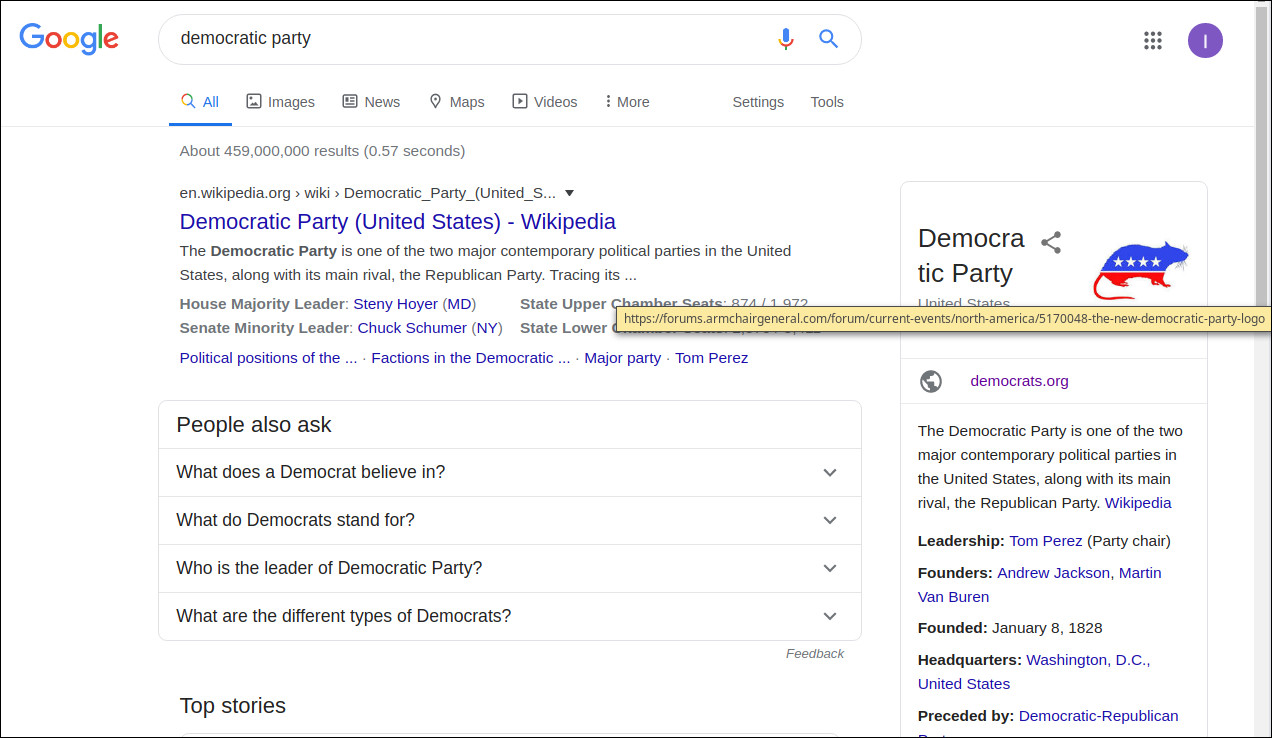
US Democratic Party Symbol Changed to a Rat in Google Search
The rat election symbol is currently being shown for all search results that show the Democratic Party symbol.
BigBrothers Articles - H 2020 1 2 3 4 5 BigBrothers List - H 2021 2020 2019 2018 BigBrother blog BigBrother blog
US Commerce Dept Shares Tips On Securing Virtual Meetings
21.3.2020 Bleepingcomputer BigBrothers
The US National Institute of Standards and Technology (NIST) today shared a number of measures that should be taken by remote workers to prevent eavesdropping and protect their privacy during virtual meetings while working from home during the current COVID-19 pandemic.
Jeff Greene, the director of the National Cybersecurity Center of Excellence (NCCoE) at the NIST said that "if virtual meetings are not set up correctly, former coworkers, disgruntled employees, or hackers might be able to eavesdrop."
"Using some basic precautions can help ensure that your meetings are an opportunity to collaborate and work effectively – and not the genesis of a data breach or other embarrassing and costly security or privacy incident."
Boost your online meetings' security
Greene suggests taking advantage of your conferencing software's built-in security features, as well as of suggestions provided by their developers to boost virtual meetings' security.
NCCoE's director recommends considering multi-factor authentication (MFA) whenever available and to make use of a dashboard to keep a close eye on your meeting's attendees.
Limiting the reuse of meeting access codes and enabling notifications on attendees joining in to be able to quickly identify those who shouldn't be attending.
The list of measures to be taken to prevent eavesdropping by unauthorized parties according to the NIST:
• Follow your organization’s policies for virtual meeting security.
• Limit reuse of access codes; if you’ve used the same code for a while, you’ve probably shared it with more people than you can imagine or recall.
• If the topic is sensitive, use one-time PINs or meeting identifier codes, and consider multi-factor authentication.
• Use a “green room” or “waiting room” and don’t allow the meeting to begin until the host joins.
• Enable notification when attendees join by playing a tone or announcing names. If this is not an option, make sure the meeting host asks new attendees to identify themselves.
• If available, use a dashboard to monitor attendees – and identify all generic attendees.
• Don’t record the meeting unless it’s necessary.
• If it’s a web meeting (with video):
- Disable features you don’t need (like chat or file sharing).
- Before anyone shares their screen, remind them not to share other sensitive information during the meeting inadvertently.
When you know that sensitive information will be shared between the attendees of a specific virtual meeting, you can also take the following additional measures to further increase security:
• Using only approved virtual meeting services.
• Issuing unique PINs or passwords for each attendee and instructing them not to share them.
• Using a dashboard feature so you can see who all the attendees are at any time.
• Locking the call once you have identified all the attendees and lines in use.
• Encrypting recordings, requiring a passphrase to decrypt them, and deleting recordings stored by the provider.
• Only conducting web meetings on organization-issued devices.
NIST provides a separate collection of telework security resources designed to assist remote workers including a guide to enterprise telework and BYOD security, an infographic on securing conference calls, guidance on mobile security, and security configurations and checklists.
CISA tips on securing enterprise VPNs
The DHS Cybersecurity and Infrastructure Security Agency (CISA) also shared tips on how to secure enterprise virtual private networks (VPNs) in response to the increasing number of employees working from home in response to the current COVID-19 pandemic.
CISA advised organizations to keep their VPN software, network devices, and user devices up to date, to alert their employees of any phishing attacks, as well as to make sure that their security teams are up to speed when it comes to security incident detection and response.
Also, CISA recommended implementing MFA on VPN connections or require users to use strong passwords as a defense measure against attacks.
Enterprises were also encouraged to test their VPN infrastructure in advance to assess its capability to support an increased number of users.
As part of its teleworking guidance, the DHS cybersecurity agency also suggested reviewing CISA documentation on how to secure network infrastructure devices, avoid social engineering and phishing attacks, as well as to choose, protect and supplement passwords.
To assist the wave of new remote workers, Software developers and service providers including Google, Microsoft, Adobe, Zoom, and LogMeIn, are also offering free licenses or enhanced versions of their software and services during Coronavirus-disease outbreak.
US Democratic Party Symbol Changed to a Rat in Google Search
21.3.2020 Bleepingcomputer BigBrothers
The election symbol of the US Democratic Party has been changed to a rat within the Google search knowledge panel that shows when searching for the party's name, instead of the usual donkey-themed one.
While no one knows how this happened, the new rat-themed symbol displayed when searching for "democratic party" on Google is now automatically loaded from a post made by a now-banned user on a history forum in January.

US Democratic Party Symbol Changed to a Rat in Google Search
The rat election symbol is currently being shown for all search results that show the Democratic Party symbol.
The Republican Party symbol remains unchanged for now. but does display the changed Democratic Party symbol in the bottom of their knowledge panel.
Republican Party Knowledge Panel
Researchers from cybersecurity intelligence company Under the Breach, who first discovered this change, say it is unclear how this was done.
BleepingComputer has reached out to Google for comment but had not heard back at the time of this publication. This article will be updated when a response is received.
This is a developing story ...
H/T Under the Breach
Update March 16, 18:41 EDT: "Most images in Knowledge Panels are automatically generated from pages on the web," a Google spokesperson told BleepingComputer.
"When errors are reported, we fix them quickly. We encourage people and organizations to claim their Knowledge Panels, which allows them to select a representative image."
The Democratic Party rat election symbol was automatically displayed in the Knowledge Panel based on a web source and Google will remove it since the image is not representative to the entity.
FBI Warns of Human Traffickers Luring Victims on Social Networks
21.3.2020 Bleepingcomputer BigBrothers
FBI's Internet Crime Complaint Center (IC3) today issued a public service announcement on human traffickers' continued usage of online platforms like dating sites and social networks to lure victims.
"The FBI warns the public to remain vigilant of the threat posed by criminals who seek to traffic individuals through force, fraud, or coercion through popular social media and dating platforms," the PSA says.
"Offenders often exploit dating apps and websites to recruit—and later advertise—sex trafficking victims. In addition, offenders are increasingly recruiting labor trafficking victims through what appears to be legitimate job offers."
Online platforms tools used against vulnerable targets
According to the FBI's investigations, victims from various different backgrounds from rural areas to large cities are being lured by human traffickers into forced labor or sex work using online platforms.
In many cases, the criminals will pose as legitimate job recruiters or agents of employment agencies and will bait potential victims with the promise of fake employment and a better life.
Individuals who share personal information on online platforms are the ones most likely to be targeted by such criminals, especially after posting about "financial hardships, their struggles with low self-esteem, or their family problems."
The traffickers will use their targets' stories as the base for well-planned attacks via the Internet, convincing them that they want to be helpful or that they are interested in a relationship.
However, their victims will subsequently be coerced into sex work or forced labor after the traffickers manage to establish a false sense of trust and they persuade them to meet in person.
Human traffickers using online platforms
During the last few years, the FBI discovered multiple cases of human traffickers using popular social networks and dating sites to recruit victims.
Among the multiple such cases identified over the years, the FBI shares the following three examples:
In July 2019, a Baltimore, Maryland, man was convicted on two counts of sex trafficking of a minor and one count of using the Internet to promote a business enterprise involving prostitution. The perpetrator targeted two girls after they posted information online about their difficult living and financial situation. After meeting them in person, the man forced the two girls into sex work.
In March 2019, a married couple was found guilty of conspiracy to obtain forced labor and two counts of obtaining forced labor. The couple employed foreign workers to perform domestic labor in their home in Stockton, California. The defendants used the Internet and an India-based newspaper to post false advertisements about the wages and nature of the employment at their home. Upon arrival, the workers were forced to work 18-hour days with little to no wages.
In October 2017, a sex trafficker was convicted on 17 counts of trafficking adults and minors. Additional charges included child pornography and obstruction of justice. The perpetrator received a 33-year sentence. A victim from the Seattle area met the sex trafficker's accomplice on a dating website. The trafficker and his accomplice later promised to help the victim with her acting career. After a few months, the victim was abused and forced into prostitution.
Report (potential) trafficking situations
"Human trafficking occurs in every area of the country and occurs in many forms, from forced labor to sexual exploitation, including the sexual exploitation of children," FBI Criminal Investigative Division Section Chief Michael Driscoll said last year.
"The FBI operates Human Trafficking and Child Exploitation Task Forces throughout the country to aggressively investigate the perpetrators and also provides resources to assist the victims of these crimes.”
Victims and those who think that they witnessed a potential human trafficking situation are encouraged by the FBI to contact their local law enforcement agencies, the local FBI field office, or to reach out to:
the National Human Trafficking Hotline—Call 1-888-373-7888 (TTY: 711) or text 233733;
file a complaint online with the FBI's Internet Crime Complaint Center at www.IC3.gov; or
contact the FBI's National Threat Operations Center at 1-800-CALL-FBI or tips.fbi.gov.
To report possible trafficking involving minors, contact the National Center for Missing and Exploited Children (NCMEC) at 1-800-THE-LOST (1-800-843-5678) or at Cybertipline.org.
Victims and witnesses are also urged by the FBI to keep as much evidence as possible including emails, text messages, or any other logs of communication with the traffickers to make it easier to identify, retain, and prosecute them.
"The FBI produced this public service announcement to alert Internet users of the continuing threat posed by human traffickers online and what you should do if you or someone you know suspects human trafficking," the PSA concludes.
US Govt Shares Tips on Securing VPNs Used by Remote Workers
15.3.2020 Bleepingcomputer BigBrothers
The Department of Homeland Security's cybersecurity agency today shared tips on how to properly secure enterprise virtual private networks (VPNs) seeing that a lot of organizations have made working from home the default for their employees in response to the Coronavirus disease (COVID-19) pandemic.
"As organizations elect to implement telework, the Cybersecurity and Infrastructure Security Agency (CISA) encourages organizations to adopt a heightened state of cybersecurity," an alert published today says.
Malicious actors expected to focus attacks on teleworkers
Since more and more employees have switched to using their org's VPNs for teleworking, threat actors will increasingly focus their attacks on VPN security flaws that will be less likely to get patched in time if work schedules will be spread around the clock.
CISA also highlights the fact that malicious actors might also increase their phishing attacks to steal the user credentials of employees working from home, with orgs that haven't yet implemented multi-factor authentication (MFA) for remote access being the most exposed.
