
Introduction List Kategorie Subcategory 0 1 2 3 4 5
Briton Pleads Guilty to Mirai Attacks in German Court
24.7.2017 securityweek BotNet
A British man pleaded guilty last week in a German court to launching a cyberattack that resulted in more than one million customers of telecommunications provider Deutsche Telekom experiencing Internet disruptions.
German media has identified the 29-year-old man as “Peter Parker” and “Spiderman,” online monikers linked to domains used to coordinate some attacks powered by the notorious Mirai malware. He was also identified by Handelsblatt as Daniel K.
A blog post published earlier this month by security blogger Brian Krebs revealed that the suspect is a British man named Daniel Kaye and the hacker known online as “BestBuy.” He has also been tied to the nickname “Popopret,” but it’s unclear if it’s the same person or a partner of BestBuy.
Krebs found links between Kaye, a massive Mirai botnet that enslaved a large number of Internet of Things (IoT) devices, and a piece of malware named GovRAT.
Reports of BestBuy’s apprehension surfaced in February when German police announced that a man suspected of carrying out the November 2016 attack on Deutsche Telekom had been arrested by the U.K. National Crime Agency (NCA) at a London airport based on a warrant issued by authorities in Germany.
According to German media reports, the 29-year-old pleaded guilty on Friday in the Regional Court of Cologne, claiming that he regretted his actions. He said his main motive was money – he was about to marry his fiance and he wanted a good start to married life. It’s worth mentioning that the social media profiles for Daniel Kaye uncovered by Krebs also showed that he had been engaged to be married.
The hacker told the court that Deutsche Telekom was not the main target of his attack. Instead, he used the Mirai malware to hijack routers – including ones belonging to Deutsche Telekom customers – and other types of devices, which he abused to launch distributed denial-of-service (DDoS) attacks. He claimed a telecommunications firm in the West African country of Liberia paid him $10,000 to attack a competitor.
At the time of his arrest, German authorities said the suspect faced between 6 months and 10 years in prison. He may be sentenced on July 28.
Stantinko botnet was undetected for at least 5 years while infecting half a million systems
23.7.2017 securityaffairs BotNet
A huge botnet dubbed Stantinko was undetected for at least 5 years, the disconcerting discovery was made by researchers from security firm ESET.
According to ESET, the Stantinko botnet has infected around half a million computers worldwide. Operators behind the botnet powered a massive adware campaign active since 2012, crooks mainly targeted users in Russia and Ukraine searching for pirated software.
The researchers discovered that the attack vector used by the cyber criminals is an app called FileTour, it is used to install a variety of programs on the victim’s machine, while also launching Stantinko in the background.
“Making heavy use of code encryption and rapidly adapting so as to avoid detection by anti-malware, Stantinko’s operators managed to stay under the radar for at least the last five years, attracting very little attention to their operations.” states the analysis published by ESET.
The botnet is mainly used to install on the infected systems browser extensions that are used to inject ad and perform click fraud.
The malicious browser extensions installed by the Stantinko malware are called The Safe Surfing and Teddy Protection. Both extensions distributed through the Chrome Web Store are used to block unwanted URLs. The botnet installs its versions of both browser extensions that are able to receive a configuration to perform click fraud and ad injection.
The researchers also noticed that the Stantinko malware could be used take full control of the target systems, it leverages on services that allow attackers conduct several malicious activities (i.e. performing massive searches on Google, performing brute-force attacks on Joomla and WordPress installs).
The malware installs two specific Windows services after compromise, each of them is able to reinstall the other if deleted. This means that in order to sanitize the system it is necessary to remove both services at the same time.

The Stantinko malware is a modular backdoor, its components embed a loader allowing them to execute any Windows executable sent by the C&C server directly in memory.
“This feature is used as a very flexible plugin system allowing the operators to execute anything on an infected system. Table 1 is a description of known Stantinko plugins.
MODULE NAME ANALYSIS
Brute-force Distributed dictionary-based attack on Joomla and WordPress administrative panels.
Search Parser Performs massive distributed and anonymous searches on Google to find Joomla and WordPress websites. It uses compromised Joomla websites as C&C servers.
Remote Administrator Backdoor that implements a full-range of actions from reconnaissance to data exfiltration.
Facebook Bot Bot performing fraud on Facebook. Its capabilities include creating accounts, liking picture or pages, and adding friends.
Experts speculate that crooks work close to the advertisers that pay for the traffic they receive from the botnet.
“On the other hand, traditional click-fraud malware relies on a series of redirections between several ad networks to launder their malicious traffic. This shows that not only are the Stantinko operators able to develop highly stealthy malware, but they are also able to abuse the traditional ad-serving economy without getting caught,” ESET points out.
TrickBot gang is back with new campaigns targeting Payment Processors and CRM Providers
20.6.2017 securityaffairs BotNet
Threat actors behind the financial trojan TrickBot have been updating its campaigns targeting Payment Processors and CRM Providers.
Threat actors behind Banking Trojan TrickBot switched from financial institutions to Payment processors and CRM providers.
TrickBot was initially observed in September 2016 by the researchers at security firm Fidelis Cybersecurity, that linked it to the Dyre banking trojan.
The security firm first spotted the TrickBot malware in September while it was used by crooks to target the customers of Australian banks (ANZ, Westpac, St. George and NAB).
The first TrickBot samples analyzed by the experts were implementing a single data stealer module, but a few weeks later, the researchers discovered a new sample including webinjects that appear to be in the testing phase.
In September 2016, Fidelis Cybersecurity was alerted to a new malware bot calling itself TrickBot that we believe has a strong connection to the Dyre banking trojan. From first glance at the loader, called TrickLoader, there are some striking similarities between it and the loader that Dyre commonly used. It isn’t until you decode out the bot, however, that the similarities become staggering.” reads the analysis published by Fidelis Cybersecurity.
“This would suggest, but is far from conclusive, that some individuals related to the development of Dyre have found their way into resuming criminal operations.”
TrickBot and Dyre have many similarities, the code of the new banking trojan seems to have been rewritten with a different coding style, but maintaining many functionalities.
The malware was used in a number of attacks at the end of 2016 targeting banks in the UK and Australia, and Asian financial institutions.
In May, TrickBot was used to target 20 new private banking brands, eight building societies in the UK, two Swiss banks, private banking platforms in Germany, and four investment banking firms in the U.S.
Researchers at F5 analyzed 26 TrickBot configurations that were active in May 2017 when crooks also targeted two payment processing providers and two Customer Relationship Management (CRM) SaaS providers.
“In the 26 TrickBot configurations F5 researchers analyzed that were active in May 2017, targets expanded beyond banks to include two payment processing providers and two Customer Relationship Management (CRM) SaaS providers.” F5 reports. “The fact that payment processors were targets was a notable change that we also observed in Marcher, an Android banking trojan in March of 2017. It appears now that CRMs are a new target of attackers; is it because of their potential for collecting valuable user data that could enhance phishing campaigns?”
The F5 experts analyze two distinct TrickBot infection campaigns that were active in May, they respectively targeted 210 URL targets and 257 URLs. Both campaigns targeted the same US payment processor (PayPal), but according to F5 only the second campaign targeted the CRM providers.
Giving a look at the campaigns the experts discovered:

The first campaign:
Banks (83% of URL targets, 18% UK banks)
PayPal (a payment processor attributed to the US). 35 different PayPal URLs were also present in the configuration used in the second campaign.
The second campaign:
Banks in UK (47% of targets).
Payment processors with the addition of a new payment processor URL in the UK.
CRMs Salesforce.com and an auto sales CRM developed by Reynolds & Reynolds in the US.
Trickbot campaign 2
F5 identified 6 C&C IP addresses belonging European web hosting provider networks, three of which are operated by hosting firms in Asia. All the IP addresses used 443 / HTTPS for communication with the infected hosts in order to avoid detection.
F5 concludes TrickBot gangs has extended their campaigns due to their success.
“It seems the success of TrickBot thus far has influenced the authors to not only repeat their previous target list of banks from previous campaigns but to expand those targets to include new banks globally as well as CRM providers. The fact that C&C servers in these two most recent campaigns reside within web hosting companies is also significant, along with the fact that the C&C servers were different from those used in previous campaigns,” F5 says.
TrickBot Targets Payment Processors, CRM Providers
20.6.2017 securityweek BotNet
Banking Trojan TrickBot is no longer hitting only banks and financial institutions, but also added payment processing and Customer Relationship Management (CRM) providers to its list of targets, F5 warns.
Supposedly developed by the same gang that previously operated the Dyre Trojan, TrickBot was first spotted in the summer of 2016, and initially detailed in October. By November, the malware was being used in widespread infection campaigns in the UK and Australia, and popped up in Asia the next month. Earlier this year, it started targeting the private banking sector.
The 26 active TrickBot configurations observed in May 2017 were targeting banks in the UK, Australia, US, Canada, New Zealand, Ireland, France, Germany, Switzerland, the Netherlands, Bulgaria, India, Singapore, and Hong Kong. All command and control (C&C) servers used as part of these campaigns were communicating with infected machines over port 443, F5 reports.
The list of Trojan’s targets now also includes two payment processing providers and two CRM SaaS providers, yet TrickBot isn’t the first to include them. In March this year, the Marcher Android banking Trojan started hitting payment processors too, the researchers say.
The F5 researchers analyzed two TrickBot infection campaigns that were active in May, with one configuration packing 210 URL targets and the other including 257 URLs. Both campaigns targeted the same US payment processor (PayPal), but the CRM targets only appeared in the second campaign.
