Try Word for free online.
As you can imagine, after tweeting about this discovery there was a wide range of opinions regarding this test.
Articles 5 - List Articles Page Articles Page 1 2 3 4 5 6
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Microsoft Tests Office 'Ads' in Windows 10 Wordpad
20.1.2020 Bleepingcomputer
Microsoft is testing promotions for the free Office web apps being displayed directly in the menu bar for the Windows 10 Wordpad application. As you can imagine, the reaction to this news has been mixed, with some not thinking it's a big deal and others not happy with this approach.
Microsoft provides free stripped-down versions of their Word, Excel, PowerPoint, and OneNote Office applications that can be used directly insider a browser. These web versions of the popular Office products were originally launched as Office Online, but are now known as simply Office.
Windows sleuth Rafael Rivera discovered that Microsoft is testing, or planning on testing, the display of 'ads' for the free Office web applications directly in the venerable Windows 10 Wordpad application.
Office web app promotions in Wordpad
Office web app promotions in Wordpad
(Click to see larger image)
When testing the feature, Rivera noticed that Microsoft was promoting the free Office web applications using 6 different variations that contain slightly different wording.
These different Office promotions are listed below:

Try Word for free online.
As you can imagine, after tweeting about this discovery there was a wide range of opinions regarding this test.
Some look at it negatively with one comment stating that this test is "Quite sad. This is why people rather stick with Windows 7 and 8." Another comment did not see an issue as "They are suggesting you use a free and better product, there is no harm in that in my opinion."
For those who are not happy with these promotions, the reality is that there is a good chance it will never be released. Microsoft commonly tests new features like this that after hearing negative feedback, decide to skip integrating them into the Release versions of Windows.
BleepingComputer has reached out to Microsoft with questions regarding this promotion, but have not heard back as of yet.
Windows EFS Feature May Help Ransomware Attackers
20.1.2020 Bleepingcomputer
Security researchers have created concept ransomware that takes advantage of a feature in Windows that encrypts files and folders to protect them from unauthorized physical access to the computer.
The lab-developed ransomware strain relies on the Encrypting File System (EFS) component in Microsoft's operating system and can run undetected by some antivirus software.
Abusing a legitimate feature
EFS allows users to encrypt specific files and folders with a symmetric key known as File Encryption Key, which is then encrypted with a public key (asymmetric encryption). This process and its reversal is done at a layer below the NT file system (NTFS).
The component is available in Professional and above editions of Microsoft's operating system starting Windows 2000. It is different than Bitlocker, which encrypts the entire drive.
Researchers at Safebreach Labs developed concept ransomware that relies on EFS to lock files on a Windows computer. The way it functions is described in the steps below:
1. The ransomware generates a key (using AdvApi32!CryptGenKey) to be used by EFS and records the file name used by CAPI for this key.
2. The ransomware generates a certificate for this key, using Crypt32!CertCreateSelfSignCertificate, and adds it to the personal (“MY”) certificate store using Crypt32!CertAddCertificateContextToStore.
3. The ransomware sets the current EFS key to this certificate using AdvApi32!SetUserFileEncryptionKey.
4. Now the ransomware can invoke AdvApi32!EncryptFile on every file/folder to be encrypted.
5. The ransomware saves the key file (whose name was recorded in step 1) to memory and deletes it from the following two folders:
◦ %APPDATA% \Microsoft\Crypto\RSA\sid\ (where sid is the user SID)
◦ %ProgramData% \Microsoft\Crypto\RSA\MachineKeys\
6. The ransomware flushes the EFS data from memory using the undocumented AdvApi32!FlushEfsCache (available since Windows Vista). At this time, the encrypted files become unreadable to the user (and operating system).
7. Ideally, the ransomware wipes the slack parts of the disk to ensure that data from the deleted the EFS key files and temporary files used by EncryptFile cannot be salvaged. This can also be done before the previous step.
8. The ransomware can now encrypt the key file data collected in step 5, for example, using an asymmetric (public) key hard-wired into the ransomware and send the encrypted data to the attacker directly (or instruct the victim to do so).
Restoring the files to their readable state requires decrypting the key files using the attacker's private key.
Viable technique
Amit Klein, VP of security research at SafeBreach, told BleepingComputer that although EFS malware seems theoretical, a live sample proves the opposite and the technique used could soon emerge in the wild.
To show that EFS ransomware could be a feasible threat, the researchers tested their sample on three security solutions with anti-ransomware capabilities from ESET (Internet Security 12.1.34.0), Kaspersky (Anti Ransomware Tool for Business 4.0.0.861a), and Microsoft (Windows 10 Controlled Folder Access on Windows 10 64-bit version 1809, build 17763).
Results showed that files on virtual Windows 10 machines infected with EFS could not be protected by the above-mentioned solutions.
This prompted the researchers to present their findings to 17 other anti-malware and anti-ransomware vendors for Windows. Many of them have already implemented a workaround or a fix that rolled out to customer endpoints. A list of their responses is available at the bottom of the article.
Kaspersky and ESET delivered last year an update to protect against this technique. Microsoft's response, sent on October 7, 2019, was thee following:
"Microsoft considers Controlled Folder Access a defense-in-depth feature. We assessed this submittal to be a moderate class defense in depth issue, which does not meet the Microsoft Security Servicing Criteria for Windows. Microsoft may consider addressing this in a future product".
One workaround to defend against ransomware that abuses the EFS component is to disable the feature completely. This is possible by changing the value of the following registry key to 1:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\EFS\EfsConfiguration
In an enterprise environment, disabling EFS can be done via Group Policy. Keep in mind that this solution is feasible only on machines where EFS is not needed or used.
Vendor responses:
Avast/AVG (Antivirus), on September 26, 2019: “we implemented a workaround for version 19.8”
Avira (Antivirus), on November 20, 2019: "While we value the reports of this potential vulnerability, we believe that this potential bypass which is dependent upon a customized use scenario is not a realistic ‘failure point.’"
Bitdefender (Antivirus Free, Internet Security, Total Security), on January 10, 2020: "As of today, the fix started rolling out on Bitdefender Antivirus, Bitdefender Total Security and Bitdefender Internet Security on version 24.0.14.85. On Bitdefender Free Edition the fix is in reporting mode only, being necessary for fine tunning [sic] in the future."
Check Point (SandBlast Agent), on January 16, 2020: a fix will become available on January 19 or January 20
D7xTech (CryptoPrevent Anti Malware): notified on July 5, status currently unknown
ESET (products with anti-ransomware technology), on January 19, 2020: "We are now rolling out an update to mitigate the bypass and would like to kindly ask all customers to refer to Customer Advisory 2020-0002 for more information on mitigation options regarding the bypass published in this report."
F-Secure (Internet Security with DeepGuard, SAFE), on July 31, 2019: technique is already detected as Suspicious:W32/Malware!Online and Trojan.TR/Ransom.Gen
GridinSoft (GS Anti-Ransomware, beta), on October 9, 2019: the program was last updated in 2016 and protects against ransomware that was popular at that time
IObit (Malware Fighter), on October 9, 2019: fix available in version 7.2
Kaspersky (Antivirus, Internet Security, Total Security, Free Antivirus, Small Office Security, Security Cloud, Endpoint Security, Anti-Ransomware Tool for Business), on October7, 2019: all products were updated to protect against this technique
McAfee (Endpoint products), on January 17, 2020: protection against the EFS technique is available since January 10, 2020 and covers enterprise and consumer products. A detection rule is also present in MVision EDR.
Microsoft (Windows Controlled Folder Access), on October 7, 2019: "Microsoft considers Controlled Folder Access a defense-in-depth feature. We assessed this submittal to be a moderate class defense in depth issue, which does not meet the Microsoft Security Servicing Criteria for Windows. Microsoft may consider addressing this in a future product"
Panda Security (Adaptive defense, Dome Advanced), on September 26 and October 11, 2019: protection in Panda products is based on classifying all the files/processes running at the end-point, allowing only trusted ones. "Thus, any attack using unknown files/processes will be detected and blocked.”
Sophos (Sophos Intercept X), on January 17, 2020: "We’ve updated Sophos Intercept X, and all customers using this product are protected."
Symantec (Symantec Endpoint Protection), on October 7, 2019: Issue mitigated through two signatures (SONAR.SuspBeh!gen697 and SONAR.SuspBeh!gen699) to all endpoints through the live update feature.
TrendMicro (Apex One, RansomBuster), on January 10, 2020: "Trend Micro is currently researching and working on implementing some enhancements to our endpoint protection products with anti-ransomware capabilities to try and prevent these types of attacks (ETA still in development). In the meantime, we recommend disabling EFS if it is not in in [sic] use."
Webroot (SecureAnywhere AV), on September 30, 2019: "Our threat discovery process and the various protection shields within the Webroot endpoint solution leverage this threat intelligence. While we haven’t seen this technique used in the wild yet, we now can arm our threat researchers with intel to combat it in the future"
BitPyLock Ransomware Now Threatens to Publish Stolen Data
20.1.2020 Bleepingcomputer
A new ransomware called BitPyLock has quickly gone from targeting individual workstations to trying to compromise networks and stealing files before encrypting devices.
BitPyLock was first discovered by MalwareHunterTeam on January 9th, 2020 and has since seen a trickle of new victims daily.
What is interesting is that we can compare the ransom notes of earlier versions with the latest versions to see a clear progression in the types of victims that are targeted.
To make matters worse, as ransomware operators begin stealing data before encrypting victims for use as leverage, BitPyLock actors claim to be adopting this tactic as well.
The BitPyLock Ransomware
Based on our analysis, when first launched, BitPyLock will attempt to terminate any processes that contain the following strings. This is done to terminate security software and close files being used by backup software, web server daemons, virtual machines, and databases so that they can be encrypted.
backup, cobain, drop, drive, sql, database, vmware, virtual, agent, anti, iis, web, server, apache
While encrypting files, BitPyLock will target 346 extensions (listed in the IOCs section) and will skip any files located in the following folders.
windows
windows.old
program files
program files (x86)
program data
$recycle.bin
system volume information
For every encrypted file, the ransomware will append the .bitpy extension as shown below. For example, a file named 1.doc will be encrypted and renamed to 1.doc.bitpy. 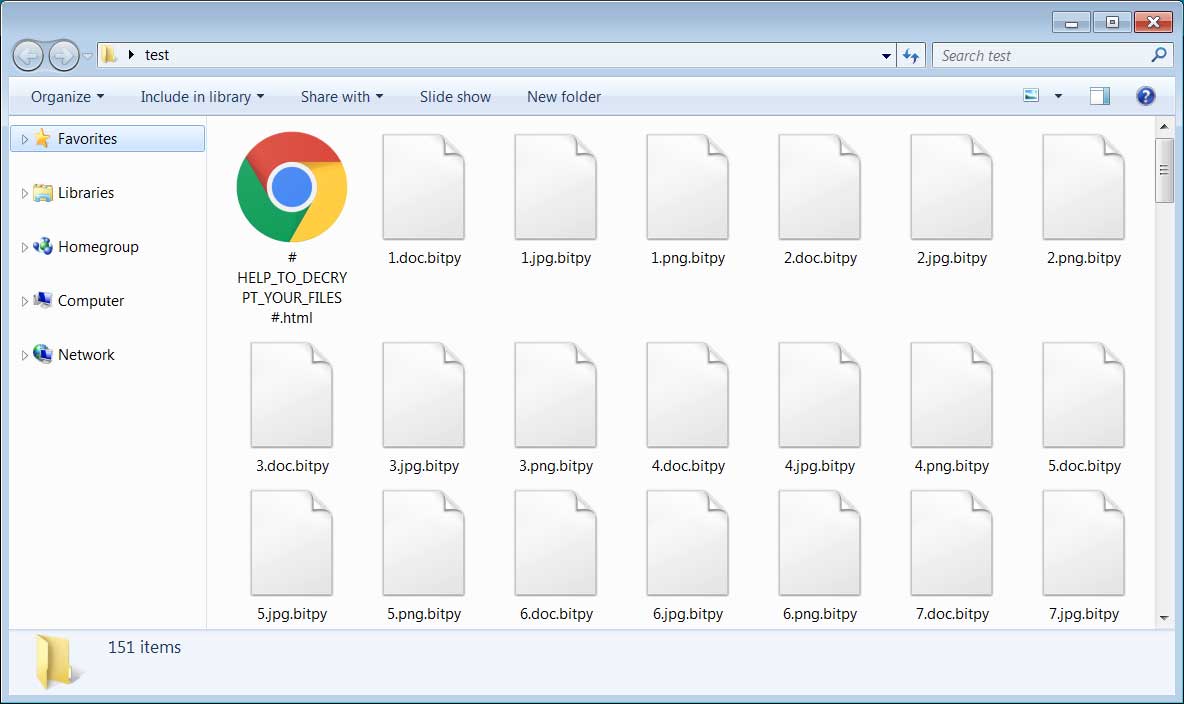
Encrypted BitPyLock files
In each folder and on the Windows desktop, BitPyLock will create a ransom note named # HELP_TO_DECRYPT_YOUR_FILES #.html that instructs the users to send a bitcoin ransom to the enclosed bitcoin address. It then instructs the victim to email the listed address to get a decryptor.
In the sample BleepingComputer analyzed, the ransom amount was hardcoded to .8 bitcoins.
The language in the original ransom note also indicated that the attackers were targeting individual machines rather than networks.
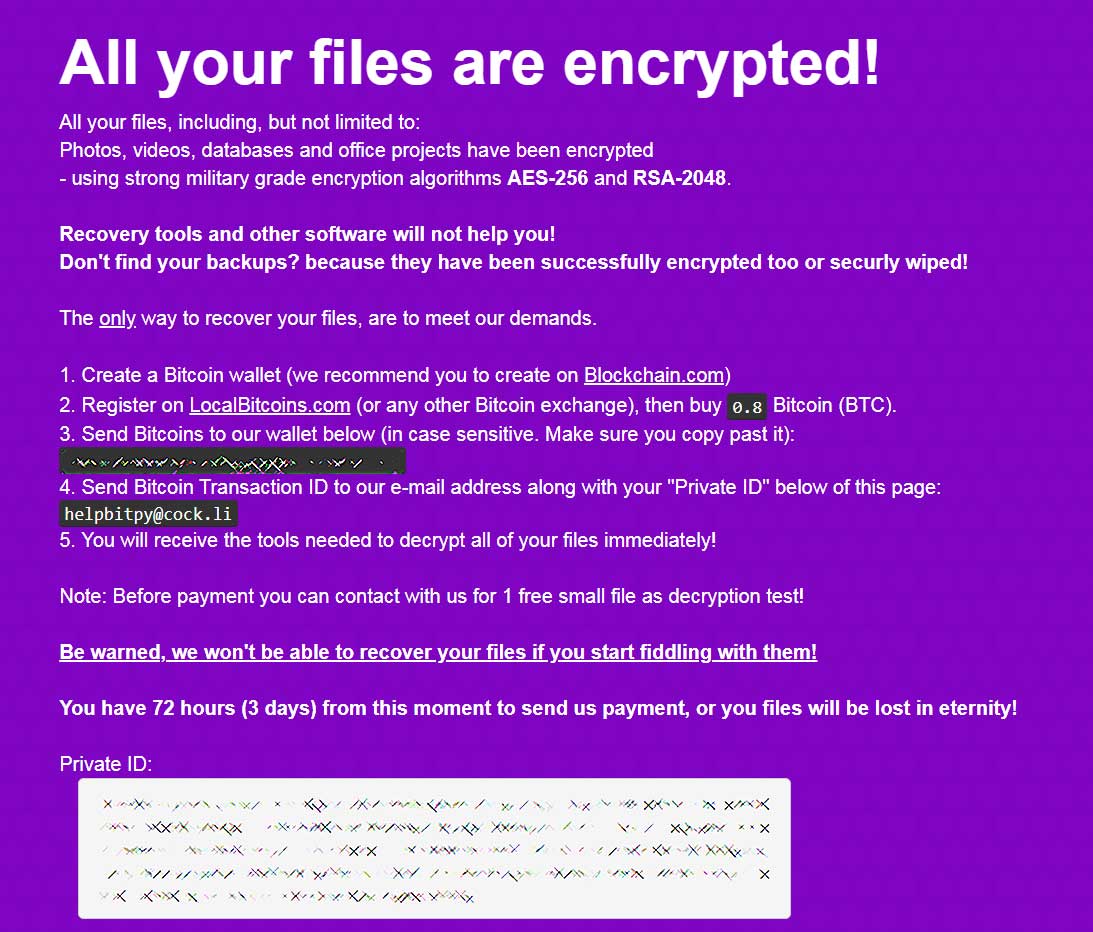
Original ransom note
Strangely, the sample that we saw had a static bitcoin address in the executable, which means every victim would have the same bitcoin address and thus it could make it impossible to determine who paid the ransom.
Evolves to network attacks and the publishing of stolen data
In a more recent version discovered by MalwareHunterTeam, the actors have changed their targeting to focus on network compromise and the claims of stealing data before encrypting devices. 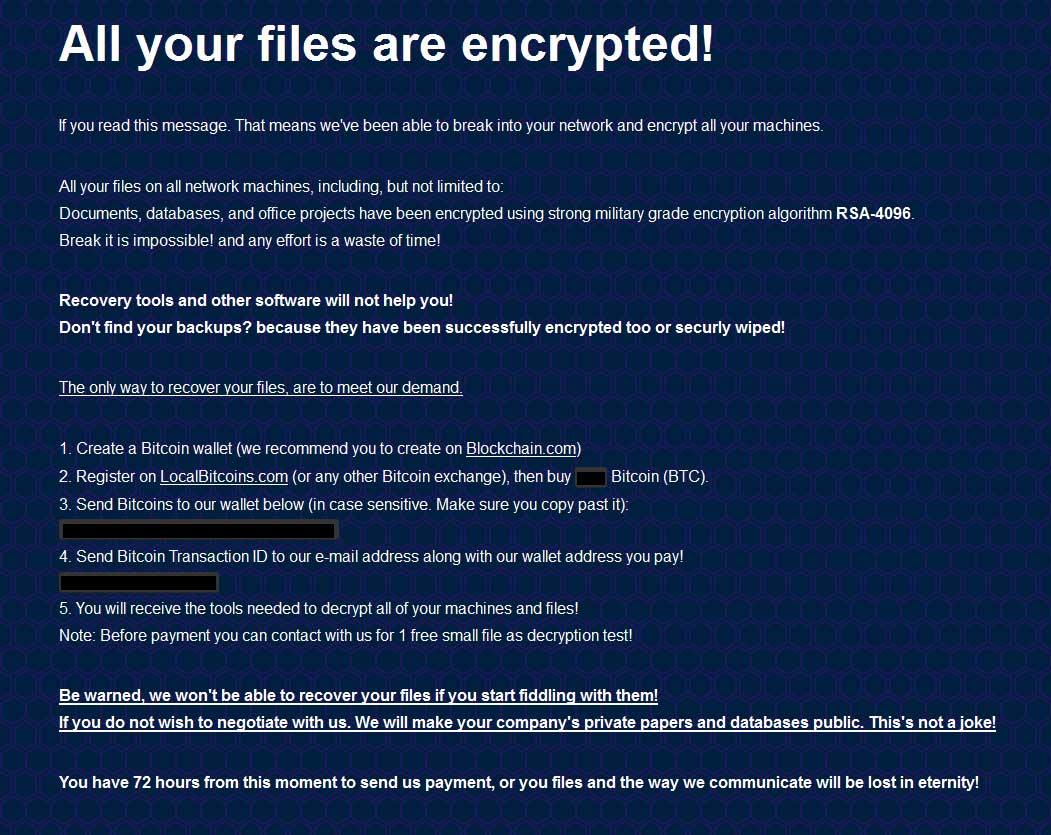
New ransom note targeting networks
In this version of the ransom note, we can see that the attackers are targeting "all your files on all network machines".
For entire network decryption, BitPyLock's ransom amounts are also fairly low compared to other targeted ransomware at only approximately 5 bitcoins for the entire network.
The ransom note further states that they will release stolen data if a ransom payment is not made.
"If you do not wish to negotiate with us. We will make your company's private papers and databases public. This's is not a joke!"
Unlike Maze Ransomware and Sodinokibi Ransomware who have already released stolen files belonging to non-paying victims, BitPyLock has not done so at this time.
This could also just be an empty threat like ransomware operators used to make in the past. Unfortunately, there is no way to tell anymore as more ransomware actors begin to actually release stolen data.
IOCs:
Hashes:
274011aaa97fd19ad6d993a5555c9306090da6a9b16c991739033ebb7673a244
Associated file names:
# HELP_TO_DECRYPT_YOUR_FILES #.html
Targeted Extensions:
.frx, .jin, .xls, .xlsx, .pdf, .doc, .docx, .ppt, .pptx, .log, .txt, .gif, .png, .conf, .data, .dat, .dwg, .asp, .aspx, .html, .tif, .htm, .php, .jpg, .jsp, .js, .cnf, .cs, .vb, .vbs, .mdb, .mdf, .bak, .bkf, .java, .jar, .war, .pem, .pfx, .rtf, .pst, .dbx, .mp3, .mp4, .mpg, .bin, .nvram, .vmdk, .vmsd, .vmx, .vmxf, .vmsn, .vmem, .gz, .3dm, .3ds, .zip, .rar, .3fr, .3g2, .3gp, .3pr, .7z, .ab4, .accdb, .accde, .accdr, .accdt, .ach, .acr, .act, .adb, .ads, .agdl, .ai, .ait, .al, .apj, .arw, .asf, .asm, .asx, .avi, .awg, .back, .backup, .backupdb, .pbl, .bank, .bay, .bdb, .bgt, .bik, .bkp, .blend, .bpw, .c, .cdf, .cab, .chm, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfp, .cgm, .cib, .class, .cls, .cmt, .cpi, .cpp, .cr2, .craw, .crt, .crw, .csh, .csl, .csv, .dac, .db, .db3, .dbf, .db-journal, .dc2, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .der, .des, .design, .dgc, .djvu, .dng, .dot, .docm, .dotm, .dotx, .drf, .drw, .dtd, .dxb, .dxf, .jse, .dxg, .eml, .eps, .erbsql, .erf, .exf, .fdb, .ffd, .fff, .fh, .fmb, .fhd, .fla, .flac, .flv, .fpx, .fxg, .gray, .grey, .gry, .h, .hbk, .hpp, .ibank, .ibd, .ibz, .idx, .iif, .iiq, .incpas, .indd, .jpe, .jpeg, .kc2, .kdbx, .kdc, .key, .kpdx, .lua, .m, .m4v, .max, .mdc, .mef, .mfw, .mmw, .moneywell, .mos, .mov, .mrw, .msg, .myd, .nd, .ndd, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nwb, .nx2, .nxl, .nyf, .oab, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .oil, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pab, .pages, .pas, .pat, .pcd, .pct, .pdb, .pdd, .pef, .pl, .plc, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .pptm, .prf, .ps, .psafe3, .psd, .pspimage, .ptx, .py, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .r3d, .raf, .rat, .raw, .rdb, .rm, .rw2, .rwl, .rwz, .s3db, .sas7bdat, .say, .sd0, .sda, .sdf, .sldm, .sldx, .sql, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .std, .sti, .stw, .stx, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxi, .sxm, .sxw, .tex, .tga, .thm, .tlg, .vob, .wallet, .wav, .wb2, .wmv, .wpd, .wps, .x11, .x3f, .xis, .xla, .xlam, .xlk, .xlm, .xlr, .xlsb, .xlsm, .xlt, .xltm, .xltx, .xlw, .ycbcra, .yuv
600 Computers Taken Down After Florida Library Cyberattack
20.1.2020 Bleepingcomputer
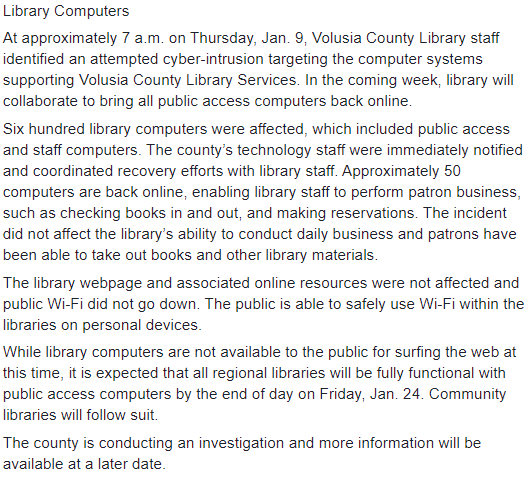
600 staff and public access computers were taken down at Volusia County Public Library (VCPL) branches from Daytona Beach, Florida, following a cyberattack that started around 7 AM on January 9.
"The county’s technology staff were immediately notified and coordinated recovery efforts with library staff," an official statement says.
"Approximately 50 computers are back online, enabling library staff to perform patron business, such as checking books in and out, and making reservations."
The library’s ability to conduct daily business was not affected in the incident allowing patrons to take out books and other library materials.
The VCPL server hosting the website was also not impacted in the attack, with the library's online presence and associated online resources remaining unaffected as a result.
While library computers are not available to the public for surfing the web at this time, it is expected that all regional libraries will be fully functional with public access computers by the end of day on Friday, Jan. 24. - VCPL
VCPL's public Wi-Fi was also not impacted by the attack and "the public is able to safely use Wi-Fi within the libraries on personal devices."
While the official statement issued by the library does not mention ransomware being used to encrypt the 600 computers that went offline after the incident, there's a high chance that this was the case and all the signs are there to point to the devices getting encrypted.
"The county is conducting an investigation and more information will be available at a later date," VCPL staff also said.
BleepingComputer asked VCPL to confirm that ransomware was what caused the computers to go down but did not hear back at the time of publication.
Volusia County Public Library statement
Some Californian libraries are also affected by a ransomware attack that encrypted computers at 26 community libraries in Contra Costa County on January 3.
"We apologize for the inconvenience this outage is causing our patrons and ask for patience as we work to get all services back online," said County Librarian Melinda Cervantes at the time. "We are working closely with law enforcement, including IT experts to gather information and prevent future attacks."
While most services have been restored since the attack according to an outage update page on the Contra Costa County Library's website last updated on January 17, several others including public printing, public WiFi, Catalog Account login, and Link+ Renewals are still down.
The county library's site is displaying a notification saying that the "network is currently down and patrons are unable to login at this time. We are investigating the issue and will establish service as soon as possible."
FBI's Internet Crime Complaint Center issued a public service announcement in October on the increasing number of high-impact ransomware attacks currently targeting both government and private U.S. organizations.
Emsisoft said in its 2019 annual ransomware report that ransomware directly impacted "at least 948 government agencies, educational establishments and healthcare providers at a potential cost in excess of $7.5 billion."
Infiltrating Networks: Easier Than Ever Due to Evil Markets
20.1.2020 Bleepingcomputer
Attackers don't always need to breach the networks of their victims themselves to plant malware as there are plenty of professional intruders offering their services on underground markets.
Various levels of access are offered for prices starting $1,000 and increasing depending on how deep the hackers have infiltrated.
All type of access is for sale
Entities from various sectors have been compromised, with managed service providers (MSPs) being the most attractive because they can act as a stepping stone for a larger set of victims.
Jim Walter from SentinelOne says that breaching an MSP can help attackers keep a low profile on the network and obtain persistence.
“Communication channels between MSPs and their clients often occur across trusted and private networks, with the boundaries between them turning into somewhat of a grey area. The traffic may remain ‘internal’ to the infrastructure of the MSP, therefore not being susceptible to traditional controls found at the perimeter (Internet facing IDS, Email Content Filters, and the like).”
An MSP with 100 customers is considered mid-sized by a network intruder looking to sell credentials for admin accounts, which could be used to get the usernames and passwords the clients use to log into the MSP’s platform.
“The price is a firm $700,” reads the post on an underground market, adding that the ad was present on other markets and setting a 48-hour deadline for the transaction.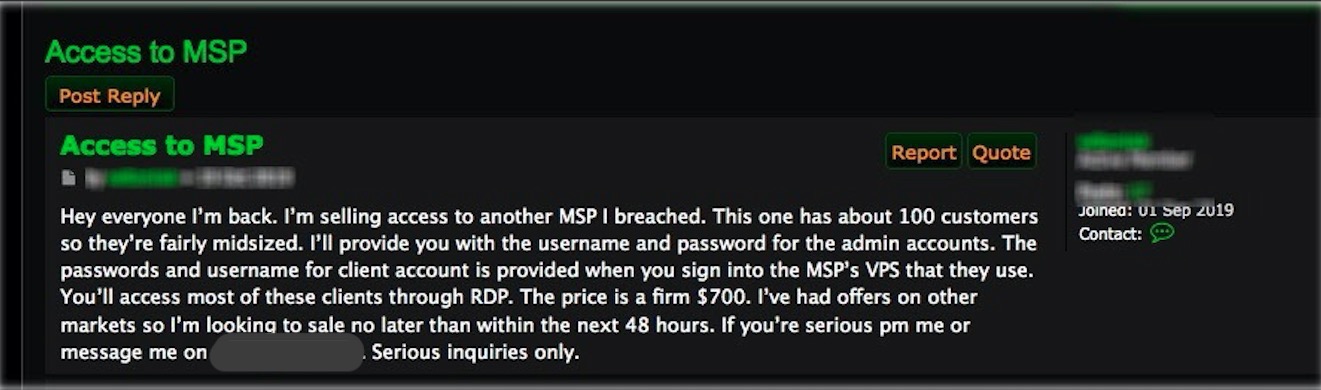
This is not an isolated case. In another post from January 6, someone was selling access to an unnamed target described as “a large tax company in the U.S.“ in the Fortune 500.
The hacker asked for $3,500 to give the keys to its internal network, from where attackers can access the company’s more than 500,000 clients through a remote connection. Getting access to an individual customer is also in the offer, for $1,000.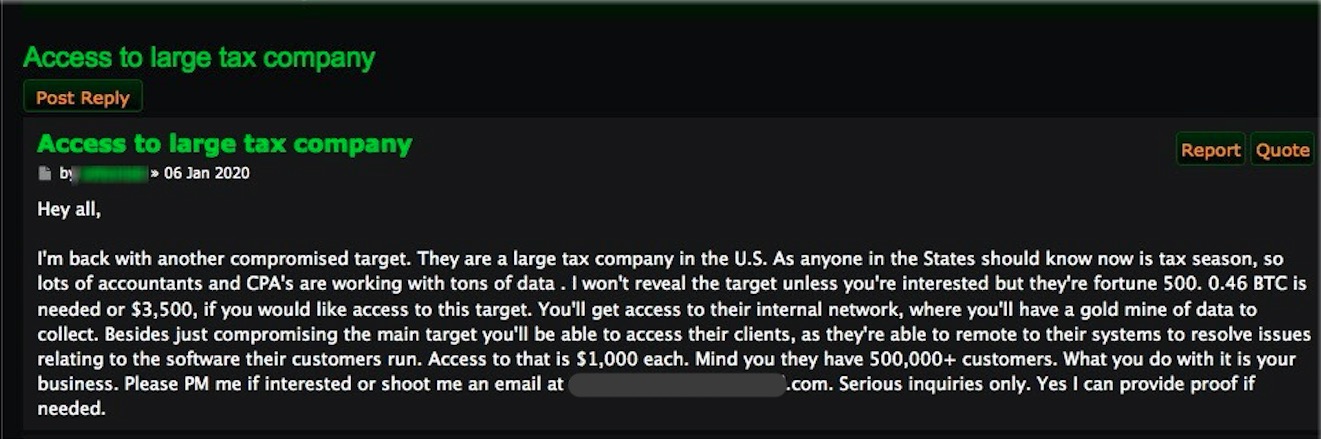
Walter says that the announcements he saw advertised access to a variety of entities in both public an private sector, including a Spanish MSP, an electronics manufacturer, and a U.S.-based utility company.
Credentials belonging to executives, access to mail servers, to content management portals used by hospitals, law firms, and schools, or root-level privileges that open all the doors are all being sold.
Other announcements seen by the researcher sold direct access to more than 20 point-of-sale (PoS) systems for $2,000 per terminal. The hacker also brags that they could hack they could breach the company network as the PoS are connected to it.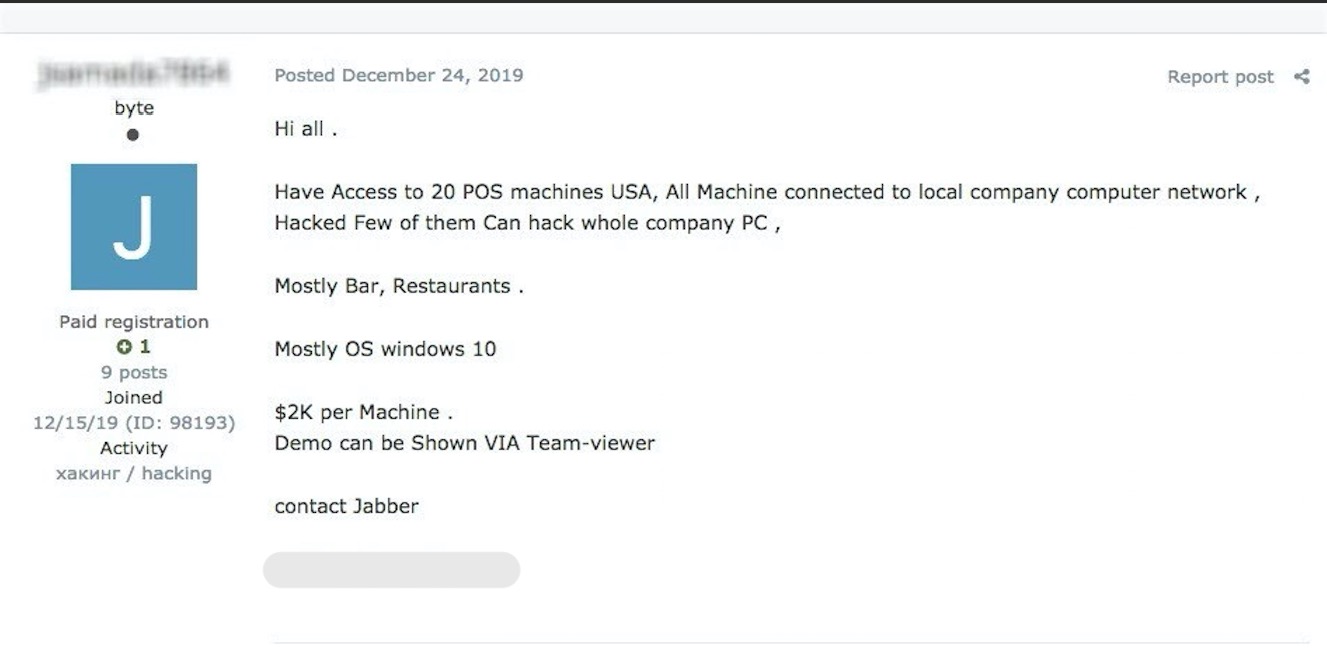
This trading happens on cybercriminal forums that do not hide in the shadows of the dark web. Some of them are closed to public view but logins can be purchased with little trouble.
This type of visibility makes it easier for less skilled attackers to drop their malware as they pay their way onto the victim’s network instead of envisaging methods to break into an environment and gain a foothold.
Defense advice
Walter lists some simple, general steps companies can take to reduce the risk of an intruder taking roots on their network or move laterally. These include the following:
enabling multi-factor authentication
network segregation
strategically placed firewalls and intrusion detection systems (IDS)
keeping an eye on traffic to and from public sharing and collaboration services
proper logging and reviewing of alerts (additional logging where possible is a plus)
restrict the use of known adversarial tools (e.g. mimikatz, wce, PStools, VNC, net, TeamViewer, WMIC, sdelete, lazagne)
For MSPs, the researcher has more specific advice:
rotate VPN authentication certificates regularly
use a dedicated VPN to communicated to client organizations
limit traffic to and from the MSP (VPNd) to specific hosts or services that are necessary
restrict rights of MSP accounts to essential tasks on client systems and remove unnecessary administrative privileges (e.g., Domain Administrator or Enterprise Administrator)
MSP accounts should connect only to the system they need to access directly for management tasks
specific service accounts are used for MSP access; consider disabling interactive logins for said accounts
allow access to ta accounts based on a specific schedule and monitor all attempts
US Retailer Hanna Andersson Hacked to Steal Credit Cards
20.1.2020 Bleepingcomputer
US children's apparel maker and online retailer Hanna Andersson disclosed that its online purchasing platform was hacked and malicious code was deployed to steal customers' payment info for almost two months.
In this type of attack dubbed Magecart, threat actors are hacking into vulnerable e-commerce platforms used by online stores and inject malicious JavaScript-based scripts into checkout pages.
The scripts known as web skimmers or e-skimmers are then used to collect the customers' payment info and send it to attacker-controlled remote sites.