Is your organization teleworking because of #COVID19? Here are some https://t.co/tcA8Kr6DTq key recommendations on enterprise VPN security. #CyberVigilance #Cyber Cybersecurity #Infosec
— US-CERT (@USCERT_gov) March 13, 2020
"Organizations may have a limited number of VPN connections, after which point no other employee can telework," CISA adds.
"With decreased availability, critical business operations may suffer, including IT security personnel’s ability to perform cybersecurity tasks."
Mitigations for boosting enterprise VPN security
Among the mitigation measures recommended for organizations considering telework options for their employees because of the Coronavirus disease (COVID-19) pandemic, CISA lists:
• Keeping VPNs, network infrastructure devices, and devices used for remote work up to date (apply the latest patches and security configs).
• Notifying employees of an expected increase in phishing attempts.
• Ensuring that IT security staff are ready for remote log review, attack detection, and incident response and recovery.
• Implementing MFA on all VPN connections or required employees to use strong passwords to defend against future attacks.
• Testing VPN infrastructure limitations in preparation for mass usage and take measures such as rate-limiting to prioritize users that will require higher bandwidths.
As part of its teleworking guidance, CISA also advises organizations to review DHS documentation on how to secure network infrastructure devices, avoid social engineering and phishing attacks, choose and protect passwords and supplement passwords, as well as the National Institute of Standards and Technology (NIST) guide to enterprise telework and BYOD security
The DHS cybersecurity agency previously warned orgs to patch Pulse Secure VPN servers against ongoing attacks trying to exploit a known remote code execution (RCE) vulnerability tracked as CVE-2019-11510.
One week later, the FBI said in a flash security alert that state-backed hackers have breached the networks of a US financial entity and a US municipal government after exploiting servers left vulnerable to CVE-2019-11510 exploits.
Unpatched Pulse Secure VPN servers remain an attractive target for malicious actors. @CISAgov released an Alert on continued exploitation of CVE-2019-11510 in Pulse Secure. Update ASAP! https://t.co/n7mx9juifv #Cyber #Cybersecurity #InfoSec
— US-CERT (@USCERT_gov) January 10, 2020
CISA also published information on how to defend against scammers who use the Coronavirus Disease 2019 (COVID-19) health crisis as bait to push their scams over the Internet.
The World Health Organization (WHO) and the U.S. Federal Trade Commission (FTC) issued warnings about ongoing Coronavirus-themed phishing attacks and scam campaigns in February.
Microsoft, Google, LogMeIn, and Cisco have also announced last week that they are offering free licenses for their meeting, collaboration, and remote work tools so that teleworkers can join virtual meetings and chat with colleagues while working remotely.
Microsoft Takes Control of Necurs U.S.-Based Infrastructure
14.3.2020 Bleepingcomputer BigBrothers
Microsoft announced today that it took over the U.S.-based infrastructure used by the Necurs spam botnet for distributing malware payloads and infecting millions of computers.
A single Necurs-infected device was observed while sending roughly 3.8 million spam messages to more than 40.6 million targets during 58 days according to Microsoft's investigation.
"On Thursday, March 5, the U.S. District Court for the Eastern District of New York issued an order enabling Microsoft to take control of U.S.-based infrastructure Necurs uses to distribute malware and infect victim computers," Microsoft Corporate Vice President for Customer Security & Trust Tom Burt said.
"With this legal action and through a collaborative effort involving public-private partnerships around the globe, Microsoft is leading activities that will prevent the criminals behind Necurs from registering new domains to execute attacks in the future."
The Necurs botnet
Necurs is today's largest spam botnet, initially spotted around 2012 and linked by some sources to the TA505 cybercrime group, the operators behind the Dridex banking trojan.
Microsoft says that the botnet "has also been used to attack other computers on the internet, steal credentials for online accounts, and steal people’s personal information and confidential data."
The botnet was also seen delivering messages pushing fake pharmaceutical spam email, pump-and-dump stock scams, and “Russian dating” scams.
The Necurs malware is also known to be modular, with modules dedicated to delivering huge numbers of spam emails as Microsoft also observed, to redirecting traffic via HTTPS and SOCKS network proxies deployed on infected devices, as well as to launching DDoS attacks (distributed denial of service) via a module introduced in 2017 — no Necurs DDoS attacks have been detected so far.
Necurs' operators also provide a botnet-for-hire service through which they will also rent the botnet to other cybercriminals who use it to distribute various flavors of info stealing, cryptomining, and ransomware malicious payloads.
Microsoft's Necurs takedown
Microsoft was able to take control of the botnet domains by "analyzing a technique used by Necurs to systematically generate new domains through an algorithm."
This allowed them to predict more than six million domains the botnet's operators would have created and used as infrastructure during the next two years.
"Microsoft reported these domains to their respective registries in countries around the world so the websites can be blocked and thus prevented from becoming part of the Necurs infrastructure," Burt added.
"By taking control of existing websites and inhibiting the ability to register new ones, we have significantly disrupted the botnet."
Redmond has also joined forces with Internet Service Providers (ISPs) and other industry partners to help detect and remove the Necurs malware from as many infected computers as possible.
"This remediation effort is global in scale and involves collaboration with partners in industry, government and law enforcement via the Microsoft Cyber Threat Intelligence Program (CTIP)," Burt said.
"For this disruption, we are working with ISPs, domain registries, government CERTs and law enforcement in Mexico, Colombia, Taiwan, India, Japan, France, Spain, Poland and Romania, among others."
NSA Warns About Microsoft Exchange Flaw as Attacks Start
14.3.2020 Bleepingcomputer BigBrothers
The U.S. National Security Agency (NSA) warned about a post-auth remote code execution vulnerability in all supported Microsoft Exchange Server servers via a tweet published on the agency's Twitter account.
NSA's tweet reminded followers to patch the CVE-2020-0688 vulnerability which would enable potential attackers to execute commands on vulnerable Microsoft Exchange servers using email credentials.
Microsoft patched this RCE security flaw as part of the February 2020 Patch Tuesday and tagged it with an "Exploitation More Likely" exploitability index assessment hinting at CVE-2020-0688 being an attractive target for attackers.
State-backed hackers already attacking Microsoft Exchange servers
The same day, researchers at security firm Volexity confirmed that exploitation of this security flaw has begun in late February, with several organizations already having had their networks compromised after state-backed advanced persistent threats (APT) groups exploited the CVE-2020-0688 flaw.
"Volexity has also observed multiple concerted efforts by APT groups to brute-force credentials by leveraging Exchange Web Services (EWS) in an effort to likely exploit this vulnerability," their report says.
"Volexity believes these efforts to be sourced from known APT groups due to IP address overlap from other attacks and, in some cases, due to the targeting of credentials that would only be known from a previous breach."
Volexity
@Volexity
Active exploitation of Microsoft Exchange servers by APT actors via the ECP vulnerability CVE-2020-0688. Learn more about the attacks and how to protect your organization here: https://www.volexity.com/blog/2020/03/06/microsoft-exchange-control-panel-ecp-vulnerability-cve-2020-0688-exploited/ …#dfir #threatintel #infosec
94
12:22 AM - Mar 7, 2020
Twitter Ads info and privacy
64 people are talking about this
A U.S. Department of Defense (DoD) source also confirmed the ongoing attacks to ZDNet, although, just like Voxelity, it didn't name the groups or the countries behind them.
As BleepingComputer previously reported, scans for unpatched Microsoft Exchange servers have started on February 25, the same day Zero Day Initiative security researcher Simon Zuckerbraun published a report on CVE-2020-0688.
After his report, a new module targeting this flaw was added by Rapid7 to the Metasploit pen-testing tool following multiple proof-of-concept exploits having surfaced on GitHub.
Sigma rules for SIEM systems provided by Nextron Systems's Florian Roth are available for detecting exploitation attempts against unpatched Exchange servers.
Microsoft Exchange Server RCE vulnerability
As Zuckerbraun explained, "any outside attacker who compromised the device or credentials of any enterprise user would be able to proceed to take over the Exchange server."
"Having accomplished this, an attacker would be positioned to divulge or falsify corporate email communications at will," he added. "Accordingly, if you’re an Exchange Server administrator, you should treat this as a Critical-rated patch and deploy it as soon as your testing is complete."
The actively exploited vulnerability was found in the Exchange Control Panel (ECP) component and it is caused by Exchange's failure to create unique cryptographic keys when installed.
After successfully exploited, it allows authenticated attackers to execute code remotely with SYSTEM privileges and fully compromise the exploited server.
Links to the security update descriptions for vulnerable Microsoft Exchange Server versions and download links are available in the table below:
Product Article Download
Microsoft Exchange Server 2010 Service Pack 3 Update Rollup 30 4536989 Security Update
Microsoft Exchange Server 2013 Cumulative Update 23 4536988 Security Update
Microsoft Exchange Server 2016 Cumulative Update 14 4536987 Security Update
Microsoft Exchange Server 2016 Cumulative Update 15 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 3 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 4 4536987 Security Update
"Fortunately, this vulnerability does require a compromised credential to exploit and, as a result, will stave off widespread automated exploitation such as those that often deploy cryptocurrency miners or ransomware," Voxelity said.
"However, more motivated attackers now have a way to compromise a critical piece of the IT infrastructure if it is not updated."
Since no mitigating factors have been identified for this vulnerability according to Microsoft, the only choice left is to patch your servers — if you're not willing to reset all users' passwords to render all previously stolen credentials useless — before hackers will get to them and manage to fully compromise your entire network.
New US Bill Aims to Protect Researchers who Disclose Govt Backdoors
14.3.2020 Bleepingcomputer BigBrothers Virus
New legislation has been introduced that amends the Espionage Act of 1917 to protect journalists, whistleblowers, and security researchers who discover and disclose classified government information.
The goal of the new legislation is to amend the Espionage Act of 1917 so it cannot be used to target reporters, whistleblowers, and security researchers who discover and publish classified government secrets.
Concerned that the current laws are being used for partisan prosecution, U.S. Representative Ro Khanna (D - California) introduced the new legislation to Congress on March 5th, 2020 and U.S. Senator Ron Wyden (D - Oregon) will soon introduce it to the Senate.
"My bill with Senator Wyden will protect journalists from being prosecuted under the Espionage Act and make it easier for members of Congress, as well as federal agencies, to conduct proper oversight over any privacy abuses. Our nation’s strength rests on the freedom of the press, transparency, and a functioning system of checks and balances. This bill is a step toward ensuring those same principles apply to intelligence gathering and surveillance operations," said Rep. Ro Khanna.
"This bill ensures only personnel with security clearances can be prosecuted for improperly revealing classified information," Senator Wyden stated.
This new legislation titled 'Espionage Act Reform Act of 2020’ ensures:
Journalists who solicit, obtain, or publish government secrets are safe from prosecution.
Every member of Congress is equally able to receive classified information, specifically from whistleblowers. Current law criminalizes the disclosure of classified information related to signals intelligence to any member of Congress, unless it is in response to a “lawful demand” from a committee. This change puts members in the minority party and those not chairing any committee at a significant disadvantage toward conducting effective oversight.
Federal courts, inspector generals, the FCC, Federal Trade Commission, and Privacy & Civil Liberties Oversight Board can conduct oversight into privacy abuses.
Cybersecurity experts who discover classified government backdoors in encryption algorithms and communications apps used by the public can publish their research without the risk of criminal penalties. The bill correctly places the burden on governments to hide their surveillance backdoors; academic researchers and other experts should not face legal risks for discovering them.
With these new amendments, security researchers are also protected from revealing classified government surveillance backdoors that have been added to encryption algorithms and communications apps that are utilized by the public.
Hacking into government systems or unlawfully obtaining nonpublic government information, though, is still off-limits and would lead to prosecution.
With these changes, researchers would be able to analyze government mobile apps, communication protocols, and algorithms and disclose any vulnerabilities and backdoors without fear of prosecution.
The current legislation can be found in chapter 37 of title 18, United States Code and the proposed amendments can be read here.
Senator Wyden has also released a summary of the bill/FAQ that provides an overview as to why the legislation is being introduced and answers some commonly asked questions.
US Govt Shares Tips to Defend Against Coronavirus Cyber Scams
7.3.2020 Bleepingcomputer BigBrothers
The Department of Homeland Security's cybersecurity agency today shared tips on how to defend against scammers who use the coronavirus health crisis as bait to push their scams over the Internet.
The Cybersecurity and Infrastructure Security Agency (CISA) warned individuals across the U.S. to remain vigilant for cyber scams related to the Coronavirus Disease 2019 (COVID-19) and to take a number of precautions to make sure that they won't be the victims of cybercriminals.
Defense measures against Coronavirus cyber scams
"Cyber actors may send emails with malicious attachments or links to fraudulent websites to trick victims into revealing sensitive information or donating to fraudulent charities or causes," CISA said.
"Exercise caution in handling any email with a COVID-19-related subject line, attachment, or hyperlink, and be wary of social media pleas, texts, or calls related to COVID-19."
Individuals are encouraged by the cybersecurity agency to:
• Avoid clicking on links in unsolicited emails and be wary of email attachments. See Using Caution with Email Attachments and Avoiding Social Engineering and Phishing Scams for more information.
• Use trusted sources—such as legitimate, government websites—for up-to-date, fact-based information about COVID-19.
