
The Floki bot is rapidly evolving, the authors implemented new features, including sophisticated anti-detection techniques and the use of the Tor network.
Introduction List Kategorie Subcategory 0 1 2 3 4 5
Floki Bot rapidly evolves and targets also PoS data
8.12.2016 securityaffairs BotNet
Cisco Talos and Flashpoint have teamed up to analyze the Floki Bot, a Zeus-based banking Trojan that is rapidly evolving in the cybercrime underground.
Security researchers from Cisco Talos and Flashpoint have conducted an investigation of the Floki Bot in a joint effort.
The Floki bot is a banking Trojan based on Zeus that has been sold on cybercrime underground since September 2016. The malware was developed starting from the Zeus source code that was leaked in 2011, it is offered for $1,000 worth of bitcoins. However, researchers determined that the malware includes some new capabilities, including anti-detection features.
“Floki Bot is a new malware variant that has recently been offered for sale on various darknet markets. It is based on the same codebase that was used by the infamous Zeus trojan, the source code of which was leaked in 2011.” reads the analysis published by the Talos Team. “Rather than simply copying the features that were present within the Zeus trojan “as-is”, Floki Bot claims to feature several new capabilities making it an attractive tool for criminals.”
The Floki bot is rapidly evolving, the authors implemented new features, including sophisticated anti-detection techniques and the use of the Tor network.
The malware researchers at Talos discovered a new source code that allows the threat to use the Tor network, but the feature seems to be still not active.
“During our analysis of Floki Bot, Talos identified modifications that had been made to the dropper mechanism present in the leaked Zeus source code in an attempt to make Floki Bot more difficult to detect. Talos also observed the introduction of new code that allows Floki Bot to make use of the Tor network.” continues the analysis.
The experts from Flashpoint speculate that the Floki Bot has a Brazilian origin, the threat actor behind the malware is currently using the “flokibot” moniker and communicates in Portuguese. It targets Brazilian IPs and domains and targeted systems have default language set to Portuguese.
The “flokibot” actor act as a sort of “connector,” he is present in several major crime communities across the world, particularly Russian and English-speaking dark web communities.
Even the analysis of its activity in the underground suggests that the actor is located in Brazil, it is most active on underground forums during hours within Brazil’s UTC -3 timezone.
“Beyond the unique intelligence obtained by Flashpoint analysts and the campaign targeting Brazil, flokibot, a Portuguese-speaking member of English and Russian-language communities, was identified by several markers as very likely to be Brazilian” states the analysis published by FlashPoint.
• Use of the Portuguese language within the actor’s communications
• Targeting computers with the default language set to Portuguese
• Targeting Brazilian domains or IP ranges
• Targeting computers with the default timezone set to Brazil UTC -03:00
• Other unique intelligence obtained by Flashpoint analysts
The presence of flokibot in several major underground communities suggests the gang import knowledge and tools into the Brazilian cybercrime underground.
“While Brazilian cybercriminals are not typically as technically sophisticated as their Russian counterparts, they will often solicit new forms of malware (to include point of sale [PoS] ransomware and banking Trojans), or offer their own services,” Vitali Kremez, senior intelligence analyst at Flashpoint, said in a blog post. “It appears that a presence on Russian [Deep and Dark Web] communities may be a likely factor in flokibot’s progression.”
Now it’s Christmas time, the best period for cyber criminals that attempt to steal credit card data, in this period we observe the proliferation of PoS malware used for this purpose.
Researchers discovered that the new strain of Floki Bot also includes the code to scrape payment card data from the memory PoS systems.
“One way in which flokibot’s technical competency has evolved is in the actor’s use of hooking methods to capture track data from PoS devices. While the malware originates from the well-known ZeuS 2.0.8.9 source code, flokibot adds this hooking method to grab track data from memory thereby extending the malware operations beyond regular banking trojan functionality making it more potent and versatile.” states FlashPoint.
A campaign analyzed by Flashpoint revealed that 225 Floki bots have collected a total of 1,375 card dumps.
Researchers have observed a spike in the number of attacks based on Floki Bot against U.S., Canadian and Brazilian banks, and insurance firms.
Both Talos and Flashpoint will continue monitoring the threat.
Experts from CloudFlare spotted a new dangerous botnet
4.12.2016 securityaffairs BotNet
Security experts from CloudFlare observed a new botnet that emerged in the wild and it could be dangerous as its predecessor Mirai.
Which is the most dreaded botnet in the current threat landscape? The Mirai botnet of course, it was used by threat actors in the wild to power massive DDoS attack, such as the one that hit the Dyn DNS service.
Now, security experts observed a new botnet is emerging in the wild and it could be dangerous as its predecessor Mirai.
The botnet was first spotted on November 23 by researchers at the content delivery network CloudFlare.
The DDoS attacks lasted 8.5 hours, attackers launched the offensive for six days at roughly the same time. The attacks were peaking at 400Gbps and hitting 320Gbps for hours on end.
“On November 23, the day before US Thanksgiving, our systems detected and mitigated an attack that peaked at 172Mpps and 400Gbps.” states the report published CloudFlare. “The attack started at 1830 UTC and lasted non-stop for almost exactly 8.5 hours stopping at 0300 UTC. It felt as if an attacker ‘worked’ a day and then went home.”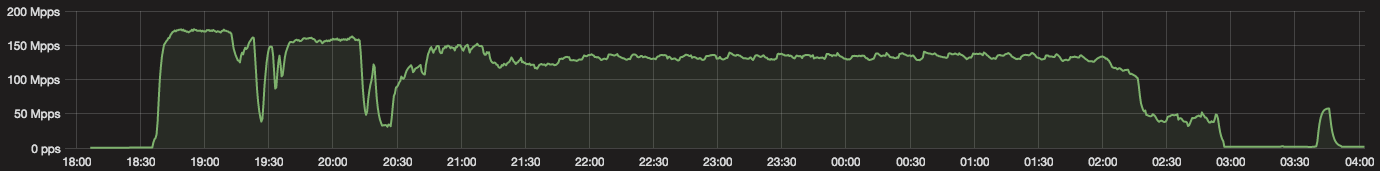
The new string of cyber attacks are not powerful such as the ones launched through the Mirai malware, but anyway, they reached a significant volume.
Researchers discovered that the attacks are not powered from the Mirai botnet because they are launched from a differed software and are very large Layer3 and Layer4 DDoS attacks.
The researchers observed that the attacks were concentrated in a small number of locations mostly on the US west coast.
CloudFlare did not disclose further details of the DDoS attacks, it is not clear if the botnet is composed of IoT devices such as Mirai.
The new botnet will likely continue to grow and most experts fear it could be combined with other malicious infrastructure powering unprecedented DDoS attacks.
Hackers offer a huge Mirai botnet as a DDoS-for-hire service
28.11.2016 securityaffairs BotNet
The hackers Popopret and BestBuy are offering a DDoS-for-hire service leveraging a Mirai botnet composed of around 400,000 compromised devices.
We have written a lot about the Mirai botnet after the clamorous attacks against the Dyn DNS service and the OVH hosting, it is a dangerous threat that was designed to target IoT devices that could be used to power massive DDoS attacks.
The Mirai botnet is becoming very popular in the criminal underground, so it is natural that crooks started offering it as a DDoS hire service to other cyber criminals.
The hackers Popopret and BestBuy are offering a DDoS-for-hire service leveraging a Mirai botnet composed of around 400,000 compromised devices.
We recognize BestBuy as the author of the GovRAT malware that offered the source code of his threat, including a code-signing digital certificate, for nearly 4.5 Bitcoin on the TheRealDeal black market.
Popopret was linked by experts from threat intelligence firm InfoArmor to Bestbuy, the researchers pointed out that Bestbuy started using also the moniker “Popopret.”
The RAT was delivered through spear-phishing and drive-by downloads attacks. Among the victims, government and military organizations. Stolen data from military organizations were also offered for sale on the black market.
Catalin Cimpanu from Bleeping Computer published an interesting post that confirms that the two monikers Popopret and BestBuy (it is not clear if they are the same person) are renting access to a Mirai botnet composed of more than 400,000 infected bots, the largest one till date offered for rent.
“Two hackers are renting access to a massive Mirai botnet, which they claim has more than 400,000 infected bots, ready to carry out DDoS attacks at anyone’s behest.” wrote Companu.
This botnet offered by Popapret and BestBuy represents an evolution of the original Mirai botnet because it included new features like SSH supported brute-force attacks to exploit zero-day vulnerabilities.
The experts at the Bleepingcomputer highlighted the fact that this Mirai botnet isn’t cheap because Popopret requests its customers to rent it for a minimum period of two weeks.
“Price is determined by amount of bots (more bots more money), attack duration (longer = more money), and cooldown time (longer = discount),” Popopret told Bleeping Computer.
Customers could get a discount if they rent the Mirai botnet for long DDoS cooldown time, which is the time between two consecutive DDoS attacks.
“DDoS botnets use cooldown times to avoid maxing out connections, filling and wasting bandwidth, but also preventing devices from pinging out and disconnecting during prolonged attack waves.” reported BleepingComputer.
Popopret provided an example of price for this Mirai Botnet, 50,000 bots with attack duration of 3600 secs (1 hour) and 5-10 minute cooldown time goes for roughly 3-4k per 2 weeks. The experts highlighted that the service is very expensive.
The botnet is controlled through a console hidden on the Tor network that could be accessed via Telnet.

