BigBrothers Articles - H 2020 1 2 3 4 5 BigBrothers List - H 2021 2020 2019 2018 BigBrother blog BigBrother blog
U.S. Treasury Sanctions Hacking Group Backed by Iranian Intelligence
18.9.20 BigBrothers Thehackernews
The U.S. government on Thursday imposed sweeping sanctions against an Iranian threat actor backed by the country's Ministry of Intelligence and Security (MOIS) for carrying out malware campaigns targeting Iranian dissidents, journalists, and international companies in the telecom and travel sectors.
According to the U.S. Treasury and the Federal Bureau of Investigation (FBI), the sanctions target Rana Intelligence Computing Company (or Rana), which the agencies said operated as a front for the threat group APT39 (aka Chafer or Remix Kitten), Iranian cyber espionage hacking collective active since 2014 known for its attacks on companies in the U.S. and the Middle East with an aim to pilfer personal information and advance Iran's national security objectives.
To that effect, 45 individuals who served in various capacities while employed at the front company, including as managers, programmers, and hacking experts, have been implicated in the sanctions, which also prohibit U.S. companies from doing business with Rana and its employees.
"Masked behind its front company, Rana Intelligence Computing Company (Rana), the Government of Iran's Ministry of Intelligence and Security (MOIS) has employed a years-long malware campaign that targeted and monitored Iranian citizens, dissidents, and journalists, the government networks of Iran's neighboring countries, and foreign organizations in the travel, academic, and telecommunications sectors," the FBI said.
Rana is also believed to have targeted Iranian private sector companies and academic institutions, including Persian language and cultural centers inside and outside the country.
APT39's Long History of Espionage Activities
Earlier this May, Bitdefender uncovered two cyberattacks directed against critical infrastructures in Kuwait and Saudi Arabia, compromising its victims via spear-phishing emails containing malicious attachments and using various intrusion tools to gain an initial foothold and collect sensitive data from infected systems.
APT39 has a history of hacking into targets spanning over 30 countries in the Middle East, North Africa, and Central Asia, and at least 15 U.S. companies in the travel sector have been compromised by Rana's malware, using the unauthorized access to track the movements of individuals whom MOIS considered a threat.
Aside from formally connecting the activities of APT39 to Rana, the FBI detailed eight separate and distinct sets of previously undisclosed malware used by the group to conduct their computer intrusion and reconnaissance activities, which comprises of:
Microsoft Office documents laced with Visual Basic Script (VBS) malware sent via social engineering techniques
Malicious AutoIt malware scripts embedded in Microsoft Office documents or malicious links
Two different versions of BITS malware to aggregate and exfiltrate victim data to an actor-controlled infrastructure
A screenshot and keylogger utility that masqueraded as legitimate Mozilla Firefox browser
A Python-based downloader to fetch additional malicious files to the victim machine from a command-and-control (C2) server
An Android implant ("optimizer.apk") with information-stealing and remote access capabilities
"Depot.dat" malware for collecting screenshots and capturing keystrokes and transmitting the information to a remote server under their control
A Series of Charges Against Iranian Hackers
The sanctions against APT39 is the latest in a string of actions undertaken by the U.S. government over the last few days against Iran, which also encompasses charges against three hackers for engaging in a coordinated campaign of identity theft and hacking on behalf of Iran's Islamic Revolutionary Guard Corps (IRGC) to steal critical information related to U.S. aerospace and satellite technology companies.
Last but not least, the Cybersecurity Security and Infrastructure Security Agency (CISA) warned of an Iran-based malicious cyber actor targeting several U.S. federal agencies by exploiting unpatched VPN vulnerabilities to amass sensitive data and even sell access to the compromised network infrastructure in an online hacker forum.

"This week's unsealing of indictments and other disruptive actions serves as another reminder of the breadth and depth of Iranian malicious cyber activities targeting not only the United States, but countries all over the world," John C. Demers, Assistant Attorney General for National Security, said in a statement.
"Whether directing such hacking activities, or by offering a safe haven for Iranian criminal hackers, Iran is complicit in the targeting of innocent victims worldwide and is deepening its status as a rogue state."
U.S. Charges Three Iranian Hackers for Attacks on Satellite Companies
18.9.20 BigBrothers Securityweek
The U.S. Department of Justice on Thursday announced charges against three Iranian nationals believed to have stolen information related to the United States’ aerospace and satellite technologies.
One of the suspects is Said Pourkarim Arabi, 34, who is said to be a member of the Islamic Revolutionary Guard Corps (IRGC), which the U.S. has designated as a terrorist organization. The other two are Mohammad Bayati, 34, and Mohammad Reza Espargham, whose age is unknown.
According to the DoJ, the men conducted cyber campaigns between at least July 2015 and February 2019, and at one point they possessed a list of over 1,800 targeted online accounts associated with satellite and aerospace companies, as well as government organizations in the U.S., Australia, U.K., Israel, and Singapore.
Authorities say the hackers used social engineering to trick people working in the aerospace and satellite sectors to hand over information that they could later use to create fake email accounts and domains. They used these resources to send out phishing emails designed to deliver a piece of malware to other individuals they targeted. The malware, often a RAT, gave them access to the victim’s computer and network.
“The defendants then used additional hacking tools to maintain unauthorized access, escalate their privileges, and steal data sought by the IRGC. Using these methods, the defendants successfully compromised multiple victim networks, resulting in the theft of sensitive commercial information, intellectual property, and personal data from victim companies, including a satellite-tracking company and a satellite voice and data communication company,” the DoJ said in a press release.
The Iranians face various charges, including conspiracy to commit computer intrusions, obtaining information by unauthorized access to protected computers, intentional damage to protected computers, aggravated identity theft, and conspiracy to commit wire fraud.
Warrants have been issued for their arrest and they could spend many years behind bars if they are ever convicted in the United States.
This is the third round of charges announced by U.S. authorities this week against alleged Iranian hackers. The DoJ previously announced charges against two hacktivists who defaced websites in response to the killing of Qasem Soleimani, and later against two state-sponsored hackers who are said to have targeted a wide range of industries since at least 2013.
The United States this week also charged two Russian cybercriminals allegedly involved in a $17 million cryptocurrency fraud scheme, and five alleged members of the China-linked threat group known as APT41.
German Hospital Hacked, Patient Taken to Another City Dies
17.9.20 BigBrothers Securityweek
German authorities said Thursday that what appears to have been a misdirected hacker attack caused the failure of IT systems at a major hospital in Duesseldorf, and a woman who needed urgent admission died after she had to be taken to another city for treatment.
The Duesseldorf University Clinic’s systems have been disrupted since last Thursday. The hospital said investigators have found that the source of the problem was a hacker attack on a weak spot in “widely used commercial add-on software,” which it didn’t identify.
As a consequence, systems gradually crashed and the hospital wasn’t able to access data; emergency patients were taken elsewhere and operations postponed.
The hospital said that that “there was no concrete ransom demand.” It added that there are no indications that data is irretrievably lost and that its IT systems are being gradually restarted.
A report from North Rhine-Westphalia state’s justice minister said that 30 servers at the hospital were encrypted last week and an extortion note left on one of the servers, news agency dpa reported. The note — which called on the addressees to get in touch, but didn’t name any sum — was addressed to the Heinrich Heine University, to which the Duesseldorf hospital is affiliated, and not to the hospital itself.
Duesseldorf police then established contact and told the perpetrators that the hospital, and not the university, had been affected, endangering patients. The perpetrators then withdrew the extortion attempt and provided a digital key to decrypt the data. The perpetrators are no longer reachable, according to the justice minister’s report.
Prosecutors launched an investigation against the unknown perpetrators on suspicion of negligent manslaughter because a patient in a life-threatening condition who was supposed to be taken to the hospital last Friday night was sent instead to a hospital in Wuppertal, a roughly 32-kilometer (20-mile) drive. Doctors weren’t able to start treating her for an hour and she died.
CISA Named Top-Level Root CVE Numbering Authority
17.9.20 BigBrothers Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has been named a Top-Level Root CVE Numbering Authority (CNA) and it will be overseeing CNAs that assign CVE identifiers for vulnerabilities in industrial control systems (ICS) and medical devices.
CNAs are responsible for issuing CVE identifiers for vulnerabilities found in their own or third-party products. A Top-Level Root CNA can not only assign CVEs, but it’s also tasked with managing CNAs in a specific domain or community.
In CISA’s case, it will be in charge of ICS and medical device vendors that are CNAs. Specifically, CISA will ensure that CVE identifiers are assigned properly, it will implement rules and guidelines of the CVE Program, it will resolve disputes, and it will recruit new CNAs.
Initially, CISA will oversee seven CNAs, including Alias Robotics, ABB, CERT@VDE, Johnson Controls, Bosch, Siemens and Gallagher Group.
“Establishing CISA as a Top-Level Root consolidates the vast expertise required to effectively assign CVE IDs to ICS and medical device vulnerabilities and enables the rapid identification and resolution of issues specific to those environments,” said CISA and MITRE.
They added, “As the Nation’s risk advisor, CISA serves the unique role as a trusted information broker across a diverse set of public and private stakeholders. In this role, CISA fosters increased information sharing to help these stakeholders make more informed decisions to better understand and manage risk from cyber and physical threats.”
Learn more about vulnerabilities in industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
CISA and MITRE are the only Top-Level Root CNAs, while Japan’s JPCERT/CC is a Root CNA.
According to MITRE, there are currently 139 CNAs across 24 countries. One of the latest additions is OT and IoT security solutions provider Nozomi Networks, which can assign CVEs to flaws found in its own products and third-party industrial and IoT products that are not covered by a different CNA.
U.S. Charges Two State-Sponsored Iranian Hackers
17.9.20 BigBrothers Securityweek
Two Iranian hackers were indicted in the United States for allegedly engaging in numerous cyberattacks, some of them conducted on behalf of the government of Iran, the U.S. Department of Justice announced on Wednesday.
The two, Hooman Heidarian (aka neo), 30, and Mehdi Farhadi (aka Mehdi Mahdavi, Mohammad Mehdi Farhadi Ramin), 34, both of Hamedan, Iran, were charged with conspiracy to commit fraud and wire fraud, unauthorized access to protected computers, unauthorized damage to protected computers, access device fraud, and aggravated identity theft.
Starting in at least 2013, the two launched coordinated attacks on an aerospace company, a defense contractor, several American and foreign universities, a think tank based in Washington, D.C., foreign governments, a foreign policy organization, non-governmental organizations (NGOs), and non-profits.
Many of the attacks were allegedly conducted in the interest of the Iranian government, targeting highly protected and extremely sensitive data related to national security communications, foreign policy, aerospace, financial and personally identifiable information, non-military nuclear data, intellectual property, and human rights activists.
Victims were selected after extensive online reconnaissance, with the information gathered at this stage often used in later phases to identify the soft spots of victim networks. Vulnerability-scanning tools were employed to identify security weaknesses.
A broad range of tools and methods were used to compromise and maintain access to victim networks, including session hijacking, SQL injection, and malware. Keyloggers and remote access Trojans were leveraged for persistence on the networks.
The defendants also created a botnet to spread malware, launch DDoS attacks, and send out spam. They also established automated forwarding rules to have new outgoing and incoming emails automatically sent to attacker-controlled accounts.
“Using these methods, the defendants stole hundreds of terabytes of data, including confidential victim work product and intellectual property, and personal identifying information, such as access credentials, names, addresses, phone numbers, Social Security numbers, and birthdates. The defendants marketed stolen data on the black market,” the DoJ says.
The defendants are also charged with defacing websites with political and other ideological content “for apparent purpose of projecting Iranian influence and threatening perceived enemies of Iran.”
Two Russians Charged Over $17M Cryptocurrency Fraud Scheme
17.9.20 BigBrothers Securityweek
The United States Department of Justice on Wednesday unsealed an indictment against two Russian nationals allegedly engaged in cryptocurrency fraud schemes.
The two, Danil Potekhin (also known as cronuswar) and Dmitrii Karasavidi (also referred to as Dmitriy Karasvidi), allegedly targeted three cryptocurrency exchanges — two in the United States and one abroad — and their customers to defraud them of at least $16.8 million in virtual currency.
According to the superseding indictment, Potekhin registered websites mimicking those of legitimate crypto-exchanges, and employed phishing and spoofing to steal users’ login credentials, email addresses, and other personal information.
Using the stolen information, Potekhin and co-conspirators accessed the victims’ cryptocurrency accounts to steal funds or manipulate virtual coin markets, the DoJ notes.
Starting July 2017, as part of one fraud scheme, Potekhin created and controlled at least 13 fake domains targeting one U.S. currency exchange, and stole the credentials of more than 150 customers of the exchange.
Furthermore, the indictment alleges that Potekhin and Karasavidi created multiple fictitious accounts with the same exchange, three of them created using stolen information of individuals from the United Kingdom. The defendants accessed victim accounts to steal digital currency.
Another attack targeting the same U.S.-based digital currency exchange was aimed at manipulating the market through accessing three victim accounts and purchasing large amounts of an inexpensive digital currency known as GAS, thus leading to an increase in demand and price.
Next, the defendants quickly converted the digital currency from GAS to other digital currencies, thus causing the value of GAS to plummet. The scheme resulted in a loss for the three victims of roughly $5 million.
The two allegedly engaged in similar schemes targeting customers of another U.S.-based digital currency exchange, as well as those of an exchange based abroad. They allegedly stole digital currency that at the time had a value of more than $11 million.
According to the indictment, the two laundered the proceeds of the attacks by transferring the funds through multiple accounts. In the end, a significant amount of the stolen funds was transferred to Karasavidi’s account.
In coordination with the DoJ, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) on Wednesday announced sanctions against the two Russians, restricting their resources and prohibiting others from dealing with them.
DoJ Indicts Two Hackers for Defacing Websites with Pro-Iran Messages
17.9.20 BigBrothers Threatpost
The two hackers allegedly hacked more than 50 websites hosted in the U.S. and vandalized them with pro-Iran messages.
The Department of Justice (DoJ) has indicted two hackers – including one teenager – for allegedly vandalizing more than 50 websites hosted in the U.S. with pro-Iran messages.
The indictment, unsealed on Tuesday, indicts Behzad Mohammadzadeh, a national of the Islamic Republic of Iran who is believed to be 19 years old, and Marwan Abusrour, a stateless national of the Palestinian Authority, who is believed to be 25 years old. Both were charged on one count of conspiring to commit intentional damage to a protected computer and one count of intentionally damaging a protected computer.
The defendants are believed to be living in Iran and Palestine and are wanted by United States authorities.
Threatpost Webinar Promo Bug Bounty
Click to register.
“These hackers are accused of orchestrating a brazen cyber-assault that defaced scores of websites across the country as a way of protesting and retaliating against the United States for killing the leader of a foreign terrorist organization,” said Joseph Bonavolonta, special agent in charge of the FBI Boston division, in a Tuesday statement. “Now, they are wanted by the FBI and are no longer free to travel outside Iran or Palestine without risk of arrest.”
The website defacement came after conflict between the U.S. and Iran peaked earlier in 2020, when U.S. drones on Jan. 3 killed Qassem Soleimani, an Iranian general with the Islamic Revolutionary Guard Corps who was highly esteemed in Iran. On the heels of Soleimani’s killing, Iranian leaders vowed retaliation.
On the heels of this incident, Mohammadzadeh and Abusrour allegedly worked together to deface 51 websites hosted in the U.S. Some of the them were hosted on computers owned by a company with corporate headquarters in Massachusetts. The two allegedly replaced the content of these websites with pictures of Soleimani against a background of the Iranian flag, along with the message, in English, “Down with America.” The two hackers allegedly took credit online for their website defacements.
The website of at least one U.S. government agency – the Federal Depository Library Program (FDLP) website – was also defaced during this time, with hackers behind the attack referencing Soleimani’s death on the FDLP landing page, and including a picture of a bloodied President Donald Trump being punched in the face and pro-Iran messages. However, it’s not clear if this website was one of the 51 allegedly targeted by Mohammadzadeh and Abusrour.
Mohammadzadeh and Abusrour were allegedly defacing websites long before the Jan. 2 incident. According to the indictment, Mohammadzadeh has publicly claimed to have personally defaced more than 1,100 websites around the world with pro-Iranian and pro-hacker messages, beginning in 2018.
Abusrour meanwhile is a self-described spammer (who sends unsolicited emails for profit), as well as an illicit trader in stolen credit cards, who has publicly claimed to have defaced at least 337 websites around the world, which he allegedly began no later than June 6, 2016, and continued through at least July of this year.
The two allegedly started working together on or about Dec. 26, when Abusrour began providing Mahammadzadeh with access to compromised websites. While the DoJ did not specify how the two allegedly accessed the websites, popular methods for compromise can include vulnerabilities in third-party plugins and stolen login credentials.
According to the DoJ, the charge of conspiring to commit intentional damage to a protected computer provides for a sentence of up to five years in prison, three years of supervised release and a fine of $250,000 or twice the gain or loss (whichever is greatest). Meanwhile, the charge of intentionally damaging a protected computer provides for a sentence of up to 10 years in prison, three years of supervised release and a fine of $250,000 or twice the gain or loss (whichever is greatest).
“Today’s indictment should send a powerful message that we will not hesitate to go after anyone who commits malicious cyber intrusions against innocent Americans in order to cause chaos, fear and economic harm,” said Bonavolonta in the statement.
NSA publishes guidance on UEFI Secure Boot customization
17.9.20 BigBrothers Securityaffairs
The US National Security Agency (NSA) published guidance on the Unified Extensible Firmware Interface (UEFI) Secure Boot customization.
The United States National Security Agency (NSA) has published guidance on how the Unified Extensible Firmware Interface (UEFI) Secure Boot feature that can be customized organizations.
The Unified Extensible Firmware Interface (UEFI) is a specification that defines a software interface between an operating system and platform firmware. UEFI replaces the legacy Basic Input/Output System (BIOS) firmware interface originally present in all IBM PC-compatible personal computers, with most UEFI firmware implementations providing support for legacy BIOS services. UEFI can support remote diagnostics and repair of computers, even with no operating system installed.
Over the years, experts observed several attacks employing rootkits that were specifically developed to target the firmware to achieve persistence and bypassing security solutions.
The Secure Boot mechanism allows the execution of only software that is trusted by the Original Equipment Manufacturer (OEM).
“Secure Boot can be customized to meet the needs of different environments. Customization enables administrators to realize the benefits of boot malware defenses, insider threat mitigations, and data-at-rest protections.”states the NSA technical report. “Administrators should opt to customize Secure Boot rather than disable it for compatibility reasons.”
NSA report revealed that several organizations often disable Secure Boot for incompatibility issues, but the Agency strongly recommends customizing it to meet the needs of the organization.
“Customization enables administrators to realize the benefits of boot malware defenses, insider threat mitigations, and data-at-rest protections. Administrators should opt to customize Secure Boot rather than disable it for compatibility reasons.” continues the report. “Customization may – depending on implementation – require infrastructures to sign their own boot binaries and drivers,”
The NSA pointed out that the Secure Boot can be configured to audit firmware modules, expansion devices, and bootable OS images (sometimes referred to as Thorough Mode). The report states that Trusted Platform Module (TPM) may be used to validate the integrity of UEFI Secure Boot.
The NSA’s report includes details on how administrators can customize Secure Boot, including information on advanced customization options that can be applied by organizations to meet their needs.
US CISA report shares details on web shells used by Iranian hackers
16.9.20 BigBrothers Securityaffairs
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a malware analysis report (MAR) that includes technical details about web shells employed by Iranian hackers.
A web shell is a code, often written in typical web development programming languages (e.g., ASP, PHP, JSP), that attackers implant on web servers to gain remote access and code execution.
According to the CISA’s report, Iranian hackers from an unnamed APT group are employing several known web shells, in attacks on IT, government, healthcare, financial, and insurance organizations across the United States. The malware used by the threat actors includes the ChunkyTuna, Tiny, and China Chopper web shells.
The Iranian hackers belong to an Iran-based threat actor that was behind attacks exploiting vulnerabilities in Pulse Secure VPN, Citrix Application Delivery Controller (ADC) and Gateway, and F5’s BIG-IP ADC products.
A few weeks ago, researchers from Crowdstrike revealed that the Iran-linked APT group tracked as Pioneer Kitten, also known as Fox Kitten or Parisite, is now trying to monetize its efforts by selling access to some of the networks it has hacked to other hackers.
The Iranian hackers have been attacking corporate VPNs over the past months, they have been hacking VPN servers to plant backdoors in companies around the world targeting Pulse Secure, Fortinet, Palo Alto Networks, and Citrix VPNs.
The CISA MAR includes technical details of 19 malicious files, including multiple components of the China Chopper web shell, such as an ASP application that listens for incoming HTTP connections from a remote operator.
CISA web shells
The web shells allow attackers to deliver and execute JavaScript code that could be used to enumerate directories, execute payloads, and exfiltrate data.
CISA experts also analyzed a program data (PDB) file and a binary which are a compiled version of the open-source project FRP. The FRP can allow attackers to tunnel various types of connections to a remote operator outside of the target’s network perimeter. The report also analyzed a PowerShell shell script that is part of the KeeThief open-source project, which allows the adversary to access encrypted password credentials stored by the Microsoft “KeePass” password management software.
“It appears this adversary utilized these malicious tools to maintain persistent remote access and data exfiltration from the victim’s network. The adversary may have used the ‘FRP’ utility to tunnel outbound Remote Desktop Protocol (RDP) sessions, allowing persistent access to the network from outside the firewall perimeter.” continues the report. “The China Chopper web shell also provides the persistent ability to navigate throughout the victim’s network when inside the perimeter. Leveraging the ‘KeeThief’ utility allows access to sensitive user password credentials and potentially the ability to pivot to user accounts outside of the victim’s network,”
The report also details additional 7 files containing malicious Hypertext Preprocessor (PHP) code that works as malicious web shells, which were identified as ChunkyTuna and Tiny web shells. Both web shells accept commands and data from a remote operator, allowing the operator C2 to remotely control the compromised system.
NSA Publishes Guidance on UEFI Secure Boot Customization
16.9.20 BigBrothers Securityweek
The United States National Security Agency (NSA) this week published guidance on how the Unified Extensible Firmware Interface (UEFI) Secure Boot feature can be customized to fit an organization’s needs.
A replacement for the legacy Basic Input Output System (BIOS), UEFI is used across multiple architectures and provides broader customization options, higher performance, improved security, and support for more devices.
Over the past couple of years, the number of attacks targeting the firmware for persistency on victim systems has increased, especially with antivirus software running on the operating system being unable to identify and block threats at the firmware level.
This is where Secure Boot comes into play, delivering a validation mechanism to mitigate early-boot vulnerabilities and the risk of firmware exploitation.
According to the NSA, however, incompatibility issues often result in Secure Boot being disabled, which the agency advises against. Furthermore, it strongly encourages customizing Secure Boot to meet the needs of the organization.
“Customization enables administrators to realize the benefits of boot malware defenses, insider threat mitigations, and data-at-rest protections. Administrators should opt to customize Secure Boot rather than disable it for compatibility reasons. Customization may – depending on implementation – require infrastructures to sign their own boot binaries and drivers,” the NSA says.
In a technical report published on Tuesday and titled “UEFI Secure Boot Customization,” the agency recommends that system admins and infrastructure owners migrate their machines to UEFI native mode, that they enable Secure Boot on all endpoints and also customize it, and that all firmware is properly secured and regularly updated.
Secure Boot, the NSA also notes, should be configured “to audit firmware modules, expansion devices, and bootable OS images (sometimes referred to as Thorough Mode),” and that a Trusted Platform Module (TPM) should be employed to ensure the integrity of both firmware and the Secure Boot configuration.
The NSA’s report includes technical information on what UEFI and Secure Boot are all about, while also delivering a broad range of details on how administrators can customize Secure Boot, including information on available advanced customization options that can be applied to meet several use cases.
More Links Found Between North Korean and Russian Hacking Operations
16.9.20 BigBrothers Securityweek
Security researchers with Intel 471 have identified connections between cyber-activities attributed to North Korean hackers and those of Russian cybercriminals.
Known as the Lazarus group, the North Korean hackers have been involved in high profile attacks, including the WannaCry outbreak in 2017, the $81 million Bangladesh bank theft, attacks on cryptocurrency exchanges, and a campaign targeting dozens of defense and governmental organizations in Israel and globally, among other incidents.
According to threat intelligence company Intel 471, the hackers from the Democratic People's Republic of Korea (DPRK) maintain a close relationship with top-tier Russian-speaking cybercriminals, including the hacking group behind the infamous Dridex Trojan, as well as the operators of TrickBot.
Referred to as TA505 and Evil Corp, the Russia-linked Dridex operator is also known for attacks involving the Locky ransomware several years ago, but its portfolio includes numerous other malware families as well: BackNet, Bart ransomware, Cobalt Strike, DoppelPaymer ransomware, FlawedAmmyy, ServHelper, SDBbot RAT, and others.
TrickBot, on the other hand, is believed to be the work of the Rusian-speaking threat actor behind the Dyre Trojan. The malware has been around for four years, with attacks earlier this year targeting telecommunications organizations in the United States and Hong Kong.
In a report published today, Intel 471 says malware that only the North Korean hackers use “was very likely delivered via network accesses held by Russian-speaking cybercriminals.”
The security researchers believe that both TA505 and the TrickBot operators are top-tier cybercriminals that have gained a reputation and are trusted by other cybercriminals on underground marketplaces and forums. The North Korean hackers themselves are top-tier cybercriminals as well.
TrickBot, the researchers say, is a private malware-as-a-service (MaaS) that only trusted customers have access to, as it is not openly advertised on cybercriminal portals.
“It is determined by Intel 471 that only top-tier cybercriminals with a proven reputation can access the service. Reputation is gained through being involved in buying and selling products, services and goods in the cybercriminal underground. Even identifying who to talk to about accessing TrickBot would require a significant amount of activity and reputation in the underground,” the researchers say.
Malware available on underground forums that North Korean hackers are known to have used, Intel 471 says, includes the Hermes ransomware (and the Ryuk ransomware, which shares code with Hermes). Moreover, previous reports have shown Lazarus infections on systems that had been infected with Emotet and TrickBot.
Furthermore, reports from NTT Security and SentinelOne show a link between TrickBot and the delivery of PowerBrace and PowerRatankba malware, which has been attributed to Lazarus. Most likely, the researchers note, TrickBot customers are linked to North Korean hackers.
“Based on the above examined links between DPRK threat and TrickBot, we assess it is likely there is a link between the operators or users of TrickBot and DPRK threat actors. TrickBot certainly appears to be a source of compromised accesses that DPRK threat actors can leverage,” Intel 471 explains.
Previous reports suggesting overlaps between TA505 infections and DPRK intrusions exist as well, including a recent alert from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which mentions that Lazarus may “be working with or contracting out to criminal hacking groups, like TA505, for initial access development.”
However, Intel 471 believes that, while there might have been some occasional interactions between TA505 and the North Korean hackers, no recent collaboration exists. However, the TrickBot operators are in contact with Lazarus, the researchers say.
“While it is hard to assess, it looks likely that the network accesses purchased by DPRK threat actors from TrickBot-linked actors were from financial institutions. It also appears that DPRK threats actors have multiple other sources of network accesses beyond just TrickBot infections and that two such additional sources are accesses sold in the cybercriminal underground and accesses obtained through social engineering,” Intel 471 notes.
CISA Shares Details on Web Shells Employed by Iranian Hackers
16.9.20 BigBrothers Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) this week released a malware analysis report (MAR) detailing web shells employed by Iranian hackers.
Web shells provide the hackers with the ability to execute code on the victim systems, enumerate directories, deploy additional payloads, steal data, and navigate the victim network. Additional components can be employed to expand the attacker’s command and control (C&C) capabilities.
CISA’s report reveals that an Iranian threat actor targeting IT, government, healthcare, financial, and insurance organizations across the United States was observed employing the ChunkyTuna, Tiny, and China Chopper web shells in their attacks.
The same actor, the report reveals, was observed targeting well-known vulnerabilities, including those in Pulse Secure virtual private network (VPN), Citrix Application Delivery Controller (ADC) and Gateway, and F5’s BIG-IP ADC products.
At the end of August, Crowdstrike revealed that the Iran-based cyber-espionage group known as PIONEER KITTEN, PARISITE, UNC757, and FOX KITTEN, which is believed to be operating on behalf of the Iranian government, has been targeting the same vulnerabilities in opportunistic attacks on numerous sectors.
CISA, which does not name the Iranian threat actor referenced in their new report, details the functionality of 19 malicious files, many of which are components of the China Chopper web shell.
The web shell supports the delivery and execution of JavaScript code, but also includes components to listen for incoming HTTP connections from the attacker server (an application service provider (ASP) application), and to enable directory enumeration, payload execution, and data exfiltration capabilities.
A version of the open source project FRP was also employed, for the tunneling of various types of connections (a February 2020 ClearSky report also revealed the use of FRP in FOX KITTEN attacks), and a PowerShell shell script was used to access encrypted credentials stored by Microsoft’s KeePass password management software.
“The adversary may have used the ‘FRP’ utility to tunnel outbound Remote Desktop Protocol (RDP) sessions, allowing persistent access to the network from outside the firewall perimeter. The China Chopper web shell also provides the persistent ability to navigate throughout the victim's network when inside the perimeter. Leveraging the ‘KeeThief’ utility allows access to sensitive user password credentials and potentially the ability to pivot to user accounts outside of the victim's network,” CISA says.
CISA’s report also details 7 additional files that were identified as ChunkyTuna and Tiny web shells, and which are meant to provide operators with the ability to pass commands and data from remote servers.
2 Hackers Charged for Defacing Sites after U.S. Airstrike Killed Iranian General
16.9.20 BigBrothers Thehackernews
The US Department of Justice (DoJ) on Tuesday indicted two hackers for their alleged involvement in defacing several websites in the country following the assassination of Iranian major general Qasem Soleimani earlier this January.
Behzad Mohammadzadeh (aka Mrb3hz4d), 19, and Marwan Abusrour (aka Mrwn007), 25, have been charged with conspiracy to commit intentional damage to a protected computer for a widespread "cyber-assault" that affected over 1,400 websites with pro-Iranian and pro-Palestinian messages.
"The hackers victimized innocent third parties in a campaign to retaliate for the military action that killed Soleimani, a man behind countless acts of terror against Americans and others that the Iranian regime opposed," said Assistant Attorney General for National Security John C. Demers in a statement.
The defendants, from Iran and Palestine, respectively, are now wanted by the US authorities and are no longer free to travel outside their countries without risking an arrest.
Although Abusrour and Mohammadzadeh have been behind a defacing spree individually on their own over the last couple of years, they began to work together starting last December, before stepping up their attacks on January 3, a day after the US forces killed Qassem Soleimani in a drone airstrike near Baghdad International Airport.
With help from Abusrour, who provided Mohammadzadeh with access to compromised websites, the latter went on to hack into at least 51 websites in the US by replacing their content with pictures of the late general against a background of the Iranian flag along with the message "Down with America," alongside the message "Suleimani was not a person/he was a belief/Beliefs never die."
In addition, visitors of the defaced websites were directed to Mohammadzadeh's Telegram and public Instagram account, which subsequently redirected users to Zone-H, a security portal that holds an archive of all web intrusions, linking the exploits to his pseudonym "Mrb3hz4d."
The indictment also highlighted a screenshot of the messages shared between the two individuals and posted on Abusrour's Instagram account that revealed the list of seven websites that were broken into, in addition to posting the results of their work on social media and other online accounts in order to publicize their defacements.
The two hackers have now been charged and risk sentences of up to 10 years in prison and fines of up to $250,000, if found guilty, according to the DoJ.
"Foreign hackers are a persistent commercial and national security threat to the United States," said US Attorney Andrew E. Lelling. "Working with our law enforcement partners worldwide, we will aggressively pursue, prosecute and apprehend those who use the internet to attack American interests.
U.S. Charges Hackers for Defacing Sites in Response to Killing of Qasem Soleimani
16.9.20 BigBrothers Securityweek
The United States on Tuesday announced charges against two men from Iran and Palestine accused of defacing websites in response to the killing of Qasem Soleimani.
Qassem Soleimani, a top Iranian military commander, was killed in early January 2020 as part of a drone strike launched by the United States. Many expected Iran to retaliate in cyberspace, but a majority of the attacks that were made public were website defacements, which are considered less sophisticated attacks.
Nevertheless, U.S. authorities have not ignored these cyberattacks and they say some of them were launched by Behzad Mohammadzadeh, aka Mrb3hz4d, who is believed to be a 19-year-old Iranian, and Marwan Abusrour, aka Mrwn007, believed to be a 25-year-old Palestinian.
The two are said to have defaced tens of websites hosted in the United States as part of a retaliation campaign over the killing of Soleimani. Some of the impacted sites were hosted by a company based in Massachusetts, and the indictment has been filed in the District of Massachusetts.
Mohammadzadeh and Abusrour have been charged with one count of conspiring to commit intentional damage to a protected computer and one count of intentionally damaging a protected computer. They face up to five years in prison for the first charge and up to 10 years for the second charge.
Prosecutors pointed out that Mohammadzadeh has claimed to have defaced more than 1,100 websites. His profile on Zone-H, a service that allows hackers to keep track of the websites they deface, shows that he targeted 1,279 sites as of September 8. Abusrour describes himself as a spammer, carder and black hat, claiming to have defaced over 300 websites.
Mohammadzadeh and Abusrour have both been added to the FBI’s Cyber’s Most Wanted list.
“The hackers victimized innocent third parties in a campaign to retaliate for the military action that killed Soleimani, a man behind countless acts of terror against Americans and others that the Iranian regime opposed,” said Assistant Attorney General for National Security John C. Demers. “Their misguided, illegal actions in support of a rogue, destabilizing regime will come back to haunt them, as they are now fugitives from justice.”