• Do not reveal personal or financial information in email, and do not respond to email solicitations for this information.
• Verify a charity’s authenticity before making donations. Review the Federal Trade Commission’s page on Charity Scams for more information.
• Review CISA Insights on Risk Management for COVID-19 for more information.
Coronavirus-themed phishing, scams, and malware
This warning comes after previous ones issued last month by the World Health Organization (WHO) and the U.S. Federal Trade Commission (FTC) about ongoing Coronavirus-themed phishing attacks and scam campaigns.
COVID-19 is a highly popular phishing bait for targeting individuals from the United States and the United Kingdom as researchers at IBM X-Force Threat Intelligence, KnowBe4, and Mimecast found in February.
A report from Imperva also highlights how "high levels of concern around the Coronavirus are currently being used to increase the online popularity of spam campaigns designed to spread fake news and drive unsuspecting users to dubious online drug stores."
Coronavirus-themed malware was also discovered by security researchers since January, with security research collective MalwareHunterTeam having previously shared malware samples with Coronavirus references including a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and a wiper.
Microsoft, Google, LogMeIn, and Cisco have also announced this week that they are offering free licenses for meeting, collaboration, and remote work tools so that remote workers can join virtual meetings and chat with their colleagues while working remotely from their homes.
FBI Warns of BEC Attacks Abusing Microsoft Office 365, Google G Suite
7.3.2020 Bleepingcomputer BigBrothers
The US Federal Bureau of Investigation (FBI) warned private industry partners of threat actors abusing Microsoft Office 365 and Google G Suite as part of Business Email Compromise (BEC) attacks.
"The scams are initiated through specifically developed phish kits designed to mimic the cloud-based email services in order to compromise business email accounts and request or misdirect transfers of funds," the FBI said in a Private Industry Notification (PIN) from March 3.
"Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling over $2.1 billion in actual losses from BEC scams targeting Microsoft Office 365 and Google G Suite."
BEC scammers in the cloud
The cybercriminals move to cloud-based email services matches organizations' migration to the same services from on-premises email systems.
Targets are redirected to the phishing kits used as part of these BEC attacks via large scale phishing campaigns, with the phishing kits being email service-aware and capable of detecting the "service associated with each set of compromised credentials."
"Upon compromising victim email accounts, cybercriminals analyze the content to look for evidence of financial transactions," the FBI explains.
"Using the information gathered from compromised accounts, cybercriminals impersonate email communications between compromised businesses and third parties, such as vendors or customers."
The scammers will then impersonate employees of the now-compromised organizations or their business partners, attempting to redirect payments between them to bank accounts under the attackers' control.
They will also steal as many partner contacts from the infiltrated email accounts that they can later use to launch other phishing attacks and compromise other businesses, pivoting to other targets within the same industry sector.
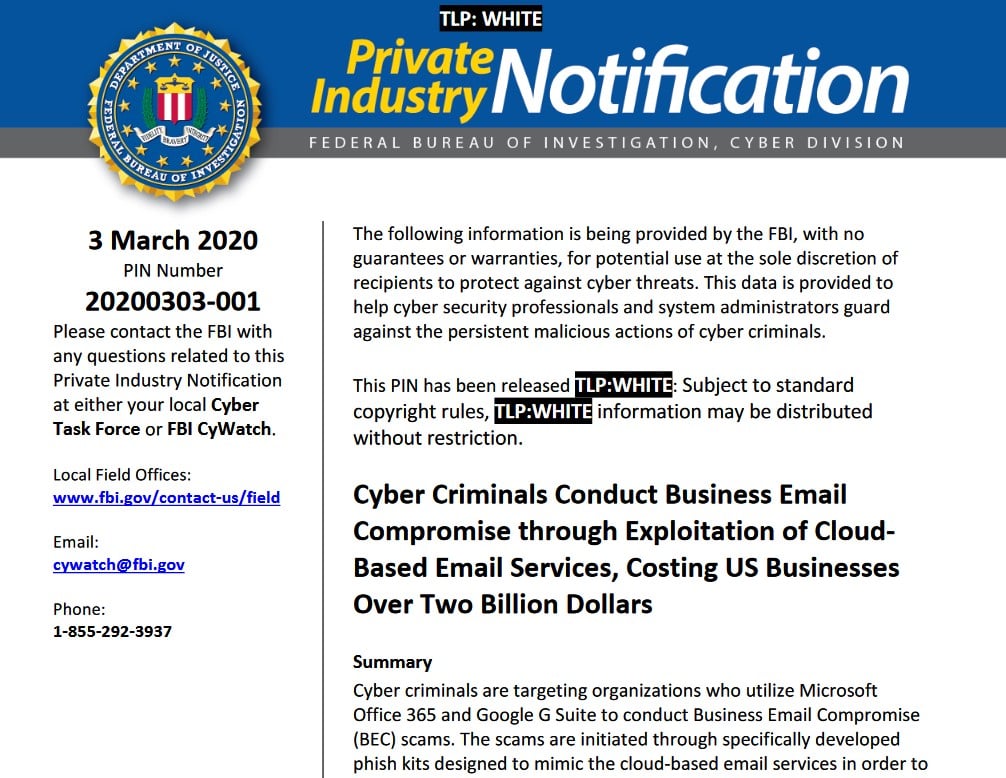
BEC defense recommendations
Even though both Microsoft Office 365 and Google G Suite come with security features that can help block BEC scam attempts, many of them have to manually configured and toggled on by IT administrators and security teams.
Because of this, "small and medium-size organizations, or those with limited IT resources, are most vulnerable to BEC scams," the FBI added.
The FBI issued a number of defense recommendations IT admins can implement on their networks to prevent BEC attacks:
• Prohibit automatic forwarding of email to external addresses.
• Add an email banner to messages coming from outside your organization.
• Prohibit legacy email protocols such as POP, IMAP, and SMTP that can be used to circumvent multi-factor authentication.
• Ensure mailbox logon and settings changes are logged and retained for at least 90 days.
• Enable alerts for suspicious activity such as foreign logins.
• Enable security features that block malicious email such as anti-phishing and anti-spoofing policies.
• Configure Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication Reporting and Conformance (DMARC) to prevent spoofing and to validate email.
• Disable legacy account authentication.
End users can also take these measures to defend against BEC scammers:
• Enable multi-factor authentication for all email accounts.
• Verify all payment changes and transactions in-person or via a known telephone number.
• Educate employees about BEC scams, including preventative strategies such as how to identify phishing emails and how to respond to suspected compromises.
The $26 billion scam
The FBI's Internet Crime Complaint Center (IC3) revealed in the 2019 Internet Crime Report published last month that cybercrime was behind individual and business losses of $1.8 billion during the last year alone.
The IC3 also issued a Public Service Announcement (PSA) in September 2019 warning that BEC scams are continuing to grow every year, with victim complaints with a total exposed dollar loss of more than $26 billion between June 2016 and July 2019, and a 100% rise in the identified global exposed losses from May 2018 to July 2019.
Even though quite hard to believe, these numbers are backed by the publicly reported losses with a Toyota Group subsidiary announcing in September 2019 that it was the victim of a BEC scam with an expected financial loss of over $37 million.
Another BEC attack affecting Nikkei, one of the largest media groups in the world, costing the company around $29 million in October 2019.
Also in October 2019, 281 people were arrested in the U.S. and other countries as part of Operation reWired, a globally-coordinated law enforcement to disrupt Business Email Compromise (BEC) schemes.
A previous and similar effort dubbed Operation Wire Wire, announced in June 2018, was the first such enforcement action designed to go after hundreds of BEC scammers and it led to the arrest of 74 individual, as well as the disruption and recovery of roughly $14 million in fraudulent wire transfers.
The FBI recommends BEC scam victims to file a complaint regardless of the amount they lost at BEC.IC3.gov.
US Govt Adds Stricter Requirements for .gov Domain Registration
7.3.2020 Bleepingcomputer BigBrothers
The U.S. government will start requiring notarized signatures as part of the registration process for .gov domains starting March 10, 2020, to prevent wire and mail fraud that might lead to such domains being registered by unauthorized organizations or individuals.
The U.S. General Services Administration (GSA) oversees the DotGov Program that operates the .GOV top-level domain (TLD) and it makes such domains available to US-based government organizations, from local municipalities to federal agencies.
Security boost for .gov domain registration
"Effective on March 10, 2020, the DotGov Program will begin requiring notarized signatures on all authorization letters when submitting a request for a new .gov domain," the DotGov Registrar says.
"This is a necessary security enhancement to prevent mail and wire fraud through signature forgery in obtaining a .gov domain.
"This step will help maintain the integrity of .gov and ensure that .gov domains continue to be issued only to official U.S. government organizations."
To request a .gov domain name, government organizations have to prepare and send an authorization letter and fill an online form after receiving a .gov registrar account.
This letter must use official letterhead stationary and it has to include a signature from the requesting organization’s authorizing authority the DotGov Program site explains.
This is the letter that will need to come with a notarized signature starting March 10, 2020, to prevent future attempts of registering .gov domains without authorization.
Anyone could register a .gov domain
The GSA says that .gov domains are exclusively granted to U.S. government organizations and they give legitimacy to government websites and online tools, ensuring the customers' trust that the content is from an official source.
However, as independent investigative journalist Brian Krebs previously reported, until the new rules are enacted, almost anyone can register a .gov domain using fake information on the authorization letter required by the GSA albeit illegally and with the risk of being indicted for wire or mail fraud if caught.
A researcher confirmed that this was possible saying that he was able to register a .gov in November 2019 using a fake Google Voice number, and a Gmail address, as well as official letterhead extracted from a legitimate government organization's documents.
"I never said it was legal, just that it was easy," the researcher said. "I assumed there would be at least ID verification. The deepest research I needed to do was Yellow Pages records."
When contacted, the GSA said that it "has already implemented additional fraud prevention controls," without detailing what were the measures taken to prevent future fraudulent .gov registration attempts.
The Cybersecurity and Infrastructure Security Agency (CISA) shared plans to take over the management of the .gov TLD from the GSA since "the .gov top-level domain (TLD) is critical infrastructure for thousands of federal, state and local government organizations across the country."
A bipartisan bill known as the "DOTGOV Act of 2019" and sponsored by US Senator Gary Peters was introduced in Senate on October 30, 2019, seeking, among other things, to provide CISA with the authority to manage the .gov TLD after assuming governance from the GSA.
UK NCSC Releases Tips on Securing Smart Security Cameras
7.3.2020 Bleepingcomputer BigBrothers
The UK National Cyber Security Centre (NCSC) has released guidance on how to correctly set up smart security cameras and baby monitors to avoid having them hacked by attackers.
This new guidance was released because so-called smart security cameras and baby monitors can put your security and privacy at risk if not configured properly.
Such devices make it possible to watch a live camera feed over the Internet, receive activity alerts when you're not around the house, and even record surveillance footage for reviewing later in case of any incidents.
By taking the steps detailed by the NCSC, users of such devices can avoid being the victim of threat actors looking to compromise them.
Change your devices' default passwords
"Smart cameras (the security cameras and baby monitors used to monitor activity in and around your house) usually connect to the internet using your home Wi-Fi," the NCSC says. "Live feeds or images from smart cameras can (in rare cases) be accessed by unauthorized users, putting your privacy at risk," the NCSC adds.
"This is possible because smart cameras are often configured so that you can access them whilst you're away from home."
The most important measure you can take to secure your smart security cameras is to change your devices' default passwords to prevent cybercriminals from gaining access via built-in default passwords seeing that many of them come with easy to guess
If not changed, criminals could access a smart security camera or a baby monitor remotely after guessing the default password and watch you or your kid via live video.
To defend against such an attack, the NCSC recommends changing the default password your device ships with a strong passphrase-based password built using three random words you would easily remember.
The FBI also recommends using passphrases that combine several words to obtain long and easy to remember passwords that are also harder to crack by an attacker.
Keep security cameras up to date, disable unneeded remote view
The NCSC also advises security camera users to always update their software and, if such an option is available, to enable automatic software updates.
This would allow keeping the devices up to date at all times while not having to worry about looking for new software releases manually.
"Using the latest software will not only improve your security, it often adds new features," the NCSC says. "Note that the software that runs your camera is sometimes referred to as firmware, so look for the words update, firmware or software within the app.
The new guidance also recommends disabling Internet access to the smart security camera if you don't use the feature allowing for viewing camera footage remotely.
"Note that doing this may also prevent you receiving alerts when movement is detected, and could stop the camera working with smart home devices (such as Alexa, Google Home or Siri)," the NCSC adds.
UK government plans to strengthen IoT security
This guidance was released following UK government plans for strengthening the security of internet-connected products that were outlined during late-January.
The new law aims to impose the following requirements from manufacturers of Internet-enabled IoT devices:
• All consumer internet-connected device passwords must be unique and not resettable to any universal factory setting
• Manufacturers of consumer IoT devices must provide a public point of contact so anyone can report a vulnerability and it will be acted on in a timely manner
• Manufacturers of consumer IoT devices must explicitly state the minimum length of time for which the device will receive security updates at the point of sale, either in store or online
In related news, Ring announced the roll-out of mandatory two-factor authentication (2FA) to all user accounts to boost security cameras' security, after a stream of incidents where attackers terrified homeowners and their children by speaking to them over their Ring devices' speakers following a series of credential stuffing attacks targeting Ring cameras.