Source: Bleeping Computer
The hackers Popopret and BestBuy declined to run a test in order to show real capabilities of their botnet.
You can monitor the Mirai botnet with the following tracker.
https://intel.malwaretech.com/botnet/mirai
Someone is Using Mirai Botnet to Shut Down Internet for an Entire Country
4.11.2016 thehackernews BotNet
Someone is trying to take down the whole Internet of a country by launching massive distributed denial-of-service (DDoS) attacks using a botnet of insecure IoT devices infected by the Mirai malware.
It all started early October when a cybercriminal publically released the source code of Mirai – a piece of nasty IoT malware designed to scan for insecure IoT devices and enslaves them into a botnet network, which is then used to launch DDoS attacks.
Just two weeks ago, the Mirai IoT Botnet caused vast internet outage by launching massive DDoS attacks against DNS provider Dyn, and later it turns out that just 100,000 infected-IoT devices participated in the attacks.
Experts believe that the future DDoS attack could reach 10 Tbps, which is enough to take down the whole Internet in any nation state.
One such incident is happening from past one week where hackers are trying to take down the entire Internet of Liberia, a small African country, using another Mirai IoT botnet known as Botnet 14.
Mirai botnet
Security researcher Kevin Beaumont has noticed that Botnet 14 has begun launching DDoS attacks against the networks of "Lonestar Cell MTN ", the telecommunication company which provides the Internet to entire Liberia via a single entry point from undersea fiber cable.
"From monitoring, we can see websites hosted in country going offline during the attacks — Additionally, a source in country at a Telco has confirmed to a journalist they are seeing intermittent internet connectivity, at times which directly match the attack," Beaumont said in a blog post published today.
According to Beaumont, transit providers confirm that the attacks were over 500 Gbps in size, but last for a short period. This volume of traffic indicates that the "Shadows Kill" Botnet, as the researcher called it, is "owned by the actor which attacked Dyn."
Why Taking Down Liberia's Internet Is easy?
ace-submarine-undersea-cables
Over a decade of civil war in Liberia destroyed the country's telecommunications infrastructure, and at that time a very small portion of citizens in Liberia had access to the internet via satellite communication.
However, some progress were made later in 2011 when a 17,000 km Africa Coast to Europe (ACE) submarine fiber-optic cable was deployed from France to Cape Town, via the west coast of Africa.
The ACE fiber cable, at depths close to 6,000 meters below sea level, eventually provides broadband connectivity to more 23 countries in Europe and Africa.
What's shocking? The total capacity of this cable is just 5.12 Tbps, which is shared between all of the 23 countries.
Since massive DDoS attack against DynDNS used a Mirai botnet of just 100,000 hacked IoT devices to close down the Internet for millions of users, one can imagine the capability of more than 1 Million hacked IoT devices, which is currently in control of the Mirai malware and enough to severely impact systems in any nation state.
This is extremely worrying because, with this capacity, not just Liberia, an attacker could disrupt the Internet services in all 23 countries in Europe and Africa, which relies on the ACE fiber cable for their internet connectivity.
The root cause? More insecure, vulnerable IoT devices, more Mirai bots.
So, in order to protect yourself, you need to be more vigilant about the security of your smart devices because they are dumber than one can ever be.
In our previous article, we provided some basic, rather effective, solutions, which would help you protect your smart devices from becoming part of the Mirai botnet. You can also check also yourself if your IoT device is vulnerable to Mirai malware. Head on to this article.
Shadows Kill Mirai Botnet caused an Internet outage in Liberia, what is the next one?
4.11.2016 securityaffairs BotNet
Mirai botnet was used to power a massive DDoS attack against Liberia causing the Internet outage in the entire country with financially devastating results.
Mirai is the malware that a few weeks ago caused a massive Internet outage in the US. Mirai was first spotted this summer by the security expert MalwareMustDie, now media reported the use of the dreaded botnet against Liberia. with financially devastating results.
The financial repercussions of the massive DDoS attack on the country are devastating.
The massive DDoS attacks began a few days ago impacting some Liberian internet providers as explained the security researcher Kevin Beaumont.

Beaumont credited the Mirai botnet for the attacks that hit the African country, he called this botnet #14 “Shadows Kill”, based on the message they sent.
Segui
Mirai Attacks @MiraiAttacks
Botnet #14 - DNS flood for 1 seconds
[Targets]
kevin.lies.in.fear (8.8.8.8/32)
00:11 - 3 Nov 2016
7 7 Retweet 10 10 Mi piace
“Over the past week we’ve seen continued short duration attacks on infrastructure in the nation of Liberia. Liberia has one internet cable, installed in 2011, which provides a single point of failure for internet access. From monitoring we can see websites hosted in country going offline during the attacks — additionally, a source in country at a Telco has confirmed to a journalist they are seeing intermittent internet connectivity, at times which directly match the attack. The attacks are extremely worrying because they suggest a Mirai operator who has enough capacity to seriously impact systems in a nation state.” Beaumont wrote in a blog post.
The Botnet #14 was able to generate a volume of traffic greater than 500 Gbps, enough to cause a massive outage in a country like Liberia.
“From monitoring, we can see websites hosted in country going offline during the attacks,” Beaumont added.
Unfortunately, it is becoming quite easy to create or rent a botnet powered by the Mirai malware due to the availability of its source code leaked online by the alleged author.
According to Flashpoint who scanned the Internet with the Shodan search engine for flawed IoT devices more than 500,000 vulnerable devices are in the wild. The countries with the highest number of vulnerable devices are Vietnam (80,000), Brazil (62,000) and Turkey (40,000).

