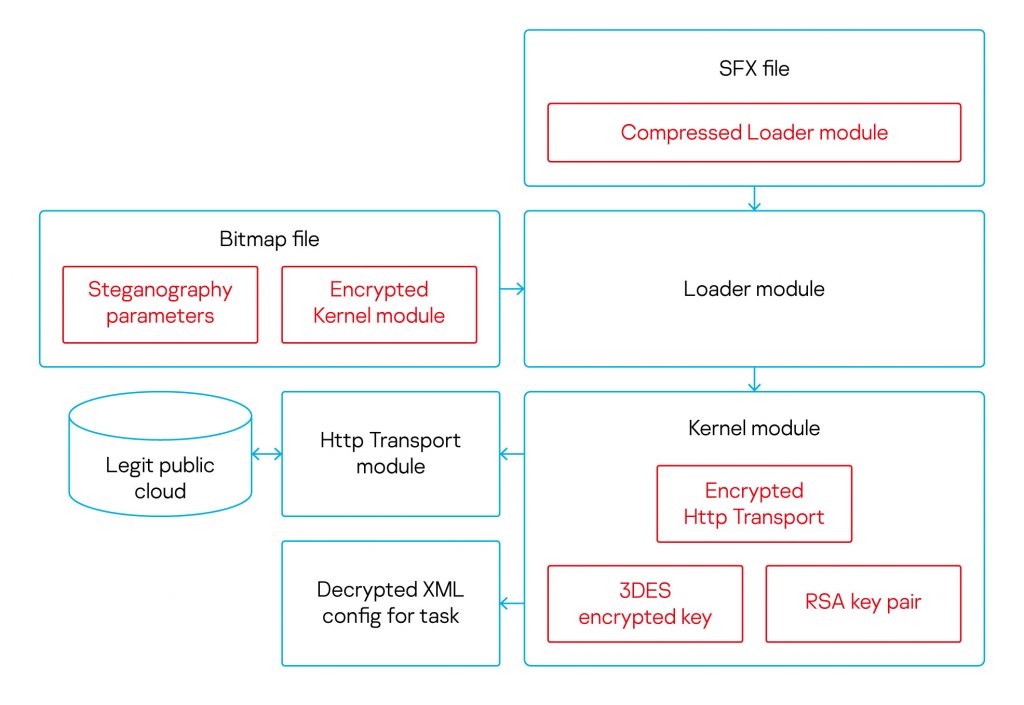
Execution flow of MontysThree’s modules
The diagram above shows the overall execution flow of the MontysThree modules. Four modules and their features are listed in the table below. The modules share common communication conventions. When dealing with shared data, such as the configuration and detailed execution log, the malware initializes the structure in thread local storage (TLS), which in its turn refers to heap structures. Interestingly, besides RAM, the execution log is stored on disk in a file, encrypted with a one-byte XOR.
The entry point DllEntryPoint() works just like a construtor, which allocates the structure with TlsAlloc() and saves it in a global variable. Modules must export a function named Open(), which takes no parameters (but could parse the command line) and returns a four-byte error code.
Module name Features
Loader This anti-detection module is in charge of custom steganography, kernel module decryption.
Kernel This kernel (main) module is in charge of decrypting the config XML, then parsing and executing the corresponding tasks in it.
HttpTransport Network module to communicate with Google, Microsoft, Dropbox legitimate public cloud services, as well as with WebDAV sources. The module is able to make requests through RDP and Citrix in a naive way using legitimate clients.
LinkUpdate Persistence module is a Windows Quick Launch .lnk modifier. With this naive persistence method users would run the Loader module by themselves every time along with the browsers from the Windows Quick Launch toolbar.
Now let’s take a look how the developers mixed strong modern cryptography standards with custom XOR-based ones.
Task Encryption in use
Steganography To decrypt the kernel module the initial loader uses a custom algorithm.
Logs encryption The malware logs exist in memory as well as in encrypted files on disk at the same time. In RAM the developers store the logs in plaintext, on disk they use one-byte XOR.
Config encryption Kernel module uses strong encryption algorithms. Configuration data is encrypted with 3DES and the key is encrypted using RSA. All the keys – RSA public/private as well as encrypted 3DES – are stored inside the module’s .data section.
Network module encryption Initially encrypted HttpTransport is made of four binary blobs stored in the kernel module. The kernel concatenates them and decrypts them with a custom XOR-based algorithm. A round key of four bytes length is used
Communications encryption The encryption algorithm is RSA using the same public and private keys stored inside the kernel module .data section.
| Module name | Features |
| Loader | This anti-detection module is in charge of custom steganography, kernel module decryption. |
| Kernel | This kernel (main) module is in charge of decrypting the config XML, then parsing and executing the corresponding tasks in it. |
| HttpTransport | Network module to communicate with Google, Microsoft, Dropbox legitimate public cloud services, as well as with WebDAV sources. The module is able to make requests through RDP and Citrix in a naive way using legitimate clients. |
| LinkUpdate | Persistence module is a Windows Quick Launch .lnk modifier. With this naive persistence method users would run the Loader module by themselves every time along with the browsers from the Windows Quick Launch toolbar. |
| Task | Encryption in use |
| Steganography | To decrypt the kernel module the initial loader uses a custom algorithm. |
| Logs encryption | The malware logs exist in memory as well as in encrypted files on disk at the same time. In RAM the developers store the logs in plaintext, on disk they use one-byte XOR. |
| Config encryption | Kernel module uses strong encryption algorithms. Configuration data is encrypted with 3DES and the key is encrypted using RSA. All the keys – RSA public/private as well as encrypted 3DES – are stored inside the module’s .data section. |
| Network module encryption | Initially encrypted HttpTransport is made of four binary blobs stored in the kernel module. The kernel concatenates them and decrypts them with a custom XOR-based algorithm. A round key of four bytes length is used |
| Communications encryption | The encryption algorithm is RSA using the same public and private keys stored inside the kernel module .data section. |
Loader module: Bitmap decryptor and next stage launcher
If the filename of the bitmap containing the steganography-encrypted data is provided to the loader as an argument, the loader decrypts the next stager from the pixel array. In the first iteration, it extracts the steganography parameter data. To do so, the algorithm takes the last bits of the bytes.
The IID, IParam and ISize parameters are kept in the first 384 bytes of the pixel array, meaning that only the last bit of every pixel array’s byte is needed. As a result, the module gathers 48 bytes of steganography configuration structure with the fields, determining the next decryption stages.
Field Offset Features
IID 0x00 Determines one or two decryption layers would apply to the following pixel array.
IParam 0x04 Determines which bits from pixel arrays bytes would form the next kernel module.
ISize 0x28 The decrypted kernel module’s resulting size.
After extracting the steganography parameters, the next stager is decrypted using a two-step algorithm. Firstly, the IParam algorithm chooses the bits from the pixel array’s bytes. Then, if IID equals 2, a custom dexoring operation using a four-byte round key is applied on the gathered bytes. The initial key for the first four-byte decryption has the hardcoded value 0x23041920. Then the formula for the round XOR key for the next bytes is:
key ^= 8 * (key ^ (key << 20))
We consider this steganography algorithm to be custom made and not taken from some open source third-party repository. Surprisingly, the decryption result is not injected into some process’s memory, but dropped to disk as a file named msgslang32.dll. The loader then simply uses the Windows API functions LoadLibraryW() and GetProcAddress() to run the next stager’s Open() function, as we previously saw with the loader module.
Kernel module: Config decryptor and tasks dispatcher
The kernel module contains three encryption keys used for configuration decryption and C2 communications. Public and private RSA keys are stored in the .data section as PUBLICKEYBLOB and PRIVATEKEYBLOB respectively. These are used to encrypt C2 communications and to decrypt the 3DES key as well. The third 3DES key is also stored in the .data section in its encrypted form; this key is used to decrypt an embedded .cab archive containing the XML config. To decompress the .cab archive the module uses Window’s standard system utility, “expand.exe”. We’ll see another common software usage in the HttpTransport module.
The XML configuration contains valuable data that helps us understand the campaign operator’s interest. It is structured using various “tasks” for the malware, such as fingerprinting the target using its OS version, process list and capturing screenshots; but also grabs the list of users’ recent documents with any of the extensions .doc, .docx, .xls, .xlsx, .rtf, .pdf, .odt, .psw, .pwd from the several recent documents directories in %USERPROFILE% and %APPDATA%, including %APPDATA%\Microsoft\Office\Последние файлы. This folder name translates to “Recent files” in Russian, suggesting that the malware is aimed at Cyrillic localised Windows versions.
Config holds the tasks scheduling (screenshot top), access tokens (here Dropbox, redacted), directories and extensions of interest. One directory exists only on Cyrillic Windows localized versions
We observed several Cyrillic text strings such as “Снимок рабочего стола” (desktop snapshot), “Системная информация” (system information), “Время выхода” (exit time).
Config tasks description starts with MT3D and contains proper short phrases in Russian
The decrypted config structure is as follows:
Field Size Content
Magic 4 bytes MT3D. All parsed files must have this as a prefix to be valid
Creation time 4 bytes Timestamp, task config creation time stored as Epoch time
Header size 4 bytes Header size has to be greater than 18. Observed value is e.g. 0x7E
XML size 4 bytes XML task description has to be greater than zero. Observed value is e.g. 0x662D
XML body XML size The task’s description and schedule in XML format
While the samples we looked at didn’t contain RTTI information, the execution logs allowed us to recover the C++ class names. After the kernel module parses the tasks from the configuration into memory, the main class that processes the instruction is CTask. CTask’s IoControl() method is in charge of handling the corresponding tasks and in turn runs the following methods:
CTask method Features
MainIoControl() Handler of “Main” task in XML. In case of a RESET command the file, serving as a “pipe”, will be deleted. Any other command here will be logged, but not executed
FileIoControl() Handler of “File” task with PUT, DEL, FIND, WATCH, WATCH_REMOVABLE, RUN and LOGS subcommands
SysInfoIoControl() Handler of “SysInfo” task with SCREENSHOT, INFO and TASKLIST subcommands
HttpIoControl() Handler of “Http” task with SENDRECV subcommand
GDriveIoControl() Handler of “GDrive” task with SENDRECV subcommand
DropboxIoControl() Handler of “Dropbox” task with SENDRECV subcommand
All methods used for external communications first decrypt the HttpTransport module and use it to transmit the corresponding data RSA-encrypted. The RSA keys in use are the same aforementioned keys used to decrypt the 3DES config key. In a separate Window procedure, the malware monitors if a USB device is plugged in, searching for files of interest.
HttpTransport module: network tasks
The HttpTransport module exists as four encrypted chunks of data inside the .text section of the kernel module. When the kernel needs to communicate, it decrypts this module and, as usual for MontysThree, runs the Open() function, passing command line arguments.
Depending on the arguments transmitted from the kernel module, the module may upload or download content using RDP, WebDAV, Citrix and HTTP protocols. Downloading data from Google and Dropbox public services using user tokens is implemented in HttpTransport as well. In case of HTTP GET/POST requests, the malware would receive a steganography bitmap picture using Windows API HTTP-related functions from a corresponding URL.
The aforementioned communication protocols themselves aren’t implemented inside the module. The malware authors make use of legitimate Windows programs like RDP, Citrix clients and Internet Explorer already installed on the target’s machine. For example, the module executes a task to send some data to a URL and receive the reply through an RDP connection as follows: edit the .rdp file to silently run Internet Explorer on the remote machine; paste the URL to the browser via the clipboard; wait and paste the contents to the opened web page via the clipboard as well; wait and receive the result through the clipboard again.
To copy data, the malware literally sends Ctrl+C, Ctrl+V and Ctrl+A. Perhaps it’s the first time we have seen such a method of “RDP communication”. The Citrix communication is done using a similar procedure: the malware doesn’t implement the protocol but rather searches for Windows Quick Launch .lnk for XenApp pnagent.exe, runs Internet Explorer remotely and communicates with it through the clipboard using special keyboard shortcuts.
Dropbox and Google data upload and download relies on another principle: its implementation uses the custom class CSimpleHttp to authenticate and send HTTP requests. For WebDAV communication, the developers simply use the “net use” Windows command.
LinkUpdate
This auxiliary module is in charge of achieving persistence on the host. It changes the .lnk files in the Windows Quick Launch panel to run the loader along with legitimate applications such as browsers when the user executes them using the modified link.
Who is behind this malware
As we mentioned at the beginning, to date we have observed no similarities or overlaps with known campaigns in terms of TTPs, infrastructure or malware code. So far, we attribute this activity and the use of MontysThree to a new actor. Some samples contain account details used for communicating with public cloud services, which pretend to be of Chinese origin. Taking into consideration all the aforementioned Cyrilic artefacts, we consider these account names to be false flags.
We assume that the actor behind MontysThree is both Russian-speaking and is going after Russian-speaking targets. Some of the filenames of the RAR SFX archives used for spreading the malware were written in Russian and referenced a Russian medical laboratory, used to entice the user to open the file. The XML configuration showcased data fields and Windows titles written in Russian, as well as specific folder paths that exist on Cyrilic localised versions of Windows. We also saw some grammatical errors in the malware’s English log message strings.
Let’s sum up
Typically we see targeted malware that is mostly going after governmental entities, diplomats and telecom operators, which are fruitful for state-sponsored actors. Industrial espionage cases like MontysThree are far more rare.
The overall campaign sophistication doesn’t compare to top notch APT actors in terms of spreading, persistence method. And some aspects of the malware – logging in RAM and files at the same time, keeping the encryption keys in the same file, running an invisible browser on the remote RDP host – seem immature and amateurish in terms of malware development.
On the other hand, the amount of code and therefore effort invested, in MontysThree is significant. The toolset demonstrates some tech-savvy decisions: Storing 3DES key under RSA encryption, custom steganography to avoid IDS and the use of legitimate cloud storage providers to hide the C2 traffic.
File Hashes
Loader
1B0EE014DD2D29476DF31BA078A3FF48
0976C442A06D2D8A34E9B6D38D45AE42
A2AA414B30934893864A961B71F91D98
Kernel
A221671ED8C3956E0B9AF2A5E04BDEE3
3A885062DAA36AE3227F16718A5B2BDB
3AFA43E1BC578460BE002EB58FA7C2DE
HttpTransport
017539B3D744F7B6C62C94CE4BCA444F
501E91BA1CE1532D9790FCD1229CBBDA
D6FB78D16DFE73E6DD416483A32E1D72
Domains and IPs
autosport-club.tekcities[.]com
dl10-web-stock[.]ru
dl16-web-eticket[.]ru
dl166-web-eticket[.]ru
dl55-web-yachtbooking[.]xyz
Data from Airlink International UAE leaked on multiple dark web forums
8.10.20 BigBrothers Securityaffairs
Cybersecurity researchers from Cyble have spotted a threat actor sharing leaked data of Airlink International UAE for free on two different platforms.
Cybersecurity researchers from Cyble have found a threat actor sharing leaked data of Airlink International UAE for free on two platforms on the dark web.
The availability of the data on the dark web could pose organizations to serious risk, threat actors could use this data to carry out multiple malicious attacks.
Cyble discovered the data leak as part of its daily monitoring.
Airlink International U.A.E. is a leading company for any travel and logistics requirements. It has more than than 200 employees with around $250 million in revenue.
The data leak is the result of a misconfigured server containing 60 directories with approximately 5,000 files each.
The data leak was first reported on May 30, 2020, the data have been posted online by the collective KelvinSecTeam.
“The files present accommodation reservations, airline tickets and other logistics services that the company provides on a global scale. In a quick inspection by sampling, it was possible to observe customers of different nationalities and services provided in Africa, Asia and Europe.” reported the media.
According to Cyble, now, another threat actor is spreading the same data on multiple dark web forums in an attempt to gain fame.
Leaked data includes 14 folders and 53,555 files divided into the following categories:
Passport scans
Flight bookings
Hotel bookings
Email communications between Airlink International Group employees and customers
Insurance policy for international travel
Cyble provides recommends the following recommendation to the organizations:
Configure server to prevent unauthorized access, directory listing
Review old backup and unreferenced files for sensitive information
Test file permissions
Enumeration of infrastructure and application administrator interfaces
Consider running scans and doing audits periodically to help detect future misconfigurations or missing patches
U.S. Seizes Domain Names Used by Iran for Disinformation
8.10.20 BigBrothers Securityweek
U.S. Seizes Domain Names Used by Iran for Disinformation
The United States this week announced that it seized a total of 92 domain names that an Iran-linked adversary was leveraging in a global disinformation campaign.
Although four of the domains pretended to be genuine news outlets, they were controlled by Iran’s Islamic Revolutionary Guard Corps (IRGC) to spread Iranian propaganda targeting the United States, while the remaining websites were spreading propaganda to other countries.
The manner in which these domains were being used was in violation of sanctions the U.S. imposed on both the government of Iran and the IRGC.
As of April 2019, the United States has designated the IRGC as a foreign terrorist organization. The organization was found to have provided material support to terrorist groups such as Hizballah, Hamas, and the Taliban.
On October 7, pursuant to a seizure warrant, the United States seized 92 domain names that were being operated in violation of federal law. Four of these were seized pursuant to the Foreign Agents Registration Act (FARA), which requires the submission of periodic registration statements about activities and income.
“The four domains purported to be independent news outlets, but were actually operated by or on behalf of the IRGC to target the United States with pro-Iranian propaganda in an attempt to influence the American people to change United States foreign and domestic policy toward Iran and the Middle East,” the U.S. Department of Justice says.
These domains, the DoJ explains, targeted an audience in the U.S. without proper registration pursuant to FARA and also failed to inform the audience that the IRGC and the government of Iran were in control of the published content.
Also masquerading as news outlets, the remaining 88 domains targeted audiences in Western Europe, the Middle East, and South East Asia, spreading pro-Iranian disinformation.
All of the domains were found to be owned and operated by companies in the U.S., but the government of Iran and the IRGC used them without a license from the Office of Foreign Assets Control (OFAC). Pursuant to the International Emergency Economic Powers Act (IEEPA), a license is required to provision services to the government of Iran.
The activity associated with these domains was initially reported on in 2018, but the Department of Justice has now linked it to the IRGC, John Hultquist, Senior Director of Analysis, Mandiant Threat Intelligence, said in an emailed comment.
“The DOJ has just linked Iranian information operations that FireEye publicly reported in 2018 to the Islamic Revolutionary Guard Corps, Iran’s aggressive security service. The IRGC is very comfortable with asymmetric tools and they have increasingly adopted cyber capabilities as a means to disrupt and manipulate their enemies abroad. Iran has become a prolific actor in the information operations space and similar to their cyberattack capability, they have evolved over a series of brash operations,” Hultquist said.
Russia-Linked Hackers Targeting Russian Industrial Organizations
8.10.20 BigBrothers Securityweek
A previously unknown threat group whose members speak Russian has been launching attacks against Russian industrial organizations in a highly targeted espionage campaign, Kaspersky reported on Thursday.
According to Kaspersky, the group calls its toolset MT3 and based on this the cybersecurity company has named the threat actor MontysThree. The campaign will be detailed on Thursday at Kaspersky’s second SAS@Home event.
MontysThree has been active since at least 2018, but Kaspersky has not found any links between this group and other known advanced persistent threats (APTs).MontysThree
Denis Legezo, senior security researcher with Kaspersky’s Global Research and Analysis Team, told SecurityWeek that the hackers have only been seen targeting the IT networks of industrial entities and there is no indication that they have also targeted industrial control systems (ICS).
MontysThree, Kaspersky says, relies on a piece of malware that has four modules. One of them has loader functionality and is responsible for delivering the main payload. The loader is hidden inside a self-extracting RAR archive that references contact lists, medical test results or technical documentation in order to convince the employees of the targeted organization to download the file.

The loader uses steganography to evade detection, with the main payload being hidden inside a bitmap image file. The main payload uses encryption to evade detection and protect C&C communications.
The malware allows the attackers to steal Microsoft Office and PDF documents, capture screenshots, and collect information on the compromised machine in order to help the hackers determine if it might be of interest to them. The stolen information is hosted on public cloud services from Google, Microsoft and Dropbox, making it more difficult to detect attacks, Kaspersky said.