German BSI Tells Local Govt Authorities Not to Pay Ransoms
7.3.2020 Bleepingcomputer BigBrothers
BSI, Germany's federal cybersecurity agency, recommends local governments and municipal institutions not to pay the ransoms asked by attackers after they get affected by ransomware attacks.
Germany's Federal Office for Information Security (aka BSI, short for Bundesamt für Sicherheit in der Informationstechnik) in collaboration with the Federal Criminal Police Office (BKA) also issued recommendations for local authorities on how to deal with ransom demands following an increasing number of such attacks.
Local authorities advised not to respond to extortionists
The presidents of the German City Council, the German District Council, and the German Association of Cities and Municipalities also issued a joint statement in support of BSI's recommendation.
"We must not give in to such ransom demands. It must be clear that municipal administrations cannot be blackmailed," they said. "Otherwise, criminals will be offered incentives to continue their actions. The attitude of our administrations must be crystal-clear and non-negotiable."
"Every attempt to extortion must be consistently reported and followed up. A zero-tolerance policy must apply to such attacks on the functionality of municipal services, the data of citizens and their tax money."
BKA President Holger Münch also said that local authorities impacted by ransomware attacks should never respond to ransom requests to avoid supporting the extortionists' 'business model'.
Münch recommended taking precautions for timely systematic prevention, detection, and response to such attacks and to report any ransomware-related incidents to the appropriate authorities.
"The best protection against ransom demands from cybercriminals is consistently implemented IT security measures," BSI President Arne Schönbohm added. "Effective emergency management can decisively minimize the effects of a cyber attack. The BSI is also happy to provide municipalities with advice."
The BSI provides government agencies and privately-held organizations with detailed guidance on how to defend against and respond to ransomware attacks, as well as first aid info in the event of serious IT security incidents.
Previous recommendations not to pay ransoms
In October 2019, the FBI Internet Crime Complaint Center (IC3) also issued a public service announcement targeted at public and private U.S. organizations about the increasing number of high-impact ransomware attacks.
"Since early 2018, the incidence of broad, indiscriminant ransomware campaigns has sharply declined, but the losses from ransomware attacks have increased significantly, according to complaints received by IC3 and FBI case information," the IC3 said at the time.
"Although state and local governments have been particularly visible targets for ransomware attacks, ransomware actors have also targeted health care organizations, industrial companies, and the transportation sector."
The FBI urged both individuals or organizations that had their systems encrypted by ransomware not to pay the ransoms requested by the extortionists behind the attacks and, instead, to contact the FBI's field offices and report the attacks to IC3 as soon as possible.
The agency advised U.S. organizations targeted by a heavy barrage of ransomware attacks to take the following defensive measures:
• Regularly back up data and verify its integrity
• Focus on awareness and training
• Patch the operating system, software, and firmware on devices
• Enable anti-malware auto-update and perform regular scans
• Implement the least privilege for file, directory, and network share permissions
• Disable macro scripts from Office files transmitted via email
• Implement software restriction policies and controls
• Employ best practices for use of RDP
• Implement application whitelisting
• Implement physical and logical separation of networks and data for different org units
• Require user interaction for end-user apps communicating with uncategorized online assets
Prevention is the new target
Taking measures to block ransomware operators from infiltrating their networks is even more important now that harvesting victims' data before encrypting systems has surfaced as the latest extortion method.
Once the data gets stolen, the ransomware gangs will start threatening to leak out the stolen data in small batches as leverage to pressure their victims to give in and paying the ransoms.
This trend was initially started by Maze Ransomware in November 2019 and it was later adopted by operators of other ransomware families such as Sodinokibi, Nemty Ransomware, and BitPyLock.
Sodinokibi (aka REvil) also shared plans to email stock exchanges like NASDAQ as a hit to the stock valuation of traded companies they compromise.
"Ransomware is not about encrypting data. It is the _current_ implementation of a methodology that coerces the victim to act as an agent for the criminal (typically to acquire BTC)," as security researcher thegrugq said three years ago. "Encrypting data just an implementation detail; it’s the 'coerced agent' part that matters."
RailWorks Corporation, one of North America’s leading railroad track providers, was the first to disclose a data breach following a ransomware attack last week showing that ransomware attacks should now also be considered data breaches, with all that it entails, including potential fines.
Chinese Security Firm Says CIA Hackers Attacked China Since 2008
7.3.2020 Bleepingcomputer BigBrothers
Chinese security vendor Qihoo 360 says that the US Central Intelligence Agency (CIA) has hacked Chinese organizations for the last 11 years, targeting various industry sectors and government agencies.
Qihoo 360 claims in the report that lacks any technical details that "the CIA hacking group (APT-C-39)" has targeted a multitude of Chinese companies between September 2008 and June 2019, with a focus on "aviation organizations, scientific research institutions, petroleum industry, Internet companies, and government agencies."
"We speculate that in the past eleven years of infiltration attacks, CIA may have already grasped the most classified business information of China, even of many other countries in the world," Qihoo 360's report says.
"It does not even rule out the possibility that now CIA is able to track down the real-time global flight status, passenger information, trade freight and other related information.
"If the guess is true, what unexpected things will CIA do if it has such confidential and important information? Get important figures‘ travel itinerary, and then pose political threats, or military suppression?"
Targeted Chinese areas
APT-C-39 used CIA and NSA attack tools
The Chinese security firm also says that its researchers connected the APT-C-39 hacking campaigns to the CIA based on malware used during the attacks spanning over 11 years, including the Fluxwire backdoor and the Grasshopper malware builder.
Documentation info on these tools was leaked by WikiLeaks in March 2017, with the leak site saying at the time it also had "the majority of its [CIA's] hacking arsenal including malware, viruses, trojans, weaponized 'zero day' exploits, malware remote control systems and associated documentation."
Qihoo 360 found that "the technical details of most samples of the APT-C-39 are consistent with the ones described in the Vault 7 documents" and that "before the Vault 7 cyber weapon was disclosed by WikiLeaks, the APT-C-39 already used relevant cyber weapons against targets in China."
Additionally, the Chinese security outfit claims that the APT-C-39 hacking campaigns also used tools connected with the US National Security Agency (NSA). The Chinese researchers were able to detect the WISTFULTOOL data exfiltration plugin used "in an attack against a large Internet company in China in 2011."
APT-C-39 group's weapons compilation time also locates the hacking group within the U.S. time zone per Qihoo 360 seeing that "yhe compilation time of the captured samples is in line with the North American business working hours."
CIA hackers also tracked by other security firms
Qihoo 360 is not the only security vendor tracking CIA hacking campaigns, with Kaspersky and Symantec also having previously labeled them as Lamberts and Longhorn, respectively.
While Kaspersky researchers have been monitoring CIA hacking activities since 2008 (matching Qihoo 360's claims), Symantec's monitoring data goes back to at least 2011 and highlighting 40 compromised targets from roughly 16 countries, across various industry sectors in across the Middle East, Europe, Asia, and Africa.
The CIA hackers were also mentioned as the ones behind attacks on domestic Chinese aviation companies from late-2018 by the Chinese cybersecurity group Qi-Anxin in a report from September 2019 as reported by ZDNet.
Qi-Anxin's researchers, just like their Qihoo 360 counterparts, made the connection to the CIA hacking groups after spotting the Fluxwire backdoor being used during the attack.
Qihoo 360's report was published after two Chinese nationals were charged yesterday by the US Dept of Justice and sanctioned by the US Treasury for allegedly laundering over $100 million worth of cryptocurrency for North Korean actors known as Lazarus Group.
US Charges Two With Laundering $100M for North Korean Hackers
7.3.2020 Bleepingcomputer BigBrothers
Two Chinese nationals were charged today by the US Dept of Justice and sanctioned by the US Treasury for allegedly laundering over $100 million worth of cryptocurrency out of the nearly $250 million stolen by North Korean actors known as Lazarus Group after hacking a cryptocurrency exchange in 2018.
According to a Department of Justice (DoJ) press release, 田寅寅 aka Tian Yinyin, and 李家东aka Li Jiadong, were charged with operating an unlicensed money transmitting business and money laundering conspiracy.
$300 million worth of crypto stolen by Lazarus Group
The almost $250 million worth of virtual currency their North Korean co-conspirators were able to steal after hacking into an unnamed virtual currency exchange was "laundered through hundreds of automated cryptocurrency transactions aimed at preventing law enforcement from tracing the funds."
"In April 2018, an employee of the exchange unwittingly downloaded DPRK-attributed malware through an email, which gave malicious cyber actors remote access to the exchange and unauthorized access to customers’ personal information, such as private keys used to access virtual currency wallets stored on the exchange’s servers," the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) explained.
"Lazarus Group cyber actors used the private keys to steal virtual currencies ($250 million dollar equivalent at date of theft) from this exchange, accounting for nearly half of the DPRK’s estimated virtual currency heists that year."
The North Korean hackers are also tied to the theft of another roughly $48.5 million worth of cryptocurrency from a South Korea-based exchange in November 2019.
In April 2018, the Lazarus Group leveraged previously used malware code from the now-defunct cryptocurrency application Celas Trade Pro — software both developed and offered by the Lazarus Group registered website called Celas Limited. Creating illegitimate websites and malicious software to conduct phishing attacks against the virtual currency sector is a pattern previously seen from North Korean cybercriminals. - OFAC
Crypto converted into Chinese yuan and Apple gift cards
Tian and Li received $91 million from DPRK-controlled accounts as the first batch of currency to launder in April 2018 and an additional $9.5 million after the Lazarus Group actors hacked a second exchange. The defendants then transferred these funds among virtual currency addresses they controlled to obfuscate their origin.
From December 2017 up until around April 2019, Tian and Li have purportedly laundered more than $100 million worth of cryptocurrency, primarily sourced from Lazarus Group's virtual currency exchange hacks.
Flow of laundered cryptocurrency funds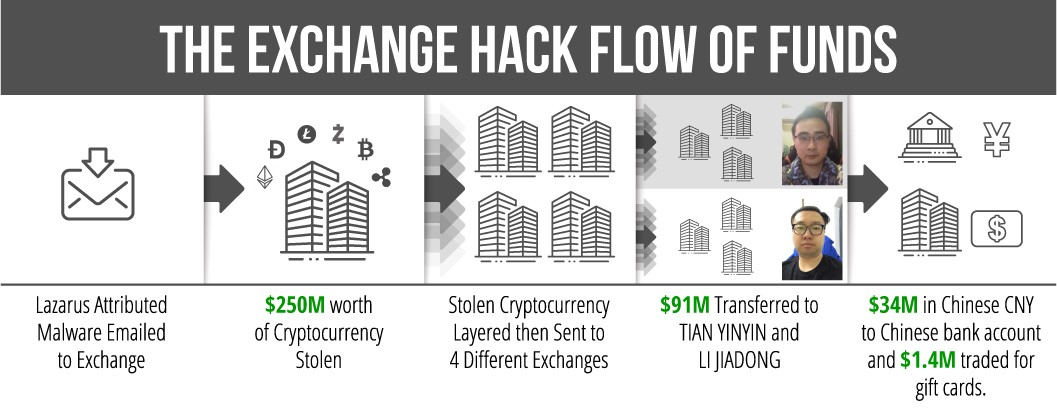
"The civil forfeiture complaint specifically names 113 virtual currency accounts and addresses that were used by the defendants and unnamed co-conspirators to launder funds," the DoJ added. "The forfeiture complaint seeks to recover the funds, a portion of which has already been seized."
"The two defendants operated through independent as well as linked accounts and provided virtual currency transmission services for a fee for customers," the OFAC added. "As a result of today’s action, all property and interests in property of these individuals that are in the United States or in the possession or control of U.S. persons must be blocked and reported to OFAC."
"The August 2019 UN Security Council 1718 Committee Panel of Experts report estimates that North Korea had attempted to steal as much as $2 billion, of which $571 million is attributed to cryptocurrency theft. This revenue allows the North Korean regime to continue to invest in its illicit ballistic missile and nuclear programs."
While the DoJ and OPAC haven't named the two hacked crypto exchanges, the two press releases hint at potential connections to Lazarus Group campaigns detected and reported by Kaspersky in 2018 and 2020.
FBI Says $140+ Million Paid to Ransomware, Offers Defense Tips
24.2.2020 Bleepingcomputer BigBrothers
Through the analysis of collected ransomware bitcoin wallets and ransom notes, the FBI states that victims have paid over $140 million to ransomware operators over the past six years.
At the RSA security conference this week, FBI Special Agent Joel DeCapua explained how he used bitcoin wallets and ransom notes that were collected by the FBI, shared by private partners, or found on VirusTotal to compute how much money was paid in ransom payments over 6 years.
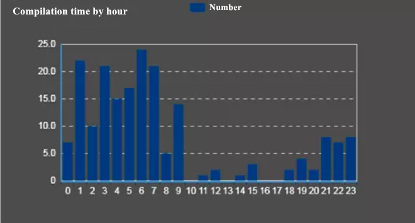
According to DeCapua between 10/0/1/2013 and 11/07/2019, there have been approximately $144,350,000 in bitcoins paid to ransomware actors as part of a ransom. This money does not include operational costs related to the attack, but purely the ransom payments.