Large-scale DDoS attacks continue to represent a serious threat for web services across the world, and IoT devices represent a privileged attack vector due to the lack of security by design. IoT manufacturers are encouraged to seriously consider the approach at the security of their products.
I reached MalwareMustDie for a comment on the real abilities of the Mirai Botnet.
Q: Which are the capabilities of the Mirai Botnet?
A: Mirai botnet can make big damage as per several “demonstration” they did, included Liberia attack. The threat is seriously powerful, as per I firstly mentioned in the Security Affair interview. The way to stop it, are, either we push the effort to arrest ‘skiddes‘ who related to this botnet, and more strict in rule/policy for DDoS abuses, or, put down be more aggressive to take down infected IoT devices. Seriously, time is critical yet many ppl still not acting faster, if we let this happen with the current pace, in this Christmas or new year some countries and services can be shut down too … and they can do that.
Q: Is it possible to use Mirai to shut down a country like the UK or France?
A: If they know which point to attack, YES. They caused a major Internet outage in the United States for some hours, and the US have the strongest internet backbone in this planet.
It is my personal opinion that who released the code online was trying to rapidly increase the size of Mirai botnet. More smoking guns make harder the attribution and this could help crooks to keep lower their profile and nation-state hackers make impossible the attribution of the attacks even against a foreign country.
It is clear that someone is using the Botnet #14 to test a large scale attack probably against some Government.
We have no time, we need a new approach to cyber security, IoT device need security by design.
New IoT Botnet Malware Discovered; Infecting More Devices Worldwide
1.11.2016 thehackernews BotNet
The whole world is still dealing with the Mirai IoT Botnet that caused vast internet outage last Friday by launching massive distributed denial of service (DDoS) attacks against the DNS provider Dyn, and researchers have found another nasty IoT botnet.
Security researchers at MalwareMustDie have discovered a new malware family designed to turn Linux-based insecure Internet of Things (IoT) devices into a botnet to carry out massive DDoS attacks.
Dubbed Linux/IRCTelnet, the nasty malware is written in C++ and, just like Mirai malware, relies on default hard-coded passwords in an effort to infect vulnerable Linux-based IoT devices.
The IRCTelnet malware works by brute-forcing a device's Telnet ports, infecting the device's operating system, and then adding it to a botnet network which is controlled through IRC (Internet Relay Chat) – an application layer protocol that enables communication in the form of text.
So, every infected bot (IoT device) connects to a malicious IRC channel and reads commands sent from a command-and-control server.
The concept of using IRC for managing the bots, according to the researchers, is borrowed from the Kaiten malware. The source code used to build the IRCTelnet botnet malware is based on the earlier Aidra botnet.
The malware uses the "leaked" vulnerable IoT device's login credential from the Mirai botnet in order to brute force exposed Telnet ports to the Internet.
The IRCTelnet malware infects insecure devices running a Linux Kernel version 2.6.32 or above and capable of launching DDoS attacks with spoofed IPv4 and IPv6 addresses, though the scanner is programmed only to find and brute-force Telnet via IPv4.
"The botnet is having DoS attack mechanism like UDP flood, TCP flood, along with other attack methods, in both IPv4 and IPv6 protocol, with extra IP spoof option in IPv4 or IPv6 too," the researchers note in a blog post.
While analyzing the malware's source code, researchers found hard-coded Italian language messages in the user's communication interface, which suggests that the author of the IRCTelnet malware could be Italian.
The security firm found around 3,400 bots infected by the IRCTelnet malware and said that this nasty malware is capable of raising almost 3,500 bot clients within only 5 days.
The initial scans that distributed the IRCTelnet malware came from IP addresses located in Turkey, Moldova, and the Philippines.
Building a legendary, massive botnet that leverages recently vulnerable threat landscape is inviting more incidents like the recent DDoS attack against Dyn that rendered major websites inaccessible, and record-breaking DDoS attack against French Internet service and hosting provider OVH.
Hacking back the Mirai botnet, technical and legal issues
30.10.2016 securityaffairs BotNet
Security researchers have found vulnerabilities in the source code of the Mirai botnet and devised a method to hack back it.
The Mirai botnet, this name is familiar to security experts due to the massive DDoS attack that it powered against the Dyn DNS service a few days ago.
The Mirai malware was first spotted by the researcher MalwareMustDie that confirmed it was designed to hack into poorly configured and vulnerable IoT devices. Its source code was leaked on the popular criminal hacker forum Hackforum by a user with moniker “Anna-senpai” giving the opportunity to anyone to compile and customize its own version of the threat.
Experts who reviewed the code have discovered a weakness that could be exploited to shut down the botnet stopping it from flooding the targets with HTTP requests, this means that it is possible to hack back the threat. The experts from Invincea discovered three vulnerabilities in the Mirai code, one of them, a stack buffer overflow, could be exploited to halt the DDoS attack powered by the botnet. The buffer overflow vulnerability affects the way Mirai parses responses from HTTP packets.
“Perhaps the most significant finding is a stack buffer overflow vulnerability in the HTTP flood attack code. When exploited it will cause a segmentation fault (i.e. SIGSEV) to occur, crash the process, and therefore terminate the attack from that bot. The vulnerable code has to do with how Mirai processes the HTTP location header that may be part of the HTTP response sent from an HTTP flood request.” reported the analysis published by the security firm Invincea.

The researchers highlighted that their attack would not have helped in the DNS-based DDoS attack against provider Dyn, but it would halt the Layer 7 attack capabilities of the Mirai botnet implemented in the coded leaked online.
The researchers at Invincea successfully tested a proof-of-concept exploit in a virtual environment setting up a debug instance of the Mirai bot, a command and control server and a target machine.
“This simple “exploit” is an example of active defense against an IoT botnet that could be used by any DDoS mitigation service to defend against a Mirai-based HTTP flood attack in real-time. While it can’t be used to remove the bot from the IoT device, it can be used to halt the attack originating from that particular device. Unfortunately, it’s specific to the HTTP flood attack, so it would not help mitigate the recent DNS-based DDoS attack that rendered many websites inaccessible.” explained the Scott Tenaglia, Research Director in the cyber capabilities team at Invincea Labs.
Tenaglia remarked that the method proposed by the company doesn’t clean the compromised devices, instead it could be effective against HTTP flooding powered by the Mirai Botnet.
The method proposed by the researchers is a form of active defense that has important legal implications because anyway, who is defending its system from the attack power a response attack against the attacker’s infrastructure.
Hacking back is illegal under the Computer Fraud and Abuse Act.
Hacking a bot means to make an unauthorized access to a computer system and such kind of operations have to be authorized by a court order.
Invincea has made an excellent work and isn’t suggesting the hacking back, but limited its analysis on the technical aspect of the Mirai botnet and its vulnerabilities.
“It’s in the gray space of active defense,” Tenaglia told to ThreatPost. “In the defense world, this is a hotly contested issue. Say if your IoT is already compromised and bad code is already running, if I do something to the bad guy’s code, am I breaking law?”
“I would never comment on the legality of this,” Tenaglia said. “I think this gives us another point to discuss with regard to active defense. Is this something we think is ok? I don’t think it would hurt the system; it might help it. If a bot is degrading performance of the Internet connection because of the packets it’s sending out, and if this attack kills the process and the connection gets better, have we helped you? That’s why this is a gray area.”
Hackers offered an loT botnet for $7,500. The recent attack may be just a test
24.10.2016 securityaffairs BotNet
The security firm RSA revealed to have discovered in early October, hackers advertising access to a huge IoT botnet on an underground criminal forum.
Last week, a massive DDoS attack against the Dyn DNS service, one of the most authoritative domain name system (DNS), caused an extended Internet outage. A large portion of internet users was not able to reach most important web services, many websites including Twitter, GitHub, PayPal, Amazon, Reddit, Netflix, and Spotify were down for netizens in the US.
The Dyn DNS Service was flooded by a devastating wave of requests originated by million of compromised IoT devices. The Dyn company reported a huge army of hijacked Internet of Things devices has been abused by attackers to power the massive DDoS attack.
The security intelligence firm Flashpoint published an interesting post on the massive DDoS in which confirm that its experts have observed the Mirai bots driving the attack against DynDNS.
“Flashpoint has confirmed that some of the infrastructure responsible for the distributed denial-of-service (DDoS) attacks against Dyn DNS were botnets compromised by Mirai malware. Mirai botnets were previously used in DDoS attacks against security researcher Brian Krebs’ blog “Krebs On Security” and French internet service and hosting provider OVH.” reads the analysis published by Flashpoint “Mirai malware targets Internet of Things (IoT) devices like routers, digital video records (DVRs), and webcams/security cameras, enslaving vast numbers of these devices into a botnet, which is then used to conduct DDoS attacks. “
Below the Key Findings of the report published by Flashpoint
Flashpoint has confirmed that some of the infrastructure responsible for the distributed denial-of-service (DDoS) attacks against Dyn DNS were botnets compromised by Mirai malware.
Mirai botnets were previously used in DDoS attacks against the “Krebs On Security” blog and OVH.
As of 1730 EST, the attacks against Dyn DNS are still ongoing. Flashpoint is coordinating with multiple vendors and law enforcement to track the infected devices that constitute the botnet being used to conduct these attacks.
Unfortunately, the situation could be worse because hackers are selling access to a huge botnet composed of compromised Internet of Things (IoT) devices.
The security firm RSA revealed to have discovered in early October, hackers advertising access to a huge IoT botnet on an underground criminal forum.
“This is the first time we’ve seen an IoT botnet up for rent or sale, especially one boasting that amount of firepower. It’s definitely a worrying trend seeing the DDoS capabilities grow,” Daniel Cohen, head of the RSA’s FraudAction business unit, told Forbes.
According to RSA the hackers advertised an IoT botnet that is able to power DDoS attack with a 1 Tbps of traffic, the same volume of traffic that flooded the French hosting provider OVH. It is not clear if the botnet was composed of devices infected by the Mirai malware.
The hackers were offering a botnet composed of 50,000 devices for $4,600, meanwhile 100,000 bots the price is $7,500.

Cohen clarified that RSA has no evidence that the botnet is linked to infrastructure that hit the Dyn DNS service on Friday.
“Hackers have long sold access to botnets, though haven’t explicitly advertised their use of IoT devices like connected cameras, fridges and kettles. The infamous LizardSquad amassed sizeable botnets for its LizardStresser “booter” – a DDoS weapon for hire – but it largely compromised vulnerable routers.” reported FORBES.
IoT vendors are warned of future risks of cyber attacks, the Chinese manufacturer of surveillance and home video devices targeted by the Mirai botnet, Xiongmai Technology (XM), has pushed out parched to avoid the hacking of its devices.
However, any device running firmware released before September 2015 that is still using the default username and password (well known in the hacker community) remains vulnerable to attacks that use the credentials to access the devices via Telnet.
Attacks like the one powered by the IoT botnet on Friday are difficult to mitigate, anyway, the adoption of a secondary, back-up DNS provider could make hard for the attacker to shut down the web service.
Other countermeasures are listed in the FORBES blog post.
The Mirai botnet is targeting also Sierra Wireless cellular data gear products
16.10.2016 securityaffairs BotNet
Sierra Wireless is warning its customers to change factory credentials of its AireLink gateway communications products due to Mirai attacks.
Sierra Wireless is warning its customers to change factory credentials of its AireLink gateway communications product.
The company is aware of a significant number of infections caused by the Mirai malware, a threat specifically designed to compromise poorly configured IoT devices.
The malware was first spotted in August by MalwareMustDie have analyzed samples of this new ELF trojan backdoor. The name of the malware is the same of the binary,”mirai.*,” and according to the experts, several attacks have been detected in the wild.
The Mirai malware scans the web searching for connected devices such as DVRs and IP-enabled cameras that use default or hard-coded credentials.