The first campaign, F5 reveals, focused mainly on banks (83% of URL targets) and PayPal (a payment processor attributed to the US), but targeted no US bank. A total of 35 unique PayPal URLs found in the configuration used in this campaign were targeted in the second campaign too, although it mainly focused on banks in the UK (47% of targets).
The second campaign expanded the list of targeted banking URLs and payment processors with the addition of a new payment processor URL in the UK. CRMs were also added to the list, namely Salesforce.com and an auto sales CRM developed by Reynolds & Reynolds in the US.
F5 identified 6 C&C IP addresses, all within European web hosting provider networks, three of which are operated by hosting firms in Asia. All use 443 / HTTPS for communication with the infected hosts, which allows them to hide the malicious traffic and evade detection, because many anti-virus solutions don’t inspect encrypted traffic.
“It seems the success of TrickBot thus far has influenced the authors to not only repeat their previous target list of banks from previous campaigns but to expand those targets to include new banks globally as well as CRM providers. The fact that C&C servers in these two most recent campaigns reside within web hosting companies is also significant, along with the fact that the C&C servers were different from those used in previous campaigns,” F5 says.
Botnets Can Exploit More Vulnerabilities in DVRs
20.6.2017 securityweek Vulnerebility BotNet
Newly discovered vulnerabilities affecting DVR systems could open the door to new, more potent Internet of Things (IoT) botnets, Pen Test Partners security researchers warn.
Following months of investigation into the hardware and software security of more than 30 DVR brands, the researchers discovered a series of flaws that Mirai and other IoT botnets didn’t use, but which could have made these threats far more destructive. These include new telnet credentials and interfaces, as well as an exploitable buffer overflow over port 80 that impacts over 1 million devices.
The researchers also discovered new DVR brands that are vulnerable to Mirai, but which researchers didn’t know about before, and say that DVRs can be used to disable house alarms. They also note that Mirai could have used more default telnet credentials (qazxsw), along with new telnet interfaces that run on port other than 23.
The researchers found the non-standard telnet port 12323 that is used by some DVRs and which uses the same default credentials targeted by Mirai, along with an interface on TCP/9527, with credentials such as admin/blank or admin/123456, or similar, which led to a shell. Via directory traversal, an attacker could abuse the interface to recover the hashed passwords and crack them offline.
The source of the Mirai issue, the researchers suggest, is represented by the manner in which DVR vendors customized the products received from a single original design manufacturer (ODM) called XiongMai. Although vendors could change default credentials, they apparently had only a limited number of credentials to shuffle, and Mirai covers all of them.
However, botnets such as Mirai and Hajime aren’t the biggest threats to DVRs, the Pen Test Partners team argues. Because on some devices the web server running on port 80 is vulnerable to a buffer overflow via the GET request, code execution is possible, and remote access is possible. A botnet exploiting the issue could be larger than Mirai, the researchers say.
A debug interface running on port 9527 and which is present on most XM-based DVRs allows shell access as root with the credentials used for DVR login. Because the interface is port-forwarded by default, it’s likely discoverable on the public Internet in a home user & SME environment. It also packs a directory traversal vulnerability (CVE-2017-7577) and easily guessable default credentials.
The researchers also suggest that BrickerBot, a piece of IoT malware targeting the same devices as Mirai but completely disabling them, was actually meant to be a healing worm, but didn’t work as intended. The issue, they say, is that DVRs run a cut-down version of busybox, which lacks commands for the functionality BrickerBot wants to use. The malware, however, was set to brick the device if it couldn’t fix its vulnerabilities.
The Pen Test Partners researchers also say they found a way to remotely fix Mirai vulnerable devices. However, they decided against publishing the underlying details because the very same method can be used to make Mirai even more potent than it already is, by providing it with persistence over reboots.
QakBot Banking malware causes massive Active Directory lockouts
4.6.2017 securityaffairs BotNet
Security experts at IBM noticed that hundreds to thousands of Active Directory users were locked out of their company’s domain by the QakBot Banking malware
Malware researchers at IBM noticed that hundreds to thousands of Active Directory users were locked out of their organization’s domain, the incident is caused by the Qbot banking malware. The malware was first discovered in 2009, it was continuously improved over the time.

The Qbot banking malware was designed to target businesses and steal money from bank accounts, it implements network wormable capabilities to self-replicate through shared drives and removable media.
The Qbot banking malware is also able to steal user data such as digital certificates, keystrokes, cached credentials, HTTP(S) session authentication data, cookies, authentication tokens, and FTP and POP3 credentials.
The recent campaigns mainly targeted the US business banking services, including treasury, corporate banking, and commercial banking.
“This is the first time IBM X-Force has seen the malware cause AD lockouts in affected organizational networks.” reads the blog post published by IBM.
“QakBot is modular, multithread malware whose various components implement online banking credential theft, a backdoor feature, SOCKS proxy, extensive anti-research capabilities and the ability to subvert antivirus (AV) tools. Aside from its evasion techniques, given admin privileges, QakBot’s current variant can disable security software running on the endpoint.”
Qbot banking malware implements singular detection circumvention mechanisms leveraging a rapid mutation to elude AV.
“Upon infecting a new endpoint, the malware uses rapid mutation to keep AV systems guessing. It makes minor changes to the malware file to modify it and, in other cases, recompiles the entire code to make it appear unrecognizable,” states IBM.
The QakBot Banking malware leverages a dropper for distribution, researchers observed it uses delayed execution (10 to 15 minutes) to evade detection.
The dropper executes an explorer.exe instance and injects the QakBot Dynamic Link Libraries (DLL) into that process, then it corrupts its original file.
The dropper uses the ping.exe utility to invoke a ping command that will repeat six times in a loop:
C:\Windows\System32\cmd.exe” /c ping.exe -n 6 127.0.0.1 & type “C:\Windows\System32\autoconv.exe” à “C:\Users\UserName\Desktop\7a172.exe
Once the pings are complete, the contents of the original QakBot dropper are overwritten by the legitimate Windows autoconv.exe command.
QakBot gains on the target machine using a Registry runkey and scheduled tasks.
Experts observed the malware targeting Active Directory domains by performing three specific actions:
lock out hundreds to thousands of accounts in quick succession; it would perform automated
it would perform automated logon attempts, some launched using accounts that do not exist;
it would deploy malicious executables to network shares and register them as a service.
To spread through the target network, the QakBot Banking malware implements lateral movements, both automatically and on-demand, using a specific command from the C&C server.
“To access and infect other machines in the network, the malware uses the credentials of the affected user and a combination of the same user’s login and domain credentials, if they can be obtained from the domain controller (DC). QakBot may collect the username of the infected machine and use it to attempt to log in to other machines in the domain.” continues the analysis. “If the malware fails to enumerate usernames from the domain controller and the target machine, the malware will use a list of hardcoded usernames instead.”
The malware used man-in-the-browser (MitB) attacks to inject malicious code into online banking sessions, it fetches the scripts from the domain it controls.
Qbot Attacks Cause Active Directory Lockouts
2.6.2017 securityweek BotNet
Recent malware-induced Active Directory (AD) lockouts impacting numerous organizations appear to have been caused by the Qbot banking malware, IBM security researchers warn.
The researchers noticed that hundreds to thousands of AD users were locked out of their company’s domain in rapid succession, thus preventing employees of impacted organizations from accessing their endpoints, company servers and networked assets.
These incidents apparently hit numerous organizations and the Qbot banking Trojan (also known as Qakbot, Quakbot, or PinkSlip) is the culprit. The financial malware was designed to target businesses and siphon money from bank accounts, while being able to spread like a worm by self-replicating through shared drives and removable media.
Discovered in 2009, the malware has received numerous improvements over time, but IBM’s Michael Oppenheim reveals that this is the first time the security team has observed Qbot causing AD lockouts in affected organizational networks. The current campaigns appear focused on U.S. business banking services, including treasury, corporate banking and commercial banking.
Although it features a worm component, the malware is a fully-functional banking Trojan, packed with “powerful information-stealing features to spy on users’ banking activity and eventually defraud them of large sums of money,” Oppenheim says.
The threat features a modular design, is multithreaded, and includes components meant to steal online banking credentials, implement a backdoor, and create a SOCKS proxy. The malware also features extensive anti-research capabilities and can disable the security program on an endpoint, provided that it has admin privileges.
The malware also uses detection circumvention mechanisms that are different than those used by other threats in its class: “Upon infecting a new endpoint, the malware uses rapid mutation to keep AV systems guessing. It makes minor changes to the malware file to modify it and, in other cases, recompiles the entire code to make it appear unrecognizable,” Oppenheim explains.
Qbot uses a dropper for distribution, and usually uses delayed execution to evade detection. Following deployment, the dropper corrupts its file, and has its content overwritten by the legitimate Windows autoconv.exe command. It uses a Registry runkey and scheduled tasks to establish persistence.
In the recent attacks, the malware was also observed targeting Active Directory domains by performing three specific actions: it would lock out hundreds to thousands of accounts in quick succession; it would perform automated logon attempts, some launched using accounts that do not exist; it would deploy malicious executables to network shares and register them as a service.
“To access and infect other machines in the network, the malware uses the credentials of the affected user and a combination of the same user’s login and domain credentials, if they can be obtained from the domain controller (DC),” Oppenheim says.
Qbot either collects the username of the infected machine and uses it for lateral movement, or uses a list of hardcoded usernames instead. The Trojan uses three password schemes in its attempt to match usernames with various passwords. It also enumerates network shares of the target machine and attempts to copy itself to them.