Joseph R. Bonavolonta, special agent in charge of the FBI Boston Division, noted, “These hackers are accused of orchestrating a brazen cyber-assault that defaced scores of websites across the country as a way of protesting and retaliating against the United States for killing the leader of a foreign terrorist organization. Now, they are wanted by the FBI and are no longer free to travel outside Iran or Palestine without risk of arrest.”
China-linked hackers target government agencies by exploiting flaws in Citrix, Pulse, and F5 systems, and MS Exchange
15.9.20 BigBrothers Securityaffairs
CISA published an advisory on China-linked groups targeting government agencies by exploiting flaws in Microsoft Exchange, Citrix, Pulse, and F5 systems.
CISA published a security advisory warning of a wave of attacks carried out by China-linked APT groups affiliated with China’s Ministry of State Security.
Chinese state-sponsored hackers have probed US government networks looking for vulnerable networking devices that could be compromised with exploits for recently disclosed vulnerabilities.
“The Cybersecurity and Infrastructure Security Agency (CISA) has consistently observed Chinese Ministry of State Security (MSS)-affiliated cyber threat actors using publicly available information sources and common, well-known tactics, techniques, and procedures (TTPs) to target U.S. Government agencies.” reads the security advisory. “CISA has observed these—and other threat actors with varying degrees of skill—routinely using open-source information to plan and execute cyber operations.”
The list of vulnerabilities targeted by the Chinese hackers are:
CVE-2020-5902: F5 Big-IP Vulnerability – CISA has conducted incident response engagements at Federal Government and commercial entities where the threat actors exploited CVE-2020-5902. This is a vulnerability in F5’s Big-IP Traffic Management User Interface that allows cyber threat actors to execute arbitrary system commands, create or delete files, disable services, and/or execute Java code.[7]
CVE-2019-19781: Citrix Virtual Private Network (VPN) Appliances – CISA has observed the threat actors attempting to discover vulnerable Citrix VPN Appliances. CVE-2019-19781 enabled the actors to execute directory traversal attacks.[8]
CVE-2019-11510: Pulse Secure VPN Servers – CISA has conducted multiple incident response engagements at Federal Government and commercial entities where the threat actors exploited CVE-2019-11510—an arbitrary file reading vulnerability affecting Pulse Secure VPN appliances—to gain access to victim networks. Although Pulse Secure released patches for CVE-2019-11510 in April 2019, CISA observed incidents where compromised Active Directory credentials were used months after the victim organization patched their VPN appliance.[9]
CVE-2020-0688: Microsoft Exchange Server – CISA has observed the actors exploiting CVE-2020-0688 for remote code execution to enable email collection of targeted networks.
CISA also warned that the threat actors are exploiting the Microsoft Exchange CVE-2020-0688 RCE vulnerability to access emails from the exchange servers found in Federal Government environments.
According to the advisory, some attacks have been successful and allowed the Chinese hackers to penetrate federal networks.
“According to a recent U.S. Department of Justice indictment, MSS-affiliated actors have targeted various industries across the United States and other countries—including high-tech manufacturing; medical device, civil, and industrial engineering; business, educational, and gaming software; solar energy; pharmaceuticals; and defense—in a campaign that lasted over ten years.[1] continues the advisory. These hackers acted for both their own personal gain and the benefit of the Chinese MSS.[2]”
Once gained a foothold in the target network, Chinese hackers make lateral movements using a variety of tools such as
Cobalt Strike: Cobalt Strike is a legitimate adversary simulation platform intended to be used by security professionals to assess a network’s security. Threat actors are using cracked versions as part of their attacks to enable backdoor access to compromised systems and deploy additional tools on the network.
China Chopper Web Shell: This tool allows threat actors to install a PHP, ASP, ASPX, JSP, and CFM webshells (backdoor) on publicly exposed web servers. Once the China Chopper Web Shell is installed, the attackers gain full access to a remote server through the exposed web site.
Mimikatz: Mimikatz is a post-exploitation tool that allows attackers to dump Windows credentials stored in a computer’s memory. This tool is commonly used by threat actors, including ransomware operations, utilize to gain access to administrator credentials, and therefore, compromise Windows domain controllers.
CISA recommends that private companies and government agencies adopt necessary countermeasures and patch the devices in their infrastructure:
“CISA and the FBI also recommend that organizations routinely audit their configuration and patch management programs to ensure they can track and mitigate emerging threats. Implementing a rigorous configuration and patch management program will hamper sophisticated cyber threat actors’ operations and protect organizations’ resources and information systems,” states the advisory.
Below the list of patches that could be installed to prevent Chinese hackers and other threat actors from exploiting them:
VULNERABILITY PATCH INFORMATION
CVE-2020-5902 F5 Security Advisory: K52145254: TMUI RCE vulnerability CVE-2020-5902
CVE-2019-19781 Citrix blog post: firmware updates for Citrix ADC and Citrix Gateway versions 11.1 and 12.0Citrix blog post: security updates for Citrix SD-WAN WANOP release 10.2.6 and 11.0.3Citrix blog post: firmware updates for Citrix ADC and Citrix Gateway versions 12.1 and 13.0Citrix blog post: firmware updates for Citrix ADC and Citrix Gateway version 10.5
CVE-2019-11510 Pulse Secure Out-of-Cycle Advisory: Multiple vulnerabilities resolved in Pulse Connect Secure / Pulse Policy Secure 9.0RX
CVE-2020-0688 Microsoft Security Advisory: CVE-2020-0688: Microsoft Exchange Validation Key Remote Code Execution Vulnerability
UK NCSC releases the Vulnerability Disclosure Toolkit
15.9.20 BigBrothers Securityaffairs
The British National Cyber Security Centre (NCSC) released a guideline, dubbed The Vulnerability Disclosure Toolkit, for the implementation of a vulnerability disclosure process.
The UK National Cyber Security Centre (NCSC) has released a guideline, dubbed The Vulnerability Disclosure Toolkit, on how to implement a vulnerability disclosure process.
The guidelines highlight the importance for any organization to encourage responsible bug reporting through specifically-defined processes.
A vulnerability disclosure process could help organizations in rapidly address vulnerabilities reported by experts and bug hunters to reduce the risk of compromise.
“The international standard for vulnerability disclosure (ISO/IEC 29147:2018) defines the techniques and policies that can be used to receive vulnerability reports and publish remediation information. The NCSC designed this toolkit for organisations that currently don’t have a disclosure process but are looking to create one.” reads the guideline.
Receiving vulnerability reports reduces the risk that flaws are discovered by adversaries and exploited in attacks in the wild, and improve the security of the products or services of the organization.
“Having a clearly signposted reporting process demonstrates that your organisation takes security seriously. By providing a clear process, organisations can receive the information directly so the vulnerability can be addressed, and the risk of compromise reduced.” states the document. “This process also reduces the reputational damage of public disclosure by providing a way to report, and a defined policy of how the organisation will respond”
The guideline is organized into three main sections, Communication, Policy, and Security.txt. The process for communicating a vulnerability must be clear and well defined, it could be useful to set up a specific path for disclosing the issues (email address or secure web form).
The use of security.txt standard could help to create an easy-to-find section of websites where it is possible to find the contacts and the policy.
The file contains two key fields, “CONTACT”, which includes references to report the flaw (i.e. email or secure web form) and POLICY, a link to the vulnerability disclosure policy of the organization.
The NCSC provided recommendations on how to respond to vulnerability disclosure, for example, it suggests to never ignore any reports and suggest companies to avoid forcing the finder to sign a non-disclosure agreement “as the individual is simply looking to ensure the vulnerability is fixed.”
Another crucial aspect of the Vulnerability Disclosure Toolkit is the policy, it must be clear and have to allow organizations to define expectation from vulnerability reports and their response. It is essential to enable the organization and the finder (the expert who reports the flaw) to confidently work within an agreed framework.
The release of “The Vulnerability Disclosure Toolkit” is just a part of the efforts of the UK Government in the definition of national legislative frameworks.
“Equally, going forward this requirement will be embedded into legislative frameworks. The UK government is currently developing legislation that will require manufacturers of smart devices to provide a public point
of contact as part of a vulnerability disclosure policy. This is also a requirement for other international efforts on smart device security including the standard EN 303 645″ concludes the guide.
Chinese Hackers Using Publicly Available Resources in Attacks on U.S. Government
15.9.20 BigBrothers Securityweek
Threat actors affiliated with the Chinese Ministry of State Security (MSS) continue to target U.S. government agencies, the Cybersecurity and Infrastructure Security Agency (CISA) says in a new alert.
Published with contribution from the FBI, the alert presents some of the tactics, techniques, and procedures (TTPs) that the Chinese state-sponsored hackers are employing in attacks on the U.S., such as the heavy use of publicly available tools to hinder attribution.
CISA’s alert arrives a couple of months after the U.S. indicted two Chinese hackers for the targeting of organizations in the defense, high-tech manufacturing, engineering, software (business, educational, and gaming), solar energy, and pharmaceuticals sectors for more than ten years.
According to CISA, threat actors affiliated with the Chinese MSS use open-source information in the planning stage of their operations, and engage target networks leveraging readily available exploits and toolkits.
Over the past 12 months, CISA says, the hackers were observed leveraging the Common Vulnerabilities and Exposure (CVE) database, the National Vulnerabilities Database (NVD), Shodan, and other information sources to identify vulnerable targets, understand specific security issues, and discover exploitable systems.
“While using these data sources, CISA analysts have observed a correlation between the public release of a vulnerability and targeted scanning of systems identified as being vulnerable. This correlation suggests that cyber threat actors also rely on Shodan, the CVE database, the NVD, and other open-source information to identify targets of opportunity and plan cyber operations,” CISA reveals.
The adversaries are continuously targeting, scanning, and probing for significant vulnerabilities and they often use the same security flaws to compromise multiple organizations in different industries, mainly due to the lack of quick mitigation of known issues.
Some of the most recent security bugs targeted by Chinese hackers are CVE-2020-5902 (vulnerability in F5 Big-IP), CVE-2019-19781 (bug in Citrix VPN appliances), CVE-2019-11510 (arbitrary file read issue in Pulse Secure VPN servers), and CVE-2020-0688 (remote code execution on Microsoft Exchange Server).
The threat actors, CISA also says, have the ability to “build and maintain relatively low-complexity capabilities” in support of attacks on federal government networks. They also employ commercial and open-source tools for these operations, including the Cobalt Strike implant, the China Chopper web shell, and the open-source credential harvesting tool Mimikatz.
CISA also notes that the adversaries continue to use low-complexity attack vectors, such as spear-phishing emails, misconfigurations, and the lack of a patch management program, to abuse common vulnerabilities.
The agency also reveals that it has observed beaconing activity on government networks compromised by Chinese actors, brute-force attacks leveraging credentials available on the Internet, suspicious network scanning activity for ports on target networks, and the targeting of CVE-2020-0688 “to collect emails from the exchange servers found in Federal Government environments.”
External proxy tools or hop points, such as commercial infrastructure as a service (IaaS) or software as a service (SaaS) products – such as the Tor browser – are also employed by the Chinese hackers. In one instance, CISA observed a network proxy tool targeting 221 unique government agency IP addresses.
“CISA asserts with high confidence that sophisticated cyber threat actors will continue to use open-source resources and tools to target networks with a low security posture. When sophisticated cyber threat actors conduct operations against soft targets, it can negatively impact critical infrastructure, federal, and state, local, tribal, territorial government networks, possibly resulting in loss of critical data or personally identifiable information,” CISA notes.
Thus, entities at risk are advised to apply patches for known vulnerabilities as soon as possible, as well as to routinely conduct security audits of their configurations and patch management process, to make sure they are not exposed and that threats can be easily mitigated.
CISA: Chinese Hackers Exploiting Unpatched Devices to Target U.S. Agencies
15.9.20 BigBrothers Thehackernews
The US Cybersecurity and Infrastructure Security Agency (CISA) issued a new advisory on Monday about a wave of cyberattacks carried by Chinese nation-state actors targeting US government agencies and private entities.
"CISA has observed Chinese [Ministry of State Security]-affiliated cyber threat actors operating from the People's Republic of China using commercially available information sources and open-source exploitation tools to target US Government agency networks," the cybersecurity agency said.
Over the past 12 months, the victims were identified through sources such as Shodan, the Common Vulnerabilities and Exposure (CVE) database, and the National Vulnerabilities Database (NVD), exploiting the public release of a vulnerability to pick vulnerable targets and further their motives.
By compromising legitimate websites and leveraging spear-phishing emails with malicious links pointing to attacker-owned sites in order to gain initial access, the Chinese threat actors have deployed open-source tools such as Cobalt Strike, China Chopper Web Shell, and Mimikatz credential stealer to extract sensitive information from infected systems.
That's not all. Taking advantage of the fact that organizations aren't quickly mitigating known software vulnerabilities, the state-sponsored attackers are "targeting, scanning, and probing" US government networks for unpatched flaws in F5 Networks Big-IP Traffic Management User Interface (CVE-2020-5902), Citrix VPN (CVE-2019-19781), Pulse Secure VPN (CVE-2019-11510), and Microsoft Exchange Servers (CVE-2020-0688) to compromise targets.
"Cyber threat actors also continue to identify large repositories of credentials that are available on the internet to enable brute-force attacks," the agency said. "While this sort of activity is not a direct result of the exploitation of emergent vulnerabilities, it demonstrates that cyber threat actors can effectively use available open-source information to accomplish their goals."
This is not the first time Chinese actors have worked on behalf of China's MSS to infiltrate various industries across the US and other countries.
In July, the US Department of Justice (DoJ) charged two Chinese nationals for their alleged involvement in a decade-long hacking spree spanning high tech manufacturing, industrial engineering, defense, educational, gaming software, and pharmaceutical sectors with an aim to steal trade secrets and confidential business information.
But it's not just China. Earlier this year, Israeli security firm ClearSky uncovered a cyberespionage campaign dubbed "Fox Kitten" that targeted government, aviation, oil and gas, and security companies by exploiting unpatched VPN vulnerabilities to penetrate and steal information from target companies, prompting CISA to issue multiple security alerts urging businesses to secure their VPN environments.
Stating that sophisticated cyber threat actors will continue to use open-source resources and tools to single out networks with low-security posture, CISA has recommended organizations to patch routinely exploited vulnerabilities, and "audit their configuration and patch management programs to ensure they can track and mitigate emerging threats.
TikTok Rejects Microsoft Offer, Oracle Sole Remaining Bidder
14.9.20 BigBrothers Securityweek
American tech giant Microsoft said Sunday its offer to buy TikTok was rejected, leaving Oracle as the sole remaining bidder ahead of the imminent deadline for the Chinese-owned video app to sell or shut down its US operations.
TikTok is at the center of a diplomatic storm between Washington and Beijing, and President Donald Trump has set Americans a mid-September deadline to stop doing business with its Chinese parent company ByteDance -- effectively compelling a sale of the app to a US company.
The Wall Street Journal and The New York Times reported that Oracle had won the bidding war, citing people familiar with the deal, although the company did not immediately confirm that to AFP.
But two Chinese state media outlets -- CGTN and China News Service -- said Monday that ByteDance will not sell TikTok to Oracle either, citing unnamed sources.
The Oracle bid would need approval from the White House and Committee on Foreign Investment in the United States, a source told the Journal, with both parties under the belief it would meet US data security concerns.
Microsoft had indicated at the beginning of August that it was interested in acquiring TikTok's US operations, but announced Sunday that bid had been rejected.
"ByteDance let us know today they would not be selling TikTok's US operations to Microsoft," it said in a statement.
"We are confident our proposal would have been good for TikTok's users, while protecting national security interests."
In early August, Trump issued an executive order stating that if a purchase agreement was not reached by September 20, the platform would have to close in the United States.
Trump claims TikTok could be used by China to track the locations of federal employees, build dossiers on people for blackmail, and conduct corporate espionage.
- Disputed dangers -
In late August, China's commerce ministry published new rules potentially making it more difficult for ByteDance to sell TikTok to a US entity by adding "civilian use" to a list of technologies that are restricted for export.
ByteDance had vowed to "strictly abide" by the new export rules.
"We believe Microsoft would only buy TikTok WITH its core algorithm which the Chinese government and ByteDance was not willing to budge," Wedbush analyst Daniel Ives said in a note.
"Given the need now to get a green light from Beijing after its export rules were changed a few weeks ago, TikTok's days in the US likely are numbered with a shutdown now the next step," the analyst said.
Downloaded 175 million times in the United States, TikTok is used by as many as a billion people worldwide to make quirky, short videos on their cellphones. It has repeatedly denied sharing data with Beijing.
Microsoft said it would have "made significant changes to ensure the service met the highest standards for security, privacy, online safety, and combatting disinformation."
A deal with Microsoft could also have included Walmart, which joined forces with the tech giant during negotiations.
Ives said that even with Microsoft out of the picture, "while Oracle is technically the remaining bidder, without willing to sell its core algorithm we see no TikTok sale on the horizon."
"Oracle could be a technology partner, but a sale/divestiture of the US operations for TikTok remains the focus."
TikTok meanwhile has filed a lawsuit challenging the US crackdown, contending that Trump's order was a misuse of the International Emergency Economic Powers Act because the platform is not "an unusual and extraordinary threat."
Controversially, Trump has demanded that the US government get a cut of any deal, which critics contend appears unconstitutional and akin to extortion.
The bidding for TikTok comes during a broader deterioration of relations between the world's top two economies in recent months, with both exchanging fierce recriminations over trade, human rights, and the origins of the coronavirus pandemic.
Iran Says US Vote Hack Allegation 'Absurd'
12.9.20 BigBrothers Securityweek
Tehran on Friday hit back at allegations by Microsoft that Iran based hackers had targeted the US presidential campaigns, declaring it does not care about the election's outcome.
Microsoft claimed that it has thwarted cyber attacks by hackers from China, Russia and Iran who have been targeting staff from the campaigns of President Donald Trump and his Democratic rival Joe Biden, ahead of the November vote.
Both the Trump and Biden campaigns have been cited by media as saying they were aware of being targeted by hackers.
"The United States, which has for decades been meddling in the elections of other countries such as Iran, is in no place to make such absurd claims," state news agency IRNA quoted Iran's foreign ministry spokesman Saeed Khatibzadeh as saying.
As an instance, he pointed to the role of the US Central Intelligence Agency in a coup in 1953, which toppled hugely popular prime minister Mohammad Mosaddegh, who had called for Iran's oil to be nationalised.
It was clear that "foreign activity groups have stepped up their efforts targeting" the November 3 election, Microsoft said on Thursday.
The firm said an Iran-based group called Phosphorus has been targeting personal accounts of people associated with the Trump campaign.
"For Tehran, it does not matter who is in the White House. What matters is Washington's commitment to international rights, rules and norms, not meddling in others' affairs and acting on their commitments," Khatibzadeh said.
Decades-old tensions between Tehran and Washington have escalated since 2018, when Trump unilaterally withdrew the US from a multinational accord that limited Iran's nuclear programme. Trump subsequently reimposed crippling sanctions on Iran's economy.
Animosity further deepened after a US drone strike near Baghdad airport killed top Iranian general Qasem Soleimani in January.
Iranian officials have repeatedly said that they favour no specific candidate in the 2020 election, while also calling for Washington's return to the 2015 nuclear deal and the lifting of sanctions.
Russian Military Hackers Targeted Credentials at Hundreds of Organizations in US, UK
11.9.20 BigBrothers Securityweek
For the past year, Russia-linked threat actor Strontium has targeted hundreds of organizations in the United States and the United Kingdom to harvest account credentials, Microsoft reveals.
Also referred to as APT 28, Fancy Bear, Pawn Storm, Sednit, and Tsar Team, Strontium is believed to be a military unit of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS).
On Thursday, Microsoft published information on a newly identified Strontium campaign that focused on harvesting Office365 credentials for tens of thousands of accounts at organizations in the US and UK, many of them directly involved in political elections.
The attacks appear to have started in September 2019, and hit more than 200 organizations by June 2020. Between August 18 and September 3, the same attacks were observed targeting 6,912 accounts at 28 organizations.
“None of these accounts were successfully compromised,” Microsoft says, underlining that not all of the targeted entities were election-related.
Previous credential-harvesting efforts from Strontium relied on spear-phishing, such as the attacks leading up to the 2016 US presidential election, but the new campaign employed brute-force/password-spray tooling instead. The shift in tactics was observed for other nation-state actors as well, as it makes attacks more difficult to attribute.
Strontium is using tools to route authentication attempts through roughly 1,100 IPs, most of which associated with the Tor anonymizing service. The pool of IPs, however, is constantly evolving, with approximately 20 IPs added/removed daily.
“STRONTIUM’s tooling alternates its authentication attempts amongst this pool of IPs approximately once per second. Considering the breadth and speed of this technique, it seems likely that STRONTIUM has adapted its tooling to use an anonymizer service to obfuscate its activity, evade tracking, and avoid attribution,” Microsoft explains.
In a two-week timeframe (August 19 – September 3), Strontium used an average of 1,294 daily IPs, associated with 536 netblocks and 273 ASNs. Some of the netblocks were more heavily used than others, and Microsoft believes that the underlying anonymization service is over-serving IPs in these specific netblocks.
“The fact that the anonymization service is over-serving specific netblocks gives defenders an opportunity to hunt for activity associated both with this STRONTIUM activity or other malicious tooling that is utilizing the same anonymization service,” the tech company says.
Strontium was also observed leveraging password-spray tools that try username-password combinations in a “low-’n-slow” manner: roughly four authentication attempts per hour for any targeted account. The attacks last days or weeks, and nearly each of the attempts originates from a different IP address.
“In brute-force mode, the tooling attempts many username: password attempts very rapidly for a much shorter time period. Organizations targeted by the tooling running in this mode typically see over 300 authentication attempts per hour per targeted account over the course of several hours or days,” the company reveals.
Strontium, Microsoft also reveals, is only one of the state-sponsored hacking groups targeting election-related organizations in the US and the UK. The China-linked Zirconium and Iran-backed Phosphorus groups were also observed engaging in such activities recently.
Iran Says US Vote Hack Allegation 'Absurd'
11.9.20 BigBrothers Securityweek
Tehran on Friday hit back at allegations by Microsoft that Iran based hackers had targeted the US presidential campaigns, declaring it does not care about the election's outcome.
Microsoft claimed that it has thwarted cyber attacks by hackers from China, Russia and Iran who have been targeting staff from the campaigns of President Donald Trump and his Democratic rival Joe Biden, ahead of the November vote.
Both the Trump and Biden campaigns have been cited by media as saying they were aware of being targeted by hackers.
"The United States, which has for decades been meddling in the elections of other countries such as Iran, is in no place to make such absurd claims," state news agency IRNA quoted Iran's foreign ministry spokesman Saeed Khatibzadeh as saying.
As an instance, he pointed to the role of the US Central Intelligence Agency in a coup in 1953, which toppled hugely popular prime minister Mohammad Mosaddegh, who had called for Iran's oil to be nationalised.
It was clear that "foreign activity groups have stepped up their efforts targeting" the November 3 election, Microsoft said on Thursday.
The firm said an Iran-based group called Phosphorus has been targeting personal accounts of people associated with the Trump campaign.
"For Tehran, it does not matter who is in the White House. What matters is Washington's commitment to international rights, rules and norms, not meddling in others' affairs and acting on their commitments," Khatibzadeh said.
Decades-old tensions between Tehran and Washington have escalated since 2018, when Trump unilaterally withdrew the US from a multinational accord that limited Iran's nuclear programme. Trump subsequently reimposed crippling sanctions on Iran's economy.
Animosity further deepened after a US drone strike near Baghdad airport killed top Iranian general Qasem Soleimani in January.
Iranian officials have repeatedly said that they favour no specific candidate in the 2020 election, while also calling for Washington's return to the 2015 nuclear deal and the lifting of sanctions.
Microsoft Warns of Cyberattacks on Trump, Biden Election Campaigns
11.9.20 BigBrothers Threatpost
Just months before the U.S. presidential election, hackers from Russia, China and Iran are ramping up phishing and malware attacks against campaign staffers.
The U.S. election campaigns of both Donald Trump and Joe Biden have been targeted in a slew of recent cyberattacks, Microsoft said on Thursday.
With the U.S. presidential election a mere two months away, in recent weeks cyberattacks targeting people and organizations involved in it have ramped up — including numerous attempts against Trump and Biden staffers, Microsoft said. The tech giant has associated the unsuccessful attacks with threat groups linked to Russia, China and Iran.
“What we’ve seen is consistent with previous attack patterns that not only target candidates and campaign staffers, but also those they consult on key issues,” said Tom Burt, corporate vice president of customer security and trust with Microsoft, in a Thursday post. “The activity we are announcing today makes clear that foreign activity groups have stepped up their efforts targeting the 2020 election as had been anticipated, and is consistent with what the U.S. government and others have reported.”
Threatpost Webinar Promo Bug Bounty
Click to Register
One threat group, which Microsoft dubs Zirconium, was spotted launching thousands of attacks between March and September, resulting in nearly 150 compromises. Microsoft said the group is operating from China.
Among those that have been targeted by Zirconium include high-profile individuals associated with the election – such as staffers on the “Joe Biden for President” campaign -and prominent leaders in the international affairs community.
The threat actors, for instance, targeted “non-campaign email accounts belonging to people affiliated with the campaign,” according to Microsoft. “The group has also targeted at least one prominent individual formerly associated with the Trump Administration.”
Zirconium’s TTPs include using web “beacons” that are tied to an attacker-controlled domain. The group then sends the URL of the domain to targets via email text (or attachment) and persuades them to click the link via social engineering.
“Although the domain itself may not have malicious content, [this] allows Zirconium to check if a user attempted to access the site,” said Microsoft. “For nation-state actors, this is a simple way to perform reconnaissance on targeted accounts to determine if the account is valid or the user is active.”
Beyond politics, Zirconium has also been targeting “prominent individuals in the international affairs community, academics in international affairs from more than 15 universities,” according to Microsoft.
On the other side of the coin, the personal email accounts of staffers associated with the “Donald J. Trump for President” campaign are also being targeted, this time by another threat group called Phosphorus, which Microsoft said is operating from Iran. The group – also known as APT 35, Charming Kitten and Ajax Security Team –was first discovered targeting campaign staffers of both Trump and Biden by Google’s Threat Analysis Group in June, with phishing attacks.
The Iran-linked hacking group has been known to use phishing as an attack vector, and in February was discovered targeting public figures in phishing attacks that stole victims’ email-account information. Earlier this year, Microsoft also took control of 99 websites utilized by the threat group in attacks. Last year, Phosphorus was also discovered attempting to break into accounts associated with the 2020 reelection campaign of President Trump. And most recently, it was seen using WhatsApp and LinkedIn messages to impersonate journalists.
Another threat group seen behind recent phishing attacks targeting officials related to the U.S. elections is a group called Strontium (also known as Fancy Bear, APT28, and Sofacy), operating from Russia, said Microsoft. Microsoft assessed with “high confidence” that the group has attacked more than 200 organizations including political campaigns, advocacy groups, parties and political consultants. These include think-tanks such as The German Marshall Fund of the United States, The European People’s Party, and various U.S.-based consultants serving Republicans and Democrats.
Microsoft said that it believes the group — responsible for election-meddling in 2016 and the attack on the Democratic National Committee — is compromising targets’ email accounts in order to gather intelligence and disrupt operations. Strontium has also shaken up its techniques since the previous 2016 election, where it relied on spear-phishing to capture people’s credentials. Now, the group has been observed launching brute-force attacks and password-spraying tactics, which Microsoft said has likely allowed them to automate aspects of their operations.
“Strontium also disguised these credential-harvesting attacks in new ways, running them through more than 1,000 constantly rotating IP addresses, many associated with the Tor anonymizing service,” according to Microsoft. “Strontium even evolved its infrastructure over time, adding and removing about 20 IPs per day to further mask its activity.”
With the 2020 U.S. Presidential Election coming up, cybersecurity concerns are under the spotlight – including worries about the integrity of voting machines, the expected expansion of mail-in voting due to COVID-19 and disinformation campaigns. Previous direct hacking efforts, including in 2016, are making many wary about security risks facing the election this time around.
“We disclose attacks like these because we believe it’s important the world knows about threats to democratic processes,” said Microsoft. “It is critical that everyone involved in democratic processes around the world, both directly or indirectly, be aware of these threats and take steps to protect themselves in both their personal and professional capacities.”
The recent slew of cyberattack attempts targeting various political entities should come as no surprise, Neal Dennis, threat intelligence specialist at Cyware, told Threatpost.
“Politicians and their support staff, along with contracted service providers, should anticipate they will at some point be a target of an advanced persistent threat, not if but when,” Dennis said. “A robust and purposefully paranoid mindset around what comes to their inboxes, phones, and other communication platforms – along with strong industry best practices for password management – would serve them well, though not mitigate 100 percent of their risk.”
Russian Hackers Target U.S. Campaigns, Parties: Microsoft
11.9.20 BigBrothers Securityweek
The same Russian military intelligence outfit that hacked the Democrats in 2016 has attempted similar intrusions into the computer systems of more than 200 organizations including political parties and consultants, Microsoft said Thursday.
Those efforts appear to be part of a broader increase in targeting of U.S. political campaigns and related groups, the company said. “What we’ve seen is consistent with previous attack patterns that not only target candidates and campaign staffers but also those who they consult on key issues,” Tom Burt, a Microsoft vice president, said in a blog post.
Most of the infiltration attempts by Russian, Chinese and Iranian agents were halted by Microsoft security software and the targets notified, he said. The company would not comment on who may have been successfully hacked or the impact.
Although U.S. intelligence officials said last month that the Russians favor President Donald Trump and the Chinese prefer former Vice President Joe Biden, the Democratic challenger, Microsoft noted Thursday that Chinese state-backed hackers have targeted “high profile individuals associated with the election,” including people associated with the Biden campaign.
China is largely an espionage threat, however, while Russia steals data and weaponizes it.
Microsoft did not assess which foreign adversary poses the greater threat to the integrity of the November presidential election. The consensus among cybersecurity experts is that Russian interference is the gravest. Senior Trump administration officials have disputed that, although without offering any evidence.
“This is the actor from 2016, potentially conducting business as usual,” said John Hultquist, director of intelligence analysis at the top cybersecurity firm FireEye. “We believe that Russian military intelligence continues to pose the greatest threat to the democratic process.”
The Microsoft post shows that Russian military intelligence continues to pursue election-related targets undeterred by U.S indictments, sanctions and other countermeasures, Hultquist said. It interfered in the 2016 campaign seeking to benefit the Trump campaign by hacking the Democratic National Committee and emails of John Podesta, the campaign manager of Hillary Clinton, and dumping embarrassing material online, congressional and FBI investigators have found.
The same GRU military intelligence unit, known as Fancy Bear, that Microsoft identifies as being behind the current election-related activity also broke into voter registration databases in at least three states in 2016, though there is no evidence it tried to interfere with voting.
Microsoft, which has visibility into these efforts because its software is both ubiquitous and highly rated for security, did not address whether U.S. officials who manage elections or operate voting systems have been targeted by state-backed hackers this year. U.S. intelligence officials say they have so far not seen no evidence of that.
Thomas Rid, a Johns Hopkins geopolitics expert, said he was disappointed by Microsoft’s refusal to differentiate threat level by state actor. “They’re lumping in actors that operate in a very different fashion, probably to make this sound more bipartisan,” he said. “I just don’t understand why.”
Microsoft said in the past year it has observed attempts by Fancy Bear to break into the accounts of people directly and indirectly affiliated with the U.S. election, including consultants serving Republican and Democratic campaigns and national and state party organizations — more than 200 groups in all.
Also targeted was the center-right European People’s Party, the largest grouping in the European Parliament. A party spokesperson said the hacking attempts were unsuccessful. The German Marshall Fund of the United States, a think tank, was another target. A spokesperson said there was no evidence of intrusion.
Microsoft did not say whether Russian hackers had attempted to break into the Biden campaign but did say that Chinese hackers from the state-backed group known as Hurricane Panda “appears to have indirectly and unsuccessfully” targeted the Biden campaign through non-campaign email accounts belonging to people affiliated with it.
The Biden campaign did not confirm the attempt, although it said in a statement that it was aware of the Microsoft report.
The blog post said Iranian state-backed hackers have unsuccessfully tried to log into accounts of Trump campaign and administration officials between May and June of this year. “We are a large target, so it is not surprising to see malicious activity directed at the campaign or our staff,” Trump campaign deputy press secretary Thea McDonald said. She declined further comment.
Tim Murtaugh, the campaign’s communications director, said: “President Trump will beat Joe Biden fair and square and we don’t need or want any foreign interference.”
In June, Google disclosed that Hurricane Panda had targeted Trump campaign staffers while Iranian hackers had attempted to breach accounts of Biden campaign workers. Such phishing attempts typically involve forged emails with links designed to harvest passwords or infect devices with malware.
Although both Attorney General William Barr and National Security Advisor Robert O’Brien have both said China represents the greatest threat to U.S. elections, the only mention of a Trump administration official targeted by Chinese hackers is “at least one prominent individual formerly associated with” the administration.
Graham Brookie, director of digital forensic research at The Atlantic Council, disputes Barr and O’Brien’s claim that China poses the greater threat to this year’s election. His lab is at the forefront of unearthing and publicizing Russian disinformation campaigns.
Brookie confirmed that his employer was among targets of Hurricane Panda but said there was no evidence the hacking attempts, which he said were unsuccessful, had anything to do with the 2020 election.
“We have every indication that this was an instance of cyber-espionage, information gathering, as opposed to electoral interference,” he said.
By contrast, Brookie said, “it’s pretty evident that the Russian attempts (Microsoft disclosed) were focused on electoral processes and groups working on that.”