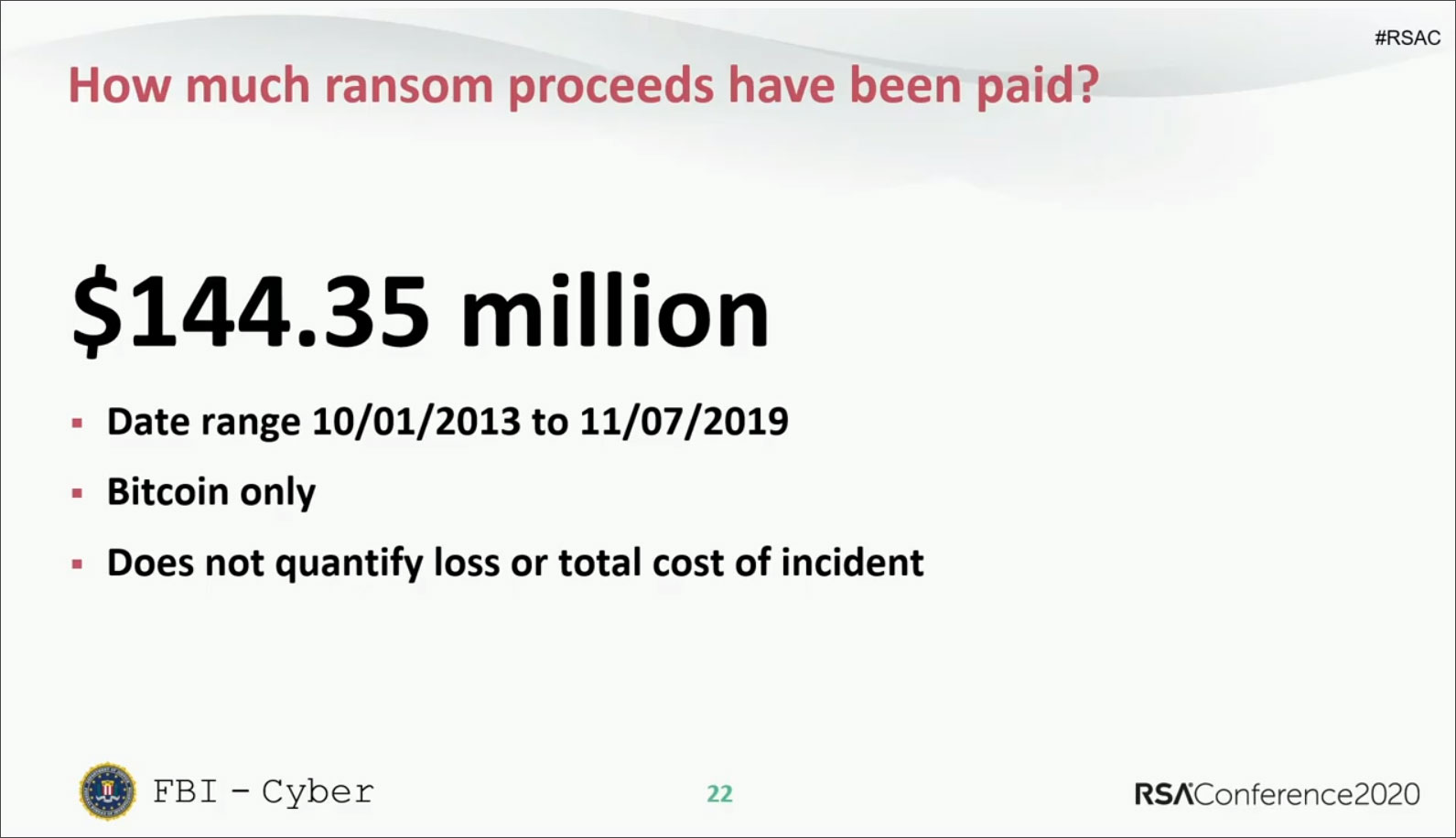
RSA Slide: Ransom paid over 6 years
When analyzing the ransomware families that the ransoms were paid, Ryuk stood out head and shoulders above the rest with payments totaling $61.26 million. The second-place spot goes to Crysis/Dharma at $24.48 million and then third place is Bitpaymer at $8.04 million.
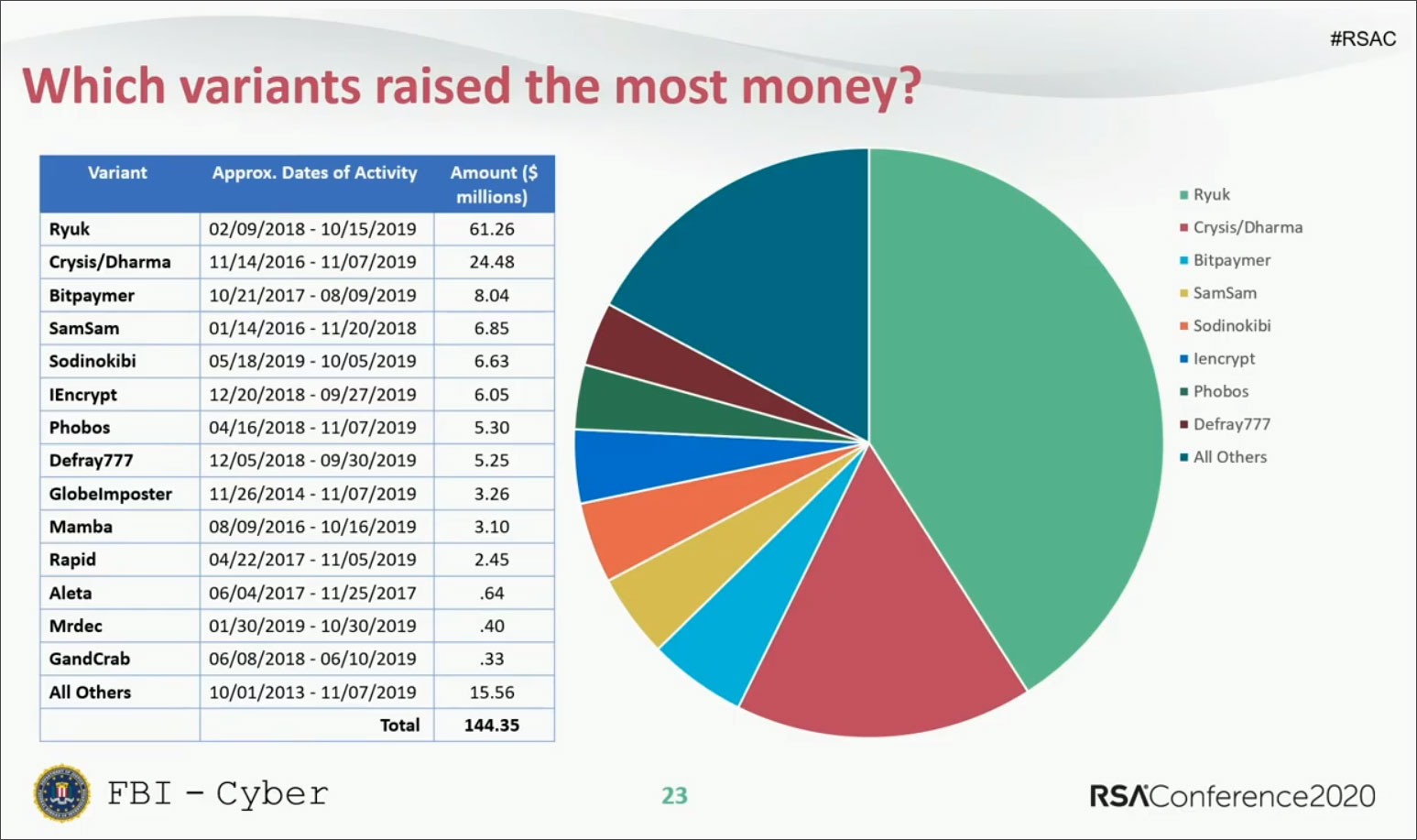
RSA Slide: Who earned the most
It should be noted that the actual amount of payments made over the 6 years is probably quite larger as there are many ransom notes and wallets that the FBI does not have access to. Furthermore, many companies keep ransomware attacks secret to prevent it from impacting stock prices.
FBI offers tips on ransomware defense
As part of his RSA talk, DeCapua also offered recommended tips on how companies can defend themselves against ransomware.

RSA Slide: FBI tips to protect against ransomware
1. RDP accounts for 70-80% of network breaches
DeCapua stated that the Windows Remote Desktop Protocol (RDP) is the most common method that ransomware attackers are gaining access to a network before deploying ransomware.
"RDP is still 70-80% of the initial foothold that ransomware actors use," DeCapua stated in his talk.
Therefore, if you use RDP in your organization it is recommended that you use Network Level Authentication (NLA), which requires clients to authenticate themselves with the network before actually connecting to the remote desktop server.
This offer increased security as it does not give the attacker access to an RDP server until they are authenticated and thus offers better protection against preauthentication exploits.
It is also suggested that you use unique and complex passwords for your RDP accounts.
BleepingComputer also suggests that you place all RDP services behind a VPN so that they are not publicly accessible on the Internet.
2. Be careful of phishing attacks
While not shown on his slide, DeCapua also mentioned that if its not RDP attacks that allow bad actors access to a network, its either phishing, following by remote code execution vulnerabilities.
All users must be wary of strange emails with attachments asking you to enable content or enable editing, which you should never do without speaking to an IT staff or system administrator.
Phishing is getting harder and more complex to detect, especially now that actors are compromising coworker's accounts and using them to phish other employees.
Always be wary of any email with attachments and if you are not 100% sure if they legitimate, reach out to the sender via phone or speak to a system admin before opening them.
3. Install software and operating system updates
Make sure to install operating system and software updates as quickly as possible after being released.
Every second Tuesday of the month, Microsoft releases security updates for its software and Windows as part of the Microsoft Patch Tuesday.
It is very common to find proof-of-concept exploits being published soon after updates are released, which are useful for administrators and researchers, but also for attackers to use in attacks.
Therefore, it is important to get those updates installed as soon as possible. This is especially true for public-facing services such as RDP, Exchange, etc.
4. Use complex passwords
Everyone knows you need to use complex passwords that are unique for every login that you have.
Unfortunately, many people do not heed this advice and just use the same password at every site.
This means if one of those sites gets hacked, your exposed credentials can then be used in credential stuffing attacks at other sites and possibly even network logins.
Use a password manager to keep track of your unique passwords and you will be far greater protected.
5. Monitor your network
DeCapua stated that invariably someone at your company is going to get phished, hacked, or compromised in some way so it is important to always monitor a network for suspicious activity.
"You're not going to prevent an intrusion, but actors get really really noisy when they are moving laterally and trying to escalate their privileges," stated DeCapua.
Invest in network monitoring tools and intrusion detection systems to detect suspicious activity and traffic in your network.
6. Have a contingency plan and backups
To be technical, things just happen. So have a contingency plan and good backups.
No matter how hard you try to protect your computers and network, someone invariably clicks on the wrong thing or a server is exposed in some manner.
So always make sure to have a tested and working nightly backup routine with file versioning. This includes offline backups that are not accessible via the cloud.
BleepingComputer routinely sees ransomware actors targeting a victim's cloud-based backup service and deleting all backups before encrypting the network.
Therefore, it is important to retain offline backups that cannot be wiped by bad actors.
You can watch FBI Special Agent Joel DeCapua's full talk below:
Russia Blocks Tutanota Email, Service Still Usable Over Tor or VPN
22.2.2020 Bleepingcomputer BigBrothers
Access to the Tutanota secure email service is currently being blocked in Russia, with the block being enacted over the weekend, starting February 14.
While Roskomnadzor, Russia's telecommunications watchdog, usually published an official statement on occasions when similar services were blocked in the country, this time the block came without warning, with the team behind the service being forced to collect proof that this was happening.
No Russian authorities contacted or notified Tutanota about this block as of yet and the team behind it still doesn't know why Tutanota is blocked in Russia according to Tutanota co-founder and developer Matthias Pfau.
Still accessible via Tor or VPN
"As the OONI Explorer - a tool to demonstrate censorship online - shows, Tutanota is blocked in parts of Russia," Pfau shared in a blog post published today.
"Tutanota is also listed in the registry of blocked sites provided by Russian activists," he added. This registry is part of a Russian initiative that wants to force all foreign internet service providers to give Russian authorities access to Russian citizens' data and encryption keys.
Russia's move to block Tutanota for all Russian users is seen as an attempt to block its citizens' access to confidential and encrypted communication, the core of the company's product, an open-source and secure email service with a free tier for private users.
Tutanota is currently blocked in Russia. If you are affected by this outage, please use the Tor browser or a vpn to access Tutanota.https://t.co/Re8lQ1uDbS#censorship #surveillance #privacy #HumanRights #FreeSpeech
— Tutanota (@TutanotaTeam) February 16, 2020
"We have not been presented with an official reason for the blockage in Russia by the authorities," Pfau told BleepingComputer in an email interview.
"We are still evaluating the situation and figuring out how we can resolve this for the users of our secure email service in Russia. For now, we ask them to use the Tor browser or a VPN to access Tutanota."
Russian users who cannot access Tutanota can use a VPN or the Tor browser to evade the ongoing block to get access to their secure Tutanota mailboxes.