The groups behind Magecart attacks have been active since at least 2010 according to a RiskIQ report, and they are known to target Magento-powered online shops, as well as OpenCart, PrismWeb, and OSCommerce-powered stores.

Hanna Andersson email (Image: Twitter)
Attack discovered after credit cards landed on the dark web
Email notifications sent to customers say that Hanna Andersson was informed by law enforcement on December 5, 2019, that "credit cards used on its website were available for purchase on a dark web site."
The following investigation confirmed that Hanna Andersson's "third-party ecommerce platform, Salesforce Commerce Cloud, was infected with malware that may have scraped information entered by customers into the platform during the purchase process.
The earliest potential date of compromise identified by forensic investigators is September 16, 2019, and the malware was removed on November 11, 2019."
While Hanna Andersson's investigation into the security incident revealed that no all of the customers who paid using their payment cards through the Salesforce Commerce Cloud (previously known as Demandware), it was not able to pinpoint the ones who were.
Because of this, the retailer will notify all customers that made purchases on the site during that period as detailed in a notice of security incident sent to the authorities.
"The incident potentially involved information submitted during the final purchase process on our website, www.hannaandersson.com, including name, shipping address, billing address, payment card number, CVV code, and expiration date," says the notice.
The company secured their site's online purchasing platform after the incident and hardened it against future compromise, and is currently helping payment card brands and law enforcement with their investigations of the attack.
In addition, as an added benefit to help protect your identity, we are offering MyIDCare identity theft protection services through ID Experts. MyIDCare services include: 12 months of credit and CyberScan monitoring, a $1,000,000 insurance reimbursement policy, and fully managed id theft recovery services. - Hanna Andersson
Salesforce Commerce Cloud hit again
"Although I don't have the details on this specific case, it's likely attackers used a vulnerability to inject malicious code within the CMS, as they did before," Malwarebytes security researcher Jérôme Segura told BleepingComputer.
The previous case Segura is referring to is that of UK retailed Sweaty Betty which also got hacked and had its customers' payment information stolen for over a week, between November 19th, 2019 and November 27th, 2019.
"Contrary to most Magecart hacks that happen on Magento, Sweaty Betty runs Demandware, which is popular among the biggest stores," Magecart security expert Willem de Groot of Sanguine Security Labs told BleepingComputer at the time.
Demandware is now known as Salesforce Commerce Cloud after the enterprise cloud commerce platform was acquired by Salesforce back in 2016.
The Salesforce Commerce Cloud platform is currently used by over 2,800 currently live websites according to BuiltWith stats.
Salesforce's cloud platform-as-a-service (Paas) Heroku is also being abused by Magecart attackers to host their skimmers as Malwarebytes' Threat Intelligence team discovered in December 2019.
FTCode Ransomware Now Steals Saved Login Credentials
20.1.2020 Bleepingcomputer
FTCode ransomware victims now have one more thing to worry about with the malware having been upgraded to also steal saved user credentials from email clients and web browsers.
FTCode is a PowerShell-based ransomware strain first spotted in 2013 by security researchers at Sophos, a malware that resurfaced in October 2019 as the final payload in a spam email campaign targeting Italian recipients.
Being fully developed in PowerShell allows it to encrypt its targets' devices without having to download additional components, while also making it very easy for its developers to add new functionality.
The 'new and improved' FTCode ransomware
The newly added info stealer functionality allows FTCode to harvest and exfiltrate the stored credentials before encrypting its victims' files.
FTCode is now capable of stealing saved credentials from both web browsers (Internet Explorer, Mozilla Firefox, Google Chrome) and email clients (Mozilla Thunderbird and Microsoft Outlook).
The way the ransomware collects the credentials is different for each of the five applications, directly accessing registry keys in the case of Internet Explorer and Microsoft Outlook, while in the case of Mozilla Firefox, Mozilla Thunderbird, and Google Chrome it goes into the folders where the apps store the credentials.
Stealing credentials saved in Google Chrome (Zscaler)
Once the information is harvested, FTCode will deliver it to its operators using a POST request sent to its command-and-control (C2) server, with the usernames and passwords being encoded using the Base64 encoding scheme.
This capability was not available in previous variants as confirmed in a report published by researchers with the Zscaler ThreatLabZ team.
An FTCode Decryptor for those who can capture the encryption keys while having their computers encrypted is available from Certego.
FTCode brought back to life
Starting September 26th, a series of reports [1, 2, 3, 4] about new ransomware being distributed via spam and named FTCode.
Security outfit Certego said that it is was the sample Sophos detected in 2013 and speculates that FTCode was revived in recent attacks because PowerShell is integrated by default on Windows devices running at least Windows 7 or Windows Server 2008 R2.
The FTCode ransomware arrives on its victims' computers via spam emails containing malicious Word documents camouflaged as invoices, document scans, and resumes, which will drop the JasperLoader malware downloader and then encrypts the device.
However, the encryption will not happen until the malware will gain persistence by adding a scheduled task and a shortcut into the Startup folder.
Right before starting to encrypt the files, FTCode will check for the C:\Users\Public\OracleKit\w00log03.tmp file that acts as a killswitch.
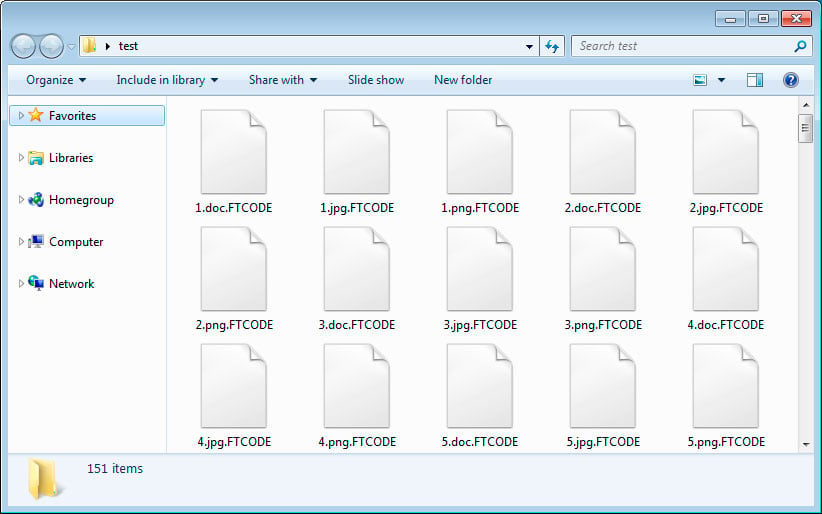
Files encrypted by FTCode
If that file is not found, FTCode generates an encryption key that gets sent to the attackers' C2 server, an encryption key that can be captured and later used with Certego's decryptor to restore files on locked computers.
In the next stage, the ransomware also disables the Windows recovery environment and deletes Shadow Volume Copies and Windows backups to make data recovery impossible without paying the ransom.
Next, FTCode starts encrypting files adding the .FTCODE extension to all locked files and READ_ME_NOW.htm ransom notes to every folder.
The attackers ask for $500 ransom to deliver the decryptor to their victims, however, as one of BleepingComputer's readers has pointed out there have been reports of paying the ransom and not getting the decryptor.
Emotet Malware Dabbles in Extortion With New Spam Template
20.1.2020 Bleepingcomputer
The Emotet malware has started using a spam template that pretends to be an extortion demand from a "Hacker" who states that they hacked the recipient's computer and stole their data.
Emotet is spread through spam emails that commonly use templates based around a particular theme such as shipping information, voice mails, scanned documents, reports, and invoices.
The threat actors will send out email templates that reflect approaching holidays, such as Christmas party and Halloween party invites, and trending current events such as an invite to a Greta Thunberg Demonstration.
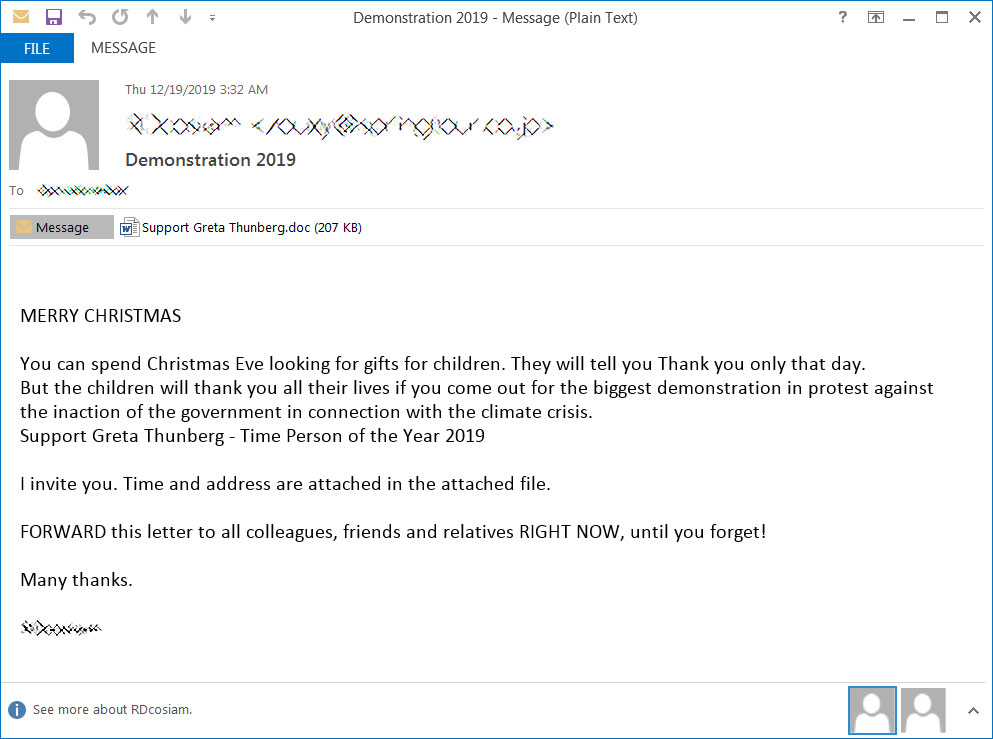
Greta Thunberg demonstration invite template
The goal of all of these emails is to trick the recipient into opening an attached Word document that will attempt to download and install the Emotet malware onto the computer.
Emotet will then use the infected computer to send further malicious spam and to download and install other malware onto the device.
Emotet starts impersonating extortion emails
Since the summer of 2018, scammers have been sending out sextortion emails that state that the recipient's computer was hacked and that an attacker recorded video of the recipient while on adult sites.
The emails then threaten to send the video to the recipient's friends and family if they don't pay the scammers a $500 to $3,000 extortion payment.
These emails are a scam and the attackers do not have any video, but it scared enough people that they made over $50 thousand in just a week.
In a new template shared with BleepingComputer by security researcher ExecuteMalware, the Emotet operators have started to use a similar extortion template that states "YOUR COMPUTER HACKED!" and that the recipient's data was stolen.
According to Emotet expert Joseph Roosen, this campaign first started around January 15th, 2020.
From the various emails seen by BleepingComputer, this new campaign is using "INF Jan 17 20.doc for [Name]" or "For [Name]" for the email subjects.
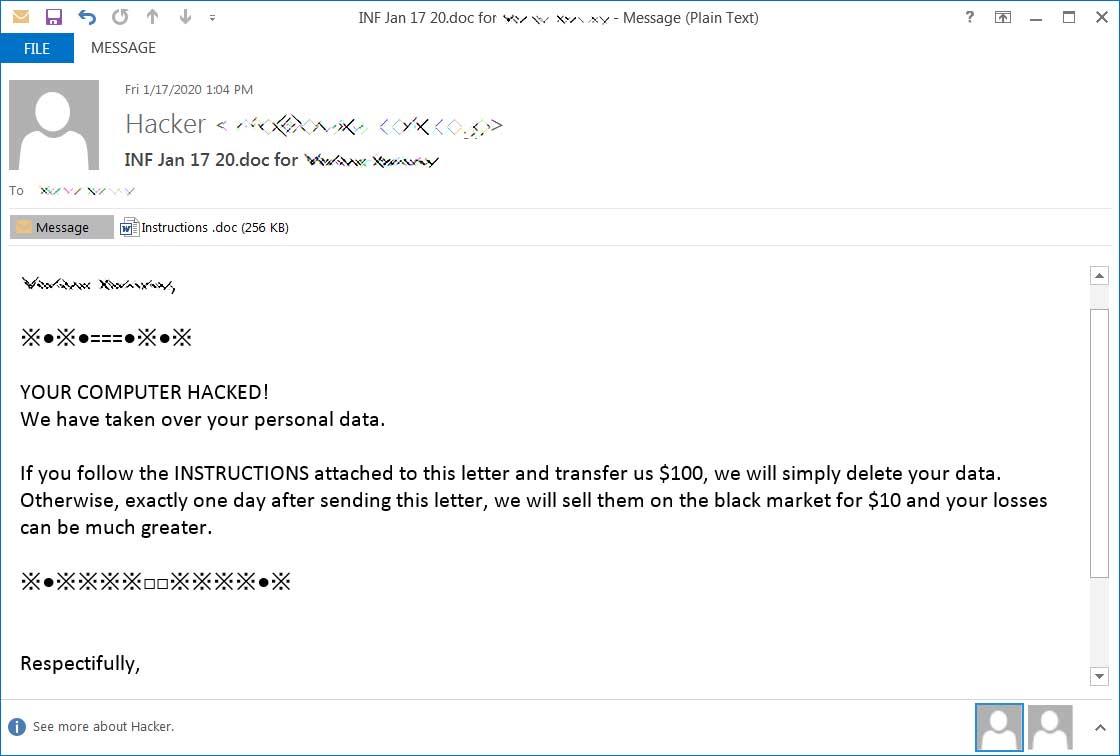
Emotet extortion spam template
The email goes on to tell the user to open the attached document for instructions on how to pay $50 or $100 or their stolen data will be sold on the black market for $10.
"YOUR COMPUTER HACKED!
We have taken over your personal data and financial data.
If you follow the instructions attached to this letter and transfer us $ 50, we will simply delete your data.
Otherwise, exactly one day after sending this letter, we will sell them on the black market for $ 10 and your losses can be much greater.
Nothing personal is just a business.
Have a nice day. I hope for your cooperation"
If the user opens the document, they will be shown the standard Emotet malicious document template that states the recipient needs to "Enable Content" to properly view the document.
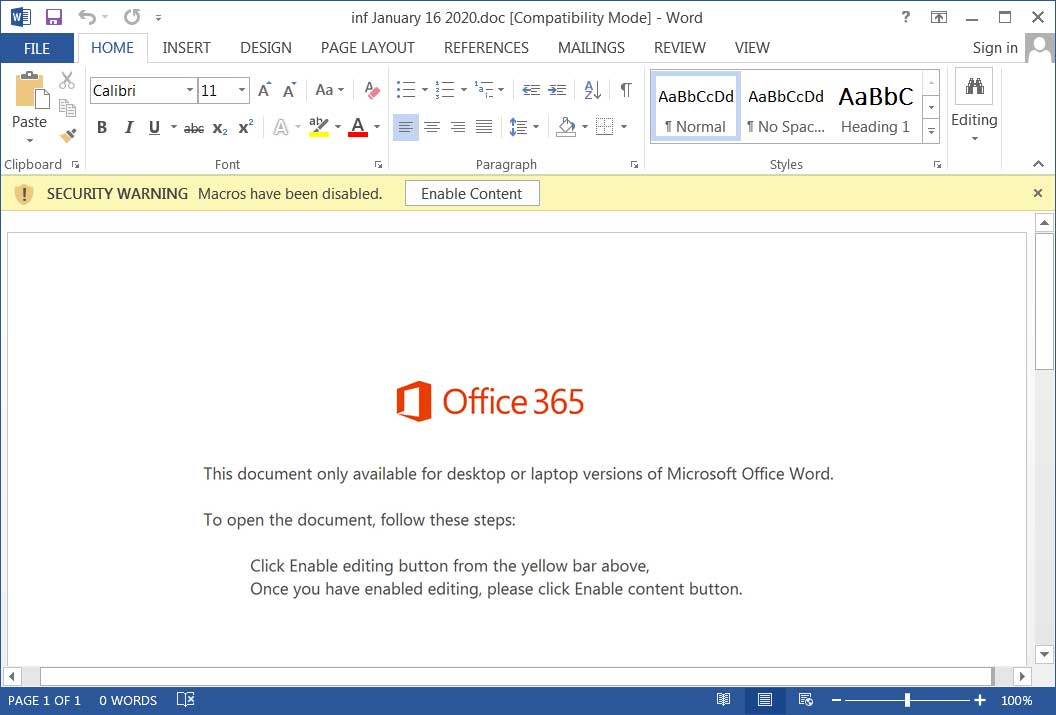
Emotet malicious document template
Once the document is opened, a PowerShell command will be executed that downloads and installs the Emotet Trojan on the computer.
Even worse, after some time Emotet will download the TrickBot information-stealing Trojan, which will begin to steal your login credentials, sensitive files, browser history, and more.
On high-value networks, TrickBot is also known to partner with the Ryuk Ransomware actors and will open a reverse shell back to them so that the Ryuk operators can encrypt the entire network.
Be wary of all unexpected attachments
Due to the severity of the Emotet infection, users need to be wary of any strange emails they receive, especially ones containing Word attachments.
Instead of opening an attachment, they should contact the sender directly to confirm they sent the email or at least share it with their network administrator first so it can be opened in a controlled environment.
For those who wish to learn more about Emotet and its latest developments, we recommend that you follow the Cryptolaemus group on Twitter.
Cryptolaemus is a group of security researchers who provide frequent updates on this malware's activity so that other researchers and network administrators can be better protected against this threat.
Mitsubishi Electric Warns of Data Leak After Security Breach
20.1.2020 Bleepingcomputer
Mitsubishi Electric, a leading global company in the manufacture and sales of electrical and electronic products, disclosed a security breach that might have caused the leak of personal and confidential corporate information.
The breach was detected almost eight months ago, on June 28, 2019, with the delay being attributed to the increased complexity of the investigation caused by the attackers deleting activity logs.
"On June 28, last year, a suspicious behavior was detected and investigated on a terminal in our company, and as a result of unauthorized access by a third party, data was transmitted to the outside," a detailed company statement published today says.
"This is an advanced method of monitoring and detection, and it took time to investigate because the log (operation record) for identifying the transmitted file was deleted by an attacker on some terminals."
Mitsubishi Electric is still continuing internal investigations into unauthorized access to its network according to a Japanese security blogger.
Chinese-backed threat group might be behind the attack
The breach began with affiliates in China and then spread to the company's internal network per an Asahi Shimbun report that prompted Mitsubishi Electric's statement.
"The hijacked account was used to gain infiltration into the company's internal network, and continued to gain unauthorized access to middle-managed PCs who had extensive access to sensitive information," the report says.
"According to people involved, Chinese hackers Tick may have been involved," Nikkei also found. "According to the company, at least tens of PCs and servers in Japan and overseas have been found to have been compromised."
Tick (also tracked as Bronze Butler and REDBALDKNIGHT) is a cyber-espionage group known for primarily going after Japanese entities, with targets ranging from critical infrastructure and heavy industry organizations to international relations and manufacturing.
Their main goal is to steal intellectual property, confidential corporate info, and product details, after compromising enterprise servers via spearphishing and abusing various zero-day vulnerabilities.
The group is also known for usually deleting evidence from compromised devices to hinder investigations following their attacks.
Sensitive information potentially stolen
Mitsubishi Electric said that it wasn't possible to know for sure if the information might have been exfiltrated by the attackers from some of the compromised terminals since the logs were deleted to erase traces.
The company provides the following list of potentially leaked info, with estimates on the "maximum number of possible leaks" (employees, applicants, and retired employees), with an estimated quantity of around 200 MB of documents:
• Personal information and recruitment applicant information (1,987)
• New graduate recruitment applicants who joined the company from October 2017 to April 2020, and experienced recruitment applicants from 2011 to 2016 and our employee information (4,566)
• 2012 Survey results regarding the personnel treatment system implemented for employees in the headquarters in Japan, and information on retired employees of our affiliated companies (1,569)
"Exchanges with government agencies such as the Ministry of Defense, the Nuclear Regulatory Commission, the Agency for Natural Resources and Energy, the Cabinet Office, and the Ministry of the Environment," as well as "transaction-related conference materials such as joint development with private companies such as electric power, railways, and telecommunications, and product orders" might also have been leaked as reported by Kyodo News.
However, an in-house investigation confirmed "that sensitive information on social infrastructure such as defense, electric power, and railways, highly confidential technical information, and important information concerning business partners did not leak."
"To date, no damage or impact related to this matter has been confirmed," Mitsubishi Electric statement also adds.
Local media also says that Japanese authorities were also notified, with Chief Cabinet Secretary Yoshii Suga confirming after the Cabinet meeting on the morning of January 20 that he "was notified that it was confirmed that there was no leak of sensitive information such as defense equipment and electric power."
Mitsubishi Electric will start delivering notifications and reports on the breach to customers who might have had their information leaked during the incident.
"We are informing the affected customers of the possible breach of trade secrets," the electrical and electronic equipment manufacturing firm also adds.
Citrix Patches CVE-2019-19781 Flaw in Citrix ADC 11.1 and 12.0
20.1.2020 Bleepingcomputer
Citrix released permanent fixes for the actively exploited CVE-2019-19781 vulnerability impacting Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances and allowing unauthenticated attackers to perform arbitrary code execution.
"Permanent fixes for ADC versions 11.1 and 12.0 are available as downloads here and here," Citrix's CISO Fermin J. Serna says in an update published today.
"These fixes also apply to Citrix ADC and Citrix Gateway Virtual Appliances (VPX) hosted on any of ESX, Hyper-V, KVM, XenServer, Azure, AWS, GCP or on a Citrix ADC Service Delivery Appliance (SDX). SVM on SDX does not need to be updated.
It is necessary to upgrade all Citrix ADC and Citrix Gateway 11.1 instances (MPX or VPX) to build 11.1.63.15 to install the security vulnerability fixes. It is necessary to upgrade all Citrix ADC and Citrix Gateway 12.0 instances (MPX or VPX) to build 12.0.63.13 to install the security vulnerability fixes."
Important updates on the #CitrixADC, Citrix Gateway vulnerability: (1) Permanent fixes for ADC v11.1 & 12. (2) We have moved forward the availability of permanent fixes for other ADC versions & SD-WAN WANOP from previous target dates. #CVE201919781https://t.co/20c9u3oh8h
— Citrix (@citrix) January 19, 2020
Accelerated firmware update timeline
Besides releasing these permanent fixes for the CVE-2019-19781 flaw, Citrix also says that it has fast-forwarded the "availability of permanent fixes for other ADC versions and for SD-WAN WANOP," with the new dates being moved to:
• ADC version 12.1, now January 24
• ADC version 13 and ADC version 10.5, now January 24
• SD-WAN WANOP fixes, now January 24
The new firmware update timeline is available below:
Citrix ADC and Citrix Gateway
Version Refresh Build Release Date
11.1 11.1.63.15 January 19, 2020
12.0 12.0.63.13 January 19, 2020
12.1 12.1.55.x January 24, 2020
10.5 10.5.70.x January 24, 2020
13.0 13.0.47.x January 24, 2020
Citrix SD-WAN WANOP
Release Citrix ADC Release Release Date
10.2.6 11.1.51.615 January 24, 2020
11.0.3 11.1.51.615 January 24, 2020
Citrix advises all customers to apply mitigation measures to ADC versions 12.1, 13, 10.5 and SD-WAN WANOP versions 10.2.6 and 11.0.3 appliances until a permanent fix will be available.
"Once complete, you can use the tool we have previously provided to ensure the mitigations have successfully been applied," Serna added.
"While all the mitigations associated with CVE-2019-19781 are effective across all known scenarios, we strongly encourage customers to apply the permanent fixes as soon as possible."
"We are urging customers to apply these fixes immediately and have amped up our support staff to help them if necessary," Citrix Corporate Communications and Media Relations Karen Master told BleepingComputer.
Vulnerable Citrix appliances under attack
An unknown threat actor is scanning for and securing Citrix ADC servers against CVE-2019-19781 exploitation attempts, at the same deploying a backdoor to maintain future access as FireEye researchers discovered.
"FireEye believes that this actor may be quietly collecting access to NetScaler devices for a subsequent campaign," the report says.
More than 25,000 vulnerable Citrix endpoints were found by security firm Bad Packets roughly a week ago, with around 1,000 of them from the U.S. and thousands more in Germany, the United Kingdom, Switzerland, and Australia.
Opportunistic scanning activity continues to target Citrix (NetScaler) servers vulnerable to CVE-2019-19781.
This critical vulnerability allows unauthenticated remote attackers to execute arbitrary commands on the targeted server. #threatintel https://t.co/Ba1muwe7ny
— Bad Packets Report (@bad_packets) January 13, 2020
Scans for Citrix appliances vulnerable to attacks started on January 8 according to security experts, while proof-of-concept (PoC) exploits were made public just two days later.
The Cybersecurity and Infrastructure Security Agency (CISA) released its own public domain tool designed to enable security staff to test if their organizations' servers are vulnerable on January 13, while the Dutch National Cybersecurity Centre (NCSC) advised companies four days ago to shut down vulnerable Citrix appliances until a reliable fix is available.
Update January 19, 17:04 EST: Added info on ongoing attacks.
Update January 22, 17:39 EST: Citrix released another series of permanent fixes for the impacted versions of Citrix SD-WAN WANOP, available for download here.
To apply the security vulnerability fix, you need to upgrade all Citrix SD-WAN WANOP versions to build 10.2.6b or 11.0.3b as appropriate. These fixes are ONLY applicable to the SD-WAN 4000-WO, 5000-WO, 4100-WO, and 5100-WO platforms. All other SD-WAN PE and SD-WAN SE platforms are not impacted by this vulnerability and do not need to be patched.
Update January 23, 17:40 EST: Citrix released another series of permanent CVE-2019-19781 fixes for Citrix ADC (NetScaler ADC) and Citrix Gateway versions 12.1 and 13.0, available for download here (ADC) and here (Gateway).
New Nest Video Extortion Scam Plays Out Like a Spy Game
20.1.2020 Bleepingcomputer
A new sextortion scam that breaks the typical mold has been detected at the beginning of the year. Fraudsters preying on the insecurity of connected devices used footage from Nest cameras, and led victims through a convoluted path of email accounts and web sites before making their ransom price known.
Compared to a typical sextortion campaign, the fraudsters put in some effort to convince the victim that they’re dealing with skilled hackers by having them access multiple email accounts and links for instructions.
Hopping from one email contact to another
The scammers do not stray away from the classic scheme and claim to have a nude video of the victim, threatening to make it public on an adult website unless they get paid.
The footage claims to have been obtained after infecting the victim’s phone with malware that also propagates to neighboring devices with recording capabilities.
It all starts with an email informing the victim of the hack and that the personal video would be distributed online. Proof of the existing footage can be found in an email stored in an email account provided by the fraudster. The address and the password are included in this initial message.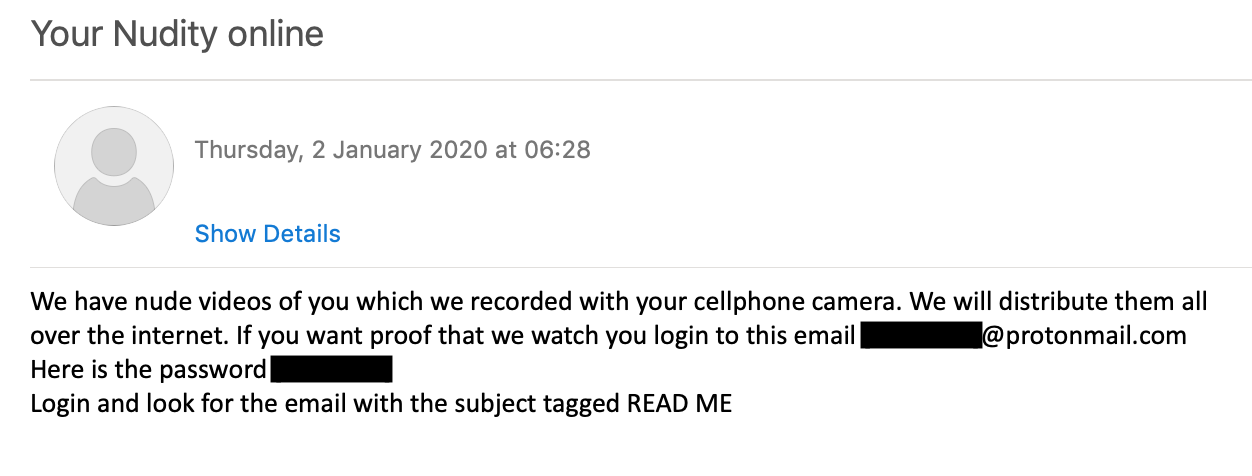
A short link is provided in that email, redirecting the victim to a website that appears to show a live feed from Nest cameras set up in public spaces, allegedly infected by the malware planted on the victim’s phone. Further instructions are also offered.
Security researchers from Mimecast, a company offering secure email cloud services, analyzed this sextortion campaign and determined that the footage is embedded from the official Nest site.
“While it doesn’t belong to the victims and their Nest cameras have not been hacked into on this occasion, the footage from Nest’s official website was used to scare the victims.” Mimecast
To increase panic and push victims into sending money, the fraudsters’ narrative is that they had been monitoring for 11 months and that they can track the victim by triangulating the signal from a mobile phone.
The threat continues by saying that nude “videos are currently being uploaded by your cell phone on several Porn websites servers and you have only a week till they are free for the public to view.”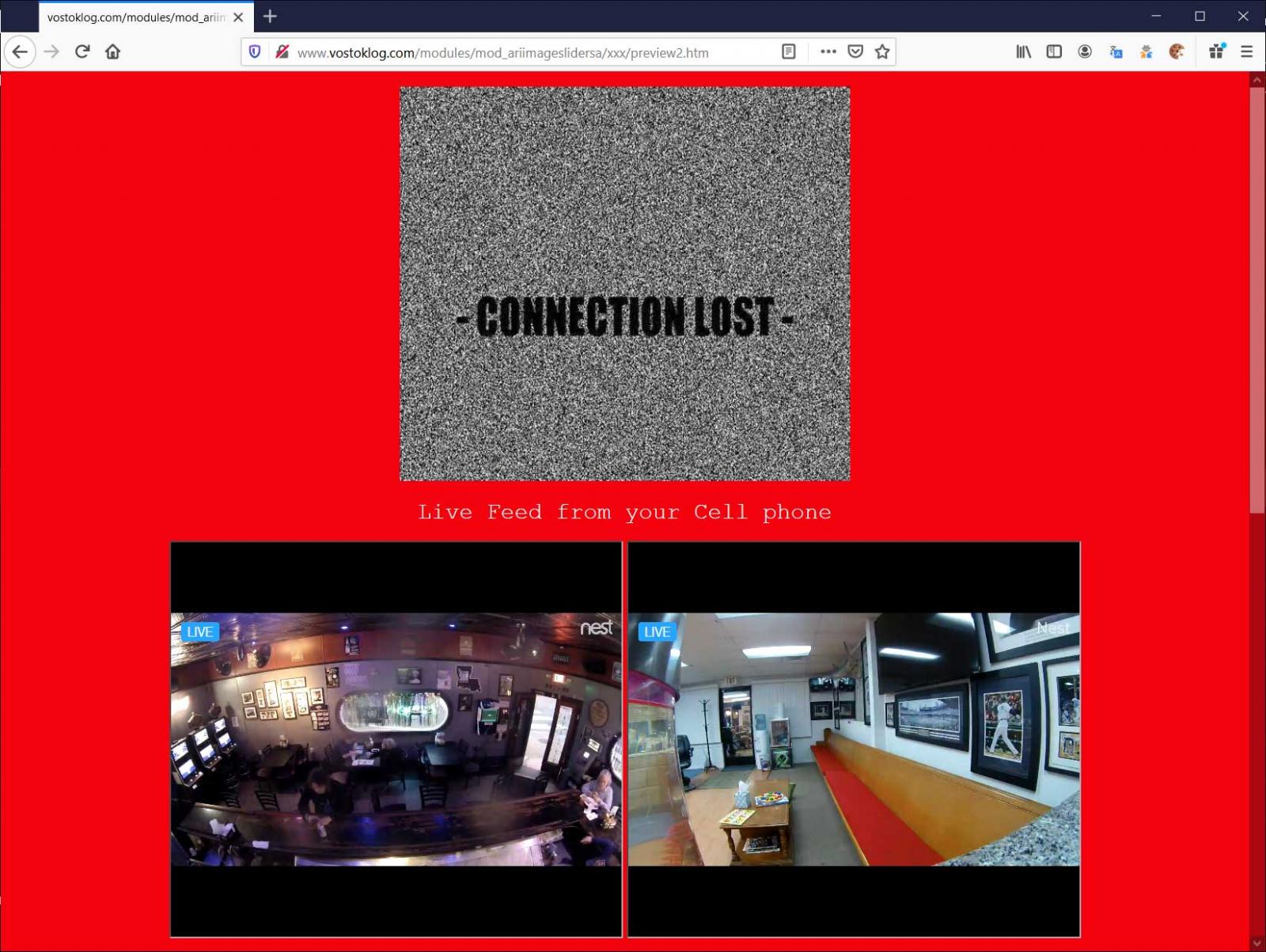
At the end of the ransom note is an email address the victim can contact to learn the fraudsters’ demands. This is just another step in this intricate scheme because the reply guides towards logging into another email address for directions. Again, the password is included.
The scammers state that it’s a hacked account, most likely in an attempt to increase the belief that they’re experienced cybercriminals, as visible in their reply below: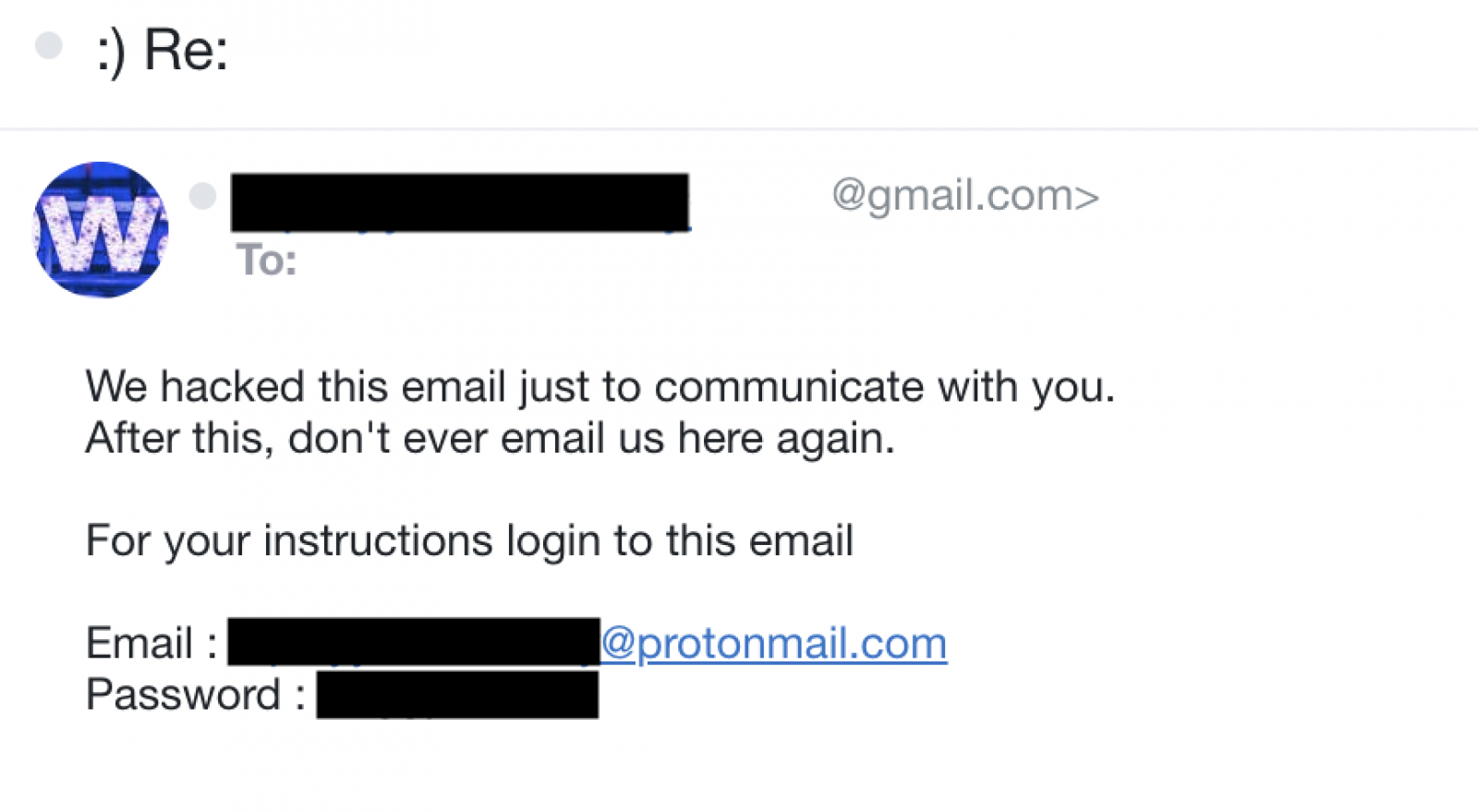
source: Mimecast
If the victim follows the trail to this stage, they get to find out how much the scammer wants to not follow through with their declared plan.