Courtesy of man-in-the-browser (MitB) functionality, the malware can inject malicious code into online banking sessions, and fetches these scripts from the domain it controls. This allows the Trojan to display fake login pages to trick users into exposing their login credentials.
The threat is also able to steal user information such as keystrokes, cached credentials, digital certificates, HTTP(S) session authentication data, cookies (including authentication tokens and Flash cookies), and FTP and POP3 credentials.
It also sends to its server information about the system, IP address, DNS name, host name, username, domain, user privileges, OS version, network interfaces (address, netmask and status), installed software, credentials from the endpoint’s protected storage, account name and webserver credentials, connection type, POP3 username, server and password, and SMTP server and email addresses.
Meant to target the business banking sector, the malware is also known to have targeted organizations in the healthcare and education sectors, as its operators have added improvements to its code, to enhance persistence mechanisms, anti-AV and anti-research capabilities.
“Researchers believe that a closed, organized cybercrime gang with roots in Eastern Europe is responsible for QakBot,” Oppenheim says.
Due to long periods of inactivity, Qbot continues to be placed at the bottom of the top 10 list of the most active malware families, despite being one of the oldest threats in its category.
Qbot Infects Thousands in New Campaign
26.5.2017 securityweek BotNet
A recent distribution campaign resulted in thousands of machines being infected with the Qbot malware, Cylance security researchers warn.
Qbot, which is also known as Qakbot or Quakbot, has been around since 2009, but multiple layers of obfuscation, server-side polymorphism and periodic improvements allow it to remain a persistent threat.
The malware is known for its credential stealing functionality and the ability to spread through network shares, but also includes backdoor capabilities. For two weeks in February last year, the threat managed to ensnare over 50,000 computers worldwide into a botnet. In July, a SentinelOne report on the Furtim-related SFG malware tied Qbot to a fast-flux proxy-based network called Dark Cloud or Fluxxy.
What’s unclear regarding the newly observed Qbot outbreak is how the malware managed to infect such a large number of machines in a short period of time. Most probably, Cylance says, updated exploit kits helped with the distribution.
The core functionality of Qbot has remained fairly consistent over the years, and the polymorphic nature of the threat helped it evade detection. Focusing on this aspect allowed the researchers to discover how often the executable code is modified.
The same as with previously observed samples, the malware continues to configure a scheduled task to request updates, with one command set to run on a weekly basis. The payload received from the server is encrypted, and “the first 20 bytes serve as the RC4 key to decrypt the data,” the security researchers say.
By creating a script to send HTTP requests to each of the three URLs the malware itself receives updates from, the security researchers discovered that files with a unique hash would be supplied every 10 minutes. They also managed to collect a total of 140 unique files supplied by the server over a period of 24 hours.
“All 141 downloaded files were 32-bit Windows executables. Across the 141 files, all have unique compile timestamps, and the earliest one occurred on May 15, 2017,” the researchers say.
Analyzing two files with the same import hash but with different file hashes revealed that, of nine PE sections each of them contains (.text, .code, .rdata, .data, .CRT, .exp, .code (again), .rsc, and .reloc), all section hashes match except those for .text, .rdata, and .data.
Different .text sections could reveal a change in executable code, and initial analysis revealed that all 27 functions identified matched 100%. Following deobfuscation, however, the security researchers discovered that nine functions had received some changes, albeit the overall Qbot functionality remained the same.
“Qakbot continues to be a significant threat due to its credential collection capabilities and polymorphic features. Unhindered, this malware family can rapidly propagate through network shares and create an enterprise-wide incident,” Cylance notes.
In an emailed comment to SecurityWeek, Michael Patterson, CEO of Plixer, pointed out that there is no shortage of vulnerabilities that malicious applications can exploit and that threats will continue to evolve. Thus, defense systems should adapt to ensure more efficient detection.
“Qakbot’s dynamic polymorphic abilities make it particularly evasive to antivirus systems. This means the virus can more easily maintain its presence without being detected," Patterson said. "It does however need to communicate on the network in order to carry out its dastardly deeds. In the case of Qakbot, it uses HTTPS to communicate with command-and-control (C&C) and FTP to upload stolen data. Network Traffic Analytics can be leveraged against flow data to watch for this one-two punch combination especially where odd FQDNs patterns are detected.”
Botnet Spread via NSA Hacking Tools for Weeks
17.5.2017 securityweek BotNet
The ransomware attack that stormed the world over the past several days wasn’t the first to leverage the leaked EternalBlue/DoublePulsar NSA hacking tools for distribution, Proofpoint researchers have discovered.
WannaCry might have gained everyone’s attention because of its destructive potential, but credit to being the first to use the EternalBlue exploit abusing a Server Message Block (SMB) vulnerability on TCP port 445 should go to the cryptocurrency miner Adylkuzz, Proofpoint says.
Similar to WannaCry, the attack leverages the EternalBlue exploit to rapidly propagate from machine to machine, along with the NSA backdoor called DoublePulsar which is used to install a malicious payload on compromised machines.
Symptoms of infection, however, aren’t as visible as with WannaCry: loss of access to shared Windows resources and degradation of PC and server performance. What’s more, the malicious code also shuts down SMB networking to prevent infections with other malware.
According to ProofPoint security researcher Kafeine, this attack might have been much larger than the ransomware outbreak. Furthermore, Kafeine suggests that, because Adylkuzz specifically patched the vulnerability targeted by WannaCry, it might have limited the latter’s infection.
What is certain, however, is that “the Adylkuzz campaign significantly predates the WannaCry attack, beginning at least on May 2 and possibly as early as April 24.” Kafeine also notes that the infection is ongoing and is potentially quite disruptive, although not as flashy as the ransomware rampage.
The Adylkuzz attack is launched from several virtual private servers. EternalBlue is abused for compromise, then the DoublePulsar backdoor is installed to download and run Adylkuzz from another host. Once up and running, the cryptocurrency miner first stops any potential instances of itself and blocks SMB communication to avoid further infection.
Next, the malware determines the public IP address of the victim and then downloads the mining instructions, the cryptominer, and cleanup tools. As it turns out, the cryptominer binaries and mining instructions are hosted on multiple command and control (C&C) servers at the same time.
As part of this attack, Adylkuzz is mining for Monero, a cryptocurrency that saw a surge in activity after the AlphaBay darknet market adopted it last year: BondNet, a Monero-mining botnet that has been active since December 2016, was detailed recently, the Sundown exploit kit was previously dropping a Monero miner, and a Go-based miner was seen last year targeting Linux systems.
Unlike Bitcoin, which now generally requires dedicated, high-performance machines, the Monero mining process can be easily distributed across a botnet, Kafeine explains.
Mining payments associated with an Adylkuzz address suggests the attacks started on April 24. On May 11, the actor supposedly switched to a new mining user address, to avoid having too many Moneros paid to a single address. Three observed addresses received around $43,000 in payments, the researcher says.
“We have currently identified over 20 hosts set up to scan and attack, and are aware of more than a dozen active Adylkuzz C&C servers. We also expect that there are many more Monero mining payment addresses and Adylkuzz C&C servers associated with this activity,” Kafeine notes.
The SMB vulnerability that both WannaCry and Adylkuzz abuse has been addressed by Microsoft in March 2017, and also resolved on unsupported platforms via an emergency patch released over the weekend. Installing these patches should prevent the malware from spreading further.
In the meantime, security researchers apparently linked the WannaCry attacks to the North Korea-linked hacking group Lazarus and suggest that more attacks might follow. Although the attacks have slowed down significantly as of Monday, even industrial systems might be at risk, experts warn.
In the light of these attacks, installing the latest Windows patches might have never been a better course of action.
“For organizations running legacy versions of Windows or who have not implemented the SMB patch that Microsoft released last month, PCs and servers will remain vulnerable to this type of attack. Whether they involve ransomware, cryptocurrency miners, or any other type of malware, these attacks are potentially quite disruptive and costly. Two major campaigns have now employed the attack tools and vulnerability; we expect others will follow and recommend that organizations and individuals patch their machines as soon as possible,” Kafeine says.
The Rakos botnet – Exploring a P2P Transient Botnet From Discovery to Enumeration
10.5.2017 securityaffairs BotNet
1. Introduction
We recently deployed a high interaction honeypots expecting it to be compromised by a specific malware. But in the first few days, instead of getting infected by the expected malware, it received a variety of attacks ranging from SSH port forwarding to “Viagra and Cialis” SPAM to XORDDoS failed deployment attempts. By the third day, it was insistently hit and compromised by Rakos, a Linux/Trojan.
Based on the expected Rakos behavior reported last December by ESET [1], our honeypot was recruited to a botnet and immediately began attempting connections to other hosts on the Internet, both to “call home” and to search for new victims. Although it wasn’t our initial plan, we noticed that this sample didn’t behave like the one ESET described, which got us curious and made us analyze it here at Morphus Labs.
After analyzing and exploiting this botnet’s communication channel and employing Crawling and Sensor Injection enumeration methods, we did find a network floating around 8,300 compromised devices per day spread over 178 countries worldwide. Considering the recent DDoS attack reported by Incapsula [2] against a US College, originated from 9,793 bots, which was able to generate 30,000 requests per second during 54 hours, we may infer how potentially threatening is Rakos botnet.