Based on the lures used by the hackers, the language artifacts found in the malware, and the fact that it only targets Windows devices configured to use Cyrillic script, Kaspersky believes the members of the MontysThree group are Russian speakers and they target Russian entities.
“Some samples contain account details used for communicating with public cloud services, which pretend to be of Chinese origin. Taking into consideration all the aforementioned Cyrilic artefacts, we consider these account names to be false flags,” Kaspersky said in its report. “We also saw some grammatical errors in the malware’s English log message strings.”
The cybersecurity firm says MontysThree is not as sophisticated as other groups it has seen, but it’s still not a threat that should be ignored.
“Some aspects of the malware – logging in RAM and files at the same time, keeping the encryption keys in the same file, running an invisible browser on the remote RDP host – seem immature and amateurish in terms of malware development,“ Kaspersky said. “On the other hand, the amount of code and therefore effort invested, in MontysThree is significant. The toolset demonstrates some tech-savvy decisions: Storing 3DES key under RSA encryption, custom steganography to avoid IDS and the use of legitimate cloud storage providers to hide the C2 traffic.”
NATO Chief Calls for New Strategy on Cyber, China
8.10.20 BigBrothers Securityweek
NATO needs a new strategic concept adjusted to the global rise of new technologies, terrorism and China to replace a plan developed a decade ago, the head of the alliance said on Wednesday.
French President Emmanuel Macron famously branded the alliance "brain dead" last year, demanding a new strategy that would, among other things, reopen dialogue with Russia -- stifled after it annexed part of Ukraine -- and refocus on the fight against Islamist terrorism.
As part of a "reflection process" triggered by the French leader's controversial remarks, NATO will revise its strategic concept -- its overarching statement of the threats it faces and how it might respond, Secretary General Jens Stoltenberg told a conference in Slovakia's capital Bratislava.
"The time has come to develop a new strategic concept for NATO, as the world has fundamentally changed," Stoltenberg said at the GLOBSEC security forum.
He dubbed the initiative "NATO 2030".
Stoltenberg urged the Western defensive alliance of 30 states to "develop common principles and standards for new technologies" to meet security challenges related to "disruptive technologies" using big data and cyber telecommunications.
The NATO chief also highlighted the need to address the "fundamental shift in the global balance of power with the rise of China" as well as the rise of a "more brutal form of terrorism, more instability to the south of our Alliance, in the Middle East and North Africa."
At a summit in London last year, NATO leaders for the first time formally recognised the "challenges" posed by China.
While the transatlantic alliance remains focused on its European and North American core, Stoltenberg has argued it is impossible to ignore Beijing's booming military investment and geopolitical assertiveness.
Stoltenberg also underscored the importance of maintaining resilient societies across the alliance, insisting that "our military cannot be strong if our societies are weak.
"So our first line of defence must be strong societies able to prevent, endure, adapt and bounce back from whatever happens," he added in an apparent nod to the unprecedented impact of the coronavirus pandemic on NATO members.
Since the Ukraine conflict erupted in 2014, NATO has sought ways to boost its members' resilience to the kind of hybrid warfare -- combining irregular forces, cyber tactics and disinformation -- seen there.
IRS COVID-19 Relief Payment Deadlines Anchor Convincing Phish
8.10.20 BigBrothers Threatpost
The upcoming deadlines for applying for coronavirus relief are the lure for a phish that gets around email security gateways by using a legitimate SharePoint page for data-harvesting.
A credential-phishing email campaign is making the rounds, using the lure of coronavirus tax relief to scam people into giving up their personal information.
The data-harvesting cybercriminals are looking to take advantage of the Internal Revenue Service (IRS) deadlines that are approaching for consumers who haven’t received an Economic Impact Payment. While most Americans got their one-time $1,200 payment in the spring, those who don’t usually file tax returns (such as those on Social Security) weren’t automatically included in that payout. These individuals have until Nov. 21 to register for their assistance check. Meanwhile, taxpayers who requested an extension of time to file their 2019 tax return have a deadline of October 15.
The emails purport to contain an important document about COVID-19 relief funds from the IRS. Clicking the link in the email leads readers to a SharePoint form that they were told to complete before accessing the document, according to Chetan Anand, co-founder and architect at Armorblox.
Threatpost Webinar Promo Retail Security
Click to Register!
The SharePoint form asks for email credentials, Social Security numbers, driver license numbers and tax ID numbers.
The sneaky use of the SharePoint form as an interim step helped the emails get past email gateways, Anand noted, in a blog posted Wednesday.
“This email got past existing Office 365 email security controls because it didn’t follow the tenets of more traditional phishing attacks,” he wrote. “When victims clicked the link in the email, they were led to a SharePoint form that asked for email credentials along with a host of other personal information…Since the phishing link pointed to a legitimate SharePoint page, it got past any email security filters designed to block known bad domains. The familiar Microsoft branding on the page might also put victims’ minds at ease as they subconsciously buy into the legitimacy of the email. It’s worth noting the irony-laden footer asking people not to share passwords or give away personal information.”
The phishing page was in fact hosted on a compromised user’s SharePoint account, lending legitimacy. Closer inspection revealed that the SharePoint account belonged to an employee of the Reproductive Medicine Associates of Connecticut (RMACT).
The campaign, which hit multiple email inboxes in the Armorblox telemetry, also used better-than-average social engineering, Anand noted, with the email language and context including multiple emotional triggers.
For instance, the email subject line read “IRS Covid Relief Fund Update,” and the sender name was “IRS Covid Relief Funds.”
“Both [are] very specific and related to topics that elicit quick actions from victims,” the researcher wrote, noting that the use of the IRS is an “authority” trigger. “Discerning readers will stop short of sharing the wealth of personal information asked in this SharePoint form. However, given the context of the communication – IRS sharing COVID relief fund details – victims might rationalize the extent of personal information asked in the form.”
The email language also included urgency triggers by talking about “important updates,” and ends with a simple but effective request: asking victims to click the link if they want to view the document – this, along with the aforementioned boilerplate confidentiality footer, makes it seem more legitimate, according to Anand.
That’s not to say that the phish is perfect – as always, some red flags pop up.
“A closer look reveals some grammatical irregularities in the email, as well as a non-capitalized ‘Irs’ in the email sender name, both of which can be red flags to anyone who stops and reads the email closely,” he noted.
To avoid falling victim, users should remain vigilant, and be wary of entering any personal information – including Social Security numbers and the like – after clicking on a link in an email.
“Perform a second factor of authentication by calling or texting the email sender to confirm the requests are legitimate,” Anand pointed out. “Whenever possible, engage with emails related to money and data in a rational manner. Subject the email to an eye test that includes inspecting the sender name, sender email address, language within the email, and any logical inconsistencies within the email.”
Feds Sound Alarm Over Emotet Attacks on State, Local Govs
8.10.20 BigBrothers Threatpost
CISA warned already-strained public-sector entities about disturbing spikes in Emotet phishing attacks aimed at municipalities.
A dramatic uptick in Emotet phishing attacks since July has led the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to issue a warning that state and local governments need to fortify their systems against the trojan.
“This increase has rendered Emotet one of the most prevalent ongoing threats,” the CISA alert, issued Tuesday, read.
The alarm comes at a time when municipalities are already strained, juggling the concurrent crises of the COVID-19 pandemic, widespread social unrest and a caustic election season. Emotet, which can load other malware and self-propagate, is the last thing they need.
Threatpost Webinar Promo Retail Security
Click to Register!
“Emotet is one of the reasons why you should never click on links in emails you don’t recognize,” Bryan Becker, product manager at WhiteHat Security, told Threatpost. “Among other things, Emotet turns your computer into a ‘bot’ or ‘zombie’ that can be controlled by the hacker group to perform other crimes — without your OS or anti-malware noticing – one of which is sending more spam emails infecting more people with Emotet.”
Since July, CISA’s executive branch security protection tool, the EINSTEIN Intrusion Detection System, has found more than 16,000 instances of Emotet activity. These attacks are being executed in phases, indicating “possible targeted campaigns,” according to CISA, using tainted .doc Word files to deliver the malware.
CISA also said that Emotet-related domains and IPs seemed to be the most common on ports 80, 8080 and 443.
“In one instance, traffic from an Emotet-related IP attempted to connect to a suspected compromised site over port 445, possibly indicating the use of Server Message Block [SMB] exploitation frameworks along with Emotet,” the CISA report added.
That attack-volume data tracks with what’s being observed across the rest of the world. According to Check Point, the Emotet trojan tops its index of the most potent threats in circulation for the third consecutive month: It impacted 14 percent of organizations globally, followed by Trickbot at 4 percent and Dridex at 3 percent.
CISA Tracks the Threat
Starting last February, CISA said cybercriminals were targeting foreign countries using COVID-19 phishing emails to deliver malware. By July, researchers saw those emails and Emotet URLs being targeted against U.S. business, once again using COVID-19 communications for cover.
In August, CISA saw a 1,000-percent spike in Emotet loader downloads, and the attacks started to include state and local governments. By September, Canada, France, Japan, New Zealand, Italy and the Netherlands had seen breaches by Emotet, which then dropped Trickbot to deliver ransomware, and Qakbot trojans to steal banking information and other sensitive data.
Researchers also have noticed that Emotet has picked up a couple of new tricks over the course of the year. First, Emotet’s attachments started to include password-protected archive files to bypass email security gateways. Soon after, Palo Alto Networks reported to CISA that researchers are now seeing instances of “thread jacking” — that is, intercepting an existing email chain via an infected host and simply replying with an attachment to deliver the malware to an unsuspecting recipient.
And the threat isn’t limited to desktop computers. Steve Banda, senior manager of security solutions at Lookout, told Threatpost Emotet has gone mobile this year.
“While the Emotet is an advanced trojan primarily seen to affect desktops, our data shows mobile users encountering phishing attacks at a rate of over 30 percent on their personal devices,” Banda said. “It’s become more evident through our threat research that adversaries are extending their attacks to mobile. In many cases, desktop and mobile malware will have connections to the same command-and-control infrastructure. Cybercriminals are taking full advantage of this expanded attack surface.”
Local municipalities, from tribal and territorial governments to state authorities, as well as private businesses, are being encouraged by CISA to review existing security protocols and make necessary updates to prepare for the next Emotet phishing attempt.
Emotet, an Evolving Threat
Emotet was first detected in 2014 as a threat targeted at banks. But it has continued to evolve into something much more widespread and sophisticated, with the ability to deliver a range of secondary malware to compromised systems. In late 2019 it re-emerged with new social-engineering tools and the novel ability to customize phishing emails with messages tied to recent holidays, headlines and happenings. This version of Emotet also added an export function.
In February, the trojan got a code makeover and gained the ability to spread over Wi-Fi Networks.
But later that same month, researcher James Quinn with Binary Defense won a brief victory over Emotet, when he was able to exploit a vulnerability and develop a killswitch, shutting the malware down until early August, Threatpost reported. There’s also an anonymous vigilante combating Emotet by replacing payloads with memes and GIFs.
Despite those, and other, efforts, Emotet continues to proliferate. In fact, earlier in October it was spotted hitting hundreds of U.S. organizations with emails purporting to come from the Democratic National Committee, in a new politically charged spear-phishing attack.
“It’s mature, having been around in various forms since 2014, but it is always mutating and continues to evade detection by antivirus (AV),” Mark Kedgley, CTO at New Net Technologies, told Threatpost. “It has strong downloader capabilities, so it’s a carrier or conduit for other hacking tools and malware, such as credential-theft or ransomware. And it has worm capabilities too, designed to spread the malware laterally within a network once it has breached defenses, usually via phishing.”
The key for local governments trying to protect their systems, Kedgley said, is to understand the nature of the threat.
“Because of the polymorphic nature of Emotet, AV and other signature-based detection technologies will not be effective,” he said. “Therefore, the best action is to harden the infrastructure and reduce functionality used to infect systems, and also to leverage breach-detection capabilities…which will place a trojan like this right in the cross-hairs.”
CISA also offered mitigation best practices like blocking email attachments associated with malware, blocking attachments which can’t be scanned by antivirus software, using multifactor authentication and restricting browser access to risky sites.
BAHAMUT Spies-for-Hire Linked to Extensive Nation-State Activity
8.10.20 BigBrothers Threatpost
Researchers uncovered a sophisticated, incredibly well-resourced APT that has its fingers in wide-ranging espionage and disinformation campaigns.
A cyberespionage group known as BAHAMUT has been linked to a “staggering” number of ongoing attacks against government officials and private-sector VIPs in the Middle East and South Asia, while also engaging in wide-ranging disinformation campaigns.
That’s according to BlackBerry researchers, who said that the highly resourced group is probably operating on a mercenary basis, offering their services to the highest bidder.
“BAHAMUT is behind a number of extremely targeted and elaborate phishing and credential-harvesting campaigns, hundreds of new Windows malware samples, use of zero-day exploits, anti-forensic/AV evasion tactics, and more,” said Eric Milam, vice president of research operations at BlackBerry, in a report issued on Wednesday.
He added, “They rely on malware as a last resort, are highly adept at phishing, tend to aim for mobile phones of specific individuals as a way into an organization, show an exceptional attention to detail and above all are patient – they have been known to watch their targets and wait for a year or more in some cases.”
Researchers also found that BAHAMUT is running reams of fake-news entities – ranging from fraudulent social-media personae to stewarding entire news websites built to include disinformation.
“The sophistication and sheer scope of malicious activity that our team was able to link to BAHAMUT is staggering,” said Milam.
BAHAMUT – the name, in Arabic lore, of a sea monster that provides the support structure that holds up the earth – focuses mainly on carrying out classic espionage activity, according to researchers.
Mobile and Phishing Cyberattacks
While it distributes custom Windows malware and uses various zero-days, the group has notably recently embraced mobile: The report uncovered nine malicious iOS applications that had been available in the Apple App Store, and an assortment of Android applications that BlackBerry said are “directly attributable” to BAHAMUT, based on unique fingerprints.
“The applications were complete with well-designed websites, privacy policies and written terms of service – often overlooked by threat actors – which helped them bypass safeguards put in place by both Google and Apple,” the researchers said.
The apps in reality functioned as backdoors, with espionage capabilities that fluctuated across samples. All of them had the ability to enumerate filetypes on the devices and upload any potential file of interest. Other functionalities included the ability to enumerate device information, access contacts, access call records, access SMS messages, record phone calls, record audio, record video, download and update the backdoor, and track GPS location, researchers said.
They added that some of the targets for the mobile apps were specific to the United Arab Emirates (downloads were region-locked to the UAE); also, they observed Ramadan-themed applications and those pertaining to a Sikh separatist movement.
Phishing is another part of the group’s core competency, and its methods are unique.
“BAHAMUT’s phishing and credential harvesting tradecraft is significantly better than the majority of other publicly known APT groups,” the firm noted. “This is principally due to the group’s speed, their dedication to single-use and highly compartmentalized infrastructure, and their ability to adapt and change, particularly when their phishing tools are exposed.”
The phishing exercises that the group carries out for credential harvesting happen only after “concerted and robust reconnaissance operations” aimed at very precise targets, researchers noted.
BAHAMUT also stands up new phishing infrastructure on an ongoing basis, with targeted spear-phishing operations lasting anywhere from a few hours to a few months, depending on the domain and success rates.
“This embrace of ever-fleeting infrastructure makes real-time detection all but impossible,” according to the report.
Fake Websites for Attacks and Disinformation
In addition to its more traditional efforts, BAHAMUT is also distinctive in its use of original, painstakingly crafted websites, applications and personae to carry out cyberattacks, as well as spread fake news and misinformation, according to researchers.
Dozens of the fake sites were seen to serve up malware or exploits; while others tied into BAHAMUT phishing servers, or acted as command-and-control domains for BAHMAUT backdoors.
On the disinformation front, several of the fake websites researchers identified deal directly with a common theme: The 2020 Sikh Referendum, which has been a hotbed issue within India since late last year. This is essentially a secessionist movement, the brainchild of an organization called “Sikhs for Justice” (SFJ), which was banned by the government of India in July of 2019.
In some cases, social-media accounts were created and linked to the news sites, to make them seem more legitimate.
One site, called Techsprouts, was once a legitimate technology news site run by a journalist from India, which is now defunct. Its purpose left researchers scratching their heads.
“The group took over the domain of what was originally an information security news website and began pushing out content focused on geopolitics, research, industry news about other hack-for-hire groups,” according to the report – along with news about exploit brokers like the NSO Group.
Fake contributor to Techsprouts. Source: BlackBerry
“Within the past year…BAHAMUT appears to have re-registered the Techsprouts domain and continued to operate it,” according to the report – which added that the new site has an impressive list of “contributors.”
“Their biographies are impressive, but upon further inspection, it is apparent that the thumbnail photos of each author seen throughout the site have been appropriated from other sites and other people with quite different names,” the report explained. “For example, the image of ‘Alice Jane,’ a senior writer, was actually that of Julie Luck, the evening anchor at the local CBS station in Greensboro, N.C.”
In this case, the content isn’t overtly fake or malicious, leaving researchers wondering what its purpose is.
“[Other researchers] posited that the group used sites like this (though not Techsprouts specifically) as a way to discern the click habits of their targets,” according to the report. “BlackBerry is unable to verify this theory, though it certainly seems well within the realm of possibility.”
Hackers for Hire
The group overall is using a wide range of tools, tactics and techniques (TTPs), and researchers said that “at least one zero-day developer reflects a skill-level beyond most other known threat-actor groups today” – all of which suggests that the group is extremely well-funded and well-resourced.
This is borne out further by BAHAMUT’s startlingly good operational security (OpSec). Notably, there is no domain or IP address cross-over between operational functions in the group’s current tradecraft.
“We find, for example, that no domains or IP addresses used to control or distribute Windows malware are used for phishing or to administer malware designed for any other operating system,” according to the report. “Similarly, it is rare that any single server is used for more than a single mobile application at any given time. BAHAMUT ensures that no hosting provider is leveraged too heavily and spreads its current active infrastructure across more than 50 different hosting providers, thereby ensuring operational continuity if any single campaign is identified or a set of malware samples is disclosed. This is likely enormously time consuming, expensive, and requires considerable attention to detail.”
As for the victimology, apart from somewhat clustered targeting in South Asia and the Middle East, the targets run the gamut in terms of political ideology, which lends credence to the “hacker for hire” theory – the targeting “is all over the place,” according to researchers.
In looking at code-based similarities and unique string-based similarities, researchers said they was able to connect the dots between shadowy, “unsolved” APT incidents that have been spotted going back for years.
“BAHAMUT leverages publicly available tools, imitates other threat groups and changes its tactics frequently, which has made attribution difficult in the past,” researchers said. “However, BlackBerry reports with high confidence that the threat group is behind exploits researched by over 20 different security companies and nonprofits.”
Specifically, the threat groups identified as EHDevel, Windshift, Urpage and the White Company, along with the unnamed threat group in Kaspersky’s 2016 “InPage zero-day” research.
In all, given the extensive capabilities, links to disparate nation-state-linked APT activity, and lack of focused targeting, researchers concluded that BAHAMUT is one sprawling group that sells services to the highest bidder, including governments.
“Operational security will become increasingly important as more and more intelligence functions are outsourced by governments, corporations, and private individuals to groups like BAHAMUT,” according to the report. “These third parties add a layer of plausible deniability for those who employ them.”
CISA Warns of Emotet Trojan Targeting State, Local Governments
8.10.20 BigBrothers Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warns of an increase in attacks targeting state and local governments with the Emotet Trojan.
Active for over a decade, Emotet is a Trojan mainly used to drop additional malware onto compromised systems. Previously, it also functioned as a banking Trojan and as an information stealer.
Emotet has been silent for nearly half a year in 2020, but resumed activity in July, with the number of attacks surrounding it surging the next month. In early August, Binary Defense security researchers revealed that a vaccine deployed in February kept Emotet away for six months.
In an alert published this week, CISA and the Multi-State Information Sharing & Analysis Center (MS-ISAC) explain that, since August, cyber-criminals have been increasingly targeting state and local governments with phishing emails meant to drop Emotet.
“Emotet is difficult to combat because of its “worm-like” features that enable network-wide infections. Additionally, Emotet uses modular Dynamic Link Libraries to continuously evolve and update its capabilities,” the alert reads.