UK Judge Refuses Assange Lawyers' Plea to Dismiss New US Allegations
10.9.20 BigBrothers Securityweek
Lawyers for WikiLeaks founder Julian Assange on Monday failed to persuade a British judge to throw out new US allegations against him, as he resumed his fight to avoid extradition to the United States for leaking military secrets.
Protesters gathered outside London's Old Bailey court as the 49-year-old Australian was brought in, brandishing placards reading "Don't Extradite Assange" and "Stop this political trial".
Inside, Assange's lawyers sought to "excise" new allegations lodged by Washington in recent weeks, saying they had not had time to formulate a proper response.
Assange faces 18 charges under the US Espionage Act relating to the 2010 release by WikiLeaks of 500,000 secret files detailing aspects of US military campaigns in Afghanistan and Iraq.
Washington claims he helped intelligence analyst Chelsea Manning to steal the documents before exposing confidential sources around the world.
If convicted, Assange -- who has been held at the high-security Belmarsh Prison for the last 16 months -- could be jailed for up to 175 years.
US authorities recently laid out new evidence against Assange alleging that he and others at the whistleblowing site recruited hackers.
In court on Monday, defence lawyer Mark Summers protested against the "11th hour" allegations, noting the difficulties Assange already had in communicating with his legal team due to coronavirus restrictions.
"What is happening is abnormal, unfair and liable to create injustice if allowed to continue," he said.
But District Judge Vanessa Baraitser said: "These are issues which must take place in the context of considering the extradition request and not before it."
- 'Abuse trial' -
Clean-shaven and wearing a dark suit and maroon tie, Assange spoke to confirm his name and date of birth, and said he did not consent to extradition.
It was the first time he has been seen in public since the first part of the hearing in February, when he appeared weak and confused.
The second part of the hearing, due in April, was delayed by the coronavirus pandemic. It is set to last three to four weeks.
Supporters of Assange gathered outside the court, including fashion designer Vivienne Westwood, who said he was "shining the light on all the corruption in the world".
His father, John Shipton, said the hearing was an "abuse trial."
Assange's partner, Stella Moris, took a 80,000-strong petition opposing his extradition to Prime Minister Boris Johnson's Downing Street office, but was turned away.
She has said she feared Assange would take his own life -- leaving their two young sons, who were conceived during his asylum in Ecuador's London embassy, without a father.
US journalism lecturer Mark Feldstein, from the University of Maryland, was the first witness to be called in the hearing, giving evidence via videolink.
He said leaks of classified information, either to the media or Congress, were commonplace.
"Leaks shed light on decision-making by the government and inform the public powerfully, but they also expose government deceit, corruption and illegality and abuse of power," he told the court.
At the February hearing, James Lewis, representing the US government, said WikiLeaks was responsible for "one of the largest compromises of classified information in the history of the United States".
"Reporting or journalism is not an excuse for criminal activities or a licence to break ordinary criminal laws," he added.
- Long-running saga -
The extradition hearing is the latest in a series of legal battles faced by Assange since the leaks a decade ago.
In 2010, he faced allegations of sexual assault and rape in Sweden, which he denied.
He was in Britain at the time but dodged an attempt to extradite him to Sweden by claiming political asylum in Ecuador's embassy in London.
For seven years he lived in a small apartment in the embassy, but after a change of government in Ecuador, Quito lost patience with its guest and turned him over to British police in April 2019.
Swedish prosecutors confirmed last year they had dropped the rape investigation, saying that despite a "credible" account from the alleged victim there was insufficient evidence to proceed.
Spyware Labeled ‘TikTok Pro’ Exploits Fears of US Ban
10.9.20 BigBrothers Social Virus Threatpost
Malware can take over common device functions as well as creates a phishing page to steal Facebook credentials.
Researchers have discovered a new Android spyware campaign pushing a “Pro” version of the TikTok app that is exploiting fears among its young and gullible users that the popular social media app is on the cusp of being banned in the United States. The malware can take over basic device functions—such as capturing photos, reading and sending SMS messages, making calls and launching apps—as well as uses a phishing tactic to steal victims’ Facebook credentials.
The rogue app called TikTok Pro is being promoted by threat actors using a variant of a campaign already making the rounds, which urges users via SMS and WhatsApp messages to download the latest version of TikTok from a specific web address, said Zscaler CISO and VP of security Shivang Desai in a report published Tuesday.
The first wave of the campaign spread a fake app, containing malware dubbed “TikTok Pro,” which asks for credentials and Android permissions–including camera and phone permissions—and resulted in the user being bombarded with advertisements, he said.
Threatpost Webinar Promo Bug Bounty
Click to Register
The new wave has leveled up with a completely new app delivering “full-fledged spyware with premium features to spy on victim with ease,” Desai wrote.
Once installed and opened, the new “Tik Tok Pro” spyware launches a fake notification which then disappears along with the app’s icon. “This fake notification tactic is used to redirect the user’s attention, meanwhile the app hides itself, making the user believe the app to be faulty,” he said in his report.
The malware also has another anti-detection capability in that it has an additional payload stored under the /res/raw/ directory, “a common technique used by malware developers to bundle the main payload inside the Android package,” Desai wrote. The payload is just a decoy rather than possesses actual app functionality, he added.
The spyware’s main execution capability comes from an Android service named MainService, which acts as the “brain” of the spyware and controls its functionality—”from stealing the victim’s data to deleting it,” Desai wrote.
In addition to having the ability to take over common smartphone functions—such as capturing photos, sending SMS messages, executing commands, capturing screenshots, calling phone numbers and launching other apps on the device—the spyware also has a unique feature it uses to steal Facebook credentials.
Similar to phishing campaigns, “Tik Tok Pro” launches a fake Facebook login page that, as soon as the victim tries to log in, stores the victim’s credentials in /storage/0/DCIM/.fdat. An additional command, IODBSSUEEZ, then sends the stolen credentials to the malware’s command and control server.
Desai noted that this type of phishing tactic can be extended to steal other critical user credentials, such as bank-account or financial log-in data, though this type of activity wasn’t seen in the observed campaign.
Moreover, the new spyware has numerous functionalities similar to other more well-known versions of this type of malware, such as Spynote and Spymax, “meaning this could be an updated version of these Trojan builders, which allow anyone, even with limited knowledge, to develop full-fledged spyware,” Desai noted.
However, the Facebook credential-stealing capability is unique to “Tik Tok Pro” and not something that’s been observed before with these spyware apps, he said.
The persistence of using the TikTok brand to spread malware is likely the result of the current controversy over the popular video-sharing app, which is owned by China’s ByteDance and has been criticized for its questionable data-collection tactics.
President Trump has threatened to ban in the app in the United States and several U.S. companies—including Microsoft and Wal-Mart—are eyeing a purchase of the app. India recently banned TikTok as well as many other Chinese apps over a political dispute.
“Users looking forward to using the TikTok app amidst the ban might look for alternative methods to download the app,” Desai wrote in his report. “In doing so, users can mistakenly install malicious apps, such as the spyware mentioned in this blog.”
Desai reiterated the usual warnings to Android users not to trust unknown links received in SMS or other messages and to only install apps from official stores like Google Play to avoid falling victim to the new spyware campaign.
Another mitigation tactic is to keep the “Unknown Sources” option disabled in the Android device, which won’t let a device install apps from unknown sources, he added.
To check to see if the new spyware is running undetected on an Android device, users can search for the app in device settings by going to Settings -> Apps -> Search for icon that was hidden and search for “TikTok Pro,” Desai advised.
US Revokes Visas For 1,000 Chinese Under Trump Order
10.9.20 BigBrothers Securityweek
The United States has revoked visas of more than 1,000 Chinese students and researchers under an order by President Donald Trump that accused some of them of espionage, the State Department said Wednesday.
Trump, in a May 29 proclamation as tensions rose with Beijing on multiple fronts, declared that some Chinese nationals officially in the United States for study have stolen intellectual property and helped modernize China's military.
The State Department, offering its first figures on the effects of Trump's order, said that more than 1,000 visas have been revoked since it began implementing the proclamation on June 1.
"The high-risk graduate students and research scholars made ineligible under this proclamation represent a small subset of the total number of Chinese students and scholars coming to the United States," a State Department spokeswoman said.
"We continue to welcome legitimate students and scholars from China who do not further the Chinese Communist Party's goals of military dominance," she said.
The State Department declined to give details on whose visas have been revoked, citing privacy laws.
Nearly 370,000 students from China were enrolled at US universities in 2018-19, the most of any country, offering a lucrative source of income to institutions that are now facing growing pressure from the coronavirus pandemic.
Some Asian American activists have warned that Trump's orders are creating a climate of suspicion on campuses, with students of Asian descent facing unfounded questions about their intentions.
But US officials say the number of espionage cases involving China has soared in recent years as part of a concerted effort by Beijing.
US officials accuse China of seeking to steal university research into Covid-19, a reason cited for the Trump administration's closing China's consulate in Houston in June.
France, Japan, and New Zealand warn of a surgein Emotet attacks
9.9.20 BigBrothers Virus Securityaffairs
Cybersecurity agencies from multiple countries are warning of the surge of Emotet attacks targeting the private sector and public administration entities.
Cybersecurity agencies across Asia and Europe are warning of Emotet spam campaigns targeting businesses in France, Japan, and New Zealand.
The French national cyber-security agency published an alert to warn of a significant increase of Emotet attacks targeting the private sector and public administration entities in France.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
Emotet malware is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
According to the French national cyber-security agency, the number of Emotet attacks increased for several days, and the attacks are targeting almost any business sector.
“For several days, ANSSI has observed the targeting of French companies and administrations by the Emotet malware,” reads the alert issued by the ANSSI (Agence Nationale de la Sécurité des Systèmes d’Information).
“Special attention should be paid to this because Emotet is now used to deploy other malicious code that may have a strong impact on the activity of victims.”
New Zealand’s Computer Emergency Response Team (CERT) also published a security alert warning of spam campaigns spreading the Emotet threat.
“CERT NZ is aware of increased Emotet activity affecting New Zealand organisations.” reads the alert published by the New Zealand CERT.
“The emails contain malicious attachments or links that the receiver is encouraged to download. These links and attachments may look like genuine invoices, financial documents, shipping information, resumes, scanned documents, or information on COVID-19, but they are fake.”
Japan’s CERT (JPCERT/CC) also issued an alert to warn of a rapid increase in the number of domestic domain (.jp) email addresses that have been infected with the infamous malware and that can be employed in further spam campaigns.
“Since September 2020, JPCERT/CC has confirmed a sharp increase in the number of domestic domain (.jp) email addresses that can be infected with the malware Emotet and used to send spam emails that attempt to spread the infection.” reads the alert. “In addition, the number of consultations regarding Emotet infections is increasing, and we understand the situation where Emotet infections are spreading.”

JPCERT/CC has posted FAQ information on the JPCERT/CC Eyes blog and a tool dubbed EmoCheck that can be used to check for the malware infection on a computer.
US Federal systems must be covered by vulnerability-disclosure policies by March 2021
8.9.20 BigBrothers Securityaffairs
A new Cybersecurity and Infrastructure Security Agency (CISA) mandate requires U.S. agencies to implement vulnerability-disclosure policies by March 2021.
The U.S. government’s cybersecurity agency CISA has issued a mandate that requires federal agencies to implement vulnerability-disclosure policies (VDPs) by March 2021.
The main purpose of vulnerability-disclosure policies is to ensure that required information, other than confidential business information, is disclosed to the public and shared with relevant parties in a timely, accurate, complete, understandable, convenient and affordable manner.
The move aims at providing government agencies a formal mechanism to receive from security researchers and white-hat hackers reports of vulnerabilities on their infrastructure.
Vulnerability-disclosure policies allow enhancing the resiliency of the government’s infrastructure by encouraging meaningful collaboration between federal agencies and the public.
“When agencies integrate vulnerability reporting into their existing cybersecurity risk management activities, they can weigh and address a wider array of concerns,” reads the CISA directive. “This helps safeguard the information the public has entrusted to the government and gives federal cybersecurity teams more data to protect their agencies. Additionally, ensuring consistent policies across the executive branch offers those who report vulnerabilities equivalent protection and a more uniform experience.”

The Vulnerability-disclosure policies would specify which systems are covered as part of the process, including those systems that were not intentionally exposed online.
The directive mandates that organizations implement VDPs with clear wording around which systems are in-scope, as well as assurances around good-faith security research.
A draft of the directive was first issued in December 2019 open to public comment, since then the agency received more than 200 recommendations from more than 40 security experts, academics, federal agencies, civil society, and members of Congress.
In the next 60 days CISA will publish further guidance regarding the implementation of the VDP into their information-security programs and within 180 days all agencies must publish their vulnerability disclosure policy.
Within 240 days, the agencies must report milestones for VDP to cover all government information systems and CISA must begin coordinating the processes implemented t the disclosure of the vulnerabilities.
“To centralize part of this effort, CISA will offer a vulnerability disclosure platform service next spring. We expect this will ease operations at agencies, diminish their reporting burden under this directive, and enhance discoverability for vulnerability reporters.” concludes the directive.
U.S. Unveils Cybersecurity Policies for Space Systems
8.9.20 BigBrothers Securityweek
A presidential memorandum made public on Friday by the White House details the cybersecurity principles that should govern space systems.
Space systems, the memorandum points out, are essential to global communications, explorations, navigation, positioning, timing, weather monitoring, national security, and other applications, and should be kept safe from cyberattacks.
These systems rely on information systems and networks for flight operations, data transmission, and more, which makes them susceptible to malicious activities varying from manipulating sensors to sending unauthorized commands, and injecting malicious code to cause data loss, loss of space vehicle control, or shortened system lifespan.
According to the memorandum (SPD-5), space systems should be governed by the same cybersecurity principles and practices that apply to terrestrial systems, although some of these principles are of particular importance to space systems, such as the ability to remotely receive updates and incident response, which should be integrated into space vehicles before launch.
“For this reason, integrating cybersecurity into all phases of development and ensuring full life-cycle cybersecurity are critical for space systems. Effective cybersecurity practices arise out of cultures of prevention, active defense, risk management, and sharing best practices,” the memorandum reads.
Principles detailed in the memorandum demand that space systems are designed in anticipation of cyberattacks, that positive control of a vehicle can be regained when necessary, that critical space vehicle functions are protected against unauthorized access and against jamming and spoofing, and that physical protections reduce vulnerabilities of specific space vehicle systems.
Ground systems, information processing systems, and operational technology should be protected as well, through cybersecurity best practices and hygiene practices, as well as physical security for automated information systems. Keeping a close eye on the supply chain should also diminish risks impacting the cybersecurity of space systems.
“Implementation of these principles, through rules, regulations, and guidance, should enhance space system cybersecurity, including through the consideration and adoption, where appropriate, of cybersecurity best practices and norms of behavior,” the memorandum reads.
Furthermore, the document encourages collaboration between space system owners and operators for promoting the development of best practices. It also states that threat, warning, and incident data should be shared within the space industry.
NSA, NCMF Lay Out Design Plans for Cyber Center for Education and Innovation
8.9.20 BigBrothers Securityweek
The National Security Agency and the National Cryptologic Museum Foundation (NCMF) last week shared information on the design plans for the proposed Cyber Center for Education and Innovation (CCEI), set to be built on the NSA-Washington (NSAW) campus at Fort Meade.
The CCEI, a state-of-the-art venue, is expected to include more than 70,000 square-feet of conference space and classrooms, delivering programs to encourage the sharing of knowledge and resources between academia, government, and industry, and aiming to strengthen cyber-security across the country.

The center will also be the home of the National Cryptologic Museum, which the NSA says aims to inspire transparency, courtesy of large open floor plans, tall glass windows and skylights, and a well-lit main room.
Founded in 1993 and enriched through a 20-year collaboration between the NSA and the NCMF, the National Cryptologic Museum is an educational tool for cryptologic professions, aiming to motivate analysts, computer scientists, engineers, linguists, and mathematicians.
The museum, which houses the nation’s cryptologic treasures, currently resides inside its original structure, near NSAW’s secure fence line.
NSA also plans on using the new venue to “serve its industry and academic engagements and cyber-security technical exchanges.” The CCEI will also be used for a multitude of unclassified events, such as ceremonies, education and training, and onboarding for new NSA hires.
“One way to increase public trust and confidence in NSA is to enhance our public and private partnerships in support of whole-of-nation cybersecurity efforts. The CCEI will be a key physical manifestation that enables NSA to notably grow and sustain public/private collaborations,” said NSA’s Engagement & Policy Director Natalie Laing.
The CCEI and National Cryptologic Museum will be built by the NCMF, which will then gift the complex to the NSA and the U.S. government.
China Launches Initiative for Global Data Security Issues
8.9.20 BigBrothers Securityweek
China has launched an initiative to address global data security issues, a countermove to the U.S. “clean network” program that is aimed at discouraging other countries from using Chinese technology.
Foreign Minister Wang Yi announced the initiative in Beijing on Tuesday at a seminar on global digital governance.
He said mounting risks for cyber security threaten national security, public interests and personal rights.
The move comes amid a deterioration in U.S.-China relations encompassing trade tensions and competition in telecommunications and artificial intelligence technologies, with the U.S. accusing Chinese technology companies of threatening American national security.
“Bent on unilateral acts, a certain country keeps making groundless accusations against others in the name of ‘clean’ networks and used security as a pretext to prey on enterprises of other countries who have a competitive edge,” Wang said, according to a transcript of his speech released by the ministry. “Such blatant acts of bullying must be opposed and rejected.”
Wang said that it was important to develop international rules on data security that will “reflect the will and respect the interests of all countries through broad-based participation.”
U.S. Secretary of State Mike Pompeo last month unveiled the “Clean Network” program, saying it is aimed at protecting citizens’ privacy and sensitive information from “malign actors, such as the Chinese Communist Party.”
More than 30 countries and territories such as Australia and Britain are participating in that initiative, which seeks to exclude Chinese telecommunications companies like Huawei and ZTE, as well as apps, cloud service providers and undersea cables from their internet networks.
The U.S. has expressed concerns over national security threats from services provided by Chinese technology companies like Huawei, Bytedance and Tencent.
Washington has dissuaded some U.S. allies from using Huawei’s technology in 5G networks, saying data potentially could be accessed by the Chinese government. Huawei vehemently denies that.
Washington also has imposed sanctions that restrict Huawei from procuring chips containing American technology. Recently, the U.S. also said it will ban Chinese company Bytedance’s popular TikTok video app in the country unless it finds an American buyer. It similarly labelled Tencent’s popular messaging app WeChat a national security threat.
The Chinese initiative opposes impairing critical infrastructure and theft of important data. It also opposes abusing technology to “conduct mass surveillance against other states,” the transcript said.
Companies should not “install backdoors in their products and services” to illegally obtain user data, should respect the sovereignty, jurisdiction and governance of data in other states,” it says.
“The Chinese government has acted in strict compliance with data security principles. We have not and will not ask Chinese companies to transfer data overseas to the government in breach of other countries’ laws,” said Wang.
“Politicization of security issues, double standards and slandering others violate the basic norms governing international relations, and seriously disrupts and hampers global digital cooperation and development,” he said.
Russian Indicted for Attempting to Recruit Tesla Employee to Install Malware
8.9.20 BigBrothers Securityweek
A Russian national has been indicted in the United States for conspiring to recruit a Tesla employee to install malware onto the company’s network.
The man, Egor Igorevich Kriuchkov, 27, was arrested on August 22, when the U.S. Department of Justice announced that he had attempted to recruit an employee of a company in Nevada, offering them $1 million to install malware within the enterprise environment.
Kriuchkov told the employee that the malware would allow Kriuchkov and co-conspirators to exfiltrate data from the organization’s network, and that the data would then be used to extort money from the company.
While the DoJ did not provide information on the targeted company, a tweet from Elon Musk confirmed that electric car maker Tesla was the intended victim of the attack.
The targeted employee is reportedly a Russian-speaking, non-US citizen working at Tesla’s Giga Nevada factory. The Justice Department believes that the cybercriminals conspired to recruit him from about July 16 until August 22.
Kriuchkov arrived in the United States at the end of July and worked for several weeks to convince Tesla’s employee to accept the payment for installing malware. Instead of accepting the bribe, however, the employee informed the company, and the FBI was alerted thereafter.
“The malware would purportedly provide Kriuchkov and his co-conspirators with access to the data within the computer system. After the malware was introduced, Kriuchkov and his co-conspirators would extract data from the network and then threaten to make the information public, unless the company paid their ransom demand,” the DoJ explained.
Kriuchkov was charged last week for participating in a conspiracy “to intentionally cause damage to a protected computer.” He remains in detention pending trial.
FBI issues second alert about ProLock ransomware stealing data
7.9.20 BigBrothers Ransomware Bleepingcomputer
The FBI issued a second warning this week to alert US companies of ProLock ransomware operators stealing data from compromised networks before encrypting their victims' systems.
The 20200901-001 Private Industry Notification seen by BleepingComputer on September 1st comes after the MI-000125-MW Flash Alert on the same subject issued by the FBI four months ago, on May 4th, 2020.
FBI's previous alert also warned private industry partners that ProLock's decryptor is not working properly and that data will be lost since files over 64MB might be corrupted as part of the decryption process.
ProLock ransomware started as PwndLocker during late 2019, slowly making a reputation for itself while targeting both US businesses and local governments.
PwndLocker rebranded itself as ProLocker in March after fixing a bug that allowed free decryption of locked files, and its activity started to escalate as it started targeting corporate networks again.
The boost in activity was most likely caused by partnering with the QakBot banking trojan gang which made it a lot easier to gain access to new victims' networks.
ProLock Tor payment site
ProLock ransoms can reach almost $700K
The operators behind the human-operated ProLock ransomware have been harvesting and exfiltrating information from their victims' devices before deploying their payloads since March 2020 according to the FBI.
The stolen data is later used by the threat actors as leverage in persuading the victim organizations into paying ransoms ranging between $175,000 to more than $660,000 depending on the size of the compromised network as BleepingComputer found.
So far, ProLock has successfully encrypted the networks of organizations around the world from multiple industry sectors including healthcare, construction, finance, and legal, including US government agencies and industrial entities.
ProLock's operators have used several attack vectors to breach their victims' systems including phishing emails with QakBot malicious attachments, using stolen credentials, and exploiting system configuration flaws.
The threat actors were observed archiving the stolen data and uploading to cloud storage platforms including OneDrive, Google Drive, and Mega with the help of the Rclone cloud storage sync command-line tool.
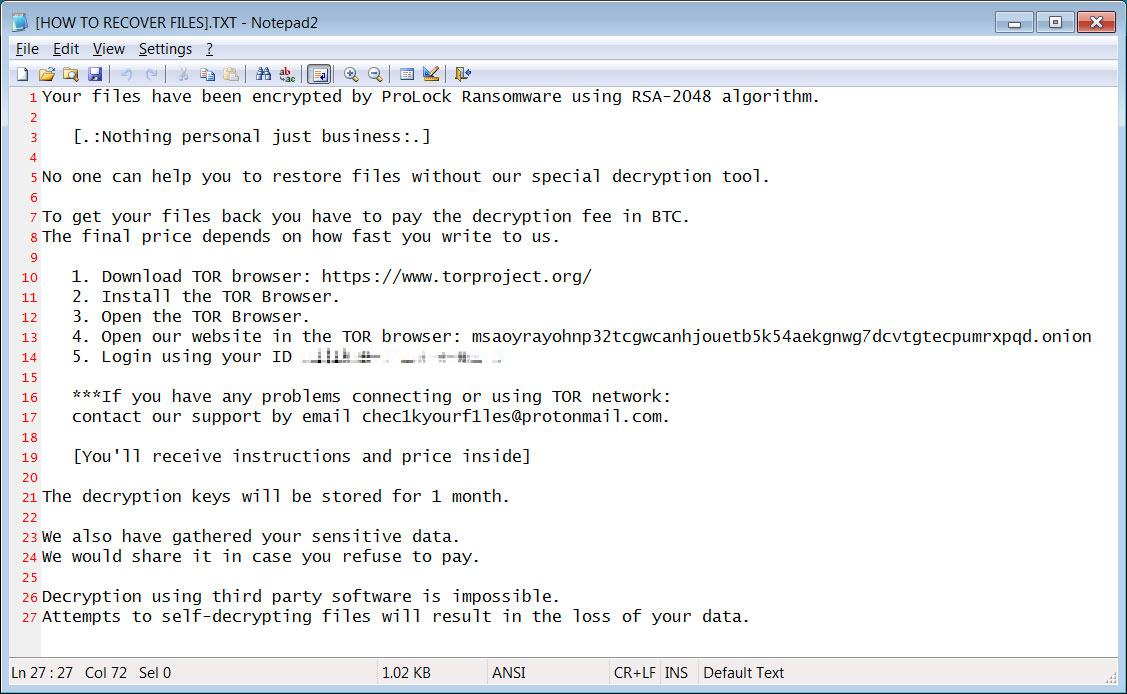
ProLock ransom note
Victims encouraged not to pay the ransoms
The FBI encourages private industry partners affected by ProLock ransomware attacks not to give in to the threat actors' demands and pay the ransoms.
Doing so would only embolden them to target other victims and will also directly fund their future illicit operations as the FBI explained.
However, the FBI recognizes the damages companies could face following such attacks and urges victims to report the attacks as soon as possible after having their systems infected with ProLock ransomware regardless of their decision to pay for a decryptor or not.
Reporting the attack to the local FBI field office to provide attack-related information such as phishing emails, recovered ransomware samples, ransom notes, and network traffic logs could help counter other attacks, as well as to identify and hold the attackers accountable for their activity.
The FBI recommends US orgs to periodically back up their data to an off-line/off-site backup location and to always keep their software up to date to patch any newly discovered security flaws the ProLock operators could exploit.
They are also recommended to make use of two-factor authentication (2FA) wherever possible, to disable unused Remote Desktop Protocol (RDP) instances, and to disable automatic attachment downloads in email clients.
A full replacement of all Huawei and ZTE hardware on American wireless networks will cost $1.837bn
6.9.20 BigBrothers Securityaffairs
The US Federal Communications Commission (FCC) estimates the cost of a full replacement of all Huawei and ZTE hardware on American wireless networks at $1.837bn.
A report published by the US Federal Communications Commission (FCC) revealed that performing a full replacement of all Huawei and ZTE equipment on American wireless networks will cost $1.837bn in total.
“Based on data Commission staff collected through the information collection, all filers report it could cost an estimated $1.837 billion to remove and replace Huawei and ZTE equipment in their networks.” reads the report published by the FCC. “Of that total, filers that appear to initially qualify for reimbursement under the Secure and Trusted Communications Network Act of 2019 report it could require approximately $1.618 billion to remove and replace such equipment.”
The report aims at promoting the security of our national communications networks by providing information from the US carriers.
The FCC pointed out that around $1.618bn of $1.837bn will be reimbursed by taxpayers according to the Secure and Trusted Communications Networks Act of 2019.
In July the FCC blocked the Chinese companies from receiving subsidies from a government fund, its decision is part of its efforts to protect the national communications networks from security risks posed by the use of Chinese equipment.
The FCC’s move definitively banned U.S. organizations from using the government Universal Service Fund for acquiring equipment or services provided by the Chinese firms.
In November 2019, the U.S. Federal Communications Commission has cut off government funding for equipment from the Chinese companies Huawei and ZTE due to security concerns. The Federal Communications Commission also requested the government to assign subsidies to the American companies that will replace any equipment from the Chinese firms that they already have in place.
The FCC fears that the Chinese firms could conduct cyber espionage for their government due to their “substantial ties to the Chinese government,”
The next step is the approval of the Congress for the $1.6bn fund to use for the reimbursements for the replacement of the Chinese equipment.
“It is a top priority of our nation and this Commission to promote the security of our country’s communications networks. That’s why we sought comprehensive information from U.S. carriers about equipment and services from untrusted vendors that have already been installed in our networks. Today’s announcement marks a critical milestone in our ongoing commitment to secure our networks,” said FCC Chairman Ajit Pai. “By identifying the presence of insecure equipment and services in our networks, we can now work to ensure that these networks—especially those of small and rural carriers—rely on infrastructure from trusted vendors. I once again strongly urge Congress to appropriate funding to reimburse carriers for replacing any equipment or services determined to be a national security threat so that we can protect our networks and the myriad parts of our economy and society that rely upon them.”
The FCC has also published a list of 51 carriers that will need to replace their Huawei and ZTE equipment benefiting from the US funds.
The U.S. has already pushed its allies for banning Huawei, ZTE and other Chinese companies.
The Chinese giant Huawei was already excluded by several countries from building their 5G internet networks. The United States, Australia, New Zealand, Romania, and Japan announced the exclusion of Huawei technology for their 5G internet networks.
In April 2018, the UK GCHQ intelligence agency warned UK telcos firms of the risks of using ZTE equipment and services for their infrastructure.
In December 2018, a Czech cyber-security agency is warned against using Huawei and ZTE technologies because they pose a threat to state security.
U.S. Department of Defense discloses details about critical and high severity issues
5.9.20 BigBrothers Securityaffairs
The U.S. Department of Defense has disclosed the details about four critical and high severity vulnerabilities in its infrastructure.
The U.S. Department of Defense has disclosed details of four vulnerabilities in its infrastructure, two high severity rating issues and other two critical flaws.
The vulnerabilities could be exploited by threat actors to hijack a subdomain, execute arbitrary code remotely, or view files on the vulnerable system.
The vulnerabilities were reported in August and July through the Department’s bug bounty program operated via HackerOne.
One of the critical issues is a subdomain takeover due to an unclaimed Amazon S3 bucket.
The ethical hacker chron0x who reported the flaw discovered that the subdomain was referencing an Amazon S3 bucket in the US East region that did no longer exists. The hackers claimed this bucket and successfully took over the subdomain.
“This is extremely vulnerable to attacks as a malicious user could create any web page with any content and host it on the deployedmedicine.com domain.” reads the advisory. “This would allow them to post malicious content which would be mistaken for a valid site. They could:
XSS
Phishing
Bypass domain security
Steal sensitive user data, cookies, etc.”
An attacker could exploit the issue to target visitors of the website with phishing and cross-site scripting attacks.
The second critical flaw is a remote code execution on a DoD server running Apache Solr that had been left unpatched since August 2019.
The vulnerability was reported by the ethical hacker Hzllaga on August 19.
The expert discovered that the server was vulnerable to CVE-2019-0192 and CVE-2019-0193, he successfully exploited CVE-2019-0193 and successfully remotely executed arbitrary code.
One of the high-severity issues disclosed by the Department is an unpatched read-only path traversal in a Cisco product used by the agency. The issue could be exploited to access arbitrary sensitive files on the system.
The second high-severity issue is a code injection on a DoD host that may lead to arbitrary code execution. The flaw was reported by e3xpl0it from Positive Technologies.
The DoD quickly addressed all the vulnerabilities.
Since the DoD launched a bug bounty program on HackerOne in November 2016, it addressed a total of 9555 security issues.
Army Cyber Command Completes its Move to Georgia Base
4.9.20 BigBrothers Thehackernews
The Army command dedicated to defending against hackers and other online threats celebrated its move into a new $366 million headquarters in Georgia on Thursday.
Created a decade ago, the Army Cyber Command had been spread across Army installations in three states before consolidating at Fortitude Hall, its new home at Fort Gordon in Augusta. Plans to bring the entire command together under one roof had been in the works for seven years.

“It’s not just a physical move. It’s not just a nice new facility,” Lt. Gen Stephen Fogarty, the commander of Army Cyber Command, told reporters on a conference call Thursday. He called the headquarters “a purpose-filled cyber weapons system.”
Fogarty was joined during a dedication ceremony by Army Under Secretary James McPherson and Gen. Paul Nakasone, who serves as commander of U.S. Cyber Command and director of the National Security Agency.
McPherson noted the move brings the Army’s cyber soldiers, commanders and trainees together at Fort Gordon, which is also home to an NSA facility.
“The cyber domain in the most recent one, it’s the one that changes the most rapidly and it it is the one we must learn to not only compete in but dominate in with our near-peer competitors,” McPherson said.
The U.S. military established the Army Cyber Command in 2010 after the Defense Department declared cyberspace a new domain for warfare, citing rising threats from hackers backed by foreign governments and online attackers acting independently. The command oversees about 16,500 soldiers, civilians and contract workers worldwide.
According to the Army, the Cyber Command headquarters will bring about 1,200 additional soldiers and civilian workers to Fort Gordon. Fogarty said all of them should be in place within the next year. Fortitude Hall spans 336,000 square feet (31,215 square meters) and is equipped with more than 300 servers.
Before the consolidation, elements of the Army Cyber Command were also based in Fort Belvoir, Virginia, and Fort Meade, Maryland. At Fort Gordon, the Army now has its electronic warfare and defense units based at the same installation used for training new cyber soldiers and providing them with continuing education.
The headquarters dedication on Thursday was largely symbolic. Army Cyber Command’s leader, Lt. Gen. Stephen G. Fogarty, and his command staff have been working at Fort Gordon since July.
NSA Mass Surveillance Program Illegal, U.S. Court Rules
4.9.20 BigBrothers Threatpost
The NSA argued its mass surveillance program stopped terrorist attacks – but a new U.S. court ruling found that this is not, and may have even been unconstitutional.
A U.S. federal appeals court ruled that the controversial National Security Agency (NSA) mass surveillance program exposed in 2013 was illegal – and may have even been unconstitutional.
The call comes seven years after former NSA contractor and whistleblower Edward Snowden outed the mass surveillance program, which enabled snooping in on millions of American’s phone calls, in a bombshell leak that drew widespread worries about privacy.