2. Botnet C&C channel analysis
To better understand this P2P Transient botnet behavior and its C&C protocol, we listened to its traffic for 24 hours, and after analyzing it, we noticed two kinds of communications: one between bots through HTTP and, the other, between bots and C&C servers through TLS/SSL. In this section, we detail the commands we mapped.
Some definitions before start:
Checker: An infected machine (“bot”) that is part of the botnet.
Skaro: C&C server
A particular node may play both roles.
2.1 Communication between Checkers and Skaros
The connections between Checkers and Skaros are made through SSL/TLS encrypted sessions. It was necessary to intercept the traffic using a classic man-in-the-middle attack to access the messages. See in Table 1 the list of captured commands and its descriptions.
Table 1 – C&C between Checkers and Skaros
COMMAND DESCRIPTION
POST /ping HTTP/1.1 This command is used by Checkers to inform a Skaro its information and stats. It includes: system architecture, operating system, a “checker” port number (used for bot to bot communication) and machine load (CPU and Memory). In the response, it receives the SSL certificate files (CA, CERT and KEY), a list of up to 30 Skaros addresses and 50 Checkers
GET /upgrade/up HTTP/1.1 Command issued by the Checker to get a new list of username/password combinations from a Skaro.
GET /upgrade/vars.yaml HTTP/1.1 Issuing this command, a Checker receives a response like the initial parameters. It’s a kind of configuration refresh.
GET /upgrade/linux-armv5 HTTP/1.1 This command is used to get a new version of the malware binary file.
2.2. Communication between Checkers
The communication between Checkers is essential to discover their own public IP address. The bots reach each other through HTTP requests using the high random TCP port they bind to.
See in Table 2 the list of commands and its descriptions.
Table 2 – C&C between Checkers
Command Description
GET / HTTP/1.1 One bot querying another to discover its own IP address.
GET /love HTTP/1.1 Like the previous command; one bot uses “/love” to query another for its own IP address and PTR (the reverse name associated with that IP address). There is a “zen” parameter we didn’t realize its function.
3. Sizing the botnet
Now that we better understand the C&C channel, let’s move on to the intelligence gathering phase. The objective here is to enumerate the population of this botnet, classify its nodes into Skaros and Checker groups and get as much information as possible about them. To this end we implemented two standard approaches to size P2P botnets, Crawling and Sensor Injection [3]
3.1. Crawling
This strategy consists of visiting as many nodes as possible and collecting information about them. The crawler starts by requesting the neighbor list from a seed node and iteratively requests neighbor lists from every newly discovered and active node until all bots are discovered [4].
To maximize our chances of finding an ‘always available and responsive’ seed node, we investigated the lists of Skaros we collected during the man-in-the-middle process and the “/ping” commands we collected to discover prevalent IP addresses. Doing this, we found a group of three IPs both present in the section “skaro” in response to the C&C command “/upgrade/vars.yaml” and in the section “proxies” in response to the C&C command “/ping”, which could make them good seed node candidates.
To validate this, we queried them manually issuing “/ping” commands. As a result, two didn’t respond, and the other answered with an SSL error message, as seen in Figure 1.
At this moment, we realized that the bots authenticate via the SSL certificate found in the C&C command responses. Using it, we issued another “/ping” to the same Skaro that, this time, answered with the expected results, including a list of up to 30 Skaros and 50 Checkers. This botnet protection/authentication mechanism indicated to us the importance of this node to the botnet and made us choose it to be our seed node. We decided to call them “Super Skaros”.
Finally, we wrote a script to automate the crawling process. The script, written in Python, iteratively requests the seed node for the Skaros it knows. Then is asks these Skaros for the Skaros they know and so on until there is no new Skaro to request. The script also creates a graph of the botnet while discovering it to make it easy to further analyze the nodes and its interconnections.
3.1. Sensor Injection
The second strategy is to inject fake nodes into the botnet as sensor nodes [5]. The objective is to offer the network fake nodes to be contacted by the others while enumerating them.
Given the restricted number of Skaros and Checkers returned by each query, the crawling approach may give us just a limited view of the whole botnet. Even when we tried to repeat the query for the same Skaro, the returned list usually included just a small number of new nodes.
To overcome this problem and to improve que quality of our enumeration process, we decided to apply the Sensor Injection method, which, for this research, consists in inserting fake nodes (Skaros and Checkers) into the botnet and collecting information about the nodes that contact them.
To insert the Checker Sensor, we basically ran the malware binary on a controlled environment preventing it from establishing any SSH outgoing connections and monitored the network traffic to enumerate all bots that contacted it. As the communication between Checkers isn’t encrypted, this strategy could give us the possibility to inspect any content posted to or from our sensor.
To insert the Skaro Sensor, we prepared a “/ping” command with manipulated “available”, “running” and “addr” parameters pointing to the IP address to one of our honeypots and sent it to a valid Skaro. Next, we issued a new “/ping” command to the same Skaro and confirmed that our Sensor Node appeared in the returned Skaro list, as seen in Figure 2
To receive and handle those HTTPS connections, we deployed a Nginx server and configured it with the botnet default SSL certificates. With this setup up and running, we started receiving POST and GET requests coming from Checkers, as seen in Figure 3.
To capture and store the data posted to the Skaro Sensor, we created a simple PHP script to append to a file the received HTTP POST parameters. In Figure 4 there is an example of a Checker posted data using the “/ping” C&C command, as always, full of information about the victim, include credentials in clear text.
Finally, to maintain our Skaro Sensor alive on the botnet, we could continually send the manipulated “/ping” command to the Skaros on the network. To implement this, we just configured the “/ping” request of the Crawling method with the appropriate values. As the Crawling would periodically visit all active Skaros, our Sensor Node would always be propagated.
3.3. Experiment environment setup
After defining the methodology and tuning the scripts, it was time to create the environment to execute the experiments, detailed in this section.
As we were dealing with a P2P botnet, distributing the Sensor Nodes in different parts of the world could give us a better view of the botnet, especially if it imposed any kind of communication restriction or load balancing based on geographic regions or IP addresses.
Thus, we distributed 5 Sensor Nodes in the following locations:
North America: Oregon
South America: São Paulo
Europe: Ireland
Southeast Asia: Singapore
Oceania: Australia
In each location, we installed a honeypot with the configurations and scripts necessary to run the Crawling and Sensor Injection experiments, which include:
Network packet capture: to capture all inbound and outbound connections;
A Nginx HTTPS server: to be our Skaro Sensor;
The Crawling Script: to run the crawling process while enumerating all Skaros and Checkers and to create graphs;
A Rakos binary: to be our Checker Sensor;
Outbound filter: all the outgoing connections on TCP port 22 (SSH) were blocked to avoid our honeypot from scanning the Internet for victims.
3.4. Running the experiments
Finally, we put our plan into action. The experiments were started simultaneously in all honeypots. Shortly after, the Crawling Process was already querying 30 to 60 Skaros and the Sensor Nodes were receiving connections from the botnet. All as expected.
After 72 hours (or 3 days), we stopped the experiment and started processing all the collected data. The results are shown in the next section.
4. Results
The experiments generated approximately 5 GB of data amongst PCAP files, HTTP requests, crawled data and graph files that were handled and inserted into an Elastic Stack [6] and Gephi [7] platforms for querying and visualization purposes. The results of both enumeration methods are summarized in Table 3.
Table 3: Results Summary
NODE TYPE / METHOD CRAWLING SENSOR INJECTION UNIQUE NODES
CHECKERS 498 24782 24967
SKAROS 281 239 299
>UNIQUE NODES 779 24839 25084
As we expected, the crawling strategy gave us just a small view of the whole picture. In fact, it accounted for just 3,15% of the total number of discovered nodes. The other part, 96,84% or 24,839 nodes, was found by the Sensor Nodes.
Each sensor discovered an average of 5,000 unique Checkers and 48 unique Skaros during the whole experiment. Comparing to the Crawling method, it’s interesting that although Sensor Injection could discover 50 times more Checkers, it discovered 15% less Skaros. It is also worth mentioning that the efficacy of Sensor Nodes depends on the continuous “/ping” to maintain the Sensor Nodes “alive”.
To make it easy to represent the botnet and its interconnections, we produced graphs for each crawler. One of those graphs, as seen in Figure 5, shows in green the discovery path from the seed node to the Checkers, in lilac, passing through Skaros, in orange. In summary, each node is connected just to the node from which it was discovered by during the crawling process.
The other graph shows the real interconnection between nodes, as seen in Figure 6. Here we can see a very thick botnet where virtually all Checkers know all Skaros.
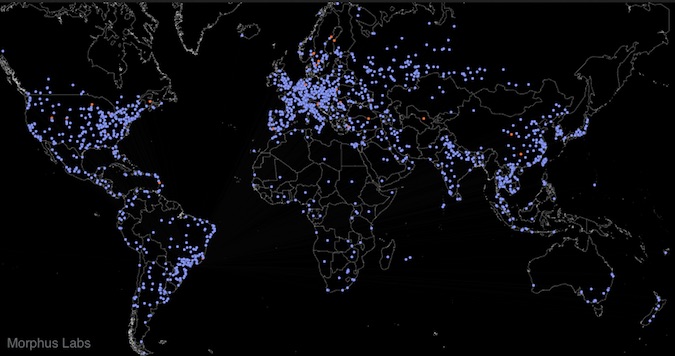
Now, plotting the discovery path graph on the world map, as seen in Figure 7, we may have an idea of the botnet worldwide. To geolocalize the nodes, we used MaxMind database [8].
Figure 8 represents all the connections received by “São Paulo” sensor. The big yellow node represents the sensor node. In lilac are the Checkers and in orange, the Skaros.