To get access to Tutanota's services using the Tor Browser you will have to follow these steps:
• Download the TOR browser for your device here: https://www.torproject.org/download/
• Install the TOR browser
• Once the browser is installed, launch it, and you will be able to access the Tutanota website again
AT&T mobile users weren't able to access Tutanota's service either starting with January 25 but, following media reports, the company reached out to Tutanota and fixed the problem saying that "the outage has been a technical issue."
According to Pfau, Tutanota is also being blocked in Egypt since October 2019 although users can still access it via VPN and Tor.
ProtonMail and StartMail also blocked
As we previously reported, Tutanota is not the first secure email service blocked by the Russian government since the start of 2020, with ProtonMail (and ProtonVPN) also becoming unreachable in Russia starting on January 29.
The ProtonMail block was prompted by Proton Technologies' opposition to register their service with Russian state authorities — something requested from all VPN providers as we reported last year — and to provide info on the owners of mailboxes used to send false bombing threats.
"In accordance with the procedure enshrined in the legislation, Roskomnadzor consistently restricts access to resources used by criminals to destabilize the situation in the country and increase tension, and expects effective interaction with all parties involved," a Roskomnadzor press release explained at the time.
The block imposed against ProtonMail was lifted roughly one week later, around February 3, as detailed in an incident recorded on the service's status page.
https://t.co/P6mbhjM7cY has been blocked in Russia. We feel that there is no justification for blocking. StartMail will continue to evaluate the technical situation to see if we can restore access for our Russian users. Read our CEO's statement: https://t.co/oLvu2OKSu3
— StartMail (@MyStartMail) January 27, 2020
Dutch encrypted email service StartMail is also blocked in Russia since January 23, 2020, "to protect the Russian segment of the Internet from disseminating inaccurate socially significant information, distributed under the guise of reliable messages."
"In this specific case, they claim that thousands of false bomb threats were sent from Startmail.com email accounts," StartMail CEO Robert Beens said in a blog post.
US Govt Updates Info on North Korean Malware
16.2.2020 Bleepingcomputer BigBrothers
The Federal Bureau of Investigation (FBI) and Cybersecurity and Infrastructure Security Agency (CISA) released new info on North Korean malware with six new and updated Malware Analysis Reports (MARs) related to malicious cyber activity from North Korea.
Each of these MARs is designed to provide organizations with detailed malware analysis information acquired via manual reverse engineering.
They are also issued to help network defenders to detect and reduce exposure to HIDDEN COBRA malicious cyber activity as the U.S. government refers to North Korean government malicious activity.
Users and administrators are urged by CISA to carefully review the seven MARs released today:
AR20-045A — BISTROMATH (a full-featured RAT)
AR20–045B — SLICKSHOES (Themida-packed malware dropper)
AR20-045C — CROWDEDFLOUNDER (Remote Access Trojan loader)
AR20-045D — HOTCROISSANT (beaconing implant with backdoor capabilities)
AR20-045E — ARTFULPIE (loads and executes a DLL from a hardcoded URL)
AR20-045F — BUFFETLINE (beaconing implant with backdoor features)
AR20-045G — HOPLIGHT (backdoor Trojan)
"The information contained in these most recent seven (7) MARs, as well as the previous work linked below, is the result of analytic efforts between the U.S. Department of Homeland Security (DHS), the U.S. Department of Defense (DOD), and the FBI to provide technical details on the tools and infrastructure used by cyber actors of the North Korean government," CISA explains.
Each MAR comes with detailed "malware descriptions, suggested response actions, and recommended mitigation techniques."
US Cyber Command also uploaded malware samples to VirusTotal, saying that "this malware is currently used for phishing & remote access by #DPRK cyber actors to conduct illegal activity, steal funds & evade sanctions."
USCYBERCOM Malware Alert
✔
@CNMF_VirusAlert
Replying to @CNMF_VirusAlert and 4 others
#ValentinesDayMemes @US_CYBERCOM
View image on Twitter
289
2:25 PM - Feb 14, 2020
Twitter Ads info and privacy
162 people are talking about this
Cyber National Mission Force "enables whole-of-government efforts to ID #NorthKorea cyber activities, including #DPRK malware that exploits financial institutions, conducts espionage & enables #cyber attacks against US & partners."
During 2019, CISA and the FBI have also released joint MARs on a malware strain dubbed ELECTRICFISH and used by the North-Korean APT group Lazarus to collect and steal data from victims, as well as on the Lazarus HOPLIGHT Trojan whose MAR was updated today.
CISA advises organizations to follow these best practices to strengthen their security posture:
• Maintain up-to-date antivirus signatures and engines.
• Keep operating system patches up-to-date.
• Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
• Restrict users' ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators group unless required.
• Enforce a strong password policy and implement regular password changes.
• Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
• Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
• Disable unnecessary services on agency workstations and servers.
• Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its "true file type" (i.e., the extension matches the file header).
• Monitor users' web browsing habits; restrict access to sites with unfavorable content.
• Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs, etc.).
• Scan all software downloaded from the Internet prior to executing.
• Maintain situational awareness of the latest threats and implement appropriate Access Control Lists (ACLs).
Additional info on how to prevent malware infections can be found in the Guide to Malware Incident Prevention and Handling for Desktops and Laptops provided by the National Institute of Standards and Technology (NIST).
More information regarding HIDDEN COBRA activity in the form of previous alerts and MARs released via the National Cyber Awareness System are available here.
US Charges Huawei With Conspiracy to Steal Trade Secrets, Racketeering
16.2.2020 Bleepingcomputer BigBrothers
The U.S. Department of Justice charged Huawei and two U.S. subsidiaries with conspiracy to steal trade secrets and to violate the Racketeer Influenced and Corrupt Organizations Act (RICO).
The defendants included in today's16-count superseding indictment are Huawei — the world’s largest manufacturer of telecommunications equipment — and four official and unofficial subsidiaries: Huawei Device Co. Ltd. (Huawei Device), Huawei Device USA Inc. (Huawei USA), Futurewei Technologies Inc. (Futurewei) and Skycom Tech Co. Ltd. (Skycom).
Huawei’s Chief Financial Officer Wanzhou Meng is also introduced as a defendant. She was previously charged together with Huawei and two Huawei affiliates — Huawei USA and Skycom - with financial fraud, money laundering, conspiracy to defraud the U.S., obstruction of justice, and sanctions violations in a 13-count indictment unsealed in January 2019.
The new charges included in this new indictment relate to the company's alleged decades-long efforts to steal intellectual property from six US tech companies.
During this time, Huawei and its US and Chinese subsidiaries purportedly misappropriated copyrighted information and trade secrets including but not limited to internet routers' manuals and software source code, as well as antenna and robot testing technology.
"The means and methods of the alleged misappropriation included entering into confidentiality agreements with the owners of the intellectual property and then violating the terms of the agreements by misappropriating the intellectual property for the defendants’ own commercial use, recruiting employees of other companies and directing them to misappropriate their former employers’ intellectual property, and using proxies such as professors working at research institutions to obtain and provide the technology to the defendants," the press release says.
US Attorney EDNY
✔
@EDNYnews
Chinese Telecommunications Conglomerate Huawei and Subsidiaries Charged in Racketeering Conspiracy and Conspiracy to Steal Trade Secrets https://www.justice.gov/usao-edny/pr/chinese-telecommunications-conglomerate-huawei-and-subsidiaries-charged-racketeering … (Announced with @TheJusticeDept and @NewYorkFBI)
265
7:04 PM - Feb 13, 2020
Twitter Ads info and privacy
233 people are talking about this
"As part of the scheme, Huawei allegedly launched a policy instituting a bonus program to reward employees who obtained confidential information from competitors. The policy made clear that employees who provided valuable information were to be financially rewarded."
According to the DoJ, Huawei and its subsidiaries were able to obtain the targeted nonpublic intellectual property which made it possible for the Chinese company to significantly decrease research and development costs, thus obtaining an unfair competitive advantage.
"The superseding indictment also includes new allegations about Huawei and its subsidiaries’ involvement in business and technology projects in countries subject to U.S., E.U. and/or U.N. sanctions, such as Iran and North Korea – as well as the company’s efforts to conceal the full scope of that involvement," the DoJ press release adds.
Huawei allegedly violated the imposed sanctions by using local affiliates in the sanctioned countries to arrange shipments of equipment and to provide services to end-users.
The Shenzen-based company also used its unofficial subsidiary Skycom to help "the Government of Iran in performing domestic surveillance, including during the demonstrations in Tehran in 2009."
FBI: Cybercrime Victims Lost $3.5 Billion in 2019
16.2.2020 Bleepingcomputer BigBrothers
FBI's Internet Crime Complaint Center (IC3) published the 2019 Internet Crime Report which reveals that cybercrime was behind individual and business losses of $3.5 billion as shown by the 467,361 complaints received during the last year.
IC3 says that it has received 4,883,231 complaints since its inception in May 2000, with an average of around 340,000 complaints per year and over 1,200 complaints per day during the last five years.
These resulted in recorded losses reported by victims of $10.2 billion over the last five years, between 2015 and 2019.
"The most frequently reported complaints were phishing and similar ploys, non-payment/non-delivery scams, and extortion," the report says,
"The most financially costly complaints involved business email compromise, romance or confidence fraud, and spoofing, or mimicking the account of a person or vendor known to the victim to gather personal or financial information."
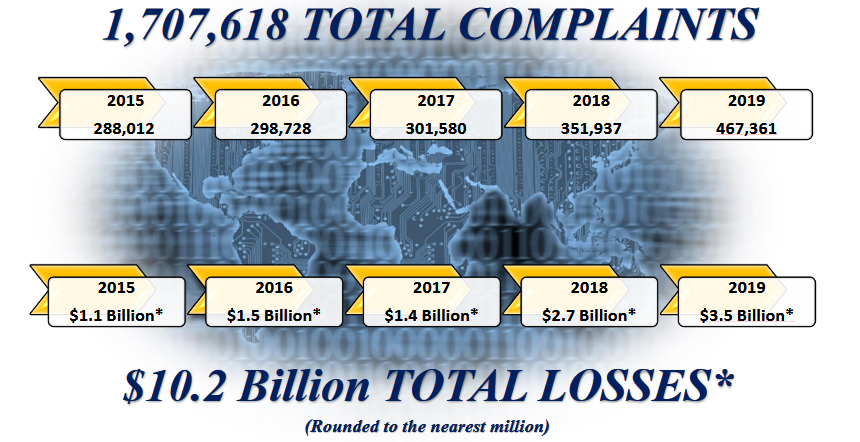
Losses to cybercrime over the last 5 years (FBI)
Donna Gregory, the chief of IC3, said that in 2019 instead of cybercriminals using new types of fraud to steal money from their victims, they were adopting new techniques and tactics to further evade detection while carrying out their scams.
"Criminals are getting so sophisticated," Gregory added. "It is getting harder and harder for victims to spot the red flags and tell real from fake."
"In the same way your bank and online accounts have started to require two-factor authentication — apply that to your life. Verify requests in person or by phone, double-check web and email addresses, and don’t follow the links provided in any messages."
The IC3 also says that the Recovery Asset Team (RAT) established in February 2018 was able to help cybercrime victims recover funds lost due to various types of Internet crimes.
"The RAT, which was established as a standalone team in 2018, completed its first full year of operation in 2019, assisting in the recovery of over $300 million lost through online scams, for a 79% return rate of reported losses," the FBI says.
BEC scams still behind most victim losses
The 2019 cybercrime type with the highest reported total victim losses, BEC (Business Email Compromise) also known as EAC (Email Account Compromise) reached almost $1.8 billion in losses according to 23,775 recorded complaints by targeting wire transfer payments of both individuals and businesses.
"These scams typically involve a criminal spoofing or mimicking a legitimate email address," the report explains. "For example, an individual will receive a message that appears to be from an executive within their company or a business with which an individual has a relationship.
"The email will request a payment, wire transfer, or gift card purchase that seems legitimate but actually funnels money directly to a criminal."
During 2019, IC3 observed an increased number of diversion of payroll funds BEC complaints where fraudsters send emails a company’s human resources or payroll department requesting direct deposit info updates while posing as an employee.
If their request is met, the employee's paycheck will generally be sent to a criminal-controlled pre-paid card account instead.