“Seven years ago, as the news declared I was being charged as a criminal for speaking the truth, I never imagined that I would live to see our courts condemn the NSA’s activities as unlawful and in the same ruling credit me for exposing them,” Snowden said on Twitter, Wednesday.
After Snowden in 2013 exposed the NSA’s phone-record collection program, many argued for the program, saying it had successfully thwarted terrorist attacks. Rep. Mike Rogers, a Michigan Republican who chairs the House Intelligence Committee, for instance said that the NSA surveillance program had stopped more than 50 terrorist attacks.
The NSA for its part echoed claims program had helped foil terrorist attacks, pointing to a specific case against Basaaly Moalin, a Somali immigrant who was convicted of conspiring to support terrorist group al-Shabaab.
However, in an appeals case for Moalin (as well as three other Somali immigrants who supported terrorist organizations), the U.S. Court of Appeals for the Ninth Circuit on Wednesday ruled that the illegally collected phone records actually did not play a pivotal role in the case.
In fact, the court ruled that the collection of Americans’ phone records was actually illegal, and may have also violated the Fourth Amendment, which gives Americans security against unreasonable searches and seizures.
“The panel affirmed the convictions of four members of the Somali diaspora for sending, or conspiring to send, $10,900 to Somalia to support a foreign terrorist organization, in an appeal that raised complex questions regarding the U.S. government’s authority to collect bulk data about its citizens’ activities under the auspices of a foreign intelligence investigation, as well as the rights of criminal defendants when the prosecution uses information derived from foreign intelligence surveillance,” according to court documents.
This week, privacy advocates, such as the ACLU, praised the ruling. “This ruling, which confirms what we have always known, is a victory for our privacy rights,” according to the American Civil Liberties Union (ACLU) on Twitter, Wednesday.
Alex Abdo, litigation director with Knight First Amendment Institute, noted on Twitter that the court held that the government must provide notice to criminal defendants prosecuted with evidence that’s been derived from NSA surveillance – in “perhaps the court’s most unprecedented and therefore significant move.”
“The work to rein in overreaching NSA surveillance is far from over, but it’s worth pausing to consider that nearly all the progress we’ve made has come because of disclosures criminalized by a law—the Espionage Act—that makes no exception for disclosures in the public interest,” he said.
Snowden, for his part, still faces of espionage charges in the U.S. In 2013 after Snowden leaked thousands of classified documents, about top-secret surveillance programs to journalists that shed light on U.S. spying efforts, the U.S. Department of Justice charged him for violating the Espionage Act and for stealing government property, for which he faces at least 30 years in jail. The U.S. has also sued Snowden over his new memoir, alleging he published the book in violation of non-disclosure agreements signed with both the CIA and NSA.
Government Backed 'MDBR' Service Blocks Connections to Malicious Domains
3.9.20 BigBrothers Securityweek
A new Malicious Domain Blocking and Reporting (MDBR) service will help organizations improve security by preventing IT systems from connecting to malicious domains.
Launched through a partnership between the U.S. Department of Homeland Security’s Cybersecurity Infrastructure Security Agency (CISA), Center for Internet Security (CIS), and Akamai Technologies, the MDBR service adds another layer of Domain Name System (DNS) security to help organizations protect applications.
Expected to improve the security of U.S. state, local, tribal, and territorial (SLTT) government organizations, the fully managed proactive domain security service will be free for members CIS Multi-State Information Sharing and Analysis Center (MS-ISAC) and Elections Infrastructure Information Sharing and Analysis Center (EI-ISAC).
Through preventing connections to harmful domains, MDBR technology aims to reduce infections with known malware and ransomware, as well as prevent phishing and other common cyber-threats. Furthermore, the technology was meant to prevent malware from communicating with the command and control (C&C) server.
Organizations looking to take advantage of MDBR simply need to point their DNS requests to Akamai’s DNS servers (MDBR is built on top of Akamai’s Enterprise Threat Protector (ETP) service). Thus, all DNS lookups are proactively compared against a list of known and suspected malicious domains.
Attempts to connect to these domains will be blocked and logged, and CIS’ security analysts will provide members with reports on these blocked requests, in addition to helping with remediation, if needed.
Any SLTT should be able to easily integrate MDBR into existing information technology (IT) infrastructure. With CIS and Akamai fully maintaining the service, organizations won’t have to worry about maintenance.
All logged data will be delivered to the CIS Security Operations Center (SOC), including details on DNS requests, either successful or blocked, which will then be used for analysis and reporting, for the betterment of the SLTT community. Each organization will also receive specific reporting and CIS will deliver regular reporting and intelligence services to SLTT members.
“MDBR will help SLTTs turbocharge their cyber defenses. It will be a key player in CIS’s growing arsenal of our defense-in-depth tool kit,” James Globe, CIS Vice President of Operations and Security Services, commented.
Minister: New Zealand Enduring Wave of Cyberattacks
3.9.20 BigBrothers Securityweek
New Zealand’s justice minister says the nation is confronting cyberattacks on an unprecedented scale, targeting everything from the stock market to the weather service.
Andrew Little said in an interview with The Associated Press on Wednesday that tracking down the perpetrators of the attacks in recent weeks would be extremely difficult, as the distributed denial of service attacks are being routed through thousands of computers.
One line of investigation is the emails sent to people in some of the targeted organizations demanding a ransom in exchange for stopping the attacks, Little said. The official advice is to never, ever pay a ransom.
Little said he’s been told that the sheer volume of data used by the attackers is unprecedented. New Zealand’s foreign spy agency, the Government Communications Security Bureau, is helping with the investigation and working to protect companies targeted in what it says appears to be part of a global campaign.
The attacks stopped share trading for up to several hours at a time over four days last week. Private company NZX, which hosts the market, said it halted trading to maintain market integrity because the attacks prevented it from publishing market announcements.
Little said the attackers had found vulnerabilities in the stock market’s operations.
“That motivated them to continue the attack, and they picked on other organizations as well,” he said.
One of those was the bank TSB, which was hit Tuesday. Chief Executive Donna Cooper said the attack disrupted some of its services but it had a plan in place and the bank remained sound.
Another bank, Westpac, said it successfully repelled an attack two weeks ago and hadn’t been hit again since. News organizations Stuff and RNZ reported they had repelled attacks over the weekend.
The weather organization MetService was also hit this week, switching its website to a stripped down version in order to stay online.
NZX said that, despite more attacks on its website, so far this week it has been able to trade uninterrupted.
“NZX has been advised by independent cyber specialists that the attacks last week are among the largest, most well-resourced and sophisticated they have ever seen in New Zealand,” chief executive Mark Peterson said in a statement.
Little said the attacks were a wake-up call to all organizations with customer-facing websites. Only a few organizations seem to have been targeted at any one time and most have been able to repel the attacks, giving him confidence the country can move past them.
Chinese Hackers Target Europe, Tibetans With 'Sepulcher' Malware
3.9.20 BigBrothers Virus Securityweek
A Chinese threat actor was observed targeting both European diplomatic entities and the Tibetan community with the same strain of malware.
Tracked as APT TA413 and previously associated with LuckyCat and ExileRAT malware, the threat actor has been active for nearly a decade, and is believed to be responsible for a multitude of attacks targeting the Tibetan community.
In a report published Wednesday, Proofpoint’s security researchers revealed a link between COVID-19-themed attacks impersonating the World Health Organization (WHO) to deliver the “Sepulcher” malware to economic, diplomatic, and legislative entities within Europe and attacks on the Tibetan community that delivered LuckyCat-linked malware and ExileRAT.
Furthermore, a July campaign targeting Tibetan dissidents was attempting to deliver the same Sepulcher malware from the same infrastructure, with some of the employed email addresses previously used in attacks delivering ExileRAT, suggesting that both campaigns are the work of TA413.
“While best known for their campaigns against the Tibetan diaspora, this APT group associated with the Chinese state interest prioritized intelligence collection around Western economies reeling from COVID-19 in March 2020 before resuming more conventional targeting later this year,” Proofpoint notes.
Targeting European diplomatic and legislative entities and economic affairs and non-profit organizations, the March campaign attempted to exploit a Microsoft Equation Editor flaw to deliver the previously unidentified Sepulcher malware.
The July campaign was employing a malicious PowerPoint (PPSX) attachment designed to drop the same malware, and Proofpoint connected it to a January 2019 campaign that used the same type of attachments to infect victims with the ExileRAT malware.
What linked these attacks, Proofpoint reveals, was the reuse of the same email addresses, clearly suggesting that a single threat actor was behind all campaigns. The use of a single email address by multiple adversaries, over the span of several years, is unlikely, the researchers say.
“While it is not impossible for multiple APT groups to utilize a single operator account (sender address) against distinct targets in different campaigns, it is unlikely. It is further unlikely that this sender reuse after several years would occur twice in a four-month period between March and July, with both instances delivering the same Sepulcher malware family,” Proofpoint says.
The security researchers believe that the global crisis might have forced the attackers to reuse infrastructure, and that some OPSEC mistakes started to occur following re-tasking.
The Sepulcher malware can conduct reconnaissance on the infected host, supports reverse command shell, and reading and writing from/to file. Based on received commands, it can gather information about drives, files, directories, running processes, and services, can manipulate directories and files, moving file source to destination, terminate processes, restart and delete services, and more.
“The adoption of COVID-19 lures by Chinese APT groups in espionage campaigns was a growing trend in the threat landscape during the first half of 2020. However, following an initial urgency in intelligence collection around the health of western global economies in response to the COVID-19 pandemic, a return to normalcy was observed in both the targets and decoy content of TA413 campaigns,” Proofpoint notes.
U.S. Voter Databases Offered for Free on Dark Web, Report
2.9.20 BigBrothers Threatpost
Some underground forum users said they’re monetizing the information through the State Department’s anti-influence-campaign effort.
Personal information for several million American voters has turned up on a Russian underground cybercrime forum, according to reports – and users are purportedly looking to monetize it using a recently launched State Department program meant to prevent election-meddling.
The personal information includes names, dates of birth, gender, physical addresses and email addresses, and election-specific data – such as when an individual registered to vote, voter registration numbers and polling stations – according to Kommersant, a Moscow-based newspaper.
The outlet reported Tuesday that several databases of voter data (including one encompassing 7.6 million voters in Michigan, and others covering between 2 million and 6 million voters each for Arkansas, Connecticut, Florida and North Carolina) turned up in an unnamed marketplace in late 2019. Now, that information is being offered for free in discussion forums by someone going by the handle Gorka9, according to Kommersant. The publication added that the hacker said the data was still valid as of this past March.
Security firm Infowatch confirmed that the databases seem authentic. A spokesperson for Infowatch said that the information could be used to mount influence campaigns bent on swaying U.S. voters towards one candidate or another — but more likely, it could be used to mount convincing phishing efforts.
“As is usual in cases like these, victims (registered voters) will need to be on the lookout for bad actors attempting to use the information gleaned from these databases to obtain even more information about their targets,” Chris Hauk, consumer privacy champion at Pixel Privacy, told Threatpost via email. “It is sad to believe that in this day and age that simply registering to exercise your right to vote can make you the target of hackers.”
Meanwhile, forum users told Kommersant that they have also been able to monetize the data through the U.S. State Department’s $10 million anti-influence program. The Rewards for Justice (RFJ) program, which is administered by the Diplomatic Security Service, is offering millions in rewards for “information leading to the identification or location of any person who works with or for a foreign government for the purpose of interfering with U.S. elections through certain illegal cyber-activities.”
One person told Kommersant that he was paid $4,000 through the program for alerting the Feds about a leaked Connecticut voter database – a claim that has not been confirmed. The State Department did not immediately respond to a request for comment.
As for how the data was obtained, one hacker told the outlet that most of the theft is carried out using server vulnerabilities that can be exploited via SQL injection, which is a method for inserting malicious code into a vulnerable, targeted database. Security researchers said that the claim is entirely plausible.
“New vulnerabilities are reported every hour and database systems are especially prone to attack due to their highly configurable and powerful interactive features,” Mark Kedgley, CTO at New Net Technologies (NNT), told Threatpost. “SQL injection is still a difficult vulnerability to test for as automated tests usually lack the knowledge of the application’s setup and operation. Encryption of data is always an unpopular route due to the heavy impact on system resources and performance. Ideally, security needs to be built in as the application is developed and then a hardened configuration applied to the database system, derived from either the CIS Benchmark or DISA STIG.”
In some cases, hacking may not even be required in order to garner the information, according to Paul Bischoff, privacy advocate with Comparitech. “It’s remarkably easy to get one’s hands on voter databases in most states,” Bischoff said via email. “Many of them are available to the public, including Michigan. Even though there are rules about how the data can be used, rules can be broken. Those who legitimately request receive voter data are responsible for securing it, and not everyone has the same standards of security. I wouldn’t be surprised if we see more voter databases in the hands of foreign threat actors before the 2020 general election.”
As a backdrop, election-meddling continues to be a security concern as the U.S. presidential election looms on the horizon. While direct hacking activity remains a concern, experts say that the bigger issue is influence campaigns bent on spreading divisiveness and disinformation — mainly through online social-media bots and troll farms. In fact, a recent Black Hat attendee survey, more than 70 percent said influence campaigns will have the greatest impact on the elections.
FBI: Ring Smart Doorbells Could Sabotage Cops
2.9.20 BigBrothers Threatpost
While privacy advocates have warned against Ring’s partnerships with police, newly unearthed documents reveal FBI concerns about ‘new challenges’ smart doorbell footage could create for cops.
The FBI is worried that Ring doorbell owners can use footage collected from their smart devices to keep tabs on police, newly uncovered documents show.
The documents – a 2019 Technical Analysis Bulletin from the FBI – was spotted by The Intercept in the BlueLeaks database, a trove of 270 gigabytes of data reportedly leaked from 200 police departments, which was released publicly in June. While unclassified, the document is “law-enforcement (LE) sensitive” according to the Feds, meaning that it has been distributed internally within the federal government and among law enforcement units, and is prohibited to those “without FBI authorization.”
The FBI document outlines how Ring surveillance footage could present new “challenges” for law enforcement. Ring owners can get an early alert if police officers are approaching their house, for instance, or the footage could give away officer locations in a standoff.
“The FBI assesses IoT devices are likely to pose new challenges to LE personnel, negatively affecting LE effectiveness and pose security challenges for LE personnel,” according to the 2019 document uncovered by The Intercept. “Most IoT devices contain sensors and cameras, which generate an alert or can be remotely accessed by the owner to identify activity in and around an owner’s property. If used during the execution of a search, potential subjects could learn of LE’s presence nearby, and LE personnel could have their images captured, thereby presenting risk to their present and future safety.”
In one 2017 incident, the FBI approached a home to issue a search warrant. The warrant subject was able to see the FBI’s presence through his smart-video doorbell, and contacted his neighbor and landlord regarding the law enforcement’s presence, the FBI said.
Access to home security camera footage could also allow users to bypass law enforcement altogether, as seen in an August 2018 incident, warned the FBI. There, homeowners posted images collected from their smart security system on social media, posting public accusations against subjects in the footage about “possible crimes” – without contacting the cops first.
The concerns of the FBI pose an ironic contrast from previous worries from privacy advocates around Amazon-owned Ring’s police partnership and what that means for surveillance and racial bias. Over the years, more than 30 consumer advocacy groups in 2019 have urged local legislators to intervene in Ring’s partnerships with law enforcement. And in 2019, Jason Kelley and Matthew Guariglia with the Electronic Frontier Foundation (EFF) also put Ring on blast, calling for the company “to immediately end the partnerships it holds” with law enforcement agencies.
Beyond Ring’s relationship with law enforcement, privacy advocates have concerns around how the smart doorbell collects and shares information. A 2020 EFF investigation found that Amazon’s Ring Doorbell app for Android is a nexus for data-harvesting, with privacy advocates alleging Ring goes so far as to silently deliver updates on Ring customer usage to Facebook, even if the Ring owner doesn’t have a Facebook account.
The FBI for its part noted that IoT devices in general have been paramount in helping assist law-enforcement efforts. For instance, last October, a Colorado man shared footage from his smart car’s motion-detecting cameras of a woman keying his car, allowing local law enforcement to identify the woman on social media.
“The FBI assesses that IoT devices very likely can be used to identify subjects of LE investigations by providing a new digital trail of evidence leading to subjects, resulting in more timely arrests,” according to the FBI document.
Facebook Nabs Russia-Linked Campaign to Fuel US Chaos
2.9.20 BigBrothers Securityweek
Facebook on Tuesday said that it caught a budding Russia-linked campaign to fuel political chaos in the US, working off a tip from the FBI in its latest take-down of coordinated inauthentic behavior at the leading social network.
The network of 13 Facebook accounts and two pages posing as journalists and targeting left-wing progressives was removed for violating a policy against "foreign interference" at the platform.
The investigation that uncovered the covert operation, which was linked to the Internet Research Agency in Russia (IRA), started with a tip from the Federal Bureau of Investigation, according to Facebook head of security policy Nathaniel Gleicher.
The network was in the early stages of building an audience, with little engagement from users, Facebook said.
"They put substantial effort into creating elaborate fictitious personas, trying to make fake accounts look as real as possible," Gleicher said while briefing reporters.
The list of topics in posts included "social and racial justice in the US and UK, NATO and EU politics, alleged Western war crimes and corruption, environmental issues, the founder of Wikileaks, tensions between Israel and Palestine, the coronavirus pandemic, criticism of fracking, French influence in Africa, the Biden-Harris campaign, QAnon, President Trump and his policies, and the US military policies in Africa.".
Unwitting freelance writers were recruited to write material to be posted online, according to Facebook.
The Facebook pages were said to be crafted to drive viewers to websites of the social network, and their operators were working diligently to get approval to run targeted ads.
"It follows a steady pattern where particularly Russian actors have gotten better at hiding who they are, but their impact is smaller and smaller and they are getting caught earlier," Gleicher said.
"These actors are caught between a rock and hard place: run a large network that gets caught quickly or run a small network that has limited reach."
- Beyond Facebook -
The campaign targeted its audience with English-language content focused heavily on a small number of political groups, including Democratic Socialists, environmentalists, and disgruntled Democrats in the US, according to an analysis by Graphika.
A consistent target of the network was left-leaning voters in Britain and the US with the potential to be dissuaded from supporting centrist leadership of the Democratic and Labour parties, Graphika determined.
The network worked to amplify a PeaceData website that posed as an independent news outlet, the analysis found.
Only about five percent of the Engiish-language articles on the website dealt primarily with the US election or candidates, but they appeared oriented to build a left-wing audience and steer it away from Democratic presidential candidate Joe Biden’s campaign, in the same way that the IRA tried to depress progressive and minority support for Hillary Clinton in 2016, according to Graphika.
The operation had a presence on Twitter and LinkedIn as well as on Facebook, according the social network analysis specialist.
Twitter said it suspended five accounts linked to Russia for "platform manipulation."
The accounts appeared to be associated with the PeaceData website and appeared to gain little traction on Twitter before being removed, according to the one-to-many messaging platform.
"Regardless of the low-level impact in this case, governments around the world must stop these practices," Twitter said in a tweet.
"They’re antidemocratic."
Twitter is blocking links to content from the PeaceData website, which could still be accessed online Tuesday.
The website began publishing in December, and the Facebook accounts were set up in May, according to Graphika.
"The network was in its infancy when it was taken down," Graphika concluded.
Hackers Attack Norway's Parliament
2.9.20 BigBrothers Securityweek
Norway's parliament said Tuesday it had been the target of a "vast" cyber attack that enabled hackers to access the emails of some lawmakers.
The hackers' identities were not immediately known.
"The parliament has recently been targetted in a vast cyber attack," the institution wrote in a statement.
"There have been intrusions in the email accounts of a few MPs and employees. Our analyses show that varying quantities of data have been downloaded," it said, providing no further details.
The website of the Storting, the single chamber parliament, was working normally on Tuesday.
The parliament's administrative director said the institution had detected "anomalies a little more than a week ago" and took steps "that were effective".
"We don't know who's behind it," Marianne Andreassen told reporters. A police report has been filed.
In its annual threat assessment published in February, Norway's domestic intelligence service PST warned of "computer network operations" which they said represented a "persistent and long-term threat to Norway".
"With no borders and no warning, a malicious actor can cause serious damage to Norwegian companies and infrastructure," PST said, adding that sensitive information could be "stolen or manipulated" and essential infrastructure "disrupted or destroyed".
In 2018, Norway arrested a Russian national suspected of gathering information on the parliament's internet network, but released him several weeks later due to lack of evidence.
At the other end of the world, the New Zealand stock exchange said it had also been the target of cyber attacks from abroad in recent days.
Iranian Hackers Target Critical Vulnerability in F5's BIG-IP
1.9.20 BigBrothers Securityaffairs
A hacking group believed to be linked to the Iranian government was observed targeting a critical vulnerability that F5 Networks addressed in its BIG-IP application delivery controller (ADC) in early July.
Tracked as CVE-2020-5902 and featuring a CVSS score of 10, the vulnerability allows remote attackers to take complete control of a targeted system. F5's BIG-IP is used by many large organizations for application acceleration, load balancing, SSL offloading, and web application firewall.
The first attacks targeting the bug were seen several days after advisories and patches were released. At the time, Positive Technologies, which discovered the bug, identified over 8,000 vulnerable devices directly exposed to the Internet.
Shortly after, attackers found ways to bypass mitigations in place for the vulnerability. At the end of July, CISA warned of adversaries exploiting the bugs in attacks on U.S. government and commercial organizations.
One threat group targeting the vulnerability, Crowdstrike notes in a blog post, is PIONEER KITTEN, an Iran-based cyber-espionage group believed to be “a contract element operating in support of the Iranian government.”
Active since at least 2017 and also tracked as PARISITE, UNC757, and FOX KITTEN, the group has been observed targeting the academic, aviation, chemical, defense, engineering, financial services, government, healthcare, insurance, media, manufacturing, consulting and professional services, retail, and technology sectors, in attacks that appear to be opportunistic in nature.
The group’s focus is on “gaining and maintaining access to entities possessing sensitive information of likely intelligence interest to the Iranian government,” Crowdstrike notes. Targets are located in Israel, Middle East North Africa (MENA), and North America.
For initial access, PIONEER KITTEN mainly relies on exploiting remote external services on assets that are accessible from the Internet. The group almost exclusively employs open-source tools in their operations.
“PIONEER KITTEN’s namesake operational characteristic is its reliance on SSH tunneling, through open-source tools such as Ngrok and the adversary’s custom tool SSHMinion, for communication with implants and hands-on-keyboard activity via Remote Desktop Protocol (RDP),” Crowdstrike reveals.
In addition to CVE-2020-5902, the adversary also exploits vulnerabilities such as CVE-2019-11510 (arbitrary file reading in Pulse Secure), CVE-2018-13379 (system file download in Fortinet FortiOS), CVE-2019-1579 (arbitrary code execution in Palo Alto Networks VPN), and CVE-2019-19781 (unauthenticated code execution in Citrix Application Delivery Controller (ADC) and Gateway).
“The widespread nature of PIONEER KITTEN’s target scope is likely a result of the adversary’s opportunistic operational model; the entities apparently of most interest to the adversary are technology, government, defense, and healthcare organizations,” Crowdstrike says.
Chinese Researcher Arrested for Destroying Evidence of Data Transfer to China
1.9.20 BigBrothers Securityweek
A Chinese national was arrested in the United States for destroying evidence of possible transfer of sensitive data to China.
The man, Guan Lei, 29, was a researcher at the University of California, Los Angeles, and was staying in the U.S. on a J-1 non-immigrant visa.
According to a criminal complaint, on July 25, the researcher was observed throwing a damaged hard drive into a trash dumpster near his residence.
Guan, who refused to allow the FBI to examine his computer, was not allowed to board a flight to China. The FBI was able to recover the damaged hard drive, but said in an affidavit that the damage to it was irreparable and that all data on it appeared “to have been removed deliberately and by force.”
The complaint also reveals that Guan was being investigated for the possible transfer of “sensitive U.S. software or technical data to China’s National University of Defense Technology (NUDT).”
Guan is also said to have denied being associated with the Chinese military – the People’s Liberation Army – when applying for a visa in 2018, as well as in interviews with federal law enforcement.
Furthermore, the complaint reveals that the researcher admitted taking part in military training, wearing military uniforms at NUDT, and having a faculty advisor in China who “was also a lieutenant general in the PLA who developed computers used by the PLA General Staff Department, the PLA General Armament Department, Air Force, military weather forecasts, and nuclear technology.”
The affidavit supporting the complaint also notes that NUDT is believed to be procuring items of U.S. origin for the building of “supercomputers with nuclear explosive applications.” The U.S. Department of Commerce placed the university on its Entity List for nuclear nonproliferation reasons.
According to the complaint, not only did Guan destroy the hard drive, but also hid digital storage devices from investigators and lied about having contact with the Chinese consulate during his stay in the U.S.
Guan was ordered detained. An arraignment was scheduled for Sept. 17, 2020. Guan is accused of destruction of evidence, an offense that carries a statutory maximum sentence of 20 years in federal prison.
France Won't Ban Huawei But Favors European 5G Systems
1.9.20 BigBrothers Securityweek
French President Emmanuel Macron says France is not excluding Chinese telecom giant Huawei from its upcoming 5G telecommunication networks but favors European providers for security reasons.
The French leader spoke after meeting with visiting Chinese Foreign Minister Wang Yi in Paris on Friday.
Macron said he had already told Chinese President Xi Jinping about his preference for companies such as Ericsson and Nokia, saying “you would do the same as me.”
“It’s normal that ... we want a European solution” because of the importance of “the security of our communication,” Macron told reporters.
France’s information security agency ANSSI said last month that Huawei Technologies Ltd. will not be banned from France, but French telecoms operators that buy its technology will only be able to get licenses limited to eight years. The French government has said it will restrict Huawei’s 5G technology to protect military bases, nuclear installations and other sensitive sites.
Huawei is at the center of a major dispute between Washington and Beijing over technology and security. U.S. officials say Huawei is a security risk, which the company denies, and are lobbying European and other allies to avoid its technology as they upgrade to next-generation networks.
China, meanwhile, is trying to encourage Europeans to guarantee access to their markets for Chinese telecom and technology companies.
US DoJ wants the funds stored by North Korea in 280 BTC and ETH
30.8.20 BigBrothers Cryptocurrency Securityaffairs
US DoJ filed a civil forfeiture complaint to seize 280 Bitcoin (BTC) and Ethereum (ETH) accounts containing funds allegedly stolen by North Korea-linked hackers
The US DoJ has filed a civil forfeiture complaint with the intent to seize control over 280 Bitcoin and Ethereum accounts that are believed to be holding funds which are the proceeds of hacking campaigns conducted by North Korea-linked APT groups against two cryptocurrency exchanges.
The complaint did not name the hacked exchanges, it only reports two attacks that took place in July 1, 2019, and September 25, 2019.
The DoJ reveals that the funds stolen in the two hacks, along with $250 million stolen from another exchange in 2018, were all laundered by the same Chinese Over-The-Counter (OTC) traders.
The first attack carried out by North Korean hackers resulted in the theft of $272,000 worth of alternative cryptocurrencies and tokens, including Proton Tokens, PlayGame tokens, and IHT Real Estate Protocol tokens. In the second attack, threat actors stole $2.5 million worth of multiple virtual currencies.
North Korean hackers used “chain hopping” to launder the stolen funds, this means that they have used the stolen funds to buy other cryptocurrencies, for example, converting Stellar to Ethereum.
“Over the subsequent months, the funds were laundered through several intermediary addresses and other virtual currency exchanges. In many instances, the actor converted the cryptocurrency into BTC, Tether, or other forms of cryptocurrency – a process known as “chain hopping” – in order to obfuscate the transaction path.” reads the press release published by DoJ. “As detailed in the pleadings, law enforcement was nonetheless able to trace the funds, despite the sophisticated laundering techniques used.”
The analysis of the blockchain allowed the US officials to follow the stolen funds from two hacked exchange back to the 280 crypto-currency accounts.

Many of these 280 addresses are currently frozen as a result of the investigation conducted immediately after the hacks.
“Today’s complaint demonstrates that North Korean actors cannot hide their crimes within the anonymity of the internet. International cryptocurrency laundering schemes undermine the integrity of our financial systems at a global level, and we will use every tool in our arsenal to investigate and disrupt these crimes,” said Special Agent in Charge Emmerson Buie Jr. of the FBI’s Chicago Field Office. “The FBI will continue to impose risks and consequences on criminals who seek to undermine our national security interests.”
In September 2019, the US Treasury put sanctions on three North Korea-linked hacking groups, the Lazarus Group, Bluenoroff, and Andarial.
The groups are behind several hacking operations that resulted in the theft of hundreds of millions of dollars from financial institutions and cryptocurrency exchanges worldwide and destructive cyber-attacks on infrastructure. Lazarus Group is also considered the threat actors behind the 2018 massive WannaCry attack.
According to the Treasury, the three groups “likely” stole $571 million in cryptocurrency from five Asian exchanges in 2017 and 2018.
Intelligence analysts believe the groups are under the control of the Reconnaissance General Bureau, which is North Korea’s primary intelligence bureau.
FBI warns of an increase in online romance scams
30.8.20 BigBrothers Securityaffairs
The FBI is warning of online romance scams and related financial losses, overall losses associated with those complaints exceeded $475 million.
The Federal Bureau of Investigation warns of online romance scams (also known as confidence fraud), an ongoing criminal activity that continues to cause large financial losses along with emotional effects with unpredictable consequences.
Crooks behind romance scams use fake online identities to establish a contact with the potential victims and gain their trust.
The main hunting spots for these scammers are the dating websites and the social media platforms, they take advantage of people looking for romantic partners with the goal of financially exploiting the victims.
“According to the FBI’s Internet Crime Complaint Center (IC3), which provides the public with a means of reporting Internet-facilitated crimes, romance scams result in greater financial losses to victims when compared to other online crimes.” reads the alert published by the FBI. “In 2019, almost 20,000 complaints categorized as romance scams were reported to IC3 (about 1,000 more than the previous year), and the losses associated with those complaints exceeded $475 million.”
Upon establishing an online romantic relationship, crooks attempt to manipulate the victims into sending them money or other sensitive or financial information that could be used later in other fraudulent activities..
According to the FBI’s 2019 Internet Crime Report the losses associated with those complaints exceeded $475 million.

The trend related to financial losses is worrisome, experts continue to observe a yearly increase in the number of victims’ reports. The financial losses associated with this kind of scams were more than $211 million in 2017 and more than $362 million in 2018.
In April, the FBI issued another alert to warn of fraudsters that were taking advantage of the uncertainty and fear surrounding the COVID-19 pandemic to steal money from the victims and in some cases using them as a money mule.
In August 2019, the FBI published a security advisory to warn of threat actors using online dating sites to conduct confidence/romance scam and recruit money mules.
If you develop a romantic relationship with someone you meet online, consider the following recommendations provided by the FBI’s alert.
Research the person’s photo and profile using online searches to see if the material has been used elsewhere.
Go slow and ask questions.
Beware if the individual seems too perfect or quickly asks you to leave a dating service or social media site to go “offline.”
Beware if the individual attempts to isolate you from friends and family or requests.
Beware if the individual promises to meet in person, but then always comes up with an excuse why he or she can’t. If you haven’t met the person after a few months, for whatever reason, you have good reason to be suspicious.
Never send money to anyone you don’t know personally.
If you believe you are a victim of a romance scam, stop all contact immediately and file a complaint online at ic3.gov.
Justice Dept: North Korean Hackers Stole Virtual Currency
28.8.20 BigBrothers Securityweek
North Korean hackers stole millions of dollars from virtual currency accounts and then laundered the stolen funds in hopes of making the crime untraceable, according to a Justice Department civil forfeiture complaint filed Thursday.
The complaint, filed in Washington’s federal court, seeks the forfeiture of 280 virtual currency accounts. It comes months after Justice Department officials accused hackers from North Korea of stealing nearly $250 million worth of virtual currency and charged two Chinese hackers with laundering more than $100 million from the hack.
Acting Assistant Attorney General Brian Rabbitt of the Justice Department’s criminal division said Thursday’s new case “publicly exposes the ongoing connections between North Korea’s cyber-hacking program and a Chinese cryptocurrency money laundering network.”
In the latest complaint, prosecutors laid out what they said were persistent North Korean efforts to attack financial institutions and cryptocurrency exchanges, which are favored for illicit transactions because they are perceived as hard to trace.
In one of the episodes they describe, a hacker gained access to the virtual currency wallets of a U.S.-based company as well as funds held on other platforms, and stole nearly $2.5 million and laundered it through more than 100 accounts.
The case is the latest Justice Department action targeting North Korea over either cyber offenses or sanctions violations. In 2018, federal prosecutors charged a computer programmer working for the North Korean government with cyberattacks that targeted Sony Pictures Entertainment and unleashed the WannaCry ransomware virus that infected computers in 150 countries and crippled parts of the British health care system.
The U.S. Cyber Command is among the federal agencies that participated in the investigation. On Wednesday, it disclosed samples of malicious software that officials said North Korean hackers have been using to target a wide variety of victims.
Assistant Attorney General John Demers, who heads the Justice Department’s national security division, said prosecutors are committed to publicly calling out foreign adversaries for cyber crime.
“Although North Korea is unlikely to stop trying to pillage the international financial sector to fund a failed economic and political regime, actions like those today send a powerful message to the private sector and foreign governments regarding the benefits of working with us to counter this threat,” he said in a statement.
Iranian Hackers Target Academic Researcher via WhatsApp, LinkedIn
28.8.20 BigBrothers Securityweek
The Iran-linked hacking group known as Charming Kitten recently switched to WhatsApp and LinkedIn to conduct phishing attacks, Clearsky security researchers reveal.