The graph for the other sensor nodes look very much like these differing basically by the geographic position of the sensor node.
The worldwide botnet distribution is shown in Figure 9. It’s clearly perceived a high node concentration in Europe, highlighting France, Italy and Spain.
The Top 10 countries are shown in Figure 10.
Another interesting finding of this research is related to the victims’ devices as seen in Figure 11. At least 45% of them are Raspberry PI followed by OpenELEC with 21.79% – which are usually deployed on Raspberries. Next, with 16,74%, comes UBNT, wireless access points devices from Ubiquiti.
This botnet relies basically on default or easy guessable passwords that devices owners fail to manage. None the less, Open ELEC systems do not even offer an easy way for users to change the default password, as shown in Figure 12 The text was extracted from Open ELEC’s website [9].
5. Indicators of Compromise
In this section are the IoCs (Indicators of Compromise) that could be used to search for this malware in your environment.
5.1. Binary hashes
Table 4: Rakos binary hashes
OS ARCH MD5 SHA256
Linux i386 4d08072825eb9e32b9736988c57050eb 7328e81a67419bba42d204a82db311db1a033c1c37d454f7adc3e1ebd635e976
Linux ARM abf87f358d265a072d3ee4a4e1ddc16f 519c236f9974279e1db3c973b2d3c4e561307cfb52dcca4b77d19004b506157d
Linux MIPS f6eed5ce7e92f4d34de98d6d262a869b f5dc3cb4d884012b8f255a4946c2914d9ecaa3382f556125124480c3c47be07e
Linux x86-64 b5cc4d3e6188cbb6a6f725b53fbf3c6b 3e538db81365c3a64af78f53cb64fd58c7843ffa690ec0996b7556fc43a876df
FreeBSD x86-64 8e9f0211e0e6448e587aaa979f311ac1 9d476b8b4326be1207e3064f0aa0e01646277722c50c8e9a61c8c87f53416075
5.2. Yara Rules
strings:
$ = “upgrade/vars.yaml”
$ = “upgrade/up”
$ = “/tmp/init”
$ = “dalek”
$ = “skaro”
condition:
4 of them
5.3. URL Filtering
GET /love
User-Agent: Go-http-client/1.1
6. Final Words
This research revealed a network of controlled devices we defined as a “Transient Botnet”. The term transient refers to the non-persistence aspect of Rakos malware which means that a single bot remains on the network after a reboot only if it gets compromised again, just like Mirai. In other words, we are dealing with a threat that, like many others, counts on the certainty of the abundance of victims and that most them will remain vulnerable – even though this vulnerability could be avoided by a password change.
This transient aspect was reflected in the results we found. During the experiments, the number of nodes floated during the period with peaks of 1,700 new IP addresses which could be existing victims we didn’t know yet or simply new infected or re-infected nodes. Considering this fluctuation, from the 25084 unique nodes discovered in 72 hours, we may consider an average of 8362 bots per 24 hours which certainly represents risks if they were used together in DDoS attacks, for example.
This individual problem that potentially leads to a global threat reminds us the difficult adoption of BCP 38 (Best Current Practices) [10] that specifies how Internet Services Provides (ISPs) could individually cooperate by configuring its routers to defeat DDoS amplification attacks over the Internet. The difference is that in password vulnerability problems we don’t have a guideline or an imposed rule; it involves much more devices and, especially, people.
Finally, it’s worth mentioning that during the 30 days we analyzed this botnet, we didn’t notice any malicious actions other them the SSH brute-force scanner itself. It seems that someone is preparing it to be sold or to offer “services” using it when it gets in the right size. Thinking this way, the innocuous-looking may be a strategy to fly under the radar.
7. References
[1] http://www.welivesecurity.com/2016/12/20/new-linuxrakos-threat-devices-servers-ssh-scan/
[2] https://www.incapsula.com/blog/new-mirai-variant-ddos-us-college.html
[3] Rossow, Christian, et al. “Sok: P2pwned-modeling and evaluating the resilience of peer-to-peer botnets.” Security and Privacy (SP), 2013 IEEE Symposium on. IEEE, 2013.
[4] J. Kang and J.-Y. Zhang. Application Entropy Theory to Detect New Peer-to-Peer Botnets with Multi-chart CUSUM. In Proceedings of the 2nd International Symposium on Electronic
[5] Karuppayah, Shankar, et al. “On advanced monitoring in resilient and unstructured P2P botnets.” Communications (ICC), 2014 IEEE International Conference on. IEEE, 2014.
[6] https://www.elastic.co/
[7] https://gephi.org/
[8] http://dev.maxmind.com/geoip/geoip2/geolite2/
[9] http://wiki.openelec.tv/index.php?title=OpenELEC_FAQ#SSH_Password_change
[10] https://tools.ietf.org/html/bcp38
[11] https://isc.sans.edu/forums/diary/Exploring+a+P2P+Transient+Botnet+From+Discovery+to+Enumeration/22392/
Thousands of Devices Hacked by Rakos Botnet
9.5.2017 securityweek BotNet
Thousands of devices have been hacked by a Linux malware named Rakos, and while researchers have yet to see any actual malicious activity involving the botnet, they believe it could be used for powerful distributed denial-of-service (DDoS) attacks.
Rakos, whose existence was brought to light in December 2016 by ESET, targets Linux systems by launching brute-force attacks via SSH. The security firm reported at the time that the compromised machines had not been leveraged for DDoS attacks or spam campaigns, as one might expect.
Brazil-based Morphus Labs recently deployed some high interaction honeypots that were quickly targeted by Rakos. A closer analysis revealed that the botnet had ensnared roughly 8,300 devices per day across 178 countries.
Rakos consists of bots and command and control (C&C) servers, but since it’s a peer-to-peer botnet some infected machines may play both these roles. Rakos bots obtain a list of IP addresses from a C&C server and attack those hosts via SSH. Each compromised device will in turn target other devices.
The botnet has been described as “transient” due to the fact that the infection is not persistent after a reboot of the hacked device.
Morphus Labs researchers analyzed the botnet by using crawlers and by injecting fake nodes to act as sensors. Data collected over the course of 72 hours revealed the existence of just over 25,000 unique infected devices, or roughly 8,300 per day. This includes nearly 300 machines that served as C&C servers.
The country with the highest number of nodes was China (3,300), followed by Vietnam, Taiwan, Thailand, Russia, India, Brazil and the United States, which had just under 1,000 unique infections.
Experts determined that more than 45 percent of the compromised devices were Raspberry Pis, followed by Open Embedded Linux Entertainment Center (OpenELEC) systems, which also typically run on Raspberry Pi. Unsurprisingly, the third most targeted systems are wireless access points from Ubiquiti Networks, which are often targeted by cybercriminals.
The Rakos botnet can hack devices because their owners have neglected to set strong passwords, but researchers pointed out that, in some cases, such as OpenELEC, default SSH passwords cannot be changed by users.
While 8,000 bots might not seem much, Morphus noted that a new Mirai variant recently used a similar number of compromised devices to launch a significant DDoS attack on a U.S. college. The attack lasted for 54 hours and peaked at 37,000 requests per second (RPS).
However, there is currently no evidence of malicious activity coming from Rakos, except for the brute-force SSH attacks.
“It seems that someone is preparing it to be sold or to offer ‘services’ using it when it gets in the right size,” explained Renato Marinho, director of research at Morphus Labs. “Thinking this way, the innocuous-looking may be a strategy to fly under the radar.”
The Bondnet botnet- From China with Love
6.5.2017 securityaffairs BotNet
The new Bondnet botnet “Bond007.01” recently discovered coming out of China and it has infected an estimated 15,000 Windows server computers world-wide.
There’s a new botnet in town and it’s named after the spy with a license to kill – James Bond. The new Bondnet botnet “Bond007.01” was discovered coming out of China by researchers at Guardicore Labs and it has infected an estimated 15,000 Windows server computers worldwide. The infected systems make up a wide variety of government, corporate, university, city and hospital computers.
So far the Bondnet botnet has not been weaponized but instead seems to be focused on using the thousands of slaved computers to mine a variety of cryptocurrencies such as ZCash, RieConin, and what appears to be its primary target, Monero.
“Operating under the name Bond007.01, the attacker can then take full control of the servers to exfiltrate data, hold it for ransom, use the server to stage further attacks and more. Active since December 2016, Bondent primarily mines Monero. Bond007.01 is financially motivated, earning around a thousand dollars a day.” states the report published by Guardicore.
Crypto-currency mining is a mechanism used to introduce more currency into the system. Miners are often paid a small transaction fee as well as a “subsidy” of newly created electronic coins. Crypto-currency mining is a very computer resource intensive effort and can consume the availability of infected machines to the point of making them useless to the owners.
The Bondnet botnet, which has been reportedly in operation since late 2016, produces over $1,000 a day in mined currency.
The prime targets for the Bondnet attacks seem to be Windows 2008 servers equipped with MySQL however, the creators have a wide variety of targets and exploits they employ to infect a targeted system. The primary attack surface appears to be Windows RDP combined with brute force attacks against weak credentials.

The attackers also used a wide range of attacks against other web server software including JBoss, Oracle web apps, MSSQL and Apache Tomcat. Researchers have confirmed the Bondnet attacks seen so far are limited to Windows based server systems with 2008 and 2012 releases facing the brunt of the assault.