Two options are offered: pay EUR 500 in bitcoin (link to instructions on how to obtain it is included) or USD 600 in gift cards from various vendors (iTunes, Amazon, Steam, Google Play, Walmart, Sephora, Best Buy, Target, eBay). In another variant, the sum demanded is EUR/USD 800 payable in either bitcoin or gift cards, with a deadline of four days.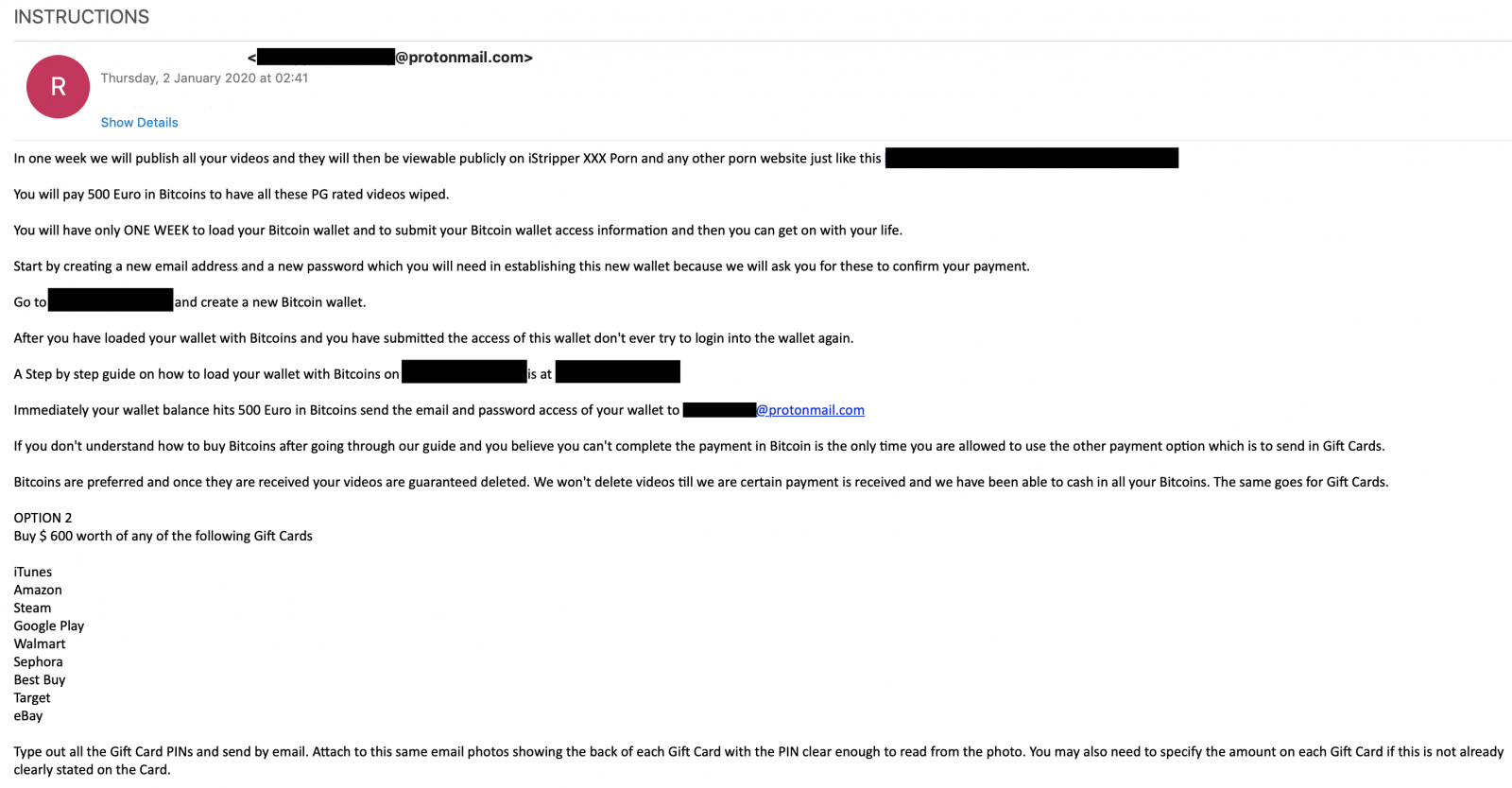
source: Mimecast
This campaign was observed in the first week of the year targeting recipients in the U.S. A total of 1,687 emails were sent between January 2-3.
The effort to make the victim go through all these hoops may be an attempt to hide the message exchange from platforms that could detect them, Mimecast told BleepingComputer.
Dr. Kiri Addison, Head of Data Science Overwatch at Mimecast says that choosing the allows the criminals to exploit a new opportunity for their extortion business.
IoT devices have been labeled as insecure and vulnerable to hacking a long time ago, so going with this narrative makes the claims more believable.
“Ensuring that users are aware of ‘sextortion’ as a phishing technique is a key part of the defense against these campaigns” - Kiri Addison
New Jersey Synagogue Suffers Sodinokibi Ransomware Attack
20.1.2020 Bleepingcomputer
Temple Har Shalom in Warren, New Jersey had their network breached by the actors behind the Sodinokibi Ransomware who encrypted numerous computers on the network.
In an email seen by BleepingComputer, Temple Har Shalom informed their congregation that they discovered the ransomware attack on January 9th after staff had trouble connecting to the Internet
After checking their servers, they found that the Temple's files were encrypted and a ransom note was left behind. Other computers on the network had been encrypted as well.
"The encryption affected all of our server-based files and electronic data. We have a mechanical back up for those files and data, but the back-up was encrypted as well. Certain computers were affected in full. Others were unaffected and remain functional," the email from Temple Har Shalom stated.
A source familiar with the matter told BleepingComputer that Sodinokibi was demanding close to $500,000 ransom to receive a decryptor for their network.
Temple Har Shalom states that they will be contacting congregation members for information needed to recreate encrypted files. This indicates that they have no intention of paying the ransom.
Like all ransomware victims, the temple feels violated by the attack but does not think they were targeted as a Jewish organization.
"The attack is violative of us as a community, though we have no reason to believe that we were targeted because we are a Jewish organization."
As Sodinokibi is known to steal files before encrypting them, they may have gained access to the personal data of congregants.
The synagogue states that this data may include a congregant's name, address, and email address, but they do not believe the attackers had access to their financial information.
"Beyond names, addresses and e-mail addresses of congregants, because of the way we segregate our files, we do not believe that confidential personal membership information (such as financial information) was accessed," the email stated. "Nonetheless, as we note above, be particularly mindful of phishing scams."
Temple members, though, should be on the lookout for targeted phishing emails using their personal information.
Sodinokibi has also started to publicly leak the stolen data of victims if a ransom is not paid. It is not known how much data, if any, was stolen from the temple or if they intend to publish it for non-payment.
BleepingComputer has contacted both the ransomware actors and the temple, but have not heard back at this time.
Microsoft Issues Mitigation for Actively Exploited IE Zero-Day
20.1.2020 Bleepingcomputer
Microsoft published a security advisory containing mitigation measures for an actively exploited zero-day remote code execution (RCE) vulnerability impacting Internet Explorer.
Redmond's advisory says that the company is aware of "limited targeted attacks" targeting this vulnerability.
"A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer," says the advisory.
"The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user."
While no patch exists for this issue so far, Microsoft says that they are currently working on a fix that could be released as an out-of-band security update, as it happened in September 2019 when a very similar Internet Explorer RCE zero-day was fixed.
Security Response
✔
@msftsecresponse
Security Advisory - Microsoft Guidance on Scripting Engine Memory Corruption - for more information please visit: https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/ADV200001 …
43
11:16 PM - Jan 17, 2020
Twitter Ads info and privacy
47 people are talking about this
Attackers who successfully exploit this security flaw can gain the same user permissions as the user logged into the compromised Windows device.
If the user is logged on with administrative permissions, the attacker can take full control of the system allowing program installation, data manipulation, or the possibility to create accounts with full user rights.
"In a web-based attack scenario, an attacker could host a specially crafted website that is designed to exploit the vulnerability through Internet Explorer and then convince a user to view the website, for example, by sending an email," Microsoft adds.
The list of Internet Explorer versions and platforms impacted by this zero-day flaw, including the impact and severity ratings, are available below.
Product Platform Impact Severity
Internet Explorer 10 Windows Server 2012 Remote Code Execution Moderate
Internet Explorer 11 Windows 10 Version 1803 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1803 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1803 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1809 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1809 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1809 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows Server 2019 Remote Code Execution Moderate
Internet Explorer 11 Windows 10 Version 1909 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1909 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1909 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1709 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1709 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1709 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1903 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1903 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1903 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1607 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1607 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows Server 2016 Remote Code Execution Moderate
Internet Explorer 11 Windows 7 for 32-bit Systems Service Pack 1 Remote Code Execution Critical
Internet Explorer 11 Windows 7 for x64-based Systems Service Pack 1 Remote Code Execution Critical
Internet Explorer 11 Windows 8.1 for 32-bit systems Remote Code Execution Critical
Internet Explorer 11 Windows 8.1 for x64-based systems Remote Code Execution Critical
Internet Explorer 11 Windows RT 8.1 Remote Code Execution Critical
Internet Explorer 11 Windows Server 2008 R2 for x64-based Systems Service Pack 1 Remote Code Execution Moderate
Internet Explorer 11 Windows Server 2012 Remote Code Execution Moderate
Internet Explorer 11 Windows Server 2012 R2 Remote Code Execution Moderate
Internet Explorer 9 Windows Server 2008 for 32-bit Systems Service Pack 2 Remote Code Execution Moderate
Internet Explorer 9 Windows Server 2008 for x64-based Systems Service Pack 2 Remote Code Execution Moderate
Redmond provides the following workaround to mitigate this vulnerability:
For 32-bit systems, enter the following command at an administrative command prompt:
takeown /f %windir%\system32\jscript.dll
cacls %windir%\system32\jscript.dll /E /P everyone:N
For 64-bit systems, enter the following command at an administrative command prompt:
takeown /f %windir%\syswow64\jscript.dll
cacls %windir%\syswow64\jscript.dll /E /P everyone:N
takeown /f %windir%\system32\jscript.dll
cacls %windir%\system32\jscript.dll /E /P everyone:N
Undoing the workaround
For 32-bit systems, enter the following command at an administrative command prompt:
cacls %windir%\system32\jscript.dll /E /R everyone
For 64-bit systems, enter the following command at an administrative command prompt:
cacls %windir%\system32\jscript.dll /E /R everyone
cacls %windir%\syswow64\jscript.dll /E /R everyone
New US Bill Wants to Assign State Cybersecurity Coordinators
20.1.2020 Bleepingcomputer
Four U.S. Senators have introduced a bipartisan bill that will require the Department of Homeland Security (DHS) to appoint cybersecurity effort coordinators in every state to orchestrate cyberattack response and remediation efforts, and to improve coordination between federal, state, and local entities.
Cybersecurity state coordinators will have to ensure that local, state, and federal entities collaborate and share resources during cybersecurity threat prevention and response processes according to the Cybersecurity State Coordinator Act of 2020 bill introduced by Senators Margaret Hassan (D-NH), John Cornyn (R-TX), Rob Portman (R-OH), and Gary Peters (D-MI) on January 16, 2020.
"Cyberattacks can be devastating for communities across our country, from ransomware attacks that can block access to school or medical records to cyberattacks that can shut down electrical grids or banking services," the bill's sponsor Senator Hassan said.
"The bipartisan bill I introduced would take a big step forward in improving communication between the federal government, states, and localities, as well as strengthening cybersecurity preparedness in communities across the country."
Senator Hassan also stated that, while officials were well prepared to respond to ransomware attacks such as the ones hitting New Hampshire’s Strafford County and the Sunapee School District, the federal government has to make sure that local and state entities have all the training and resources to mitigate and defend against future attacks.
Cybersecurity state coordinator responsibilities
Hassan's press release explains that the federally funded Cybersecurity State Coordinator program will be housed in DHS's Cybersecurity and Infrastructure Security Agency (CISA).
A CISA employee would be appointed by the Director to act as Cybersecurity State Coordinators according to the just introduced bill's text, to have several duties including to:
• Improve coordination within federal entities and between federal and non-federal entities, including state and local governments and other organizations
• Support preparation, response, and remediation efforts relating to cybersecurity risks and incidents, including ransomware
• Facilitate the sharing of cyber threat information
• Raise awareness of financial, technical, and operational resources that the federal government offers to non-federal entities to help prevent cyber threats
Senator Portman added that "cybersecurity for state and local governments is just as important as federal cybersecurity, and frequently, they lack the resources, technical know-how, and situational awareness to secure their systems, or respond in the event of an attack.
This bipartisan bill, which creates a Cybersecurity State Coordinator position, would help bolster state and local governments’ cybersecurity by facilitating their relationship with the federal government to ensure they know what preventative resources are available to them as well as who to turn to if an attack occurs."
Senator Peters also stated that U.S. states need someone to take control in case of cyberattacks to coordinate efforts with federal government experts given the increasing sophistication of current cyber threats.
"These coordinators would help states better understand relevant threats, access federal cybersecurity resources and respond to potential attacks," he added.
DHS cyber response teams to ransomware, cyberattacks
Senator Hassan introduced another bill on January 31, 2019, known as the DHS Cyber Hunt and Incident Response Teams Act, to authorize DHS cyber hunt and incident response teams following the increasing number of cyberattacks targeting US entities during 2018.
The bill enacted and signed by the President on December 20, 2019, allows the newly established teams to provide technical support and advice to government and private sector organizations on how to properly reinforce their IT systems against such attacks.
Per the DHS Cyber Hunt and Incident Response Teams Act, the DHS makes these teams responsible for:
• assistance to asset owners and operators in restoring services following a cyber incident;
• identification of cybersecurity risk and unauthorized cyber activity;
• mitigation strategies to prevent, deter, and protect against cybersecurity risks;
• recommendations to asset owners and operators for improving overall network and control systems security to lower cybersecurity risks, and other recommendations, as appropriate;
The Senator previously worked on other bipartisan bills focused on cybersecurity, including the Hack Department of Homeland Security (DHS) Act and the Public-Private Cybersecurity Cooperation Act as part of a package of bills signed into law on December 21, 2018.
The FBI's Internet Crime Complaint Center issued a public service announcement in October 2019 on the growing number of high-impact ransomware attacks against both public and private US organizations.
How Malware Gains Trust by Abusing the Windows CryptoAPI Flaw
20.1.2020 Bleepingcomputer
The new Windows CryptoAPI CVE-2020-0601 vulnerability disclosed by the NSA can be abused by malware developers to sign their executables so that they appear to be from legitimate companies. This creates trust in the program, which may cause a user to be more willing to execute them.
Most of the coverage of this vulnerability illustrates how the vulnerability can be exploited to spoof certificates used for TLS connections to web sites and perform MiTM attacks.
For example, Kudelski Security illustrated how they used the vulnerability to create a fake certificate that impersonates github.com. To protect users, Chrome added protections that block users from accessing sites using these spoofed certificates.
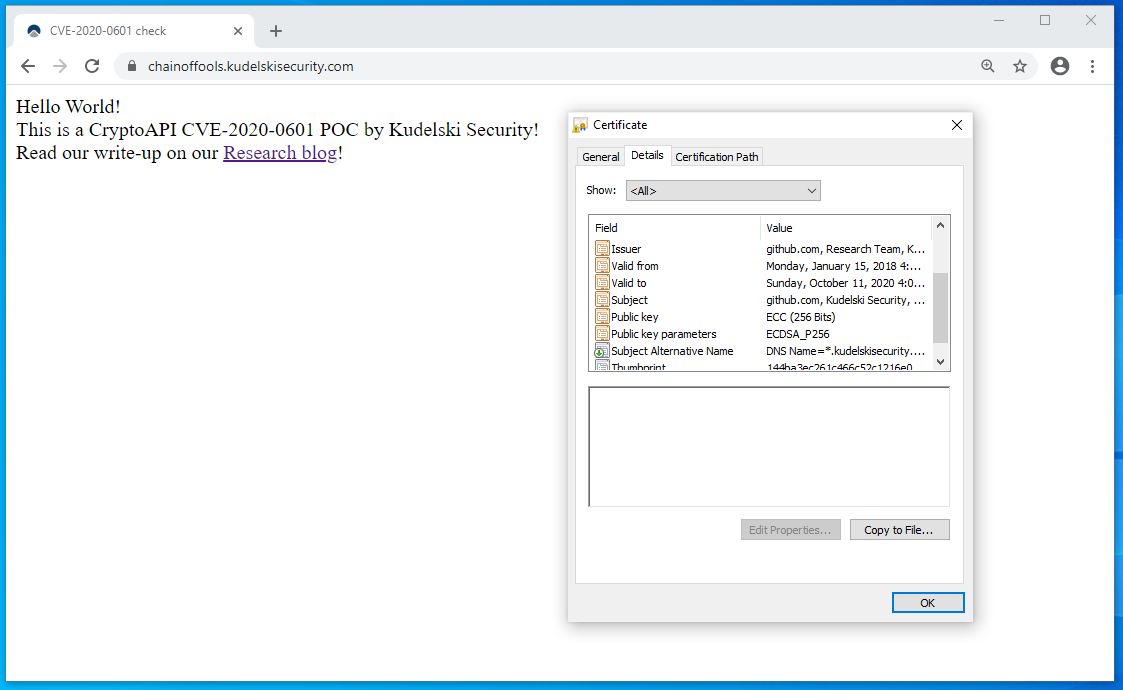
Spoofing web site certificates
This vulnerability, though, can also be used to spoof code-signing certificates.
When a developer releases a program, they can digitally sign the executables to assure users that the program is from a trusted source. If that user trusts the company, then their signed executables are most likely trustworthy as well and would be more apt to execute them.
Antivirus software may also whitelist software from being detected as malware if they utilize trusted and well-known digital signatures.
Using this new CryptoAPI vulnerability, malware distributors can create code-signing certificates that spoof legitimate companies so that their signed malware executables appear to be from a trusted company like Microsoft.
It's about trust
When running an executable in Windows that requires elevated, or administrative, privileges the operating system will display a User Account Control (UAC) prompt asking you to confirm if the permission should be granted.
If the executable has been code-signed, the UAC prompt will display a blue banner, the product name of the executable, its icon, and the name of the developer listed in the code-signing certificate. The user can then use this information to decide if they should grant elevated privileges to the program.
UAC Prompt for the Windows Registry Editor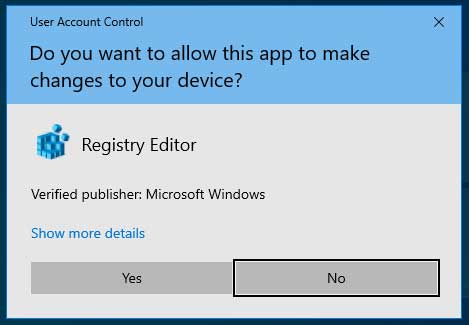
When this same executable is unsigned, Windows will display a UAC prompt with a yellow banner that specifies the publisher is 'Unknown' and once again asking if you would like to give elevated privileges.
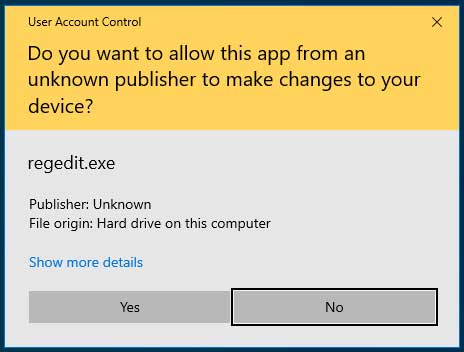
UAC Prompt from an unsigned executable
As you can see from the two prompts above, the one for the unsigned executable is intended to make the user more wary about providing administrative privileges.
Due to this, malware distributors are commonly creating fake companies to purchase code-signing certificates or stealing certificates from other companies. These certificates are then used to sign their malware executables.
The problem for attackers, though, is that once a certificate is reported to be used with malware, the certificate authority responsible for this cert will revoke it so that it no longer works.
Using CVE-2020-0601 to spoof trusted publishers
Using the CVE-2020-0601 vulnerability, malware distributors can easily create certificates that spoof legitimate companies such as Microsoft.
This allows them to sign their executables so that they appear as the same code signing certificate as seen in Windows executables. Even worse, as these certificates are exploiting a vulnerability, they cannot be revoked by certificate authorities or blocked on unpatched Windows devices.
By signing an executable as a trusted publisher, it could also allow malware to bypass antivirus engines that have whitelisted the trusted certificate.
To illustrate this, BleepingComputer found an executable on VirusTotal that is signed with a certificate exploiting the CVE-2020-0601 vulnerability. This certificate spoofs the ones used by Microsoft to sign Windows executables.
On an unpatched system, Windows does not see anything wrong with the certificate when it is opened.
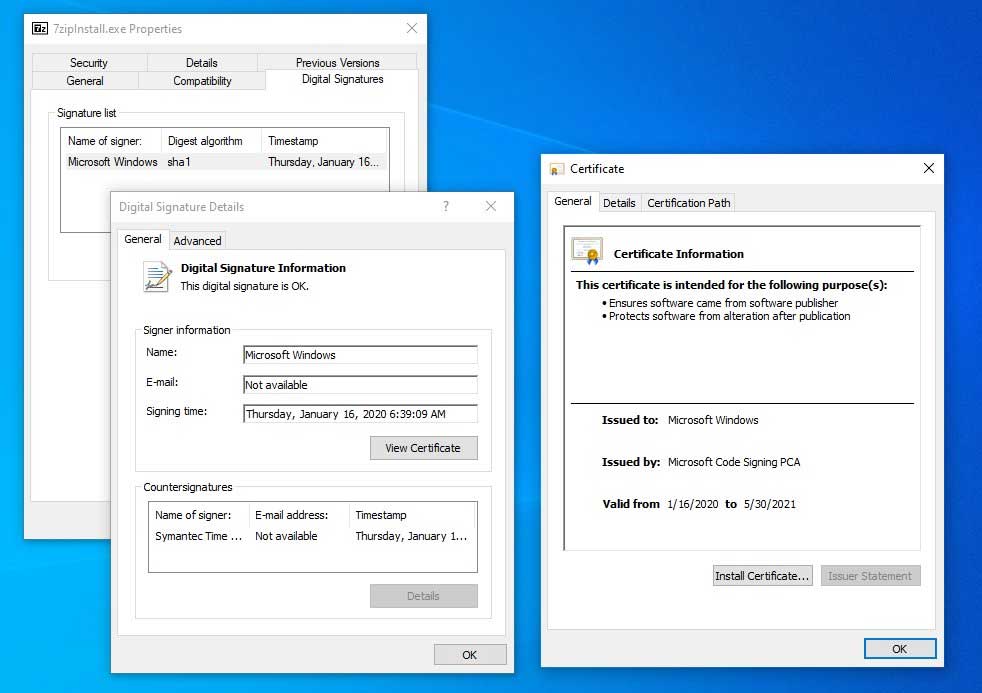
Certificates on an unpatched system
Even when you run the program, it displays a UAC prompt indicating it was signed by Microsoft.
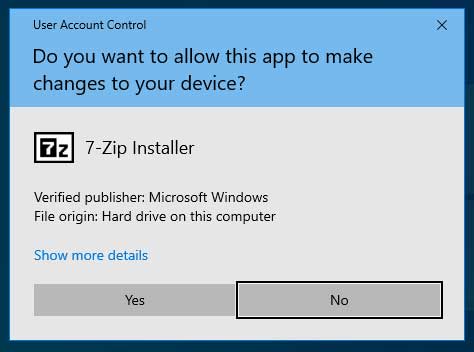
UAC prompt on an unpatched system
On a patched system, though, Windows will see that this certificate is spoofed and display a warning stating "A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider."
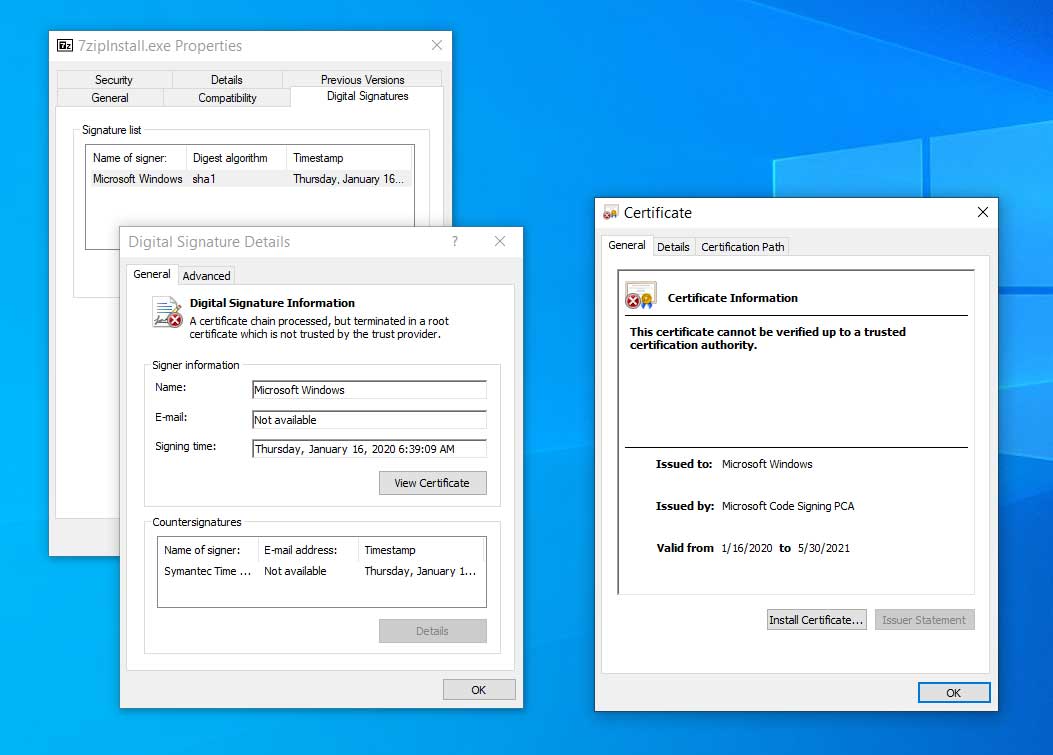
Certificates on a patched system
UAC prompts on a patched system will also ignore the spoofed certificate and treat the application as untrusted.
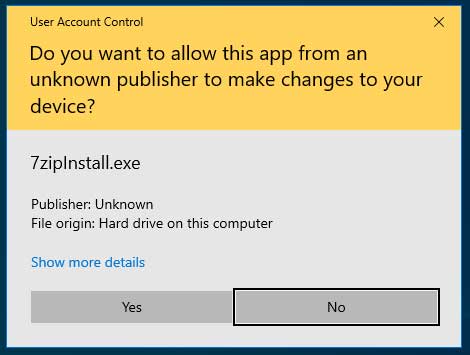
UAC prompt on a patched system
It is not a question as to whether malware will exploit this vulnerability, but a question as to when.
Already on VirusTotal, we see researchers uploading executables [1, 2, 3] signed with spoofed certificates and can expect to see malware using it in the wild soon.
With easy to use proof-of-concepts available, this vulnerability allows attackers to generate signed malware that looks trusted and possibly bypass antivirus software.
Even better, it allows them to do so without the cost or hardship of acquiring a legitimate code-signing certificate that can easily be revoked.
"This is an immediate high-impact scenario for malware bypass. For the past year, malware deliveries have reused a signed malware to bypass AV systems relying on this check rather than their own. At its best, the criminals would leverage this vulnerability against unpatched Windows 10 as part of "free" malware signing bypassing static and/or trust-based detection," Head of SentinelLabs Vitali Kremez told BleepingComputer in a conversation about this vulnerability.
Windows Defender detects malicious certificates
The good news is that antivirus software, web browsers, and Microsoft have been hard at work implementing detections for these spoofed certificates.
Windows Defender will now detect programs signed with certificates that exploit this vulnerability as Exploit:Win32/CVE-2020-0601.
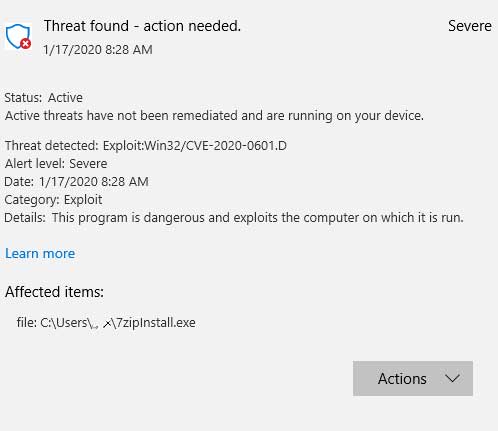
Windows Defender detected CVE-2020-0601
Microsoft is also utilizing the CveEventWrite function to log attempts to exploit the CVE-2020-0601 vulnerability to the Event Viewer.
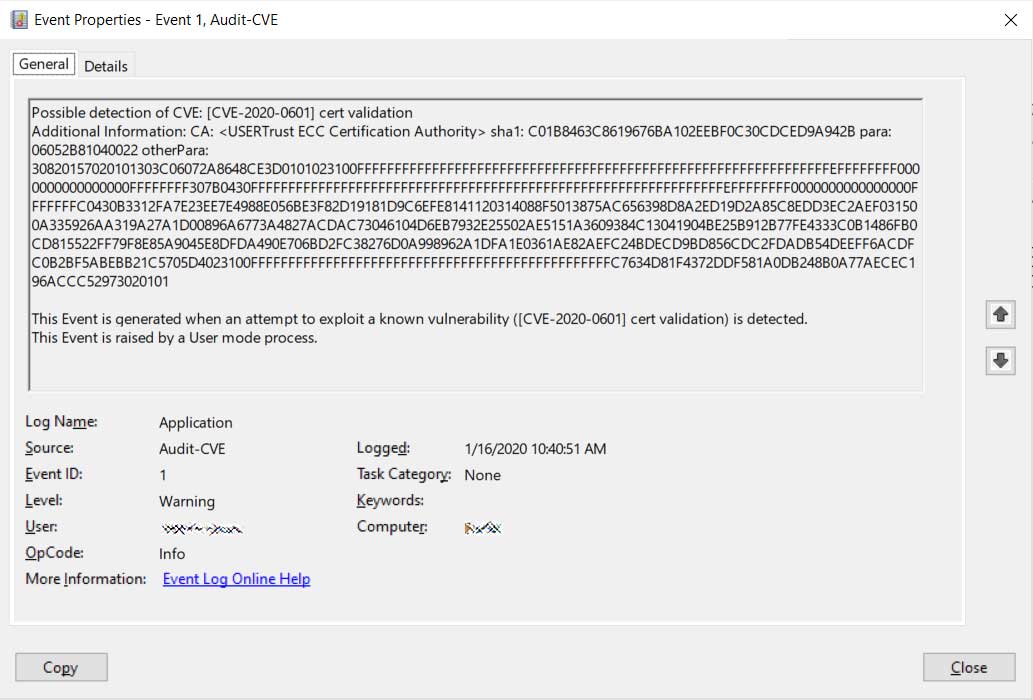
Logging exploit attempts to Event Viewer
Google Chrome added new protections in Chrome 79.0.3945.130 that prevent you from accessing sites using spoofed certificates.
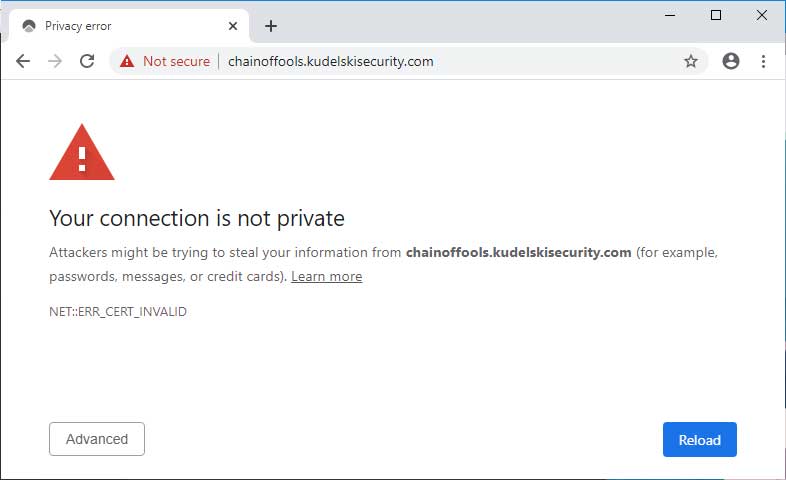
Chrome with CVE-2020-0601 detection
Finally, antivirus engines such as ones from McAfee, Kaspersky, ZoneAlarm, and GData have added detections for this vulnerability and others will do the same.
If so many security companies and software developers are taking this vulnerability seriously, so should you.
Be sure to install the patch as soon as possible to become protected.
FBI Says State Actors Hacked US Govt Network With Pulse VPN Flaw
20.1.2020 Bleepingcomputer
FBI said in a flash security alert that nation-state actors have breached the networks of a US municipal government and a US financial entity by exploiting a critical vulnerability affecting Pulse Secure VPN servers.
The US Cybersecurity and Infrastructure Security Agency (CISA) previously alerted organizations on January 10 to patch their Pulse Secure VPN servers against ongoing attacks trying to exploit the flaw tracked as CVE-2019-11510.
This bug enables unauthenticated remote attackers to send a specially crafted URIs to connect to vulnerable servers and read sensitive files containing user credentials. These can later be used to take control of an organizations' systems and more.
On unpatched systems, the vulnerability "allows people without valid usernames and passwords to remotely connect to the corporate network the device is supposed to protect, turn off multi-factor authentication controls, remotely view logs and cached passwords in plain text (including Active Directory account passwords)," security researcher Kevin Beaumont explained.
US entities breached in Pulse Secure VPN attacks
The FBI says that unidentified threat actors have used the CVE-2019-11510 flaw "to exploit notable US entities" since August 2019.
In August 2019, attackers were able to gain access to a US financial entity’s research network by exploiting servers unpatched against CVE-2019-11510.
During the same month, a US municipal government network was also breached following an attack that exploited the same vulnerability.
Based on the sophistication of the Tactics, Techniques, and Procedures (TTPs) used in the two attacks, "the FBI believes unidentified nation-state actors are involved in both compromises; however, it remains unclear if these are isolated incidents."
US govt network hacked
The attack that targeted and compromised the US municipal government network took place in mid-August 2019 according to the FBI.
"In this case, the operators were able to enumerate and exfiltrate user accounts, host configuration information, and session identifiers that could allow them to gain further access to the internal network.
At this time, the FBI is continuing to gather indicators of compromise on the incident."
Attackers infiltrate US financial entity's research network
"The intruder(s) remotely exploited a Pulse Secure VPN appliance by using CVE-2019-11510," the flash alert says. "The vulnerability in Pulse Secure allowed directory transversal and access to a file where login credentials were written in plain text. In addition, the Pulse Secure appliance may have been vulnerable to a buffer overflow and command injection.
After breaching the network, the nation-state actors gained access to the Active Directory, harvesting and exfiltrating user credentials (usernames and passwords) for the VPN client
Following attempts to enumerate and gaining access to other network segments, the hackers were only able to infiltrate the exploited segment which was the only one on the network using single-factor authentication.
"The intruder(s) attempted to access several Outlook web mail accounts but were unsuccessful due to the accounts being on separate domains
requiring different credentials not obtained by the intruder(s).
While the intruder(s) performed additional enumeration, there was no evidence that any data was compromised or exfiltrated, and the intruder(s) seemingly did not install any persistence capability or foothold in the network."

Possible Iran connection and mitigation measures
While the FBI did not directly connect these attacks to Iranian-backed hackers, a Private Industry Notification (PIN) detailing Iranian Cyber Tactics and Techniques shared a day later mentions "information indicating Iranian cyber actors have attempted to exploit Common Vulnerability and Exposures (CVEs) 2019-11510 [..]"
"The FBI assesses this targeting, which has occurred since late 2019, is broadly scoped and has affected numerous sectors in the United States and other countries.
The FBI has observed actors using information acquired from exploiting these vulnerabilities to further access targeted networks, and establish other footholds even after the victim patched the vulnerability."
Municipalities are advised by the FBI to review this National Security Agency (NSA) cybersecurity advisory on mitigating VPN vulnerabilities.