Back to the to the Sierra Wireless alert, the company is warning its customers that of Mirai attacks against the AirLink Cellular Gateway devices (LS300, GX400, GX/ES440, GX/ES450 and RV50).
“Sierra Wireless has confirmed reports of the ‘Mirai’ malware infecting AirLink gateways that are using the default ACEmanager password and are reachable from the public internet. The malware is able to gain access to the gateway by logging into ACEmanager with the default password and using the firmware update function to download and run a copy of itself,” Sierra Wireless wrote in a security bulletin . “Devices attached to the gateway’s local area network may also be vulnerable to infection by the Mirai malware.”
The Mirai botnet was involved in a number of severe attacks, according to the experts it powered DDoS attacks against the website of the popular investigator Brian Krebs and the OVH hosting provider that reached 1Tbps.
Unfortunately, the number of malware specifically designed to infect IoT systems continue to increase. This week, Security Affairs published in exclusive the discovery of a new threat, dubbed NyaDrop, made by experts at MalwareMustDie.
“There is evidence that ‘Internet of Things’-type devices have been infected with the Linux malware Mirai, which attackers used in the recent DDoS attacks against the web site Krebs on Security,” reads a security bulletin published by the US ICS-CERT.
Inside the DDoS attacks powered by large IoT botnets
12.10.2016 securityaffairs BotNet
Cloudflare firm has published a report that analyzes two recent attacks that were powered by large IoT botnets based on the Mirai Threat.
The IoT botnets represent one the most dangerous threats in the security landscape, recently we have assisted to cyber attacks powered by these infrastructures that reached magnitude never seen before.
The recent DDoS attacks powered by IoT botnets hit target websites with HTTP traffic, in some cases reaching more than one million requests per second. These IoT botnets leveraged on the Mirai malware specifically designed to scan the Internet for vulnerable IoT devices.
Cloudflare firm has published a report that analyzes two recent attacks that represent a sort of milestone in the DDoS attacks because the attackers switched from SYN flood- and ACK flood-based attacks at Layer 3, to HTTP-based attacks at Layer 7.
The company observed the DDoS attacks through their automatic DDoS mitigation systems examining specific features of the attacks such as the number of HTTP requests per second.
Cloudflare confirmed that two attacks peaked at more than 1 million HTTP requests per second. In one case the DDoS attack involved more than 52,000 IP addresses peaking at 1.75 million requests per second.

“This attack continued for 15 minutes. Multiple recent attacks had >1 Mrps and lasted for minutes.” states the report published by Cloudflare.
“This particular attack peaked at 1.75 Mrps. It was composed of short HTTP requests (around 121 bytes per request), without anything unusual in the HTTP headers. The requests had a fixed
Cookie
header. We counted 52,467 unique IP addresses taking part in this attack.”
According to Cloudflare the attack was powered through hundreds of autonomous systems networks, the biggest sources in the Ukraine (AS15895) and Vietnam (AS45899).
Cloudflare reported also data related to a second attack that peaked at 360 Gbps and leveraged on longer HTTP requests.
The attack lasted roughly one hour and was launched from 128,833 unique IP addresses, most of the attack concentrated on Frankfurt.
“It’s the long payload sent after the request headers that allowed the attackers to generate substantial traffic. Since this attack we’ve seen similar events with varying parameters in the request body,” states Cloudflare.“Sometimes these attacks came as GET requests, sometimes as POST. Additionally, this particular attack lasted roughly one hour, with 128,833 unique IP addresses.”

The analysis of the IoT devices involved in both attacks revealed that they have port 23 (telnet) open (closing connection immediately) or closed. Never filtered.
The vast majority of the IoT devices from the Vietnamese networks are connected CCTV cameras, most of them having open port 80 with presenting “NETSurveillance WEB” page.
What will happen in the future?
IoT devices will continue to be exploited by threat actors in the wild, “as more and more devices (fridges, fitness trackers, sleep monitors, …) are added to the Internet they’ll likely be unwilling participants in future attacks.”
It’s time to consider seriously the security of IoT devices.
Which are principal cities hostages of malicious botnets?
8.10.2016 securityaffairs BotNet
Which are principal cities hostages of malicious botnets? Symantec has tried to reply the difficult questions with an interesting study.
It is not a mystery, there is a strict link between cybercrime and Geography. Cyber criminal organization used different tactics and offer different products depending on the country where they operate. Russian criminal communities specialize in the sale of payment card data and hacking services, the Chinese ones focus on mobile meanwhile the Brazilian crooks shows great expertise in the banking trojan.
Today I desire to present the findings of an interesting research conducted by Symantec on the botnet diffusion. Let me highlight that botnet location doesn’t mean that the country also hosts control infrastructure neither that criminal organizations live in the same area.
“This map reveals which countries and cities unwittingly played host to the most bot-infected devices, such as PCs, Macs, smartphones, tablets and connected home devices, across Europe, the Middle East and Africa (EMEA) in 2015.” states Symantec. “The rankings, tables and percentages are determined by total bot volumes for each country and city. The measure of ‘Bot density’ refers to a comparison of the bot population to the number of internet users in any given country or city, and calculated by dividing the amount of internet users, as reported by Internet World Stats on September 20, 2016, by total number of unique bot infections detected in a given city or country in 2015.”
The experts of the security firm discovered that the Turkey (18.5% of EMEA’s total bot population) there is the highest number of infected machines recruited in botnets, Istanbul and the capital city Ankara contain the highest number of botnet controlled devices in EMEA.
Bad news for my country, Italy is at the second place (9.8% of EMEA’s total bot population) followed by the Hungary at the third place (9.1%
of EMEA’s total bot population), Rome is third in the ranking of places with highest bot population, followed by Budapest and Szeged.

The availability of botnets for sale and rent is a precious commodity for cyber criminal organizations that could use them for many illegal activities, such as DDoS attacks and spam campaigns.
In many cases, botnets are composed of compromised IoT devices (i.e. Cameras, routers, modems, and sensors) that could be used to launch powerful attacks.
Hungary ranks as the top country for bot density, Hungarian Internet users have a one in 393 chance of using a compromised device that is part of a botnet, meanwhile, in Italy the experts have found one bot for every 1829 internet users.
It is curious the data related to the principality of Monaco where people have the second largest chance of one of their devices being recruited in a botnet. Internet users in the principality have a one in 457 chance of owning a bot.
Give a look at the interactive map, by clicking on a country it is possible to see all the data collected in the study.
More than 500,000 IoT devices potentially recruitable in the Mirai Botnet
8.10.2016 securityaffairs BotNet
Security experts have discovered more than 500,000 vulnerable Internet of Things (IoT) devices that could be potentially recruited in the Mirai botnet.
In the last weeks, security experts observed two of the powerful DDoS attacks of ever that hit the hosting provider OVH and the websites of the popular security expert Brian Krebs.
Malware researchers believe that the attacks were launched by at least a couple of botnets, one of them is the dreaded Mirai botnet.
The Mirai ELF trojan was first spotted by experts from MalwareMustDie in August, the threat was targeting IoT devices in the wild.
Researchers believe that the attack against the OVH was powered by a botnet composed of a large number of compromised IoT devices, including DVRs and cameras.
Last week, the author of Mirai botnet released the source code of the malware that includes a list of 60 couples of usernames and passwords used by the malware to compromise the IoT devices.
The list of login credentials includes the default username/password combination root/xc3511 that according to the experts at Flashpoint allowed the hack in the majority of devices composing the Mirai botnet.
The botnet was mainly composed of video surveillance devices manufactured by Dahua Technology.
“While investigating the recent large-scale distributed denial-of-service (DDoS) attacks, Flashpoint identified the primary manufacturer of the devices that utilize the default username and password combination known as root and xc3511.” reads a report published by Flashpoint.
“These types of credentials exist all across the Internet and are commonly used via Telnet to access numerous types of DVRs. In fact, countless DVR manufacturers buy parts preloaded with Linux and rudimentary management software from a company called XiongMai Technologies, located in Hangzhou, China.”
Many device manufacturers use components of the Chinese company XiongMai Technologies. According to the experts, there are at least half a million devices worldwide using these vulnerable components that could be accessed with default credentials.
“Default credentials pose little threat when a device is not accessible from the Internet. However, when combined with other defaults, such as web interfaces or remote login services like Telnet or SSH, default credentials may pose a great risk to a device.” continues the report. “In this case, default credentials can be used to “Telnet” to vulnerable devices, turning them into “bots” in a botnet.”
The major risk related the firmware provided by the Chinese manufacturer is related to the combination of default hardcoded credentials and the availability of a Telnet service that is active by default and which allows remote access to the devices.
“The Dahua devices were identified early because of their distinctive interface and recent use in other botnets. Utilizing the “botnets. Utilizing the “Low Impact Identification Tool” or LIFT, Flashpoint was able to identify a large number of these devices in the attack data provided.” states the report.
“The issue with these particular devices is that a user cannot feasibly change this password. The password is hardcoded into the firmware, and the tools necessary to disable it are not present. Even worse, the web interface is not aware that these credentials even exist. Further exacerbating the issue, the Telnet service is also hardcoded into /etc/init.d/rcS (the primary service startup script), which is not easy to edit. The combination of the default service and hard-coded credentials has led to the assignment of has led to the assignment of CVE-2016-1000245 by the Distributed Weakness Filing Project.”
Flashpoint scanned the internet with the Shodan search engine for flawed IoT devices.
FlashPoint spotted more than 500,000 vulnerable devices in the wild, the countries with the highest number of vulnerable devices are Vietnam (80,000), Brazil (62,000) and Turkey (40,000).