According to CISA, approximately 16,000 Emotet-related alerts were observed since July, with the malware being executed in phases in what appear to be targeted campaigns. Malicious Word documents attached to phishing emails were used as the initial attack vector.
The agency also observed Emotet-related traffic over ports 80, 8080, and 443, as well as one instance where an Emotet-related IP attempted to connect over port 445, suggesting the possible use of Server Message Block (SMB).
In February and July, CISA says, Emotet was using COVID-19-themed phishing to target victims in the United States and abroad. In August, the malware operators changed tactics to improve campaign efficiency, and the number of attacks in the United States increased.
In September, the number of Emotet attacks surged worldwide, with the malware dropping Trickbot to deliver ransomware in some cases, or Qakbot to steal banking credentials and other information from victims.
Emotet operators also switched to using password-protected archives as attachments, to bypass email security gateways and security researchers noticed that hackers leveraged thread hijacking for the delivery of Emotet.
In their alert, CISA and MS-ISAC also provide a list of ATT&CK techniques that Emotet employs, along with Snort signatures to help with detection, and recommendations to network defenders (regardless of whether in federal, local, state, territorial, or tribal governments, or from the private sector) on how to improve security posture.
A sophisticated cyberattack hit the International Maritime Organization (IMO)
7.10.20 BigBrothers Securityaffairs
The United Nations International Maritime Organization (IMO) disclose a cyber attack that disrupted its IT systems.
The United Nations International Maritime Organization (IMO) is a global standard-setting authority for the safety, security and environmental performance of international shipping. The UN Maritime Organization is the United Nations that develops a regulatory framework that is adopted on a global scale to ensure the safety and security of shipping and the prevention of marine and atmospheric pollution by ships.
According to the agency, a first cyberattack caused the unavailability of the IMO website, and other web services on September 30.
The agency initially attributed the problem to technical issues, but on October 2, it revealed that the real cause of the problems was a cyberattack.
“A number of IMO’s web-based services became unavailable on Wednesday 30 September. The systems impacted included the IMO public website and other web-based services.” reads a statement published by the organization on its website.
“The email system, including other Internal and external collaboration platforms, are working as normal. The platform used for virtual meeting with simultaneous interpretation has been unaffected and continued to function, without issue, during Wednesday’s Facilitation Committee (FAL) session and is expected to continue to function during today’s final FAL session.”
The access to the website www.imo.org has been restored on Friday 2 October. Initial investigation revealed that the IT systems at the IMO was hit by a sophisticated cyber-attack.
“The interruption of web-based services was caused by a sophisticated cyber-attack against the Organization’s IT systems that overcame robust security measures in place.” continues the statement.
IMO did not share technical details about the attack, the Secretariat is working with international security experts to identify the source of the attack, and further enhance the security of its infrastructure.
At the end of September, the French maritime transport and logistics giant CMA CGM S.A. revealed it was the victim of a malware attack that affecting some servers on its network.
The company currently ranks fourth behind Maersk Line, MSC, and COSCO Shipping Lines, all companies that have been curiously hit by malware attacks in the past.
CISA alert warns of Emotet attacks on US govt entities
7.10.20 BigBrothers Securityaffairs
The CISA agency is warning of a surge in Emotet attacks targeting multiple state and local governments in the US since August.
The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
During that time, the agency’s EINSTEIN Intrusion Detection System has detected roughly 16,000 alerts related to Emotet activity.
According to the experts from CISA the Emotet attacks were targeted on US government entities.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
The alert published by CISA was based on data provided by the Multi-State Information Sharing & Analysis Center (MS-ISAC) and the CISA itself since July 2020.
“Since August, CISA and MS-ISAC have seen a significant increase in malicious cyber actors targeting state and local governments with Emotet phishing emails. This increase has rendered Emotet one of the most prevalent ongoing threats.” reads that alert published by CISA.
“To secure against Emotet, CISA and MS-ISAC recommend implementing the mitigation measures described in this Alert, which include applying protocols that block suspicious attachments, using antivirus software, and blocking suspicious IPs.”
According to CISA, the surge in the attacks has rendered this malware one of the most prevalent ongoing threats.
In mid-September, cybersecurity agencies across Asia and Europe warned of Emotet spam campaigns targeting businesses in France, Japan, and New Zealand. At the end of September, agencies in Italy and the Netherlands, and researchers from Microsoft issued new alerts about the spike in Emotet activity.
CISA and MS-ISAC recommend admins and users to use antimalware solutions to block suspicious attachments and to block suspicious IPs addresses.
The report includes mitigations, Indicators of Compromise (IoCs) and MITRE ATT&CK Techniques.
EU Court Curbs Mass Phone Data Grab by Spy Agencies
6.10.20 BigBrothers Securityweek
The EU's top court on Tuesday put limits on how European spy and security agencies could harvest troves of personal data, but said this could be done under a serious threat to national security.
At the request of the courts in France, Belgium and Britain, the European Court of Justice confirmed that "EU law precludes national legislation" that requires telcos and tech companies to carry out the "indiscriminate retention" of data, a statement said
However, it does allow for exemptions in cases of "serious threat to national security" or the "fight against serious crime", under the supervision of a judge or an independent administrative authority.
This lifting of the ban would have to be "limited in time to what is strictly necessary," the court added.
The decision will be closely looked at by privacy activists who fear wide loopholes that would allow unfettered data spying by state agencies.
Data privacy is a highly sensitive issue in Europe, where activists have put the legality of Facebook and other big tech operations into jeopardy over similar concerns.
The legal onslaught began after revelations by Edward Snowden of mass digital spying by US agencies that also revealed cooperation with Washington by the UK's spy agencies.
The mass harvesting of data is a central part of anti-terror laws passed in several Western countries in the wake of September 11 and other attacks.
Second-ever UEFI rootkit used in North Korea-themed attacks
6.10.20 BigBrothers Securityaffairs
A China-linked threat actor used UEFI malware based on code from Hacking Team in attacks aimed at organizations with an interest in North Korea.
Researchers from Kaspersky have spotted a UEFI malware that was involved in attacks on organizations with an interest in North Korea.
The experts were investigating several suspicious UEFI firmware images when discovered four components, some of which were borrowing the source code a Hacking Team spyware.
In 2015, the hacker who breached the systems of the Italian surveillance firm Hacking Team leaked a 400GB package containing hacking tools and exploits codes. The archive included a number of zero-day exploits for Adobe Flash Player and Microsoft IE, these codes are just part of the hacking arsenal of the surveillance firm, which developed the popular Remote Control System (RCS) spyware, also known as Galileo. RCS has a modular structure that allows it to compromise several targets by loading the necessary zero-day exploits.
Trend Micro was the first security firm to discover the availability of a UEFI BIOS rootkit in the arsenal of the Hacking Team that allowed the company’s spyware to ensure the persistence even if the victims had formatted their hard disk to reinstall the Operating System.
“Hacking Team uses a UEFI BIOS rootkit to keep their Remote Control System (RCS) agent installed in their targets’ systems. This means that even if the user formats the hard disk, reinstalls the OS, and even buys a new hard disk, the agents are implanted after Microsoft Windows is up and running.” stated Trend Micro.
The firmware malware is based on code associated with HackingTeam’s VectorEDK bootkit, with minor changes.
Experts revealed that they were not able to determine the exact infection vector that allowed the attackers to overwrite the original UEFI firmware.
Experts speculate that the threat actors need to have physical access in order to deploy the implant into the victim’s machine. However, researchers don’t exclude that a rogue firmware was pushed remotely through a supply chain attack.
“Of course, we cannot exclude other possibilities whereby rogue firmware was pushed remotely, perhaps through a compromised update mechanism. Such a scenario would typically require exploiting vulnerabilities in the BIOS update authentication process. While this could be the case, we don’t have any evidence to support it,” reads the analysis published by Kaspersky.
The UEFI implant spotted by Kaspersky was used to deploy a new piece of malware that experts classified as a variant derived from a wider framework that they tracked as MosaicRegressor.
The MosaicRegressor framework was developed for cyber espionage purposes, its modular architecture allows operators to perform multiple actions.
Kaspersky researchers revealed to have found MosaicRegressor components at several dozen entities between 2017 and 2019. The list of victims included NGOs and diplomatic entities in Asia, Africa and Europe.
Researchers speculate the threat actors behind these attacks are linked with the Winnti APT.
“The attacks described in this blog post demonstrate the length an actor can go in order to gain the highest level of persistence on a victim machine. It is highly uncommon to see compromised UEFI firmware in the wild, usually due to the low visibility into attacks on firmware, the advanced measures required to deploy it on a target’s SPI flash chip, and the high stakes of burning sensitive toolset or assets when doing so.” concludes the report.
“With this in mind, we see that UEFI continues to be a point of interest to APT actors, while at large being overlooked by security vendors.”
China-Linked Hackers Used UEFI Malware in North Korea-Themed Attacks
6.10.20 BigBrothers Securityweek
A threat actor linked to China has used UEFI malware based on code from Hacking Team in attacks aimed at organizations with an interest in North Korea, Kaspersky reported on Monday.
Kaspersky researchers analyzed the malware and the malicious activity after stumbling upon several suspicious UEFI firmware images. A deeper investigation revealed the existence of four components, many of which were based on source code leaked in 2015 by a hacker who had breached the systems of the now-defunct Italian surveillance solutions provider Hacking Team. The firmware implant appeared to be based on code associated with the Vector-EDK bootkit, with only some minor modifications.
Kaspersky has not been able to determine how the attackers managed to rewrite the firmware on targeted machines. However, considering that the firmware implant is based on Hacking Team code, it’s possible that deployment involved physical access to the targeted device and attaching a USB key — Hacking Team’s Vector-EDK bootkit was designed to be deployed via a USB key.
“Of course, we cannot exclude other possibilities whereby rogue firmware was pushed remotely, perhaps through a compromised update mechanism. Such a scenario would typically require exploiting vulnerabilities in the BIOS update authentication process. While this could be the case, we don’t have any evidence to support it,” Kaspersky researchers said.
The implant’s main bootkit component is designed to act as a persistent dropper for a piece of Windows malware. This allows the attackers to ensure that the Windows malware cannot be removed from the compromised system — the malware is rewritten to disk if removed, unless the malicious firmware is also removed.
The malware delivered by the bootkit was determined to be a variant from a framework that Kaspersky has dubbed MosaicRegressor, which is designed for espionage. The framework is modular, enabling the attackers to carry out various tasks, such as stealing documents from the compromised computer.
Kaspersky detected MosaicRegressor components at “several dozen” entities between 2017 and 2019. Victims included NGOs and diplomatic entities in Asia, Africa and Europe, and one thing they had in common was a connection to North Korea — in some cases they had a presence in the country, while others were involved in non-profit activity related to North Korea. However, only two of these victims were targeted with the UEFI implant.
Evidence uncovered by Kaspersky suggests that the hackers behind these attacks are Chinese speakers, and a connection has been found to Winnti, but no definitive links have been found to a known threat actor.
There aren’t too many known attacks involving UEFI malware. ESET reported in 2018 that the Russia-linked threat group Fancy Bear had been using a UEFI rootkit in its attacks.
DoD, DHS Warn of Attacks Involving SLOTHFULMEDIA Malware
6.10.20 BigBrothers Securityweek
The U.S. Department of Defense’s Cyber National Mission Force (CNMF) and the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) last week published a malware analysis report for what they described as a new malware variant named SLOTHFULMEDIA.
SLOTHFULMEDIA is described as a dropper that deploys two files when executed, including a RAT designed to allow hackers to control compromised devices, and a component that removes the dropper once the RAT achieves persistence on the targeted computer.
The RAT is capable of running arbitrary commands, terminating processes, taking screenshots, modifying the registry, and making changes to files.
The U.S. government’s malware analysis report includes technical details about how the malware works, indicators of compromise (IoC) and recommendations for securing systems against such threats.
“Users or administrators should flag activity associated with the malware and report the activity to the CISA or the FBI Cyber Watch (CyWatch), and give the activity the highest priority for enhanced mitigation,” the agencies said.
It’s not uncommon for these types of malware analysis reports made public by U.S. agencies to include information about the threat actor believed to be behind the attacks, including if it’s a nation-state actor. However, the report on SLOTHFULMEDIA doesn’t provide any information on the possible origin of the attackers.
CISA and CNMF say the malware has been used in attacks launched by a sophisticated threat actor against entities in India, Kazakhstan, Kyrgyzstan, Malaysia, Russia, and Ukraine.
A sample of the malware was also made available on VirusTotal by the U.S Cyber Command, which regularly posts samples of malware linked to foreign threat actors. A majority of the samples shared by USCYBERCOM have been linked to North Korea, and some have been attributed to Russia and Iran, but this summer it also started sharing Chinese samples.
ESET last week published a report on XDSpy, a previously unknown threat actor that has been active for at least 9 years and which has also targeted Russia and Ukraine, as well as Belarus, Moldova and Russia. This group has mainly targeted government organizations, and its main goal appears to be the theft of sensitive documents.
SecurityWeek has asked ESET if it has found any links between XDSpy and SLOTHFULMEDIA given the timing of the reports and the fact that they both target Russia and Ukraine. However, the cybersecurity firm says SLOTHFULMEDIA is actually related to PowerPool, a threat actor whose activities were detailed by the company back in 2018 after it was spotted exploiting a Windows zero-day vulnerability.
ESET at the time reported seeing attacks against a relatively small number of users located in the US, UK, Germany, Ukraine, Chile, India, Russia, Poland and the Philippines.
UN Maritime Agency Hit by 'Sophisticated Cyberattack'
6.10.20 BigBrothers Securityweek
The United Nations’ International Maritime Organization (IMO) last week said some of its systems were disrupted as a result of a cyberattack.
IMO describes itself as the “global standard-setting authority for the safety, security and environmental performance of international shipping.” The organization says its main role is to develop a fair and effective regulatory framework that is universally adopted and implemented.
IMO’s website and other web services were first disrupted on September 30, when the agency announced on Twitter that its team was working on fixing some “technical issues.” Then, on October 2, it admitted that the problems were caused by a cyberattack, and said that it was working on restoring impacted systems.
“IMO has ISO/IEC 27001:2013 certification for its information security management system. IMO was the first UN organization to get this certification in 2015,” IMO stated. “The IMO Headquarters file servers are located in the UK, with extensive backup systems in Geneva. The backup and restore system is regularly tested.”
It added, “Following the attack the Secretariat shut down key systems to prevent further damage from the attack.”
IMO has not shared any technical information about the attack. It may have been a distributed denial-of-service (DDoS) attack, a ransomware attack, or a different type of breach.
While it has described it as a “sophisticated cyberattack against the Organization’s IT systems that overcame robust security measures in place,” it’s not uncommon for organizations to describe even DDoS attacks as “sophisticated.”
SecurityWeek has reached out to IMO to find out exactly what type of attack it was and we will update this article if the organization responds.
The news came less than a week after French shipping giant CMA CGM was hit by a cyberattack that forced it to shut down some systems. According to reports, the attack involved a piece of file-encrypting ransomware named Ragnar Locker.
German Privacy Watchdog Fines H&M $41M for Spying on Workers
2.10.20 BigBrothers Securityweek
A German privacy watchdog said Thursday that it is fining clothing retailer H&M 35.3 million euros ($41 million) after the company was found to have spied on some of its employees in Germany.
Hamburg’s data protection commissioner said in a statement that the Swedish company collected private information about employees at a customer service center in Nuremberg, “ranging from rather harmless details to family issues and religious beliefs.”
The information was recorded on a network drive accessible to up to 50 managers and “used, among other things, to obtain a detailed profile of employees for measures and decisions regarding their employment.”
The data protection commissioner, Johannes Caspar, said that “the combination of collecting details about their private lives and the recording of their activities led to a particularly intensive encroachment on employees’ civil rights.”
The privacy violation was discovered after the data briefly became visible to all people on the company network, resulting in news reports about the information gathering.
H&M said in a statement that the practices in Nuremberg didn’t correspond to company guidelines but that it nevertheless took full responsibility and had apologized unreservedly to the employees. The company said it would examine the fine issued.
Casper welcomed H&M’s decision to pay compensation to employees at the Nuremberg service center and take measures to prevent future privacy breaches, saying the steps “show the intention to give the employees the respect and appreciation they deserve as dependent workers in their daily work for their company.”
FBI, CISA Say DDoS Attacks Won't Prevent Voting
1.10.20 BigBrothers Securityweek
While they might hinder access to information, distributed denial-of-service (DDoS) attacks against election infrastructure won’t prevent voting, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) said in an alert issued this week.
DDoS attacks would either slow down election-related public-facing websites or render them inaccessible, thus preventing voters from staying updated with voting information or from accessing voting results.
Such attacks are meant to disrupt activities for a period of time through flooding Internet-accessible servers with requests and preventing legitimate users from connecting to online resources, such as online accounts or websites.
“The public should be aware that if foreign actors or cyber criminals were able to successfully conduct DDoS attacks against election infrastructure, the underlying data and internal systems would remain uncompromised, and anyone eligible to vote would still be able to cast a ballot,” the FBI and CISA note.
Furthermore, the two agencies warn that threat actors might falsely claim that they successfully compromised voting systems through DDoS attacks and that they were able to prevent voters from casting their ballots or that they managed to modify already-cast votes.
Such disinformation attempts, the two agencies say, would undermine the public’s trust in the country’s democratic institutions and seek to discredit the electoral process. Two other similar alerts issued over the past couple of weeks warn of disinformation regarding the security of voting systems and the validity of election results.
“The FBI and CISA have no reporting to suggest a DDoS attack has ever prevented a registered voter from casting a ballot, or compromised the integrity of any ballots cast,” the alert reads.
The agencies also note that they’ve worked closely with election officials to identify additional channels through which they could keep voters informed, including traditional media, verified social media accounts, and other resources.
“Election officials have multiple safeguards and plans in place to limit the impact and recover from a DDoS incident with minimal disruption to the voting process,” the agencies say.
Citizens are advised to get informed on vote procedures and polling places ahead of election day, to make sure that information comes from trustworthy sources only, and to only rely on state and local government election officials when it comes to details on how to vote, on polling locations, and on final election results.
Russian Sentenced to Prison for Hacking LinkedIn, Dropbox
30.9.20 BigBrothers Securityweek
A Russian national was sentenced to 88 months in prison in the United States for hacking LinkedIn, Dropbox, and Formspring in 2012.
The man, Yevgeniy Aleksandrovich Nikulin, who will turn 33 next month, was charged in 2016 for using stolen employee credentials to access without authorization the systems of LinkedIn, Dropbox and Formspring. He was arrested in the Czech Republic the same year and was extradited to the U.S. two years later.
In April 2019, the Czech Republic’s highest court said that Nikulin’s rights were violated when he was extradited to the United States in March 2018, before a separate asylum case went through the court system.
Nikulin, who lived a luxury life, owning expensive cars and watches, was also linked to the 2013 theft of cryptocurrency from BitMarket.eu and is believed to have made more money from this attack than from the trading of usernames and passwords.
He is said to have stolen the credentials of roughly 117 million Americans, which he then attempted to sell on underground portals for €5,500 (roughly $6,200).
Evidence presented in court revealed that Nikulin managed to hack into the computers of LinkedIn, Dropbox, and Formspring employees, and then install malware to remotely control the machines and steal the employees’ login information.
Investigators were able to trace at least one intrusion back to an IP address associated with a Moscow location where Nikulin lived at the time.
The hacker was found guilty by a United States jury in early July.
Prior to the sentencing hearing, which was scheduled for September 29, prosecutors sought a sentence of 145 months in prison, three years of supervised release, and restitution.
Nikulin’s lawyers, Adam Gasner and Valery Nechay, disputed the amount of loss caused by the intrusions and also argued that the hacker had been in custody for a total of 48 months already, asking the court to sentence him to time served.
The hacker was sentenced to 88 months in prison (64 months for trafficking in unauthorized access devices and damaging a protected computer, and 60 months for computer intrusion and conspiracy, which will be served concurrently, and 24 months for aggravated identity theft), of which he will serve 85%, or 74.8 months, minus the time already served.