They're also recommended to take the following measures to defend against the impact of potential attacks targeting domains connected to municipality networks, including "local infrastructure managing emergency services, transportation, or elections:"
• Be alert to and immediately install patches released by the vendors, especially for web-facing appliances;
• Block or monitor the malicious IP addresses above, as well as any other IP addresses conducting remote logins at odd hours;
• Reset credentials before reconnecting the upgraded devices to an external network;
• Revoke and create new VPN server keys and certificates;
• Use multifactor authentication as a measure of security beyond passwords, which allows you to differentiate a user from an attacker;
• Review your accounts to ensure adversaries did not create new accounts;
• Implement network segmentation where appropriate;
• Ensure that administrative web interfaces are not accessible from the internet.
Ongoing attacks targeting unpatched Pulse Secure VPN servers
According to an NSA advisory from October 2019, "Exploit code is freely available online via the Metasploit framework, as well as GitHub. Malicious cyber actors are actively using this exploit code."
While on August 25, 2019, security firm Bad Packets discovered 14,528 unpatched Pulse Secure servers, a scan from today yielded 3,328 results with the U.S. being the first on the "leaderboard" with over 1,000 unpatched VPN servers.
Bad Packets Report
@bad_packets
Week 21 CVE-2019-11510 Scan Results
• Vulnerable Pulse Secure VPN servers detected: 3,328
Our latest vulnerability scan results are freely available for authorized government CERT, CSIRT, and ISAC teams.
Submit request here: https://forms.gle/nkVd1xNkACobo2Zt6 …#cybersecurity #threatintel
9
9:41 AM - Jan 17, 2020
Twitter Ads info and privacy
See Bad Packets Report's other Tweets
The two US entities the FBI says were compromised are not the only examples of such successful attacks targeting CVE-2019-11510.
While not yet officially confirmed, a high-profile case could be that of the international foreign currency exchange Travelex which was hit by Sodinokibi ransomware on December 3 after not patching their Pulse Secure VNP servers, with the attackers asking for a $3 million ransom.
Travelex was one of the companies Mursch warned of having vulnerable servers in September 2019. Travelex did not reply to his email at the time.
Scott Gordon (CISSP), Pulse Secure Chief Marketing Officer, told BleepingComputer that attackers are actively exploiting "unpatched VPN servers to propagate malware, REvil (Sodinokibi), by distributing and activating the Ransomware through interactive prompts of the VPN interface to the users attempting to access resources through unpatched, vulnerable Pulse VPN servers."
Hackers Are Securing Citrix Servers, Backdoor Them for Access
20.1.2020 Bleepingcomputer
An unknown threat actor is currently scanning for and securing vulnerable Citrix ADC servers against CVE-2019-19781 exploitation attempts, while also backdooring them for future access.
The actor deploys a payload dubbed NOTROBIN by FireEye researchers who discovered this campaign, an implant designed to clean the Citrix ADC appliances of malware strains known to target such devices and to mitigate the CVE-2019-19781 flaw to block subsequent exploitation efforts.
NOTROBIN also plants a backdoor that provides access to the now secured Citrix ADC server to actors that know a secret hardcoded passphrase, unique for each compromised device.
The NOTROBIN payload was also observed while adding cron syslog entries to gain persistence on compromised servers.
Further exploitation blocked on 'secured' devices
"FireEye believes that this actor may be quietly collecting access to NetScaler devices for a subsequent campaign," the report adds.
While monitoring one of the devices where NOTROBIN was dropped, the researchers were able to observe more than a dozen attacks being blocked over three days, with the attackers being served with 404 errors after their malicious templates containing commands were deleted in real-time.
"The mitigation works by deleting staged exploit code found within NetScaler templates before it can be invoked," FireEye explains.
"However, when the actor provides the hardcoded key during subsequent exploitation, NOTROBIN does not remove the payload. This lets the actor regain access to the vulnerable device at a later time."
While this actor hasn't yet dropped any other malware on the Citrix servers it secured against future CVE-2019-19781 exploitation, FireEye's researchers are skeptical about his future goals seeing that, on the whole, this entire campaign looks like a staging operation hoarding Citrix appliances for yet unknown purposes.
Citrix still working on a patch for vulnerable appliances
The CVE-2019-19781 vulnerability affects Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances, and it enables unauthenticated attackers to perform arbitrary code execution via directory traversal after exploitation.
Currently, over 25,000 Citrix endpoints are vulnerable to attacks targeting this flaw, with almost 1,000 found in the U.S. and thousands more in Germany, United Kingdom, Switzerland, and Australia as Bad Packets reported almost a week ago.
Scans for vulnerable Citrix appliances began on January 8 according to security experts, and proof-of-concept (PoC) exploits were made public two days later.
The PoC exploits allow attackers to take control of vulnerable Citrix Application Delivery Controller (NetScaler ADC) and Citrix Gateway (NetScaler Gateway) devices by creating reverse shells and executing malicious commands on the compromised servers.
Although Citrix disclosed the bug almost a month ago, a patch available for the Citrix ADC CVE-2019-19781 flaw is not yet available. Instead, the company provides mitigations and has shared a timeline of expected release dates for firmware updates to address the issue, starting with January 20th, 2020.
Fermin J. Serna
@fjserna
We just published further information around the Citrix ADC/Gateway vulnerability with fix release dates. If I can recommend something, apply the mitigation ASAP if you have the management IP exposed and not firewall protected. It stops the attack on known vulnerable scenarios. https://twitter.com/CitrixNetwork/status/1216153467926073349 …
Citrix Networking
@CitrixNetwork
Blog post from @Citrix CISO @fjserna about updates to the Citrix ADC, Citrix Gateway #CVE201919781 vulnerability - https://bit.ly/36LRITI
122
1:43 AM - Jan 12, 2020
Twitter Ads info and privacy
90 people are talking about this
Citrix also noted in an updated advisory yesterday, the mitigations are ineffective for Citrix ADC Release 12.1 builds before 51.16/51.19 and 50.31 because a "bug exists that affects responder and rewrite policies bound to VPN virtual servers causing them not to process the packets that matched policy rules."
For these cases, the company recommends updating to an unaffected build and then applying the mitigation steps to fully protect devices.
Four days ago, the Cybersecurity and Infrastructure Security Agency (CISA) also released a public domain tool that allows security staff to test if their organizations' servers are vulnerable.
The Dutch National Cybersecurity Centre (NCSC) issued a warning yesterday advising companies to shut down their Citrix ADC and Gateway servers until a reliable solution for protecting all Citrix appliance versions against CVE-2019-19781 will be available.
The full timeline of expected release dates for firmware updates is available below:
Citrix ADC and Citrix Gateway
Version Refresh Build Expected Release Date
10.5 10.5.70.x 31st January 2020
11.1 11.1.63.x 20th January 2020
12.0 12.0.63.x 20th January 2020
12.1 12.1.55.x 27th January 2020
13.0 13.0.47.x 27th January 2020
Citrix SD-WAN WANOP
Release NetScaler Release Expected Release Date
10.2.6 11.1.63.x 27th January 2020
11.0.3 11.1.63.x 27th January 2020
Fraudsters Set Up Site Selling Temporary Social Security Numbers
20.1.2020 Bleepingcomputer
Some fraudsters have set up a scam site claiming to be for a data protection fund created by the U.S. Federal Trading Commission (FTC) to offer financial compensation to users whose personal data appeared in information leaks.
This is a reinterpretation of the classic advance-fee scam where the victim makes a small payment inebriated by the promise of getting a much larger sum in return.
Despite posing as a site associated with the FTC, this money-making scheme accepts victims from any country and offers to sell "temporary social security numbers (SSNs)" to those that don't have one.
Bait: cash for data leak victims
Named "Official Personal Data Protection Fund," the website promises to pay users of any geography if their personal data was used by an unauthorized third party.
A fake verification service can help users find out if their data ever leaked. The results of the check dictate if the user is entitled to compensation and the exact value.
This "verification" requires some personal data, though. At least the name (first and last) and phone number are required for the check to begin.
There are three specific sources to choose from - social networks, messengers, and ad networks, and details for the selected one are also needed.
The form accepts any information, Kaspersky's Tatyana Sidorina writes in a blog post on Thursday.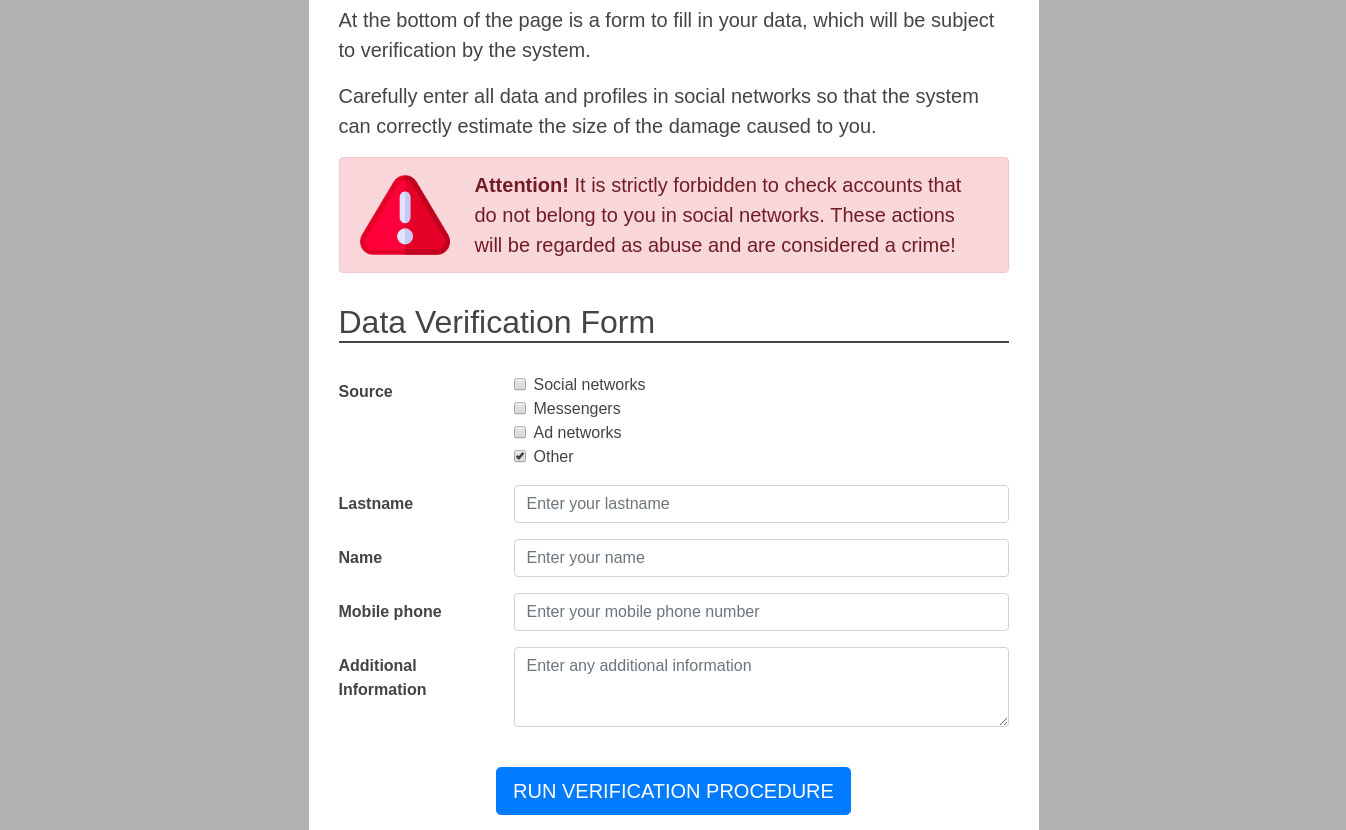
Regardless of what you enter in the form, results are returned and, as expected, they claim that personal data was found in leaks and that financial compensation was available.
While analyzing the fraudulent website, Kaspersky typed "fghfgh fghfgh" for the name of the user. The results returned showed that photos, videos, and contact information "repeatedly appeared in information leaks."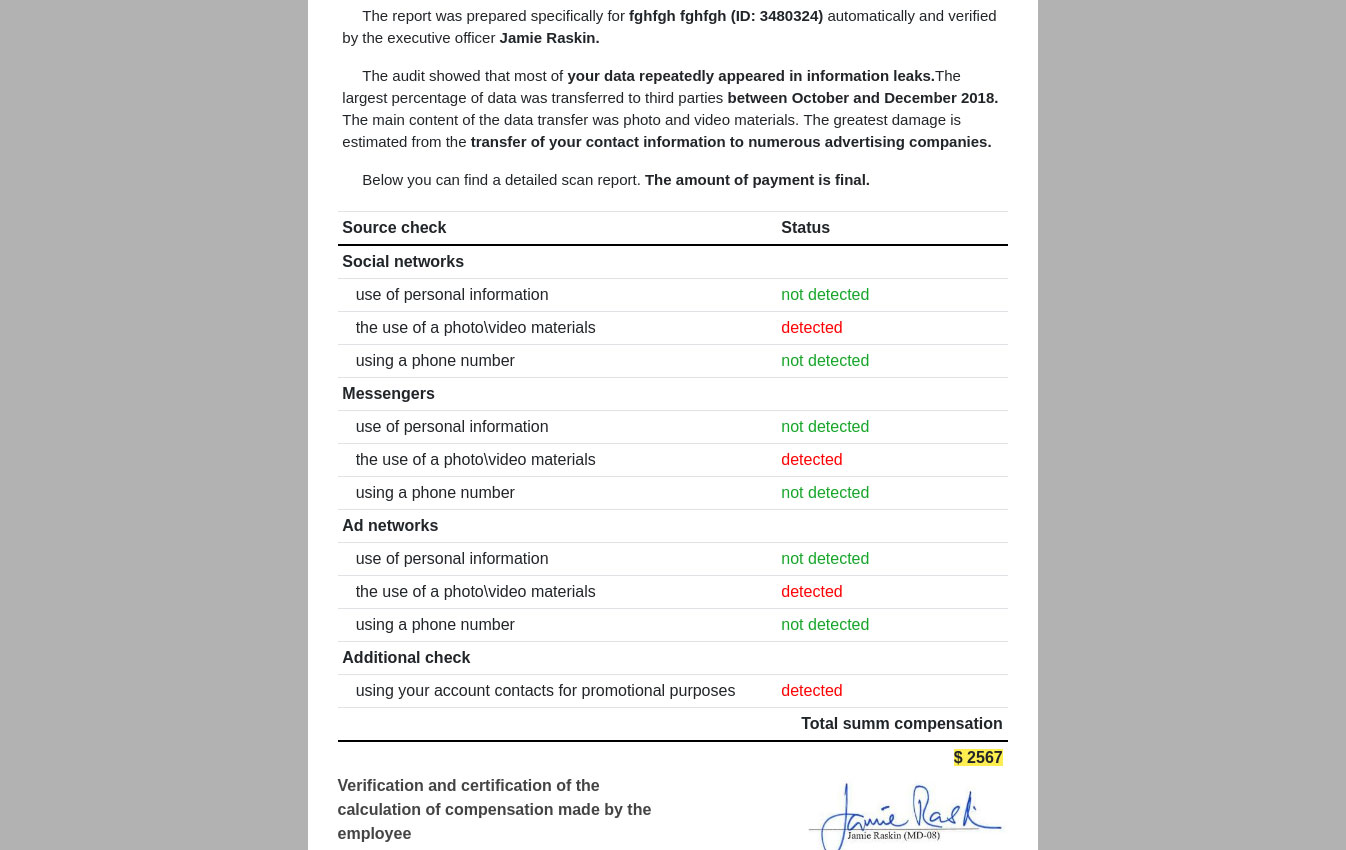
The compensation calculated by the fraudsters was $2,567, a sum sufficiently large to keep victims interested in how they can get it: provide a card number and the SSN.
The fact that this program is associated with the FTC and users of any geography are eligible should ring the alarm in the first place. Spelling mistakes are also a good clue that this is a scam and should keep you from sending personal information.
Since users of any geography are accepted, not all have an SSN. The solution is to buy a temporary SSN valid for two days, for the low price of $9.32.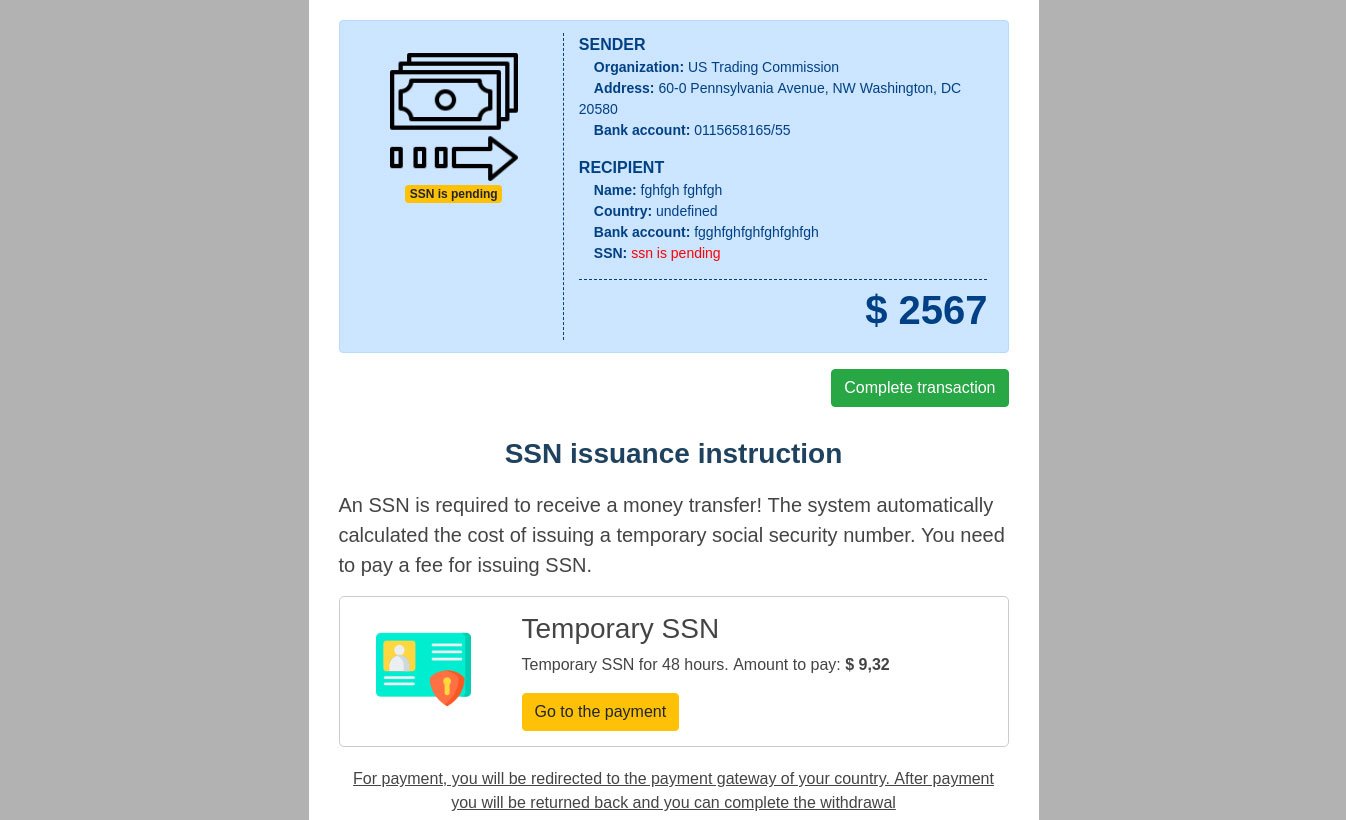
Even if a real SSN is provided, the website will still ask you to get a temporary one. Sidorina notes that the payment page is localized, at least for Russian IP addresses, and the price is converted to rubles.
"This is strange. Why would a U.S. government agency require payment in a foreign currency?"
Kaspersky believes that Russian speakers are behind this, as the similarity with other schemes running in Russia and the Commonwealth of Independent States (CIS) and the ruble payment form seems to suggest so.
WeLeakInfo.com Seized For Selling Info from Data Breaches, 2 Arrested
20.1.2020 Bleepingcomputer
As a clear indication of how law enforcement views the commercial disclosure of stolen information, the FBI has seized the WeLeakInfo.com domain and international law enforcement arrested two individuals for selling subscriptions to data exposed in breaches. These accessed credentials were then used to conduct attacks in the UK, Germany, and the US.
In coordination with the UK NCA, the Netherlands National Police Corps, the German Bundeskriminalamt, and the Police Service of Northern Ireland. the FBI took ownership of the WeLeakInfo.com domain name and added a notice stating it was seized.
WeLeakInfo.com Seizure Notice
According to a U.S. Department of Justice announcement, the domain was seized for offering subscriptions that allowed subscribers to search for specific information exposed in data breaches.
"The website had claimed to provide its users a search engine to review and obtain the personal information illegally obtained in over 10,000 data breaches containing over 12 billion indexed records – including, for example, names, email addresses, usernames, phone numbers, and passwords for online accounts. The website sold subscriptions so that any user could access the results of these data breaches, with subscriptions providing unlimited searches and access during the subscription period (one day, one week, one month, or three months)."
As part of this operation, two individuals were arrested in the Netherlands and Ireland who are suspected to be involved in the site and are believed to have made £200,000 from its operation. Online payments traced back to these individual's IP addresses indicate that they may be heavily involved in the site's operation.
The UK's NCA states that they have established links between We Leak Info and the purchase of further malware such as RATs and Cryptors.
"Law enforcement activity in the UK last year established links between the purchase of cyber crime tools, such as remote access Trojans (RATs) and cryptors, and weleakinfo.com."
The commercialization of stolen data
We Leak Info claimed to have compiled almost 12.5 billion records stolen from data breaches and allowed users to pay to access it.
To access this data, visitors could subscribe to various plans ranging from a $2 trial to a $70 three-month unlimited access account. These plans would then allow a user to perform searches that retrieve information exposed in these data breaches.
WeLeakInfo Plans
The actual disclosure of the stolen data compared to just allowing users to be notified if their info was exposed is a clear distinction between how We Leak Info and a service like HaveIBeenPwned utilize data breaches.
In We Leak Info's case, threat actors commonly subscribed to search for exposed usernames and passwords and then used that info to perform credential stuffing attacks, phishing attacks, and potentially network breaches.
On the other hand, HaveIBeenPwned will just tell you if an entered email is part of a data breach, but does not provide any other information.
Seizure notice thought to be a joke, even by owners
When the news that weleakinfo.com was seized, people were not sure if this was a prank being conducted by the owners or an actual seizure by law enforcement.
To illustrate this confusion, a poll on Twitter showed that 70% of the 492 respondents felt that this was a joke.
Voting on whether it was a prank
At the time, even We Leak Info indicated that they had no idea what was going on and tweeted that they "are currently investigating this issue."
Tweet from We Leak Info
With the press releases from law enforcement, we now have a clear picture that this was not a joke and that their operation has been shut down.
Update 1/17/20: Included information revealed in today's press release from the UK NCA.
Dutch Govt Suggests Turning Off Citrix ADC Devices, Mitigations May Fail
20.1.2020 Bleepingcomputer
Mitigation recommendations for CVE-2019-19781, a currently unpatched critical flaw affecting Citrix Application Delivery Controller (ADC) and Citrix Gateway, do not have the expected effect on all product versions.
In an updated advisory today, the software company informs that it found a new product that is vulnerable to the same security issue and that the advised actions do not work on some versions of Citrix ADC.
Bug makes mitigation ineffective on some Citrix ADC
Until patches become available, the company sticks to the original advice but notes that it is ineffective for Citrix ADC Release 12.1 builds before 51.16/51.19 and 50.31 because “bug exists that affects responder and rewrite policies bound to VPN virtual servers causing them not to process the packets that matched policy rules.”
The recommended course in this case is to first update to an unaffected build and then apply the mitigation steps.
Further analysis of the vulnerability and its impact on Citrix products revealed that it is also present in the Wan Optimization (WANOP) edition of the Citrix SD-WAN appliance.
The updated list of Citrix products affected by CVE-2019-19781 now looks like this:
Citrix ADC and Citrix Gateway version 13.0 all supported builds
Citrix ADC and NetScaler Gateway version 12.1 all supported builds
Citrix ADC and NetScaler Gateway version 12.0 all supported builds
Citrix ADC and NetScaler Gateway version 11.1 all supported builds
Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
Citrix SD-WAN WANOP software and appliance models 4000, 4100, 5000, and 5100 all supported builds
Turn off Citrix appliance, if possible
In a warning today, the Dutch National Cybersecurity Centre (NCSC) says that companies should consider turning off Citrix ADC and Gateway servers if the impact is acceptable. Given the latest update, the organization assesses that at the moment there is no reliable solution to protect all versions of Citrix ADC and Citrix Gateway servers against CVE-2019-19781.
If turning off the appliances is not possible, NCSC strongly recommends monitoring the network for potential abuse. Further limiting the risk of exploitation is possible by whitelisting specific IP addresses or IP blocks.
Threat actors are currently exploiting the bug, both Citrix and the Dutch National Cybersecurity Center (NCSC) warn. Scanning for vulnerable Citrix ADC and Gateway appliances started in the first week of the year and multiple working exploits are available in the public space.
Firmware updates that fix the problem in all supported builds of Citrix ADC, Citrix Gateway, and SD-WAN WANOP are expected to be released by the end of January. Below is a timeline of the expected release dates:
Citrix ADC and Citrix Gateway
Version Refresh Build Expected Release Date
10.5 10.5.70.x 31st January 2020
11.1 11.1.63.x 20th January 2020
12.0 12.0.63.x 20th January 2020
12.1 12.1.55.x 27th January 2020
13.0 13.0.47.x 27th January 2020
Citrix SD-WAN WANOP
Release NetScaler Release Expected Release Date
10.2.6 11.1.63.x 27th January 2020
11.0.3 11.1.63.x 27th January 2020
Citrix recommends customers to upgrade all their vulnerable appliances to a fixed firmware version when it becomes available.
The vulnerability has a severity score of 9.8 out of 10 and was publicly disclosed by Positive Technologies on December 23, 2019. Exploiting it does not require authentication and can allow arbitrary code execution to an attacker that is already on the internal network.
Windows 10 Insider Build 19546 Adds Graphing Mode to Calculator
20.1.2020 Bleepingcomputer
Windows 10 Build 19013 Out With New DirectX 12 Features for Insiders
Microsoft has released Windows 10 Insider Preview Build 19546 to Insiders in the Fast ring, which has added a new Graphing Mode to the Windows Calculator and fixed bugs in Timeline, Outlook search, and more.
If you are a Windows Insider in the Fast ring, you can update to the Insider Preview Build 19546 by going into Settings -> Update & Security -> Windows Update and then checking for new updates.
To see the full release notes and fixes for this Windows 10 insider build, you can read the blog post.
The most notable changes found in this new build released to Windows Insiders in the Fast ring are detailed below.
New Graphing Mode in Windows Calculator
The biggest change in this build is a new Graphing Mode being added to the Windows Calculator.
"Adding support for graphing is one of our top feature requests in Feedback Hub, and we’re excited to bring this feature to our users. Graphing capabilities are also essential for students who are beginning to explore linear algebra. With this feature, we hope to empower students to learn mathematics by improving their conceptual understanding and attitudes towards math."
New Graphing Mode in Windows Calculator
This new mode allows users to:
Plot one or more equations on the graph
Add equations with variables.
Analyze the graph.
For those who are interested in testing the app, Microsoft is asking that you post suggestions and feedback in the Feedback Hub.
The new Indexer Diagnostics app
Microsoft has also released a new tool that helps you diagnose Windows search issues called the Indexer Diagnostics app.
If you are having issues with finding your content in Windows Search, you can use this tool to check if a file is indexed, look for failed queries, and check what content is being indexed.
Indexer Diagnostics app
This app is available to anyone running Windows 10 and can be downloaded here.
General changes, improvements, and fixes for PC
We fixed an issue resulting in Timeline not showing any activities.
We fixed an issue resulting in Outlook search not working for some.
We fixed an issue significantly impacting Task View reliability for some.
We fixed an issue where pressing Spatial Sound -> Off in the sound menu caused Explorer.exe to crash.
Known issues
BattlEye and Microsoft have found incompatibility issues due to changes in the operating system between some Insider Preview builds and certain versions of BattlEye anti-cheat software. To safeguard Insiders who might have these versions installed on their PC, we have applied a compatibility hold on these devices from being offered affected builds of Windows Insider Preview. See this article for details.
We are aware Narrator and NVDA users that seek the latest release of Microsoft Edge based on Chromium may experience some difficulty when navigating and reading certain web content. Narrator, NVDA and the Edge teams are aware of these issues. Users of legacy Microsoft Edge will not be affected.
The cloud recovery option for Reset this PC isn’t working on this build. Please use the local reinstall option when performing Reset this PC.
We’re looking into reports of the update process hanging for extended periods of time when attempting to install a new build.
We’re investigating reports that some Insiders are unable to update to newer builds with error 0x8007042b.
We’re looking into reports of certain external USB 3.0 drives not responding with Start Code 10 after they’re attached.
The Optimize Drives Control Panel is incorrectly reporting that optimization has never run on some devices. Optimization is completing successfully, even though it is not reflected in the UI.
The Documents section under Privacy has a broken icon (just a rectangle).
Remote Desktop Connection crashes when attempting to connect to multiple sessions.
Snipping isn’t working on secondary monitors.
The IME candidate window for East Asian IMEs (Simplified Chinese, Traditional Chinese, and the Japanese IME) may not open sometimes. We are investigating your reports. As a workaround if you encounter this, please change the focus to another application or editing area and back to the original and try again. Alternatively, you can go to Task Manager and end the “TextInputHost.exe” task from the Details tab, and it should work afterwards.
FBI to Warn State Officials of Election Infrastructure Cyber Threats
20.1.2020 Bleepingcomputer
The Federal Bureau of Investigation (FBI) today announced a change in policy requiring the timely notification of state officials of potential cyber threats to election infrastructure.
"Protecting the integrity of elections in the United States against criminal activity and national security threats is among the top priorities of the Department of Justice (DOJ) and the FBI," says a press release published today.
"Cyber intrusions affecting election infrastructure have the potential to cause significant negative impacts on the integrity of elections."
State election officials now on FBI's notification list
The new internal policy was prompted by the need to make sure that such incidents can be mitigated promptly, something that directly depends on cyber incident notifications being delivered as soon as possible and to the right people after a cyber threat is detected.
Previously, the FBI would only alert the direct victims like counties of hacks affecting election equipment which, unfortunately, wouldn't always translate into immediate reactions because of their limited resources to respond to such attacks.
However, this just introduced policy will allow for speedier responses to cyber intrusions into election systems.
Chief state election officials "with ultimate authority over elections held in the state" that will be alerted by the FBI following such incidents will be able to take more suitable mitigation measures than local officials based on higher authority alone.
"Each state has a designated person to serve as its chief state election official with ultimate authority over elections held in the state, which often includes certifying election results," the FBI explains.
Understanding that mitigation of such incidents often hinges on timely notification, the FBI has established a new internal policy outlining how the FBI will notify state and local officials responsible for administering election infrastructure of cyber activity targeting their infrastructure. - FBI
More importantly, keeping both state and local election officials in the loop will allow for increased reaction times as their cybersecurity defense resources can pull together to fight cyber threats.
"Decisions surrounding notification continue to be dependent on the nature and breadth of an incident and the nature of the infrastructure impacted," the FBI concluded.
"It is the intent of the FBI that this new policy will result in increased collaboration between all levels of government for the integrity and security of U.S. elections."
Election systems part of U.S. critical infrastructure
The U.S. Department of Homeland Security (DHS) designated the country's voting and election systems as critical infrastructure in January 2017 following sanctions announced by White House, the FBI, DHS, and US Treasury against 35 Russian diplomats for Russia's involvement in the 2016 United States elections.
In more recent developments, during October 2019, the FBI updated and expanded a collection of resources and tools designed to help political campaigns, private businesses, and individuals to better recognize and mitigate risks posed by foreign entities' cyber intrusions and disinformation efforts during this year's U.S. election season.
"We’ve created these Protected Voices videos to showcase the methods these adversaries might use, and to help campaigns practice good cyber hygiene, because the foundation of election security is cybersecurity," Director of the FBI Chris Wray said at the time.
The DHS Incident Response Team and the Cybersecurity and Infrastructure Security Agency (CISA) also provide a list of best practices for securing elections systems as part of CISA's Security Tip ST19-002.
All these precautions are important with Microsoft saying in July 2019 that Russian-backed actors attempted to hack into the campaigns of three congressional candidates during the 2018 midterm elections.
Google Chrome Adds Protection for NSA's Windows CryptoAPI Flaw
20.1.2020 Bleepingcomputer
Google just released Chrome 79.0.3945.130, which will now detect certificates that attempt to exploit the NSA discovered CVE-2020-0601 CryptoAPI Windows vulnerability.
As part of Microsoft's January 2020 Patch Tuesday, security updates were released for a vulnerability discovered by the NSA in the Windows CryptoAPI library Crypt32.dll.
This vulnerability allows attackers to create TLS and code-signing certificates that spoof, or impersonate, other companies to perform man-in-the-middle attacks or create phishing sites.
With PoCs for the CVE-2020-0601 vulnerability already released that allow attackers to easily create spoofed certificates, it is only a matter of time before we start to see them used in attacks.
The new version of Chrome blocks spoofed certificates
Today, Google released Chrome 79.0.3945.130, which adds new code by Google's Ryan Sleevi to further check the integrity of a web site's certificate before allowing a visitor to access the site.
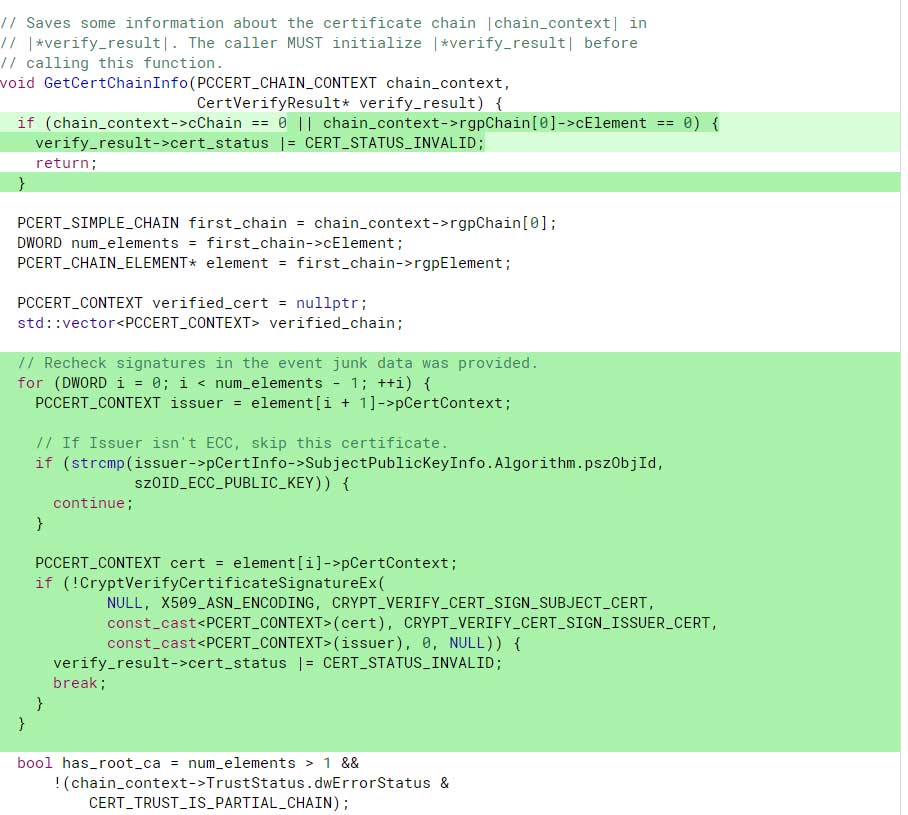
Added CVE-2020-0601 detections to Google Chrome
To show the new protections at work, using Kudelski Security's CVE-2020-0601 test site we can see the vulnerability being exploited on an unpatched Windows 10 PC using an older version of Google Chrome.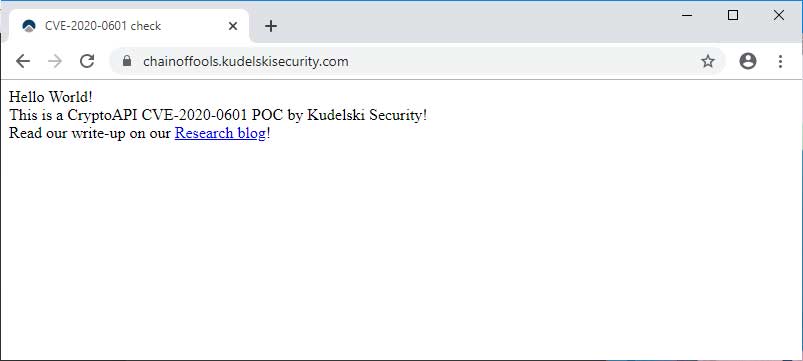
CVE-2020-0601 exploited in
On the same unpatched Windows 10 machine using Google Chrome 79.0.3945.130, when you visit the site again the browser now warns that "Attackers might be trying to steal your information".