Once the Bondnet intruder has broken through into the Windows system it then installs a series of Visual Basic programs, DLLs and Windows management programs to act as a Remote Access Trojan (RAT) and the crypto-currency mining system. The RAT allows back door access for the Bondnet controllers and the mining system reports back with its results so the controllers can profit from the stolen computer usage.
While the Bondnet botnet creators are stealing computer time and resources to obtain their digital bounty, there are darker forces that can be unleashed. The Bondnet botnet is managed and controlled remotely by the unknown users and thus can also be weaponized to form a DOS attack network, a ransomware net or be used for simple passive surveillance.
Guardicore and other researchers have not seen any indication that the Bondnet operators are interested in data stored on the infected systems. Instead, they are concentrating their efforts on stealing the computer time for the crypto-currency mining operations. The speculation is that the amount of money earned by the Bondnet stealthy mining techniques exceeds what could be obtained via extortion by ransomware or DOS attacks.
However, the added usage and power consumption inflicted by Bondnet botnet reportedly costs victims as much as $2,000 a month and the potential of the Bondnet to be weaponized into something more sinister shows just how dangerous it is.
“While organisations can treat this as an issue of increased electric bills which can annually result in additional costs of 1000-2000$ per server, this may only be the beginning.” warns the analysis. “With relatively simple modifications the Bondnet can use its complete control over compromised organization servers, many of which contain sensitive information, to spread evil and perform other illegal actions. Today’s mining may easily become a ransomware campaign, data exfiltration or lateral movement inside the victim’s network.”
Owners of Windows server based systems are advised to monitor usage carefully, update their software to the latest versions to close security holes, raise the level of their password and credential employment and run a complete check for the Bondnet using AV security products.
Guardicore has released a full technical report on the Bondnet, a removal tool and an analysis of its operations at.
An Army of Thousands of Hacked Servers Found Mining Cryptocurrencies
5.5.2017 thehackernews BotNet
A new botnet consisting of more than 15,000 compromised servers has been used to mine various cryptocurrencies, earning its master around $25,000 per month.
Mining cryptocurrencies can be a costly investment, as it requires an enormous amount of computing power, but cybercriminals have found an easy money-making solution.
Dubbed BondNet, the botnet was first spotted in December 2016 by GuardiCore researchers, who traced back the botnet malware developer, using online handle Bond007.01, to China.
According to the GuardiCore researchers, Bond007.01 is currently using BondNet for mining cryptocurrencies — primarily Monero, but also ByteCoin, RieCoin, and ZCash — but they warn that the hacker could easily take full control of compromised servers for malicious purposes, like mounting Mirai-style DDoS attacks.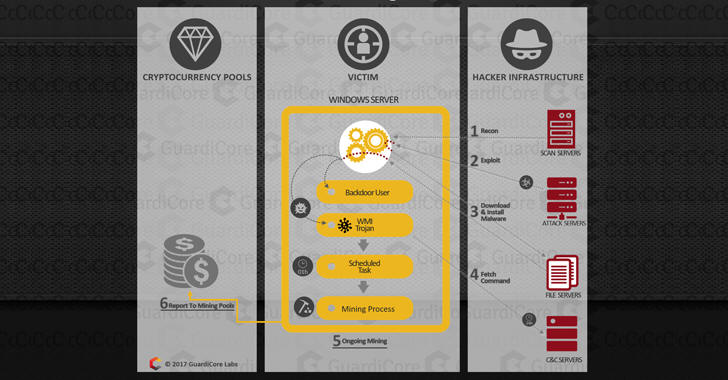
BondNet Attacks only Windows Server Machines
Since mining cryptocurrencies require large amounts of CPU/GPU power, the botnet master goes after Windows Server machines; instead of consumer IoT devices.
However, in order to compromise Windows Server machines, the botnet master relies on different attack techniques. Researchers say the hacker uses a combination of old vulnerabilities and weak user/password combinations to attack mostly old and unsupported Windows Server machines.
The most common flaws exploited by the botnet operator include known phpMyAdmin configuration flaws, exploits in JBoss, and bugs in Oracle Web Application Testing Suite, MSSQL servers, ElasticSearch, Apache Tomcat, Oracle Weblogic, and other services.
Once the hacker gain access to a Windows Server machine, he deploys Visual Basic files to gather information about the infected system and then install a Remote Access Trojan (RAT) and a cryptocurrency miner to make a huge profit from the hacked servers.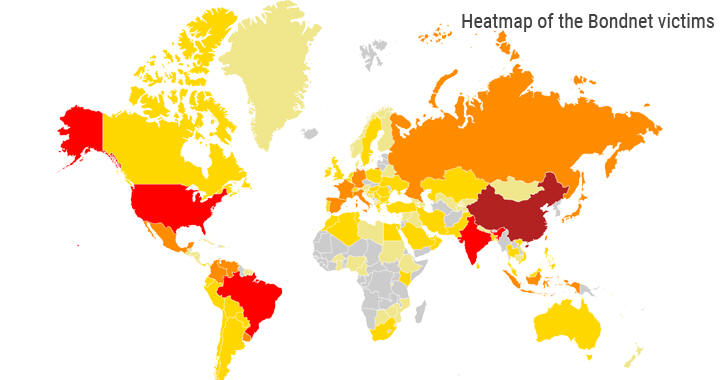
BondNet's Botnet Infrastructure
One thing that's worth noticing is that the botnet operator does not use all infected machines for mining cryptocurrencies. The operator has built its botnet infrastructure of compromised servers with various roles:
1. Some infected machines serve as scanning servers to check for vulnerable systems on the Internet by going through a list of IP addresses with open ports that have been compiled with the WinEggDrop TCP port scanner.
2. Some servers are used as file servers to host the mining software.
3. Other infected servers are turned into command-and-control (C&C) servers after they have been equipped with a fork of goup — a small open source HTTP server written in Golang.
"Building an attack infrastructure on top of victim machines helps conceal the attacker’s true identity and origin of the attack," the GuardiCore researchers explained in their report published Thursday.
"It also provides high availability infrastructure, which is very helpful when relying on compromised servers, providing infinite backup options in case one of the servers fails or loses connectivity to the internet."
BondNet has already infected more than 15,000 server machines at major institutions around the world, including high-profile global companies, universities, and city councils, while the majority of them runs Windows Server 2008 R2.
Additionally, the BondNet botnet adds around 500 new machines to its network each day, and an approximately the same number of servers are delisted.
Here's How to Detect the Threat and How to Mitigate:
To prevent your machines from getting hacked, server admins are advised to secure their systems by regularly applying security patches for all software, updating the firmware, and employing stronger passwords.
Meanwhile, GuardiCore has also provided network and file indicators of compromise systems to help server administrators check whether their machines are among compromised ones.
The researchers have also released a detection & cleanup tool (registration is required to download it) to help admins find and remove BondNet bots from their servers, as well as instructions on how to clean the system manually, without using the script.
Botnet of Thousands of Servers Mines for Crypto-Currency
5.5.207 securityweek BotNet
A botnet comprised of more than 15,000 servers is currently being used for mining crypto-currency, but attackers could easily take full control of the compromised machines if they choose, GuardiCore warns.
Dubbed BondNet, the botnet appears to have been active since December 2016 and is mainly focused on mining Monero, a crypto-currency highly popular among cybercriminals. The botnet’s operator is estimated to be earning around $1,000 a day, or more than $25,000 a month, the security researchers say.
To breach servers, the attackers use a variety of public exploits, after which they install a Windows Management Interface (WMI) backdoor to establish communication with the command and control (C&C) server. This also allows attackers to take full control of the servers and steal data on them, hold it for ransom, or stage further attacks.
The security firm determined that BondNet has penetrated more than 15,000 machines to date and says that around 2,000 of the compromised servers report to the C&C each day. Additionally, the botnet adds around 500 new machines to the network daily, while delisting around the same number of servers. The oldest server breached has an uptime of over 7.5 years.
The botnet operators use a mix of vulnerabilities and weak credentials to breach Windows Server machines, including known phpMyAdmin configuration bugs, exploits in JBoss, Oracle Web Application Testing Suite, ElasticSearch, MSSQL servers, Apache Tomcat, Oracle Weblogic and other common services.
Common to all attacks is the use of Visual Basic files to download and install a remote access Trojan (RAT) and a crypto-currency miner. The compromised machines are then used to expand the botnet infrastructure, to conduct attacks, or serve up malware files such as miner executables. Other machines would host the C&C servers, the researchers say.
Although the crooks appear focused on mining Monero, miners such as ByteCoin, RieCoin or ZCash (all convertible to USD) are also dropped in some cases. Up-to-date versions of the mining programs are downloaded and installed, and scheduled task, triggered hourly, ensure that the miner process can survive reboots.
The backdoor used by the botnet is a WMI RAT downloaded from an Amazon S3 bucket (mytest01234), and is installed using a known MOF file method. Set to run every night at 11PM, the backdoor defines a new WMI provider class, which allows the attacker to execute code as a result of a WMI event and to hide the activity behind the WMI service process.
The backdoor enables the Guest account and resets its password, so that the attacker can remotely connect using Remote Desktop Protocol (RDP), Server Message Block (SMB), or Microsoft Remote Procedure Call (RPC).
Next, it collects information about the machine, including computer name, RDP port, guest username, OS version, number of active processors, uptime measured in hours, original infection vector, whether the victim is running a Chinese version of Windows, OS language, and CPU architecture (x86/x64), and sends it to the C&C encoded, over HTTP. The malware also downloads a command file and executes it (the commands are obfuscated Visual Basic code and are executed “in memory”).