Active since at least 2011, the adversary is also tracked as Ajax Security Team, APT35, ITG18, NewsBeef, Newscaster, and Phosphorus, and was previously observed targeting a U.S. presidential candidate, media organizations, government officials, and prominent expatriate Iranians, using an updated spear phishing technique.
In July, only a couple of months after Google revealed that the Iranian hackers targeted the WHO, the threat actor accidentally leaked 40Gb of data. In early 2020, the hackers were observed posing as journalists in a phishing campaign that targeted at least five individuals around the world.
Now, security firm Clearsky reveals that the adversary continues phishing attacks in which they impersonate journalists, this time from ‘DeutscheWelle’ and the ‘Jewish Journal’, and it employed both email and WhatsApp to approach the target and trick them into clicking on a malicious link. Fake LinkedIn profiles were used to gain victims’ trust.
The most recent campaign targeted Israeli scholars (via their institutional email account), and US government employees. The hackers used a personalized URL, tailored to the victim’s email address, to trick them into accessing the malicious link, and also attempted to send a malicious ZIP file to the victim.
“Clearsky alerted ‘Deutsche Welle’ about the impersonation and the watering hole in their website. A ‘Deutsche Welle’ representative confirmed that the reporter which Charming Kitten impersonated, did not send any emails to the victim nor any other academic researcher in Israel in the past few weeks,” the security firm says.
As part of the campaign, the attackers used a well-developed LinkedIn account in support of their email spear-phishing attacks, and showed willingness to speak to the victim on the phone, over WhatsApp, using a legitimate German phone number.
The hackers approached Israeli researchers from Haifa and Tel Aviv Universities, to ask them to participate in a webinar about Iran and other subjects, nominating the victim as the main speaker in the webinar. The attackers sent multiple, repeated messages, until the victim responded.
The Charming Kitten attackers messaged the victim repeatedly for ten days, claiming they were interested in engaging in a direct phone call, and attempted to lure the victim into “activating their account” on the site "Akademie DW" (their phishing page).
“If the victim is not willing to share their personal phone number, the attacker will send him a message from the fake LinkedIn account. This message will contain a promise that the webinar is secured by Google, as they sent to the victim on the tenth day,” Clearsky says.
In another attack, the hackers created a fake LinkedIn account for ‘Helen Cooper’, a senior researcher at Hudson Institute and sent email messages that contained either a malicious link or a malicious attachment. Sending malicious files via email is uncommon for this threat actor.
North Korean Hackers Are Back at Targeting Banks
28.8.20 BigBrothers Securityweek
Since February 2020, North Korean state-sponsored hackers have been targeting banks in multiple countries, the Cybersecurity and Infrastructure Security Agency (CISA), the Department of the Treasury, the Federal Bureau of Investigation (FBI) and U.S. Cyber Command (USCYBERCOM) warn in a joint advisory.
Active since at least 2014, and referred to as BeagleBoyz, the hacking group is responsible for numerous attacks on financial institutions worldwide, such as the $81 million heist from a Bangladeshi bank, the FASTCash ATM cash-out scheme, and attacks on cryptocurrency exchanges.
BeagleBoyz, the advisory notes, represents a subset of HIDDEN COBRA, the cyber-activity the United States associates with North Korea hackers, and is also known as Lazarus, APT38, Bluenoroff, and Stardust Chollima.
Since 2015, the group has been abusing compromised bank-operated SWIFT system endpoints and has attempted to steal an estimated $2 billion to date.
“The BeagleBoyz’s bank robberies pose severe operational risk for individual firms beyond reputational harm and financial loss from theft and recovery costs. […] Equally concerning, these malicious actors have manipulated and, at times, rendered inoperable, critical computer systems at banks and other financial institutions,” the joint advisory reads.
The US notes that the BeagleBoyz often leave anti-forensic tools on the computer networks of victim institutions, that they deployed a wiper against a bank in Chile in 2018, and also warns that the hackers’ ability to “exploit critical banking systems may erode confidence in those systems and presents risks to financial institutions across the world.”
The hackers performed fraudulent ATM withdrawals in multiple countries, including the United States, affecting over 30 countries in total.
Since the FASTCash scheme was publicly detailed in October 2018, the hackers have updated their capability to perform the attacks. They have developed malware for the targeting of switch applications on Windows servers, and also expanded the campaign to target interbank payment processors.
Following initial intrusion, the hackers selectively exploit systems within the compromised environment, and employ a variety of methods to run code, maintain access to the compromised systems, leverage privileges, and evade defenses.
Once inside the network of a financial institution, the adversaries look for the SWIFT terminal and for the server where the organization’s payment switch application is stored. They also map out the network to learn about the available systems and move laterally, and perform reconnaissance and administration operations.
The BeagleBoyz use a variety of malware in their attacks, including the CROWDEDFLOUNDER and HOPLIGHT remote access Trojans (RATs), which allow for remote access and data exfiltration, ECCENTRICBANDWAGON for keylogging, and the VIVACIOUSGIFT and ELECTRICFISH network proxy tunneling tools.
In attacks on cryptocurrency exchanges, the hacking group prefers the COPPERHEDGE full-featured RAT, which allows them to run arbitrary commands, perform information harvesting, or exfiltrate data, the U.S. agencies said.
After gaining access to SWIFT terminals and switch application servers, the threat actor monitors the system to gain knowledge of configurations and legitimate use patterns, and then performs illicit transactions that allow for fraudulent ATM cash outs.
The FASTCash malware, which can intercept financial request messages and inject fraudulent messages, is used in these attacks against both UNIX and Windows machines. The Windows variant reveals the use of modified publicly available code for the hashmaps and hook functions and the parsing of ISO 8583 messages.
FASTCash for Windows, the advisory reveals, was designed to inject itself into running software and take control of send and receive functions, to manipulate ISO 8583 messages. Two variants of the malware were observed, supporting ASCII encoding and Extended Binary Coded Decimal Interchange Code (EBCIDC) encoding, respectively.
The U.S. provides full technical details on both FASTCash and FASTCash for Windows, and has included in the joint advisory various recommendations for financial institutions and other organizations looking to keep their systems protected from the BeagleBoyz group.
Elon Musk Confirms Russian Hackers Attempted to Recruit Tesla Employee
28.8.20 BigBrothers Securityweek
The failed attempt by Russian hackers to recruit an employee to install malware onto an enterprise network was targeting electric car maker Tesla, a tweet from Elon Musk confirms.
The scheme was publicly detailed earlier this week, when the U.S. Department of Justice announced the arrest of Egor Igorevich Kriuchkov, 27, of Russia, who offered $1 million to an employee of an unnamed U.S. company in Nevada in exchange for installing malware onto the organization’s systems.
The targeted company, Teslarati revealed on Thursday, was Tesla. Replying to a Teslarati tweet, Elon Musk has confirmed the attack.
According to the criminal complaint the DoJ made public earlier this week, Tesla’s employee was approached by Kriuchkov in July, and the two met socially in early August, after Kriuchkov arrived in Nevada on a tourist visa.
The employee, Teslarati says, is a Russian-speaking, non-US citizen working at Tesla-owned lithium-ion battery and electric vehicle subassembly factory Giga Nevada, also referred to as Gigafactory 1.
A few days after meeting the employee, Kriuchkov revealed his true intentions: he asked the employee to install malware onto Tesla’s network, offering between $500,000 and $1,000,000 for that. The malware would provide Kriuchkov and co-conspirators with the ability to steal information from Tesla.
The hackers were planning on exfiltrating information from Tesla’s network during a distributed denial of service (DDoS) attack that was supposed to draw the attention of security teams within the company.
The employee, however, warned Tesla and the company contacted the FBI. Details of the planned attack were revealed in several more meetings, which were surveilled by the FBI. Kriuchkov was arrested on August 22.
FBI arrested a Russian national for recruiting employee of US firm to plant malware
27.8.20 BigBrothers Securityweek
FBI authorities arrested a Russian national in the U.S. after attempting to recruit an employee at a targeted company to plant a malware.
US authorities arrested the Russian national Egor Igorevich Kriuchkov (27) after attempting to recruit an employee at a targeted company to plant a piece of malware. The man was arrested on August 22 and appeared in court on August 24. Kriuchkov offered $1 million to the unfaithful employee of the US company.
“Egor Igorevich Kriuchkov, 27, a citizen of Russia, was charged in a complaint with one count of conspiracy to intentionally cause damage to a protected computer. He was arrested on Aug. 22, 2020, in Los Angeles and had his initial appearance before U.S. Magistrate Judge Alexander F. MacKinnon in U.S. District Court in Los Angeles, California, who ordered Kriuchkov detained pending trial.” states the DoJ’s press release.
“According to the complaint and statements made in court, from about July 15, 2020 to about Aug. 22, 2020, Kriuchkov conspired with associates to recruit an employee of a company to introduce malware.”
Kriuchkov conspired with other criminals to recruit the employee of an unnamed company in Nevada.
Kriuchkov entered the United States on July 28 using his Russian passport and a tourist visa.
The Russian man and his co-conspirators were planning to exfiltrate data from the network of the company and blackmail the organization to leak stolen data, unless the company paid a ransom demand.
Kriuchkov exposed his plan to the employee after multiple meeting, he also told the employee that the previous victim organizations had paid millions of dollars to avoid the public release of the stolen data.
“He explained the malware attacks the systems in two ways. Firstly, the malware appears to be an external DDoS attack. This attack occupies the
company’s computer security staff and conceals the second attack.” complete the reason. “The second attack exfiltrates data from the computer network and into the possession of the “group.” The “group” later contacts the company and threatens to make the data public if the company does not pay a large ransom.”
The crooks were planning to launch a DDoS attack as a diversionary tactic, then to exfiltrate the data.
The Russian national provided the employee with a burner phone, instructed him to communicate through a TOR browser, to set up a Bitcoin wallet to receive payment. The man asked the employee to leave the burner phone in airplane mode until the money transfer was completed.
The FBI was able to physically witness some of the meetings between Kriuchkov and the employee.
“After being contacted by the FBI, Kriuchkov drove overnight from Reno, Nevada, to Los Angeles. Kriuchkov asked an acquaintance to purchase an airline ticket for him in an attempt to fly out of the country.” concludes the DoJ. “The charges and allegations contained in a complaint are merely accusations. The defendant is presumed innocent unless and until proven guilty beyond a reasonable doubt in a court of law.”
Ghanaian Extradited to U.S. for Cybercrimes That Caused Millions in Losses
27.8.20 BigBrothers Securityweek
A man from the African country of Ghana was recently extradited to the United States over his role in various types of cybercrime schemes that authorities say caused millions of dollars in losses.
The Ghanaian, 27-year-old Maxwell Peter, was charged along with several other individuals, back in 2017, by a federal grand jury with wire fraud, computer fraud, money laundering and identity theft.
According to prosecutors, the suspect was part of an Africa-based cybercrime group involved in business email compromise (BEC), romance scams, gold-buying scams, fraudulent-check scams, advance-fee scams, and credit card scams.
In one BEC attack, the cybercriminals hacked into the systems of a Memphis-based real estate firm back in 2016. They used spoofed email addresses and VPNs to trick the company into wiring funds to their US-based money mules, which forwarded the money to Africa.
As for the other scams, the Justice Department said, “The indictment alleges that the proceeds of these criminal activities, both money and goods, were shipped and/or transferred from the United States to locations in Africa through a complex network of both complicit and unwitting individuals that had been recruited through the various Internet scams. The defendant is specifically alleged to have created and used the alias ‘Sandra Lin’ in furtherance of these crimes.”
While some of the individuals involved in these schemes are still at large, seven others have already been prosecuted. Some of the suspects have been sentenced to years in prison, while others await sentencing. One man’s trial is underway.
Russian Arrested After Offering $1 Million to U.S. Company Employee for Planting Malware
27.8.20 BigBrothers Thehackernews
Hackers always find a way in, even if there's no software vulnerability to exploit.
The FBI has arrested a Russian national who recently traveled to the United States and offered $1 million in bribe to an employee of a targeted company for his help in installing malware into the company's computer network manually.
Egor Igorevich Kriuchkov, 27-year-old, entered the United States as a tourist and was arrested in Los Angeles after meeting with the unnamed employee of an undisclosed Nevada-based company numerous times, between August 1 to August 21, to discuss the conspiracy.
"On or about July 16, EGOR IGOREVICH KRIUCHKOV used his WhatsApp account to contact the employee of victim company and arranged to visit in person in the District of Nevada," the court documents say.
"On or about July 28, EGOR IGOREVICH KRIUCHKOV entered the United States using his Russian Passport and a B1/B2 tourist visa."
Kriuchkov also asked the employee to participate in developing tailored malware by sharing information about the company's infrastructure.
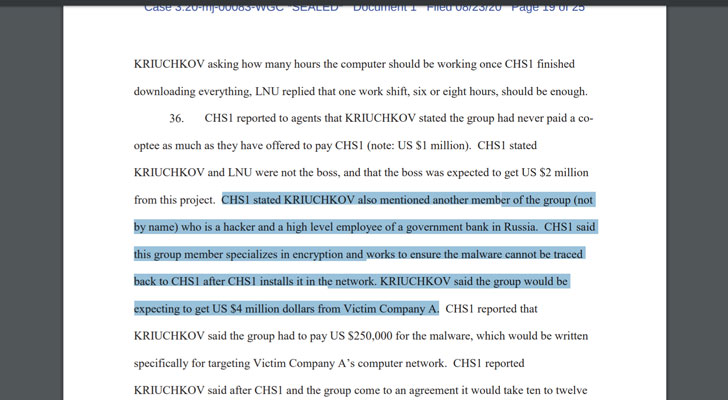
According to court documents released by the US Justice Department, the malicious software Kriuchkov asked to install aims to extract data from the company's network, allowing attackers to threaten it later to make the information public unless it pays a ransom.
Kriuchkov and his co-conspirators in Russia promised the employee to pay $1 million in Bitcoins after successfully planting the said malware and offered to launch a DDoS attack on the company's network to divert attention from the malware.
"If CHS1 [employee] agreed to this arrangement, the group would provide the malware to CHS1 [employee] in either a thumb drive to be inserted into a computer's USB drive or an email with an attachment containing malware."
"The unidentified co-conspirator discussed various means by which to pay the employee, including payments using cryptocurrency, a guarantor security deposit, or cash."
"After being contacted by the FBI, Kriuchkov drove overnight from Reno, Nevada, to Los Angeles. Kriuchkov asked an acquaintance to purchase an airline ticket for him in an attempt to fly out of the country," the United States agencies say.
After getting arrested by the FBI, who was conducting physical surveillance of Kriuchkov and his meetings, he listed prior companies the gang had targeted and also revealed that each of these targeted companies had a person working at those companies who installed malware on behalf of the gang.
To be noted, it's quite possible that a few high-profile ransomware and data breach attacks might have been executing in the same way by conspiring with the insiders.
Kriuchkov has been charged with one count of conspiracy to cause damage to a protected computer intentionally.
CISA Details Strategy for Secure 5G Deployment
26.8.20 BigBrothers Securityweek
The U.S. Department of Homeland Security’s (DHS) Cybersecurity and Infrastructure Security Agency (CISA) has published details on its strategy for the secure deployment of 5G networks within the country.
The fifth-generation (5G) of wireless technology is expected to bring numerous benefits, including higher data rates, low latency, and high network capacity, thus allowing for advancements in fields such as smart cities, autonomous vehicles, and much more.
Initially, 5G will operate on a non-standalone (NSA) network, but should transition to standalone (SA) 5G within several years, allowing users to take full advantage of the benefits the technology brings along.
“5G networks and future communications technologies (e.g., SDN, network slicing, edge computing) will transform the way we communicate, introducing a vast array of new connections, capabilities, and services. However, these developments introduce significant risks that threaten national security, economic security, and impact other national and global interests,” CISA says.
Last year, over 30 countries developed The Prague Proposals, a document that identifies recommendations on 5G roll-out, which the US used to develop the National Strategy to Secure 5G, a document that details the manner in which the U.S. will secure 5G infrastructure domestically and abroad.
CISA’s own 5G strategy aligns with this document, providing information on five strategic initiatives aimed at ensuring that secure and resilient 5G infrastructure is being deployed.
“Each of the strategic initiatives address critical risks to secure 5G deployment, such as physical security concerns, attempts by threat actors to influence the design and architecture of the network, vulnerabilities within the 5G supply chain, and an increased attack surface for malicious actors to exploit weaknesses,” the agency explains.
The five strategies are centered around the development of 5G policy and standards, increasing awareness on 5G supply chain risks and promoting security measures, securing existing infrastructure to pave the way for future 5G deployments, encouraging innovation to foster trusted 5G vendors, and analyzing use cases and detailing risk management strategies.
Each with its own set of objectives, these strategies are meant to ensure that threat actors won’t be able to influence 5G networks at an architectural level, that vulnerabilities at the supply chain level are prevented or addressed, that 5G deployments are secure, that there are enough vendors in the 5G marketplace to ensure competition, and that any security issues introduced by 5G are understood.
“With increased capabilities like faster download speeds and ultra-reliable connectivity, 5G networks will spark an industrial revolution that will enable the development of many new and enhanced services like autonomous vehicles, smart cities, augmented reality, and remote surgery. Given the potential for various applications and reliance of the network for future infrastructure, the stakes for safeguarding the network against these vulnerabilities could not be higher,” CISA concludes.
The agency, which says it will focus on ensuring that established critical infrastructure sector partnerships will be used for 5G deployments, also published an infographic to help easily understand the benefits and risks associated with 5G.
Military's Top Cyber Official Defends More Aggressive Stance
26.8.20 BigBrothers Securityweek
The U.S. military’s top cyber official is defending the government’s shift toward a more aggressive strategy in cyberspace, saying the mission has evolved over the last decade from “a reactive and defensive posture” to keep pace with sophisticated threats.
Gen. Paul Nakasone, the commander of U.S. Cyber Command and the director of the National Security Agency, says in a piece being published Tuesday by the magazine Foreign Affairs that the military’s cyber fighters are increasingly prepared to engage in combat with online adversaries rather than wait to repair networks after they’ve been penetrated.
“We learned that we cannot afford to wait for cyber attacks to affect our military networks. We learned that defending our military networks requires executing operations outside our military networks. The threat evolved, and we evolved to meet it,” wrote Nakasone in a piece co-authored with Michael Sulmeyer, his senior adviser.
As an example, Nakasone cited a mission from last October in which Cyber Command dispatched an elite team of experts to Montenegro to join forces with the tiny Balkan state targeted by Russia-linked hackers. The “hunt forward” mission helped protect an ally but was also an opportunity for the U.S. to improve its own cyber defenses before the 2020 election, Nakasone wrote.
The proactive strategy is a change from a decade ago when Cyber Command was first established in the wake of a punishing cyber attack on the Defense Department’s classified and unclassified networks. Cyber Command, created in 2010 to protect U.S. military networks, was initially more focused on “securing network perimeters.”
In recent years, though, Cyber Command has gone on the offensive, as 68 cyber protection teams “proactively hunt for adversary malware on our own networks rather than simply waiting for an intrusion to be identified,” Nakasone said. It’s also doing more to combat adversaries on an ongoing basis and to broadly share information about malicious software it uncovers to make it a less effective threat.
“Some have speculated that competing with adversaries in cyberspace will increase the risk of escalation — from hacking to all-out war. The thinking goes that by competing more proactively in cyberspace, the risk of miscalculation, error, or accident increases and could escalate to a crisis,” Nakasone wrote.
He said that while Cyber Command takes those concerns seriously, “We are confident that this more proactive approach enables Cyber Command to conduct operations that impose costs while responsibly managing escalation. In addition, inaction poses its own risks: that Chinese espionage, Russian intimidation, Iranian coercion, North Korean burglary, and terrorist propaganda will continue unabated.”
Cybercriminal greeners from Iran attack companies worldwide for financial gain
24.8.20 BigBrothers Securityaffairs
Group-IB has detected financially motivated attacks carried out in June by newbie threat actors from Iran.
The attackers used Dharma ransomware and a mix of publicly available tools to target companies in Russia, Japan, China, and India. All the affected organizations had hosts with Internet-facing RDP and weak credentials. The hackers typically demanded a ransom between 1-5 BTC. The newly discovered hacker group suggests that Iran, which has been known as a cradle of state-sponsored APT groups for years, now also accommodates financially motivated cybercriminals.
Group-IB researchers have recently observed increased activities around Dharma ransomware distribution. Dharma, also known as Crysis, has been distributed under a ransomware-as-a-service (RaaS) model at least since 2016. Its source code popped up for sale in March 2020 making it available to a wider audience. During an incident response engagement for a company in Russia, Group-IB’s DFIR team established that Persian-speaking newbie hackers were behind a new wave of Dharma distribution. Even though the exact number of victims is unknown, the discovered forensic artifacts allowed to establish the geography of their campaigns and the toolset, which is far behind the level of sophistication of big league Iranian APTs.
It was revealed that the operators scanned ranges of IPs for hosts with Internet-facing RDP and weak credentials in Russia, Japan, China, and India. To do so, they used a popular software called Masscan – the same technique was employed by Fxmsp, an infamous seller of access to corporate networks. Once vulnerable hosts were identified, the attackers deployed NLBrute to brute-force their way into the system and to check the validity of obtained credentials on other accessible hosts in the network. In some attacks, they attempted to elevate privileges using exploit for CVE-2017-0213.
Interestingly, the threat actors likely didn’t have a clear plan on what to do with the compromised networks. Once they established the RDP connection, they decide on which tools to deploy to move laterally. For instance, to disable built-in antivirus software, the attackers used Defender Control and Your Uninstaller. The latter was downloaded from Iranian software sharing website – the Google search query in Persian language “دانلود نرم افزار youre unistaller” was discovered in the Chrome artifacts. Other tools were downloaded by the attackers from Persian-language Telegram channels when they were already present in the network.
To scan for accessible hosts in the compromised network, threat actor used Advanced Port Scanner – another publicly available tool. After the network reconnaissance activities were completed, the adversary used collected information to move laterally through the network using the RDP protocol. The end goal of the attackers was to drop and execute a variant of Dharma ransomware: the adversary connected to the targeted hosts, dropped Dharma executable, and executed it manually. On average, the ransom demand was between 1-5 BTC.
“The fact Dharma source code has been made widely available led to the increase in the number of operators deploying it,” said Oleg Skulkin, senior DFIR analyst at Group-IB. “It’s surprising that Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage. Despite that these cybercriminals use quite common tactics, techniques and procedures they have been quite effective. Therefore, we believe it’s important to provide some recommendations on how to protect against them and give a complete outline of the MITRE ATT&CK mapping.”
The pandemics exposed a great number of vulnerable hosts with many employees working from homes and the vector became increasingly popular among cybercriminals. Therefore, the default RDP port 3389 should be edited by changing it to any other. As the attackers usually need several attempts to brute force passwords and gain access to the RDP, it is important to enable account lockout policies by limiting the number of failed login attempts per user. Threat intelligence solutions enable organizations to mitigate risks and further damage by quickly identifying stolen data and tracking down the source of the breach, while specialized threat detection systems allow to discover unwanted intrusions, traffic anomalies within the corporate network, and attempts to gain unauthorized access to any data.

CISA, FBI Alert Warns of Vishing Campaign
24.8.20 BigBrothers Securityweek
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have issued an alert to warn of a voice phishing (vishing) campaign targeting the employees of multiple organizations.
As part of the attacks, which started in mid-July, adversaries were attempting to gain access to employee tools via phishing phone calls. Once they were in the possession of credentials, the attackers would access the databases of victim companies to harvest information on their customers and conduct further attacks.
“The monetizing method varied depending on the company but was highly aggressive with a tight timeline between the initial breach and the disruptive cash-out scheme,” the two agencies reveal.
In preparation of the attacks, the adversaries registered bogus domains and created fake pages mimicking the internal login pages for virtual private networks (VPNs) at the targeted companies. These pages were also meant to bypass multi-factor authentication methods by capturing two-factor authentication (2FA) codes or one-time passwords (OTP).
To ensure they were successful, the attackers used Secure Sockets Layer (SSL) certificates for the bogus domains, along with various domain naming schemes, to trick victims into believing they were accessing support, ticket, or employee websites within their organizations.
According to the two agencies, the attackers used social media, recruiter and marketing tools, open-source research, and publicly available background check services to harvest information on employees at the targeted organizations, including their names, addresses, and phone numbers, along with information on their position and duration at the company.
Using unattributed Voice over Internet Protocol (VoIP) numbers and spoofing the phone numbers of offices and employees within the victim company, the attackers then started calling the employees, attempting to trick them into revealing their VPN login information by accessing a new VPN link.
“The actors used social engineering techniques and, in some cases, posed as members of the victim company’s IT help desk, using their knowledge of the employee's personally identifiable information—including name, position, duration at company, and home address—to gain the trust of the targeted employee,” the alert reads.
Once the employees revealed their login information, the adversaries used it in real-time to access corporate tools. In some cases, the employees approved the 2FA or OTP prompts, while in others SIM-swap attacks were used to bypass the additional authentication factor.
Leveraging the fraudulently obtained access, the attackers gathered additional information on victims, or attempted to steal funds using various methods.
The campaign was successful mainly because of the mass shift toward working from home during the COVID-19 pandemic, which led to an increase in the use of corporate VPN. Similar campaigns observed prior to the pandemic exclusively targeted telecommunications and Internet service providers.
To stay protected, organizations are advised to restrict VPN connections to managed devices only, restrict VPN access hours, monitor applications for unauthorized access, use domain monitoring to identify phishing domains, improve 2FA and OTP messaging, and educate employees on vishing and other phishing techniques.
Grandoreiro campaign impersonates Spanish Agencia Tributaria
24.8.20 BigBrothers Securityaffairs
Operators of Grandoreiro Latin American banking trojan have launched a new campaign using emails posing as the Agencia Tributaria in order to infect new victims.
Operators behind the Grandoreiro banking trojan, which is popular in Latin America, have been using emails posing as the Agencia Tributaria to trick victims into installing the malware.
The campaign began on August 11th, 2020, when many many Spanish people receiving messages claiming to be from the Agencia Tributaria. The emails attempted to trick users into believing they were a communication from the tax agency, the messages used sender info like “Servicio de Administración Tributaria” and come from the email address contato@acessofinanceiro[.]com.
The message includes a link that points to a ZIP archive that claims to contain a digital tax receipt and inform the users that they have to fill a document to be submitted to the Agencia Tributaria along with a fee to pay.
“Although the message offers no guarantee of being an official communication, it is likely that some recipients have been tricked into downloading the linked ZIP file via the provided link.” reads the analysis published by ESET.
“The link redirects to a domain that was registered on the same day, August 11. However, looking at the information provided by whois – a service that provides identifying information about domain name registrants – the registrant’s country is listed as Brazil, which could perhaps indicate the whereabouts of the operators of this campaign.”
The researchers noticed other Latin American banking trojan campaigns in the same period, some of the malware distributed was Mekotio.
The malicious file has been hosted by threat actors either on a compromised domain or in a cloud storage service like Dropbox. In the case of the cloud storage, the link points to a Dropbox folder containing the ZIP file.
“This ZIP payload contains an MSI file and a GIF image. Homing in on the properties of the MSI file reveals that it was compiled the day before, August 10. It should also be noted that the ZIP filename has the country code “ES” at the end. ESET researchers also detected other files in Dropbox with very similar sizes and dates of compilation, but with different country codes – possibly indicating that this campaign is targeting victims in various countries at the same time.” continues ESET.
The MSI file is as a variant of Win32/TrojanDownloader.Delf.CYA, which is a downloader employed in other campaigns spreading Latin American banking trojans, including Grandoreiro, Casbaneiro, Mekotio and Mispadu.
“Impersonating Spain’s Agencia Tributaria or other similar agencies is an old trick in the attackers’ book that has been used for a long time, especially during tax season. However, even when high season for income taxes has already concluded, this year has seen this technique being used by Latin American banking trojans and other threats specialized at stealing data.” concludes ESET.
Hackers are targeting teleworkers with vishing campaign, CISA and FBI warn
21.8.20 BigBrothers Securityaffairs
The FBI and CISA issued a joint alert to warn teleworkers of an ongoing vishing campaign targeting entities from multiple US sectors.
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have issued a joint security advisory to warn teleworkers of an ongoing vishing campaign targeting organizations from multiple US industry industries.
Voice phishing is a form of criminal phone fraud, using social engineering over the telephone system to gain access to private personal and financial information for the purpose of financial reward.
Hackers aim at collecting login credentials for networks of the target organizations, then they attempt to monetize their efforts by selling access to corporate resources in the cybercrime underground.
The campaign is worrisome due to the ongoing COVID-19 pandemic that caused the spike in the number of employees working from home and the increase in the use of corporate VPN and elimination of in-person verification.
“In mid-July 2020, cybercriminals started a vishing campaign — gaining access to employee tools at multiple companies with indiscriminate targeting—with the end goal of monetizing the access,” reads the alert.
“Using vished credentials, cybercriminals mined the victim company databases for their customers’ personal information to leverage in other attacks. The monetizing method varied depending on the company but was highly aggressive with a tight timeline between the initial breach and the disruptive cashout scheme.”
The agencies provide technical details about the attack technique used by cybercriminals.
Threat actors initially registered domains and created phishing pages that look like the company’s internal VPN login page, the hackers also attempt to trick victims into providing two-factor authentication (2FA) or one-time passwords (OTP). Attackers also obtained Secure Sockets Layer (SSL)
certificates for the domains they registered and used a variety of domain naming schemes, including the following examples:
support-[company]
ticket-[company]
employee-[company]
[company]-support
[company]-okta
Threat actors compiled dossiers on the employees working for the companies they wanted to target, they gathered their data by scraping of public profiles on social media platforms, recruiter and marketing tools, publicly available background check services, and open-source research.
Attackers collected information such as name, home address, personal cell/phone number, the position at the company, and duration at the company.
Then threat actors directly called employees on their personal cellphones using random Voice-over-IP (VoIP) phone numbers or by spoofing the phone numbers of other company employees.
“The actors used social engineering techniques and, in some cases, posed as members of the victim company’s IT help desk, using their knowledge of the employee’s personally identifiable information—including name, position, duration at company, and home address—to gain the trust of the targeted employee,” continues the alert.
“The actors then convinced the targeted employee that a new VPN link would be sent and required their login, including any 2FA or OTP.”
When the victim provided their data through the phishing site, including 2FA or OTP, the attackers used it in real-time to gain access to the corporate account. In some cases,
bad actors used a SIM-Swap attack on the employees obtain the 2FA and OTP authentication code sent to the victims’ phones.
“The actors then used the employee access to conduct further research on victims, and/or to fraudulently obtain funds using varying methods dependent on the platform being accessed,” the FBI and CISA said.
The two agencies shared a series of recommendations for companies and their employees:
Organizational Tips:
Restrict VPN connections to managed devices only, using mechanisms like hardware checks or installed certificates, so user input alone is not enough to access the corporate VPN.
Restrict VPN access hours, where applicable, to mitigate access outside of allowed times.
Employ domain monitoring to track the creation of, or changes to, corporate, brand-name domains.
Actively scan and monitor web applications for unauthorized access, modification, and anomalous activities.
Employ the principle of least privilege and implement software restriction policies or other controls; monitor authorized user accesses and usage.
Consider using a formalized authentication process for employee-to-employee communications made over the public telephone network where a second factor is used to authenticate the phone call before sensitive information can be discussed.
Improve 2FA and OTP messaging to reduce confusion about employee authentication attempts.
End-User Tips:
Verify web links do not have misspellings or contain the wrong domain.
Bookmark the correct corporate VPN URL and do not visit alternative URLs on the sole basis of an inbound phone call.
Be suspicious of unsolicited phone calls, visits, or email messages from unknown individuals claiming to be from a legitimate organization. Do not provide personal information or information about your organization, including its structure or networks, unless you are certain of a person’s authority to have the information. If possible, try to verify the caller’s identity directly with the company.
If you receive a vishing call, document the phone number of the caller as well as the domain that the actor tried to send you to and relay this information to law enforcement.
Limit the amount of personal information you post on social networking sites. The internet is a public resource; only post information you are comfortable with anyone seeing.
Evaluate your settings: sites may change their options periodically, so review your security and privacy settings regularly to make sure that your choices are still appropriate.
For more information on how to stay safe on social networking sites and avoid social engineering and phishing attacks, visit the CISA Security Tips below:
Avoiding Social Engineering and Phishing Attacks
Staying Safe on Social Networking Sites
Transparent Tribe Mounts Ongoing Spy Campaign on Military, Government
20.8.20 BigBrothers CyberSpy Threatpost
The group has added a management console and a USB worming function to its main malware, Crimson RAT.
The APT group Transparent Tribe is mounting an ongoing cyberespionage campaign, researchers said, which is aimed at military and diplomatic targets around the world. The effort features a worm that can propagate from machine to machine while stealing files from USB removable drives.
Transparent Tribe (a.k.a. ProjectM and Mythic Leopard), is a prolific group that has been active [PDF] since at least 2013, specializing in widespread spy-craft. In the latest campaign, Kaspersky has observed spearphishing emails going out with malicious Microsoft Office documents containing a custom remote-access trojan (RAT) called Crimson. So far, researchers have found 1,093 targets across 27 countries, with the most-affected being Afghanistan, Germany, India, Iran and Pakistan.

Crimson is executed by way of embedded macros, according to Kaspersky research released on Thursday. It’s a .NET RAT that has a slew of malicious capabilities, including managing remote file systems, capturing screenshots, keylogging, conducting audio surveillance using built-in microphones, recording video streams from webcams, stealing passwords and stealing files.
Transparent Tribe has updated Crimson RAT for this campaign, the firm said, adding a server-side component used to manage infected client machines as well as a new USBWorm component developed for stealing files from removable drives, spreading across systems by infecting removable media, and downloading and executing a thin-client version of Crimson from a remote server.