Google Chrome 79.0.3945.130 with CVE-2020-0601 detection
Sleevi states that this check is "not perfect", but is good enough for now as users roll out the security updates to their operating systems and Google switches to better verifiers.
"This isn't perfect, but is enough of a safety check until we switch to our verifier or tighten down the blocking of 3P modules, even for CAPI."
It would not be surprising to find other browser and security software start integration detection for CVE-2020-0601 into their products so that even if a company can't immediately install the security patches, they will have a modicum of protection against the vulnerability.
WordPress Plugin Bugs Let Hackers Wipe or Takeover Your Site
20.1.2020 Bleepingcomputer
Critical bugs found in the WordPress Database Reset plugin used by over 80,000 sites allow attackers to drop all users and get automatically elevated to an administrator role and to reset any table in the database.
The open-source WP Database Reset WordPress plugin maintained by WebFactory Ltd is designed to help reset databases to default settings with a few mouse click, wiping all the data stored in the database including posts, pages, users, and more.
WP Database Reset makes it possible to choose between resetting a website's entire database or to reset only specific tables.
Using the WP Database Reset plugin (WebFactory Ltd)
Unauthenticated database reset and privilege escalation
The two vulnerabilities tracked as CVE-2020-7048 and CVE-2020-7047, rated as Critical and High severity, were patched with the release of WP Database Reset 3.15, a week after the initial disclosure from WordFence, the WordPress security firm that discovered the flaw.
During the last two days since the patched version was released, a little over 8,300 users have already updated their installations, with more than 71,000 still having to secure their websites from potential attacks.
"One of these flaws allowed any unauthenticated user to reset any table from the database to the initial WordPress set-up state, while the other flaw allowed any authenticated user, even those with minimal permissions, the ability to grant their account administrative privileges while dropping all other users from the table with a simple request," WordFence's Chloe Chamberland says.
Successful exploitation of the two flaws on unpatched WordPress sites could lead to full site takeover and/or database reset.
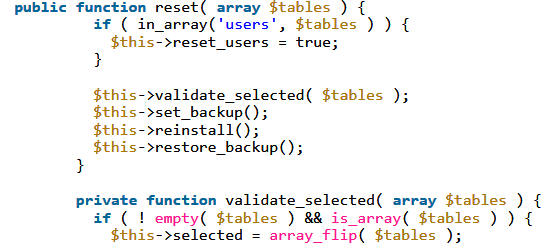
Vulnerable database reset function (WordFence)
The CVE-2020-7048 authentication bypass flaw is caused by improper authentication stemming from missing capability checks or security nonce protection.
Poorly implemented privilege management is behind CVE-2020-7047, a bug that allows site users with subscriber or higher permissions to reset the wp_users table and, after dropping all other users with a simple request, and automatically getting elevated to an admin role.
"A site owner allowing open registration on a site with a vulnerable version of the WP Database Reset plugin could lose control of their site," the Wordfence Threat Intelligence team report adds.
To defend against attacks abusing these flaws, the security outfit advises admins to update to WP Database Reset 3.15 immediately and to keep up to date site backups stored on a different server than the one hosting their WordPress installation.
WordFence also created a video demonstration of how an exploit targeting these vulnerabilities would work.
TrickBot Now Uses a Windows 10 UAC Bypass to Evade Detection
20.1.2020 Bleepingcomputer
The TrickBot Trojan has received an update that adds a UAC bypass targeting the Windows 10 operating system so that it infects users without displaying any visible prompts.
A UAC bypass allows programs to be launched without displaying a User Account Control prompt that asks users to allow a program to run with administrative privileges.
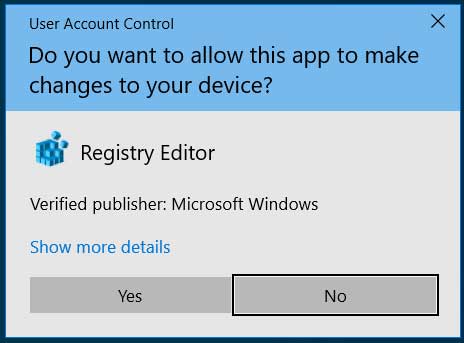
Example of UAC prompt
In a new TrickBot sample, Head of SentinelLabs Vitali Kremez discovered that the trojan is now using the Windows 10 Fodhelper bypass.
Using Windows 10 UAC bypass
When executed, TrickBot will check if the operating system is Windows 7 or Windows 10.
If it is Windows 7, TrickBot will utilize the CMSTPLUA UAC bypass and if Windows 10, will now use the Fodhelper UAC Bypass.
The Fodhelper bypass was discovered in 2017 and uses the legitimate Microsoft C:\Windows\system32\fodhelper.exe executable to execute other programs with administrative privileges.
"Fodhelper.exe is a trusted binary on Windows 10 that TrickBot uses to execute the malware stage bypassing UAC via the registry method," Kremez told BleepingComputer in a conversation.
When properly configured, when executed Fodhelper will also launch any command stored in the default value of the HKCU\Software\Classes\ms-settings\shell\open\command key.
As Fodhelper is a trusted Windows executable, it allows auto-elevation without displaying a UAC prompt. Any programs that it executes will be executed without showing a UAC prompt as well.
TrickBot utilizes this bypass to launch itself without a warning to the user and thus evading detection by the user.
Command executed by the Fodhelper UAC bypass
As more users move to Windows 10 and as Windows Defender matures, more malware has begun to target the operating system and its security features.
In September 2019 we reported how the GootKit banking Trojan also added the Fodhelper bypass in 2019 to execute a command that whitelists the malware executable's path in Windows Defender.
In July 2019, TrickBot also targeted Windows Defender by trying to disable various scan options. With the inclusion of Fodhelper, we continue to see the malware developers attempt to reduce the security features found in Windows 10.
PoCs for Windows CryptoAPI Bug Are Out, Show Real-Life Exploit Risks
20.1.2020 Bleepingcomputer
Proof-of-concept exploit code is now available for the Windows CryptoAPI spoofing vulnerability tracked as CVE-2020-0601 and reported by the National Security Agency (NSA), just two days after Microsoft released a patch.
The PoC exploits for the flaw now known as CurveBall (per security researcher Tal Be'ery) were publicly released during the last 24 hours by Swiss cybersecurity outfit Kudelski Security and ollypwn.
British hardware hacker Saleem Rashid also developed a CurveBall PoC exploit but only tweeted screenshots of his exploit code abusing CVE-2020-0601.
Saleem Rashid
@saleemrash1d
CVE-2020-0601
View image on TwitterView image on Twitter
2,570
6:16 PM - Jan 15, 2020
Twitter Ads info and privacy
1,209 people are talking about this
What's next? Well, after these working PoC exploits were released, users and organizations should patch their systems by applying the security updates Microsoft released during this month's Patch Tuesday.
While the NSA and Microsoft stated that the flaw hasn't yet been exploited in the wild, the agency's advisory recommends installing the patches as soon as possible to block attackers from defeating "trusted network connections and deliver executable code while appearing as legitimately trusted entities."
DHS' Cybersecurity and Infrastructure Security Agency (CISA) also strongly recommended agencies to "patch all affected endpoints within 10 business days" in its second-ever Emergency Directive.
Kudelski Security
@KudelskiSec
On Jan 14. @Microsoft addressed a critical flaw discovered by the #NSA in the #Windows10, Windows Server 2016 and 2019 versions of crypt32.dll, the library implementing Windows' CryptoAPI. @AnomalRoil explains the flaw, and demonstrates it with a POC. https://hubs.ly/H0mCq570
34
4:15 PM - Jan 16, 2020
Twitter Ads info and privacy
25 people are talking about this
What's the potential impact of an attack exploiting CVE-2020-0601?
The spoofing vulnerability impacts Windows 10, Windows Server 2016 and 2019 versions of CRYPT32.DLL, while "an attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear the file was from a trusted, legitimate source," according to Microsoft.
On compromised systems, attackers can launch man-in-the-middle attacks, as well as decrypt confidential info from network connections to impacted software and endpoints.
CERT/CC vulnerability analyst Will Dormann also revealed that "by exploiting this vulnerability, an attacker may be able to spoof a valid X.509 certificate chain on a vulnerable Windows system.
This may allow various actions including, but not limited to, interception and modification of TLS-encrypted communications or spoofing an Authenticode signature."
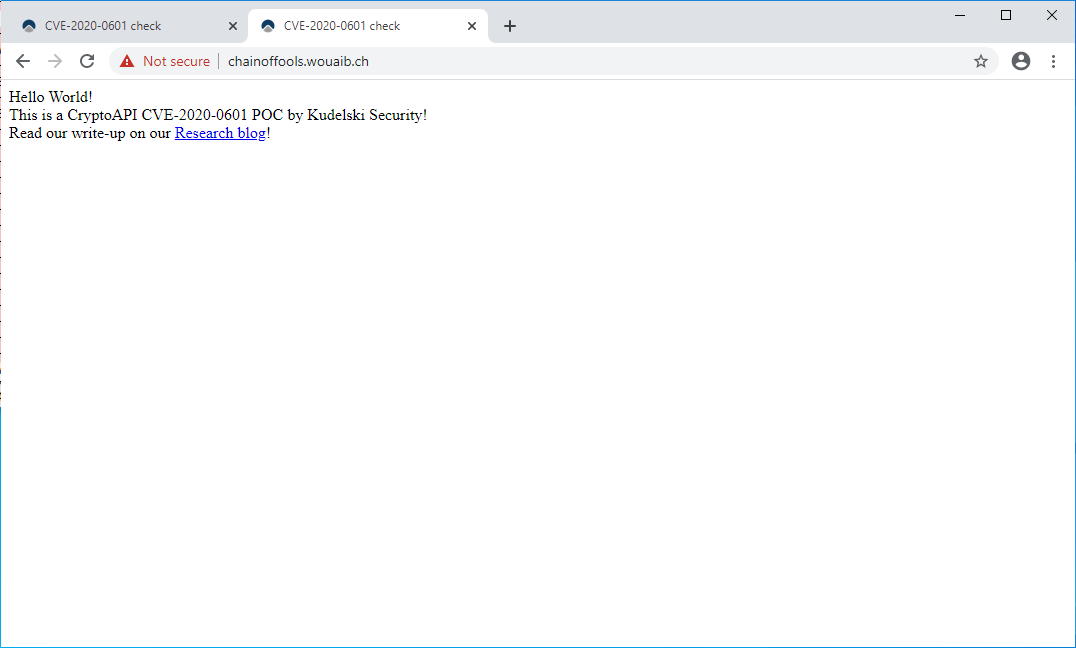
Chrome PoC on patched system
Chrome PoC on unpatched system
As Crowdstrike co-founder Dmitri Alperovitch further explained, the potential impact of CVE-2020-0601 includes remote code execution (due to auth bypass), compromise of HTTPs authentication, spoofing code signing (in user-mode), and spoofing content signing.
The code execution was also confirmed by the NSA: "The certificate validation vulnerability allows an attacker to undermine how Windows verifies cryptographic trust and can enable remote code execution."
Updated Windows logs exploitation attempts
Crowdstrike's head of EDR, Alex Ionescu and former Project Zero member Matt Tait confirmed yesterday that the Windows Update (WU) system — which was initially thought to have been also impacted — is not affected.
This is because the updates are signed with RSA certificates rather than ECC-based ones, preventing attackers from abusing as part of MiTM attacks to serve malicious code.
Luckily, as security researcher and co-director of the Open Crypto Audit Project (OCAP) Kenneth White noticed, some vendors including Crowdstrike already updated their security solutions to detect CurveBall exploitation attempts, while Microsoft updated Windows Defender to detect "files w/crafted certificates exploiting the certificate validation vulnerability," per Microsoft Defender ATP Product Manager Amitai Rottem.
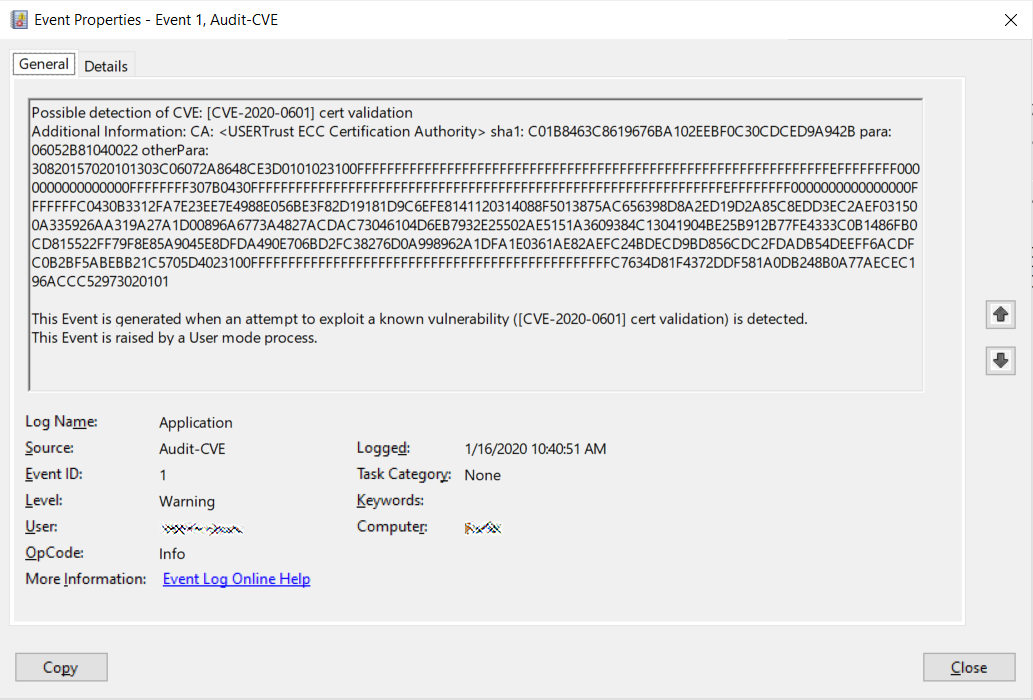
Windows Event Viewer logging exploit attempts
To sum it all up, per the NSA "the consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available.
Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners."
"In the end, please keep in mind that such a vulnerability is not at risk of being exploited by script kiddies or ransomware," Kudelski Security also added.
"While it is still a big problem because it could have allowed a Man-in-the-Middle attack against any website, you would need to face an adversary that owns the network on which you operate, which is possible for nation-state adversaries, but less so for a script kiddie.
This is why we are releasing this PoC, the exploitability of this vulnerability is not good enough to lead to a sudden ransomware threat (unlike the one we had with Wannacry)."
Google to Kill Chrome Apps Across All Platforms
20.1.2020 Bleepingcomputer
Google announced that it will slowly phase out support for Chrome apps on all operating systems until they will completely stop working in June 2022 for all users.
Chrome apps are HTML5, CSS, and JavaScript-based web apps that can be installed via the Google Chrome browser for a user experience comparable to that of native applications.
They were officially introduced and made available for download in the Chrome Web Store in May 2013 as "Chrome packaged apps," following the unveiling of a Chrome app launcher developer preview in February 2013.
Chrome Apps phase-out timeline
While this might come as a surprise for some Chrome apps users, this was an announcement expected for a while now given that Google already said in 2016 that "in the second half of 2017, the Chrome Web Store will no longer show Chrome apps on Windows, Mac, and Linux [..]"
This move was prompted by the fact that, as Google revealed three years ago, only roughly 1% of users on Windows, Mac, and Linux were actively using Chrome apps.
Google encouraged web developers at the time to migrate their Chrome apps to the web and, if not possible, to convert them into Chrome extensions or use platforms such as Electron or NW.js.
Expanding on previous announcements, Google has now published a timeline for the full phase-out of Chrome apps during the next two years:
March 2020: Chrome Web Store will stop accepting new Chrome Apps. Developers will be able to update existing Chrome Apps through June 2022.
June 2020: End support for Chrome Apps on Windows, Mac, and Linux. Customers who have Chrome Enterprise and Chrome Education Upgrade will have access to a policy to extend support through December 2020.
December 2020: End support for Chrome Apps on Windows, Mac, and Linux.
June 2021: End support for NaCl, PNaCl, and PPAPI APIs.
June 2021: End support for Chrome Apps on Chrome OS. Customers who have Chrome Enterprise and Chrome Education Upgrade will have access to a policy to extend support through June 2022.
June 2022: End support for Chrome Apps on Chrome OS for all customers.
As the timeline shows, Chrome apps will stop working on Windows, Mac, and Linux in December 2020, with a full shut down for all Chrome OS users in June 2022.
"This change does not impact support for Chrome Extensions. Google will continue to support and invest in Chrome Extensions on all existing platforms," Chrome Platform Team Technical Director Anthony Laforge said.
"Fostering a robust ecosystem of extensions is critical to Chrome's mission and we are committed to providing a useful extension platform for customizing the browsing experience for all users."
Google also provides developers with a Chrome Apps migration site with details on how to build Progressive Web Apps that work on both desktop and mobile platforms, extension-enhanced web pages, and converting Chrome apps into extensions.
Customer-Owned Bank Informs 100k of Breach Exposing Account Balance, PII
20.1.2020 Bleepingcomputer
P&N Bank in Western Australia (WA) is informing its customers that hackers may have accessed personal information stored on its systems following a cyber attack.
The data, some of it sensitive in nature, was stored on the bank’s customer relationship management (CRM) platform that is completely separated from the core banking system.
Plenty of info exposed
A division of Police & Nurses Limited, P&N Bank operates under a Operating under a customer-owned or mutual model, which does not distinguish between members and shareholders as they are one and the same. It is the largest of its kind in the state.
The financial organization says in the breach notification sent to customers that the compromised system contained the following information: names, addresses, emails, age, customer and account numbers, as well as the account balance. All this counts as personally identifiable information that is protected under the Privacy Act in Australia.
Funds, social security numbers, and data in identification documents (driver’s license, passport) were stored on a different system and are safe.
source: @vrNicknack
As many as 100,000 individuals may be impacted by the incident, which was labeled as “sophisticated” by Andrew Hadley, the bank’s chief executive officer.
The attack did not target P&N Bank directly. It occurred during a server upgrade around December 12, 2019, at a third-party that was offering hosting services to the organization.
In a statement for The West Australian, Hadley says that one of the Big Four accounting firms (Deloitte, PricewaterhouseCoopers, Ernst & Young or KPMG) has been commissioned to audit the bank’s IT systems.
“Upon becoming aware of the attack, we immediately shut down the source of the vulnerability,” the bank wrote to customers. The West Australian Police (WAPOL) and federal authorities are on the case.
In the time since discovering the attack and informing its customers, the bank assessed the extent of the incident and allowed the police investigation to develop without alerting the intruder.
P&N Bank assures its customers that protecting their information and funds is a priority, stressing that accounts are kept safe with "highly sophisticated security measures and controls."
Ako Ransomware Uses Spam to Infect Its Victims
20.1.2020 Bleepingcomputer
It has been discovered that the network-targeting Ako ransomware is being distributed through malicious spam attachments that pretend to be a requested agreement.
Last week we reported on the Ako Ransomware and how it was targeting companies with the intent to encrypt their entire network. At the time, it was not known how it was being distributed and when we asked the ransomware operators they told us it was a "secret".
Since then, the ransomware identification site ID-Ransomware has seen an increasing amount of victims.
ID Ransomware Submissions
David Pickett, a Senior Cybersecurity Analyst at AppRiver, reached out to BleepingComputer yesterday to tell us that his company saw the Ako ransomware being distributed through spam email.
These emails pretend to contain an agreement requested by the recipient and use mail subjects such as "Agreement 2020 #1775505".
Spam email distributing the Ako Ransomware
Attached to these emails is a password-protected zip file named agreement.zip with the password '2020' being given in the email.
The extracted archive will contain an executable renamed as agreement.scr that when executed will install the ransomware.
Agreement.zip Archive
As shown by this report from JoeSandbox, when Ako is executed it will encrypt the victim's files and leave them with a ransom note named ako-readme.txt.
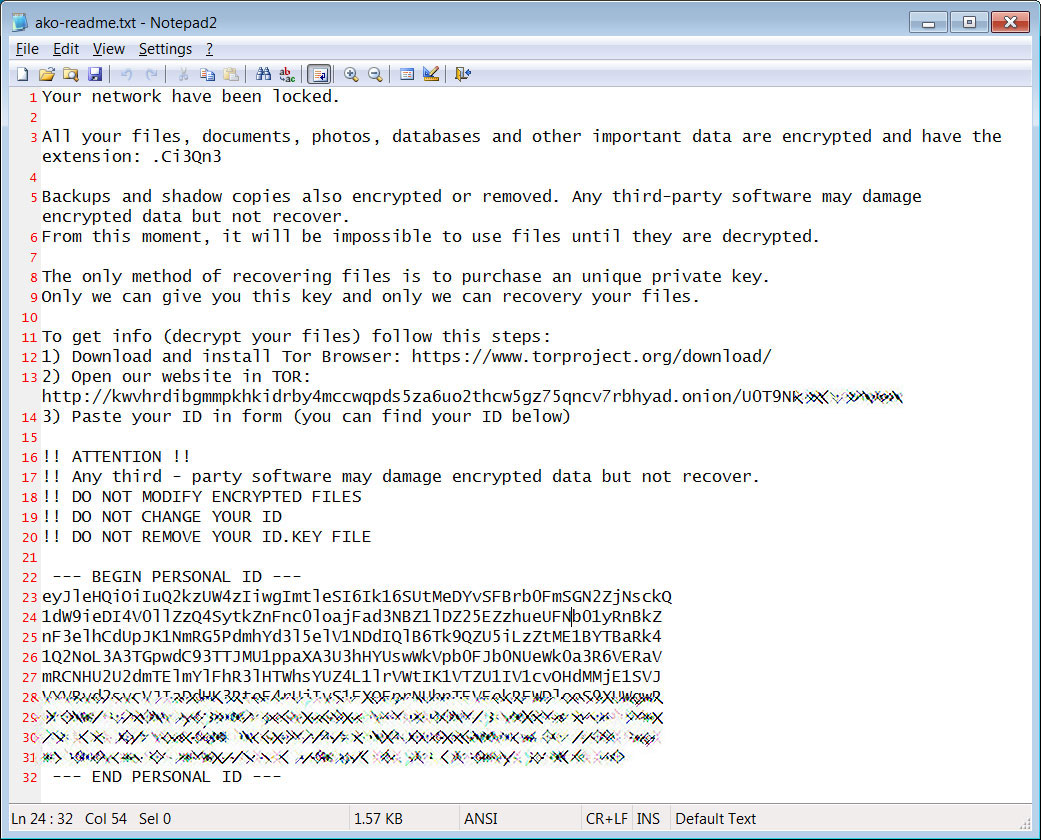
Ako Ransom Note
As spam is being used to spread the Ako Ransomware, everyone must be is trained on how to properly identify malicious email and not open any attachments without first confirming who and why they were sent.
This is especially true for email attachments that are in password-protected archives as they commonly used to avoid being detected by secure email gateways and antivirus software.
Online Pharmacy PlanetDrugsDirect Discloses Security Breach
20.1.2020 Bleepingcomputer
Canadian online pharmacy PlanetDrugsDirect is emailing customers, notifying them of a data security incident that might have impacted some of their sensitive personal and financial information.
PlanetDrugsDirect (also known as Planet Drugs Direct) is an active Canadian International Pharmacy Association (CIPA) member, and association of licensed, retail pharmacies that sell medication to Canadian and U.S. citizens, and more
PlanetDrugsDirect describes itself as an "online prescription referral service which provides our customers with direct access to affordable prescription and non-prescription medications" with roughly 400,000 customers.
Online pharmacy security breach
The Canadian online prescription referral service informed a yet unknown number of customers via email of a recent data security incident that may have impacted some of their data.
"Our investigation to date indicates that your exposed data may include your name, address, e-mail address, phone number, medical information including prescription(s), and payment information," PlanetDrugsDirect says in the breach notification.
"At this moment, there is no evidence to suggest passwords for online account access has been compromised," the online pharmacy adds.
PlanetDrugsDirect also states that the incident is currently under investigation and that additional details will be provided as soon as possible.
"We assure you that we are working diligently to complete the investigation and to rectify the situation," the alert also says.
PlanetDrugsDirect security breach notification
PlanetDrugsDirect's site says that the online pharmacy collects several types of personal, financial, and medical information "necessary for providing service and arranging to fill your orders through our contracted pharmacies and government approved dispensaries."
The collected information usually includes the following: "name, mailing address, e-mail address, telephone number(s), occupation, employment status, referral source, the name of your primary physician (and his or her contact information), age, height, weight, sex, date of birth, the existence and types of drug allergies, medications requested, family medical history information, your personal medical history information, details of your existing medications, credit card information (including card type and number, expiry date and name of card holder) and prescription information."
Clients warned to track bank account and credit card activity
Customers are also advised in PlanetDrugsDirect's security incident notification to keep a close eye on their bank account and credit card activity.
In the event of any unusual activity, customers should immediately notify their bank and credit card company, as well as PlanetDrugsDirect's staff.
Clients can contact the company at 1-888-791-3784 or via e-mail at info@planetdrugsdirect.com.
"We take the privacy and protection of your data very seriously and we are doing everything we can to ensure that you're not impacted further by this incident," PlanetDrugsDirect concludes.
BleepingComputer confirmed the security incident after calling PlanetDrugsDirect's call center to ask for more details. The company's representative was unable to provide additional info other than customers being notified by email of the incident.
We have also reached out via email asking for more details regarding the reported security breach incident but did not hear back at the time of publication.
iPhones Can Now Double As a Security Key for Google Accounts
20.1.2020 Bleepingcomputer
Approving sign-ins to a Google Account from an iPhone (Google)
Google announced that iPhones running iOS 10 or later can now be used as security keys to protect Google accounts against phishing attacks by verifying sign-ins on Chrome OS, iOS, macOS and Windows 10 devices without pairing.
This couldn't have come at a better time given that, according to a recent study conducted by Google and The Harris Poll, 74% out of 500 high-risk US users surveyed - including politicians, activists, executives, and influencers — reported being targeted or compromised by a phishing attack.
The free email service Gmail also automatically blocks over 100 million phishing emails every day according to Google, warning those attacked by government-backed actors of phishing attempts.
By enabling iPhone users to defend against phishing attacks using their phone's security key, Google effectively brought the strongest phishing-resistant two-factor authentication (2FA) to Google accounts on the iOS platform.
Unlike other two-factor authentication (2FA) methods that try to verify your sign-in, security keys are built with FIDO standards that provide the strongest protection against automated bots, bulk phishing attacks, and targeted phishing attacks. - Google
Your iPhone as a Google account security key
This comes after Google also made using the security key built-in Android phones running Android 7.0+ (Nougat) generally available last year, and previously allowing iOS users to verify sign-ins into Google and Google Cloud services with the help of Android phones set up as security keys.
The security key in your iPhone works the same: it uses Bluetooth to verify sign-ins on Chrome OS, iOS, macOS and Windows 10 devices without the need to pair your devices.
This way, you can protect your Google account against hacking attempts on any device with your iPhone's help, even when sensitive information like your user credentials has been stolen.
"This makes it easier and more convenient for you to unlock this powerful protection, without having to carry around additional security keys," Google said. "Use it to protect your personal Google Account, as well as your Google Cloud Accounts at work."
Before setting up your iPhone as a Google account security key you will also be prompted to install the Google Smart Lock app and allow it to send notifications.
Setting up your iPhone
You can set up your phone as a security key for your Google Account using the following steps:
Make sure you have 2-Step Verification or Advanced Protection turned on.
Visit myaccount.google.com/security using a supported browser, like Chrome.
Under "Signing in to Google," select 2-Step Verification. You might need to sign in.
Click Add security key and then Select your iPhone and thenAdd.
Follow the on-screen instructions and turn on your iPhone’s built-in security key by tapping Yes, I’m in when prompted to in the Smart Lock app.
To utilize your iPhone's inbuilt security key to sign in to your Google account on new devices you have to:
Make sure Bluetooth is turned on for both devices.
Sign in to your Google Account on a Chrome OS (version 79 and above), iOS, macOS, or Windows 10 device.
Check your iPhone for a Smart Lock notification. Tap the notification.
To verify your sign-in, tap Yes.
Google also recommends registering a backup security key to your Google account to use in the event that you lose your iPhone.
Use your iPhone to enroll in Google's Advanced Protection Program
"You can now use your mobile phone as a security key in the Advanced Protection Program for the enterprise," Google also announced today.
"This means you can use your Android or iOS device’s built-in security key for 2-Step Verification, which makes it easier and quicker to protect high-risk users with our strongest account security settings."
iPhone users can learn more about signing up for the Advanced Protection Program by going to g.co/advancedprotection.
"With attacks on the rise, and many major events on the horizon this year like the U.S. elections in November, the Advanced Protection Program offers a simple way to incorporate the strongest account protection that Google offers," Google Advanced Protection Program PM Shuvo Chatterjee concluded.
Microsoft's Indexer Diagnostics Helps Troubleshoot Windows Search
20.1.2020 Bleepingcomputer
Microsoft released an Indexer Diagnostics utility to help users troubleshoot and, in some cases, fix Windows Search problems they might experience on their Windows 10 devices.
The tool, which is still in Beta, does this by allowing you to detect potential issues affecting the Search Indexer service by making it possible to check if your files are indexed and what paths are indexed.
"Indexing is the process of looking at files, email messages, and other content on your PC and cataloging their information, such as the words and metadata in them," Microsoft says. "When you search your PC after indexing, it looks at an index of terms to find results faster."

Indexer Diagnostics was developed by Microsoft to make some Windows indexing aspects more readily available without having to deal with the restrictions of an update cadence a source familiar with the matter told BleepingComputer.
Its main purpose is to improve understanding for both users and developers the capabilities of Windows Search, as well as boost the troubleshooting ability and support for general issues affecting Windows Search.
Windows Search troubleshoot helper
By allowing them to look for specific issues affecting the Search Indexer service, the Indexer Diagnostics utility boosts your ability to spot potential issues when Windows Search becomes unresponsive or when search results don't appear as expected on your computer.
Advanced users such as system admins also have the option to track a device's resource usage by collecting resource traces when the indexer uses too many resources from the app's Performance tab, as well as functional traces and application logs when it is not working correctly — these can be attached to bug reports that can .be filed from within the app.
Restart and reset the search service
However, Indexer Diagnostics' most important feature is its capability to help you fix several problems that might affect Windows Search by restarting the search service or resetting it.
These built-in one-click fixes, available on the 'Search is not working' tab in the app's sidebar almost mirror a list of solutions for Search issues published by Microsoft in September 2019 after fixing a Windows Desktop Search known issue on Windows 10, version 1903 devices where searching did not return any results.
Delivered through the MS Store for faster updates
Since the Indexer Diagnostics tool enables you to restart and reset the Windows Search service with a simple mouse click as opposed to the multi-step procedures needed to do it manually, it should help fix search problems faster.
When this is not possible and Windows Search keeps misbehaving by failing to index your files or failing to show results to your queries, it allows you to file a bug report, together with all the relevant information Microsoft needs to analyze and create a fix for your specific problem.
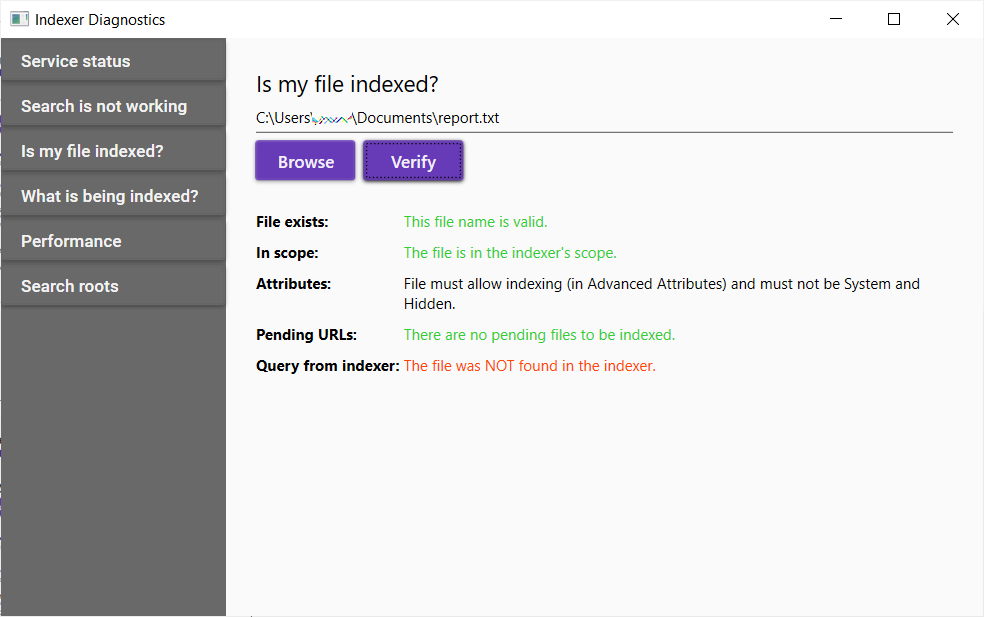
File not being indexed
Failed search query
If we take into account the number of Windows 10 users, having reports coming right after problems are detected through the app's inbuilt feedback channel will allow Redmond's developers to react faster and have a resolution ready a lot quicker.
Microsoft uses the MS Store to ship Indexer Diagnostics updates faster without adding weight to the OS and to take advantage of a newly added mechanism designed to deliver functionality to users who need it without affecting those that won't use it as BleepingComputer was also told.
In addition, Redmond will continue adding functionality to the Indexer Diagnostics app in the future, with the end goal of helping Windows 10 customers experiencing search issues to fix them easier or to report them to the development team for faster patches.
Microsoft's New Edge Browser Released, What You Need to Know
20.1.2020 Bleepingcomputer
Microsoft's Chromium-based Edge browser is officially released and is now available for download. This new browser ditches Microsoft's home-grown EdgeHTML rendering engine for Google's open-sourced platform called 'Chromium' and the Blink rendering engine, which will add greater compatibility and performance.
This first Stable release is Microsoft Edge 79 and can be downloaded immediately from the Microsoft Edge site for both Windows and Mac. Otherwise, Microsoft Edge will be installed automatically over the next coming months via Windows Update.
Microsoft plans on first releasing Microsoft Edge to Windows Insiders in the Release preview ring and then slowly expanding to all other Windows 10 users via Windows Update.
When the new Microsoft Edge is installed, it will replace the existing Edge browser that normally comes with Windows 10. If you do not wish to replace this browser and want to block its install via Windows Update, please see the last section of this article.
It is also possible to run both the classic Edge and the new Microsoft Edge side-by-side using these instructions.
Below we have outlined many of the new features in the new Microsoft Edge browser.
What's new in Microsoft Edge
The new Microsoft Edge is based on Google Chrome so it has many similar features.
Microsoft, though, has also added some features to their browser that makes it stand out from the rest, which we have outlined below.
Block potentially unwanted apps (PUAs)
Chromium-based Microsoft Edge blocks Potentially Unwanted Programs (PUPs) that may display unwanted ads, modify the search engine of the browser, or claim to update your drivers when actually performing malicious or unwanted behavior.
This 'Block potentially unwanted apps' feature blocks Edge from downloading or installing potentially unwanted programs on Windows 10 systems. The feature is not enabled by default and can be enabled from Edge's privacy settings, as highlighted below:
Open Edge settings.
Navigate to Privacy and services settings.
Locate "Block potentially unwanted apps" section and enable the feature.
Media Autoplay Blocking
Like the classic Edge, Chromium Edge also comes with a setting to block media autoplay. This prevents videos on random websites with audio from playing in the background without user permission or interaction.
Media autoplay block settings can be configured from Edge > Settings > Content (edge://settings/content/mediaAutoplay).
Tracking Prevention
Microsoft Edge includes a Tracking prevention feature that blocks third-party tracking scripts on web sites you visit to improve your privacy.
![]()
You can disable this feature off from Edge > Privacy settings or enable the advanced settings to block all trackers.
Use Collections to stay organized
The browser includes a new feature called 'Collections' that helps users organize similar data and save it under one collection.
This is helpful when comparing shopping items from different stores like Amazon or Microsoft or collect or combine information from multiple sites for a project.
To enable Collections in Microsoft Edge, follow these steps:
In the address bar, enter edge://flags or edge://flags#edge-collections. If you open edge://flags menu, you will have to search for Collections.