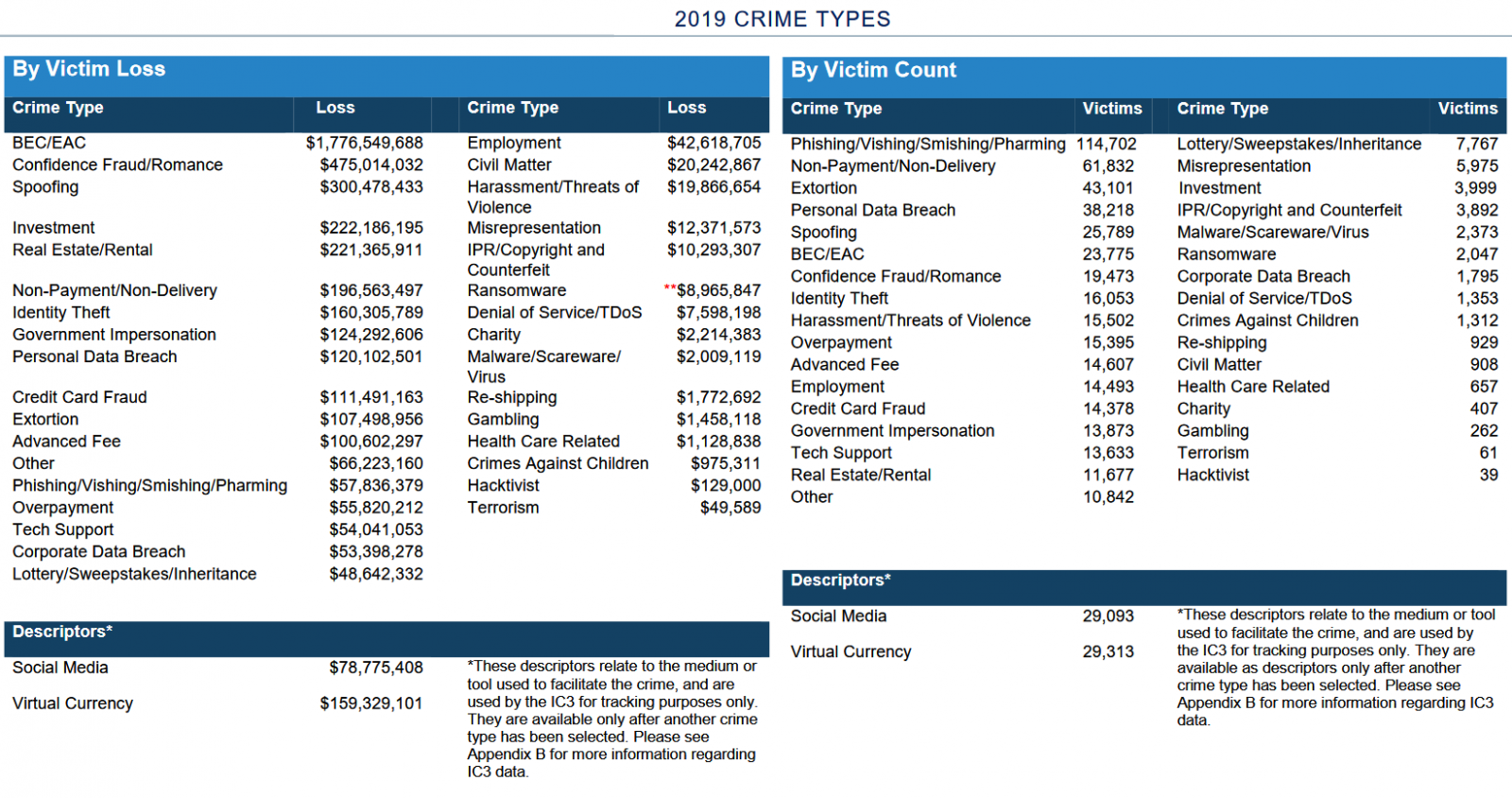
Image: FBI
Victims encouraged to report malicious activity
Also during 2019, the IC3 received 13,633 Tech Support Fraud complaints from victims residing in 48 countries, with recorded losses amounting to over $54 million, representing a tremendous 40 percent increase when compared to 2018.
According to IC3, the vast majority of victims that sent complaints reporting tech support fraud scams were over 60 years of age.
In 2019, the IC3 also received 2,047 complaints related to ransomware incidents, with adjusted losses of over $8.9 million.

Image: FBI
"Information reported to the IC3 plays a vital role in the FBI’s ability to understand our cyber adversaries and their motives, which, in turn, helps us to impose risks and consequences on those who break our laws and threaten our national security," assistant director of the FBI’s Cyber Division Matt Gorham said.
"It is through these efforts we hope to build a safer and more secure cyber landscape," Gorham added, encouraging both businesses and individuals to contact the local FBI field office to report any malicious activity.
U.S. Charges Chinese Military Hackers for Equifax Breach
15.2.2020 Bleepingcomputer BigBrothers
The U.S. Department of Justice announced today that four members of the Chinese People’s Liberation Army (PLA) 54th Research Institute were charged for hacking the credit reporting agency Equifax in 2017.
On January 28, 2020, a federal grand jury in Atlanta returned an indictment alleging that Wu Zhiyong (吴志勇), Wang Qian (王乾), Xu Ke (许可), and Liu Lei (刘磊) broke into Equifax's computing systems and stole sensitive personal info of nearly half of all U.S. citizens and Equifax trade secrets.
Under the global settlement agreed upon with the Federal Trade Commission, the Consumer Financial Protection Bureau, and 50 U.S. states and territories on July 22, Equifax said that it will spend up to $425 million to help the breach victims.
According to the indictment, "The PLA hackers obtained names, birth dates, and social security numbers for the 145 million American victims, in addition to driver's license numbers for at least 10 million Americans stored on Equifax's databases.

Image: The FBI
"The hackers also collected credit card numbers and other personally identifiable information belonging to approximately 200,000 American consumers. Accordingly, in a single breach, the PLA obtained sensitive personally identifiable information for nearly half of all American citizens.
"In addition, the PLA hackers obtained personally identifiable information belonging to nearly a million citizens of the United Kingdom and Canada."
They were able to infiltrate Equifax's network by exploiting a vulnerability in the Apache Struts framework used by Equifax’s online dispute portal.
After hacking the digital portal, they moved through the network for weeks, stealing credentials and infecting systems with malware.
Following the initial reconnaissance stage, they used roughly 9,000 queries on Equifax’s databases to find and collect login credentials, PII, and financial data.
During one of the times the hackers downloaded the stolen Equifax info, everything was then packaged into an archive that was later split into more manageable 600 MB segments, later exfiltrated to a Dutch server via HTTP.
The defendants also did their best to evade detection throughout their intrusion by routing traffic through roughly 34 servers located in 20 countries to hide their true location.
They also used encrypted channels within Equifax’s network to mix their communications with normal network activity, as well as deleted generated archives containing stolen data after exfiltration and wiped server log files daily.
"This was one of the largest data breaches in history," Attorney General William P. Barr said in a press conference today. "It came to light in the summer of 2017, when Equifax announced the theft.
"This kind of attack on American industry is of a piece with other Chinese illegal acquisitions of sensitive personal data.
"For years, we have witnessed China’s voracious appetite for the personal data of Americans, including the theft of personnel records from the U.S. Office of Personnel Management, the intrusion into Marriott hotels, and Anthem health insurance company, and now the wholesale theft of credit and other information from Equifax."
"In short, this was an organized and remarkably brazen criminal heist of sensitive information of nearly half of all Americans, as well as the hard work and intellectual property of an American company, by a unit of the Chinese military," Barr added.
The four defendants were charged with three counts of conspiracy to commit economic espionage, to commit computer fraud, and to commit wire fraud.
Also, they were charged with two counts of unauthorized access and intentional damage to a protected computer, three counts of wire fraud, and one count of economic espionage.
AG Barr also said that roughly "80 percent of our economic espionage prosecutions have implicated the Chinese government, and about 60 percent of all trade secret theft cases in recent years involved some connection to China."
The US Department of Justice previously charged five Chinese military hackers for computer hacking and espionage targeting six American entities in the U.S. nuclear power, metals and solar products industry sectors.
Another Chinese national was sentenced for being part of a conspiracy with Chinese military officers that led to the hacking into the computer networks of major U.S. defense contractors.
Japanese Defense Contractors Kobe Steel, Pasco Disclose Breaches
9.2.2020 Bleepingcomputer BigBrothers Incindent
Japanese defense contractors Pasco Corporation (Pasco) and Kobe Steel (Kobelco) today disclosed security breaches that happened in May 2018 and in June 2015/August 2016, respectively.
The geospatial provider and the major steel manufacturer also confirmed unauthorized access to their internal network during the two incidents, as well as malware infections affecting their computing systems following the attacks.
No damage such as information leakage has been discovered so far during the following investigations per the official statement issued today by Pasco.
However, while Kobelco's official statement doesn't mention it, Nikkei reports that 250 files with data related to the Ministry of Defense and personal info were compromised after the company's servers were hacked.
It is also possible that the threat actors behind the attacks might have targeted the companies' defense information, but the data that might have been leaked did not include defense secrets.
Kobe Steel is a known supplier of submarine parts for the Japan Self-Defense Forces (SDF), while Pasco is a provider of satellite data.
Two of four hacked Japanese defense contractors
The two companies are the last of the four defense-related firms that were hacked between 2016 and 2019, as Japanese Defense Minister Taro Kono said during a press conference on January 31.
Kono also stated that no hints are pointing at the attacks being related to each other and that the Japanese Ministry of Defense coordinated the disclosures because "it should be publicly disclosed. It is necessary to get the world to know and think about defenses."
The other two defense contractors that were infiltrated by attackers are Mitsubishi Electric and NEC. Both of them confirmed that their systems were breached in statements published on January 20 and January 30, respectively.
Mitsubishi Electric disclosed that the security breach might have caused the leak of personal and confidential corporate info, with about 200 MB worth of documents being exposed during the attack that took place on June 28, 2019.
The eight months delay disclosing the incident was attributed by Mitsubishi Electric to the complexity of the investigation caused by the activity logs being deleted after the attack.
NEC said that servers belonging to its defense business unit were accessed without authorization in December 2016 by third parties, but "no damage such as information leakage has been confirmed so far." 27,445 files were accessed illegally during the incident according to an NEC statement to BleepingComputer.
Chinese hackers suspected in at least two of the attacks
"According to people involved, Chinese hackers Tick may have been involved," Nikkei reported after Mitsubishi Electric disclosed the breach.
"According to the company, at least tens of PCs and servers in Japan and overseas have been found to have been compromised."
"The hijacked account was used to gain infiltration into the company's internal network, and continued to gain unauthorized access to middle-managed PCs who had extensive access to sensitive information," an Asahi Shimbun report added.
A Pasco official was also quoted as saying that the attackers behind the May 2018 security breach might be linked to China per a Kyodo News report from today.
Tick (also tracked as Bronze Butler and RedBaldNight) is a state-backed hacking group with Chinese ties with a focus on cyberespionage and information theft.
The group is known for primarily targeting Japanese organizations from several sectors including but not limited to manufacturing, critical infrastructure, international relations, and heavy industry.
Their end goal is to steal confidential intellectual property and corporate info after breaching enterprise servers via spearphishing attacks and exploiting various zero-day vulnerabilities — including one affecting Trend Micro's OfficeScan in the case of Mitsubishi Electric as reported by ZDNet.
According to research, Tick also usually wipes all evidence from hacked servers as part of an effort to delay investigations after their operations are eventually discovered.
DoJ Asks Victims of the Quantum DDoS Service to Come Forward
9.2.2020 Bleepingcomputer BigBrothers
The U.S. Department of Justice (DoJ) today issued a notification to raise awareness among victims of the Quantum Stresser Distributed Denial of Service (DDoS) for-hire service operated by David Bukoski.
DDoS-for-hire services known as booters or stressers are used by malicious actors, pranksters, or hacktivists to launch large-scale DDoS cyberattacks against a targeted site or online service, triggering a denial of service that leads to the service being taken down or working a lot slower than usual.
"Due to the large number of potential victims in this case, Chief U.S. District Judge Timothy M. Burgess issued an order directing the government to employ alternative victim notification procedures so that any member of the community at large who believes they may be a crime victim is made aware of their potential rights," the DoJ statement says.
"The government is asking that members of the community who believe they may be a victim of Bukoski’s criminal activities, to please contact (907) 271-3041 to reach the Victim-Witness Unit at the U.S. Attorney’s Office, District of Alaska."
This notification was the result of a motion for alternative victim notification filed on February 3 which also says that there are "plans to notify – to the extent possible – those ISPs providing services to victim networks, who may be able to conduct additional notification of their own customers. "
The DoJ has scheduled a restitution hearing on May 5, 2020, at 10:30 A.M. in Anchorage.
Quantum Stresser seizure notification
Quantum Stresser had more than 80,000 customer subscriptions on November 29, 2018, dating back to 2012 per stats shared by the DoJ and it was seized on December 20, 2018, together with 14 other booter sites following an FBI investigation.
"In 2018 alone, Quantum was used to launch over 50,000 actual or attempted DDoS attacks targeting victims worldwide, including victims in Alaska and California," the DoJ said.
"From at least on or about March 2011 through at least on or about November 29, 2018, in the District of Alaska and elsewhere, the defendant, DAVID BUKOSKI, operating a service called 'Quantum Stresser,' knowingly caused and knowingly and intentionally aided and abetted unlawful computer intrusions and attempted unlawful computer intrusions," says the indictment unsealed on December 18, 2018.
According to the DoJ notification advisory, Bukoski pleaded guilty to aiding and abetting computer intrusions in August 2019 and he was sentenced to five years in prison on February 4, 2020.
DDoS booter users also under investigation
The FBI's Internet Crime Complaint Center issued a public service announcement in October 2017 about the increasing number of DDoS attacks launched using booter and stresser services against US companies and government assets.
Besides taking down stresser services and seizing their domains, law enforcement agencies are now also hunting down their users, with several hundred individuals being investigated as a result of Operation Power Off, a collaboration between Europol and law enforcement partners.
This operation took down the WebStresser booter/stresser website in April 2018, a service that had 151,000 registered users when it was taken down.
Following WebStresser's takedown, DDoS attacks went down roughly 60% across Europe according to a report from DDoS mitigation firm Link11.