“Coming in two versions, it was compiled in 2017, 2018 and 2019, indicating that this software is still under development and the APT group is working on ways to improve it,” according to the research.
Server-Side Management Interface
The server component gives attackers a handy control panel, which provides a list of infected machines and shows basic information about the victims’ systems as well as geolocation information retrieved from a legitimate website using a remote IP address as the input.
“At the top, there is a toolbar that can be used for managing the server or starting some actions on the selected bot,” Kaspersky said. “At the bottom, there is an output console with a list of actions performed by the server in the background. It will display, for example, information about received and sent commands.”
The bot panel is an interface with 12 tabs, which can be used to manage a remote system and collect information. The tabs match up with various Crimson components – for instance, there are tabs for explore the remote file system; downloading, uploading and deleting files; keylogging; and monitoring the remote screen and checking what the user is doing on their system.
In the remote-screen tab, “the attacker can retrieve a single screenshot or start a loop that forces the bot to continuously send screenshots to the server, generating a live stream of sorts. The attacker can also configure the RAT component to record the images on the remote system,” according to the analysis.
USBWorm Component
The freshly added USBWorm component in Crimson RAT behaves as a downloader, infector and USB stealer.
“When started, it checks if its execution path is the one specified in the embedded configuration and if the system is already infected with a Crimson client component,” explained Kaspersky researchers. “If these conditions are met, it will start to monitor removable media, and for each of these, the malware will try to infect the device and steal files of interest.”
The infection procedure for USBWorm starts with cataloging all directories on the victim device, the analysis details. The malware then creates a copy of itself in the drive root directory for each one, using the same directory name. It changes the legitimate directories’ attribute to “hidden” – which results in all the actual directories being replaced with a copy of the malware using the same directory name. USBWorm also uses an icon that mimics a Windows directory, tricking the user into executing the malware when trying to access it.
“This simple trick works very well on default Microsoft Windows installations, where file extensions are hidden and hidden files are not visible,” according to Kaspersky. “The victim will execute the worm every time he tries to access a directory. Moreover, the malware does not delete the real directories and executes ‘explorer.exe’ when started, providing the hidden directory path as argument. The command will open the Explorer window as expected by the user.”
The data theft procedure lists all files stored on the device and copies those with an extension matching a predefined list: .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pps, .ppsx and .txt.
“Our investigation indicates that Transparent Tribe continues to run a high amount of activity against multiple targets,” said Giampaolo Dedola, security expert at Kaspersky, in a media statement. “During the last 12 months, we have observed a very broad campaign against military and diplomatic targets, using a big infrastructure to support its operations and continuous improvements in its arsenal. The group continue to invest in its main RAT, Crimson, to perform intelligence activities and spy on sensitive targets. We don’t expect any slowdown from this group in the near future and we’ll continue to monitor its activities.”
U.S. Details North Korean Malware Used in Attacks on Defense Organizations
20.8.20 BigBrothers Securityweek
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have shared details on a piece of malware North Korean threat actors likely used in attacks targeting employees of defense organizations in Israel and other countries.
Dubbed BLINDINGCAN, the malware was apparently used in “Dream Job,” a campaign active since the beginning of this year, which hit dozens of defense and governmental companies in Israel and globally by targeting specific employees with highly appealing job offerings.
According to U.K. cybersecurity firm ClearSky, the operation appears to have been the main offensive campaign orchestrated by the North Korea-linked threat group Lazarus in 2020. Previously, the Israeli defense ministry claimed to have successfully prevented the attacks.
Also referred to as Hidden Cobra, Lazarus has been involved in numerous high profile attacks, such as the WannaCry outbreak in 2017, the $81 million Bangladesh bank theft, or the recent attacks on crypto-currency exchanges.
Over the past couple of years, the United States Cyber Command (USCYBERCOM) has shared various malware samples associated with the group, but only a malware analysis report (MAR) has been published for the BLINDINGCAN remote access Trojan (RAT).
The malware, the two agencies reveal, can collect various types of information on the victim system, including OS and processor details, system name, local IP information, and MAC address, and also provides attackers with remote capabilities, such as the ability to retrieve information on available disks, manipulate processes, files and directories, execute code, and erase itself.
The report reveals that the HIDDEN COBRA actors “are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation.” Moreover, the FBI and CISA reveal that North Korean hackers have been observed targeting government contractors this year, to harvest data on military and energy technologies.
“The malicious documents employed in this campaign used job postings from leading defense contractors as lures and installed a data gathering implant on a victim's system. This campaign utilized compromised infrastructure from multiple countries to host its command and control (C2) infrastructure and distribute implants to a victim's system,” the report reads.
The MAR was released after the analysis of two DLLs and four DOCX files. The documents would attempt to fetch a payload from an external domain, while a DLL was observed unpacking and executing a variant of the Hidden Cobra RAT.
In their report, CISA and the FBI also included a series of recommendations on how system admins can improve security and keep systems protected, such as ensuring that machines and applications are kept up to date, applying best practices when it comes to email attachments, user permissions, and removable drives, and enforcing a strong password policy.
Over 6,000 email accounts belonging to Taiwan government agencies hacked by Chinese hacked
20.8.20 BigBrothers Securityaffairs
Chinese hackers have hacked thousands of Taiwan Government email accounts belonging at least 10 Taiwan government agencies, officials said.
Chinese hackers have gained access to around 6,000 email accounts belonging to at least 10 Taiwan government agencies, officials said.
According to a top Taiwan cyber official, the attacks are part of a cyber espionage campaign. The government of Taipei is still investigating the campaign and assessing its impact, although the cyber official told AFP press agency that the damage done was “not small.”
The Taiwanese Government accuses the Chinese government of continues cyber incursions since 2016 when President Tsai Ing-wen was elected.
“Taipei has accused Beijing of stepping up a cyber campaign since 2016 when Taiwan elected President Tsai Ing-wen, who refuses to acknowledge Beijing’s insistence that the self-ruled democratic island is part of “one China”.” reads the AFP press.
President Tsai always claimed the independence of its country and thanks to its position against Beijing it was voted by its population.
According to the Taiwan Investigation Bureau’s Cyber Security Investigation Office, the China-linked cyberespionage groups tracked as Blacktech and Taidoor have been targeting government agencies and information service providers since 2018.
“We know for sure that these 6,000 emails have been compromised. We are still assessing the extent of the damage,” the office’s deputy director, Liu Chia-zung, told AFP.
“As far as we know, the damage done by this infiltration is not small.”
“We are making this public because we want to alert everyone of the threat and stop further damage.”
The Chinese government has increased diplomatic and economic pressure on Taiwan, it also showed the muscles increasing military drills near the country in recent weeks.
CISA’s MAR warns of North Korean BLINDINGCAN RAT
20.8.20 BigBrothers Securityaffairs
US CISA published an alert related to a new North Korean malware, dubbed BLINDINGCAN, used in attacks on the US defense and aerospace sectors.
The US Cybersecurity and Infrastructure Security Agency (CISA) has published a Malware Analysis Report (MAR) that includes technical details about a new strain of malware, tracked as BLINDINGCAN, that was attributed to North Korea.
According to the government experts, the BLINDINGCAN malware was employed in attacks aimed at US and foreign companies operating in the military defense and aerospace sectors.
Some of the attacks were attributed by the researchers to cyber espionage campaigns tracked as Operation North Star and Operation Dream Job.
The attack chain is similar to the one used in past campaigns, threat actors pose as recruiters at big corporations to establish contact with employees at the target organizations. The attackers use job offerings from prominent defense and aerospace entities as bait to trick victims into opening weaponized Office or PDF documents that are used to deploy malware on the victim’s computers.
According to the CISA alert, the attackers used the above technique to deliver the BLINDINGCAN remote access trojan (RAT) (aka DRATzarus) and access the victim’s system for reconnaissance purpose.
“FBI has high confidence that HIDDEN COBRA actors are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation. A threat group with a nexus to North Korea targeted government contractors early this year to gather intelligence surrounding key military and energy technologies.” reads the CISA’s MAR report. “The malicious documents employed in this campaign used job postings from leading defense contractors as lures and installed a data gathering implant on a victim’s system.”
The BLINDINGCAN RAT implements the following built-in functions-:
Retrieve information about all installed disks, including the disk type and the amount of free space on the disk
Get operating system (OS) version information
Get Processor information
Get system name
Get local IP address information
Get the victim’s media access control (MAC) address.
Create, start, and terminate a new process and its primary thread
Search, read, write, move, and execute files
Get and modify file or directory timestamps
Change the current directory for a process or file
Delete malware and artifacts associated with the malware from the infected system
The CISA MAR also indicators of compromise (IoCs), Yara rules, and other technical info that could be used by system administrators to discover compromise systems within their networks.
In April, the U.S. Departments of State, the Treasury, and Homeland Security, and the Federal Bureau of Investigation released a joint advisory that is warning organizations worldwide about the ‘significant cyber threat’ posed by the North Korean nation-state actors to the global banking and financial institutions.
The advisory contains comprehensive resources on the North Korean cyber
threat that aims at helping the international community, industries, and other governments to protect their infrastructure from state-sponsored attacks. The document also includes a list of recent attacks attributed to North Korean state-sponsored hackers.
The U.S. government is also offering a monetary reward of up to $5 million to anyone who can provide ‘information about the activities carried out by North Korea-linked APT groups. The offer also includes information about past hacking campaigns.
Thousands of Taiwan Government Email Accounts 'Hacked by China'
20.8.20 BigBrothers Securityweek
Chinese hackers infiltrated at least 10 Taiwan government agencies and gained access to around 6,000 email accounts in an attempt to steal data, officials said Wednesday.
The damage done was "not small", according to a top Taiwan cyber official, who said the full impact was still being assessed.
Taipei has accused Beijing of stepping up a cyber campaign since 2016 when Taiwan elected President Tsai Ing-wen, who refuses to acknowledge Beijing's insistence that the self-ruled democratic island is part of "one China".
Tsai, who views Taiwan as de facto independent, won re-election by a landslide in January in what was seen as a strong rebuke to Beijing's campaign to influence the island.
According to the Taiwan Investigation Bureau's Cyber Security Investigation Office, two well-known Chinese hacking groups -- Blacktech and Taidoor -- have been targeting government departments and information service providers since 2018.
"We know for sure that these 6,000 emails have been compromised. We are still assessing the extent of the damage," the office's deputy director, Liu Chia-zung, told AFP.
"As far as we know, the damage done by this infiltration is not small," Liu added.
"We are making this public because we want to alert everyone of the threat and stop further damage."
The announcement comes a week after US health secretary Alex Azar wrapped up a historic trip to the self-ruled island as China warned Washington not to "play with fire".
Beijing has ramped up diplomatic and economic pressure on Taiwan as well as increasing military drills near the island, including its jets breaching Taiwan's air defence zone with unprecedented frequency in recent weeks.
Senate: WikiLeaks Knowingly Assisted Russian Influence Effort Before 2016 Election
19.8.20 BigBrothers Securityweek
A new report from the Senate intelligence committee on Russia’s interference in the 2016 presidential election in the United States says WikiLeaks knowingly assisted the Kremlin’s influence efforts.
The United States has concluded that Russia conducted an extensive influence campaign leading up to the 2016 election, and a significant part of that campaign involved breaking into the computer systems of the Democratic party and Hilary Clinton’s campaign and leaking information via the whistleblower website WikiLeaks.
WikiLeaks has been accused of meddling in the election through its actions, but a Senate report published on Tuesday claims that “WikiLeaks actively sought, and played, a key role in the Russian influence campaign and very likely knew it was assisting a Russian intelligence influence effort.”
Some parts of the 966-page report, including in the “Hack and Leak” section, are redacted, but the Senate committee said it had determined that Russian President Vladimir Putin ordered the cyberattacks on the Democratic National Committee (DNC) and the Clinton campaign in an effort to harm the Clinton campaign and help the Trump campaign. It was previously reported that Putin allegedly personally ordered the hacking and disinformation campaign aimed at the 2016 election.
WikiLeaks’ founder, Julian Assange, is currently being held in Britain. The United States is hoping to have him extradited to face hacking-related charges.
Earlier this year, Assange’s lawyer told a court that Trump had offered to pardon him if he accepted to say that Russia had nothing to do with the DNC leaks, a claim that the White House has denied.
SecurityWeek has reached out to WikiLeaks for comment.
Republican senator Marco Rubio, chairman of the committee that released the report, stated that while the investigation did find irrefutable evidence of Russian meddling, it “found absolutely no evidence that then-candidate Donald Trump or his campaign colluded with the Russian government to meddle in the 2016 election.”
However, the report noted, “While the GRU and WikiLeaks were releasing hacked documents, the Trump Campaign sought to maximize the impact of those leaks to aid Trump’s electoral prospects. Staff on the Trump Campaign sought advance notice about WikiLeaks releases, created messaging strategies to promote and share the materials in anticipation of and following their release, and encouraged further leaks.”
It added, “The Trump Campaign publicly undermined the attribution of the hack-and-leak campaign to Russia and was indifferent to whether it and WikiLeaks were furthering a Russian election interference effort.”
The report also noted that Trump’s campaign chairman, Paul Manafort, had been in communication with several individuals tied to Russia, including a Russian intelligence officer who may have been connected to the hack and leak operation targeting the 2016 election. Manafort at one point pushed the idea that Ukraine, not Russia, was behind the cyberattack on the DNC.
China Slams US 'Abuse' Over New Huawei Sanctions
19.8.20 BigBrothers Securityweek
Beijing on Tuesday hit out at new US sanctions against telecom giant Huawei, accusing Washington of an "abuse of national power" to block the rise of Chinese companies.
A US Commerce Department statement Monday barred an additional 38 Huawei affiliates from buying American computer chips and other technology.
Tensions were already high between the two powers, and Washington has claimed that Chinese firms are used to spy for Beijing -- an accusation the Chinese government and the companies deny.
Chinese foreign ministry spokesman Zhao Lijian on Tuesday said there was no evidence that Huawei products contained security loopholes or backdoors.
The sanctions have "completely punctured the last pretence of market principles and fair competition that the US has always touted", he added.
Washington has engaged in "abuse of national power to apply all sorts of restrictions on Huawei and other Chinese enterprises," he said at a regular press briefing.
US officials have argued that Huawei poses a security risk because of its links to the Beijing government, a claim denied by the company.
Commerce Secretary Wilbur Ross said Huawei and its affiliates "have worked through third parties to harness US technology in a manner that undermines US national security and foreign policy interests".
The Trump administration has banned Huawei from 5G wireless networks in the United States and pressed allies to do the same.
Huawei became the largest global smartphone manufacturer in the past quarter, largely due to sales in the Chinese market, even as Washington moves to deny the company access to much of the Google Android system.
Zhao on Tuesday urged the US to "correct its mistakes," saying China would "continue to take necessary measures to protect the legitimate rights and interests of Chinese companies".
US President Donald Trump has also sought to ban the wildly popular mobile application TikTok if it is not divested by its Chinese parent firm ByteDance, and ordered a ban on the Chinese messaging app WeChat, owned by tech giant Tencent.
U.S. Army Report Describes North Korea's Cyber Warfare Capabilities
18.8.20 BigBrothers Securityweek
A report published recently by the U.S. Army describes North Korea’s cyber warfare capabilities and provides information on various units and their missions.
The 332-page report, titled “North Korean Tactics,” details North Korean forces and their actions, and one chapter focuses on electronic intelligence warfare, which Pyongyang allegedly uses to collect information on its enemies, deceive its enemies, and launch disruptive and destructive attacks, particularly ones aimed at communication and information systems and infrastructure.
North Korea’s electronic warfare includes both lethal and non-lethal methods. Non-lethal methods include electronic jamming and signals reconnaissance, while lethal methods can include physical destruction of targets supporting its enemy’s decision-making process.
In terms of computer warfare, the Army says North Korea primarily conducts these types of attacks because they represent a low-cost and low-risk method for targeting the enemy’s computers, they can be used to counter the enemy’s superior conventional military capabilities, and they can “upset the status quo with little fear of retaliation.”
“North Korean computer warfare activities may be conducted prior to or during a military action. For example, by damaging or destroying networks related to an enemy’s projected force deployments and troop movements, the [Korean People’s Army (KPA)] can effectively disrupt planning and misdirect movement, producing substantial confusion and delays. As modern armies increasingly rely on ‘just-in-time’ logistics support, targeting logistics-related computers and databases can produce delays in the arrival of important material such as ammunition, fuel, and spare parts during critical phases of a conflict,” the report reads.
The unit responsible for cyber warfare is called the Cyber Warfare Guidance Unit, and it’s often referred to as Bureau 121. The Army says Bureau 121 has more than 6,000 members, with many operating from countries such as China, Russia, India, Malaysia and Belarus.
It’s worth pointing out that South Korea’s defense ministry estimated in 2015 that North Korea had an elite cyber warfare unit with up to 6,000 members.
The Army says Bureau 121 has four main subordinate groups. One of them is Lazarus, which has an unknown number of members and which is believed to be responsible for many of the high-profile cyberattacks launched by North Korea over the past years.
Another group is called Andarial (Andariel), which has roughly 1,600 members and whose mission is to conduct reconnaissance operations in preparation of further attacks.
The Bluenoroff group has approximately 1,700 members and it focuses on financially-motivated campaigns.
The U.S. Treasury Department last year placed sanctions on Andarial, Lazarus, and Bluenoroff.
The fourth and final group is the Electronic Warfare Jamming Regiment, which focuses on jamming enemy communications.
Surveillance Bill Vote Scrapped After Opposition From Trump, DoJ
28.5.2020 Securityweek BigBrothers
House Democrats on Wednesday decided to abandon a vote on the reauthorization of several government surveillance programs under the Foreign Intelligence Surveillance Act (FISA).
FISA, the USA PATRIOT Act, and similar legislation is amended under the USA FREEDOM Act, which was enacted in June 2015 and expired on March 15, 2020, after being silently extended for several months.
An amendment to the USA FREEDOM Act that would limit the government’s access to Americans’ Internet browsing and search history was rejected in the Senate earlier this month, falling short of a single vote.
A similar amendment proposed earlier this week by Representatives Zoe Lofgren (D-CA) and Warren Davidson (R-OH) saw broad support in the House of Representatives, but the vote on the USA FREEDOM Reauthorization Act was abandoned on Wednesday, after both the Department of Justice and President Donald Trump publicly opposed the bill.
In a statement published on Wednesday morning, Assistant Attorney General Stephen E. Boyd underlined that the DoJ opposes the Lofgren-Davidson amendment, saying that it would limit the DoJ’s ability to pursue terrorists and spies.
“Given the cumulative negative effect of these legislative changes on the Department’s ability to identify and track terrorists and spies, the Department must oppose the legislation now under consideration in the House. If passed, the Attorney General would recommend that the President veto the legislation,” Boyd said.
In a tweet on Tuesday, President Donald Trump urged Republicans to vote against the FISA bill, at least until light is shed into the FBI’s surveillance of his presidential campaign in 2016.
“I hope all Republican House Members vote NO on FISA until such time as our Country is able to determine how and why the greatest political, criminal, and subversive scandal in USA history took place!,” President Trump tweeted.
In a tweet on Wednesday, the president made it clear that he would veto the FISA reauthorization, should it pass the House.
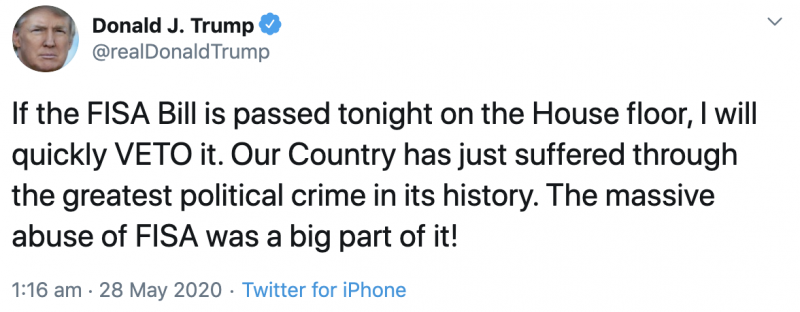
Since FISA reauthorization failed, the FBI and others can no longer use the now-expired authorities for data collection in newly opened investigations. The abandoned vote also impacts the National Security Agency’s surveillance program, which was suspended in early 2019.
Boris Johnson to reduce Huawei’s role in national 5G network
27.5.2020 Securityaffairs BigBrothers
UK Government will reduce the presence of the equipment manufactured by Chinese Huawei in its 5G network in the wake of the coronavirus outbreak.
UK Government will reduce the presence of the equipment manufactured by the Chinese tech firm Huawei in its 5G network in the wake of the Coronavirus outbreak.
Early this year, the UK Government agreed on the involvement of Huawei in the national 5G network, while the United States expressed its disappointment for the Johnson decision and threatened to limit intelligence sharing with the ally.
“The Prime Minister plans to reduce Huawei’s involvement in Britain’s 5G network in the wake of the coronavirus outbreak, the Telegraph has learned.” reported The Telegraph.
“Boris Johnson has instructed officials to draw up plans that would see China’s involvement in the UK’s infrastructure scaled down to zero by 2023.”
Prime Minister Boris Johnson has tacked officials to draft plans that would define the way Chinese firms will be involved in Britain’s infrastructure end by 2023.
Next month Mr Johnson will visit the US to participate at the G7 summit, he aims at confirming that the UK jhas reduced its dependecy from the China provisioning of 5G network equipment, a circumstance that could ramp up trade talks with US President Donald Trump.
In January, the EU’s executive Commission presented a set of rules and technical measures aimed at reducing cybersecurity risks from the adoption of 5G. The Commission’s recommendations included blocking high-risk equipment suppliers from “critical and sensitive” components of 5G infrastructures, such as the core.
The EU’s executive Commission did not explicitly mention companies, but a clear reference is to the Chinese firm Huawei.
In January, the British Government also agreed to assign a limited role for Huawei in the country’s 5G network, but highlighted that “high-risk vendors” would be excluded from the building of “sensitive” core infrastructure.
US Government continues to push hard for countries to ban Chinese companies from building their next-generation 5G network, claiming Chinese equipment can be exploited by the Chinese government for cyber espionage.
MPs in Johnson’s party doesn’t agree with the involvement of Huawei in building 5G network.
“He has taken a great many soundings from his own MPs on this issue and shares their serious concerns. The deal was struck before the pandemic hit but coronavirus has changed everything,” an unnamed source told The Telegraph.
French Privacy Watchdog Okays Coronavirus Tracing App
27.5.2020 Securityweek BigBrothers
France's privacy watchdog gave the green light Tuesday to a government-backed cellphone app that will alert users if they have been in contact with an infected person.
Use of the app called StopCovid will be voluntary, and will keep track of users who had been in close proximity of one another over a two-week period. If any become infected, they inform the platform, which alerts the others.
Privacy defenders have expressed fears that the app marks the first step towards a society under constant online surveillance.
But the CNIL watchdog, which gave provisional approval for StopCovid in April, said Tuesday that the app met the legal requirements for privacy protection, with ample safeguards to prevent abuse.
It nevertheless made a number of recommendations to make it even safer, including improving the quality of information provided to users, allowing users to object to information shared, and providing an option for erasing stored data.
The app will not rely on geolocation, but instead use Bluetooth technology which allows mobile phones to communicate with each other over short distances.
The French parliament, which must vote on the rolling out of the app, will debate the matter on Wednesday.
If it says yes, StopCovid could be available in app stores from this weekend.
France started reemerging on May 11 from a two-month lockdown to curb coronavirus spread. Public transport has resumed, though many people are still working from home and most schools have yet to reopen.
Bars, restaurants and public parks remain shuttered.
The issue of how to track coronavirus spread with mobile technology has sparked privacy concerns in several countries now lifting strict home confinement measures as they hope to kickstart their economies.
As a result of the lockdowns, few people in most countries have been exposed to the virus, and thus do not have immunity and remain at risk of infection, raising fears of a second wave once people start mixing again.
The European Commission has recommended that data harvested through contact-tracing apps be stored only on users' own phones and that it be encrypted.
US Lawmakers Push for Internet Privacy Amendments to USA Freedom Act
27.5.2020 Securityweek BigBrothers
United States lawmakers this week will vote on an amendment to the surveillance bill known as the USA FREEDOM Reauthorization Act that would limit law enforcement access to people’s search and browsing histories.
Enacted in June 2015, the USA FREEDOM Act amends, among others, the Foreign Intelligence Surveillance Act of 1978 (FISA), and USA PATRIOT Act, imposing limits on the bulk collection of data on U.S. citizens by the National Security Agency (NSA) and other intelligence agencies.
If renewed, the USA Freedom Act would reauthorize several surveillance programs, allowing the Federal Bureau of Investigation, among others, to gain access to an individual’s Internet browsing and search history (from their Internet services provider) without a warrant.
An amendment introduced by Senator Ron Wyden (D - OR) and Senator Steve Daines (R - MT) to the USA FREEDOM Reauthorization Act (H.R. 6172), which aimed to prohibit the use of Section 215 of the USA PATRIOT Act to access such data without a warrant, was rejected in the Senate, one vote short of the 60 needed for approval.
This week, the House of Representatives will vote on the bipartisan amendment proposed by Representatives Zoe Lofgren (D-CA) and Warren Davidson (R-OH) to the USA FREEDOM Reauthorization Act, which seeks to prohibit the warrantless collection of such data. If the amendment is approved, the Senate would have to consider it too.
“After extensive bicameral, bipartisan deliberations, there will be a vote to include a final significant reform to Section 215 that protects Americans’ civil liberties,” Congresswoman Lofgren commented.
The amendment is supported by Reps. Adam Schiff, Chair of the House Permanent Select Committee on Intelligence, and Jerrold Nadler, Chair of the House Judiciary Committee.
“Representatives will be able to vote to prevent the government from using Section 215 to collect the websites we visit, the videos we watch and the searches we make. Without this prohibition, intelligence officials can potentially have access to information such as our personal health, religious practices, and political views without a warrant. As such, I urge my colleagues to support the Lofgren-Davidson amendment and Americans’ Fourth Amendment rights,” Rep. Lofgren continued.
Senator Wyden, one of the authors of the amendment that was ultimately rejected by the Senate, praised the Lofgren-Davidson initiative, underlining that it should eliminate law misinterpretations by making it clearer that Americans’ search and browsing histories cannot be collected pursuant to Section 215 of the PATRIOT Act.
“I applaud Rep. Lofgren for securing a vote on my amendment to ban warrantless collection of Americans’ internet activity. There are few things more private than where a person goes on the internet, or what they search for online, so the government must obtain a warrant to get that information. I urge the House to pass it, and the Senate to follow suit,” Sen. Wyden said.
The amendment clearly prohibits the collection of U.S. person records, of Virtual Private Networks that might be used by U.S. persons, and prevents the U.S. government from learning who accessed a website or online video unless it can guarantee that no U.S. person accessed that resource. Basically, the amendment fully eliminates the ‘incidental’ collection of the records of U.S. persons.
Governments Asked to Stop Cyberattacks on Healthcare Systems
27.5.2020 Securityweek BigBrothers
More than 40 current and former leaders from around the world have signed a letter asking governments to prevent and stop cyberattacks on healthcare systems amid the COVID-19 pandemic.
The initiative is led by the CyberPeace Institute, a non-governmental organization dedicated to enhancing peace and stability in cyberspace, and supported by the Red Cross.
The letter addressed to governments is also signed by the leaders of major tech and cybersecurity companies (including Microsoft, Kaspersky and Trend Micro), university professors, religious figures, NGOs and non-profit organizations, research organizations, healthcare organizations, former state presidents and ministers, and other officials.
There have been several reports of campaigns launched by profit-driven cybercriminals that use the coronavirus outbreak as a lure. There have also been reports of sophisticated threat groups targeting healthcare entities and organizations involved in the national and international response to the coronavirus outbreak.
The attacks range from ransomware to disinformation campaigns, and they have targeted hospitals, government organizations, health authorities, and testing and vaccine research facilities.
“We call on the world’s governments to take immediate and decisive action to stop all cyberattacks on hospitals, healthcare and medical research facilities, as well as on medical personnel and international public health organizations. To this end, governments should work together, including at the United Nations, to reaffirm and recommit to international rules that prohibit such actions,” the letter reads.
“This will not be the last health crisis. For now and for the future, governments should assert in unequivocal terms: cyber operations against healthcare facilities are unlawful and unacceptable.
“We don’t tolerate attacks on health infrastructure in the physical world, and we must not tolerate such attacks in cyberspace – whether in times of peace or in times of conflict. We stand with the International Committee of the Red Cross in support of its call to protect medical services and medical facilities against cyberattacks of any kind. We call on governments to work together and to join forces with civil society and the private sector to ensure that medical facilities are respected and protected, and to hold perpetrators accountable. Above all, governments should take action and stop cyberattacks on hospitals and medical facilities,” the letter adds.
The Australian Red Cross reported this week that it has observed nearly 900 attempts by cyber threat actors to access the hundreds of millions of dollars it raised for bushfire victims.
Qatar Tracing App Flaw Exposed 1 Mn Users' Data: Amnesty
27.5.2020 Securityweek BigBrothers Incindent
A security flaw in Qatar's controversial mandatory coronavirus contact tracing app exposed sensitive information of more than one million users, rights group Amnesty International warned Tuesday.
The glitch, which was fixed on Friday after being flagged by Amnesty a day earlier, made users' ID numbers, location and infection status vulnerable to hackers.
Privacy concerns over the app, which became mandatory for residents and citizens on pain of prison from Friday, had already prompted a rare backlash and forced officials to offer reassurance and concessions.
Users and experts had criticised the array of permissions required to install the app including access to files on Android devices, as well as allowing the software to make unprompted phone calls.
Despite insisting the unprecedented access was necessary for the system to work, officials said they would address privacy concerns and issued reworked software over the weekend.
"Amnesty International's Security Lab was able to access sensitive information, including people's name, health status and the GPS coordinates of a user's designated confinement location, as the central server did not have security measures in place to protect this data," the rights group said in a statement.
"While Amnesty International recognises the efforts and actions taken by the government of Qatar to contain the spread of the COVID-19 pandemic and the measures introduced to date, such as access to free healthcare, all measures must be in line with human rights standards."
More than 47,000 of Qatar's 2.75 million people have tested positive for the respiratory disease -- 1.7 percent of the population -- and 28 people have died.
Like other countries, Qatar has turned to mobiles to trace people's movements and track who they come into contact with, allowing officials to monitor coronavirus infections and flag possible contagion.
"The Ehteraz app's user privacy and platform security are of the utmost importance," Qatar's health ministry said in a statement on Tuesday.
"A comprehensive update of the app was rolled out on Sunday May 24 with expanded security and privacy features for all users."
But Etheraz, which means "Precaution", continues to allow real-time location tracking of users by authorities at any time, Amnesty said.
"It was a huge security weakness and a fundamental flaw in Qatar's contact tracing app that malicious attackers could have easily exploited," said Claudio Guarnieri, head of the group's security lab.
"The Qatari authorities must reverse the decision to make use of the app mandatory," he said.
Hacker Behind 'Doxxing' of German Politicians Charged
27.5.2020 Securityweek BigBrothers
German prosecutors said Tuesday they had brought charges against a 22-year-old hacker who released personal data of dozens of politicians, journalists and other public figures online, embarrassing national authorities.
The German man -- arrested in January last year -- is accused of multiple computer crimes, as well as making false reports to the police and attempted blackmail.
Police at the time of his arrest said he had confessed to stealing and leaking online private data -- so-called "doxxing" -- from hundreds of politicians and public figures, among them Chancellor Angela Merkel.
The accused said his motive was being "annoyed" at some of their public statements.
The 2018 case prompted German authorities to promise beefed-up IT security, coming just three years after the federal parliament's computer network was crippled by a hacking attack since pinned on the Russian state by Berlin's intelligence services.
Tuesday's charges cover 73 cases where the accused acquired "personal data, especially telephone numbers, addresses, credit card data, photos and communications" belonging to his targets.
Investigators said he used email providers' password reset facilities to gain access to the people's accounts, as well as trawling a "hacker website" shut down by American authorities in January 2020 for login details already acquired by third parties.
When arrested, officials said the suspect had made a "comprehensive" confession and shown "clear remorse" for his hacking attacks on around 1,000 people.
Between December 1 and December 24, 2018, he released a drip-feed of personal data on his Twitter account with the display name "G0d" in a so-called "advent calendar".
He repeated the data drop the following month using the Twitter account of a YouTube personality to which he had acquired access.
Further charges include a blackmail attempt against six German MPs, in which the hacker demanded Bitcoin payments worth around 900 euros ($1,000) in exchange for withholding their personal data.
He is also accused of making three false reports to the police of imminent bomb attacks or mass shootings between June 2016 and December 2018, as well as triggering two investigations against other people with false crime reports in the same period.
FTC Settles With Canadian Smart Lock Maker Over Security Practices
27.5.2020 Securityweek BigBrothers
The Federal Trade Commission (FTC) has approved a settlement with Canadian smart lock maker Tapplock, which allegedly falsely claimed that its devices were designed to be “unbreakable.”
Toronto-based Tapplock, Inc. is an Internet of Things (IoT) technology company that provides smart security solutions for both business and end-users alike. It sells Internet-connected smart fingerprint padlocks that interact with users’ mobile devices when within Bluetooth range.
According to the FTC, although the company advertises its locks as highly secure, these devices are not secure. Moreover, the commission claims that Tapplock hasn’t taken reasonable precautions, and failed to follow industry best practices and keep collected consumer data secure.
Personal information collected by the Tapplock app includes usernames, email addresses, profile photos, and the smart lock’s precise location.