Click the dropdown and choose Enabled.
Click the Restart button located at the bottom banner to relaunch Microsoft Edge with the Collections feature.
Stream 4K Netflix Video
Microsoft Edge is the first Chromium browser to stream Netflix content at 4K resolution. This is done through Microsoft's PlayReady DRM implementation.
Google Chrome, on the other hand, can only stream Netflix at 1080p HD only.
Edge can Read Web Pages in 24 Different Voices
Microsoft is updating Edge's built-in Read Aloud feature with 24 male and female voices from different parts of the world including the United States, United Kingdom, and India.
The accents of China, Japan, the UK, France, Germany, and Mexico are also supported.
Block Microsoft Edge forced installation
If you want to continue using the Classic Microsoft Edge, Microsoft has released a tool called the 'Microsoft Edge Blocker Toolkit' to prevent the forced installation of Chromium Edge.
With Blocker Toolkit, you can prevent Microsoft from replacing the current Edge browser on your Windows 10 Home, Pro or Enterprise systems.
The Blocker Toolkit only prevents the browser from being automatically installed via Windows Update on Windows 10 RS4 and newer.
The Blocker Toolkit will not prevent users from manually installing Microsoft Edge after you have blocked Windows Update.
Organizations do not need to deploy the Blocker Toolkit in environments managed with an update management solution such as Windows Server Update Services or System Center Configuration Manager. Organizations can use those products to fully manage the deployment of updates released through Windows Update and Microsoft Update, including Microsoft Edge (Chromium-based), within their environment.
Microsoft says Blocker Toolkit may create a Registry value that blocks the automatic installation of the new Microsoft Edge on Windows 10 April 2018 Update (version 1803) or newer.
The Registry value is created under the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate key and value is called DoNotUpdateToEdgeWithChromium.
When you use the tool, the value is set to 1 and Edge installation via Windows Update will be blocked. If the value is 0 or not set, Edge will be automatically downloaded and installed.
You can learn more about this process in our dedicated article: How to Block Windows 10 Update Force Installing the New Edge Browser.
Microsoft Office January Security Updates Fix Code Execution Bugs
20.1.2020 Bleepingcomputer
Microsoft released the January 2019 Office security updates, bundling a total of seven security updates and three cumulative updates for five different products, six of them patching flaws allowing remote code execution.
Redmond also released the January 2020 Patch Tuesday security updates, with security updates for 49 vulnerabilities, seven of them being classified as Critical and 41 as Important.
Unlike previous Patch Tuesday releases, Microsoft did not publicly disclose any vulnerabilities found to be actively exploited in the wild.
To download Microsoft Office security updates on your device, you have to click on the corresponding Knowledge Base article in the table below and then scroll down to the "How to download and install the update" section to grab the update packages for each product.
Patched Microsoft Office vulnerabilities
Out of the seven security updates released by Microsoft for several Office products, six patch remote code execution (RCE) bugs detailed in the CVE-2020-0650, CVE-2020-0651, and CVE-2020-0652 security advisories, and impacting Office 2016, Office 2013, Office 2010, Excel 2016, Excel 2013, and Excel 2010.
The RCE security vulnerabilities patched today received a severity rating of 'Important' from Microsoft given that they could allow potential attackers to execute arbitrary code and/or commands after successfully exploiting vulnerable Windows devices.
Attackers could then install programs, view, change, and delete data, or create new accounts with full user rights on the compromised computers.
The other security update tracked as CVE-2020-0647 is a Microsoft Office Online spoofing vulnerability impacting Office Online Server and is caused by incorrect validation of origin in cross-origin communications.
"The attacker who successfully exploited the vulnerability could then perform cross-origin attacks on affected systems," Microsoft explains.
"These attacks could allow the attacker to read content that the attacker is not authorized to read, and use the victim's identity to take actions on the site on behalf of the victim. The victim needs to be authenticated for an attacker to compromise the victim."
January 2020 Microsoft Office security updates
The January Microsoft Office security updates are available via the Download Center and the Microsoft Update platform.
Additional info on each of them is available within the linked knowledge base articles.
Microsoft Office 2016
Product Knowledge Base article title and number
Excel 2016 Security update for Excel 2016: January 14, 2020 (KB4484217)
Office 2016 Security update for Office 2016: January 14, 2020 (KB4484221)
Microsoft Office 2013
Product Knowledge Base article title and number
Excel 2013 Security update for Excel 2013: January 14, 2020 (KB4484234)
Office 2013 Security update for Office 2013: January 14, 2020 (KB4484227)
Microsoft Office 2010
Product Knowledge Base article title and number
Excel 2010 Security update for Excel 2010: January 14, 2020 (KB4484243)
Office 2010 Security update for Office 2010: January 14, 2020 (KB4484236)
Microsoft SharePoint Server 2019
Product Knowledge Base article title and number
Office Online Server Security update for Office Online Server: January 14, 2020 (KB4484223)
Microsoft SharePoint Server 2013
Product Knowledge Base article title and number
Project Server 2013 January 14, 2020, cumulative update for Project Server 2013 (KB4484230)
SharePoint Enterprise Server 2013 January 14, 2020, cumulative update for SharePoint Enterprise Server 2013 (KB4484232)
SharePoint Foundation 2013 January 14, 2020, cumulative update for SharePoint Foundation 2013 (KB4484228)
Windows 7 Begins to Show Full Screen Windows 10 Upgrade Alerts
20.1.2020 Bleepingcomputer
When users log into Windows 7 today, they should not be surprised if they see a full-screen alert telling them that the operating system is no longer supported, they are vulnerable to viruses, and that they should upgrade to Windows 10 to fix all of these issues.
Yesterday, January 14th, 2020, Windows 7 officially reached the end of life, which means it will no longer be supported, receive free security updates, and bug fixes.
As a way of warnings users and promoting Windows 10 at the same time, Microsoft installed a program called EOSNotify in the December Windows 7 KB4530734 Monthly Rollup.
Since then, every time a Windows 7 user logged into their computer and at noon every day, a scheduled task was started that launched the %windir%\system32\EOSNotify.exe program.
Once the date reached January 15th, 2020, instead of lying dormant and not displaying anything, the program began to show full-screen alerts that cover your entire screen, including the desktop, on all Windows 7 machines around the world. What you see below, is all you will see on your monitor when the alert is displayed as it covers the entire screen.
Windows 7 End of Life alert
For users who do not have the time to read it, they can click on the "Remind me later" button to close the alert and have it be shown again at a later date.
If users never want to see this alert again, they can click on the 'Don't remind me again' button.
For users who have not been shown this alert yet, they can configure the following registry key to prevent it from ever being displayed in the first place.
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\EOSNotify]
"DiscontinueEOS"=dword:00000001
For those who want more technical information about how this alert works, you can read our original reporting on the EOSNotify application.
While most of us who commonly use computers already known that Windows 7 is no longer supported, many have no idea.
As annoying and intrusive as this alert is, it makes sense to display it to let everyone know that their system will no longer be adequately protected.
This allows them to make an educated decision as to whether they want to upgrade to Windows 10, which can still be done for free, switch to a Mac, or even give Linux and its Windows 7 theme a try.
Google Chrome Aims to Make Browser User-Agents Obsolete
20.1.2020 Bleepingcomputer
To enhance the privacy of its users and reduce the complexity of updating User-Agent strings, Google Chrome plans to move to a new system that web sites can use to identify information about their visitors.
When connecting to a web site, a browser will send a User-Agent string to the webserver that can be used to identify the name of the browser, its version, the operating system, and its rendering engine.
Web sites can use this browser information to determine what type of content they will send back or if their site even supports the browser.
As time has gone on and browsers have integrated various technology from other companies, User-Agent strings have become convoluted and unwieldy.
For example, below is the user-agent for Chrome 79.0.3945.117, which as you can see also includes confusing references to other browsers such as Safari and Mozilla.
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.117 Safari/537.36
Even worse, due to the specific information contained in them, User-Agents are a privacy risk as Google states they are commonly used by fingerprinter scripts to track users.
Google wants to freeze the User-Agent and switch to Client Hints
To increase the privacy of their users and still allow web sites to get information about a client, Chrome developer Yoav Weiss intends to move away from user-agent strings and instead adopt the HTTP specification called 'UA Client Hints'.
"The User-Agent string is an abundant source of passive fingerprinting information about our users. It contains many details about the user’s browser and device as well as many lies ("Mozilla/5.0", anyone?) that were or are needed for compatibility purposes, as servers grew reliant on bad User Agent sniffing.
On top of those privacy issues, User-Agent sniffing is an abundant source of compatibility issues, in particular for minority browsers, resulting in browsers lying about themselves (generally or to specific sites), and sites (including Google properties) being broken in some browsers for no good reason."
What Weiss proposes is to eventually freeze the User-Agent string of Google Chrome so that they always send the same string regardless of the browser's version.
For example, the Chrome Mobile User-Agent would be frozen at:
Mozilla/5.0 (Linux; Android 9; Unspecified Device) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/71.1.2222.33 Mobile Safari/537.36
The Chrome Desktop User-Agent would be frozen at:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.1.2222.33 Safari/537.36
When a user visits a web site, the request will contain the frozen UA string as well as a special 'Sec-UA' header that contains basic information about the client as shown below.
Sec-CH-UA: "Examplary Browser 73"
If a web site needs more than this basic information, they would request it in an 'opt-in' response header that asks for more detailed information such as the minor version and the operating system of the visitor.
This could be done via the following header request:
Accept-CH: UA, Platform
As the web site has not opted into this information being sent, the browser would respond on all subsequent requests with headers containing the requested information:
Sec-CH-UA: "Examplary Browser 73.3R8.2H.1"
Sec-CH-Platform: "Windows 10"
Ultimately, though, it will be up to the browser whether they will honor these requests for more information and what information is being sent to the website.
This means that if a request comes from a site that is known to be abusive, Google can decide not to send any further client information back to them.
To use Client Hints, a web site must first satisfy the following requirements:
Server opt-ins must be delivered on a top-level navigation request, over a secure connection.
Hints are only delivered with same-origin requests, over a secure connection.
If the first party wants hints to be delivered to certain third-party hosts, the first-party can explicitly delegate specific hints to specific hostnames.
Hints are Sec- prefixed, to provide servers with more confidence regarding the values they deliver, as well as to avoid legacy server bugs.
As part of this plan, Google hopes to remove access to the navigator.userAgent JavaScript property in Chrome 81, freeze the browser's User-Agent string in Chrome 83, and unify all desktop and mobile versions to the same string in Chrome 85.
Milestone
Stable date
Action
M81
Mid March ‘20
Deprecate access to `navigator.userAgent`
M83
Early June ‘20
Freeze browser version and unify OS versions
M85
Mid September ‘20
Unify desktop OS string as a common value for desktop browsers.
Unify mobile OS/device strings as a similarly common value for those at M85 (*)
Other vendors, such as Microsoft and Mozilla, have indicated that they support this change, while Safari already froze their UA string to some degree other than operating system version changes.
Concerns about using Client Hints
Switching to Client Hints as a method for web sites to gain information about a client appears to be a good idea but does have some issues.
As Client Hints will only be usable by the top-level navigation request, third-parties scripts that require User-Agent information will need to work with websites to receive this information.
Furthermore, as the browser does not send detailed information about the client in the first request, there will be a delay in getting detailed information for sites that need it.
Windows BSOD Betrays Cryptominer Hidden in WAV File
20.1.2020 Bleepingcomputer
The infamous blue screen of death (BSOD) on computers belonging to a company in the medical tech sector was the tell for a malware infection that spread across more than half the network.
The malware was hiding its modules in WAV audio files and spread to vulnerable Windows 7 machines on the network via EternalBlue, the exploit for SMBv1 used in the devastating WannaCry and NotPetya cyber attacks from 2017.
EternalBlue and cryptojacking
Security researchers providing incident response services found that more than 800 computers had been compromised starting October 14, 2019. The discovery was possible by investigating systems that experienced a BSOD crash since that date.
With the lack of kernel memory dumps, which would have pointed to what triggered the error, the researchers from Guardicore relied on attack residue data to determine the cause.
They found that infected machines accessed data in a registry key (HKLM\Software\Microsoft\Windows\CurrentVersion\Shell) and executed a rather long command, which turned out to be an unclassified, but publicly available, PowerShell script encoded with base-64.
C:\Windows\System32\WindowsPowershell\v1.0\PowerShell.exe -NonInteractive -WindowStyle Hidden -EncodeCommand JABTAEUAZgA4AGMAYQBXAGoAIAA9ACAAIgBIAEsATABNADoAXABTAG8AZgB0AHcAYQByAGUAXABNAG…==
An endpoint detection and response (EDR) platform the company installed in its attempt to solve the problem revealed that the malware-loading process consisted of deploying two processes named cscdll.dll and cscomp.dll, tasked with "compiling C# and executed when C# code is loaded and executed from memory."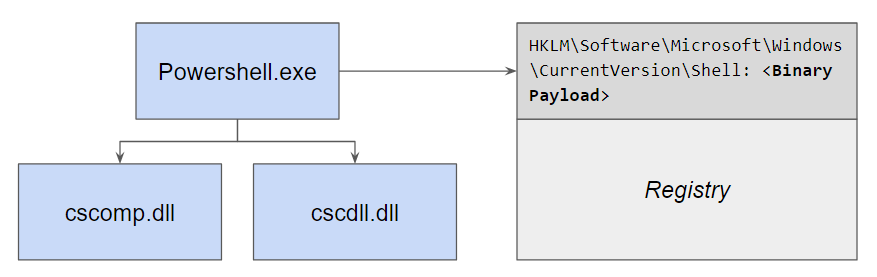
The payload was a module that mines for Monero cryptocurrency using the CryptonightR algorithm. To evade detection, the authors resorted to steganography to embedded it in WAV audio files. As a result, the files seem harmless but carry an extra load that is later extracted and executed on an infected host.
This exact technique was reported on October 16 last year by researchers at BlackBerry Cylance, who said that some of the audio could be played and “had no discernible quality issues or glitches.” However, Guardicore saw it integrated in a full attack flow.
Another module hidden this way was tasked with scanning the network and for lateral movement. “The code implements the infamous EternalBlue exploit and spreads the malware over SMB,” reads Guardicore Lab Team’s analysis.
Weak spots
While this attack is not sophisticated, it shows that some mid-size organizations are ill-prepared to defend against a cybersecurity incident and set up the environment to support post-infection analysis efforts.
For this particular case, the victim company used Windows 7, an operating system that on Tuesday received its last batch of updates and is no longer supported by Microsoft.
This may have not been relevant for the attack but leaving the systems unpatched for almost three years is what provided the opportunity to spread to over 50% of the network computers.
Guardicore hit some bumps during their investigation because the computers analyzed had not been configured to save kernel memory dumps, “which could have been helpful in forensics analysis and in understanding the root cause of the [BSOD] errors.”
Intel Patches High Severity Flaw in VTune Performance Profiler
20.1.2020 Bleepingcomputer
Intel patched six security vulnerabilities during the January 2020 Patch Tuesday, including a high severity vulnerability in VTune and a bug affecting the Intel Processor Graphics drivers for Windows and Linux.
The security issues addressed today are detailed in the six security advisories published on Intel's Product Security Center.
According to Intel, these vulnerabilities could allow authenticated users to potentially trigger denial of service states and escalate privileges via local access, while others could lead to information disclosure.
"This month, consistent with our commitment to transparency, we are releasing 6 security advisories addressing 6 vulnerabilities," Intel's Director of Security Communications Jerry Bryant said.
"Three of these, including the one with the highest CVSS severity rating of 8.2, were internally found by Intel, and the others were reported through our Bug Bounty program."
Intel's January 2020 Patch Tuesday advisories
Below you can find all the advisories published by Intel during 2020's first Patch Tuesday, together with links to download pages where you can get the updates needed to patch the security flaws.
While Intel says that they are not aware of any of the security issues being exploited in the wild, users are advised to install the updates as soon as possible.
Out of the six vulnerabilities patched today two stand out. The first one tracked as CVE-2019-14613 is a high severity one impacting the Intel VTune Amplifier for Windows that may allow authenticated local attackers to potentially escalate privileges.
The other one is a medium severity information disclosure flaw tracked as CVE-2019-14615 that affects the Windows and Linux graphics drivers on a wide range of processors including the company's latest 10th Generation 'Ice Lake' Intel Core Processors.
Advisory Number Advisory CVE ID Severity rating Updates
INTEL-SA-00325 Intel VTUNE CVE-2019-14613 8.2 DOWNLOAD
INTEL-SA-00308 Intel RWC 3 for Windows CVE-2019-14601 6.7 DOWNLOAD
INTEL-SA-00300 Intel SNMP Subagent Stand-Alone for Windows CVE-2019-14600 6.5 DISCONTINUED
INTEL-SA-00314 Intel Processor Graphics CVE-2019-14615 6.3 DOWNLOAD
INTEL-SA-00306 Intel Chipset Device Software INF Utility CVE-2019-14596 5.9 DOWNLOAD
INTEL-SA-00332 Intel DAAL CVE-2019-14629 3.9 DOWNLOAD
"Intel has released security updates to address vulnerabilities in multiple products," the Cybersecurity and Infrastructure Security Agency (CISA) said today in a notification. "An authenticated attacker with local access could exploit some of these vulnerabilities to gain escalation of privileges."
The agency encourages both users and administrators to review the security advisories published today by Intel and apply the necessary updates to defend against potential exploitation attempts.
Each of the linked advisories comes with a detailed list of all affected products and recommendations for vulnerable products, as well as contact info for users and researchers who would want to report other vulnerabilities found in Intel branded tech or products.
Windows Terminal Adds Retro CRT Effects and Console Search
20.1.2020 Bleepingcomputer
Microsoft released Windows Terminal Preview v.08 today and with it comes useful improvements that include a console search feature, tab sizing, and a new retro option that makes consoles look like an old CRT.
The Windows Terminal app is a new multi-tab console application being developed by Microsoft that allows users to have multiple console tabs open in one window. These tabs can be a mix of CMD prompts, PowerShell consoles, and different shells from Linux distributions installed via the Windows Subsystem for Linux (WSL).
Below we have outlined the major features added in this build.
New Search feature
With this release, users can now search for text within an open console window by using the Ctrl+Shift+F keyboard combination.
New search feature
If you are like me and wish the Find feature used the Ctrl+F keyboard combination, you can change it by adding a new keybinding like the following:
"keybindings": [
{ "command": "find", "keys": [ "ctrl+f" ] }
]
New Tab width setting
By default, Windows Terminal will display equal width tabs for every open tab.
Version 0.8 introduces a new tabWidthMode global setting that can be set to either 'equal' or 'titleLength'. If set to titleLength, the width of the tabs will be equal (with a little padding) to the title of the tab as shown below.
New tabWidthMode setting
Retro
Finally, Microsoft added a fun experimental feature that emulates a retro CRT when displaying the console.
This feature is controlled by the 'experimental.retroTerminalEffect' setting that when set to true will cause the fonts to glow and the console to show scanlines.
This is illustrated in a Linux shell running Midnight Commander below.
New retro mode with scanlines and glowing fonts
To enable the retro Terminal effect, you can add the following setting to a profile:
"experimental.retroTerminalEffect": 1,
For the above example, Windows Terminal Program Manager Kayla Cinnamon told BleepingComputer that she set her "color scheme to Vintage and am using the PxPlus IBM VGA8 font from here: https://int10h.org/oldschool-pc-f."
For those who do not have the Vintage color scheme, it is:
{
"name": "Vintage",
"foreground": "#C0C0C0",
"background": "#000000",
"black": "#000000",
"red": "#800000",
"green": "#008000",
"yellow": "#808000",
"blue": "#000080",
"purple": "#800080",
"cyan": "#008080",
"white": "#C0C0C0",
"brightBlack": "#808080",
"brightRed": "#FF0000",
"brightGreen": "#00FF00",
"brightYellow": "#FFFF00",
"brightBlue": "#0000FF",
"brightPurple": "#FF00FF",
"brightCyan": "#00FFFF",
"brightWhite": "#FFFFFF"
}
More information about these settings and other changes can be read in v0.8's release notes.
NSA's First Public Vulnerability Disclosure: An Effort to Build Trust
20.1.2020 Bleepingcomputer
The U.S. National Security Agency (NSA) started a new chapter after discovering and reporting to Microsoft a vulnerability tracked as CVE-2020-0601 and impacting Windows 10 and Windows Server systems.
In a phone conference that Bleeping Computer joined, NSA's Director of Cybersecurity Anne Neuberger said that this is the first time the agency decided to publicly disclose a security vulnerability to a software vendor.
"We thought hard about that. When Microsoft asked us, 'Can we attribute this vulnerability to NSA?' we gave it a great deal of thought. And then we elected to do so and here is why," Neuberger explained.
She added that "part of building trust is showing the data" and, as a result, "it's hard for entities to trust that we indeed take this seriously and ensuring that vulnerabilities can be mitigated is an absolute priority."
Neuberger also said during the media call that the agency will make efforts towards becoming an ally to the cybersecurity community and private sector entities, and will begin to share vulnerability data with its partners instead of accumulating it and using it in future offensive operations.
"Sources say this disclosure from NSA is planned to be the first of many as part of a new initiative at NSA dubbed 'Turn a New Leaf,' aimed at making more of the agency's vulnerability research available to major software vendors and ultimately to the public," journalist Brian Krebs reported.
NSA redefining itself
"We believe in Coordinated Vulnerability Disclosure (CVD) as proven industry best practice to address security vulnerabilities," MSRC's Principal Security Program Manager Mechele Gruhn added.
"Through a partnership between security researchers and vendors, CVD ensures vulnerabilities are addressed prior to being made public."
NSA's new approach to building trust with the public and its partners redefines the agency's cybersecurity mission as US Army General and NSA Director Paul M. Nakasone stated in July 2019.
"The Cybersecurity Directorate will reinvigorate our white hat mission opening the door to partners and customers on a wide variety of cybersecurity efforts," he added at the time.
"It will also build on our past successes such as Russia Small Group to operationalize our threat intelligence, vulnerability assessments, and cyber defense expertise to defeat our adversaries in cyberspace."
The NSA-reported vulnerability
The CVE-2020-0601 spoofing vulnerability reported by the NSA affects the Windows CryptoAPI and is caused by the way Elliptic Curve Cryptography (ECC) certificates are validated.
"The certificate validation vulnerability allows an attacker to undermine how Windows verifies cryptographic trust and can enable remote code execution," the NSA says.
CVE-2020-0601 hasn't yet been exploited in the wild according to Microsoft's security advisory, and the US agency advises users and organizations to install the patches released as part of Microsoft's January 2020 Patch Tuesday as soon as possible to block attackers from defeating "trusted network connections and deliver executable code while appearing as legitimately trusted entities."
NSA/CSS
✔
@NSAGov
This #PatchTuesday you are strongly encouraged to implement the recently released CVE-2020-0601 patch immediately. https://media.defense.gov/2020/Jan/14/2002234275/-1/-1/0/CSA-WINDOWS-10-CRYPT-LIB-20190114.PDF …


2,792
7:31 PM - Jan 14, 2020
Twitter Ads info and privacy
2,562 people are talking about this
"This vulnerability is one example of our partnership with the security research community where a vulnerability was privately disclosed and an update released to ensure customers were not put at risk," Gruhn added.
The NSA security advisory also comes with mitigation measures for systems where installing the patches released by Microsoft today is not immediately possible.
"Properly configured and managed TLS inspection proxies independently validate TLS certificates from external entities and will reject invalid or untrusted certificates, protecting endpoints from certificates that attempt to exploit the vulnerabilities," the agency reveals.
"Ensure that certificate validation is enabled for TLS proxies to limit exposure to this class of vulnerabilities and review logs for signs of exploitation."
The consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available. Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners. - NSA
Windows 7 Gets Final Monthly Rollup Update Before End Of Life
20.1.2020 Bleepingcomputer
Windows 7 has just received its last set of security updates. After today, Windows 7 won't receive any security or non-security updates from Microsoft, and it is now considered an unsupported operating system.
The new monthly rollup and non-security update for Windows 7 come with a couple of security fixes. Microsoft says KB4534310 for Windows 7 has resolved security issues affecting Windows Cryptography, Windows Input and Composition, Windows Management, and other components.
The full changelog of the update includes:
Security updates to Windows App Platform and Frameworks, Windows Input and Composition, Windows Management, Windows Cryptography, Windows Storage and Filesystems, the Microsoft Scripting Engine, and Windows Server.
Microsoft has also published Servicing Stack Update (SSU) KB4536952 to improve Windows Update performance on Windows 7.
The last update for Windows 7 applies to all its editions or versions including Windows 7, Service Pack 1, Windows Server 2008 R2 Service Pack 1, Windows Embedded Standard 7 Service Pack 1, Windows Embedded, POSReady 7, and Windows Thin PC.
You can download and install the latest patches by checking for updates in Control Panel. You can also grab the offline installer by downloading the package from the Microsoft Update website.
Windows 7 EoL
After January 14, devices with Windows 7 will need to be upgraded to Windows 10 for continued support, updates and patches from Microsoft. Consumers or businesses will miss out the latest technologies, apps, security updates, and support if they use Windows 7 despite its EoL (End of Life).
In a support doc, Microsoft has stated that it will display a full-screen upgrade warning notification on Windows 7 PCs from January 15. The notification will remain on the screen until you interact with it on your PC running:
Starter.
Home Basic.
Home Premium.
Professional (No such notifications if you have purchased the Extended Security Update).
Ultimate.
It's also important to note that Microsoft has never blocked the free upgrades to Windows 10, and you can upgrade to Windows 10 today for free by following our guide.
Windows 7 Extended Security Updates (ESUs)
Companies, organizations and small businesses may pay Microsoft and extend support by up to three years. According to Microsoft's Windows 7 ESUs policy, enterprise customers may pay $50, $100, or $200 per year get security updates for Windows 7 Pro or Enterprise.
Security company 0Patch is also planning to release security updates for Windows 7 for free in the coming weeks.
Microsoft's January 2020 Patch Tuesday Fixes 49 Vulnerabilities
20.1.2020 Bleepingcomputer
Today is Microsoft's January 2020 Patch Tuesday and also the Windows 7 end of life. This is going to be a stressful day for your Windows administrators, so be nice!
With the release of the January 2020 security updates, Microsoft has released fixes for 49 vulnerabilities. Of these vulnerabilities, 7 are classified as Critical, 41 as Important, and 1 as Moderate.
One of the 'Critical' vulnerabilities fixed today was discovered by the NSA and could allow attackers to spoof digital certificates or perform man-in-the-middle (MiTM) attacks.
More information about the 'CVE-2020-0601 - Windows CryptoAPI Spoofing' vulnerability can be found below and in our dedicated article: Microsoft Fixes Windows CryptoAPI Spoofing Flaw Reported by NSA.
The good news is that there were no vulnerabilities publicly disclosed or found being actively exploited in the wild.
Users should still install these security updates as soon as possible to protect Windows from known security risks.
For information about the non-security Windows updates, you can read about today's Windows 10 January 2020 Cumulative Updates.
CVE-2020-0601 - Windows CryptoAPI Spoofing Vulnerability
The big news of the day is the first Windows vulnerability being publicly attributed as discovered by the United State's National Security Agency (NSA).
While more detailed information is found in our dedicated article, this Patch Tuesday security update article would not be complete without a summary of the vulnerability.
The CVE-2020-0601 vulnerability is a flaw in how the Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates.
Using this flaw attackers could cause malware to appear as code-signed by legitimate companies, conduct man-in-the-middle attacks, and decrypt encrypted information over network connections.
This is a critical vulnerability and all Windows users are advised to install this patch immediately.
Critical Windows Remote Desktop Gateway vulnerabilities
The January 2020 Patch Tuesday also fixes three vulnerabilities in the Windows Remote Desktop Gateway (RD Gateway).
Two of the vulnerabilities (CVE-2020-0609 and CVE-2020-0610) could allow an unauthenticated attacker to perform remote code execution on a vulnerable system.
"A remote code execution vulnerability exists in Windows Remote Desktop Gateway (RD Gateway) when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. This vulnerability is pre-authentication and requires no user interaction. An attacker who successfully exploited this vulnerability could execute arbitrary code on the target system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
To exploit this vulnerability, an attacker would need to send a specially crafted request to the target systems RD Gateway via RDP."
The third vulnerability (CVE-2020-0612) could allow an attacker to perform a denial of service (DoS) on an RDP system and cause it to stop responding.
"A denial of service vulnerability exists in Windows Remote Desktop Gateway (RD Gateway) when an attacker connects to the target system using RDP and sends specially crafted requests. An attacker who successfully exploited this vulnerability could cause the RD Gateway service on the target system to stop responding."
If you use RD Gateway in your organization you must install this update.
The January 2020 Patch Tuesday Security Updates
Below is the full list of resolved vulnerabilities and released advisories in the January 2020 Patch Tuesday updates. To access the full description of each vulnerability and the systems that it affects, you can view the full report here.
Tag CVE ID CVE Title Severity
.NET Framework CVE-2020-0606 .NET Framework Remote Code Execution Vulnerability Critical
.NET Framework CVE-2020-0605 .NET Framework Remote Code Execution Vulnerability Critical
.NET Framework CVE-2020-0646 .NET Framework Remote Code Execution Injection Vulnerability Critical
Apps CVE-2020-0654 Microsoft OneDrive for Android Security Feature Bypass Vulnerability Important
ASP.NET CVE-2020-0603 ASP.NET Core Remote Code Execution Vulnerability Critical
ASP.NET CVE-2020-0602 ASP.NET Core Denial of Service Vulnerability Important
Common Log File System Driver CVE-2020-0615 Windows Common Log File System Driver Information Disclosure Vulnerability Important
Common Log File System Driver CVE-2020-0634 Windows Common Log File System Driver Elevation of Privilege Vulnerability Important
Common Log File System Driver CVE-2020-0639 Windows Common Log File System Driver Information Disclosure Vulnerability Important
Microsoft Dynamics CVE-2020-0656 Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability Important
Microsoft Graphics Component CVE-2020-0622 Microsoft Graphics Component Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0607 Microsoft Graphics Components Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0642 Win32k Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0643 Windows GDI+ Information Disclosure Vulnerability Important
Microsoft Office CVE-2020-0650 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0652 Microsoft Office Memory Corruption Vulnerability Important
Microsoft Office CVE-2020-0653 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0651 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0647 Microsoft Office Online Spoofing Vulnerability Important
Microsoft Scripting Engine CVE-2020-0640 Internet Explorer Memory Corruption Vulnerability Moderate
Microsoft Windows CVE-2020-0644 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0624 Win32k Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0635 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0620 Microsoft Cryptographic Services Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0616 Microsoft Windows Denial of Service Vulnerability Important
Microsoft Windows CVE-2020-0608 Win32k Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0601 Windows CryptoAPI Spoofing Vulnerability Important
Microsoft Windows CVE-2020-0621 Windows Security Feature Bypass Vulnerability Important
Microsoft Windows Search Component CVE-2020-0633 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0623 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0613 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0614 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0632 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0627 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0628 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0625 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0626 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0629 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0631 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0630 Windows Search Indexer Elevation of Privilege Vulnerability Important
Windows Hyper-V CVE-2020-0617 Hyper-V Denial of Service Vulnerability Important
Windows Media CVE-2020-0641 Microsoft Windows Elevation of Privilege Vulnerability Important
Windows RDP CVE-2020-0610 Windows Remote Desktop Gateway (RD Gateway) Remote Code Execution Vulnerability Critical
Windows RDP CVE-2020-0609 Windows Remote Desktop Gateway (RD Gateway) Remote Code Execution Vulnerability Critical
Windows RDP CVE-2020-0637 Remote Desktop Web Access Information Disclosure Vulnerability Important
Windows RDP CVE-2020-0612 Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability Important
Windows RDP CVE-2020-0611 Remote Desktop Client Remote Code Execution Vulnerability Critical
Windows Subsystem for Linux CVE-2020-0636 Windows Subsystem for Linux Elevation of Privilege Vulnerability Important
Windows Update Stack CVE-2020-0638 Update Notification Manager Elevation of Privilege Vulnerability Important
Windows 10 Cumulative Updates KB4528760 & KB4534273 Released
20.1.2020 Bleepingcomputer
Windows 10's January 2020 cumulative updates are now rolling out with important fixes for Windows 10 November 2019 Update, May 2019 Update, and October 2018 Update.
Like every other cumulative update, January 14 cumulative update for Windows 10 version 1909, 1903, and version 1809 include security fixes for core components and as well as Windows Cryptography.
To grab the update, go to the Windows Update page and click on the 'Check for updates' button to install the patches. If you own multiple PCs or if you would like to patch the PCs manually, you can learn more about it here.
Builds 18362.592 and 18363.592
If you are using the November 2019 Update, you'll be getting 18363.592 (KB4528760). Those who are using Windows 10 May 2019 Update will receive Build 18362.592 with the following changes:
Security updates to Windows App Platform and Frameworks, Windows Input and Composition, Windows Management, Windows Cryptography, Windows Storage and Filesystems, the Microsoft Scripting Engine, and Windows Server.
The update also improves security storing, managing files, and when using input devices such as a mouse or keyboard.
Build 17763.973
Windows 10 KB4534273 (Build 17763.973) for Windows 10 version 1809, Windows Server version 1809, and Windows Server 2019 comes with the following bug fixes:
Addresses an issue to support new SameSite cookie policies by default for release 80 of Google Chrome.
Security updates to Windows App Platform and Frameworks, Windows Input and Composition, Windows Management, Windows Cryptography, Windows Virtualization, the Microsoft Scripting Engine, and Windows Server.
Known issues in this update
Symptom Workaround
Certain operations, such as rename, that you perform on files or folders that are on a Cluster Shared Volume (CSV) may fail with the error, “STATUS_BAD_IMPERSONATION_LEVEL (0xC00000A5)”. This occurs when you perform the operation on a CSV owner node from a process that doesn’t have administrator privilege.
Do one of the following:
Perform the operation from a process that has administrator privilege.
Perform the operation from a node that doesn’t have CSV ownership.
Microsoft is working on a resolution and will provide an update in an upcoming release.
After installing KB4493509, devices with some Asian language packs installed may receive the error, "0x800f0982 - PSFX_E_MATCHING_COMPONENT_NOT_FOUND."
Uninstall and reinstall any recently added language packs. For instructions, see Manage the input and display language settings in Windows 10.
Select Check for Updates and install the April 2019 Cumulative Update. For instructions, see Update Windows 10.
Note If reinstalling the language pack does not mitigate the issue, reset your PC as follows:
Go to the Settings app > Recovery.
Select Get Started under the Reset this PC recovery option.
Select Keep my Files.
Microsoft is working on a resolution and will provide an update in an upcoming release.
When setting up a new Windows device during the Out of Box Experience (OOBE), you might be unable to create a local user when using Input Method Editor (IME). This issue might affect you if you are using the IME for Chinese, Japanese, or Korean languages.
Note This issue does not affect using a Microsoft Account during OOBE.
To mitigate this issue, set the keyboard language to English during user creation or use a Microsoft Account to complete OOBE. You can set the keyboard language back to your preferred language after user creation. Once the OOBE is done and you are at the desktop, you can rename the current user using these instructions. If you prefer to create a new local user, see KB4026923.
Microsoft is working on a resolution and will provide an update in an upcoming release.
Microsoft Fixes Windows CryptoAPI Spoofing Flaw Reported by NSA
20.1.2020 Bleepingcomputer
Microsoft patched a spoofing vulnerability present in the Windows usermode cryptographic library, CRYPT32.DLL, on Windows 10, Windows Server 2016, and Windows Server 2019 systems.
In a media call with the NSA that Bleeping Computer joined, the National Security Agency (NSA) stated that they discovered this vulnerability and immediately reported it to Redmond's security team.
Both NSA and Microsoft say that the vulnerability hasn't yet been exploited in the wild, while the agency recommends in its own advisory to install the patches delivered with Microsoft's January 2020 Patch Tuesday as soon as possible to block attackers from defeating "trusted network connections and deliver executable code while appearing as legitimately trusted entities."
In its second-ever Emergency Directive, DHS' Cybersecurity and Infrastructure Security Agency (CISA) also "strongly recommends agencies initiate patching immediately, with a focus on patching the Windows 10 and Server 2016/2019 systems impacted by CVE-2020-0601.
Agencies should prioritize patching mission-critical systems and High-Value Assets (HVAs), internet-accessible systems, and servers. Agencies should then apply the patch to the remaining endpoints."
The consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available. Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners. - NSA
Spoofing ECC certificate chains' validity
"A spoofing vulnerability exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates," says Microsoft's security advisory. "An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear the file was from a trusted, legitimate source.
The user would have no way of knowing the file was malicious, because the digital signature would appear to be from a trusted provider," Microsoft adds.
After successfully exploiting unpatched systems, attackers can launch man-in-the-middle attacks, as well as decrypt confidential info from user connections to the impacted software.