Large-scale DDoS attacks continue to represent a serious threat for web services across the world, and IoT devices represent a privileged attack vector due to the lack of security by design. IoT manufacturers are encouraged to seriously consider the approach at the security of their products.
The source code of the Mirai IoT botnet leaked online. Do you trust it?
3.10.2016 securityaffairs BotNet
A hacker released the source code of the Mirai malware that powered the record-breaking DDoS attack against the Brian Krebs Website, but …
A couple of weeks ago the unknown hackers launched a massive Distributed Denial of Service (DDoS) attack against the website of the popular cyber security investigator Brian Krebs.
Further investigation revealed the involvement of a powerful botnet composed of more than 1 million Internet of Things used to launch the DDoS attack, the devices were infected by a certain malware that is now in the headlines because its code was publicly disclosed.
A reference to the malicious code was spotted by Brian Krebs on the popular criminal hacker forum Hackforum. The Hackforum user with moniker “Anna-senpai” shared the link to the source code of the malware “Mirai.”
“The leak of the source code was announced Friday on the English-language hacking community Hackforums. The malware, dubbed ‘Mirai’ spreads to vulnerable devices by continuously scanning the Internet for IoT systems protected by factory default or hard-coded usernames and passwords.” reported Krebs.

The Mirai malware was specifically designed to infect Internet of Things (IoT) devices using the credential factory settings, a circumstance that is quite common in the wild.
The first group of research that published a detailed analysis of the Mirai malware is the MalwareMustDie crew.
Experts from MalwareMustDie analyzed in August samples of a particular ELF trojan backdoor, dubbed ELF Linux/ Mirai, which was targeting IoT devices. The name of the malware is the same of the binary,”mirai.*,” and according to the experts, several attacks have been detected in the wild.
The ELF Linux/Mirai is very insidious, when the MalwareMustDie team discovered it many antivirus solutions were not able to detect the threat.
“The reason for the lack of detection is because of the lack of samples, which are difficult to fetch from the infected IoT devices, routers, popular brands of DVR or WebIP Camera, the Linux with Busybox binary in embedded platform, which what this threat is aiming.” states the analysis from MalwareMustDie Blog.
The last ELF examined by Security Affairs was the Linux Trojan Linux.PNScan that has actively targeting routers based on x86 Linux in an attempt to install backdoors on them.
But MalwareMustDie tells us that Linux/Mirai “is a lot bigger than PnScan”.
And continues: “The threat was starting campaign in early August even if this ELF is not easy to be detected since it is not showing its activity soon after being installed: it sits in there and during that time, no malware file will be left over in system, all are deleted except the delayed process where the malware is running after being executed.”
“The reason why not so many people know it”, says MalwareMustDie – “is that antivirus thinks it is a variant of Gafgyt or Bashlite or Bashdoor, or what hackers refer as LizKebab/Torlus/Gafgyt/Qbots. Then, the real samples of this malware is hard to get since most malware analysts have to extract it from memory on an infected device, or maybe have to hack the CNC to fetch those.”
This means that also the forensic analysis can be difficult if we switch off the infected device: all the information would be lost and maybe it would be necessary start again with a new infection procedure, in case.
Back to the present, let’s read the announcement made by Anna-senpai.
“When I first go in DDoS industry, I wasn’t planning on staying in it long. I made my money, there’s lots of eyes looking at IOT now, so it’s time to GTFO,” Anna-senpai wrote. “So today, I have an amazing release for you. With Mirai, I usually pull max 380k bots from telnet alone. However, after the Kreb [sic] DDoS, ISPs been slowly shutting down and cleaning up their act. Today, max pull is about 300k bots, and dropping.”
“So, I am your senpai, and I will treat you real nice, my hf-chan,” Anna-senpai added, cheekily using the Japanese honorific for a fellow classmate.”
While many experts are investigating the reason why the hacker published the code of the Mirai Malware online, authoritative experts have doubts about its authenticity.
Someone speculate that the hackers behind the threat intend to spread the Mirai malware code around to make hard the investigation of the last string of DDoS attacks, including the one against Brian Krebs’s website.
“Miscreants who develop malicious software often dump their source code publicly when law enforcement investigators and security firms start sniffing around a little too close to home,” wrote Krebs“Publishing the code online for all to see and download ensures that the code’s original authors aren’t the only ones found possessing it if and when the authorities come knocking with search warrants.”
I contacted the MalwareMustDie research team for a comment.
“When the Mirai malware was we firstly published on the Internet, it was widespread news, almost everyone knows that, including the Mirai herder/seller actor who just “released” the malicious code. He didn’t act anything that time. The code was originally coded by a third-party and was used to run services by the mentioned actor w/modification etc. We suspect, it is NOT the original one, but it is partial or modified version with the intent to leak it. He is not sharing it generously. If a blackhat actor leaks such level of codes with that kind of disclosure, experiences has tons of proof that must be something not right behind it. He wanted to believe it is legit, I ask you now: “How would you trust a criminal actor?’s statement”” “If you see the forum well, NO ONE in the thread was successfully can build the Mirai botnet service as per instruction the bad actor “generously leaked”.. So, what is the purpose of leaking something that doesn’t work as per expected? What was leaked then? Yes, the “leaked code” was partially looked like Mirai functionality, but is that all of the code? I surely don’t think so.”
The statement above looks making much sense, looking at the thread in the forum where the source was published, there was hardly found successfully built test as per instruction that the bad actor “generously leaked.”
Then I asked MalwareMustDie, what is the purpose of leaking something that doesn’t work as per expected? What was leaked then?”
“Yes, the “leaked code” was partially looked like Mirai functionality, but is that all of the code? I suspiciously don’t think so..” said MalwareMustDie.
” He furtherly added: “Who would trust the blackhat bad actor’s statement? I urge him to surrender himself to the law before he makes some more announcement”
Necurs botnet: the resurrection of the monster and the rising of spam
29.9.2016 securityaffairs BotNet
Necurs botnet, the monster is resurrected. Banking Trojans and Ransomware propagated via spam is bring backing the high-volume spam campaign
Botnets are like monsters that surface back after some period of inactivity, this time, the monster it the dreaded Necurs botnet. The Necurs Botnet is one of the world’s largest malicious architectures, used to spread the dreaded threats, that vanished since June 1.
The Necurs Botnet was used by crooks to deliver the Dridex banking malware and the dreaded Locky ransomware, but now many security experts wondered about its end.
“We can only tell that the Dridex and Locky spam campaigns stopped since June 1 in our observation. We cannot confirm how the botnet was brought down yet,” Joonho Sa, a researcher for FireEye confirmed to Motherboard.
When it was first spotted earlier 2015, the experts classified the malicious infrastructure used to spread the threat as high-complex and efficient, “a masterpiece of criminality.”