Security researchers have identified both physical and electronic vulnerabilities in Tapplock’s devices, allowing easy access to attackers. Moreover, users cannot effectively revoke access to their locks and the account authentication process can be bypassed, resulting in leaked personal information.
In its complaint, the FTC also alleges that Tapplock failed to take the necessary measures that would have helped it identify electronic vulnerabilities in its locks.
Last week, the agency approved a settlement initially announced in April. The settlement requires Tapplock to implement a security program and prohibits the company from misrepresenting its privacy and security practices.
Furthermore, the IoT provider is required to subject its information security program to third-party assessments every two years, and the commission has authority to approve the assessor for each two-year period.
“After receiving no comments, the Commission voted 5-0 to finalize the settlement,” the FTC announced.
Internet Organizations Ask US House to Limit Access to Search, Browsing History
27.5.2020 Securityweek BigBrothers
In a letter to the U.S. House of Representatives, several Internet organizations are urging for an amendment to the surveillance bill known as the USA FREEDOM Reauthorization Act to prohibit warrantless collection of search and browsing history.
Signed by Mozilla Corporation, Engine, Reddit, Reform Government Surveillance, Twitter, i2Coalition, and Patreon, the letter asserts that the Internet browsing and search history provide a detailed picture of a person’s life, and that legislation should ensure that this information is well protected.
“We urge you to explicitly prohibit the warrantless collection of internet search and browsing history when you consider the USA FREEDOM Reauthorization Act (H.R. 6172),” the letter reads.
Privacy and security are essential to “our economy, our businesses, and the continued growth of the free and open internet,” the signing organizations say, adding that Congress can help preserve user trust by “clearly reaffirming these protections.”
Such privacy concerns are addressed in an amendment introduced by Senator Ron Wyden (D - OR) and Senator Steve Daines (R - MT) to H.R. 6172, which aims to expressly prohibit “the use of Section 215 of the USA PATRIOT Act for the warrantless collection of search and browsing history.” The Senate voted on the amendment earlier this month, but came one vote short of approving it.
The majority of Senate supports the amendment, the same as consumer groups and businesses across America, the letter notes. Broadly supported by members of the House of Representatives too, the provision “should be included if the House reauthorizes the USA FREEDOM Act,” the signing organizations point out.
Effective legal safeguards, they say, are required to protect information from search and browsing history, which may reveal medical conditions, religious beliefs, and personal relationships.
The organizations also note that such information should only be produced with a warrant, and some of them have already asked for the adoption of a higher standard for this data.
“Congress should take this opportunity to resolve any potential ambiguity and provide strong legal protections for all search and browsing history. […] We respectfully urge you to include the text of the Wyden/Daines amendment as part of the USAFREEDOM Reauthorization Act,” the letter concludes.
UK Set to Scale Back Huawei Role in 5G Network: Report
26.5.2020 Thehackernews BigBrothers
Britain will reduce Chinese tech giant Huawei's controversial involvement in its 5G network in the wake of the coronavirus outbreak, the Daily Telegraph reported Saturday.
Prime Minister Boris Johnson gave the green light to Huawei's participation in January, despite widespread domestic opposition and pressure from the United States.
But he has now instructed officials to draft plans that would see China's involvement in Britain's infrastructure end by 2023, according to the report.
Washington has pushed hard for countries to bar Huawei from building their next generation 5G mobile networks, claiming its equipment can be used to spy for Beijing.
Johnson is due to meet US President Donald Trump next month for the G7 summit, with Britain hoping to scale up talks over a bilateral trade deal.
MPs in Johnson's own party have led the charge against Huawei's involvement, a movement that has gathered pace following China's actions during the coronavirus crisis.
"He has taken a great many soundings from his own MPs on this issue and shares their serious concerns. The deal was struck before the pandemic hit but coronavirus has changed everything," an unnamed source told the paper.
Bitter Israel-Iran Rivalry Takes New Forms Online
22.5.2020 Securityweek BigBrothers
Hacked websites in Israel, a reported cyberattack in Iran and a Twitter war between their leaders: the arch foes' animosity is flaring up online.
The latest volleys in Israel and Iran's longstanding rivalry coincide with the 20th anniversary of the Israeli army's withdrawal from southern Lebanon, forced out by Iranian-backed militant group Hezbollah.
They also come before Jerusalem Day on Friday, which often sees increased tensions.
While Israelis celebrate their 1967 capture of the eastern part of the holy city, Iran commemorates the day with events marking Palestinian and Muslim connections to the holy city, expounding its opposition to Zionism -- the founding ideology of Israel.
"We will support and assist any nation or any group anywhere who opposes and fights the Zionist regime," Iran's supreme leader Ayatollah Ali Khamenei tweeted Wednesday.
He called for the "defence" of Palestinians and for "thugs like (Israeli Prime Minister Benjamin) Netanyahu" to be overthrown.
"The nature of the Zionist regime is incompatible with peace, because the Zionists seek to expand their territories," he added.
Netanyahu blasted Khamenei in a response on Twitter on Wednesday night.
"He should know that any regime that threatens Israel with extermination will find itself in similar danger," the Israeli premier wrote on his official account in Hebrew.
The lead-up to Jerusalem Day also saw a poster go up on Khamenei's website, proclaiming that "Palestine will be Free", with the tagline "The final solution: Resistance until referendum".
An accompanying post explained that a plebiscite could decide "the government to rule over the land of Palestine".
Iran's Foreign Minister Mohammad Javad Zarif shot back at Netanyahu on Thursday.
"Disgusting that those whose civilization found a 'Final Solution' in gas chambers attack those who seek a real solution at the ballot box, through a REFERENDUM," he tweeted.
"Why are US and West so afraid of democracy?"
US Secretary of State Mike Pompeo slammed Khamenei's "disgusting and hateful anti-Semitic remarks", while a German foreign ministry source said "such anti-Israeli statements are absolutely unacceptable. Israel's right to exist is non-negotiable".
- Hacker threats -
The morning after the Twitter barbs, Israelis woke to a series of cyberattacks targeting websites of businesses, municipalities and NGOs with a message in Hebrew and English: "the countdown to the destruction of Israel began long ago".
An accompanying link led to a video showing Israeli commercial capital Tel Aviv in flames, with the words "be ready for a big surprise".
There were no immediate details on the group that claimed the attack, naming itself in English "Hackers of Saviour".
Earlier this week, The Washington Post reported Israel had launched a cyberattack against the Iranian port of Shahid Rajaee, located on the Strait of Hormuz, a vital route for international oil traffic.
This attack was thought to be in retaliation for a cyberattack against civil hydraulic installations in Israel.
Israeli authorities have not confirmed either attack, but allowed doubt to linger through indirect and sometimes metaphorical language.
"The Iranian octopus is sending its tentacles to grab us from every direction," outgoing Defence Minister Naftali Bennett said this week.
"We must increase the diplomatic, economic, military and technological pressure, and act in other dimensions as well."
The next day, army chief Aviv Kohavi said: "We are preparing varied means and unique combat techniques to mortally harm the enemy."
The attacks, if confirmed, add a cyber dimension to a series of Israeli air strikes targeting Iranian interests in Syria.
Tehran supports Syrian President Bashar al-Assad's regime and has backed it militarily.
Israel has launched hundreds of strikes in Syria since the start of the civil war in 2011, targeting Syrian government troops as well as allied Iranian forces and Hezbollah fighters.
On Thursday, the Israeli army said it had detected a desire among Iranian forces to withdraw somewhat from the front lines in Syria, putting it down in part to the coronavirus pandemic and economic crisis in Iran.
"The main thing we see on the ground is a general vector of withdrawal... not massive, but a general posture of withdrawal," the army said.
But, it added, "the Iranians are definitely trying different additional ways to engage with Israel."
Tens of thousands Israeli websites defaced
22.5.2020 Securityaffairs BigBrothers
Thousands of Israeli websites have been defaced earlier today, hackers published an anti-Israeli message on their homepage and attempted to implant malicious code.
A massive hacking campaign defaced thousands of Israeli websites, attackers published an anti-Israeli message on their homepage and attempted to inject a malware seeking permission to access visitors’ webcams.
“Be ready for a big surprise” “The countdown of Israel destruction has begun since a long time ago,” reads the message published in in Hebrew and English on the defaced Israeli websites.
A video published by the hackers shows explosions in Tel Aviv and a battered and bloodied Prime Minister Benjamin Netanyahu swimming away from a burning city.
The hackers also added a link on some websites, asking users to click on the link and activate their camera

The list of hacked websites belong to local municipalities, several NGOs, popular restaurant chains, and a left-wing Member of parliament.
The attacks were carried out by a group calling itself the “Hackers of Saviour” most of the hacked websites were hosted on the Israeli WordPress hosting service uPress. The hacker group’s YouTube channel describes the crew as collective seeking on avenging Israel’s policy on the Palestinian situation.
“Early this morning we detected a widespread cyber attack against many websites stored on our servers. It is a case of a malicious and far-ranging attack carried out by anti-Israel (Iranian) sources. We detected a weakness in a WordPress add on that enabled the hack and are working closely with the National Cyber Bureau to research the breach and fix the affected sites.” reads a statement from the company sent to Ynet News.
The hosting provider confirmed the attack and revealed that the hackers exploited a vulnerability in a WordPress plugin to compromise the Israeli websites. Below the message published by the company on Facebook:
The company said it was working with Israeli authorities to investigate the hack. uPress also took down all defaced websites and pulled the file hackers were exploiting. The company is working to restore all the defaced websites.
“The Israel National Cyber Bureau, the government agency tasked with protecting Israel from hacking attacks confirmed that “a host of Israeli websites were hacked in the morning hours in a suspected Iranian cyber-attack.”” reported the website Calcalistech.
“The matter is being handled by the Bureau. We recommend users refrain from pressing any links on compromised sites,”.
The hosting provider reported the incident to the authorities that launched an investigation into the attacks.
The Israeli National Cyber-Directorate (INCD), the Israeli cyber-security agency, warned users against visiting and interacting with the hacked websites.
Israeli press outlets blame Iranian hackers for the attacks, but at the time there is no concrete evidence to support this attribution.
Surveillance Fears Drive Business Use of Secure Collaboration Tools
22.5.2020 Securityweek BigBrothers
Fear of Government Surveillance Overreach is Driving the Adoption of Secure Collaboration Platforms
The COVID-19 pandemic and associated upsurge in remote working has expanded the threat landscape for all enterprises. The security of communications and collaboration tools is a hot topic, with online conferencing tools being among the relatively few beneficiaries of the pandemic.
Wickr is one such product, with a tag line of leaving no trace. While it can legally be instructed to hand over user data, it has none to hand over. In an attempt to understand what drives user behavior, the company has analyzed use of its Pro/business collaboration platform during the COVID-19 epoch. "We saw a big spike," said the firm in its analysis. "It makes sense, since demand for remote work solutions has certainly increased over the past few months. We also noticed that some countries had much larger spikes than others and wondered if something else could be driving the increases."
If it were just the increased operation of working from home driving the increased use of the Wickr platform, it could be expected to be fairly uniform -- which isn't the case. There is, however, a secondary 'privacy' issue over the same period -- the development and use of coronavirus contact tracing apps.
Looking more closely at its figures, Wickr detected a correlation between the more draconian use of contact apps and the uptake of its platform. Turkey, for example, where coronavirus patients are required to use a tracing app capable of alerting enforcement authorities if they leave their home or other quarantined area, has seen a 4,486% growth in the use of the Wickr platform from February 2020 to April 2020. Turkey has in the past also detained thousands of citizens for using an encrypted app, and requires service providers to add intercept functionalities.
Israel, where security agencies can track the phone data of people with suspected coronavirus, has seen a 2,336% increase. Hungary, which has proposed government mandated encryption backdoors and has recently granted its prime minister an indefinite power to rule by decree, has seen a 1,502% increase,
In contrast, privacy-conscious Germany, which is adopting the least intrusive form of contact tracing, has seen a mere 25% increase. It seems clear from these figures that something more than, or in addition to, remote working is driving the rapid adoption of secure collaboration tools. The implication is that concern over privacy is a major factor -- but this isn't proven by these figures alone.
Wickr checked back over its historical figures, and found another correlation to government activity. In December 2018, the Australian government passed the Telecommunications Access and Assistance Act, which allows the Australian government to compel cooperation and surveillance assistance from companies. Local use of Wickr increased by 100% at this time.
In March 2019, a local government bill in Hong Kong enabled extraditions to mainland China for the first time. Local use of the Wickr Pro/business platform increased by 200%. In Russia, in May 2019 when the sovereign internet law was signed, tightening Moscow's grip on internet communications, use of Wickr again increased by 200%.
It seems likely from these figures that the primary motivation for adopting secure collaboration platforms is concern over government interference in privacy. The figures are dramatically higher today because of the privacy implications of the COVID-19 contact tracing apps. It would seem that many people are concerned that governments will not easily abandon their increased surveillance powers following the end of the pandemic. Comparisons between 9/11 and the Patriot Act, and COVID-19 and contact tracing and surveillance are common.
What remains somewhat surprising, however, is that the increased adoption analyzed by Wickr is not in its consumer-oriented chat program, but in its business-oriented communication and collaboration tool. It is easier to understand individuals being concerned about their personal privacy than in businesses being concerned about government surveillance -- yet that is what these figures suggest.
There are two possible reasons for this. Even though business is already subject to considerable government surveillance in many different forms, nevertheless business is led by individuals with individuals' attitudes towards privacy. The second reason may be more pragmatic. Business is global and there are many different data protection and privacy laws with different degrees of severity in place around the world. If any one government acquires excessive surveillance rights, this could be seen as a threat to international trade.
However, whatever the causes, the one thing that cannot be denied is a sudden and dramatic uptake in the use secure collaboration tools that appears to correlate with fears of increasing government surveillance capabilities. It would seem that the backlash against government surveillance that started with Edward Snowden's revelations about the Five Eyes' surveillance practices has not waned over the years.
Israeli Websites Targeted in Major Cyber Attack
21.5.2020 Securityweek BigBrothers
Many Israeli websites were hit by a coordinated cyber attack Thursday, with the home pages replaced by images of the country's commercial capital Tel Aviv in flames.
Israel's National Cyber Directorate said private companies using a particular operating system were targeted, but said the damage was "superficial".
It did not state the number of pages targeted but Israeli media reported it was more than 1,000, including those of major firms.
The pages were replaced with the slogan "the countdown to the destruction of Israel started long ago".
A link led to a computer-generated video of Tel Aviv and other Israeli cities on fire, seemingly after a series of attacks.
There were no immediate details on the group which claimed the attack called Hackers of Saviour.
The attack came a day before Israelis celebrate Jerusalem Day -- signifying the country's capture of the eastern part of the disputed city in 1967.
Iran, Israel's long-time rival, also commemorates the day but highlights the Palestinian and Muslim connection to the holy city.
Their animosity has flared in a war of words on Twitter.
Iran's supreme leader Ayatollah Ali Khamenei recently attacked Israel's founding ideology Zionism, charging that Zionists have "been acting like a cancerous tumour, furthering their goals by massacring children, women and men".
Israeli Prime Minister Benjamin Netanyahu replied Wednesday evening, saying Khamenei "should know that any regime that threatens Israel with extermination will find itself in similar danger".
The attack on Israeli websites came days after a cyber attack on computer systems at an Iranian port was blamed on Israel.
US Secretary of State Mike Pompeo made an eight-hour visit to Israel last week, during which he accused Iran of using its resources to "foment terror" even as its people face the Middle East's deadliest novel coronavirus outbreak.
Pompeo also tweeted that "the United States condemns Supreme Leader Khamenei's disgusting and hateful anti-Semitic remarks.
"They have no place on Twitter or on any other social media platform."
Israel is suspected to be behind the cyberattack on Iranian port
21.5.2020 Securityaffairs BigBrothers
Israel is likely behind the recent cyberattack which disrupted some operations at Iran’s Shahid Rajaei Port, located near the Strait of Hormuz.
A couple of weeks ago, Iranian officials announced that hackers damaged a small number of systems at the port of Shahid Rajaei in the city of Bandar Abbas.
Bandar Abbas is the capital of Hormozgān Province on the southern coast of Iran, on the Persian Gulf. The city occupies a strategic position on the narrow Strait of Hormuz, and it is the location of the main base of the Iranian Navy. Bandar Abbas is also the capital and largest city of Bandar Abbas County.
Iranian officials did not reveal details of the cyber attack that took place on May 9, two days before Iranian officials disclosed the incident.
Local authorities, including the Ports and Maritime Organization (PMO) in the state of Hormozgan, confirmed that operations at the port were impacted by the cyber attack.
Initially, officials denied the cyber-attack, but due to media pressure that later admitted the cyber intrusion.
The authorities did not attribute the attack to a specific threat actor, Iran’s Deputy Minister of Roads and Urban Development stated that he did not have any information about the origin of the attack.
“Currently, the distribution of cargo in northern ports is good; although the performance of all southern ports is negative.” Mohammad Rastad.
Rastad told Fars News Agency that the attack was carried out by a foreign governenment.
Now a foreign government security official said the attack was “highly accurate” and the damages caused to the Iranian infrastructure were greater than described in official Iranian accounts.
The news was reported by The Washington Post, which blamed Israel for the cyber attack that was launched in retaliation for an earlier cyberattack on rural water distribution systems in Israel.
In April, the Israeli government has issued an alert to organizations in the water sector following a series of cyberattacks that targeted the water facilities.
Earlier May, Israel’s security cabinet discussed alleged Iranian cyberattack on Israeli water and sewage facilities that fortunately did not cause serious damage. The attack demonstrates an escalation by the Iranians, because they targeted civilian infrastructure.
“This was a very unordinary cyberattack against civilian water facilities which is against every ethic and every code even in times of war,” a senior Israeli official told Channel 13. “We didn’t expect this even from the Iranians. It is just not done.”Iran reported three cyberattacks within one week back in December. At least one of the attacks was allegedly “state-sponsored.”
Israel’s National Cyber Directorate announced to have received reports of cyber attacks aimed at supervisory control and data acquisition (SCADA) systems at wastewater treatment plants, pumping stations and sewage facilities.
The recent attack could be a response of the Israeli cyber army against the wave of attacks that targeted Israely water sector.
“Israel appears to be behind a cyberattack earlier this month on computers at Iran’s Shahid Rajaee port that caused massive backups on waterways and roads leading to the facility, the Washington Post reported on Monday.” reads the report published by the Reuters.
“Citing unnamed U.S. and foreign government officials, the Post said the May 9 disruption of Iranian computers was presumably in retaliation for an earlier attempted cyberattack on rural water distribution systems in Israel.”
The Reuters agency contacted the Israeli Embassy in Washington for a comment by it has yet to respond.
In December 2019, Iran foiled two massive cyber-attacks in less than a week, the country’s telecommunications minister Mohammad Javad Azari-Jahromi revealed.
The news was reported by both the ISNA and Mehr news agencies, the Iranian minister defined the attacks as “really massive” and attributed them to a nation-state actor.
Canada Fines Facebook Over Misleading Privacy Claims
20.5.2020 Securityweek BigBrothers
Facebook has agreed to pay a Can$9 million (US$6.5 million) fine for making false or misleading claims about its privacy settings, Canada's competition watchdog announced Tuesday.
An investigation of the social media network's practices from 2012 to 2018 found that the company gave Canadians the impression that users could control who saw their personal information on Facebook and Messenger.
But it allowed their data to be shared with third party developers, the Competition Bureau said in a statement.
"Canadians expect and deserve truth from businesses in the digital economy, and claims about privacy are no exception," said competition commissioner Matthew Boswell.
He noted that Facebook had vowed publicly to stop the practice in 2015 but continued to allow third-party access to its users messages and posts until 2018.
As part of the settlement, Facebook has agreed not to make false or misleading representations about the disclosure of personal information, and pay the Competition Bureau's Can$500,000 investigation costs.
The company has about 24 million users in Canada.
In February, Canada's privacy commissioner took Facebook to court for violating privacy laws. The company has called it overreach and has asked a judge to quash the case.
Fake U.S. Dept of Treasury emails spreads new Node.js malware
19.5.2020 Bleepingcomputer BigBrothers
A new Node.js based remote access trojan and password-stealing malware is being distributed through malicious emails pretending to be from the U.S. Department of the Treasury.
This new spam campaign was discovered by Abuse.ch that says payment for a government contract was not paid due to incorrect banking information.
The email then prompts the user to examine the document for any mistakes, as if they do not hear back, the money will be used of the government's Coronavirus disaster relief.
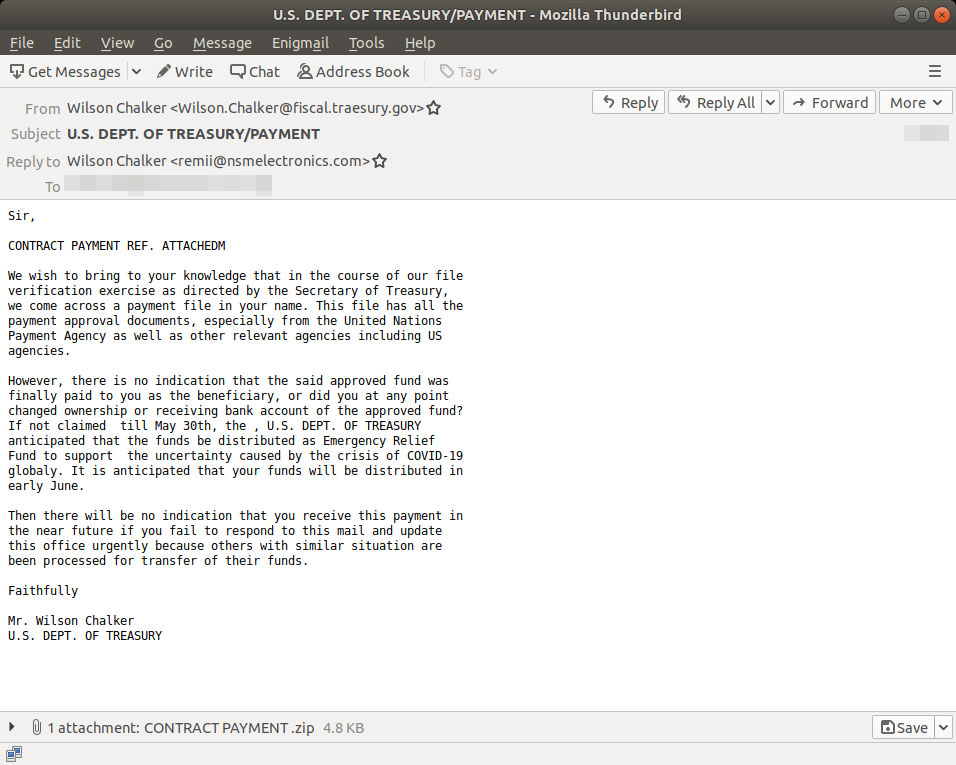
Fake Dept of Treasury email
"However, there is no indication that the said approved fund was finally paid to you as the beneficiary, or did you at any point changed ownership or receiving bank account of the approved fund? If not claimed till May 30th, the , U.S. DEPT. OF TREASURY anticipated that the funds be distributed as Emergency Relief Fund to support the uncertainty caused by the crisis of COVID-19 globaly. It is anticipated that your funds will be distributed in early June," the phishing email states.
Attached to this email is an archive named 'CONTRACT PAYMENT.zip' containing a file named 'CONTRACT PAYMENT.jar'.
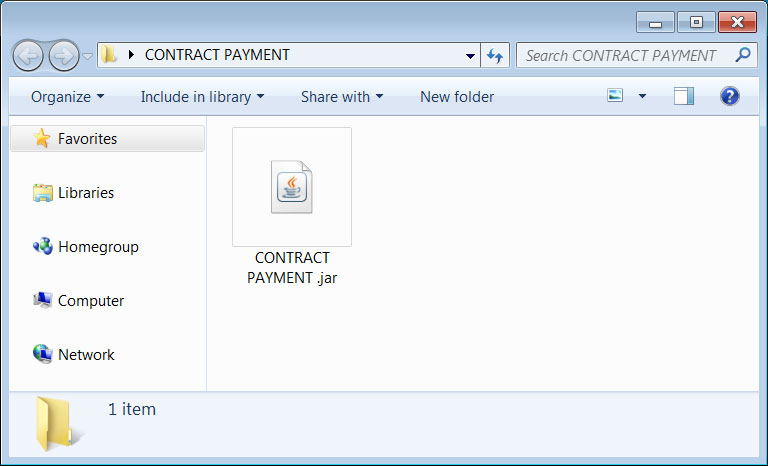
Attached File
This malware is a new Node.js malware called QNodeService that was discovered by MalwareHunterTeam and later analyzed by TrendMicro.
When executed, this JAR file will download Node.js and a script called wizard.js and stored the packages in a folder named %UserProfile\qnodejs-node-v13.13.0-win-x64, as seen below.
Qnodejs-node-v13.13.0-win-x64 folder
So that the malware is run every time the victim logs into Windows, a Windows Registry Run value will be created.
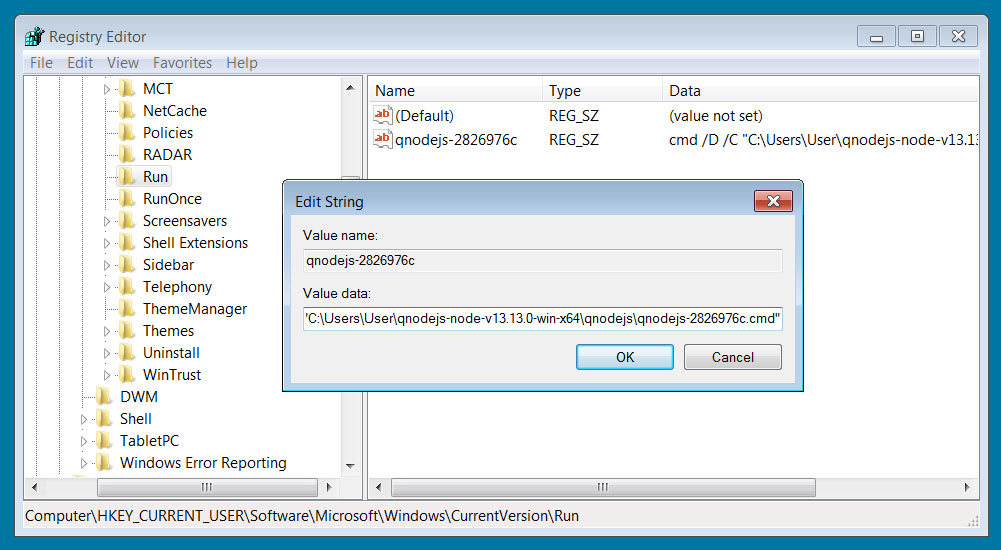
Configured Run key for persistence
According to TrendMicro's report, once the QNodeService is installed, it will have full control over the computer and further compromise it to steal data.
This further compromise is made through the following features built into the QNodeService malware:
Update itself
Get machine information such as IP address, machine name, location, user name, and OS version.
Execute commands, including the download of further payloads.
Delete and write files
Steal passwords from various applications such as Chrome and Firefox.
If you have fallen victim to this malware, you should immediately assume that your data and passwords have been compromised.
It is also possible that the malware was used to gain access to other devices on your network.
Due to this, you should immediately change any passwords that you have saved in your browser's or other applications.
Network, system, and security administrators should then perform an audit of the rest of the network to confirm that no other devices were compromised.
Court Curbs German Spies' Foreign Internet Surveillance
19.5.2020 SecuritryWeek BigBrothers
Germany's foreign intelligence service violated the constitution by spying on internet data from foreigners abroad, the nation's top court ruled Tuesday in a victory for overseas journalists who brought the case.
The BND agency's surveillance violates "the fundamental right to privacy of telecommunications" and freedom of the press, judges at the Constitutional Court in Karlsruhe said in their verdict.
But given the "great importance" of foreign surveillance to German security, the court gave the BND until the end of 2021 to change its practices and comply with the law.
The ruling marked the first time the Constitutional Court clearly stated that the BND must respect fundamental rights accorded by the Germany's Basic Law constitution even when operating abroad.
German intelligence services are already not allowed to monitor the internet traffic of Germans in such a vast way.
The case was brought by journalists and civil society groups who were outraged after the BND was granted sweeping new powers to carry out "strategic telecommunications surveillance" under amended legislation in 2016.
This allowed the BND to tap into internet traffic from non-Germans abroad, often through monitoring the use of keywords, phone numbers or email addresses, and to share this information with other secret services.
One of the plaintiffs, media watchdog Reporters Without Borders (RSF), argued that this allowed the agency to spy on journalists "almost without restrictions".
"The journalists' mission of monitoring the activities of the state is rendered ineffective if these states are listening in on their conversations while they do their research," said RSF on its website.
The mass surveillance also deterred sources from contacting reporters covering topics such as corruption, tax fraud and human rights abuses, it argued.
The group hailed Tuesday's verdict, saying it set a new benchmark for human rights and press freedom.
"We're very pleased that Karlsruhe has clamped down on the escalating surveillance practices of the federal intelligence service abroad," said Christian Mihr, RSF's Germany director.
- Stricter oversight -
"The big victory is that German authorities cannot get out of their constitutional obligations by going abroad and working there," said Nora Markard from the GFF Society for Civil Rights, another of the co-plaintiffs.
Crucially, the judges agreed that foreign intelligence gathering was necessary to keep Germany safe and was in theory not incompatible with the constitution.
But it had to be justified and proportional, they warned, whereas the BND's current snooping is "not tied to specific grounds or suspicions".
The judges called for stricter rules to govern the BND's overseas internet monitoring, including clearly defined thresholds to decide who should be targeted, and limits on sharing and storing the collected data.
An independent body should be created "that allows for comprehensive oversight and control of the surveillance process", they said.
Legislators have until December 31, 2021 to make the necessary changes to German law.
DoJ Again Asks for Encryption Backdoors After Hacking US Naval Base Shooter's iPhones
19.5.2020 SecuritryWeek BigBrothers
The U.S. Department of Justice announced on Monday that the FBI managed to gain access to the data stored on two iPhones belonging to an individual who last year killed and wounded several people at a United States naval base.
On December 6, 2019, Mohammed Saeed Alshamrani launched a terrorist attack on the Naval Air Station Pensacola in Florida, killing three people and injuring eight others. The shooter was a member of the Royal Saudi Air Force and he had been taking part in a training program sponsored by the Pentagon.
Alshamrani was killed during the attack and he attempted to destroy his iPhones before being shot. The FBI asked Apple for help in accessing the locked devices in an effort to find out more about the attacker’s activities and associations prior to the incident.
U.S. Attorney General William Barr and FBI Director Christopher Wray announced on Monday that the FBI managed to access the data stored on the two locked iPhones.
“The phones contained important, previously-unknown information that definitively established Alshamrani’s significant ties to Al Qaeda in the Arabian Peninsula (AQAP), not only before the attack, but before he even arrived in the United States. The FBI now has a clearer understanding of Alshamrani’s associations and activities in the years, months, and days leading up to the attack,” the DoJ said.
AG Barr took the opportunity to highlight that Apple was asked for assistance in accessing the information on the two iPhones, but “the company declined to do so.”
“Thanks to the great work of the FBI – and no thanks to Apple – we were able to unlock Alshamrani’s phones,” Barr stated. “The trove of information found on these phones has proven to be invaluable to this ongoing investigation and critical to the security of the American people. However, if not for our FBI’s ingenuity, some luck, and hours upon hours of time and resources, this information would have remained undiscovered. The bottom line: our national security cannot remain in the hands of big corporations who put dollars over lawful access and public safety. The time has come for a legislative solution.”
Apple has denied refusing to assist the FBI and says the government’s false claims are an “excuse to weaken encryption and other security measures.”
“It is because we take our responsibility to national security so seriously that we do not believe in the creation of a backdoor — one which will make every device vulnerable to bad actors who threaten our national security and the data security of our customers,” Apple stated. “There is no such thing as a backdoor just for the good guys, and the American people do not have to choose between weakening encryption and effective investigations.”
Apple claimed it did give authorities access to Alshamrani’s iCloud backups. However, the encryption and security mechanisms present on iPhones make it difficult to recover data from a locked device.
The FBI has been known to rely on the services of third-parties specializing in mobile forensics. One such company is Israel-based Cellebrite, which is believed to have helped the FBI hack locked phones in the past. According to some reports, the company helped the FBI access the iPhone of Syed Rizwan Farook, the terrorist behind the 2015 San Bernardino attack.
Authorities have been trying to convince tech companies — and in some cases force them through proposed legislation — to implement encryption backdoors that would make it easier to investigate crimes. However, security and privacy experts argue that such backdoors could be abused, including by the cybercriminals they are meant to protect users against.
Facebook Chief Wants EU Not China to Lead on Tech Rules
18.5.2020 Securityweek BigBrothers Social
Facebook founder Mark Zuckerberg on Monday urged the European Union to take the lead in setting global standards for tech regulation or risk seeing countries follow China as a model.
"I think right now a lot of other countries are looking at China... and saying: 'Hey, that model looks like maybe it might work. Maybe it gives our government more control?'," Zuckerberg said, during a video debate with EU commissioner Thierry Breton.
Under the Beijing model, "you don't have to respect human rights quite as much in how the society gets run," he added.
"I just think that that's really dangerous and I worry about that kind of model spreading to other countries," Zuckerberg said in the talk, organised by the Centre on Regulation in Europe
"I think that the best antidote to that is having a clear regulatory framework that comes out of Western democratic countries, and that can become a standard around the world," he argued.
"When Europe sets policies, they often become the standards around the world," he said, citing the EU's GDPR data protection legislation, which has been widely replicated.
Breton, one of the EU's top officials on tech policy, said that Facebook and other big tech companies must also live up to certain values.