"By exploiting this vulnerability, an attacker may be able to spoof a valid X.509 certificate chain on a vulnerable Windows system," CERT/CC vulnerability analyst Will Dormann explains.
"This may allow various actions including, but not limited to, interception and modification of TLS-encrypted communications or spoofing an Authenticode signature."
Will Dormann
@wdormann
Replying to @wdormann
Now that it's all public:
1) CVE-2020-0601 - Windows doesn't properly validate X.509 certificate chains. https://www.kb.cert.org/vuls/id/849224/
2) CVE-2020-0609, CVE-2020-0610 - Windows Remote Desktop Gateway (not to be confused with RDP proper) unauthenticated RCE.https://www.kb.cert.org/vuls/id/491944/
188
7:14 PM - Jan 14, 2020
Twitter Ads info and privacy
182 people are talking about this
Microsoft's security update addresses the vulnerability tracked as CVE-2020-0601 and reported by the NSA by making sure that the Windows CryptoAPI completely validates ECC certificates.
"This vulnerability is classed Important and we have not seen it used in active attacks," Microsoft Security Response Center' Principal Security Program Manager Mechele Gruhn added.
"This vulnerability is one example of our partnership with the security research community where a vulnerability was privately disclosed and an update released to ensure customers were not put at risk."
Microsoft encourages security researchers and organizations to report other potential vulnerabilities using the company's MSRC Researcher Portal.
Mitigation, prevention, and detection options
The NSA security advisory also provides mitigation measures for systems where immediately installing the patches Microsoft released as part of its January 2020 Patch Tuesday.
"Network devices and endpoint logging features may prevent or detect some methods of exploitation," says the agency's advisory.
"Properly configured and managed TLS inspection proxies independently validate TLS certificates from external entities and will reject invalid or untrusted certificates, protecting endpoints from certificates that attempt to exploit the vulnerabilities.
Ensure that certificate validation is enabled for TLS proxies to limit exposure to this class of vulnerabilities and review logs for signs of exploitation."
The NSA also recommends using capture analysis tools like Wireshark and tools such as OpenSSL and the Windows certutil utility to extract and analyze certificates to detect any malicious properties.
Certutil can be used to examine an X509 certificate by running the following command:
o certutil –asn
OpenSSL can be used to examine an X509 certificate by running the following command:
o openssl asn1parse –inform DER –in –i –dump
or
o openssl x509 –inform DER –in –text
Certutil can be used to list registered elliptic curves and view their parameters by running the following commands:
o certutil –displayEccCurve
o certutil –displayEccCurve
OpenSSL can be used to view standard curves enabled/compiled into OpenSSL by running the following commands:
o openssl ecparam –list_curves
o openssl ecparam –name –param_enc explicit –text
"Certificates with named elliptic curves, manifested by explicit curve OID values, can be ruled benign," the NSA explains.
However, "certificates containing explicitly-defined elliptic curve parameters which only partially match a standard curve are suspicious, especially if they include the public key for a trusted certificate, and may represent bona fide exploitation attempts."
Critical WordPress Plugin Bug Allows Admin Logins Without Password
20.1.2020 Bleepingcomputer
A critical authentication bypass vulnerability allows anyone to log in as an administrator user on WordPress sites running an affected version of the InfiniteWP Client because of logical mistakes in the code.
Based on the active installations tracked by the WordPress plugin library, the open-source InfiniteWP plugin is currently installed on over 300,000 websites, while the plugin's site claims that it's installed on over 513,000 sites.
Upon installation, InfiniteWP Client is designed to allow its users to manage an unlimited number of WordPress sites from a central location with "one-click updates for WordPress, plugins, and themes across all your sites" and "one-click updates for WordPress, plugins and themes across all your sites."
Critical authentication bypass flaw
The vulnerability was patched by Revmakx, the plugin's maker, on January 8 with the release of InfiniteWP Client 1.9.4.5, one day after researchers at web app security outfit WebARX disclosed the vulnerability on January 7.
Since the InfiniteWP Client version including the security fix was released, a little over 167,000 users have already updated their installation, with around 130K left to patch to secure their websites from potential future attacks.
"In order for the request to even get to the vulnerable part of the code, we first must encode the payload with JSON, then Base64, then send it raw to the site in a POST request," WebARX says.
"All we need to know is the username of an administrator on the site. After the request has been sent, you will automatically be logged in as the user."
The issue was found in the iwp_mmb_set_request function found in the init.php file, a function designed to check if actions attempted by a user are authenticated.
However, the researchers found that the readd_site and add_site don't have an authorization check, a flaw that can be exploited with the correct payload to have the InfiniteWP server automatically log any user as an admin.
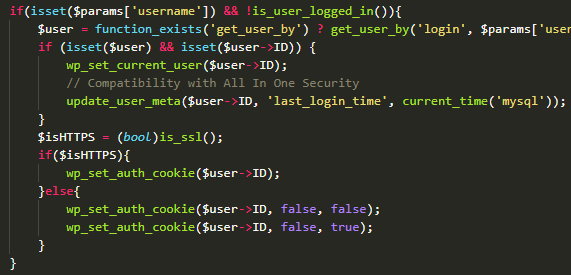
Image: WebARX
"Once the payload meets these conditions, the username parameter that is supplied will be used to login the requester as that user without performing any further authentication," WebARX adds.
Admins who are still using InfiniteWP client version 1.9.4.4 or earlier are advised to update their installations as soon as possible to prevent having their websites compromised.
Another auth bypass caused by Improper Authentication logic and allowing users to login as admins was found in the WordPress plugin dubbed WP Time Capsule.
The WP Time Capsule plugin is also developed by Revmakx and is active on more than 20,000 websites. The flaw was also patched by the developer on January 8, with almost all users (~19,180) having already patched their installations since.
Adobe Releases Their January 2020 Security Updates
20.1.2020 Bleepingcomputer
Adobe has released its monthly security updates that fix vulnerabilities in Adobe Experience Manager and Adobe Illustrator CC. All users are advised to install the applicable updates as soon as possible to resolve these vulnerabilities.
This is the first security update from Adobe in 2020 and surprisingly does not contain any fixes for Adobe Flash Manager, which is typically in the top spot when it comes to the number of vulnerabilities fixed.
There are, though, four vulnerabilities in Adobe Experience Manager and five in Adobe Illustrator CC, with the vulnerabilities in Illustrator being more critical as they can lead to arbitrary code execution.
Below are the Adobe December 2019 security updates:
APSB20-01 Security update available for Adobe Experience Manager
This update fixes four vulnerabilities in the Adobe Experience Manager.
Of the 4 vulnerabilities that were fixed by this update, three are classified as 'Important' and one as 'Moderate'. These vulnerabilities allow an attacker to gain view information on the computer that they would normally not have access to.
Vulnerability Category
Vulnerability Impact
Severity
CVE Number
Affected Versions Download Package
Reflected Cross-Site Scripting
Sensitive Information disclosure
Important CVE-2019-16466
AEM 6.3
AEM 6.4
AEM 6.5
Cumulative Fix Pack 6.3.3.7
Service Pack 6.4.7.0
Service Pack 6.5.3.0
Reflected Cross-Site Scripting Sensitive Information disclosure Important CVE-2019-16467
AEM 6.3
AEM 6.4
AEM 6.5
Cumulative Fix Pack 6.3.3.7
Service Pack 6.4.7.0
Service Pack 6.5.3.0
User Interface Injection
Sensitive Information Disclosure
Moderate
CVE-2019-16468
AEM 6.3
AEM 6.4
AEM 6.5
Cumulative Fix Pack 6.3.3.7
Service Pack 6.4.7.0
Service Pack 6.5.3.0
Expression Language injection Sensitive Information Disclosure Important CVE-2019-16469 AEM 6.5 Service Pack 6.5.3.0
Users should download the latest version of Acrobat and Reader to resolve these vulnerabilities.
APSB20-03 Security update available for Adobe Illustrator CC
This security update resolves five 'Critical' vulnerabilities in Adobe Illustrator that could lead to remote code execution. This would allow attackers to use these vulnerabilities in the software to execute almost any command they wish on the computer.
Vulnerability Category Vulnerability Impact Severity CVE Numbers
Memory Corruption Arbitrary Code Execution Critical
CVE-2020-3710
CVE-2020-3711
CVE-2020-3712
CVE-2020-3713
CVE-2020-3714
Users are advised to upgrade to Adobe Illustrator CC 24.0.2 to resolve these vulnerabilities.
United Nations Targeted With Emotet Malware Phishing Attack
20.1.2020 Bleepingcomputer
Pretending to be the Permanent Mission of Norway, the Emotet operators performed a targeted phishing attack against email addresses associated with users at the United Nations.
Yesterday, the Emotet trojan roared back to life after a 3-week vacation with strong spam campaigns that targeted countries throughout the world.
While Emotet's normal spam campaigns pretended to be fake accounting reports, delivery notices, and invoices, the malware operators had something special in mind for the United Nations.
Impersonating the "Permanent Mission of Norway"
In a sample of a phishing email shared with BleepingComputer by email security firm Cofense, the Emotet operators pretend to be representatives of Norway at the United Nations in New York, who state that there is a problem with an attached signed agreement.
According to Cofense, this phishing campaign had "highly specific targeting" and was seen being sent to 600 unique email addresses at the United Nations.
The email states that the representatives of Norway found a problem with a signed agreement and that the recipient should review it to learn the issue.
Emotet spam targeting the United Nations
The full text of this targeted phishing email can be read below:
Hi,
Please be advised that the new problem has been appeared today.
See below our info for this question.
Please let me know if you need anything else.
Regards
Permanent Mission of Norway to the United Nations in New York
Attached to these emails is a Microsoft Word document that starts with "Doc_01_13" that pretends to be the signed agreement being sent by the Permanent Mission of Norway.
While there was room for Emotet to send a more convincing Word document template, they instead sent the same one that is used for all of the malspam campaigns.
This template pretends to be a warning that the "document only available for desktop or laptop versions of Microsoft Office Word." It then prompts the user to click on 'Enable editing' or 'Enable Content' to view the document.
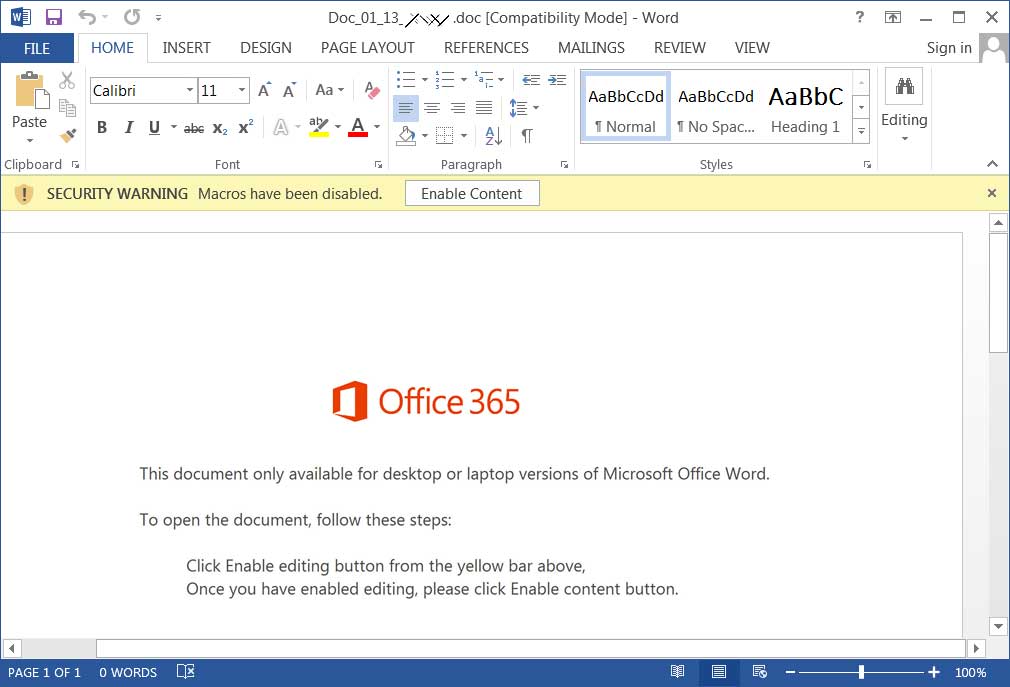
Malicious Email Attachment
If a user opens the document and enables its content, malicious Word macros will be executed that downloads and installs Emotet on the computer.
Emotet will now run in the background while sending out spam emails to other victims.
Eventually, Emotet will also install other payloads such as Trickbot, which would be when things get really bad for the compromised UN workstation.
Emotet can lead to a full network compromise
When Emotet is installed on a machine, one of the malware payloads that is invariably installed is the TrickBot trojan.
The TrickBot trojan will attempt to harvest data from the computer such as cookies, login credentials, files from the computer, and possibly spread to other computers on the network.
After the harvesting of information is finished, TrickBot is known to open a reverse shell back to the operators of Ryuk Ransomware.
These operators will proceed to infiltrate the network, gain administrator credentials, and ultimately deploy Ryuk so that it encrypts every device on the network.
This is particularly worrisome for a UN network as ransomware operators are known to steal data before encrypting files, which could expose extremely sensitive diplomatic or government information.
While there are no known victims of this phishing attack, this targeted attack illustrates that bad actors are constantly trying to get access to the networks of organizations and government networks.
This is why it is imperative for all employees regardless of what sector they work in to be properly trained on how to recognize phishing emails.
Furthermore, before opening any attachments and enabling macros, users should notify their network administrator and contact the alleged user who sent the email to confirm its authenticity.
BleepingComputer has contacted the Permanent Mission of Norway about this attack but has not heard back at this time.
Ryuk Ransomware Uses Wake-on-Lan To Encrypt Offline Devices
20.1.2020 Bleepingcomputer
The Ryuk Ransomware uses the Wake-on-Lan feature to turn on powered off devices on a compromised network to have greater success encrypting them.
Wake-on-Lan is a hardware feature that allows a powered down device to be woken up, or powered on, by sending a special network packet to it. This is useful for administrators who may need to push out updates to a computer or perform scheduled tasks when it is powered down.
According to a recent analysis of the Ryuk Ransomware by Head of SentinelLabs Vitali Kremez, when the malware is executed it will spawn subprocesses with the argument '8 LAN'.
Spawning subprocess with 8 Lan argument
When this argument is used, Ryuk will scan the device's ARP table, which is a list of known IP addresses on the network and their associated mac addresses, and check if the entries are part of the private IP address subnets of "10.", "172.16.", and "192.168."
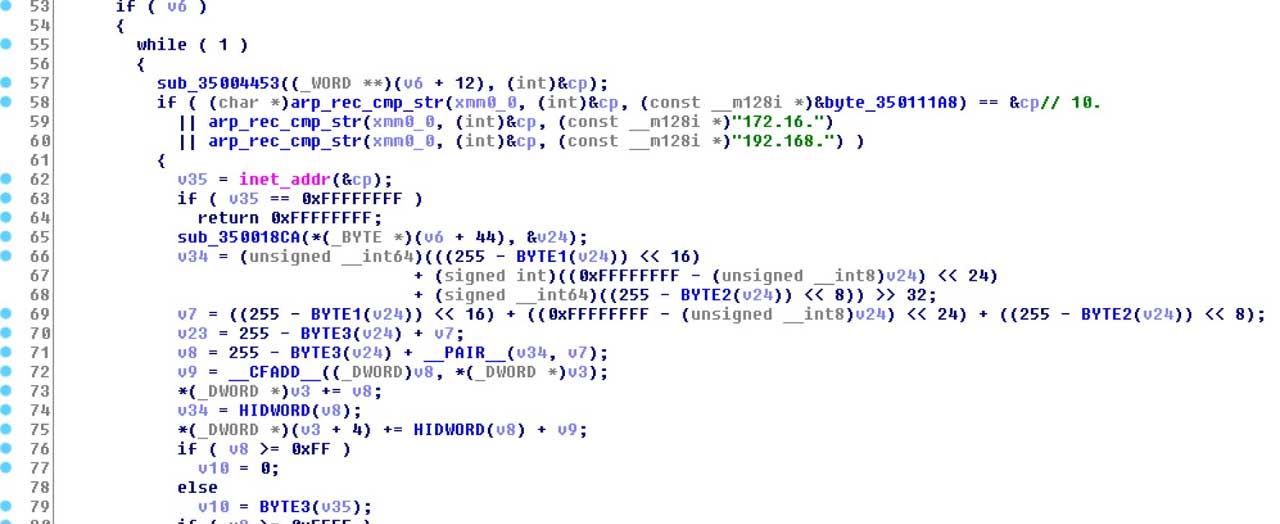
Checking for private network
If the ARP entry is part of any of those networks, Ryuk will send a Wake-on-Lan (WoL) packet to the device's MAC address to have it power up. This WoL request comes in the form of a 'magic packet' containing 'FF FF FF FF FF FF FF FF'.
Ryuk sending a WoL packet
If the WoL request was successful, Ryuk will then attempt to mount the remote device's C$ administrative share.
Mount drive to the Remote C$ Share
If they can mount the share, Ryuk will encrypt that remote computer's drive as well.
In conversations with BleepingComputer, Kremez stated that this evolution in Ryuk's tactics allow a better reach in a compromised network from a single device and shows the Ryuk operator's skill traversing a corporate network.
"This is how the group adapted the network-wide ransomware model to affect more machines via the single infection and by reaching the machines via WOL & ARP," Kremez told BleepingComputer. "It allows for more reach and less isolation and demonstrates their experience dealing with large corporate environments."
To mitigate this new feature, administrators should only allow Wake-on-Lan packets from administrative devices and workstations.
This would allow administrators to still benefit from this feature while adding some security to the endpoints.
At the same time, this does not help if an administrative workstation is compromised, which happens quite often in targeted ransomware attacks.
Update 1/14/20 11:28 AM: CrowdStrike also has analysis of this feature here.
Windows 7 Reaches End of Life Tomorrow, What You Need to Know
20.1.2020 Bleepingcomputer
It's the end of an era: Windows 7 will reach end of support tomorrow, on January 14, a decade after its initial release, with Microsoft to no longer provide users with software updates and security updates or fixes.
"The specific end of support day for Windows 7 will be January 14, 2020," Microsoft says. "After that, technical assistance and software updates from Windows Update that help protect your PC will no longer be available for the product.
Therefore, it's important that you upgrade to a modern operating system such as Windows 10, which can provide the latest security updates to help keep you and your data safer."
For products that have reached their end of support, Microsoft stops providing bug fixes for issues that are discovered, security fixes for newly found vulnerabilities, or technical support.
Customers who still use end of service software are advised by Redmond to move to a new Windows 10 device or to upgrade as soon as possible to avoid falling victim to malware infections and attacks exploiting newly discovered security risks.
Security updates after the end of support
However, as Microsoft says on its support website, "for customers requiring more time to move to the latest product, the Extended Security Update (ESU) program is available for certain legacy products as a last resort option.
The ESU program provides security updates only for up to 3 years, after the End of Support date. Contact your account manager, partner or device manufacturer for more information."
The Extended Security Updates program is available for Windows 7 Professional, Windows 7 Enterprise, and Windows 7 Ultimate through volume licensing programs, and it does not include or provide customers with user-requested non-security updates, new features, or design change requests.
"If an organization waits and purchases ESU for the first time in year two or year three, they will have to pay for the preceding years also," Microsoft adds. "This is because the security updates that are offered under the ESU program are cumulative."
Windows IT Pro
✔
@MSWindowsITPro
Windows 7 will reach end of support on January 14, 2020. If you have questions about obtaining, deploying, or managing Windows 7 Extended Security Updates (ESU) for your org, make sure to join our #AMA next Tuesday (12/17)!! http://aka.ms/ama/Windows7ESU pic.twitter.com/LDmd8wU6vC
56
8:22 PM - Dec 10, 2019
Twitter Ads info and privacy
46 people are talking about this
Besides the ESU program, Redmond also provides the Windows Virtual Desktop program, enabling orgs to continue using Windows 7 with free extended security updates through January 2023.
After Windows 7's end of support, the 0Patch platform will also continue to ship patches to its agents for vulnerabilities rated as high-risk.
"Each Patch Tuesday we'll review Microsoft's security advisories to determine which of the vulnerabilities they have fixed for supported Windows versions might apply to Windows 7 or Windows Server 2008 and present a high-enough risk to warrant micropatching," 0Patch said.
End of support reminders and free Windows 10 upgrades
Microsoft will start displaying full-screen notifications on Windows 7 devices on January 15 to remind users that their operating system is no longer supported and that they should upgrade to the latest Windows 10 version.
Windows 7 Professional customers who have enrolled in the Extended Security Updates program, use domain-joined machines, or machines in kiosk mode will not be shown this reminder.
While Microsoft says that upgrading to Windows 10 from Windows 7 for free was only available until July 29, 2016, free Windows 10 upgrades are still a thing.
You can do so using this step by step Windows 10 upgrade procedure that involves running the Media Creation Tool and choosing the 'Upgrade this PC now' option on your Windows 7 computer.
Windows 7 end of support notification
Chrome and Edge to support Windows 7 after EoL
Google announced that they will keep supporting Google Chrome in Windows 7 through July 15, 2021 (at least), to give companies more time to upgrade to Windows 10.
"We have enterprises covered, even if they haven’t yet made the full move to Windows 10,"Google said. "We will continue to fully support Chrome on Windows 7 for a minimum of 18 months from Microsoft’s End of Life date, until at least July 15, 2021.
So if you haven’t started your move to Windows 10 yet, or even if your organization is mid-way through migration, you can still benefit from the enterprise capabilities of Chrome."
This means that Google Chrome users will still receive browser security updates after Windows 7 end of support, with management tools and enterprise policies to continue to work.
Today, Microsoft also said that they will continue to support their new Microsoft Edge web browser in Windows 7 for as long as Google does.
Other Microsoft products reaching EoL in 2020
Windows 7 is not the only Microsoft product reaching end of support this year, with several other major Microsoft products including Office 2010, Visual Studio 2010, Windows Server 2008 (including 2008R2), and multiple Windows 10 versions also being retired.
A list of some of the most prominent ones and links to more details for each of them is available below.
Product End of Support date
SQL Server 2008 and 2008 R2 07/09/19
Windows Server 2008 and 2008 R2 01/14/20
Exchange Server 2010
Office 2010 client 10/13/20
SharePoint Server 2010
Project Server 2010
Windows 7 currently has a market share of over 26% according to StatCounter and NetMarketShare, with Windows 10 being installed on more than 65% of Windows devices.
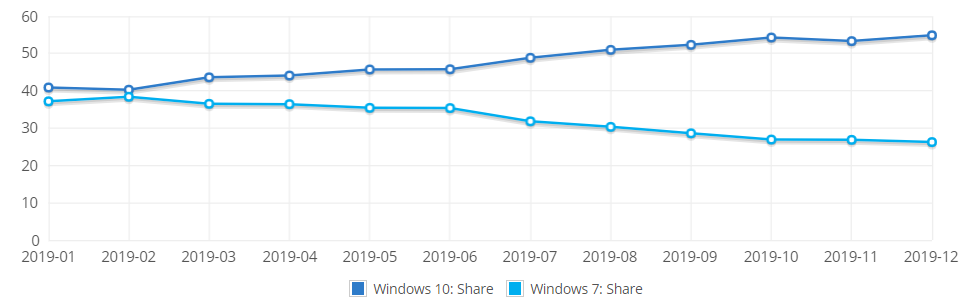
Windows 7 market share (NetMarketShare)
In related news, the KDE Community said last week that it wants Windows 7 users to migrate to the Plasma desktop environment after Microsoft's 10-year-old OS reach end of support.
The KDE Community announces at the moment that it wants to help Windows 7 refugees to migrate to one of the 25 Linux distributions with Plasma support.
"Instead of migrating to Windows 10 and putting up with hours of updates, intrusions on your privacy and annoying ads built into your apps, install a Linux operating system with Plasma," KDE said.
"In 30 minutes you will be up and running and you will have all the security and stability of a Linux system, with all the features and ease of use of Plasma."
Out of Windows' current 77% market share, more than 26% are Windows 7 users amounting to almost one billion people that can't let go of the decade-old OS because they either are scared of the change or don't like Windows 10.
Microsoft to Support the New Edge Browser After Windows 7 EOL
20.1.2020 Bleepingcomputer
Microsoft will continue to support the new Microsoft Edge in Windows 7 even after the operating system reaches the end of life tomorrow.
With tomorrow being the last day that Windows 7 will receive any security and operating system updates from Microsoft, it was not 100% clear if Microsoft would also continue to support Microsoft Edge in the operating system.
Google announced last week that they will continue to support Google Chrome in Windows 7 through at least July 15th, 2021 to give organizations time to upgrade to Windows 10.
"We have enterprises covered, even if they haven’t yet made the full move to Windows 10. We will continue to fully support Chrome on Windows 7 for a minimum of 18 months from Microsoft’s End of Life date, until at least July 15, 2021. So if you haven’t started your move to Windows 10 yet, or even if your organization is mid-way through migration, you can still benefit from the enterprise capabilities of Chrome."
According to a report by Neowin, Microsoft has told them that they will continue to support the new Microsoft Edge in Windows 7 for as long as Google does.
This is because the new Microsoft Edge is a Chromium-based browser, which is the same engine used by Google Chrome. If one works on Windows 7, for the most part, the other will as well.
This is a smart move by both companies as there is no technical reason that either of these browsers should not be able to run in all Windows versions from Windows 7 through Windows 10.
Unless there is a core change in the Windows operating system, I also do not see this changing soon.
With that said, Windows 7 users should upgrade to Windows 10 as soon as possible to keep their operating system secure.
Without security updates, users are at risk from new vulnerabilities that will not be patched and could lead to malware infections, such as ransomware, or the full compromise of a vulnerable computer.
If your hardware supports Windows 10, I strongly suggest you take advantage of Microsoft's free upgrade offer while it is still available.
Update 1/13/20: Microsoft issued us the following vague statement regarding how long they would support Microsoft edge:
"We’re going to continue to support Windows 7 users with the new Microsoft Edge."
CISA Releases Test Tool for Citrix ADC CVE-2019-19781 Vulnerability
20.1.2020 Bleepingcomputer
DHS CISA released a public domain tool designed to help security staff to test if their organizations are vulnerable to ongoing attacks that might target the CVE-2019-19781 security flaw impacting the Citrix Application Delivery Controller (NetScaler ADC) and Citrix Gateway (NetScaler Gateway) products.
"The Cybersecurity and Infrastructure Security Agency (CISA) has released a utility that enables users and administrators to test whether their Citrix Application Delivery Controller (ADC) and Citrix Gateway software is susceptible to the CVE-2019-19781 vulnerability," says the DHS agency.
CISA also strongly recommends all organizations to review CERT/CC’s U#619785 vulnerability note and the Citrix CTX267027 security bulletin to apply the described mitigation measures until new versions of the software will be released.
According to the CTX267027 bulletin, Citrix will be releasing new Citrix ADC and Citrix Gateway versions to patch the CVE-2019-19781 vulnerability starting with January 20, 2020.
US-CERT
✔
@USCERT_gov
Is your Citrix ADC and Gateway software susceptible to CVE-2019-19781? Visit CISA to find out how to test it. https://go.usa.gov/xdqGV #Cyber #Cybersecurity #InfoSec
95
9:03 PM - Jan 13, 2020
Twitter Ads info and privacy
100 people are talking about this
Attackers are probing, exploits already available
The vulnerability makes it possible for unauthenticated attackers to perform arbitrary code execution via directory traversal if successfully exploited.
Several working proof-of-concept (PoC) exploits for the CVE-2019-19781 vulnerability are already publicly available (we won't be linking to them for obvious reasons) from numerous locations.
The PoC exploits allow attackers to create reverse shells back to their machines and execute malicious commands on the compromised devices, effectively enabling the attacker to gain full control over the machines.
Two days earlier, we reported about ongoing scans for vulnerable Citrix hosts following warnings coming from security researchers, coupled with the additional warning that an exploit is imminent and that admins must apply mitigation measures as soon as possible.
Fermin J. Serna
@fjserna
We just published further information around the Citrix ADC/Gateway vulnerability with fix release dates. If I can recommend something, apply the mitigation ASAP if you have the management IP exposed and not firewall protected. It stops the attack on known vulnerable scenarios. https://twitter.com/CitrixNetwork/status/1216153467926073349 …
Citrix Networking
@CitrixNetwork
Blog post from @Citrix CISO @fjserna about updates to the Citrix ADC, Citrix Gateway #CVE201919781 vulnerability - https://bit.ly/36LRITI
122
1:43 AM - Jan 12, 2020
Twitter Ads info and privacy
90 people are talking about this
A technical deep dive for this vulnerability was published by security outfit MDSec, providing a demo of how a working PoC can be used.
TrustedSec also provides a guide that can be followed to check your devices for evidence of a compromise, with Citrix ADC admins being advised to monitor their devices for attacks.
Additionally, Nextron Systems's Florian Roth provided Sigma detection rules for SIEM systems for detecting CVE-2019-19781 exploit attempts on Citrix ADC (NetScaler) and Citrix Gateway devices.
Finally, a list of the estimated dates that patches for the Citrix Application Delivery Controller (ADC) and Citrix Gateway CVE-2019-19781 vulnerability will be published are available below.
Version Refresh Build Expected Release Date
10.5 10.5.70.x 31st January 2020
11.1 11.1.63.x 20th January 2020
12.0 12.0.63.x 20th January 2020
12.1 12.1.55.x 27th January 2020
13.0 13.0.47.x 27th January 2020
BEC Scammers Use Aging Report Phishing to Find New Targets
20.1.2020 Bleepingcomputer
A group tracked as Ancient Tortoise is targeting accounts receivable specialists tricking them into sending over aging reports and thus collecting info on customers they can scam in later attack stages.
Aging reports (aka schedule of accounts receivable) are collections of outstanding invoices designed to help a company's financial department to keep track of customers who haven't yet paid for goods or services they bought on credit.
These sets of invoices allow accounts and management to get an overview of the company's credit and collection processes by breaking down the outstanding debts into increments going from thirty to more than ninety days overdue.
Going beyond BEC scams
While BEC aka EAC (short for Email Account Compromise) scammers are known for using social engineering or hacking to switch the bank accounts used by an organization's financial department to wire out funds, the Ancient Tortoise actors go beyond that.
A report shared exclusively with BleepingComputer that will go live tomorrow shows how researchers at Agari Cyber Intelligence Division (ACID) observed the new threat group impersonating a company's CFO and requesting an updated aging report together with up to date contact information for each of the customers that had unpaid overdue invoices.
Not asking the company's employees to change payment accounts is a tactic used by Ancient Tortoise to gain their trust and trick them into following up to their demands for company records.
The attackers also made use of name deception and free email accounts designed to mimic the firm's CFO to further strengthen their hoax.
Aging report phishing attack (Agari)
However, Agari's research team was the one who connected with them, continuing the email exchange to further understand the inner workings of Ancient Tortoise's fraud scheme.
According to Crane Hassold, senior director of threat research at Agari, the research team "happily obliged and sent them a fake aging report containing the names of purported customers, the amounts of overdue payments, and the names and contact details for each of the 'customers' accounts payable points of contact."
The threat actors collected all the fake customer data delivered by Agari's researchers and, two days after the email exchange, they started contacting all the fake customers, "requesting payment for the outstanding invoices referenced in the aging report" and asking for the outstanding invoices to be paid via ACH or wire to a new account.
To make their email look legitimate, Ancient Tortoise registered a new domain about an hour and a half before sending the messages that closely mimicked our fake employee’s domain. Of course, the display name and username used by the scammer also matched our persona as well. - Agari
Given that the attackers now had all the info they needed to create emails that would perfectly match a supplier's messages, the damages following a real-world attack were Ancient Tortoise would have legitimate information on their hands could prove to be severe for some of their victims.
This also allows the group to launch attacks that are a lot more convincing (the phishing emails contain info like order numbers, debt amounts, company details) than your run-of-the-mill BEC attack were the threat actors have to rely on their social engineering skills to deceive their targets.
In the next stage of their attack, Ancient Tortoise actors sent details on the bank account they controlled for the outstanding payments to be delivered.
Attacker-controlled account details (Agari)
When requested, Ancient Tortoise also sent the fake customers overdue payment invoices altered to show the attackers' bank account details. This only happened after the actors quickly sent an email to the fake vendor's employee posing as the CFO to have all outstanding invoices delivered "as soon as possible."
The BEC scammers delivered the fake within a time span of roughly 45 minutes from the initial request, showing both resourcefulness and speed when it came to making sure that their victims don't catch on to their scam.
"An analysis of the fake invoice also showed that the scammer’s computer was set to a +4 GMT timezone," Agari also found. "This information lines up nicely with additional intelligence collected during our engagements that indicates the Ancient Tortoise actor was likely located in Dubai, United Arab Emirates."
This is just one of the BEC scammer groups Agari is tracking, with others such as Silent Starling, Curious Orca, and Scattered Canary previously being observed running elaborate BEC schemes that led to the compromise of hundreds of employees from hundreds of companies from all over the world.
"In one case, Silent Starling received a consolidated aging report that included details for more than 3,500 customers with past due payments totaling more than $6.5 million," Agari adds.
Original invoice on the left, Ancient Tortoise-altered invoice on the right (Agari)
When it comes to defense against such attacks, Agari says that "for vendors and suppliers, where the initial malicious email usually impersonates a company executive, a multi-layered approach to email security is essential, which includes implementing strong anti-phishing email and email authentication protections that specialize in defending against advanced identity deception attacks and brand spoofing.
For companies that work with external suppliers, in addition to utilizing identity deception defenses—for aging reports, attackers impersonate vendors rather than executives—having a formal process for handling outgoing payments (especially if supplier’s normal payment account has changed) is one of the best ways to prevent these types of attacks."
BEC scammers everywhere
According to FBI's Internet Crime Complaint Center (IC3) Internet Crime report published in April 2019, BEC scams were the cybercrime with the highest reported total losses in 2018, with BEC victims losing over $1,2 billion.
The Financial Crimes Enforcement Network (FinCEN) also released a report in July saying that BEC SAR filings (short for suspicious activity reports) grew from a monthly average of $110 million in 2016 to over $301 million per month in 2018.
The IC3 also issued a PSA in September saying that BEC scams are continuing to grow every year, with a 100% rise in the identified global exposed losses between May 2018 and July 2019, and victim complaints with a total exposed dollar loss of more than $26 billion and related to 166,349 incidents being received between June 2016 and July 2019.
While hard to believe, these figures are somewhat backed by incidents such as the one in which Nikkei, one of the largest media organizations in the world, reported a BEC scam that cost the group roughly $29 million in October.
One month earlier, a member of the Toyota Group also announced that it was scammed in a BEC attack, with an expected financial loss of over $37 million.
Nemty Ransomware to Start Leaking Non-Paying Victim's Data
20.1.2020 Bleepingcomputer
The Nemty Ransomware has outlined plans to create a blog that will be used to publish stolen data for ransomware victims who refuse to pay the ransom.
A new tactic started by the Maze Ransomware and now used by Sodinokibi is to steal files from companies before encrypting them. If a victim does not pay the ransom, then the stolen data will be leaked little-by-little until payment has been made or it has all been released.
The theory behind this is that companies may be more apt to pay a ransom if it costs less than the possible fines, data breach notification costs, loss of trade and business secrets, tarnishing of brand image, and potential lawsuits for the disclosing of personal data.
To facilitate this publishing of stolen data, the Maze operators have created a web site that they use to publish information about their non-paying victims and links to the leaked data.
Nemty plans on creating a leaked data site
In the Nemty Ransomware affiliate panel, the ransomware developers have a news feed where they post their plans, bug fixes, and upcoming changes coming to their ransomware-as-a-service.
According to a recent 'News' post shared with BleepingComputer, Nemty plans to create a web site where they will leak stolen data if ransoms are not paid.
Newsfeed from Nemty Ransomware affiliate panel
Nemty is already configured for network attacks with a builder mode that is used to create executables that target an entire network rather than individual computers.
According to this mode, the created ransomware executables are "only for corporations". This means there will be one key used to decrypt all the devices in the network and victims will not be able to decrypt individual machines.
Nemty Targeted attack ransomware builder
With this functionality already in place, evolving the RaaS to incorporate data exfiltration and further extortion tactics would not be a laborious change.
If remains to see if this new extortion method is paying off for the ransomware actors, but one thing is for sure, we will continue to see more threat actors adopting this new tactic.
Even worse, this also means that these types of attacks are not only affecting the company but are causing personal and third-party information to be disclosed to unauthorized users.
While that means that victims should treat these as attacks like data breaches, from existing cases, it does not appear that they are doing so.
Emotet Malware Restarts Spam Attacks After Holiday Break
20.1.2020 Bleepingcomputer
After almost a three-week holiday vacation, the Emotet trojan is back and targeting the over eighty countries with malicious spam campaigns.