On October 2015, an international joint effort of law enforcement agencies, including the FBI and the NCA, destroyed the botnet, but it resurrected after and was used to mainly spread the Locky ransomware. Experts called it Necurs and confirmed it was the world’s largest botnet.Ba
Back to the present, it’s like watching a sequel to a monster movie where the monster actually resurrected. Normally a sequel is made for profit and sometimes in the case of botnets as well these monsters are brought back to life for sequels as well.
Consider the recent increase in Spam volumes. The average of 200K IP addresses was listed under SpamCop Block list till before 2016. Just this year the list has doubled to 400K IP addresses even spiking to 450K. Yes, we might be seeing a sequel to an old monster flick.
Using obsolete tactic of high-volume spam which is currently well blocked by updated spam filters. Now the tactic of a huge amount of spam in a short interval of time has been replaced by stealthier tactics, but the operators behind the Necurs botnet have changed their attack variation from persistence to speed. To shed better light on the situation lets consider the spam filters as automatic jail doors and spams as convicts trying to escape. The idea is to use the small delay in the jail doors closing to put through as many convicts as possible . In this case, the convicts which make it through are emails which can land malware payloads to the targets.
Experts from the Cisco Talos Labs published an interesting analysis on the “Rising Tides of Spam” that is affordable to the operators of malicious infrastructures, like the Necurs botnet.
“This year, 2016, has seen overall spam volumes creep back up to a level that we have not seen for a very long time. I present to you “Exhibit A”: The ten year volume graph from the Composite Block List (CBL). According to CBL, the last time spam volumes were this high was back in mid-2010.” states the blog post published by the Talos team.

It’s more like the short term campaigns are giving better turnover to the attackers.
The Lurk takedown has contributed to some extra prey to the attackers behind the Necurs botnet and has been a win-win for them ever since. Since the campaign has been profitable to the malicious attacker, researchers caution that the attack model maybe would be copied by other botnet operators.
“Email threats, like any other, constantly evolve. As we grow our techniques to detect and block threats, attackers are simultaneously working towards evading detection technology. Unfortunately there is no silver bullet to defending against a spam campaign. Organizations are encouraged to build a layered set of defenses to maximize the chances of detecting and blocking such an attack” explained the Talos Team.
Hence monster movie reboots and sequels are in the forecast. The question is are you buying tickets or preparing your spam protection mechanism.
Cisco Talos profiled the GozNym botnet after cracking the trojan DGA
28.9.2016 securityaffairs BotNet
The Talos team published a detailed analysis of the GozNym botnet, it was possible because the experts cracked the DGA algorithm used by the malware.
In April 2015, the researchers from the IBM X-Force Research discovered a new banking Trojan dubbed GozNym Trojan that combines best features of Gozi ISFB and Nymaim malware.
The GozNym has been seen targeting banking institutions, credit unions, and retail banks. Among the victims of the GozNym Trojan there are 24 financial institutions in North America and organizations in Europe, including a Polish webmail service providers, investment banking and consumer accounts at 17 banks in Poland and one bank in Portugal.
Now experts from Cisco’s Talos team who have analyzed the threat have identified four variants that differ in the usage of the Domain generation algorithm (DGA).
A DGA is an algorithm that allows malware to periodically generate a large number of domain names that are used as rendezvous points with their C&C servers.
The crooks used spear phishing messages containing specially crafted Word documents as an attack vector. Once the victims open the documents and enable the macro, a VBA code download and execute the GozNym.
Once the malware has infected a system, it checks Internet connectivity through a DNS query for google.com and microsoft.com records. In presence of a connection, it contacts the command and control (C&C) domains generated by the DGA via a simple gethostbyname API call or via a complex DNS protocol implementation either 8.8.4.4 or 8.8.8.8 as its server.
The GozNym banking Trojan hijacks victims’ browsing sessions redirecting them to a phishing website.
The experts from the Talos group identified several DGA variants, below the description of one of them published by the malware researchers.
“In the first stage of DGA, a variation of the XORShift Pseudo-Random Number Generator (PRNG) is used to create a list of fifteen domains. The PRNG is seeded with a bit-shifted value of the current day, as well as two hard coded DWORDs. Each domain is between 5 and 12 lowercase letters long, followed by a randomly selected TLD of .net, .com, .in, or .pw. GozNym then uses Google’s DNS server to query each domain, and checks if the IP responses are publicly routable. Once it resolves 2 different IPs, it uses those in the second stage of the DGA.” reads the analysis published by the Talos group.
In the second stage, the malware creates a list of 128 domain names using the same methods of stage 1, but it replaces the hardcoded DWORD seeds with the IP addresses obtained in the first stage. The GozNym DGA is complex, but Cisco researchers have identified flaws that allowed them to predict domain names using brute force.
The researchers from Talos have discovered vulnerabilities in the DGA that allowed them to predict domain names used by the threat, an information that precious for malware hunters that can use DNS sinkholes to analyze the malware.
The experts were able to profile the botnet, the sinkhole server they used, received 23,062 beacons within the first 24 hours. This means that the botnet is roughly composed of 23,062 machines because each of the would only send just one beacon, except the cases of sandboxes, which may beacon out several times from a small set of IPs.
The number of unique IPs belonging to the botnet is 1854.
A loot at the top countries from which beacons were received reveals that most of them are from Germany (47%) and the United States (37%).

I suggest reading the analysis published by the Talos team that also include some scripts that can be used to analyze the GozNym samples:
DGA_release.py which simulates the DGA used by GozNym.
Extract_parameters_from_http_post.py which extracts parameters from the HTTP POST requests that are sent to C2 servers.
Decrypt_response.py which allows for a decryption of the response payload.
BASHLITE Botnets peaked 1 Million Internet of Thing Devices
1.9.2016 securityaffeirs BotNet
A joint research conducted by Level 3 Communications and Flashpoint allowed the identification of a million devices infected by the BASHLITE malware.
Do you remember the BASHLITE malware? It was a strain of malware (also known as Lizkebab, Torlus and Gafgyt) detected by experts at Trend Micro shortly after the public disclosure of the ShellShock bug.
The BASHLITE malware includes the code of the ShellShock exploit and it had been used by threat actors in the wild to run distributed denial-of-service (DDoS) attacks.
It could infect multiple Linux architectures, for this reason, crooks used it to target Internet of Things devices.
In June, experts from the security firm Sucuri spotted a botnet composed of tens of thousands of CCTV devices that had been used by crooks to launch DDoS attacks against websites.
The BASHLITE source code was leaked online in early 2015, malware developers used it to create their own variant.
Now experts from Level 3 and Flashpoint confirmed the overall number of devices infected by the BASHLITE malware is more than 1 million.
The number includes compromised devices belonging to several botnets, according to the experts, almost every infected device are digital video recorders (DVRs) or cameras (95%), the remaining is composed of routers (4%), and Linux servers (1%).
“Of the identifiable devices participating in these botnets, almost 96 percent were IoT devices (of which 95 percent were cameras and DVRs), roughly 4 percent were home routers and less than 1 percent were compromised Linux servers. This represents a drastic shift in the composition of botnets compared to the compromised server- and home router-based DDoS botnets we’ve seen in the past.” states a blog post published by Level 3 firm.
The researchers have been tracking more than 200 C&C worldwide used by the BASHLITE botnets. Fortunately, the IP addresses of the C&C servers was found hardcoded in the instance of malware detected in the wild making easy for experts to shut down them.
The researchers provided interesting details about the Global Distribution of the gafgyt Bots, the vast majority of infected devices are located in Brazil, Taiwan and Colombia.
“Of the bots we’ve observed participating in attacks, peaking at more than 1 million devices, a large percentage are located in Taiwan, Brazil and Colombia. A large majority of these bots were using white-labeled DVRs generically described as “H.264 DVRs” and DVRs manufactured by the company Dahua Technology.” continues the post. “We have contacted Dahua Technology to make them aware of this issue. Our investigation shows more than one million of these two types of devices are accessible on the internet, providing a large pool of potential bots.”