"A further 400 users of the service are now being targeted by the NCA and partners," NCA said in an announcement at the time, while Europol added that WebStresser users are not the only ones that police forces have in their sights.
FBI Warns of DDoS Attack on State Voter Registration Site
9.2.2020 Bleepingcomputer BigBrothers
The US Federal Bureau of Investigation (FBI) warned of a potential Distributed Denial of Service (DDoS) attack that targeted a state-level voter registration and information site in a Private Industry Notification (PIN) released today.
"The FBI received reporting indicating a state-level voter registration and voter information website received anomalous Domain Name System (DNS) server requests consistent with a Pseudo Random Subdomain (PRSD) attack," according to the FBI PIN seen by BleepingComputer.
PRSD attacks are a type of DDoS attack used by threat actors to disrupt DNS record lookups by flooding a DNS server with large amounts of DNS queries against non-existing subdomains.
The FBI says that the state voter registration website was not affected by the DDoS siege due to properly set up rate-limiting on the target's DNS servers.
DDoS attack details
A high volume of DNS requests consistent with a PRSD DDoS attack hit the DNS server of the voter registration website over a month, with short periods of time where the amount of DNS requests increased tenfold.
"The requests occurred over the course of at least one month in intervals of approximately two hours, with request frequency- peaking around 200,000 DNS requests during a period of time when less than 15,000 requests were typical for the targeted website," the FBI explains.
"The DNS requests had source IP addresses belonging to recursive DNS servers, obfuscating the originating host(s) or attacker, and were largely for non-existent subdomains of the targeted website.
During a sample three minute window, 24 IP addresses used by recursive DNS servers made 2,121 DNS requests.
A small sample of the DNS request traffic contained roughly 1,020 requests for unique subdomains, of which 956 were single requests for non-existent subdomains which appeared to be randomly generated."
The FBI also shared a number of examples of requests for nonexistent subdomains for the targeted attack, all of them sharing the same keyword added to the target domain.
DDoS mitigation measures
The FBI also provided potential targets with a series of precautionary measures to be taken to successfully mitigate DDoS attacks including but not limited to:
• Implement an incident response plan, including a DDoS mitigation strategy, and practice this plan prior to an actual incident.
• If the incident response plan involves external organizations, ensure the appropriate contacts with the external organizations are established prior to an incident.
• Enable automated patches for your operating system, Web browser(s), and software to the extent possible. When necessary, manually apply as soon as possible.
• Maintain a timeline of attacks, recording all relevant details.
The DHS Cybersecurity and Information Security Agency (CISA) also provides DDoS guidance, with details on how to avoid becoming a DDoS victim, how to know if an attack is happening, and what to do when you are experiencing an attack.
The FBI also encouraged PIN recipients to report any related suspicious activity to their local FBI field office or to file an online complaint with the Internet Crime Complaint Center.
Previous FBI alerts
In January, the FBI issued a flash security alert with additional IOCs and TTPs from recent defacement attacks operated by Iranian threat actors, as well as one regarding state-backed actors that hacked a US municipal government and a US financial entity by exploiting a Pulse Secure VPN server flaw.
On the same day, the FBI also notified private industry partners that nation-state threat actors were able to breach two other US municipalities by abusing the CVE-2019-0604 SharePoint vulnerability per ZDNet.
A Private Industry Notification (PIN) from November 2019 released by the FBI Cyber Division warned of cyberattacks against the US automotive industry with the end of sensitive corporate and enterprise data theft.
The FBI's Internet Crime Complaint Center (IC3) also published a public service announcement (PSA) in October about the increasing number of high-impact ransomware attacks targeting U.S. organizations.
DoD to Require Cybersecurity Certification From Defense Contractors
8.2.2020 Bleepingcomputer BigBrothers
The United States Department of Defense (DoD) announced that defense contractors will have to meet a basic level of cybersecurity standards when replying to a government acquisition program's request for proposals by 2026.
The Cybersecurity Maturity Model Certification (CMMC) framework version 1.0 was released on January 31 and it is "a unified cybersecurity standard for future DoD acquisitions."
Cyber requirements for some contractors will appear later this year and, by 2026, all new DoD contracts will come with the new CMMC requirements, DoD's Under Secretary of Defense for Acquisition and Sustainment Ellen M. Lord said.
With the introduction of the CMMC, the DoD wants to enhance the protection of supply chain unclassified information — Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) — by increasing the Defense Industrial Base (DIB) subcontractors' cybersecurity readiness.
Today, Under Secretary of Defense Ellen Lord announced new cybersecurity certification standards for government acquisition. This first DOD cybersecurity certification model will strengthen & secure the defense
industrial base. pic.twitter.com/VRlGxqquBF
— Department of Defense (@DeptofDefense) January 31, 2020
The CMMC provides the DoD with a straightforward mechanism designed to make it easier to certify the cyber readiness of the large and small defense contractors using 5 levels of certification that focus on both cybersecurity practices and processes.
Meeting CMMC level 1 requirements will confirm that the DIB contractor is qualified to safeguard FCI, level 3 that it can protect DoD CUI, while levels 4 and 5 shows that it al can reduce risk of Advanced Persistent Threats (APTs).
"Something ... simple in Level 1 would be, 'Does your company have antivirus software? Are you updating your antivirus software? Are you updating your passwords?'" said DoD's chief information security officer for acquisition Katie Arrington explained.
"CMMC Level 1 is the basic cyber hygiene skills we should be doing every day. They are there to protect yourself, your company and your own information."
Image: DoD
Defense contractors will not be certified for CMMC by the DoD alone, as CMMC "third-party assessment organizations" or C3PAOs will be designated by the department to conduct these assessments once everything is in place.
Cybersecurity risks are threatening the national security of the U.S. government and that of the defense industry, including partners and allies, with an estimated $600 billion equating to 1% of the total global gross domestic product being lost to cyber thieves every year according to a study from McAfee and the Center for Strategic and International Studies.
The DIB sector consists of over 300,000 companies that support the warfighter and contribute towards the research, engineering, development, acquisition, production, delivery, sustainment, and operations of DoD systems, networks, installations, capabilities, and services. The aggregate loss of intellectual property and certain unclassified information from the DoD supply chain can undercut U.S. technical advantages and innovation as well as significantly increase risk to national security. - The DoD
"Adversaries know that in today's great-power competition environment, information and technology are both key cornerstones," Lord added. "Attacking a sub-tier supplier is far more appealing than a prime [supplier]."
"We need to make sure our industry partners are prepared to take on the work, and our third-party auditors will ensure that they are implementing the practices that we need in place to secure that national defense and our industrial base," Arrington said.
The CMMC model in tabular form with all practices organized by Domain, Capability, and Level is available here, together with maturity level processes, and process and practice descriptions.
Russia Blocks ProtonMail and ProtonVPN, Tor to the Rescue
2.2.2020 Bleepingcomputer BigBrothers
Proton Technologies' security-focused ProtonMail end-to-end encrypted email service and ProtonVPN VPN service have been blocked by the Russian government since yesterday.
"On January 29, based on the requirements of the General Prosecutor's Office of the Russian Federation, Roskomnadzor will restrict access to the mail service Protonmail.com (Switzerland)," Roskomnadzor, Russia's telecommunications watchdog, said in a press release.
"This email service was used by cybercriminals both in 2019 and especially actively in January 2020 to send false messages under the guise of reliable information about mass mining of objects in the Russian Federation," Roskomnadzor added.
The block was prompted by Proton Technologies' refusal to register their services with state authorities — something that was asked from all VPN providers operating in the country as we reported last year — and to provide information about the owners of the mailboxes used to send the bombing threats per Roskomnadzor's statement.
"In accordance with the procedure enshrined in the legislation, Roskomnadzor consistently restricts access to resources used by criminals to destabilize the situation in the country and increase tension, and expects effective interaction with all parties involved," the press release further explains.
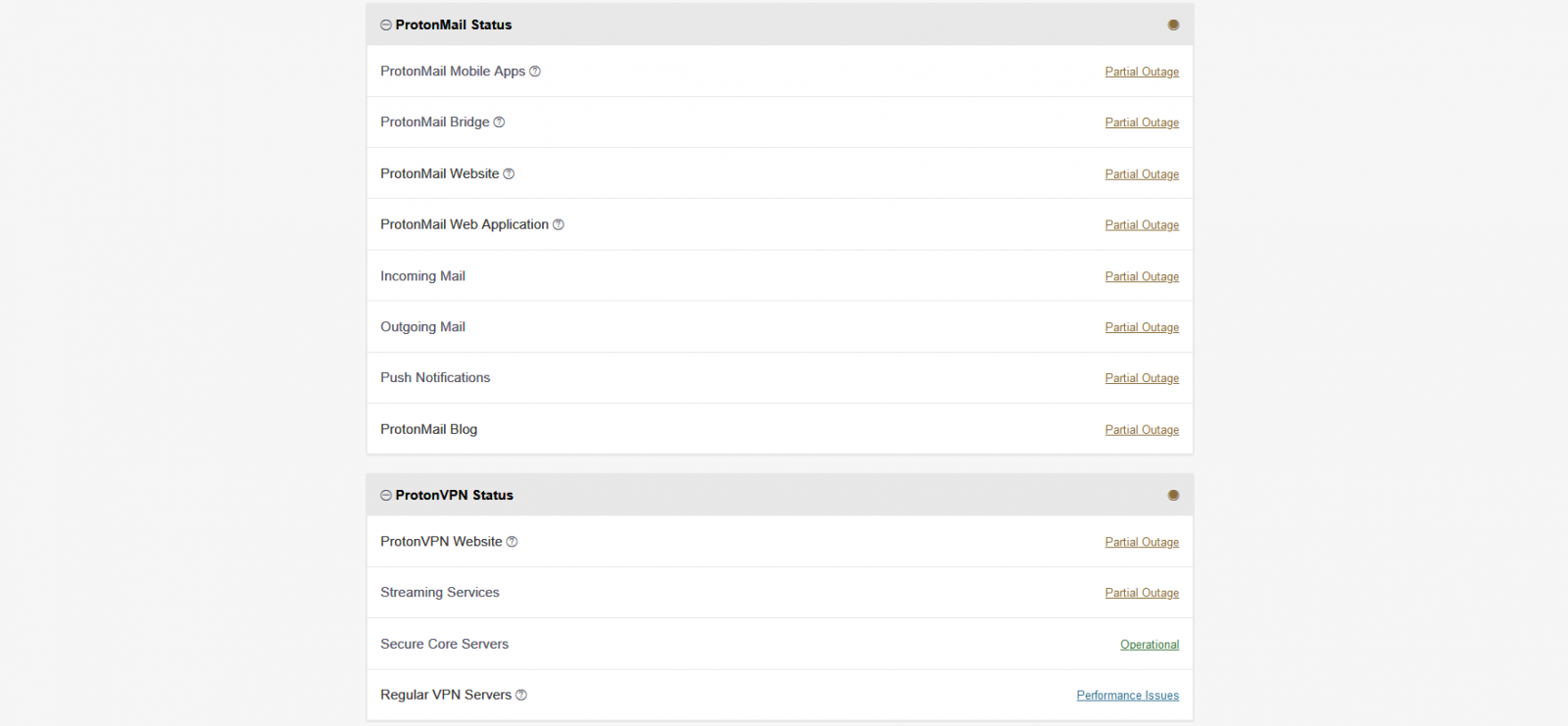
ProtonMail and ProtonVPN service status
Proton Technologies' response
The Swiss company behind ProtonMail and ProtonVPN published an incident on its status page, which currently lists partial outages for most services needed by the company's products to work properly.
"We have received reports that Proton is currently blocked in Russia. We are reaching out to the appropriate authorities to get the block lifted as soon as possible," the company says.
"This block affects ProtonMail and ProtonVPN users who were not logged in before the block was implemented. For now, we recommend using the TOR network (via the TOR Browser) to access our services."
ProtonMail also said in a statement to Reuters that they "condemn this block as a misguided measure which only serves to harm ordinary people."
ProtonMail
✔
@ProtonMail
(1/2) The Russian government has blocked ProtonMail and ProtonVPN within Russia. We are reaching out to the appropriate authorities to get the block lifted as soon as possible. https://www.reuters.com/article/us-russia-protonmail/russia-blocks-encrypted-email-service-protonmail-idUSKBN1ZS1K8 …
552
4:16 PM - Jan 29, 2020
Twitter Ads info and privacy
342 people are talking about this
Although access to both services is restricted for any Russian users, Proton Technologies says that ways to get around this block are available.
ProtonMail and ProtonVPN users are advised to access the two services using the Tor service specifically is designed to help circumvent censorship.
To get access to Proton's services using the Tor Browser you will have to follow these steps:
Download the TOR browser for your device here: https://www.torproject.org/download/
Install the TOR browser
Once the browser is installed, launch it and you will be able to access the Proton websites
ProtonVPN users who cannot log in into the app will have to manually set up an OpenVPN connection for their device until the block is lifted:
Open the TOR browser
Navigate to the ProtonVPN Knowledge Base: https://protonvpn.com/support/
Search for the OpenVPN guide for your OS, for instance type "Windows OpenVPN"
Open the guide and follow the steps to set up a manual connection on your device
Connect using your OpenVPN/IKEv2 credentials