Nikulin was also sentenced to three years of supervised release (provided that he is not deported to Russia as soon as released from prison) and ordered to pay restitution of $1 million to LinkedIn, $514,000 to Dropbox, $20,000 to Formspring, and $250,000 to WordPress parent company Automattic (although he was not charged for this hack as well).
FBI and CISA warn of disinformation campaigns about the hack of voter systems
29.9.20 BigBrothers Securityaffairs
The FBI and the US CISA issued a joint public service announcement about the threat of disinformation campaigns targeting the 2020 US election.
The Federal Bureau of Investigation (FBI) and the US Cybersecurity and Infrastructure Security Agency (CISA) issued a joint public service announcement to warn of the threat of disinformation campaigns targeting the upcoming 2020 US election season.
Threat actors aim at delegitimate the result of the vote by actively spreading false information about successfully compromised voting systems and voter registration databases.
“During the 2020 election season, foreign actors and cyber criminals are
spreading false and inconsistent information through various online
platforms in an attempt to manipulate public opinion, sow discord, discredit the electoral process, and undermine confidence in U.S. democratic institutions.” reads the joint announcement. “These malicious actors could use these forums to also spread disinformation suggesting successful cyber operations have compromised election infrastructure and facilitated the “hacking” and “leaking” of U.S. voter registration data.”
The goal is to manipulate public sentiment and discredit the electoral process to weaken the trust in the US Government.
“During the 2020 election season, foreign actors and cyber criminals are
spreading false and inconsistent information through various online
platforms in an attempt to manipulate public opinion, sow discord, discredit the electoral process, and undermine confidence in U.S. democratic institutions.” continues the announcement. “These malicious actors could use these forums to also spread disinformation suggesting successful cyber operations have compromised election infrastructure and facilitated the “hacking” and “leaking” of U.S. voter registration data.”
The Government agencies confirmed that the availability of voter registration information in the past did not impact the voting process or election results.
Both agencies have no information “suggesting any cyberattack on U.S. election infrastructure has prevented an election from occurring, prevented a registered voter from casting a ballot, compromised the accuracy of voter registration information, or compromised the integrity of any ballots cast.”
The FBI and CISA recommend the US citizens to critically evaluate any information on the election, validating the sources and verifying the news they received.
Below the list of recommendations provided by the agencies to the American public to unmask disinformation attempts about cyberattacks on US election infrastructure and voter info:
• Seek out information from trustworthy sources, verify who produced the content, and consider their intent.
• Rely on state and local election officials for information about voter registration databases and voting systems.
• View early, unverified claims with a healthy dose of skepticism.
• Verify through multiple reliable sources any reports about compromises of voter information or voting systems, and consider searching for other reliable sources before sharing such information via social media or other avenues.
• Report potential election crimes—such as disinformation about the manner, time, or place of voting—to the FBI.
• If appropriate, make use of in-platform tools offered by social media companies for reporting suspicious posts that appear to be spreading false or inconsistent information about voter information or voting systems.
In early August, the Director of the U.S. National Counterintelligence and Security Center (NCSC) William Evanina shared information on ongoing operations aimed at influencing the 2020 U.S. election.
“Many foreign actors have a preference for who wins the election, which they express through a range of overt and private statements; covert influence efforts are rarer. We are primarily concerned about the ongoing and potential activity by China, Russia, and Iran” reads the press release published by the Office of the Director of the National Intelligence.
Evanina linked the efforts to Russia, China, and Iran, he explained, for example, that Russian actors are supporting President Trump’s candidacy with a coordinated effort on both Russian television and media.
According to US intelligence, Russia is carrying out campaigns to denigrate former Vice President Biden that is considered hostile by the Kremlin.
FBI, CISA Warn of Disinformation Campaigns Regarding Hacked Voting Systems
29.9.20 BigBrothers Securityweek
Threat actors are expected to spread false information regarding hacked voter information and voting systems, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) say in an alert.
Last week, the two agencies issued a warning on possible campaigns aimed at distributing false information about the election results, urging the population to double check all sources of information to ensure their validity and make sure the data they receive comes from reliable sources, such as state and local election officials.
At the time, the agencies noted that disinformation campaigns might leverage websites, social media, and other venues to disseminate false information about voter suppression, cyber-attacks on election infrastructure, fraud, and other issues.
In a new alert, the FBI and CISA reiterate the warning, noting that “foreign actors and cyber criminals are spreading false and inconsistent information through various online platforms in an attempt to manipulate public opinion, sow discord, discredit the electoral process, and undermine confidence in U.S. democratic institutions.”
During the current election season, these actors are expected to spread false information claiming that hacking groups successfully compromised the election infrastructure and compromised U.S. voter registration data.
The reality, the two agencies point out, is that much of the U.S. voter information is available for purchase through publicly available sources. Although threat actors might have acquired voter registration information, the voting process and the election results are not impacted by this, the FBI and CISA say.
They also point out that there’s no indication that cyber-attacks have so far “prevented an election from occurring, prevented a registered voter from casting a ballot, compromised the accuracy of voter registration information, or compromised the integrity of any ballots cast.”
The same as before, the population is advised to ensure information comes from trustworthy sources, to only rely on state and local election officials when it comes to information on voter registration and voting systems, and verify through reliable sources any reports about compromises of voting systems or databases containing voter information.
Furthermore, citizens are encouraged to report potential election crimes, including disinformation, and use the tools available on social media platforms to report suspicious posts that might be “spreading false or inconsistent information about voter information or voting systems.”
“The FBI and CISA coordinate closely with federal, state, and local election partners and provide services and information to safeguard U.S. voting processes and maintain the integrity of U.S. elections. Both organizations urge the American public to critically evaluate the sources of the information they consume and to seek out reliable and verified information,” the alert also notes.
Putin proposes new information security collaboration to US, including no-hack pact for election
28.9.20 BigBrothers Securityaffairs
Putin is proposing a new cyber security collaboration with the United States, including a no-hack pact for the upcoming Presidential election.
Russian Government has published a statement by President Vladimir Putin that proposes to the United States a comprehensive program of measures for restoring the Russia – US cooperation in information security.
Russia was accused of interfering in the 2016 US presidential election, in February 2018 the special prosecutor Robert Mueller accused thirteen Russian nationals of tampering with the election and charged them with conspiring against the United States.
The measures proposed by Putin aim at building up a mutual trust between the two Governments, the collaboration will contribute to ensure global peace in the information space.
“One of today’s major strategic challenges is the risk of a large-scale confrontation in the digital field. A special responsibility for its prevention lies on the key players in the field of ensuring international information security (IIS).” reads the statement. “In this regard, we would like to once again address the US with a suggestion to agree on a comprehensive program of practical measures to reboot our relations in the field of security in the use of information and communication technologies (ICTs).”
Putin suggested four actions to set up a prolific collaboration on Information security.
To restore a regular full-scale bilateral interagency high-level dialogue on the key issues of ensuring IIS.
To maintain a continuous and effective functioning of the communication channels between competent agencies of our States through Nuclear Risk Reduction Centers, Computer Emergency Readiness Teams and high-level officials in charge of the issues of IIS within the bodies involved in ensuring national security, includig that of information.
To jointly develop and conclude a bilateral intergovernmental agreement on preventing incidents in the information space similarly to the Soviet-American Agreement on the Prevention of Incidents On and Over the High Seas in force since 25 May 1972.
To exchange, in a mutually acceptable format, guarantees of non-intervention into internal affairs of each other, including into electoral processes, inter alia, by means of the ICTs and high-tech methods.
Recently, the FBI warned that foreign actors and cybercriminals could spear disinformation aimed at discrediting the electoral process and undermine confidence in U.S. democratic institutions
The proposal of collaboration in information security is not new, the two states already discussed on the topic in 2017.
At the time, Putin and Trump discussed the creation of a joint Cyber Security unit, but the event and the tensions between the two states halted any joint initiative.
Hacker Uploads Documents to WHO, UNESCO Websites
28.9.20 BigBrothers Securityweek
A hacker has found a way to upload PDF files to the websites of several organizations, including the World Health Organization (WHO) and UNESCO.
The attack, first reported by Cyberwarzone.com, does not appear particularly sophisticated and its impact is likely low, but the same vulnerabilities could have been exploited by more advanced threat actors for more serious attacks.
The files were uploaded by a hacker who uses the online moniker m1gh7yh4ck3r. A search for “m1gh7yh4ck3r” on Google shows that in recent days they uploaded files to official websites of UNESCO, WHO, the Georgia Institute of Technology, and a Cuban government website.
Georgia Tech and the WHO have apparently removed the files uploaded by the hacker, but the files are still present on the UNESCO and the Cuban government websites at the time of writing.
Reached by SecurityWeek, UNESCO representatives said they will launch an investigation. The WHO and Georgia Tech did not immediately respond to our inquiry.
The PDF files uploaded by the hacker are related to online game hacks and hacking Facebook and Instagram accounts. The documents contain links that point to various hacking services and tools. These services and tools appear to be fake and they lead users to various types of scammy websites.
One of the antivirus engines on VirusTotal detects some of the PDF files as containing a trojan, and one file is detected as “suspicious.”
It’s unclear how the hacker managed to upload the files, but it was likely an unsophisticated method considering that the documents were uploaded to domains that appear to be designed to allow users to upload files. They may have exploited known or unknown file upload or authentication bypass vulnerabilities — in the case of the UNESCO website the login page is easy to access.
While in this case the attack likely had a low impact, the ability to upload arbitrary files to the websites of organizations such as the WHO and UNESCO can be highly useful to sophisticated state-sponsored actors.
There have been many malicious campaigns since the start of the pandemic where financially-motivated cybercriminals and state-sponsored groups sent malicious emails impersonating the WHO. Exploiting a vulnerability such as the one leveraged by m1gh7yh4ck3r could have been highly useful to them.
Researchers Uncover Cyber Espionage Operation Aimed At Indian Army
28.9.20 BigBrothers Thehackernews
Cybersecurity researchers uncovered fresh evidence of an ongoing cyberespionage campaign against Indian defense units and armed forces personnel at least since 2019 with an aim to steal sensitive information.
Dubbed "Operation SideCopy" by Indian cybersecurity firm Quick Heal, the attacks have been attributed to an advanced persistent threat (APT) group that has successfully managed to stay under the radar by "copying" the tactics of other threat actors such as the SideWinder.
Exploiting Microsoft Equation Editor Flaw
The campaign's starting point is an email with an embedded malicious attachment — either in the form of a ZIP file containing an LNK file or a Microsoft Word document — that triggers an infection chain via a series of steps to download the final-stage payload.
Aside from identifying three different infection chains, what's notable is the fact that one of them exploited template injection and Microsoft Equation Editor flaw (CVE-2017-11882), a 20-year old memory corruption issue in Microsoft Office, which, when exploited successfully, let attackers execute remote code on a vulnerable machine even without user interaction.
Microsoft addressed the issue in a patch released in November 2017.
As is often the case with such malspam campaigns, the attack relies on a bit of social engineering to bait the user into opening a seemingly realistic Word document that claims to be about the Indian government's defense production policy.
What's more, the LNK files have a double extension ("Defence-Production-Policy-2020.docx.lnk") and come with document icons, thereby tricking an unsuspecting victim into opening the file.
Once opened, the LNK files abuse "mshta.exe" to execute malicious HTA (short for Microsoft HTML Applications) files that are hosted on fraudulent websites, with the HTA files created using an open-sourced payload generation tool called CACTUSTORCH.
A Multi-stage Malware Delivery Process
The first stage HTA file includes a decoy document and a malicious .NET module that executes the said document and downloads a second-stage HTA file, which in turn checks for the presence of popular antivirus solutions before copying Microsoft's credential back and restore utility ("credwiz.exe") to a different folder on the victim machine and modifying the registry to run the copied executable every time upon startup.
Consequently, when this file gets executed, not only does it side-load a malicious "DUser.dll" file, it also launches the RAT module "winms.exe," both of which are obtained from the stage-2 HTA.
"This DUser.dll will initiate the connection over this IP address '173.212.224.110' over TCP port 6102," the researchers said.
"Once successfully connected, it will [...] then proceed for performing various operations based on the command received from C2. For example, if C2 sends 0, then it collects the Computer Name, Username, OS version etc. and sends it back to C2."
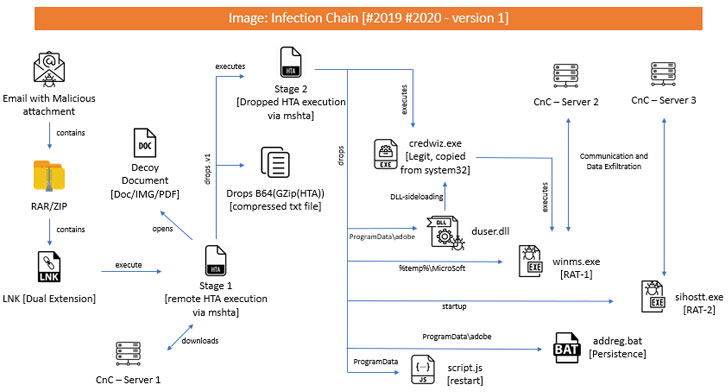
Stating the RAT shared code-level similarities with Allakore Remote, an open-sourced remote-access software written in Delphi, Quick Heal's Seqrite team noted that the Trojan employed Allakore's RFB (remote frame buffer) protocol to exfiltrate data from the infected system.
Possible Links to Transparent Tribe APT
In addition, a few attack chains are also said to have dropped a previously unseen .NET-based RAT (called "Crimson RAT" by Kaspersky researchers) that comes equipped with a wide range of capabilities, including access files, clipboard data, kill processes, and even execute arbitrary commands.
Although the modus operandi of naming DLL files shares similarities with the SideWinder group, the APT's heavy reliance on the open-sourced toolset and an entirely different C2 infrastructure led the researchers to conclude with reasonable confidence that the threat actor is of Pakistani origin — specifically the Transparent Tribe group, which has been recently linked to several attacks targeting the Indian military and government personnel.
"Thus, we suspect that the actor behind this operation is a sub-division under (or part of) Transparent-Tribe APT group and are just copying TTPs of other threat actors to mislead the security community," Quick Heal said.
Microsoft Says China-Linked Hackers Abused Azure in Attacks
28.9.20 BigBrothers Securityweek
Microsoft Reports Evolution of China-Linked Threat Actor GADOLINIUM
Microsoft this week announced that it recently removed 18 Azure Active Directory applications that were being abused by China-linked state-sponsored threat actor GADOLINIUM.
Also known as APT40, TEMP.Periscope, TEMP.Jumper, Leviathan, BRONZE MOHAWK, and Kryptonite Panda, the adversary has been active since at least 2013, mainly operating in support of China’s naval modernization efforts, through targeting various engineering and maritime entities, including a U.K.-based company.
The threat actor was recently observed leveraging Azure cloud services and open source tools in attacks employing spear-phishing emails with malicious attachments.
“As these attacks were detected, Microsoft took proactive steps to prevent attackers from using our cloud infrastructure to execute their attacks and suspended 18 Azure Active Directory applications that we determined to be part of their malicious command & control infrastructure,” the tech company says.
According to Microsoft, GADOLINIUM has expanded its target list to include the Asia-Pacific region, as well as other targets in higher education and regional government organizations. Previously employing custom malware, the threat actor has added open-source tools to their toolset over the past year, making tracking more difficult.
The group has been experimenting with the use of cloud services for years, starting with a Microsoft TechNet profile in 2016. In 2018, the hackers abused GitHub to host commands, and 2019 and 2020 attacks employed similar techniques.
Over the past year, similar to other state-sponsored threat groups, GADOLINIUM has included open-source tools in its portfolio, which also results in lower overall costs for the attackers, in addition to making attribution more difficult.
In April this year, the adversary adopted COVID-19 lures in their spear-phishing emails. The multi-stage infection process would result in a modified version of the open-source PowershellEmpire toolkit being delivered.
The toolkit enables the threat actor to load additional payloads onto the victim’s machine, including a command and control module that leverages OneDrive to execute commands and retrieve results. As part of the attacks, GADOLINIUM leveraged an Azure Active Directory application for data exfiltration to OneDrive.
“From an endpoint or network monitoring perspective the activity initially appears to be related to trusted applications using trusted cloud service APIs and, in this scenario, no OAuth permissions consent prompts occur,” Microsoft explains.
Microsoft Kills 18 Azure Accounts Tied to Nation-State Attacks
26.9.20 BigBrothers Threatpost
An APT group has started heavily relying on cloud services like Azure Active Directory and OneDrive, as well as open-source tools, to obfuscate its attacks.
Microsoft has suspended 18 Azure Active Directory applications that were being leveraged for command-and-control (C2) infrastructure by what it says is a Chinese nation-state actor.
While Microsoft services like Azure Active Directory (AD) – its cloud-based identity and access management service – are popular among enterprises, cybercriminals are also swooping in on these services to enhance the weaponization of their malware payload, attempt to gain command and control all the way to the server, and obfuscate detection. One such threat group recently spotted leveraging these cloud services and open source tools is what Microsoft calls Gadolinium, a Chinese nation-state activity group that has been compromising targets for nearly a decade.
After compromising victim devices, Gadolinium was setting up AD accounts to receive commands from and send stolen data to its C2 server. But beyond that, the threat group has also stored stolen data in Microsoft’s file hosting service and synchronization service, OneDrive; launched attacks using the open source PowershellEmpire toolkit and used GitHub to host commands.
“Gadolinium has been experimenting with using cloud services to deliver their attacks to increase both operation speed and scale for years,” said Ben Koehl and Joe Hannon, with Microsoft’s Threat Intelligence Center, in a report posted Thursday.
Evolved Attacks
Gadolinium is also known as APT40, which researchers like FireEye have assessed with “moderate confidence” is a state sponsored espionage actor attributed to China. While previously Gadolinium has targeted worldwide maritime and health industries, Microsoft said recently it has observed newly expanded targeting for the threat group to include the Asia Pacific region and other targets in higher education and regional government organizations.
In mid-April 2020 the threat actors were detected sending spear-phishing emails with malicious attachments, with lures relating to the COVID-19 pandemic. When opened, the attached PowerPoint file (20200423-sitrep-92-covid-19.ppt), would drop a file, doc1.dotm, which then has two payloads that run in succession.
These include a payload that turns off a type check (DisableActivitySurrogateSelectorTypeCheck), while the second loads an embedded .Net binary that downloads a .Png image file.
“The .png is actually PowerShell which downloads and uploads fake png files using the Microsoft Graph API to https://graph.microsoft.com/v1.0/drive/root:/onlinework/contact/$($ID)_1.png:/content where $ID is the ID of the malware,” said researchers.
Behind the scenes, these attacks relied on a bundle of Microsoft services and open source tooling – which Microsoft said has been a steady trend in recent years for several nation-state activity groups migrating to open source tooling.
Gadolinium Leveraging Cloud Services
Researchers said that historically Gadolinium has leveraged custom-crafted malware families – but analysts have been able to identify these and defend against them.
In response, the threat actor has started experimenting with cloud applications to help it sidestep detection of its attacks, starting in 2018, when the threat group chose to use GitHub to host commands. Many cloud services frequently offer a free trial or one-time payment account offering (via PayGo), and malicious actors have found ways to take advantage of these legitimate business offerings, said researchers.
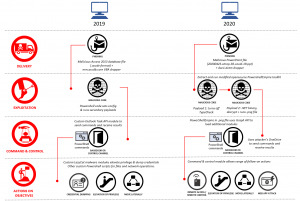
Gadolinium’s attack vectors. Credit: Microsoft
“By establishing free or PayGo accounts, they can use cloud-based technology to create a malicious infrastructure that can be established quickly then taken down before detection or given up at little cost,” said researchers.
This past year, Gadolinium has also started modifying portions of its attack vector, instead using open-source toolkits to obfuscate its activity and make it more difficult for analysts to track.
Microsoft said that the 18 Azure Active Directory applications that were suspended were part of Gadolinium’s PowerShell Empire infrastructure, which is a modified version of the open source PowershellEmpire toolkit. This is a toolkit that allows attackers to load additional modules to infected computers via Microsoft Graph API calls. It provides a command and control module that uses the attacker’s Microsoft OneDrive account to execute commands and retrieve results between attacker and victim systems.