It is quite easy for hackers to compromise DVRs that are affected by multiple critical vulnerabilities. In many cases, the same flawed software is used by multiple vendors for their devices.
“Most of these devices run some flavor of embedded Linux. When combined with the bandwidth required to stream video, they provide a potent class of DDoS bots,” continues the post.
According to the experts, crooks behind the botnets have used some of the C&C servers to launch more than 100 attacks per day.
“Most attacks are short-lived, with the median duration just over 2 minutes, and 75 percent of attacks shorter than 5 minutes.”
“The use of IoT devices in botnets is not new, but as they become more common, we expect these types of botnets to increase in number and power,” Level 3 said in a blog post. “The security of IoT devices poses a significant threat. Vendors of these devices must work to improve their security to combat this growing threat. ”
Redirector.Paco, a Million-Machine Clickfraud Botnet
17.5.2016 BotNet
According to the experts at Bitdefender an HTTPS hijacking click-fraud botnet dubbed Redirector.Paco infected almost 1 million devices since now.
Security experts at Bitdefender spotted a new click fraud botnet dubbed Redirector.Paco that has been around at least since September 2014 and has already infected more than 900,000 devices over the years.
Crooks behind the Redirector.Paco aimed to create a clickbot that is able to redirect all traffic performed when using a search engine (i.e. Google, Yahoo or Bing) and to replace the legitimate results with others decided by hackers to earn money from the AdSense program.
“To redirect the traffic the malware performs a few simple registry tweaks. It modifies the “AutoConfigURL” and “AutoConfigProxy” values from the “Internet Settings” registry key so that for every request that a user makes, a PAC (Proxy auto-config) file will be queried. This file tells the browser to redirect the traffic to a different address.” states a blog post from BitDefender.
The experts highlighted the existence of some indicators that could be associated with the fraudulent activity of the botnet, including:
Displaying messages like “Waiting for proxy tunnel” or “Downloading proxy script” in the status bar of the browser.
Long page loading time for Google page.
Missing “o” characters above the number of search result pages.
The threat actors behind the Redirector.Paco botnet used to deliver the malware by bundling it with installers for benign applications, such as WinRAR and YouTube Downloader.
In one of the attacks spotted by the experts at Bitdefender, the installers dropped JavaScript files that modify the “Internet Settings” registry key in order to change the behavior of the web browser and force it into using a proxy auto-configuration (PAC) file created by the attacker to provide fake search results. The attackers also rely on a root certificate so that any connection that goes through the server specified in the PAC file looks private without raising suspicion.
“As shown, any request to any page that starts with https://www.google or https://cse.google will be redirected to the IP 93.*.*.240 on port 8484. However, at this point, since the requests are made on the HTTPS protocol, they will be accompanied by a warning that alerts the user that there is a problem with the certificate.” continues the post. “Update.txt downloads and installs a root certificate so that any connection that goes through the server specified in the PAC file looks private.”
The experts also spotted a variant of the Redirector.Paco botnet that relies on a .NET component that modifies search results locally by setting up a local server without redirecting traffic to an external server.
Most infected devices are located in India, but experts observed several infections also in the United States, Malaysia, Greece, Italy, Brazil and other African countries.
Redirector.Paco botnet infections

Journey of a ‘Hacked Computer’ : From Torrents to Botnets
8.5.2016 BotNet
One out of every three websites were involved in transmitting malware to their users, which was found attached to their digital content.
Suppose, there is a movie, released last month. You didn’t have the time to watch it in the theatre and you also want to save some money. What would you do? Go to any one of the torrent sites and download it.It’s THAT simple. Isn’t it?
Have you ever wondered why is that is so simple? Here’s the answer.
It’s all about money. When you downloaded a movie/a cracked software or any kind of pirated material for free from torrent sites. They may provide you that cracked software or a 1080p HD movie and a malware bound with it. This malware is mostly ‘Trojans’ which steal every sensitive information they can, from your computer including your passwords, pictures from webcam, other documents and can also lock your computer in exchange for a ransom or mine bitcoins using your computer!
Apart from stealing critical information, this malware are capable of making your device part of a ‘Botnet Army’ along with millions of other victims like you. Botnets are controlled by their command and control servers, also called as ‘C&C Servers’ or ‘C2 Servers’. Access to these millions of devices is also given to the black hats for rent .The rent depends upon the number of systems, their hardware configuration, operating systems and the duration of their usage. Black hats / cyber-criminal groups such as ‘APT29’ use them as digital slaves for spamming, performing DDOS attacks, harvesting credentials and for other malicious operations.
According to RiskIQ, a San Francisco-based cybersecurity company, which was authorized by the Digital Citizens Alliance (DCA) to conduct the study titled as “Digital Bait” which scanned 800 websites with pirated content.” It was realized, one out of every three websites were involved in transmitting malware to their users, which was found attached to their digital content”.
The earning of these pirate websites is estimated to be around $70 Million a year.once a device is a part of the ‘botnet army’, also called as a ‘zombie’ it can be used for many malicious activities such as DDOS attack, spreading of other malware etc. without the user’s consent. The banking information stolen from these victims are sold in the ‘black market’ for around $2 – $130 per credential.
Here are some screenshots, I acquired from social media that may give you an idea on the working of botnets and their command and control servers.


Typical botnet topologies include:
Star, in which the bots are controlled by a central server.
Multi-server, in which there are multiple C&C servers for redundancy.
Hierarchical, in which there are multiple C&C servers.They are organized into tiered groups.
Random, in which there is no C&C server at all. Co-opted computers communicate as a peer-to-peer botnet (P2P botnet).
For example, The SpyEye and Zeus botnets have also been extremely profitable and widespread for their commanders. Both steal banking credentials from victims and automate the process of grabbing money from accounts. The creators of Zeus botnet sold it to various criminal gangs who infected more than 13 million computers with it from 2008 on, and used it to steal more than $100 million. The cyber security firms estimate that botnets, over time, have resulted in more than $110 Billion in losses to victims all over the world. An estimated 500 Million computer devices are infected via botnet attackers annually, which is around 18 victims infected per second.
There is always a ray of hope. According to Symantec’s Internet Security Threat Report, Volume 21 (Apr 2016), There are 1.1M bots in 2015, decreased 42%, while comparing to the number of bots in 2014, which was 1.9M.
Various CERTs,IT security firms and law enforcement agencies are working together to fight global cyber crime. In December,2015 the INTERPOL took down a ‘Dorkbot’ botnet in coordination with Microsoft,CERT Polska, ESET,US Department of Homeland Security’s United States Computer Emergency Readiness Team(US-CERT), the Indian Central Bureau of Investigation(CBI), Europol, Canadian Radio-television and Telecommunications Commission, US Federal Bureau of Investigation(FBI), the Royal Canadian Mounted Police, National Central Bureau in Russia, the Russian Ministry of Interior Department K and the Turkish National Police.
Dorkbot was used to carry out the following activities using its victims’ computers.
Stealing keystrokes from banking websites or online payment websites.
Performing Distributed denial of service attacks.
Providing a mechanism to download other dangerous malwares.
Same as many botnets, Dorkbot was spread via USB Flash drives, social networks and instant messaging software,you are advised to scan your computers with anti-virus software regularly.
Just like Dorkbot,there are several botnets taken down by joint efforts of the law enforcement agencies and cyber security companies.which involves takedown of Simda botnet,Dridex botnet and Ramnit botnet.some of them may continue to propagate.
You can always stay safe using up-to-date anti-virus software, firewalls etc.if you suspect a file to be malicious, always use a sandbox to execute it. According to the industry’s estimated infection reports, in the few minutes it took you to read this article, more than 3,000 new computers have joined the botnet army.
Security experts shut down the dreaded Linux Mumblehard botnet
10.4.2016 BotNet
Researchers and law enforcement in a joint effort shut down the Mumblehard botnet composed of more than 4000 Linux machines.
Security experts have shut down a spam botnet, known as Mumblehard, composed of more than 4,00o Linux machines.
In May 2015, researchers from ESER revealed the sophisticated Mumblehard spamming malware infected thousands of Linux and FreeBSD servers going under the radar for at least five years.
The infected machines were part of a botnet used, in the preceding five years, to run spam campaign, a version of the Mumblehard malware was uploaded for the first time to the VirusTotal online malware checking service in 2009.
At that time, security experts at ESET have monitored the botnet during the previous 7 months by sinkholing one of its C&C servers and observing 8,867 unique IP addresses connected to it, with 3,000 of them joining in the past three weeks.

Today the botnet was dismantled, the experts speculate that operators behind the Mumblehard botnet are highly skilled developers that designed a custom “packer” to conceal the Perl-based source code that made it run, a backdoor, and a mail daemon that was able to send large volumes of spam messages.
The experts that accessed the C&C infrastructure used for the Mumblehard botnet, discovered an interesting automatic delisting mechanism from Spamhaus’ Composite Blocking List (CBL)
“Another interesting aspect of the Mumblehard operation revealed by our access to the C&C server was the automatic delisting from Spamhaus’ Composite Blocking List (CBL).” reported a blog post published by ESET. “There was a script automatically monitoring the CBL for the IP addresses of all the spam-bots. If one was found to be blacklisted, this script requested the delisting of the IP address. Such requests are protected with a CAPTCHA to avoid automation, but OCR (or an external service if OCR didn’t work) was used to break the protection.”
Researchers from ESET worked with Estonian law enforcement and an industry partner to shut down the Mumblehard botnet, a complex operation conducted by “sinkholing” the control infrastructure.
In February the experts took control of the Internet address belonging to the command server, by analyzing the incoming traffic they were able to estimate that the malicious infrastructure was composed at least of 4,000 machines.