On victim-turned-C&C servers, the attackers install a fork of goup, which is a small open source HTTP server written in Golang. The attackers’ webserver can track victims and encrypt files on disk using AES. The use of .asp and .zip extensions for the files served by the C&C server allows the attackers to avoid auditing and firewall alerts.
The attackers deploy new command and control instances manually by connecting over RDP to the victim machine and copying a ZIP file that contains the server, an open source service manager (nssm), and command files. The server is installed using an included batch script, is named w3wp, the same as the Microsoft IIS host process, and runs at startup. Because the attackers sometimes forget to save all.asp, some C&C servers don’t save the information the Trojans send.
The botnet’s infrastructure is built of compromised servers with various roles: C&C servers, file servers, scanning servers etc. The attackers use the TCP port scanner WinEggDrop to scan the Internet for new targets. The scanning servers also check for public, unpatched vulnerabilities in different frameworks, and store those IPs for attack servers to attempt to compromise.
Many of the victims are used as file servers to serve up mining software, and they have the same web server as the C&Cs. The WMI Trojan files, however, are hosted on an Amazon S3 bucket.
“While organizations can treat this as a minor issue of increased electric bills, with relatively simple modifications this backdoor is capable of taking complete control of thousands of victim machines, many of which contain sensitive information like mail servers. Today's mining may easily become a ransomware campaign, data exfiltration or lateral movement inside the victim's network,” GuardiCore concludes.
WordPress Attacks Powered by Router Botnet Drop Rapidly
3.5.2017 securityweek BotNet
A botnet powered by compromised home routers has been apparently shut down. It is unclear if the botnet operators decided to pull the plug on their operation or if the disruption was caused by law enforcement.
Security firm Wordfence warned last month that tens of thousands of vulnerable routers from dozens of ISPs worldwide had been abused for brute-force and other types of attacks aimed at WordPress websites.
Researchers said the attackers may have hijacked the devices by exploiting some known vulnerabilities that users and ISPs had failed to patch, including the flaw dubbed “Misfortune Cookie.”
However, on Tuesday, Wordfence reported that the volume of attacks had started to drop significantly over the weekend, particularly on Sunday night, Pacific time. By Monday evening, the 30,000 or 40,000 attack attempts coming every hour from some ISPs had dropped to less than 5,000, and the frequency of the attacks continued to decrease.
Wordfence has not been able to determine what caused the apparent shut down of the botnet and it’s unclear if the situation is permanent or just temporary. However, the company believes we might know exactly in the next few weeks.
One possible scenario is that the attackers themselves decided to end their operation for some reason. Another possibility is that law enforcement or other entities managed to take down the command and control (C&C) servers used by the botnet.
Law enforcement agencies have been very busy targeting cybercriminal operations in recent weeks. In April, U.S. authorities announced efforts to disrupt and dismantle the Kelihos botnet. Two weeks later, Interpol reported that authorities in the ASEAN region worked with private companies to identify nearly 9,000 C&C servers and hundreds of compromised websites.
The recent attacks originating from routers had caused Wordfence and organizations such as Spamhaus to blacklist the offending IP addresses, which resulted in users being unable to access certain online services.
“By reducing these attacks, this ensures those ISP customers have full internet access again,” said Wordfence’s Mark Maunder.
Cloud-Hosted Botnet Controllers on the Rise: Report
2.5.2017 securityweek BotNet
The number of botnet controllers hosted in the cloud has spiked in recent months, data from international nonprofit organization Spamhaus reveals.
Cloud computing has become highly popular lately, and it appears that cybercriminals are also adopting it for their nefarious operations. Because of advantages such as low-cost and scalability, an increasing number of malicious actors are abusing legitimate services to deploy botnet command and control (C&C) servers, researchers say.
Starting in January 2017, several large botnet operators were found using cloud services from Amazon AWS (Amazon Web Services), with Google Compute Engine becoming increasingly popular as well.
A chart provided by Spamhaus shows that the uptick in the use of Amazon AWS for the hosting of botnet controllers started in November 2016 and reached its peak in January 2017. While the number of newly detected botnet controllers on these platforms has decreased, more and more instances of C&C servers hosted on Google Compute Engine have started to emerge.
Spamhaus has been considering only botnet controllers for the creation of the said chart, but warns that other fraudulent infrastructure, including payment sites for ransomware (TorrentLocker, Locky, Cerber etc) or malware distribution sites are also increasingly abusing Amazon and Google services.
“Neither Amazon nor Google are handling abuse reports about botnet controllers, malware distribution sites, and other types of criminal activity on their clouds in a timely manner. Both allow botnet controllers to remain online for weeks at a time, despite multiple abuse reports and reminders,” Spamhaus’ Thomas Morrison notes.
He also notes that Spamhaus has reached out repeatedly to both Amazon and Google to report these abuse issues, but that “no relevant response from either” has been received so far. The researcher also speculates that the root cause of this problem might be a weak or non-existent customer verification process. A weak Acceptable Use Policy, or a corporate culture and management not supporting of Abuse Desk policy enforcement might also contribute to the issue, Morrison notes.
Currently, the Spamhaus Block List (SBL), which is “a database of IP addresses from which Spamhaus does not recommend the acceptance of electronic mail,” contains 159 items for Amazon.com and 53 addresses for Google.com.
“We encourage Amazon and Google to take the appropriate actions to stop all outstanding abuse problems on their networks, just as all responsible hosting networks must do. In addition, Amazon and Google must take necessary and appropriate steps to prevent further abuse of all types from being generated on their network. That includes reacting to abuse reports from many sources including, but not limited to, SBL listings, and effectively prohibiting all services to spammers and other abusive users,” the researcher notes.
Contacted by SecurityWeek, a Google spokesperson provided the following statement: "Google Cloud Platform has many precautions in place to prevent, detect, and stop abusive behavior. A team of engineers is dedicated to investigating and addressing potential security and abuse incidents 24/7, and we suspend activity that violates our Acceptable Use Policy. Our team identifies the vast majority of abuse before we are notified. When third parties notify us of potential abuse, we investigate claims to verify them before taking action. Potential abuse on Google Cloud Platform can be reported here."
Hajime ‘Vigilante Botnet’ Growing Rapidly; Hijacks 300,000 IoT Devices Worldwide
27.4.2017 thehackernews BotNet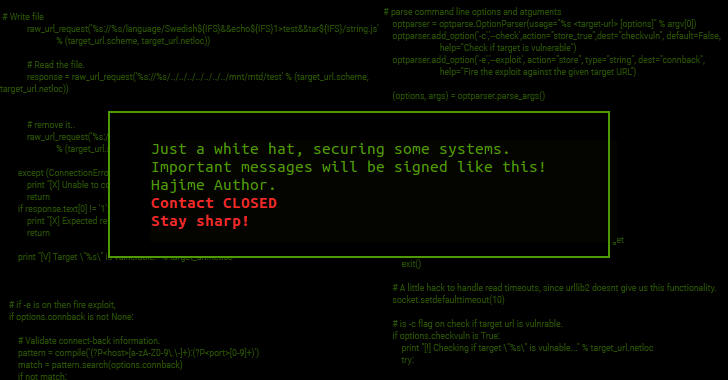
Hajime ‘Vigilante Botnet’ Growing Rapidly; Hijacks 300,000 IoT Devices Worldwide
Last week, we reported about a so-called 'vigilante hacker' who hacked into at least 10,000 vulnerable 'Internet of Things' devices, such as home routers and Internet-connected cameras, using a botnet malware in order to supposedly secure them.
Now, that vigilante hacker has already trapped roughly 300,000 devices in an IoT botnet known as Hajime, according to a new report published Tuesday by Kaspersky Lab, and this number will rise with each day that passes by.
The IoT botnet malware was emerged in October 2016, around the same time when the infamous Mirai botnet threatened the Internet last year with record-setting distributed denial-of-service (DDoS) attacks against the popular DNS provider Dyn.
How the Hajime IoT Botnet Works
Hajime botnet works much like Mirai by spreading itself via unsecured IoT devices that have open Telnet ports and uses default passwords and also uses the same list of username and password combinations that Mirai is programmed to use.
However, the interesting part of Hajime botnet is that, unlike Mirai, once Hajime infects an IoT devices, it secures the devices by blocking access to four ports (23, 7547, 5555, and 5358) known to be the most widely used vectors for infecting IoT devices, making Mirai or other threats out of their bay.
Hajime also uses a decentralized peer-to-peer network (instead of command-and-control server) to issue updates to infected devices, making it more difficult for ISPs and Internet providers to take down the botnet.
One of the most interesting things about Hajime is the botnet also displays a cryptographically signed message every 10 minutes or so on infected device terminals, describing its creators as "just a white hat, securing some systems."
Unlike Mirai and other IoT botnets, Hajime lacks DDoS capabilities and other hacking skills except for the propagation code that lets one infected IoT device search for other vulnerable devices and infects them.
But What if…?
What's not known is: What the Hajime Botnet is for? or Who is behind it?
"The most intriguing thing about Hajime is its purpose," says Kaspersky security researchers. "While the botnet is getting bigger and bigger, partly due to new exploitation modules, its purpose remains unknown. We haven’t seen it being used in any type of attack or malicious activity, adding that "its real purpose remains unknown."
Also, the researchers believe that this might not happen, because Hajime botnet takes steps to hide its running processes and files on the file system, making the detection of infected systems more difficult.
So far, the purpose behind building this botnet is not entirely clear, but all signs yet point to a possible white-hat hacker, who is on his/her mission to secure open and vulnerable systems over the Internet.