“The attacker uses an Azure Active Directory application to configure a victim endpoint with the permissions needed to exfiltrate data to the attacker’s own Microsoft OneDrive storage,” said researchers. “From an endpoint or network monitoring perspective the activity initially appears to be related to trusted applications using trusted cloud service APIs and, in this scenario, no OAuth permissions consent prompts occur.”
Polish police shut down major group of hackers in the country
25.9.20 BigBrothers Securityaffairs
Polish police dismantled a major group of hackers that was behind several criminal activities, including ransomware attacks, and banking fraud.
Polish authorities have dismantled a major hacker group that was involved in multiple cybercrime activities, including ransomware attacks, malware distribution, SIM swapping, banking fraud, running rogue online stores, and even making bomb threats at the behest of paying customers.
The gang, composed of four suspects, in believed to be among the most active groups in the country.
“Today, the Polish authorities are announcing the arrest of 4 suspected hackers as part of a coordinated strike against cybercrime. Those arrested are believed to be among the most active cybercriminals in the country.” reads the press release published by the Europol.
“This operation was carried out by the Polish Police Centre Bureau of Investigation (Centralne Biuro Œledecze Policji) under the supervision of the Regional Prosecutor’s Office in Warsaw (Prokuratura Regionalna w Warszawie), together with the cybercrime departments of provincial police headquarters and Europol.”
The arrests are the result of an investigation that begun in May 2019, when the group sent a first bomb threat to a school in £êczyca after being paid by an individual named Lukasz K..
According to local media, the hackers spoofed the email of a businessman that was a rival of the victim, for this reason, the police arrested him and detained the man for two days in prison. Once the police understood that he was extraneous to the attack, the man was released out of jail and hired a private investigator to discover who was behind the bomb alert.
When the group of hackers discovered that the man was released, they hacked a Polish mobile operator and generated invoices for thousands of zlotys in the name of both the detective and the businessman.
The group is behind several bomb threats that targeted multiple organizations, including the Western Railway Station in Warsaw and 1,066 kindergartens across the country.
According to Europol’s press release, the gang was involved in many other criminal activities, including:
Malware distribution: two members of the gang were involved in the distribution of malware, such as Remote Access Tools (RAT) and mobile malware, to over 1000 people across Poland. The malware was distributed through phishing messages impersonating government institutions. According to the news site Zaufana Trzeciastrona, the hackers distributed both Windows and Android malware, including Cerberus, Anubis, Danabot, Emotet, and njRAT.
SIM swapping: Personal data, including bank account credentials, stolen with malware were used by hackers in SIM SWAPPING attacks. Crooks were able to steal over €147 000 (PLN 662 000) from their victims’ bank accounts.
E-commerce fraud: one member of the gang was running 50 fake online shops and defrauded approximately 10,000 people.
Zaufana Trzeciastrona revealed the name of the individuals arrested by the police:
Kamil S., once, during the ToRepublic times, known as Razzputin (now he used other pseduonyms),
Pawe³ K., operating under the pseudonym Manster_Team, until recently the role of a “banker”,
Janusz K., one of the most active and versatile perpetrators of most of the crimes described below, IT technician
£ukasz K., also an important figure in the underground world
as well as Mateusz S., Rados³aw S., Joanna S. and Beata P.
CISA says federal agency compromised by malicious cyber actor
25.9.20 BigBrothers Securityaffairs
Cybersecurity and Infrastructure Security Agency (CISA) revealed that a hacker breached a US federal agency and exfiltrated data.
Cybersecurity and Infrastructure Security Agency (CISA) revealed that a hacker breached a US federal agency and threat actors exfiltrated data.
CISA published a detailed incident report related to the incident but didn’t disclose the name of the hacked agency. Threat actors implanted a malware in the network of an unnamed federal agency that was able to avoid detection.
“The Cybersecurity and Infrastructure Security Agency (CISA) responded to a recent threat actor’s cyberattack on a federal agency’s enterprise network.” reads the analysis report published by CISA. “By leveraging compromised credentials, the cyber threat actor implanted sophisticated malware—including multi-stage malware that evaded the affected agency’s anti-malware protection—and gained persistent access through two reverse Socket Secure (SOCKS) proxies that exploited weaknesses in the agency’s firewall.”
The intrusion was detected by the EINSTEIN, the CISA’s intrusion detection system that is used to monitor federal civilian networks.
The threat actors initially leveraged compromised credentials for Microsoft Office 365 (O365) accounts, domain administrator accounts, and credentials for the agency’s Pulse Secure VPN server.
“First the threat actor logged into a user’s O365 account from Internet Protocol (IP) address 91.219.236[.]166 and then browsed pages on a SharePoint site and downloaded a file (Data from Information Repositories: SharePoint [T1213.002]). The cyber threat actor connected multiple times by Transmission Control Protocol (TCP) from IP address 185.86.151[.]223 to the victim organization’s virtual private network (VPN) server (Exploit Public-Facing Application [T1190]).” continues the report.
CISA analysts speculate the attackers obtained the credentials from an unpatched agency VPN server by exploiting the CVE-2019-11510—in Pulse Secure.
Once the attackers logged into Office 365 accounts, they attempted to view and download help desk email attachments with “Intranet access” and “VPN passwords” in the subject line. The attackers have done it to gather additional information on the target network, they also enumerated the Active Directory and Group Policy key and changed a registry key for the Group Policy.
In order to establish Persistence and Command and Control on the federal agency network, the attackers created a persistent Secure Socket Shell (SSH) tunnel/reverse SOCKS proxy.
The intruders connected a hard drive in the agency’s network they controlled as a locally mounted remote share.
“The mounted file share allowed the actor to freely move during its operations while leaving fewer artifacts for forensic analysis,” the report continues.
The attacker created a local account on the network that allowed them to browse the local network, run PowerShell commands, and exfiltrate data stored in compressed Zip files with several files and directories on them. CISA couldn’t confirm if the attacker exfiltrated these ZIP archives.
According to CISA, the malware installed on the network of the federal agency was able to overcome the agency’s anti-malware protection, and inetinfo.exe escaped quarantine.
Additional technical details, including Indicators of Compromise (IoCs) are included in the Analysis Report published by CISA.
CISA Says Threat Actor Breached Federal Agency's Network
25.9.20 BigBrothers Securityweek
A threat actor was able to compromise the network of a federal agency and create a reverse proxy and install malware, the Cybersecurity and Infrastructure Security Agency (CISA) reported on Thursday.
The attack, CISA explains, relied on compromised credentials for initial access, and resulted in multi-stage malware being installed on the affected agency’s systems, without triggering in-place anti-malware protections.
Credentials for multiple Microsoft Office 365 (O365) and domain administrator accounts were employed in the attack, CISA says. Using the Transmission Control Protocol (TCP), the attackers were able to connect multiple times to the victim organization’s virtual private network (VPN) server.
CISA could not determine how the adversary obtained the credentials, but says that they might have gotten them from an unpatched VPN server by exploiting a known vulnerability in Pulse Secure, namely CVE-2019-11510, which was patched in April 2019.
“CISA has observed wide exploitation of CVE-2019-11510 across the federal government,” the agency notes.
Following initial access, the threat actor started gathering information of interest from email accounts, enumerated the Active Directory and Group Policy key, modified a registry key for the Group Policy, and enumerated compromised systems.
The attackers connected to the compromised network using various methods, including Remote Desktop Protocol (RDP), a Windows Server Message Block (SMB) client, and through plink.exe, a command-line version of PuTTy.
Furthermore, the adversary achieved persistence through a Secure Socket Shell (SSH) tunnel/reverse SOCKS proxy (two Scheduled Tasks were created for them), and executed a unique, multi-stage malware to drop files. Additionally, they created a locally mounted remote share.
The threat actor also created a local account to browse directories on a file server, copy a file to the locally mounted remote share, interact with other files on users’ home directories (although CISA could not confirm whether exfiltration occurred), create a reverse SMB SOCKS proxy, interact with a PowerShell module, steal data from an account directory and file server directory, and create ZIP archives containing files and directories (CISA could not confirm that the ZIP files were exfiltrated).
To overcome the agency’s anti-malware protection, the threat actor accessed the “anti-malware product’s software license key and installation guide and then visited a directory used by the product for temporary file analysis,” after which they were able to run their malware executable.
CISA, which has provided indicators of compromise (IoC) associated with the attack, recommends that all federal agencies monitor network traffic to identify unusual activity such as unusual open ports, large outbound files, and unexpected and unapproved protocols.
The agency also recommends that organizations deploy an enterprise firewall, that they identify and block all ports that are not necessary, implement multi-factor authentication, separate administrative accounts on administrative workstations and apply the principle of least privilege, secure RDP, and ensure that anti-malware software and operating systems are up to date.
TikTok Urges Court to Block Trump's Ban on App in US
24.9.20 BigBrothers Securityweek
TikTok is urging a federal court to block US President Donald Trump from banning the video app, arguing the move is motivated by election politics rather than legitimate national security concerns.
The Chinese-owned app -- which is wildly popular in the US -- has come under fire as tensions escalate between Beijing and Washington, with Trump threatening a ban if it is not sold to an American company.
Attorneys are set to argue the case on Thursday before a judge who will decide whether to put Trump's order on hold until a lawsuit over the ban is resolved.
Citing "confusing and contradictory statements about TikTok" by the president and other agencies, the motion for a preliminary injunction argues a ban is not motivated by "genuine national security concern, but rather by political considerations relating to the upcoming general election."
TikTok, which became a global phenomenon with its brand of short, addictive phone videos, has some 100 million US users.
A deal to restructure ownership of the app was thrown into doubt Monday when Trump vowed to block a deal that allows its Chinese parent firm ByteDance to retain any control.
The comments cast doubt over an agreement that had appeared to cut a way through the threatened ban.
The deal would make Silicon Valley giant Oracle the data partner for TikTok, with retail giant Walmart also taking a minority stake in a new entity to be called TikTok Global.
As competing statements deepened the mystery over the app's future, ByteDance earlier said TikTok Global plans to launch a "small round of pre-IPO financing" after which it would become an 80 percent-owned subsidiary of ByteDance.
But Trump told Fox News om Monday that TikTok's Chinese parent firm "will have nothing to do with it."
Oracle and Walmart "are going to own the controlling interest," he added. "Everything is going to be moved into a cloud done by Oracle... and it's going to be controlled -- totally controlled by Oracle."
ByteDance said Thursday that it had applied for an export license with the commerce ministry, although it did not link the move to TikTok or any potential sale.
China's commerce ministry published new rules in August that added "civilian use" to a list of technologies that are restricted for export and require permission, which could complicate any sale.
Winning a temporary injunction typically involves convincing a judge that not intervening would allow irreparable harm to be done to a party likely to win the case.
TikTok would suffer "devastating harm" from which it could not recover if Trump's ban is found to be unlawful, the motion argued.
As US relations with China grew more contentious, Trump began targeting TikTok, the filing read.
The motion also speculated that TikTok had irked the president because of reports the app was used by his critics to snatch up tickets to a Trump rally in Tulsa to which they had no intention of going -- an event which belly flopped with significantly fewer people in attendance.
Russian Hackers Target Russian Companies With Ransomware
24.9.20 BigBrothers Securityweek
A hacking group whose members are Russian speakers is targeting organizations in Russia and post-Soviet countries with ransomware, Group-IB’s security researchers have discovered.
Dubbed OldGremlin, the new cyber-crime group is actively targeting banks, medical organizations, software developers, and industrial enterprises, among others, and has launched at least seven campaigns since spring.
The adversary employs phishing as means to compromise enterprise networks, and has been observed impersonating the self-regulatory organization Mikrofinansirovaniye i Razvitiye (SRO MiR); the Minsk Tractor Works plant in Belarus; a Russian metallurgical holding company; the Russian media group RBC; and a dental clinic, Group-IB explains.
In March and April 2020, the hackers leveraged the COVID-19 crisis to impersonate SRO MiR and distribute a self-developed Trojan called TinyPosh. In late April, they impersonated dental clinic Novadent, employing the same tactics.
In May, OldGremlin leveraged a fake email allegedly from a Russian RBC journalist that offered a bank employee an interview. The email, which accurately imitated the media holding's style, enticed the victim into clicking a link leading to TinyPosh.
In mid-August, the group launched two large-scale malicious campaigns impersonating RBC and a mining and metallurgical company. Roughly 250 malicious emails were sent to Russian companies in the financial and industrial sectors. Days later, the theme of the emails was changed to the protests in Belarus, with over 50 malicious messages sent.
A successful attack carried out in August targeted a large medical company with a phishing email allegedly sent by RBC. In the initial stage of the attack, a backdoor called TinyNode was deployed, providing remote access to compromised systems and a way to collect valuable information and spread across the network.
The attackers moved laterally across the network, obtained domain administrator credentials, and created an additional privileged account. A few weeks later, they deleted all backups and installed the TinyCryptor ransomware on hundreds of computers, blocking the organization’s regional branches.
The cybercriminals demanded a $50,000 ransom from the victim company in exchange for decrypting the data.
"OldGremlin is the only Russian-speaking ransomware operator that violates the unspoken rule about not working within Russia and post-Soviet countries. They carry out multistage targeted attacks on Russian companies and banks using sophisticated tactics and techniques similar to those employed by APT groups,” Oleg Skulkin, senior digital forensics analyst at Group-IB, commented.
Russia-linked APT28 targets govt bodies with fake NATO training docs
23.9.20 BigBrothers Securityaffairs
Russia-linked cyberespionage group APT28 uses fake NATO training documents as bait in attacks aimed at government bodies.
The Russia-linked cyberespionage group APT28 is behind a string of attacks that targeting government bodies with Zebrocy Delphi malware. The malicious code was distributed using fake NATO training materials as bait and had a very low detection rate of 3/61 on VirusTotal.
Even today, less than half of the known antivirus engines are flagging the infection on VirusTotal, as observed by BleepingComputer:
The APT28 group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
Threat intelligence firm QuoIntelligence uncovered a campaign on Government bodies on August 9, the attacks likely started on August 5.
“On 9 August, QuoIntelligence disseminated a Warning to its government customers about a new APT28 (aka Sofacy, Sednit, Fancy Bear, STRONTIUM, etc.) campaign targeting government bodies of NATO members (or countries cooperating with NATO).” reads the report published QuoIntelligence. “In particular, we found a malicious file uploaded to VirusTotal, which ultimately drops a Zebrocy malware and communicates with a C2 in France.”
The command and control infrastructure was hosted in France, for this reason, QuoIntelligence had reported their findings to the French law enforcement agencies.
The same campaign was also reported in August by the Qi’anxin Red Raindrops.
The researchers analyzed files (Course 5 – 16 October 2020.zipx) containing the malicious code. Upon renaming the file as a JPG, they were showing the logo of the Supreme Headquarters Allied Powers Europe (SHAPE), which is the NATO’s Allied Command Operations (ACO) located in Belgium
The malicious file distributed by APT28 is titled, “Course 5 – 16 October 2020.zipx”

Experts revealed the sample has a Zip file concatenated. Experts pointed out that the technique works because JPEG files are parsed from the beginning of the file while some Zip implementations parse Zip files from the end of the file ignoring the signature at the beginning.
According to QuoIntelligence researchers, the campaign targeted some NATO countries and at least one Middle Eastern country, Azerbaijan that cooperates with the North-Atlantic alliance.
After decompressing the ZIP file, the following two samples are dropped:
Course 5 – 16 October 2020.exe (Zebrocy malware) SHA256: aac3b1221366cf7e4421bdd555d0bc33d4b92d6f65fa58c1bb4d8474db883fec
Course 5 – 16 October 2020.xls (Corrupted file) SHA256: b45dc885949d29cba06595305923a0ed8969774dae995f0ce5b947b5ab5fe185
The Excel file (XLS) is corrupted and cannot be opened by Microsoft Excel, it contains information about military personnel involved in the military mission “African Union Mission for Somalia,” but researchers were not able to determine if the information contained in the file is legitimate or not.
The Zebrocy malware employed in this campaign is a persistent backdoor that can be used by threat actors to perfor system reconnaissance and take full control of the target systems.
The Zebrocy payload (present in “Course 5 – 16 October 2020.exe”) replicates itself into “%AppData%\Roaming\Service\12345678\sqlservice.exe” and further adds a randomized 160-byte blob to the newly generated file to make harder the detection by signature-based antivirus engines.
The malicious code creates a Windows scheduled task that runs every minute and sends data in obfuscated and encrypted form to the C2 server with post requests.
“The task runs regularly and tries to POST stolen data (e.g. screenshots) to hxxp://194.32.78[.]245/protect/get-upd-id[.]PHP” continues the report.”The malware sends POST requests about once per minute without getting a response back. Additionally, the server closes the connection after waiting for about 10 more seconds. It is possible that this unresponsive behavior is due to the C2 determining the infected machine as not interesting.”
The report includes the list of Indicators of Compromise (IOCs), IDS detection rule(s), and technical details about the campaign.
HOW DO PROVIDERS IMPLEMENT INTERNET BLOCKING IN BELARUS?
23.9.20 BigBrothers Securityaffairs
Researchers at Qurium Media Foundation analyzed the blocking implemented by four different operators in Belarus.
September 23, 2020
Qurium analyzes the blocking implemented by four different operators in Belarus
Belarus operators use their own infrastructure to implement the blocking
Block techniques include transparent web proxies, injection of HTTP responses, stateless and stateful SSL DPI and fake DNS responses
In August 2020, mass anti-government protests erupted in Belarus against the re-election of the president Alexander Lukashenko and the arrest of opposition political candidates. The Internet was shutdown several days and more than 80 websites, most of them news and political sites, were blocked. They still remain blocked.
Qurium Media Foundation, in collaboration with the Belarusian human rights organization Human Constanta, has been looking into some of the implementation details of the Internet blocking in Belarus, focusing on a few selected providers (Business Network, Beltelecom, A1 and MTS), to look deeper into the nature of the hardware used for the blocking and understand how it is working.
According to Qurium’s report, providers use their own infrastructure to implement the blocking and blocking is therefor not implemented on a central level. Some of the blocking techniques used include Domain Name System spoofing, transparent proxies with hijacked HTTPS certificates and Deep Packet Technology (DPI) implementations.
Qurium forensics report: Internet blocking in Belarus
New Zebrocy Campaign Suggests Russia Continues Attacks on NATO
23.9.20 BigBrothers Securityweek
QuoINT security researchers have identified a new Zebrocy campaign targeting countries associated with the North Atlantic Treaty Organization (NATO).
Detailed for the first time in 2018, Zebrocy has been associated with the Russia-linked state-sponsored threat actor APT28 (also known as Fancy Bear, Pawn Storm, Sednit, and Strontium), which has been active since at least 2007.
While some security researchers see Zebrocy as a separate adversary, others have shown connections between various threat actors operating out of Russia, including a link between GreyEnergy and Zebrocy attacks.
The recently observed campaign, which likely started on August 5, employed the Delphi version of the Zebrocy malware and a command and control (C&C) infrastructure hosted in France, QuoINT’s security researchers reveal.
Lures employed in these attacks had a NATO-related theme, a recurring motif in APT28 campaigns — the adversary used a similar theme in attacks in 2017. The intended victim in the new attacks was a specific government body in Azerbaijan, but other NATO members or countries involved in NATO exercises might have been targeted as well.
The attackers distributed what appeared to be a JPEG image that, instead, turned out to be a ZIP archive concatenated to evade detection. The file drops the Zebrocy executable and a corrupted Excel file, likely in an attempt to lure the intended victim into executing the malware.
Once executed, the malware creates a scheduled task to regularly attempt to send stolen data to a remote domain. On machines that the C&C server appears to find uninteresting, the connection is terminated by the server.
“QuoINT concludes with medium-high confidence that the campaign targeted a specific government body, at least in Azerbaijan. Although Azerbaijan is not a NATO member, it closely cooperates with the North-Atlantic organizations and participates in NATO exercises. Further, the same campaign very likely targeted other NATO members or countries cooperating with NATO exercises,” QuoINT says.