Despite the researchers shut down the botnet, they are still investigating how the attackers composed a so large infrastructure. The researchers initially suspected that attackers compromised websites running WordPress CMS, but further analysis excluded this hypothesis.
“We knew some of the victims had been compromised through an unpatched CMS such as WordPress or Joomla, or one of their plugins. Forensic analysis of the C&C server suggests that computers running the Mumblehard bot agents were not initially compromised from that specific server.” states the report.
“The scripts we found were only to be run where PHP shells had already been installed. Perhaps Mumblehard’s operators were buying access to these compromised machines from another criminal gang?”
The GM Bot v2 released after source leak, it is more expensive of v2
15.3.2016 BotNet
After the source code of the Android banking Trojan GM Bot was leaked online, the new version GM Bot v2 was offered for sale.
The availability of the source code of a malware in the criminal underground represents a great opportunity for crooks that can customize the threat allowing its evolution in an unpredictable way.
After the source code of the Android banking Trojan GM Bot was leaked online, a new version of the threat appeared in the wild.
In February, the experts at IBM X-Force threat intelligence discovered the source code for Android malware GM Bot was leaked on an underground. The source code was leaked in December 2015, it includes the bot component and the control panel.
Of course, the code rapidly spread within the criminal ecosystem, it now that is available online for free malware developers started to work on it.
GM Bot appeared in the wild in 2014, when the authors were offering it in the Russian underground as a powerful instrument for mobile phishing.
android malware GM Bot v2
The malware implements a number of features to target Android users, including intercepting SMS messages. The malware allows attackers to gain control of the targeted device, including the customization of fake screens.
In short, mobile banking Trojans such as GM Bot are a one-stop fraud shop for criminals:
They launch fake overlay windows that mimic bank applications to steal user credentials and payment card details.
They control the device’s SMS relay to eavesdrop, intercept and send out SMS messages.
They can forward phone calls to a remote attacker.
They have spyware features and can control the device via remote commands.
The original creator of the Android malware sold the rights to distribute GM Bot v1 (aka MazarBot) to other cyber criminal organizations that are offering it for $5000.
Other variants of GM Bot are known as MazarBot, SlemBunk, Bankosy, Acecard and Slempo.
The new GM Bot v2 variant, which is currently in a testing phase, was developed from scratch by the original developer using the moniker “GanjaMan.”
“After news from IBM X-Force about the leak of Android malware GM Bot’s source code, the author of GM Bot released a second version of the malware. News of v2 came from the official GM Bot developer and vendor, a user going by the alias GanjaMan in venues where the malware is sold.” wrote Limor Kessem, cybersecurity evangelist at IBM.
“According to an underground forum post authored by GM Bot’s vendor, it took six months’ worth of work for this updated version of GM Bot. GanjaMan adds that v2 was “written from scratch,” perhaps in order to emphasize that it does not use the previous version’s code, which was recently leaked by one of its dubious customers.”
According to the experts at the IBM Security, GanjaMan explained that GM Bot v2 includes three different Android exploits that can be used to infect mobile devices. The exploits have been already fixed by Google, so it is likely GanjaMan will add other exploits in the coming variants.
The developer announced also significant improvements for the malware, including rootkit features and the use of the Tor communication channel.
The new GM Bot v2 variant that includes all the available packages and exploits costs $15,000 and an additional $2,000 monthly rental fee that must be paid starting with the second month of use.
Cybercriminals can decide to not pay for the exploits, in this case GM Bot v2 goes for $8,000 and a $1,200 monthly rental fee.
“Judging by past cases of underground malware vendors, the monthly rental fees are most likely technical support fees. Trojan vendors have been known to run into debilitating operational issues as a result of having to provide support to their buyers without getting paid for the extra time spent on resolving issues, bugs and technical questions. The monthly fee concept helps the developers hire tech support agents to handle requests while they continue to develop and sell the malware,” continues Kessem.
GanjaMan is also searching for peers pay-per-install accomplices and cybercriminals who can help with directing Web traffic in countries his buyers would be interested in targeting.
Stay Tuned.
Mazar Bot actively targeting Android devices and wiping them
15.2.2016 BotNet
A new malware dubbed Mazar Bot is threatening Android users and has the ability to gain root access to the mobile device and completely wipe it.
A new threat is threatening Android users, its name is Mazar BOT and has the ability to gain root access to the mobile device and completely wipe its storage.
Mazar BOT could be used by threat actors to recruit victims’ Android devices in a mobile botnet.
The experts at Heimdal Security spotted the Mazar BOT in live attacks while they were investigating an SMS message sent to random mobile numbers and locations. Mazar BOT spreads via a spam SMS or MMS that arrives with the following link (sanitized by Heimdal Security) to a malicious APK:
You have received a multimedia message from +[country code] [sender number] Follow the link http: //www.mmsforyou [.] Net / mms.apk to view the message.”
Once the victim clicks the link above, he will download the APK file on their Android devices. When the file is executed it prompts the user to install a new application with a generic name, MMS Messaging, that asks for admin level privileges … and most of the users give them to the app.

The admin privileges allow the threat actors to perform the following operations:
Gain boot persistence to help survive device restarts
Send and Read your SMS messages
Make Calls to your contacts
Read the phone’s state
Plague phone’s control keys
Infect your Chrome browser
Change phone settings
Force the phone into sleep mode
Query the network status
Access the Internet
Wipe your device’s storage (the most critical capabilities of all)
The researchers at Heimdal Security observed that Mazar BOT is also able to download and install a legitimate TOR Android app on the infected device, even without the user’s interaction.
“In the next phase of the attack, the infection will unpack and run the TOR application, which will then be used to connect to the following server: http: // pc35hiptpcwqezgs [.] Onion.
After that, an automated SMS will be sent to the number 9876543210 (+98 is the country code for Iran) with the text message: “Thank you”. The catch is that this SMS also includes the device’s location data.” continues the post.
The mobile malware can use the Tor app to surf the Internet anonymously. The experts also noticed that Mazar BOT also installs an Android app called Polipo Proxy which acts as a local proxy for the user’s traffic. The Polipo Proxy could be used by attackers malware’s author to spy on victim’s Web traffic and carry out Man-in-the-Middle (MitM) attacks.
The experts believe that the Mazar BOT is operated by a Russian cyber criminal gang, it is curious that the malware cannot be installed on Android smartphones in Russia. The analysis of the source code of the malware revealed the presence of instructions on how to stop the malware installation process on phone configured with the Russian language.
Another clue that suggests the involvement of Russian bad actors is that the Mazar BOT is offered for sale on several Russian underground forums.
In order to protect mobile devices from this threat follow these simple suggestions:
Don’t click on links in SMS or MMS messages sent to your phone.
Go to Settings → Security → Disable the option “Allow installation of apps from sources other than the Play Store.”
Install and keep an up-to-date Anti-virus solution on your Android device.
Avoid unsecured Wi-Fi hotspots and keep your Wi-Fi turned OFF when not in use.
Someone has pwned the Dridex botnet serving the Avira Antivirus
5.2.2016 BotNet
Unknowns have pwned the Dridex botnet and are using it to spread a legitimate copy of the Avira Antivirus software instead the malicious payload.
This story is very intriguing, someone has hacked a portion of the dreaded Dridex botnet and replaced malicious links with references to installers for the Avira Antivirus. The Antivirus company denies any involvement and speculate the involvement of an unknown white hat hacker.
Spam campaigns relying on the Dridex malware are threatening banking users across the world despite the operations conducted by law enforcement on a global scale. We left Dridex malware spreading across the Europe, in particular targeting the customers of the banks in the UK. In October, the NCA has uncovered a series of cyber attacks based on a new strain of the Dridex banking trojan that allowed crooks to steal £20m in the UK alone.

Now Dridex is once again in the headlines, spam emails containing the famous malware are continuing to target netizens despite the arrest of one of its botmasters in August.
In October the experts at Palo Alto Networks confirmed that the overall volume of Dridex emails peaked nearly 100,000 per day, the campaign rapidly reached 20,000 emails, mostly targeting emails accounts in the UK.
Spam messages often include malicious Word documents embedded with macros, when victims open the macros download the Dridex payload from a hijacked server. Dridex is a banking trojan that relies on web injection to manipulate banking websites and use a keylogger component to monitor victim’s activity.
Now someone has pwned the Dridex botnet and is using it to spread a legitimate Antivitus software instead the malicious payload. Despite the noble intent, even the action of this unknown is illegal because he is spreading an installer on the victims’machine without their consensus.
“The content behind the malware download URL has been replaced, it’s now providing an original, up-to-date Avira web installer instead of the usual Dridex loader,” explained Moritz Kroll, a malware researcher at Avira.
“We still don’t know exactly who is doing this with our installer and why – but we have some theories,” said Kroll. “This is certainly not something we are doing ourselves.”
“A whitehat may have hacked into infected web servers using the same vulnerabilities the malware authors used in the first place and has replaced the bad stuff with the Avira installer,” added Kroll.
Avira was involved in a similar case in the past when the installer has been included into the CryptoLocker and Tesla ransomware.