However, the most concerning issue of all — Is there any guarantee that the Hajime author will not add attack capabilities to the worm to use the hijacked devices for malicious purposes?
Maybe today the Hajime author is in the mission to secure the world, but tomorrow, when he would realize he could make money online by renting his/her botnet to others, he could be another Adam Mudd.
Mudd, a 19-year-old teenager, has recently been sentenced to 2 years in prison for creating and running a DDoS-for-hire service called 'Titanium Stresser' that made more than 1.7 million victims of DDoS attacks since 2013.
Secondly, What if the well-intentioned botnet is hijacked by some malicious actor?
If this happens, the vigilant IoT botnet could be used for malicious purposes, such as conducting DDoS attacks against online sites and services, spreading malware, or instantly bricking the infected devices at one click.
Radware researchers also believe that the flexible and extensible nature of the Hajime botnet can be used for malicious purposes, like those mentioned above and conducting real-time mass surveillance from Internet-connected webcams, according to a new threat advisory published Wednesday by Radware.
Last but not the least: Do we seriously need some vigilante hackers to protect our devices and network?
This solution could be temporary, trust me. For example, the latest Hajime botnet is nothing but a band-aid.
Since Hajime has no persistence mechanism, as soon as the infected device is rebooted, it goes back to its previously unsecured state, with default passwords and the Telnet port open to the world.
How to Protect your IoT devices?
The only true solution is You — Instead of just sitting over there, doing nothing and waiting for some vigilante hackers to do miracles, you can protect your IoT devices in a way Hajime or any well-intentioned botnet can't do.
So go and update the firmware of your devices, change their default passwords, put them behind a firewall, and if any device is by default vulnerable and cannot be updated, throw it and buy a new one.
Just keep in mind: Once a single IoT of yours gets compromised, your whole network falls under risk of getting compromised and so all your devices which are connected to that network.
The Hajime Botnet continues to grow and implements a new attack technique
27.4.2017 securityaffairs BotNet
The mysterious Hajime Botnet continues to grow and reached 300,000 IoT Devices, the author also implemented a new attack method.
Recently experts from Symantec spotted a new IoT botnet dubbed Hajime that is spreading quickly in the last months, mostly in Brazil and Iran.
The Hajime malware was first spotted in October 2016, it implements the same mechanism used by the Mirai botnet to spread itself. The threat targets unsecured IoT devices with open Telnet ports and still used default passwords. Researchers discovered Hajime uses the same list of username and password combinations that Mirai, plus two more.
Unlike Mirai, Hajime doesn’t use C&C servers, instead, it implements a peer-to-peer network.
“There isn’t a single C&C server address, instead the controller pushes command modules to the peer network and the message propagates to all the peers over time. This is typically considered a more robust design as it makes takedowns more difficult.” reads the analysis published by Symantec.
Hajime is more sophisticated than Mirai, it implements more mechanisms to hide its activity and running processes. The threat has a modular structure allowing operators to add new capabilities on the fly.
The analysis of the Hajime reveals that it doesn’t implement denial of service (DDoS) capabilities or any other attacking code. Symantec researchers noticed that Hajime fetches a statement from its controller and displays it on the terminal every 10 minutes. The message is:
Just a white hat, securing some systems. Important messages will be signed like this!
Hajime Author.
Contact CLOSED
Stay sharp!
The message is digitally signed and the worm will only accept messages signed by a hardcoded key. Once infected a system, the worm blocks access to ports 23, 7547, 5555, and 5358, in order to prevent attacks from other IoT threats, including Mirai.
Experts believe Hajime could be the work of a cyber vigilante, in the past we have observed similar codes like the Linux.Wifatch discovered by Symantec in October 2015.
According to a research conducted by a new research conducted by Kaspersky Lab, the Hajime botnet continues to grow, it has already recruited up to 300,000 IoT devices.
The author of the Hajime is continuing to update the code, researchers at Kaspersky observed that he made recent changes in the attack module introducing the TR-069 exploitation. Currently, the bot implements three different attack methods: TR-069 exploitation, Telnet default password attack, and Arris cable modem password of the day attack.
“Technical Report 069 is a standard published by the Broadband Forum, which is an industry organization defining standards used to manage broadband networks. Many ISPs and device manufacturers are members of the Broadband Forum. TR-069 allows ISPs to manage modems remotely. TCP port 7547 has been assigned to this protocol, but some devices appear to use port 5555 instead.” reads the analysis published by Kaspersky.
“The TR-069 NewNTPServer feature can be used to execute arbitrary commands on vulnerable devices.”
The TR-069 attack was implemented last year when hackers compromised more than 900.000 routers of the from Deutsche Telekom.
Experts at Kaspersky discovered that the Hajime botnet targets any device on the Internet with the exception of specific networks and devices. The author of the threat recently improved the detection logic of the malicious code.
“Once the attack successfully passes the authentication stage, the first 52 bytes of the victim’s echo binary are read. The first 20 bytes, which is the ELF header, hold information about the architecture, operating system and other fields. The victim’s echo ELF header is then compared against a predefined array, containing the Hajime stub downloader binaries for different architectures.” states Kaspersky. “This way the correct Hajime-downloader binary that works on the victim’s machine, can be uploaded from the attacker (which is actually the infected device that started the attack).”
A honeypot set up by Kaspersky registered during a 24-hour period 2,593 successful telnet Hajime attacks. 2,540 of them originated from unique IP addresses, 949 of the hosts provided a payload, and 528 of them had an active web server running at port 80/tcp.
Most attacks were powered by compromised devices located in Vietnam (20.04%), Taiwan (12.87%) and Brazil (8.94%).

“The most intriguing thing about Hajime is its purpose. While the botnet is getting bigger and bigger, partly due to new exploitation modules, its purpose remains unknown. We haven’t seen it being used in any type of attack or malicious activity. Nevertheless, we advise owners of IoT devices to change the password of their devices to one that’s difficult to brute force and to update the firmware if possible,” concluded Kaspersky.
Mysterious Hajime Botnet Grows to 300,000 IoT Devices: Kaspersky
26.4.2017 securityweek BotNet
Hajime, a piece of Internet of Things (IoT) malware that emerged in October 2016, has already ensnared roughly 300,000 devices in a botnet, Kaspersky Lab researchers say.
The malware emerged around the same time the infamous Mirai botnet started making the rounds, and is targeting the same devices that this threat does, but without using them to launch distributed denial of service (DDoS) attacks. Instead, it simply closes some ports to keep the infected devices away from Mirai and similar threats.
Called Hajime to keep the naming scheme in line with Mirai (they mean “beginning” and “future” in Japanese, respectively), the worm managed to build a peer-to-peer (P2P) botnet, but researchers aren’t sure about its purpose right now. Symantec said recently that a white hat hacker could have created the malware, but suggested that the botnet could be easily repurposed for nefarious operations.
What’s certain, however, is that Hajime’s author continues to update the code, as recently made changes were seen in the attack module. At the moment, the worm supports three different attack methods: TR-069 exploitation, Telnet default password attack, and Arris cable modem password of the day attack. The TR-069 exploit was implemented only recently, Kaspersky reveals.
TR-069 (Technical Report 069), a standard published by the Broadband Forum, is used by ISPs to manage modems remotely via TCP port 7547 (some devices use port 5555). By abusing the TR-069 NewNTPServer feature, attackers can execute arbitrary commands on vulnerable devices. Late last year, the TR-069 attack was used to crash nearly 1 million modems from Deutsche Telekom.
According to Kaspersky, Hajime attacks any device on the Internet with the exception of several networks, and its author recently improved the architecture detection logic. Thus, after passing the authentication stage, the malware reads the first 52 bytes of the victim’s echo binary (information about architecture and operating system is in the first 20 bytes), and then compares the echo ELF header against a predefined array, so as to fetch the correct Hajime-downloader binary.
On the other hand, despite Hajime being able to attack any device, the authors focused on some specific brands/devices, as the worm uses only specific username-password combinations to brute-force its way into vulnerable devices. The threat uses one combination or the other based on words contained in the welcome message when opening a telnet session.
Instead of the telnet passwords, the malware uses a specially crafted password of the day when it encounters Arris cable modems. Although the ARRIS password of the day is a remote backdoor known since 2009, many ISPs don’t bother changing the default seed at all. After successfully compromising these devices, Hajime gains access to a remote shell and can execute commands.
During a 24-hour period, Kaspersky’s honeypot registered 2,593 successful telnet Hajime attacks. 2,540 came from unique IP addresses, 949 of the hosts provided a payload, and 528 of them had an active web server running at port 80/tcp. Most attacking devices (which were themselves victims to Hajime) were located in Vietnam (20.04%), Taiwan (12.87%) and Brazil (8.94%).
Looking at infected peers as DHT seeders, the researchers discovered 15,888 unique infected boxes, most located in Iran (14.38%), Vietnam (11.45%) and Brazil (6.94%). When looking at infected peers as DHT leechers, however, the researchers found 297,499 unique infected hosts, all of which were requesting Hajime config. Iran (19.65%), Brazil (8.80%), and Vietnam (7.87%) are affected the most.
“The most intriguing thing about Hajime is its purpose. While the botnet is getting bigger and bigger, partly due to new exploitation modules, its purpose remains unknown. We haven’t seen it being used in any type of attack or malicious activity. Nevertheless, we advise owners of IoT devices to change the password of their devices to one that’s difficult to brute force and to update the firmware if possible,” Kaspersky notes.