When Emotet sends spam campaigns the threat actors utilize various email templates that pretend to be invoices, reports, voice mails, holiday party invites, or even invites to a Greta Thunberg climate change demonstration.
These emails include malicious attachments that when opened will install the Emotet trojan.
Once installed, Emotet will use the victim's computer to send further spam and will also download other infections such as TrickBot, which may ultimately lead to a Ryuk Ransomware infection depending on the target.
Emotet expert Joseph Roosen told BleepingComputer that on December 21st, 2019, Emotet stopped sending spam campaigns even though their command and control servers continued to run and issue updates.
At around 8:30 AM EST today, Roosen told us that Emotet began spewing forth spam campaigns again that target recipients around the world, with a strong focus on the United States.
Emotet is back from the holidays
Current Emotet campaigns being seen today include regular emails and reply-chain attacks pretending to be proof-of-delivery documents, reports, agreements, and statements.
Email security firm Cofense told BleepingComputer that they have seen spam campaigns targeting 82 countries, with a heavy targeting against the United States.
Examples of Emotet spam shared by Cofense with BleepingComputer pretend to be various reports being sent to the victim for their review as shown below. These emails will either include attached documents or links that can be used to download them.
Reply-chain Emotet Spam
Security researcher James also saw the renewal of Emotet's campaigns in the form of proof of delivery documents being sent from alleged account departments.
Proof of delivery spam
For all of the seen campaigns, when a user opens the attachment they will be presented with a message stating that this "document only available for desktop or laptop versions of Microsoft Office Word." It then prompts the user to click on 'Enable editing' or 'Enable Content' to view the document.
Malicious Word doc
When a user opens the document, malicious macros will be executed that download the Emotet trojan from a remote server and executes it.
Emotet will now quietly run in the background while using the infected device to send out further malicious spam. Eventually, Emotet will also install other payloads such as Trickbot, which will then be used to compromise the entire network and the devices on it.
As always, never open attachments from anyone without confirming over the phone that they did indeed send you the file. You should also always be cautious of enabling content or macros on any attachment you receive.
To be safe, it is advised that you also upload suspicious attachments to VirusTotal to check for malicious macros before opening it.
Android Trojan Steals Your Money to Fund International SMS Attacks
20.1.2020 Bleepingcomputer
An Android banking Trojan dubbed Faketoken has recently been observed by security researchers while draining its victims' accounts to fuel offensive mass text campaigns targeting mobile devices from all over the world.
Faketoken is an Android malware strain first introduced in an F-Secure report from 2012 as a Mobile Transaction Authentication Number (mTAN) interceptor camouflaged as a mobile token generator, a Trojan that later added ransomware capabilities in December 2016.
Besides using fake logins and phishing overlay screens to steal credentials and exfiltrating mTAN numbers used by banks to validate online transactions, the malware can also generate customized phishing pages targeting over 2,200 financial apps, and can steal device information such as the IMEI and IMSI numbers, the phone number, and more.
This Trojan is also capable of mimicking apps used for taxi service ride-hailing and for paying traffic tickers with the end goal of collecting payment card data as Kaspersky Lab discovered in August 2017.
Faketoken phishing screens (Kaspersky)
Banking malware turned offensive mass texting tool
"Not long ago, our botnet activity monitoring system — Botnet Attack Tracking — detected that some 5,000 smartphones infected by Faketoken had started sending offensive text messages," says Alexander Eremin, malware analyst at Kaspersky Lab. "That seemed weird."
While the vast majority of mobile malware comes with SMS capability out of the box and it uses it for various purposes including intercepting text messages and spreading to other devices, banking malware using it to send mass texts is quite unusual.
Once it manages to infect a target's device, Faketoken will check if their bank accounts have enough money and it will use the stolen payment cards to add credit to the victim's mobile account.
After making sure that the funds are ready to be exhausted, Faketoken will proceed to send offensive text messages to local and international phone numbers to infect devices from all over the world on your dime.
"Faketoken’s messaging activities are charged to the infected device owners," Eremin adds. "Before sending anything out, it confirms that the victim's bank account has sufficient funds.
If the account has the cash, then the malware uses the card to top up the mobile account before proceeding with messaging."
This tactic allows it to siphon the victims' bank accounts and, given that Kaspersky Lab's researchers were able to detect roughly 5,000 smartphones infected with this Faketoken variant, the attackers can quickly add to their cash pile if others will also get infected.
Besides draining your bank account to fund its mass attacks against mobile devices from all over the world, Faketoken can also perform a wide array of other actions as instructed by the attackers:
• Change masks to intercept incoming text messages;
• Send text messages to a specified number with a specified text;
• Send text messages with a specified text to a specified list of recipients;
• Send a specified text message to all contacts;
• Upload all text messages from the device to the malicious server;
• Upload all the contacts from the device to the malicious server;
• Upload the list of installed applications to the malicious server;
• Reset the device to factory settings;
• Make a call to a specified number;
• Download a file to the device following a specified link;
• Remove specified applications;
• Create a notification on the phone to open a specified page or run a specified application;
• Start overlaying specified applications with a specified phishing window;
• Open a specified link in its own window;
• Run an application;
• Block the device in order to extort money for unblocking it. This command may include an option indicating the need to encrypt files.
Faketoken defense measures
To defend against Faketoken's recent attacks, Kaspersky Lab recommends only installing apps distributed through Google's official Play Store block installs from unknown sources by going into Settings -> Security and unchecking 'Unknown sources'.
Android users are also advised to always pay attention to the access permissions requested by apps during their installation seeing that even apps downloaded from the Google Play Store can come with malware.
And, more importantly in the case of this particular Faketoken variant, according to Kaspersky Lab you should "not follow links from messages unless you are sure they are safe — even messages from people you know.
For example, if someone who normally posts photos on social media or sends them through instant messaging apps instead sends you a text message with a link, that’s a red flag."
Windows 7 Reminder: Get a Free Windows 10 Upgrade While You Can
20.1.2020 Bleepingcomputer
With the Windows 7 end of life fast approaching, users need to decide whether they want to upgrade them to Windows 10 or just get a new PC.
Starting next Tuesday, January 14th, 2020, Windows 7 will reach its end of life, which means Microsoft will release the last cumulative update for all editions of the operating system.
This means no more security updates going forward. unless you purchase Extended Security Updates. and your computer will become vulnerable to any security vulnerabilities that are discovered in the future.
To remind people of the end of support, on January 15th, Microsoft will start displaying alerts in Windows 7 reminding them that the operating system is no longer supported and that they should upgrade to Windows 10.

Windows 7 End of Support Ad
The good news is that if you wish to upgrade to Windows 10, you can still do so for free using the steps in the following section.
Microsoft was supposed to remove this offer a long time ago, but it is still live.
There is, though, no idea how long this method will work, so if you wish to upgrade a device from Windows 7 to Windows 10 for free, you should do so as soon as possible.
How to upgrade to Windows 10 for free
You can grab a free copy of Windows 10 by running the Media Creation Tool on your Windows 7/8.1 PC. After performing the upgrade, you have to connect to the internet and your Windows 7 license will be converted to a digital entitlement of Windows 10.
Go to Microsoft's Windows 10 download page from here.
Click the 'Download Tool now' button and Media Creation Tool will download
Open the Media Creation Tool and agree to the license.
Select the 'Upgrade this PC now' option and click Next.
Select 'Keep all apps and files' and continue. Click on the Install button to begin the installation process of Windows.
During the installation, the computer will restart numerous times. This process can take a while, so please be patient.
After Windows 10 is finished installing and you're connected, you can verify your Windows 10 activation from Settings > Windows Update > Activation.
We don't know when Microsoft will close this free upgrade method, but you should hurry up if you don't want to lose your free copy of Windows 10.
Sodinokibi Ransomware Publishes Stolen Data for the First Time
12.1.2020 Bleepingcomputer
For the first time, the operators behind the Sodinokibi Ransomware have released files stolen from one of their victims because a ransom was not paid in time.
Since last month, the representatives of the Sodinokibi, otherwise known as REvil, have publicly stated that they would begin to follow Maze's example and publish data stolen from victims if they do not pay a ransom.
While there have been threats made against Travelex and CDH Investments, they have not carried through with them.
This all changed today when the public representative of Sodinokibi stated they beginning to "keep promises" as they posted links to approximately 337MB of allegedly stolen victim files on a Russian hacker and malware forum.
Sodinokibi publishing victim's data
Source: Damien
They claim this data belongs to Artech Information Systems, who describe themselves as a "minority- and women-owned diversity supplier and one of the largest IT staffing companies in the U.S", and that they will release more if a ransom is not paid.
"This is a small part of what we have. If there are no movements, we will sell the remaining, more important and interesting commercial and personal data to third parties, including financial details."
At this time, Artech's site is down and it is not known if it is due to this attack. BleepingComputer has reached out to Artech with questions related to the ransomware attack, but have not heard back.
As we have been saying over and over, ransomware attacks need to be treated with transparency and as a data breach.
By trying to hide these attacks, and the theft of employee, company, and customer data, companies are not only risking fines and lawsuits but are also putting personal data at risk.
This practice of using stolen data as leverage is not going to go away and is only going to get worse.
Expect to see more ransomware operators began to utilize this practice as it becomes the norm in attacks.
Android Trojan Kills Google Play Protect, Spews Fake App Reviews
12.1.2020 Bleepingcomputer
Android Trojan Kills Google Play Protect, Spews Fake App Reviews
An Android malware strain camouflaged as a system app is used by threat actors to disable the Google Play Protect service, generate fake reviews, install malicious apps, show ads, and more.
The heavily obfuscated malware dubbed Trojan-Dropper.AndroidOS.Shopper.a uses a system icon and the ConfigAPKs name which closely resembles the name of a legitimate Android service responsible for app configuration the first time a device is booted.
"Trojan-Dropper.AndroidOS.Shopper.a was most widespread in Russia, where the largest share of infected users (28.46%) was recorded in October – November 2019," Kaspersky Lab researcher Igor Golovin said. "Second place went to Brazil (18.70%) and third to India (14.23%)."
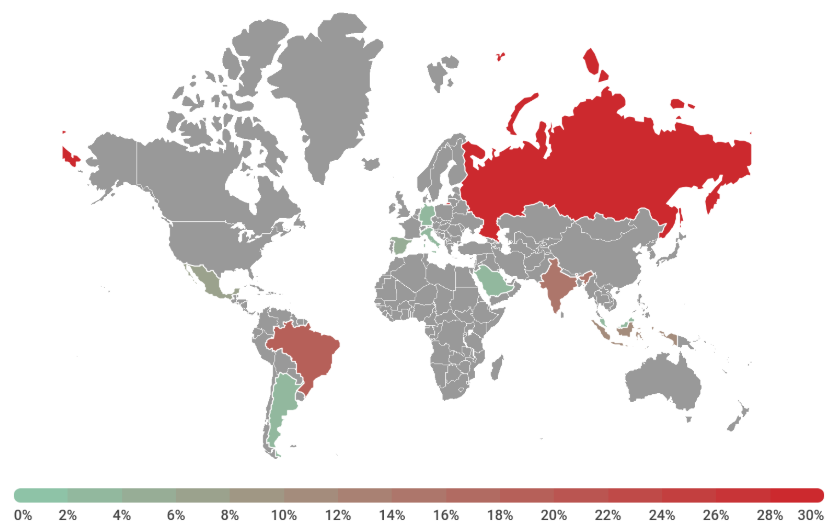
Image: Kaspersky Lab
Malicious Play Store promotion services
Once it infects a victim's Android device, the malware downloads and decrypts the payload, then goes straight to information harvesting, collecting device info such as country, network type, vendor, smartphone model, email address, IMEI, and IMSI.
All this data is then exfiltrated to the operators' servers which will send back a series of commands to be run on the infected smartphone or tablet.
The attackers will utilize the Shopper.a Trojan to boost other malicious apps' ratings on the Play Store, post fake reviews on any apps' entries, install other apps from the Play Store or third-party app stores under the cover of an "invisible" window.
All this is done by abusing the Accessibility Service, a known tactic used by Android malware to perform a wide range of malicious activities without needing user interaction [1, 2, 3, 4]. If it has no permissions to access the service, the Trojan will use phishing to get them from the compromised device's owner.
The malware also disables the Google Play Protect mobile threat protection service, Google's built-in Android malware protection, so that it can go about its business undisturbed.
"Google Play Protect scans over 50 billion apps every day across more than two billion devices," according to the Android Security & Privacy 2018 Year In Review report published in March 2019.
Shopper.a receiving commands (Kaspersky Lab)
"The lack of installation rights from third-party sources is no obstacle to the Trojan — it gives itself the requisite permissions through Accessibility Service," Kaspersky Lab researcher Igor Golovin explained.
"With permission to use it, the malware has almost limitless possibilities for interacting with the system interface and apps. For instance, it can intercept data displayed on the screen, click buttons, and emulate user gestures."
Depending on what commands it receives from its masters, Shopper.a can perform one or more of the following tasks:
• Open links received from the remote server in an invisible window (whereby the malware verifies that the user is connected to a mobile network).
• After a certain number of screen unlocks, hide itself from the apps menu.
• Check the availability of Accessibility Service rights and, if not granted, periodically issue a phishing request to the user to provide them.
• Disable Google Play Protect.
• Create shortcuts to advertised sites in the apps menu.
• Download apps from the third-party “market” Apkpure[.]com and install them.
• Open advertised apps on Google Play and “click” to install them.
• Replace shortcuts to installed apps with shortcuts to advertised sites.
• Post fake reviews supposedly from the Google Play user.
• Show ads when the screen is unlocked.
• Register users through their Google or Facebook accounts in several apps.
"Cybercriminals use Trojan-Dropper.AndroidOS.Shopper.a to boost certain app’s rating and increase the number of installations and registrations," Golovin added.
"All this can be used, among other things, to dupe advertisers. What’s more, the Trojan can display advertising messages on the infected device, create shortcuts to ad sites, and perform other actions."
In related news, Google disclosed that Play Protect detected and removed around 1,700 applications infected with the Joker Android malware (also known as Bread) from the Play Store since the company started tracking this strain in early 2017.
To put things into perspective, while the Android Security & Privacy 2018 yearly review did not provide the exact number of removed malicious apps, the 2017 one states that the company "took down more than 700,000 apps that violated the Google Play policies, 70% more than the apps taken down in 2016."
Citrix ADC CVE-2019-19781 Exploits Released, Fix Now!
12.1.2020 Bleepingcomputer
Numerous working exploits for the Citrix ADC (NetScaler) CVE-2019-19781 vulnerability are finally here and have been publicly posted in numerous locations. There is no patch available for this vulnerability, but Citrix has provided mitigations, which should be applied now!
If successfully exploited, this vulnerability allows unauthenticated users to utilize directory traversal to perform arbitrary code execution.
Since late December, we have been reporting and security professionals have been warning that an exploit for this vulnerability is imminent and that administrators must apply mitigations to their devices as soon as possible.
Two days after reporting that attackers were attempting to exploit, or at least scan, for vulnerable devices, numerous exploits have been made public that allow attackers to take control of vulnerable Citrix Application Delivery Controller (NetScaler ADC) and Citrix Gateway (NetScaler Gateway) devices.
The public proof-of-concept (PoC) exploits that have been released allow attackers to easily create reverse shells back to their machines and execute commands on the vulnerable devices. This essentially allows an attacker to gain full control over these devices.
Security company MDSec published a technical nose dive for this vulnerability and provided a demonstration of how a working PoC can be used to create a reverse shell back to an attacker.
BleepingComputer will not be providing links to any of these exploits as we have too many readers who may use it for malicious reasons.
Mitigate your Citrix ADC devices now!
Even though Citrix disclosed this vulnerability almost a month ago, there is still no patch available for the Citrix ADC CVE-2019-19781 vulnerability.
Instead, Citrix has released a series of steps administrators can use to mitigate the problem.
These steps are different depending on how the system was installed, but you can use the following steps for a standalone system:
enable ns feature responder
add responder action respondwith403 respondwith "\"HTTP/1.1 403 Forbidden\r\n\r\n\""
add responder policy ctx267027 "HTTP.REQ.URL.DECODE_USING_TEXT_MODE.CONTAINS(\"/vpns/\") && (!CLIENT.SSLVPN.IS_SSLVPN || HTTP.REQ.URL.DECODE_USING_TEXT_MODE.CONTAINS(\"/../\"))" respondwith403
bind responder global ctx267027 1 END -type REQ_OVERRIDE
save config
Users are also advised to sign up for security alerts from Citrix to be notified when patches become available.
In the meantime, all administrators should apply the mitigation steps and also configure IDS systems to monitor for this threat.
According to TrustedSec, you can test if the mitigations have been applied properly, you can use the following command (replace host with the IP/hostname of your server):
curl https://host/vpn/../vpns/cfg/smb.conf --path-as-is
If you receive a 403 response, it means you properly applied the mitigations. If you can see the smb.conf, the the mitigations were not done correctly and the device is still vulnerable.
TrustedSec has also provided a guide that can be used to check your devices for evidence of a compromise.
"With the recent Citrix ADC (NetScaler) CVE-2019-19781 Remote Code Execution vulnerability, the TrustedSec Incident Response team has been working closely with our offensive and research teams as they created a working exploit. This has allowed us to create a list of locations and indicators to search for on potentially compromised Citrix ADC hosts."
It is recommended that all Citrix ADC administrators become familiar with TrustedSec's forensics guide and monitor their devices for attacks.
Finally, Nextron Systems's Florian Roth has provided Sigma detection rules for SIEM systems that can be used to detect attempts to exploit the CVE-2019-19781 vulnerability against Citrix ADC (NetScaler) and Citrix Gateway devices.
Expected patch release dates
Citrix has contacted BleepingComputer to share a blog post containing the estimated dates that patches for the Citrix Application Delivery Controller (ADC) and Citrix Gateway CVE-2019-19781 vulnerability will become available.
The current schedule for these patches and their corresponding versions are below.
Version Refresh Build Expected Release Date
10.5 10.5.70.x 31st January 2020
11.1 11.1.63.x 20th January 2020
12.0 12.0.63.x 20th January 2020
12.1 12.1.55.x 27th January 2020
13.0 13.0.47.x 27th January 2020
Updated 1/11/20 11:05 PM EST: Updated article to include estimated patch dates for various versions of the affected Citrix software.
Australia Bushfire Donors Affected by Credit Card Skimming Attack
12.1.2020 Bleepingcomputer
Attackers have compromised a website collecting donations for the victims of the Australia bushfires and injected a malicious script that steals the payment information of the donors.
This type of attack is called Magecart and involves hackers compromising a web site and injecting malicious JavaScript into eCommerce or checkout pages. These scripts will then steal any credit cards or payment information that is submitted and send it off to a remote site under the attacker's control.
The Malwarebytes Threat Intelligence Team has discovered a legitimate web site collecting donations for the tragic bushfires in Australia that has been compromised by a Magecart script.
While the donors were probably not targeted by this attack, they are unfortunately caught in the cross fire.
When a visitor of the site adds an item to their cart, such as a donation, a malicious credit-card skimmer script named ATMZOW will be loaded into the checkout pages.
Donation page with the ATMZOW skimmer
When a user submits their payment information as part of the checkout process, the malicious script will steal the submitted information and send it to the vamberlo[.]com domain. This domain is obfuscated in the script as shown below.
The obfuscated domain that payment information is sent to
Malwarebytes' Jérôme Segura has told BleepingComputer that once they became aware of the compromised site they were able to get the vamberlo[.]com shut down.
For now, this means that any visitors to the site will no longer have their payment information stolen.
As the code is still active on the site, though, it could be modified by the hackers to utilize a new domain that will enable the skimming script again.
Malwarebytes has contacted the site about the malicious script injected into their eCommerce store but has not heard back at this time.
Skimmer active on other sites
Using the PublicWWW tool, Troy Mursch of Bad Packets Report has also discovered that this same script is currently active on 39 other web sites
Skimmer active on other sites
It is not known if those sites are utilizing the same domain to send payment information.
If they are, then with the shutdown of the vamberlo[.]com domain, they will no longer be active as well.
Maze Ransomware Publishes 14GB of Stolen Southwire Files
12.1.2020 Bleepingcomputer
The Maze Ransomware operators have released an additional 14GB of files that they claim were stolen from one of their victims for not paying a ransomware demand.
In December the Maze Ransomware operators attacked Southwire, a wire and cable manufacturer out of Georgia, and allegedly stole 120GB worth of files before encrypting 878 devices on the network.
Maze then demanded $6 million in bitcoins or they would publicly release Southwire's stolen files.
When Southwire did not make a payment, the Maze operators uploaded some of the company's files to a "News" site that they had created to shame non-paying victims.
This led to Southwire filing a lawsuit against Maze in Georgia courts and asking for an injunction in the courts of Ireland against a web hosting provider who was hosting the Maze news site. This injunction led to the site being taken down and Southwire's stolen data being accessible.
"Not in retaliation"
Yesterday, the Maze operators released an additional 14.1GB of stolen files that they claim belong to Southwire on a Russian hacking forum. They further state that they will continue to release 10% of the data every week unless the ransom is paid.
"But now our website is back but not only that. Because of southwire actions, we will now start sharing their private information with you, this only 10% of their information and we will publish the next 10% of the information each week until they agree to negotiate. Use this information in any nefarious ways that you want", the Maze operators stated in their post.
When we asked the Maze operators if they released this additional data out of retaliation for the lawsuit, BleepingComputer was told:
" Before lawsuit it was just few files as a proof. Now it is 10% of 120GB, but not in retaliation. It was planned if they don't negotiate. We will post new parts every week if they don't change their mind.
So the next week another 10%, after 2 weeks another 10% and so on while 100% (120GB) is not published. They can stop this process by negotiating with us and revert it to full data destruction after payment.
In retaliation we have something more interesting ;)
But retaliation doesn't come if they begin negotiate with us."
When we asked what they meant by "something more interesting", they would not elaborate any further.
Ultimately, all companies should never pay a ransom as it only encourages this type of criminal behavior to continue. It is also easy to say that when you are not in Southwire's predicament.
Southwire now needs to weigh the cost of their data being exposed versus the cost of paying the ransom.
If their data contains third-party information, including personal information about employees or customers, then this attack would need to be classified also as a data breach.
This would then require additional costs for government notifications, customer and employee notifications, and potentially fines depending on any privacy laws that may have been violated.
As the data is being released in small batches, each one would constitute a separate data breach but could also potentially be reported under one breach notification.
BleepingComputer has contacted Southwire regarding the release of additional files, but have not heard back at this time.
Sodinikibi Ransomware Hits New York Airport Systems
12.1.2020 Bleepingcomputer
Albany International Airport's staff announced that the New York airport's administrative servers were hit by Sodinokibi Ransomware following a cyberattack that took place over Christmas.
Airport operations were not impacted by the ransomware attack and customers' financial or personal information was not accessed by the attackers according to a statement from airport officials per WNYT-TV.
No airline or TSA servers were affected in the incident, with airport officials saying that the vast majority of encrypted files being administrative documents and archived data.
The Albany County Airport Authority alerted the FBI and the New York State Cyber Command as soon as the attack was discovered, and also hired the services of ABS Solutions to help with the investigation.
MSP's breached systems used as a stepping stone
The attackers were able to infiltrate the New York airport's systems through the maintenance server of its managed service provider (MSP) Logical Net, a Schenectady, NY-based data center services and hosted cloud solutions provider.
The Sodinokibi Ransomware malware spread through the Albany County Airport Authority's network and also reached the backup servers.
Following the attack, airport CEO Philip Calderone told Times Union that "We have severed our relationship with LogicalNet."
Left without backups, the airport paid the "under six figures" ransom the attackers demanded. Albany International Airport's insurer reimbursed part of the ransom payment, with a $25,000 deductible to be recovered from Logical Net.
"Thanks to the fast action by our IT department, airport operations during one of the busiest travel periods of the year were not impacted and no passenger or airline data was acquired or accessed," Calderone added.
"Within hours the authority was able to resume all administrative functions with systems functioning as normal. We are grateful for the assistance provided by the New York State Cyber Command, the FBI and our consultant ABS."
BleepingComputer has contacted the Albany International Airport, Logical Net, and the Sodinokibi actors asking for more details but has not yet heard back.
High-profile Sodinokibi victims
International foreign currency exchange Travelex is another company hit by Sodinokibi on New Year's Eve, with the company being forced to shut down all its systems "to protect data and prevent the spread of the virus."
Following the complete systems shut down, customers were unable to use the site or the app for transactions at around 1,500 Travelex locations across the world.
While Travelex said in a statement that there is no evidence that any of its data was stolen in the attack, the Sodinokibi crew later told BleepingComputer that they copied over 5GB of personal and financial data, including but not limited to names, dates of birth, social security numbers, payment card info.
They also said that Travelex's backup files were also deleted and they will start publishing the stolen data if the company doesn't pay the $3 million ransom in seven days.
U.S. data center provider CyrusOne also had some of its systems encrypted by Sodinokibi Ransomware in early December 2019, while hundreds of dental practices using the online backup product DDS Safe had their files locked in August after the software's developer got infected through its cloud management provider, PercSoft.
Beware of Amazon Prime Support Scams in Google Search Ads
12.1.2020 Bleepingcomputer
A malicious ad campaign is underway in Google Search results that lead users to fake Amazon support sites and tech support scams.
A security researcher reached out to BleepingComputer today about search keywords such as "amazon prime" and "amazon prime customer support" that leads to ads pretending to be Amazon Prime support.
For example, in the image below simply searching for "amazon prime" resulted in a fake and shady-looking support ad hosted on sites.google.com.
Scam ads in Google Search results
BleepingComputer performed these searches and was able to verify that these malicious ads were being displayed.
When a user clicks on the ad they will be brought to a page that attempts to impersonate Amazon and includes a phone number to call to receive help. This number is 1-844-325-7794, which is different from the legitimate Amazon support number of 1 (888) 280-4331.
Fake Amazon Support Site
When BleepingComputer attempted to call the number, we received a busy signal each time we called.
In addition to Amazon support scams, other ads discovered by the researcher were for the search keywords "my account" and "login" that lead to a variety of different tech support scams like the one below.
Tech Support Scam ads in Google Search
Clicking on these ads lead to tech support scams located on sites such as sites.google.com, Azure, and other providers.
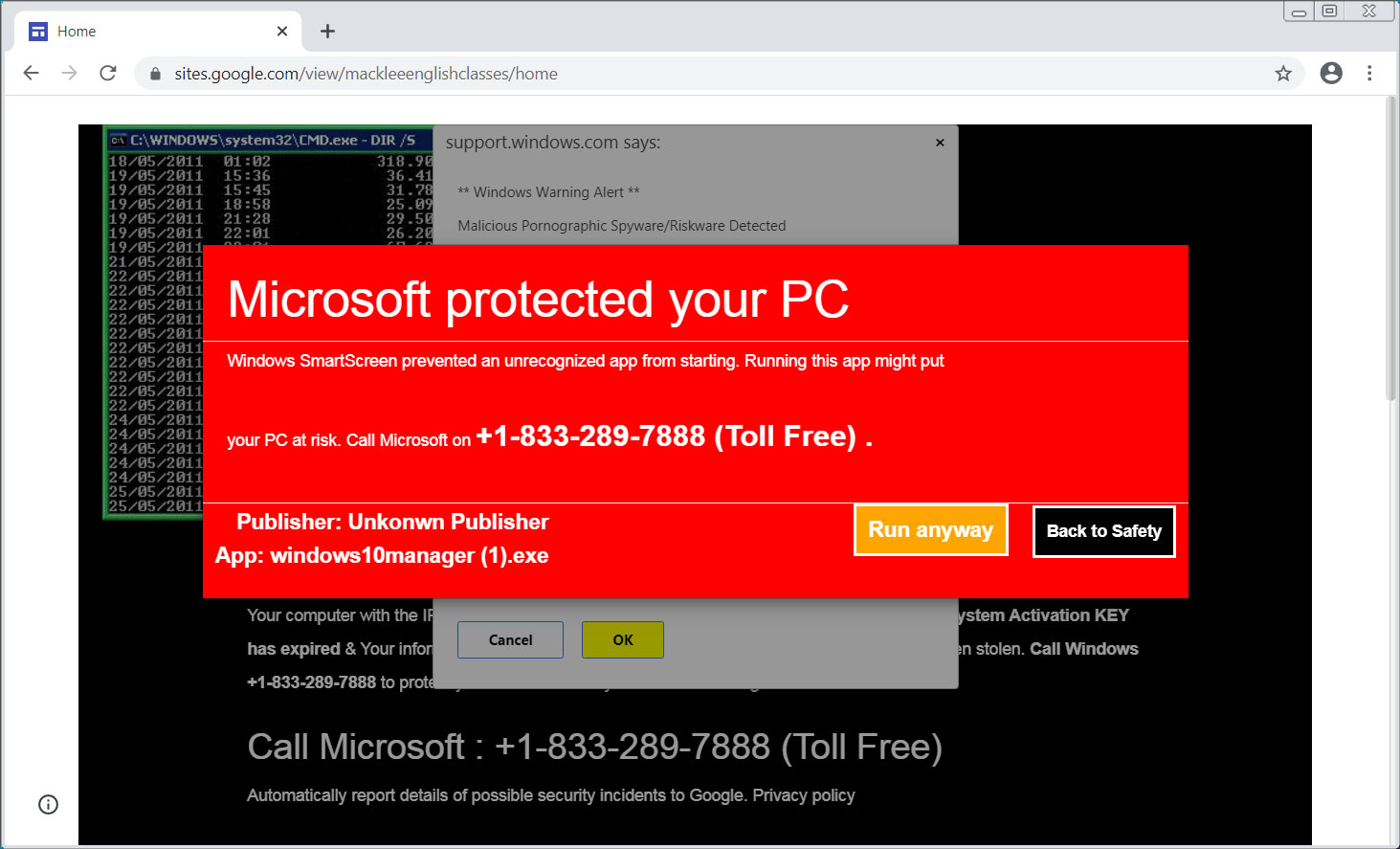
Tech Support Scam via Google Ads
Now many of you may look at these ads and wonder how anyone could fall for them.
The reality is that there are many people, especially older people, who are not comfortable with computers, the Internet, and receiving support via online chat and email.
These types of people are more apt to search for a support phone number and then click on a link without properly analyzing the ad for suspicious characteristics.
Users need to be very careful of the sites that they click on in search results because in many cases they are not vetted properly and can lead to malicious sites.
This is especially true during the holiday or right after as users are commonly looking for support numbers for presents that they have received.
US Govt Warns of Attacks on Unpatched Pulse VPN Servers
12.1.2020 Bleepingcomputer
The US Cybersecurity and Infrastructure Security Agency (CISA) today alerted organizations to patch their Pulse Secure VPN servers as a defense against ongoing attacks trying to exploit a known remote code execution (RCE) vulnerability.
This warning follows another alert issued by CISA in October 2019, and others coming from the National Security Agency (NSA), the Canadian Centre for Cyber Security, and UK's National Cyber Security Center (NCSC).
Pulse Secure reported the vulnerability tracked as CVE-2019-11510 and disclosed by Orange Tsai and Meh Chang from the DEVCORE research team, and by Jake Valletta from FireEye in an April 2019 out-of-cycle advisory.
The company also issued software updates to patch all affected Pulse Connect Secure and Pulse Policy Secure versions.
"CISA expects to see continued attacks exploiting unpatched Pulse Secure VPN environments and strongly urges users and administrators to upgrade to the corresponding fixes," today's DHS alert warns.
Unpatched Pulse Secure VPN servers remain an attractive target for malicious actors. @CISAgov released an Alert on continued exploitation of CVE-2019-11510 in Pulse Secure. Update ASAP! https://t.co/n7mx9juifv #Cyber #Cybersecurity #InfoSec
— US-CERT (@USCERT_gov) January 10, 2020
If left unpatched, CVE-2019-11510 could allow remote unauthenticated attackers to compromise vulnerable VPN servers and "gain access to all active users and their plain-text credentials" and execute arbitrary commands.
On unpatched systems, the flaw "allows people without valid usernames and passwords to remotely connect to the corporate network the device is supposed to protect, turn off multi-factor authentication controls, remotely view logs and cached passwords in plain text (including Active Directory account passwords)," security researcher Kevin Beaumont explains.
According to an NSA advisory from October 2019, "Exploit code is freely available online via the Metasploit framework, as well as GitHub. Malicious cyber actors are actively using this exploit code."
"Actors will take advantage of the vulnerability that was reported on Pulse Secure, Fortinet and Palo Alto VPN products – and in this case, exploit unpatched VPN servers to propagate malware, REvil (Sodinokibi), by distributing and activating the Ransomware through interactive prompts of the VPN interface to the users attempting to access resources through unpatched, vulnerable Pulse VPN servers," Pulse Secure Chief Marketing Officer Scott Gordon told Bleeping Computer.
Week 19 CVE-2019-11510 Scan Results
• Vulnerable Pulse Secure VPN servers detected: 3,825
Our latest vulnerability scan results are freely available for authorized CERT, CSIRT, and ISAC teams.
Submit request here: https://t.co/vlS08kyQo2#cybersecurity #infosec #threatintel
— Bad Packets Report (@bad_packets) January 4, 2020
While on August 25, 2019, cyber threat intelligence outfit Bad Packets was able to discover 14,528 unpatched Pulse Secure servers, this month a subsequent scan yielded 3,825 results showing that a vast majority of orgs patched their VPN gateways.
Since August 2019, Bad Packets Chief Research Officer Troy Mursch reached out to organizations that haven't yet patched their assets, alerting them of the serious damage attackers could inflict on their systems if they leave their servers unpatched.
While not yet confirmed, a high-profile case of an organization directly affected by not patching their Pulse Secure servers could be the international foreign currency exchange Travelex which had its systems infected with Sodinokibi ransomware after an attack that took place on December 31.
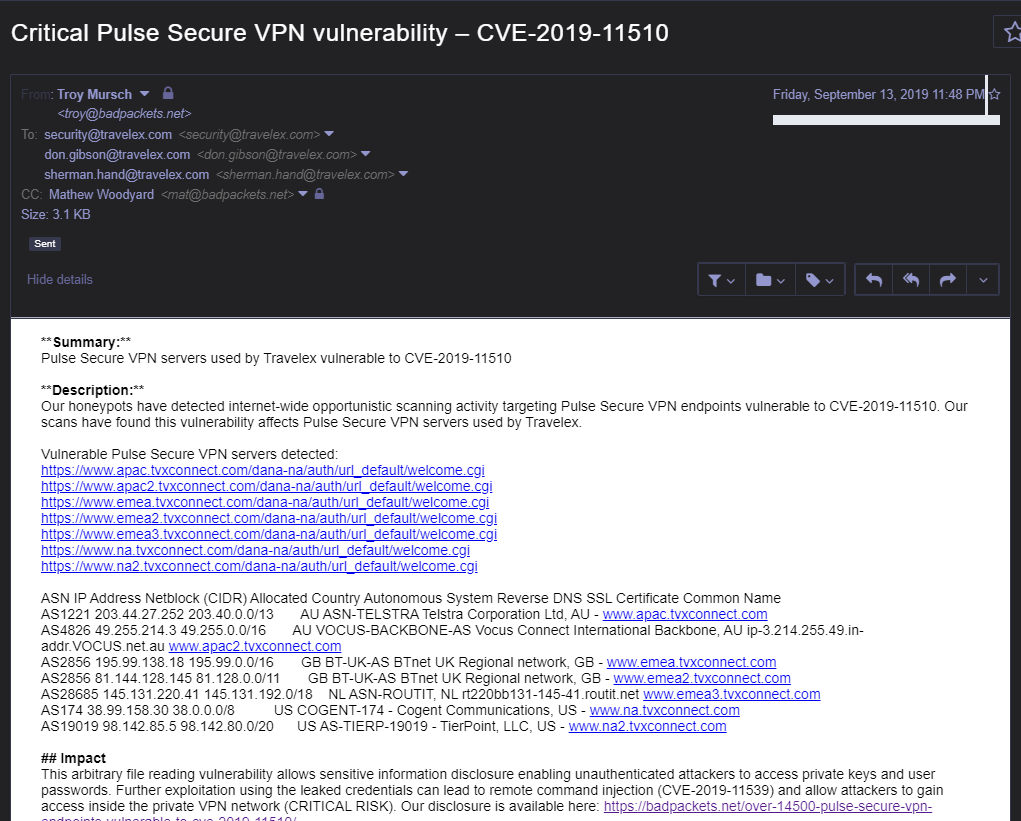
Image: Bad Packets
As it happens, Travelex was one of the organizations that Mursch warned of the issue in September 2019. Unfortunately, Travelex did reply to his email.
Beaumont also found several Internet-exposed Windows servers with RDP enabled and the Network Level Authentication feature toggled off on Travelex's AWS platform. This could allow potential attackers to connect before authenticating.