The security researchers also note that this APT28 attack shows striking similarities with a ReconHellcat/ BlackWater attack uncovered last month: the compressed Zebrocy malware and the lure in the BlackWater attack were both uploaded on August 5 by the same user in Azerbaijan (highly likely by the same organization), the attacks happened simultaneously, and victimology is similar in both attacks.
Furthermore, the researchers point out that APT28 previously targeted both NATO and the Organization for Security and Co-operation in Europe (OSCE) — the ReconHellcat campaign was employing OSCE-themed lures — but that there’s no “strong causation link […] or solid technical link between the two attacks.”
“We assessed ReconHellcat as a high-capability APT group, like APT28,” QuoINT concludes.
Facebook Says Fake Accounts From China Aimed at US Politics
23.9.20 BigBrothers Social Securityweek
Facebook said Tuesday it derailed a network of fakes accounts out of China that had recently taken aim at the US presidential race.
The takedown came as part of the social networks fight against "coordinated inauthentic behavior" and marked the first time Facebook had seen such a campaign based in China targeting US politics, according to head of security policy Nathaniel Gleicher.
Facebook did not connect the campaign to the Chinese government, saying its investigation found links to individuals in the Fujian province of China.
In the takedown, Facebook removed 155 accounts, 11 Pages, 9 Groups and 6 Instagram accounts for violating its policy against foreign interference in deceptive schemes.
The campaign out of China focused primarily on the Philippines and South East Asia more broadly, and just a bit on the US, according to Gleicher.
Posts particularly commented about naval activity in the South China Sea, including US Navy ships, Facebook said.
The account holders would have had to use techniques to circumvent China's "Great Firewall," which bans the US social network. Gleicher said the people running the pages posed as locals in places they targeted, and tried to hide their locations using virtual private network software.
The network posted in South East Asia about Beijing's interest in the South China Sea; Hong Kong, and in support of Philippines President Rodrigo Duterte, Facebook said.
The network had evidently been active since at least 2018, only recently starting to post content both in for and against US President Donal Trump and his Democratic challenger Joe Biden, according to Gleicher.
"The operation had been running a while aimed at Southeast Asia; its aim at the US seemed nascent and ineffective," Gleicher said during a briefing with journalists.
"These actors had hardly posted anything; it looked like audience building."
About 133,000 people followed one or more of the campaigns Facebook pages, and around 61,000 people had joined one or more of its online Groups, according to the California-based social network.
The campaign had only spent about $60 on ads at Facebook, paid for in Chinese yuan, Gleicher said.
FBI, CISA Warn of Disinformation Campaigns Targeting 2020 Election Results
23.9.20 BigBrothers Securityweek
Threat actors are expected to launch disinformation campaigns targeting the results of the 2020 elections in the United States, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) said in an alert this week.
Spreading disinformation on the results of the elections represents a threat to the credibility of the electoral process, meant to undermine confidence in the democratic institutions in the United States, the alert reads.
According to the FBI and CISA, both foreign actors and cybercriminals are expected to target the 2020 elections through newly created websites, changes made to existing websites, as well as through the creation and sharing of corresponding social media content containing false information.
Election results, the two agencies note, are typically validated within several days or weeks, to ensure that every legally cast vote has been accurately counted. This year, however, the COVID-19 pandemic has resulted in an increase in the use of mail-in ballots, which leads to incomplete results on election night.
“Foreign actors and cybercriminals could exploit the time required to certify and announce elections’ results by disseminating disinformation that includes reports of voter suppression, cyberattacks targeting election infrastructure, voter or ballot fraud, and other problems intended to convince the public of the elections’ illegitimacy,” the alert reads.
Thus, the FBI and CISA advise towards evaluating sources of information to ensure they are reliable (such as state and local election officials) and that they provide verified information. What’s more, the agencies say, the public should also keep in mind that, even if threat actors may successfully alter election-related websites, the underlying data and internal systems remain uncompromised.
The public is also advised to verify who produced the content they are accessing, verify through multiple sources any reports on issues related to voting or election results before sharing such content on social media or other venues, and rely on election officials for information on final election results.
Furthermore, the public is encouraged to report potential election crimes, such as disinformation on the election process, to the FBI, or use the tools offered by social media companies to report posts that might be spreading false or inconsistent election-related information.
Operation DisrupTor: police arrested 179 vendors engaged in the sale of illicit good
23.9.20 BigBrothers Securityaffairs
A global police sting dubbed Operation DisrupTor targeted vendors and buyers of illicit goods on the dark web, Europol announced.
A coordinated operation conducted by law enforcement agencies across the world, dubbed Operation DisrupTor, targeted vendors and buyers of illicit goods on the dark web.
The operation, led by the German federal criminal police, saw the participation of law agencies from Austria, Britain, Germany, the Netherlands, Sweden, and the United States.
This operation follows the takedown in May of last year of Wall Street Market that took place in May 2019. The Wall Street Market marketplace was considered one of the most important points of aggregation in the cybercrime underground for trading in cocaine, heroin, cannabis and amphetamines as well as digital goods (i.e. stolen data, malware, and fake documents). The Tor-based marketplace had more than one million registered accounts, more than 5,000 registered sellers and more than 60,000 sales offers.
Operation DisrupTor resulted in the arrest of 179 vendors who engaged in tens of thousands of sales of illicit good were arrested across Europe and the United States.
“Today, a coalition of law enforcement agencies across the world announced the results of a coordinated operation known as DisrupTor which targeted vendors and buyers of illicit goods on the dark web.” reads the press release published by the Europol. “As a result, 179 vendors who engaged in tens of thousands of sales of illicit good were arrested across Europe and the United States. Over $6.5 million were seized in both cash and virtual currencies, alongside some 500 kilograms of drugs, including fentanyl, oxycodone, hydrocodone, methamphetamine, heroin, cocaine, ecstasy, MDMA, and medicine containing addictive substances; and 64 firearms.”
The police arrested 121 people in the US, 42 in Germany, 8 in the Netherlands, 4 in the UK, 3 in Austria and 1 in Sweden.
The Europol confirmed that multiple investigations are still ongoing.

“Law enforcement is most effective when working together, and today’s announcement sends a strong message to criminals selling or buying illicit goods on the dark web: the hidden internet is no longer hidden, and your anonymous activity is not anonymous.” the Head of Europol’s European Cybercrime Centre (EC3), Edvardas Šileris said. “Law enforcement is committed to tracking down criminals, no matter where they operate – be it on the streets or behind a computer screen.”
German investigators blame Russian DoppelPaymer gang for deadly hospital attack
23.9.20 BigBrothers Securityaffairs
The investigation of German authorities on the recent attack on the Dusseldorf hospital reveals the possible involvement of Russian hackers.
Last week, German authorities revealed that a cyber attack hit a major hospital in Duesseldorf, the Duesseldorf University Clinic, and a woman who needed urgent admission died after she had to be taken to another city for treatment.
“The Duesseldorf University Clinic’s systems have been disrupted since last Thursday.” stated the Associated Press.
The treatment for the women was delayed for an hour that caused the death of the patient.
Now, in an update to lawmakers shared this week, prosecutors revealed that the malware family that hit the German hospital was the infamous Doppelpaymer ransomware.
The same ransomware family was involved in numerous attacks in the last months, including the security breach suffered early this month by UK research university Newcastle University.
DoppelPaymer ransomware has been active since June 2019, in November Microsoft Security Response Center (MSRC) warned customers of the DoppelPaymer ransomware and provided useful information on the threat.
Experts pointed out that the DoppelPaymer ransomware operators “according to private security firms, is based in Russia.”
Investigators believe that the real targey of the ransomware operators was the Heinrich Heine University in Duesseldorf that was affiliated with the hospital.
The attack caused systems gradually crashing, it paralyzed the operations at the hospital and emergency patients were hijacked in other structures while surgical operations postponed.
The hospital confirmed that there was no concrete ransom demand and reported that there are no indications that data is irretrievably lost.
The news agency dpa cited a report from North Rhine-Westphalia state’s justice minister that revealed the hospital was hit by a ransomware attack, which infected 30 servers at its network and an extortion note was found on one of the systems. The ransom note includes details to contact the attackers but doesn’t contain any sum.
Duesseldorf law enforcement contacted the ransomware gang and told them the hospital had been affected, endangering the life of patients. The ransomware operators then decided to withdraw the extortion attempt and provided a digital key to decrypt the data.
The justice minister’s report confirmed that the perpetrators are no longer reachable.
CISA’s advisory warns of notable increase in LokiBot malware
23.9.20 BigBrothers BotNet Securityaffairs
US Cybersecurity and Infrastructure Security Agency (CISA) is warning of a notable increase in the use of LokiBot malware by threat actors since July 2020.
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued a new security advisory warning federal agencies and the private sector of a surge in the attacks employing the LokiBot malware since July 2020.
The Agency’s EINSTEIN Intrusion Detection System has detected persistent malicious activity associated with the LokiBot malware.
“CISA has observed a notable increase in the use of LokiBot malware by malicious cyber actors since July 2020. Throughout this period, CISA’s EINSTEIN Intrusion Detection System, which protects federal, civilian executive branch networks, has detected persistent malicious LokiBot activity.” reads the CISA’s advisory.
The Lokibot malware has been active since 2015, it is an infostealer that was involved in many malspam campaigns aimed at harvest credentials from web browsers, email clients, admin tools and that was also used to target cryptocoin-wallet owners.
The malware is able to steal sensitive information (a variety of credentials, including FTP credentials, stored email passwords, passwords stored in the browser, as well as a whole host of other credentials)
The original LokiBot malware was developed and sold by online by a hacker who goes online by the alias “lokistov,” (aka Carter).
The malicious code was initially advertised on many hacking forums for up to $300, later other threat actors started offering it for less than $80 in the cybercrime underground.
Across time, the author of the threat implemented new features such as real-time key-logging to capture keystrokes, desktop screenshot and functionalities.
The CISA LokiBot advisory includes detection signatures and mitigation recommendations for LokiBot attacks.
Below the list of mitigations:
Maintain up-to-date antivirus signatures and engines. See Protecting Against Malicious Code.
Keep operating system patches up to date. See Understanding Patches and Software Updates.
Disable file and printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
Enforce multi-factor authentication. See Supplementing Passwords for more information.
Restrict users’ ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators’ group unless required.
Enforce a strong password policy. See Choosing and Protecting Passwords.
Exercise caution when opening email attachments, even if the attachment is expected and the sender appears to be known. See Using Caution with Email Attachments.
Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
Disable unnecessary services on agency workstations and servers.
Scan for and remove suspicious email attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
Monitor users’ web browsing habits; restrict access to sites with unfavorable content.
Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs).
Scan all software downloaded from the internet prior to executing.
Maintain situational awareness of the latest threats and implement appropriate access control lists.
Visit the MITRE ATT&CK Techniques pages (linked in table 1 above) for additional mitigation and detection strategies.
German Experts See Russian Link in Deadly Hospital Hacking
22.9.20 BigBrothers Securityweek
German authorities probing a cyber attack on a hospital's IT system that led to a fatal delay in treatment for a critically ill woman believe the software used can be traced back to Russian hackers.
In an update to lawmakers published on Tuesday, prosecutors wrote that hackers used malware known as "Doppelpaymer" to disable computers at Duesseldorf University Hospital on September 10, aiming to encrypt data and then demand payment to unlock it again.
The same ransomware has been used in cyber attacks around the world carried out "by a group of hackers that, according to private security firms, is based in Russia", the report said.
The attack saw the hospital's computer system become disconnected from the ambulance network.
A severely ill woman was therefore admitted to a hospital further away in Wuppertal and died shortly afterwards.
The longer distance that the ambulance had to travel led to an hour's delay before medical staff were able to treat her.
Cologne prosecutors last week opened an investigation into involuntary manslaughter against unknown suspects over the woman's death.
If charges are brought, it would be a rare case of a hacking with deadly consequences.
Investigators suspect that the hackers had not meant to hit the hospital, with the actual target thought to have been the affiliated Heinrich Heine University in Duesseldorf.
Local police were able to contact the hackers during the attack to tell them patients' lives were at risk, prompting the hackers to hand over a decryption key before breaking off communication.
Germany has seen several hacker attacks on research and higher education institutions in recent months, including the University of Giessen, the University of Cologne and the Ruhr University Bochum.
The German government has in recent years blamed Russia for several high-profile attempts by hackers to spy on lawmakers or leading politicians, including Chancellor Angela Merkel.
British Hacker Sentenced to 5 Years for Blackmailing U.S. Companies
22.9.20 BigBrothers Thehackernews

A UK man who threatened to publicly release stolen confidential information unless the victims agreed to fulfill his digital extortion demands has finally pleaded guilty on Monday at U.S. federal district court in St. Louis, Missouri.
Nathan Francis Wyatt , 39, who is a key member of the infamous international hacking group 'The Dark Overlord,' has been sentenced to five years in prison and ordered to pay $1,467,048 in restitution to his victims.
Wyatt, who was extradited to the United States late last year after being held for over two years in the United Kingdom, has pleaded guilty to conspiring to commit aggravated identity theft and computer fraud.
U.K. police first arrested Wyatt in September 2016 during an investigation into the hacking of an iCloud account belonging to Pippa Middleton, the younger sister of the British royal family member Duchess of Cambridge, and stealing 3,000 images of her.
Though he was released in that case without charge due to lack of evidence, Wyatt was again arrested in September 2017 over hacking companies, credit card frauds, and blackmailing schemes to extort money from the victims.
According to court documents, Wyatt has attacked multiple healthcare providers and accounting firms in Missouri, Illinois, and Georgia states as a member of The Dark Overlord since February 2016, but the court documents do not name the companies.
The Dark Overlord (TDO) is infamous for remotely accessing the computer networks of victim companies in the United States and then stealing sensitive data, like patient medical records and personal identifying information.
"The Dark Overlord has victimized innumerable employers in the United States, many of them repeatedly," said U.S Attorney Jeff Jensen. "I am grateful to the victims who came forward despite ransom threats and to the prosecutors and agents who were the first to catch and punish a member of The Dark Overlord in the United States."
Wyatt admitted that his hacking gang members typically worked by obtaining sensitive data from victim companies and then threatening them to release the stolen data unless they paid a ransom of between $75,000 and $350,000 in bitcoin.
Wyatt's role at TDO was directly contacting victims and maintaining communication, payment, and virtual private network accounts that he used to send threatening and extortionate messages to victims and their family and friends.
In one such threatening message, Wyatt sent to the victims involved the daughter of one of the owners of the Farmington company, asking her, "hi ... you look peaceful ... by the way did your daddy tell you he refused to pay us when we stole his company files?," adding that "In four days we will be releasing for sale thousands of patient info. including yours."
"Nathan Wyatt used his technical skills to prey on Americans' private data and exploited the sensitive nature of their medical and financial records for his own personal gain," said Acting Assistant Attorney General Brian C. Rabbitt of the DOJ's Criminal Division.
"Today's guilty plea and sentence demonstrate the department's commitment to ensuring that hackers who seek to profit by illegally invading the privacy of Americans will be found and held accountable, no matter where they may be located."
The Dark Overload has previously been attributed to several hacking events, including leaking ten unreleased episodes of the 5th season of ' Orange Is The New Black' series from Netflix and hacking Gorilla Glue , Little Red Door cancer service agency, among others.
DHS Issues Dire Patch Warning for ‘Zerologon’
22.9.20 BigBrothers Threatpost
The deadline looms for U.S. Cybersecurity and Infrastructure Security Agency’s emergency directive for federal agencies to patch against the so-called ‘Zerologon’ vulnerability.
Federal agencies that haven’t patched their Windows Servers against the ‘Zerologon’ vulnerability by Monday Sept. 21 at 11:59 pm EDT are in violation of a rare emergency directive issued by the Secretary of Homeland Security.
With only hours until the deadline for the directive, issued on Friday, to be executed, what is at stake is a “vulnerability [that] poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action,” according to the Cybersecurity and Infrastructure Security Agency (PDF).
Microsoft released a patch for the vulnerability (CVE-2020-1472) as part of its August 11, 2020 Patch Tuesday security updates. However, earlier this month the stakes got higher for risks tied to the bug when four public proof-of-concept exploits for the flaw were released on Github.
The bug is located in a core authentication component of Active Directory within the Windows Server OS and the Microsoft Windows Netlogon Remote Protocol (MS-NRPC). Exploiting the bug allows an unauthenticated attacker, with network access to a domain controller, to completely compromise all Active Directory identity services, according to Microsoft.
“This attack has a huge impact: It basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain,” said researchers with Secura, in a whitepaper published earlier this month.
As previous reported, the flaw stems from the Netlogon Remote Protocol, available on Windows domain controllers, which is used for various tasks related to user and machine authentication.
“The issue exists in the usage of AES-CFB8 encryption for Netlogon sessions. The AES-CFB8 standard requires that each ‘byte’ of plaintext have a randomized initialization vector (IV), blocking attackers from guessing passwords. However, Netlogon’s ComputeNetlogonCredential function sets the IV to a fixed 16 bits – not randomized – meaning an attacker could control the deciphered text,” according to earlier reporting.
Since the flaw was first identified it has been under active attack. Calls for immediate patching have been unanimous. However, the Monday deadline for patching by CISA suggests still too many systems have not been updated.
“This emergency directive remains in effect until all agencies have applied the August 2020 Security Update (or other superseding updates) or the directive is terminated through other appropriate action,” according to CISA.
The directive is part of the Department of Homeland Security’s “Section 3553(h) of title 44” U.S. Code of Laws.
The directive requires security teams at those affected federal civilian and executive branch departments to update all Windows Servers with the domain controller role by midnight EDT Sept. 21. “If affected domain controllers cannot be updated, ensure they are removed from the network,” the agency said.
Next, agencies must ensure “technical and/or management controls are in place to ensure newly provisioned or previously disconnected domain controller servers are updated before connecting to agency networks,” CISA wrote.
“The availability of the exploit code in the wild increasing likelihood of any upatched domain controller being exploited,” the agency said. It added the widespread presence of the vulnerable domain controllers across the federal enterprise is a concern, coupled with the high potential for agency information systems to be compromised.
The CISA directive orders those agencies, by 11:59 PM EDT, Wednesday, Sept. 23, 2020, to submit a “completion report” to DHS.
“Beginning Oct. 1, 2020, the CISA Director will engage the CIOs and/or Senior Agency Officials for Risk Management of agencies that have not completed required actions, as appropriate and based on a risk-based approach,” read the CISA directive signed by Christopher Krebs, Director, Cybersecurity and Infrastructure Security Agency, within the Department of Homeland Security.
FERC, NERC joint report on cyber incident response at electric utilities
22.9.20 BigBrothers Securityaffairs
The US FERC and NERC published a study on cyber incident response at electric utilities that also includes recovery best practices.
The U.S. Federal Energy Regulatory Commission (FERC) and the North American Electricity Reliability Corporation (NERC) released a study on cyber incident response and recovery best practices for electric utilities.
The report is based on information shared by experts at eight U.S. electric utilities. The idea behind the study is to improve the incident response and incident recovery plans ensuring the reliability of the electric system in case of a cybersecurity incident.
A cyber attack could have a severe impact on the operations of the utilities and consequent economical losses. The incident response and recovery (IRR) plan describes the way the staff at the utility will responds to a incident.
“Establishing clear procedures for handling incidents is a complex undertaking and, though individualized to an organization’s mission, size, structure, and functions, generally contain common elements: (1) they define their scope (to whom they apply, what do they cover, and under what circumstances); and (2) they define computer security events and incidents, staff roles and responsibilities, levels of authority for response (e.g., authority to disconnect equipment), reporting requirements, requirements and guidelines for external communications and information sharing, and procedures to evaluate performance.” reads the study.
While incident response and recovery (IRR) plans provided by the utilities that contributed to the study present many similarities, such as the compliance NIST framework (SP 800-61), there isn’t an optimal model.
Each utility has developed separate plans for responding to the cyber incident depending on the impact on their operational and business networks.
The goal of the NERC and FERC teams were to identify and consolidate a set of practices that could be adopted by electric utilities as best practices for the development of an IRR plan.
In the preparation phase, an effective IRR plan has to include a clear definition of personnel roles, promote accountability, and, where appropriate, empower personnel to take action without unnecessary delays.
An effective IRR plan leverages technology and automated tools along with well-trained personnel.