If you want to have the right regulation "you have to have a clear set of values and in Europe we have these values," he said, hinting Facebook sometimes fell short, especially on controlling illegal content or paying fair taxes.
"At the end of the day, if we cannot find a way, we will regulate, of course," he warned
- Lobbying drive -
"It is extremely important that when you are CEO, at the end of the day, you are the only one to be responsible," Breton said.
"The mission of a CEO is to listen to everyone and then to take the decision. At the end of the day, it will be Mark who will be responsible, nobody else."
The debate came as Facebook embarks on a European lobbying campaign.
The European Commission is ramping up towards a Digital Service Act, a major piece of EU lawmaking intended to curb the powers of US big tech.
The law would include all aspects of the digital world, including cracking down on hate speech, protecting user data and preventing big companies from abusing their dominant market positions.
Silicon Valley firms are preparing a furious lobbying counterattack to limit its reach.
Left unchecked, the law could force Facebook, Google, Amazon or Apple to split their businesses, provide rivals access to their data and act more as public utilities and not profit-seeking innovators.
The law would also make the giants liable for illegal content -- such as hate speech or pirated music -- reversing a laissez faire policy they say fueled the internet revolution.
FBI warns US organizations of ProLock ransomware decryptor not working
18.5.2020 Securityaffairs BigBrothers
The FBI issued a flash alert to warn organizations in the United States that the ProLock ransomware decryptor doesn’t work properly.
Early this month, the FBI issued a flash alert to warn organizations of the new threat actor targeting healthcare, government, financial, and retail industries in the US.
“The decryption key or ‘decryptor’ provided by the attackers upon paying the ransom has not routinely executed correctly,” states the alert.
“The decryptor can potentially corrupt files that are larger than 64MB and may result in file integrity loss of approximately 1 byte per 1KB over 100MB.”
Threat actors are attempting to take advantage of the ongoing Coronavirus pandemic and are using COVID-19 lures in their attacks.
Experts reported several ransomware attacks against businesses and organizations, the ProLock ransomware is just is yet another threat to the list.
The FBI is recommending victims of ransomware attacks to avoid paying the ransom to decrypt their files. Feds warned that the decryptor for the ProLock is not correctly working and using it could definitively destroy the data. The descriptor could corrupt files larger than 64MB during the decryption process.
Emsisoft
@emsisoft
Fabian Wosar, Emsisoft’s CTO, said if Diebold’s claims about not paying their assailants are true, it’s probably for the best: That’s because current versions of ProLock’s decryptor tool will corrupt larger files such as database files - via @briankrebs https://krebsonsecurity.com/2020/05/ransomware-hit-atm-giant-diebold-nixdorf/ …
12
7:34 PM - May 11, 2020
Twitter Ads info and privacy
See Emsisoft's other Tweets
The PwndLocker ransomware first appeared in the threat landscape by security researchers in late 2019, operators’ demands have ranged from $175,000 to more than $660,000 worth of Bitcoin.
According to the FBI, operators behind the threat gain access to hacked networks via the Qakbot (Qbot) trojan, but experts from Group-IB added that they also target unprotected Remote Desktop Protocol (RDP)-servers with weak credentials. It is still unclear if the ProLock ransomware was managed by the Qakbot gang, or if the ProLock operators pay to gain access to hosts infected with Qakbot to deliver their malware.
“ProLock operators used two main vectors of initial access: QakBot (Qbot) and unprotected Remote Desktop Protocol (RDP)-servers with weak credentials.” reads the report published by Group-IB.
“The latter is a fairly common technique among ransomware operators. This kind of access is usually bought from a third party but may be obtained by group members as well.”
In March, threat actors behind PwndLocker changed the name of their malware to ProLock, immediately after security firm Emsisoft released a free decryptor tool.
According to the popular investigator Brian Krebs, the systems at Diebold Nixdorf were recently infected by the ProLock ransomware (aka PwndLocker), the same piece of ransomware involved in the attack against Lasalle County, Ill. in March.
“Fabian Wosar, Emsisoft’s chief technology officer, said if Diebold’s claims about not paying their assailants are true, it’s probably for the best: That’s because current versions of ProLock’s decryptor tool will corrupt larger files such as database files.” reads the analysis published by Krebs.
“As luck would have it, Emsisoft does offer a tool that fixes the decryptor so that it properly recovers files held hostage by ProLock, but it only works for victims who have already paid a ransom to the crooks behind ProLock.
“We do have a tool that fixes a bug in the decryptor, but it doesn’t work unless you have the decryption keys from the ransomware authors,” Wosar said.”
Australian Steel Maker BlueScope Hit by Cyberattack
18.5.2020 Securityweek BigBrothers
Australian steel producer BlueScope was recently hit by a cyberattack that caused disruptions to some of the company’s operations.
The company said on Friday that it responded to a “cyber incident” detected at one of its US-based businesses. While BlueScope did not share any information about the type of attack, iTnews reported that the company was hit by ransomware and that it was working to restore systems from backups.
BlueScope said the incident impacted some of its IT systems, mainly affecting manufacturing and sales operations in Australia.
“Some processes have been paused, whilst other processes including steel despatches continue with some manual processes and workarounds,” the company stated.
The firm’s North Star, Asian and New Zealand units have only experienced minor disruptions and continued to operate “largely unaffected.”
“In the affected areas the Company has reverted to manual operations where possible while it fully assesses the impact and remediates as required, in order to return to normal operations as quickly as possible,” BlueScope said.
BlueScope is not the only major Australian company hit by ransomware in recent weeks. Shipping giant Toll revealed earlier this month that some of its systems were infected with ransomware — this was the second ransomware incident disclosed by the company this year.
Toll initially said there was no evidence that the attackers stole any information, but later admitted that the hackers did manage to download information on current and former employees and details on commercial agreements with enterprise customers.
The attack on Toll involved Nefilim ransomware, whose operators are known to steal data and threaten to make it public unless a ransom is paid.
Transportation Agency Hacked in 2nd Texas Government Attack
18.5.2020 Securityweek BigBrothers
Texas’ transportation agency has become the second part of the state government to be hit by a ransomware attack in recent days.
On Thursday, someone hacked into the Texas Department of Transportation’s network in a “ransomware event,” according to a statement the department posted on social media Friday.
The departments’ website says some features are unavailable due to technical difficulties, but it is not clear what functions were affected by the attack. Agency officials did not respond to emailed questions Sunday.
The hack comes days after another ransomware attack took down the websites and case management systems of Texas’ appellate and high courts. The courts and transportation agency both said they are working with the FBI to investigate.
Hackers use ransomware to invade computer systems and encrypt files in an effort to extort payments to unlock them.
Upon detecting the hack, staff at the transportation department “immediately” isolated the affected parts of the network and “shut down further unauthorized access,” according to the statement. James Bass, the department’s executive director, said his staff is “working to ensure critical operations continue during this interruption.″ The hacks follow a ransomware attack of unprecedented size that hit more than 20 local governments in Texas last summer.
U.S. Restriction on Chipmakers Deals Critical Blow to Huawei
18.5.2020 Securityweek BigBrothers
The latest U.S. sanctions on tech giant Huawei threaten to devastate the company and escalate a feud with China that could disrupt technology industries worldwide.
Huawei Technologies Ltd. is one of the biggest makers of smartphones and network equipment, but that $123 billion-a-year business is in jeopardy after Washington announced further restrictions on use of American technology by foreign companies that make its processor chips.
Huawei spent the past year scrambling to preserve its business after an earlier round of U.S. restrictions imposed last May cut off access to American components and software.
“Our business will inevitably be impacted,” Huawei’s chairman, Guo Ping, said at a conference Monday with industry analysts.
“In spite of that, the challenges over the past year have helped us develop a thicker skin, and we are confident about finding solutions soon,” Guo said.
The company said Monday that it would need some time to “understand the impact” of the latest restrictions.
The conflict is politically explosive because Huawei is more than just China’s most successful private company. It is a national champion among industries the ruling Communist Party is promoting in hopes of transforming China into a global competitor in profitable technologies.
On Monday, China’s Ministry of Commerce warned it will protect “the legitimate rights and interests of Chinese enterprises,” but gave no details of potential retaliation. Beijing has threatened in the past to issue an “unreliable entities list” that might restrict operations of American companies in China.
Friction over Huawei adds to a broader deterioration of U.S.-Chinese relations.
The two sides have declared a truce in a trade war, but arguments over the origin of the coronavirus pandemic that is roiling the global economy have raised worries that agreement might fall apart.
Huawei is at the center of the U.S.-Chinese conflict over Beijing’s technology ambitions, which Washington worries might erode American industrial leadership.
Huawei has few alternatives if Washington refuses to allow its suppliers to use U.S. technology. The company has developed some of its own chips but even the biggest non-U.S. manufacturers such as Taiwanese giant TSMC need American components or production equipment.
“Every electronics system that Huawei produces could be negatively impacted,” Jim Handy, semiconductor analyst for Objective Analysis, said in an email. “Most China-based alternatives haven’t yet been established.”
New curbs announced Friday are the third round of sanctions aimed at cutting off Huawei’s access to U.S. technology and markets.
In a statement, Huawei criticized the U.S. decision as “arbitrary and pernicious” and warned it will affect operation and maintenance of networks installed by the company in more than 170 countries.
“The U.S. government has intentionally turned its back on the interests of Huawei’s customers and consumers,” it said.
The statement said the decision “will damage the trust and collaboration within the global semiconductor industry,” harming other industries that depend on it.
The Trump administration says Huawei is a security risk, which the company denies, and is trying to persuade European and other allies to shun its technology for next-generation telecom networks.
Chinese officials accuse Washington of raising phony security concerns to hurt a rising competitor to American tech companies.
The potential impact extends far beyond Huawei. The company spends tens of billions of dollars a year on components and technology from U.S. and other suppliers, purchases that might be disrupted if output of smartphones and other products is blocked.
U.S. suppliers already have complained to Washington that restrictions imposed last May on Huawei’s access to American components and other technology will cost them billions of dollars in lost potential sales.
The company’s telecoms market in the U.S. evaporated after a congressional panel in 2012 labeled Huawei and its Chinese competitor ZTE Corp. security risks and told phone carriers to avoid them.
Last year’s sanctions require U.S. companies to obtain government permission to sell chips and other technology to Huawei. The company can keep using Google’s Android operating system on its smartphones but lost the ability to pre-install music, maps and other Google services customers expect on phones.
Huawei has launched its own smartphone operating system and is paying developers to create apps to run on it. But the company says sales have suffered.
Despite that, Huawei reported a 2019 profit of 62.7 billion yuan ($8.8 billion) and said total sales rose 19% over a year earlier.
The sanctions highlight Huawei’s reliance on technology suppliers despite having one of the world’s biggest corporate research and development budgets.
Huawei has its own semiconductor unit, HiSilicon, but needs manufacturers including TSMC to make the most advanced chips.
Beijing has spent the past two decades and billions of dollars to create a Chinese semiconductor industry. But its biggest producer, SMIC, can only make chips that are two generations behind TSMC.
“Huawei had already begun to shift some production from TSMC to SMIC, although SMIC cannot yet produce Huawei’s latest Kirin 980 chipset,” said Neil Thomas, a research associate at U.S. think tank Paulson Institute. “But SMIC can probably manufacture earlier-generation Huawei chipsets.”
Then-chairman Eric Xu warned in March that more U.S. pressure on Huawei might provoke Chinese retaliation that could disrupt its global industry.
Beijing will not “just stand by and watch Huawei be slaughtered,” Xu said. “The impact on the global industry would be astonishing.”
Elexon, a middleman in the UK power grid network hit by cyber-attack
17.5.2020 Securityaffairs BigBrothers
Elexon, a middleman in the UK power grid network, recently reported it was hit by a cyber attack.
Elexon, a middleman in the UK power grid network, was the victim of a cyber attack, the incident impacted only affected the internal IT network, including the company’s email server, and employee laptops
“Hackers have targeted a critical part of the UK’s power network, locking staff out of its systems and leaving them unable to send or receive emails.” reads a post published by The Telegraph.
“Elexon – a key player in the energy market between power station operators and firms that supply households and businesses – said in a statement that its internal systems and company laptops had been affected by the cyberattack. It declined to give further details.”
The company manages electricity supply and demand and distributes the power around the network according to the demand.
“We are advising you that today that ELEXON’s internal IT systems have been impacted by a cyber attack. BSC Central Systems and EMR are currently unaffected and working as normal. The attack is to our internal IT systems and ELEXON’s laptops only.” reads a post published by the company on its website. “We are currently working hard to resolve this. However please be aware that at the moment we are unable to send or receive any emails.”
The company has taken down the email server in response to the attack.
According to Elexon, the systems use to manage the UK’s electricity transit were not impacted.
The company published a second message to announce that it has discovered the root cause of the incident, and that is was working to restore the internal network and employee laptops. Elexon also added that the BSC Central Systems (and their data) and EMR were not impacted and are continuing to work as normal.
Even if the company did not reveal any details on the attack, experts speculate the involvement of a ransomware.
Experts from security firm Bad Packets reported that Elexon had been running an outdated version of Pulse Secure VPN server, if confirmed threat actors could have exploited it to access the internal network.
In January, the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) warned organizations that attackers continue to exploit the well known Pulse Secure VPN vulnerability tracked as CVE-2019-11510.
The CVE-2019-11510 flaw in Pulse Connect Secure is a critical arbitrary file read vulnerability, it could be easily exploited by using publicly available proof-of-concept code. The flaw can be used in combination with the CVE-2019-11539 remote command injection issue gain access to private VPN networks.
In October, the UK’s National Cyber Security Centre (NCSC) reported that advanced persistent threat (APT) groups have been exploiting recently disclosed VPN vulnerabilities in enterprise VPN products in attacks in the wild. Threat actors leverage VPN vulnerabilities in Fortinet, Palo Alto Networks and Pulse Secure, to breach into the target networks.
The UK agency reported that APT groups target several vulnerabilities, including CVE-2019-11510 and CVE-2019-11539 in Pulse Secure VPN solutions, and CVE-2018-13379.
NSA also warned of multiple state-sponsored cyberespionage groups exploiting enterprise VPN Flaws
Despite Pulse Secure addressed the flaw in April, thousands of Pulse Secure VPN endpoints are yet to be fixed. In January 2020, Bad Packets reported that there were still 3,623 vulnerable Pulse Secure VPN servers, 1,233 of which were in the United States. The security firm confirmed, Elexon was still running an outdated Pulse Secure VPN installation.
The UK’s National Grid agency publicly announced that the incident did not affect electricity supply across the nation.
National Grid ESO
@ng_eso
We’re aware of a cyber attack on ELEXON’s internal IT systems. We’re investigating any potential impact on our own IT networks. Electricity supply is not affected. We have robust cybersecurity measures across our IT and operational infrastructure to protect against cyber threats. https://twitter.com/ELEXONUK/status/1260943958374522880 …
ELEXON UK
@ELEXONUK
Our internal IT systems have been impacted by a cyber-attack. BSC Central Systems and EMR are currently unaffected. Please note that we are currently unable to send or receive any emails. See more information here: https://bit.ly/2WTP22C . Apologies for any inconvenience.
27
8:13 PM - May 14, 2020
Twitter Ads info and privacy
27 people are talking about this
US warns of Chinese hackers targeting COVID-19 research orgs
17.5.2020 Bleepingcomputer BigBrothers
Threat actors affiliated to the People’s Republic of China (PRC) are attempting to compromise and collect COVID-19 information from organizations in the US health care, pharmaceutical, and research industry sectors.
The ongoing attacks are currently investigated by the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) as stated in a joint public service announcement published today (1, 2, 3).
"China’s efforts to target these sectors pose a significant threat to our nation’s response to COVID-19," the FBI said.
"This announcement is intended to raise awareness for research institutions and the American public and provide resources and guidance for those who may be targeted.
"These actors have been observed attempting to identify and illicitly obtain valuable intellectual property (IP) and public health data related to vaccines, treatments, and testing from networks and personnel affiliated with COVID-19-related research.
"The potential theft of this information jeopardizes the delivery of secure, effective, and efficient treatment options."
Rumors confirmed
Today's warning confirms rumors saying that US authorities will raise awareness this week that PRC-affiliated threat actors are trying to US-based organizations involved in COVID-19-related research.
Last week, CISA and the UK's National Cyber Security Centre (NCSC) issued another advisory warning of organizations involved in international COVID-19 responses, healthcare, and essential services being targeted by government-backed hacking groups.
While they didn't name the country sponsoring those attacks, the end goal was the same, with the threat actors seeking "to obtain intelligence on national and international healthcare policy, or acquire sensitive data on COVID-19-related research."
CISA and NCSC said that they were also investigating APT campaigns using large-scale password spraying in attacks against international and national healthcare care entities from multiple countries including but not limited to the US and the UK.
The FBI also said last month in a joint flash alert coordinated with CISA that phishing campaigns were targeting US healthcare providers with COVID-19 themed lures to distribute malicious attachments to create "an initial intrusion vector to enable follow-on system exploitation, persistence, and exfiltration."
FBI
✔
@FBI
The #FBI and @CISAgov have observed PRC-affiliated actors attempting to obtain public health research related to #COVID19 treatments. The potential theft of this information jeopardizes the delivery of secure, effective, and efficient treatment options. http://ow.ly/F1WL50zF63n
648
4:15 PM - May 13, 2020
Twitter Ads info and privacy
426 people are talking about this
Defense recommendations
The full public service advisory (1, 2) also provides recommendations for US COVID-19 research organizations to defend against attacks and information on how to report suspicious or criminal activity.
"The FBI and CISA urge all organizations conducting research in these areas to maintain dedicated cybersecurity and insider threat practices to prevent surreptitious review or theft of COVID-19-related material," the PSA reads.
Targeted COVID-19 research and response organizations are advised to take defensive measures to block potential attacks:
Assume that press attention affiliating your organization with COVID-19-related research will lead to increased interest and cyber activity.
Patch all systems for critical vulnerabilities, prioritizing timely patching for known vulnerabilities of internet-connected servers and software processing internet data.
Actively scan web applications for unauthorized access, modification, or anomalous activities.
Improve credential requirements and require multi-factor authentication.
Identify and suspend access of users exhibiting unusual activity.
US govt shares list of most exploited vulnerabilities since 2016
16.5.2020 Bleepingcomputer BigBrothers
US Government cybersecurity agencies and specialists today have released a list of the top 10 routinely exploited security vulnerabilities between 2016 and 2019.
Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the broader US Government issued the AA20-133A alert through the National Cyber Awareness System to make it easier for organizations from the public and private sector to prioritize patching in their environments.
"The public and private sectors could degrade some foreign cyber threats to U.S. interests through an increased effort to patch their systems and implement programs to keep system patching up to date," CISA said.
"A concerted campaign to patch these vulnerabilities would introduce friction into foreign adversaries’ operational tradecraft and force them to develop or acquire exploits that are more costly and less widely effective."
A PDF version of CISA's alert on the top 10 most exploited security vulnerabilities between 2016 and 2019 is available here.
Most exploited: Microsoft’s OLE and Apache Struts
Based on the US Government's analysis of cyberattacks abusing security vulnerabilities, threat actors have most often exploited bugs in Microsoft’s Object Linking and Embedding (OLE) technology, with the Apache Struts web framework being the second-most-reported exploited technology.
"Of the top 10, the three vulnerabilities used most frequently across state-sponsored cyber actors from China, Iran, North Korea, and Russia are CVE-2017-11882, CVE-2017-0199, and CVE-2012-0158," CISA says. "All three of these vulnerabilities are related to Microsoft’s OLE technology."
However, Chinese hackers have been frequently exploiting CVE-2012-0158 starting with December 2018 showing that organizations have failed to patch it and that malicious actors will continue abusing such flaws as long as they're not fixed.
In 2020, CISA says that attackers have been hard at work exploiting unpatched Citrix VPN (CVE-2019-11510) and Pulse Secure VPN (CVE-2019-19781) vulnerabilities after the move to remote working caused by the COVID-19 pandemic, as well as taking advantage of hasty deployments of cloud collaboration services like Microsoft Office 365.
The top 10 routinely exploited security flaws since 2016
The full list of the top 10 most exploited security flaws between 2016 and 2019 is embedded in the table below, with links to National Vulnerability Database entries and associated malware.
CVE Associated Malware
CVE-2017-11882 Loki, FormBook, Pony/FAREIT
CVE-2017-0199 FINSPY, LATENTBOT, Dridex
CVE-2017-5638 JexBoss
CVE-2012-0158 Dridex
CVE-2019-0604 China Chopper
CVE-2017-0143 Multiple using the EternalSynergy and EternalBlue Exploit Kit
CVE-2018-4878 DOGCALL
CVE-2017-8759 FINSPY, FinFisher, WingBird
CVE-2015-1641 Toshliph, Uwarrior
CVE-2018-7600 Kitty
The AA20-133A CISA alert also provides mitigations for each of the top vulnerabilities detailed above.
Additionally, CISA, FBI, and the broader U.S. Government recommend organizations to transition away from any end-of-life software as soon as possible as the easiest way to mitigate old unpatched security issues in their environments.
Earlier today, the US Government also released info on three new malware variants (two trojans and a Remote Access Tool) associated with North Korean government malicious cyber activity tracked as HIDDEN COBRA.
US govt exposes new North Korean malware, phishing attacks
16.5.2020 Bleepingcomputer BigBrothers
The US government today released information on three new malware variants used in malicious cyber activity campaigns by a North Korean government-backed hacker group tracked as HIDDEN COBRA.
The new malware is being used "for phishing and remote access by #DPRK cyber actors to conduct illegal activity, steal funds & evade sanctions" according to the information published by Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Defense (DoD).
U.S. Cyber Command has also uploaded five samples of the newly discovered malware variants onto the VirusTotal malware aggregation repository.
USCYBERCOM Malware Alert
✔
@CNMF_VirusAlert
5 New malware samples attributed to DPRK by @FBI:https://virustotal.com/gui/user/CYBERCOM_Malware_Alert … . These malware are used for phishing and remote access by #DPRK cyber actors to conduct illegal activity, steal funds & evade sanctions. @US_CYBERCOM @CISAgov
297
3:51 PM - May 12, 2020
Twitter Ads info and privacy
210 people are talking about this
Besides the malware samples shared by the U.S. Cyber Command, CISA has also published detailed malware analysis reports (MARs) on its website containing indicators of compromise (IOCs) and YARA rules for each of the detected samples.
The cybersecurity agency also provides mitigation measures in the form of Snort rules, as well as recommendations for system owners and administrators to strengthen the security posture of their organization's systems.
The MARs are issued to help network defenders detect and reduce exposure to HIDDEN COBRA malicious cyber activity as the United States government cybersecurity agencies refer to North Korean government malicious activity.
Three new North Korean malicious tools
The first of the new malware variants, COPPERHEDGE, is described as a Remote Access Tool (RAT) "used by advanced persistent threat (APT) cyber actors in the targeting of cryptocurrency exchanges and related entities."
This RAT is known for its capability to help the threat actors perform system reconnaissance, run arbitrary commands on compromised systems, and exfiltrate stolen data.
TAINTEDSCRIBE is a trojan that acts as a full-featured beaconing implant with command modules and designed to disguise as Microsoft’s Narrator.
The trojan "downloads its command execution module from a command and control (C2) server and then has the capability to download, upload, delete, and execute files; enable Windows CLI access; create and terminate processes; and perform target system enumeration."
Last but not least, PEBBLEDASH is yet another North Korean trojan acting like a full-featured beaconing implant and used by North Korean-backed hacking groups "to download, upload, delete, and execute files; enable Windows CLI access; create and terminate processes; and perform target system enumeration."
USCYBERCOM Malware Alert
✔
@CNMF_VirusAlert
Replying to @CNMF_VirusAlert
#ICYMI 21 malware samples already in Virus Total also attributed to DPRK by @FBI. #CNMF enables a whole of government effort to seek out DPRK malicious cyber activity. Check out the 3 latest MARs https://www.us-cert.gov/northkorea released by @CISAgov to better defend your networks.
63
3:20 PM - May 12, 2020
Twitter Ads info and privacy
55 people are talking about this
More information on HIDDEN COBRA
Last month, the U.S. government has also issued guidance on North Korean hacking activity and offered a reward of up to $5 million for any information on DPRK hackers' cyber activity, including past or ongoing operations if it leads to the identification or location of North Korean actors or to the disruption of DPRK-related illegal activities.
North Korean backed hacking groups were also behind cryptocurrency heists that led to losses of $571 million during 2017 and 2018, and the U.S. Treasury signed sanctions against three DPRK-sponsored hacking groups (Lazarus, Bluenoroff, and Andariel) in September 2019.
Two Chinese nationals were also charged during March 2020 with the laundering over $100 million worth of cryptocurrency out roughly $250 million stolen by the Lazarus Group in 2018 in a cryptocurrency exchange hack,
The US govt issued six other Malware Analysis Reports of North Korean malware in mid-February including:
• BISTROMATH (full-featured RAT),
• SLICKSHOES (Themida-packed malware dropper),
• CROWDEDFLOUNDER (Remote Access Trojan loader),
• HOTCROISSANT (beaconing implant with backdoor capabilities),
• ARTFULPIE (malware that loads and executes a DLL from a hardcoded URL),
• BUFFETLINE (beaconing implant with backdoor features).
In 2019, CISA and the FBI have also released information on another malware strain dubbed ELECTRICFISH and used by the North-Korean APT group Lazarus to steal data, as well as on the Lazarus HOPLIGHT trojan used to mask malicious traffic.
More info about North Korean HIDDEN COBRA malicious cyber activity in the form of previous MARs and alerts released via the National Cyber Awareness System is available here.
Interserve UK defense contractor hacked, up to 100,000 past and present employees details exposed
16.5.2020 Securityaffairs BigBrothers
Britain’s Ministry of Defence contractor Interserve has been hacked, intruders have stolen up to 100,000 past and present employees’ details.
Interserve, a contractor for the Britain’s Ministry of Defence suffered a security breach, hackers have stolen up to 100,000 of past and current employees details. The company currently has around 53,000 employees. Stolen data includes payment information and details of their next of kin.
“Outsourcing group Interserve is recovering from a cyberattack which took place over the weekend that may have seen the details of up to 100,000 people stolen.” reported The Telegraph.
“Hackers broke into a human resources database owned by the outsourcing firm, which recently helped build the Birmingham Nightingale Hospital, on May 9 and stole information on current and former Interserve employees, a company insider said.”
Attackers might have accessed to names, addresses, bank details, payroll information, next of kin details, HR records, dates of absences, and pension information.
The security breach took place early May, at the time there are no details about the attack and it is unclear the number of affected individuals.
“Interserve was the target of a cyber security attack earlier this month.” reads a press release published by the company on its website.
“Interserve is working closely with the National Cyber Security Centre (NCSC) and Strategic Incident Response teams to investigate, contain and remedy the situation. This will take some time and some operational services may be affected. Interserve has informed the Information Commissioner (ICO) of the incident. We will provide further updates when appropriate.”
The defense contractor is investigating the incident with the help of the National Cyber Security Centre.
According to the defense contractor’s website, Interserve is present on 35 MoD sites, the company also announced that it is supporting the NHS during COVID-19.
Chinese Hackers Target Air-Gapped Military Networks
16.5.2020 Securityweek BigBrothers
A threat actor believed to be operating out of China has been targeting physically isolated military networks in Taiwan and the Philippines, Trend Micro reports.
Tracked as Tropic Trooper and KeyBoy, and active since at least 2011, the threat actor is known for the targeting of government, military, healthcare, transportation, and high-tech industries in Taiwan, the Philippines, and Hong Kong.
Previously, the group was observed targeting victims with spear-phishing emails containing malicious attachments designed to exploit known vulnerabilities, such as CVE-2017-0199.
Now, Trend Micro reveals that, since December 2014, the threat actor has been leveraging a piece of malware referred to as USBferry to target entities such as military/navy agencies, government institutions, military hospitals, and even a national bank.
USBferry is a piece of stealthy USB malware capable of executing various commands on specific targets, and designed to steal critical data through USB storage.
To ensure the success of their attacks, the hackers would first target organizations related to military or government, which might employ less robust security, and use these as jumping-off points for attacks. In one instance, the group compromised a military hospital and used it to move to the military’s physically isolated network.
USBferry was initially mentioned in a 2017 PricewaterhouseCoopers report, but without a technical analysis. Trend Micro’s investigation into the malware revealed the use of at least three versions, each with different variants and components.
The activities the malware performs on the compromised systems differ from one environment to another: it can execute commands, source target files or folder lists, and copy files from air-gapped machines to compromised hosts.
“The group achieves infection by employing the USB worm infection strategy and ferrying a malware installer via USB into an air-gapped host machine,” Trend Micro explains.
The malware checks for network connectivity and, if none is found, it proceeds to collect information from the machine and copy the data to the USB drive.
The security researchers also discovered that the hackers have employed several different backdoors in a recent incident, including WelCome To Svchost (the first version dated 2011), Welcome To IDShell, and Hey! Welcome Server.
Other tools the hackers have employed in their attacks include a command-line remote control listener/port relay tool, backdoor payload/steganography payload execution loaders, and port scanning tools available on the Internet.
The group was also observed using steganography to mask backdoor routines and evade anti-malware and network perimeter detections. The technique was used to send information to the command and control server, in addition to delivering payloads.
“Tropic Trooper seems to have been targeting air-gapped environments over the past six years; in particular, the group prefers to target military hospitals and national banks as initial footholds. It could be difficult for some military and government offices to have sufficient security controls; protections can be challenged and thus make incident response trickier,” Trend Micro notes.
US Seeks to Cut Off China's Huawei From Global Chip Suppliers
16.5.2020 Securityweek BigBrothers
US officials moved Friday to cut off Chinese tech giant Huawei from global chipmakers, ramping up sanctions on the company seen by Washington as a national security risk.
The Commerce Department said it was broadening its sanctions enforcement to include semiconductor designs that are developed using US software and technology.
Officials said Huawei had been circumventing sanctions by obtaining chips and components that are produced around the world based on US technology.
"This announcement cuts off Huawei's efforts to undermine US export controls," the Commerce Department said in a statement.
The department said it would "narrowly and strategically target Huawei's acquisition of semiconductors that are the direct product of certain US software and technology."
Commerce Secretary Wilbur Ross said in a statement that even as Huawei seeks to develop its own components in response to US sanctions, "that effort is still dependent on US technologies."
The move is the latest aimed at Huawei, one of the world's biggest tech and smartphone firms, which US officials say has been stealing American trade secrets and aiding Beijing's espionage efforts.
Huawei has denied links to the Chinese government, and the sanctions have heightened US-China trade tensions.
The latest action "puts America first, American companies first and American national security first," a senior Commerce Department official said in a statement.
US officials said the new rules would have a 120-day grace period. After that, any chips destined for Huawei or its affiliates would be required to have a license.
A senior State Department official, who joined a call with journalists on the new actions, said the move would not necessarily deny Huawei access to these products but require a license allowing Washington to keep track of the technology.
"One shouldn't jump to conclusions on what the impact will be," the official said.
- Taiwan chipmaker in US -
In a separate announcement, US officials announced the Taiwan Semiconductor Manufacturing Corporation intends to invest $12 billion in a US-based nanometer semiconductor foundry.
The deal "is a game changer for the US semiconductor industry that will bolster American national security and our economic prosperity," Secretary of State Mike Pompeo said in a statement.
Officials said the two announcements were unrelated. But analyst Patrick Moorhead of Moor Insights & Strategy said both were related to efforts to cut off China and Huawei from key US technologies.
"The US is concerned with 'feeding' Huawei, who they consider a threat with US technologies that could turn around and spy on them or their allies," Moorhead said.
"With TSMC, the fear was that China could physically or electronically intrude on Taiwan based TSMC."
Washington last year said it would blacklist Huawei from the US market and from buying crucial American components, though it has extended a series of reprieves to allow US businesses that work with Huawei time to adjust.
On Friday it extended this reprieve by another 90 days but said these exceptions are not likely to be extended further.
The Commerce Department senior official said the grace period was aimed at easing the transition for those using Huawei equipment but warned that "entities who rely on that equipment are urged to make preparations" to transition away from that by August.
Washington has been especially active in aiming to keep Huawei from developing 5G or fifth generation wireless networks in the US and allied countries, claiming these systems would be a security risk.
China Rejects US Claim of Attempted Vaccine Theft as 'Smearing'
15.5.20 Securityweek BigBrothers
Beijing accused the United States on Thursday of smearing China after Washington alleged Chinese hackers were attempting to steal research on developing a vaccine against the coronavirus.
The claims have added fuel to tensions between the global superpowers, who have traded barbs over the origin of the pandemic that has killed 300,000 people.
US authorities said Wednesday that Chinese hackers were trying to obtain coronavirus data on treatments and vaccines, warning the effort involved Chinese government-affiliated groups and others.
The FBI and the Cybersecurity and Infrastructure Security Agency said China's efforts posed a "significant threat" to the US response to COVID-19.
"China expresses strong dissatisfaction and firm opposition to such smearing," foreign ministry spokesman Zhao Lijian told a regular press briefing.
"Judging from past records, the US has carried out the largest cybertheft operations worldwide," Zhao said.
He stressed that Beijing has significant achievements of its own in the fight against the pandemic.
China is "also leading the world in COVID-19 vaccine research and treatment", and therefore has more reason to worry about cyber espionage itself, Zhao said.
He added that the country has cracked down on cyber-hacking, and that any cyber attack hindering the global fight against the pandemic should be condemned by people around the world.
Responding to US President Donald Trump's reference to COVID-19 as the "Plague from China", Zhao said the US should stop blaming and discrediting others, and focus on their own prevention and control work.
The virus first emerged in the central Chinese city of Wuhan late last year.





