In the detection and analysis phase, the study recommends the use of baselining to detect potential cyber incidents, and the adoption of a decision tree or flowchart to quickly assess if a specific risk threshold is reached and if certain circumstances qualify as an event.
In the containment and eradication phase, the IRR plan should analyze the impact of the decision taken in the previous phases. The organization should have a deep knowledge of the potential threats, their potential impact, and the countermeasures to deploy to mitigate them.
The IRR plans should consider the resource implications of incident responses of indeterminate length.
In the post-incident activity an effective IRR plans implement lessons-learned from previous incidents and simulated activities identifying clear shortfalls in the IRR plan.
NSA Issues Cybersecurity Guidance for Remote Workers, System Admins
22.9.20 BigBrothers Securityweek
The National Security Agency (NSA) has published two cybersecurity information sheets (CSIs) with recommendations for National Security System (NSS) and Department of Defense (DoD) workers and system administrators on securing networks and responding to incidents during the work-from-home period.
Titled Compromised Personal Network Indicators and Mitigations, the first of the CSIs is meant to deliver details on how teleworkers can identify and mitigate the compromise of their personal networks and to secure data and the equipment provided by the government when working remotely.
Furthermore, the CSI provides a series of indicators of compromise (IoC), along with the mitigation techniques that teleworkers can apply to prevent future compromises. The CSI is meant for government employees, but anyone can use the provided information to identify and prevent network breaches, the NSA points out.
“While there is no way to ensure that personal networks will be completely secured from attacks—attackers are persistent and continue to find ways to circumvent security controls—users can still take steps to help prevent future attacks,” the CSI reads.
Should the indicators of compromise outlined in the document be observed, users are advised to apply the provided mitigations to any computer, mobile device, or IoT device connected to their personal network.
Recommended steps to mitigate the compromise, the NSA says, include rebooting and resetting routers, disabling their remote administration functionality and updating the firmware; disconnecting infected machines from the network, resetting passwords on a different device and running anti-malware software; and removing ransomware infections and restoring a previously backed-up good state.
The document details a series of more aggressive actions as well, all meant to help users eliminate threats from their personal devices or network, in addition to mitigating the compromise.
The NSA’s second CSI, which is titled Performing Out-of-Band Network Management, provides system admins information on how to isolate management traffic from operational traffic to ensure that a compromised device or malicious traffic won’t affect network operations or compromise network infrastructure.
“OoB [Out-of-Band] management creates a framework that enables administrators to improve the security of their networks by segmenting management traffic from operational traffic, and ensuring that management traffic only comes from the OoB communication path,” the NSA explains.
The document provides information on the architecture design of OoB management and recommends that a vulnerability and risk assessment should be performed first, to decide whether a virtually or physically segmented OoB network architecture should be implemented.
The NSA recommends using encryption protocols and strong encryption algorithms and key sizes, managing devices using strong virtual private networks (VPNs) only, hardening network management devices, continuously monitoring the network and reviewing logs, and establishing a configuration review and check-in process, which will allow easily identifying malicious changes.
DHS CISA orders federal agencies to fix Zerologon flaw by Monday
21.9.20 BigBrothers Securityaffairs
DHS CISA issued an emergency directive to tells government agencies to address the Zerologon vulnerability (CVE-2020-1472) by Monday.
The Department of Homeland Security’s CISA issued an emergency directive to order government agencies to address the Zerologon vulnerability (CVE-2020-1472) by Monday.
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
Administrators of enterprise Windows Servers have to install the August 2020 Patch Tuesday to mitigate “unacceptable risk” posed by the flaw to federal networks.
“CISA has determined that this vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action.” reads the emergency directive. “This determination is based on the following:
the availability of the exploit code in the wild increasing likelihood of any upatched domain controller being exploited;
the widespread presence of the affected domain controllers across the federal enterprise;
the high potential for a compromise of agency information systems;
the grave impact of a successful compromise; and
the continued presence of the vulnerability more than 30 days since the update was released.
CISA requires that agencies immediately apply the Windows Server August 2020 security update to all domain controllers.”
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
The only limitation on how to carry out a Zerologon attack is that the attacker must have access to the target network.
Secura researchers released a Python script that uses the Impacket library to test vulnerability for the Zerologon exploit, it could be used by admins to determine if their domain controller is still vulnerable.
“By simply sending a number of Netlogon messages in which various fields are filled with zeroes, an attacker can change the computer password of the domain controller that is stored in the AD. This can then be used to obtain domain admin credentials and then restore the original DC password.” concludes the research paper.
“This attack has a huge impact: it basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain. The attack is completely unauthenticated”
The ZeroLogon attack could be exploited by threat actors to deliver malware and ransomware on the target network.
CISA officials state that Windows Servers that can’t be patched have to be shut down and removed from the government network.
This emergency directive requires the following actions:
Update all Windows Servers with the domain controller role by 11:59 PM EDT, Monday, September 21, 2020,a. Apply the August 2020 Security Update to all Windows Servers with the domain controller role. If affected domain controllers cannot be updated, ensure they are removed from the network.b. By 11:59 PM EDT, Monday, September 21, 2020, ensure technical and/or management controls are in place to ensure newly provisioned or previously disconnected domain controller servers are updated before connecting to agency networks.
“In addition to agencies using their vulnerability scanning tools for this task, CISA recommends that agencies use other means to confirm that the update has been properly deployed.
These requirements apply to Windows Servers with the Active Directory domain controller role in any information system, including an information system used or operated by another entity on behalf of an agency, that collects, processes, stores, transmits, disseminates, or otherwise maintains agency information.“
Report information to CISAa. By 11:59 PM EDT, Wednesday, September 23, 2020, submit a completion report using the provided template. Department-level Chief Information Officers (CIOs) or equivalents must submit completion reports attesting to CISA that the applicable update has been applied to all affected servers and provide assurance that newly provisioned or previously disconnected servers will be patched as required by this directive prior to network connection (per Action 1).
FERC, NERC Conduct Study on Cyber Incident Response at Electric Utilities
21.9.20 BigBrothers Securityweek
The U.S. Federal Energy Regulatory Commission (FERC) and the North American Electricity Reliability Corporation (NERC) last week released a report outlining cyber incident response and recovery best practices for electric utilities.
The report is based on a study conducted by staff at FERC, NERC and NERC regional entities. The study is based on information provided by experts at eight U.S. electric utilities of various sizes and functions, and its goal was to help the industry improve incident response and incident recovery plans, which authors of the study say help ensure the reliability of the bulk electric system in the event of a cybersecurity incident.Incident response for electric utilities
The study found that there is no best incident response and recovery (IRR) plan model. The IRR plans of the targeted utilities share many similarities — they are based on the same NIST framework (SP 800-61) — but there are also differences, and some organizations have developed separate plans for incidents impacting their operational and business networks.
However, staff at NERC and FERC have identified some practices that all electric utilities should consider when developing an IRR plan.
In the preparation phase, they recommend a clear definition of personnel roles and empowering staff to take action without unnecessary delays, recognizing the importance of people while also leveraging technology and tools, ensuring that employees are well trained and are always updating their skills, and incorporating lessons learned from past incidents and tests.
In the incident detection and analysis phase, the report recommends the use of baselining to detect potential incidents, and using a decision tree or flowchart to quickly assess if a specific risk threshold is reached and if certain circumstances qualify as an event.
In the containment and eradication phase, IRR plans should take into account the impact of the steps taken. The organization should have a thorough understanding of the potential impact of, for example, isolating operational networks in case of an incident. It should also take into consideration the possibility that a piece of malware present in the environment may initiate destructive actions that are automatically triggered by the containment strategy.
Another important factor that needs to be considered in this phase is related to the resource implications of an incident response of indeterminate length.
As for post-incident activities, the report recommends using lessons learned from incidents and simulations to improve IRR plans and address possible shortfalls.
DHS Orders Federal Agencies to Immediately Patch 'Zerologon' Vulnerability
21.9.20 BigBrothers Securityweek
The Department of Homeland Security (DHS) on Friday issued an Emergency Directive that requires federal agencies to install fixes for a Netlogon elevation of privilege vulnerability for which Microsoft released patches in August 2020.
Tracked as CVE-2020-1472 and discovered by researchers at cybersecurity firm Secura, the issue exists in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC) “when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller,” Microsoft explains in its advisory.
An unauthenticated attacker can exploit the bug through a specially crafted application that runs on a device on the network. The attacker connecting to a domain controller via Netlogon would be granted domain administrator access.
Referring to the issue as Zerologon, Secura researchers explain that the vulnerability has been assigned a CVSS score of 10. They also published technical details on the security flaw, along with a tool to check for vulnerable systems, and recommend installing the available patches on all Active Directory domain controllers.
“The patch that addresses Zerologon also implements some additional defense-in-depth measures that forces domain-joined machines to use previously optional security features of the Netlogon protocol. An update in February 2021 will further tighten these restrictions, which may break some third-party devices or software,” Secura says.
Several proof-of-concept (PoC) exploits have already been published for the Zerologon vulnerability.
In its Emergency Directive 20-04, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA) warns all federal agencies that applying Microsoft’s patches is the only available mitigation for this critical vulnerability, aside from removing affected domain controllers from the environment.
“CISA has determined that this vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action,” the Emergency Directive reads.
Agencies are required to apply the Windows Server August 2020 security update to all domain controllers by Monday, September 21, 2020, at 11:59 PM EDT. In addition to installing the August 2020 patches, agencies are also required to ensure that even newly provisioned or previously disconnected domain controller servers have the updates before they are connected to agency networks.
Furthermore, CISA recommends that agencies use their vulnerability scanning tools along with additional means to ensure that the necessary patches have been deployed.
“These requirements apply to Windows Servers with the Active Directory domain controller role in any information system, including an information system used or operated by another entity on behalf of an agency, that collects, processes, stores, transmits, disseminates, or otherwise maintains agency information,” CISA says.
Agencies are also required to submit completion reports by 11:59 PM EDT, Wednesday, September 23, 2020.
“This emergency directive remains in effect until all agencies have applied the August 2020 Security Update (or other superseding updates) or the directive is terminated through other appropriate action,” CISA says.
While some experts have described the Zerologon flaw as “scary,” Microsoft has assigned it an exploitability assessment score of “2- exploitation less likely.”
Trump Backs Proposed Deal to Keep TikTok Operating in US
21.9.20 BigBrothers Securityweek
President Donald Trump said Saturday he’s given his “blessing” to a proposed deal that would see the popular video-sharing app TikTok partner with Oracle and Walmart and form a U.S. company.
Trump has targeted Chinese-owned TikTok for national security and data privacy concerns in the latest flashpoint in the rising tensions between Washington and Beijing. The president’s support for a deal comes just a day after the Commerce Department announced restrictions that if put in place could eventually make it nearly impossible for TikTok’s legions of younger fans to use the app.
Trump said if completed the deal would create a new company likely to be based in Texas.
“I have given the deal my blessing,” he said. “If they get it done, that’s great. If they don’t, that’s OK too.”
Trump said the new company will be hiring at least 25,000 people and making a $5 billion contribution to a fund dedicated to education for Americans. “That’s their contribution that I’ve been asking for,” he said.
TikTok said Oracle and Walmart could acquire up to a cumulative 20% stake in the new company in a financing round to be held before an initial public offering of stock, which Walmart said could happen within the next year. Oracle’s stake would be 12.5%, and Walmart’s would be 7.5%, the companies said in separate statements.
The deal will make Oracle responsible for hosting all TikTok’s U.S. user data and securing computer systems to ensure U.S. national security requirements are satisfied. Walmart said it will provide its ecommerce, fulfillment, payments and other services to the new company.
“We are pleased that the proposal by TikTok, Oracle, and Walmart will resolve the security concerns of the U.S. administration and settle questions around TikTok’s future in the U.S.,” TikTok said in a statement.
Trump has been demanding that the U.S. operations of TikTok be sold to a U.S. company or else be shut down. He’s also been targeting WeChat, another Chinese-owned app.
The administration contends that the user data collected by the two apps could be shared with the Chinese government. On Saturday, Trump said the U.S.-based TikTok “will have nothing to do with China.” TikTok says it has 100 million U.S. users.
On Friday, the U.S. Commerce Department said it would bar TikTok from U.S. app stores as of late Sunday. Further restrictions that would prevent TikTok from accessing essential internet services in the country would go into effect on Nov. 12. Commerce said Saturday that it will delay the barring of TikTok from U.S. app stores until Sept. 27 at 11:59 p.m.
Commerce is imposing similar restrictions on WeChat, although all of the restrictions on that app are set to go into effect Sunday night at 11:59 p.m.
Earlier Saturday, WeChat users asked a U.S. judge to block the government’s actions, saying they would restrict free speech. WeChat is an all-in-one app with instant-messaging, social media and other communication tools. The U.S. government argued that it is not restricting free speech because WeChat users still “are free to speak on alternative platforms that do not pose a national security threat.”
U.S. Magistrate Judge Laurel Beeler asked lawyers for the government and WeChat users whether the prohibitions would cripple WeChat as soon as the clock ticked from Sunday night into Monday morning without a resolution. An attorney for the government said they would likely lead to a “degradation” of WeChat over time.
Judge Beeler did not rule immediately on the motion.
WeChat has millions of U.S. users who rely on the app to stay in touch and conduct business with people and companies in China and around the world. In court filings, the founder of the Mental Health Association for Chinese Communities, who is a U.S. citizen in California, said that the group’s primary tool to reach out and provide services to Chinese Americans is WeChat.
“Since many of the Chinese community members we serve are not fluent in English, WeChat is the only online tool that they rely on,” Elaine Peng said.
The Trump administration’s aggressive tactics are part of its latest attempt to counter the influence of China, a rising economic superpower. Since taking office in 2017, Trump has waged a trade war with China, blocked mergers involving Chinese companies and stifled the business of Chinese firms like Huawei, a maker of phones and telecom equipment.
China-backed hackers, meanwhile, have been blamed for data breaches of U.S. federal databases and the credit agency Equifax, and the Chinese government strictly limits what U.S. tech companies can do in China.
China’s ministry of commerce condemned the U.S. moves and urged it to stop what it called bullying behavior. It also said China may take “necessary measures” to protect Chinese companies.
The U.S. Treasury Department said Saturday that TikTok’s deal still needs to close with Oracle and Walmart, and it also needs documentation and conditions to be approved by the Committee on Foreign Investment in the United States.
That, of course, also leaves the potential for more roller coasters of emotion for TikTok users, such as Haley Hoffman Smith, a 24-year-old who moved to Manhattan this year to pursue her dream of becoming a talk-show host. She said she had just hit 100,000 followers on TikTok and was crushed on Friday to hear it may be headed for a shutdown.
“TikTok is an inextricable part of my dream chasing story,” she said, “and to lose it forever would not only be an inconvenient setback, but an absolute heartbreak.”
As Trump Holds Back, Tech Firms Step in on Election Security
21.9.20 BigBrothers Securityweek
Adam Schiff was in the audience at the 2018 Aspen Security Forum when a Microsoft executive mentioned an attempted hacking of three politicians up for reelection. It was the first that Schiff, then the top Democrat on the House Intelligence Committee, had ever heard of it.
Schiff said he thought it was “odd” that Congress hadn’t been briefed. He got in touch with high-ranking officials in the intelligence agencies, and they didn’t know about it, either. It turned out that Russian hackers had unsuccessfully tried to infiltrate the Senate computer network of then-Sen. Sen. Claire McCaskill, D-Mo., and other unidentified candidates.
Two years later, Schiff says that breakdown is still emblematic of the disjointed effort among government agencies, Congress and private companies as they try to identify and address foreign election interference. But this year, with President Donald Trump adamant that Russia is not interfering and his administration often trying to block what Congress learns about election threats, it’s those private companies that often are being called upon to fill the breach.
Lawmakers welcome the help from the private sector and say the companies have become increasingly forthcoming, but it’s a haphazard way to get information. It allows the companies to control much of what the public knows, and some are more cooperative than others.
“If a company wants to publicize it, that’s great,” says Virginia Sen. Mark Warner, the top Democrat on the Senate Intelligence Committee. “But what happens when they don’t want to bring it to the attention of the government?”
That’s what happened in 2016, when Russia spread disinformation through social media, including Facebook, Twitter and YouTube. Those companies were slow to recognize the problem and they initially balked at government requests for more information. But after Congress pushed them publicly, they gradually became more cooperative.
Now, Facebook and Twitter give Congress regular briefings to the intelligence committees, issue frequent reports about malicious activity and are part of a group that regularly meets with law enforcement and intelligence officials in the administration.
Microsoft, which is part of that group, announced last week that Russian hackers had tried to breach computers at more than 200 organizations, including political campaigns and their consultants. Most of the hacking attempts by Russian, Chinese and Iranian agents were halted by Microsoft security software and the targets notified. But the company would not say which candidates or entities may have been breached.
Lawmakers say the private sector can only do so much.
“It’s certainly important that the social media companies participate and cooperate, which they have not always done in the past, but that does not in any way replace the analysis that is done by the intelligence community, and I believe that analysis should be shared with Congress,” says Sen. Susan Collins, R-Maine, a member of the Senate Intelligence Committee.
That relationship between intelligence agencies and Congress has grown strained since Trump took office. He has has doubted the agencies’ conclusions about Russian interference in 2016 and he fired, demoted and criticized officials who shared information he didn’t like.
The current director of national intelligence, John Ratcliffe, a close Trump ally, tried to end most in-person election security briefings — a decision he later reversed after criticism from lawmakers from both parties. But Ratcliffe maintains that his office will not provide “all member” briefings for all lawmakers, citing what he says were leaks from some of those meetings this year.
Lawmakers say that in restricting what’s given to Congress, the administration is effectively restricting what it tells the public about election security and misinformation. That threatens to sow confusion, just as foreign adversaries such as Russia are hoping for.
Schiff, now chairman of the House Intelligence Committee, has pressured the companies to act more quickly, including taking down misinformation before it goes viral, not after. He has particular concerns about Google, which owns YouTube, and says it has been less transparent than others. Schiff and other lawmakers have stepped up concerns about doctored videos and foreign-owned news outlets spreading fake news on the video platform.
At a hearing with tech companies in June, Schiff pressed Google, saying that it “has essentially adopted a strategy of keeping its head down and avoiding attention to its platform while others draw heat.”
Richard Salgado, Google’s director for law enforcement and information security, told Schiff: “I certainly hope that is not the perception. If it is, it is a misperception, Mr. Chairman.”
Google has made some disclosures, including recently revealing a Chinese effort to target Trump campaign staffers and an Iranian group’s attempt to target the Biden campaign. But the company gave little detail on the attacks, including when they took place or how many were targeted.
Still, the companies have stepped up in many cases.
Facebook and Microsoft have been making disclosures to the public while also working behind the scenes with the federal government and the intelligence committees. Facebook issues a monthly release on foreign and domestic election activity, and Microsoft has publicly disclosed more than a dozen instances of threat activity since Schiff was caught unaware at the Aspen event in 2018.
The executive who revealed the Russian activity at that event, Microsoft’s Tom Burt, says the company has learned to be more proactive with the federal government. He says the attempted hackings were not something he had planned to announce at the security forum, but he answered honestly when asked a question by the moderator. Today, Burt says the company gives federal and congressional authorities a heads-up when they have announcements about election interference.
Foreign attackers “are persistent, they are skilled, they are super well-resourced, and they are going to continue to try and interfere with the electoral process and try to sow distrust with the American people,” Burt said.
As lawmakers pursue other channels of information, there are still places where the private sector cannot help. Florida Rep. Stephanie Murphy, a Democrat, has been fighting for more than a year to have the administration publicly identify two Florida counties where Russian hackers gained access to voter databases before the 2016 election. People living in those counties are still unaware.
“The only way you can fight that disinformation is with transparency, and the U.S. government has to be transparent about the attacks on our democracy by providing the public with the information they need to push back against this foreign interference,” Murphy said. “I think maybe companies are accustomed to disclosing when they have had data breaches, and that is why you are seeing corporate America lead in providing the American public with information about meddling in our election.”
German encrypted email service Tutanota suffers DDoS attacks
20.9.20 BigBrothers Securityaffairs
The popular encrypted email service Tutanota was hit with a series of DDoS attacks this week targeting its website fist and its DNS providers later.
Encrypted email service, Tutanota suffered a series of DDoS attacks that initially targeted the website and later its DNS providers.
The company currently has over 2 million users, some of them were not able to access the service for several hours.
The first DDoS attacks targeted Tutanota on the weekend before September 14th, following the attacks a few hundred users were not able to access the service. The company quickly mitigated the attacks by restricting an “overreacting IP-block” responsible for the attack.
“This weekend continuous DDoS attacks and an infrastructure issue led to donwtimes for hundreds of users. While we were able to mitigate most of the DDoS, an overreacting IP-block to fight the attacks led to hundreds of users not being able to access Tutanota for multiple hours this Sunday. ” reads a blog post published by Tutanota.
The company explained it has enhanced anti-DDoS measures which should make it quicker to such kinds of attacks in the future.
“We are now able to mitigate most attacks within short times,” continues the post.
In the second wave of attacks, threat actors hit the DNS provider which hosts records for Tutanota, instead of the company servers.
“After multiple direct attacks on Tutanota, the attacker yesterday aimed at two providers that host the Tutanota DNS records.” reads a second post published by the German company.
“As a result these providers went down. We quickly tried to update our DNS records and host them at another provider. This did not work initially because the DNS entries got locked at one of the DNS hosting providers.”
Due to the DDoS attacks, the DNS providers were down and the company was not able to change the DNS entries for its domain. Millions of users were not able to access their Tutanota accounts.
“While we were moving another domain to a different registrar, our tutanota.com domain got unlocked again. We then registered our domain on a third, more robust DNS hosting provider that is able to hold against the ongoing attacks.” continues the post. “We have updated our DNS records, and universal access has finally been restored Thursday morning around 7:30 CET.”
The company explained that due to the intermittent outages several emails sent to its users may have not been delivered.
Tutanota confirmed that no user data was compromised following the attacks, it also added that it is still suffering accessibility issues.
“Issues that are remaining now are caused by caching and propagation: Each DNS server does not ask for the next update, until the old DNS entry expires. Some servers cached old nameservers during the time that our domain was locked.” concluded the post.
“This is the reason why Tutanota is still not accessible for some users, even though our status page says that everything is up and running. DNS entries are slowly propagating so that soon all users can access Tutanota again.”
Researchers Uncover 6-Year Cyber Espionage Campaign Targeting Iranian Dissidents
20.9.20 BigBrothers Thehackernews
Capping off a busy week of charges and sanctions against Iranian hackers, a new research offers insight into what's a six-year-long ongoing surveillance campaign targeting Iranian expats and dissidents with an intention to pilfer sensitive information.
The threat actor, suspected to be of Iranian origin, is said to have orchestrated the campaign with at least two different moving parts — one for Windows and the other for Android — using a wide arsenal of intrusion tools in the form of info stealers and backdoors designed to steal personal documents, passwords, Telegram messages, and two-factor authentication codes from SMS messages.
Calling the operation "Rampant Kitten," cybersecurity firm Check Point Research said the suite of malware tools had been mainly used against Iranian minorities, anti-regime organizations, and resistance movements such as the Association of Families of Camp Ashraf and Liberty Residents (AFALR), Azerbaijan National Resistance Organization, and citizens of Balochistan.
Windows Info-Stealer Targets KeePass and Telegram
Per Check Point, the infection chain was first traced to a malware-laced Microsoft Word document ("The Regime Fears the Spread of the Revolutionary Cannons.docx"), which, when opened, executes a next-stage payload that checks for the presence of the Telegram app on the Windows system, and if so, drop three additional malicious executables to download auxiliary modules and exfiltrate relevant Telegram Desktop and KeePass files from the victim's computer.
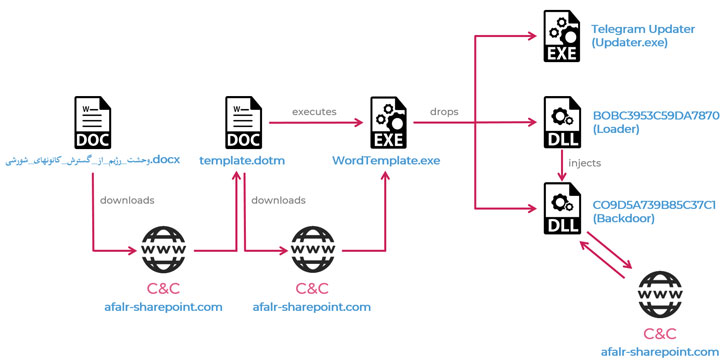
In doing so, the exfiltration allows the attacker to hijack the individual's Telegram account and steal the messages, as well as amass all files with specific extensions to a server under their control.
The research also confirms an advisory from the US Cybersecurity and Infrastructure Security Agency (CISA) earlier this week, which detailed the use of PowerShell scripts by an Iranian cyber actor to access encrypted password credentials stored by the KeePass password management software.
What's more, information from Telegram accounts was stolen using a separate tactic that involved hosted phishing pages impersonating Telegram, including using fake feature update messages to gain unauthorized access to accounts.
Capture Google SMS 2FA Codes
On the other hand, the Android backdoor, which comes equipped with capabilities to record the infected phone's surroundings and retrieve contact details, is installed through an app that masquerades as a service to help Persian-language speakers in Sweden get their driver's license.
Especially, the rogue app is engineered to intercept and transmit all SMS messages that begin with the prefix 'G-' — typically used for Google's SMS-based two-factor authentication (2FA) — to a phone number that it receives from a command-and-control (C2) server, thus allowing the bad actor to capture the victim's Google account credentials using a legitimate Google account login screen and bypass 2FA.
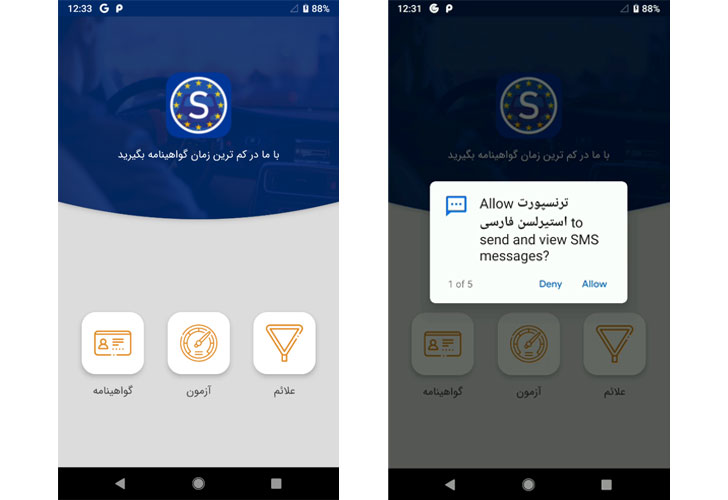
Check Point said it uncovered multiple malware variants dating back to 2014, with some of the versions used simultaneously and featuring significant differences between them.
"We noticed that while some of the variants were used simultaneously, they were written in different programming languages, utilized multiple communication protocols and were not always stealing the same kind of information," the cybersecurity firm noted.
A Surveillance Campaign Targeting Dissidents
Given the nature of targets handpicked for Rampant Kitten, like the Mujahedin-e Khalq (MEK) and the Azerbaijan National Resistance Organization (ANRO), the hackers are likely to be working at the behest of the Iranian government, as has been found in the recent series of indictments unsealed by the US Department of Justice.
"The conflict of ideologies between those movements and the Iranian authorities makes them a natural target for such an attack, as they align with the political targeting of the regime," Check Point said.
"In addition, the backdoor's functionality and the emphasis on stealing sensitive documents and accessing KeePass and Telegram accounts shows that the attackers were interested in collecting intelligence about those victims, and learning more about their activities."
Chinese hackers stole info from Spanish centers working on Covid19 vaccine
19.9.20 BigBrothers Securityweek
Chinese hackers have stolen information from Spanish laboratories working on a vaccine for COVID19, El Pais newspaper revealed.
The El Pais newspaper reported that Chinese hackers have stolen information from Spanish laboratories working on a vaccine for COVID19.
While pharmaceutical companies worldwide are working on the research of a vaccine for the ongoing COVID19 pandemic, threat actors are conducting cyber espionage campaigns in the attempt of stealing information on the work.
Regarding the specific attacks reported by El Pais, the are no technical details about the alleged intrusion and their extent.
“The cyberattacks were conducted against Spain and several other countries competing to develop a coronavirus vaccine, said Paz Esteban, the head of Spain’s National Intelligence Center (CNI).” reported El Pais.
“The CNI director said that “sensitive sectors such as health and pharmaceutics” had been targeted, and that there has been “a particularly virulent campaign, and not just in Spain, against laboratories working on a vaccine for Covid-19.”
Most of these attacks came from China and Russia, according to the newspaper, and were launched by nation-state actors.
In July, the British National Cyber Security Centre revealed that Russia-linked group APT29 is conducting cyberespionage campaigns targeting UK, US, and Canadian organizations working on the development of a COVID-19 vaccine.
The cyberattack against Spanish research labs came from China, but it is not clear which is the nature of the information stolen.
According to Spain’s secret service chief Paz Esteban, the laboratories were hit by “a particularly virulent campaign,” the hackers hit centers working on the development of vaccine in Spain and abroad.
Speaking at a seminar organized by the Association of European Journalists (AEJ) on Thursday, Esteban explained that the frequency and the level of sophistication increased during the lockdown.
The official warned of a “qualitative and quantitative growth” in the cyberattacks during the coronavirus confinement period, he explained that people working remotely are more exposed to cyber threats
Chinese officials denied any involvement in the attacks explaining that their country is ahead in the research on the COVID19 vaccine.
“China’s research and development on vaccines against Covid-19 is ahead of other countries’. We have no need to steal what others are doing in order to have access to a vaccine,” said Wang Wenbin, the spokesperson for China’s Foreign Ministry.
In July, US DoJ charged two Chinese hackers working with China’s Ministry of State Security with hacking into computer systems of government organizations and companies worldwide.
The hackers targeted companies and organizations from multiple countries including the United States, Australia, Belgium, Germany, Japan, Lithuania, the Netherlands, Spain, South Korea, Sweden, and the United Kingdom.
According to prosecutors, the defendants also probed for vulnerabilities in computer networks of companies developing COVID-19 vaccines and treatments.
“A CSIC spokesperson said that no theft has occurred at its Madrid research centers. Sources at Clinic Hospital in Barcelona said they were not aware of any intrusion into the computers storing the results of an experimental vaccine based on coronavirus genetic material.” concludes the report. “Similar responses were provided by the National Institute of Agricultural and Food Research and Technology (INIA) and by the University of Santiago de Compostela, where a team led by José Manuel Martínez Costas is working on an original angle based on a strategy involving bird virus.”
Chinese Hackers 'Stole Data From Spanish Vaccine Labs': Report
19.9.20 BigBrothers Securityweek
Chinese hackers have stolen information from Spanish laboratories working on a vaccine for Covid-19, El Pais newspaper reported Friday.
The report emerged as drug companies around the world race to produce an effective jab to counter a virus that has now killed more than 940,000 people and infected 30 million.
It was not clear what information was taken, when it happened, nor how important it was, with the paper citing sources privy to the attack.
Quoted in the article, Spain's secret service chief Paz Esteban said hackers had mounted "a particularly virulent campaign targeting laboratories working on the search for a vaccine" not only in Spain but elsewhere.
Speaking to journalists on Thursday, Esteban who heads the CNI intelligence services, said there had been a "qualitative and quantitative" increase in attacks during lockdown, with hackers targeting "sensitive sectors such as healthcare and pharmaceuticals".
Such attacks had multiplied in other countries involved in efforts to develop a vaccine, prompting an exchange of information between their respective spy services, she said.
Most attacks were carried out by hackers from China and Russia, often from state organisations, but also by criminal organisations and universities who trade in hacked data, security sources said.
But the attack in which Spanish data were stolen was launched by Chinese hackers, they said.
The CNI was not immediately available to comment on the report.
In July, a court in the US state of Washington charged two Chinese nationals with stealing terabytes of data from hundreds of computer systems all over the world, in some cases on behalf of Chinese government agencies.
The hacking, which took place over a decade, had more recently involved looking for vulnerabilities in the systems of firms developing Covid-19 vaccines, testing technology, and treatments, the US justice department said.
Spain was one of 11 countries named in the indictment as being targeted by the attacks.
Hackers Collecting Intelligence on Potential Opponents to Iranian Regime
19.9.20 BigBrothers Securityweek
An Iran linked group, named Rampant Kitten by researchers, has been discovered targeting anti-regime organizations in a campaign that has likely been running since 2014.
The primary targets include supporters of Mujahedin-e Khalq (MEK) and the Azerbaijan National Resistance Organization, two prominent resistance movements that advocate the liberation of Iranian people and minorities within Iran. These targets, together with WHOIS records suggesting that associated malicious websites had been registered by Iranian individuals, and the discovery of one registrant's email address linked to Iranian hacking forums, is enough for the Check Point researchers to conclude that Rampant Kitten is an Iranian group, which itself implies a link to the Iranian government. Its purpose is to seek intelligence on members of the dissident groups and their activities.
The attack vectors used in the campaign, which has largely remained under the radar for six years, include four variants of Windows infostealers (stealing documents, and Telegram Desktop and KeePass account information); an Android backdoor used to steal 2FA codes from SMS messages and take voice recordings; and Telegram phishing pages distributed using fake Telegram service accounts.
The campaign was initially uncovered by the discovery of a document targeting the MEK in Albania. The MEK had originally been headquartered in Iraq, but following mounting political tensions had moved to Albania. The malicious document uses an external template downloaded from a remote server. The template contains a macro that executes a batch script that attempts to download the next stage payload. The payload checks to see if Telegram is installed, and if so, extracts three additional executables from its resources. These are the Loader, which injects the main payload into explorer.exe; an infostealer payload; and updater.exe, which is a modified Telegram updater.
The last provides a unique persistence mechanism, based on Telegram's internal update procedure. Periodically, the malware copies the Telegram main executable into 'Telegram Desktop\tupdates'. This triggers an update procedure for the Telegram application once it starts. However, the default updater file (Telegram Desktop\Updater.exe) has already been amended, most notably to run the payload again.
Analysis of this payload led to the discovery of multiple variants dating back to 2014. This uncovered further websites operated by the same group. Some of these websites hosted phishing pages impersonating Telegram. Surprisingly, this phishing attack seems to have been known to Iranian Telegram users -- several Iranian Telegram channels sent out warnings against the phishing sites, claiming that the Iranian regime is behind them. The channels suggested that the phishing messages were sent by a Telegram bot. The messages warned the recipients that they were making an improper use of Telegram's services, and that their account will be blocked if they do not enter the phishing link.
The researchers also discovered a malicious Android app tied to the same attack group. The app masquerades as a service to help Persian speakers in Sweden get their driver's license. Two versions have been discovered -- one apparently compiled as a test version, and the other the release version to be deployed on the target device.
The Android backdoor can steal existing SMS messages; forward 2FA SMS messages to a phone number provided by the attacker-controlled C&C server; retrieve personal information like contacts and accounts details; initiate a voice recording of the phone's surroundings; perform Google account phishing; and retrieve device information such as installed applications and running processes.
Lotem Finkelsteen, Manager of Threat Intelligence at Check Point, commented, "After conducting our research, several things stood out. First, there is a striking focus on instant messaging surveillance. Although Telegram is un-decryptable, it is clearly hijackable. Instant messaging surveillance, especially on Telegram, is something everyone should be cautious and aware of. Second, the mobile, PC and web phishing attacks were all connected to the same operation. These operations are managed according to intelligence and national interests, as opposed to technological challenges."
Rampant Kitten appears to have been running this campaign largely undetected for at least six years. The targets seem to be dissidents associated with a number of anti-regime Iranian groups. It seems almost certain that this is another example of Iranian threat actors -- quite possibly with some affiliation to the Iranian regime -- collecting intelligence on potential opponents to the regime.
US DoJ charges Iranian hackers for attacks on US satellite companies
18.9.20 BigBrothers Securityaffairs
The US Department of Justice announced the indictment of three Iranian hackers for hacking US aerospace and satellite companies.
Three Iranian hackers residing in Iran have been indicted for stealing data from aerospace and satellite tracking companies.
The hackers were employed in a coordinated campaign of identity theft and hacking on behalf of Iran’s Islamic Revolutionary Guard Corps (IRGC), a designated foreign terrorist organization. The campaign aimed at stealing critical information related to United States aerospace and satellite technology and resources.
The indictment charged Said Pourkarim Arabi, 34, Mohammad Reza Espargham, 25, and Mohammad Bayati, 34.
The hacking campaign has been active since July 2015 and continued until at least February 2019.
“The defendants at one time possessed a target list of over 1,800 online accounts, including accounts belonging to organizations and companies involved in aerospace or satellite technology and international government organizations in Australia, Israel, Singapore, the United States, and the United Kingdom.” reads the DoJ’s press release.
The campaign targeted multiple organizations from both the US and abroad, hackers focus on the theft of commercial information and intellectual property.
The three hackers used fake online profiles and email accounts to impersonate US citizens working in the satellite and aerospace fields.
The threat actors used fake identities to target individuals at the organizations of interest. Upon clicking on a link included in the spear-phishing messages the infection process started.
The Iranian hackers targeted individuals included in a list of 1,800 online accounts belonging to people working with aerospace and satellite companies, and government organizations. Targeted entities are in Australia, Israel, Singapore, the US, and the UK.
“Today’s charges are yet another example of the FBI’s dedication to investigating those who target and attempt to steal data and proprietary information from the United States,” said James A. Dawson, Assistant Director in Charge of the FBI’s Washington Field Office. “Today’s charges allege that these individuals conspired in a coordinated campaign with known IRGC members and acted at their direction. The defendants targeted thousands of individuals in an attempt to steal critical information related to United States aerospace and satellite technology. The FBI remains dedicated to protecting the United States, and we continue to impose risk and consequences on cyber adversaries through our unique authorities, world-class capabilities, and enduring partnerships.”
According to a recently published CISA’s report, Iranian hackers from an unnamed APT group are employing several known web shells, in attacks on IT, government, healthcare, financial, and insurance organizations across the United States. The malware used by the threat actors includes the ChunkyTuna, Tiny, and China Chopper web shells.
The Iranian hackers belong to an Iran-based threat actor that was behind attacks exploiting vulnerabilities in Pulse Secure VPN, Citrix Application Delivery Controller (ADC) and Gateway, and F5’s BIG-IP ADC products.
A few weeks ago, researchers from Crowdstrike revealed that the Iran-linked APT group tracked as Pioneer Kitten, also known as Fox Kitten or Parisite, is now trying to monetize its efforts by selling access to some of the networks it has hacked to other hackers.
The Iranian hackers have been attacking corporate VPNs over the past months, they have been hacking VPN servers to plant backdoors in companies around the world targeting Pulse Secure, Fortinet, Palo Alto Networks, and Citrix VPNs.
The CISA MAR includes technical details of 19 malicious files, including multiple components of the China Chopper web shell, such as an ASP application that listens for incoming HTTP connections from a remote operator.
Once infected hackers used multiple tools to steal sensitive data and maintain a foothold in the target networks. The list of tools in the arsenal of the group includes Metasploit, Mimikatz, NanoCore, and a generic Python backdoor.
The leader of the group was Arabi, the man was identified by US officials as a member of Iran’s Islamic Revolutionary Guard Corps (IRGC). The man participated in many other operations against US and US firms.
According to investigators, Arabi lived in IRGC housing.
The second member of the group was Espargham, a well known white-hat security researcher and member of the OWASP Foundation.
Espargham also used the online moniker “Reza Darkcoder” and “M.R.S.CO,” and he was known to be the leader of the Iranian Dark Coders Team, a group of website defacers.
Arabi and Espargham collaborated to target aerospace and satellite companies. The white-hat hacker provided Arabi with malware and supported him in hacking operations. He also created a tool named VBScan that scanned vBulletin forums for vulnerabilities.
The third hacker also provided the group with malware to use in their cyber attacks.
All three remain at large in Iran and have been added to the FBI’s Cyber Most Wanted List.